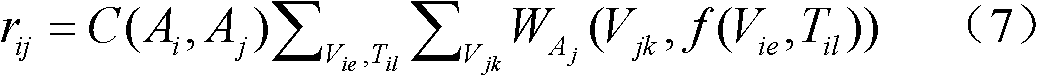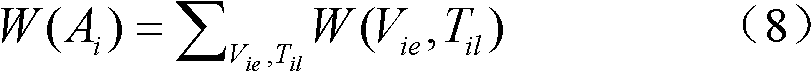Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
529 results about "Large scale network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Large scale brain networks are collections of widespread brain regions showing functional connectivity by statistical analysis of the fMRI BOLD signal or other signal fluctuations. An emerging paradigm in neuroscience is that cognitive tasks are performed not by individual brain regions working in isolation,...
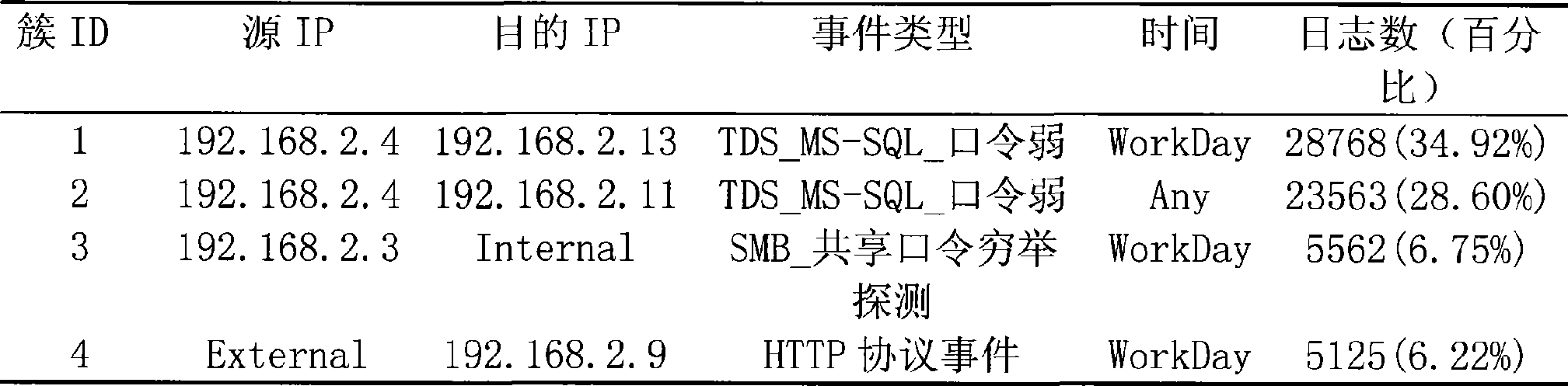
Peer-to-peer based network performance measurement and analysis system and method for large scale networks
ActiveUS7194002B2Improve balanceSlowed network performanceSpecial service provision for substationDigital computer detailsSelf formingGroup method
A network performance (e.g., latency and bandwidth) measurement infrastructure for large scale networks based on self-organized probing groups of devices. Each group of devices has a lead device that measures network characteristics, and then shares the measurement information with other devices. This grouping method reduces the amount of network bandwidth needed for adequate measurements, while still providing necessary information to individual devices. The system utilizes a novel multicast-based algorithm that is adopted for both intra-group and inter-group performance measurement. The measurement groups (MeGroups) are dynamic and self-forming, and use a set of heuristic algorithms to optimize the dynamic groupings.
Owner:MICROSOFT TECH LICENSING LLC
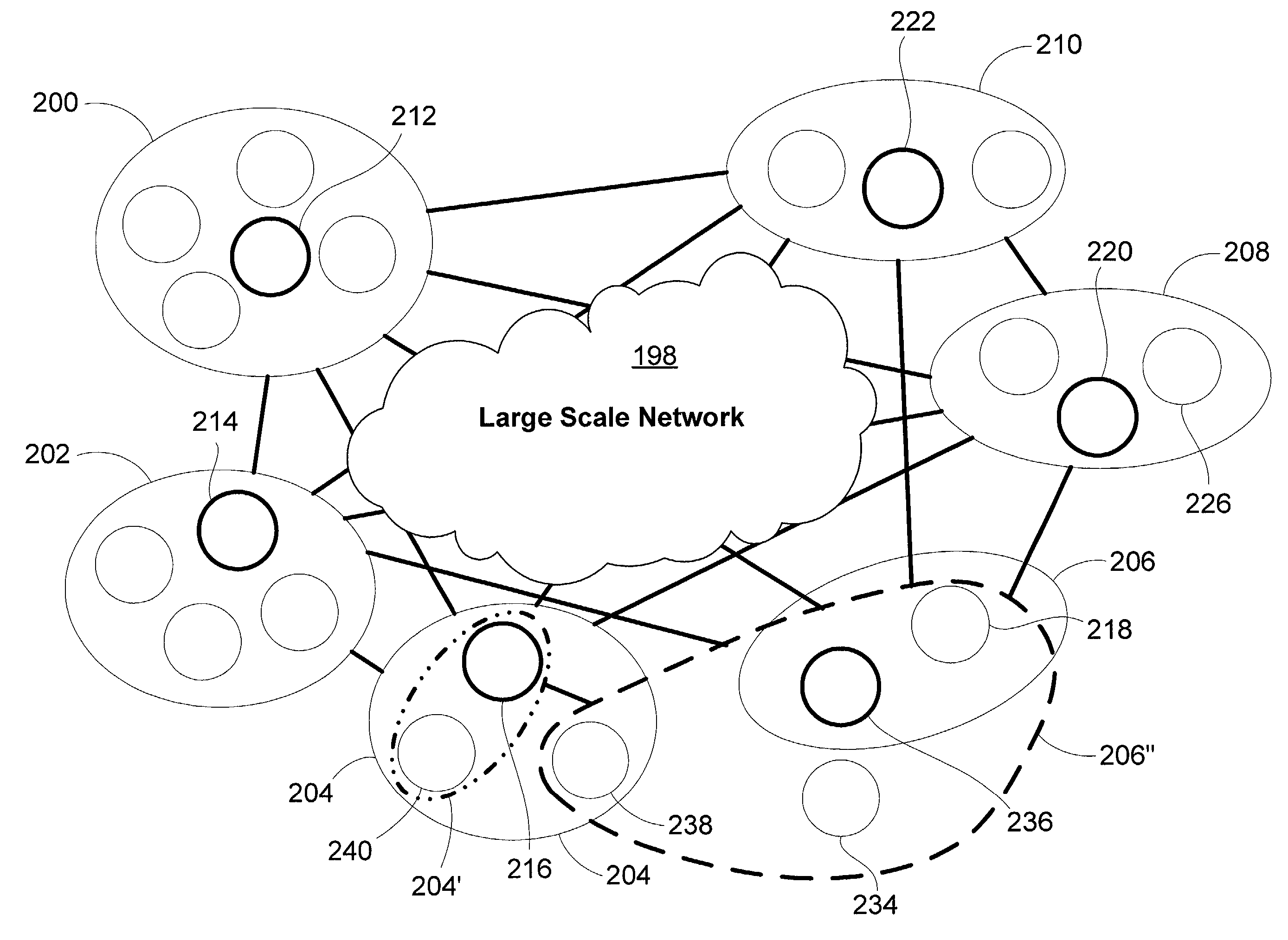
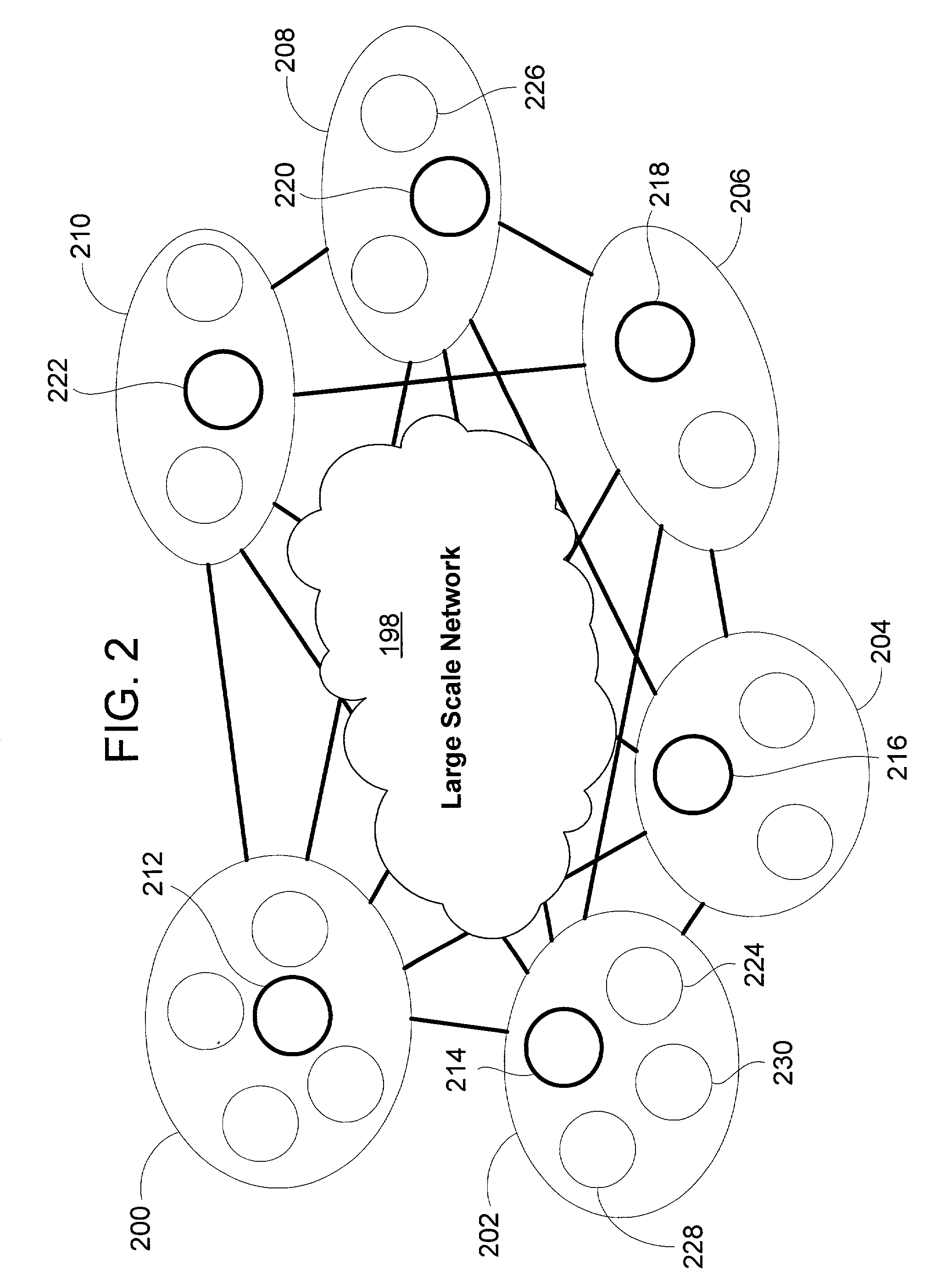
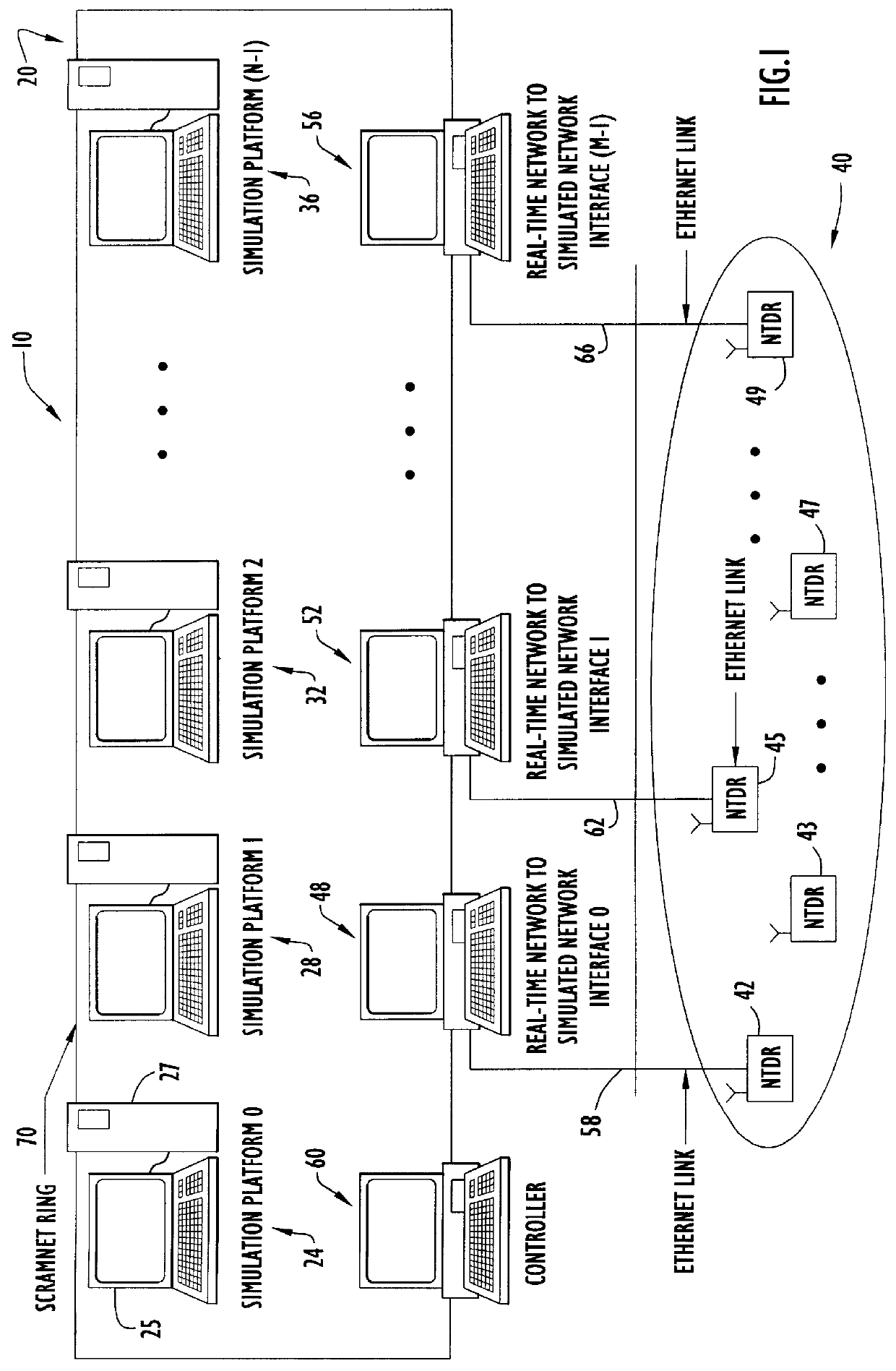
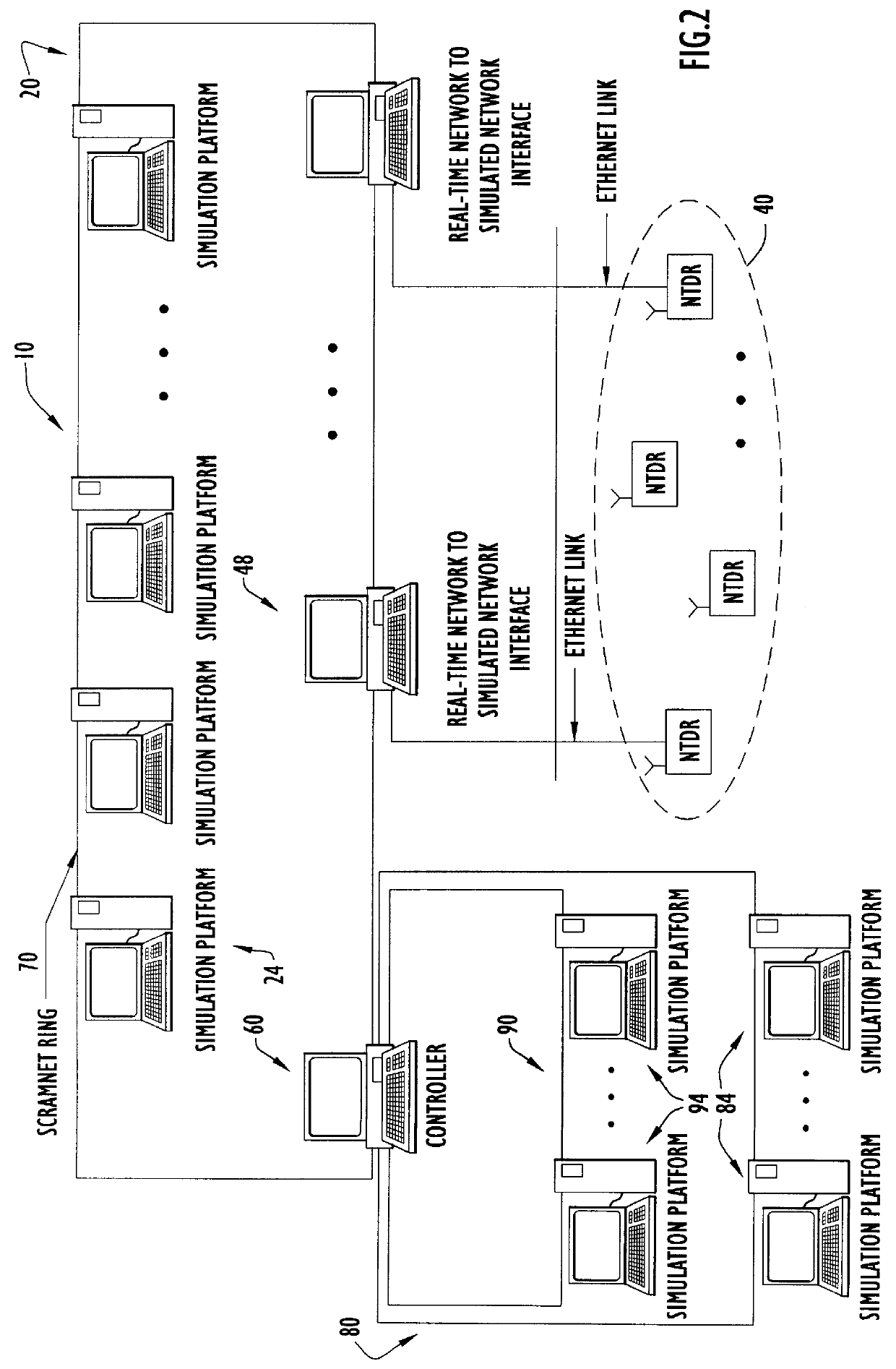
Large-scale network simulation method and apparatus
InactiveUS6134514AAnalogue computers for electric apparatusData switching networksTelecommunications linkChronological time
A distributed discrete-event simulation system operable for processing time-stamped events in chronological order for simulating a multinode communications network, the simulation system comprising a plurality of subsystem platforms (SPs) operable for transmitting message packets to other SPs for simulating node to node communications; and a system controller coupled via a communication link to the plurality of SPs for controlling synchronization and message packet processing associated with the plurality of SPs; wherein when a time-stamped event is received by one of the SPs, the receiving SP responsive to the time-stamped event triggers execution of tasks associated with the time-stamped event in the other SPs via the message packets to provide parallel task processing for the particular time-stamped event among the plurality of SPs.
