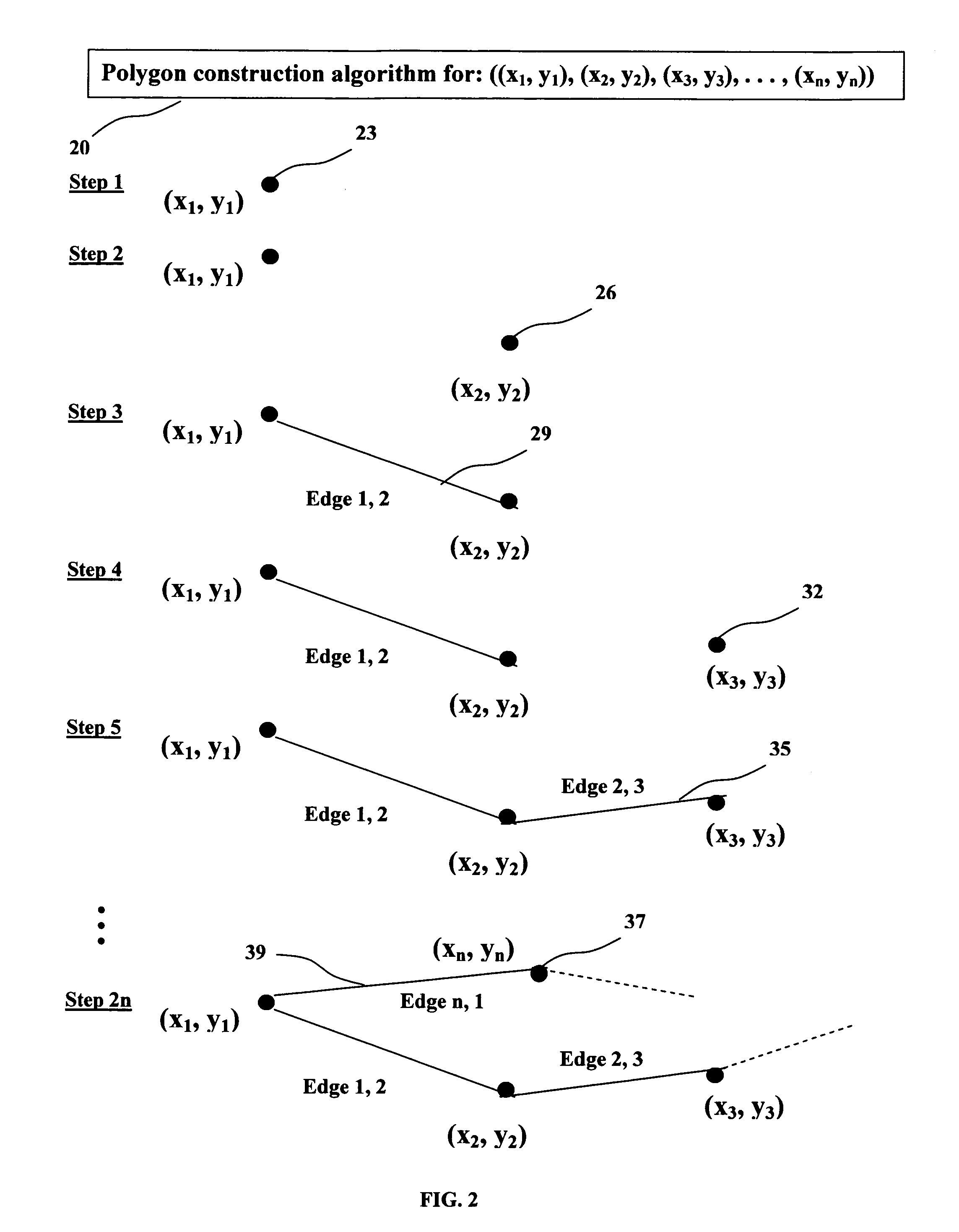
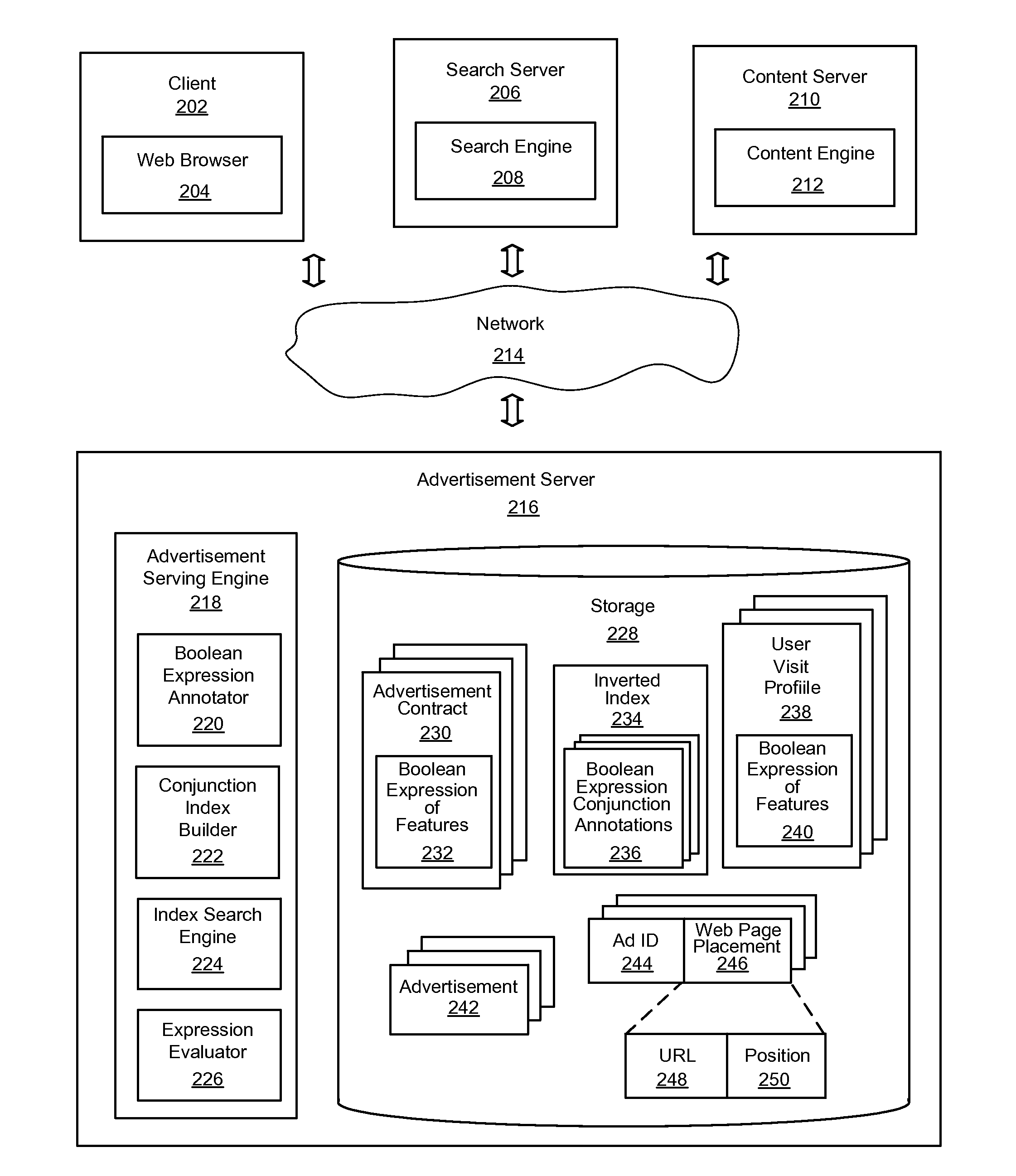
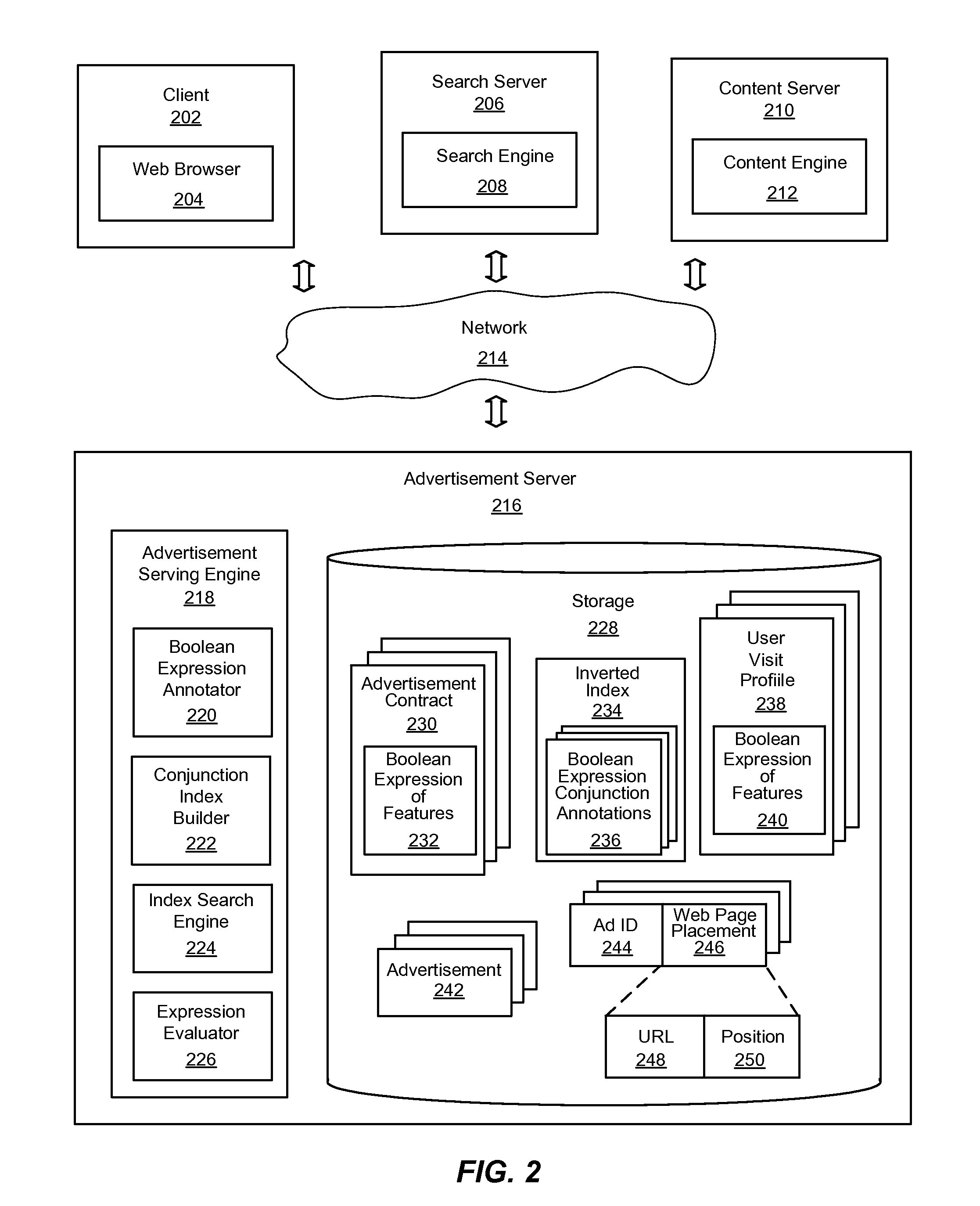
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
133 results about "Boolean expression" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, a Boolean expression is used expression in a programming language that produces a Boolean value when evaluated, that is one of true or false. A Boolean expression may be composed of a combination of the Boolean constants true or false, Boolean-typed variables, Boolean-valued operators, and Boolean-valued functions.
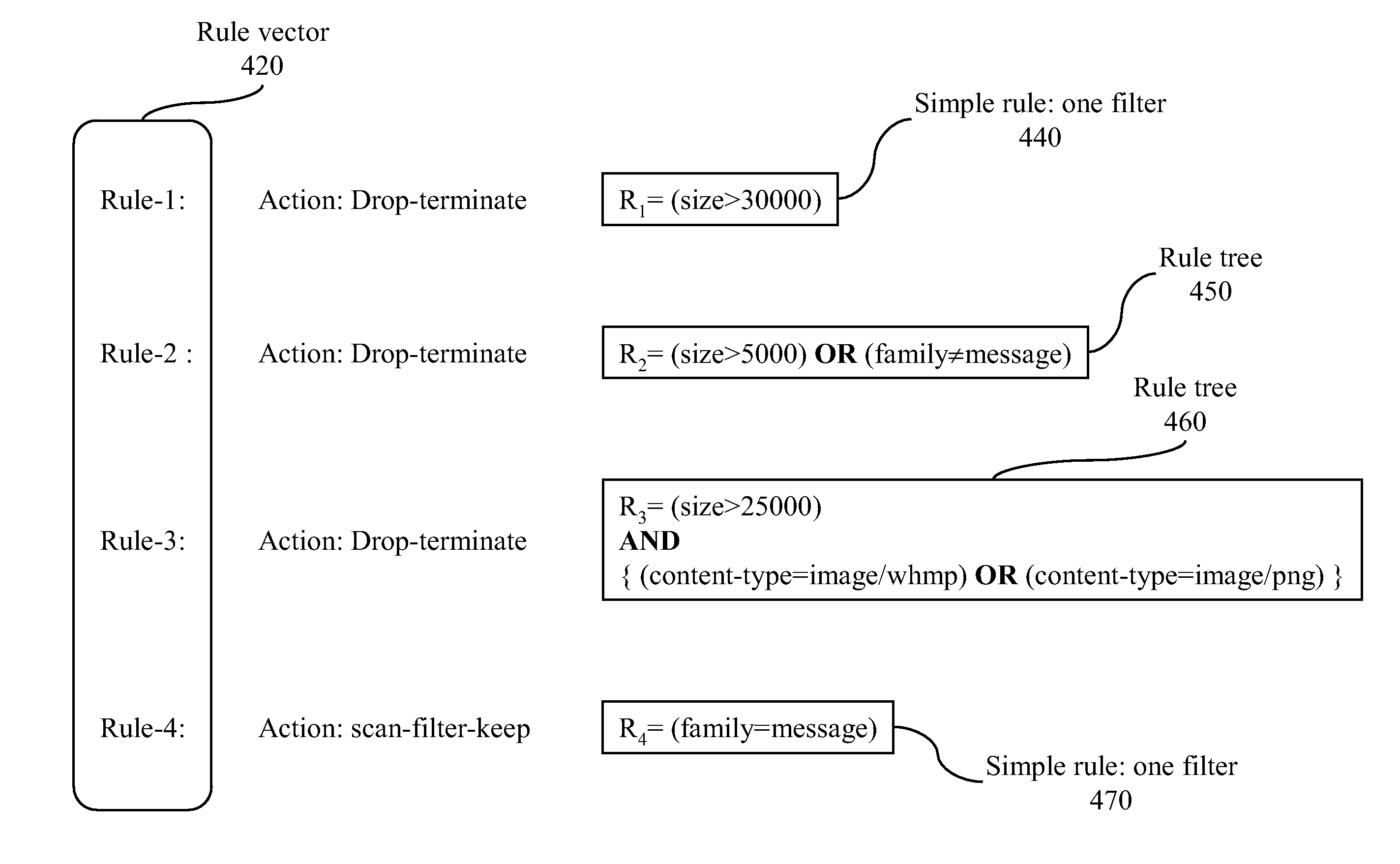
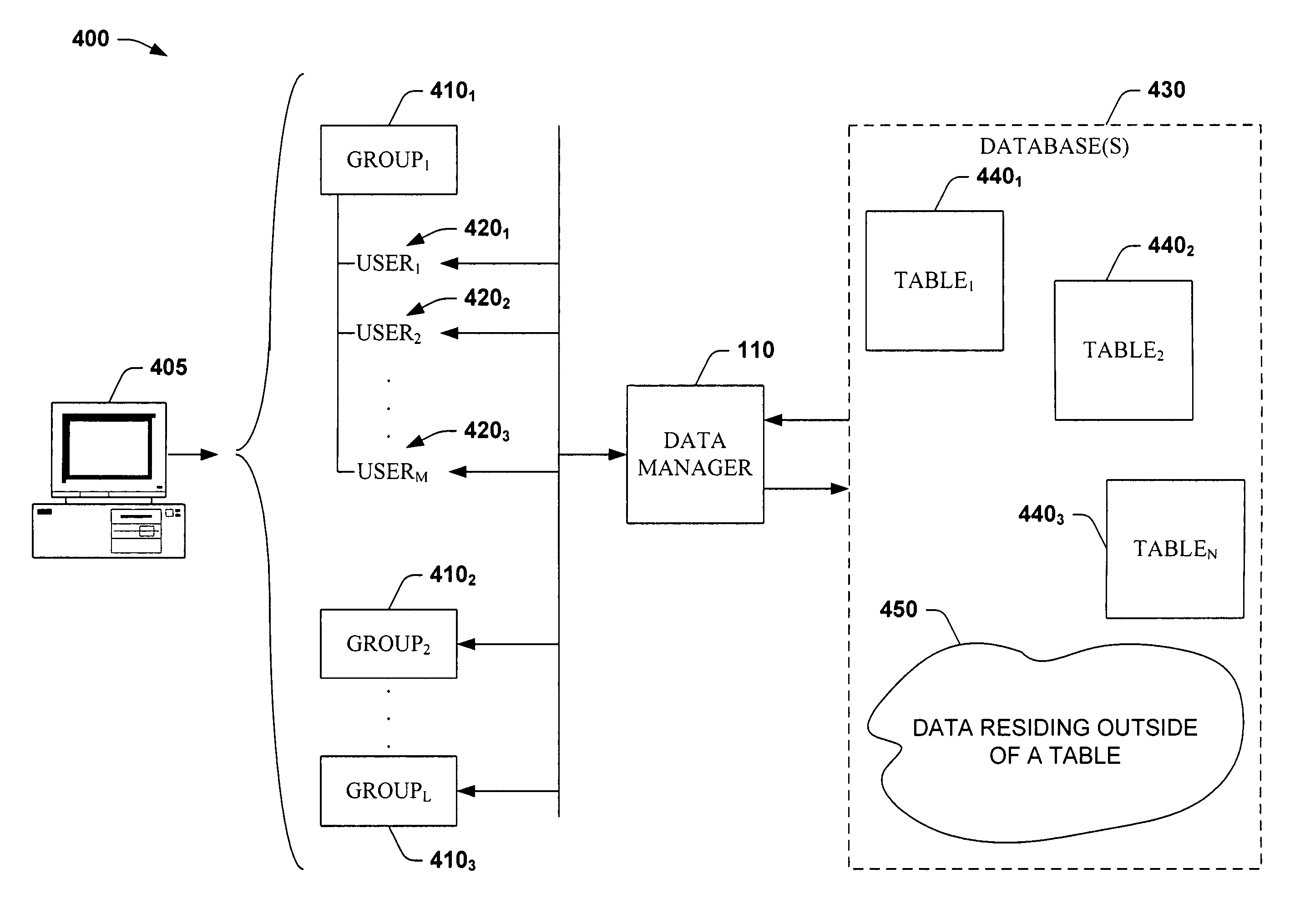
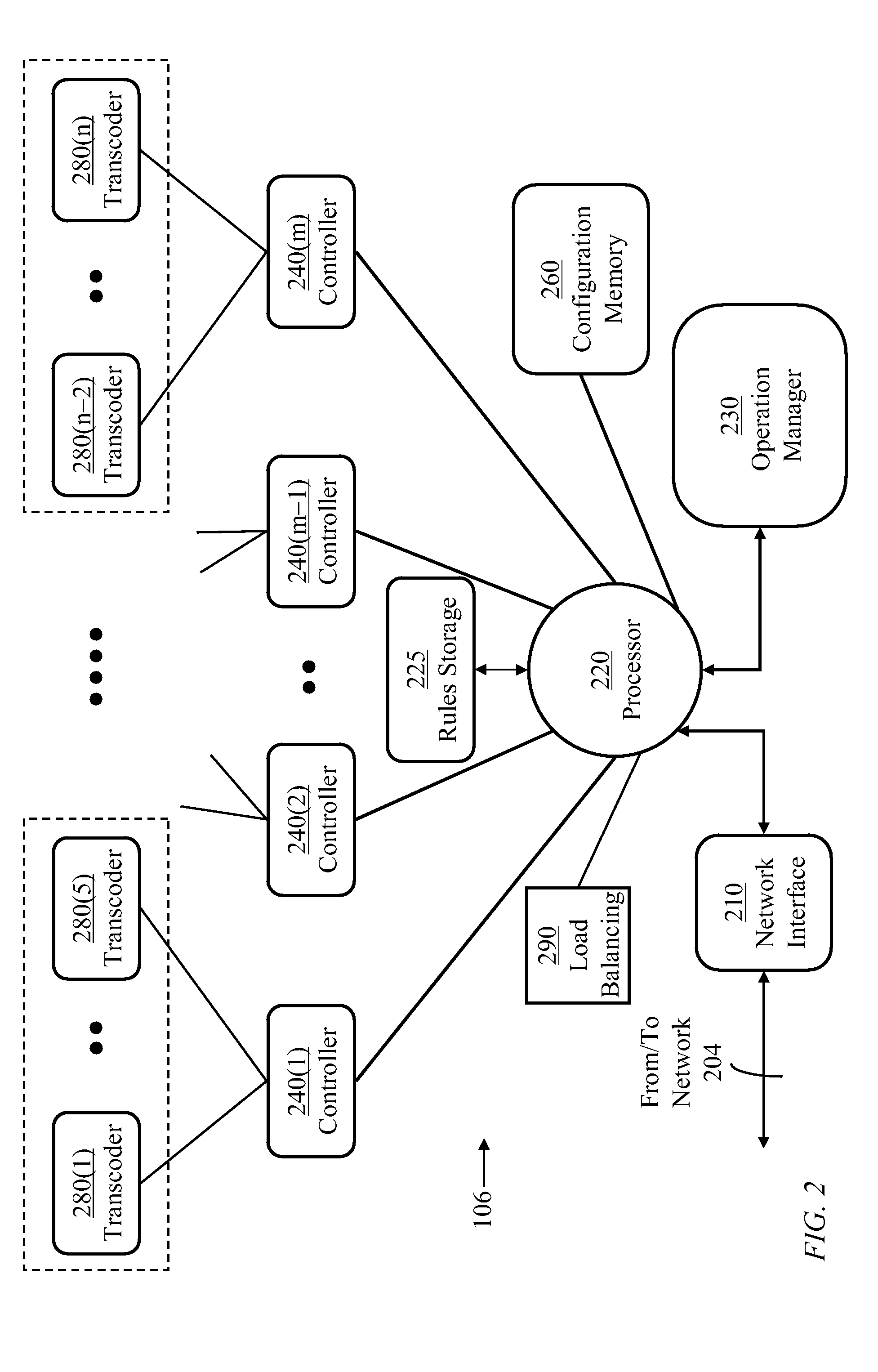
Method and system for rule-based content filtering
ActiveUS20090125459A1Comprehensive and efficient and economical systemGuaranteed economic efficiencyDigital computer detailsDigital dataContent adaptationData mining
A system and method for content-filtering of data containers in a network supporting versatile communications services are disclosed. The content-filtering system is integrated with a content-adaptation system. Several server units handle data containers formulated at source according to different protocols. A content filtering process relies on characterizing each component of a container to produce a set of content descriptors and producing a set of binary conditions for each component according to a preset criterion for each descriptor. A set of rules is devised where each rule applies a respective Boolean expression to a subset of the conditions to prescribe a respective content-editing action. Methods of specifying and evaluating a rule's Boolean expression are disclosed. A formal graph is used to define inter-dependence of rules.
Owner:MASIMO CORP
System and method for performance complex heterogeneous database queries using a single SQL expression
InactiveUS6341277B1Easy to implementEasy maintenanceDigital data information retrievalData processing applicationsDatabase queryClient-side
