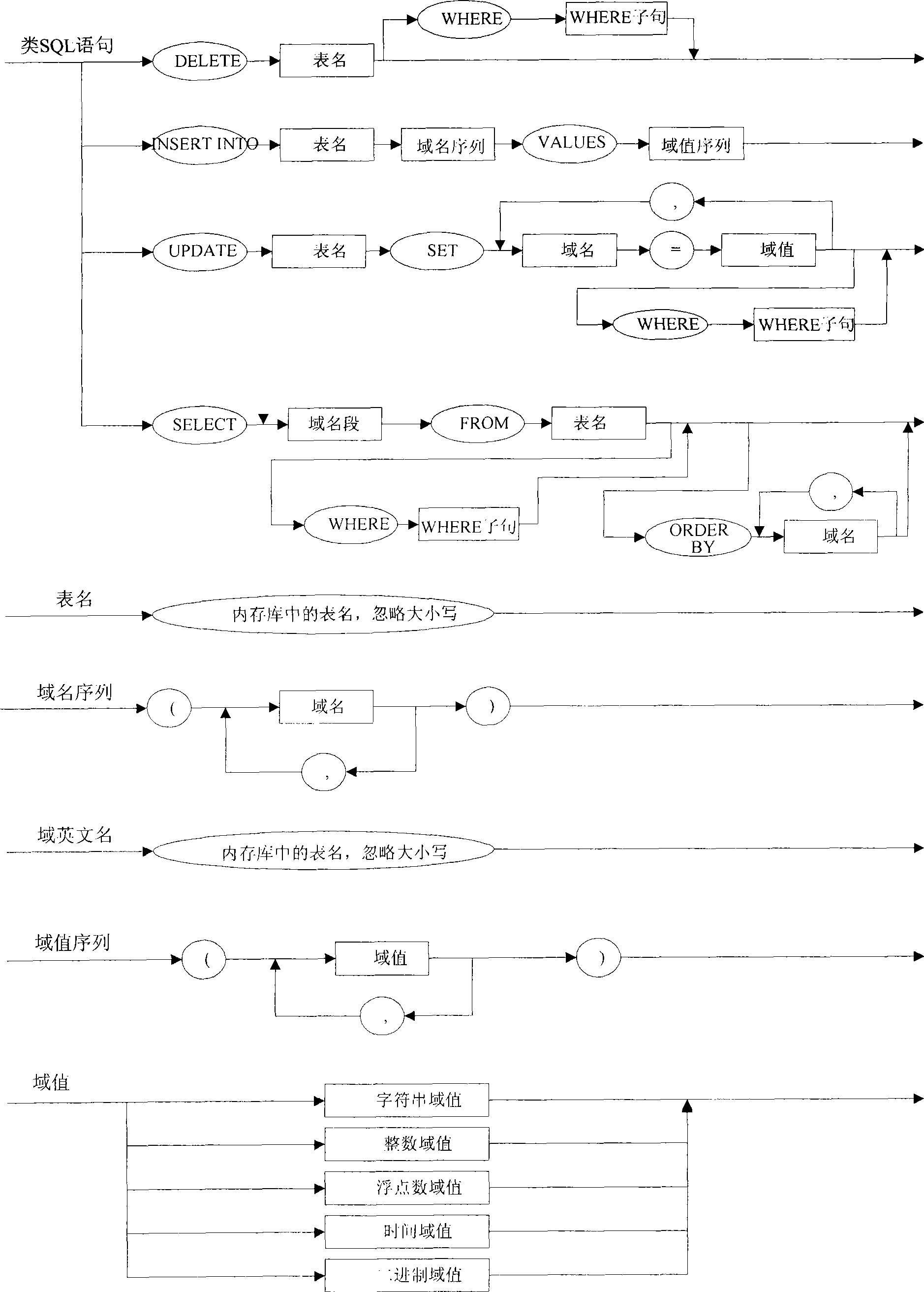Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
80 results about "Unix operating system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
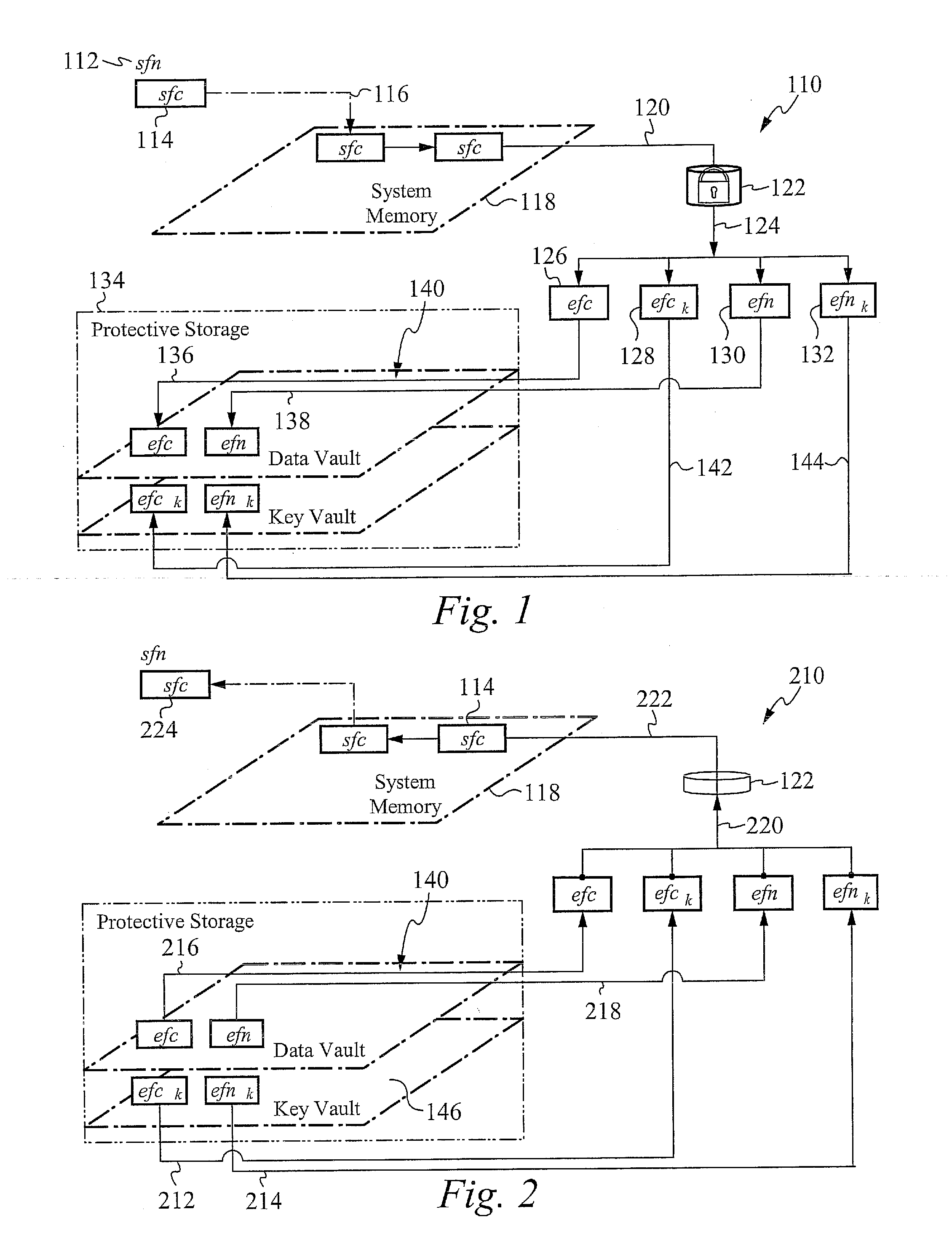
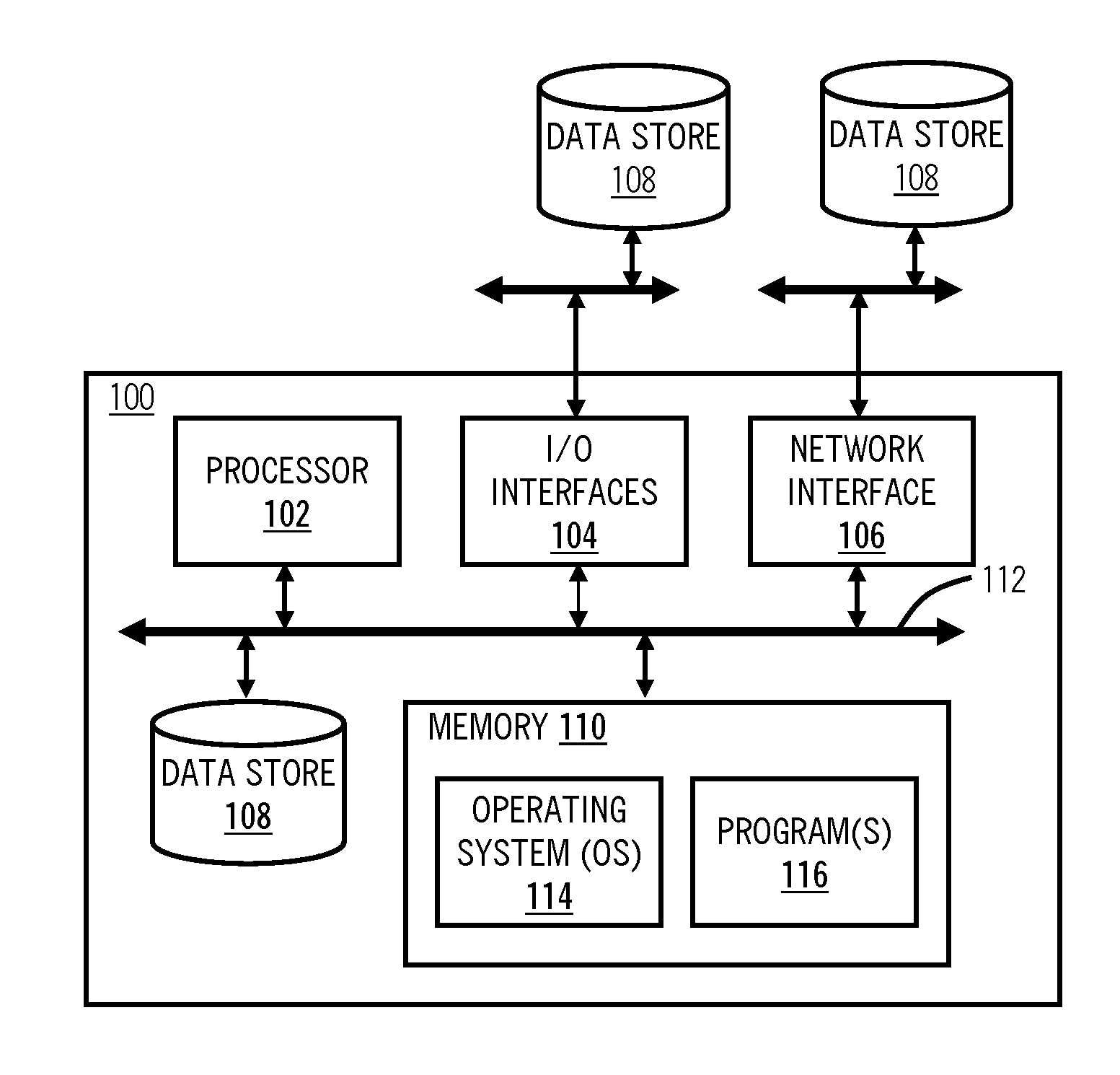
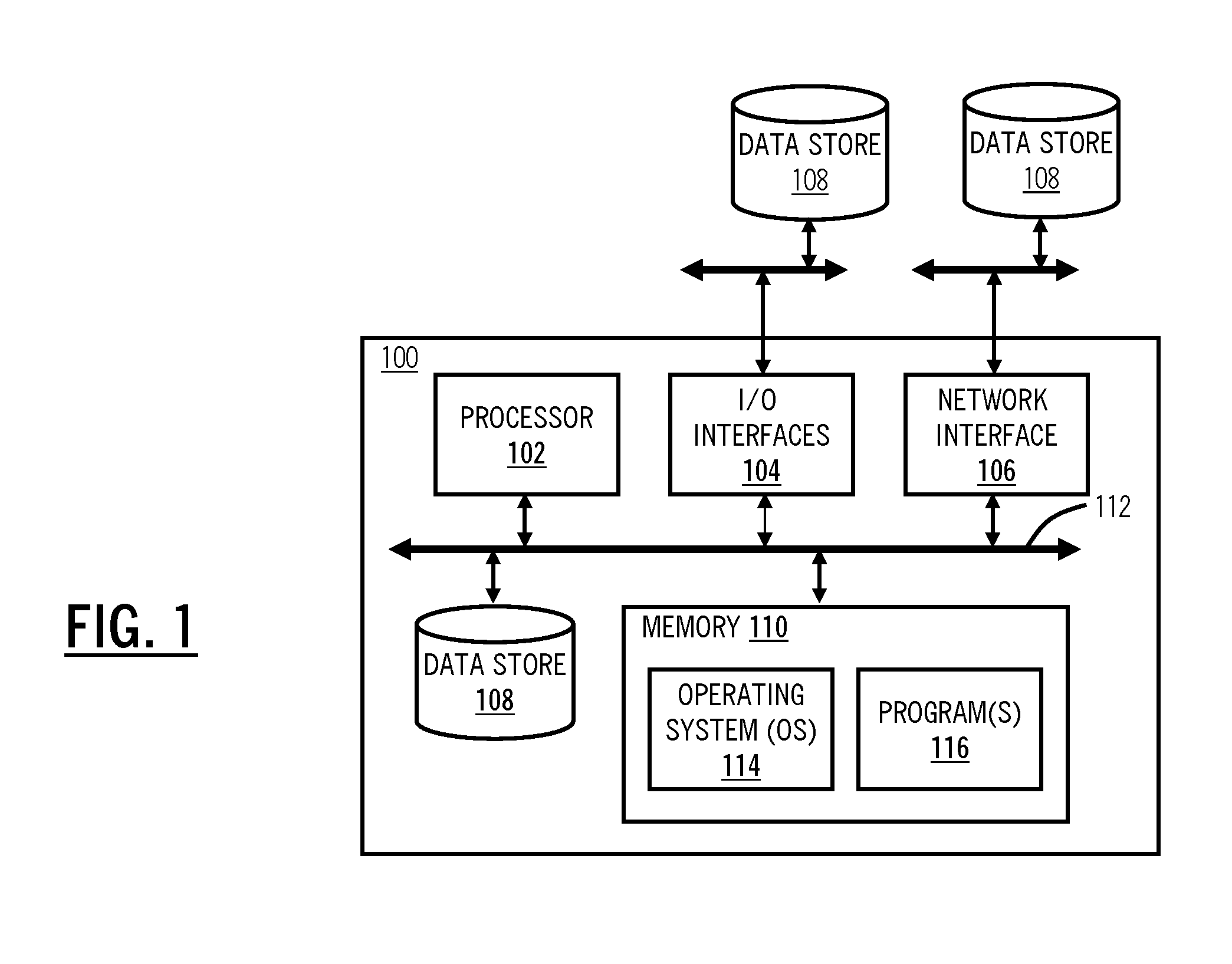
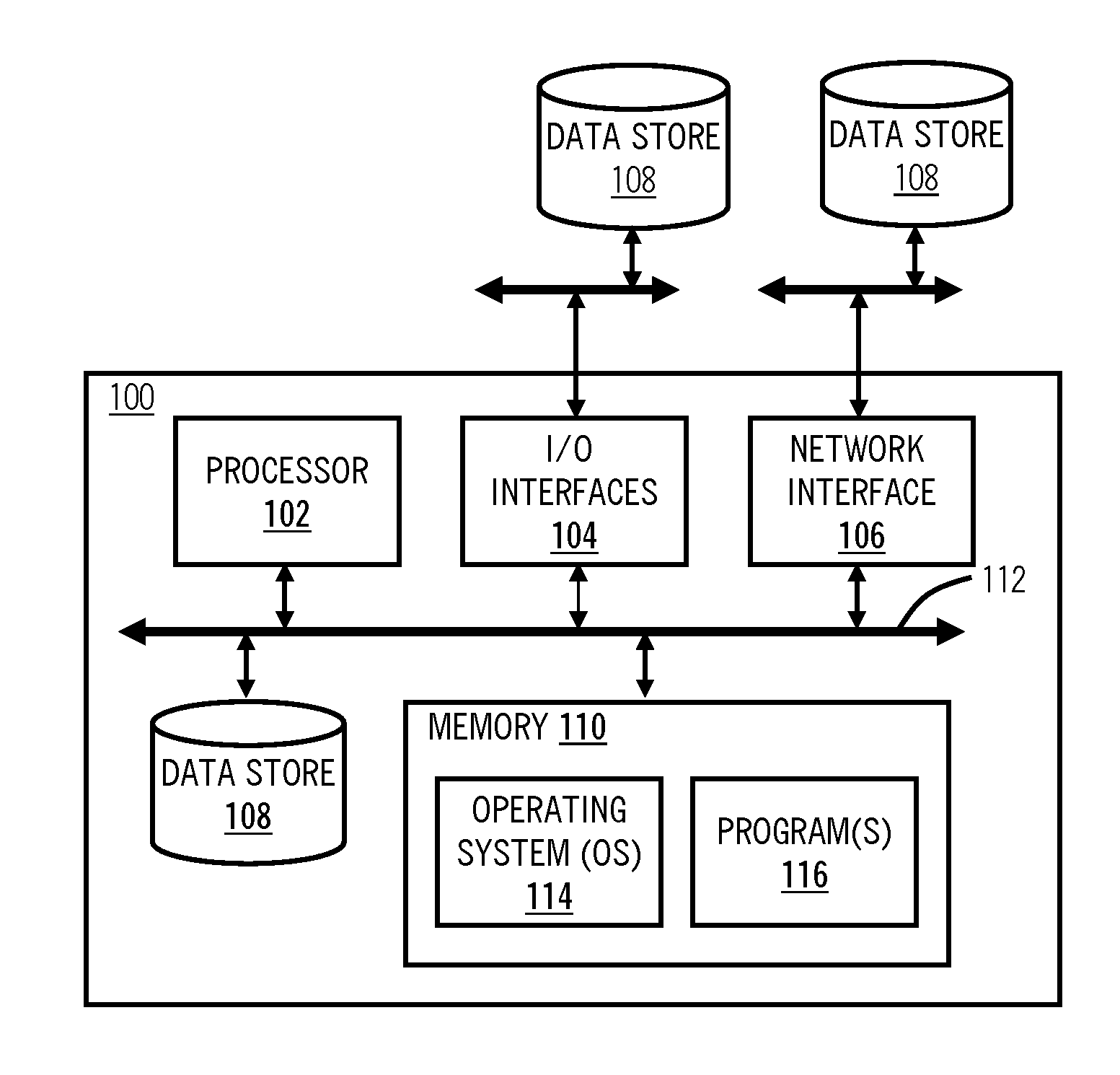
Encrypting operating system
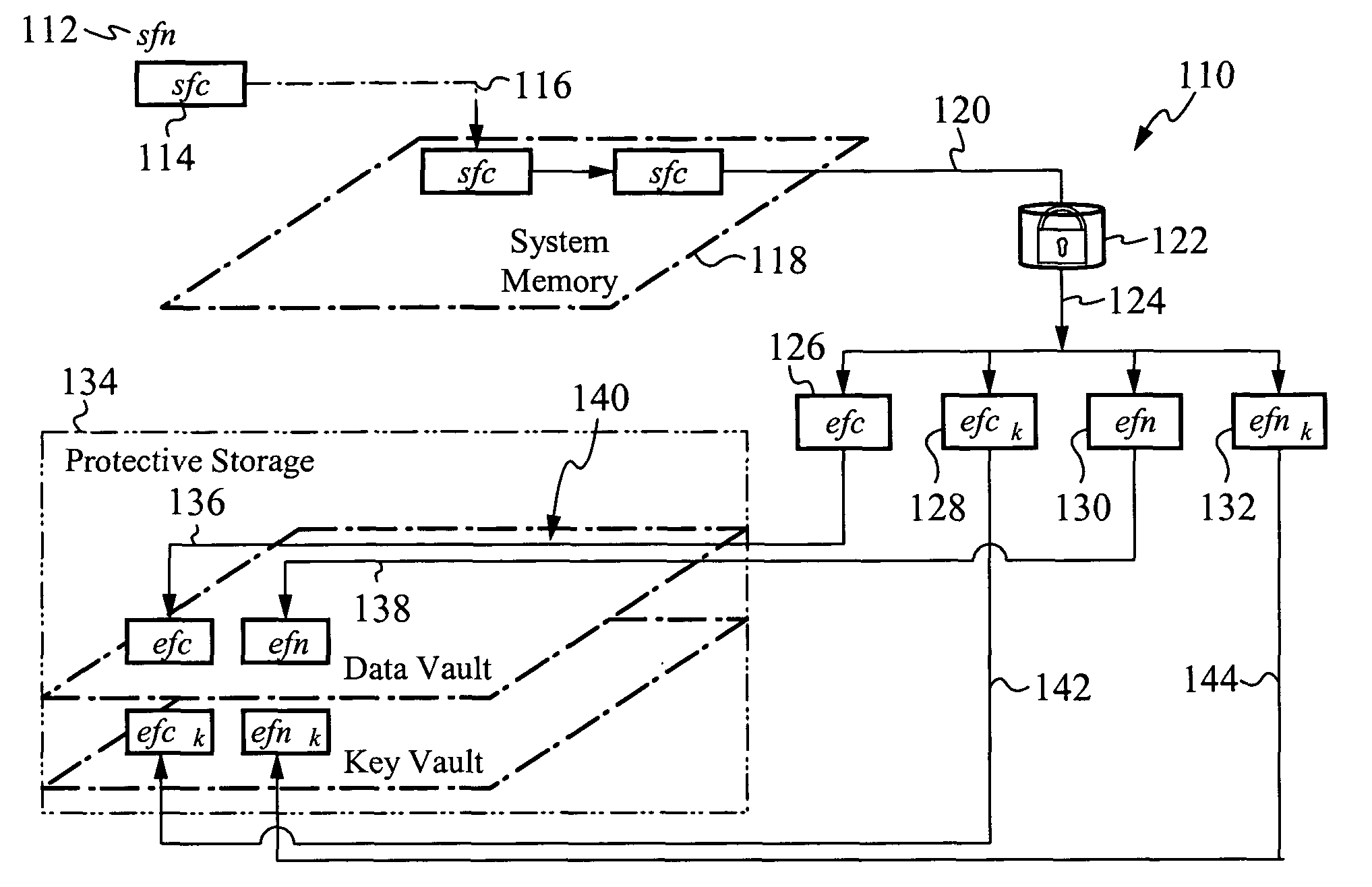
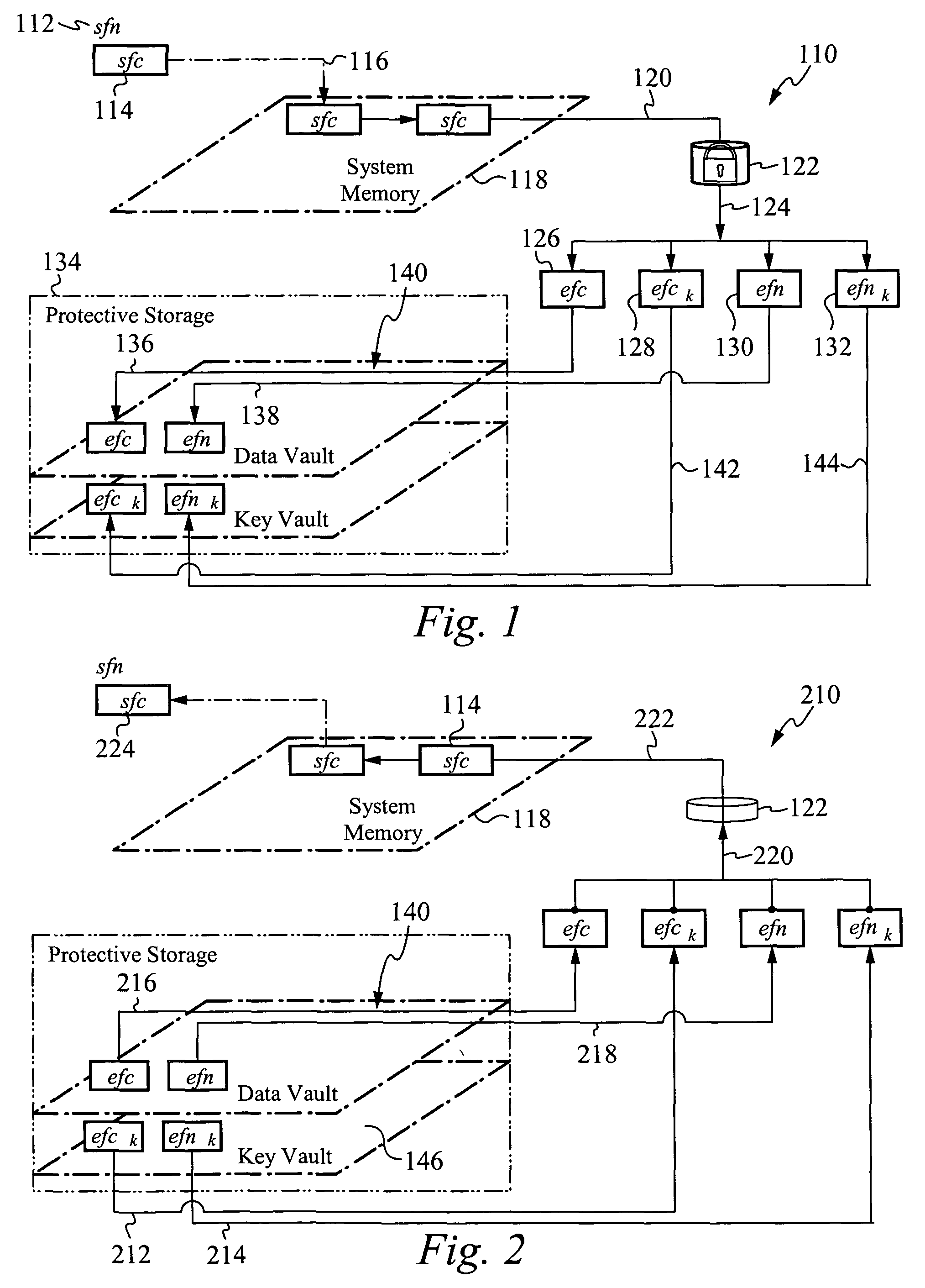
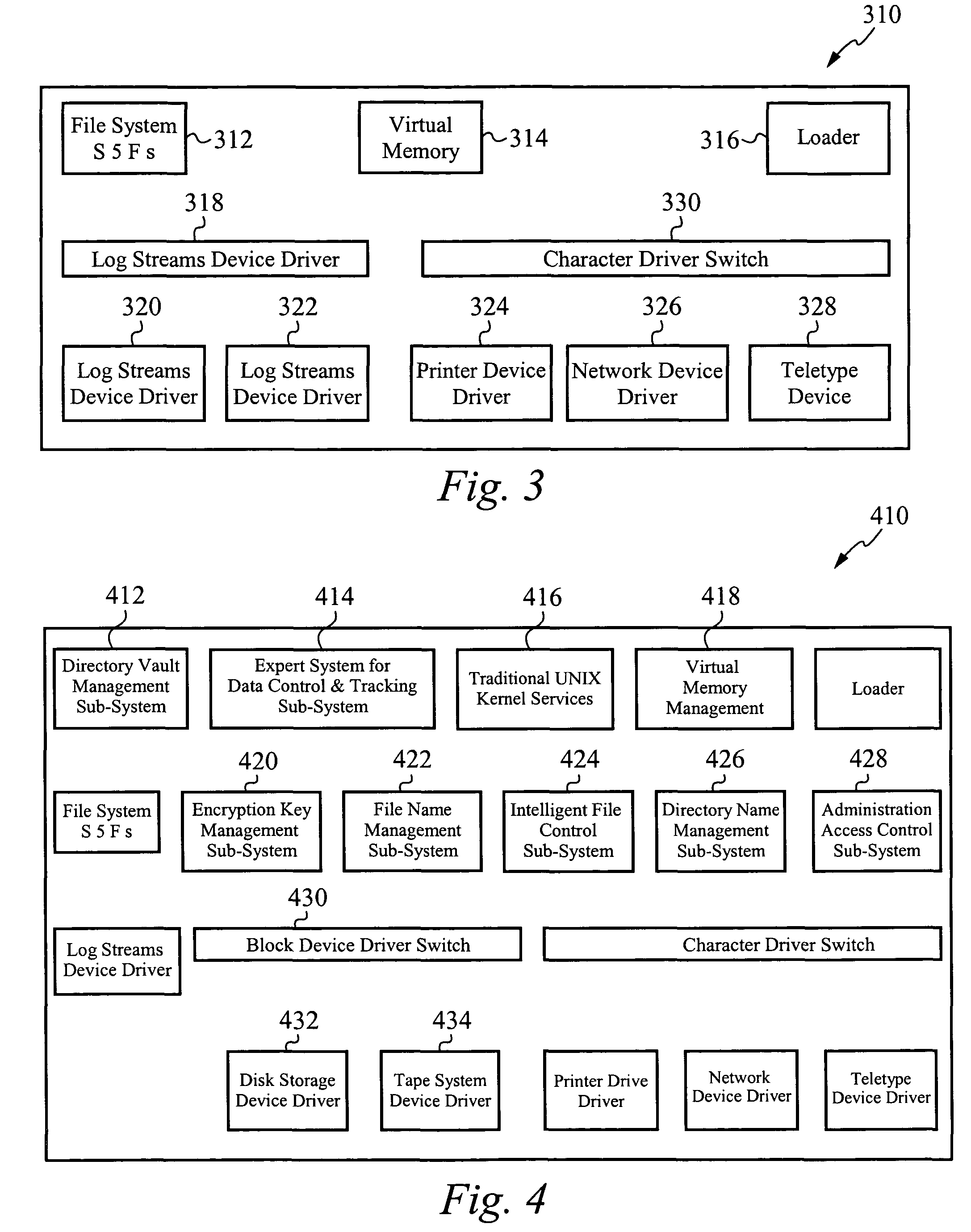
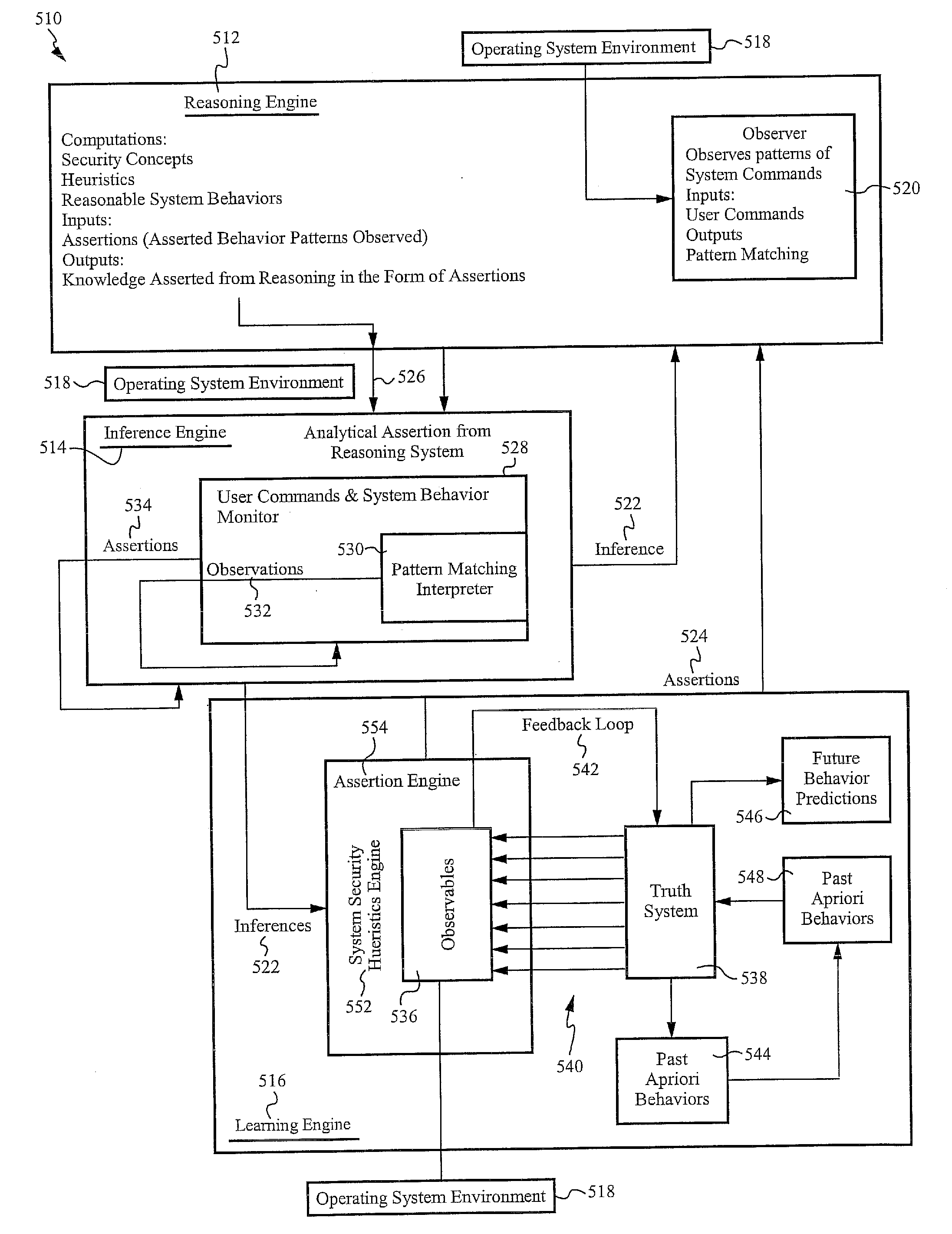
InactiveUS7810133B2Effective meanEncryption apparatus with shift registers/memoriesDigital data processing detailsOperational systemFile system
A method of and system for encrypting and decrypting data on a computer system is disclosed. In one embodiment, the system comprises an encrypting operating system (EOS), which is a modified UNIX operating system. The EOS is configured to use a symmetric encryption algorithm and an encryption key to encrypt data transferred from physical memory to secondary devices, such as disks, swap devices, network file systems, network buffers, pseudo file systems, or any other structures external to the physical memory and on which can data can be stored. The EOS further uses the symmetric encryption algorithm and the encryption key to decrypt data transferred from the secondary devices back to physical memory. In other embodiments, the EOS adds an extra layer of security by also encrypting the directory structure used to locate the encrypted data. In a further embodiment a user or process is authenticated and its credentials checked before a file can be accessed, using a key management facility that controls access to one or more keys for encrypting and decrypting data.