Owner:HARRIS CORP
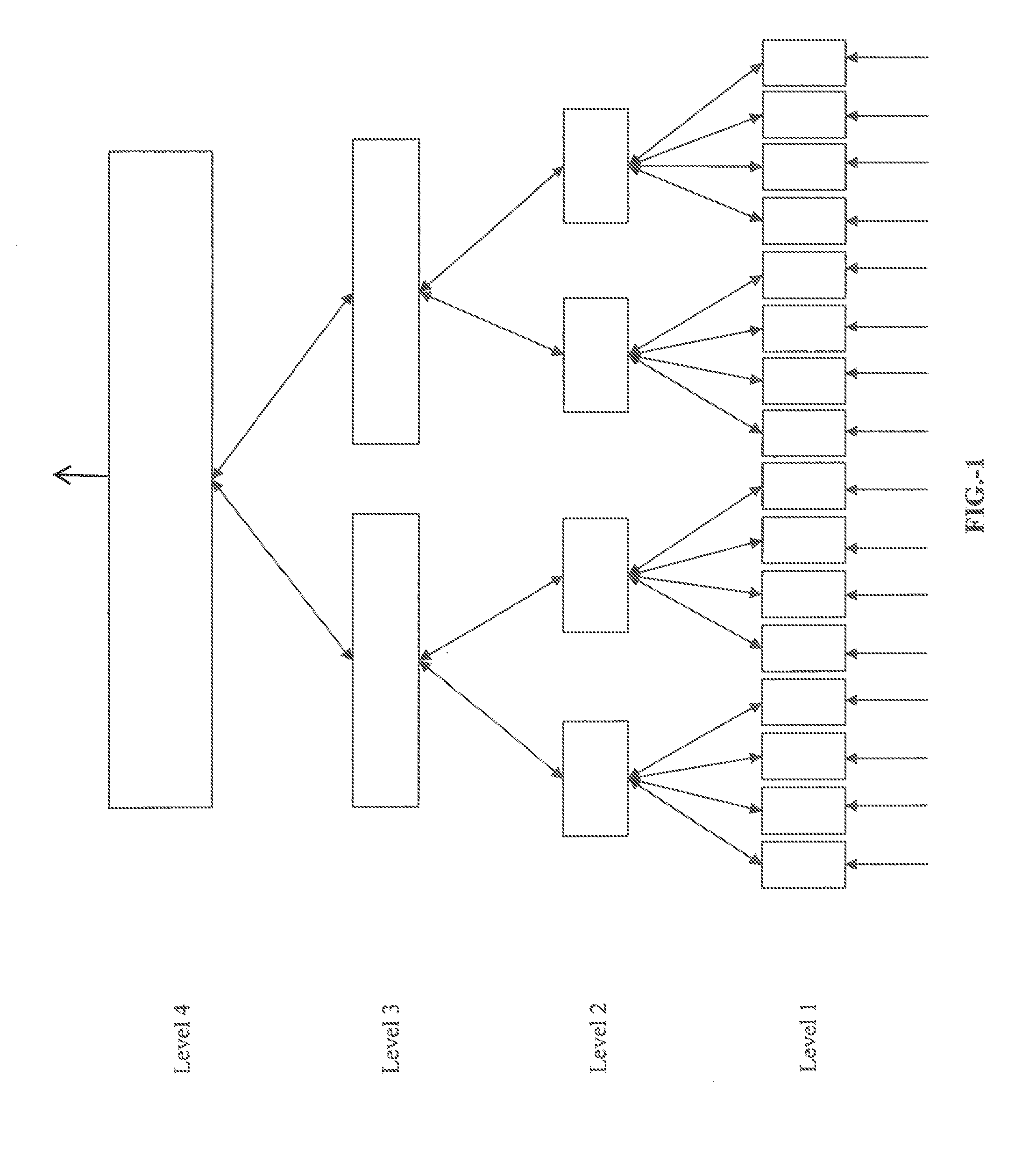
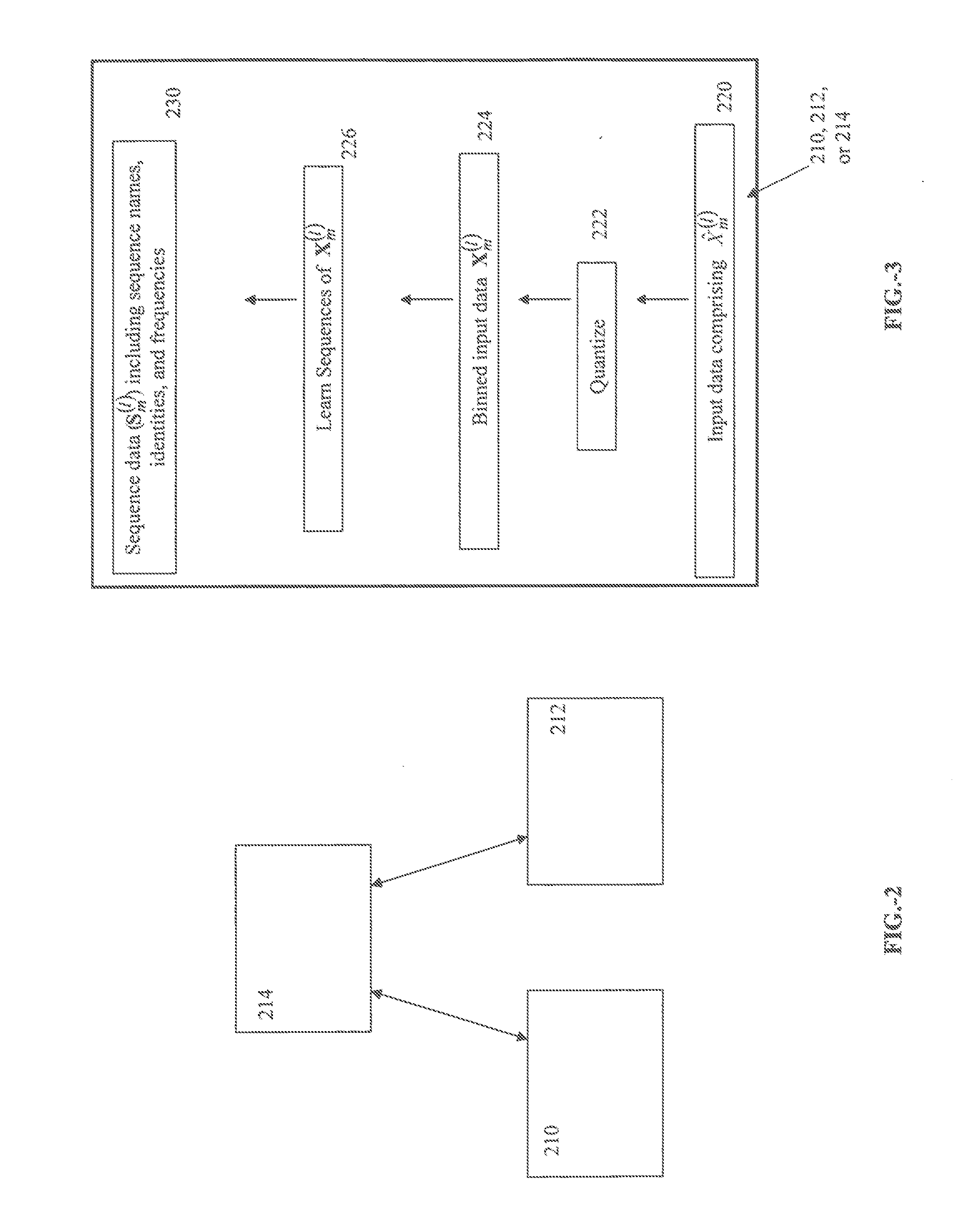
Trainable hierarchical memory system and method
Memory networks and methods are provided. Machine intelligence is achieved by a plurality of linked processor units in which child modules receive input data. The input data are processed to identify patterns and / or sequences. Data regarding the observed patterns and / or sequences are passed to a parent module which may receive as inputs data from one or more child modules. the parent module examines its input data for patterns and / or sequences and then provides feedback to the child module or modules regarding the parent-level patterns that correlate with the child-level patterns. These systems and methods are extensible to large networks of interconnected processor modules.
Owner:NUMENTA INC
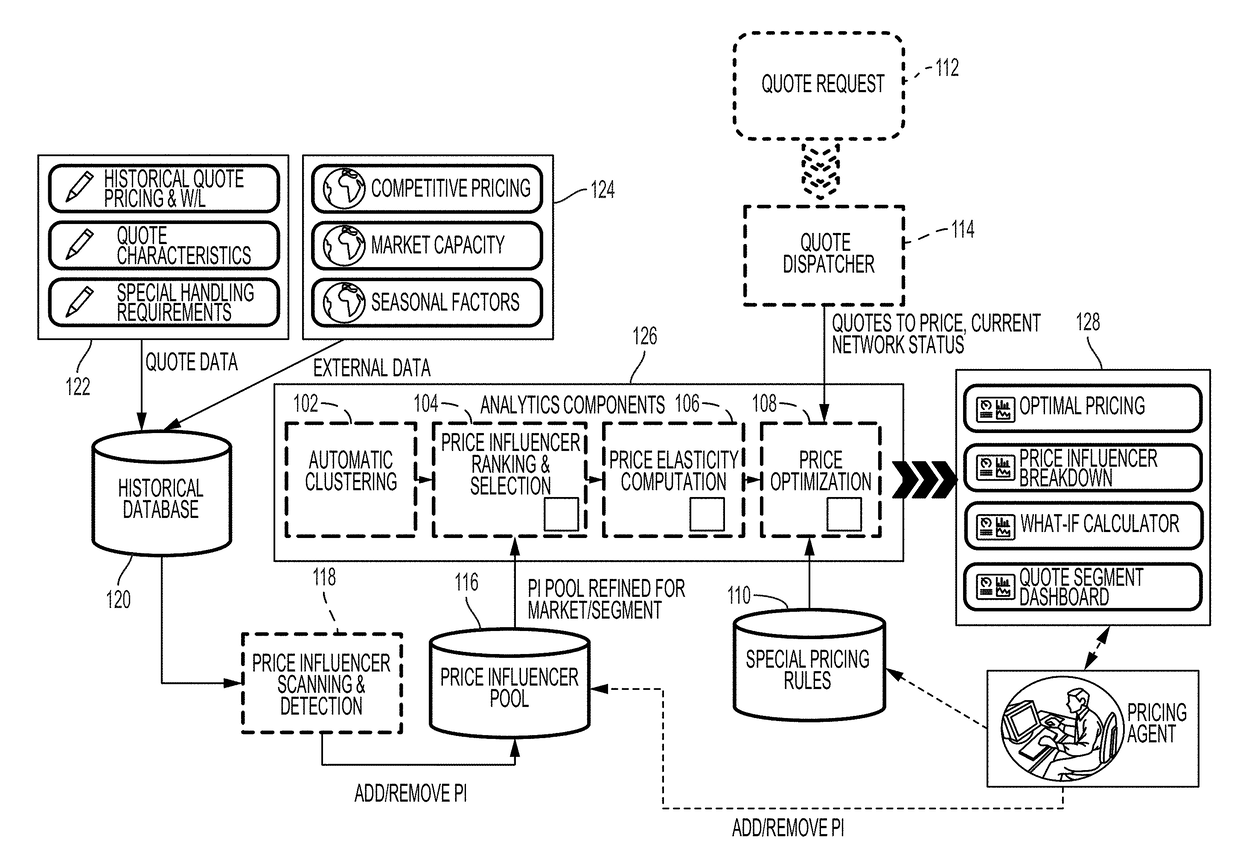
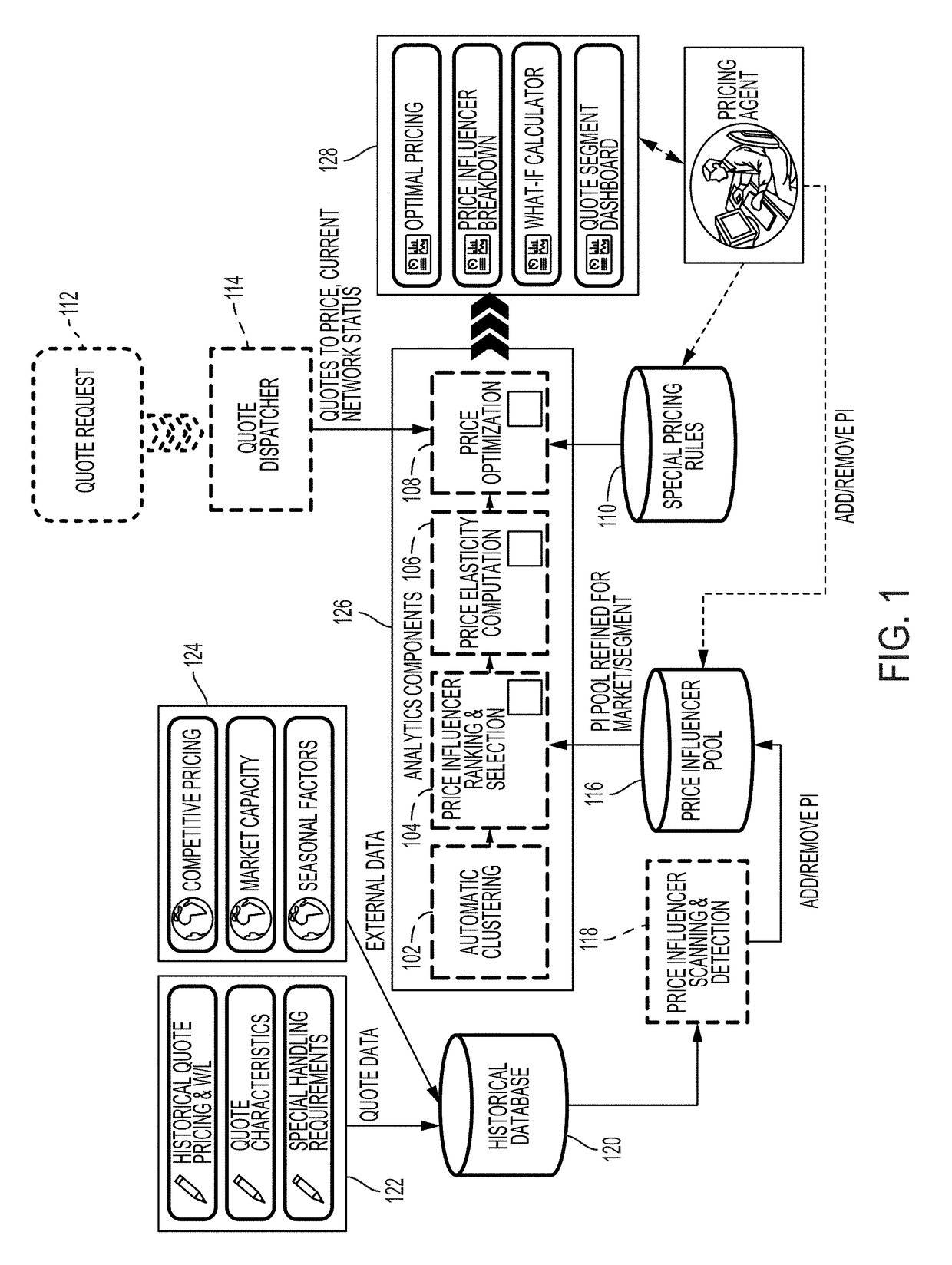
Training a machine to automate spot pricing of logistics services in a large-scale network
A machine learning algorithm is trained to learn to cluster a plurality of original-destination routes in a network for transporting cargo into a plurality of clusters based on similarities of the original-destination routes, and to learn to cluster the plurality of clusters into a plurality of subgroups based on customer behavior. Influencing criteria associated with each of the subgroups may be determined and based on the influencing criteria, a price elasticity curve for each of the subgroups may be generated. Based on the price elasticity curve and current network traffic, cargo transportation price associated with each of the subgroups may be determined.
Owner:IBM CORP
Community division method in complex network
InactiveCN101383748AEmbody the essential characteristicsReflect the interactionStar/tree networksSpecial data processing applicationsMacroscopic scaleGranularity
The invention provides a community classification method in complex network, a plurality of different nodes having partial influences are taken as the cores, the influences of the nodes are caused to evenly diffuse from the core outwards layer by layer, finally the node having the greatest influence becomes the core, the influences of the nodes in layer-by-layer expansion continuously attenuate, the interconnection of the nodes form a local region which expands until the method stops, the influences of the nodes are slight and can reach the edge of the network of the local region. For a large-scale unordered complex network, the positions of the nodes having different importance degrees can be rapidly located, a great deal of more fine-granularity information is dug out, simultaneously the original structural character of the network is kept unchanged, and the original large-scale complex network is simplified and downsized, so that not only the efficiency of search can be improved, but also the structure of the large-scale network from macroscopic view can be more clearly analyzed.
Owner:BEIHANG UNIV
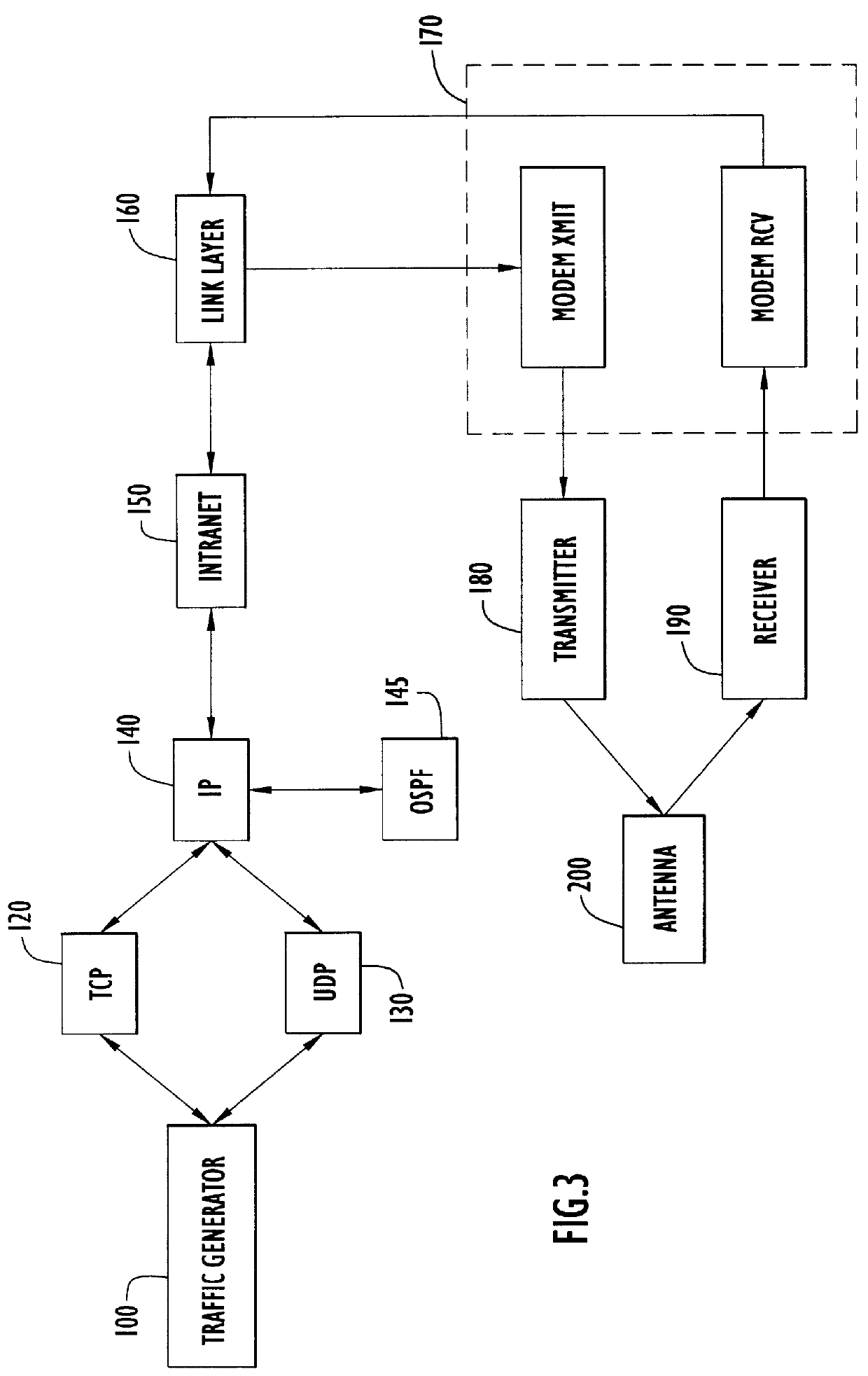
Modeling link throughput in IP networks
A model is given for performance evaluation of IP computer networks that are dominated by congestion-controlled traffic. The model includes heterogeneous TCP flows, UDP flows, short-lived TCP flows, and TCP flows in a differentiated services network. The performance of large-scale networks is estimated where flows may encounter multiple congested links.
Owner:AVAYA INC
Dynamic coordination and control of network connected devices for large-scale network site testing and associated architectures
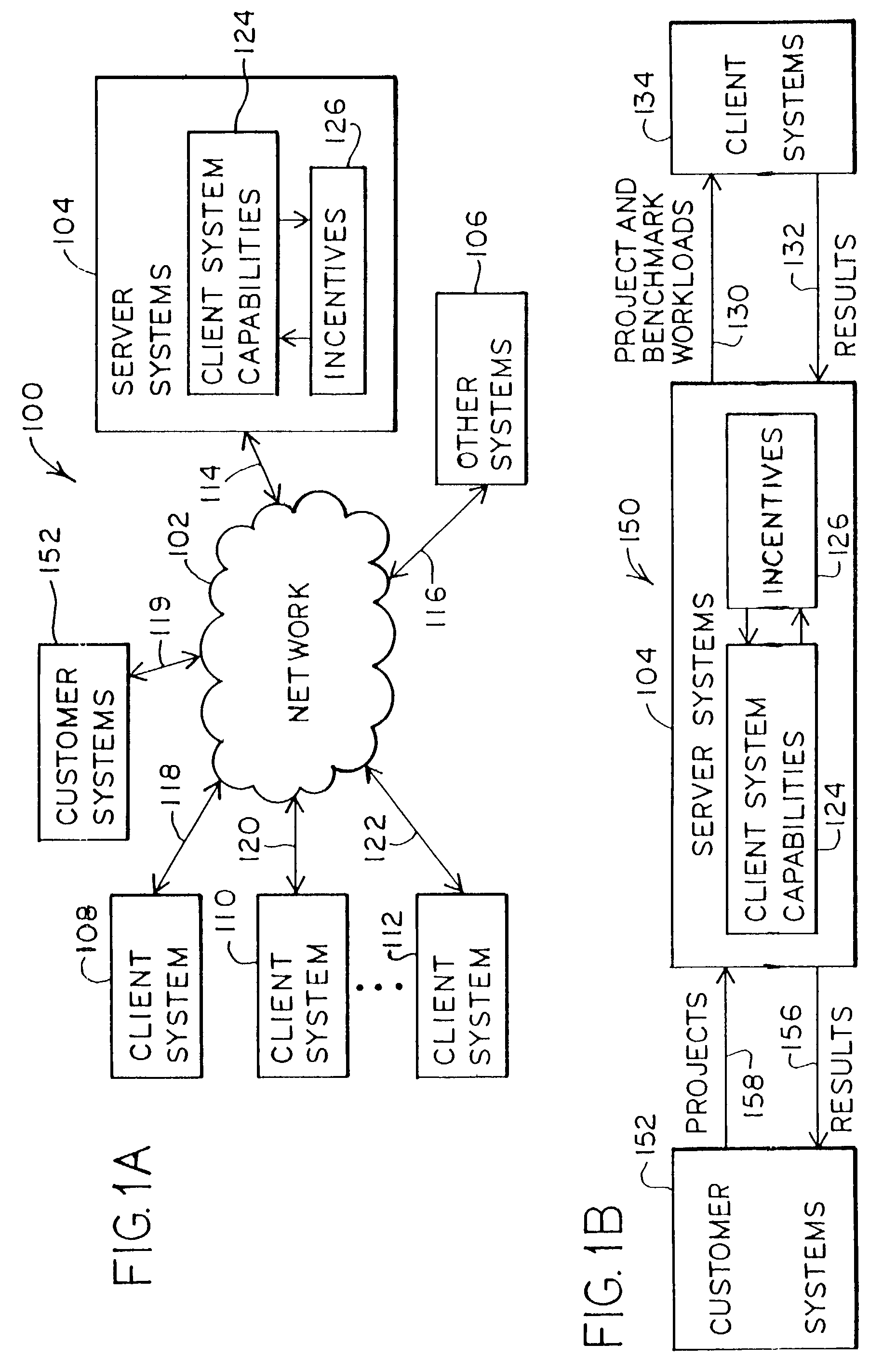
InactiveUS7254607B2Error detection/correctionMultiple digital computer combinationsClient agentCommunications system
Dynamic coordination and control of network connected devices within a distributed processing platform is disclosed for large-scale network site testing, or for other distributed projects. For network site testing, the distributed processing system utilizes a plurality of client devices which are running a client agent program associated with the distributed computing platform and which are running potentially distinct project modules for the testing of network sites or other projects. The participating client devices can be selected based upon their attributes and can receive test workloads from the distributed processing server systems. In addition, the client devices can send and receive poll communications that may be used during processing of the project to control, manage and coordinate the project activities of the distributed devices. If desired, a separate poll server system can be dedicated to handling the poll communication and coordination and control operations with the participating distributed devices during test operations, thereby allowing other server tasks to be handled by other distributed processing server systems. Once the tests are complete, the results can be communicated from the client devices to the server systems and can be reported, as desired. Additionally, the distributed processing system can identify the attributes, including device capabilities, of distributed devices connected together through a wide variety of communication systems and networks and utilize those attributes to organize, manage and distribute project workloads to the distributed devices.
