Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
42 results about "New Executable" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
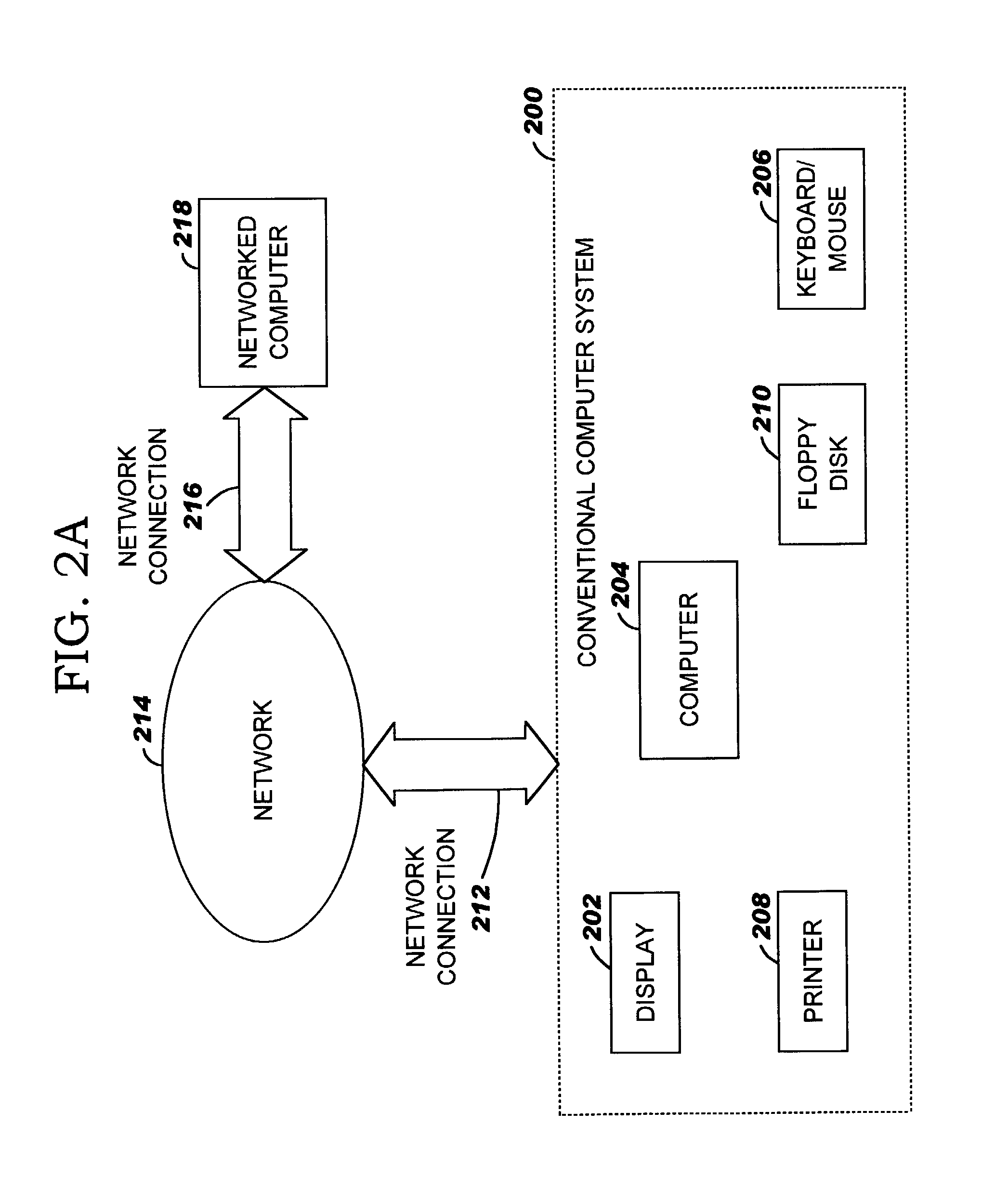
The New Executable (abbreviated NE or NewEXE) is a 16-bit .exe file format, a successor to the DOS MZ executable format. It was used in Windows 1.0–3.x, multitasking MS-DOS 4.0, OS/2 1.x, and the OS/2 subset of Windows NT up to version 5.0 (Windows 2000). A NE is also called a segmented executable.
System, method, and service for detecting improper manipulation of an application
InactiveUS20060195906A1Eliminate loopholesMore robustnessDigital data processing detailsUser identity/authority verificationObfuscationApplication procedure
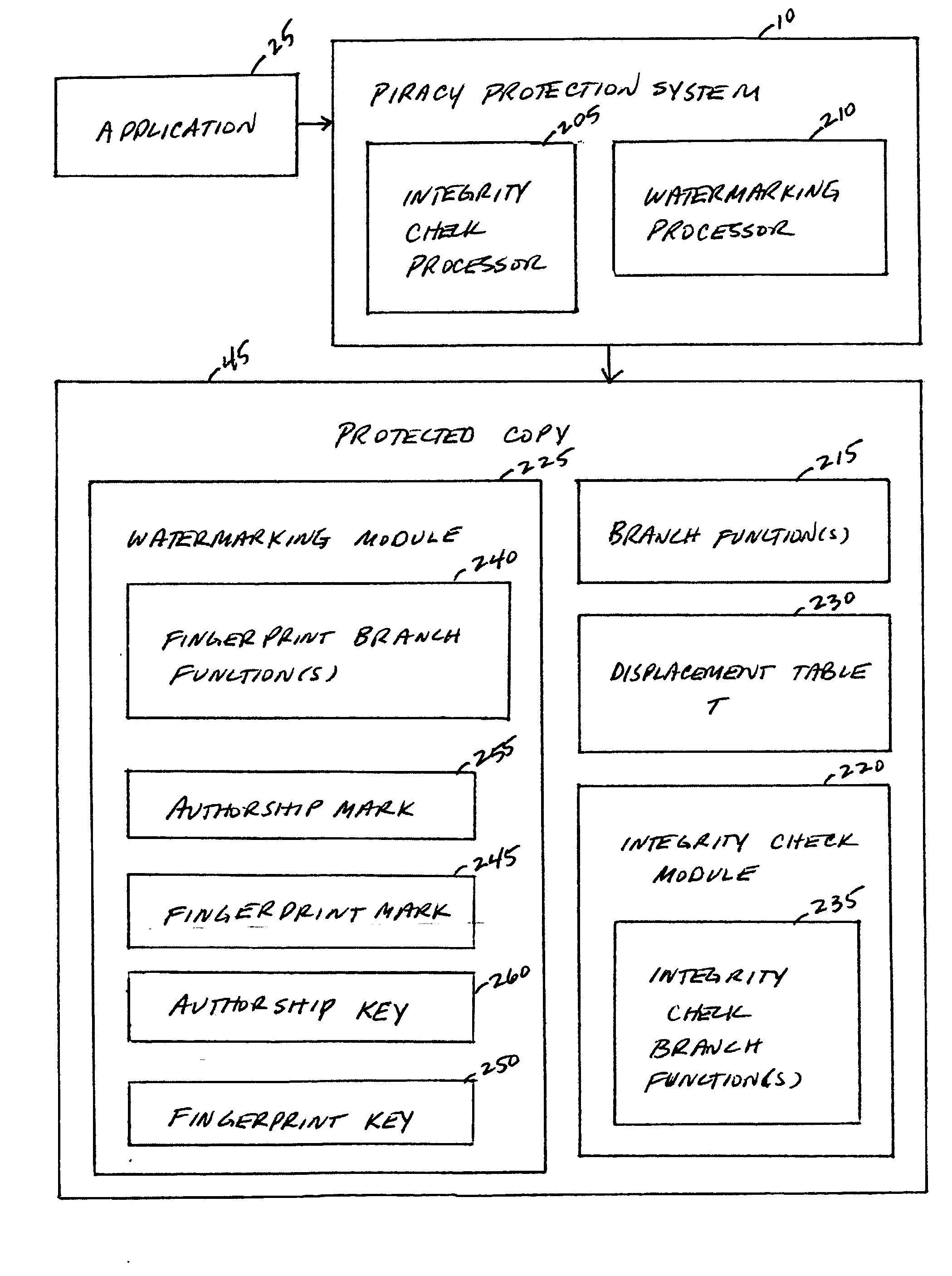
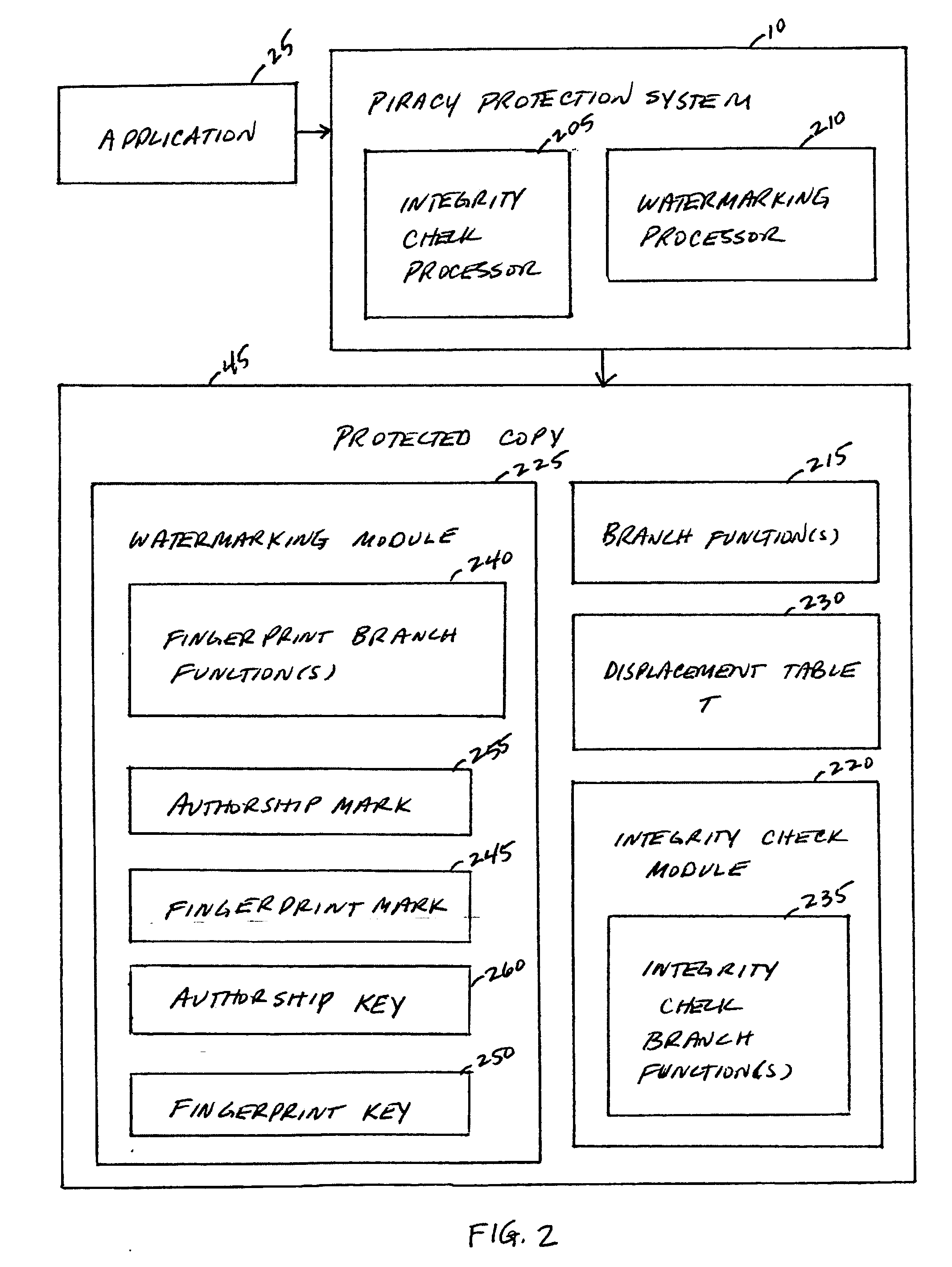
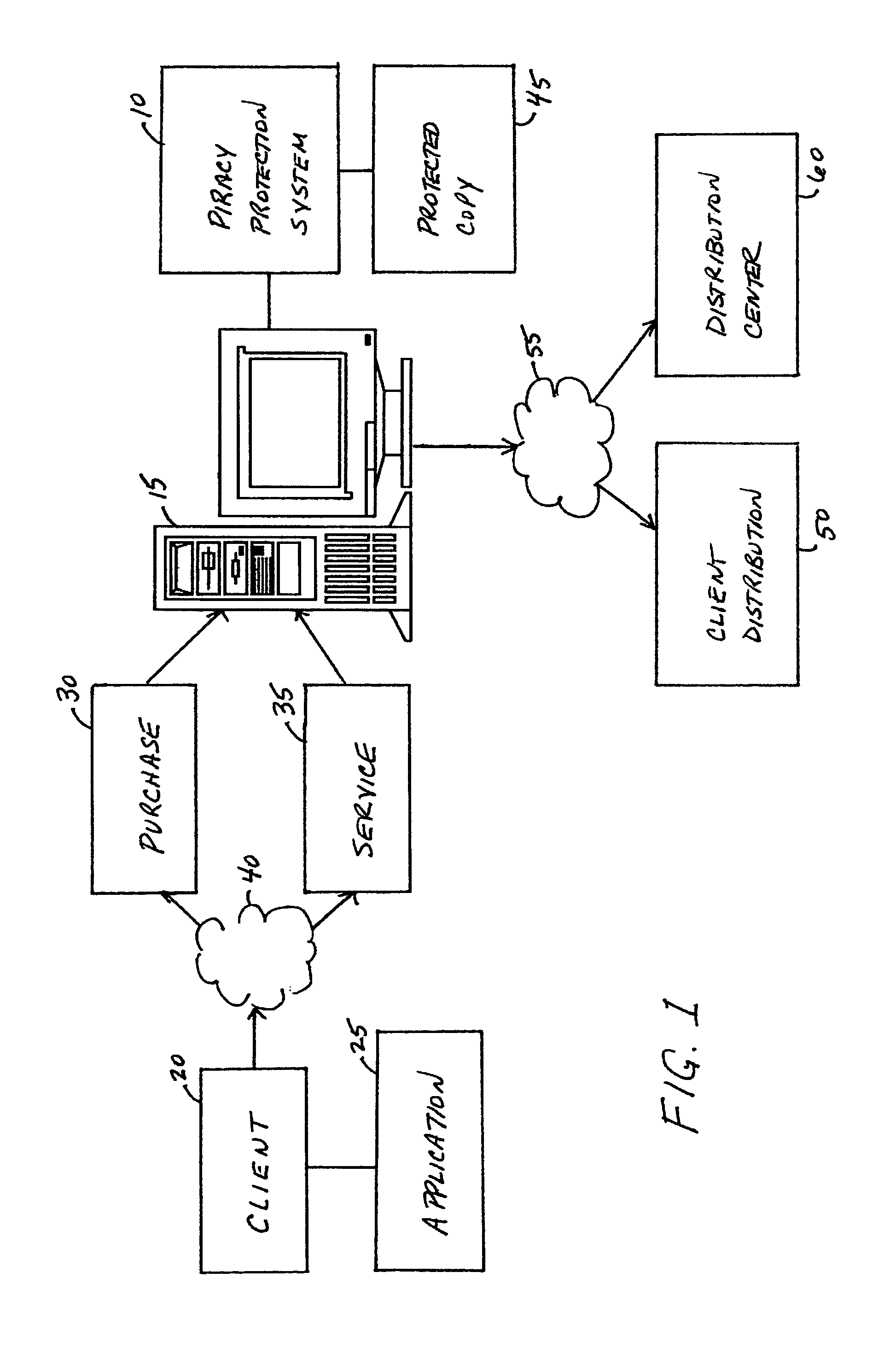
A piracy protection system incorporates tamper detection capabilities into a protected copy of an application by disassembling a statically linked binary of the application, modifying some of the instructions in the application, and then rewriting all of the modified and unmodified instructions to a new executable file, a protected copy. The piracy protection system comprises an offline tamper detection technique in which the software itself detects the tampering and causes the program to fail, therefore protecting itself from malicious attacks. The system further comprises a dynamic software-watermarking process that incorporates code obfuscation to prevent reverse engineering.
