Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
355results about How to "Implement backup" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
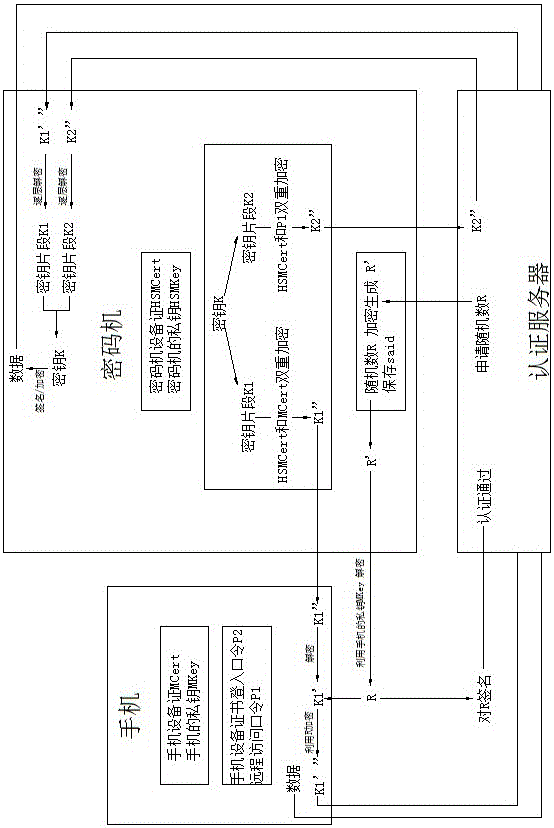
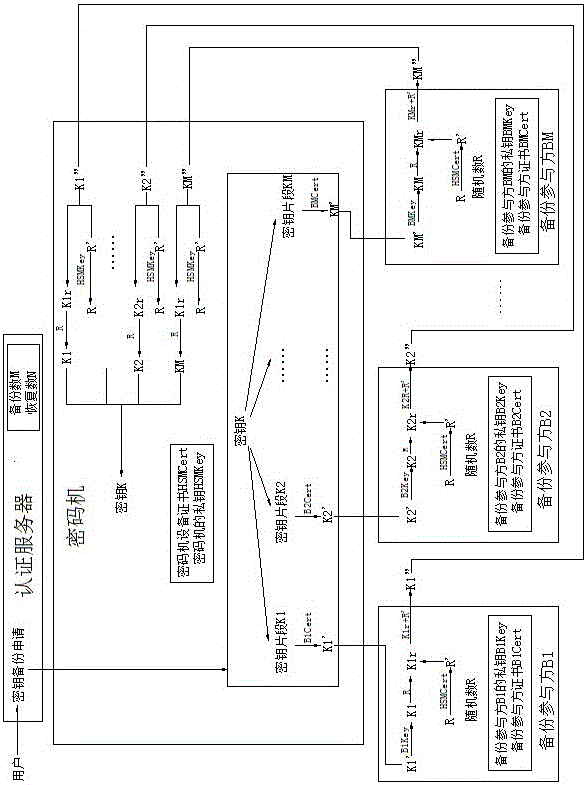
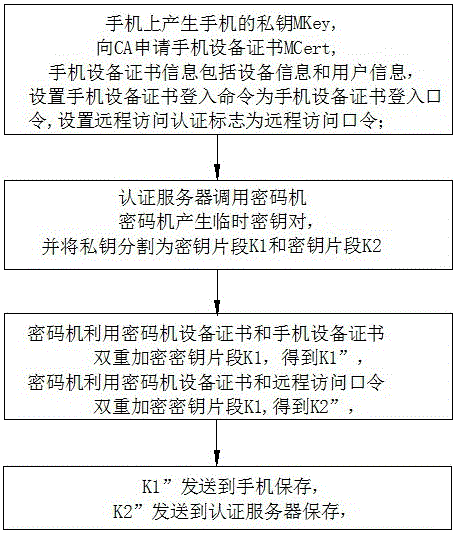
Method and system for realizing block chain private key protection based on key segmentation
ActiveCN106548345AImprove securityAvoid Permission RisksKey distribution for secure communicationPayment protocolsPasswordStructure of Management Information
The invention discloses a method and a system for realizing block chain private key protection based on key segmentation, and aims to solve a technical problem that a private key of a block chain is lack of security and cannot be retrieved. The method for realizing block chain private key protection based on key segmentation comprises that hard encryption for a block chain private key supporting mobile phone equipment certificate authentication and password authentication is realized by taking a mobile phone as a terminal carrier and using a cipher machine and an authentication server of the cloud; and the block chain private key is segmented by using a threshold algorithm, and multi-party participating key backup and key recovery / retrieval is realized. The method comprises (1) a registration procedure, (2) a private key utilization procedure, (3) a private key backup procedure, and (4) a private key recovery / retrieval procedure. The system structurally comprises a cipher machine and an authentication server of the cloud and a mobile phone acting as the terminal carrier. The method and the system disclosed by the invention can realize safe storage, safe utilization, multi-party participating backup and multi-party participating retrieval of the block chain private key.
Owner:北京信任度科技有限公司
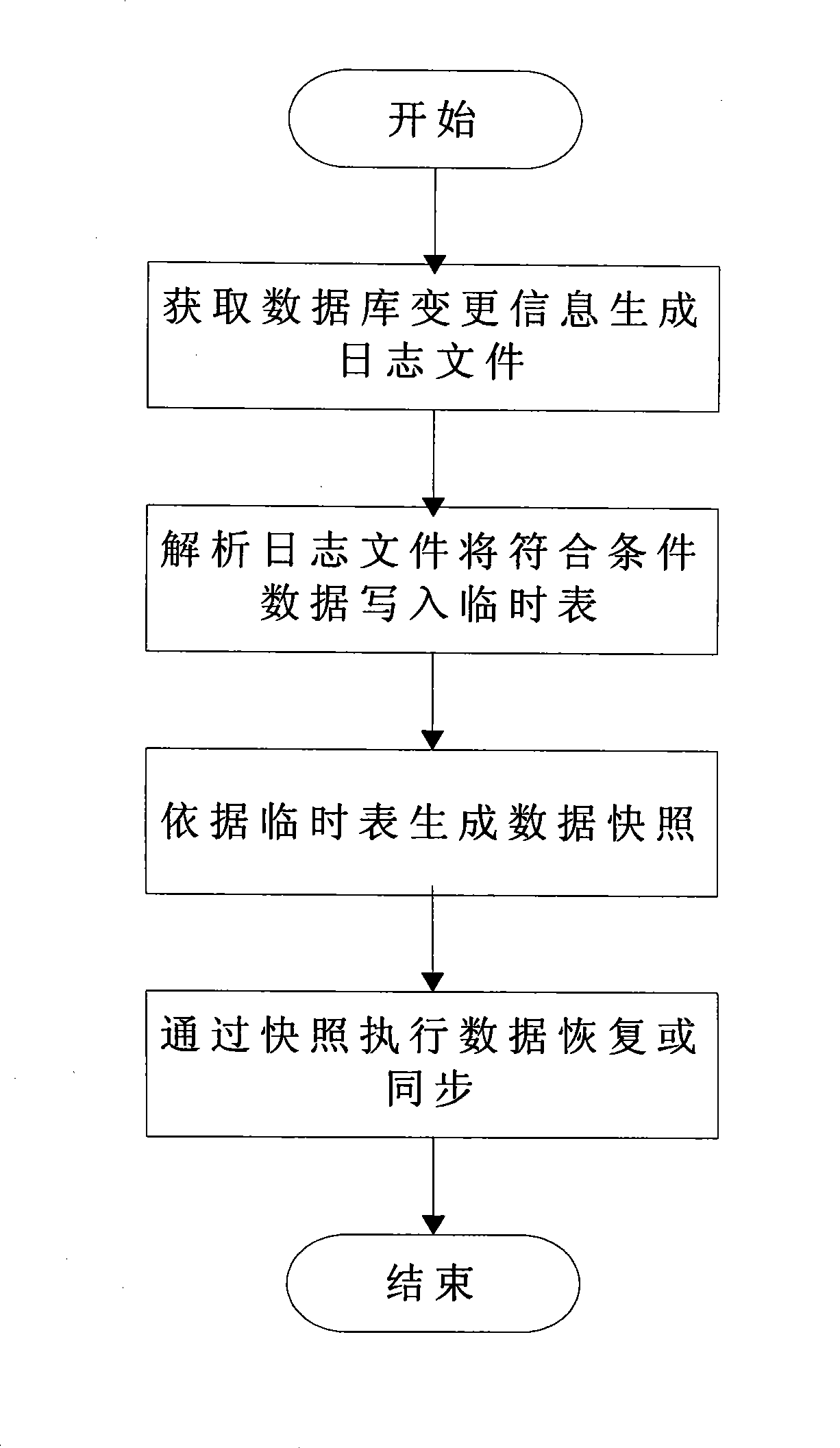
Data restoring and synchronizing method based on log snapshot
InactiveCN101436207AReduce storage overheadReduce system costSpecial data processing applicationsLogfileData memory
The invention relates to the field of occupation of the mass data memory space and backup and recovery of historical data, and in particular provides a data recovery and synchronization method based on log snapshots. The data recovery and synchronization method based on the log snapshots adopts log files with given format to record changed information of data of databases each time; the changed information is formatted, positioned and stored into the log files; an analytic program calls an approximate algorithm to acquire effective data on set time points by means of multithreading; the data is temporarily stored into a temporary table, and abstract data snapshots are generated according to the temporary table; and data recovery and synchronization is realized by utilization of the snapshots. The data recovery and synchronization method based on the log snapshots can greatly reduce the burden of a database system, obviously improve the efficiency of the database system and an application system, save a great deal of memory space, and reduce the operation cost of the systems.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
File backup recovery method based on sector recombination
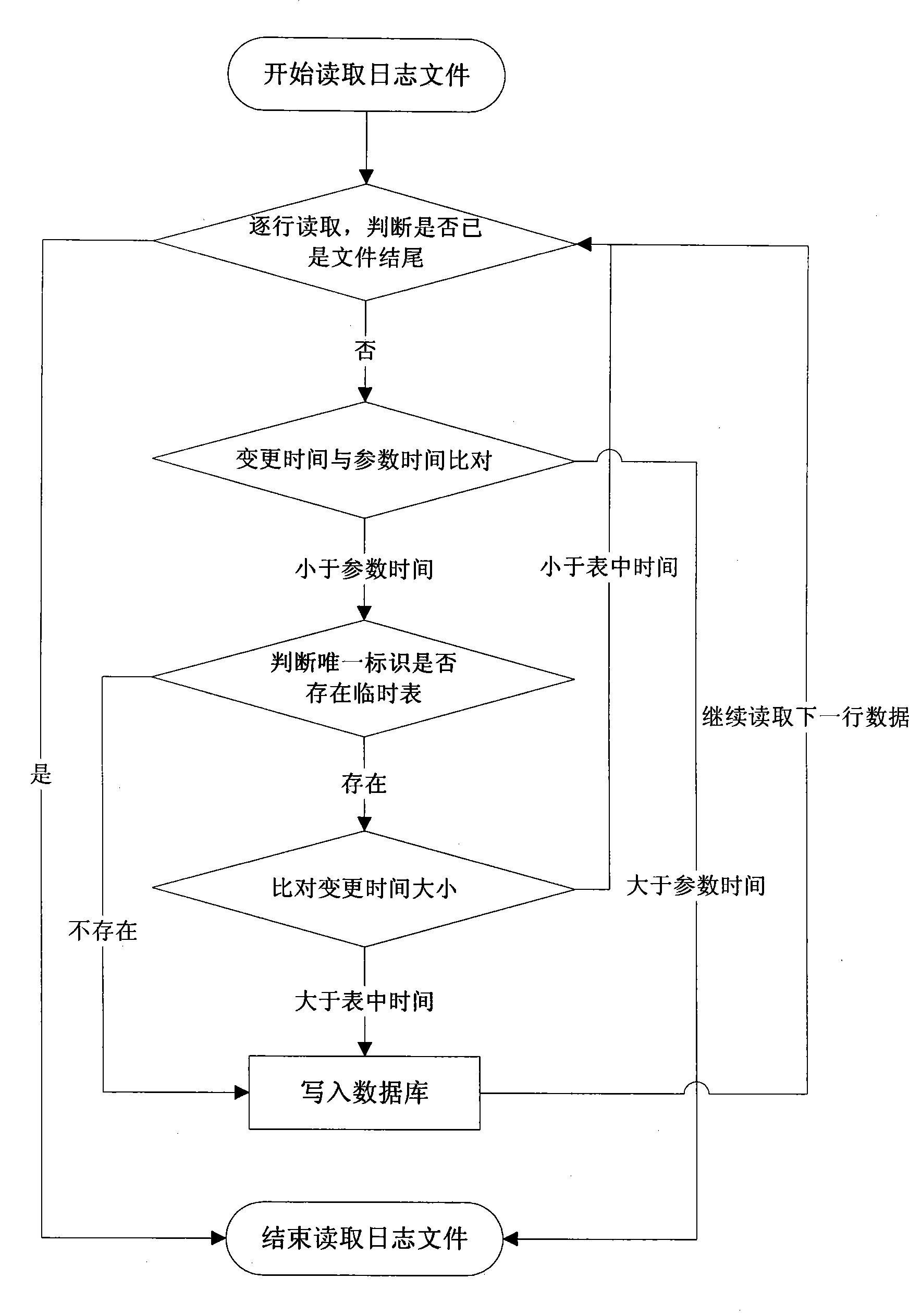
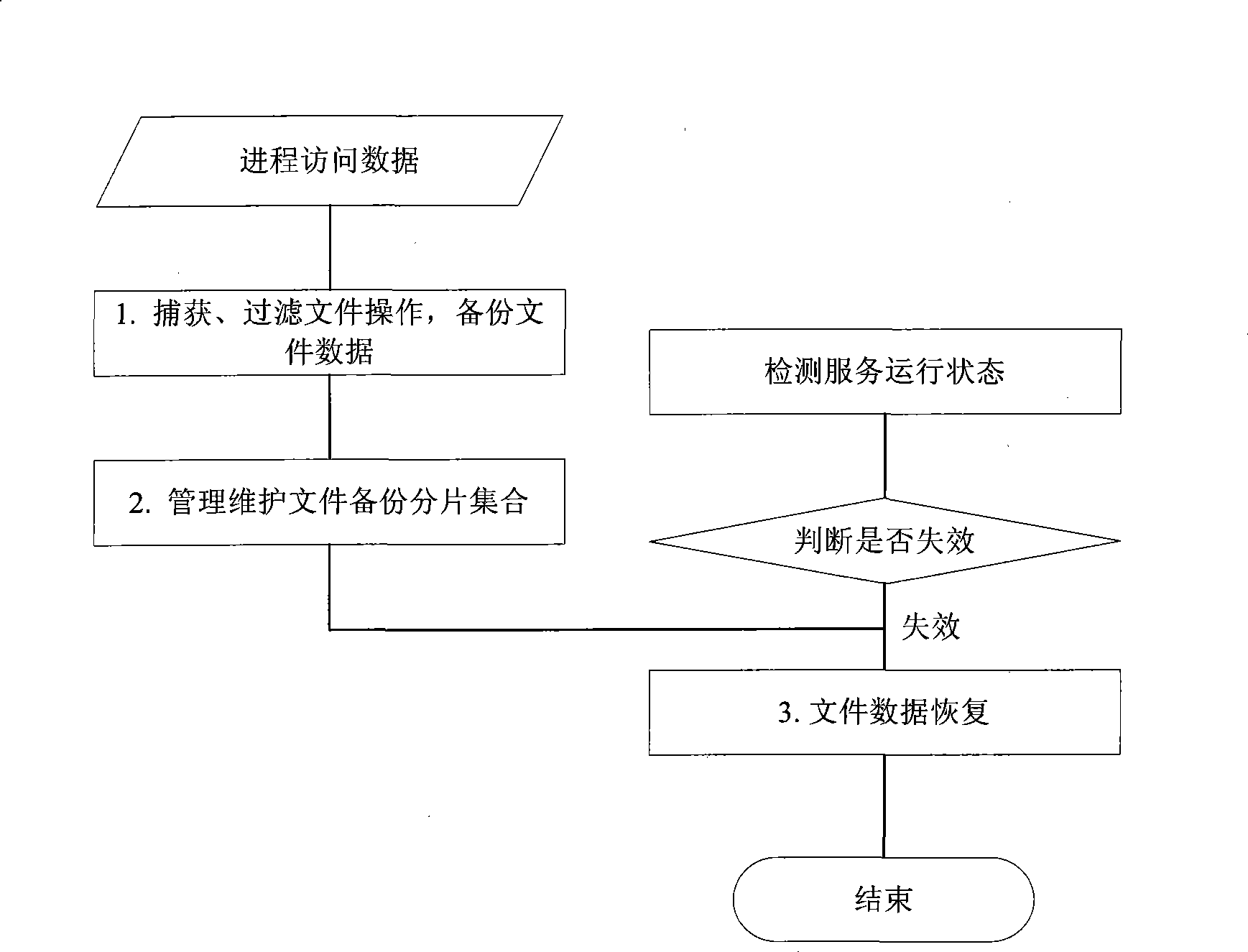
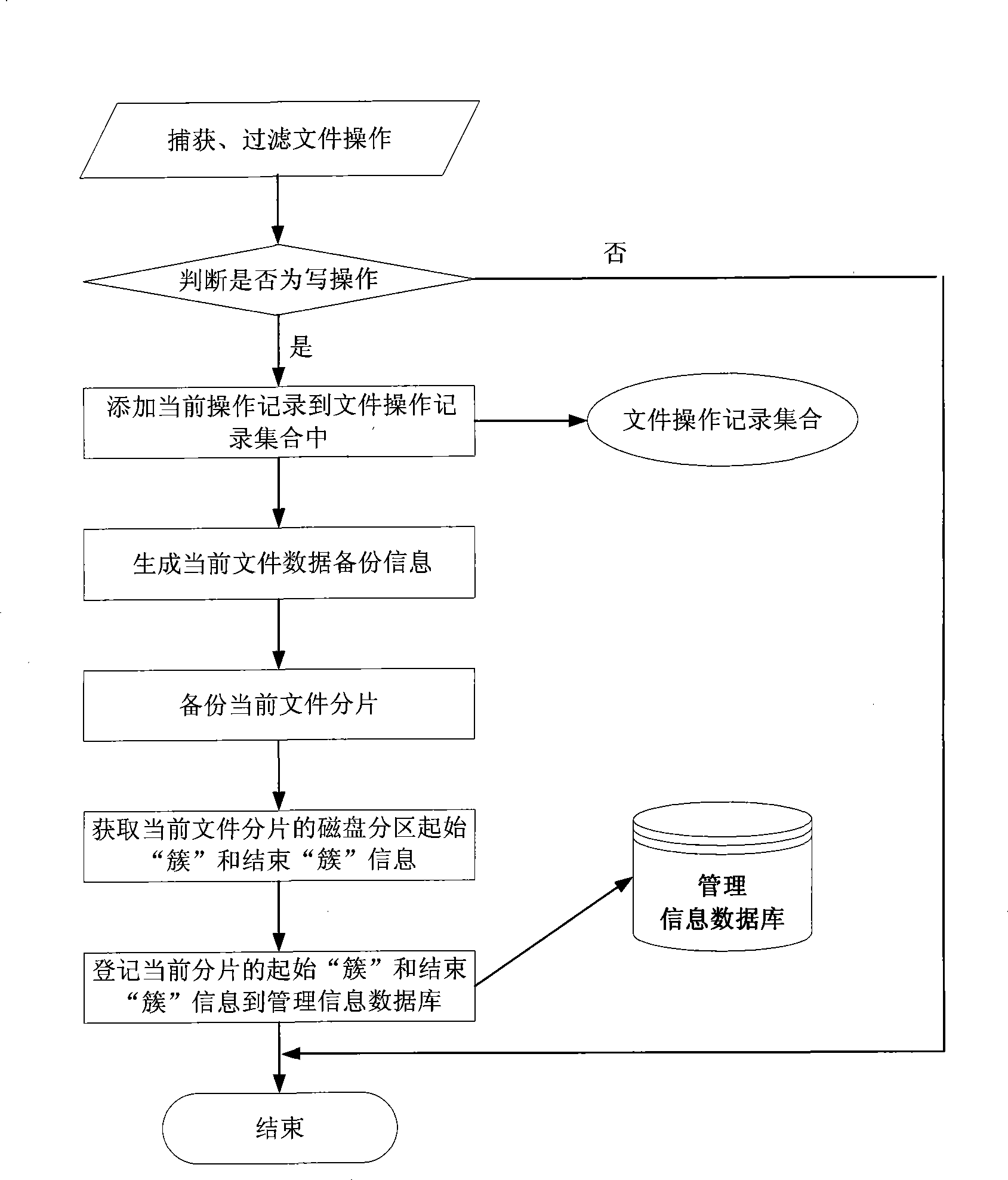
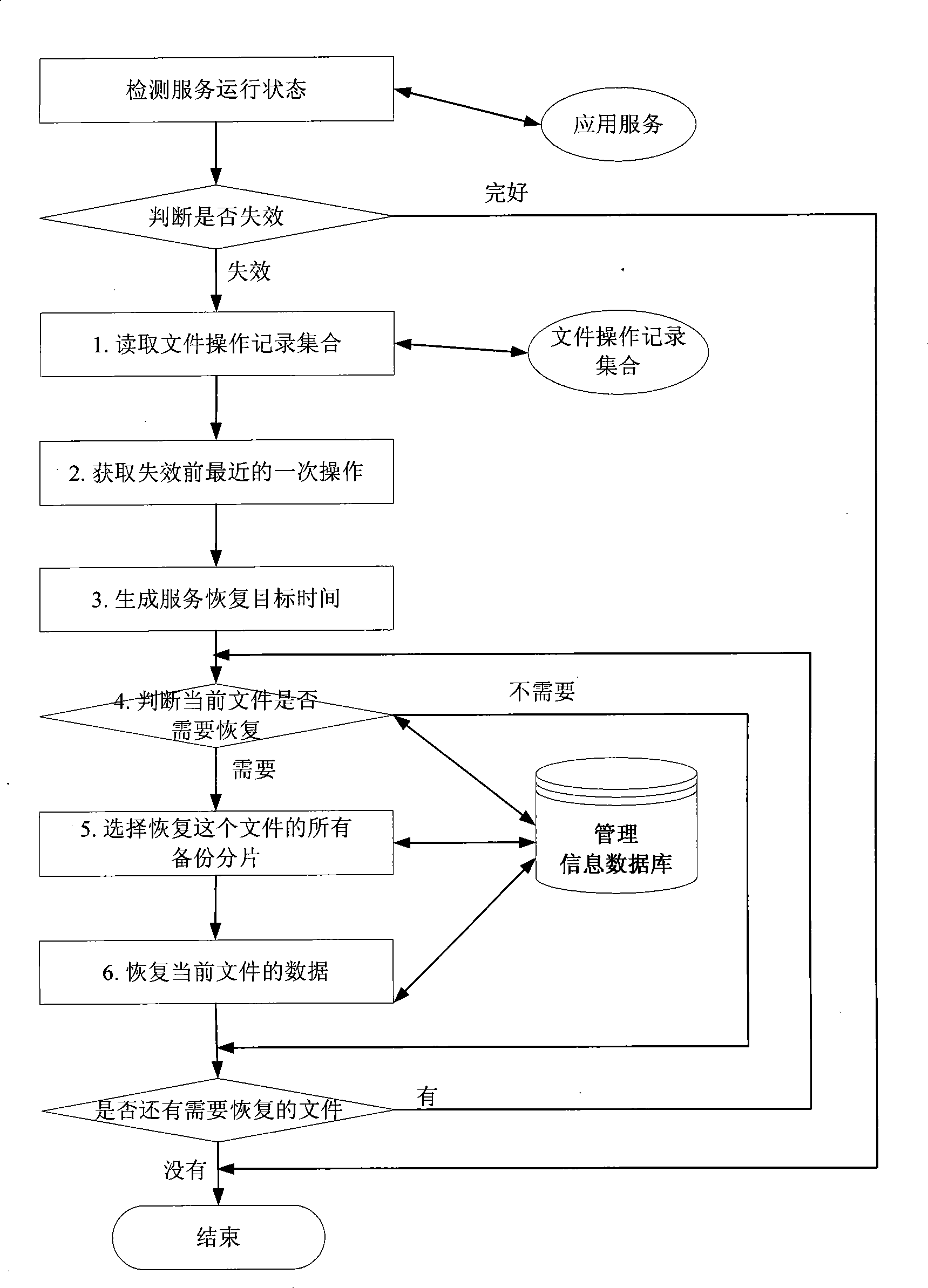
InactiveCN101477486AImprove unityReduce read and write access timesSpecial data processing applicationsRedundant operation error correctionRecovery methodRestoration method
The invention discloses a method for file backup recovery based on sector recombination, and aims to achieve the purpose that on the premise that the file data recovery result is correct, the file data recovery is accelerated, and the real-time and accuracy requirements of the recovery are satisfied. The technical scheme of the invention is as follows: obtaining and filtering to get the write operation information conducted by a procedure to all files in a disc; conducting splice type initiative backup according to the file data corresponding to the information; opening space NBS in a local disc to store the backup data in the file original state and the subsequent backup slicing data; and conducting operation level recovery to the served file data when the information system service crashes or is damaged, specifically, selecting all backup slices used for recovering the file and recovering the file through adopting the method of slice data sector recombination. The invention does not need the operation of data copy or move, can greatly increase the speed of data recovery, and has the advantages of both incremental backup mode and log backup mode.
