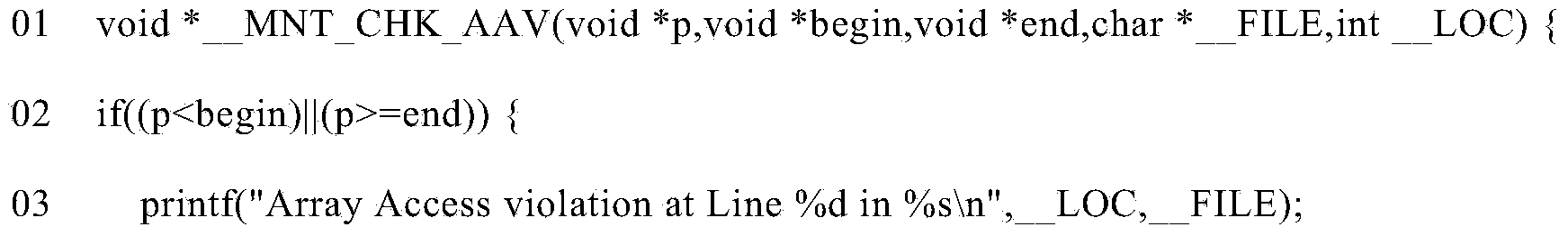Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
187 results about "Function definition" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
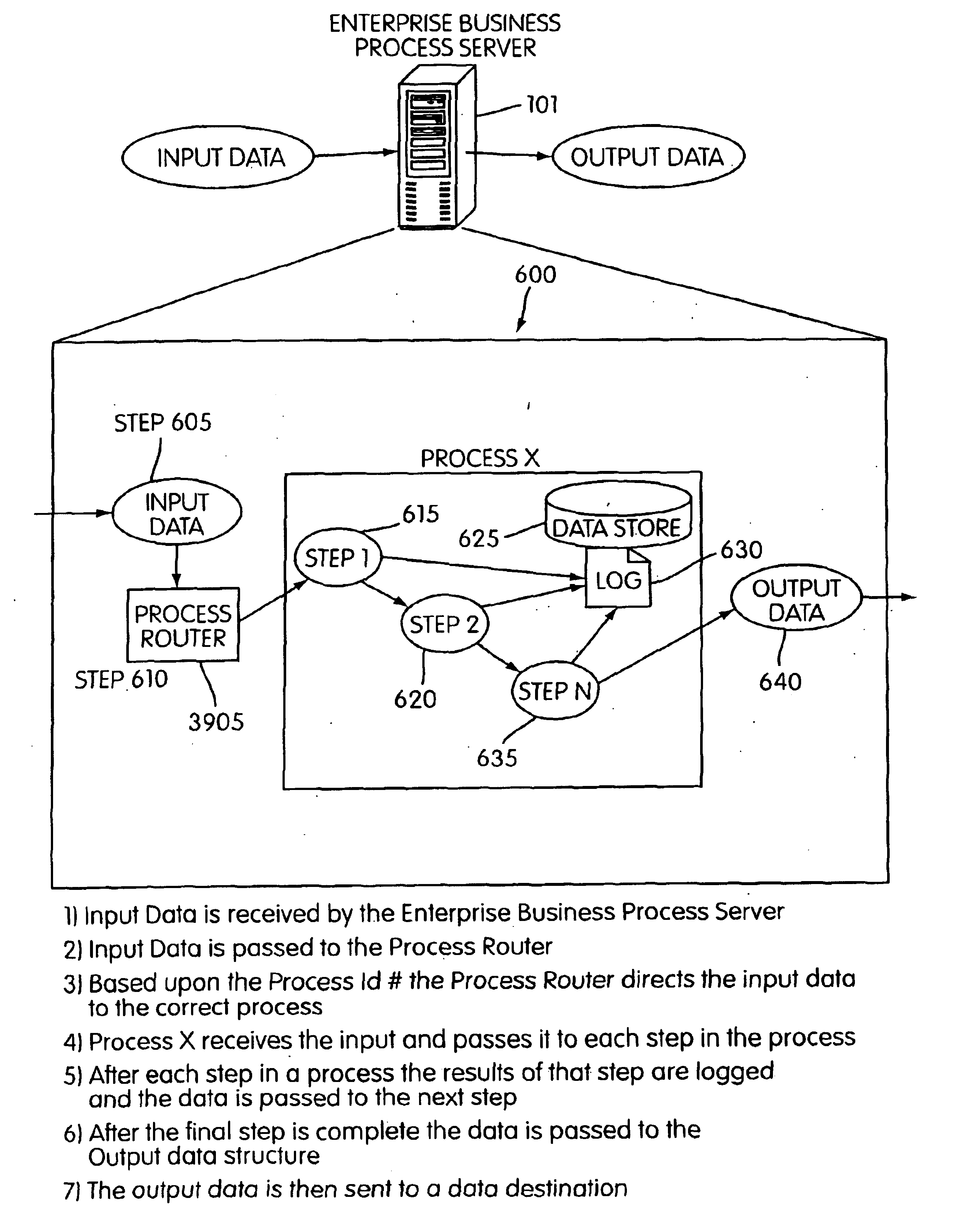
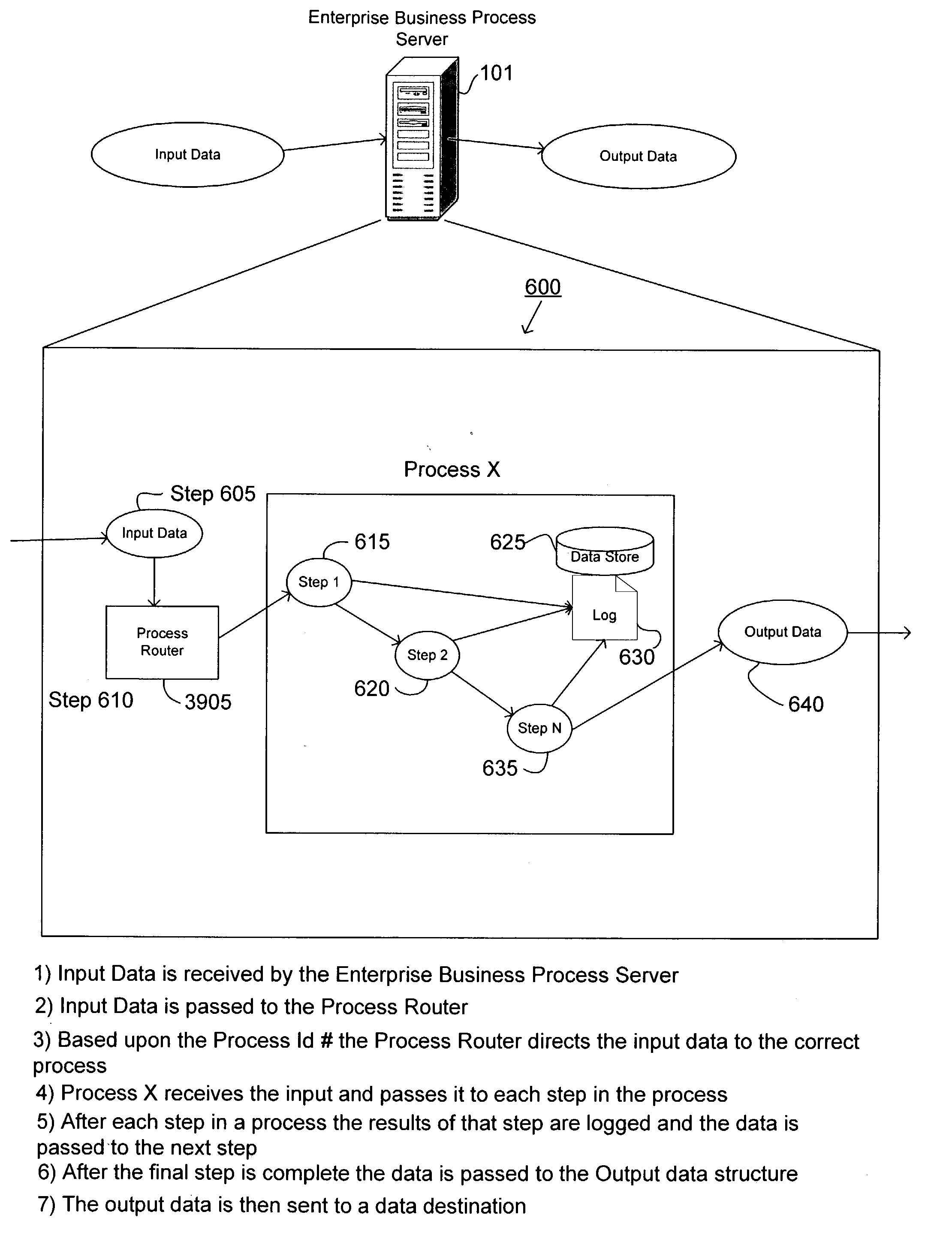
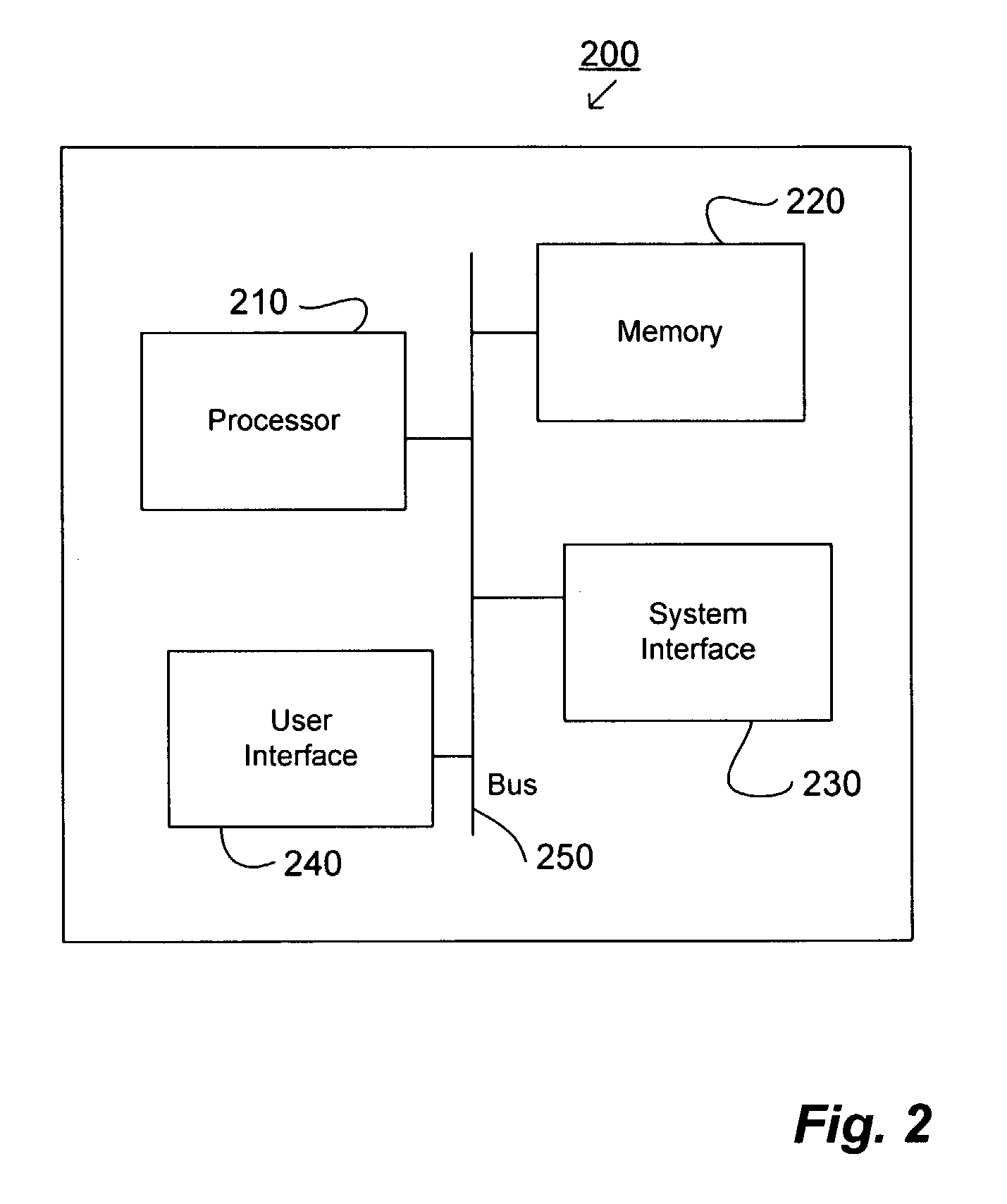
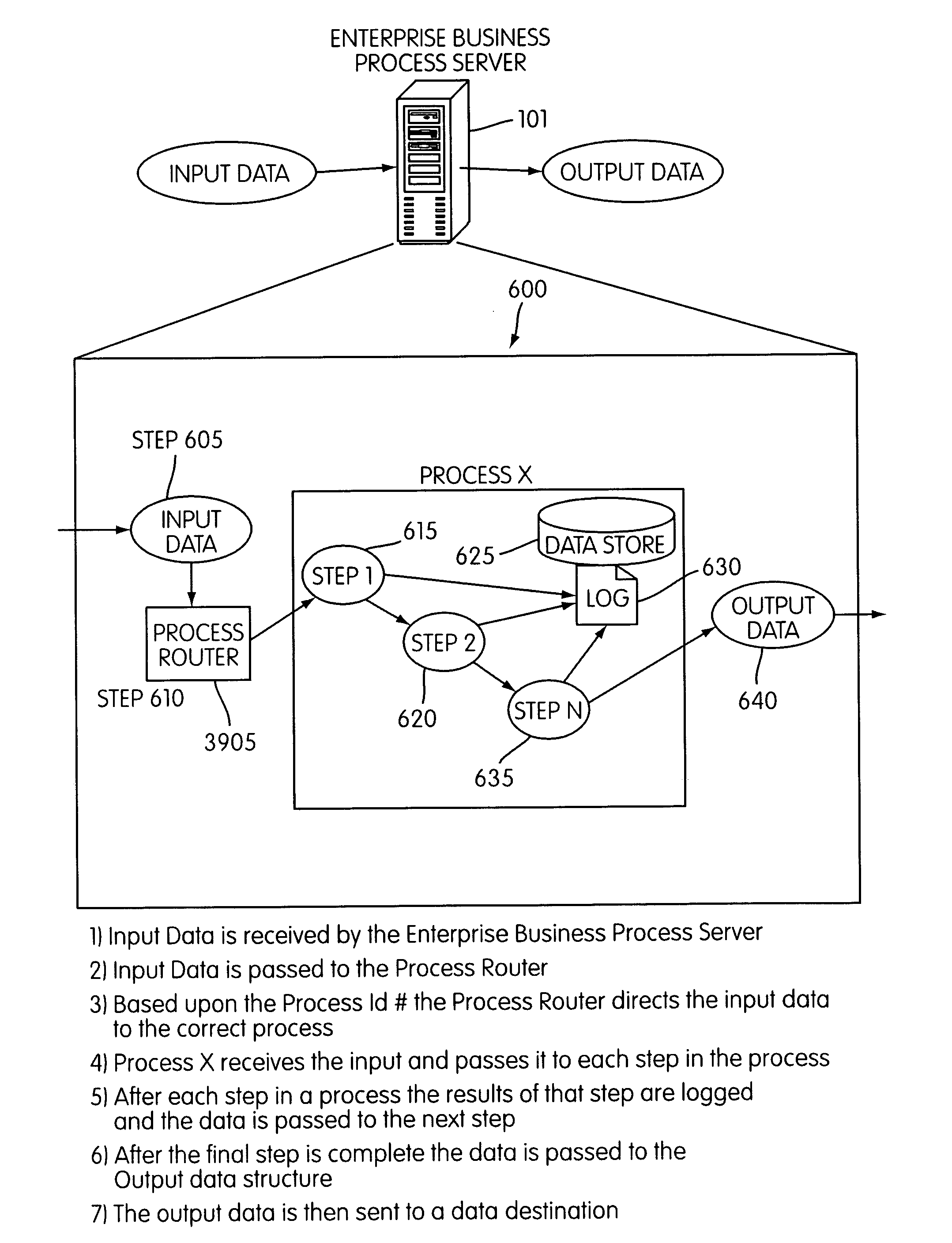
Method and system for enterprise business process management
InactiveUS6920474B2Shorten development timeSimple processMultiple digital computer combinationsOffice automationFunction definitionApplication software
An enterprise business process management system and method for definition and execution of business processes formed from portions of one or more business applications present in an enterprise. The enterprise business process management system includes a server, a router, and an interface for defining and executing such business processes. A data quality business process detects, corrects, analyzes, and reports quantitative and qualitative characteristics of application data and transactional data present in the enterprise. An interface module is provided by which a user may select and define function definition information for a business process.