Owner:CALLAHAN CELLULAR L L C
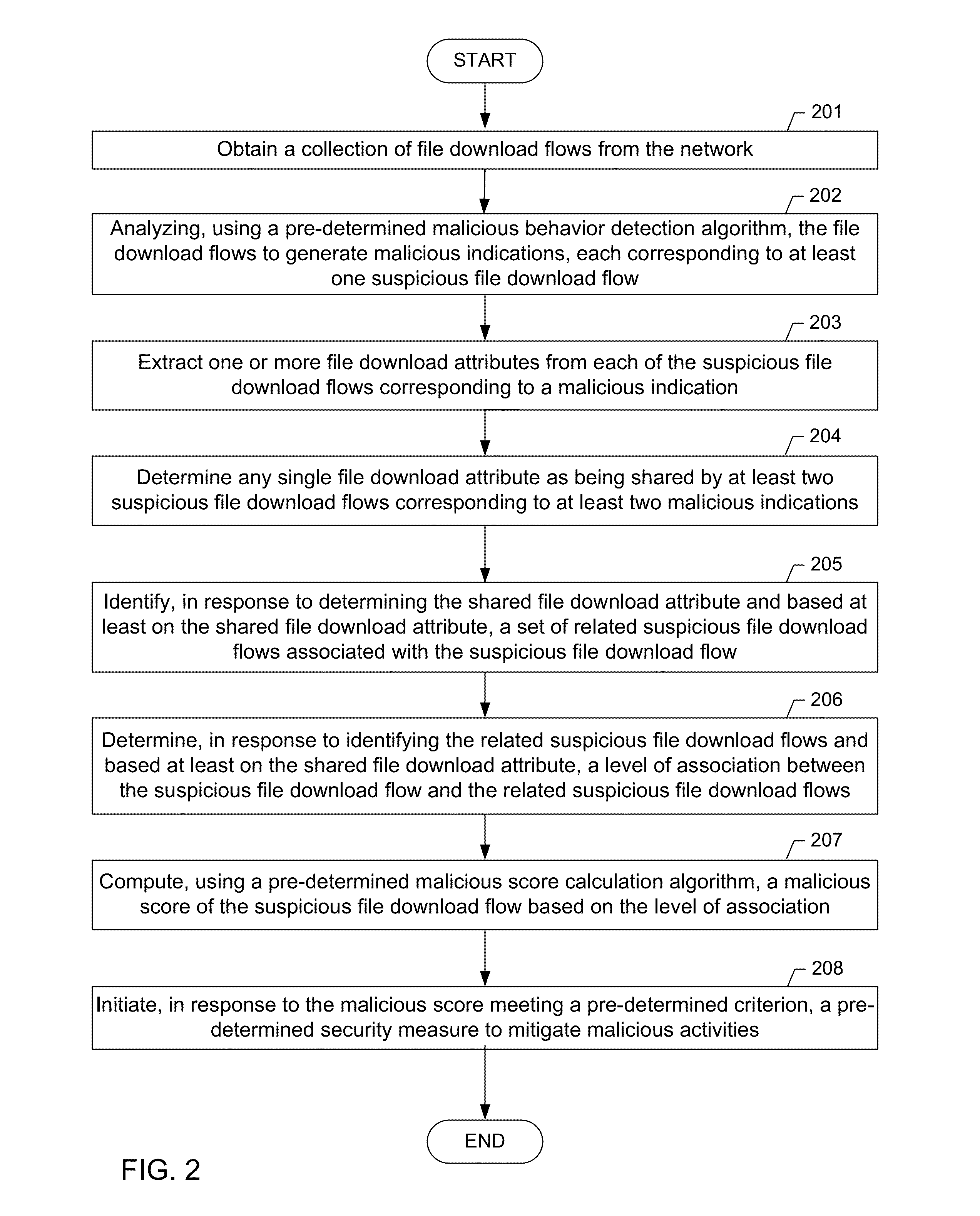
Detecting malware infestations in large-scale networks
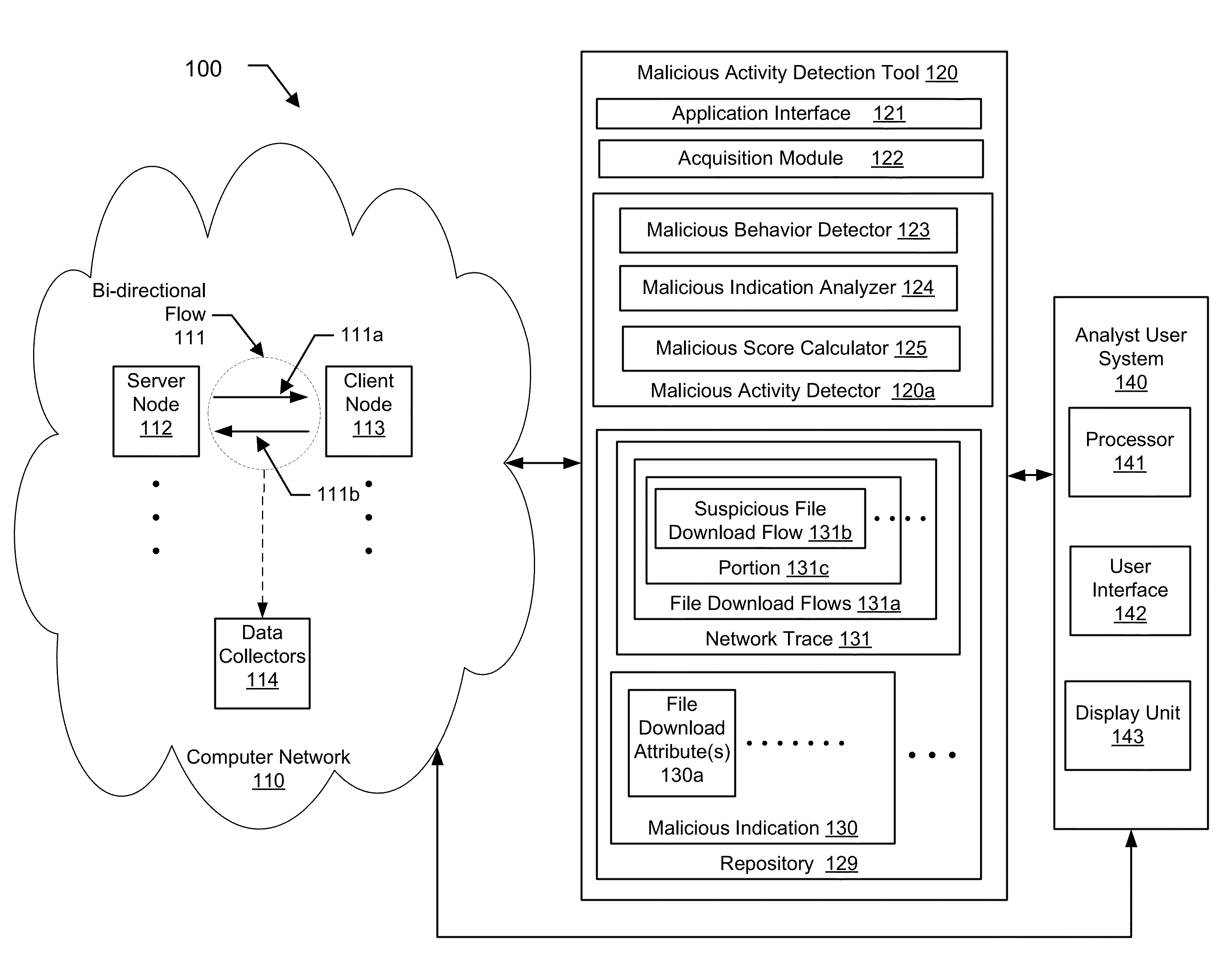
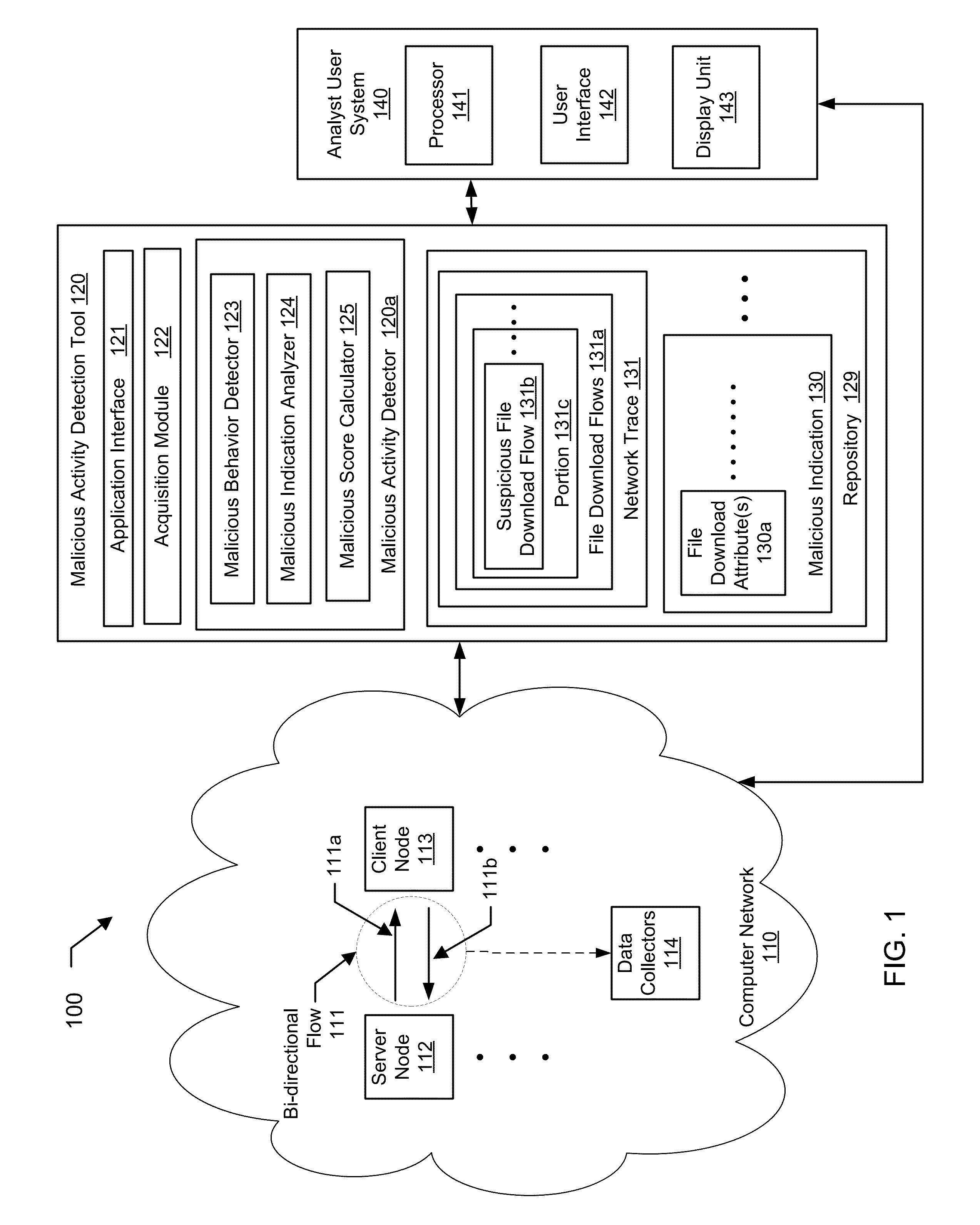
A method for detecting a malicious activity in a network. The method includes obtaining file download flows from the network, analyzing, the file download flows to generate malicious indications using a pre-determined malicious behavior detection algorithm, extracting a file download attribute from a suspicious file download flow of a malicious indication, wherein the file download attribute represents one or more of the URL, the FQDN, the top-level domain name, the URL path, the URL file name, and the payload of the suspicious file download flow, determining the file download attribute as being shared by at least two suspicious file download flows, identifying related suspicious file download flows and determining a level of association between based at least on the file download attribute, computing a malicious score of the suspicious file download flow based on the level of association, and presenting the malicious score to an analyst user of the network.
Owner:THE BOEING CO
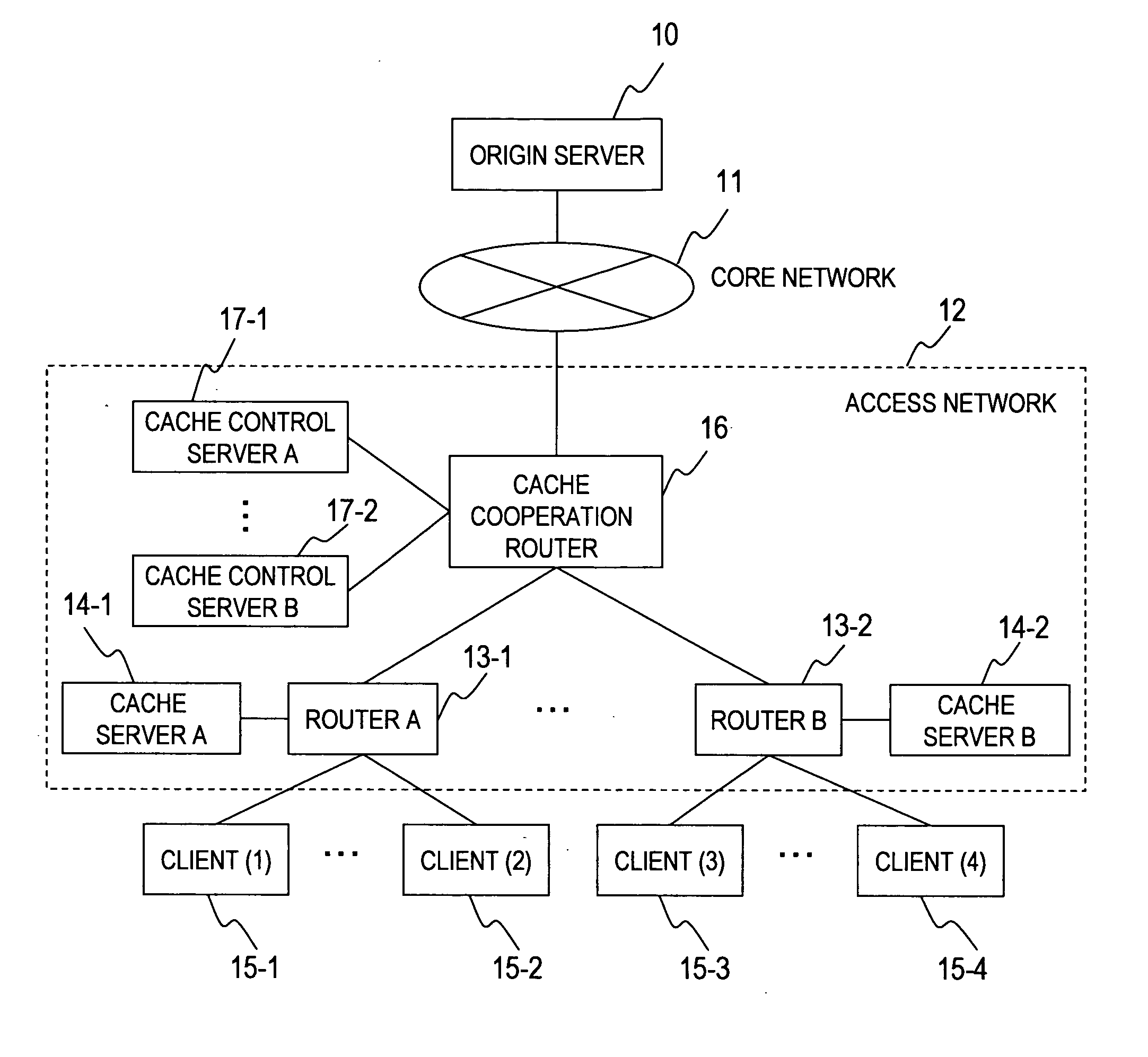
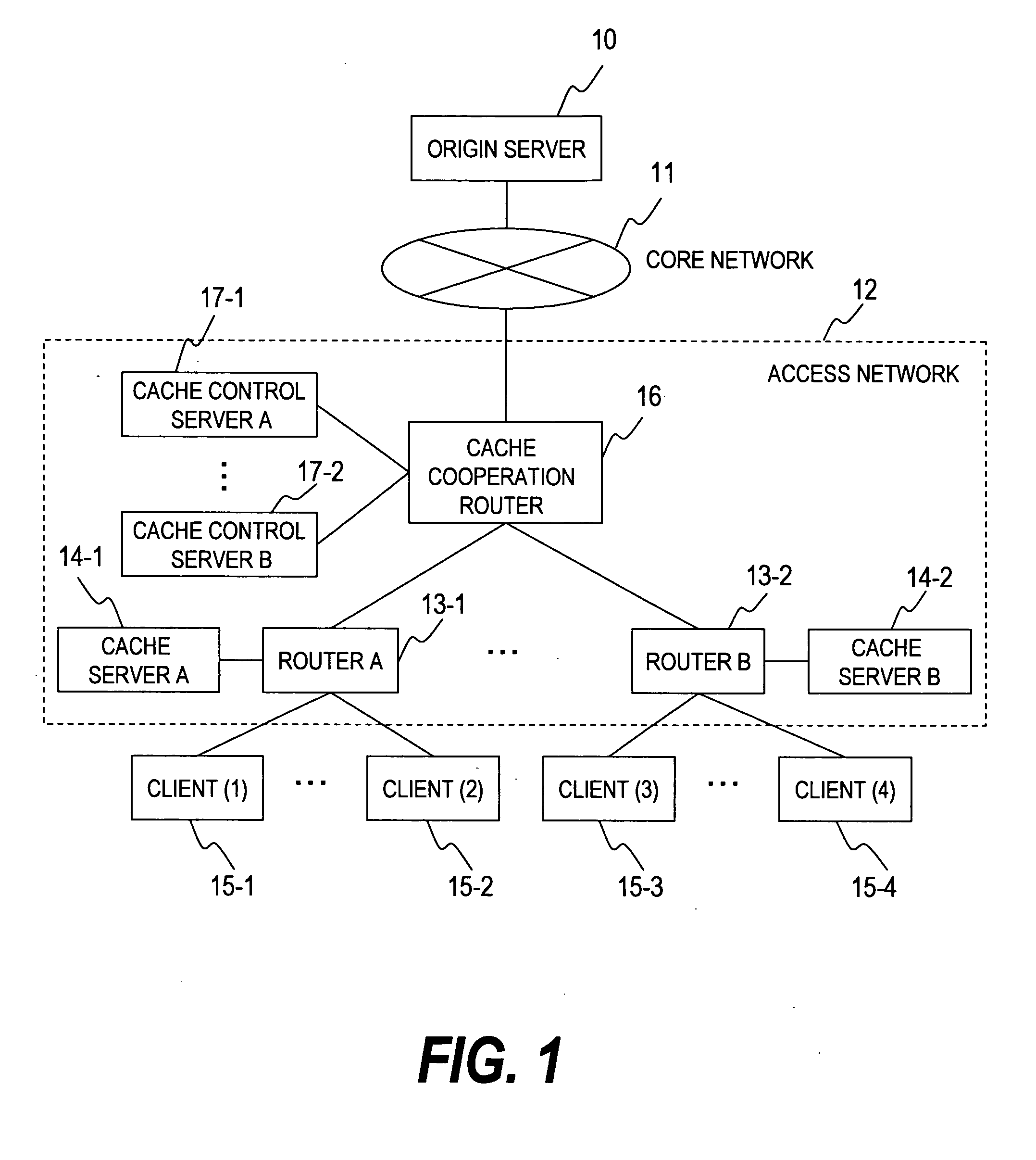
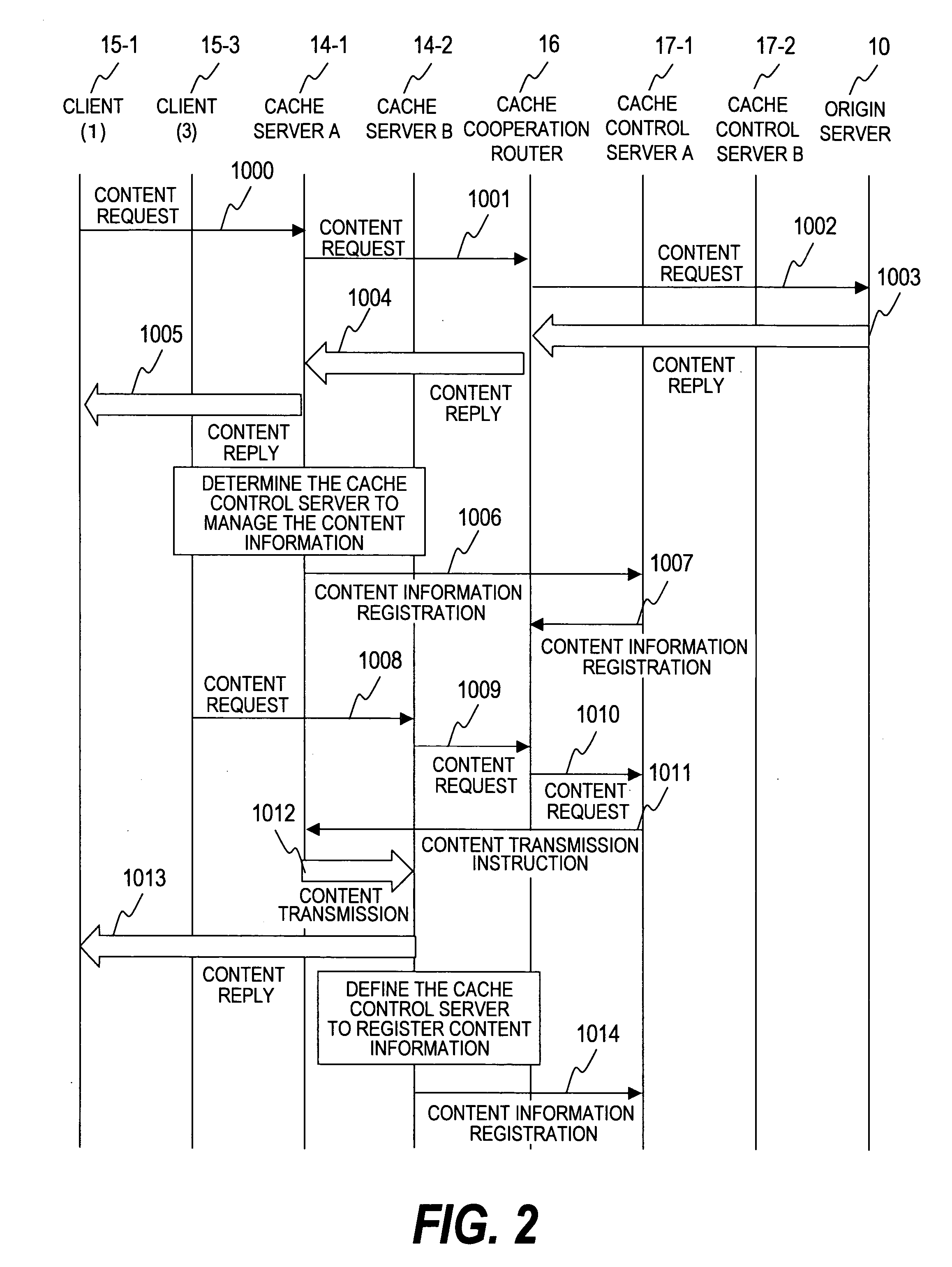
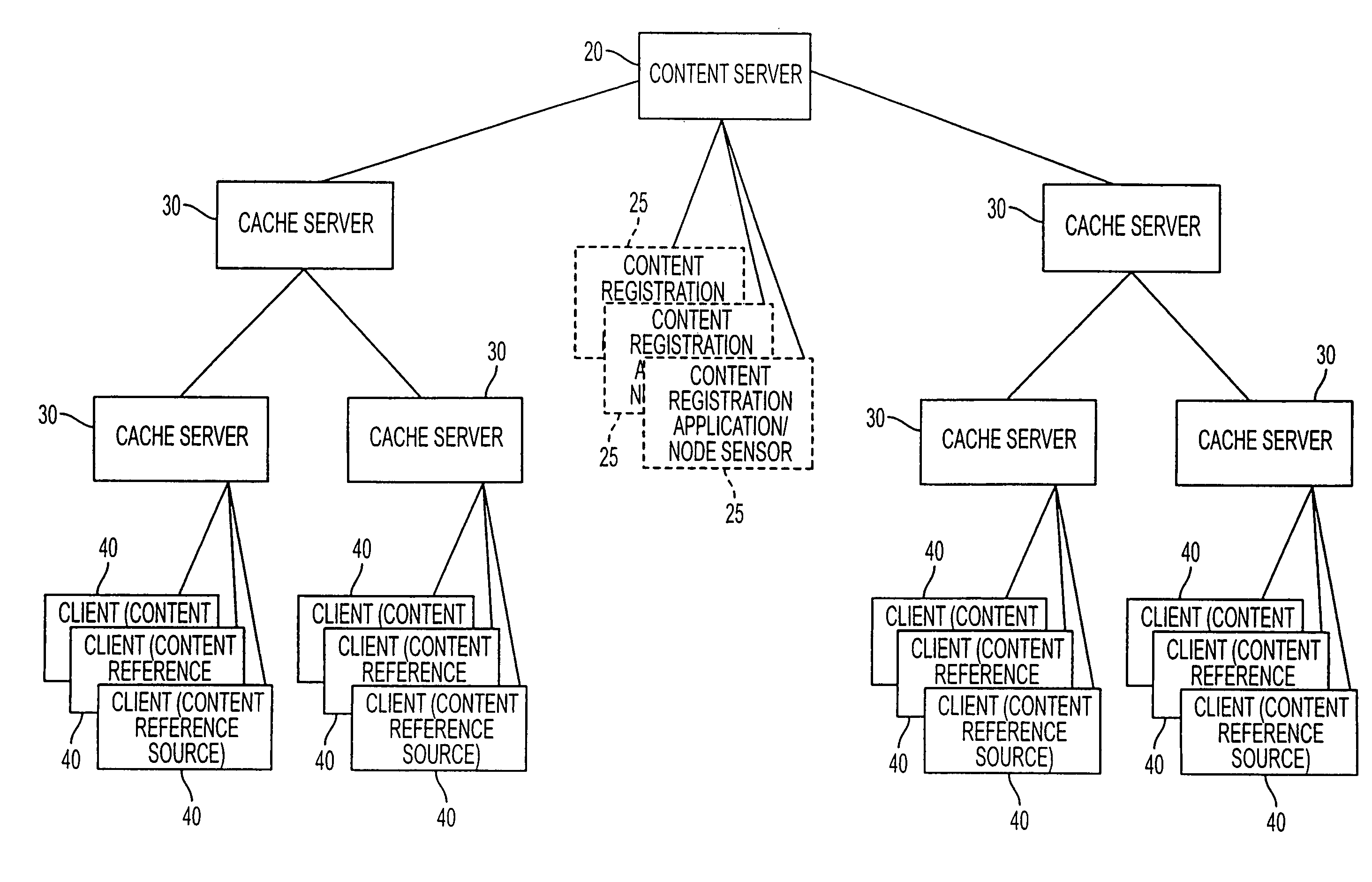
Cache system
InactiveUS20070050491A1Easily adapted to large-scale networkDigital computer detailsTransmissionCache serverParallel computing
The purpose of the invention is to provide a distributed cache system applicable to a large-scale network having multiple cache servers. In a distributed cache system including multiple cache control servers, the content information is divided and managed by each cache control server. When content requested from a client is stored in the distributed cache system, a cache cooperation router forwards the content request to the cache control server which manages the information of the requested content. A cache control server has a function to notify its own address to the distributed cache system when the cache control server is added to the distributed cache system. When a cache control server receives the notification, it sends content information to the new cache control server and synchronizes the content information. Thus, a cache control server can be added to the system with ease.