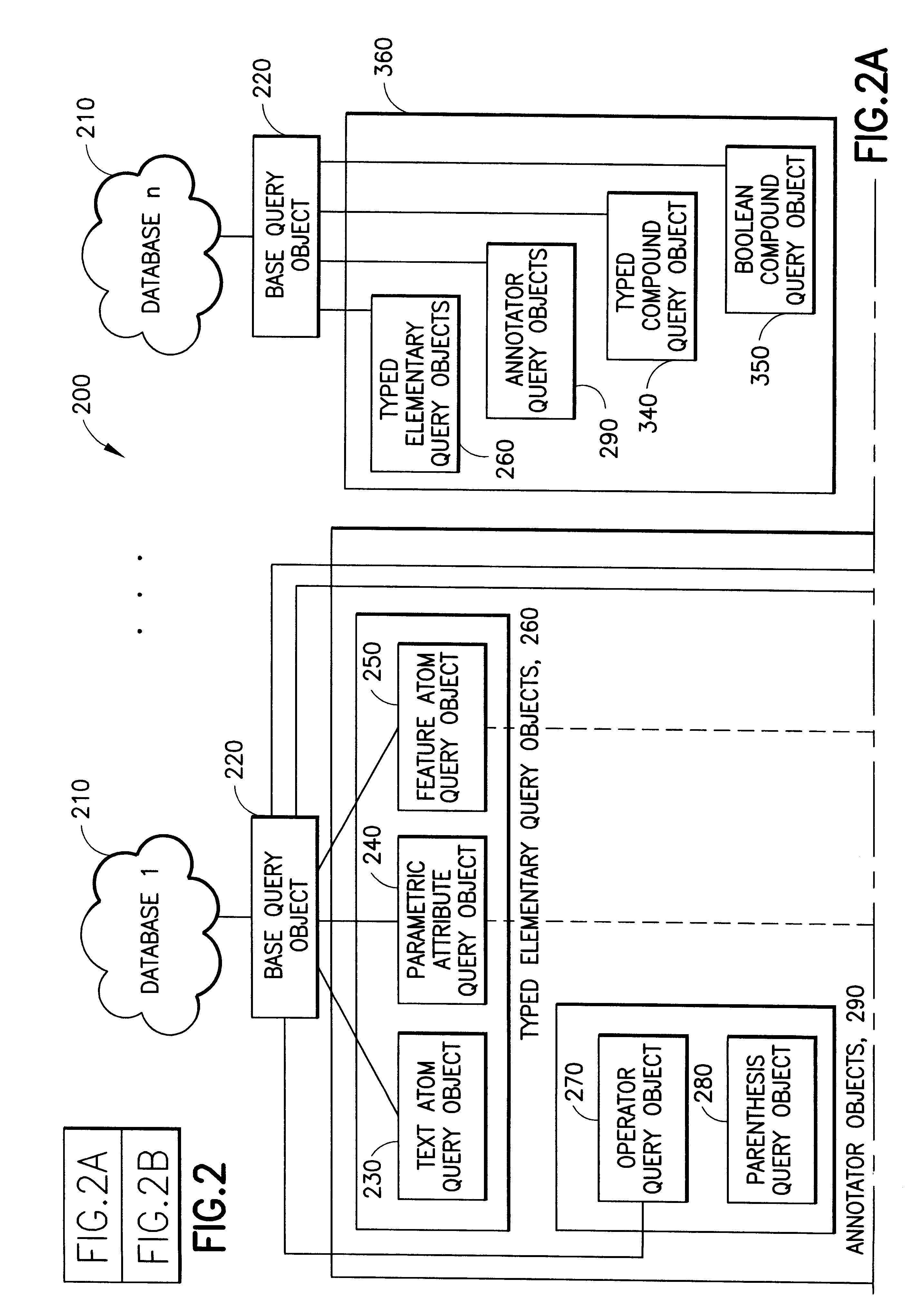
Query objects are created by a client process. The query objects have one or more sub-query objects and one or more execute methods that are capable of operating on their respective query object to produce one or more query expressions. All of the execute methods are capable of producing the respective query expression that is compatible with a structured query language. A compound query contains one or more boolean expressions of one or more of the query objects. The compound query has one or more compound execute methods which invoke one or more the execute methods of each of the query objects. Each of the execute methods returns their respective query expression and the compound execute method uses one or more common table expressions to combine the query expressions to form a single compound query expression that represents the boolean expression. This single expression can be execute against a database to return a result without executing any of the query expressions against the database individually.
Owner:IBM CORP
User interface for providing third party content as an RSS feed
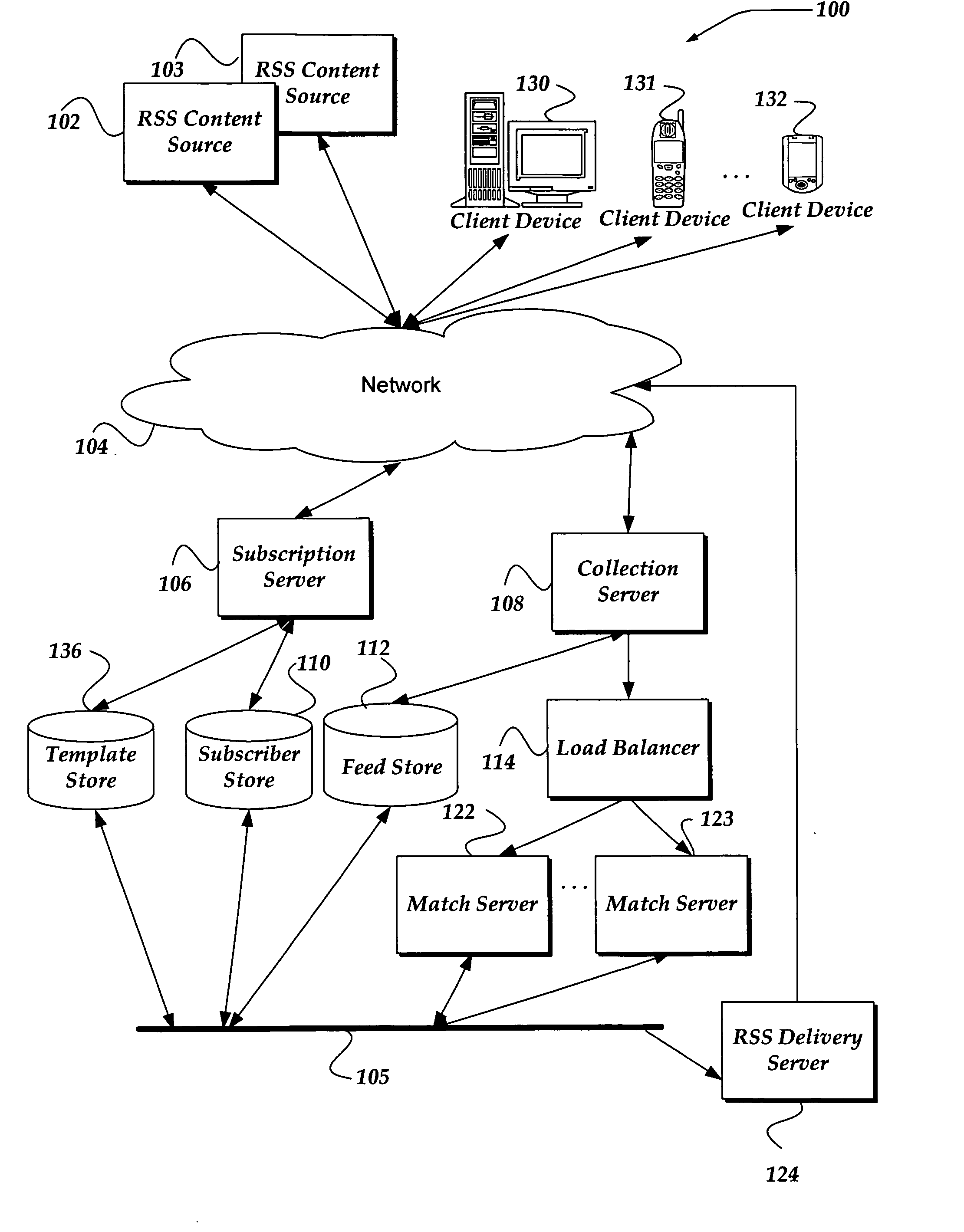
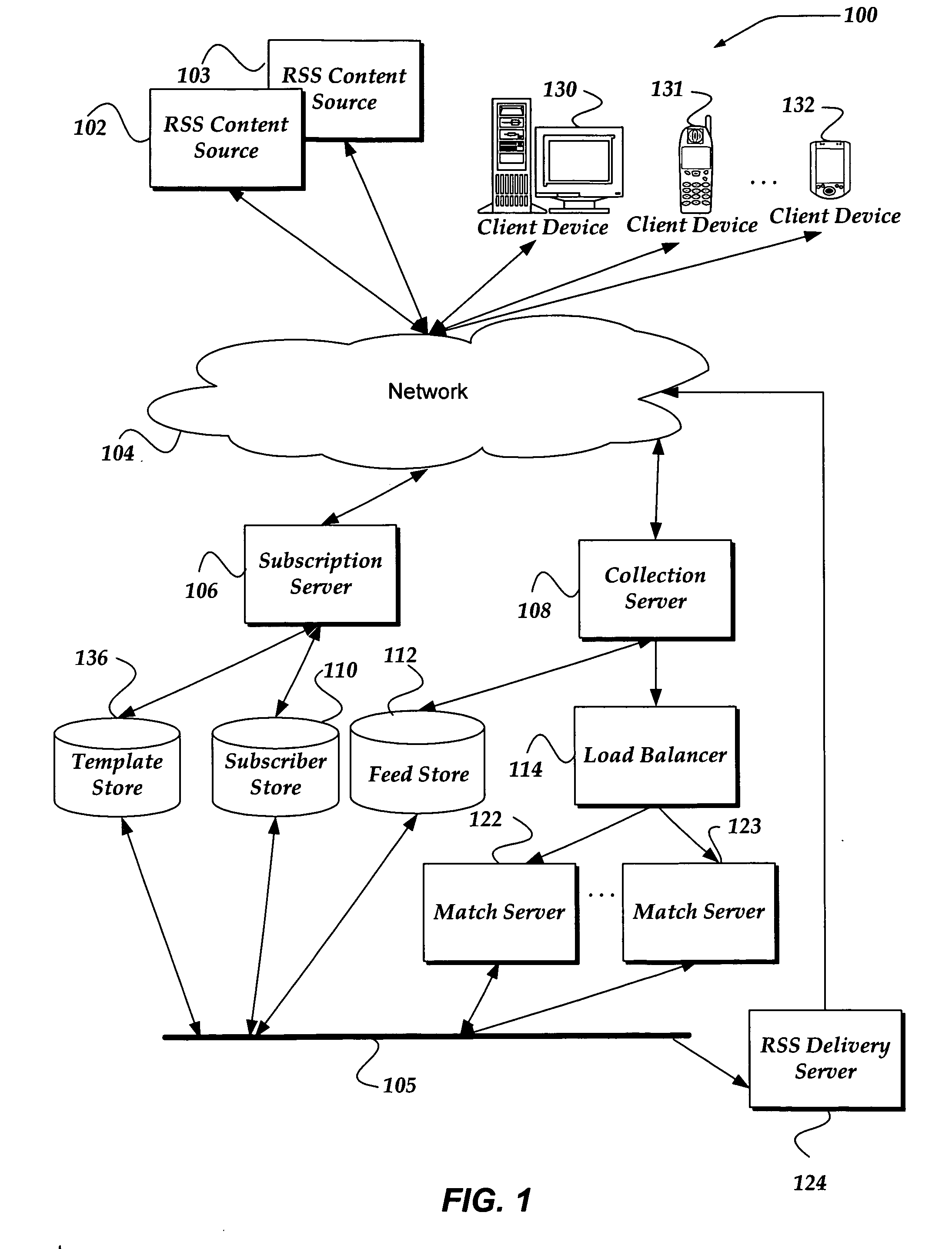
A system, method, and apparatus are directed to managing a subscription to an RSS feed. A search component enables searching over a network for content associated with an RSS feed. In one embodiment, the search component receives a search query in the form of a structured query language (SQL), Boolean expression, or the like. The search component may search for content based on the search query and validate the RSS feed associated with the results from the search. A list of validated RSS feeds may be sent to the user. The user may then select from the list and subscribe to a validated RSS feed. In addition, the user may employ the search query as an RSS feed. Thus, the same search may be performed automatically and the results compared to the previous search results. If a change in the search results is detected, the user may be alerted.