Owner:NAT UNIV OF DEFENSE TECH
Key generation, backup and migration method and system based on trusted computing
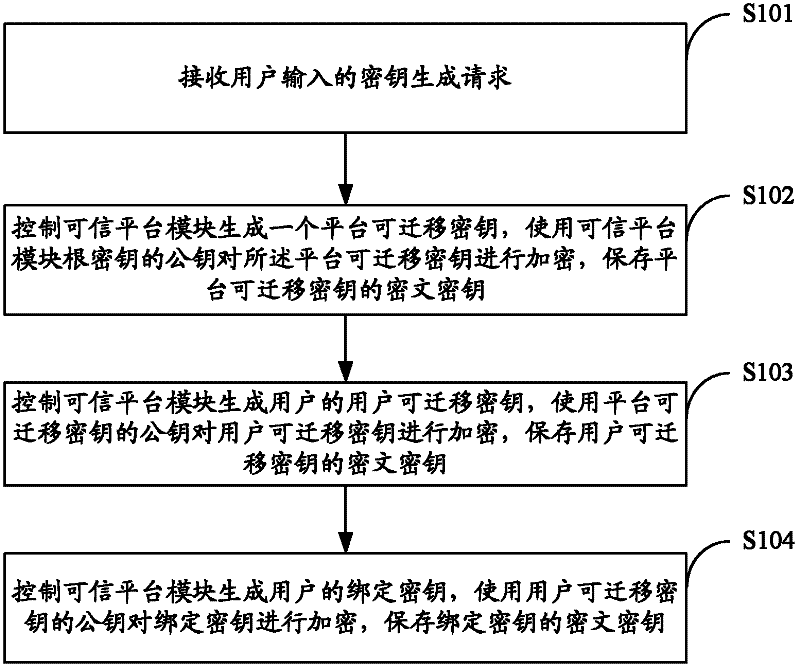
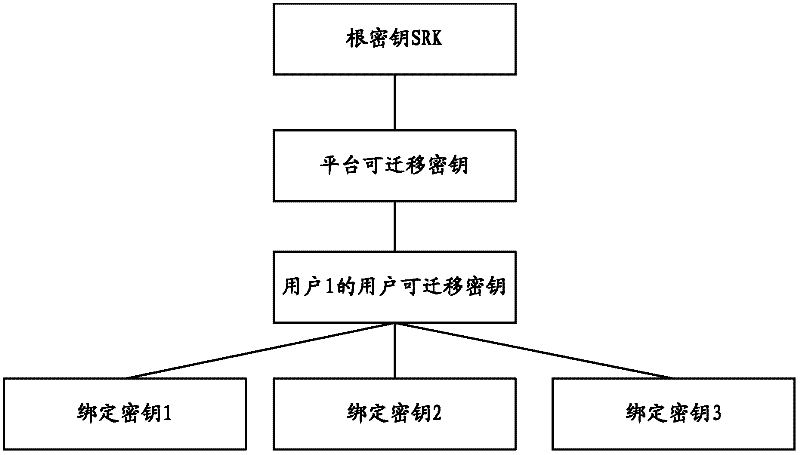
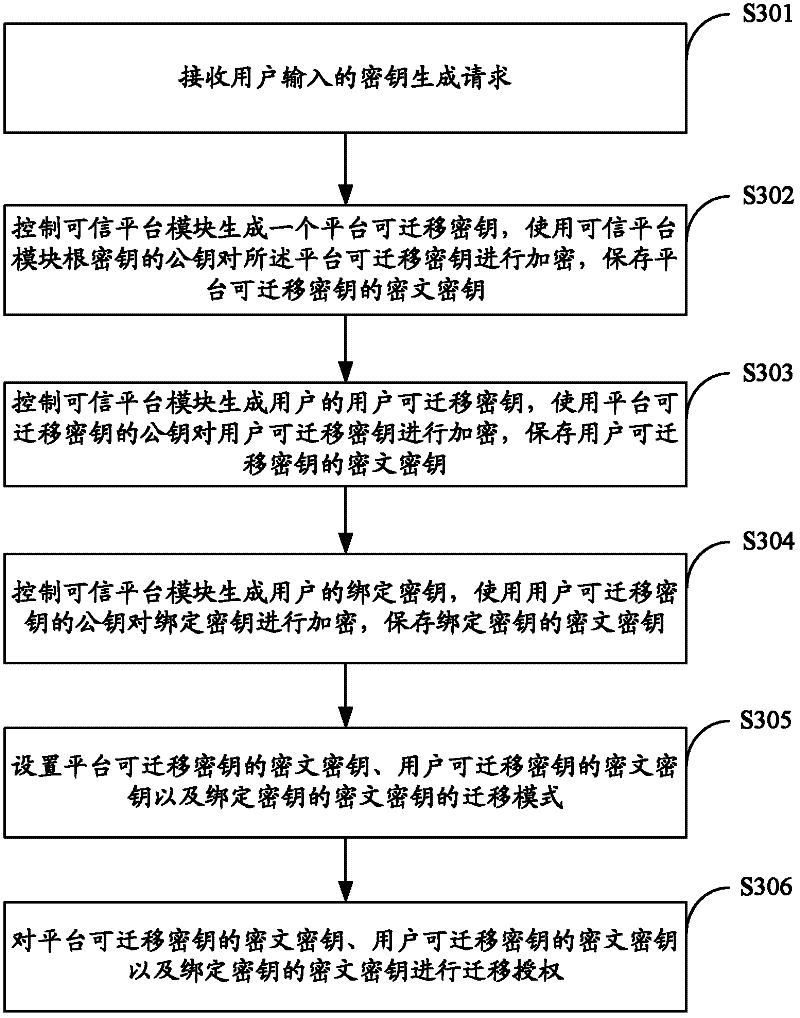
InactiveCN102355351ARealize generationImplement backupKey distribution for secure communicationMultiple keys/algorithms usageUser inputCiphertext
The invention is suitable for the technical field of computers, and provides a key generation, backup and migration method and system based on trusted computing. The method comprises the following steps of: receiving a key generation request input by a user; controlling a trusted platform module to generate a platform migratory key, encrypting the platform migratory key by a public key of a root key of the trusted platform module, and storing a cipher text key of the platform migratory key; controlling the trusted platform module to generate a user migratory key, encrypting the user migratory key by using the public key of the platform migratory key, and storing the cipher text key of the user migratory key; and controlling the trusted platform module to generate a binding key of the user, and encrypting the binding key by using the public key of the user migratory key, and storing the cipher text key of the binding key. According to the method and the system, the generation, backup, recovery and migration of the key are realized based on a trusted computing module in the trusted computing, and the security of the key in the generation, backup, recovery and migration processes is improved.
Owner:HUAWEI TECH CO LTD +1
Method for using quantum keys to improve safety of electric power information transmission in power system WiMAX wireless communication network
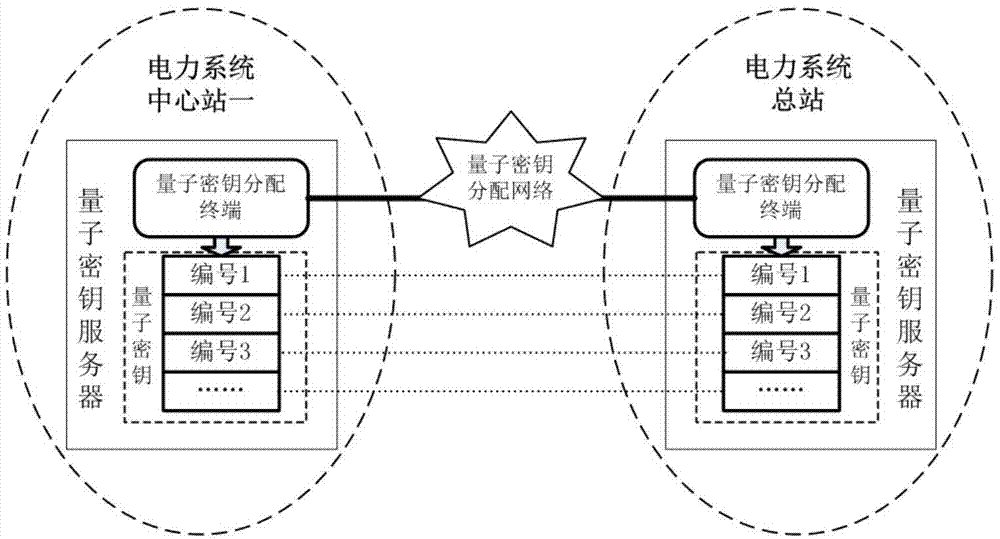
ActiveCN103491531AEasy retrievalImprove securityEnergy efficient ICTSecurity arrangementData needsWiMAX
The invention discloses a method for using quantum keys to improve safety of electric power information transmission in a power system WiMAX wireless communication network. According to the method for using the quantum keys to improve safety of electric power information transmission in the power system WiMAX wireless communication network, due to the fact that the quantum key distribution technology is applied to the power system WiMAX wireless communication network, safety of information transmission of a power system is improved; the scheme that a quantum key distribution network and the power system WiMAX wireless communication network are combined is adopted, the unconditionally safe quantum keys are applied to the power system WiMAX wireless communication network, pre-encryption is carried out on data needing to be transmitted by using the quantum keys on the premise that the IEEE802.16 protocol in the WiMAX technology is not modified, another encryption is carried out on a ciphertext generated through pre-encryption by using the encryption technology in the WiMAX wireless network, the effect of double protection on information transmission in the electric power system is achieved, convenience and rapidness are achieved, and safety of wireless communication of the electric power system is improved to the maximum extent.
Owner:UNIV OF SCI & TECH OF CHINA +2
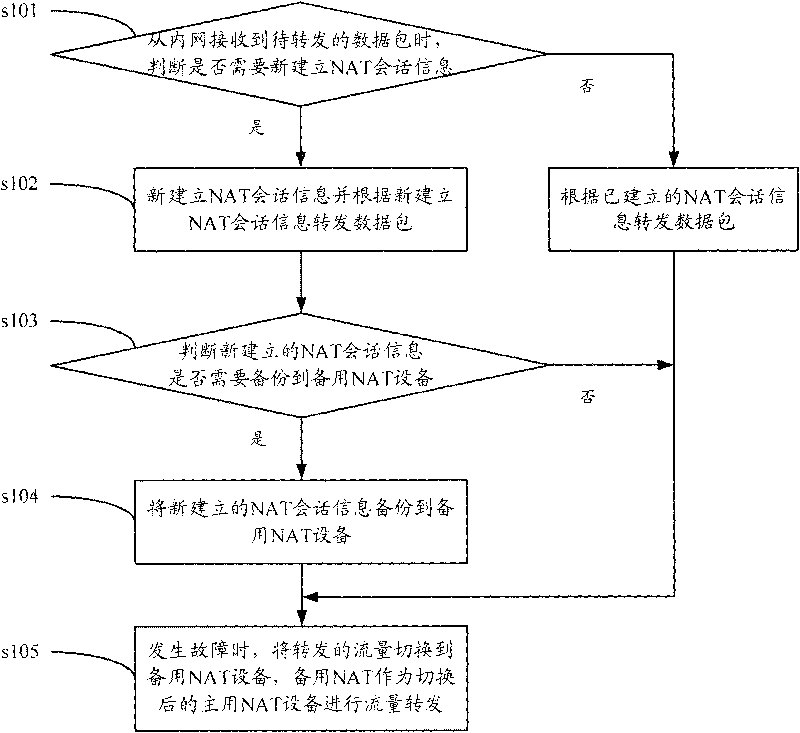
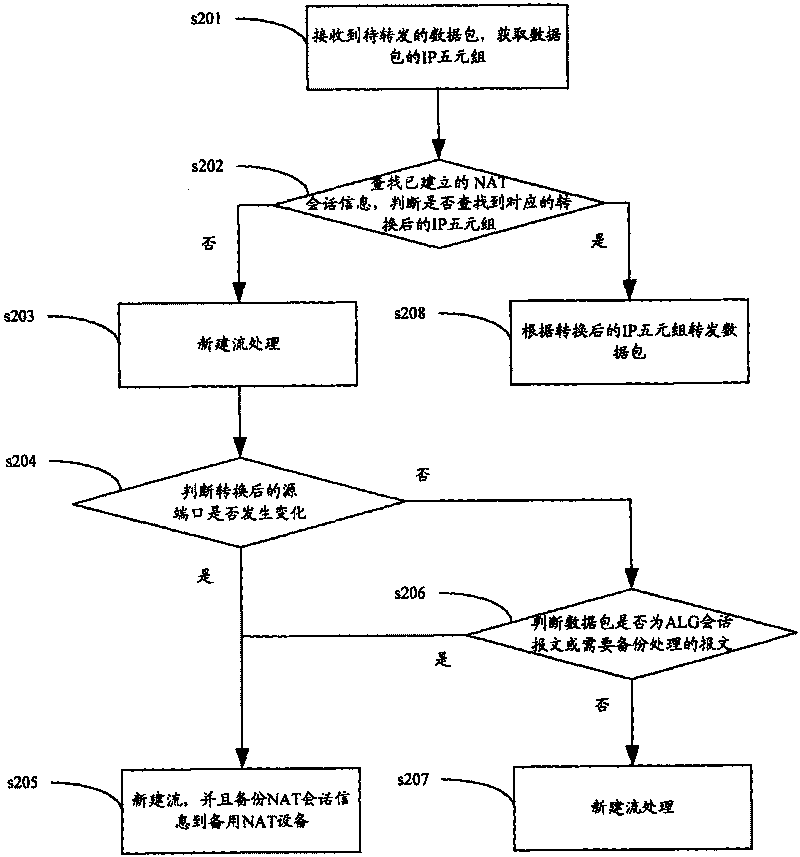
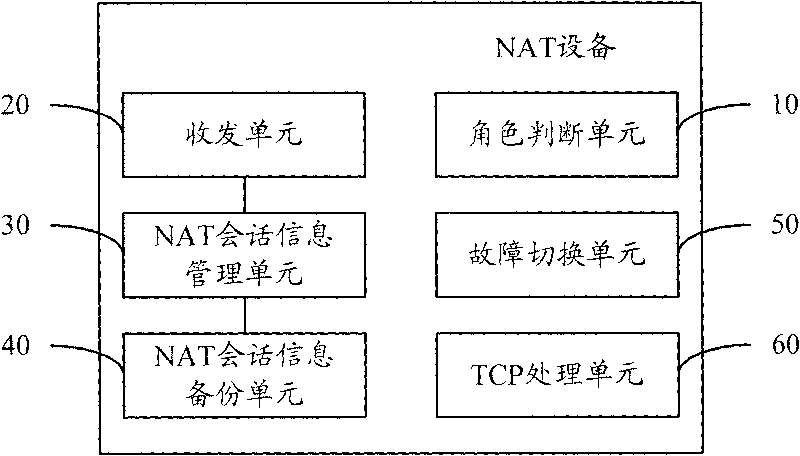
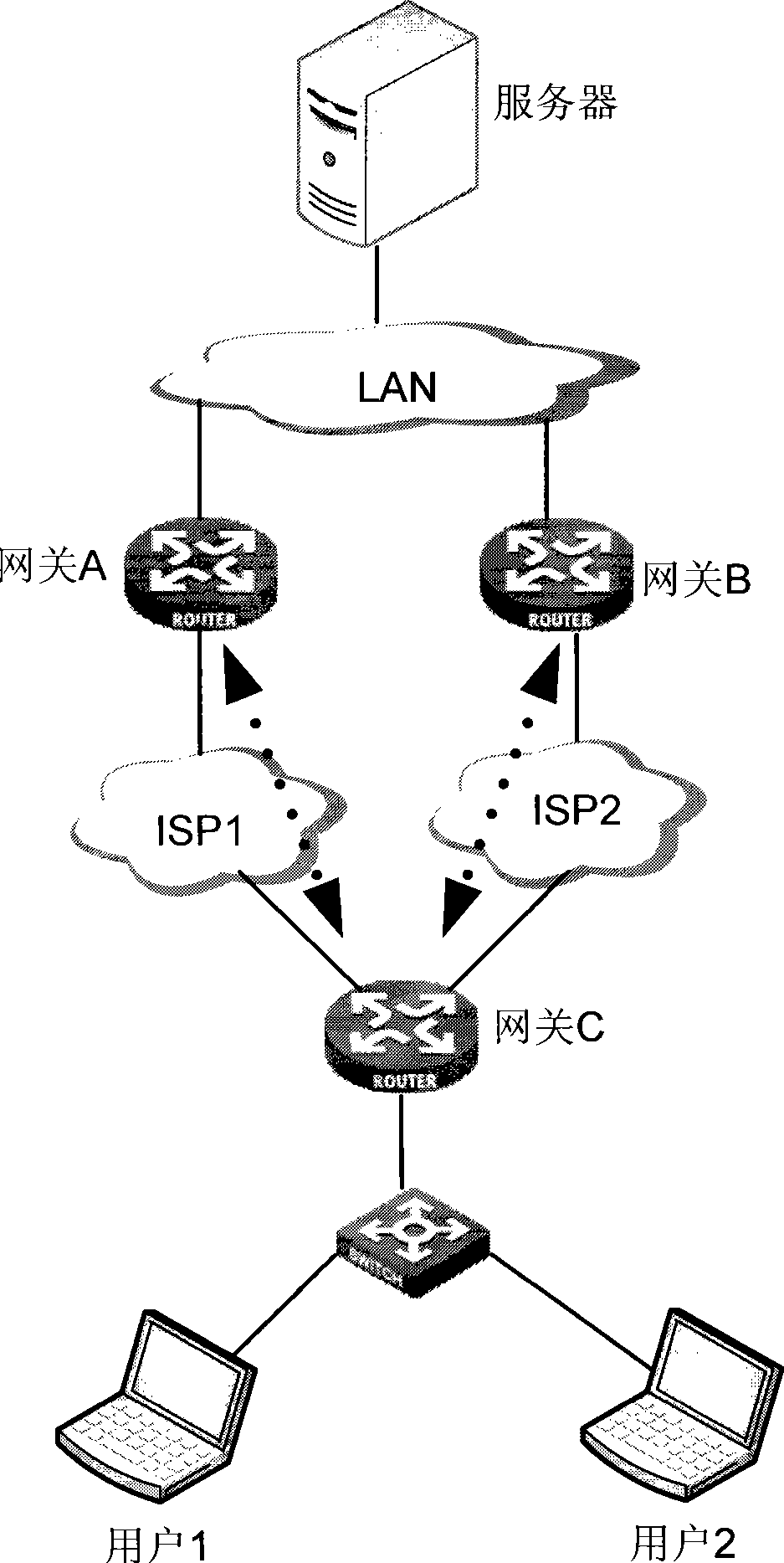
Hot backup method of NAT service and equipment
InactiveCN101702657AReduce in quantityPerformance is not affectedError preventionData switching networksNetwork addressingNetwork address
The invention discloses a hot backup method of an NAT service converted by a network address and equipment. NAT session information in the equipment is screened, backup is carried out only on the NAT session information which conforms to conditions; if the addresses of the NAT equipment in a public network address pool are more, the quantity of the NAT session information needing backup is less, so that the performance of the newly established session on the NAT device is not influenced, and many-for-one backup can be realized.
