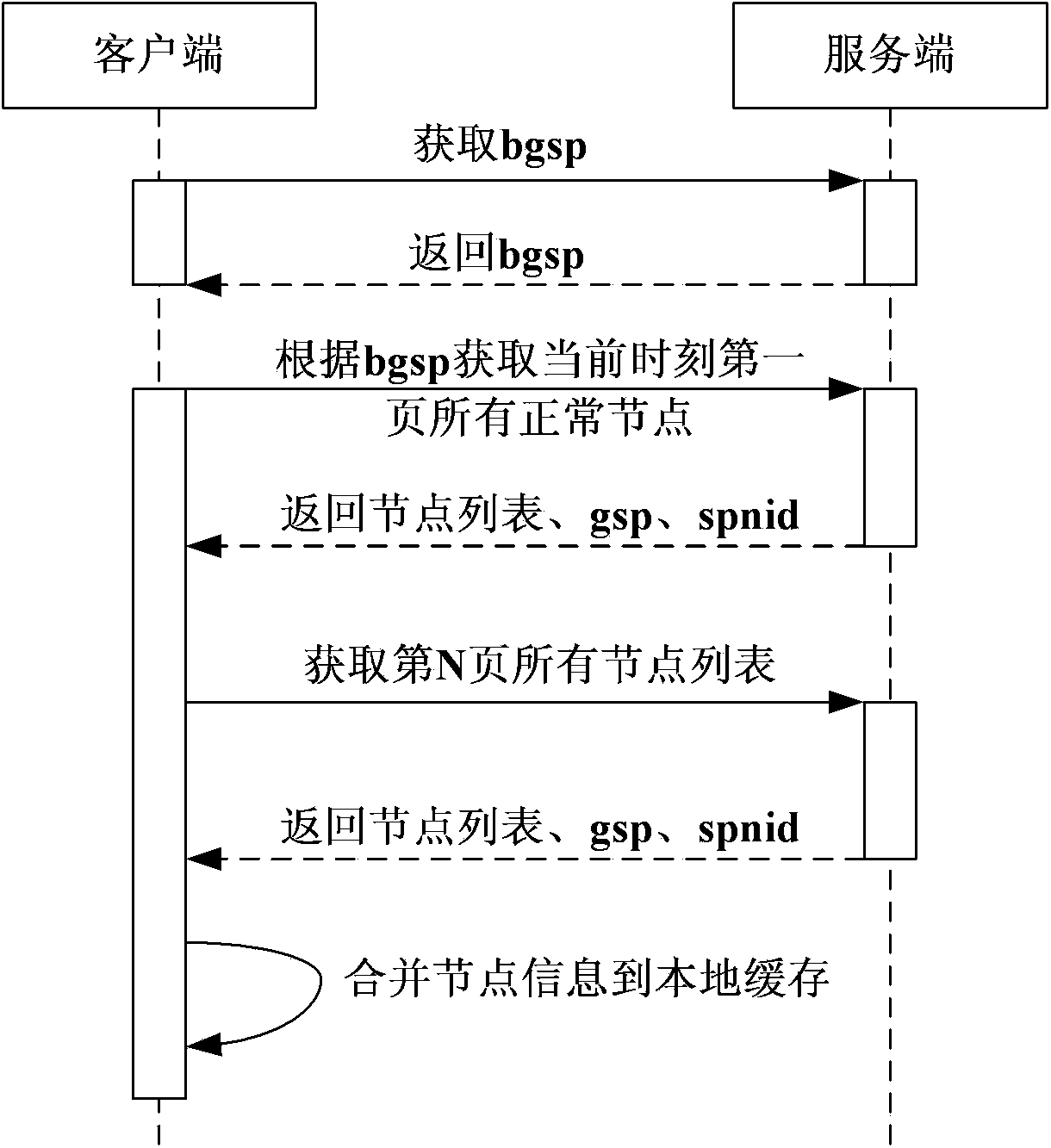
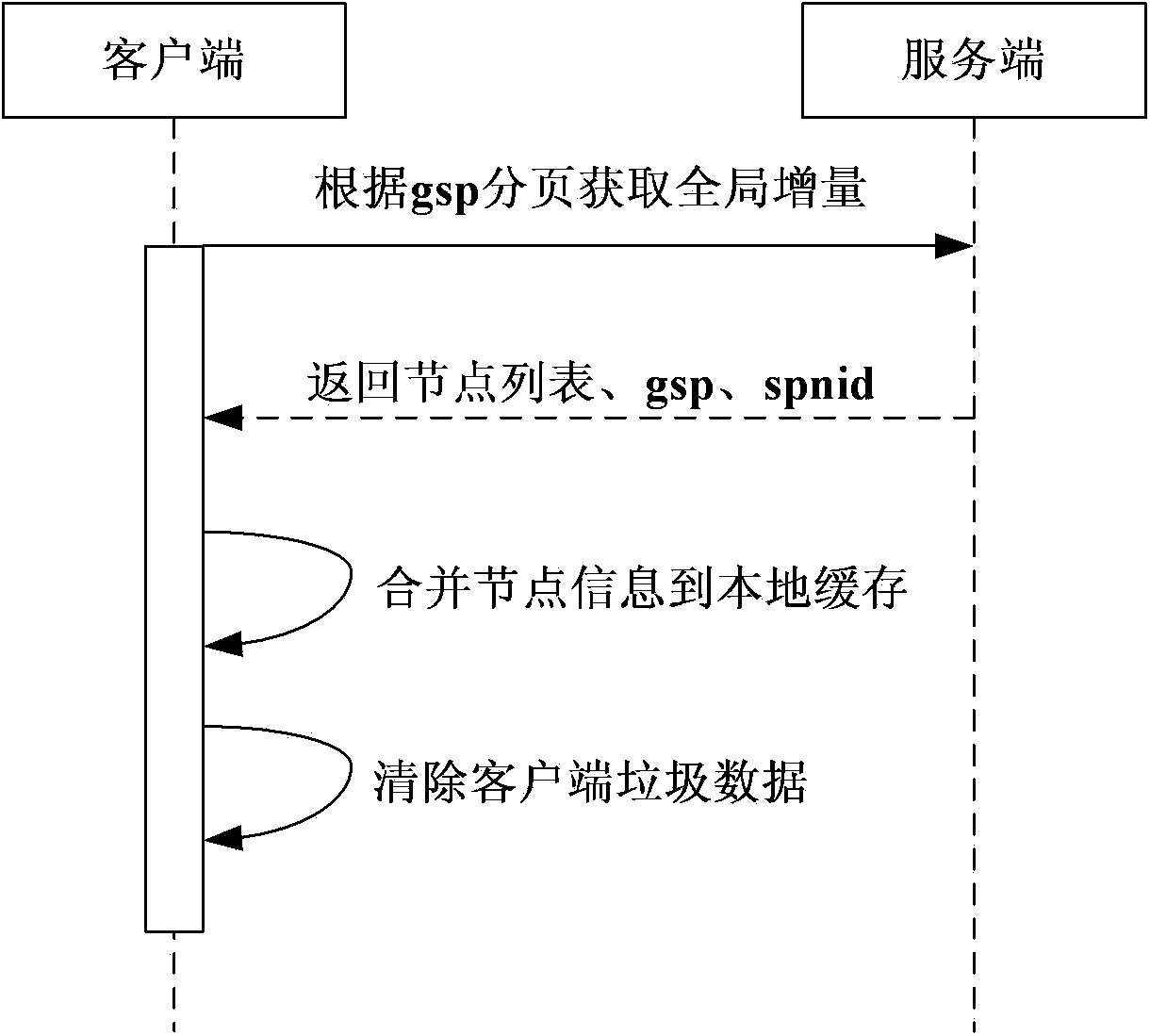
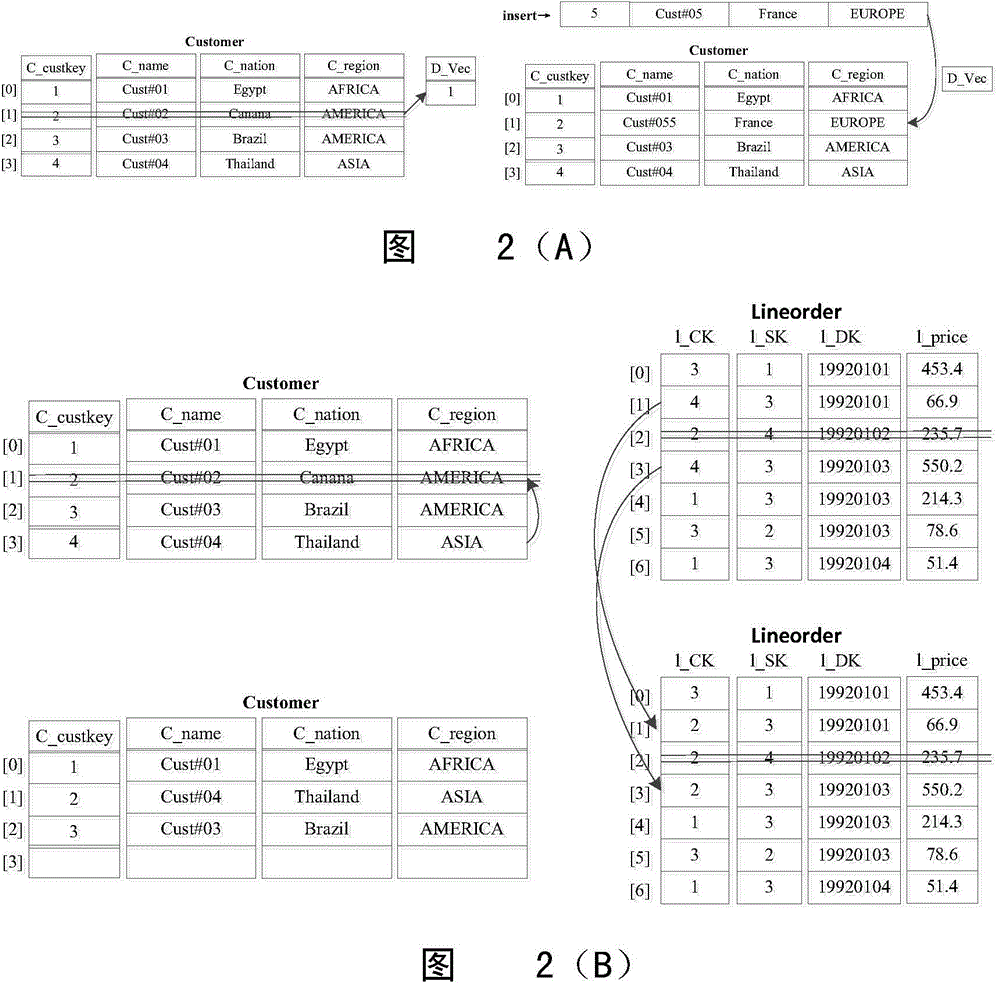
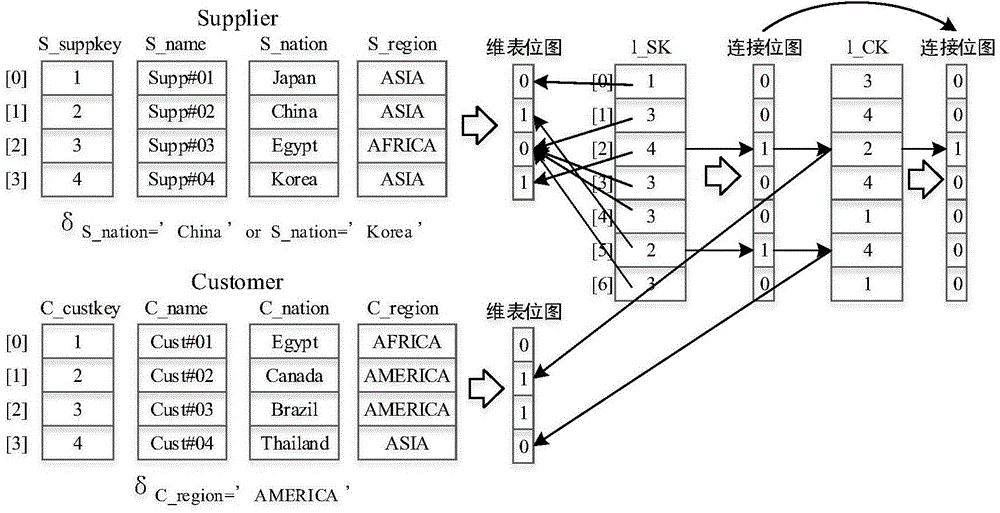
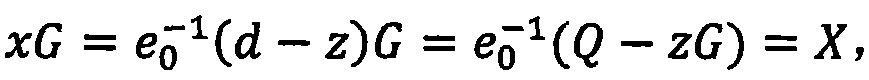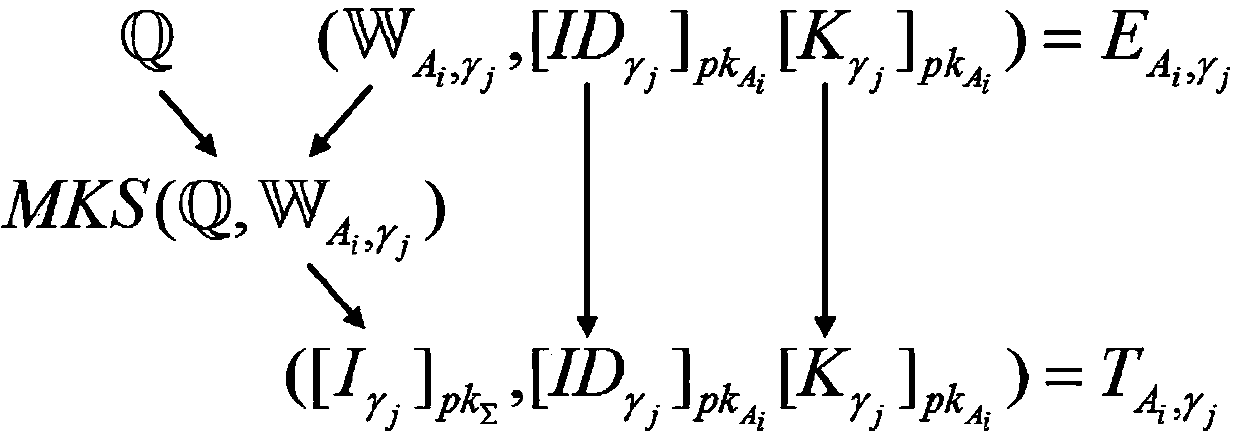Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
634results about How to "Reduce storage overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
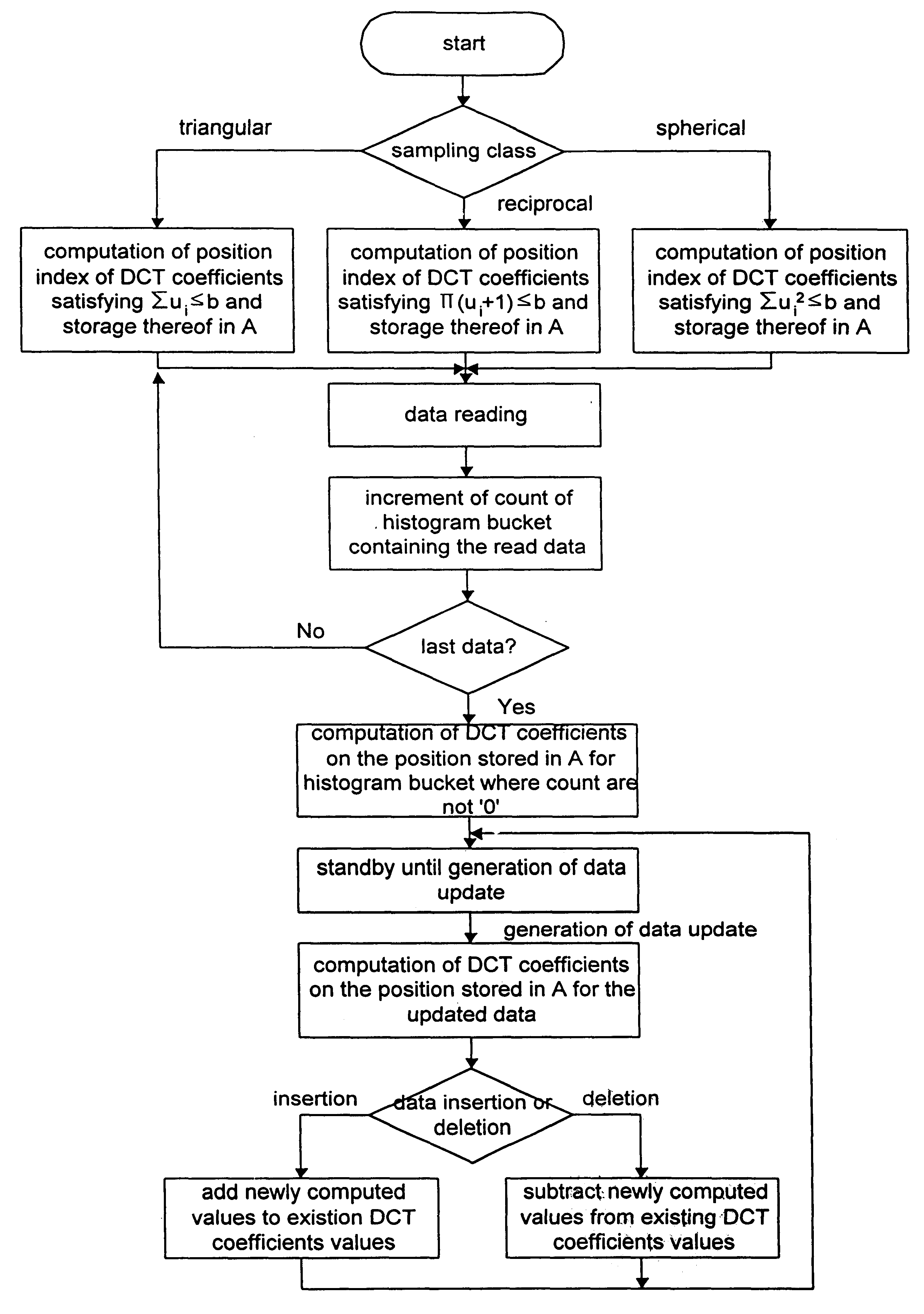
Multi-dimensional selectivity estimation method using compressed histogram information
InactiveUS6311181B1Reduce error rateReduce storage overheadData processing applicationsDigital data processing detailsExecution planHigh probability
Disclosed is a multi-dimensional selectivity estimation method using compressed histogram information which the database query optimizer in a database management system uses to find the most efficient execution plan among all possible plans. The method includes the several steps to generate a large number of small-sized multi-dimensional histogram buckets, sampling DCT coefficients which have high values with high probability, compressing information from the multi-dimensional histogram buckets using a multi-dimensional discrete cosine transform(DCT) and storing compressed information, and estimating the query selectivity by using compressed and stored histogram information as the statistics.