Owner:OATH INC
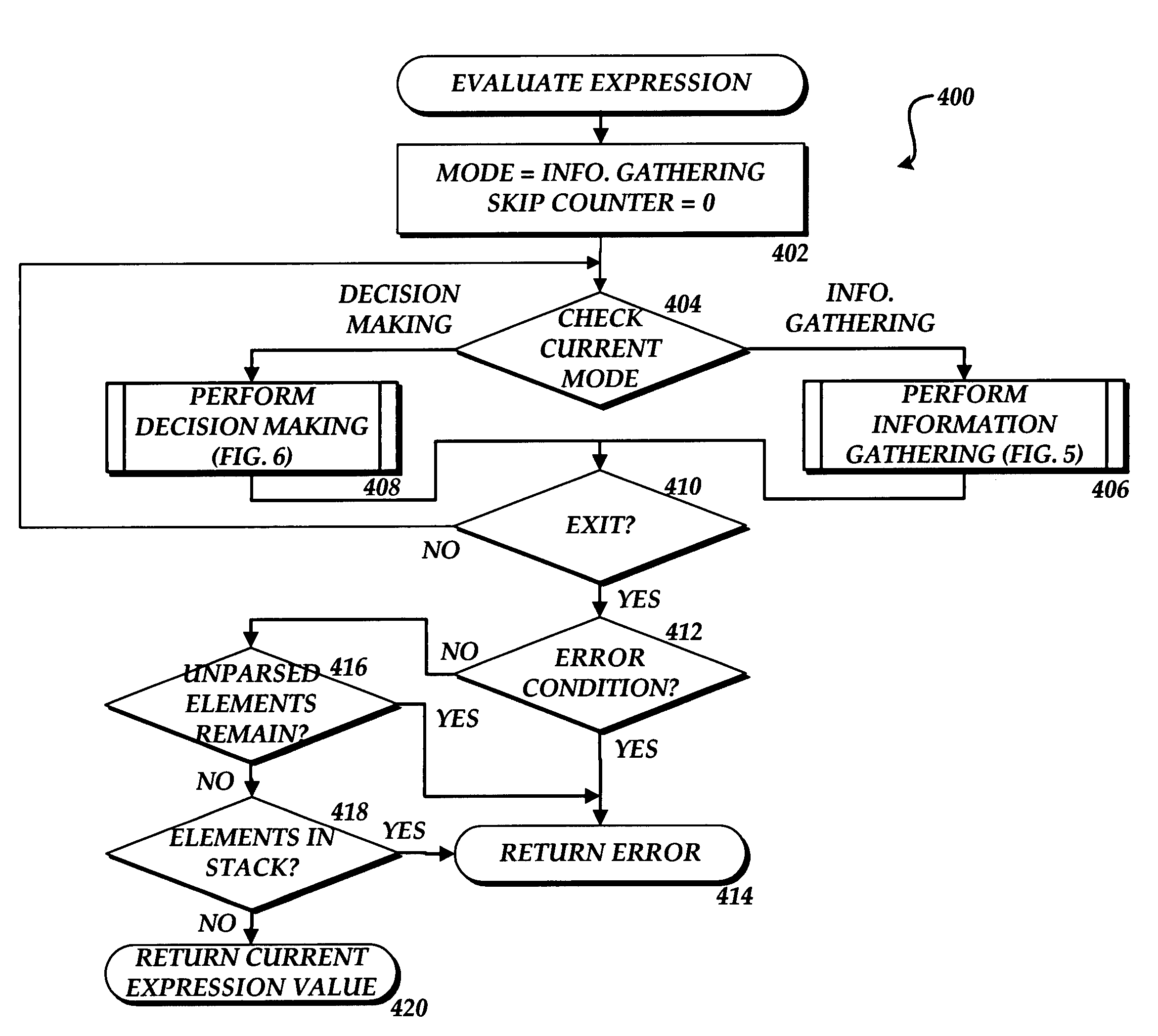
Method, system, and apparatus for efficient evaluation of boolean expressions
ActiveUS7406592B1Effective evaluationEvaluated more quicklySoftware engineeringDigital computer detailsOperandOperating system
Methods, systems, and computer-readable media are provided for efficiently evaluation Boolean expressions. According to the method, the Boolean expression is expressed using pre-fix notation. Each element in the pre-fix expression is then parsed. For each first operand for a Boolean operation, the value of the operand is determined. This may include evaluating a GUID. When an operator and a second operand are encountered, a decision is made as to whether the second operand should be evaluated. The determination as to whether the second operand should be evaluated is made based upon the value of the first operand and the type of operator. If the second operand need not be evaluated, no evaluation is performed thereby saving time and memory space. The evaluation of the Boolean expression continues in this manner until the entire expression has been evaluated. If the Boolean expression is evaluated as true, the program module associated with the Boolean expression may be loaded. Otherwise, the program module will not be loaded.
Owner:AMERICAN MEGATRENDS
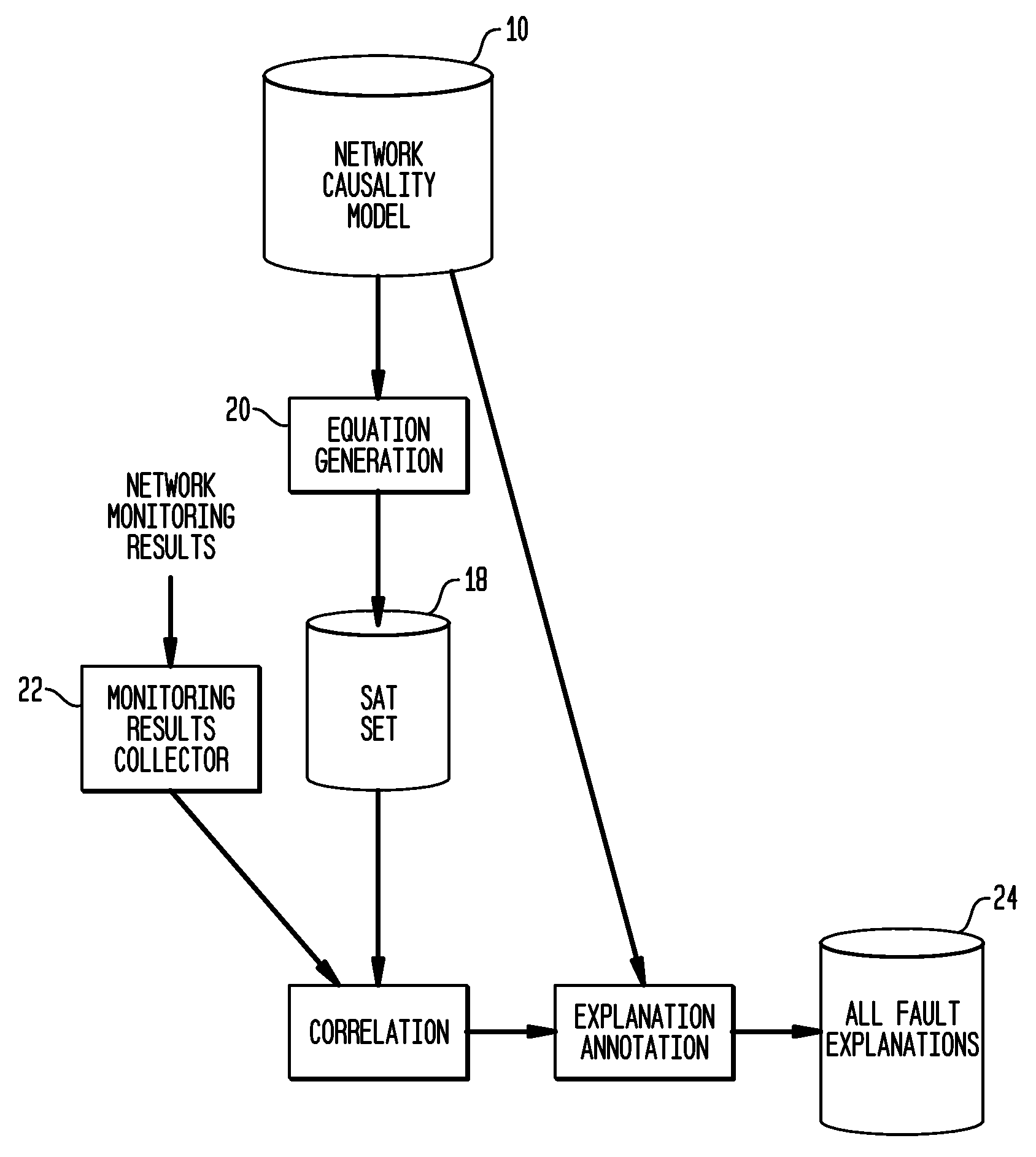
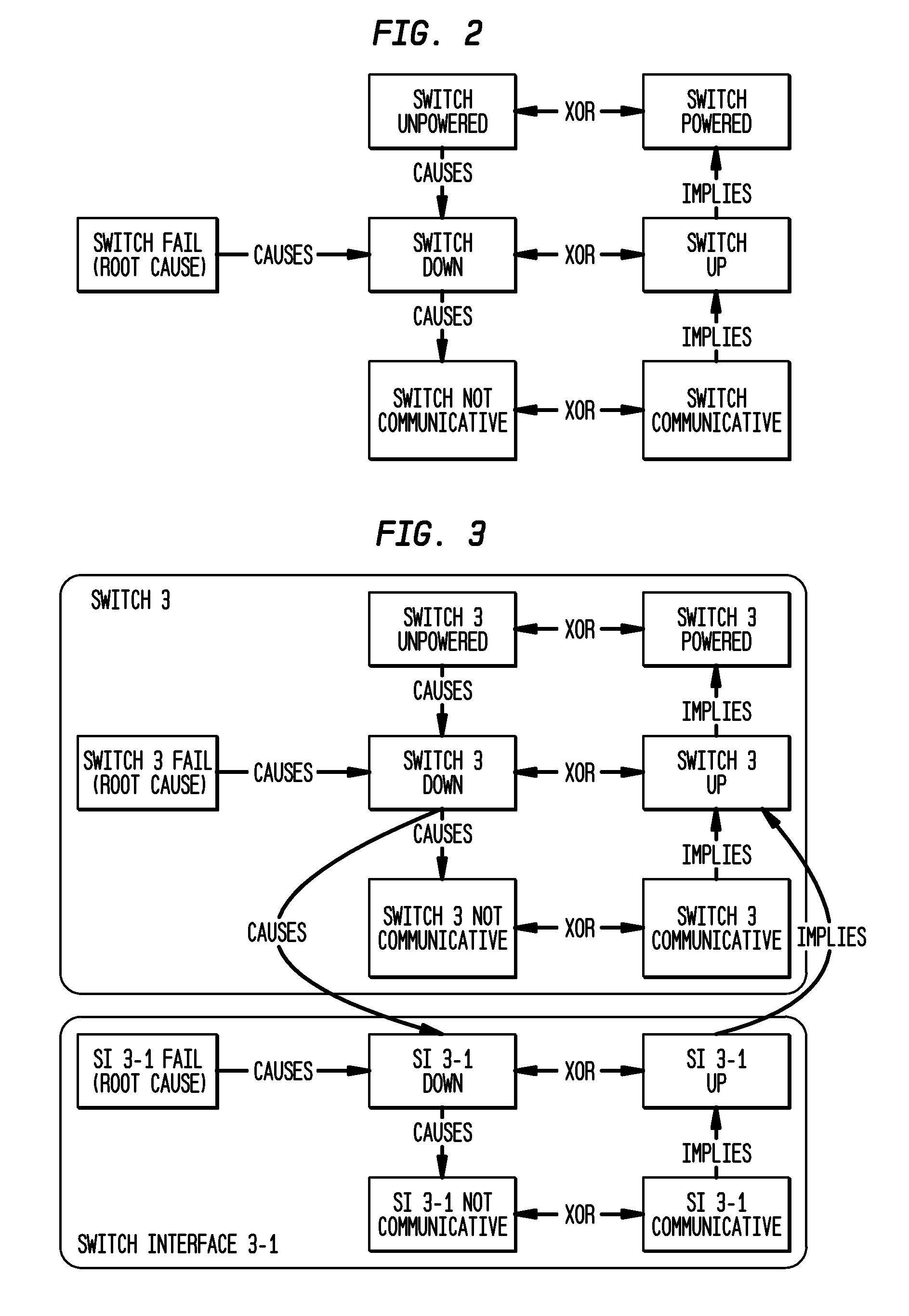
Computing diagnostic explanations of network faults from monitoring data
InactiveUS20100115341A1Digital computer detailsNon-redundant fault processingDisease causationCausality
A system and method for network fault diagnosis in a network having network elements is presented. The method comprises creating a network causality model, generating Boolean expressions from the network causality model, converting the Boolean expressions into SAT sets, receiving network monitoring results, correlating these monitoring results with the SAT sets, and enumerating all possible diagnostic explanations of potential faults, properly annotated. Creating a network causality model can comprise creating, for each network element, an element-specific causality model, stitching together all network elements using the element-specific causality models and a network topology, retrieving monitoring state and propagation information, and generating the network causality model using the stitched together network elements and the monitoring state and propagation information. Stitching together network elements can comprise adding causes and implies dependency between appropriate network elements and / or adding and connecting reachable and not-reachable states. The network causality model can comprise network element states.
Owner:TT GOVERNMENT SOLUTIONS
Systems and methods that optimize row level database security
ActiveUS20050177570A1Improve securityEnhanced syntaxDigital data processing detailsCheck valvesDatabase securityBoolean expression
The systems and methods of the present invention facilitate database row-level security by utilizing SQL extensions to create and associate named security expressions with a query initiator(s). Such expressions include Boolean expressions, which must be satisfied by a row of data in order for that data to be made accessible to the query initiator. In general, a query is augmented with security expressions, which are aggregated and utilized during querying rows of data. The systems and methods variously place security expressions within a query in order to optimize query performance while mitigating information leaks. This is achieved by tagging security expressions as special and utilizing rules of predicate to pull or push non-security expressions above or below security expressions, depending on the likelihood of a non-security being safe, as determined via a static and / or dynamic analysis.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods that optimize row level database security
ActiveUS7661141B2Facilitate row-level securityEnhanced syntaxDigital data processing detailsCheck valvesDatabase securityData bank
The systems and methods of the present invention facilitate database row-level security by utilizing SQL extensions to create and associate named security expressions with a query initiator(s). Such expressions include Boolean expressions, which must be satisfied by a row of data in order for that data to be made accessible to the query initiator. In general, a query is augmented with security expressions, which are aggregated and utilized during querying rows of data. The systems and methods variously place security expressions within a query in order to optimize query performance while mitigating information leaks. This is achieved by tagging security expressions as special and utilizing rules of predicate to pull or push non-security expressions above or below security expressions, depending on the likelihood of a non-security being safe, as determined via a static and / or dynamic analysis.
