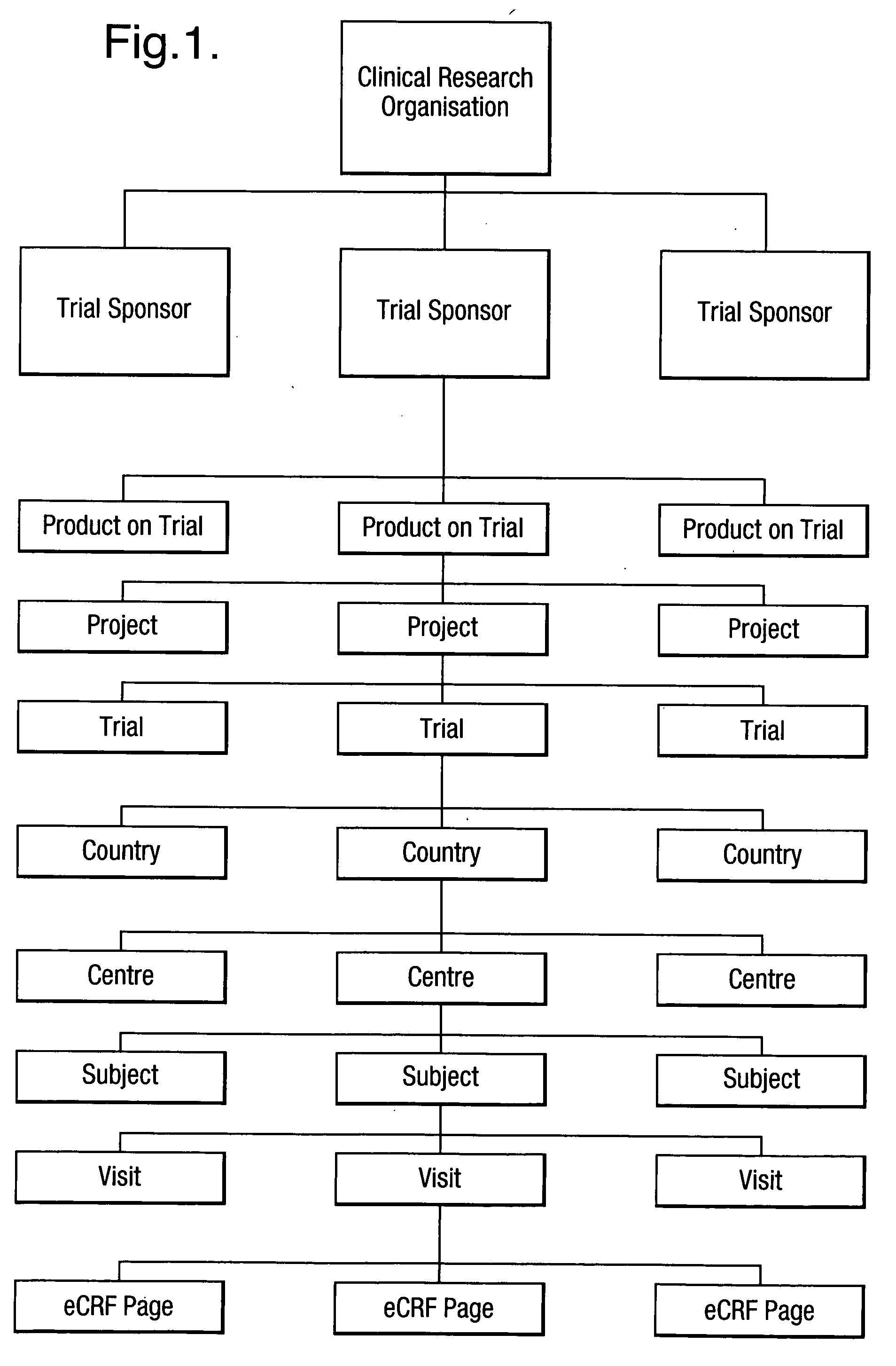
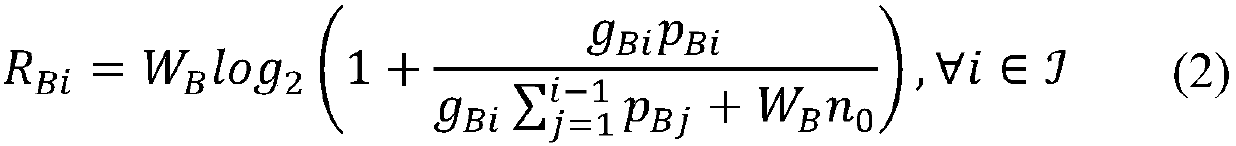Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
192 results about "Efficient algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Algorithm efficiency A measure of the average execution time necessary for an algorithm to complete work on a set of data. Algorithm efficiency is characterized by its order. Typically a bubble sort algorithm will have efficiency in sorting N items proportional to and of the order of N2, usually written O( N2 ).
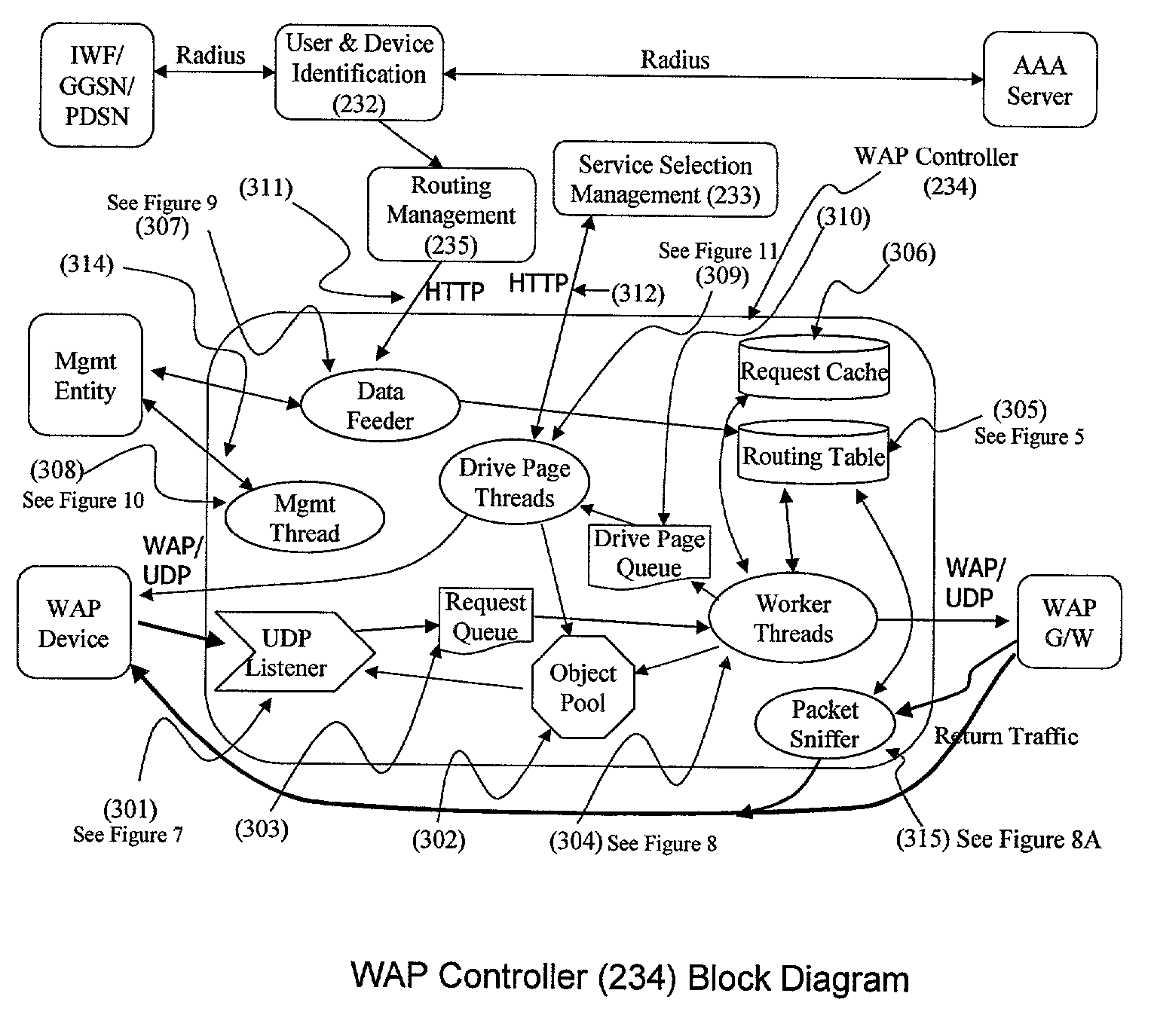
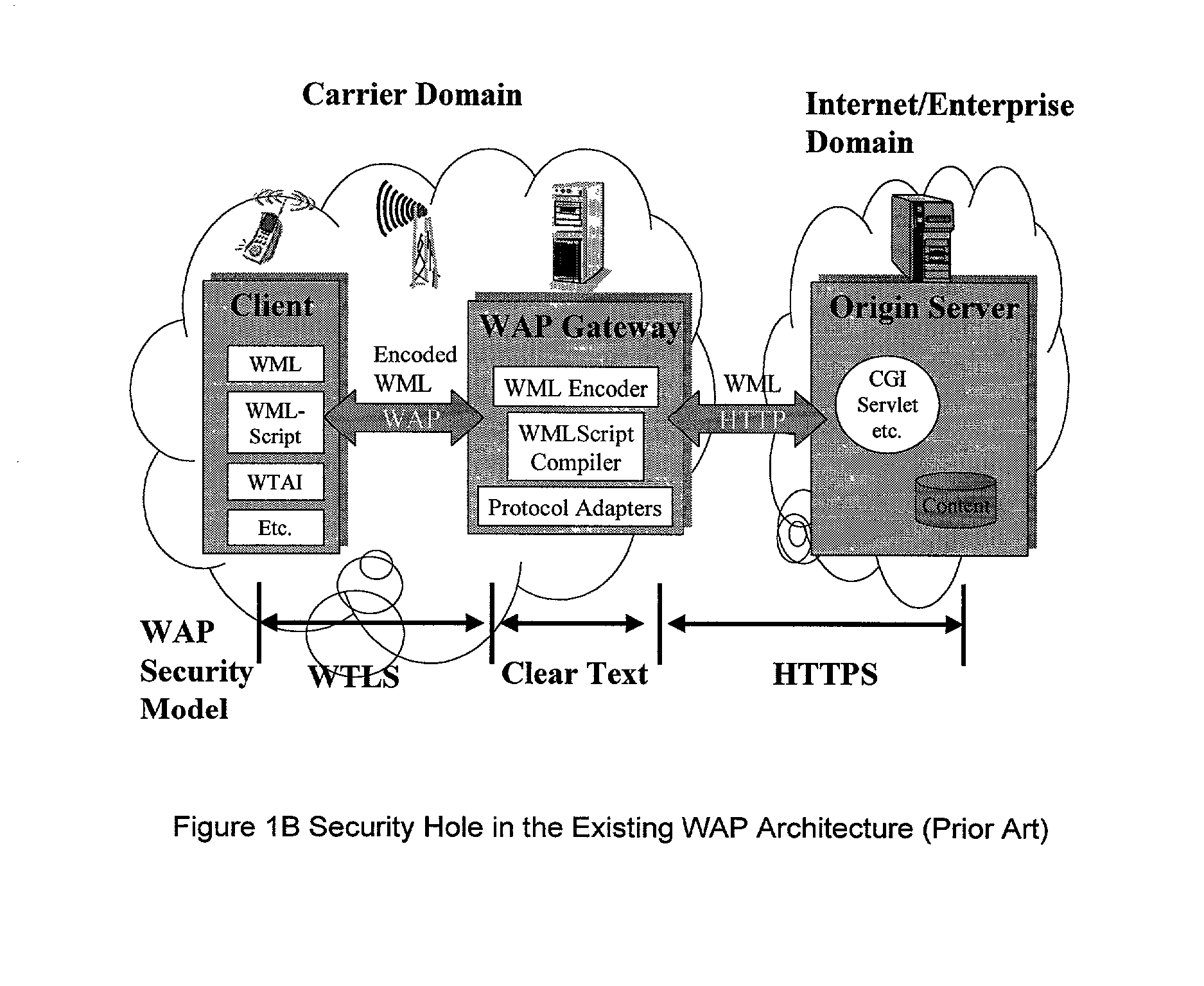
Method and apparatus for providing service selection, redirection and managing of subscriber access to multiple WAP (Wireless Application Protocol) gateways simultaneously
ActiveUS7039037B2Time-division multiplexData switching by path configurationCyber operationsComputer network
A method (FIG. 5) and apparatus (FIG. 3) to provide control and policy enforcement of WAP (Wireless Application Protocol) services in a wireless data networks is taught herein. WAP traffic is inspected with efficient algorithms to intercept un-registered WAP access and intercept dynamic change of user service selection. The intercepted WAP requests are modified with value-added parameters (such as QoS and subscriber identifiers) as per user and service provider agreement and table data. A series of strategies are described to blend wireless intelligence, user preference and service subscription, network operator requirements and service provider or enterprise preferences into routing and drive page generation. The means to dynamically provision users' service choices to wireless network elements are also presented without having to break the session within the system. This enables innovative data services such as pay-per-use, smart routing, and enterprise secured WAP services unlike any current conventional system.
Owner:MAVENIR SYST INC
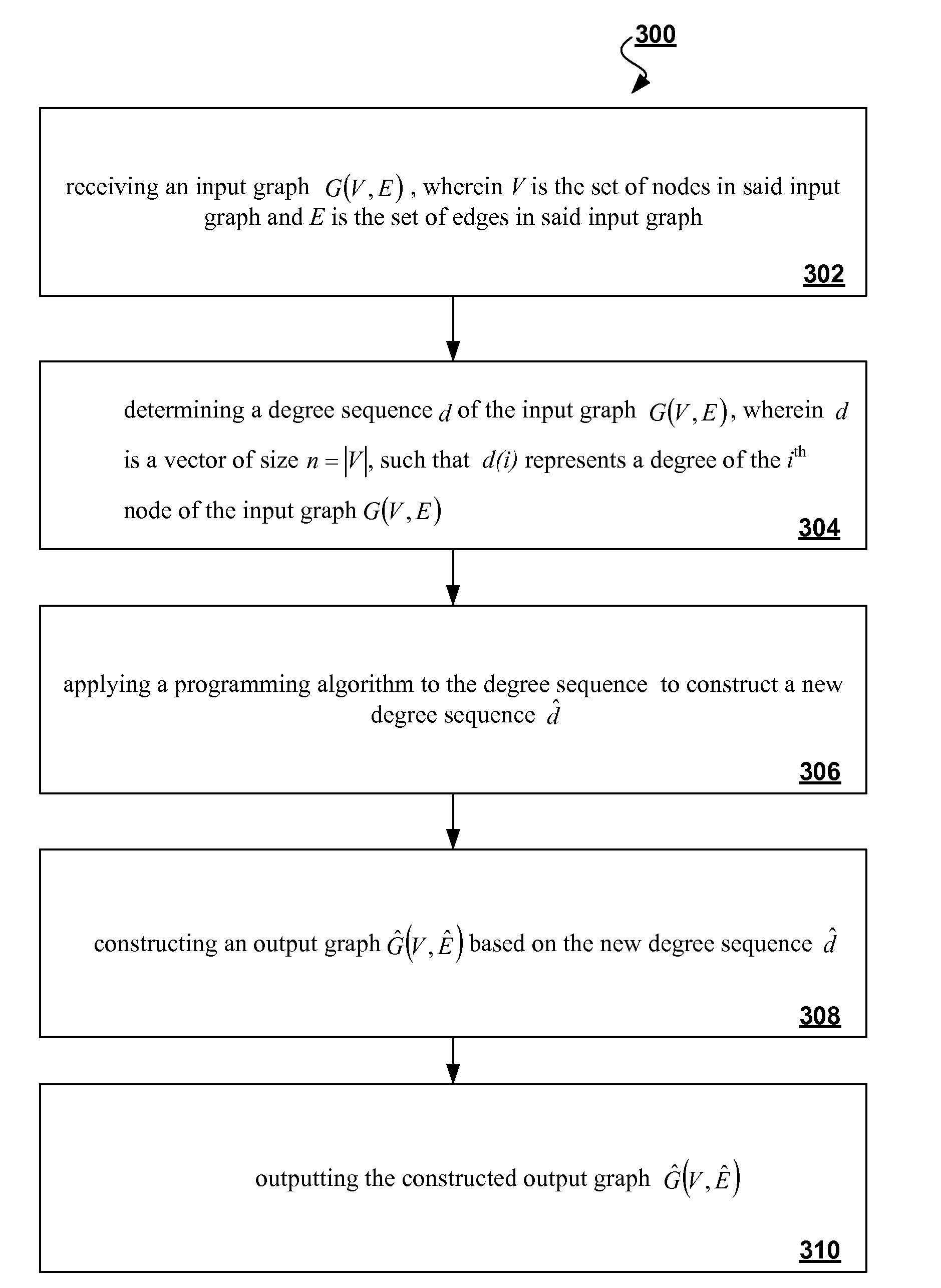
Algorithms for identity anonymization on graphs
InactiveUS20090303237A1Preserving individual privacy and basic structure of networkDrawing from basic elementsTransmissionGraphicsRe identification
The proliferation of network data in various application domains has raised privacy concerns for the individuals involved. Recent studies show that simply removing the identities of the nodes before publishing the graph / social network data does not guarantee privacy. The structure of the graph itself, and in is basic form the degree of the nodes, can be revealing the identities of individuals. To address this issue, a specific graph-anonymization framework is proposed. A graph is called k-degree anonymous if for every node v, there exist at least k−1 other nodes in the graph with the same degree as v. This definition of anonymity prevents the re-identification of individuals by adversaries with a priori knowledge of the degree of certain nodes. Given a graph G, the proposed graph-anonymization problem asks for the k-degree anonymous graph that stems from G with the minimum number of graph-modification operations. Simple and efficient algorithms are devised for solving this problem, wherein these algorithms are based on principles related to the realizability of degree sequences.
Owner:IBM CORP
Method and apparatus for providing service selection, redirection and managing of subscriber access to multiple WAP (Wireless Application Protecol) geteways simultaneously
ActiveUS20030035409A1Time-division multiplexData switching by path configurationCyber operationsTraffic capacity
A method (FIG. 5) and apparatus (FIG. 3) to provide control and policy enforcement of WAP (Wireless Application Protocol) services in a wireless data networks is taught herein. WAP traffic is inspected with efficient algorithms to intercept un-registered WAP access and intercept dynamic change of user service selection. The intercepted WAP requests are modified with value-added parameters (such as QoS and subscriber identifiers) as per user and service provider agreement and table data. A series of strategies are described to blend wireless intelligence, user preference and service subscription, network operator requirements and service provider or enterprise preferences into routing and drive page generation. The means to dynamically provision users' service choices to wireless network elements are also presented without having to break the session within the system. This enables innovative data services such as pay-per-use, smart routing, and enterprise secured WAP services unlike any current conventional system.