Owner:KOREA ADVANCED INST OF SCI & TECH
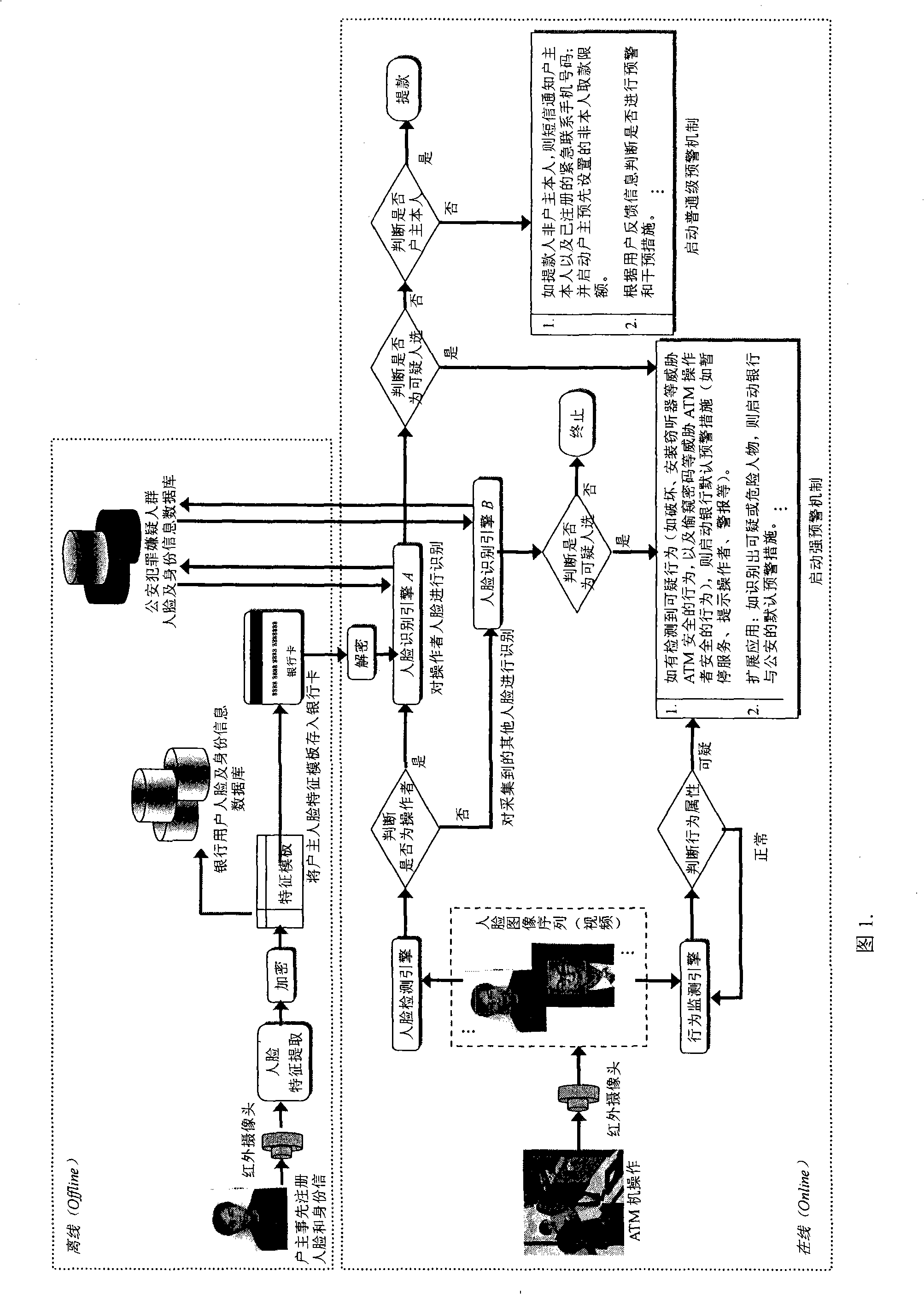
ATM secure authentication and pre-alarming method based on face recognition
ActiveCN101266704AEnsure safetyGuaranteed privacyCharacter and pattern recognitionAlarmsComputer networkAcquisition apparatus
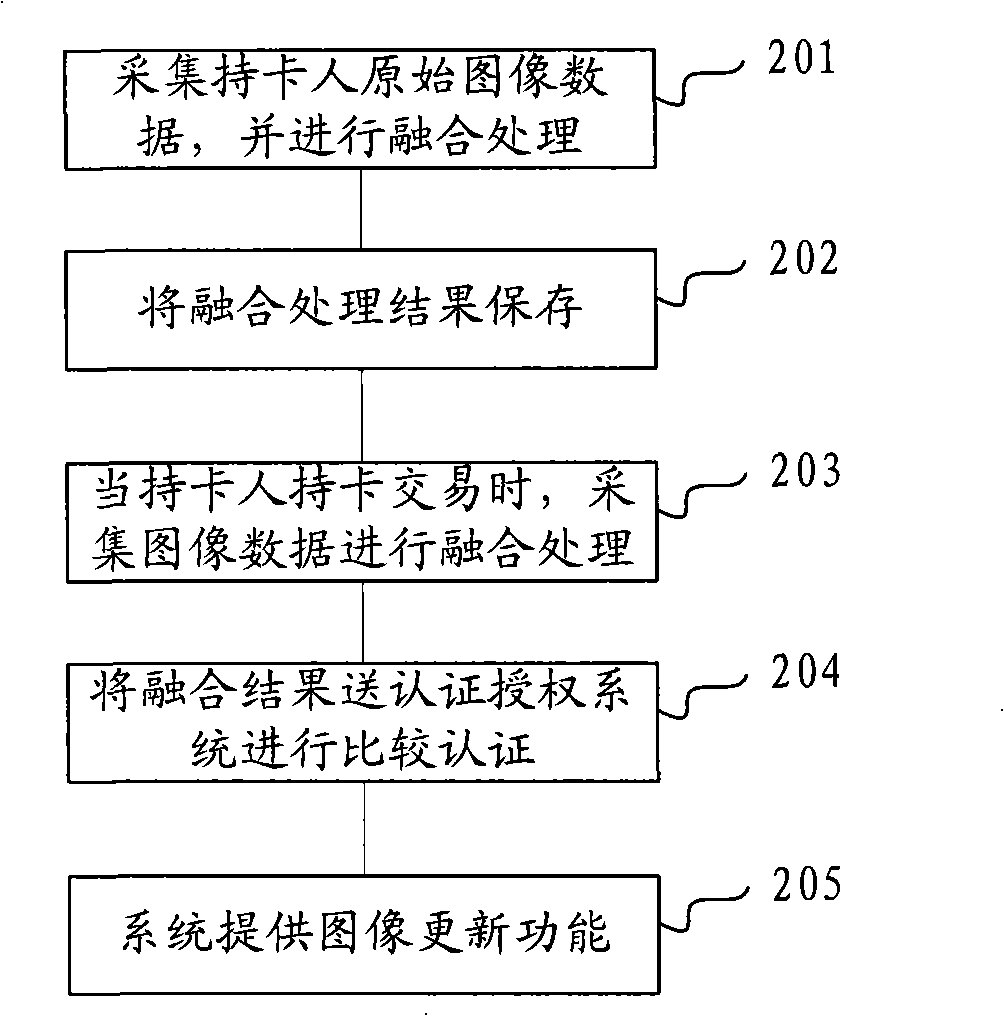
The invention discloses an ATM security certificate and a pre-warning method based on face recognition. The invention introduces face recognition and video detection into the applications of ATM and bank card business for the first time, which can obviously improve the security of ATM financial system, effectively reduce and overawe various ATM fraud and criminal activities. The complete system operation process in the method of the invention is: firstly, registering the face information of a holder at a service window which arranges an infrared face acquisition equipment or with the registration by the users themselves on ATM in bank, and saving the encrypted face information to a bank database and a bank card. Then, determining whether the ATM operator to be recognized is the holder of the bank card or not through verifying the user's identity by a face recognition engine; determining and recognizing whether existing behaviors that threaten ATM and the users though a behavior monitoring engine; and determining whether to trigger corresponding pre-warning mechanism or not according to the recognition result. The invention can extend to the applications of bank book business, public security monitoring and pursuing escaped criminals, etc.