Owner:IBM CORP
Method for compiling program components in a mixed static and dynamic environment
InactiveUS6973646B1Simple methodReduce the amount requiredUser identity/authority verificationProgram controlProgramming languageDynamic compilation
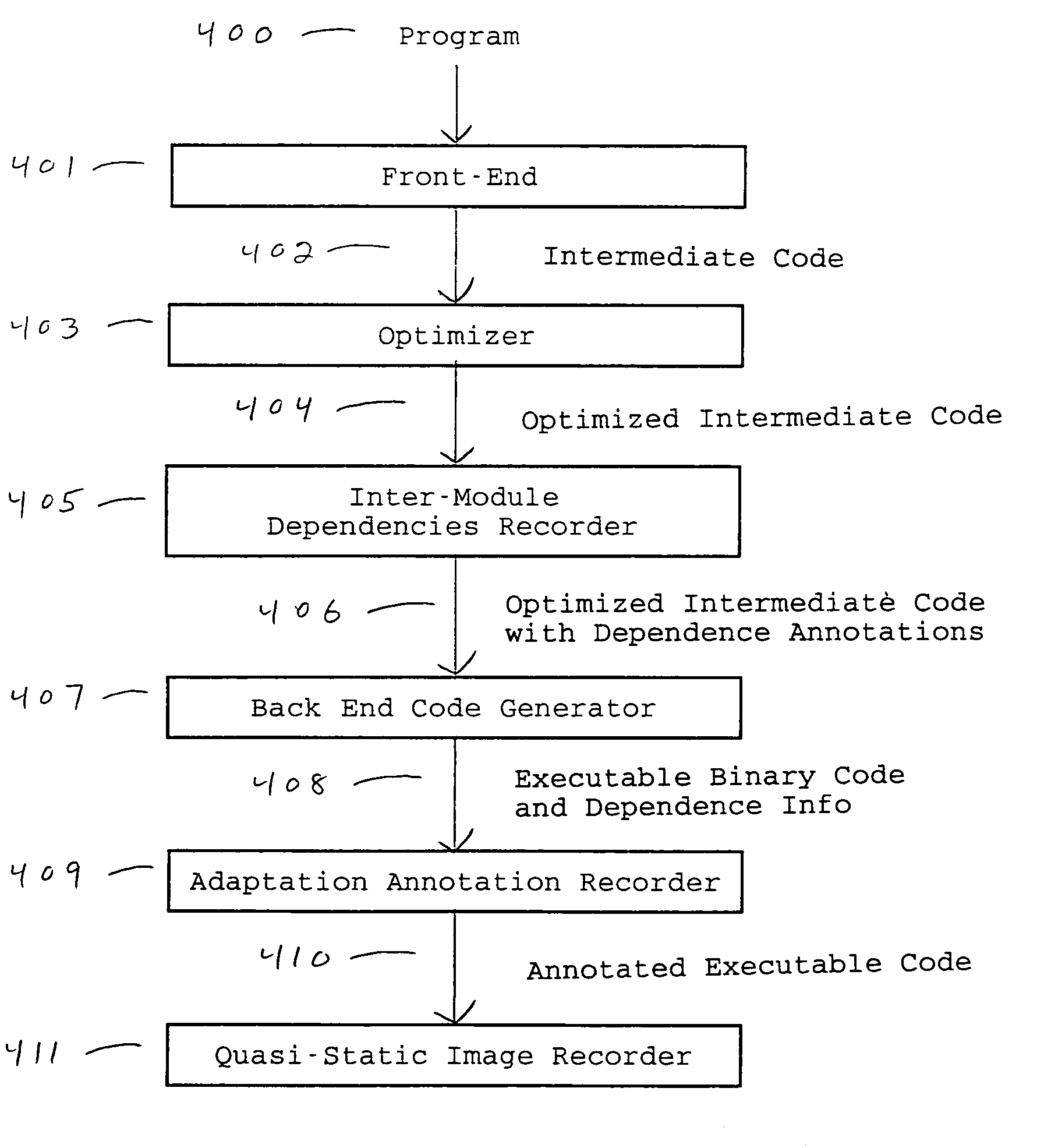
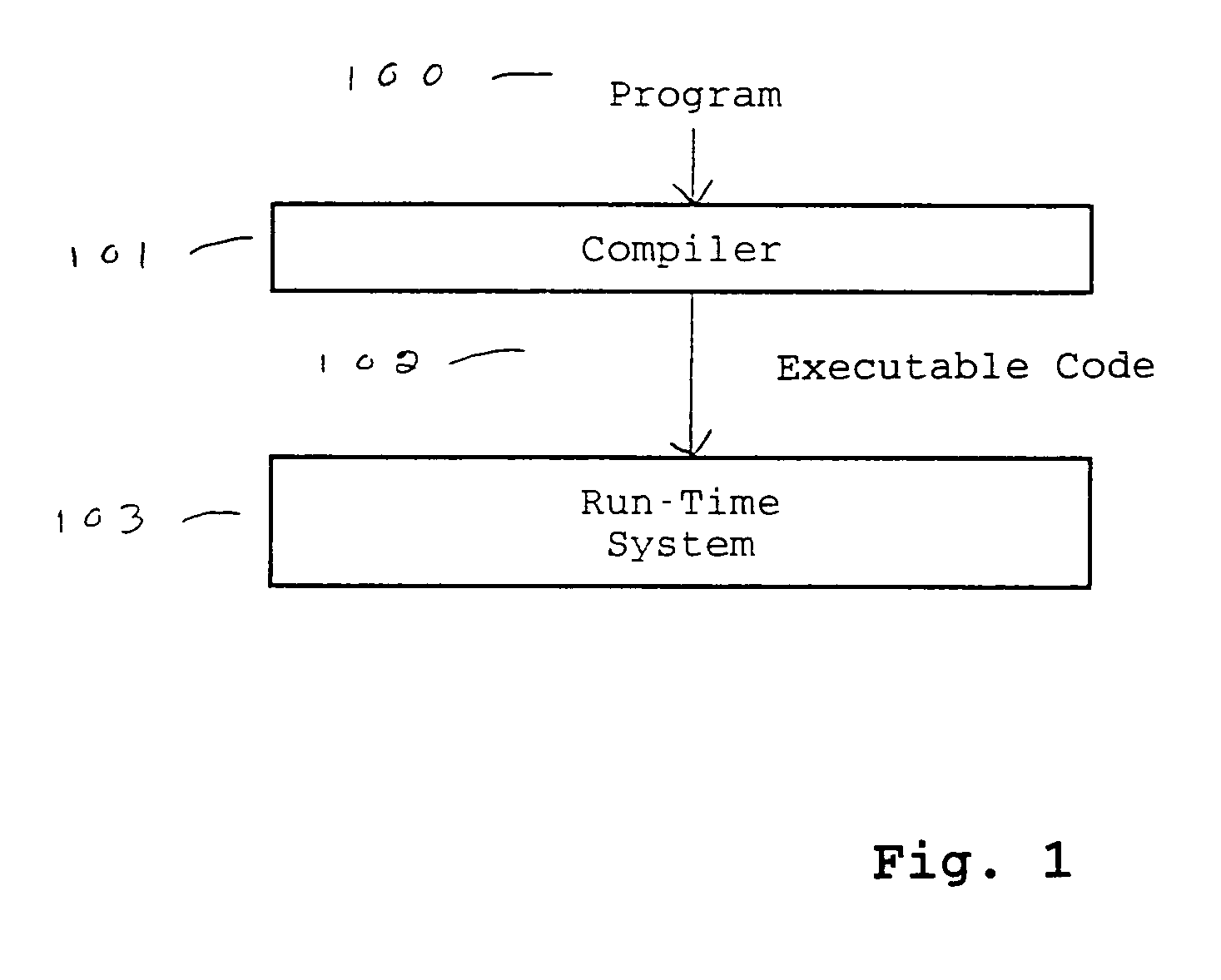
This invention describes a method and several variants for compiling programs or components of programs in a mixed static and dynamic environment, so as to reduce the amount of time and memory spent in run-time compilation, or to exercise greater control over testing of the executable code for the program, or both. The invention involves generating persistent code images prior to program execution based on static compilation or dynamic compilation from a previous run, and then, adapting those images during program execution. We describe a method for generating auxiliary information in addition to the executable code that is recorded in the persistent code image. Further, we describe a method for checking the validity of those code images, adapting those images to the new execution context, and generating new executable code to respond to dynamic events, during program execution. Our method allows global interprocedural optimizations to be performed on the program, even if the programming language supports, or requires, dynamic binding. Variants of the method show how one or several of the features of the method may be performed. The invention is particularly useful in the context of implementing Java Virtual Machines, although it can also be used in implementing other programming languages.
Owner:IBM CORP
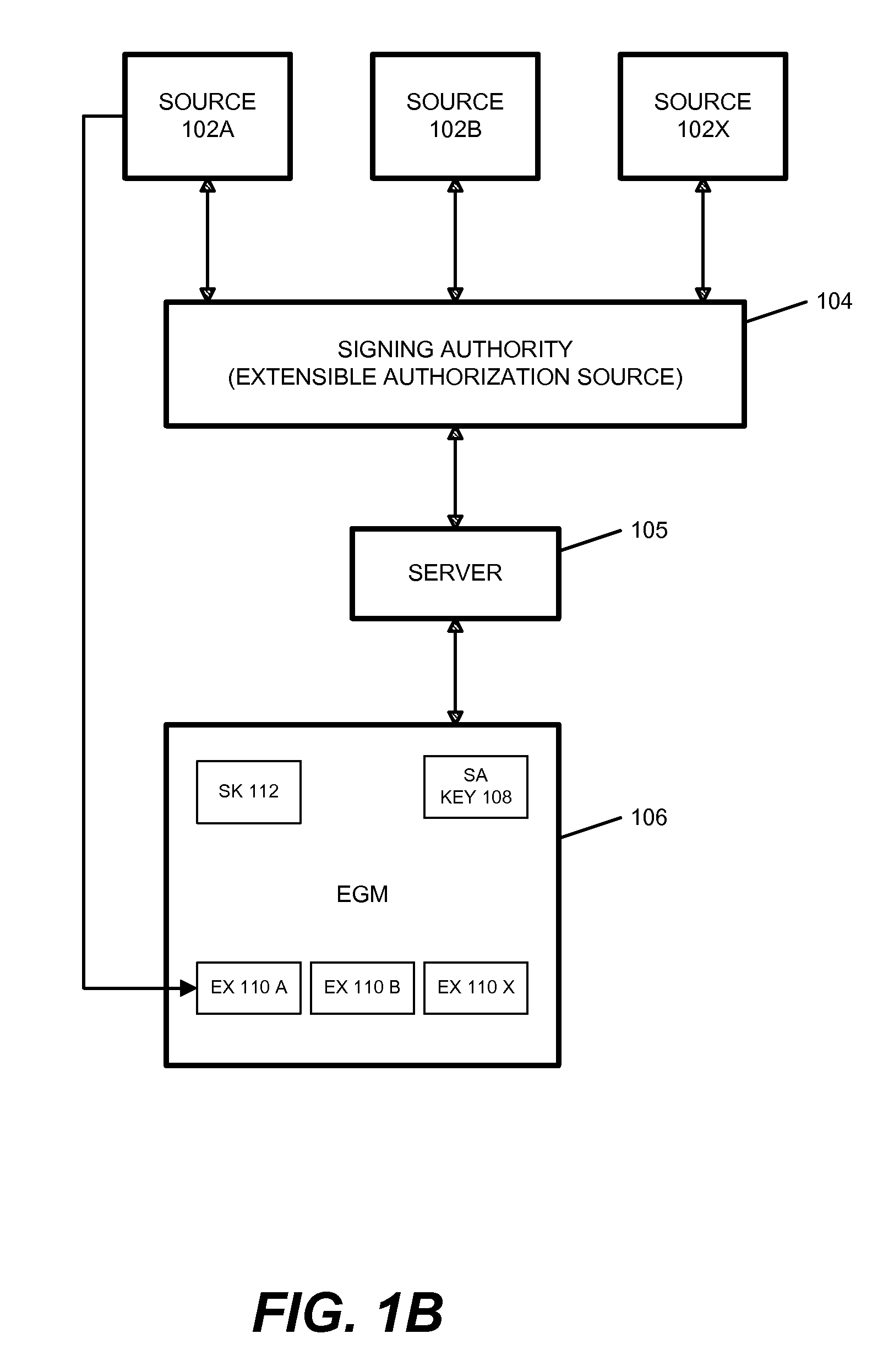
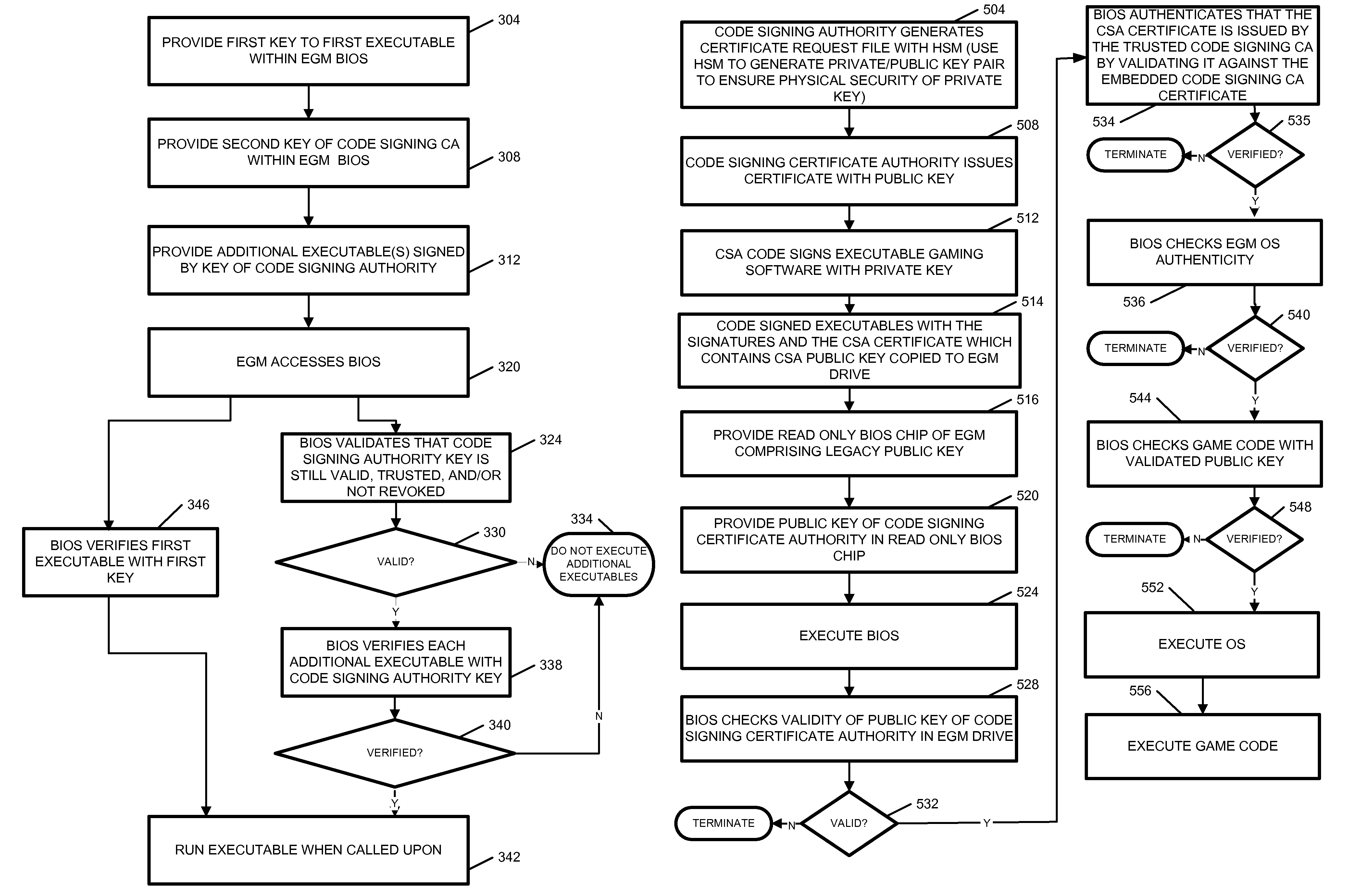
Egm authentication mechanism using multiple key pairs at the BIOS with pki
Executable applications on a gaming machine are verified before they can be executed, for security purposes and to comply with jurisdictional requirements. Unlike in prior systems for authenticating the executable applications, embodiments allow for new executable applications to be provided and verified over time with different private and public key pairs, even after the operating code of the gaming machine is certified by the jurisdiction and deployed in the field.
Owner:IGT
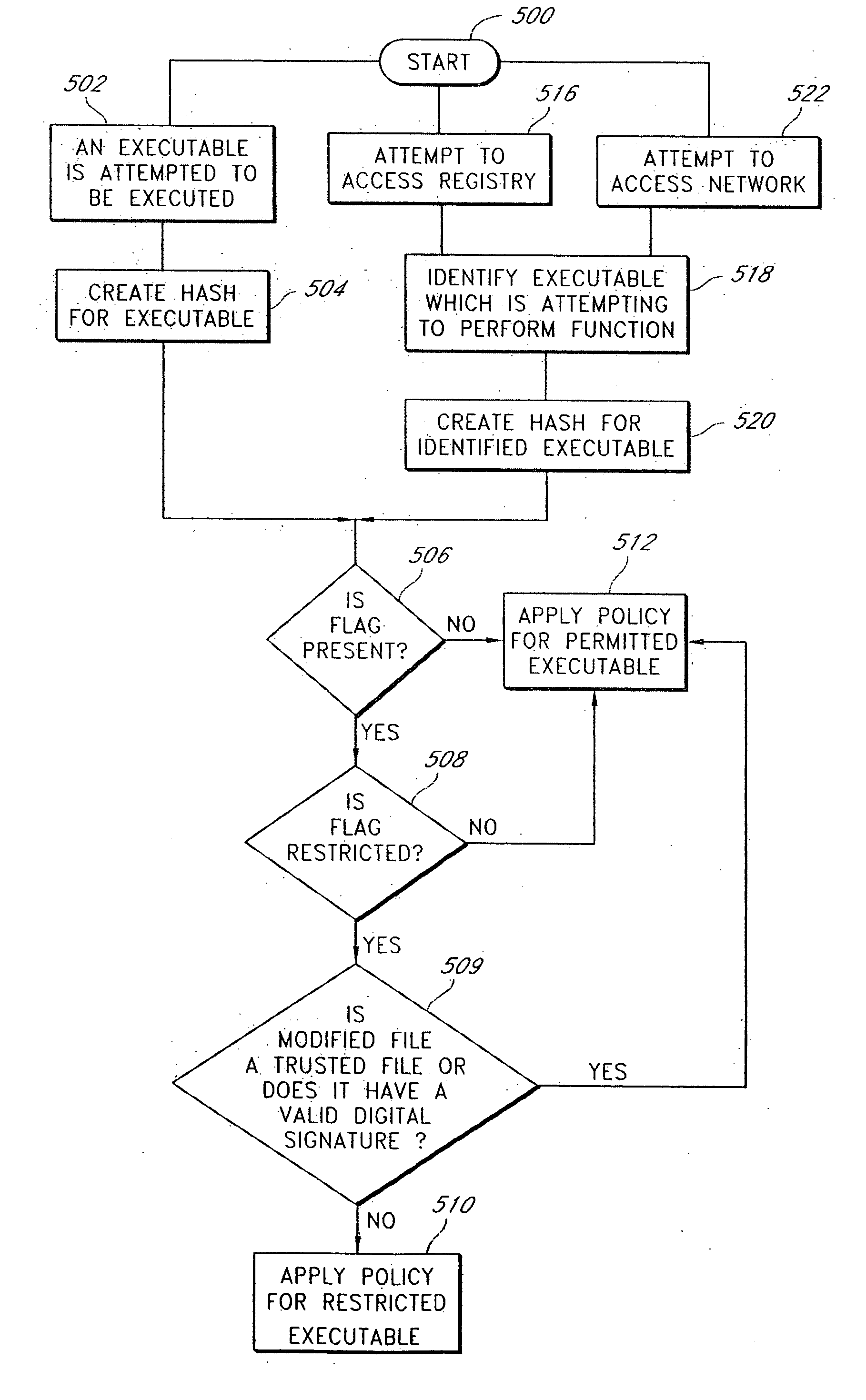
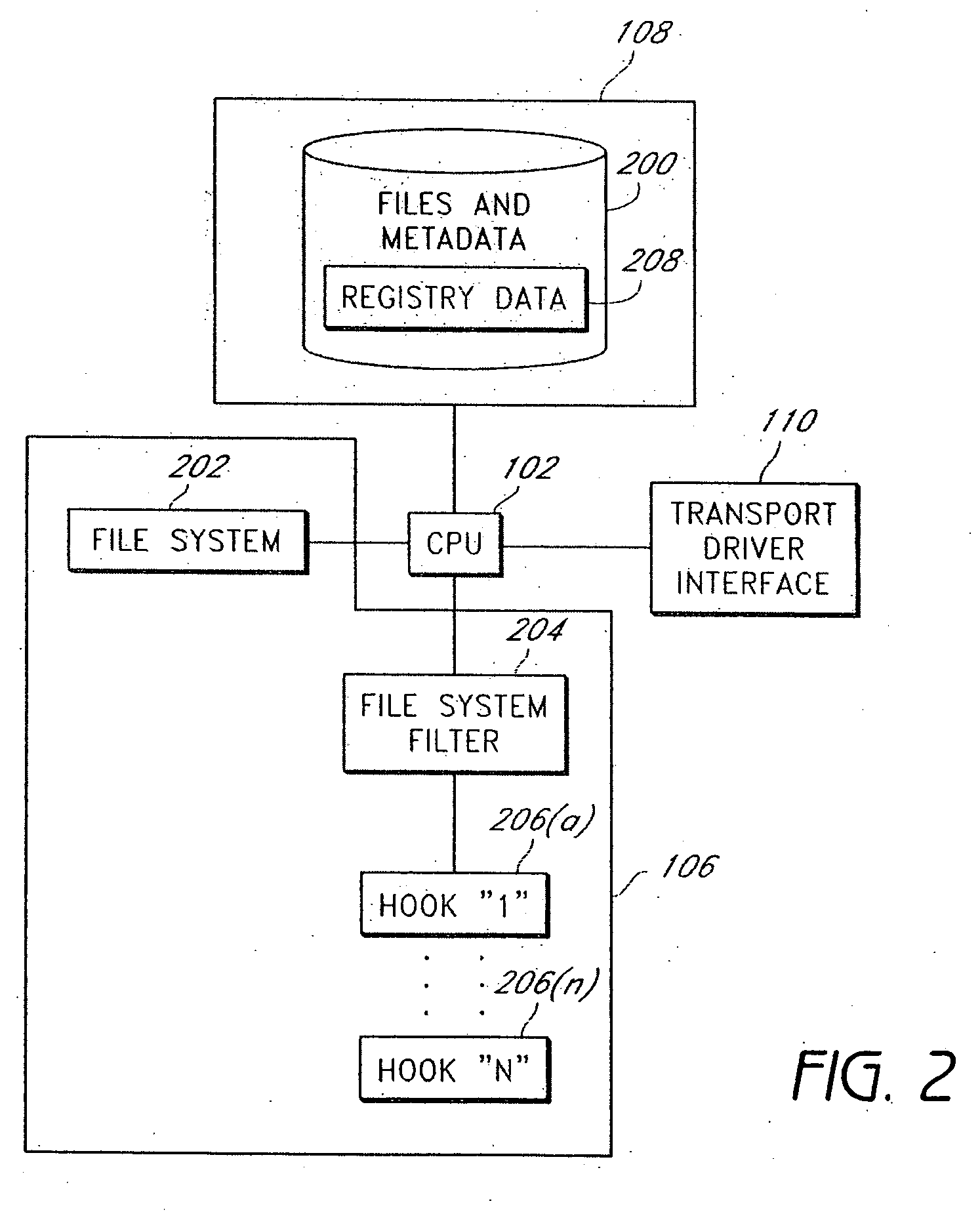
Real time lockdown
ActiveUS20070150956A1Preventing executionMemory loss protectionDigital data processing detailsFile systemNew Executable
A system and method that trusts software executables existent on a machine prior to activation for different types of accesses e.g. execution, network, and registry. The system detects new executables added to the machine as well as previously existent executables that have been modified, moved, renamed or deleted. In certain embodiments, the system will tag the file with a flag as modified or newly added. Once tagged, the system intercepts particular types of file accesses for execution, network or registry. The system determines if the file performing the access is flagged and may apply one or more policies based on the requested access. In certain embodiments, the system intercepts I / O operations by file systems or file system volumes and flags metadata associated with the file. For example, the NT File System and its extended attributes and alternate streams may be utilized to implement the system.