Owner:EXIT CUBE HONG KONG
Encrypting operating system
InactiveUS20100217970A1Effective meanEncryption apparatus with shift registers/memoriesUnauthorized memory use protectionComputer hardwareOperational system
A method of and system for encrypting and decrypting data on a computer system is disclosed. In one embodiment, the system comprises an encrypting operating system (EOS), which is a modified UNIX operating system. The EOS is configured to use a symmetric encryption algorithm and an encryption key to encrypt data transferred from physical memory to secondary devices, such as disks, swap devices, network file systems, network buffers, pseudo file systems, or any other structures external to the physical memory and on which can data can be stored. The EOS further uses the symmetric encryption algorithm and the encryption key to decrypt data transferred from the secondary devices back to physical memory. In other embodiments, the EOS adds an extra layer of security by also encrypting the directory structure used to locate the encrypted data. In a further embodiment a user or process is authenticated and its credentials checked before a file can be accessed, using a key management facility that controls access to one or more keys for encrypting and decrypting data.
Owner:EXIT CUBE HONG KONG
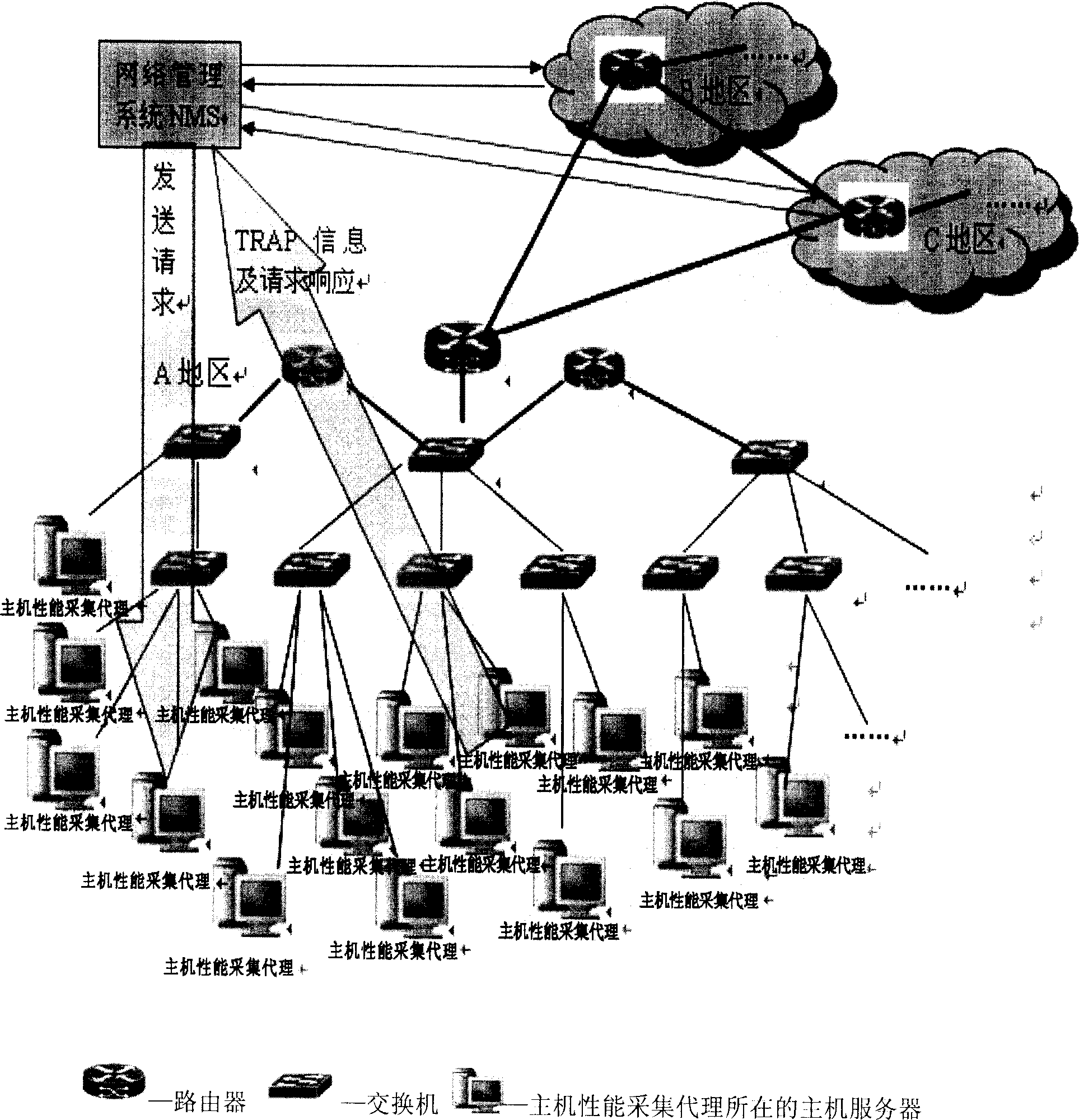
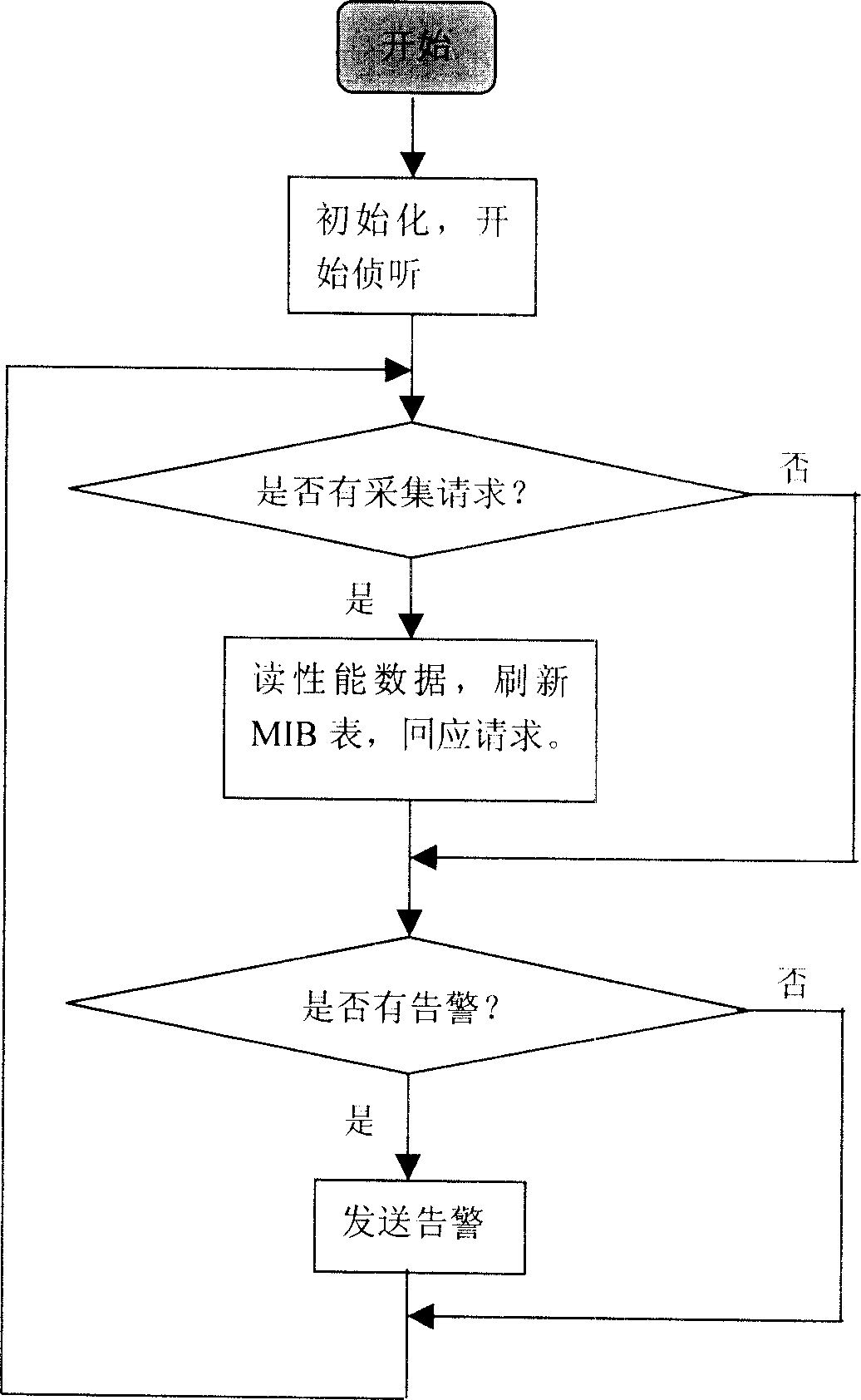
Host performance collection proxy in large-scale network
InactiveCN1756257ALive UpdateEffective monitoringData switching networksReal-time dataOperational system
The invention discloses a performance collection agent for large internet host computer. Wherein, obtaining basic performance information and statistic data from host computer information acquisition module; providing standard SNMP interface to response acquisition request and provide real time data; TRAP alarm-generating module and MIB table update condition set and real time detect data to active send alarm contained SNMP TRAP information if performance index over alarm threshold. This invention fits to host computer with Linux, Solaris and other like-Unix OS.
Owner:BEIHANG UNIV
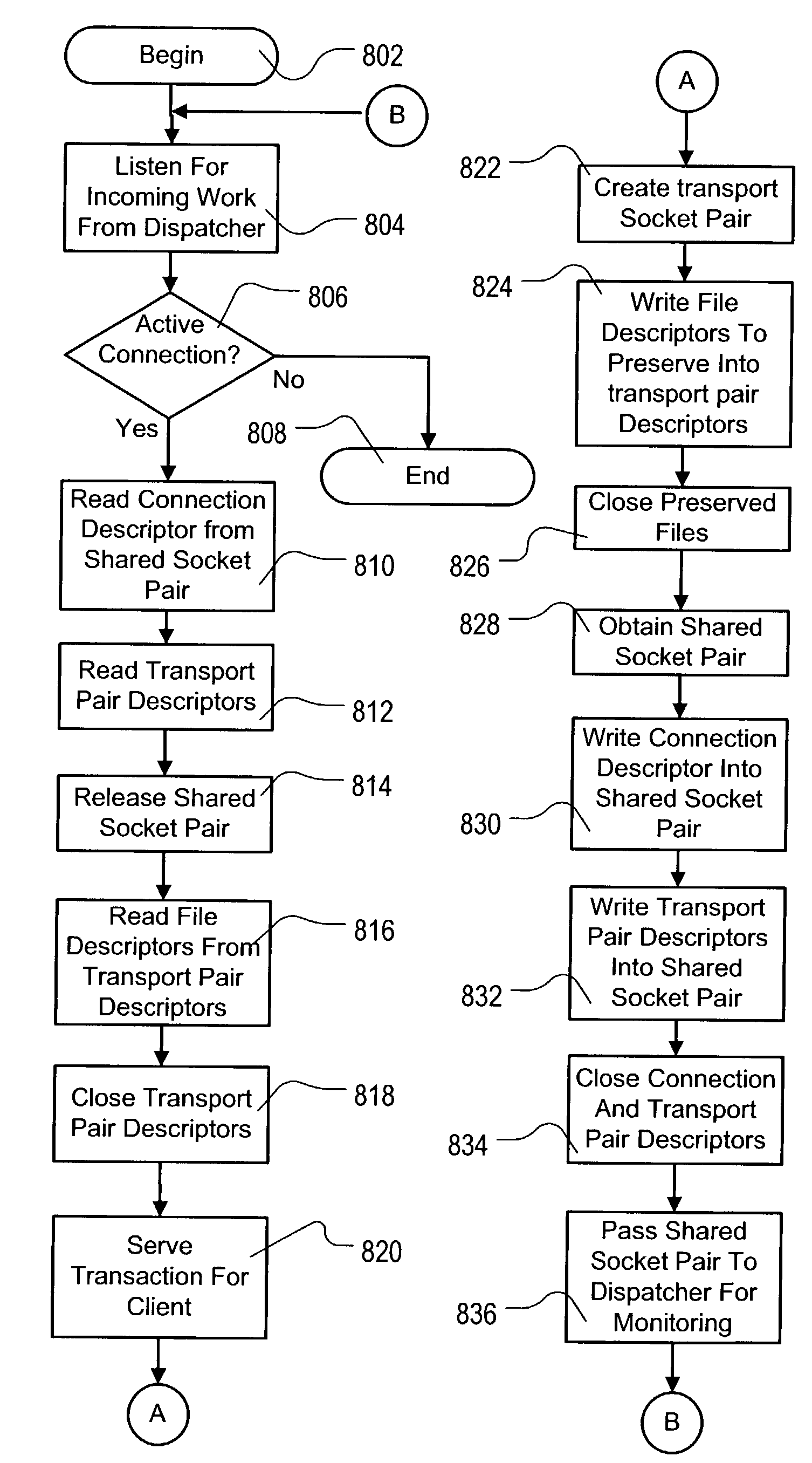
Method and system for optimizing file table usage
InactiveUS7373647B2Easy to useMultiprogramming arrangementsSpecific program execution arrangementsUnix domain socketOperational system
An operating system directed to using special properties of a common inter-process communications mechanism (IPC), namely UNIX domain socket-pairs or stream-pipes alternatively as a storage medium for file-descriptors of UNIX processes. When a file-descriptor is written into a socket-pair, and closed in the UNIX process, the file remains open, but occupies no space in the process' file-table. The file-descriptor may later be read out of the socket-pair to reestablish it in the file-table, and access it. This property is implemented in an IPC mechanism of UNIX operating system whereby a process such as a dispatcher may manage more connections and processes than its file-table size allow. This provides scalability improvements of the UNIX operating system.
Owner:IBM CORP
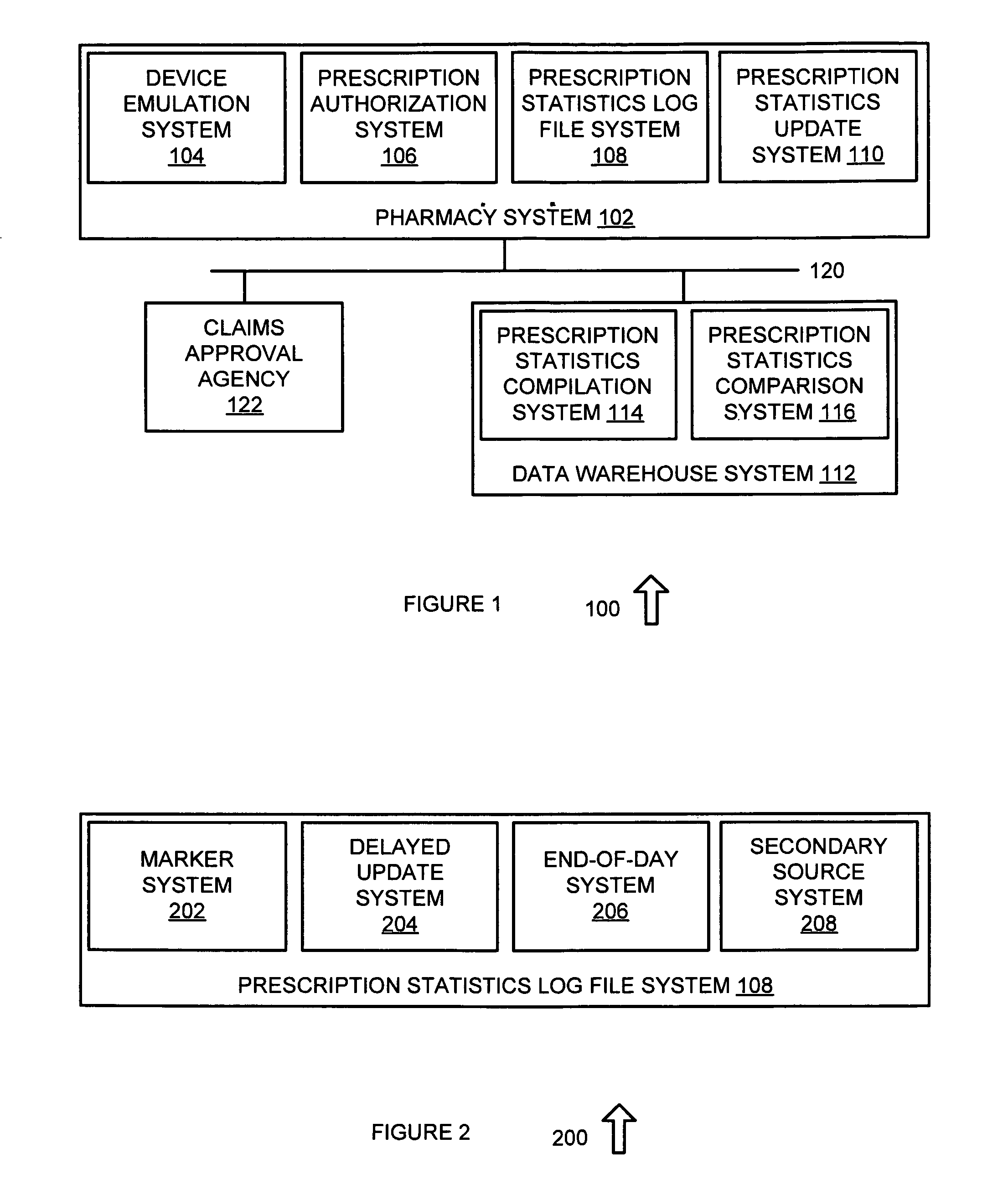
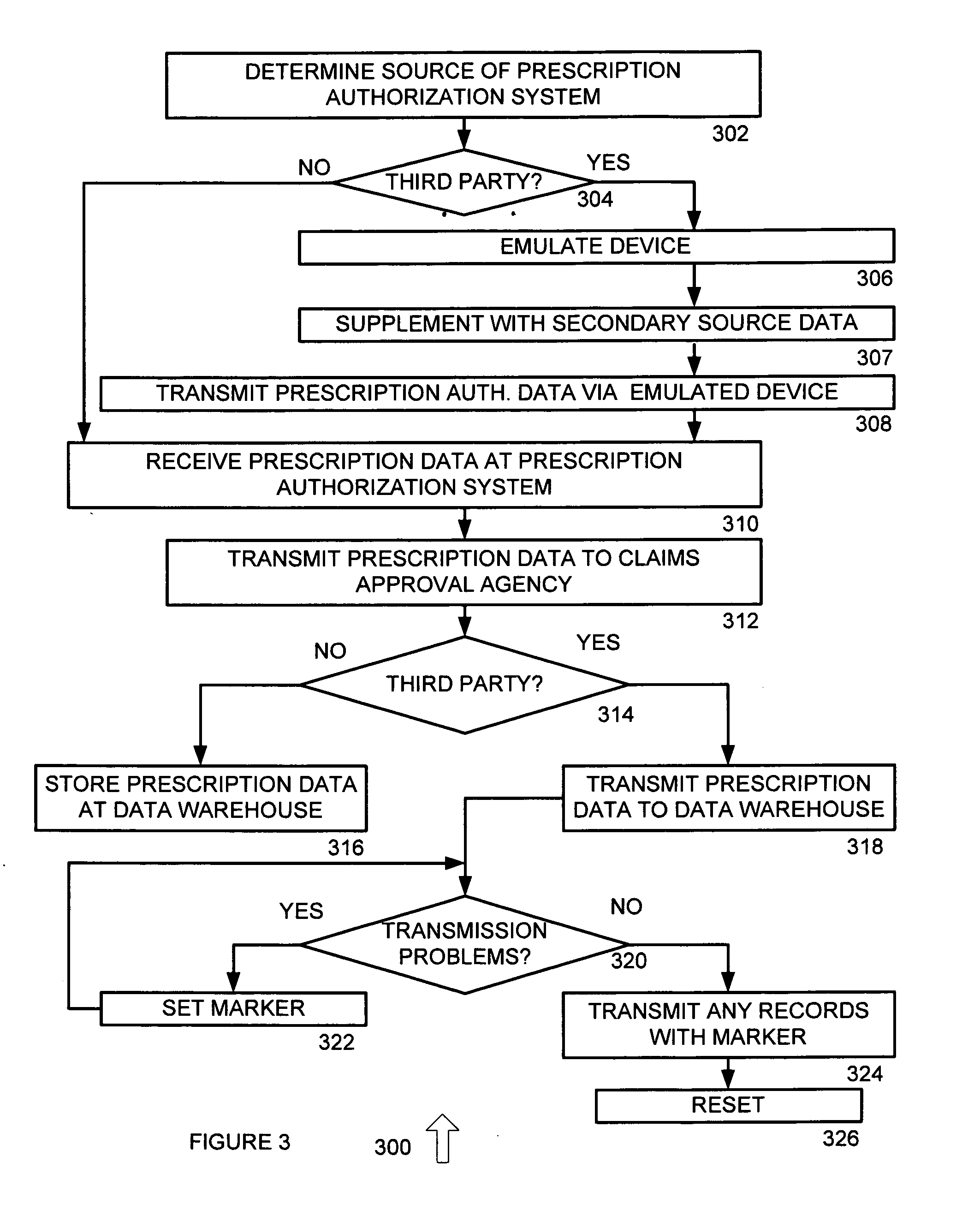
Pharmacy system data interface system and method
A method for receiving prescription data from a pharmacy is provided. The method includes emulating a device, such as using a pseudo TTY feature of a Unix operating system or a pseudo device of a Windows operating system. A prescription authorization system is then set to transmit data to the emulated device when the prescription data is provided to a claims approval agency by the prescription authorization system. The data can be supplemented with data from a secondary source, such as a system that acquires data in accordance with the Health Insurance Portability and Accountability Act or other suitable systems. The prescription data and any supplemental data is then received at the prescription authorization system, and is transmitted to the emulated device. The prescription data is also stored in a local log file, and is transmitted to a data warehouse over a network using the emulated device.
Owner:TDS OPERATING INC
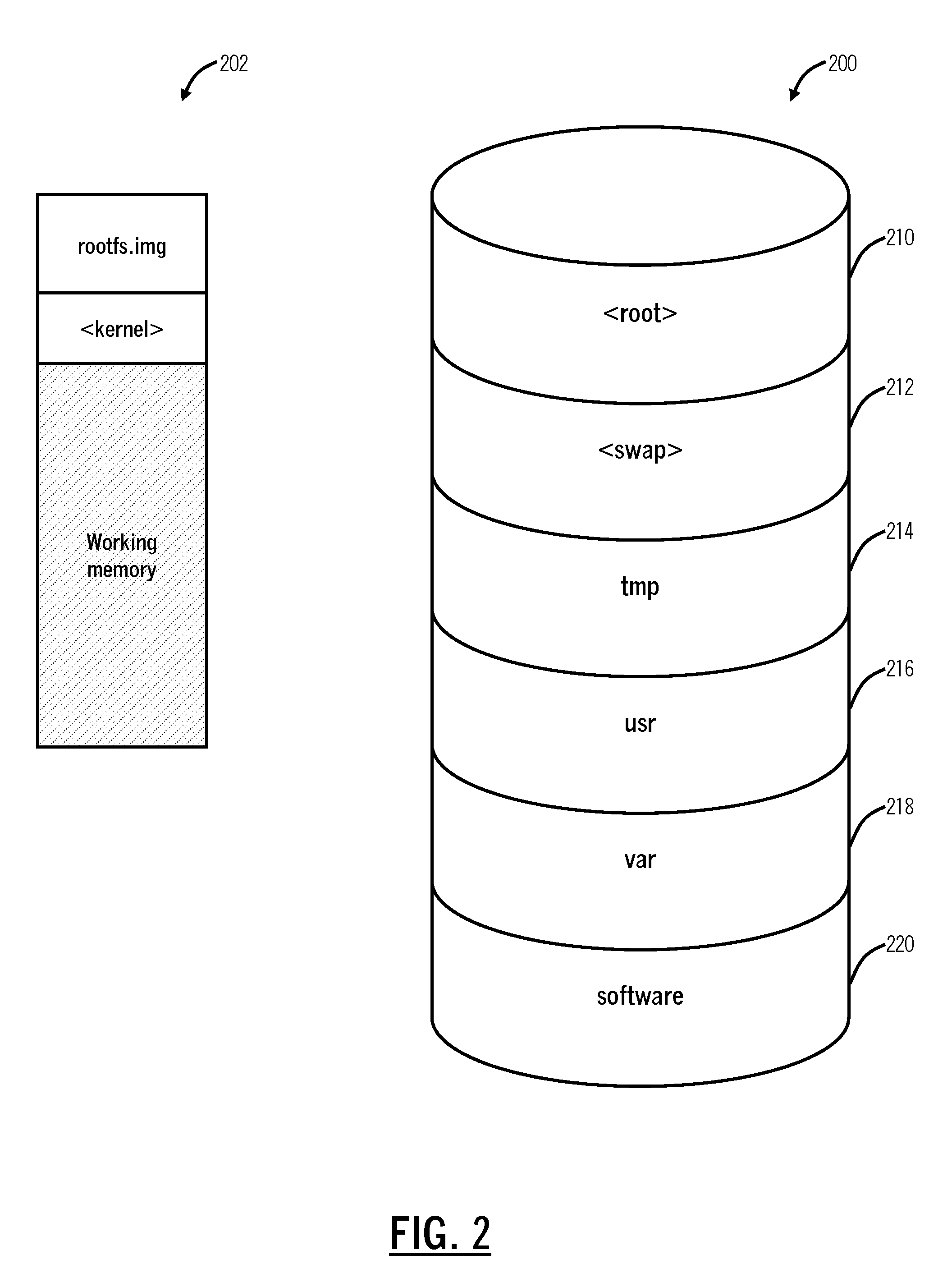
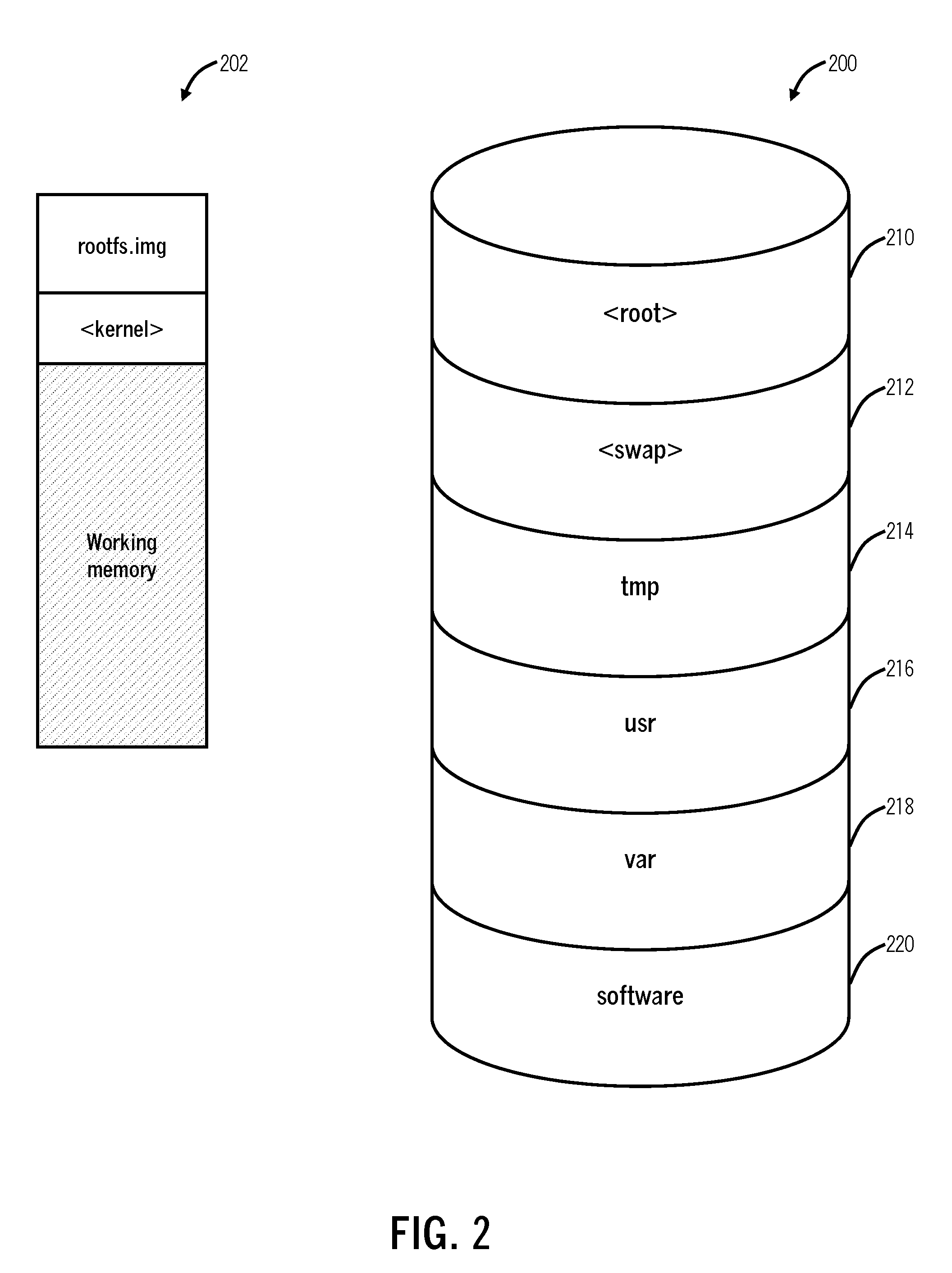
Systems and methods for live operating system upgrades of inline cloud servers
An upgrade method for a Unix or Unix-like operating system, a server, and a cloud-based system include operating a server with an old operating system with a partition structure for media, wherein the partition structure includes a root partition and a usr partition; copying media to the root partition and the usr partition associated with a new operating system while the old operating system is operating; rebooting the server with the new operating system set to load; and subsequent to the rebooting, making the root partition persistent using memory and the usr partition persistent using a NULL file system.
