Safe log analyzing method and system
An analysis method and log technology, applied in the field of information security, can solve problems such as large number of alarms, many irrelevant alarms, and difficulty in achieving expected results, so as to avoid interference and reduce workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
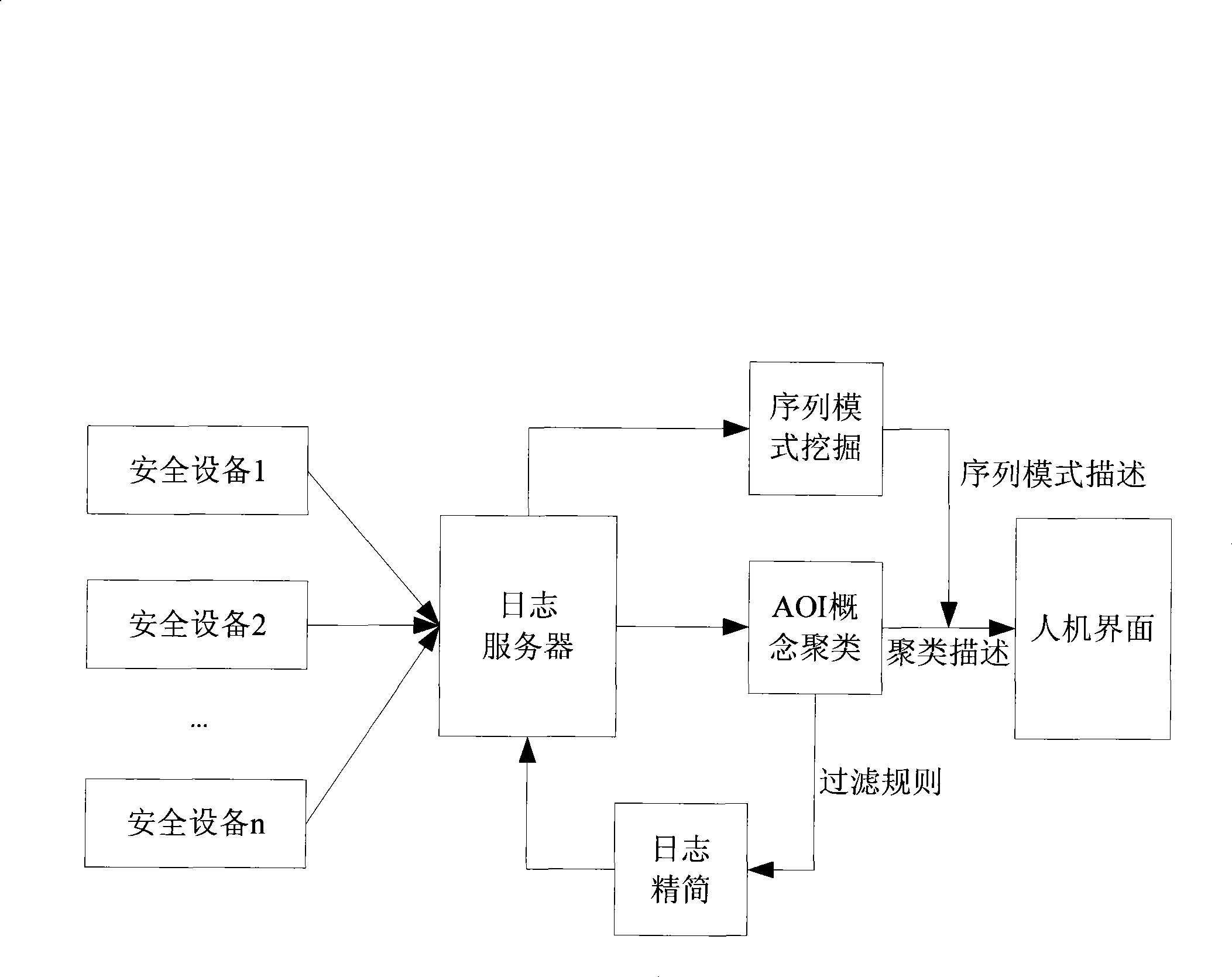
[0031] This embodiment is the workflow of the log analysis system, such as figure 1 shown, including the following steps:
[0032] 1. The IDS detectors distributed in each protected network report the observed intrusion events to the unified log server, complete the summary of the logs, and predict the logs according to the set clustering threshold requirements and set attribute divisions. deal with.