Owner:MICROSOFT TECH LICENSING LLC
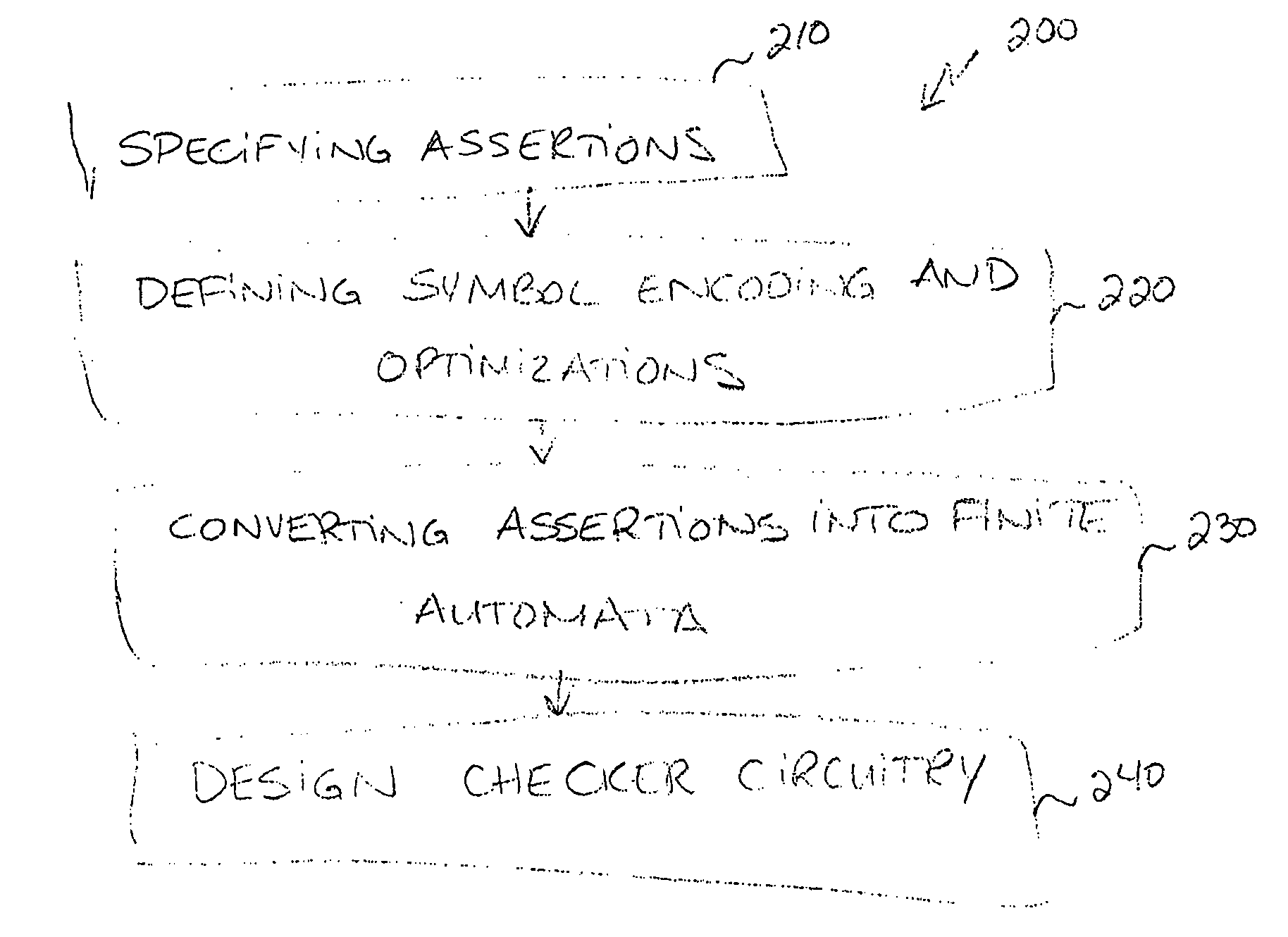
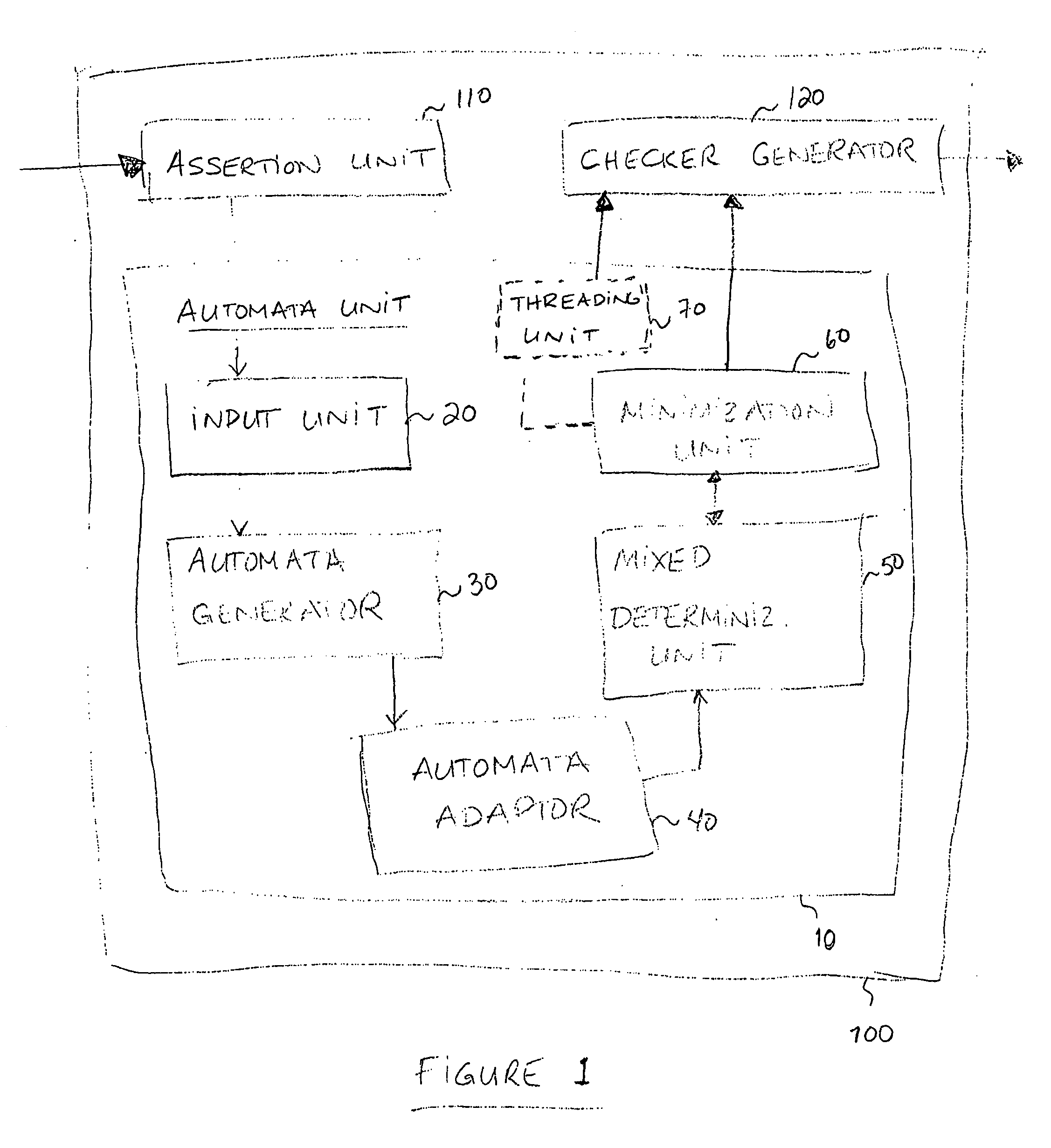
Automata unit, a tool for designing checker circuitry and a method of manufacturing hardware circuitry incorporating checker circuitry
InactiveUS20080082946A1Computer aided designSoftware simulation/interpretation/emulationAutomatonDual layer
The present invention relates to an automata unit, a tool for designing circuitry and / or checker circuitry, and a method for manufacturing hardware circuitry. The automata unit includes an input unit for receiving assertions using Boolean expressions, an automata generator for translating the assertions into automata, and an automata adaptor. The automata generator uses a dual layer symbolic alphabet for representing the assertions, and the automata adaptor adapts automata algorithms so as to support the symbolic alphabet in the generated automata. The tools for designing circuitry and checker circuitry rely on the automata unit, and further include an assertion unit and either a circuit generator or a checker generator.
Owner:MCGILL UNIV
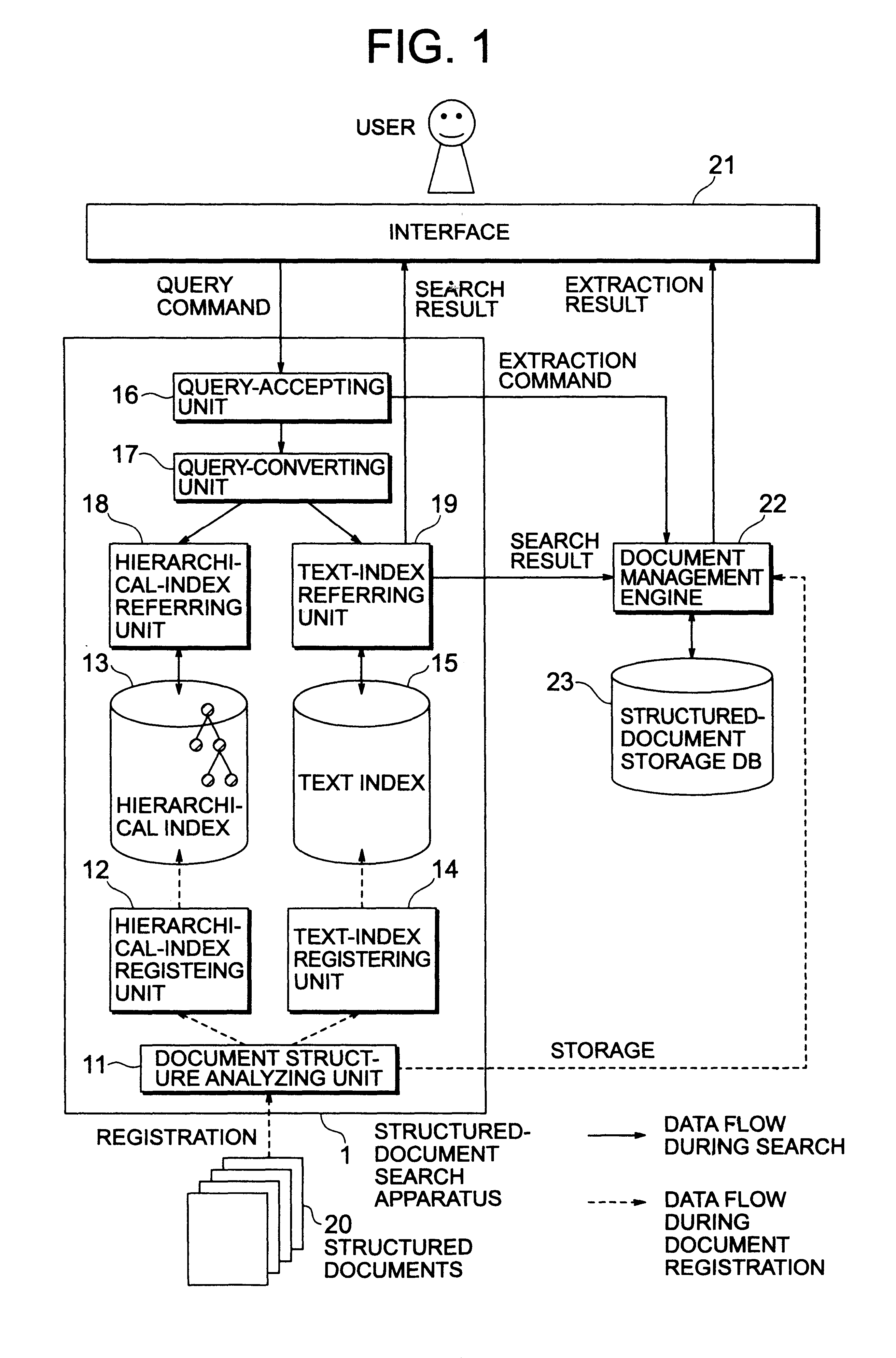
Structured-document search apparatus and method, recording medium storing structured-document searching program, and method of creating indexes for searching structured documents
InactiveUS6853992B2Increase speedData processing applicationsDigital data processing detailsDocument preparationDocumentation
A query in which a sibling relationship among document parts, which are elements of a structured document, can be designated as a search condition is input, and a query tree which represents the query in a tree structure is created. A query converting unit refers to a hierarchical index in which a hierarchical relationship among document parts of each structured document to be searched is expressed in a tree structure, and converts the query tree to a Boolean expression. A text-index referring unit refers to a text index in which is registered information representing a relationship between each set including a character string in text data and a part-ID of a meta part and a document-ID of a document, thereby searching a document corresponding to the Boolean expression converted from the query tree.
Owner:FUJITSU LTD
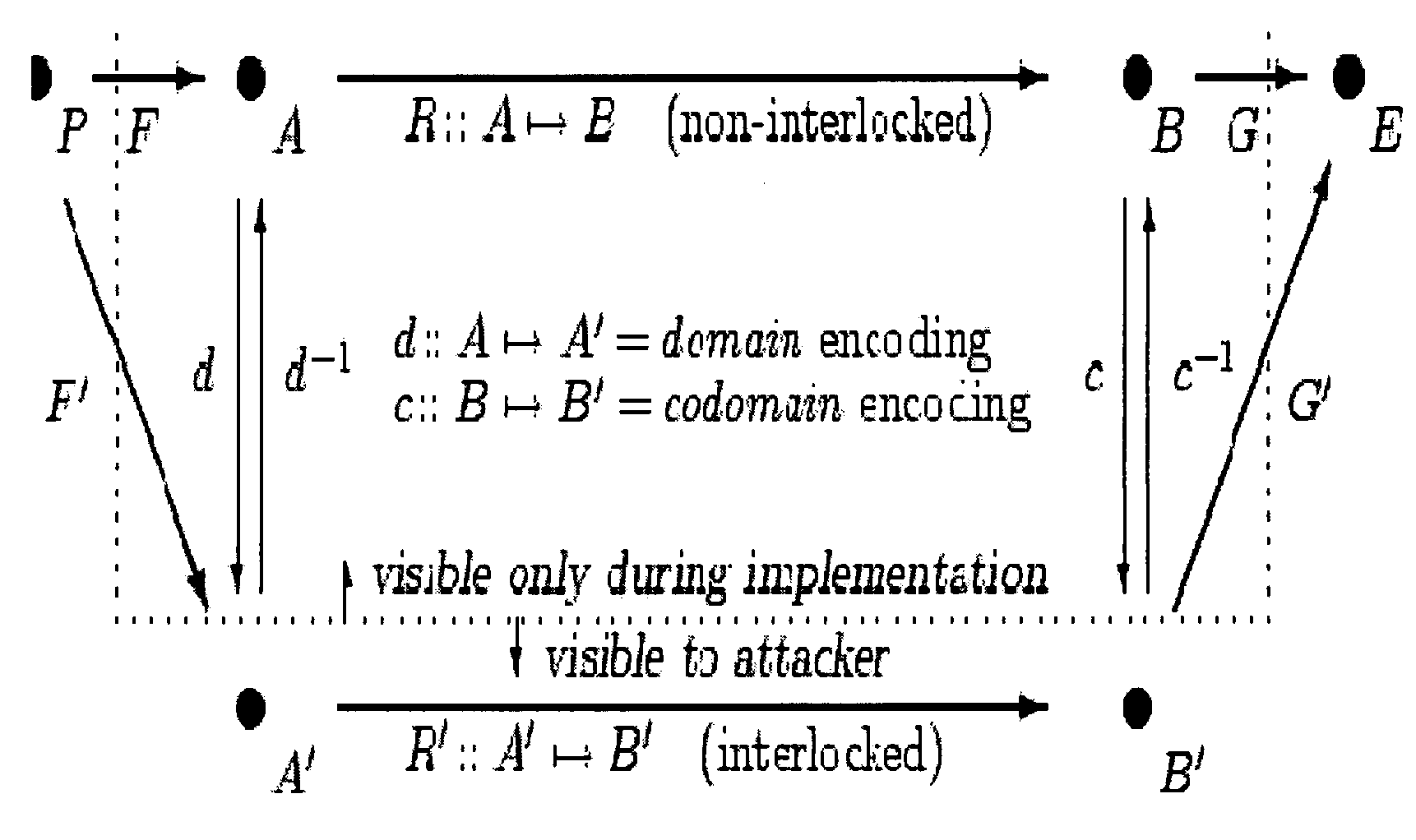
System and method of interlocking to protect software - mediated program and device behaviors
A method for rendering software resistant to reverse engineering. Replace at least one first constant (mathematical expression, etc.) in a computational expression with a second mixed mathematical and bitwise-Boolean expression, the first constant being simpler than the second expression and the second expression being based on the value or the variables found in the first constant (or expression). Evaluation of the second mixed mathematical and bitwise-Boolean expression produces a value preserving the value of the first constant, either: with the original value of the first constant or the original value of the result of the first expression, in which case the second mixed mathematical and bitwise-Boolean expression is obtained from the first constant by converting the first constant by mathematical identities; or, in an encoded form, as a new value, which can be converted back to the original value of the first constant by applying an information-preserving decoding function, in which case the second mixed mathematical and bitwise-Boolean expression is obtained from the first constant by modifying the first constant by a combination of conversion according to mathematical identities and transformation according to an information preserving encoding function.
Owner:CLOAKWARE CORP +1
Systems and methods that specify row level database security
ActiveUS7711750B1Consumes spaceReduce disadvantagesDigital data processing detailsComputer security arrangementsClustered dataContext data
The present invention specifies database security at a row level and, optionally, at a column and table level. The systems and methods cluster one or more sets of rows with similar security characteristics and treat them as a named expression, wherein clustered data is accessed based on associated row-level security. The systems and methods specify a syntax that invokes row(s), column(s) and / or table(s) security via programming statements. Such statements include arbitrary Boolean expressions (predicates) defined over, but not restricted to table columns and / or other contextual data. These statements typically are associated with query initiators, incorporated into queries therefrom, and utilized while querying data. Rows of data that return “true” when evaluated against an aggregate of associated security expressions are said to “satisfy” the security expressions and enable access to the data stored therein. Such security expressions can be created and invoked via the Structured Query Language (SQL) database programming language.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for rule-based content filtering
ActiveUS8019709B2Guaranteed economic efficiencyDigital computer detailsDigital dataContent adaptationData mining
A system and method for content-filtering of data containers in a network supporting versatile communications services are disclosed. The content-filtering system is integrated with a content-adaptation system. Several server units handle data containers formulated at source according to different protocols. A content filtering process relies on characterizing each component of a container to produce a set of content descriptors and producing a set of binary conditions for each component according to a preset criterion for each descriptor. A set of rules is devised where each rule applies a respective Boolean expression to a subset of the conditions to prescribe a respective content-editing action. Methods of specifying and evaluating a rule's Boolean expression are disclosed. A formal graph is used to define inter-dependence of rules.
Owner:MASIMO CORP
Methods and systems for group authentication using the naccache-stern cryptosystem in accordance with a prescribed rule
A method for group authentication using a public key cryptosystem that includes a public key and a private key, comprising the steps of providing a Private Key Share to a Tool of each Entity of each Group encompassed by a Boolean Expression of a prescribed Rule based upon the private key, encrypting a random number using the public key of the public key cryptosystem to generate a ciphertext challenge at a Verification Device, conveying the ciphertext challenge to the Tool of each Entity in communication with the Verification Device, generating a response to the ciphertext challenge using the Private Key Share of the Tool of each Entity in communication with the Verification Device, transmitting the response generated by each Entity in communication with the Verification Device to the Verification Device, combining the responses received from the Entities in communication with the Verification Device, determining whether any combination of the responses equals the random number wherein any combination that equals the random number identifies an Authenticated Group and any combination that does not equal the random number identifies a non-authenticated Group, and effecting an apposite course of action with respect to an Operation governed by the prescribed Rule based upon the outcome of the determining step.