Owner:ZSCALER INC
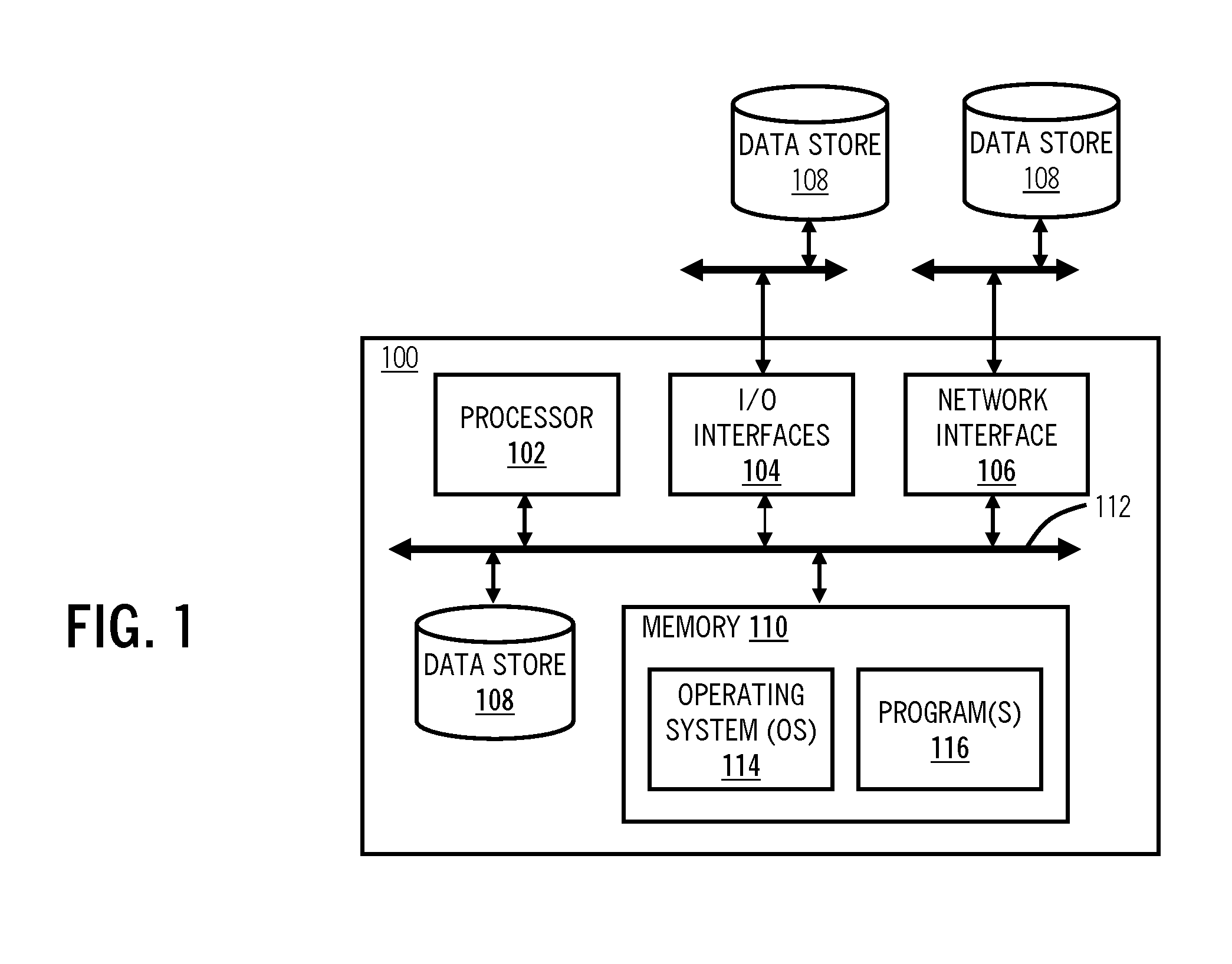
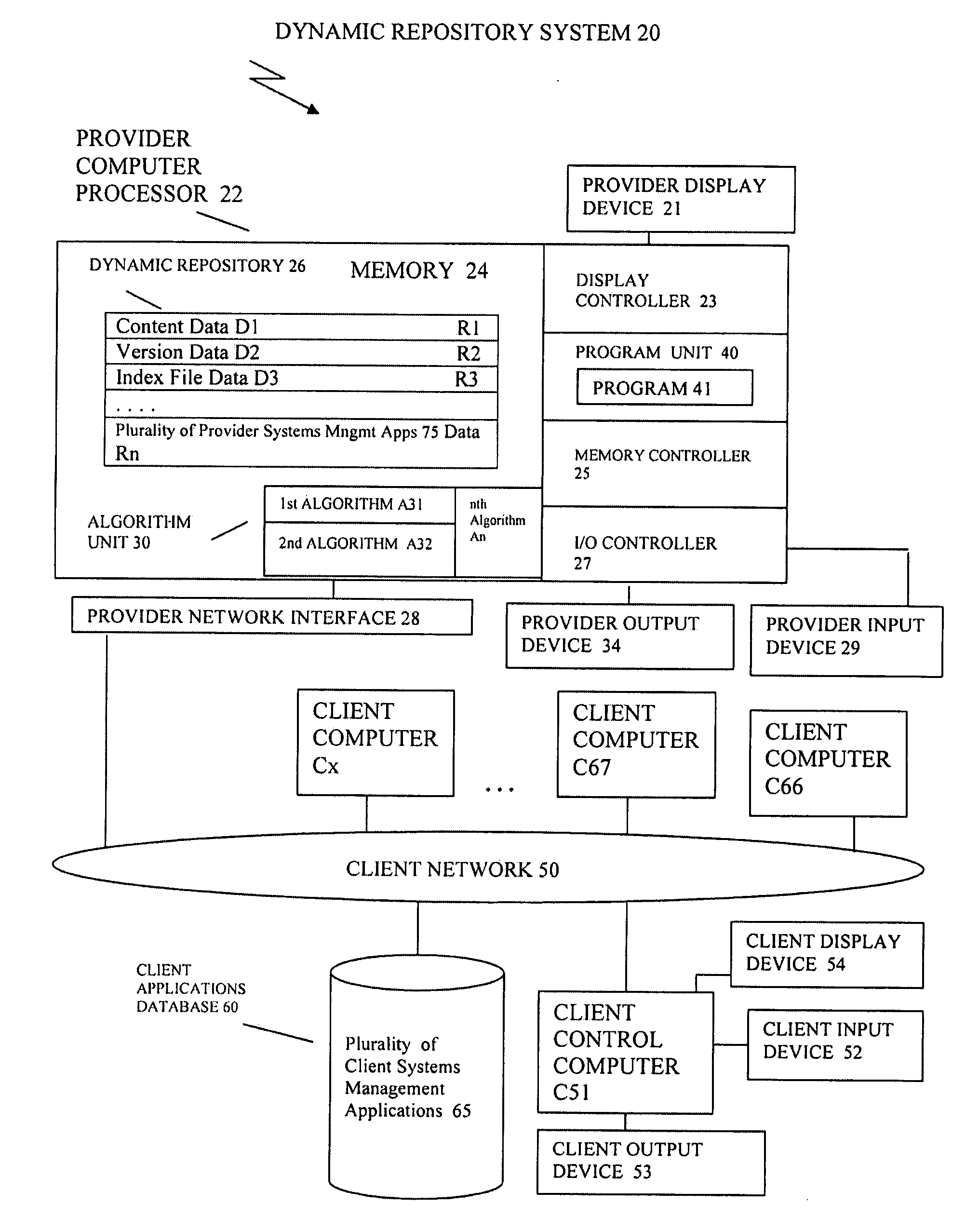
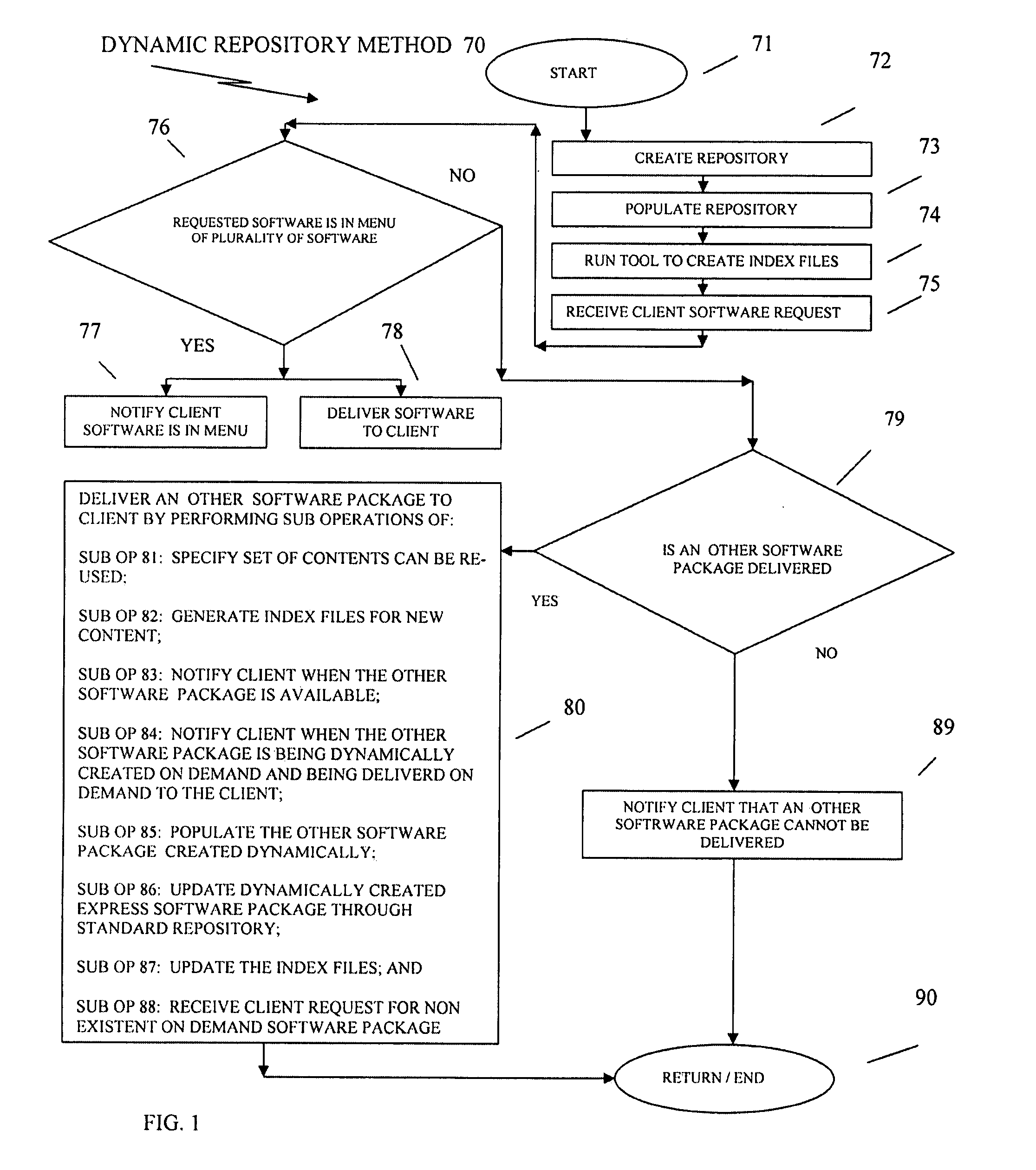
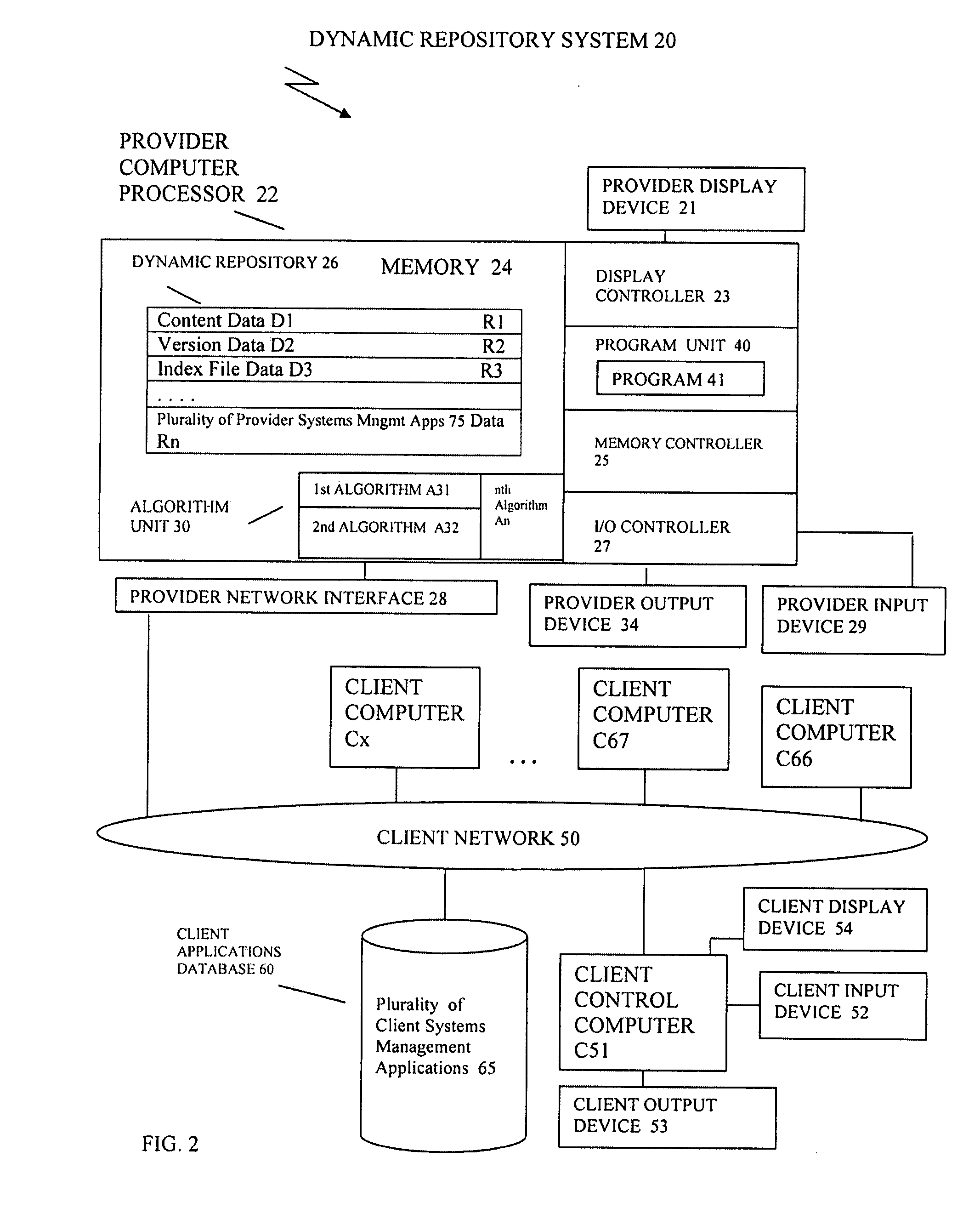
Methods, systems and computer products for a dynamic repository
InactiveUS20090070757A1Create efficientlyProgram code adaptionProgram loading/initiatingOperational systemGNU/Linux
A software development service offering of generating and installing software applications packages on computer systems running a set of operating systems including LINUX and UNIX operating systems, by creating a dynamic repository; populating a plurality software packages; running a tool that creates a set of index files, wherein the set of index files includes a menu of the plurality of software packages, wherein each software package in the plurality of software packages contains a set of contents; determining whether a software package is included in a menu of the plurality of software packages; and delivering to a client system the software package requested in a selection request, or delivering to the client system an other software package, when the software package is not included in the menu of the plurality of software packages.
Owner:IBM CORP
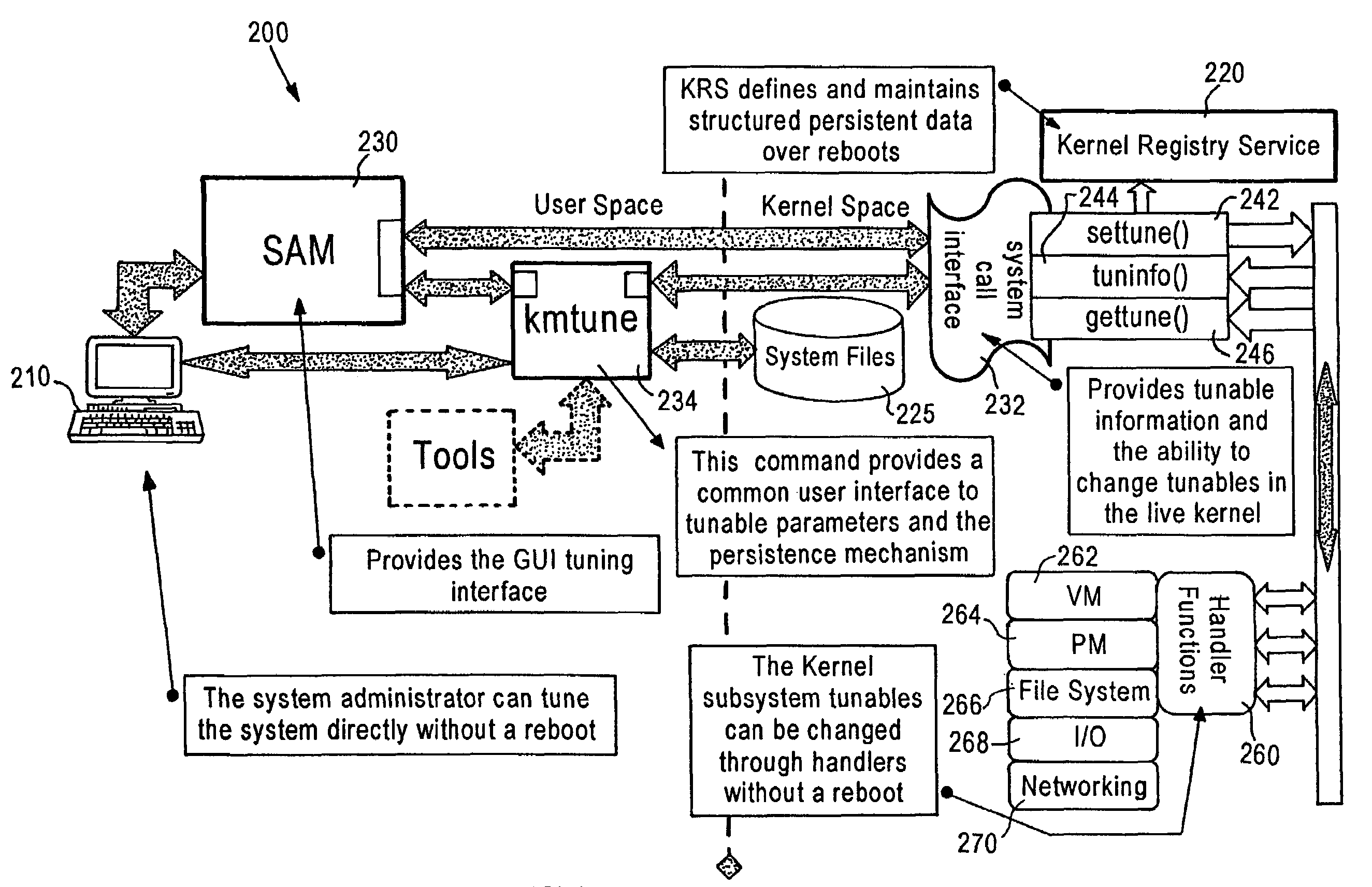
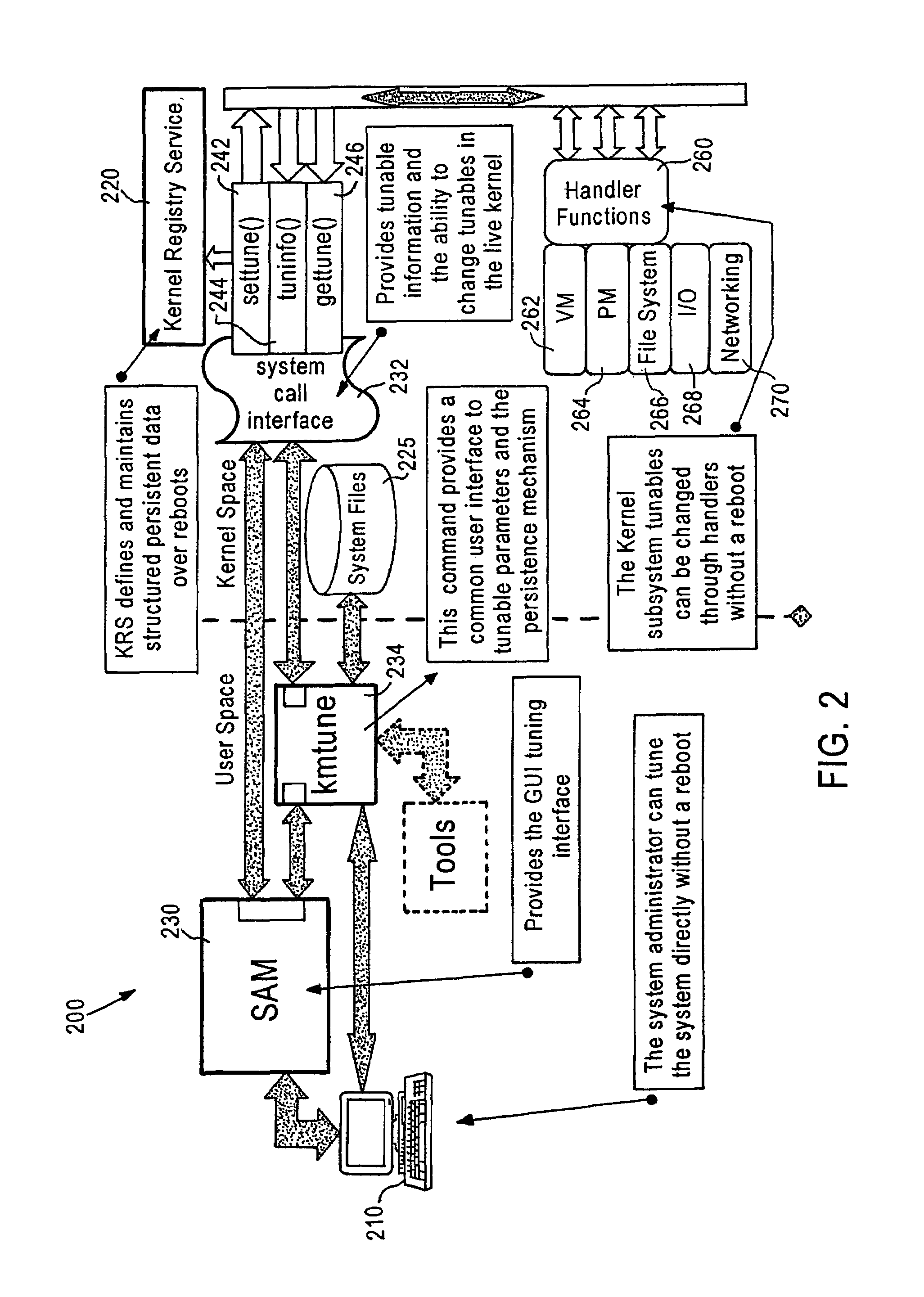
Dynamic kernel tunables
InactiveUS7076647B2Improve usabilityEasier to patch softwareData resettingProgram loading/initiatingGraphicsGraphical user interface
The present invention is directed to a method and apparatus in which a UNIX operating system can be configured or tuned without rebooting the system. Advantageously, the present invention is directed to a dynamic mechanism for updating kernel parameters which is persistent and lasts across reboots. The present invention provides a dynamic kernel tunable framework for changing tunables in a kernel without rebooting. A graphical user interface displays and is used to change graphical values and settings of dynamic tunables.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
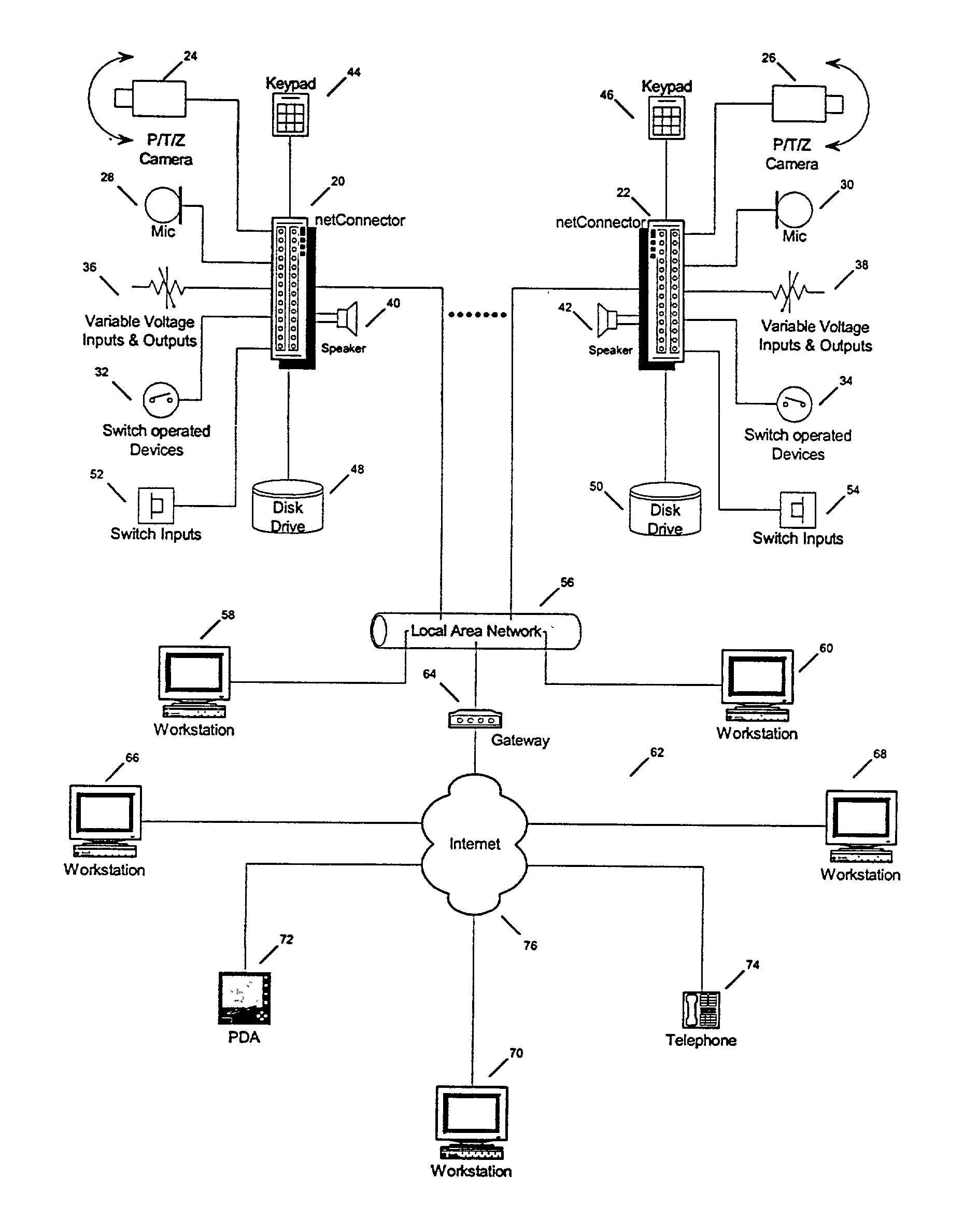
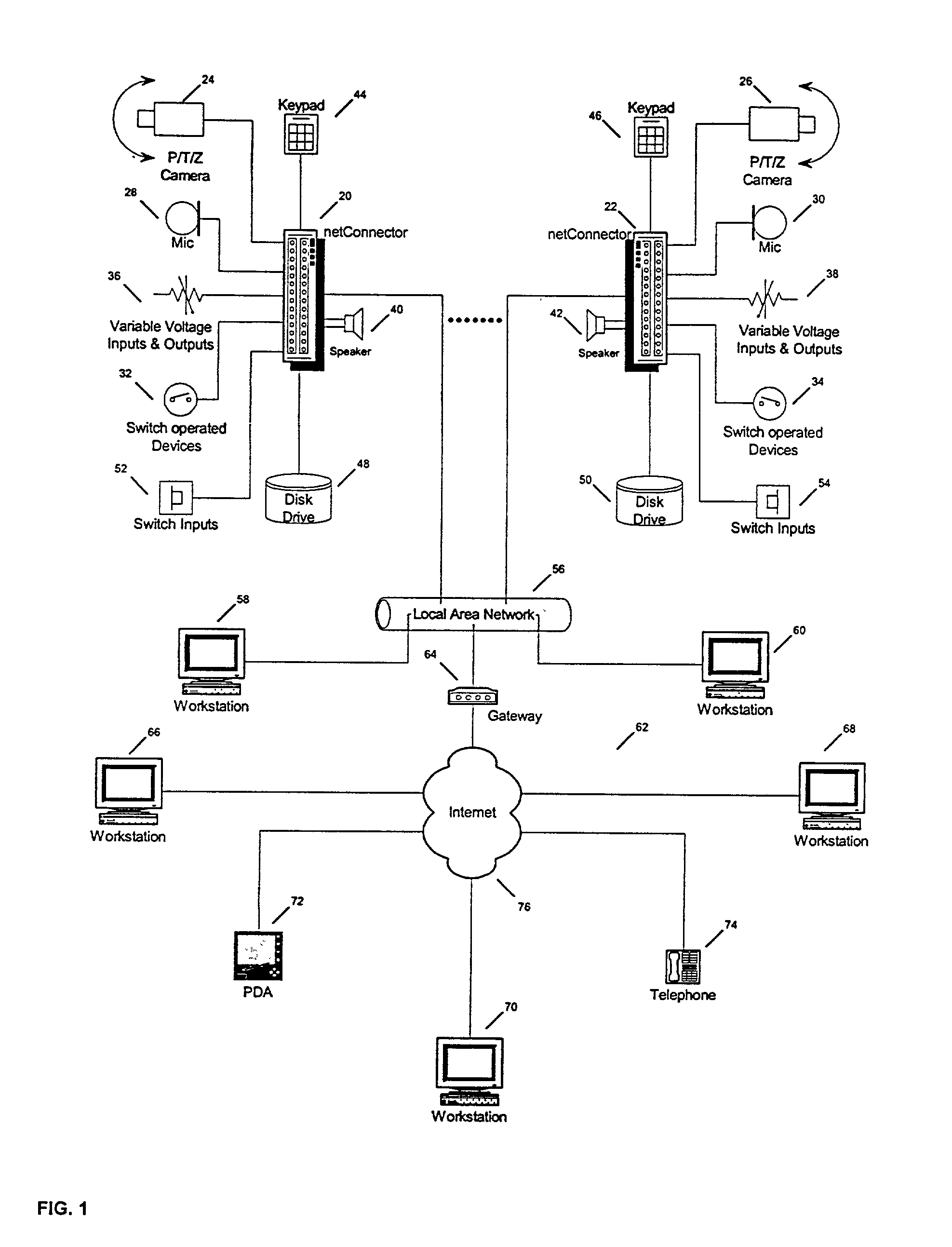
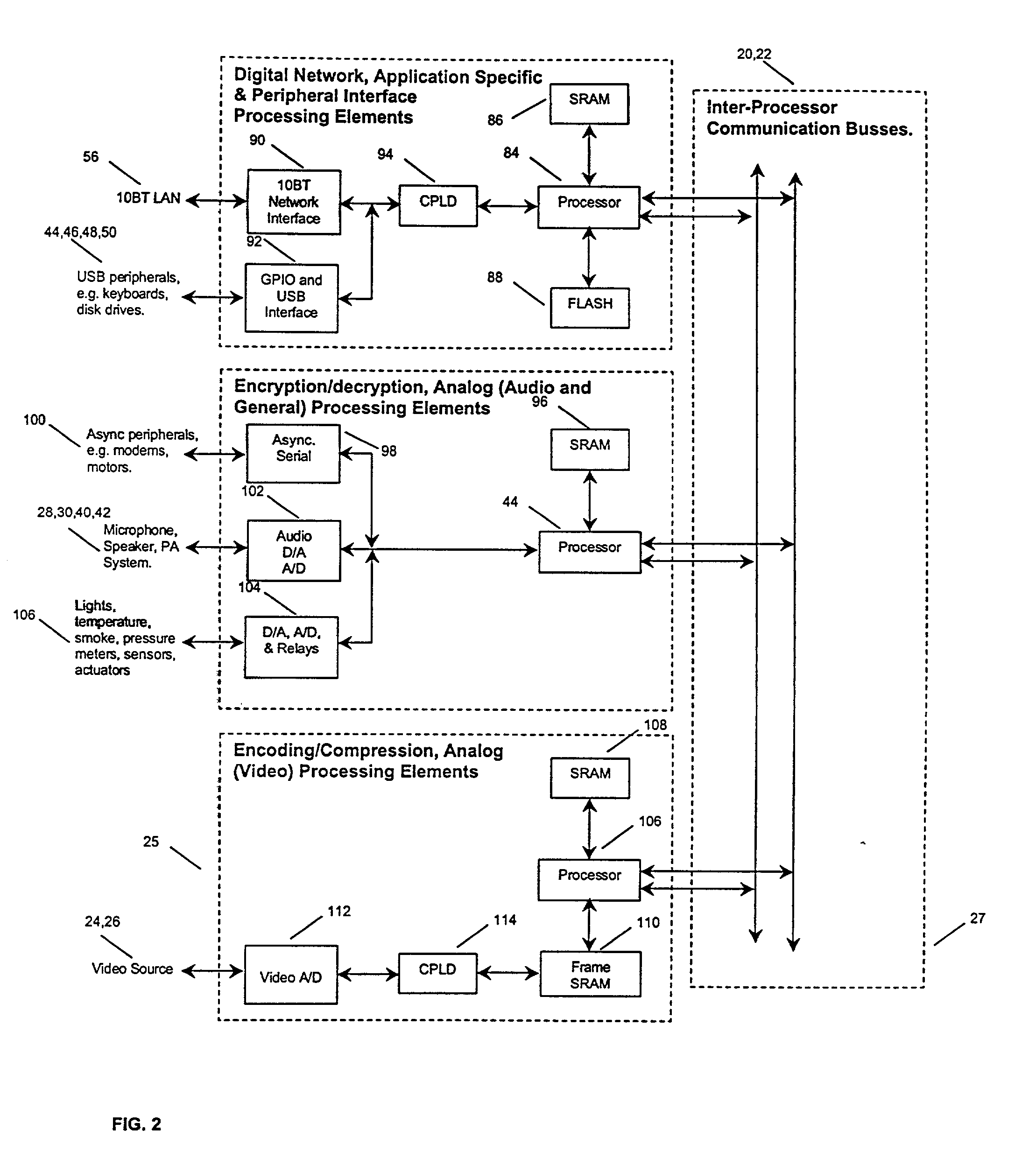
Analog gateway
ActiveUS7260090B2Eliminate needIncreased memory storageTime-division multiplexData switching by path configurationOperational systemNetwork connection
A secure analog gateway is configured with a pipelined architecture for interfacing various types of analog devices with a digital communication network and enabling asynchronous bi-directional communication between the analog device and the digital communication network using, for example, standard transmission control protocol over internet protocol (TCP / IP) in a network mode of operation. The analog gateway is also capable of operation in a stand-alone mode of operation in which data from an analog device is stored locally for later retrieval by way of a network. The functionality of the analog gateway is segregated among multiple processing elements which each perform a specific part of the gateway's function. In accordance with an important aspect of the invention, the analog gateway utilizes relatively inexpensive digital signal processors (DSP) to perform gateway functions, thus eliminating the need for relatively more expensive microprocessors and increased memory storage for storing Microsoft Windows or Unix operating systems and web-browsers as in known systems. In one embodiment of the invention, the analog gateway is configured to provide secure communications using standard TCP / IP over the world-wide web.