Owner:NEW H3C TECH CO LTD
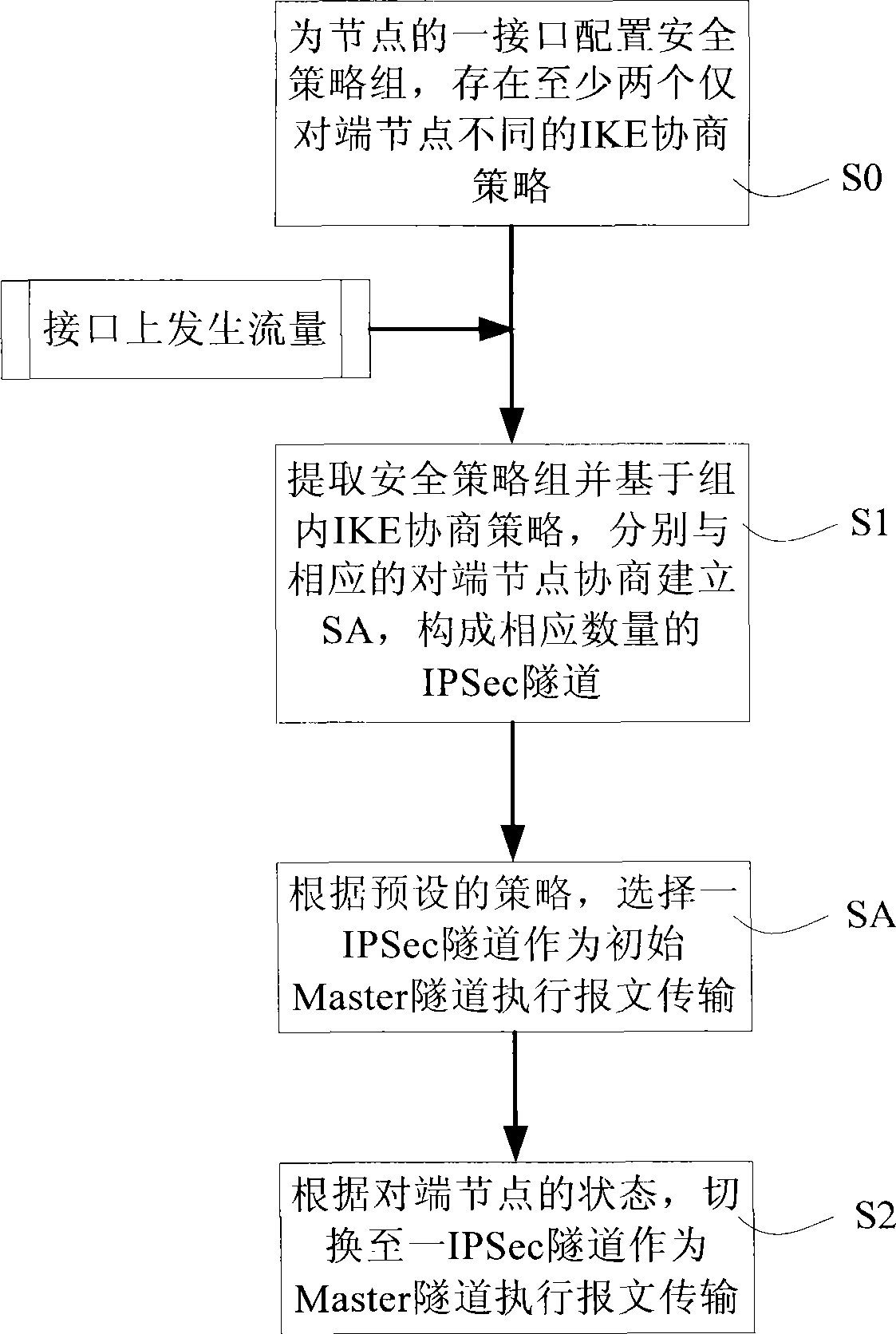
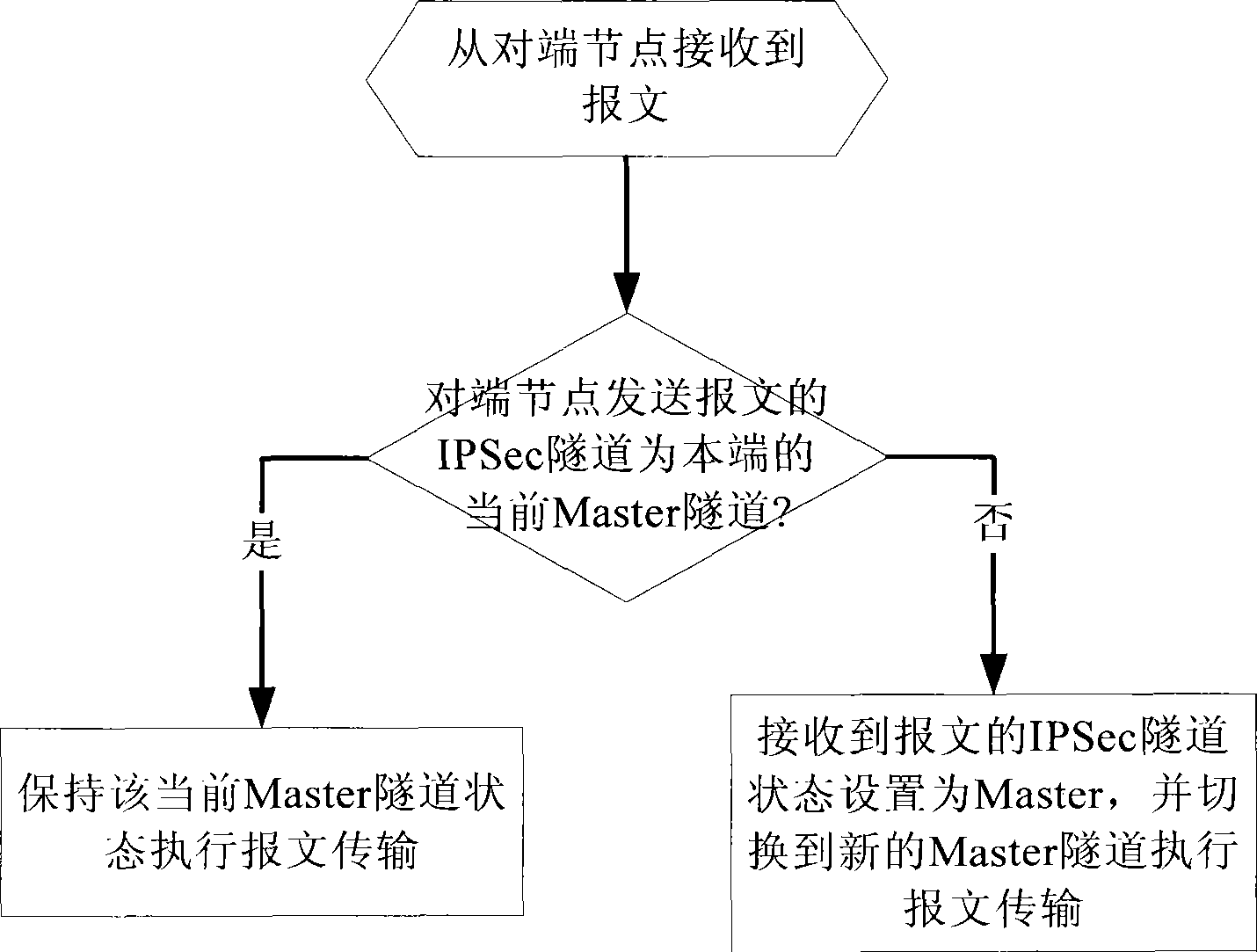
Method for implementing backup and switch of IPSec tunnel, system and node equipment, networking architecture
InactiveCN101442471AImplement backupLow costError preventionNetworks interconnectionTraffic capacityNetwork architecture
The invention discloses a method and a system for realizing backup and switching of IPSec tunnel. The method comprises the following steps: configuring a security strategy group for an interface of nodes, wherein the security strategy group at least has two IKE negotiation policies only with different opposite end nodes; and when flow rate generates on the interface, performing the following steps: extracting the security strategy group; and based on the IKE negotiation policy in the group, respectively negotiating with the corresponding opposite end nodes to establish SA for forming IPSec tunnels with corresponding quantity; according to the states of the opposite end nodes, switching to an IPSec tunnel to be used as a Master tunnel to perform message transmission. The invention also discloses node equipment and a network framework. The invention can support IPSec of core node provided with a plurality of breakout gateways to protect communication, thereby effectively reducing cost, shortening time of service interruption, and improving usability of system.
Owner:NEW H3C TECH CO LTD
Information transmission method of spacecraft
ActiveCN102932049AImprove reliabilityImplement backupError preventionTransmission systemsNumerical controlInformation transmission
The invention discloses an information transmission method of a spacecraft. The information transmission method comprises the following steps that: when a numerical control computer works normally, the numerical control computer receives telemeasuring data acquired by a remote unit and telemeasuring data provided by the control computer per se, the numerical control computer also receives telemeasuring data of a loading task processing unit, carries out telemeasuring formatting on all the received telemeasuring data to generate whole spacecraft telemeasuring data and outputs the whole spacecraft telemeasuring data to the remote unit A, and the remote unit A finishes information source encryption of the whole spacecraft telemeasuring data and outputs the encrypted information sources to a measurement and control responder; and when the numerical control computer works abnormally, the remote unit A directly outputs the acquired telemeasuring data and the telemeasuring data generated by the remote unit A per se to the measurement and control responder for downloading all the telemeasuring data. The information transmission method disclosed by the invention realizes backup of a key telemeasuring information transmission path of the spacecraft, thereby ensuring continuous monitoring of the ground on working states of key equipment of the spacecraft and improving the information transmission reliability.
Owner:BEIJING INST OF SPACECRAFT SYST ENG
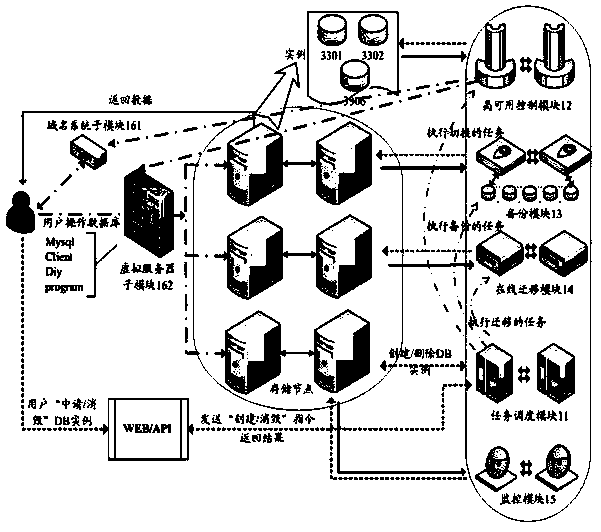
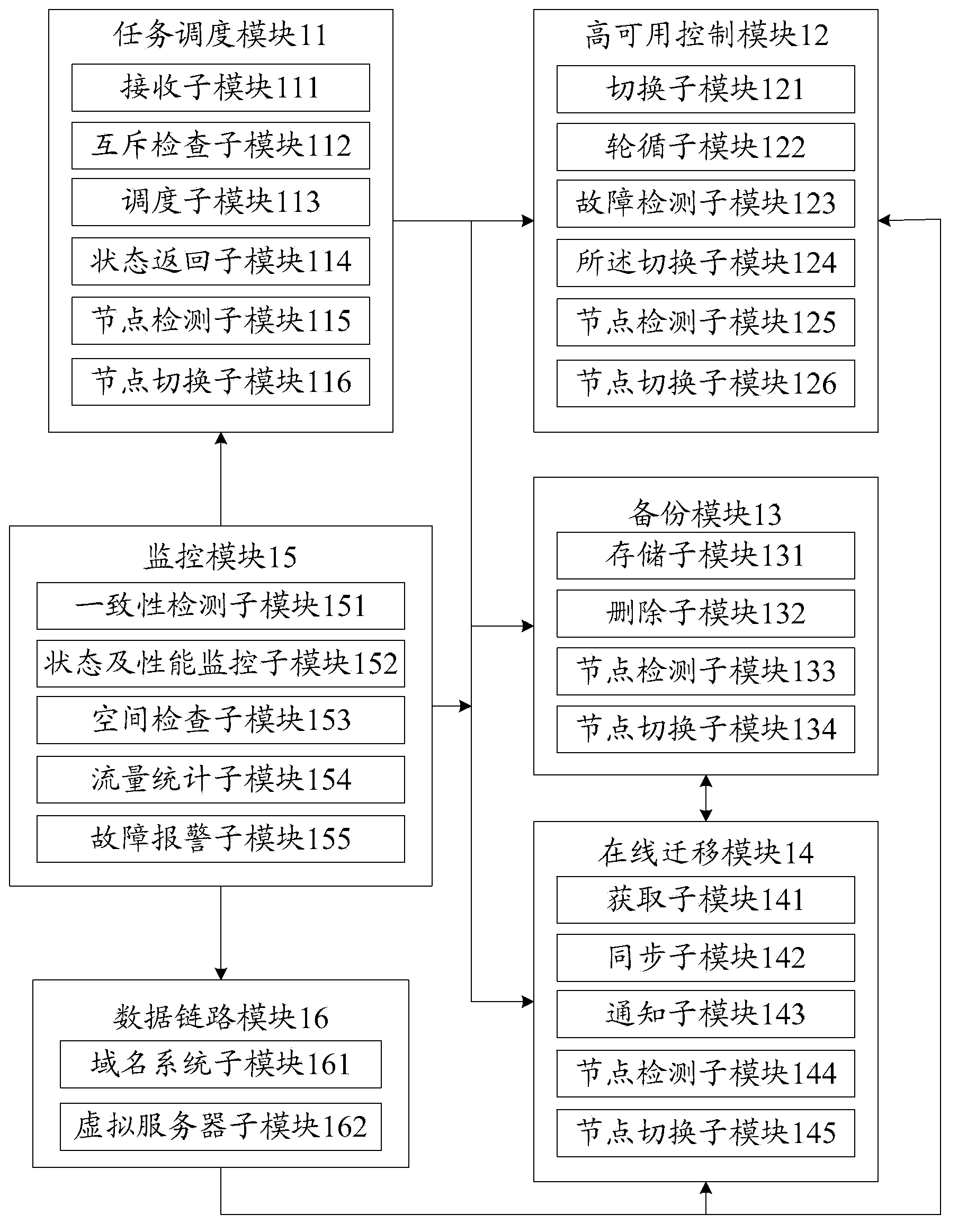
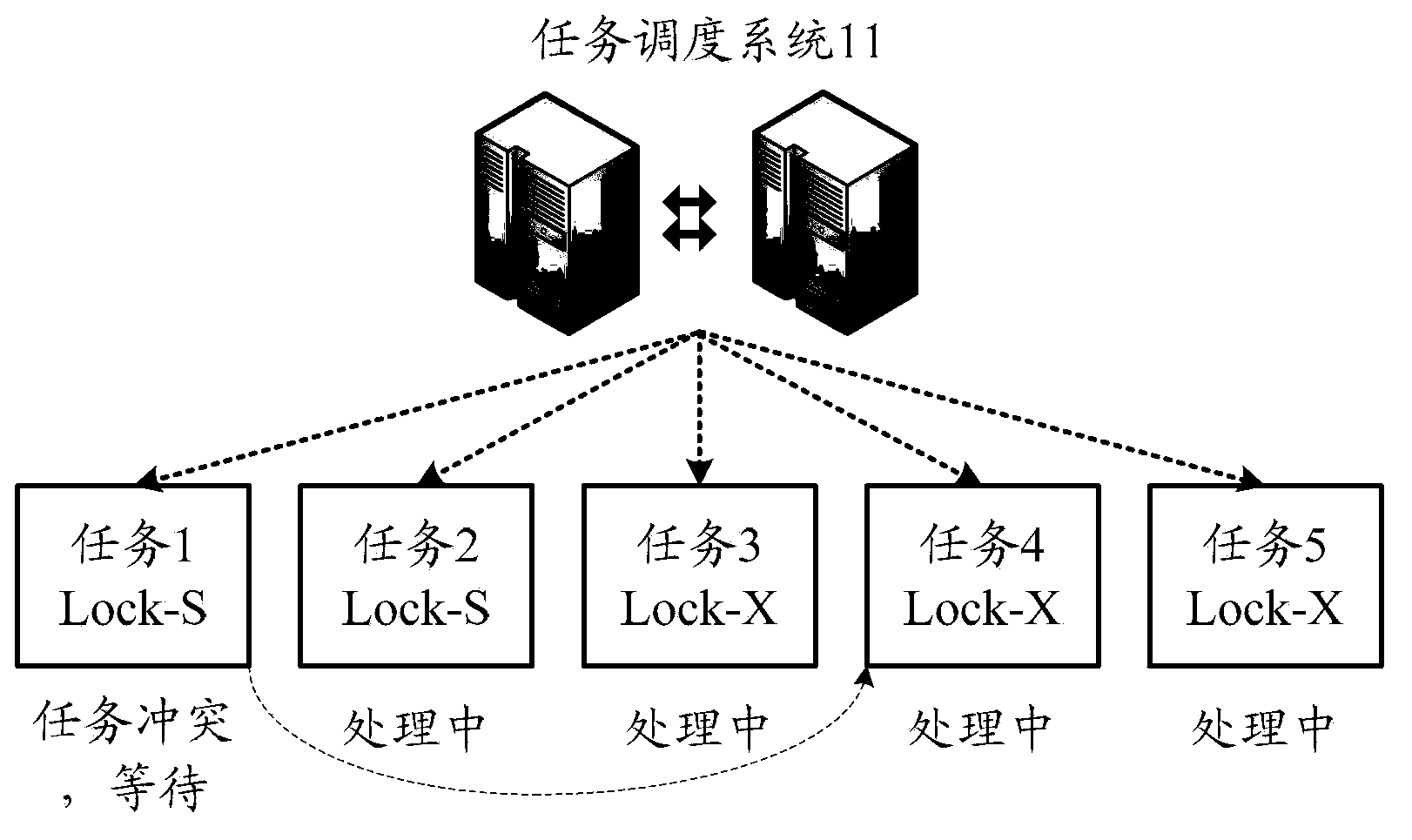
Remote data service system of data base and task scheduling method
ActiveCN103677967AUnder pressureDon't worry about backupMultiprogramming arrangementsSpecial data processing applicationsOperating systemRemote Data Services
The invention provides a remote data service system of a data base and a task scheduling method of the remote data service system. The remote data service system comprises a task scheduling module, a high-availability control module, a backup module and an on-line migration module. For a user, self-construction of a server and a data base is not needed by the adoption of the remote data service system and the task scheduling method, so that time is saved, and efficiency is improved; in addition, under the condition that the service amount of the user is increased, the user just needs to add storage nodes, data migration and the like can be completed by the system, as a result, use is convenient, and efficiency is high.