Owner:哈尔滨维科智能系统有限公司
Improved positioning method of indoor fingerprint based on clustering neural network
InactiveCN102932738AReduce calculationReduce storage overheadCharacter and pattern recognitionLocation information based servicePattern recognitionCluster algorithm
The invention discloses the technical field of wireless communication and wireless network positioning, and in particular relates to an improved positioning method of an indoor fingerprint based on a clustering neural network. According to the technical scheme, the positioning method is characterized by comprising the following steps of: an offline phase: constructing a fingerprint database by fingerprint information collected from a reference point, sorting fingerprints in the fingerprint database by utilizing a clustering algorithm, and training the fingerprint and position information of each reference point by utilizing a artificial neural network model to obtain an optimized network model; and an online phase: carrying out cluster matching on the collected real-time fingerprint information and a cluster center in the fingerprint database to determine a primary positioning area, and taking the real-time fingerprint information in the primary positioning area as an input end of the neural network model of the reference point to acquire final accurate position estimation. The method has the advantages that low calculation and storage cost for the clustering artificial neural network fingerprint positioning method can be guaranteed, the positioning accuracy of the clustering artificial neural network fingerprint positioning method can be improved, and accurate positioning information is provided for users.
Owner:BEIJING JIAOTONG UNIV
User-oriented cloud storage data integrity protection method
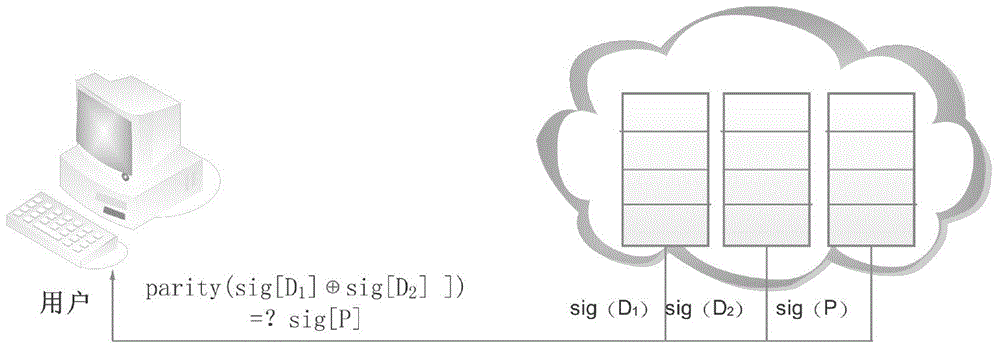
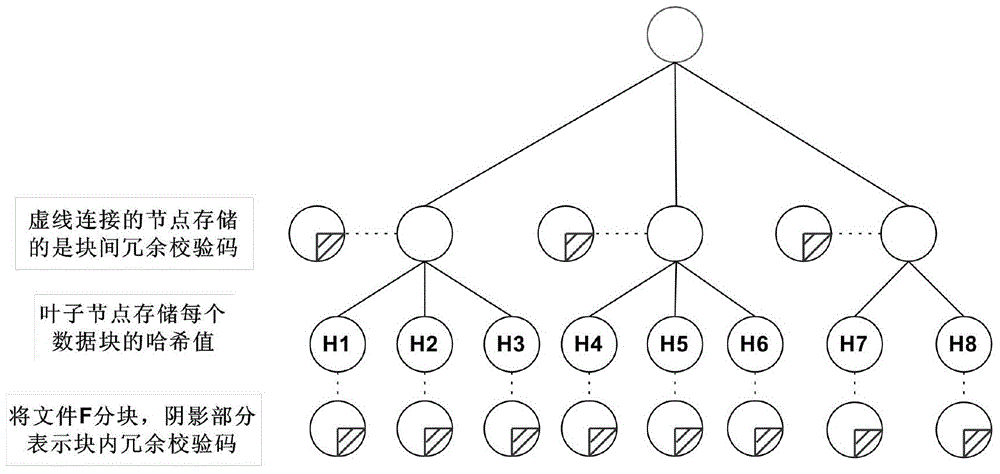
InactiveCN105320899ASave storage spaceAvoid Lost Security RisksDigital data protectionData integrityOriginal data
The invention discloses a user-oriented cloud storage data integrity protection method. The method includes the steps of 1, uploading, wherein a user side segments and numbers a file to generate intra-block redundancy check codes, the hash value of each file block is calculated and saved as a range-based 2-3 tree, the hash values are linked into one value and signed with private keys, and inter-block redundancy check codes are generated and encrypted with stream substitution secret keys; 2, verification, wherein a cloud management node sends a verification request to a corresponding cloud storage server, corresponding original data and algebraic signatures of the inter-block redundancy check codes corresponding to the original data are calculated and returned to the user side for data integrity verification, and the step 3 is executed if data destruction is found; 3, recovery, wherein the user side acquires all the file blocks on corresponding branch trees from a cloud side according to tree information and performs error recovery on the file blocks through erasure codes of the file blocks. According to the method, integrity verification and recovery are performed on the dynamic data stored in the cloud side from the user perspective.
Owner:PEKING UNIV
Parity protection for data chunks in an object storage system
The present invention relates to a method and system for providing parity protection in an object storage system. The present invention allows for tracking the storage requirements for chunks in a distributed storage cluster when transitioning from replica-based protection to parity or erasure coding-based protection and when transitioning from parity or erasure coding-based protection to replica-based protection.
Owner:NEXENTA BY DDN INC
Route exchange method suitable for GEO/LEO double layered constellation network
InactiveCN103905306AReduce overheadShorten convergence timeData switching networksOn boardBoundary values
The invention discloses a route exchange method suitable for a GEO / LEO double layered constellation network. According to the method, a system period is divided into equal-duration time sections based on a dynamic boundary value; a GEO layer satellite high in on-board processing capacity is used for calculating the best route and the second best route for each LEO satellite; in the processes of information transmission and exchange, when loads of the LED satellites are large, the GEO satellite shares part of low priority services in time for the LED satellites, and it is guaranteed that important information is reliably transmitted in real time; when link congestion, node ineffectiveness and other emergency conditions happen in the satellite network, in order to avoid rerouting of the whole network, and the GEO satellite only calculates rerouting for affected routes; after link congestion is eliminated, the LED satellites recover route information in time before congestion in order to avoid link resource waste in the network. In the network that topology time varying happens, links are prone to congestion, on-board resources are limited, continuous high-load flows are prone to being generated, and nodes are prone to being ineffective at the special period, the method can reduce constellation system cost, shorten convergence time, save the on-board resources, increase the utilization rate of the link resources, guarantee that important information is reliably transmitted in real time and improve invulnerability and robustness of the satellite network.
