Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
240 results about "Unix" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Unix (/ˈjuːnɪks/; trademarked as UNIX) is a family of multitasking, multiuser computer operating systems that derive from the original AT&T Unix, development starting in the 1970s at the Bell Labs research center by Ken Thompson, Dennis Ritchie, and others.
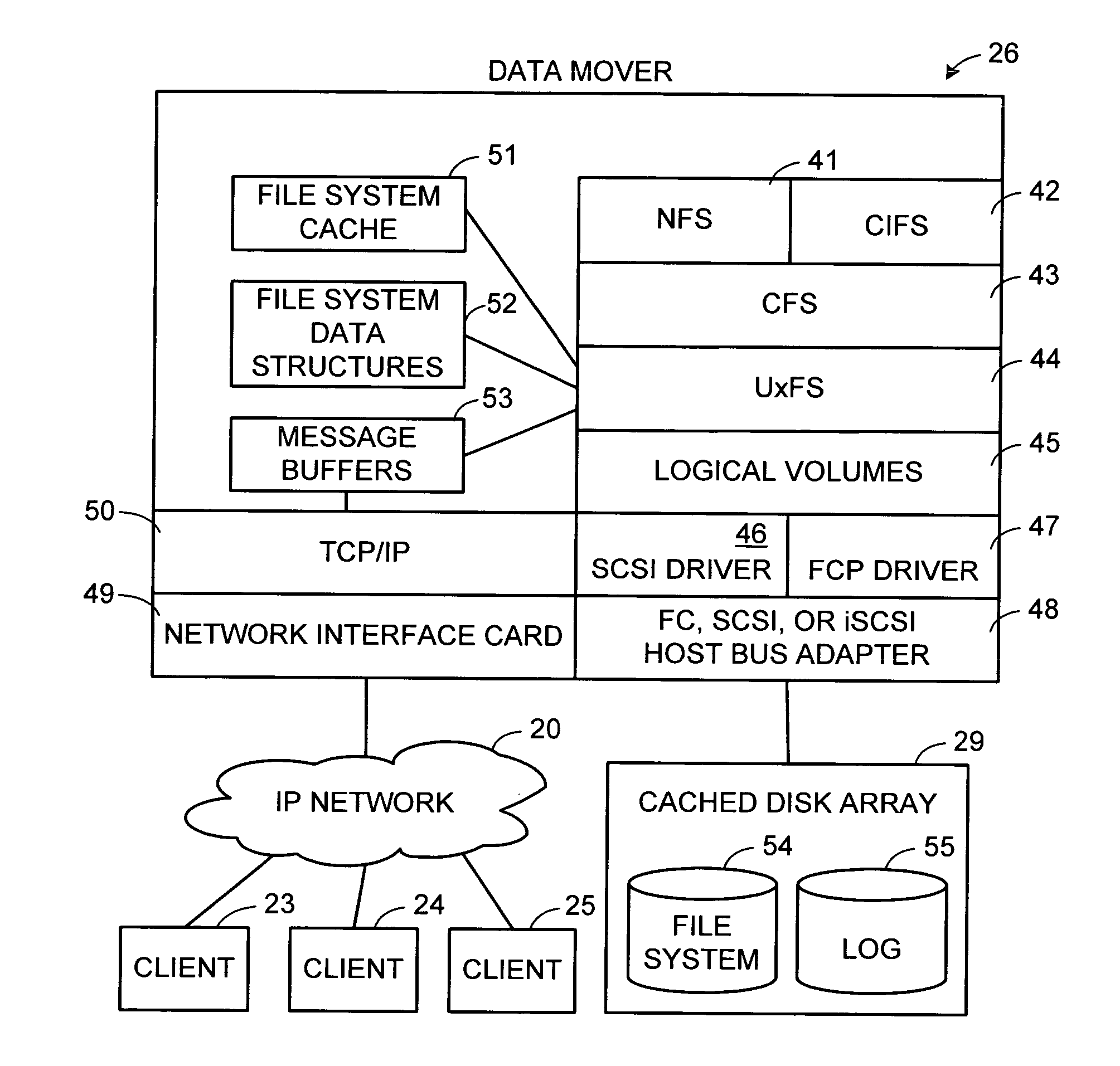
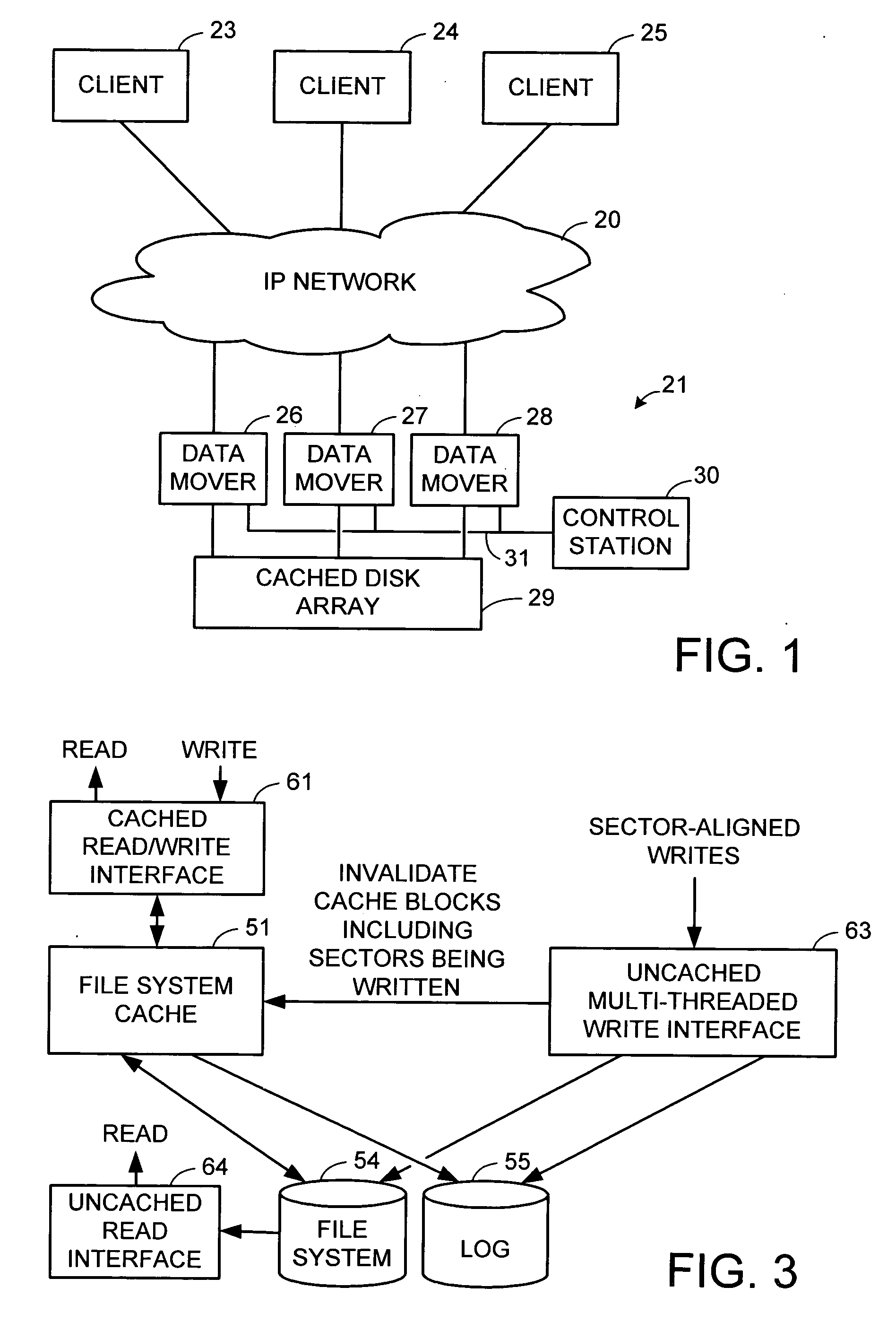
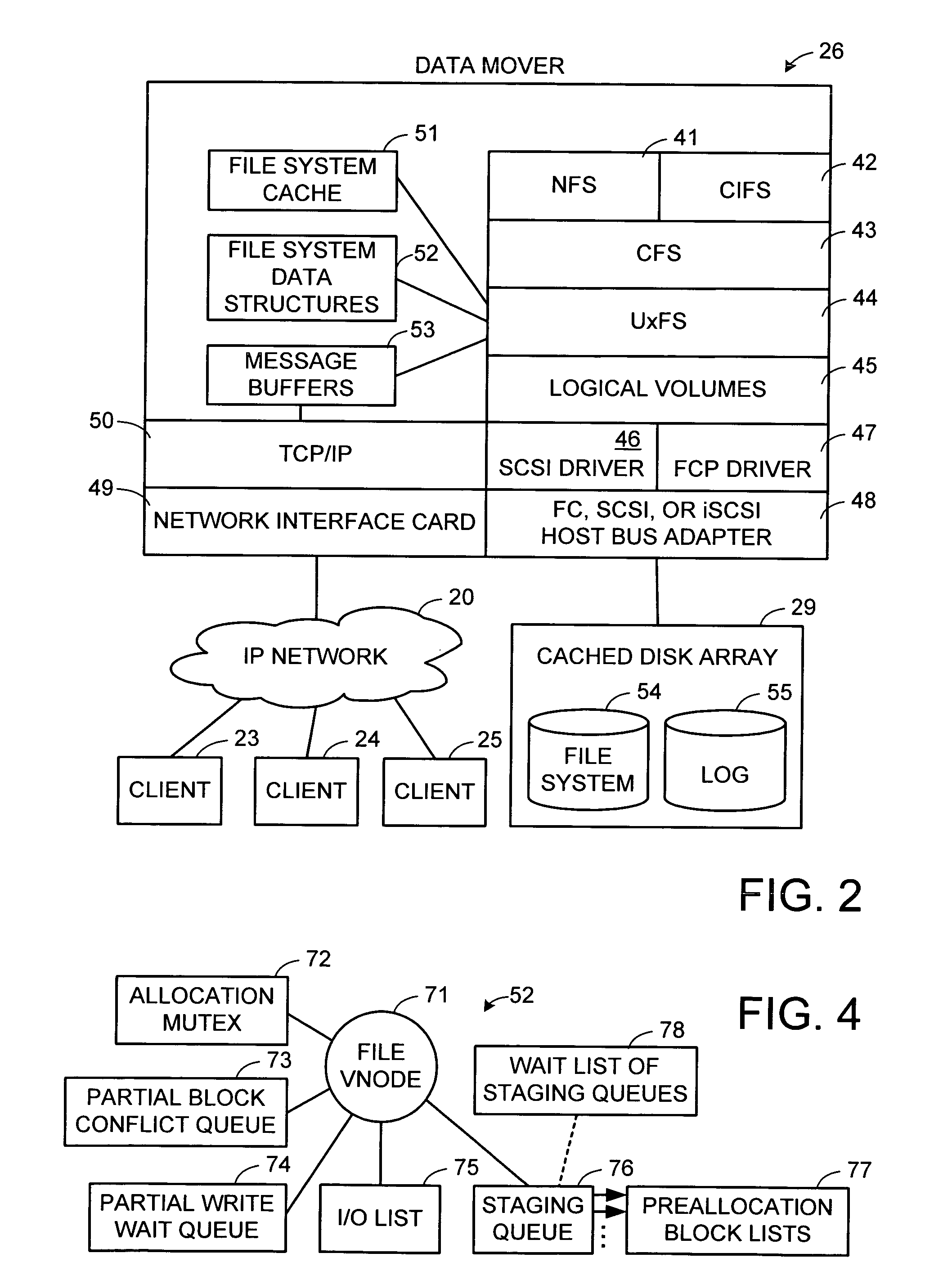
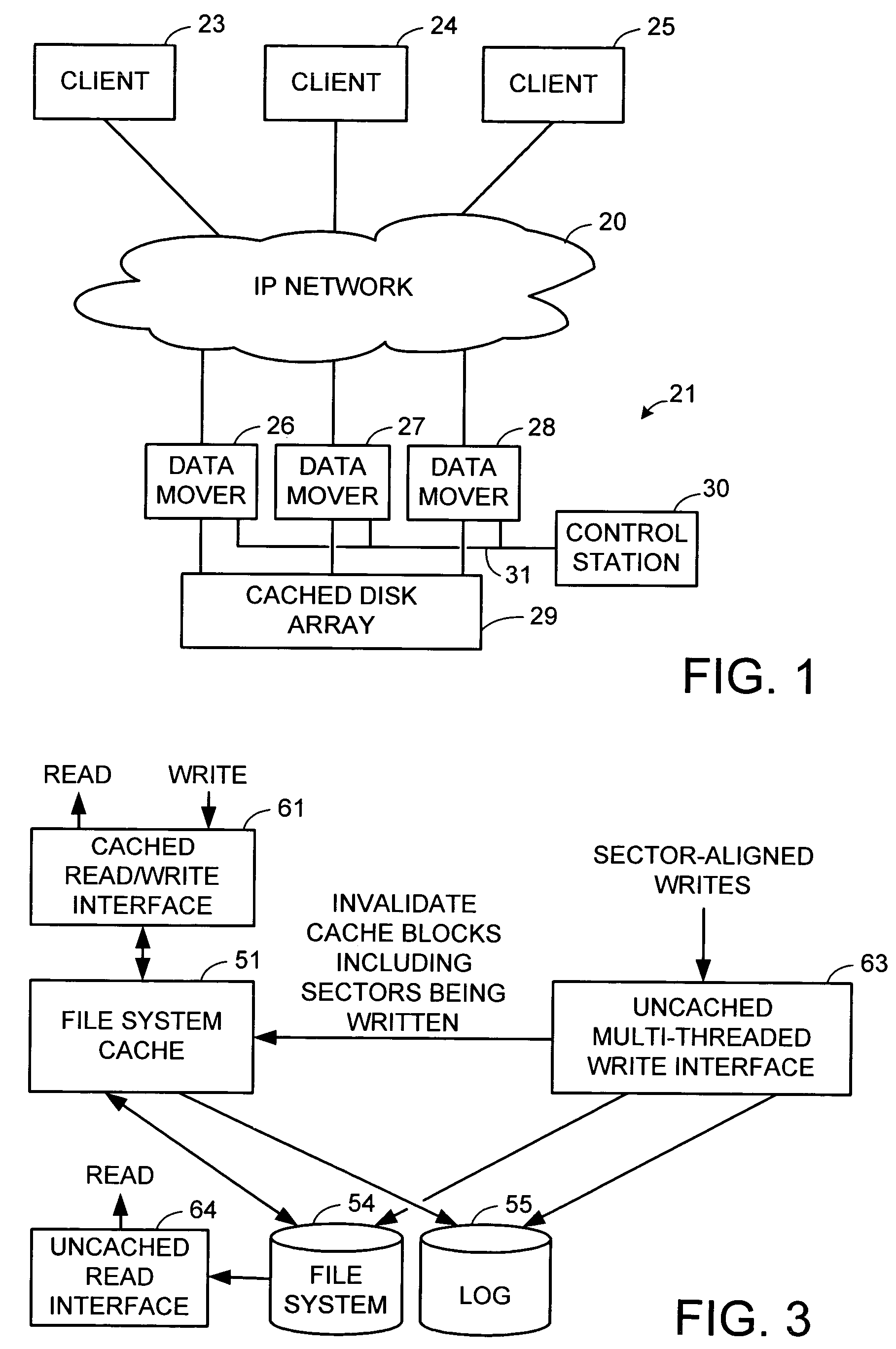
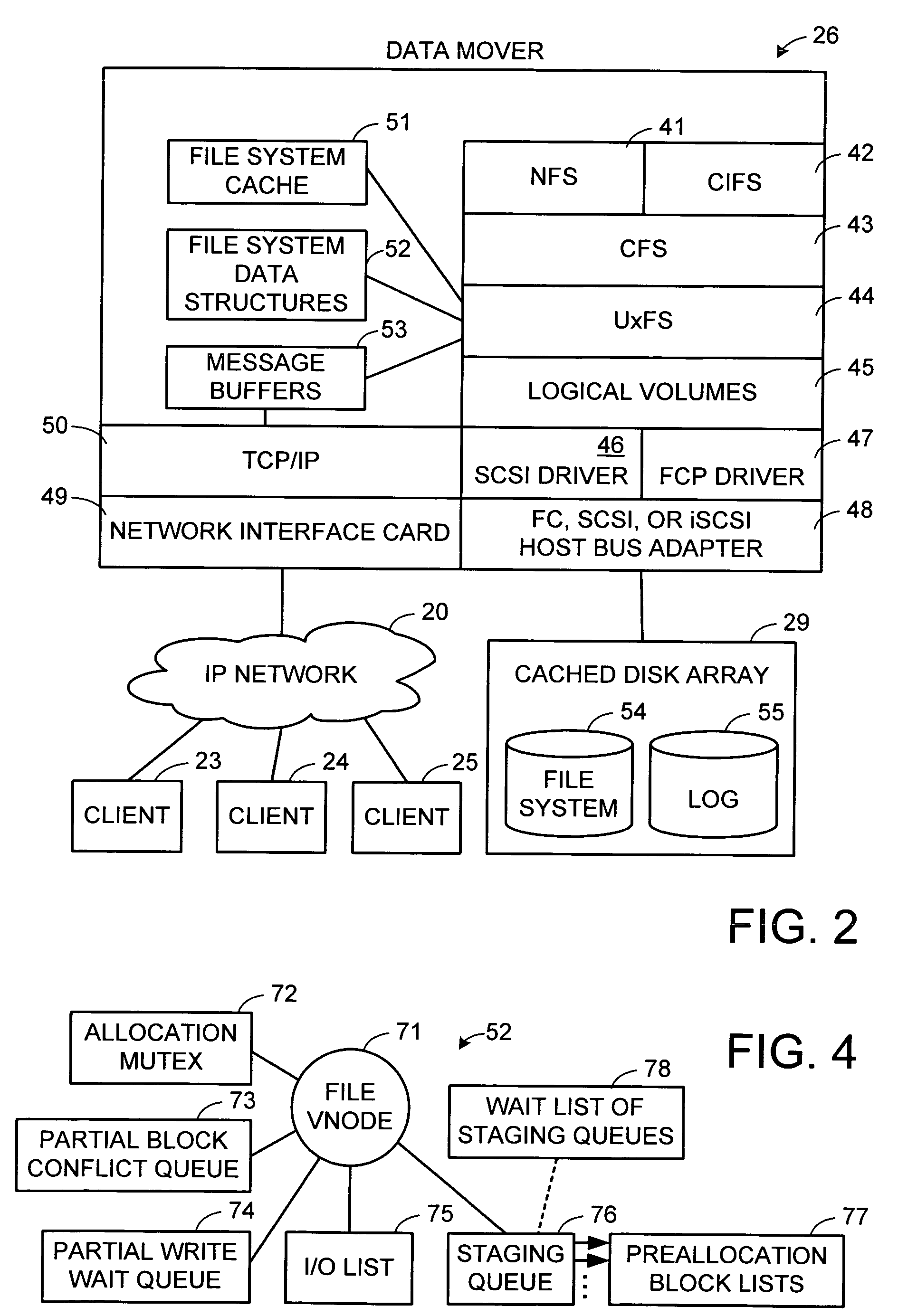
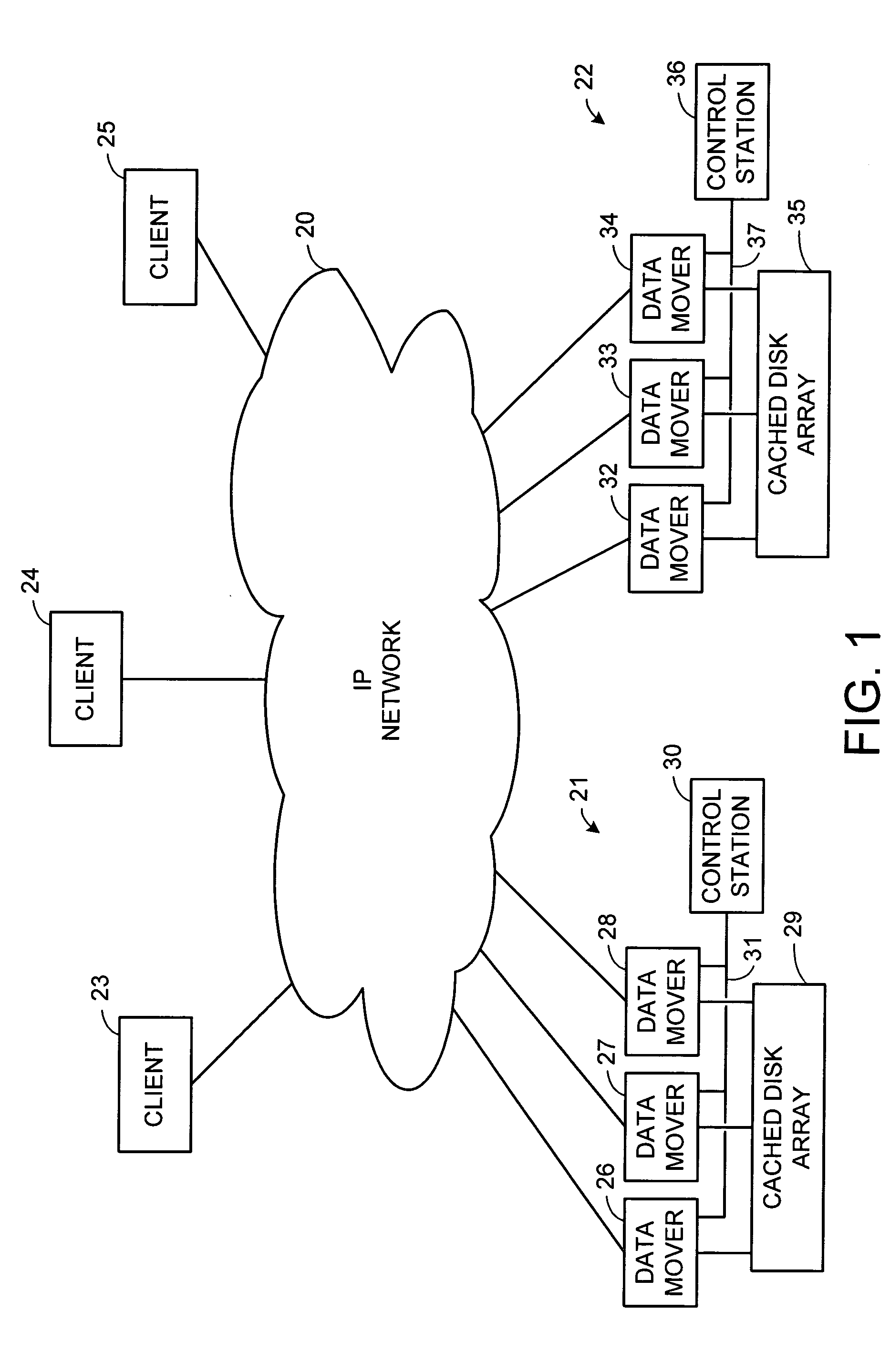
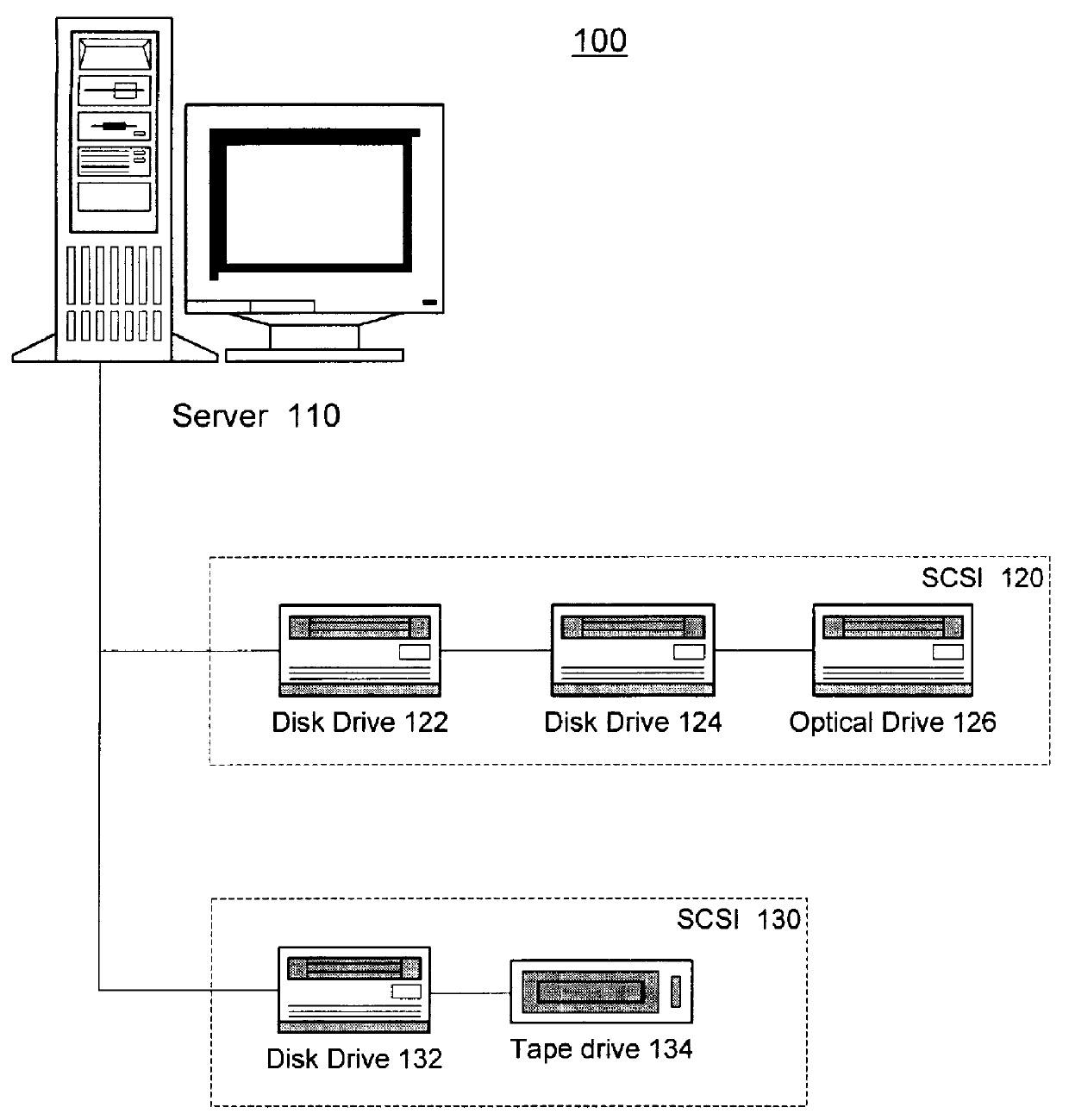
Maintenance of a file version set including read-only and read-write snapshot copies of a production file
Read-only and read-write snapshot copies of a production file in a Unix-based file system are organized as a version set of file inodes and shared file blocks. Version pointers and branch pointers link the inodes. Initially the production file can have all its blocks preallocated or it can be a sparse file having only an inode and its last data block. A protocol is provided for creating read-only and read-write snapshots, deleting snapshots, restoring the production file with a specified snapshot, refreshing a specified snapshot, and naming the snapshots. Block pointers are marked with a flag indicating whether or not the pointed-to block is owned by the parent inode. A non-owner marking is inherited by all of the block's descendants. The block ownership controls the copying of indirect blocks when writing to the production file, and also controls deallocation and passing of blocks when deleting a read-only snapshot.
