Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
130 results about "Stack trace" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
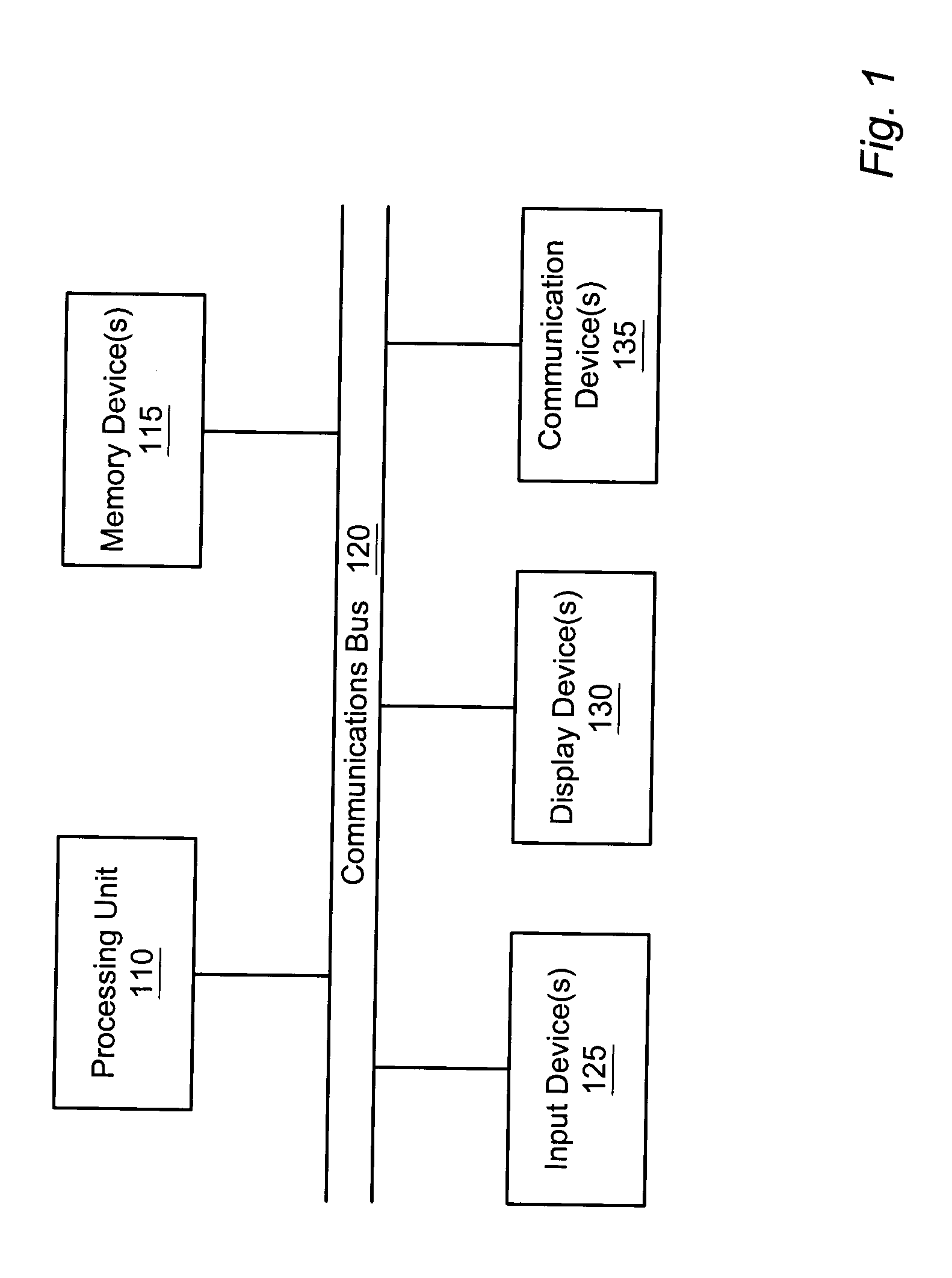
In computing, a stack trace (also called stack backtrace or stack traceback) is a report of the active stack frames at a certain point in time during the execution of a program. When a program is run, memory is often dynamically allocated in two places; the stack and the heap. Memory is continuously allocated on a stack but not on a heap, thus reflective of their names. Stack also refers to a programming construct, thus to differentiate it, this stack is referred to as the program's runtime stack. Technically, once a block of memory has been allocated on the stack, it cannot be easily removed as there can be other blocks of memory that were allocated before it. Each time a function is called in a program, a block of memory is allocated on top of the runtime stack called the activation record (or stack pointer.) At a high level, an activation record allocates memory for the function's parameters and local variables declared in the function.
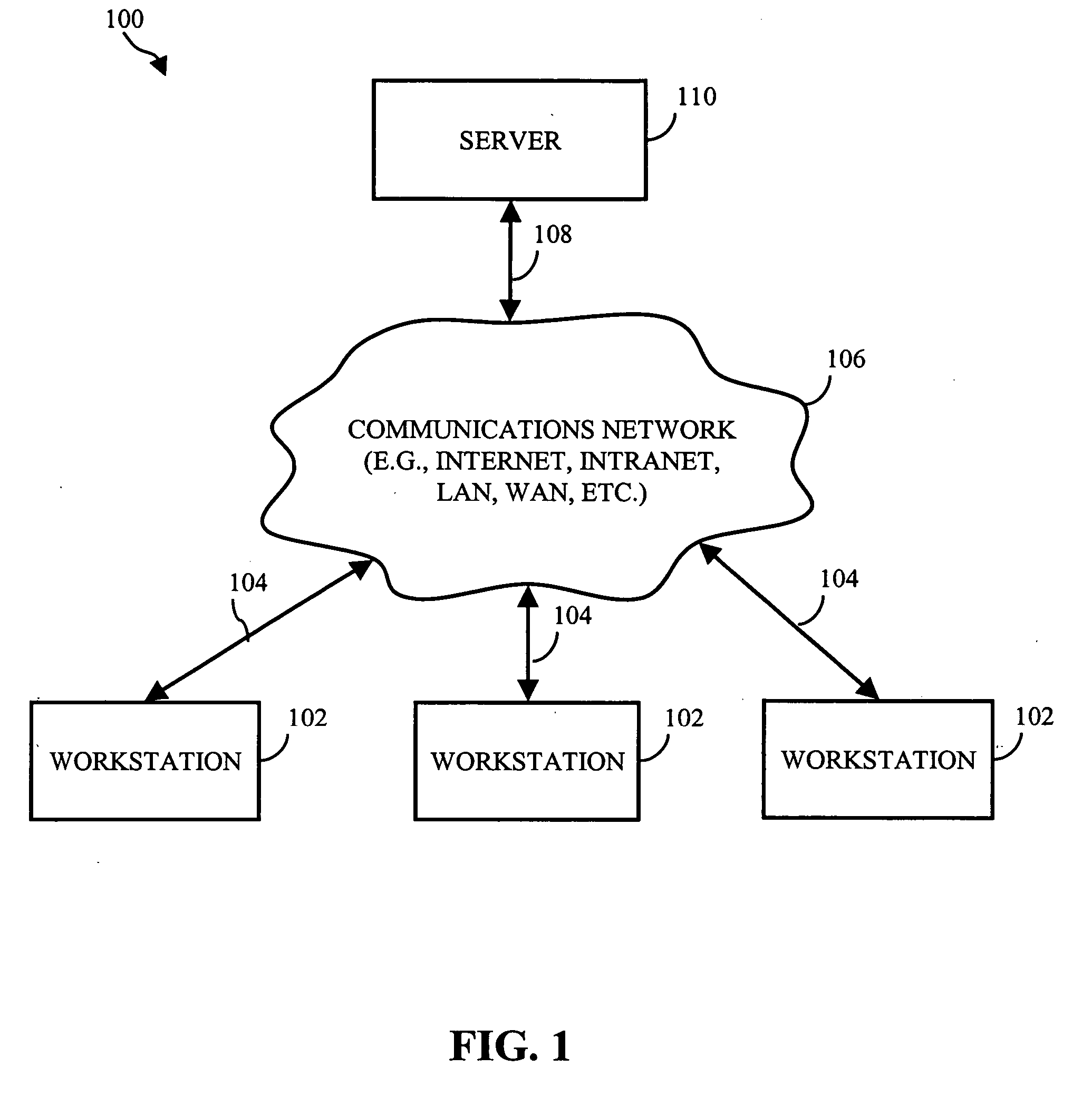
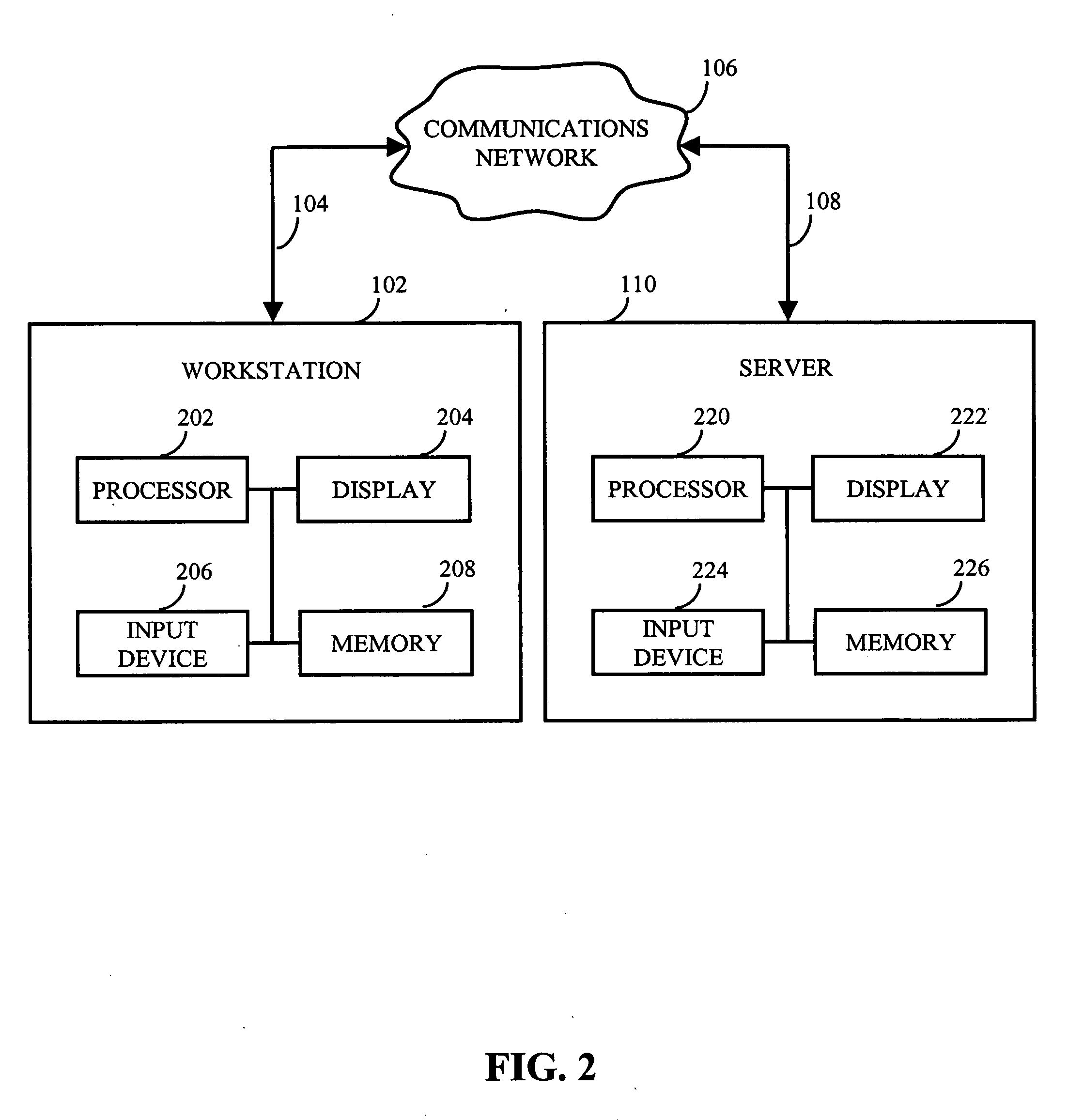
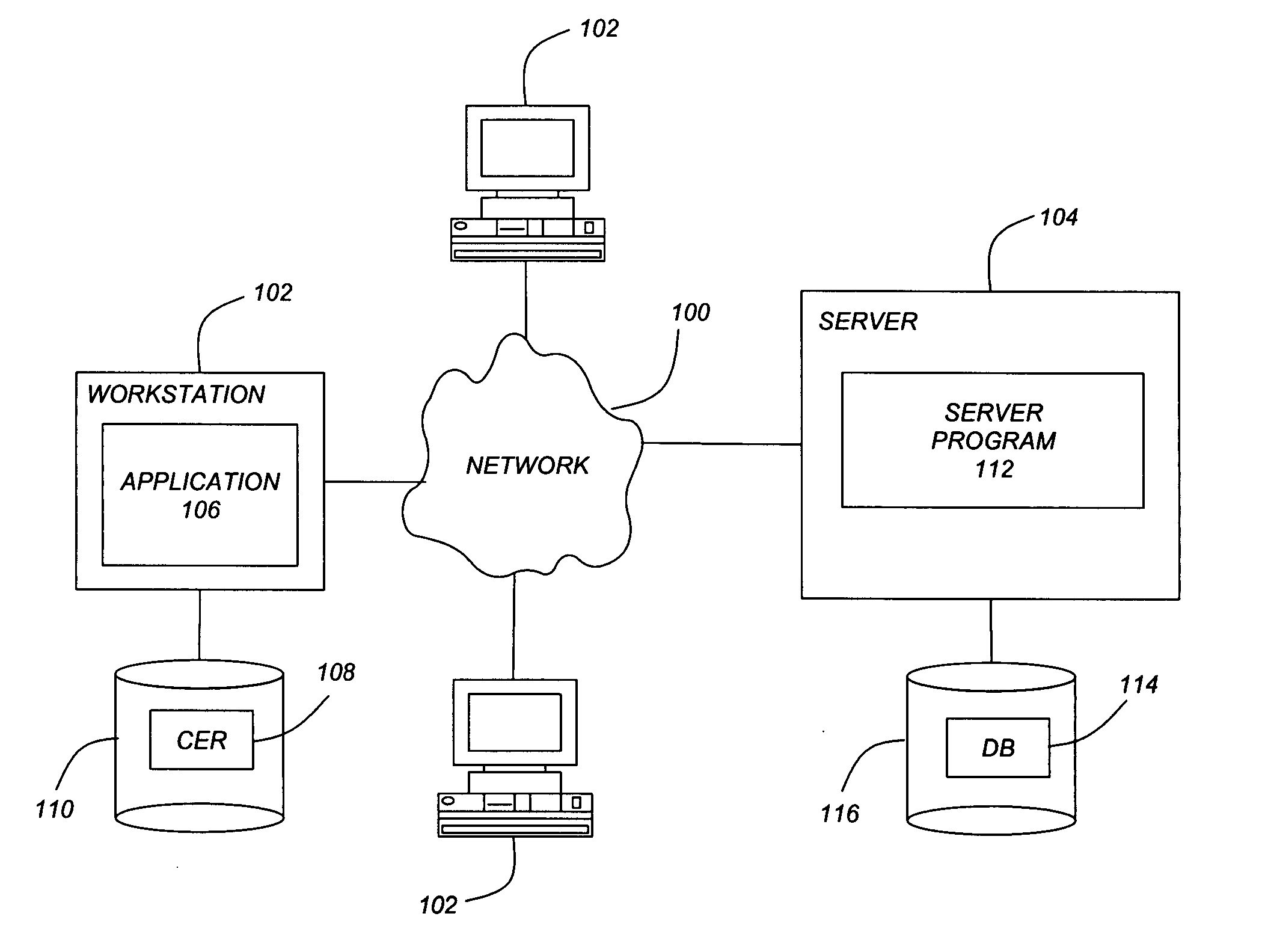
Method and apparatus for breaking down computing tasks across a network of heterogeneous computer for parallel execution by utilizing autonomous mobile agents
InactiveUS7082604B2Ease of parallel processingProgram initiation/switchingResource allocationApplication softwareLarge applications
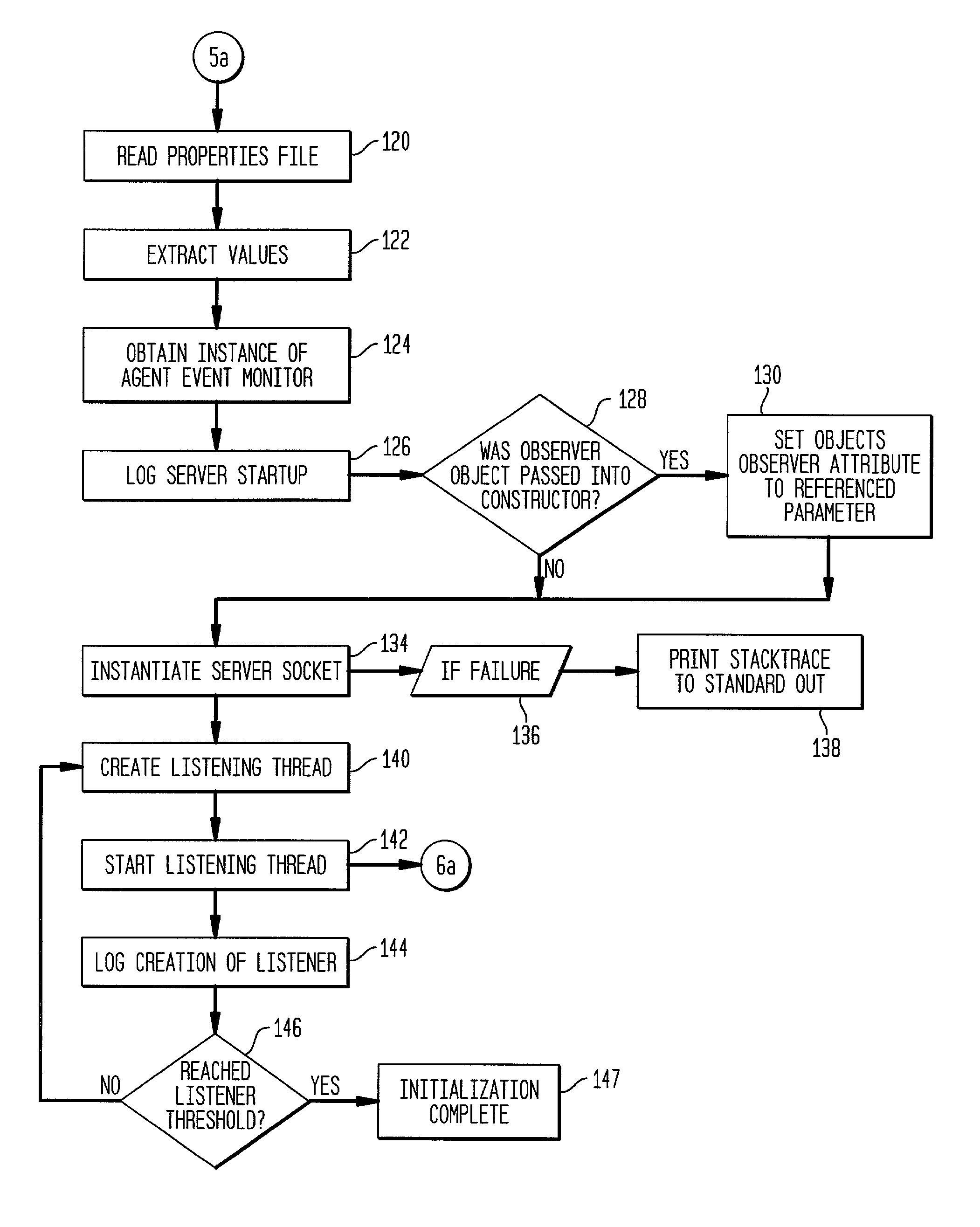
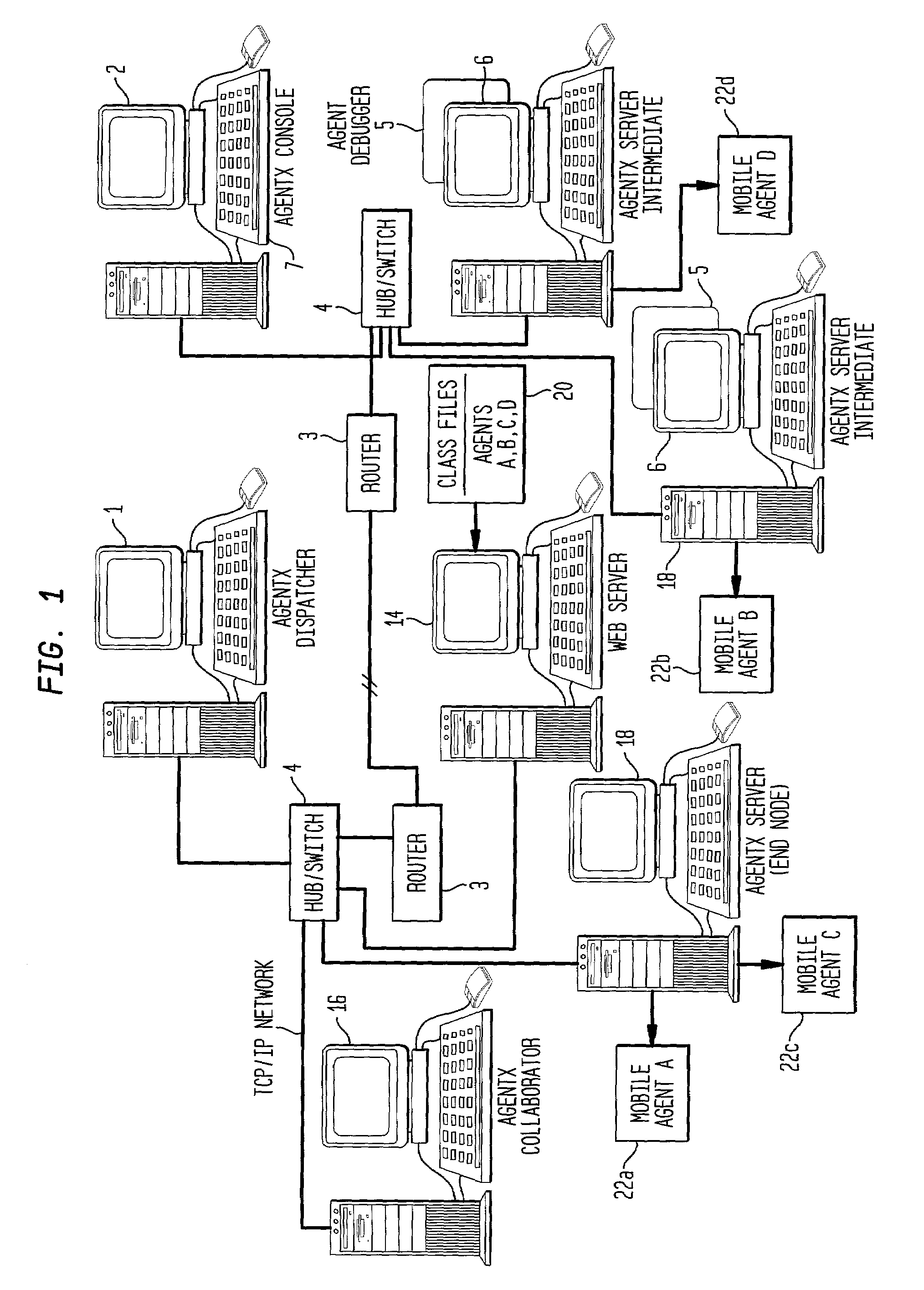
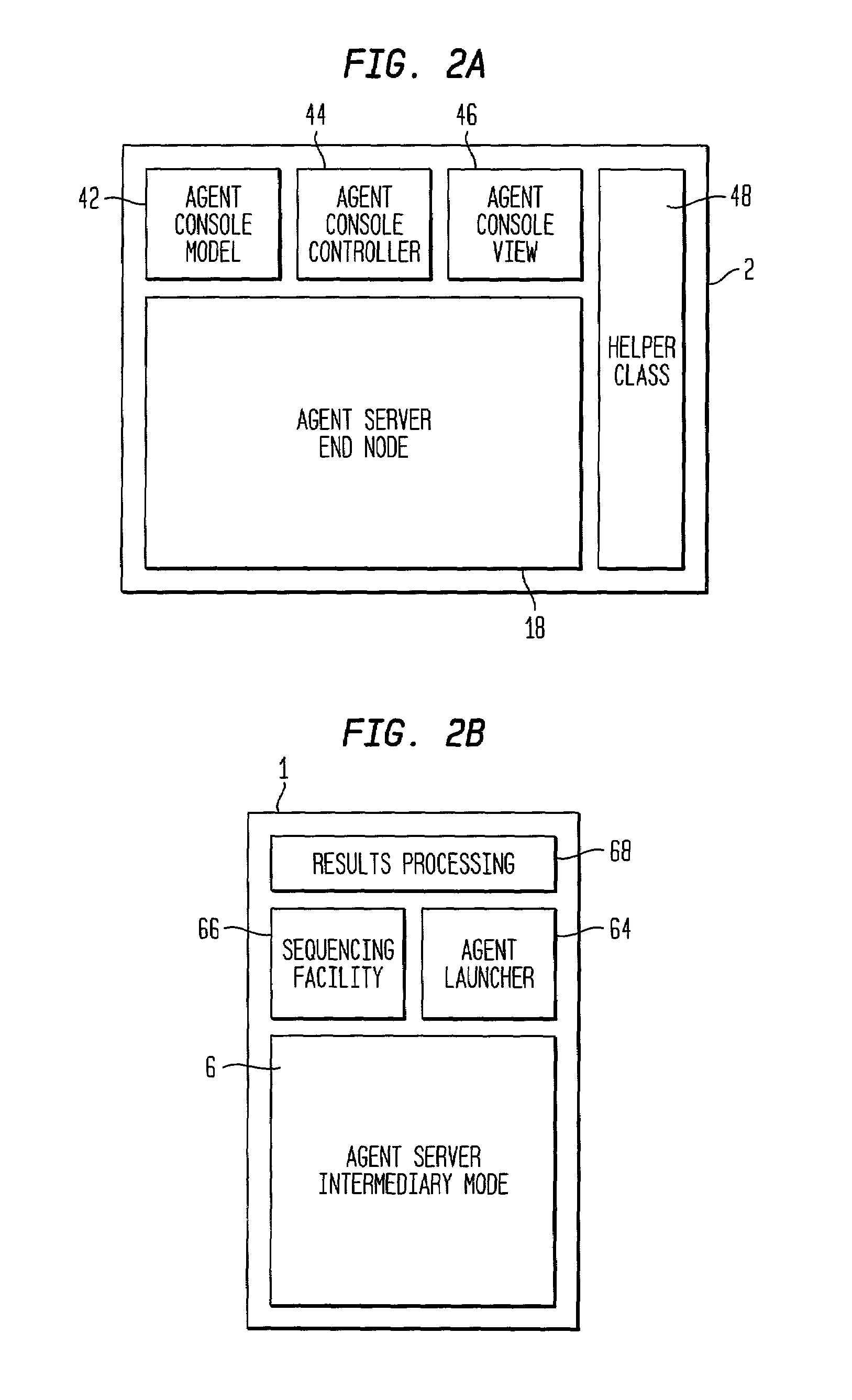
A method and apparatus is provided for breaking down computing tasks within a larger application and distributing such tasks across a network of heterogeneous computers for simultaneous execution. The heterogeneous computers may be connected across a wide or local area network. The invention supports mobile agents that are self-migrating and can transport state information and stack trace information as they move from one host to another, continuing execution where the mobile agents may have left off. The invention includes a server component for providing an execution environment for the agents, in addition to sub-components which handle real-time collaboration between the mobile agents as well as facilities monitoring during execution. Additional components provide realistic thread migration for the mobile agents. Real-time stack trace information is stored as the computing tasks are executed, and if over-utilization of the computing host occurs, execution of the computing task can be halted and the computing task can be transferred to another computing hosts where execution can be seamlessly resumed using the stored, real-time state information and stack trace information.