Owner:HON HAI PRECISION IND CO LTD +1
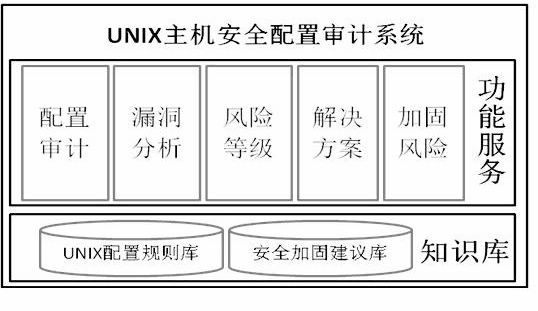
UNIX host safety configuration auditing method based on configurable knowledge base
ActiveCN102306258ASave the workload of manual item-by-item inspectionAvoid duplication of effortPlatform integrity maintainanceOperational systemSoftware engineering
Owner:STATE GRID ELECTRIC POWER RES INST +2
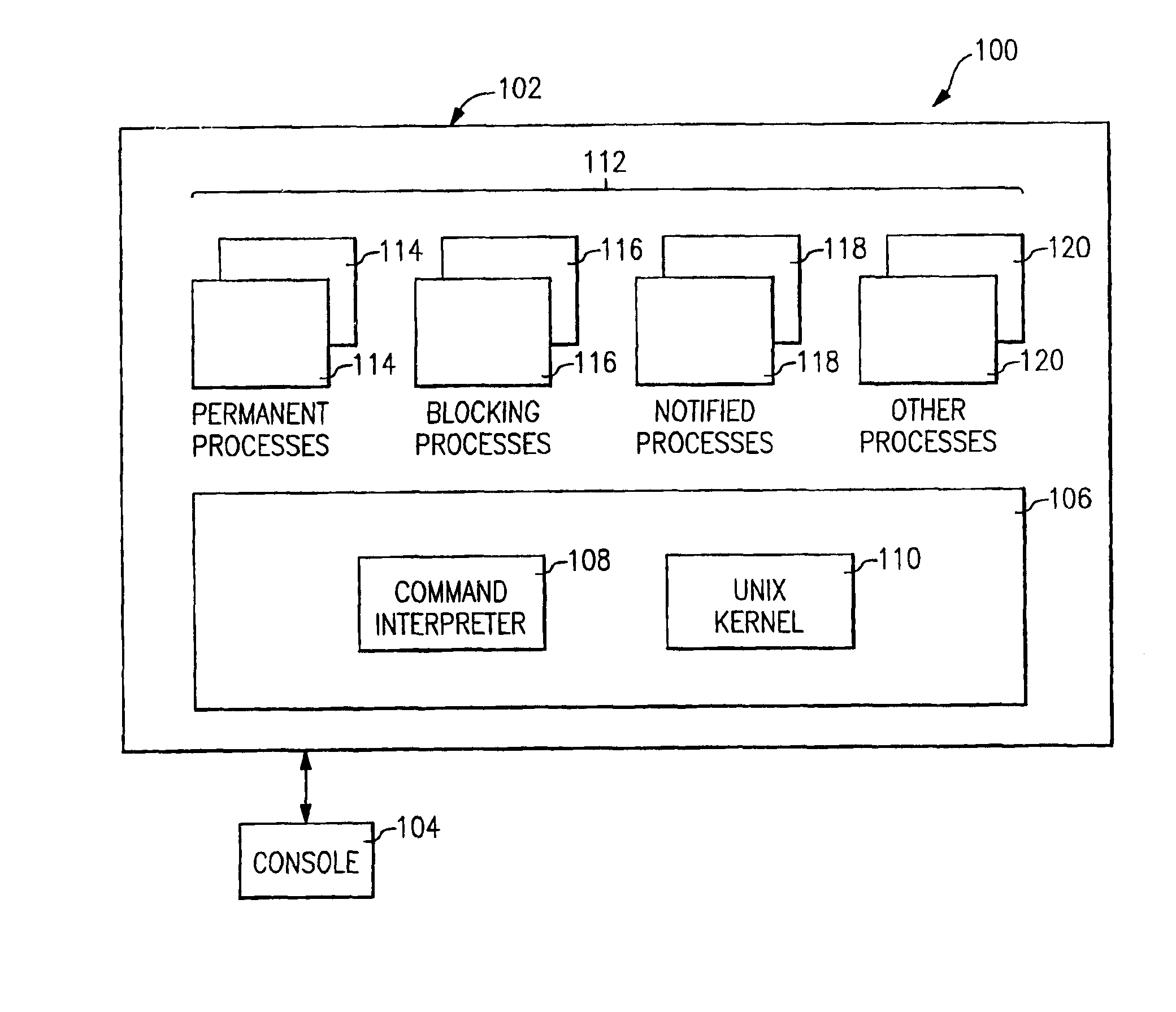
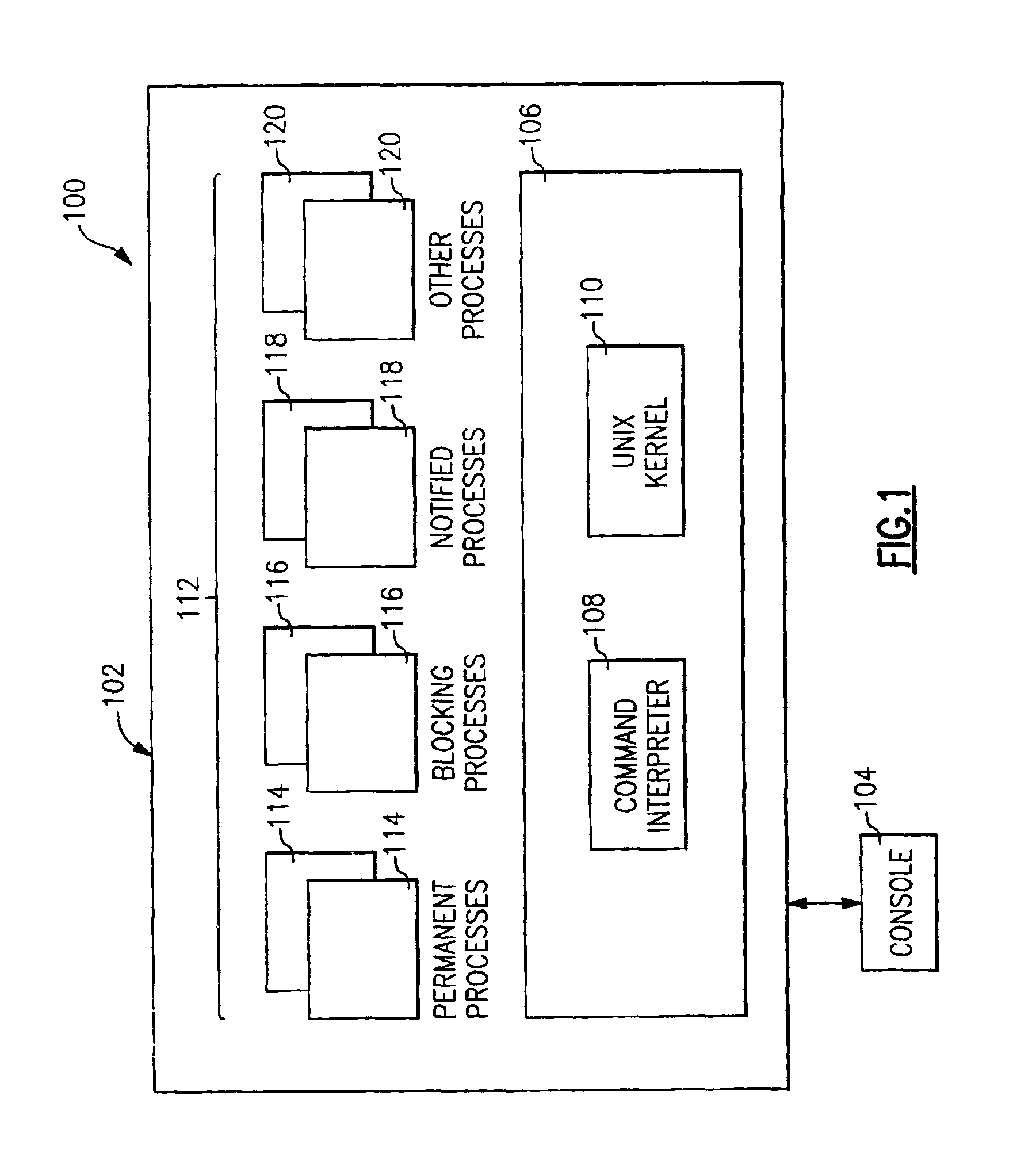
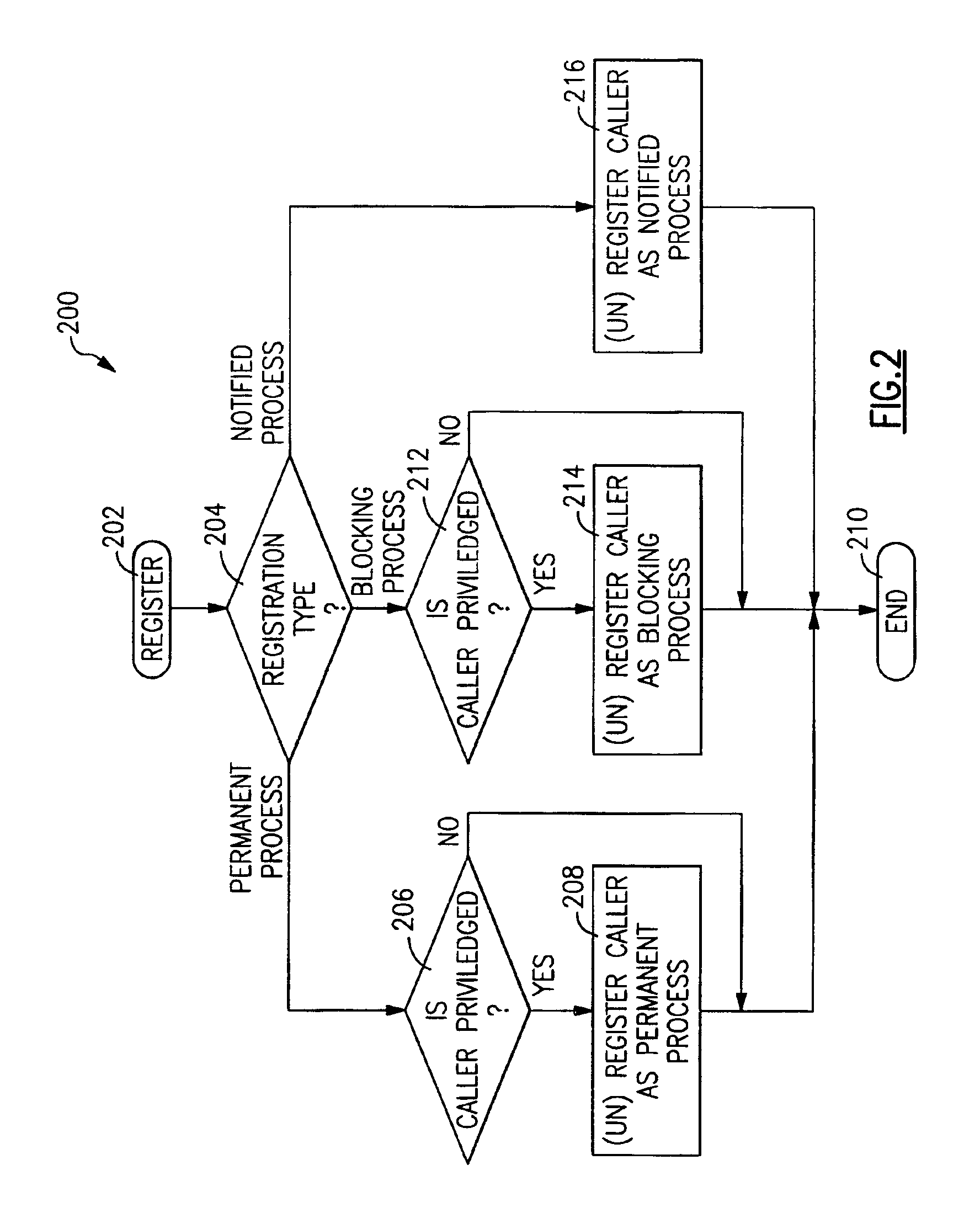
Method and apparatus for controlling the termination of processes in response to a shutdown command
InactiveUS6957363B2Program initiation/switchingDigital data processing detailsOperational systemHandling system
A method and apparatus for controlling the termination of one or more processes in an information handling system, such as UNIX processes running under the control of an UNIX operating system kernel, in response to a shutdown command. Processes may optionally register with a registration facility of the operating system kernel as permanent processes ineligible for process termination or as blocking processes entitled to advance notification of process termination. In response to receiving a shutdown command, a shutdown facility of the operating system kernel notifies each process that has registered as a blocking process of an impending shutdown. Upon the expiration of a predetermined time interval, the shutdown facility determines whether all of the processes that have registered as blocking processes have concurred in the shutdown, either by unregistering as blocking processes or by terminating. If all of the processes that have registered as blocking processes have concurred in the shutdown, the shutdown facility terminates processes that have not registered as permanent processes while allowing processes that have registered as permanent processes to continue to run. Otherwise, the shutdown facility aborts the shutdown without terminating any of the processes and generates a message identifying processes that have not concurred in the shutdown.
Owner:IBM CORP
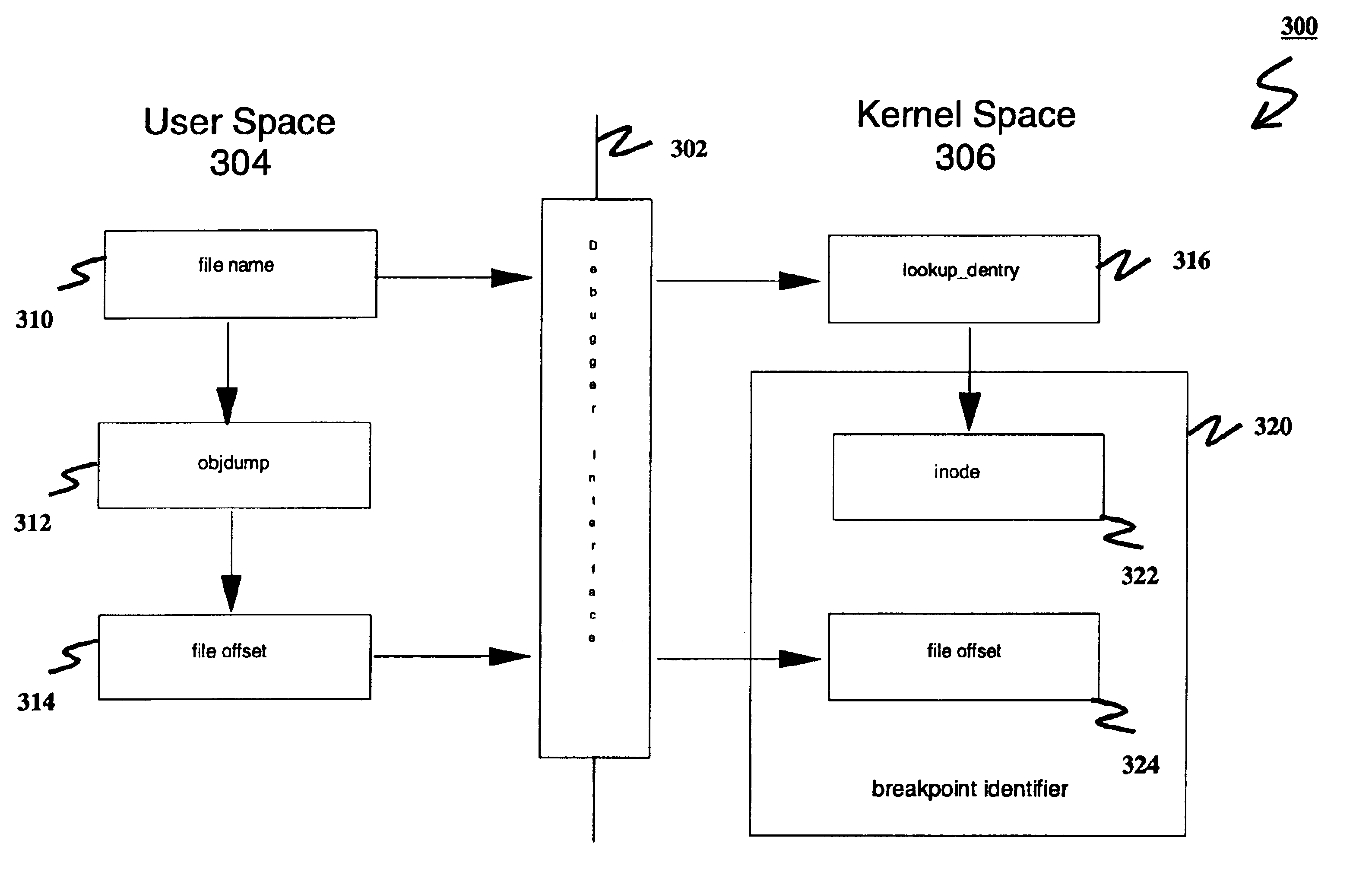
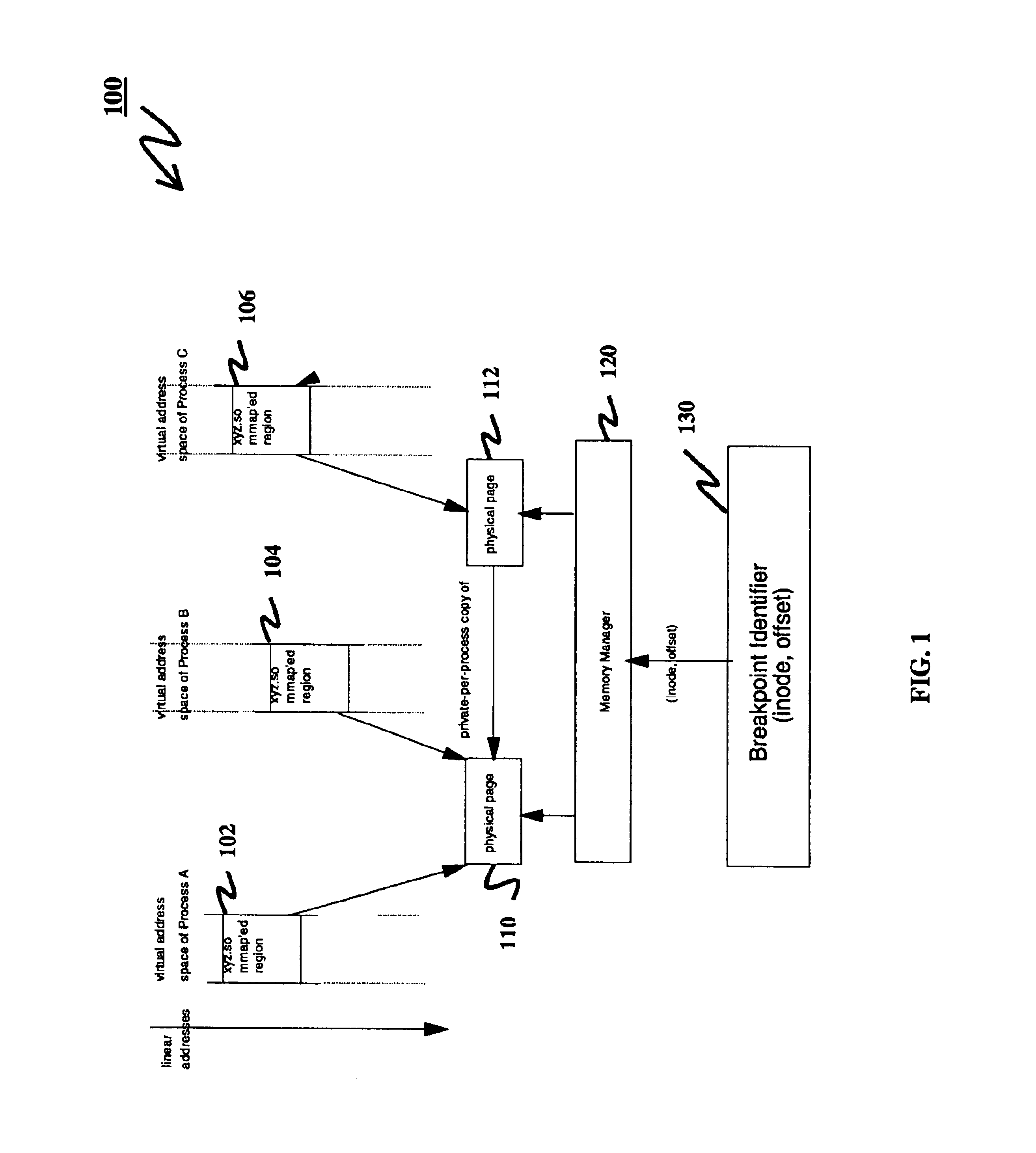
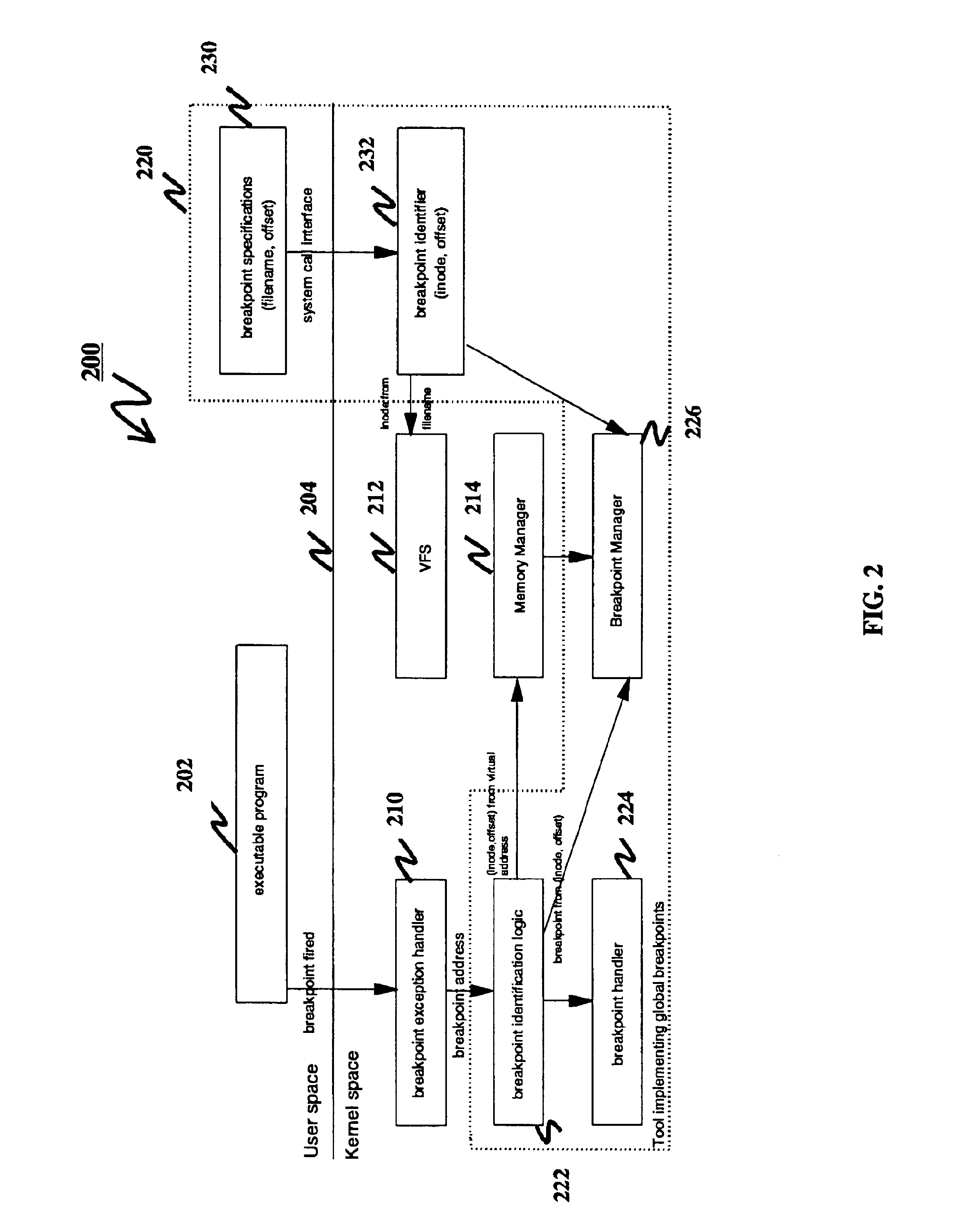
Method for global breakout identification
InactiveUS6842893B1Error detection/correctionSpecific program execution arrangementsOperational systemInode
A method, a computer-implemented apparatus, and a computer program product for identifying a global breakpoint for debugging computer software are disclosed. The method includes the step of representing the global breakpoint in software code using an identifier of an executable file and an offset in the executable file. Preferably, the file identifier is an inode of a Unix or Unix-like operating system.