Owner:EMC IP HLDG CO LLC
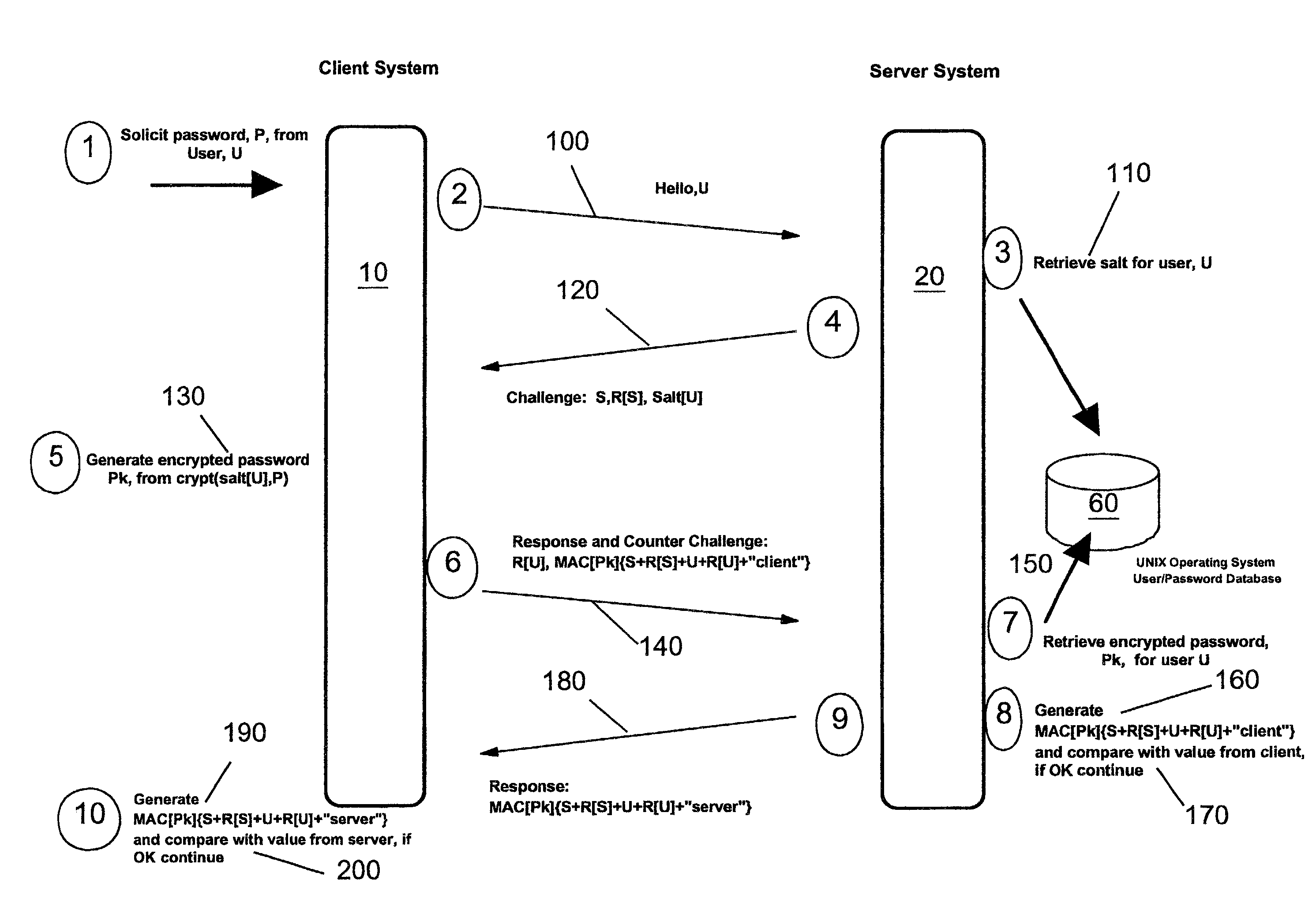
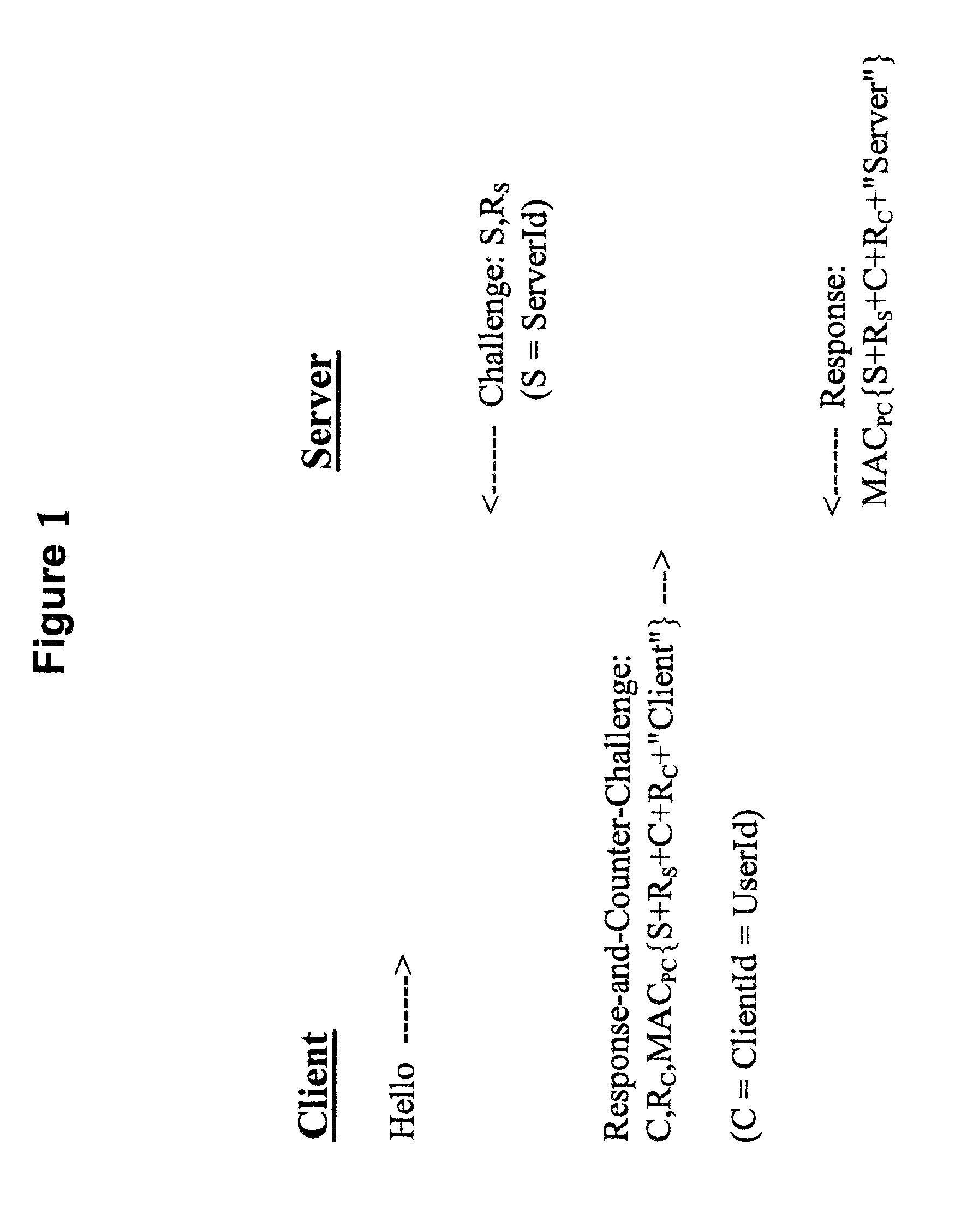
Methods, apparatus and computer programs performing a mutual challenge-response authentication protocol using operating system capabilities
InactiveUS20030093680A1Avoids security exposureMeet growth requirementsKey distribution for secure communicationDigital data processing detailsOperational systemCrypt
A client-server authentication method for use where a server process has access to a repository storing cipher-protected client passwords. The method includes applying the same cipher function to the client's copy of its password as was previously applied to generate the stored cipher-protected client passwords. This ensures that both the client and server have access to an equivalent cipher-protected client password-providing a shared secret for driving a mutual challenge-response authentication protocol without having to convert the password into cleartext at the server. The invention can be implemented without significant additional software infrastructure in a UNIX environment. Client passwords are typically stored in the UNIX password repository under the protection of the crypt( ) function applied to the combination of the password and a random number (a "salt'). By sending the salt to the client system together with the server's initial challenge of the authentication protocol, a process at the client is able to apply the crypt( ) function to the client password with the same salt such that the client and server have a shared secret for use as, or to generate, a common session key for the authentication.
Owner:IBM CORP
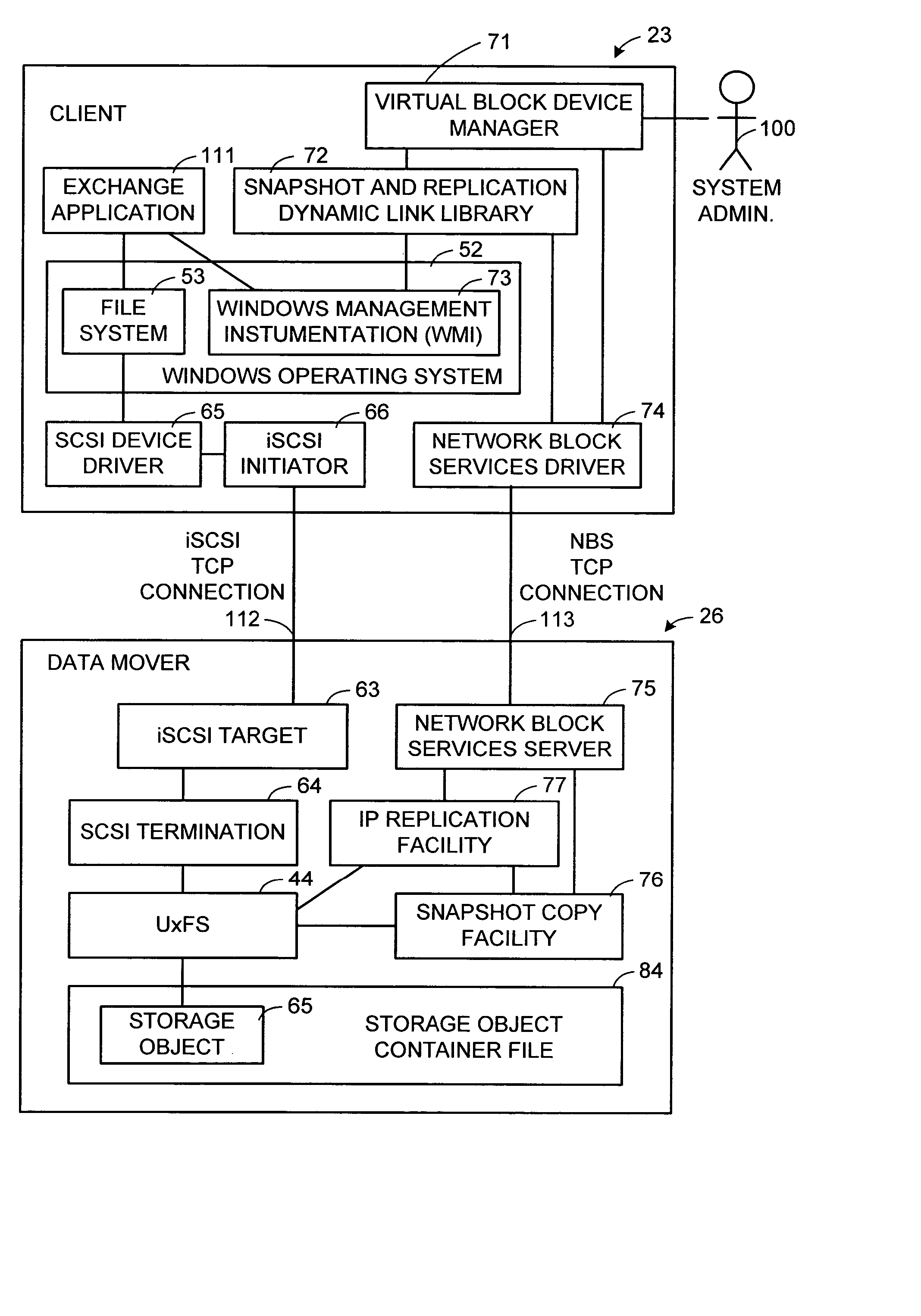
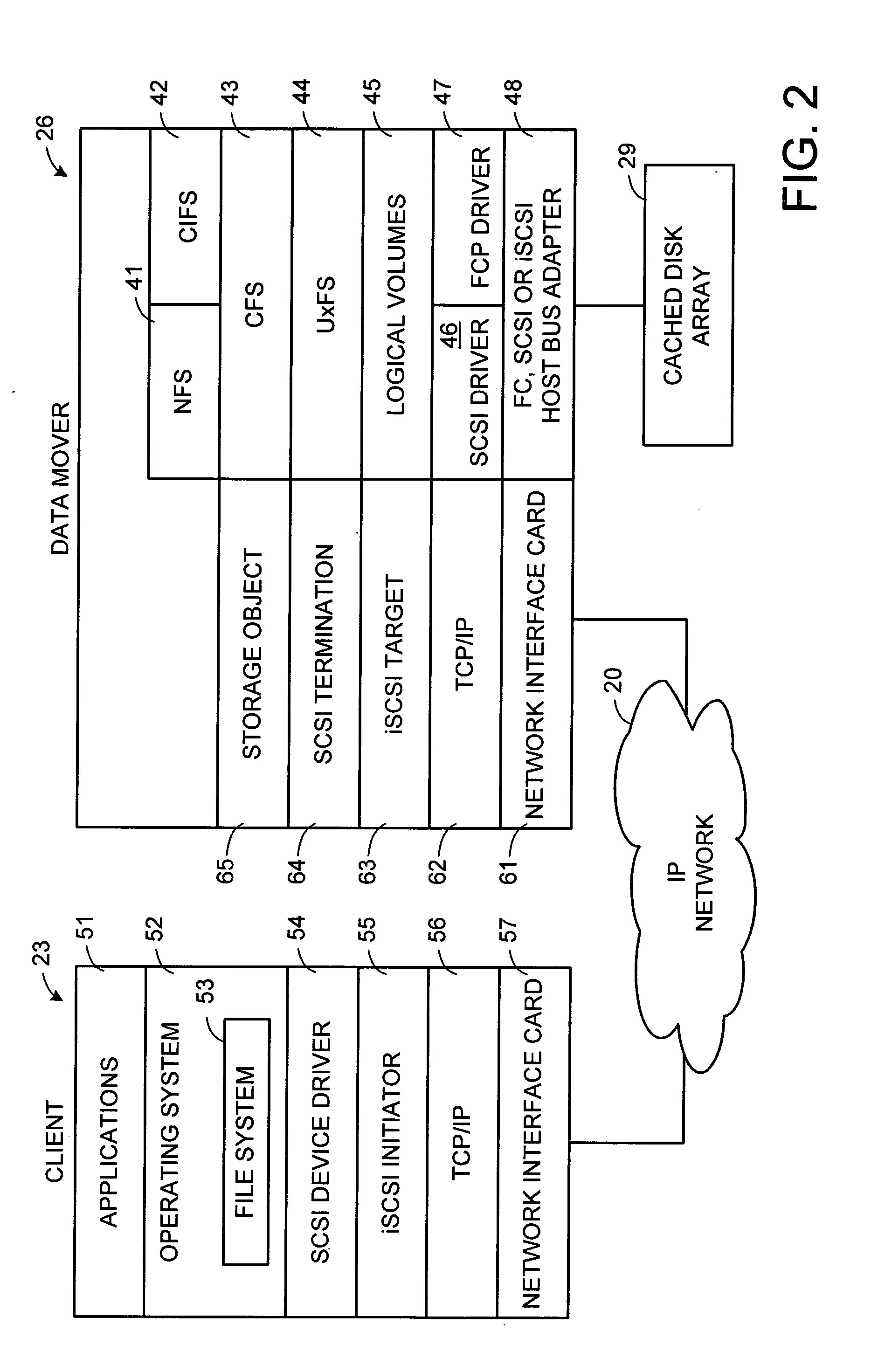
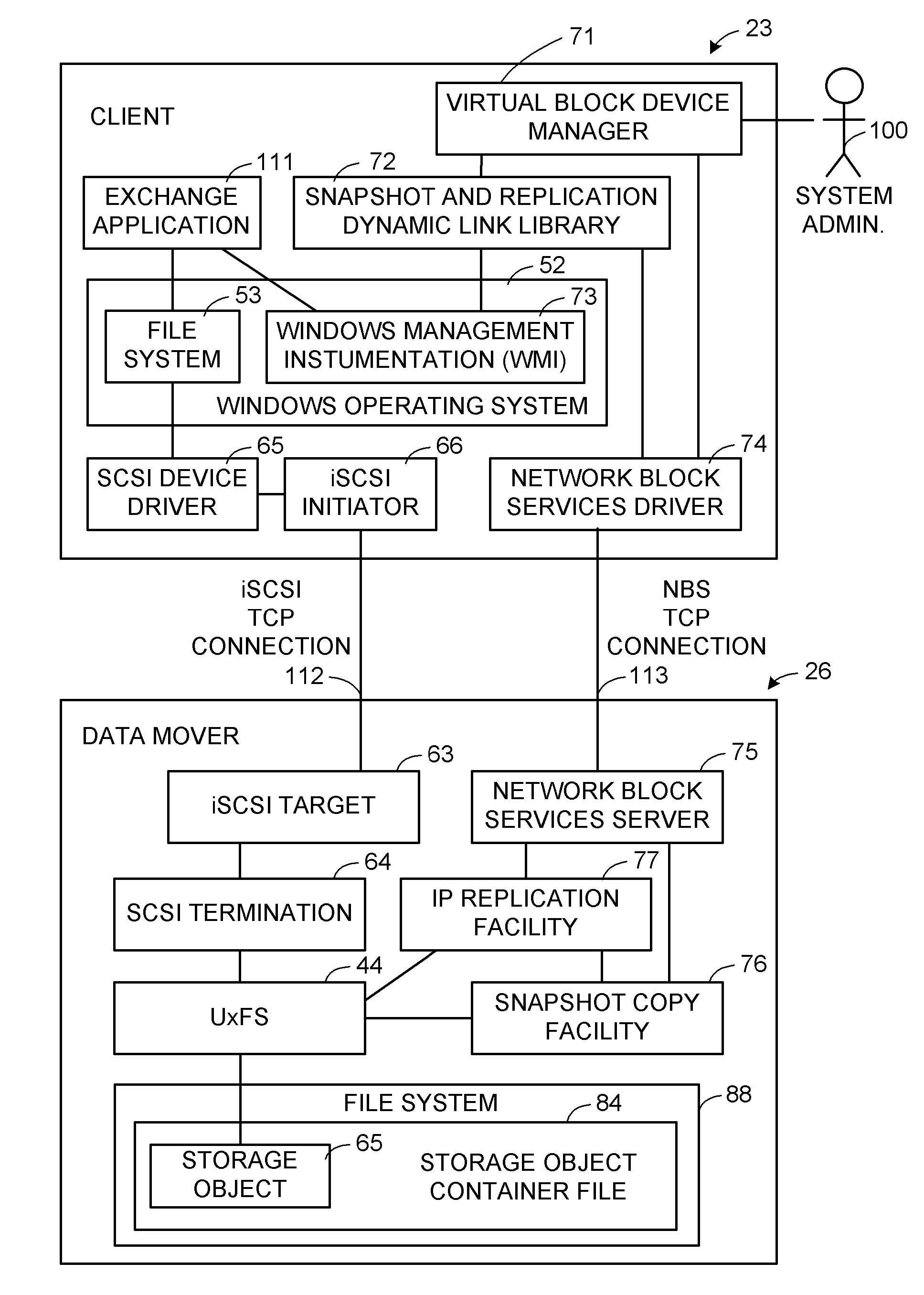
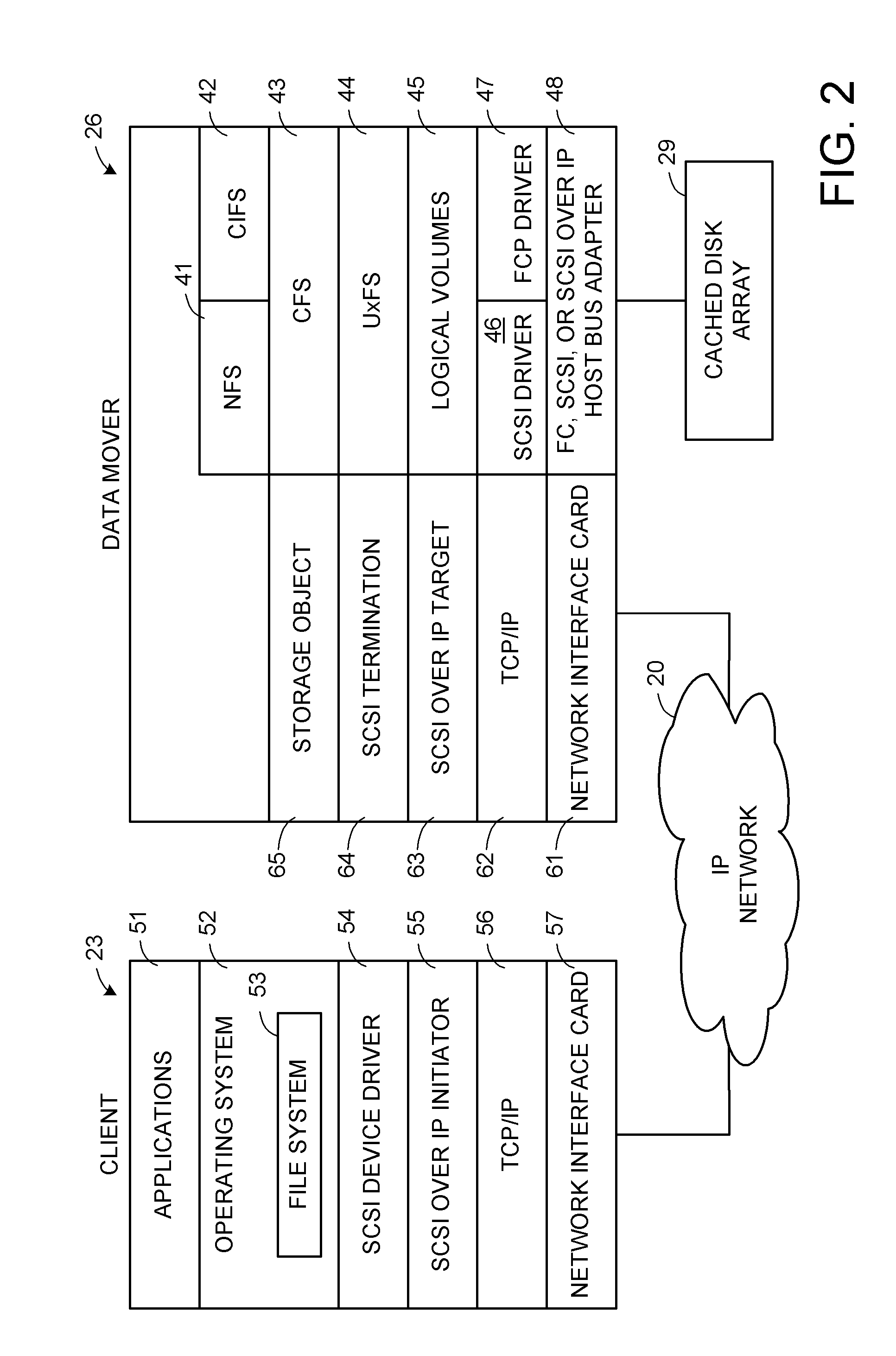
Multi-protocol sharable virtual storage objects
ActiveUS20050044162A1Digital data processing detailsMultiple digital computer combinationsUnixFile replication
A storage object such as a virtual disk drive or a raw logical volume is contained in a UNIX compatible file so that the file containing the storage object can be exported using the NFS or CIFS protocol and shared among UNIX and MS Windows clients or servers. The storage object can be replicated and backed up using conventional file replication and backup facilities without disruption of client access to the storage object. For client access to data of the storage object, a software driver accesses the file containing the storage object. For example, a software driver called a virtual SCSI termination is used to access a file containing a virtual SCSI disk drive. Standard storage services use the iSCSI protocol to access the virtual SCSI termination. An IP replication or snapshot copy facility may access the file containing the virtual SCSI disk drive using a higher-level protocol.
Owner:EMC IP HLDG CO LLC
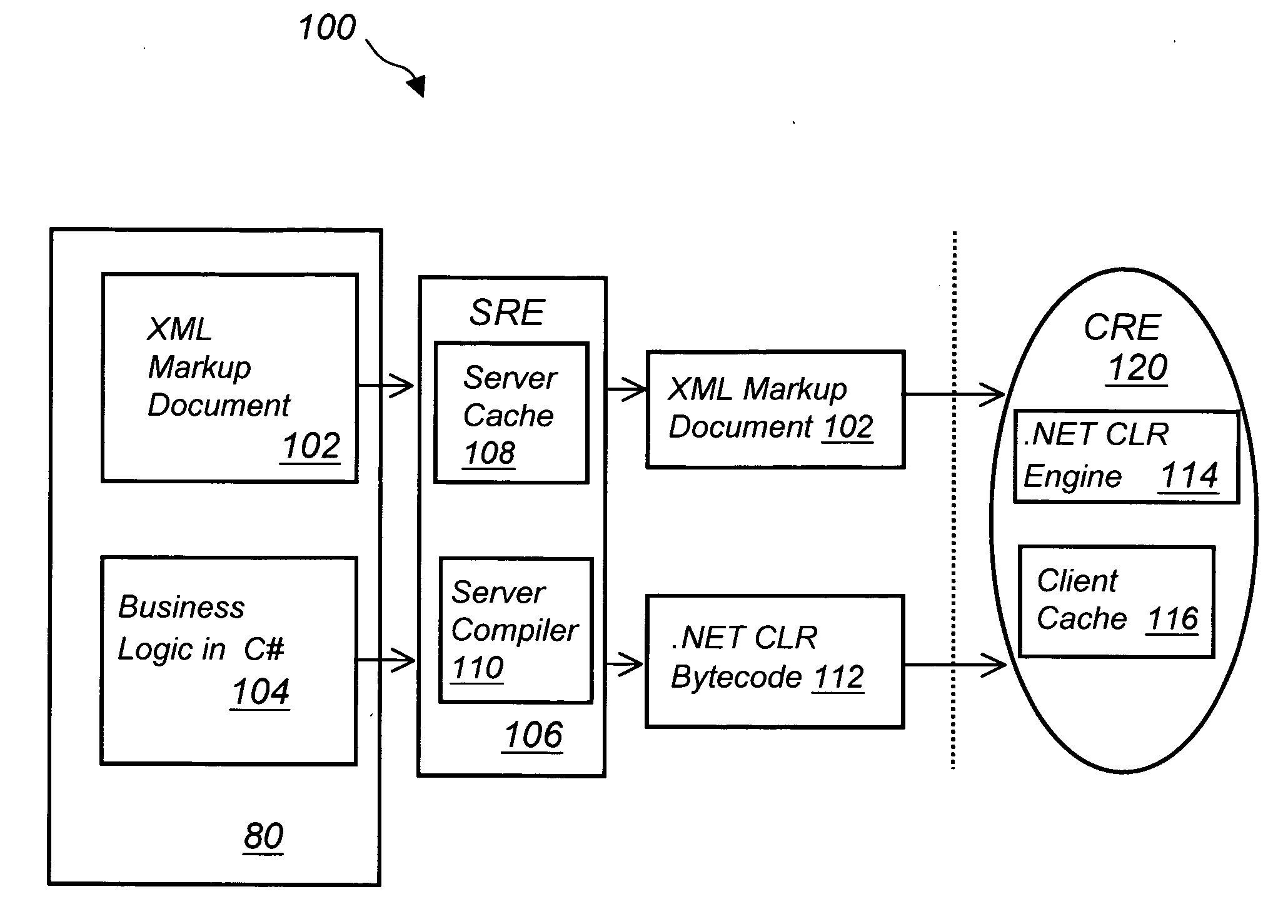
System and method for developing and deploying computer applications over a network
InactiveUS20050155027A1Reduce bandwidth costsReduce maintenance costsNatural language data processingProgram loading/initiatingVisual BasicOperational system
A method of developing a computer application by coding a markup document in an XML markup language, coding a business logic component using any programming language, compiling the business logic component into a specific executable code, converting the XML document into a specific markup language document and deploying the converted markup document and the executable code to a client machine running a specific operating system via a network connection. The XML markup document can be converted in any markup language including XUL, SVG, Xforms, XML related languages, HTML, HTML related languages, text, and combinations thereof. The business logic component can be written using any programming language including Java, JavaScript, J#, C#, C, C++, Visual Basic, ActionScript, XSL, XQuery, and XPath, among others. The computer application can run in any operating system including next generation Windows Longhorn, Windows 2000, Linux, Unix, Apple or Palm operating systems, among others.
Owner:NEXAWEB
Log collection, structuring and processing
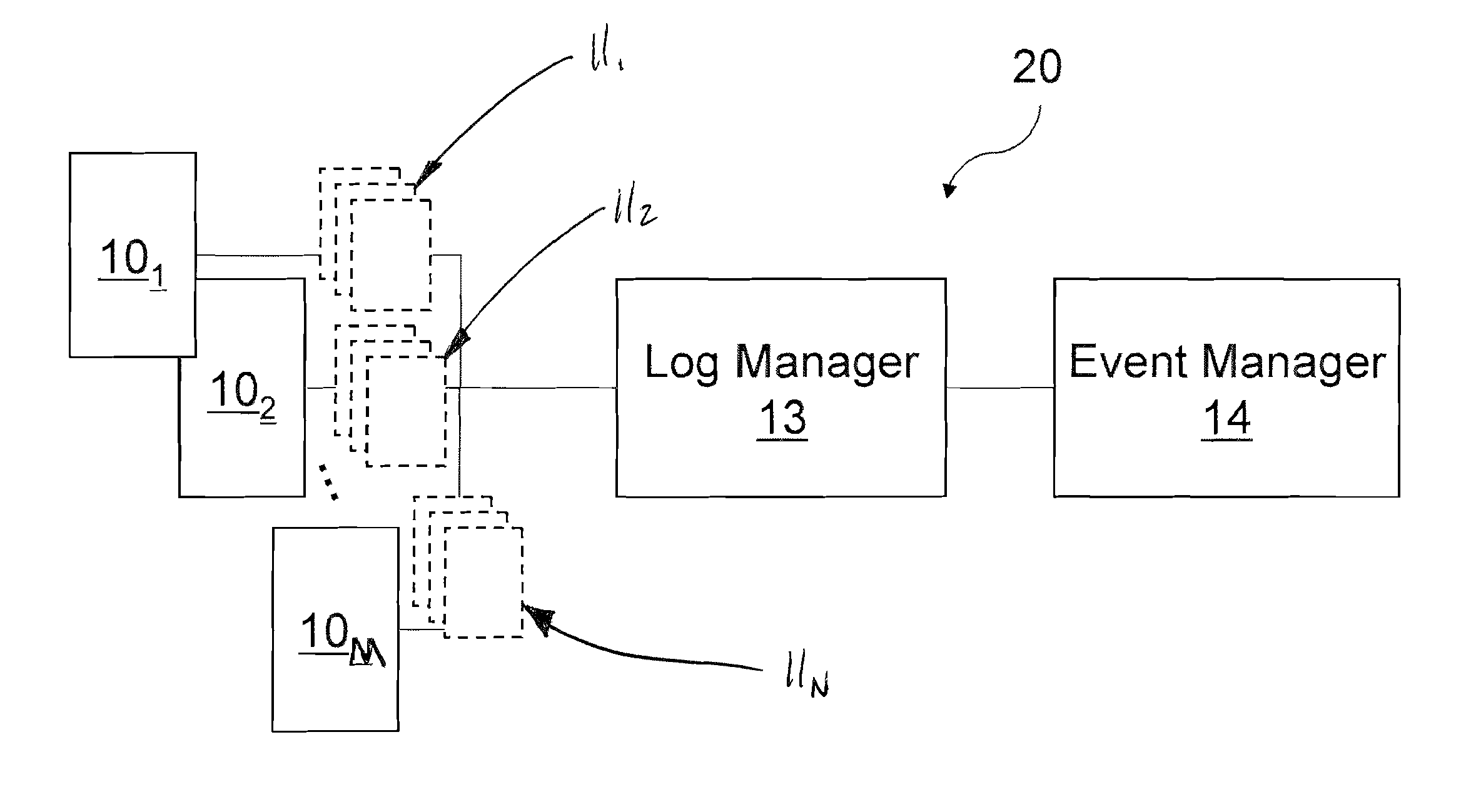
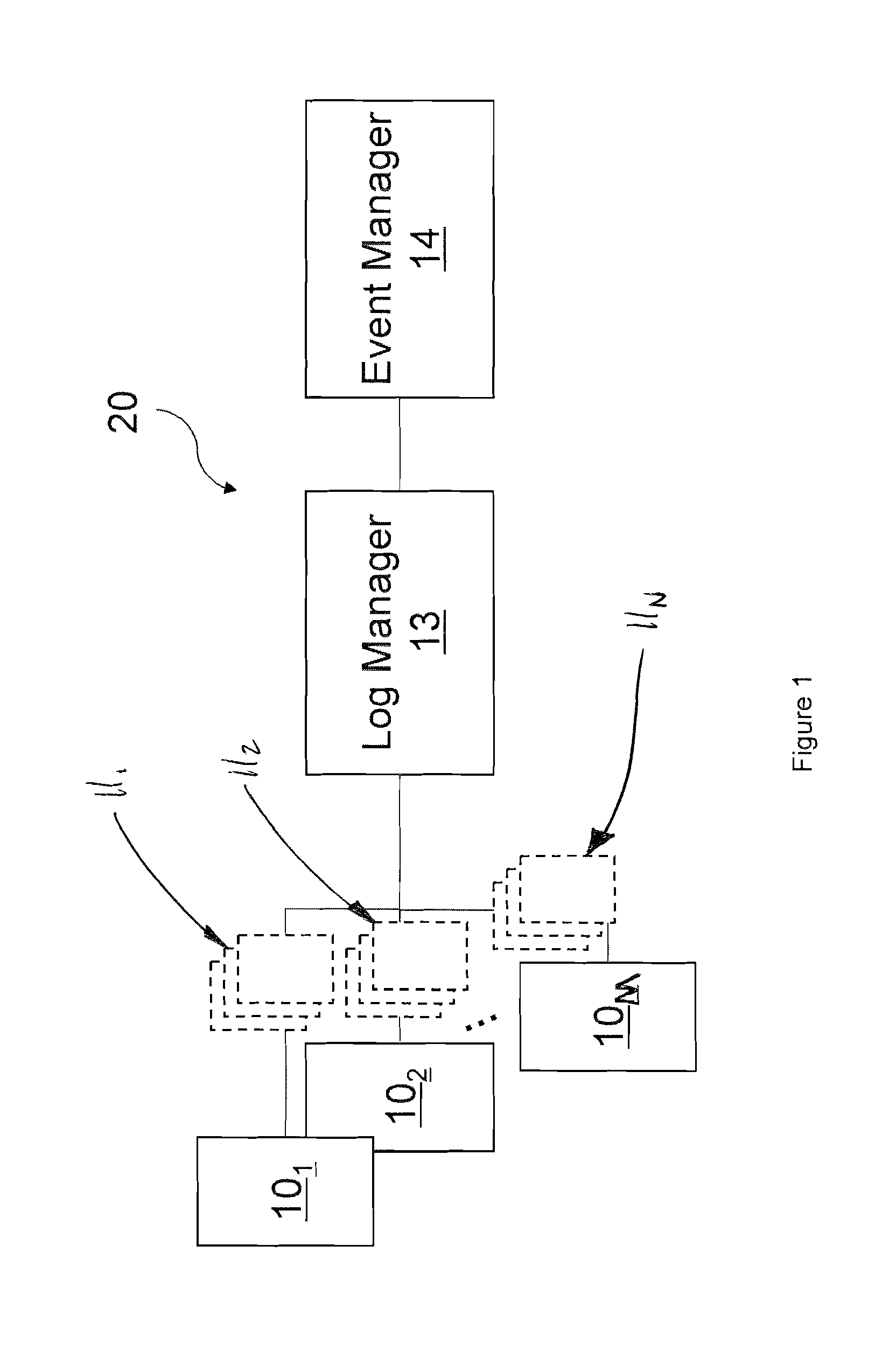
ActiveUS7653633B2Facilitates automated selective accessEasy to processMultiplex system selection arrangementsError detection/correctionUnixLog management
The present invention generally relates to log message processing such that events can be detected and alarms can be generated. For example, log messages are generated by a variety of network platforms (e.g., Windows servers, Linux servers, UNIX servers, databases, workstations, etc.). Often, relatively large numbers of logs are generated from these platforms in different formats. A log manager described herein collects such log data using various protocols (e.g., Syslog, SNMP, SMTP, etc.) to determine events. That is, the log manager may communicate with the network platforms using appropriate protocols to collect log messages therefrom. The log manager may then determine events (e.g., unauthorized access, logins, etc.) from the log data and transfer the events to an event manager. The event manager may analyze the events and determine whether alarms should be generated therefrom.