Owner:FORCEPOINT LLC
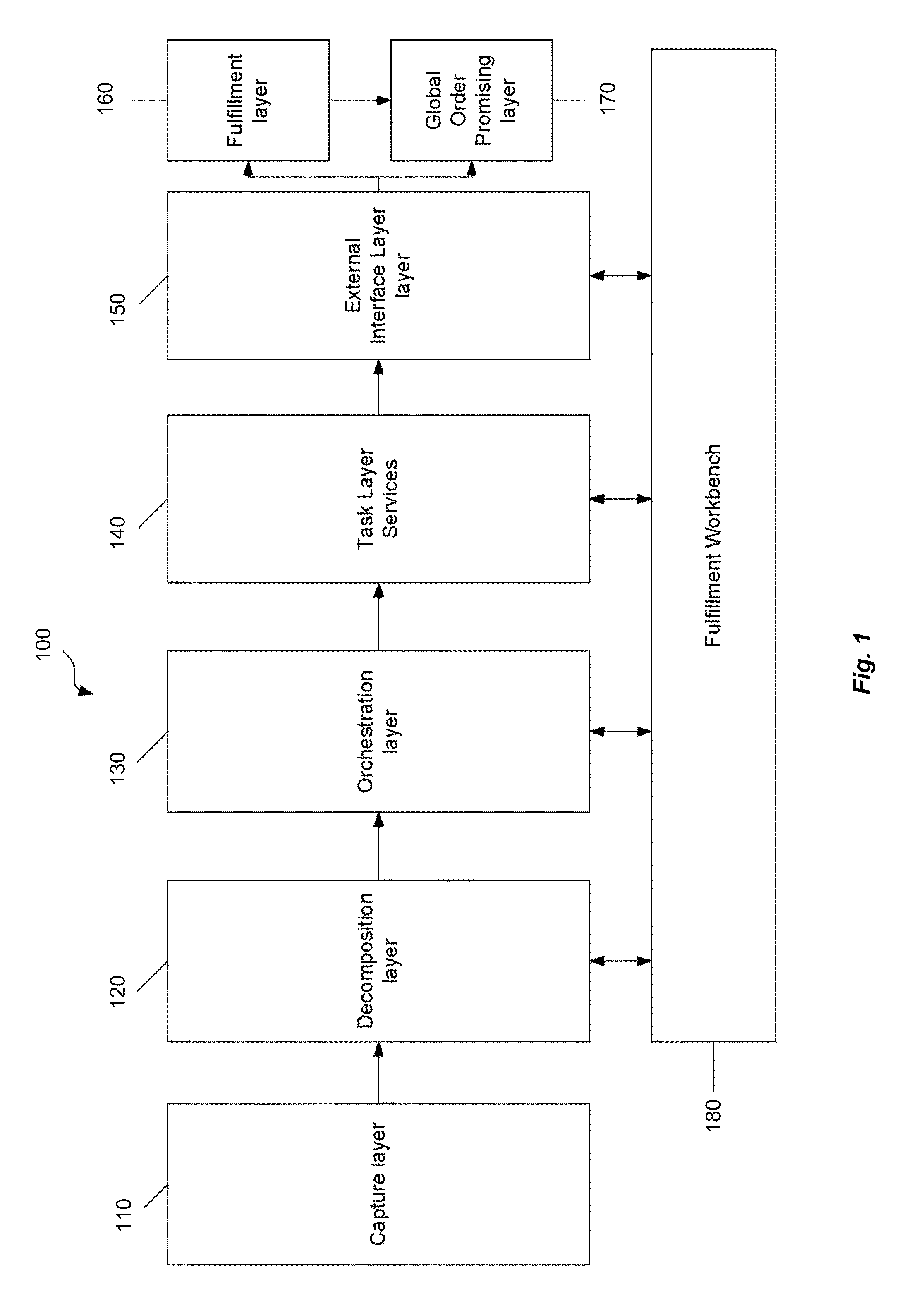
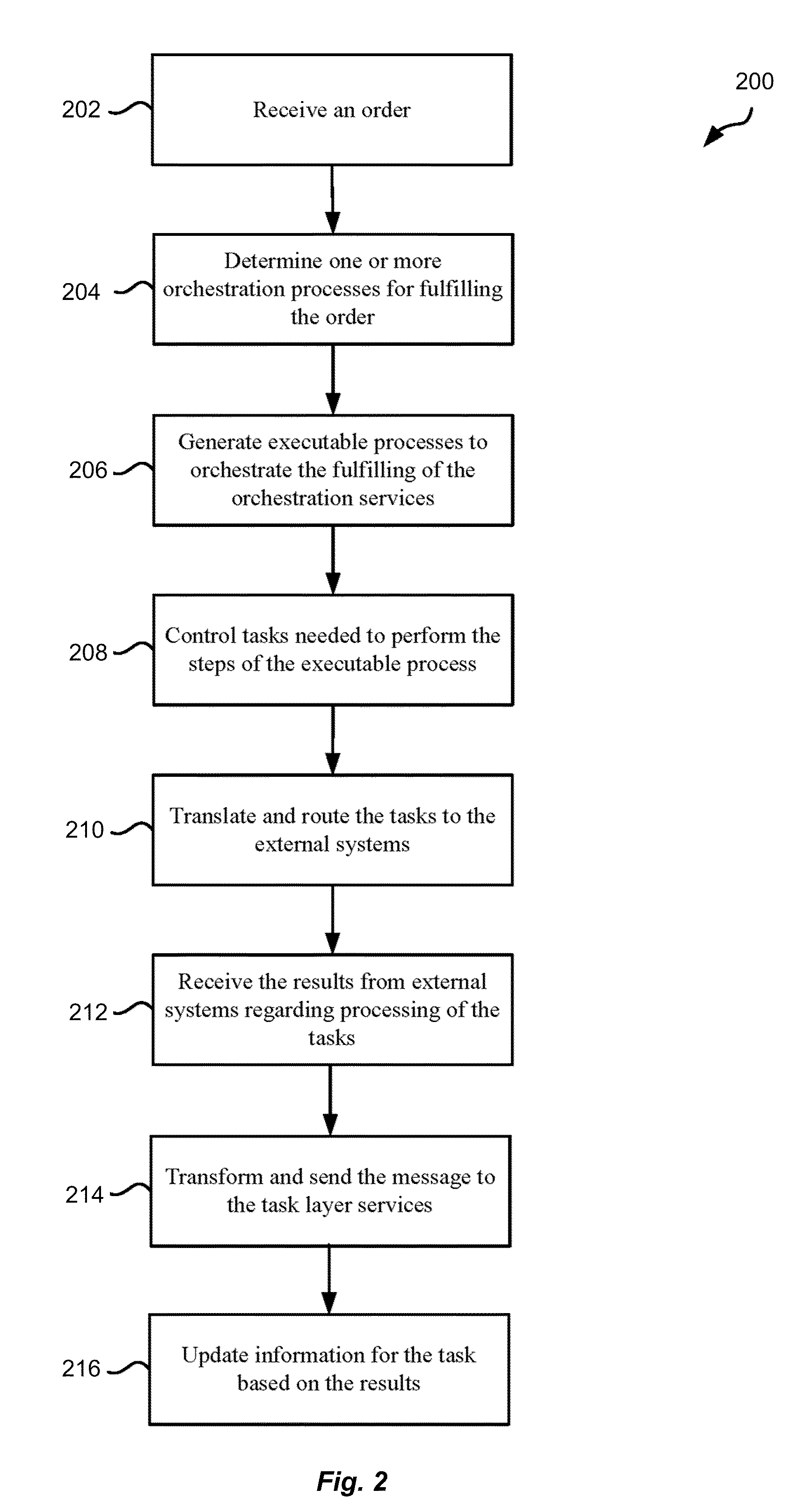
Change management framework in distributed order orchestration system
A computer-readable medium, computer-implemented method, and system are provided. In one embodiment, an original executable process is executed in a regular mode. When a change request is received, the original executable process is stopped, and a new executable process is created. The new executable process is then executed in a change mode.
Owner:ORACLE INT CORP
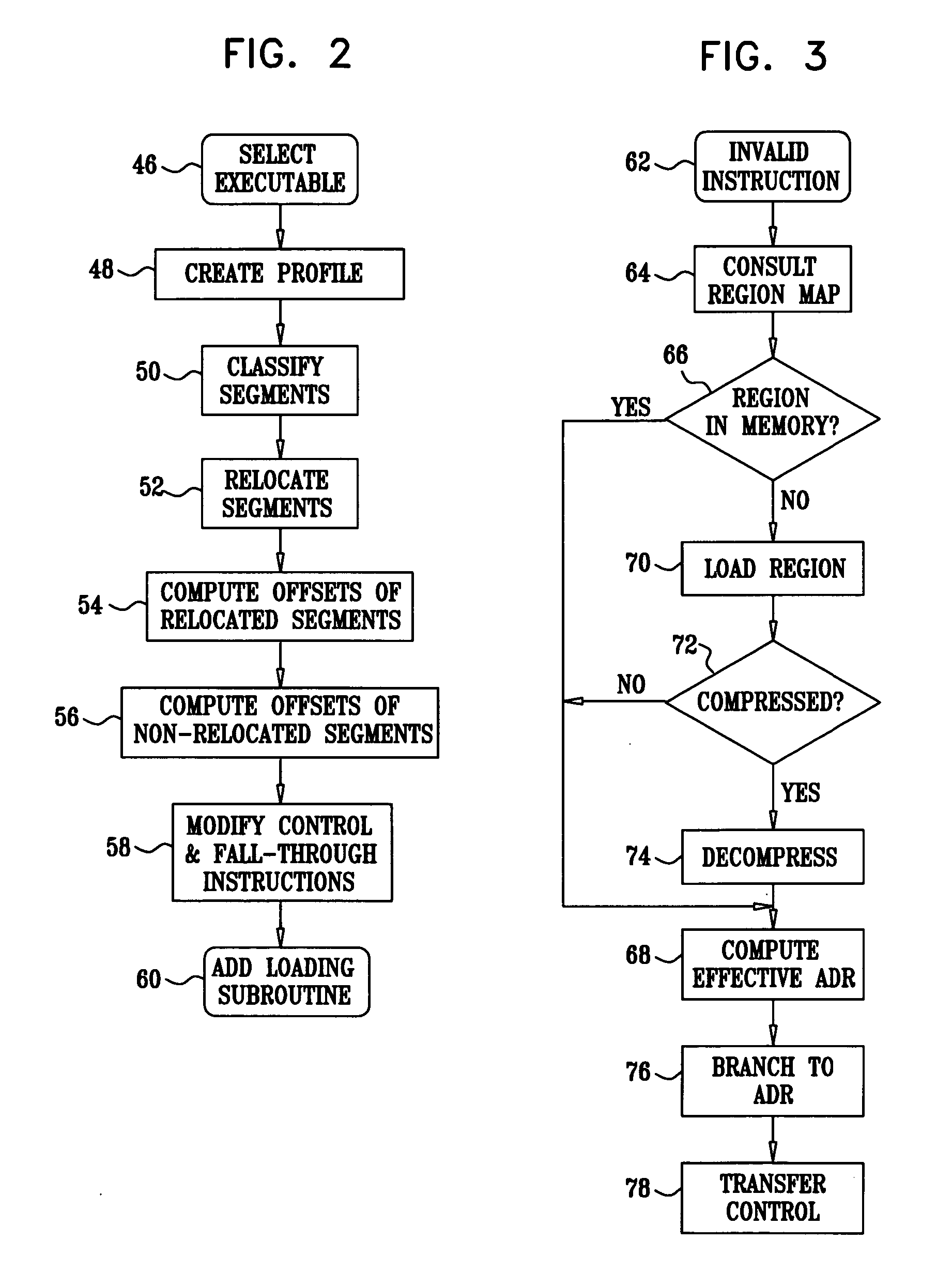
Link-time profile-based method for reducing run-time image of executables
InactiveUS20060048106A1Image is often very smallImprove performanceProgram loading/initiatingMemory systemsNew ExecutableRunning time
An executable program file is produced, which has a reduced run-time image size and improved performance. Profiling information is obtained from an original executable program. Both the original executable code and the profiling information are used to generate the new executable program file. All frozen basic blocks are grouped together and relocated in a separate non-loading module. Each control transfer to and from the relocated code is replaced by an appropriate interrupt. An interrupt mechanism invokes an appropriate handler for loading the relevant code segments from the non-loading module containing the targeted basic blocks. Since the relocated basic blocks are frozen, the time-consuming interrupt mechanism is rarely if ever invoked during run-time, and therefore, has no significant effect on performance.
Owner:IBM CORP
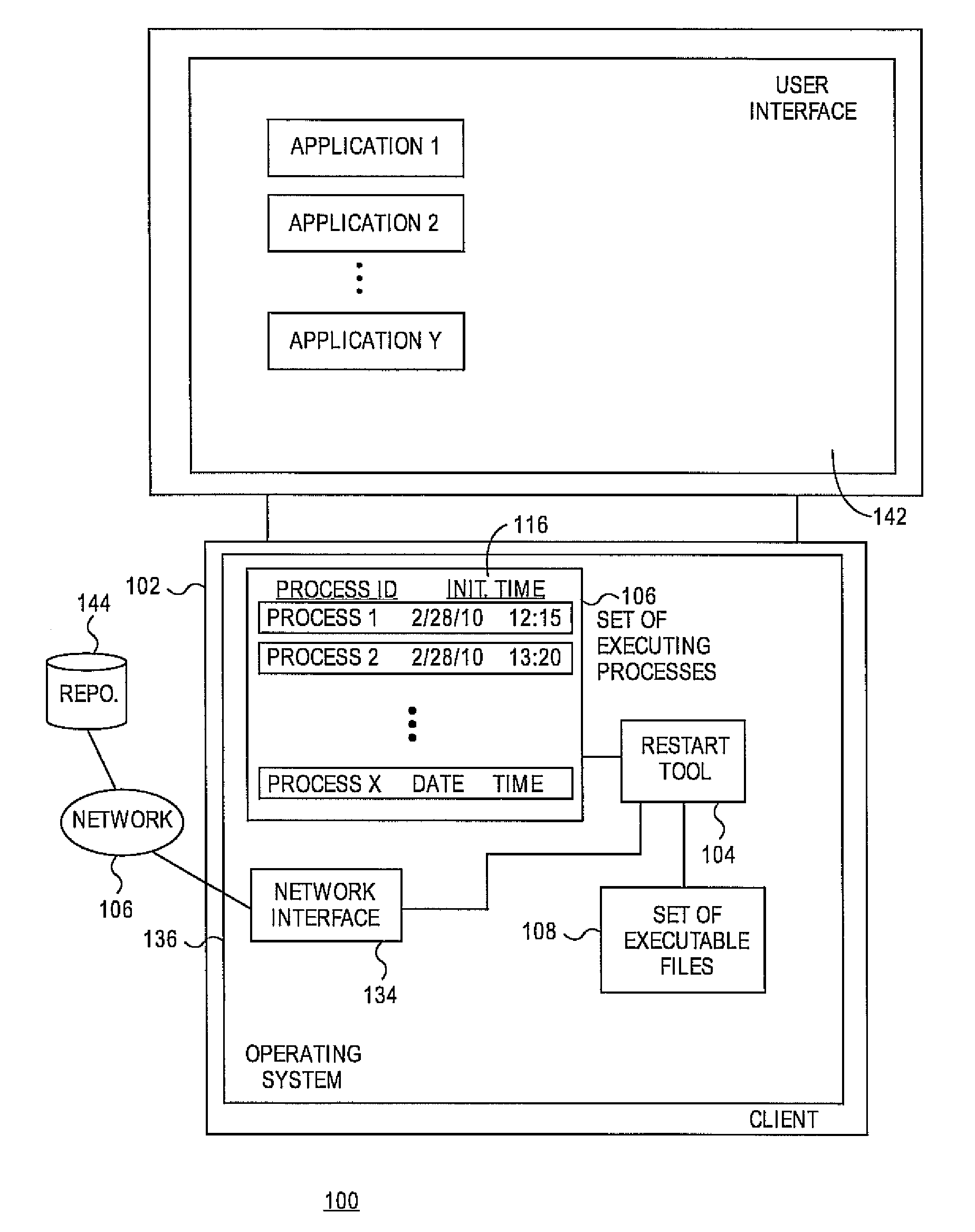
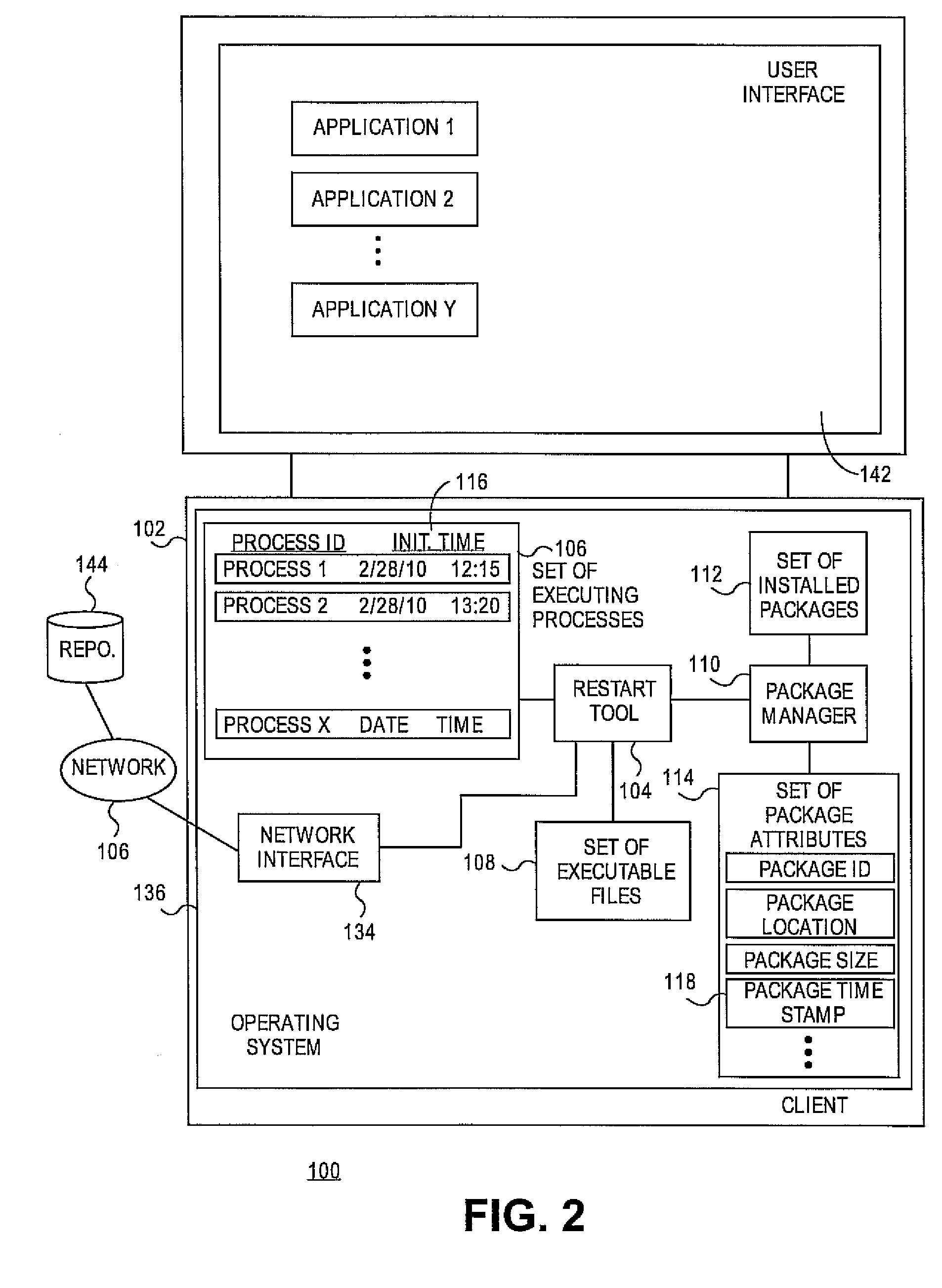
Systems and methods for detecting computing processes requiring reinitialization after a software package update
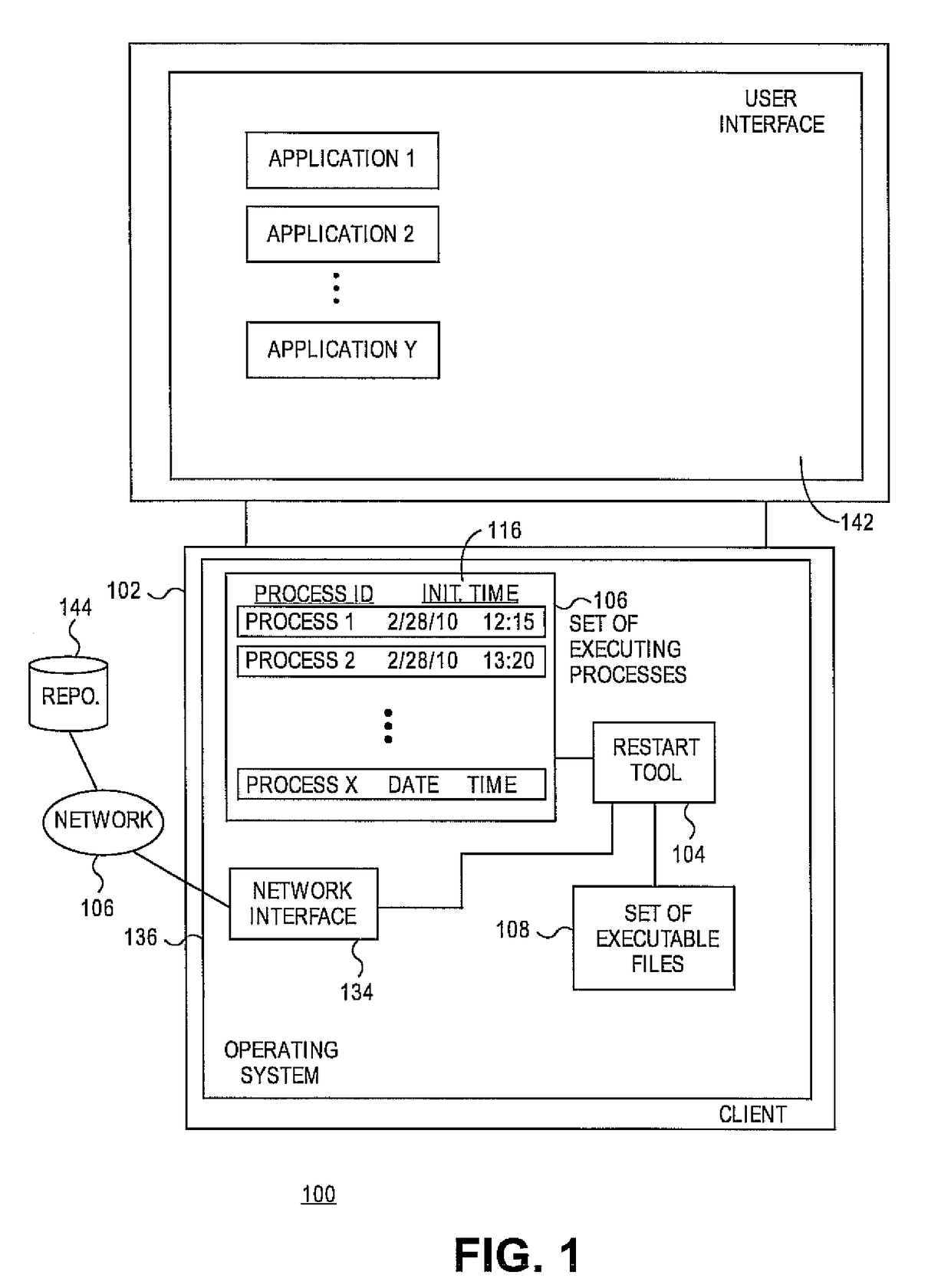
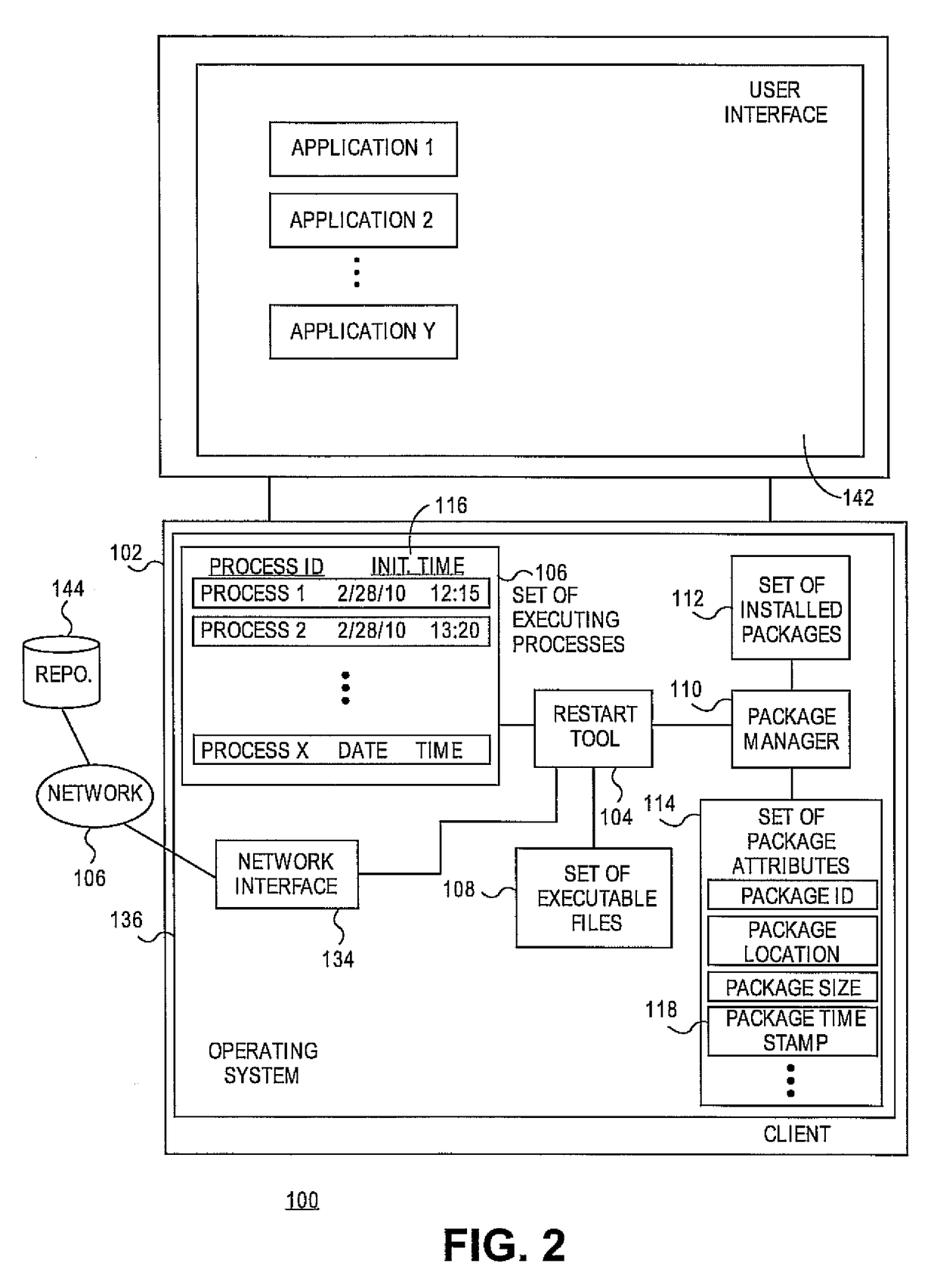