Owner:IBM CORP
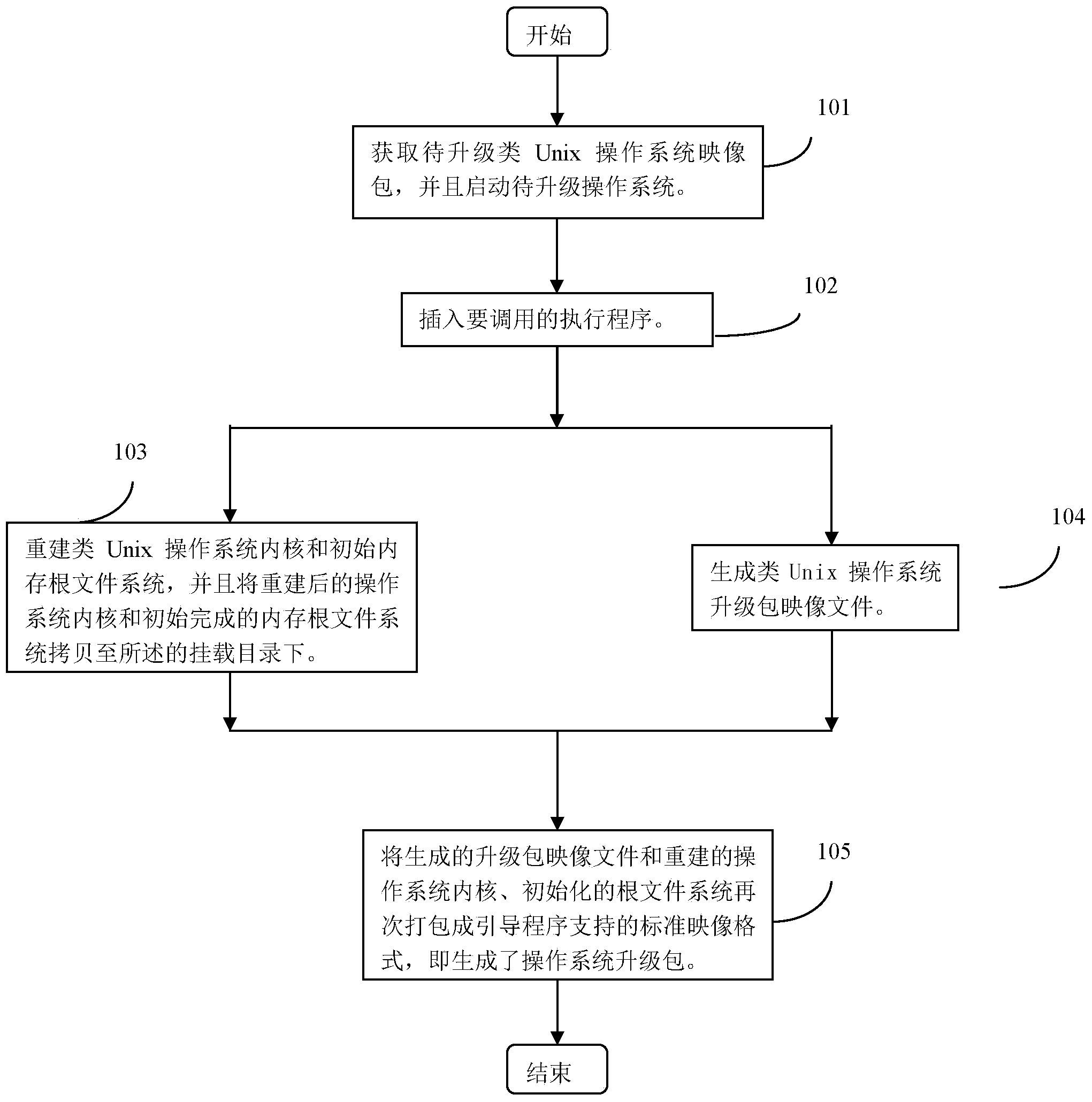
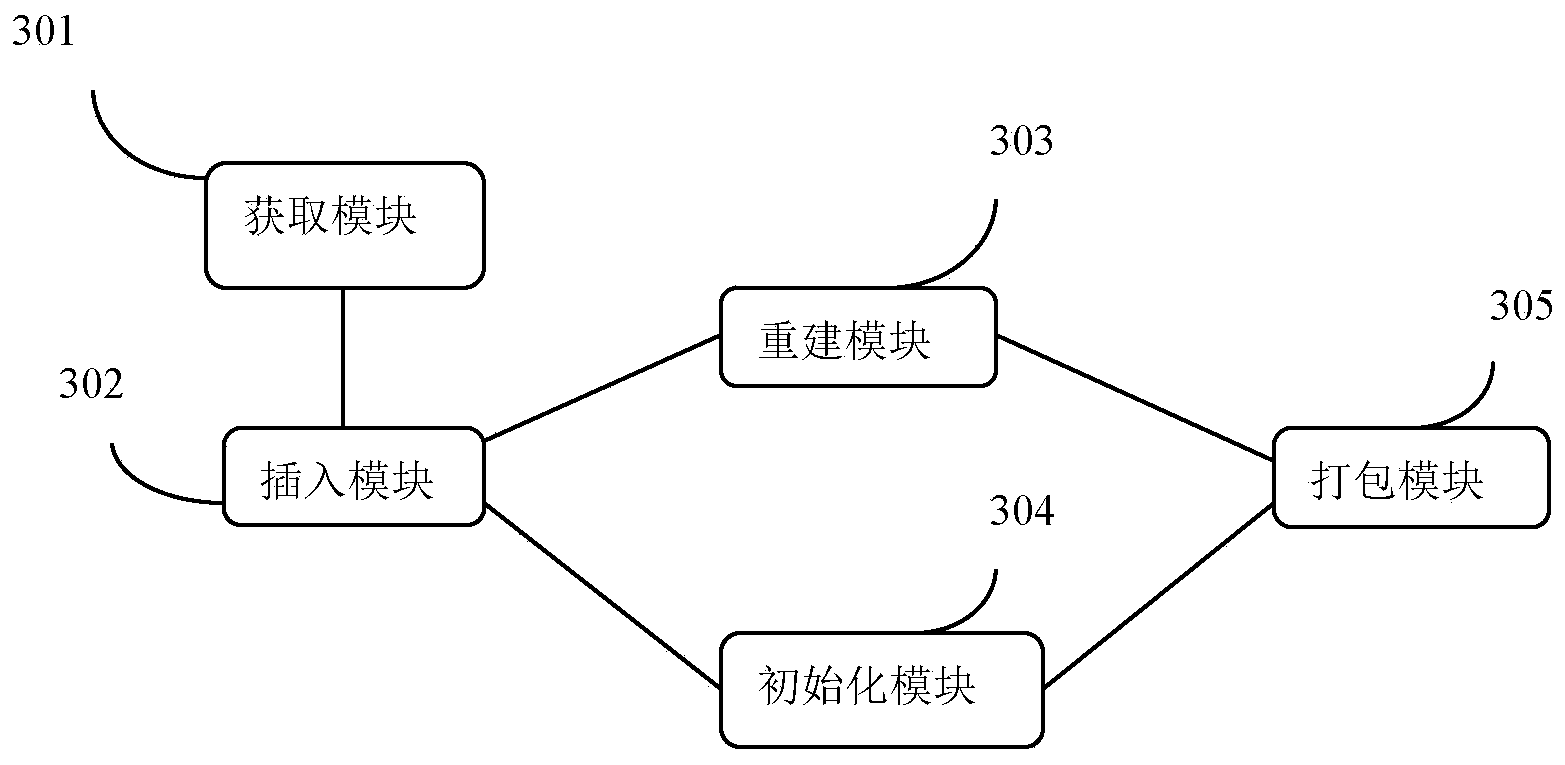
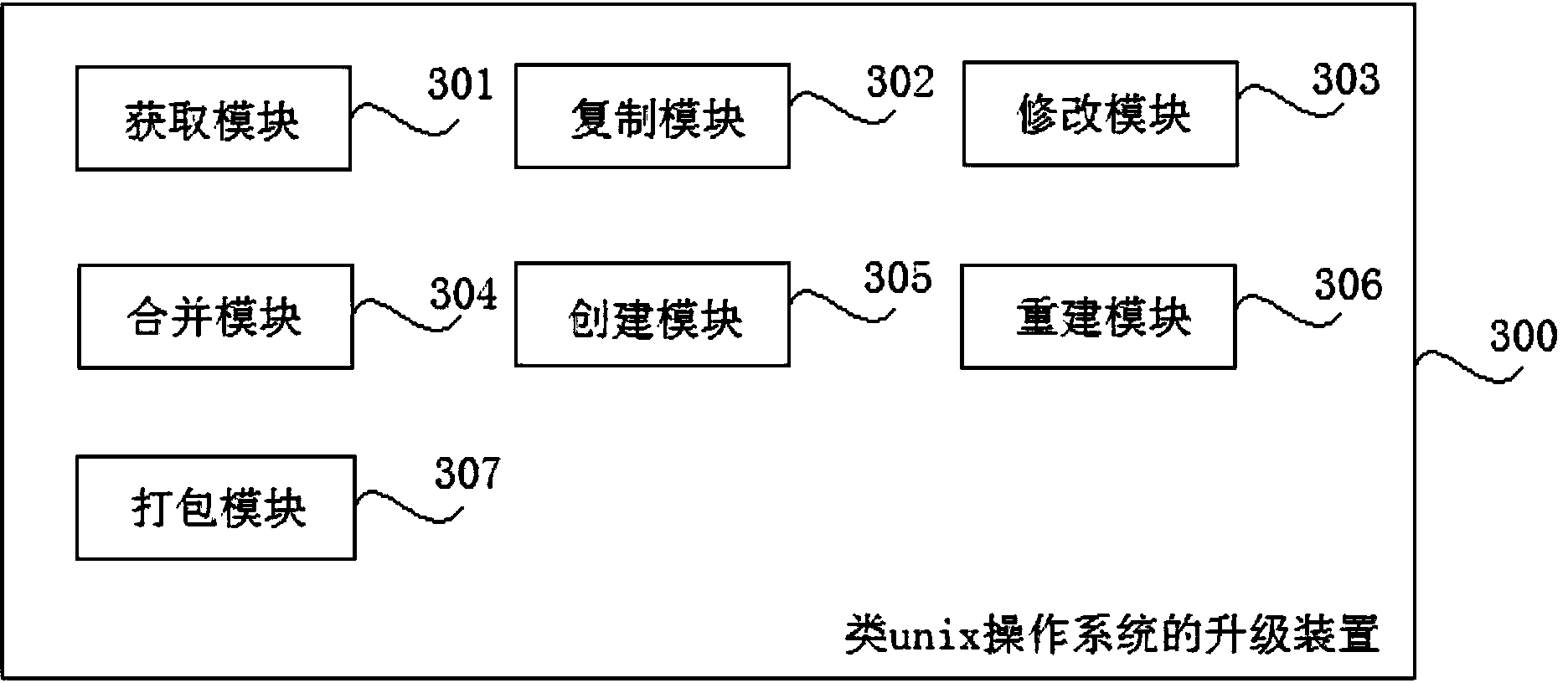
Method and device for manufacturing Unix-like operating system upgrade patch
ActiveCN103777953AImprove upgrade experienceSpecific program execution arrangementsOperational systemFile system
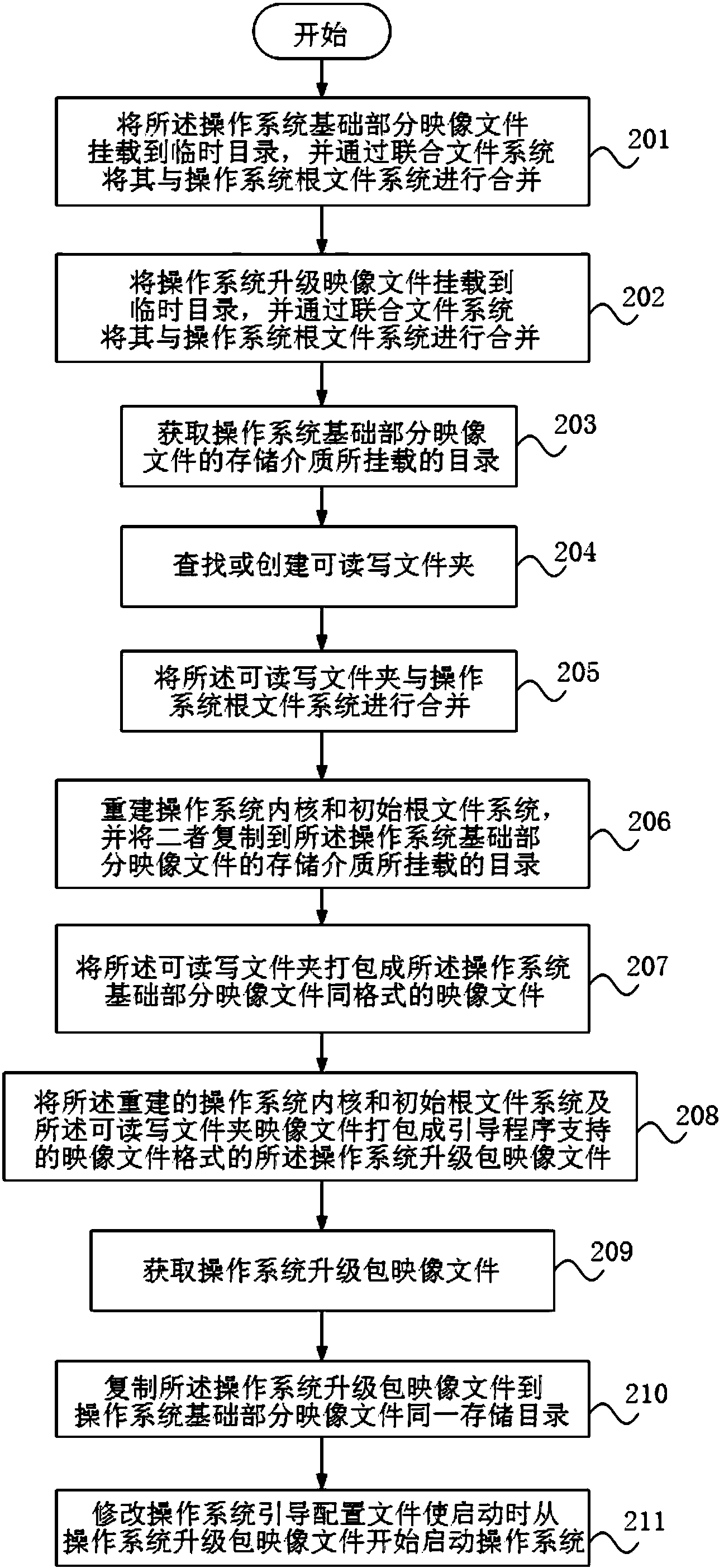
The invention discloses a method and a device for manufacturing a Unix-like operating system upgrade patch. The method comprises the following steps of obtaining a Unix-like operating system mapping patch to be updated, and starting an operating system to be updated; rebuilding a Unix-like operating system core, initializing a memory root file system, and copying the rebuilt operating system core and the initialized memory root file system to a mounting catalogue; generating a Unix-like operating system upgrade patch mapping file; packaging the generated upgrade patch mapping file, the rebuilt operating system core and the initialized root file system once more to generate a standard mapping format which guides program support, namely generating the operation system update patch. The manufacturing process of the operating system upgrade patch is greatly simplified, and the adaptability and the flexibility of the operation system are improved.
Owner:BEIJING GUODIANTONG NETWORK TECH CO LTD +1
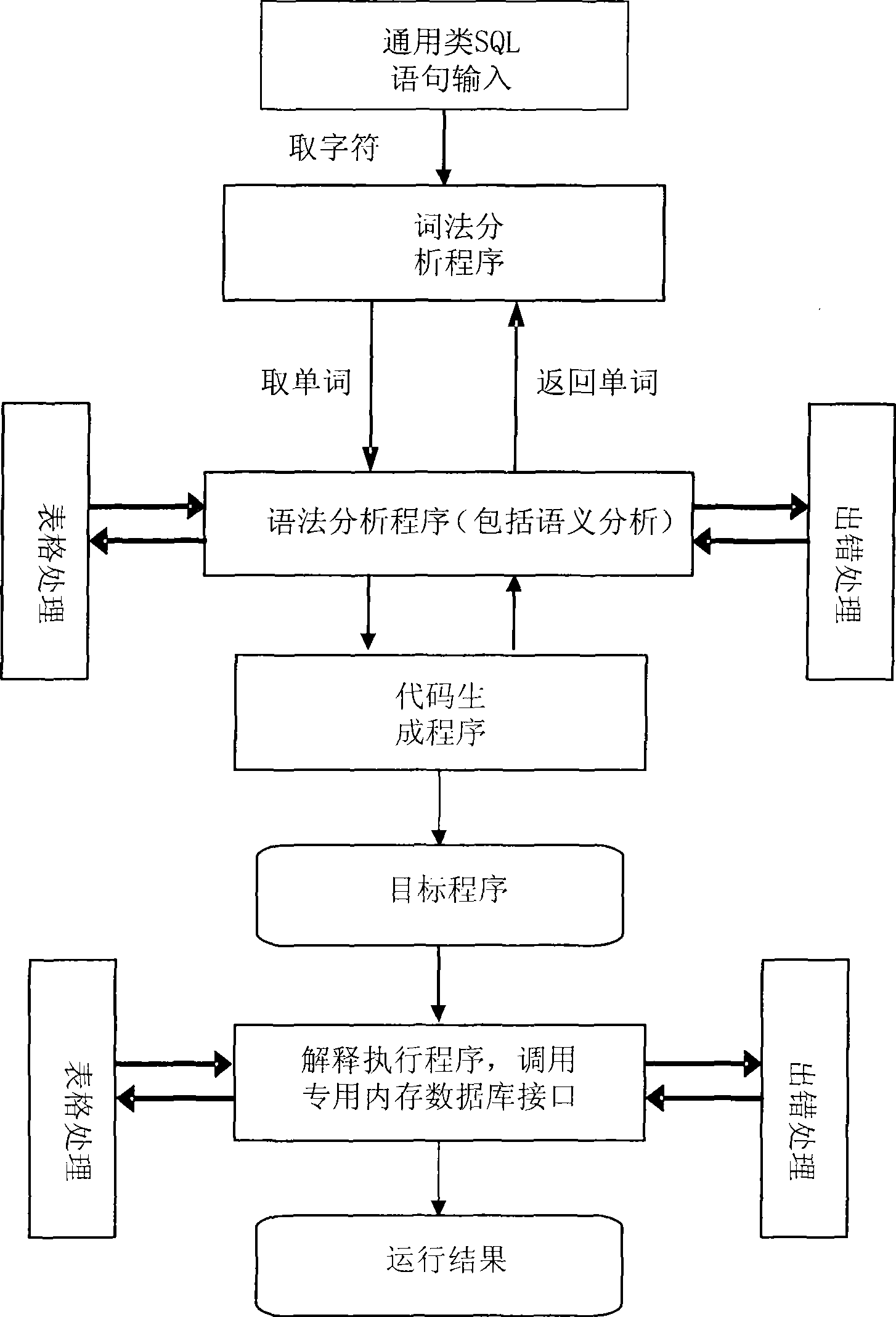
Universal interaction method for internal memory database of monitoring system
InactiveCN101499093AImprove general performanceSpecial data processing applicationsInternal memoryOperational system
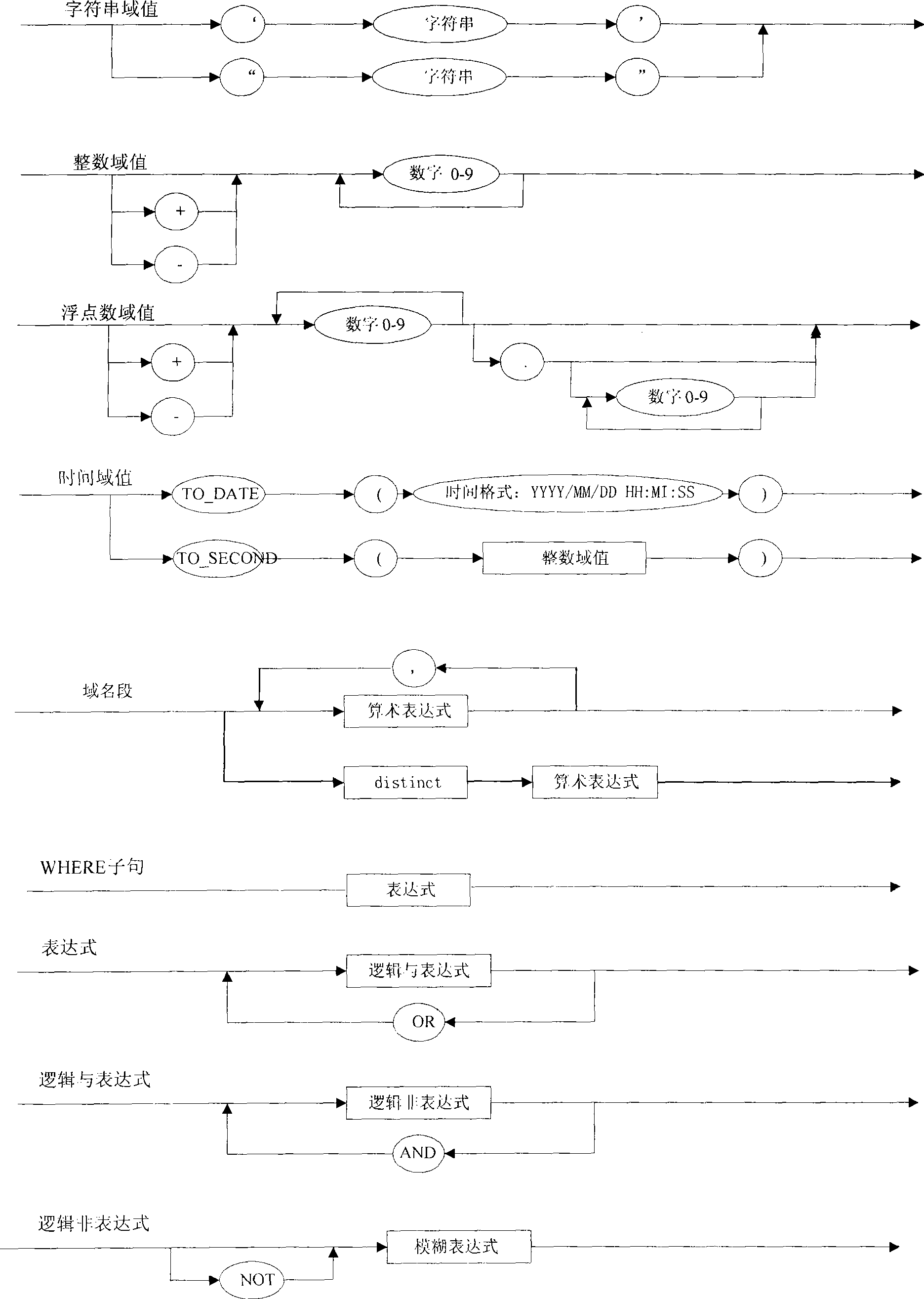
The invention discloses a monitor system memory database universal interactive method which has characteristic in including steps as follows: 1) defining a similar SQL language, inputting needed similar SQL sentence; 2) translating the input similar SQL sentence into an object code; 3) executing the object code generated by translating and calling an interface special for the memory database for processing interacting. The method uses uniform similar SQL sentence for processing interacting with various maker memory database that is suitable for various UNIX operation system, LINUX operation system and WINDOWS operation system, has strong commonality; in additional, all functions are realized in an application layer and need not get help to any operation system software itself.
Owner:NARI TECH CO LTD
System and method for realizing VPN protocol at application layer
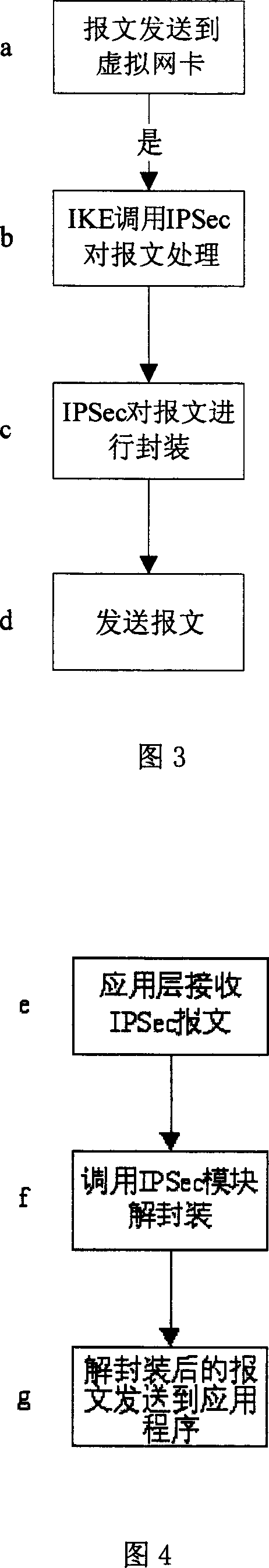
InactiveCN1937571AAvoid confictImprove adaptability to network environmentNetworks interconnectionOperational systemNetwork communication
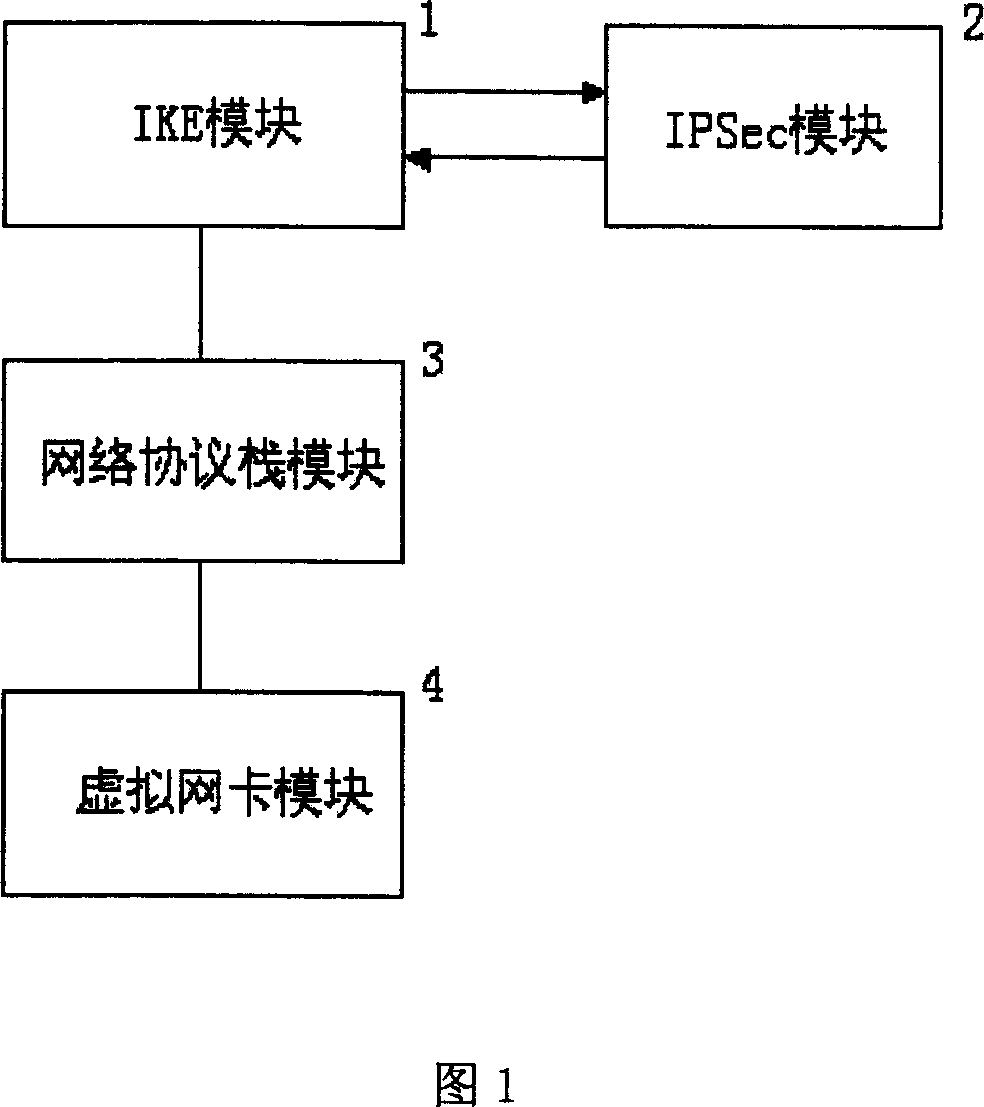
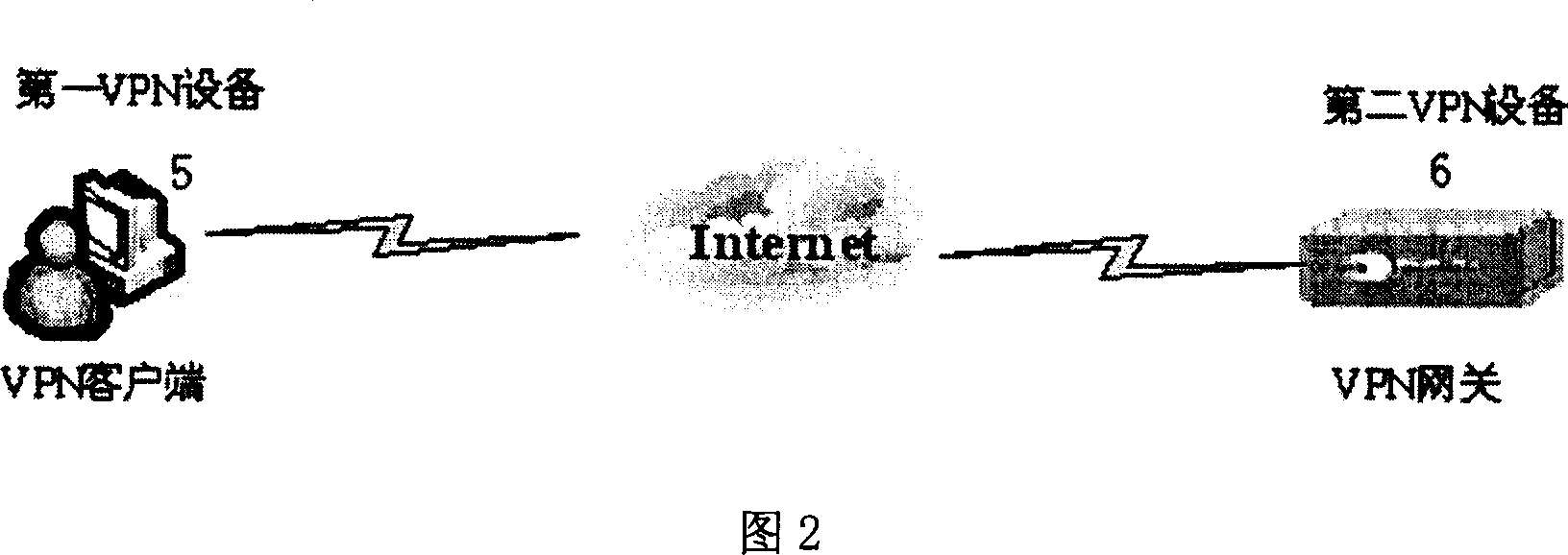
The invention discloses a system and method for implementing VPN protocol at application layer, relating to a network communication packing method, and especially relating to a method for implementing IPSec protocol packing at system application layer; and the method can prevent IPsec message being blocked by other programs at system kernel layer, thus assuring the IPSec message smoothly passes through the system and implementing safety communication. And the system comprises VPN card module, network protocol stack module, IKE module and IPSec module, connected in series in order, where the IKE module and the IPSec module call each other, so do the IKE module and the network protocol stack module, and so do the network protocol stack module and the VPN card module. And the method encrypt and decrypt VPN message at the system application layer, thus improving the adaptability of VPN client-end system to network environments, applied to making VPN system development in Windows and Unix operating systems.
Owner:武汉思为同飞网络技术股份有限公司
Reinforcing system
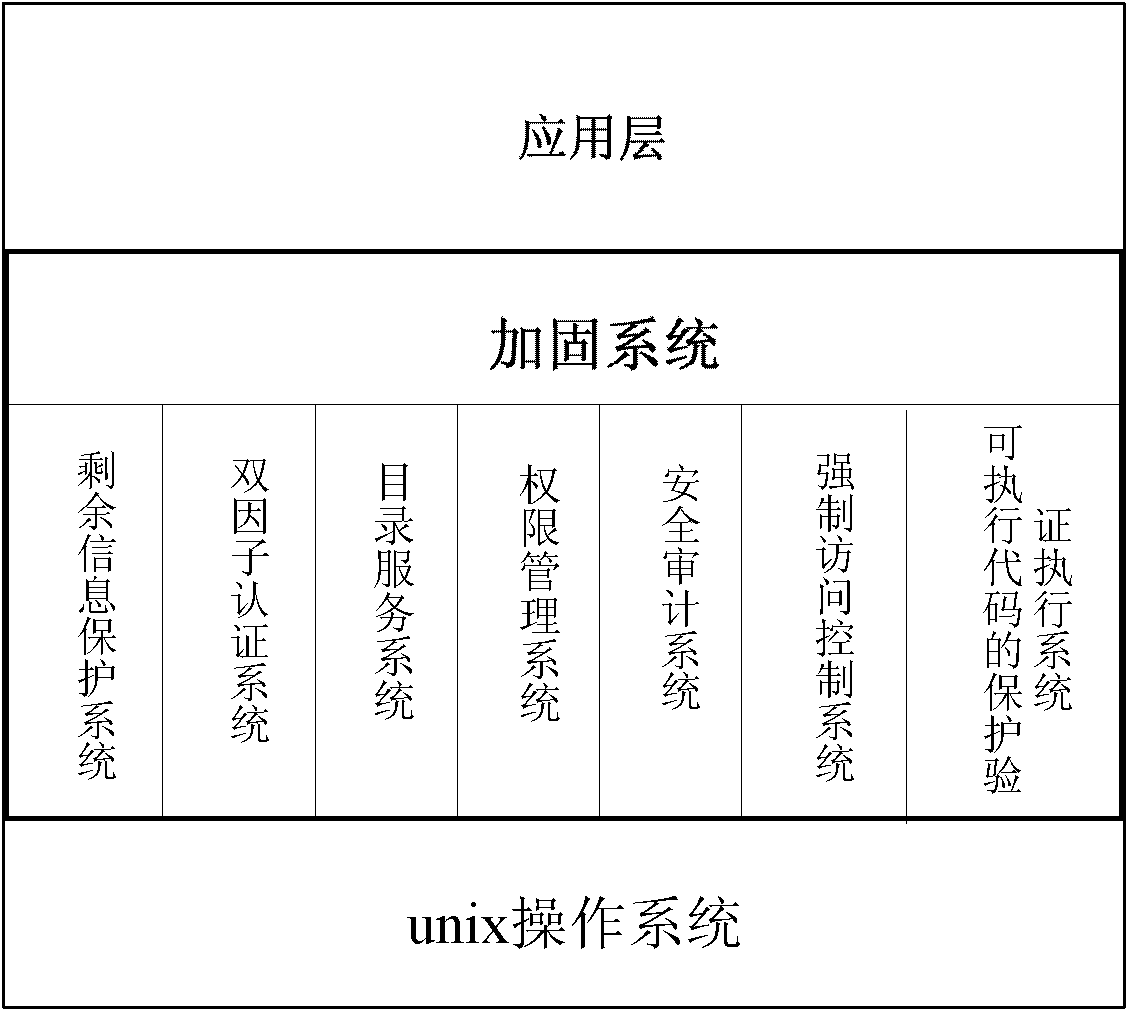
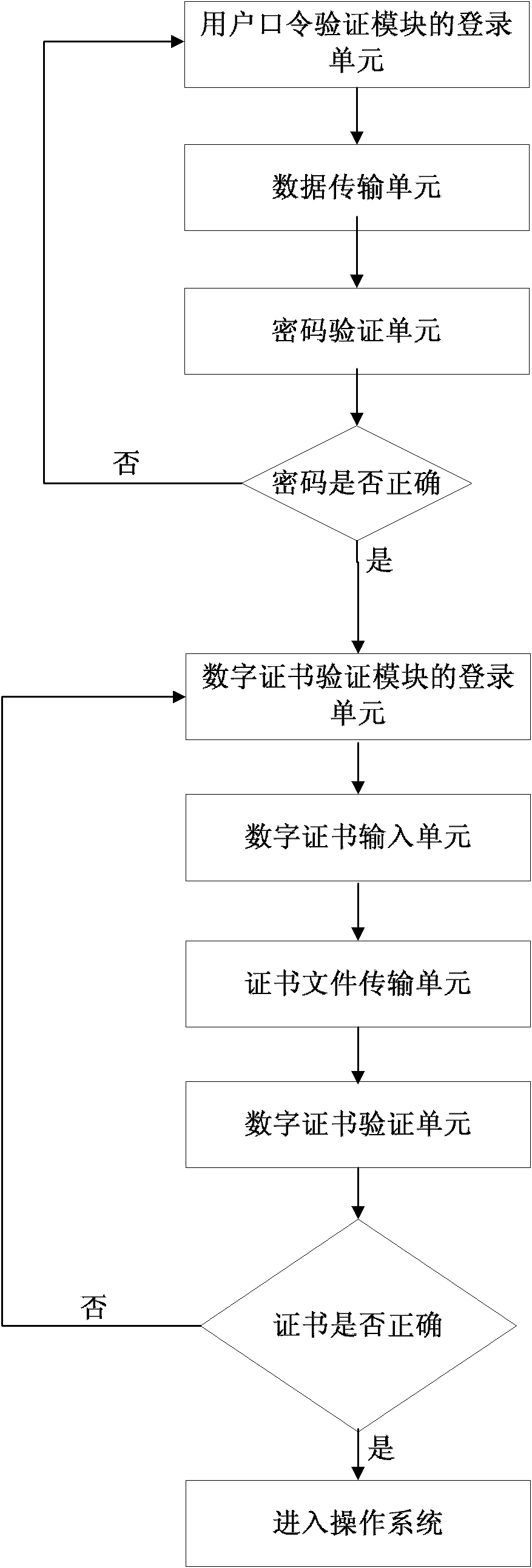
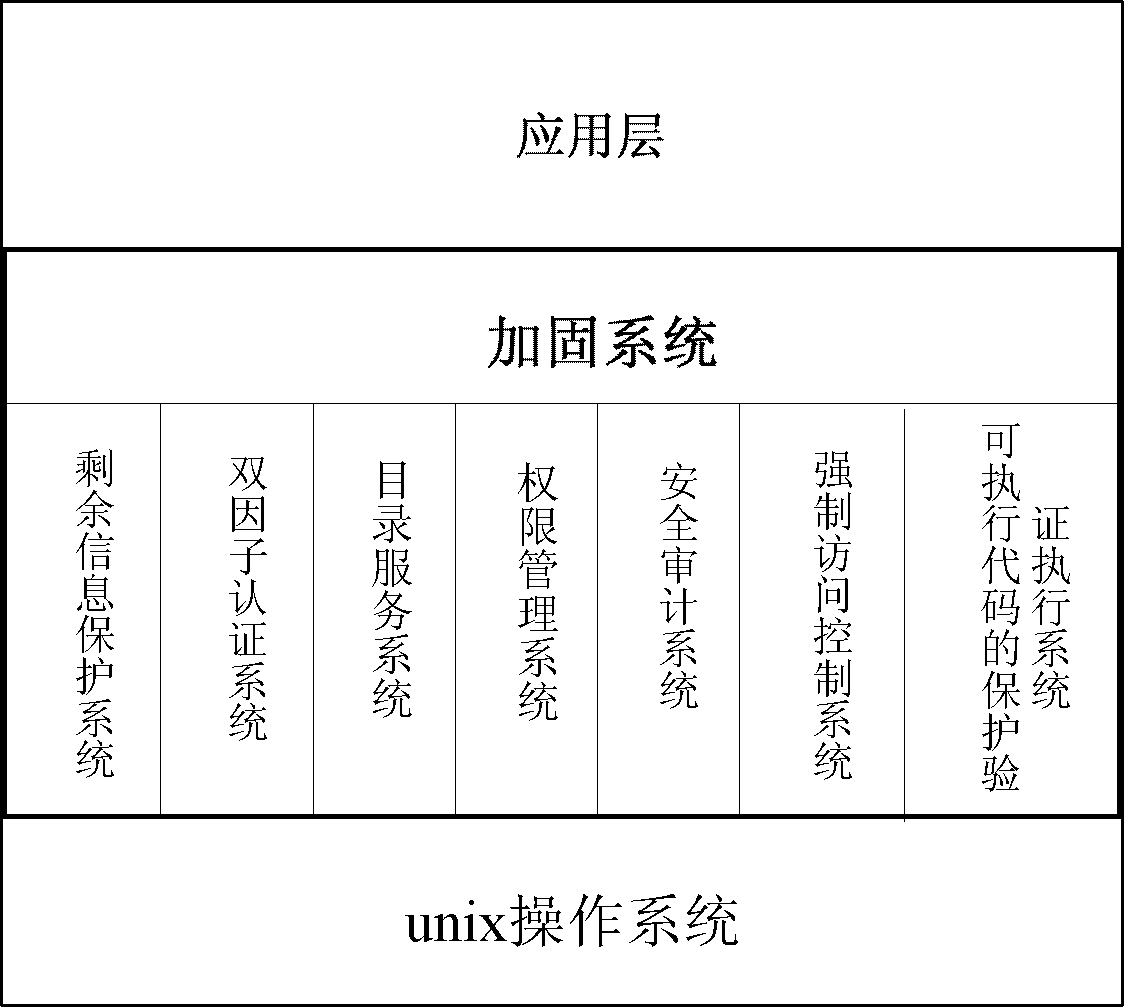
ActiveCN102486819AMeet the technical requirements of grade protectionDigital data authenticationOperational systemApplication software
The invention discloses a reinforcing system, which comprises a dual-factor authentication sub system, a mandatory access control sub system based on safety marks, a protection verification executing sub system capable of executing codes, a remaining information protection sub system, an authority management sub system based on roles, a security auditing sub system and a built-in lightweight directory access protocol (LDAP) directory service sub system. Under the simultaneous effects of the sub systems, security functions such as mandatory access control, dual-factor authentication, object reuse prevention, system and application program completeness protection and important data protection which are not realized by an ordinary commercial uniplexed information and computering service (UNIX) operation system, the classification protection technical requirements of important information systems of railways, electric power and the like are met, and the reinforcing system belongs to the security reinforcing system providing safe and reliable operation environment for key business application.