Owner:HITACHI LTD
Server and connecting destination server switch control method
InactiveUS7904562B2Reduce loadModified dynamicallyMultiple digital computer combinationsTransmissionCache serverServer allocation
Owner:FUJITSU LTD
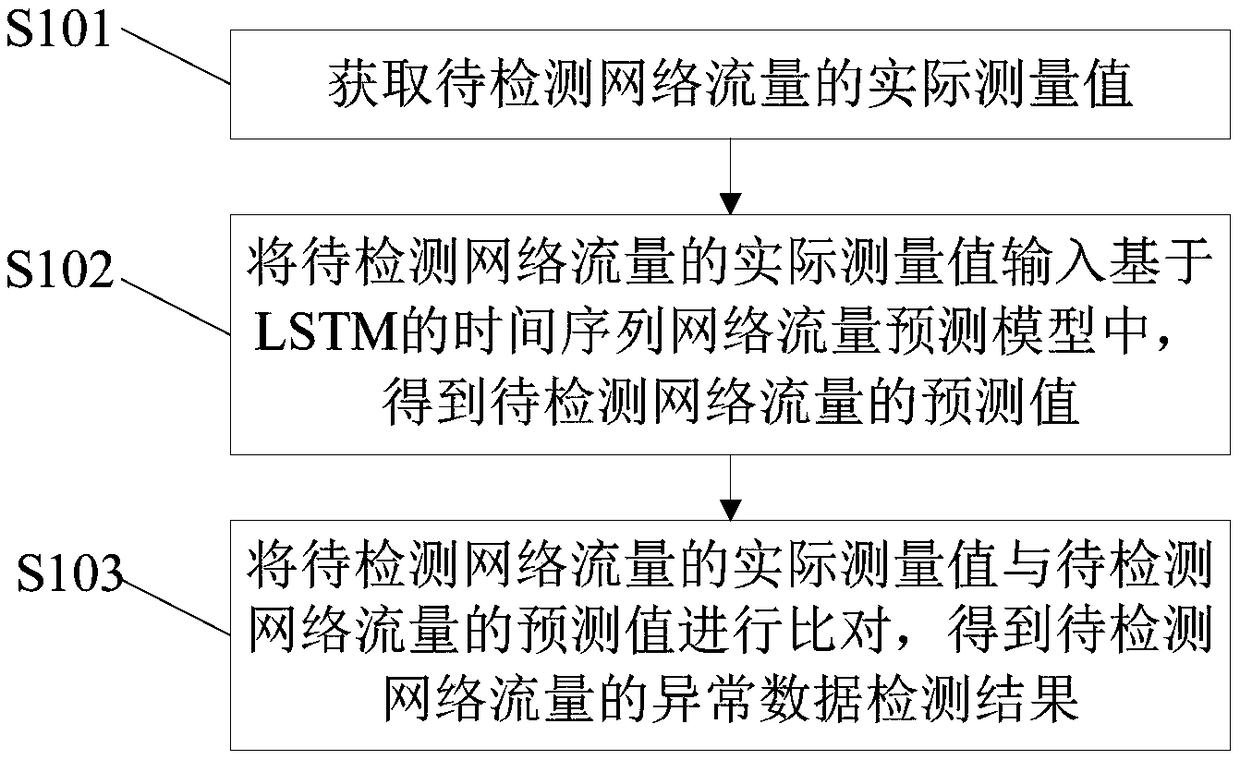
LSTM (Long Short-Term Memory) based time sequence network anomaly detection method and device
InactiveCN108900546AImprove Anomaly Detection EfficiencyGood exception recognitionData switching networksInformation securityData detection
The invention provides LSTM (Long Short-Term Memory) based time sequence network anomaly detection method and device, and relates to the technical field of information security. The method comprises the following steps: acquiring an actual measured value of the to-be-detected network traffic; inputting the actual measured value of the to-be-detected network traffic into a LSTM based time sequencenetwork traffic prediction model, to obtain a predicted value of the to-be-detected network traffic; comparing the actual measured value of the to-be-detected network traffic with the predicted valueof the to-be-detected network traffic, to obtain an anomaly data detection result of the to-be-detected network traffic. The LSTM based time sequence network anomaly detection method provided by the invention can detect one-dimensional time sequence traffic data anomaly data and provide early warning in a large-scale network environment, thus improves the network anomaly detection efficiency, realizes a good effect of identifying network traffic anomaly, ensures relatively complete development fitting and can visually and obviously distinguish the anomaly information.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
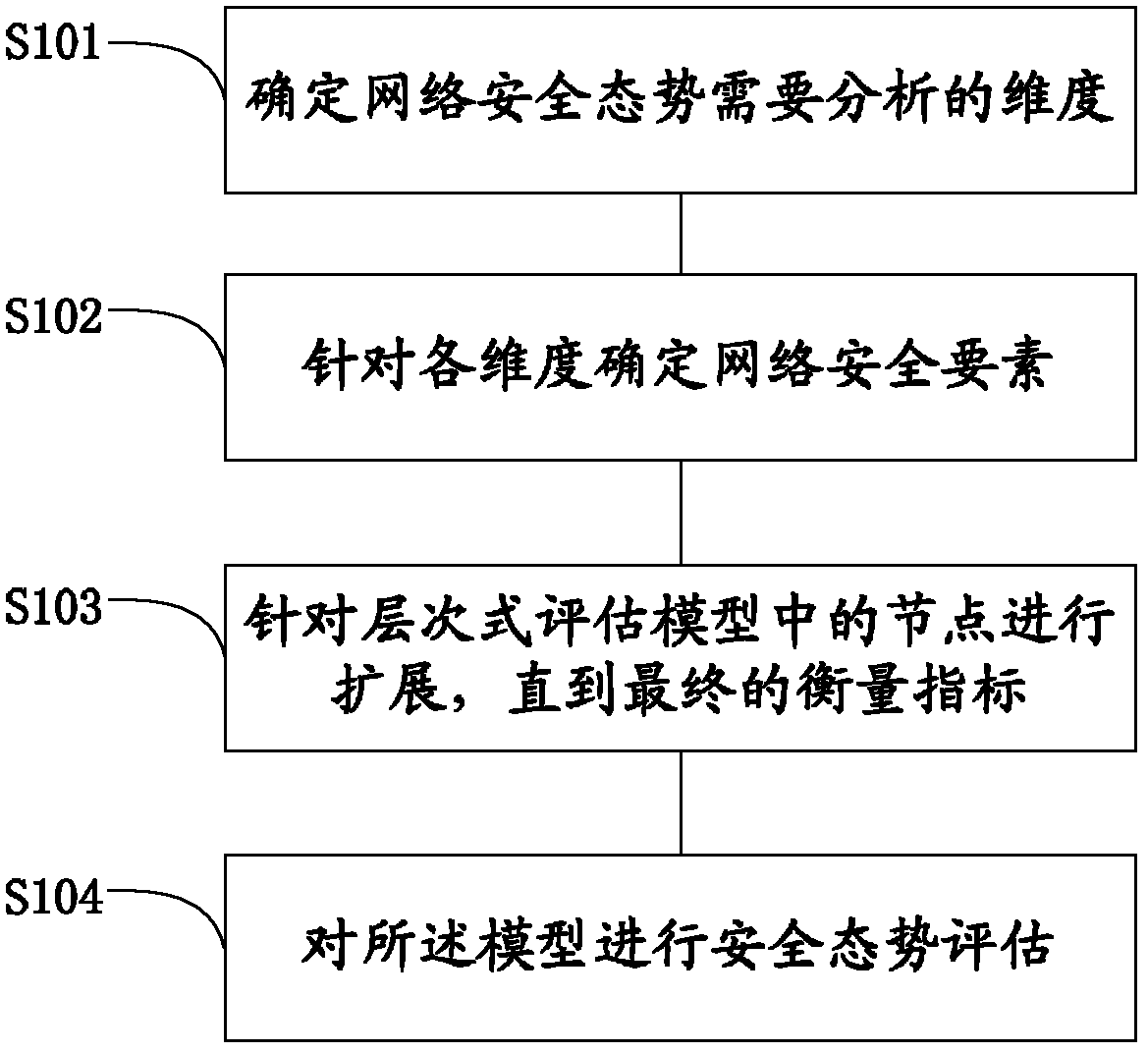
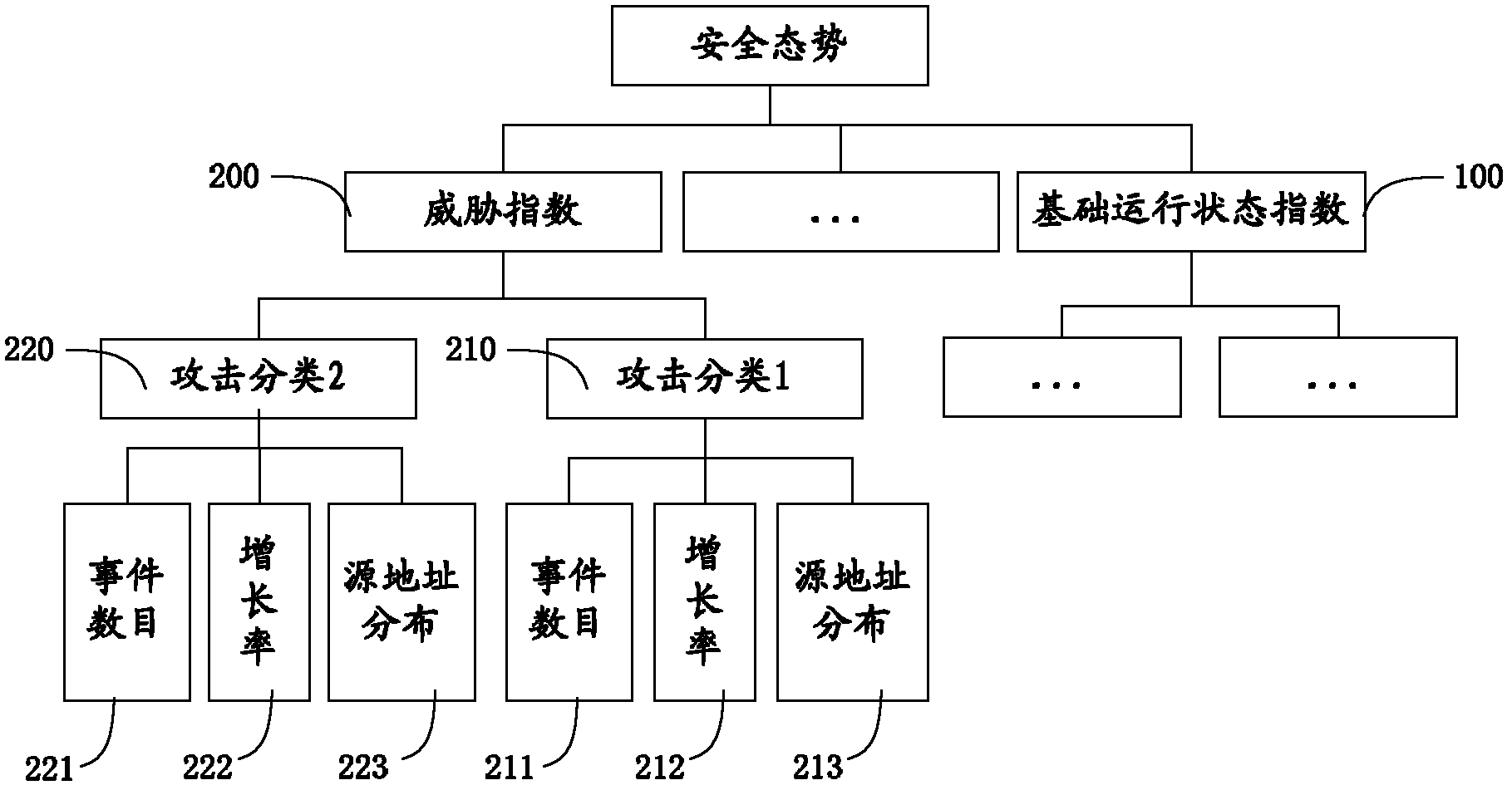
Large-scale network security situation evaluation method based on index system
The invention provides a large-scale network security situation evaluation method based on an index system. The method comprises the following steps: step one, determining dimensions that are needed to be analyzed for a network security situation; step two, determining network security factors according all the dimensions; step three, determining concrete indexes according to all the network security factors, wherein the dimensions, the security factors, and the concrete indexes are all-level nodes of a hierarchical evaluation model; and the step four, carrying out security situation evaluation on the hierarchical evaluation model to obtain a network security value. According to the method provided in the invention, efficiency of large-scale network security situation evaluation can be improved.
Owner:NAT UNIV OF DEFENSE TECH
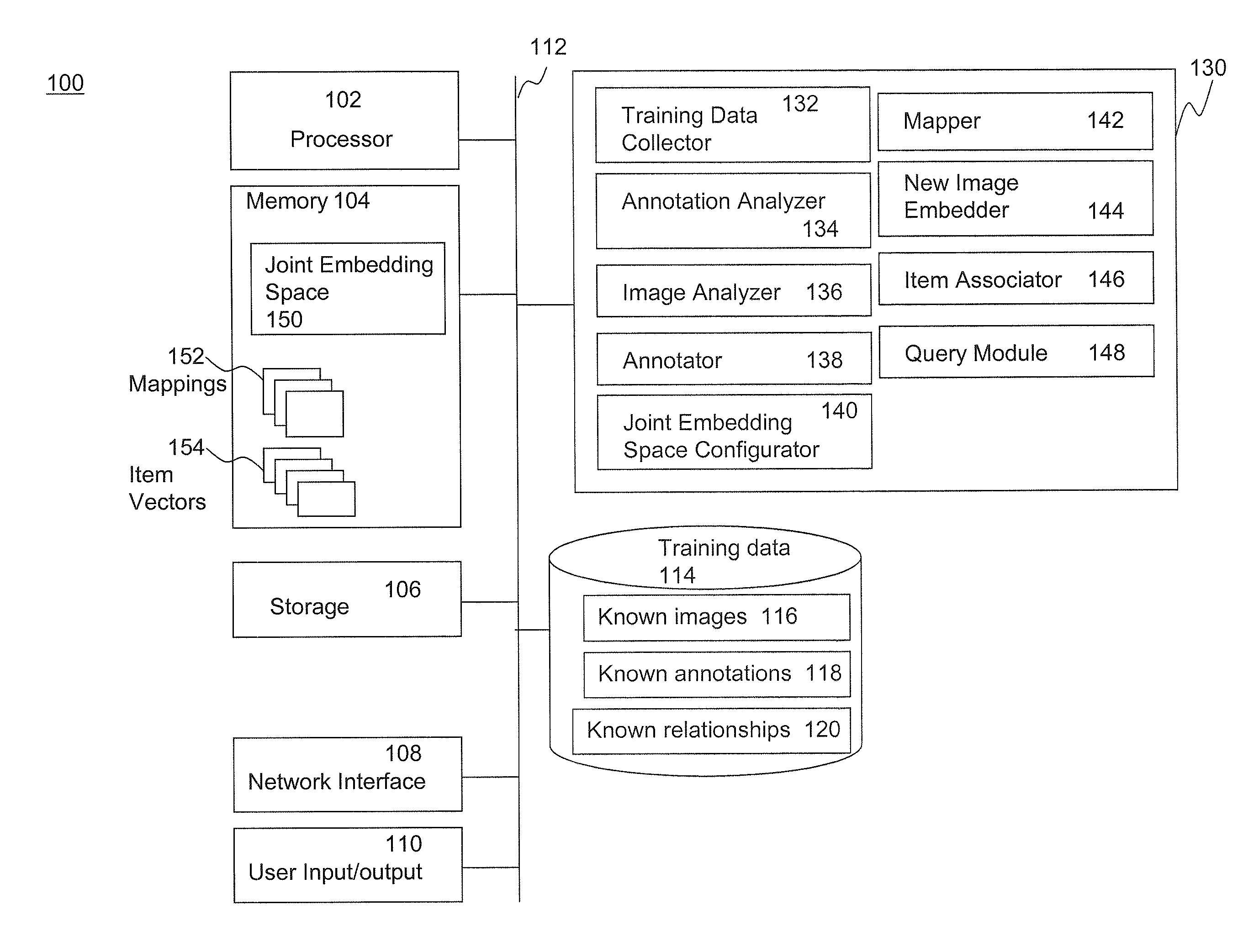
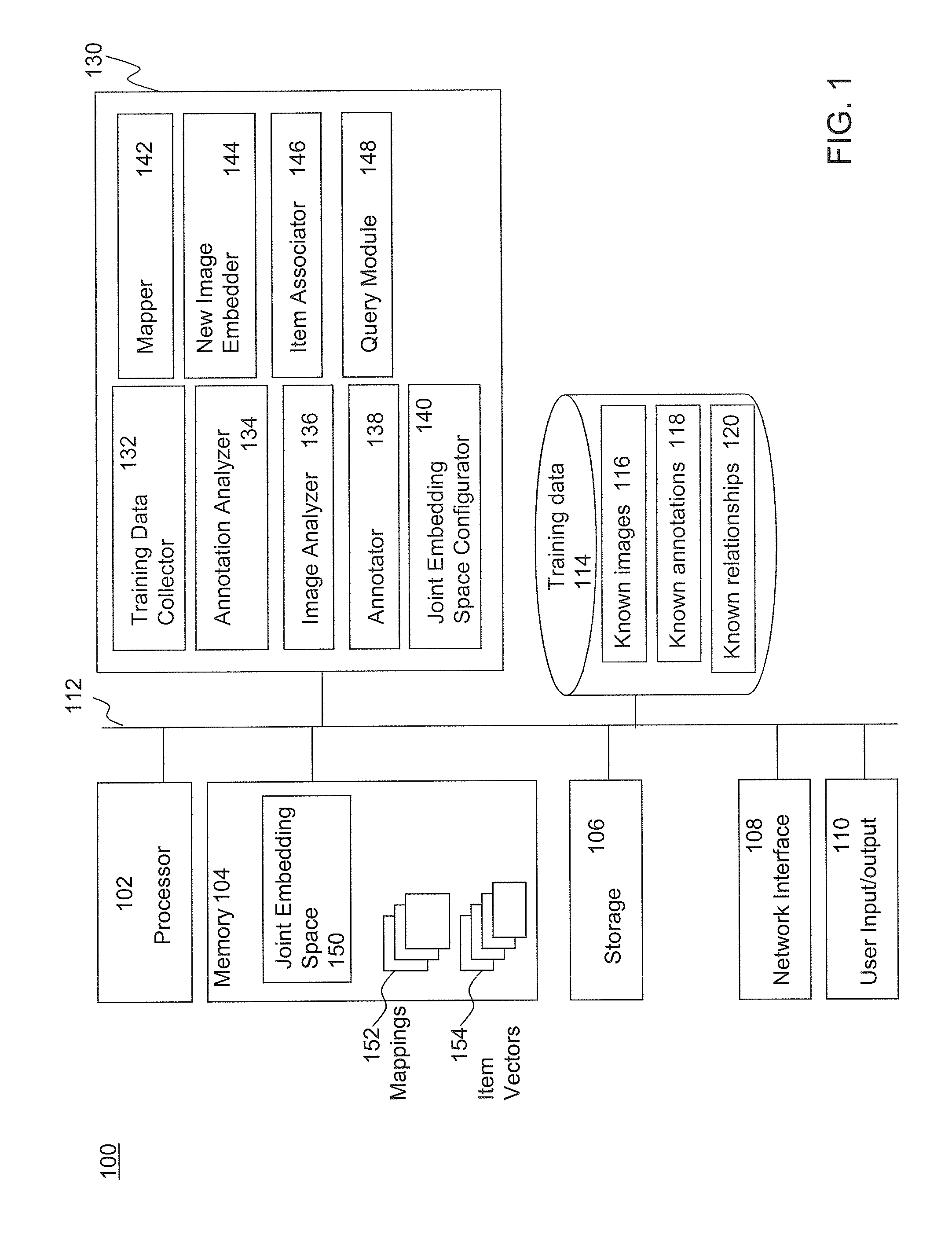
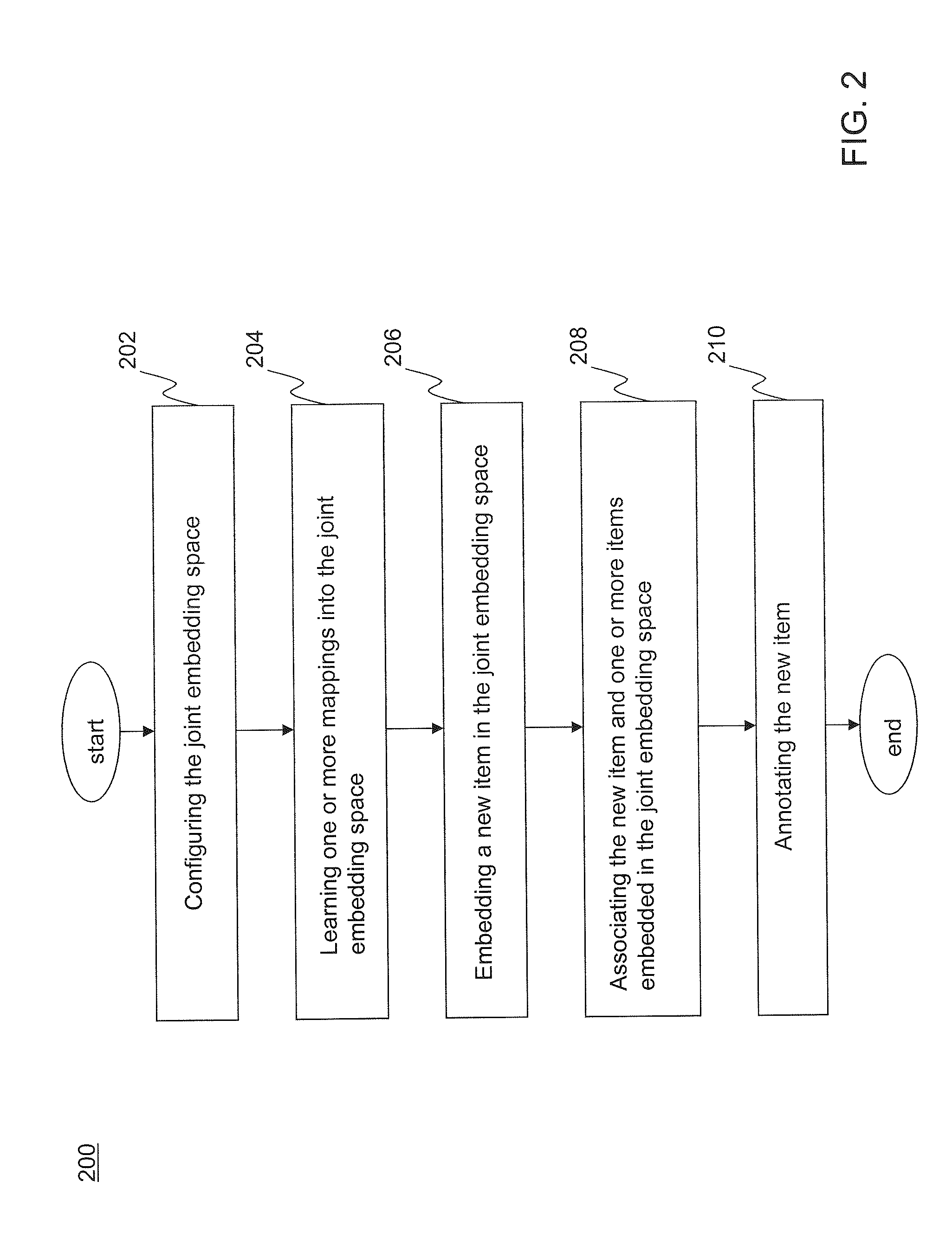
Joint Embedding for Item Association
Methods and systems to associate semantically-related items of a plurality of item types using a joint embedding space are disclosed. The disclosed methods and systems are scalable to large, web-scale training data sets. According to an embodiment, a method for associating semantically-related items of a plurality of item types includes embedding training items of a plurality of item types in a joint embedding space configured in a memory coupled to at least one processor, learning one or more mappings into the joint embedding space for each of the item types to create a trained joint embedding space and one or more learned mappings, and associating one or more embedded training items with a first item based upon a distance in the trained joint embedding space from the first item to each said associated embedded training items. Exemplary item types that may be embedded in the joint embedding space include images, annotations, audio and video.
