Key generation, backup and migration method and system based on trusted computing
A key generation and trusted computing technology, applied in the computer field, can solve problems such as inability to provide data security and low security of cloud storage data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
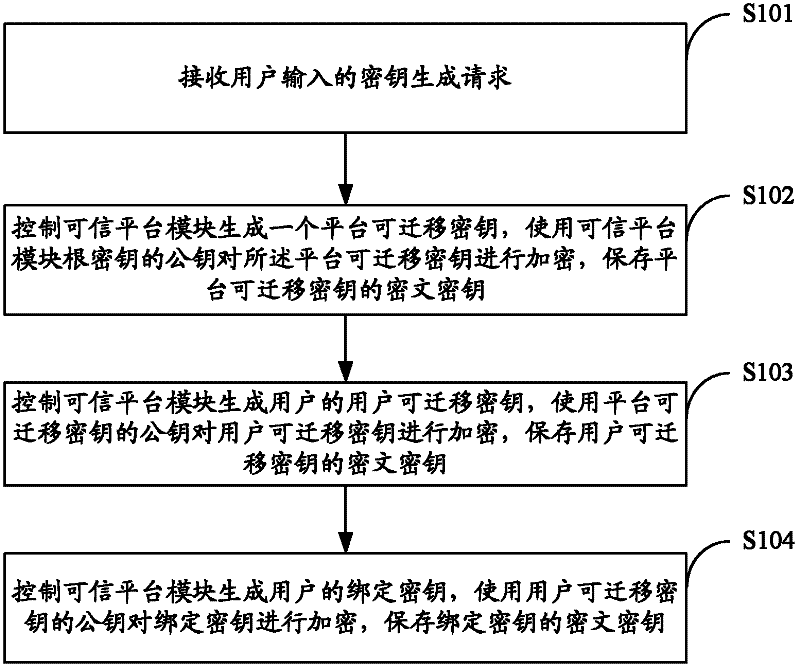
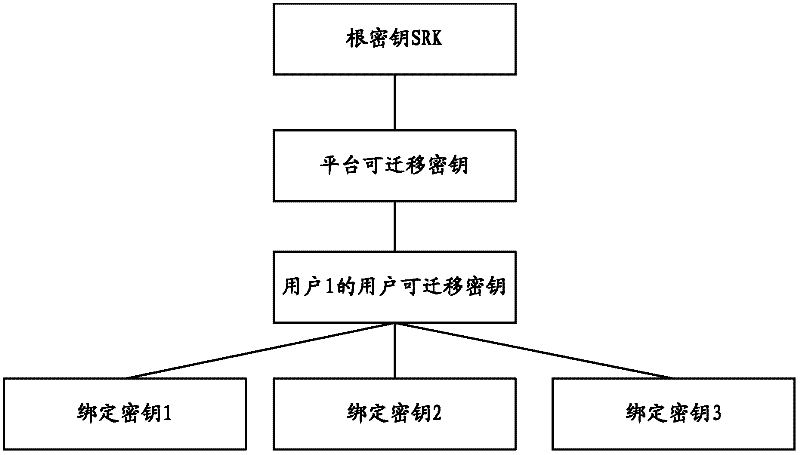
[0069] Trust Platform Module (TPM for short) is a new embedded security subsystem placed in the computer, which protects the security of the terminal platform through functions such as public key authentication, integrity measurement, and remote authentication. The keys in the trusted platform module can be divided into migratory keys and non-migratory keys. The root key SRK is a non-migratory key, which is the basis for establishing a trust relationship. The binding key is a migratory key. These keys are all asymmetric keys RSA. In the embodiment of the present invention, the root key is used as the parent key to encrypt and save the generated platform migration key, and then the platform migration key is used as the parent key to the user. The transferable key is encrypted and stored, thereby constructing a key tree. There is a trust relationship between each node. Finally, the security of the key in the entire tree is guaranteed by the root key.
[0070] figure 1 The imple...