Owner:MOBILE AGENT TECH
Methods and systems for repairing applications
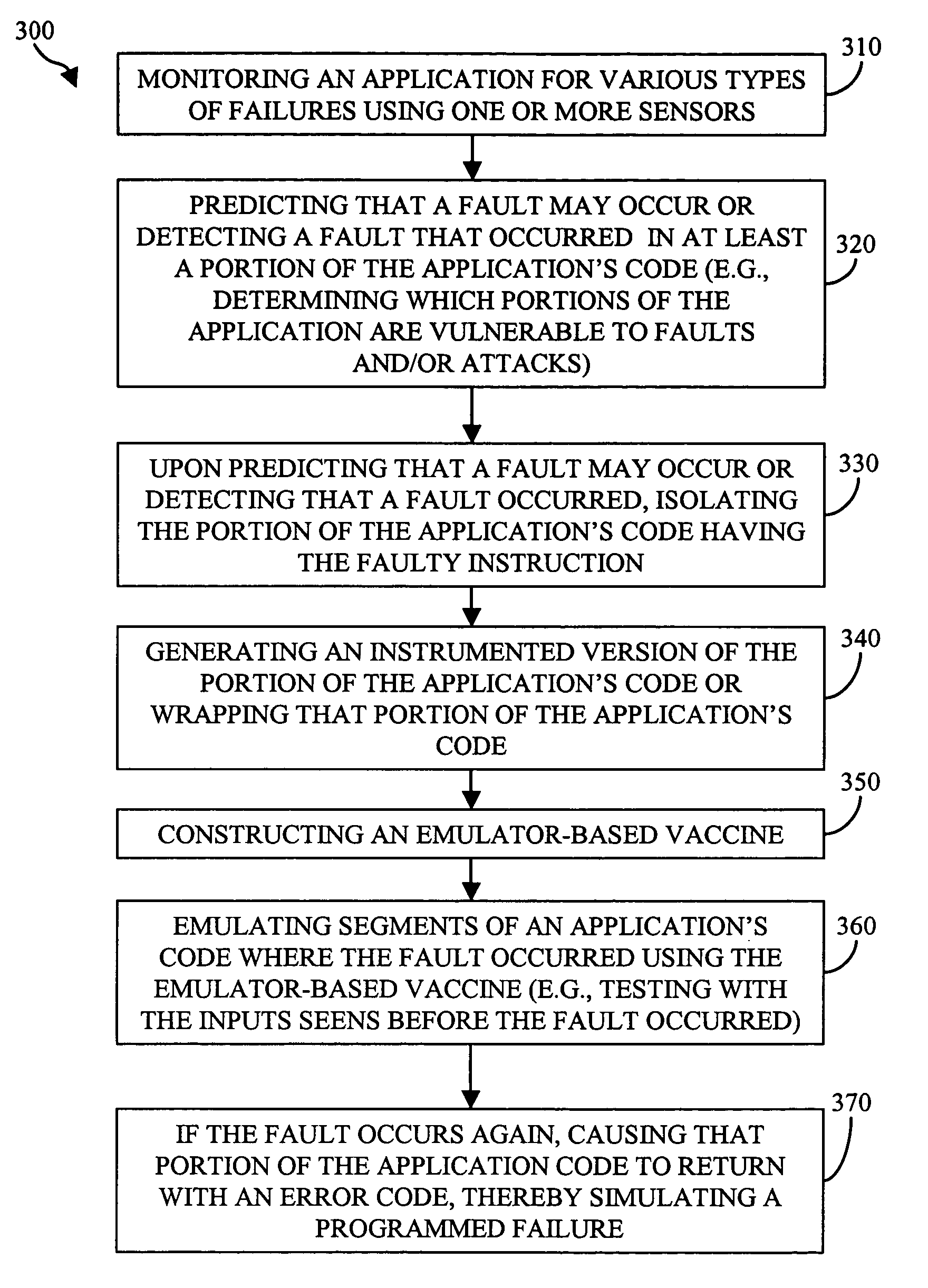
ActiveUS20060195745A1Improve usabilityEasy to useElectronic circuit testingNon-redundant fault processingCore dumpSoftware failure
In accordance with the present invention, computer implemented methods and systems are provided that allow an application to automatically recover from software failures and attacks. Using one or more sensors, failures may be detected in the application. In response to detecting the failure, the portion of the application's code that caused the failure is isolated. Using the input vectors that caused the failure, information regarding the failure (e.g., the type of failure), a core dump file (e.g., stack trace), etc., an emulator-based vaccine that repairs the failure is constructed. In response to verifying that the vaccine repaired the failure, the application is automatically updated with the emulator-based vaccine without user intervention. Application community features that efficiently use the resources available in software monoculture is also provided. An application community may be defined that includes a plurality of devices and the application's code may be divided into smaller portions of code, which are assigned to each of the plurality of devices for monitoring. Each device also notifies the other devices of the failure.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
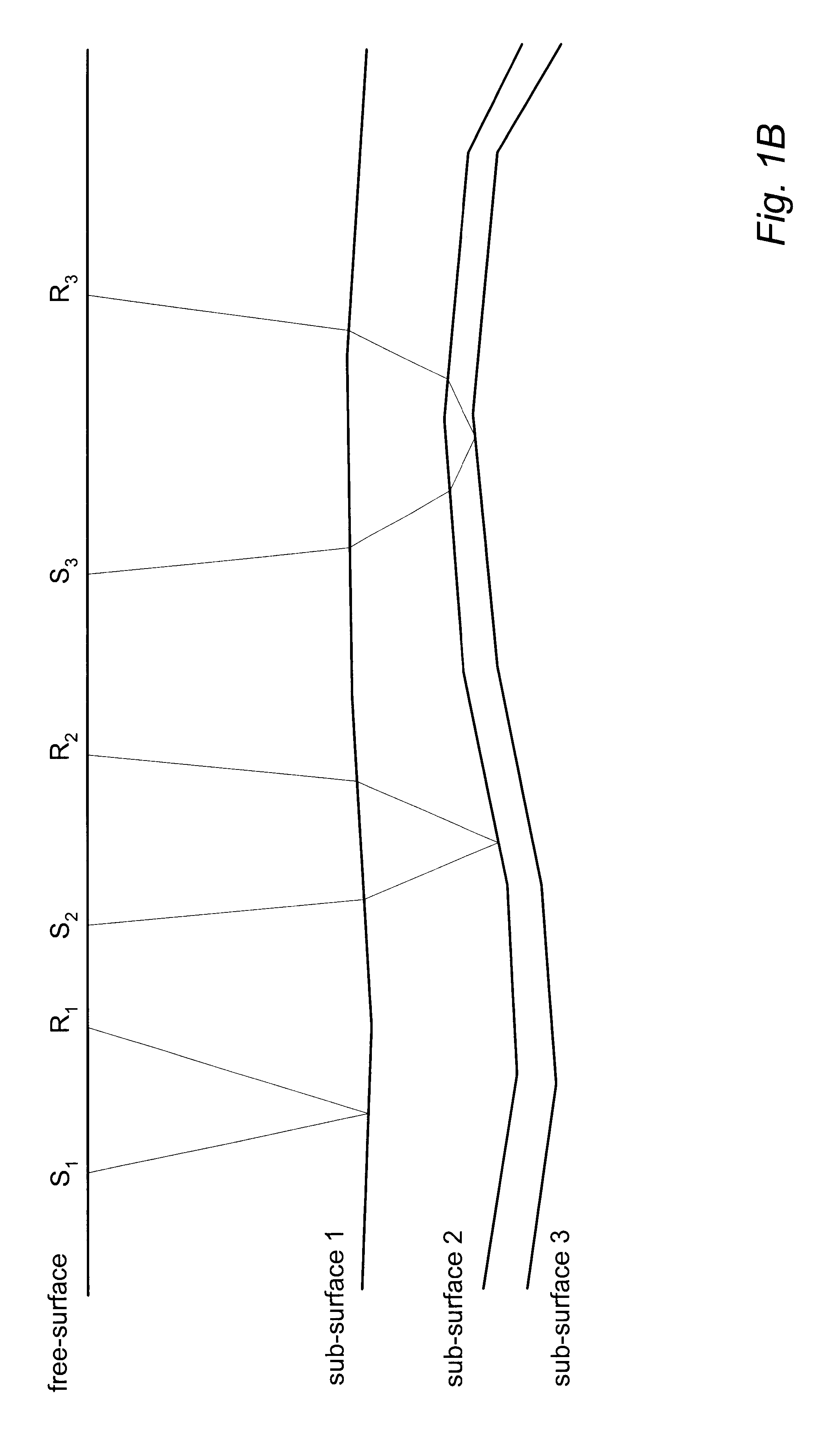
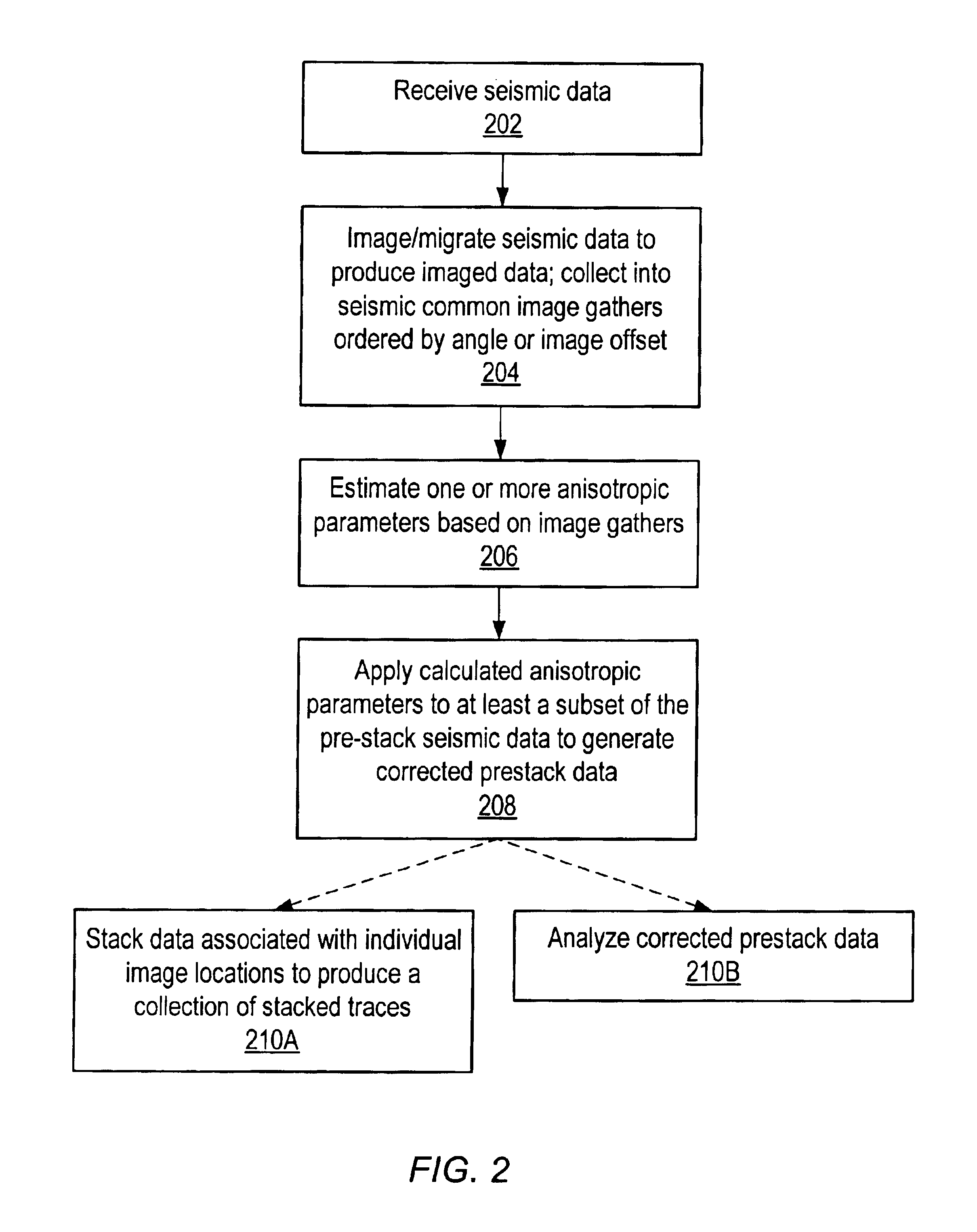
3-D prestack/poststack multiple prediction
InactiveUS6735527B1Seismic signal processingSpecial data processing applicationsNormal moveoutCommon depth point
System and method for analyzing seismic data from a formation. Stacked seismic data are provided, including a plurality of stack traces, e.g., by collecting seismic data from source and receiver locations and stacking the collected seismic data to produce the stacked seismic data. 3-dimensional (3-D) prestack traces are generated from the plurality of stack traces, e.g., by performing inverse moveout of stack traces, e.g., in a specified neighborhood, at common-depth-points, e.g., by inverse normal moveout, ray tracing, spike synthesis, etc. The inverse moveout corrected traces are convolved to compute predicted multiples which are useable in analyzing the formation. The multiples may be adaptively subtracted from the stacked seismic data, or optionally, from prestack data, to generate processed seismic data useable in analyzing the formation, e.g., for petroleum production potential. Dip moveout (DMO) corrected seismic data may be used, where DMO velocities are adjusted by dividing by cosine of the dip angle.
Owner:LANDMARK GRAPHICS
Methods and systems for repairing applications
ActiveUS7490268B2Easy to useProvide protectionNon-redundant fault processingPlatform integrity maintainanceCore dumpSoftware failure
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
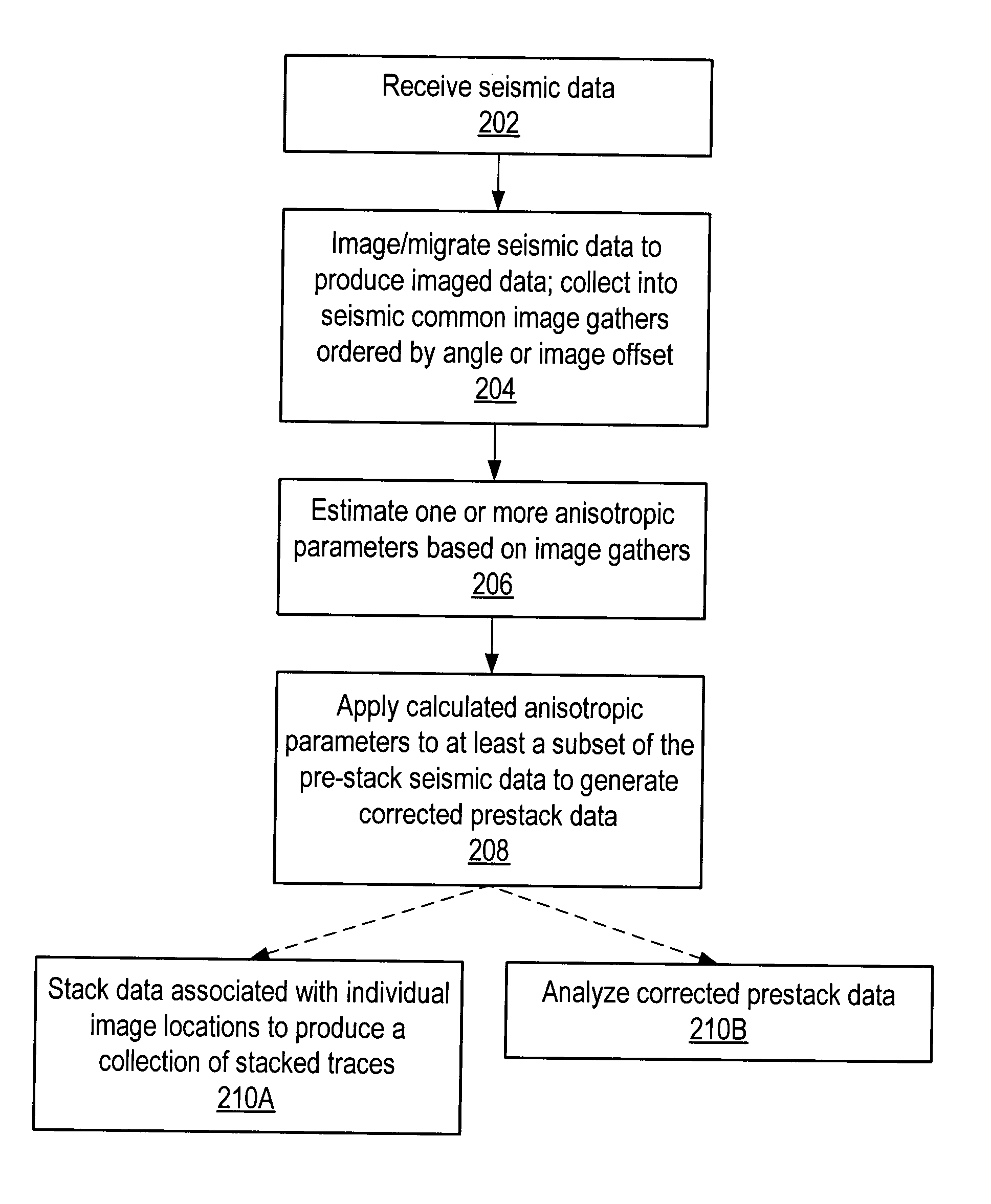
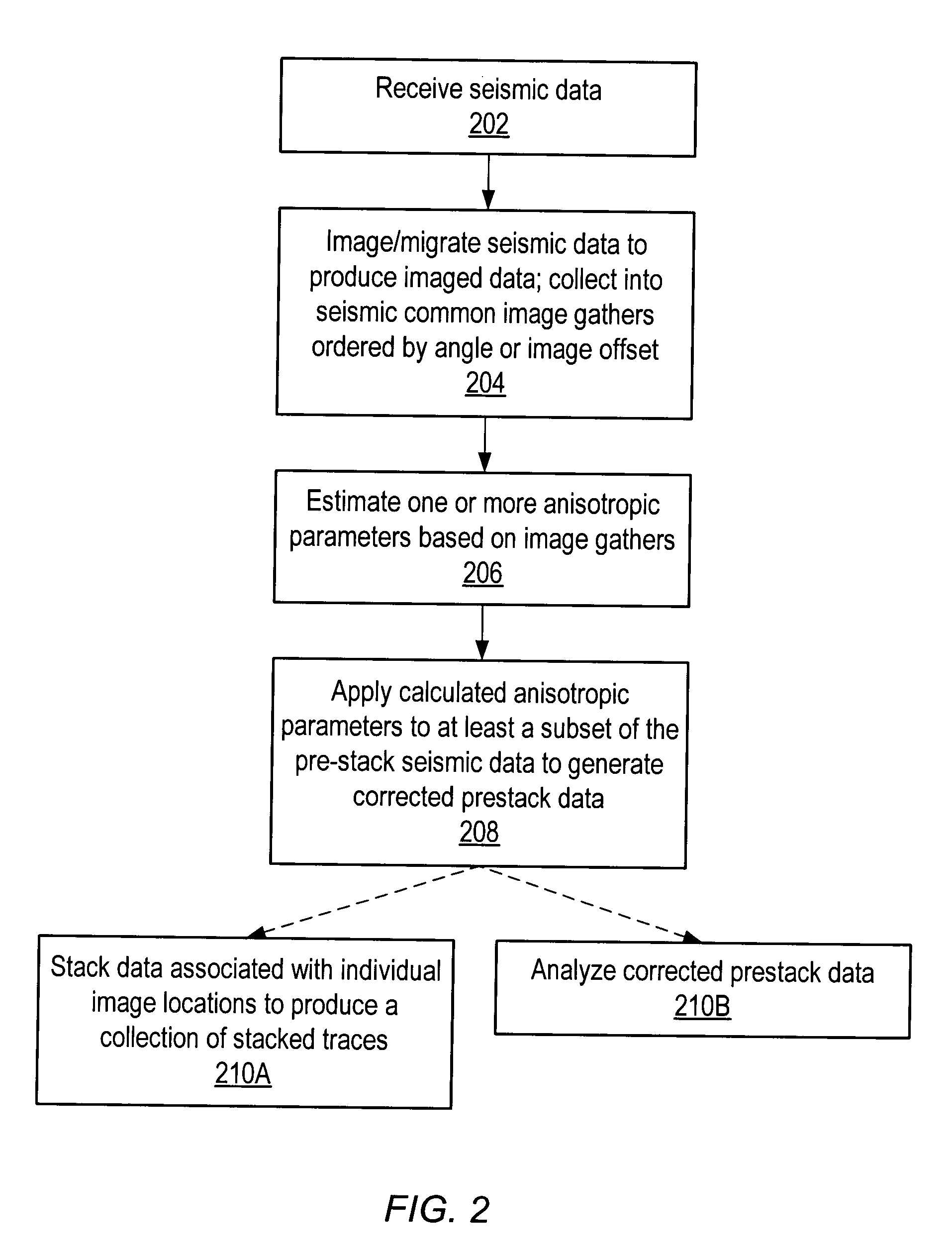
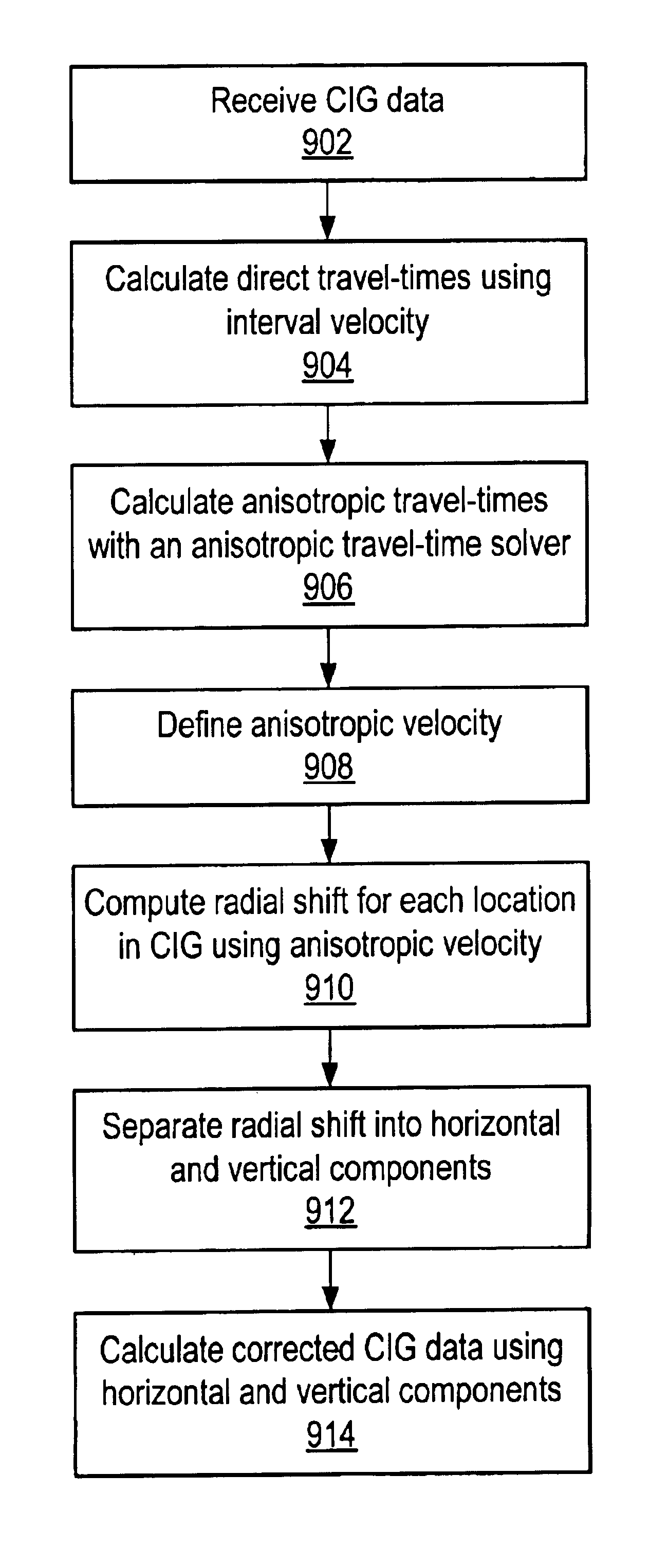
Seismic analysis using post-imaging seismic anisotropy corrections
ActiveUS20040093163A1Seismic signal processingSpecial data processing applicationsSeismic anisotropySeismic analysis
System and method for performing anisotropy corrections of post-imaging seismic data for a subsurface formation. The method may receive seismic data, preferably pre-stack seismic data comprising a plurality of traces, e.g., collected from a plurality of source and receiver locations. The seismic data may be imaged / migrated to produce imaged seismic data, which is organized into an arrangement that preserves aspects of the relative seismic propagation angle in the subsurface. One or more anisotropic parameters and corresponding corrections may be determined by analyzing the organized imaged seismic data. The determined parameters or corrections may be used to correct at least a subset of the imaged seismic data, thereby producing corrected seismic data which is useable in analyzing the formation. The corrected data may then optionally be stacked to produce a collection of corrected stacked traces, and / or analyzed as desired. The pre-stack data and / or the corrected seismic data may optionally be displayed.
Owner:LANDMARK GRAPHICS
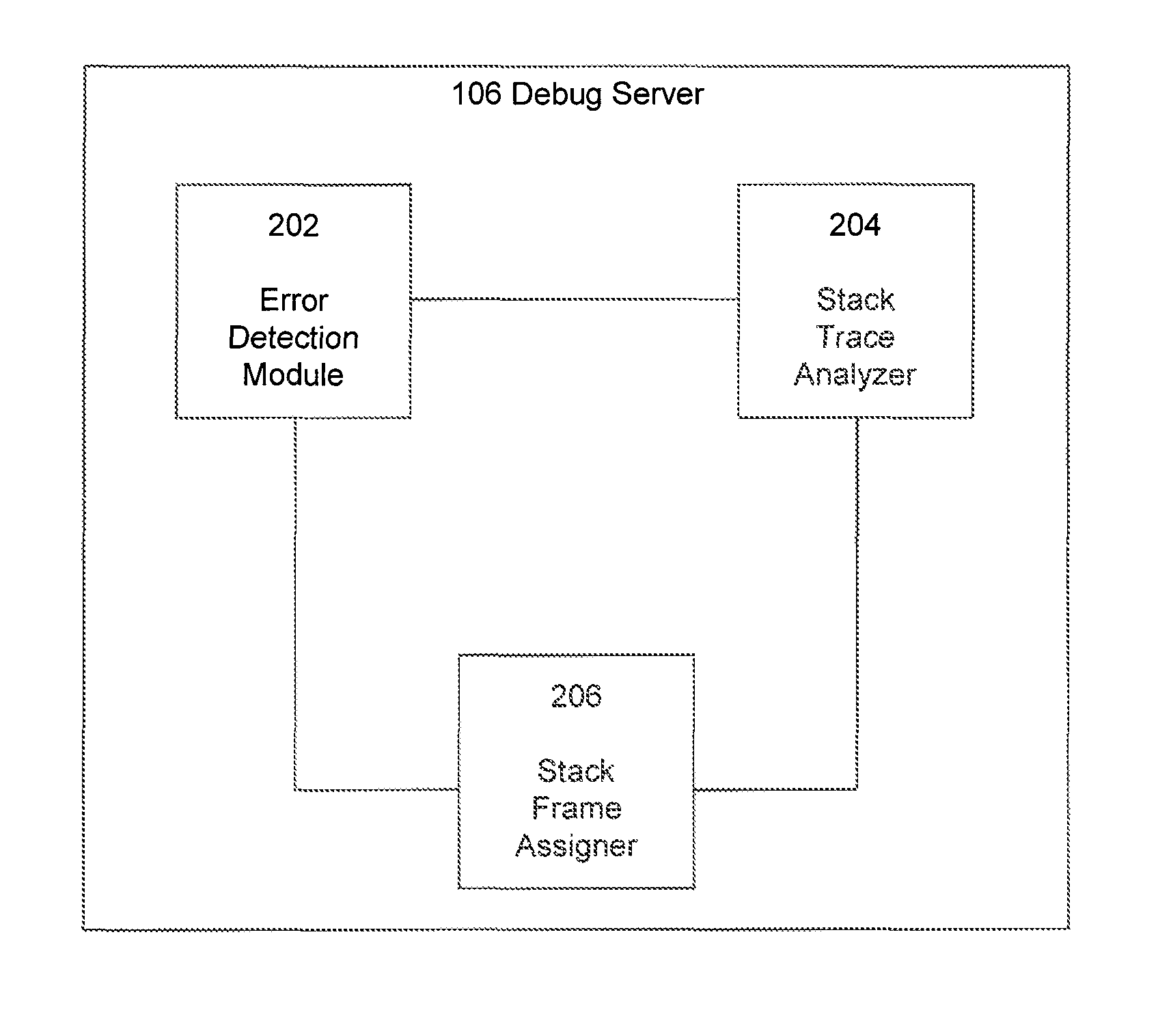
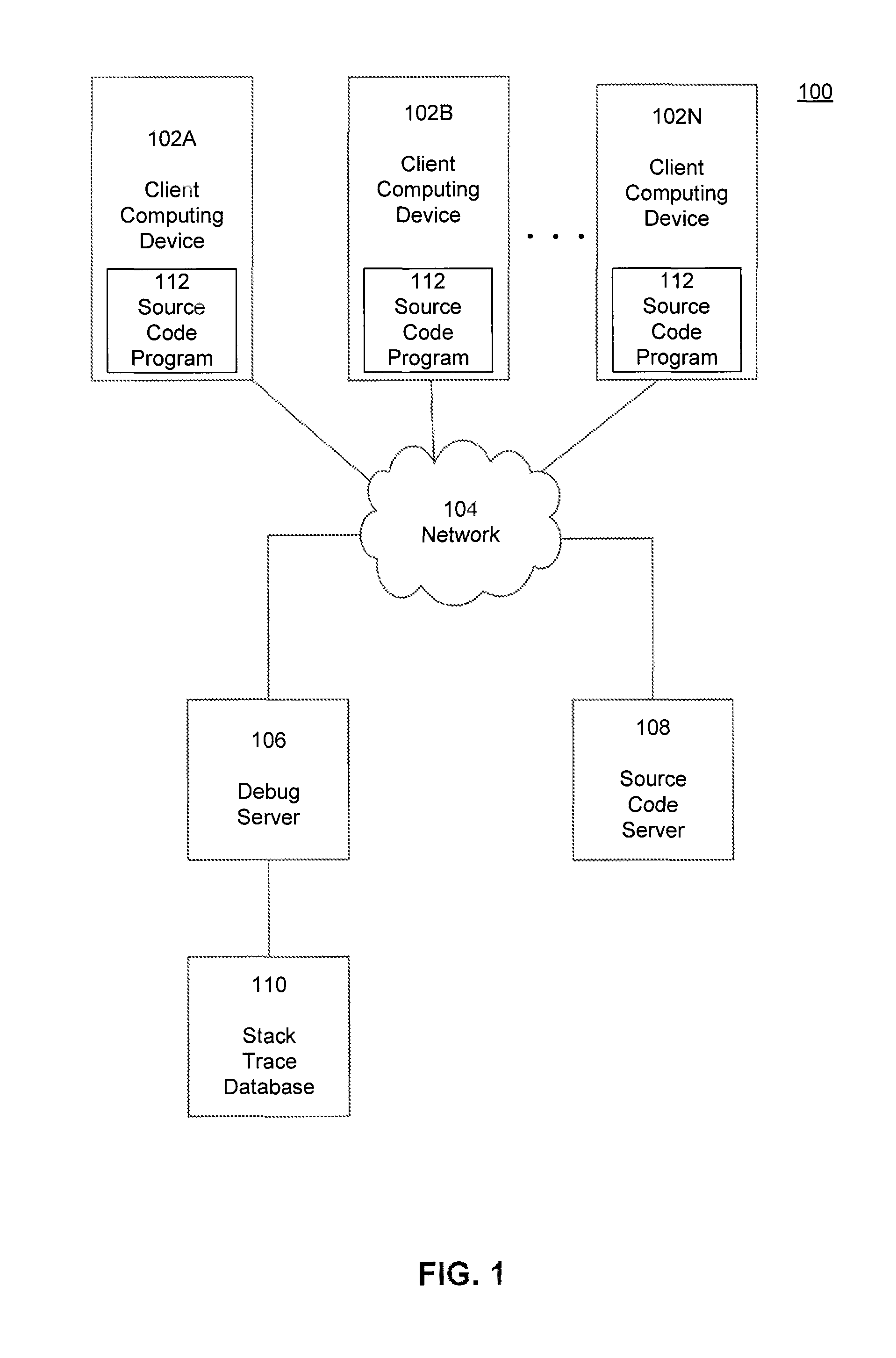
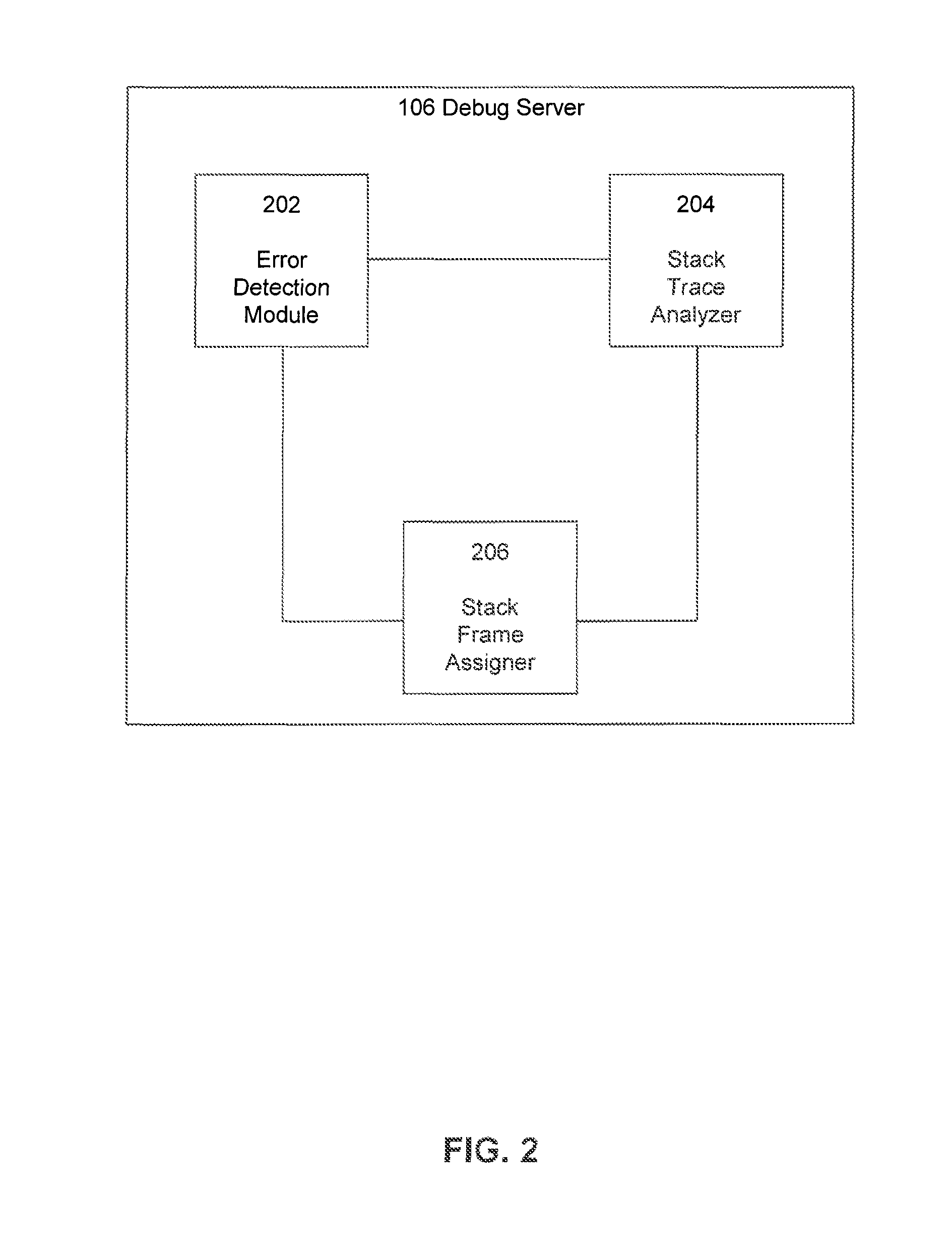
Display of aggregated stack traces in a source code viewer
InactiveUS8719791B1Software testing/debuggingSpecific program execution arrangementsSource codeStack trace
Embodiments described herein relate to systems and methods for displaying aggregated stack traces in a source code viewer. One or more execution identifiers are received in response to an execution of a first program executing on one or more client computing devices. Each execution identifier can include one or more stack frames, which correspond to a function call within the first program. An error-likeliness score is identified for each execution identifier. An error-weight is determined for each of the execution identifiers based on the identified error-likeliness scores for instances of the execution identifiers.