[0033] 2. The AOI hierarchical clustering module divides according to the attributes specified by the administrator, performs clustering analysis on the summarized logs, and derives the clustering rules. The generated clustering rules are divided into three categories: for the description of large-scale network security events (such as DDOS), the administrator can take corresponding measures to deal with them; It is set as a filtering rule; the event description that the administrator thinks needs to be further processed may not be processed.
[0034] 3. According to the clas...
Embodiment 2
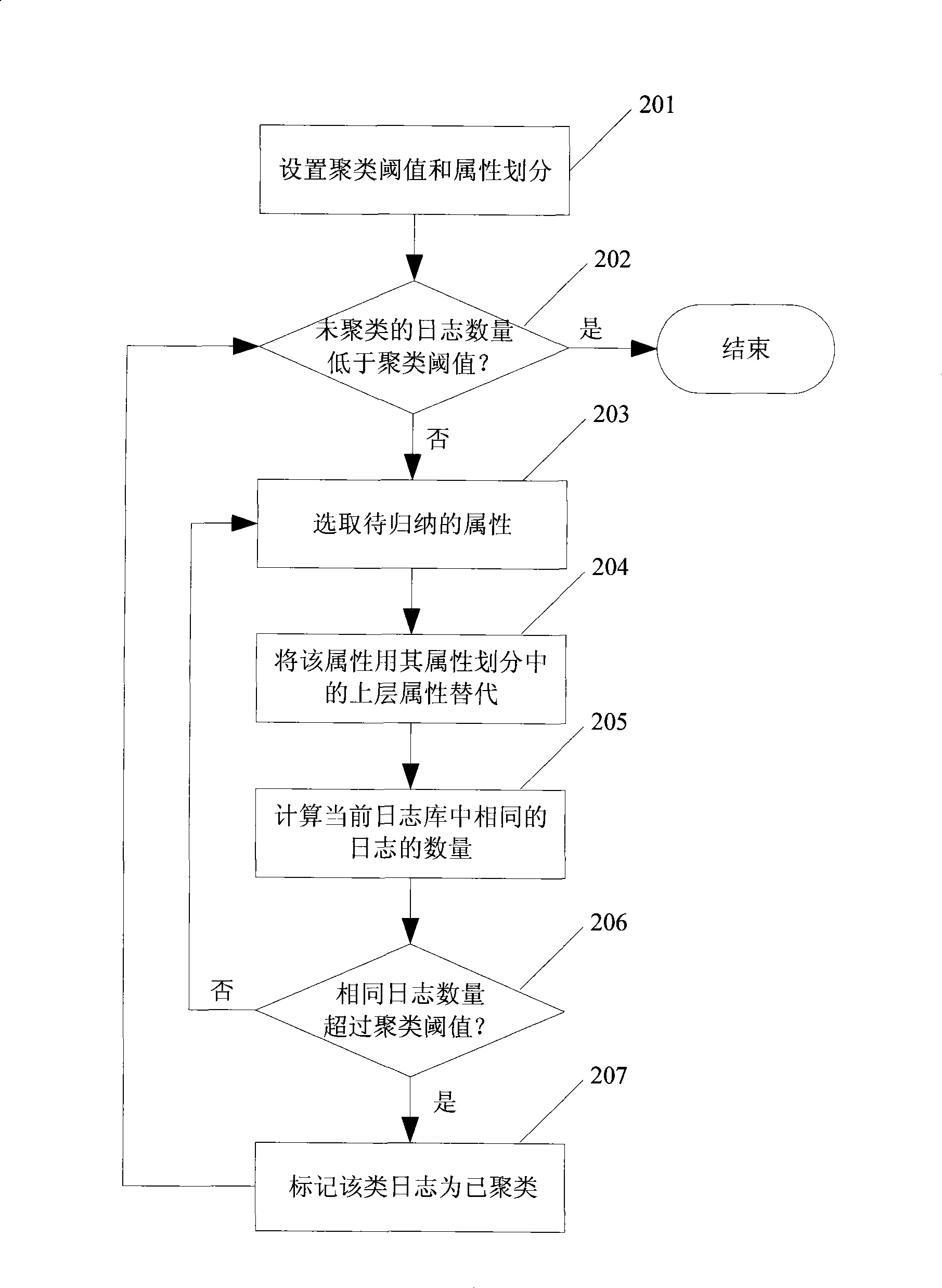
[0038] This embodiment is the processing flow of the AOI hierarchical clustering module, such as figure 2 shown, including the following steps:
[0039] Step 201: Set clustering threshold and attribute division. The clustering threshold refers to the conditions under which the number of logs contained in a cluster can be processed as a whole, and the attribute division refers to the hierarchical relationship on the log attributes participating in the clustering.
