Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
268 results about "File descriptor" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In Unix and related computer operating systems, a file descriptor (FD, less frequently fildes) is an abstract indicator (handle) used to access a file or other input/output resource, such as a pipe or network socket. File descriptors form part of the POSIX application programming interface. A file descriptor is a non-negative integer, generally represented in the C programming language as the type int (negative values being reserved to indicate "no value" or an error condition).
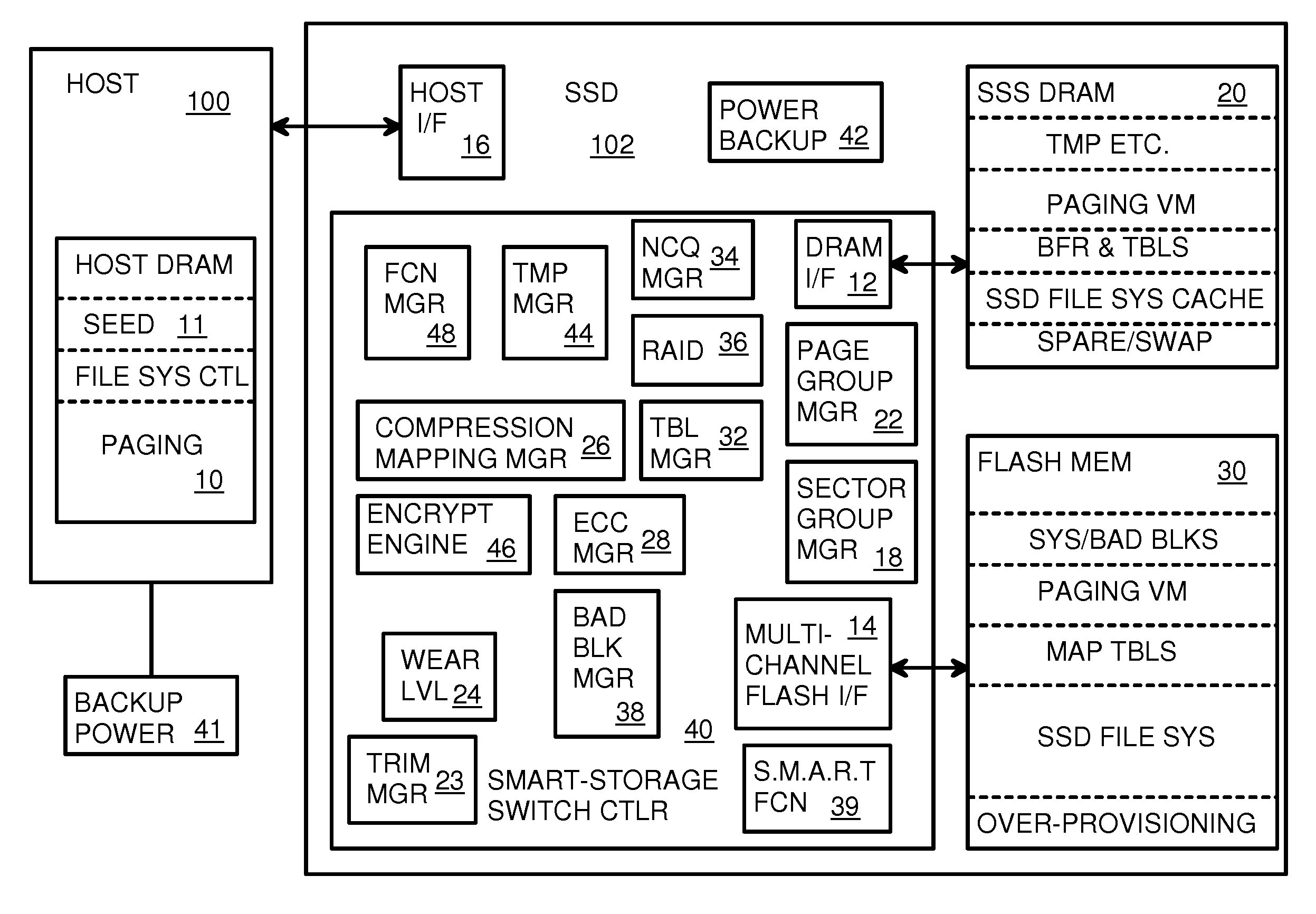
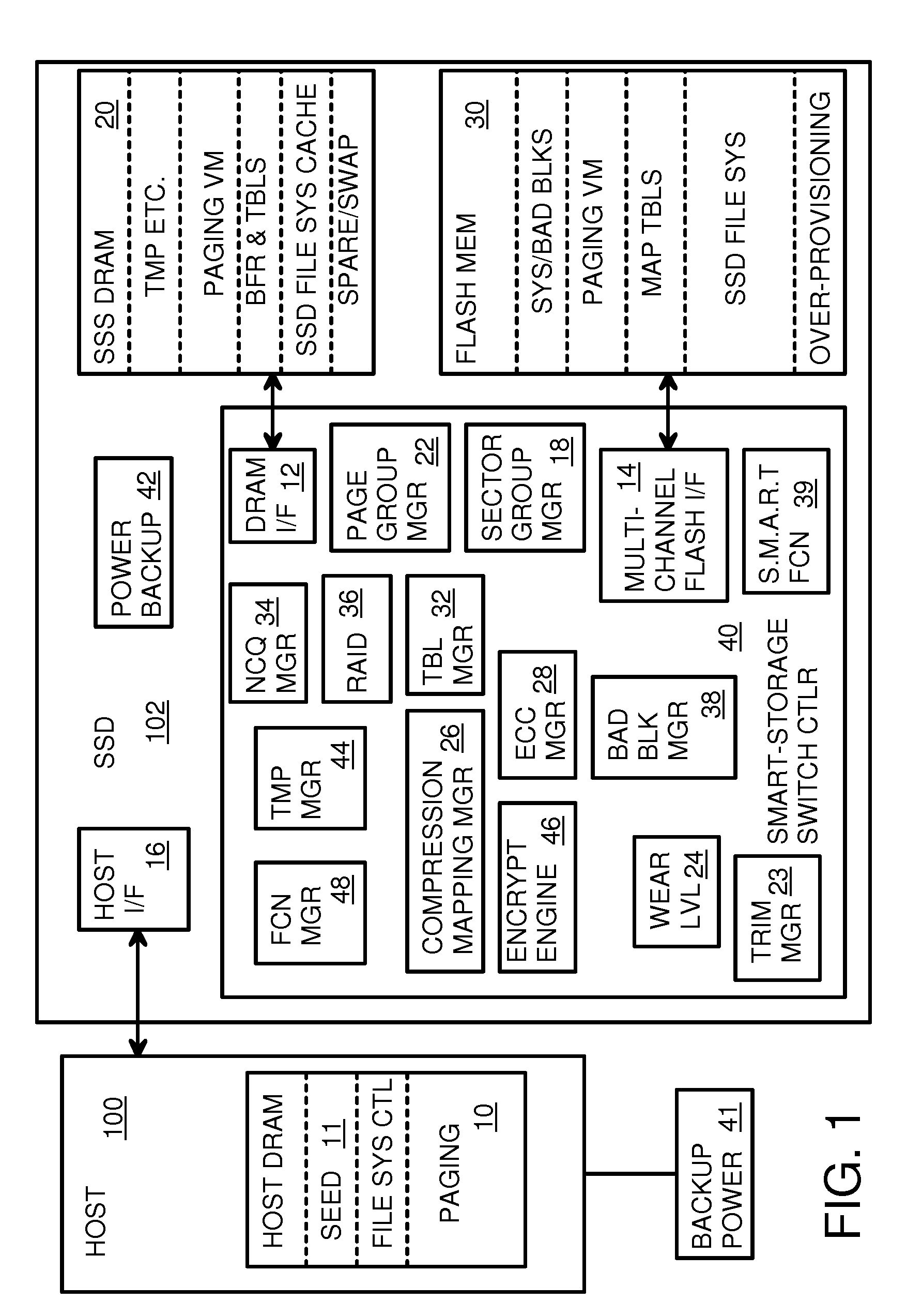
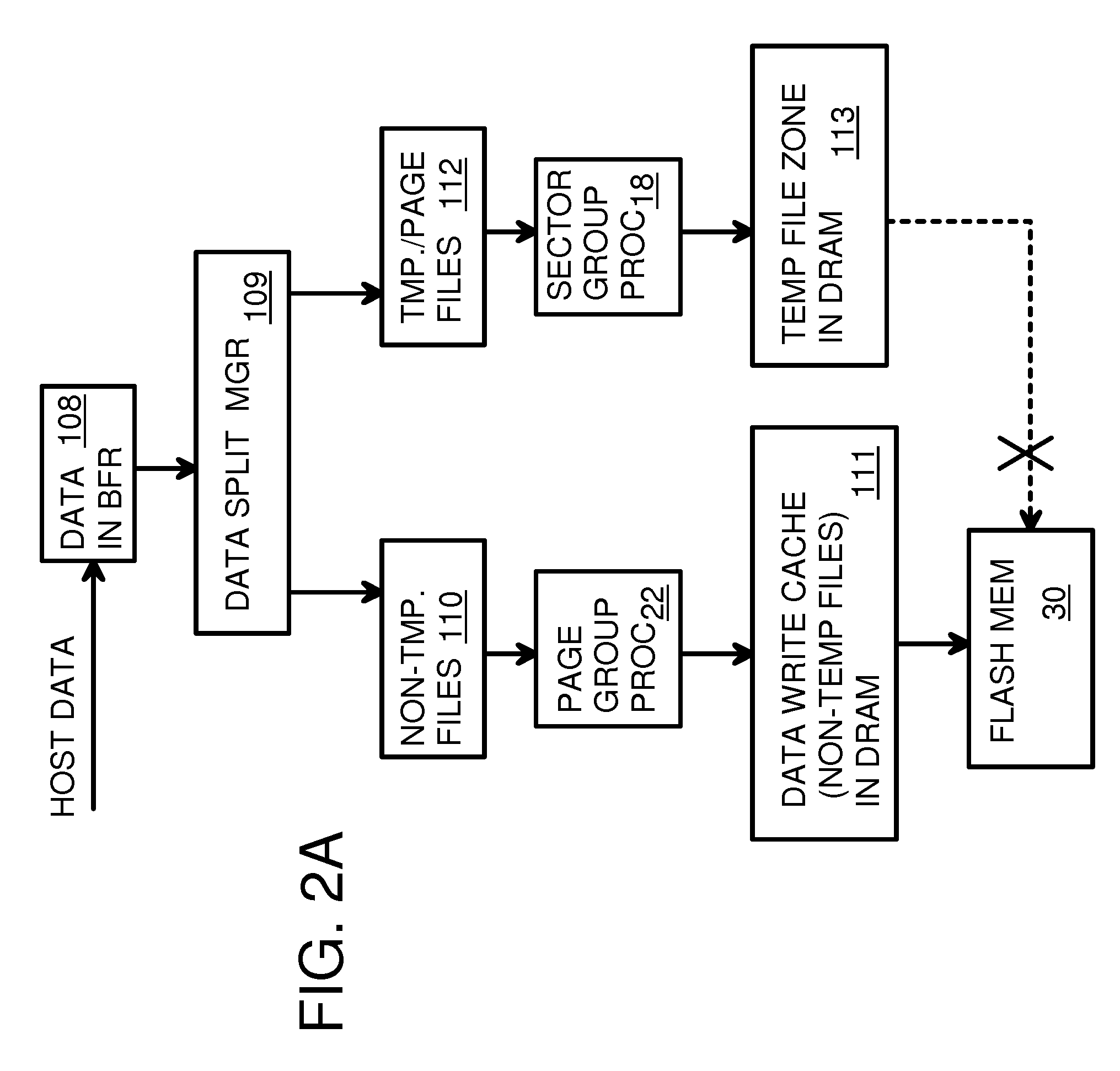
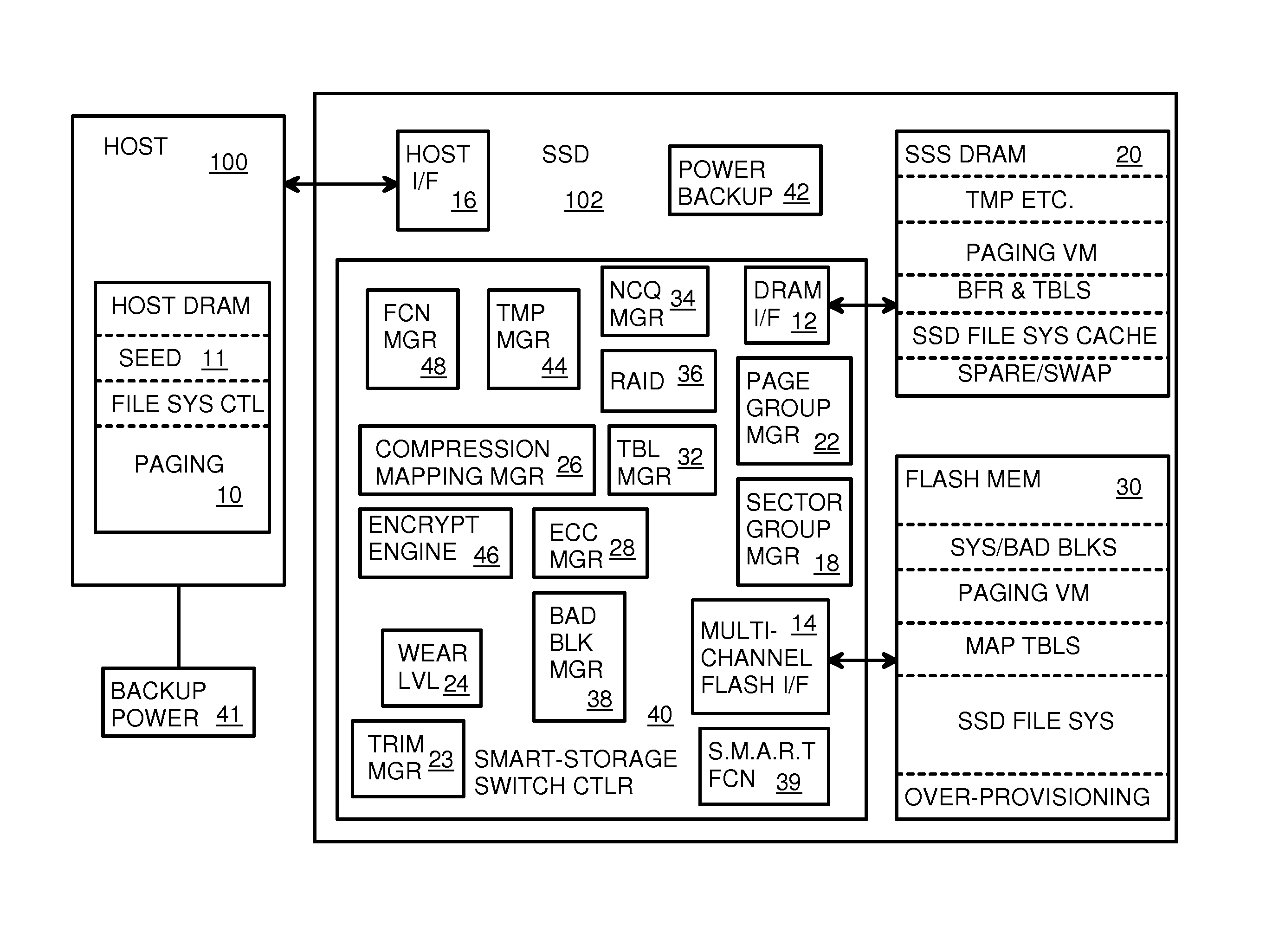
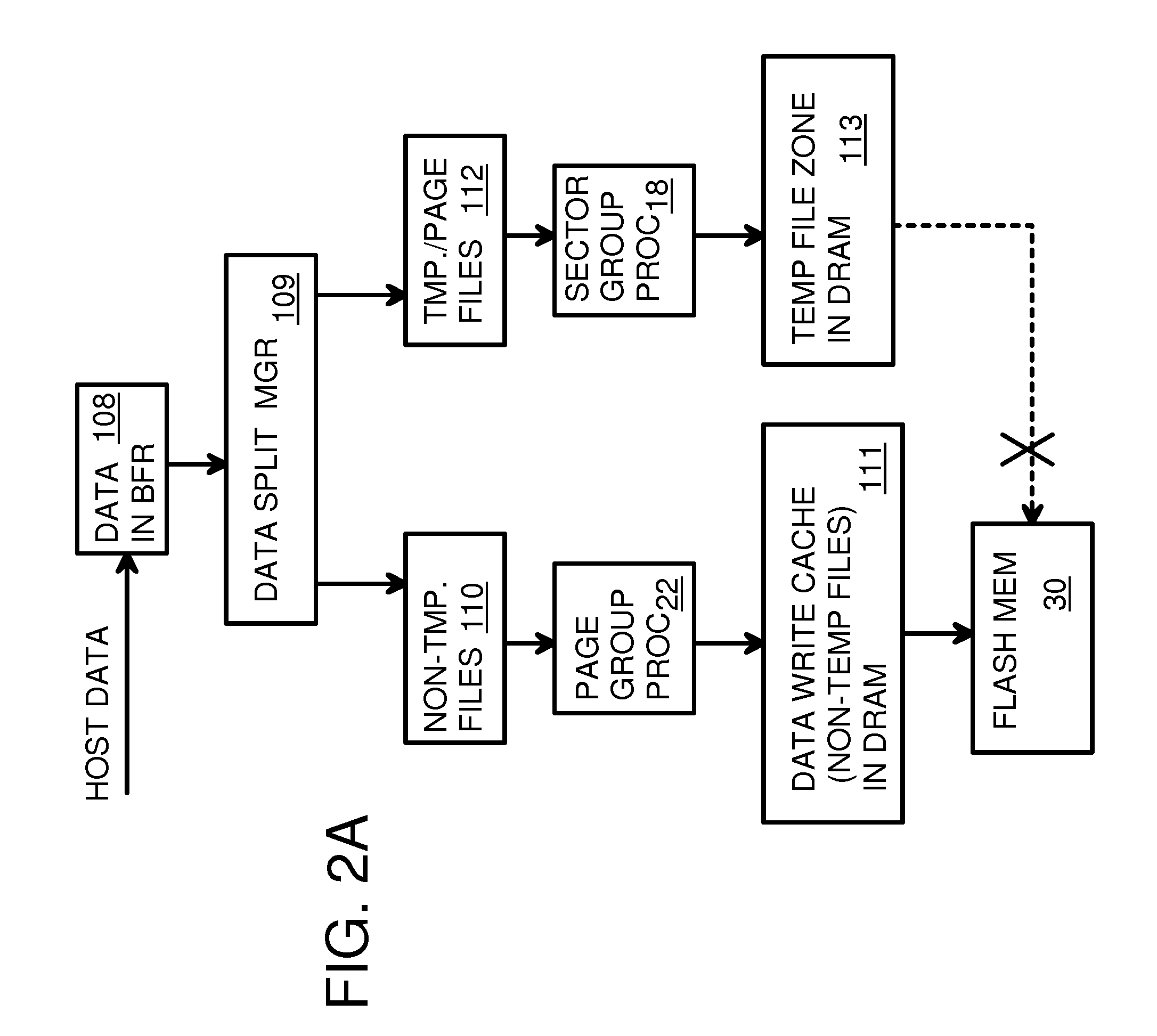
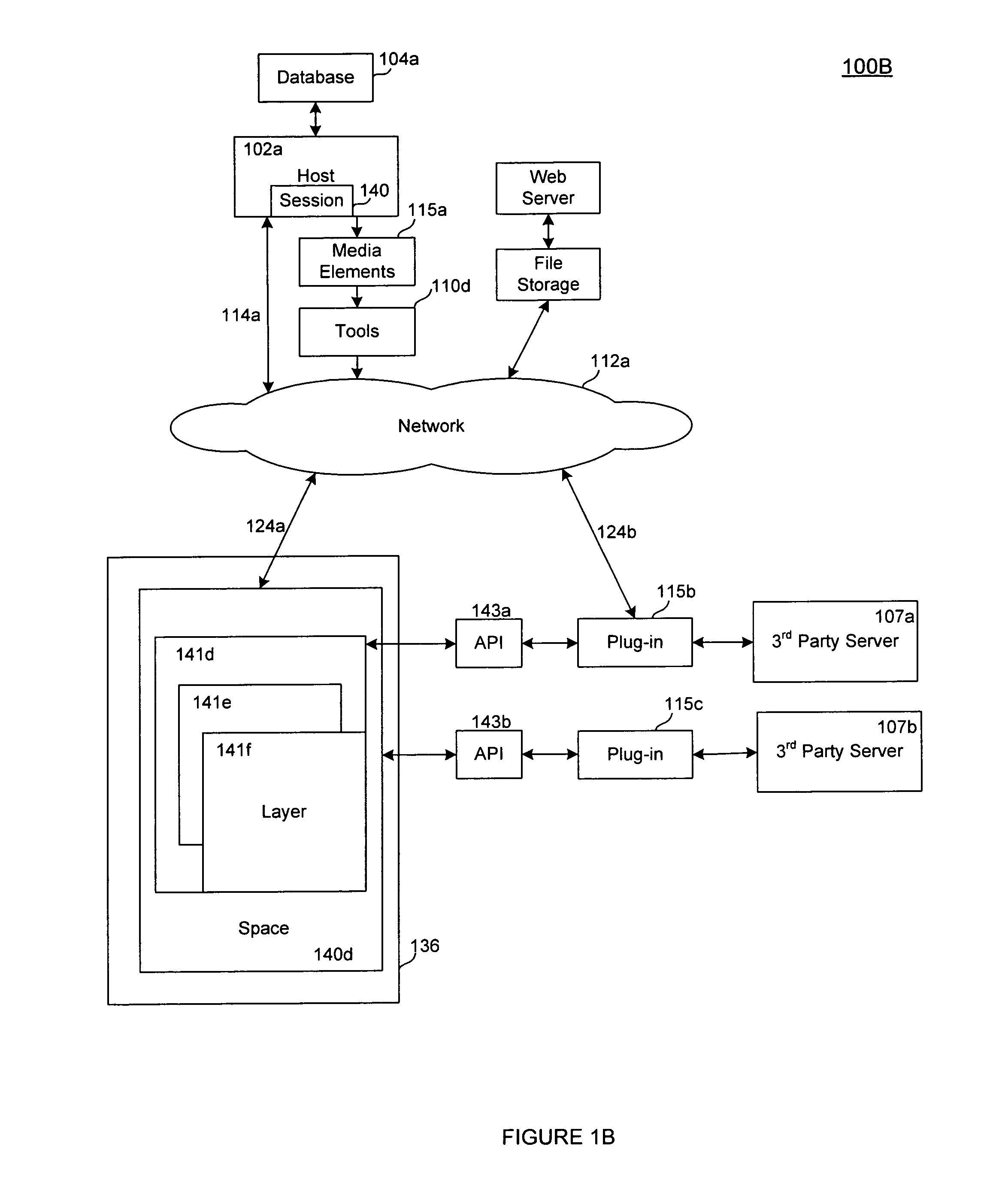
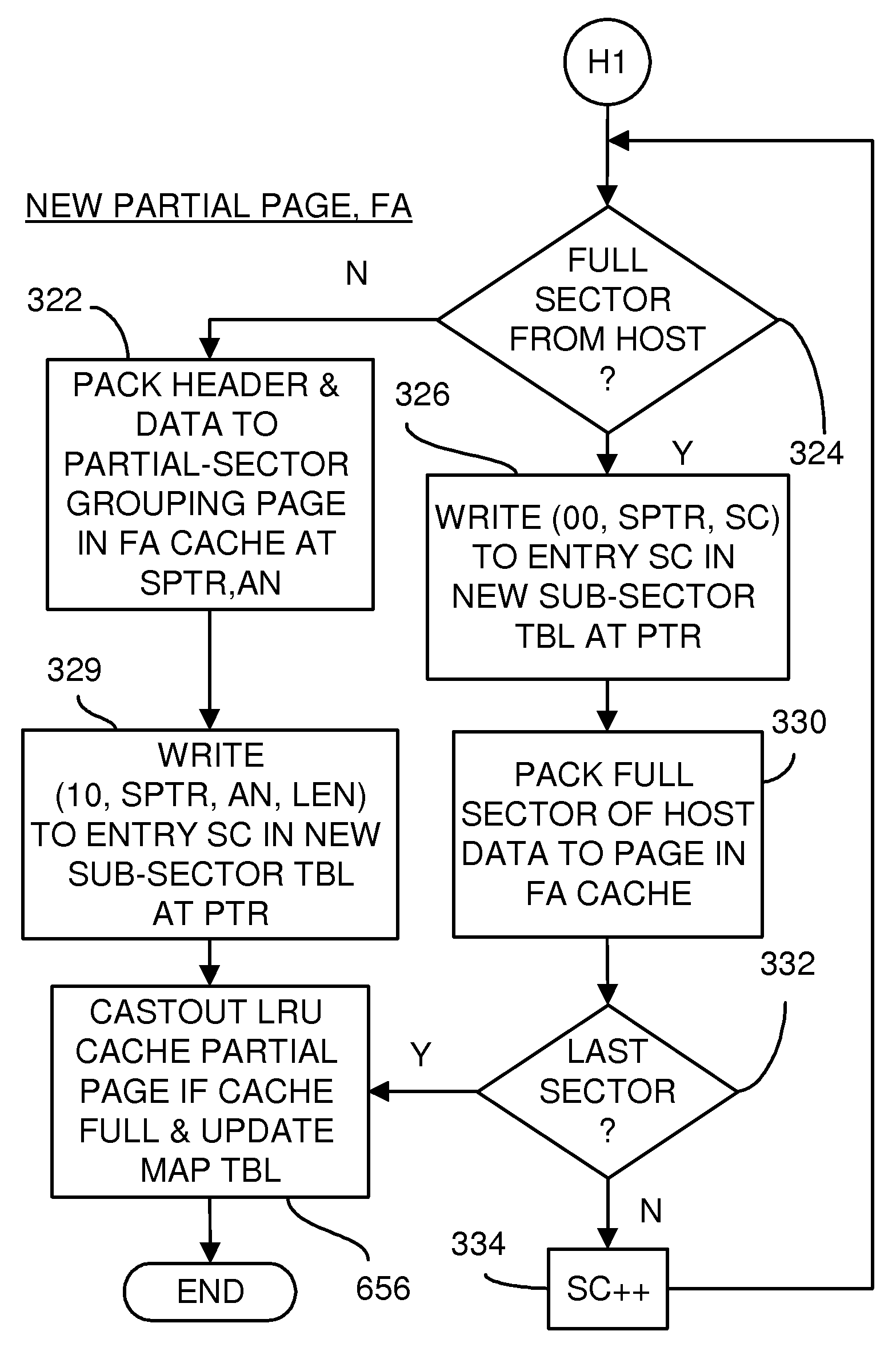
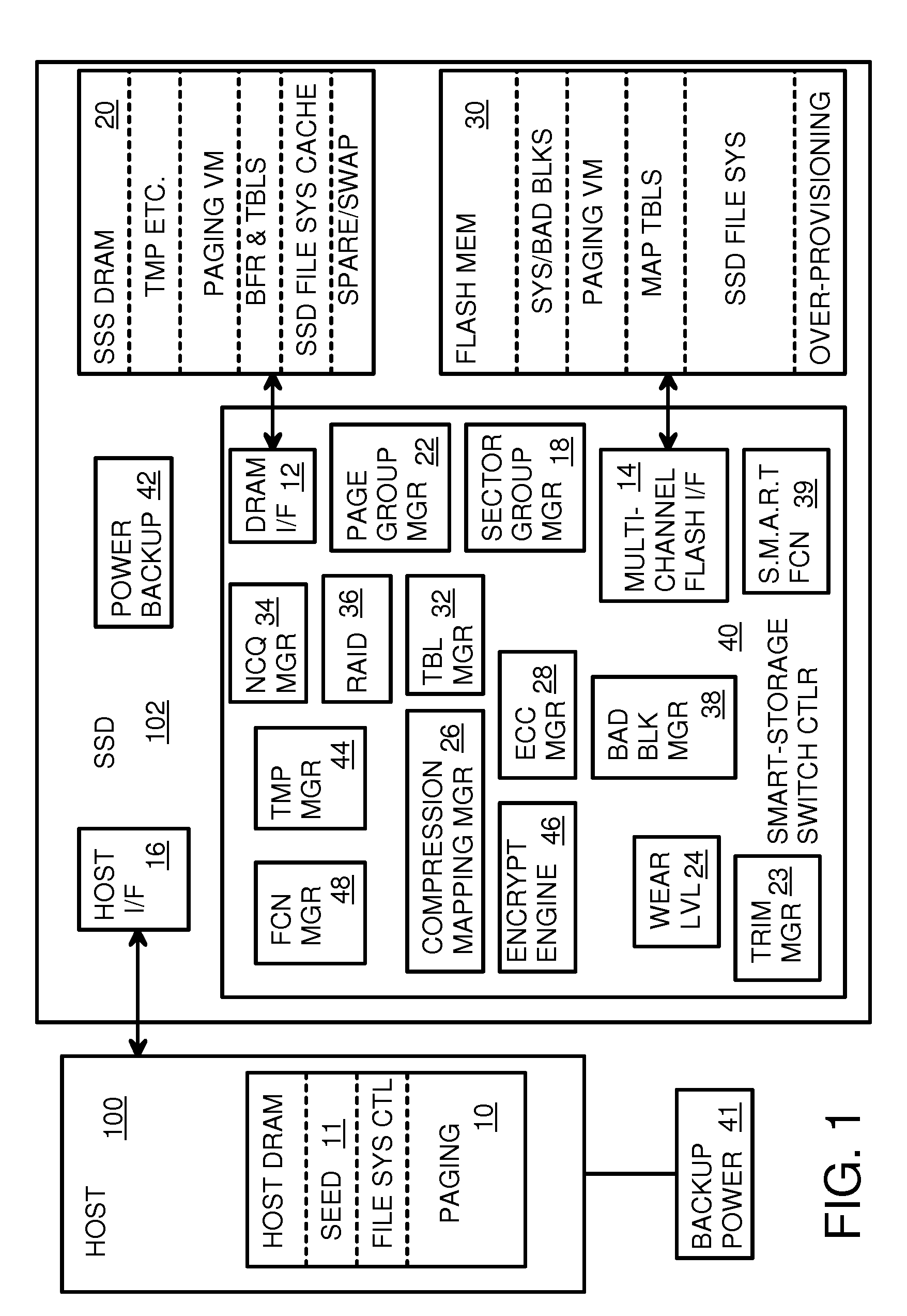
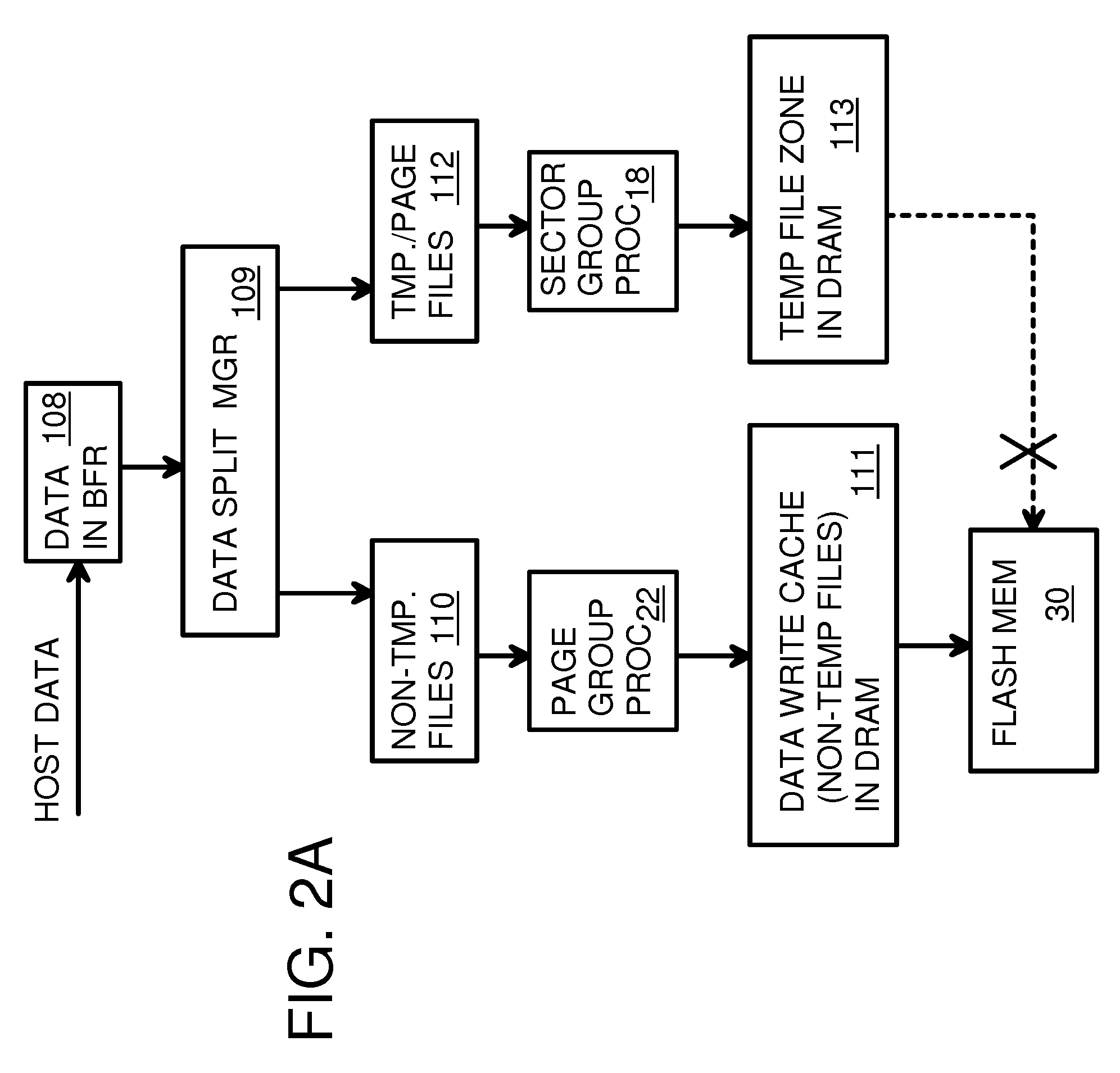
Super-Endurance Solid-State Drive with Endurance Translation Layer (ETL) and Diversion of Temp Files for Reduced Flash Wear
ActiveUS20120284587A1Memory architecture accessing/allocationDigital storageFilename extensionData file
A flash drive has increased endurance and longevity by reducing writes to flash. An Endurance Translation Layer (ETL) is created in a DRAM buffer and provides temporary storage to reduce flash wear. A Smart Storage Switch (SSS) controller assigns data-type bits when categorizing host accesses as paging files used by memory management, temporary files, File Allocation Table (FAT) and File Descriptor Block (FDB) entries, and user data files, using address ranges and file extensions read from FAT. Paging files and temporary files are never written to flash. Partial-page data is packed and sector mapped by sub-sector mapping