Owner:LOGRHYTHM INC
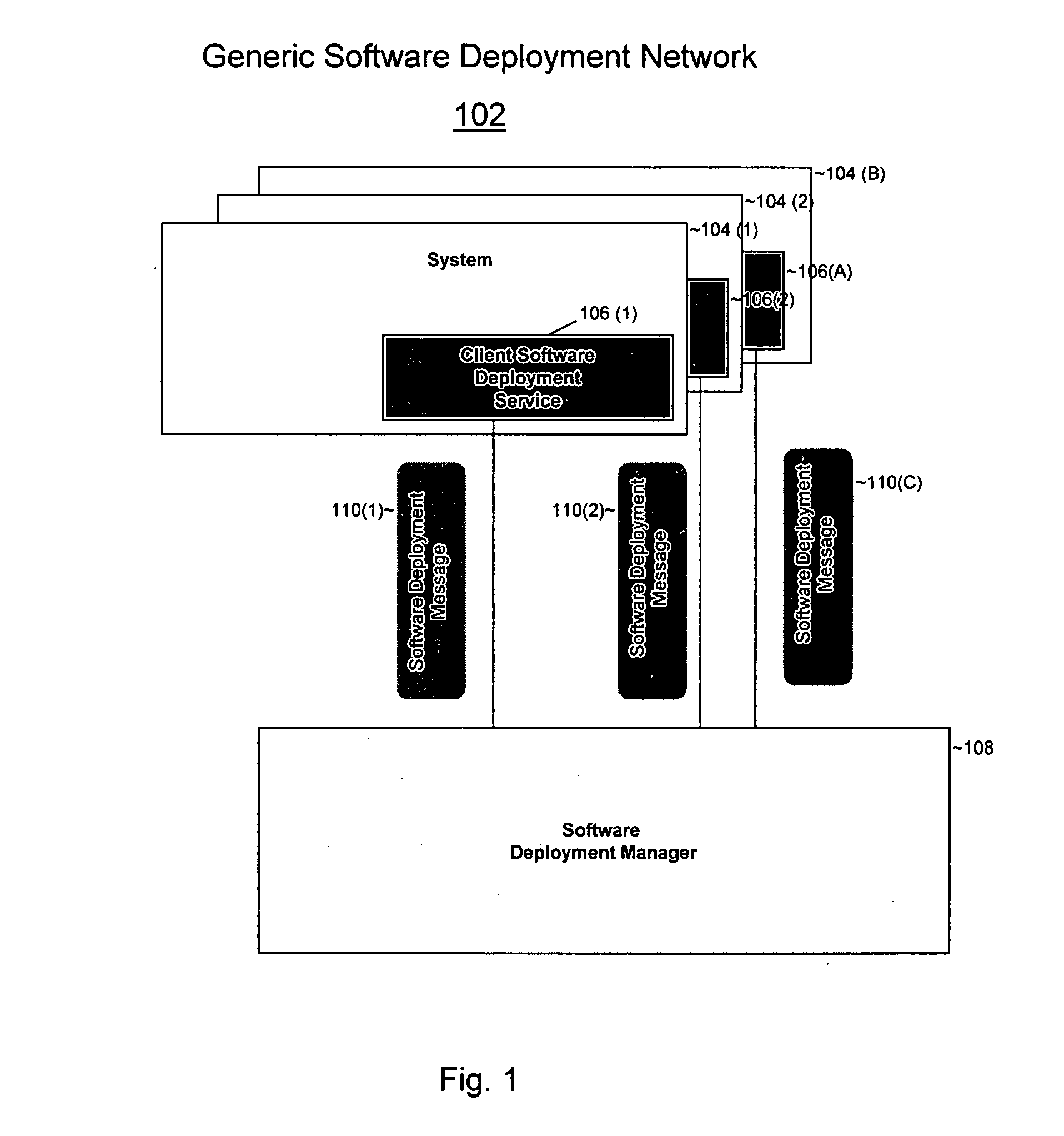
Software deployment system
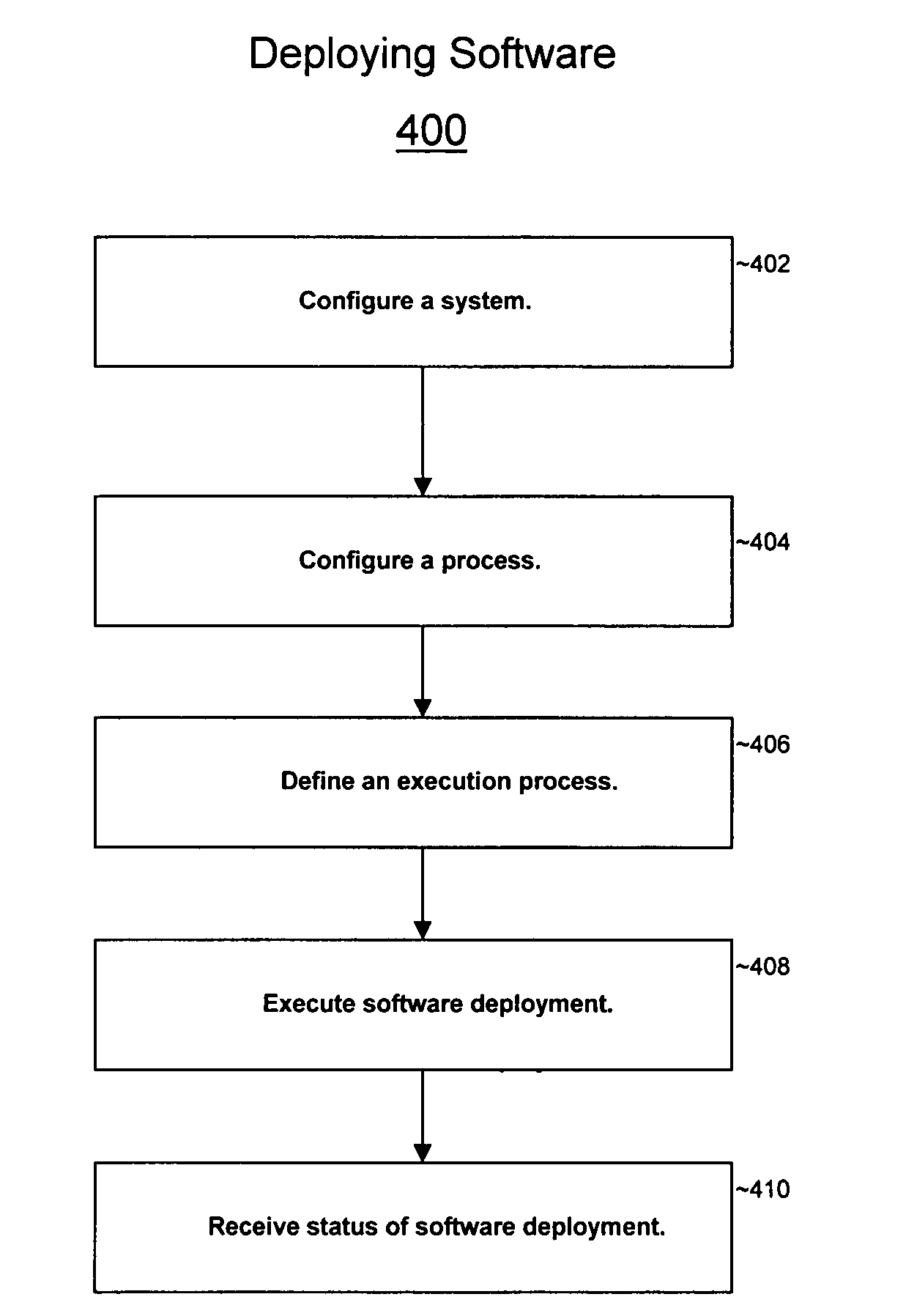
The present invention provides a system and method for deploying software onto multiple heterogeneous systems at the same time. A generic software deployment manager may deploy software by communicating with client software deployment services residing on the systems that are receiving the software deployment. The software deployment manager can operate independent of the software and the operating system on which software is being deployed by communicating with the client software deployment service. To execute a software deployment, the software deployment manager may send software deployment messages containing generic commands that signify operations to be performed to deploy software. The client software deployment service provides an interface between the software deployment manager and the recipient system by translating these generic commands to commands that are compatible with the local operating system. The software deployment manager may transmit software deployment messages simultaneously to each of the systems within a system group or an environment so that software can be efficiently deployed without incompatibilities in the network. The software deployment manager may deploy software in Linux, Windows, Unix, Macatosh, Java, or any other operating system and may deploy any software.
Owner:SAP AG
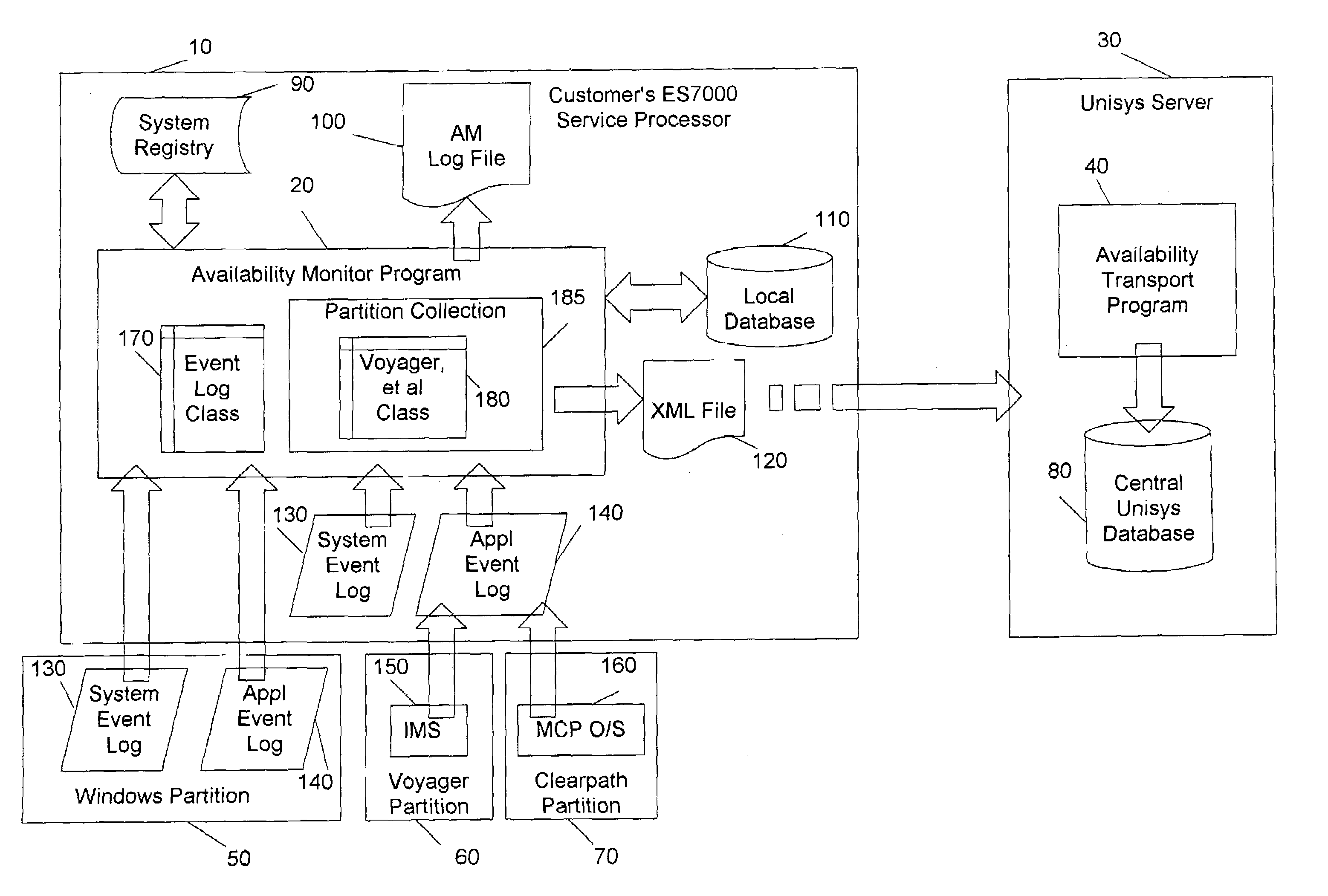
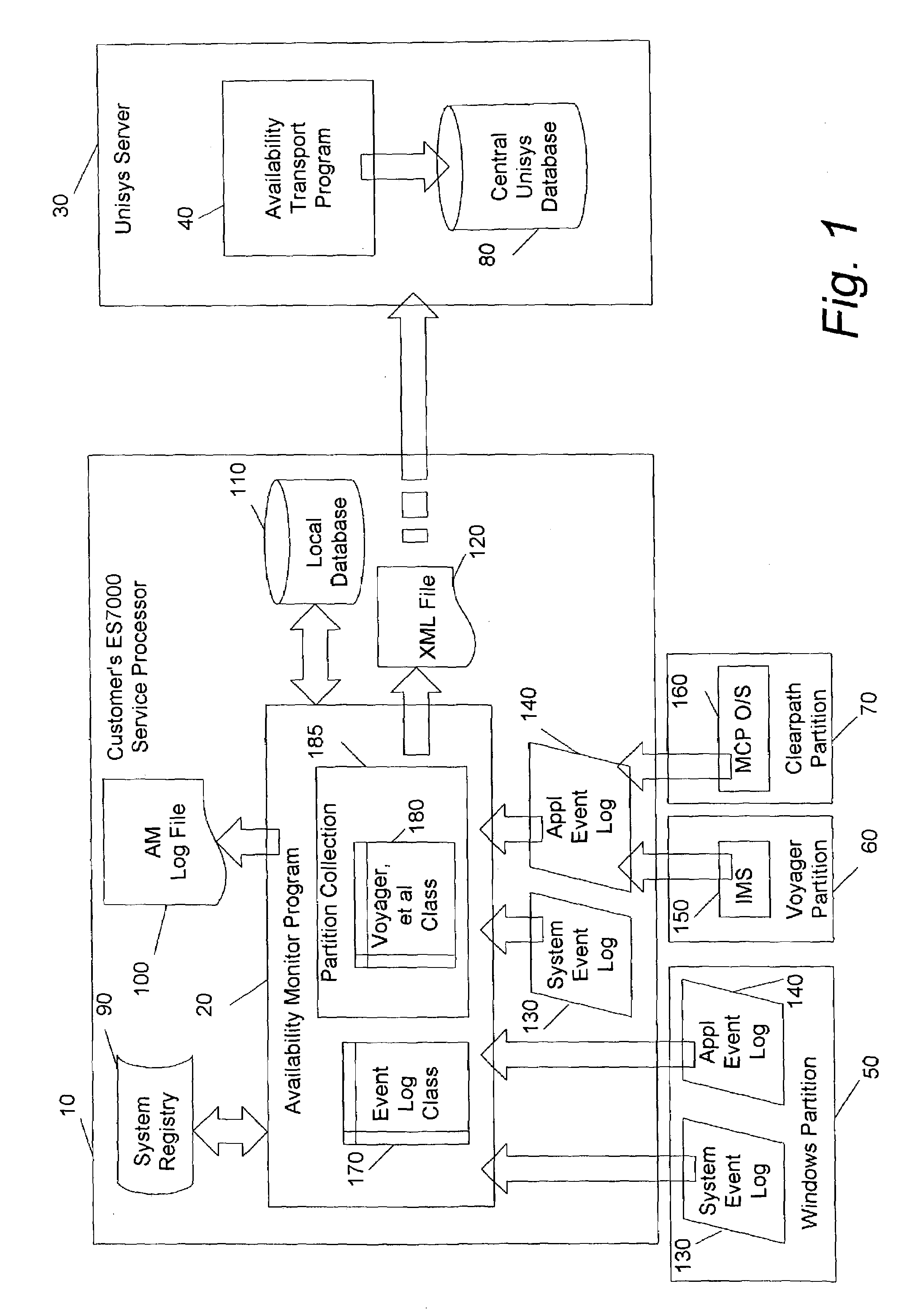
Method variation for collecting stability data from proprietary systems
ActiveUS7043505B1Improve integrityUniform compatibilityData processing applicationsError detection/correctionUnixPresent method
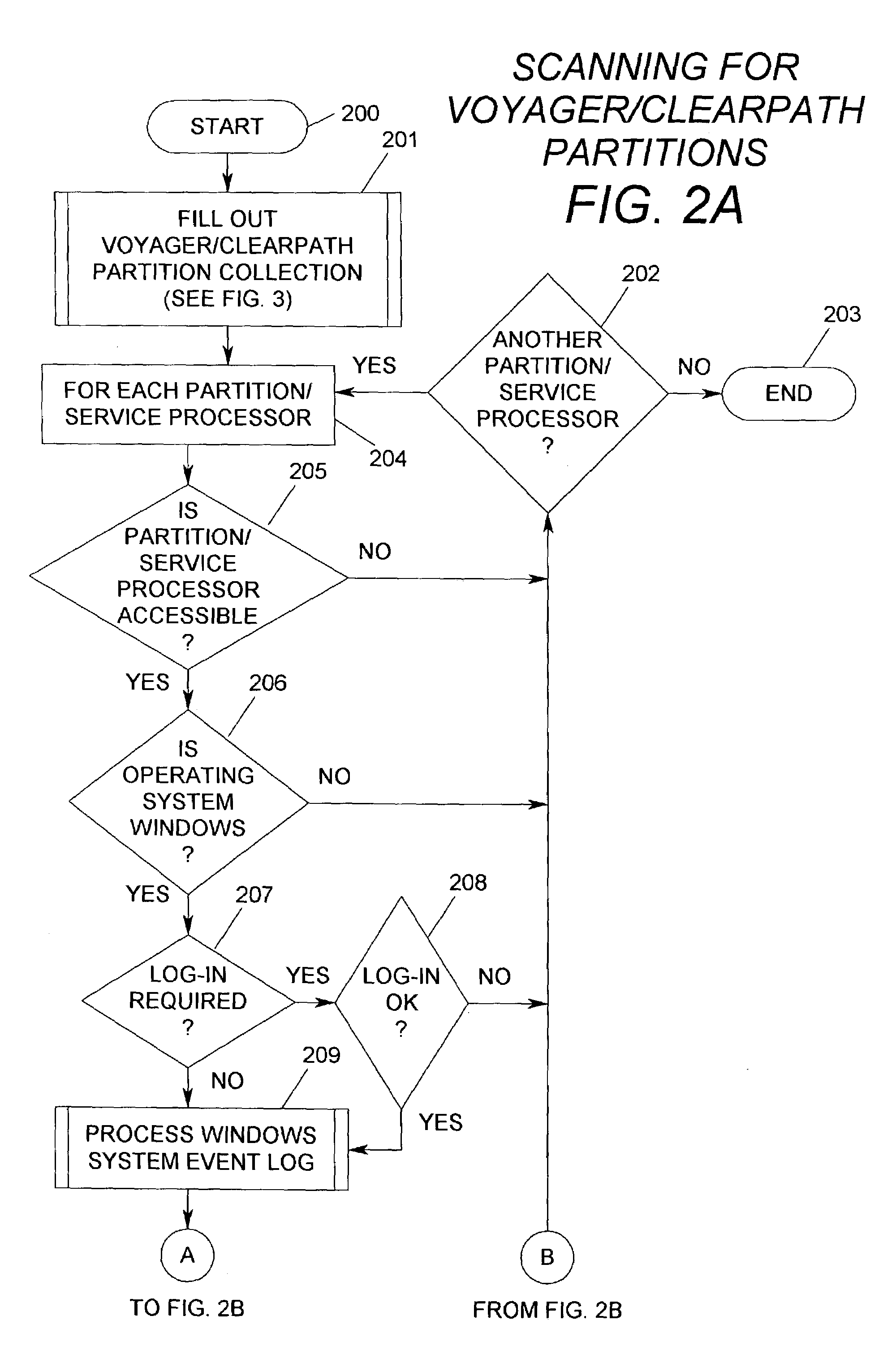
A Cellular Multi-Processor Serve provides partitions having different Operating Systems such as Windows, Unix OS2200 (Unisys), Master Control Program (Unisys) or other Operating Systems, which could be designated as OS-A or OS-B. The present method and system collects and scans availability and reliability information which involve non-windows partitions with respect to planned and unplanned stops, system starts and different categories of error conditions.
Owner:UNISYS CORP
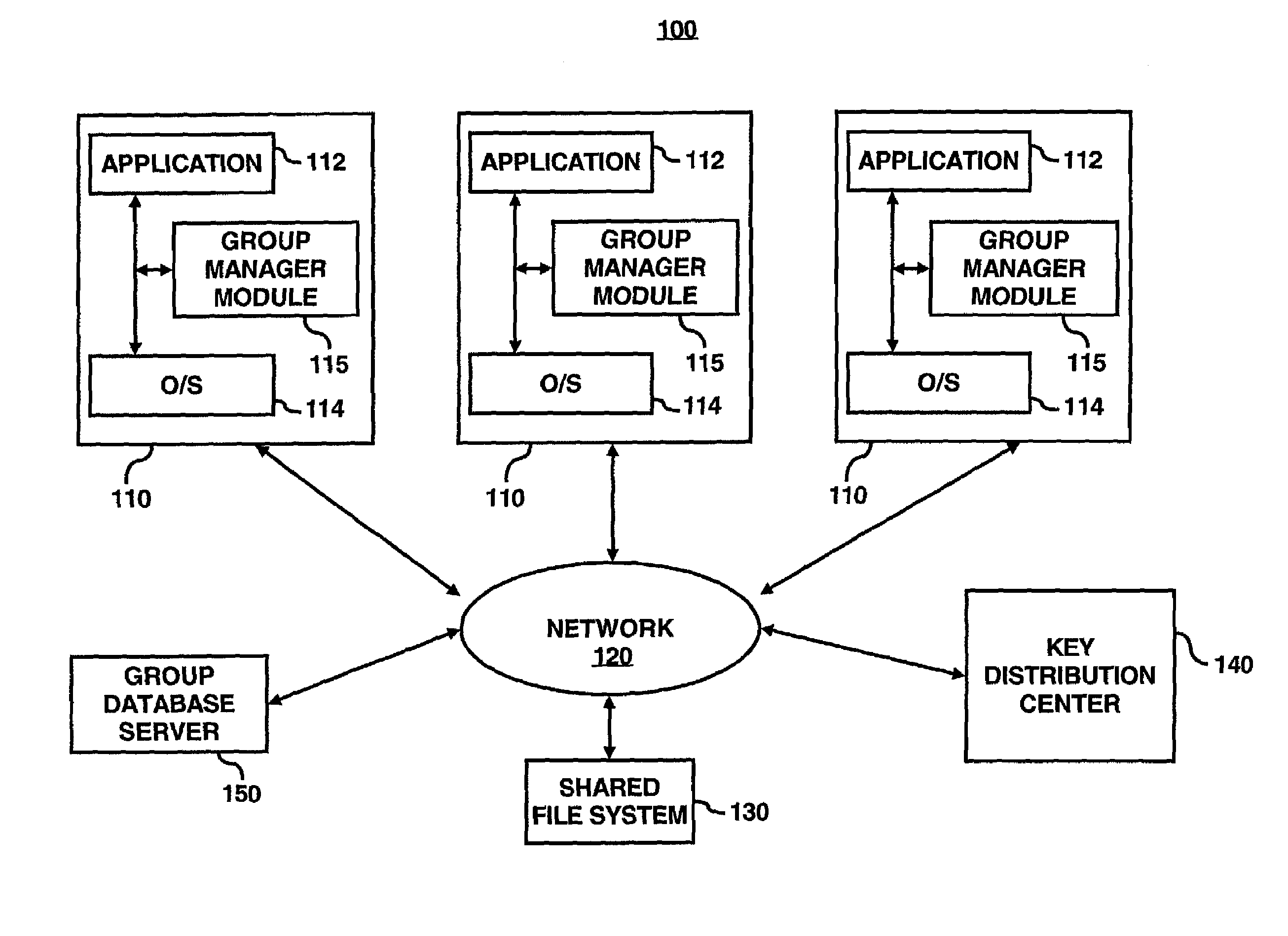
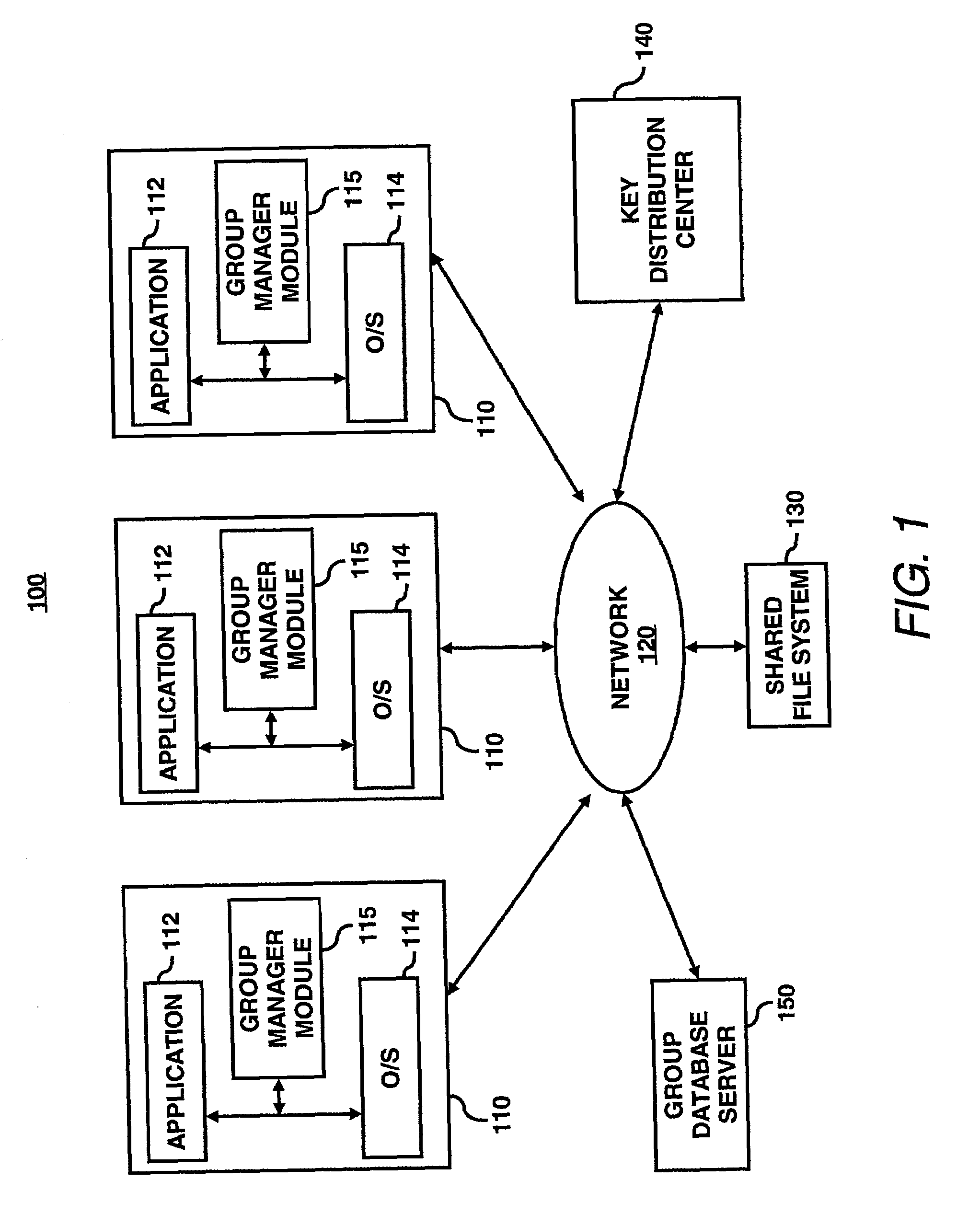
System for optimized key management with file groups
A group manager module may provide the capability to segregate or associate files into file encryption groups. A file may be placed into a file encryption group based on the attributes of the file. The attributes may be characteristics / parameters that describe who has access to a file such as UNIX permission / mode bits (group-read / write / executable bit, owner-read / write / executable bits, users-read / write / executable bits) or other system for access control lists (ACLs). Once associated with a file encryption group, the file may be encrypted with the encryption (or write) key of the selected file encryption group, and thus, decrypted with the decryption (or read) key of the file encryption group. A user may have membership into multiple file encryption groups as long as the user possesses the appropriate read / write key pairs. Membership of a file in a file encryption group is determined automatically by the system based on the permission attributes assigned by the system—groups are not explicitly created by administrators or other centralized authority. It is not users that belong to groups based on their access rights, but files which belong to groups based on their permission attributes.
