Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
40 results about "Data dependency graph" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
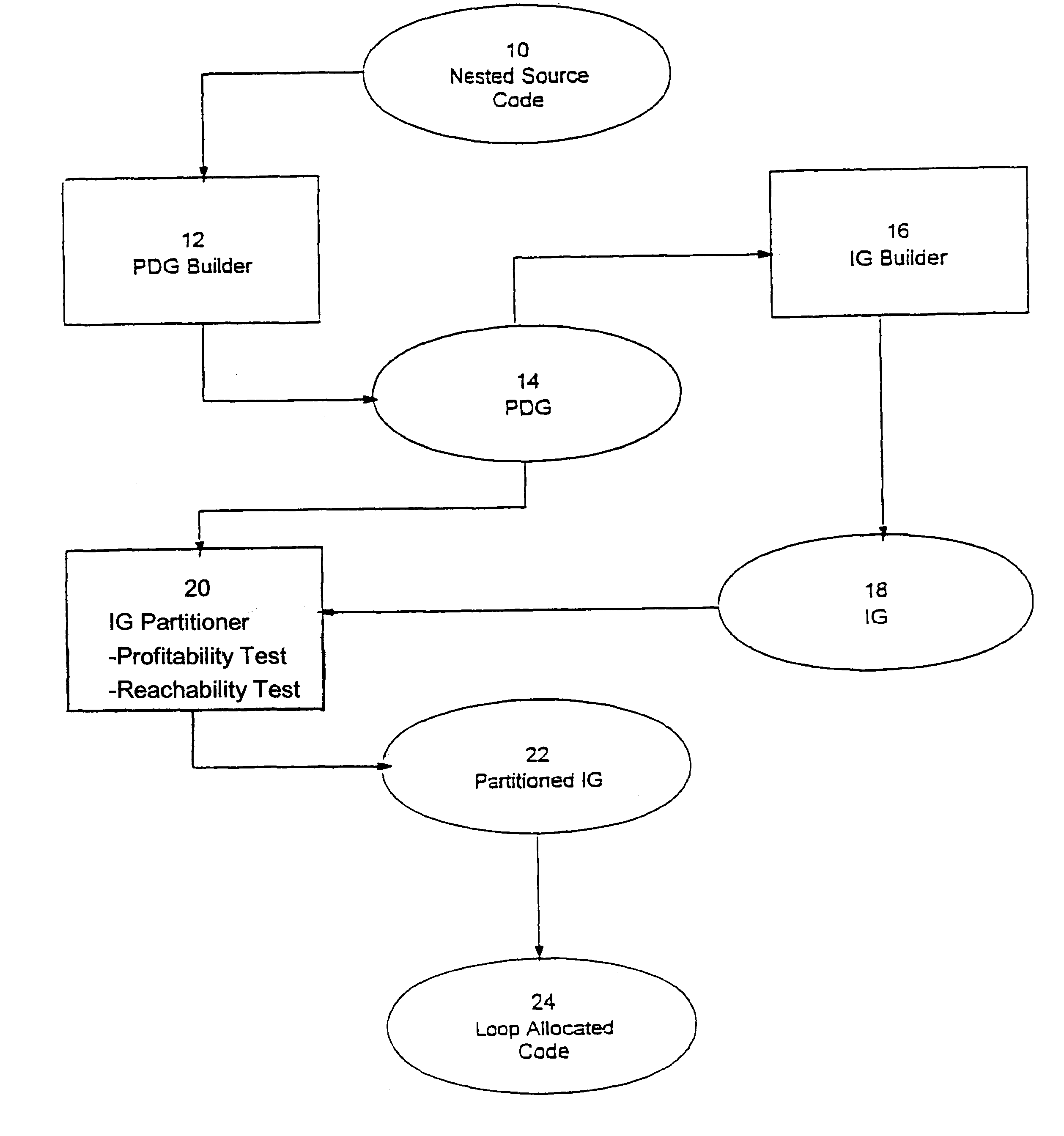
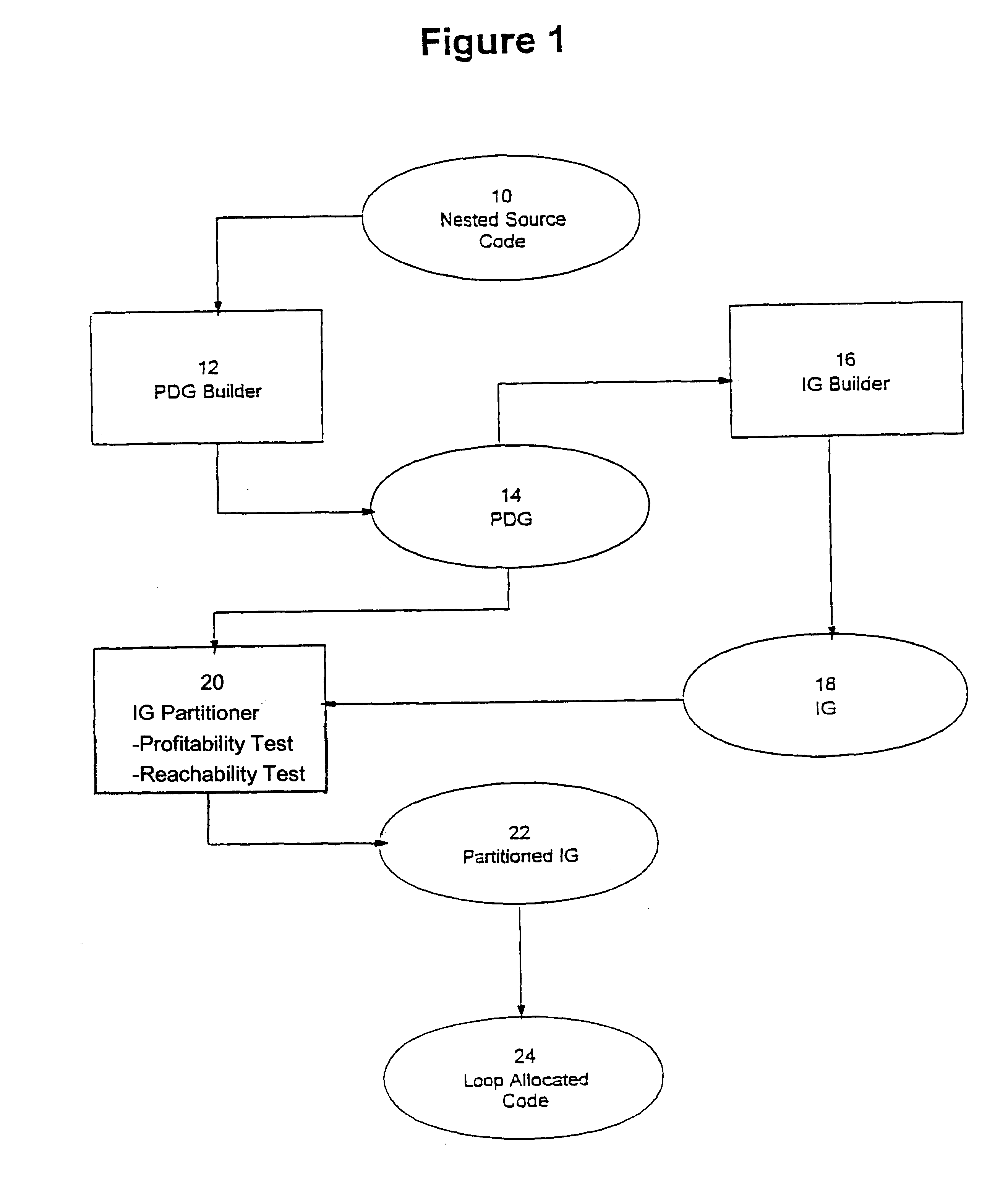
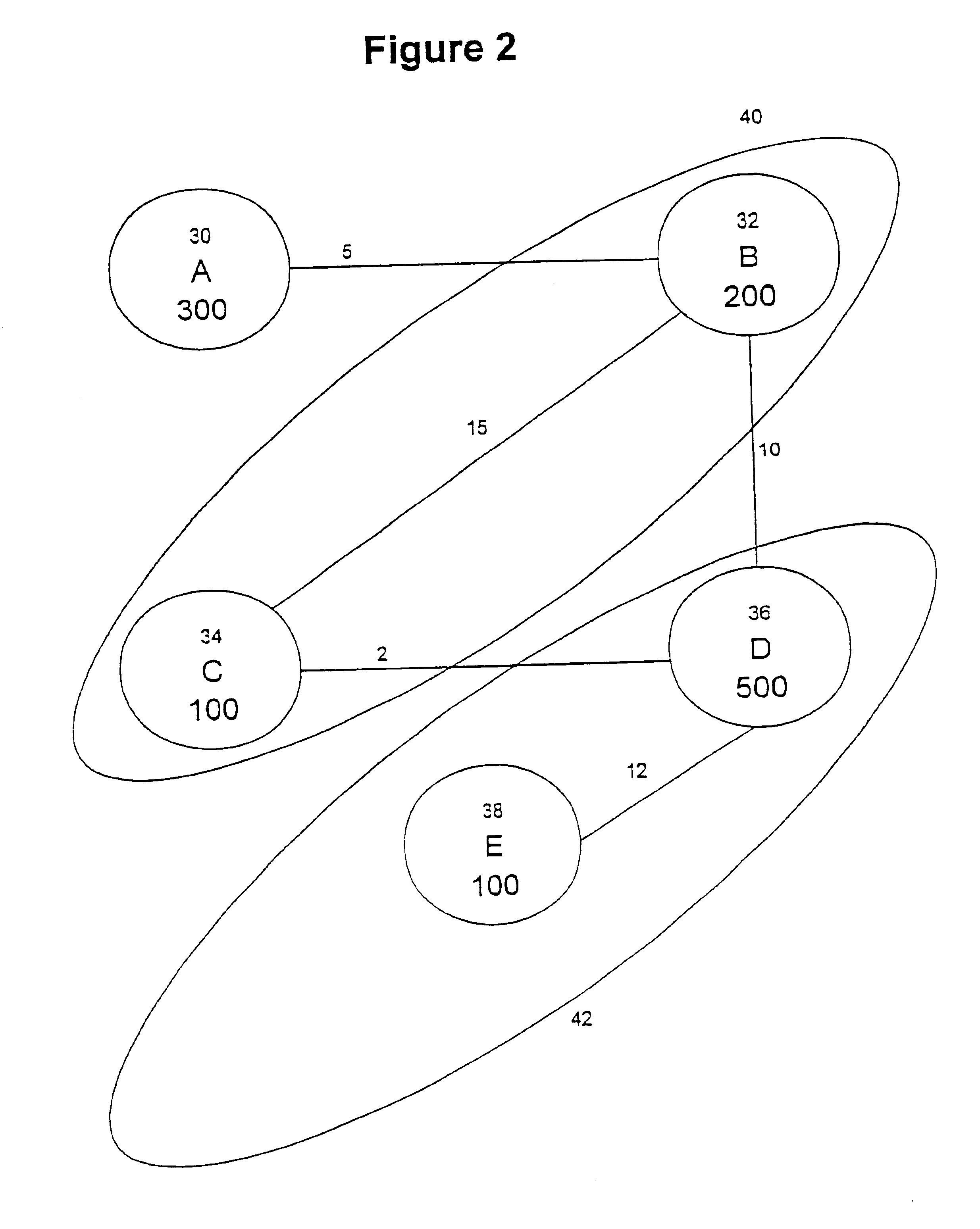
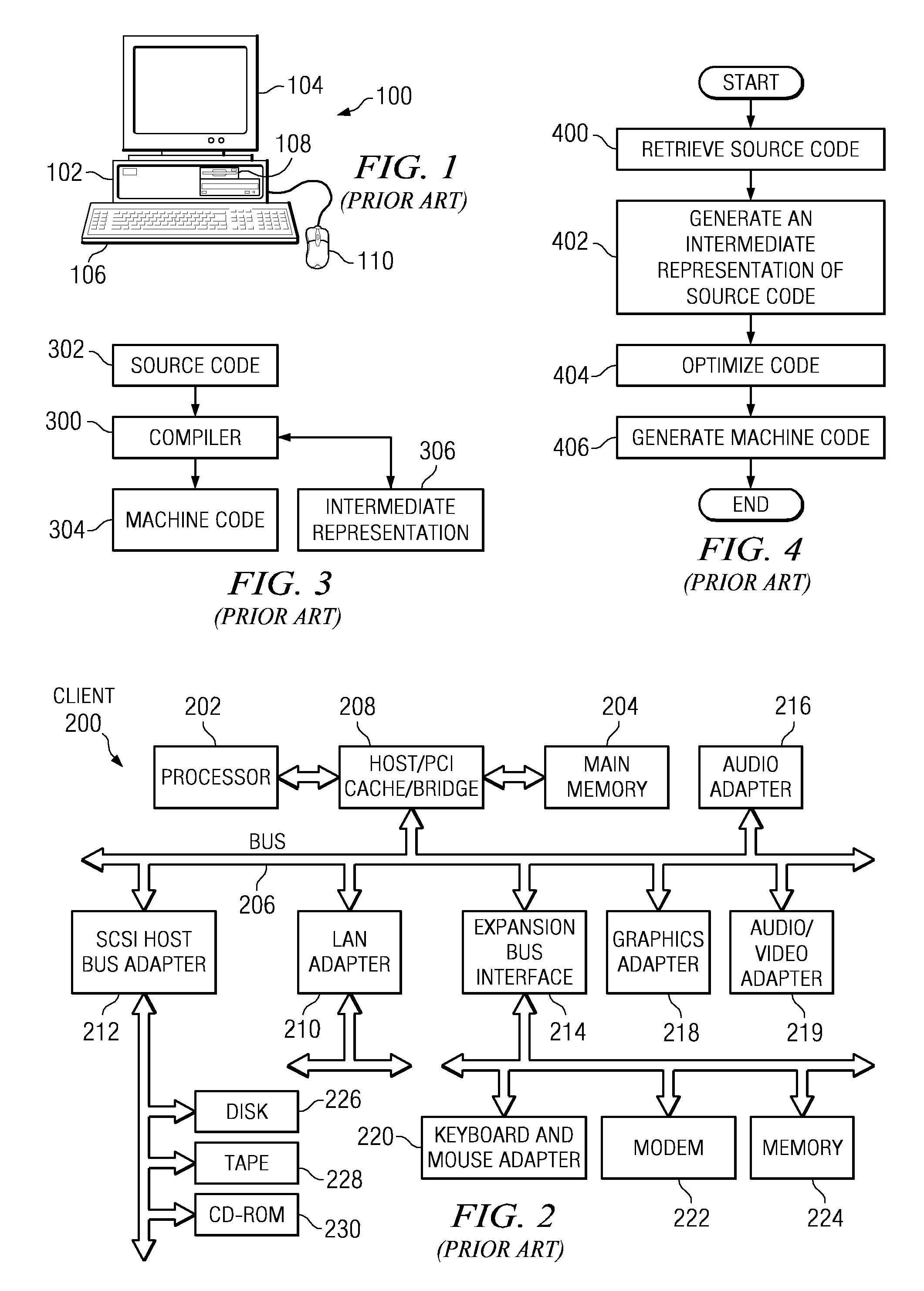
Loop allocation for optimizing compilers
Loop allocation for optimizing compilers includes the generation of a program dependence graph for a source code segment. Control dependence graph representations of the nested loops, from innermost to outermost, are generated and data dependence graph representations are generated for each level of nested loop as constrained by the control dependence graph. An interference graph is generated with the nodes of the data dependence graph. Weights are generated for the edges of the interference graph reflecting the affinity between statements represented by the nodes joined by the edges. Nodes in the interference graph are given weights reflecting resource usage by the statements associated with the nodes. The interference graph is partitioned using a profitability test based on the weights of edges and nodes and on a correctness test based on the reachability of nodes in the data dependence graph. Code is emitted based on the partitioned interference graph.
Owner:IBM CORP
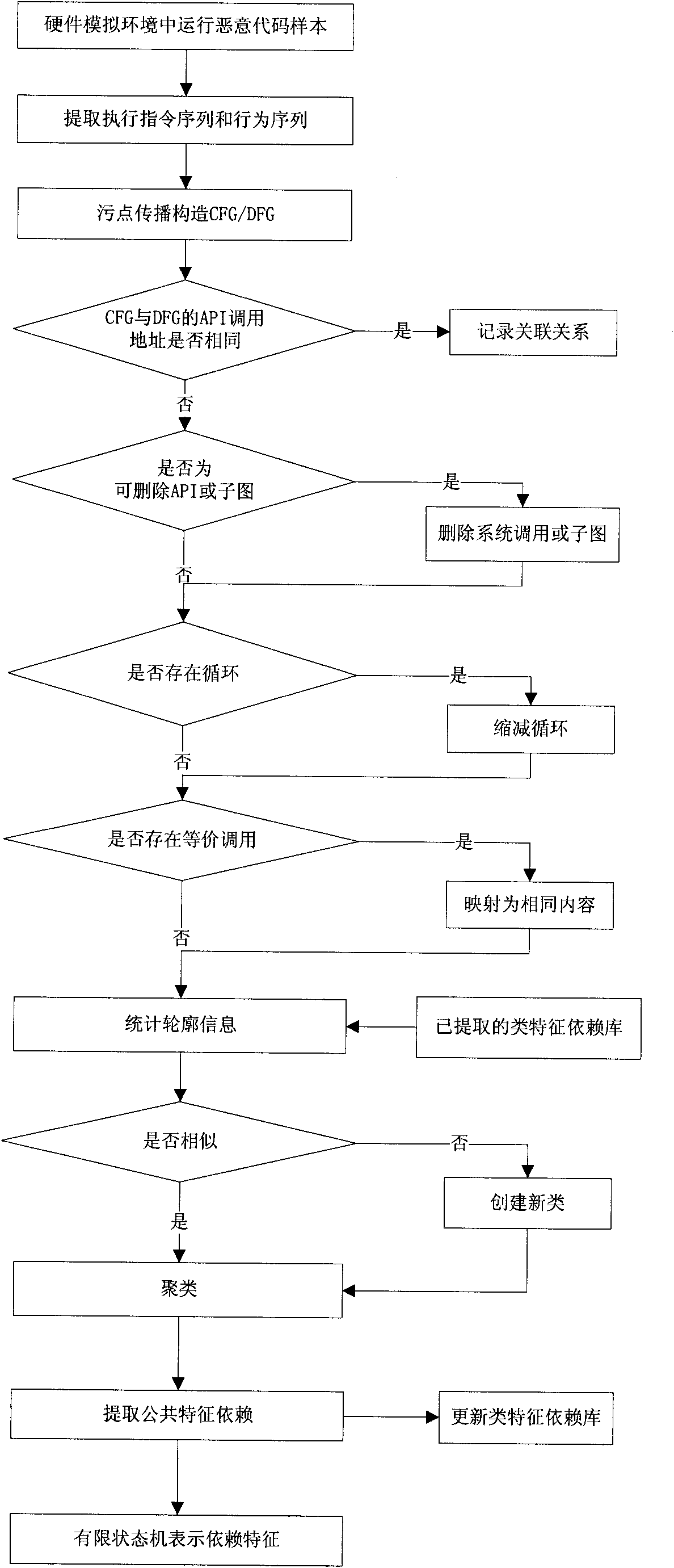
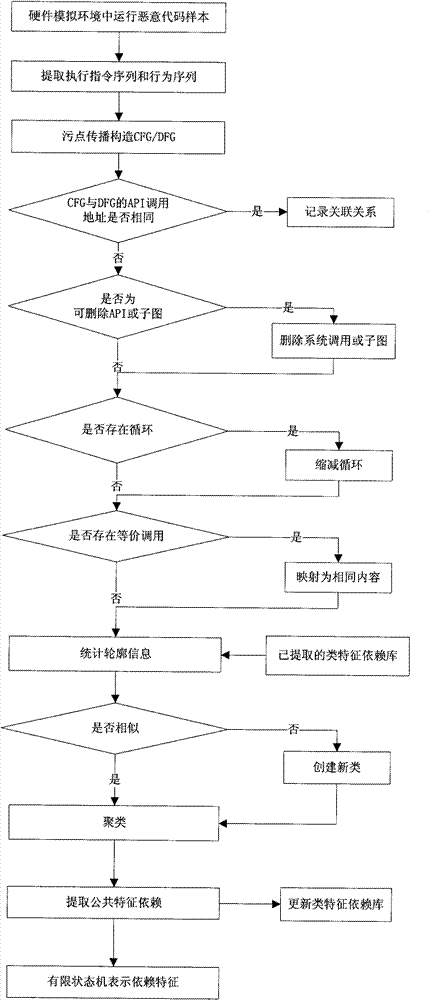
Method for extracting malicious code behavior characteristic
InactiveCN102054149AComprehensive information extractionImprove anti-interference abilityPlatform integrity maintainanceData dependency graphSingle sample
The invention discloses a method for extracting a malicious code behavior characteristic, which belongs to the technical field of network security. The method comprises the following steps of: 1) running a malicious code and extracting executive information of the malicious code, wherein the executive information comprises an executive instruction sequence and a behavior sequence of the maliciouscode; 2) constructing a control dependence graph and a data dependence graph for executing the code according to the executive information; 3) comparing relevance of the control dependence graph and the data dependence graph and recording related relevance information; and 4) comparing the control dependence graphs and the data dependence graphs of different malicious codes and extracting characteristic dependency of each type of samples according to similarity clustering. Compared with the prior art, the method has the characteristics of complete information extraction, high anti-interference performance, certain applicability to varieties of a single sample characteristic, small-sized characteristic library and wide application range.
Owner:GRADUATE SCHOOL OF THE CHINESE ACAD OF SCI GSCAS
Modification of swing modulo scheduling to reduce register usage
InactiveUS20060048123A1Software engineeringProgram controlData dependency graphDistributed computing
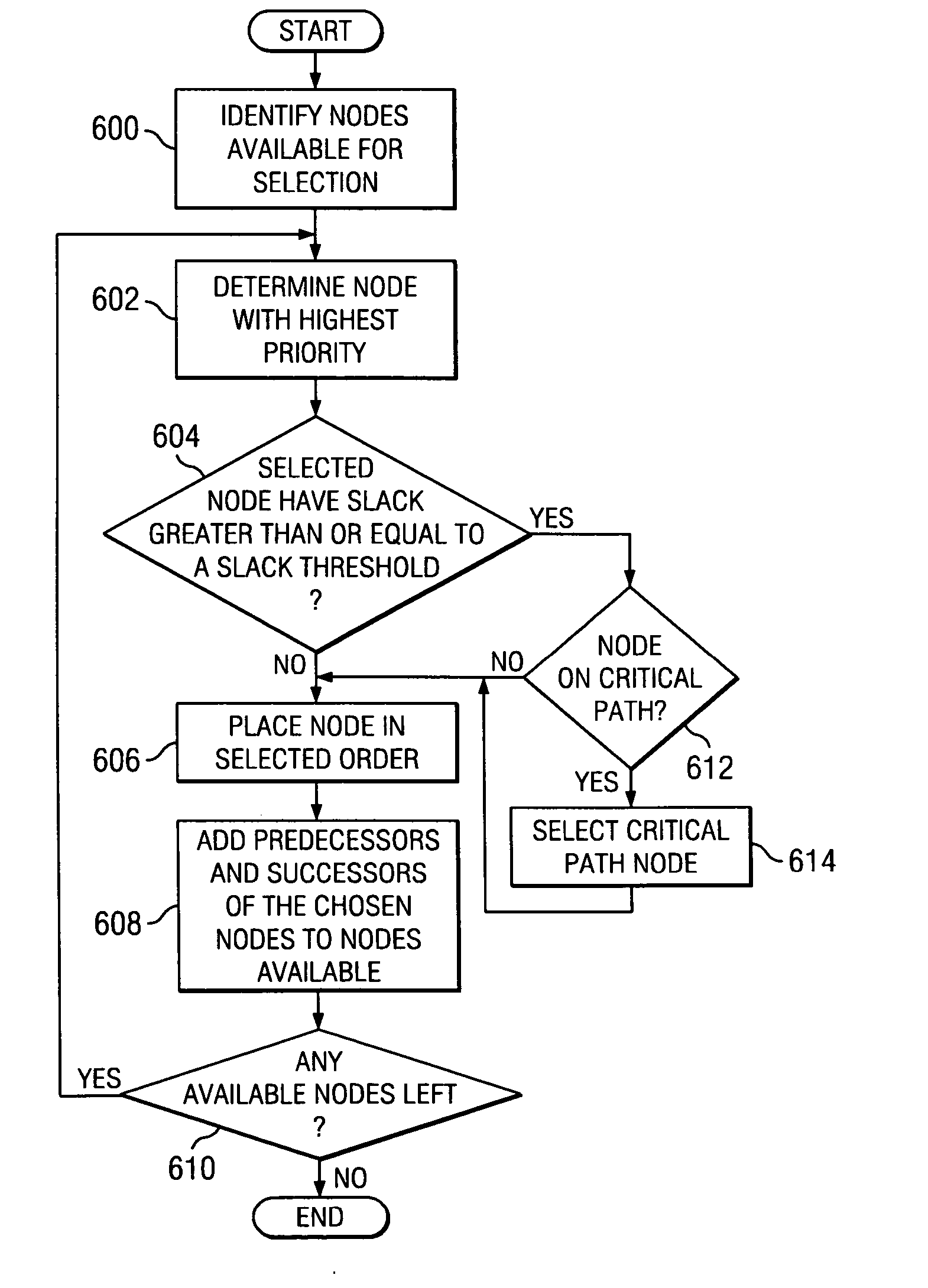
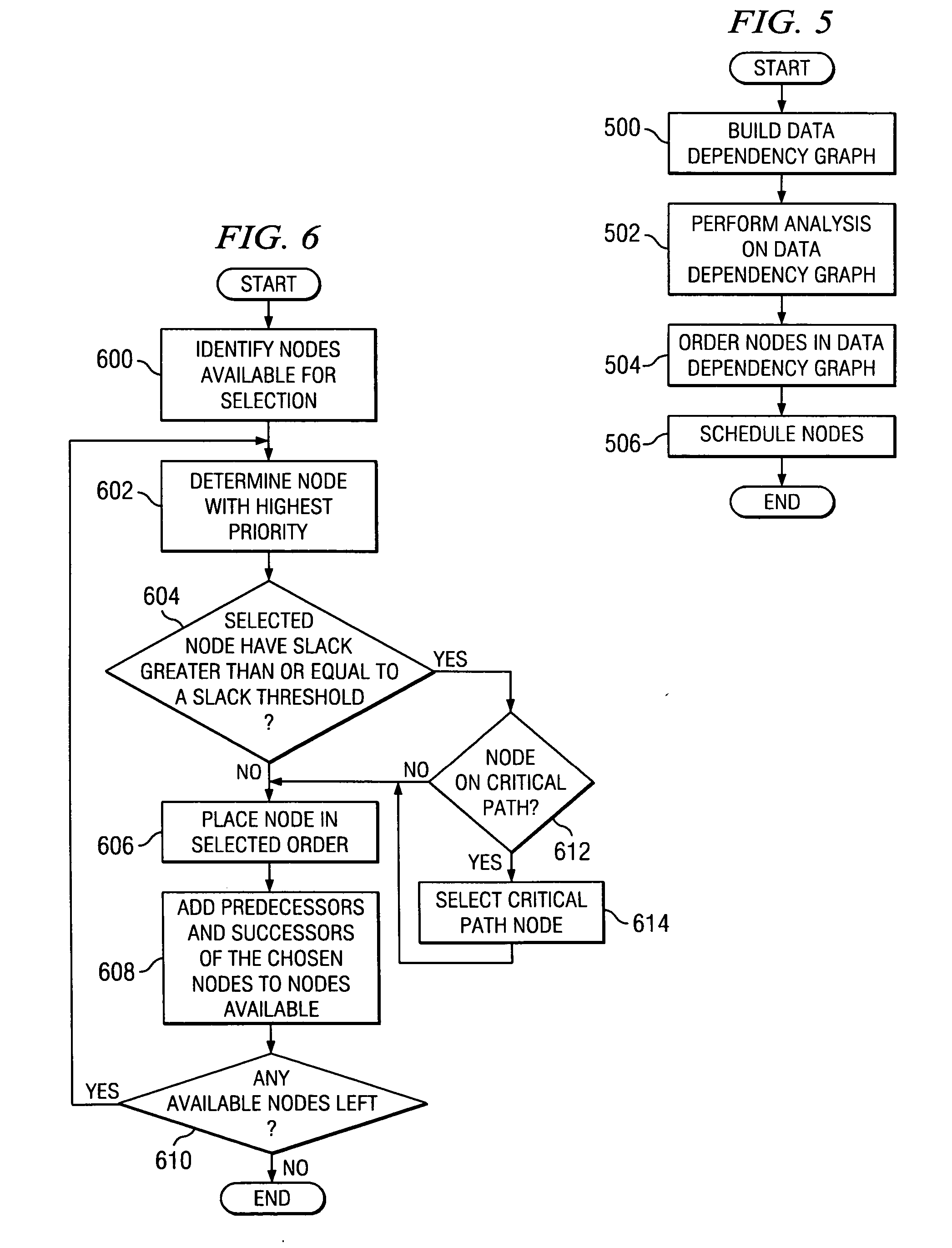
A method, apparatus, and computer instructions for optimizing loops in code during swing modulo scheduling of the code. Nodes in the data dependency graph are given a prioritized ordering for placement, using height / depth as the primary prioritization characteristic. When a node is selected with highest priority based on height / depth the node is then tested to see if it has significant slack, in which case a determination is made if there are any available nodes that lie on the critical path. Nodes from the critical path are thus taken as higher priority than nodes with significant slack, and are placed earlier in the prioritized ordering.