tables that are pointed to by a unified mapping table that stores the data-type bits and pointers to data or tables in DRAM. Partial sectors are packed together to reduce DRAM usage and flash wear. A spare / swap area in DRAM reduces flash wear. Reference voltages are adjusted when error correction fails.
Owner:SUPER TALENT TECH CORP
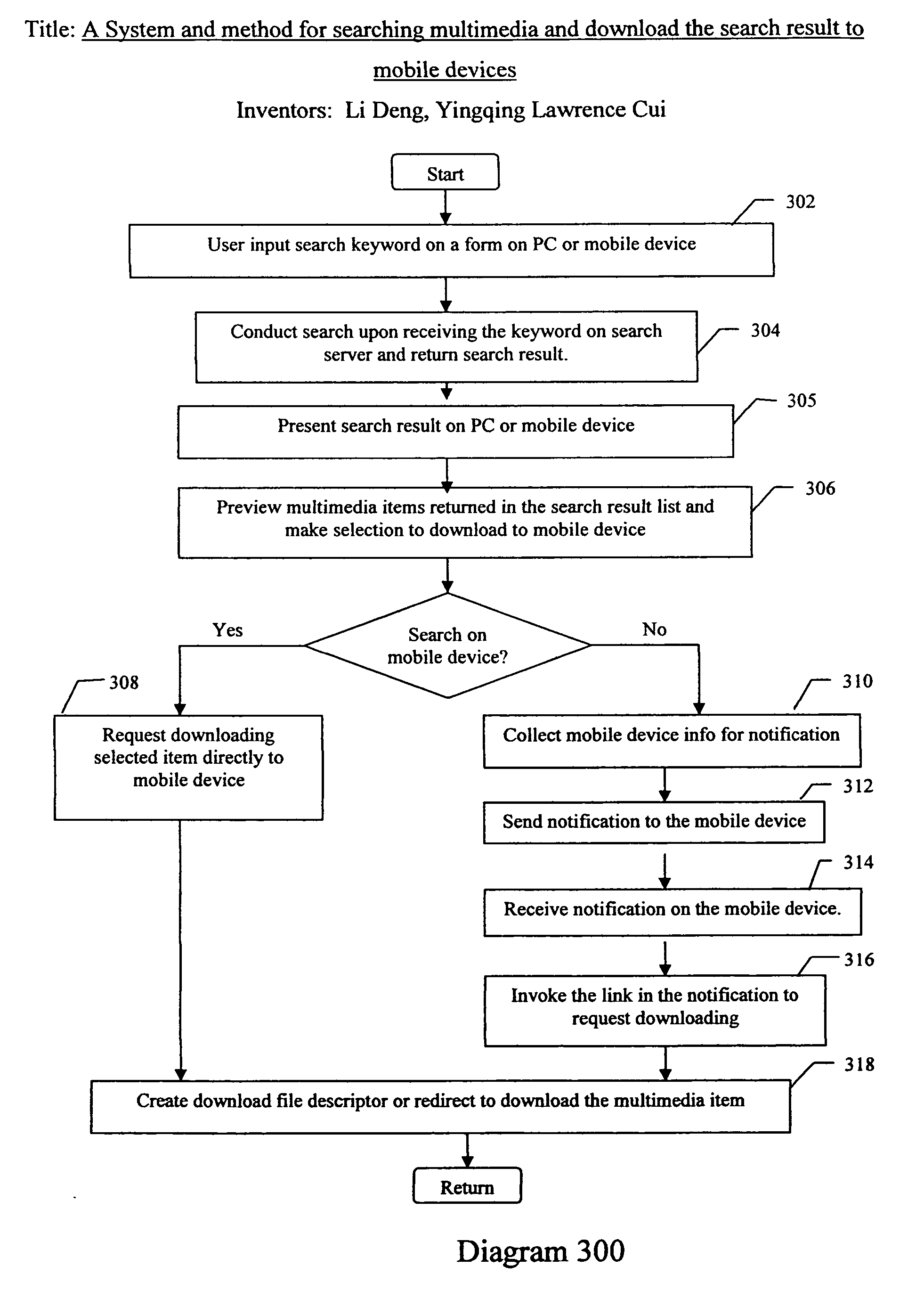
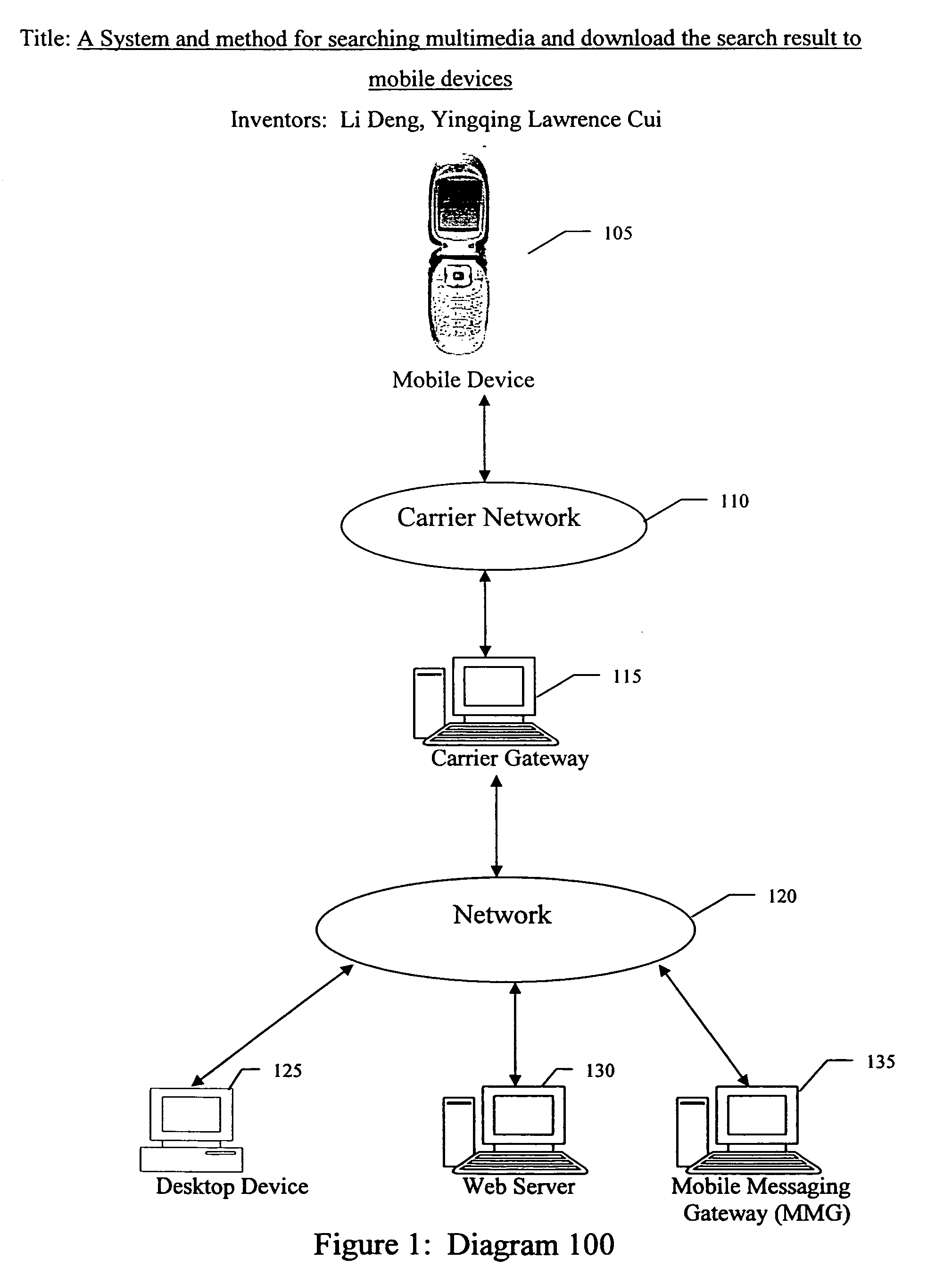
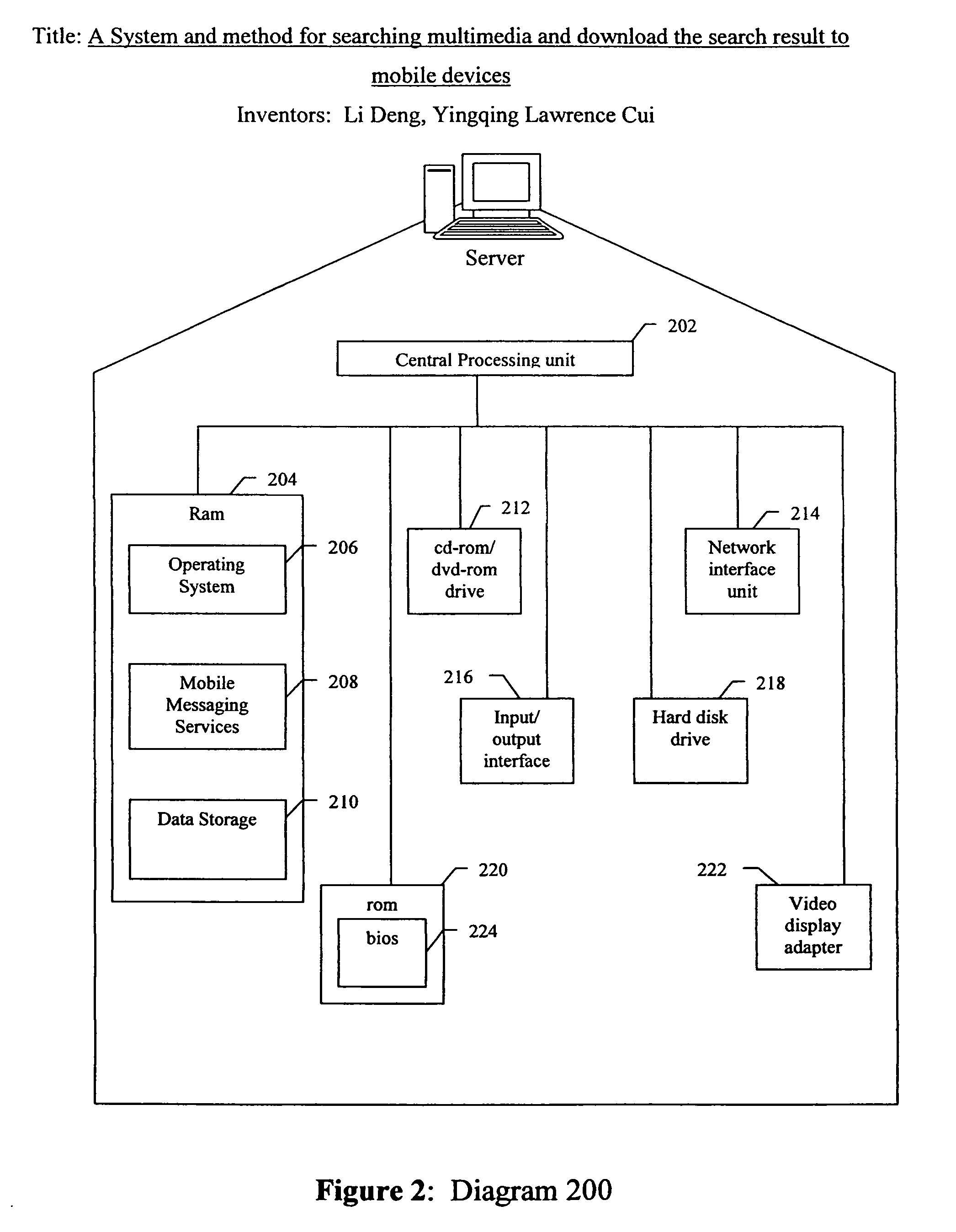
System and method for searching multimedia and download the search result to mobile devices
InactiveUS20070027857A1Metadata multimedia retrievalSpecial data processing applicationsWireless Application ProtocolThe Internet
A method and system for searching multimedia files from multimedia content sites on the internet and downloading search result to mobile devices. The system and method includes a crawling server for indexing multimedia items, a search server, a data storage server, a download server and a wireless messaging server in data communication with the internet and in wireless communication with SS7 wireless networks, and a wireless mobile device having circuitry for establishing data communications with the wireless application protocol network and a display for displaying information generated by the search server. The methods further include crawling the Internet to index multimedia items; enabling search from both desktop PC and mobile devices to find desired multimedia items; providing options to send search result to mobile devices; downloading search result directly on a mobile device; detecting downloading method from downloading request; delivering notification message to mobile device and invoking the link on the mobile device to initiate download; creating file descriptor for downloading; and downloading the multimedia item to mobile devices.
