A c source code vulnerability detection method based on bert model and bilstm
A vulnerability detection and source code technology, applied in code compilation, program code conversion, neural learning methods, etc., can solve problems such as lack of semantic information, inability to effectively learn complex graph nodes, and low detection accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below in combination with specific embodiments.
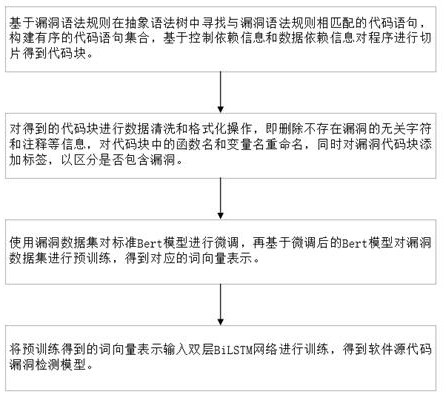
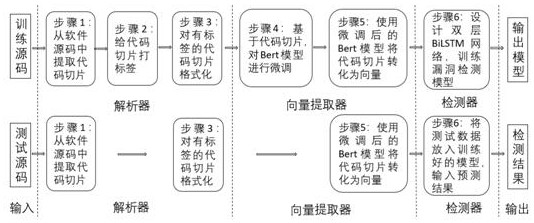
[0030] A C source code vulnerability detection method based on the Bert (Bidirectional Encoder Representations from Transformers) model and bidirectional long-term short-term memory network BiLSTM (Bi-directional Long Short-Term Memory), which mainly includes the following steps:
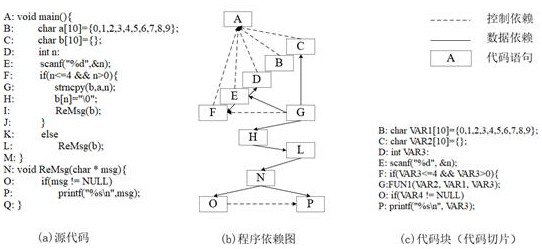
[0031] Step A: Generate program slices, based on the source code of the software, use the Joern tool to generate the program dependency graph PDG (Program Dependence Graph) and abstract syntax tree AST (Abstract Syntax Tree) corresponding to the source code. PDG contains the control dependency graph CDG between codes (Control Dependence Graph) and data dependency graph DDG (Data Dependence Graph), AST contains grammatical information between program statements; based on the control dependency information and data dependency information in the control dependency graph CDG and data dependency graph ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com