Owner:41 WINDING
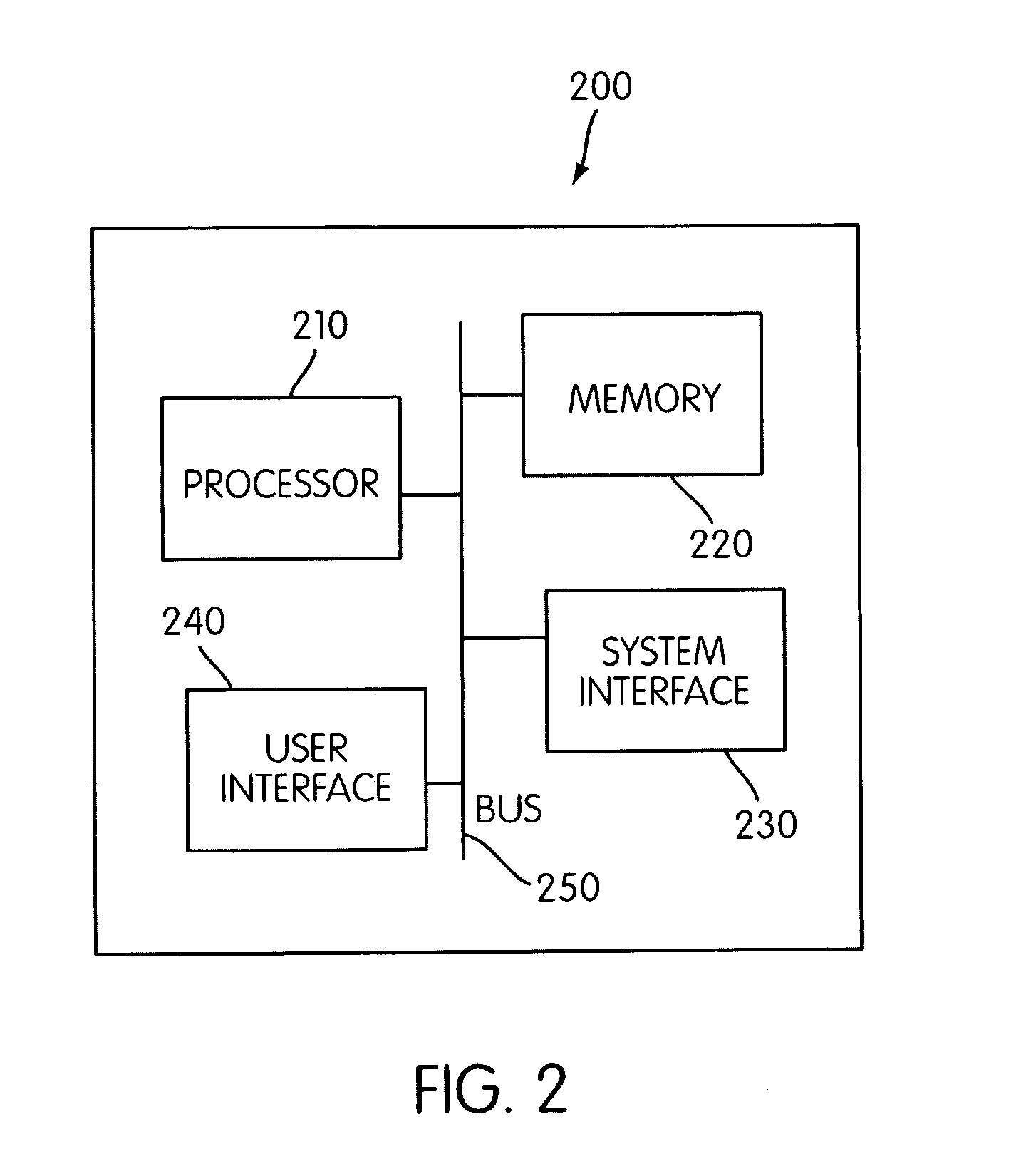
Method and system for enterprise business process management
ActiveUS20030233249A1Shorten development timeSimple processOffice automationResourcesFunction definitionApplication software
An enterprise business process management system and method for definition and execution of business processes formed from portions of one or more business applications present in an enterprise. The enterprise business process management system includes a server, a router, and an interface for defining and executing such business processes. A data quality business process detects, corrects, analyzes, and reports quantitative and qualitative characteristics of application data and transactional data present in the enterprise. An interface module is provided by which a user may select and define function definition information for a business process.
Owner:41 WINDING
Method and system for managing a plurality of enterprise business systems
InactiveUS20050114201A1Allow reuseNew functionOffice automationResourcesFunction definitionKnowledge management
An enterprise business process management system and method for definition and execution of business processes formed from portions of one or more business applications present in an enterprise. The enterprise business process management system includes a server, a router, and an interface for defining and executing such business processes. A data quality business process detects, corrects, analyzes, and reports quantitative and qualitative characteristics of application data and transactional data present in the enterprise. An interface module is provided by which a user may select and define function definition information for a business process.
Owner:41 WINDING
Method and system for managing a plurality of enterprise business systems
InactiveUS7246144B2Shorten development timeSimple processMultiple digital computer combinationsOffice automationFunction definitionApplication software
An enterprise business process management system and method for definition and execution of business processes formed from portions of one or more business applications present in an enterprise. The enterprise business process management system includes a server, a router, and an interface for defining and executing such business processes. A data quality business process detects, corrects, analyzes, and reports quantitative and qualitative characteristics of application data and transactional data present in the enterprise. An interface module is provided by which a user may select and define function definition information for a business process.
Owner:41 WINDING
Multi-modality medical data three-dimensional visual method
InactiveCN1818974ANarrow searchHigh speedImage analysis2D-image generationDiagnostic Radiology ModalityNormalized mutual information
The invention involves a multi-mode medical body data three-dimensional video-method. Most the existing technologies are based on two-two-dimensional lay or two-three dimensional lay, which do not realize the integrated display course of medical body data aligning and amalgamation. The said method includes standardization mutual information-way aligning based on multi resolution ratio and single drop multi-mode straight body protracting-way amalgamation display. The previous one includes three approaches, such as coordinate transform, orientation criterion and multi resolution ratio optimize; the latter includes five approaches, such as impress function definition, the calculation of illumination model, image composition, single drop multi-mode show of the multi-mode data and amalgamation display. The invention can realize the integrated display course of medical body data aligning and amalgamation, and is a real two-three dimensional multi-mode video-method.
Owner:HANGZHOU DIANZI UNIV
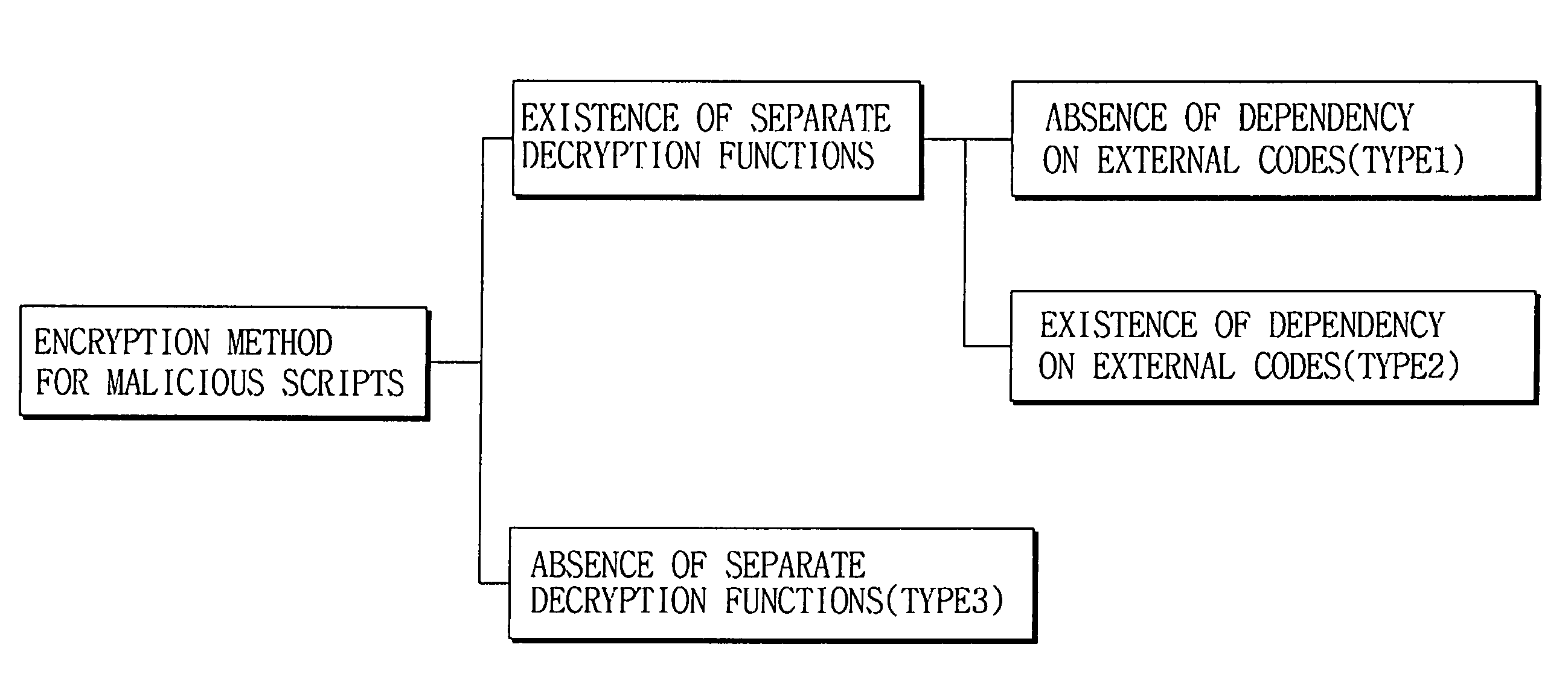
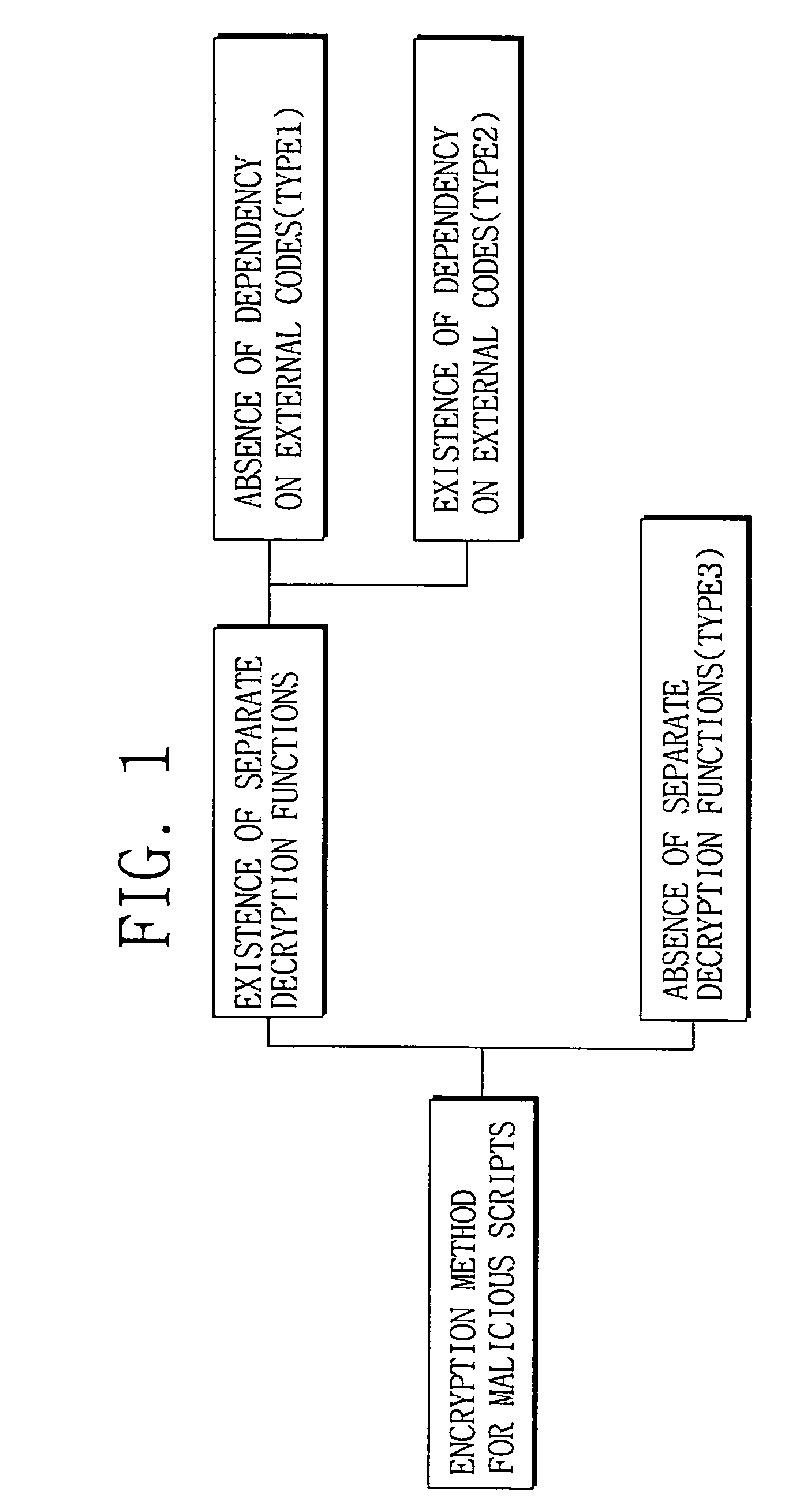
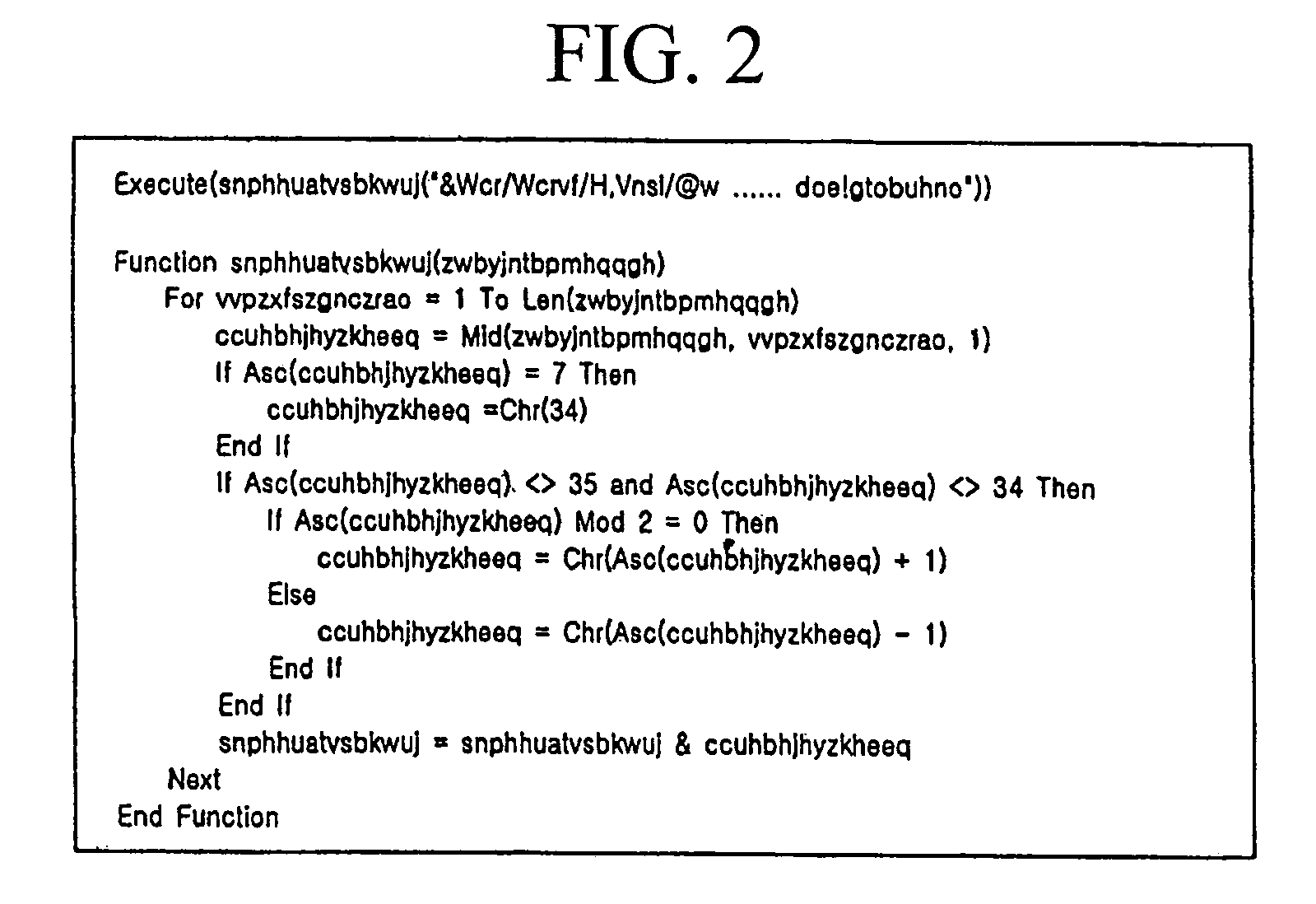
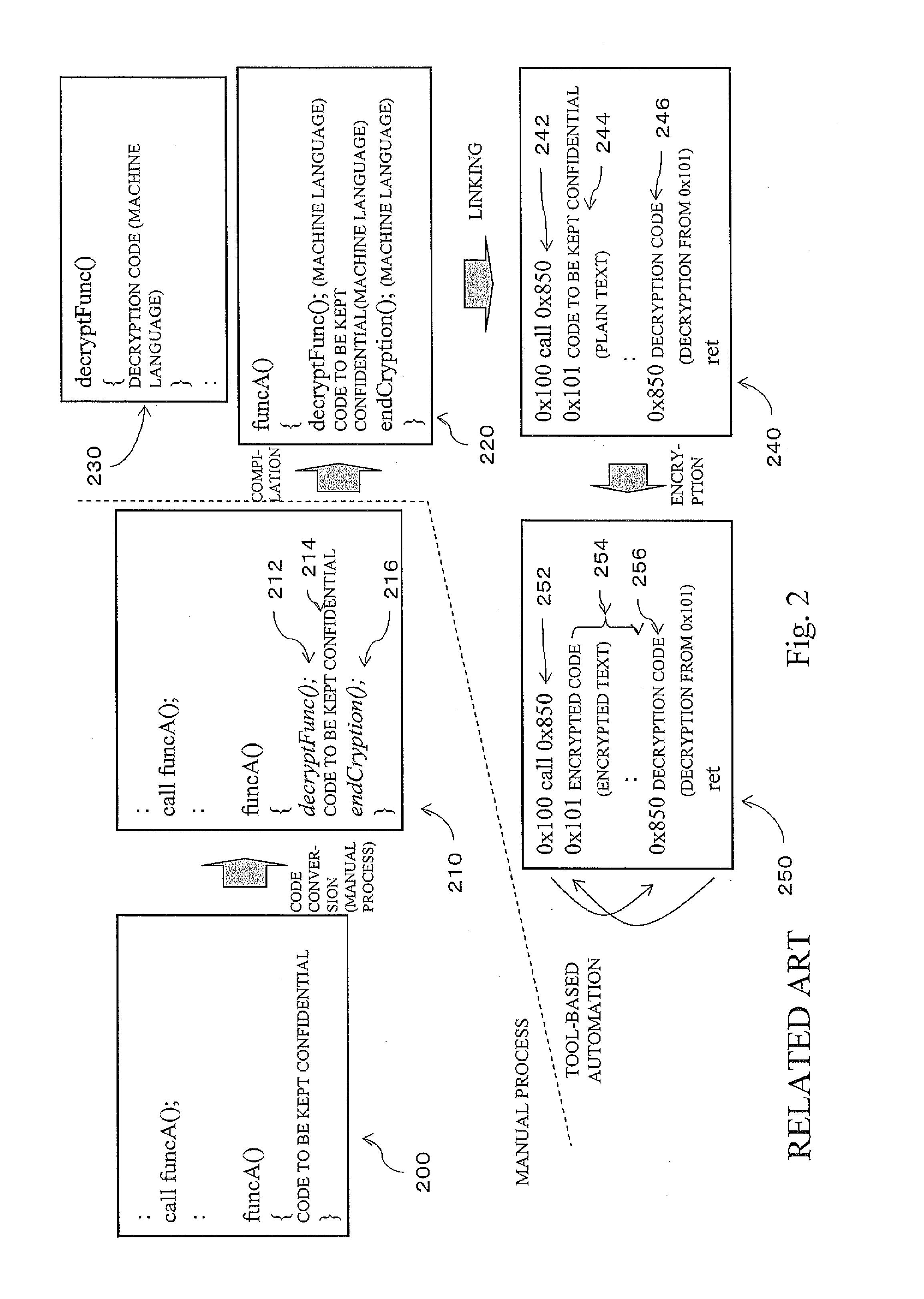
Method of decrypting and analyzing encrypted malicious scripts
ActiveUS7409718B1Flexible responseMemory loss protectionError detection/correctionProgramming languageFunction definition