Owner:STRAGENT
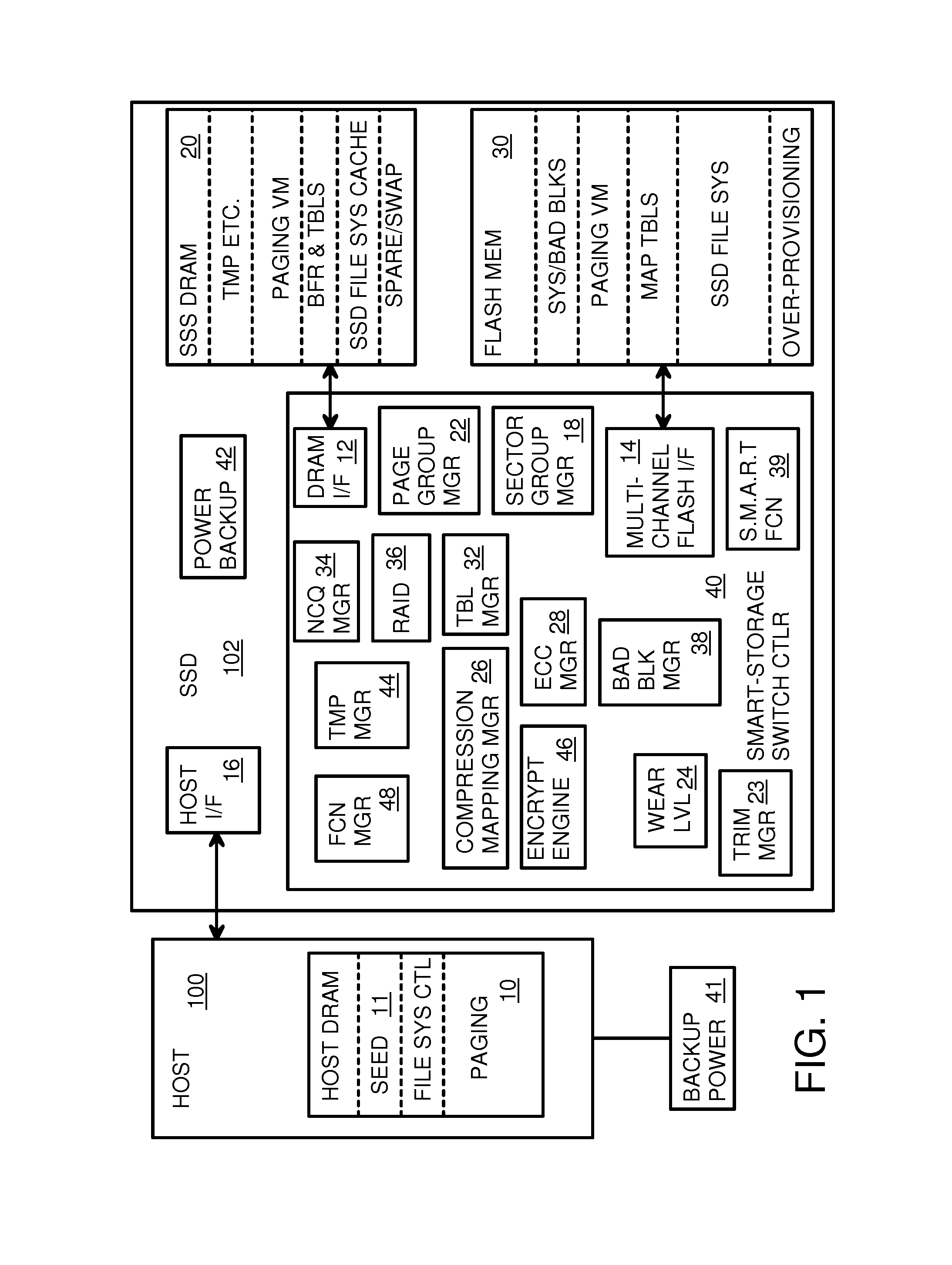
Endurance Translation Layer (ETL) and Diversion of Temp Files for Reduced Flash Wear of a Super-Endurance Solid-State Drive
ActiveUS20150106556A1Memory architecture accessing/allocationMemory adressing/allocation/relocationFilename extensionData file
A flash drive has increased endurance and longevity by reducing writes to flash. An Endurance Translation Layer (ETL) is created in a DRAM buffer and provides temporary storage to reduce flash wear. A Smart Storage Switch (SSS) controller assigns data-type bits when categorizing host accesses as paging files used by memory management, temporary files, File Allocation Table (FAT) and File Descriptor Block (FDB) entries, and user data files, using address ranges and file extensions read from FAT. Paging files and temporary files are never written to flash. Partial-page data is packed and sector mapped by sub-sector mapping tables that are pointed to by a unified mapping table that stores the data-type bits and pointers to data or tables in DRAM. Partial sectors are packed together to reduce DRAM usage and flash wear. A spare / swap area in DRAM reduces flash wear. Reference voltages are adjusted when error correction fails.
Owner:SUPER TALENT TECH CORP
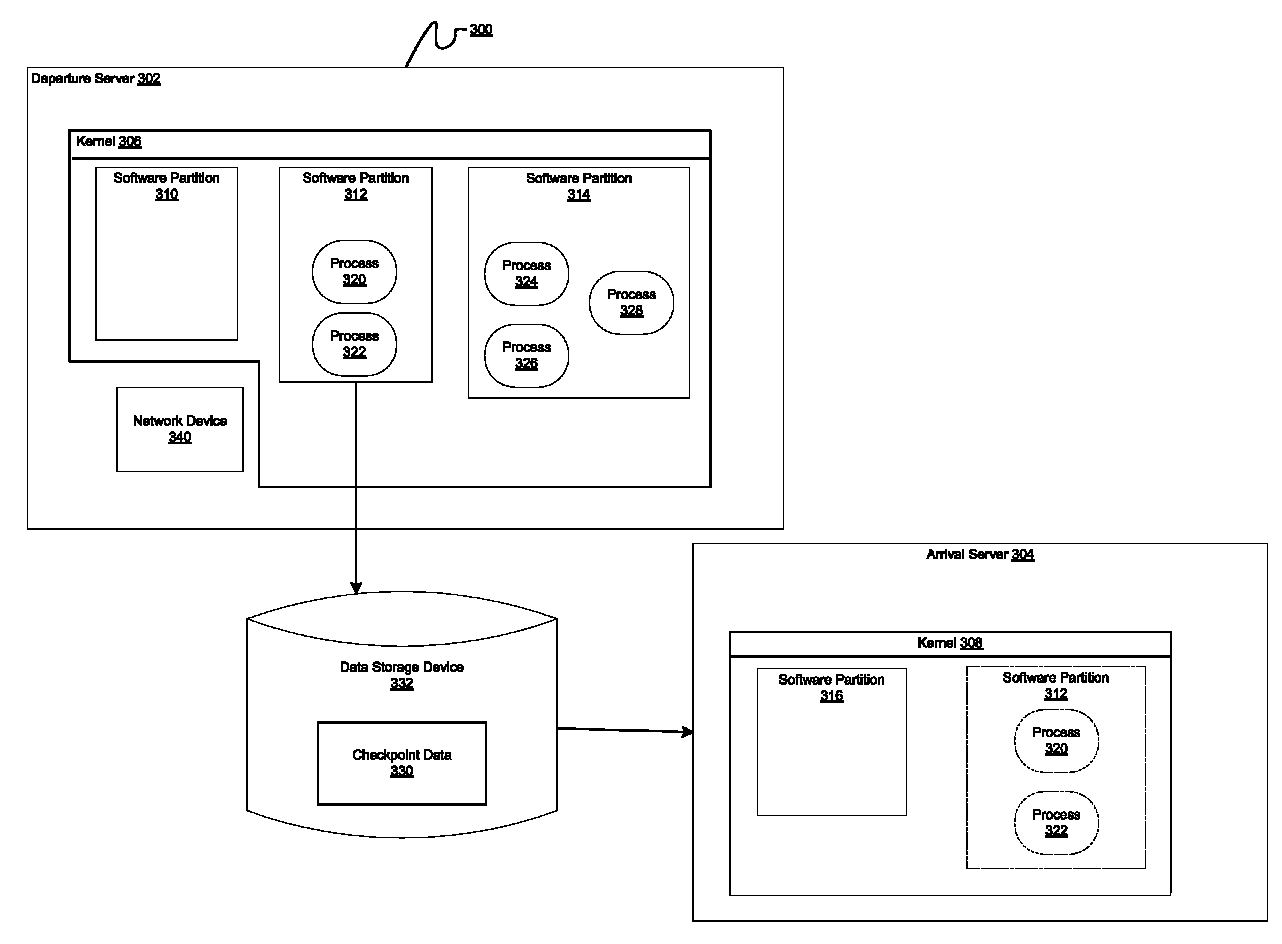
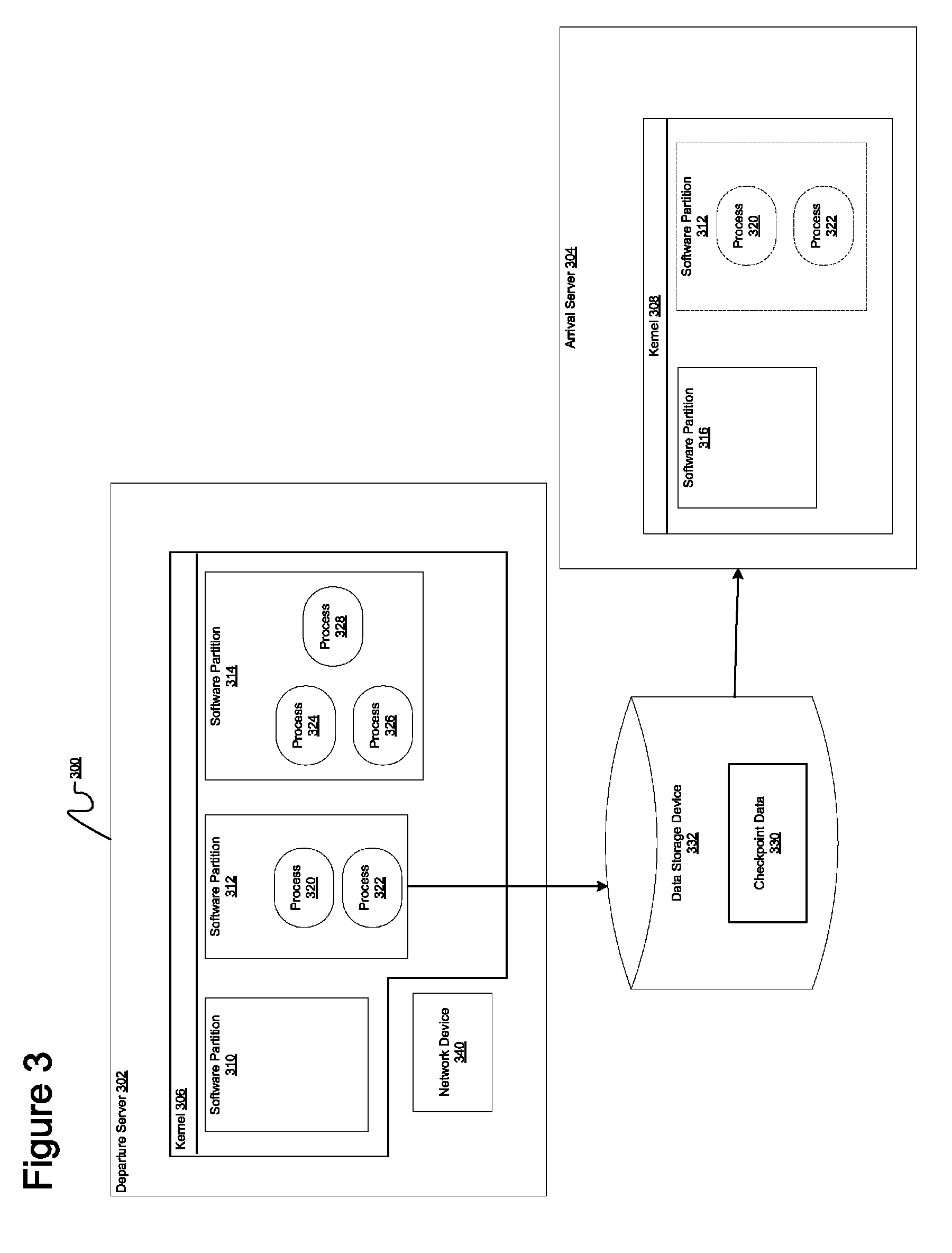
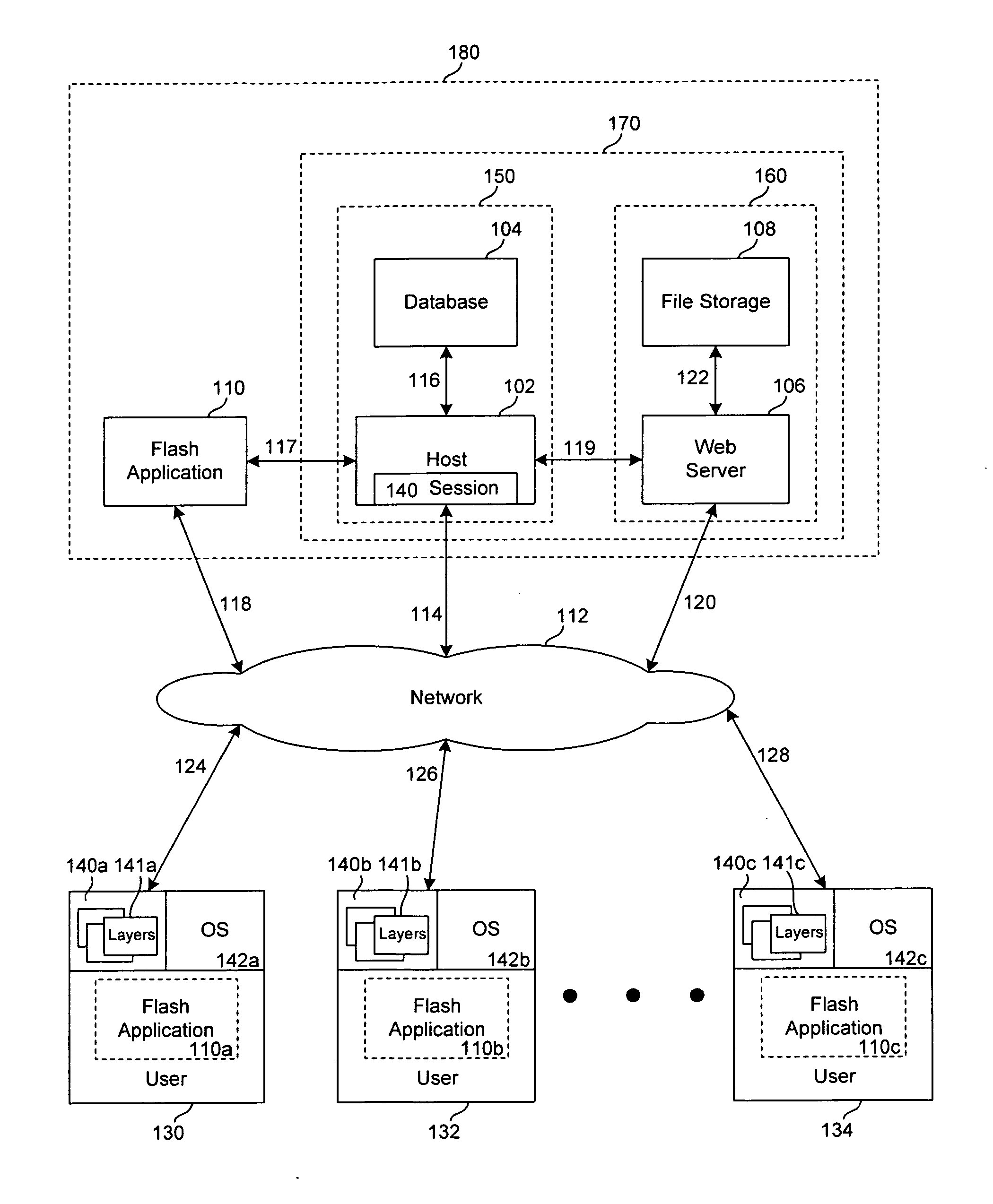
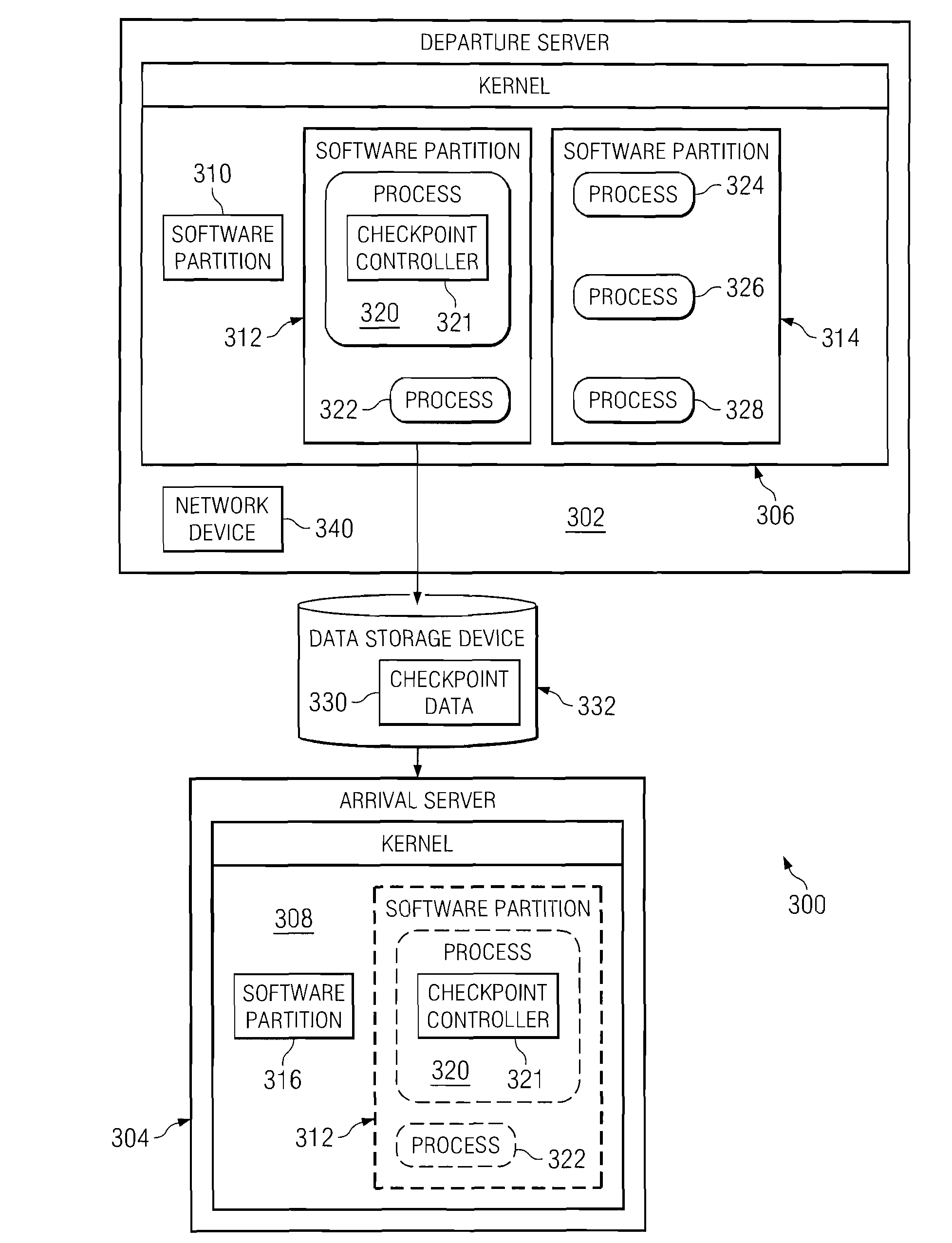
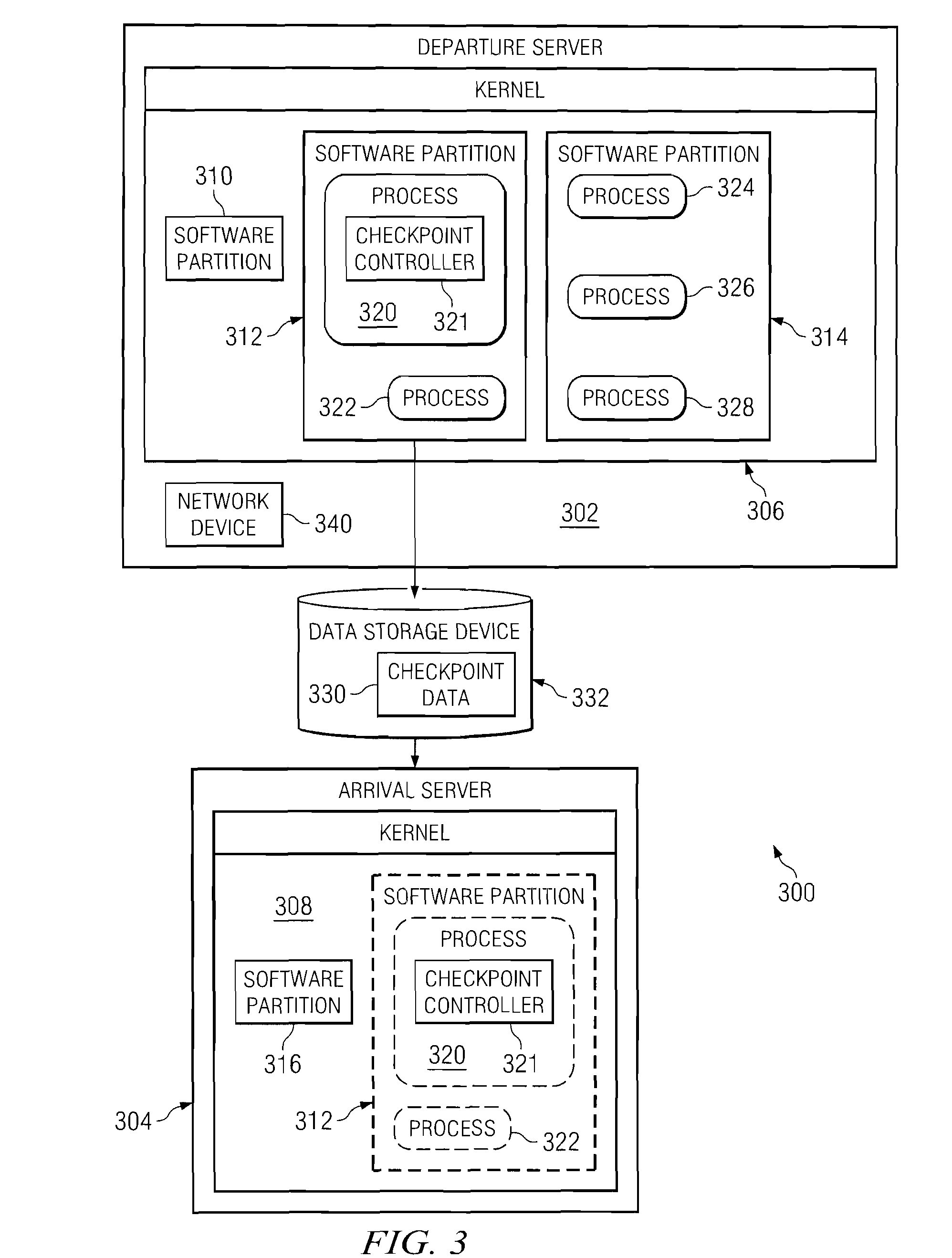
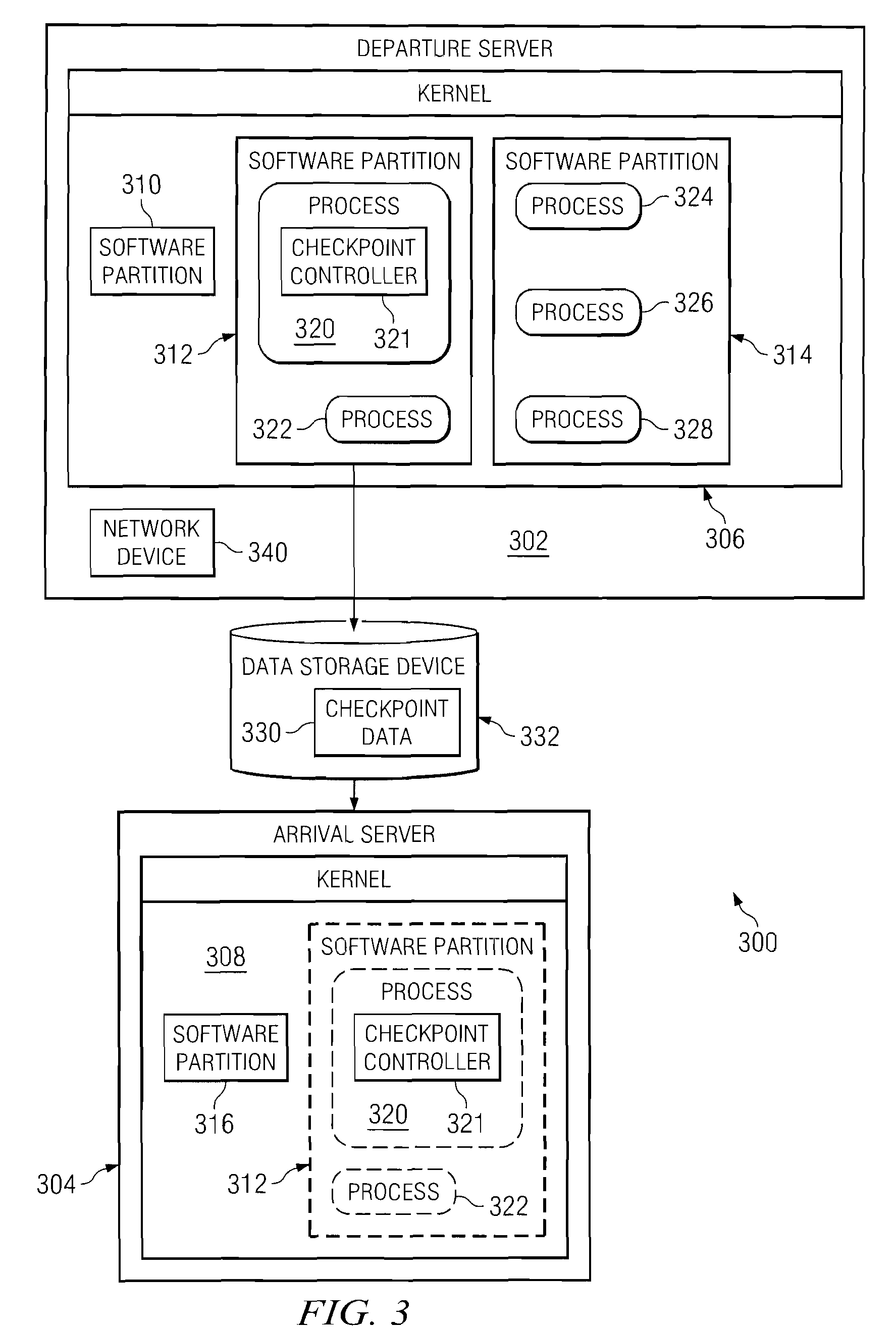
Method and apparatus for obtaining the absolute path name of an open file system object from its file descriptor
InactiveUS7930327B2Digital data processing detailsSpecial data processing applicationsFile systemFile descriptor
A computer implemented method, apparatus, and computer program product for obtaining an absolute path name for an open file system object. A file descriptor for the open file system object is identified in response to a process in a first software partition opening a file system object to form the open file system object. The absolute path name for the open file system object is cached in a path name field in a file structure associated with the file descriptor for the open file system object. The absolute path name for the open file system object in the path name field is used during migration of the first software partition to restore the open file system object in a second software partition.