Owner:GOOGLE LLC
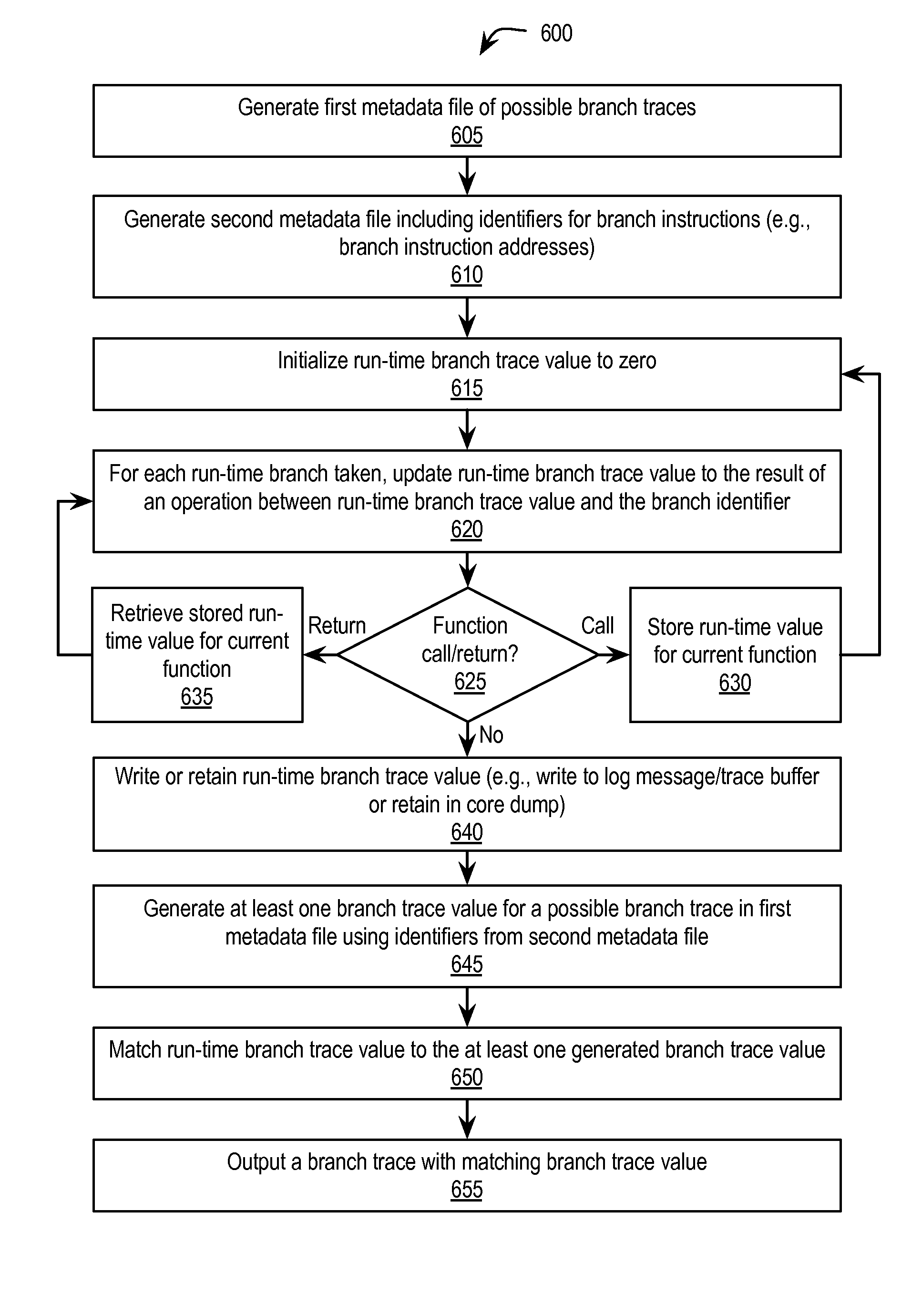
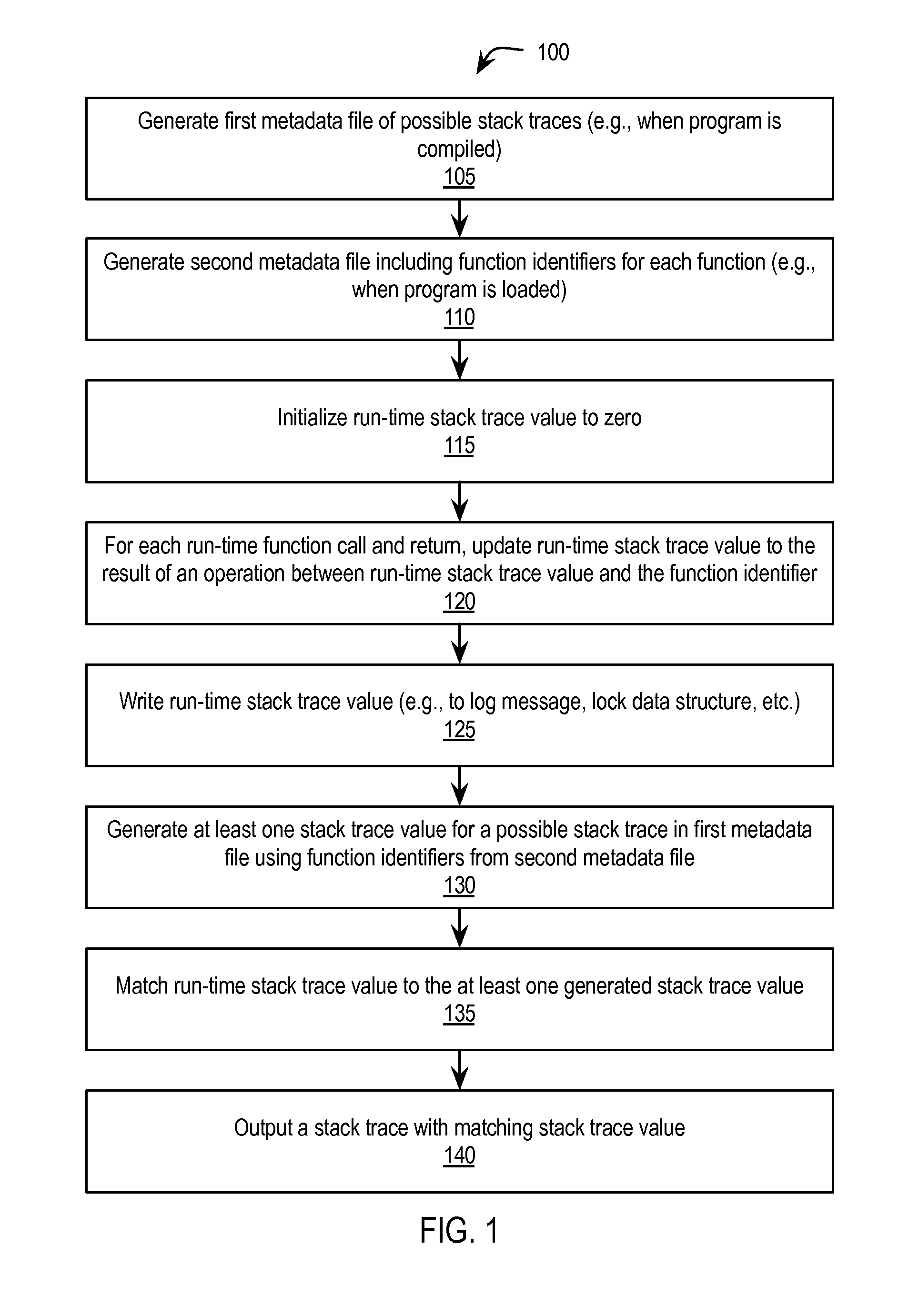
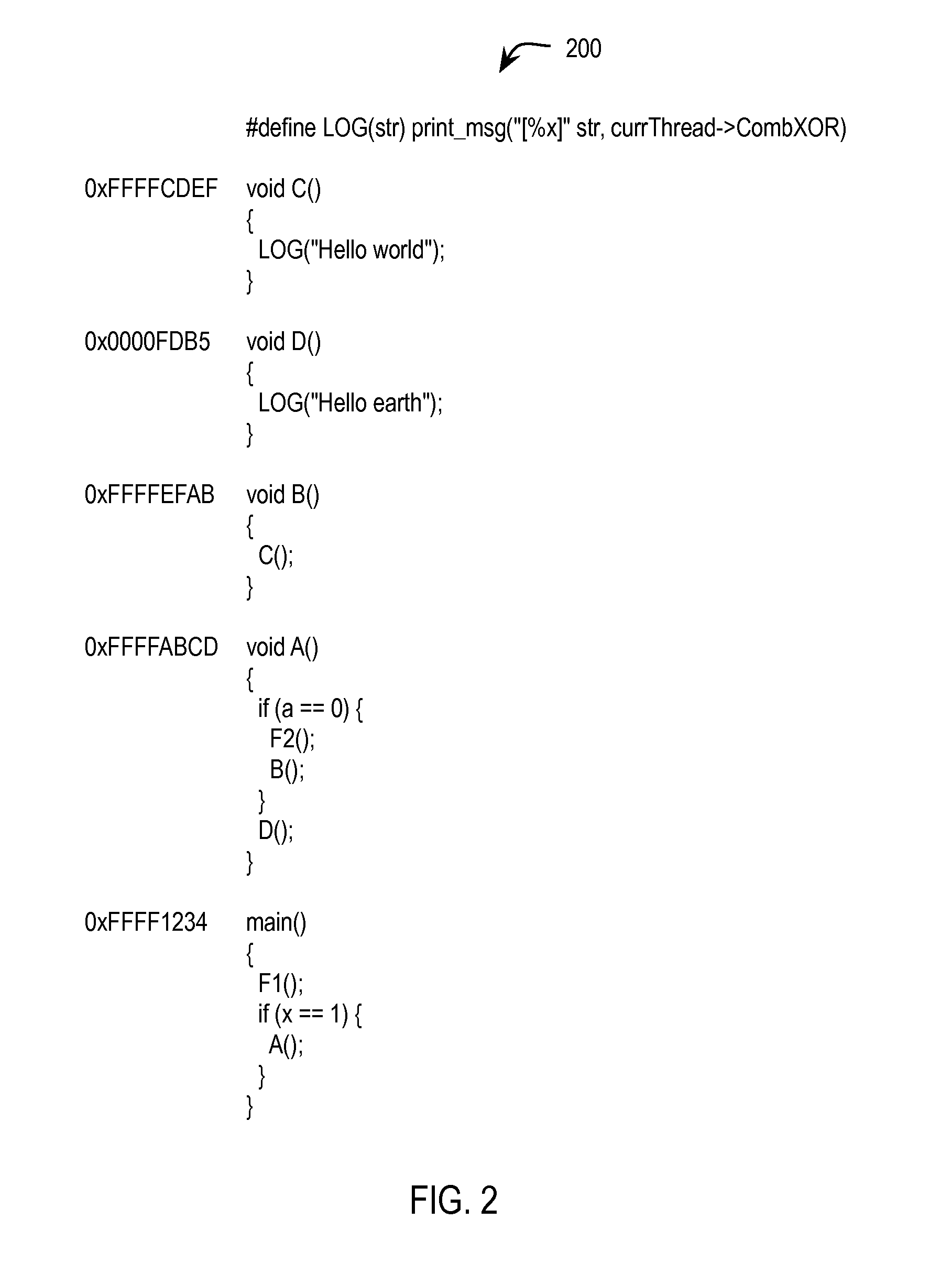
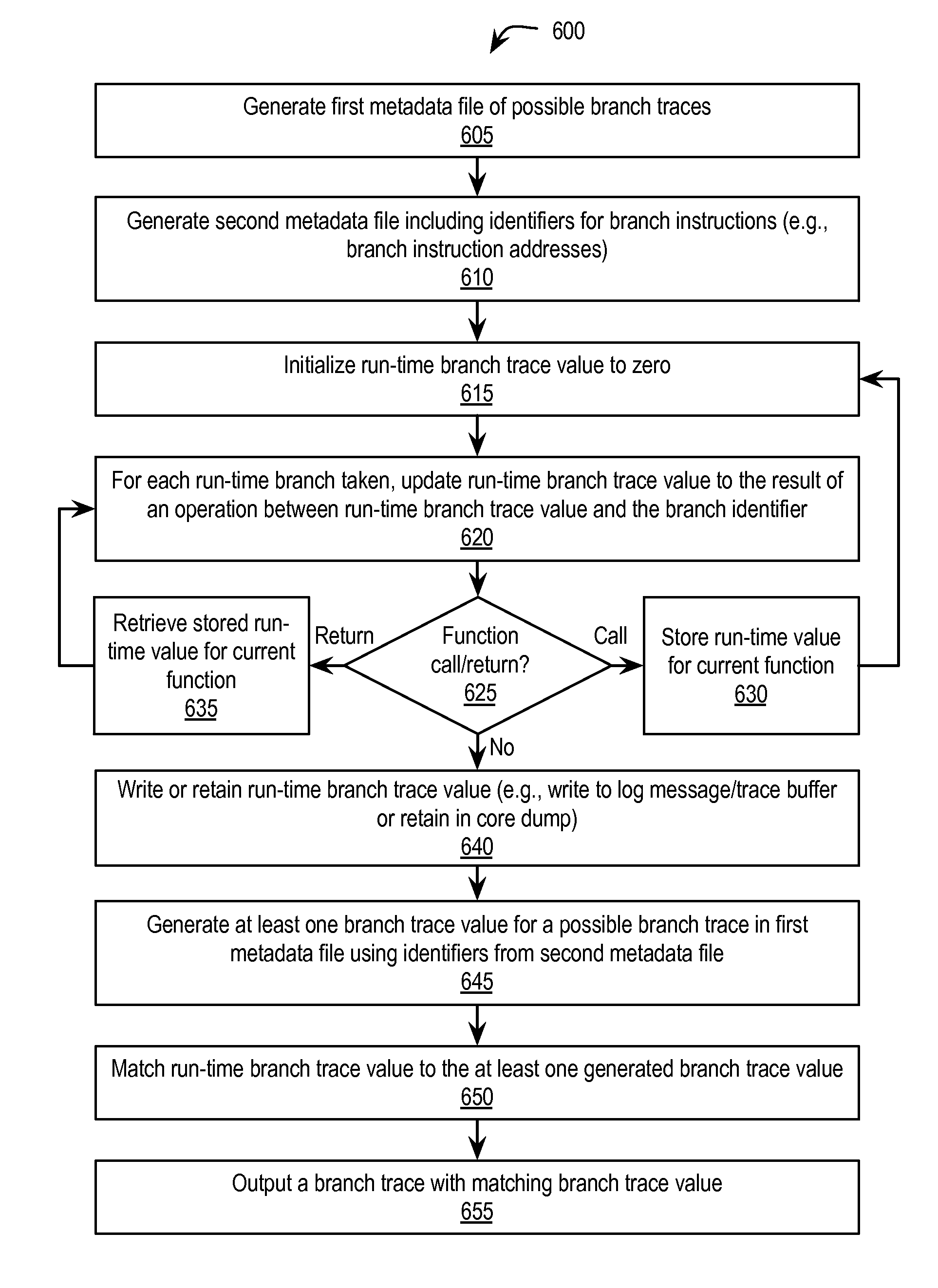
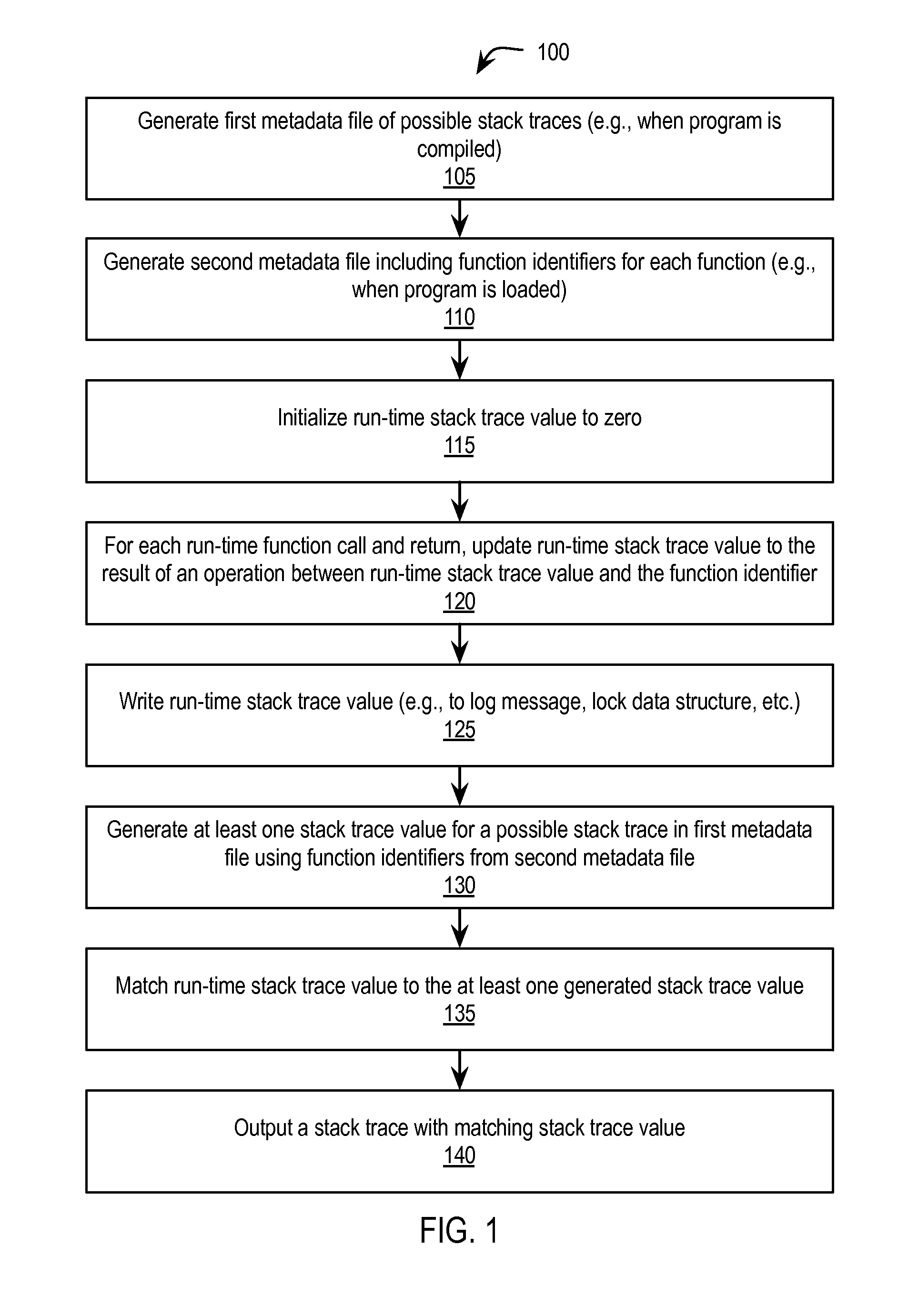
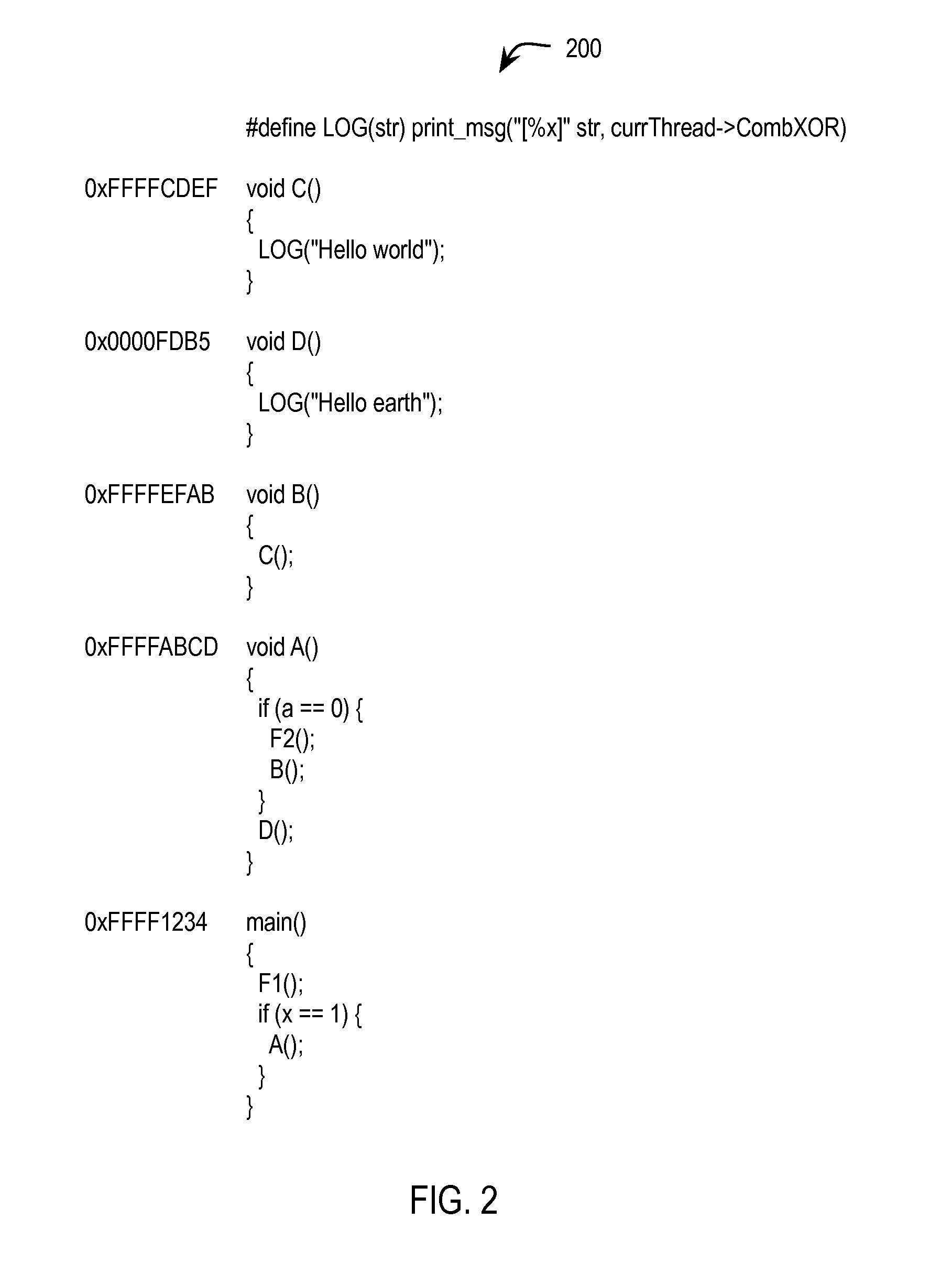
Stack trace compression
Exemplary methods, apparatuses, and systems generate a plurality of possible stack traces for a computer program. Each possible stack trace represents functions that may be active while the computer program is running. Each function has a corresponding function identifier. A value for at least one of the plurality of possible stack traces is generated. Generating the value for each stack trace includes performing a series of one or more mathematical or logical operations between the function identifiers of the possible stack trace. A stack trace is generated as an output based upon a match between a run-time stack trace value and the at least one generated stack trace value.
Owner:VMWARE INC
Seismic analysis using post-imaging seismic anisotropy corrections
InactiveUS6904368B2The result is accuratePrecise positioningSeismic signal processingSpecial data processing applicationsSeismic anisotropySeismic analysis
System and method for performing anisotropy corrections of post-imaging seismic data for a subsurface formation. The method may receive seismic data, preferably pre-stack seismic data comprising a plurality of traces, e.g., collected from a plurality of source and receiver locations. The seismic data may be imaged / migrated to produce imaged seismic data, which is organized into an arrangement that preserves aspects of the relative seismic propagation angle in the subsurface. One or more anisotropic parameters and corresponding corrections may be determined by analyzing the organized imaged seismic data. The determined parameters or corrections may be used to correct at least a subset of the imaged seismic data, thereby producing corrected seismic data which is useable in analyzing the formation. The corrected data may then optionally be stacked to produce a collection of corrected stacked traces, and / or analyzed as desired. The pre-stack data and / or the corrected seismic data may optionally be displayed.
