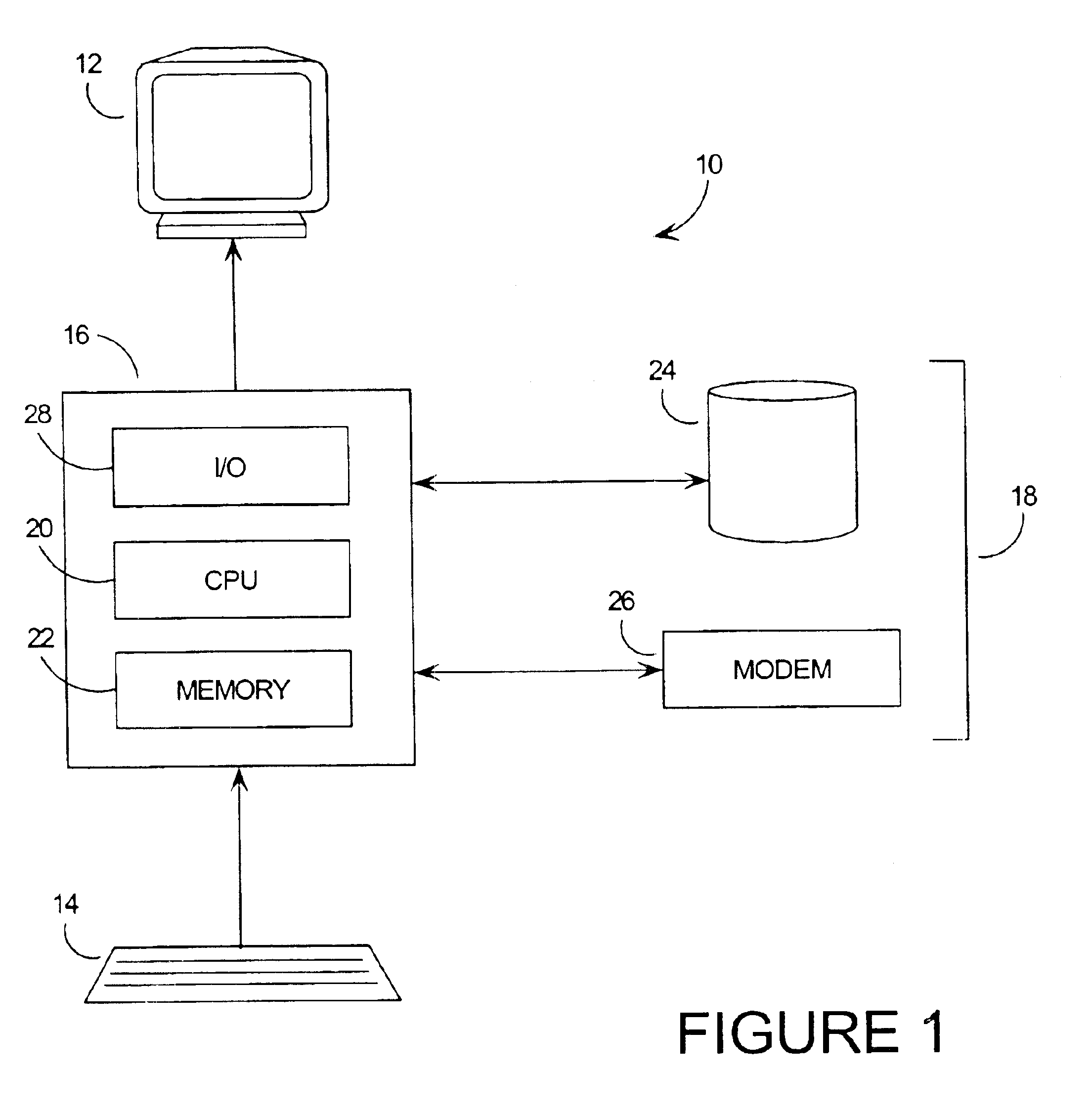
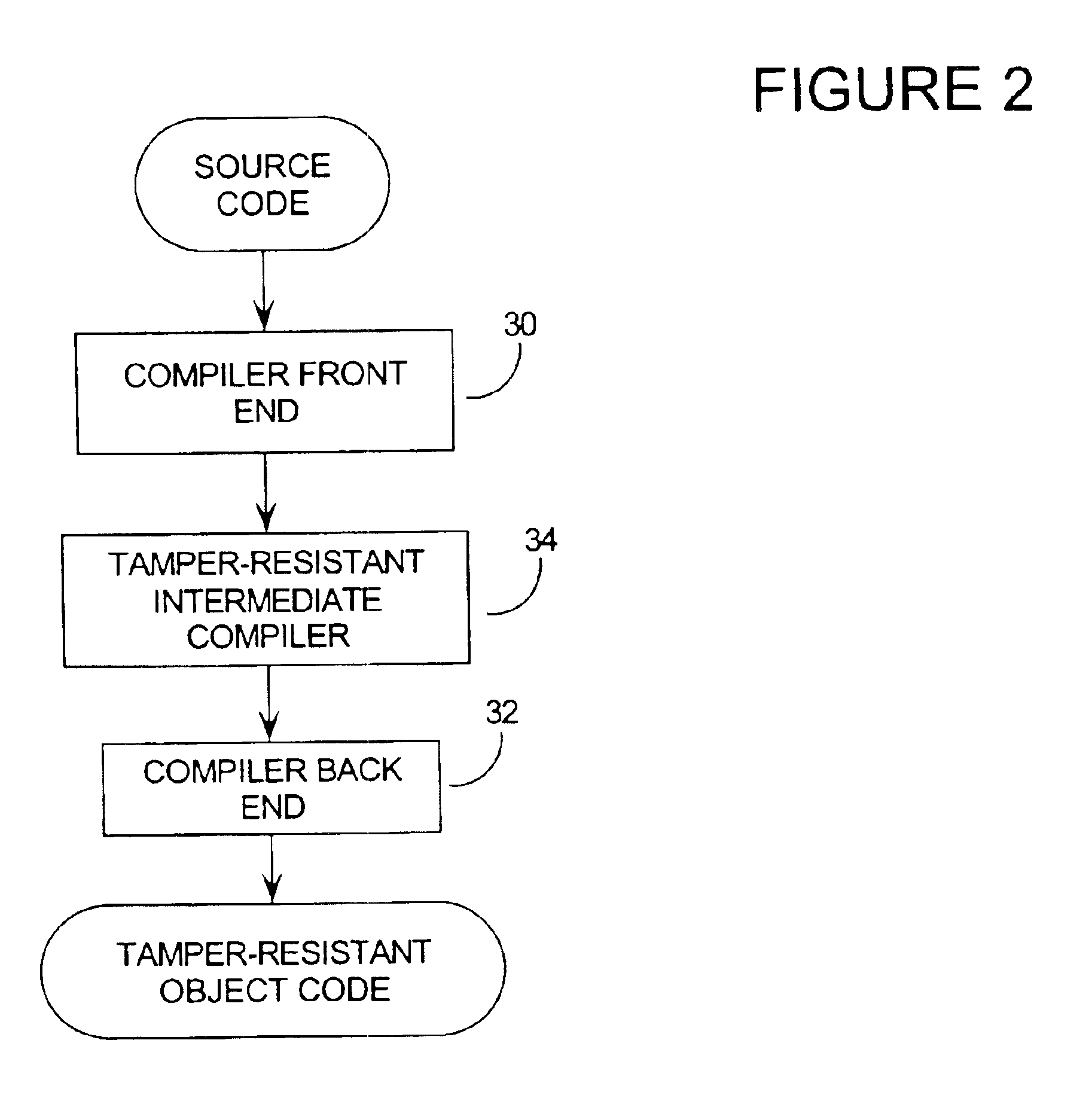
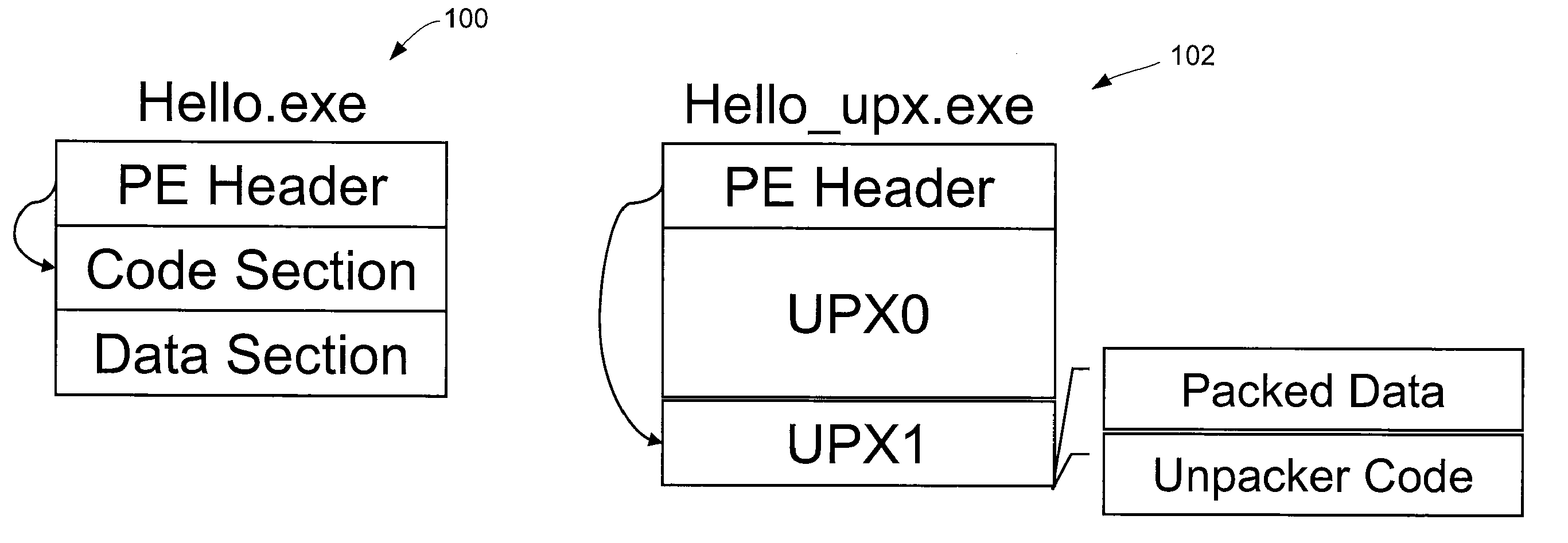
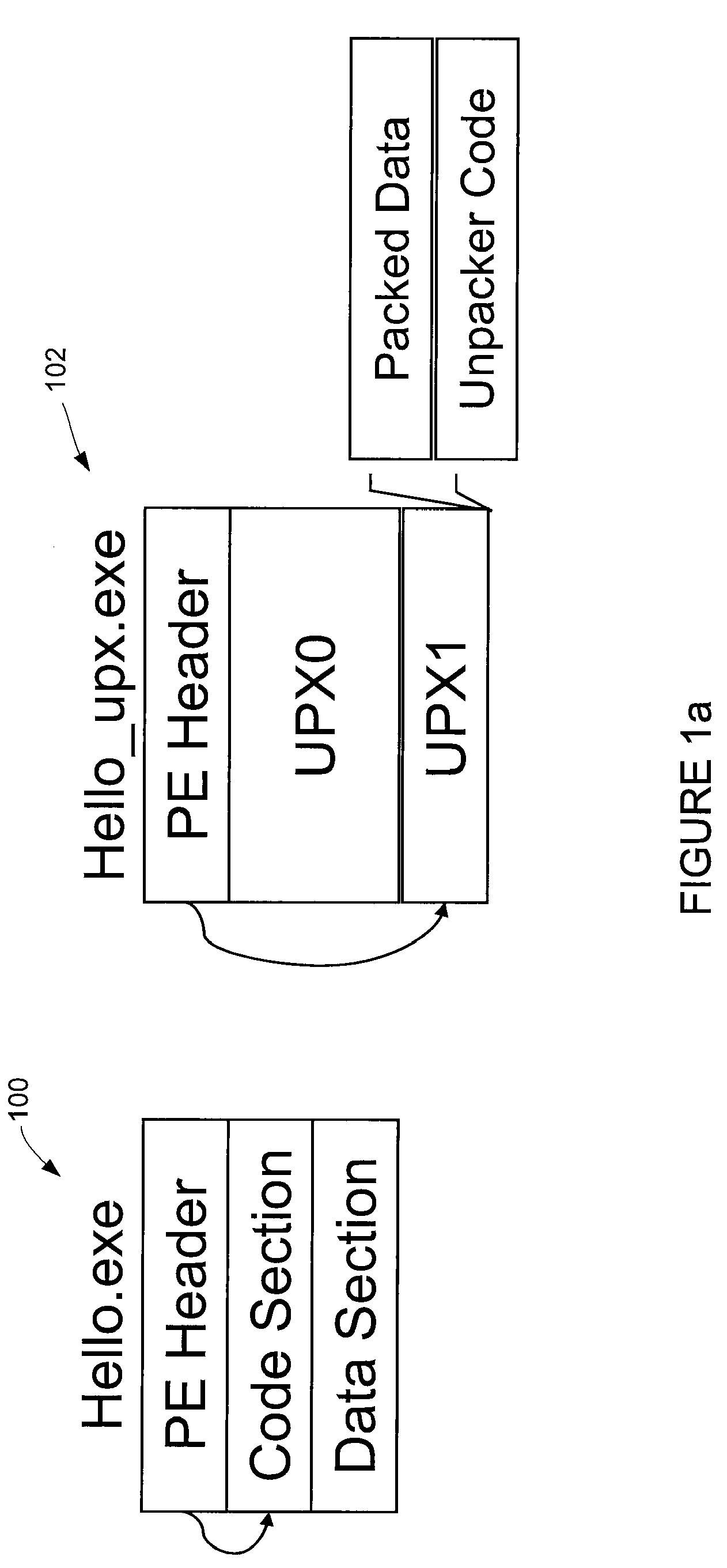
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
790 results about "Reverse engineering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Reverse engineering, also called back engineering, is the process by which a man-made object is deconstructed to reveal its designs, architecture, or to extract knowledge from the object; similar to scientific research, the only difference being that scientific research is about a natural phenomenon.
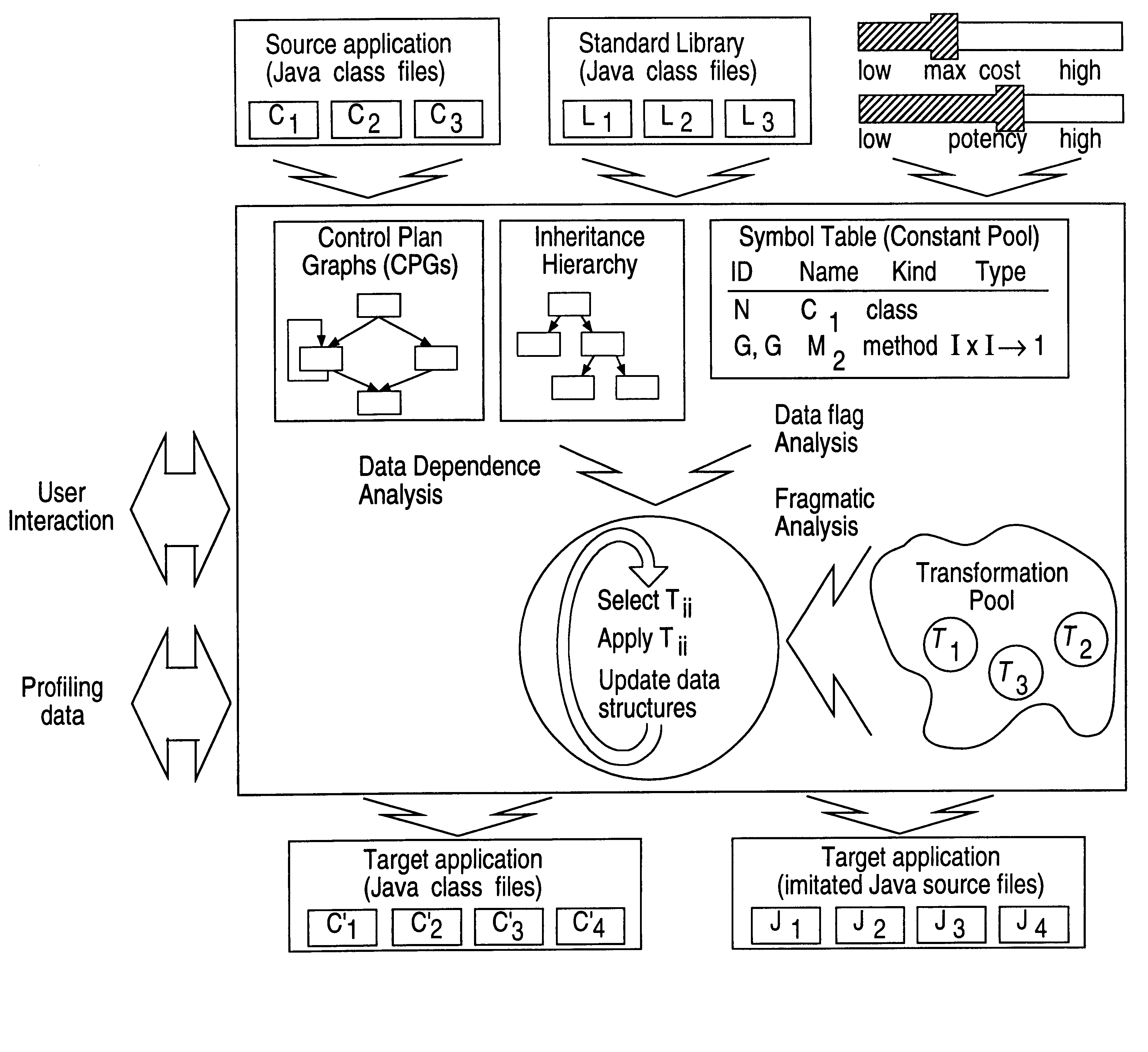
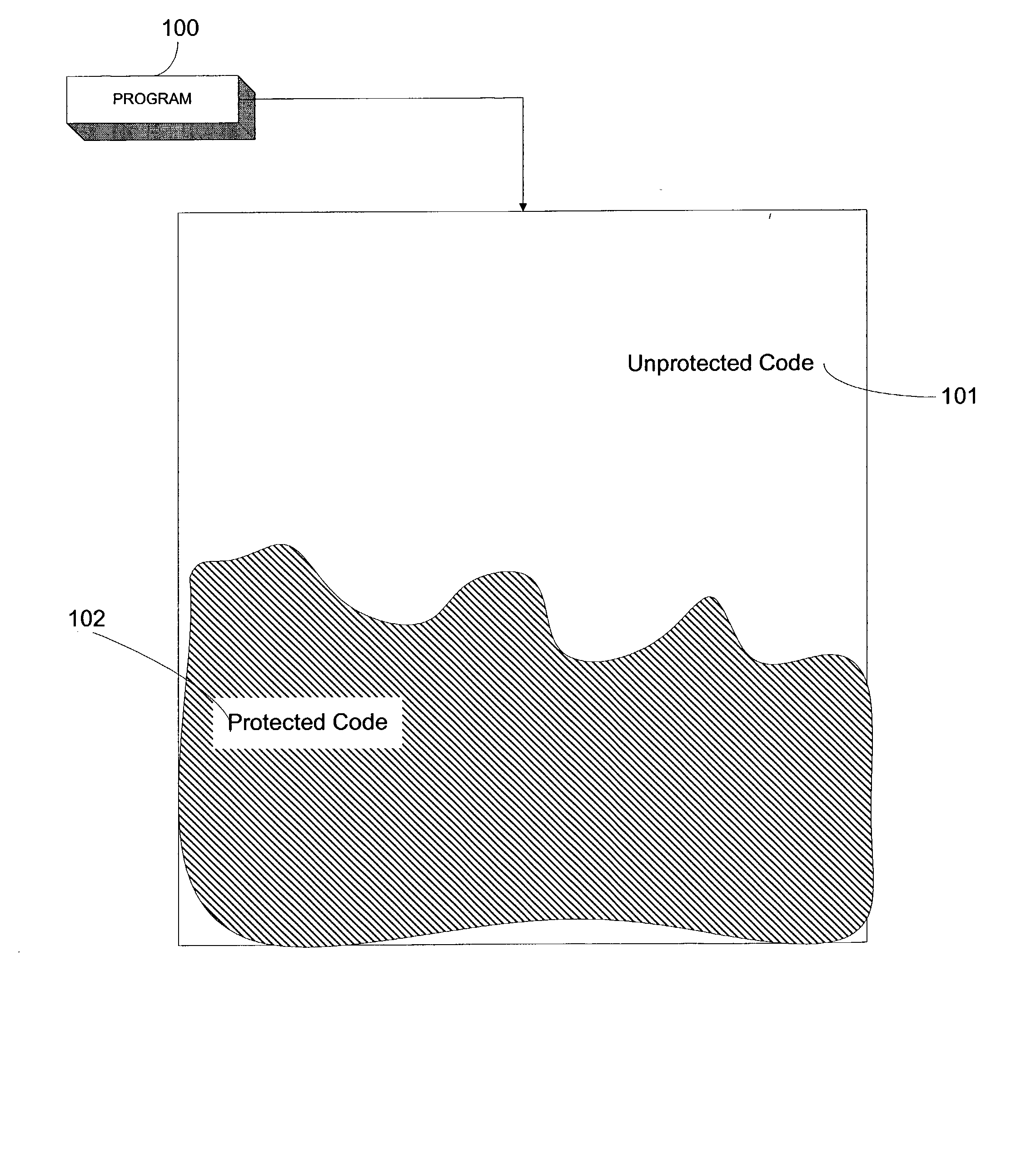
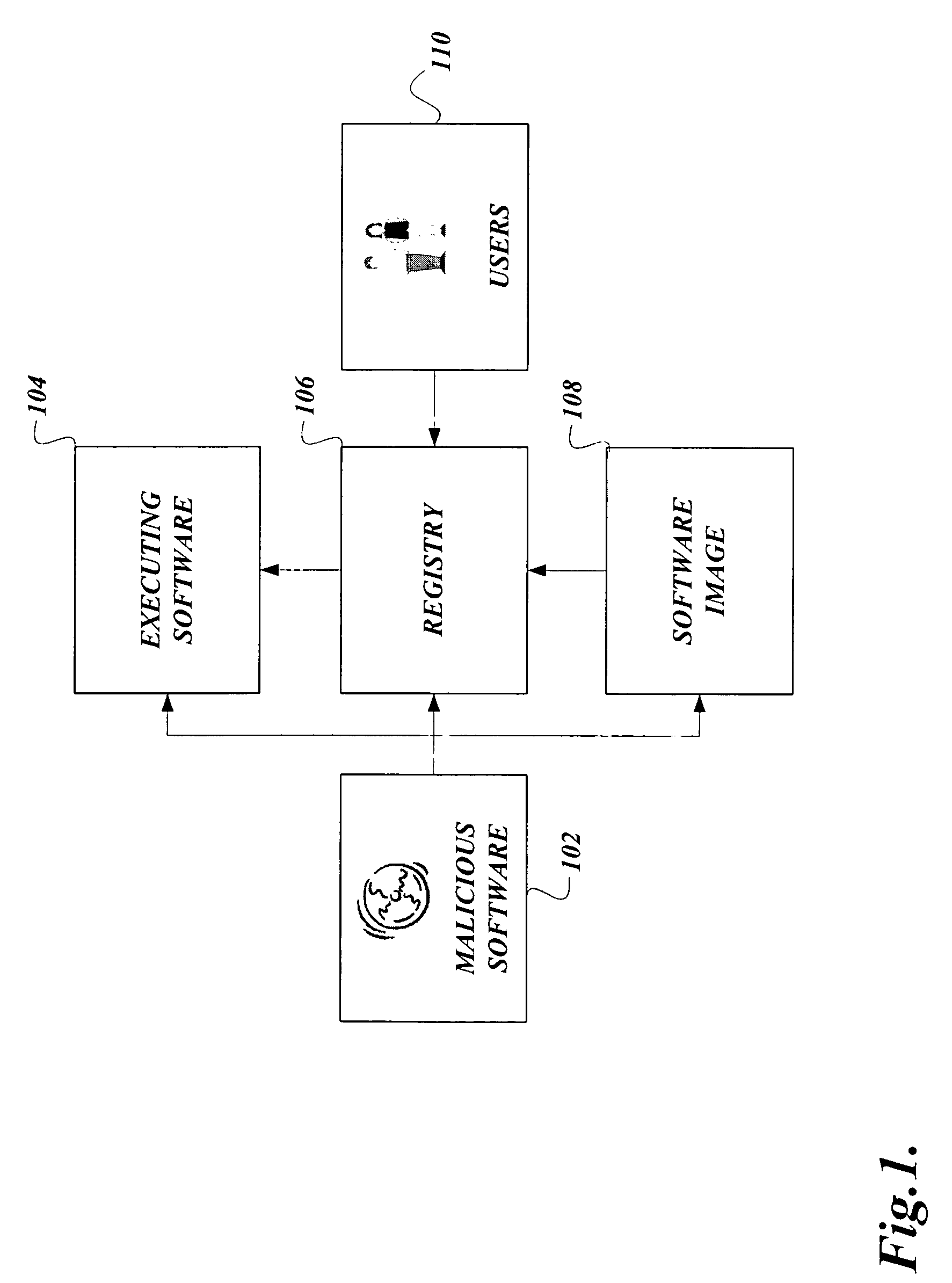
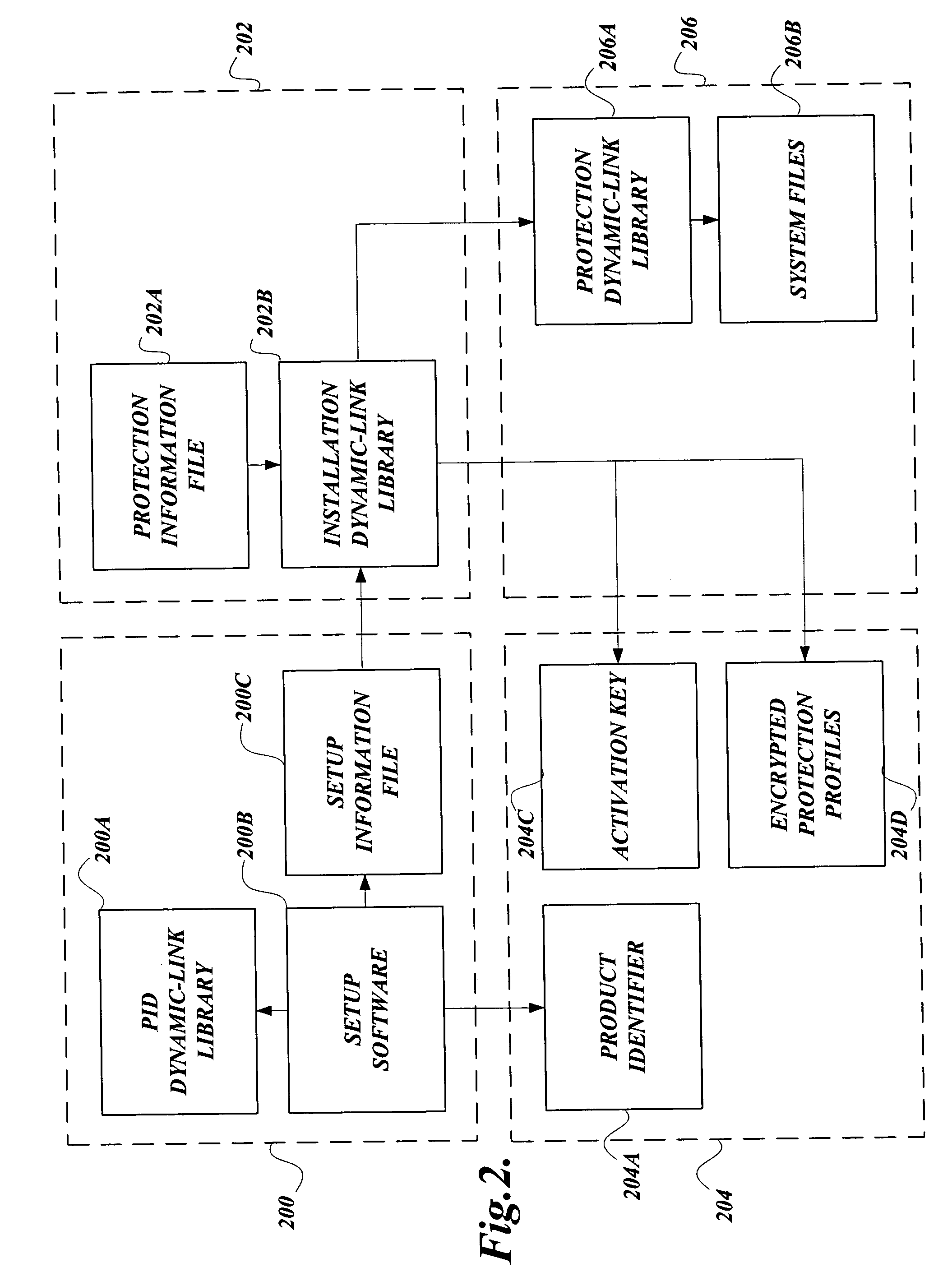
Obfuscation techniques for enhancing software security
InactiveUS6668325B1Guaranteed maximum utilizationDigital data processing detailsUnauthorized memory use protectionObfuscationTheoretical computer science
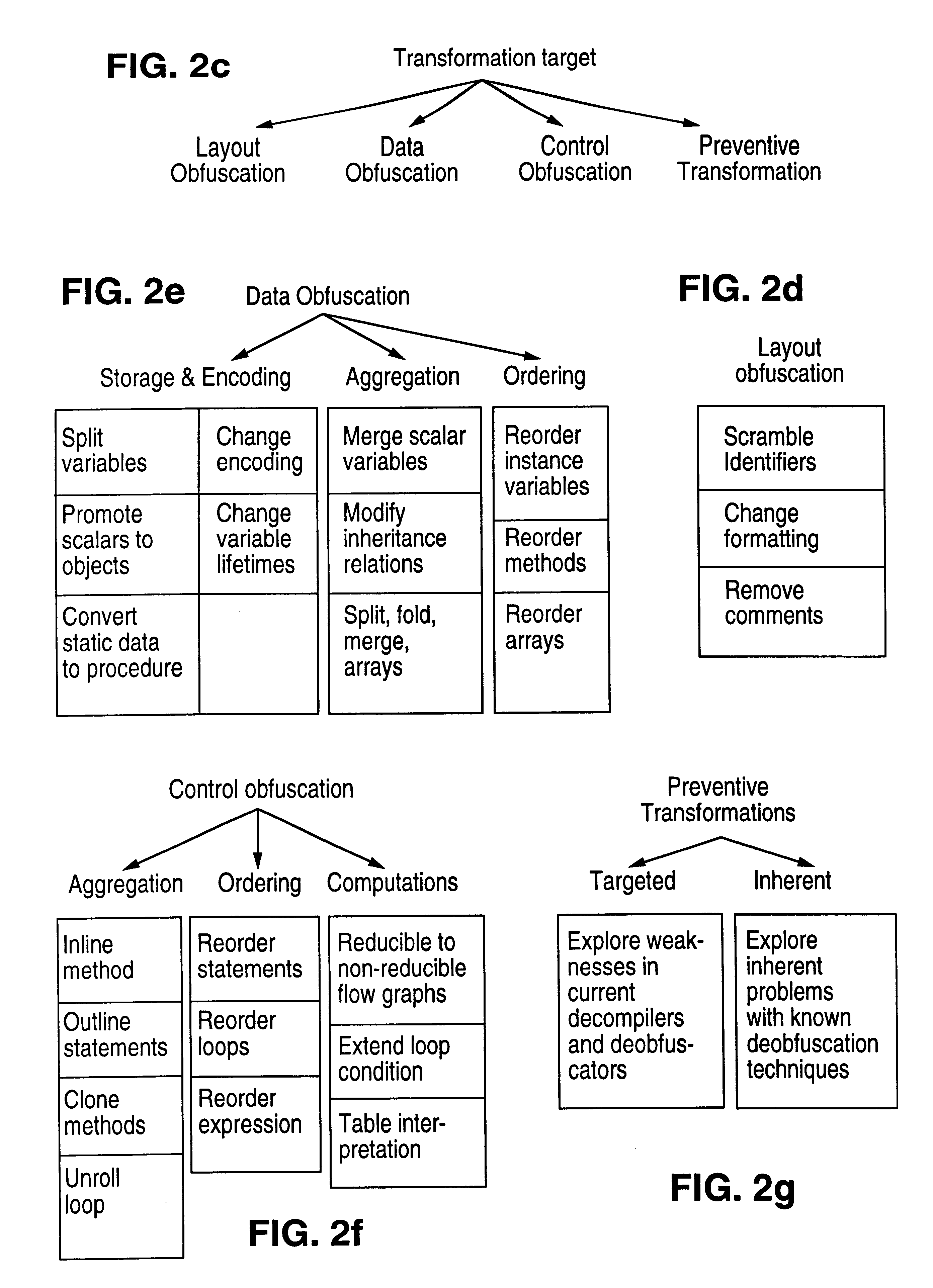
The present invention provides obfuscation techniques for enhancing software security. In one embodiment, a method for obfuscation techniques for enhancing software security includes selecting a subset of code (e.g., compiled source code of an application) to obfuscate, and obfuscating the selected subset of the code. The obfuscating includes applying an obfuscating transformation to the selected subset of the code. The transformed code can be weakly equivalent to the untransformed code. The applied transformation can be selected based on a desired level of security (e.g., resistance to reverse engineering). The applied transformation can include a control transformation that can be creating using opaque constructs, which can be constructed using aliasing and concurrency techniques. Accordingly, the code can be obfuscated for enhanced software security based on a desired level of obfuscation (e.g., based on a desired potency, resilience, and cost).
Owner:INTERTRUST TECH CORP
Tamper resistant software encoding
InactiveUS6842862B2Improvement in tamper-resistanceIncreased complexityMemory loss protectionUnauthorized memory use protectionTamper resistancePassword
The present invention relates generally to computer software, and more specifically, to a method and system of making computer software resistant to tampering and reverse-engineering. “Tampering” occurs when an attacker makes unauthorized changes to a computer software program such as overcoming password access, copy protection or timeout algorithms. Broadly speaking, the method of the invention is to increase the tamper-resistance and obscurity of computer software code by transforming the data flow of the computer software so that the observable operation is dissociated from the intent of the original software code. This way, the attacker can not understand and decode the data flow by observing the execution of the code. A number of techniques for performing the invention are given, including encoding software arguments using polynomials, prime number residues, converting variables to new sets of boolean variables, and defining variables on a new n-dimensional vector space.
Owner:IRDETO ACCESS
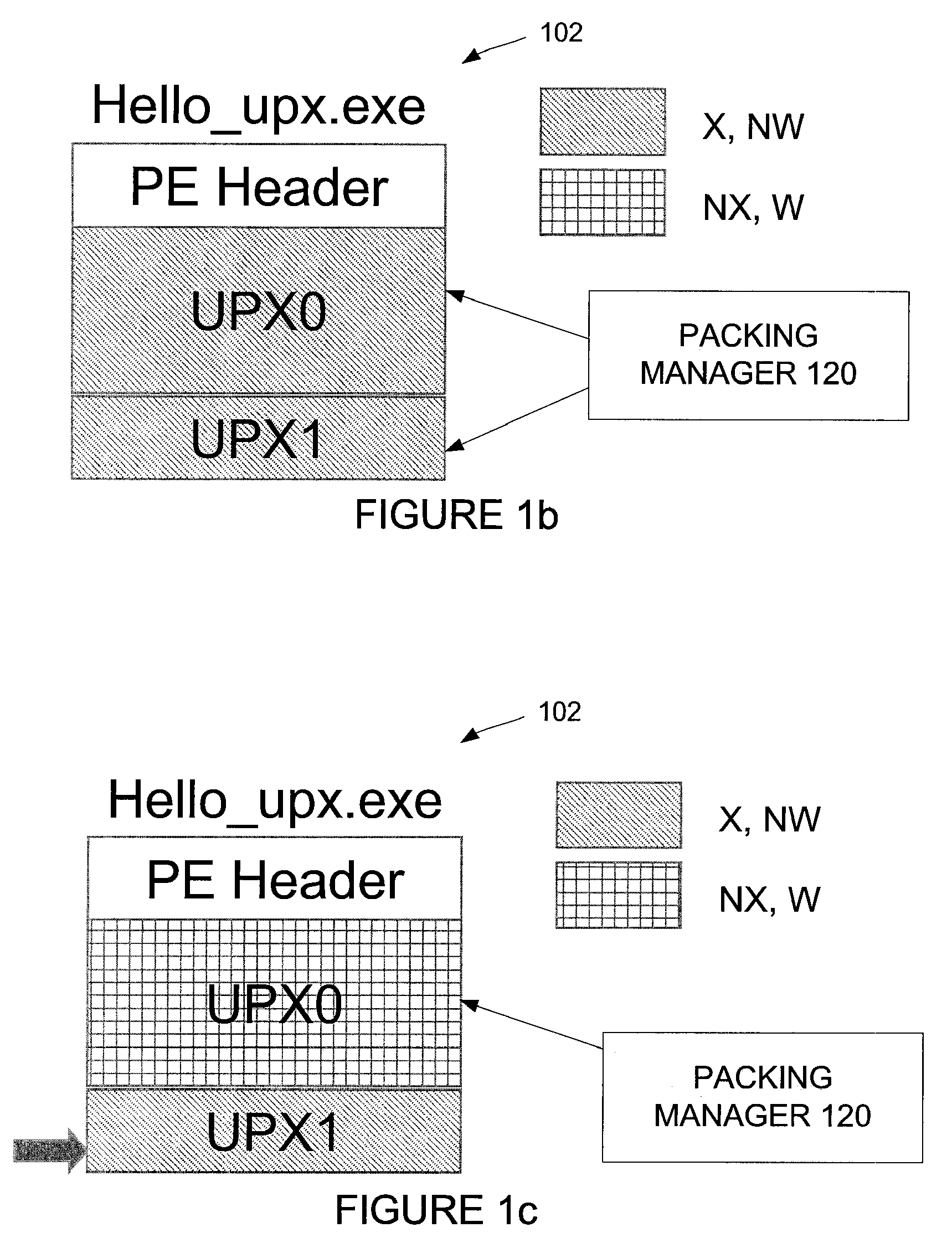
Automated unpacking of executables packed by multiple layers of arbitrary packers