Owner:IBM CORP
System and method to create a collaborative web-based multimedia layered platform
InactiveUS20070198534A1Multimedia data browsing/visualisationMultiple digital computer combinationsFile descriptorTemporal correlation
The present invention relates to a system and method to allow multiple users to collaborate on tasks and interact in a shared space session within a network in real-time; using a media application to manage media-layers. Each media-layer serves as a container for multimedia programs or plug-ins. The invention allows which media-layer to display via organization metaphors and filtering criteria. When multiple users are logged into the same shared space, each user can invoke and observe modifications to media-layers with the browser based or client based application. All events are synchronized among all users in that shared space, where the system is a communication conduit. The media-layers in the shared space maintains spatial and temporal correlation by a media application stage manager tool and described as a collection file descriptor such as an XML file. The ability to invoke events that affect media-layers can be supported in a synched or non synched mode on demand.
Owner:SIMULAT
Method and apparatus for obtaining the absolute path name of an open file system object from its file descriptor
InactiveUS20080294703A1Digital data processing detailsSpecial data processing applicationsFile systemFile descriptor
A computer implemented method, apparatus, and computer program product for obtaining an absolute path name for an open file system object. A file descriptor for the open file system object is identified in response to a process in a first software partition opening a file system object to form the open file system object. The absolute path name for the open file system object is cached in a path name field in a file structure associated with the file descriptor for the open file system object. The absolute path name for the open file system object in the path name field is used during migration of the first software partition to restore the open file system object in a second software partition.
Owner:IBM CORP
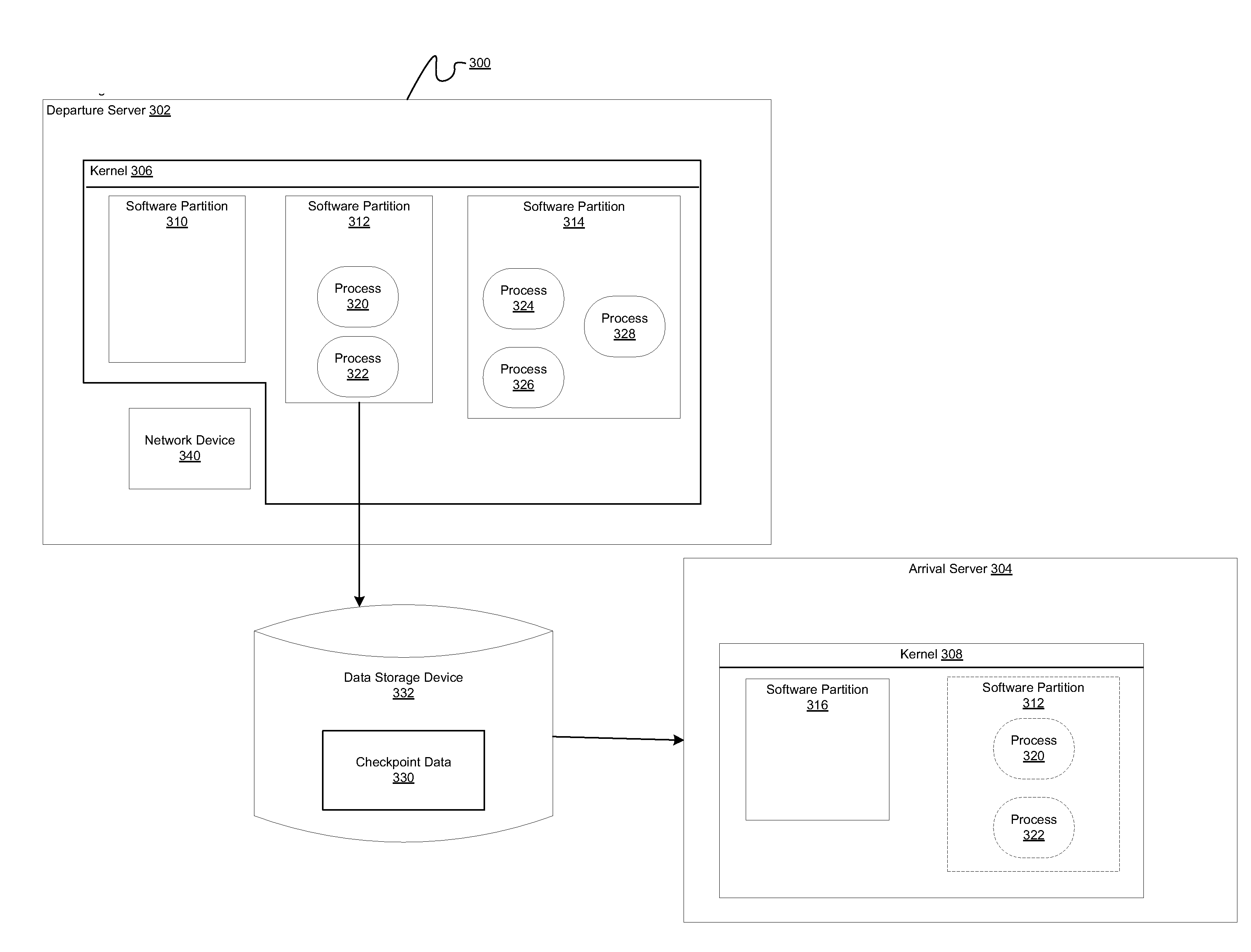
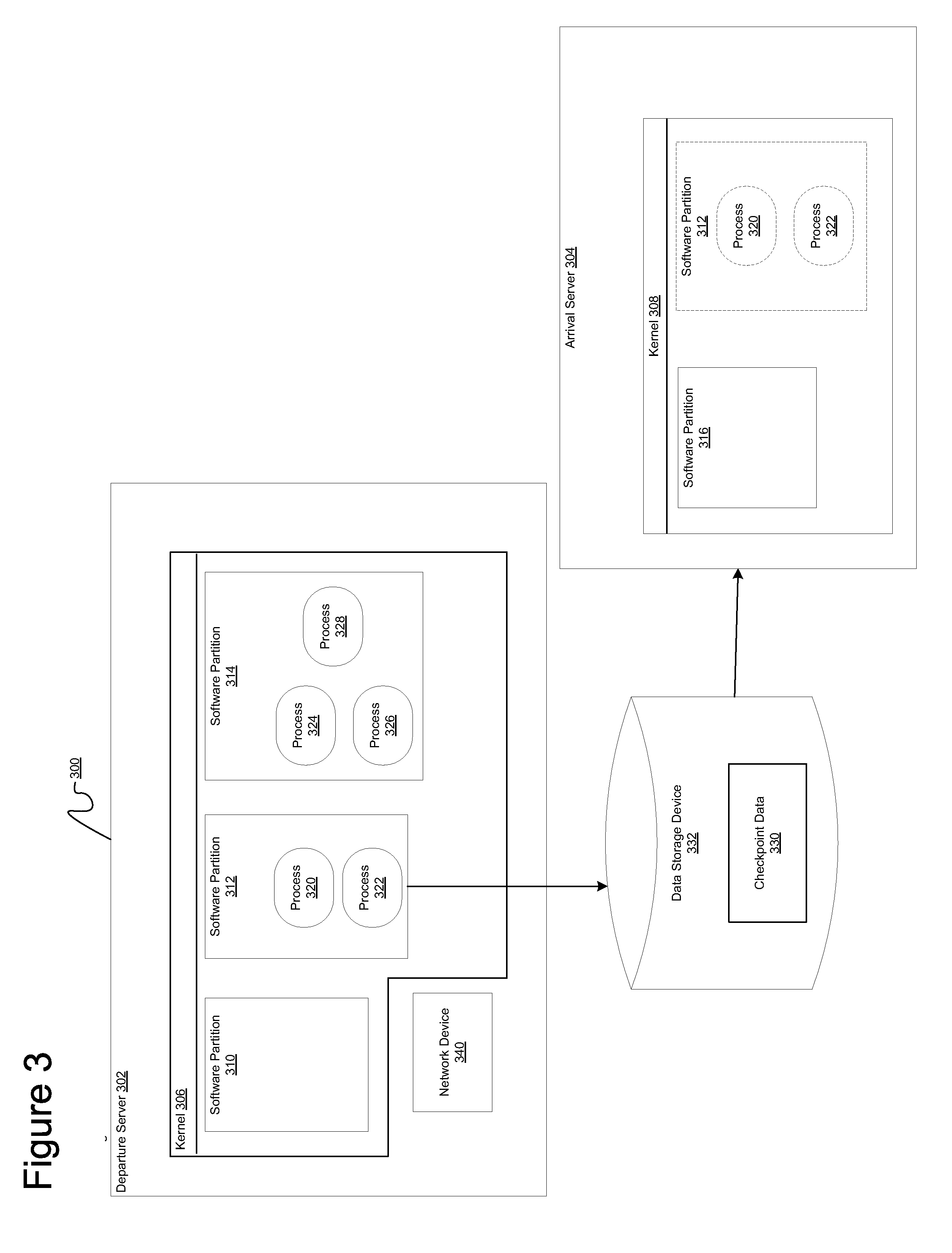
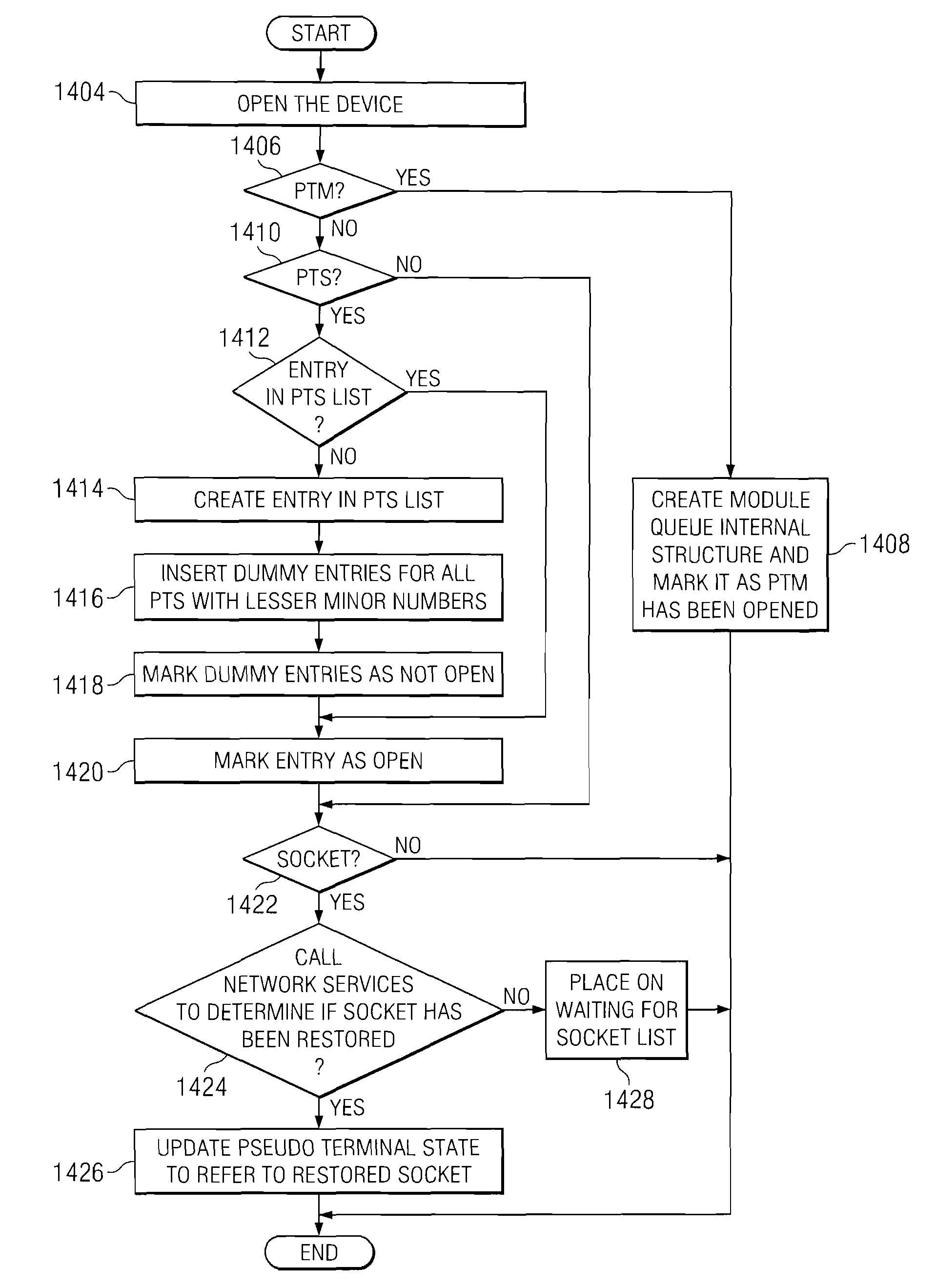
Method and apparatus for checkpoint and restart of pseudo terminals
InactiveUS20090037550A1Error detection/correctionMultiple digital computer combinationsComputer hardwareRandom order
A computer implemented method, apparatus, and computer program product for restarting pseudo terminal streams. In one embodiment, a device associated with a file descriptor in a set of file descriptors is opened. The set of file descriptors are identified in checkpoint data for restarting the pseudo terminal streams. In response to identifying the device as a pseudo terminal slave device, an entry for the identified pseudo terminal slave device is added to a list of open pseudo terminal slave devices. The entry for the identified pseudo terminal slave device is marked as an open pseudo terminal slave device. The list of open pseudo terminal slave devices permit pseudo terminal master devices and pseudo terminal slave devices to be restored and restarted in random order during a restart of the pseudo terminal streams.
Owner:LINKEDIN
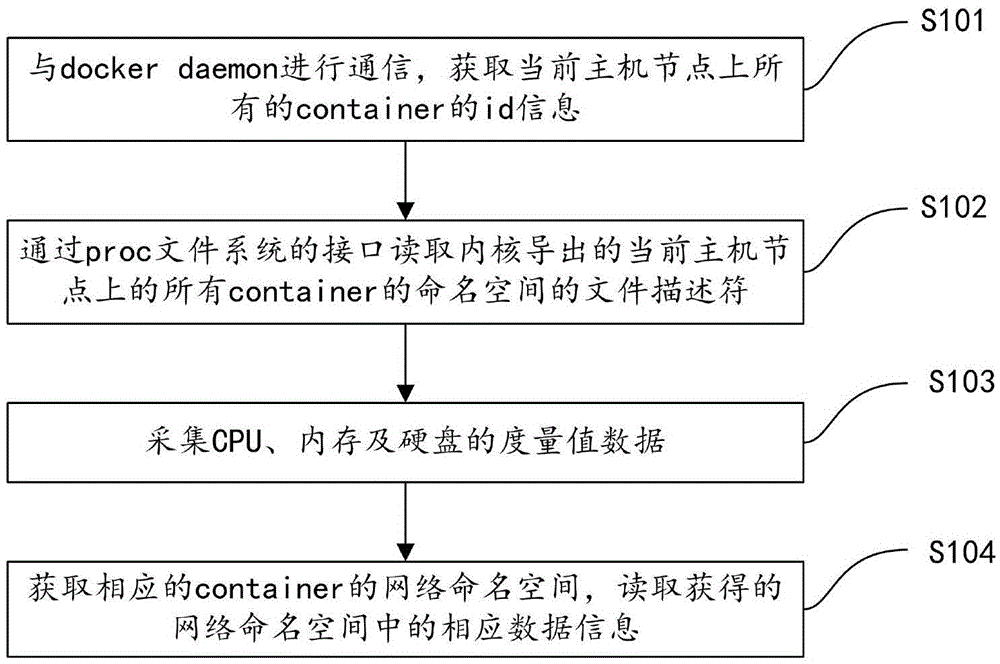
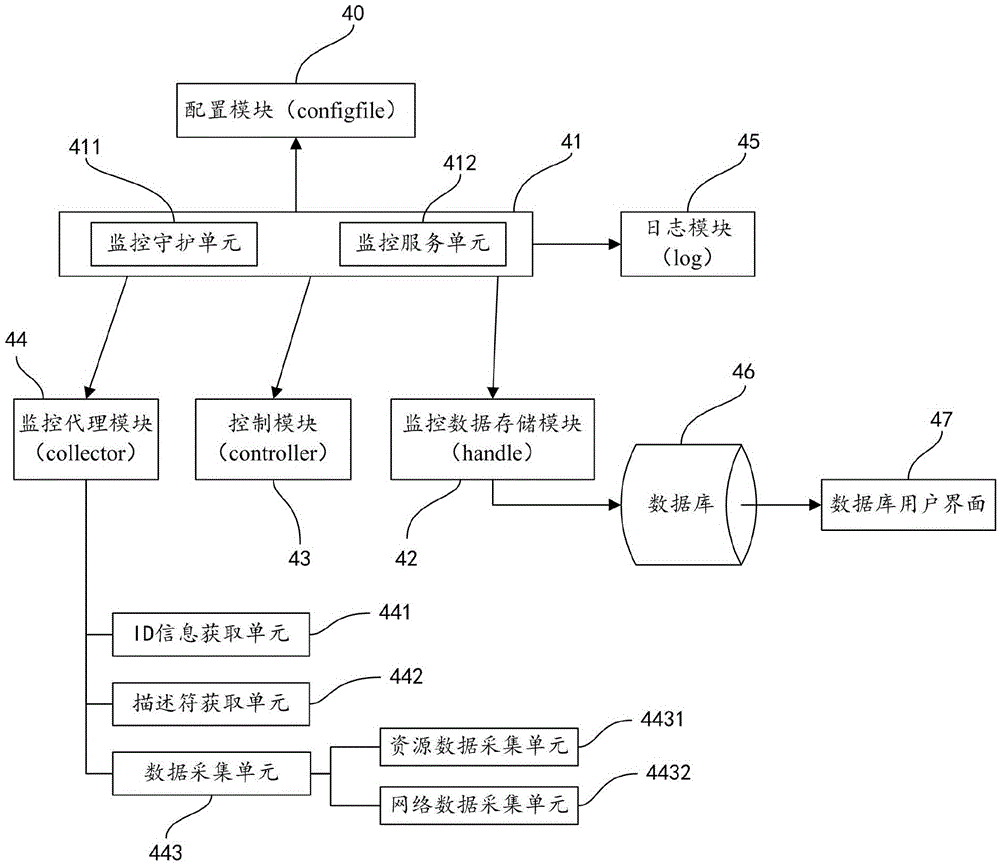
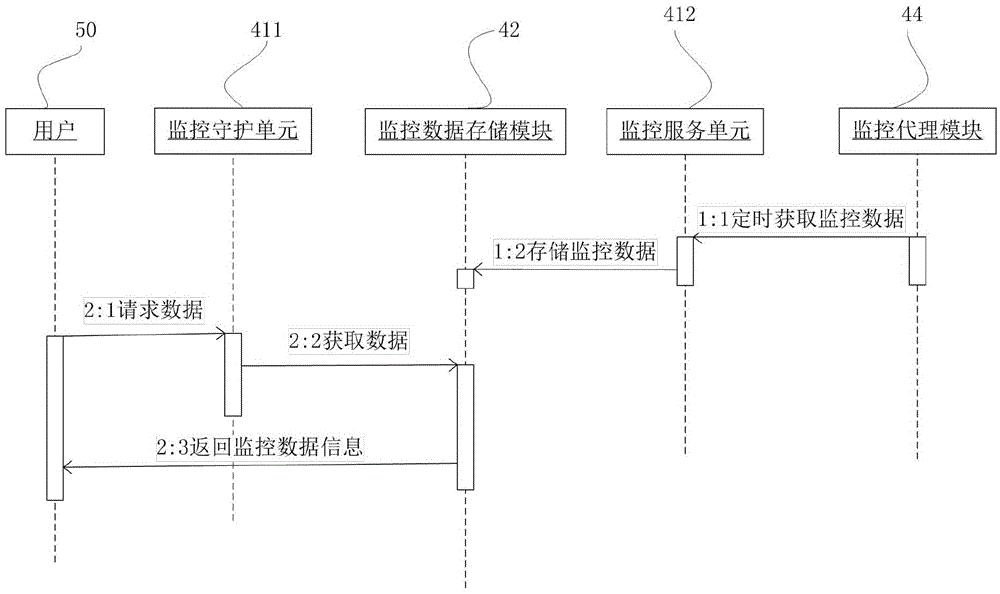
Method and system for monitoring containers created based on docker
The invention provides a method and a system for monitoring containers created based on docker. The monitoring method comprises the steps of obtaining id information of all containers in a current host; obtaining file descriptors of namespaces of all the containers in the current host, exported by a kernel; and according to the id information of the containers and the file descriptors of the namespaces, acquiring measurement value data of the containers. Through the method and system provided by the invention, the containers created by the docker 1.0 can be monitored, the underlying measurement value data of the containers can be acquired, and the usage states resources by applications in the containers can be monitored.