Owner:LANDMARK GRAPHICS CORP
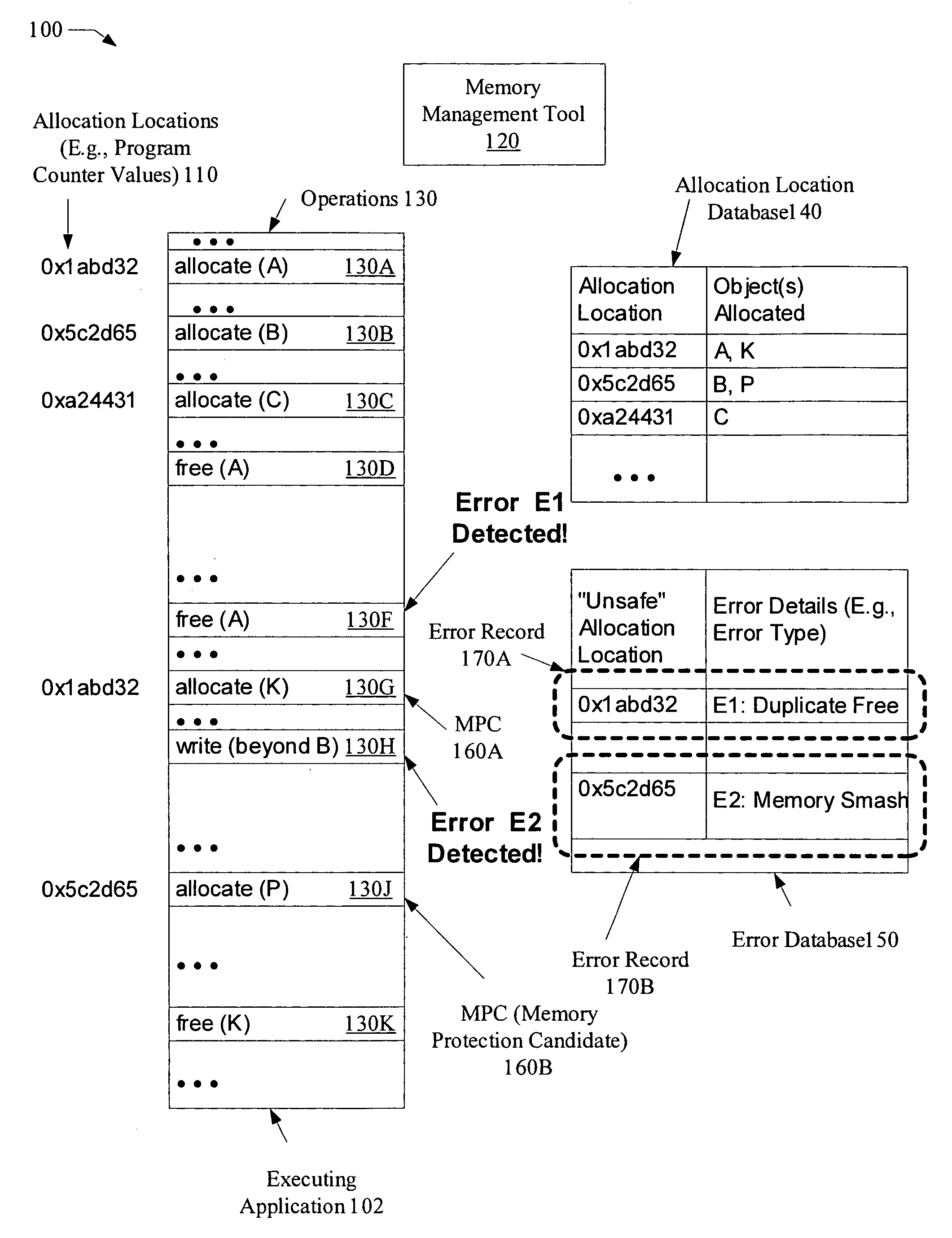
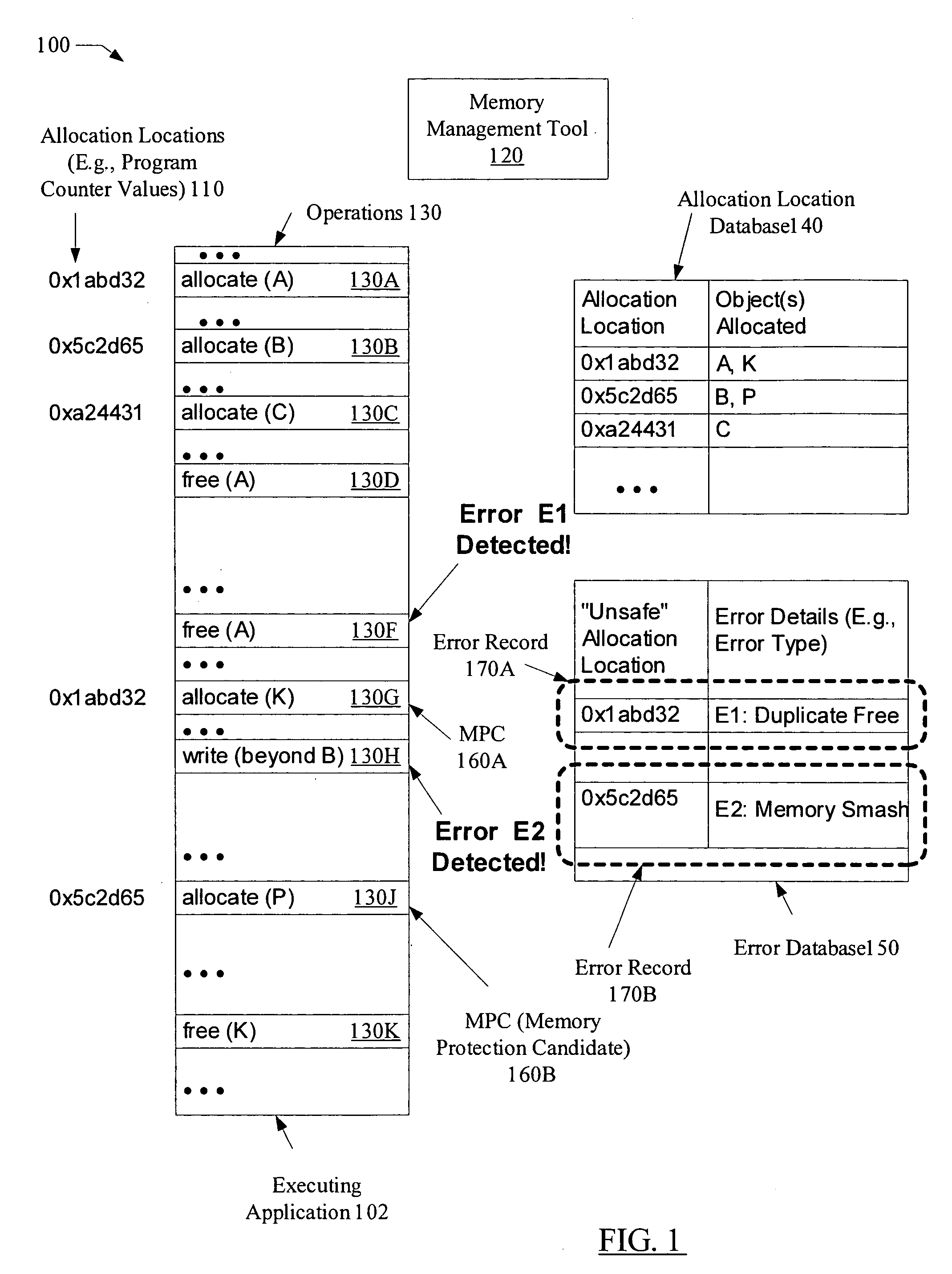
Selective self-healing of memory errors using allocation location information
ActiveUS7434105B1Reduce overheadNon-redundant fault processingMemory systemsSelf-healingMemory protection
A system for selective self-healing of memory errors comprises a processor coupled to a memory, where the memory stores instructions executable by the processor to store an error record for each memory management error detected during an execution of the application. The error record identifies an allocation location (e.g., a portion of a stack trace corresponding to the invocation of a memory allocation function such as malloc( )) of an object associated with the memory management error. The instructions are executable to use the error record to identify, during subsequent execution, memory operations performed on objects allocated from the allocation location, and to perform corresponding memory protection operations (e.g., operations to prevent re-occurrences of the memory errors) for the memory operations identified using the error record.
Owner:SYMANTEC OPERATING CORP
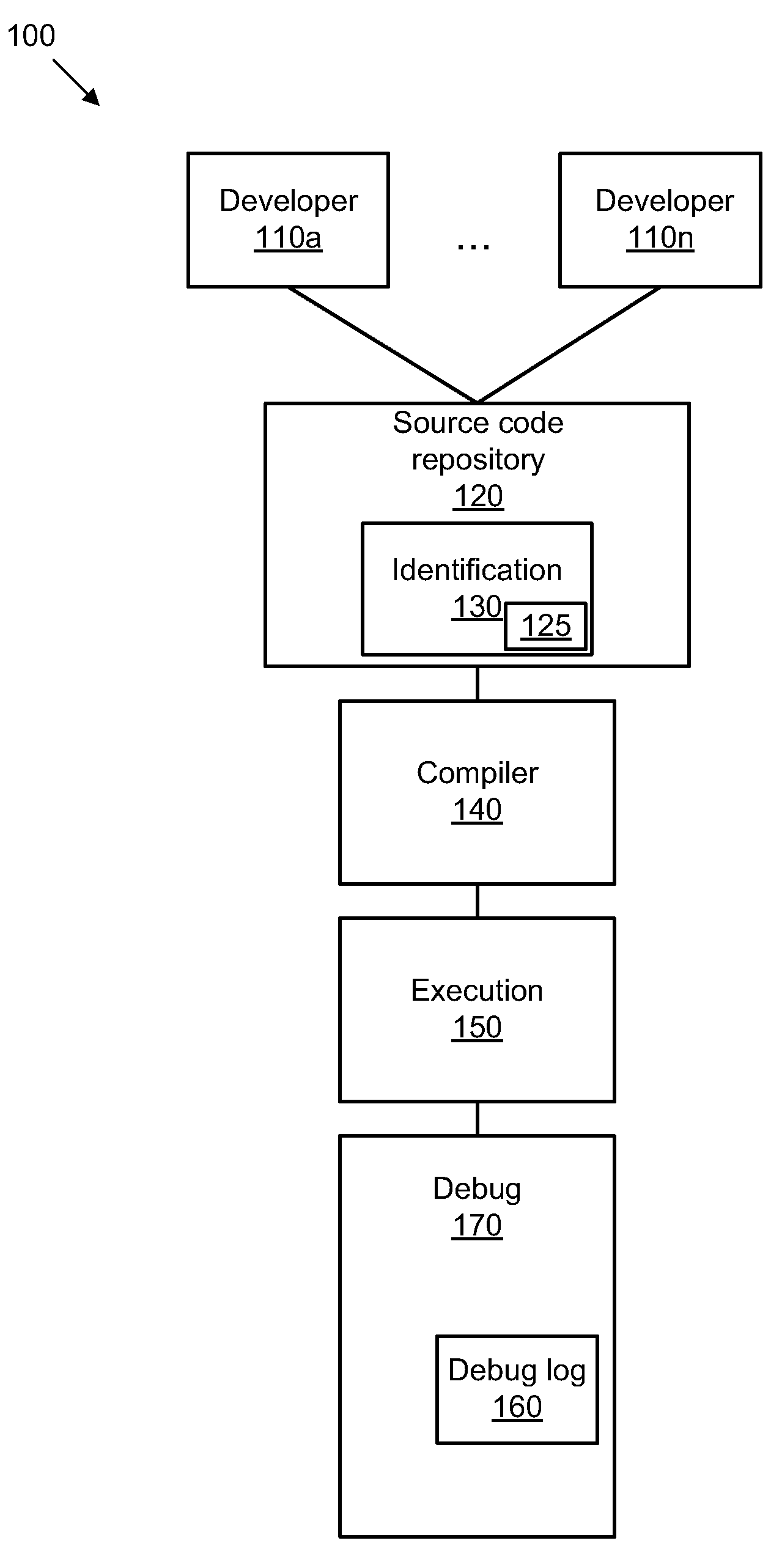
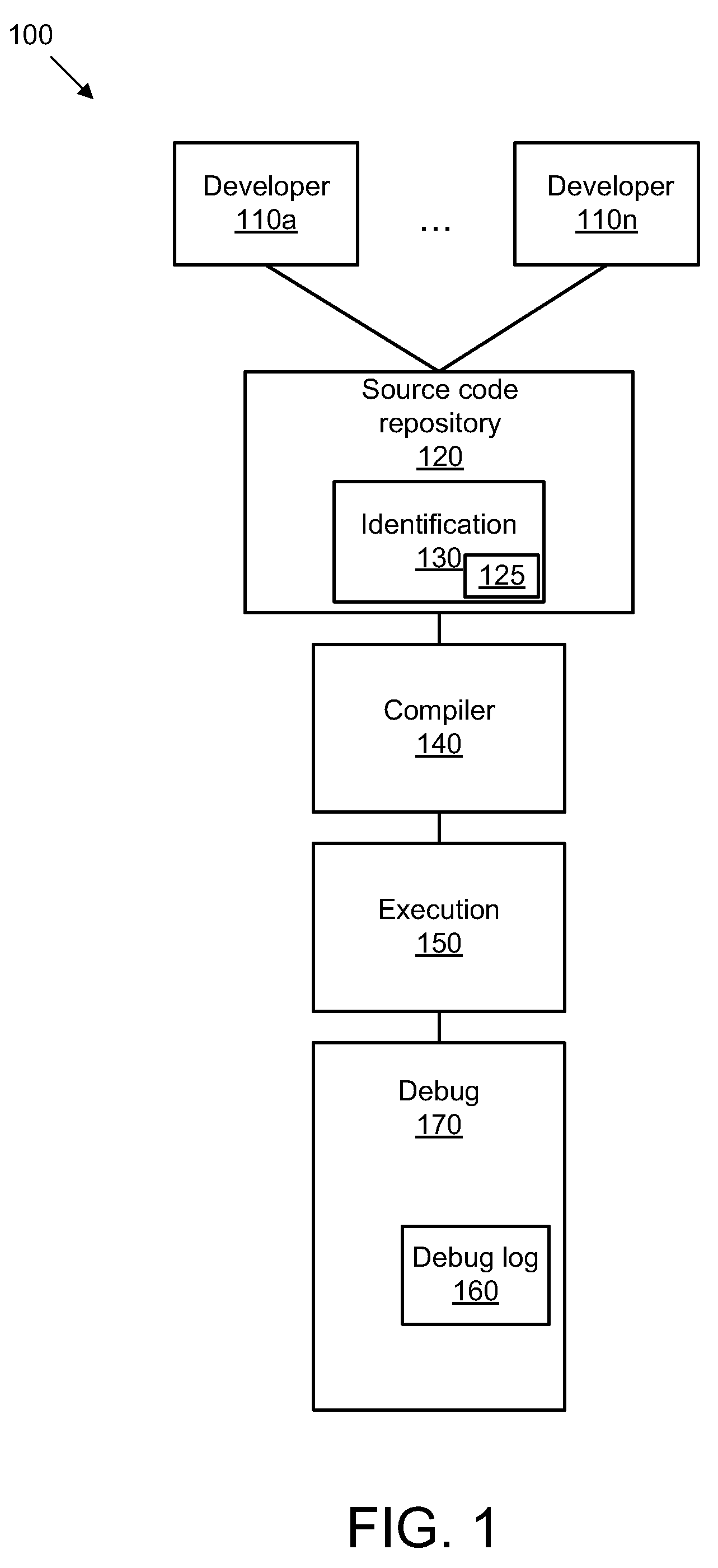
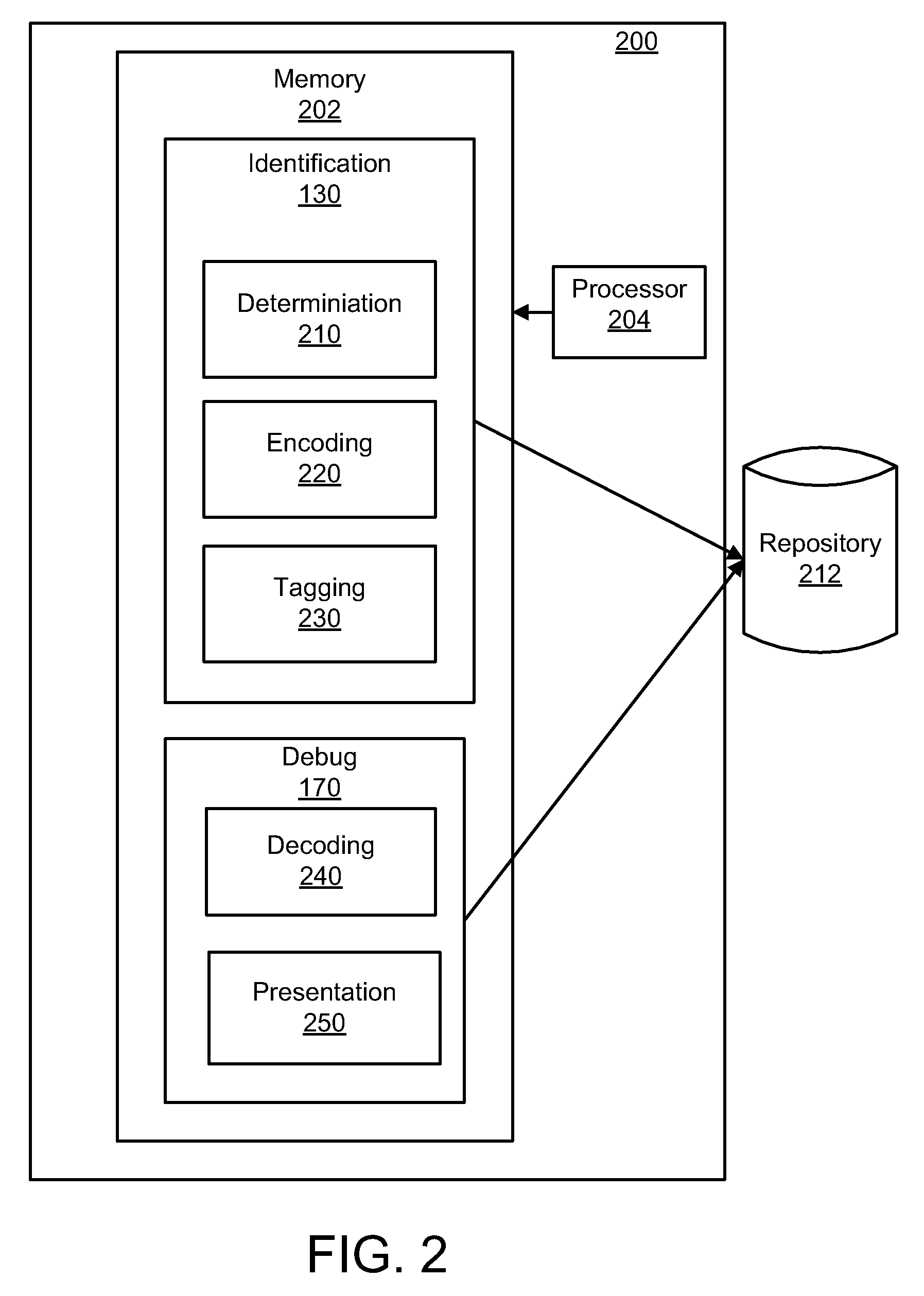
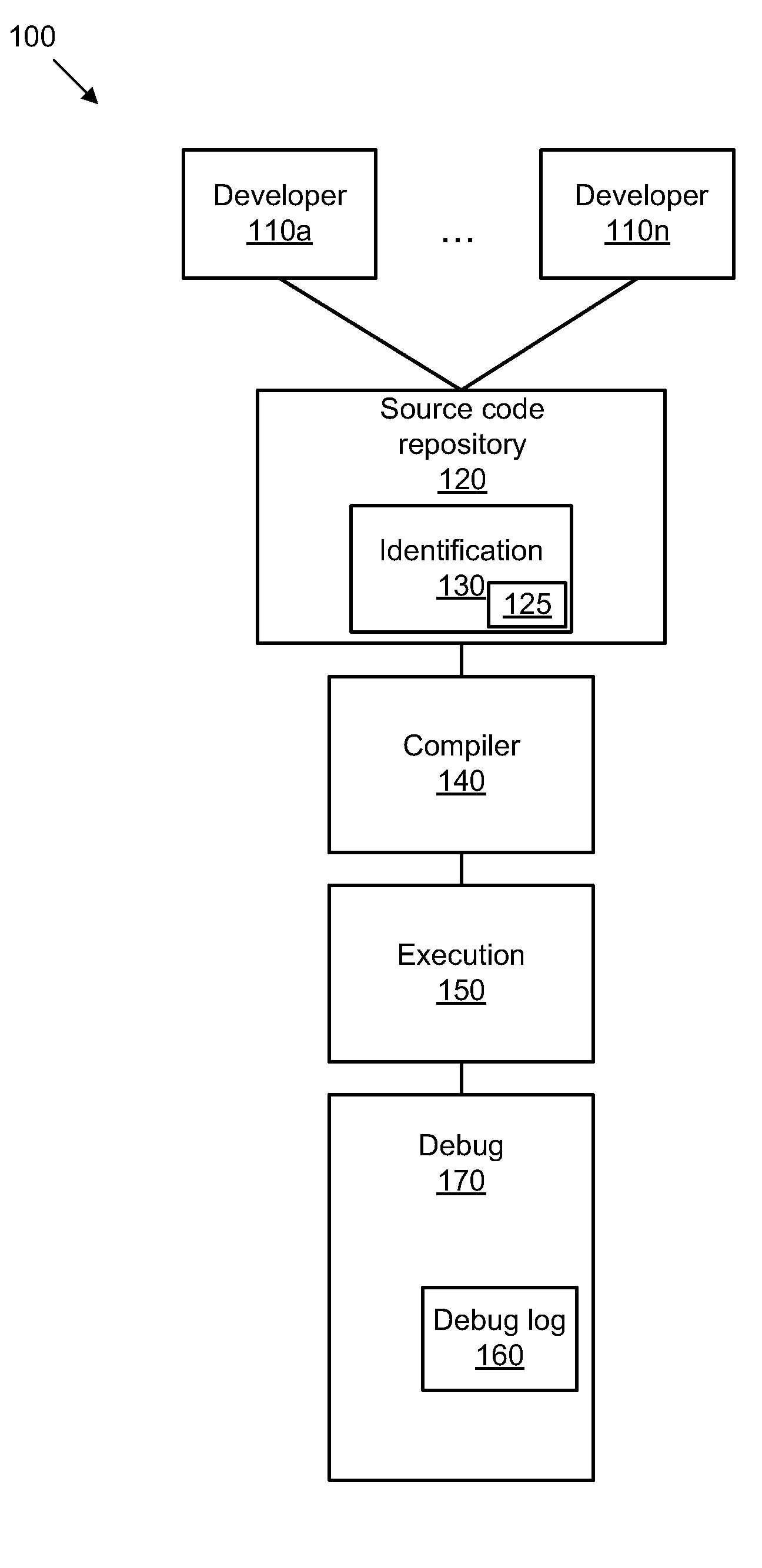
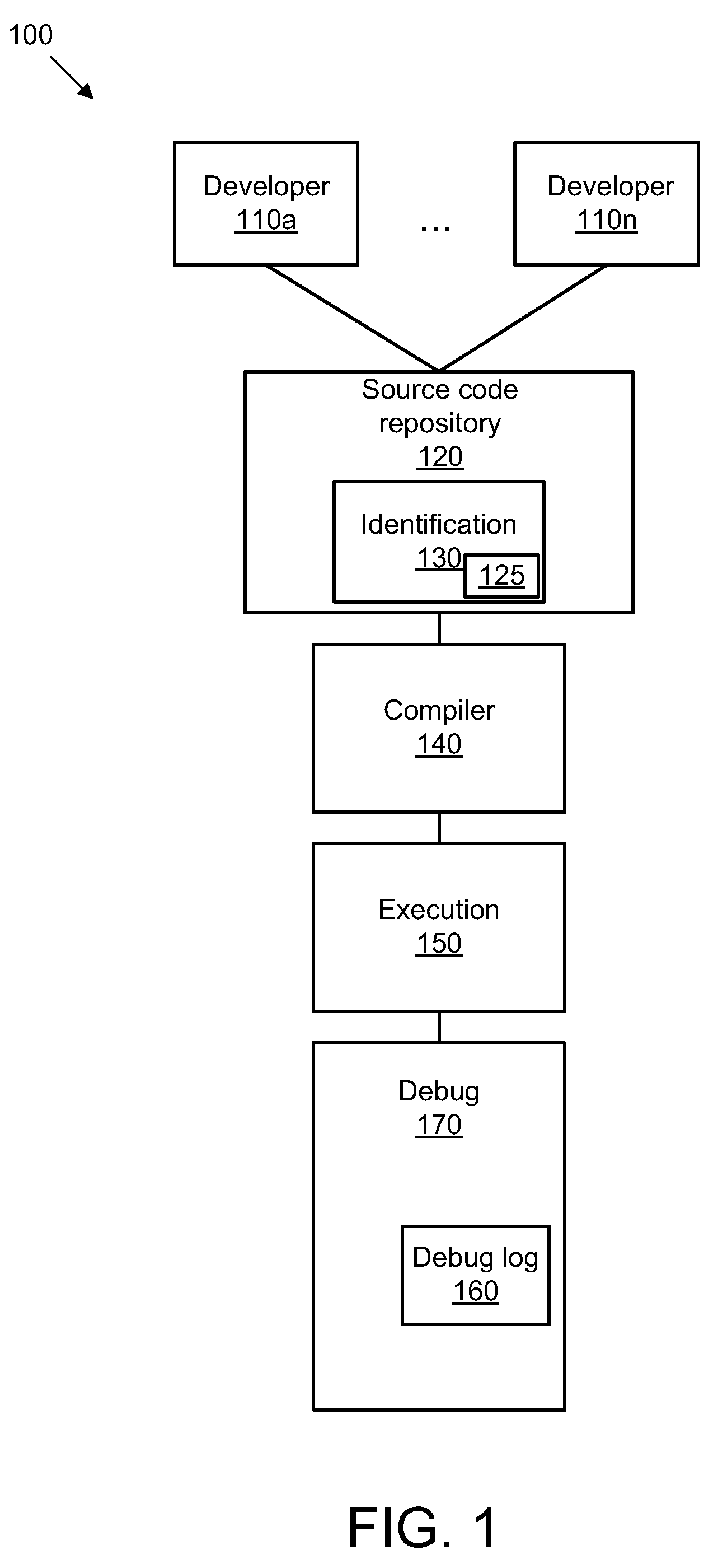
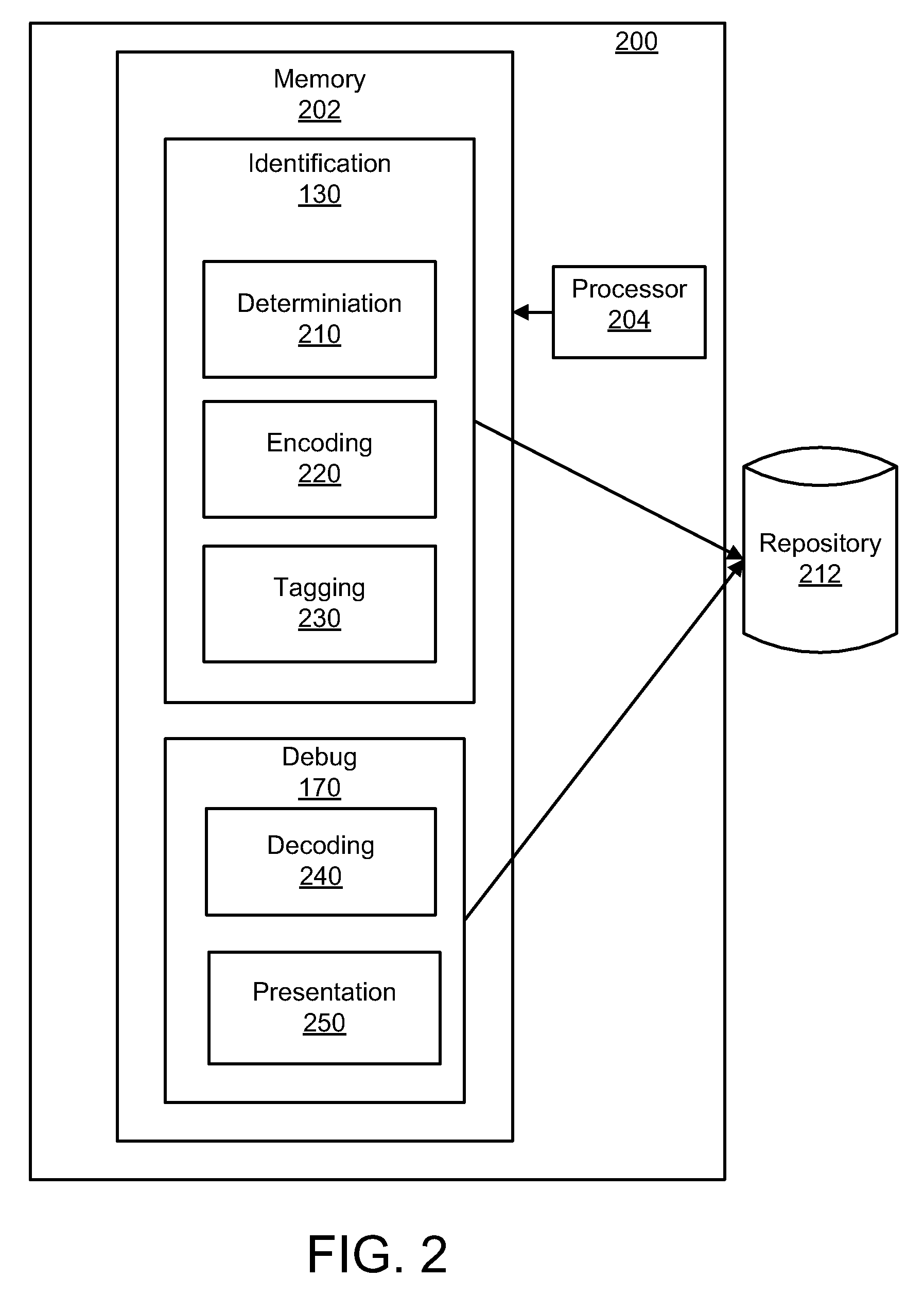
Identifying a software developer based on debugging information
InactiveUS20100211932A1Software testing/debuggingSoftware designSoftware engineeringSoftware development
A solution for identifying a software developer based on debugging information includes an identification module configured to identify a developer of a line of source code, a determination module configured to determine a developer contact tag for the developer, an encoding module configured to encode the developer contact tag, a tagging module configured to automatically tag the line of source code with the developer contact tag associated with the developer. The solution also includes a debug module configured to provide debug information, a decoding module configured to decrypt the developer contact tag, and a presentation module configured to present the debug stack trace in human readable form.