Owner:中铁信息工程集团有限公司 +1
Computer operating system safety protecting method
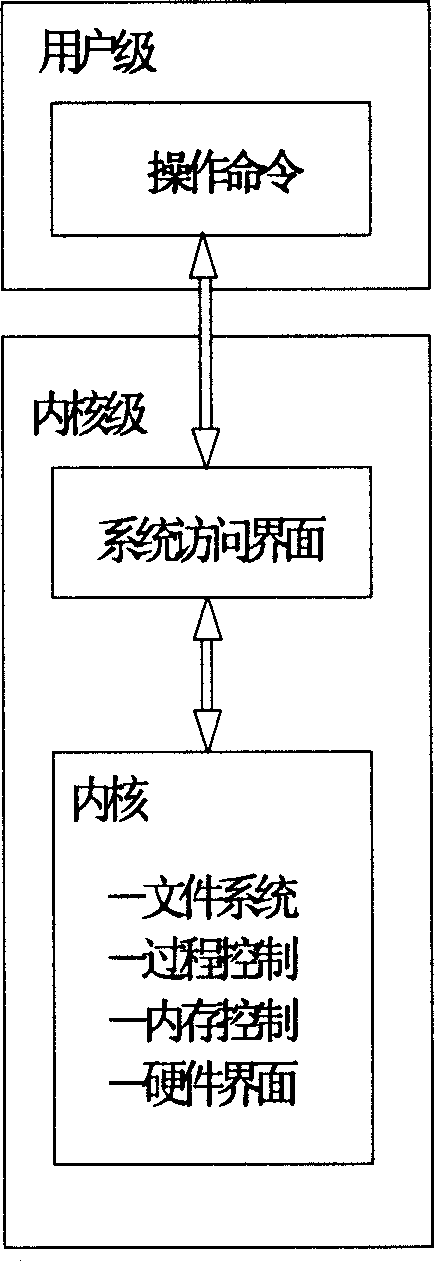
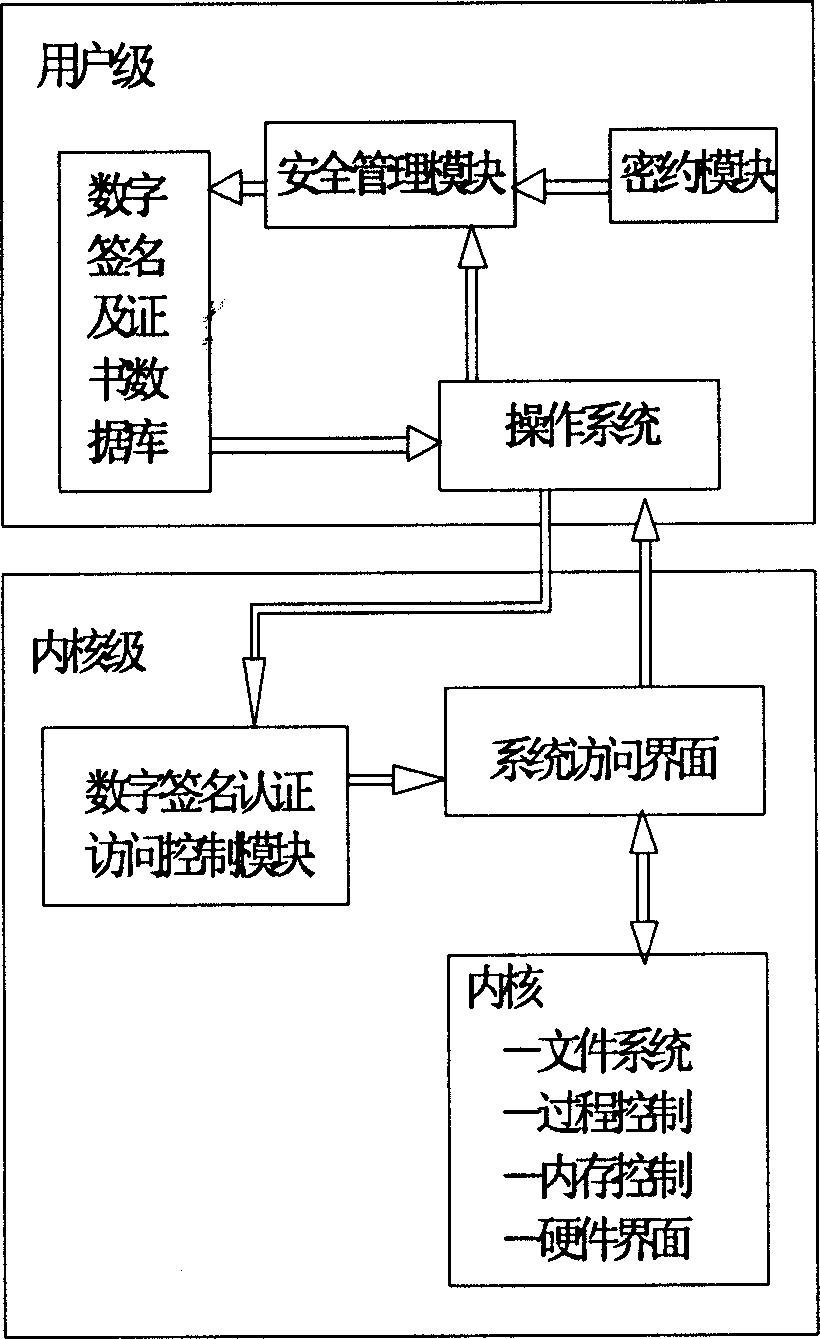
The method adds database of digital signature and certificate, module of security management and module of security agreement on Unix operating system (OS) at user level, and adds an access control module of digital signature authentication on Unix OS at kernel level. Without changing executable files of system and kernel, the method makes the each added module become an effective section of OS so as to be able to carry out security protection and effective control for whole Unix OS under condition of without rewriting operation and condition of transparence. Advantages are: simple, safety, practical and reliable.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Method and device for upgrading unix-like operating system
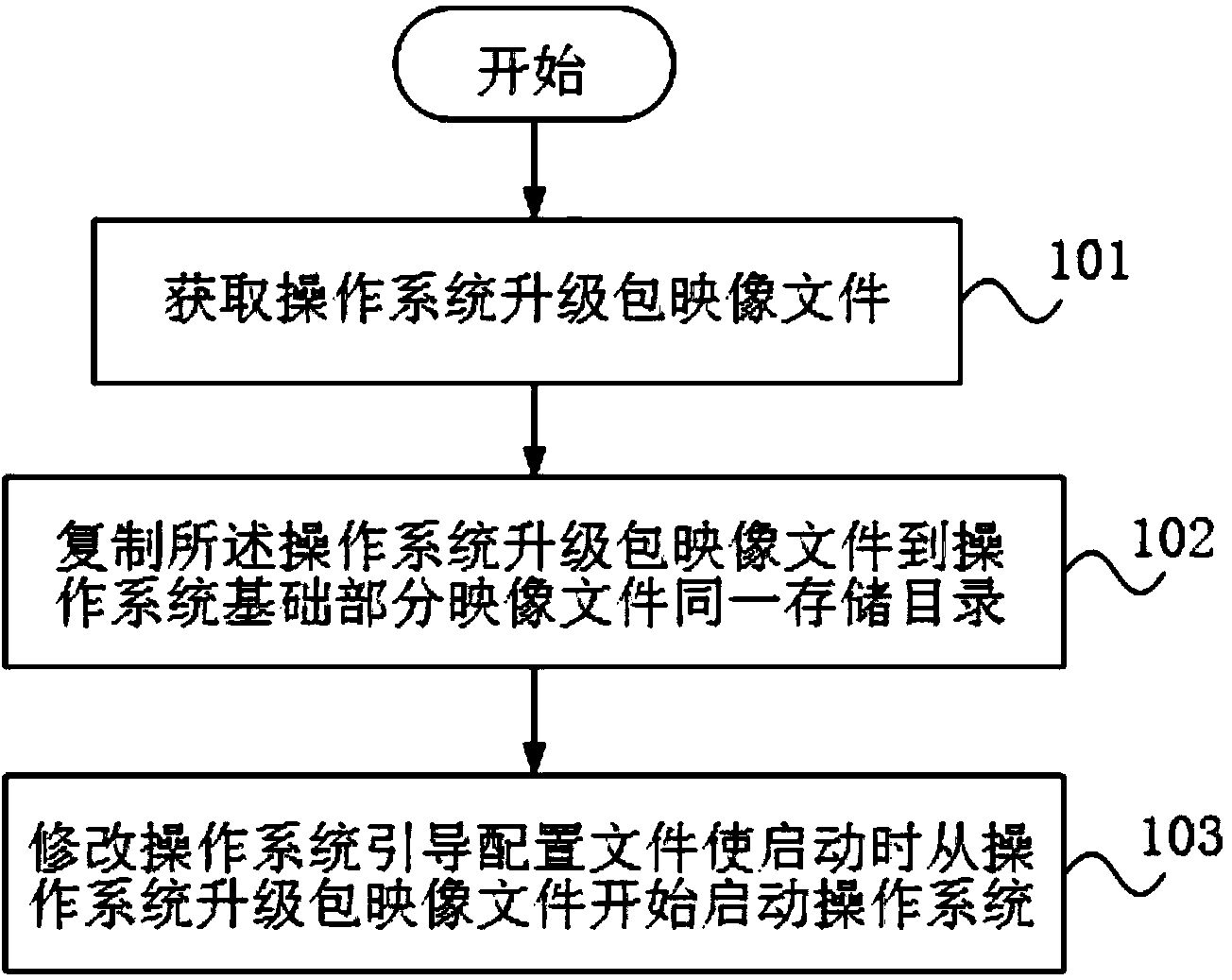
The invention discloses a method for upgrading a unix-like operating system. The method comprises the following steps of acquiring an operating system upgrade patch image file; copying the operating system upgrade patch image file to the same storage directory for an operating system base component image file; modifying an operating system bootstrap configuration file to begin starting the operating system from the operating system upgrade patch image file during start. The invention also discloses a device for upgrading a unix-like operating system. The device comprises an acquisition module used for acquiring the operating system upgrade patch image file, a copying module used for copying the operating system upgrade patch image file to the same storage directory for the operating system base component image file, and a modification module used for modifying the operating system bootstrap configuration file to begin starting the operating system from the operating system upgrade patch image file during start.
Owner:BEIJING GUODIANTONG NETWORK TECH CO LTD +1
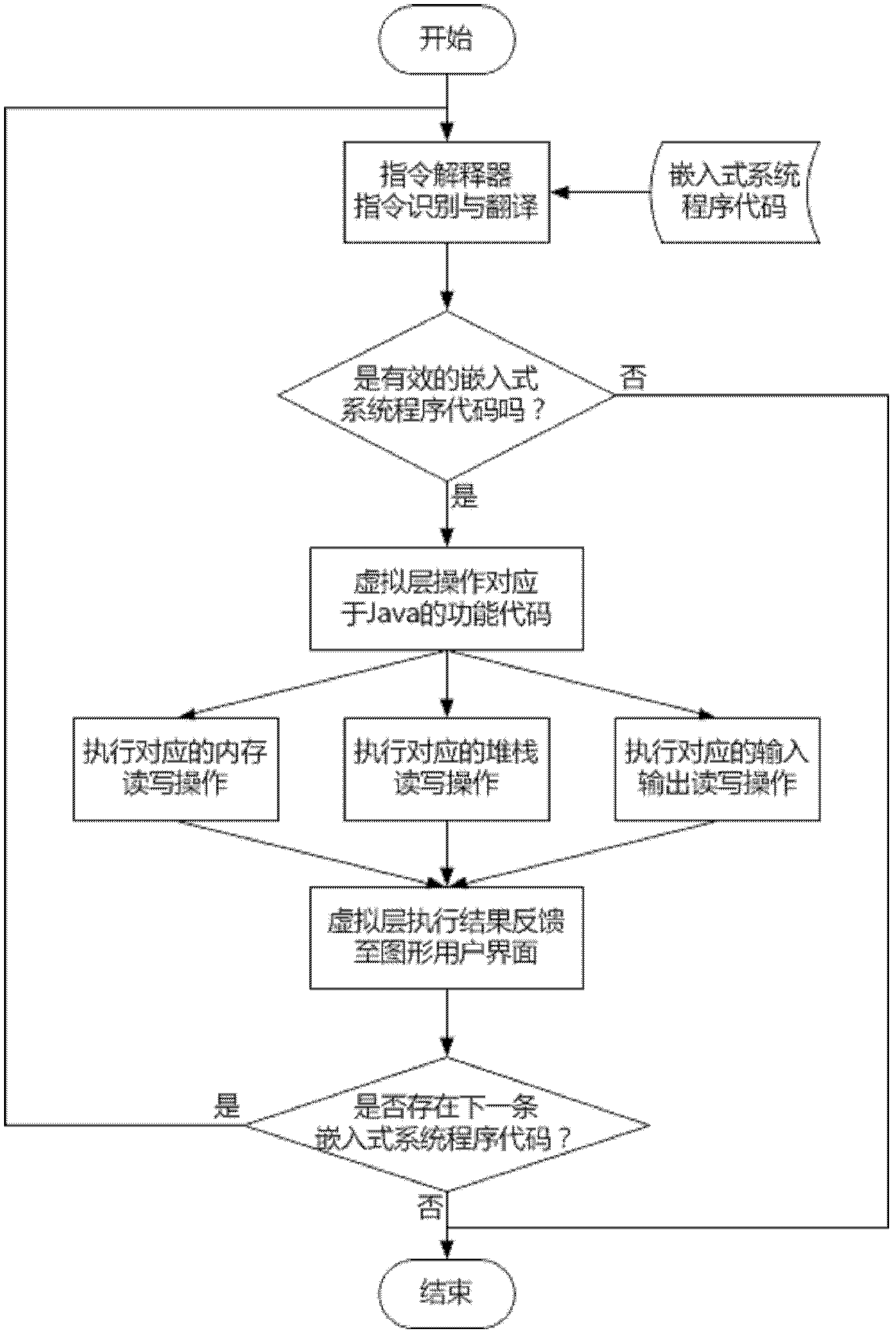
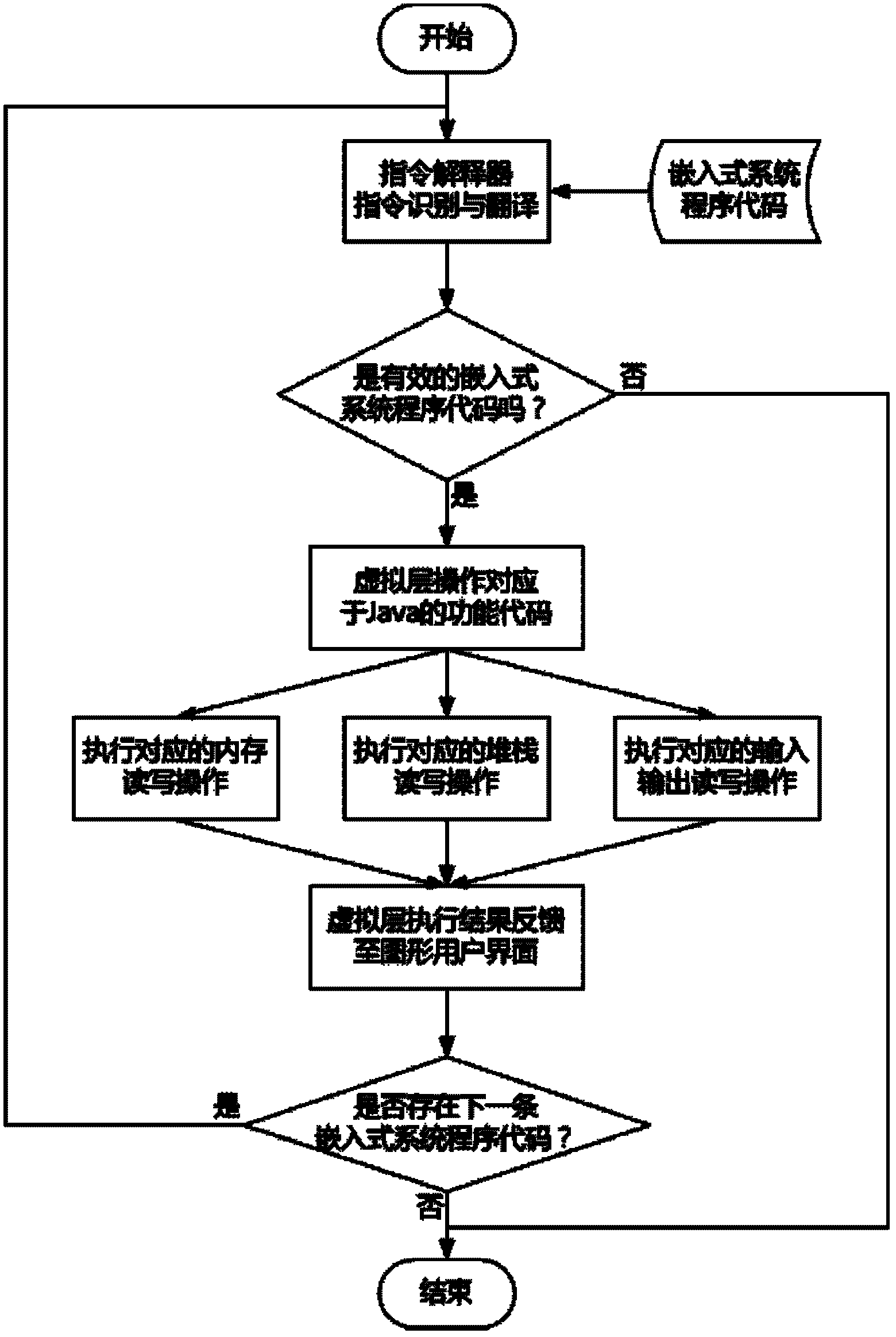
Method for realizing 8-bit embedded CPU (central processing unit) simulation running environment by aid of Java
ActiveCN102508697AImprove efficiencyImprove development efficiencySoftware simulation/interpretation/emulationSystems designUser interface
A method for realizing an 8-bit embedded CPU (central processing unit) simulation running environment by the aid of Java comprises an embedded system program code instruction interpreter, a virtual embedded processor, a virtual memory, a virtual stack manager and virtual input and output equipment. The virtual embedded processor is realized based on corresponding Java function codes. Simultaneously, an embedded system program instruction stack is realized by the aid of the Java and is used for managing execution sequence of embedded system programs, and finally, a visual embedded system simulation running result is provided for a user by the aid of a Java graphical user interface. The method supports Windows / Linux / Unix operation environments, and can be easily deployed in a PC (personal computer), online debugging is carried out via a network by the aid of advantages of the Java network, design, development and debugging efficiency of an embedded system is greatly improved, and the method is widely applicable to design, development, debugging and maintenance of industrial automatic embedded systems, and is an effective technical means for simulation development and testing.
Owner:武汉武钢绿色城市技术发展有限公司
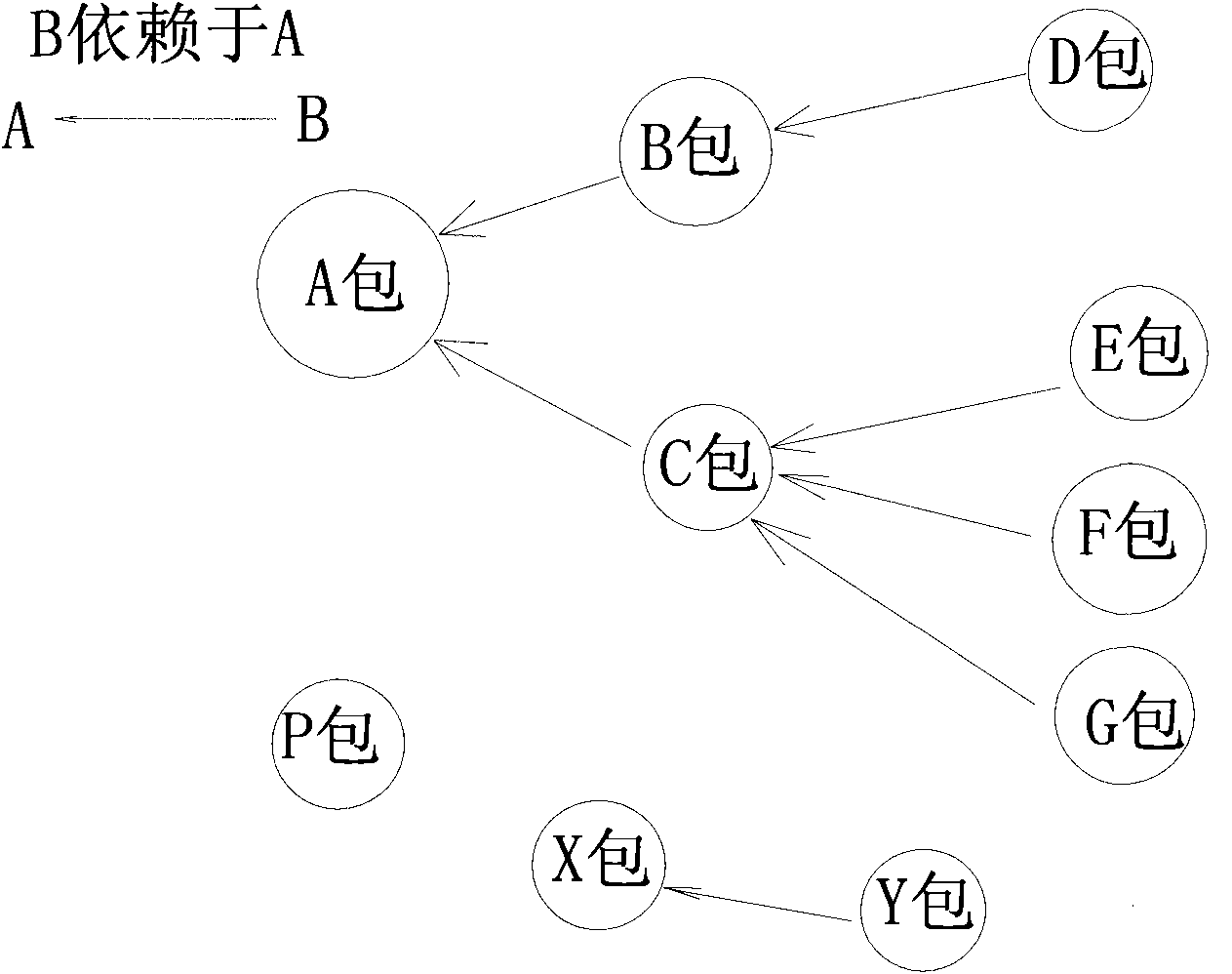
Method for reversely searching packet depended relationship in unix operating system
ActiveCN101826103AEasy to findFast customizationSpecial data processing applicationsOperational systemContrarian
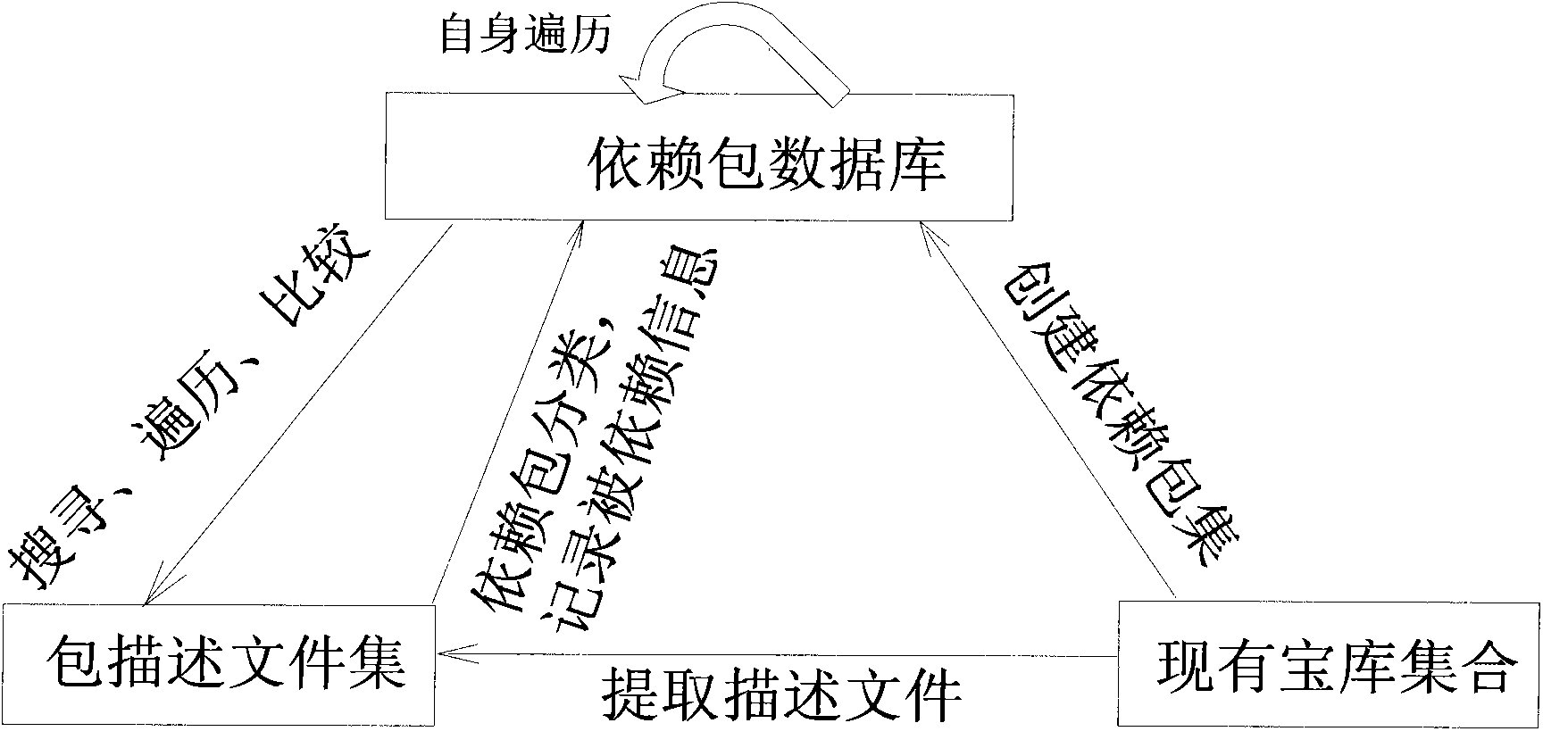
The invention provides a method for reversely searching a packet depended relationship in a unix operating system. The method comprises the following steps of searching the interdependent relationships of all the packets in the same version based on a packet storage IPS; and effectively performing customized work on the system according to the dependent relationships of the packets, wherein the reversely searching process of the whole packet comprises 1) a packet storage technique IPS, 2) a packet organization technique and 3) a method for reversely searching the packet. The packet storage technique IPS is an important part of a packet management technique and comprises the following steps of: organizing all the functional packets together according to a certain rule to form a set according to a release version; and releasing to an internet server for all the developers and users to use, wherein a client is provided with a corresponding client tool; the user accesses the IPS through network and performs operation comprising installing, uninstalling and updating the packets and viewing the description characteristics of the packets; and the characteristics comprise: a directory in which the packet is installed, the name of the packet after installation and required dependent files of the system.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
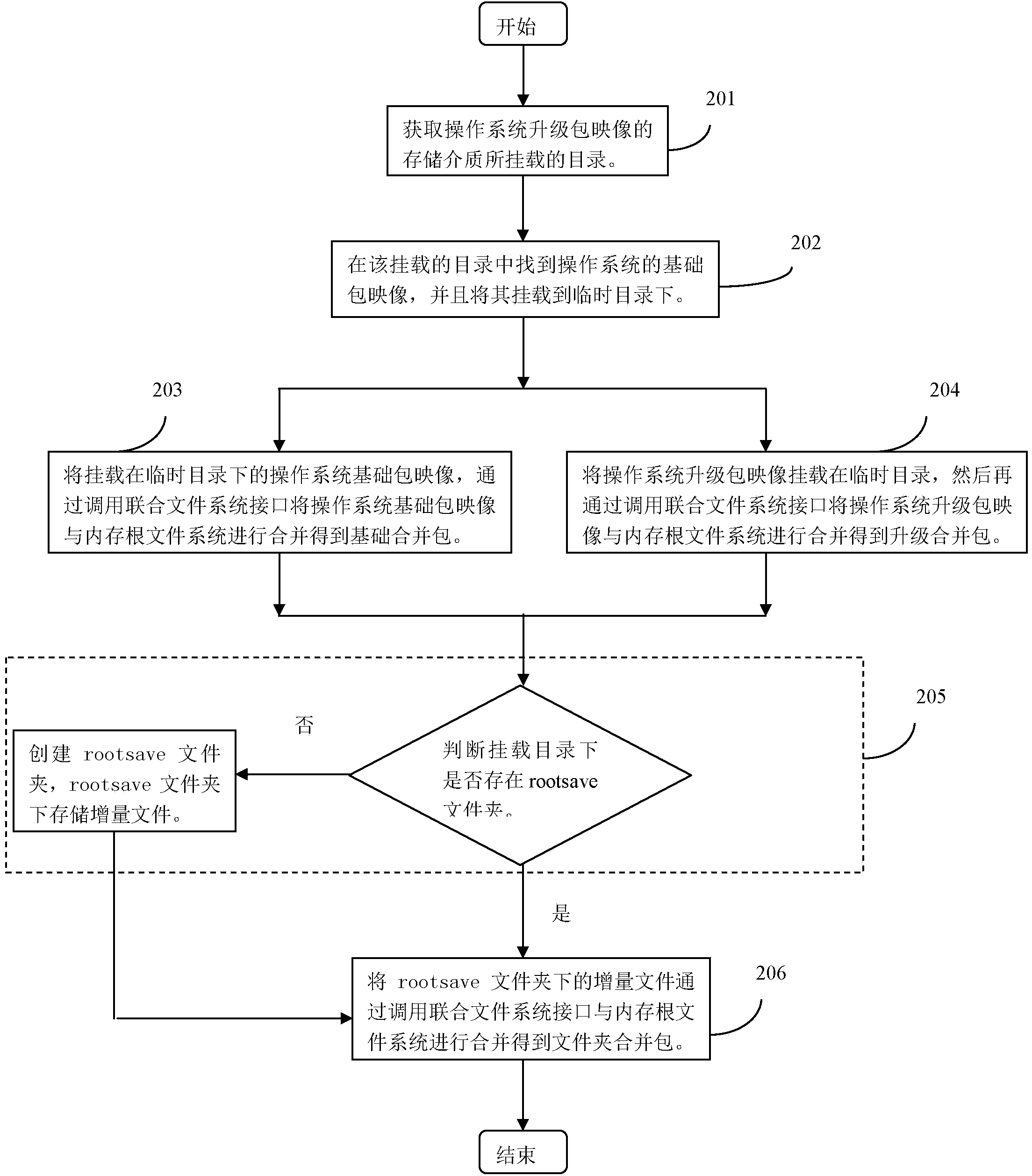
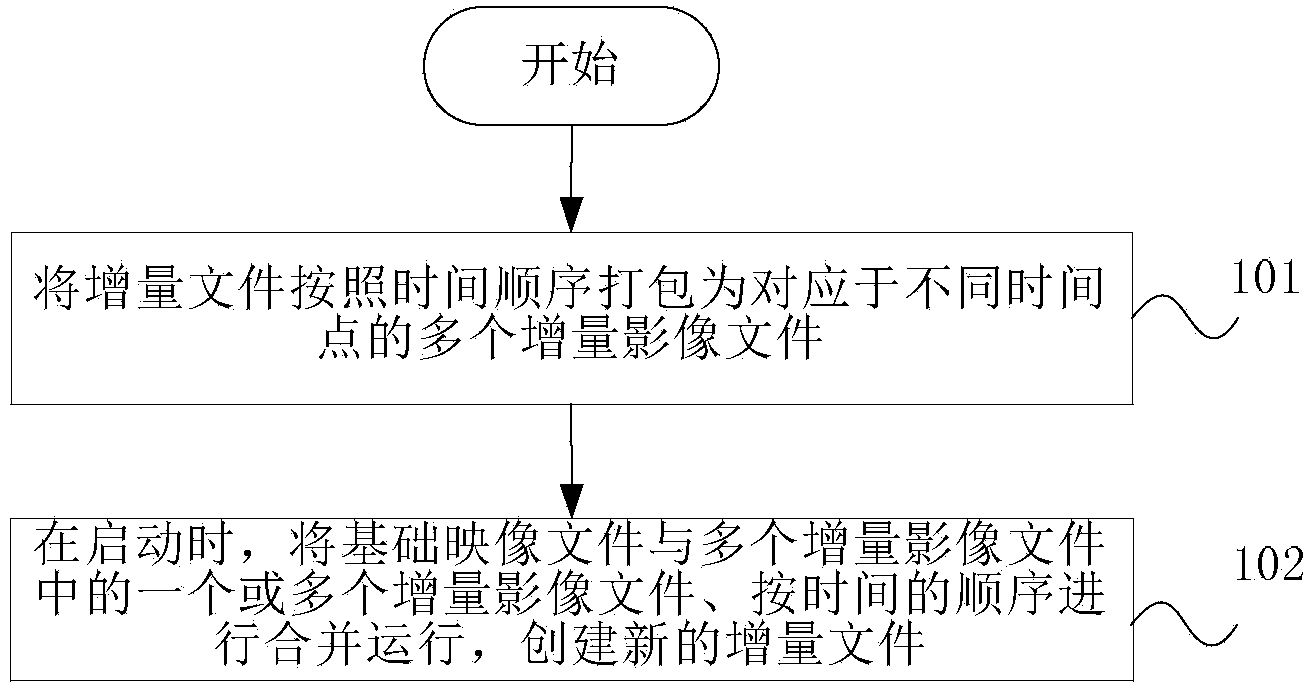
Unix-like operating system backup method and device
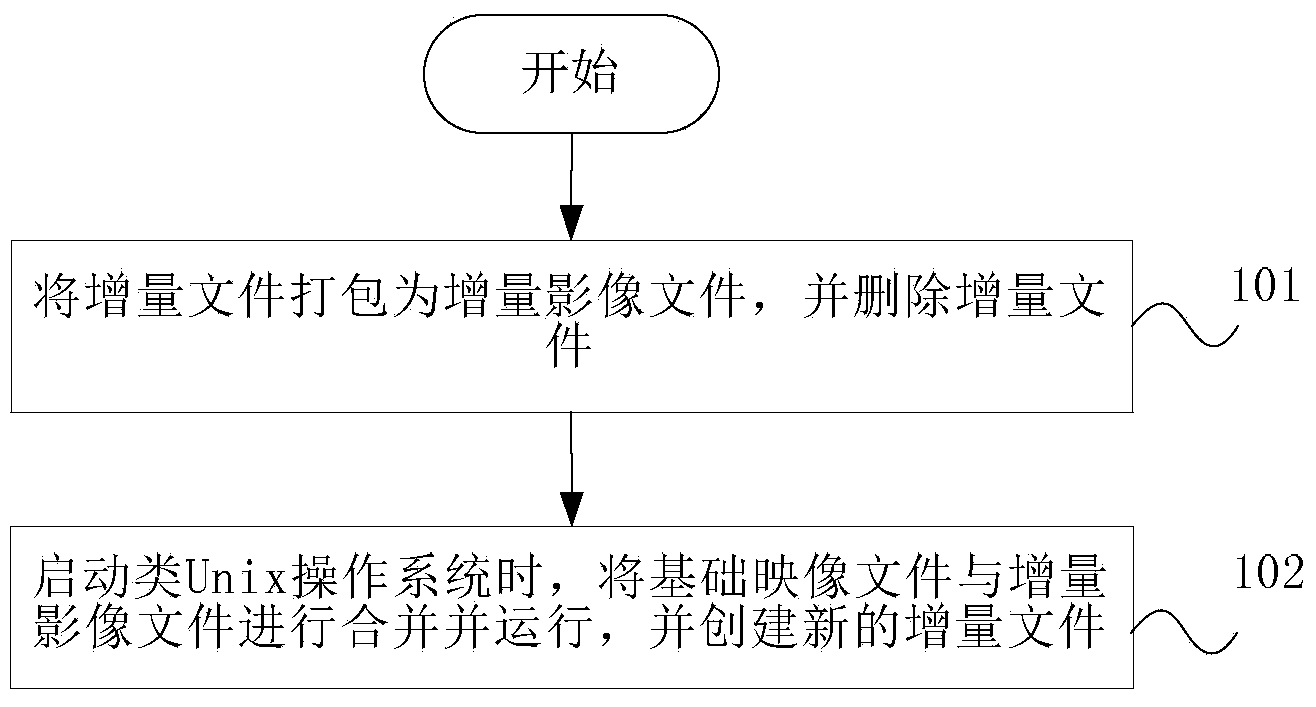
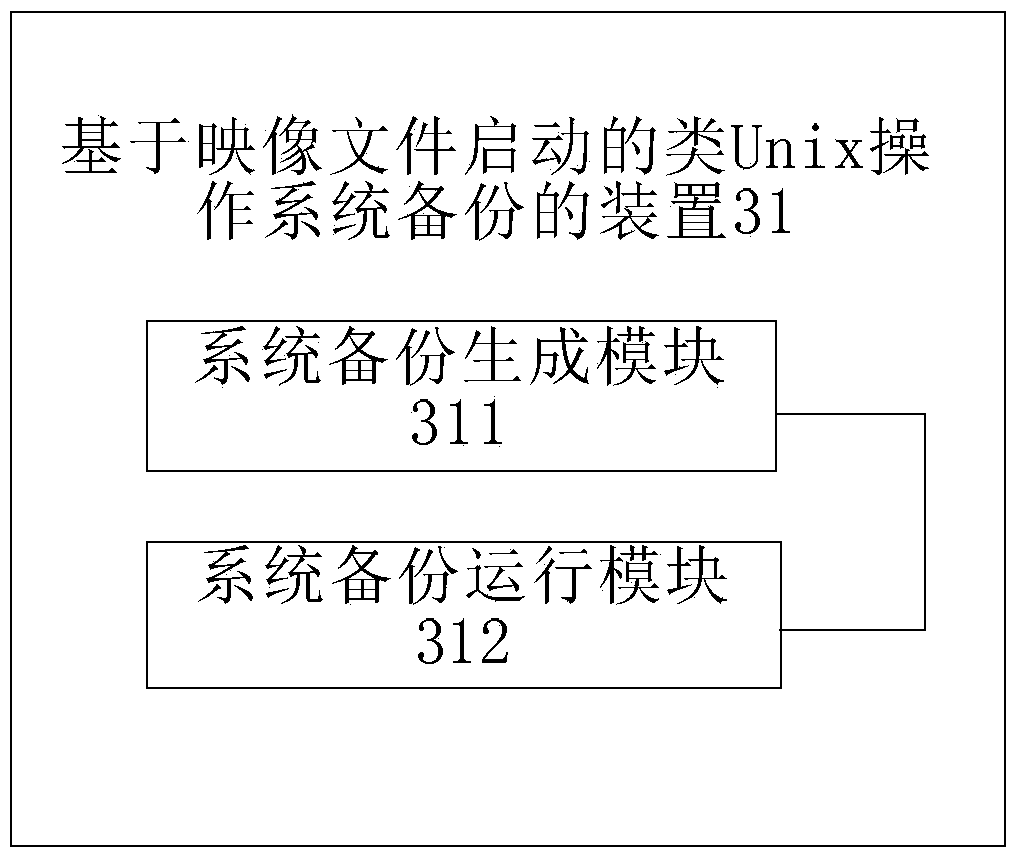
InactiveCN103778032AImplement backupSimplify the backup processProgram loading/initiatingRedundant operation error correctionOperational systemBackup
The invention discloses an image file start-based Unix-like operating system backup method and an image file start-based Unix-like operating system backup device. The method comprises the following steps of packing an increment file into an increment image file, and deleting the increment file; when the Unix-like operating system is started, carrying out merged running on a base image file and the increment image file and creating a new increment file. By the image file start-based Unix-like operating system backup method and the image file start-based Unix-like operating system backup device, the backup of the Unix-like operating system is realized through the increment image file, the backup process of the operating system is greatly simplified and a simple method is provided for implementing instant and quick one-key reset.