Owner:IBM CORP
Memory access abnormity detecting method and memory access abnormity detecting device
ActiveCN104636256AImplement detection operationsRealize the detection operation of memory access out of boundsSoftware testing/debuggingPlatform integrity maintainanceData dependency graphLexical analysis
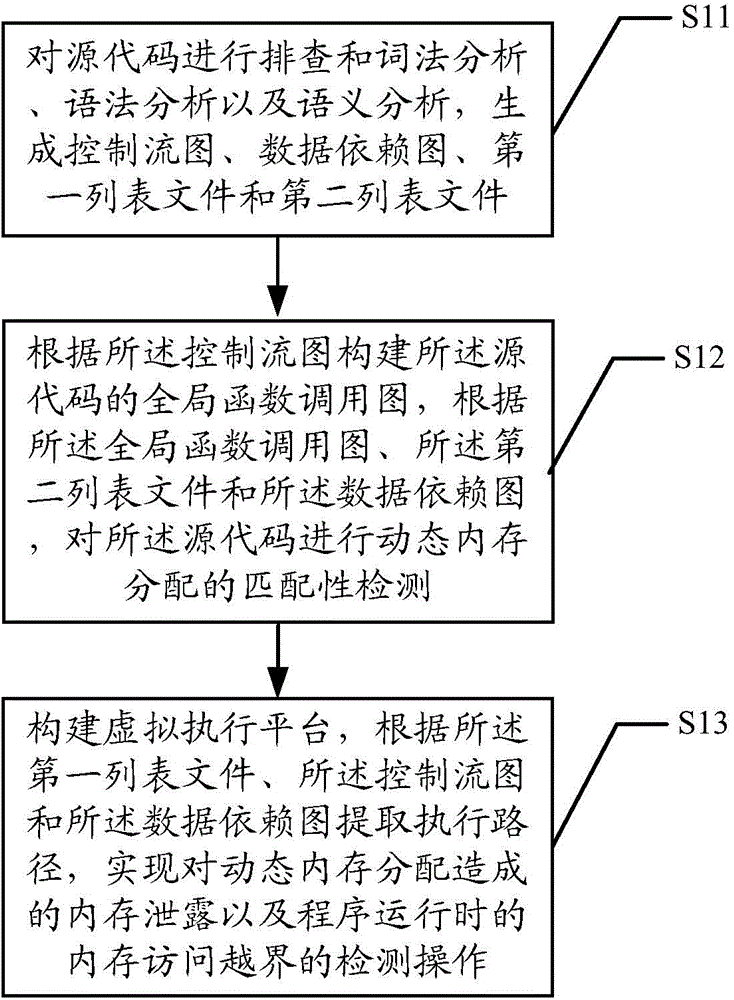
The invention discloses a memory access abnormity detecting method and a memory access abnormity detecting device. The memory access abnormity detecting method comprises the following steps of checking source codes and analyzing the morphology, the grammar and the semanteme of the source codes to generate a control flow diagram, a data dependence diagram, a first list file and a second list file; establishing a global function invocation diagram of the source codes according to the control flow diagram; performing matching detection on dynamic memory allocation of the source codes according to the global function invocation diagram, the second list file and the data dependence diagram; and establishing a virtual executing platform; and extracting an executing path according to the first list file, the control flow diagram and the data dependence diagram so as to detect memory leakage caused by dynamic memory allocation and memory access violation during running of a program. Memory access abnormity in the source codes can be sufficiently dug by analyzing the first list file, the second list file, the control flow diagram, the data dependence diagram and the global function invocation diagram, establishing the virtual executing platform and extracting the executing path, and the memory access abnormity can be detected efficiently.
Owner:AGRICULTURAL BANK OF CHINA
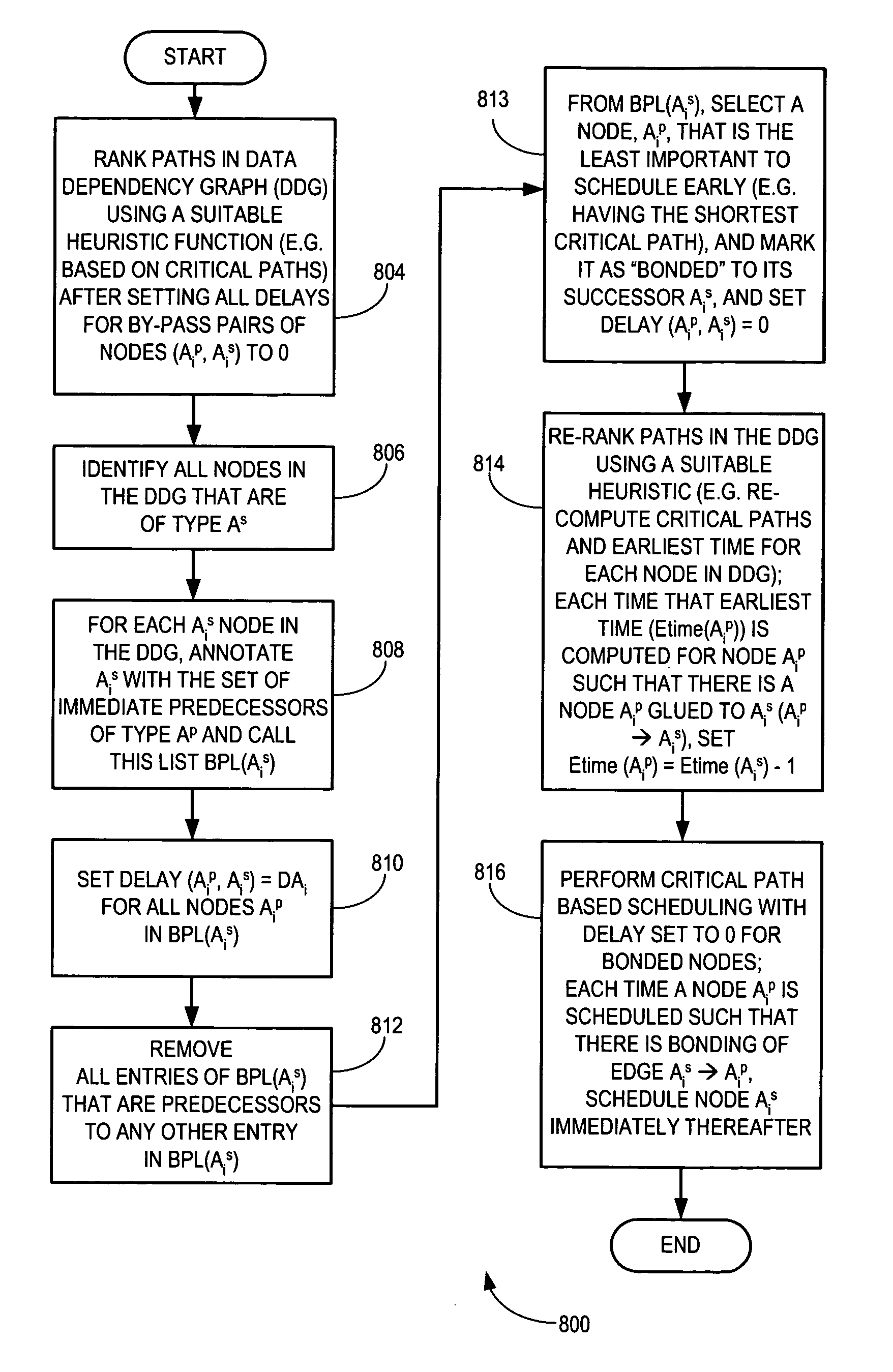
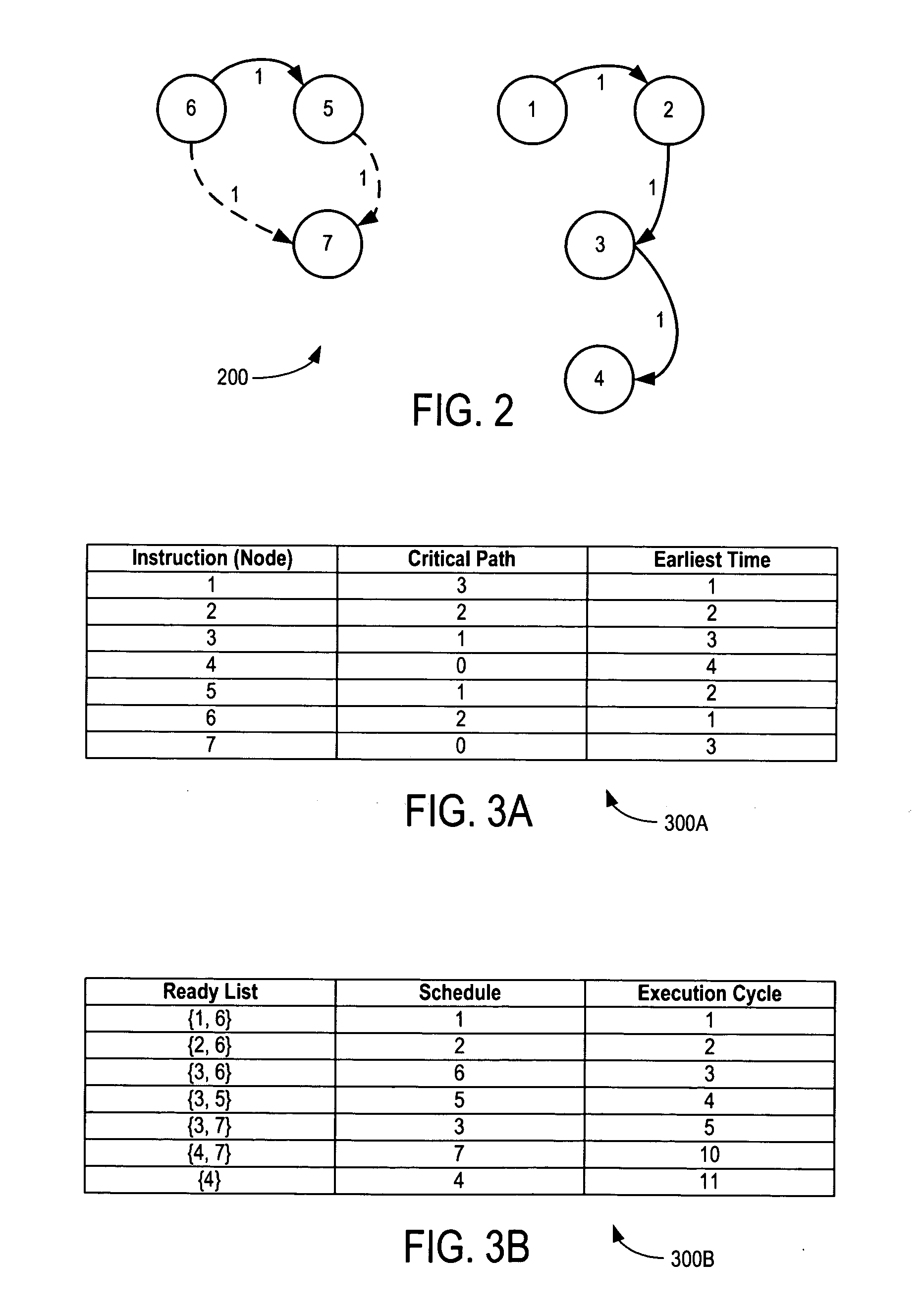
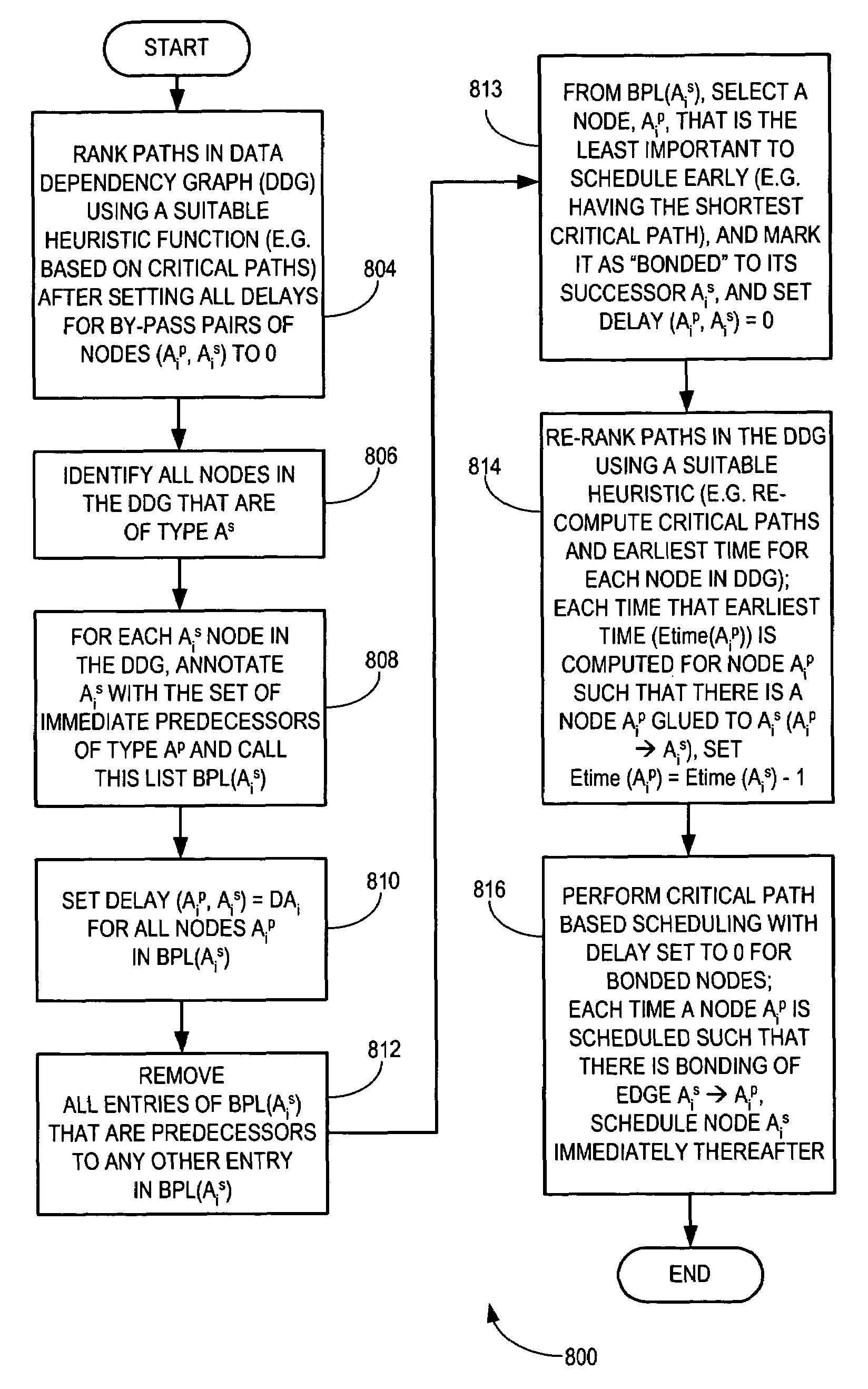
Method and system for configuring a dependency graph for dynamic by-pass instruction scheduling
ActiveUS20060031823A1Software engineeringProgram controlData dependency graphScheduling instructions
There is disclosed a method and system for configuring a data dependency graph (DDG) to handle instruction scheduling in computer architectures permitting dynamic by-pass execution, and for performing dynamic by-pass scheduling utilizing such a configured DDG. In accordance with an embodiment of the invention, a heuristic function is used to obtain a ranking of nodes in the DDG after setting delays at all identified by-pass pairs of nodes in the DDG to 0. From among a list of identified by-pass pairs of nodes, a node that is identified as being the least important to schedule early is marked as “bonded” to its successor, and the corresponding delay for that identified node is set to 0. Node rankings are re-computed and the bonded by-pass pair of nodes are scheduled in consecutive execution cycles with a delay of 0 to increase the likelihood that a by-pass can be successfully taken during run-time execution.
Owner:META PLATFORMS INC
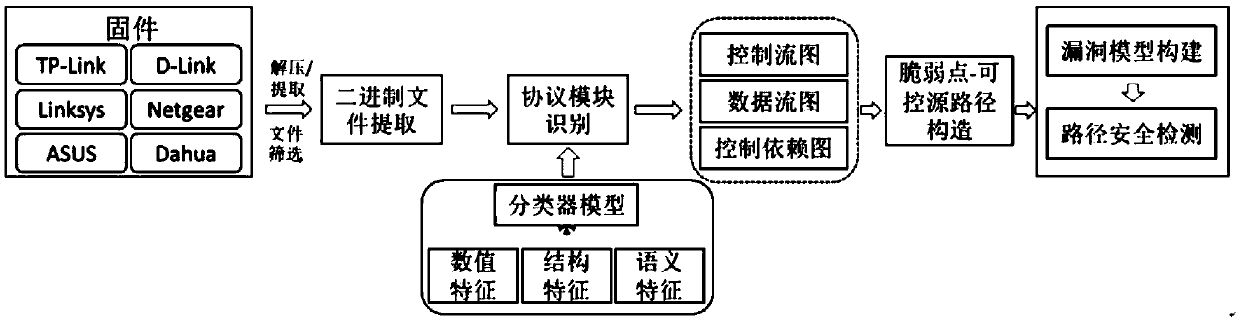
Lightweight method and system for determining protocol vulnerabilities in embedded system firmware
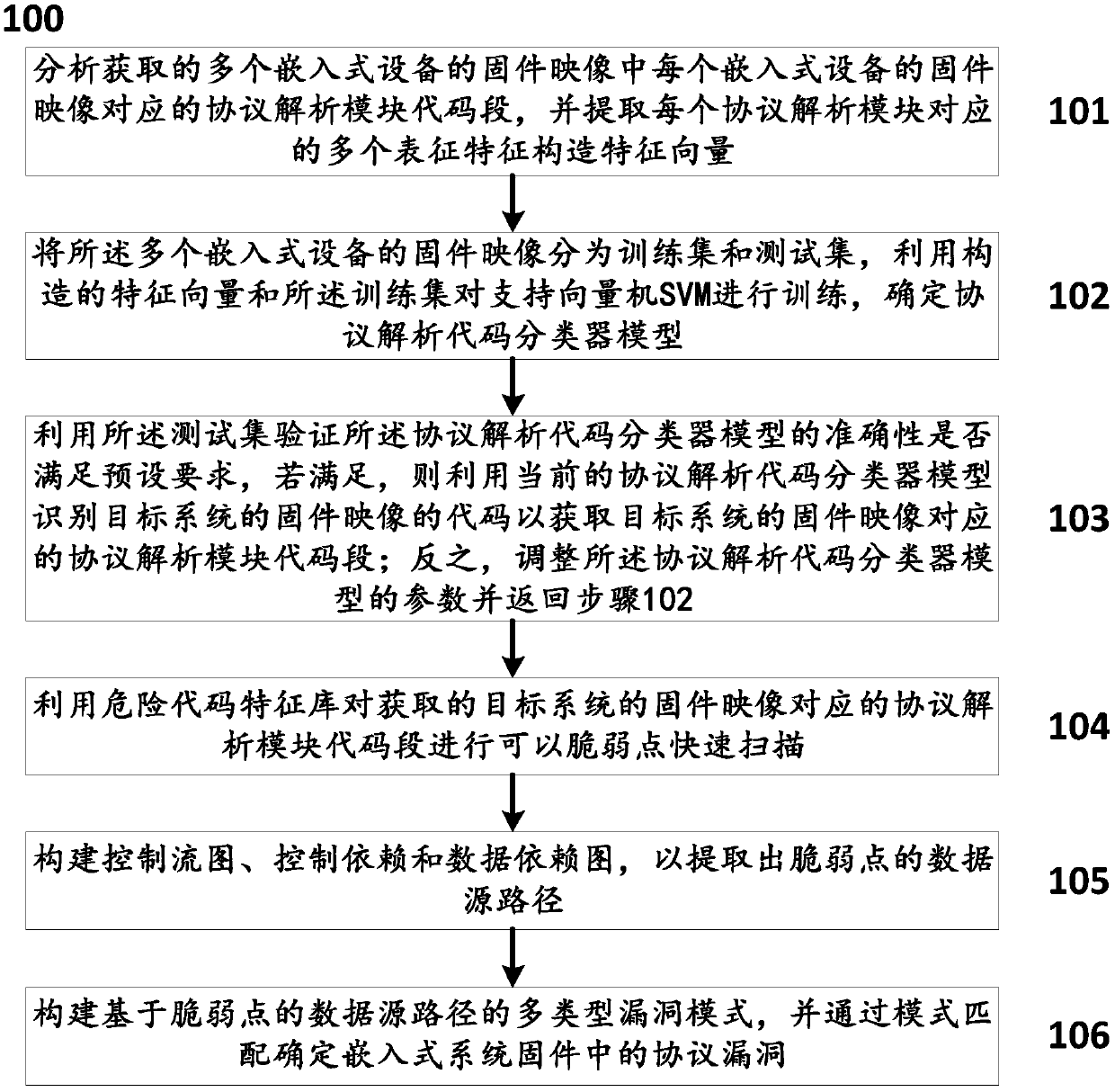
ActiveCN109525556ACharacter and pattern recognitionPlatform integrity maintainancePattern matchingGoal system
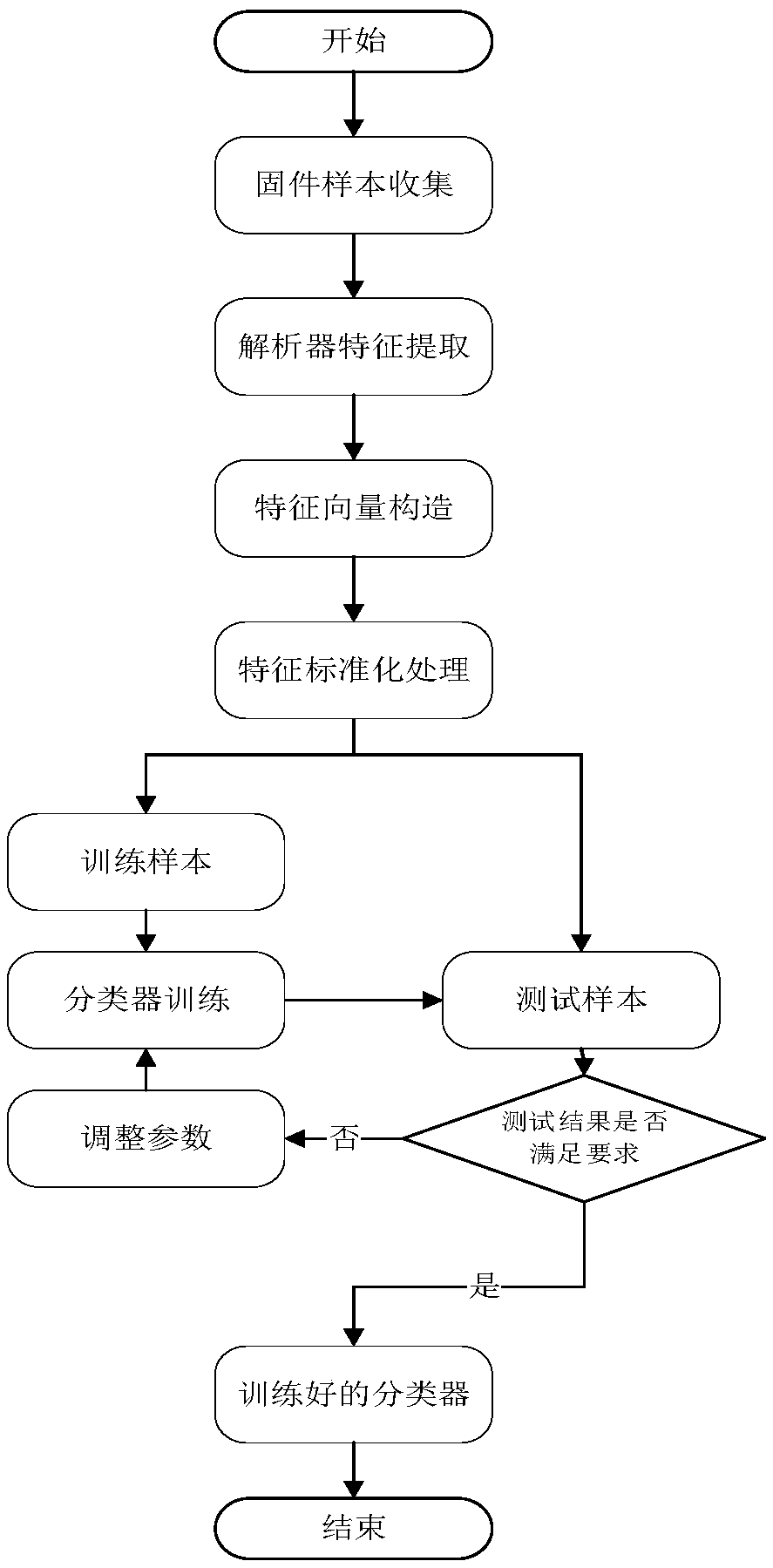
The invention discloses a lightweight method and a system for determining protocol vulnerabilities in an embedded system firmware. The method comprises the following steps: constructing a feature vector by analyzing a protocol and parsing code feature; using the constructed feature vector and a training set to train a support vector machine SVM, determining a protocol parsing code classifier modelfor identifying a protocol parsing module; using the trained protocol parsing code classifier model to identify the protocol parsing module in the firmware image code of a target system; for the identified protocol parsing module, using a dangerous code feature library to quickly scan the suspected vulnerable points of the protocol parsing module; extracting the data source paths of the vulnerable points on the basis of constructing a control flow graph, a control dependency graph, and a data dependency graph; and constructing a multi-type vulnerability mode based on a vulnerable-point-baseddata source path, and determining protocol vulnerabilities in the embedded system firmware by pattern matching. The lightweight method and the system for determining protocol vulnerabilities in the embedded system firmware can provide a technical support for network protocol security, Internet of Things / Industrial Control System security, and security testing.