Owner:CALLAHAN CELLULAR L L C
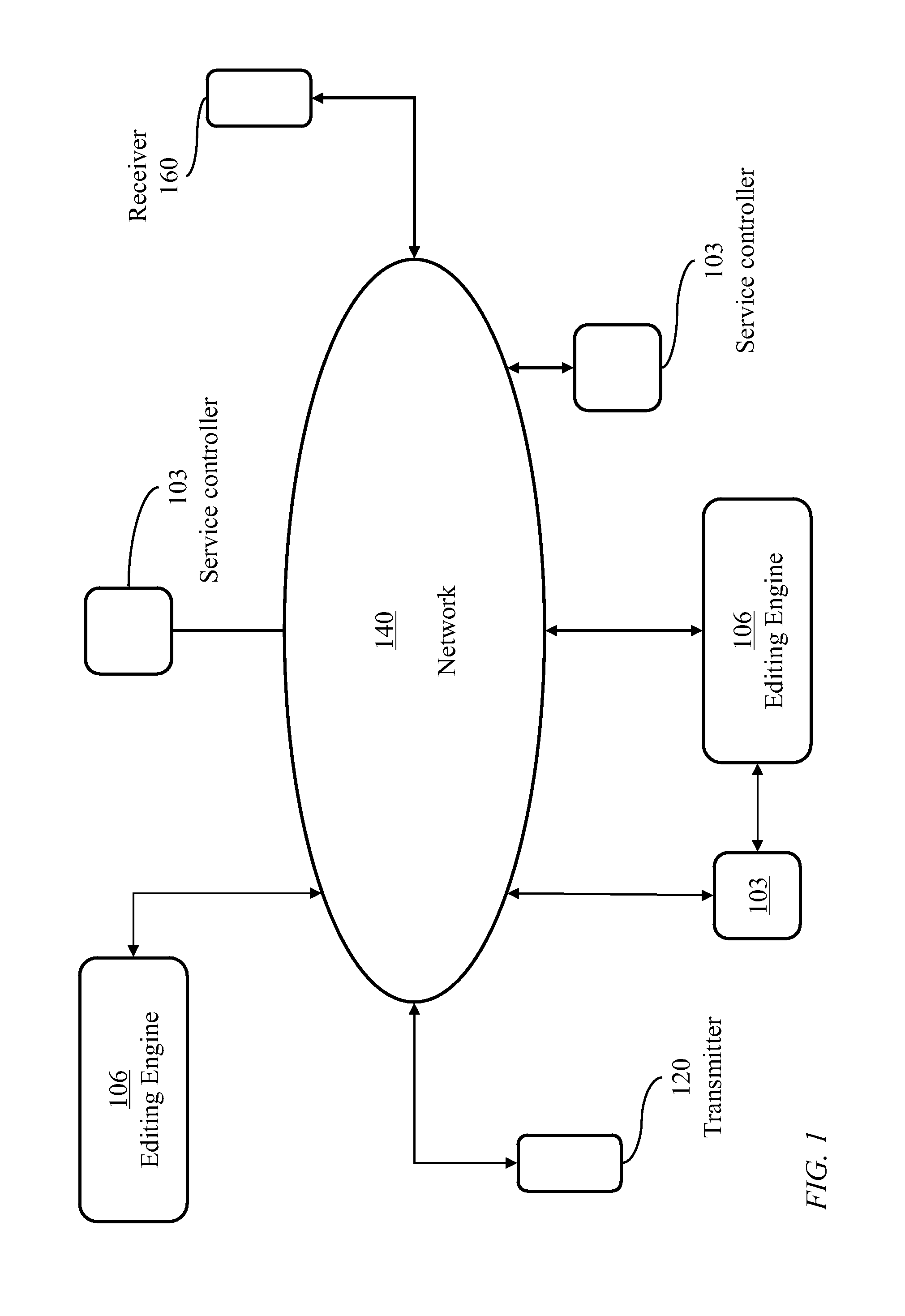
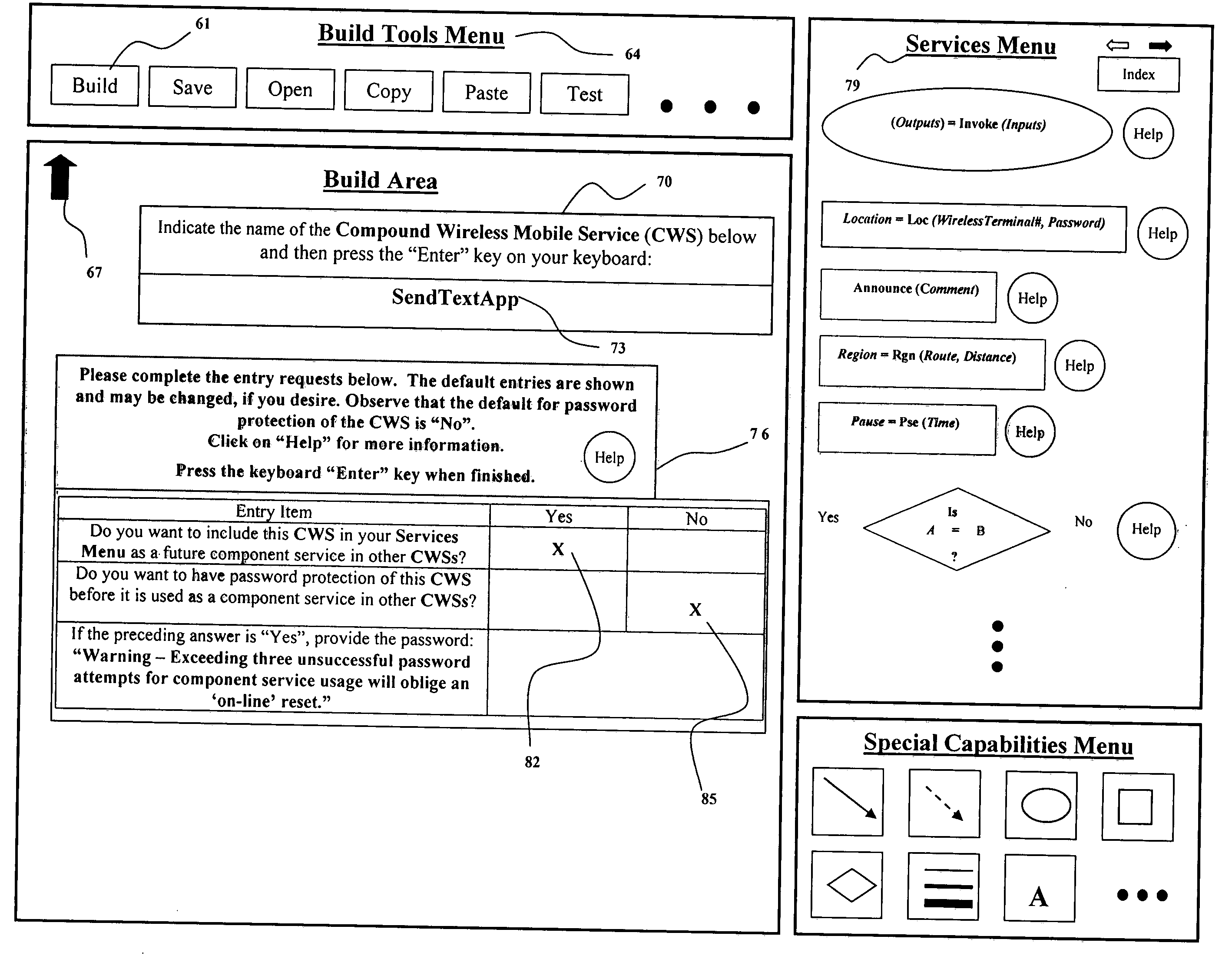
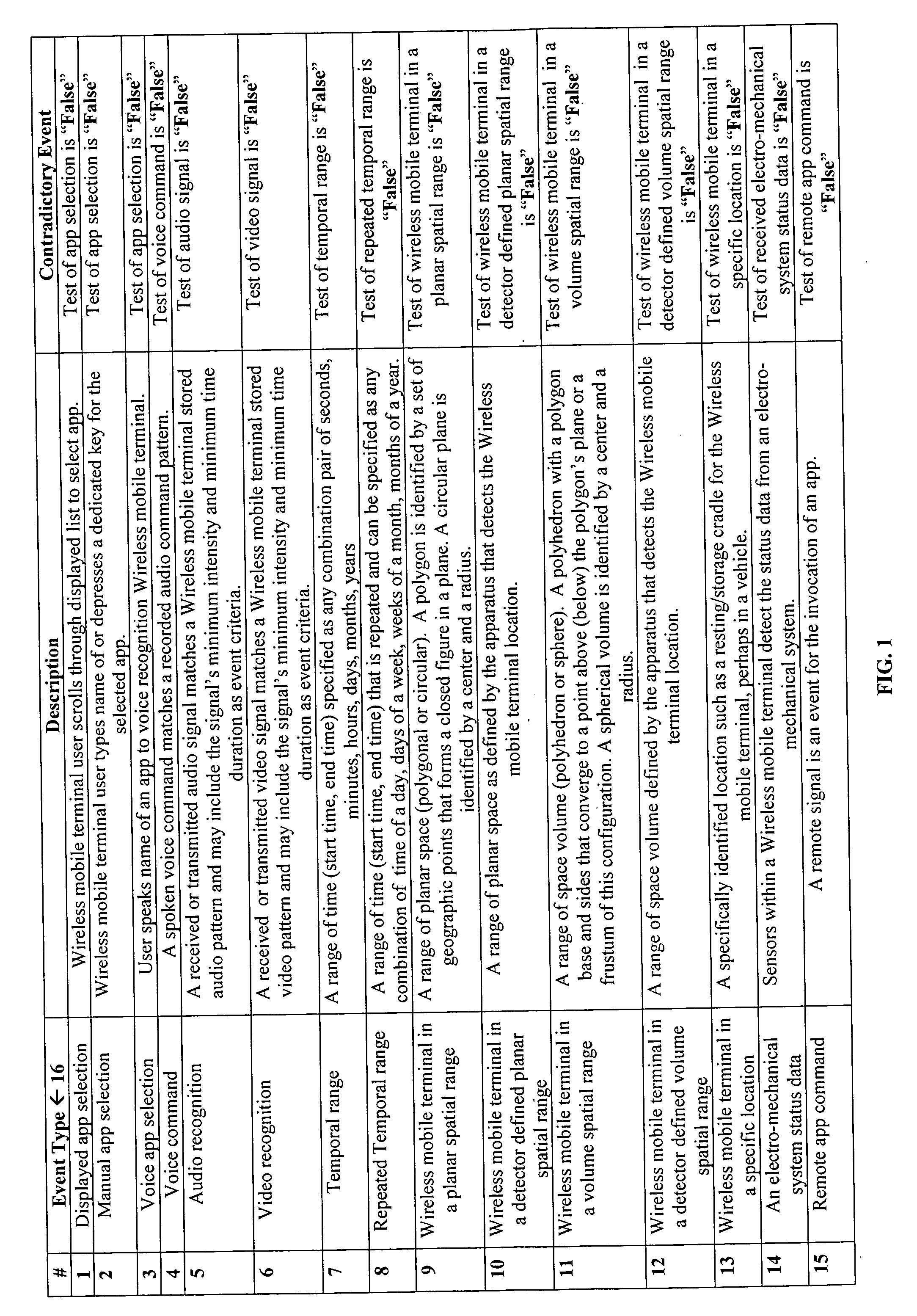
Application of the invoke facility service to restrict invocation of compound wireless mobile communication services
This invention provides a mechanism for enhancing safe use of wireless mobile terminals (smartphones) in a moving vehicle. The Invoke facility service's Boolean expression controls the conditions which invoke smartphone apps into execution. Smartphone apps, which are dangerous to execute in a moving vehicle, are prevented from invocation. Elimination of all smartphone apps in moving vehicles is inadvisable. An app, deploying an accelerometer to sense the impact of a serious collision to call “911” with a recorded message and provides the vehicle's GPS location, is an example. This invention allows an app builder to select invocation conditions for apps. Significant is the use manner of the operation “Not”. The contradiction of an event is also an event meaning that if an event is false, its contradictory event is true. Another important aspect is the conjunctive operation “And Then”. This operation implies an efficient algorithm to evaluate Boolean expressions.
Owner:KOBYLARZ THADDEUS JOHN
System and Method for Efficiently Evaluating Complex Boolean Expressions
InactiveUS20110225038A1Effective evaluationImprove indexing speedDigital data information retrievalDigital data processing detailsTheoretical computer scienceInverted index
An improved system and method for efficiently evaluating complex Boolean expressions is provided. Leaf nodes of Boolean expression trees for objects represented by Boolean expressions of attribute-value pairs may be assigned a positional identifier that indicates the position of a node in the Boolean expression tree. The positional identifiers of each object may be indexed by attribute-value pairs of the leaf nodes of the Boolean expression trees in an inverted index. Given an input set of attribute-value pairs, a list of positional identifiers for leaf nodes of virtual Boolean expression trees may be found in the index matching the attribute-value pairs of the input set. The list of positional identifiers of leaf nodes may be sorted in order by positional identifier for each contract. An expression evaluator may then verify whether a virtual Boolean expression tree for each contract is satisfied by the list of positional identifiers.