Owner:HEWLETT PACKARD DEV CO LP
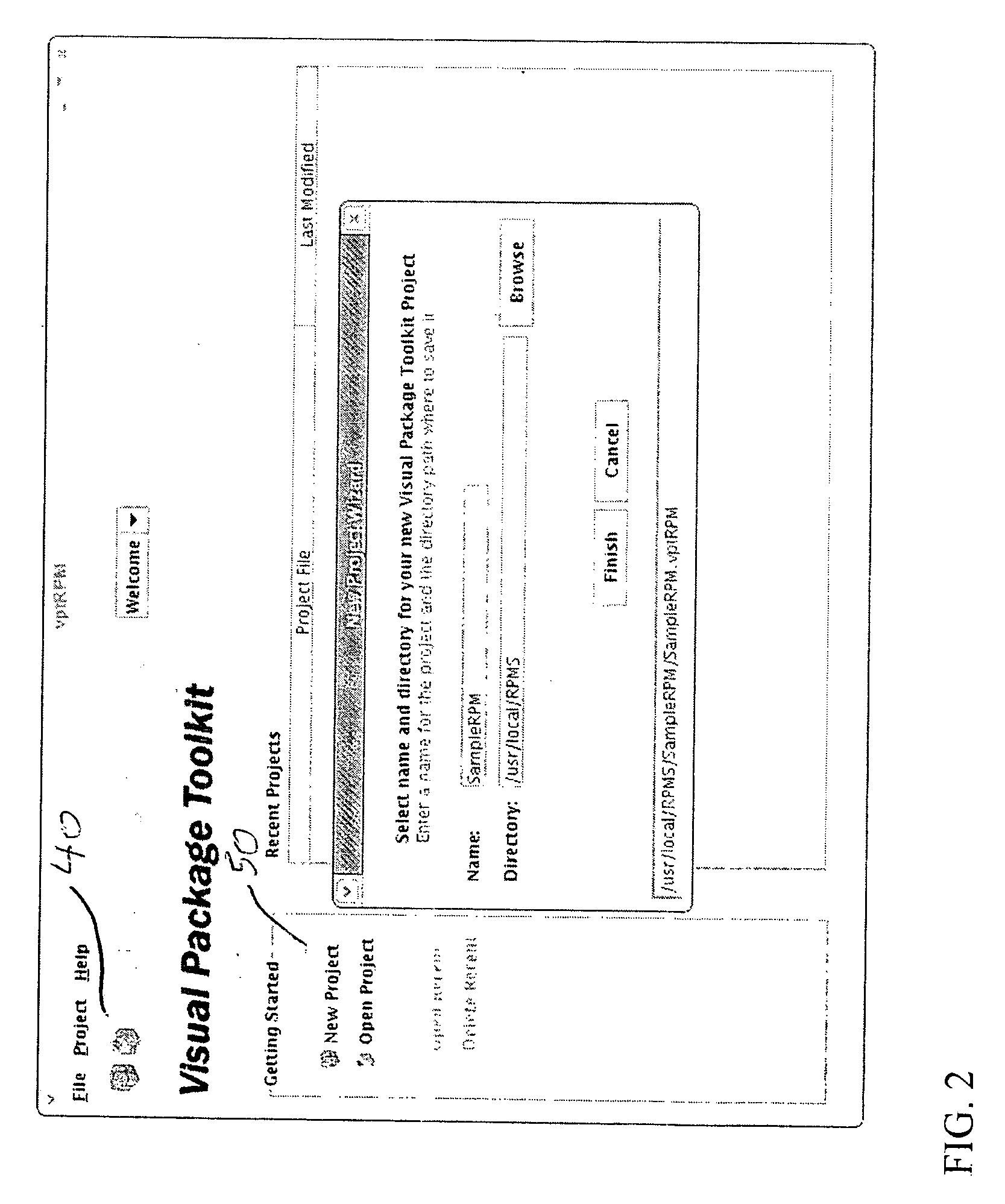
System and method for packaging software
A method and system for packaging software using a graphical user interface (GUI) to simplify the creation and modification of System V and Red Hat Package Manager (RPM) software packages. The software packaging system provides a fully interactive graphical interface portable across many platforms including Linux, Unix System V, Solaris, and AIX. RPM is a popular and powerful packaging system that installs and removes system software, enforces dependencies, and is freely available on a number of different platforms. The software packaging system of the present invention simplifies and speeds the creation of deployable RPM software packages, a complex and time consuming task if created using the RPM command line method. The GUI provides for the collection of information required for RPM software package creation, modification, and feature manipulation reducing the skill level and time that needed to perform these functions using the RPM command line.
Owner:NEXONE
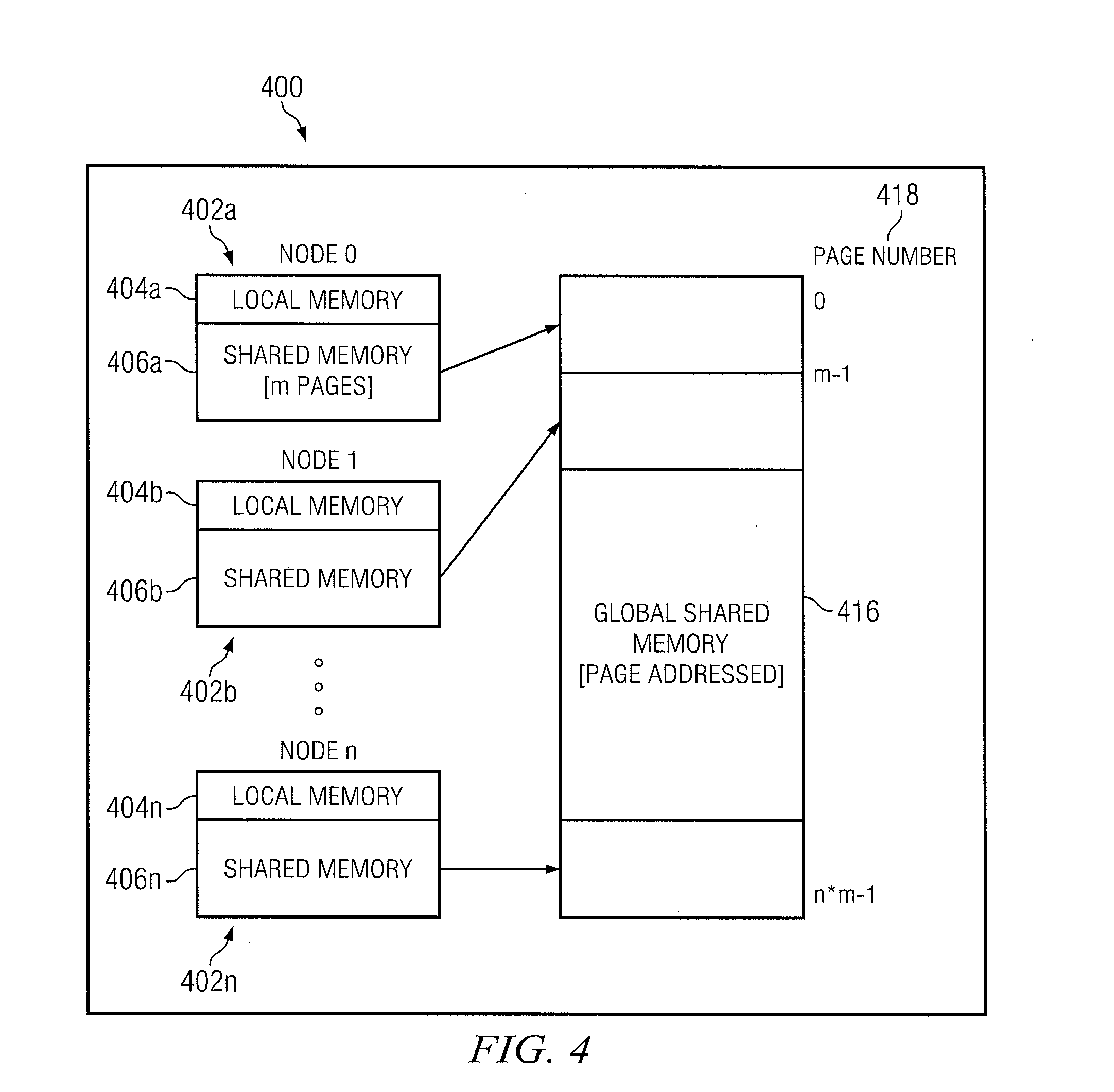
Distributed symmetric multiprocessing computing architecture
ActiveUS20110125974A1Shorten the progressMemory adressing/allocation/relocationDigital computer detailsSupercomputerGlobal address space
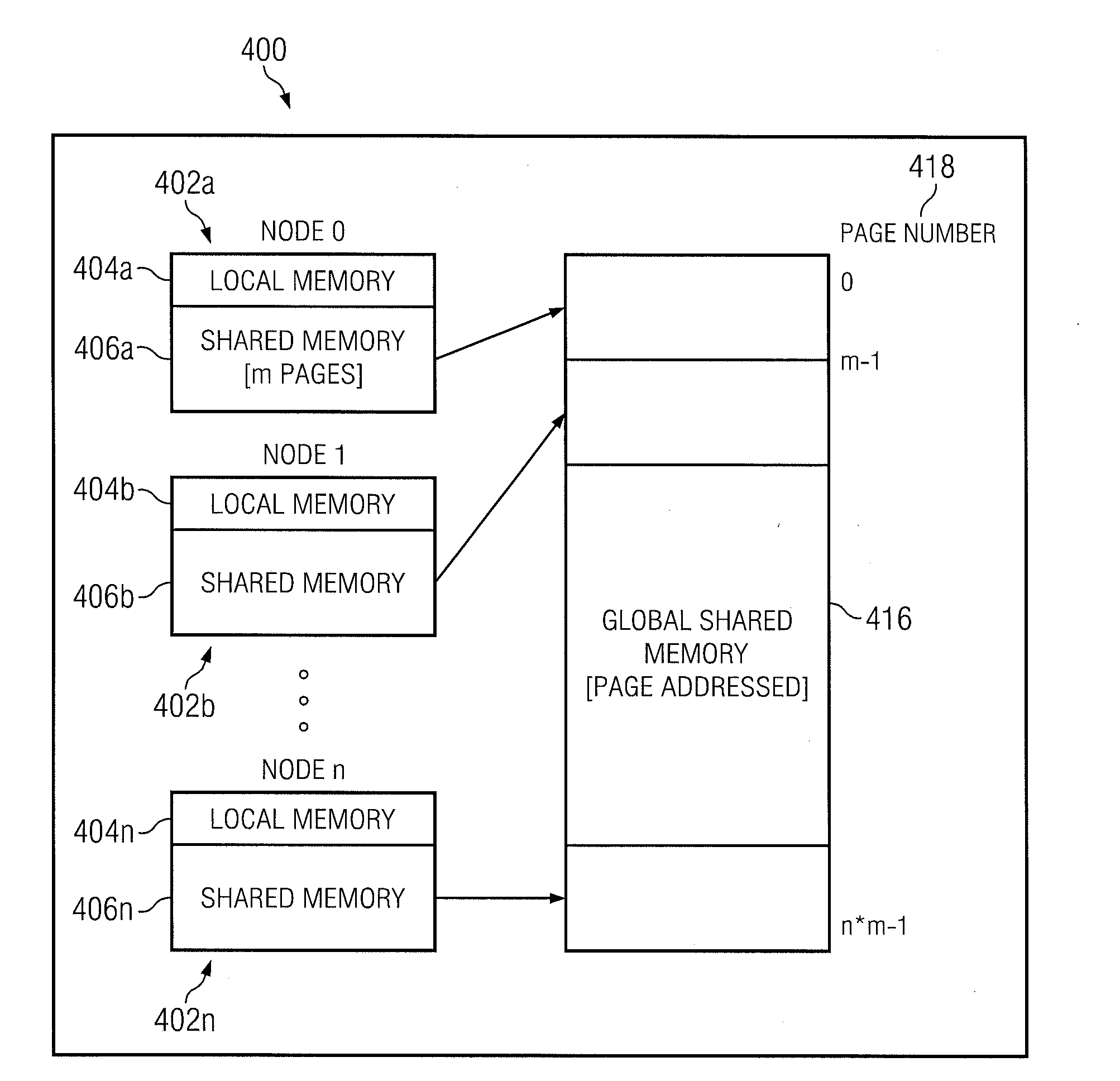
Example embodiments of the present invention includes systems and methods for implementing a scalable symmetric multiprocessing (shared memory) computer architecture using a network of homogeneous multi-core servers. The level of processor and memory performance achieved is suitable for running applications that currently require cache coherent shared memory mainframes and supercomputers. The architecture combines new operating system extensions with a high-speed network that supports remote direct memory access to achieve an effective global distributed shared memory. A distributed thread model allows a process running in a head node to fork threads in other (worker) nodes that run in the same global address space. Thread synchronization is supported by a distributed mutex implementation. A transactional memory model allows a multi-threaded program to maintain global memory page consistency across the distributed architecture. A distributed file access implementation supports non-contentious file I / O for threads. These and other functions provide a symmetric multiprocessing programming model consistent with standards such as Portable Operating System Interface for Unix (POSIX).
Owner:ANDERSON RICHARD S
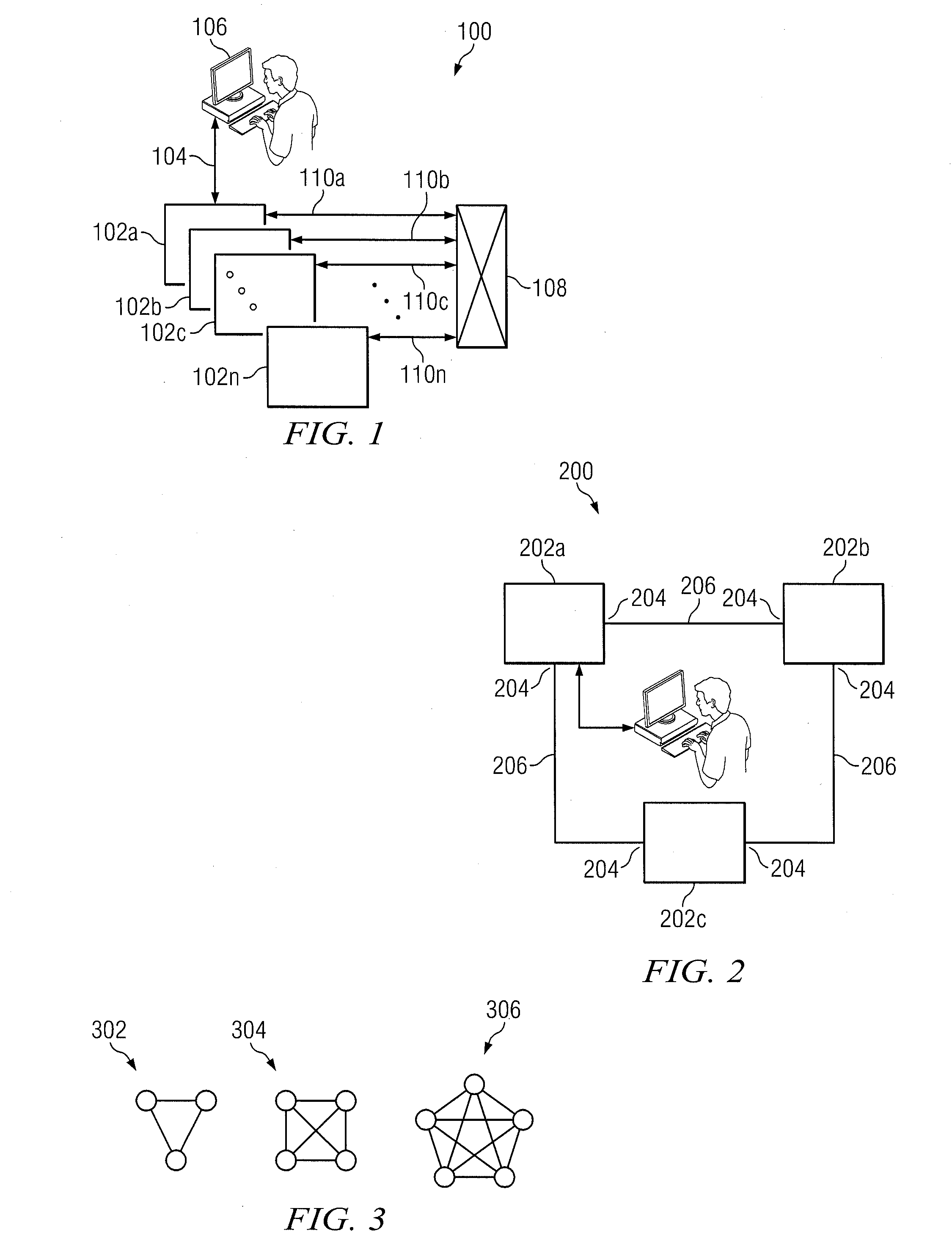
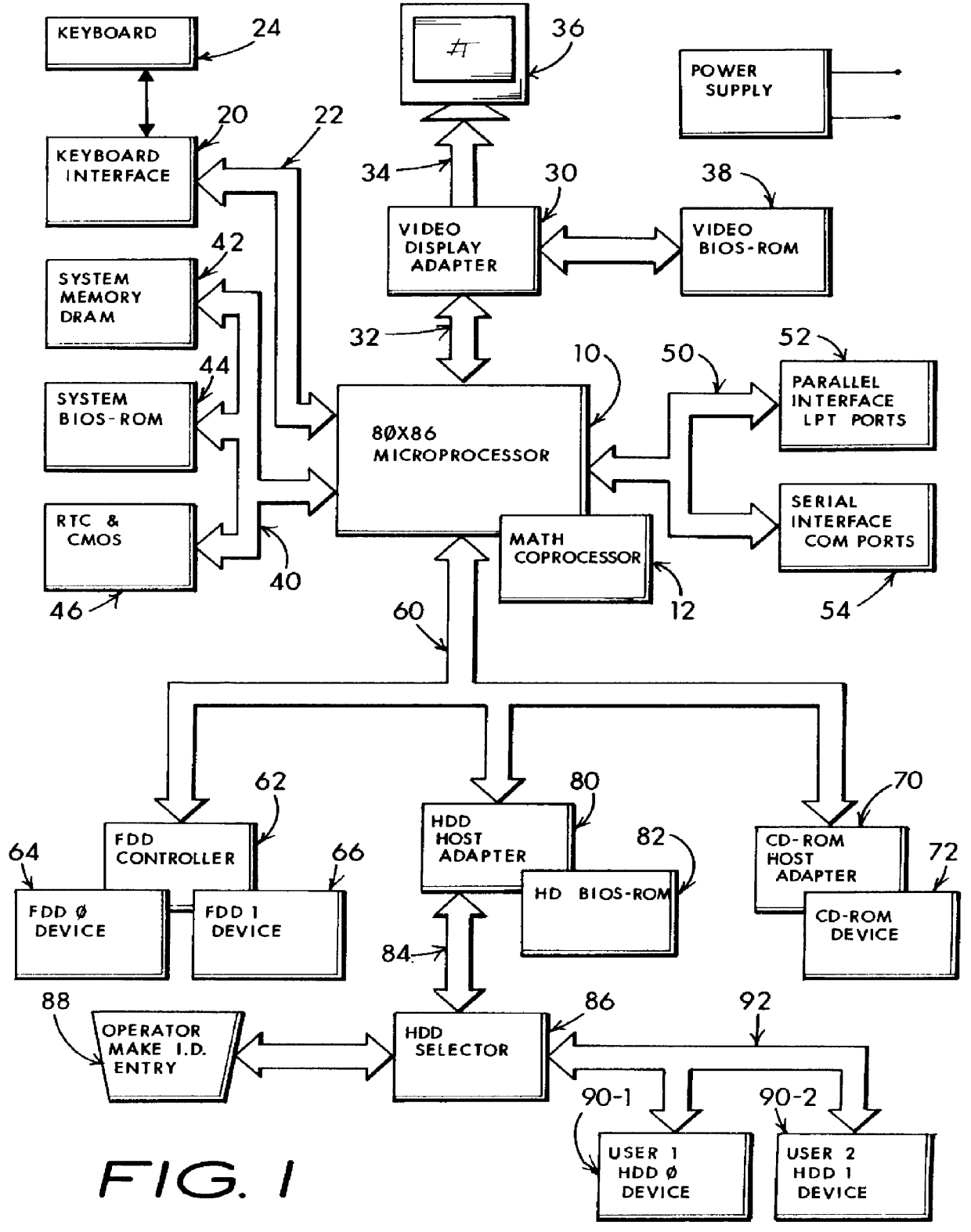
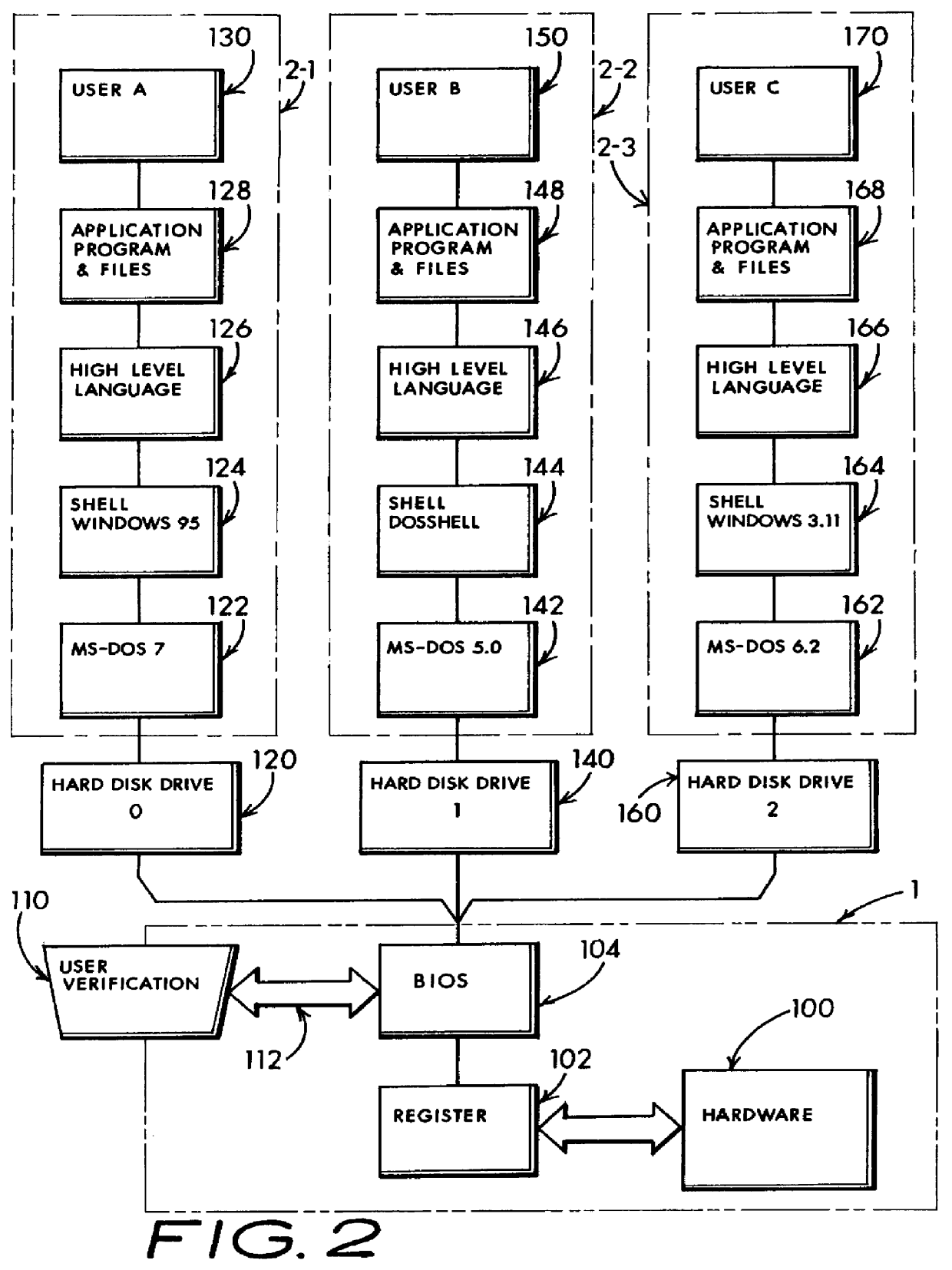
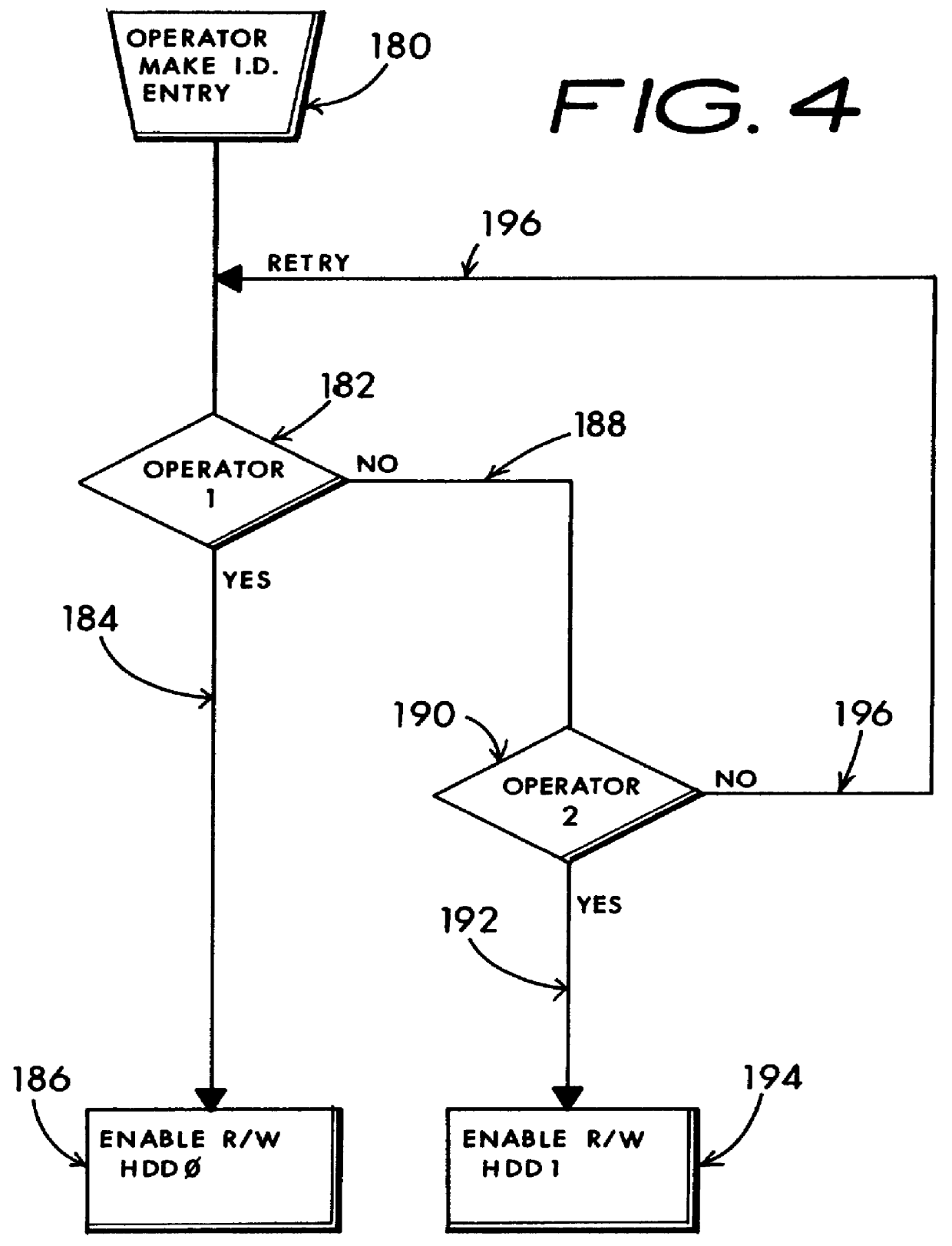
Multiple user computer including anti-concurrent user-class based disjunctive separation of plural hard drive operation
InactiveUS6052781ALow costSame level of securityMemory loss protectionError detection/correctionUnixHard disc drive
A computer sharing system which adapts a computer's hardware resources to providing virtual dual system operation for several non-concurrent system users. A separate hard disk drive including a full complement of boot, operating system, program and data file software is provided for each of the non-concurrent system users. Access by one system user to another system user's hard disk drive and attendant files is absolutely denied thereby preventing corruption of one user's hard disk dive files by another user's carelessness or malicious intent, or through unique setup adaptation of one user's program files which may otherwise interact with and impose unwanted changes on another's program file's operational performance. Each of the separate hard disk drives may be uniquely formatted to service totally different operating systems, including boot track code, in support of various operating systems including MS-DOS, Windows-NT, OS / 2, Unix and others. By definition, each separate hard disk drive may be a physically distinct hard disk drive unit, or be more economically embodied as several separately utilized media platters driven by a common hard disk drive mechanisim and having user distinctive READ and WRITE channel control for each media platter. The absolute denial of a system user's access to another system user's assigned hard disk drive may be cracked open to an limited extent whereby READ-ONLY access may be permitted. Additionally, a third hard disk drive may be enabled to be shared by one or more system users in any combination of READ-ONLY, and READ and WRITE modes. My objective is to deliver the independent performance which until now was proffered only by two completly separate computers in the economic form of one set of computer hardware offering at least two virtually separate operating systems and sets of supporting software whereby one system user is absolutely blocked from corrupting another system user's uniquely configured software and data files.
