Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
59 results about "Contrarian" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A contrarian is a person that takes up a contrary position, especially a position that is opposed to that of the majority.
Method and system for providing interactive adversing cross reference to related application
InactiveUS20040133468A1Satisfies needSpecial data processing applicationsMarketingThe InternetContrarian
A method and system of providing interactive advertising via the Internet, print, radio and other mediums. According to one embodiment, the method comprises presenting an advertisement to a user; presenting questions to the user, the questions related to the advertisement; providing an amount of credits to the user, the amount based on a number of the questions answered correctly by the user. Such advertisements may be provided via the Internet, print, radio and other mediums. The credits may take any form, including monetary, coupons, merchandise credits and the like.
Owner:BRANDPORT
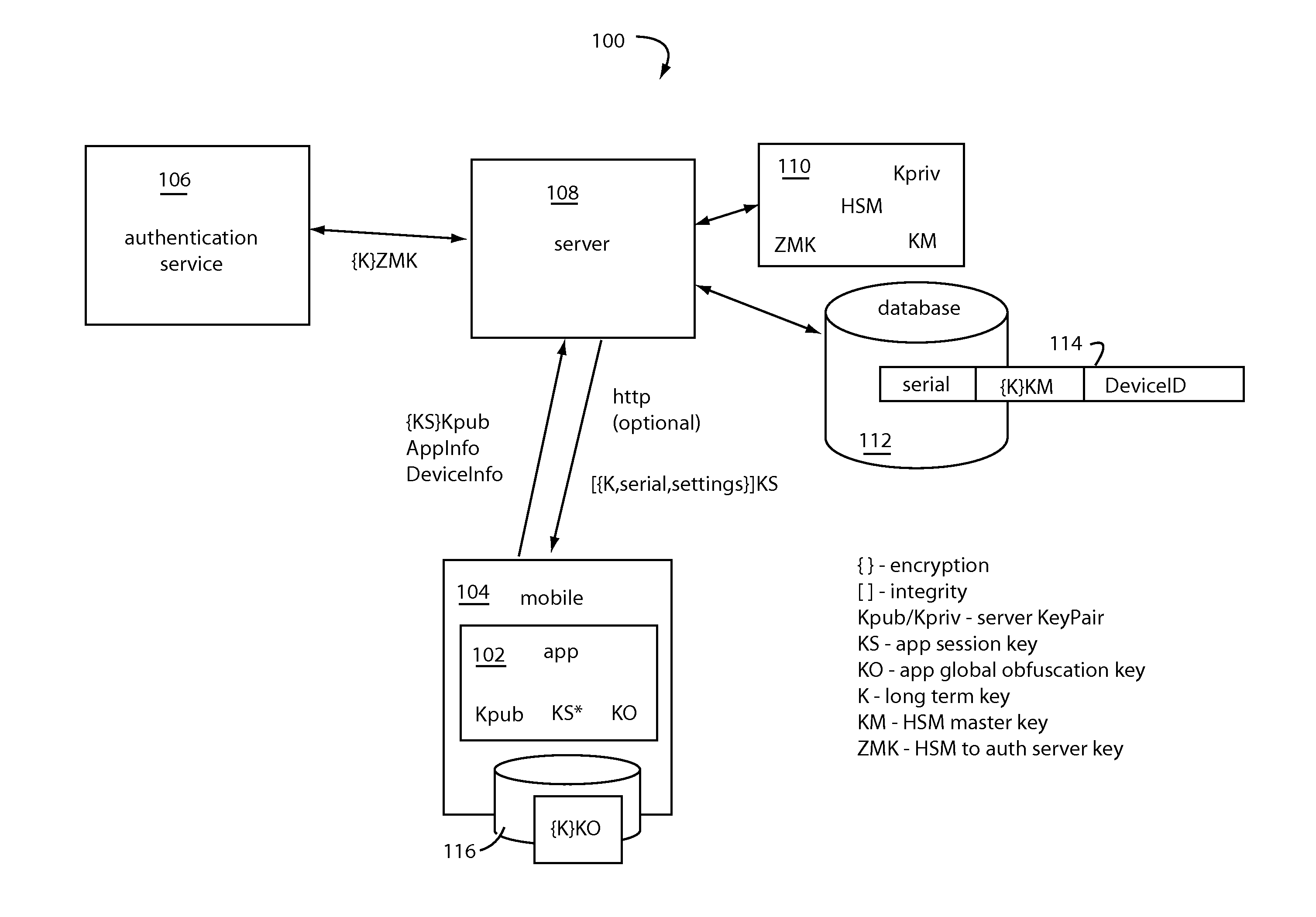
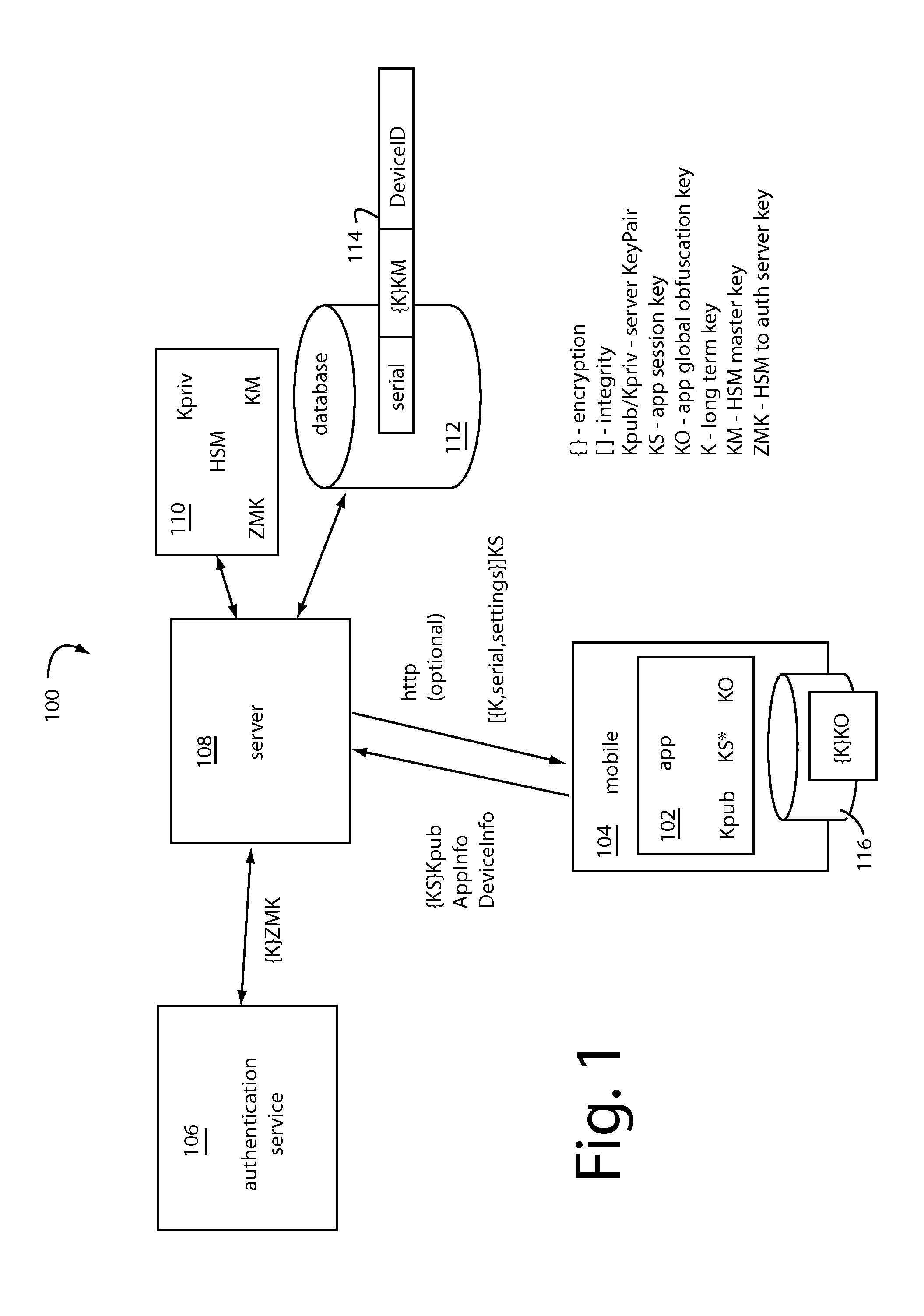
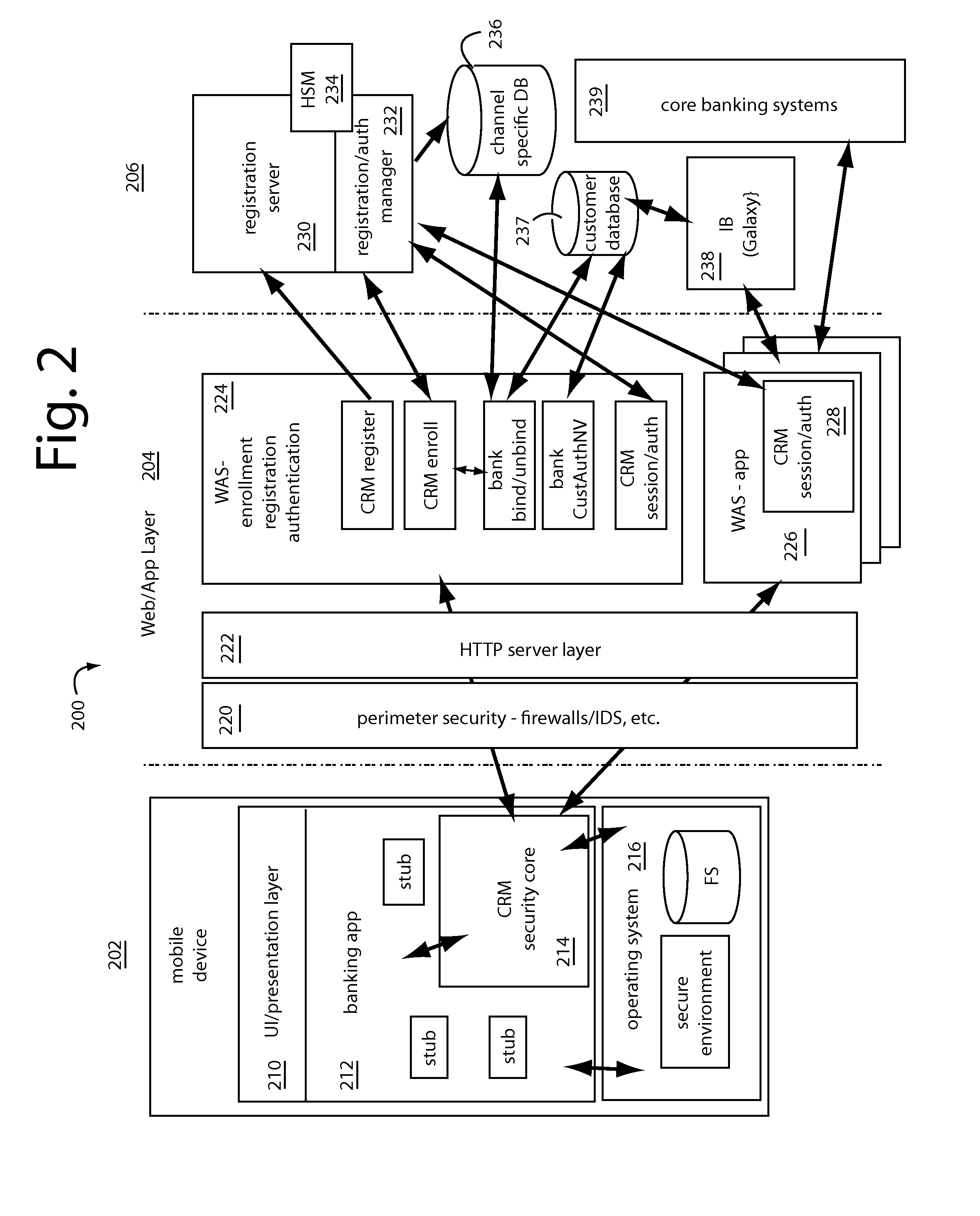
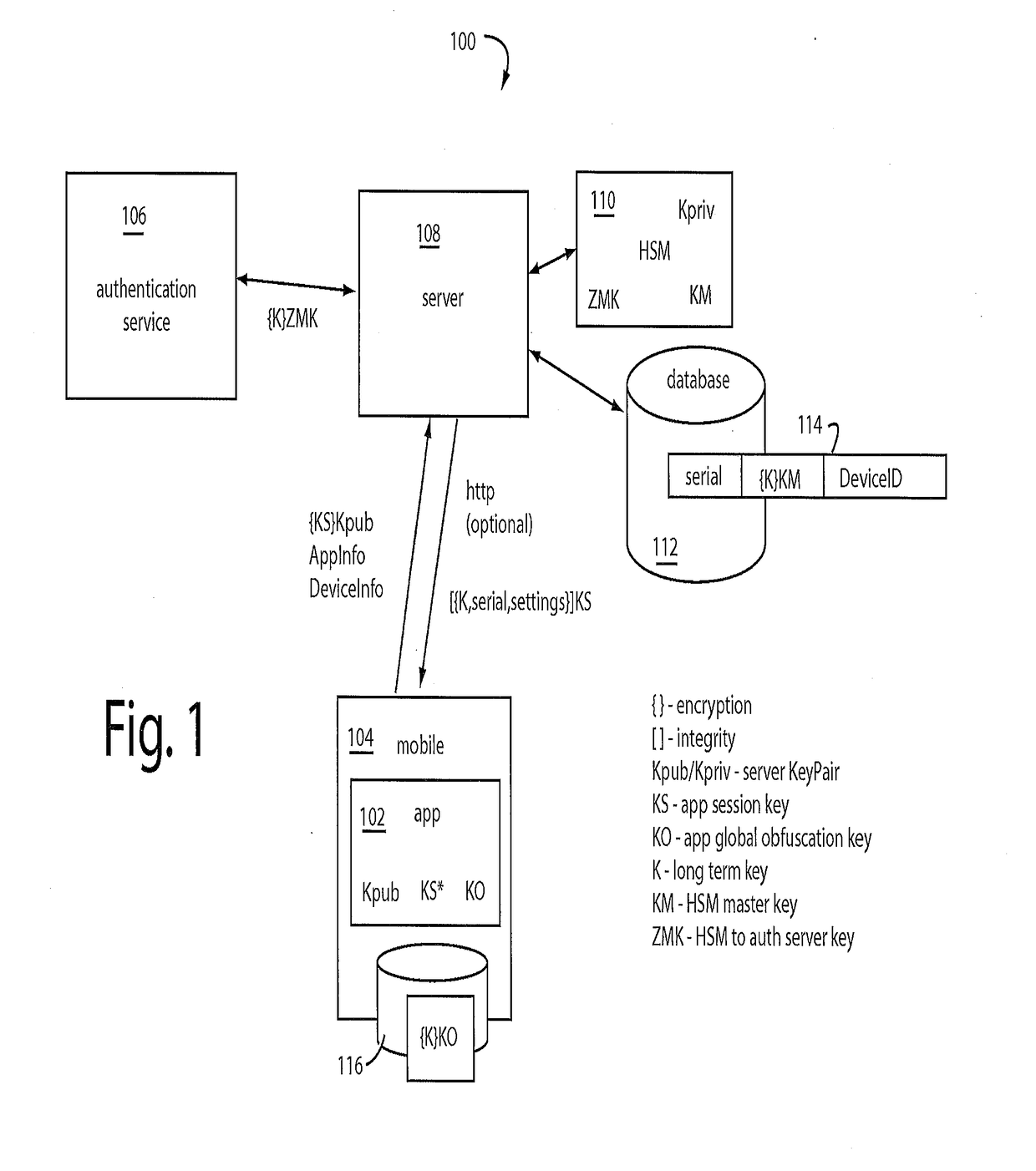
CRM Security Core
A security core supports a networked banking app for a client application device communicating with a server, such as e.g. a smartphone. It provides a secure environment for the banking app to conduct registration, enrollment, and transaction workflows with corresponding back-end servers on the network. It includes defenses against static analysis, attempts at reverse engineering, and real-time transaction fraud. A principal defense employed is obfuscation of the protocols, APIs, algorithms, and program code. It actively detects, thwarts, misdirects, and reports reverse engineering attempts and malware activity it senses. A routing obfuscator is configured to operate at the outer layer. Previous core designs are retained as camouflage. An internal TLS library is used rather than the OS TLS layer. Cookies are managed internally in the core rather than in the webkit-browser layer.