Owner:BAOLONG COMP SYST HUNAN
Calculating software monitoring system based on UNIX operating system
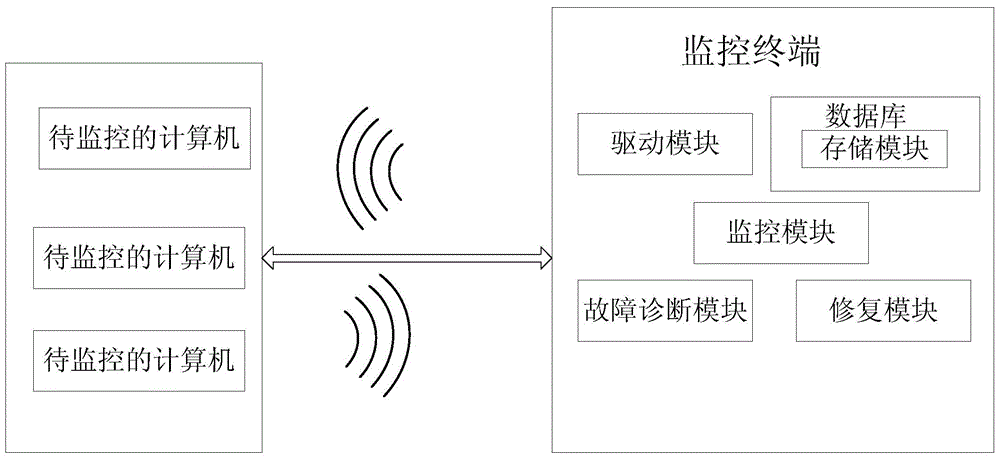
InactiveCN104699597AWork lessNormal work does not affectSoftware testing/debuggingOperational systemWireless data
The invention discloses a calculating software monitoring system based on a UNIX operating system. The calculating software monitoring system comprises a plurality of to-be-monitored computers and a monitor terminal, wherein the to-be-monitored computers are in wireless data communication with the monitor terminal; a driving module, a database, a monitoring module, a fault diagnosis module and a repairing module are arranged in the monitor terminal; the UNIX operating system, a test program and test software are installed in the database. According to the calculating software monitoring system based on the UNIX operating system disclosed by the invention, by operating the UNIX operating system in to-be-monitored computers, computer software is monitored in real time by using the monitoring module. If faults are found, the system immediately diagnoses and repairs the faults so as to ensure normal operation of the computers.
Owner:DALIAN HONGQI TECH DEV
A method for the operation of device maintenance
InactiveCN101217757AImprove work efficiencySupervisory/monitoring/testing arrangementsRadio/inductive link selection arrangementsOperational systemAutomatic control
The invention relates to an equipment maintenance operation method. The proposal is that an automatic control to the equipment maintenance operation is executed by adopting a Unix operation system platform, a shell script which comprises corresponding maintenance instruction sets is compiled according to the equipment to be maintained, the shell script is automatically called by a Unix timing function and the equipment to be maintained is remotely logged in, the maintenance instructions in the shell script are executed for the equipment to be maintained, the maintenance instruction execution results are collected and stored, and the execution results are stored to an appointed equipment according to the requirement. The invention executes the maintenance operation plan of the mobile data communication equipment by adopting an automation method, automatically achieves various detection projects and system backup, replaces manual work with technical means, improves working efficiency, and provides preconditions for the execution results of further intelligent analysis and maintenance operation.
Owner:XIANGYANG BRANCH CHINA MOBILE GRP HUBEI CO LTD
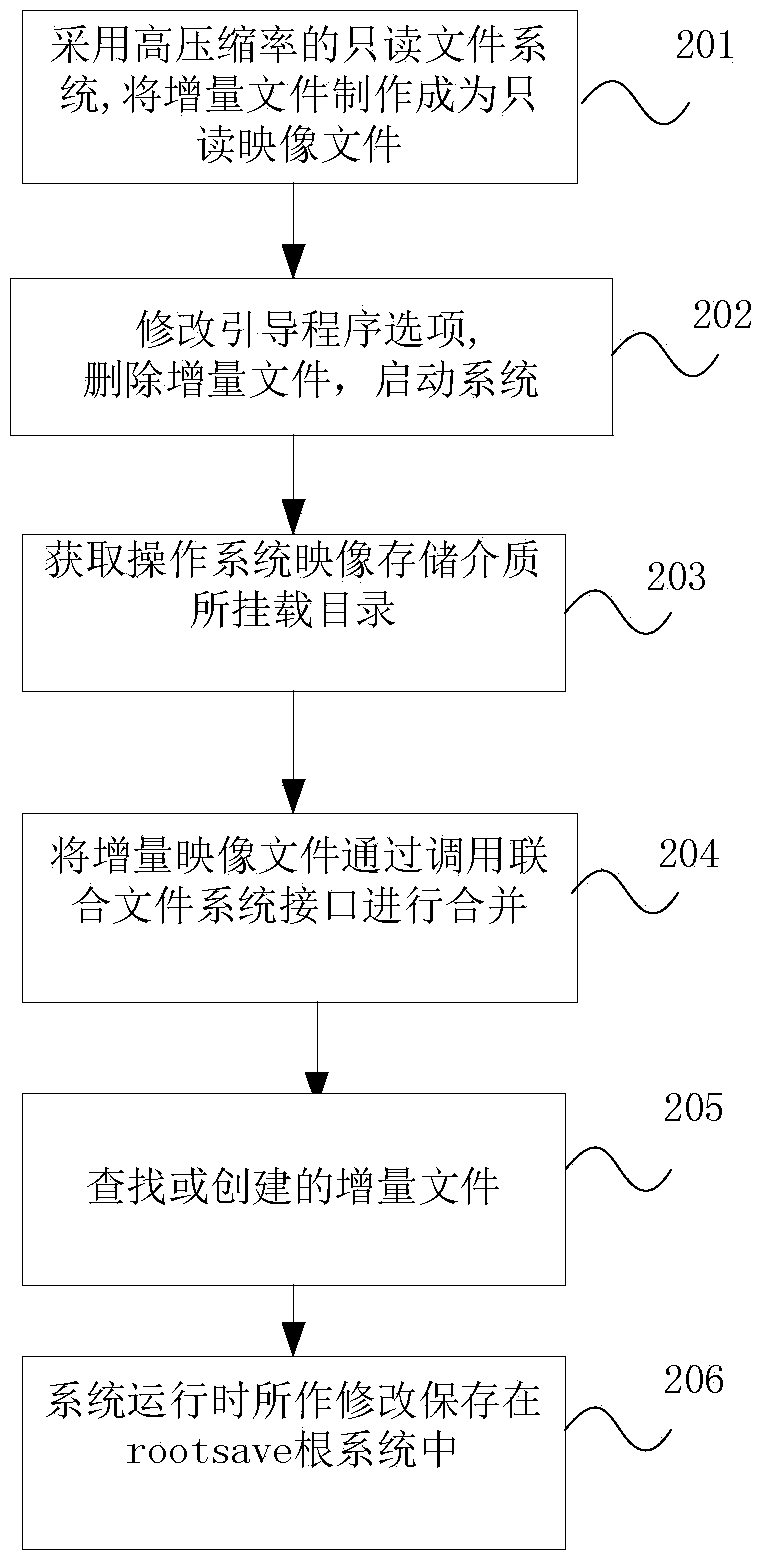
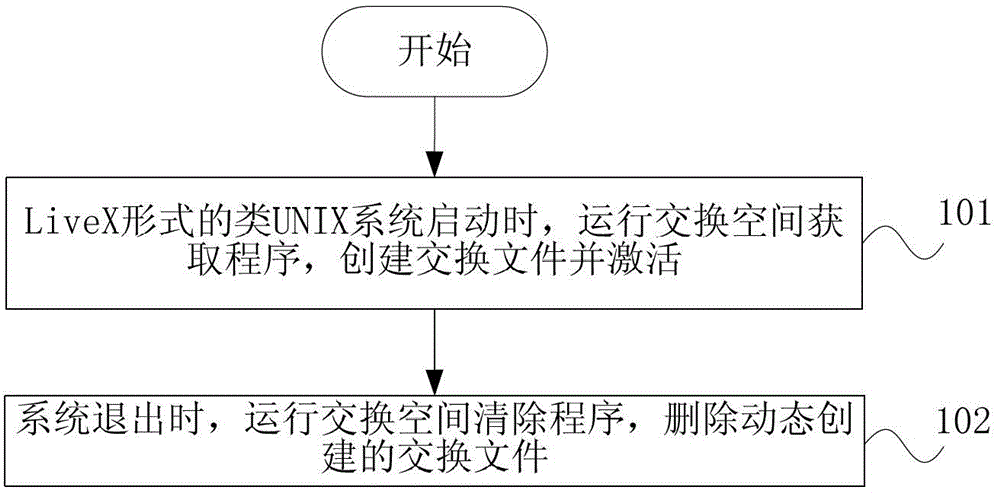
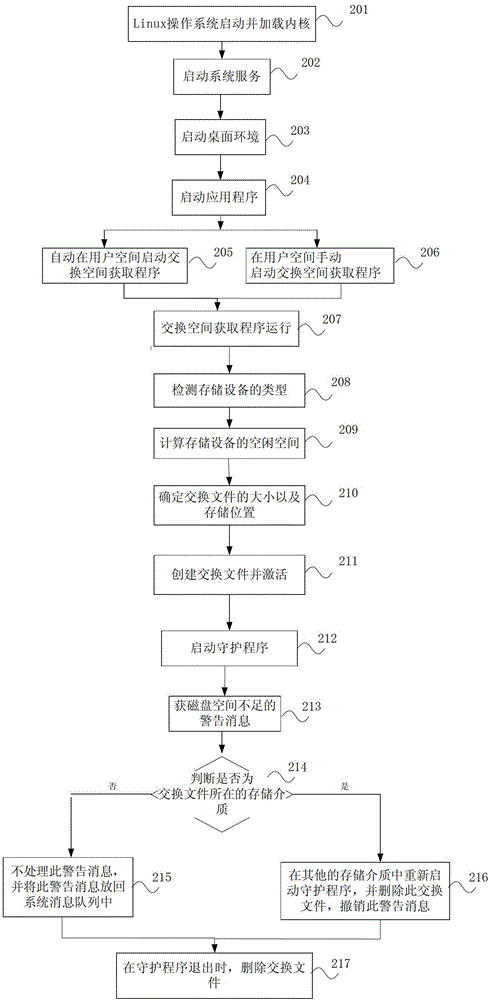
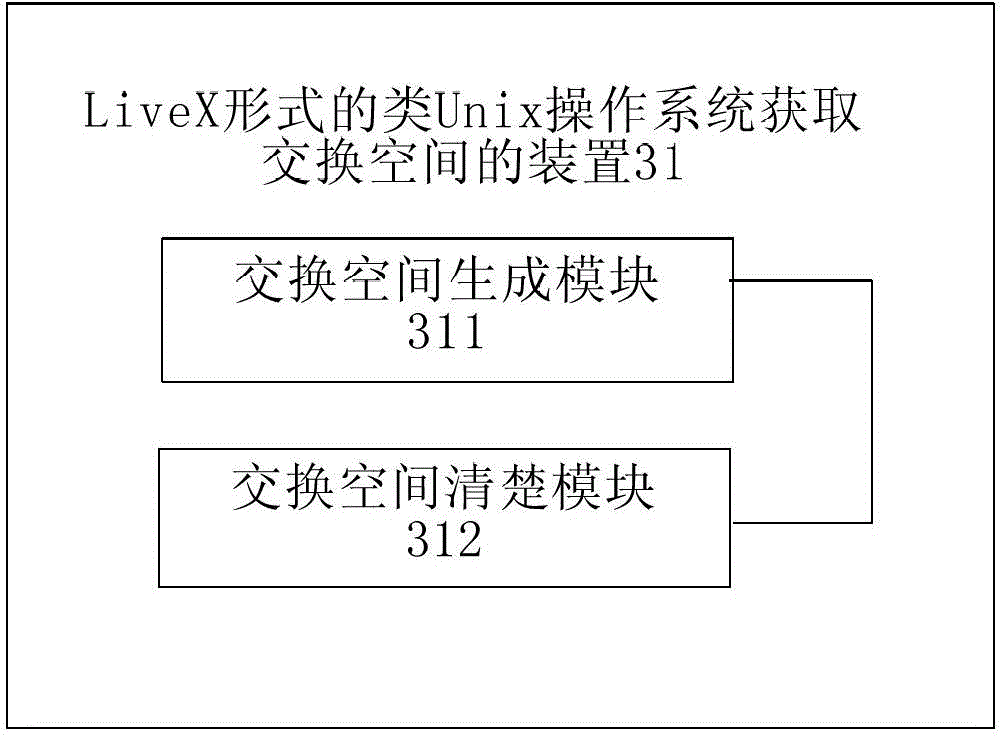
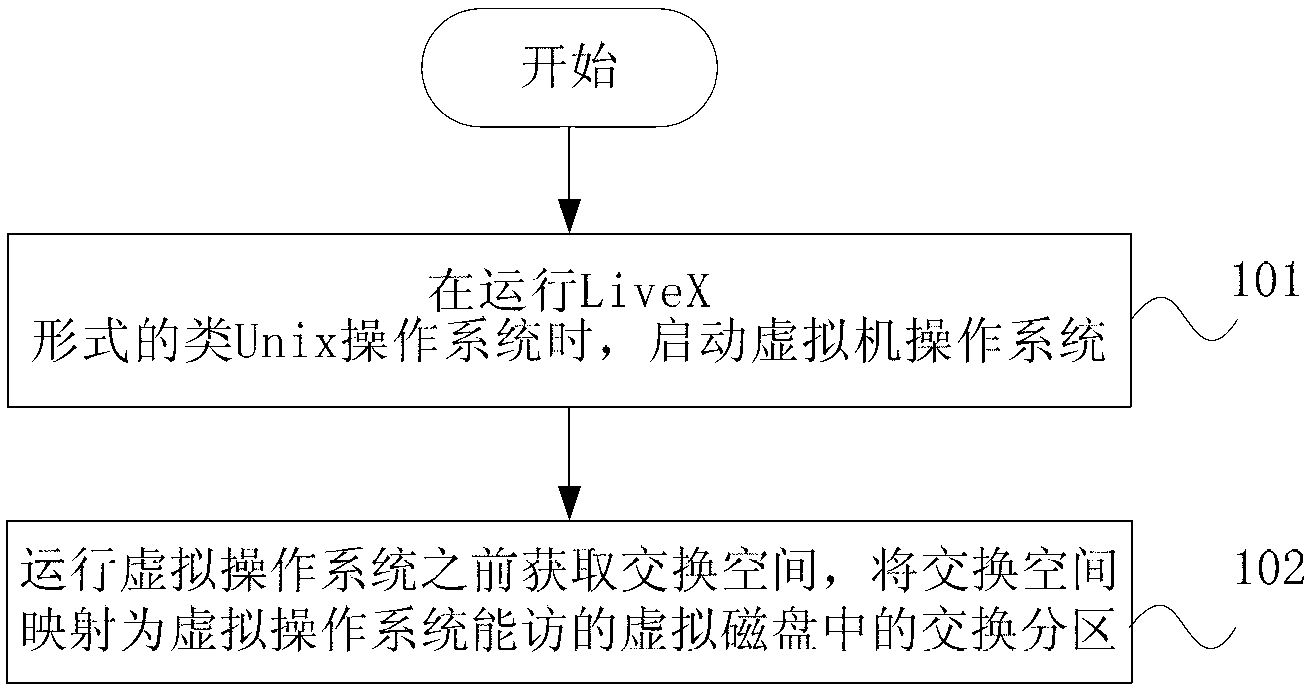
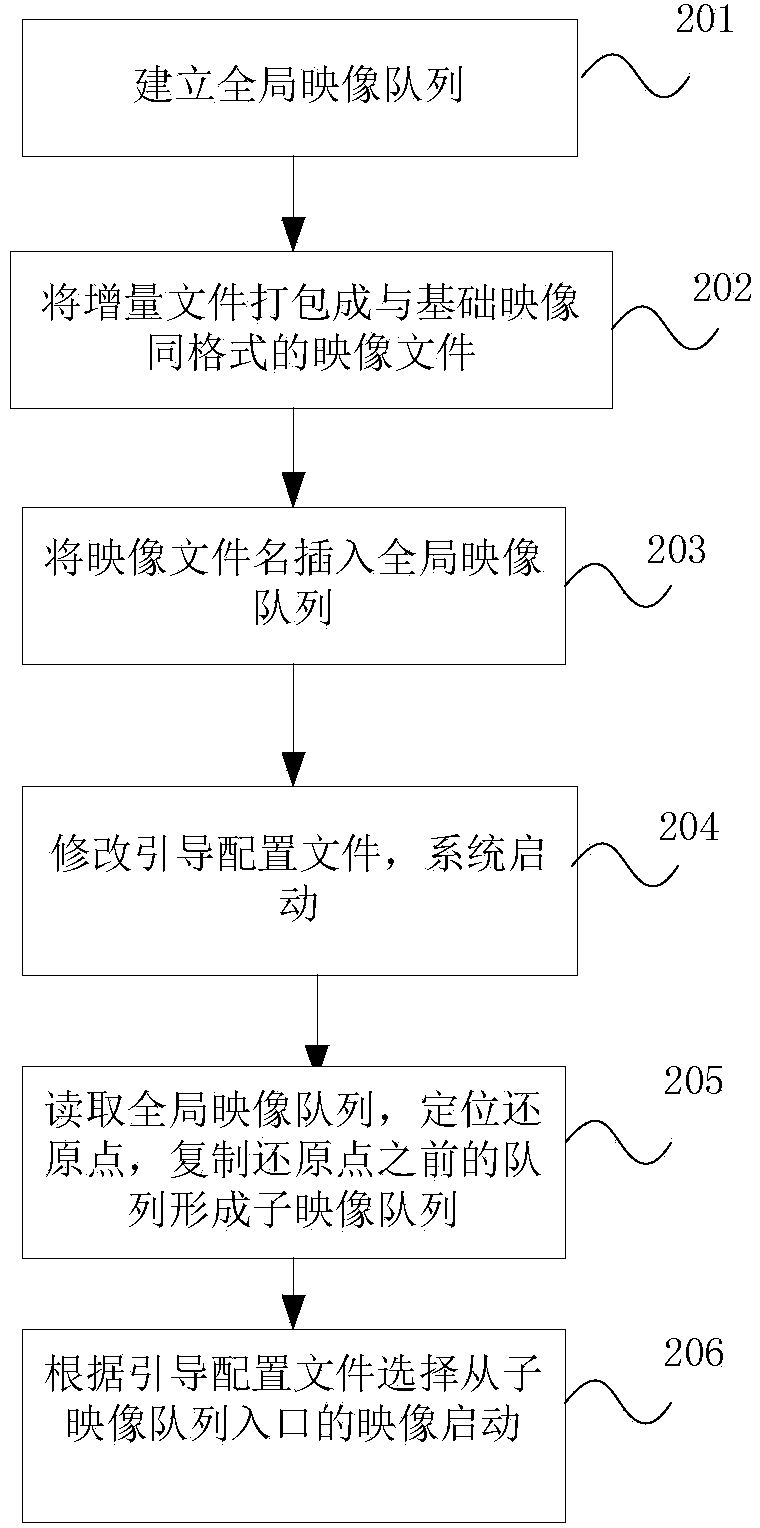
Method and device for obtaining swap space in UNIX-like operation system
The invention discloses a method and a device for obtaining a swap space in a UNIX-like operation system adopting a LiveX form. When the UNIX-like operation system adopting the LiveX form is in operation, a swap space acquisition program is operated, and a swap file is dynamically created and activated; when the UNIX-like operation system exits, a swap file purging program is operated, and the swap file created dynamically is deleted. According to the method and the device, the swap space is created for operating the UNIX-like operation system adopting the LiveX form, the problem that software with large memory requirement is in operation is solved, file swap space is dynamically created on storage equipment accessed to a host machine, so that the UNIX-like operation system can entirely pack a practical system into a practical Live system, and the large application program can be operated.