The packing manager provides an automated method that allows existing AV scanning technology to be applied to detect known malware samples packed by one or more packers that are potentially proprietary. The packing manager tracks the memory areas to which an executable binary writes and executes, and so can unpack programs packed by multiple arbitrary packers without requiring reverse-engineering of the packers or any human intervention. By tracking page modification and execution of an executable binary at run time, the packing control module can detect the instant at which the program's control is first transferred to a page whose content is dynamically generated, so AV scanning can then be invoked. Thus, code cannot be executed under the packing control manager without being scanned by an AV scanner first.
Owner:NORTONLIFELOCK INC
Session-state manager
InactiveUS6877095B1Improve securityOvercome limitationsDigital data processing detailsComputer security arrangementsSession stateEncryption
Without actually storing session-state information, the described exemplary implementations of session-state manager identify a user, validate the user's current logon state, and determine whether the user's session should expire. User identification and logon validation are checked by a server in a stateless network by generating a mathematically session-state token and sending that token to a user. Subsequently, the server receives a mathematically session-state token from the user and checks that token. If that token checks out, then the user is allowed continuing access under the same session. If it doesn't check out, then the user may be forced to start a new session by logging-on again. Alternatively, the server may check to see if the token would check out if it had come at an earlier time block. The session-state tokens are mathematical encoded and are generated using a one-way encryption scheme. Such a one-way encrypted token is scientifically impossible to reverse-engineer. Furthermore, logon expiration is checked by the server using the same mathematically session-state token. The token is checked to determine whether a predetermined number of time blocks have past. If so, then the server will terminate the user's session.
Owner:MICROSOFT TECH LICENSING LLC
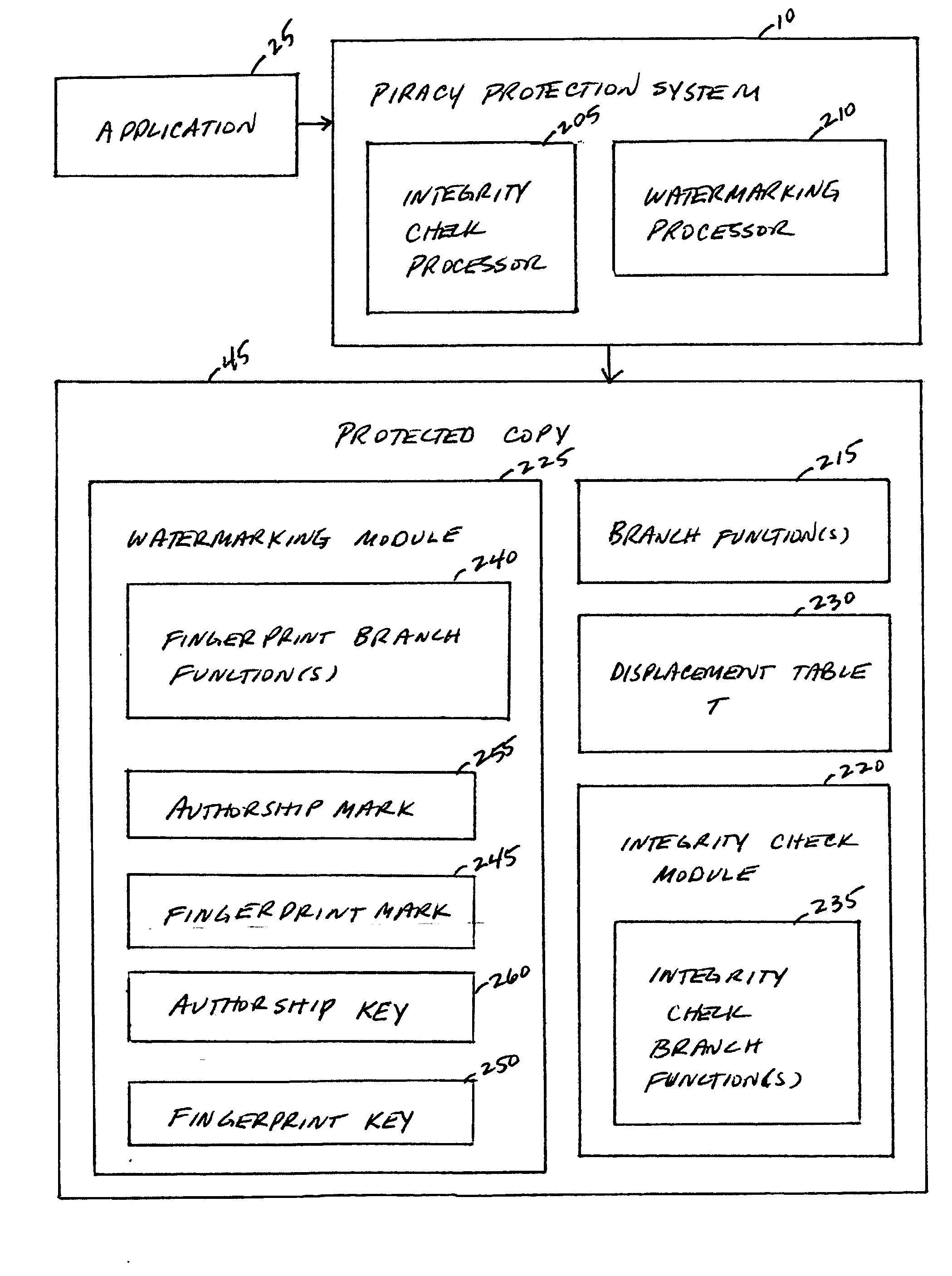
System, method, and service for detecting improper manipulation of an application
InactiveUS20060195906A1Eliminate loopholesMore robustnessDigital data processing detailsUser identity/authority verificationObfuscationApplication procedure
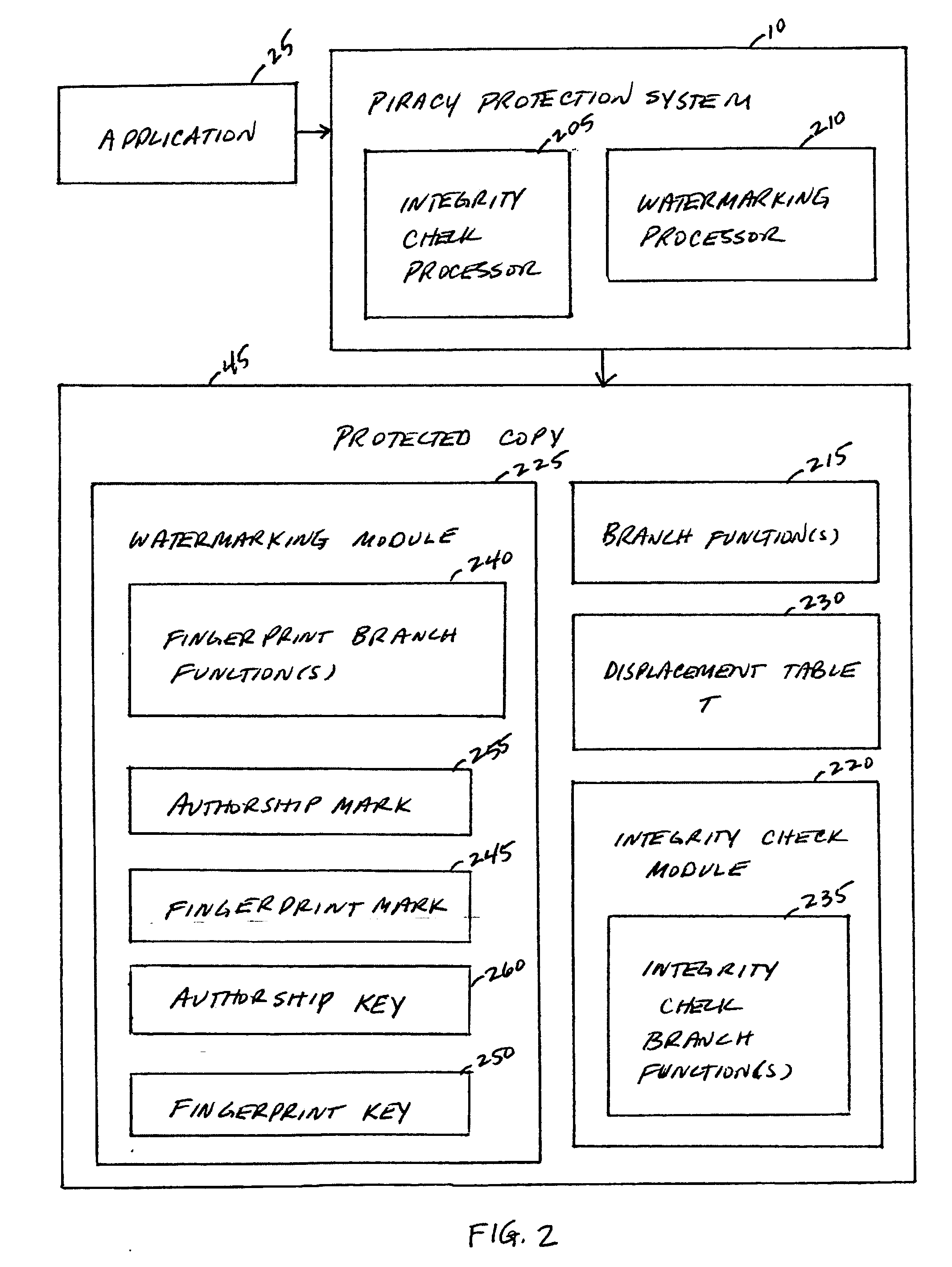
A piracy protection system incorporates tamper detection capabilities into a protected copy of an application by disassembling a statically linked binary of the application, modifying some of the instructions in the application, and then rewriting all of the modified and unmodified instructions to a new executable file, a protected copy. The piracy protection system comprises an offline tamper detection technique in which the software itself detects the tampering and causes the program to fail, therefore protecting itself from malicious attacks. The system further comprises a dynamic software-watermarking process that incorporates code obfuscation to prevent reverse engineering.