Owner:IBM CORP +1
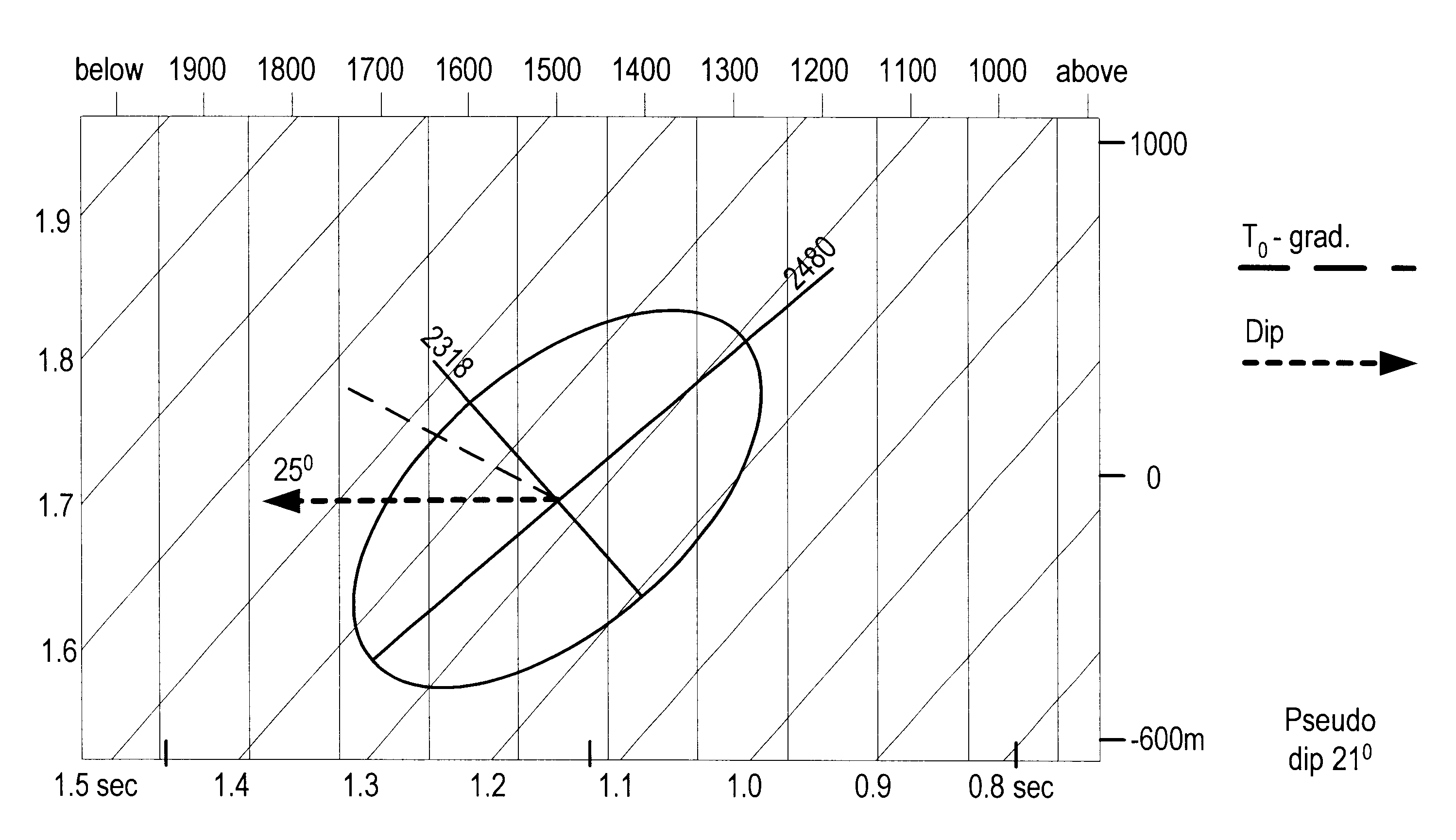
Visualization method for the analysis of prestack and poststack seismic data
InactiveUS6989841B2Weighing apparatus using counterbalance2D-image generationDisplay deviceFinite time
A method for presenting seismic data in a multidimensional visualization. Specifically, in the visualization technique of the current invention, seismic data is displayed in a multidimensional plan view utilizing at least four dimensions associated with the seismic data, such as for example, x, y, time / depth and offset. In the method of the invention, a plurality of time or depth windows are defined along a reflector or any other time or depth surface of interest on the prestack data as presented in standard CMP displays. In one embodiment of the invention, for each CMP gather, a window is defined around the data representing the reflector of interest. Passing through each window are individual seismic traces. The window, being defined on the seismic display, is associated with a finite time / depth segment and will contain several offsets. In addition, since each CMP gather has a constant x and y coordinate, the window is associated with specific spatial coordinates. These spatial coordinates are used to plot the window on an x-y plan view. Each window represents a segment of the seismic data associated with a reflector or other time / depth window. The data within each window can be analyzed to determine such things as, for example, the accuracy of the particular velocity model selected for data processing methods, such a migration. Furthermore, as multiple windows are plotted on the plan view, trends in the data become more prevalent to an observer. The resulting multidimensional plan view thereby permits presentation of the data utilizing at least four dimensions of the data. In another embodiment, additional information can be extracted from the multidimensional plan view by overlaying this plan view on additional representations of the data, such as for example, the underlying seismic structure. In addition, the visualization techniques could be used on poststack data to visualize several stacked traces around a point of interest.
Owner:FAIRFIELD INDUSTRIES INC
Hierarchical categorization of customer error reports
A method, apparatus and article of manufacture for prioritizing customer error reports for a software application. A sub-bucketing algorithm is performed in a computer to sort stack traces associated with the customer error reports by a plurality of lines or entries in the stack traces, in order to create a hierarchy for categorization of the customer error reports.
Owner:AUTODESK INC
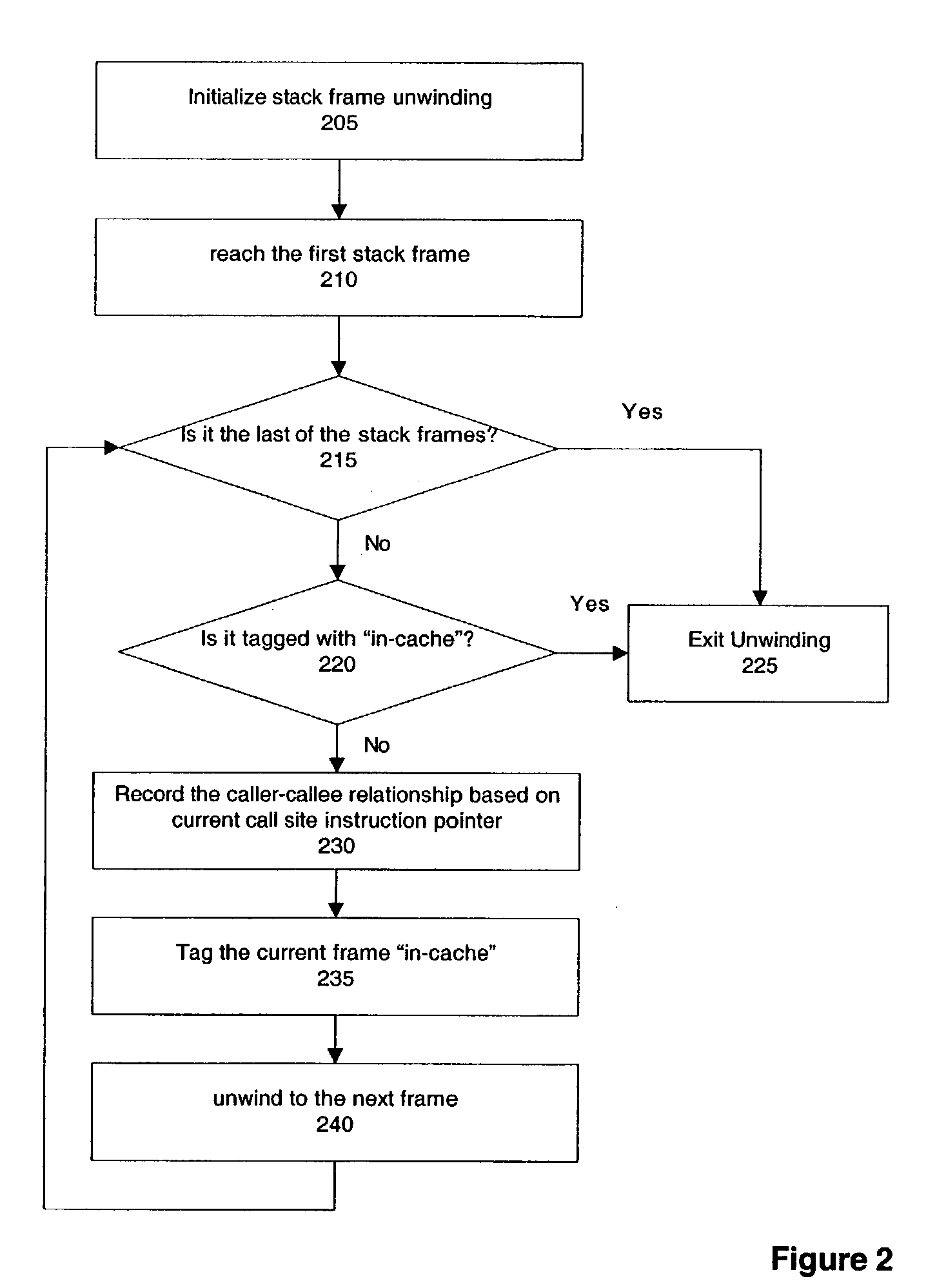
Inlining with stack trace cache-based dynamic profiling
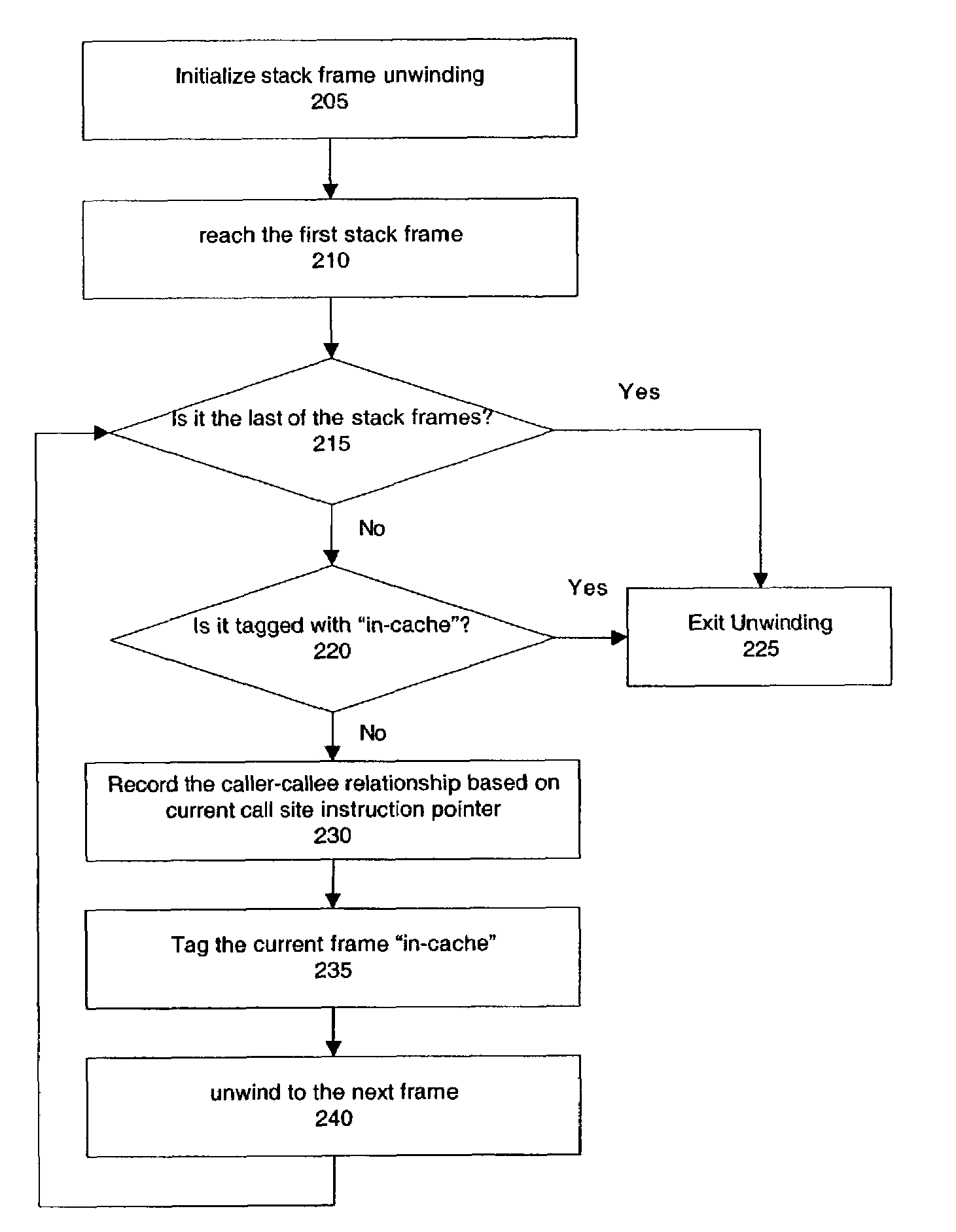
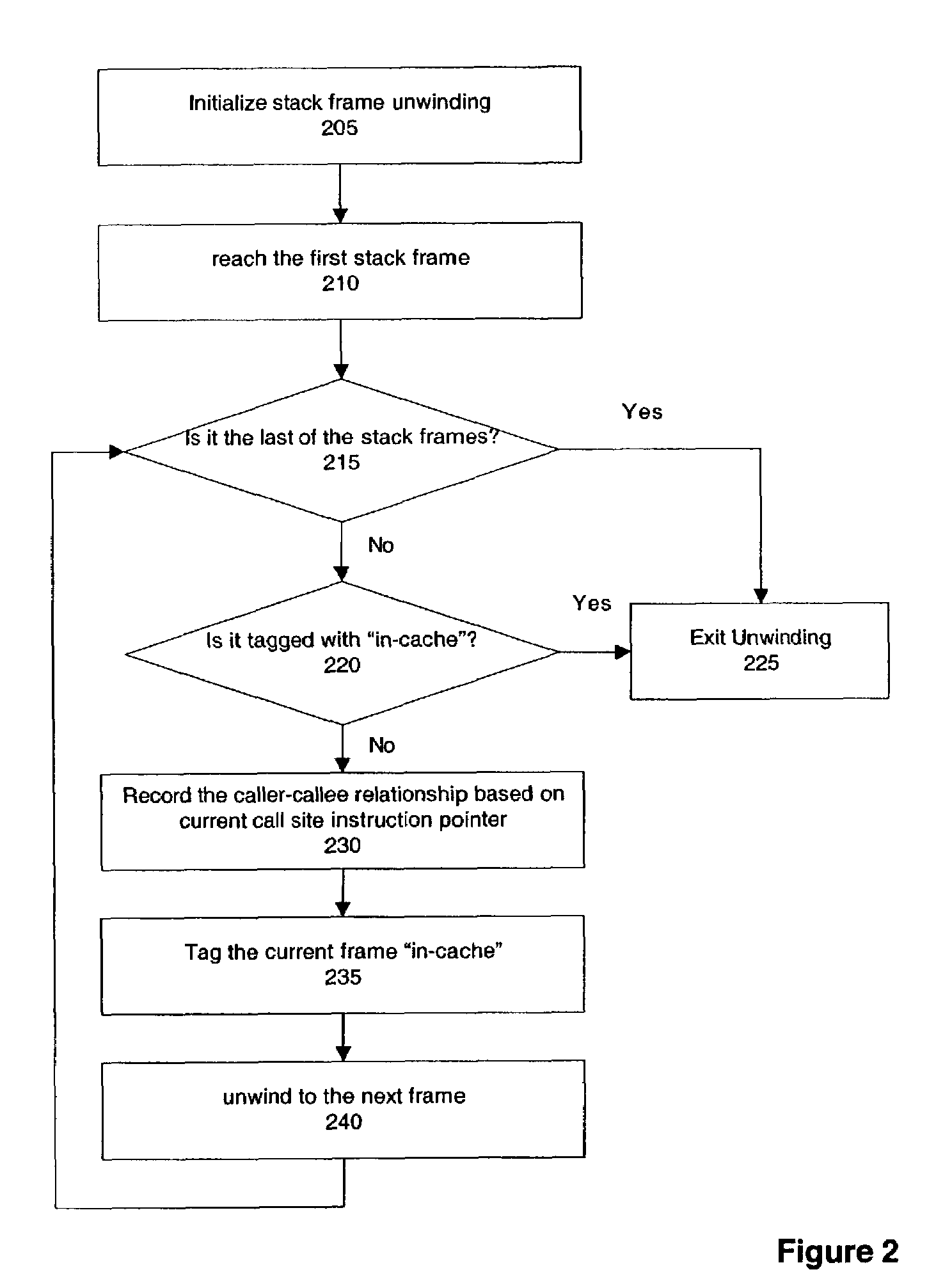
ActiveUS20040205409A1Improving inliningImprove analytical performanceSoftware engineeringError detection/correctionParallel computingStack trace
A method, system, and apparatus are described for inlining using stack trace cache. According to one embodiment, whether a last stack frame of a stack frame trace is not cached is determined, and if the last stack frame is not cached, a caller-callee relationship is recorded, and a relationship map is updated with the recorded caller-callee relationship.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
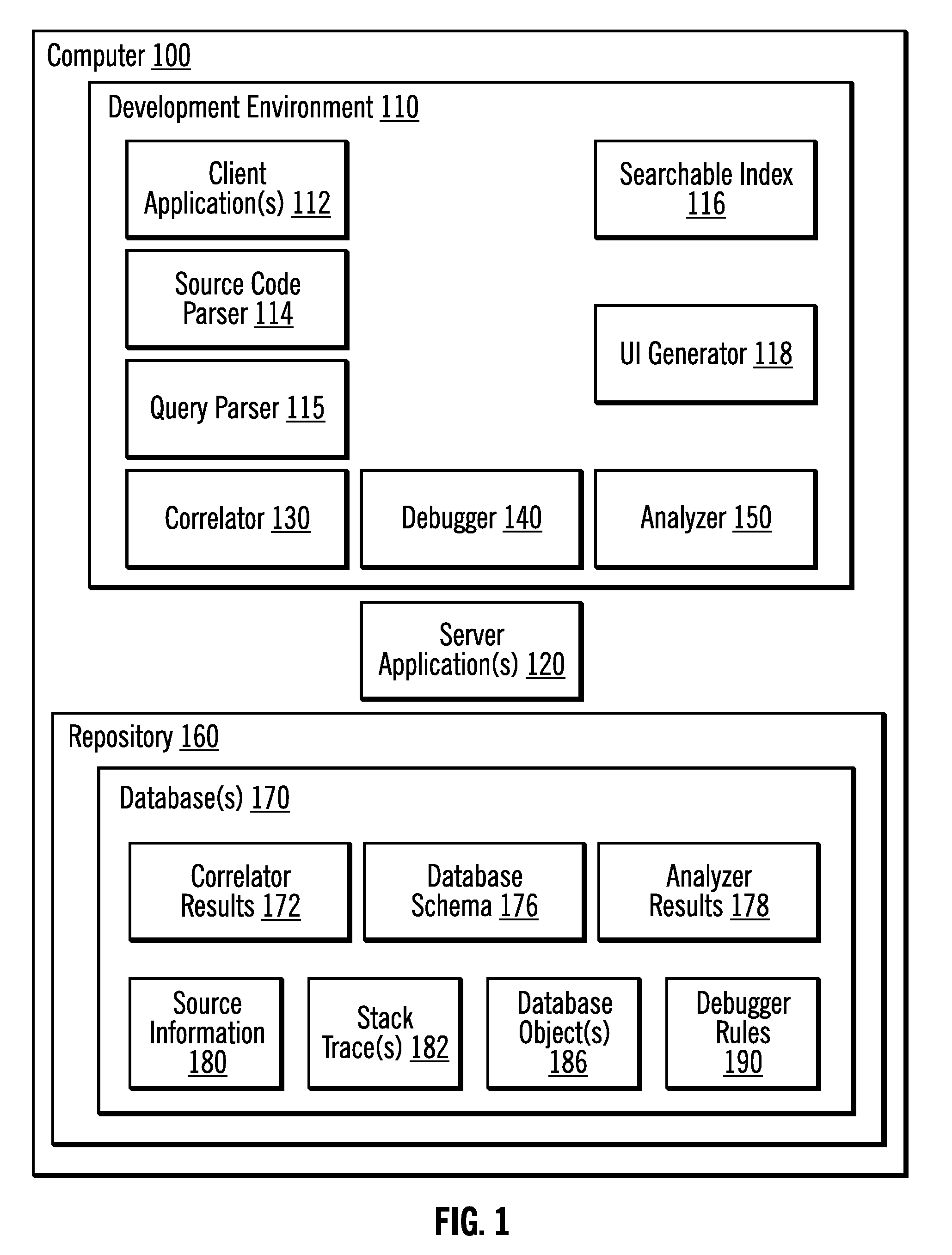
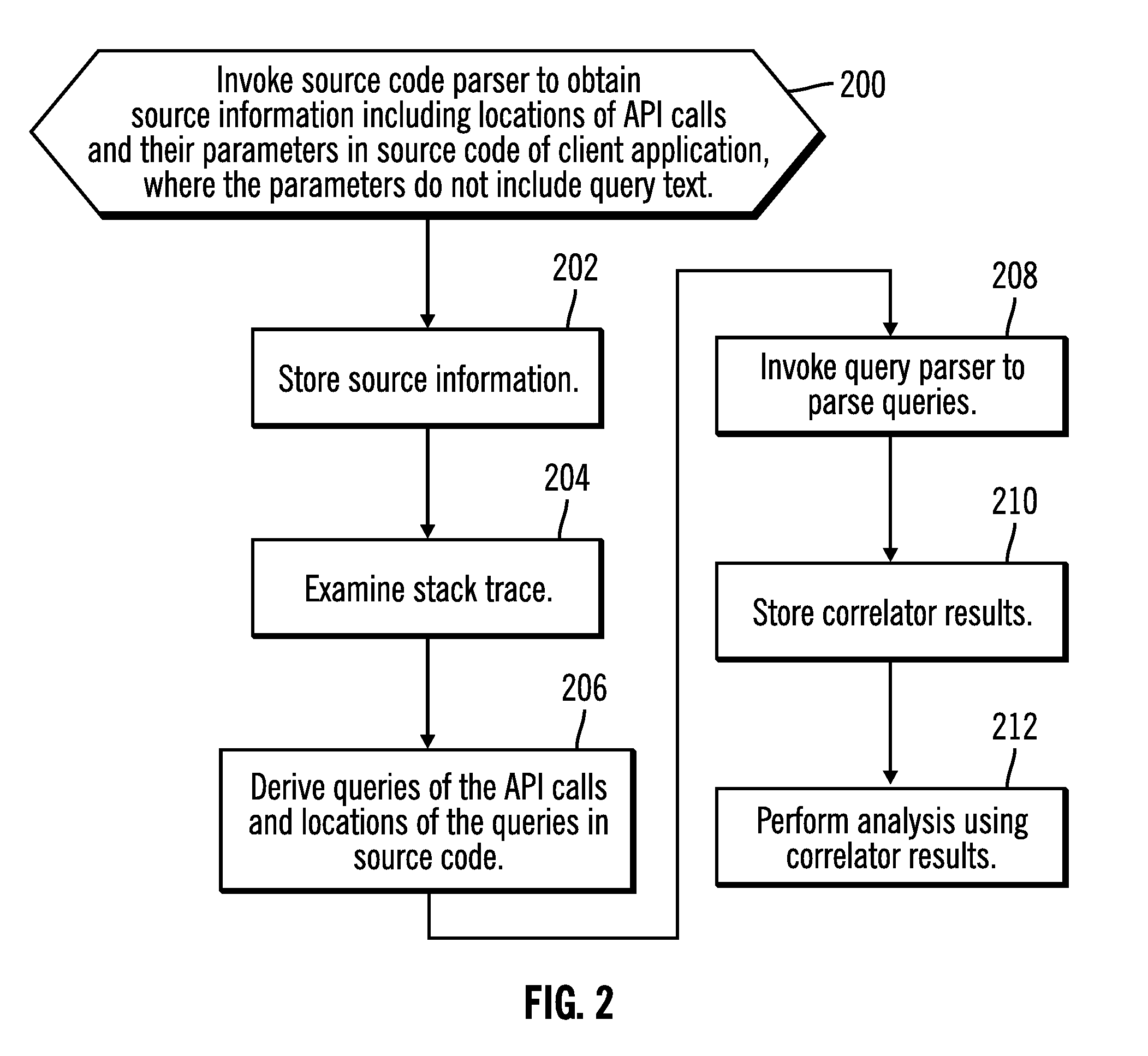
Correlating queries issued by applications with their source lines and analyzing applications for problem determination and where used analysis
InactiveUS20100332473A1Easy to doDigital data processing detailsError detection/correctionApplication programming interfaceClient-side
Provided are techniques for invoking with a processor executing on a computer a source code parser to obtain source information that includes a first location of an Application Programming Interface (API) call and parameters of the API call in source code of a client application, where the parameters the API call do not include query text for a query that is to be used to access a database; examining a stack trace to determine a second location of the API call in the stack trace; and deriving the query of the API call and a third location of the query in the source code by identifying the query in the stack trace at the location of the API call in the stack trace.
Owner:IBM CORP
Stack trace generated code compared with database to find error resolution information
InactiveUS7039833B2Avoid duplication of workLess boringSoftware testing/debuggingNon-redundant fault processingSoftware bugStack trace
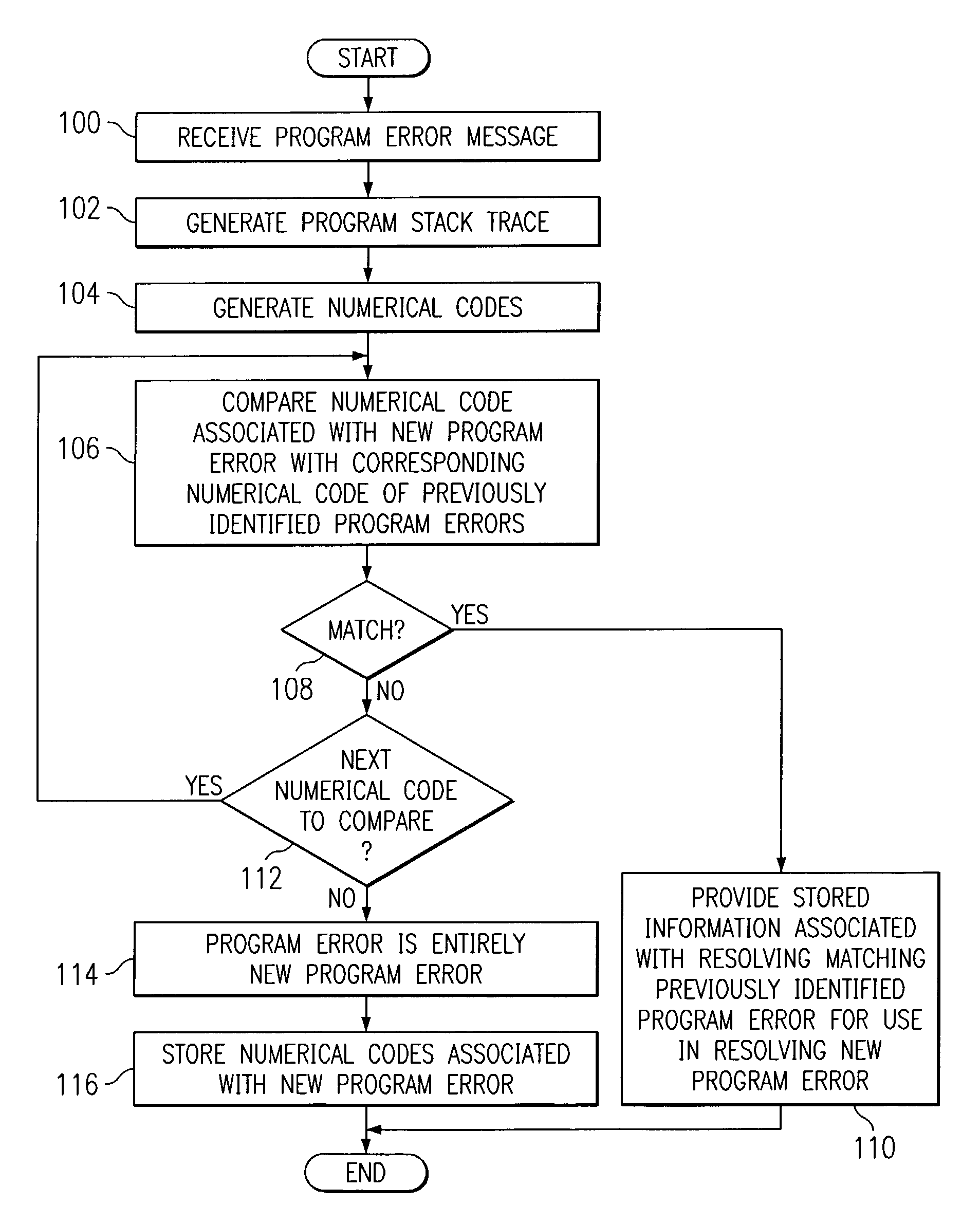
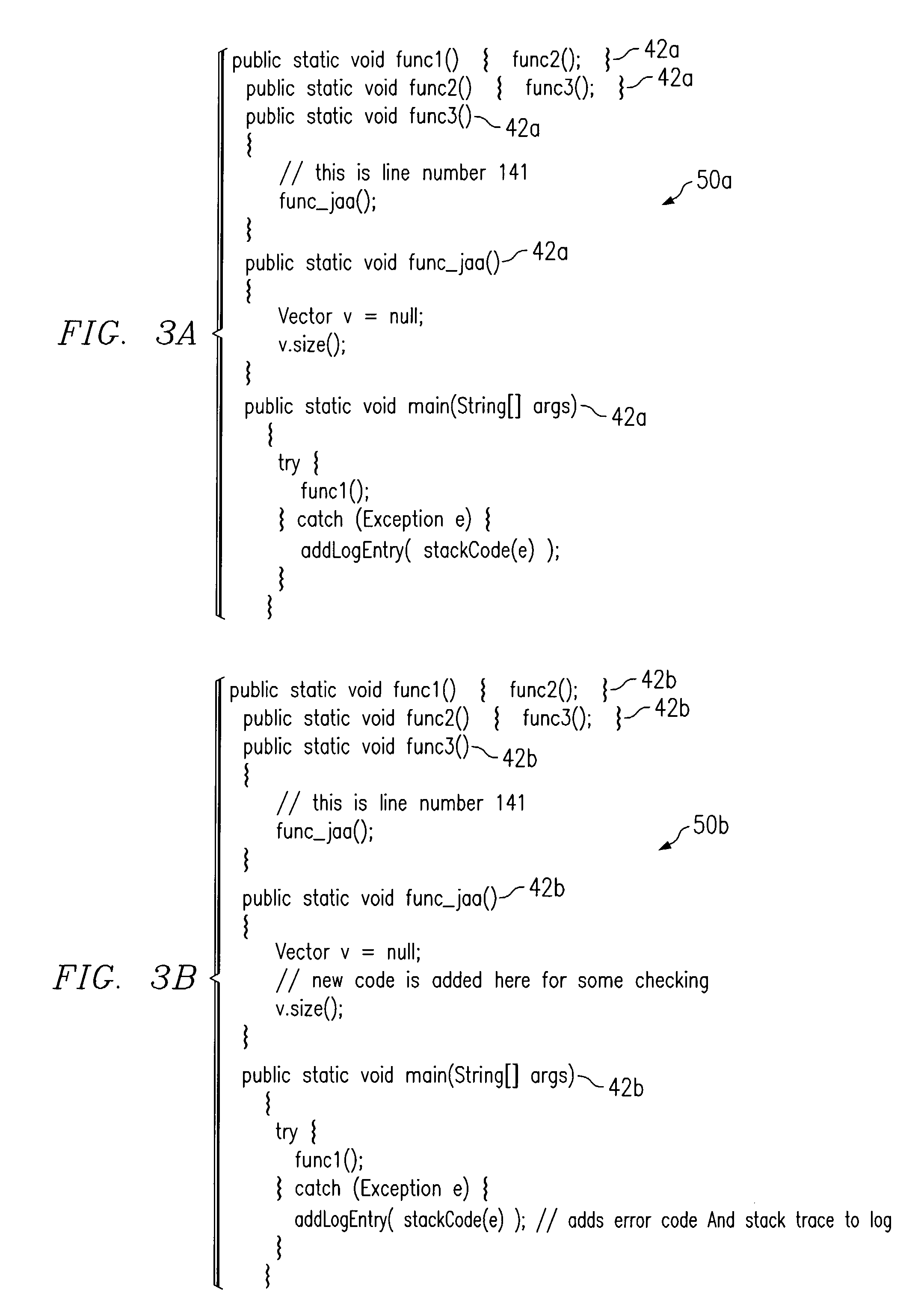
In one embodiment, a method for automatically identifying a program error in a computer program includes receiving a program error message indicating that a new program error has occurred during execution of the program and generating a program stack trace for the new program error indicating the source of the new program error within the program. A first operation is applied to a portion of the program stack trace to generate a first numerical code associated with the new program error. The first numerical code associated with the new program error is compared to one or more stored first numerical codes associated with previously identified program errors to determine whether the new program error is the same as a previously identified program error. If so, stored information associated with resolving the previously identified program error is provided for use in resolving the new program error.