Owner:YAHOO INC
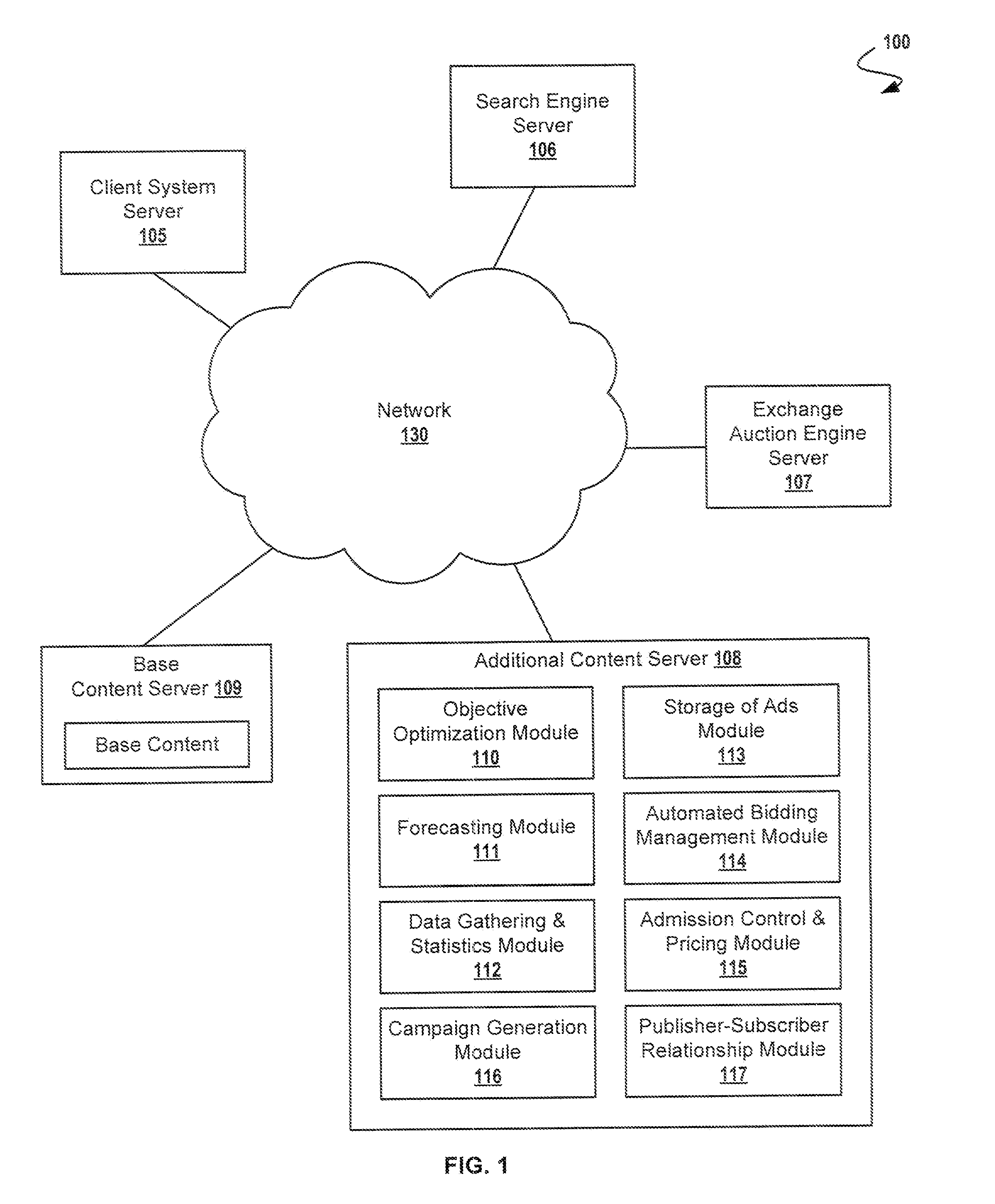
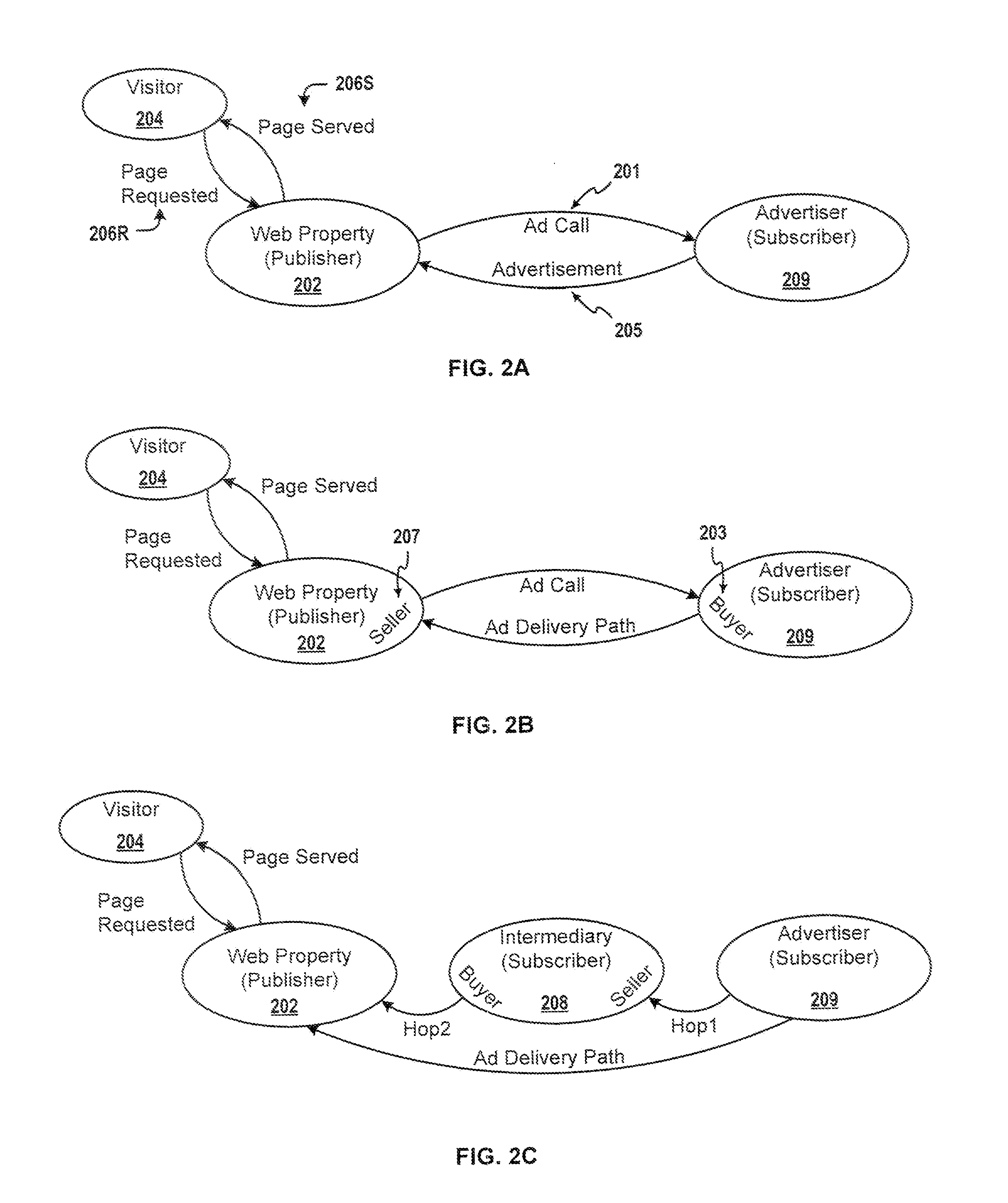
Automatic Management of Networked Publisher-Subscriber Relationships
Automatic management of networked publisher-subscriber relationships in an advertising server network. The method comprises steps for constructing a directed graph representation comprising at least one publisher node (e.g. an Internet property), at least one subscriber node (e.g. an Internet advertiser), at least one intermediary node (e.g. an Internet advertising agent), and at least one edge (e.g. an advertising target predicate) wherein any one of the edges is directly associated with at least one target predicate. The directed graph representation is used in conjunction with an inverted index for retrieving a valid node list comprising only nodes having at least one target predicate that matches at least one event predicate. The event predicate (as well as any target predicate) is any arbitrarily complex Boolean expression, and is used in producing a result node list comprising only nodes that concurrently match the event predicate with an advertising target predicate and are reachable.
Owner:BROADCOM CORP +1
Method and system for filtering information
A system and method for filtering data is provided, including identifying a target portion of a data source, dividing the target portion into one or more elements of a set, receiving one or more search requests as a filter specification, interpreting the filter specification as a Boolean logic expression, evaluating the elements of the set based on the Boolean expression, and displaying the elements which match the search request on a display.
Owner:GILL TIMOTHY DAVID +1
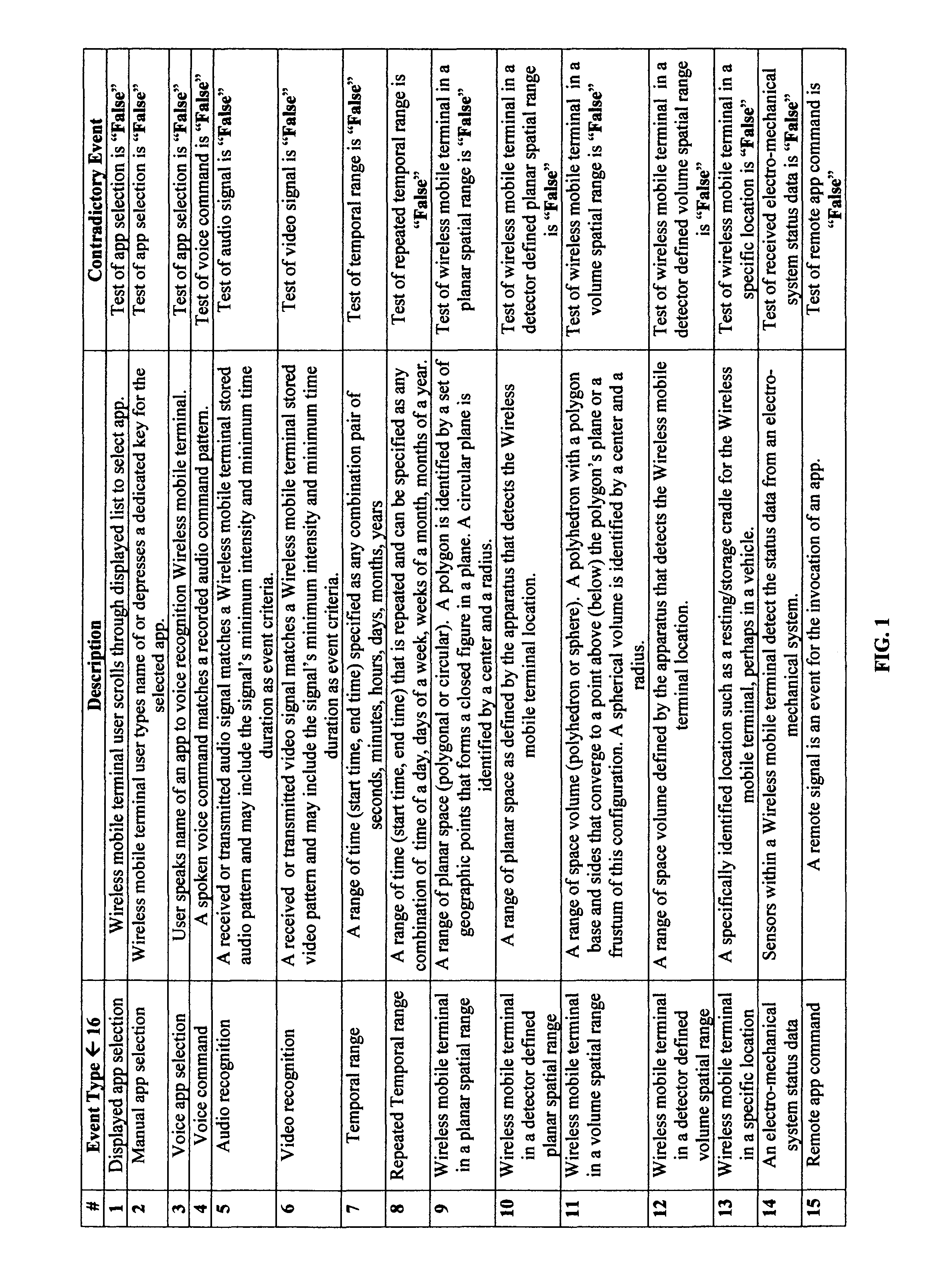
Application of the invoke facility service to restrict invocation of compound wireless mobile communication services
ActiveUS20120220276A1Save livesImprove securityService provisioningSpecial service for subscribersMobile vehicleAccelerometer
The principal purpose of this invention is to provide the mechanism for enhancing the safe use of a wireless mobile terminal (smartphone) in a moving vehicle. The Invoke facility service's Boolean expression controls the conditions for which a smartphone app will be invoked into execution. Hence, smartphone apps, which create dangerous circumstances when executed in a moving vehicle, can be prevented from invocation. The total elimination of smartphone use in a moving vehicle is inadvisable. For example, an app that deploys an accelerometer to sense the impact of a vehicle's serious collision and thereby calls “911” to transmit a recorded message that includes the vehicle's GPS location should be allowed to execute when a vehicle is moving. This invention allows an app builder to select suitable invocation conditions for an app.Significant and pertinent to the invention is the manner in which the Boolean logic operation “Not” is used. Whereas conventional apps are invoked by a positive assertion of an event; the use of the operation “Not” avails negative event assertions in the Boolean expression of an Invoke facility service. That is, the contradiction of an event is also an event; meaning that if an event is false, its contradictory event is true. Another important Boolean logic aspect of this invention is the conjunctive operation of “and then”. The “And Then” operation possesses the same functionality as the conjunctive operation of “And”, but “And Then” also possesses a sequential implication for determining the occurrence of events. The sequential implication provides an efficient means to evaluate the Boolean expressions of the Invoke facility service.
Owner:KOBYLARZ THADDEUS JOHN
Automata unit, a tool for designing checker circuitry and a method of manufacturing hardware circuitry incorporating checker circuitry
InactiveUS8024691B2Computer aided designSoftware simulation/interpretation/emulationAutomatonBoolean expression
Owner:MCGILL UNIV
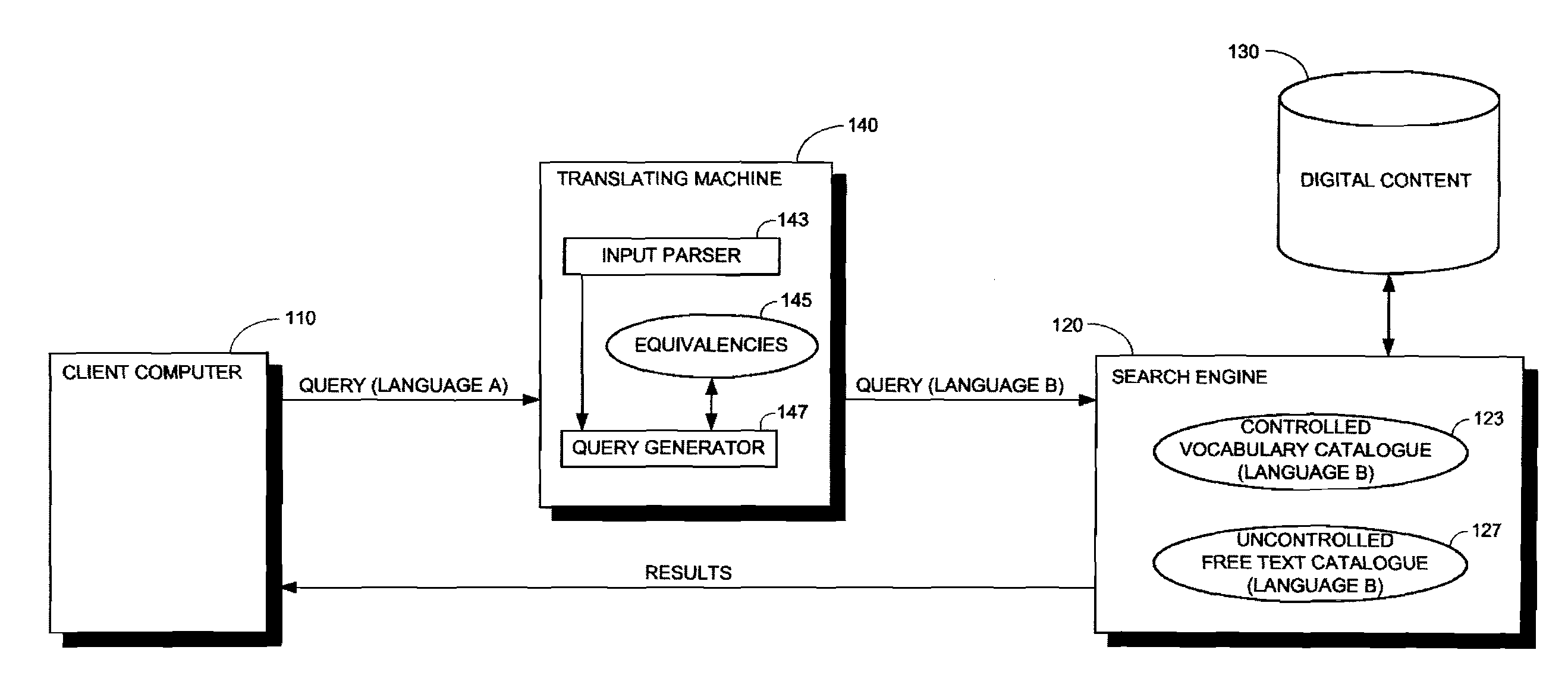
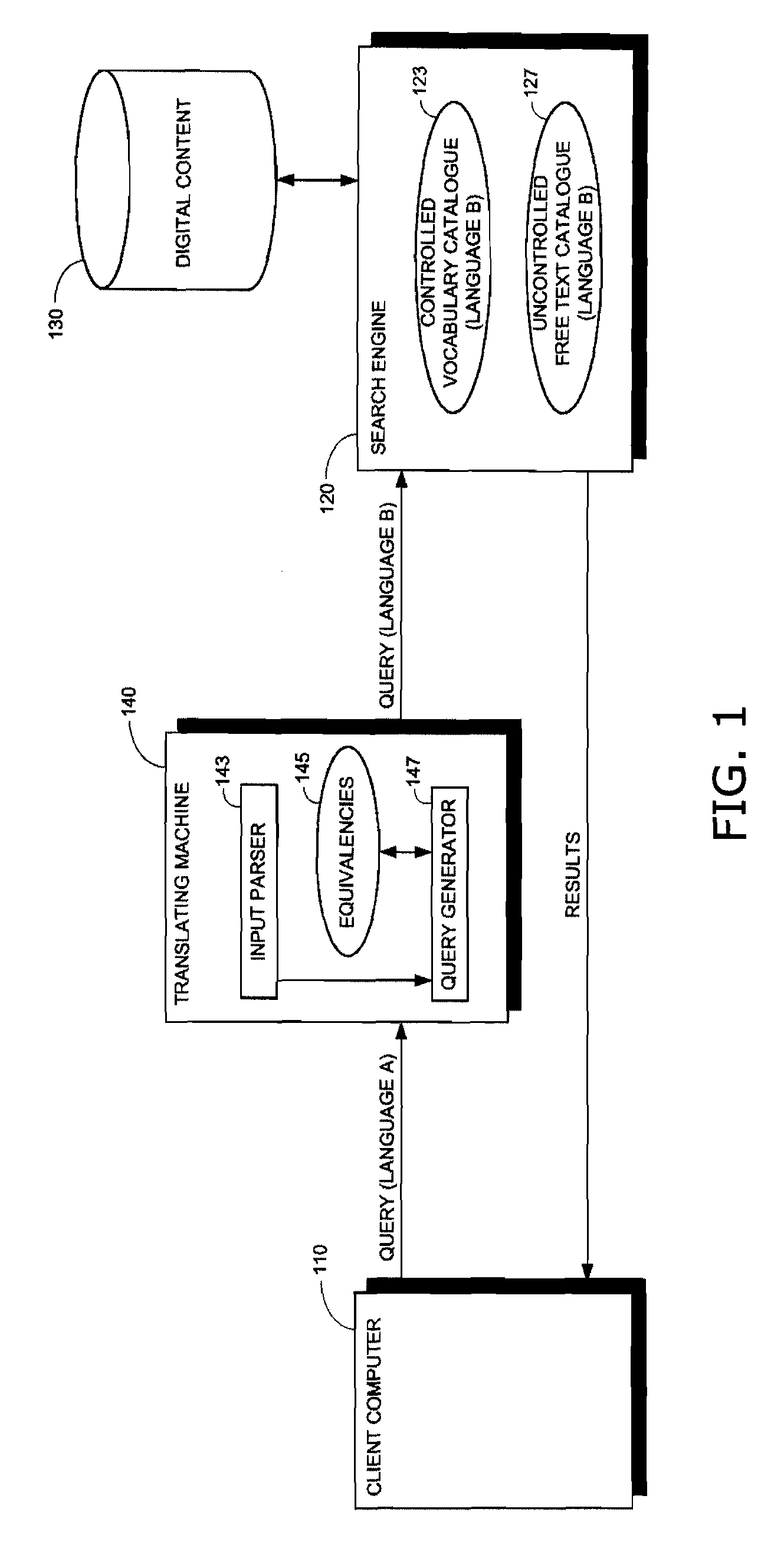
Cross-lingual information retrieval
InactiveUS20080275691A1Natural language translationDigital data information retrievalWord listSynonym
Multi-lingual search and retrieval of digital content. Embodiments are generally directed to methods and systems for creating an English language database that associates non-English terms with English terms in multiple categories of metadata. Language experts use an interface to create equivalencies between non-English terms and English terms, Boolean expressions, synonyms, and other forms of search terms. Language dictionaries and other sources also create equivalencies. The database is used to evaluate non-English search terms submitted by a user, and to determine English search terms that can be used to perform a search for content. The multiple categories of metadata may comprise structured data, such as keywords of a structured vocabulary, and / or unstructured data, such as captions, titles, descriptions, etc. Weighting and / or prioritization can be applied to the search terms, to the process of searching the multiple categories, and / or to the search results, to rank the search results.