Owner:CRYPTOMATHIC LTD
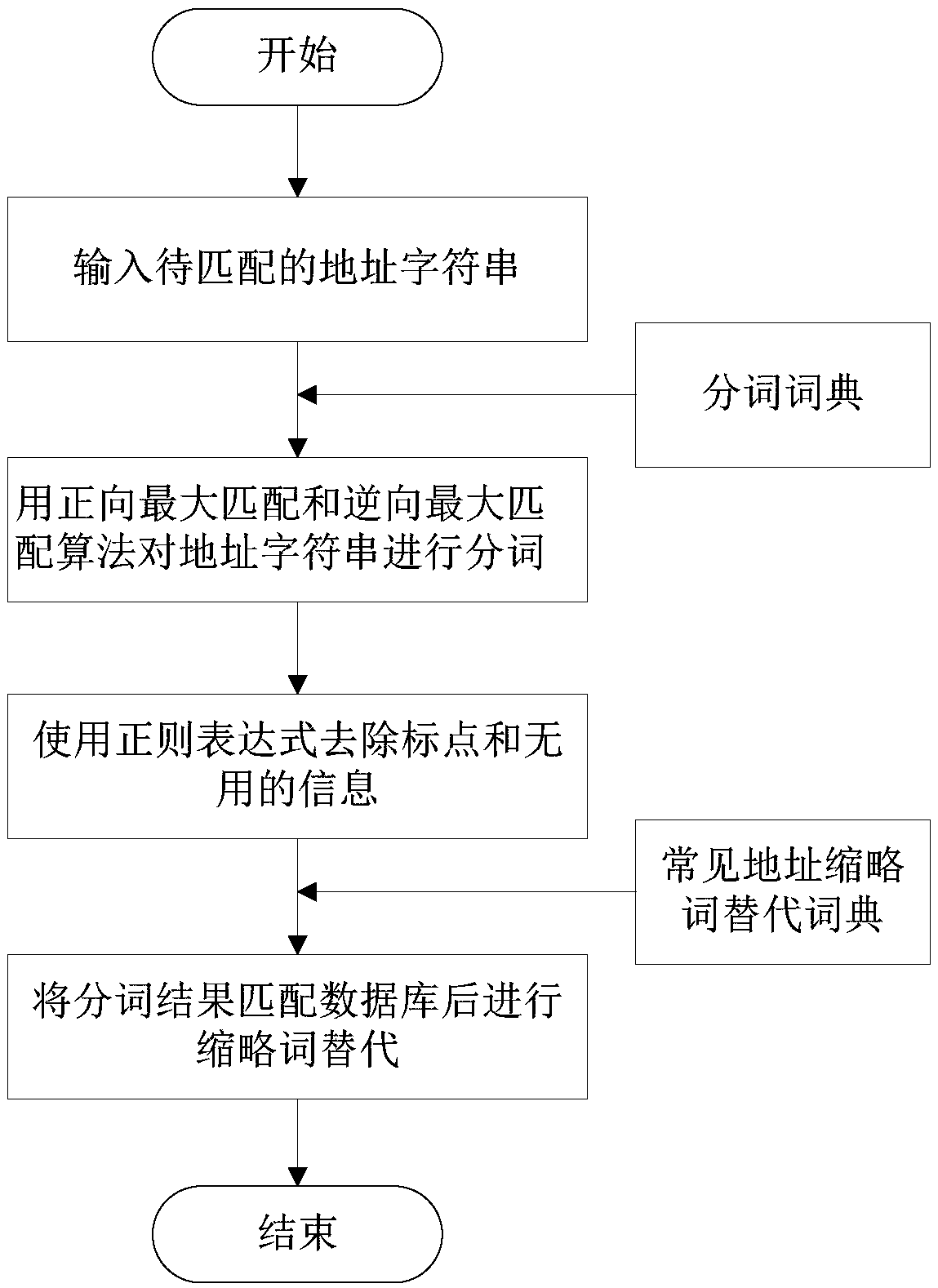
Chinese word segmentation algorithm based on reverse maximum matching
InactiveCN102999534AGuaranteed accuracySpeed up the loading processSpecial data processing applicationsChinese charactersContrarian
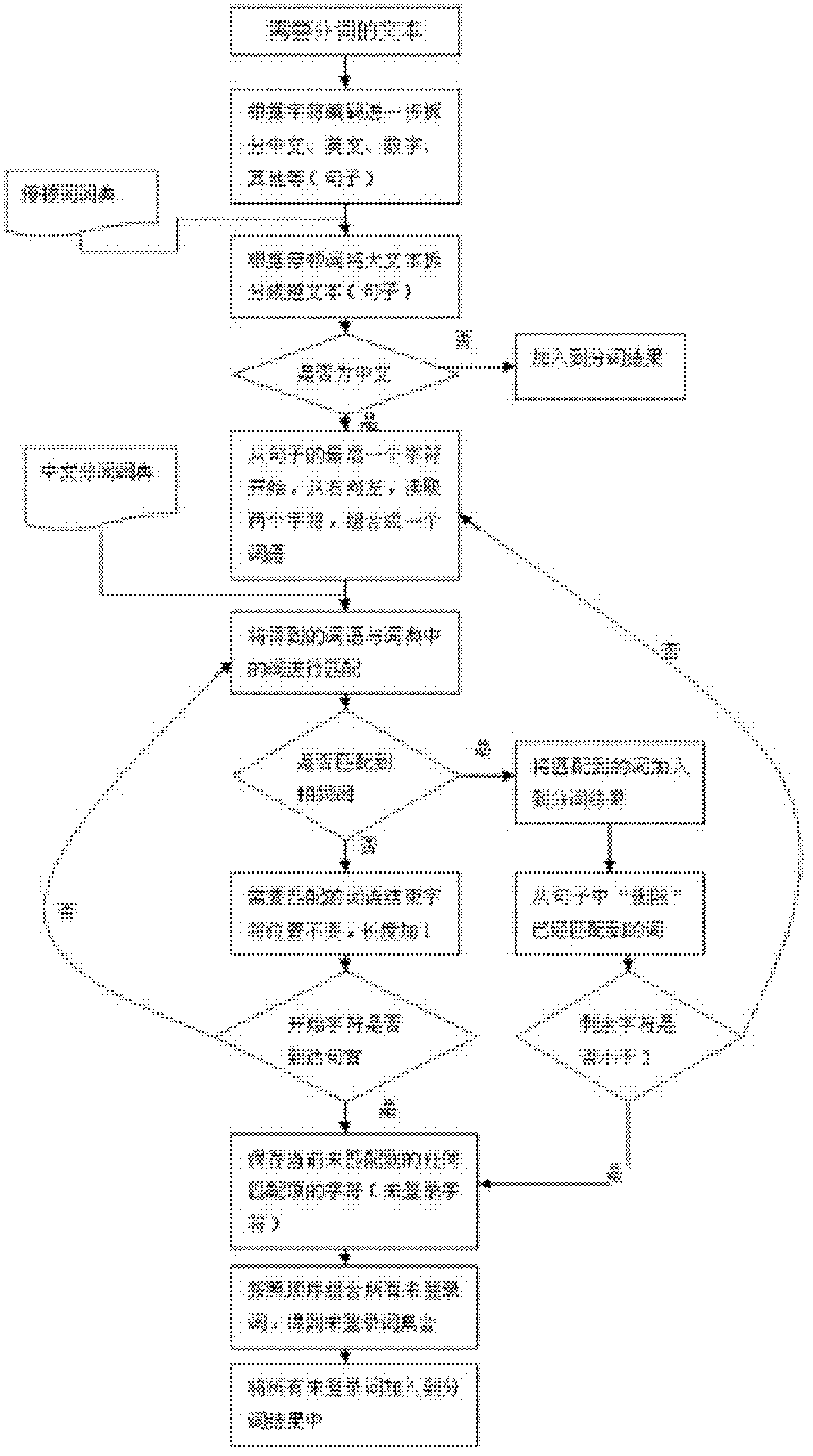
The invention discloses a Chinese word segmentation algorithm based on reverse maximum matching, which comprises the following steps: initializing three objects in a memory; inputting the contents of a text which needs word segmentation; splitting characters in the text into different types according to character codes; directly adding characters which are not Chinese characters to word segmentation results according to the character codes after the text is segmented into short sentences; splitting the short sentences into character sets according to a character string matching and decision-making mechanism; matching the character sets with character sets in a word segmentation dictionary based on the reverse maximum matching algorithm; storing matched character sets into a word segmentation result set; combining consecutive unmatched characters; and adding the consecutive unmatched characters to the word segmentation results to complete word segmentation. A quick word segmentation algorithm based on dictionaries is provided, and the dictionary loading efficiency and the word segmentation efficiency are greatly improved while word segmentation accuracy is ensured.
Owner:BEIJING JINHER SOFTWARE
Chinese word segmentation method based on hash table dictionary structure
ActiveCN103646018AImprove efficiencyImprove matching efficiencySpecial data processing applicationsContrarianChinese word
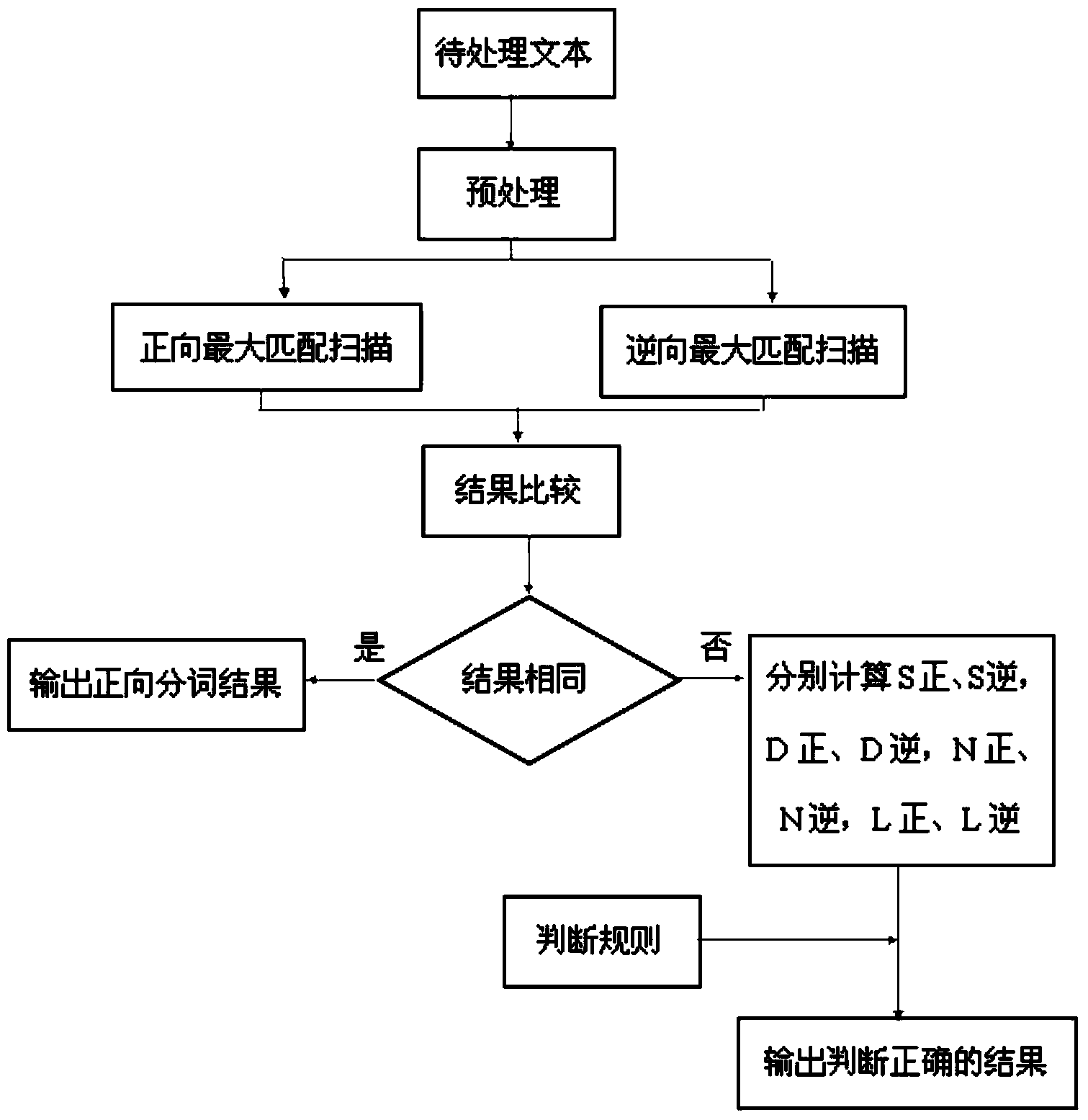
The invention discloses a Chinese word segmentation method based on a hash table dictionary structure. The Chinese word segmentation method comprises the following steps: A, performing pretreatment to a to-be-treated document; B, performing positive maximum matching scanning segmentation and negative maximum matching scanning segmentation to each treatment block; C, comparing the results of two scanning of each treatment block, if the segmentation results of the two scanning are the same, outputting a positive segmentation result, if the segmentation results are different, respectively calculating the segmentation numbers S, the separate word dictionary word numbers D, the non-dictionary word numbers N and the maximum word lengths L of the positive maximum scanning result and the negative maximum scanning result respectively; D, comparing and analyzing data produced in step 3 in combination with the method and then outputting a right result. The Chinese word segmentation method has the benefits that the matching efficiency in the segmentation process is improved, the comparison rate after positive and negative scanning can be improved, and the efficiency of two-way maximum matching algorithm is improved fundamentally.
Owner:DALIAN UNIV
Method and device for protecting JAVA executable program through virtual machine
ActiveCN103413075AProtection logicProtection processProgram/content distribution protectionCode snippetContrarian
The invention discloses a method and device for protecting a JAVA executable program through a virtual machine. The method comprises the step of creating a local dynamic link library file, the step of enumerating a .class file in protected JAVA software, the step of analyzing a JVM code in the .class file, the step of drawing a code snippet at random, the step of replacing a home position with the calling to a native method, the step of generating a derived function in the local dynamic link library file, and the step of achieving the function of drawing the code snippet by using the user-defined virtual machine. By means of the method, codes and logic of the JAVA software can be effectively prevented from being reversed and decoded, and the safety intensity of the software is improved.