Owner:JDA SOFTWARE GROUP
Method for reducing access to main memory using a stack cache
InactiveUS7065613B1Reduce in quantityEfficient stack cache logicMemory systemsParallel computingComputer science
Owner:MAXTOR
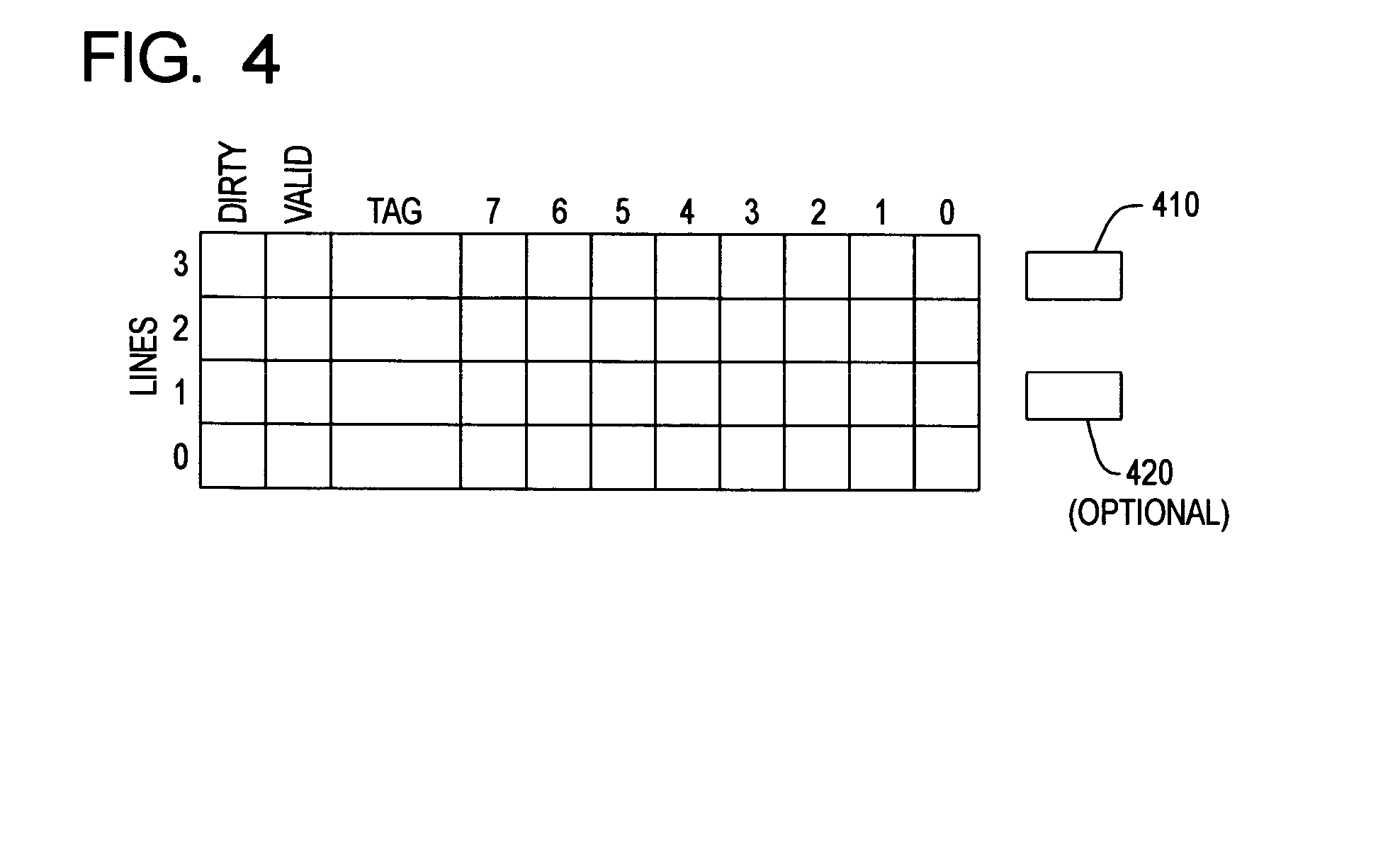
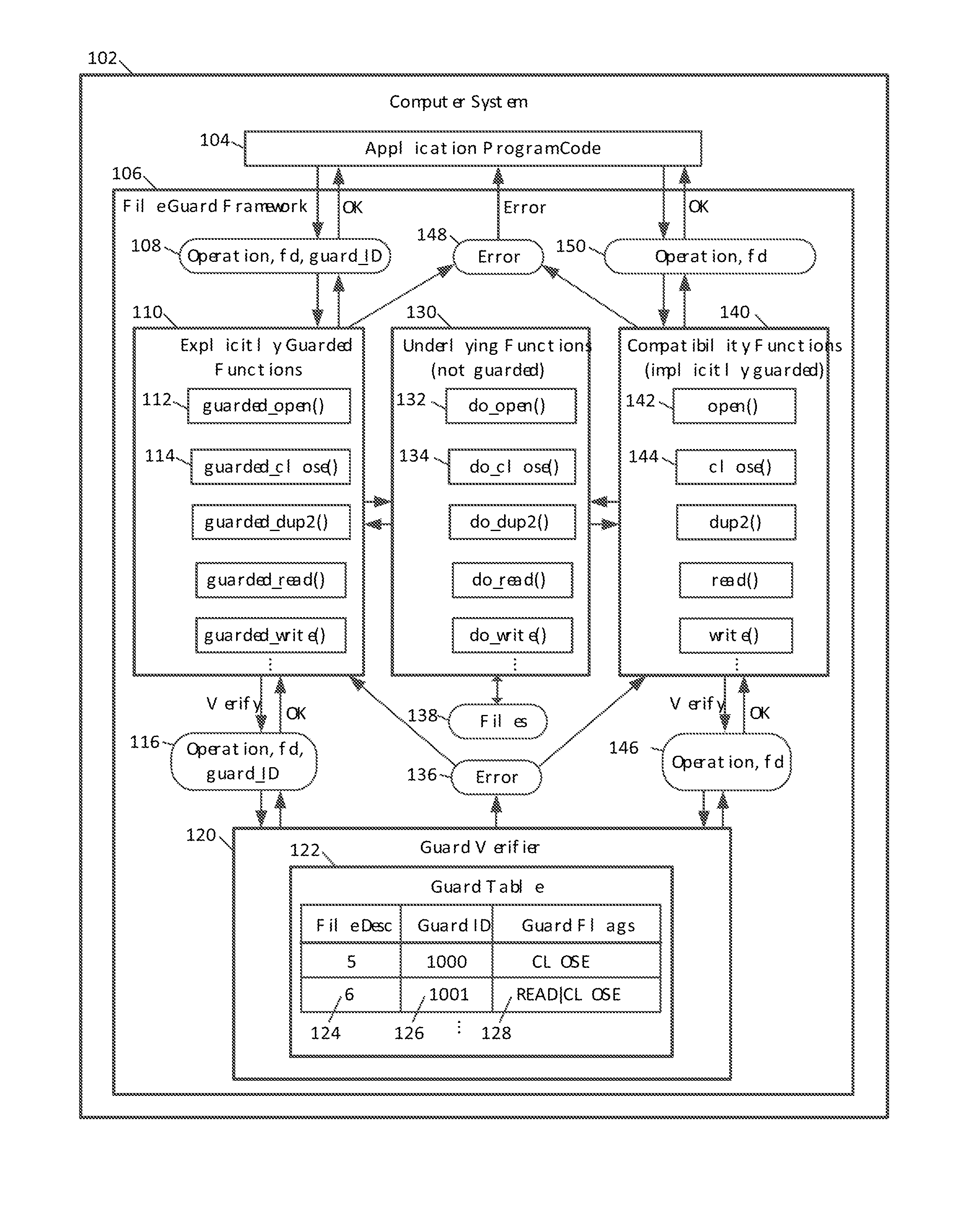
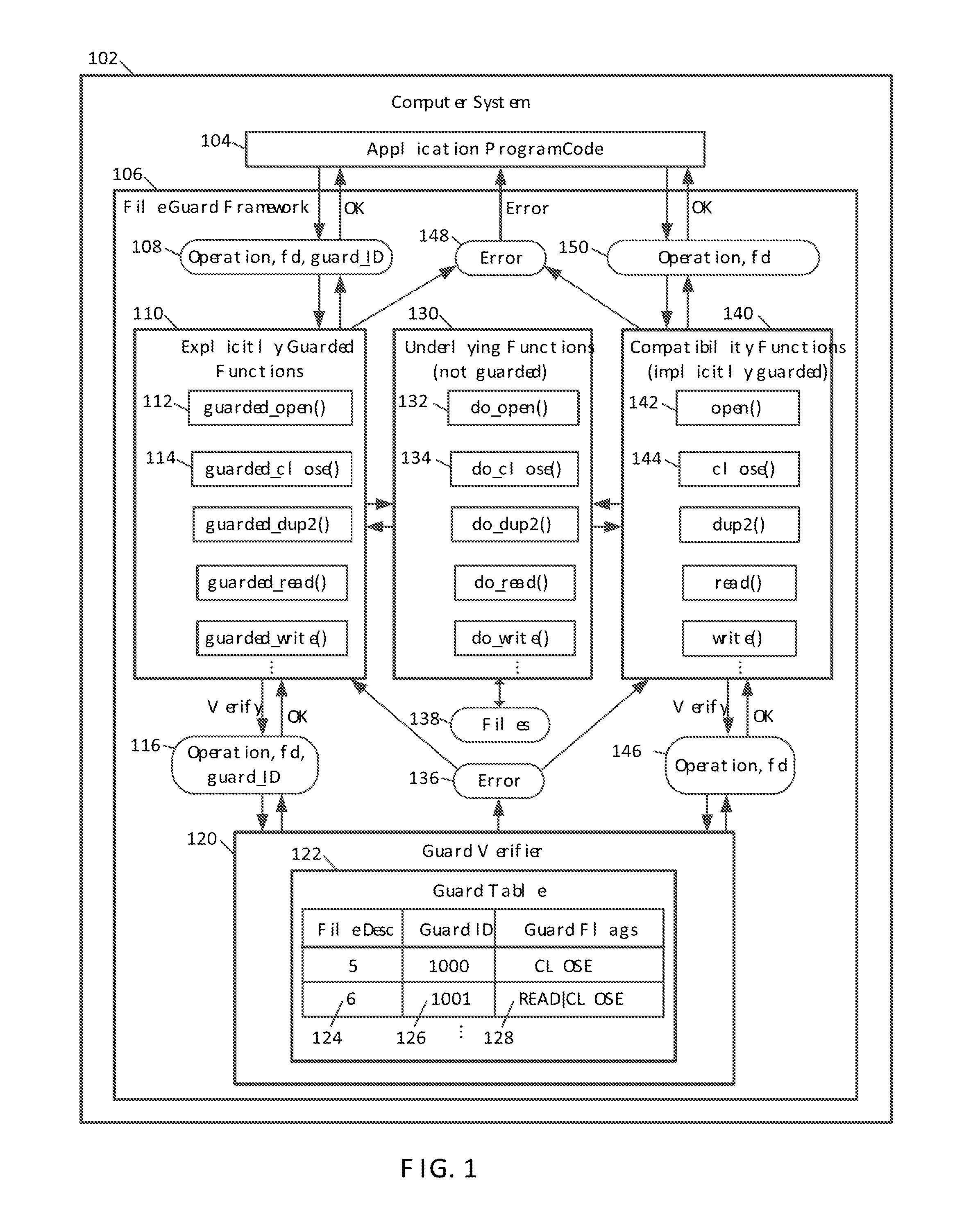
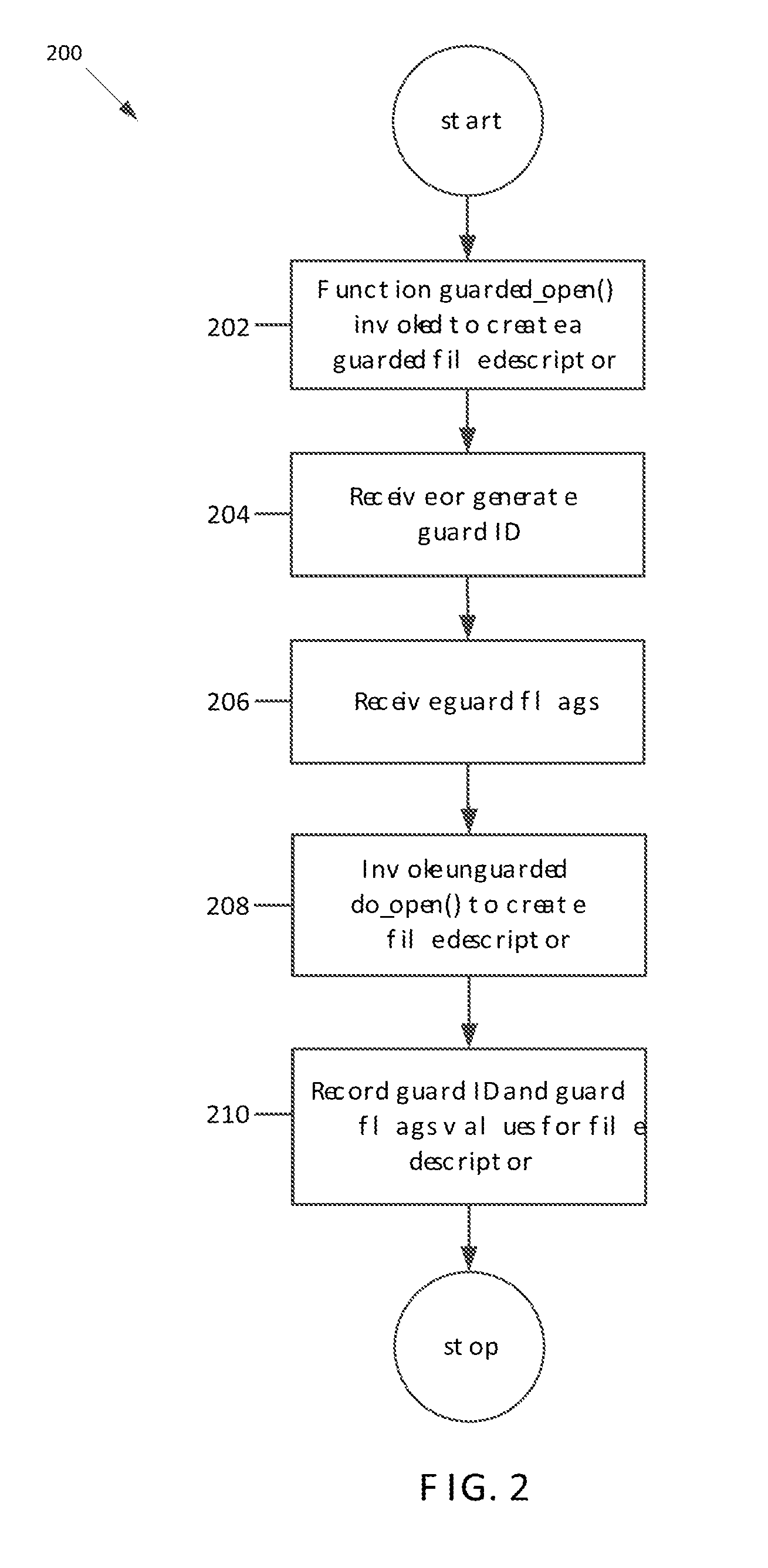
Guarded file descriptors
ActiveUS20130339313A1Preventing executionDigital data information retrievalDigital data processing detailsFile descriptorDatabase
Guarded file access operations are provided for creating and using guarded file descriptors, which can detect and prevent erroneous file access operations in computer programs. A file descriptor can be associated with a guard identifier to create a guarded file descriptor. The association can be established when the file is opened, and can be maintained independently of the computer program, which ordinarily maintains its own association between files, file descriptors, and guard identifiers. Subsequent file operations using the guarded file descriptor check that the guard identifier previously associated with that file descriptor is presented, and generate errors without performing the requested file operations if the correct guard identifier is not presented. This check serves as a validation of the computer program's use of file descriptors. An error and stack trace can be generated for use in analyzing a cause of the guard violation.
Owner:APPLE INC
Inlining with stack trace cache-based dynamic profiling
ActiveUS7386686B2Improving inlining with stack trace cache-basedImprove analytical performanceError detection/correctionSoftware engineeringCall siteParallel computing
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Method and machine for efficient simulation of digital hardware within a software development environment
InactiveUS20050066305A1Reducing CPU branch mis-predictionEasy to useCAD circuit designSpecial data processing applicationsSoftware development processParallel computing
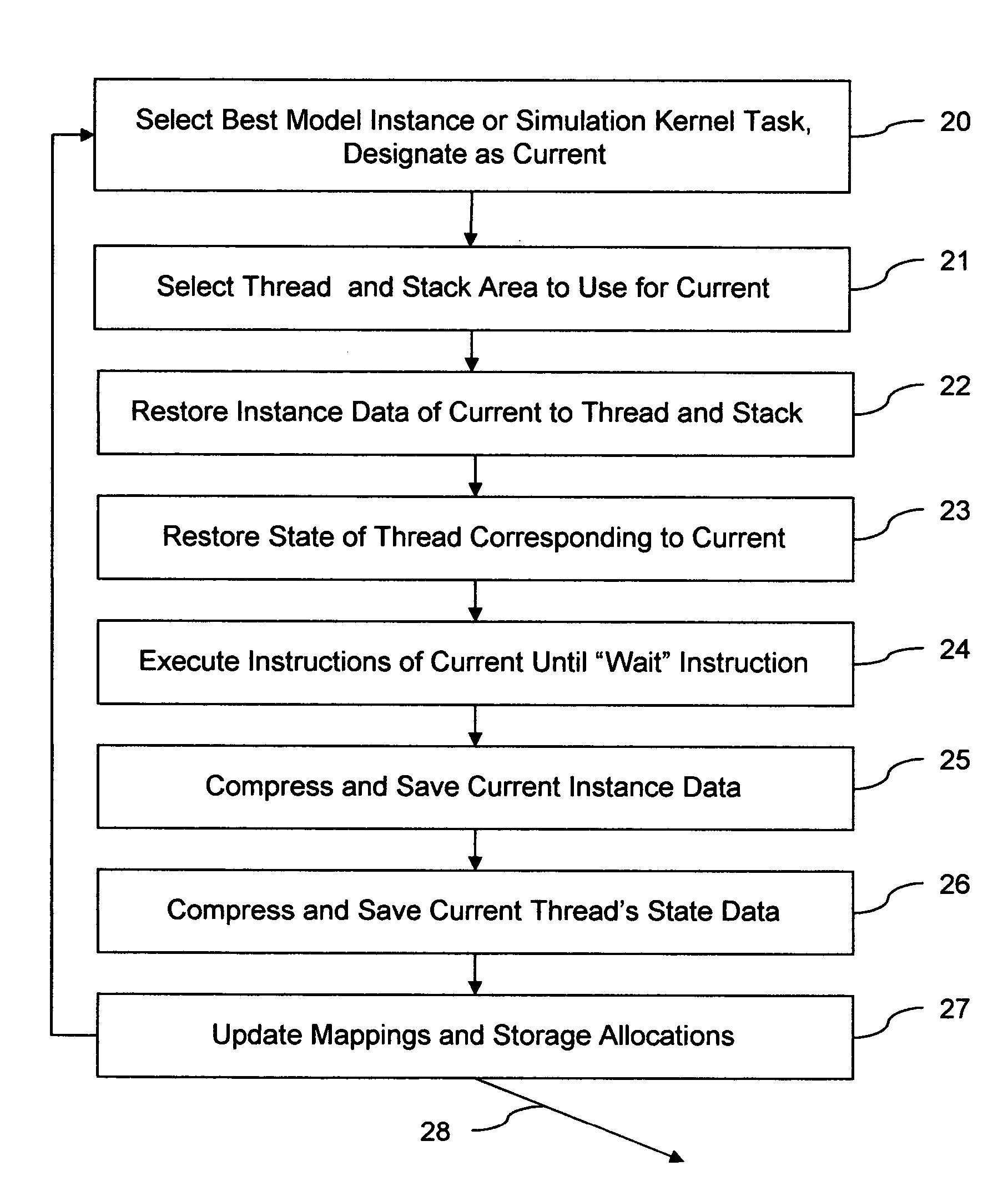
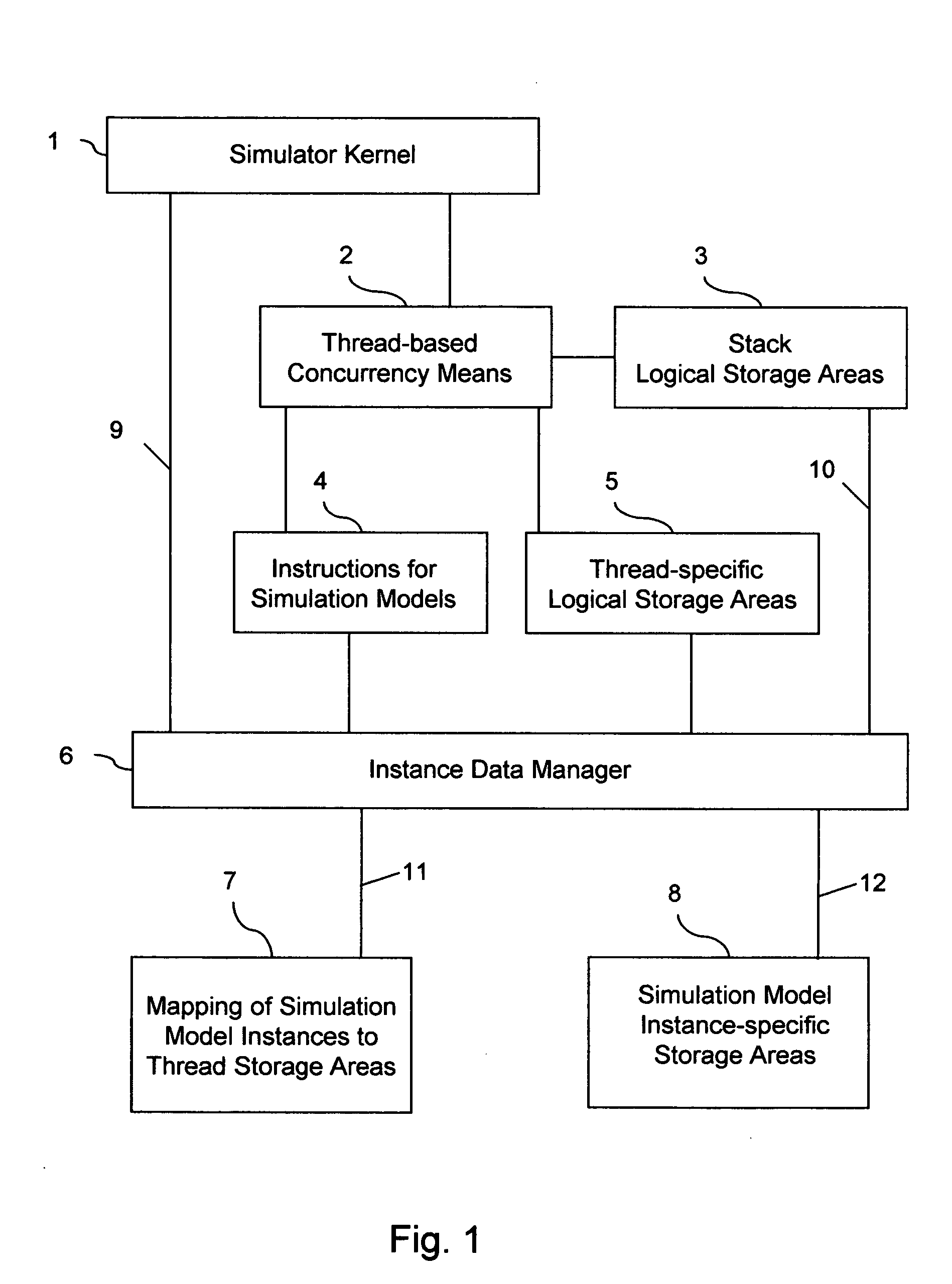
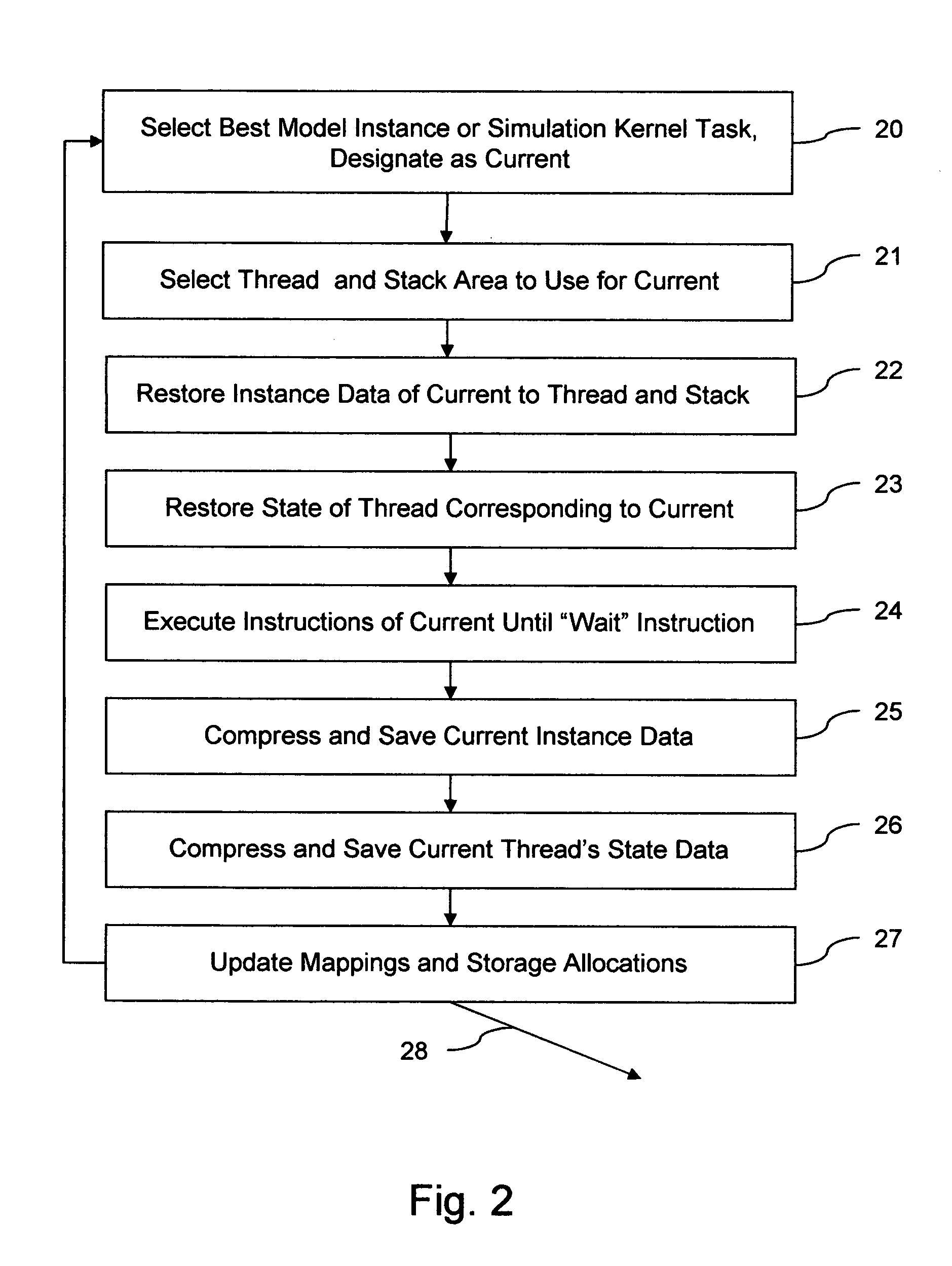
The invention provides run-time support for efficient simulation of digital hardware in a software development enviromnent, facilitating combined hardware / software co-simulation. The run-time support includes threads of execution that minimize stack storage requirements and reduce memory-related run-time processing requirements. The invention implements shared processor stack areas, including the sharing of a stack storage area among multiple threads, storing each thread's stack data in a designated area in compressed form while the thread is suspended. The thread's stack data is uncompressed and copied back onto a processor stack area when the thread is reactivated. A mapping of simulation model instances to stack storage is determined so as to minimize a cost function of memory and CPU run-time, to reduce the risk of stack overflow, and to reduce the impact of blocking system calls on simulation model execution. The invention also employs further memory compaction and a method for reducing CPU branch mis-prediction.