Owner:BEN GRP INC
SQL statement optimization method based on constant substitution
ActiveCN103678621AEliminate dependenciesEliminate join conditionsSpecial data processing applicationsLinked listSQL
The invention discloses an SQL statement optimization method based on constant substitution. The SQL statement optimization method based on constant substitution comprises the following steps: step 1, a substitution chain table is created according to a Boolean expression of WHERE clauses in a target SQL statement; step 2, the substitution chain table is traversed and a driving expression is searched for, wherein the driving expression is an equivalent expression, one side of the equivalent condition is a column, the other side of the equivalent condition is a constant, the next step continues to be executed if the driving expression is found through searching, and the step 2 is ended otherwise; step 3, according to the current driving expression, constant substitution is conducted on the target SQL statement, the substitution chain table is adjusted, and the current driving expression is marked; step 4, a next driving expression continues to be searched for, the step 3 is executed again if the next driving expression is found through searching, and the step 4 is ended otherwise. The SQL statement optimization method based on constant substitution has the advantages of being high in optimization level, and capable of improving system performance substantially.
Owner:SHANGHAI DAMENG DATABASE
Method and system for processing electronic search expressions
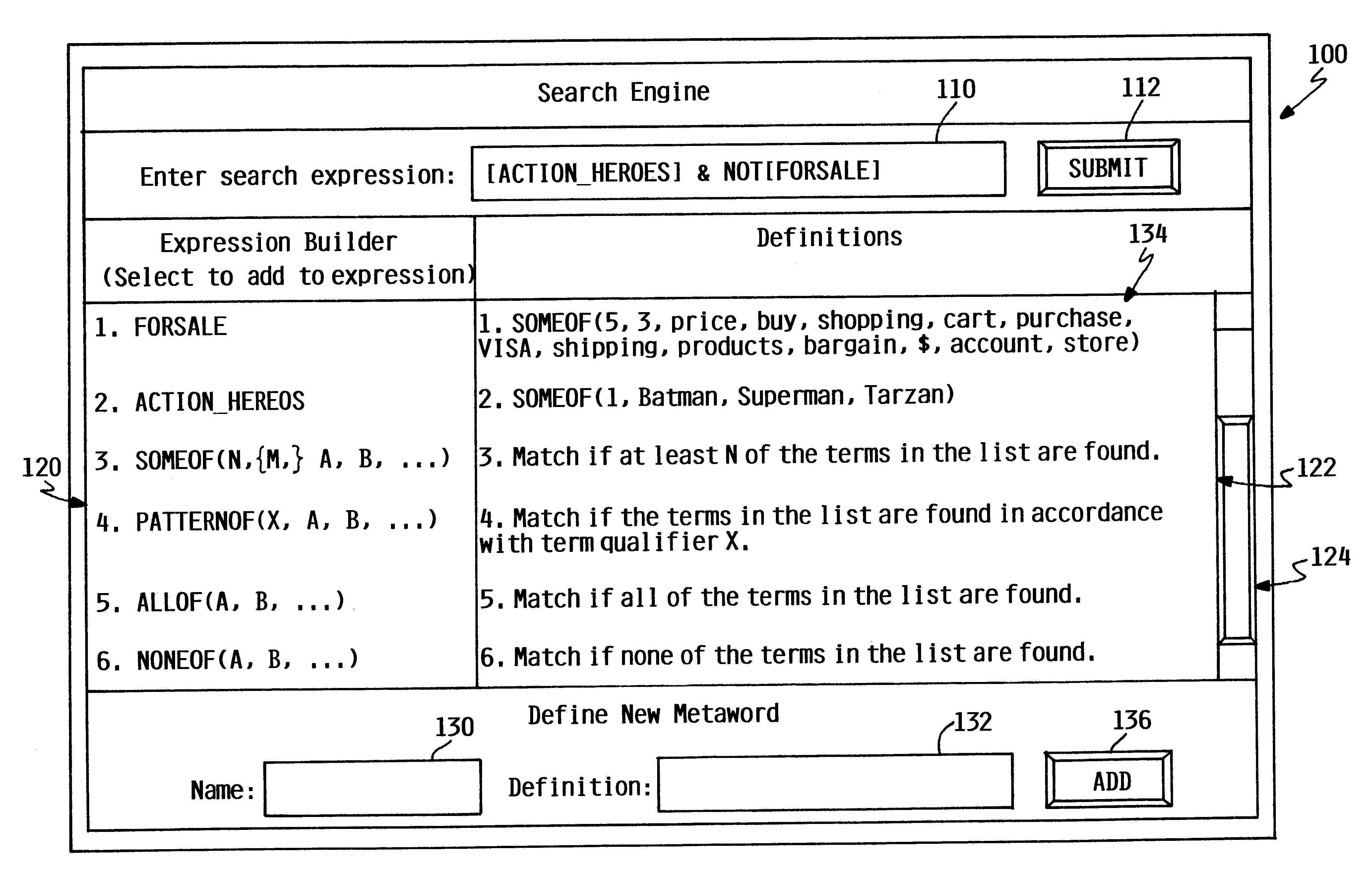
InactiveUS6598040B1Data processing applicationsDigital data information retrievalElectronic documentThreshold number
The present invention relates to a method, system, and program product for utilizing metawords to find electronic documents. According to the method of the present invention, a user specifies an initial search expression that includes at least one metaword. It is determined that the at least one metaword corresponds to a boolean expression, and, in response, an expanded search expression is generated. The expanded search expression includes the boolean expression in lieu of the at least one metaword, such that the expanded search expression is utilized in lieu of the initial search expression to find the electronic documents. In an illustrative embodiment, the determining step includes the step of determining that one or more terms and a count qualifier are associated with the at least one metaword. The count qualifier specifies a threshold number of occurrences of the one or more terms within a single electronic document.
Owner:GOOGLE LLC
System and method of evaluating network asserts
A method and apparatus of a device that evaluates multiple network asserts in response to changing network of network elements is described. In an exemplary embodiment, the device receives the multiple network asserts, where each of the plurality of network asserts represents a Boolean expression regarding a condition of at least one characteristic of at least one of the network elements. The device further detects a change in the network. In response to the detected change, the device, for one or more of the network asserts, evaluates this network assert to determine if this network asserts raises an action associated with this network assert. The device further performs the action associated this network assert if the network assert was raised.
Owner:ARISTA NETWORKS
Method and system for Boolean expression query optimization
ActiveUS7730053B2Efficient selectionReduce condition numberDigital data information retrievalDigital data processing detailsQuery optimizationComputerized system
Owner:SAP AG
System for automatically generating interlocking software based on Boolean logic
ActiveCN104049976AShorten development timeImprove work efficiencySpecific program execution arrangementsRelay logicDatabase analysis
The invention discloses a system for automatically generating interlocking software based on Boolean logic. The system comprises a database analysis module, a class module, a logic variable module, a logic tree module, a logic script generating module and a binary file generating module. The database analysis module receives original trackside data and screens out information needed by interlocking logic. The class module defines different types in the interlocking logic. The logic variable module defines class member variables and attributes of the class member variables. An interlocking logic rule base module defines grammatical rules based on the interlocking logic. The logic tree module is used for transforming a Boolean expression into a multi-fork tree structure. The logic script generating module is used for generating instantiated interlocking station interlocking scripts. The binary file generating module is used for generating instantiated interlocking station binary files. According to the automatically-generated interlocking software, a relay logic expression familiar to signal technicians serves as an expression form of codes, a rule base can be modified only in the mode similar to a natural language in the modification process, a large amount of development time is saved, and work efficiency is improved.
Owner:SHANGHAI ELECTRIC THALES TRANSPORTATION AUTOMATION SYST CO LTD
Method and apparatus for optimizing boolean expression evaluation
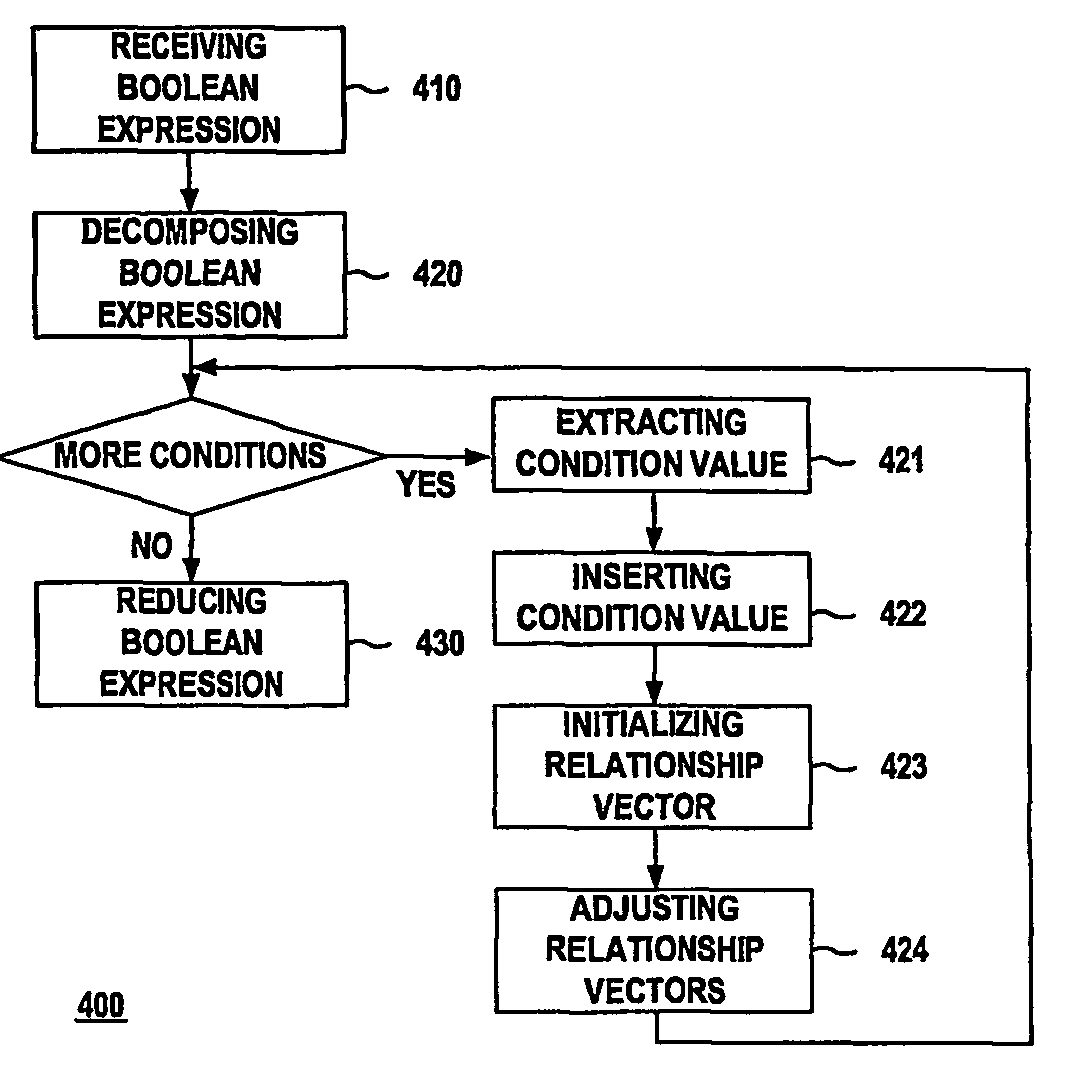
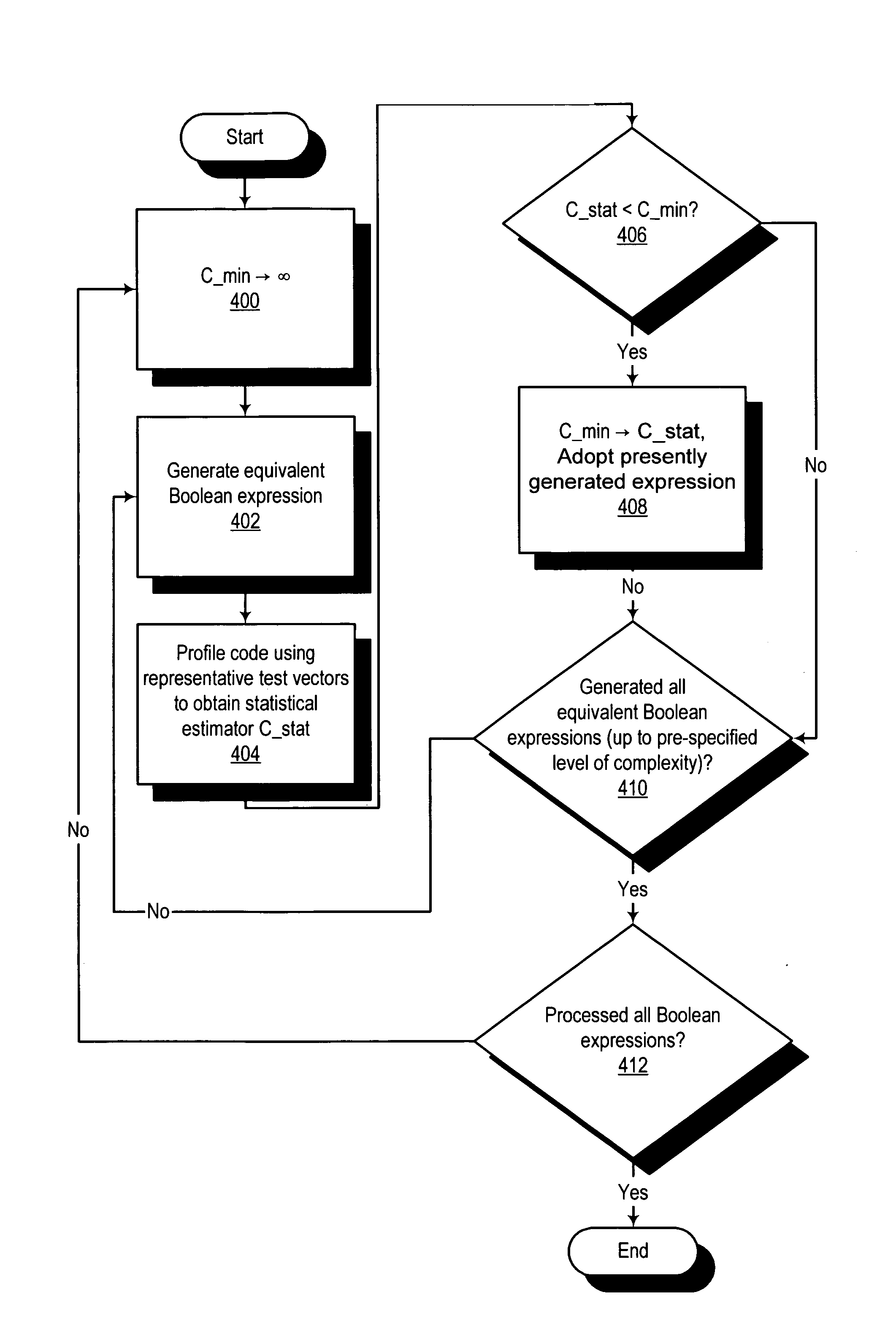
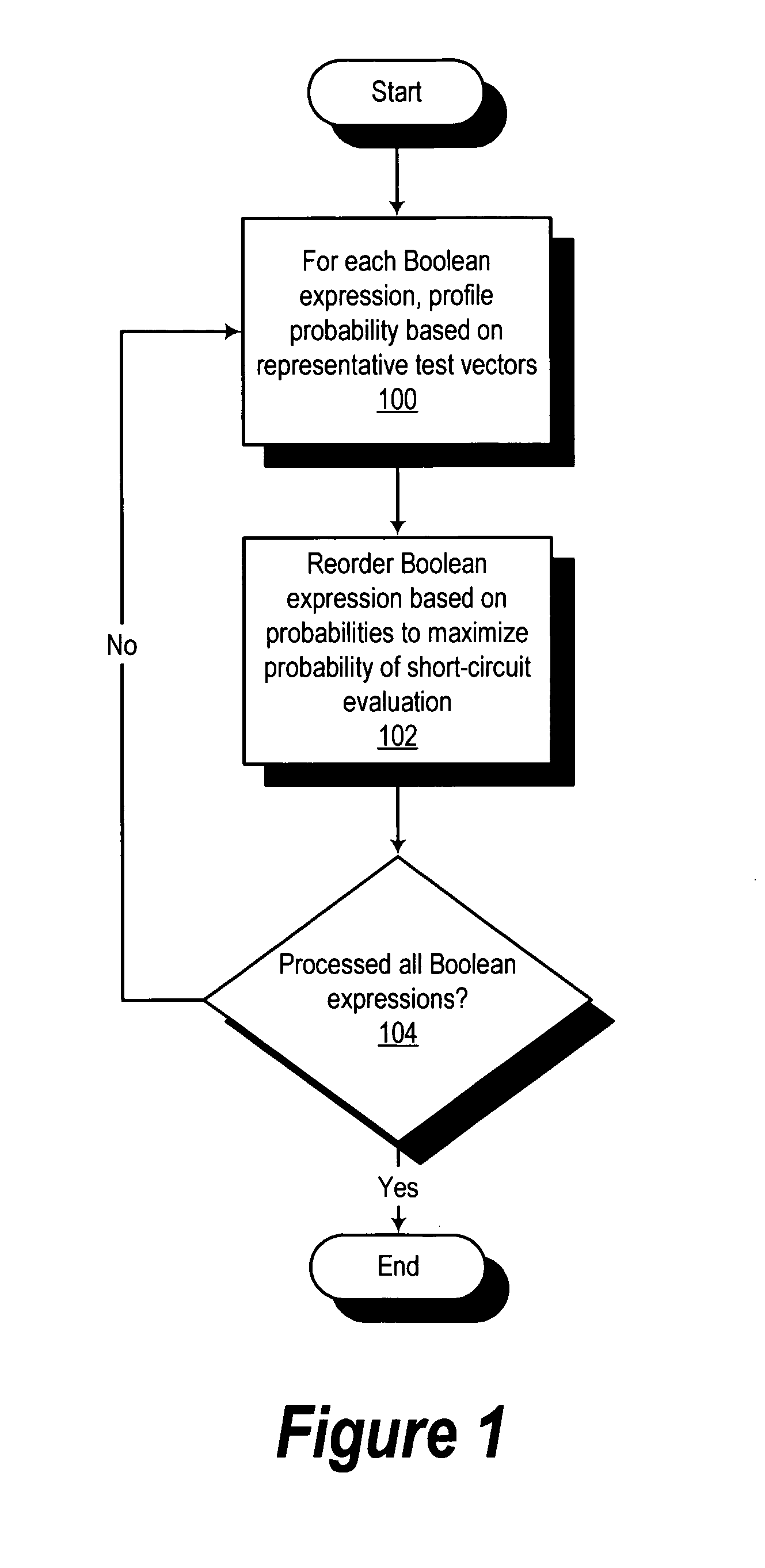
ActiveUS20070174830A1Software engineeringSpecific program execution arrangementsData processing systemTheoretical computer science
A method, computer program product, and data processing system for performing automated optimization of a control processing flow containing Boolean conditional expressions is disclosed. Each conditional expression is profiled using a representative set of test vectors to determine the probabilities of individual conditions and combinations of conditions in the expression. Next, the expression is restructured or reordered, including selective computation of subexpressions, based on the probability information, so as to maximize the probability of a short-circuit termination of evaluation of the expression and / or to minimize the statistical execution time of the expression. This process is performed for all Boolean conditional expressions related to the control processing flow.