Disclosed herein is a method of analyzing and decrypting encrypted malicious scripts. The method of the present invention comprises the steps of classifying a malicious script encryption method into a case where a decryption function exists in malicious scripts and is an independent function that is not dependent on external codes such as run time library, a case where a decryption function exists and is a dependent function that is dependent on external codes, and a case where a decryption function does not exist; and if the decryption function exists in malicious scripts and is the independent function that is not dependent on the external codes, extracting a call expression and a function definition for the independent function, executing or emulating the extracted call expression and function definition for the independent function, and obtaining a decrypted script by putting a result value based on the execution or emulation into an original script at which an original call expression is located. According to the present invention, unknown malicious codes can be promptly and easily decrypted through only a single decryption algorithm without any additional data. In addition to the decryption of encrypted codes, complexity of later code analysis can also be reduced by substituting constants for all values that can be set as constants in a relevant script.
Owner:AJOU UNIV IND ACADEMIC COOP FOUND
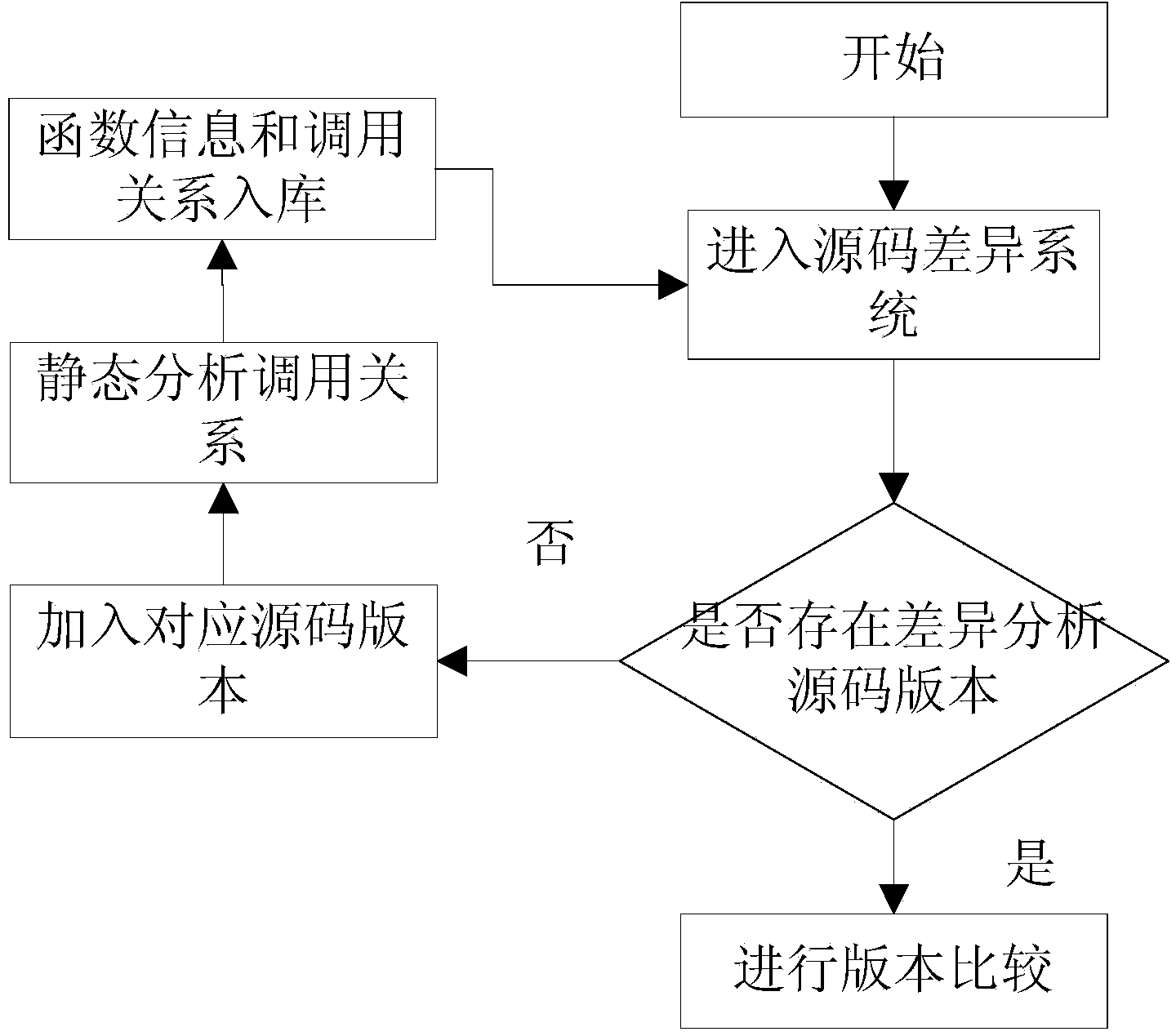
Static analysis based source code multi-versionfunction call relation difference identification method
InactiveCN104035772AAnalysis threshold is highSpecial data processing applicationsSpecific program execution arrangementsStatic timing analysisUser needs
The invention relates to a static analysis based source code multi-versionfunction call relation difference identification method. Firstly, information defined in a source code, like a function list and a static call relation between functions, is acquired through a source code static analysis technique; then source codes of two versions are chosen to carry out Diff, then the function definition list and the call relation that are acquired through static analysis are combined to identify the changed difference part, the state of the changed part is carefully analyzed, the change status, the new addition status and the deletion status defined and called by a function are respectively identified and put in storage, and finally, the call relation betweena single version and the call relation difference view of more versions are displayed in combination with the user need and the status data stored in a database. The internal call relation of single version is analyzed and displayed, and the call relation difference of more versions is also analyzed and displayed, so that an efficient auxiliary method is provided for the analysis, development, uploading and maintenance of open source software.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
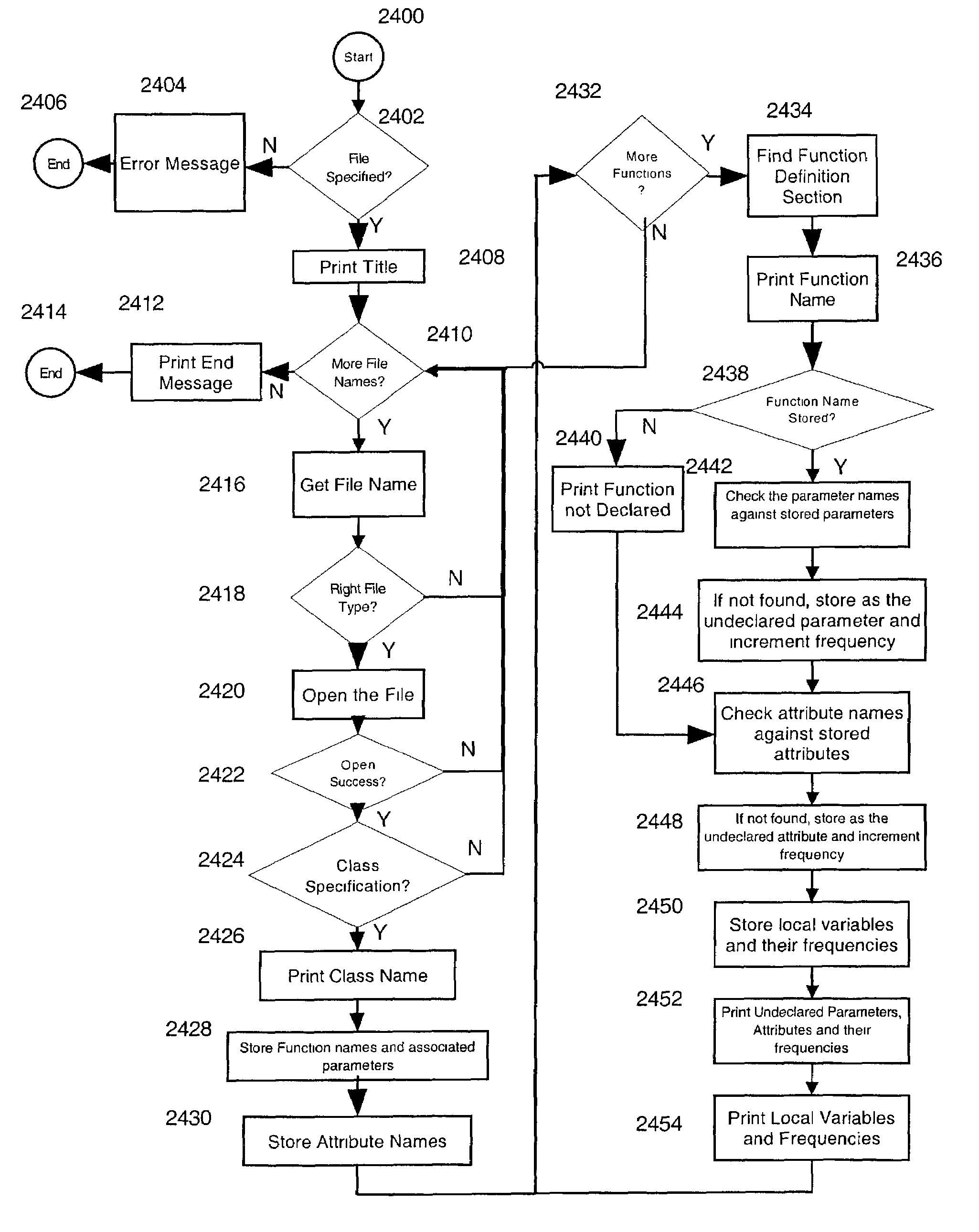
Software development environment with design specification validation tool
InactiveUS20060265690A1Errors can be reduced and avoidedSoftware testing/debuggingRequirement analysisFunction definitionLocal variable
An automated software class specification validation tool automatically determines, for functions defined in a function definition section of a class specification, whether the function is properly declared throughout one or more other sections of the same class specification. Further, it can be determined whether variables, i.e., attributes, parameters, and local variables, associated with respective functions in the function definition section are properly specified throughout one or more other sections of the same class specification. The functions and variables that are validated include attributes and functions that are specified for structures and nested classes defined in a defined type section of the class specification. The validation tool is accessible over a network via a web page, and results of the validation process are also displayed on a web page.