Owner:BEIJING SENSESHIELD TECH
Lexical item weight labeling method and device
ActiveCN105975459AImprove the effect of weight labelingDeepen connectionWeb data indexingDigital computer detailsSearch wordsLexical item
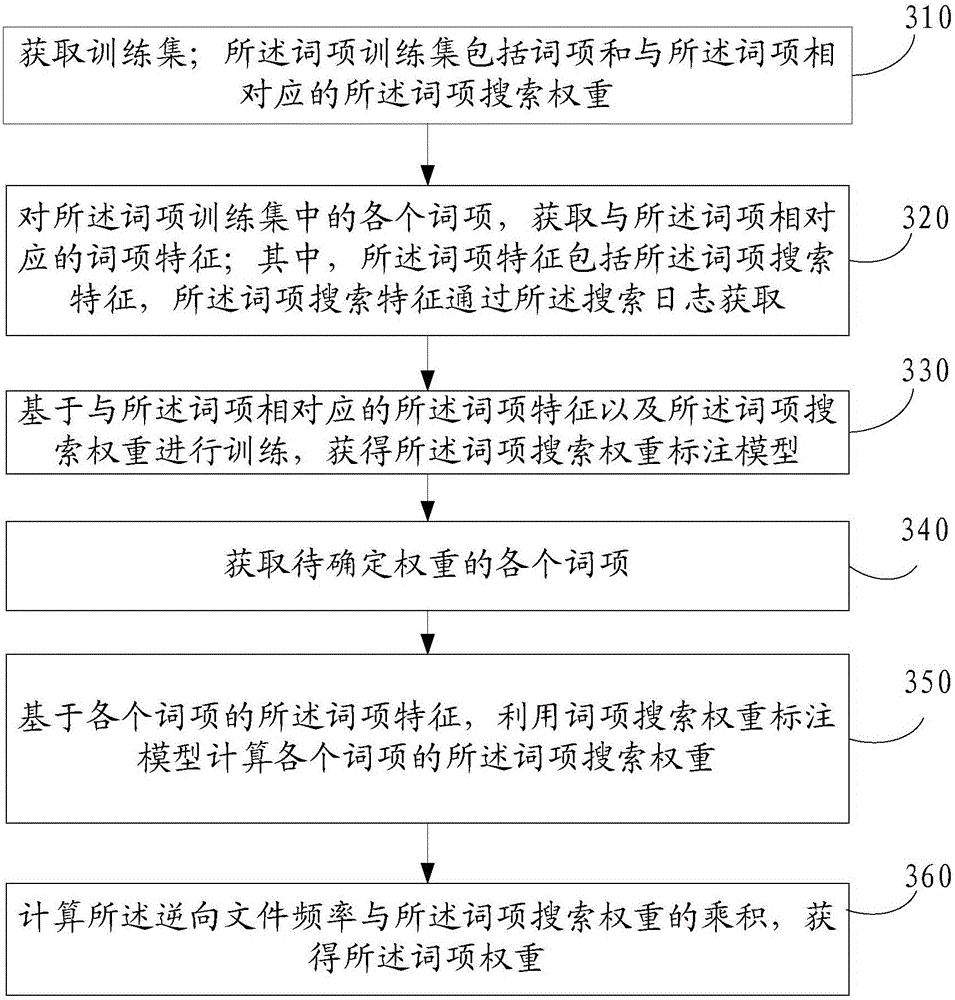
The embodiment of invention provides a lexical item weight labeling method and device, and relates to the technical field of internet search. The method includes the steps that all lexical items with weights to be determined are obtained; lexical item search weights of all the lexical items are calculated by combining search logs; according to occurrence frequencies of all the lexical items in a document set, reverse documents frequencies of all the lexical items are calculated; according to the lexical item search weights and reverse documents frequencies of all the lexical items and the, lexical item weights are calculated. The problem that in the method of using TF-IDF for calculating the lexical item weights in the internet search field, when a search task with a short text as the principal thing based on search words is implemented, important lexical items are marked with smaller weights is solved, the lexical item weights are calculated mainly based on the search logs, while connection between the lexical items and the search words is deepened, precision of correlation calculation between the lexical items and documents is improved in the search environment, and the search ranking quality is improved.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
Method and system for reverse pricing of buyer based on block chain
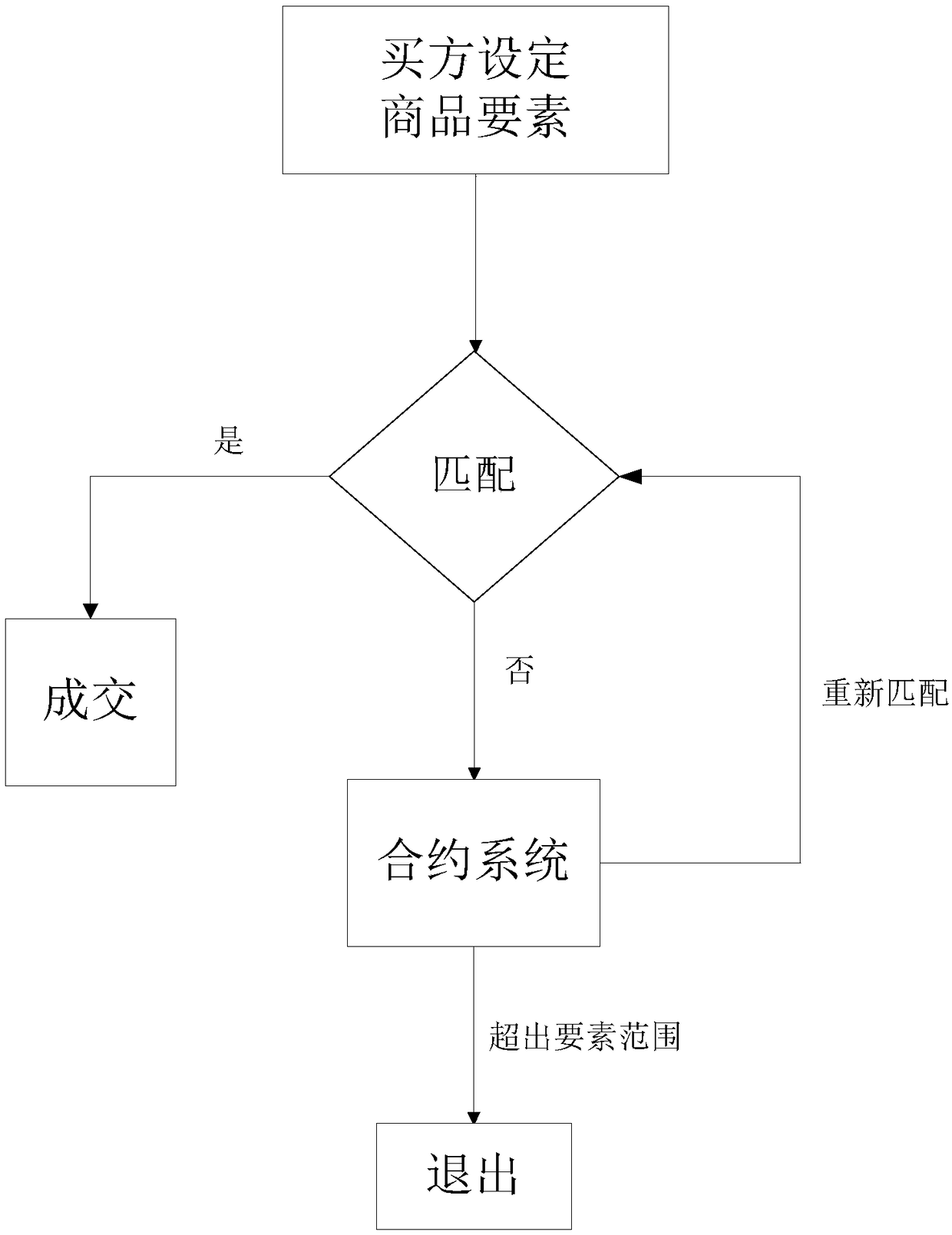
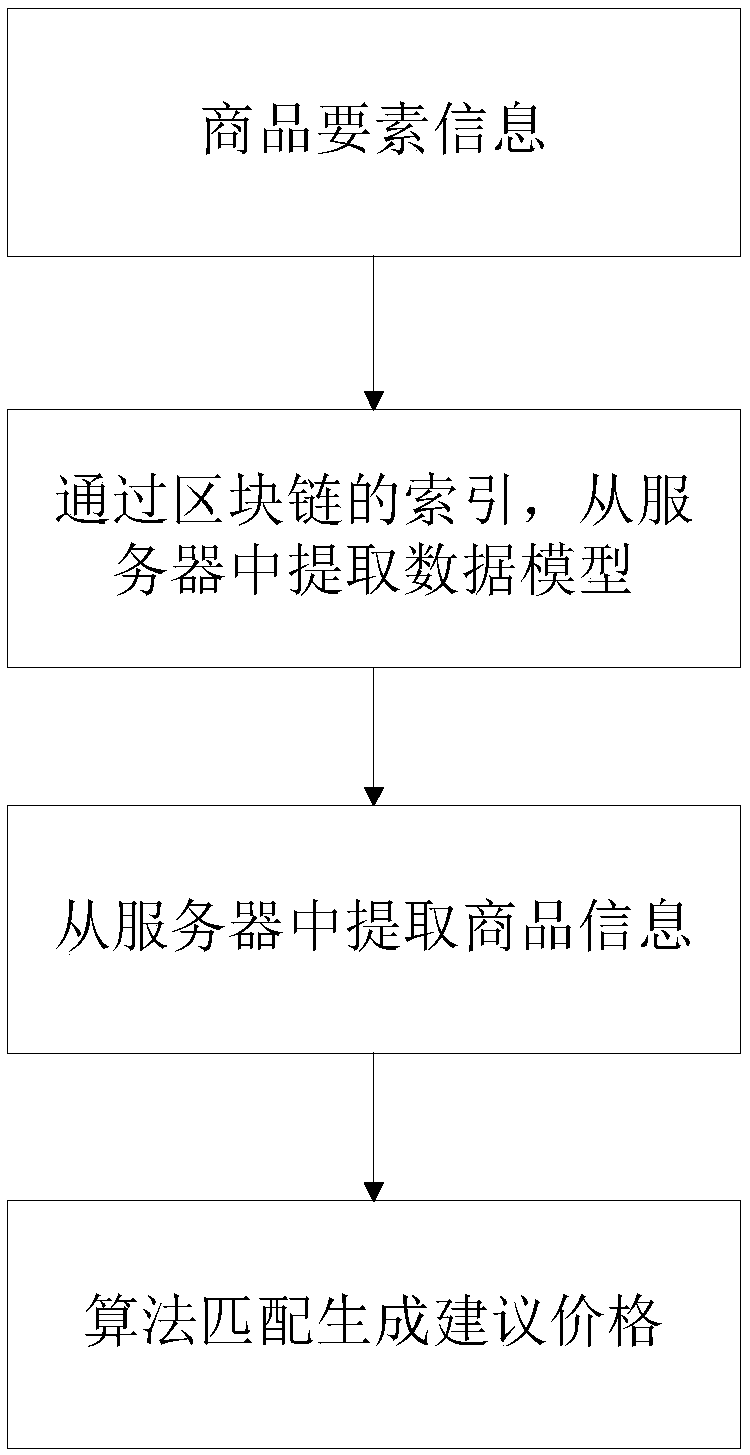
ActiveCN108805602AAvoid controlSolve the problem of mutual trustMarketingSystems managementContrarian
The invention relates to the field of reverse pricing of a buyer, and provides a method and a system for reverse pricing of a buyer based on a block chain. The method comprises the following steps: receiving a buyer element by a first client, generating a buyer contract according to the buyer element, and recording the buyer contract in a block chain, the buyer element comprising a first element and a buyer price, and the first element comprising a to-be-purchased commodity name; receiving a seller element by at least one second client, generating a seller contract according to the seller element, and recording the seller contract in the block chain, the seller element comprising a second element, a seller price, and the second element comprising a to-be-sold commodity name; and judging whether the seller contract read from the block chain conforms to the buyer contract or not by a server, if yes, generating an intelligent contract for concluding a transaction, and recording the intelligent contract in the block chain, and if not, notifying the first client and the second client of a message characterizing the transaction failure. The invention avoids the control right of a centralized system management platform to the transaction between the buyer and the seller.
Owner:朱志强 +1
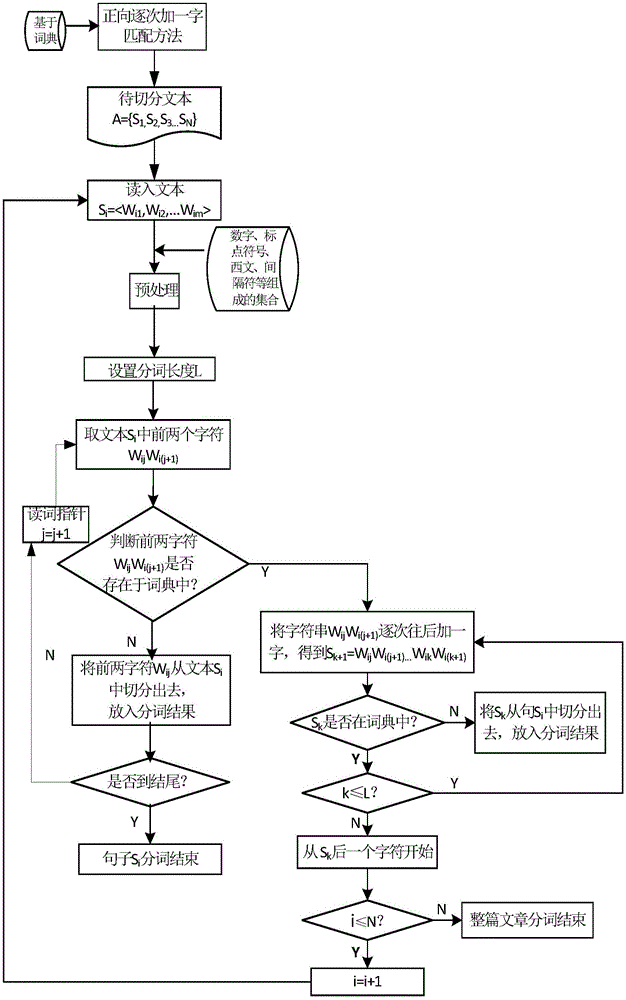
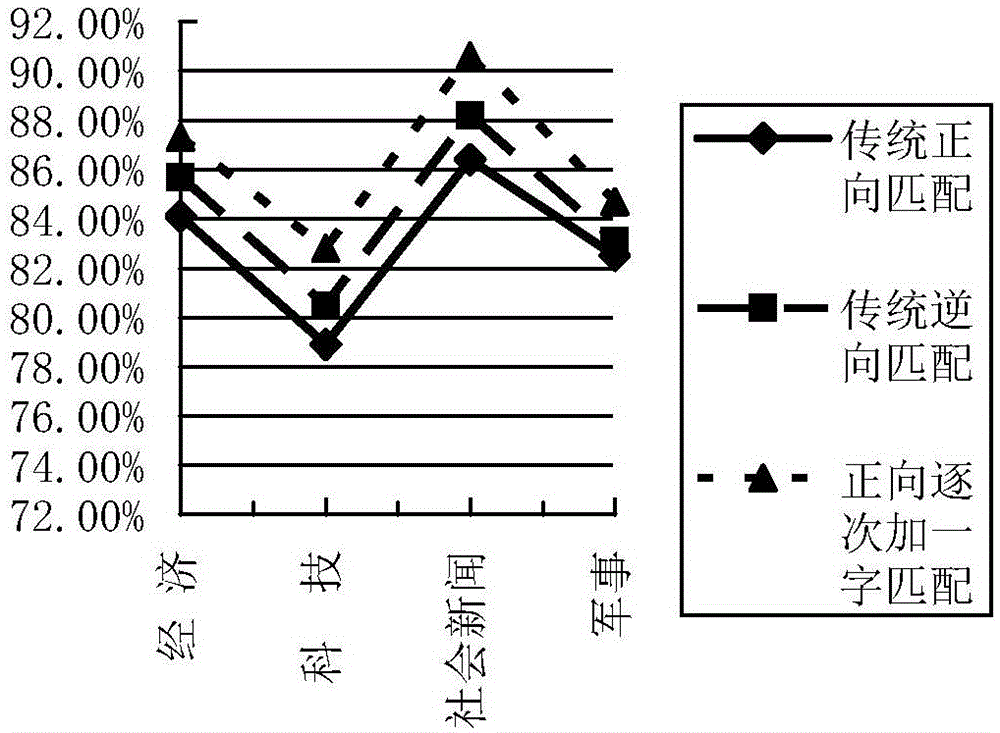
Dictionary-based method for maximum matching of Chinese word segmentations through successive one word adding in forward direction
ActiveCN105138514AConvenient timeImprove accuracySpecial data processing applicationsContrarianChinese word
The invention relates to a dictionary-based method for maximum matching of Chinese word segmentations through successive one word adding in the forward direction, and belongs to the technical field of computer Chinese text processing. The method comprises the steps that a text to be segmented is read in at first, and the input text is coarsely segmented according to obvious separators such as punctuations, figures, western languages and charts into independent short texts; the coarsely-segmented short texts are used as objects to be further segmented, and the further word segmentation search length is set; the coarsely-cut short texts are matched with the dictionary for word segmentation in the way of successive one word adding in the forward direction until word segmentation of all the short texts is finished. The defect that traditional forward-direction maximum matching word segmentation speed and accuracy are difficult to balance is avoided, and the word segmentation speed and accuracy are improved compared with traditional forward-direction and reverse-direction maximum matching word segmentation algorithms.
Owner:KUNMING UNIV OF SCI & TECH
Music reorganization-based music score automatic formation method
InactiveCN104992712AMeet the requirements of multi-tone recognitionEasy to operateSpeech analysisCharacter and pattern recognitionFrequency spectrumContrarian
The invention discloses a music reorganization-based music score automatic formation method. The method includes the following steps that: (1) audios are recognized, the changes of the whole frequency spectrum of the audios are tracked, and sound emitting trends are checked in real time; (2) the frequency spectrum changes of each pitch are tracked, and pitches requiring sound emitting are checked in real time; (3) the frequency spectrum changes of pitches of which the sound emitting has been completed are further tracked, and whether judgment on sound emitting of the previous pitches is wrong is checked; and (4) the speed, tone and note type of a music score are estimated according to sound-emitting pitch data and sound-emitting time data obtained in the above steps, so that the music score can be composed. According to the music reorganization-based music score automatic formation method, an original music score can be estimated reversely according to pitch reorganization results, and thus, audio music can be automatically identified, and a music score can be automatically formed. The music reorganization-based music score automatic formation method has the advantages of simple calculation, robustness in sound emission number, compatibility with requirements of a variety of musical instruments as well as being efficient and reliable. The music reorganization-based music score automatic formation method can be applied to mobile phone software and embedded equipment, and can be also applied to occasions such as composition creation automatic music score formation and musical instrument playing exercise check.
Owner:MEET STUDIO
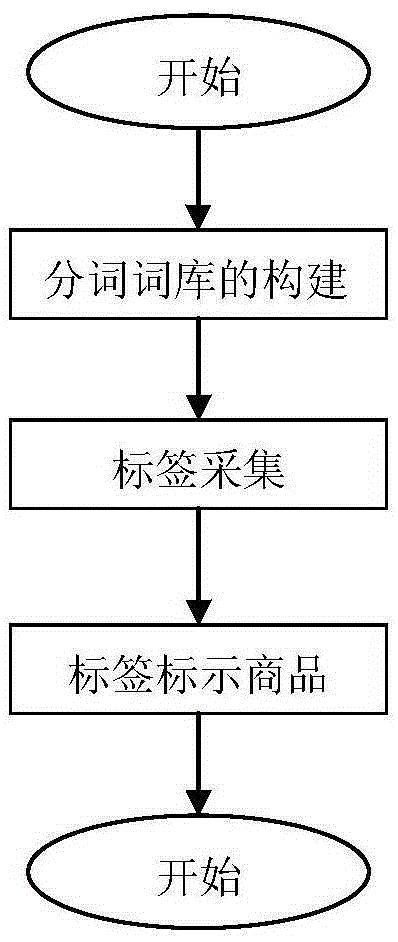
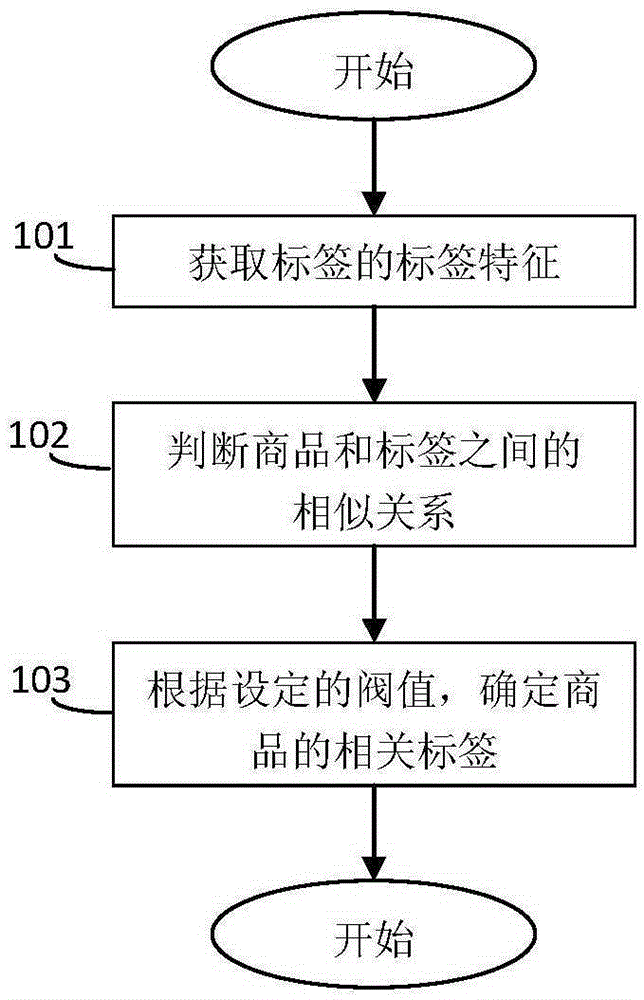
Commodity labeling method suitable for electronic commerce Chinese website
ActiveCN105320778AGuaranteed accuracyLock accuratelyWeb data indexingWebsite content managementChinese charactersData set
A commodity labeling method suitable for an electronic commerce Chinese website includes the step of building a word segmentation lexicon, the step of collecting labels and the step of marking commodities with the labels. According to the step of building the word segmentation lexicon, based on frequency statistics, in different commodity descriptions, of all commodity key words in the electronic commerce Chinese website, the commodity key words with the frequency larger than three are reserved, and the key words with the number of Chinese characters of the commodity key words smaller than or equal to five are screened from the commodity key words to serve as lexicon data. According to the step of collecting the labels, based on the built word segmentation lexicon, word segmentation processing is carried out on all commodity names in the electronic commerce Chinese website through a reverse maximum matching word segmentation algorithm, after word segmentation processing is carried out through the reverse maximum matching word segmentation algorithm, the last word formed by word segmentation processing of each commodity is selected as the commodity label of the commodity, and finally all the labels form a label data set. According to the step of marking the commodities with the labels, relations between commodity attributes and the labels are found by using a text mining algorithm.