Owner:中国人民解放军西安通信学院
Method for detecting and classifying all-network flow abnormity on line
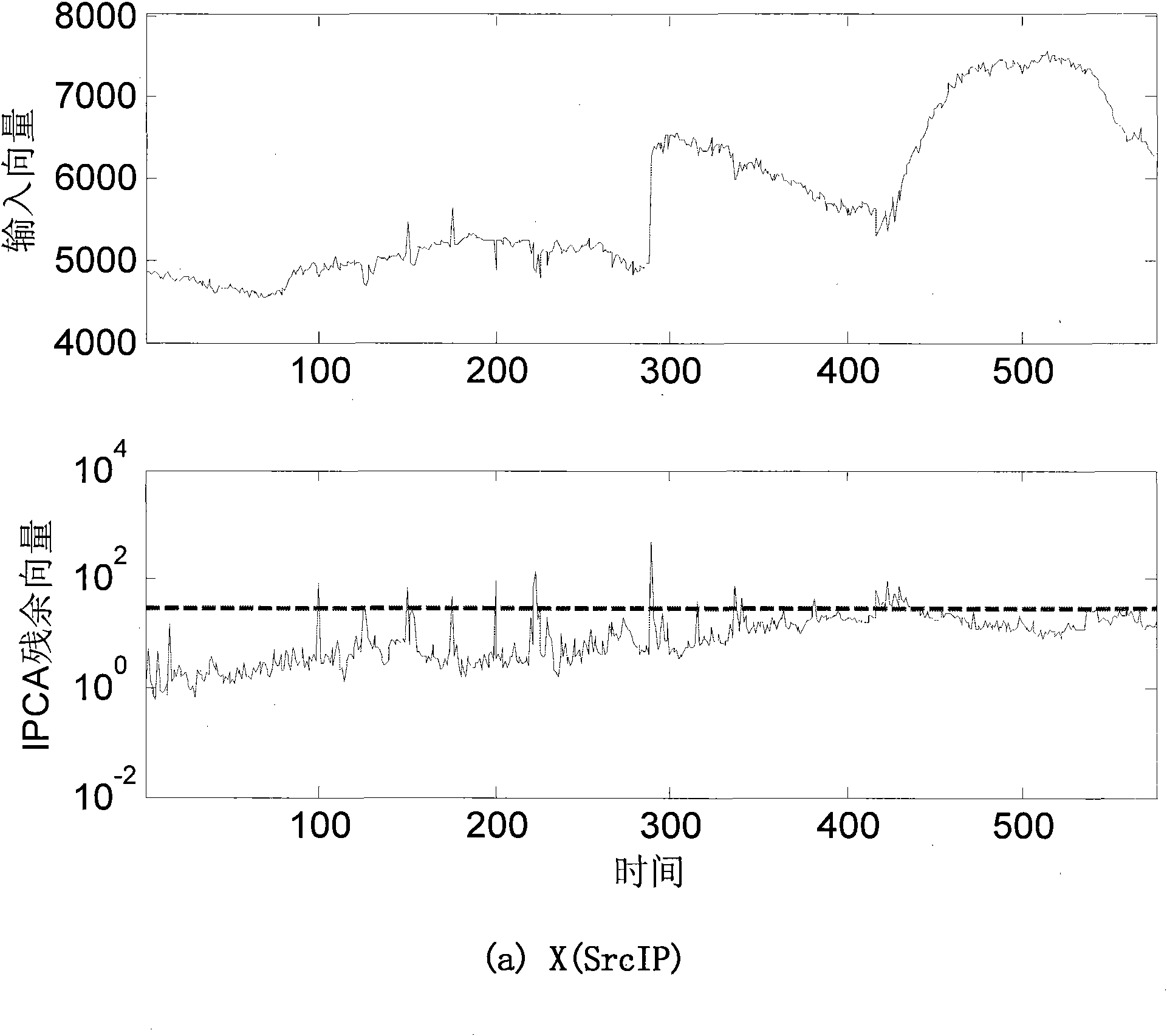
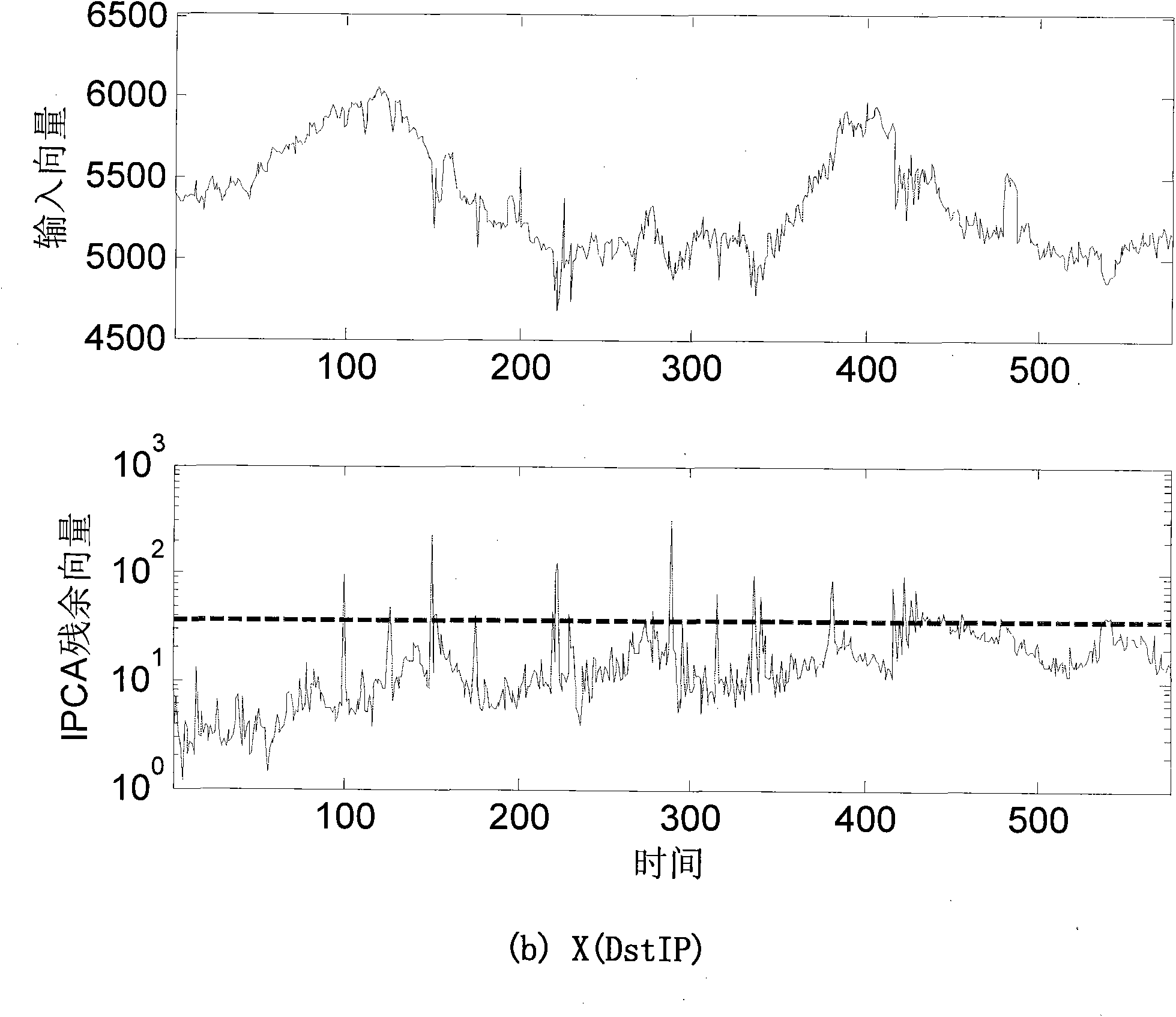
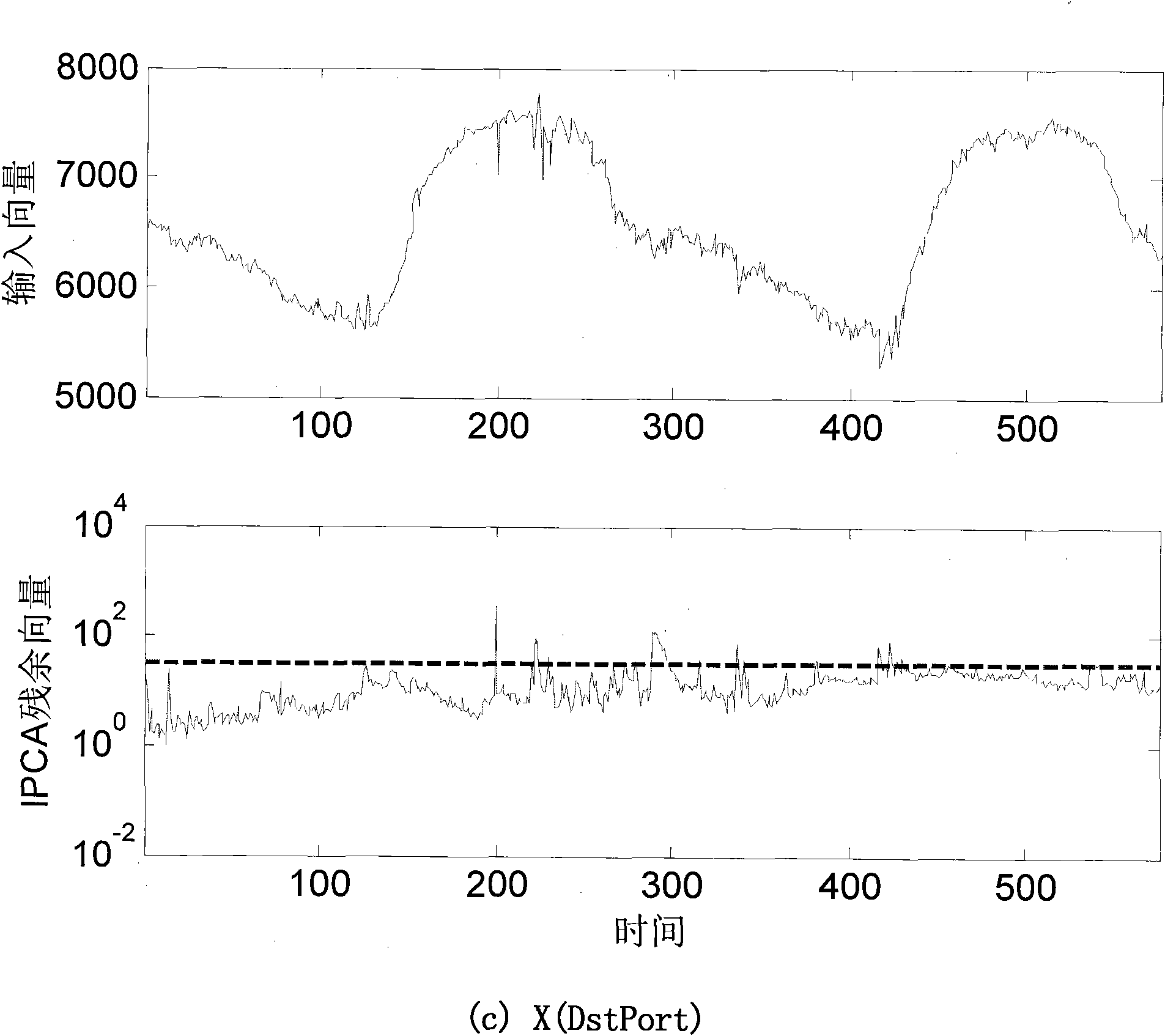
ActiveCN101848160ALow time complexityReduce storage overheadData switching networksTraffic volumeAggregate data
The invention discloses a method for detecting and classifying all-network flow abnormity on line. The method comprises the following steps of: (I) acquiring network flow (NetFlow), namely, receiving a NetFlow data packet transmitted from a border router by adopting a NetFlow collector, resolving the data packet and aggregating data streams to form data suitable for statistical analysis, and transmitting the data to a central control board through network to store in a database; (II) building a flow matrix taking the entropy of flow characteristics as measure; (III) detecting the flow abnormity on line by adopting a main increment component analyzing method; and (IV) constructing sample points in four-dimensional space by utilizing residual vector acquired through on-line detection and classifying the flow abnormity on line by adopting an increment k-mean value clustering method. The method has the advantages of detecting the flow abnormity on line, classifying the flow abnormity on line in real time, meeting the