Owner:RICOH KK
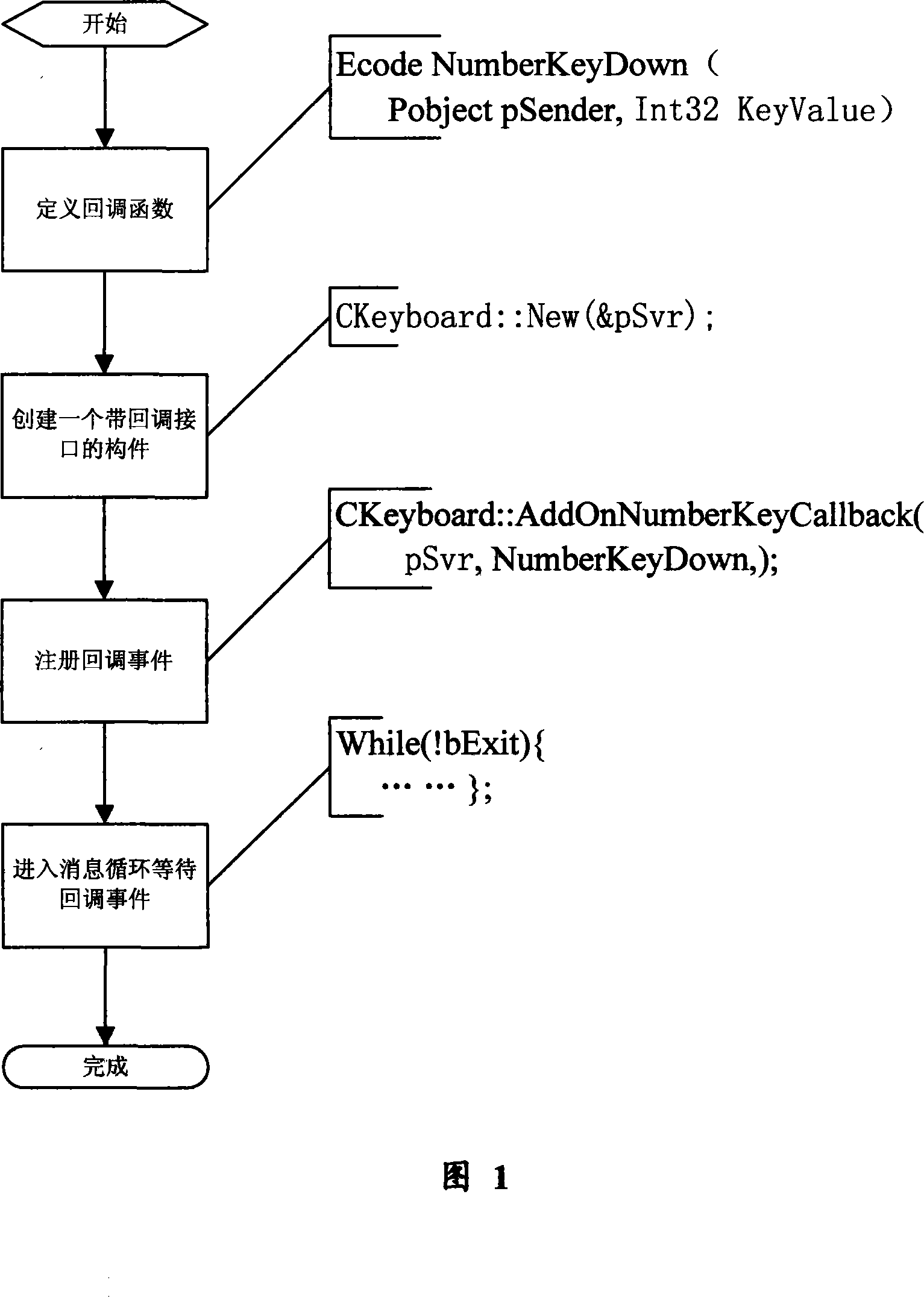
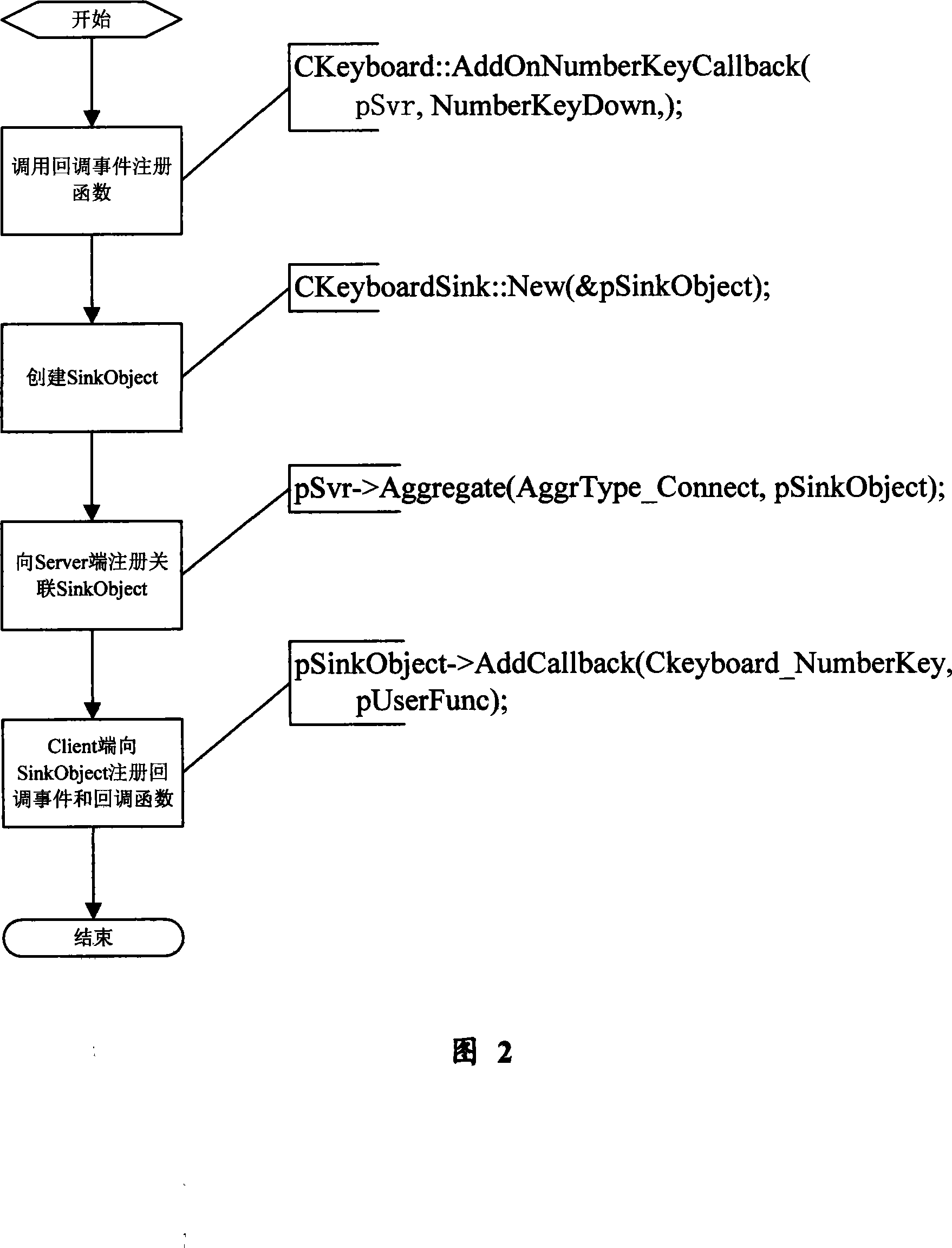
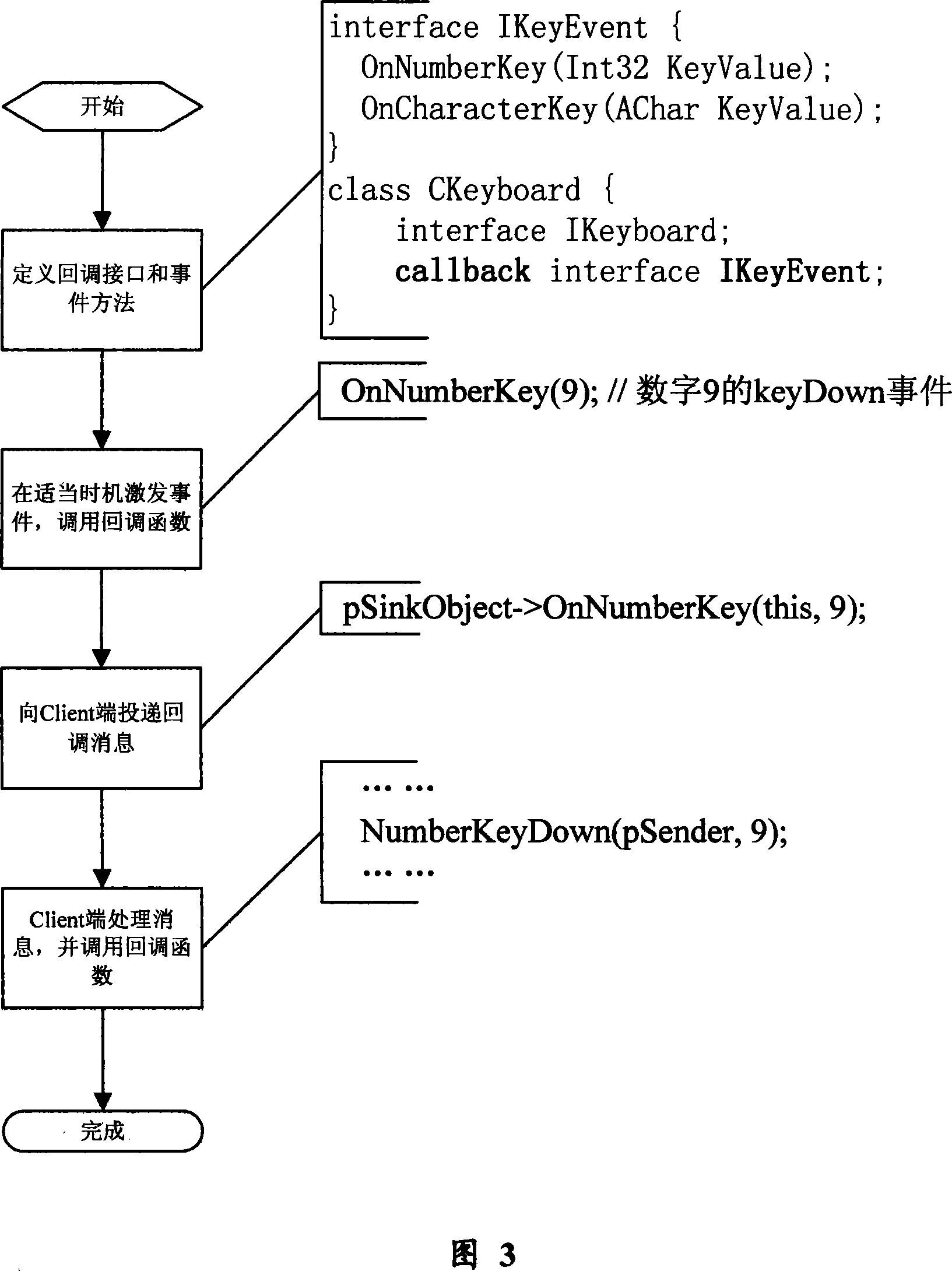
Method for implementing event call-back based on component interface in computer software system
InactiveCN101196813AEasy to implementFlexible useSpecific program execution arrangementsTerra firmaFunction definition
The invention relates to a method of realizing event callback based on a component interface in a computer software system, which comprises that: a definition information of a callback interface and an event method in the callback interface of target component class is generated at service end, a callback function definition information corresponding to the event method in the callback interface of the component class is generated at client end, an object example of the target component class is established at service end, a correlation registration processing operation is carried through between the callback event of the object example of the target class at service end and the callback function at client end, the backcall event is excitated and the callback function registered in correlation with the callback event is called according to the operation of the object example of the target component class. By adopting the method of realizing event callback based on the component interface in the computer software system, the invention has simple and convenient realization, flexible operation, powerful function, stable and reliable performance and relatively wide application scope, as well as establishes a steady basis to the further development of the computer component software system.
Owner:上海科泰华捷科技有限公司
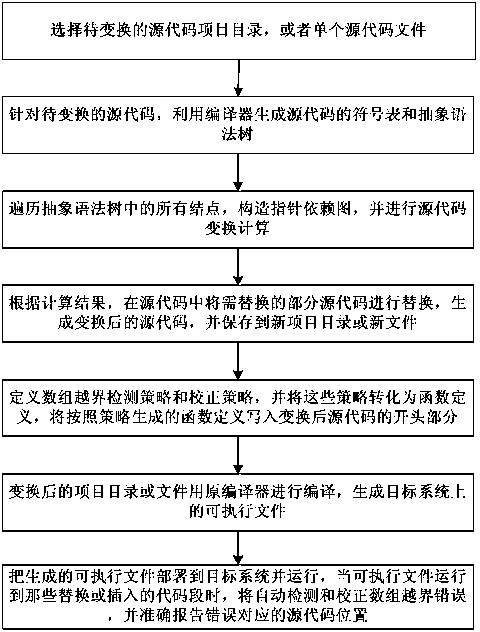
Automatic detection and correction method for array out-of-bound errors
ActiveCN103778061ASmall scaleSimplify complexitySoftware testing/debuggingArray data structureFunction definition
The invention provides an automatic detection and correction method for array out-of-bound errors. The automatic detection and correction method comprises the following steps of selecting source codes to be transformed; utilizing a compiler to generate a symbol table and an abstract syntax tree of the source codes; traversing the abstract syntax tree, constructing a pointer dependence graph and carrying out transformation calculation on the source codes; carrying out replacement on partial source codes needing to be replaced in the source codes; writing into initial parts of the transformed source codes according to function definition generated by an array out-of-bound detection strategy and an array out-of-bound correction strategy; using the original compiler to compile the transformed source codes; deploying generated executable files to a target system for operation, automatically detecting and correcting the array out-of-bound errors, and accurately reporting the positions of the source codes corresponding to the errors. The automatic detection and correction method provided by the invention has the advantages that the error positioning function is more accurate, the efficiency and the performance in operation are better, and the error correction function in operation is more automated.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Fabric operation controller
InactiveCN101349943AReduce weightImprove reliabilityInput/output for user-computer interactionLayered productsElectrical resistance and conductanceFunction definition
The invention relates to a fabric operation controller, which is characterized by comprising a fabric operation and control interface and a control circuit, wherein the fabric operation and control interface comprises a function definition layer, an upper conductive fabric layer, an isolated barrier layer, a lower conductive fabric layer and a protective layer from up to down, the upper conductive fabric adopts the conductive fabric whose surface resistance is lower than 100omega, the lower conductive fabric layer adopts the conductive fabric whose surface resistance is 100omega to 50000omega, the isolation barrier layer adopts the isolation fabric with gate holes, the protective layer adopts a waterproof insulation textile material, the control circuit comprises an interface circuit, a data processing circuit and an output interface control circuit of the fabric operation and control interface, the control circuit and the electrodes on the upper and lower conductive fabric layers are electrically connected via fine wires. The invention uses pure fabric to form the man-machine operation control interface, to provide enough operation area in use and the fabric operation and control interface in idle can be folded freely to reduce volume effectively.