Owner:GOOGLE LLC
Performance evaluation and traffic engineering in IP networks
InactiveUS6909693B1Error preventionTransmission systemsDifferentiated servicesDifferentiated service
A model is given for performance evaluation of IP computer networks that are dominated by congestion-controlled traffic. The model includes heterogeneous TCP flows, UDP flows, short-lived TCP flows, and TCP flows in a differentiated services network. The performance of large-scale networks is estimated where flows may encounter multiple congested links.
Owner:AVAYA INC
Double chain-type cross chain trading Internet of blockchains model core algorithm
InactiveCN107248076AJoin easyEasy to leaveFinanceCryptography processingFault toleranceNetwork architecture
The invention discloses a double chain-type cross chain trading Internet of blockchains model (golden monkey model) core algorithm. Different from the traditional centralized architecture, the model has a fully-distributed and multi-chain network architecture. Due to the fully-distributed architecture, easier expansion, easier extension and easier fault tolerance are realized than the existing architecture. Each chain maintains the self consistency, the consistency between chains does not need to be managed by a central organization but is maintained by a fully-distributed mechanism. Limitations from the previous centralized Internet of blockchains (chain network, in short) are broken, all chains can operate in parallel on the model, and the trading efficiency and the network operation speed are improved. The model has a new financial market architecture, extensibility is realized, a financial unit can randomly and easily enter or leave the network, and the large-scale network and a high transaction volume are supported. The model comprises participant blockchains and inter-chain blockchains, the participant blockchains or the inter-chain blockchains can be one or one group of financial institutions, the inter-chain blockchain has a double-chain structure, a trading record and a balance account are separated, and cross chain trading is realized. A core algorithm for trading between chains, particularly, a protocol algorithm of enabling the inter-chain blockchains to assist two or more than two participant blockchains for mutual trading is provided, no centralized mechanism is needed, and the consistency of the whole network is maintained.
Owner:ZEU CRYPTO NETWORKS INC
Server and connecting destination server switch control method
InactiveUS20090248871A1Reduce loadModified dynamicallyDigital computer detailsTransmissionCache serverNetworked system
A connecting destination server switch control method for switching a server and the connecting destination of the server is provided, the method realizing a larger-scaled network system by distributing a load to each cache server, thus reducing the total load and dynamically modifying a logical network according to the load of each cache server even when there is a plurality of content servers that are content distributors. In a situation where cache servers whose management sources differ are connected in many steps, the total load caused by content acquisition can be reduced by modifying the content acquisition source server of a cache server for each piece of content.
Owner:FUJITSU LTD
System and method for detecting routing security
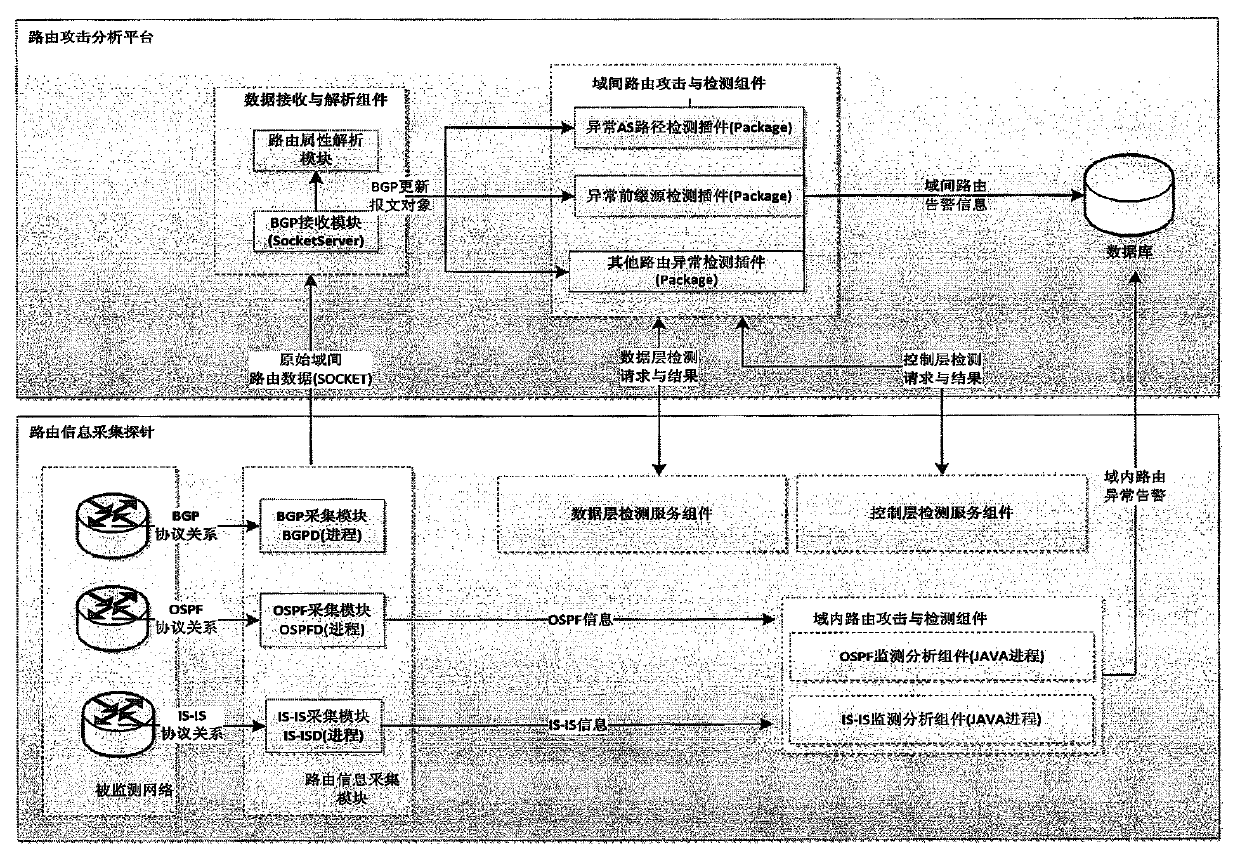
ActiveCN103442008AReduce false negative rateReduce false alarm rateData switching networksIp addressComputer science
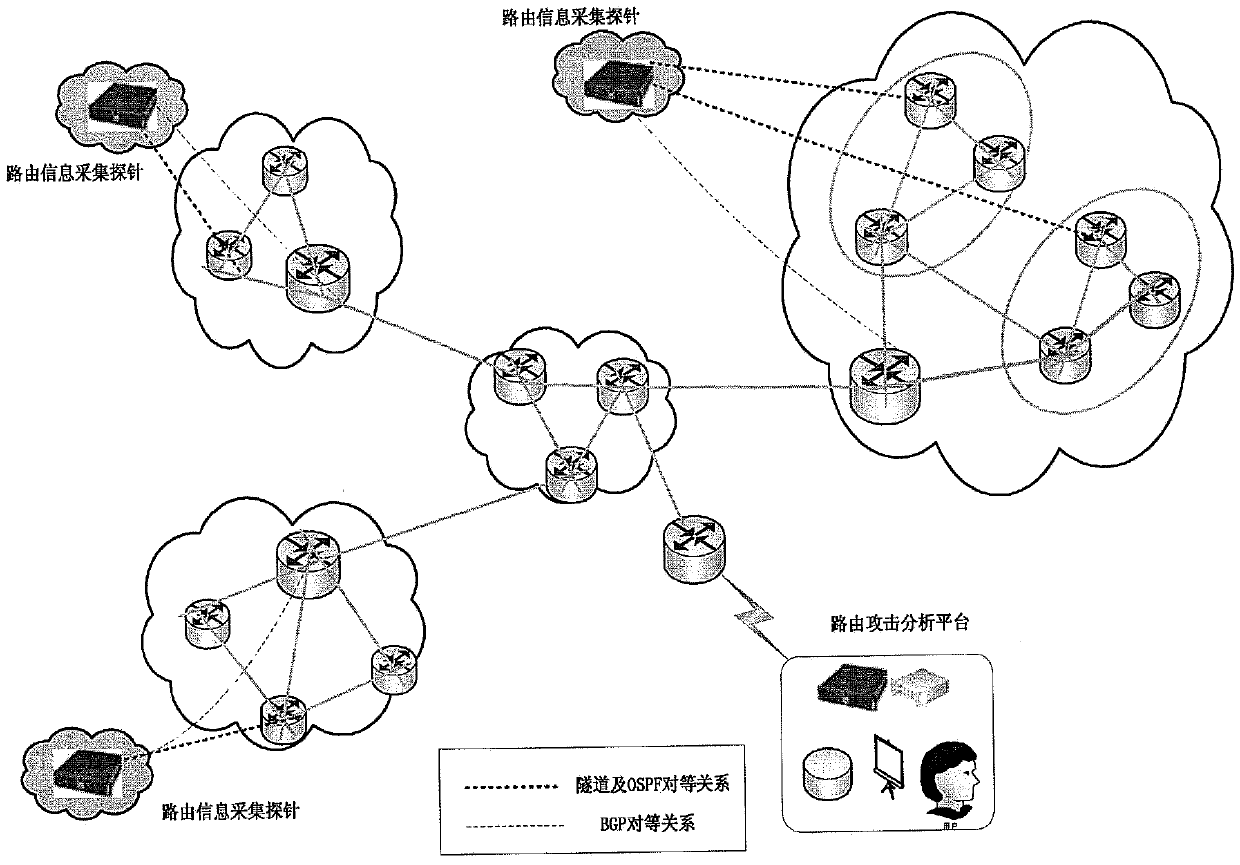
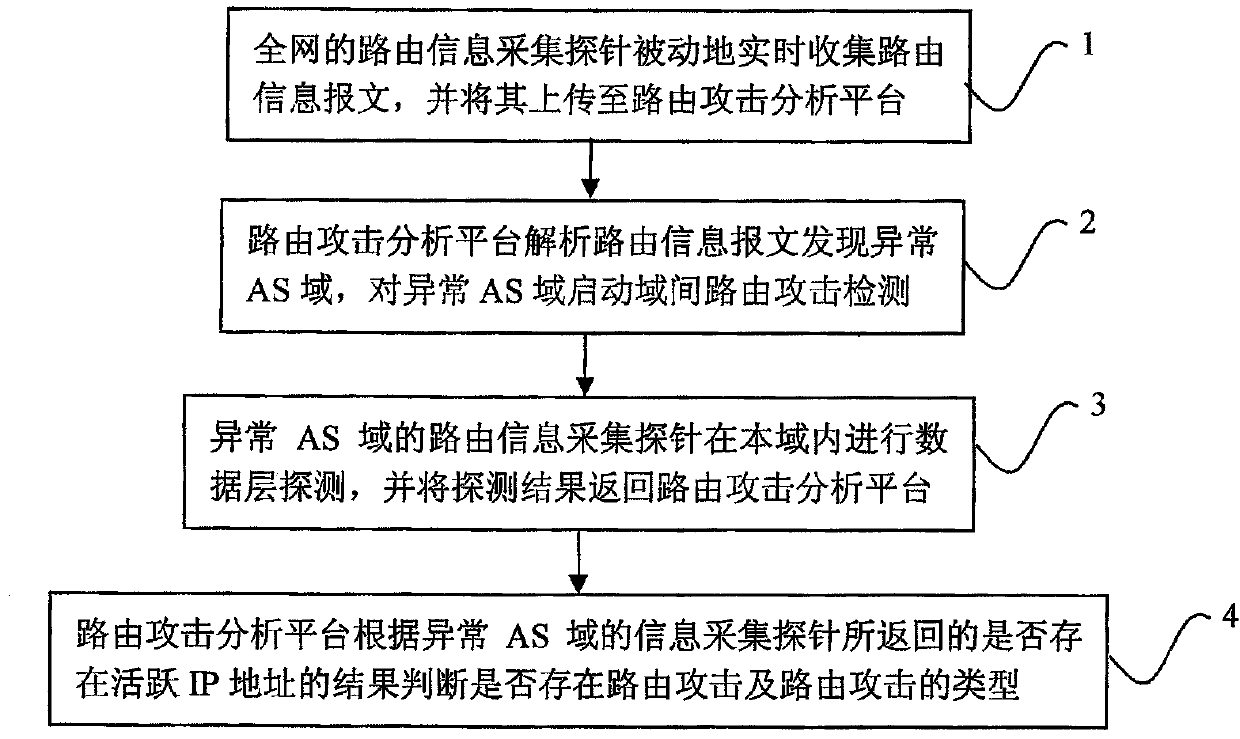
The invention provides a system for detecting routing security. The system for detecting the routing security comprises routing information collecting probes and a routing attack analyzing platform, wherein the routing information collecting probes are used for passively collecting routing information messages in real time and uploading the routing information messages to the routing attack analyzing platform, the routing information collecting probes are also used for receiving instructions of the routing attack analyzing platform to detect whether active IP addresses exist in the domain where the routing information collecting probes are located and feeding back a detection result, the routing attack analyzing platform is used for analyzing the routing information messages reported by the routing information collecting probes to discover abnormal AS domains and sending detection instructions to the routing information collecting probes in the abnormal AS domains, and the routing attack analyzing platform is also used for judging whether routing attack exits according to results fed back by the routing information collecting probes of the abnormal AS domains. The system and method for detecting routing security have the advantages that the missing report rate and false report rate of the routing attack detection can be reduced, real-time monitoring of a large-scale network system is achieved on the premise that cost is quite low, and the routing attack can be found out as early as possible.
Owner:上海星地通讯工程研究所
Safe log analyzing method and system
InactiveCN101399658AEfficient discoveryRealize detectionSecuring communicationInformation processingSerial pattern
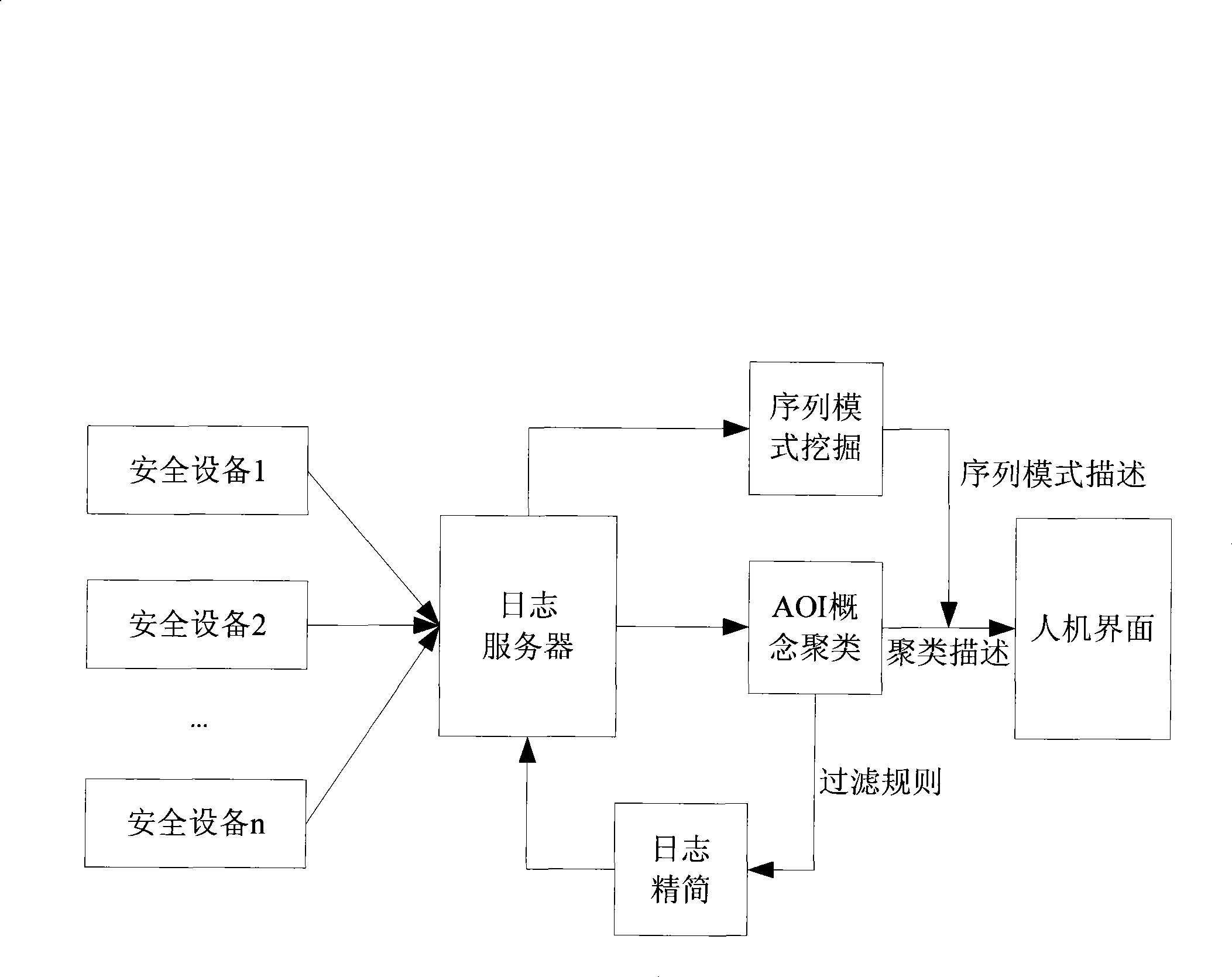
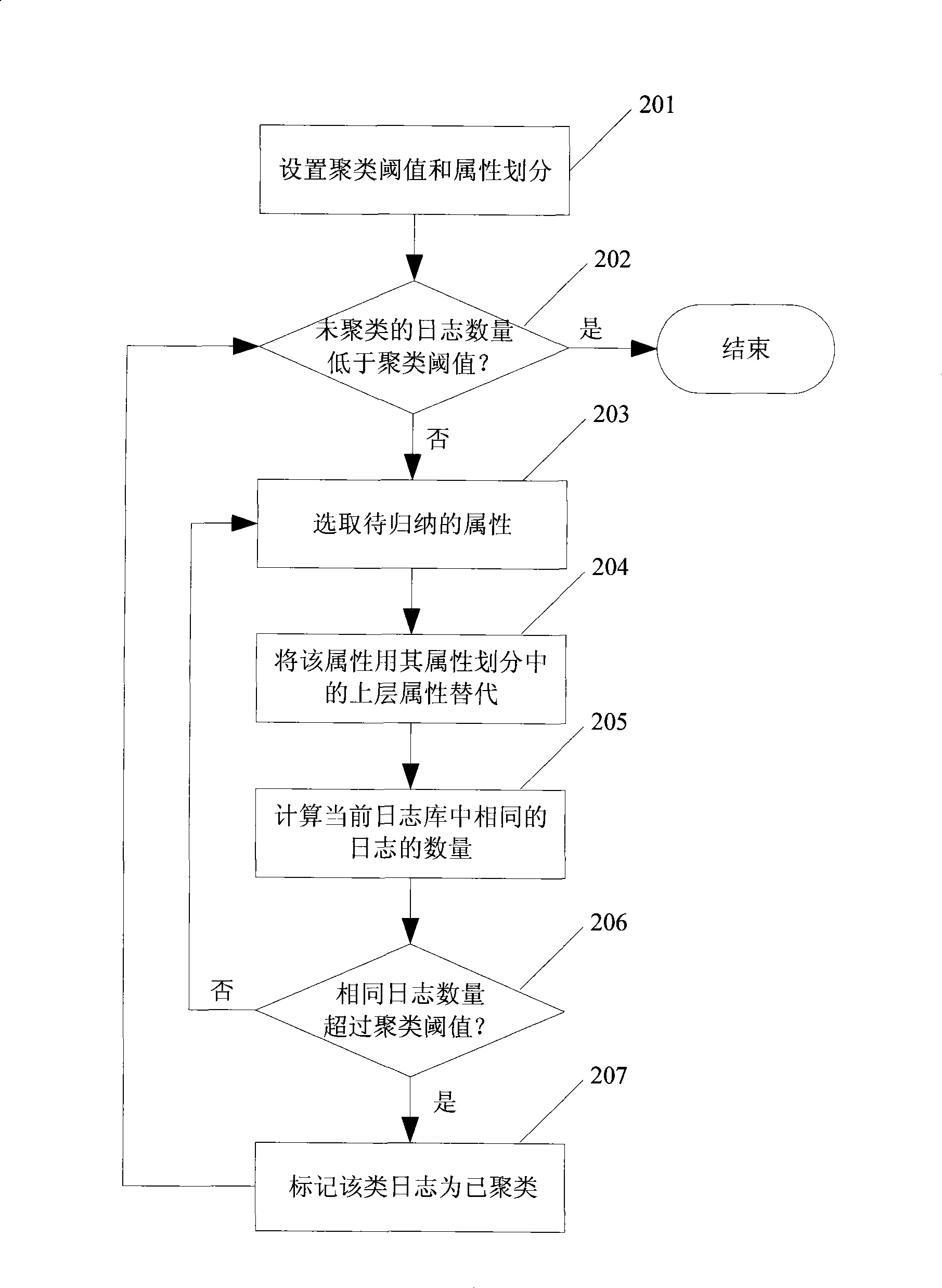
The invention discloses a method for analyzing a security log and a system thereof, which realizes filtration of invalid logs and misreported logs in mass logs, and discovers large-scale network security events and common attack sequences. The method comprises the following steps: the mass logs are subject to cluster analysis by the attribute-oriented inductive algorithm so as to generate class description of each class of log after clustering; an administrator sets filtration regulations according to the clustered class description, unrelated and misreported logs are removed from the current log base so as to simplify the mass logs; Internet Worms, distributed denial of service attacks and other large-scale network security events characteristics are extracted; the simplified log is subject to sequential pattern mining to find attack behavior sequence description commonly used by attackers to be finally submitted to the administrator. The system comprises a clustering analysis module, a filtration module and a sequential pattern mining module. The method and the system can be applied to information processing of the mass logs of security products.