Owner:CHINA ELECTRIC POWER RES INST +2
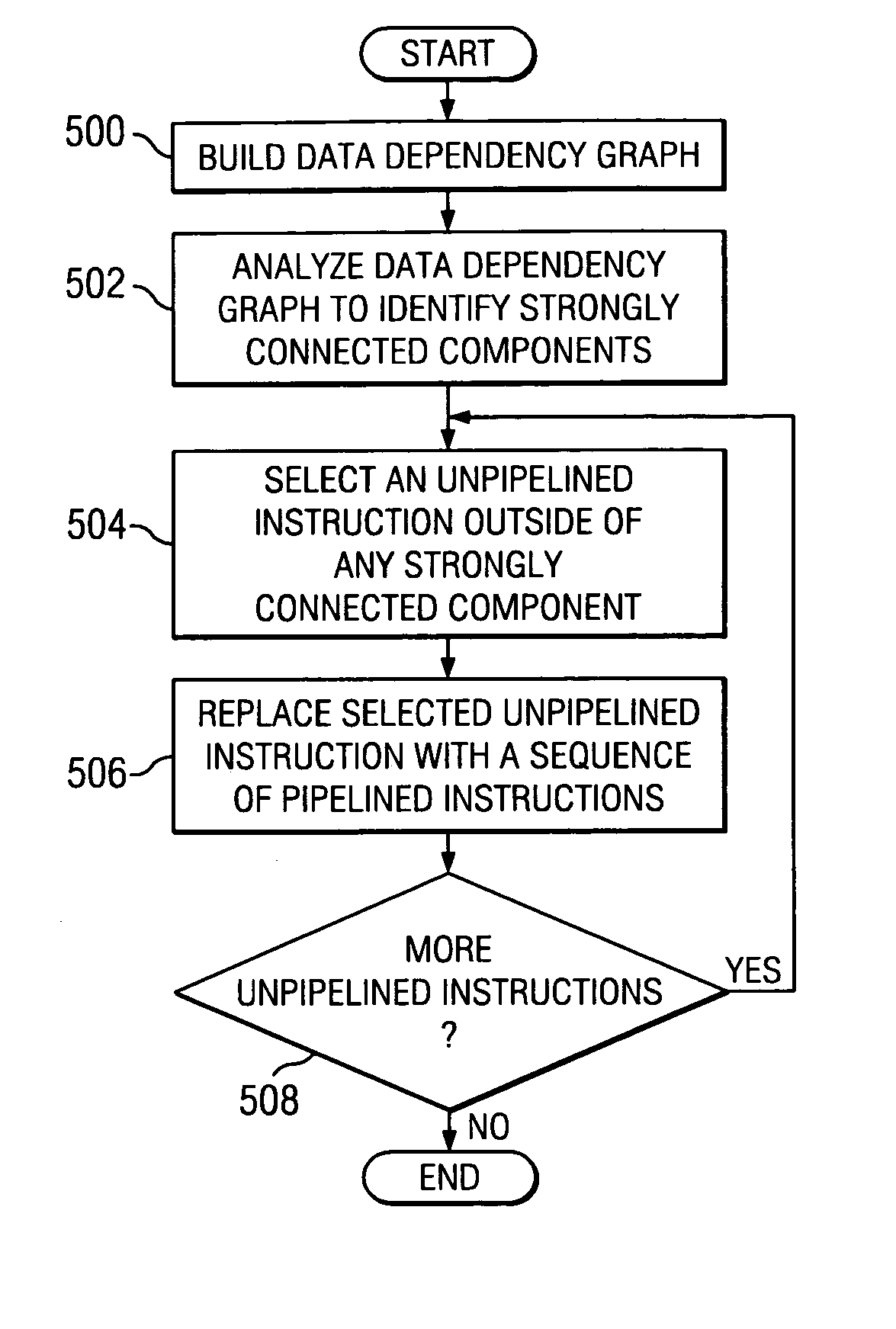
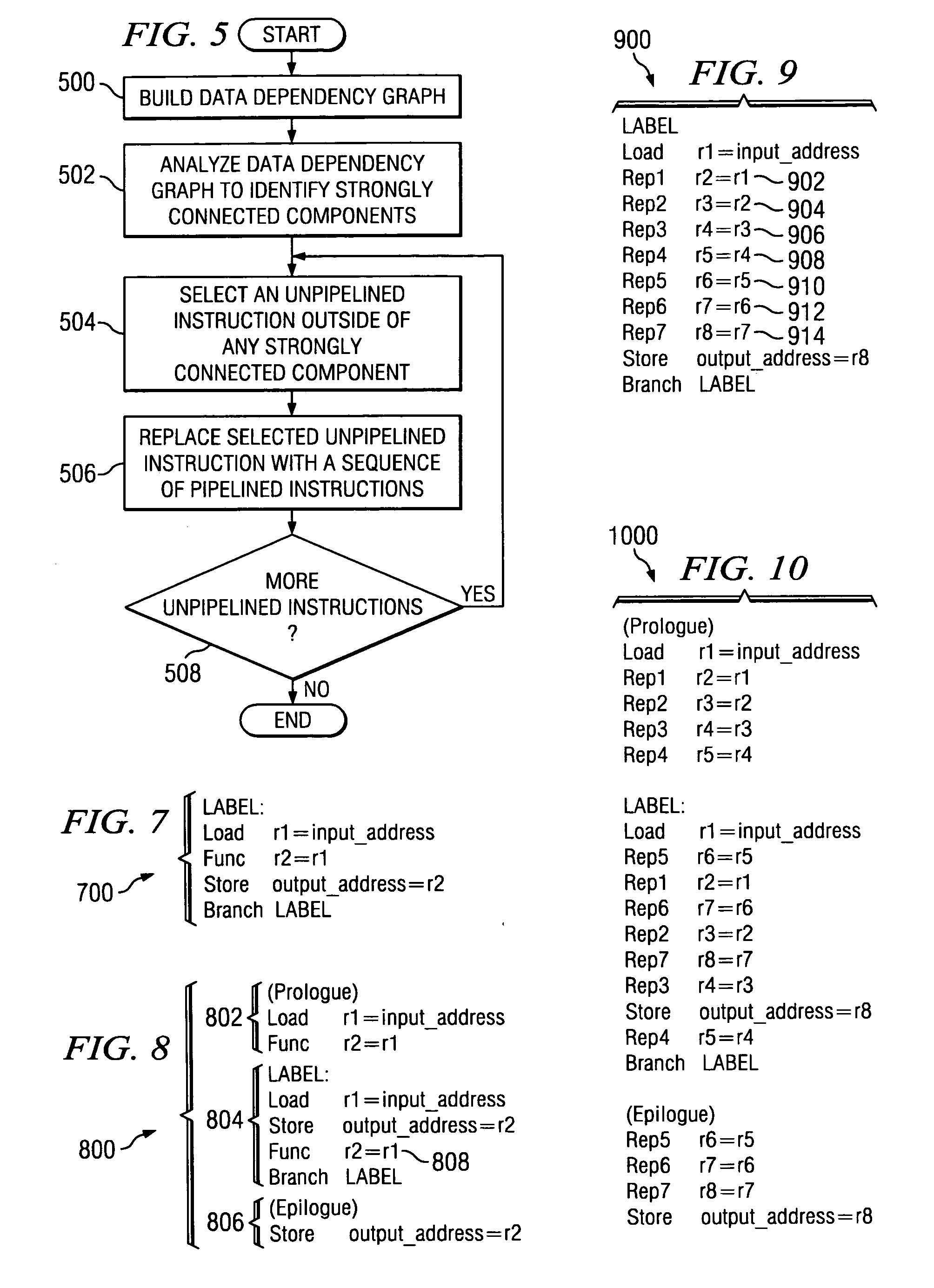
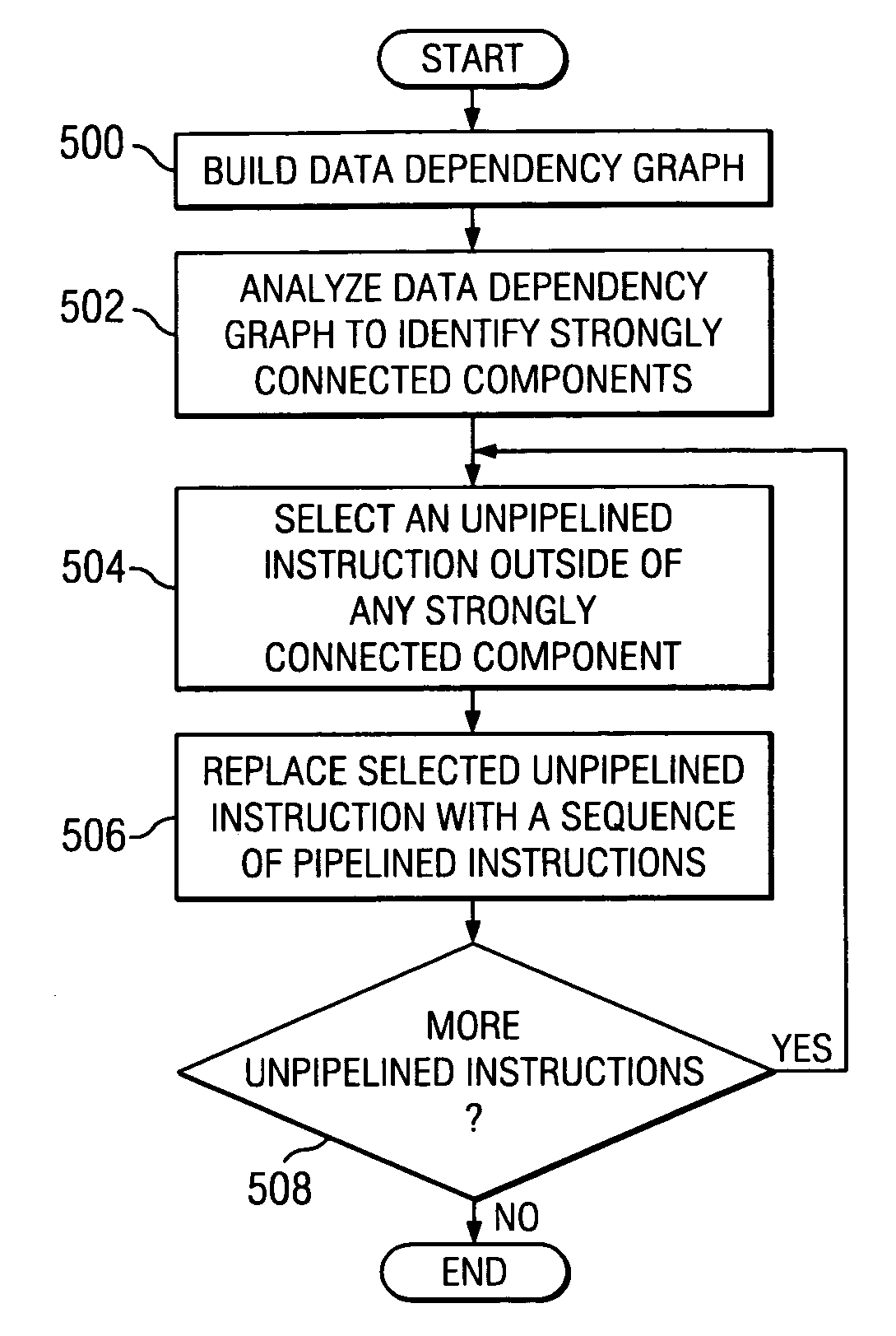
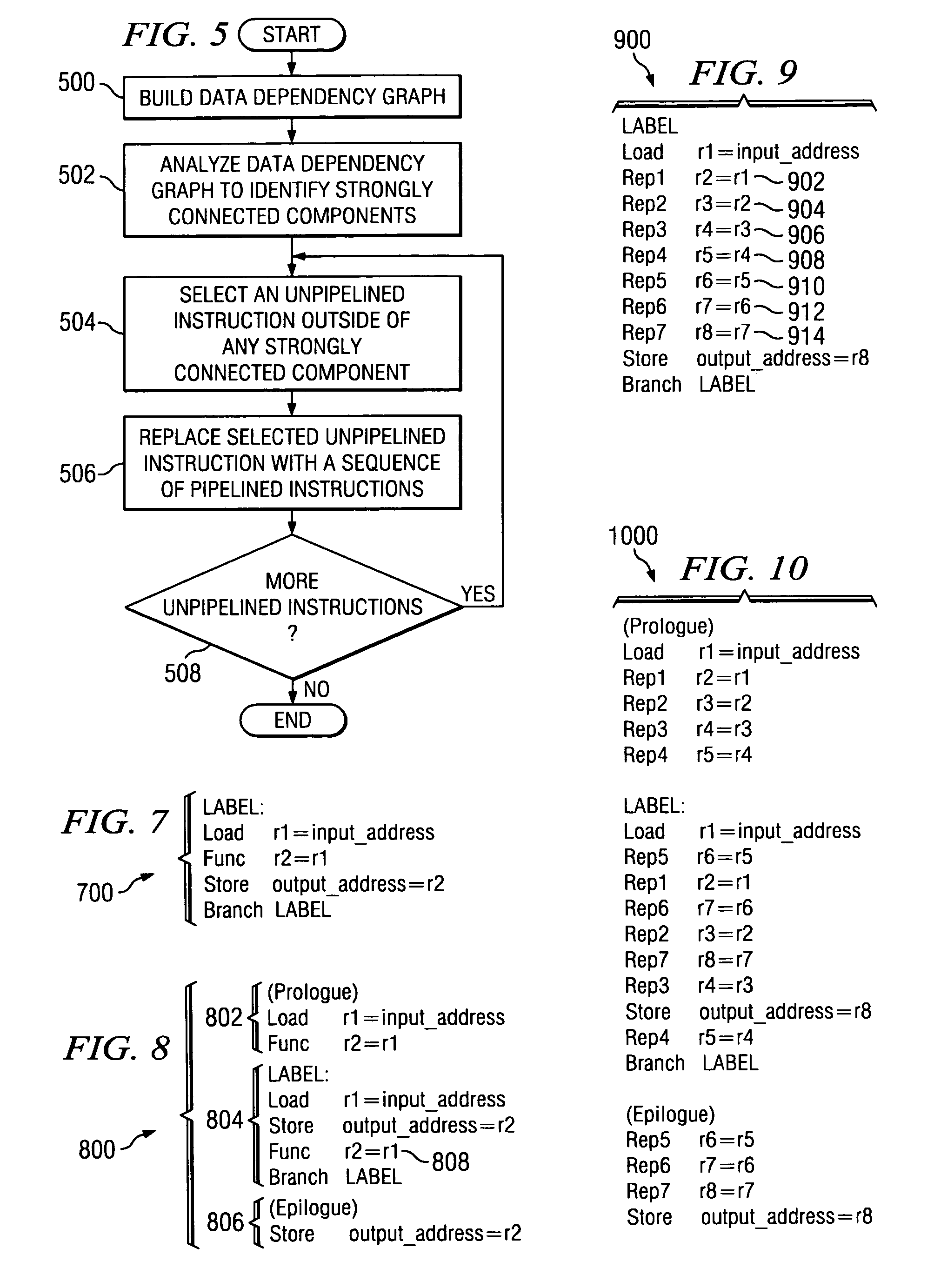
Method and apparatus for determining the profitability of expanding unpipelined instructions
InactiveUS20060048111A1Software engineeringProgram controlProcessing InstructionData dependency graph
A method, apparatus, and computer instructions for processing instructions. A data dependency graph is built. The data dependency graph is analyzed for recurrences, and unpipelined instructions that lie outside of the recurrences are expanded.