Owner:NXP USA INC
Private key fixed-length ciphertext-policy attribute-based encryption method
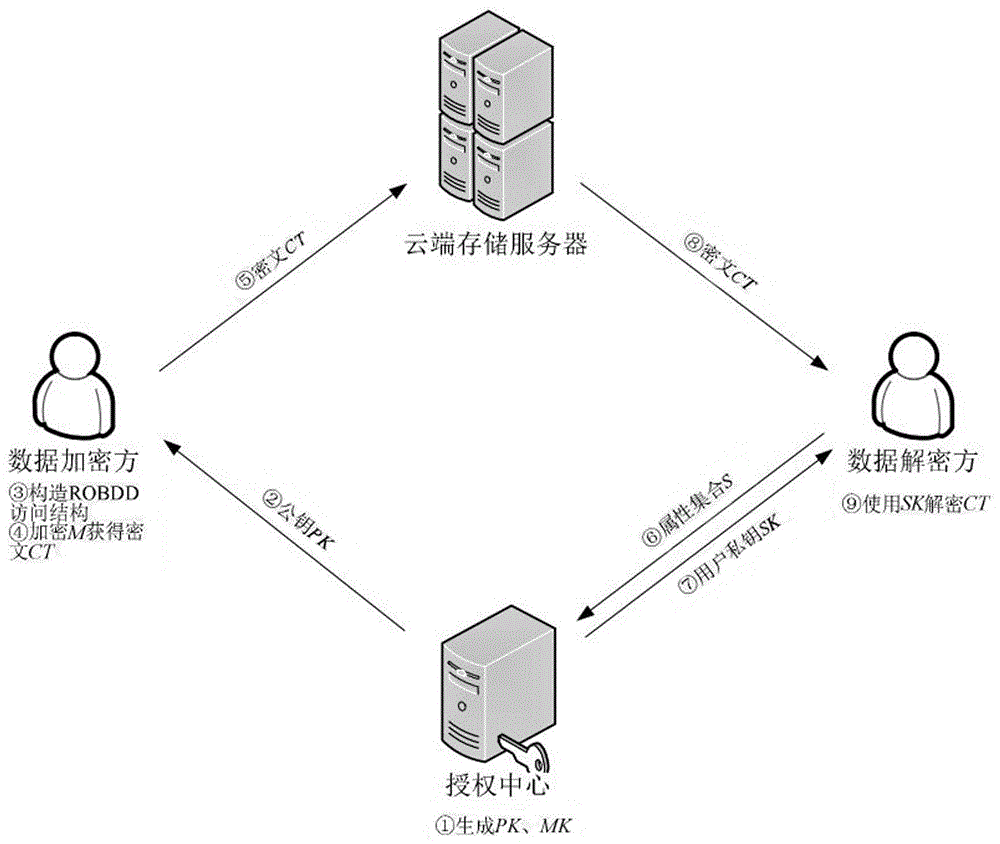
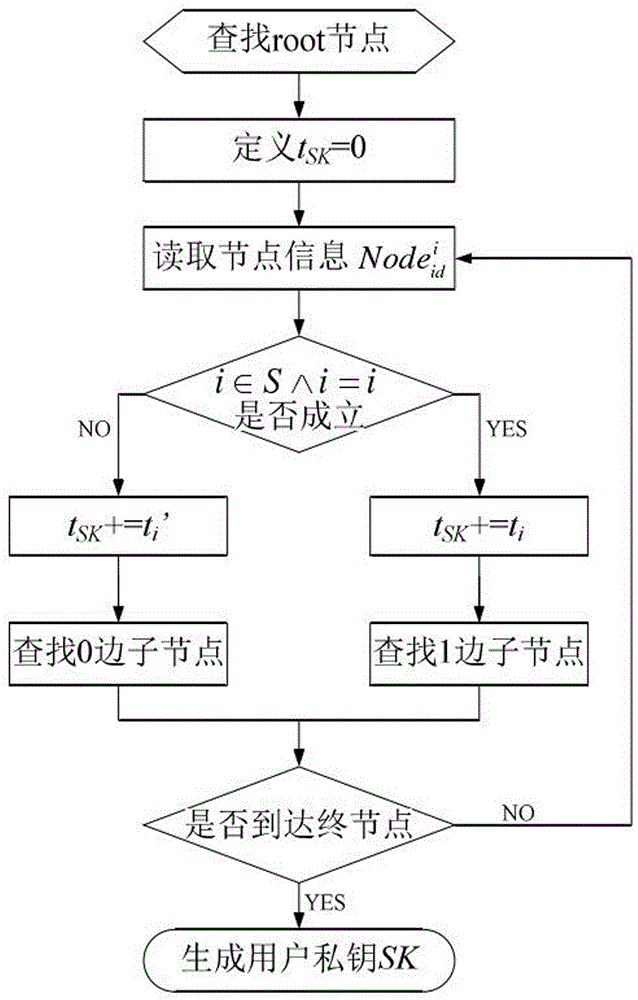
ActiveCN106850224AEnhance expressive abilityQuick decryptionPublic key for secure communicationPlaintextCiphertext
The invention discloses a private key fixed-length ciphertext-policy attribute-based encryption method. The method comprises two parts of core content of an access structure based on a simplified ordering binary decision diagram and a ciphertext-policy attribute-based encryption method based on the access structure, and implementation of the two parts of the content mainly comprises four entities of a data encryption party, a data decryption party, an authorization center and a cloud storage server; the implementation process comprises the following four steps of 1 system establishment, 2 plaintext encryption (including construction of the access structure), 3 private key generation and 4 ciphertext decryption. The access structure included in the technical scheme can support access policies represented by any Boolean expressions, and the higher working capacity and the higher working efficiency are achieved; the encryption method in the technical scheme has the advantages of being high in access structure working performance, extremely small in user private key occupied space, fixed in length, capable of achieving rapid decryption and the like, and the overall performance is more flexible and efficient.
Owner:GUILIN UNIV OF ELECTRONIC TECH
General method for generating station data
InactiveCN101593226AImprove work efficiencyRailway traffic control systemsSpecial data processing applicationsData miningObject oriented technology
The invention relates to a general method for generating station data, which comprises the following steps: sequentially acquiring names of rule bases from a time table, such as Name 1; finding out rule entries having a rule base name of the Name 1 in the rule base; finding out corresponding configuration parameters in a parameter declaration table through type codes in the rule entries; selecting a mode of continuous generation by using key words in a rule description; and after one role is generated, continuing to generate Name 2 according to the time table. Compared with the prior art, the method adopts object-oriented technology ensuring what you see is what you get, uses a traversal method for automatically generating an interlocked route sheet and adopts an open customizable mode that allows a user to make certain corrections of the rule base when a Boolean expression is generated automatically and improves working efficiency in application.
Owner:CASCO SIGNAL
Computerized information search and indexing method, software and device
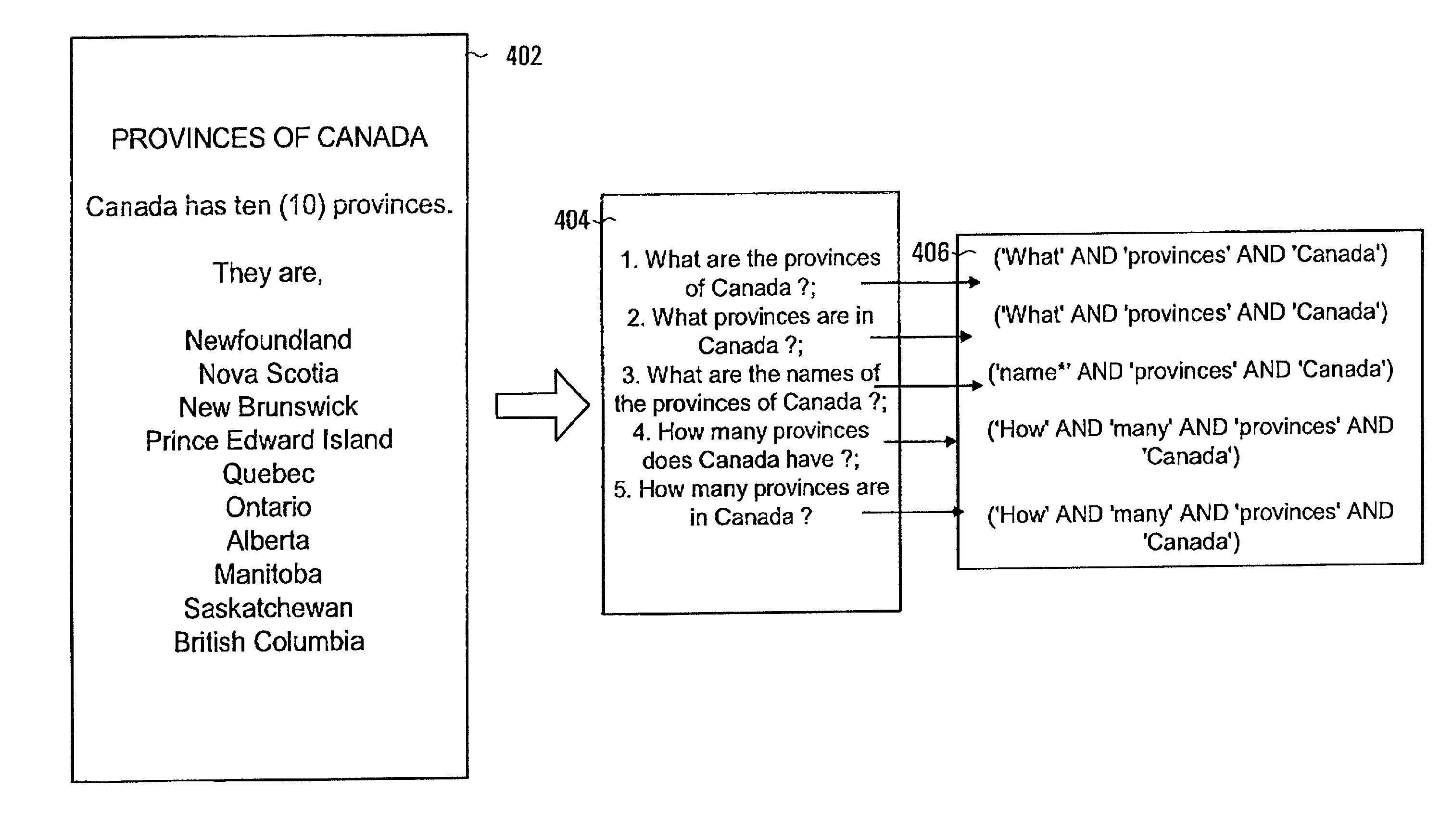
InactiveUS7171409B2Data processing applicationsDigital data information retrievalInformation searchingSoftware
Methods, software and devices for searching and indexing information are disclosed. Information to be searched is organized as a plurality of responses to queries. A Boolean expression is associated with each response. The Boolean expression for each response is applied to a received query for information. Which of the responses is or are presented is based on the results of the application of the Boolean expressions to the query.
Owner:INTELLIRESPONSE SYST
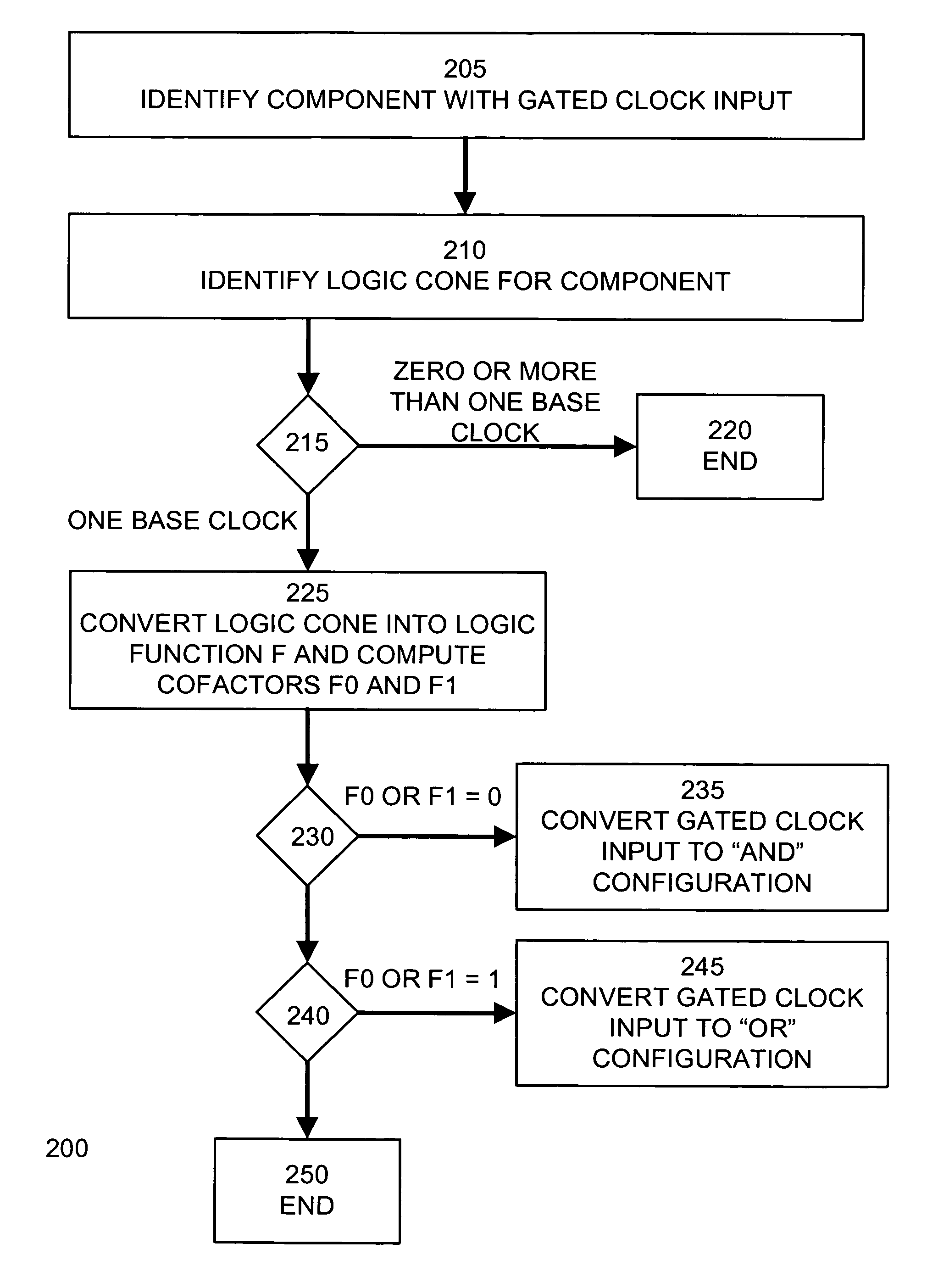
Gated clock conversion
InactiveUS7424689B1Reduce expressionCAD circuit designSoftware simulation/interpretation/emulationData signalComputer science
Gated clock signals in ASIC designs are automatically optimized for implementation with a programmable device. Components having gated clock signals are identified and converted to operate directly from the base clock signal. To maintain compatibility, the data signal to the component is modified to connect with additional input logic responsive to a clock enable signal. The input logic modifies the signal received by the component's data input so that the component's output in response to the clock enable signal is unchanged. To this end, a system and method may identify the logic cone associated with a gated clock signal, convert this logic cone into a Boolean expression, and determine cofactors of the base clock signal from this Boolean expression. The input logic and clock enable logic are derived from an analysis of the cofactors of the base clock signal.
Owner:ALTERA CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com