Owner:FOCUS TECH
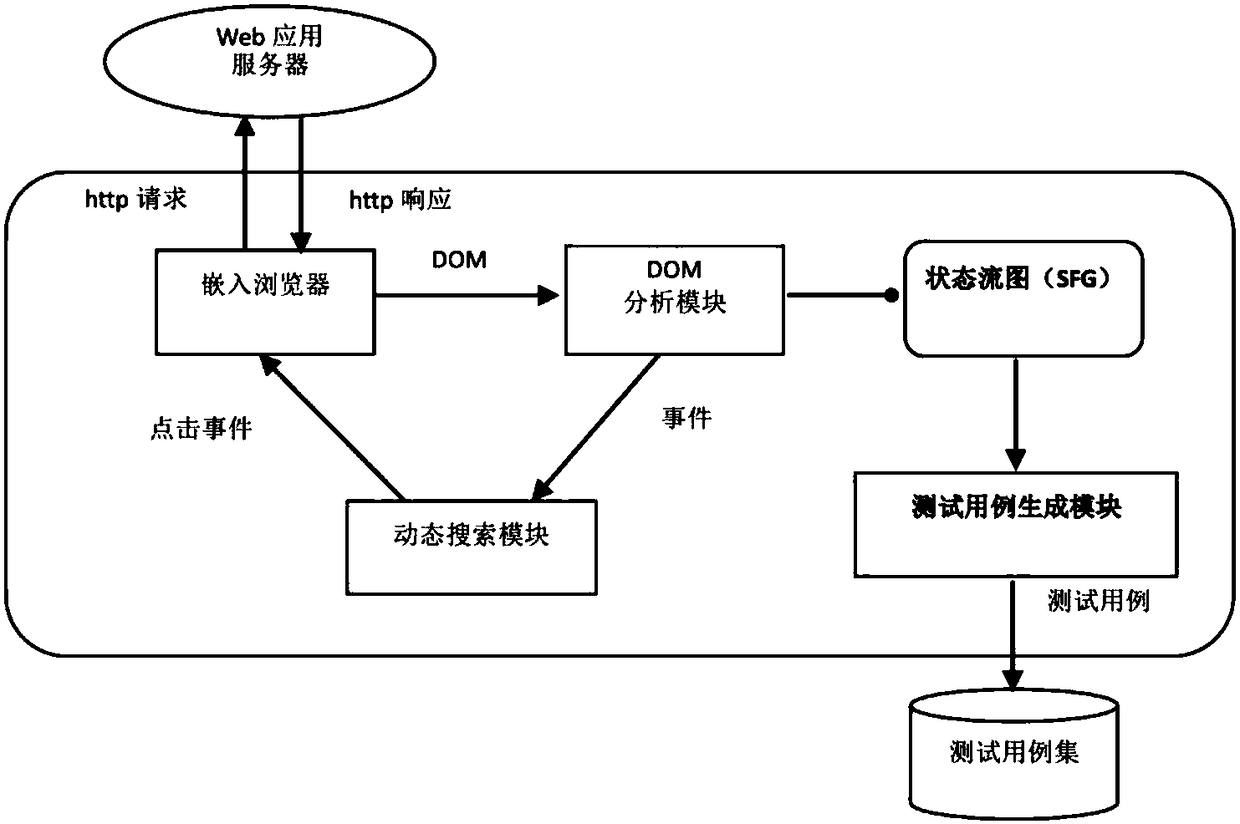
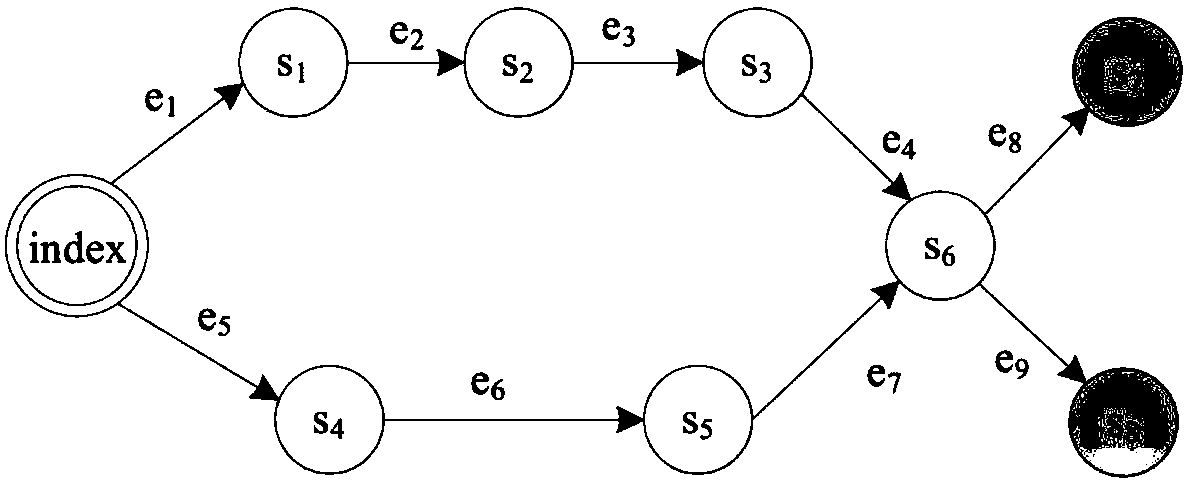
Web application test case generation method based on user interface state flow graph
The invention discloses a web application test case generation method based on a user interface state flow graph. The method includes: using the dynamic searching technology to generate the user interface state flow graph (SFG) to serve as a Web application test model, and performing reverse depth-first traversal on the SFG starting from a final-state node to obtain event sequence on a complete path from an initial-state node to the final-state node so as to generate Web application test cases, wherein visiting nodes are marked during the reverse traversal of the SFG, and the shortest paths from the initial nodes to the marked nodes are used to replace depth traversal during subsequent test case generation. By the method, test case set scale can be reduced under the premise that SFG edge coverage is guaranteed, Web application testing cost is lowered, and Web application testing efficiency is increased.
Owner:SOUTHEAST UNIV
Crm security core
InactiveUS20170243203A1Service provisioningKey distribution for secure communicationObfuscationContrarian
A security core supports a networked banking app for a client application device communicating with a server, such as e.g. a smartphone. It provides a secure environment for the banking app to conduct registration, enrollment, and transaction workflows with corresponding back-end servers on the network. It includes defenses against static analysis, attempts at reverse engineering, and real-time transaction fraud. A principal defense employed is obfuscation of the protocols, APIs, algorithms, and program code. It actively detects, thwarts, misdirects, and reports reverse engineering attempts and malware activity it senses. A routing obfuscator is configured to operate at the outer layer. Previous core designs are retained as camouflage. An internal TLS library is used rather than the OS TLS layer. Cookies are managed internally in the core rather than in the webkit-browser layer.
Owner:CRYPTOMATHIC LTD
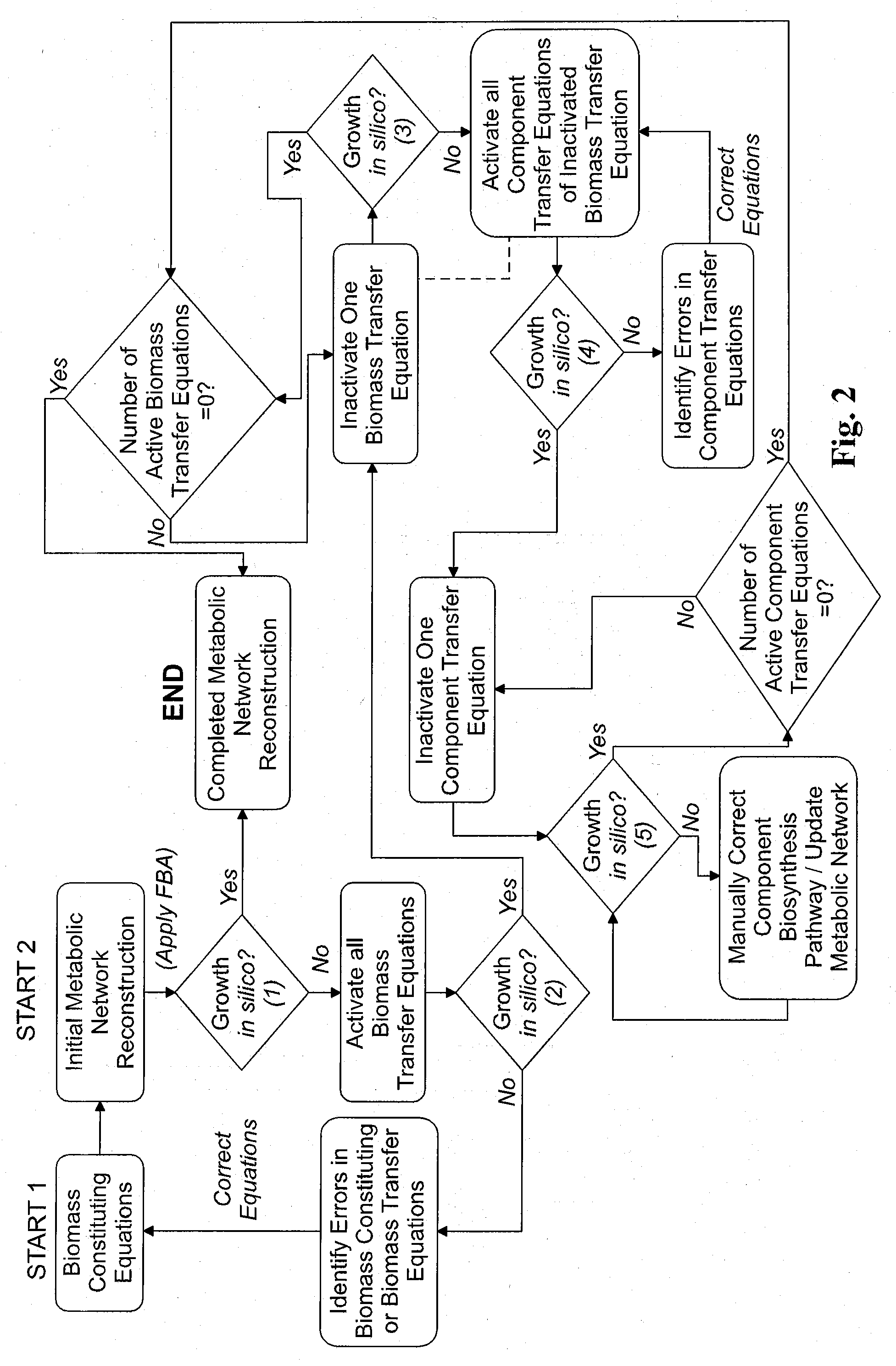
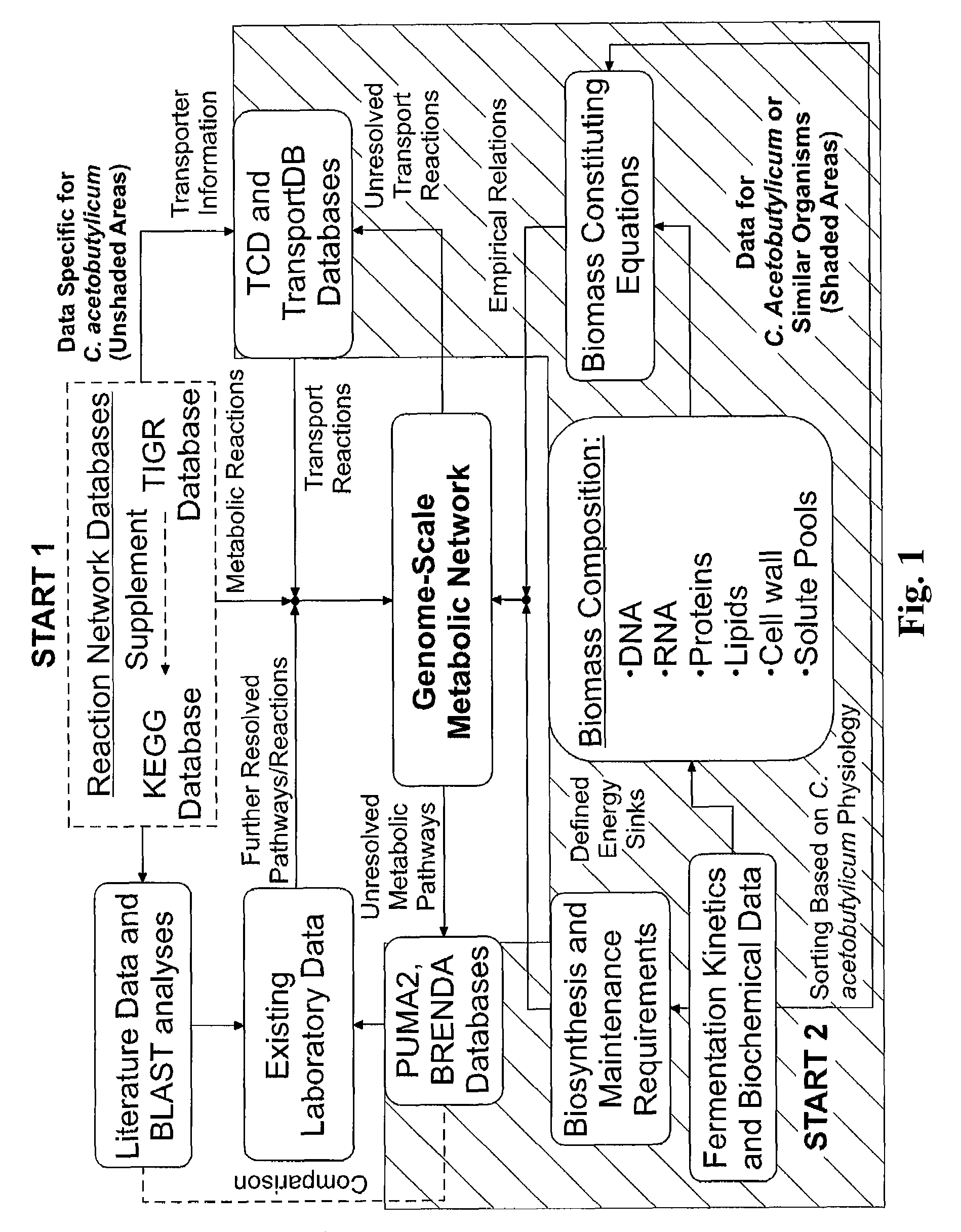
Reverse engineering genome-scale metabolic network reconstructions for organisms with incomplete genome annotation and developing constraints using proton flux states and numerically-determined sub-systems
InactiveUS20090259451A1Reduce in quantityAnalogue computers for chemical processesBiological testingUnderdetermined systemIn silico
A genome-scale metabolic network reconstruction for Clostridium acetobutylicum (ATCC 824) was created using a new semi-automated reverse engineering algorithm. This invention includes algorithms and software that can reconstruct genome-scale metabolic networks for cell-types available through the Kyoto Encyclopedia of Genes and Genomes. This method can also be used to complete partial metabolic networks and cell signaling networks where adequate starting information base is available. The software may use a semi-automated approach which uses a priori knowledge of the cell-type from the user. Upon completion, the program output is a genome-scale stoichiometric matrix capable of cell growth in silico. The invention also includes methods for developing flux constraints and reducing the number of possible solutions to an under-determined system by applying specific proton flux states and identifying numerically-determined sub-systems. Although the model-building and analysis tools described in this invention were initially applied to C. acetobutylicum, the novel algorithms and software can be applied universally.
Owner:UNIVERSITY OF DELAWARE
Method for finding topological neighbors in sampled data of physical surface
InactiveCN104850712AQuick access to initial reference dataImprove query efficiencySpecial data processing applications3D modellingNeighbor findingHigh probability
The invention provides a method for finding topological neighbors in sampled data of physical surface and belongs to the technical field of reverse product engineering. The method is characterized in that constructing a dynamic spatial index for physical surface sample points through an R* tree; subjecting the index to depth-first traversal to quickly acquire a k-nearest neighbor point set of target sample points, using the k-nearest neighbor point set as initial reference data for topological neighbors of the target sample points, describing distribution law of the sample points by kernel density estimation according to a relation between neighbor finding and sample point distribution, ranking the sample points in the initial reference data according to their probability densities, selecting Omega sample points of highest probability density to define a maximum point of local probability densities, determining a finding direction according to the maximum point, allowing the initial reference data to extend moderately to a sparse area so as to reduce the degree of neighbor information loss, and performing iterative computing so as to acquire complete topological neighbor data of the target sample points. The method has the advantages that topological neighbor data of uniform or non-uniform sampled data of a complex profile can be acquired fast, finding results include k neighbors, Voronoi neighbors and other effective neighbor data, and the local profile features of the sampled data of can be better indicated.