Owner:BEIJING VENUS INFORMATION TECH
Proactive controller for failure resiliency in communication networks
ActiveUS20150195190A1Reduce the impact of failureHardware monitoringReliability/availability analysisTraffic capacityReal-time data
Network devices and systems relating to prevention of large-scale network failure and determining a probability of a large-scale network failure for a network. The network devices may control rerouting of network traffic from failed network paths to preventative paths with probabilities of failure below determined thresholds. The network devices monitor and process real time data for dynamic and proactive rerouting when large-scale network failure occurs or is likely to occur.
Owner:UNIV OF ONTARION INST OF TECH
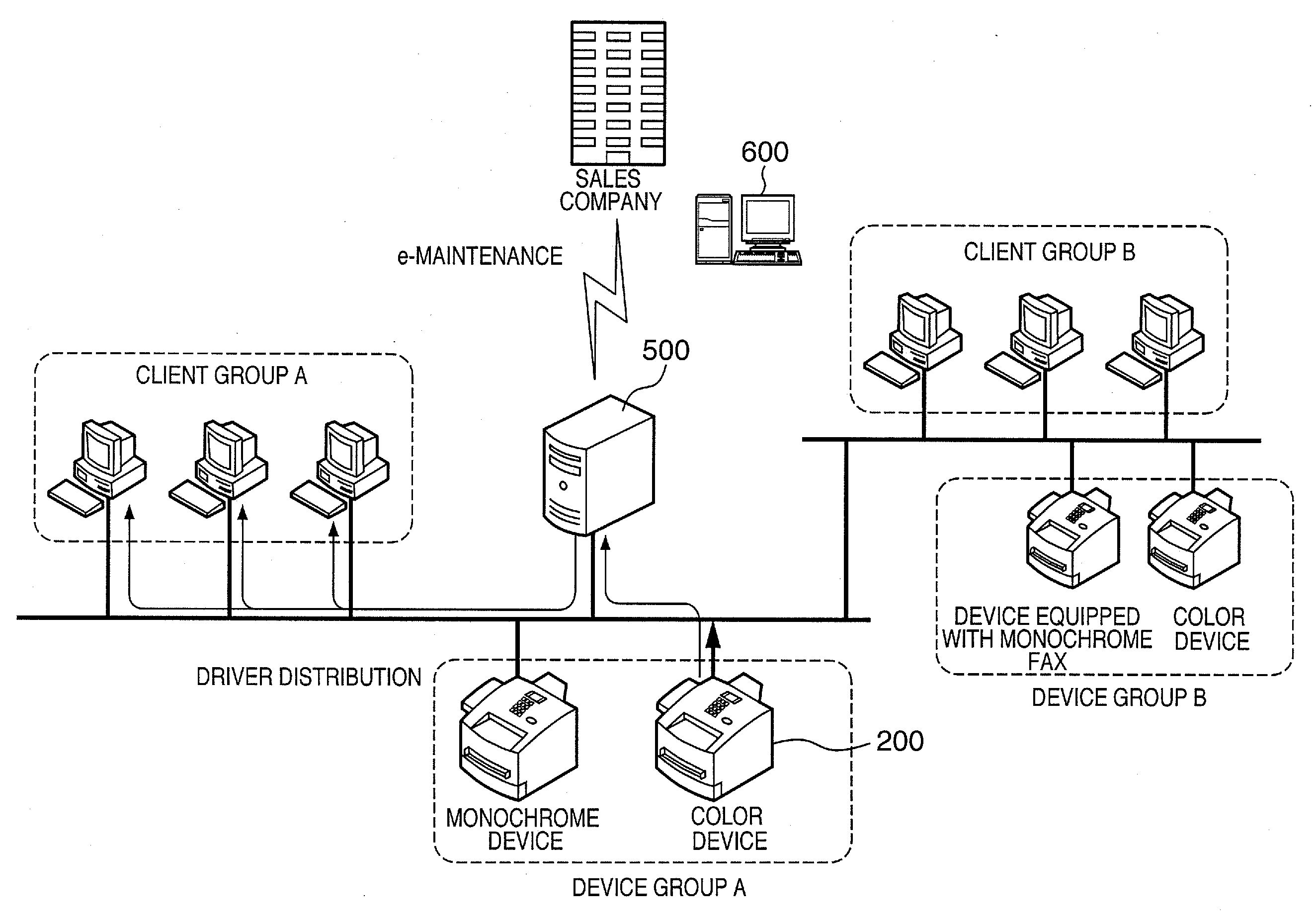
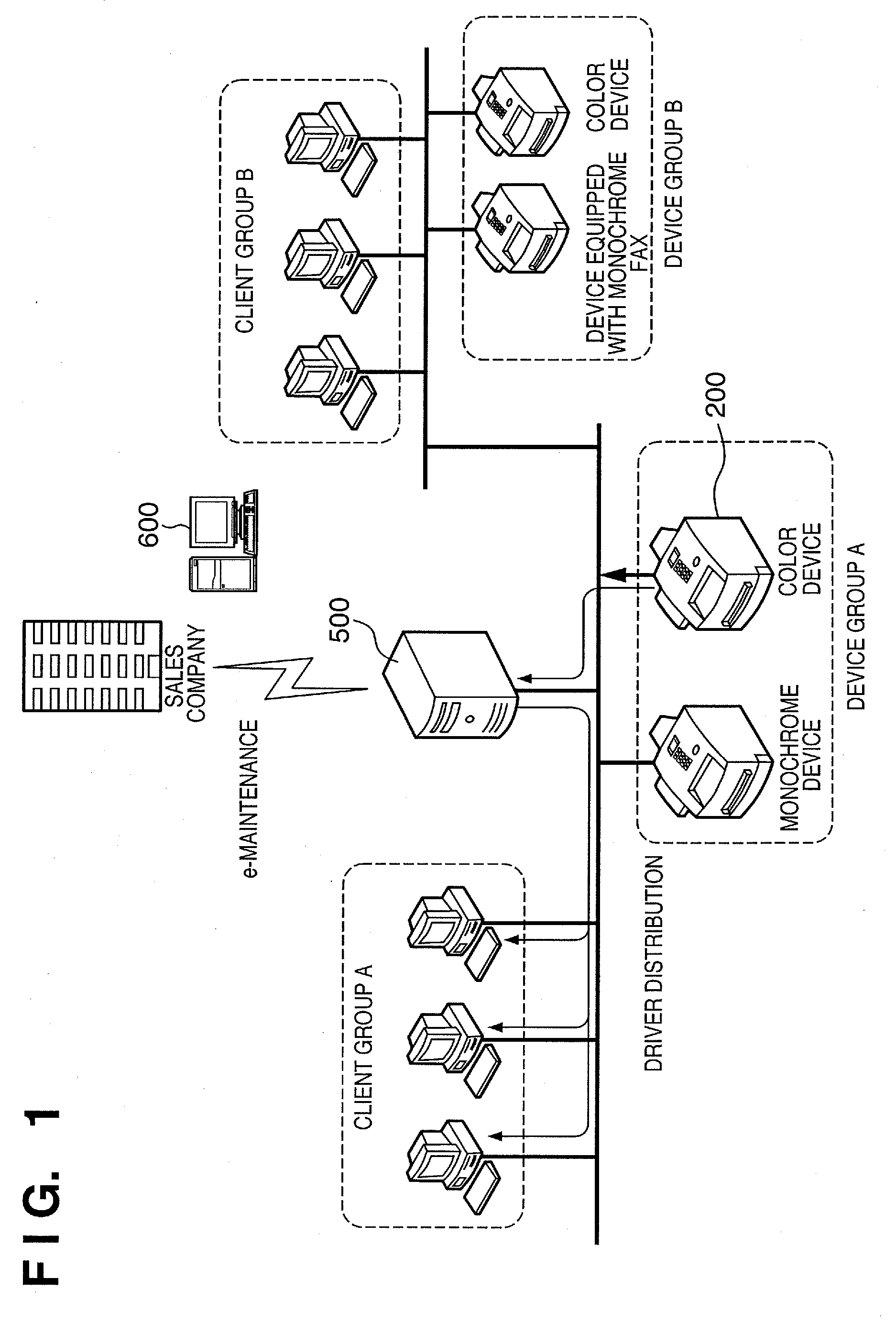
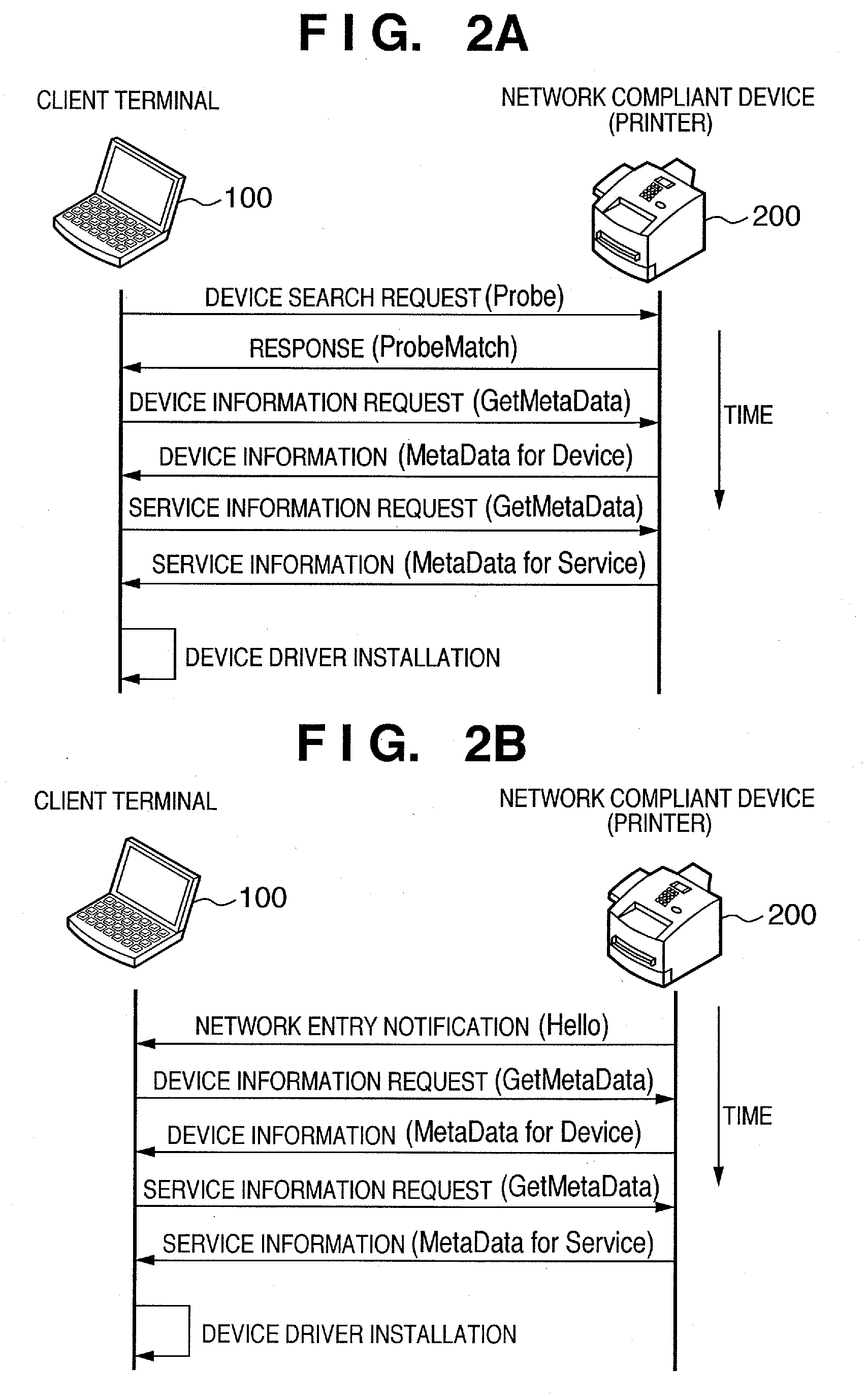
Network management server, control method, computer program, computer readable storage medium, and network system
Even in a large-scale network environment in which many clients and many devices exist on a network, this invention allows the network to function as an aggregation of logical small-scale networks in the execution of device driver setup. For this purpose, a management server manages a plurality of clients on the network as client groups, and a plurality of network devices as device groups. The management server then associates each client group with each device group. When a network device belonging to the device group A is newly installed and the power supply is turned on, the network device issues a Hello message indicating entry to the network. Upon receiving the Hello message, the management server transmits a setup request message for a device driver for the network device to only each client belonging to the client group A.
Owner:CANON KK
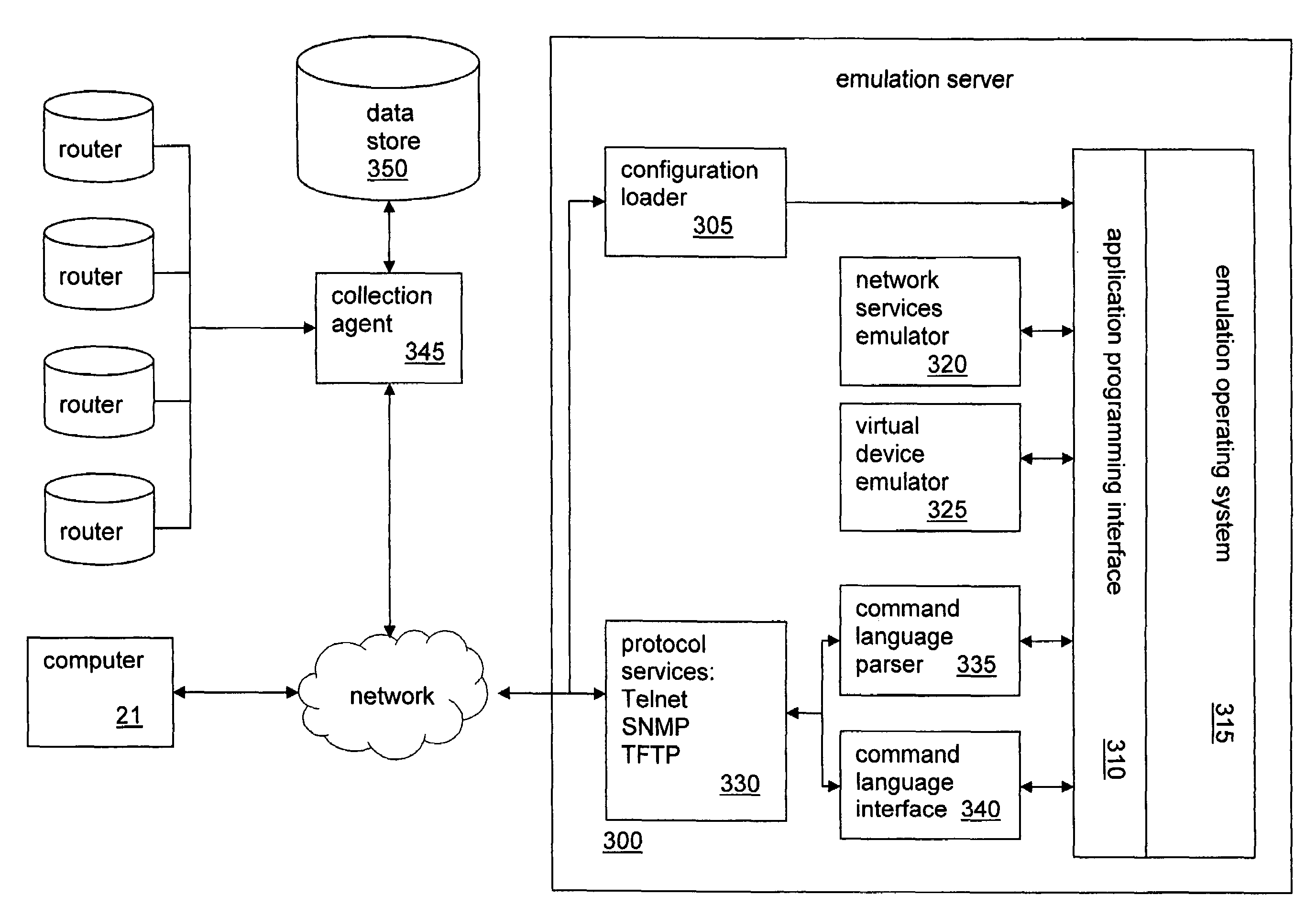
Device emulation for testing data network configurations
ActiveUS7555421B1Digital computer detailsData switching networksLarge scale networkNetwork Access Device
A system and method for providing a virtual implementation of a large scale network of devices. The invention emulates an entire network of network devices using the configuration information obtained from the actual devices to meet the needs of testing configuration changes across the entire network.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Printers with positional sensors
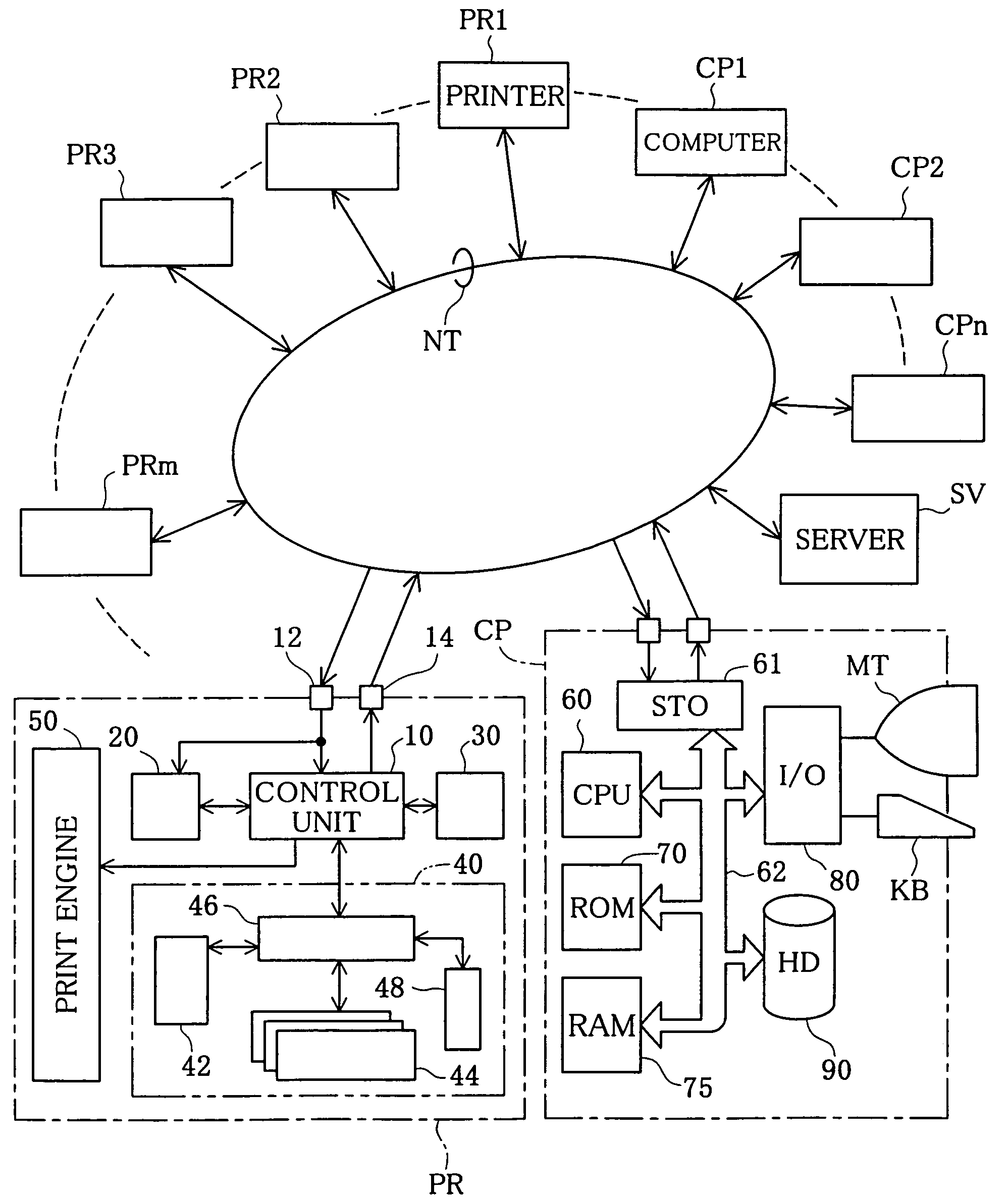
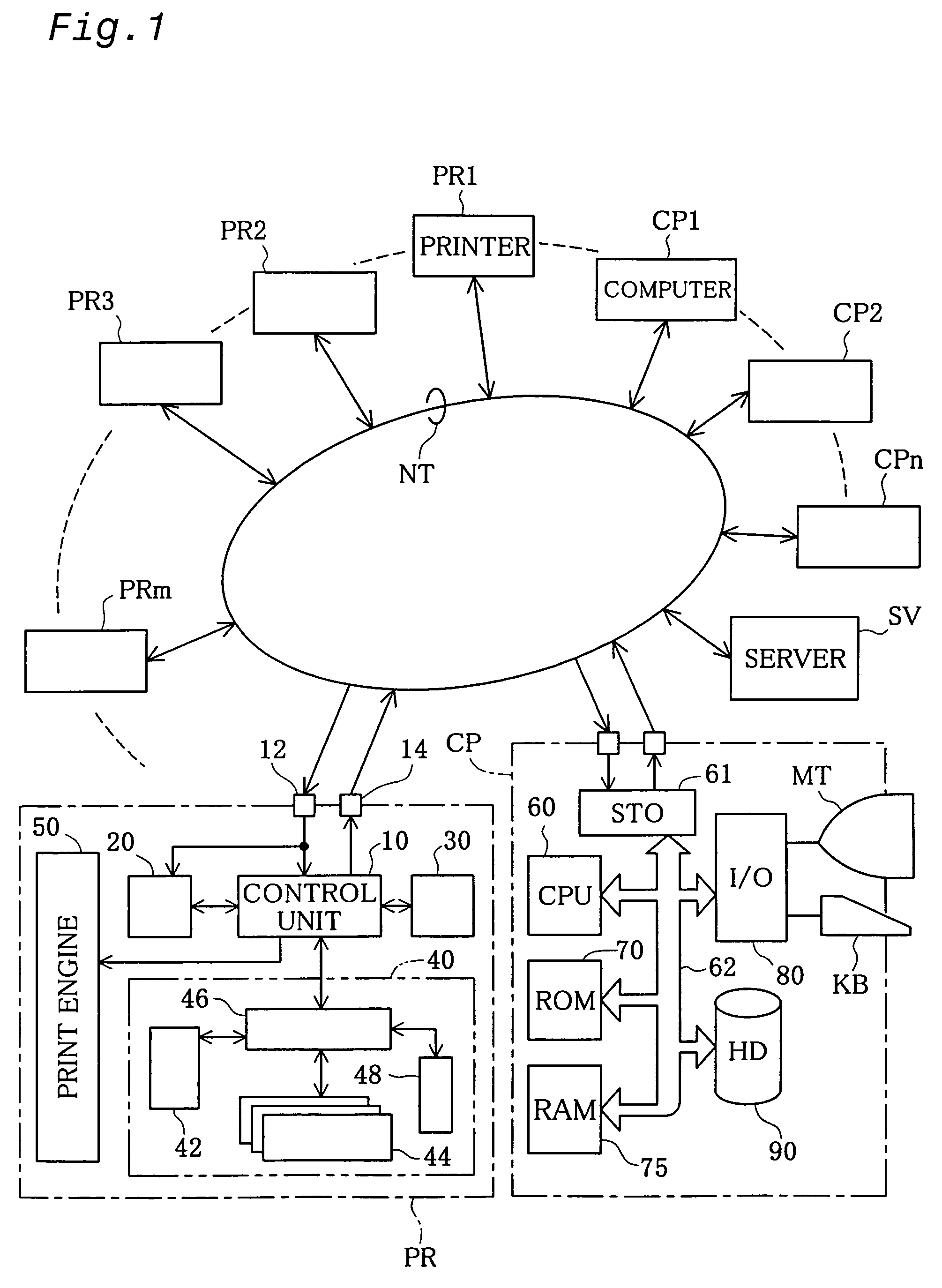
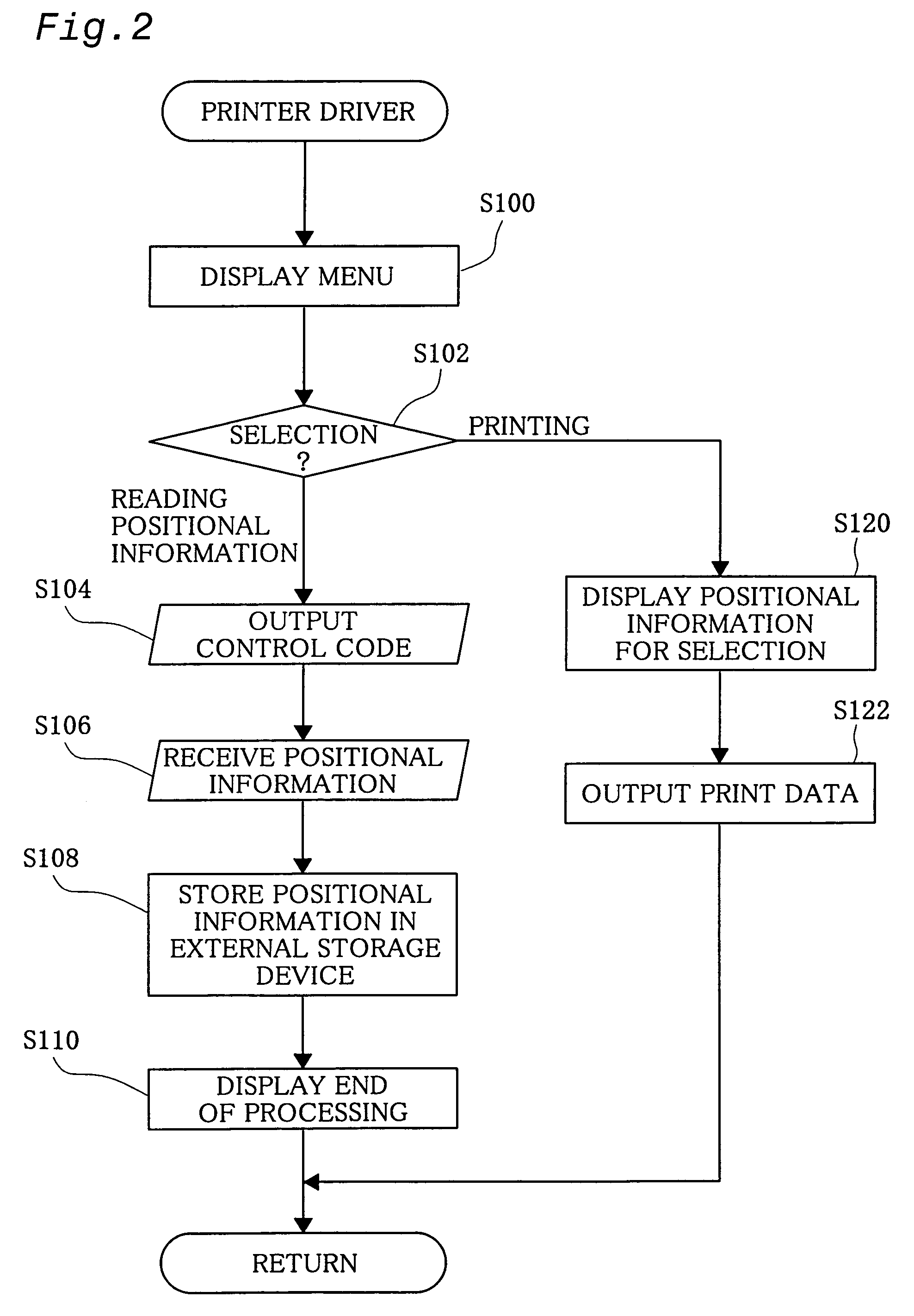
InactiveUS7256900B1Digitally marking record carriersDigital computer detailsGeolocationComputer science
The technique of the present invention ensures efficient management of printers in a large-scaled network even under a condition that some printer shifts its position on the network. A positioning unit included in each printer connected to the network recognizes positional information, which represents its own geographical position where the printer is located and includes, for example, a latitude and a longitude. Each of computers connected to the network obtains the positional information from each of the printers and specifies a printer, to which print data are output to carry out printing, based on the positional information thus obtained. This arrangement extremely facilitates the management of the printers on the network and enables the user to carry out printing with a selected printer that is located at a desired position.
Owner:SEIKO EPSON CORP
Trainable hierarchical memory system and method
Memory networks and methods are provided. Machine intelligence is achieved by a plurality of linked processor units in which child modules receive input data. The input data are processed to identify patterns and / or sequences. Data regarding the observed patterns and / or sequences are passed to a parent module which may receive as inputs data from one or more child modules. the parent module examines its input data for patterns and / or sequences and then provides feedback to the child module or modules regarding the parent-level patterns that correlate with the child-level patterns. These systems and methods are extensible to large networks of interconnected processor modules.
Owner:NUMENTA INC
Structuring system and method of network community dynamic list
ActiveCN1949220ARealize dynamic creationEasy to findSpecial service provision for substationSpecial data processing applicationsStructure systemLarge scale network