Owner:MAVENIR SYSTEMS
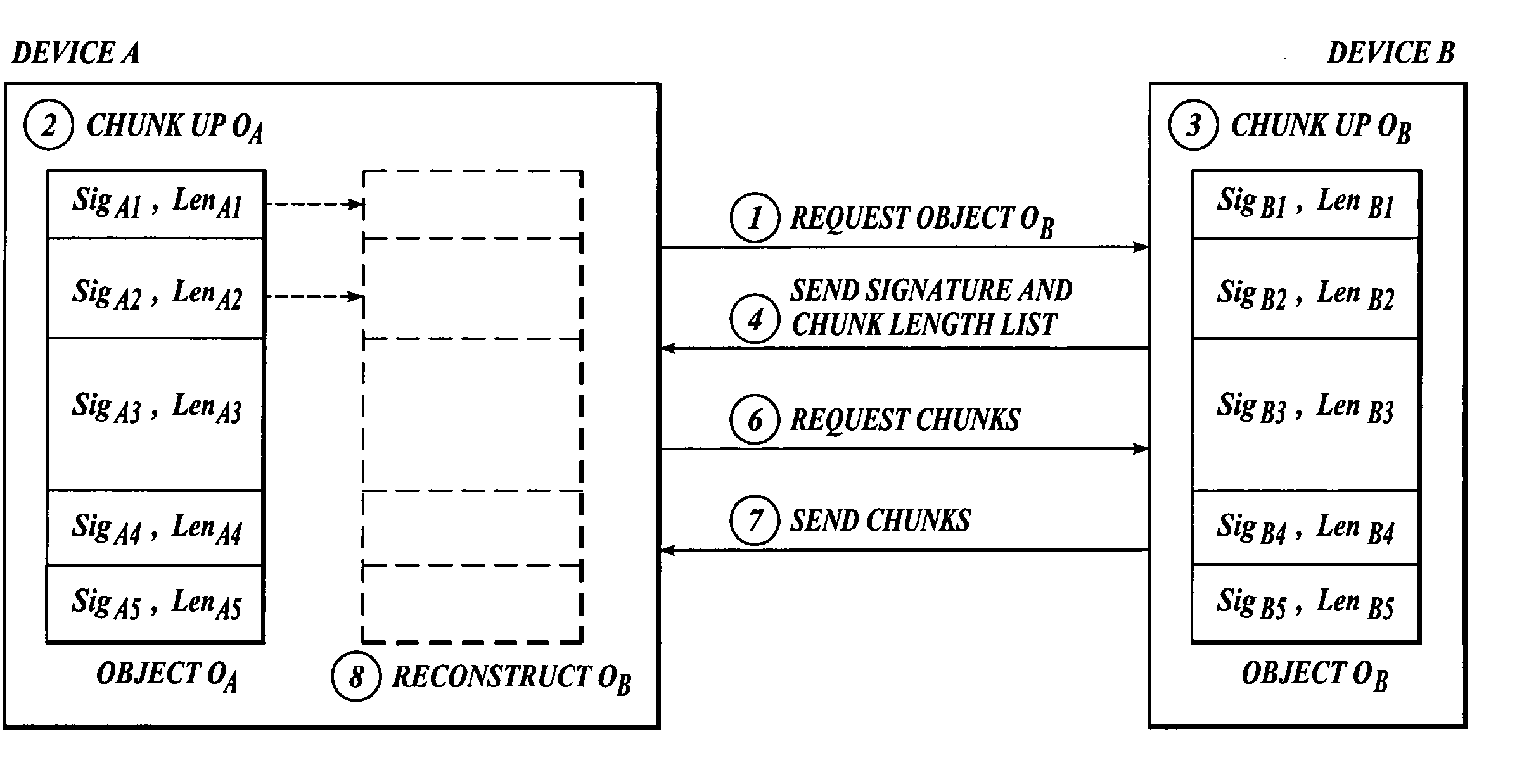
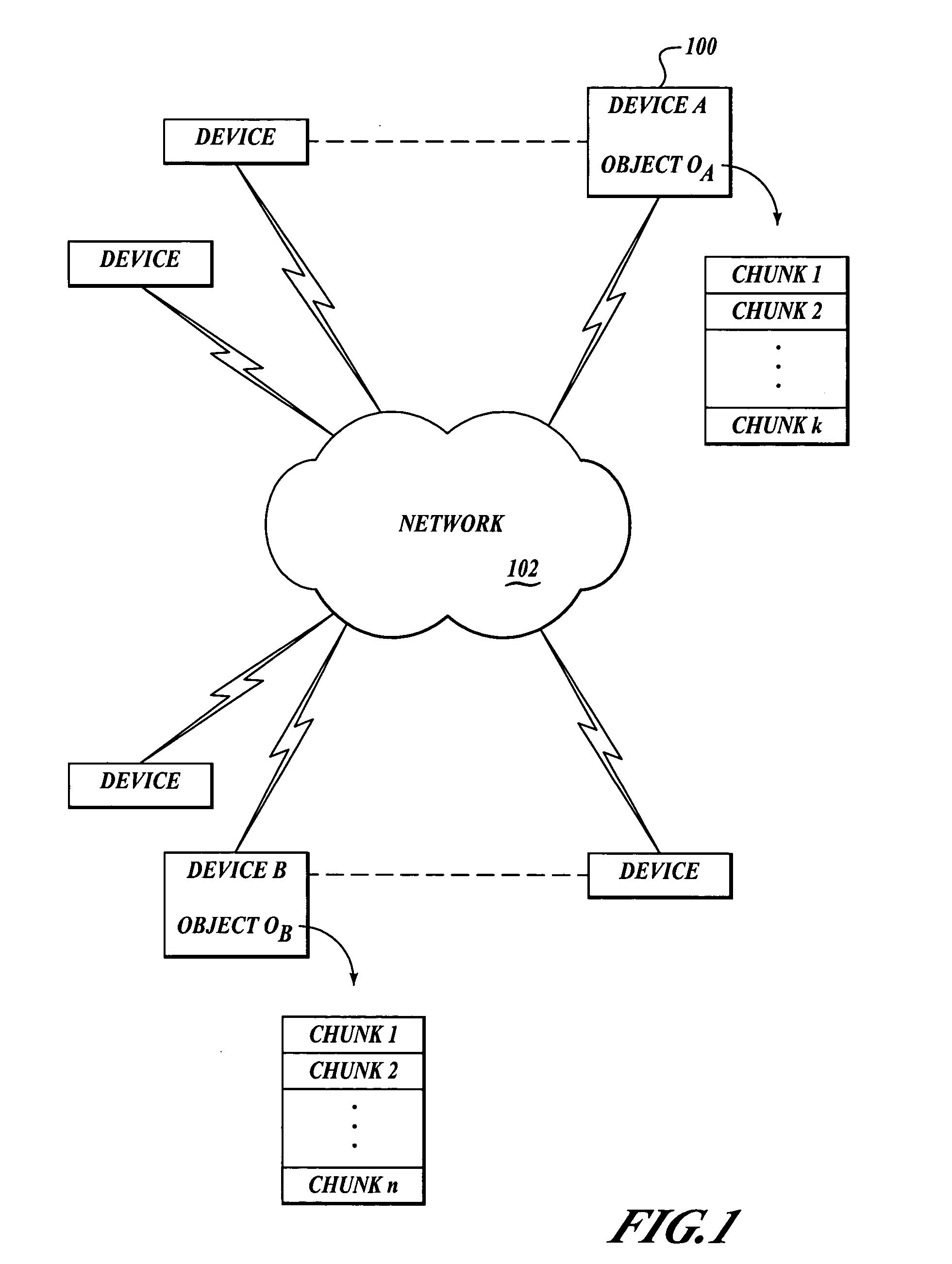
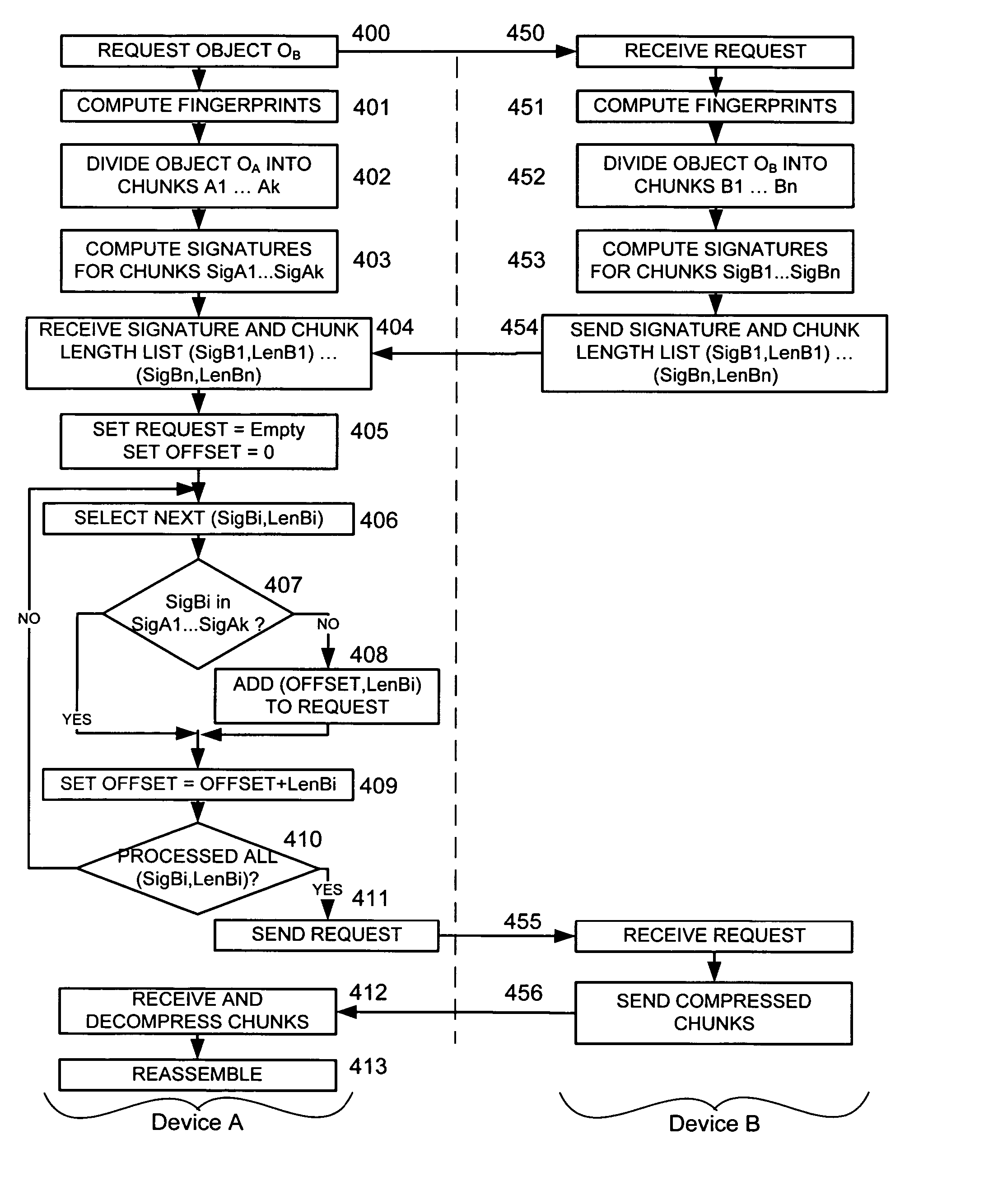
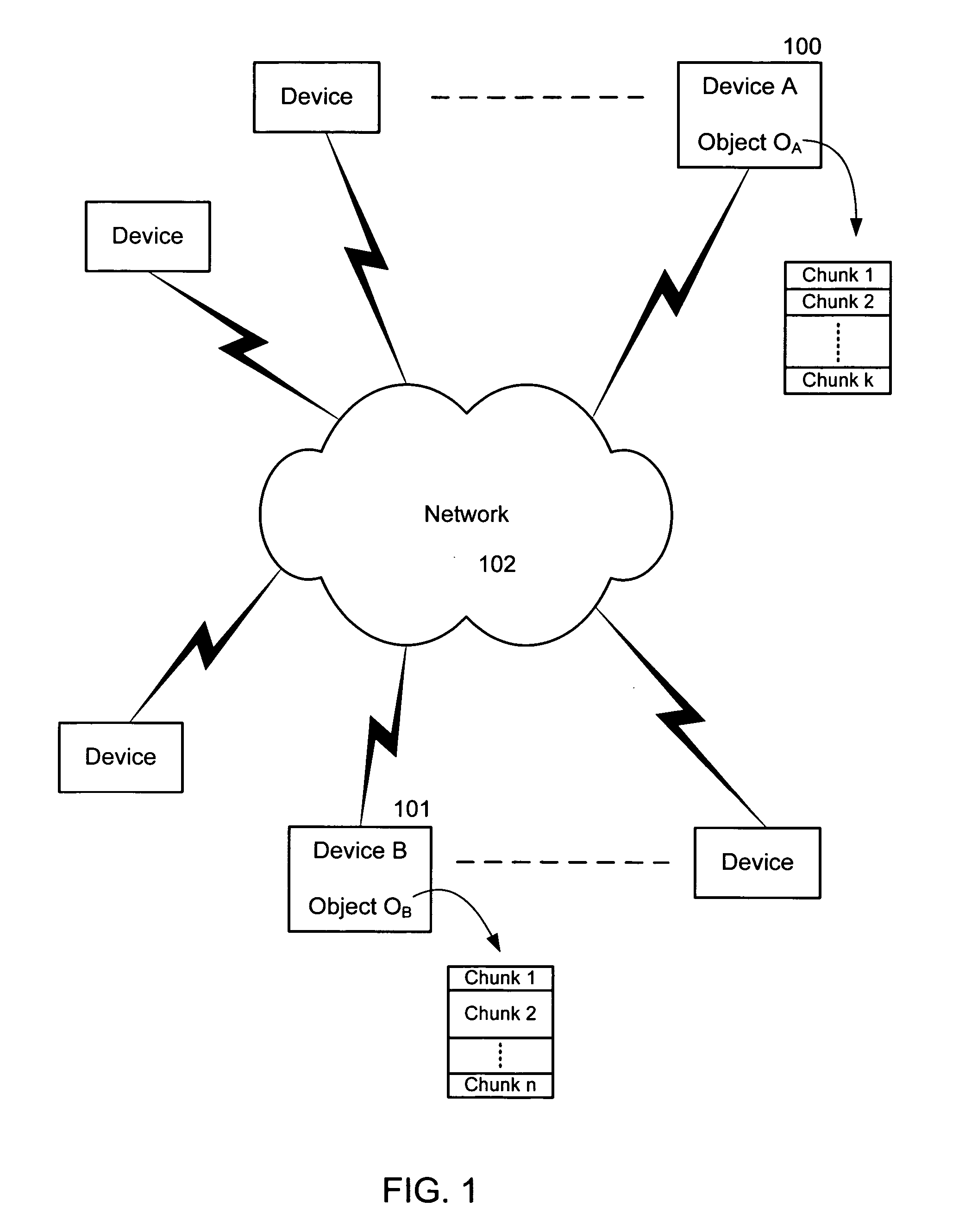
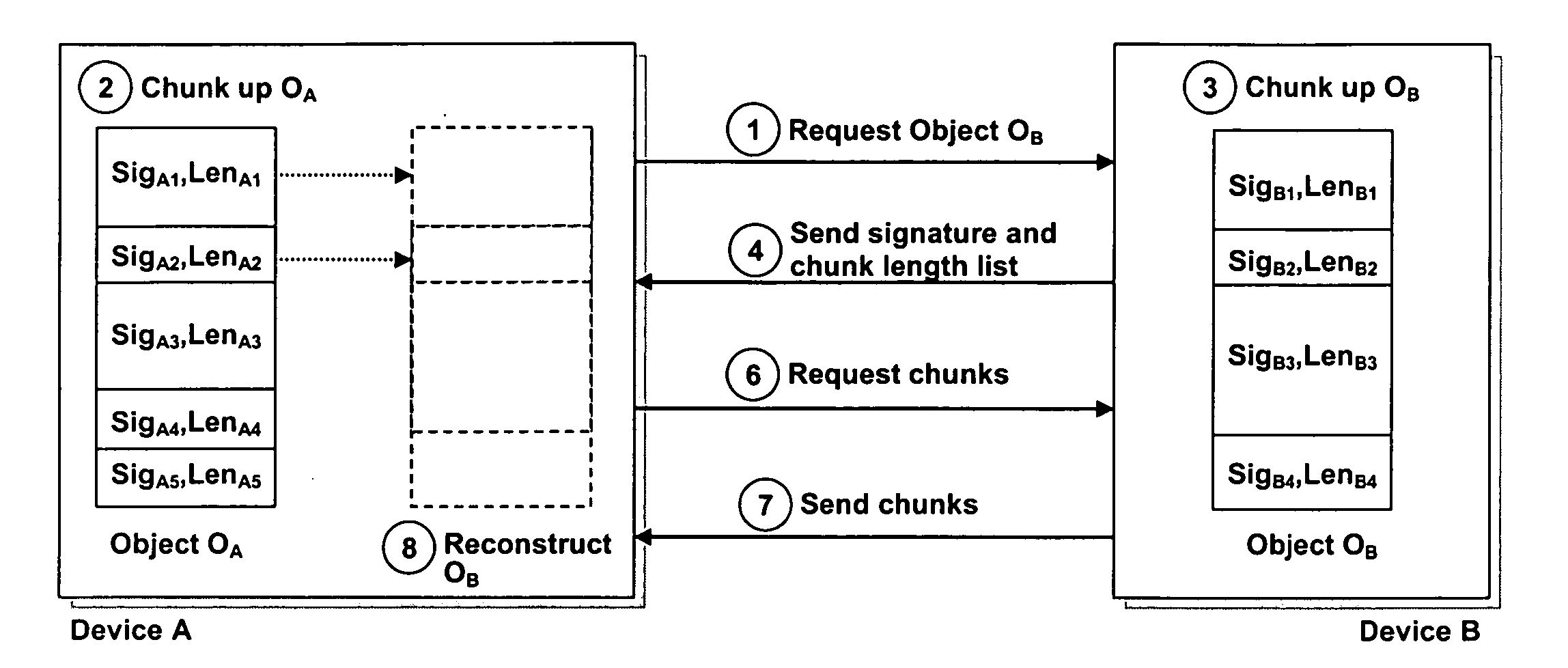
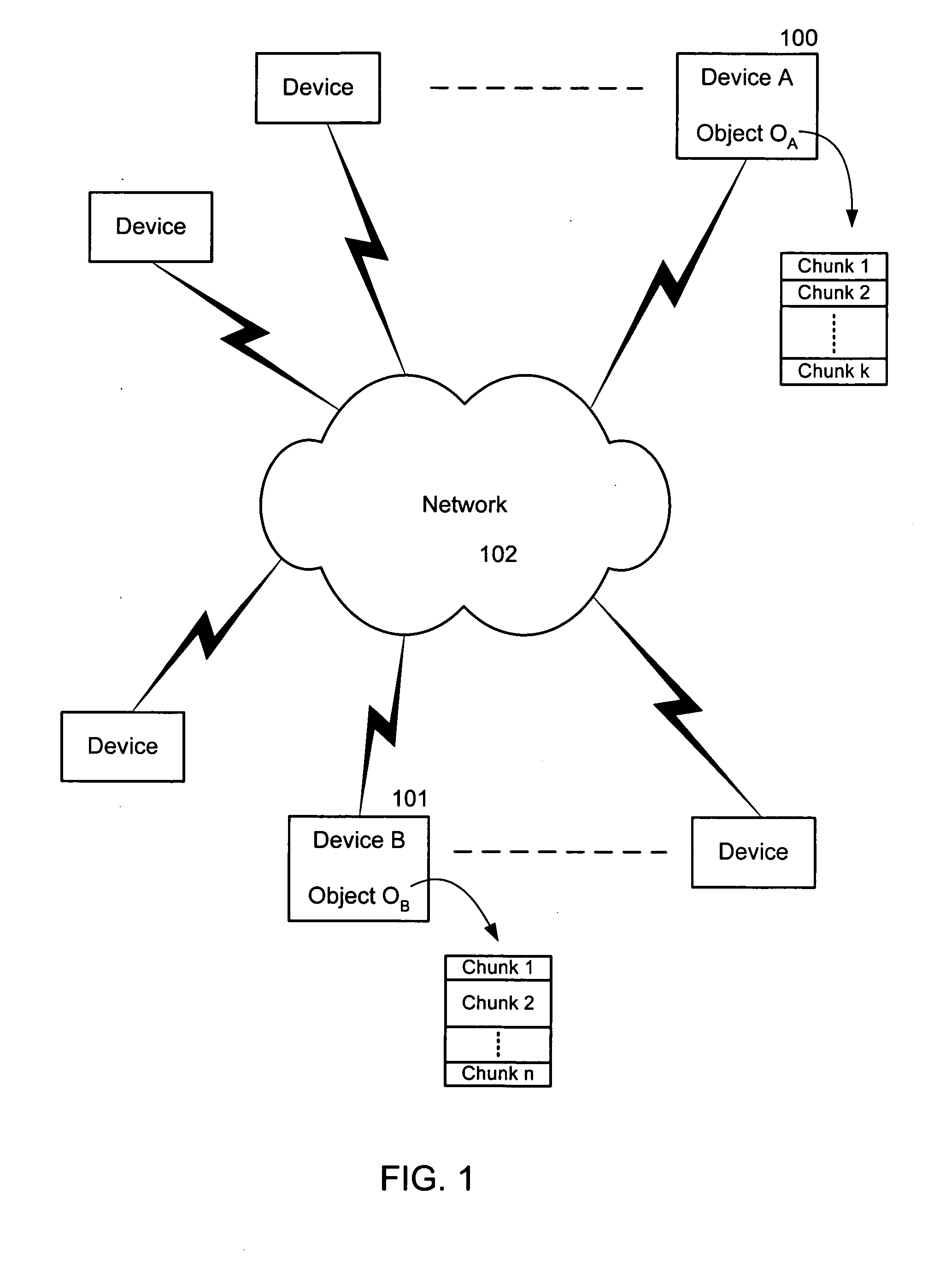
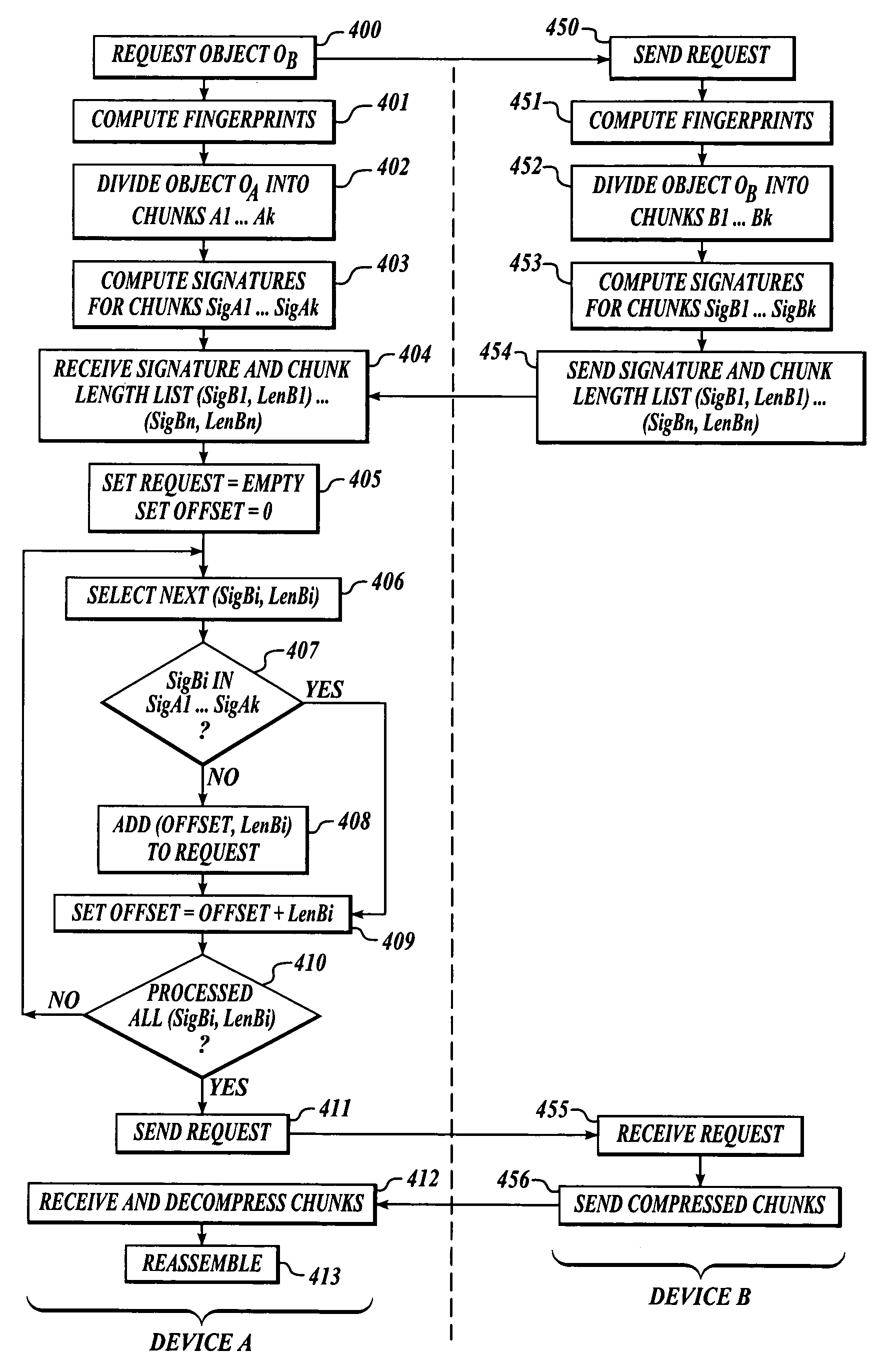
Efficient algorithm and protocol for remote differential compression
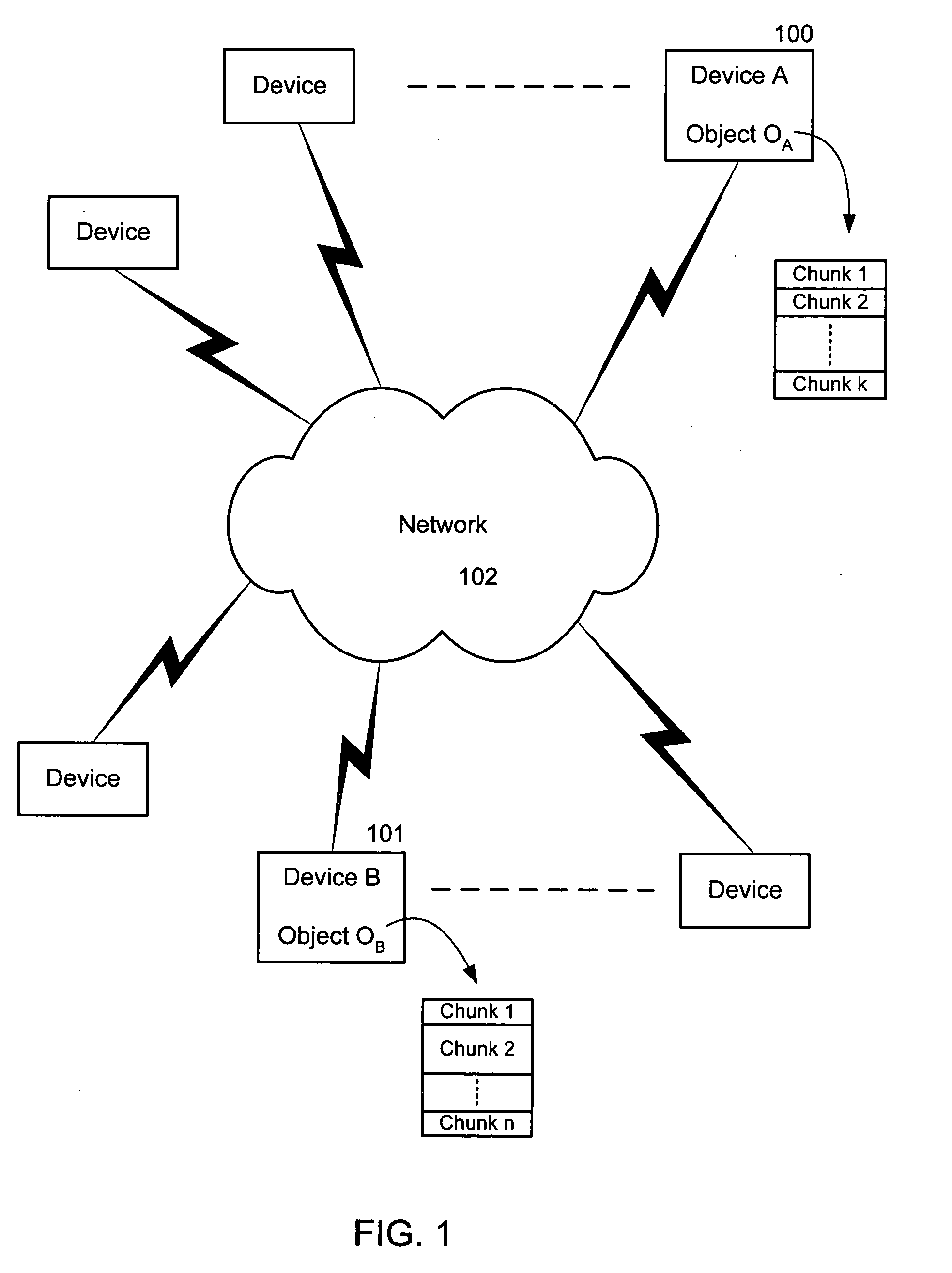
A method and system are related to updating objects over limited bandwidth networks. Objects are updated between two or more computing devices using remote differential compression (RDC) techniques such that required data transfers are minimized. In one aspect, efficient large object transfers are achieved by recursively applying the RDC algorithm to its own metadata; a single or multiple recursion step(s) may be used in this case to reduce the amount of metadata sent over the network by the RDC algorithm. Objects and / or signature and chunk length lists can be chunked by locating boundaries at dynamically determined locations. A mathematical function evaluates hash values associated within a horizon window relative to potential chunk boundary. The described method and system is useful in a variety of networked applications, such as peer-to-peer replicators, email clients and servers, client-side caching systems, general-purpose copy utilities, database replicators, portals, software update services, file / data synchronization, and others.