Owner:IBM CORP
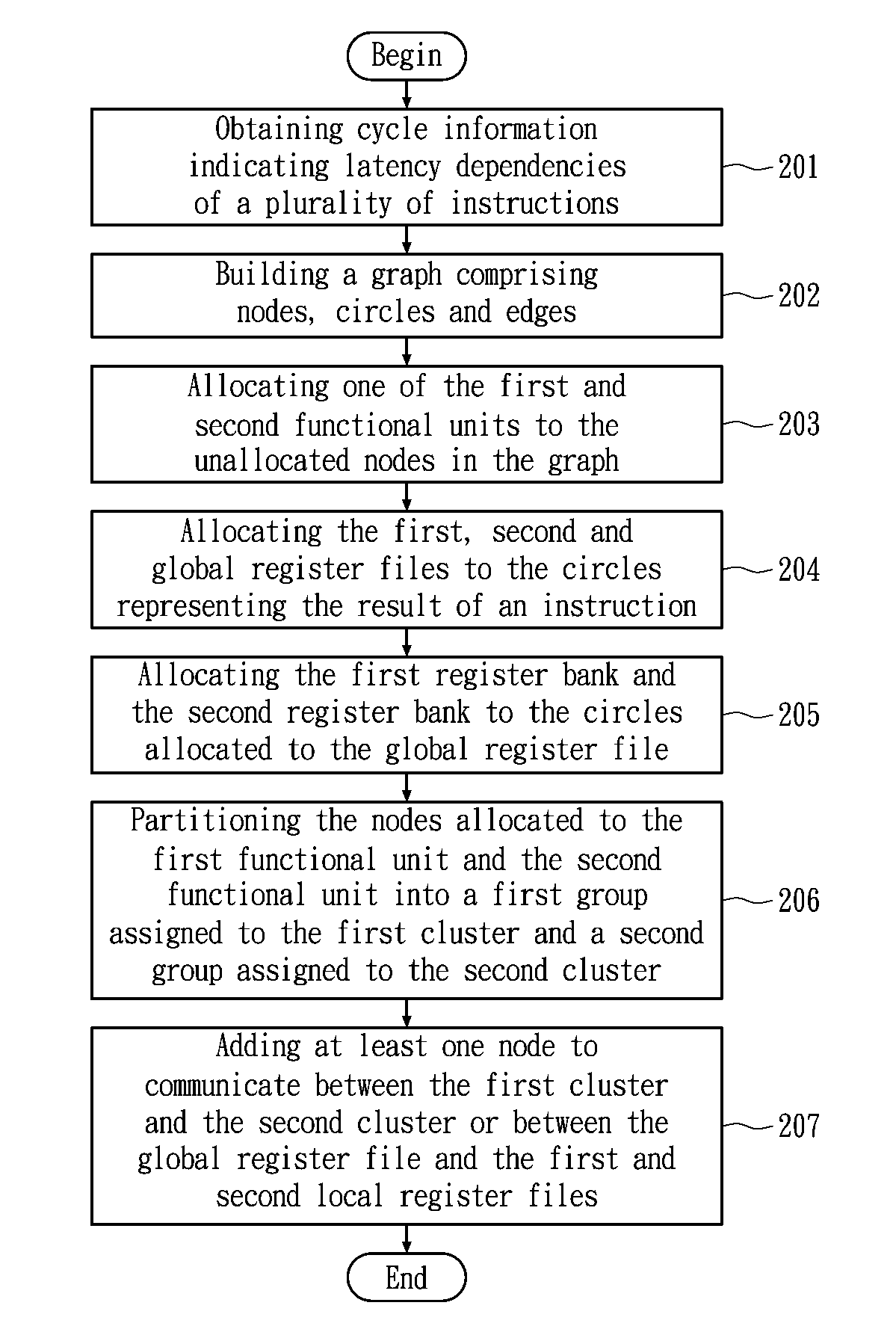
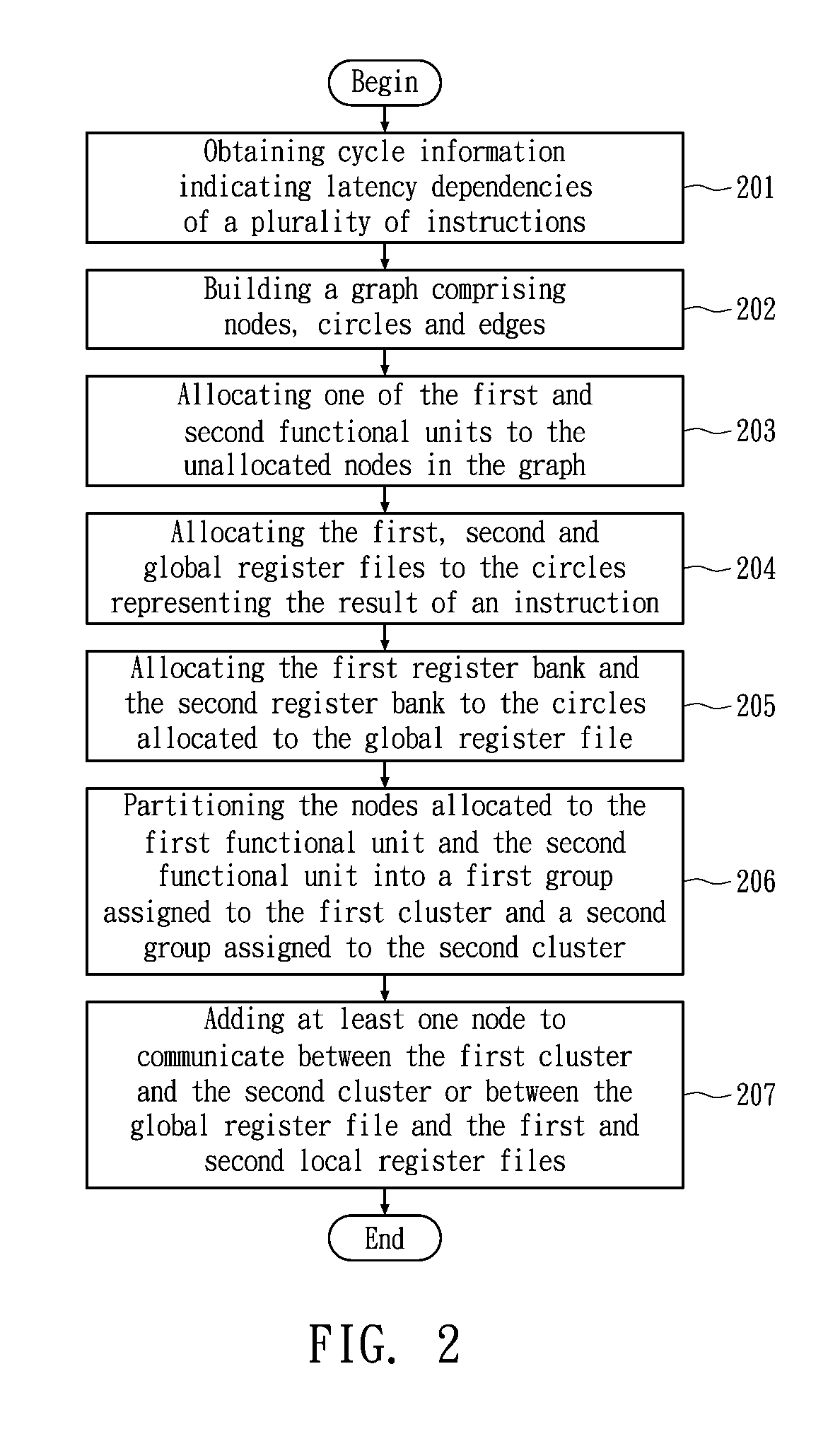
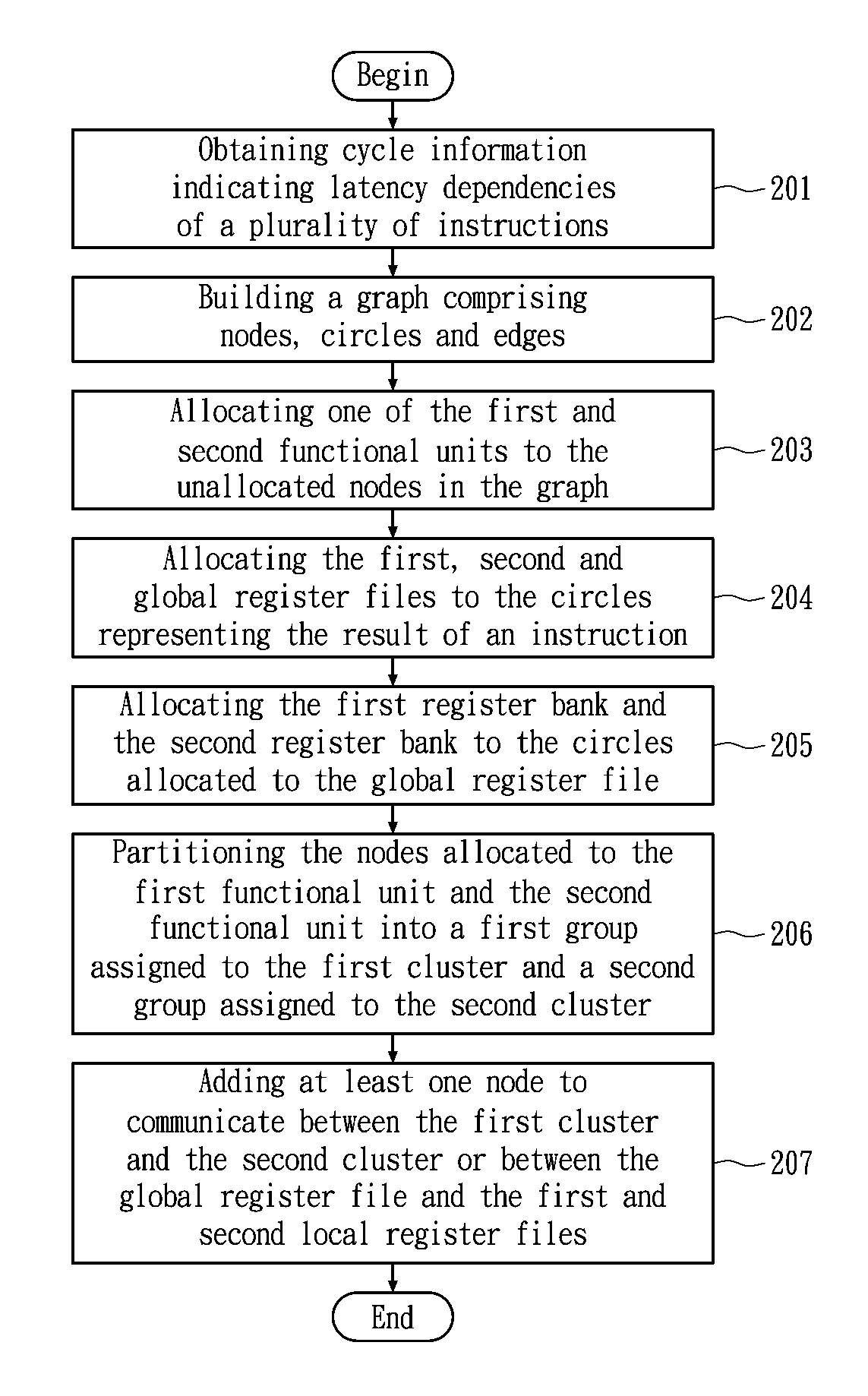
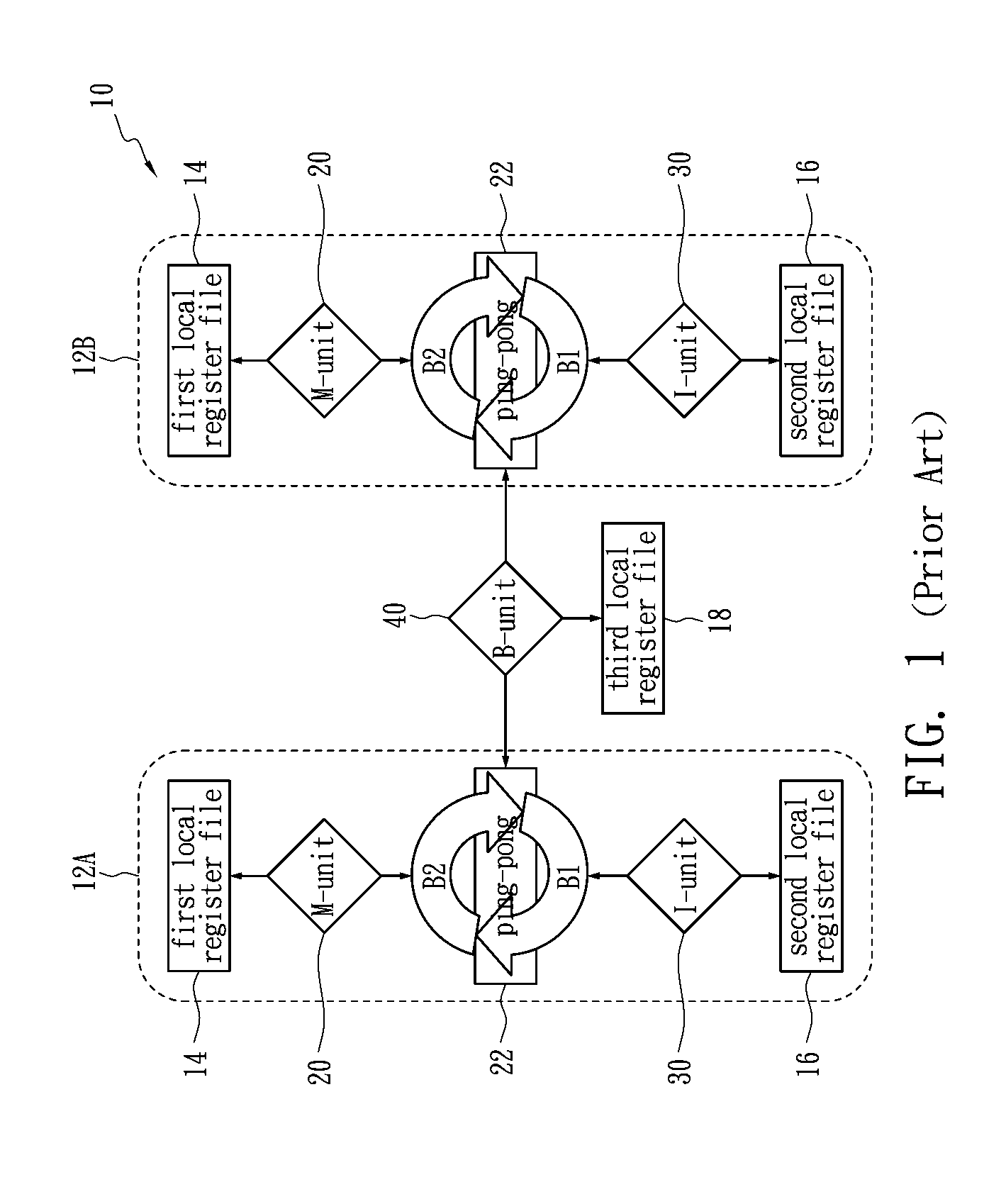
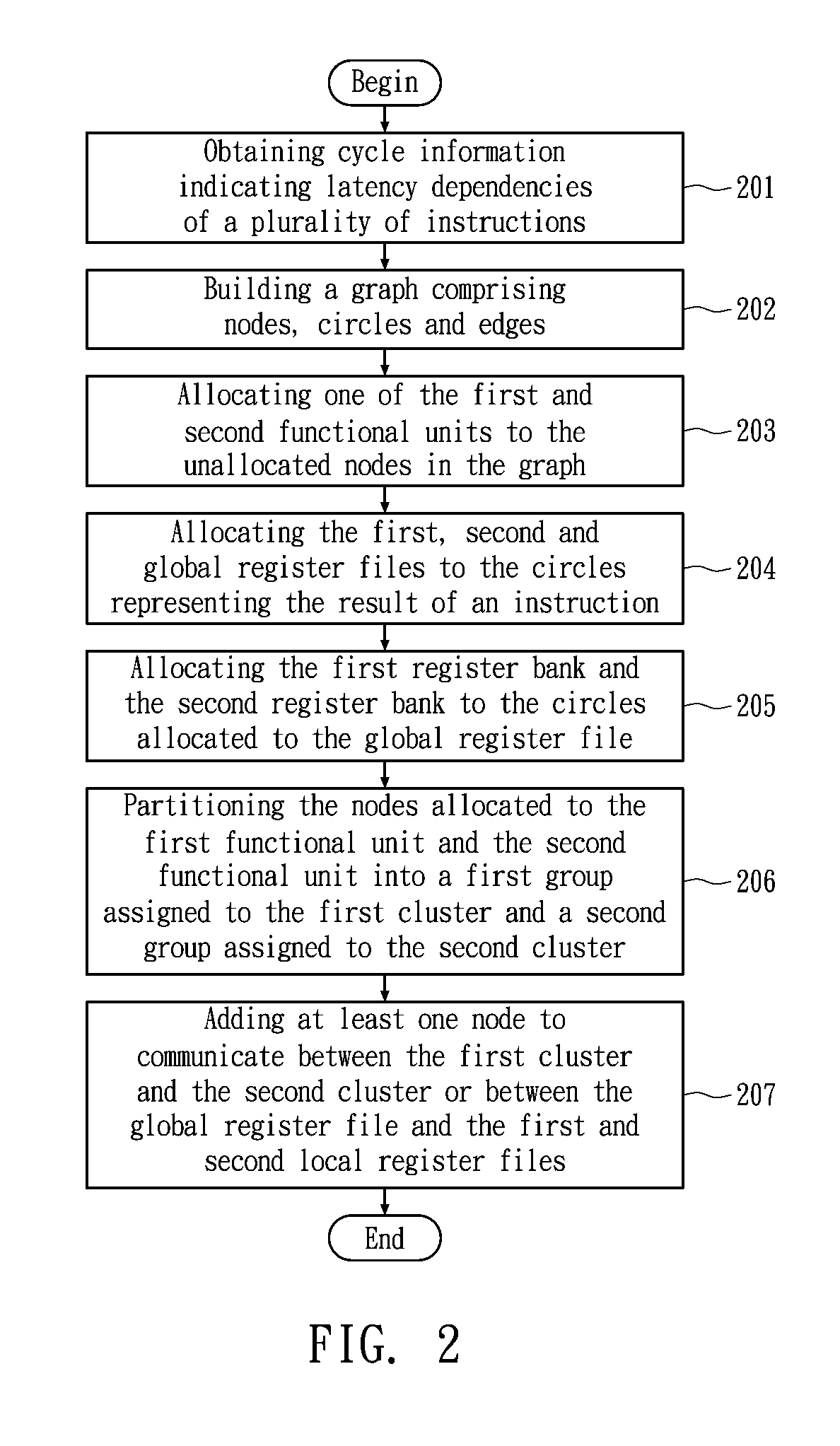
Method for allocating registers for a processor based on cycle information
ActiveUS20120159110A1Memory adressing/allocation/relocationProgram controlData dependency graphComputer architecture
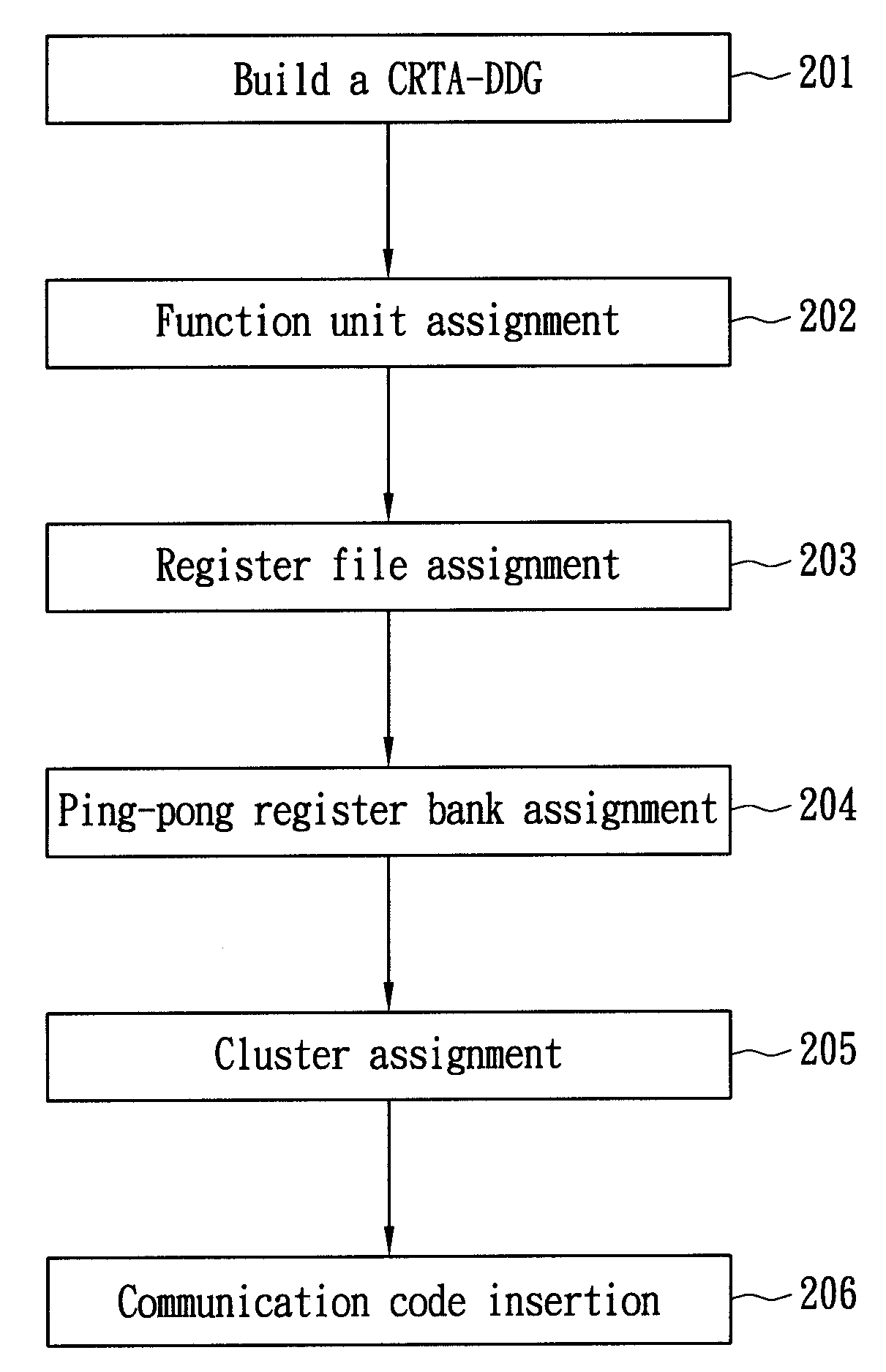
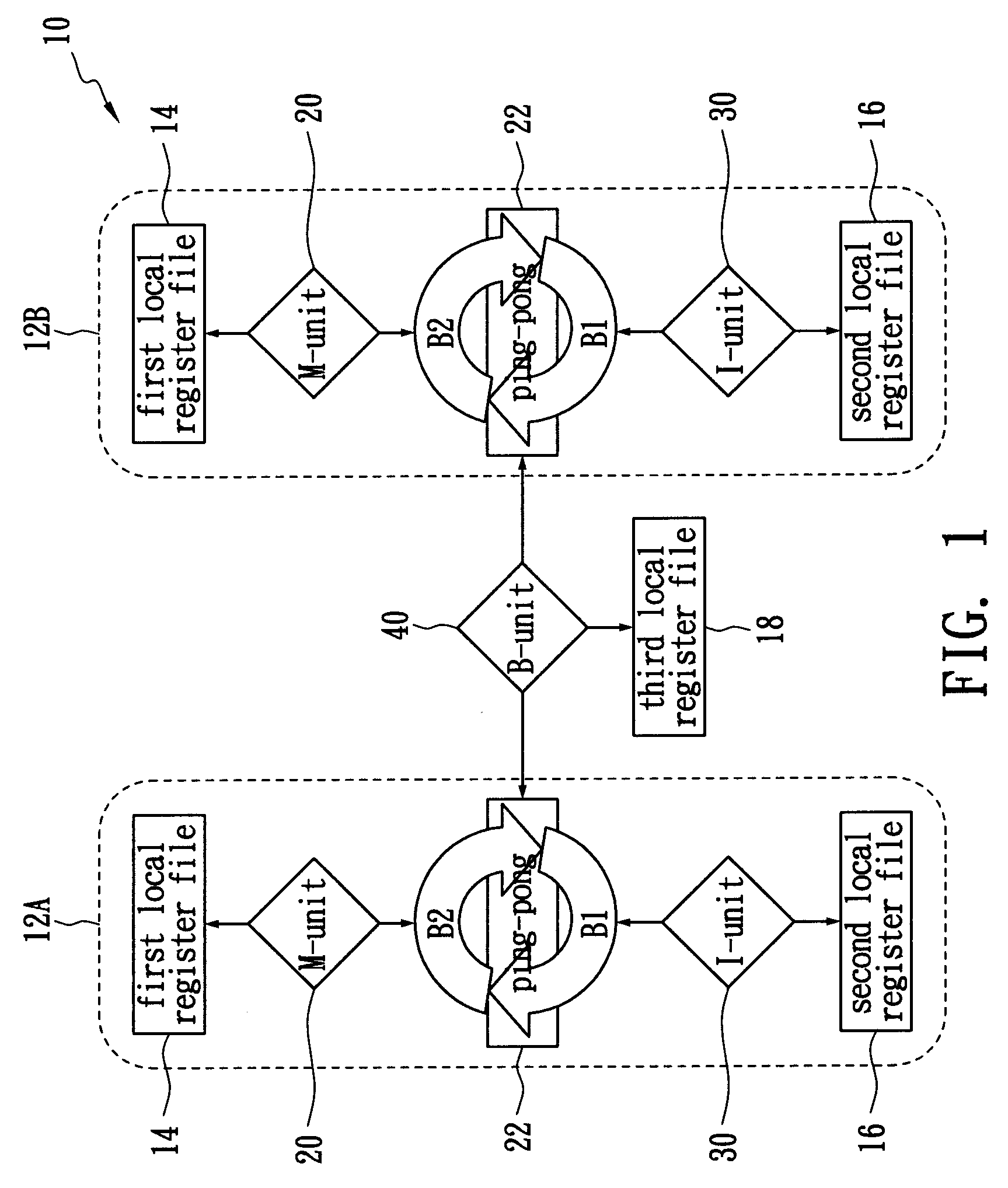
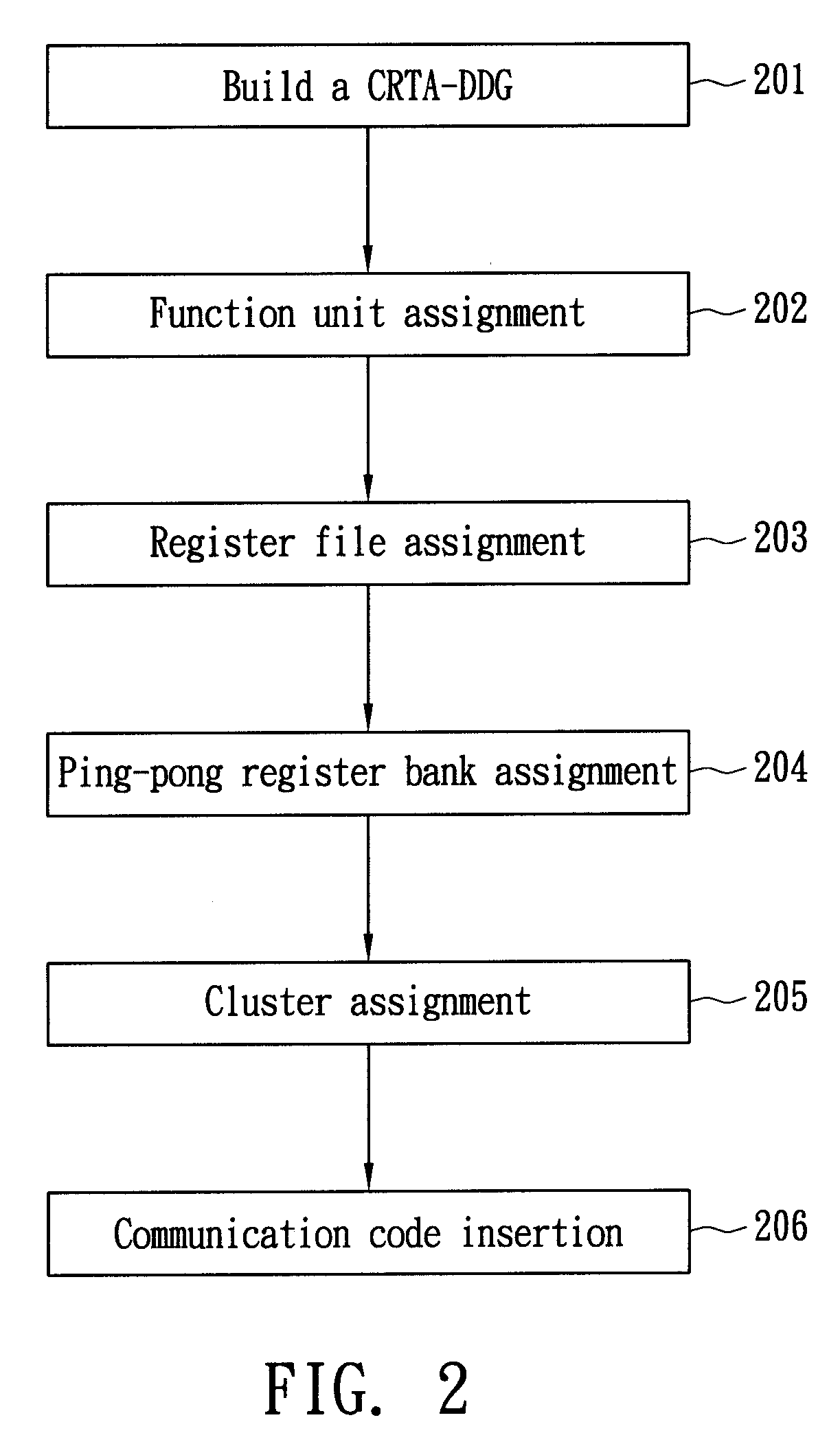
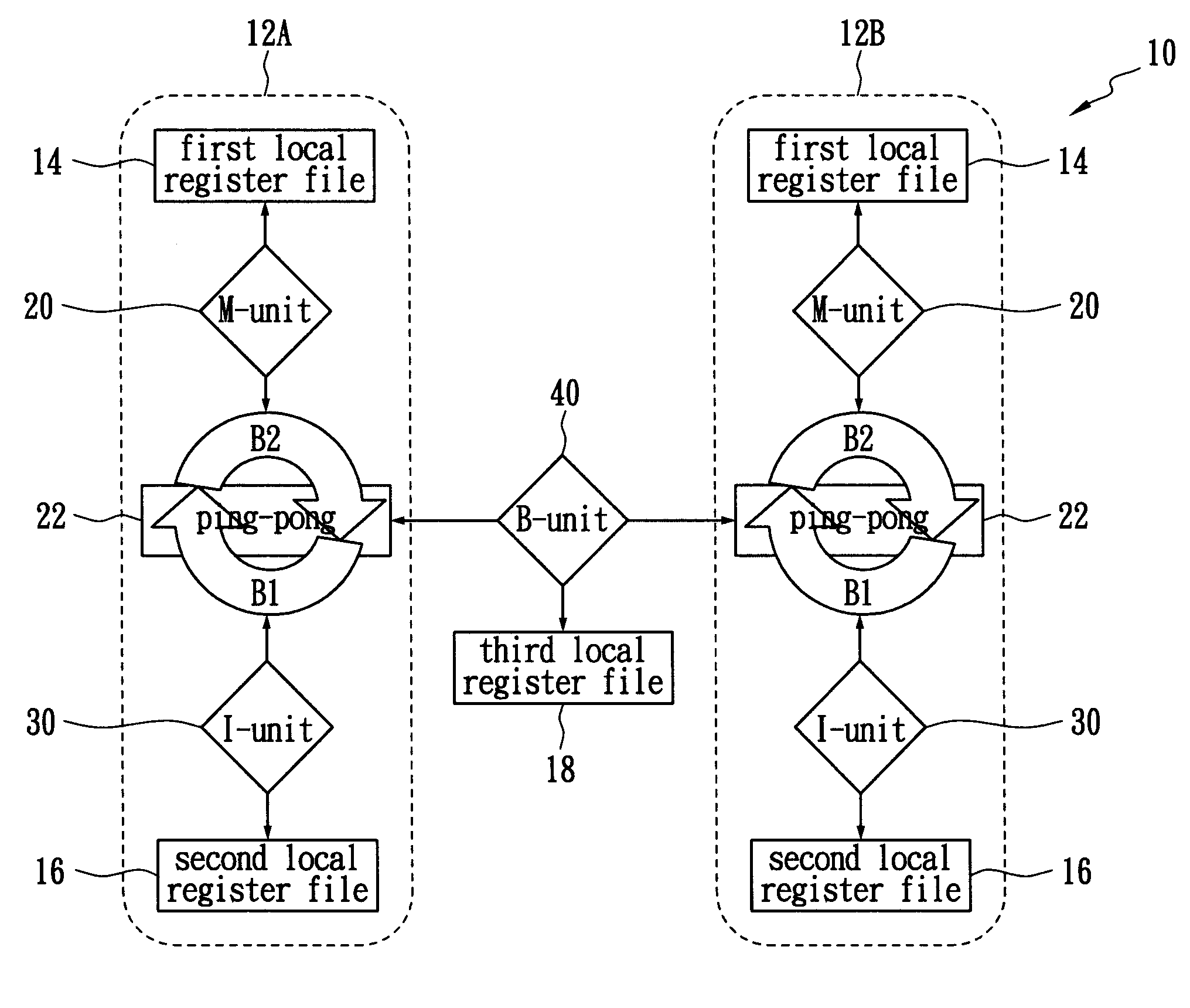
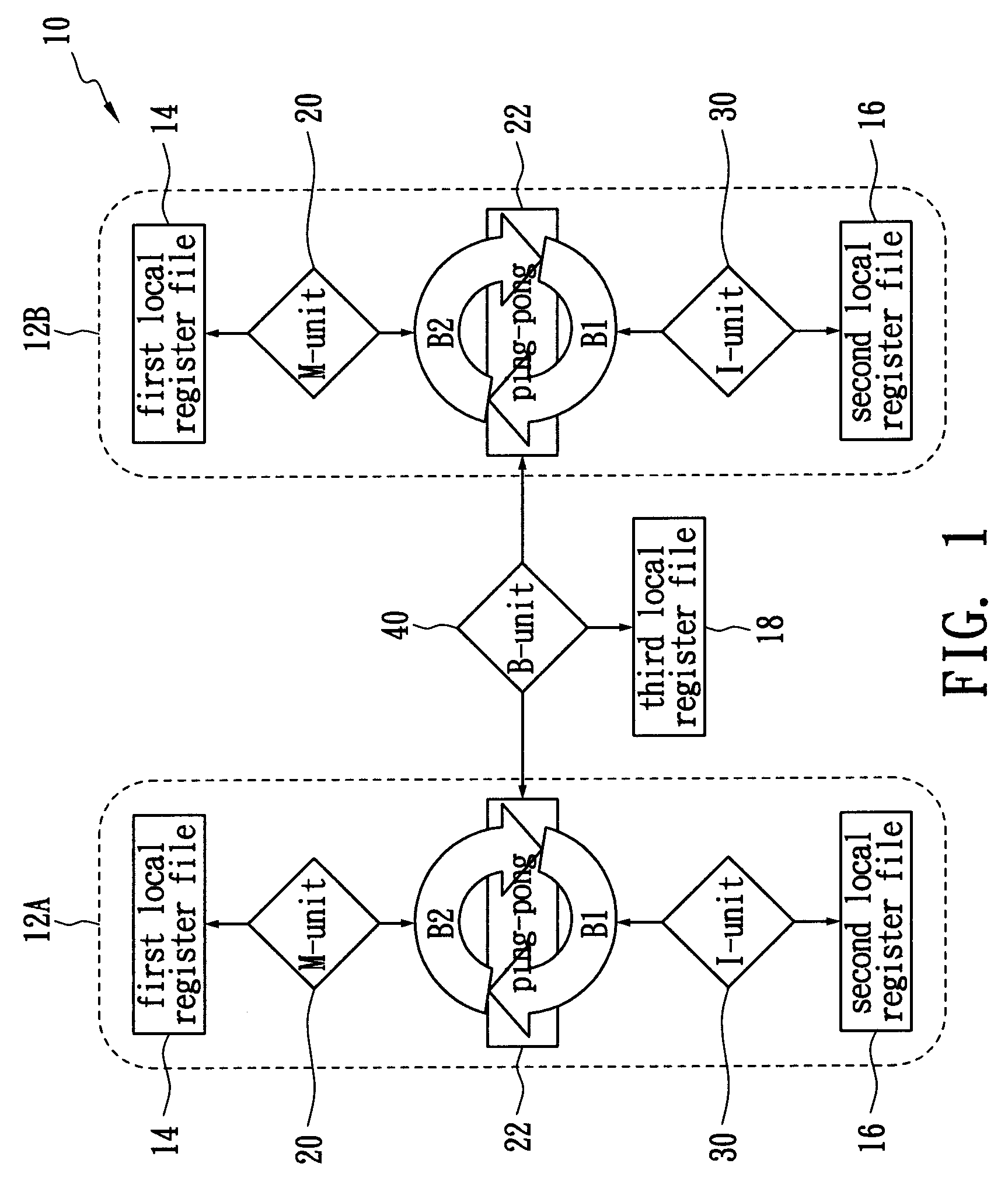
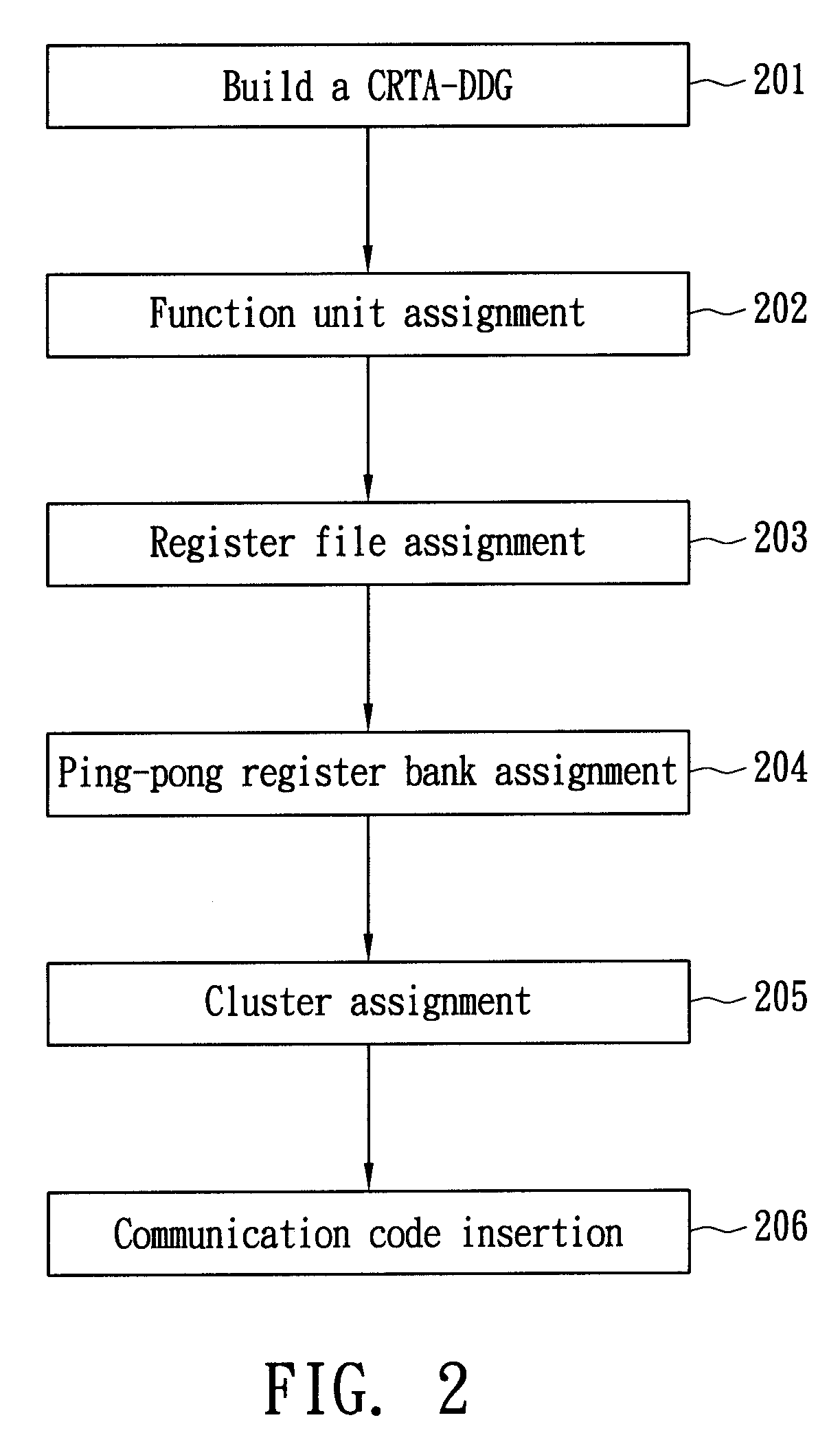
A method of allocating registers for a processor based on cycle information is disclosed. The processor comprises a first cluster and a second cluster. Each cluster comprises a first functional unit, a second functional unit, a first local register file connected to the first functional unit, a second local register file connected to the second register file, and a global register file having a ping-pong structure formed by a first register bank and a second register bank. After building a Component / Register Type Associated Data Dependency Graph (CRTA-DDG), a functional unit assignment, register file assignment, ping-pong register bank assignment, and cluster assignment are performed to take full advantage of the properties of a processor as well as cycle information.
Owner:NATIONAL TSING HUA UNIVERSITY
Instruction scheduling method and device
ActiveCN104424026AGuaranteed uptimeImprove accuracyProgram initiation/switchingSoftware engineeringData dependency graphScheduling instructions
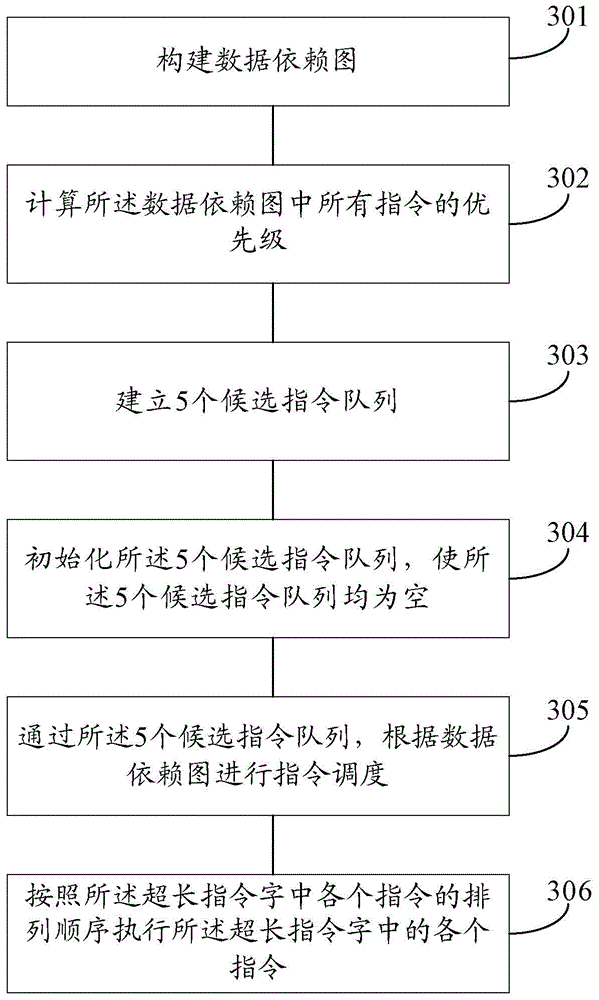
An instruction scheduling method and device for scheduling instructions, relating to the field of communications, that enable a processor or an assembly line to function normally and enhance the accuracy of scheduling. The method comprises: establishing a data dependency graph; extracting from the data dependency graph k instructions to conduct scheduling to obtain m very long instruction words (VLIW) for each cycle such that the VLIW in a same cycle can be executed parallelly and that for any two adjacent cycles, there is no dependency between the instruction at the t-th instruction slot of any VLIW in the latter cycle and the instruction at the (t+1)-th instruction slot of any VLIW in the former cycle, where 0≤k≤m*n, n is the number of instruction slots in a VLIW, n is an integer greater than or equal to 1, m is the number of VLIW in each cycle, m is an integer greater than or equal to 1, and t is an integer greater than or equal to 1 and smaller than or equal to n-1.