Owner:HANGER SOLUTIONS LLC
Universal method for submitting gaming machine source code software to a game certification laboratory
InactiveUS20060122937A1Data processing applicationsUser identity/authority verificationOperational systemGeneral purpose computer
A universal computer-implemented method for submitting source code to an authorized game certification laboratory. Initial source code and subsequent source code patches may be transferred from the manufacturer's software development environment into the laboratory's software development environment in a controlled fashion using packaging installation technology normally used for deploying software applications. The packaging technology contains automation actions for automating the synchronization and / or management of the source code and related files between the two software development environments. The entirety of the source code or any source code patch sequence may be removed by executing the corresponding uninstall function. The package containing the original source code or the source code patch sequences and related files may be code signed such as to provide persistent proof of origin which may be verified at any time. The method may be implemented under any operating system such as Microsoft Windows, Linux, UNIX and Apple Mac OS without the laboratory having to learn a complex source code configuration management software.
Owner:MUDALLA TECH INC THOITS LOVE HERSHBERGER & MCLEAN
Maintenance of a file version set including read-only and read-write snapshot copies of a production file
Owner:EMC IP HLDG CO LLC
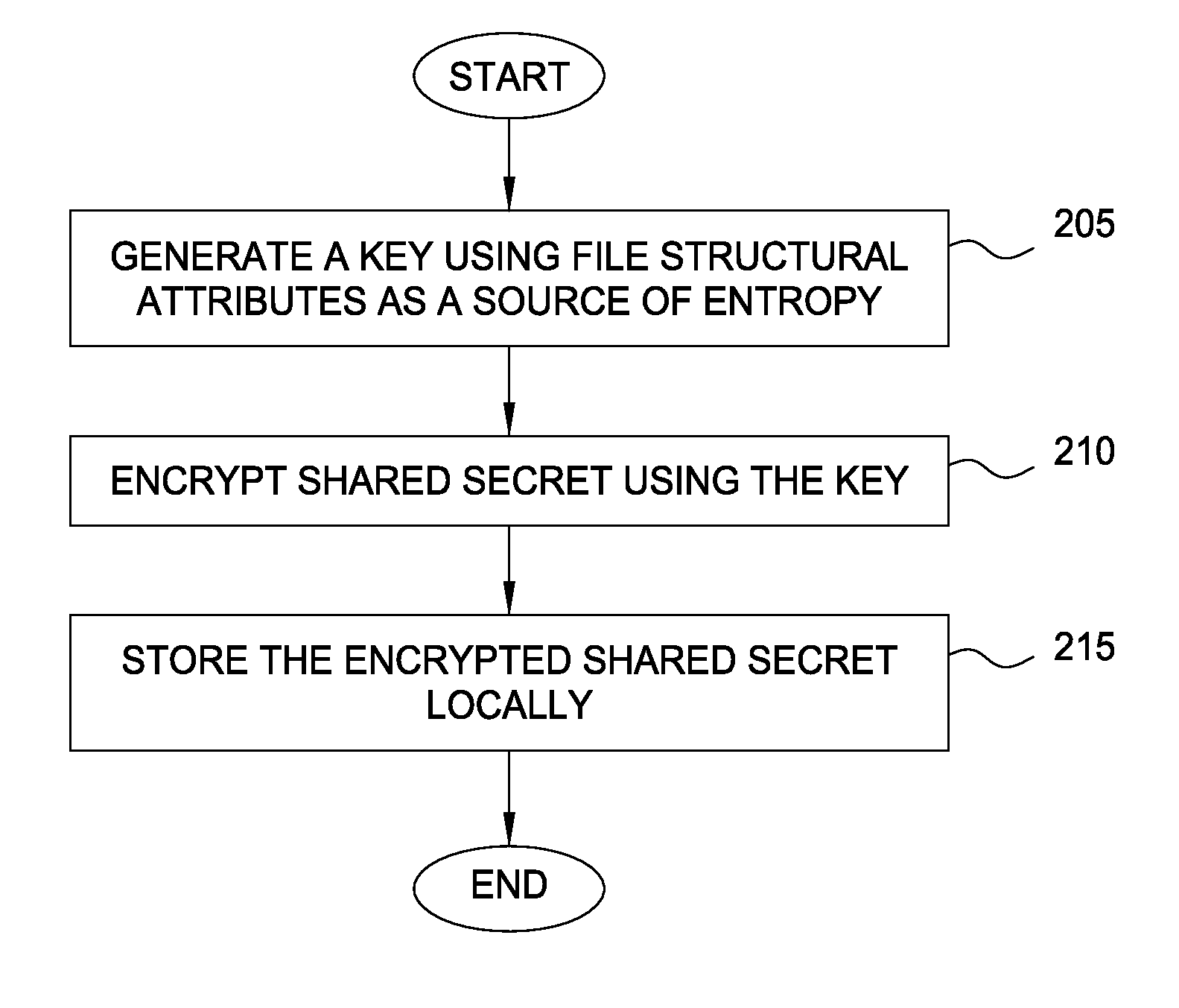
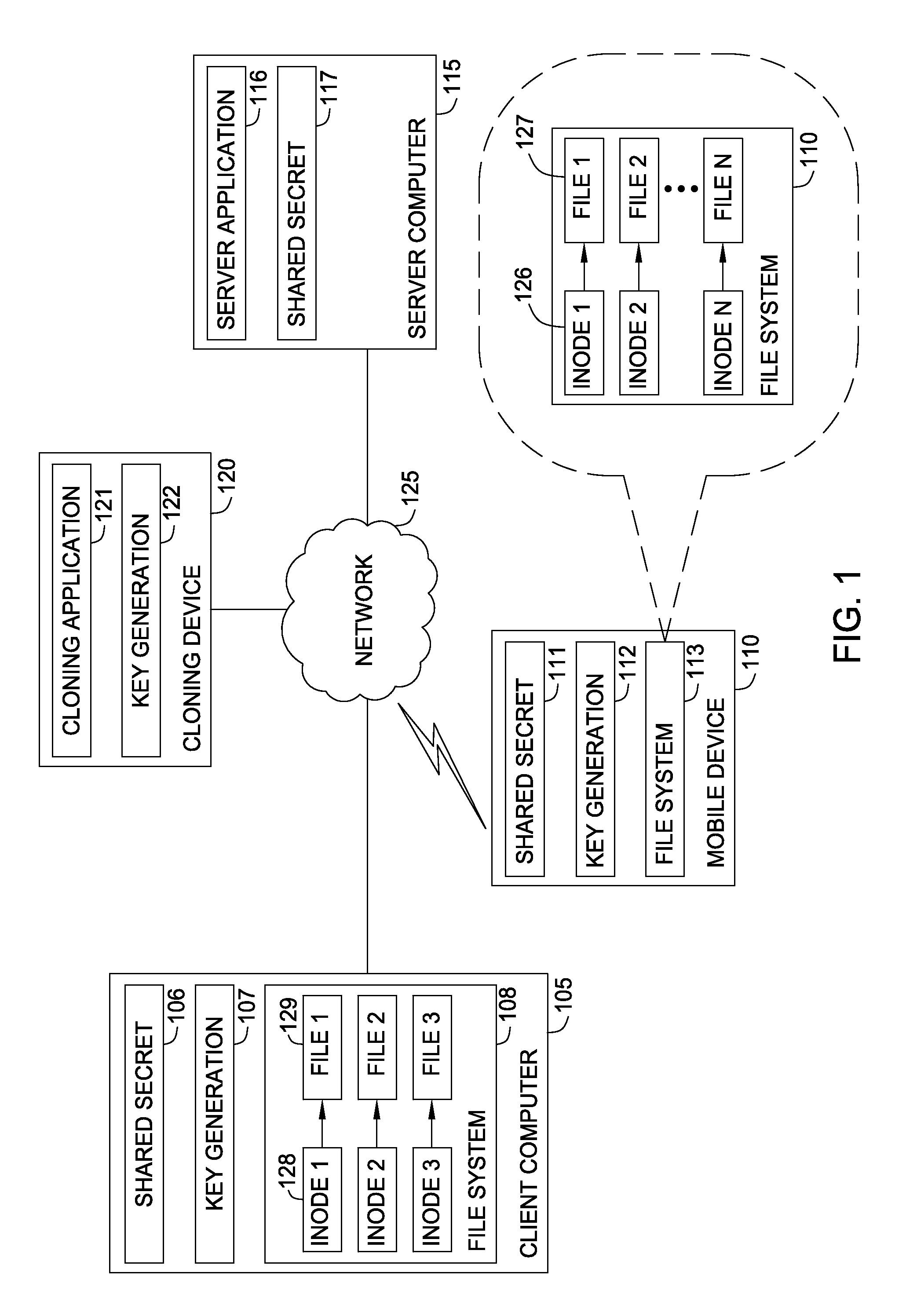
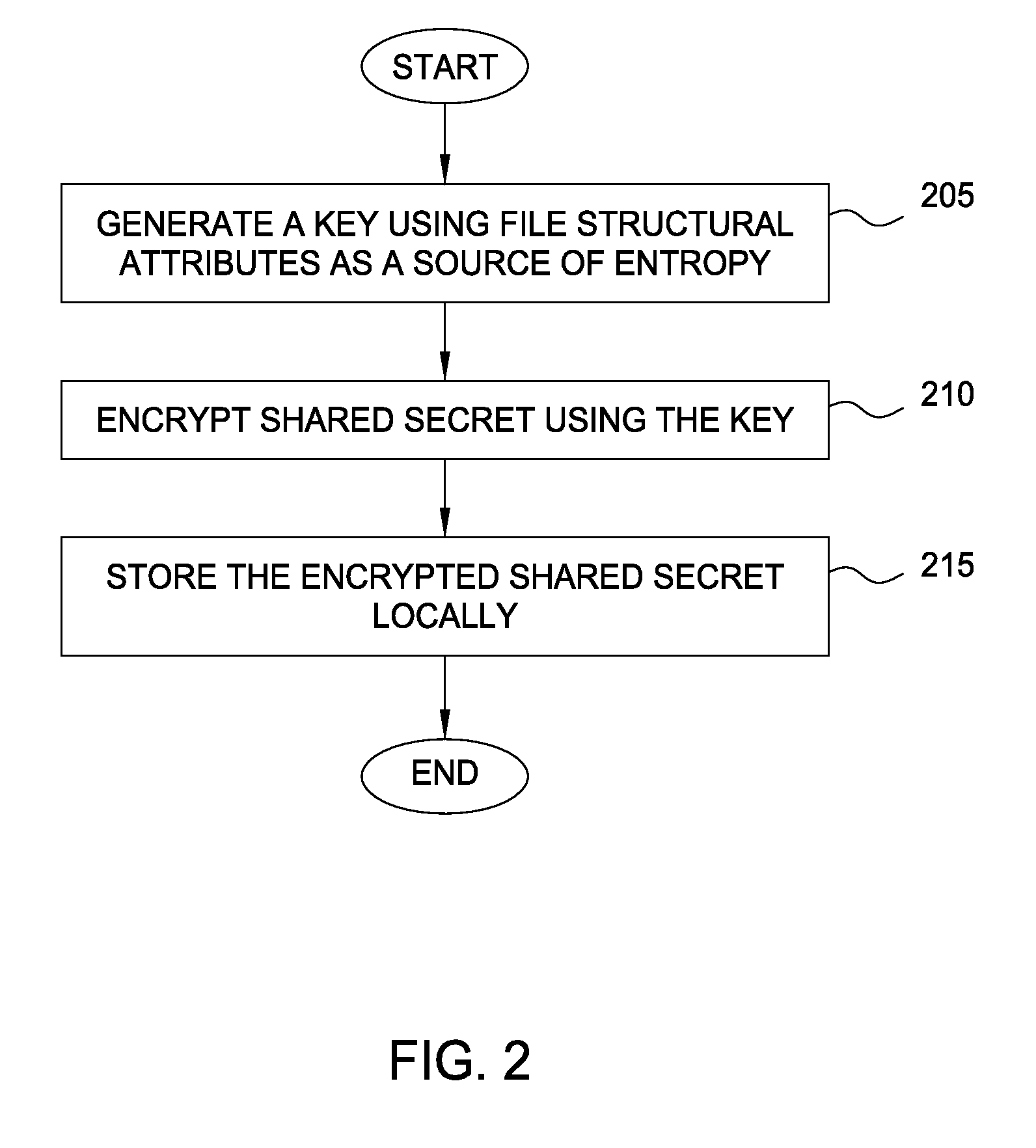
Protecting cryptographic secrets using file system attributes
Techniques are disclosed for protecting cryptographic secrets stored locally in a device, such as a mobile phone. A client device creates or downloads a shared secret to be used in a server transaction. To protect this shared secret locally, the client device encrypts the shared secret using a key generated a file system attributes value, along with other sources of entropy. The file system attributes value may correspond to the inode of a file in a UNIX-based file system. Thereafter, when the shared secret is required for logical computation, the client device reconstructs the key using the file system attributes value and the other previous sources of entropy. The client device may use the key to decrypt the information and use the shared secret for its required purpose, e.g., in generating a one-time password for a login session.
Owner:CA TECH INC
Methods and systems for implementing a test automation framework for testing software applications on unix/linux based machines
This disclosure describes, generally, methods and systems for implementing a test automation framework. The method may include receiving test scenarios. Each of the test scenarios may include at least one test case. The method may further include spawning a process for each of the test scenarios. The processes may be executed in parallel on a Linux based operating system. The method may parse each of the test cases using a parser, execute the parsed test cases using an execution module, and generate test results for each of the test scenarios. Further, the method may display the test results on a Windows based graphical user interface (GUI).
Owner:ORACLE INT CORP
Method for across-platform monitoring enterprise application system performance
InactiveCN101436274ATimely notificationSimple installation and deploymentInstrumentsMulti platformData acquisition
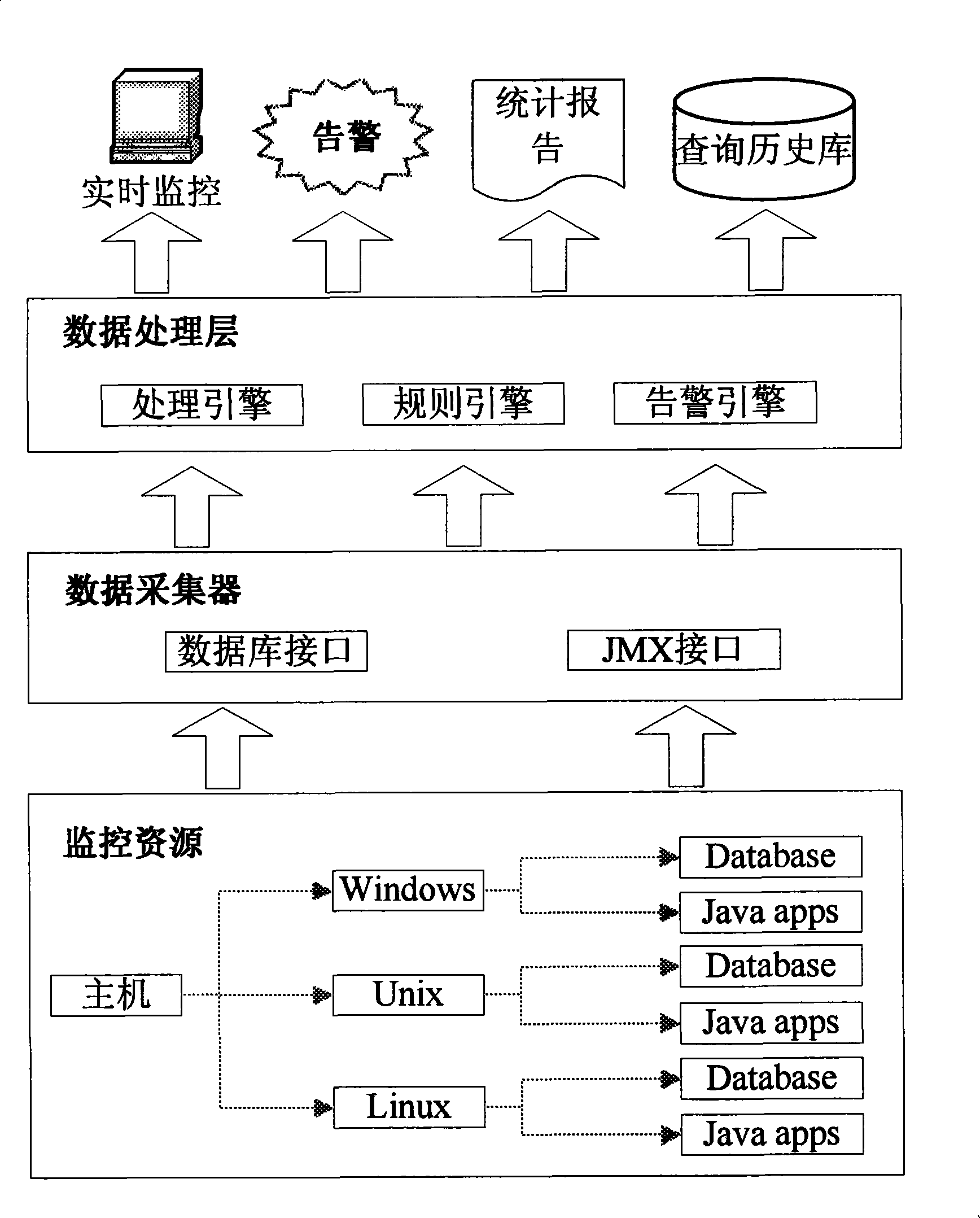
The invention provides a method for realizing the cross-platform performance monitoring of a J2EE architecture enterprise application system, which is a real-time monitoring method with a B / S structure for a J2EE architecture. The method divides the realization of performance monitoring to the application system into three layers: a data acquisition layer, a data processing layer, and a data exhibition layer; an enterprise can define key performance indices (KPI) of the enterprise according to the demand of IT operation and maintenance management of the enterprise; the realization method also internally defines a set of key performance indices which meet the demand of a plurality of enterprises at the same time; a data analysis engine is used to analyze acquired data through the acquisition to needed performance data of the key performance indices, and an analysis result is sent for alarm notification. Most enterprise-level application systems are deployed under the complex environment of various platforms, such as Unix, Windows and linux; and the development of different monitoring softwares aiming at different platforms is a complex and huge job. The data acquisition layer of the method adopts universal interface technology, and can realize the performance monitoring to multi-platform databases and application middlewares.
Owner:INSPUR SOFTWARE CO LTD
Patch management automation tool for unix, aparxml
InactiveUS20080163192A1Conserve costLow costSpecific program execution arrangementsMemory systemsEarly warning systemUnix
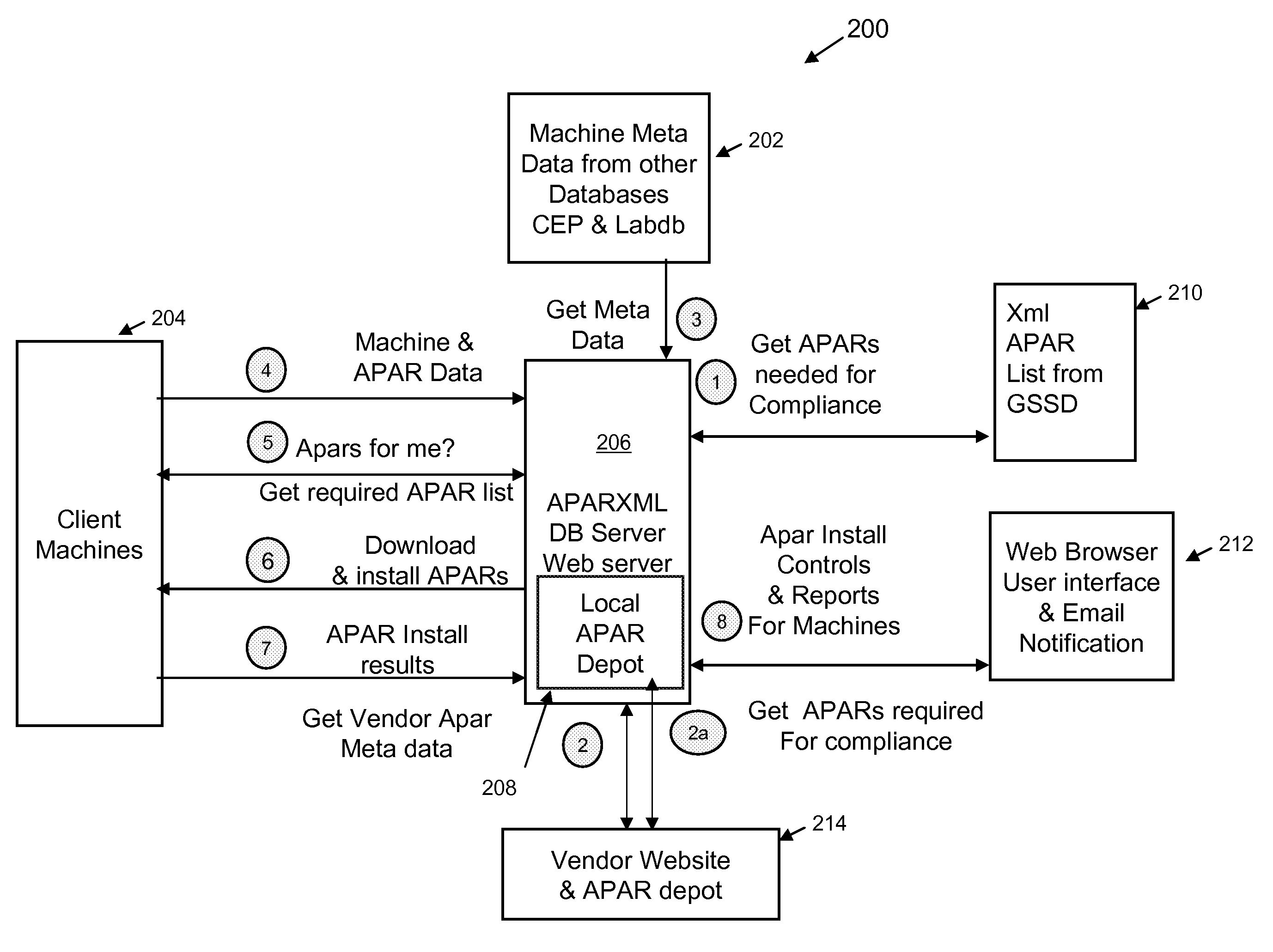
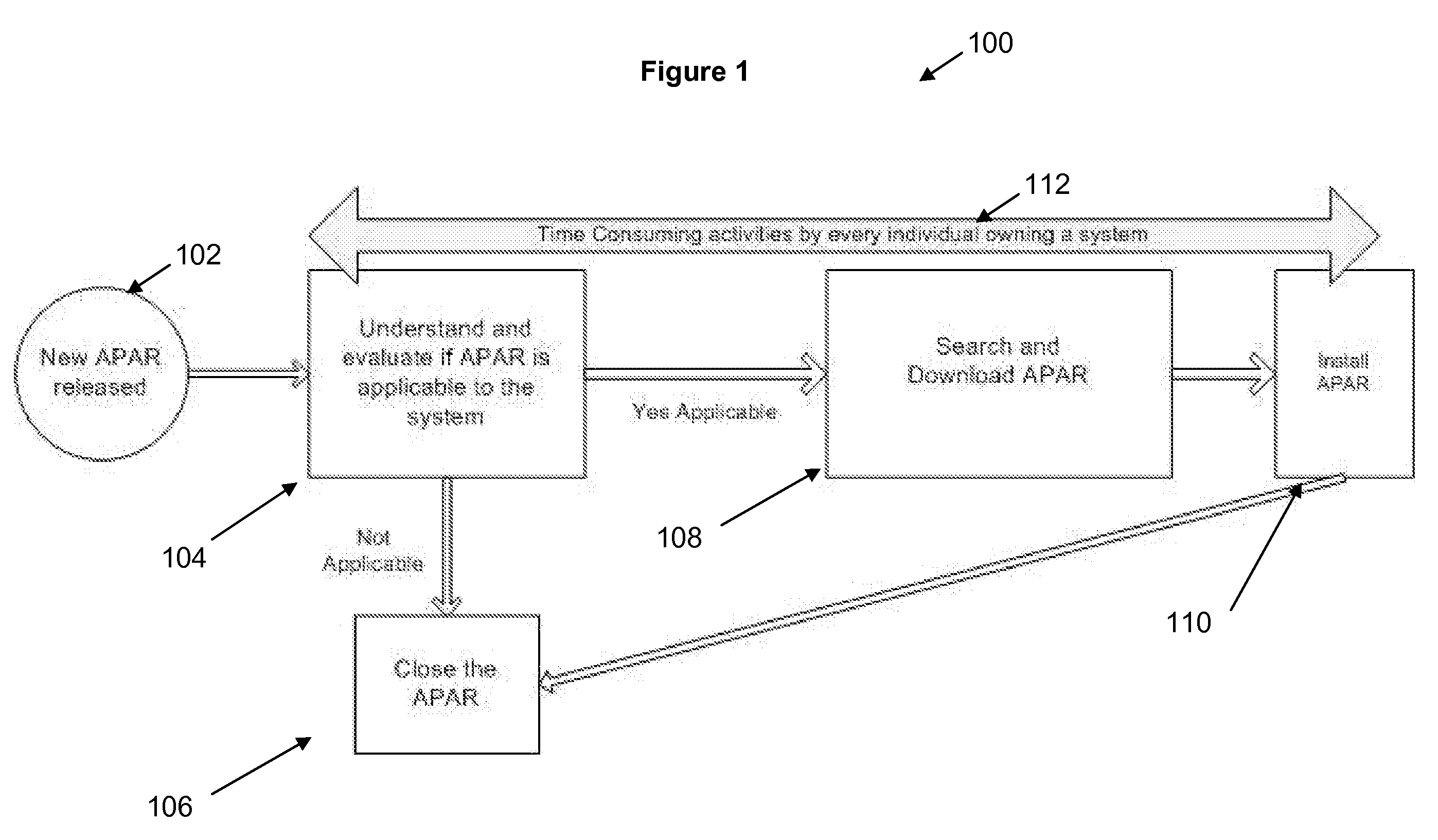
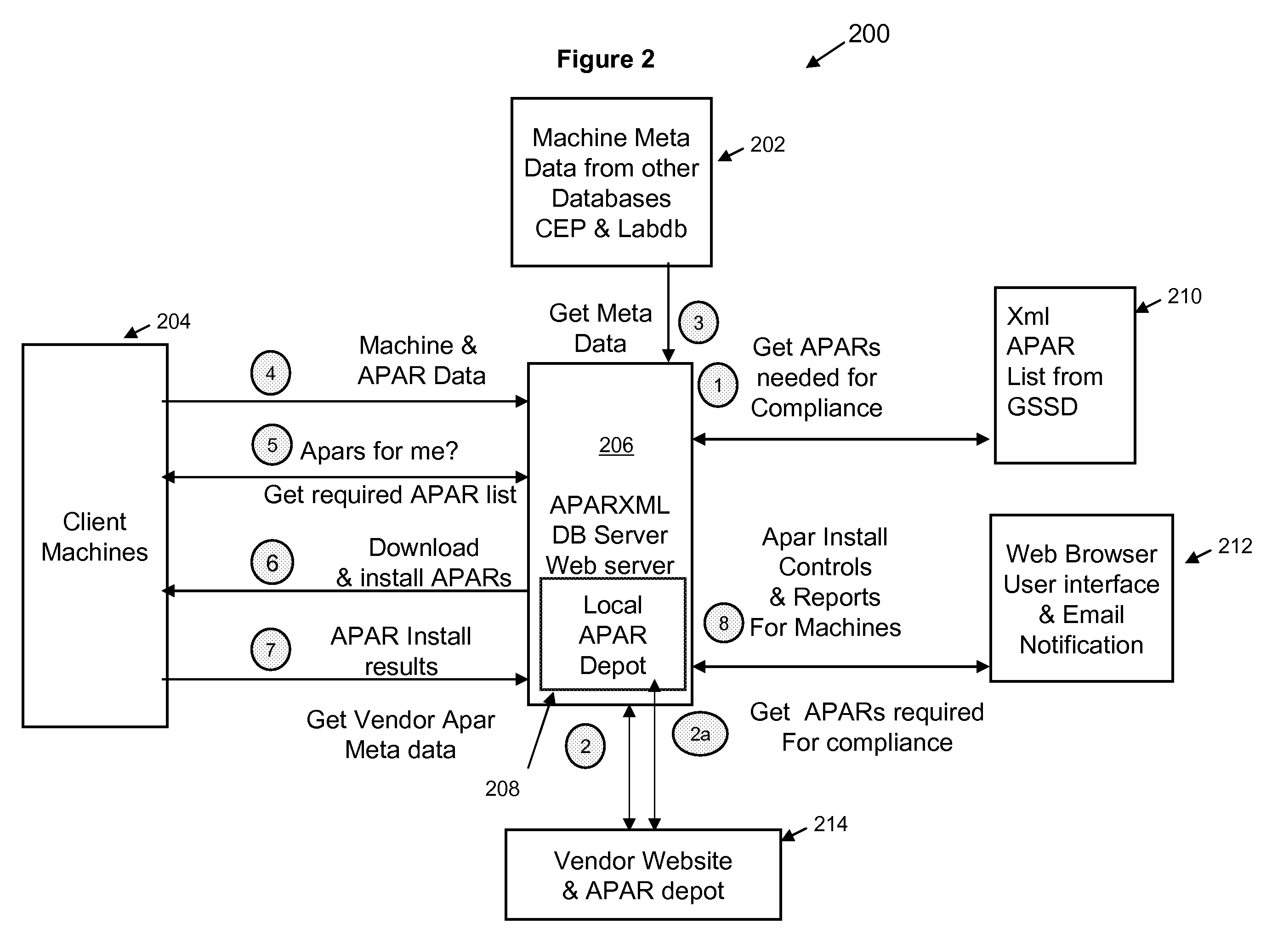
The present invention provides a common framework to determine if machines are patched and automatically applies patches as required. It provides an automated tool to assess patch levels and apply patches on several different UNIX machine types. Further, it provides a centralized, consistent method of providing patches to multiple roles within an organization while automatically managing large quantities of machines. It can manage multiple security standards, machine classifications, and patch security levels and be customized to interface with existing asset management tools. It evaluates the most suitable patch to satisfy the minimal patch requirements and is an early warning system that will tell a user when the user's machine will go out of compliance. The tool is composed of two parts: a server component and client component. The server collects data reported by client machines and stores it in a database; collects patch, machine and owner data from other databases, including internal databases and vendor web sites; downloads vendor patches to a depot area; and evaluates compliance and generates a list of patches that are missing, applied late, and patches that are satisfied. An overall compliance verdict is calculated for each machine. The server sends the client a list of patches to be installed as needed. The server receives installation status from the client, reports it onto the web, and sends the user email. The client gathers machine data and sends it to server; queries the server to see if patches are needed, and receives a patch list. The client downloads patches from APAR depot; and installs patches and reports status back to the server.