Embodiments relate to systems and methods for detecting computing processes requiring reinitialization after a software package update. A physical or virtual client machine can host a set of installed software packages, including operating system, application, and / or other software. An restart tool can track the set of executing processes on the client, and identify both corresponding executable files which spawned those processes, and any installed package updates which correspond to those executable files. The restart tool can compare the timestamp or other indicator of the version of the executable file which spawned currently running processes, and the timestamp or other indicator of any newer executable files which may have been installed after the application or other process was initiated. A user can be alerted to terminate and restart any processes running off of out-of-date executable files, or in embodiments those reinitializations can be set to be performed automatically.
Owner:RED HAT
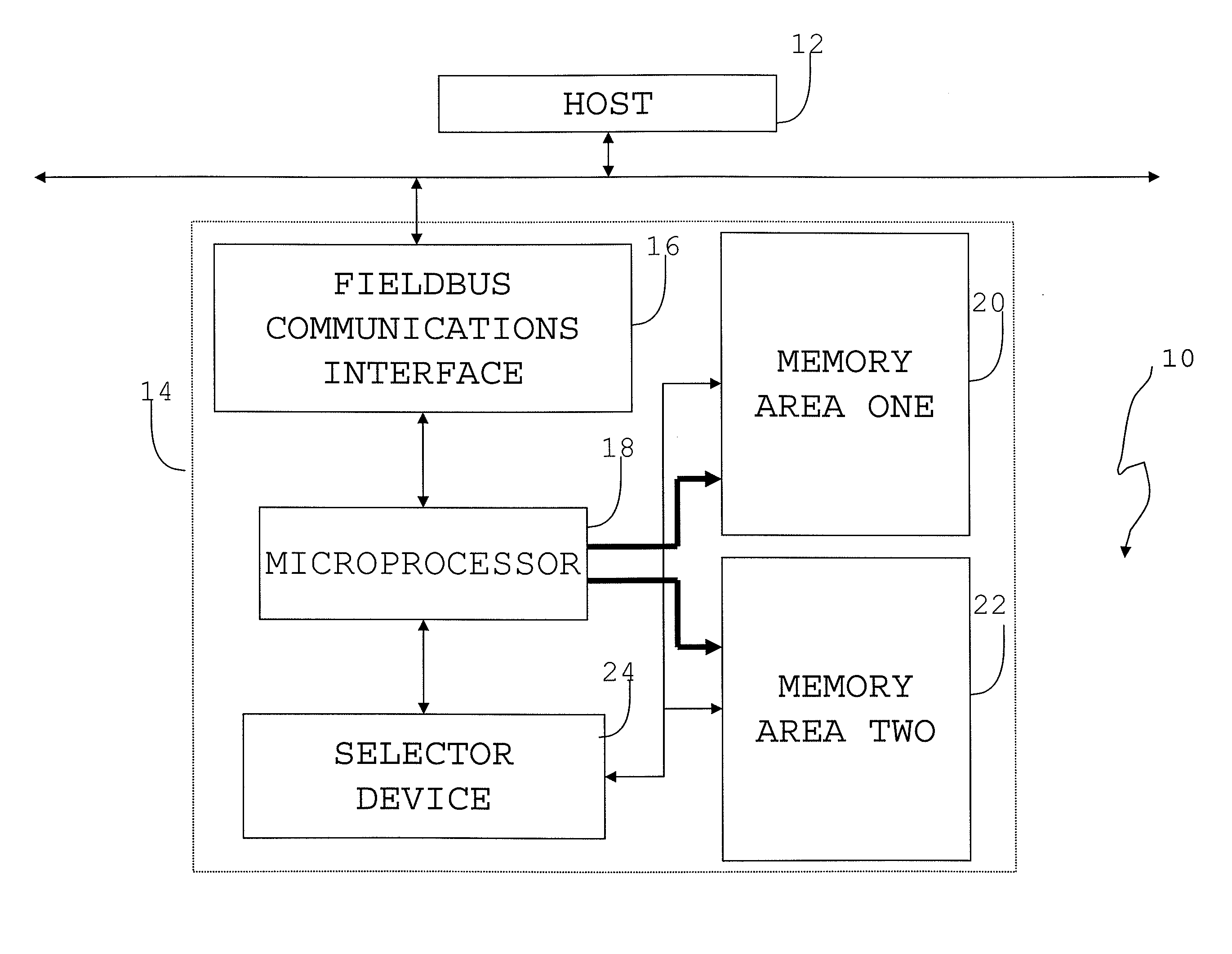
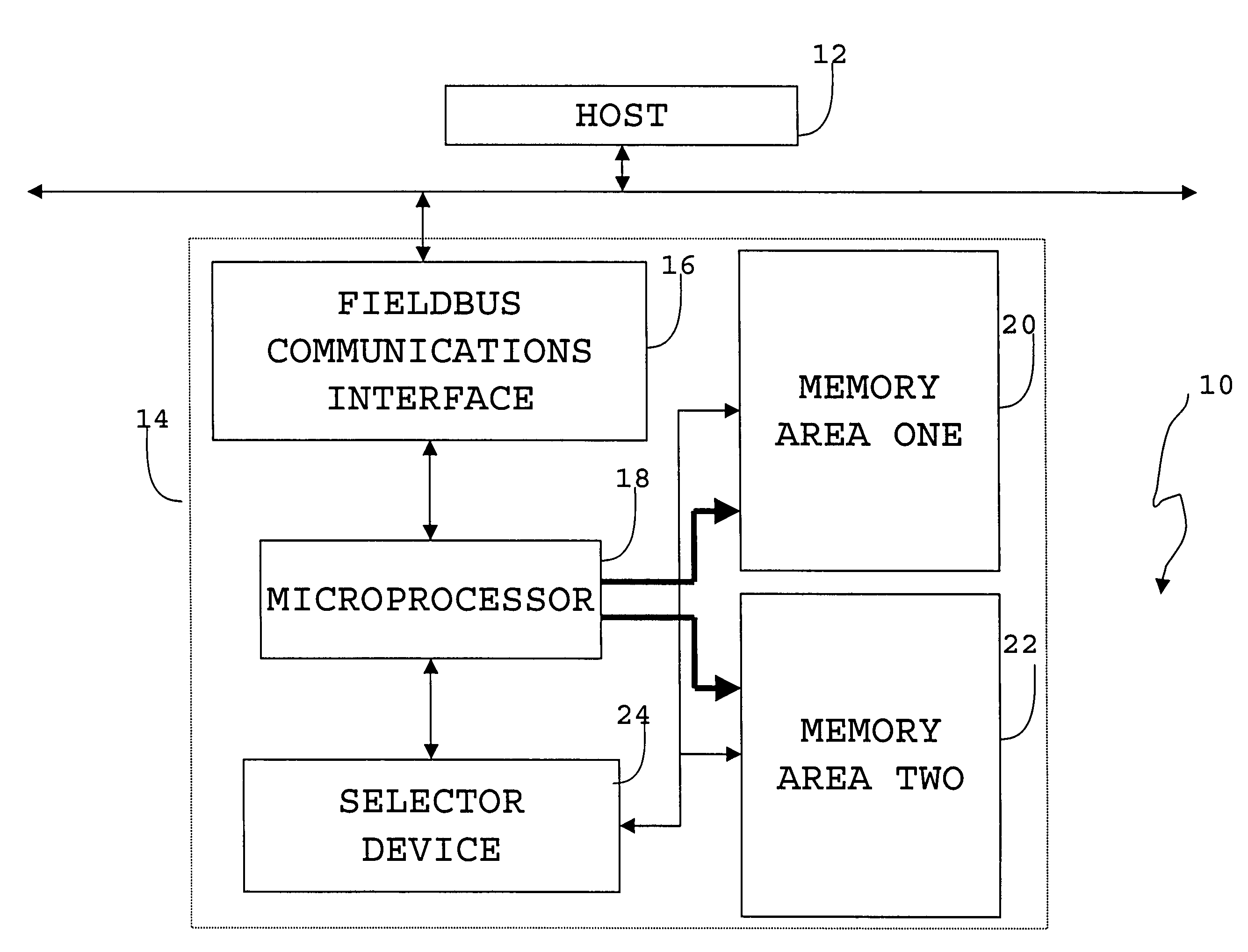
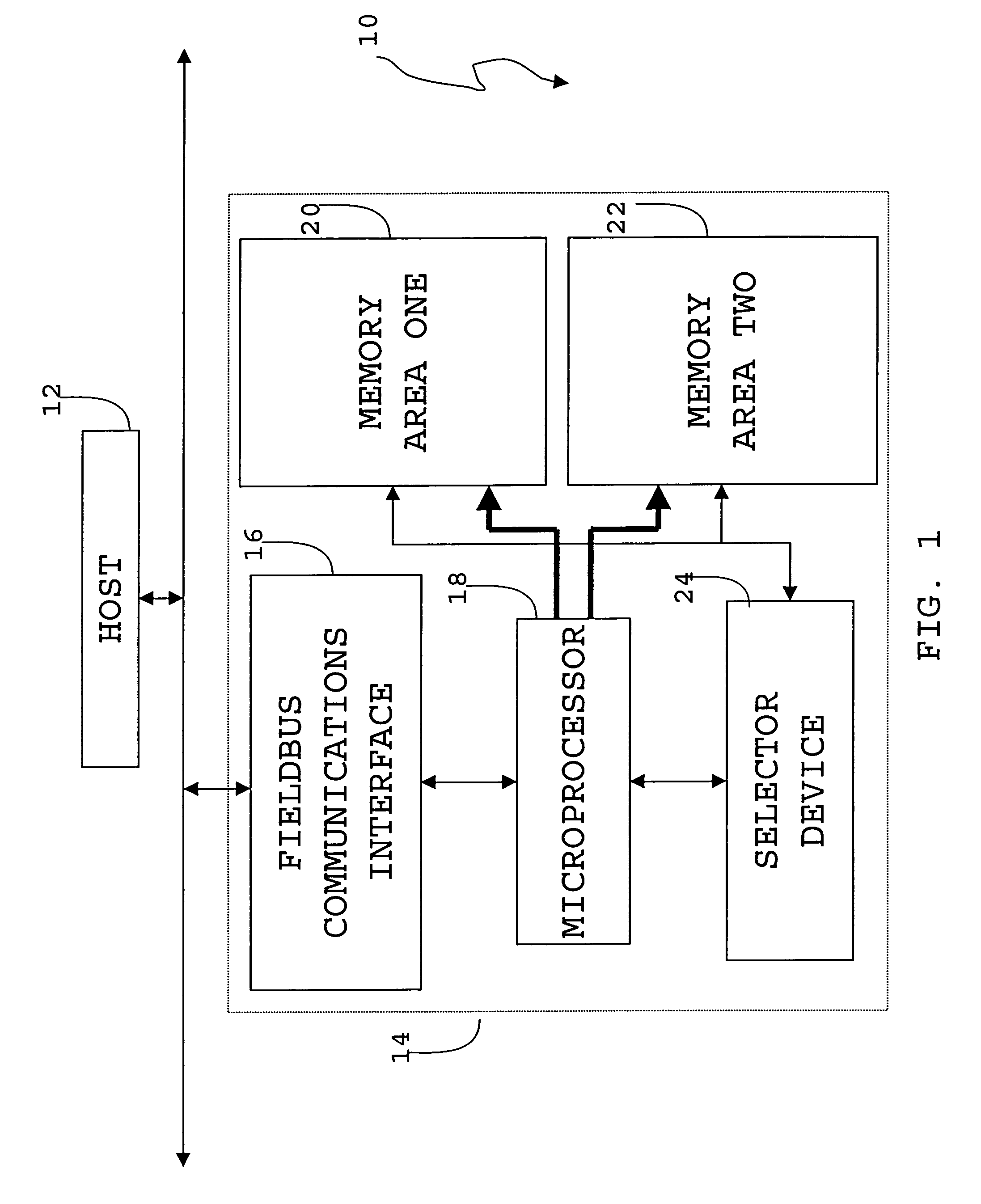
Fieldbus upgradable apparatus and method
InactiveUS20070234339A1Avoid disturbanceFunction increaseData processing applicationsSoftware engineeringOperational systemEntry point
Owner:INVENSYS
Rule based engine for validating financial transactions
A method and system for checking whether customer orders for transactions of financial instruments conform to business logic rules. Executable rule files are created and stored in a repository. New executable rule files can be created by scripting the new business logic rules in a script file which is converted into a corresponding source code file written in a computer programming language. The source code file is compiled to create an individual executable rule file. A rule selection repository contains identification of groups of selected executable rule files. The invention determines the category of the customer order and reads, from the rule selection repository, a group of executable rule files that correspond to the identified category of the customer order. The selected executable rule files are executed to check the conformance of the customer order. Execution results are stored in a status repository for subsequent retrieval and analysis.