Owner:HUAWEI TECH CO LTD +1
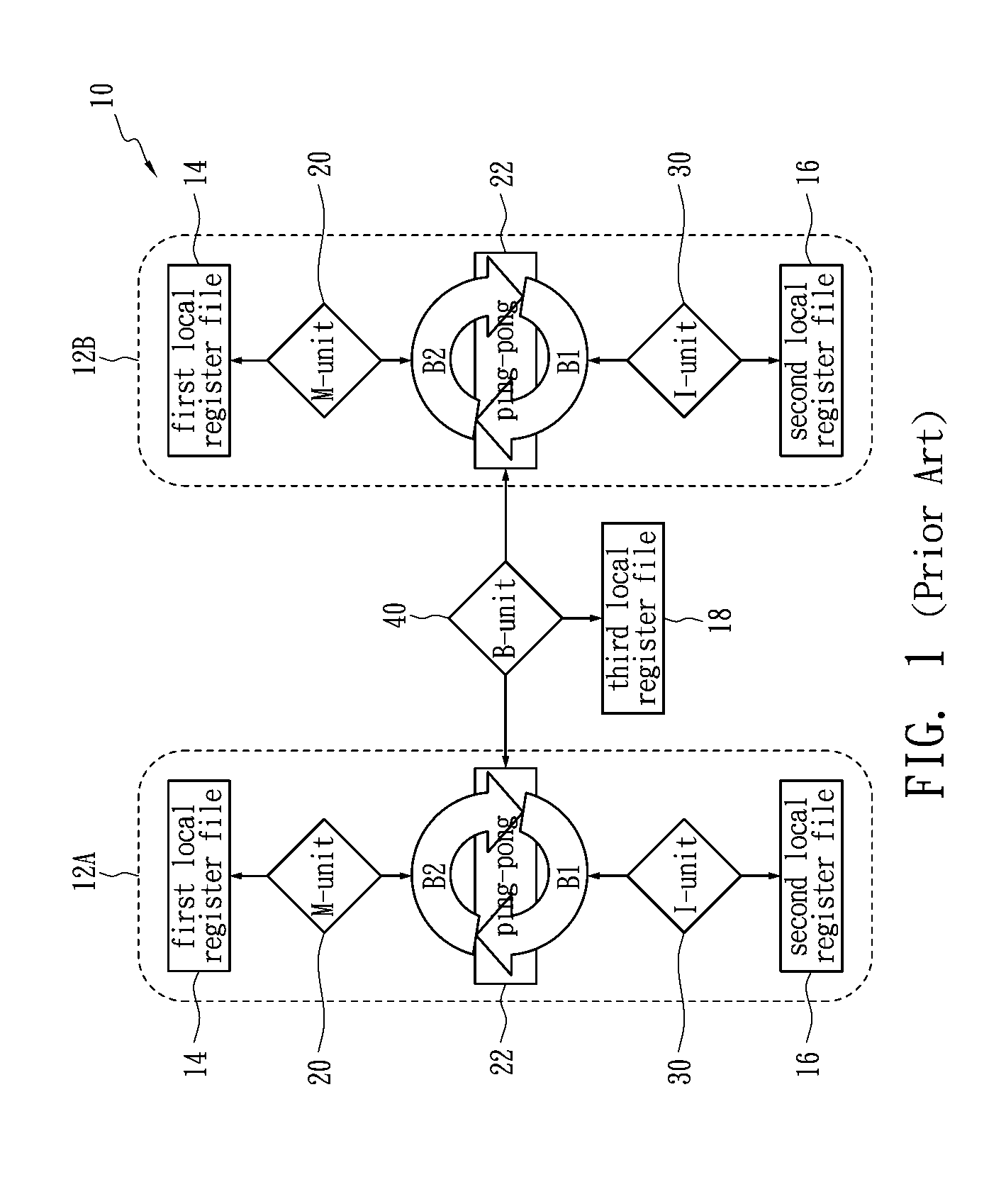
Method for allocating registers for a processor
ActiveUS20080052694A1Improve performanceClarifies allocation and schedule restrictionSoftware engineeringProgram controlData dependency graphProcessor register
A method of allocating registers for a PAC processor. The PAC processor has a first cluster and a second cluster. Each cluster includes a first functional unit, a second functional unit, a first local register file connected to the first functional unit, a second local register file connected to the second register file, and a global register file having a ping-pong structure formed by a first register bank and a second register bank. After building a Component / Register Type Associated Data Dependency Graph (CRTA-DDG), a functional unit assignment, register file assignment, ping-pong register bank assignment, and cluster assignment of the invention are performed to take full advantage of the properties of a PAC processor.
Owner:NATIONAL TSING HUA UNIVERSITY
APT detection method based on context behavior analysis
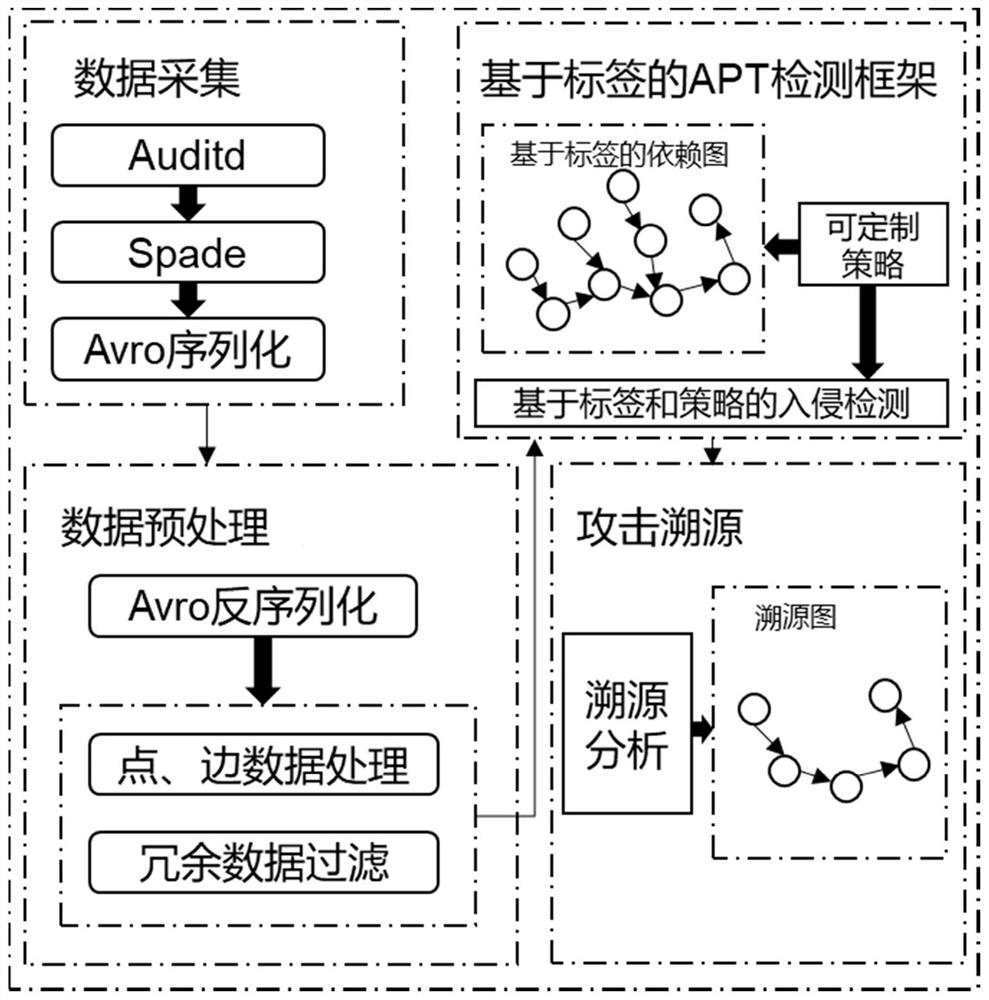
PendingCN113779574AImprove detection efficiencyReduce memory overheadSemantic analysisPlatform integrity maintainanceData dependency graphBehavioral analytics
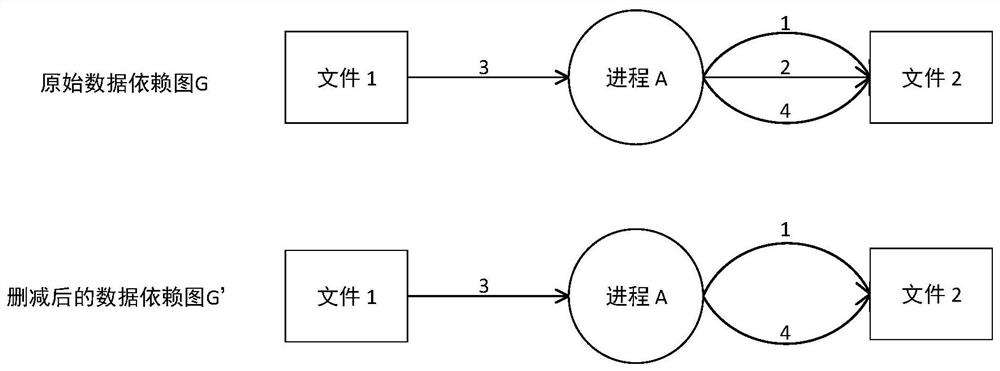
The invention discloses an APT (Advanced Persistent Threat) detection method based on context behavior analysis, which comprises the following steps: collecting log data in real time, objects related to the log data comprising processes, files and events; then preprocessing the collected log data; performing intrusion detection based on context behavior analysis according to the simplified data dependency graph; and taking the newest data dependence graph, and tracing according to the process carrying the threat tag contained in the newest data dependence graph to obtain a complete APT attack chain. The APT detection method based on context behavior analysis has good adaptability and high detection success rate.