Owner:IBM CORP
System and method for inhibiting the decryption of a nucleic acid probe sequence used for the detection of a specific nucleic acid
InactiveUS20060073487A1Reduce or impede a person's ability to designAvoid identificationSugar derivativesMicrobiological testing/measurementGenetic AnomalyNucleic Acid Probes
Sequence-specific nucleic acid hybridization assays are used for the detection of specific genetic sequences as indicators of genetic anomalies, mutations, and disease propensity. In addition, they are used for the detection of various biological agents and infectious pathogens. Because a complementary probe or nucleic acid sequence is required to detect a sequence of interest in a hybridization-based assay, nucleic acid sequencing techniques can rapidly determine the specific probe sequence being used for detection. This allows reverse engineered assays to be produced rapidly. In addition, it enables the circumvention of hybridization-based assays for biological agent or infectious pathogen detection by providing the information necessary to create or alter nucleic acid sequences to produce false positives or false negatives. The present invention provides methods and compositions for inhibiting the identification of specific detection sequences. More specifically, the invention provides masking sequences that mask the identity of specific detection sequences.
Owner:RADIX BIOSOLUTIONS
Systems and methods for preventing unauthorized use of digital content
InactiveUS7237123B2Reduce eliminate broadly disseminated effectivenessNontrivial taskRandom number generatorsUser identity/authority verificationDigital contentProtection mechanism
Theft, distribution, and piracy of digital content (software, video, audio, e-books, any content of any kind that is digitally stored and distributed) is generally accomplished by copying it, if possible, or, if it is protected from being copied in any fashion, such piracy is based upon a number of reverse engineering techniques. Aside from the straightforward copying of unprotected content, all of these other methods require first an understanding of the protective mechanism(s) guarding the content, and finally an unauthorized modification of that protection in order to disable or subvert it. Methods that prevent a skilled individual from using reverse engineering tools and techniques to attain that level of understanding and / or prevent anyone from performing such modifications can offer significant advantages to content creators who wish to protect their products.
Owner:IPLA HLDG
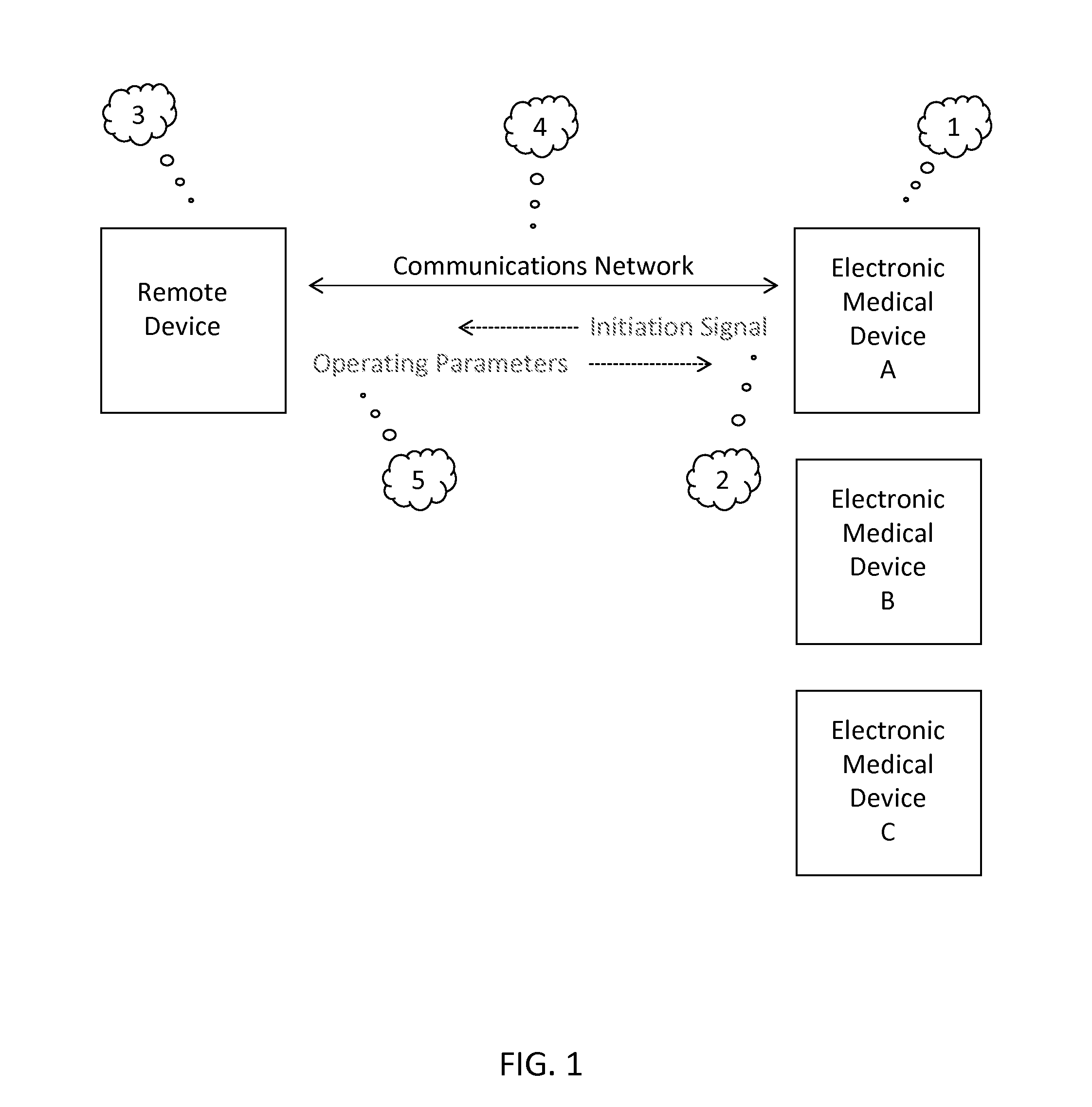
Method for External Storage of Medical Device Program Design Parameters
ActiveUS20130291116A1Easy to findPreserving a greater degree of design secrecyDigital data processing detailsAnalogue secracy/subscription systemsExternal storageMostly True
Many electronic medical devices include program design features that direct the operation of the device. The program design features of most electronic medical devices reside in the device itself and therefore are easily discovered by reverse engineering. In most cases, however, these features can be introduced into the device from an external source for only so long as necessary for each operation of the device, thereby making the reverse engineering of these features more difficult (or even impossible) and preserving a greater degree of design secrecy.
Owner:HOMER GREGG S
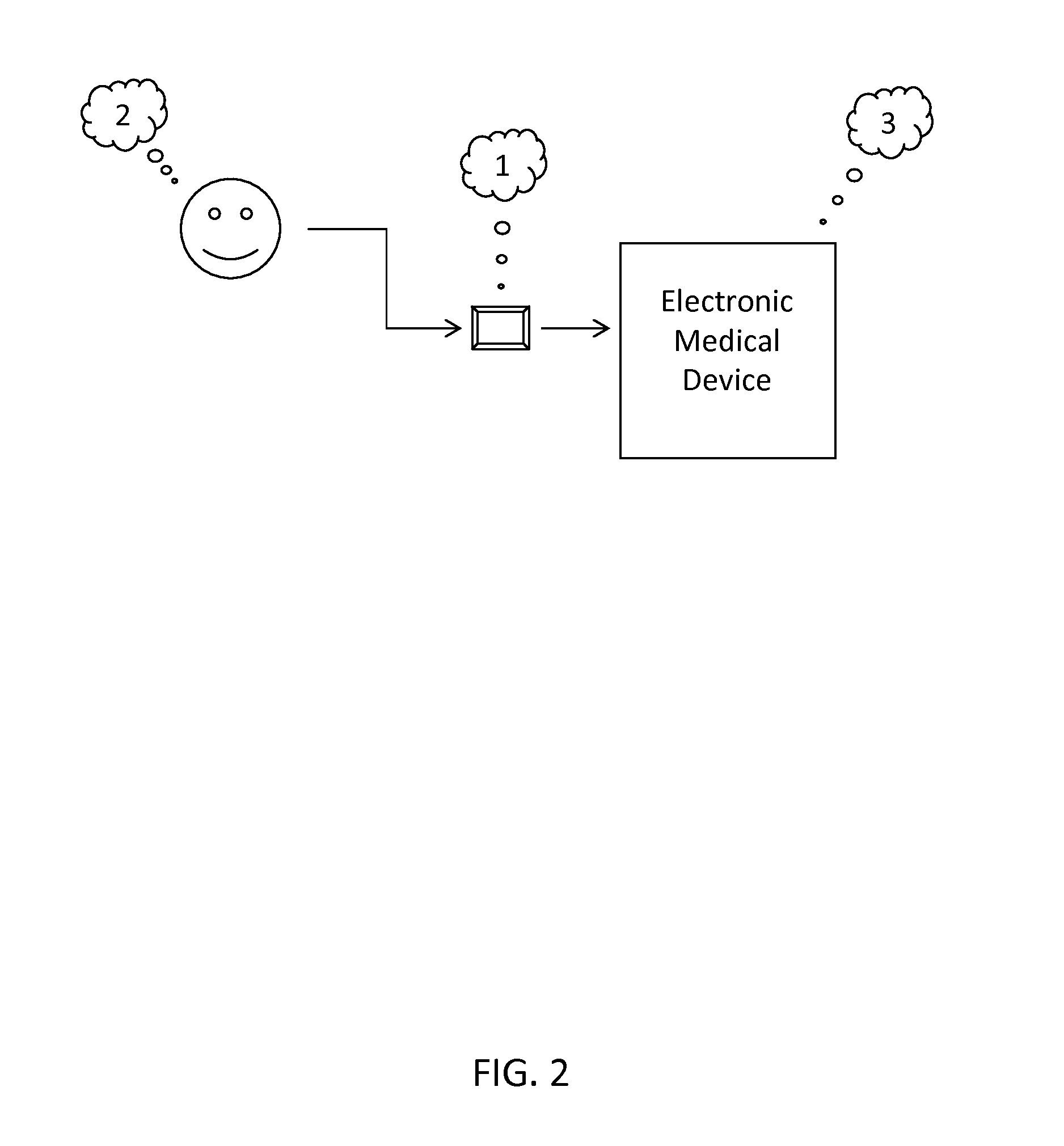
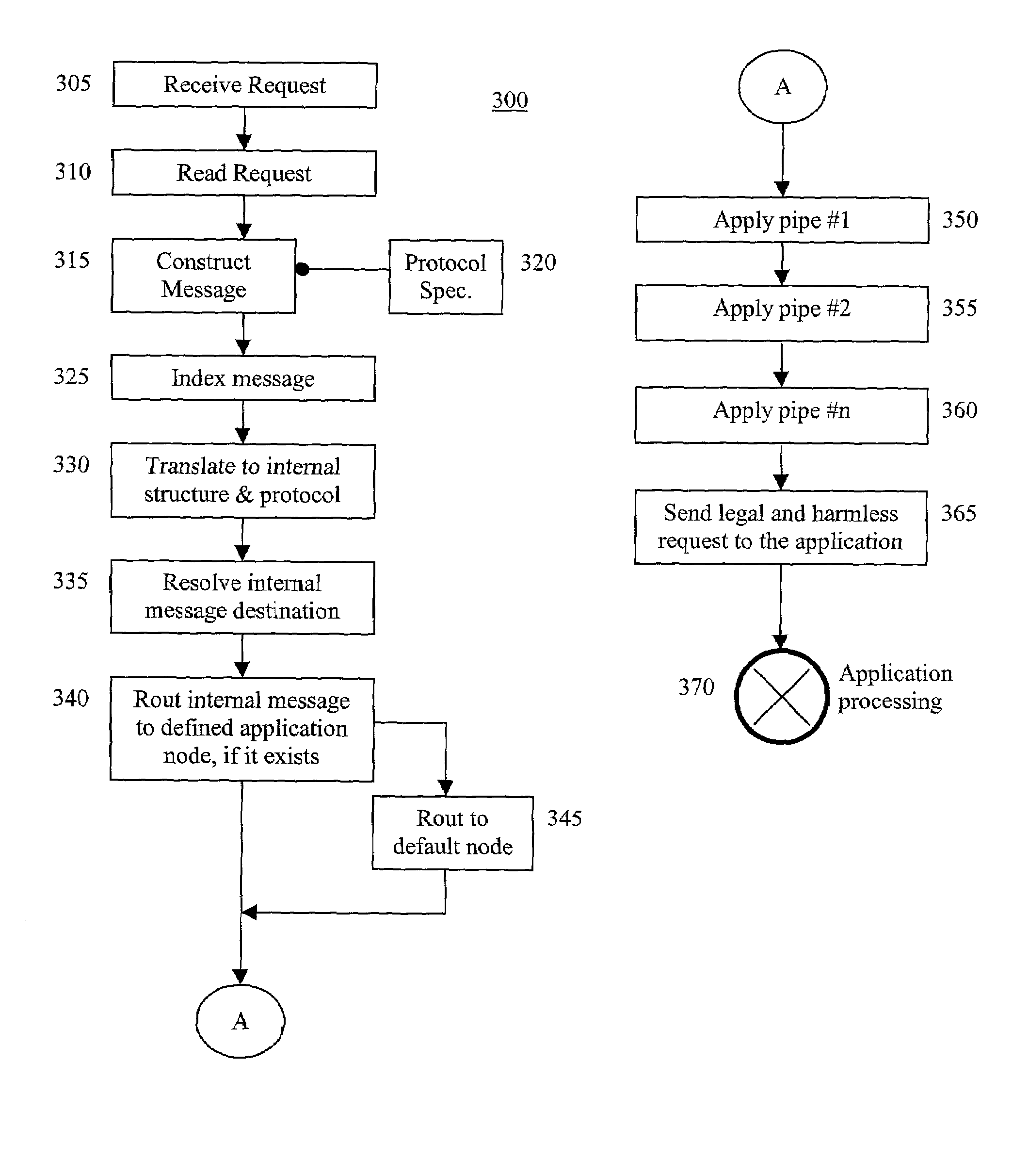
Application-layer security method and system
InactiveUS7313822B2Avoid attackMemory loss protectionUnauthorized memory use protectionConfidentialityApplication software
The present invention secures applications from executing illegal or harmful operation requests received from a distrusted environment, thereby, preventing an application from damaging itself, other applications, performance, files, buffers, databases, and confidentiality of information. An operation reverse engineering layer is positioned in front of an application in a trusted environment and between the application and the incoming application operation requests that are received from an unknown or distrusted environment. The operation reverse engineering layer checks the requests for either form, content, or both, to insure that only legal and harmless requests will pass to the given application. Hardware, software, or both, are employed to implement the operation reverse engineering layer.
Owner:KAVADO
Method and apparatus for camouflaging a standard cell based integrated circuit with micro circuits and post processing
ActiveUS20120139582A1Solid-state devicesCAD circuit designComputer architectureIntegrated circuit layout
A method and apparatus for camouflaging an application specific integrated circuit (ASIC), wherein the ASIC comprises a plurality of interconnected functional logic is disclosed. The method adds functionally inert elements to the logical description or provides alternative definitions of standard logical cells to make it difficult for reverse engineering programs to be used to discover the circuit's function. Additionally, post processing may be performed on GDS layers to provide a realistic fill of the empty space so as to resemble structural elements found in a functional circuit.