Owner:THE QUARTERMASTER EQUIPMENT RESEARCH INSTITUTE OF THE GENERAL LOGISITIC DEPARTME
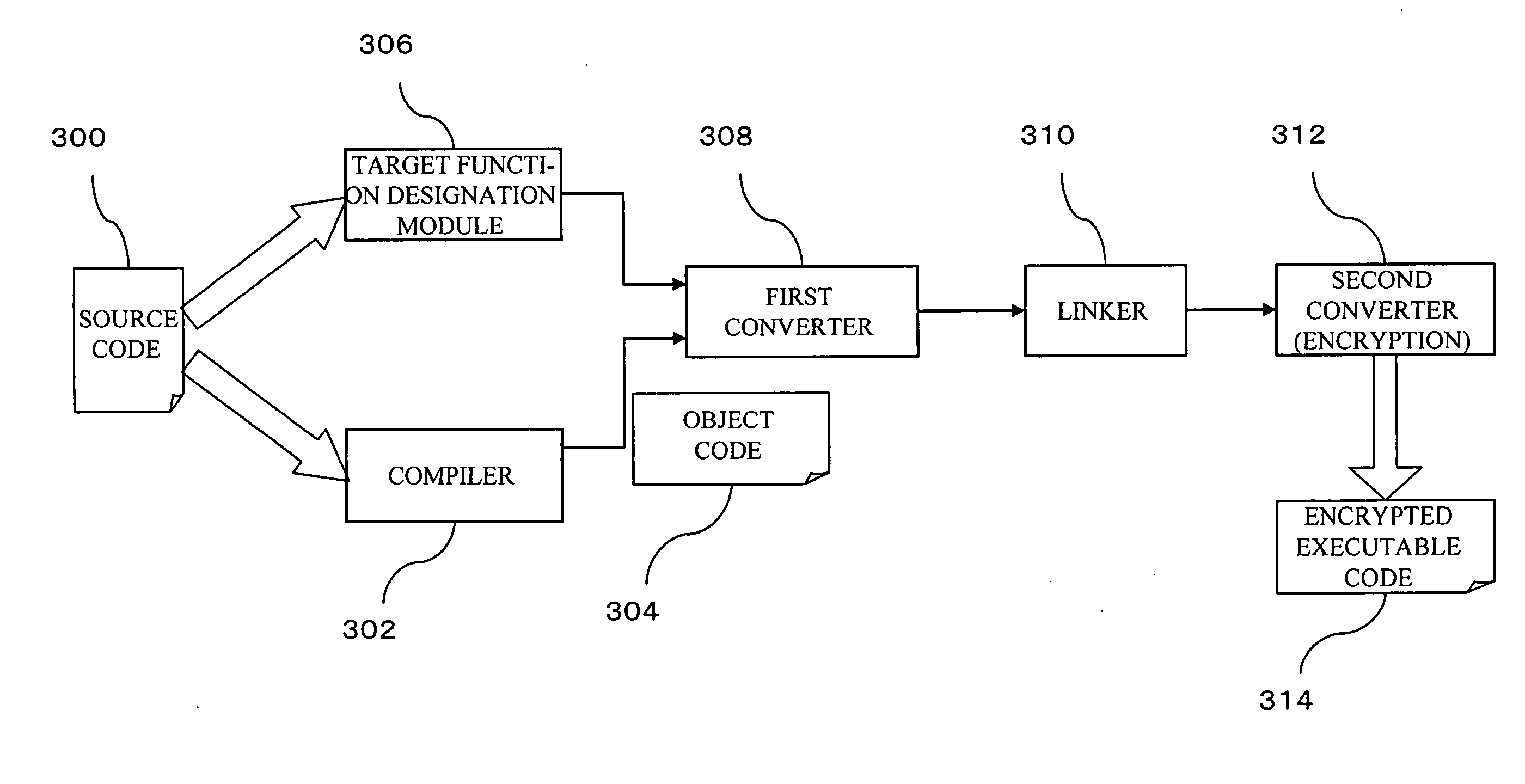
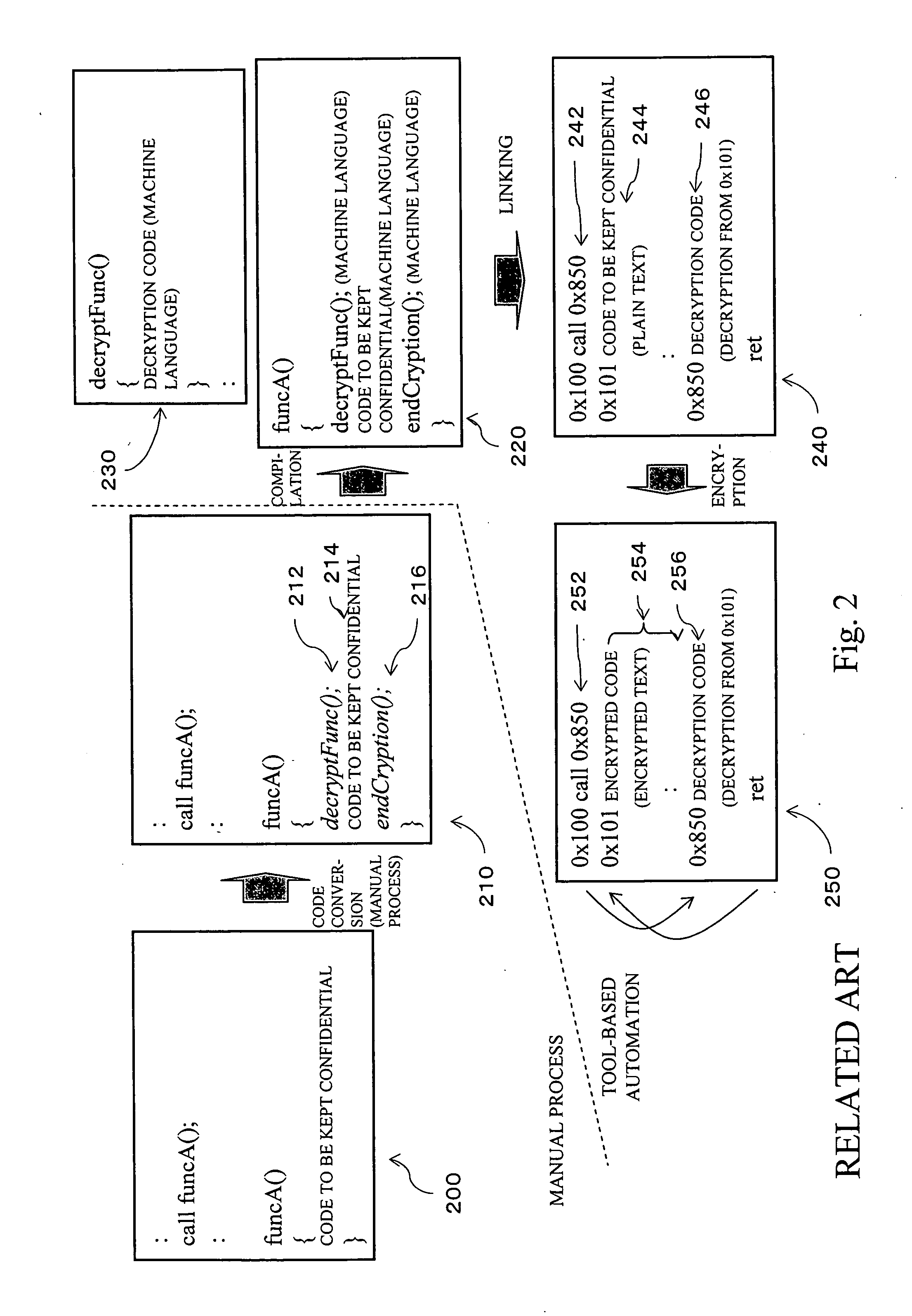
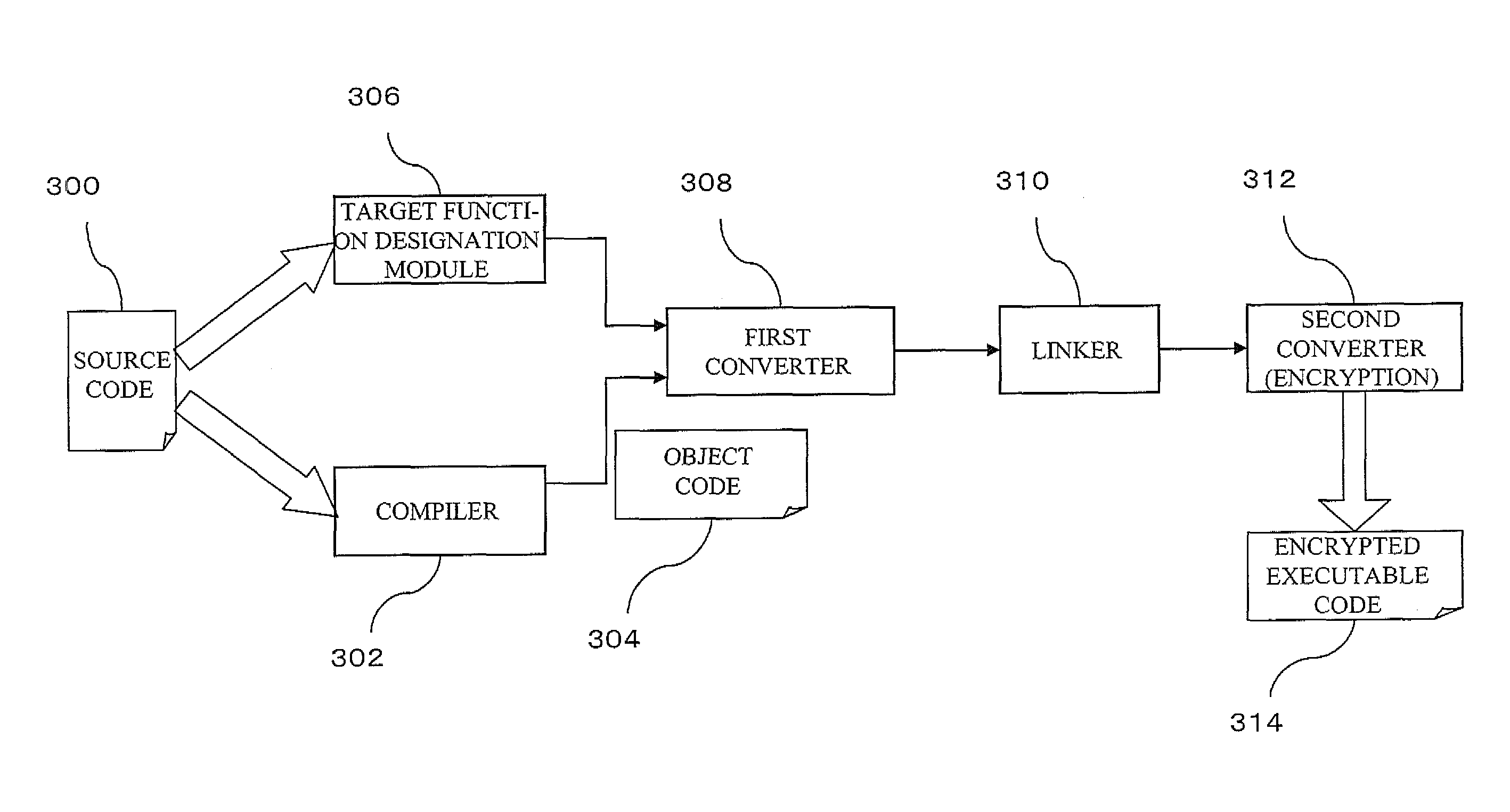
Storage medium, method, and apparatus for creating a protected executable program
InactiveUS20070118763A1User identity/authority verificationUnauthorized memory use protectionProgramming languageFunction definition
A storage medium readable by a computer is provided. The storage medium stores a program of instructions executable by the computer to perform a function for protecting a target function. The function includes generating an inserted function, having a function name identical to the function name of the target function, that includes code for a process relating to protection of the target function and a call instruction for calling the target function after this process, and generating a protected executable code on the basis of an object code, in which the function name of a function definition of the target function has been changed to a second function name, and the inserted function.
Owner:FUJIFILM BUSINESS INNOVATION CORP
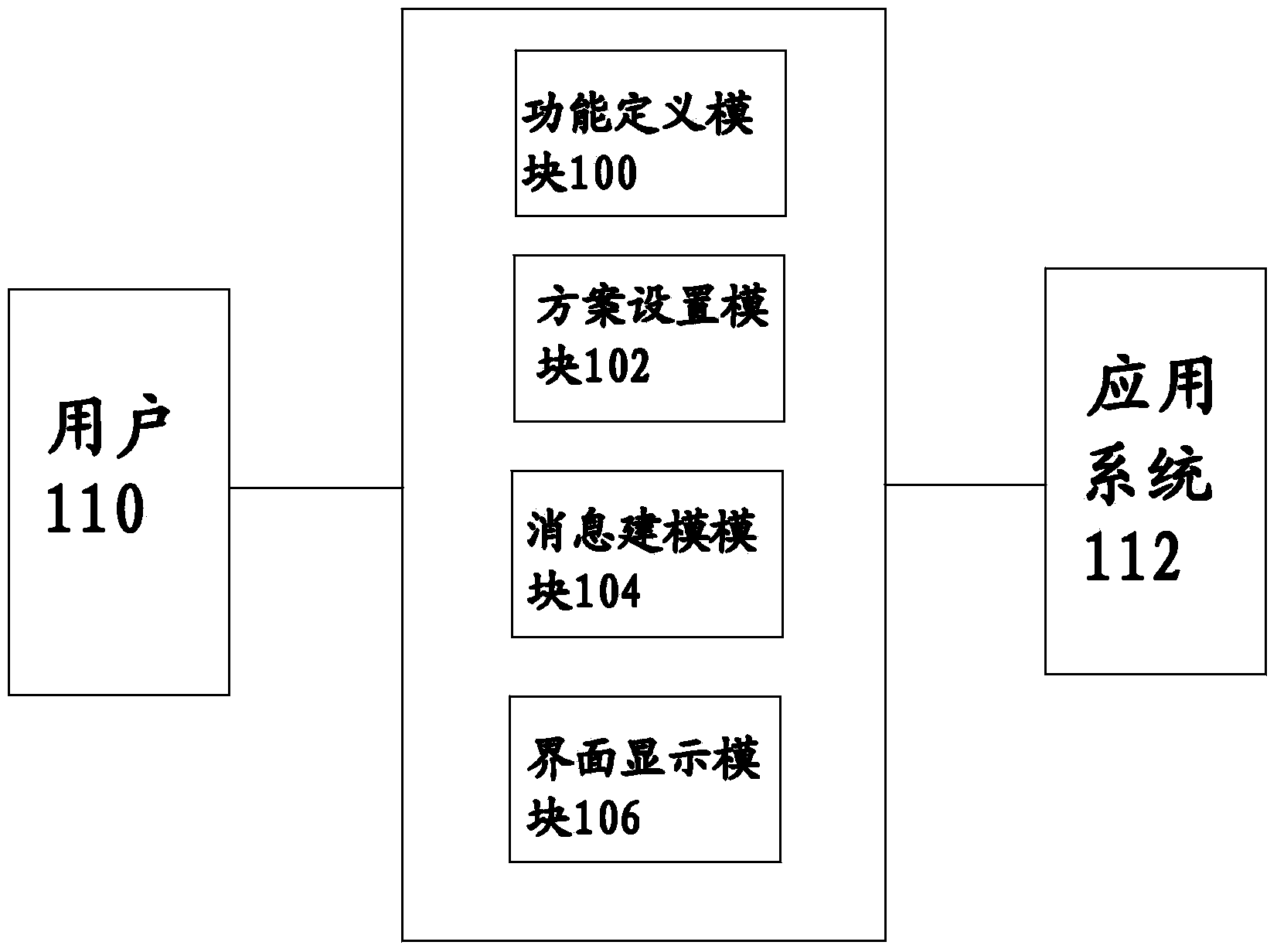
Interface integration method and system thereof
InactiveCN103631598ASupport single sign-onSupported Display ResolutionsSpecific program execution arrangementsFunction definitionComputer module
The invention discloses an interface integration method and a system thereof. The system comprises a function definition module for defining application functions comprised in the system, a scheme setting module for setting physical screen resources which are used for system displaying according to stations, a message modeling module for enabling all application systems to schedule and transmit information through message communication and an interface displaying module for displaying interfaces of the application systems into a scheme screen. According to the interface integration method and the system, interface displaying and work scheduling of a plurality of different application systems can be integrated, and the technical architecture of a constructed application system does not need to be changed; due to a message bus, the dependency among all the application systems is greatly reduced; therefore, all the application systems have functions of uniformly organizing the interfaces and are complete in original system function.