Owner:ZHEJIANG UNIV OF TECH
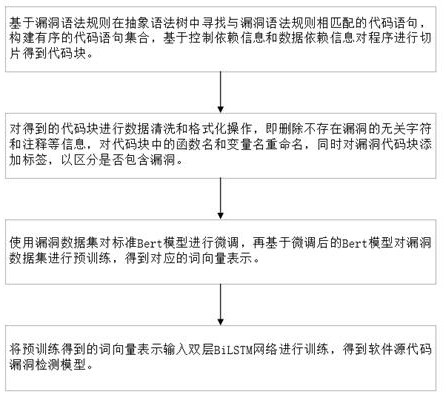
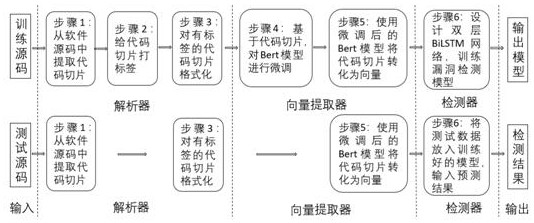
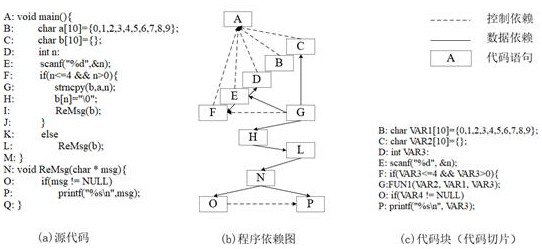
C source code vulnerability detection method based on Bert model and BiLSTM
ActiveCN113420296AImprove accuracyReduce false alarm ratePlatform integrity maintainanceNeural architecturesAlgorithmTheoretical computer science
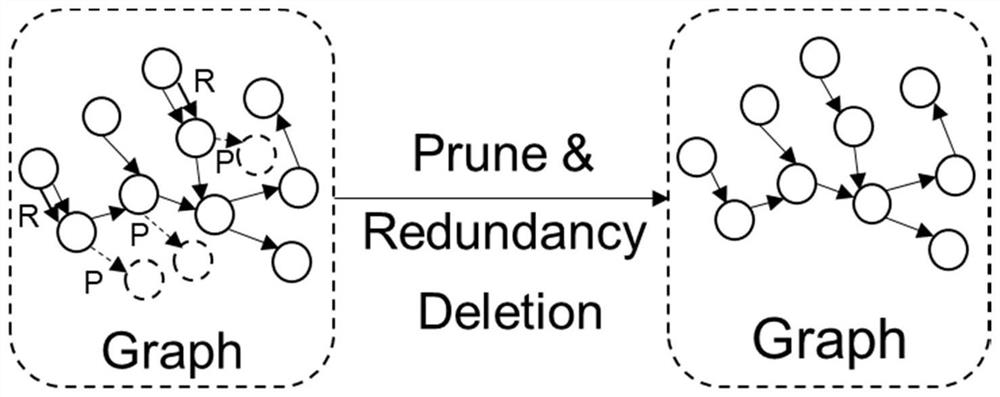
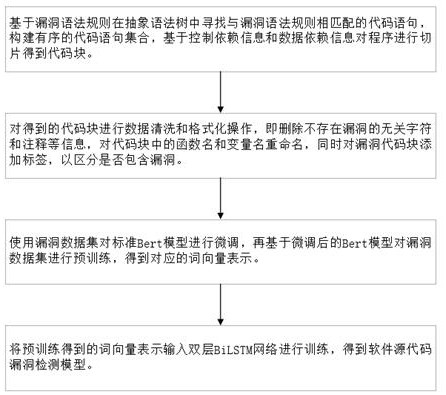
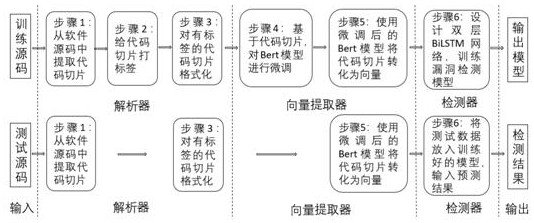
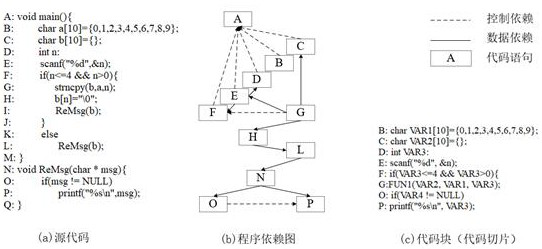
A C source code vulnerability detection method based on a Bert model and BiLSTM comprises the steps that software source codes are analyzed, a control dependency graph and a data dependency graph are constructed, the codes are sliced according to the control dependency relation and the data dependency relation between the codes, slice-level code blocks are generated, then the generated code blocks are subjected to data cleaning and preprocessing, and each generated code block is labeled to distinguish whether the code block contains vulnerability information or not. Secondly, the processed code blocks serve as a training set to be input into the Bert pre-training model to conduct fine adjustment on the standard Bert model, and a new Bert model is obtained; and the code blocks are input into a new Bert model to learn semantic information and context relationships between codes in an unsupervised manner, and word embedding coding is performed on the code blocks to obtain word vectors with maximized code semantic information and context relationships. And finally, the obtained word vector is input into BiLSTM to train a detection model, and a source code vulnerability detection model is obtained. The vulnerability detection accuracy can be improved, and the false alarm rate can be reduced.
Owner:STATE GRID GASU ELECTRIC POWER RES INST +2
Method for allocating registers for a processor
ActiveUS7650598B2Clarifies allocation and schedule restrictionSoftware engineeringProgram controlData dependency graphProcessor register
A method of allocating registers for a PAC processor. The PAC processor has a first cluster and a second cluster. Each cluster includes a first functional unit, a second functional unit, a first local register file connected to the first functional unit, a second local register file connected to the second register file, and a global register file having a ping-pong structure formed by a first register bank and a second register bank. After building a Component / Register Type Associated Data Dependency Graph (CRTA-DDG), a functional unit assignment, register file assignment, ping-pong register bank assignment, and cluster assignment of the invention are performed to take full advantage of the properties of a PAC processor.
Owner:NATIONAL TSING HUA UNIVERSITY
Method for reducing intraframe coding time delay in HEVC encoder
ActiveCN105100799AReduce encoding delayResolve dependenciesDigital video signal modificationCode moduleData dependency graph
The invention discloses a method for reducing intraframe coding time delay in an HEVC encoder. The method includes the following steps: S1 making mode decision to a largest code unit to be coded to obtain the segmentation result of all of the sub-coding units and predicted mode decision results; S2 sending the results selected by the largest code unit to be coded to a scheduler; S3 generating a data dependence graph of the basic unit of the current largest code unit by the scheduler through a method of reverse triggering of labels; S4 driving an intraframe coding unit to perform operation based on the data dependence graph; and S5 preparing the data needed by a next intraframe coding unit by the scheduler based on the operation result and triggering the next intraframe coding unit to operate. The method reduces the time delay of a largest code module in an intraframe coding mode, the streamline processing can be carried out, and the problem that how to determine the dependency of the code units in high efficient video coding is solved by the method of reverse triggering of labels.
Owner:芯原微电子(北京)有限公司 +2
Method and system for configuring a dependency graph for dynamic by-pass instruction scheduling
There is disclosed a method and system for configuring a data dependency graph (DDG) to handle instruction scheduling in computer architectures permitting dynamic by-pass execution, and for performing dynamic by-pass scheduling utilizing such a configured DDG. In accordance with an embodiment of the invention, a heuristic function is used to obtain a ranking of nodes in the DDG after setting delays at all identified by-pass pairs of nodes in the DDG to 0. From among a list of identified by-pass pairs of nodes, a node that is identified as being the least important to schedule early is marked as “bonded” to its successor, and the corresponding delay for that identified node is set to 0. Node rankings are re-computed and the bonded by-pass pair of nodes are scheduled in consecutive execution cycles with a delay of 0 to increase the likelihood that a by-pass can be successfully taken during run-time execution.
Owner:META PLATFORMS INC
Method and apparatus for modulo scheduling
ActiveUS20160070594A1Reducing total modulo scheduling timeEfficient executionDigital data information retrievalProgram initiation/switchingData dependency graphRecursion
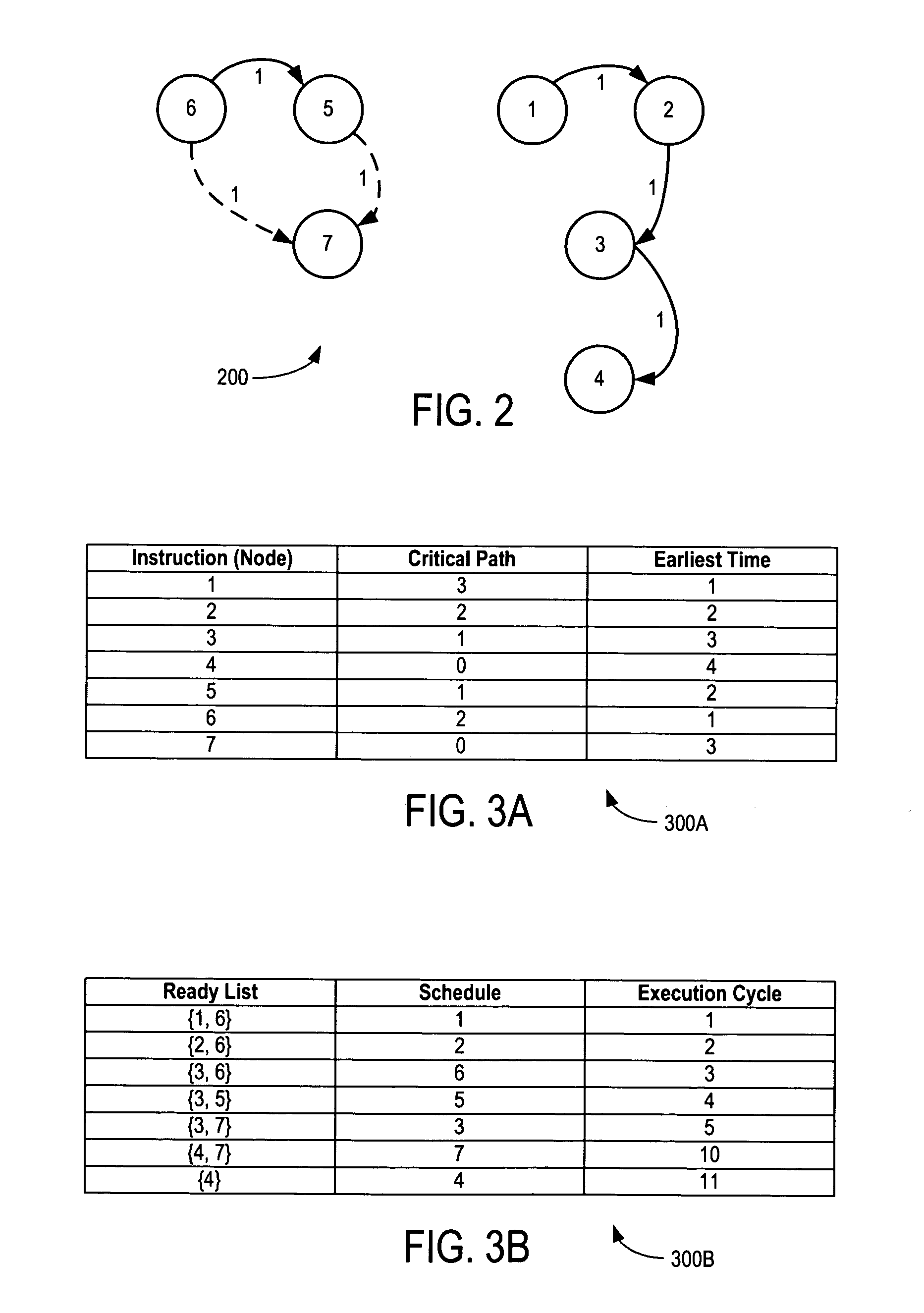
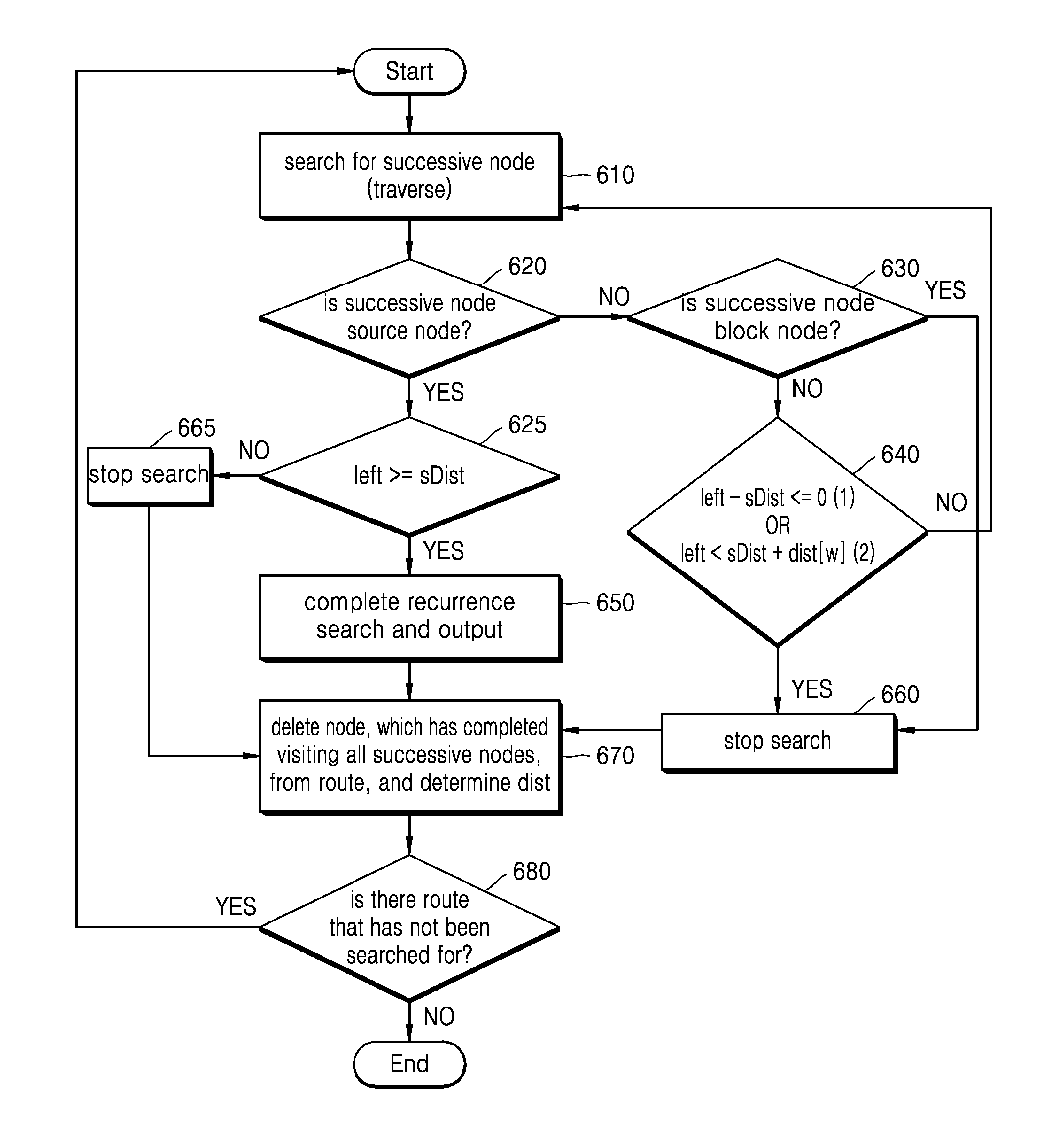
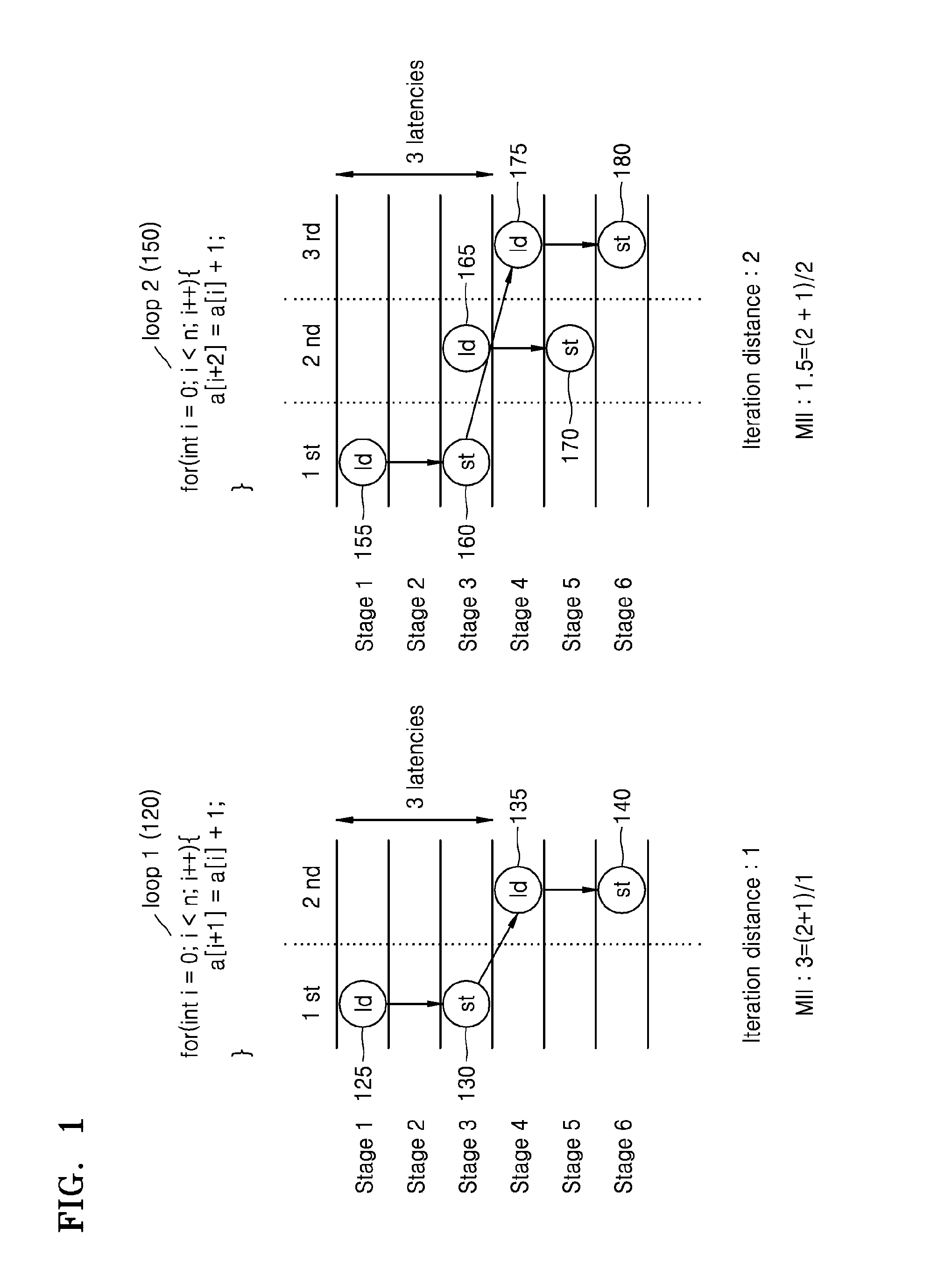
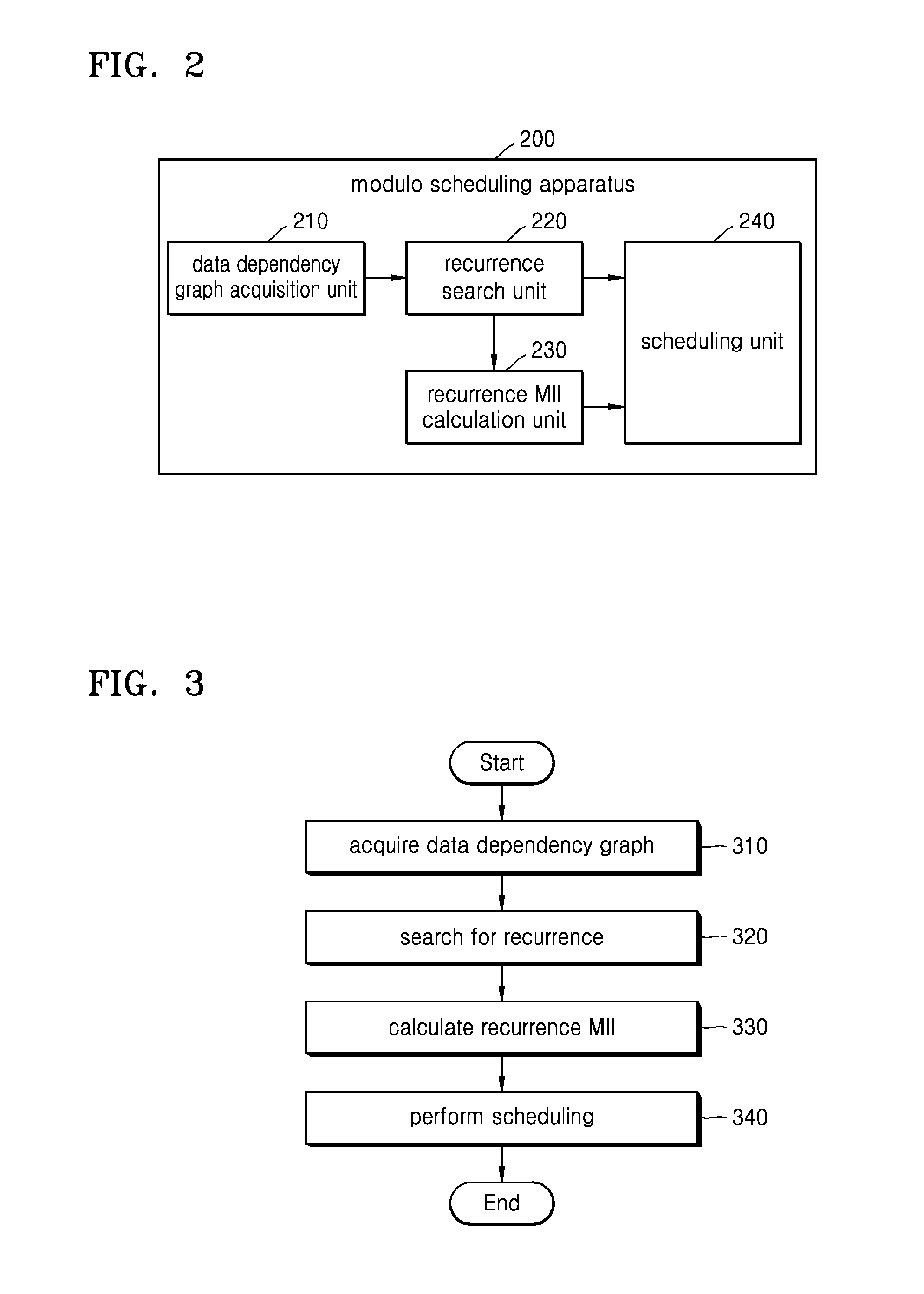
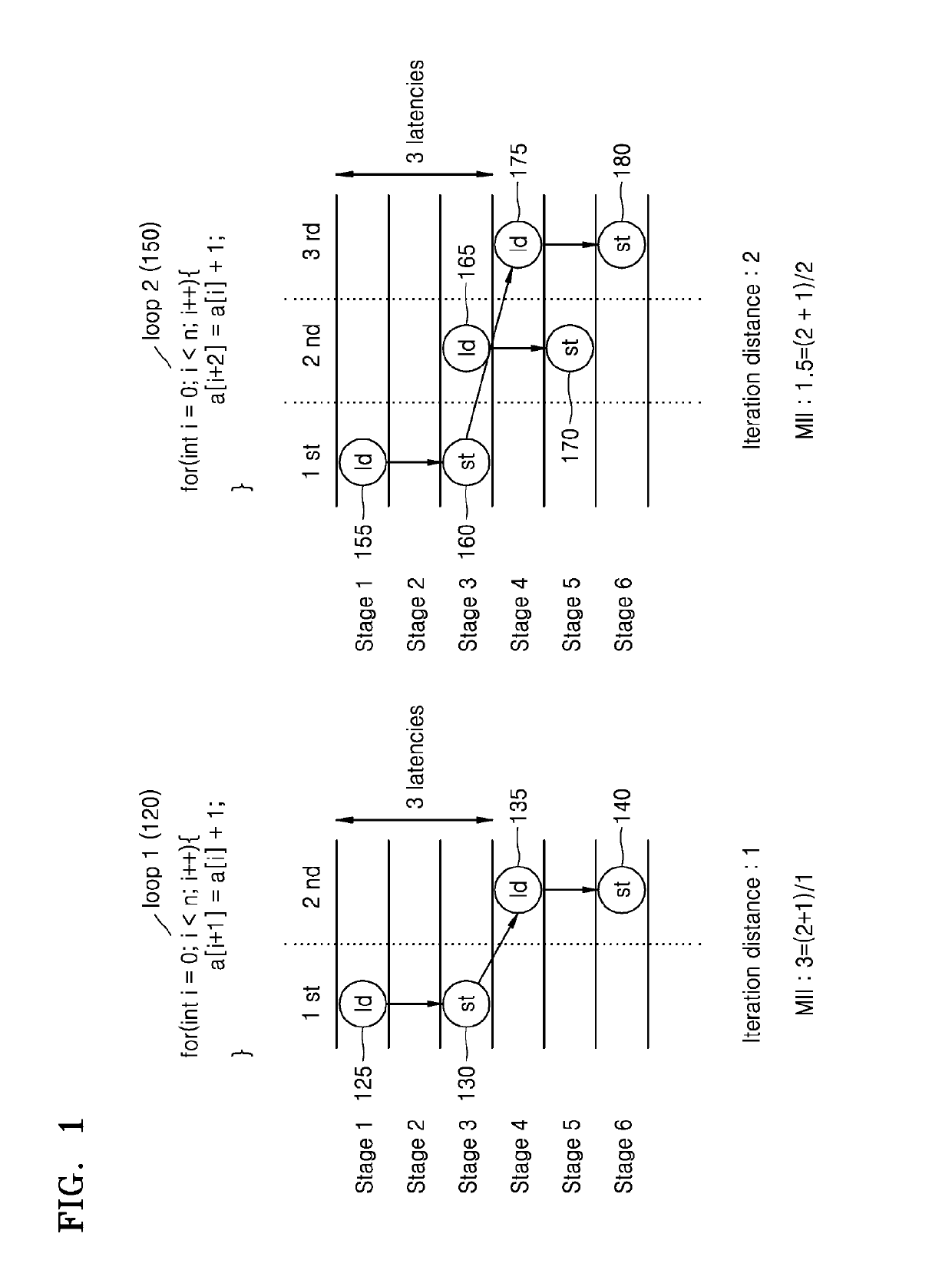
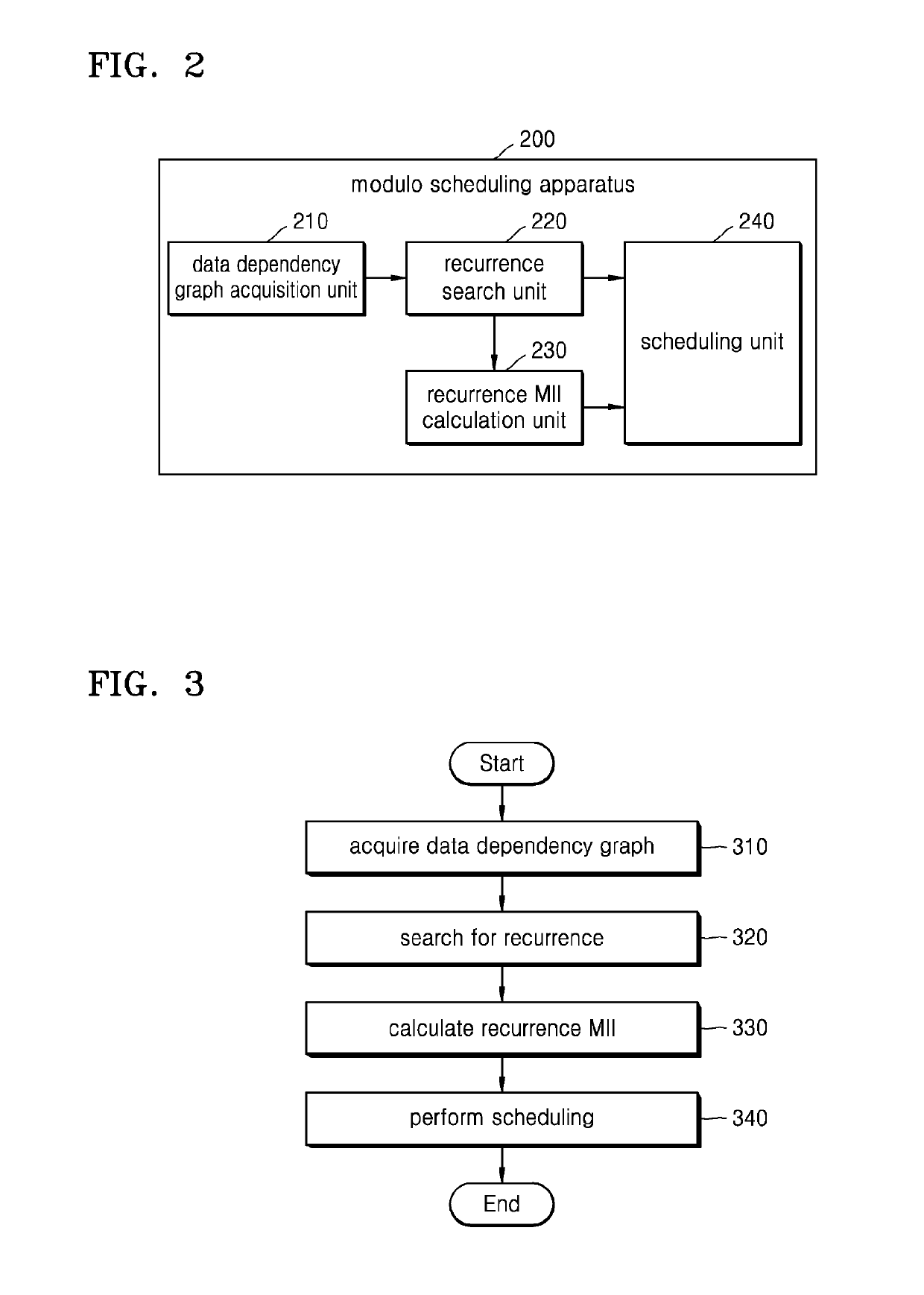
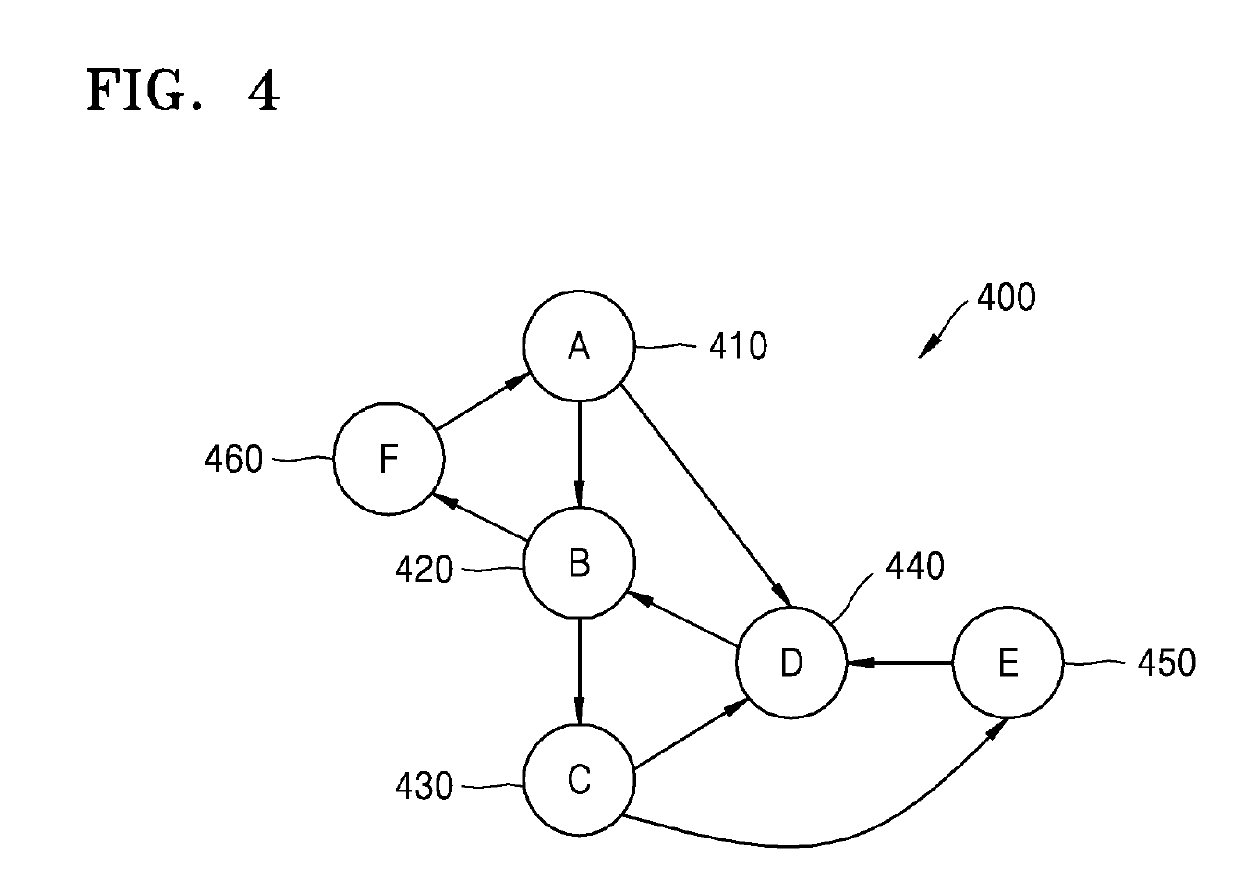
Provided is a modulo scheduling method. The modulo scheduling method includes conducting a search, based on a data dependency graph of a loop, for a recurrence in which a sum of iteration distances between command nodes is less than a predetermined critical value; and determining a processing order of the recurrence.