Owner:MICROSOFT TECH LICENSING LLC
Efficient algorithm for finding candidate objects for remote differential compression
ActiveUS20060085561A1Improve efficiencyMinimize data transferDigital data information retrievalMultiple digital computer combinationsData transmissionEfficient algorithm
The present invention finds candidate objects for remote differential compression. Objects are updated between two or more computing devices using remote differential compression (RDC) techniques such that required data transfers are minimized. An algorithm provides enhanced efficiencies for allowing the receiver to locate a set of objects that are similar to the object that needs to be transferred from the sender. Once this set of similar objects has been found, the receiver may reuse any chunks from these objects during the RDC algorithm.
Owner:MICROSOFT TECH LICENSING LLC
Efficient algorithm and protocol for remote differential compression on a local device
InactiveUS20050262167A1Structured data retrievalSpecial data processing applicationsHorizonTheoretical computer science
The present invention is used to update objects over limited bandwidth networks. Objects are updated between two or more computing devices using remote differential compression (RDC) techniques such that required data transfers are minimized. In one aspect, efficient large object transfers are achieved by recursively applying the RDC algorithm to its own metadata; a single or multiple recursion step(s) may be used in this case to reduce the amount of metadata sent over the network by the RDC algorithm. Objects and / or signature and chunk length lists can be chunked by locating boundaries at dynamically determined locations. A mathematical function evaluates hash values associated within a horizon window relative to potential chunk boundary.
Owner:MICROSOFT TECH LICENSING LLC
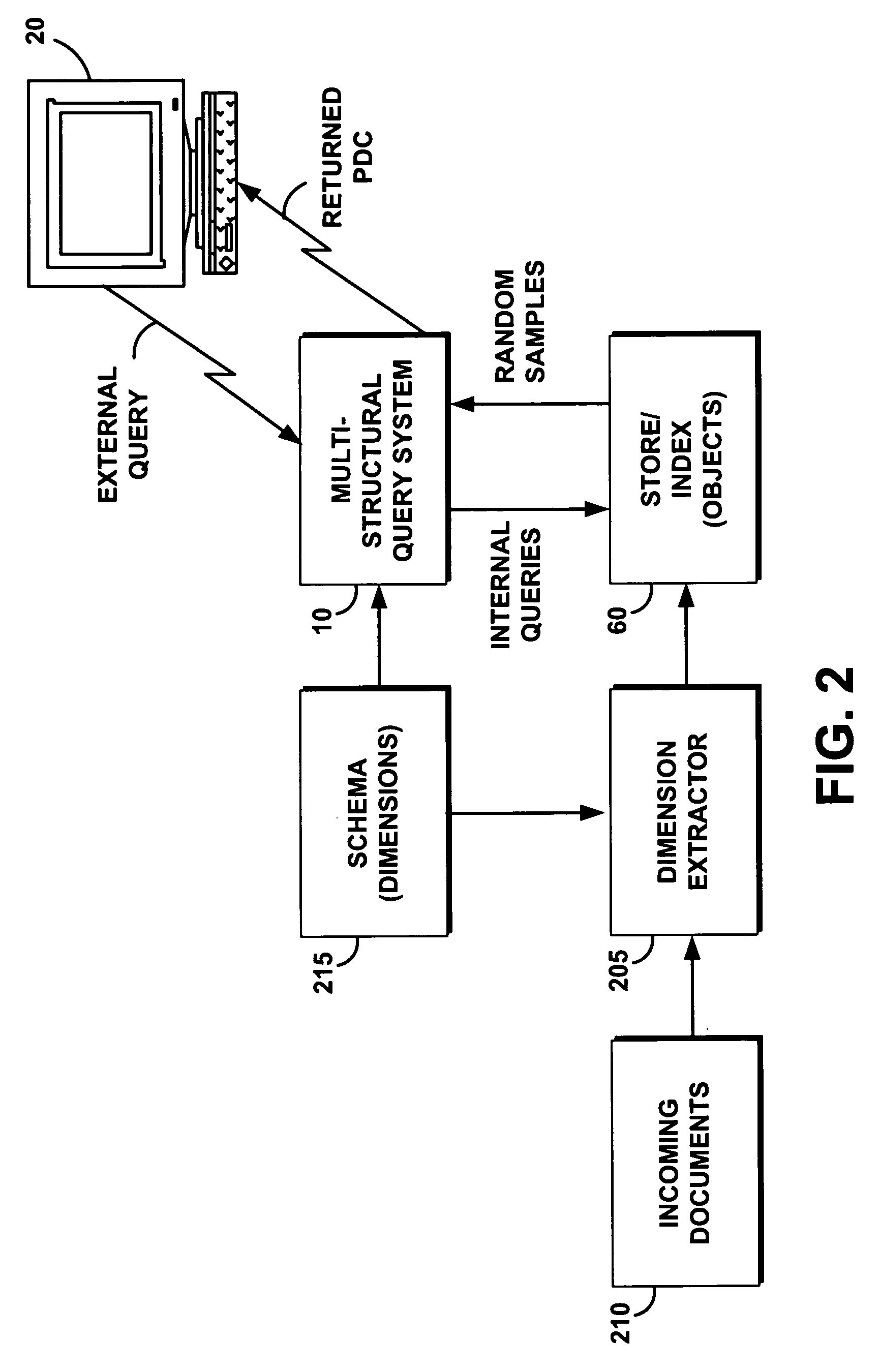
System and method for performing a high-level multi-dimensional query on a multi-structural database
InactiveUS20060282411A1Easy to solveMulti-dimensional databasesSpecial data processing applicationsData setMulti dimensional
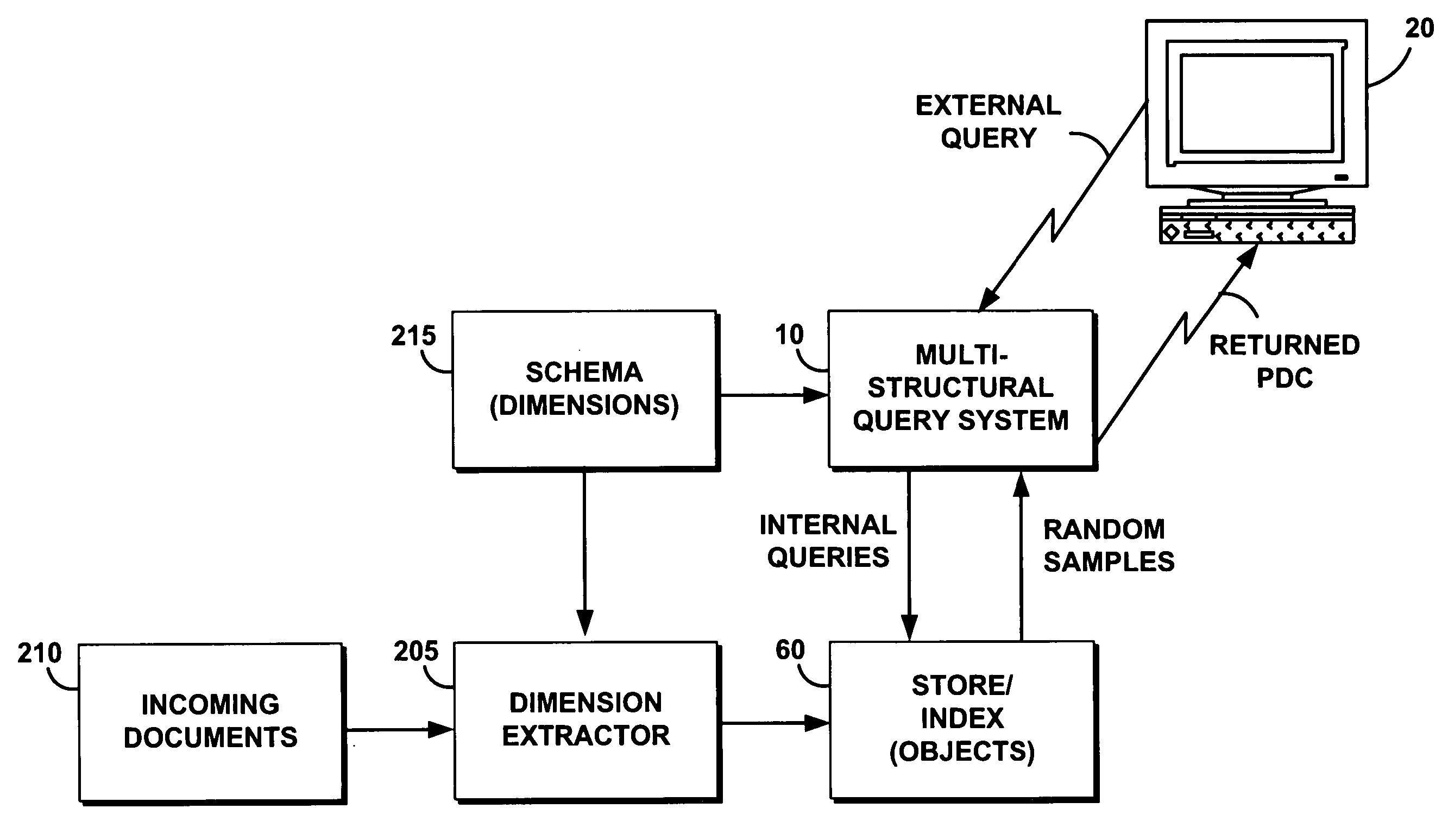
A multi-structural query system performs a high-level multi-dimensional query on a multi-structural database. The query system enables a user to navigate a search by adding restrictions incrementally. The query system uses a schema to discover structure in a multi-structural database. The query system leaves a choice of nodes to return in response to a query as a constrained set of choices available to the algorithm. The query system further casts the selection of a set of nodes as an optimization. The query system uses pairwise-disjoint collections to capture a concise set of highlights of a data set within the allowed schema. The query system further comprises efficient algorithms that yield approximately optimal solutions for several classes of objective functions.
Owner:IBM CORP
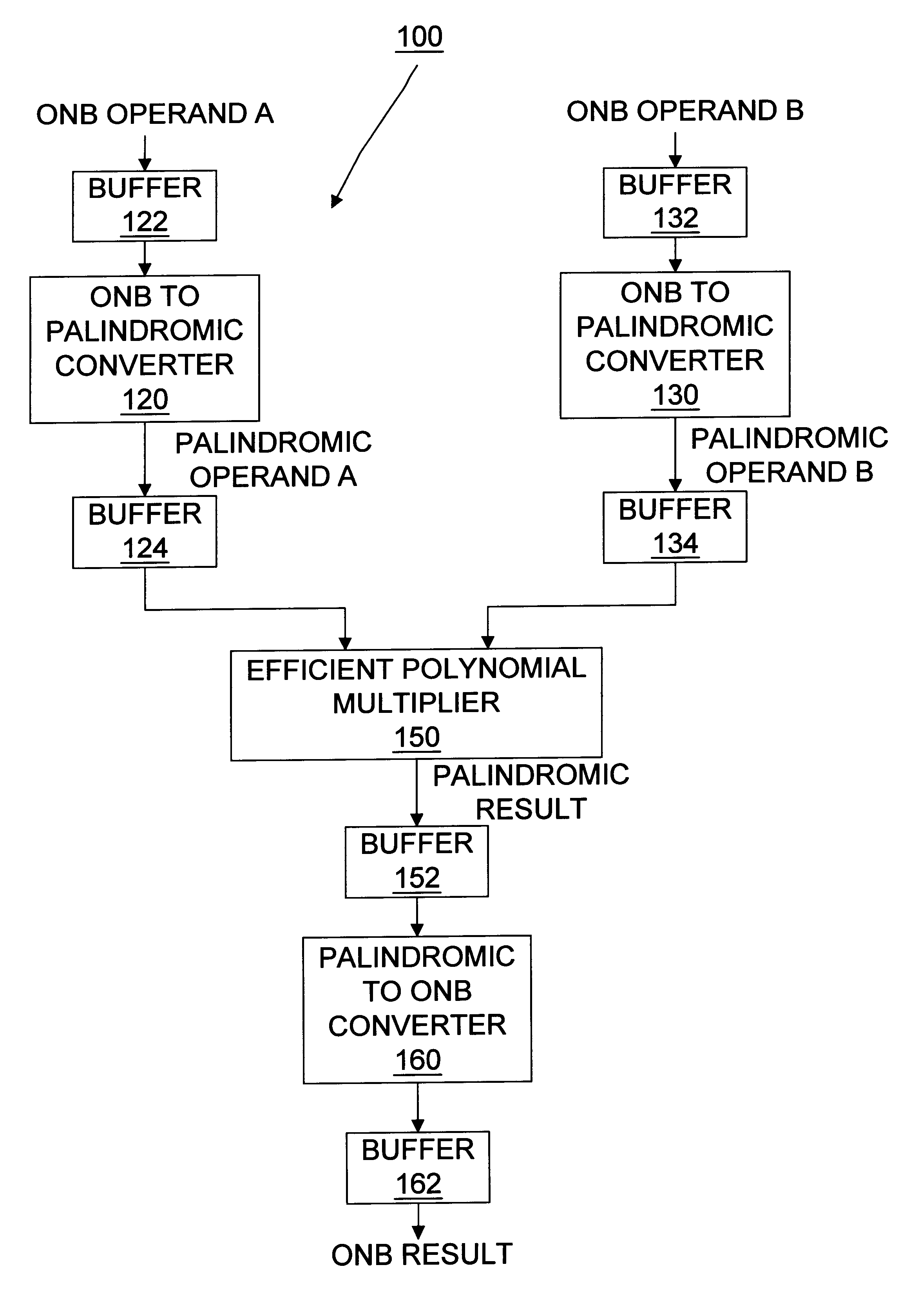
Apparatus and method for efficient arithmetic in finite fields through alternative representation
InactiveUS6199087B1Digital computer detailsComputations using residue arithmeticTheoretical computer scienceOperand
A method and apparatus are shown for performing efficient arithmetic on binary vectors in a finite field. Typically, there is an efficient algorithm within an execution context, such as hardware or software, for performing a selected arithmetic operation on an operand. When the operand is in a first representative format and the efficient algorithm operates in an alternative representation format, then the operand is permutated from the first representative format to the alternative representation format. The efficient algorithm is then performed on the operand in the alternative representation format in order to obtain a result in the alternative representation format. The result is then permutated from the alternative representation format to the first representation format. Thus, efficient arithmetic is obtained by using the most efficient algorithm available in either the first representation format or the alternative representation format and permuting operands and results to the representation format corresponding to the most efficient algorithm available.