Owner:RAMBUS INC
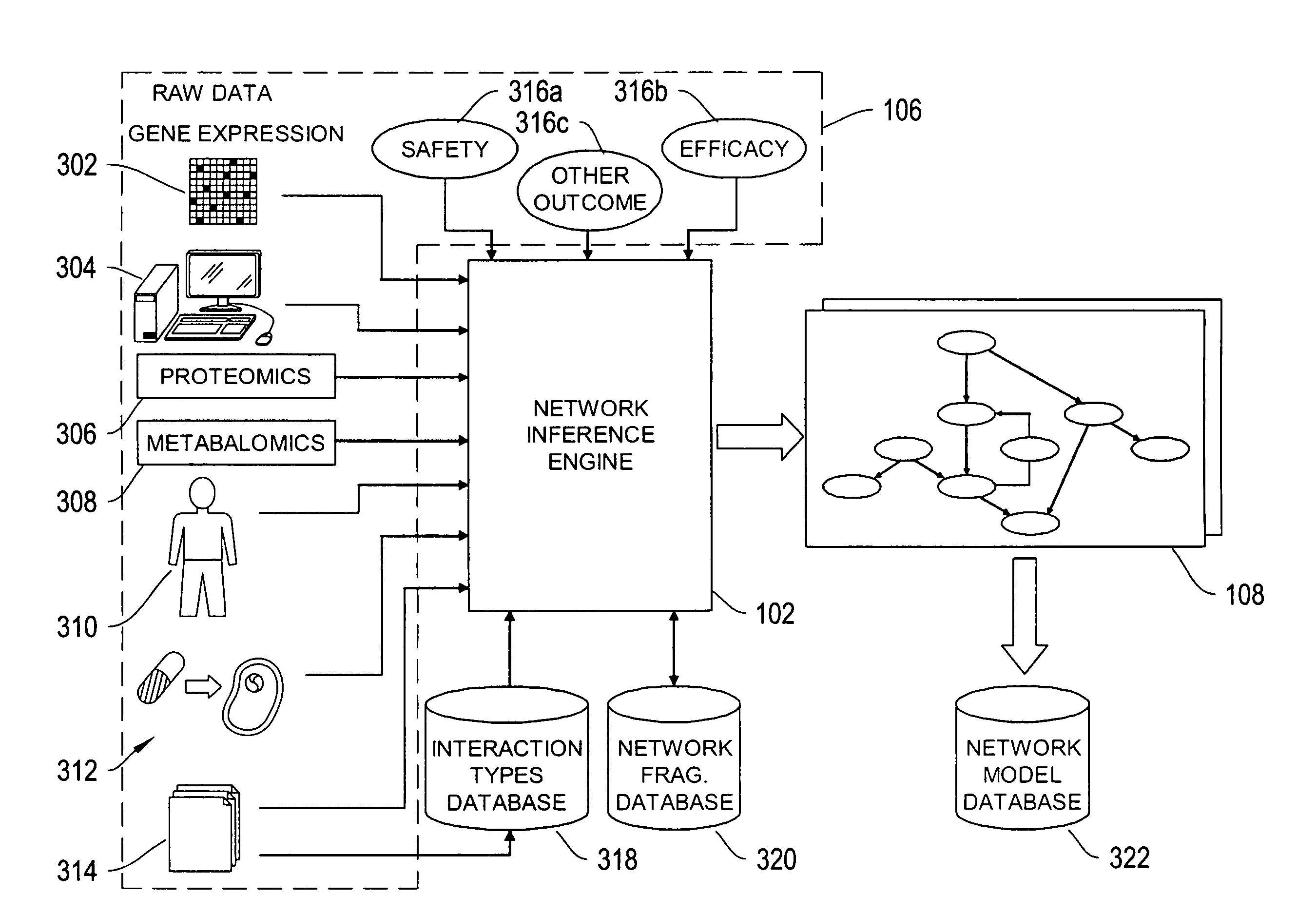
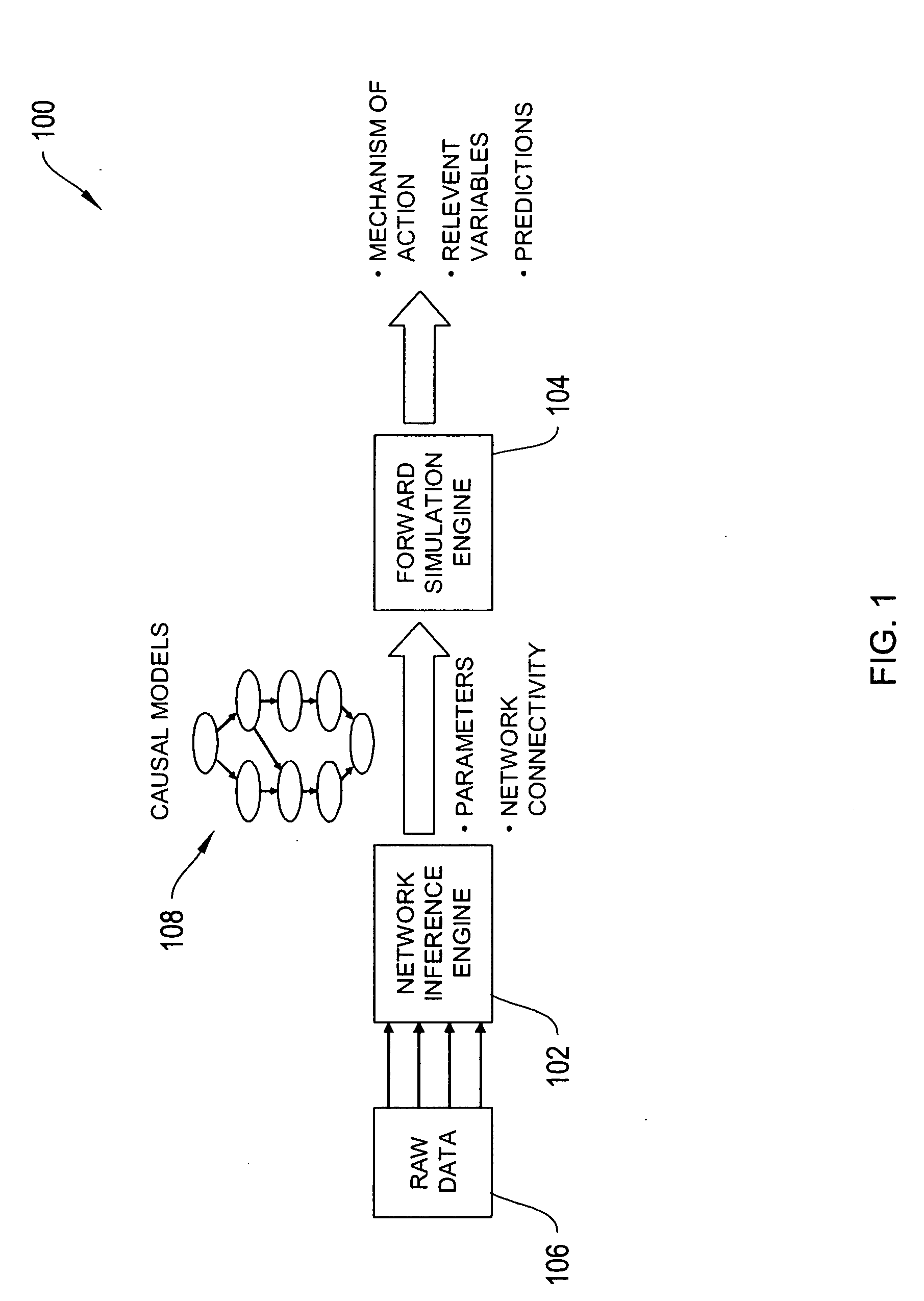
Systems and methods for modeling and analyzing networks
The systems and methods described herein utilize a probabilistic modeling framework for reverse engineering an ensemble of causal models, from data and then forward simulating the ensemble of models to analyze and predict the behavior of the network. In certain embodiments, the systems and methods described herein include data-driven techniques for developing causal models for biological networks. Causal network models include computational representations of the causal relationships between independent variables such as a compound of interest and dependent variables such as measured DNA alterations, changes in mRNA, protein, and metabolites to phenotypic readouts of efficacy and toxicity.
Owner:GENE NETWORK SCI
System and method for debugging computer program based on execution history
ActiveUS8935673B1Easy to debugEasy to navigateMemory loss protectionNuclear monitoringCode spaceSystem of record
A system and method are provided for enhanced navigation along execution time and code space in a debugger to assist a user in remediating errors, streamlining, or reverse engineering a computer program and the source code thereof. Snapshots of system states are recorded, a causality tree of commands is constructed through execution of the program to be debugged, and an intelligent display of system states captured during runtime and indexed or cross-referenced by time are displayed to the user in an intelligent manner to aid the user with certain debugging tasks. Additionally, further features in assisting the user to locate a root cause of an error or unexpected value and remediate that cause are also provided.
Owner:CADENCE DESIGN SYST INC
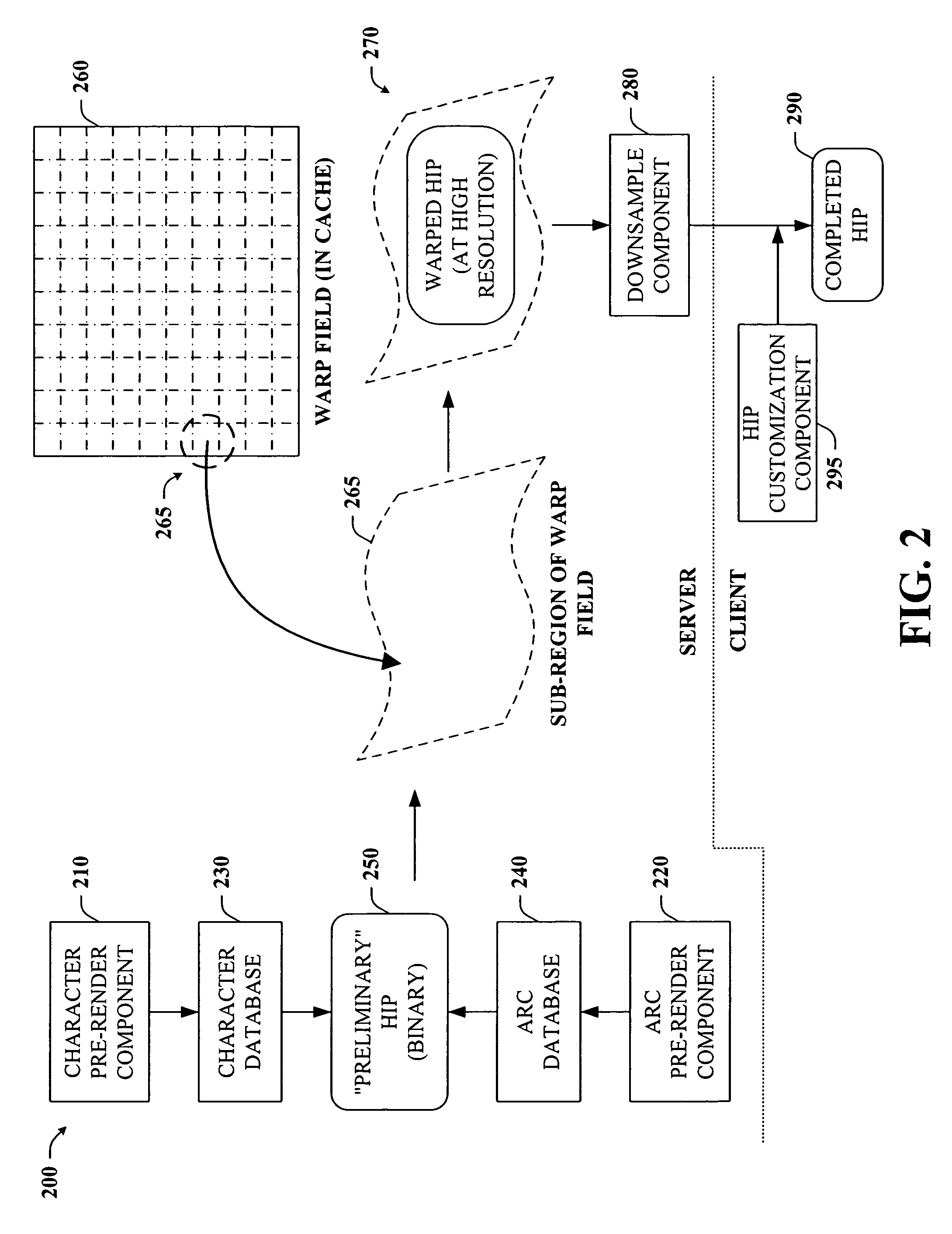
High performance content alteration architecture and techniques
ActiveUS20050229251A1Improve effectivenessIncrease speedGeometric image transformationDigital data processing detailsComputer scienceBitmap
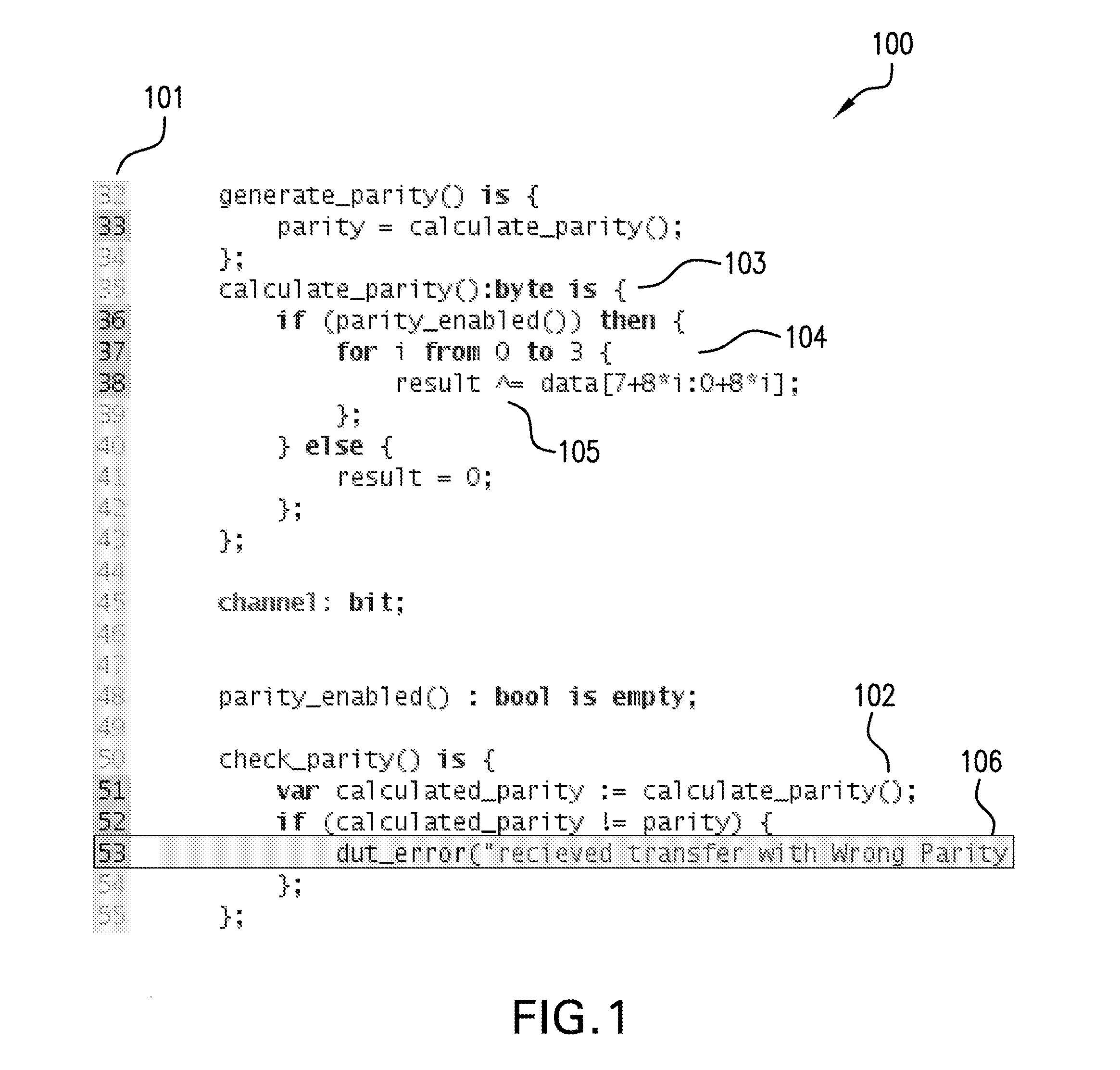
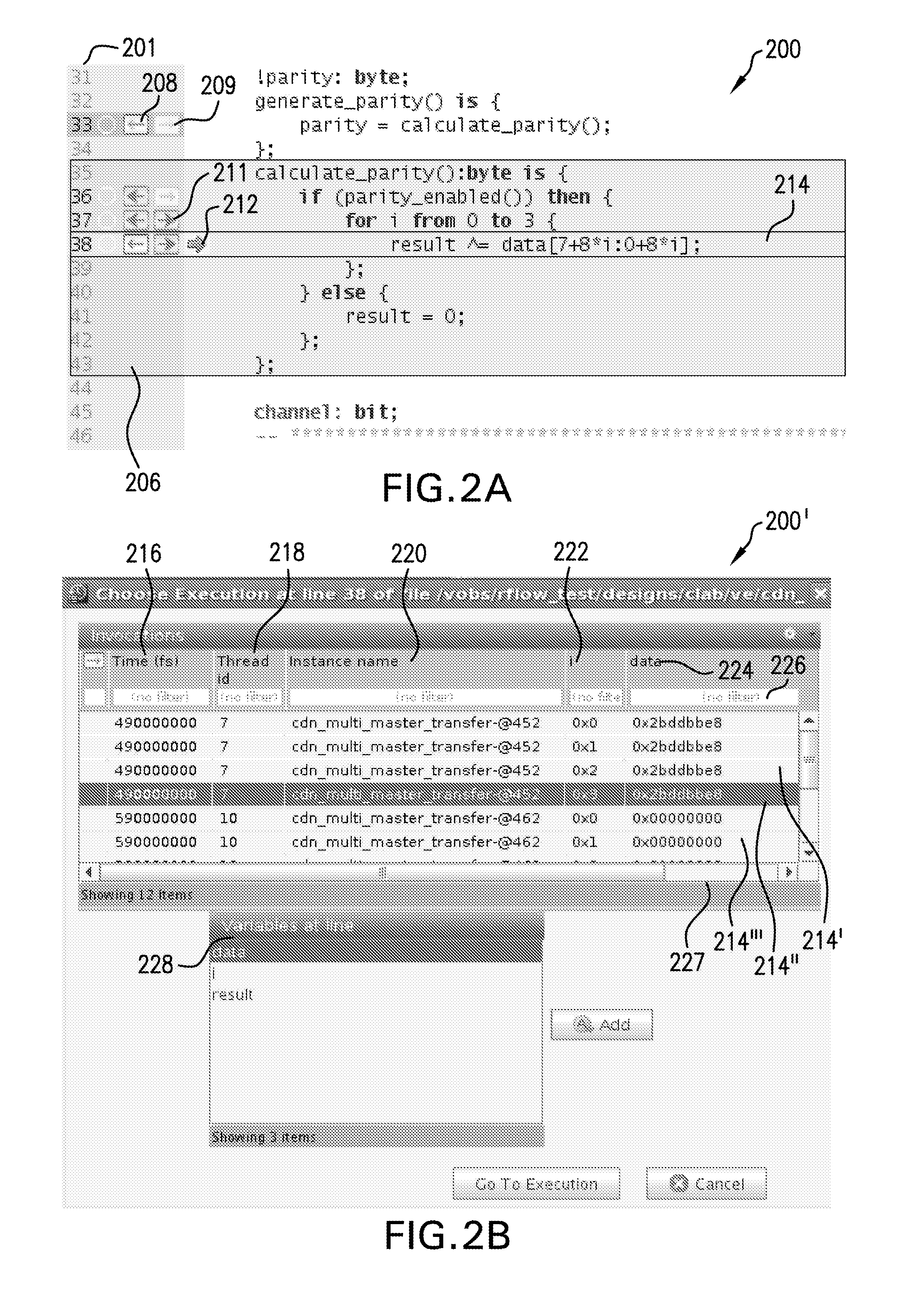
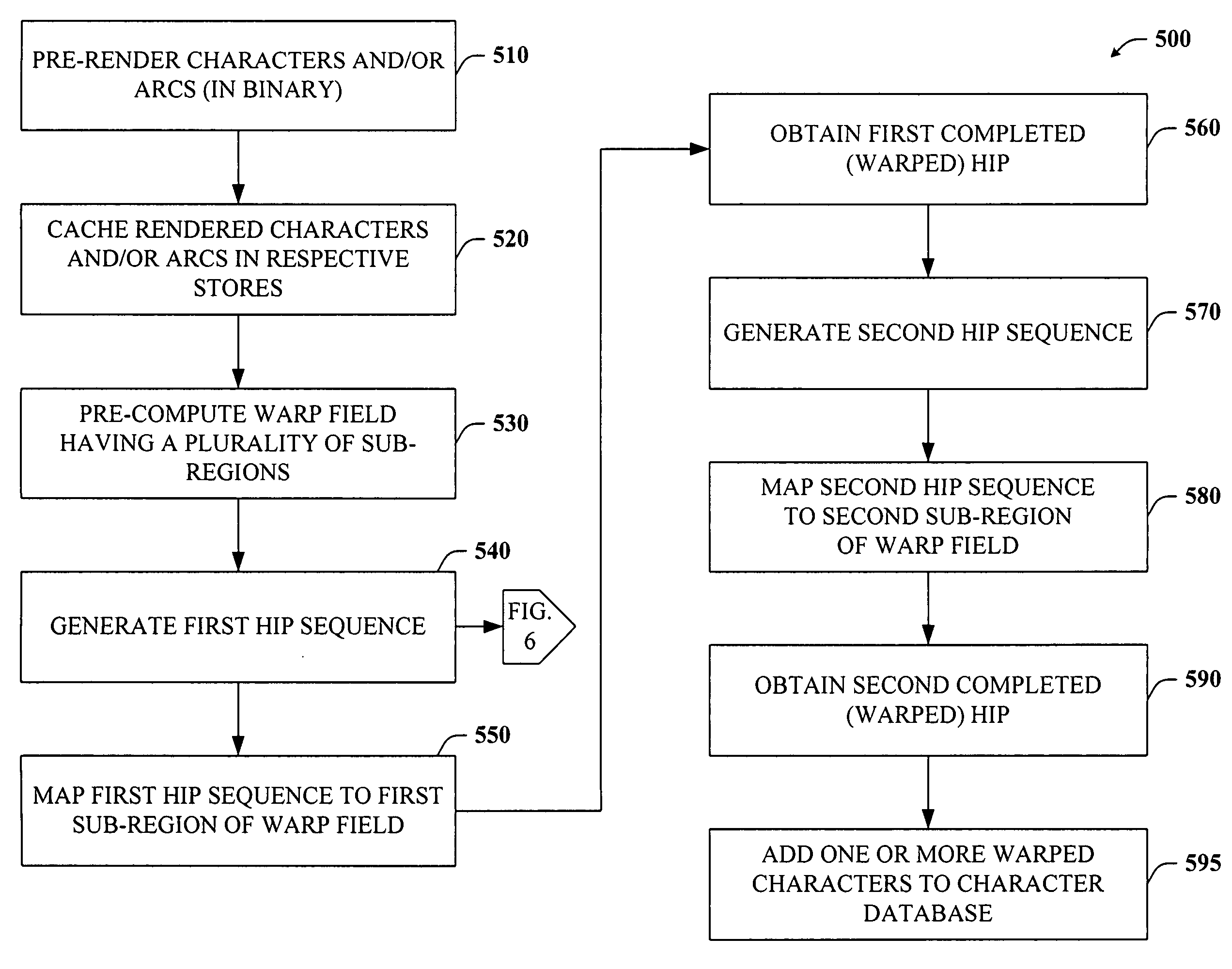
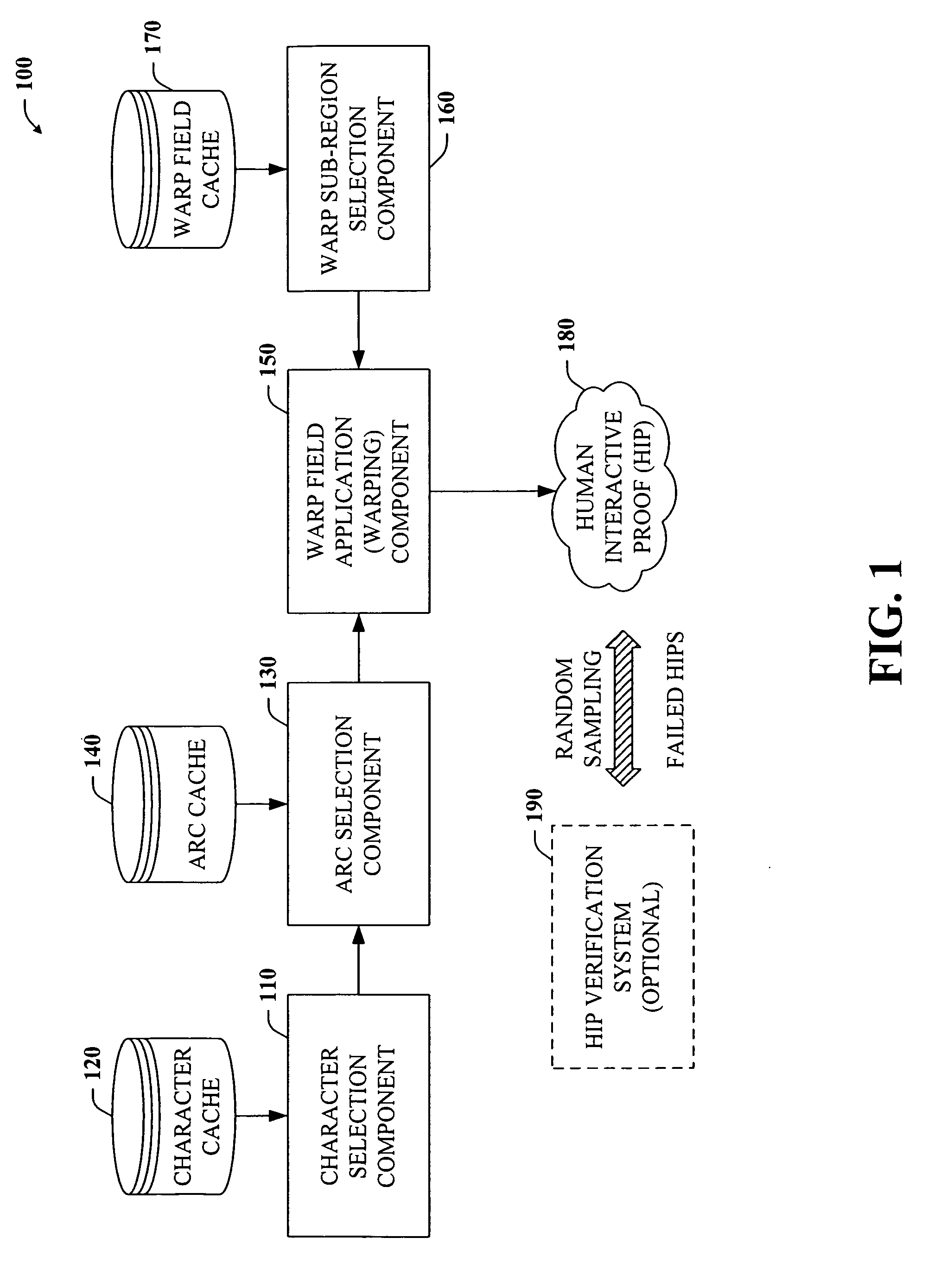
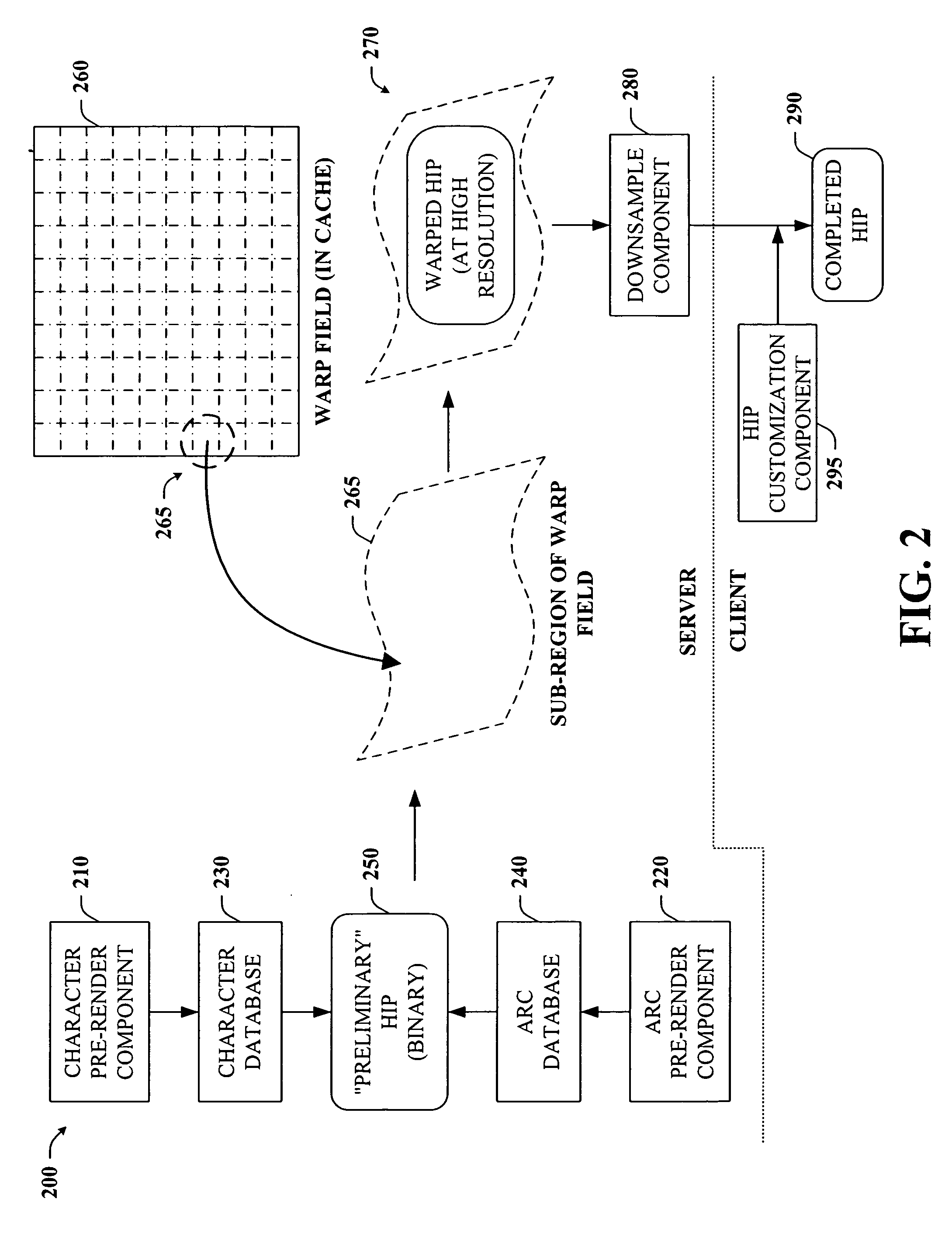
The present invention provides a unique system and method that facilitates obtaining high performance and more secure HIPs. More specifically, the HIPs can be generated in part by caching pre-rendered characters and / or pre-rendered arcs as bitmaps in binary form and then selecting any number of the characters and / or arcs randomly to form a HIP sequence. The warp field can be pre-computed and converted to integers in binary form and can include a plurality of sub-regions. The warp field can be cached as well. Any one sub-region can be retrieved from the warp field cache and mapped to the HIP sequence to warp the HIP. Thus, the pre-computed warp field can be used to warp multiple HIP sequences. The warping can occur in binary form and at a high resolution to mitigate reverse engineering. Following, the warped HIP sequence can be down-sampled and texture and / or color can be added as well to improve its appearance.