Owner:STATE GRID CORP OF CHINA +3
Software development environment with design specification verification tool
InactiveUS7171652B2Avoid prolonged useErrors can be reduced and avoidedSoftware testing/debuggingRequirement analysisSoftware development processFunction definition
An automated design specification verification tool automatically determines, for one or more functions defined in a first section of a design specification, whether a respective function name is declared in a second section of the same design specification. Further, it can be determined whether parameter names associated with respective functions in the first section are declared in the second section, and whether class attribute names associated with respective functions in the first section are described in a third section. Results of the verification process can be reported. In embodiments, the first section is a function definition section, the second section is a function list section, and the third section is a class attributes section; each being part of a class specification of a design specification document.
Owner:RICOH KK
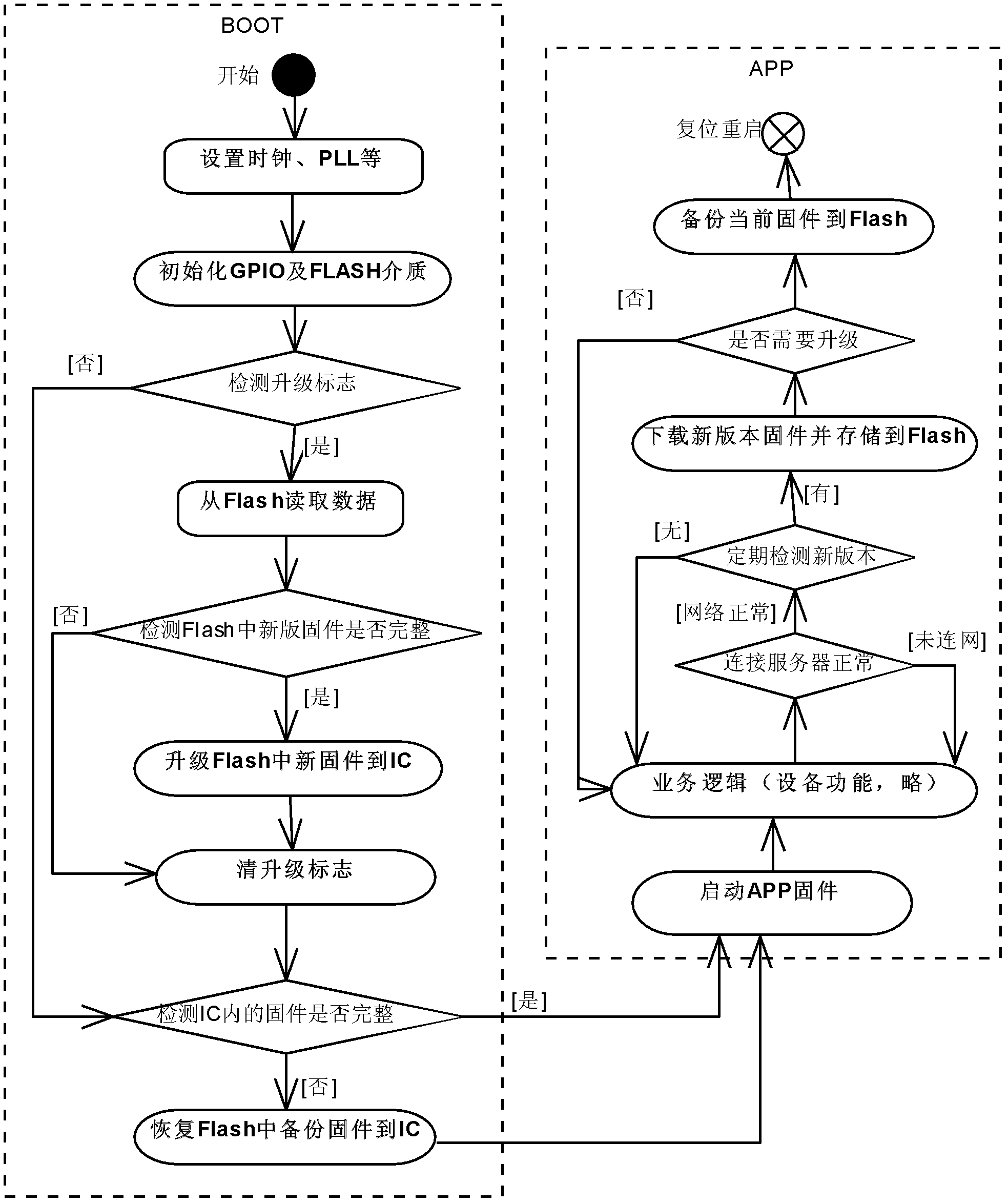
Method for remotely reliably upgrading XIP (execute in place) chip software
InactiveCN102662706ALow costSimplified function definitionProgram loading/initiatingGeneral Packet Radio ServiceFunction definition
The invention discloses a method for remotely reliably upgrading XIP (execute in place) chip software. The method aims to upgrade products designed on the basis of an XIP chip and provided with a GPRS (general packet radio service) or 3G (third generation) network or a WIFI (wireless fidelity) module. When upgrading firmware of the products, the firmware can be upgraded directly remotely through the network, and upgrading failure caused by power outage or other factors during upgrading can be avoided, and reliable upgrading can be guaranteed. Meanwhile, by the method, BOOT function definition is simplified, and downloading the firmware from a server in the BOOT area is omitted. The method can remotely reliably upgrade the XIP chip, and cost for field upgrading by operators can be evidently reduced, and the problem that the firmware cannot be reset caused by power outage during upgrading is avoided.
Owner:XIAN UNISTRONG NAVIGATION TECH CO LTD
Template compilation method
InactiveUS20050097530A1Generate efficientlySuppresses increase in code sizeProgram controlMemory systemsProgramming languageFunction definition
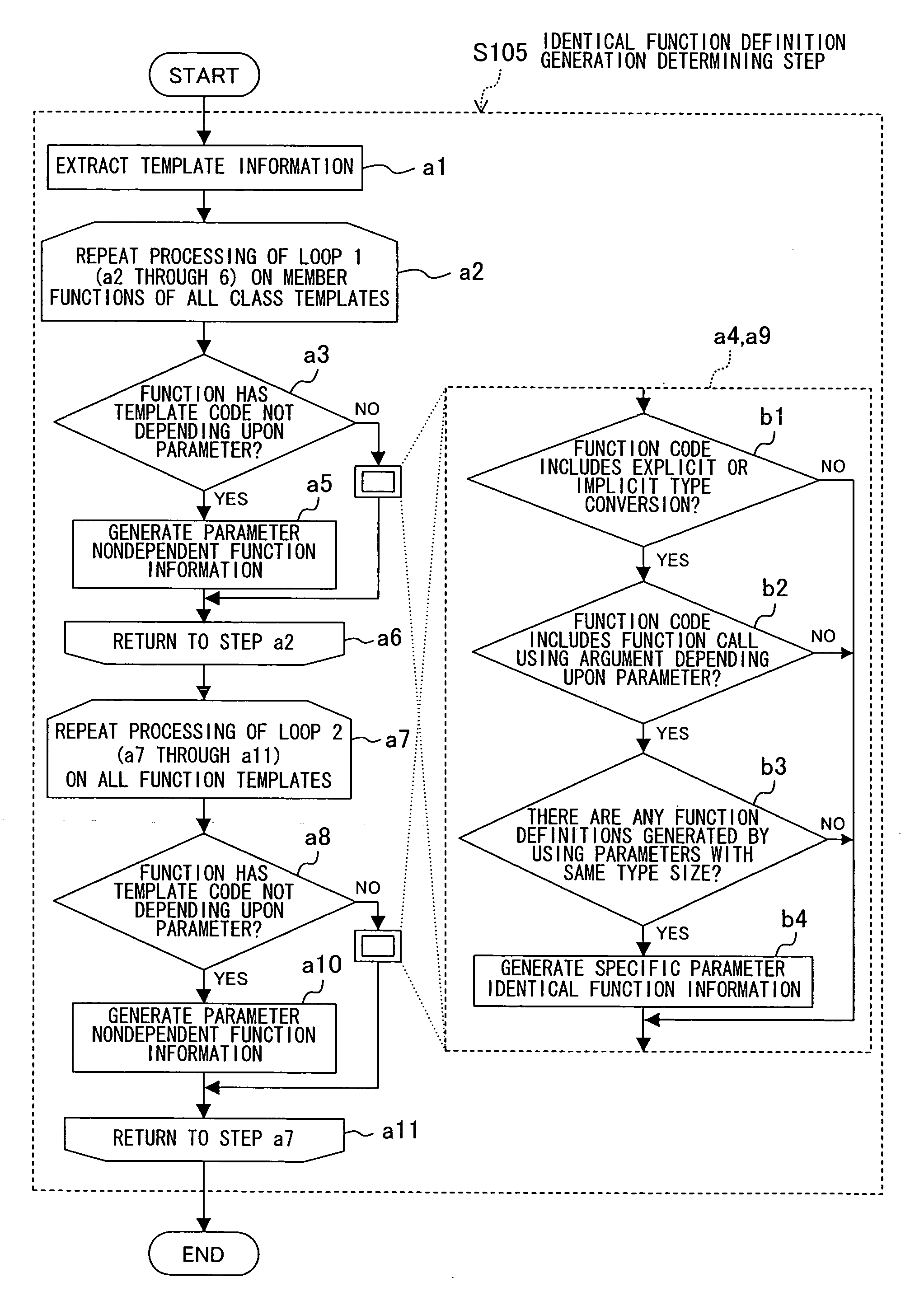
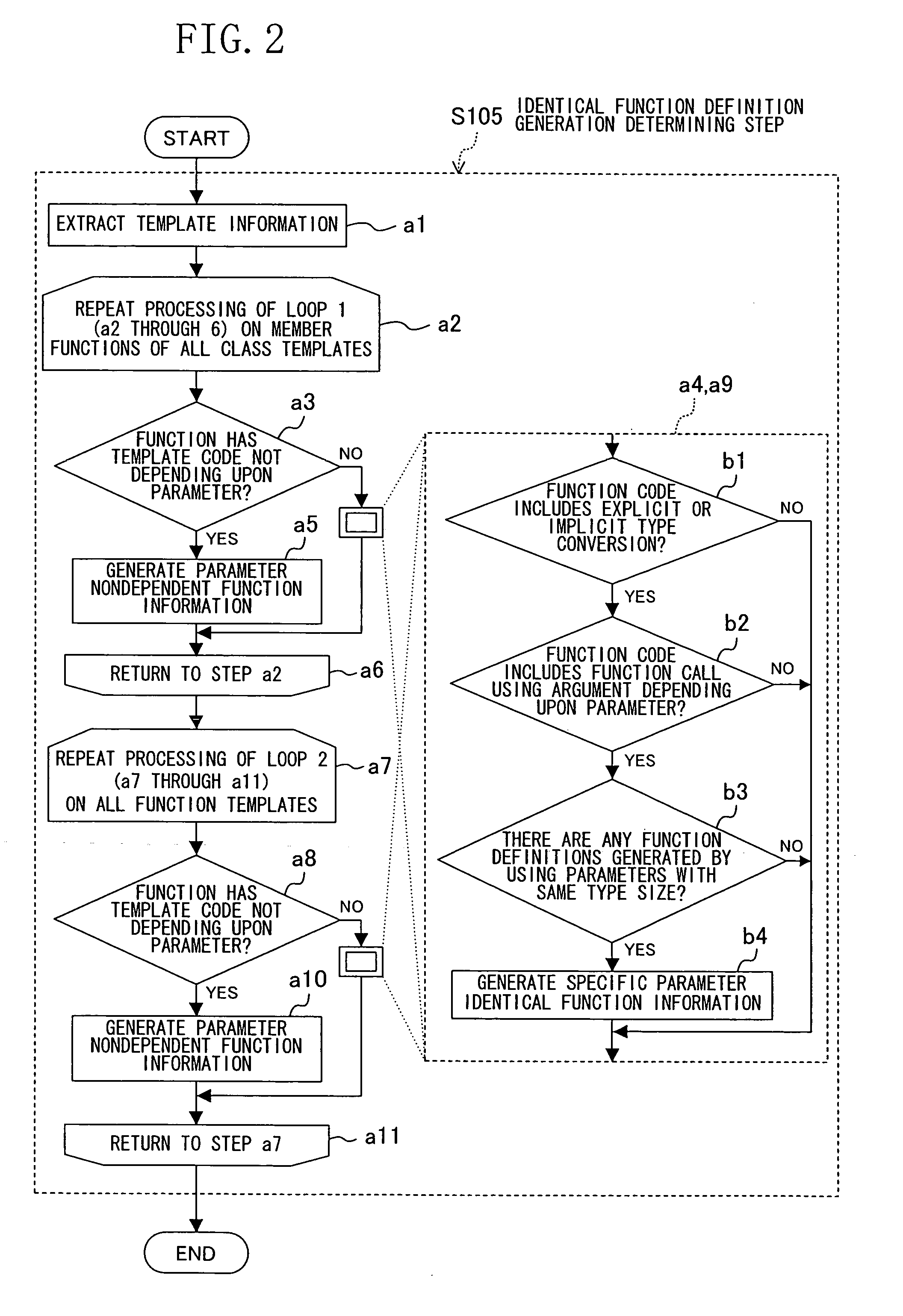
In an identical function definition generation determining step of a template compilation method, dependency between a function definition code and a template parameter is analyzed, and when there is no dependency, a common function is defined and a plurality of function definitions obtained before defining the common function are deleted in a function definition sharing step. Thereafter, a function call obtained before defining the common function is replaced with a call of the common function in a function call replacing step. Accordingly, among a plurality of function definition codes generated from a template, function definition codes generated as the identical code are shared, so as to reduce the code size that generally increases due to template facilities.
Owner:PANASONIC CORP
Extending data access and analysis capabilities via abstract, polymorphic functions
InactiveUS20060074873A1Digital data information retrievalSpecial data processing applicationsFunction definitionData access
An abstract database is an effective way to reduce the complexity of a large database management system. Abstract databases allow a user to compose queries based on the logical relationships among data items, without requiring a user to understand the underlying database schema used to store the data in the database system. Embodiments of the invention generally provide methods, systems, and articles of manufacture that extend the capabilities of an abstract database to include “late bound” polymorphic functions in an abstract data layer. Abstract functions are “late bound” because the function definition (i.e., the execution logic) is not determined until the function is actually invoked. They are polymorphic because same function may operate using many different many data input types. Additionally, abstract functions are generally transparent to the end user. That is, they are presented to the user as an additional object that may be used to compose queries of data represented by the abstract data layer undifferentiated from other data elements used to compose an abstract query.
Owner:IBM CORP
Intelligent electricity terminal plug and play method based on self recognition
InactiveCN104701984ADealing with Interconnection IssuesRealize automatic identificationCircuit arrangementsSustainable buildingsElectricityFunction definition
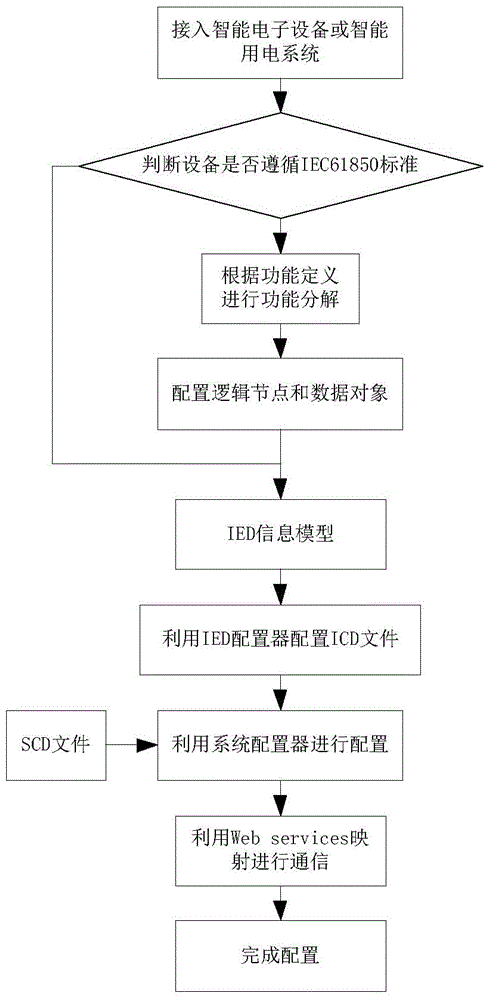
The invention discloses an intelligent electricity terminal plug and play method based on self recognition. The intelligent electricity terminal plug and play method based on the self recognition includes: connecting an intelligent electricity terminal into an intelligent electricity utilization automatic system; using a monitor master station of the intelligent electricity utilization automatic system to judge whether to follow an IEC61850 modeling standard, if yes, not acting, or if no, performing functional decomposition according to the IEC61850 modeling standard so as to obtain a logic device, a logic node and a data object according to function definition of the intelligent electricity terminal; building an IED information model; performing configuration through an IED configuration tool and a system configuration tool according to the IED information model so a to obtain ICD, CID and SCD configuration files, and then completing the configuration for IED; using wed service for mapping, and using an HTTP (hyper text transport protocol) to achieve communications. Accordingly, the intelligent electricity utilization automatic system can obtain login information of the intelligent electricity terminal, and a plug and play function of the intelligent electricity terminal and information interaction between the intelligent electricity terminal and the intelligent electricity utilization automatic system are achieved.