Owner:HEWLETT PACKARD CO
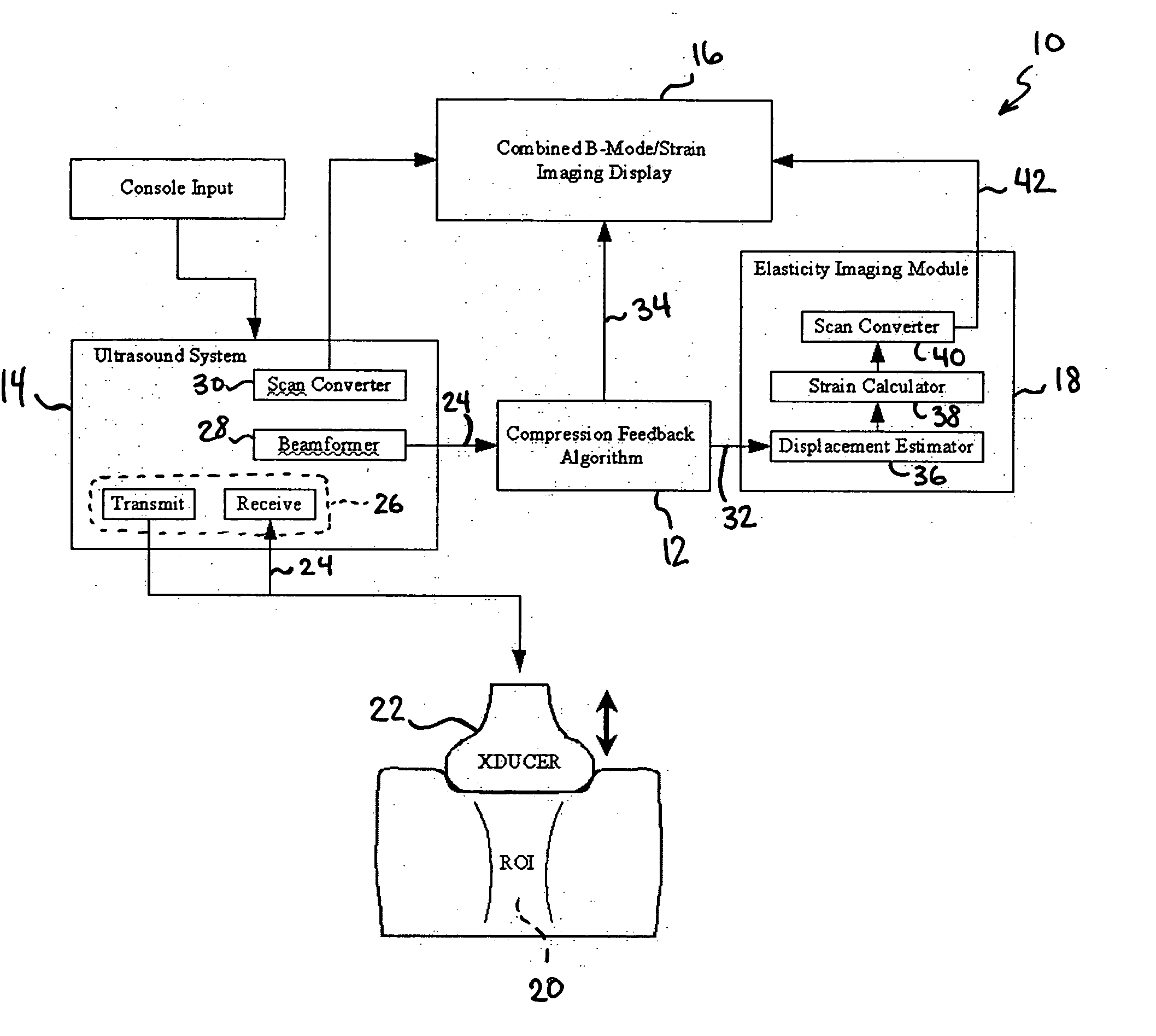
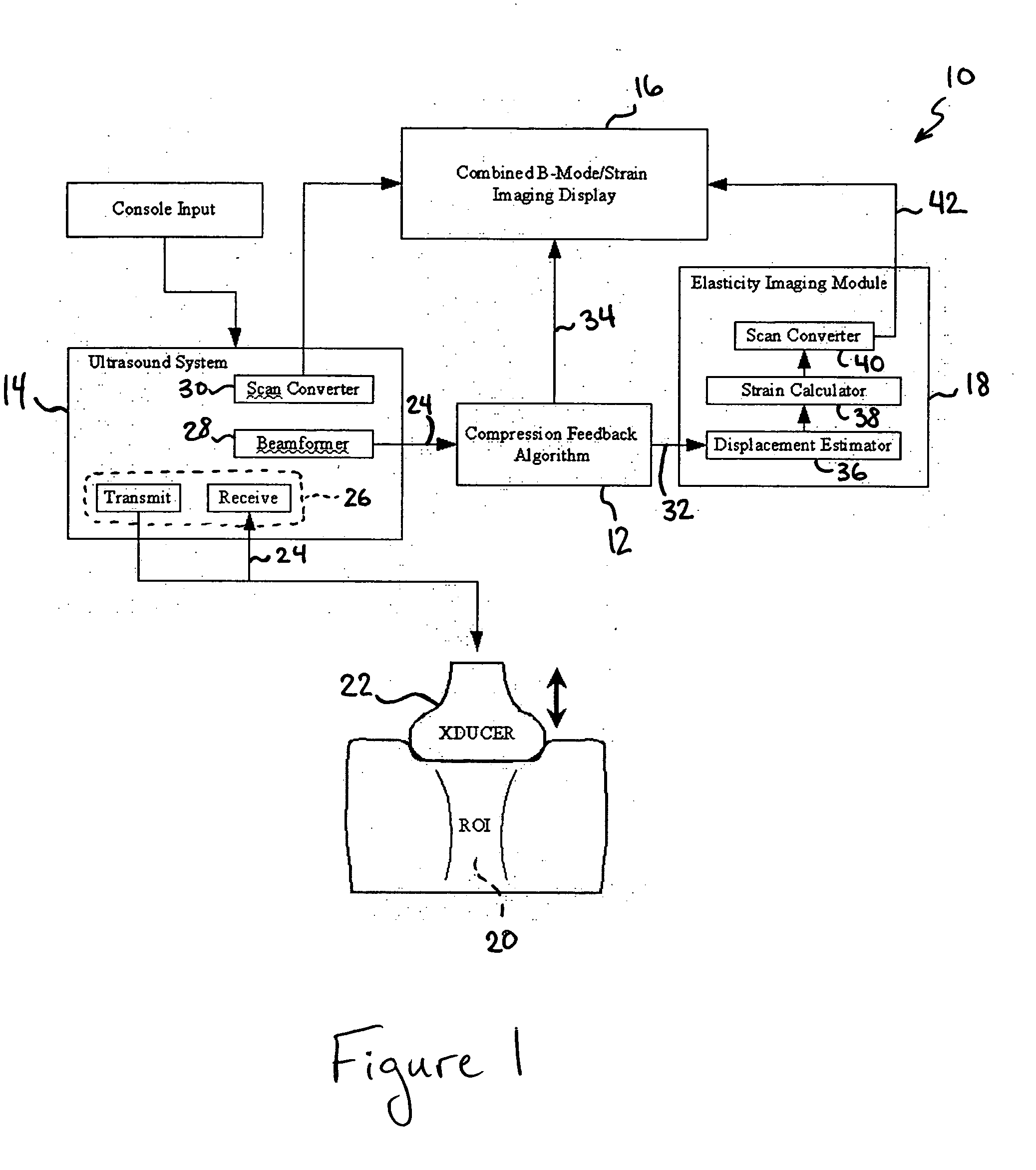
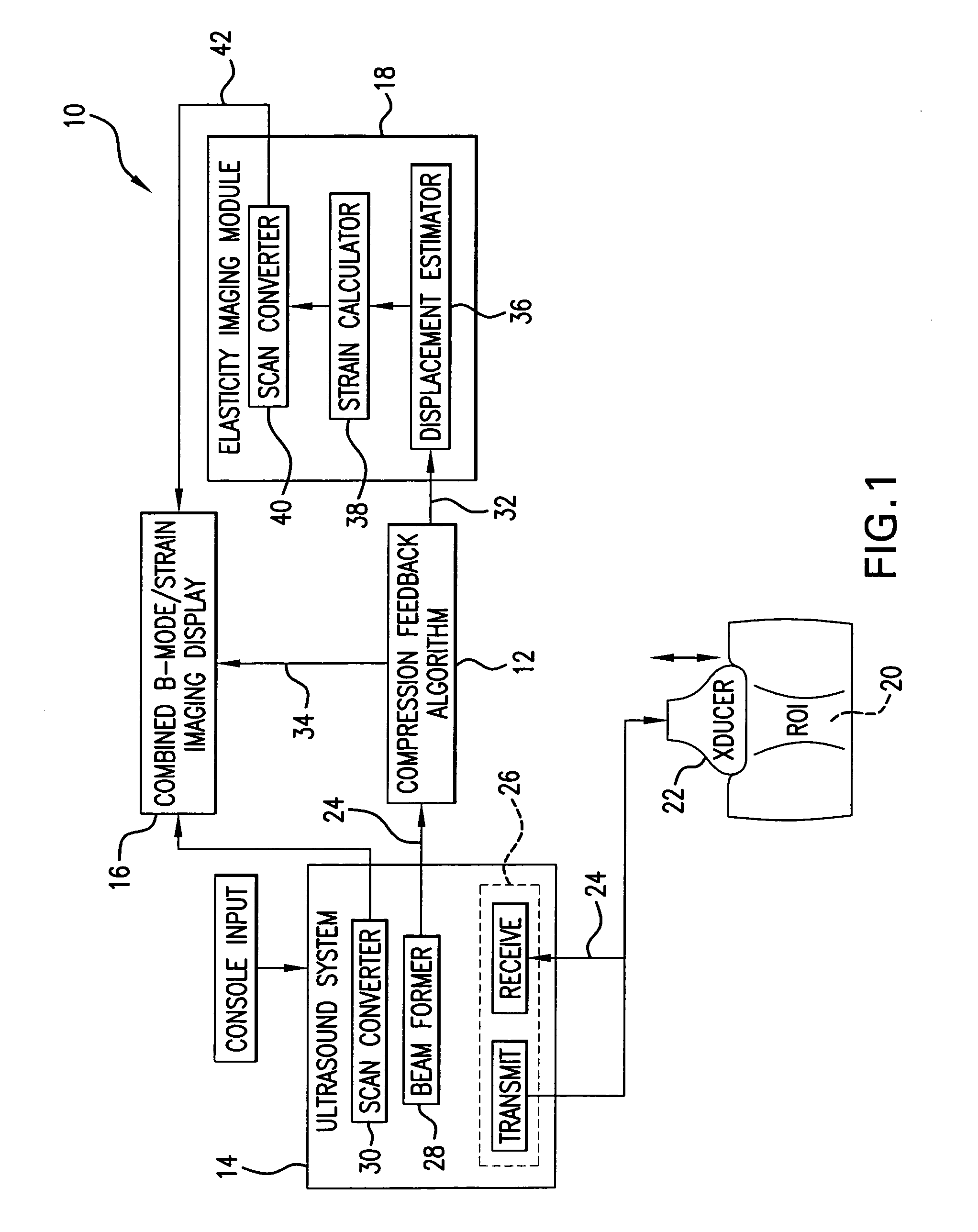
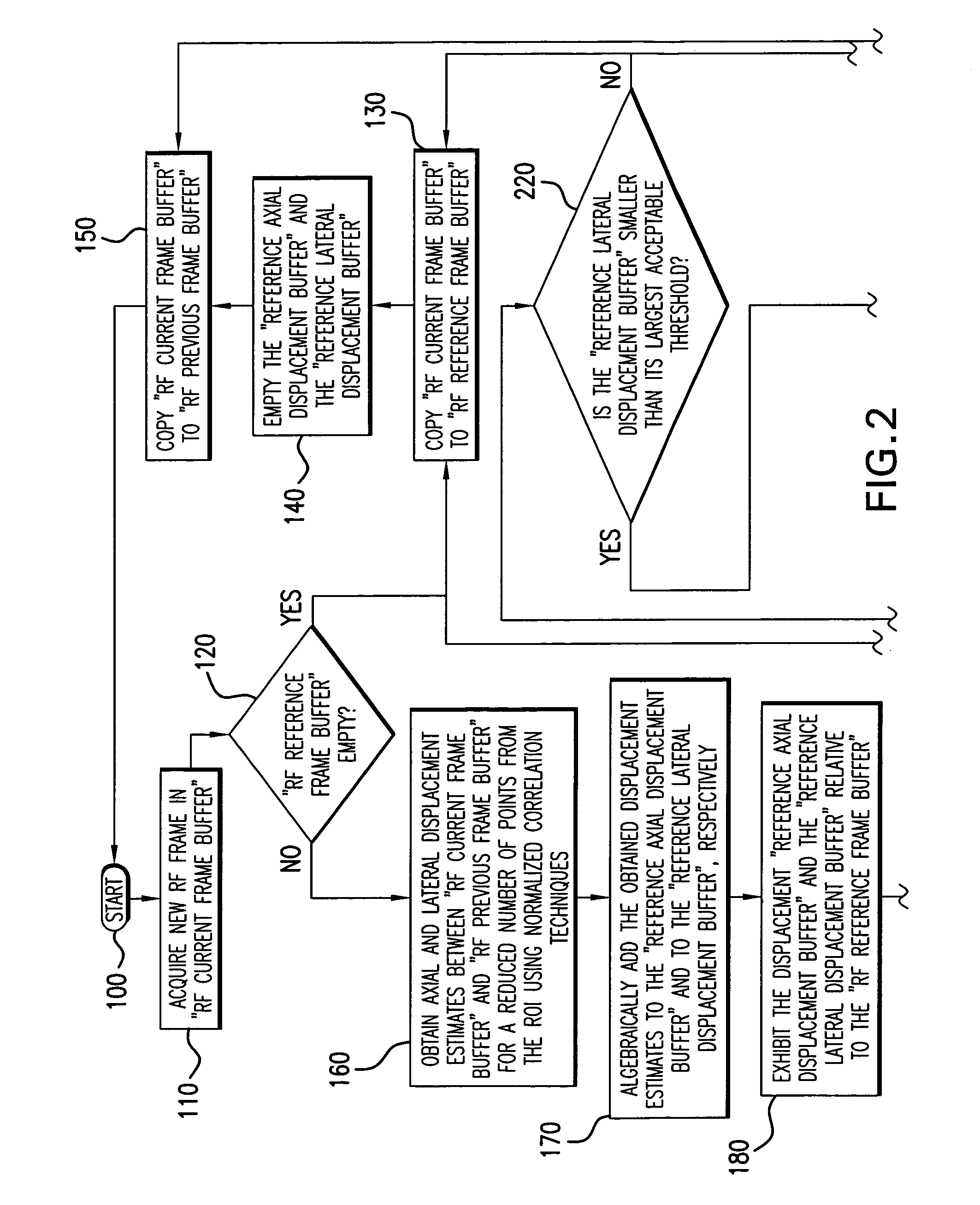
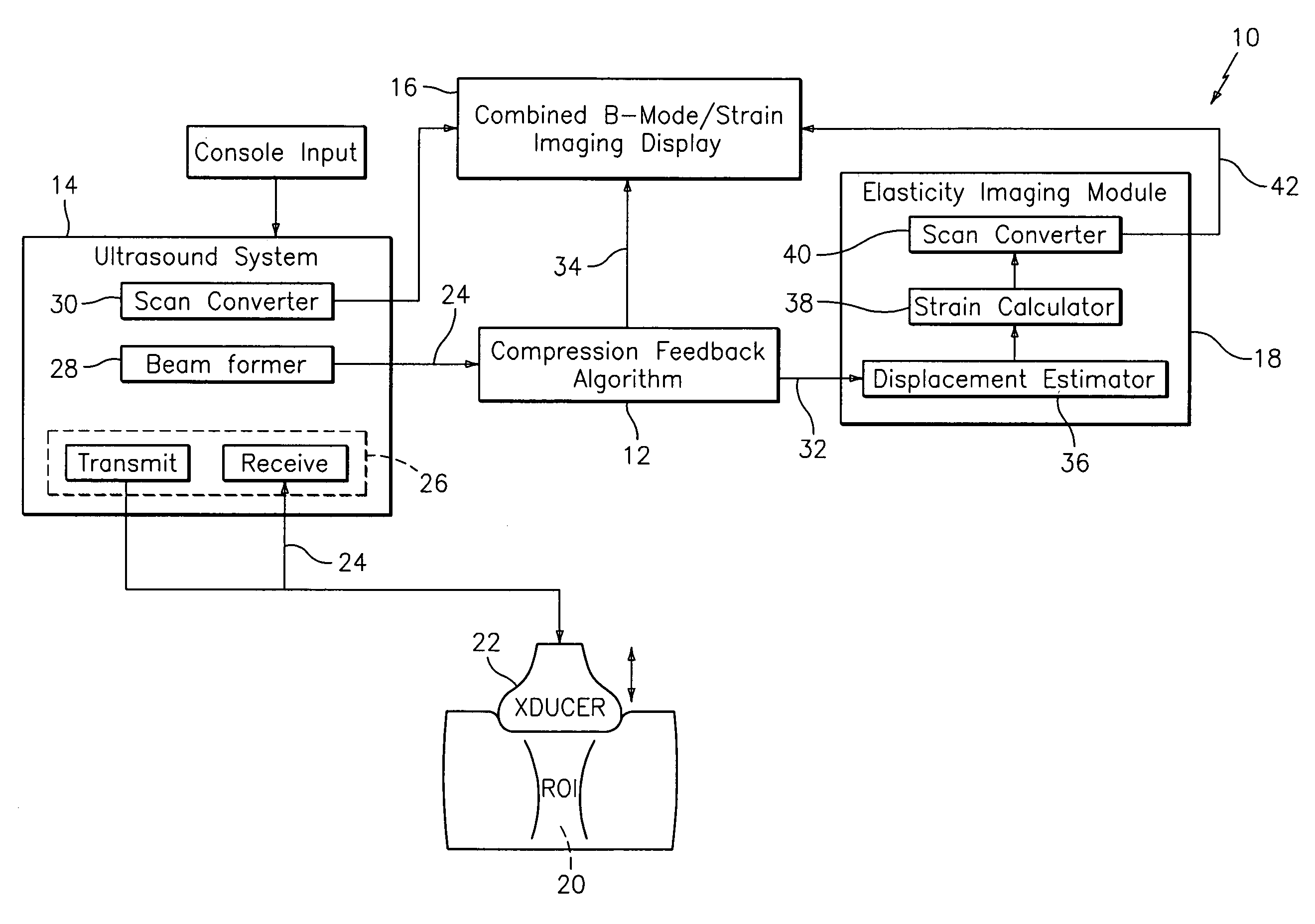
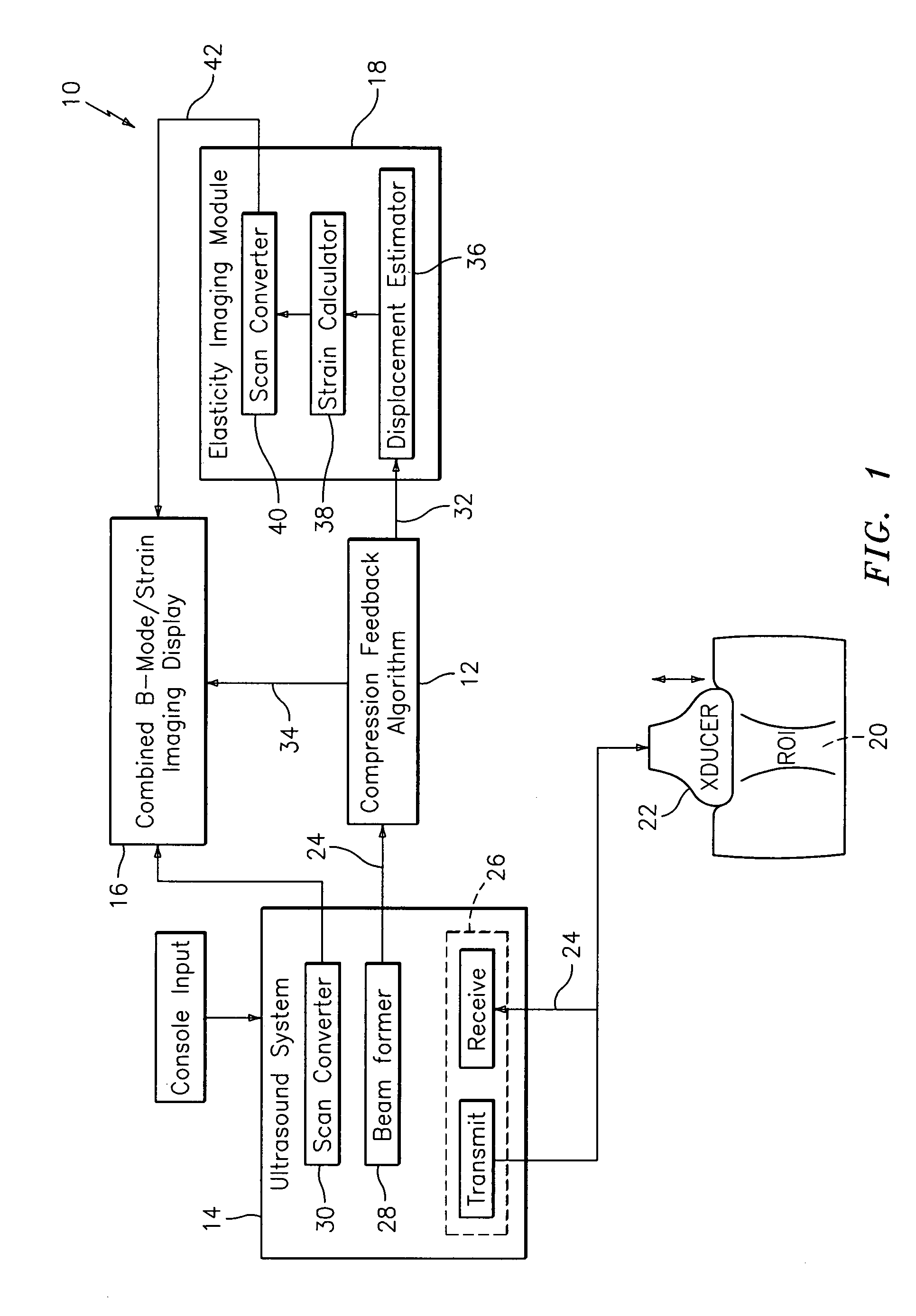
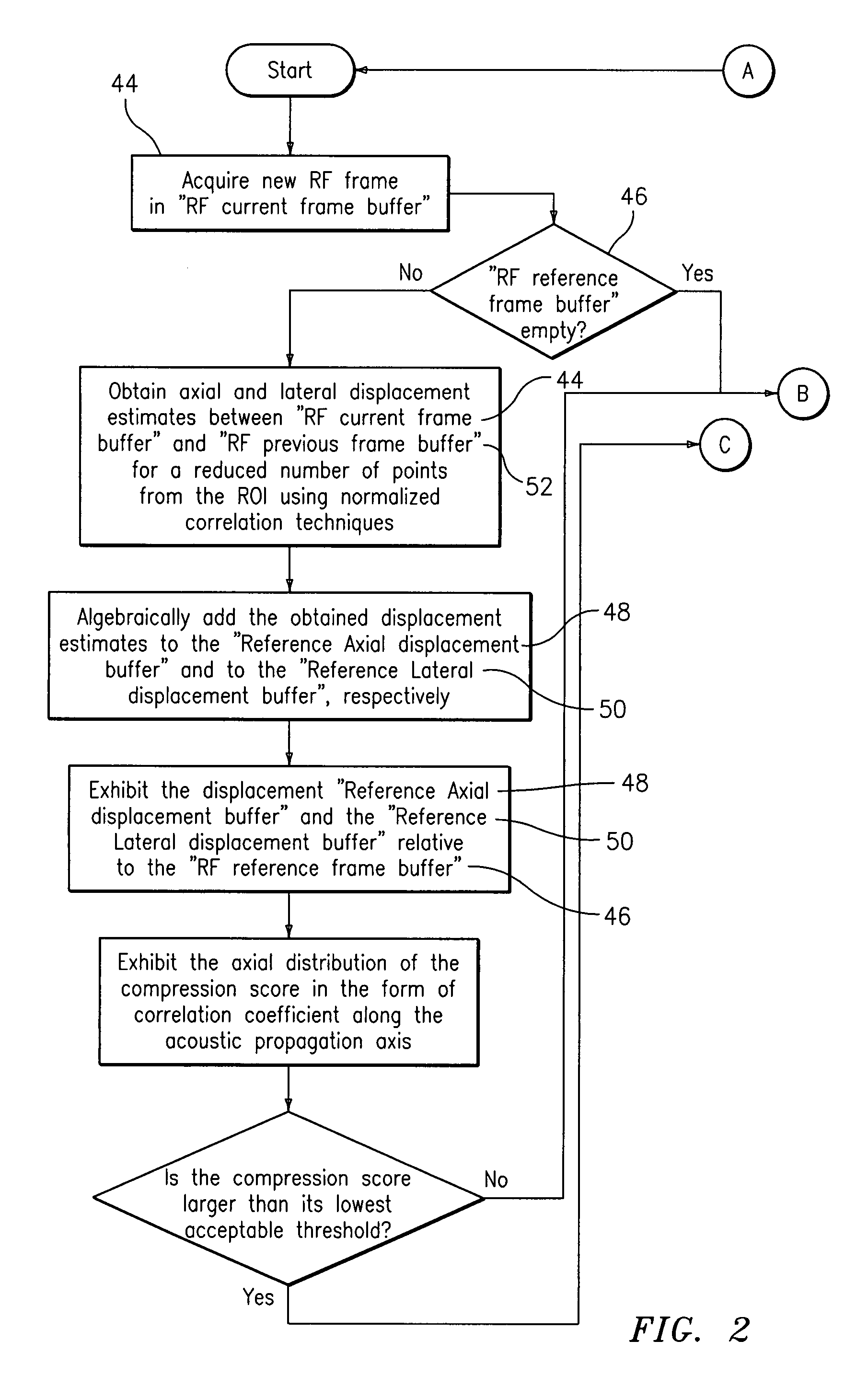
Method and apparatus for elasticity imaging
InactiveUS20060173320A1Organ movement/changes detectionInfrasonic diagnosticsUltrasound imagingElastography
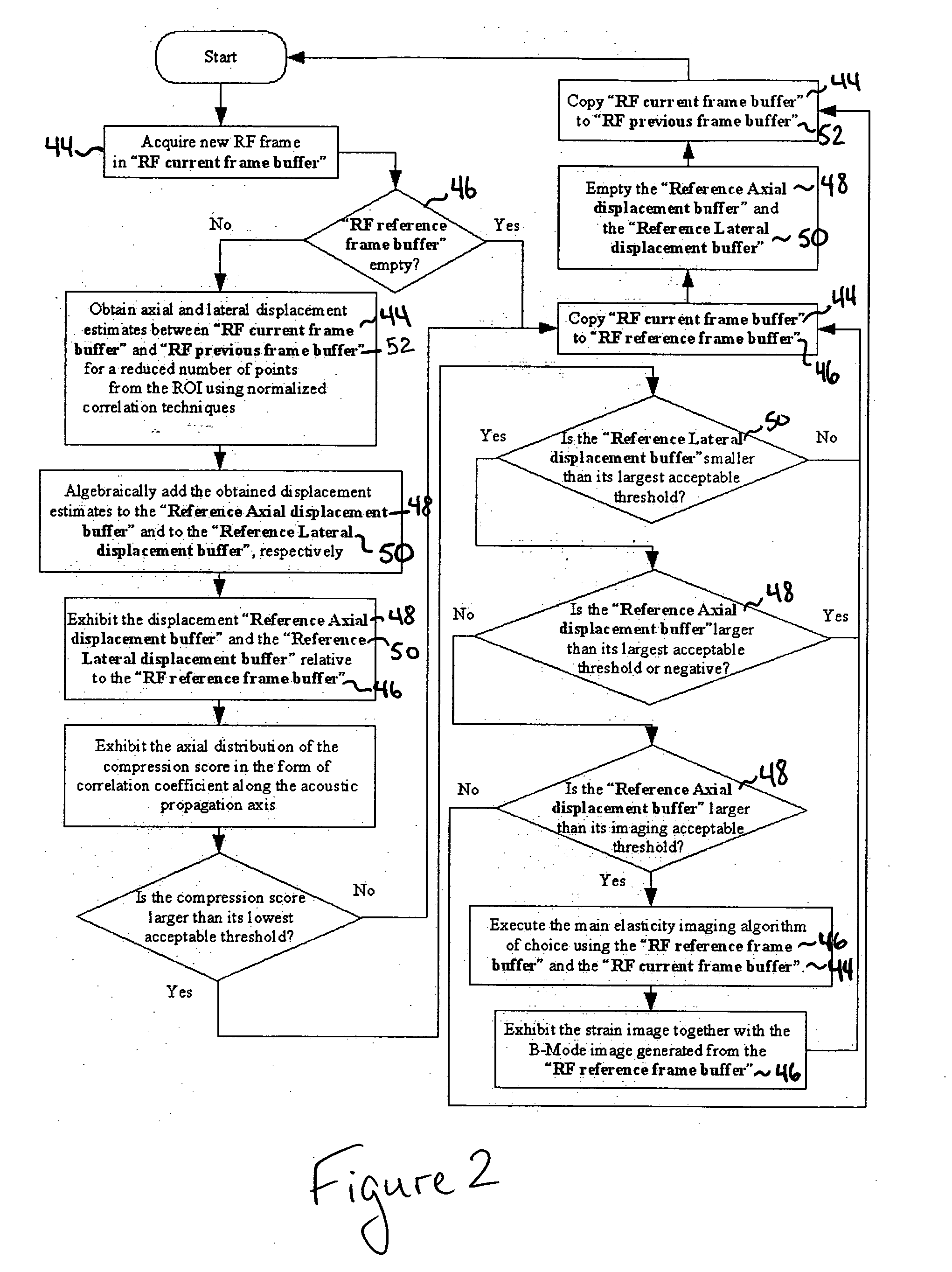
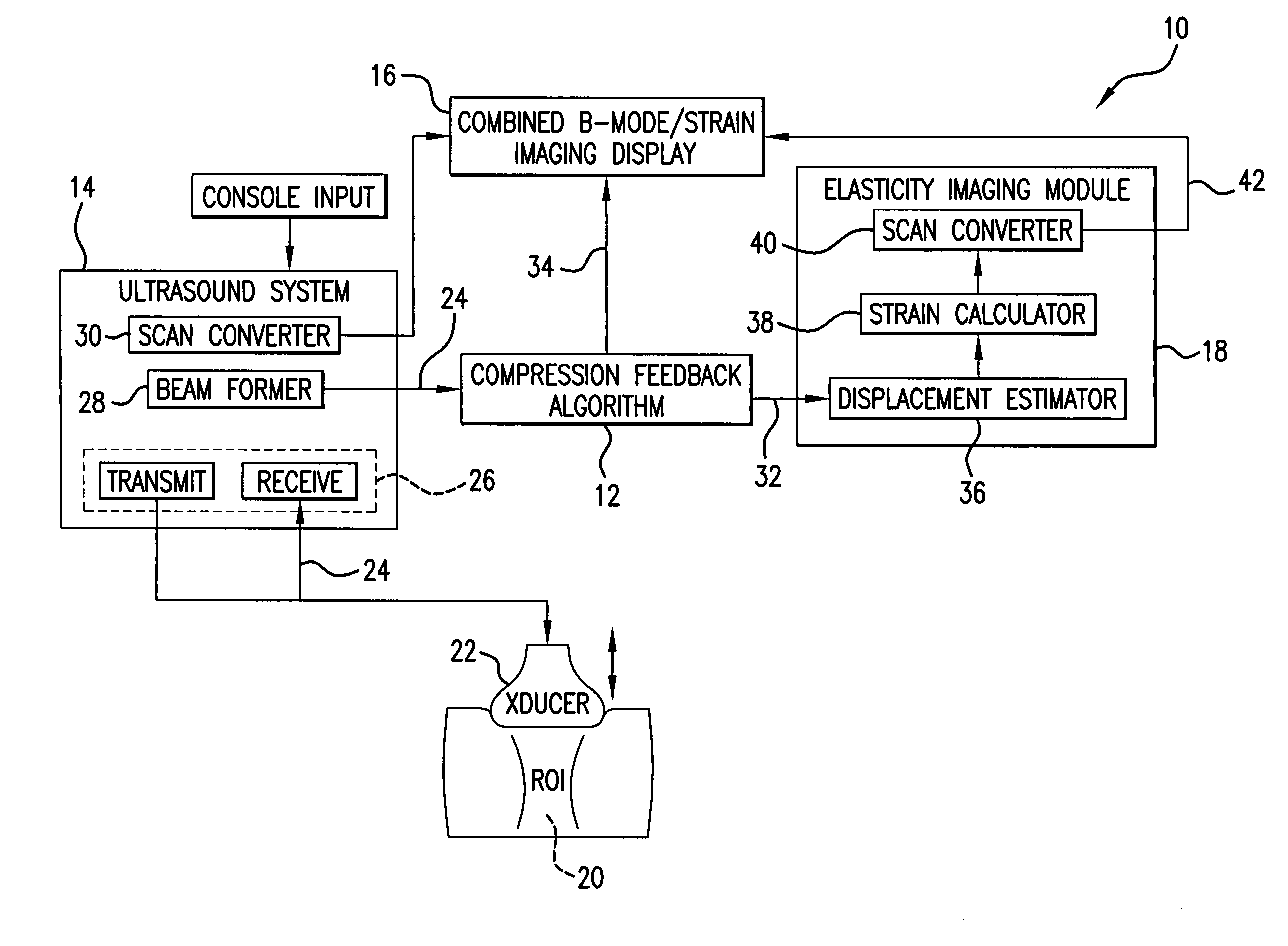
A computational efficient algorithm for compression analysis of free-hand static elasticity imaging performed using medical diagnostic ultrasound imaging equipment offers tissue compression quality and quantity feedback to the operator. The algorithm includes a criterion for automatic selection of the most advantageous pre- and post- compression frame pairs delivering elasticity images of optimal dynamic ranges (DR) and signal-to-noise ratios (SNR). The use of the algorithm in real time eases operator training and reduces significantly the amount of artifact in the elasticity images while lowering the computational burden.