Owner:MICROSOFT TECH LICENSING LLC
System and method for generating EJB components from reusable business logics in servlet program
InactiveUS6847981B2Data processing applicationsReverse engineeringMulti languageApplication software
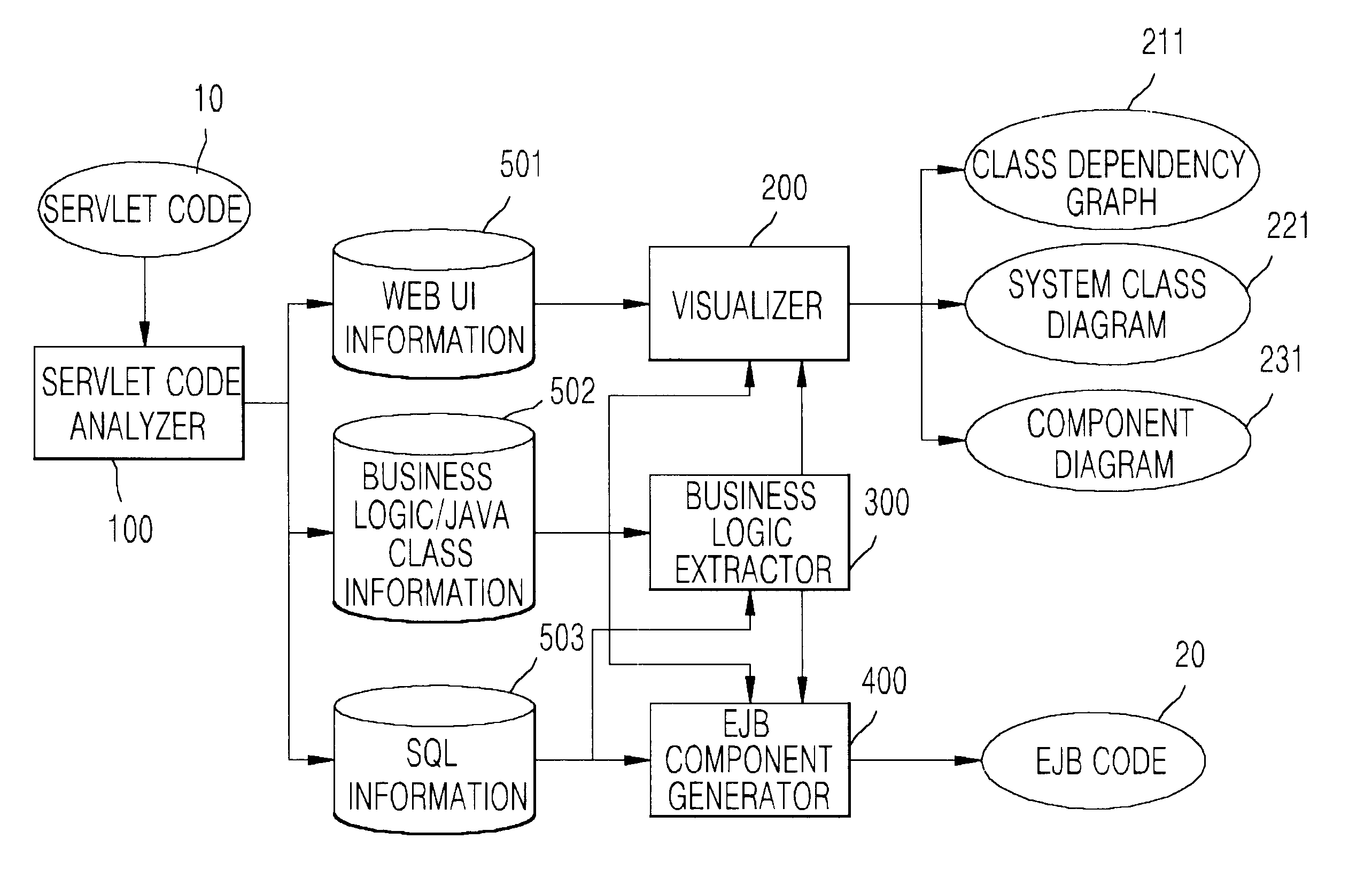
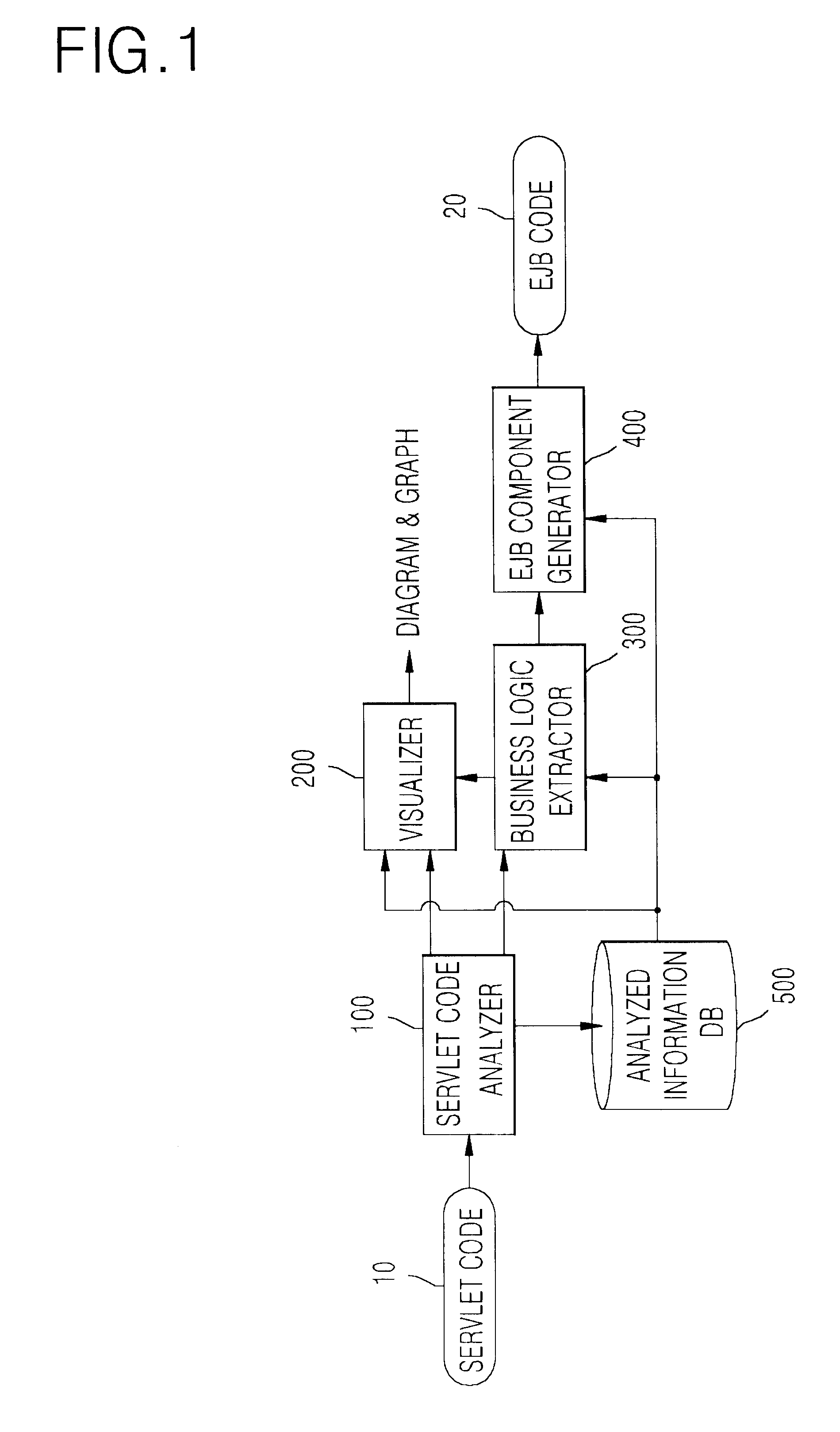
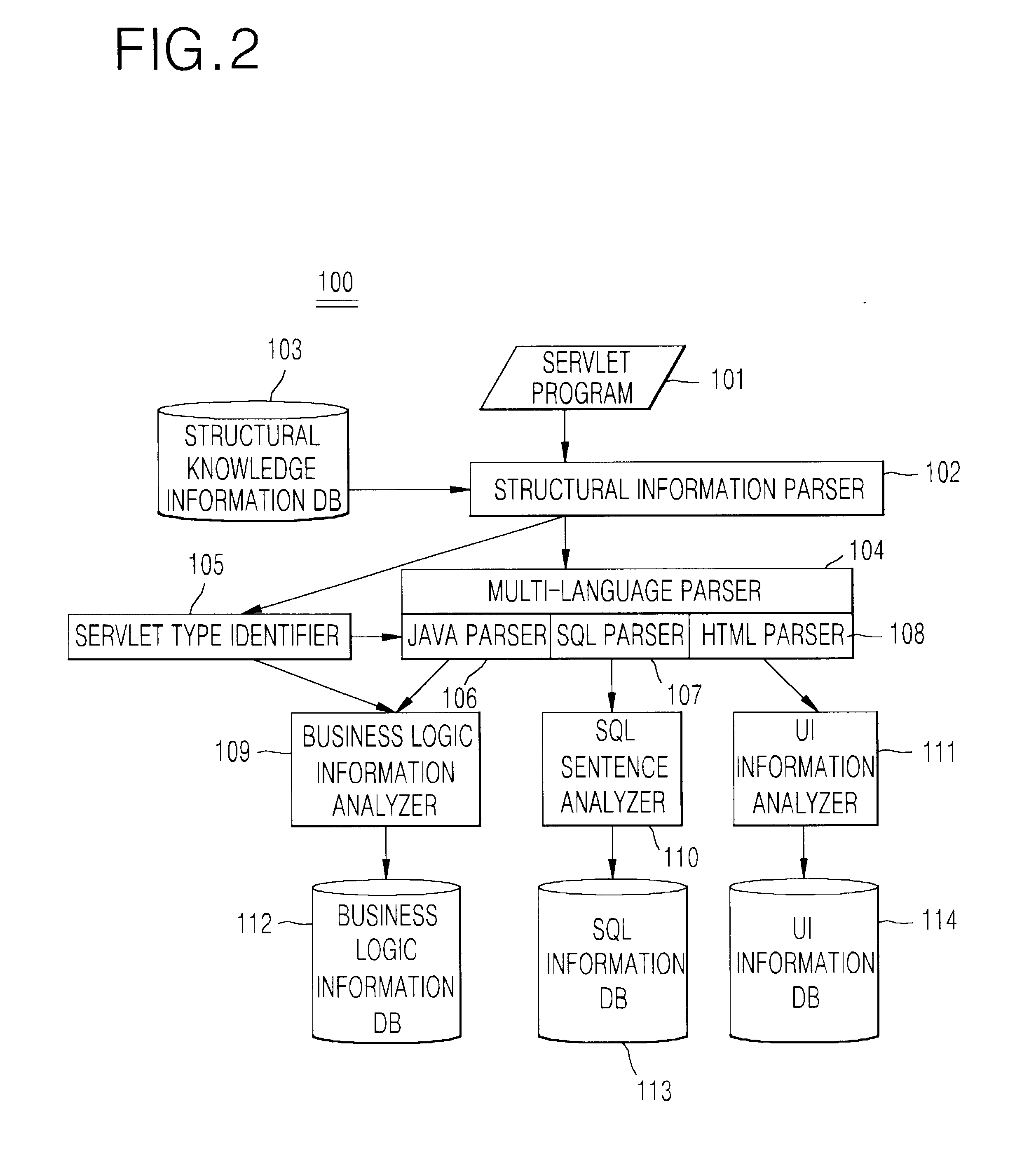
Disclosed is a system and method for generating EJB components by extracting reusable business logic from servlet programs that is one of web program languages used in web-based applications. The system a servlet code analyzer that is a reverse engineering module for analyzing the existing servlet program source, a visualizer for visualizing the analyzed information, a business logic extractor for extracting a reusable business logic, and an EJB component generator for generating the EJB components using the extracted information. The servlet code analyzer considers the flexibility of coding permitted by the servlet program and the use of a multi-language, and the visualizer helps the understanding of the existing legacy program. The business logic extractor extracts the reusable module by extracting the business logic within many user interface related codes, and thus enable the reuse of software. The EJB component generator generates java codes in a jar file that can be deployed.
Owner:ELECTRONICS & TELECOMM RES INST
Complete denture designing and manufacturing method based on CAD/RP technology
InactiveCN101548911ARestore accuratelySimplify complicated proceduresDiagnostic recording/measuringSensorsWaxGraphics
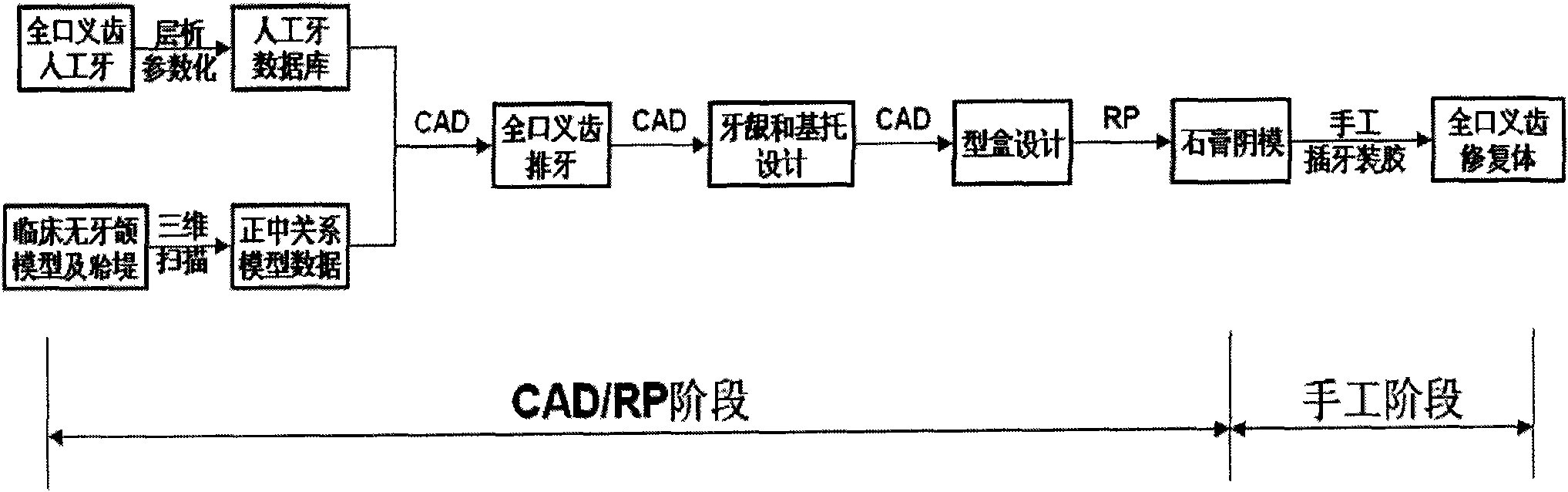
The invention discloses a neutral zone complete denture manufacturing method based on a Computer Aided Design / RapidPrototyping (CAD / RP) technology. The method comprises the following steps: a complete denture artificial tooth three-dimensional image database is established on the basis of the parameterized positioning; the data of upper and lower edentulous jaws with centric relation and neutral zone jaw is collected on the basis of the three-dimensional laser scanning technology with spatial position relation; the complete denture artificial articulation conforming to the theory of neutral zone and complete denture balanced occlusion tooth arrangement is designed on the basis of reverse engineering software, the gum and the base conforming to the complete denture neutral zone theory and the aesthetic principle are designed on the basis of the reverse engineering software; a complete denture flask is designed and processed on the basis of the CAD / RP technology; and the complete denture restoration is finished through the manual tooth inserting and the adhesive applying. The invention creates the concept of a two-step method, finishes the manual tooth arrangement and the wax pattern preparation with the highest technical content and the most complex operation in the traditional fabrication by using the computer and rapid prototyping technology, can finish the full fabrication of the complete denture only by being finally aided with the simple manual step, i.e., the second step of the two-step method, greatly simplifies the complex working procedures of the traditional handwork process, improves the efficiency and the accuracy of restoration and realizes the transformation of the designing and manufacturing process of the complete denture from the manual mode to the digital mode.