The invention relates to network community dynamic contents establishing system. It includes interconnected network community data storage module, and browse page generating module, contents ordering module. The invention also relates to the method based on the system that it computes each page ordering information value, processes ordering for chaining bit in contents list, realize network community dynamic establishment, make large scale network community contents distribute reasonably. In addition, the user can search discussion zone according to the page attribute to enter the page.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Mobile AD Hoc network self-adapting secure routing method based on reliability
ActiveCN102158864AGuaranteed validityIntegrity guaranteedNetwork topologiesSecurity arrangementRouting decisionNetwork size
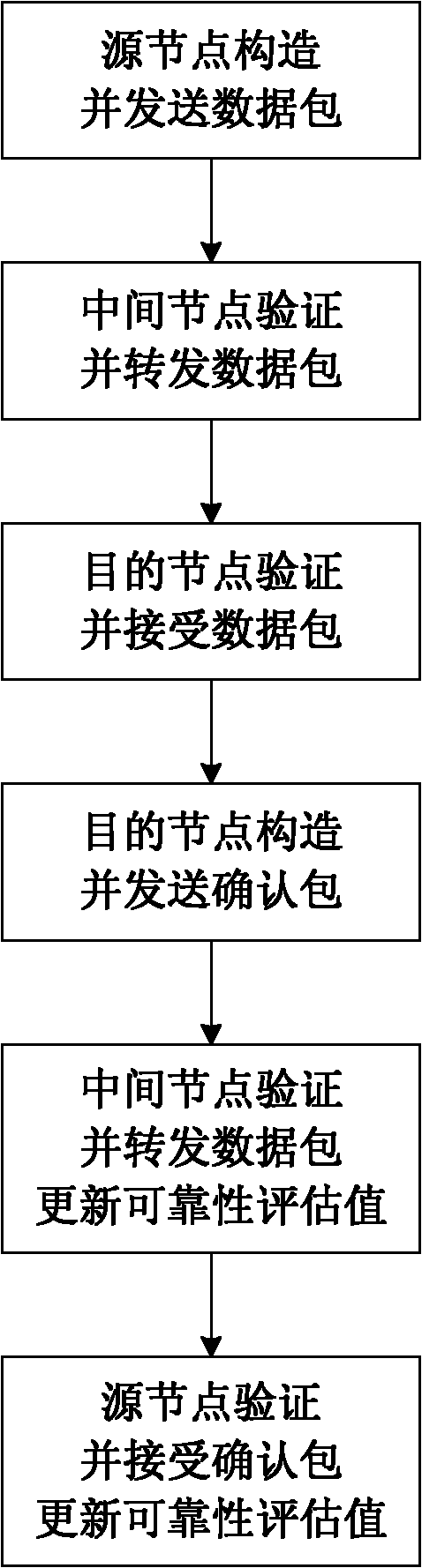
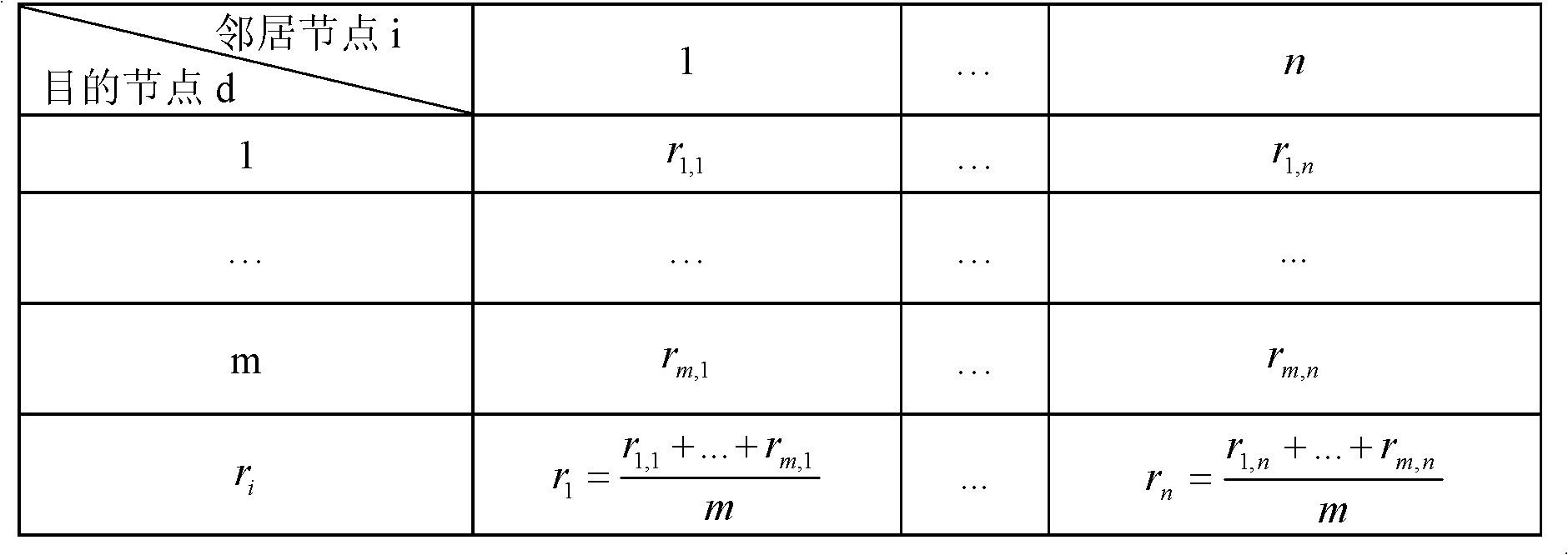
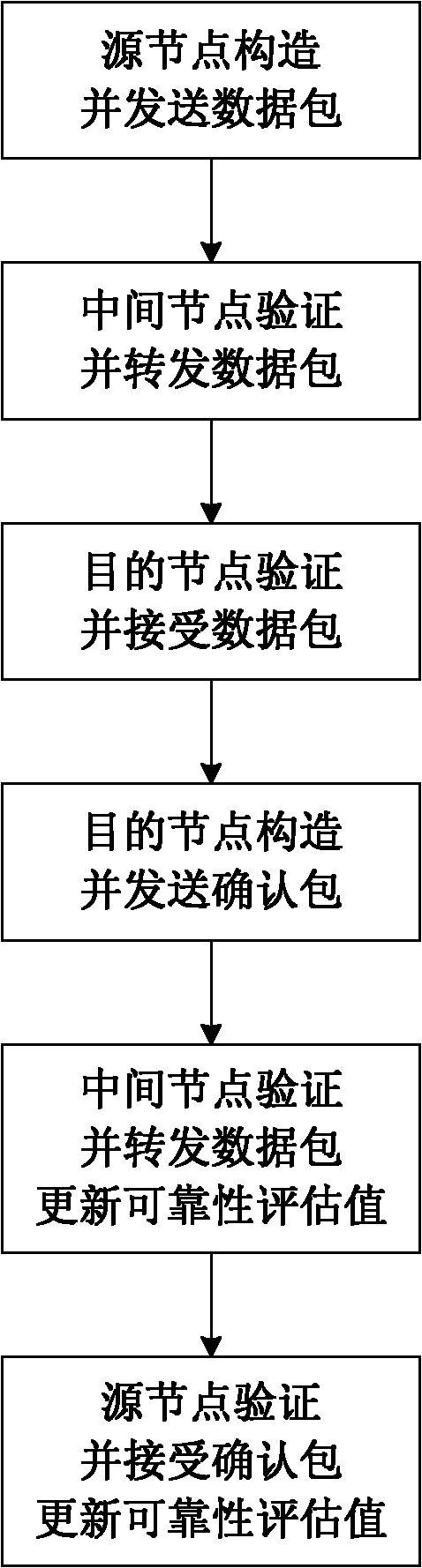
The invention discloses a mobile AD Hoc network self-adapting secure routing method based on reliability. The method comprises the following four major steps: step I, a source node transmits data packets; step II, an intermediate node forwards the data packets; step III, a destination node receives the data packets; and step IV, the data packets are transmitted and confirmed and reliability is updated. The method integrates route discovery and data transmission into a whole process, each node evaluates the reliability of adjacent nodes reaching the destination node through a response feedbackmechanism, and independently makes a route decision according to reliability evaluation level, so that unreliable nodes are avoided and a reliable path is selected from a plurality of alternative paths, the method solves secure and reliable data transmission and symmetrical secret key transmission while solving secure routing discovery problem, and improves the security and the adaptability of the network. Compared with an existing AD Hoc network routing method, the method can resist attack to a greater extent on the basis that higher expense is not needed, still has good restorability when anetwork size is changed, nodes rapidly moves and even attack in a large scope exists and error of nodes exists, and is applicable to large-scale network with rapidly moving nodes. The method has a higher practical value and a wide application prospect in the technical field of mobile AD Hoc network security.
Owner:BEIHANG UNIV
Network attack path analysis method based on incidence matrixes
InactiveCN102098306AImprove comprehensive risk analysis capabilitiesEnsure safetyData switching networksNetworked systemNetwork attack
The invention discloses a network attack path analysis method based on incidence matrixes, which is characterized in that potential attack paths in a network system are acquired by acquiring network topology information, threat information and vulnerability information of devices and interrelation between the threat and the vulnerability, and building incidence matrix models. The method provided by the invention is utilized to greatly improve comprehensive analysis capacity of network risks and effectively ensure safety of network information systems. The method is applied to large-scale network environments.
Owner:INFORMATION SECURITY METASOFT BEIJING
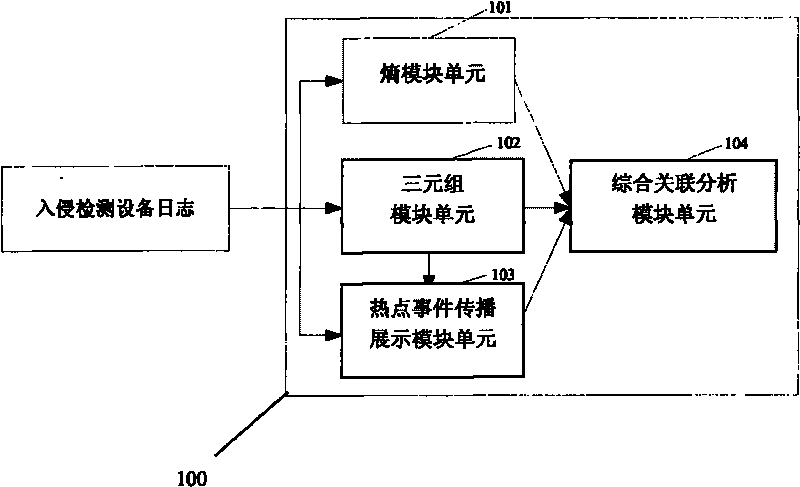
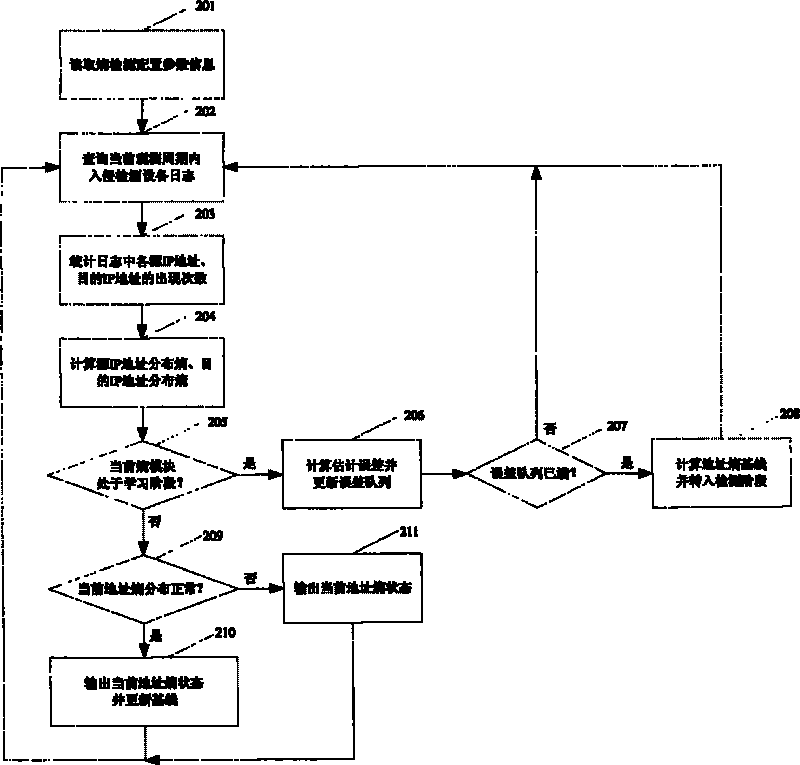
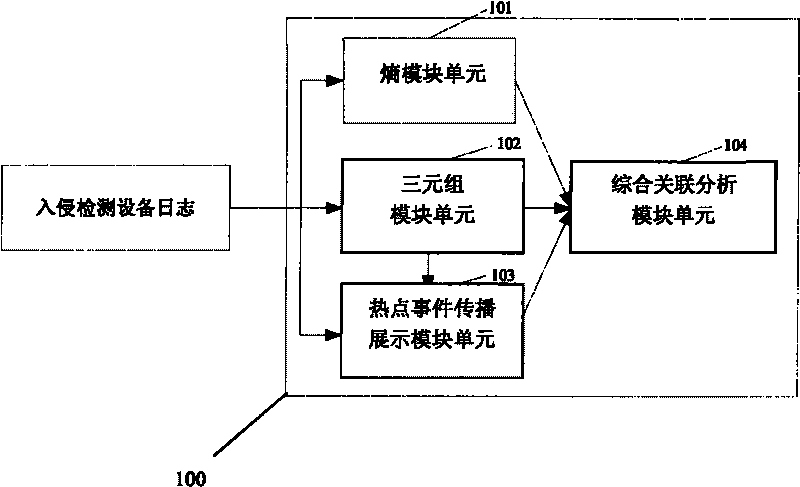
Association analysis method and system for massive logs
The invention discloses an association analysis method and an association analysis system for massive logs to evaluate the current network security condition and describe the attack condition which is paid most attention currently according to the massive logs generated by an intrusion detecting device. The method comprises the following steps: acquiring the logs of the intrusion detecting device, and judging whether a large-scale network security event exists or not by calculating the distribution condition of source addresses and destination addresses of the logs of the intrusion detecting device; merging the logs of the intrusion detecting device according to the source addresses, the destination addresses and event types, and detecting and reporting abnormal addresses and hot events; counting and displaying a propagation process of the hot events in a specific time period through graphics; and associating output results, and giving comprehensive evaluation on the current network security condition. The system comprises an entropy module unit, a triple module unit, a hot event propagation display module unit, and a comprehensive association analysis module unit.