Embodiment 2
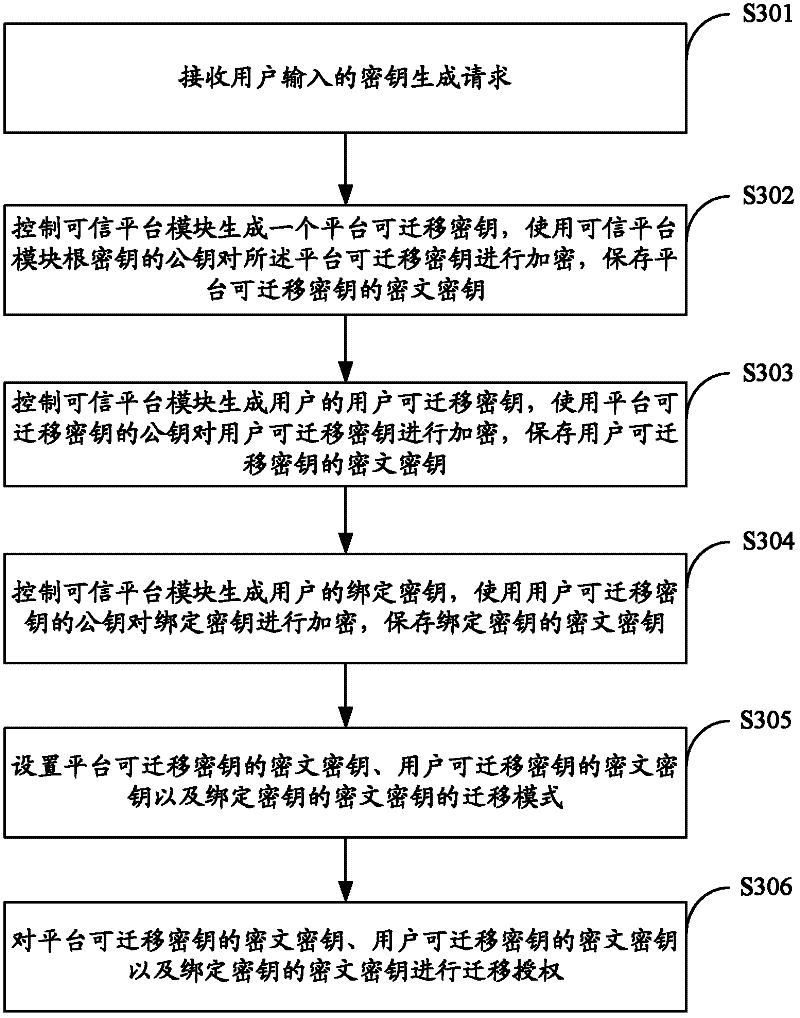
[0080] In the embodiment of the present invention, by setting the migration mode of the key and performing migration authorization on the generated key, the security characteristics of the generated key are ensured, and unauthorized users are prevented from migrating the generated key, and further Improved key security.
[0081] image 3 The implementation process of a key generation method based on trusted computing provided by the second embodiment of the present invention is shown, and the details are as follows:
[0082] In step S301, a key generation request input by a user is received.
[0083] In step S302, the trusted platform module is controlled to generate a platform transferable key, the platform transferable key is encrypted using the public key of the root key of the trusted platform module, and the ciphertext key of the platform transferable key is saved.
[0084] In step S303, the trusted platform module is controlled to generate the user's transferable key o...
Embodiment 3
[0103] Figure 4 The structure of a key generation system based on trusted computing provided by the third embodiment of the present invention is shown. For the convenience of description, only the parts related to the embodiment of the present invention are shown, wherein:
[0104] The generation request receiving unit 41 receives a key generation request input by the user. The first key generation unit 42 controls the trusted platform module to generate a platform transferable key, encrypts the platform transferable key with the public key of the root key of the trusted platform module, and saves the ciphertext of the platform transferable key. key.
[0105] The second key generation unit 43 controls the trusted platform module to generate the user's transferable key of the user, encrypts the user's transferable key with the public key of the platform's transferable key, and saves the ciphertext key of the user's transferable key. .
[0106] The third key generation unit ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com