Owner:IBM CORP
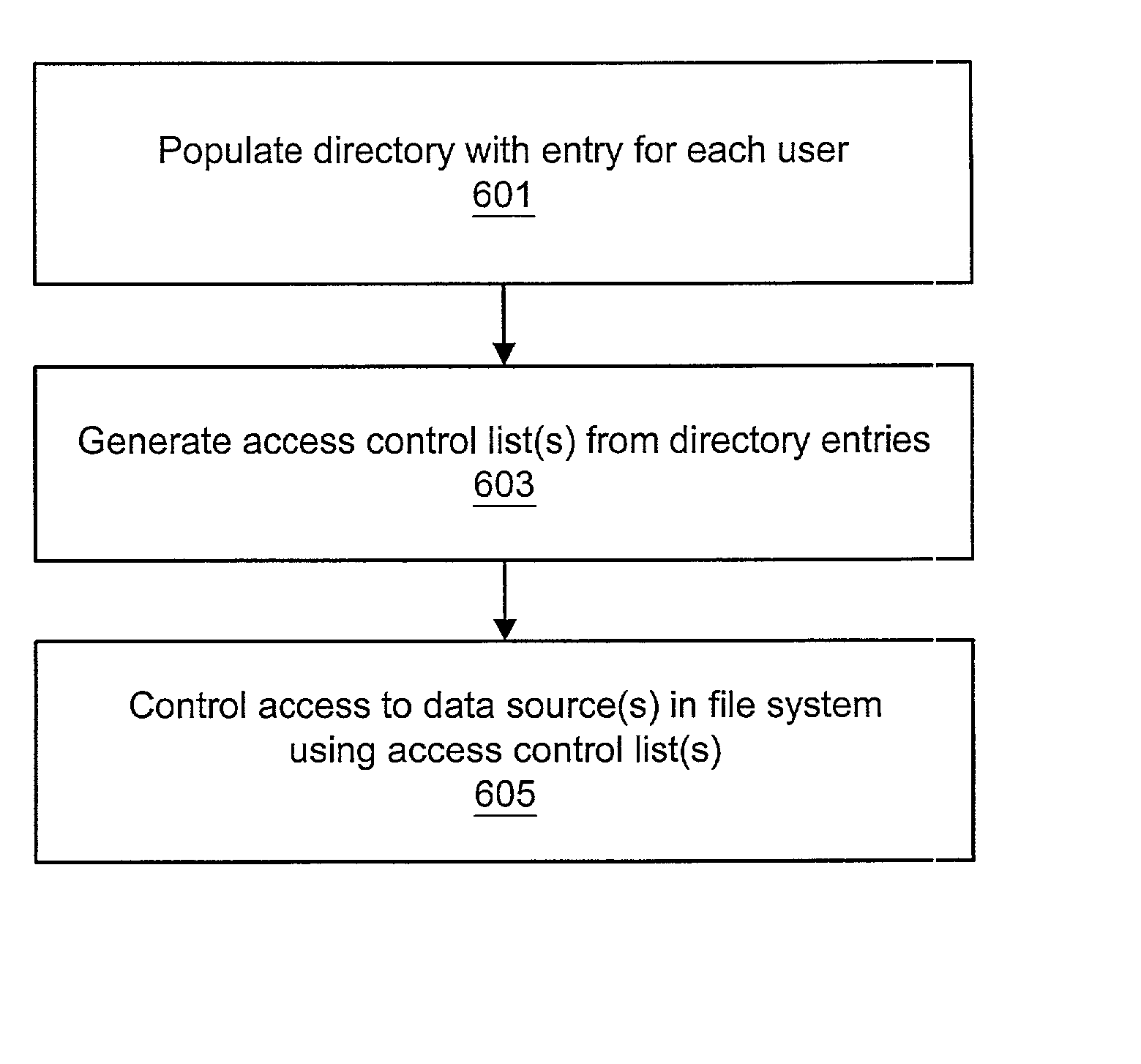
System and method for controlling UNIX group access using LDAP
InactiveUS20030041154A1Computer security arrangementsMultiple digital computer combinationsUnixOperational system
A system and method for controlling UNIX group access using an LDAP directory are disclosed. The system and method may be used to overcome a limitation on the size of groups that may be encountered in certain UNIX-based operating systems. A directory may be populated with entries for each of a plurality of users. Each entry in the directory may include information such as a user ID, user password, one or more group names, and optionally one or more hostnames. One or more access control lists may be generated from the directory entries. The operating system may check the access control list(s) to restrict access to the appropriate files or directories (i.e., data sources). For each data source which permits access by a particular group name, access may be granted to the data source to the users in the appropriate group access control list. Likewise, access may be denied to users who are not listed in the appropriate group access control list and who are not otherwise entitled to access (e.g., are not an owner of the data source). Access may include, for example, read, write, and / or execute access.
Owner:SUN MICROSYSTEMS INC
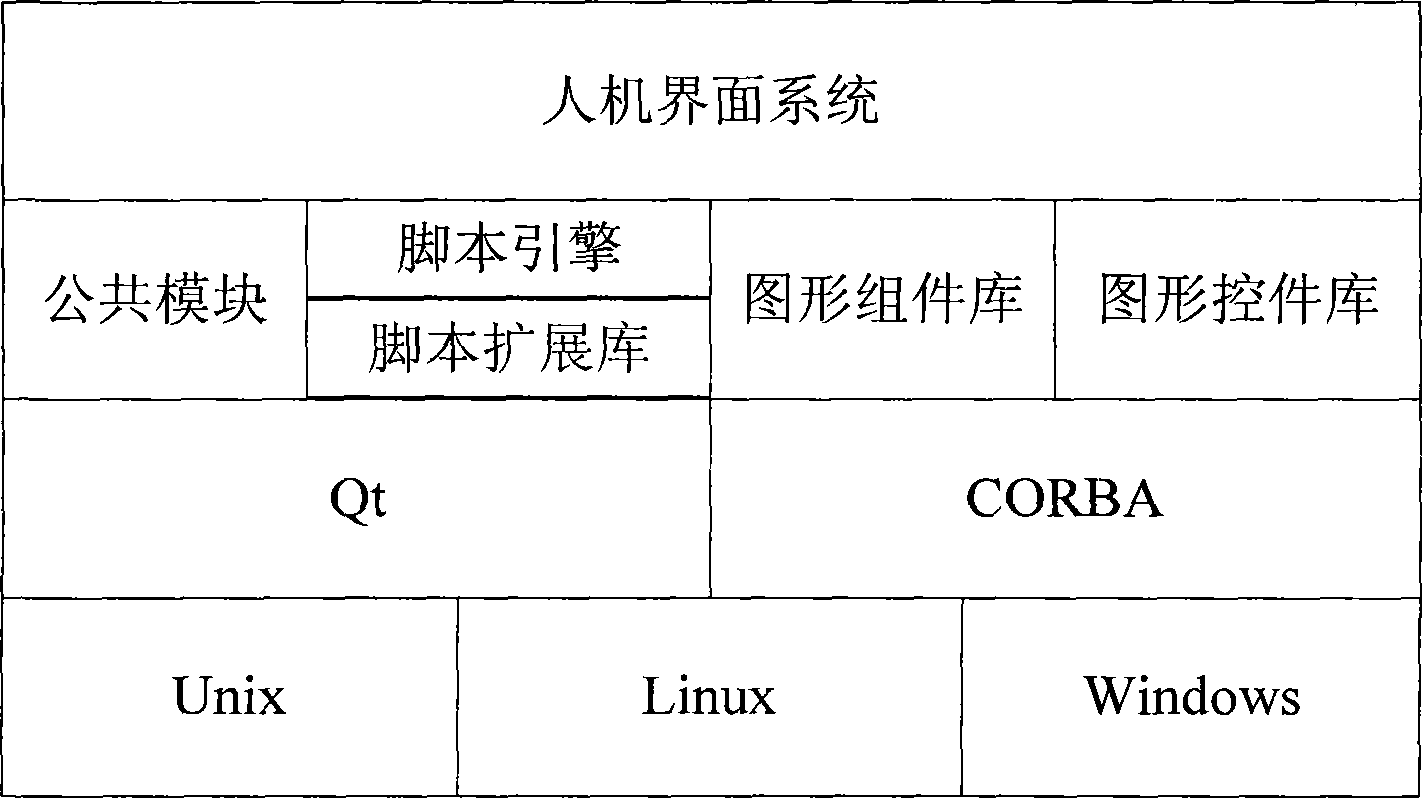
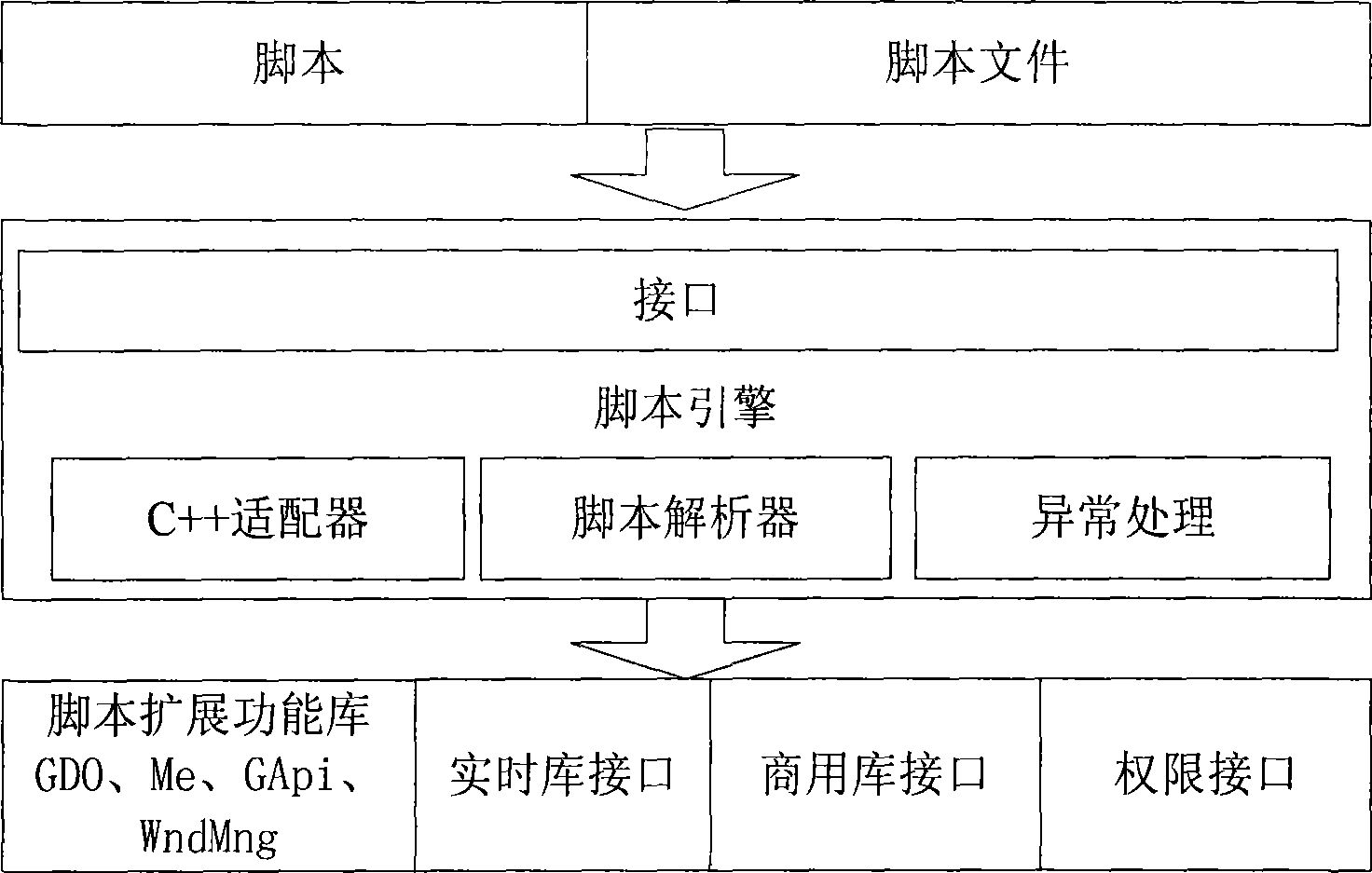
Synthesis monitoring cross-platform configuration human-machine interface system
InactiveCN101510151ATroubleshoot hardware platform issuesRealize resource sharingProgramme controlComputer controlGraphicsUnix
The invention discloses an integrated monitor cross platform configuration human-computer interface system, which comprises a server and a workstation, wherein the server and the workstation are internally provided with operating systems and a human-computer interface system framework; the human-computer interface system framework is characterized by being an MVC architecture and supporting the operating systems of Unix, Linux and Windows; the system also comprises a graphical component module encapsulated with a set of basal graphic objects in an inheritance way; a graphical control module encapsulated with a set of graphic interactive controls; and a script engine system which comprises a script engine module used for parsing the script, driving a script extended function library and dynamically executing the script and a script extension module used for accessing a real time database and a historical data base and judging authority. The integrated monitor cross platform configuration human-computer interface system realizes resource sharing and interconnection requirement, and solves the hardware platform problems of a hybrid platform and a heterogeneous platform of the integrated monitor system.
Owner:NARI TECH CO LTD
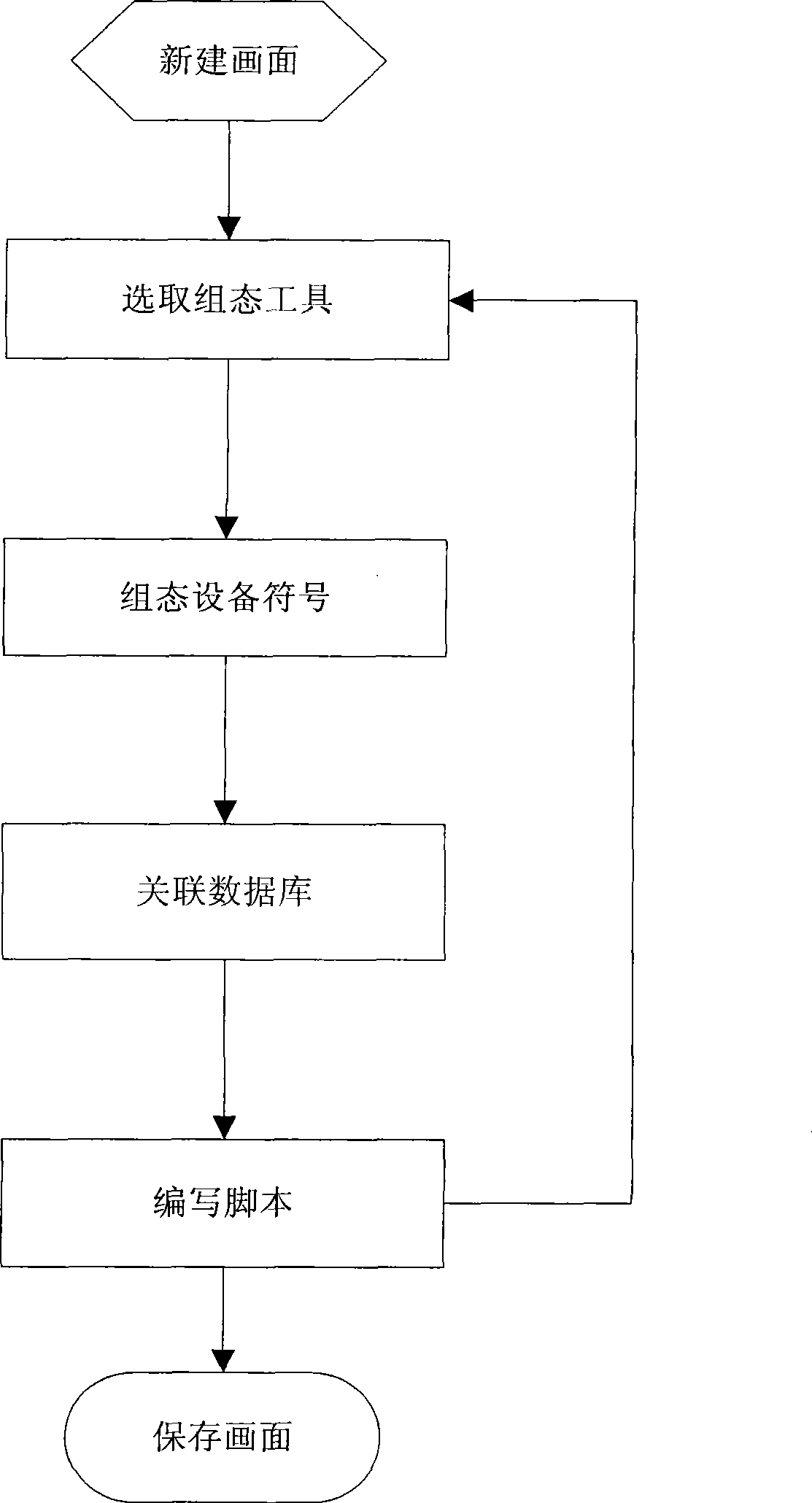
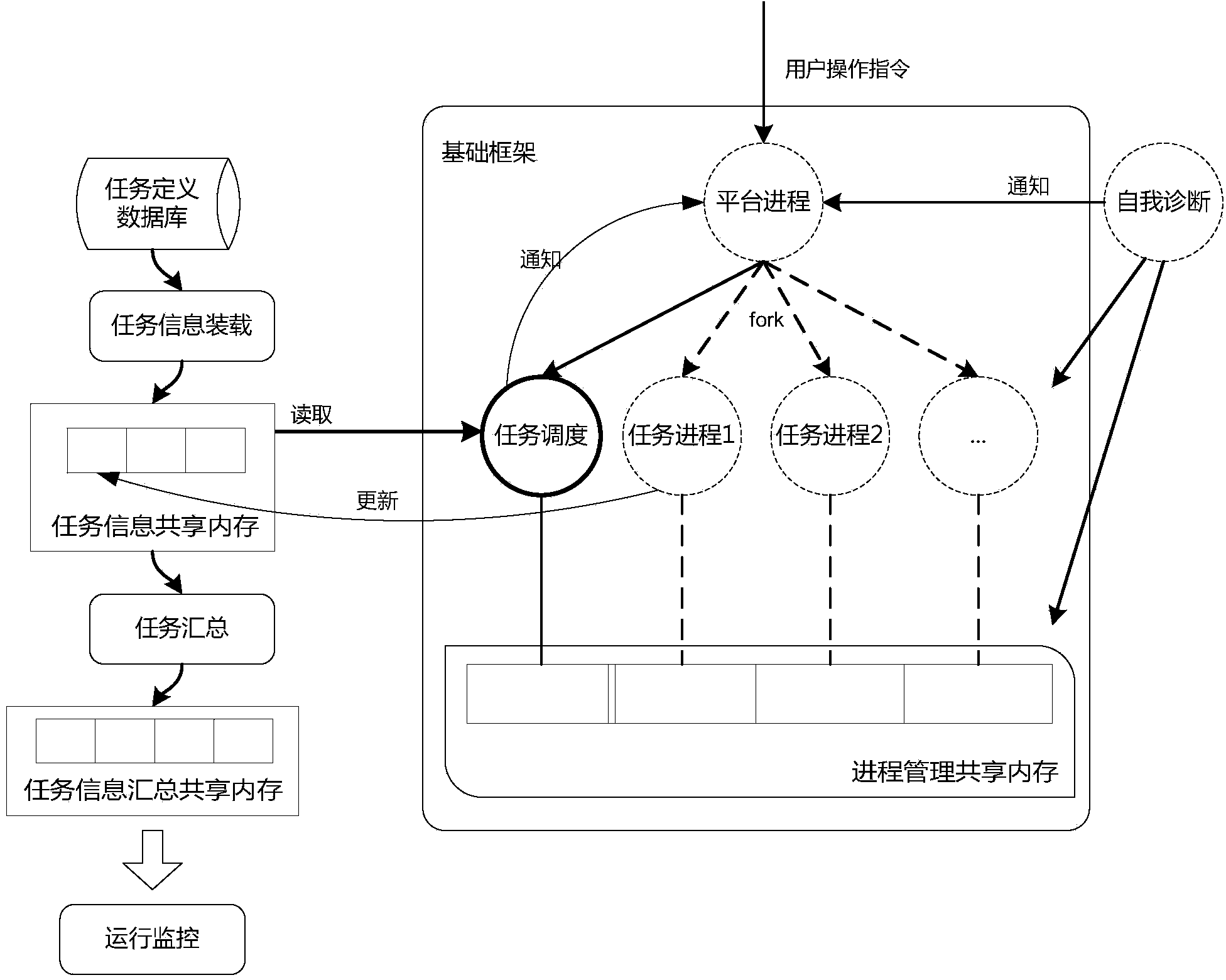
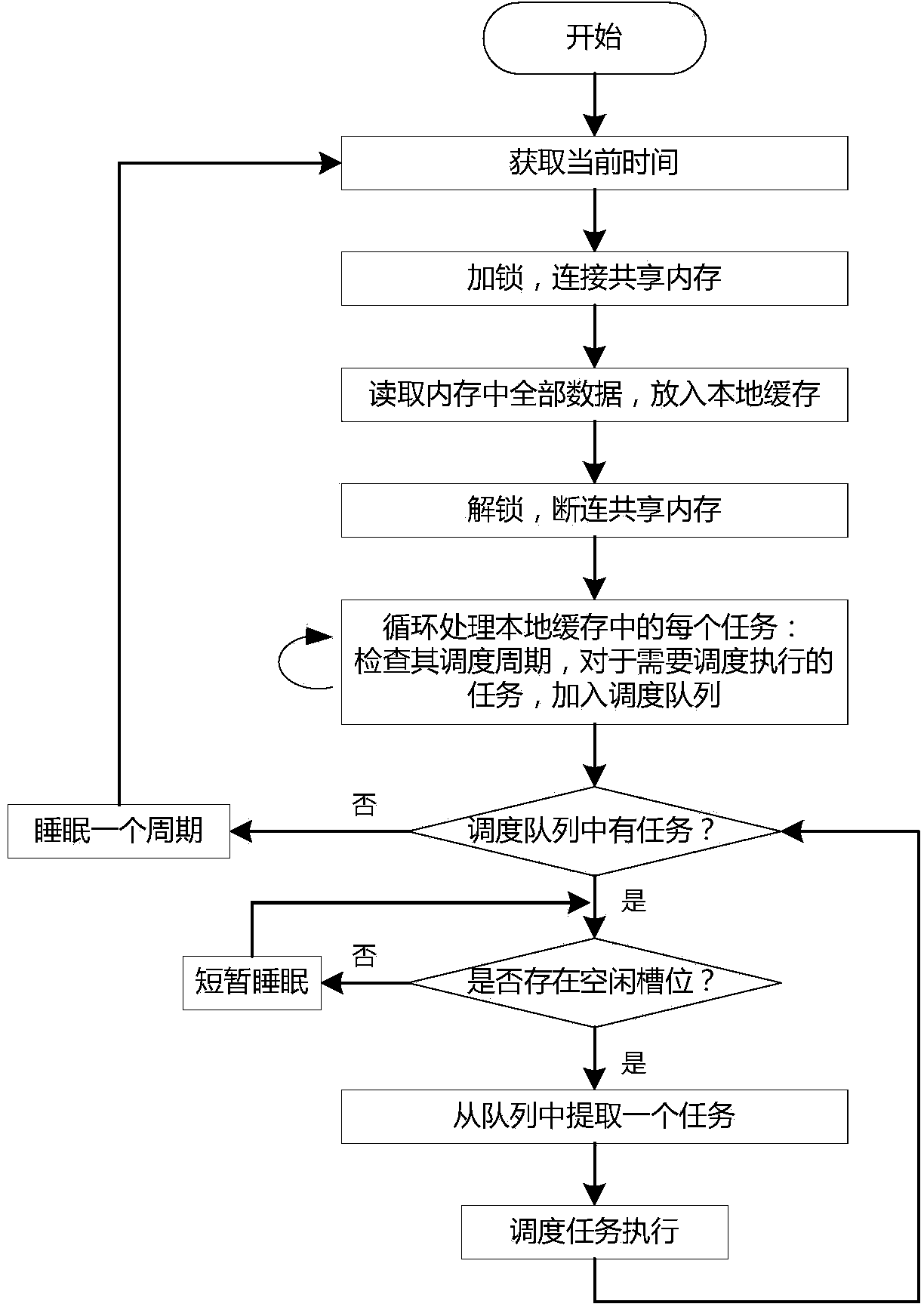
Optimization method and optimization system for task scheduling in large-scale virtualization environment
ActiveCN104331327ASimplify configuration managementReal-time visual monitoring of running statusProgram initiation/switchingInterprogram communicationVirtualizationUnix
The invention discloses an optimization method and an optimization system for task scheduling in a large-scale virtualization environment. The optimization method, as a friendly and efficient operation interface for task scheduling, includes task centralized management, distributed execution, smooth control for concurrency, execution time limit control, priority definition, operation monitoring, self-diagnosis, etc. The method is realized in accordance with crond program in a UNIX system, which enhances fine control function and supports cooperation between hosts to realize distributed execution and centralized monitoring of tasks. Task definitions managed by multiple hosts are under centralized management through a database to simplify configuration operation, so as to relieve burden of the database; the tasks are guided into a shared memory after being defined, and the database is not visited in subsequent scheduling. A scheduling platform has self-diagnosis ability, to guarantee sustained and steady scheduling work.
Owner:MASSCLOUDS
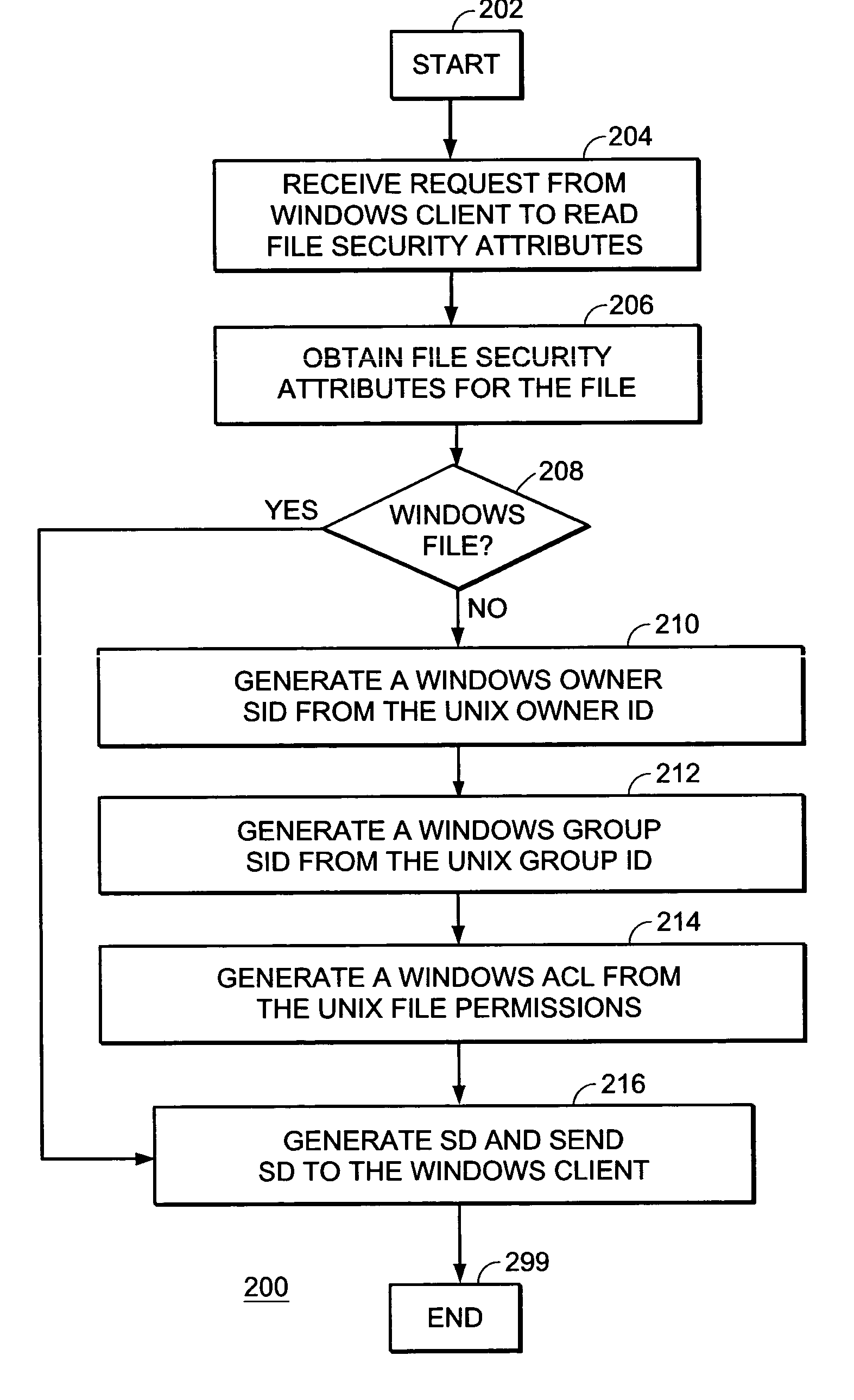
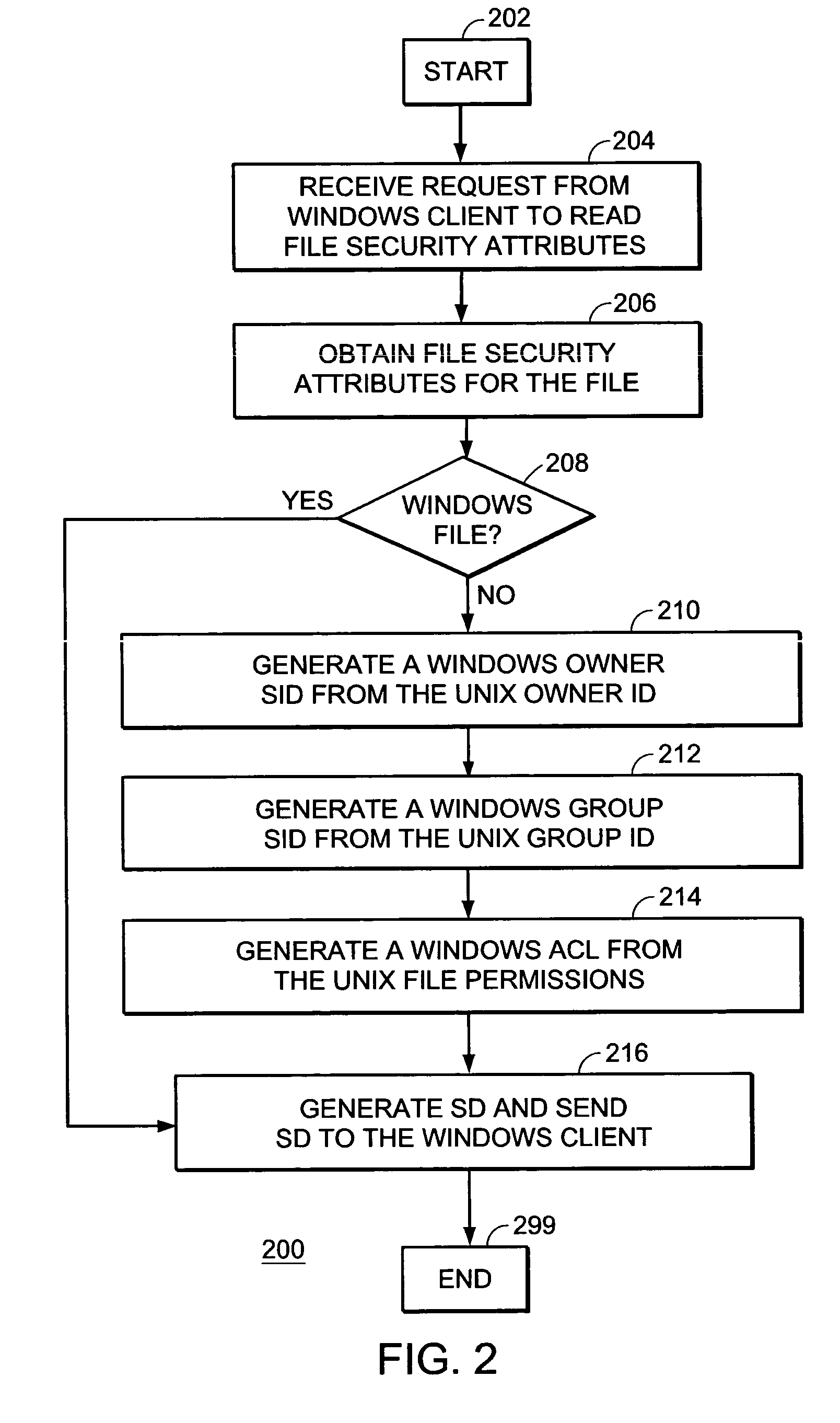
System, device, and method for managing file security attributes in a computer file storage system
A system, device, and method for managing file security attributes in a computer file storage system generates a set of Windows file security attributes from a set of UNIX file security attributes. The set of Windows file security attributes includes a UNIX-specific SID for a UNIX name that could not be translated into a Windows name. The set of Windows file security attributes also includes a set of Windows file permissions derived from a set of UNIX file permissions.