Owner:HITACHI LTD
Scalable Multi-Query Optimization for SPARQL
ActiveUS20140156633A1Minimize timeHigh expressionDigital data processing detailsRelational databasesExecution planQuery optimization
Multiquery optimization is performed in the context of RDF / SPARQL. Heuristic algorithms partition an input batch of queries into groups such that each group of queries can be optimized together. The optimization incorporates an efficient algorithm to discover the common sub-structures of multiple SPARQL queries and an effective cost model to compare candidate execution plans. No assumptions are made about the underlying SPARQL query engine. This provides portability across different RDF stores.
Owner:IBM CORP
Method and apparatus for elasticity imaging
InactiveUS20070093716A1Wave based measurement systemsDiagnostics using vibrationsUltrasound imagingElastography
A computational efficient algorithm for compression analysis of free-hand static elasticity imaging performed using medical diagnostic ultrasound imaging equipment offers tissue compression quality and quantity feedback to the operator. The algorithm includes a criterion for automatic selection of the most advantageous pre- and post-compression frame pairs delivering elasticity images of optimal dynamic ranges (DR) and signal-to-noise ratios (SNR). The use of the algorithm in real time eases operator training and reduces significantly the amount of artifact in the elasticity images while lowering the computational burden.
Owner:ALOKA CO LTD
Frequency resolution using compression
InactiveUS20080123731A1Frequency domain resolutionImprove detection accuracySpectral/fourier analysisCode conversionSpectrum analyzerImage resolution
In a frequency analysis system, such as a signal detection system or a spectrum analyzer, the frequency domain resolution is enhanced by compression and decompression of the signal samples. The limited capacity of the data storage and / or data transfer resources limit the number of samples that can be stored or transferred. A compressor forms a compressed signal prior to data transfer or storage. A decompressor decompresses the compressed signal prior to transformation to the frequency domain, by a fast Fourier transform or other frequency domain transform. The frequency domain resolution is enhanced because more decompressed samples are available for the frequency domain transform. The compressor and decompressor apply computationally efficient algorithms that can be implemented to operate in real time.
Owner:ALTERA CORP
Monocular vision AGV accurate positioning method and system based on multi-window real-time range finding
ActiveCN105955259ARealize the real-time ranging functionRealize reasonable obstacle avoidancePosition/course control in two dimensionsTime rangeAutomated guided vehicle
The invention discloses a monocular vision AGV (Automated Guided Vehicle) accurate positioning method and system based on multi-window real-time range finding. The method comprises according to a camera slanting installation mode, calibrating and measuring camera parameters and establishing a visual system real-time measuring model; setting a circular color lump on the ground to be used as the reference substance for parking positioning, identifying the circular color lump through the efficient algorithm of the visual system, and accurately extracting central position information; and in a view filed, setting a plurality of windows to process images a far-end window is used for an AGV to predetermine ground information so as to gradually decelerate; an intermediate window is used as a coarse positioning window, and used for adjusting poses; and a near-end window is used for accurate range finding and parking. The method allows an AGV to sense depth information, and has the advantages of high characteristic recognition rate, excellent arithmetic instantaneity, low cost and great extendibility. The horizontal distance deviation of AGV parking is stabilized at +-1 mm, the angle deviation is stabilized at +-1 DEG, and the parking error is stabilized at +- 2mm.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Scratch pad for storing intermediate loop filter data
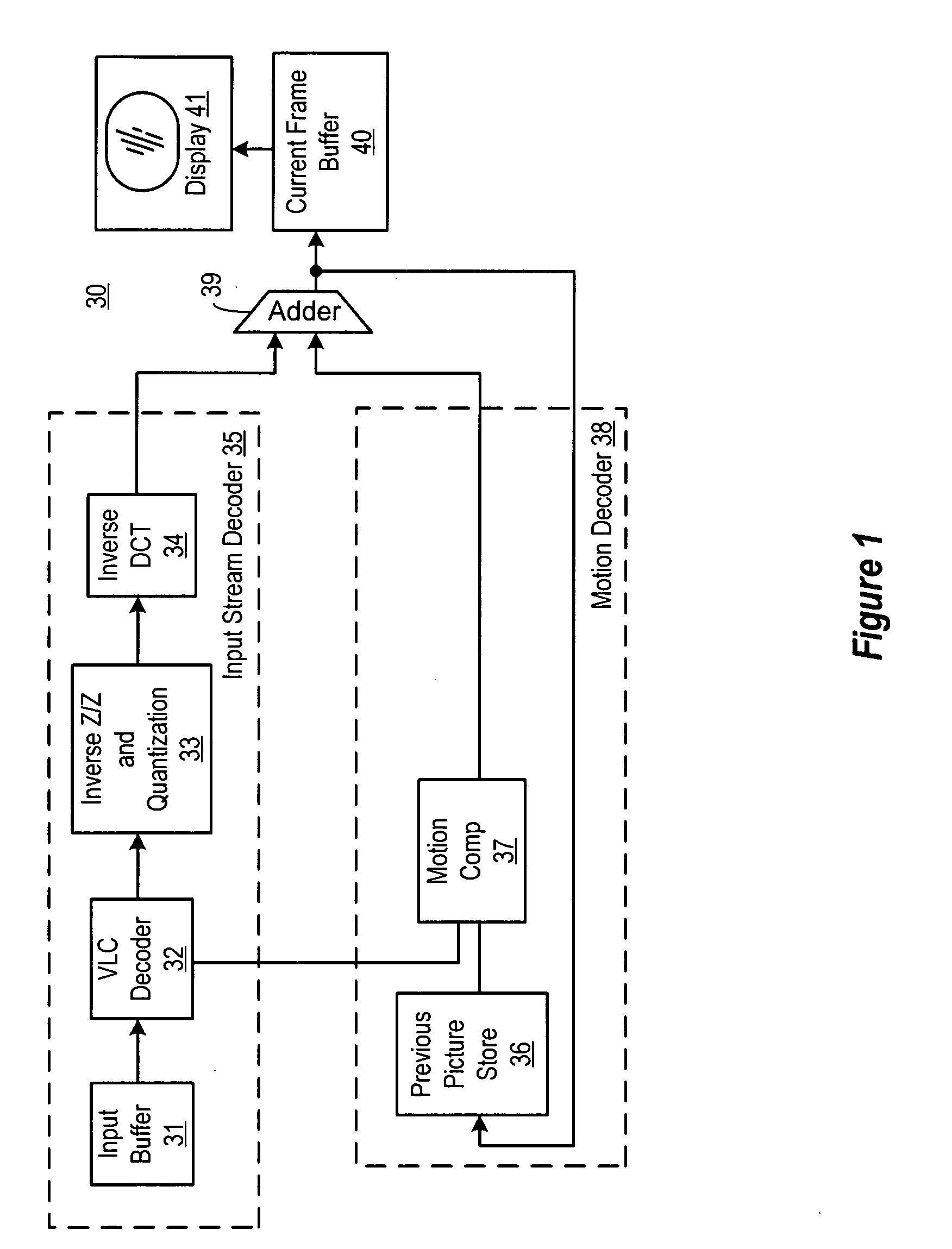
ActiveUS20060165164A1Quickly and efficiently processMeet cutting requirementsColor television with pulse code modulationColor television with bandwidth reductionLoop filterFrame based
A video processing apparatus and methodology are implemented as a combination of a processor and a video decoding hardware block to decode video data by providing the video decoding block with an in-loop filter and a scratch pad memory, so that the in-loop filter may efficiently perform piecewise processing of overlap smoothing and in-loop deblocking in a macroblock-based fashion which is a much more efficient algorithm than the frame-based method.
Owner:MEDIATEK INC +1
Long Range Path Prediction and Target Classification Algorithm using connected vehicle data and others
ActiveUS20180257660A1Instruments for road network navigationParticular environment based servicesAccurate estimationSelf driving