Owner:LETV CLOUD COMPUTING CO LTD
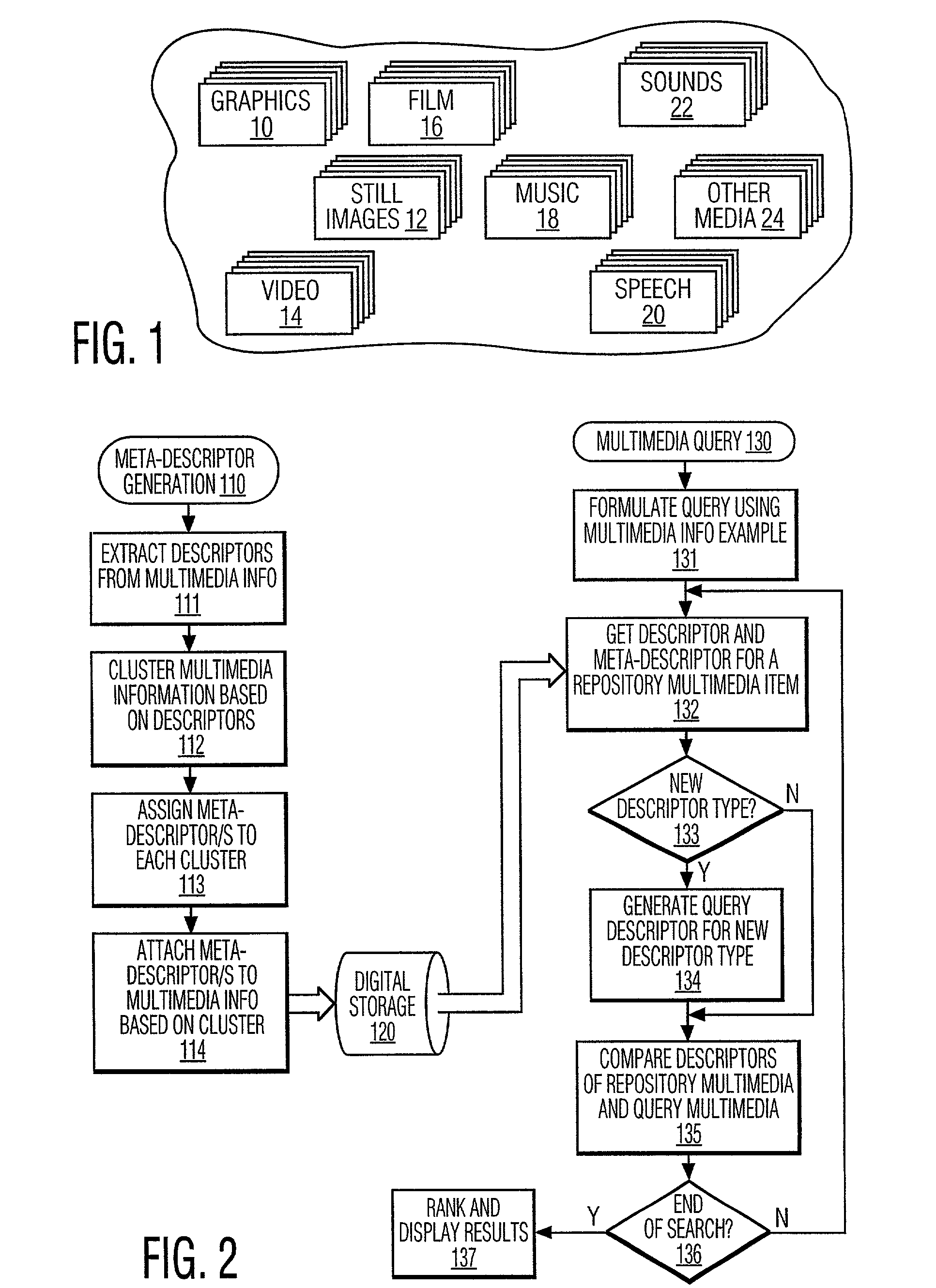
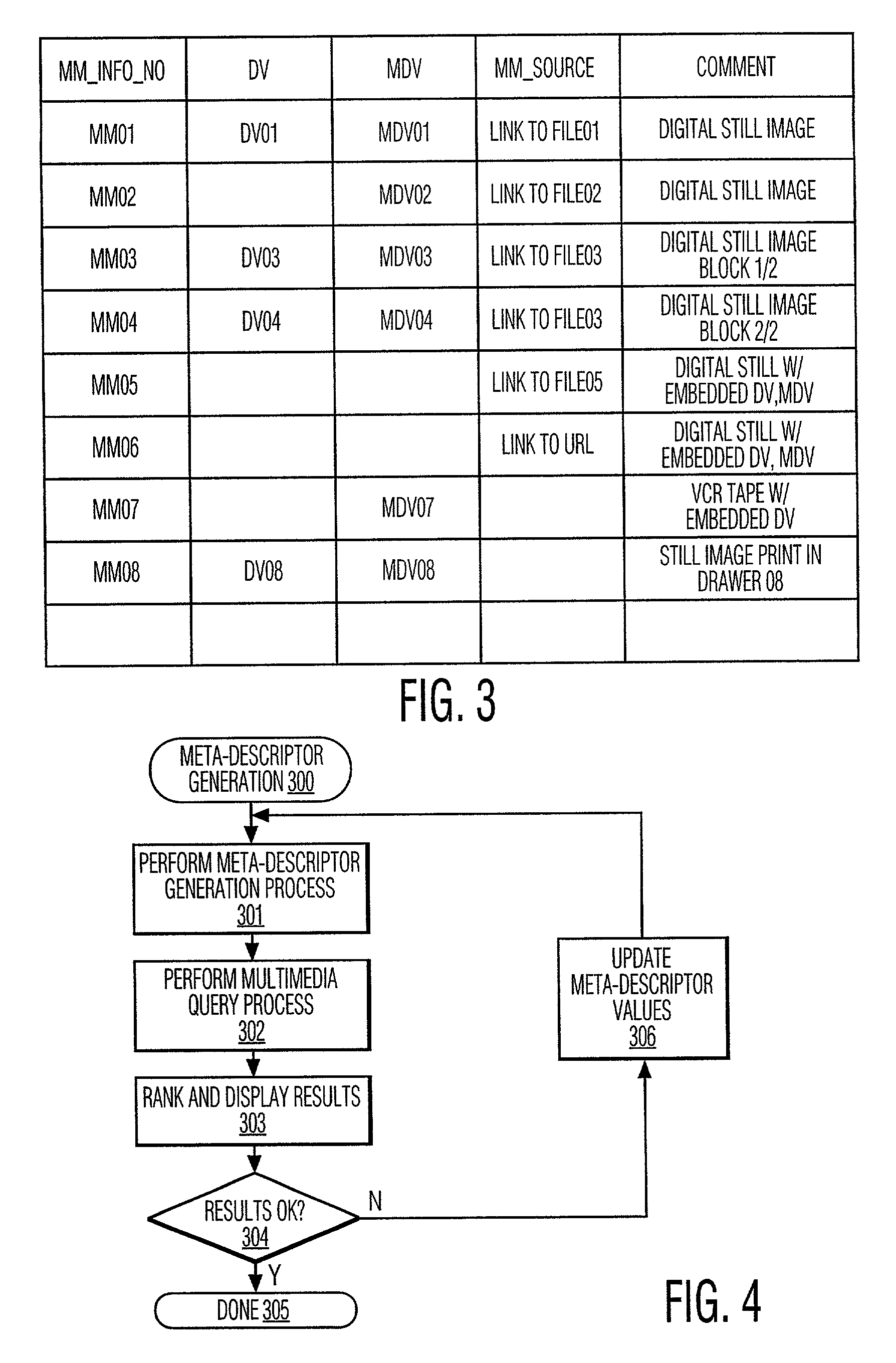
Meta-descriptor for multimedia information
InactiveUS7340458B2Improve efficiencyIncrease speedTelevision system detailsData processing applicationsQuery by ExampleFile descriptor
Multimedia information retrieval is performed using meta-descriptors in addition to descriptors. A “descriptor” is a representation of a feature, a “feature” being a distinctive characteristic of multimedia information, while a “meta-descriptor” is information about the descriptor. Meta-descriptors are generated for multimedia information in a repository (10, 12, 14, 16, 18, 20, 22, 24) by extracting the descriptors from the multimedia information (111), clustering the multimedia information based on the descriptors (112), assigning meta-descriptors to each cluster (113), and attaching the meta-descriptors to the multimedia information in the repository (114). The multimedia repository is queried by formulating a query using query-by-example (131), acquiring the descriptor / s and meta-descriptor / s for a repository multimedia item (132), generating a query descriptor / s if none of the same type has been previously generated (133, 134), comparing the descriptors of the repository multimedia item and the query multimedia item (135), and ranking and displaying the results (136, 137).
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Method and system for scheduling user-level I/O threads
InactiveUS20060075404A1Efficiently determineReduce in quantityMultiprogramming arrangementsMemory systemsThread schedulingKernel level
The present invention is directed to a user-level thread scheduler that employs a service that propagates at the user level, continuously as it gets updated in the kernel, the kernel-level state necessary to determine if an I / O operation would block or not. In addition, the user-level thread schedulers used systems that propagate at the user level other types of information related to the state and content of active file descriptors. Using this information, the user-level thread package determines when I / O requests can be satisfied without blocking and implements pre-defined scheduling policies.
Owner:IBM CORP
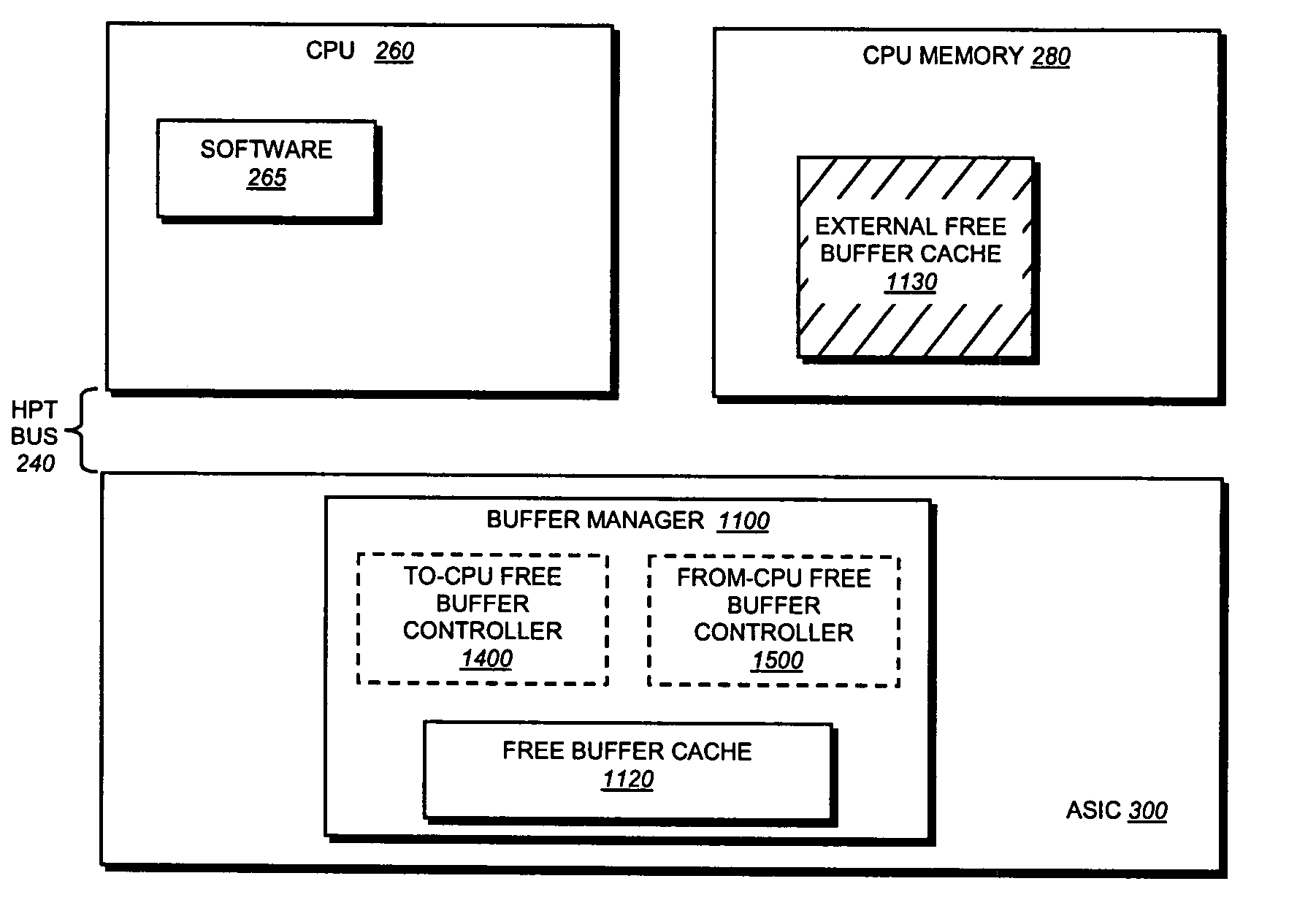
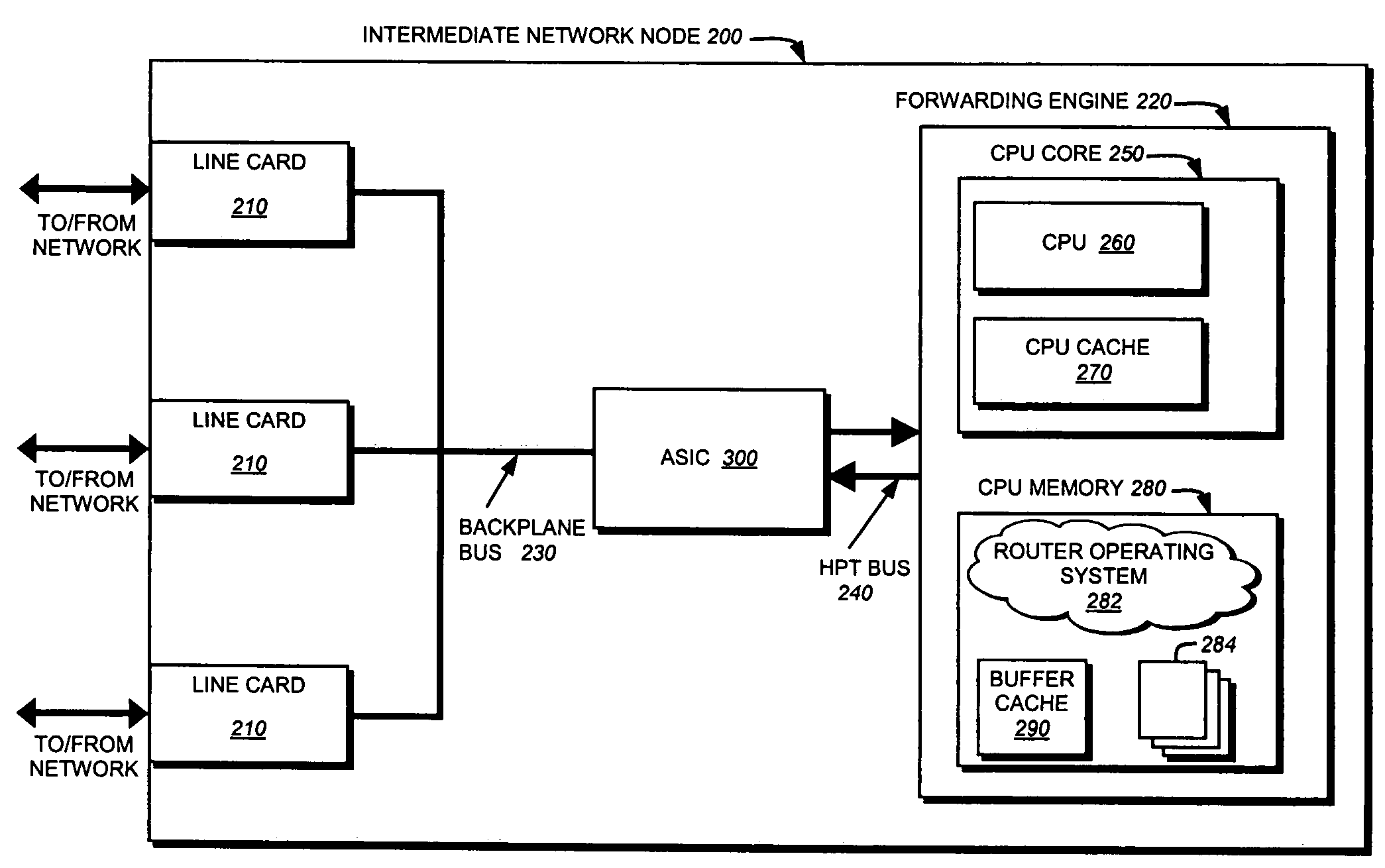
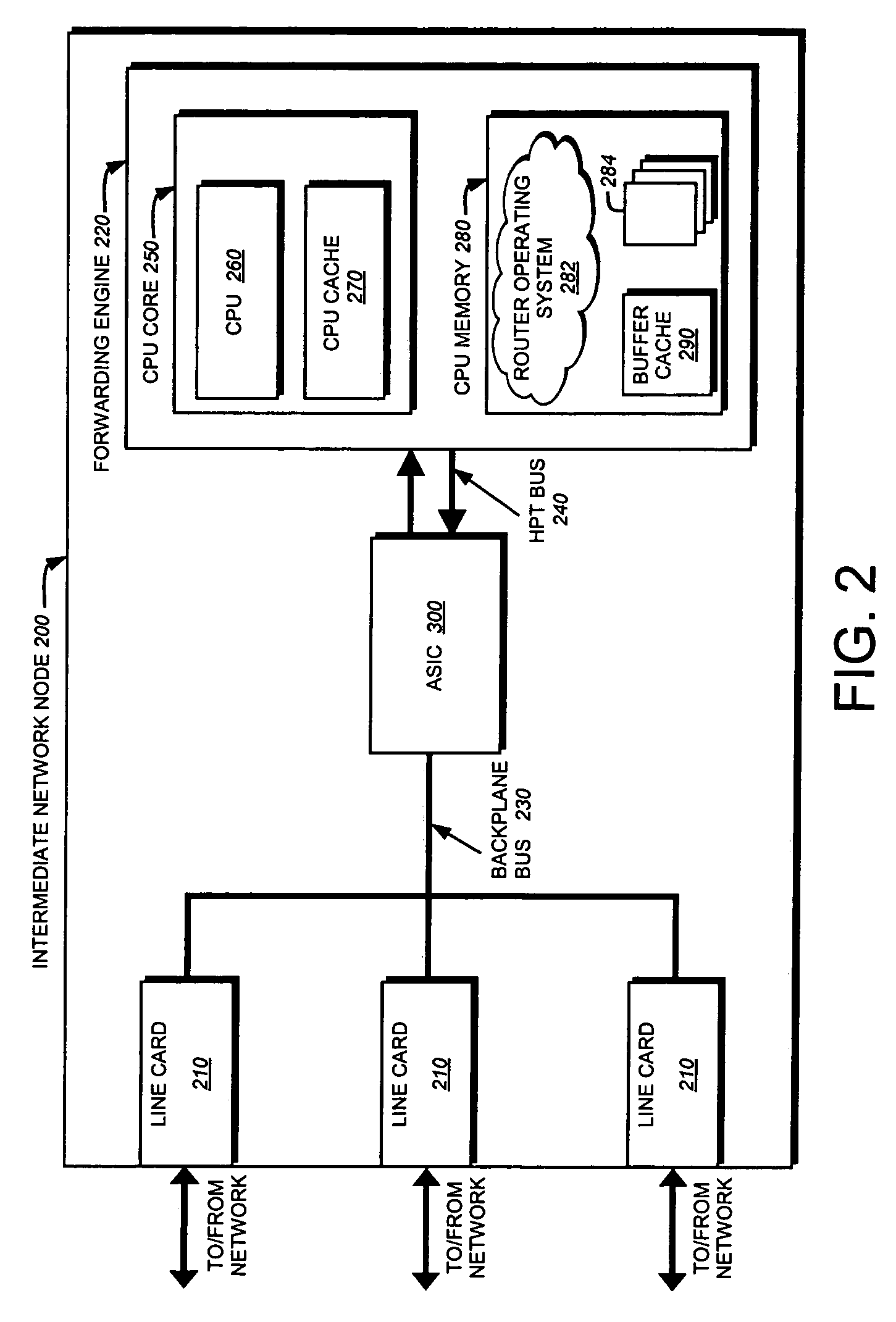
Buffer management technique for a hypertransport data path protocol
ActiveUS7111092B1Efficient managementReduce the amount of processingData switching by path configurationStore-and-forward switching systemsFile descriptorHyperTransport
A buffer-management technique efficiently manages a set of data buffers accessible to first and second devices interconnected by a split transaction bus, such as a Hyper-Transport (HPT) bus. To that end, a buffer manager controls access to a set of “free” buffer descriptors, each free buffer descriptor referencing a corresponding buffer in the set of data buffers. Advantageously, the buffer manager ensures that the first and second devices are allocated a sufficient number of free buffer descriptors for use in a HPT data path protocol in which the first and second devices have access to respective sets of free buffer descriptors. Because buffer management over the HPT bus is optimized by the buffer manager, the amount of processing bandwidth traditionally consumed managing descriptors can be reduced.
Owner:CISCO TECH INC
System and method to create a collaborative web-based multimedia layered platform
InactiveUS7933956B2Multimedia data browsing/visualisationMultiple digital computer combinationsFile descriptorApplication software
Owner:SIMULAT
Staggered polling of buffer descriptors in a buffer descriptor ring direct memory access system
InactiveUS6182165B1Radio transmissionInput/output processes for data processingMicrocontrollerDirect memory access
A microcontroller implements a buffer descriptor ring direct memory access (DMA) unit that polls buffer descriptors when in idle mode. This polling is to determine whether the software has set up a buffer or group of buffers transmission and transfer ownership of those buffers to the DMA unit. To reduce interrupt latency and bandwidth occupation, the polling of these buffer descriptor ownership flags is staggered for the DMA channels. For example, if eight DMA channels are implemented, the polling of their buffer descriptors can be distributed throughout a 1.28 millisecond polling interval.
Owner:GLOBALFOUNDRIES INC
Super-endurance solid-state drive with endurance translation layer (ETL) and diversion of temp files for reduced flash wear
ActiveUS8959280B2Memory architecture accessing/allocationInput/output to record carriersFilename extensionData file
Owner:SUPER TALENT TECH CORP
Method and apparatus for checkpoint and restart of pseudo terminals
InactiveUS7792983B2Error detection/correctionMultiple digital computer combinationsComputer hardwareRandom order
A computer implemented method, apparatus, and computer program product for restarting pseudo terminal streams. In one embodiment, a device associated with a file descriptor in a set of file descriptors is opened. The set of file descriptors are identified in checkpoint data for restarting the pseudo terminal streams. In response to identifying the device as a pseudo terminal slave device, an entry for the identified pseudo terminal slave device is added to a list of open pseudo terminal slave devices. The entry for the identified pseudo terminal slave device is marked as an open pseudo terminal slave device. The list of open pseudo terminal slave devices permit pseudo terminal master devices and pseudo terminal slave devices to be restored and restarted in random order during a restart of the pseudo terminal streams.
Owner:LINKEDIN
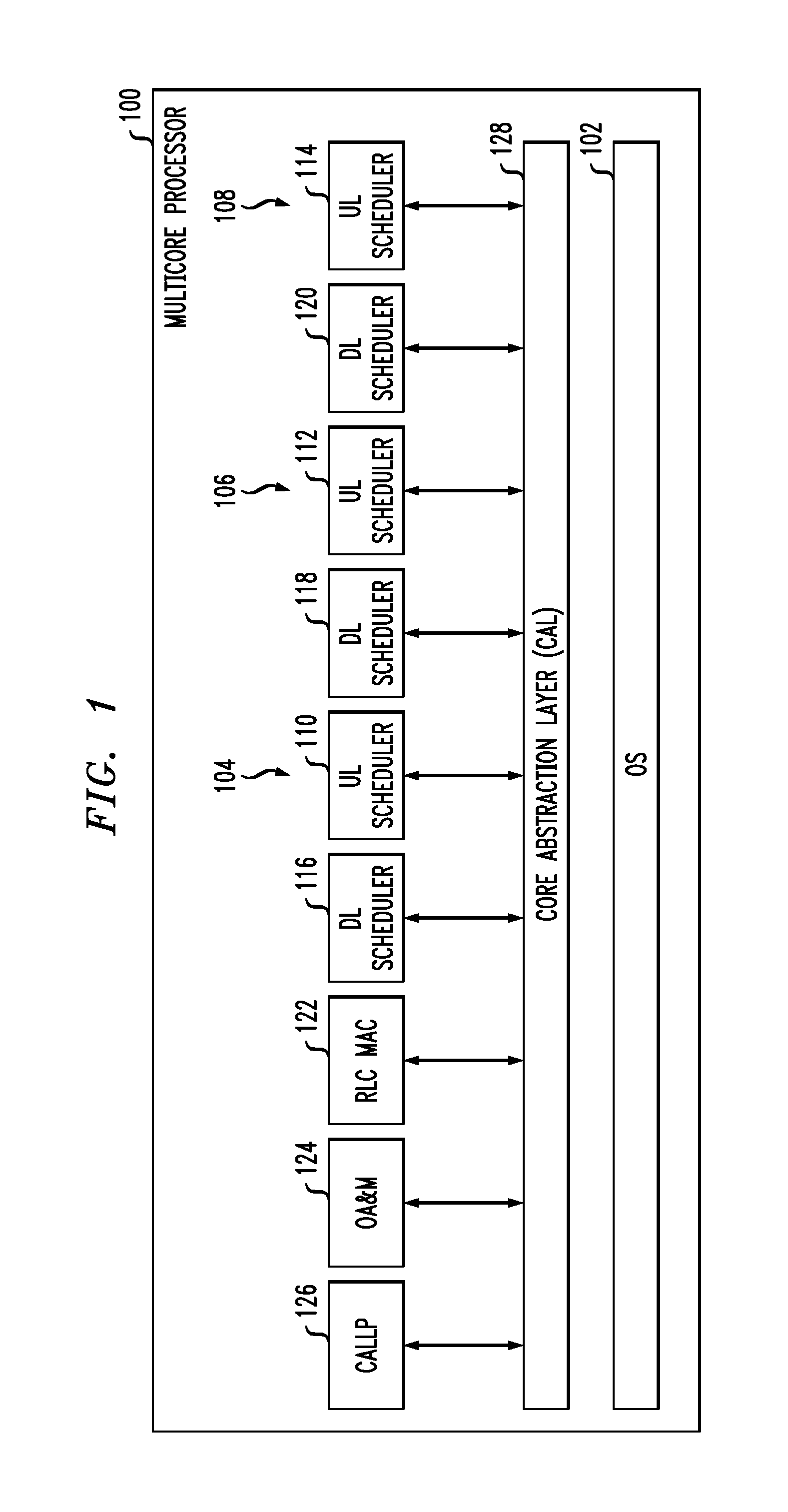
Lock-less and zero copy messaging scheme for telecommunication network applications
A computer-implemented system and method for a lock-less, zero data copy messaging mechanism in a multi-core processor for use on a modem in a telecommunications network are described herein. The method includes, for each of a plurality of processing cores, acquiring a kernel to user-space (K-U) mapped buffer and corresponding buffer descriptor, inserting a data packet into the buffer; and inserting the buffer descriptor into a circular buffer. The method further includes creating a frame descriptor containing the K-U mapped buffer pointer, inserting the frame descriptor onto a frame queue specified by a dynamic PCD rule mapping IP addresses to frame queues, and creating a buffer descriptor from the frame descriptor.