Owner:STATE GRID CORP OF CHINA +2
Interprocedural dead store elimination
InactiveUS7100156B2Improvement in code optimizationReduce needSoftware engineeringDigital computer detailsProgramming languageFunction definition
A system for optimizing computer code generation by carrying out interprocedural dead store elimination. The system carries out a top down traversal of a call graph in an intermediate representation of the code being compiled. Live on exit (LOE) sets are defined for variables at call points for functions in the code being compiled. Bit vectors representing the LOE sets for call points for functions are stored in an LOE table indexed or hashed by call graph edges. For each function definition reached in the call graph traversal, a LOE set for the function itself is generated by taking the union of the LOE call point sets. The entries in the LOE table for the LOE call point sets are then removed. The LOE set for each function is used to determine if variables that are the subject of a store operation in a function may be subject to a dead store elimination optimization.
Owner:IBM CORP
System and method for ranking and grouping results of code searches
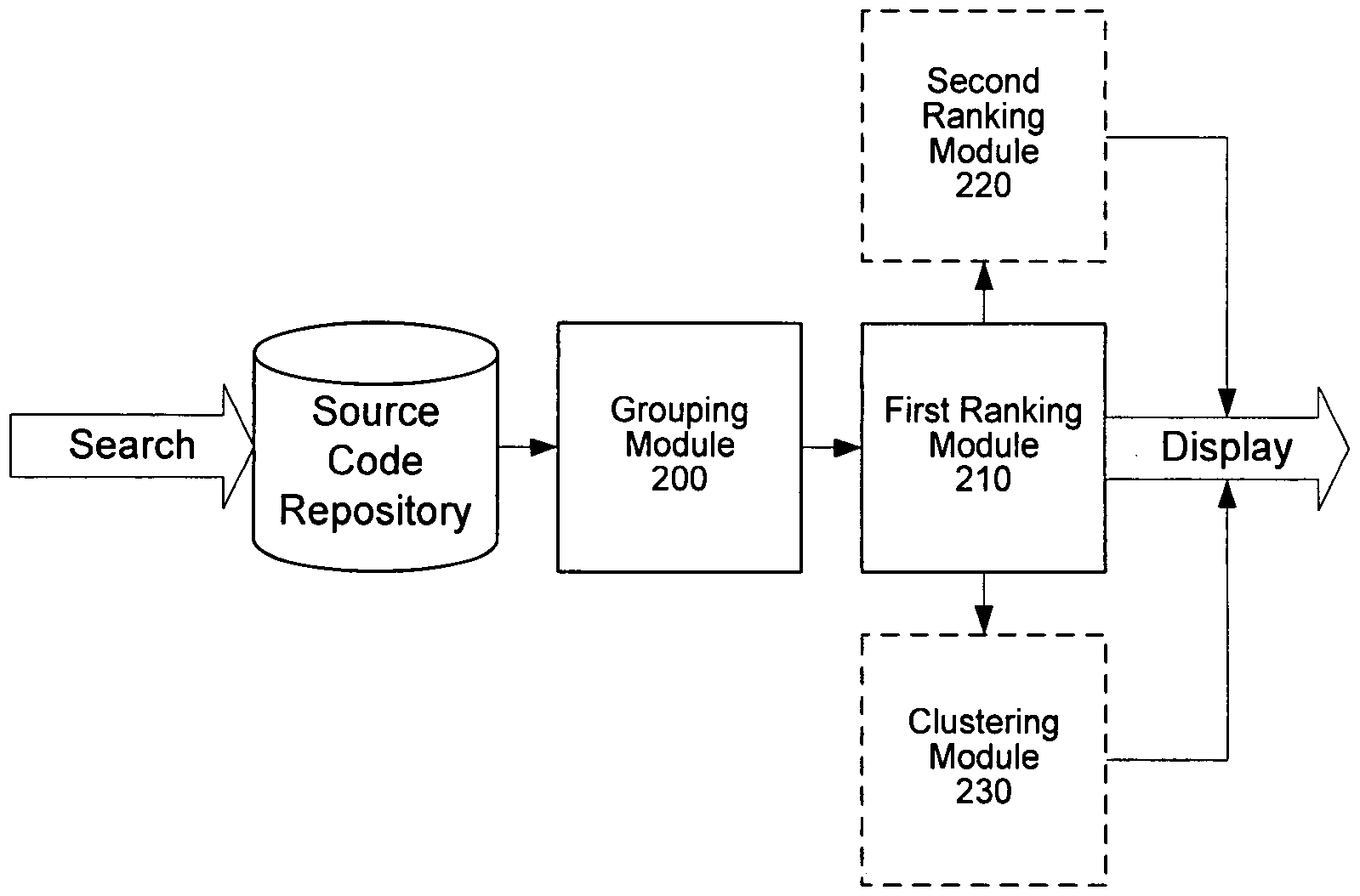
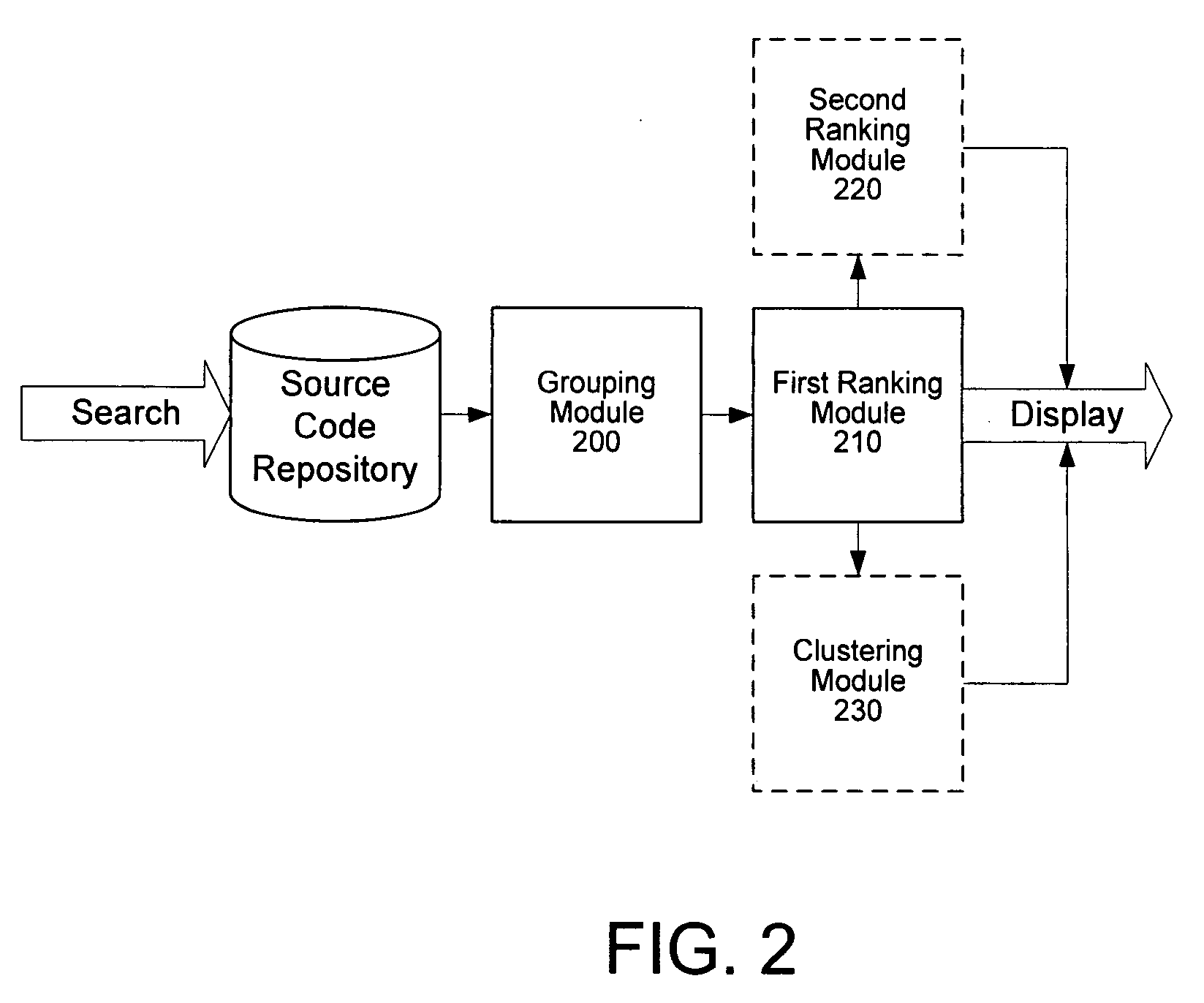
InactiveUS20100131517A1Web data indexingDigital data processing detailsFunction definitionSource code
A method of sorting search results associated with a function search performed on a source code repository comprises receiving the search results, wherein each search result is either a function definition or a function usage, grouping the search results into groups according to a grouping function, ranking the groups according to a ranking function, and displaying the grouped and ranked search results.
Owner:OATH INC
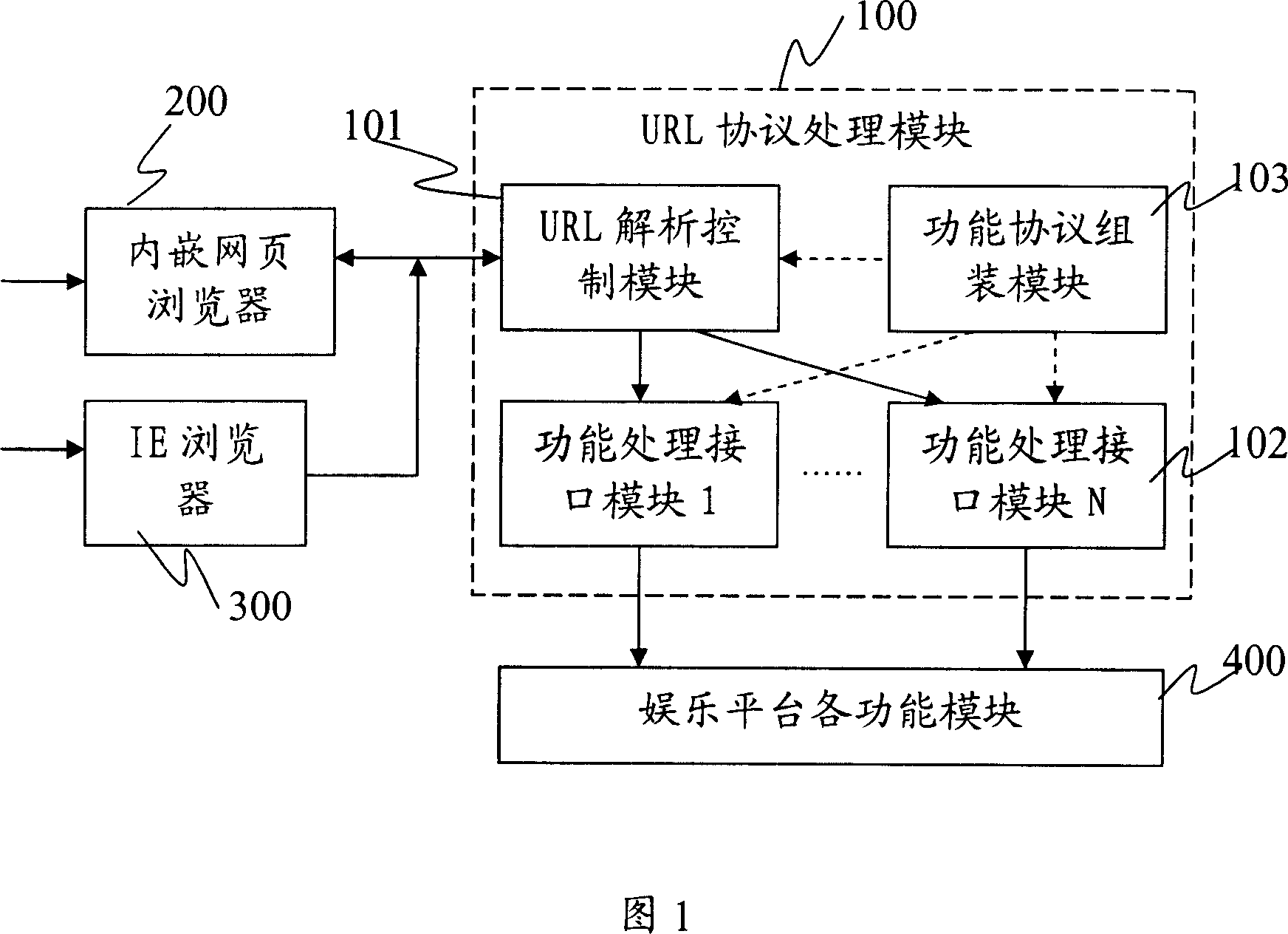
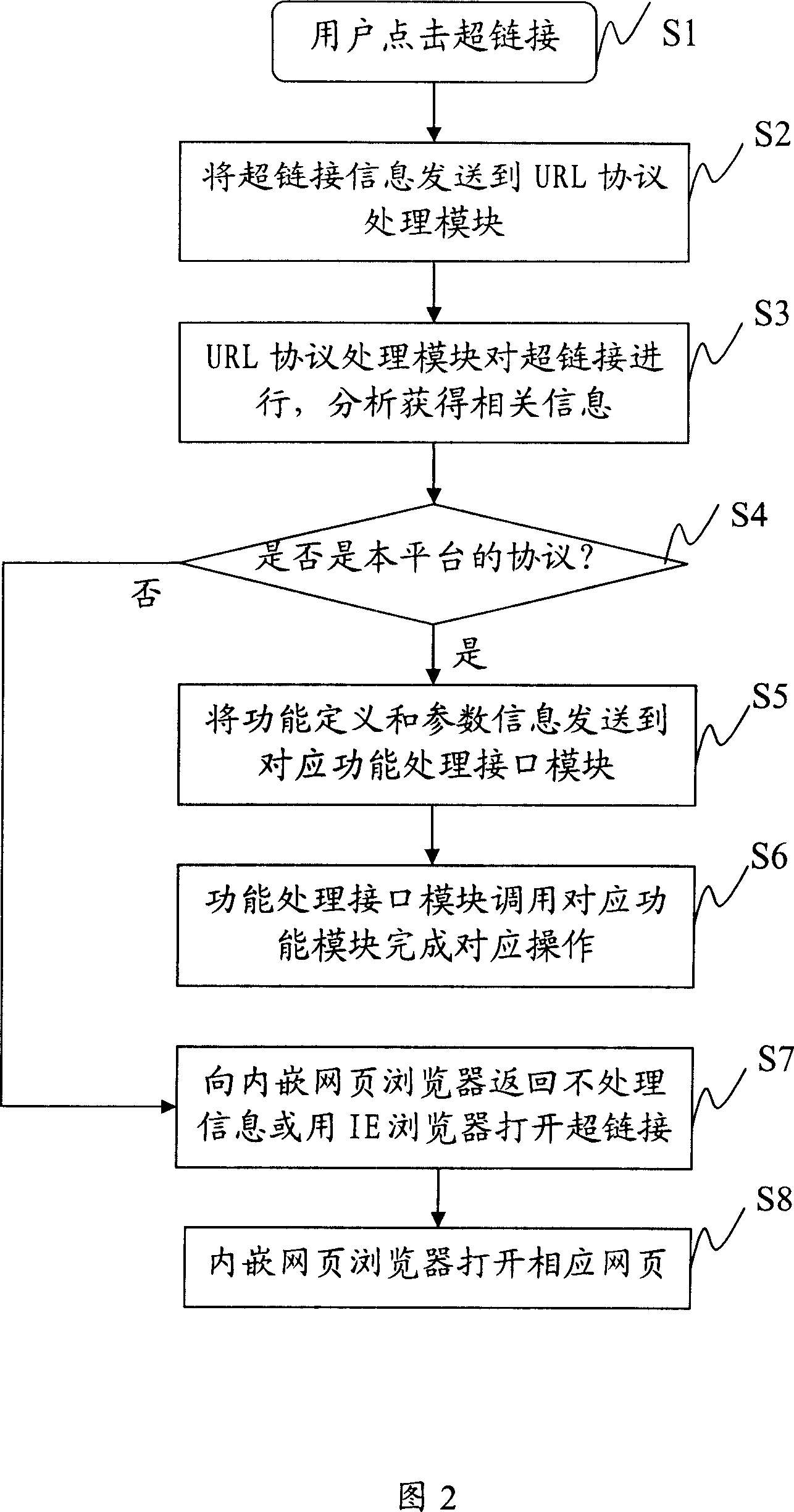
Method and system for controlling amusement platform through configuring hyperlink
ActiveCN101079047AIncrease contentExpressiveSpecial data processing applicationsHyperlinkFunction definition
The invention relates to a method and a system of controlling entertainment flat base by configuring hyperlink in the computer communication technology field, which comprises the following steps: A1 configuring uniform resource position mark URL; A2 regarding the URL as the hyperlink object, making hyperlink and showing the hyperlink on the entertainment flat base, wherein making URL protocol head corresponding the designation of the entertainment flat base; regarding function definition and parameter as the protocol content. The invention also discloses a system of controlling entertainment flat base by configuring hyperlink. The words and pictures with hyperlink in the invention can show on the any place of the entertainment flat base (dialog box, chat section or the like) and can send to the entertainment flat base on fixed time by the server, the user can come in the room, open the stage property shop and buy the stage property by hitting hyperlink. The invention simplifies the operation of using game flat base function for users, which improves the mutual environment between the users and entertainment flat base.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method, program, and storage medium for acquiring logs
InactiveUS20050171731A1Reduce in quantityEasy to getTime indicationSynchronous motors for clocksFunction definitionMan-hour
A log acquisition method is provided that allows a processing log of software to readily be acquired and reduces the man-hours needed for analyzing a bug. The method for acquiring a runtime log of a program including at least one function for performing a predetermined process, comprising changing the address of said at least one function to the address of a function for log acquisition, wherein said function for log acquisition comprises: calling said at least one function to cause said predetermined process to be executed, receiving the result of the execution and passing said result to said program; determining whether or not a pointer parameter the type of which is specified in a predetermined manner is defined in a function definition in said program; if yes, recording a memory content pointed to by said pointer parameter as data of the specified data type. The type of the pointer parameter may defined by an index structure, and the determining step includes judging the type of the pointer parameter by referring to the specified member of the index structure. The types of the members of the index structure may be various kinds of unexported functions and various kinds of structures and etc.