Self-driving and autonomous vehicles are very popular these days for scientific, technological, social, and economical reasons. In one aspect of this technology, path prediction and target classifications are main pillars and enablers for safety and mobility applications. Accurate Estimation of the lane assignment of the remote vehicle with respect to the host vehicle lane results in the accurate threat assessment. V2X and C-V2X are emerging technology for safety applications, and they cover relatively long range. Long range means more room for error in path prediction / target classification. Therefore, here, we offer an efficient path prediction and target classification algorithm to enable these technologies performing safety and mobility applications. The method fuses target vehicles data and host vehicle data in an efficient algorithm to perform this task. Other variations are also presented here.
Owner:HARMAN INT IND INC
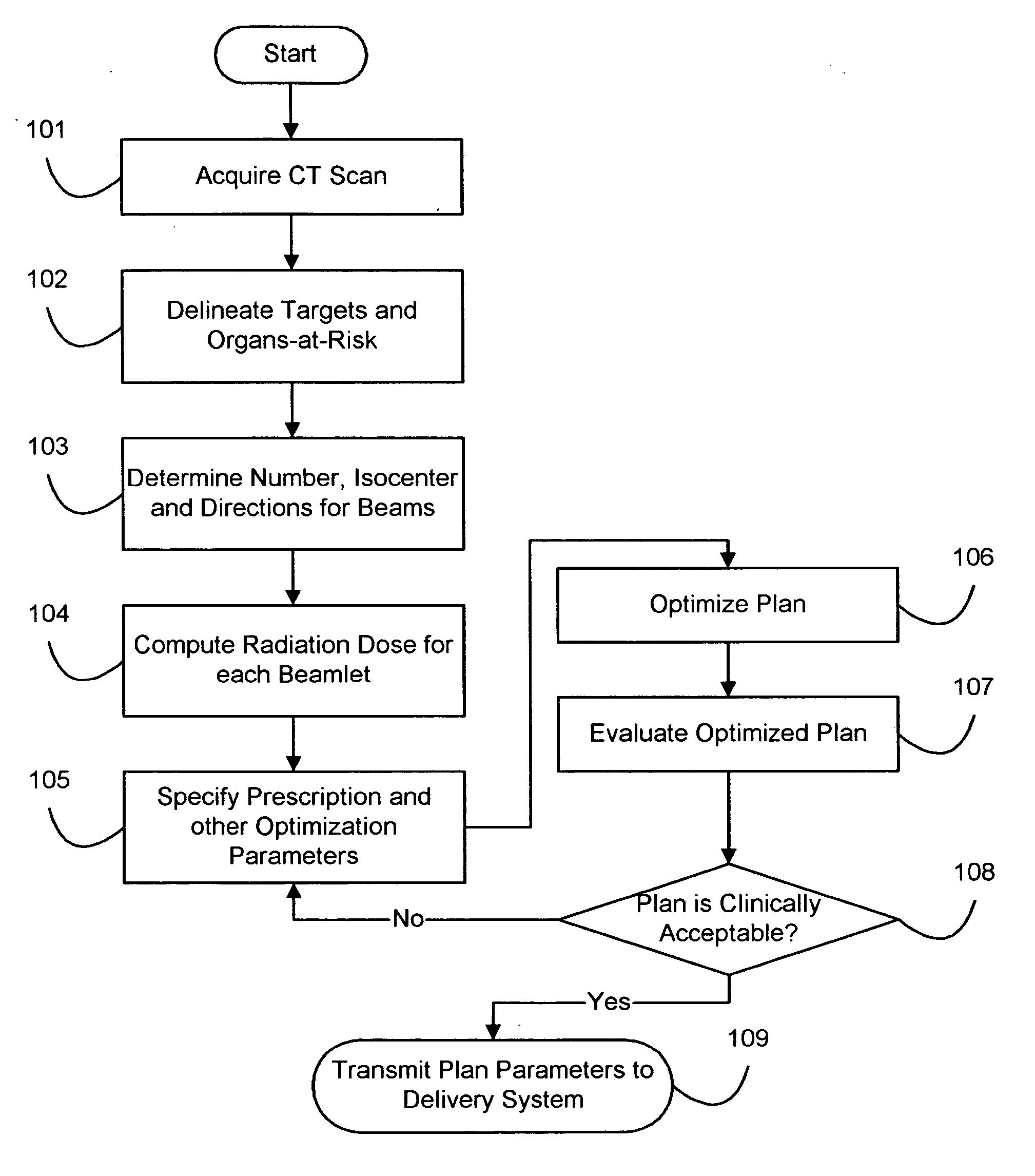
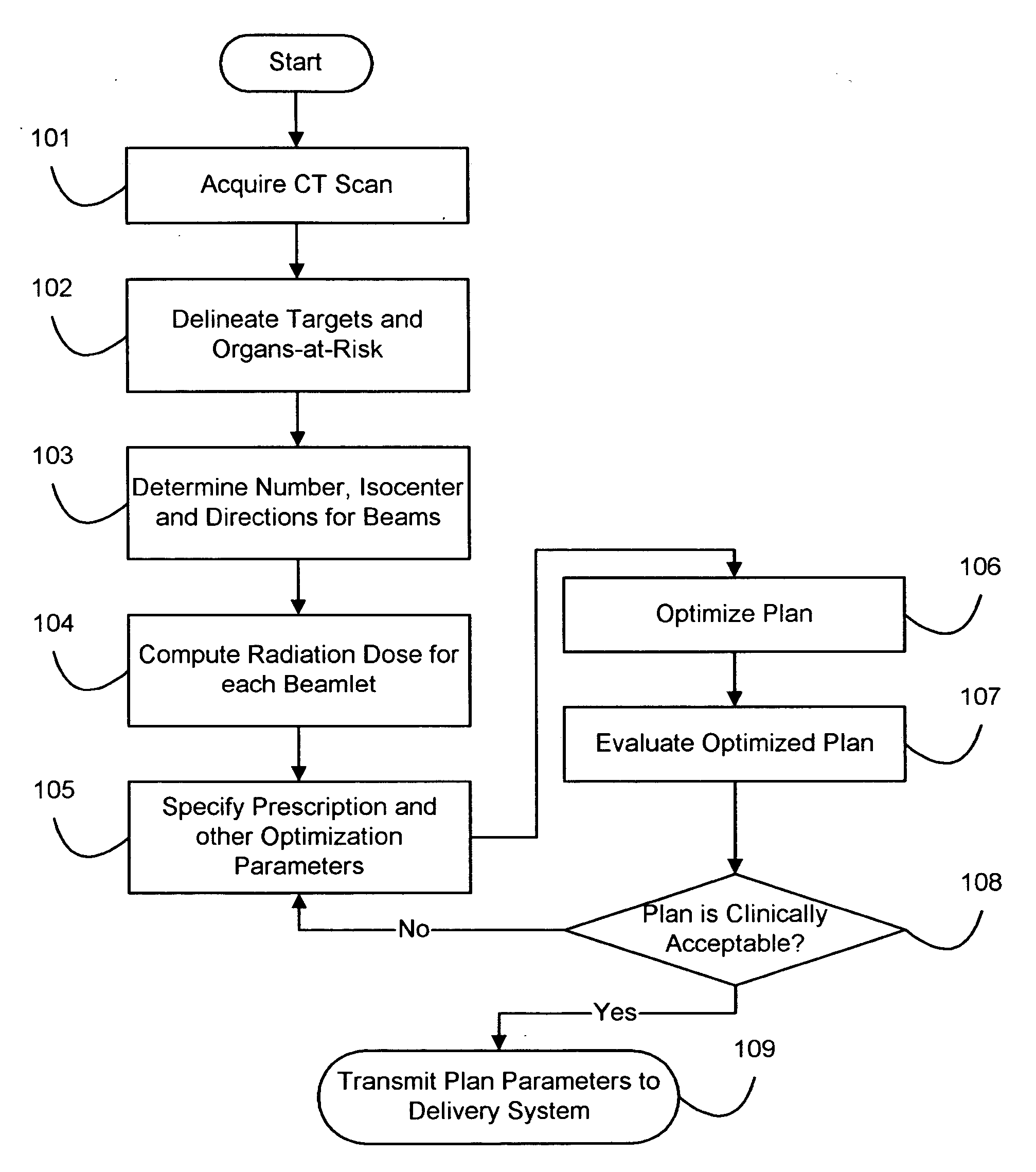
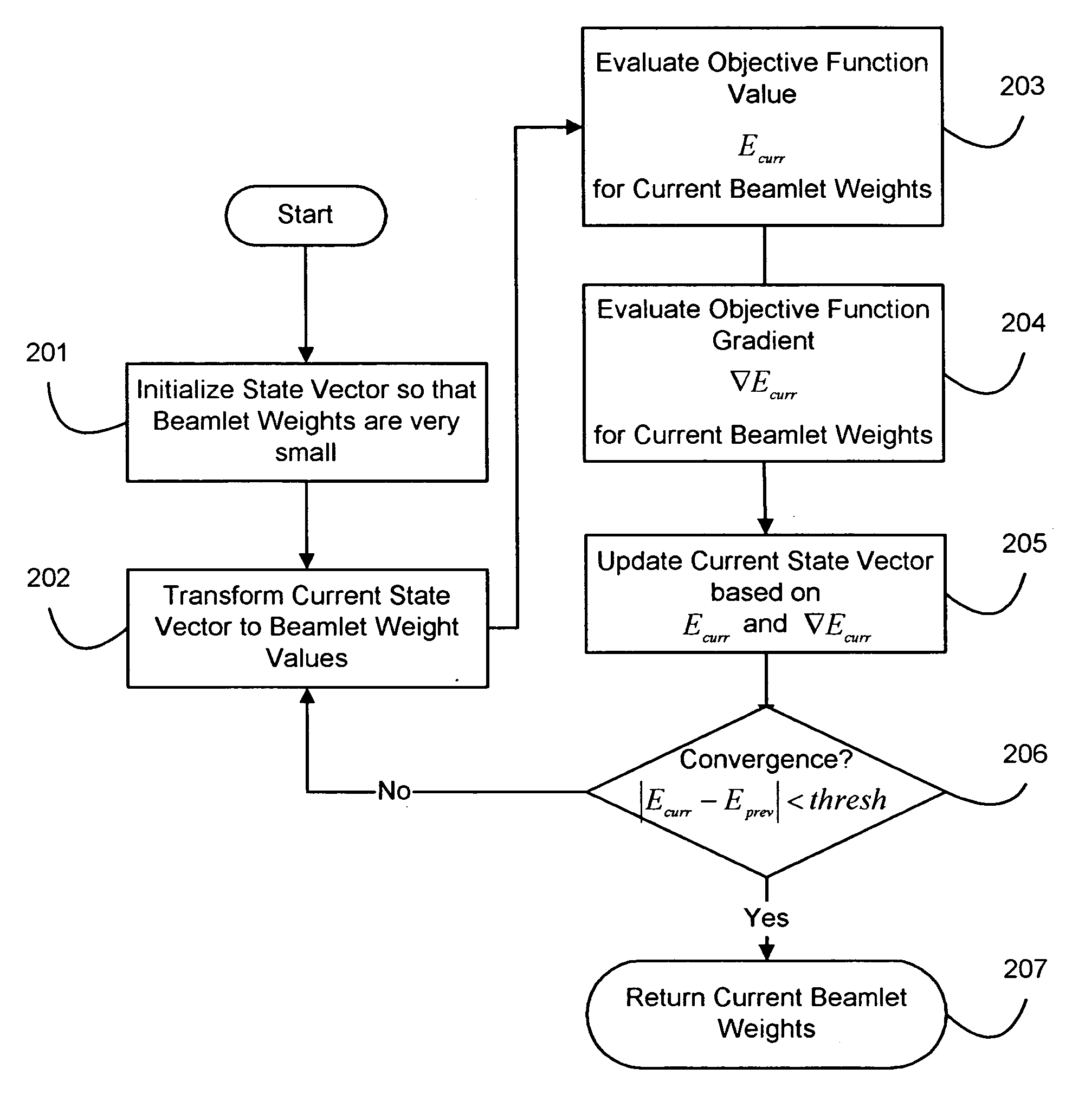
Information theoretic inverse planning technique for radiation treatment
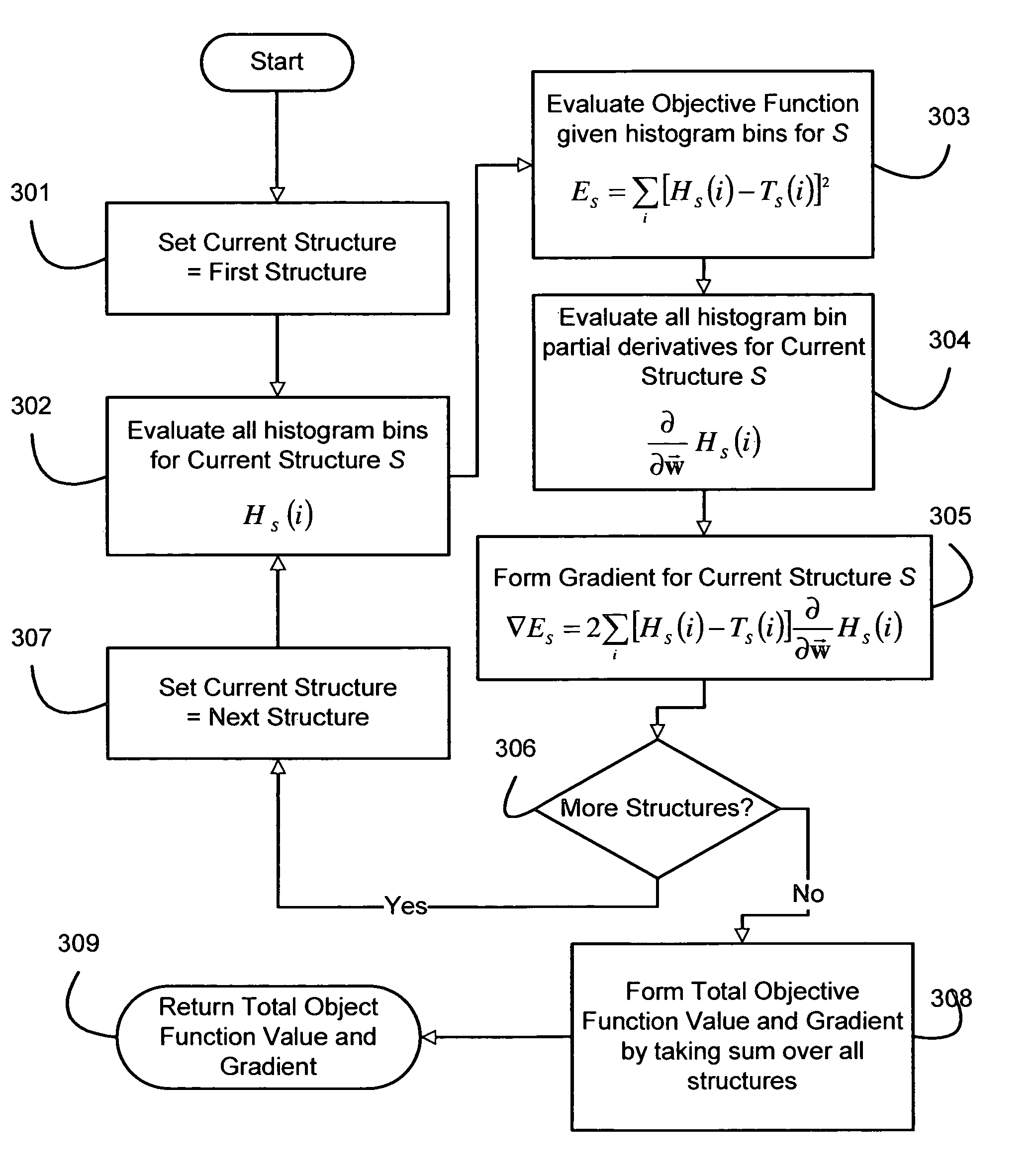
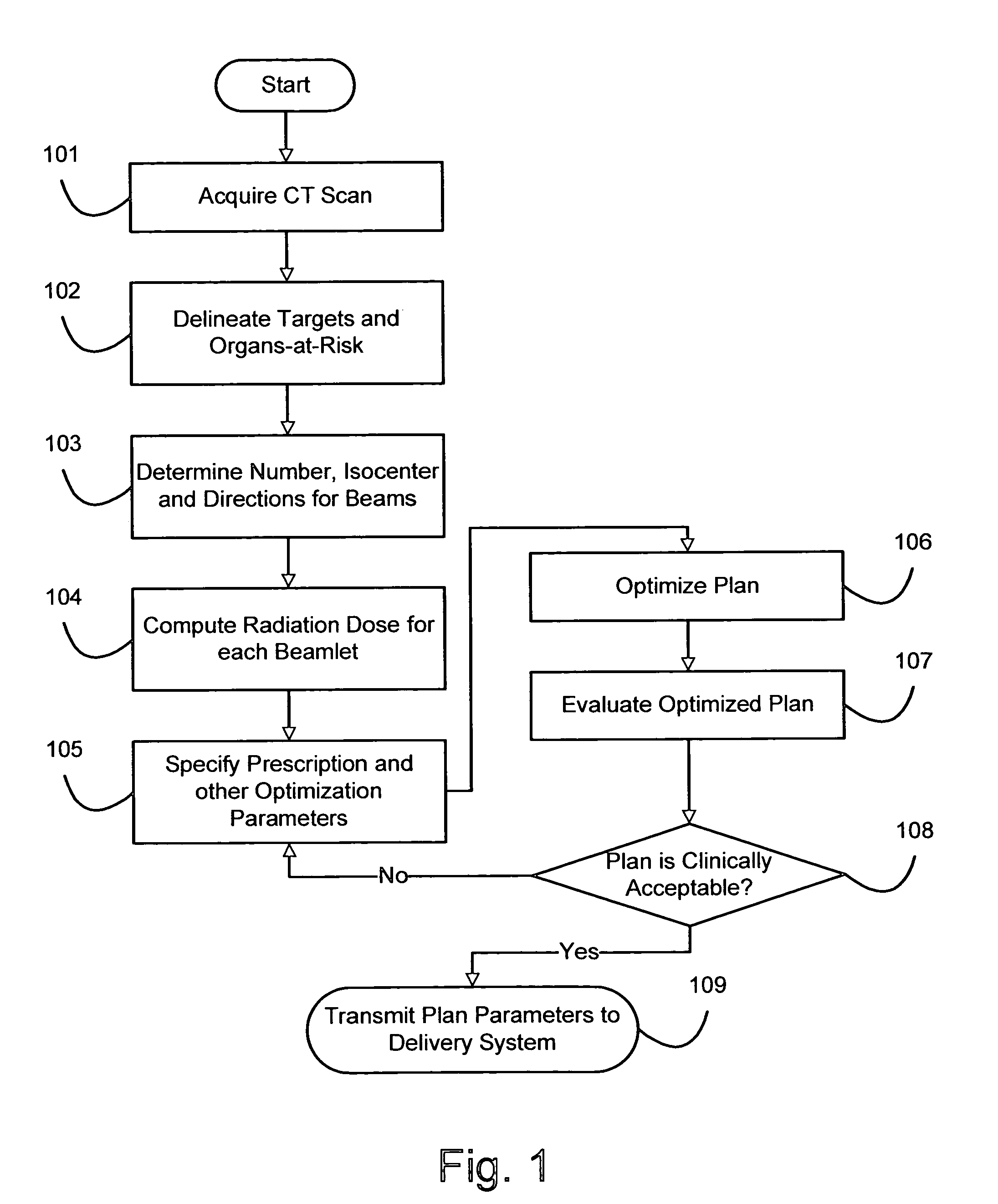
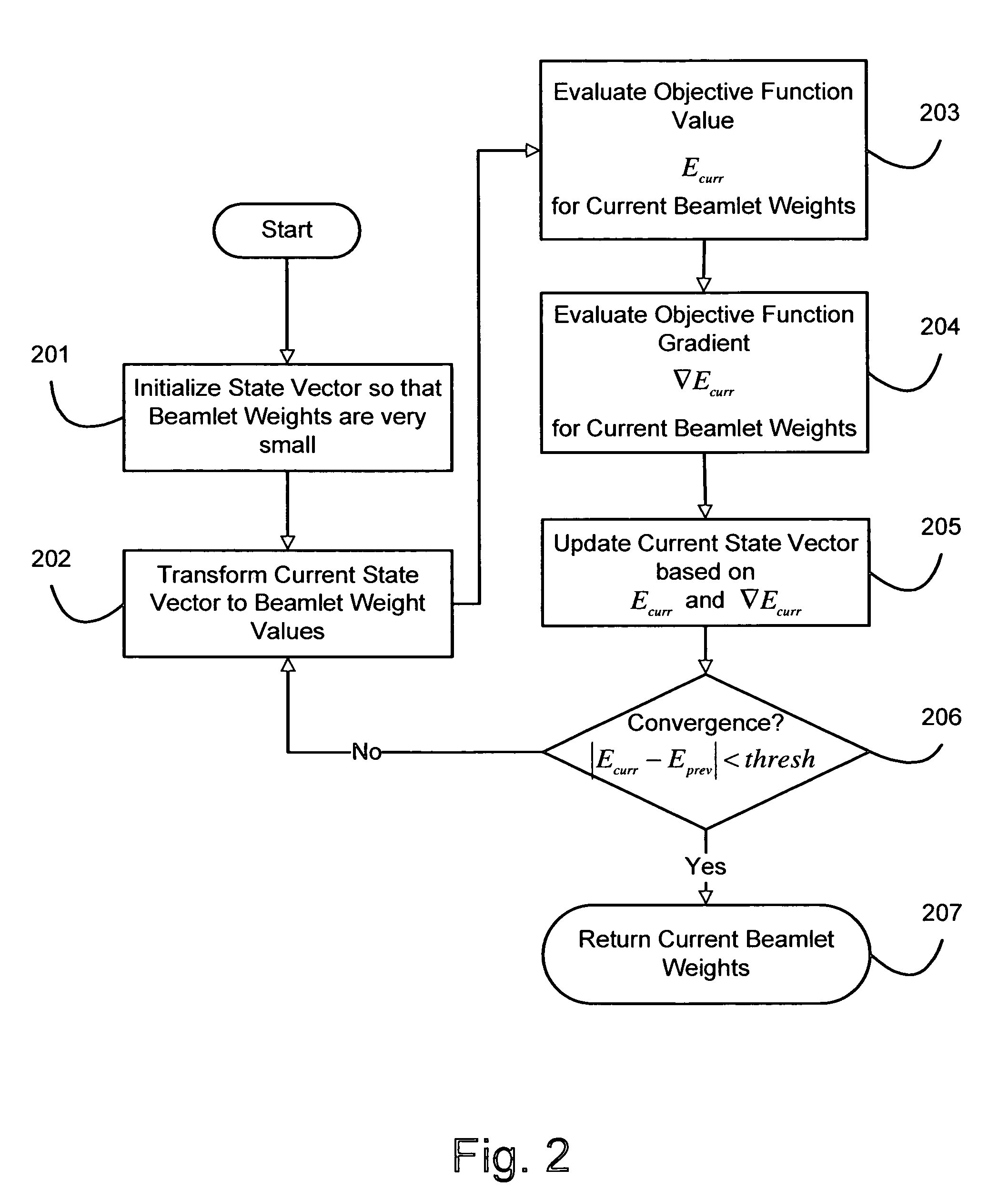
InactiveUS7369645B2Effective evaluationShorten the timeX-ray/gamma-ray/particle-irradiation therapyImaging processingRadiation treatment planning
A method for fast inverse planning of IMRT treatment plans is disclosed. The method relies on a computationally efficient algorithm for evaluating the gradient of a general class of objective functions, and also on the efficient optimization that is realized due to the directional conjugacy of the objective functions. Several types of clinically relevant objective functions that belong to this class are described. The computational evaluation relies on operations that are commonly used for signal- and image-processing, and so can benefit from a number of well-known acceleration techniques.
Owner:LANE DEREK GRAHAM
Method and apparatus for elasticity imaging
InactiveUS7223241B2Organ movement/changes detectionInfrasonic diagnosticsUltrasound imagingElastography
A computational efficient algorithm for compression analysis of free-hand static elasticity imaging performed using medical diagnostic ultrasound imaging equipment offers tissue compression quality and quantity feedback to the operator. The algorithm includes a criterion for automatic selection of the most advantageous pre- and post-compression frame pairs delivering elasticity images of optimal dynamic ranges (DR) and signal-to-noise ratios (SNR). The use of the algorithm in real time eases operator training and reduces significantly the amount of artifact in the elasticity images while lowering the computational burden.
Owner:HITACHI LTD
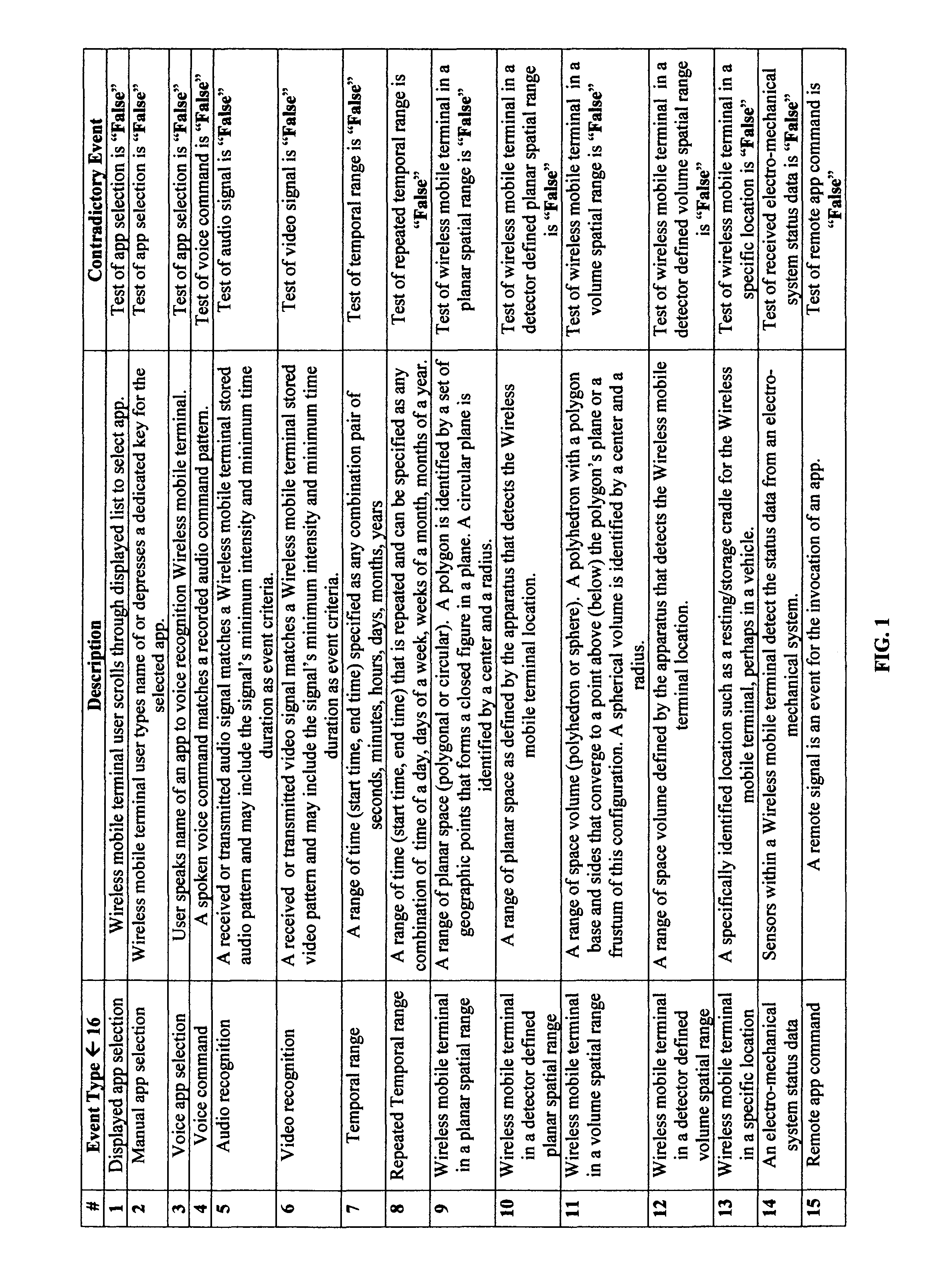
Application of the invoke facility service to restrict invocation of compound wireless mobile communication services
This invention provides a mechanism for enhancing safe use of wireless mobile terminals (smartphones) in a moving vehicle. The Invoke facility service's Boolean expression controls the conditions which invoke smartphone apps into execution. Smartphone apps, which are dangerous to execute in a moving vehicle, are prevented from invocation. Elimination of all smartphone apps in moving vehicles is inadvisable. An app, deploying an accelerometer to sense the impact of a serious collision to call “911” with a recorded message and provides the vehicle's GPS location, is an example. This invention allows an app builder to select invocation conditions for apps. Significant is the use manner of the operation “Not”. The contradiction of an event is also an event meaning that if an event is false, its contradictory event is true. Another important aspect is the conjunctive operation “And Then”. This operation implies an efficient algorithm to evaluate Boolean expressions.
Owner:KOBYLARZ THADDEUS JOHN
Fast gradient-histogram inverse planning technique for radiation treatment
InactiveUS20070003011A1Enhanced interactionRobust solutionX-ray/gamma-ray/particle-irradiation therapyImaging processingRadiation therapy
A method for fast inverse planning of IMRT treatment plans is disclosed. The method relies on a computationally efficient algorithm for evaluating the gradient of a general class of objective functions, and also on the efficient optimization that is realized due to the directional conjugacy of the objective functions. Several types of clinically relevant objective functions that belong to this class are described. The computational evaluation relies on operations that are commonly used for signal- and image-processing, and so can benefit from a number of well-known acceleration techniques.
Owner:LANE DEREK GRAHAM
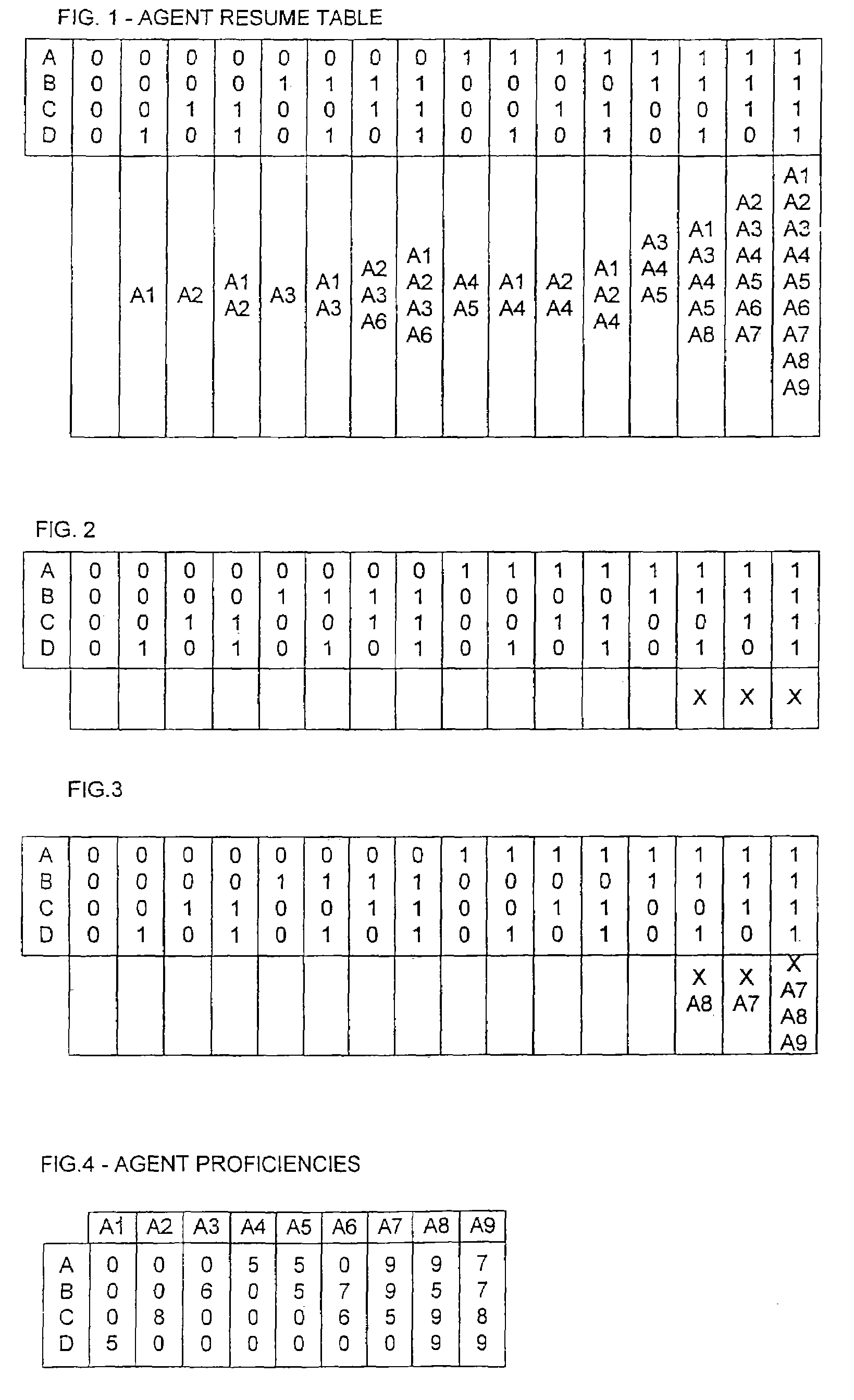
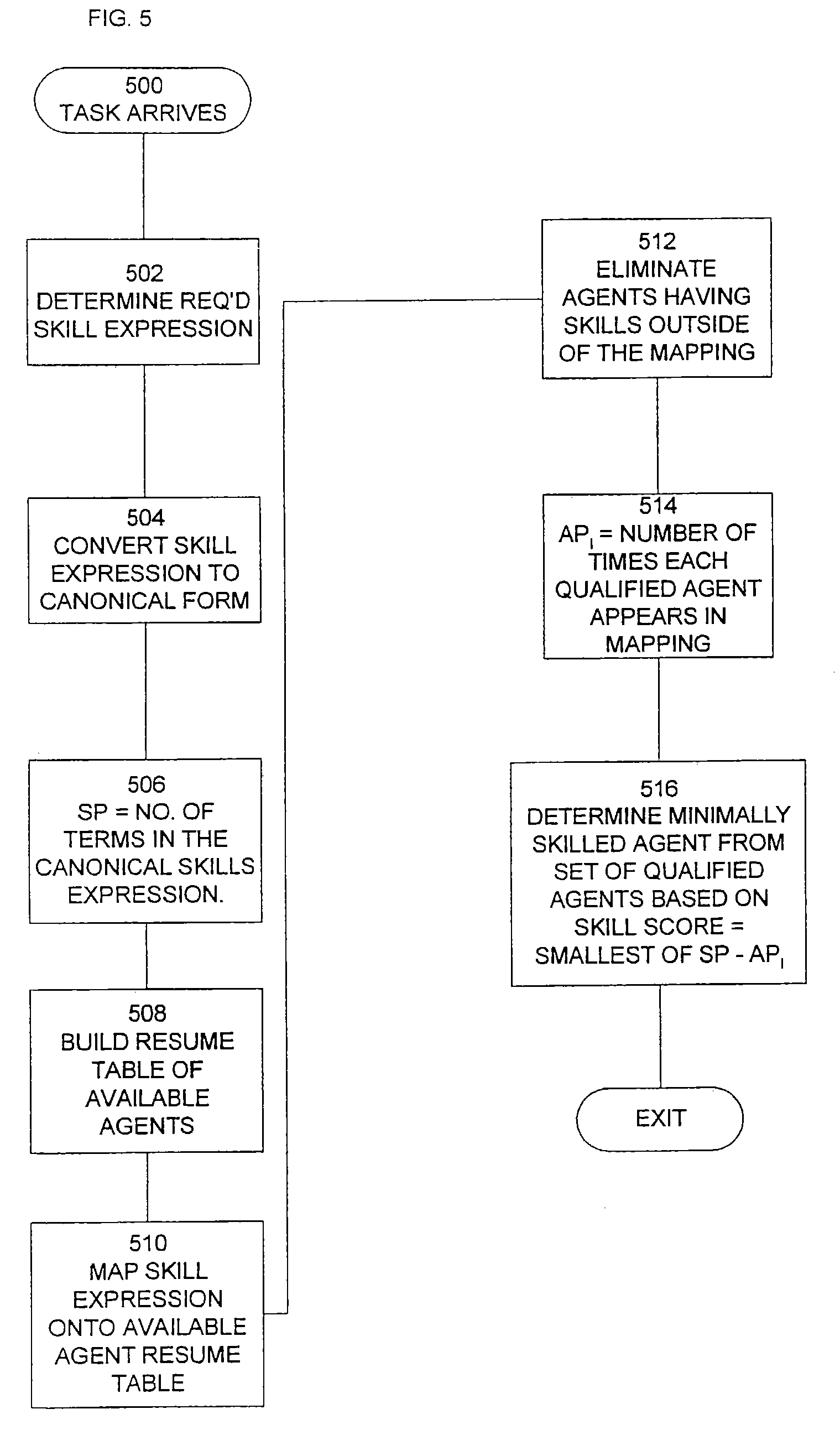
Method and apparatus for skills-based task routing
An efficient algorithm is presented for selecting an agent to service a task in a skills-based routing system. A set X is determined of all states of the boolean variables that contain the required skills for a task. A resume table of available agents is built, organized by the states of the N variables; each agent is represented in each state that includes all skills possessed by the agent. All available and qualified agents are determined from the resume table; those agents associated with a state of the resume table outside of the set X are disqualified. An agent is selected from those remaining. Preferably, an agent is selected having a minimum qualification level to service the task. One preferred way of doing this is to subtract from the number of terms in a canonical form of the required skills expression a number equal to the number of times the agent appears in the set of states X and picking an agent with the lowest result. In the preferred embodiment, however, proficiency levels of each required skill are taken into account in making the final selection.