Owner:ALCATEL LUCENT SAS
Hypertransport data path protocol
A data path protocol eliminates most of the conventional read transactions required to transfer data between devices interconnected by a split transaction bus, such as a HyperTransport (HPT) bus. To that end, each device is configured to manage its own set of buffer descriptors, unlike previous data path protocols in which only one device managed all the buffer descriptors. As such, neither device has to perform a read transaction to retrieve a “free” buffer descriptor from the other device. As a result, only write transactions are performed for transferring descriptors across the HPT bus, thereby decreasing the amount of traffic over the bus and eliminating conventional latencies associated with read transactions. In addition, because descriptors are separately managed in each device, the data path protocol also conserves processing bandwidth that is traditionally consumed by managing ownership of the buffer descriptors within a single device.
Owner:CISCO TECH INC
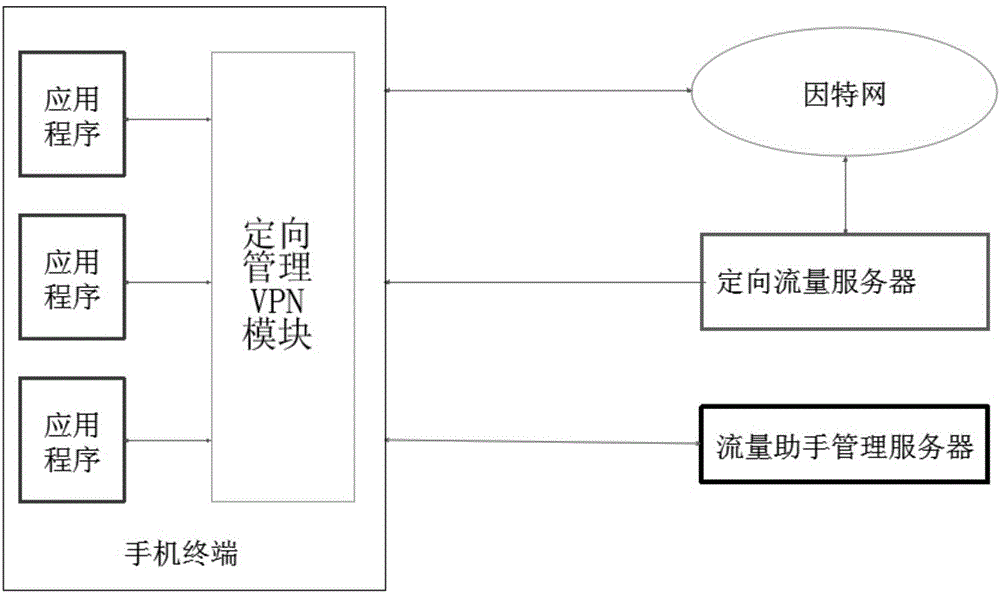
Directional traffic monitoring method based on Android terminal device
ActiveCN104468269AAddressing the Shortcomings of Directed Traffic PolicingData switching networksTraffic capacityNetwork addressing
The invention provides a directional traffic monitoring method based on an Android terminal device. The directional traffic monitoring method comprises the following steps that a directional management VPN module is established; a virtual network interface identical with a network interface of the terminal device is established through a VPNServer, so that network access of the VPN module is achieved; read-write operation of the network interface is executed by establishing file descriptors, so that the operation that the directional management VPN module reads and writes the network interface is achieved; a pointing path is established for the directional management VPN through a VPNServer.Builder type, wherein the pointing path comprises a path pointing to a network address, a path pointing to a DNS server and a path pointing to a network route; the purpose that the directional management VPN module monitors the directional traffic of the Android terminal device is achieved by calling an establish() function and feeding back a ParcelFileDescriptor object. By the adoption of the directional traffic monitoring method, traffic is monitored through the VPNServer service, and the defect that in the prior art, monitoring of the directional traffic of the Android terminal device is achieved only by obtaining the root authority is overcome.
Owner:HANGZHOU GSCOPE TECH
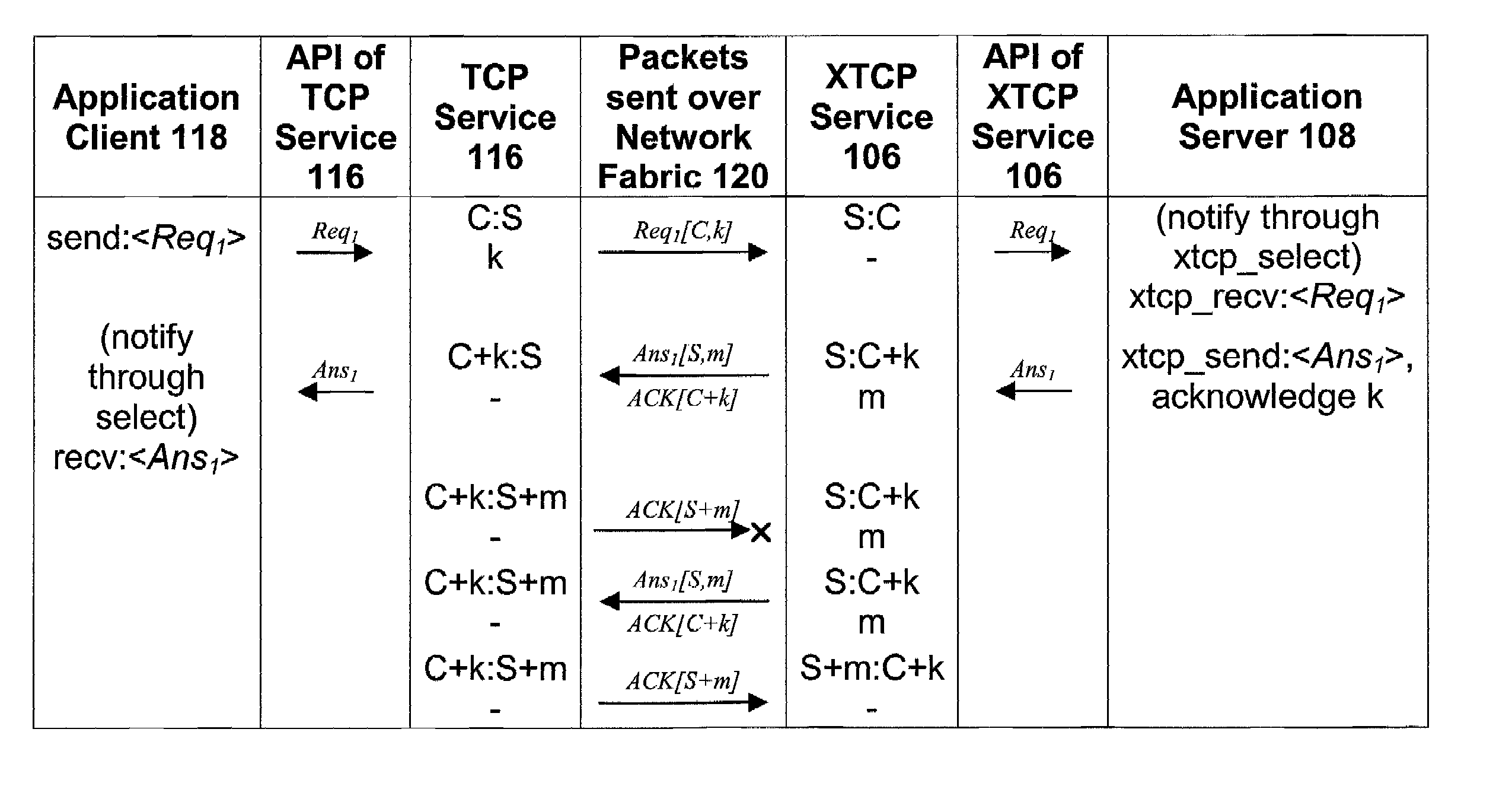
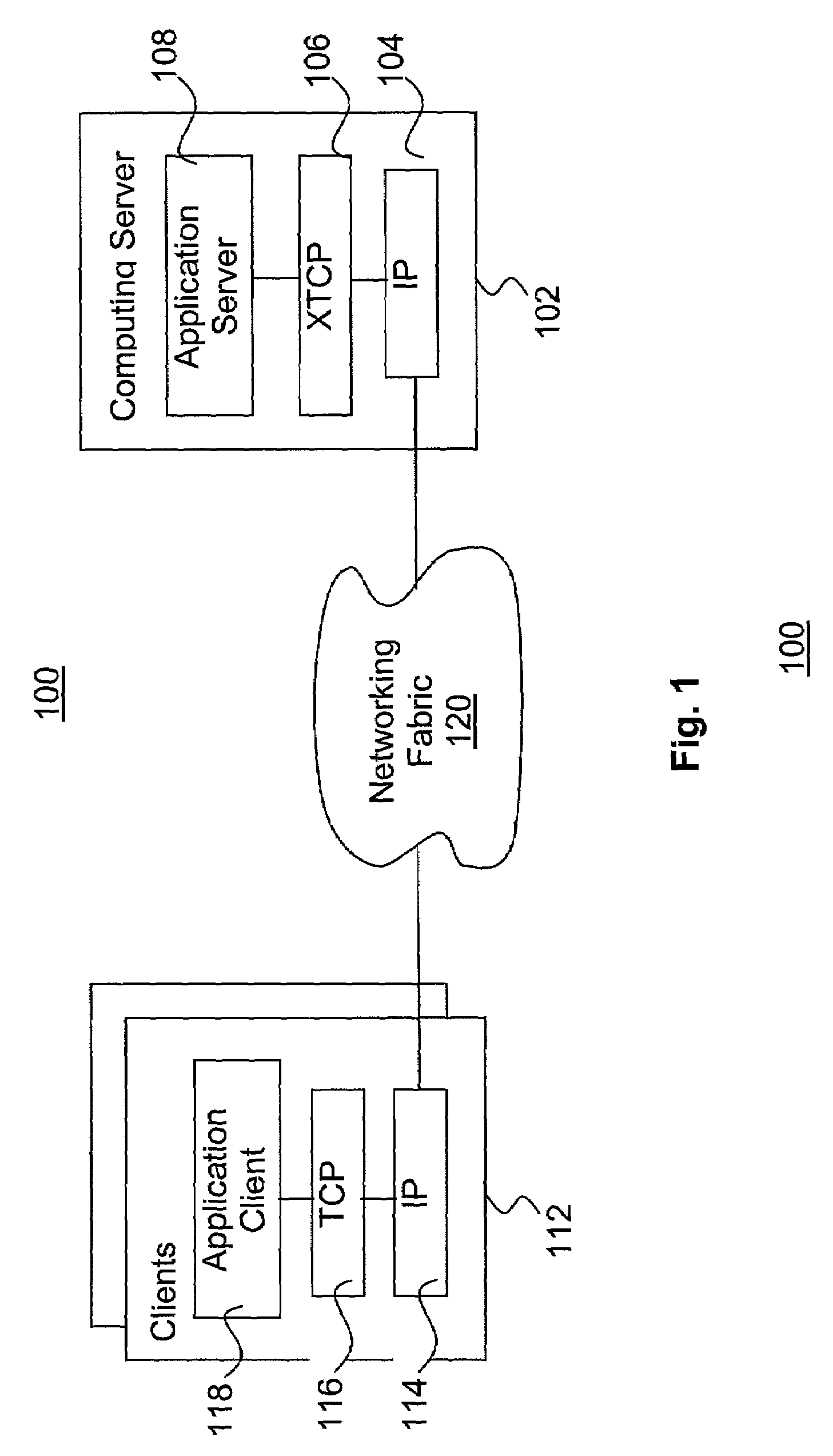
Transmission control protocol
ActiveUS7143131B1Easy to operateReduce the amount requiredError prevention/detection by using return channelFrequency-division multiplex detailsApplication serverNetwork Communication Protocols
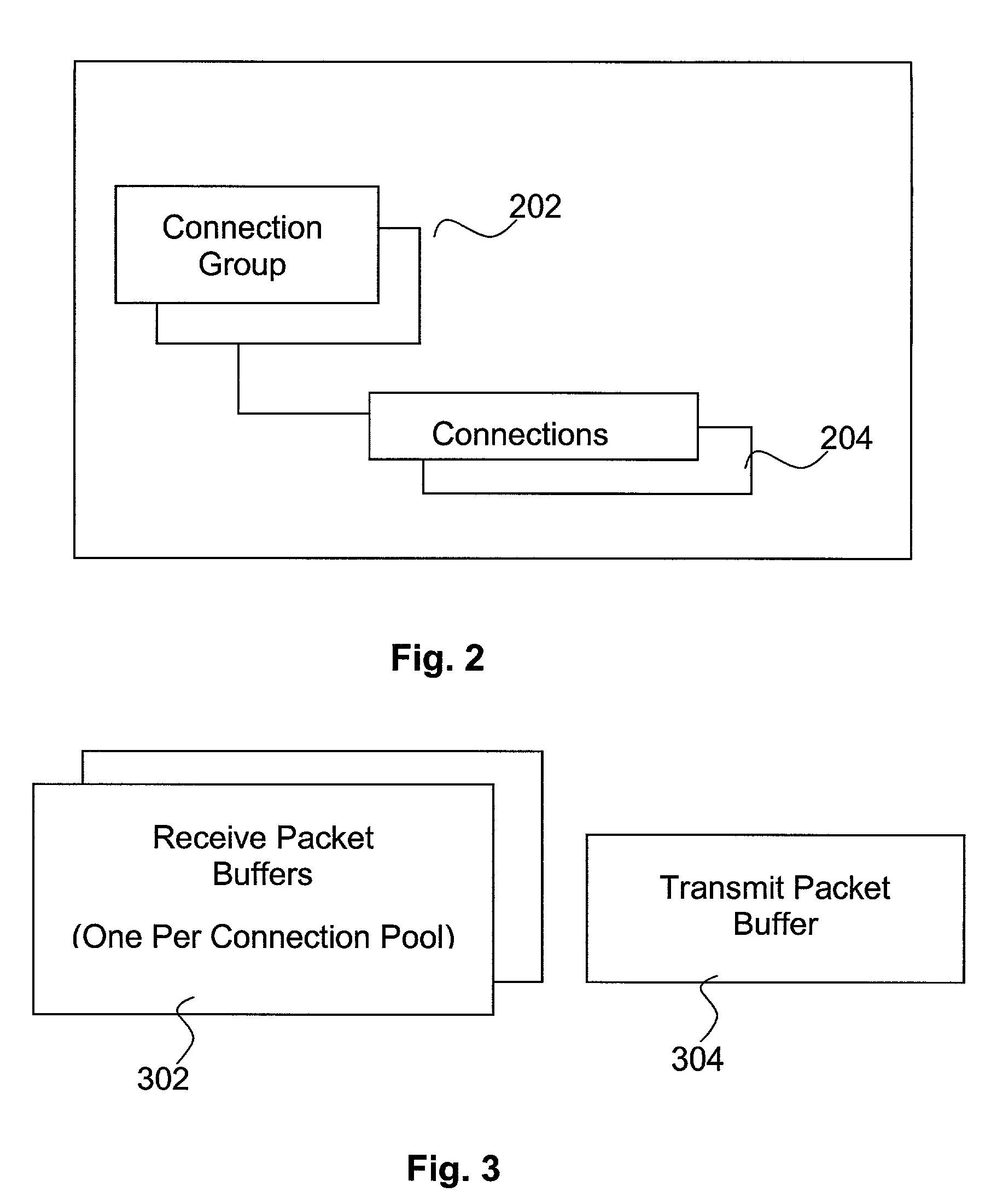
A communication protocol service in support of TCP based communication is modified to improve the operational efficiency of a server for a particular type of client-server application. The service is modified to support connection pools and connection groups within the connection pools, to enable connections with clients to be grouped and share a common file descriptor. The service is provided with an API to allow an application server to create the connection pools, connection groups and connections. The API also include receive and send services adapted to support the connection pool and connection group architecture, and to allow explicit acknowledgement of received transmissions under control of the application server. Further, in various embodiments, the buffering architecture of the service, as well as acknowledgement of request packets by the service are also modified.
Owner:MICROSOFT TECH LICENSING LLC
Parametric Analysis of Media Metadata
ActiveUS20100125586A1Data processing applicationsDigital data processing detailsFile descriptorMetadata
A method is disclosed that includes receiving a request to transmit a first multimedia file. The first multimedia file is associated with a first file descriptor. The method includes automatically generating a first generated content descriptor by analyzing the first multimedia file using a first set of analysis parameters. The method also includes comparing the first generated content descriptor to the first file descriptor and determining a first score based on a deviation of the first generated content descriptor from the first file descriptor.
Owner:AT&T INTPROP I L P
Snapshoot management method and device
ActiveCN104714755AEasy to manageInput/output to record carriersSoftware simulation/interpretation/emulationTrace fileFile system
The invention discloses a snapshoot management method and device. The snapshoot management method includes the steps that a server receives a snapshoot identification request from a client side, wherein a snapshoot identification is used for identifying a snapshoot generated by a client side file system; a latest snapshoot number of the whole file system is generated and fed back to the client side as the snapshoot identification, and a file descriptor structure of the file system is updated; a track file corresponding to the snapshoot generated by the file system is built and used for tracking files and recording the change information of the file system after the snapshoot is generated. In this way, the snapshoot management method and device can realize any catalogue snapshoot for the distribution type file system without a file layout or an overall file descriptor structure table.
Owner:XFUSION DIGITAL TECH CO LTD
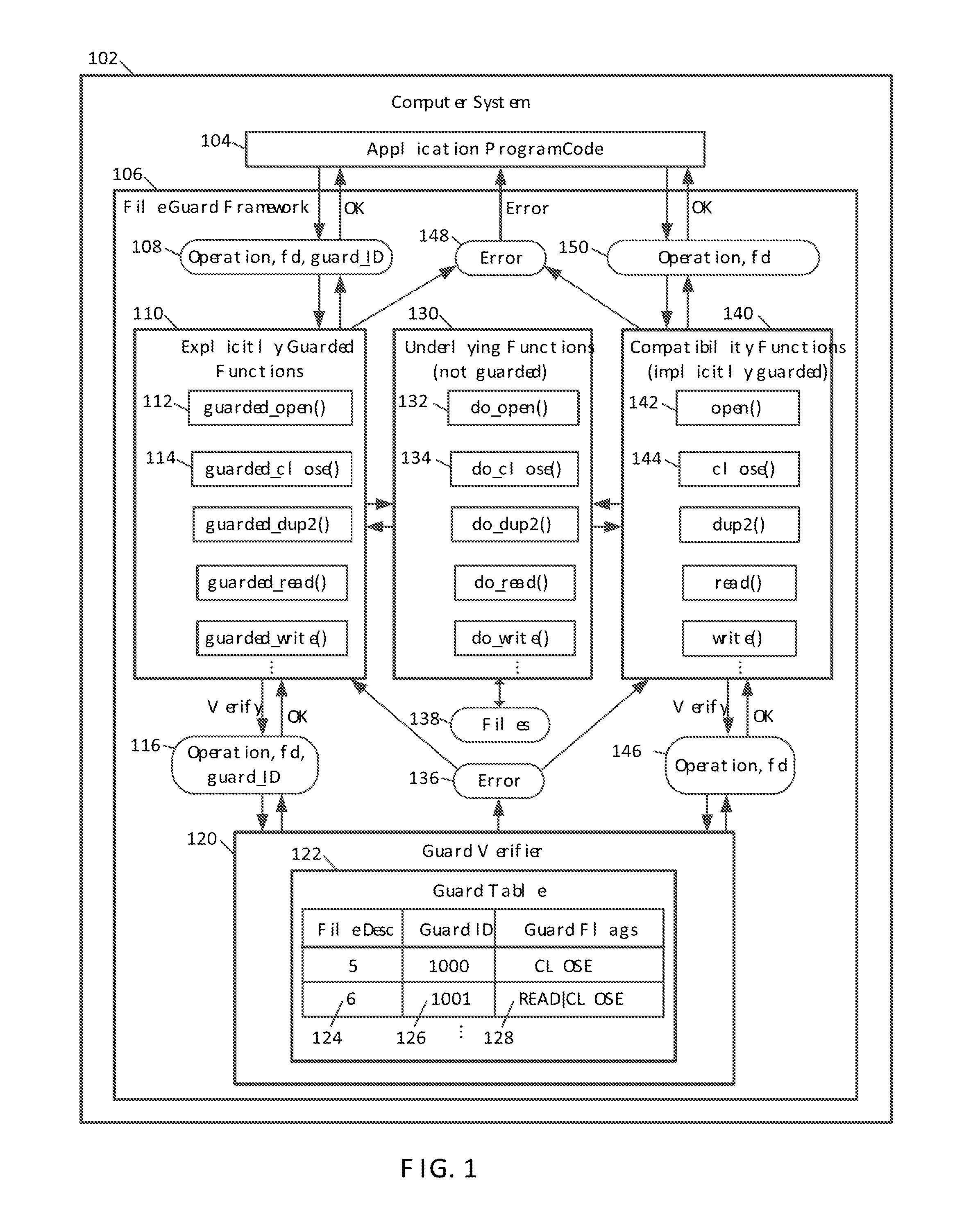
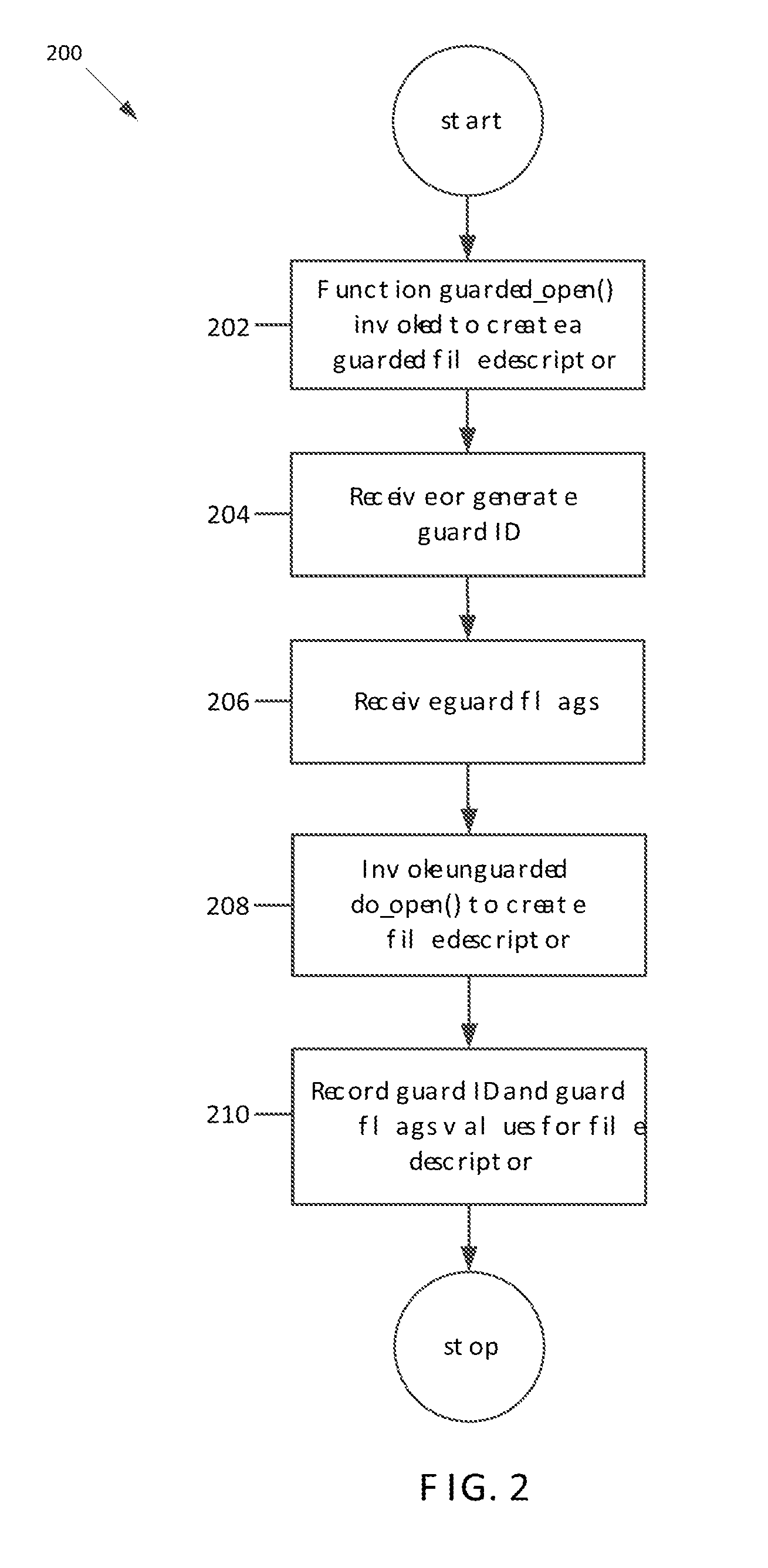
Guarded file descriptors
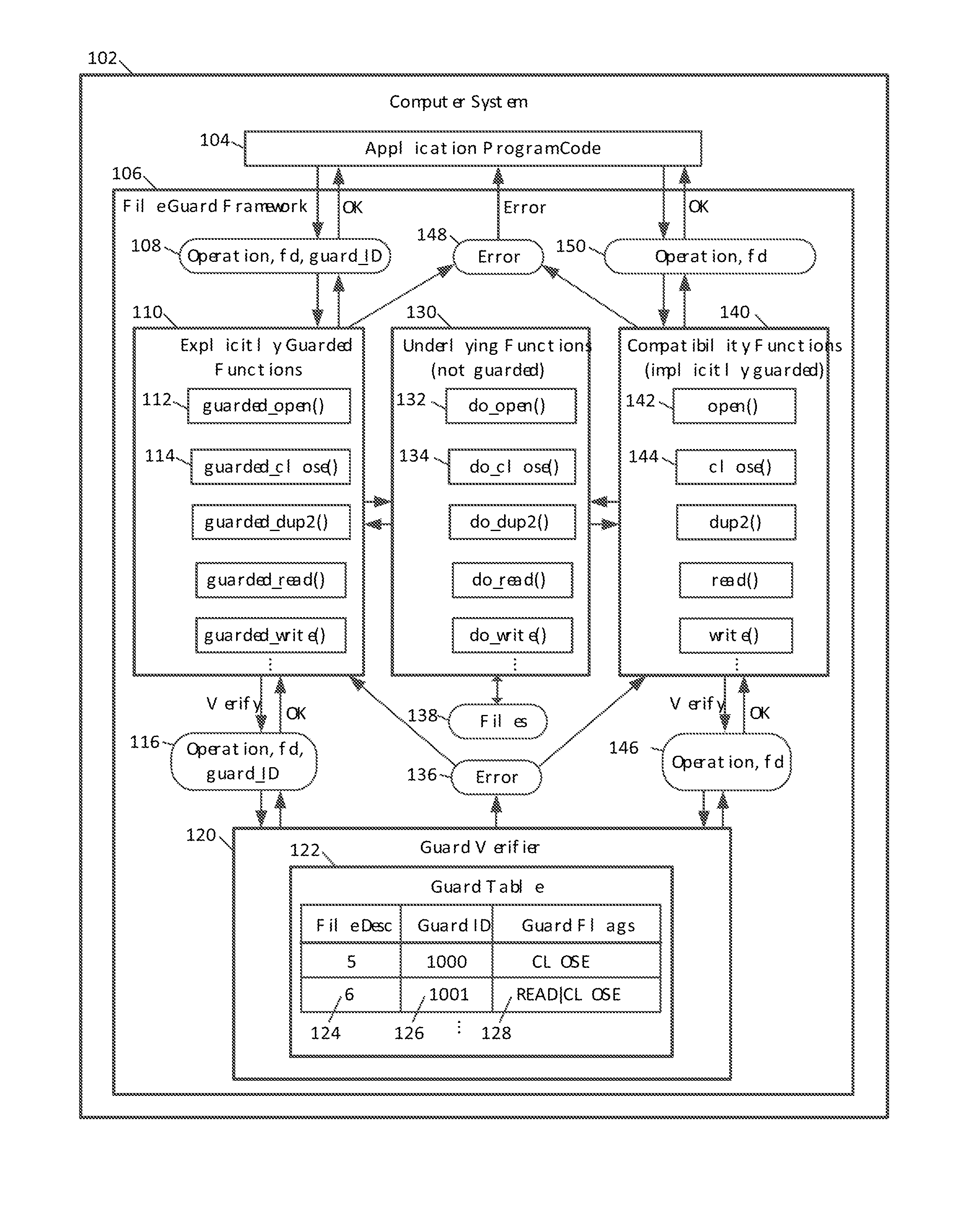
ActiveUS20130339313A1Preventing executionDigital data information retrievalDigital data processing detailsFile descriptorDatabase
Guarded file access operations are provided for creating and using guarded file descriptors, which can detect and prevent erroneous file access operations in computer programs. A file descriptor can be associated with a guard identifier to create a guarded file descriptor. The association can be established when the file is opened, and can be maintained independently of the computer program, which ordinarily maintains its own association between files, file descriptors, and guard identifiers. Subsequent file operations using the guarded file descriptor check that the guard identifier previously associated with that file descriptor is presented, and generate errors without performing the requested file operations if the correct guard identifier is not presented. This check serves as a validation of the computer program's use of file descriptors. An error and stack trace can be generated for use in analyzing a cause of the guard violation.