Owner:SHANDONG UNIV OF TECH
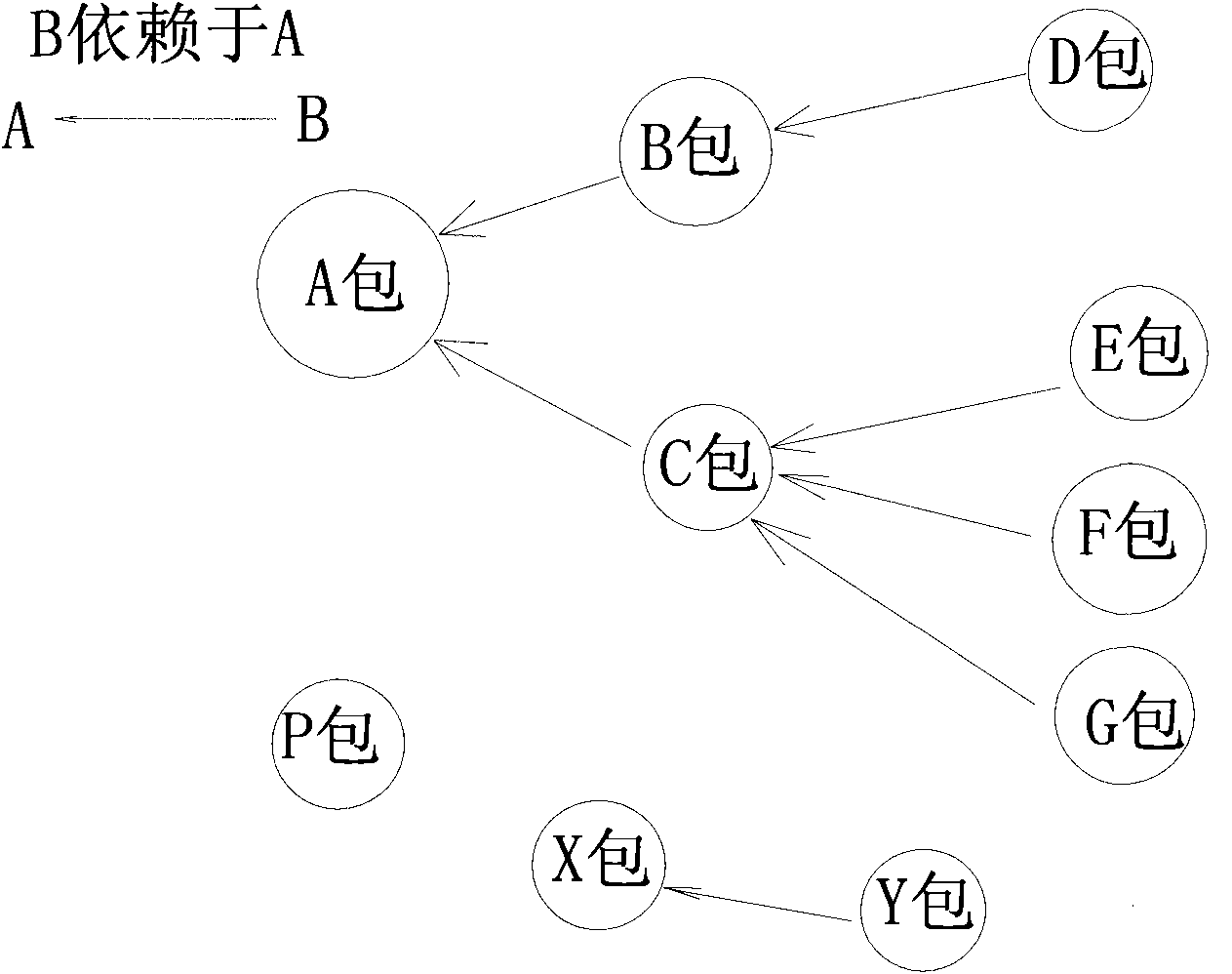
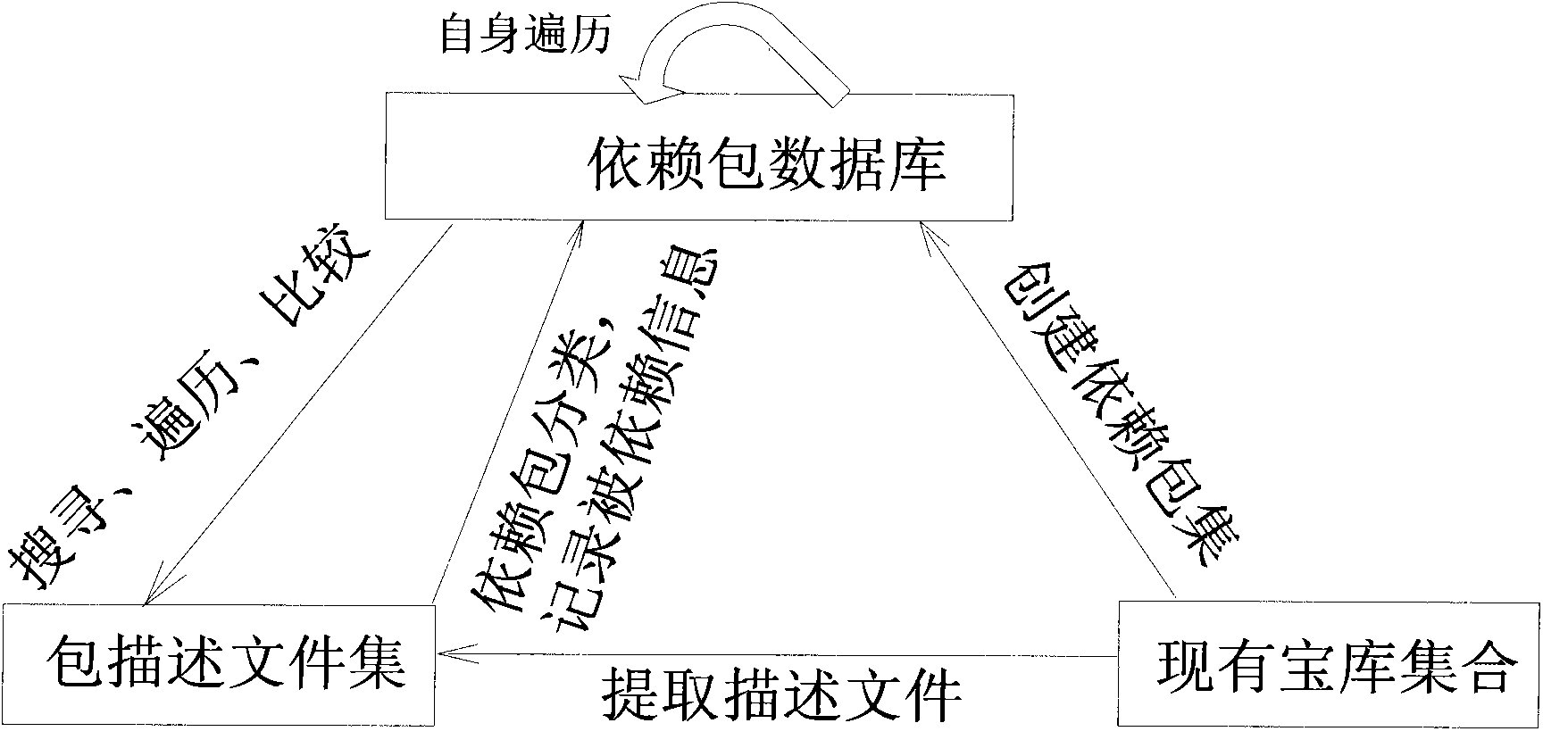
Method for reversely searching packet depended relationship in unix operating system
ActiveCN101826103AEasy to findFast customizationSpecial data processing applicationsOperational systemContrarian
The invention provides a method for reversely searching a packet depended relationship in a unix operating system. The method comprises the following steps of searching the interdependent relationships of all the packets in the same version based on a packet storage IPS; and effectively performing customized work on the system according to the dependent relationships of the packets, wherein the reversely searching process of the whole packet comprises 1) a packet storage technique IPS, 2) a packet organization technique and 3) a method for reversely searching the packet. The packet storage technique IPS is an important part of a packet management technique and comprises the following steps of: organizing all the functional packets together according to a certain rule to form a set according to a release version; and releasing to an internet server for all the developers and users to use, wherein a client is provided with a corresponding client tool; the user accesses the IPS through network and performs operation comprising installing, uninstalling and updating the packets and viewing the description characteristics of the packets; and the characteristics comprise: a directory in which the packet is installed, the name of the packet after installation and required dependent files of the system.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
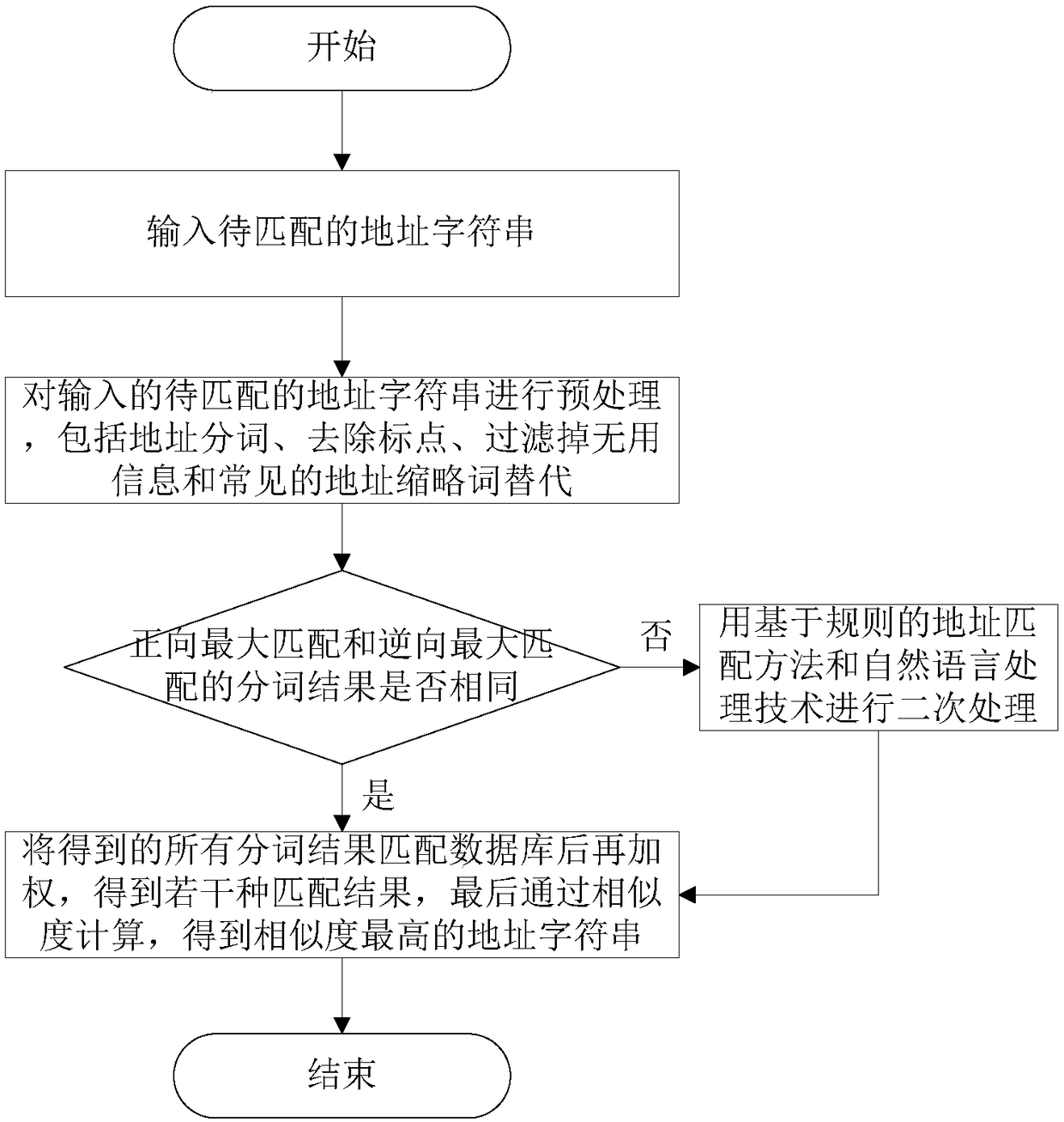
Address matching method
ActiveCN109344263AResolve ambiguityReduce the recognition rateDigital data information retrievalSpecial data processing applicationsAmbiguityContrarian
The invention relates to an address matching method, belonging to the technical field of geographic information data processing. The method comprises the steps of firstly establishing a dictionary ofword segmentation, a hierarchical dictionary of address and an alternative dictionary of common address abbreviations; and then preprocessing the input address string to be matched; carrying out the secondary processing on the different segmentation results based on forward maximum matching and reverse maximum matching in the pre-procesing by a rule-based address matching method and a natural language processing technology; finally matching all the segmentation results with the database and weighting again to obtain several matching results, finally obtaining the address string with the highest similarity through similarity calculation. The invention mainly solves the ambiguity segmentation of a single address matching method and the low recognition rate of the new words by fusing the address matching method based on dictionary and the address matching method based on rule and combining the natural language processing technology, so that the low accuracy phenomenon of the address matching results is avoided, and the accuracy of address matching is improved.
Owner:KUNMING UNIV OF SCI & TECH
Spacing query method for triangular gridding curve model
InactiveCN101430693AEnhance aggregation abilityReduce difficultySpecial data processing applications3D modellingPoint objectContrarian
The invention provides a method for searching space of a triangular mesh surface model. The method comprises the following steps: first, triangular patch data expressing product surface information and a node in an index structure are both expressed into corresponding four-dimensional point objects; the four-dimensional point objects are subject to space clustering partition by selecting an insert position, realizing node split by four-dimensional clustering method, adjusting an axial bounding box of the node in the index structure and the corresponding four-dimensional point subjects, and other steps; and space clustering partition of the triangular patch in the triangular mesh surface is realized so as to establish the index structure of the triangular mesh surface model. Based on the structure, efficiency of various space searching operations of the discrete triangular mesh surface model can be improved, the speed for processing reverse engineering data of a product can be effectively improved, and stability and accuracy of a processing result is ensured.
Owner:SHANDONG UNIV OF TECH
Method and system for reverse approval of workflow
InactiveCN106651112AReduce process design complexityImprove usabilityOffice automationResourcesContrarianUsability
The present invention discloses a method and a system for the reverse approval of a workflow. The method comprises the steps of acquiring the approval item information of a current approval node; judging whether the approval item information is consistent with a preset rejected item condition or not; if the approval item information is consistent with the preset rejected item condition, acquiring a historical flow path pre-stored in the current approval item; searching available rejected nodes according to the historical flow path; according to the selection information of a user, determining a target rejected node; reversely circulating the approval task of the current approval node to the target rejected node. Based on the arrangement of the rejected item condition, during the design of the approval process, only one rejected item is needed for each approval node. Meanwhile, the above-described method is adopted as a reverse rejection flow. Therefore, redundant rejected items and redundant rejected connection lines are eliminated. The process design complexity of the workflow reverse approval is reduced. Moreover, the usability and the use efficiency of the approval system are improved.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
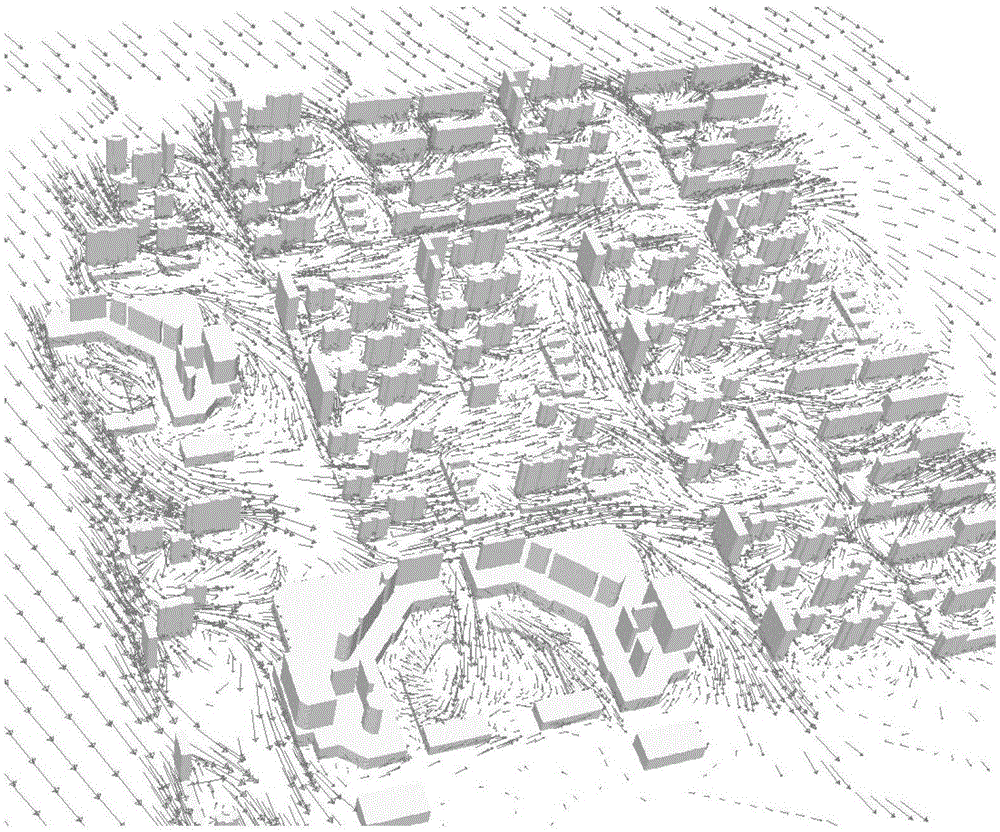
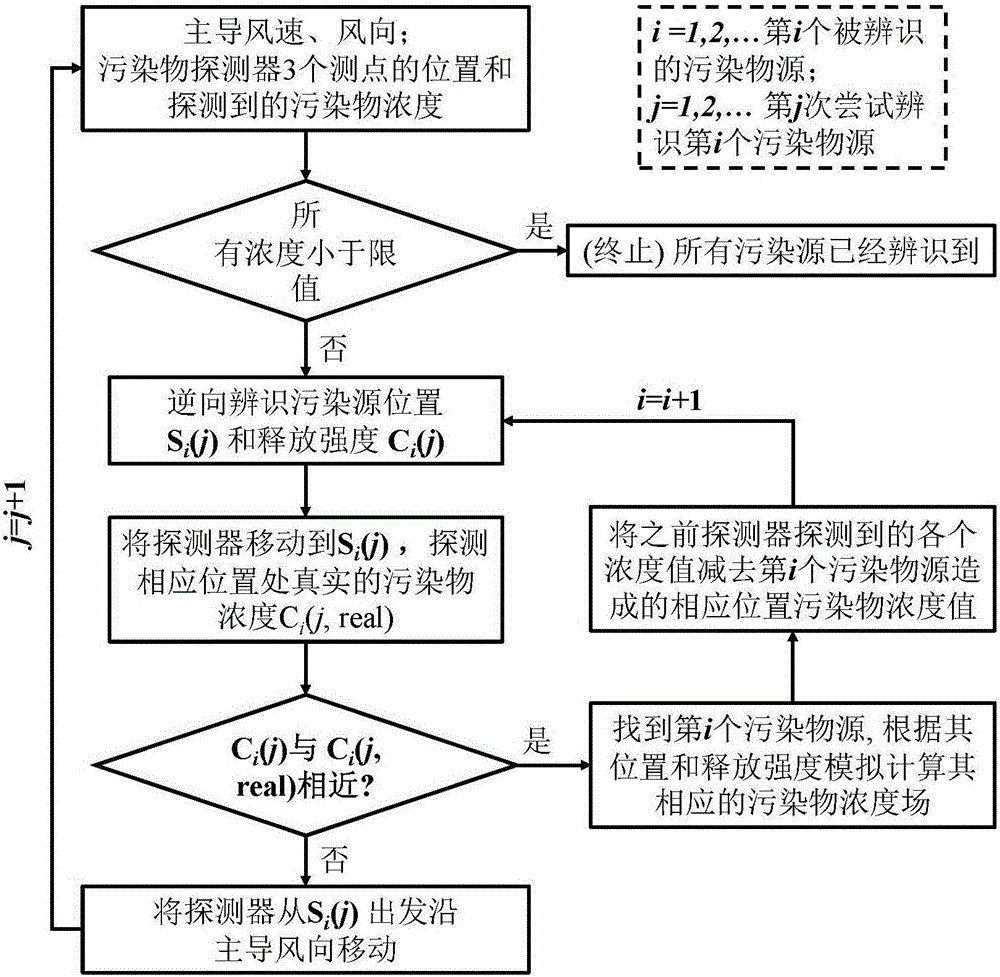
Method for identifying multiple pollution sources in city space by using moveable pollutant detector
InactiveCN106777893AReal-time monitoringRapid diagnosisInformaticsSpecial data processing applicationsContrarianTrial and error
The invention belongs to the technical field of atmosphere pollutant source identifying, and in particular relates to a method for identifying multiple pollution sources in a city space by using a moveable pollutant detector. The invention discloses a rapid reverse identification method different from conventional trial-and-error methods for multiple pollutant sources for a first time, multiple pollutant sources can be rapidly identified by using a single moveable pollutant detector, the initial investment is low, the speed is high, the result is accurate, real-time monitoring and rapid diagnosis of a city atmosphere environment can be achieved, and an economic and efficient technical scheme can be provided for government and decision of city atmosphere pollution. To verify the accuracy of the result, after the steps are completed and all pollutant sources are identified, the pollutant sources are repeatedly identified at moments, and at the moments, main air speeds and air directions are remarkably different from those, thereby ensuring that all pollutant sources can be found.