Owner:META PLATFORMS INC
Generation method and device of executable file
InactiveCN102508660AEnsure safetySpeed up productionSpecific program execution arrangementsOriginal dataNew Executable
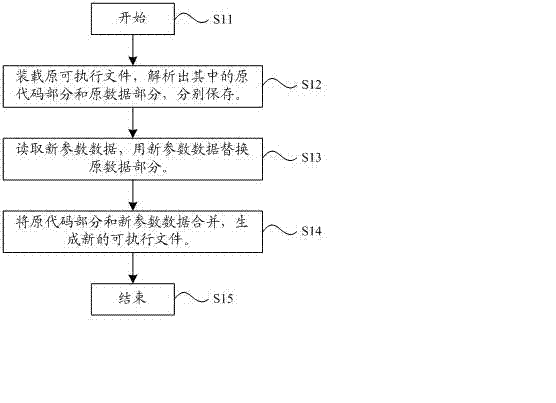
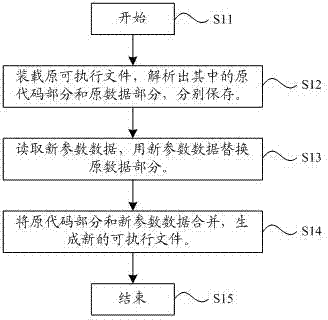
The invention discloses a generation method and device of an executable file. The generation method comprises the following steps: loading the original executable file and parsing out an original code part and an original data from the original executable file according to the creation rules of the original executable file; reading new parameter data which is required for the executable file to be generated and substituting the new parameter data for the original data part; and merging the original code part with the new parameter data and generating the new executable file. According to the method disclosed by the invention, data parameters can be modified on the basis of not modifying program codes, then the new executable file can be obtained, the participation of design staff of a source program is not required during the whole process, codes are less prone to being modified mistakenly, and the whole product production scheduling can be improved.
Owner:HISENSE BROADBAND MULTIMEDIA TECH
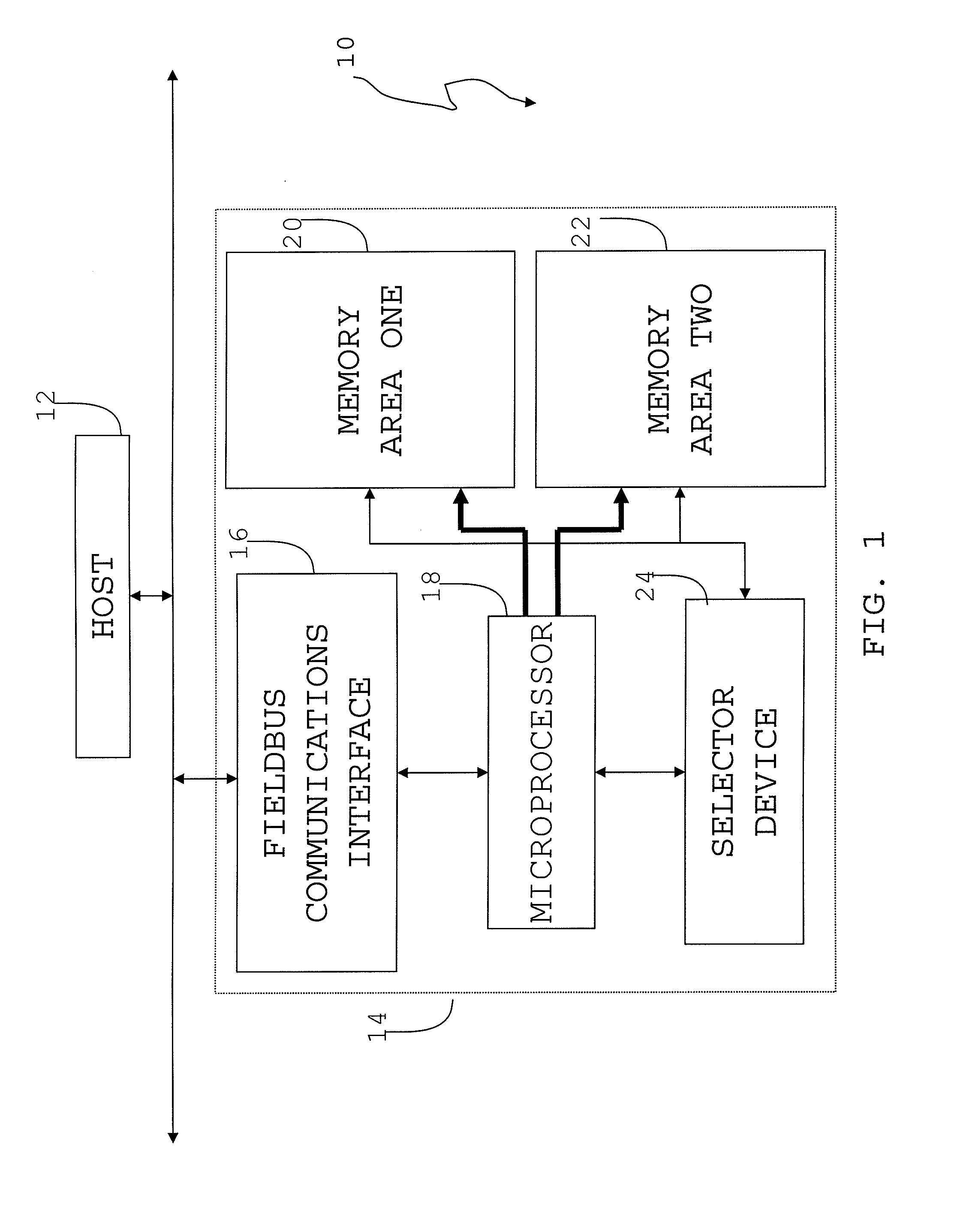
Fieldbus upgradable apparatus and method
InactiveUS7263546B1Avoid disturbanceFunction increaseData processing applicationsSoftware engineeringOperational systemEntry point
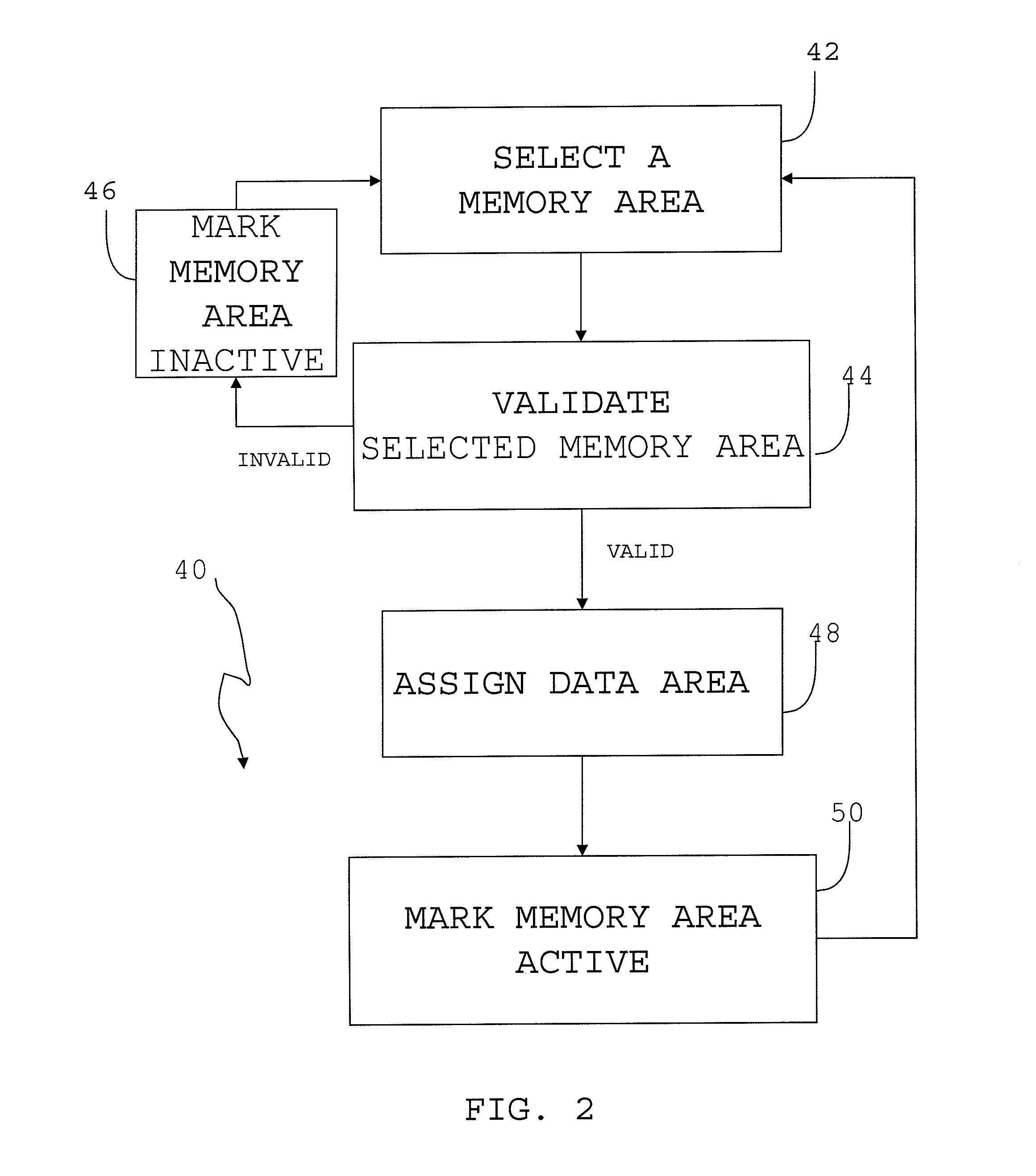
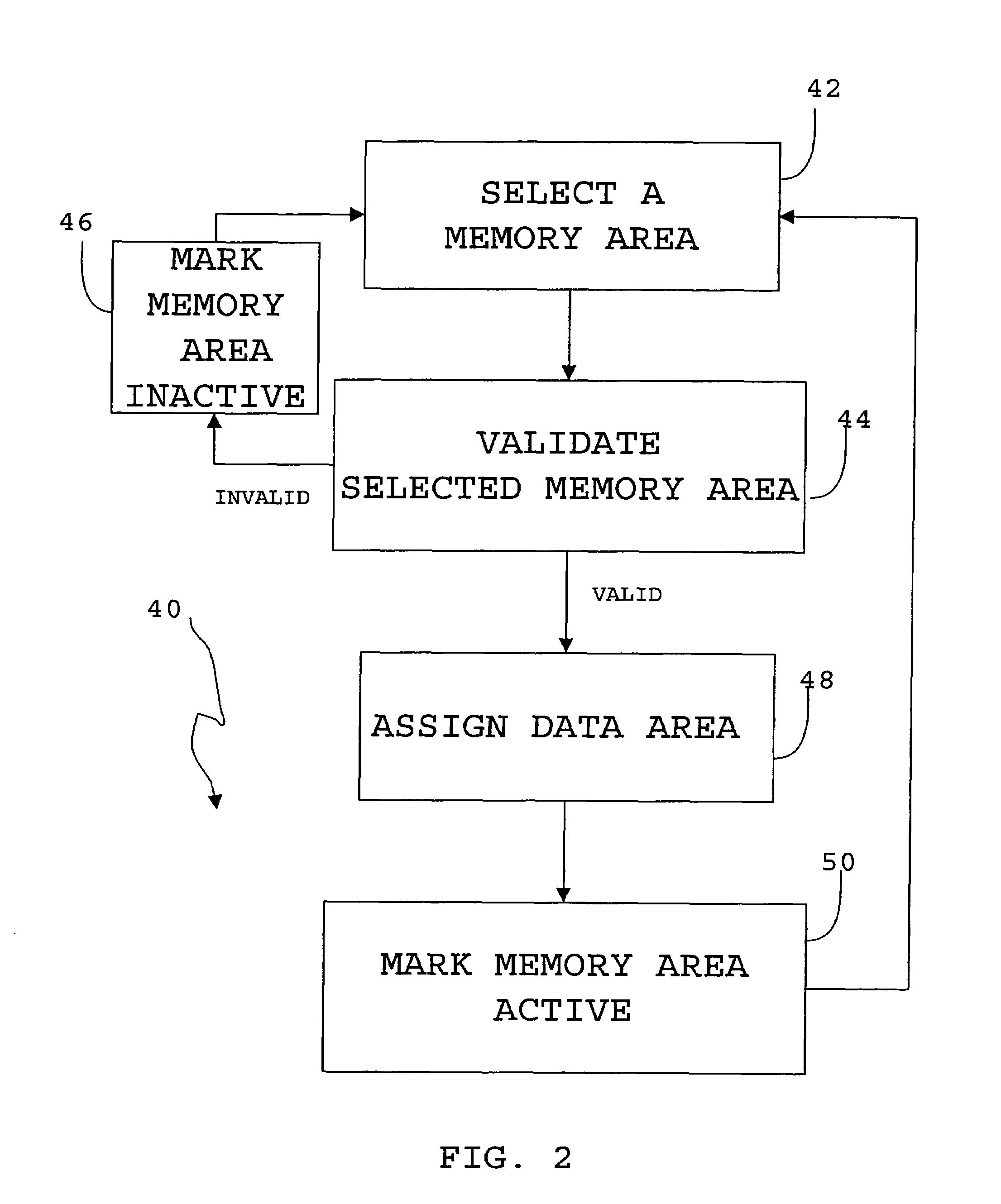
A method and apparatus to modify control devices residing on a Fieldbus communications network, without interrupting the operation of the control devices. The control device updating may further be controlled and monitored by a remotely located host that also communicates on the Fieldbus network. The control device may comprise at least two distinct memory areas, wherein at least one memory area must be active, and at least one memory area must be inactive. Active memory areas provide the control device microprocessor operating system with executable instructions or data. The host downloads new executable instructions or data to inactive memory areas, with associated data entry points, during unscheduled communications periods wherein data input / output is not being performed between the control device and the host or another control device. Upon a full data transfer and proper verification of the new data, the host may issue an activation command that causes a selector device to activate the previously inactive memory area by directing the microprocessor to the entry points of the newly downloaded executable instructions or data. The memory activation must occur while the microprocessor is not performing application execution, application input / output, or application communications. By timing the memory activation in this manner, the microprocessor may be redirected to the newly downloaded executable instructions or data without microprocessor interruption.
Owner:INVENSYS +1
System, method, and service for detecting improper manipulation of an application
InactiveUS8056138B2More robustnessEliminate loopholesDigital data processing detailsUser identity/authority verificationObfuscationNew Executable
Owner:INT BUSINESS MASCH CORP
Software protection
InactiveCN101151617AAvoid identificationProgram/content distribution protectionOperational systemNew Executable
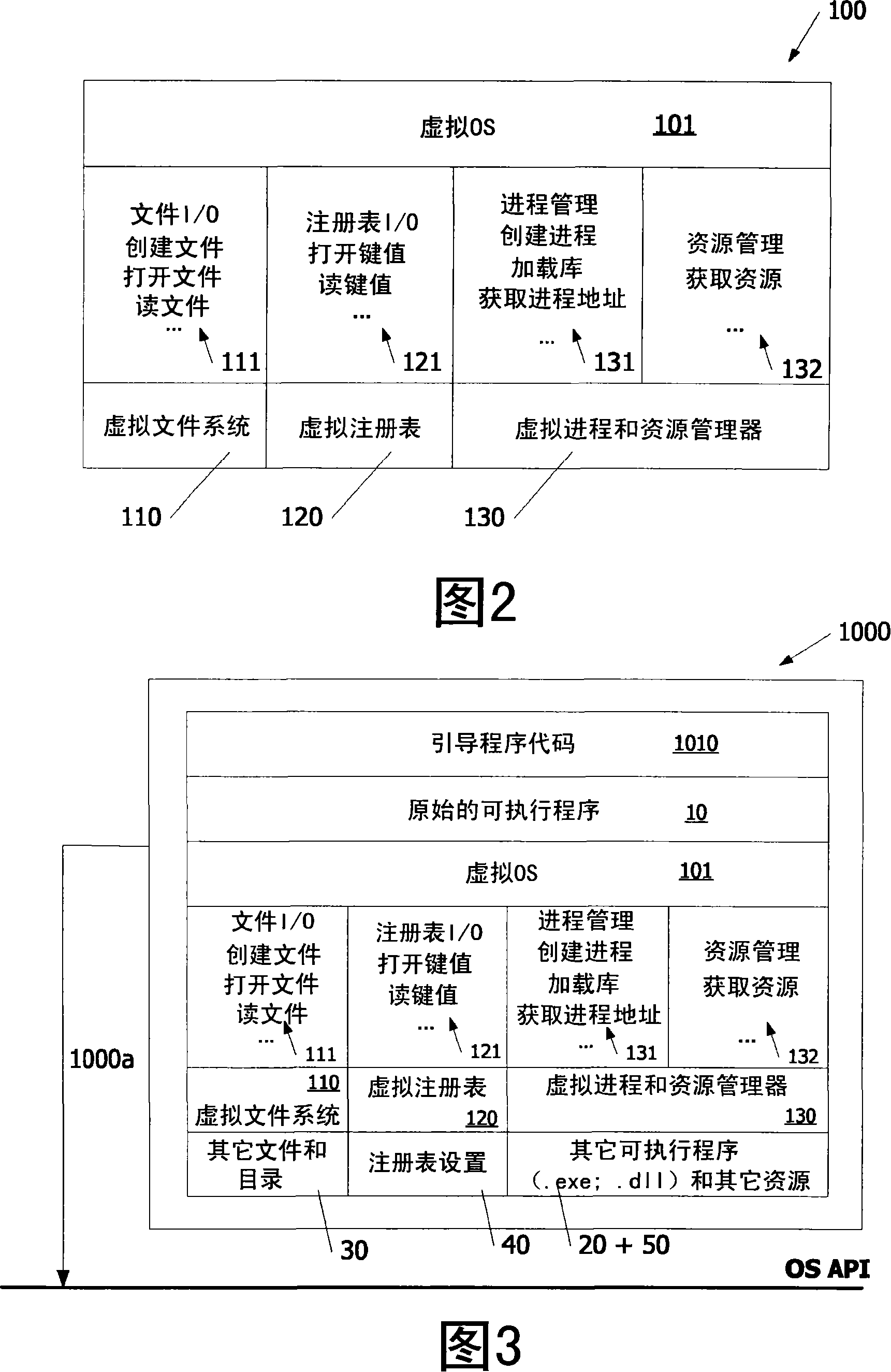
The invention relates to software protection. A method is disclosed whereby an original executable, which can be run on a computer device with an execution environment, is wrapped in an alternative execution environment for thereby forming a new executable, and thus calls from the original executable to the operating system of the computer devices can no longer be inspected or manipulated. Hereby, the executable is protected against examination and reverse engineering.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Hot patch realization method and device
InactiveCN105786537ASmall sizeReduce reserved memory spaceProgram loading/initiatingNew ExecutableObject file
The invention provides a hot patch realization method and device. The method comprises following steps of obtaining file information of a substitute function from an object file, wherein the substitute function is used for substituting a function at an object side needing to be patched; generating a new executable file for the function needing to be patched according to the file information; determining corresponding address information when the new executable file is operated at the object side; generating corresponding substitute instruction information when the new executable file is operated at the object side according to the address information; and informing the object side of operating the new executable file by utilizing the substitute instruction information.