Owner:PEKING UNIV SCHOOL OF STOMATOLOGY
Method of securing software against reverse engineering
InactiveUS20030120938A1User identity/authority verificationUnauthorized memory use protectionSoftwareReverse engineering
A method of securing software against reverse engineering replaces portions of software code with tokens. A key is created in which the functionality of each such token is indicated. The key is stored in memory, separate from the software. The key may be encrypted for added security. When an authorized user seeks to run the software, the key is recalled from memory and decrypted, if previously encrypted. The corresponding functionalities indicated by the key are substituted in the software whenever tokens are encountered.
Owner:MULLOR MIKI
White-box cryptographic system with input dependent encodings
ActiveUS20120002807A1Simplified brokenImprove propertiesSecret communicationCryptographic attack countermeasuresComputer hardwareData encoding
A white-box cryptographic system is presented wherein at least one of its internal values is represented using an input dependent encoding. The system comprises a network of a plurality of basic blocks arranged for collectively performing a cryptographic operation. An encoder is arranged for encoding output data of a first one of the plurality of basic blocks into an encoder-output according to a selected one of a plurality of encoding schemes, said selection depending on an input-message to the system. A compensator is arranged for recoding intermediate data to compensate for the effect of the encoding according to a selected one of a plurality of recoding schemes. Using variable encodings instead of fixed encodings complicates reverse engineering the white-box cryptographic system.
Owner:IRDETO ACCESS
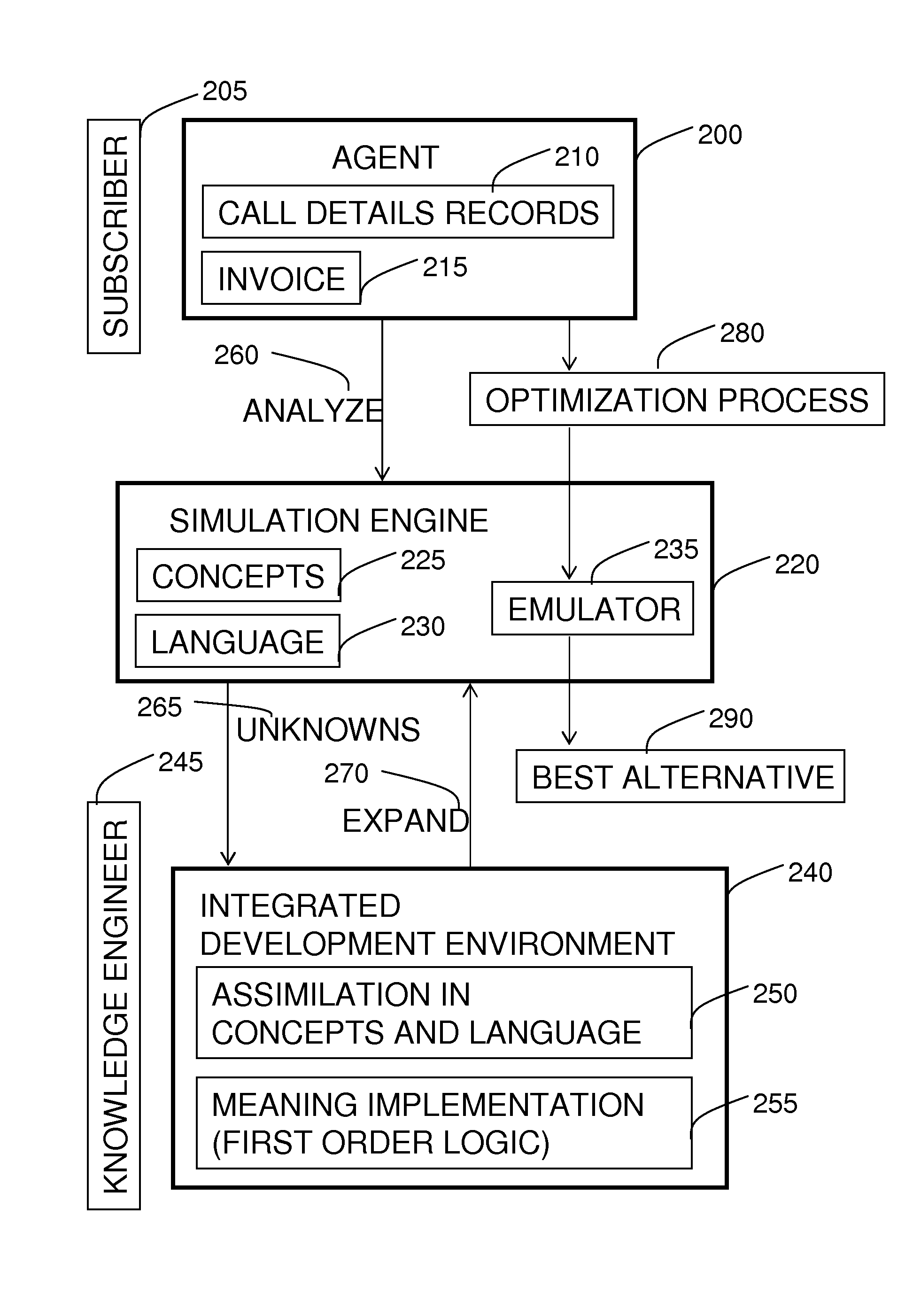
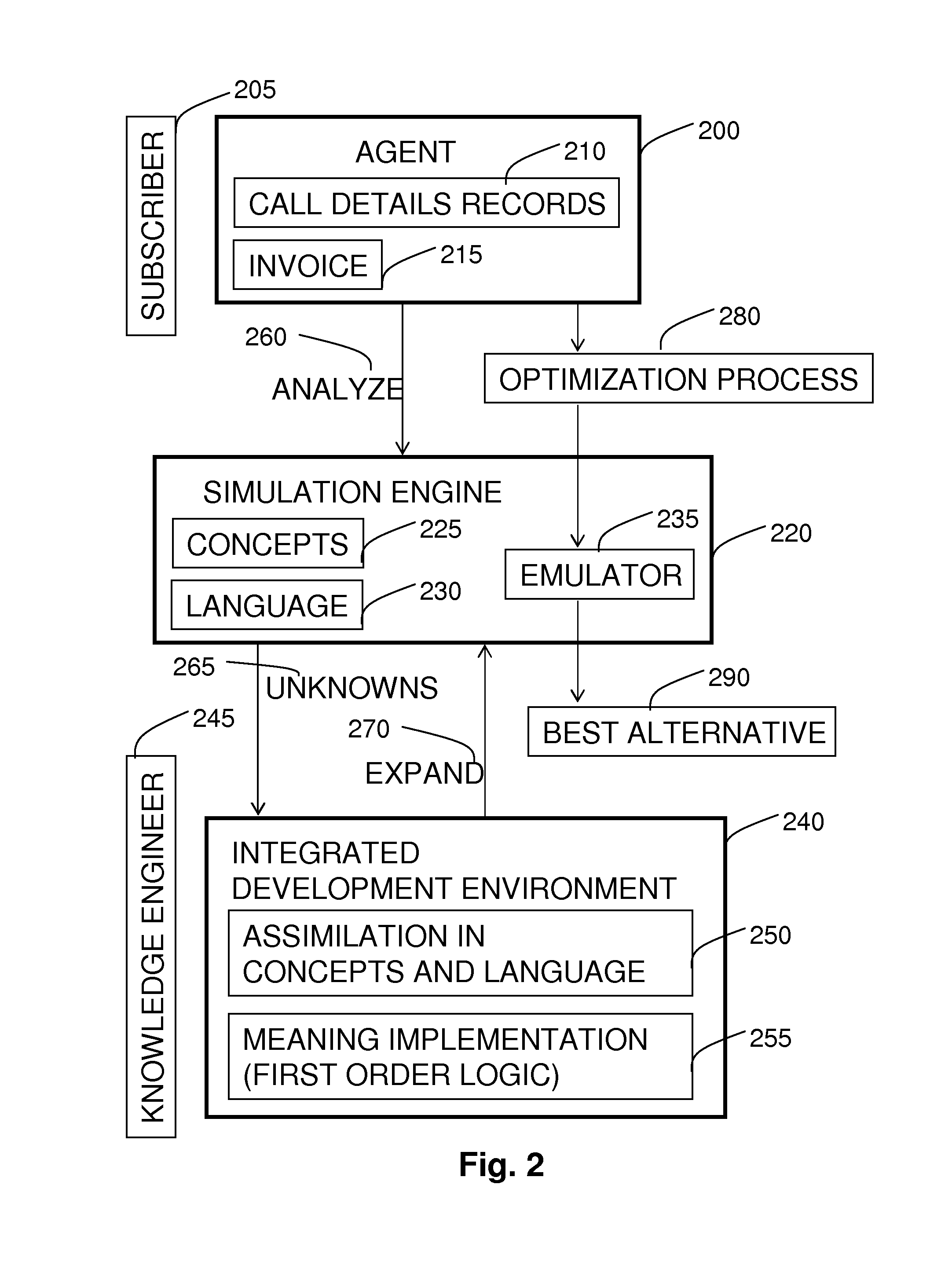
Method for Capturing the Essence of Product and Service Offers of Service Providers
InactiveUS20100169234A1Reduce the differenceAccounting/billing servicesGenetic modelsProgram planningService provision
A computer implemented method of constructing a computer implemented knowledge base, of evaluating a plurality of invoices, of knowledge refinement and generation, as well as a computer implemented knowledge base for analyzing a plurality of invoices. The methods comprise receiving the invoices, semantic and logically analyzing them to identify the invoice items (parameters and algorithms of service providers, billing plans, user profile, consumption pattern and debits) and relations connecting them and construct the knowledge base. The knowledge base comprises a hierarchic taxonomy of billing plans related to services of any domain (telecommunications services, banking, insurance, utilities etc.) and a computer implemented generic invoice constructed in reverse engineering logic for simulating debits. Debit simulations are done in order to achieve: 1. recommendations for optimal billing plans. 2. Recommendations for possible detected billing errors. 3. recommendations concerning new plans and / or services, and their financial implications Improving the knowledge base may use genetic algorithms based on an analogous hierarchic structure of the taxonomy to a genetic hierarchy, and may proceed by refining billing plans and comparing the resulting debits. Novel Semantic-web and Artificial Intelligence (AI) methods are used.
Owner:WIZBILL
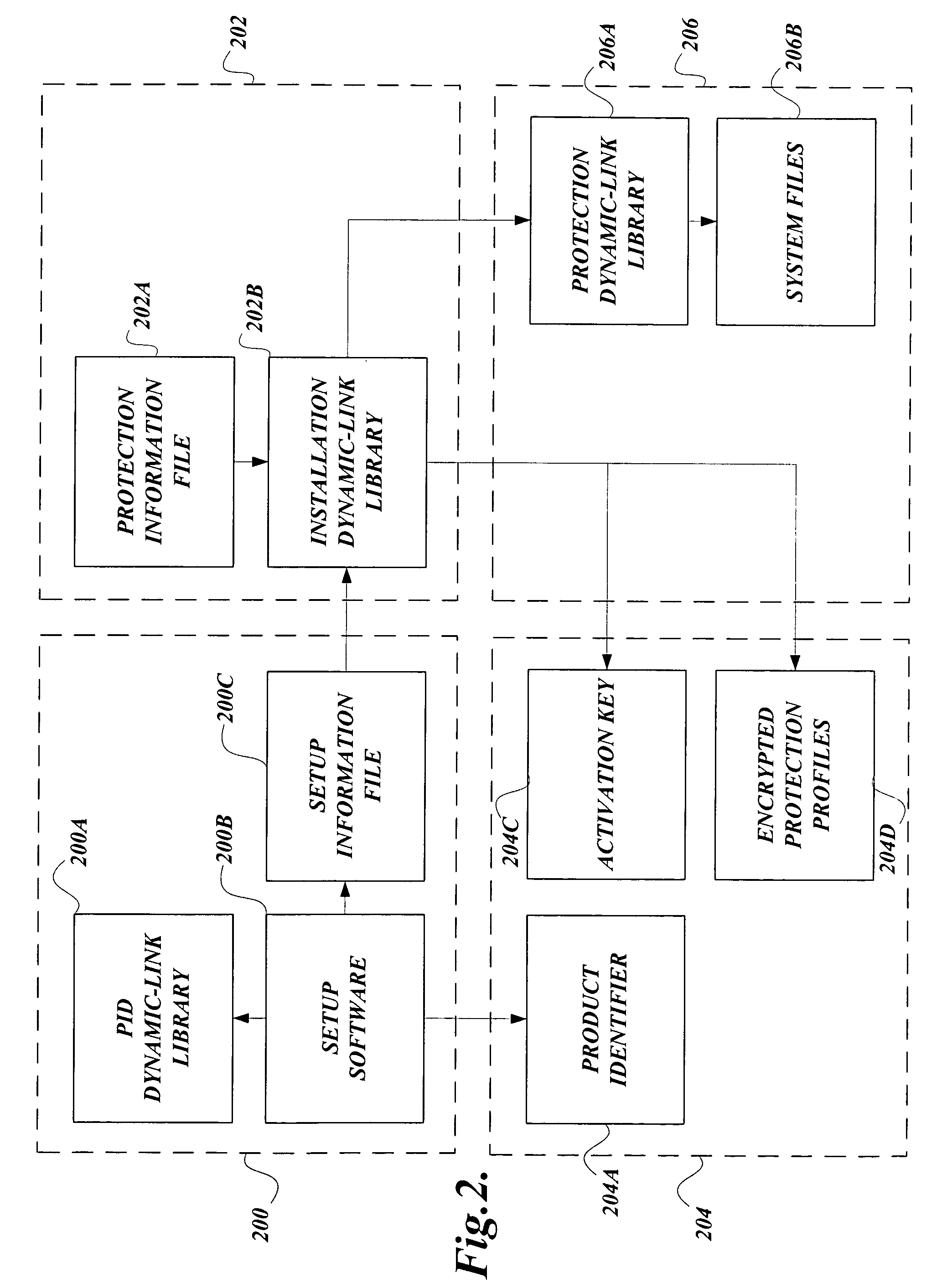
Software obfuscation
InactiveUS20060005250A1Key distribution for secure communicationDigital data processing detailsObfuscationConfigfs
Tampering with pieces of software is inhibited. Software obfuscation inhibits reverse engineering by hackers by manipulating names of functions and adding jump instructions into various pieces of software. Profiles are stored in a central hierarchical database and such profiles are protected from tampering. The obfuscation of a software image so as to becloud the comprehension of hackers in reverse engineering pieces of software comprising the software image is provided.
Owner:MICROSOFT TECH LICENSING LLC
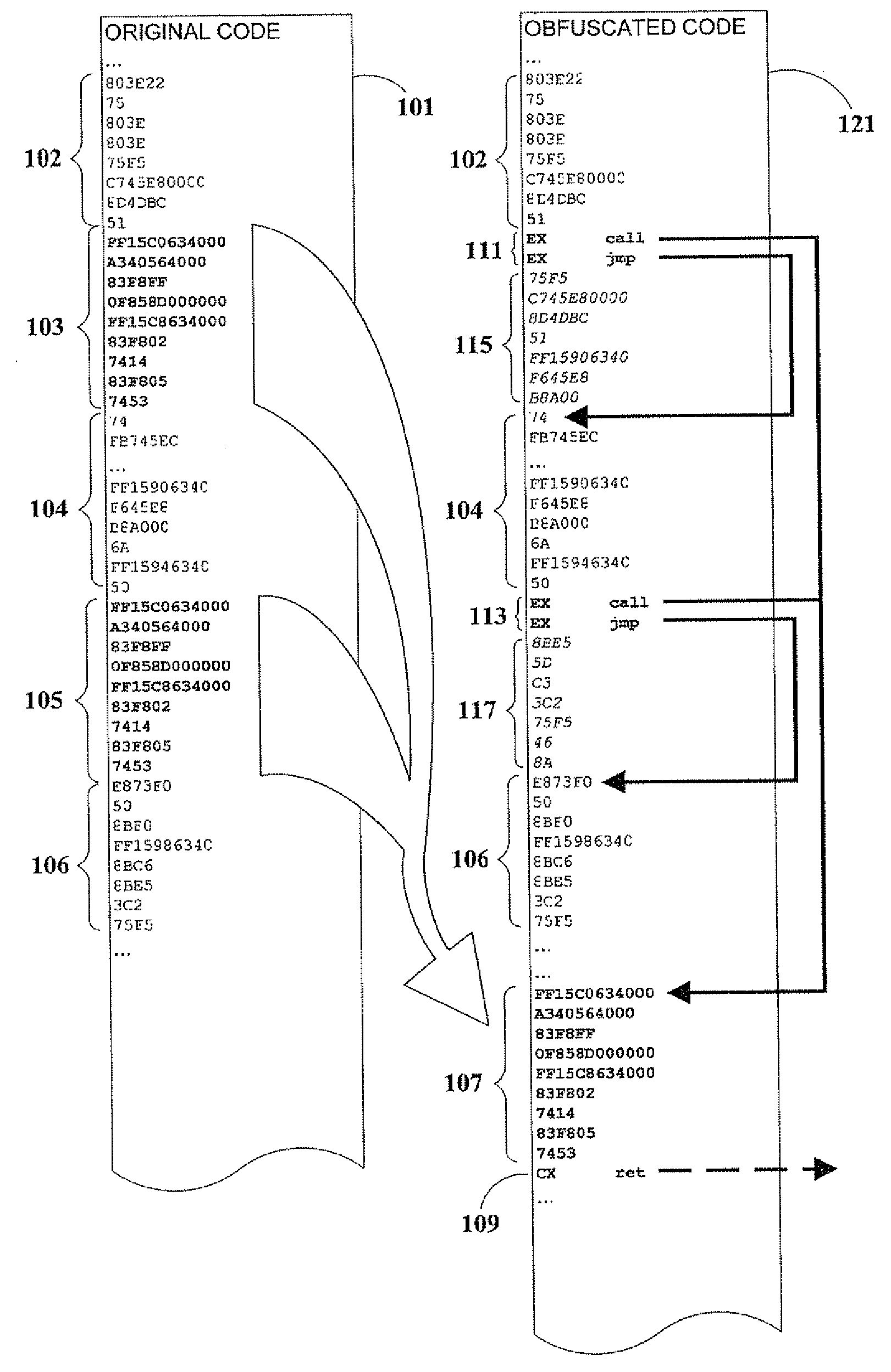
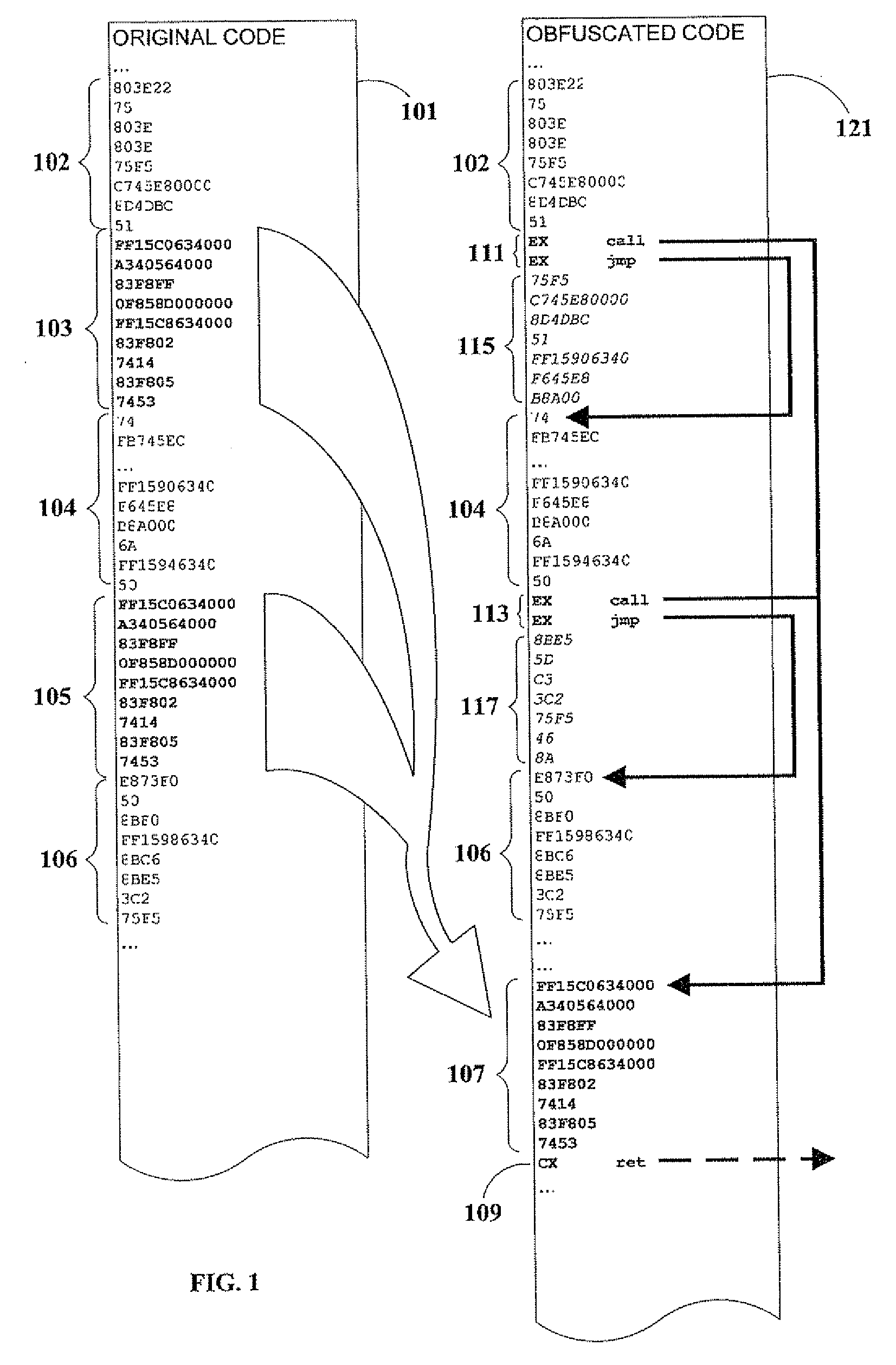
Code Obfuscation By Reference Linking
InactiveUS20090049425A1Improve efficiencyMinimize inflationProgram/content distribution protectionSpecific program execution arrangementsObfuscationDecoy
A method of obfuscating executable computer code to impede reverse-engineering, by interrupting the software's execution flow and replacing in-line code with calls to subroutines that do not represent logical program blocks. Embodiments of the present invention introduce decoy code to confuse attackers, and computed branching to relocated code so that actual program flow cannot be inferred from disassembled source representations.