Owner:DALIAN UNIV OF TECH
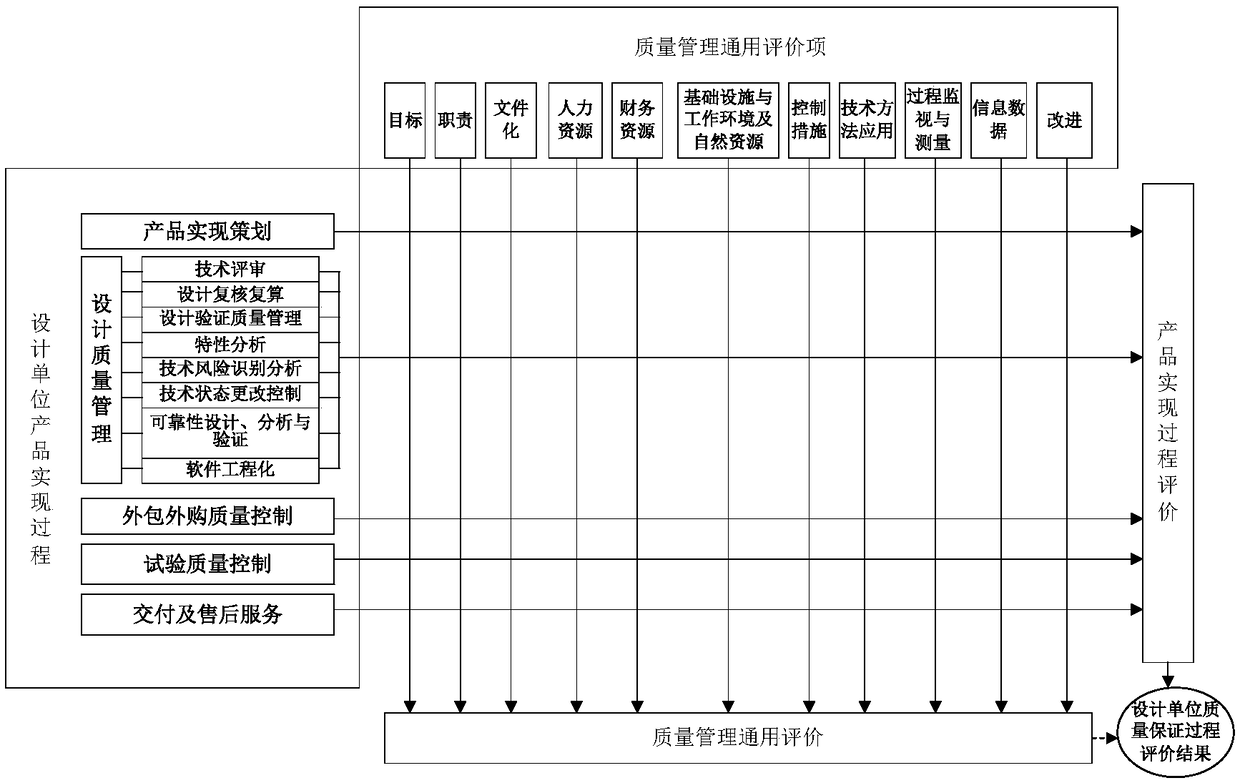
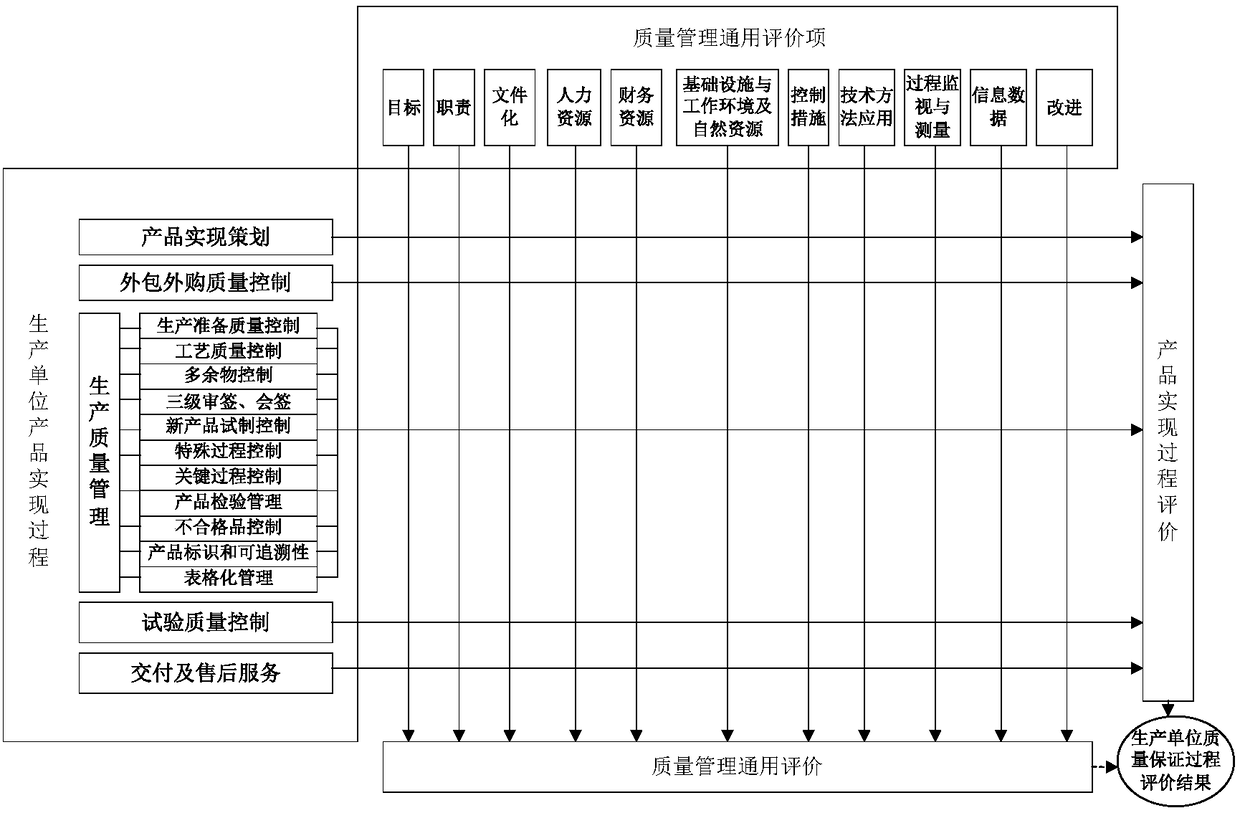
Validity evaluation method of spaceflight quality management system with positive and reverse combination
InactiveCN108305011AEmphasize the importanceGuide quality assurance capability improvementResourcesQuality dataModel quality
The invention relates to a validity evaluation method of a spaceflight quality management system with positive and reverse combination. The method includes: step 1, constructing a quality management system evaluation model based on spaceflight model quality data; step 2, analyzing a mutual relation between the system and models, and defining quality data for validity evaluation of the system; step3, determining evaluation elements of the system, and compiling an evaluation criterion of the system in a classified manner; and step 4, proposing the validity evaluation method and process of the quality management system with positive and reverse combination. Finally, a positive scoring result and a reverse scoring result are added to obtain a total score value of the quality management system, and the overall maturity grade of the quality management system is finally evaluated according to the score and the existence of a veto item. According to the method, on one hand, advanced theory and method support can be provided for more accurate measurement of the validity of the quality management system; on the other hand, support is provided for effective improvement of the validity of thequality management system and guarantee of the model development quality through implementation of system evaluation.
Owner:CHINA AEROSPACE STANDARDIZATION INST
Fault online evaluation method for unmanned aerial vehicle bee colony collaborative navigation
ActiveCN110146108ATimely and accurate identification of relative measurement valuesWide applicabilityMeasurement devicesContrarianNavigation system
The invention discloses a fault online evaluation method for unmanned aerial vehicle bee colony collaborative navigation. According to the method, reverse extrapolation is carried out on the multipletime sequences of relative measurement innovation between one member and other members during collaborative navigation, so that fault judgment is carried out; and a fault evaluation value is built comprehensively by means of a cumulative effective extrapolation epoch number and the test statistic quantity of cumulative reverse extrapolation. According to the collaborative navigation fault online evaluation method, the levels and emergency degrees of faults are comprehensively considered; the accurate on-line evaluation of the influence degrees of the faults in a collaborative navigation process can be effectively realized; and an accurate basis can be provided for an unmanned aerial vehicle bee colony collaborative navigation system in achieving fault-tolerant reconstruction.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
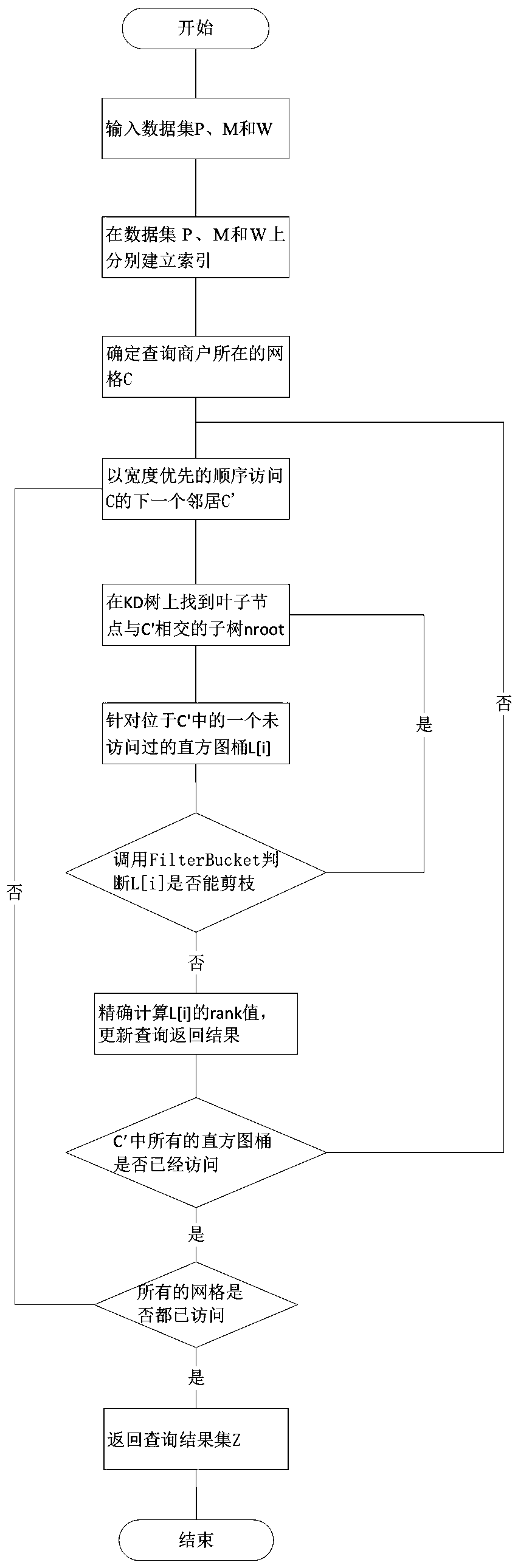
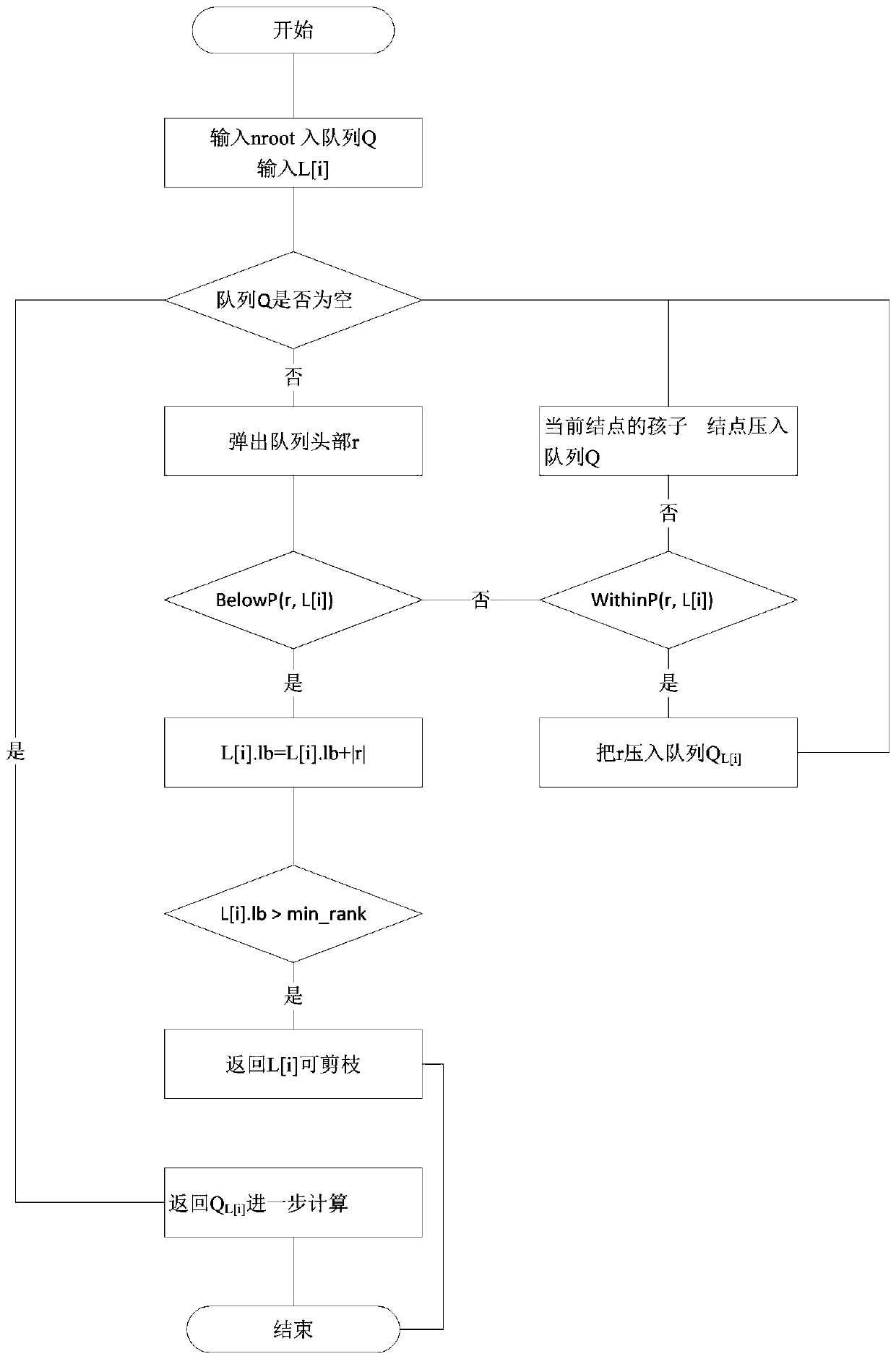
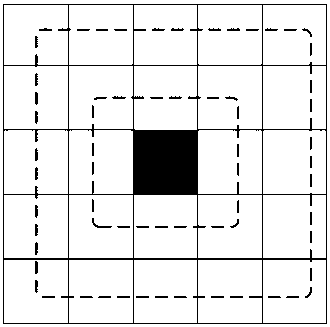
Distance-based reverse k ranking query method
ActiveCN107908722AGuaranteed real-timeNarrow down the search spaceBuying/selling/leasing transactionsSpecial data processing applicationsPersonalizationContrarian
The invention discloses a distance-based reverse k ranking query method. According to the method, first, network indexes are used to perform indexing on current positions of a merchant and mobile users, a KD tree is used to perform indexing on all dimensions of the merchant, and an equi-width histogram is used to perform indexing on user preferences; and then based on the three indexes, a method based on lower bound pruning is used to quickly find k users who are most interested in the designated merchant. The method overcomes the natural defect in distance-based reverse ranking query, can return k potential clients to any merchant and is suitable for a mobile environment, and potential client orientation with the merchant being a center provides a solution to personalized precise marketing based on position services.