Owner:GENESYS TELECOMM LAB INC AS GRANTOR +3
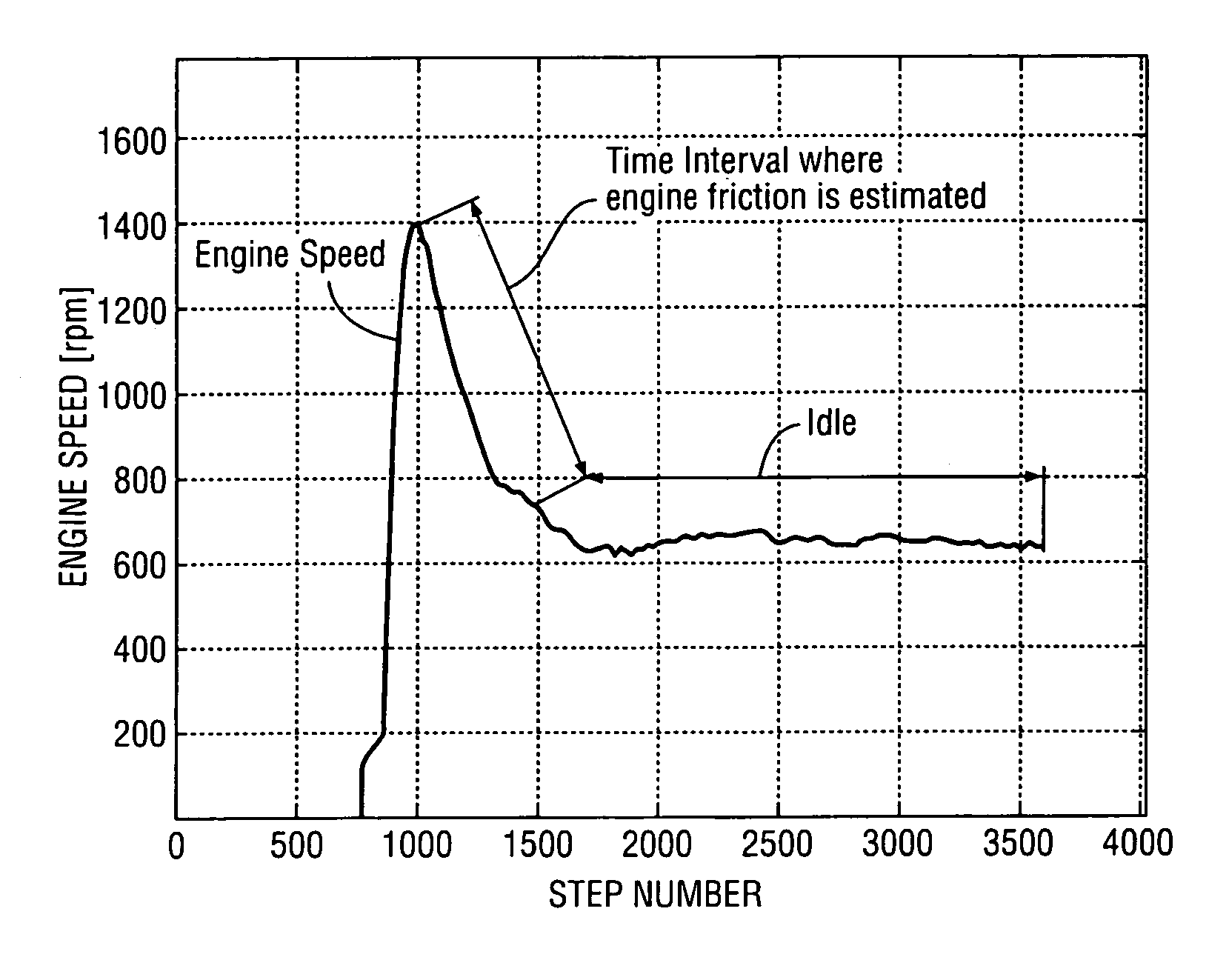
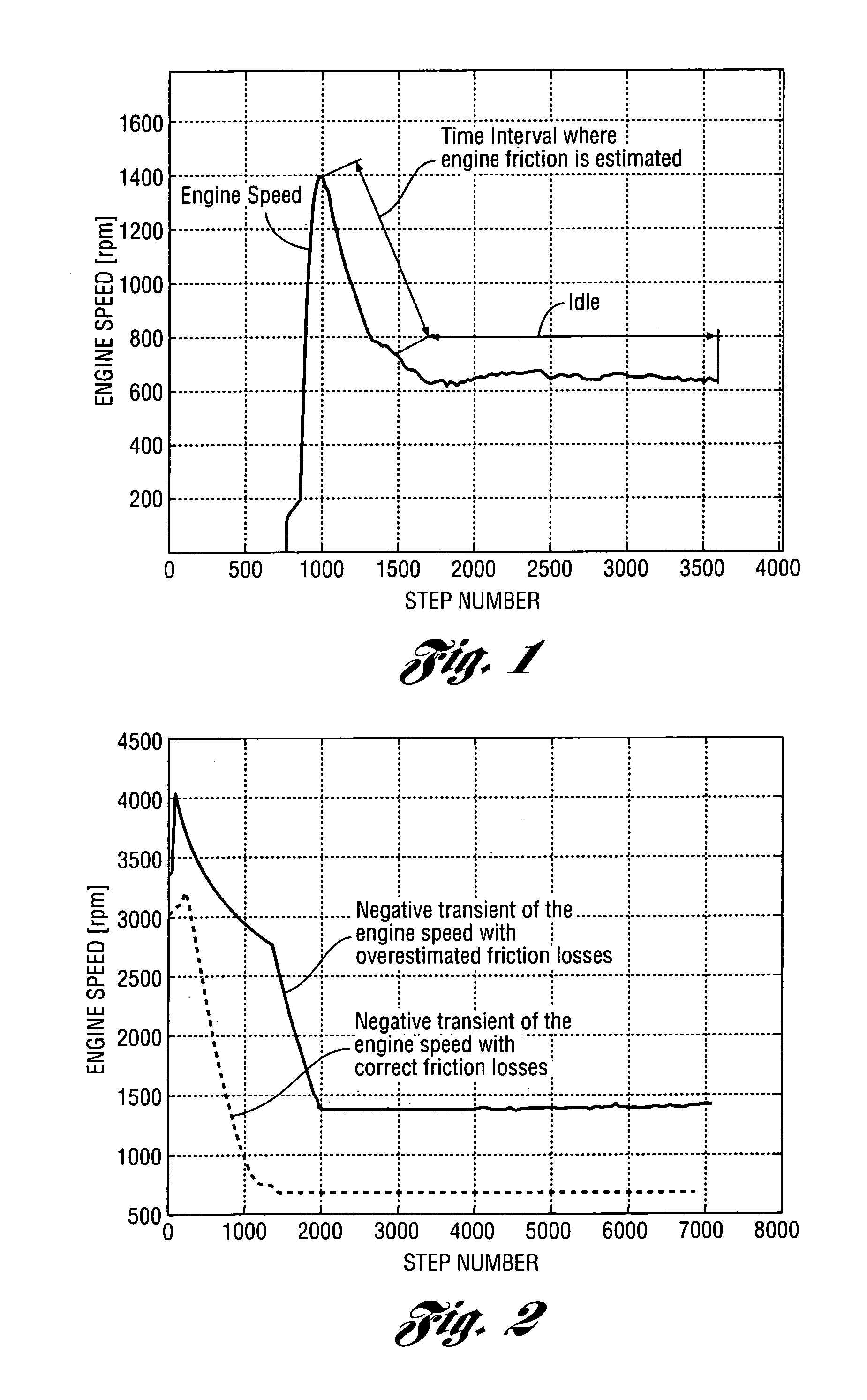
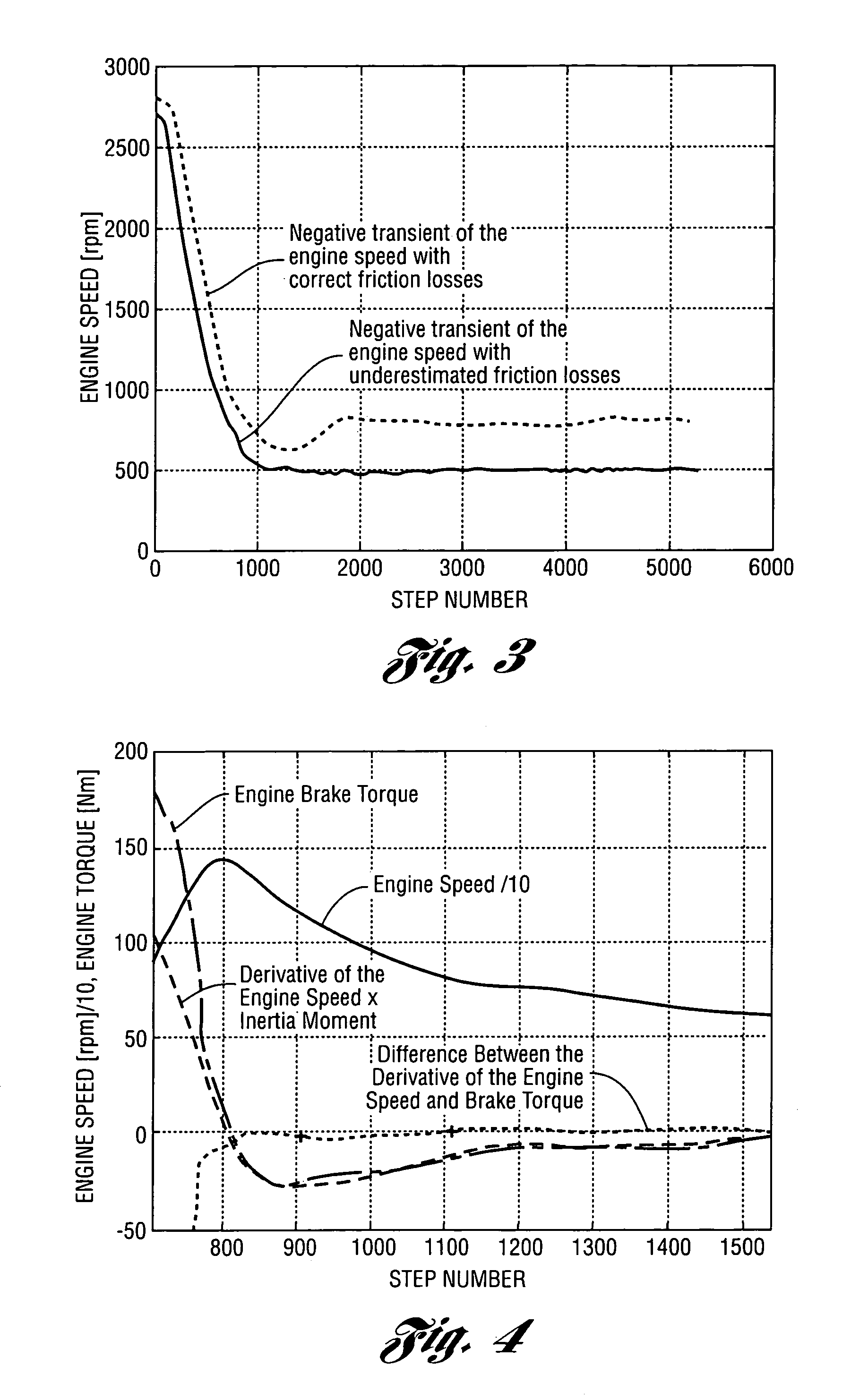
Method for estimating engine friction torque
ActiveUS7054738B1Lighten the computational burdenAnalogue computers for vehiclesElectrical controlFriction torqueEngineering
Algorithms for real-time estimation of the engine friction torque in a vehicle powertrain are disclosed. Engine friction torque is estimated at start and at engine idle. Recursive and computationally efficient algorithms allow prediction of friction torque for a wide range of speeds and loads even with few new measured points by taking into account physical dependencies used for adaptation of the sites of the look-up tables (static maps). The algorithms make it possible to avoid drivability problems that could result from errors in estimating engine friction torque.
Owner:VOLVO CAR CORP
Efficient algorithm and protocol for remote differential compression on a remote device
InactiveUS20050256974A1Efficient large object transferReduce the amount requiredMultiple digital computer combinationsTransmissionHorizonTheoretical computer science
The present invention is used to update objects over limited bandwidth networks. Objects are updated between two or more computing devices using remote differential compression (RDC) techniques such that required data transfers are minimized. In one aspect, efficient large object transfers are achieved by recursively applying the RDC algorithm to its own metadata; a single or multiple recursion step(s) may be used in this case to reduce the amount of metadata sent over the network by the RDC algorithm. Objects and / or signature and chunk length lists can be chunked by locating boundaries at dynamically determined locations. A mathematical function evaluates hash values associated within a horizon window relative to potential chunk boundary.
Owner:MICROSOFT TECH LICENSING LLC
Efficient algorithm and protocol for remote differential compression
A method and system are related to updating objects over limited bandwidth networks. Objects are updated between two or more computing devices using remote differential compression (RDC) techniques such that required data transfers are minimized. In one aspect, efficient large object transfers are achieved by recursively applying the RDC algorithm to its own metadata; a single or multiple recursion step(s) may be used in this case to reduce the amount of metadata sent over the network by the RDC algorithm. Objects and / or signature and chunk length lists can be chunked by locating boundaries at dynamically determined locations. A mathematical function evaluates hash values associated within a horizon window relative to potential chunk boundary. The described method and system is useful in a variety of networked applications, such as peer-to-peer replicators, email clients and servers, client-side caching systems, general-purpose copy utilities, database replicators, portals, software update services, file / data synchronization, and others.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for optimizing forward error correction of multimedia streaming over wireless networks
The loss of packets in a communication system can be minimized in an optimal manner by adapting a set of error correction (EC) parameters in response to a calculated probability of packet loss. The calculated probability is obtained from derived algorithms that are applied to a set of communication parameters. Algorithms are derived from Bernoulli-distributed traffic models and constant bit rate (CBR) traffic models of the communication system. A collapsed-state model is used to derive a very efficient algorithm that calculates an approximate probability of packet loss. Alternate applications for the algorithms are also disclosed.
Owner:DOLBY LAB LICENSING CORP
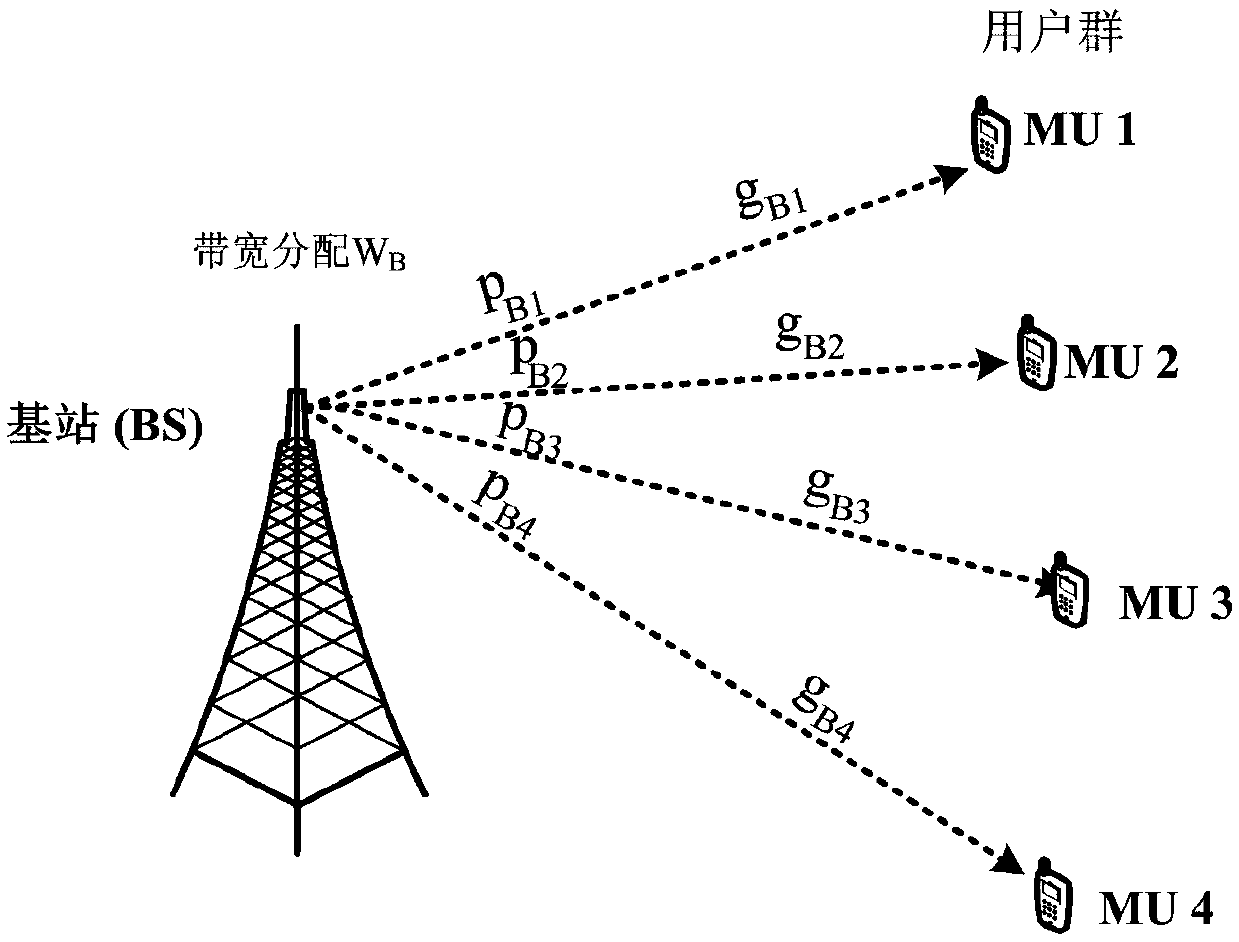
Linear search method of joint allocation of channel bandwidth and power in non-orthogonal multiple access link
InactiveCN108040364AImprove efficiencyMinimal resource consumptionPower managementResource consumptionAccess technology
The invention provides a linear search method of joint allocation of channel bandwidth and power in a non-orthogonal multiple access link. The method comprises the following steps: 1) providing, by abase station, data flow service for a mobile user through the non-orthogonal multiple access technology; 2) analyzing system characteristics to equivalently transform a problem; and 3) designing an efficient algorithm solution according to the characteristics of the finally converted problem, and finally substituting an output result of the algorithm to a top layer problem to obtain an optimal bandwidth and power allocation value. The invention provides a feasible and efficient optimization method that not only guarantees the data demand of mobile users, but also minimizes the total system resource consumption, so as to improve the utilization rate of system resources and optimize the configuration of system resources.