Owner:APPLE INC
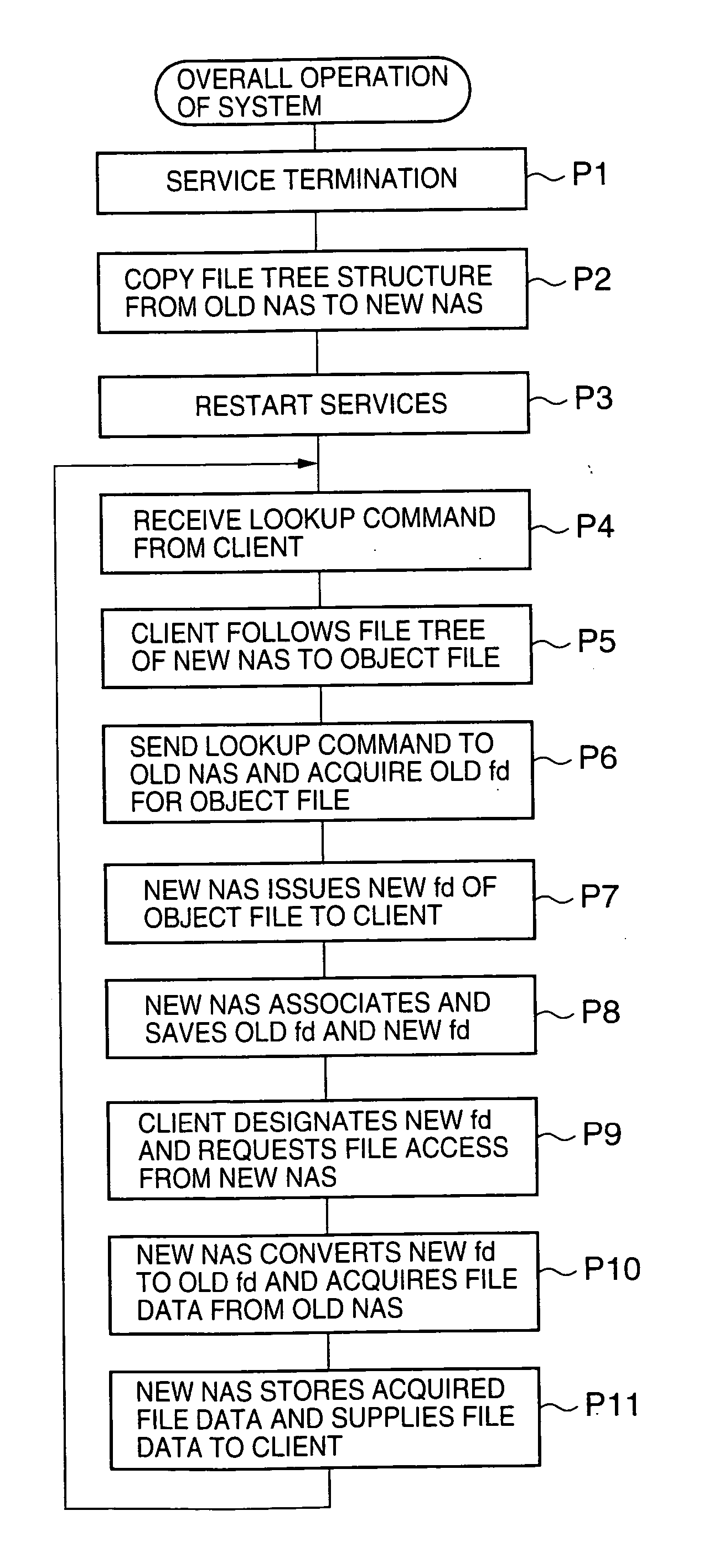
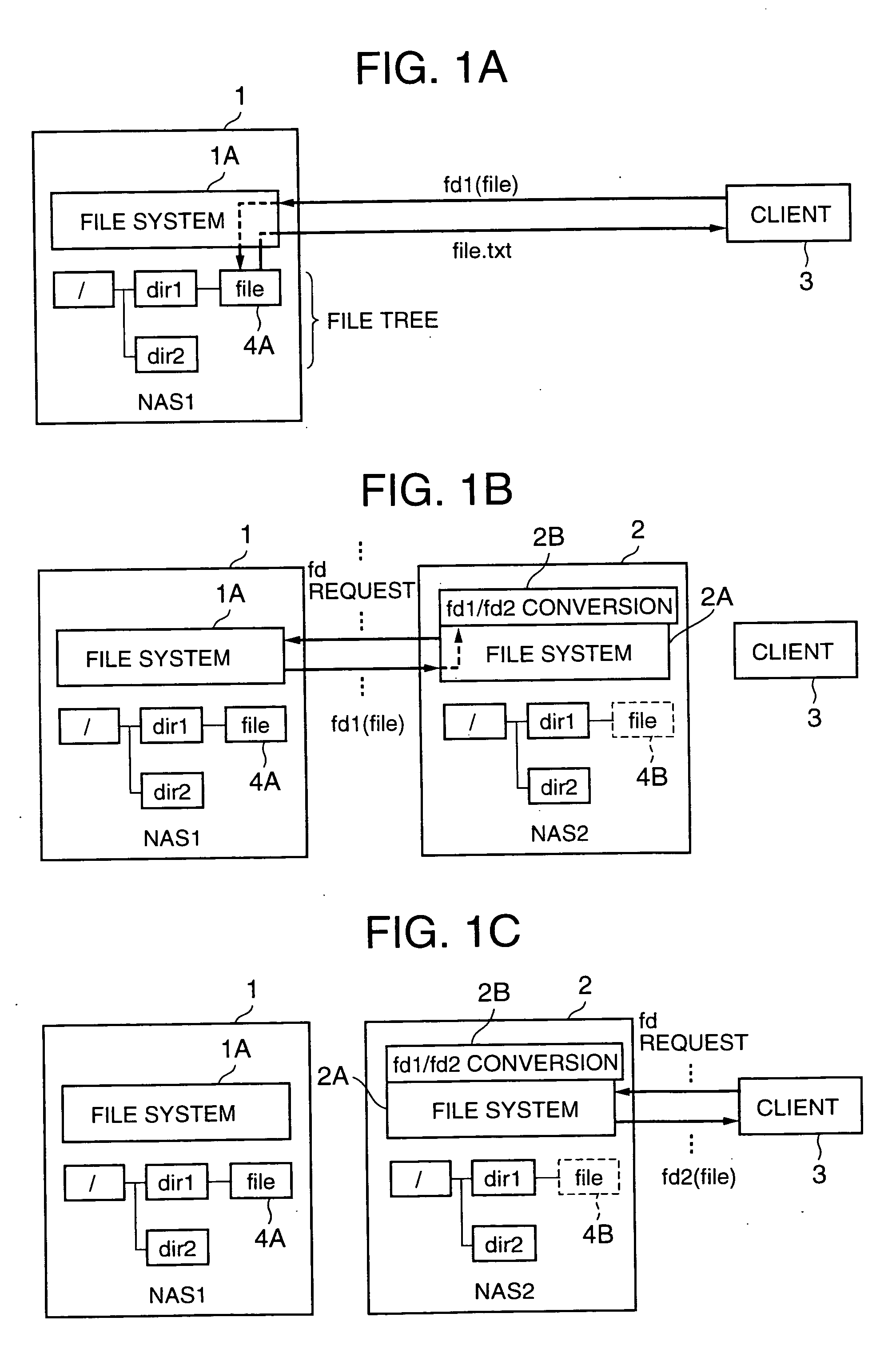
Network storage system and handover method between plurality of network storage devices
ActiveUS20060020636A1Short maintenance periodData processing applicationsDigital computer detailsClient-sideFile descriptor
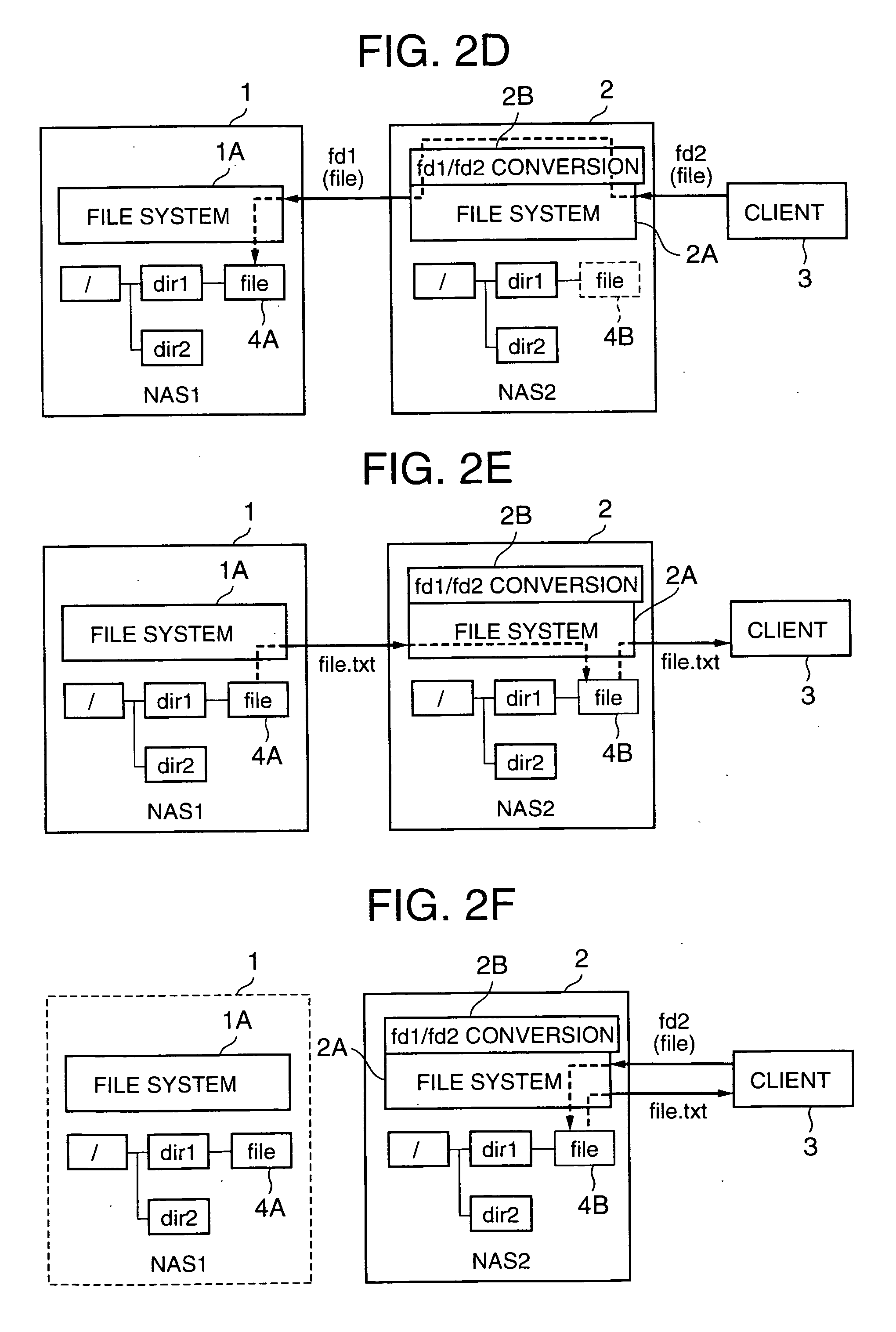
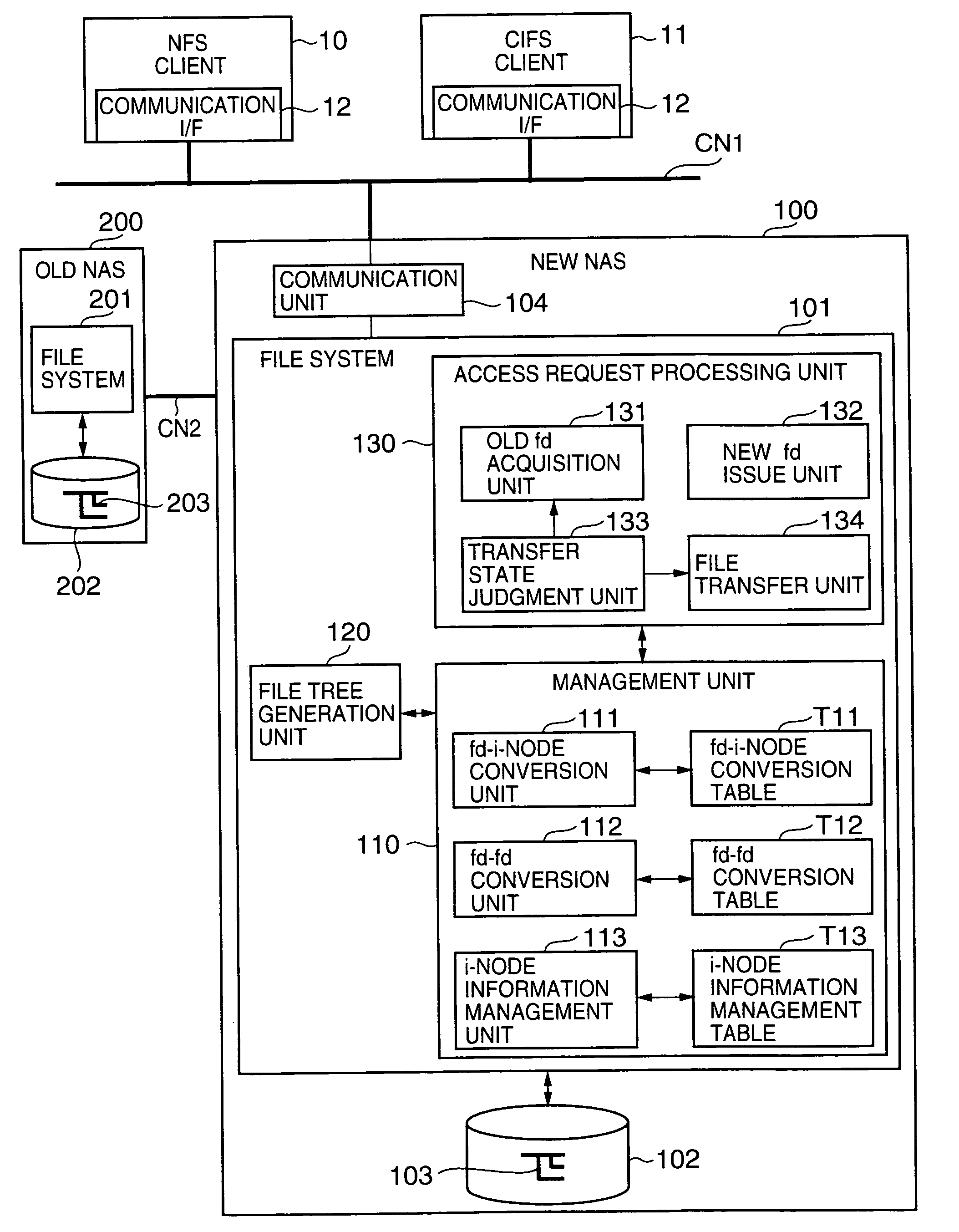
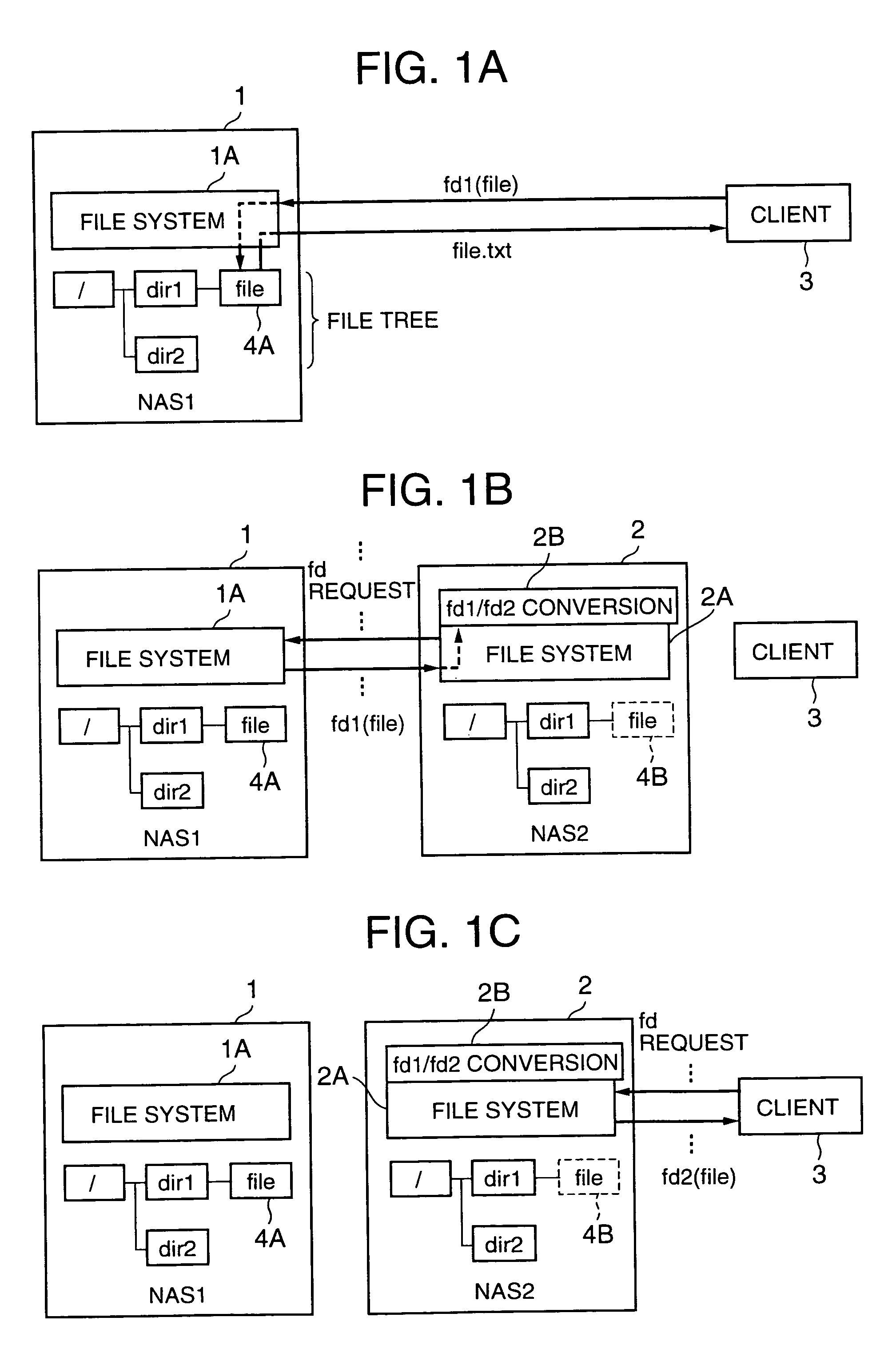
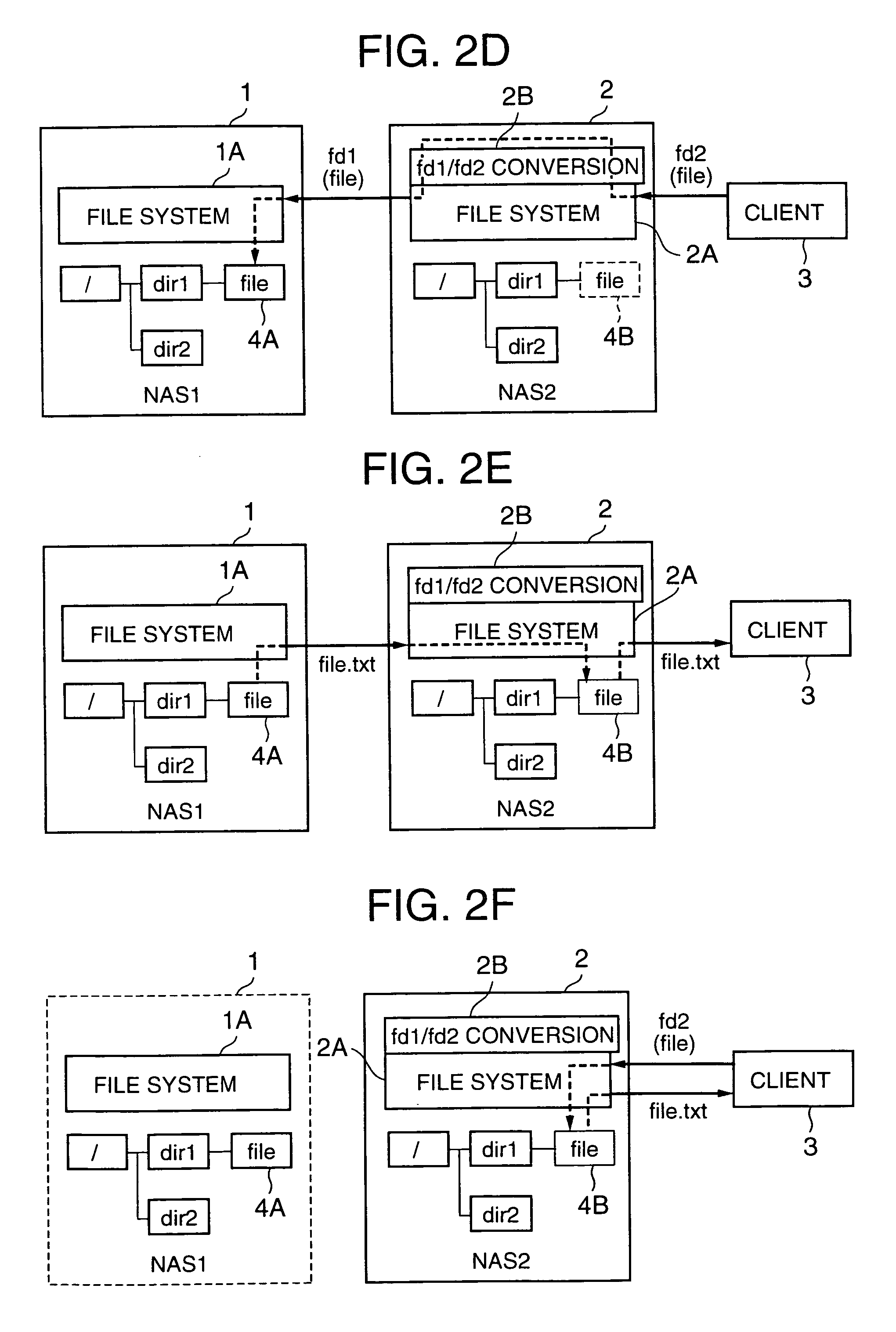
The present invention shortens service termination times and permits rapid transfers. A file tree with the same structure as that of the file tree of a first NAS is formed in a second NAS beforehand. File data is not transferred to the tree. The second NAS saves an association between a file descriptor fd1 managed by the first NAS and fd2 managed by the second NAS. Services for a client are restarted when the transfer of the tree structure is complete. When the client requests access to a desired file by designating fd2, the second NAS converts fd2 to fd1 and requests file data from the first NAS. When the first NAS reads the file data, the second NAS stores the file data in a predetermined location and supplies the file data to the client. In cases where the client desires file access once again, the second NAS reads the transferred file data and supplies same to the client.