Owner:EAST CHINA NORMAL UNIV
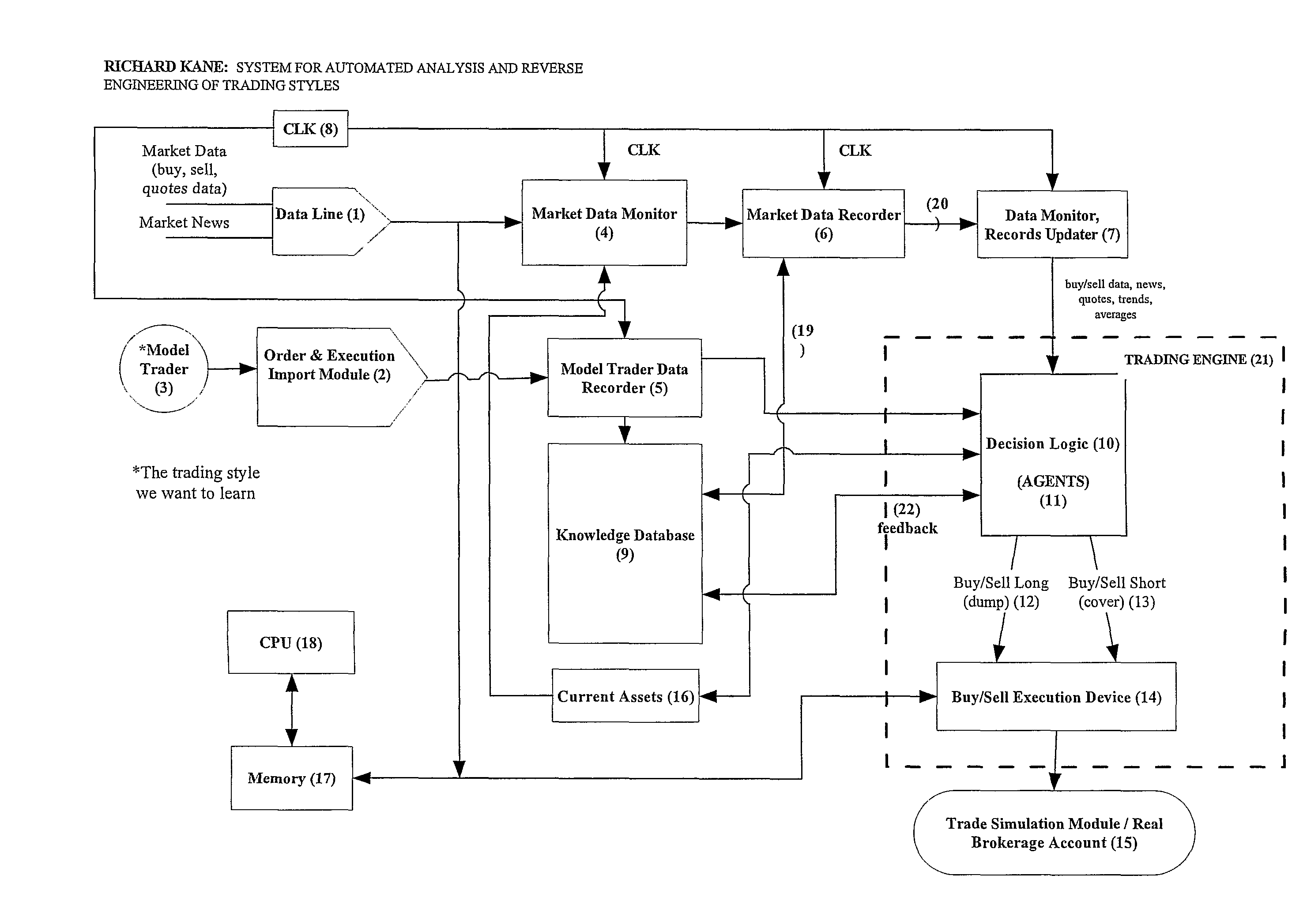
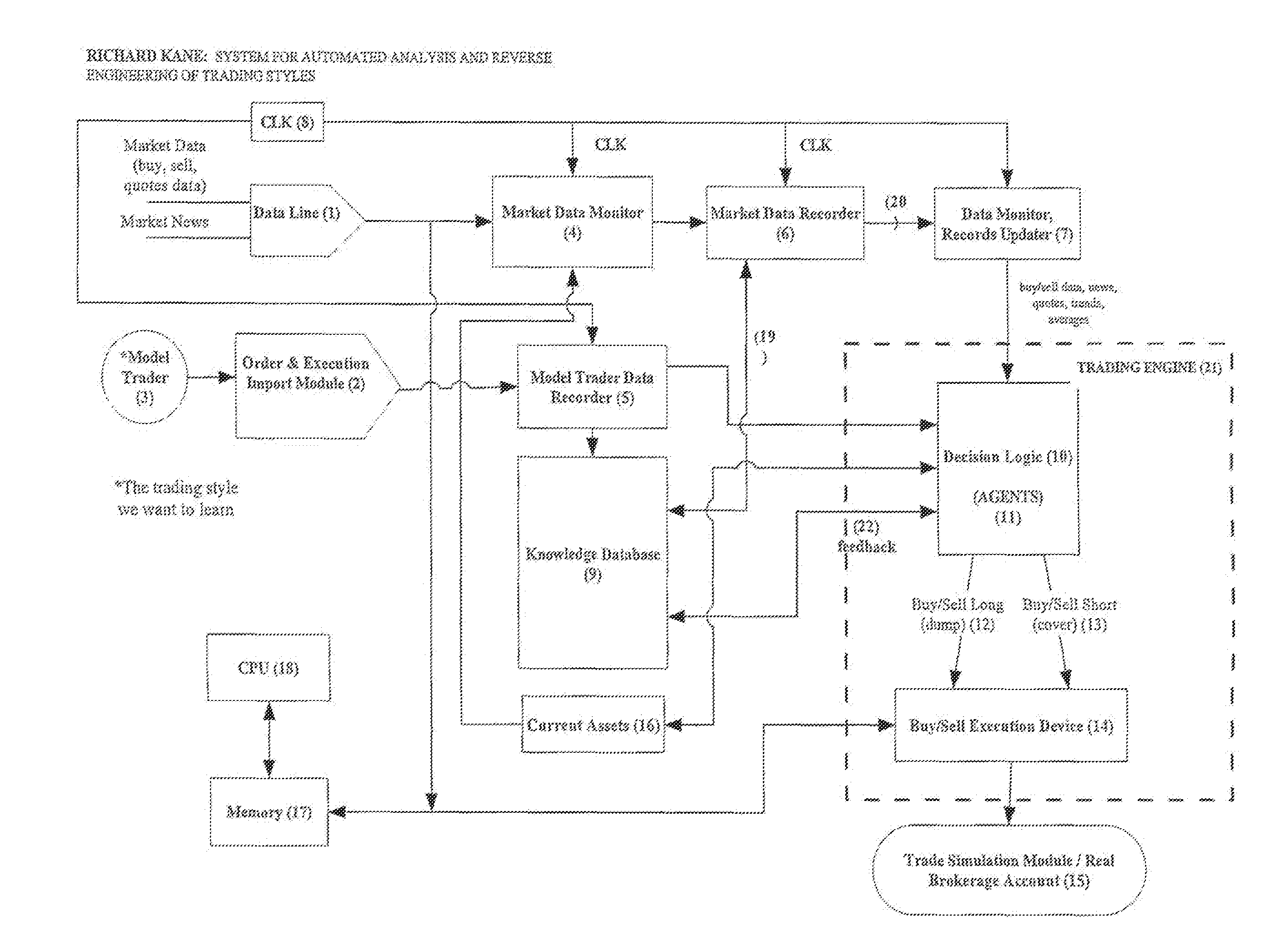
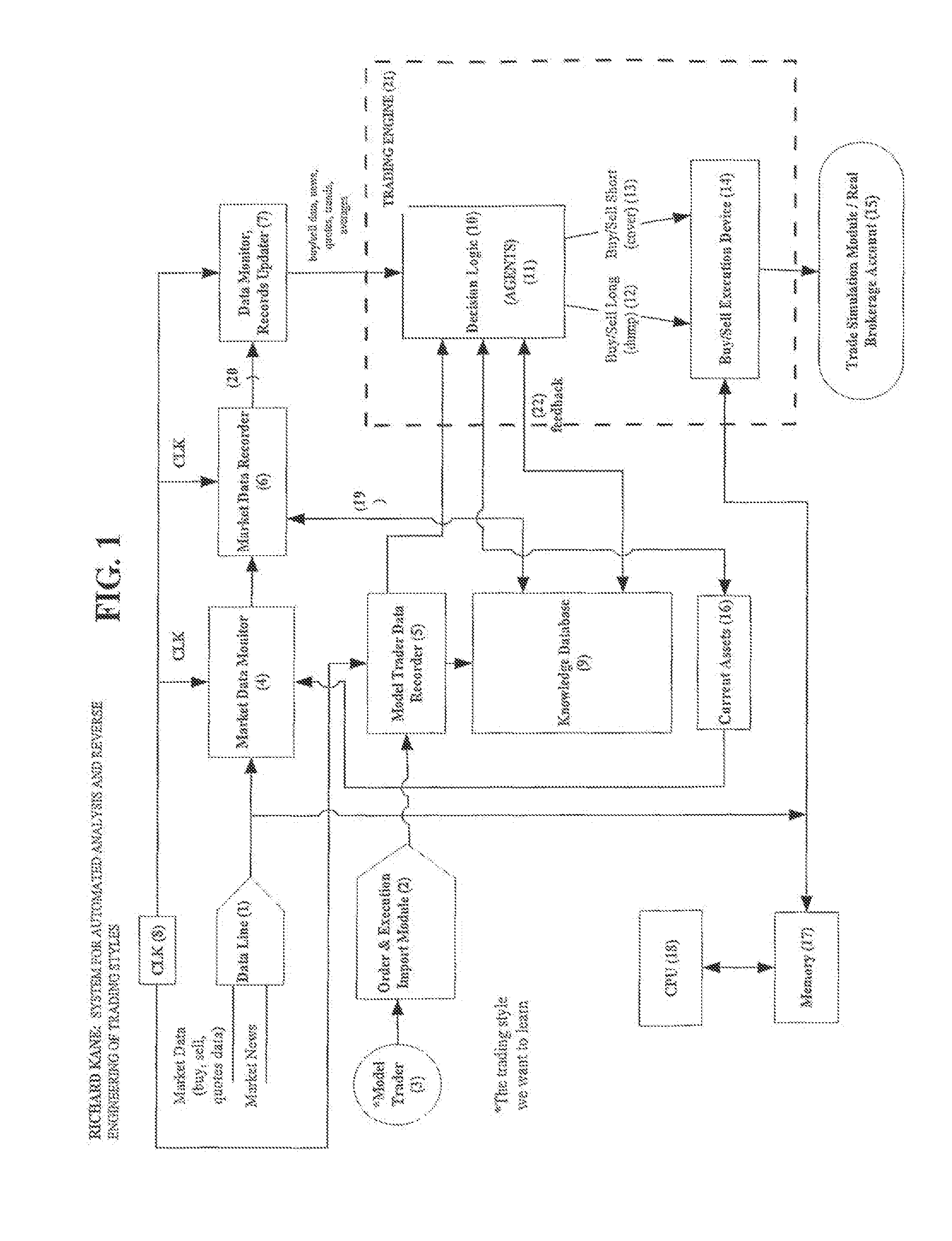
Trading style automated analysis and reverse engineering
A trading style reverse engineering system capable of learning specific trading styles by automated analysis and reverse engineering comprising: a data acquisition system having an input communicating with a securities exchange and various market news sources for receiving buy / sell data and market news data; an order and execution import module having an input communicating with model trader's trading interface for acquiring model trader order and execution data; a clock for generating clock times; a decision logic having a repository for storing a set of buy / sell rules for buying and selling securities in response to said buy / sell data, said market news data, and said order and execution data with said clock times; a knowledge database having inputs for receiving data from said order and execution import module, said data acquisition system, and said decision logic; a processing logic having inputs respectively communicating with said data acquisition systems, said order and execution module, and with said clock for assigning respective clock times to said market data and model trader data.
Owner:KANE RICHARD
Reverse engineering genome-scale metabolic network reconstructions for organisms with incomplete genome annotation and developing constraints using proton flux states and numerically-determined sub-systems
InactiveUS8311790B2Analogue computers for chemical processesSystems biologyInformation repositoryMetabolic network
A genome-scale metabolic network reconstruction for Clostridium acetobutylicum (ATCC 824) was created using a new semi-automated reverse engineering algorithm. This invention includes algorithms and software that can reconstruct genome-scale metabolic networks for cell-types available through the Kyoto Encyclopedia of Genes and Genomes. This method can also be used to complete partial metabolic networks and cell signaling networks where adequate starting information base is available. The software may use a semi-automated approach which uses a priori knowledge of the cell-type from the user. Upon completion, the program output is a genome-scale stoichiometric matrix capable of cell growth in silico. The invention also includes methods for developing flux constraints and reducing the number of possible solutions to an under-determined system by applying specific proton flux states and identifying numerically-determined sub-systems. Although the model-building and analysis tools described in this invention were initially applied to C. acetobutylicum, the novel algorithms and software can be applied universally.
Owner:UNIVERSITY OF DELAWARE
Trading style automated analysis and reverse engineering
Trading style reverse engineering system for learning trading styles by automated analysis and reverse engineering comprising:a data acquisition system communicating with a securities exchange and market news sources for receiving securities buy / sell data and market news data;an order and execution import module communicating with a model trader's trading interface for acquiring the model trader's order and execution data;a clock;a processing logic communicating with said data acquisition system, said order and execution module, and said clock for assigning clock times to data from said data acquisition system and said order and execution import module;a decision logic communicating with said processing logic, said decision logic having a repository for storing a set of buy / sell rules for buying and selling securities in response to said buy and sell data, said market news data, and said model trader order and execution data.
Owner:KANE RICHARD
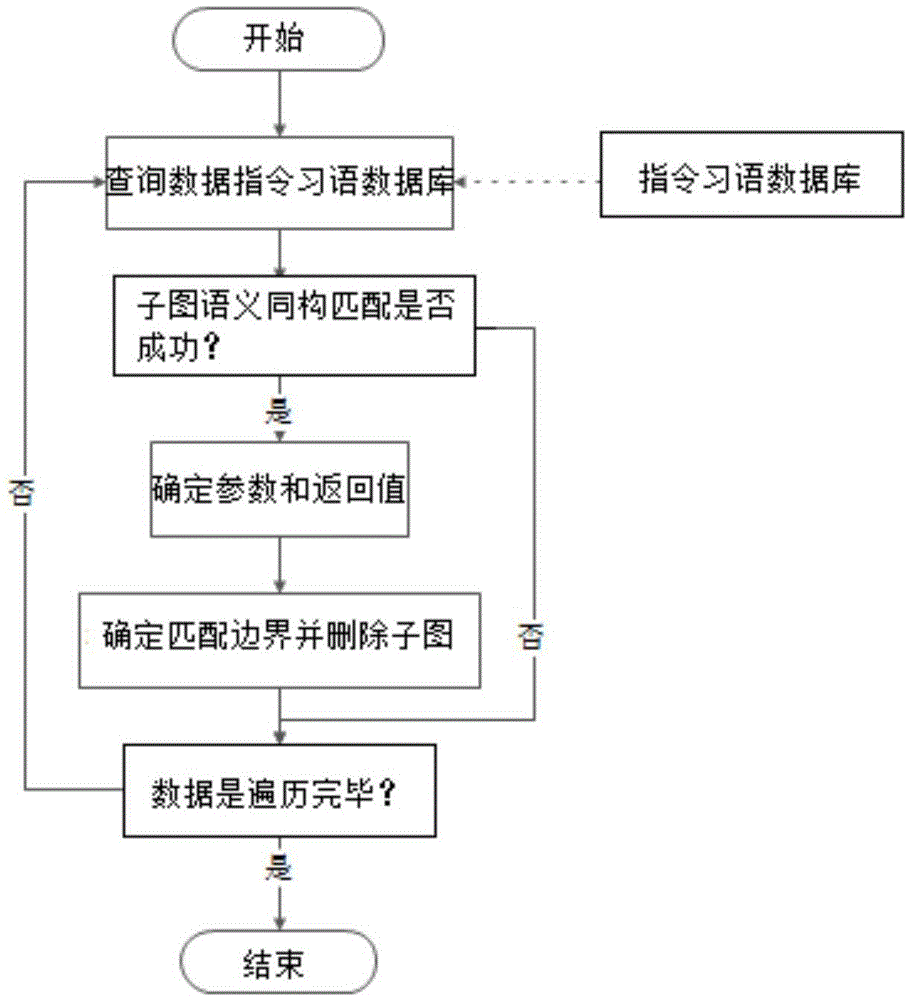
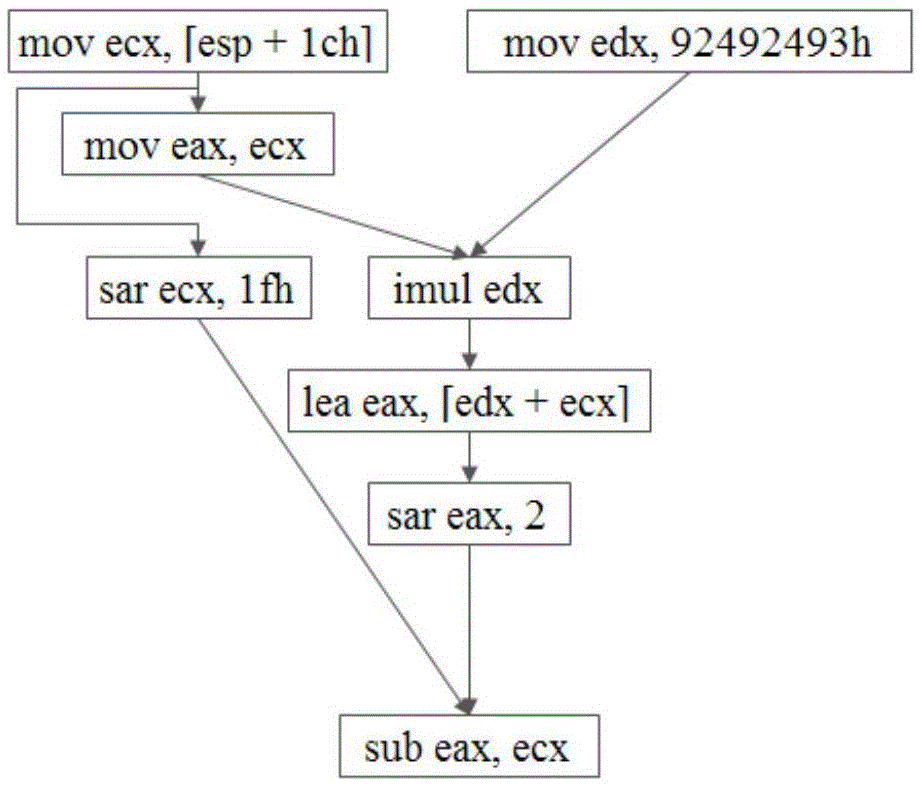
Sub-graph semantic isomorphism based instruction idiom identification method
ActiveCN105589728AHigh precisionImprove recognition accuracyDecompilation/disassemblyProgram controlData dependency graphReverse analysis
The invention discloses an analysis method of instruction idioms in reverse analysis. The analysis method of the instruction idioms in reverse analysis comprises the steps of performing data stream analysis for an assembly instruction sequence stream in a basic block; constructing a data dependence graph of the instruction sequence stream based on a definition-use relationship; then performing sub-graph semantic isomorphism matching for each connection sub-graph in the data dependence graph and a template in a template library; discovering a semantic isomorphism sub-graph; performing regulated reduction for the isomorphism sub-graph; and analyzing abstract operation of the sub-graph and corresponding operands. The analysis method of the instruction idioms in reverse analysis can efficiently increase the abstraction level of intermediate codes in the reverse analysis and improve code analysis efficiency.