Owner:HITACHI VANTARA LLC
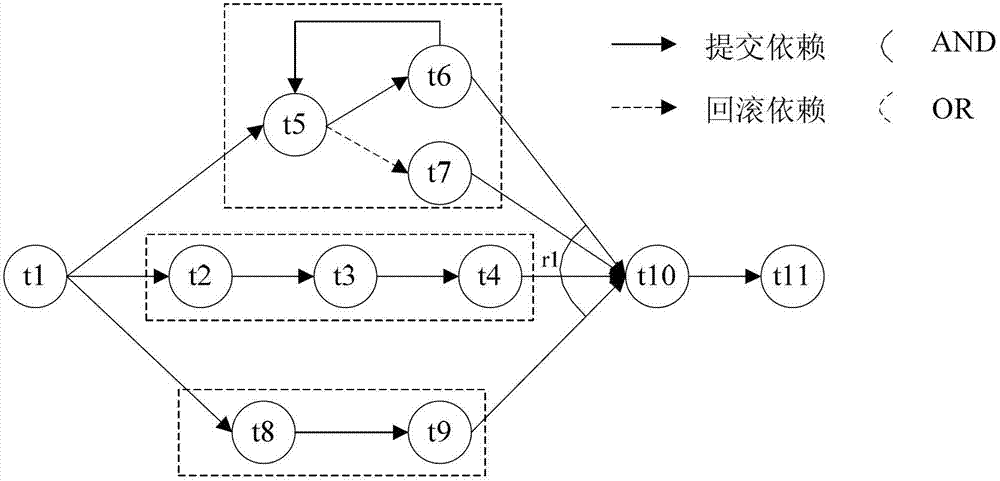
Multithreading-based parallel executing method for long transaction
A long transaction is a transaction which contains multiple atomic transactions and is longer in executing time. The serial execution for the atomic transactions not only costs longer executing time for the long transaction but also occupies more system resources and causes the reduction of the running efficiency of the system. The invention discloses a multithreading-based parallel executing method for a long transaction, which comprises the following steps: (1) formally describing the long transaction as an expanding directed graph; (2) cutting LT (Language Transaction) into a plurality of sub-transactions LT capable of being executed in a parallel form and giving a cutting algorithm; (3) deriving a plurality of sub-threads on the basis of POSIX (Portable Operating System Interface of Unix) threading library (or Windows threading API (Application Program Interface)), so as to execute the long transaction in a parallel embedding mode; and (4) running paralleled codes on a multi-core processor (or a multi-CPU (Central Processing Unit) processor). According to the multithreading-based parallel executing method for the long transaction, the executing time for the long transaction is obviously shortened, the executing efficiency for the long transaction is increased, and the method can be applied to the fields, such as SOA (Service Oriented Architecture), service combination, transaction treatment, and the like.
Owner:杭州久碳科技有限公司
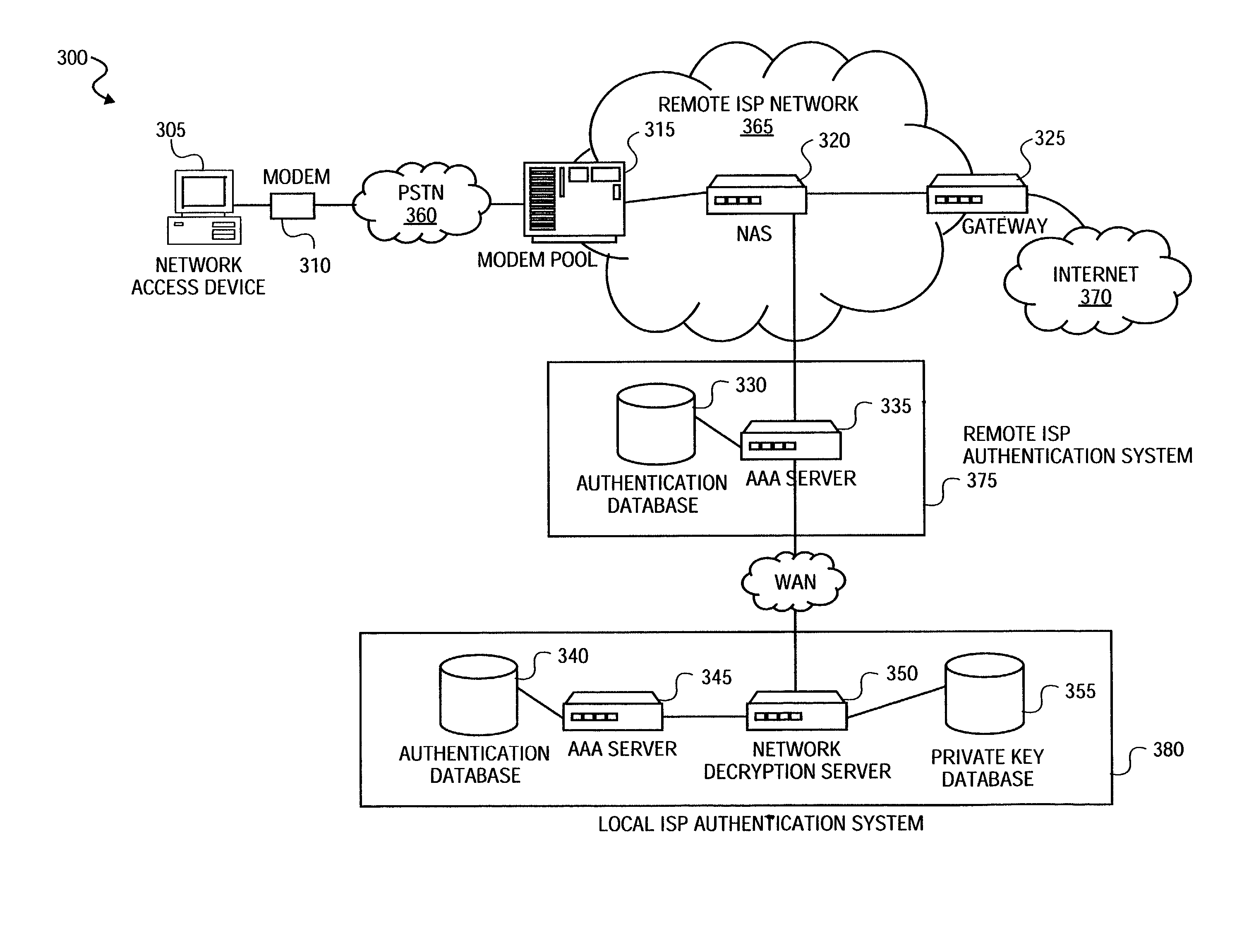
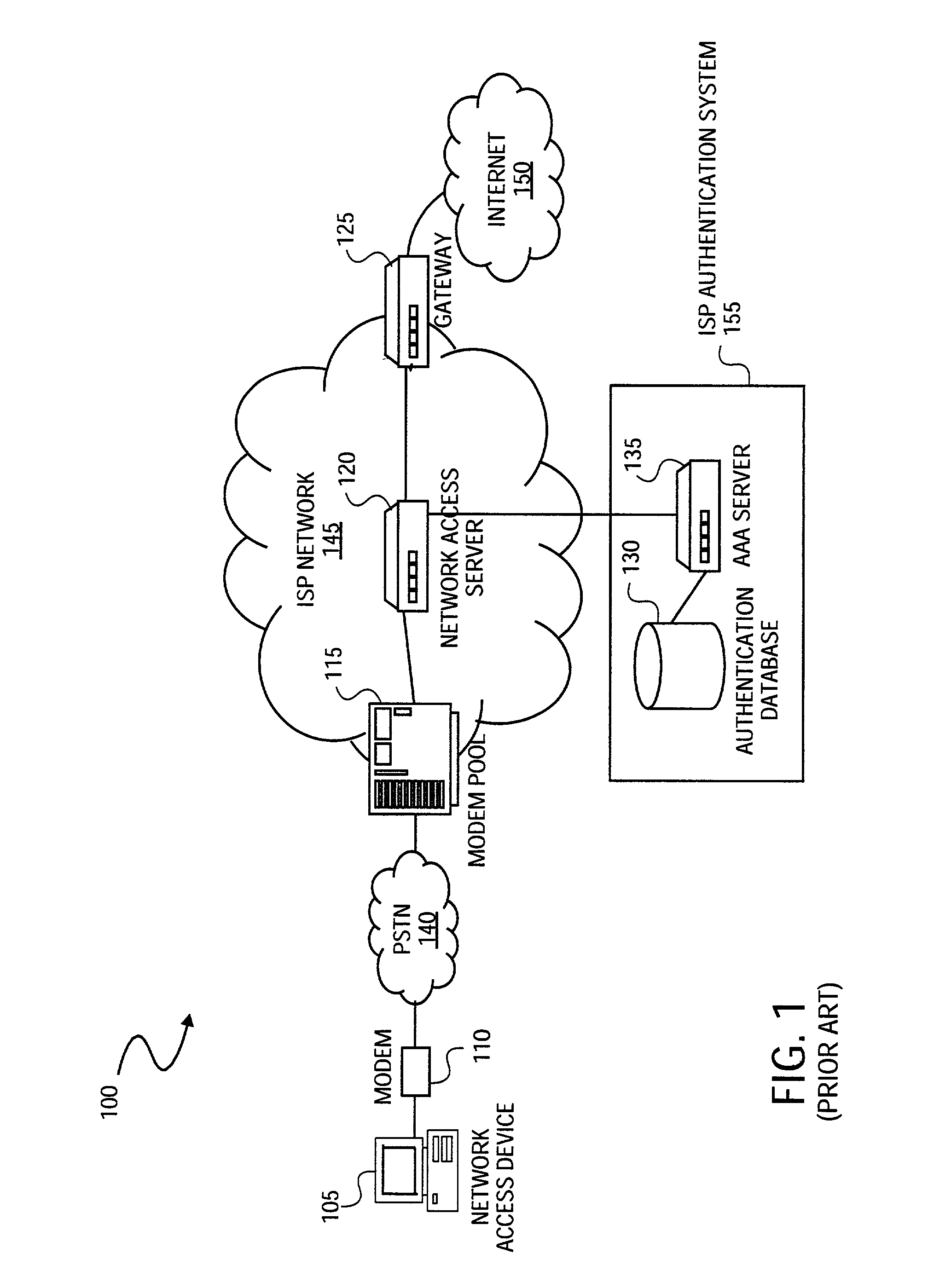
Method and system for securely authenticating network access credentials for users
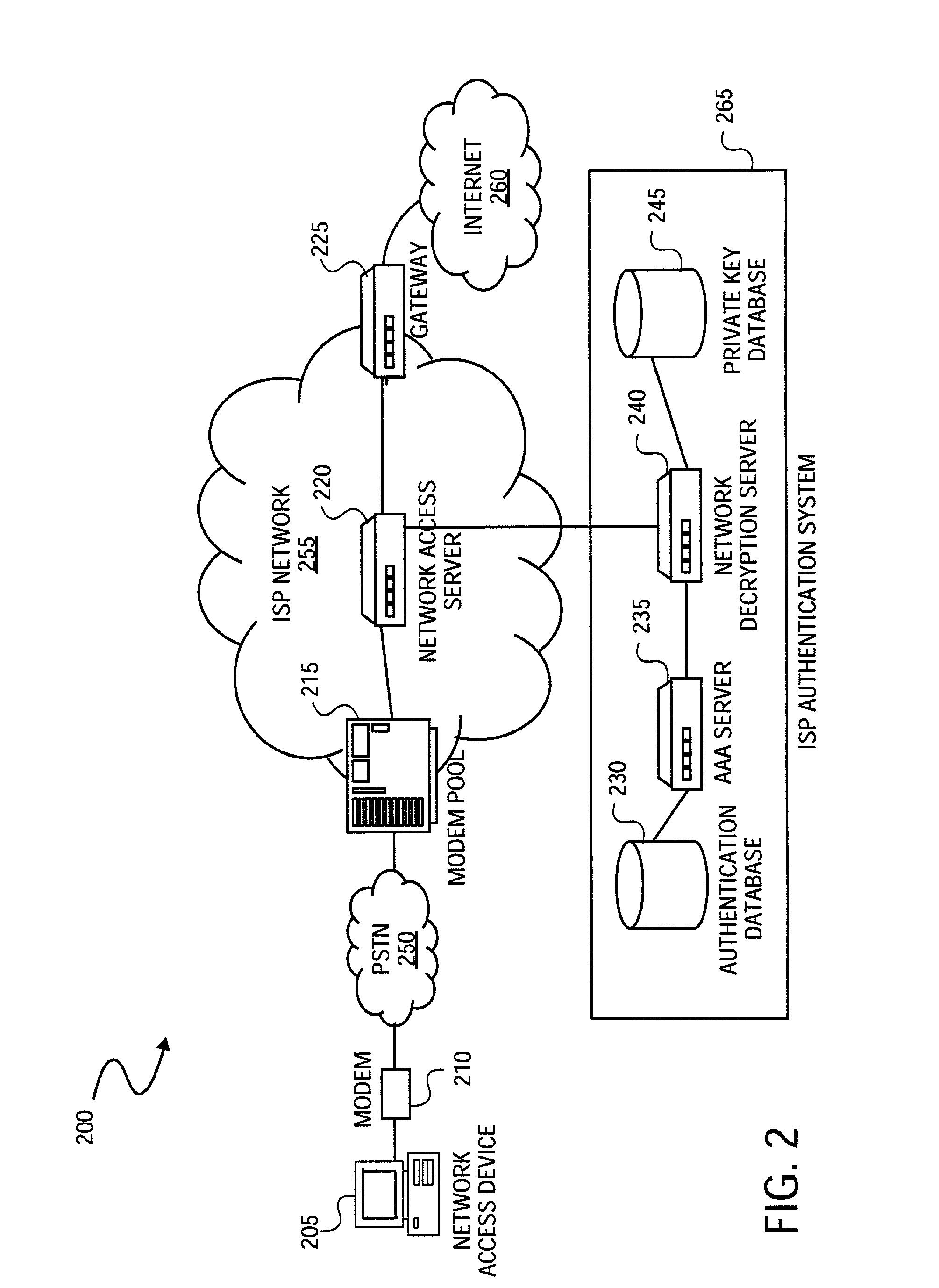
InactiveUS7921290B2Digital data processing detailsUser identity/authority verificationHypertext Transfer Protocol over Secure Socket LayerDirectory Access Protocol
A method is provided to securely authenticate user credentials. The method includes encrypting a user credential with a public key at an access device wherein the public key is part of a public / private key pair suitable for use with an encryption algorithm. The encrypted network user credential is transmitted from the access device to a decryption server where it is decrypted with a private key, the private key being part of the public / private key pair suitable for use with the encryption algorithm. The decrypted user credential is then transmitted from the decryption server to an authentication server for verification. The decryption server typically forms part of a multi-party service access environment including a plurality of access providers, the method including decrypting the user credential of a user proximate an access provider associated with the user credential. The method can be used in legacy protocols such as Point-to-Point protocol (PPP), Password Authentication Protocol (PAP), Challenge-Handshake Authentication Protocol (CHAP), Remote Authentication Dial In User Service (RADIUS) protocol, Terminal Access Controller Access Control System (TACACS) protocol, Lightweight Directory Access Protocol (LDAP), NT Domain authentication protocol, Unix password authentication protocol, HyperText Transfer Protocol (HTTP), HyperText Transfer Protocol over Secure sockets layer (HTTPS), Extended Authentication Protocol (EAP), Transport Layer Security (TLS) protocol, Token Ring protocol and / or Secure Remote Password protocol (SRP).
Owner:CHANNEL IP BV
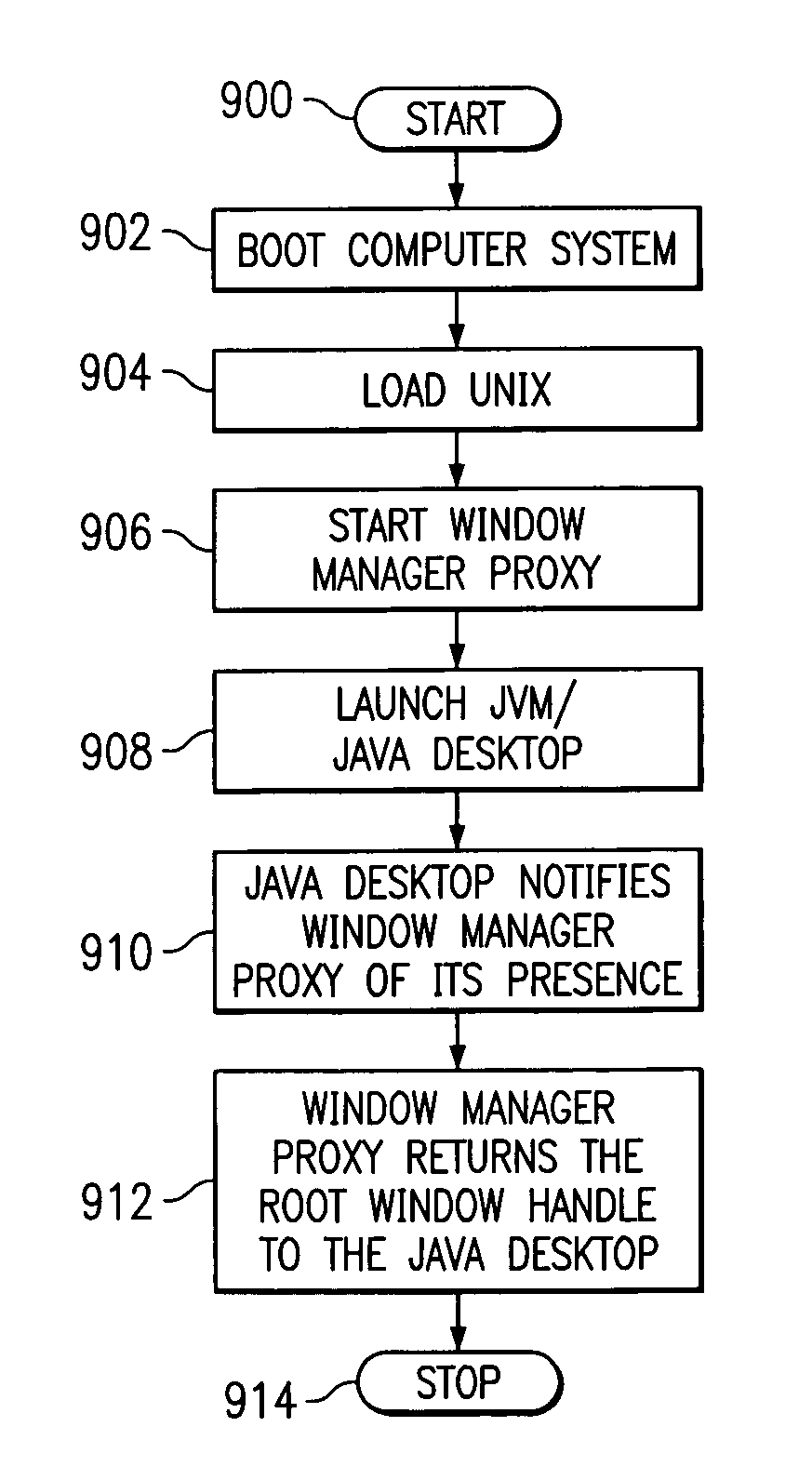
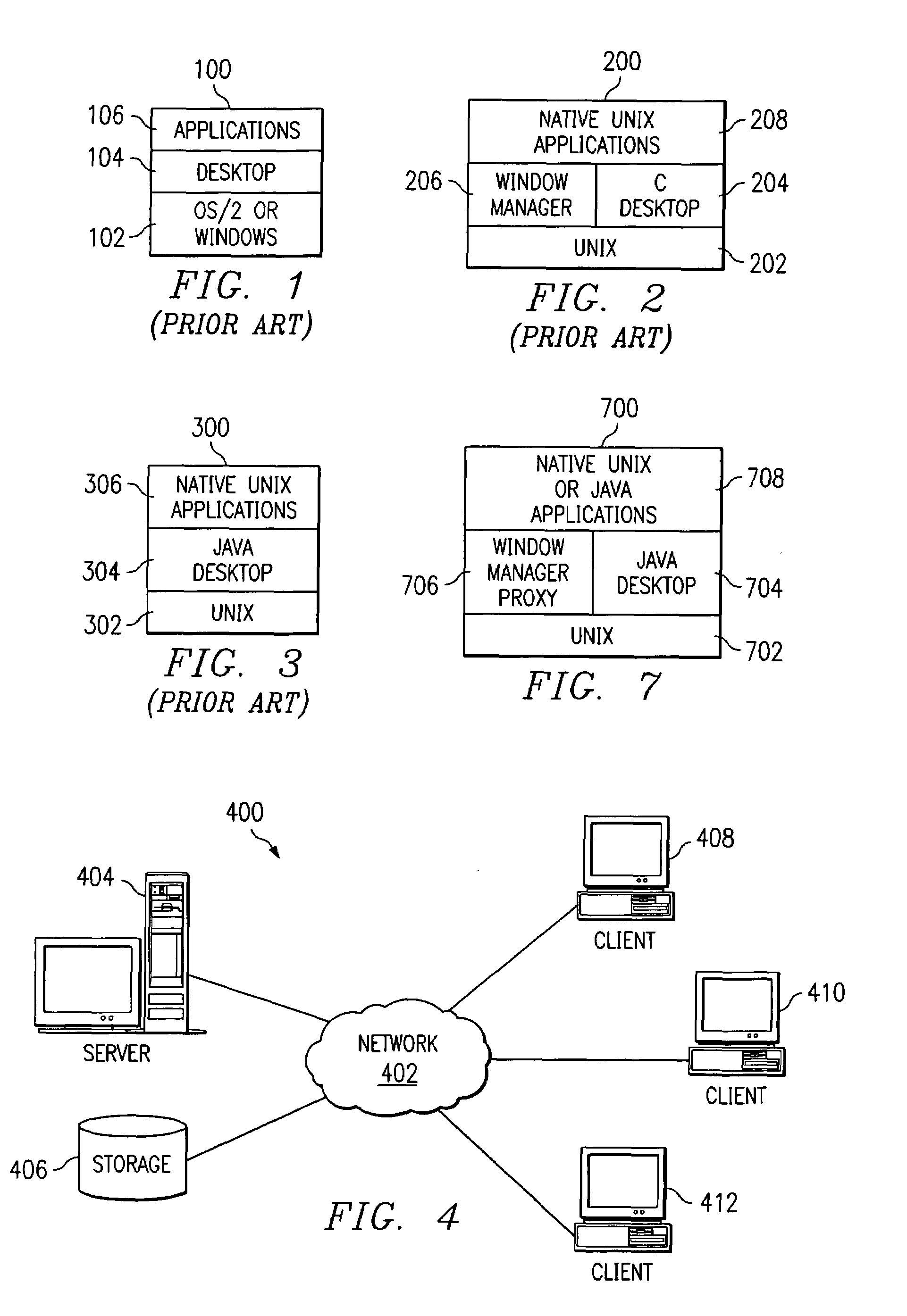
Method, system, and product for a java-based desktop to provide window manager services on UNIX
A window manager proxy method, system, and product are described allowing a Java based desktop to provide window manager services on UNIX. A computer system executes a UNIX-based operating system and a desktop implemented in Java. The computer system does not include a separate window manager. Java applications are presented by the computer system utilizing a graphical user interface. Native UNIX applications are also presented by the computer system utilizing the same graphical user interface. Native UNIX applications interact with the window manager proxy in the same manner in which they would interact with a traditional window manager. The window manager proxy forwards frame window activity related to the desktop to the Java desktop, and is the native interface from the Java desktop to the native platform for frame window activities. Native UNIX applications, Java applications, and the Java desktop are thus rendered and managed in a consistent manner providing the end user with the look and feel as configured within the Java desktop.
Owner:TWITTER INC
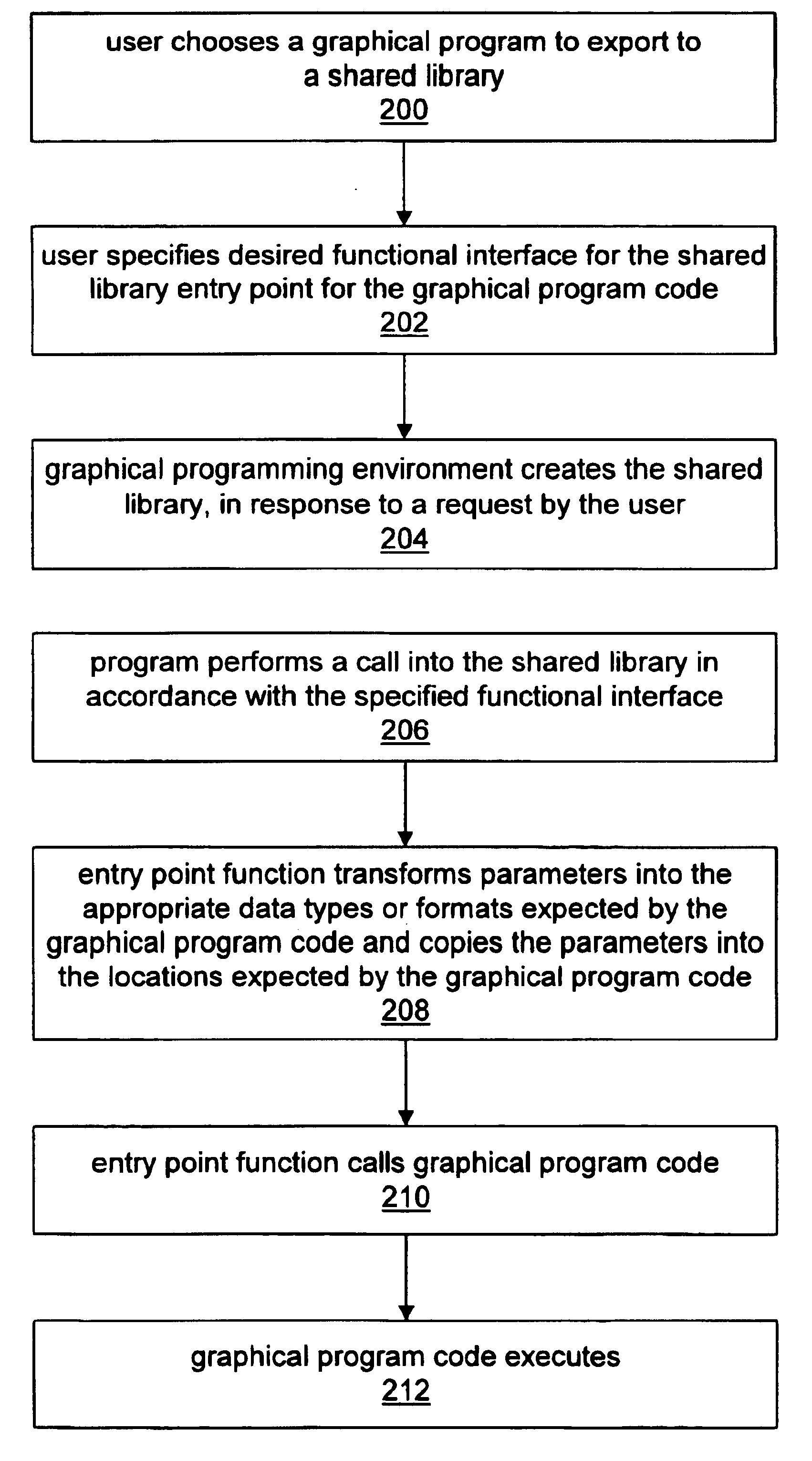
System and method for exporting a graphical program to a shared library
System and method for enabling a program to call into graphical program code via a shared library. A graphical programming system may export a graphical program to a shared library, such as a Windows Dynamic Link Library (DLL), Unix Shared Library, etc. A program, e.g. a text-based program, may then use the shared library to call into the graphical program. Graphical programs or subprograms may have associated inputs or outputs of various data types. When creating a shared library, a functional interface specifying parameterized versions of these inputs and outputs may be specified, either automatically or interactively. A program may then utilize this functional interface to construct an appropriate call into the shared library. A user interface enabling users to specify the mapping of graphical program inputs and outputs onto parameters of the functional interface is described. Multiple graphical programs or subprograms may be exported to a shared library. The shared library may include an entry point function associated with each graphical program or subprogram. When a program calls into the entry point associated with a particular graphical program, the entry point function may manipulate or copy the parameters passed by the calling program into a representation expected by the graphical program.