Owner:ALIBABA GRP HLDG LTD
Link backup method and apparatus for computer network
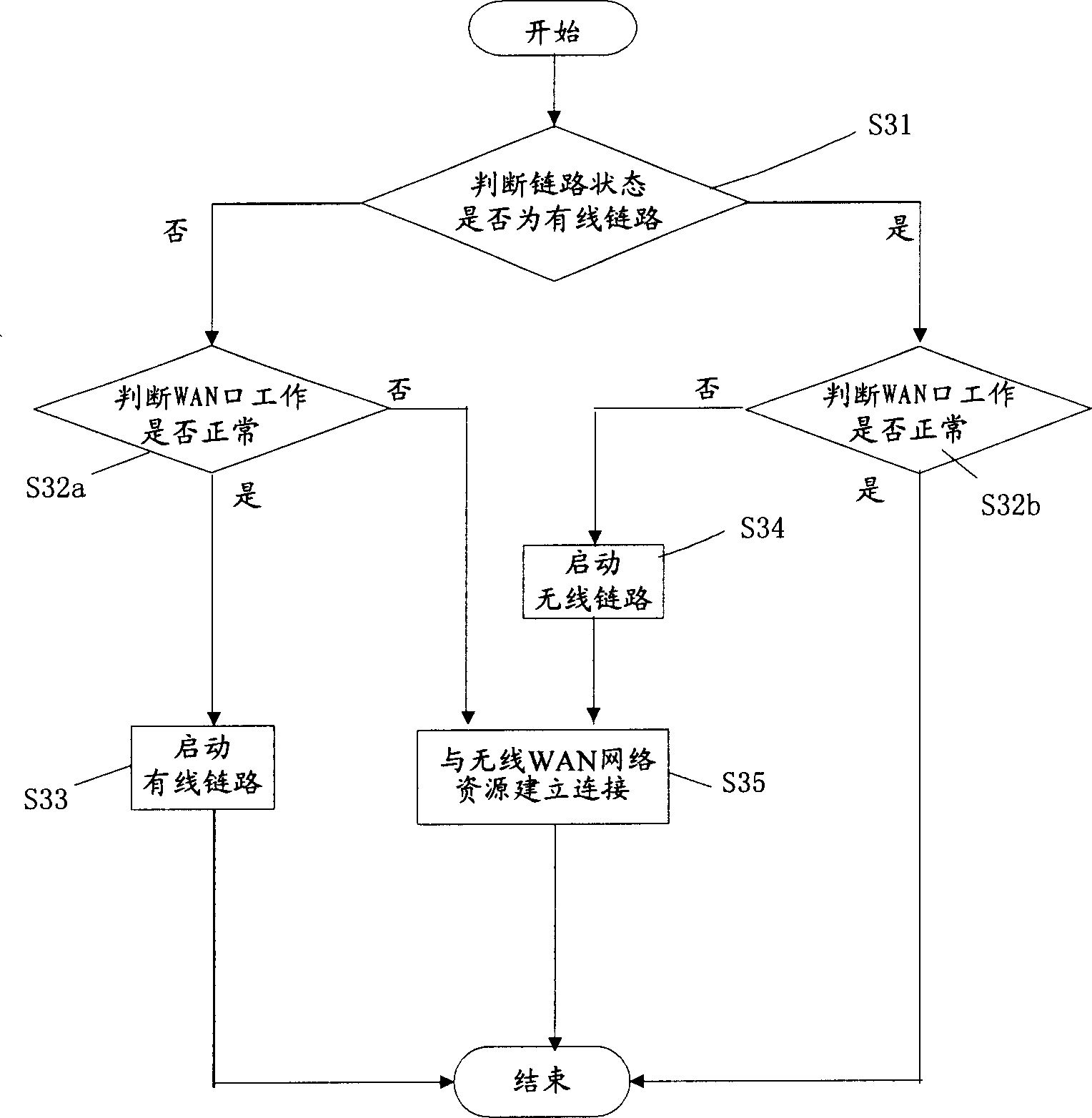
InactiveCN1812342ALess investmentExpand coverageData switching by path configurationWireless WANWireless
This invention discloses a kind of backup method for computer network links. It concludes: (1) the wireless links alternate device judges whether wired WAN links are normal operated. If they are, the links backup will stop. If they are not, the step (2) will be carried out; (2) the said wireless links alternate device switches wired links into wireless links. Wireless WAN port is started; (3) wireless WAN port accesses internet. In addition, this invention also discloses a kind of corresponding backup apparatus for computer network links. It avoids the questions that backup links are east to destroy, hard to recover and inconvenient to repair when using wired links to backup.
Owner:BELLNET TECH
Wireless controller service information backup method and equipment
ActiveCN101583144AImplement backupImprove stabilityWireless communicationService informationWireless
The invention discloses a wireless controller configuration information backup method and equipment, which are applied to a system comprising an active wireless controller, at least one standby wireless controller and at least one wireless access point, wherein the active wireless controller is configured with the address information of the at least one standby wireless controller, and active communication linkage is established between the at least one wireless access point and the active wireless controller. By the method, the wireless access point in the system maintains communication linkage with the active-standby wireless controllers simultaneously and realizes switch when failure occurs so as to guarantee the continuous implementation of services. With the invention, the backup of the configuration resources of the wireless controller can be realized under the condition that the wireless controller does not need to independently establish backup channels among the wireless controllers.
Owner:NEW H3C TECH CO LTD
Equipment configuration information management method and its system
InactiveCN1968133AImprove work efficiencyImplement backupData switching networksInformation typeInformation management
The invention relates to a method for managing device setting information, wherein said method comprises that: presetting setting mark of setting information type, when user uses client to manage the device setting information, the client obtains setting mark and operation mark, and one or more marks of manage targets to be sent to server; the server operates setting information relative to the manage target and setting mark. The invention can manage and maintain the setting information of one or more devices, to improve working efficiency.
Owner:HUAWEI TECH CO LTD
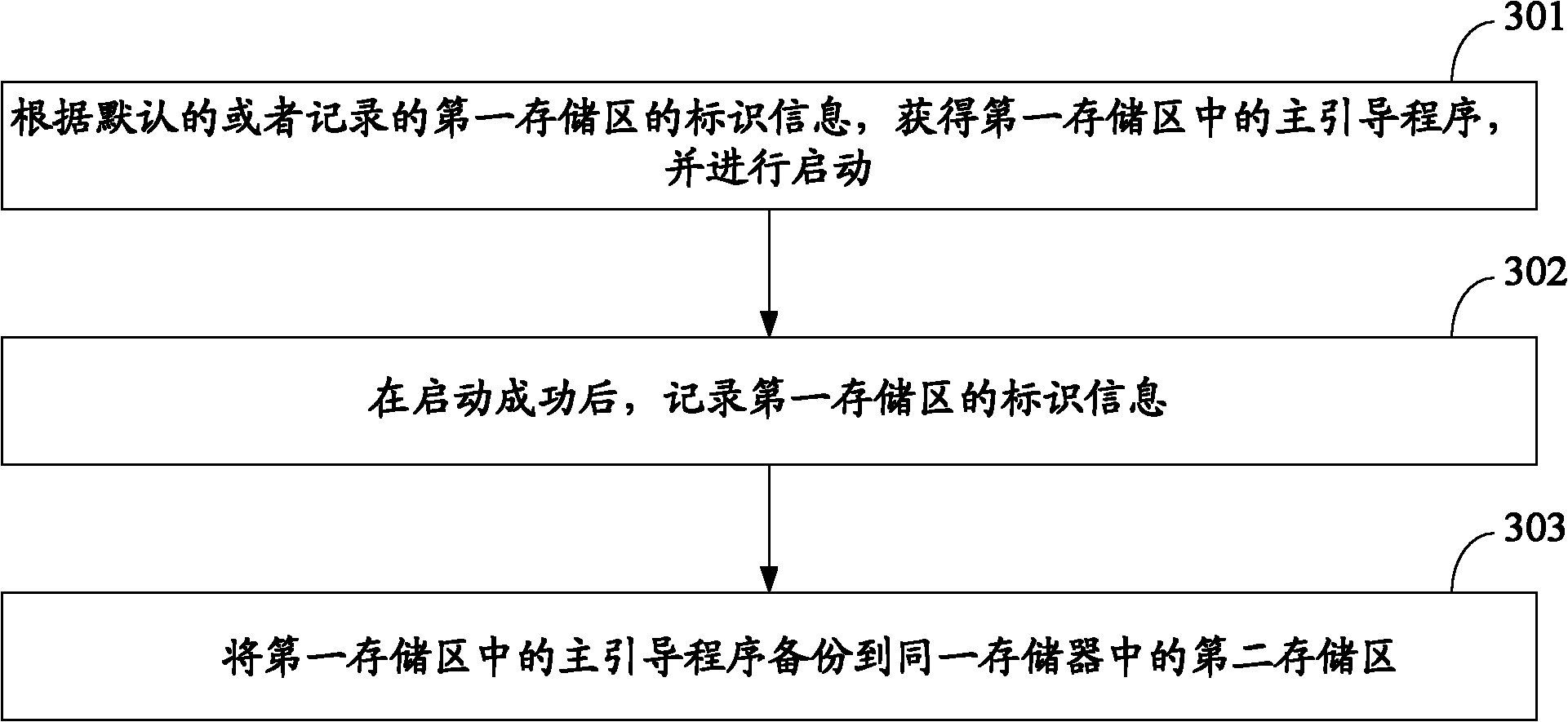
Method and device for backing up boot program
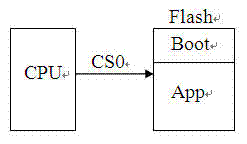
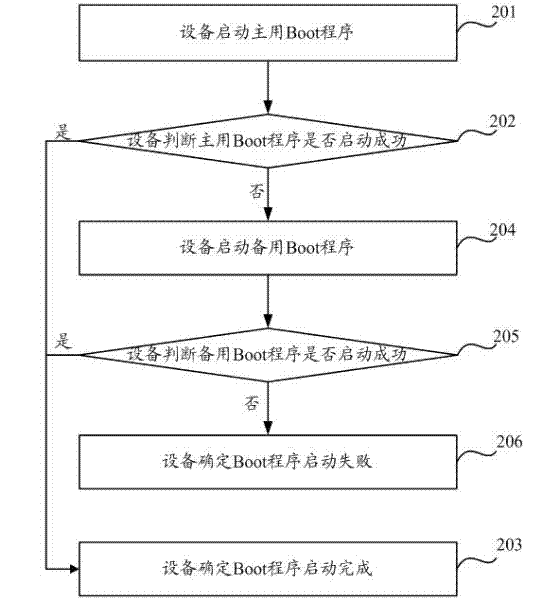
ActiveCN102023908AImplement backupGuaranteed correctnessProgram loading/initiatingRedundant operation error correctionBootingStart up
The invention discloses a method for backing up a boot program, which is used for realizing backup of the boot program and improving the reliability of system startup. The method comprises the following steps: obtaining a main boot program in a first memory area according to the default or recorded identification information in the first memory area, and starting up the main boot program, wherein the first memory area is the current memory area; after the main boot program is successfully started up, recording the identification information in the first memory area; and backing up the main boot program in the first memory area to a second memory area in the same memory. The invention also discloses a method for upgrading a boot program, which is used for realizing upgrading of the boot program. The method comprises the following steps: determining whether the boot program is needed to be upgraded after the main boot program in the first memory area is started up; if so, obtaining upgrading information; and upgrading the boot program backed up to the second memory area according to the obtained upgrading information. The invention also discloses a device for realizing the method.
Owner:ZTE CORP
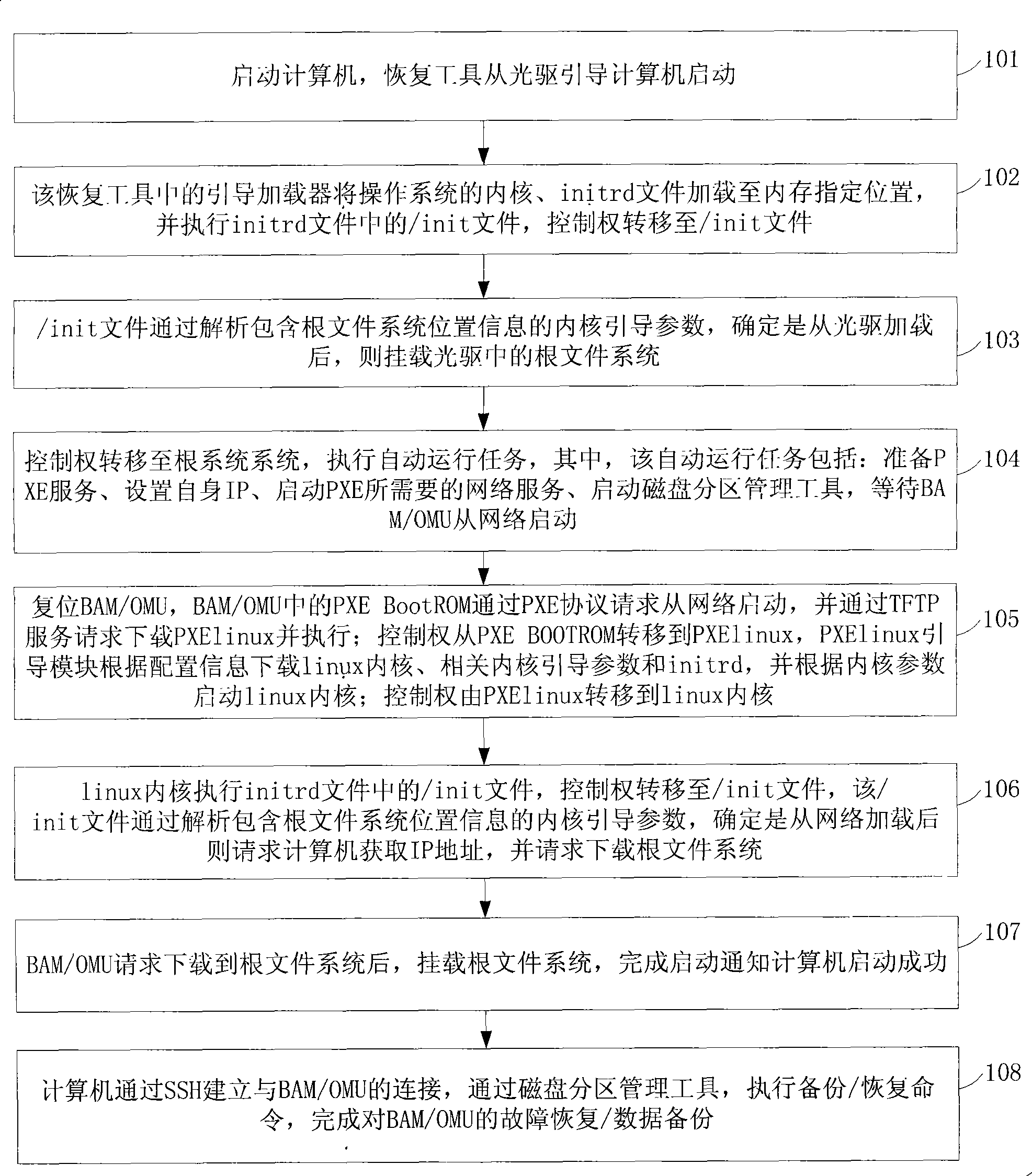
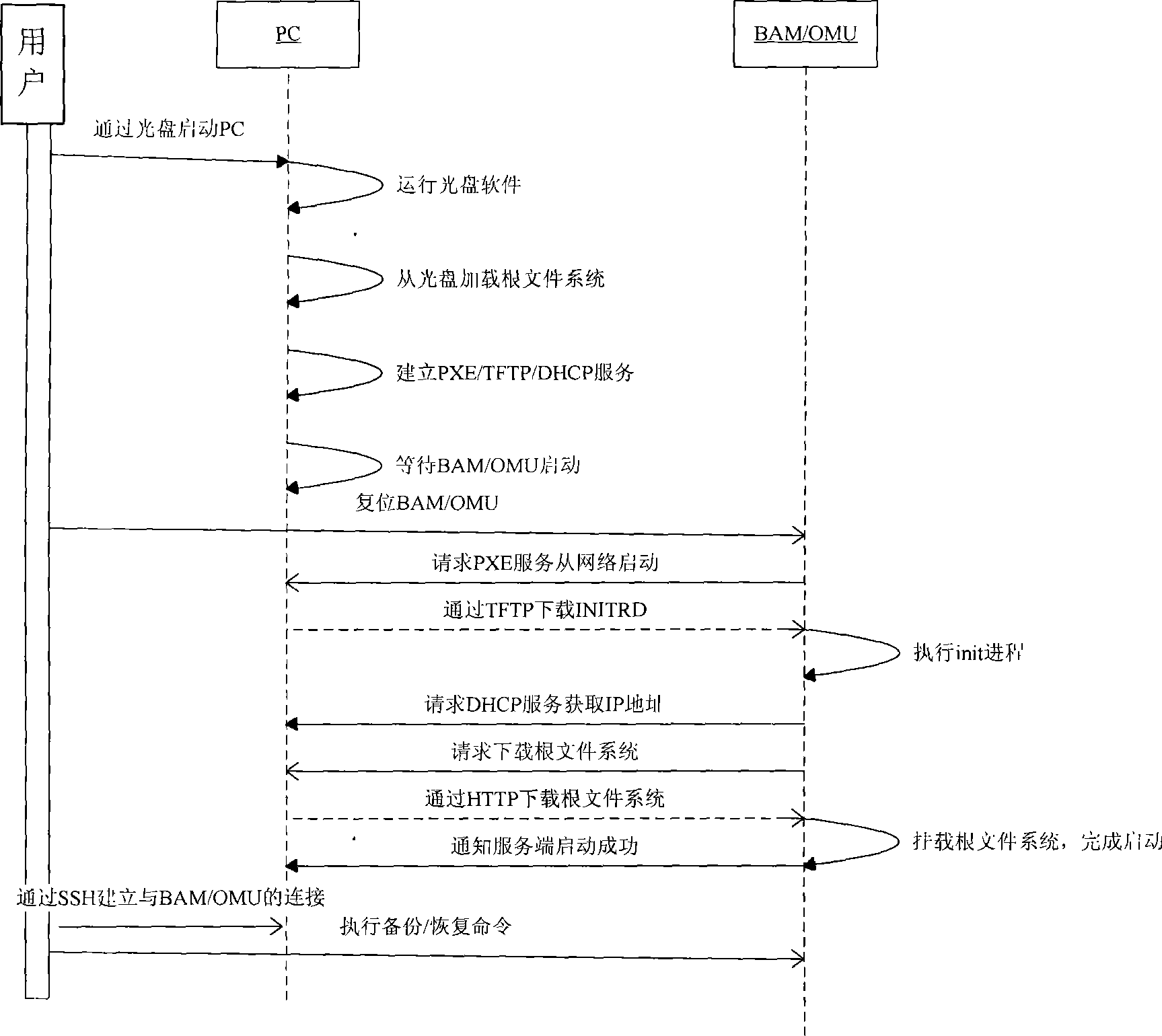
Method, system and apparatus for implementing failure restoration and data backup
InactiveCN101420326AImplement backupQuick backupData switching networksRedundant operation error correctionOperational systemFile transmission
The present invention, pertaining to the field of communication, discloses a method for realizing fault recovery and data backup, a system and an apparatus thereof. Wherein, the method comprises the steps of starting a recovery tool, the recovery tool loading a customized root file system, establishing a pre-boot execution environment (PXE) support service, a file transmission service and a disk image management service, wherein, the PXE support service and the file transmission service are used for supporting the device to be recovered to realize the starting of an operating system through a network, and the disk image management service is used for performing disk image backup and / or a recovery operation to the device to be recovered; after receiving an information that the starting of the operating system through a network by the device to be recovered is successful, remotely logging in the device to be recovered, and performing disk image backup and / or a recovery operation to the device to be recovered by the disk image management service. When the device to be recovered is not configured with a CD-ROM, a display and a keyboard, the fault recovery of the device can be realized rapidly by using the method, and also the data backup is realized, therefore, time cost by the fault recovery of the device to be recovered is greatly shortened.
Owner:HUAWEI TECH CO LTD
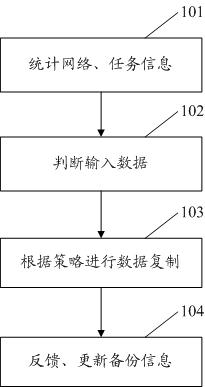
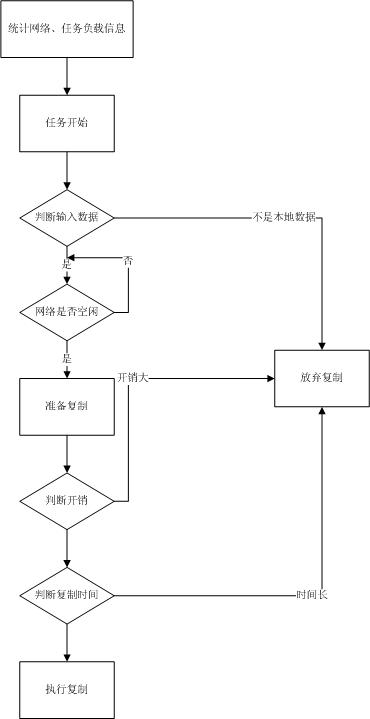
Fault tolerance optimizing method of intermediate data in cloud computing environment
InactiveCN102104496AImprove system performanceBackup is expensiveData switching networksCloud computingControl parameters
The invention relates to a fault tolerance optimizing method of intermediate data in a cloud computing environment. The method comprises the following four steps of: 1. collecting a network load, task execution progress and position information; 2. judging and analyzing task input data and mainly judging a data generating position; 3. classifying working modes according to the current environmentand adjusting recourse allocation according to a control parameter; and 4. feeding back a backup condition and updating data backup information. In the invention, the frequency of node failure in thecloud computing environment is taken into consideration at first, the intermediate data is replicated according to the task finishing time requirement and the resource use condition, and real-time monitoring and flexible management are carried out on the network load and task execution progress so as to ensure that the replication of the intermediate data is realized for the system under the condition that performance is free from influence. The fault tolerance optimizing method provided by the invention has wide practical value and application prospect in the field of cloud computing data management.