Owner:弘毅视界(北京)科技有限公司
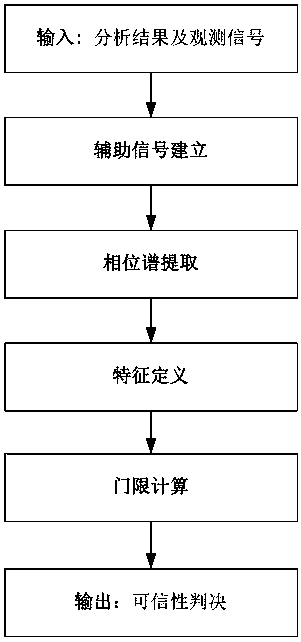
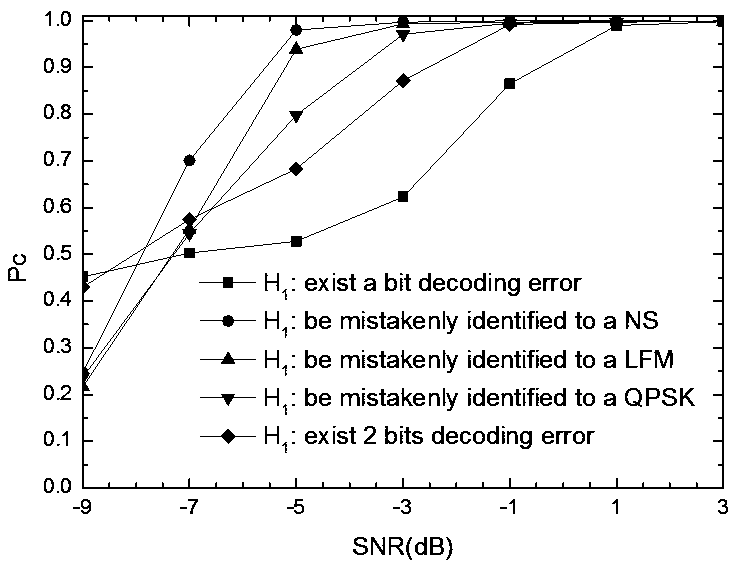
Credibility evaluation method for BPSK blind analysis result based on CFAR criterion
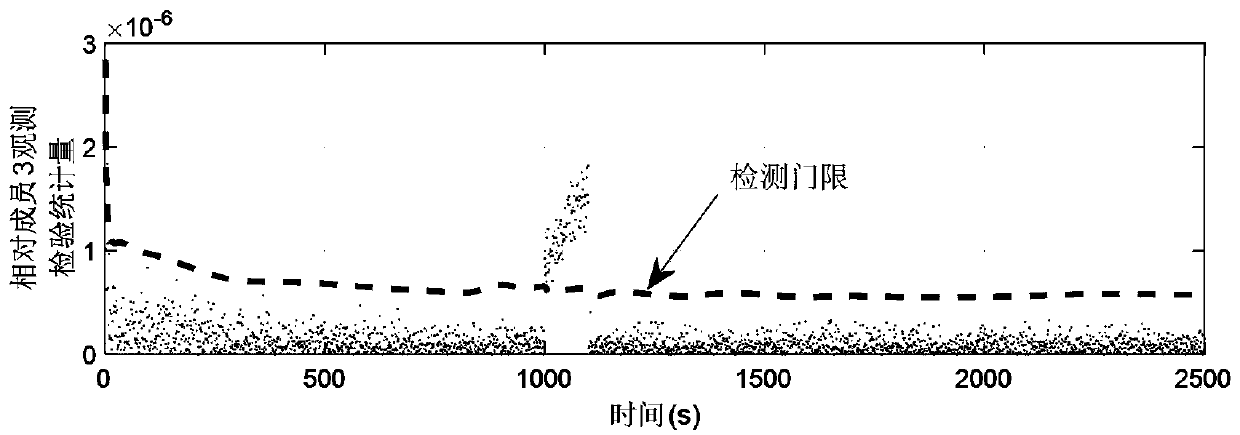
ActiveCN110602009AEffectively complete the credibility testWave based measurement systemsModulation type identificationSmall sampleSignal-to-noise ratio (imaging)
The invention provides an evaluation method based on a CFAR (Constant False Alarm Rate) in order to solve the problem of credibility evaluation of a blind analysis result of a BPSK signal. In the method, based on the phase spectrum of a correlation sequence between a specific auxiliary signal and an observation signal, the maximum value of the modulus square of the phase spectrum is extracted as atest statistic, and the test statistic is compared with a specific judgment threshold based on a CFAR criterion to judge whether an analysis result is credible or not. Computer simulation results show that the method can effectively complete credibility check of BPSK signal blind processing results in a proper signal-to-noise ratio range under a certain channel mismatch condition. Besides, compared with several existing processing algorithms, the method is more suitable for occasions of fading channels and small samples, and has certain theoretical and practical application values in occasions of electronic warfare signal processing, signal reverse engineering and the like.
Owner:JINLING INST OF TECH
Defense reverse engineering encryption method based on Camellia algorithm
ActiveCN108768624AAvoid attackImprove protectionKey distribution for secure communicationCryptographic attack countermeasuresComputer hardwareIntellectual property
The invention discloses a defense reverse engineering encryption method based on a Camellia algorithm. A confused finite state machine is built and then loaded into the Camellia algorithm, then an authorization key which is the same as a 4-bit binary authorization key set in the confused finite state machine is input into the Camellia algorithm, so that the confused finite state machine in the Camellia algorithm outputs a 64-bit binary number Ot, and three times of iterative encryption operations are performed on to-be-encrypted data of a to-be-encrypted circuit on the basis of the 64-bit binary number Ot to obtain encrypted data. The defense reverse engineering encryption method based on the Camellia algorithm provided by the invention has the advantages that when an attacker extracts encrypted data in the circuit through reverse engineering, since the attacker does not know the correct authorization key and the 64-bit binary number Ot corresponding to the correct authorization key, errors in the decryption process can be caused, and therefore incorrect data can be decrypted, so that attacks such as reverse engineering can be effectively prevented, and the protection strength of the hardware intellectual property is improved.
Owner:COLLEGE OF SCI & TECH NINGBO UNIV
Converse solved multidimensional Hash table method
InactiveCN101465755AFeatures that enable reversible solvingThe reverse solution process is efficient and simpleData switching networksContrarianMulti dimensional
Disclosed is a multi-dimensional hash table method for inverse solution, which is widely applied to real-time measurement and monitoring in large scale network. As the inverse solution is unavailable for multi-dimensional hash table technology in prior art, when network traffic abnormity is detected through multi-dimensional hash table, only the corresponding position of abnormity in multi-dimensional hash table is acquired, and the abnormity is unable to be accurately positioned on corresponding network traffic rapidly; so great obstacle is brought to the application of multi-dimensional hash table technology in large-scale network real-time monitoring field. The invention adopts the hash function group which is the key part of multi-dimensional hash table to solve the inverse solution problem. The corresponding inverse solution process is simple, efficient and has accurate results.
Owner:XI AN JIAOTONG UNIV
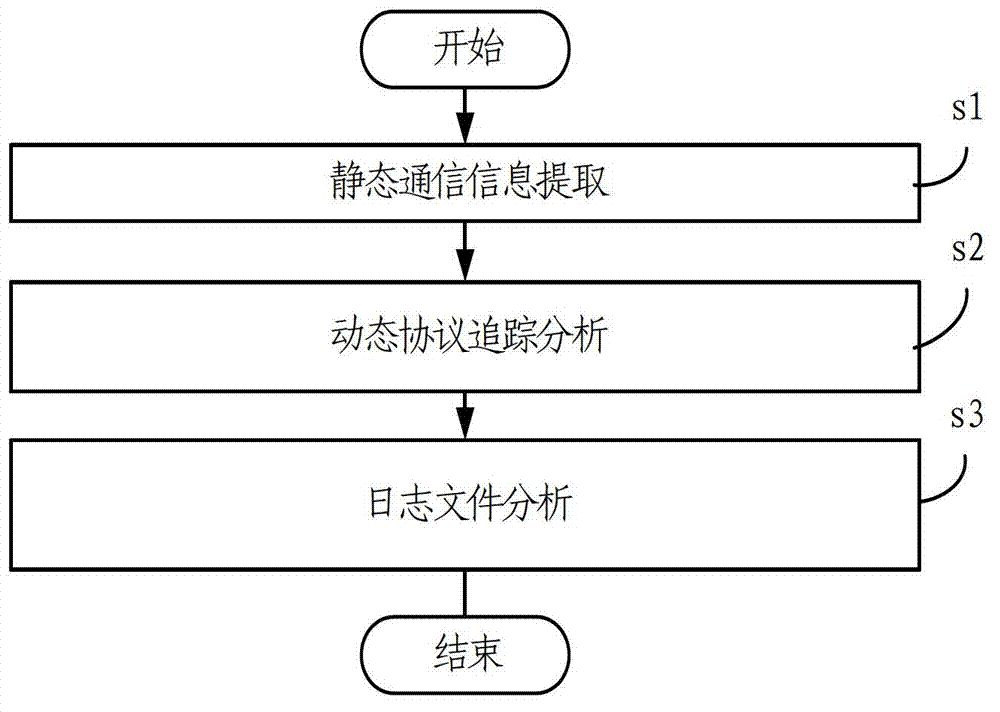
Automated reverse network protocol analysis method
ActiveCN103716284AThorough analysisCompletely crackedTransmissionInformation analysisReverse analysis
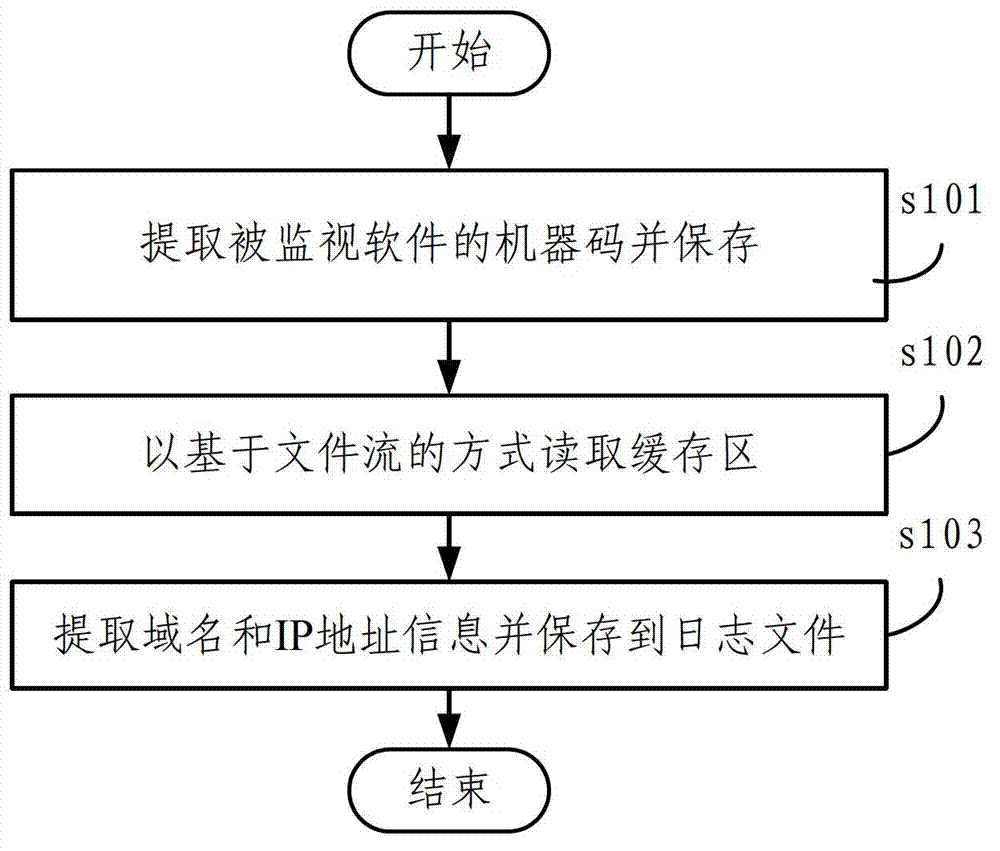
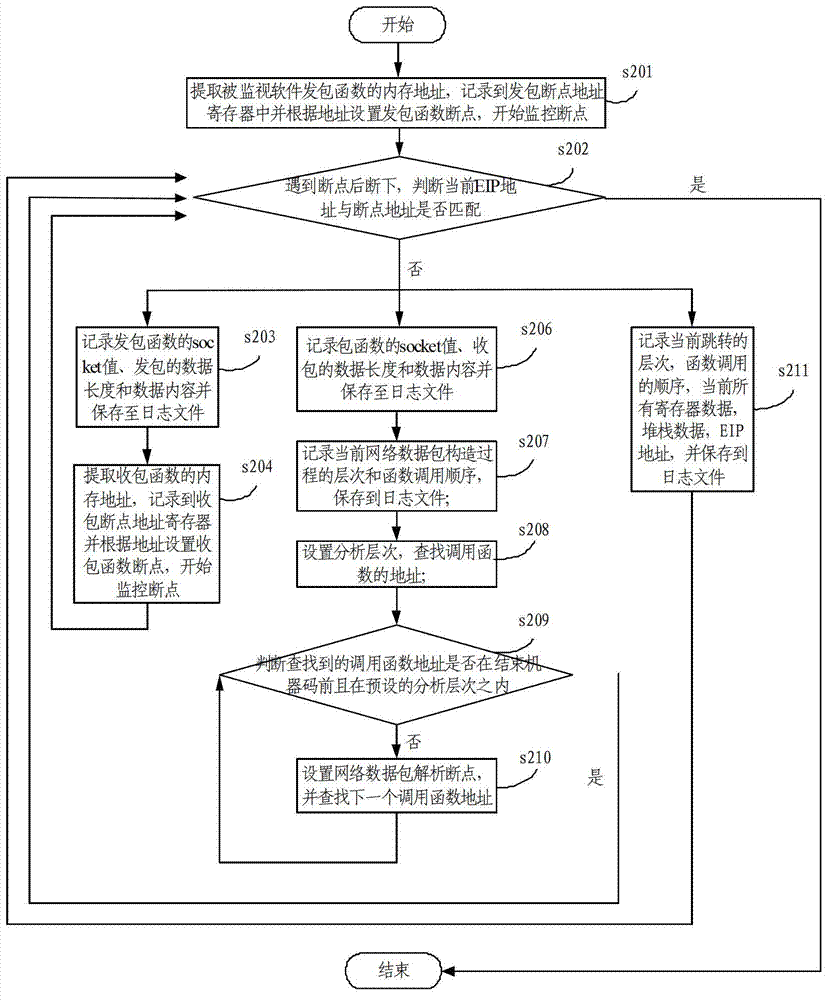
The invention relates to the technical field of network communication and particularly relates to an automated reverse network protocol analysis method. The automated reverse network protocol analysis method comprises the following steps: S1, static communication information extraction: extracting key information among information loaded in communication of C / S-end monitored software and saving the key information to a log file; S2, dynamic protocol tracking and analysis: setting a breakpoint according to the key information and capturing log information related to packet transmitting and receiving functions of the monitored software through breakpoint analysis, analyzing the construction and parsing process of a network protocol packet of the C / S-end monitored software and saving an obtained result to the log file; and S3, information analysis: analyzing and organizing the log file to obtain a needed reverse analysis result. Through fully-automated reverse network protocol analysis, a target application can be completely analyzed and cracked, manpower and time are saved, and negligence and deficiency of artificial reverse analysis are compensated.
Owner:TSINGHUA UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com