Owner:NATIONAL INSTRUMENTS
Multi-protocol sharable virtual storage objects
ActiveUS7953819B2Digital data processing detailsMultiple digital computer combinationsUnixFile replication
Owner:EMC IP HLDG CO LLC
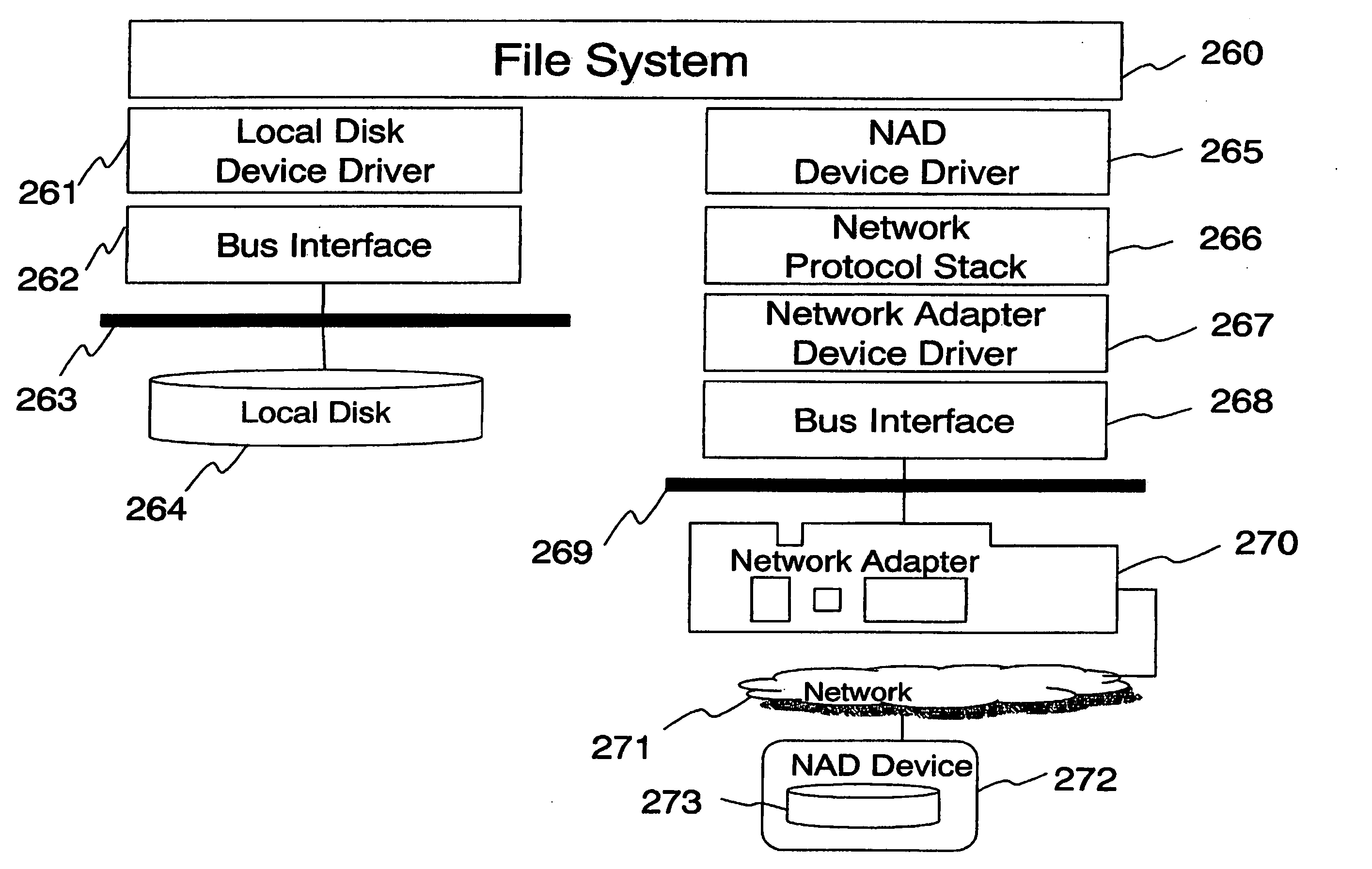
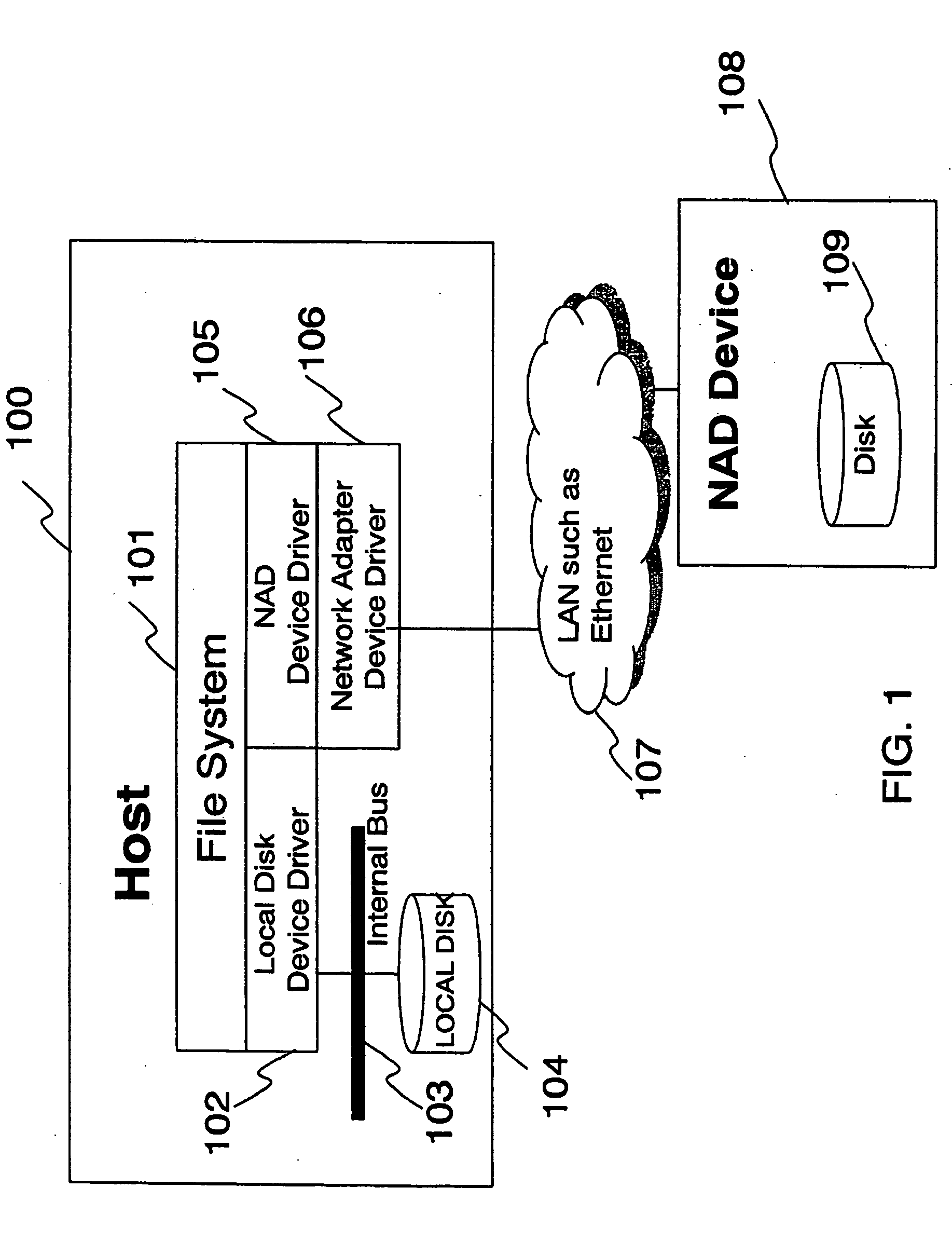
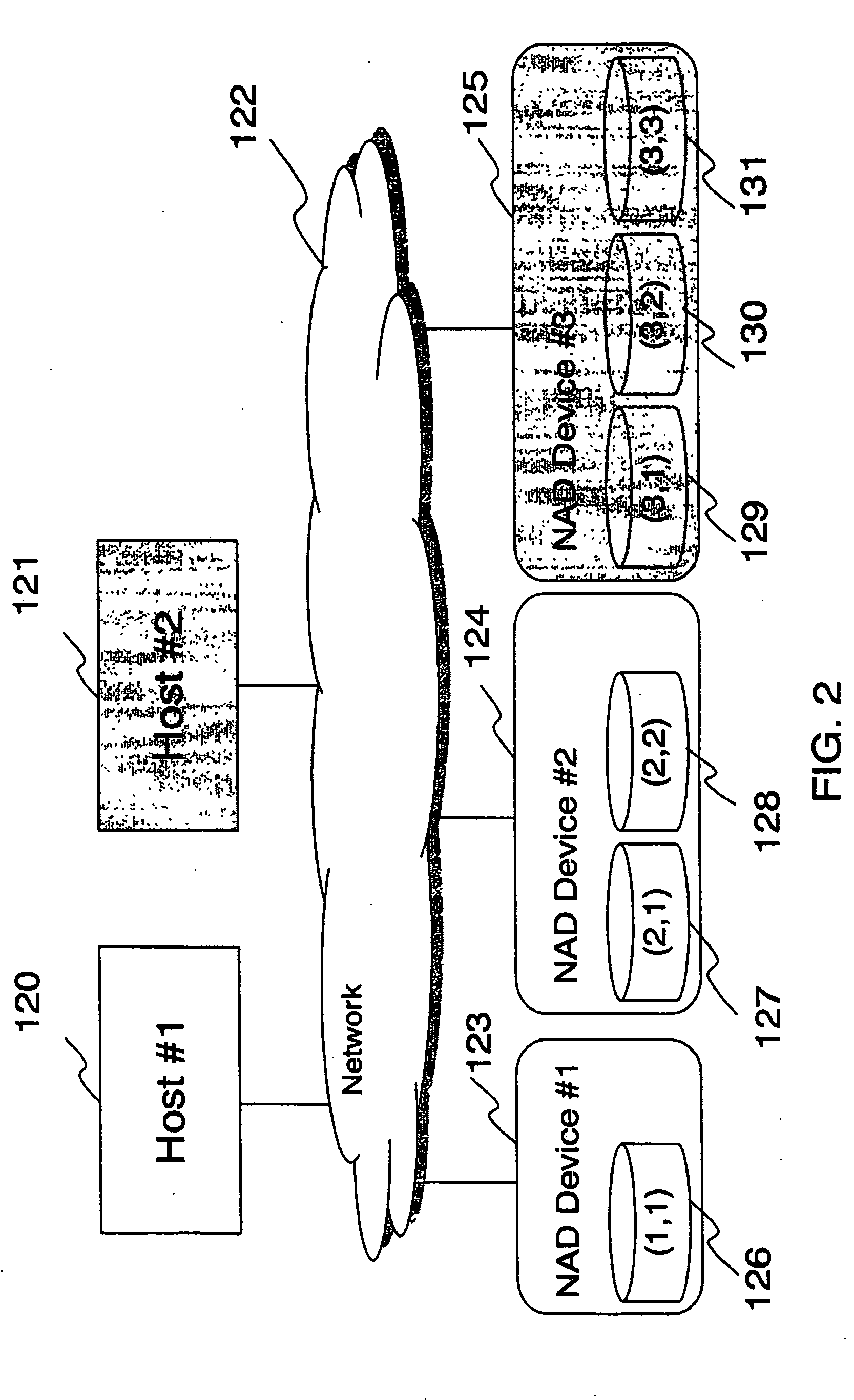
Disk system adapted to be directly attached
ActiveUS20060010287A1Conveniently connected to serverSimple processInput/output to record carriersMultiple digital computer combinationsUnixOperational system
A network-attached disk (NAD) system is disklosed that includes an NAD device for receiving a disk access command from a host through a network, and a device driver at the host for controlling the NAD device through the network, where the device driver creates a virtual host bus adapter so that the host recognizes the NAD device as if it is a local device to the host. The host may run the UNIX or Windows family of operating systems. The NAD device includes a disk for storing data, a disk controller for controlling the disk, and a network adapter for receiving a disk access command from the host through a network port.
Owner:SYNKLOUD TECH LLC
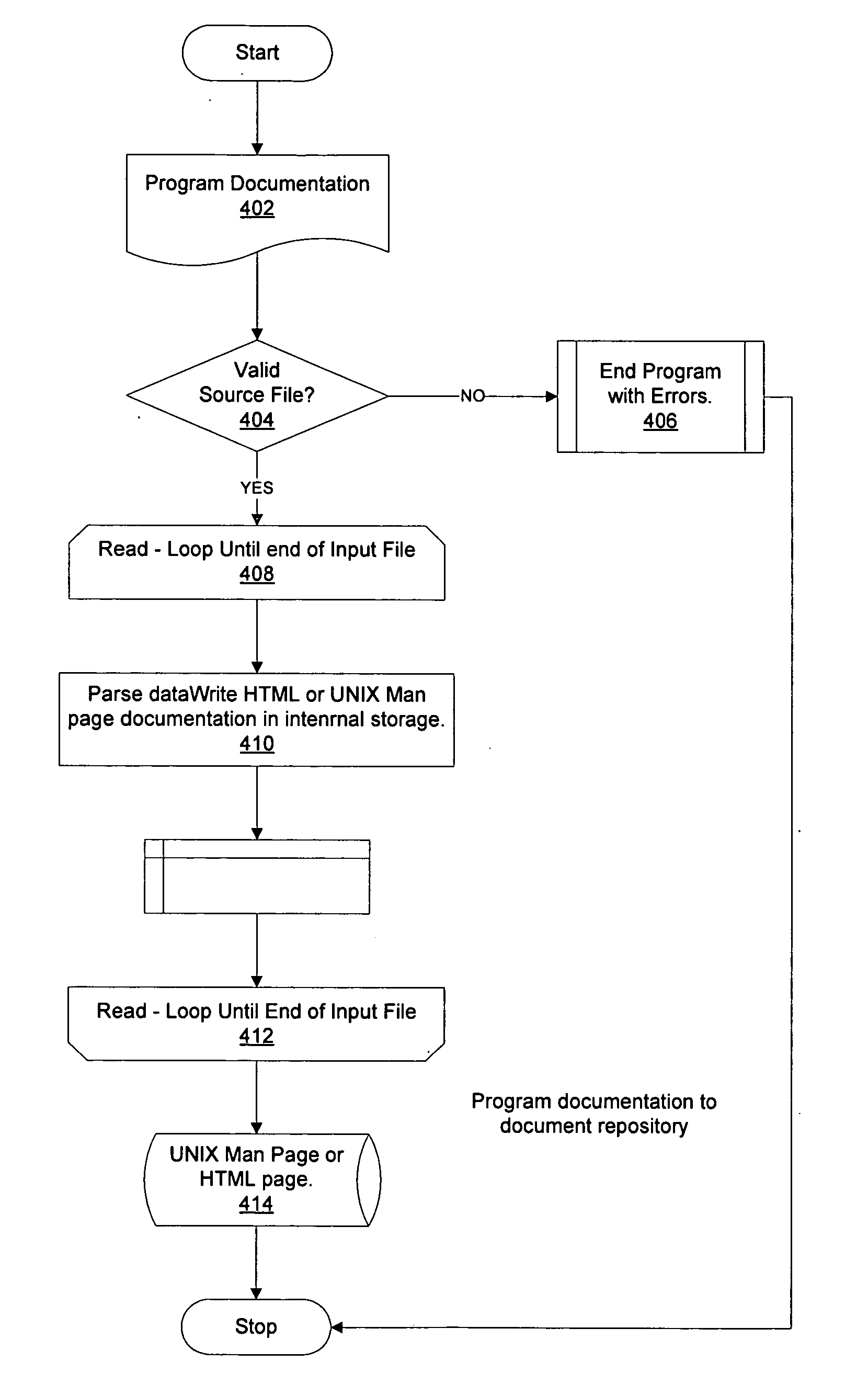
Automated source code software programmer's manual generator
InactiveUS20050060688A1Program documentationSpecific program execution arrangementsUnixSource code file
A method, system, and computer program product for generating a software documentation file from a software source code file is provided. In one embodiment, the source code file for the software is read by the automatic program documentation generation tool. The tool extracts software documentation from the source code file, by for example, locating documentation begin and end indicia within the source code and extracting the data contained within the indicia. The documentation has been previously written into the source code by a software developer, programmer, or engineer. The tool then creates a software documentation file, such as, for example, a UNIX Man Page or an HTML page, from the extracted software documentation extracted from the source code. The software documentation file is typically stored in a central repository.
Owner:ELECTRONICS DATA SYST CORP
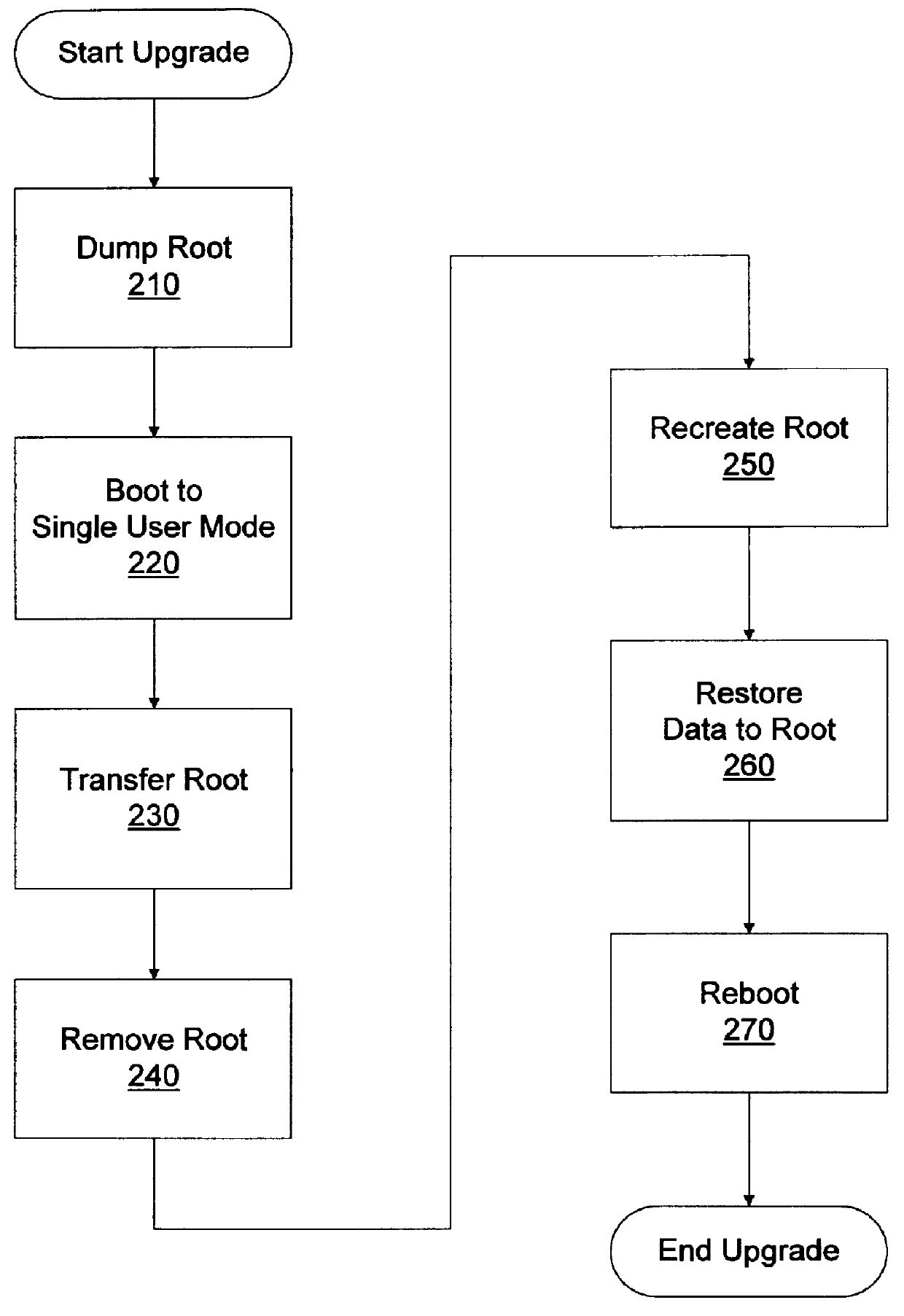
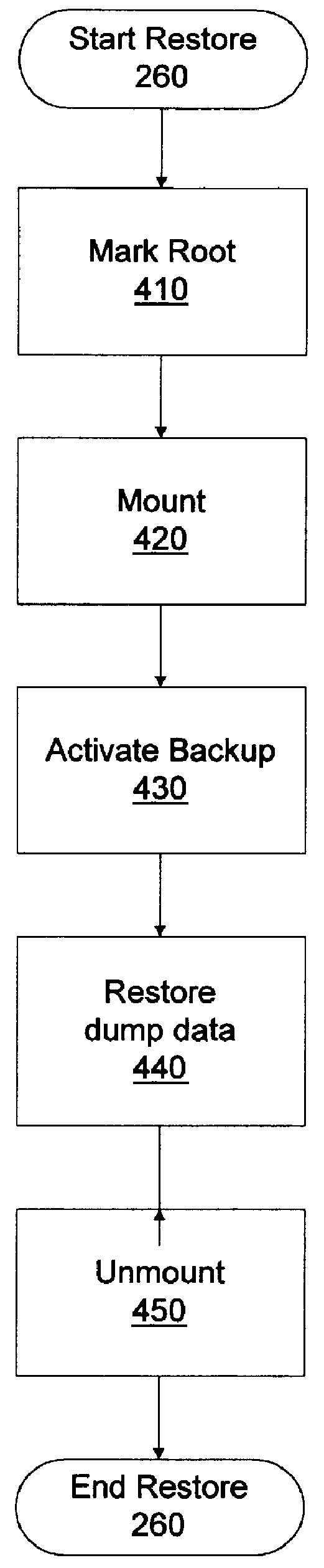
Root size decrease on a UNIX based computer system
InactiveUS6119212AMemory adressing/allocation/relocationDigital computer detailsUnixOperational system
A method for decreasing the size of a root partition on a computer system operating under control of a UNIX type operating system without reinstalling the operating system. The computer system includes a first storage device. The first storage device includes the root partition which has a first size. The root partition includes a root file system. The method includes backing up the root file system to a backup file system, booting the computer system to a maintenance mode, deactivating the root partition, activating the root partition at a second size smaller than the first size, and restoring the root file system from the backup file system.
Owner:ADVANCED MICRO DEVICES INC
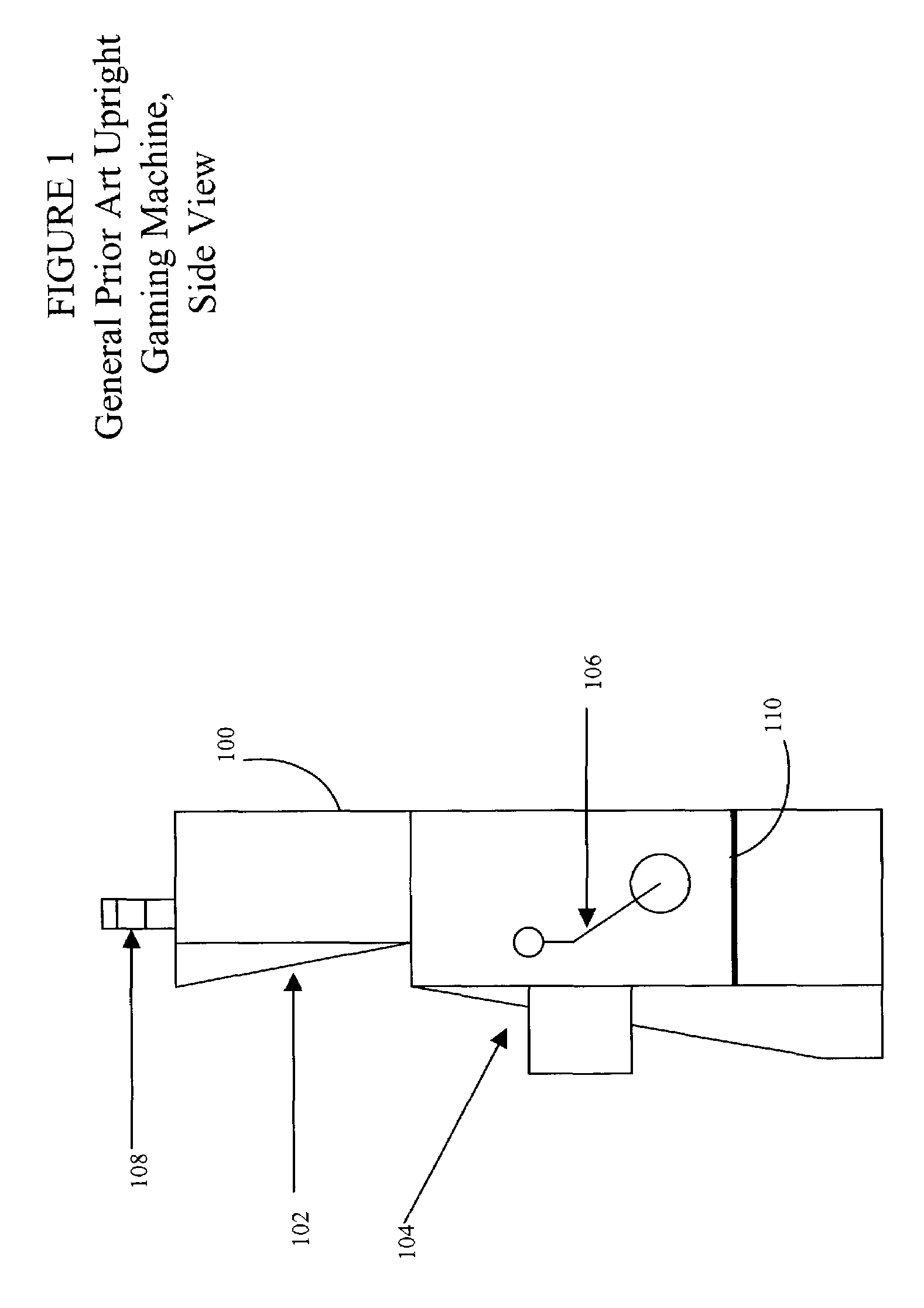
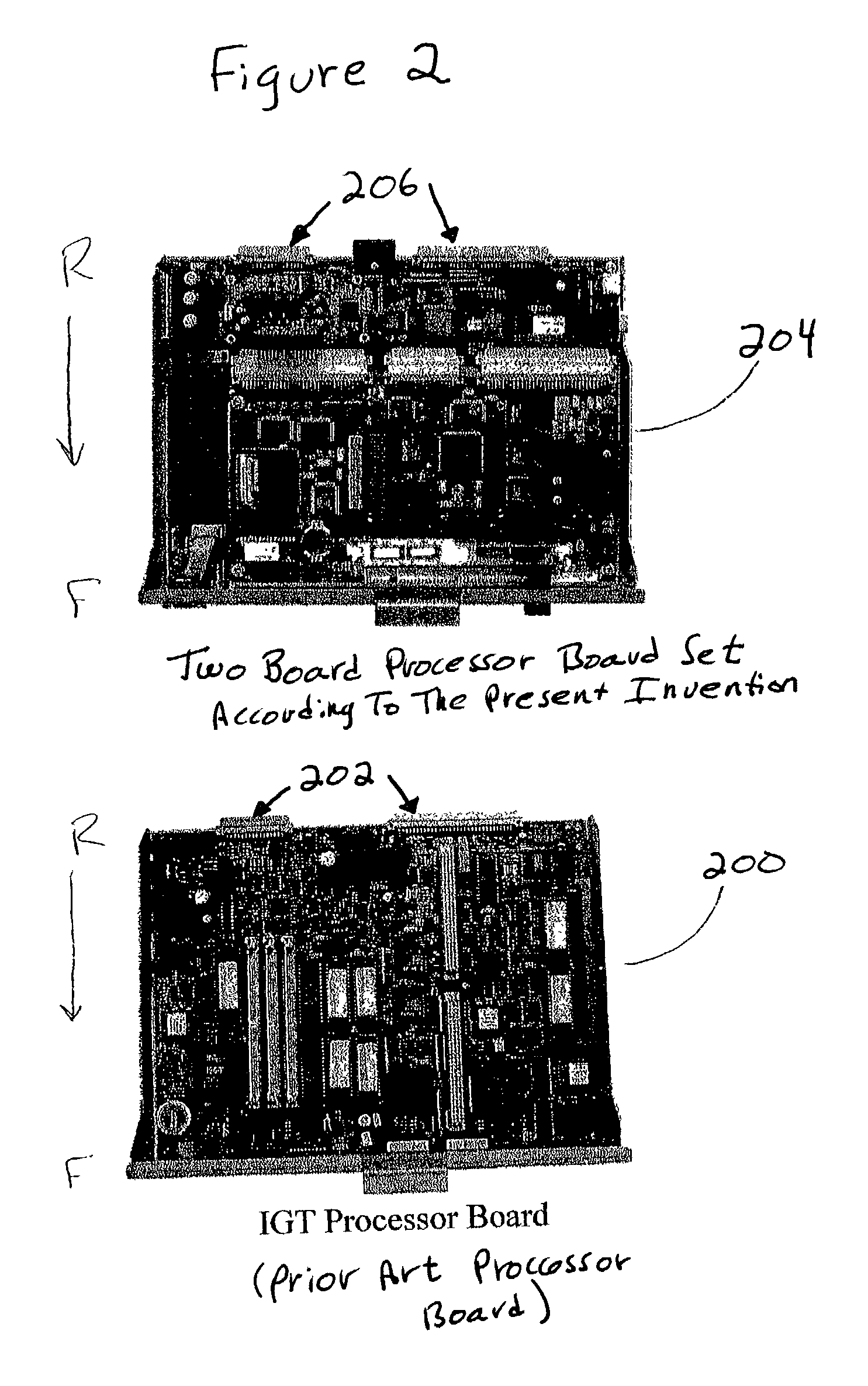
Gaming board set and gaming kernel for game cabinets
InactiveUS7351151B1Easy to useOvercome limitationsApparatus for meter-controlled dispensingVideo gamesUnixOperational system
The present invention is a method and apparatus enabling a low cost hardware upgrade path and low cost processor board retrofit for gaming machines. The enabling features include a two-board set made up of an industry standard form factor processor board (a single board system, able to support an operating system) coupled to an I / O adapter board, and further having a specially architected game kernel based on a UNIX-compatible operating system. The game kernel provides a consistent API to game applications, enabling quick and easy use of new hardware features while providing backward compatibility for existing game applications.
Owner:BALLY GAMING INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com