Owner:BEIJING VENUS INFORMATION TECH +3
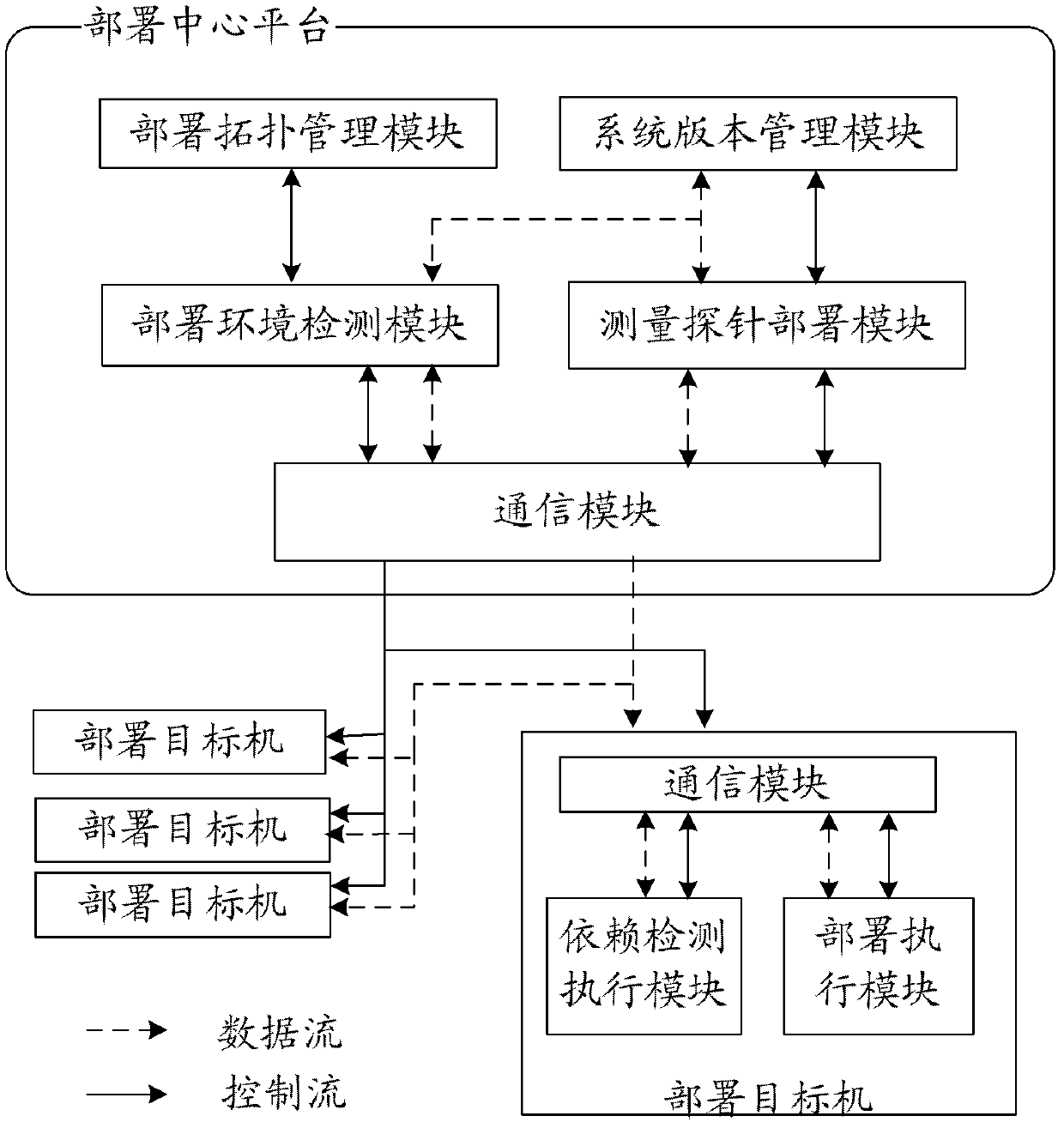
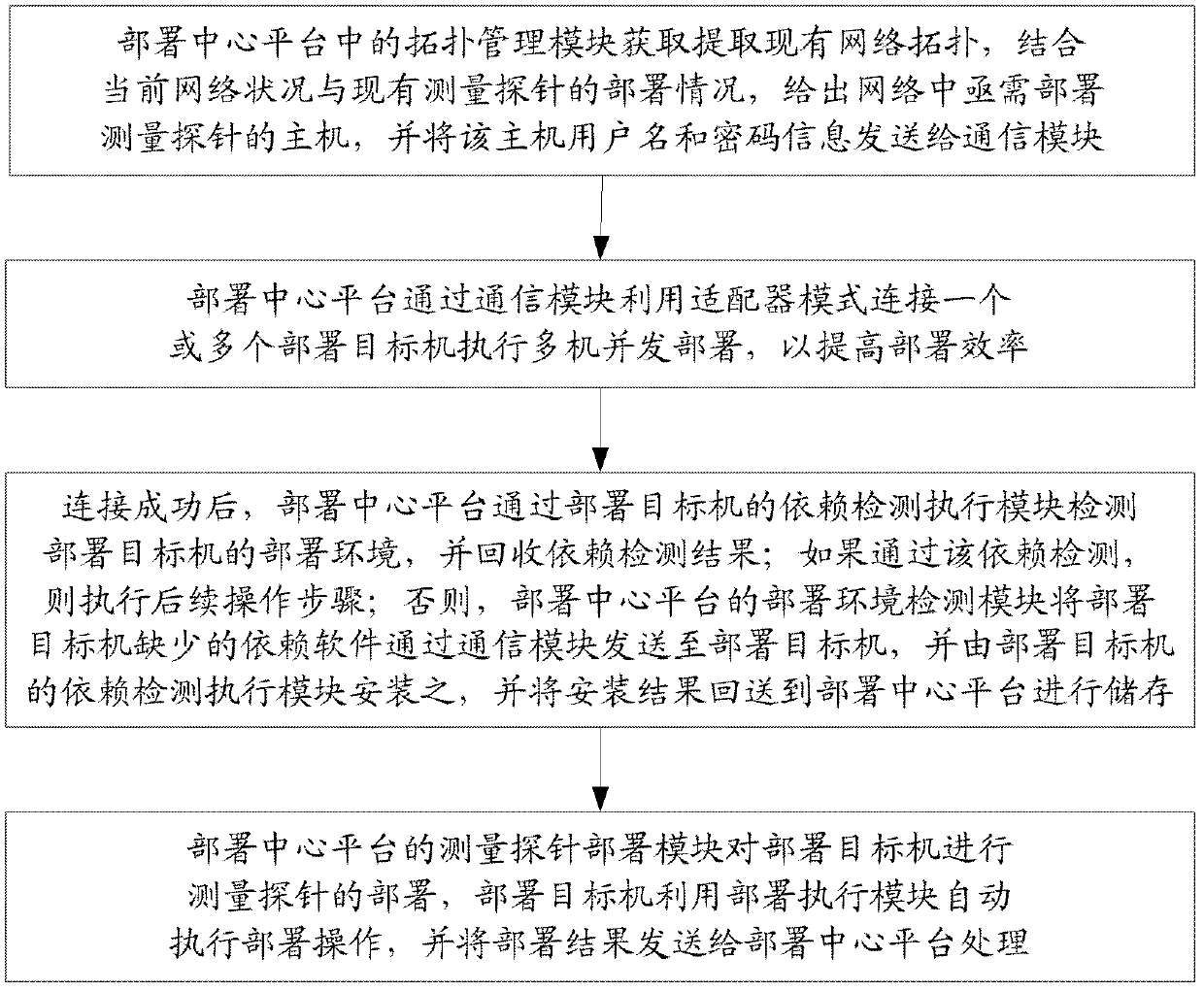
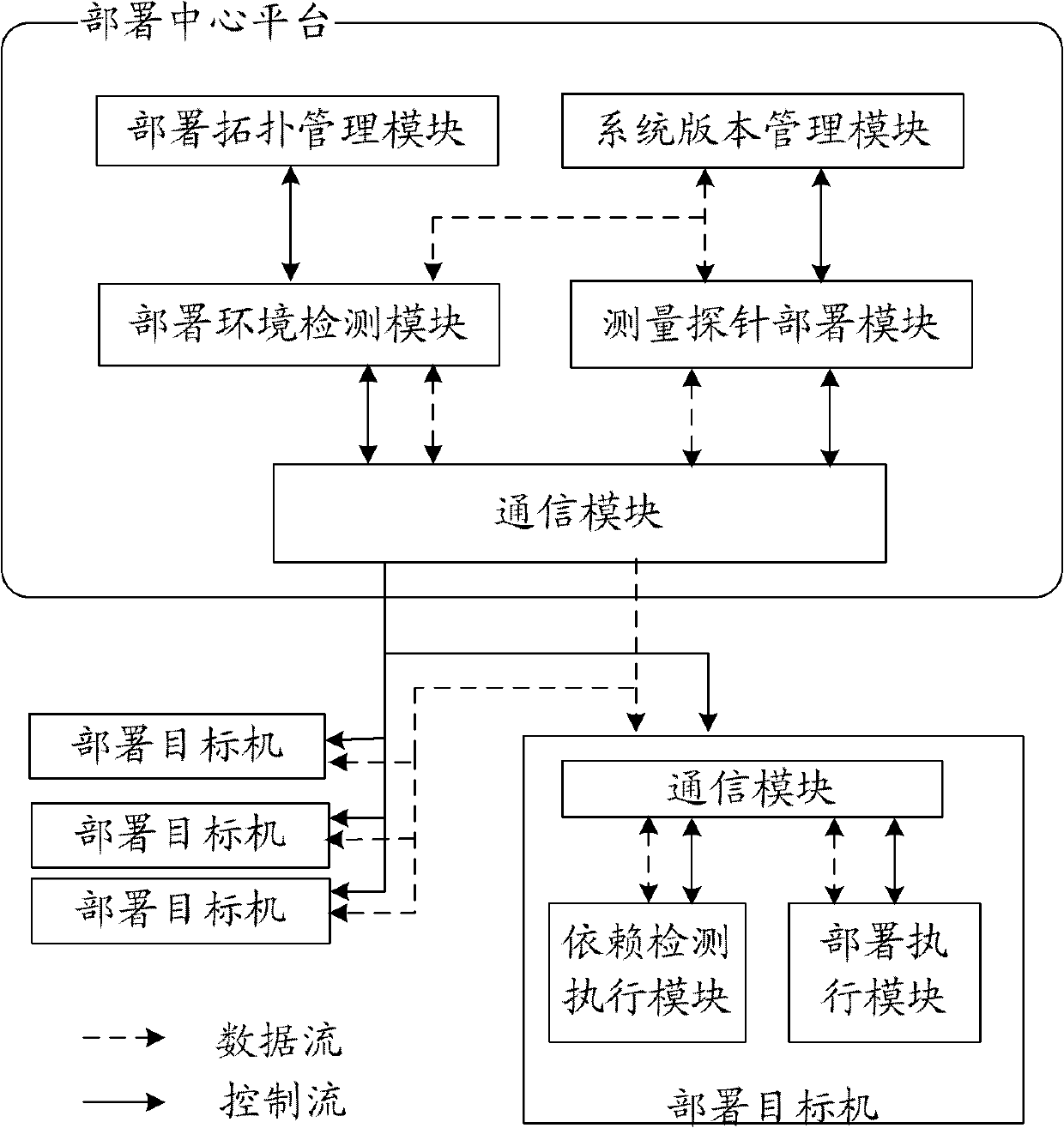
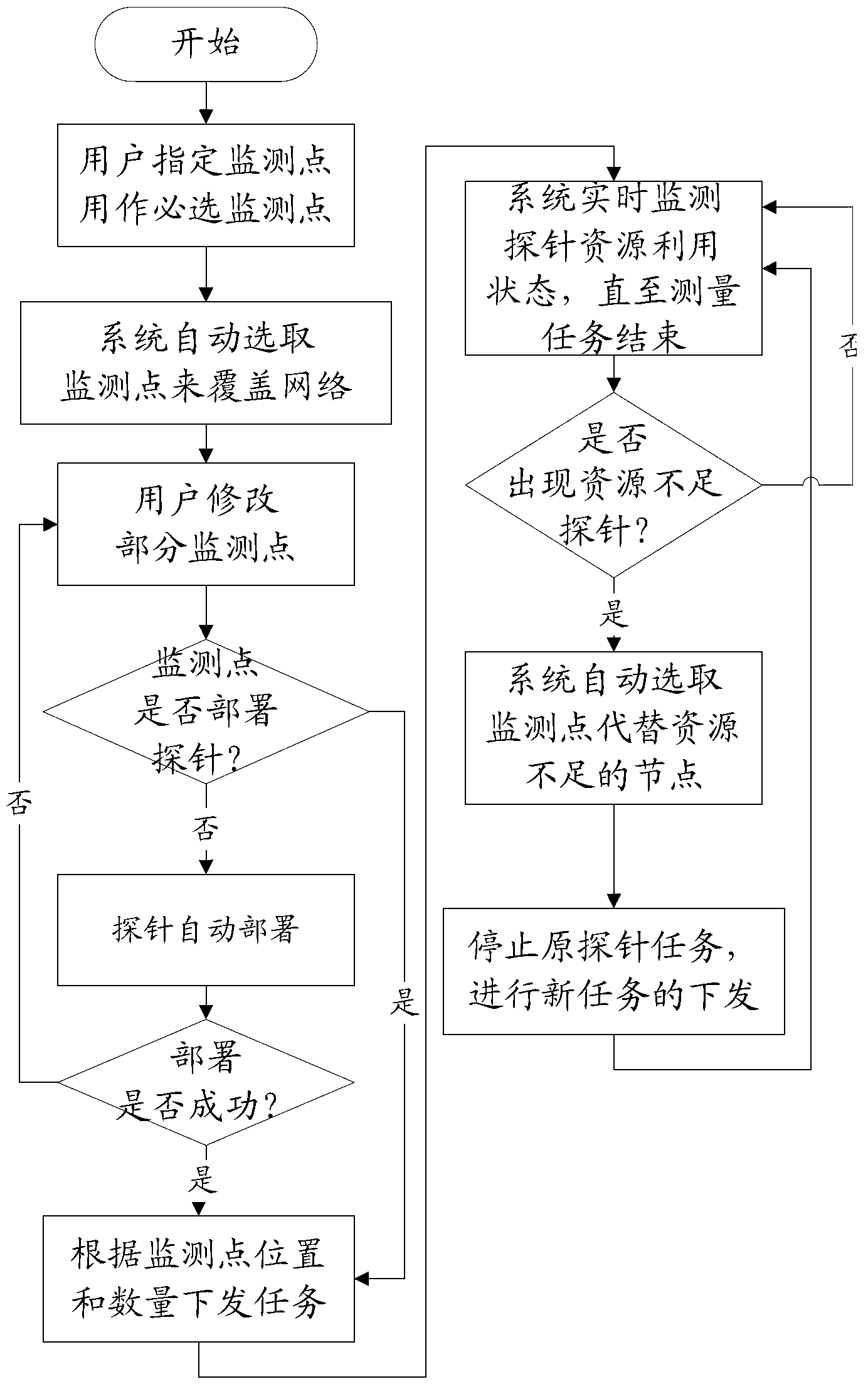
Large-scale network monitoring oriented virtual deployment system and method
InactiveCN102437938AImprove work efficiencyImprove scalabilityData switching networksVirtualizationMatch rule
The invention discloses a large-scale network monitoring oriented virtual deployment system and method. The system is provided with a deployment center platform and a plurality of deployment target machines communicated with the deployment center platform via a network. The deployment center platform is responsible for uniformly planning and managing a topology structure of measurement probe deployment in an entire computer network, issuing a deployment task according to the existing measurement probe deployment condition and network congestion condition, and executing management and version control on the deployed measurement probes. The deployment target machines receive and execute commands from the deployment center platform, and automatically execute corresponding operations so as to enable the measurement probes to be usable in the network; and a software dependency detection mechanism and a process matching rule are respectively used for realizing the platform independency of deployment and verifying the achievement of deployment. The system and the method can be used for solving a plurality of problems, such as dependency detection for deployment environment of the target machines, upgrading and maintaining of a management system version, concurrent deployment, automatic installation and detection of the plurality of target machines, dynamic scheduling and the like, in the prior art, and have better promotion and application prospects.
Owner:BEIJING UNIV OF POSTS & TELECOMM
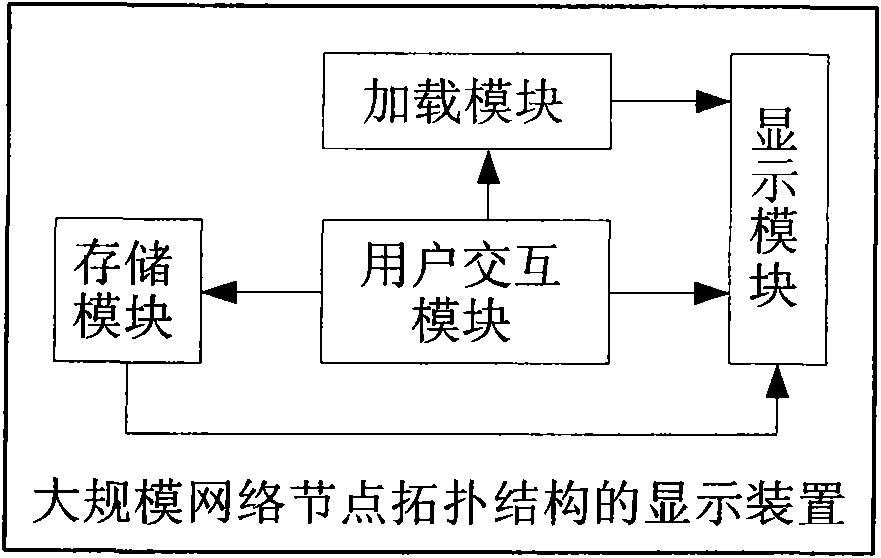
Display method and display device of large-scale network node topological structure
InactiveCN101834735AImplement Auto LayoutAchieve efficiencyData switching networksData displayRelationship - Father
The invention discloses a display method and a display device of a large-scale network node topological structure. The display method comprises the following steps of: loading node data and relational data of nodes in a network, wherein the node data comprises nodes of all levels and subordination relations among the nodes, and the relational data is used for indicating connection relations among the nodes; when a user selects a node as an attention node, displaying child nodes of the attention node, same-level nodes which have connection relations with the attention node and belong to the same father node and nodes which have connection relations with the attention node and the levels higher than that of the attention node according to the node data; and displaying connection relations among the displayed nodes according to the relational data. The invention can visually show the topological structure of the attention node, and enable the showing efficiency to improve.
Owner:BEIJING VENUS INFORMATION TECH +1
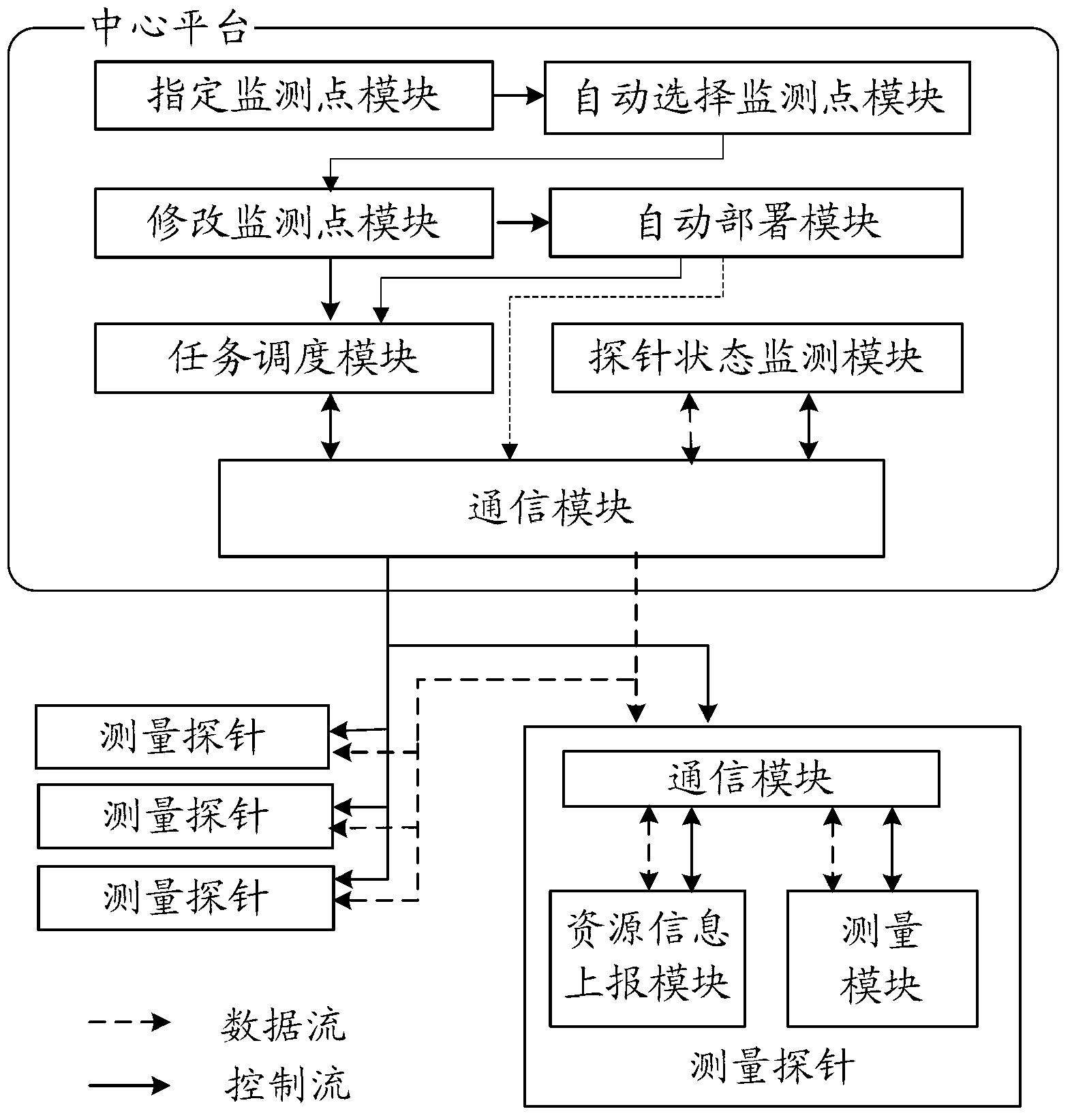
Large-scale network-oriented virtualized monitoring system and dynamic monitoring method thereof
InactiveCN102801587AImprove deployment efficiencyAcquisition speed is fastData switching networksVirtualizationResource information
The invention relates to a large-scale network-oriented virtualized monitoring system and method. The large-scale network-oriented virtualized monitoring system is provided with a central platform and a plurality of measuring probes connected with the central platform through a network. The central platform is responsible for carrying out unified planning and management on a topological structure of the measuring probes in the whole network, automatically deploying the measuring probes and selecting monitoring points and issuing a measuring task by combining service and user requirements; and in the monitoring process, the positions of the monitoring points can be flexibly and timely adjusted according to real-time resource utilization information of the measuring probes. The measuring probes report the resource utilization state information in real time in the measuring process and take corresponding operations according to instructions of the central platform. According to the large-scale network-oriented virtualized monitoring system and method, the problems of monitoring a large-scale network, acquiring the resource information of the measuring points, adjusting the positions of the measuring points in real time, taking a strategy how to select the monitoring points by a user are solved, full chains of the network can be covered with fewer monitoring points, and the acquiring speed and efficiency and data acquisition accuracy of the measuring probes are effectively improved. Therefore, the large-scale network-oriented virtualized monitoring system and method have favorable popularization and application prospect.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com