[0040] Step 202: Determine whether the number of unclustered logs is lower than the clustering threshold, if yes, end the clustering process, otherwise go to step 203.
[0041] Step 203: Select the attributes to be summarized from the attributes participating in the clustering.
[0042] Step 204: For the selected attribute, the value of the log in the log database on the attribute is represented by the value of the upper layer attribute in the attribute division.
[0043] Step 205: Classify the logs with the same...
Embodiment 3
[0046] This embodiment is a specific processing flow of the log analysis system.
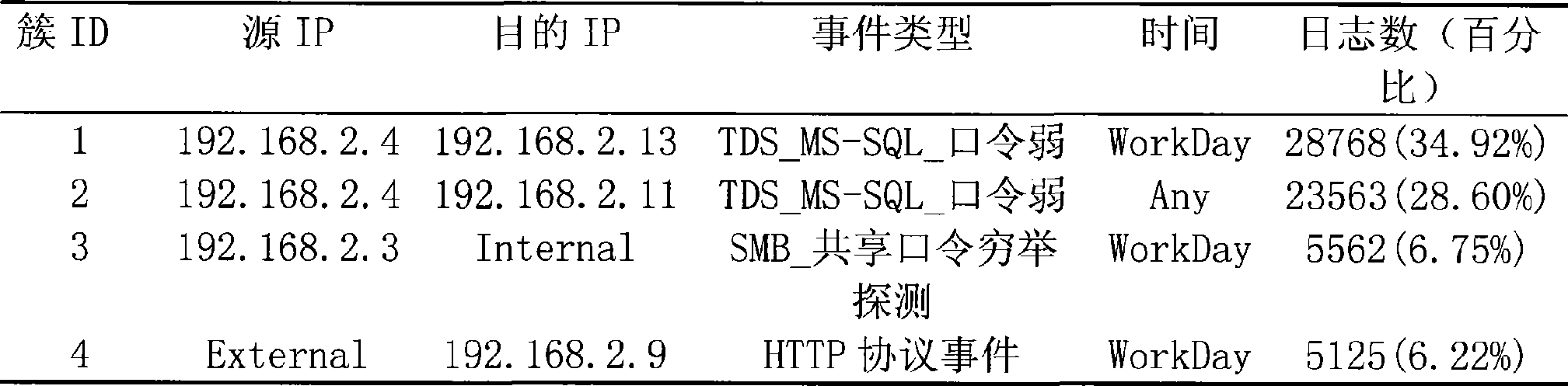
[0047] In this embodiment, the logs generated by a network intrusion detection system running continuously for one month in a real network environment are used, with a total of 82,383 entries. Processing includes the following steps:
[0048] 1. Set the clustering threshold to 5% of the total log volume, that is, when the number of logs contained in a cluster obtained by clustering exceeds 5% of the total log volume, further induction of the cluster will be stopped.
[0049] Set the division of each attribute: the division of the source address and the destination address are the same, both of which are divided by IP address. Divide the IP address into two parts: the internal network and the external network. The internal network is the address of the 192.168.2.0 network segment, and the external network is other addresses except the internal network address. Divide events into different types b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com