Owner:SEOUL NAT UNIV R&DB FOUND
Method and apparatus to achieve maximum outer level parallelism of a loop
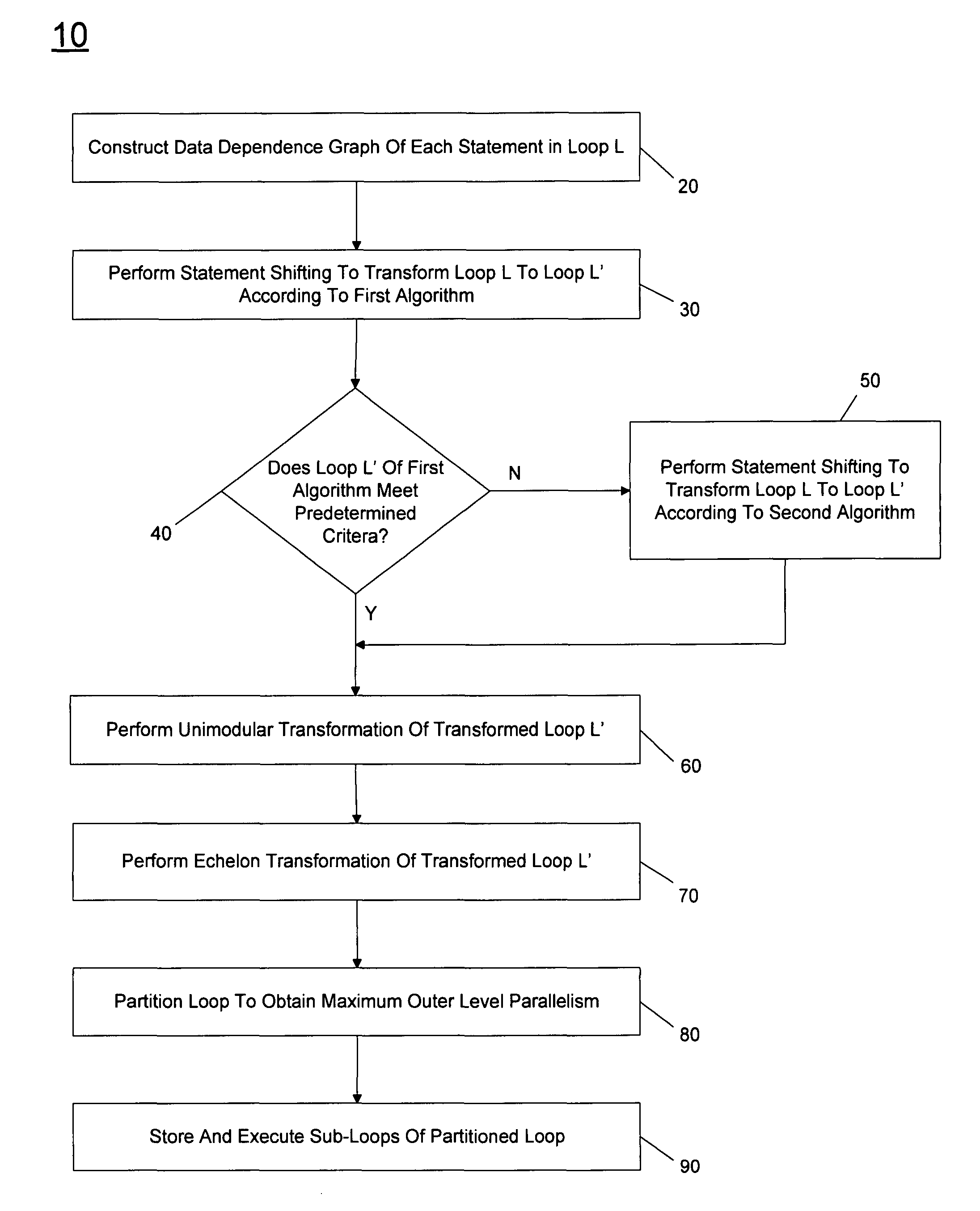
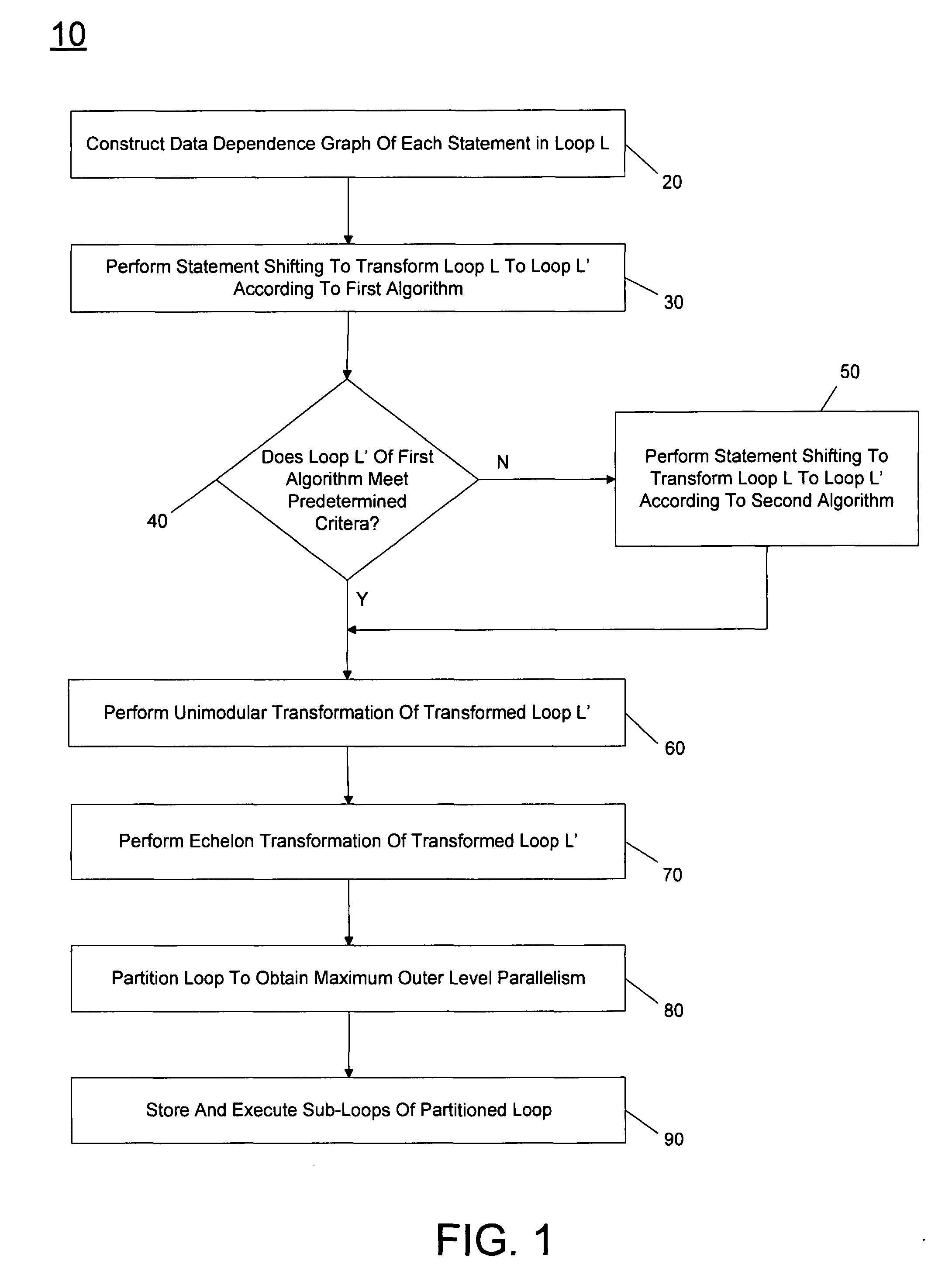
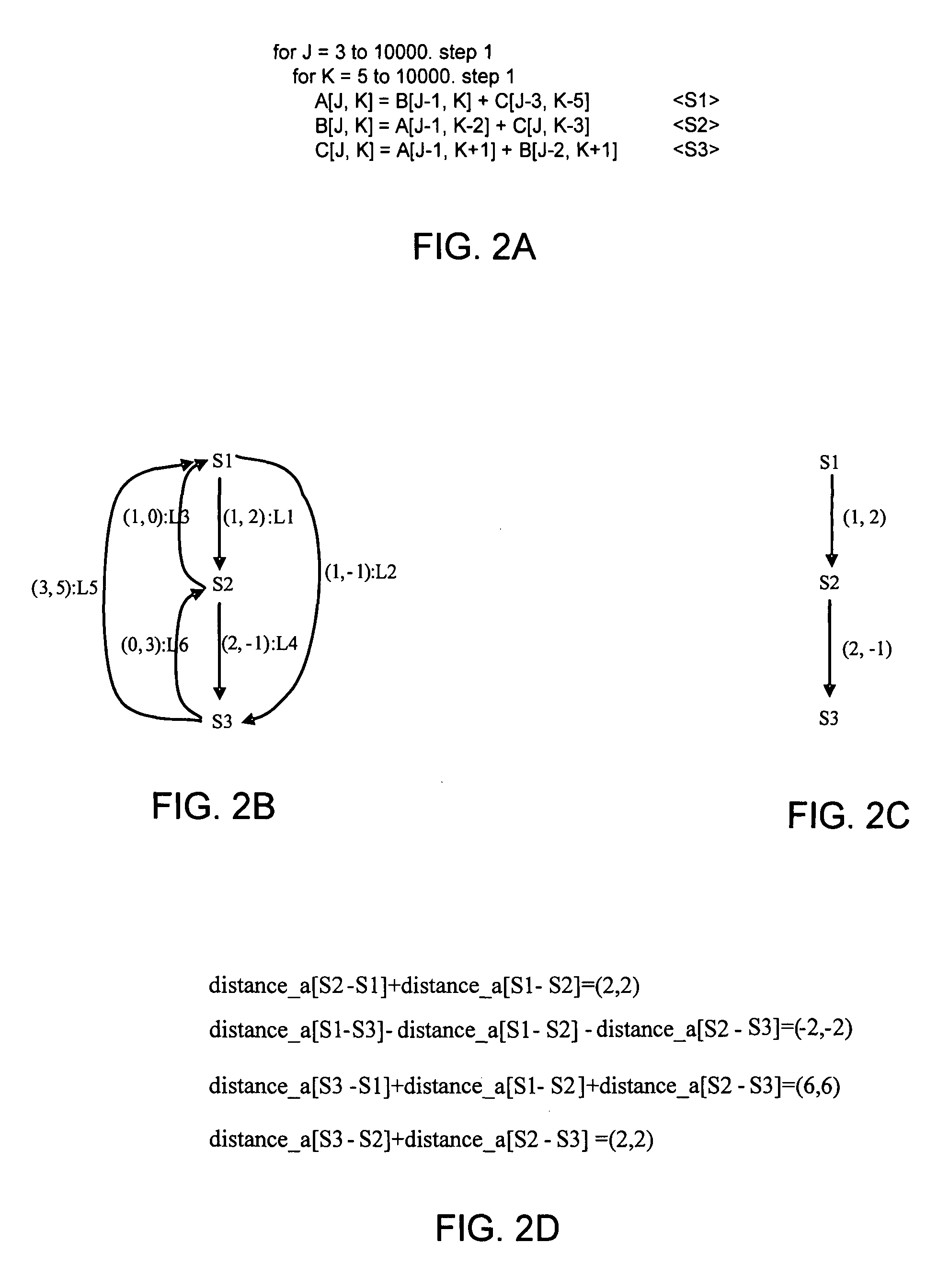
In one embodiment, the present invention includes a method for constructing a data dependency graph (DDG) for a loop to be transformed, performing statement shifting to transform the loop into a first transformed loop according to at least one of first and second algorithms, performing unimodular and echelon transformations of a selected one of the first or second transformed loops, partitioning the selected transformed loop to obtain maximum outer level parallelism (MOLP), and partitioning the selected transformed loop into multiple sub-loops. Other embodiments are described and claimed.
Owner:INTEL CORP
Method and apparatus for determining the profitability of expanding unpipelined instructions
A method, apparatus, and computer instructions for processing instructions. A data dependency graph is built. The data dependency graph is analyzed for recurrences, and unpipelined instructions that lie outside of the recurrences are expanded.
Owner:INT BUSINESS MASCH CORP
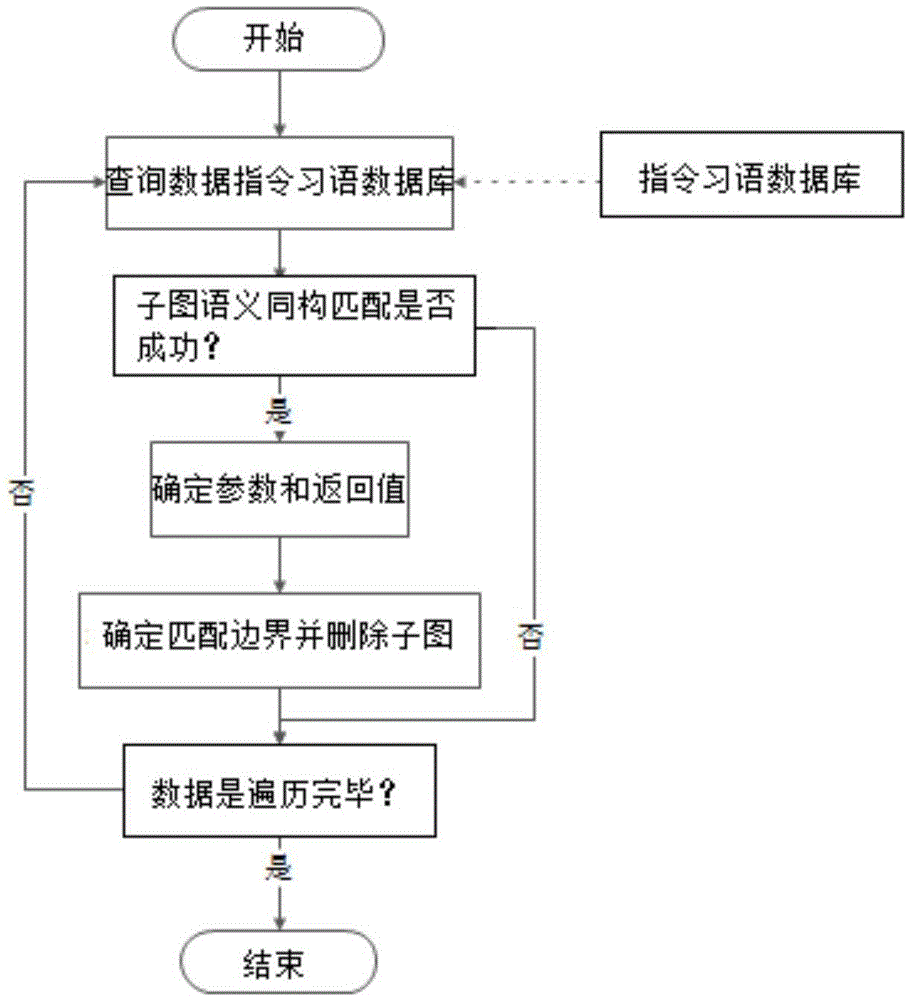
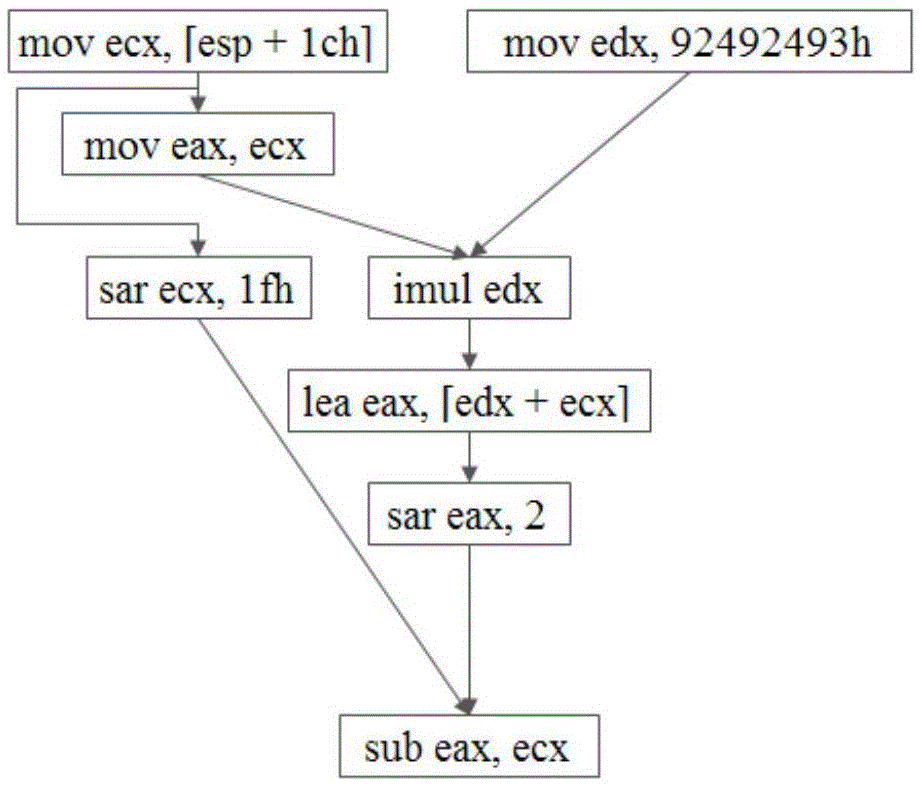
Sub-graph semantic isomorphism based instruction idiom identification method
ActiveCN105589728AHigh precisionImprove recognition accuracyDecompilation/disassemblyProgram controlData dependency graphReverse analysis
The invention discloses an analysis method of instruction idioms in reverse analysis. The analysis method of the instruction idioms in reverse analysis comprises the steps of performing data stream analysis for an assembly instruction sequence stream in a basic block; constructing a data dependence graph of the instruction sequence stream based on a definition-use relationship; then performing sub-graph semantic isomorphism matching for each connection sub-graph in the data dependence graph and a template in a template library; discovering a semantic isomorphism sub-graph; performing regulated reduction for the isomorphism sub-graph; and analyzing abstract operation of the sub-graph and corresponding operands. The analysis method of the instruction idioms in reverse analysis can efficiently increase the abstraction level of intermediate codes in the reverse analysis and improve code analysis efficiency.
Owner:弘毅视界(北京)科技有限公司
Evolution influence set prediction method based on evolution slices
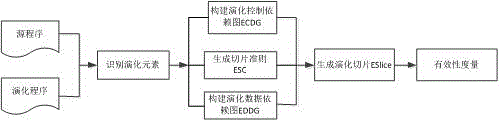
ActiveCN106844218AImprove recallLow survival rateSoftware testing/debuggingData dependency graphAlgorithm
The invention provides an evolution influence set prediction method based on evolution slices. The method is mainly used for establishing an evolution influence set to assist a software developer and a maintainer to make an evolution strategy and comprises the following steps that evolution elements are identified; an evolution slice criterion is generated; an evolution data dependence drawing is established; an evolution control dependence drawing is established; the evolution slices are generated to form an evolution influence se; the evolution influence set is measured. The evolution influence set prediction (ESISP) method based on the evolution slices has higher recall ratio and lower pseudo ratio and can effectively assist the software developer and the maintainer to make relevant decisions.