Owner:SHANGHAI JUNESH INFORMATION TECH CO LTD
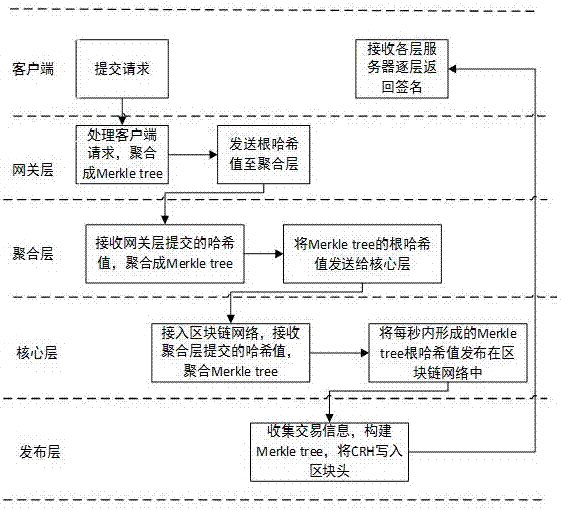
Non-key signature infrastructure building method based on block chain
InactiveCN107171812AStrong throughput and scalabilitySmall storage and network load requirementsUser identity/authority verificationDigital data protectionChain networkBlockchain
Owner:光载无限(北京)科技有限公司
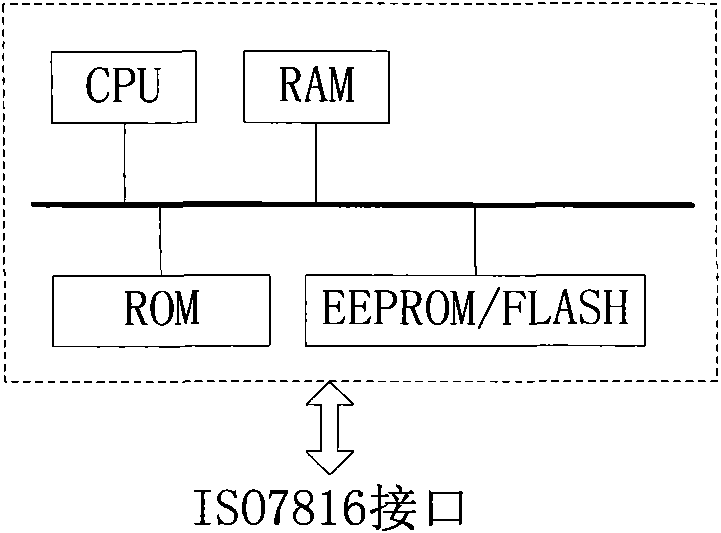
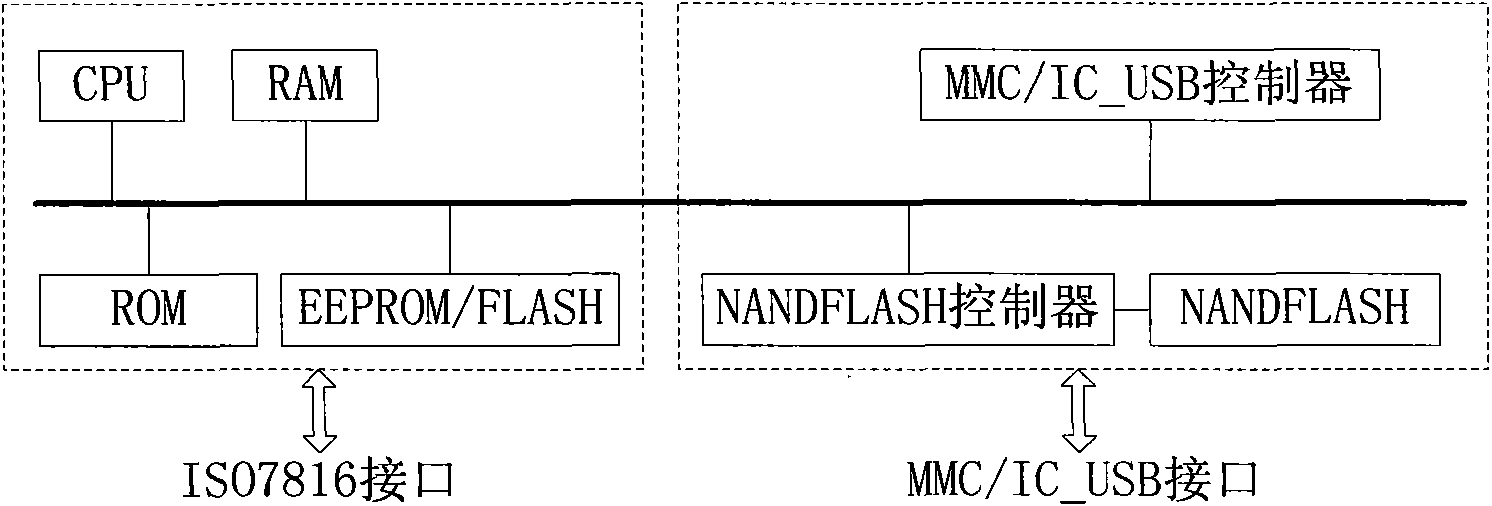
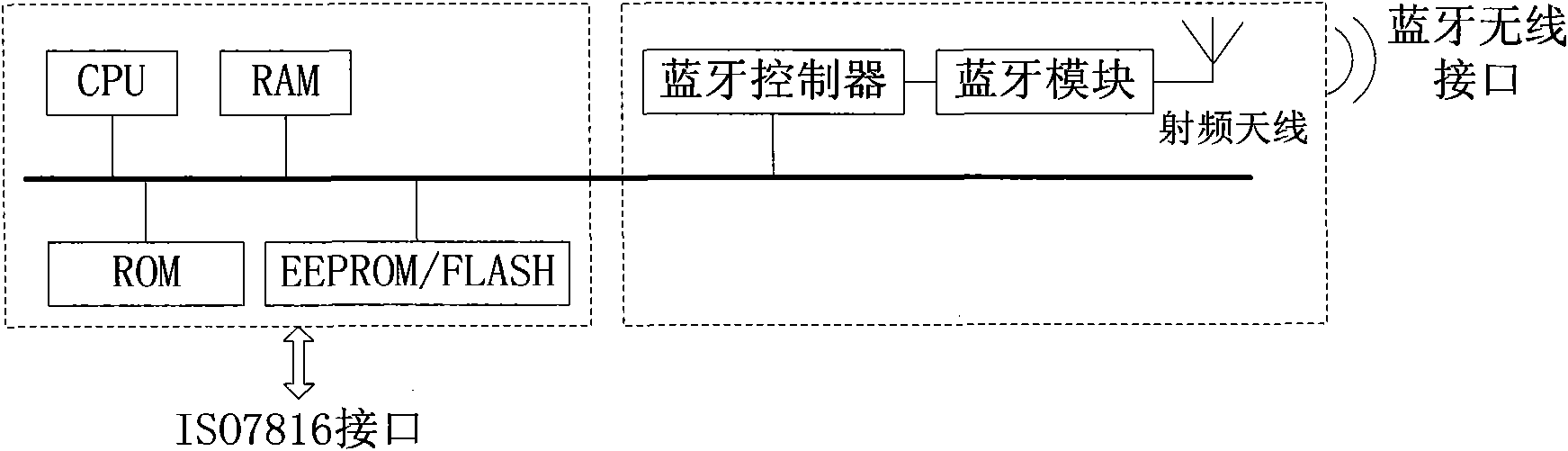
Subscriber identification module and transmission method and system based on subscriber identification module
ActiveCN102026187AMeet the interface characteristicsHigh speed data exchangeNear-field systems using receiversSensing record carriersCommunication controlRadio frequency
The invention relates to a subscriber identification module and a transmission method and system based on the subscriber identification module. The subscriber identification module comprises a bus, a processing module and a storage module, wherein the processing module and the storage module are connected with the bus. The subscriber identification module further comprises a short distance wireless communication controller, a short distance wireless communication module and a radio frequency antenna, wherein the short distance wireless communication controller is connected with the bus; the short distance wireless communication module is connected with the short distance wireless communication controller; the radio frequency antenna is connected with the short distance wireless communication module; and the short distance wireless communication controller is used for controlling the short distance wireless communication module to carry out data interaction with an external entity through driving the radio frequency antenna, writing the data which is received by the short distance wireless communication module from the external entity into the storage module through the processing module, and reading the data through the processing module from the storage module, wherein the data is sent to the external entity by the short distance wireless communication module. In the invention, the high-speed data exchange between an external entity and the subscriber identification module can be supported without needing to chang a terminal.
Owner:DATANG MICROELECTRONICS TECH CO LTD
Data backup/recovery system under cold start mode and implementing method therefor
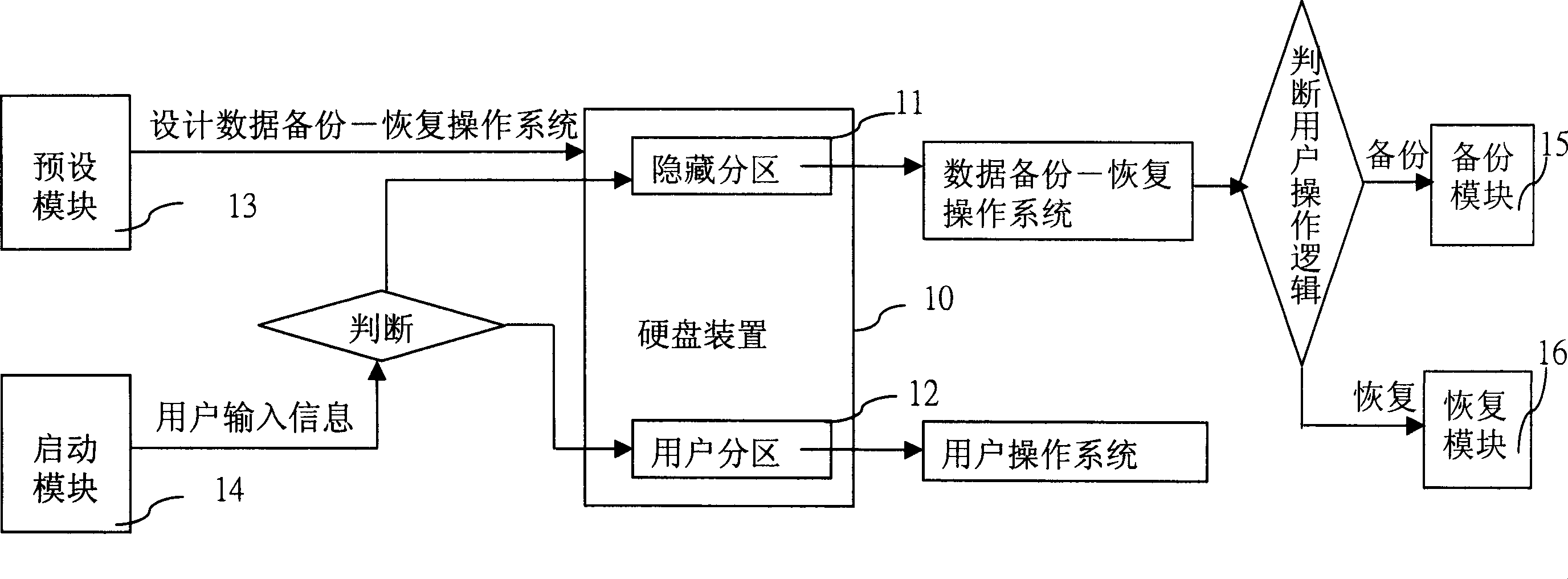
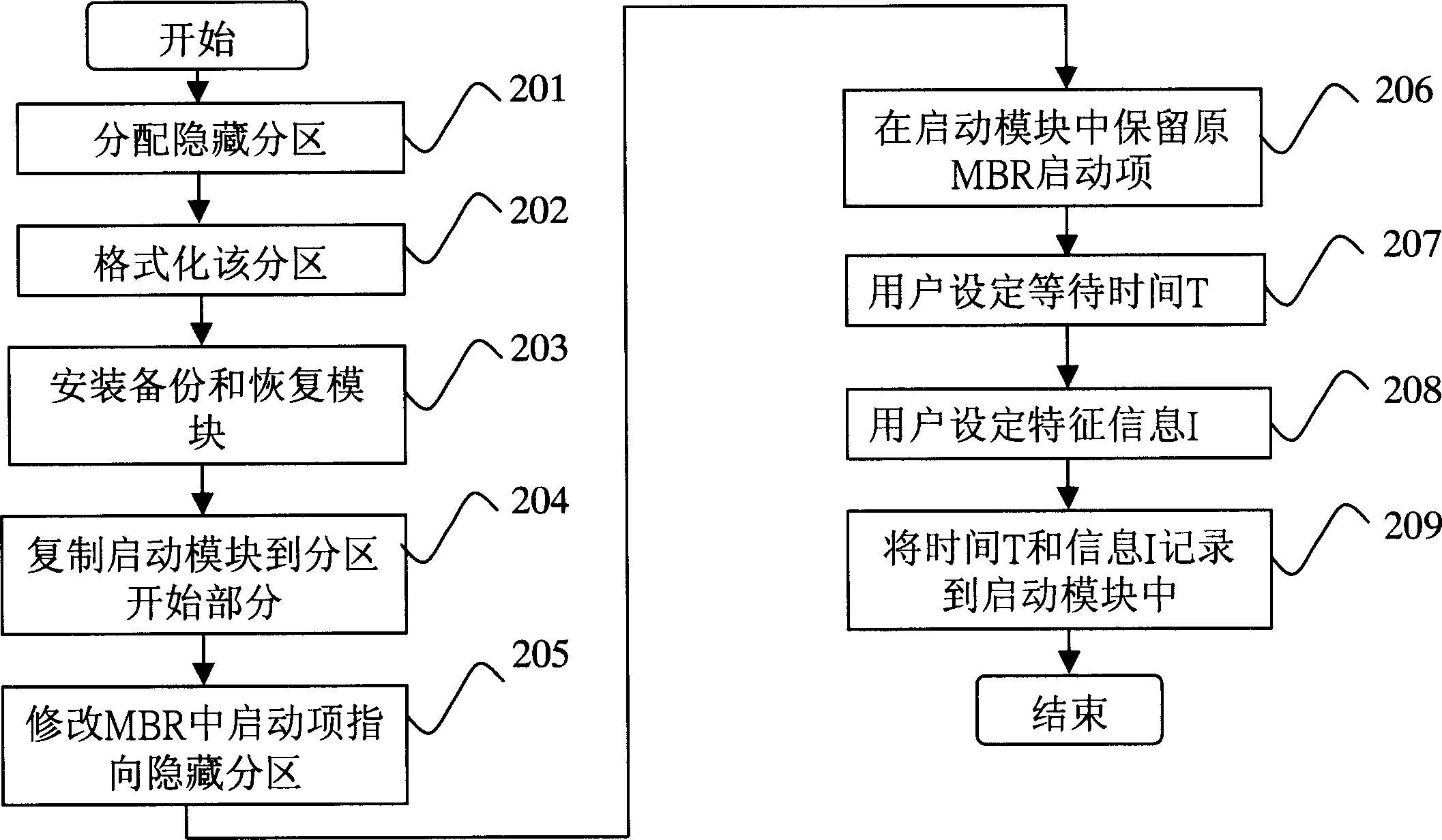
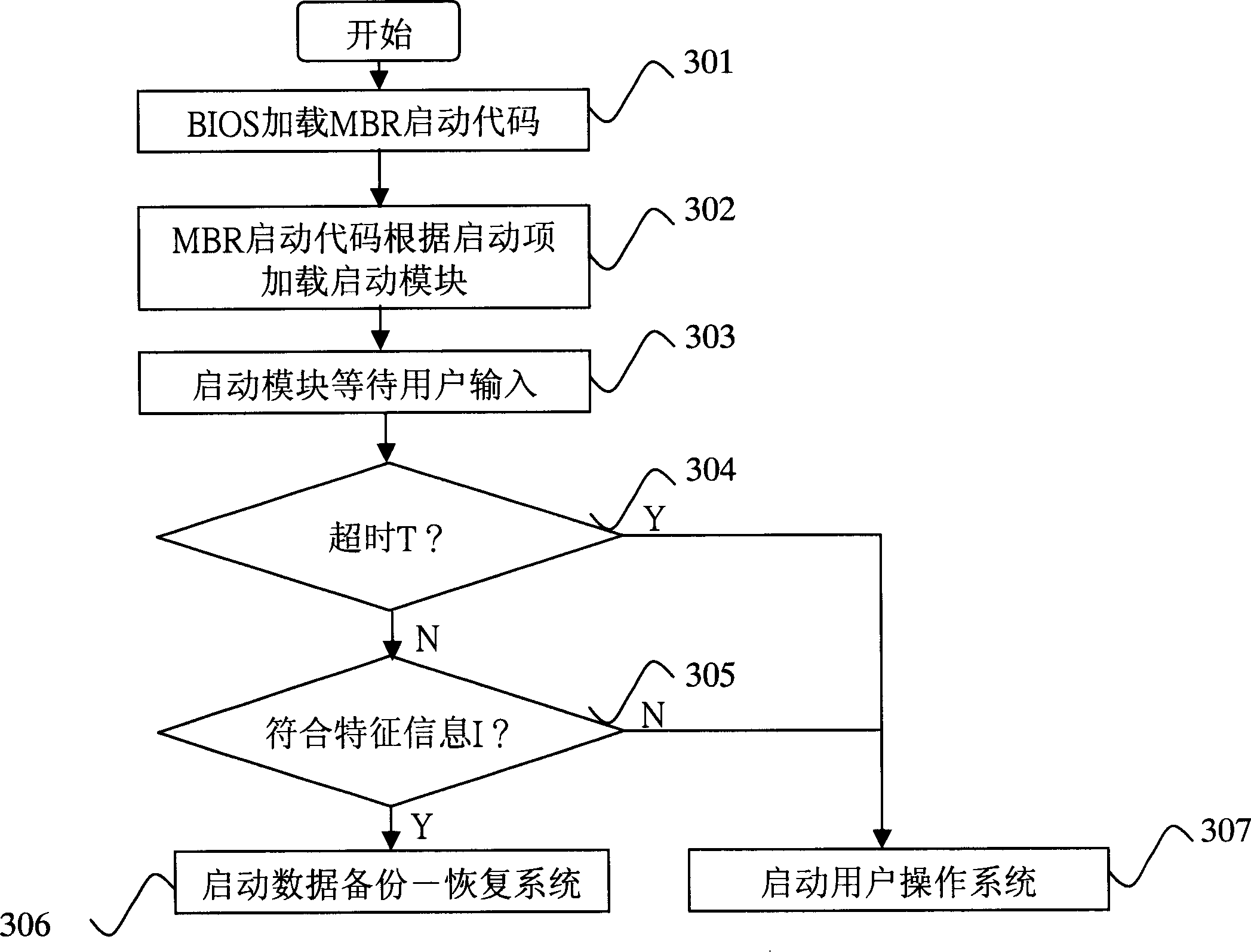
InactiveCN1877539AImplement backupAchieve recoveryProgram loading/initiatingRedundant operation error correctionStaringData information
The invention discloses a system and a method for copying and restoring data in cold-starting mode. The method comprises separating the hard disk into hidden partitions and customer partitions for copying and restoring user data information. The inventive system comprises a pre-setting module for setting a data copy / restore system on the hidden partitions; a starting module for judging computer staring type according to user inputting information after system BIOS starting, and deciding whether to start data copy / restore system according to the judging results; a copy module set in the data copy / restore system for copying data information in customer partition into the hidden partition; and a restore module set in the data copy / restore system for restoring data information in the hidden partition to the customer partition.
Owner:INVENTEC CORP
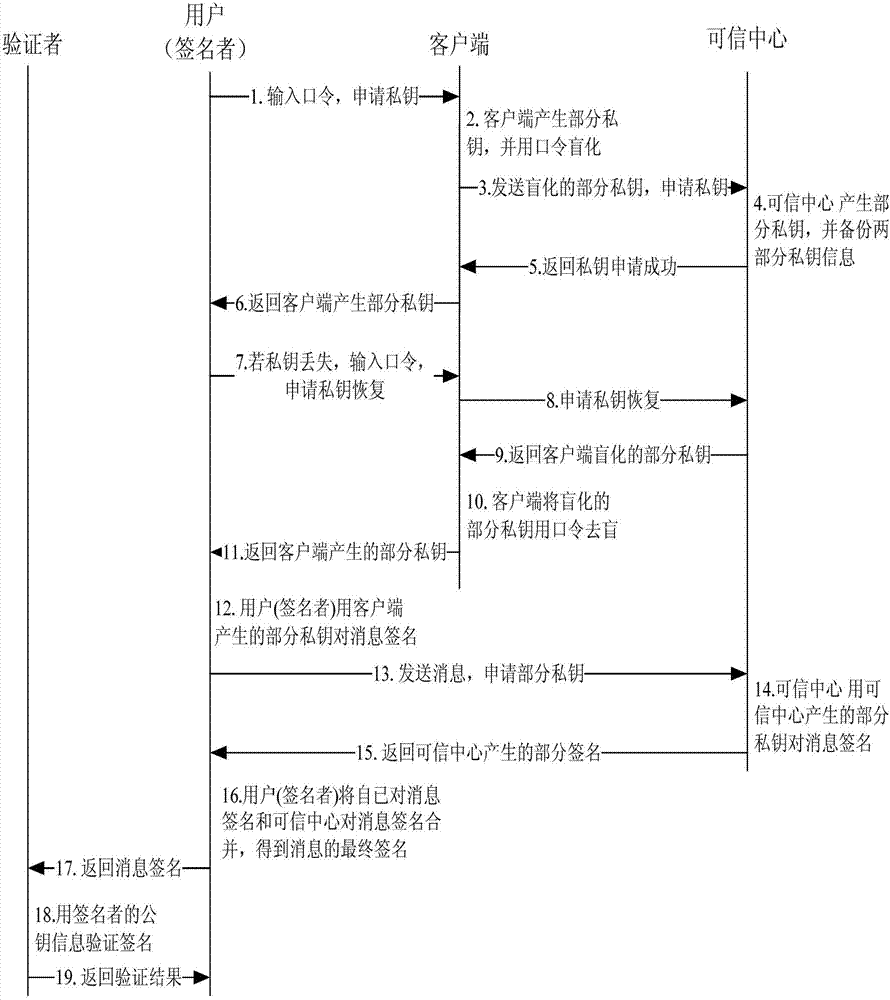
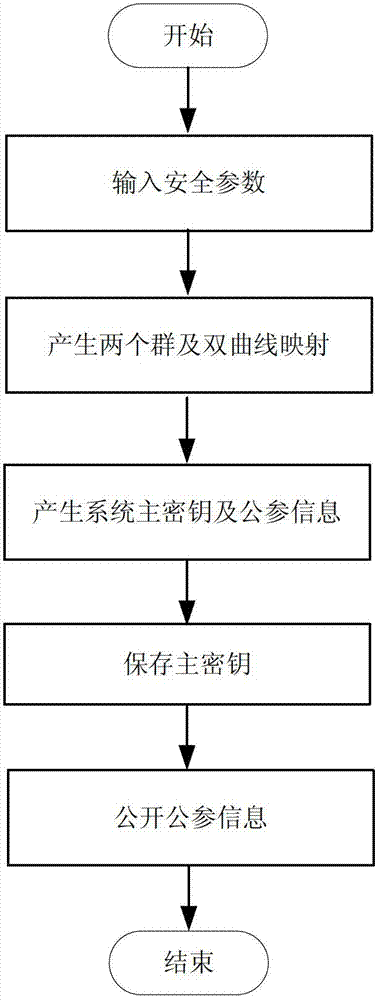
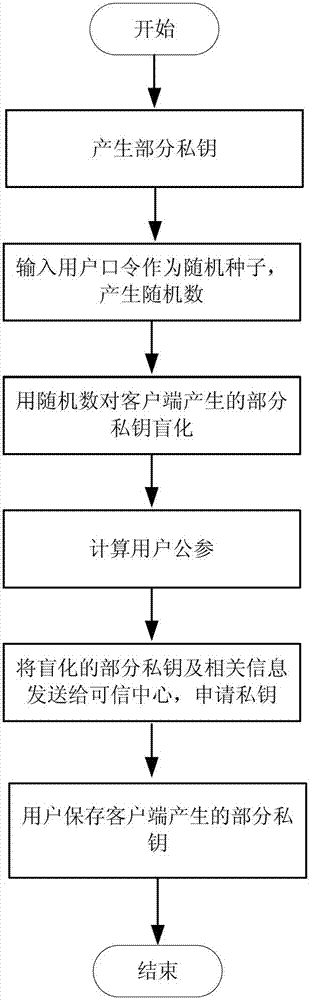
Private key safety management method based on identity public key cryptography system
InactiveCN102739401ATroubleshoot hosting issuesImplement backupPublic key for secure communicationUser identity/authority verificationPasswordCryptosystem
The invention discloses a private key safety management method based on an identity public key cryptography system. The private key safety management method comprises the steps of: system parameter establishment; private key generation algorithm; private key recovery algorithm; signature algorithm; and authentication algorithm. Through the combination of password blinding and private key slicing, in the process of distribution, storage, backup and recovery, the private key is sliced, and part of the private key is subjected to password blinding in the backup process, even in the use process, the authentic private key of a user is not needed to be calculated, and the private key is used in a slicing manner, so that the safety of the private key is ensured. Compared with the prior art, the private key is subjected to password blinding only in the backup process, the safety of the private key can be ensured without any safety measure in the distribution, storage and use processes, on one hand, the escrow problem of the private key is solved, on the other hand, the backup and the recovery of the private key can be realized easily, and for users, the private key safety management method is convenient in use and low in cost.