Owner:ZTE CORP
Rule based engine for validating financial transactions
InactiveUS20080250411A1Reduce needFinanceDigital computer detailsSource code fileFinancial transaction
A method and system for checking whether customer orders for transactions of financial instruments conform to business logic rules. Executable rule files are created and stored in a repository. New executable rule files can be created by scripting the new business logic rules in a script file which is converted into a corresponding source code file written in a computer programming language. The source code file is compiled to create an individual executable rule file. A rule selection repository contains identification of groups of selected executable rule files. The invention determines the category of the customer order and reads, from the rule selection repository, a group of executable rule files that correspond to the identified category of the customer order. The selected executable rule files are executed to check the conformance of the customer order. Execution results are stored in a status repository for subsequent retrieval and analysis.
Owner:META PLATFORMS INC
Patch generation method, device and equipment and storage medium
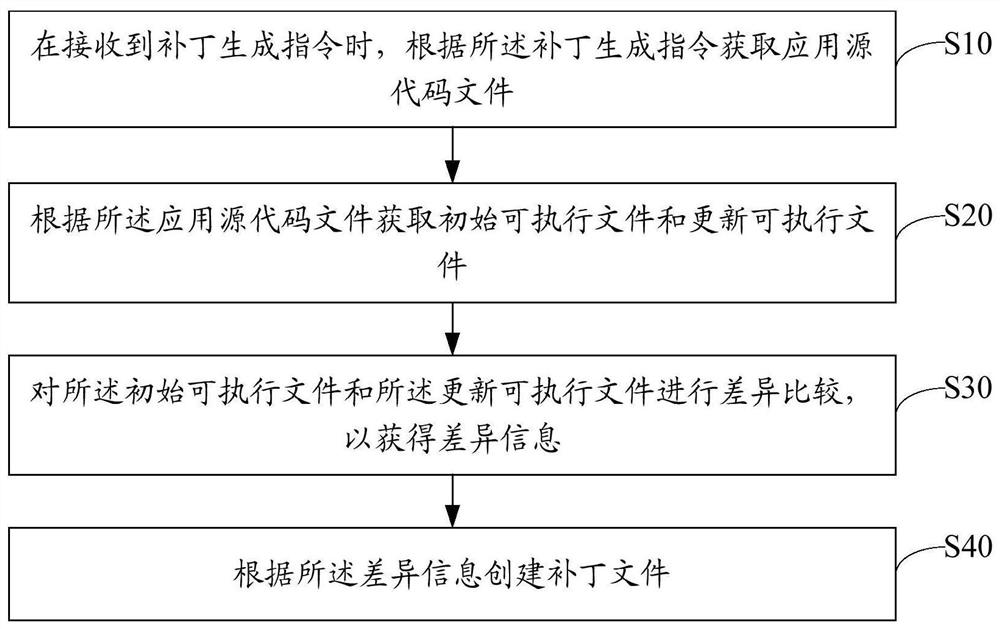
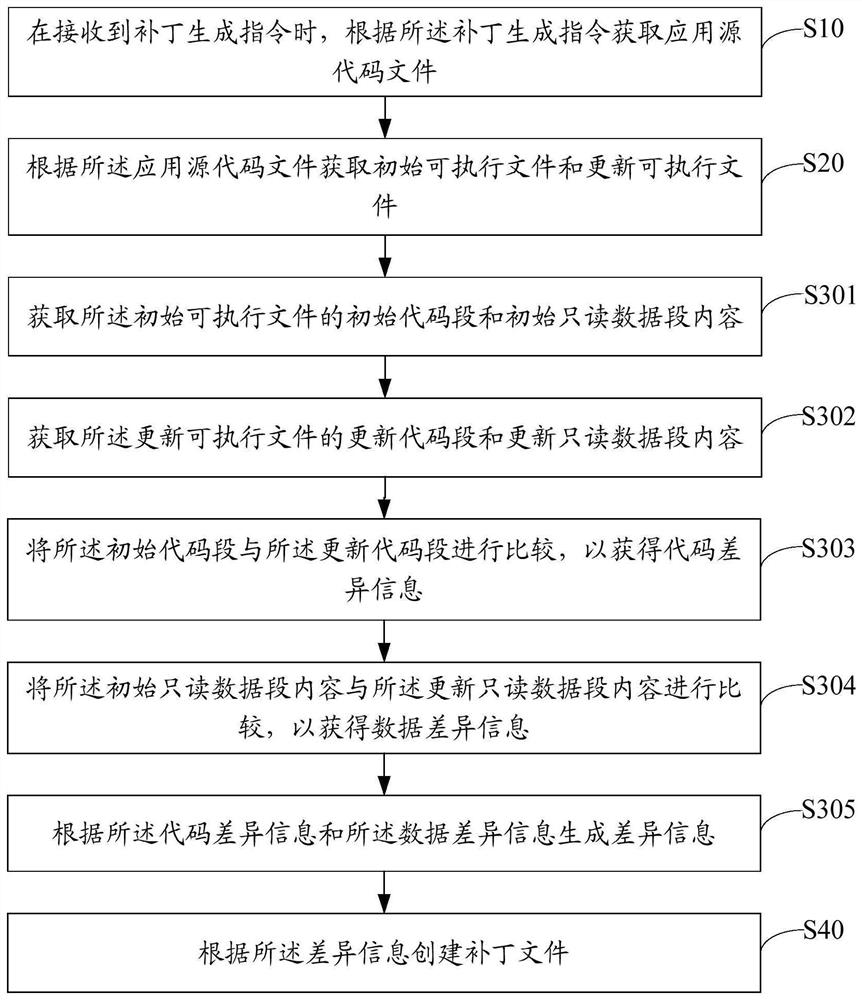
PendingCN112612502ASolve technical problems that make it difficult to generate patch filesVersion controlCode compilationSource code fileSoftware engineering
The invention belongs to the technical field of computers, and discloses a patch generation method, device and equipment and a storage medium, and the method comprises the steps: obtaining an application source code file according to a patch generation instruction when the patch generation instruction is received; obtaining an initial executable file and an updated executable file according to the application source code file; performing difference comparison on the initial executable file and the updated executable file to obtain difference information; and creating a patch file according to the difference information. Compared with an existing mode that source codes need to be provided to generate patches, difference comparison is conducted on the initial executable file and the updated executable file obtained according to the application source code file, the patch file is created, and by adopting the mode that the file is compiled, namely the application source code file, the patch file can be created under the condition that the source code is not provided, and the technical problem that the patch file is difficult to generate when the source code cannot be obtained in an existing patch generation mode is solved.
Owner:苏州三六零智能安全科技有限公司
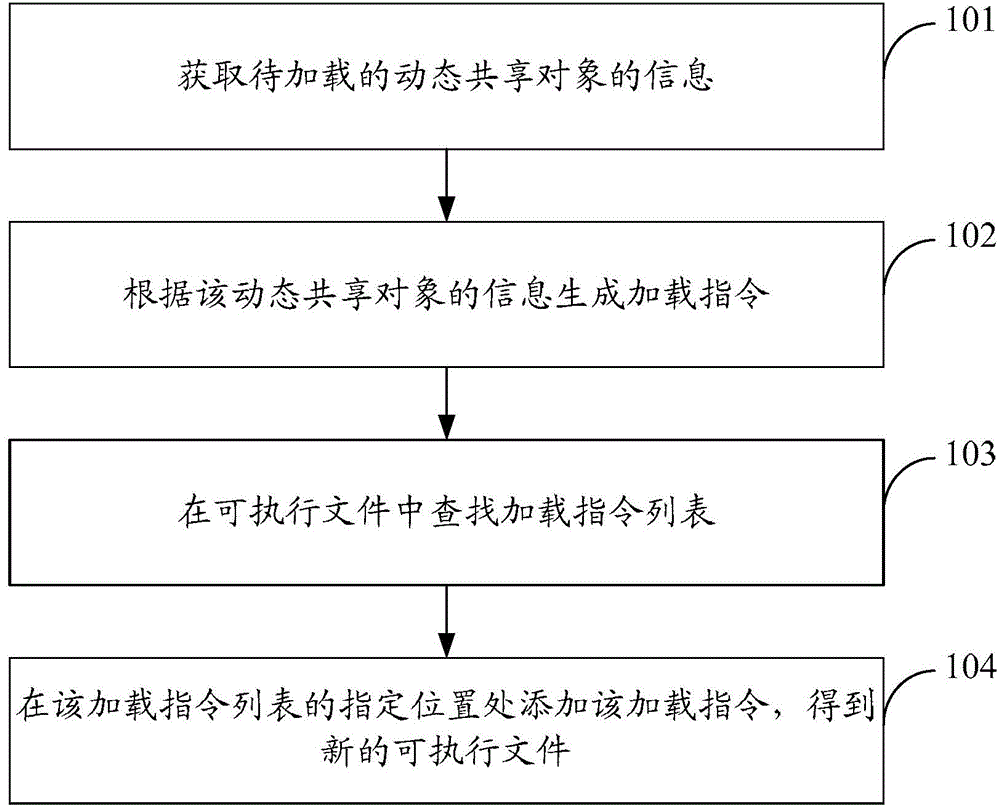
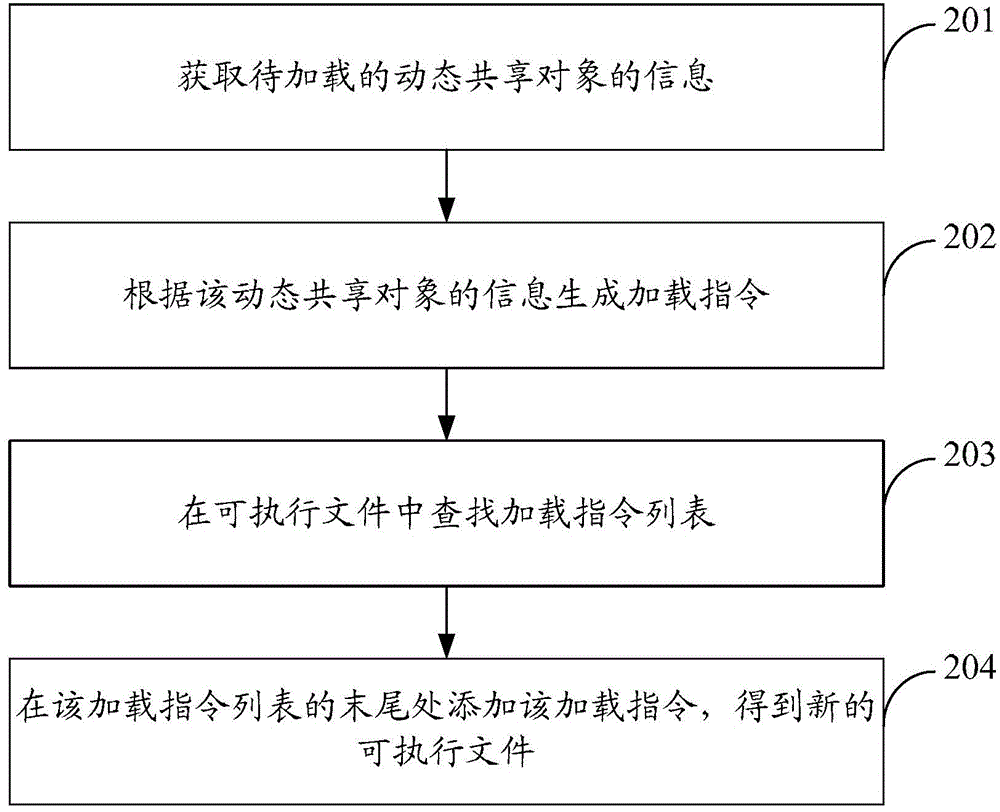
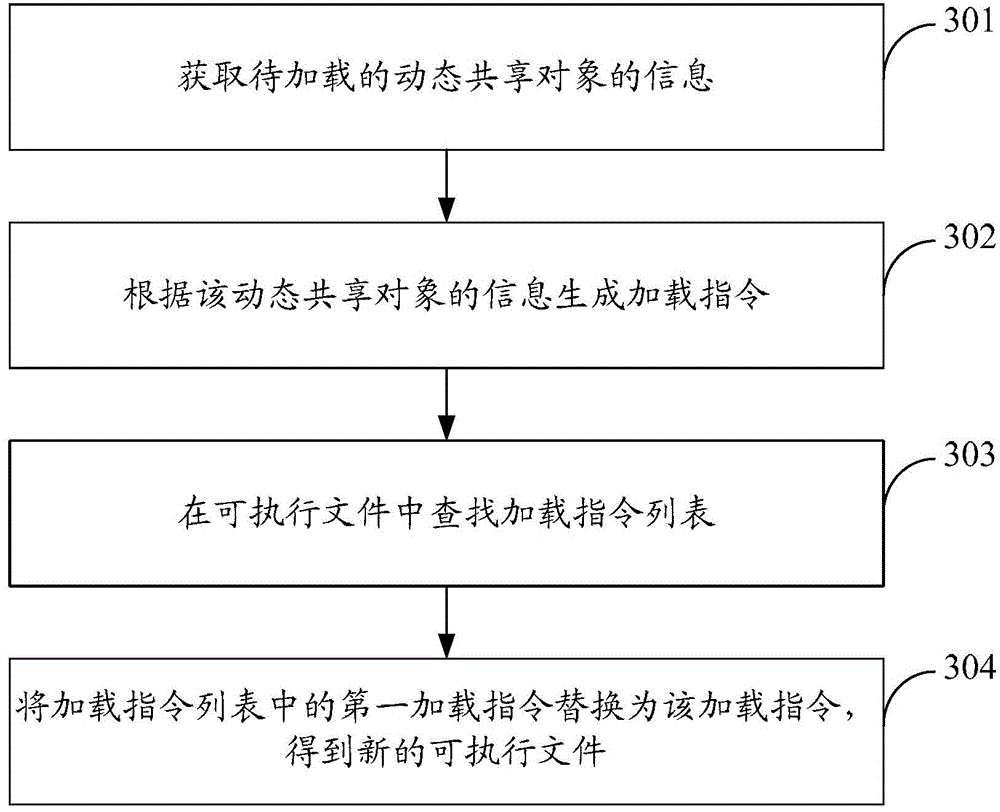
Method and apparatus for loading dynamic shared object
The invention discloses a method and apparatus for loading a dynamic shared object, and belongs to the communication field. The method comprises following steps: acquiring the information of a dynamic shared object to be loaded; generating a loading command according to the information of the dynamic shared object; searching for a loading command list in an executable file; and adding the loading command to the designated position in the loading command list so as to obtain a new executable file. The apparatus comprises an acquisition module, a generation module, a search module and a modification module. According to the embodiment of the invention, a new dynamic shared object can be loaded under a condition that source codes of the executable file is unknown, so that the source codes of the executable file are not needed, recompilation through a compiler is not needed, the dependence on the source codes of the executable file can be eliminated, and therefore the method and the apparatus are highly practical and can be more widely applied.
Owner:TENCENT TECH (SHENZHEN) CO LTD
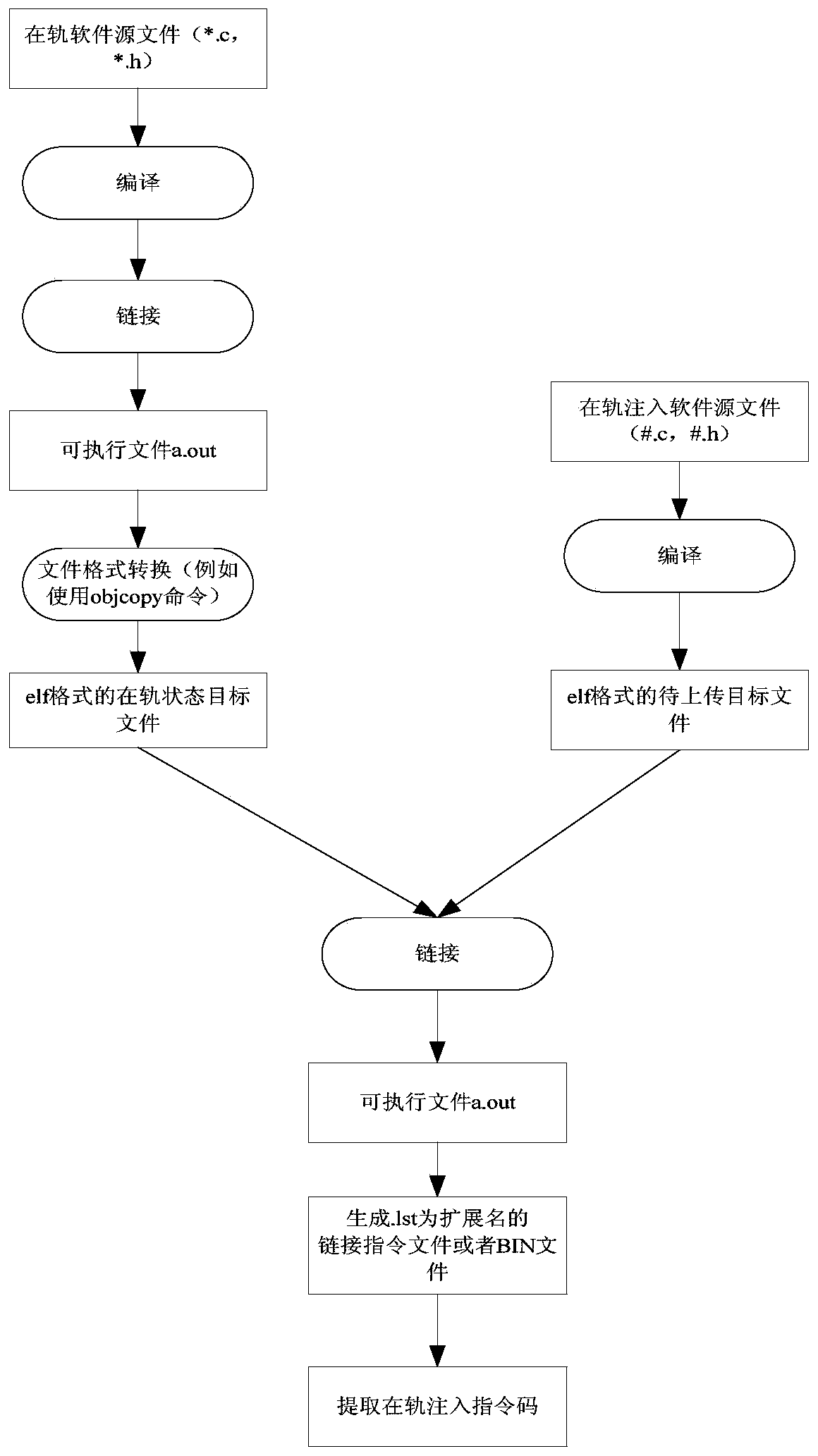
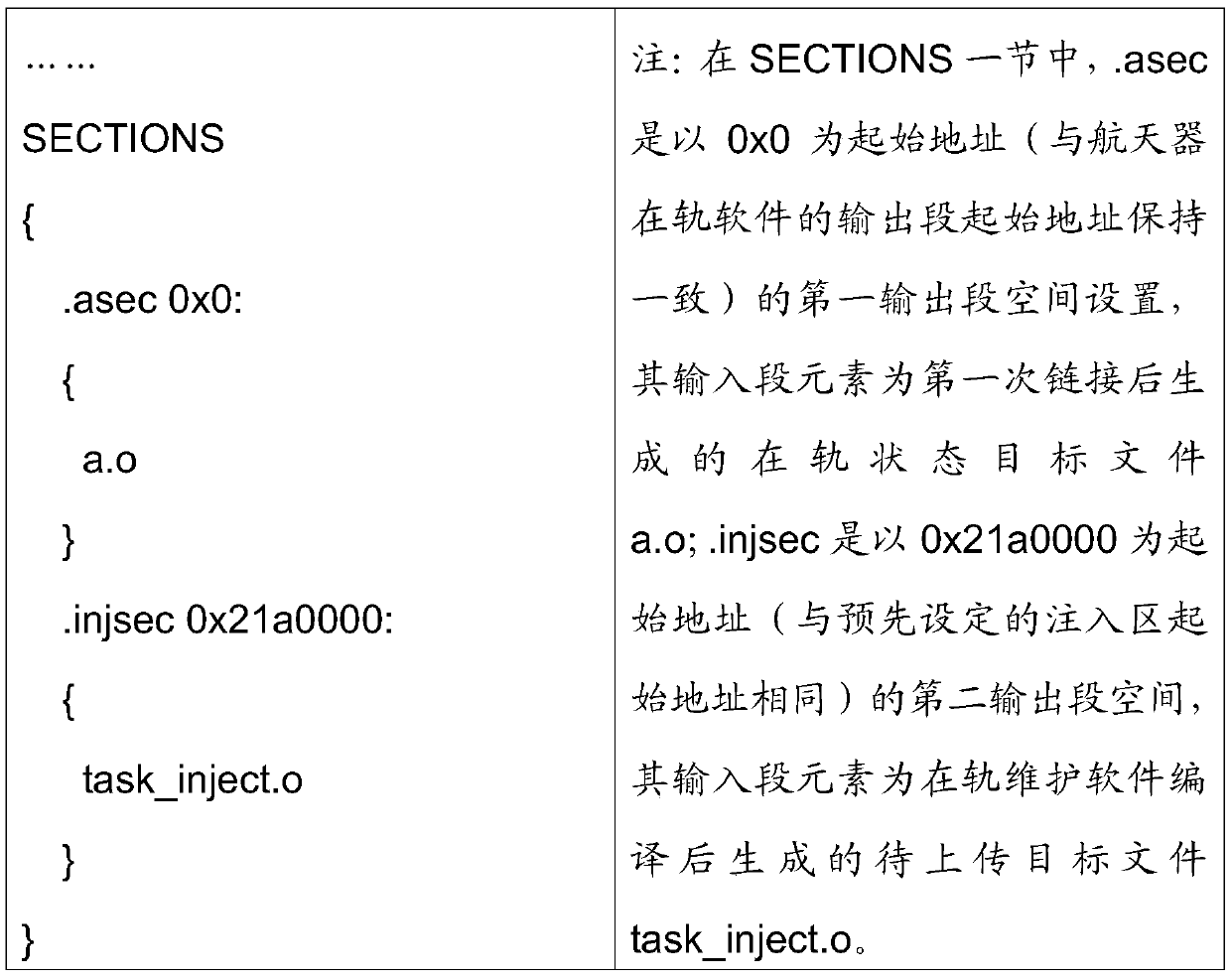
Spacecraft on-orbit maintenance injection code generation method based on secondary linking
ActiveCN107315587AImprove efficiencyImprove accuracySpecific program execution arrangementsCompiler constructionNew ExecutableOrbit
The invention provides a spacecraft on-orbit maintenance injection code generation method based on secondary linking. The method comprises the steps that (1) the state of spacecraft on-orbit running software is restored, and an on-orbit state target file is generated; (2) an on-orbit maintenance source code is written; (3) a compiler is used to independently compile the written on-orbit maintenance source code, and a to-be-uploaded target file is generated; (4) a script file for secondary linking is newly created; (5) the on-orbit state target file and the to-be-uploaded target file are linked based on the established script file for secondary linking, and a new executable file is generated; and (6) the new executable file is converted into a linking instruction file or a BIN file, and an injection code instruction with a designated initial address is directly extracted from the linking instruction file or the BIN file. Through the method, on the premise of guaranteeing that an original on-orbit software binary code does not change, a relocation process of all address relevant items in on-orbit maintenance software is automatically realized, and therefore the generation efficiency and correctness of a spacecraft on-orbit maintenance injection code are greatly improved.