Owner:LISANKE ROBERT JOHN
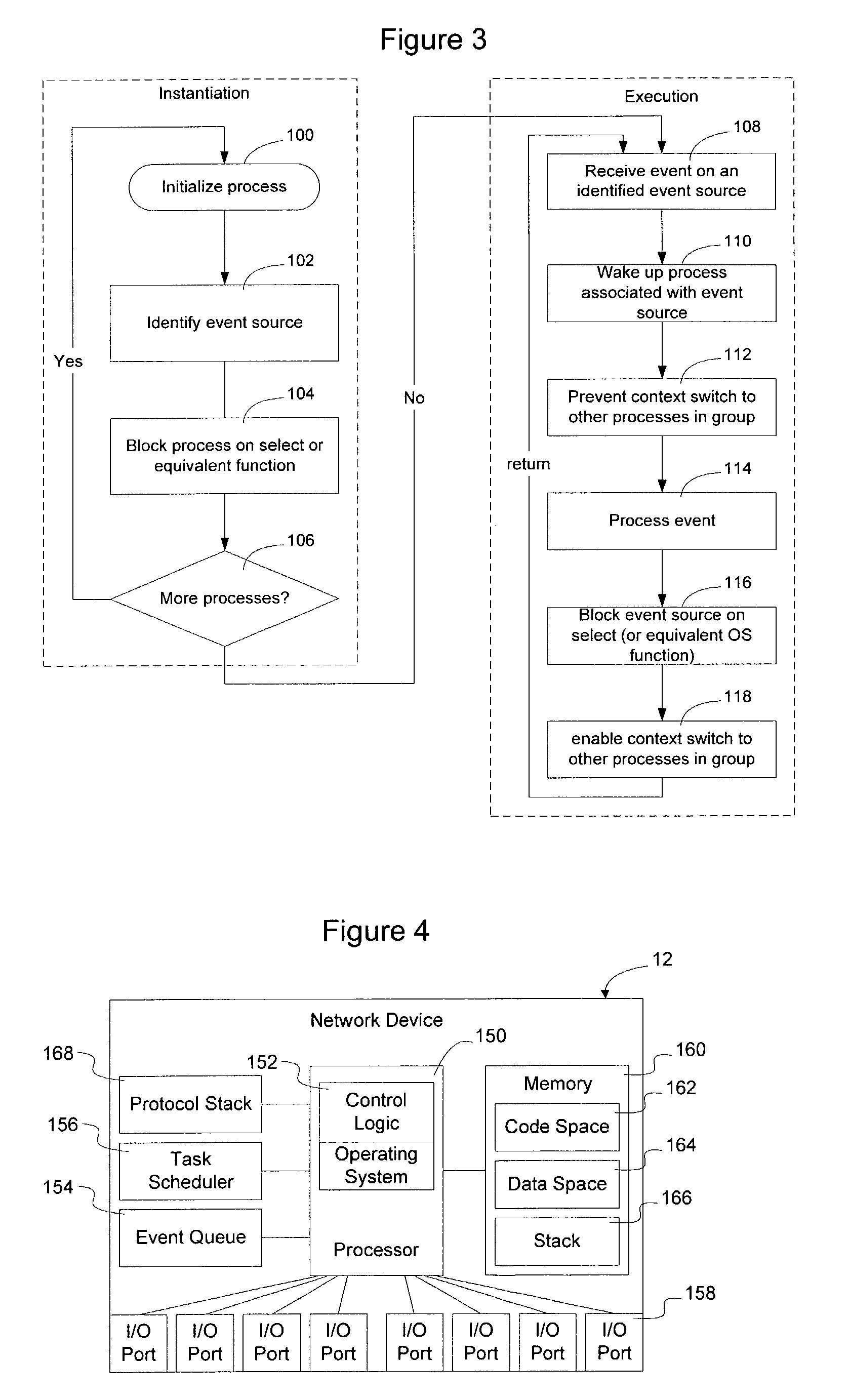
Method and apparatus for sharing stack space between multiple processes in a network device
ActiveUS7373646B1Lower requirementReduces stack requirementProgram initiation/switchingResource allocationOperational systemEvent loop
Network processes within a group of network processes are configured to share stack space by controlling when a context switch may be performed between processes in the group. Since a context switch will not be performed between group members during execution of the event loop, the dedicated stack requirements of the process are limited to that required to store state information when the process is idling on a select function. This reduces system stack requirements by allowing a large portion of the stack to be shared by multiple network processes without creating unintended dependencies between the processes. A semaphore may be used to control access to the shared stack space to prevent unintended context switches between group members. If there is more than one group of processes, the operating system may perform context switches between processes in different groups since each group has its own dedicated area of shared stack.
Owner:AVAYA MANAGEMENT LP
Memory debugging tool
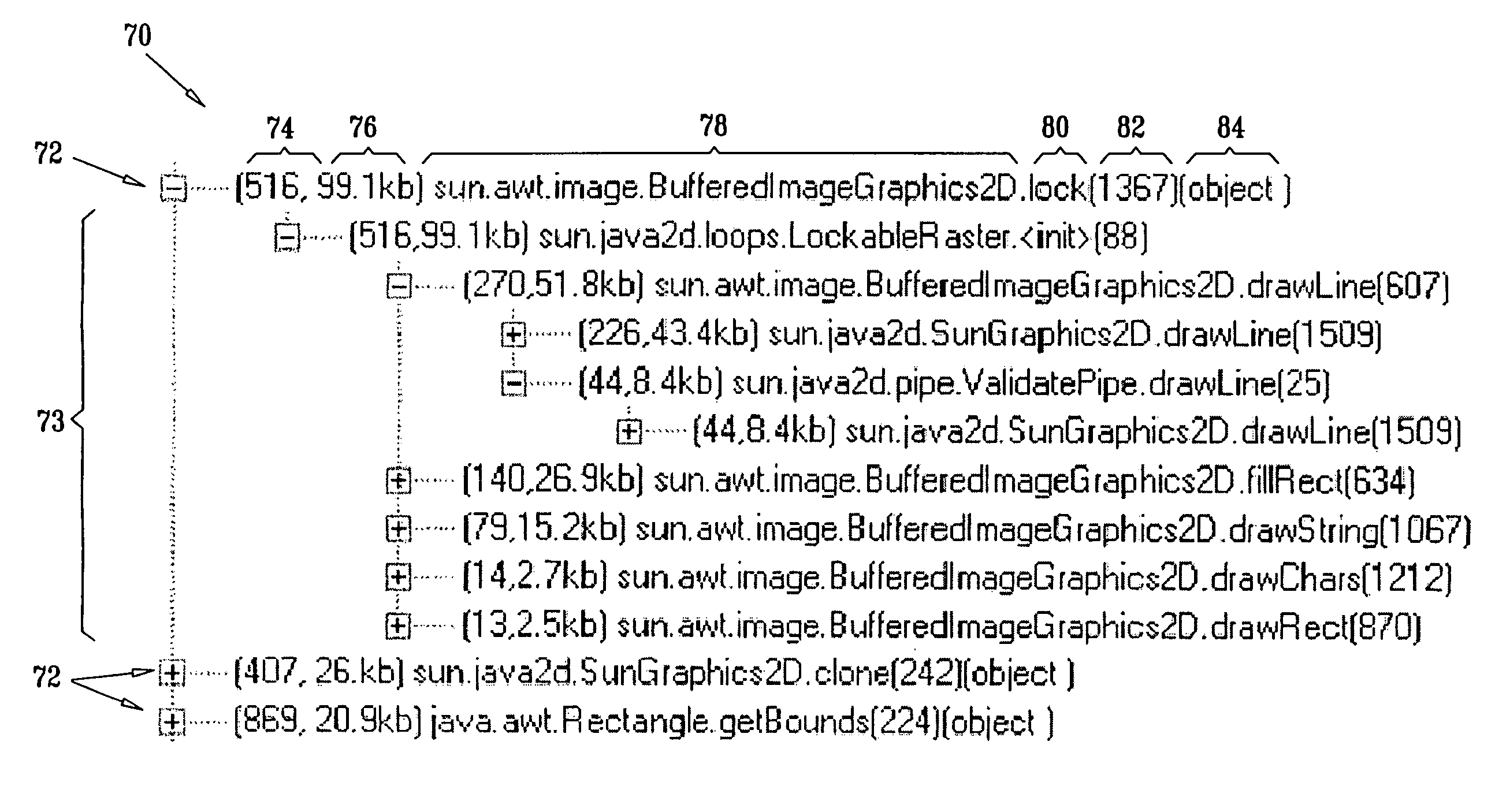
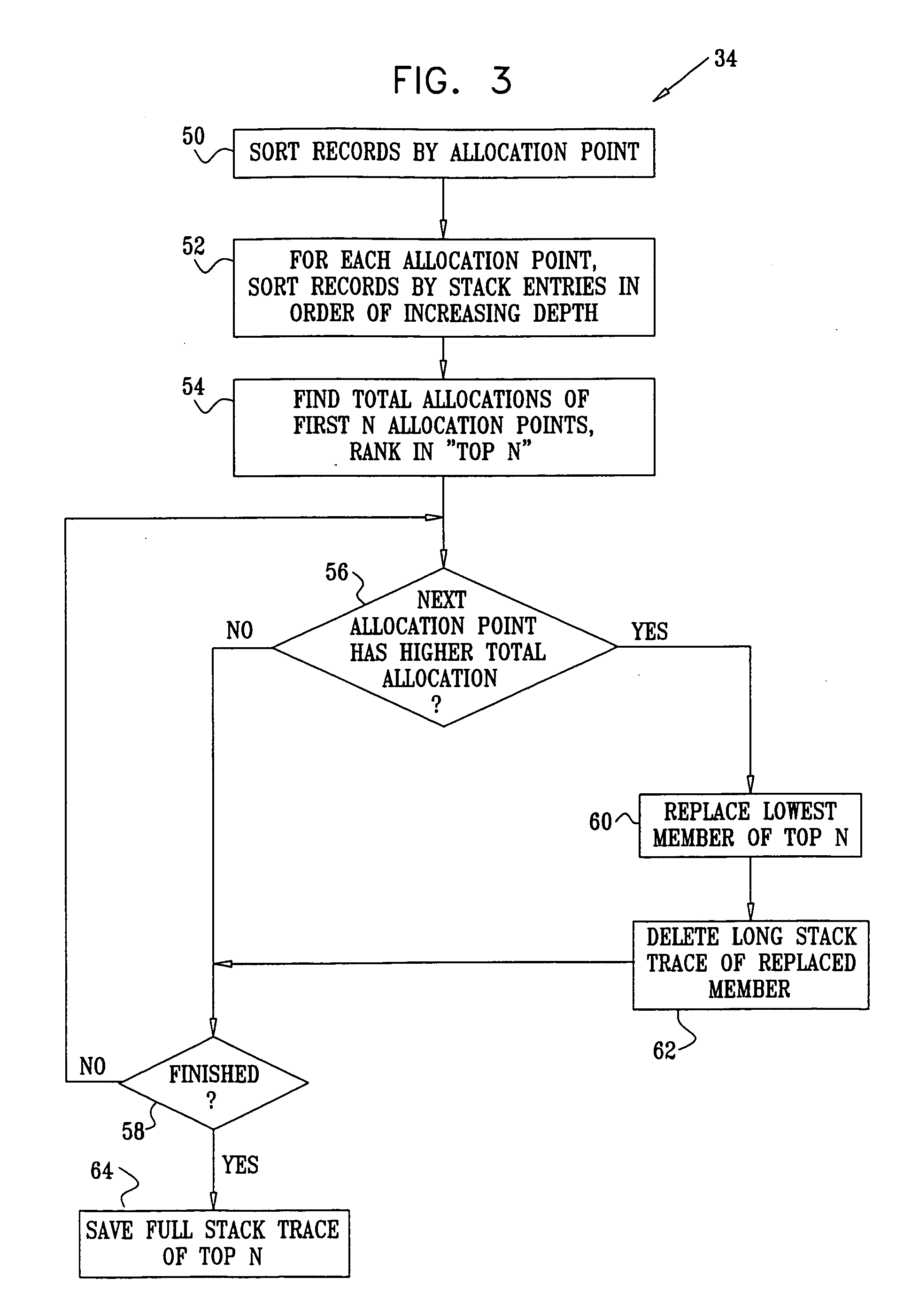
ActiveUS20060195823A1Big amount of dataError detection/correctionSpecific program execution arrangementsParallel computingTerm memory
A method for assessing memory use of a software program includes collecting records of memory allocations while running the program, the records indicating respective allocation points in the program. The records are sorted according to the respective allocation points, and the sorted records are displayed so as to enable a user to observe totals of the memory allocations at the respective allocation points. In a disclosed embodiment, stack traces are collected at the allocation points, and information regarding the stack traces is displayed for at least some of the allocation points.
Owner:SAP PORTALS ISRAEL
Anomaly detection in real-time multi-threaded processes on embedded systems and devices using hardware performance counters and/or stack traces
An aspect of behavior of an embedded system may be determined by (a) determining a baseline behavior of the embedded system from a sequence of patterns in real-time digital measurements extracted from the embedded system; (b) extracting, while the embedded system is operating, real-time digital measurements from the embedded system; (c) extracting features from the real-time digital measurements extracted from the embedded system while the embedded system was operating; and (d) determining the aspect of the behavior of the embedded system by analyzing the extracted features with respect to features of the baseline behavior determined.
Owner:NEW YORK UNIV
Method frame storage using multiple memory circuits
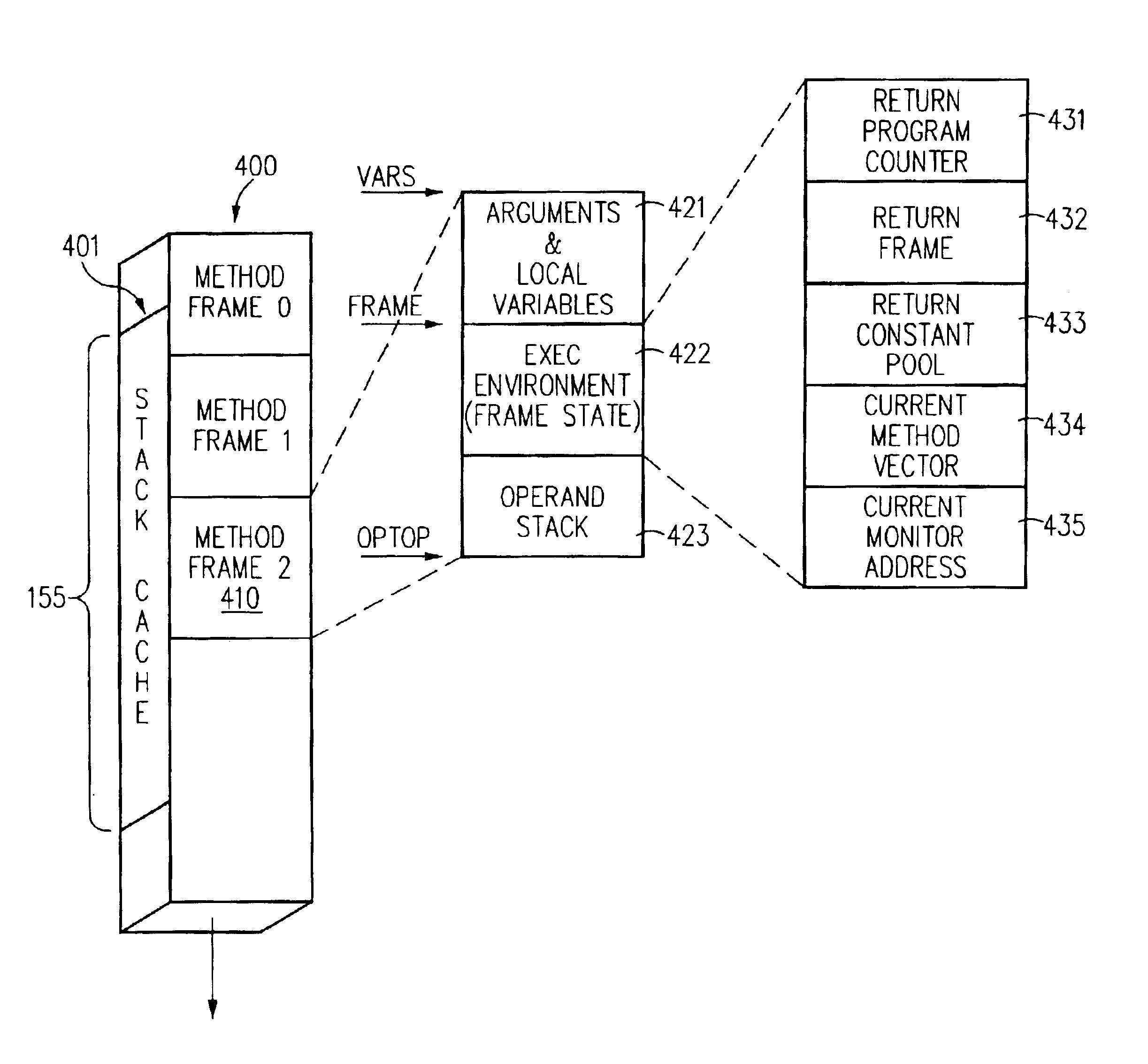
InactiveUS6950923B2Increase speedMemory architecture accessing/allocationProgram control using stored programsManagement unitMemory circuits
A memory architecture in accordance with an embodiment of the present invention improves the speed of method invocation. Specifically, method frames of method calls are stored in two different memory circuits. The first memory circuit stores the execution environment of each method call, and the second memory circuit stores parameters, variables or operands of the method calls. In one embodiment the execution environment includes a return program counter, a return frame, a return constant pool, a current method vector, and a current monitor address. In some embodiments, the memory circuits are stacks; therefore, the stack management unit to cache can be used to cache either or both memory circuits. The stack management unit can include a stack cache to accelerate data transfers between a stack-based computing system and the stacks. In one embodiment, the stack management unit includes a stack cache, a dribble manager unit, and a stack control unit. The dribble manager unit includes a fill control unit and a spill control unit. Since the vast majority of memory accesses to the stack occur at or near the top of the stack, the dribble manager unit maintains the top portion of the stack in the stack cache. When the stack-based computing system is popping data off of the stack and a fill condition occurs, the fill control unit transfer data from the stack to the bottom of the stack cache to maintain the top portion of the stack in the stack cache. Typically, a fill condition occurs as the stack cache becomes empty and a spill condition occurs as the stack cache becomes full.
Owner:SUN MICROSYSTEMS INC
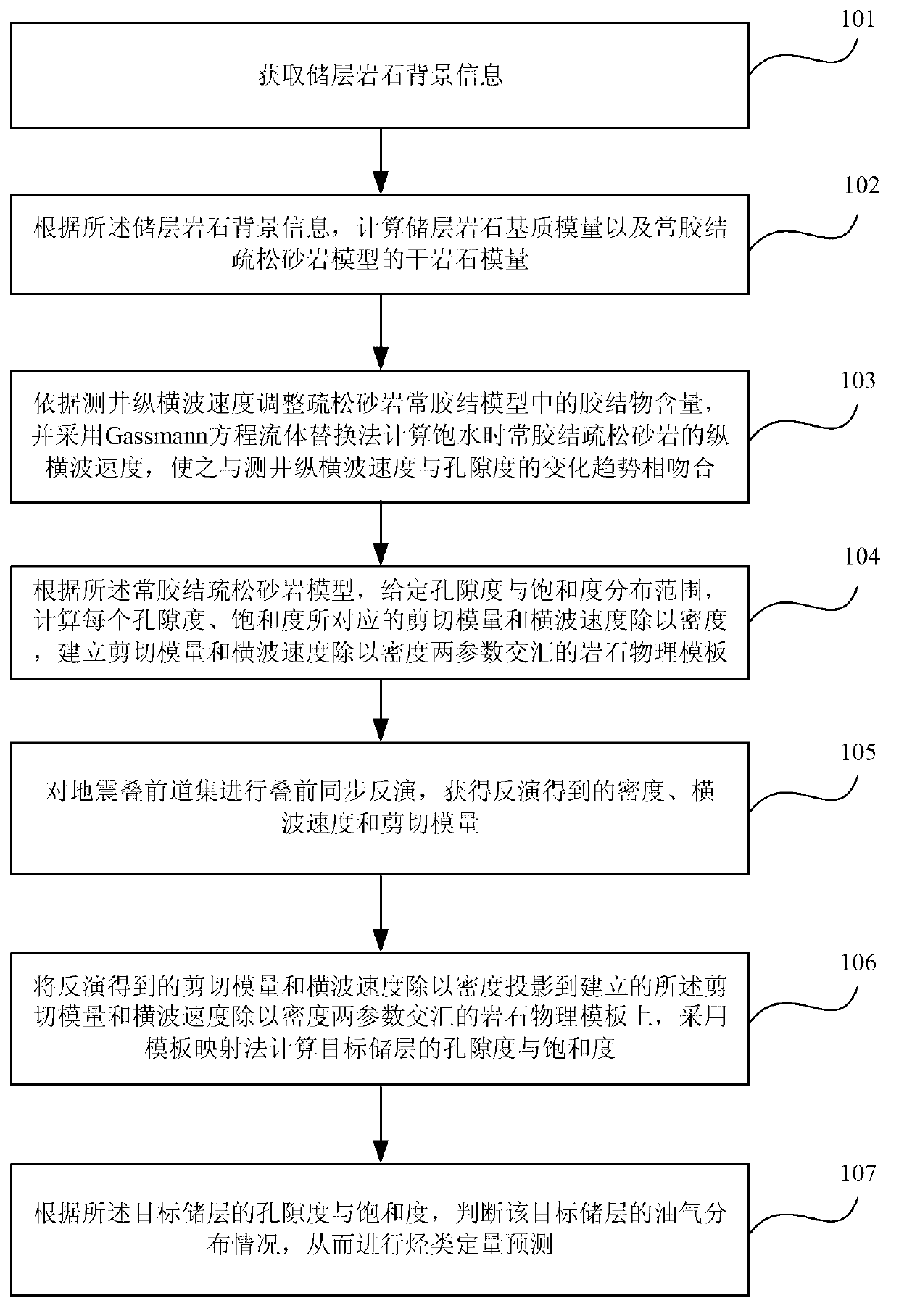
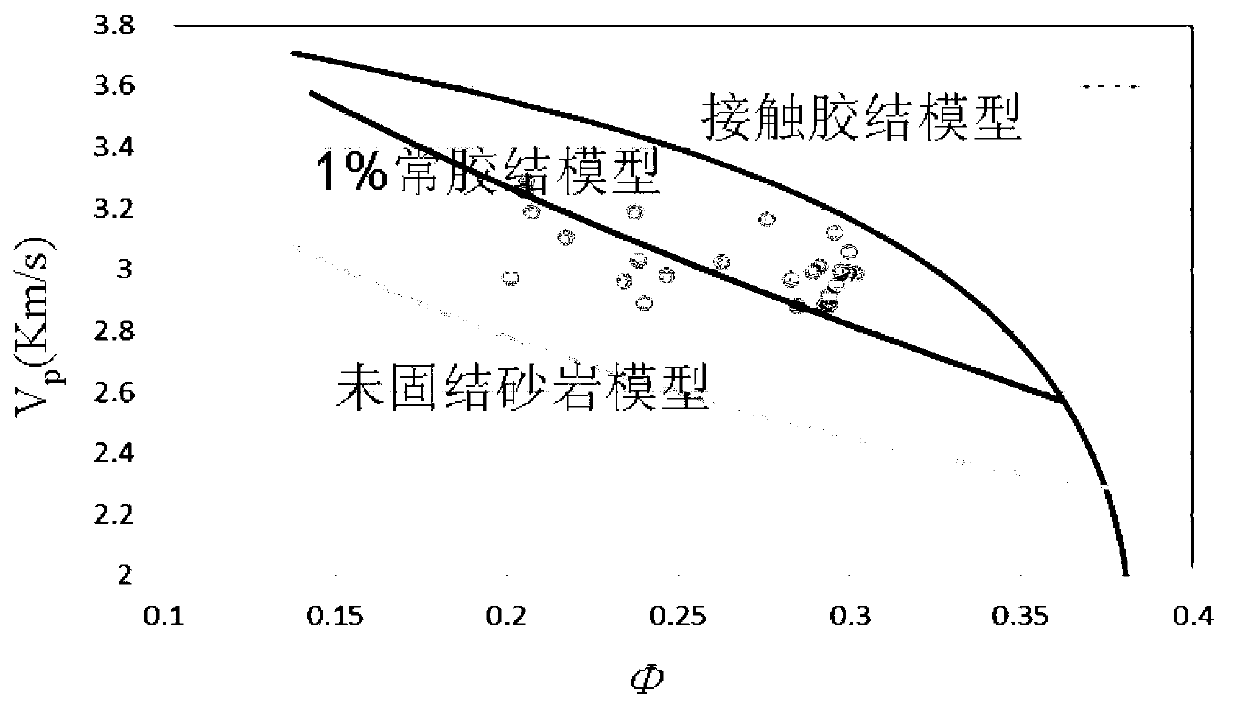
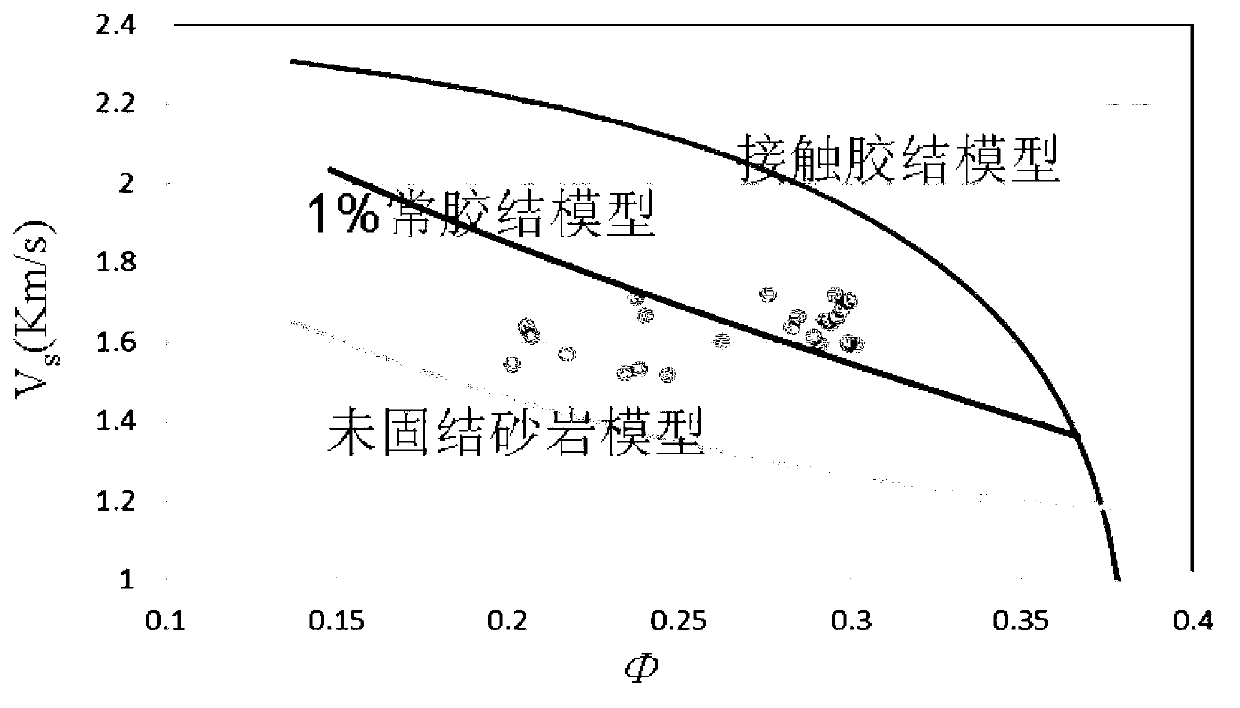
Method and device used for hydrocarbon quantitative prediction and based on unconsolidated sandstone model
ActiveCN103135135AReduce ambiguityImprove forecast accuracySeismic signal processingShear modulusPorosity
The invention provides a method and a device used for hydrocarbon quantitative prediction and based on an unconsolidated sandstone model. The method comprises the steps of obtaining background information of reservoir rock, according to the background information of the reservoir rock, calculating a dried rock modulus of the constant-cement unconsolidated sandstone model, calculating vertical and horizontal wave speeds of constant-cement unconsolidated sandstone when water is saturated, arranging a porosity degree and saturation level distribution range according to the constant-cement unconsolidated sandstone model, calculating formulas that a shear modulus corresponding to each porosity degree and saturation level and the horizontal wave speed are divided by density, building a rock physical template where a parameter that the shear modulus is divided by the density and a parameter that the horizontal wave speed is divided by the density are jointed, carrying out pre-stack synchronous inversion on earthquake pre-stack trace gathering, enabling the obtained shear modulus and the horizontal wave speed during the inversion to be divided by the density and projected to the rock physical template where the parameter that the shear modulus is divided by the density and the parameter that the horizontal wave speed is divided by the density are jointed, calculating the porosity degree and the saturation level of a target reservoir by a template mapping method, and judging an oil-gas distribution condition of the target reservoir. The method and the device used for the hydrocarbon quantitative prediction and based on the unconsolidated sandstone model improve prediction accuracy of the effective reservoir.