Owner:韶山高新创业投资有限公司
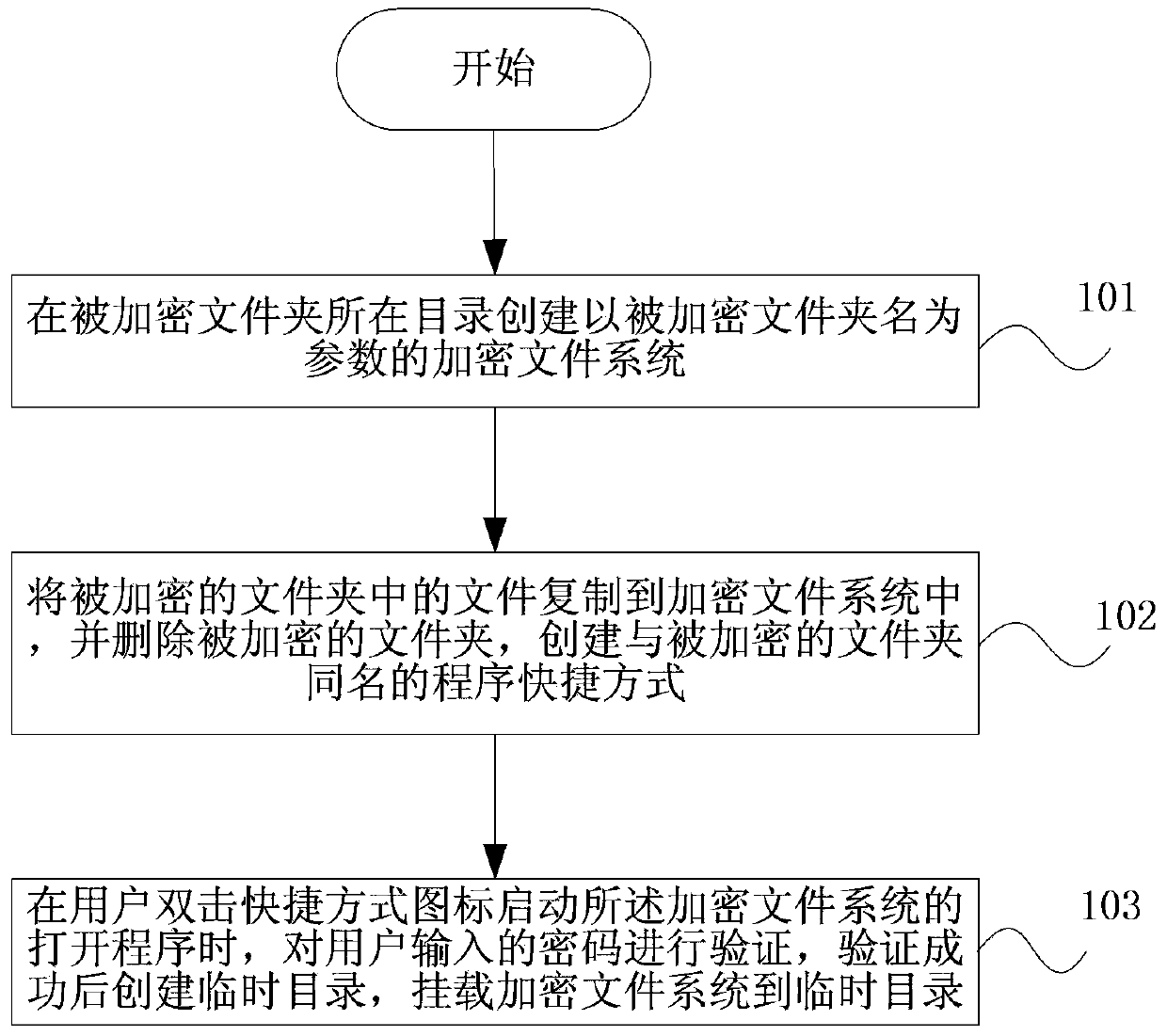
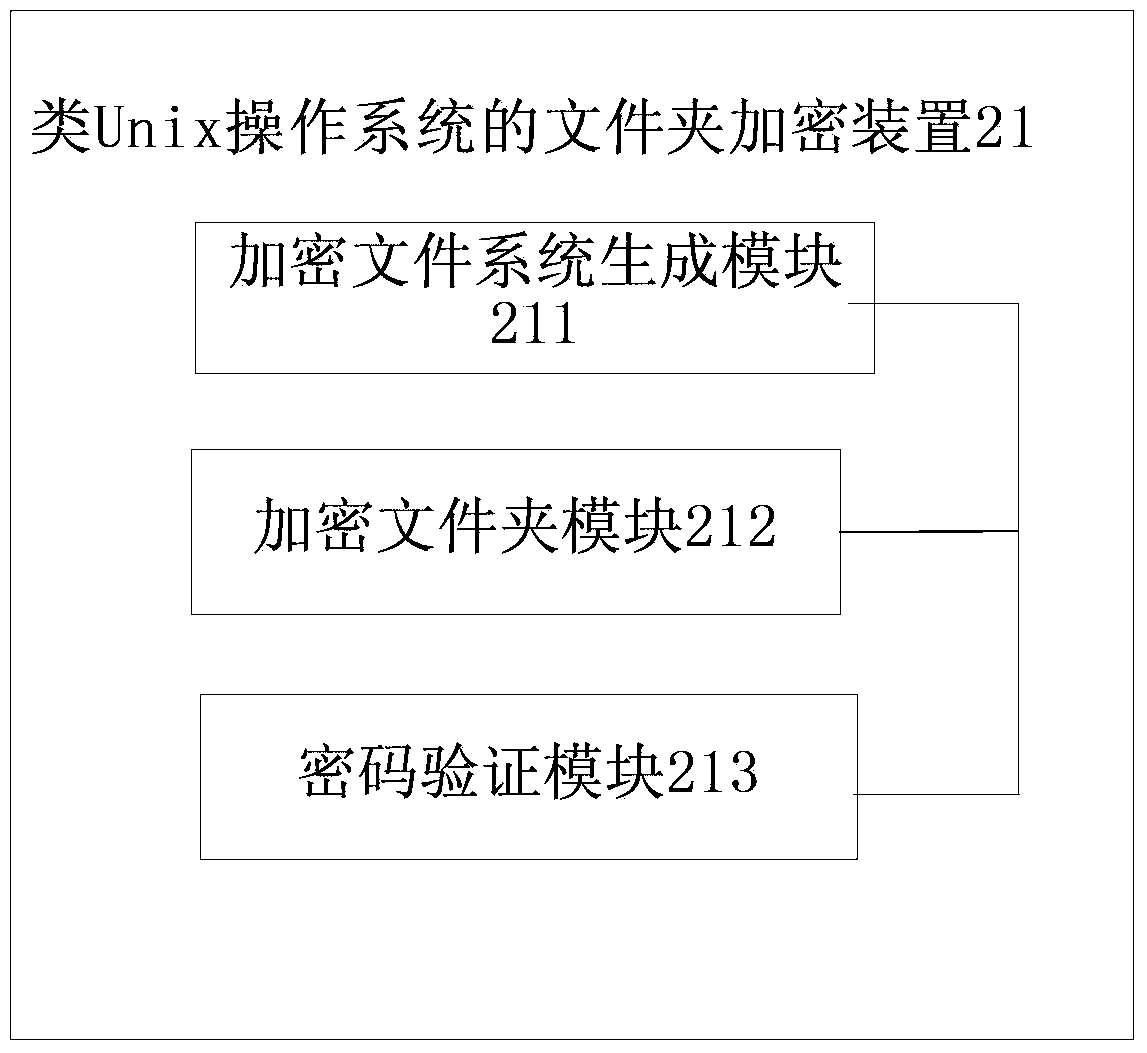
Folder encryption method and device for Unix-like operating system
InactiveCN103425938AIntuitive EncryptionWork intuitivelyDigital data protectionOperational systemPassword
The invention discloses a folder encryption method and device for a Unix-like operating system. An encrypted file system is created in a catalog where an encrypted folder is located, wherein the name of the encrypted folder is used as a parameter of the encrypted file system; files in the encrypted folder are copied to the encrypted file system, the encrypted folder is deleted, and a routine shortcut with the same name as the encrypted folder is created; when a user double clicks a shortcut icon to enable a start routine of the encrypted file system, a password input by the user is verified, a temporary catalogue is created after the verification succeeds, and the encrypted file system is mounted to the temporary catalogue. The folder encryption method and device for the Unix-like operating system can encrypt folders and achieve the effect that encrypted files can be in a protection state under both a dynamic condition and a static condition by loading and unloading the encrypted file system.
Owner:亚太宝龙科技(湖南)有限公司
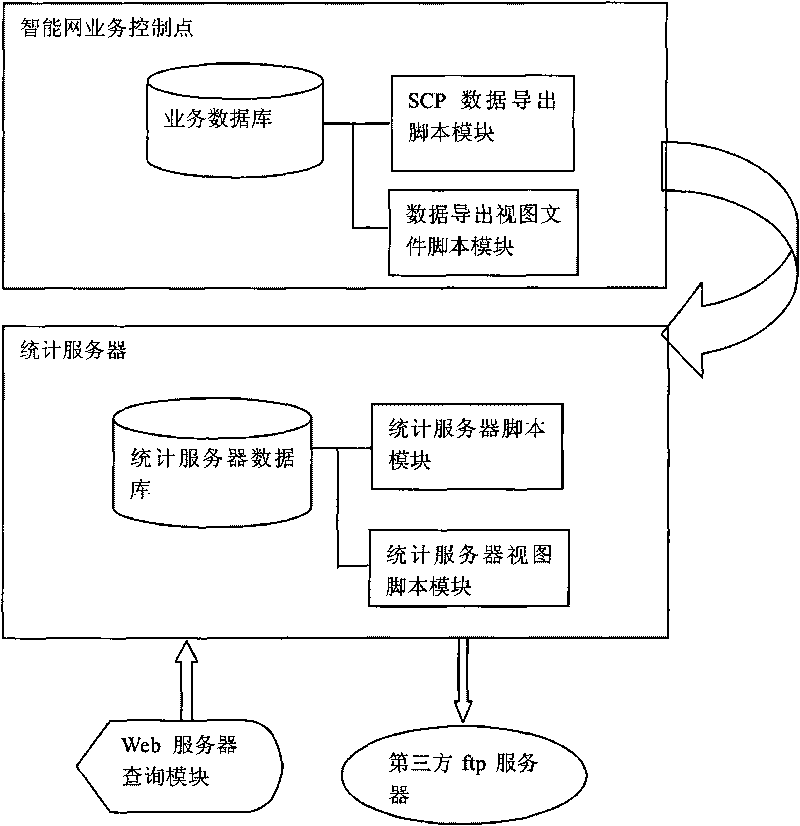
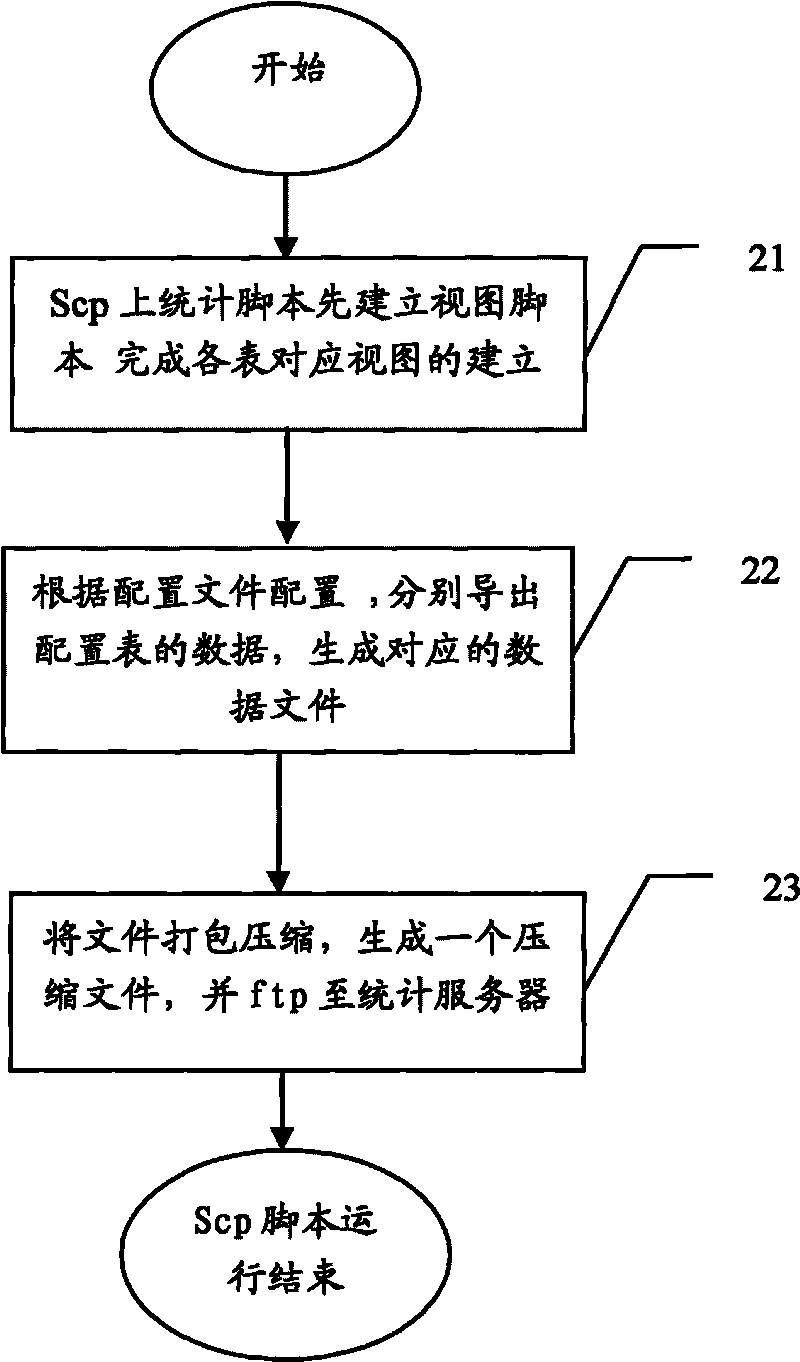
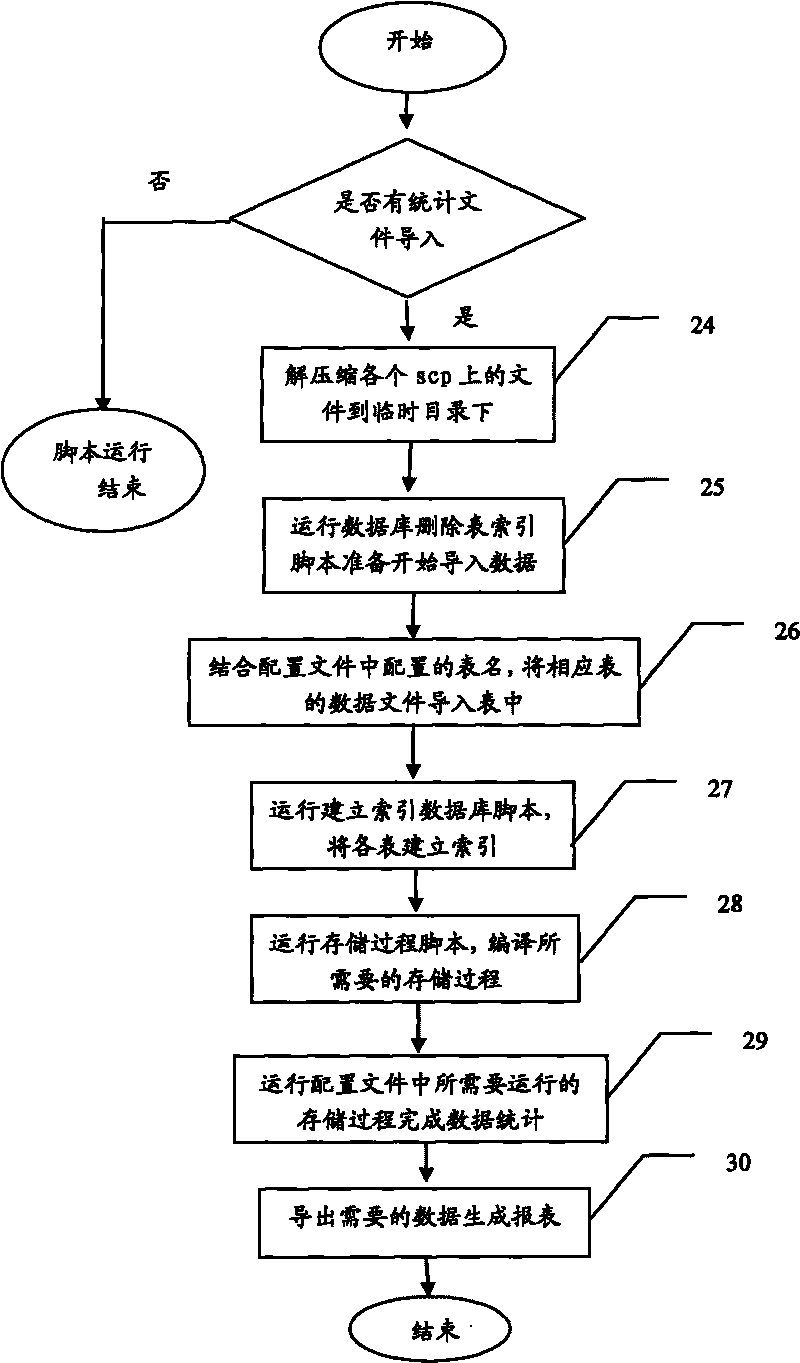
Method and device for automatically analyzing and processing polyphonic ringtone data
ActiveCN101697600AReduce loadAutomatic export implementationAutomatic exchangesTransmissionOperational systemStatistical analysis
The invention discloses a method and a device for automatically analyzing and processing polyphonic ringtone data. A polyphonic ringtone data statistical server is set, the polyphonic ringtone data are educed by each service control point according to the set parameters, and the polyphonic ringtone data are sent to the statistical server so as to finish automatic analysis and processing of the polyphonic ringtone data. The method and the device implement flexible automatic statistical analysis for the polyphonic ringtone data, reduce the load of SCP, and can well finish the analysis and processing of the multi-SCP mass polyphonic ringtone data. Moreover, the efficiency of educing, analyzing and processing the polyphonic ringtone data is improved by setting statistical demand classification parameters of the polyphonic ringtone data. For the operating environments of linux and unix operating systems, the automatic timing eduction mechanism of the polyphonic ringtone data is realized without additionally increasing the cost of the system in a mode of periodically calling a script through a control command.
Owner:徐助霞
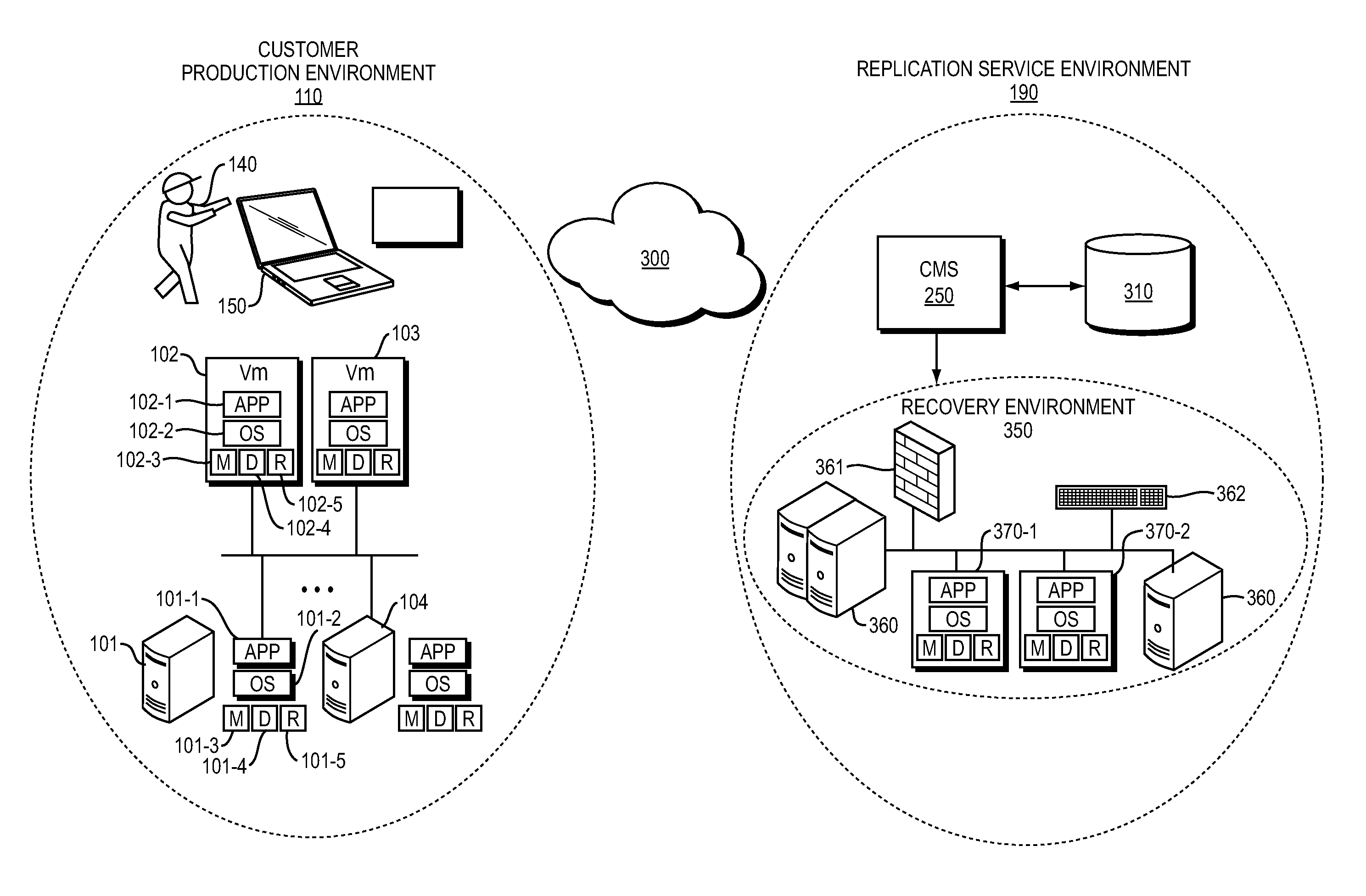
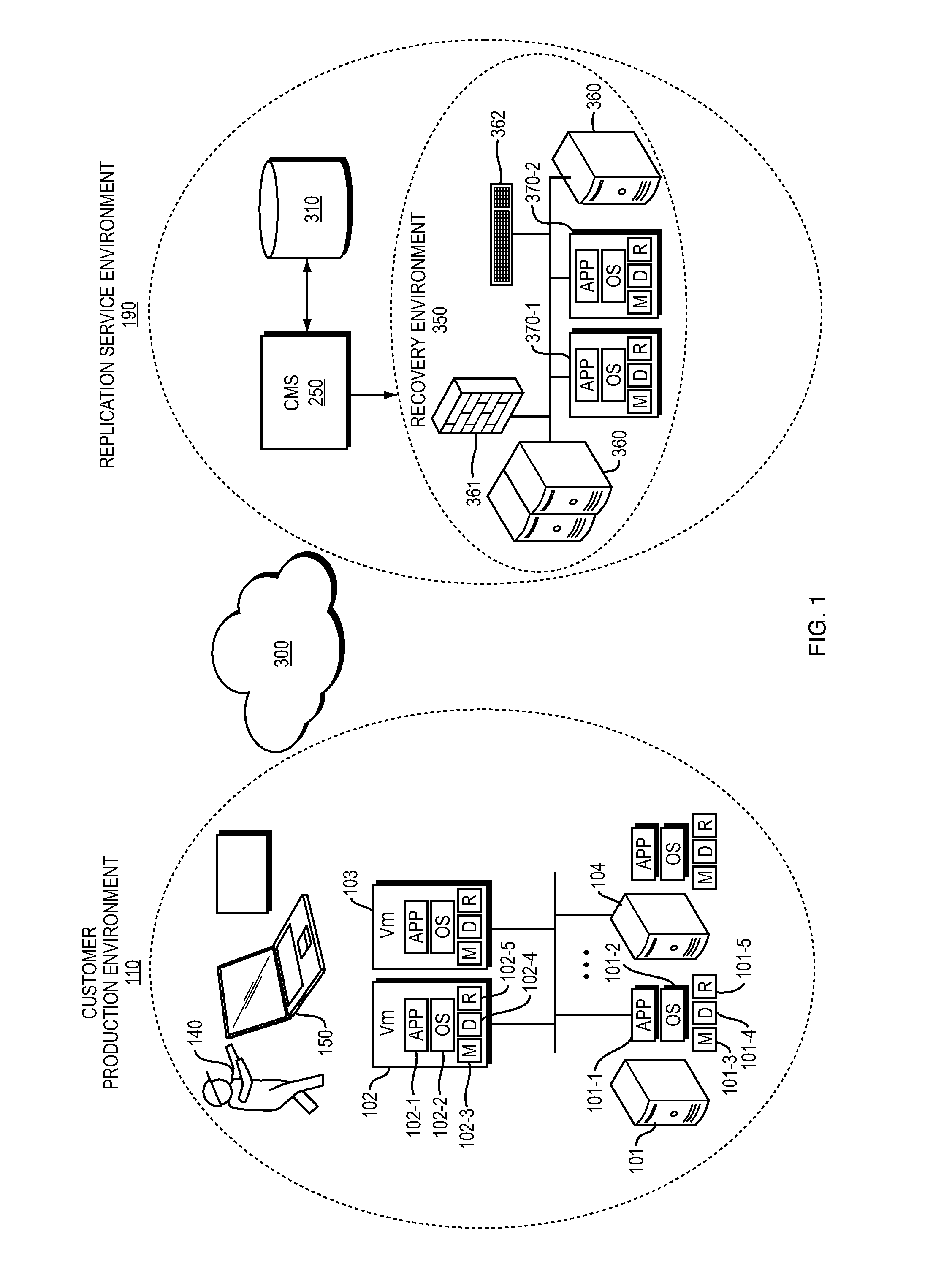
XML based generic UNIX discovery framework
Services that support recovery of a data center require collecting information concerning the service customer's physical and virtual infrastructure, and specifically the configuration of their operating systems such as UNIX operating systems. Here an automatic discovery tool executes within the context of a secure browser program. Once a user is authenticated, a JavaScript or HTML program seamlessly retrieves a file that is specific to the type and version of the UNIX operating system on the host; the file contains commands and parsing logic for the commands to retrieve configuration data. Once parsed, the program forwards that data to a database so that the replication service provider may then correctly provision recovery systems.
Owner:11 11 SYST INC
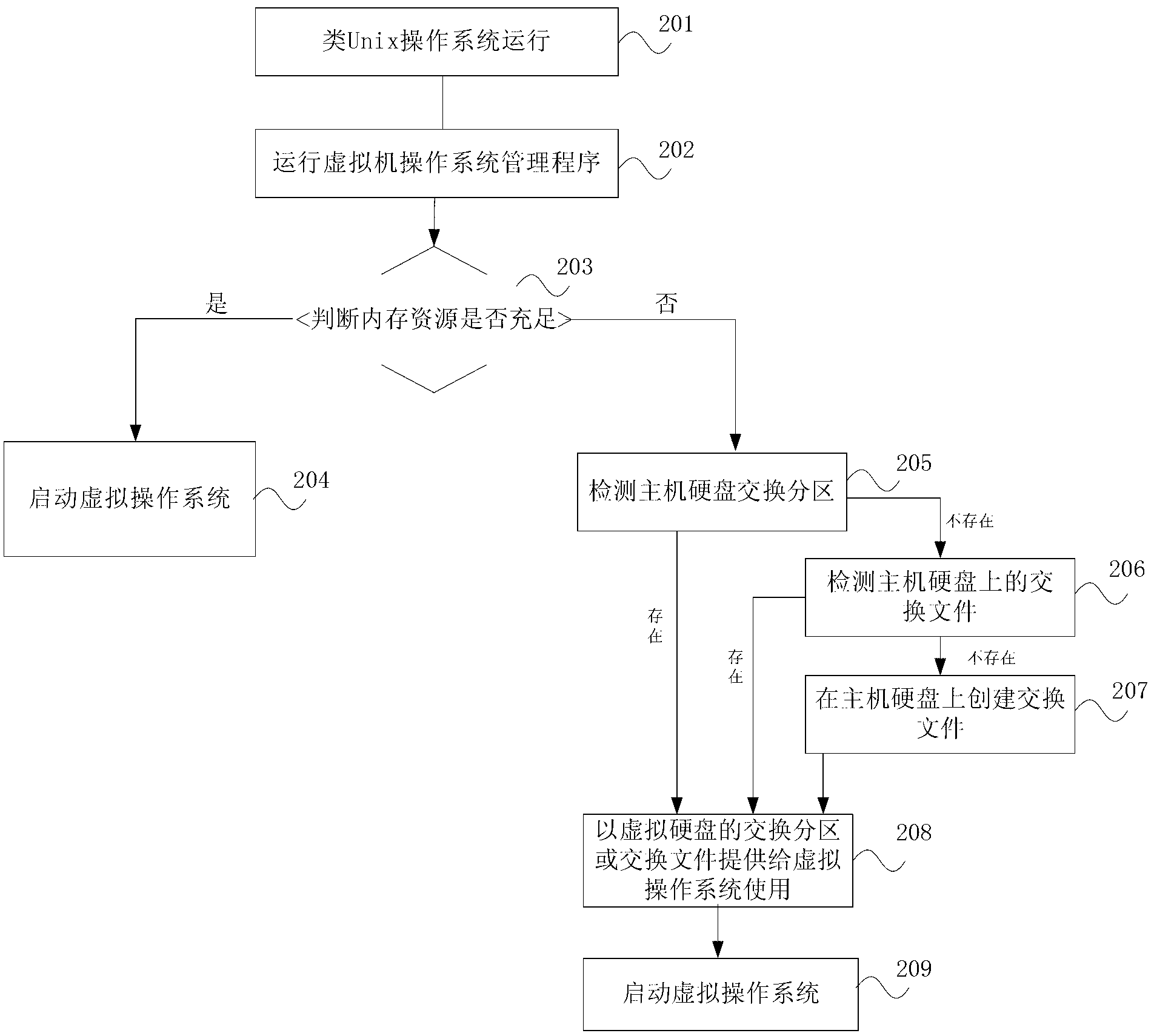
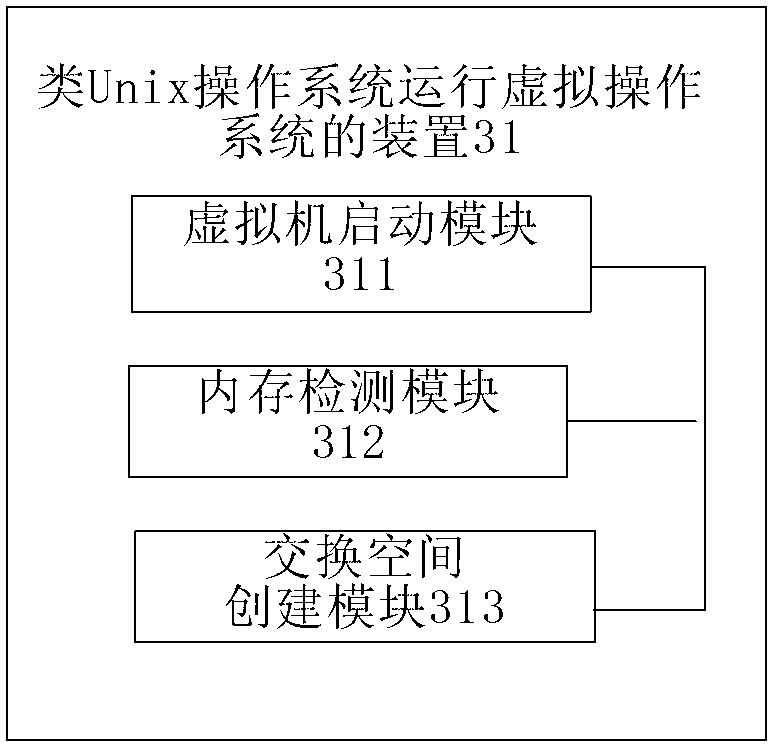
Method of similar UNIX operation system running virtual operation system and device of similar UNIX operation system running virtual operation system
InactiveCN103176832AImprove convenienceIncrease flexibilityProgram loading/initiatingSoftware simulation/interpretation/emulationOperational systemSpace mapping
The invention discloses a method of a similar UNIX operation system running virtual operation system and a device of the similar UNIX operation system running virtual operation system. When a similar UNIX operation system in a LiveX form is run, a virtual machine program is started, and a virtual operation system is run; and swap spaces are obtained before the virtual operation system is run and mapped into swap partitions of a virtual disk can be visited by the virtual operation system. According to the method of the similar UNIX operation system running virtual operation system and the device of the similar UNIX operation system running virtual operation system, before the virtual operation system is run, the existing swap partitions are searched, or existing swap files are searched, or the swap files are directly established, the swap spaces are obtained through one of three modes, then the swap spaces are mapped into the swap partitions or the swap files of the virtual disk can be visited by the to-be-run virtual operation system, then the other virtual operation system can be smoothly started and run in the similar UNIX operation system, and convenience and flexibility of using the virtual operation system in running the similar UNIX operation system in the LiveX form are improved.
Owner:湖南天下为公信息科技有限公司
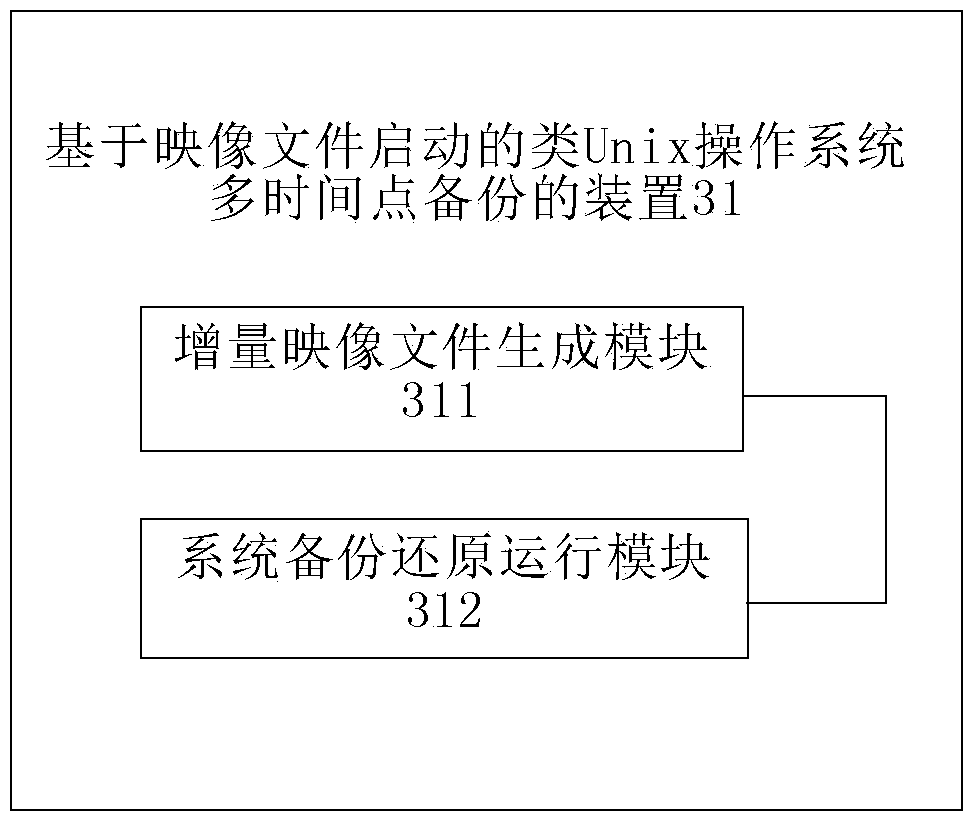
Method and device for backing up Unix-like operating system at multiple time points
InactiveCN103778033AImplement bidirectional restoreRedundant operation error correctionOperational systemChronological time
The invention discloses a method and a device for backing up a Unix-like operating system at multiple time points. The method comprises the following steps of packing increment files into a plurality of increment image files corresponding to different time points according to time sequence; when the Unix-like operating system is started, performing merged running on a basic image file and one or more increment image files in the increment image files according to time sequence to establish new increment files. By the method and the device, different backups can be selected for running the operating system according to different time points, the modification made by the system can be saved, the backup and recovery at multiple state points can be implemented according to time, bidirectional recovery can be realized, and the system can be recovered to a front time point, and can also be recovered from the front time point to a back time point.
Owner:BAOLONG COMP SYST HUNAN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com