Owner:BEIJING INST OF CONTROL ENG
APK (Android Package) signature verification method in Android system
InactiveCN103473500AMonitor illegal behaviorPlatform integrity maintainanceNew ExecutableInformation leakage
The invention provides an APK signature verification method in an Android system. The APK signature verification method in the Android system is based on APK signature verification methods in the prior art and comprises respectively putting a file needing execution and an original executable file into two folders; putting the two folders into the same folder compression package and meanwhile guaranteeing that the position of the file needing execution in the folder compression package is in front of executable files and that the position of the original executable file is at the back of the executable files. Therefore, not only is the signature verification is passed, but also new executable files can be executed. By means of the APK signature verification method in the Android system, monitoring can be performed on behavior of users of electronic products based on Android systems, such as cellphones, to prevent unsafe factors such as information leakage, or monitoring can be performed on illegal practices to meet requirements of security departments of public security bureaus and the like.
Owner:成都三零瑞通移动通信有限公司
EGM authentication mechanism using multiple key pairs at the BIOS with PKI
ActiveUS8768843B2Reduce riskPayment protocolsProgram/content distribution protectionNew ExecutableApplication software
Executable applications on a gaming machine are verified before they can be executed, for security purposes and to comply with jurisdictional requirements. Unlike in prior systems for authenticating the executable applications, embodiments allow for new executable applications to be provided and verified over time with different private and public key pairs, even after the operating code of the gaming machine is certified by the jurisdiction and deployed in the field.
Owner:IGT
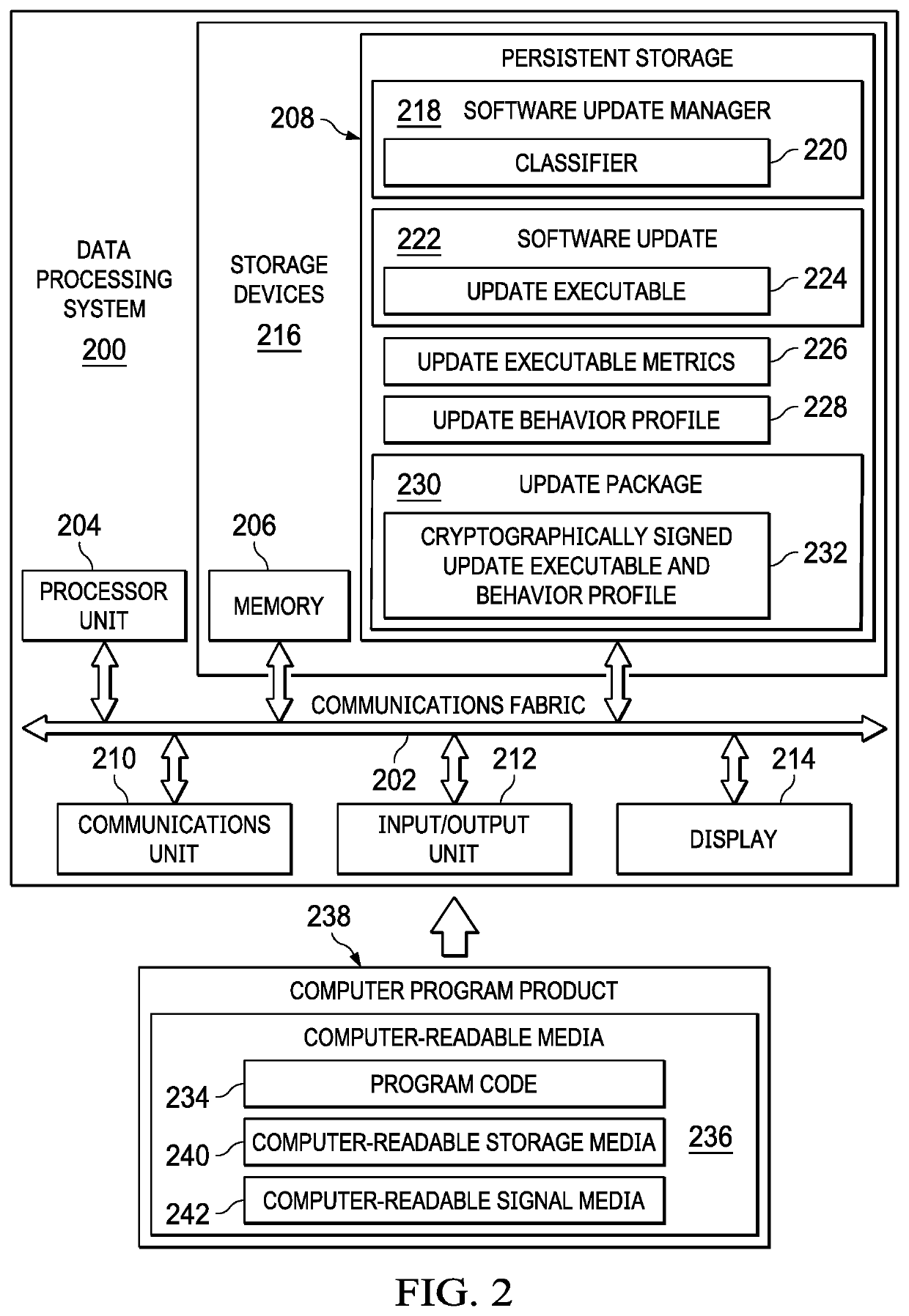
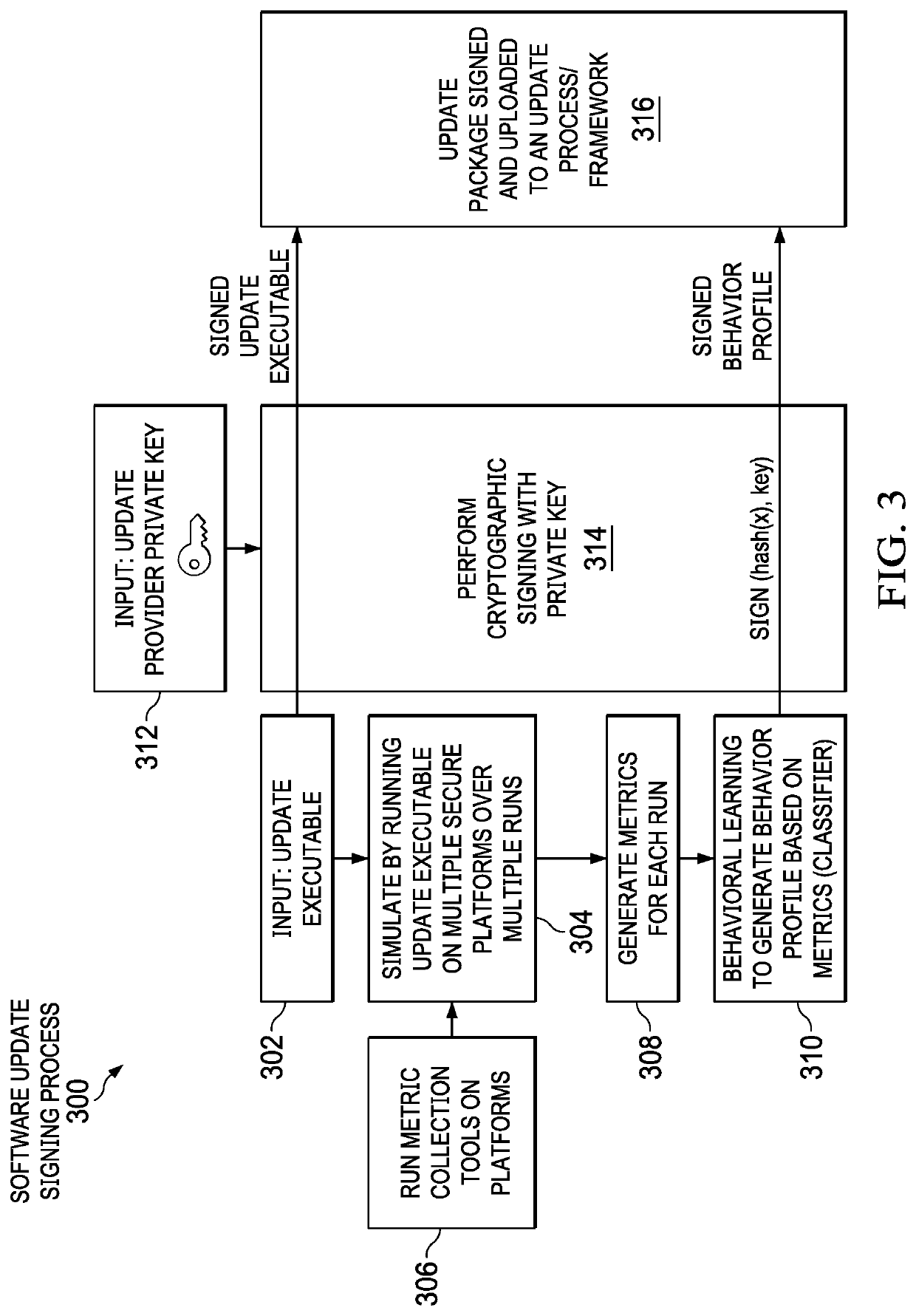
Verifying Updates Based on Update Behavior-Based Profiles
ActiveUS20200279044A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesCryptographic hash functionAlgorithm
Verifying authenticity of software updates is provided. An update executable and an update behavior profile corresponding to a software update are hashed using a cryptographic hash function. A hash of the update executable and the update behavior profile is signed using a private key to form a hashed update digital signature.
Owner:IBM CORP
Method for generating executable file used for debugging display parameters
The invention discloses a method for generating an executable file used for debugging display parameters. The method comprises the following steps: S1, loading an original executable file and analyzing an original code and original data in the original executable file; S2, modifying the analyzed original data in the original executable file and replacing the original data with new data; S3, combining the original code with the new data and generating a new executable file. The executable file is an executable bin file or an executable hex file in a display. The method for generating the executable file used for debugging the display parameters can obtain types and number of screens from the .bin file, automatically obtain an initial data flag position and a completion data flag position and prompt related information. Besides, a program can realize the same function as a Debug mode and normally display a two-dimensional array of a string type.
Owner:TIANJIN SAMSUNG ELECTRONICS CO LTD +1
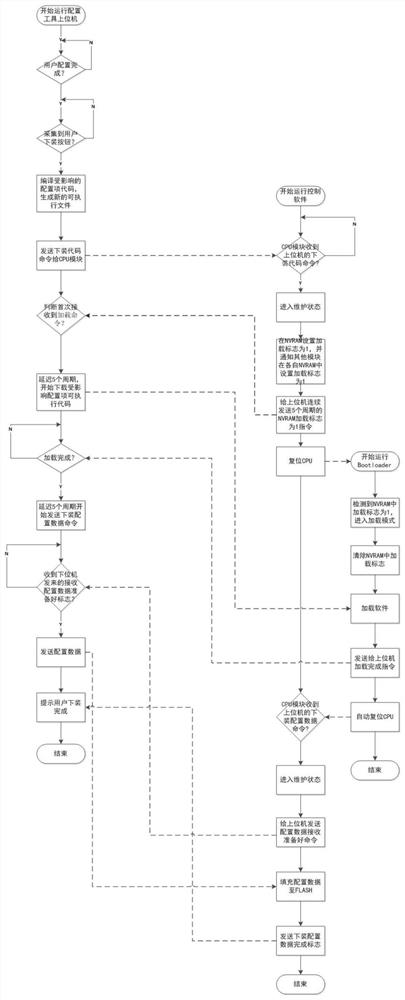
Automatic compiling, linking and loading method for distributed control software source codes
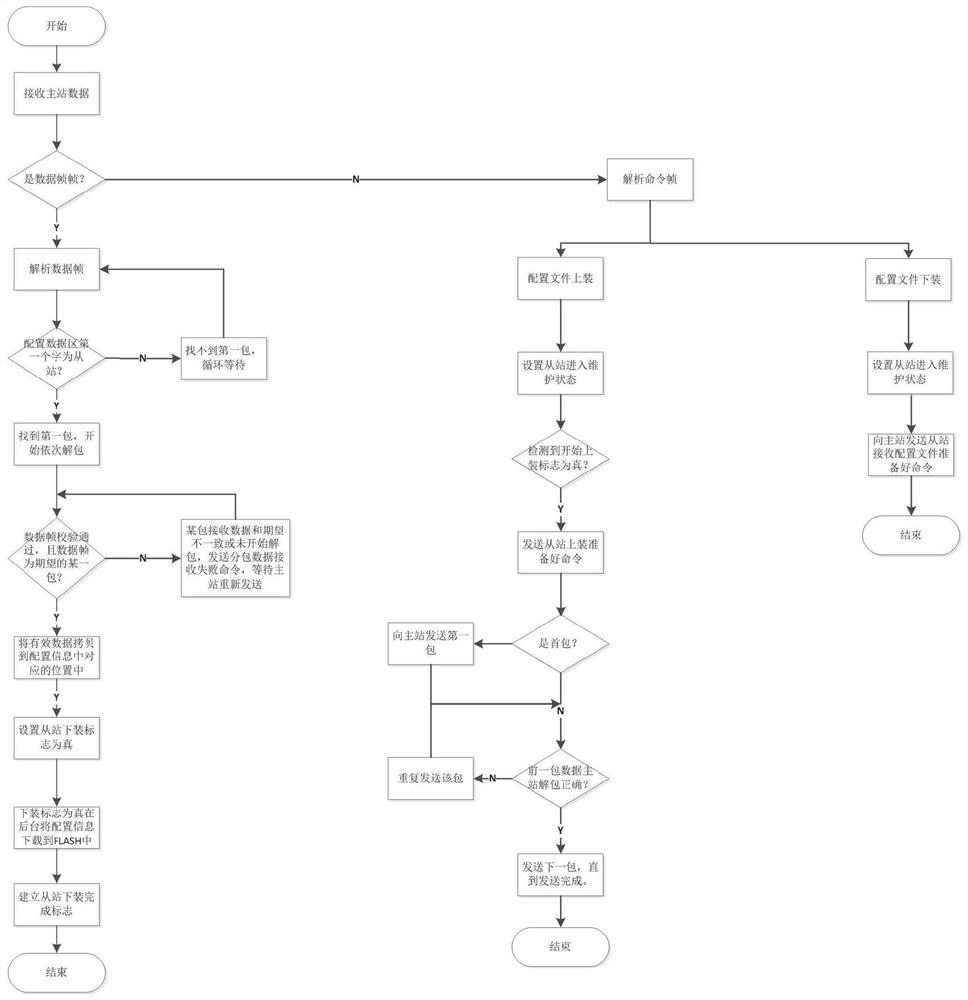
ActiveCN111880830AReduce risks such as missing loadingProgramme controlLink editingConfiguration itemNew Executable
The invention relates to an automatic compiling, linking and loading method for distributed control software source codes. The method comprises the following steps: 1, executing configuration operation by a user; 2, collecting state information of a button installed by the user; 3, generating a new executable file, and sending a code downloading command to an affected configuration item module; 4,after a code downloading command of the upper computer is received, entering a maintenance mode; 5, downloading the executable file to be downloaded to a Flash memory of the lower computer; 6, afterdownloading of the executable file is completed, enabling a BootLoader program to reply that loading of the upper computer is completed; 7, enabling the affected configuration item module of the uppercomputer to send a downloading data instruction; 8, enabling a lower computer related to the affected configuration item module to receive the downloading data instruction of the upper computer, entering a maintenance mode and receiving user configuration data. According to the invention, the software target code can be loaded to the corresponding target machine, and the risks of missing loadingof the configuration data file and the like are reduced.