Owner:BEIJING UNIV OF TECH
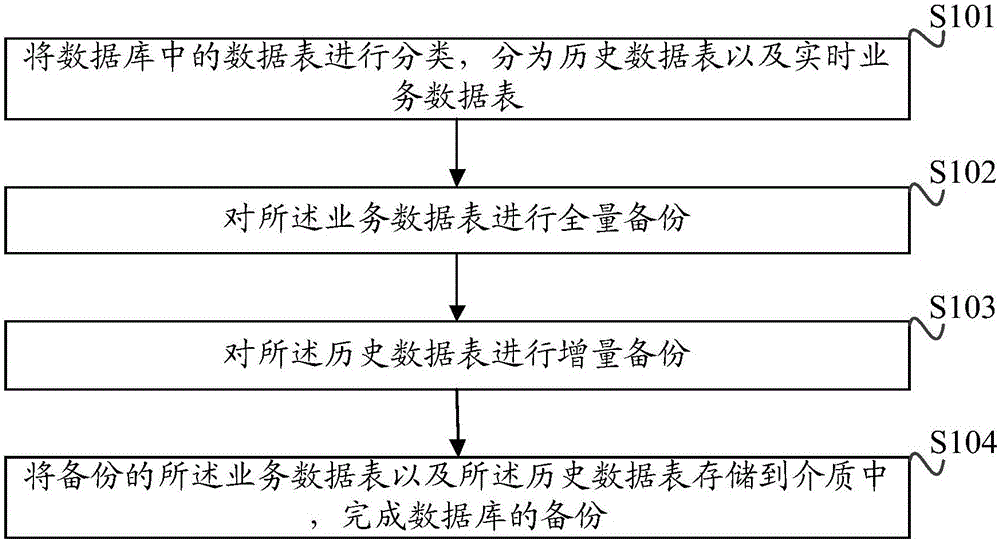
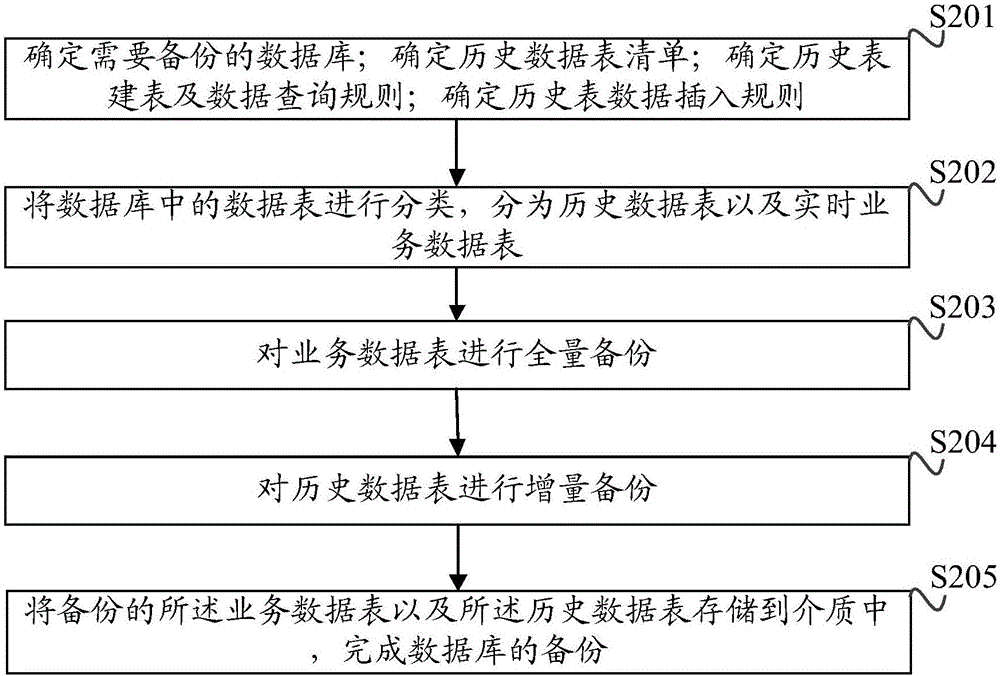
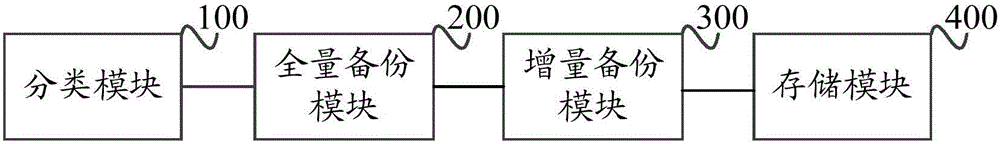
Database backup method and device
ActiveCN106445738AImplement backupImprove securitySpecial data processing applicationsRedundant operation error correctionReal time servicesDatabase backup
The invention discloses a database backup method and device. Data tables in a database are classified into historical data tables and real-time service data tables; full-volume backup is conducted on the service data tables; incremental backup is conducted on the historical data tables; the backed-up service data tables and historical data tables are stored in a medium to complete backup of the database. Due to the fact that historical data in a large mysql database occupies a large amount of storage space and real-time service data is less, the historical data tables and the real-time service data tables are backed up in a separated mode, the data volume each time of backup can be decreased, the backup time and recovery time can be shortened, and the backup speed can be improved. It is thus clear that backup of the database in a large mysql database scene is rapidly achieved, the backup recovery time is decreased, backup file space occupation is decreased, and the backup recovery efficiency and the safety guarantee capability of the database are improved.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
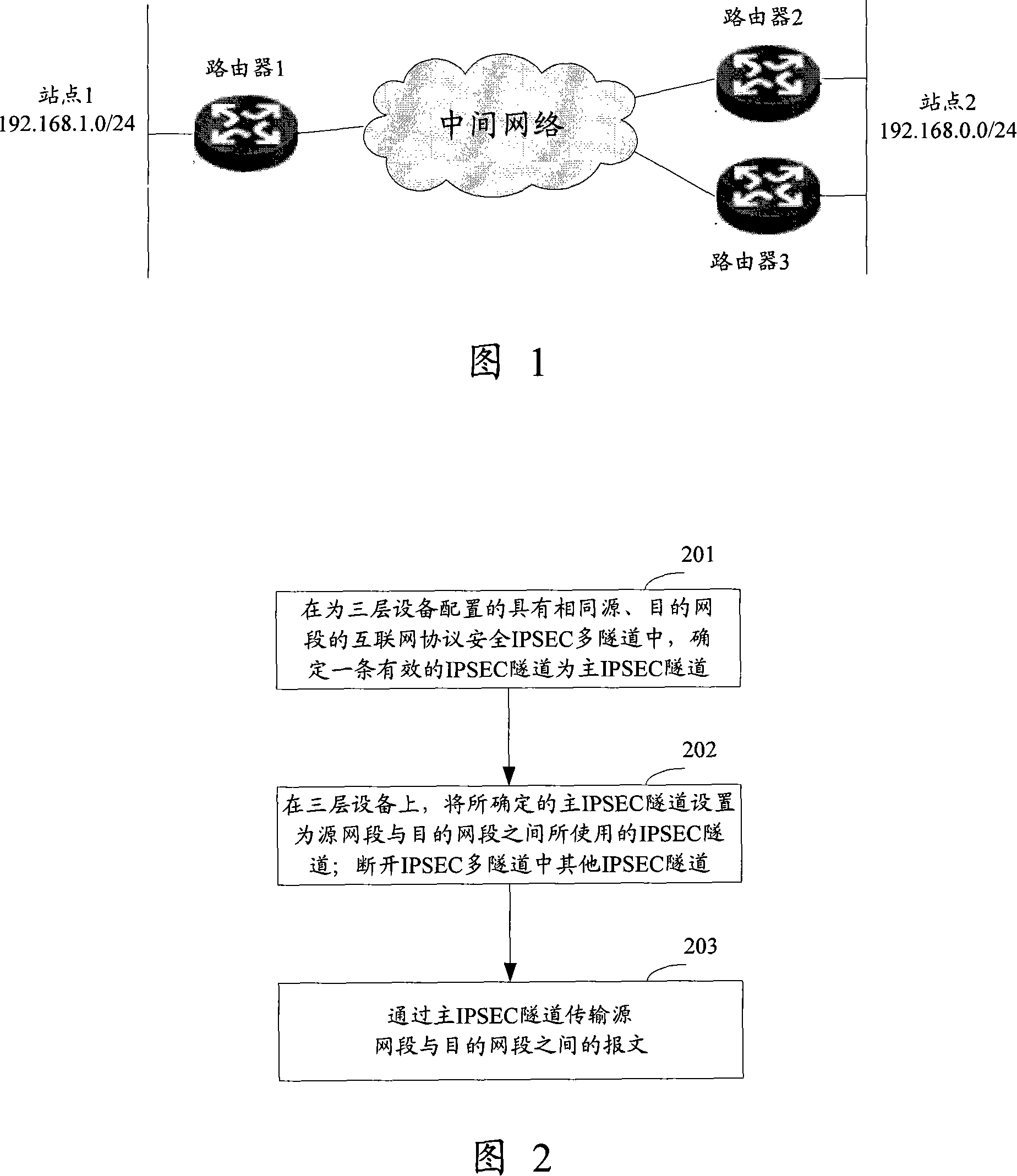
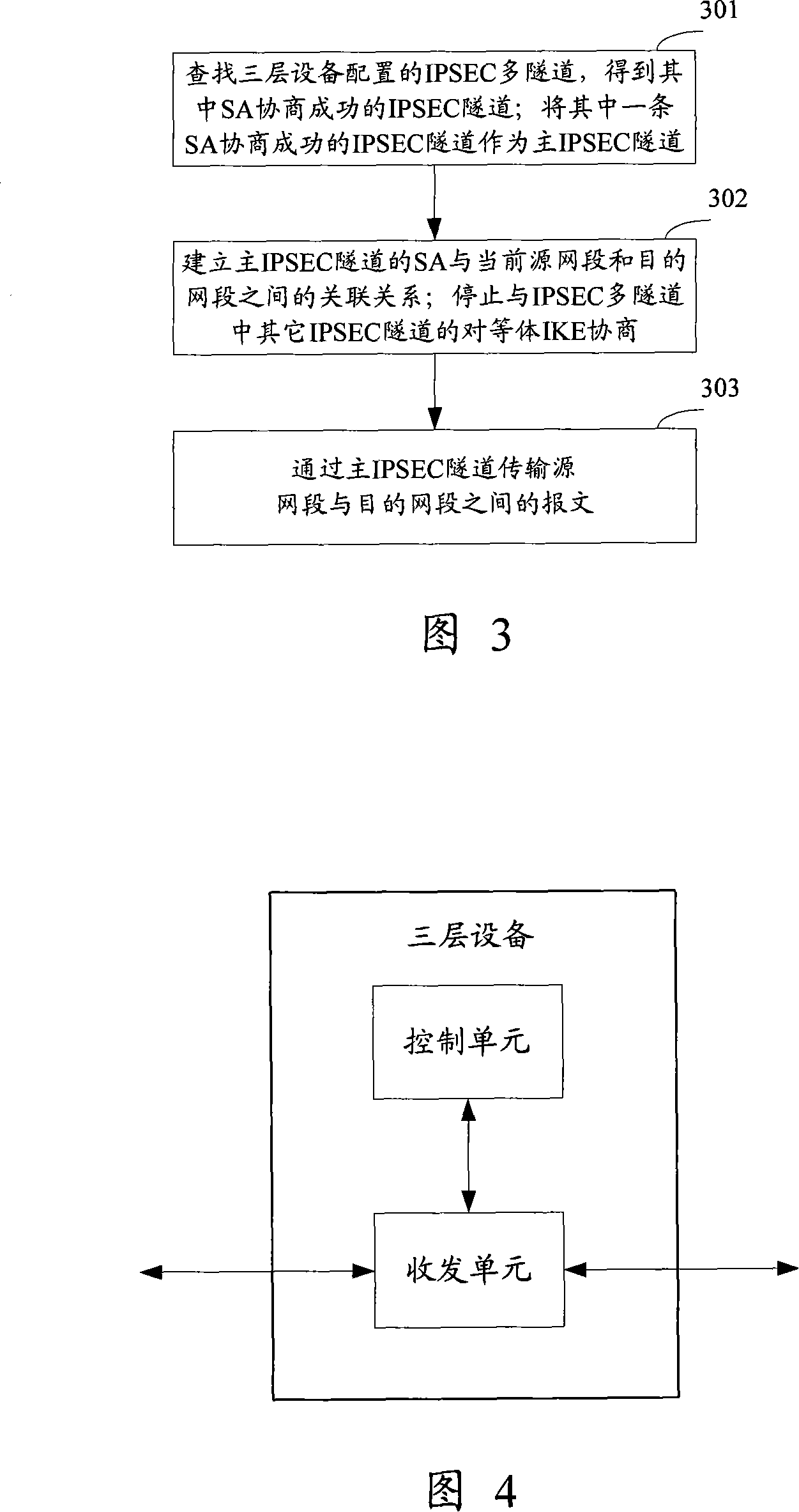
Safe multiple tunnel method using internet protocol and three-layer equipment thereof
InactiveCN101132406AShort switching timeImplement backupNetworks interconnectionInternet protocol suiteIPsec
This invention discloses a technological plan for using safety multiple tunnels of Internet protocol, which determines an effective IPSEC tunnel as the master one from multiple IPSEC tunnels with a same source and a destinated segment to transmit messages between the source and the destinated segment via the master IPSEC tunnel to realize the aim of using configured IPSEC multiple tunnels on the three-layer devices, besides, after the current IPSEC tunnel is faulty, one master tunnel is decided again from the multiple tunnels, so backup can be realized among multiple tunnles of IPSec.
Owner:NEW H3C TECH CO LTD
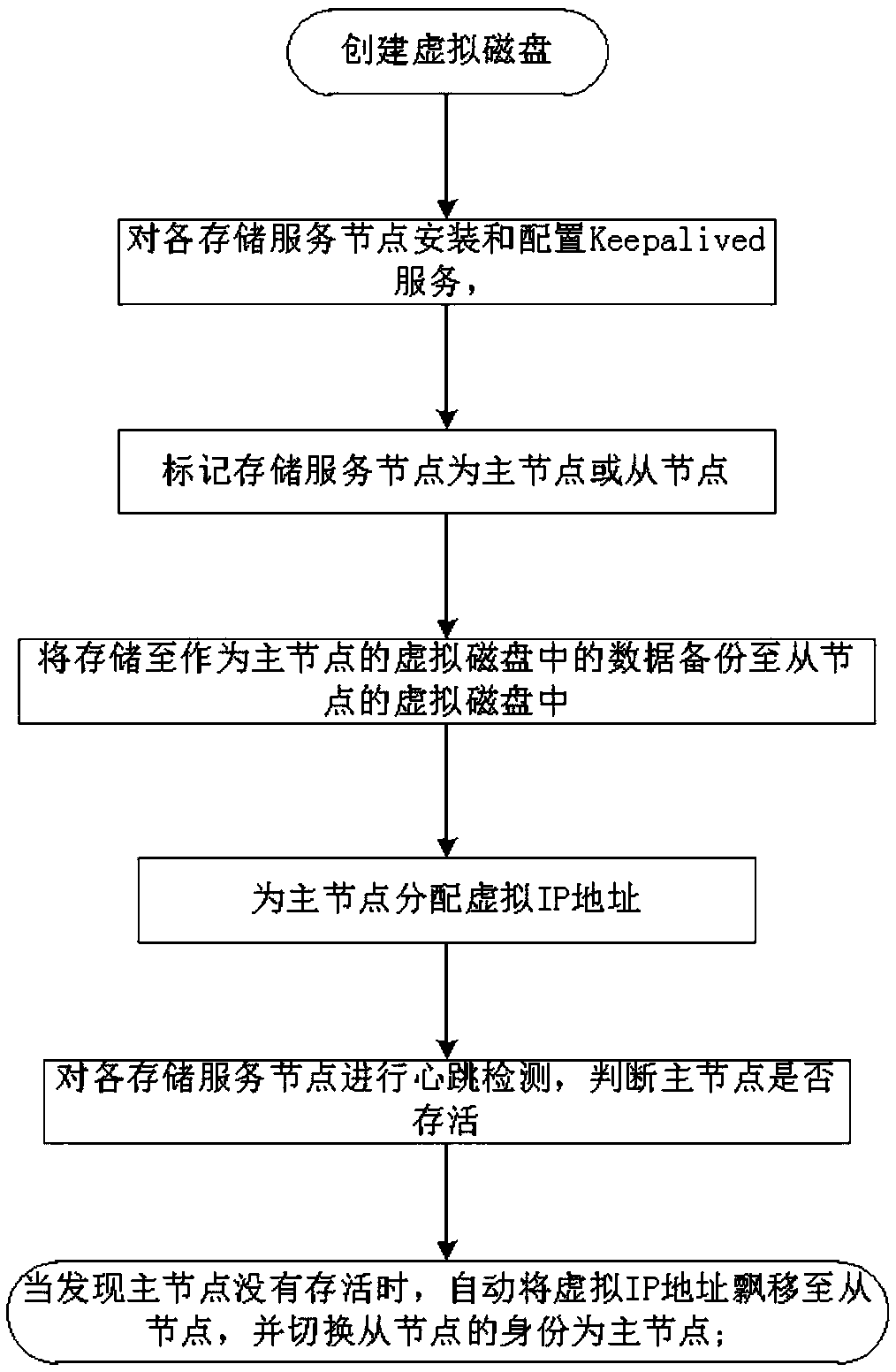
Storage fault fast switching processing method
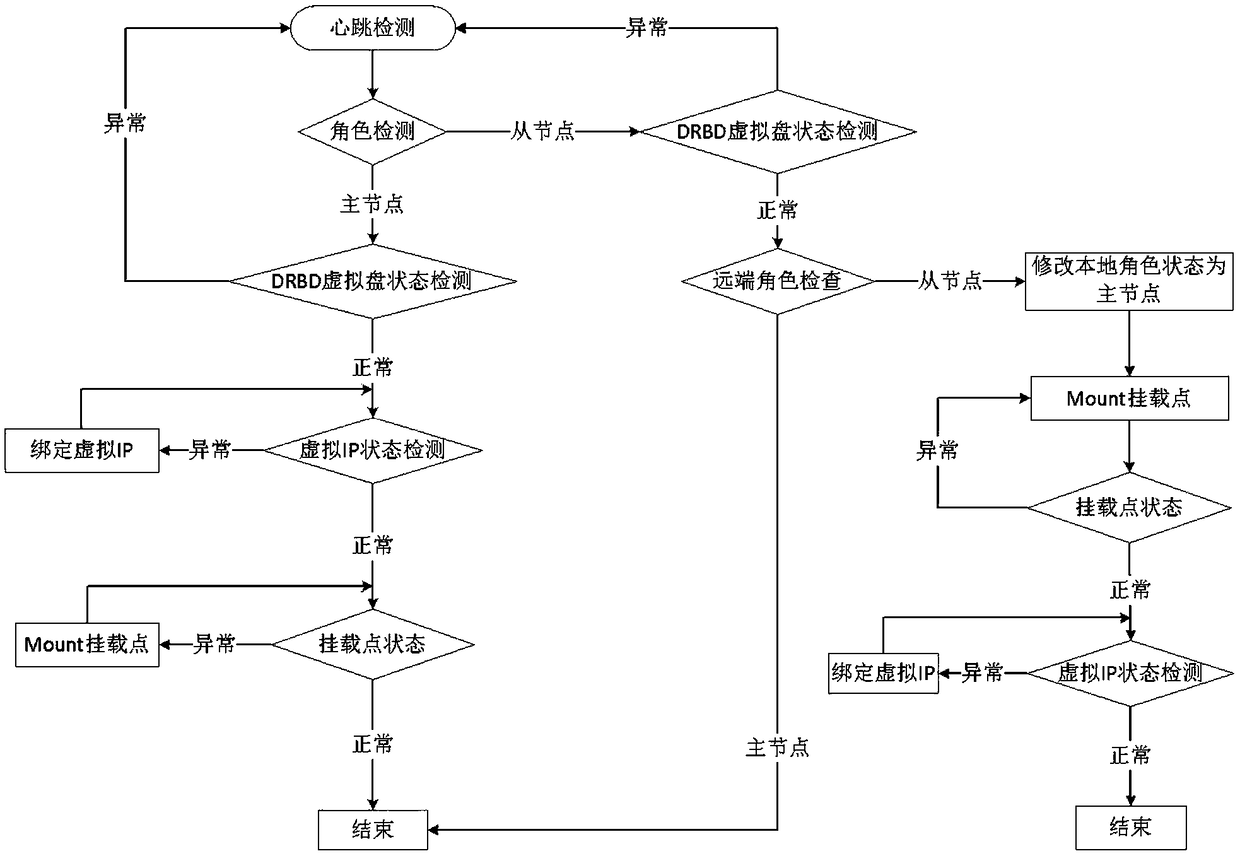
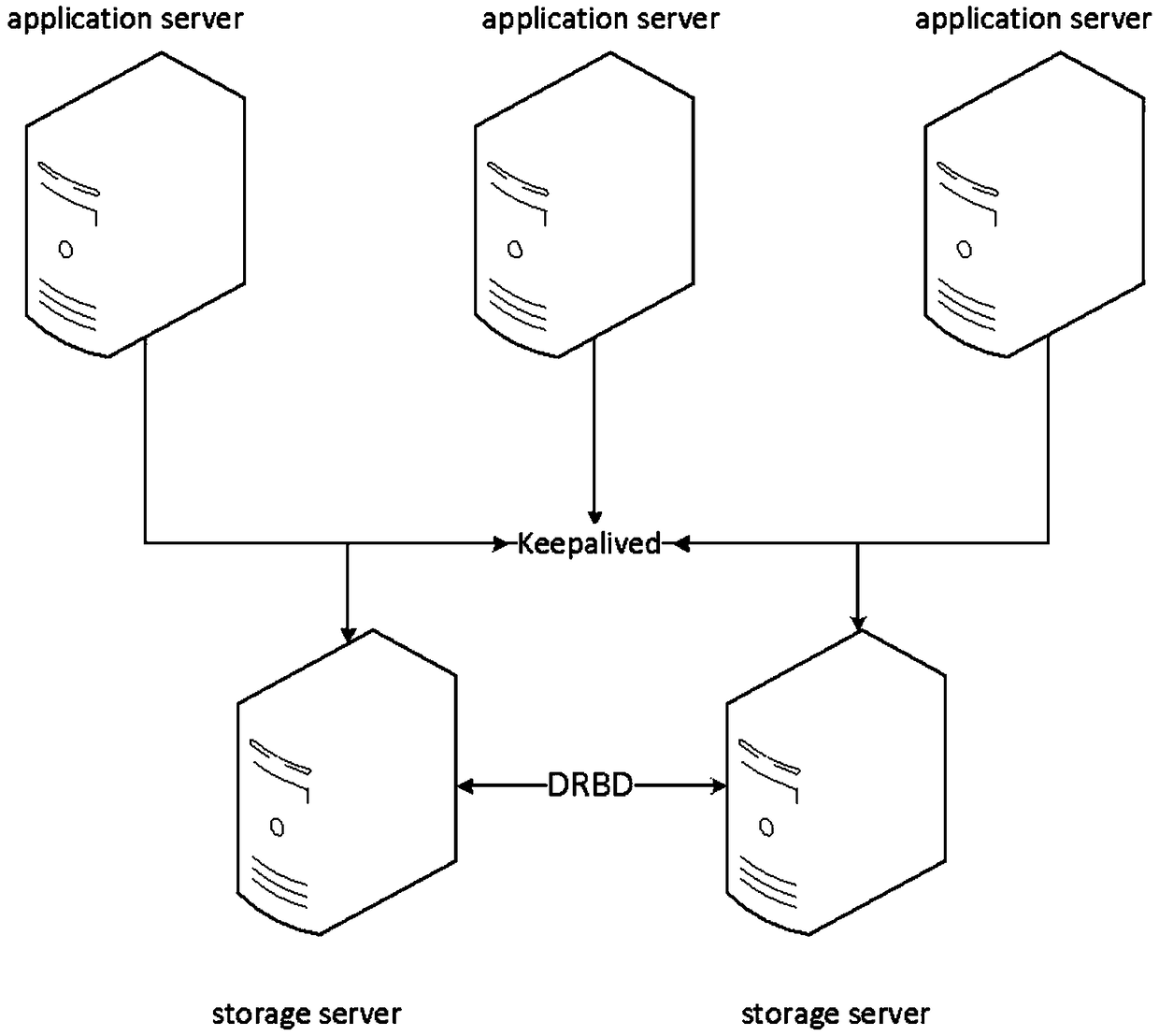
InactiveCN109271280AGuaranteed continuityImprove securityDatabase distribution/replicationData switching networksHeartbeat detectionOperating system
The invention discloses a storage fault fast switching processing method, which relates to the technical field of information storage. The method comprises the following steps: defining node roles: installing and configuring Keepalived service to each storage service node; marking the storage service node as a master node or a slave node; and setting up a storage service node as a master node or aslave node; virtual IP allocation step: allocating a virtual IP address to a primary node; Heartbeat detection step: detecting heartbeat of each storage service node, and judging whet that master node is alive or not; Node switching step: when the master node is not found to be alive, automatically shifting the virtual IP address to the slave node, and switching the identity of the slave node tothe master node. The invention solves the problem of low data switching efficiency between the existing master device and the slave device.
