File system operation intercepting method based on event monitoring mechanism
A file system operation and mechanism technology, applied in computer security devices, special data processing applications, instruments, etc., can solve problems such as lack of fine control, inaccessibility, and large granularity of protection means
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] In order to make the purpose, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments:
[0022] The file system operation interception method based on the event monitoring mechanism described in the present invention comprises the following steps:
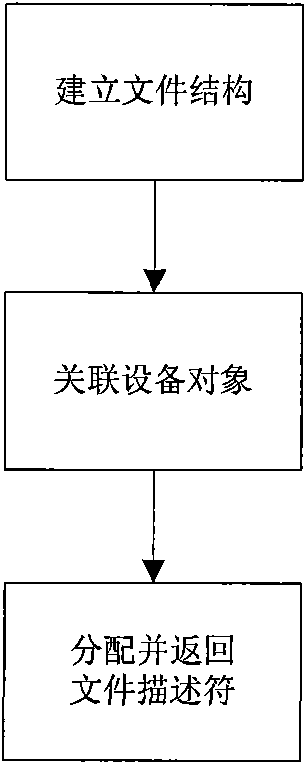
[0023] 1) A user-trusted management program calls iauth_init to start an interception service. The process calling this function must have administrator privileges. This function will return a file descriptor.
[0024] 2) The management program calls iauth_add_watch to monitor the key parts of the system. When calling this function, the management program must specify a callback function to judge whether an access is legal.
[0025] 3) If necessary, the management program can call iauth_remove_watch to remove the watch.
[0026] 4) When other applications try to read and write...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com