Owner:中国航发控制系统研究所
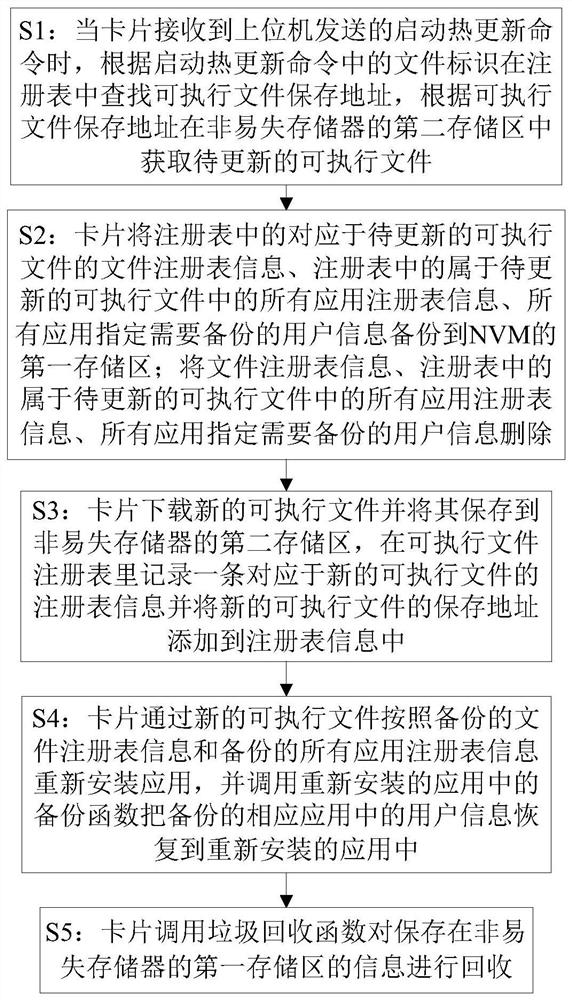
A method and a device for realizing hot updating of executable files of an intelligent card
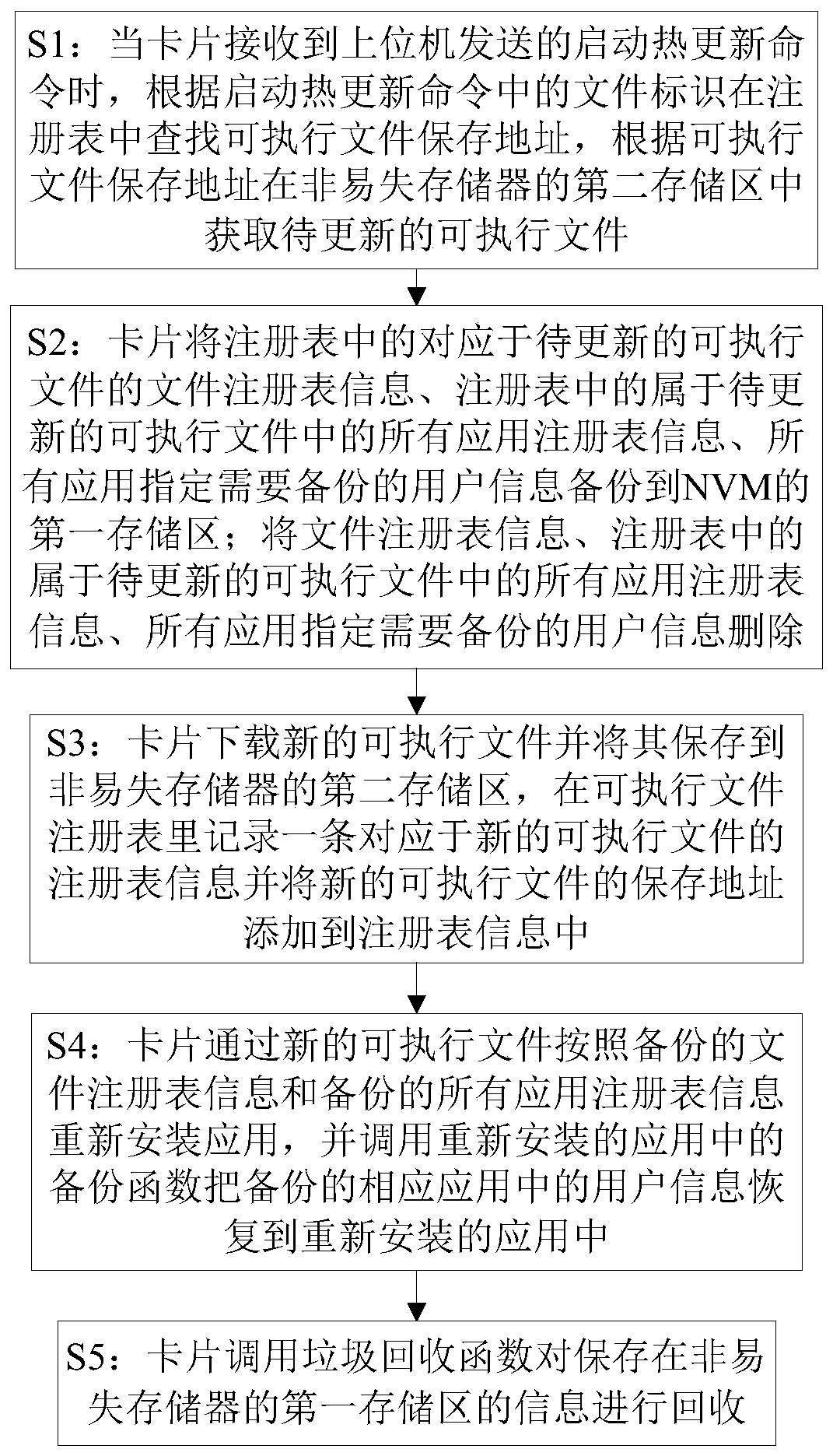
ActiveCN109819018AEasy to useImprove experienceKey distribution for secure communicationVersion controlSoftware engineeringSmart card
The invention discloses a method and device for realizing hot update of executable files of an intelligent card, and the method comprises the steps: obtaining an executable file to be updated when a card receives a hot update starting command sent by an upper computer; Backing up file registry information corresponding to the executable file to be updated in the registry, all application registryinformation belonging to the executable file to be updated in the registry and user information designated to be backed up by all applications to a first storage area of the nonvolatile memory; Downloading a new executable file, reinstalling the application according to the backup file registry information and all the backup application registry information through the new executable file, and calling a backup function in the reinstalled application to restore the user information in the backup corresponding application to the reinstalled application. According to the method, the executable file and the application to be updated can be updated, previous data of an application user are reserved, the user can use the method conveniently, and the user experience is improved.
Owner:FEITIAN TECHNOLOGIES
Detecting computing processes requiring reinitialization after a software package update
Embodiments relate to systems and methods for detecting computing processes requiring reinitialization after a software package update. A physical or virtual client machine can host a set of installed software packages, including operating system, application, and / or other software. An restart tool can track the set of executing processes on the client, and identify both corresponding executable files which spawned those processes, and any installed package updates which correspond to those executable files. The restart tool can compare the timestamp or other indicator of the version of the executable file which spawned currently running processes, and the timestamp or other indicator of any newer executable files which may have been installed after the application or other process was initiated. A user can be alerted to terminate and restart any processes running off of out-of-date executable files, or in embodiments those reinitializations can be set to be performed automatically.
Owner:RED HAT
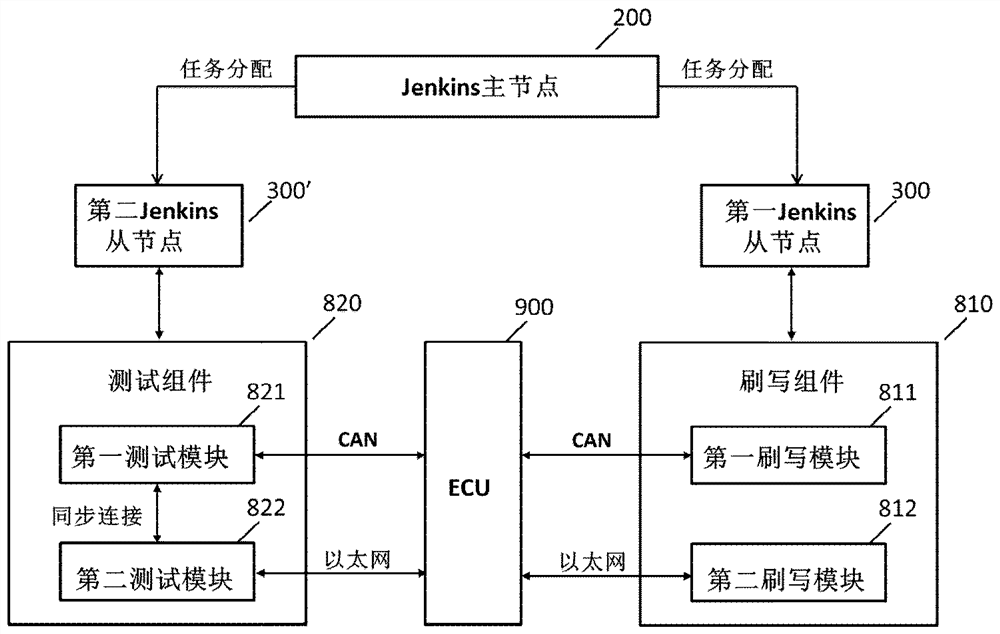
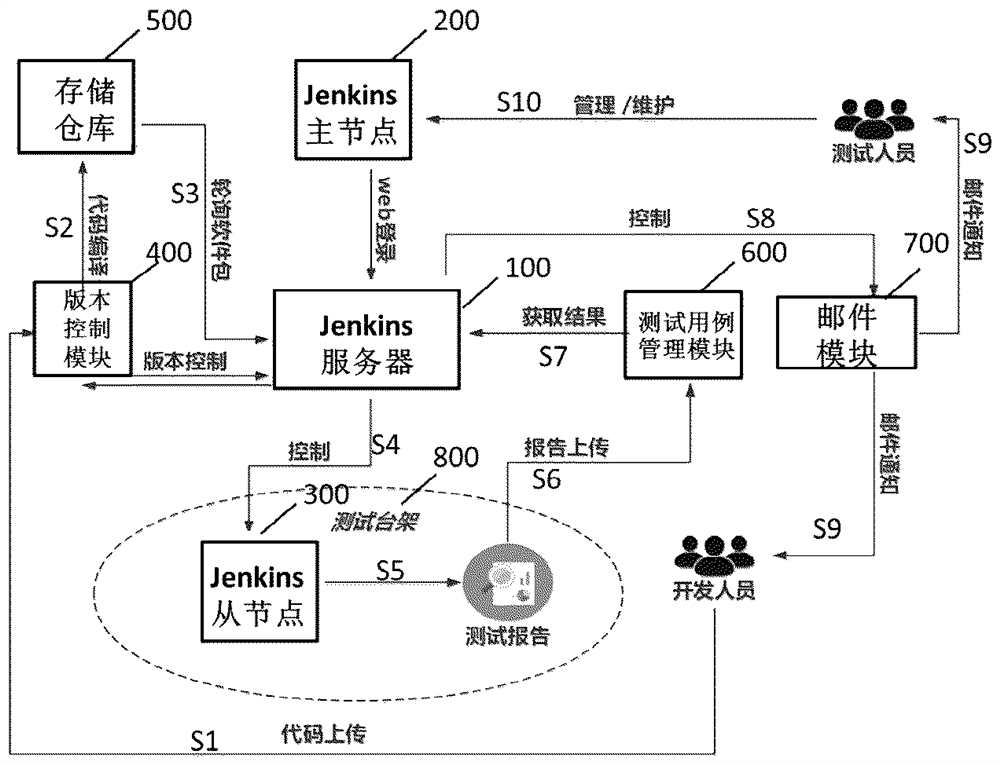
ECU software test system and method
PendingCN113177004AImprove work efficiencyReduce the burden onSoftware testing/debuggingSoftware engineeringNew Executable
The invention relates to an ECU software test system and method. The system comprises a Jenkin server, a version control module, a storage warehouse and a test bench, the version control module is used for generating an executable software package, and the storage warehouse is used for storing the executable software package generated by the version control module. The Jenkin server is used for triggering and generating a test task when a new executable software package is detected to be generated in the storage warehouse in a polling manner, and the test bench is used for executing the brushing and testing of ECU software based on the test task to generate a test report. According to the method and the system, the test task can be automatically constructed, and a developer and a tester can be notified after the test result is sorted.
Owner:NIO TECH ANHUI CO LTD
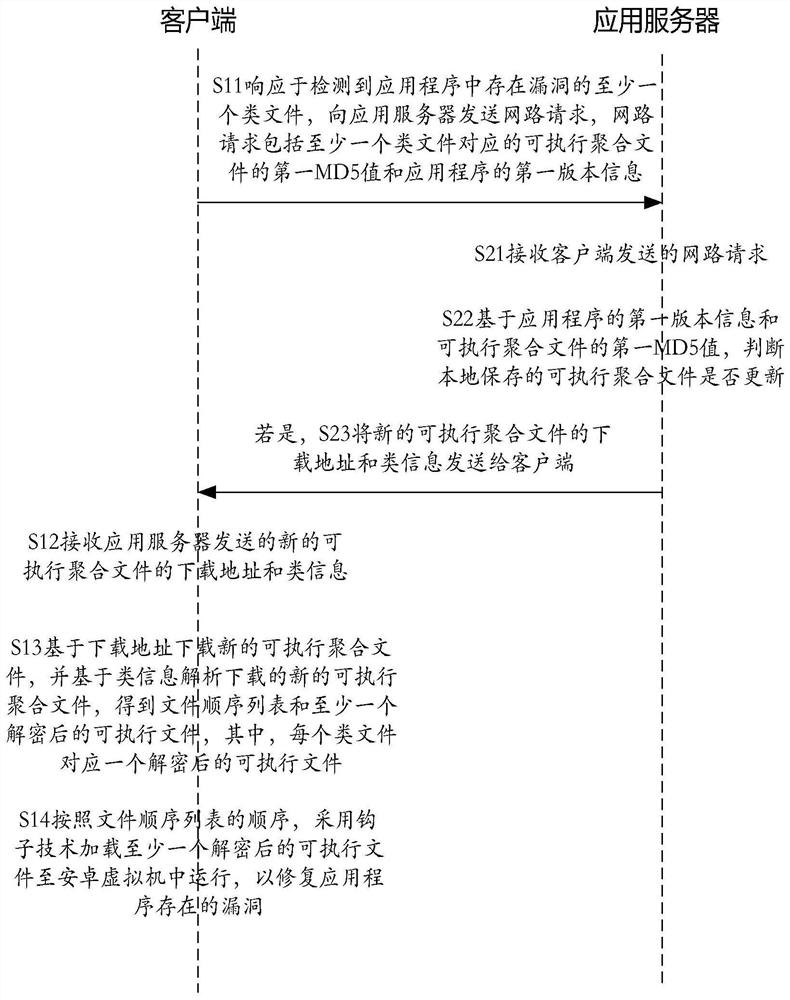
Method and equipment for repairing code bugs
ActiveCN111953475AAchieve replacementAchieve the purpose of repairEncryption apparatus with shift registers/memoriesPlatform integrity maintainanceApplication serverSoftware engineering
The invention aims to provide a code bug repairing method and device, and the method comprises the steps: responding to at least one class file, with bugs, in an application program through a client,and transmitting a network request to an application server, requesting the application server to return a downloading address and class information of a new executable aggregate file to the client; the client downloads a new executable aggregate file based on the download address, analyzes the downloaded new executable aggregate file based on the class information to obtain a file sequence list and at least one decrypted executable file, and sends the decrypted executable file to the server according to the sequence of the file sequence list; at least one decrypted executable file is loaded into the Android virtual machine for running by adopting a hook technology, so that the bugs existing in the application program are repaired, the instantaneity of online bug repair is improved, an application server does not need to send a version again, technical support is provided for better user experience, the user experience is improved, and meanwhile, the user experience is improved. And the retention degree of the user is enhanced.
Owner:SHANGHAI LIANSHANG NETWORK TECHNOLOGY CO LTD
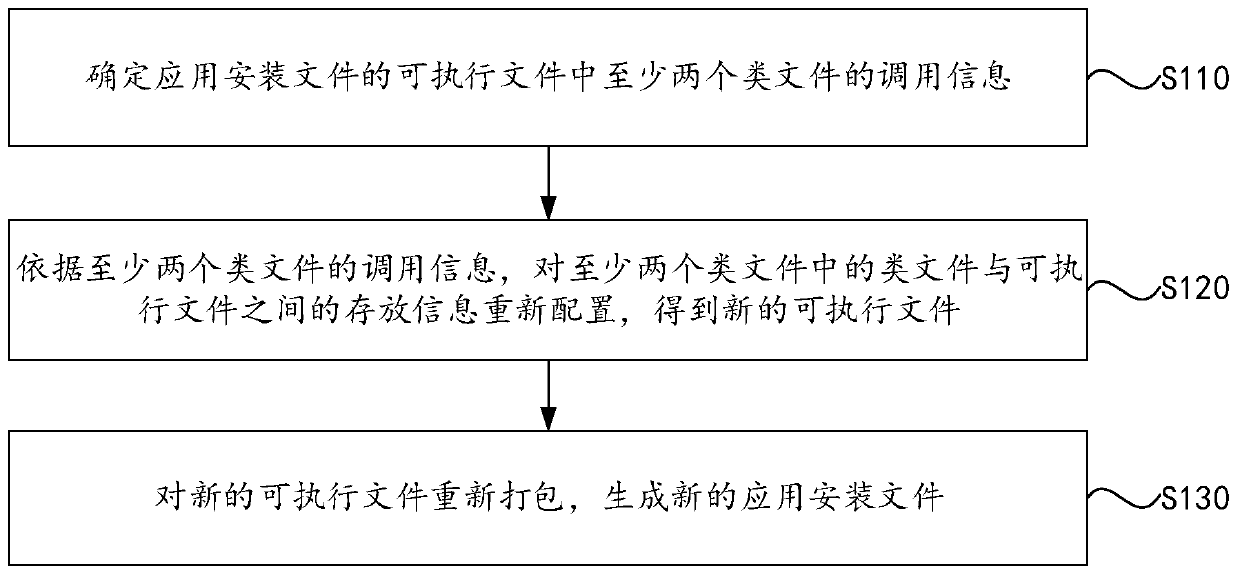
File processing method and device, equipment and medium
PendingCN111240738AOverall small sizeVersion controlFile/folder operationsFunction definitionSoftware engineering
The embodiment of the invention discloses a file processing method and device, equipment and a medium. The method comprises the steps: determining calling information of at least two types of files inan executable file of an application installation file; according to the calling information of the at least two class files, reconfiguring storage information between the class files in the at leasttwo class files and the executable file to obtain a new executable file; and repackaging the new executable file to generate a new application installation file. By the adoption of the scheme, the storage positions of the class files with the calling relation can be adjusted, function definition and function calling of the same function in different executable files are integrated into the same executable file, and the size of the application installation file is reduced.
Owner:BEIJING YOUZHUJU NETWORK TECH CO LTD
A hot update method and device for implementing smart card executable files
ActiveCN109819018BEasy to useImprove experienceKey distribution for secure communicationVersion controlSoftware engineeringSmart card
The invention discloses a method and device for implementing hot update of executable files of a smart card. The method includes: when the card receives a start hot update command sent by a host computer, acquiring the executable file to be updated; The file registry information of the executable file to be updated, the registry information of all applications belonging to the executable file to be updated in the registry, and the user information specified by all applications to be backed up are backed up to the first storage area of the non-volatile memory ;Download the new executable file and reinstall the application according to the backup file registry information and the backup application registry information through the new executable file, and call the backup function in the reinstalled application to save the User information is restored to the reinstalled app. The invention can update executable files and applications to be updated, and retain the previous data of application users, which is convenient for users to use and improves user experience.
Owner:FEITIAN TECHNOLOGIES
A Method of Injection Code Generation for On-orbit Maintenance of Spacecraft Based on Secondary Link
ActiveCN107315587BImprove efficiencyImprove accuracyCompiler constructionParser generationCode generationSoftware engineering
The invention provides a spacecraft on-orbit maintenance injection code generation method based on secondary linking. The method comprises the steps that (1) the state of spacecraft on-orbit running software is restored, and an on-orbit state target file is generated; (2) an on-orbit maintenance source code is written; (3) a compiler is used to independently compile the written on-orbit maintenance source code, and a to-be-uploaded target file is generated; (4) a script file for secondary linking is newly created; (5) the on-orbit state target file and the to-be-uploaded target file are linked based on the established script file for secondary linking, and a new executable file is generated; and (6) the new executable file is converted into a linking instruction file or a BIN file, and an injection code instruction with a designated initial address is directly extracted from the linking instruction file or the BIN file. Through the method, on the premise of guaranteeing that an original on-orbit software binary code does not change, a relocation process of all address relevant items in on-orbit maintenance software is automatically realized, and therefore the generation efficiency and correctness of a spacecraft on-orbit maintenance injection code are greatly improved.
Owner:BEIJING INST OF CONTROL ENG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com