Owner:PETROCHINA CO LTD
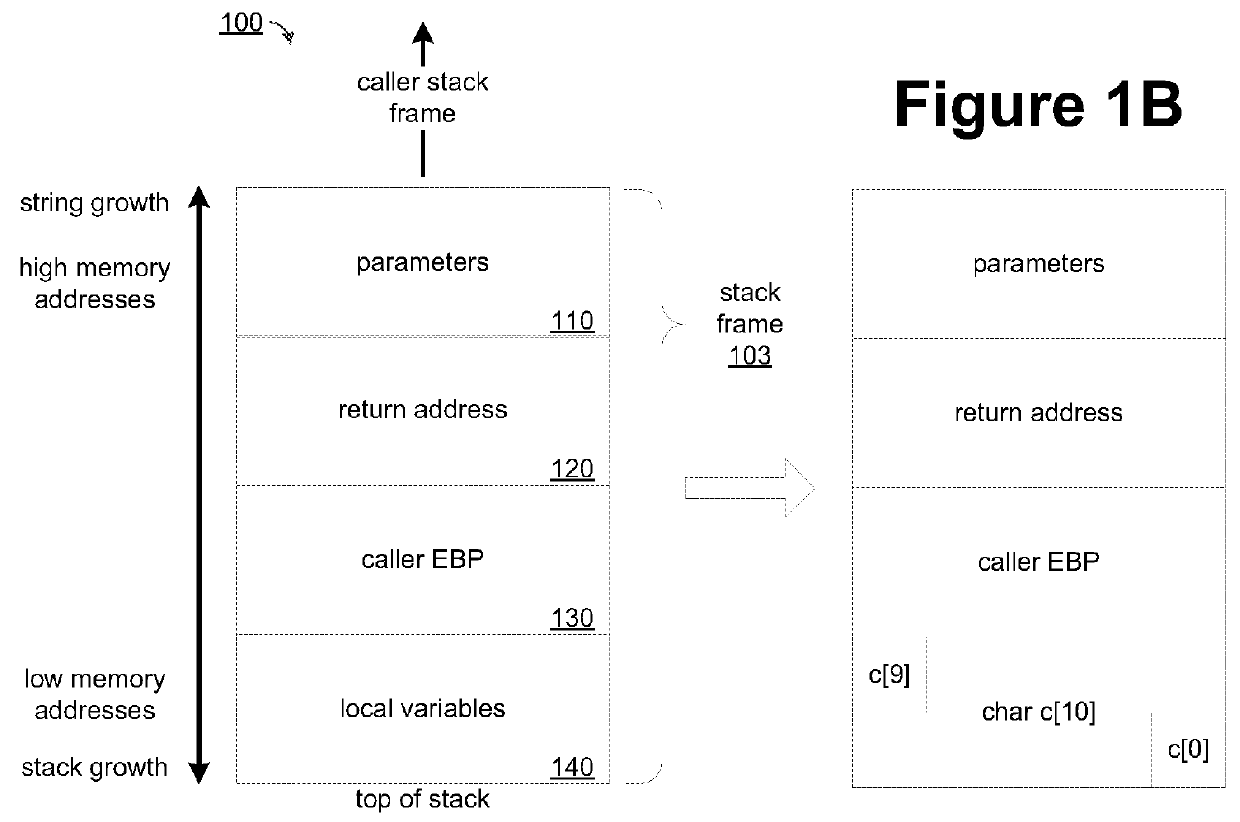
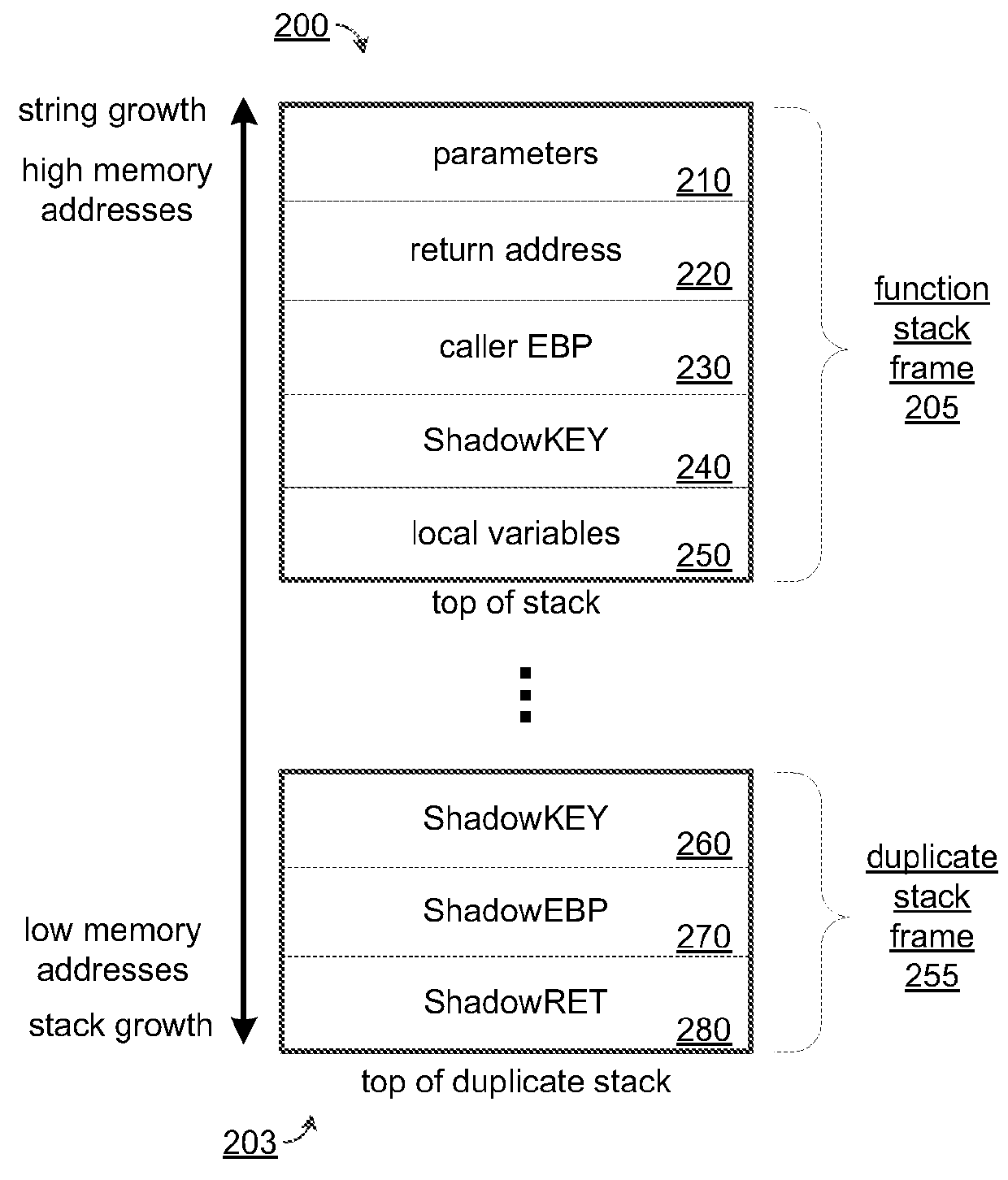
Preventing stack buffer overflow attacks
InactiveUS9251373B2Digital data protectionPlatform integrity maintainanceCall stackBuffer overflow protection
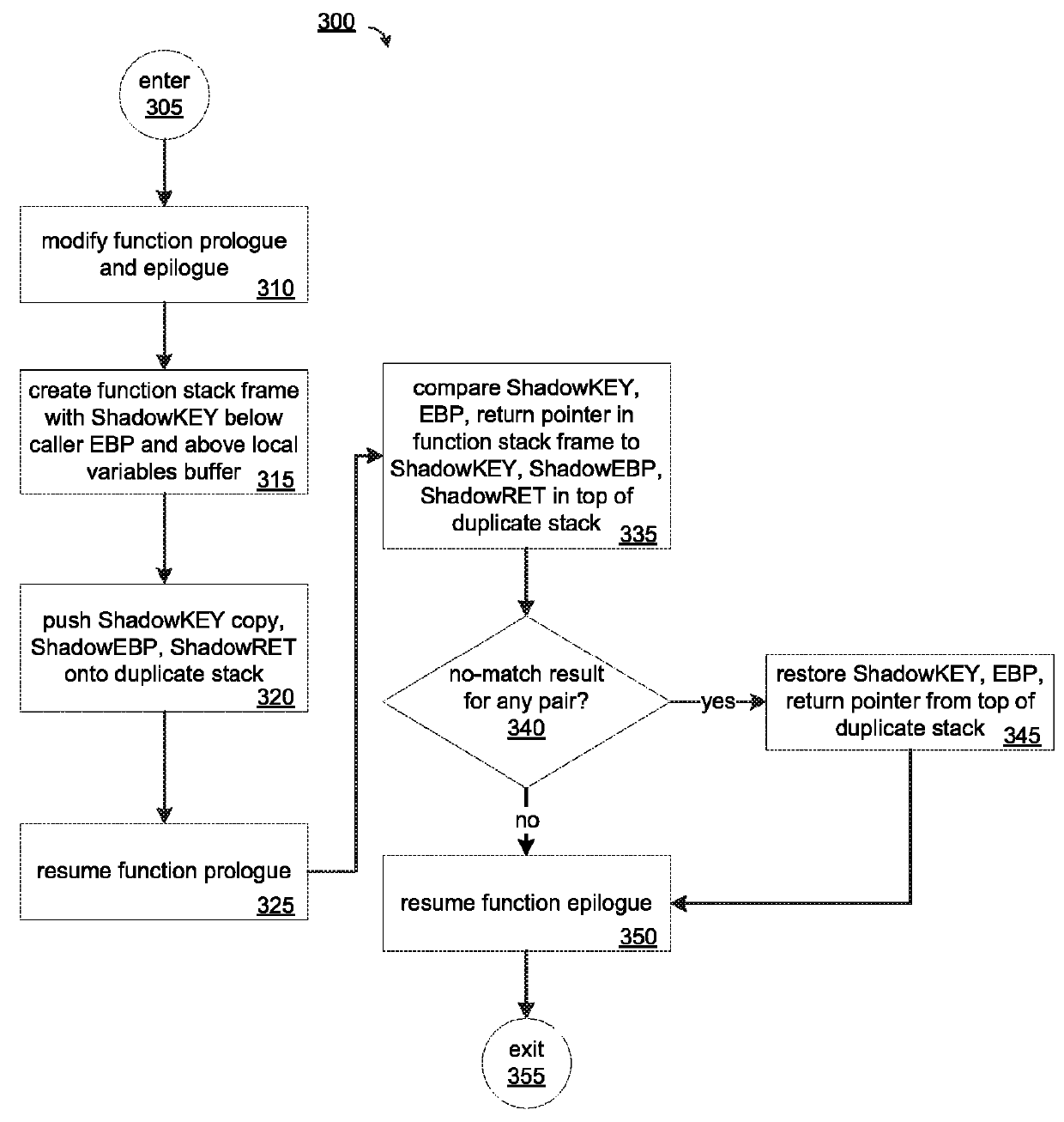
Improved buffer overflow protection for a computer function call stack is provided by placing a predetermined ShadowKEY value on a function's call stack frame and copying the ShadowKEY, a caller EBP, and a return pointer are pushed onto a duplicate stack. The prologue of the function may be modified for this purpose. The function epilogue is modified to compare the current values of the ShadowKEY, caller EBP, and the return pointer on the function stack to the copies stored on the duplicate stack. If they are not identical, an overflow is detected. The preserved copies of these values may be copied back to the function stack frame thereby enabling execution of the process to continue. A function prologue and epilogue may be modified during compilation of the program.
Owner:NORTHERN BORDERS UNIV
Inversion method of frequency dispersion amplitude versus offset (AVO)
ActiveCN102478667AEliminate the effects ofImprove mining efficiencySeismic signal processingFrequency spectrumInterface waves
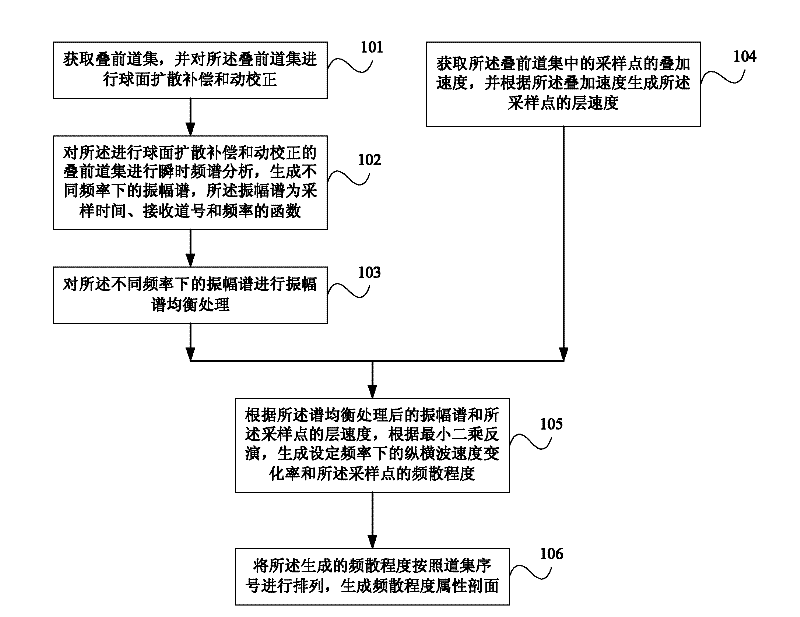
The invention discloses an inversion method of frequency dispersion amplitude versus offset (AVO). The inversion method comprises the following steps: acquiring a pre-stack trace gather; carrying out spherical diffusion compensation and dynamic correction on the pre-stack trace gather, and carrying out instant spectrum analysis on the pre-stack trace gather, so as to generate amplitude spectra under different frequencies; carrying out amplitude spectrum balancing on the amplitude spectra; acquiring a stacking velocity of sampling points in the pre-stack trace gather; generating a layer velocity of the sampling points according to the stacking velocity; generating speed variation rate of the velocity of vertical and horizontal waves under a set frequency and frequency dispersion degree of the sampling points according to the amplitude spectra after amplitude spectrum balancing, the layer velocity of the sampling points, and least square inversion; and ranking the generated frequency dispersion degree according to the trace gather serial number, so as to generate an attribute section of the frequency dispersion degree. By utilizing the inversion method of frequency dispersion AVO provided by the embodiment of the invention, the influence of a strong amplitude energy group caused by impedance difference of an elastic interface wave can be eliminated, and the false 'frequency abnormality' caused by the stacking when post-stack seismic data spectrum is analyzed can be avoided, so that the obtained result is more reliable.
Owner:BC P INC CHINA NAT PETROLEUM CORP +1
Method of parallel regulating multi-task of imbedding system
InactiveCN1564137ADoes not affect the task scheduling processEasy to implementSoftware testing/debuggingComputer hardwareApplication software
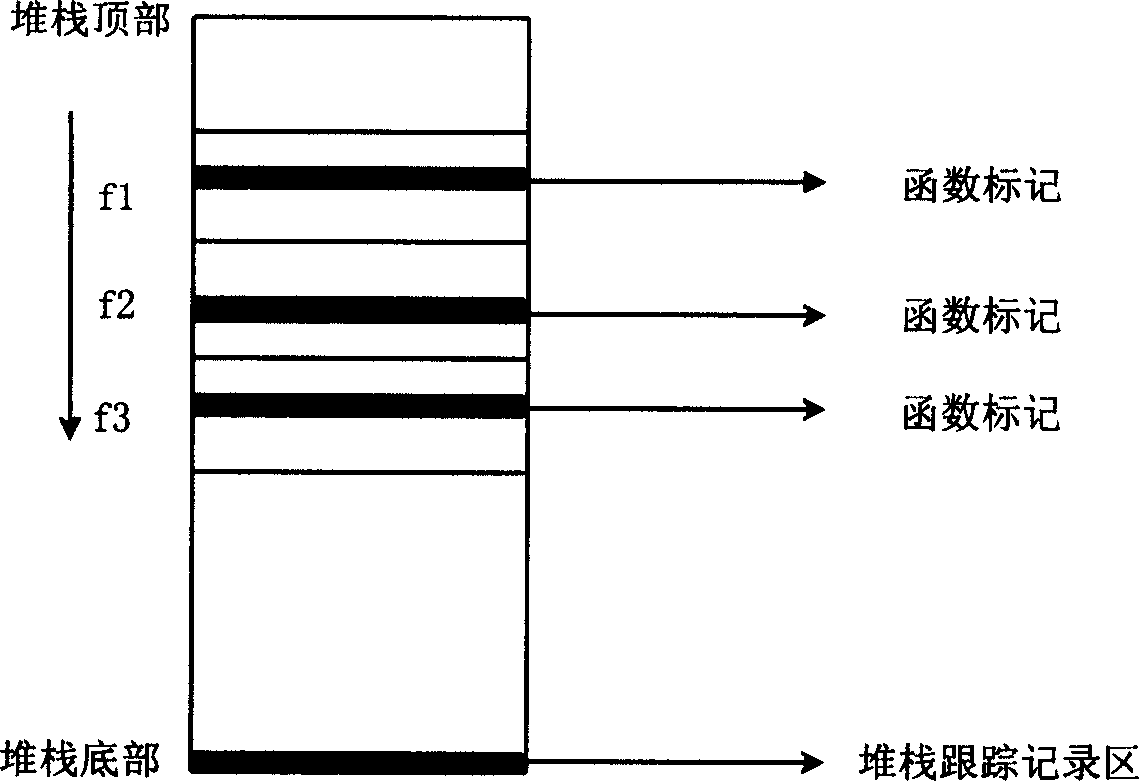
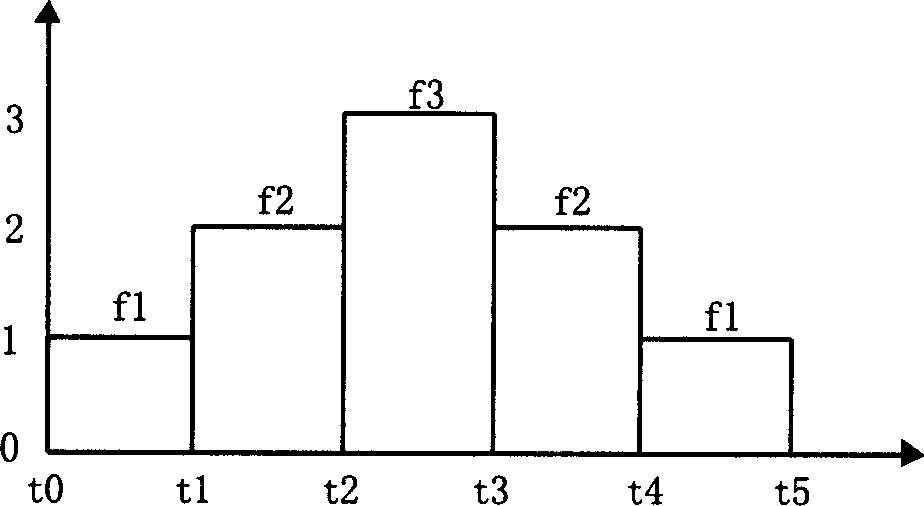
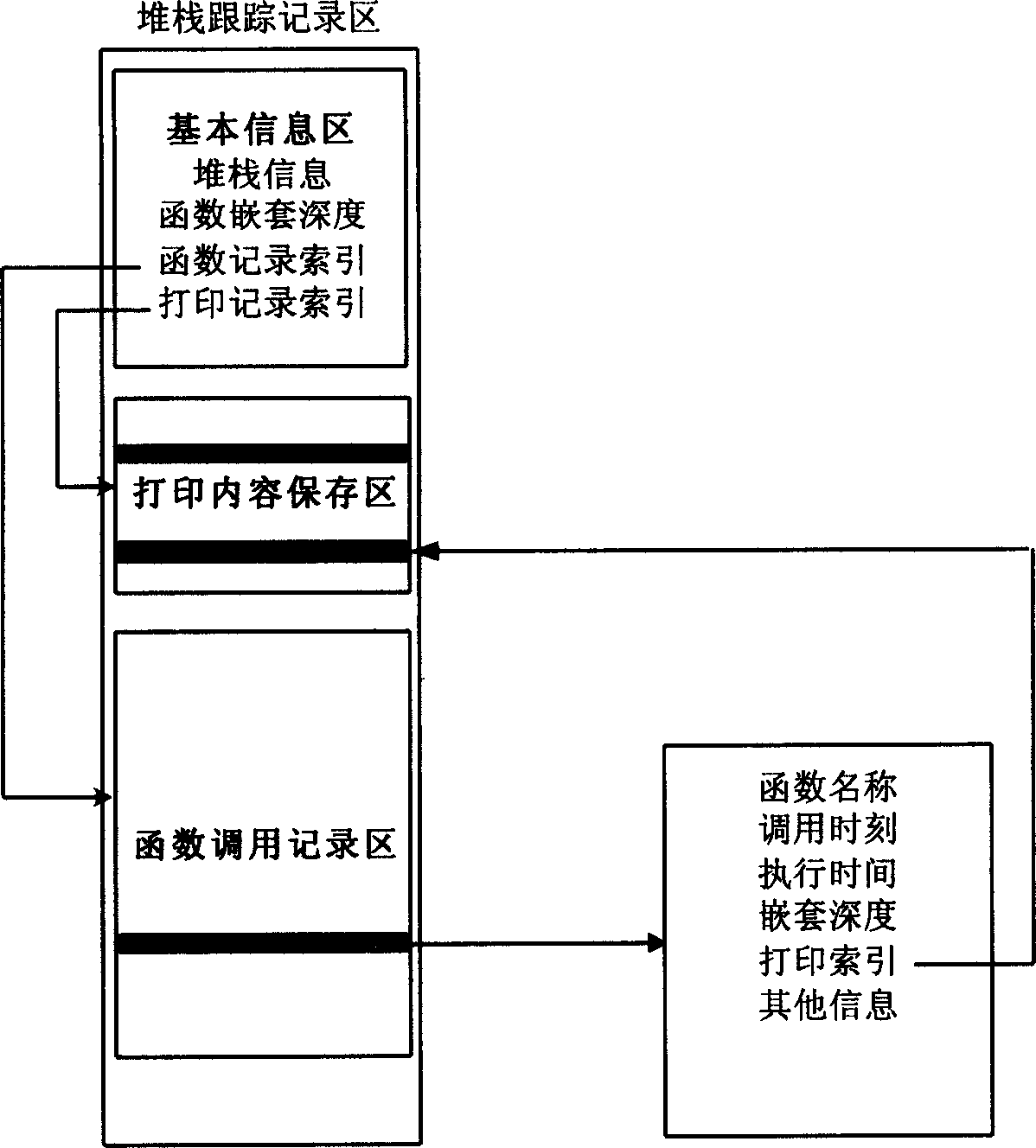
The method includes steps: setting up at least one stack trace record area on memory for each stack, and initializing the area; executing printing information recording function, in printing procedure, calling printing contents saving function to save printing information to the said trace record area; executing a entrance trace record function at entrance; executing a exit trace record function at exit, embedding stubs at entrance and exit of functions in application program; calling analysis debugging function in use for stack trace record area to display all basic information in the stack trace record area, as well as procedures of function call and saved printing contents. The invention does not inference on task dispatching procedure of software to be tested, analyzes abnormity of software by using information recorded in stack trace record area without need of hardware analysis.
Owner:ZTE CORP
Stack trace compression
ActiveUS20150058825A1Hardware monitoringSoftware testing/debuggingParallel computingLogical operations
Exemplary methods, apparatuses, and systems generate a plurality of possible stack traces for a computer program. Each possible stack trace represents functions that may be active while the computer program is running. Each function has a corresponding function identifier. A value for at least one of the plurality of possible stack traces is generated. Generating the value for each stack trace includes performing a series of one or more mathematical or logical operations between the function identifiers of the possible stack trace. A stack trace is generated as an output based upon a match between a run-time stack trace value and the at least one generated stack trace value.
Owner:VMWARE INC
Identifying a software developer based on debugging information
InactiveUS8589880B2Error detection/correctionSoftware designSoftware engineeringSoftware development
A solution for identifying a software developer based on debugging information includes an identification module configured to identify a developer of a line of source code, a determination module configured to determine a developer contact tag for the developer, an encoding module configured to encode the developer contact tag, a tagging module configured to automatically tag the line of source code with the developer contact tag associated with the developer. The solution also includes a debug module configured to provide debug information, a decoding module configured to decrypt the developer contact tag, and a presentation module configured to present the debug stack trace in human readable form.
Owner:INT BUSINESS MASCH CORP +1
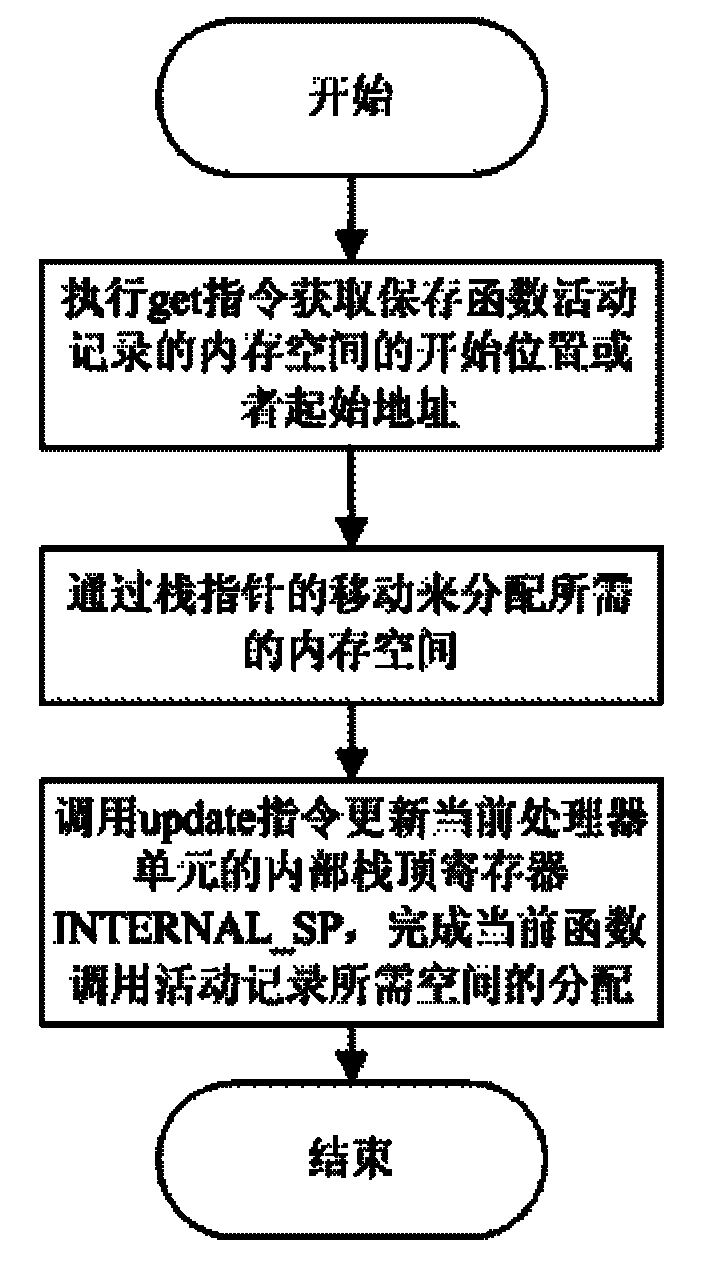
Independent stack function calling method based on CMP speculation multi-thread mechanism
InactiveCN101833476AAvoid waitingOptimize allocationMultiprogramming arrangementsShared memoryStack trace
The invention discloses an independent stack function calling method based on CMP speculation multi-thread mechanism, overcoming stack locking problem of shared stack function calling method and ensuring program calling function to be executed correctly and efficiently under speculation multi-thread. When a processor is initialized, a private memory space is divided as stack space for each processor unit in the shared memory space, an interior stack top register for recording corresponding stack space stack top thereof is set for each processor unit; function stack frame allocation is completed by calling instruction get, moving stack pointer and calling instruction update; and function stack frame is released by returning of stack pointer of processor unit and calling of instruction update.
Owner:XI AN JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com