Owner:ZHEJIANG UNIV OF TECH
Frequency division multiplexing multi-user MIMO energy efficiency optimization method
ActiveCN103997775AReduce productionImprove universalityEnergy efficient ICTPower managementFrequency-division multiplexingProcess engineering
The invention discloses a frequency division multiplexing multi-user MIMO energy efficiency optimization method which can be applied to a multi-user MIMO system. The optimization goal is to design a precoding scheme for each user to maximize a total energy efficiency utility function. The frequency division multiplexing multi-user MIMO energy efficiency optimization method is implemented through the following steps that firstly, optimization preprocessing is conducted on energy efficiency functions of all the users, wherein the optimization preprocessing process is specifically divided into three steps of noise whitening and channel diagonalization, determination of a water-filling solution of a link power allocation scheme and acquisition of the optimized energy efficiency functions; secondly, the energy efficiency functions optimized in advance are used for determining the sending power of each user to maximize the total energy efficiency utility function of the multiple users; finally, a user group energy efficiency utility maximization algorithm is used for solving the problem. According to the frequency division multiplexing multi-user MIMO energy efficiency optimization method, the definition of the multi-user energy efficiency utility function has universality and can cover various indexes including the weighted average, the exponentiation product, the weighed harmonic average, the weighed minimum value and the like for maximizing the energy efficiency of all the users, and the efficient algorithm put forward later is applicable to all the indexes.
Owner:上海瀚芯实业发展合伙企业(有限合伙)
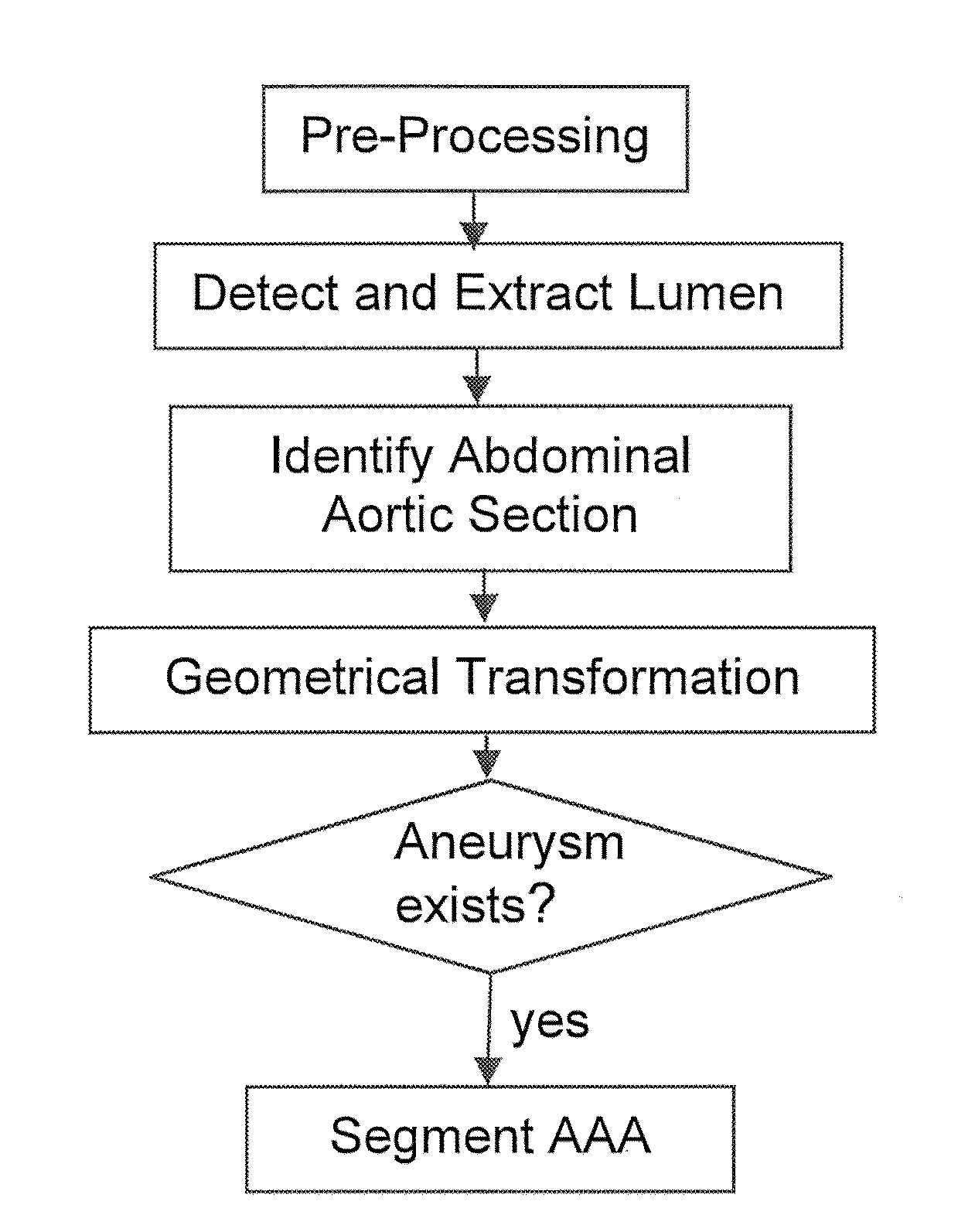
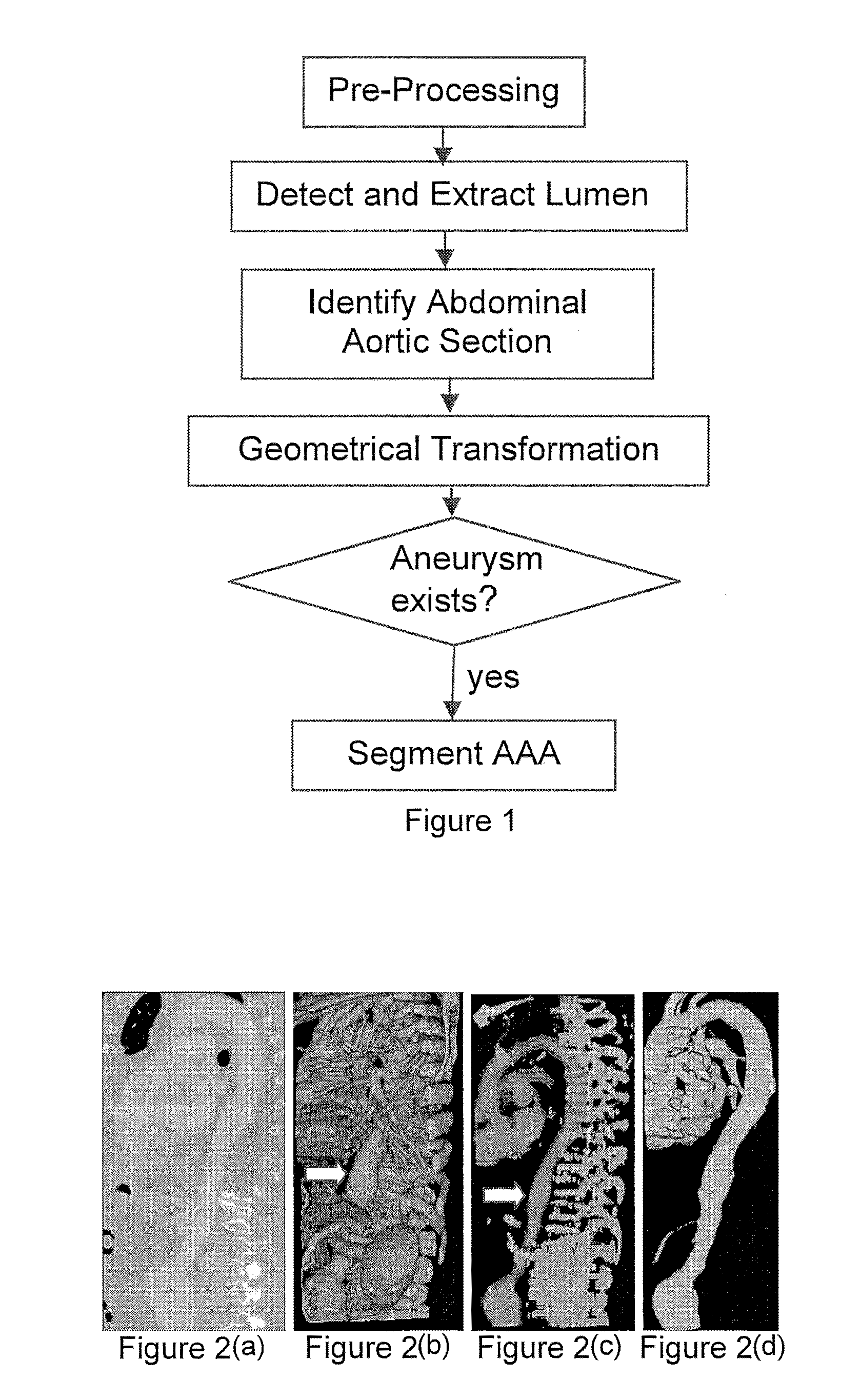
Automatic detection and accurate segmentation of abdominal aortic aneurysm
InactiveUS20110206257A1Fast resultsSimple methodImage enhancementImage analysisEfficient algorithmAccurate segmentation
This invention concerns an efficient algorithm for automatic and accurate segmentation of Abdominal Aortic Aneurysm (AAA). The algorithm first identifies the location of the lumen (the inner portion of aorta) and then segments it. The abdominal portion of the lumen is then found using anatomical and geometrical features. This portion of the lumen is straightened using geometrical transformation based on the smoothed centreline. The transformed lumen is then passed through a number of filters, based on geometrical, intensity, gradient and texture features, to search for the existence of the aneurysm. If aneurysm is detected, a deformable model is first initialized to the approximate borders of the aneurysm which are then refined using global and location information.
Owner:UNIVERSITY OF LAUSANNE
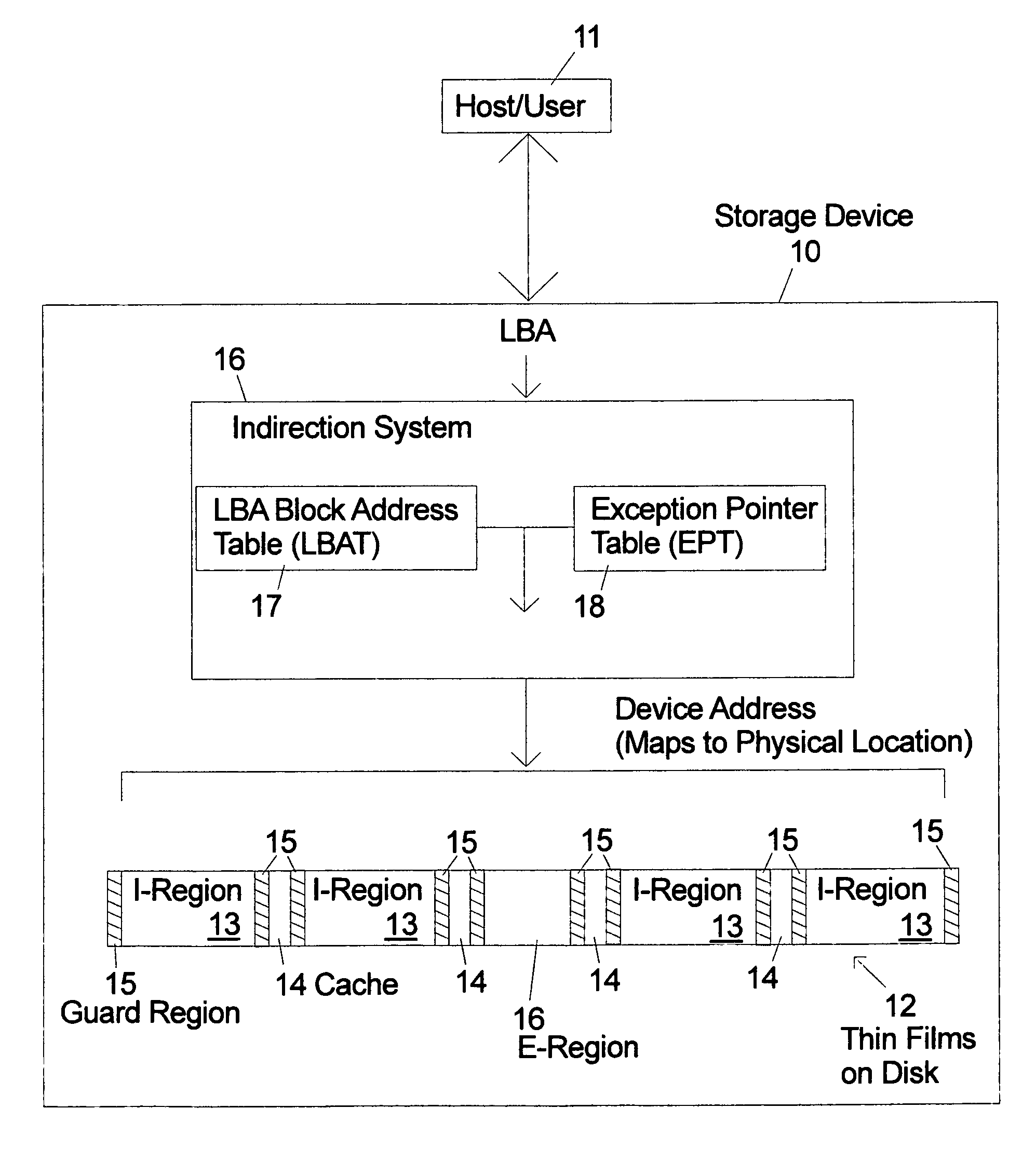
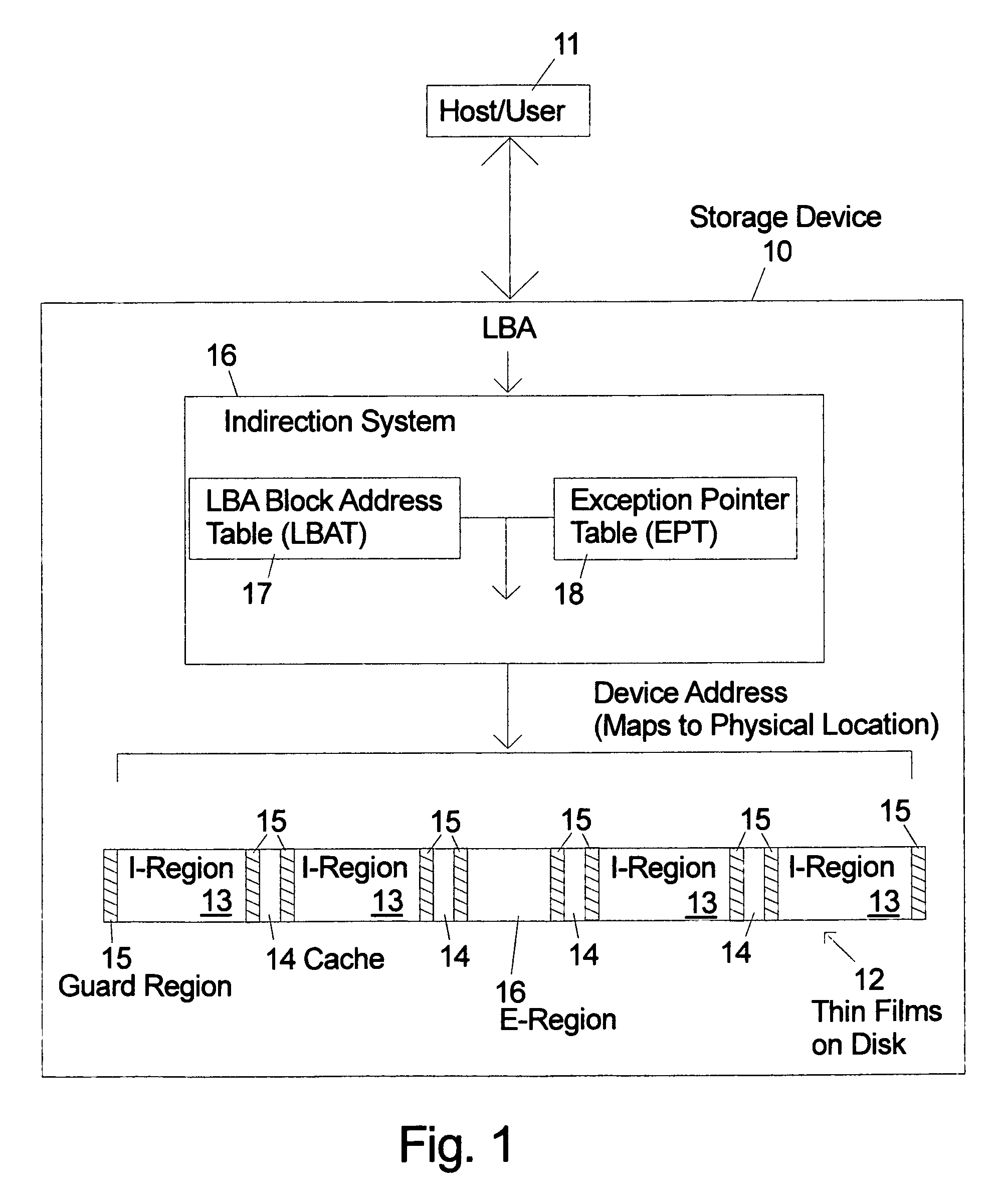
Indirection memory architecture with reduced memory requirements for shingled magnetic recording devices
ActiveUS20120303930A1Small sizeEfficient algorithmMemory adressing/allocation/relocationRecording on magnetic disksShingled magnetic recordingTheoretical computer science
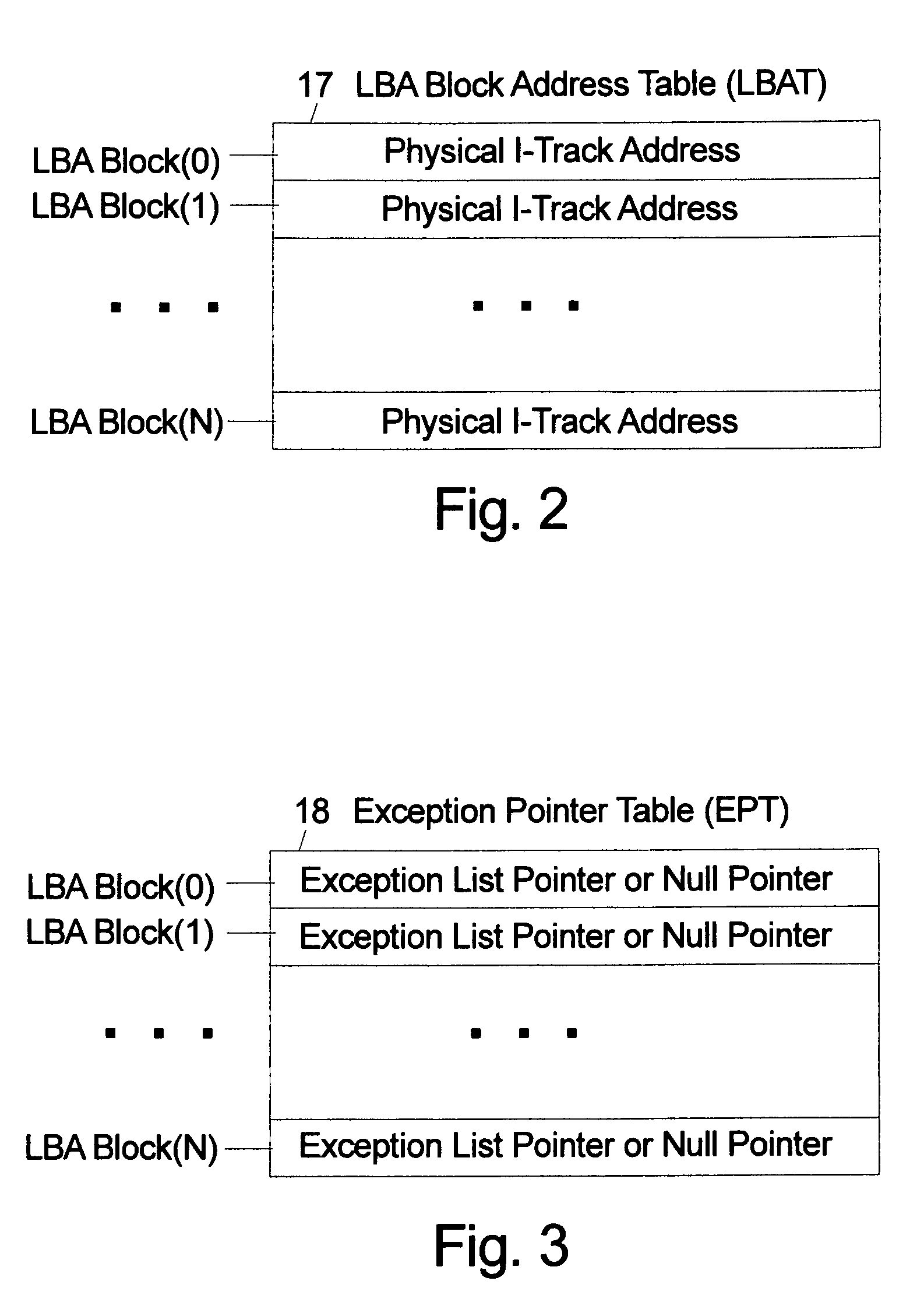
An indirection system in a shingled storage device is described that uses an efficient algorithm to map LBAs to DBAs based on a predetermined rule or assumption and then handles as exceptions LBAs that are not mapped according to the rule. The assumed rule is that a fixed-length set of sequential host LBAs are located at the start of an I-track. Embodiments of the invention use two tables to provide the mapping of LBAs to DBAs. The mapping assumed by the rule is embodied in the LBA Block Address Table (LBAT) which gives the corresponding I-track address for each LBA Block. The LBA exceptions are recorded using an Exception Pointer Table (EPT), which gives the pointer to the corresponding variable length Exception List for each LBA Block. The indexing into the LBAT and the EPT is made efficient by deriving the index from the LBA by a simple arithmetic operation.
Owner:WESTERN DIGITAL TECH INC
Database system
InactiveUS20040177090A1Easily exposedReduce distanceObject oriented databasesSpecial data processing applicationsData storingData store
A database system which uses a hierarchical structure of data nodes. The nodes are of two types, tag nodes forming the hierarchical structure, each tag node having one or more data storing audit nodes as children. Data entered into the database is stored in the audit nodes and changes to the stored data are made by the addition of new versions of the audit nodes such that the audit nodes form an audit trail for the database. Current data is viewed by supplying via the tag node the most recently added child, and older versions of the database are similarly supplied via the tag nodes transparently presenting older versions of the time-stamped audit nodes. The tag nodes may store data which has been automatically deduced from the data in the audit nodes. Both data and the data structure may be selectively replicated throughout the database using an efficient algorithm.
Owner:CMED GROUP
Track geometric irregularity inspection method based on two-dimensional laser displacement sensors
ActiveCN107554553AImprove anti-interference abilityEasy to handleUsing optical meansRailway auxillary equipmentGyroscopeAccelerometer
The invention discloses a detection method for track geometric irregularity based on a two-dimensional laser displacement sensor. A left laser sensor, a right laser sensor, a longitudinal inclinometer, a lateral inclination meter, a gyroscope, a lateral accelerometer, and a left vertical acceleration are installed on the detection beam. meter, right vertical accelerometer, the left laser sensor and the right laser sensor are two-dimensional laser sensors; perform the following measurements: track gauge detection, height detection, rail direction detection, horizontal superhigh detection, twist detection, curvature detection, Rail vertical as well as side wear measurements. The present invention adopts a high-speed two-dimensional laser displacement sensor, which has strong anti-interference ability. Based on the two-dimensional sensor, there is no complicated image processing step, and with simple and effective back-end algorithm processing, it has higher detection and calculation speed. It can effectively eliminate the influence of vehicle body vibration on the detection result, the detection result has high repeatability, can compensate the detection result, and has higher detection accuracy.
Owner:CHANGZHOU LUHANG RAILWAY TRANSPORTATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com