Owner:SAFENET DATA SECURITY ISRAEL
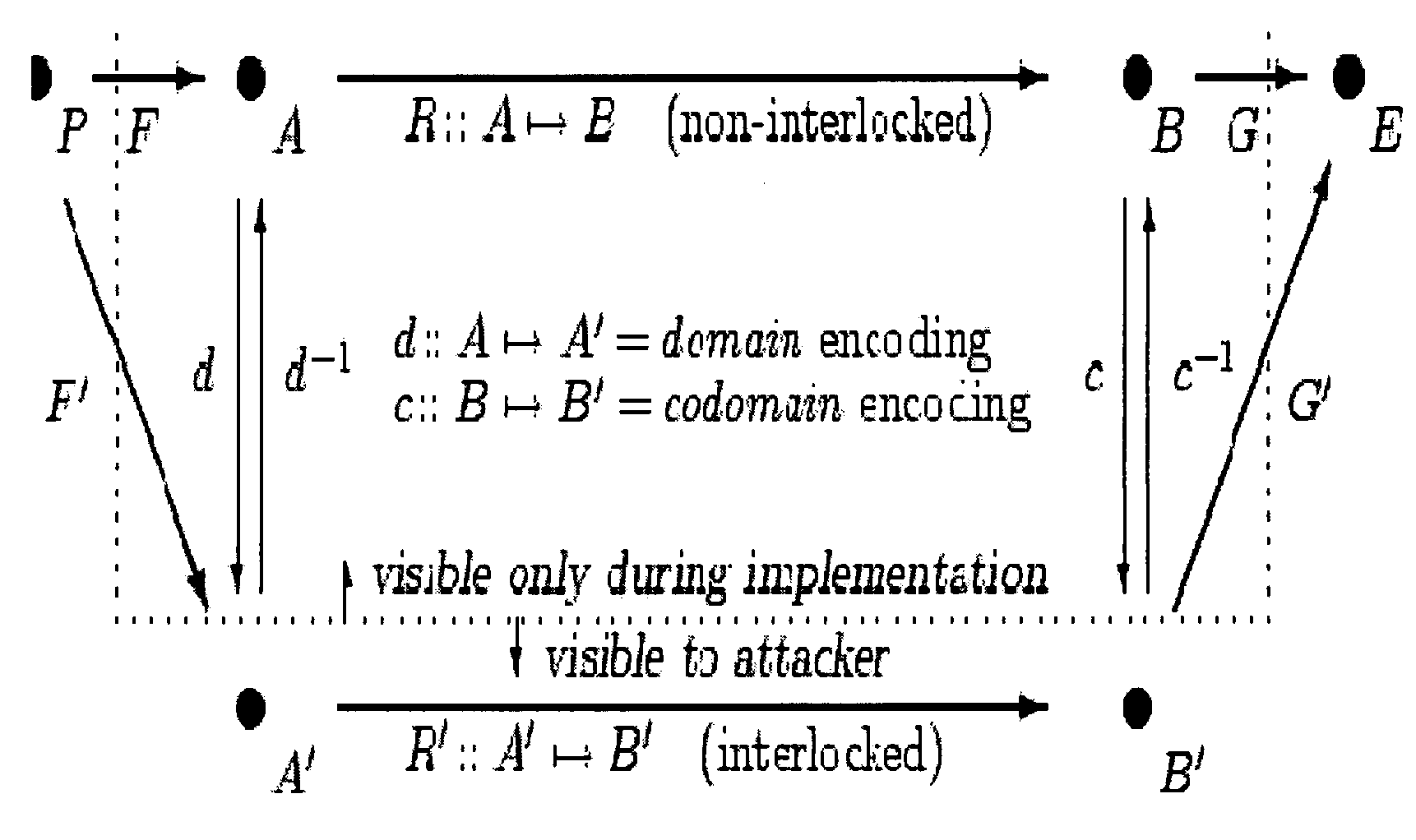
System and method of interlocking to protect software - mediated program and device behaviors
A method for rendering software resistant to reverse engineering. Replace at least one first constant (mathematical expression, etc.) in a computational expression with a second mixed mathematical and bitwise-Boolean expression, the first constant being simpler than the second expression and the second expression being based on the value or the variables found in the first constant (or expression). Evaluation of the second mixed mathematical and bitwise-Boolean expression produces a value preserving the value of the first constant, either: with the original value of the first constant or the original value of the result of the first expression, in which case the second mixed mathematical and bitwise-Boolean expression is obtained from the first constant by converting the first constant by mathematical identities; or, in an encoded form, as a new value, which can be converted back to the original value of the first constant by applying an information-preserving decoding function, in which case the second mixed mathematical and bitwise-Boolean expression is obtained from the first constant by modifying the first constant by a combination of conversion according to mathematical identities and transformation according to an information preserving encoding function.
Owner:CLOAKWARE CORP +1
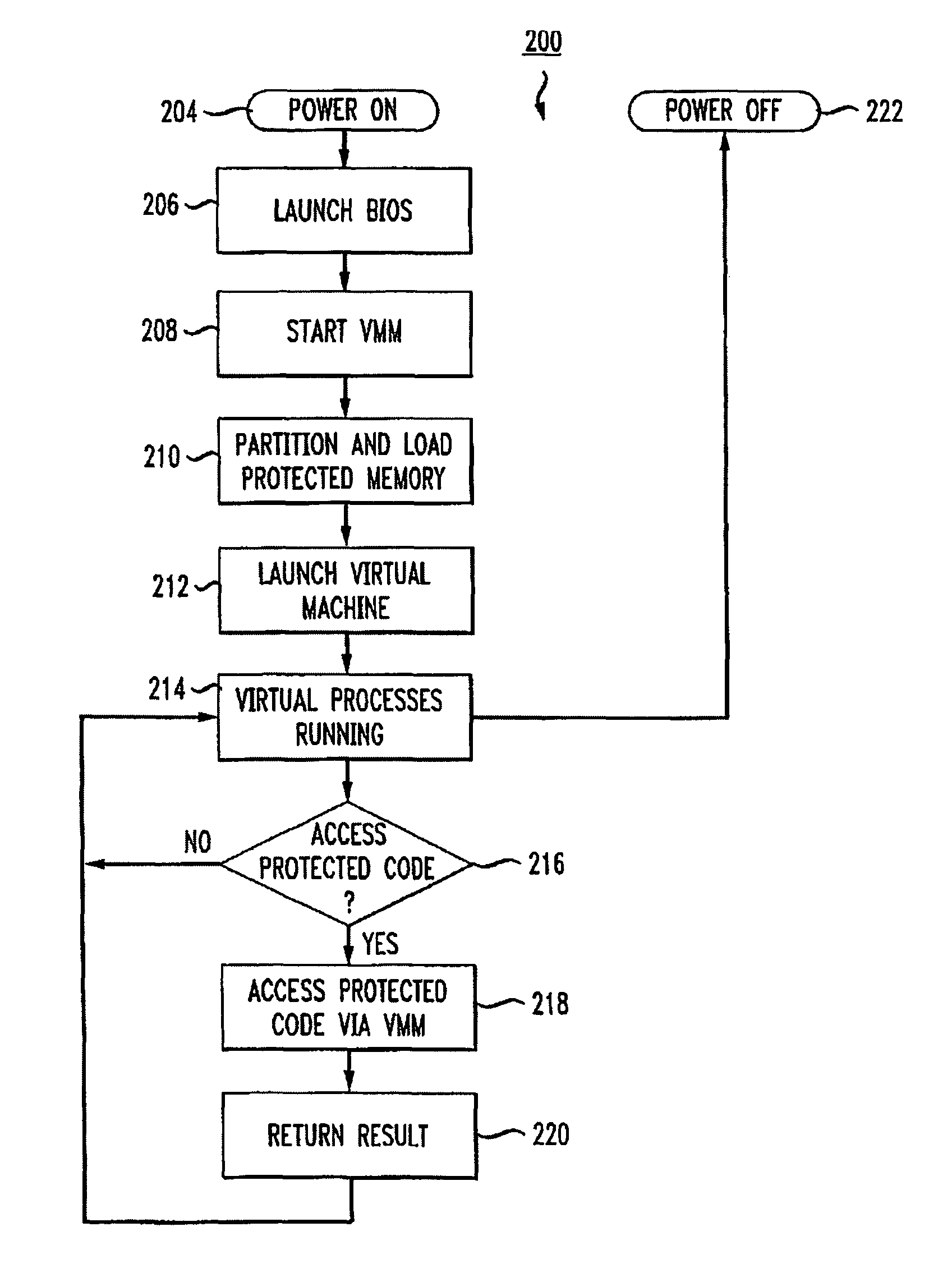
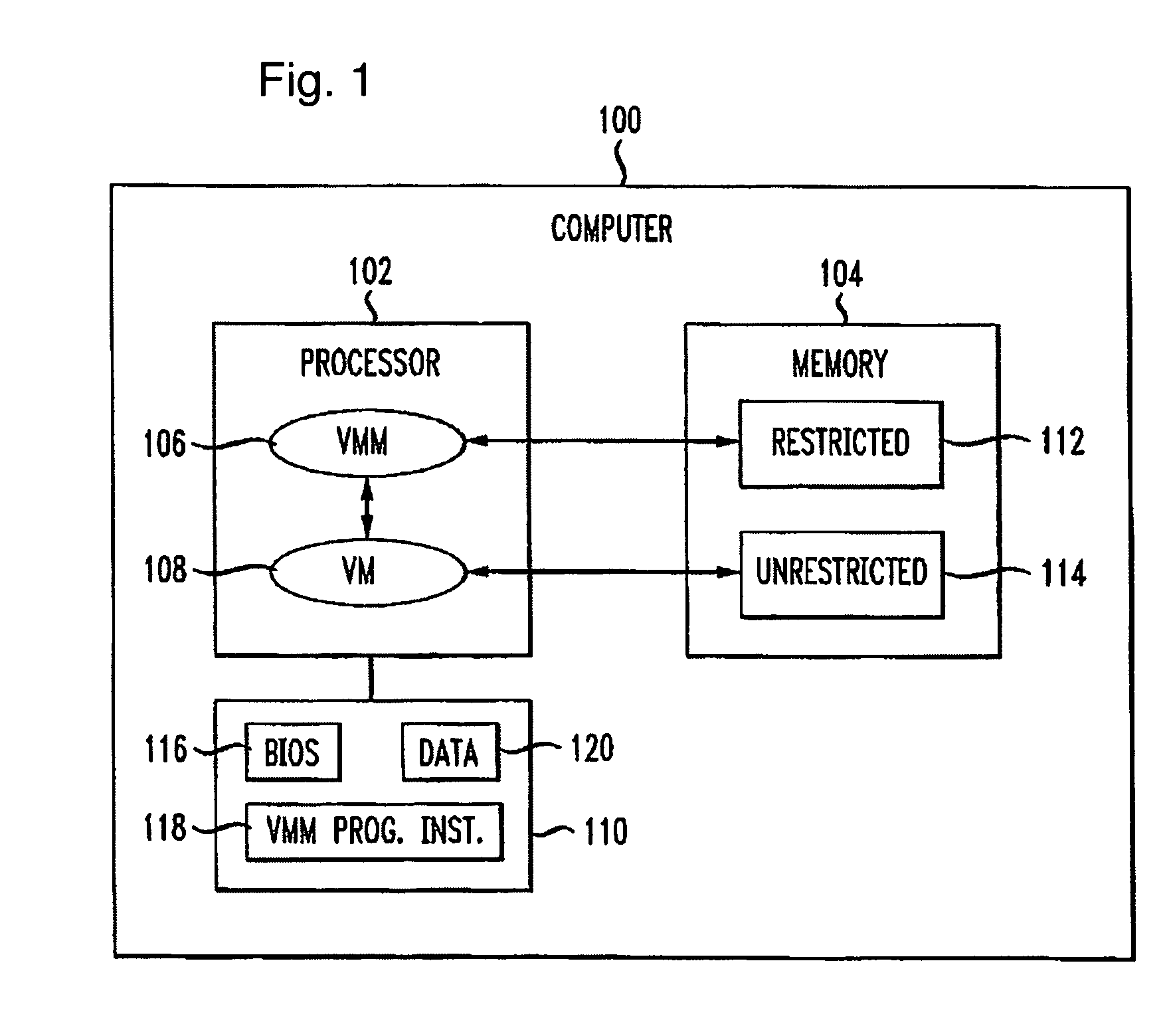
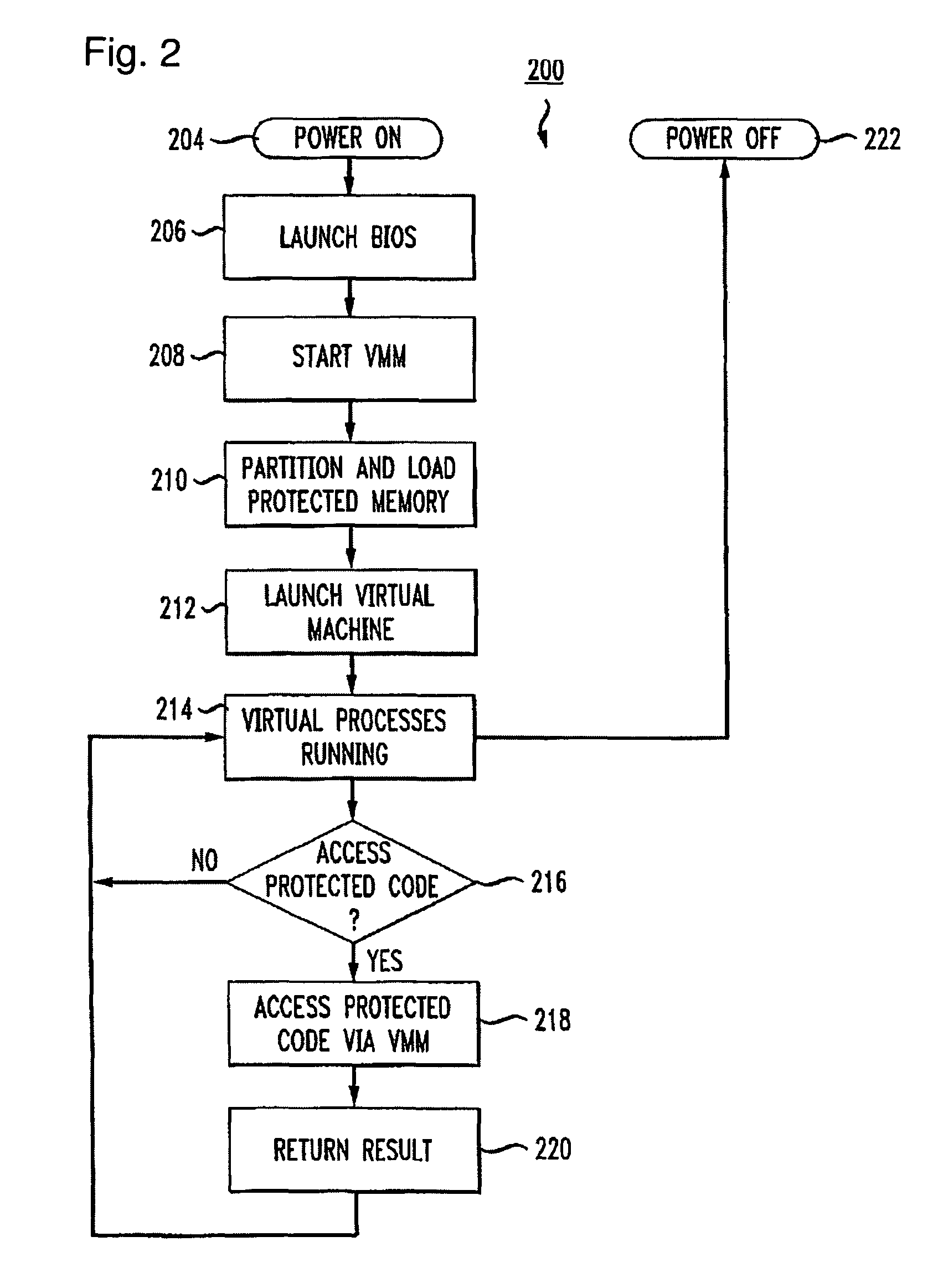
Virtualization-based security apparatuses, methods, and systems
InactiveUS8156298B1Avoid disadvantagesAvoid problemsMemory architecture accessing/allocationComputer security arrangementsOperational systemProtection mechanism
Apparatuses, devices, and methods for protecting content on a computer are disclosed that employ a novel hypervisor configured to segregate, or partition, hardware resources or portions thereof into protected and unprotected areas and devices. The partitioning, effectively hides protected hardware resources, such as the BIOS device, etc., from operating systems running on the computer. The hypervisor controls access resources into the protected area and limits the manner in which the operating systems on the computer can access the protected resources and content. The hypervisor can be configured to physically partition entire hardware resource or to employ virtualization technology to partition hardware resources, such as memory devices, into protected and unprotected areas that are virtually partitioned. The hypervisor of the present invention provides a new concept in employing anti-forensic techniques to bring about a protection mechanism that prevents unauthorized users including remote attackers who have obtained administrative access from accessing, reverse engineering, or otherwise exposing content protected. The content can generally be anything that can be maintained in a computer including data, algorithms, code, information and processes in general, etc., such as personal, sensitive, confidential and proprietary information and algorithms, and cryptographic keys.