Owner:重庆富民银行股份有限公司
Storage battery powered train and train network control system
PendingCN106945564ARealize emergency power supply interlockAchieve traction braking force distributionElectric devicesElectrodynamic brake systemsAutomotive engineeringPower storage
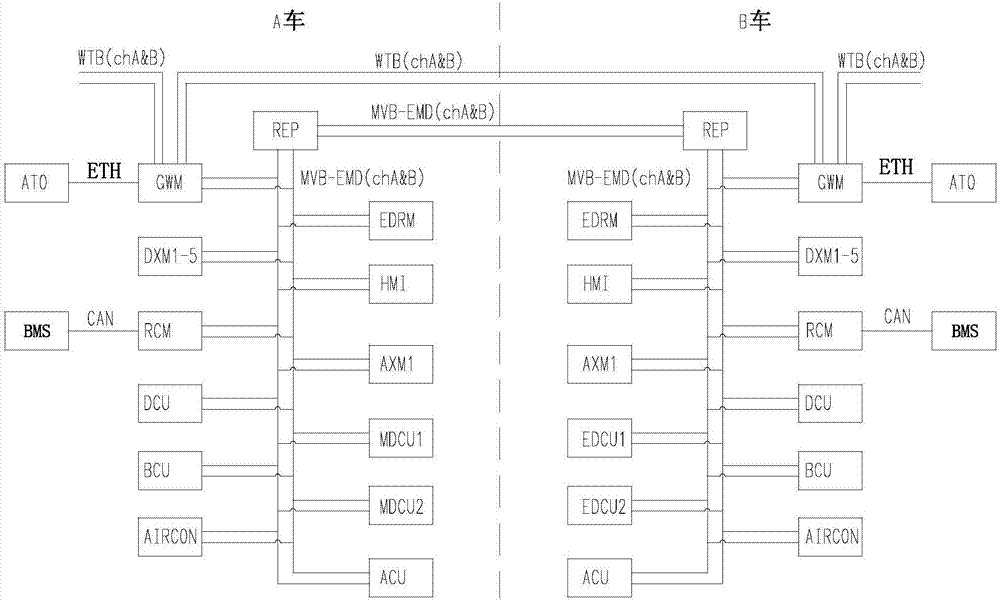
The invention provides a storage battery powered train and a train network control system. A main transmission system of the train comprises a power storage battery, a traction converter cabinet and a traction motor. The power storage battery is connected with the input end of the traction converter cabinet, and the traction motor is connected with the output end of the traction converter cabinet. The control system comprises that a train automatic driving system is connected with a train control module, and a storage battery management system is connected with the CAN gateway module in each train carriage. An event recorder, a display, an analog input module, a first door controller, a second door controller, a train control module, a digital input and output module, a CAN gateway module, a traction control unit, a brake control unit and an air conditioning control unit are connected to a communication bus, and the communication bus is connected to a MVB repeater. The storage battery powered train has a special network control system.
Owner:CRRC ZIYANG CO LTD
Method for implementing long connection changeover of network
InactiveCN1665206AEnsure safetyImplement backupData switching by path configurationTraffic capacityNetwork connection
The invention discloses a method for implementing the switching of long network connection, comprising: establishing at least a virtual server corresponding to a server group with the same servicing function, composed of at least a real server; setting an identification word for the virtual server to identify the state change of the real server in the server group; according to the identification word, judging if the state of the real server changes: if the state is normal, establishing the connection between a client and the real server; otherwise, implementing the switching of long connection according to the identification word. The invention can still evenly allocate the whole flow to different servers as the state of the real server changes and assure the implementation of the switching of long connection by network load balancing equipment after the state of the real server is normal.
Owner:HUAWEI TECH CO LTD
Boot program backup method and Boot program backup device
InactiveCN102520979AGuaranteed reliabilityImplement backupProgram loading/initiatingRedundant operation error correctionEngineeringDouble boot
The invention discloses a Boot program backup method and a Boot program backup device. The method includes the following steps: booting a master Boot program, and judging whether the master Boot program is successfully booted; if the master Boot program is successfully booted, then determining that the booting of the master Boot program is completed; if the master Boot program is not successfully booted, then booting a standby Boot program, and judging whether the standby Boot program is successfully booted; and if the standby Boot program is successfully booted, then determining that the booting of the Boot program is completed. In the embodiment of the invention, the backup mechanism of the master Boot program and the standby Boot program is utilized to realize double-Boot program backup, consequently, the problem of the failure of the booting of a device, which is caused by the damage of the Boot program, can be effectively prevented, and the reliability of the booting of the Boot program is guaranteed.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Multi-channel bus data simulation system
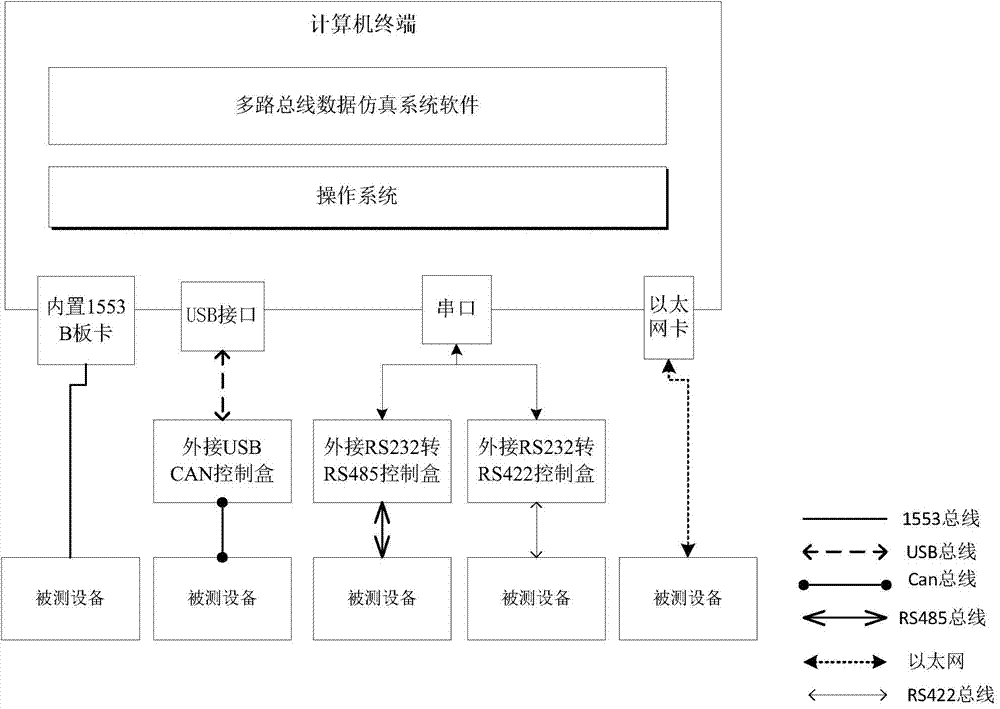
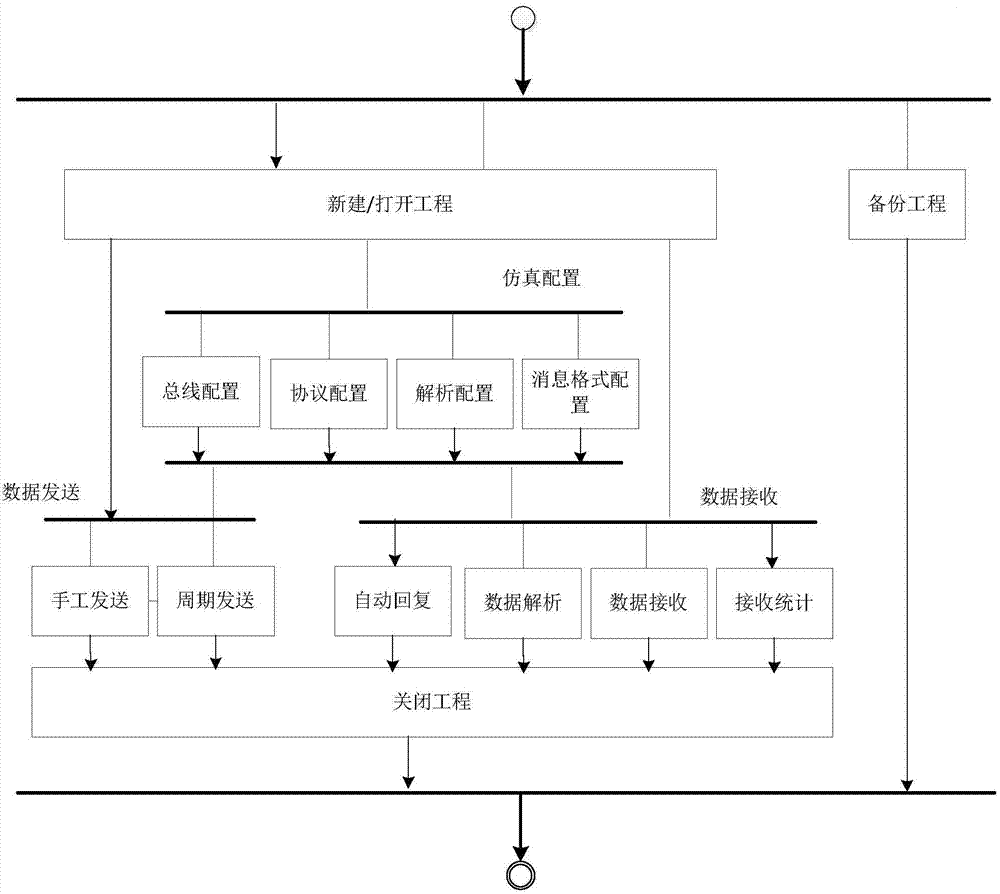
ActiveCN104765709AReliable supportImprove work efficiencyElectric digital data processingData simulationData type
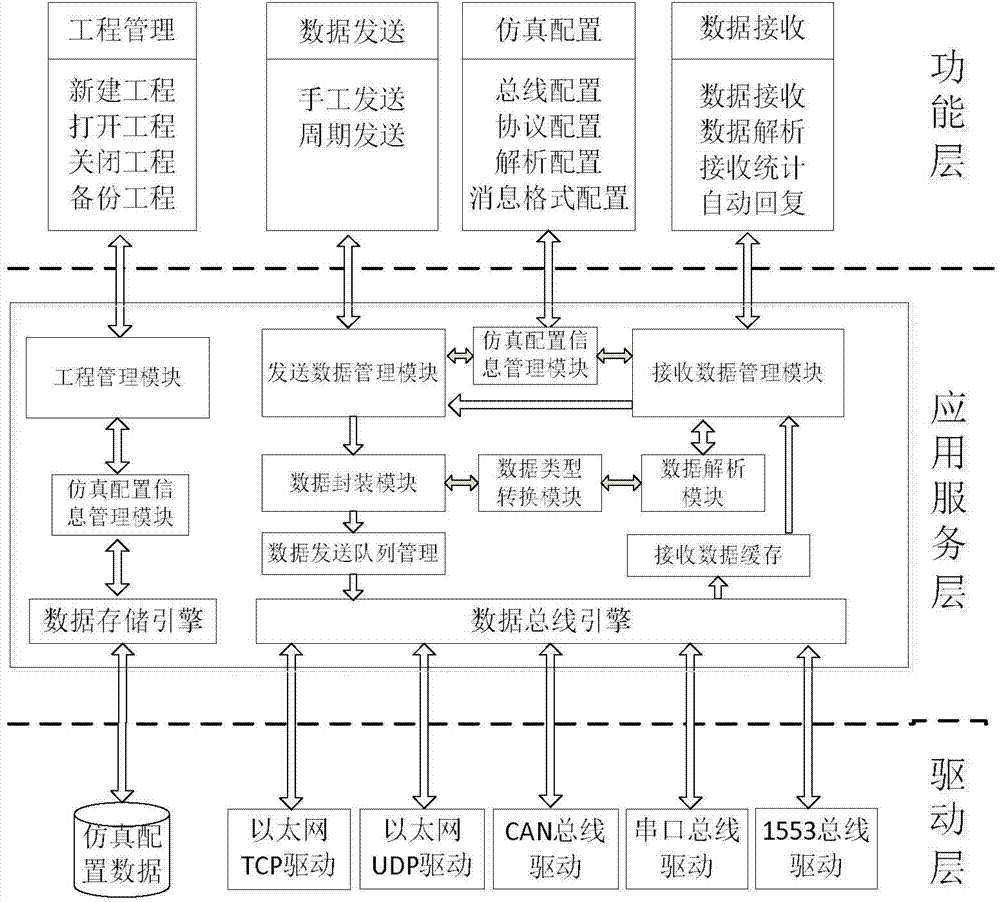
The invention discloses a multi-channel bus data simulation system to help development or test personnel achieve zero encoding and common bus different information formulas rapidly. According to the technical scheme, multi-channel bus data simulation software operating at a computer terminal assembles information and messages according to a bus formula and data, a data packaging module pushes the data to a data sending queue management module to be sent, and a data analysis module calls Ethernet TCP drive according to bus configuration information and sends sending queue data to corresponding bus data bus engines corresponding to bus Ethernet. An engineering management module calls a data storage engine to achieve data reading and writing and pushes the received bus data to a receiving data cache. A receiving data management module calls a simulation configuration information management module to return analysis formulas and transmit to a data analysis module after receiving notices. The data analysis module calls a data type conversion module to achieve data receiving and analysis.