Owner:CANON KK
Storage medium, method, and apparatus for creating a protected executable program
InactiveUS7870396B2Unauthorized memory use protectionHardware monitoringProgramming languageFunction definition
Owner:FUJIFILM BUSINESS INNOVATION CORP
Interactive image segmentation method of android system
ActiveCN104463843AImprove computing efficiencyEliminate area itemsImage analysisFunction definitionImage segmentation algorithm
The invention provides an interactive image segmentation method of an android system. The interactive image segmentation method is a new method for extracting image foreground objects and includes the steps that an energy function definition of a traditional image segmentation algorithm is improved, a region item is canceled, and a boundary item is enhanced, so that the influence on a segmentation result by boundary item parameters is eliminated, and the improved method is realized on an android platform; on the android platform, the setting of iterations with the highest cost performance is obtained aiming at the influence on the segmentation accuracy by the iterations of the interactive image segmentation algorithm; by means of the iteration interactive image segmentation algorithm, aiming at certain conditions of inaccurate segmentation, an interactive correction link is added to ensure the accuracy of image segmentation, and extracted scenery bodies are integrated into other background images. Due to the improvement of the interactive image segmentation algorithm, the region item of an original energy function is eliminated, so that the calculation efficiency of the algorithm is improved, the improved algorithm is applied to the android platform, and a user can segment images on android equipment easily.
Owner:NANJING UNIV OF POSTS & TELECOMM
A radar signal processing trunking platform and a software easy-to-expand implementation method
InactiveCN109101348AAchieve layeringImprove reusabilityWave based measurement systemsInterprogram communicationFault toleranceFunction definition
The invention relates to the field of radar signal processing software, in particular to a radar signal processing cluster platform and a method for realizing software expansion. The invention provides a radar signal processing trunking platform and a software easy-to-expand realization method. The method of the invention comprises the development of system layer software, the development of middle layer software, the development of application layer software, the realization of radar signal processing software and the expansion of signal processing software. The method of the invention has the advantages of universality, high fault tolerance rate, short development period, etc., and can realize the function definition, resource allocation and mode expansion of radar signal processing software.
Owner:WUHAN BINHU ELECTRONICS
Python software fuzzy test method based on dynamic type perception
ActiveCN110399300AImprove maintainabilityImprove robustnessSoftware testing/debuggingCode compilationFunction definitionMaintainability
The invention provides a Python software fuzzy test method based on dynamic type perception. The Python software fuzzy test method comprises the following steps: 1) obtaining a source program code ofan open source Python software project from a gyhub; 2) generating an abstract syntax tree corresponding to the source program code; 3) identifying and extracting a function definition node from the abstract syntax tree; 4) generating parameters by using a dynamic type sensing strategy according to the information of the function definition nodes, and generating a test case set corresponding to the function definition; and 5) executing the test case to generate a test result report, carrying out variation-based fuzzy test according to the result of the test report, and providing a test case with potential defects. According to the method, the problem that a fuzzy test method for Python software is lacked at present is solved, input for triggering potential defects can be provided. A developer is helped to debug and repair the defects. The maintainability and robustness of the software are improved, and therefore the quality of a software product can be better controlled.
Owner:NANJING UNIV
Method for identifying number and size of wood veneer knots based on image processing
ActiveCN103942816AEasy to separateFilter impactImage enhancementImage analysisWood veneerFunction definition
A method for identifying the number and size of wood veneer knots based on image processing comprises the steps that (a) images are collected; (b) the images are converted to gray images; (c) a gray valve corresponding to the one-dimensional maximum entropy is obtained according to an entropy function definition formula and is set to be a threshold value; (d) the images are subjected to binarization processing according to the threshold value, only the black color and white color are displayed, N primarily-selected knots are separated from a background, and N is larger than or equal to zero; (e) a morphological closed operation is used for eliminating insolated points outside the knots and peripheral interference features; (f) all primarily-selected knots are processed respectively, wherein the step (f) further comprises the steps that (1) contour points are searched for and judged if having communication areas, if not, the contours are filtered out, and if yes, a fitting ellipse is obtained and the next step can be executed; (2) the lengths of a major axis and a minor axis of the fitting ellipse and the ratio of the lengths are calculated, if the ratio is smaller than 0.5 or the ratio is larger than 2.0, the contour point is filtered out, and if the ratio is larger than 0.5 and smaller than 2.0, the next step is executed; (3) interference factors are filtered out according to the matching degree of all points of the communication area and the obtained fitting ellipse; (g) the number of the knots is counted, and the area of the largest knob is calculated.
Owner:INST OF WOOD INDUDTRY CHINESE ACAD OF FORESTRY
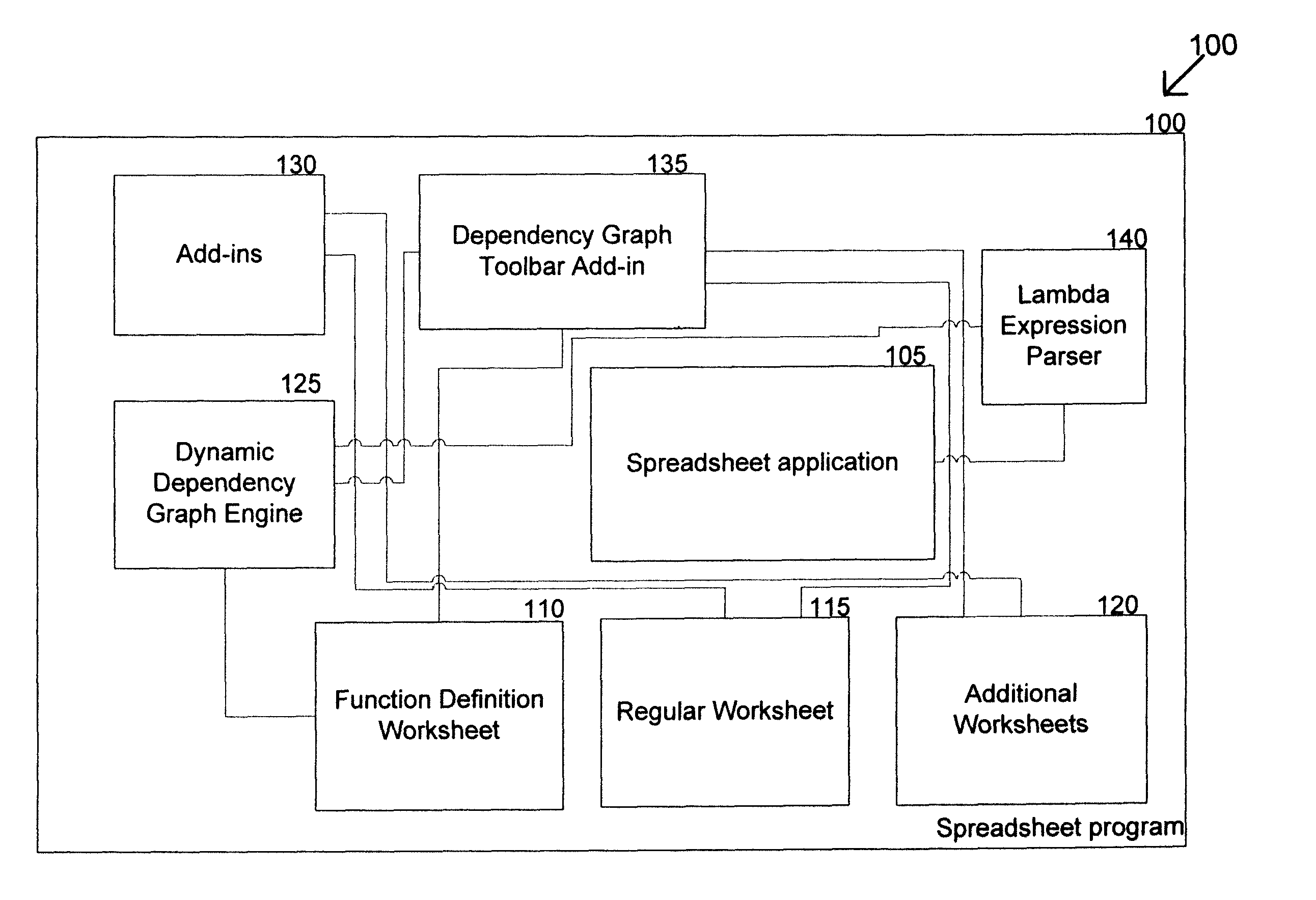
System and method for storing a series of calculations as a function for implementation in a spreadsheet application
InactiveUS9037961B1Text processingSpecial data processing applicationsProgramming languageFunction definition
The dependency graph spreadsheet system allows for the capture of a sequence of calculations or formulas as a function. The function is stored as a function definition in a spreadsheet application. The function definition provides the ability to call or select a name or code associated with the function or function definition in the spreadsheet application by placing the name in a cell of the spreadsheet application. If the form of the calculation needs to be verified or modified, the function is reviewed and / or modified in the function definition worksheet, eliminating the need to seek out each invocation of the function in the spreadsheet application. The dependency graph spreadsheet system also provides the ability to invoke a higher order function that uses a defined function as an input and generates an output from the higher order function on a range of data inputs for the defined function in the spreadsheet.
Owner:CREDIT SUISSE
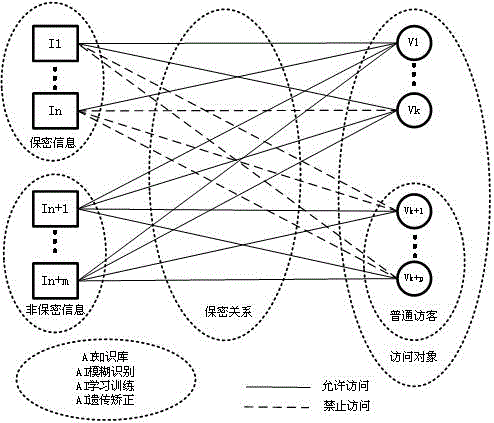
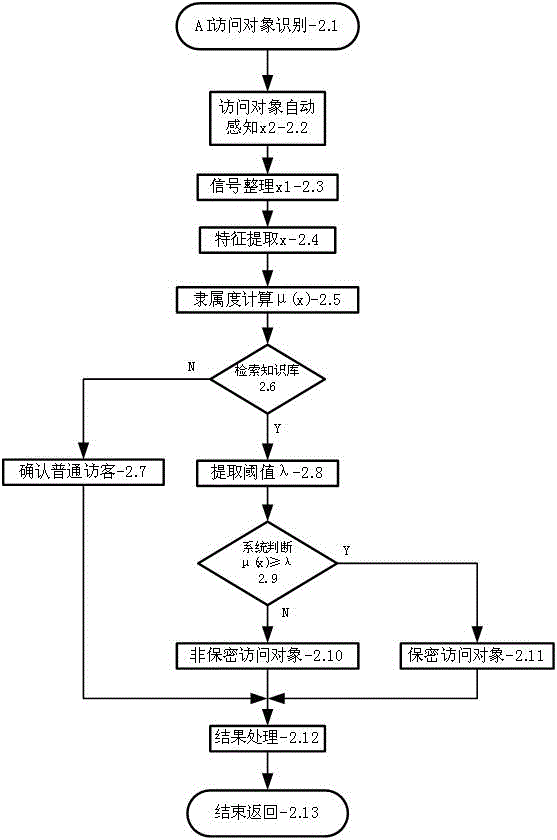
CMS object-oriented artificial intelligence information secrecy system
InactiveCN106022018AImprove confidentialityAccurate and confidentialDigital data protectionDigital data authenticationPrivacy protectionPerson recognition
The invention relates to a CMS object-oriented artificial intelligence information secrecy system. A corresponding accurate secrecy relationship between information and an access object is established to eliminate defects of ''rigid uniformity and one lock'' of a conventional secrecy method. The system performs fuzzy recognition and automatic judgment in three aspects of the information, the access object and the secrecy relationship. Functions of automatic sensing, information acquisition, information recognition, object recognition, signal conditioning, characteristic extraction, fuzzy recognition function definition, membership degree definition, threshold definition, learning training, genetic correction, new person recognition learning, new information recognition, secrecy relationship editing, result processing and the like are set in AI access object recognition, AI information recognition and AI secrecy relationship recognition. The system is suitable for personal privacy protection, is especially suitable for application to VR / AR / MR (Virtual Reality / Augmented Reality / Mix reality) and mobile phones, and is suitable for security mobile storage and instant messaging products.
Owner:丁贤根
Browser-independent pop-up windows
InactiveUS20050183076A1Natural language data processingExecution for user interfacesFunction definitionXML
A development tool for generating interactive help windows from SGML or XML definition files. The development tool supports the use of a defined keyword in link definitions in the definition files. The development tool adding a JavaScript function definition to an output HTML file, the function generating a new window having content defined by a file specified by a parameter for the function. The development tool replacing the link definitions including the defined keyword with calls to the JavaScript function. The development tool generating a pop-up definition HTML file having window content based on an SGML or XML definition provided to the development tool. The calls to the JavaScript function being defined in the HTML output file to pass the name of the pop-up definition HTML file as a parameter.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com