Owner:NANTONG UNIVERSITY
Method for allocating registers for a processor based on cycle information
A method of allocating registers for a processor based on cycle information is disclosed. The processor comprises a first cluster and a second cluster. Each cluster comprises a first functional unit, a second functional unit, a first local register file connected to the first functional unit, a second local register file connected to the second register file, and a global register file having a ping-pong structure formed by a first register bank and a second register bank. After building a Component / Register Type Associated Data Dependency Graph (CRTA-DDG), a functional unit assignment, register file assignment, ping-pong register bank assignment, and cluster assignment are performed to take full advantage of the properties of a processor as well as cycle information.
Owner:NATIONAL TSING HUA UNIVERSITY
Method for extracting malicious code behavior characteristic
InactiveCN102054149BComprehensive information extractionImprove anti-interference abilityPlatform integrity maintainanceData dependency graphSingle sample
The invention discloses a method for extracting a malicious code behavior characteristic, which belongs to the technical field of network security. The method comprises the following steps of: 1) running a malicious code and extracting executive information of the malicious code, wherein the executive information comprises an executive instruction sequence and a behavior sequence of the malicious code; 2) constructing a control dependence graph and a data dependence graph for executing the code according to the executive information; 3) comparing relevance of the control dependence graph and the data dependence graph and recording related relevance information; and 4) comparing the control dependence graphs and the data dependence graphs of different malicious codes and extracting characteristic dependency of each type of samples according to similarity clustering. Compared with the prior art, the method has the characteristics of complete information extraction, high anti-interference performance, certain applicability to varieties of a single sample characteristic, small-sized characteristic library and wide application range.
Owner:GRADUATE SCHOOL OF THE CHINESE ACAD OF SCI GSCAS
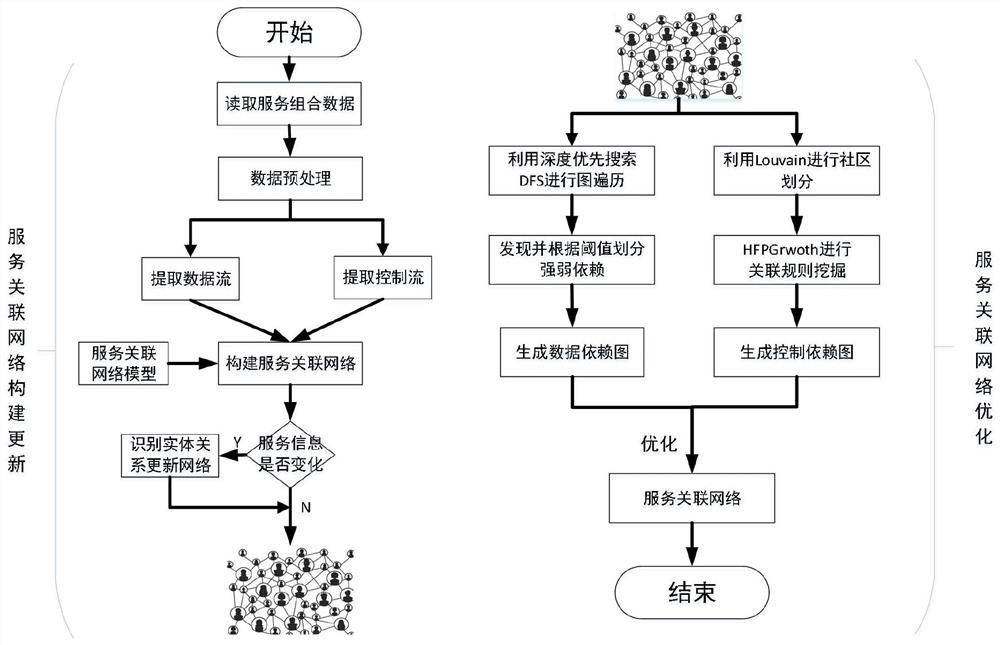
Scientific and technological service association network construction method, dependency relationship identification method and computer product
PendingCN113239127AEffective serviceEfficient managementDatabase updatingRelational databasesData dependency graphState of art
The invention provides a scientific and technological service association network construction method, a dependency relationship identification method and a computer product, and overcomes the defect that the prior art only pays attention to single data dependency or control dependency and cannot be directly applied to a complex and changeable large service environment. According to the invention, a service data set of a sample file is obtained and labeled, meanwhile, node pairs with an association relationship are extracted to construct a science and technology service association network, and then updating of the association network is maintained through five control structures; a science and technology service association network is traversed through DFS to obtain a data dependency graph, community division is carried out on the network through Louvain, the situation of edge single nodes is eliminated, then an original FPGrowth algorithm is transformed, a new Hmark is added to the position of an item header table, and the construction time of an fp tree is shortened. According to the invention, massive heterogeneous services can be effectively managed, and support is provided for distributed deployment and efficient execution of science and technology service combinations.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
Data updating method, device and equipment and storage medium
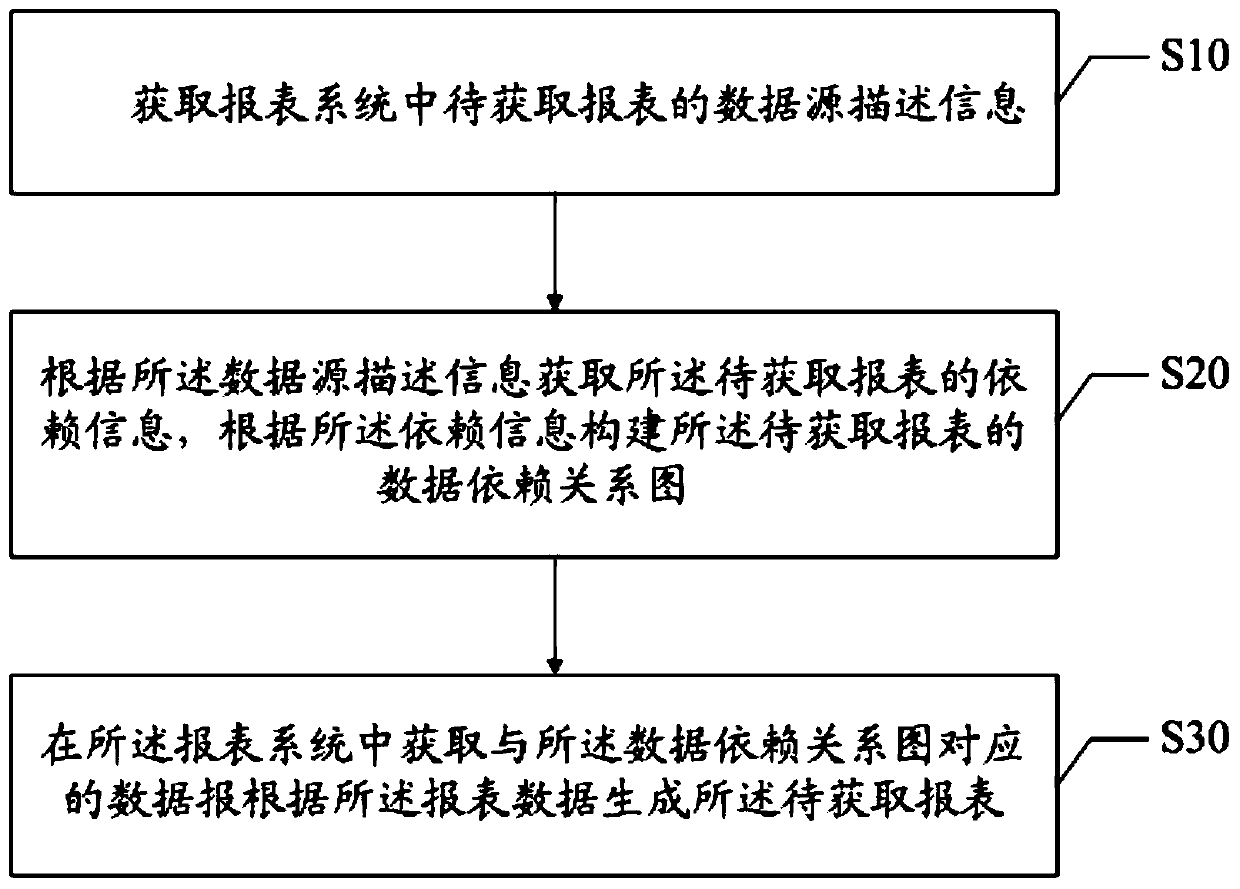
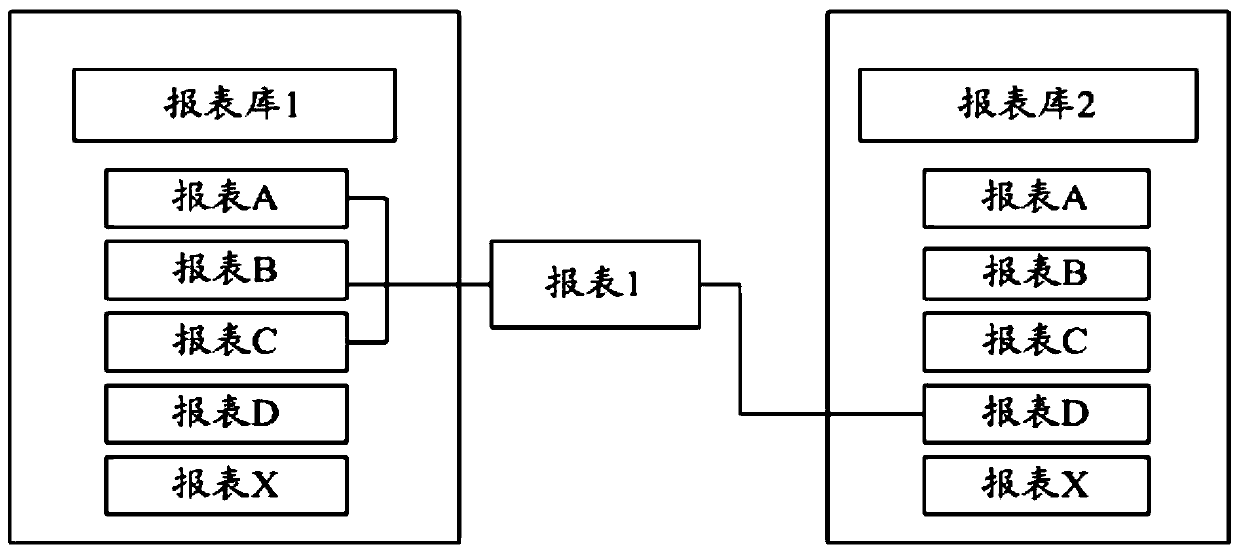
PendingCN111352947ARealize automatic acquisitionImprove update efficiencyDatabase updatingSpecial data processing applicationsData dependency graphData source
The invention discloses a data updating method, device and equipment, and a storage medium, and relates to the field of financial science and technology. The method comprises the steps: obtaining datasource description information of a to-be-obtained report in a report system; obtaining dependence information of the to-be-obtained report according to the data source description information, and constructing a data dependence relation graph of the to-be-obtained report according to the dependence information; and obtaining report data corresponding to the data dependency graph in the report system, and generating the to-be-obtained report according to the report data. According to the invention, the report data can be updated in the updating process; the report system automatically acquires updated report data in the report system according to the dependence information of the report data; the required report is automatically generated according to the updated report data, so the report data can be automatically acquired and updated in the report system without waiting for periodic updating of the report system, and the updating efficiency and timeliness of the report data are improved.
Owner:WEBANK (CHINA)
A Method for Reducing Intra-frame Coding Delay in HEVC Encoder
ActiveCN105100799BResolve dependenciesReduce encoding delayDigital video signal modificationData dependency graphCode module
Owner:芯原微电子(北京)有限公司 +2
Method and apparatus for modulo scheduling
ActiveUS10423607B2Reduce dispatch timeDatabase updatingOther databases indexingData dependency graphRecursion
Provided is a modulo scheduling method. The modulo scheduling method includes conducting a search, based on a data dependency graph of a loop, for a recurrence in which a sum of iteration distances between command nodes is less than a predetermined critical value; and determining a processing order of the recurrence.
Owner:SEOUL NAT UNIV R&DB FOUND
Instruction scheduling method and device, equipment, storage medium and program product
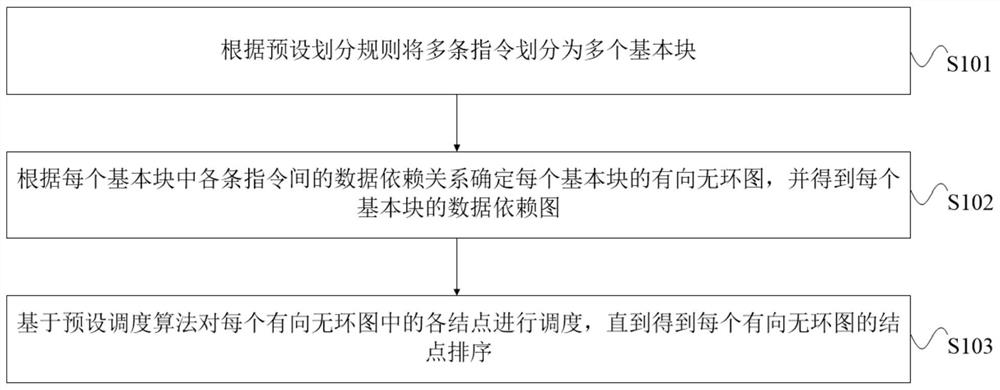
PendingCN113296788AReduce capacity sizeReduce the quantity requiredCode compilationMachine execution arrangementsData dependency graphScheduling instructions
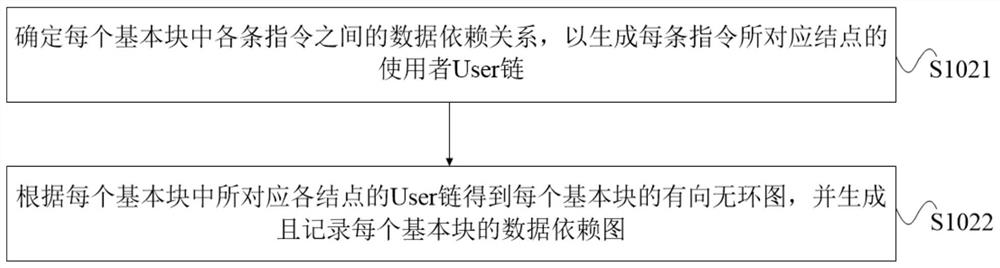
The invention provides an instruction scheduling method and device, equipment, a storage medium and a program product. The method comprises the following steps: firstly, dividing a plurality of instructions into a plurality of basic blocks according to a preset division rule, then determining a directed acyclic graph of each basic block according to a data dependency relationship among the instructions in each basic block, and obtaining a data dependency graph of each basic block; and scheduling each node in each directed acyclic graph based on a preset scheduling algorithm until a node sequence of each directed acyclic graph is obtained. Due to the fact that the instructions in the same basic block have the data dependency relationship, the node sequence is obtained after scheduling according to the preset scheduling algorithm based on the directed acyclic graph, the capacity of a memory occupied by a program can be effectively reduced, meanwhile, the number of required memories and registers is reduced, the phenomenon of register overflow is effectively avoided, the required development technology threshold and cost are low, and the realizability is high.
Owner:SHANGHAI EASTSOFT MICROELECTRONICS
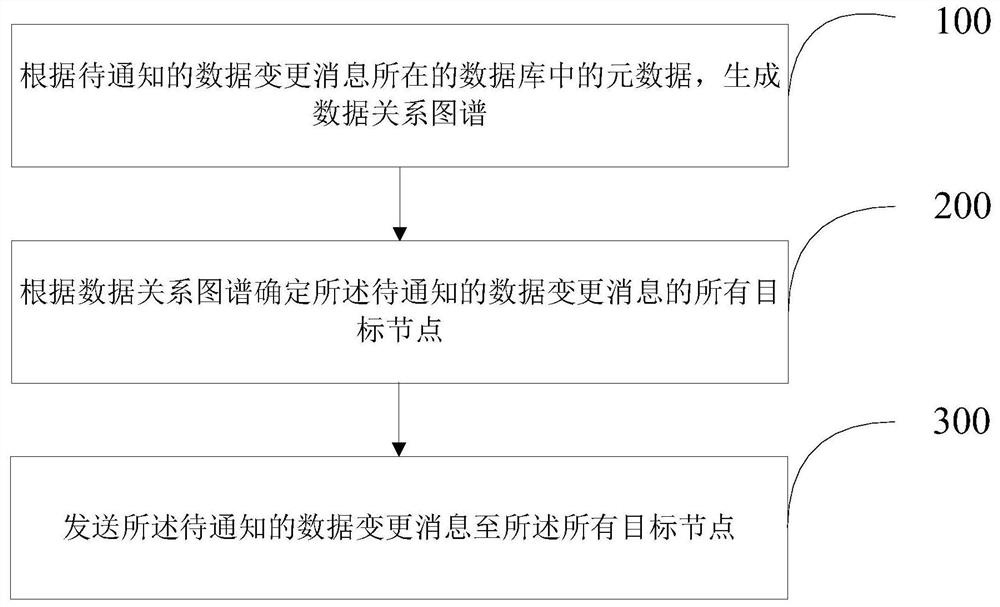
Data change message notification method and device
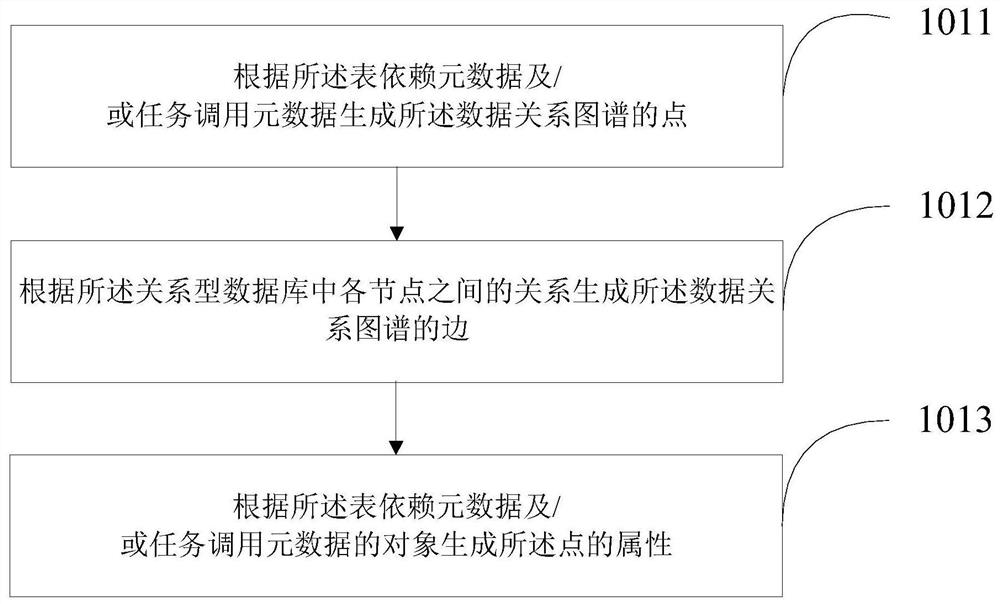
The invention belongs to the technical field of big data, and provides a data change message notification method and device, and the method comprises the steps: generating a data relation graph according to metadata in a database where a to-be-notified data change message is located; determining all target nodes of the to-be-notified data change message according to a data relationship graph; andsending the to-be-notified data change message to all the target nodes. According to the method, a task calling relationship and a table dependency relationship are fused to construct a complete'datadependency graph '. Based on the data dependence graph, a traversal algorithm of the graph is utilized to carry out change notification, and the effects of accurately notifying without omitting any person in charge and controlling a notification level to notify in place at one time are achieved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
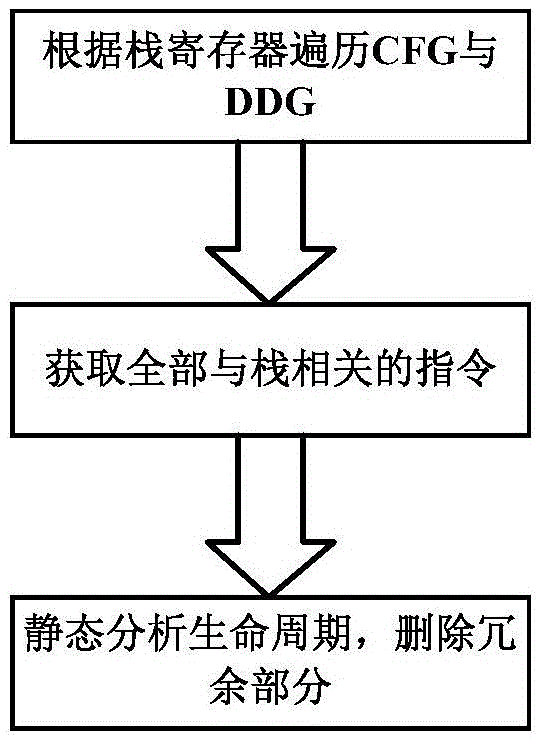
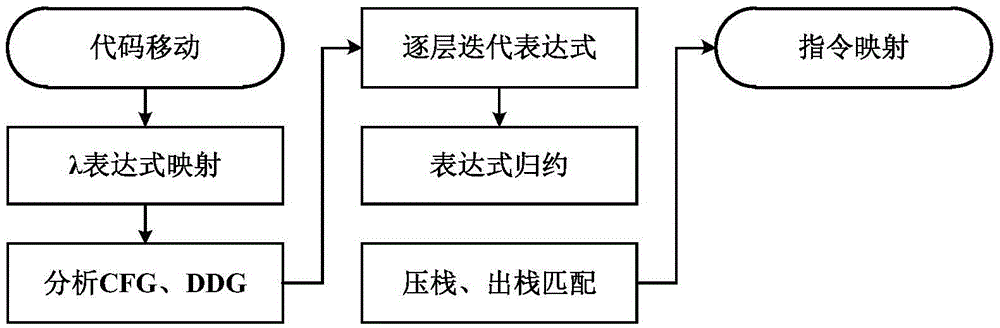
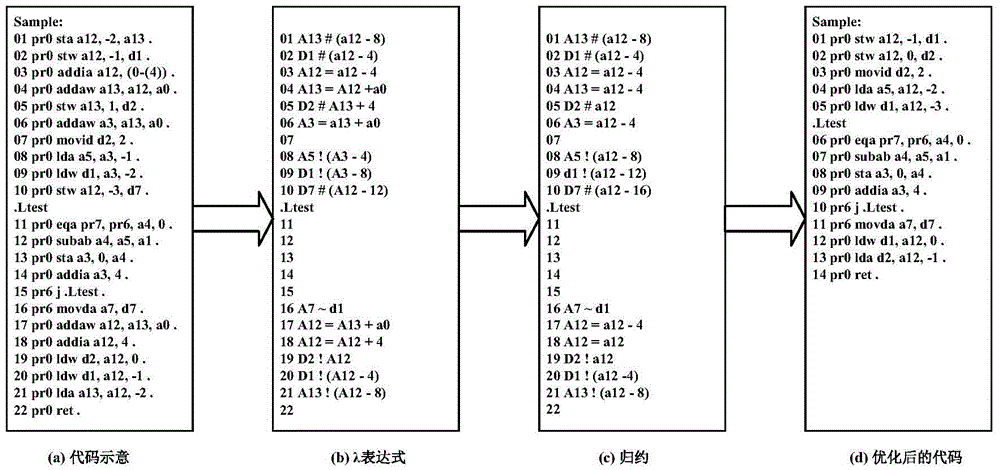
An Algebraic System-Based Cross-File Process Optimization Method
InactiveCN103559069BEffective mergerEfficient releaseProgram controlMemory systemsData dependency graphProcess optimization
The invention discloses a cross-file inter-process optimization method based on an algebraic system. The method includes the following steps: according to the characteristics of the target machine, select instructions related to stack operations and logic operations, construct an algebraic system, and provide these instructions with the algebraic system. Establish a mapping relationship; traverse the program call graph PCG from the program entrance, and judge whether the nodes connected by edges belong to different source files, if so, continue to the next step, otherwise continue to traverse PCG; start from the function call instruction and follow The control flow graph CFG in the current function starts to traverse the data dependency graph DDG, generates the algebraic expression of the instruction stack operation, and performs expression reduction; analyzes the pop operation of the subsequent node function, reads the constant value from it, and passes it on in sequence , optimize and calculate, and finally delete redundant instruction fragments. The invention effectively merges and releases the optimizeable part in the function stack frame. In addition, the present invention also achieves better effects in cross-file process optimization, constant propagation and constant calculation.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
A c source code vulnerability detection method based on bert model and bilstm
ActiveCN113420296BImprove accuracyReduce false alarm ratePlatform integrity maintainanceNeural architecturesAlgorithmTheoretical computer science
A C source code vulnerability detection method based on the Bert model and BiLSTM. By analyzing the software source code, a control dependency graph and a data dependency graph are constructed, and the code is sliced according to the control dependency relationship and data dependency relationship between codes to generate slices. Level code blocks, then perform data cleaning and preprocessing on the generated code blocks, and label each generated code block to distinguish whether the code block contains vulnerability information. Second, input the processed code block as a training set into the Bert pre-training model to fine-tune the standard Bert model to obtain a new Bert model. Then input the code block into the new Bert model to learn the semantic information and contextual relationship between the codes in an unsupervised manner, perform word embedding encoding on the code block, and obtain a word vector with maximized code semantic information and contextual relationship. Finally, input the obtained word vector into BiLSTM to train the detection model, and obtain the source code vulnerability detection model. The invention can improve the accuracy rate of loophole detection and reduce the false alarm rate.
Owner:STATE GRID GASU ELECTRIC POWER RES INST +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com