Owner:NULLRING
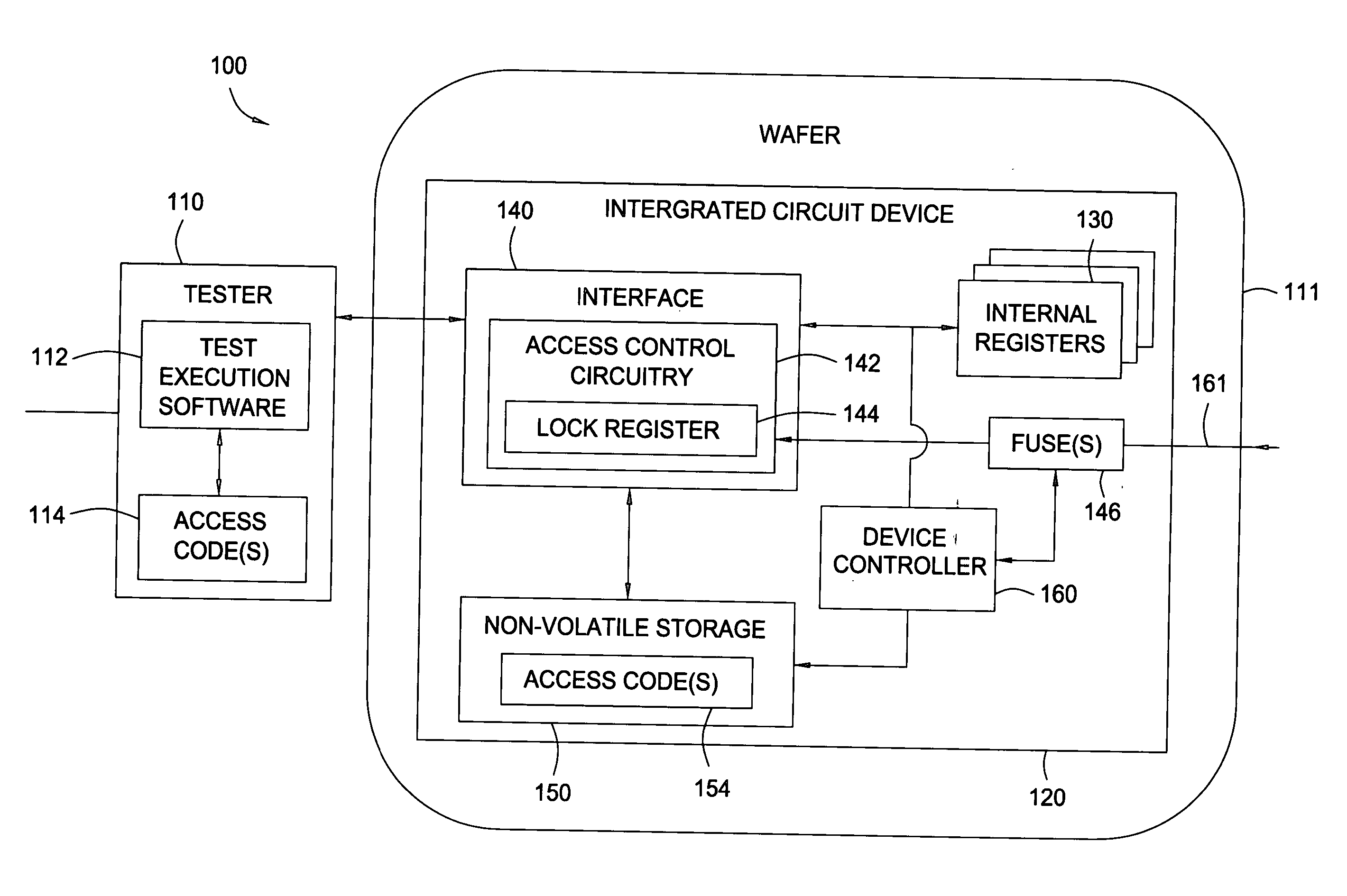
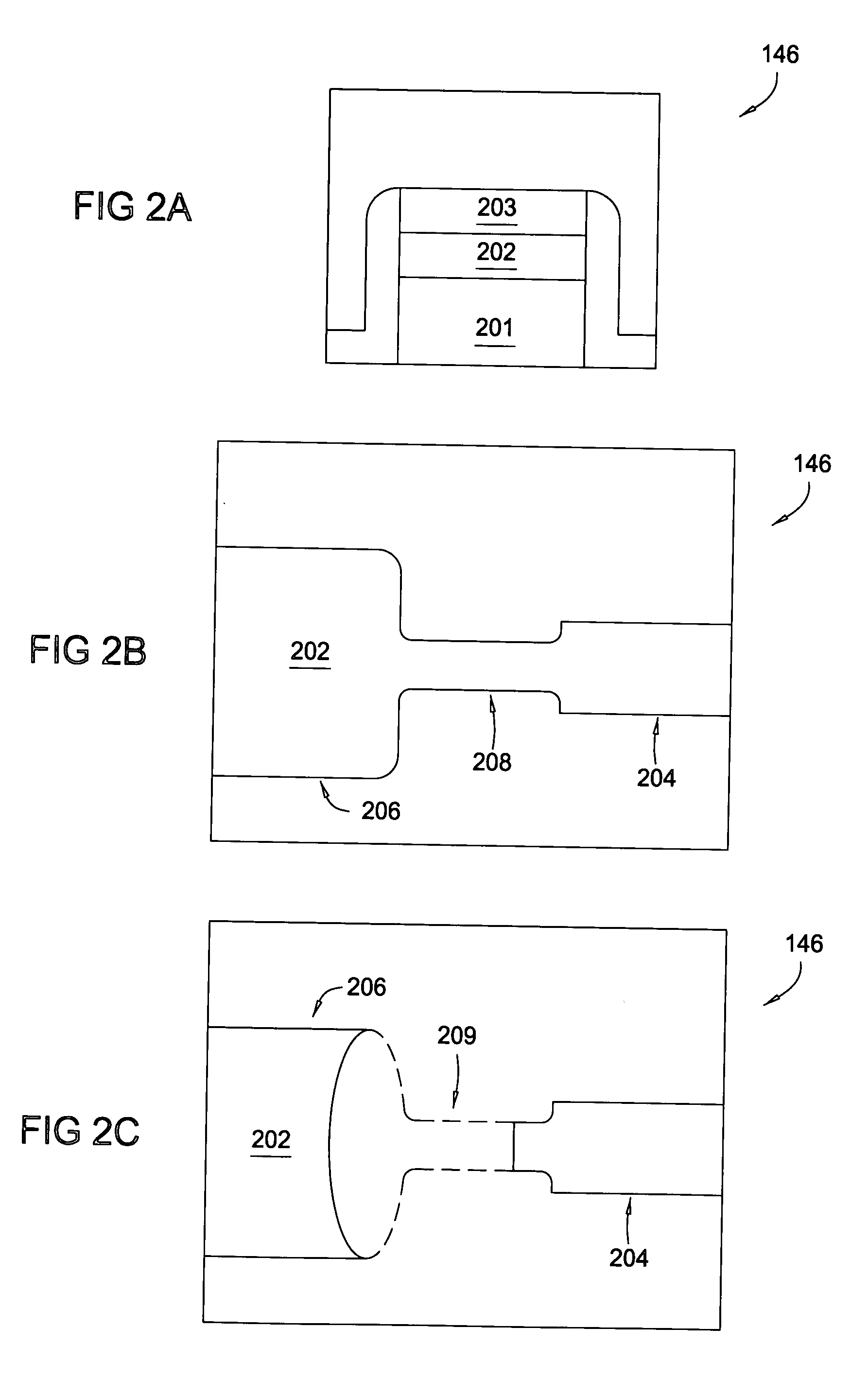
Using electrically programmable fuses to hide architecture, prevent reverse engineering, and make a device inoperable
ActiveUS20060136751A1Prevent unauthorized accessPrevent copyingUnauthorized memory use protectionHardware monitoringElectricityControl electronics
Owner:MARVELL ASIA PTE LTD
Creating and customizing a workflow process from a document
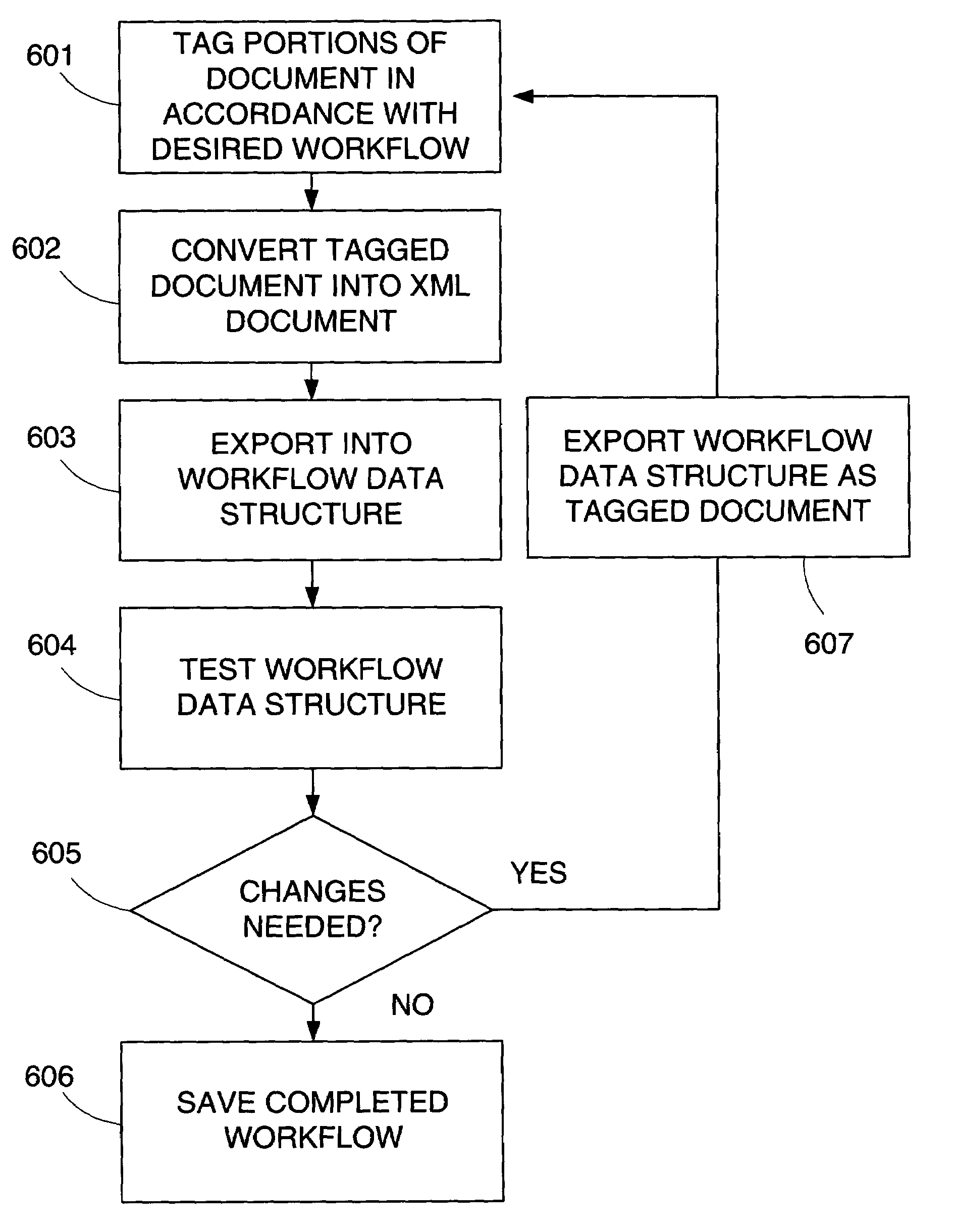
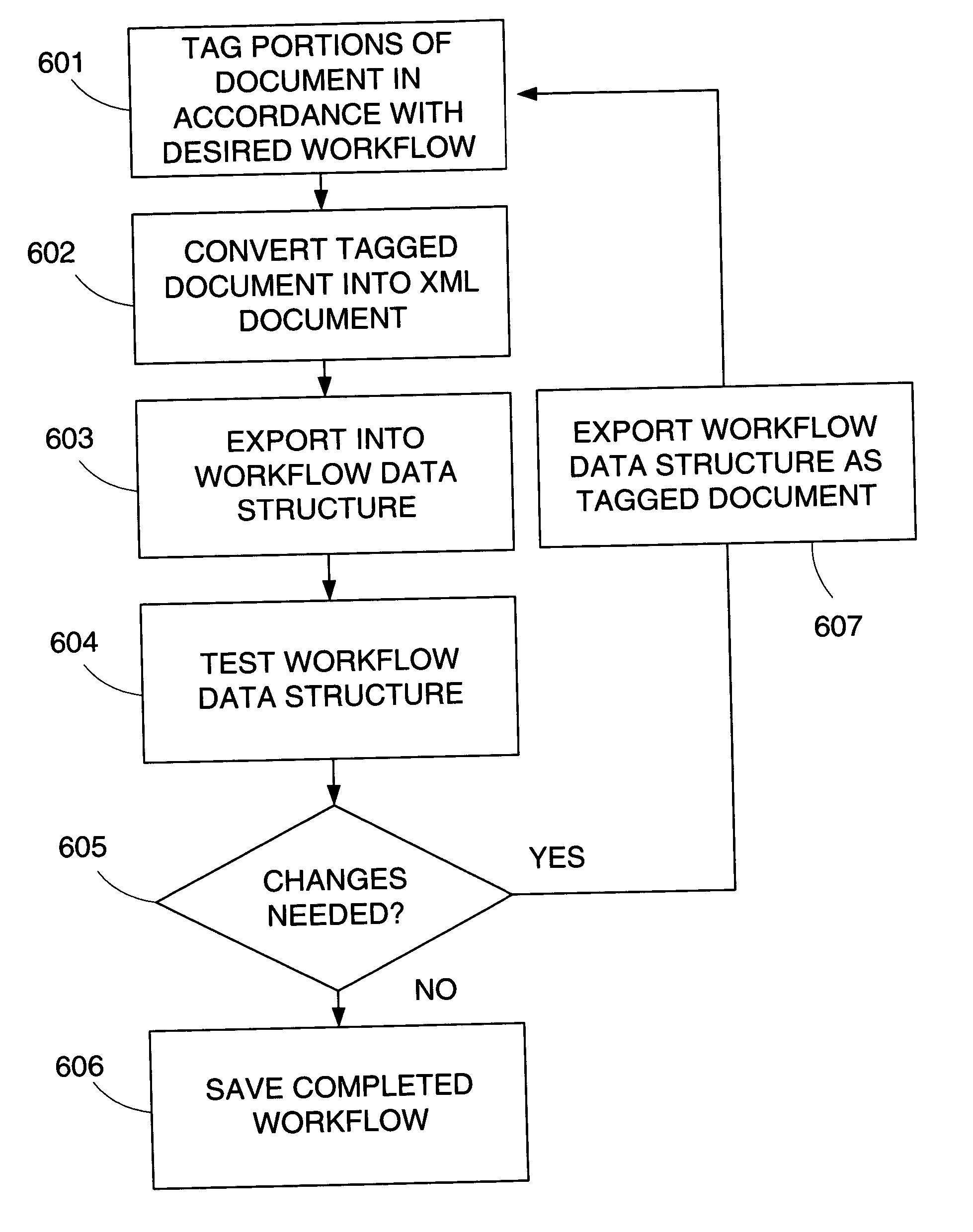
InactiveUS7657831B2Digital data processing detailsNatural language data processingDocument preparationDocumentation
An apparatus and method is provided for deconstructing or “reverse engineering” one or more documents into a workflow process by identifying various phases, steps, and questions that arise from the document. Using an editing tool, a user selects text portions of a document and specifies one or more workflow parameters associated with the text, such as a question that will be generated to elicit information corresponding to the selected text. The document is tagged and used to generate a data structure used to execute the workflow process at a later time. The data structure can be modified to change the workflow structure.
Owner:J J DONAHUE
CRM Security Core
A security core supports a networked banking app for a client application device communicating with a server, such as e.g. a smartphone. It provides a secure environment for the banking app to conduct registration, enrollment, and transaction workflows with corresponding back-end servers on the network. It includes defenses against static analysis, attempts at reverse engineering, and real-time transaction fraud. A principal defense employed is obfuscation of the protocols, APIs, algorithms, and program code. It actively detects, thwarts, misdirects, and reports reverse engineering attempts and malware activity it senses. A routing obfuscator is configured to operate at the outer layer. Previous core designs are retained as camouflage. An internal TLS library is used rather than the OS TLS layer. Cookies are managed internally in the core rather than in the webkit-browser layer.
Owner:CRYPTOMATHIC LTD
Creating and customizing a workflow process from a document
ActiveUS20050027733A1Digital data processing detailsNatural language data processingPaper documentDocument preparation
An apparatus and method is provided for deconstructing or “reverse engineering” one or more documents into a workflow process by identifying various phases, steps, and questions that arise from the document. Using an editing tool, a user selects text portions of a document and specifies one or more workflow parameters associated with the text, such as a question that will be generated to elicit information corresponding to the selected text. The document is tagged and used to generate a data structure used to execute the workflow process at a later time. The data structure can be modified to change the workflow structure.
Owner:J J DONAHUE
Profile protection
InactiveUS20050278535A1Prevent tamperingKey distribution for secure communicationDigital data processing detailsObfuscationSoftware engineering
Tampering with pieces of software is inhibited. Profiles are stored in a central hierarchical database and such profiles are protected from tampering. The obfuscation of a software image so as to becloud the comprehension of hackers in reverse engineering pieces of software comprising the software image is provided. A process of verifying whether the pieces of software together constitute a software package that requires protection from tampering is also provided.
Owner:MICROSOFT TECH LICENSING LLC
High performance content alteration architecture and techniques
ActiveUS7505946B2Improve effectivenessIncrease speedDigital data processing detailsGeometric image transformationComputer scienceBitmap
The present invention provides a unique system and method that facilitates obtaining high performance and more secure HIPs. More specifically, the HIPs can be generated in part by caching pre-rendered characters and / or pre-rendered arcs as bitmaps in binary form and then selecting any number of the characters and / or arcs randomly to form a HIP sequence. The warp field can be pre-computed and converted to integers in binary form and can include a plurality of sub-regions. The warp field can be cached as well. Any one sub-region can be retrieved from the warp field cache and mapped to the HIP sequence to warp the HIP. Thus, the pre-computed warp field can be used to warp multiple HIP sequences. The warping can occur in binary form and at a high resolution to mitigate reverse engineering. Following, the warped HIP sequence can be down-sampled and texture and / or color can be added as well to improve its appearance.
Owner:MICROSOFT TECH LICENSING LLC
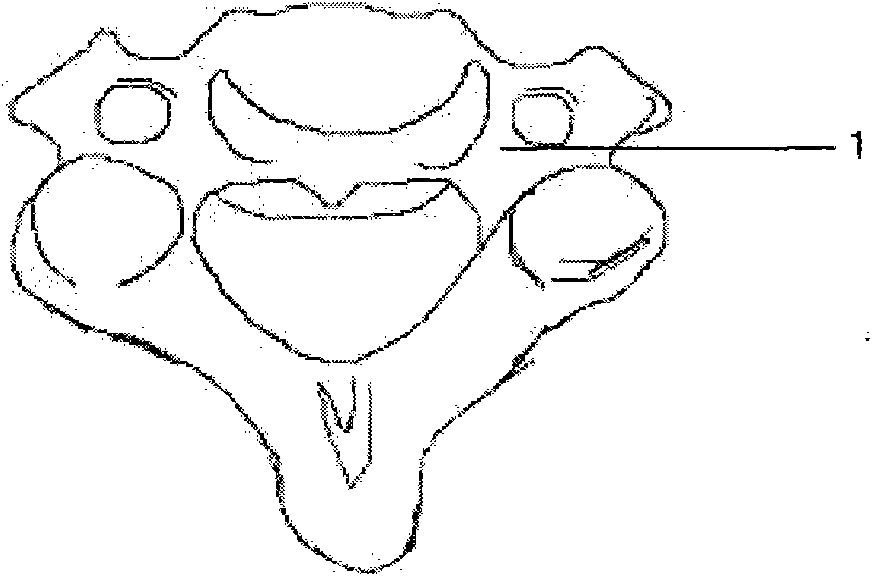
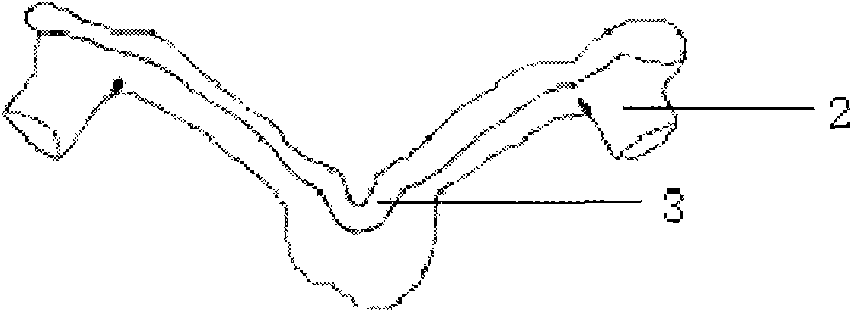
Navigation template capable of being used for positioning vertebral pedicle
The invention discloses a navigation template capable of being used for positioning vertebral pedicle. A manufacture method of the navigation template comprises the following steps of: firstly, acquiring original data and establishing a three-dimensional vertebra model on a computer; secondly, carrying out three-dimensional analysis on a vertebral pedicle needle-entering channel, extracting an outline of the rear part of a vertebral plate, establishing a virtual reverse template coincide to the outline at the rear part of the vertebral plate in a system; thirdly, fitting the virtual reverse template with the vertebral pedicle needle-entering channel, establishing a virtual needle-entering template; and fourthly, manufacturing the needle-entering template by using a quick forming technology, wherein the needle-entering template is a reverse navigation template coincide to the outline of the rear part of the vertebral plate. The invention organically integrates a digital technology, reverse engineering and the quick forming technology, thereby achieving the purpose of rapidly, cheaply and efficiently accurately positioning the vertebral pedicle.
Owner:陆声
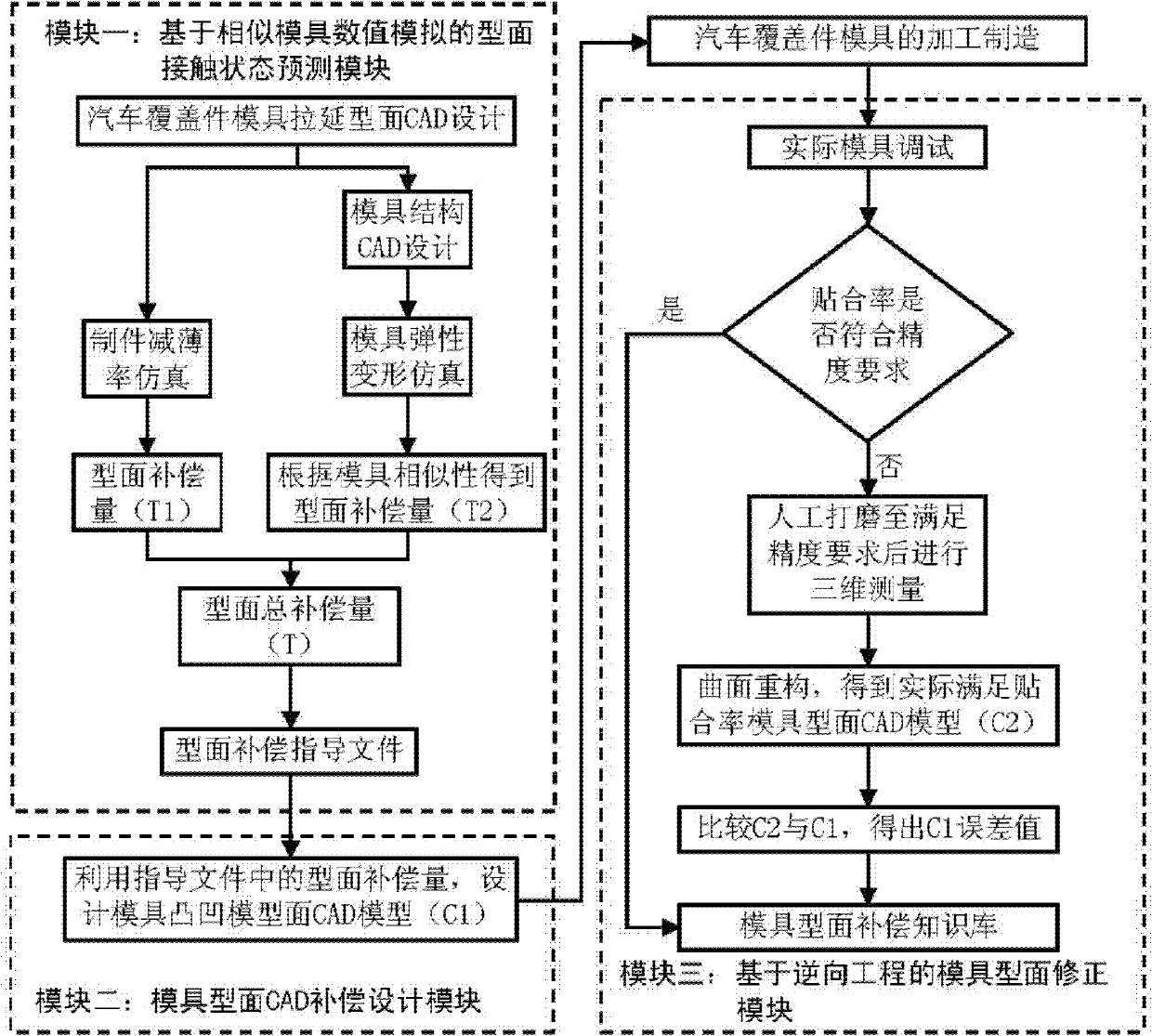
Design method for molded surface of automobile cover part die based on molded surface deformation compensation
InactiveCN102169521ASimple designQuality improvementSpecial data processing applicationsComputer Aided DesignCapability Maturity Model
The invention discloses a design method for a molded surface of an automobile cover part die based on molded surface deformation compensation, which comprises the steps of predicting the contact state of the molded surface based on similar die numerical value simulation, outputting a compensation guide document for the molded surface of the die based on the dethickness of a manufactured piece and the elastic deformation of the die, using CAD (computer aided design) software to design the compensation molded surface of the die based on the guide document and outputting the CAD compensation molded surface, and outputting the repaired actual molded surface of the die by using a method based on reverse engineering. Under the premises of reasonable technical conditions and die structures, a CAE-CAD-CMM (computer aided engineering-computer aided design-capability maturity model) integration system for the molded surface of the automobile cover part die based on the dethickness of the manufactured piece and the elastic deformation compensation of the die is formed. The method can be adopted for quickening the design process of the molded surface of the automobile cover part die, reducing the manual grinding time, guarantees the fit precision of the molded surface of the die and the forming precision of the automobile cover part, and provides a new method for the high-quality short-period debugging work of the automobile cover panel die.
Owner:TIANJIN UNIV OF TECH & EDUCATION TEACHER DEV CENT OF CHINA VOCATIONAL TRAINING & GUIDANCE +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com