Owner:GOOGLE LLC
Network storage system and handover method between plurality of network storage devices
The present invention shortens service termination times and permits rapid transfers. A file tree with the same structure as that of the file tree of a first NAS is formed in a second NAS beforehand. File data is not transferred to the tree. The second NAS saves an association between a file descriptor fd1 managed by the first NAS and fd2 managed by the second NAS. Services for a client are restarted when the transfer of the tree structure is complete. When the client requests access to a desired file by designating fd2, the second NAS converts fd2 to fd1 and requests file data from the first NAS. When the first NAS reads the file data, the second NAS stores the file data in a predetermined location and supplies the file data to the client. In cases where the client desires file access once again, the second NAS reads the transferred file data and supplies same to the client.
Owner:GOOGLE LLC
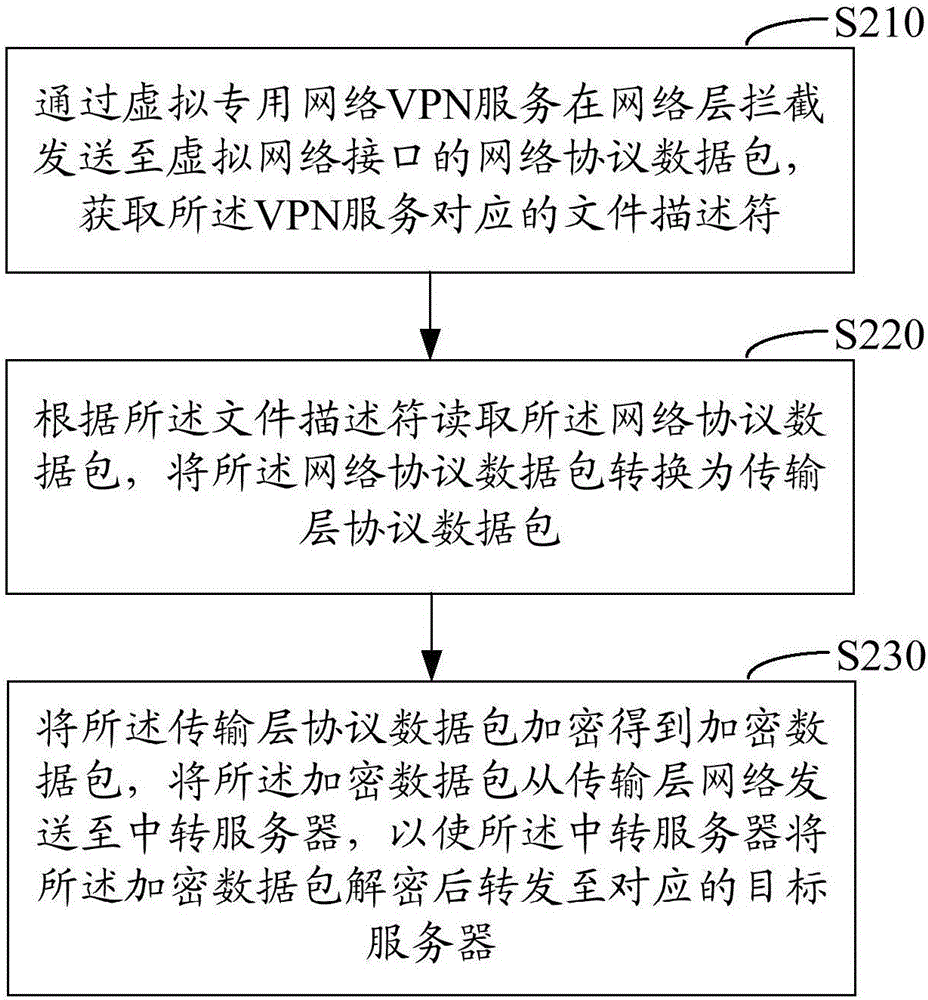
Terminal data transmission method and device
The invention relates to a terminal data transmission method and device. The terminal data transmission method comprises the steps of: intercepting a network protocol data packet sent to a virtual network interface on a network layer by a VPN (Virtual Private Network) service, and acquiring a file descriptor corresponding to the VPN service; according to the file descriptor, reading the network protocol data packet, and converting the network protocol data packet into a transmission layer protocol data packet; and encrypting the transmission layer protocol data packet to obtain an encrypted data packet, and sending the encrypted data packet to a transit server from a transmission layer network, so that the transit server forwards the encrypted data packet to a corresponding target server after decrypting the encrypted data packet. Safety of terminal data transmission also can be improved without acquiring a system permission.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Distributed collection and storage method of journal
InactiveCN103036961AImprove transmission efficiencyImprove throughputTransmissionUsabilityComputer terminal
The invention discloses a distributed collection and storage method of a journal. The method adopts transmission control protocol (TCP) / internet protocol (IP) to interchange data, a sending terminal serializes the data, and a receiving terminal deserializes the data. In order to maintain long connection, a client terminal sends heartbeat packet at regular intervals to determine whether a journal server terminal is on line, and when the journal server terminal corresponds the heartbeat packet when the journal server terminal is on line. A first speed regulator controls a connected FD (file descriptor) integrally and storages the processed data in a data-caching pool. A second speed regulator reads a certain amount of data from the data-caching pool and sends the data to a remote terminal. After the remote terminal of a computer receives the data, the remote terminal writes the data in a data base. By means of the distributed collection and storage method of the journal, the transmission efficiency of the client terminal and the journal server are improved, the handling capacity operation of the journal server and the data base is improved, and the instantaneity and the usability of the system are improved.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
Method and system for realizing access for a great amount of terminals for helix server
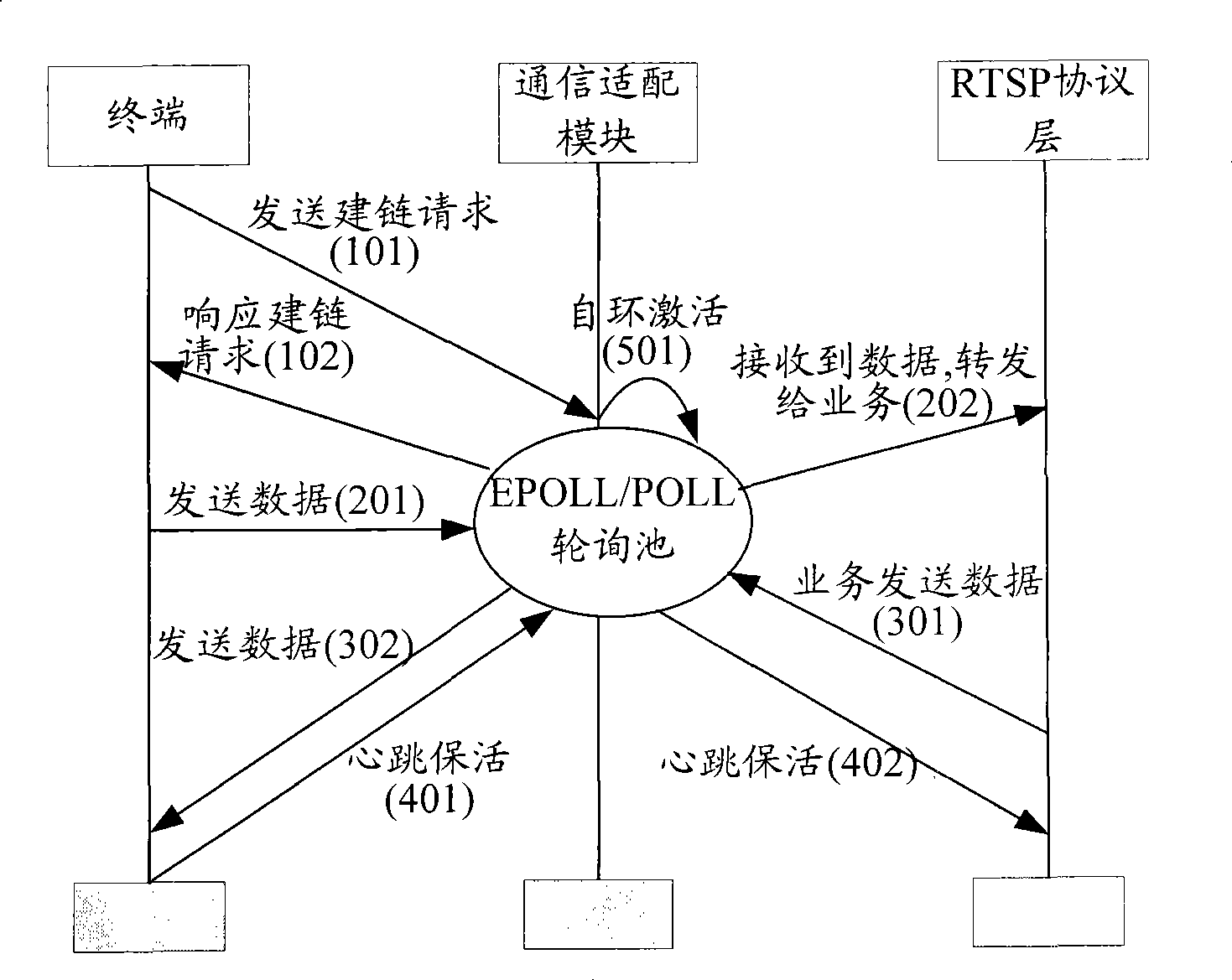
InactiveCN101448006ALarge number of concurrent video streamsImprove the efficiency of communication processingSpecial service provision for substationSelective content distributionMedia serverFile descriptor
The invention discloses a method and a system for realizing access for a great amount of terminals for a helix server, which belongs to the technical field of the IPTV and is used for solving the technical problems in the prior art that when a great number of terminals are accessed, the treatment efficiency of the helix server is low, and the TCP short connection accessed with a great number of terminals cannot be reliably supported. The invention adopts an EPOLL / POLL event polling interface to perform event polling to the linked link circuit, thereby enhancing the capability of the system to access a great amount of terminals, and the invention adopts the socket file descriptor as the index entry of the polling list, thereby improving the retrieval efficiency of the link circuit during the process of accessing a great amount of terminals. The processing capacity of the helix server can be enhanced, so that the TCP short connection accessed with a great amount of terminals can be reliably supported by the helix server.
Owner:ZTE CORP
File system operation intercepting method based on event monitoring mechanism
ActiveCN101556608AAdd monitoring at willAdd any interceptioPlatform integrity maintainanceSpecial data processing applicationsSystems managementFile system
The invention relates to a file system operation intercepting method based on an event monitoring mechanism. The method comprises the following steps: a supervisor program which is trusted by a user calls function iauth_init to start the intercept service, and the function returns a file descriptor; the supervisor program calls function iauth_add_watch to monitor the key part of a system, and when the function is called, the supervisor program is required to specify a call back function so as to judge whether an access is illegal; when other application programs try to read and write monitored files, the call back function provided by the supervisor program can be called and decides the validity of the reading and writing so as to judge whether to let the reading and writing to pass or reject the reading and writing, and the action can lead the file operation of the application program which is tried to be read and written to be successful or failed. The invention has the advantages that the method provides user-friendly system call to lead a system manager to arbitrarily add monitoring, intercepting and preventing functions to the file system operation of the computer. The function can provide convenience for the application software on the system security aspect.
Owner:INSIGMA TECHNOLOGY CO LTD
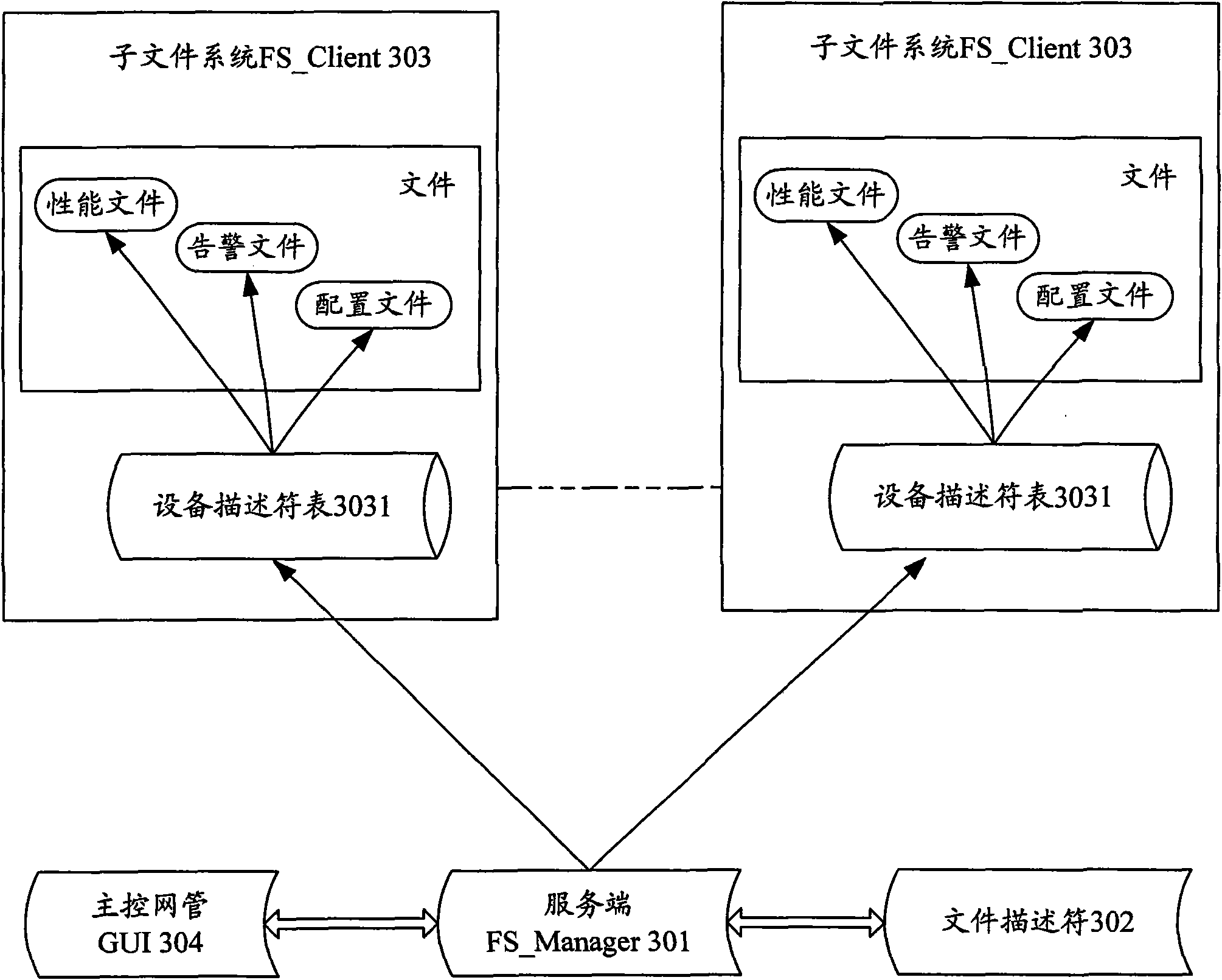
Distributed type management monitoring system, monitoring method and establishing method thereof
ActiveCN101621405AReduce communicationFast communication speedDigital data information retrievalData switching networksFile systemMonitoring system
The invention discloses an establishing method of a distributed type management monitoring system, establishing the distributed type management monitoring system based on a distributed type file system. Furthermore, the invention also discloses a monitoring method of the distributed type management monitoring system, comprising the following steps: a subfile system of the distributed type management monitoring system updates a file recording monitoring information at fixed time and correspondingly updates an equipment descriptor table; the subfile system updates the equipment descriptor table and informs a service terminal of updating a file descriptor table; and the service terminal finds the equipment descriptor table corresponding to an appointed network element by traversing the file descriptor table and reads an appointed file according to the equipment descriptor table. Correspondingly, the invention provides the distributed type management monitoring system comprising the service terminal, the file descriptor table and the subfile system. Therefore, by the invention, the self and independent monitoring of each network element is realized, unnecessary communication between the network elements is reduced, and the stability of the distributed type management monitoring system is enhanced.
Owner:北京中兴光泰软件有限责任公司
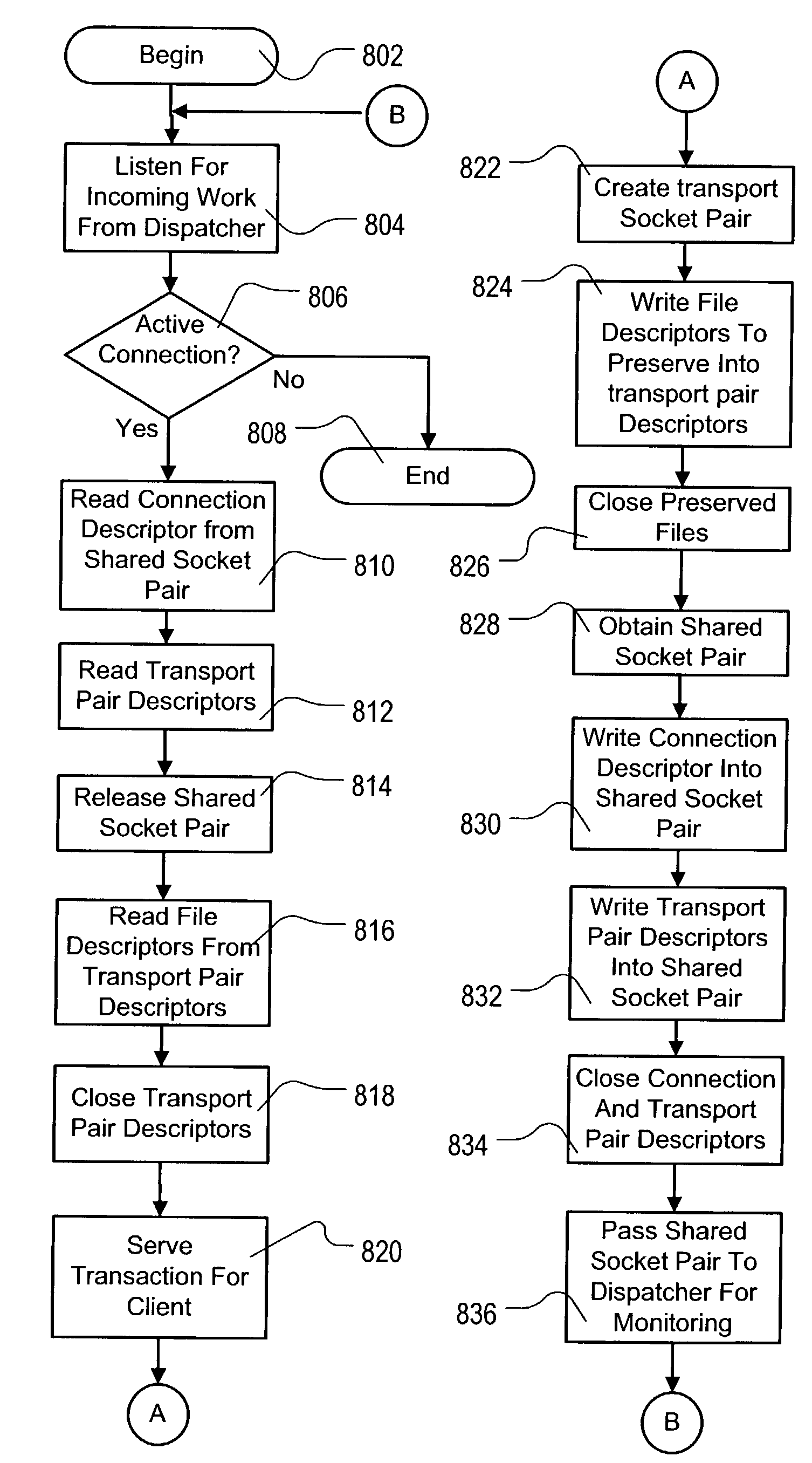
Method and system for optimizing file table usage
InactiveUS7373647B2Easy to useMultiprogramming arrangementsSpecific program execution arrangementsUnix domain socketOperational system
An operating system directed to using special properties of a common inter-process communications mechanism (IPC), namely UNIX domain socket-pairs or stream-pipes alternatively as a storage medium for file-descriptors of UNIX processes. When a file-descriptor is written into a socket-pair, and closed in the UNIX process, the file remains open, but occupies no space in the process' file-table. The file-descriptor may later be read out of the socket-pair to reestablish it in the file-table, and access it. This property is implemented in an IPC mechanism of UNIX operating system whereby a process such as a dispatcher may manage more connections and processes than its file-table size allow. This provides scalability improvements of the UNIX operating system.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com