Owner:10TH RES INST OF CETC
Data backup system and method based on memory database
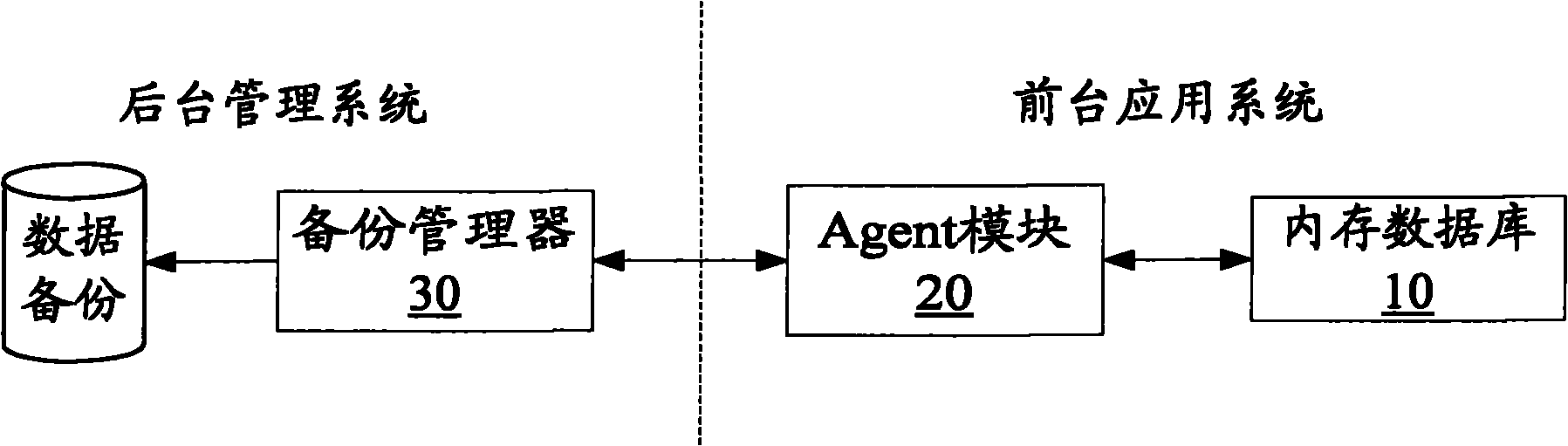
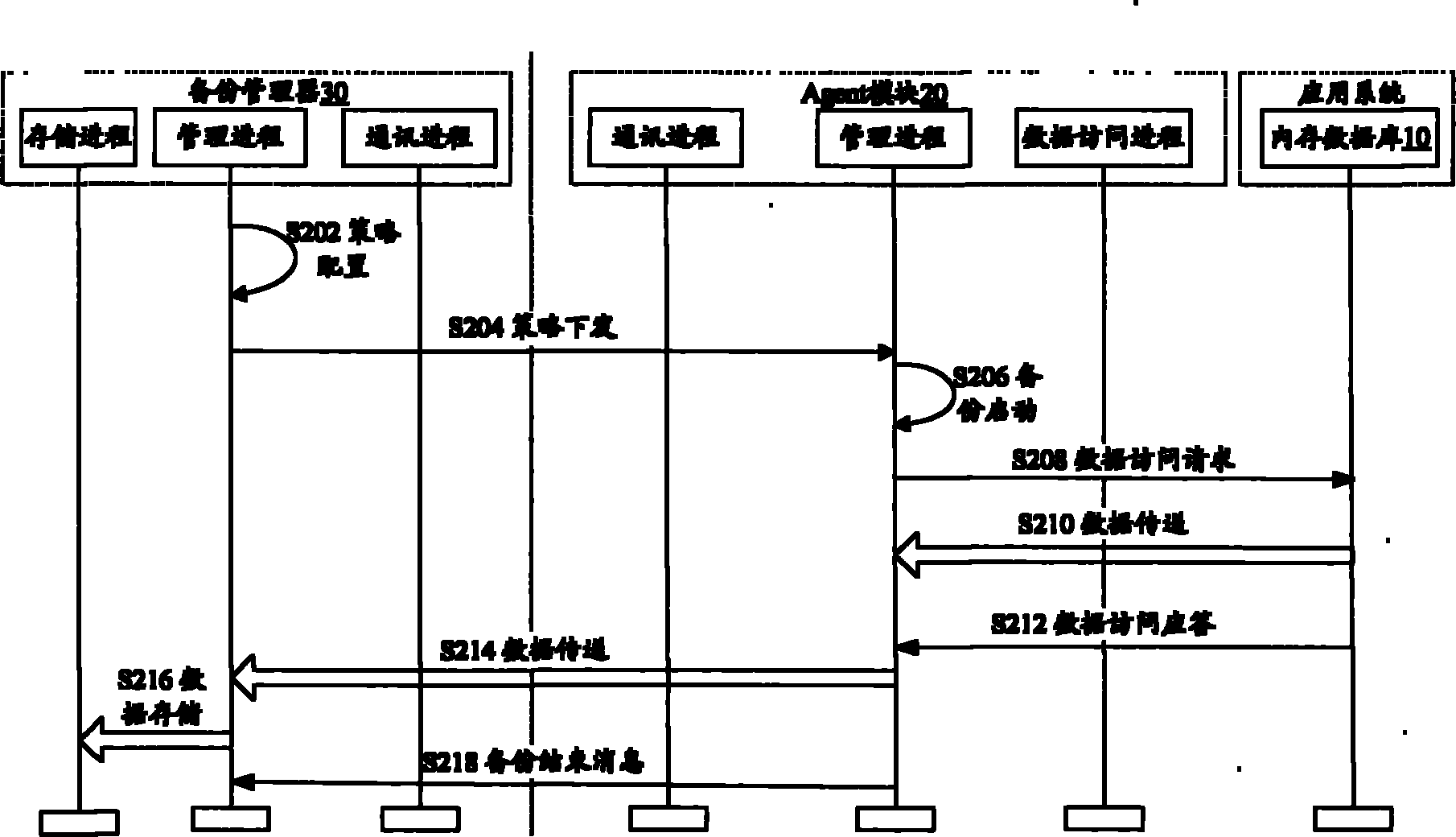
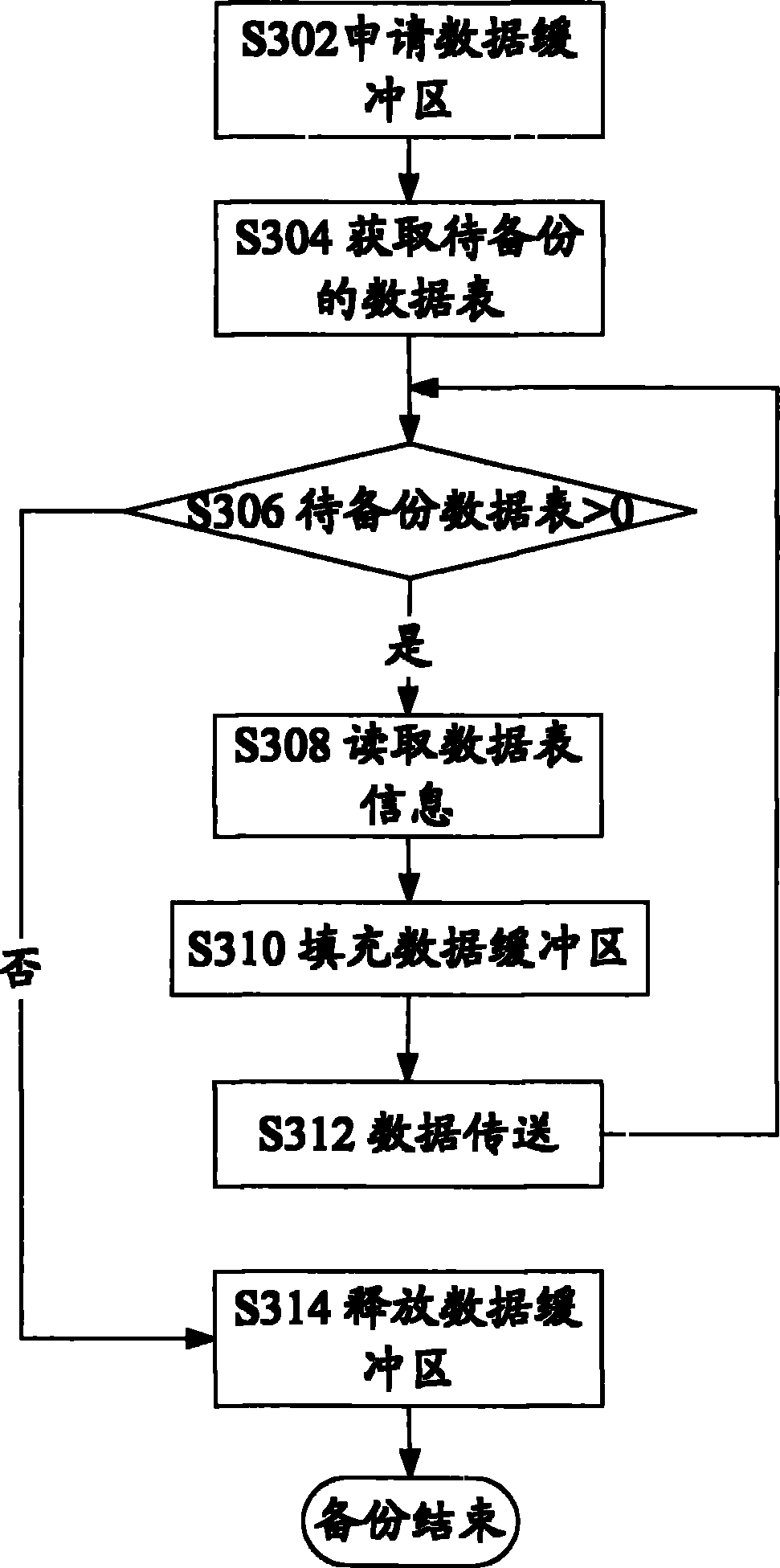
ActiveCN101887388AAvoid interferenceImplement backupSpecial data processing applicationsRedundant operation error correctionIn-memory databaseData shipping
The invention discloses data backup system and method based on a memory database. The system comprises the memory database, a proxy module and a backup manager, wherein the backup manager is used for issuing a backup strategy to the proxy module, wherein the backup strategy contains data that needs to be backed-up; and the proxy module is used for accessing data in the memory database according to the backup strategy through an application program interface (API) provided by the memory database and transmitting the accessed data into the backup manager so as to carry out backup. The invention avoids the problems of the interference on the saving operation of the memory database and the occupying of read-write (IO) resource of the memory database and realizes the backup to designated object data.
Owner:ZTE CORP
File backup method and device
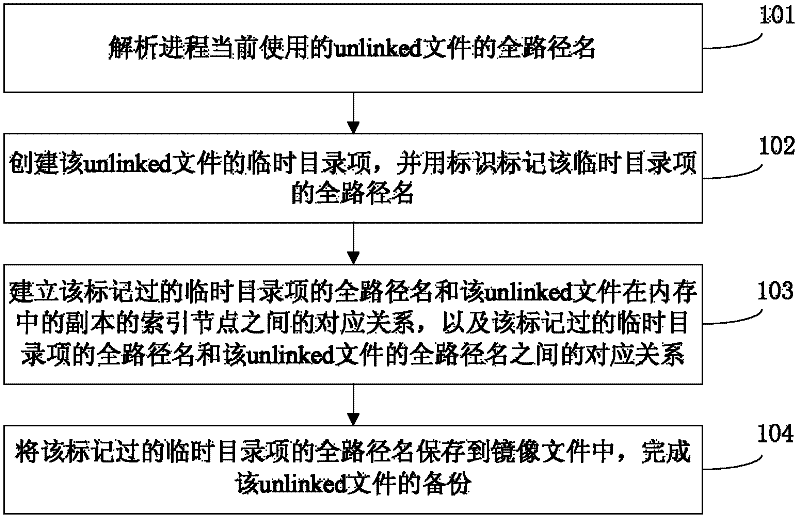
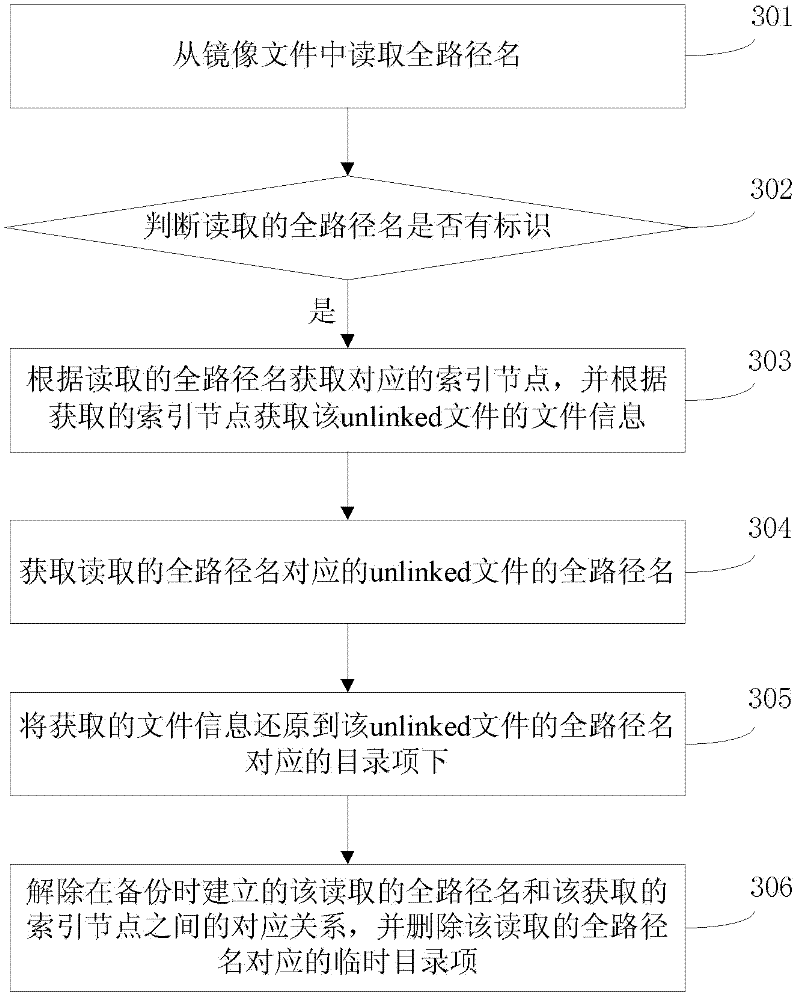
InactiveCN102331957AImplement backupProtect functional integrityDigital data information retrievalRedundant operation error correctionInternal memoryComputerized system
The invention discloses a file backup method and device and belongs to the field of a computer system. The method comprises the following steps: analyzing an entire path name of an unlinked file which is used by a process currently; establishing a temporary directory entry of the unlinked file and marking the entire path name of the temporary directory entry with an identifier; establishing a congruent relationship between the marked entire path name of the temporary directory entry and an index node of a copy of the unlinked file in an internal memory and a congruent relationship between themarked entire path name of the temporary directory entry and the entire path name of the unlinked file; and storing the marked entire path name of the temporary directory entry into an image file, thereby finishing the back-up of the unlinked file. According to the method, the back-up of the unlinked file is realized by correctly analyzing the entire path name of the unlinked file and establishing the temporary directory entry of the unlinked file.
Owner:HUAWEI TECH CO LTD
Security and protection device and cloud service system and safety method of wide band video
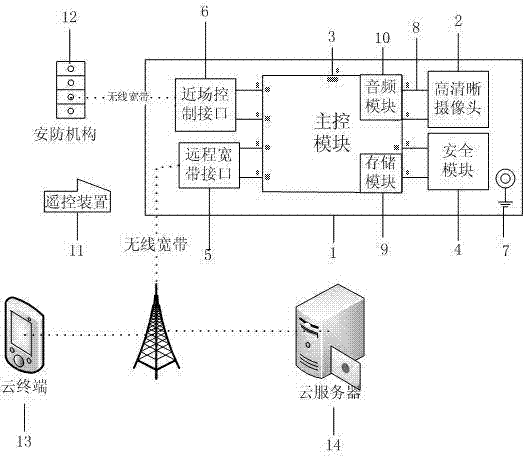
InactiveCN103096036AImplement backupImprove efficiencyClosed circuit television systemsTransmissionProtection mechanismBroadband
The invention relates to a security and protection device of a wide band video. The security and protection device of the wide band video comprises a shell body, a high definition camera connected with a main control module, a long-distance wide band joint, a near field control joint and a safety module used for storing a digital certificate and / or biological characteristics. A cloud service system is composed of the security and protection device, a cloud terminal, a cloud server and a security and protection mechanism. Video and image information is transmitted through a wind band. Warning information is sent by the cloud server through a multimedia message by the cloud server. Two-way multiple-factor certification is adopted by the cloud terminal, the safety module and the cloud server so that safety of data is guaranteed. A highly confidential safety device based on a financial integrated circuit (IC) card is reused for security and protection service of a wisdom family and a wisdom city so that business process reengineering is performed, operation and maintenance cost is reduced and repeated construction is avoided.
Owner:潘铁军
Port binding method and device
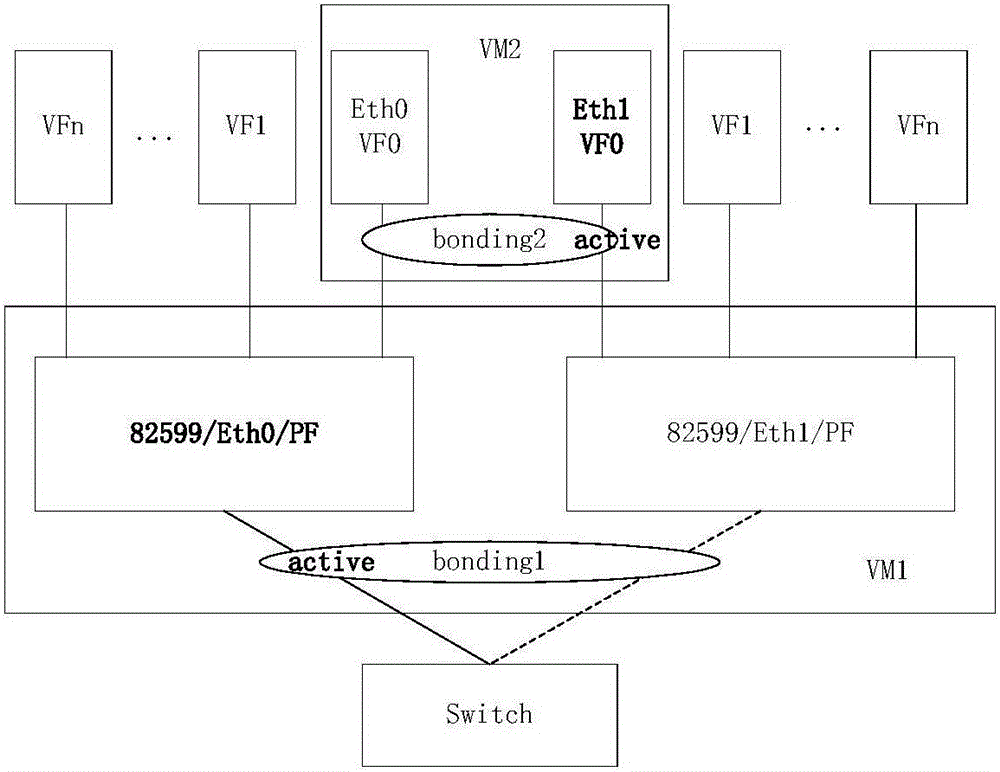
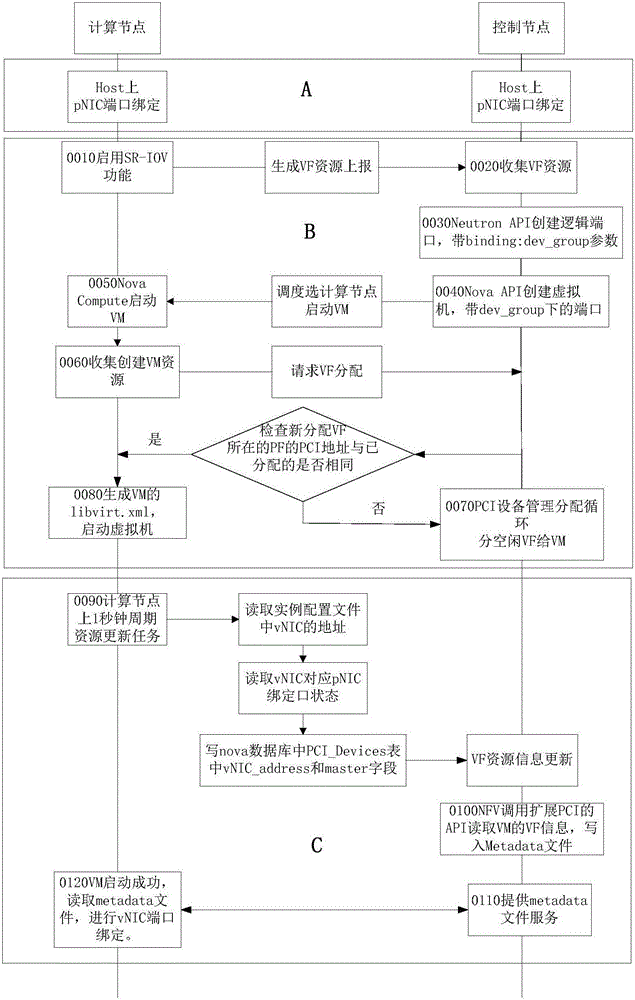
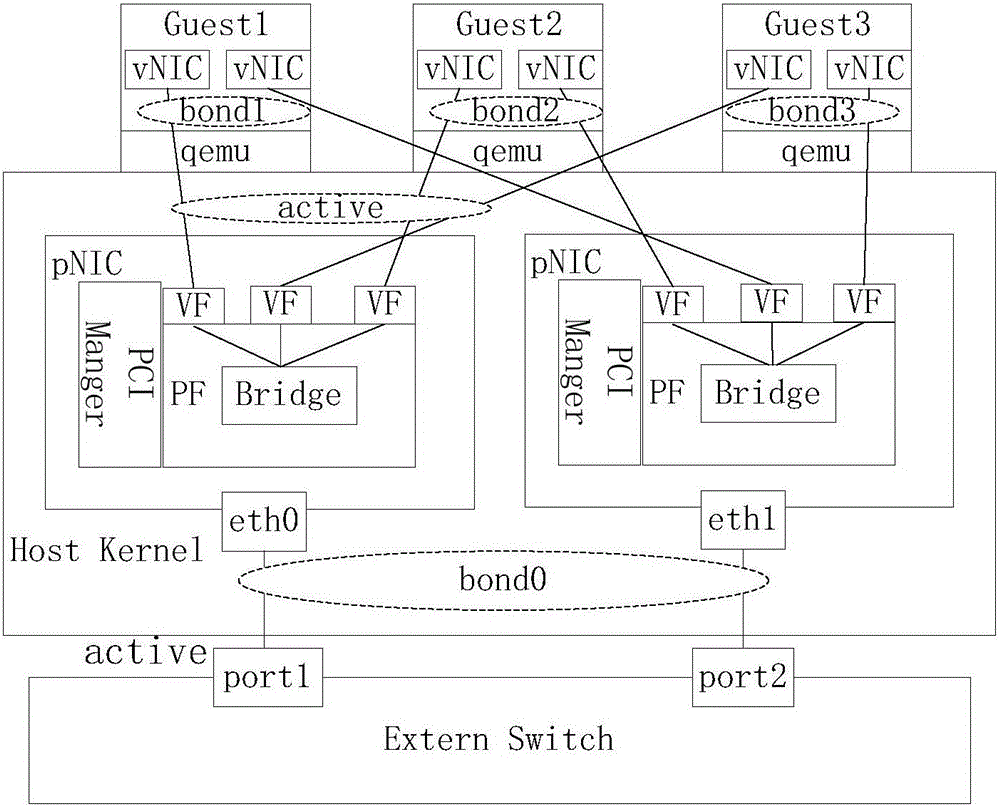
InactiveCN107181679AImplement link backupOvercome issues from the same PFData switching networksVirtual machineVirtual function
The invention provides a port binding method and device, and belongs to the technical field of communication. The method comprises that an SR-IOV logic port is created, and logic ports under the same aggregation port belong to the same binding group; and a virtual machine is created, a virtual function VF is selected and distributed to the virtual machine, so that physical functions (PFs), where the VFs of the same binding group are located, are different. By means of the technical solution of the present invention, the problem that VFs come from the same PF during aggregation binding of a vNIC port of the virtual machine can be overcome.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com