requirement on the real-time detection and classification of the flow abnormity better and laying the technical foundation for subsequently defending against network attack, along with lower time complexity and storage expenditure.
Owner:中国人民解放军陆军炮兵防空兵学院
Data restoring and synchronizing method based on log snapshot
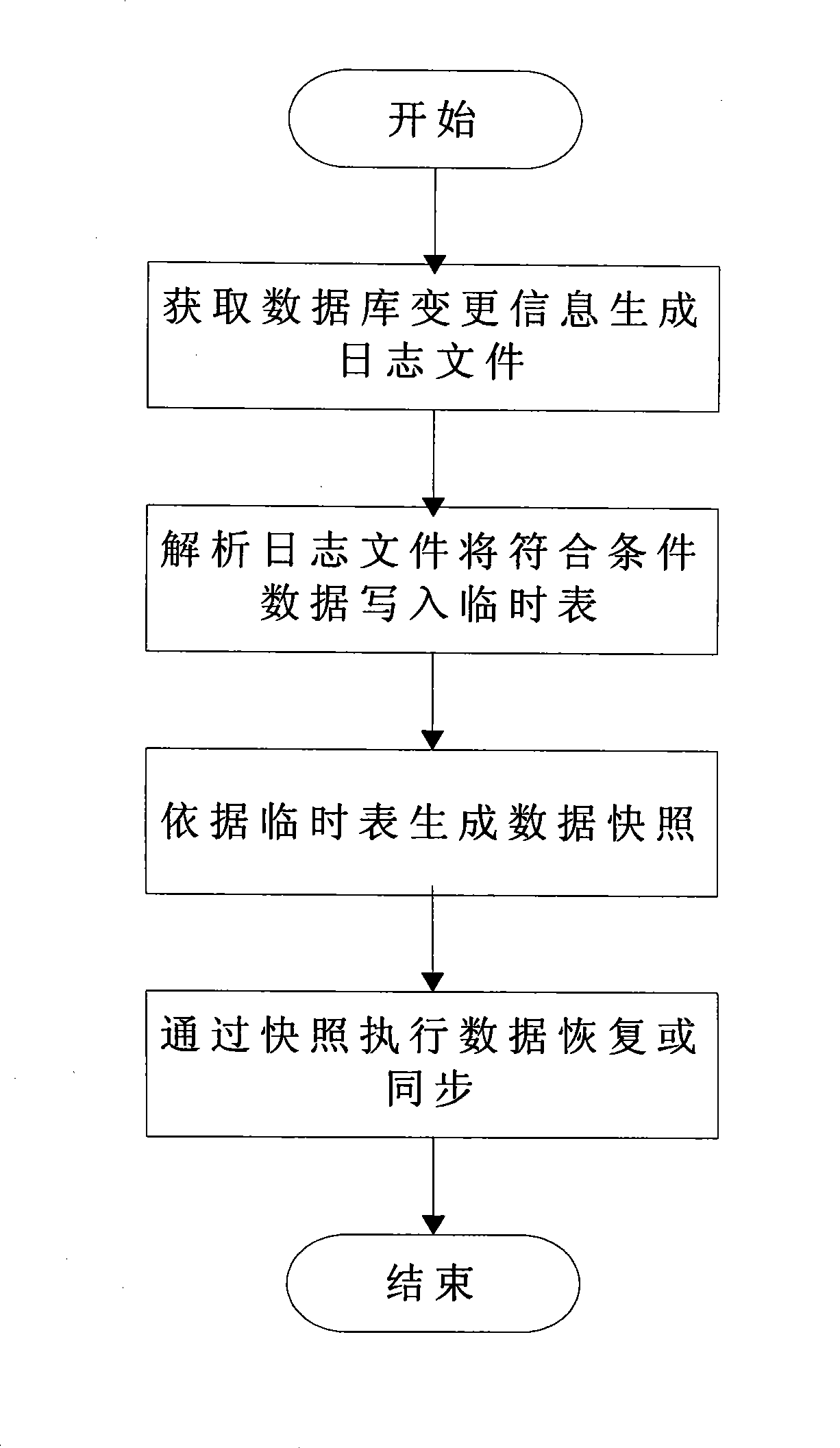
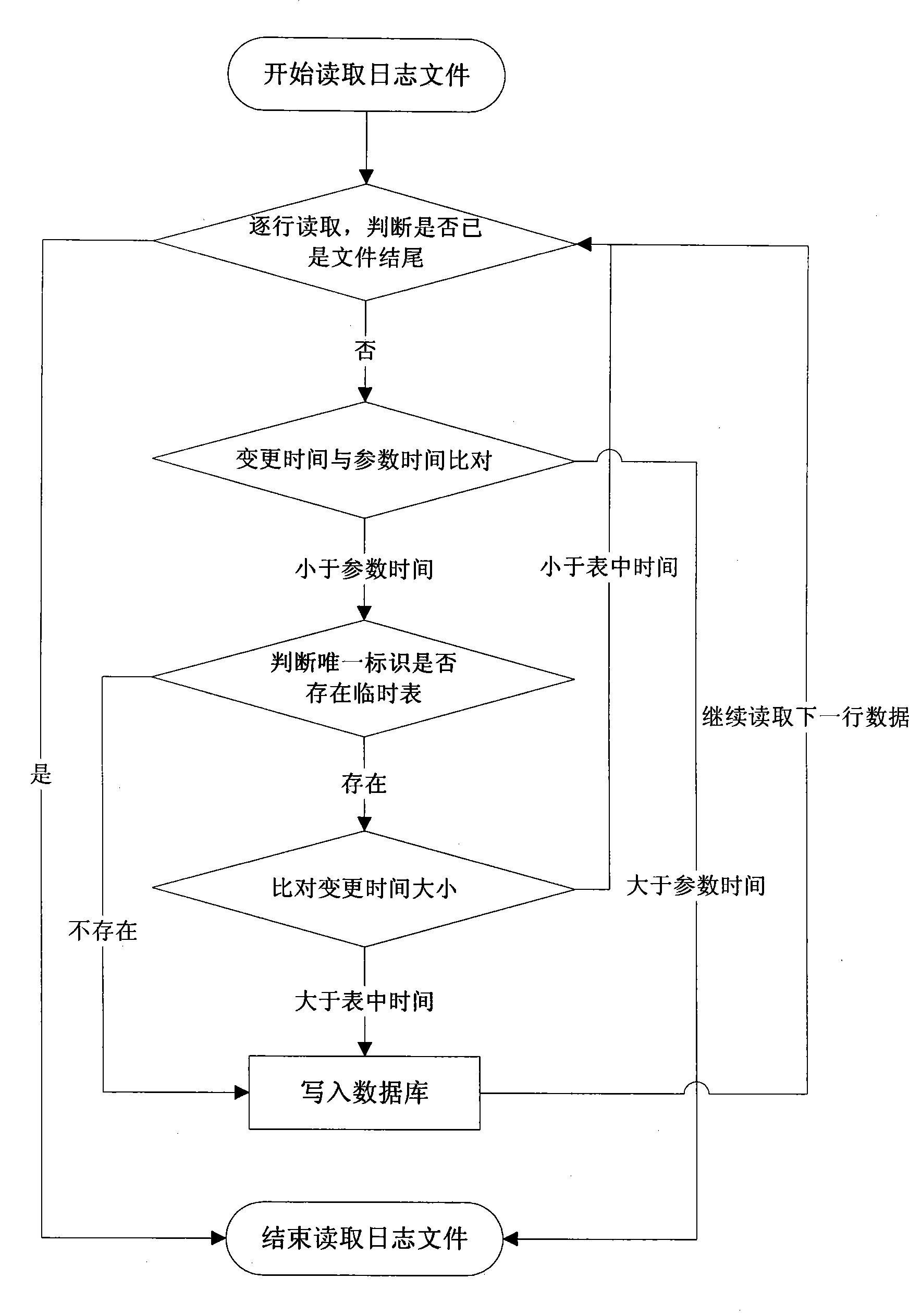
InactiveCN101436207AReduce storage overheadReduce system costSpecial data processing applicationsLogfileData memory
The invention relates to the field of occupation of the mass data memory space and backup and recovery of historical data, and in particular provides a data recovery and synchronization method based on log snapshots. The data recovery and synchronization method based on the log snapshots adopts log files with given format to record changed information of data of databases each time; the changed information is formatted, positioned and stored into the log files; an analytic program calls an approximate algorithm to acquire effective data on set time points by means of multithreading; the data is temporarily stored into a temporary table, and abstract data snapshots are generated according to the temporary table; and data recovery and synchronization is realized by utilization of the snapshots. The data recovery and synchronization method based on the log snapshots can greatly reduce the burden of a database system, obviously improve the efficiency of the database system and an application system, save a great deal of memory space, and reduce the operation cost of the systems.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
Cluster fault-tolerance system, apparatus and method
InactiveCN101369241AGuaranteed to recover correctlyQuick checkError detection/correctionExtensibilityFault tolerance
The invention discloses a cluster fault tolerance system, a device and a method. The system includes: a remote checkpoint server which is used to respond the remote checkpoint request from a faulty node and execute the checkpoint operation; a node faulty checking module which is used to monitor the operating system of a local node and the running state of an assigned process and to trigger a remote checkpoint; and a communication system checkpoint module which is used to realize the checkpoint of the communication device and support the recovery function of communication breakpoint. The invention provides localized fast fault restoration for the parallel processing cluster, has a lower overhead and good expansibility, and makes ideal availability for the cluster system with ten billions and hundred billions calculation scale.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
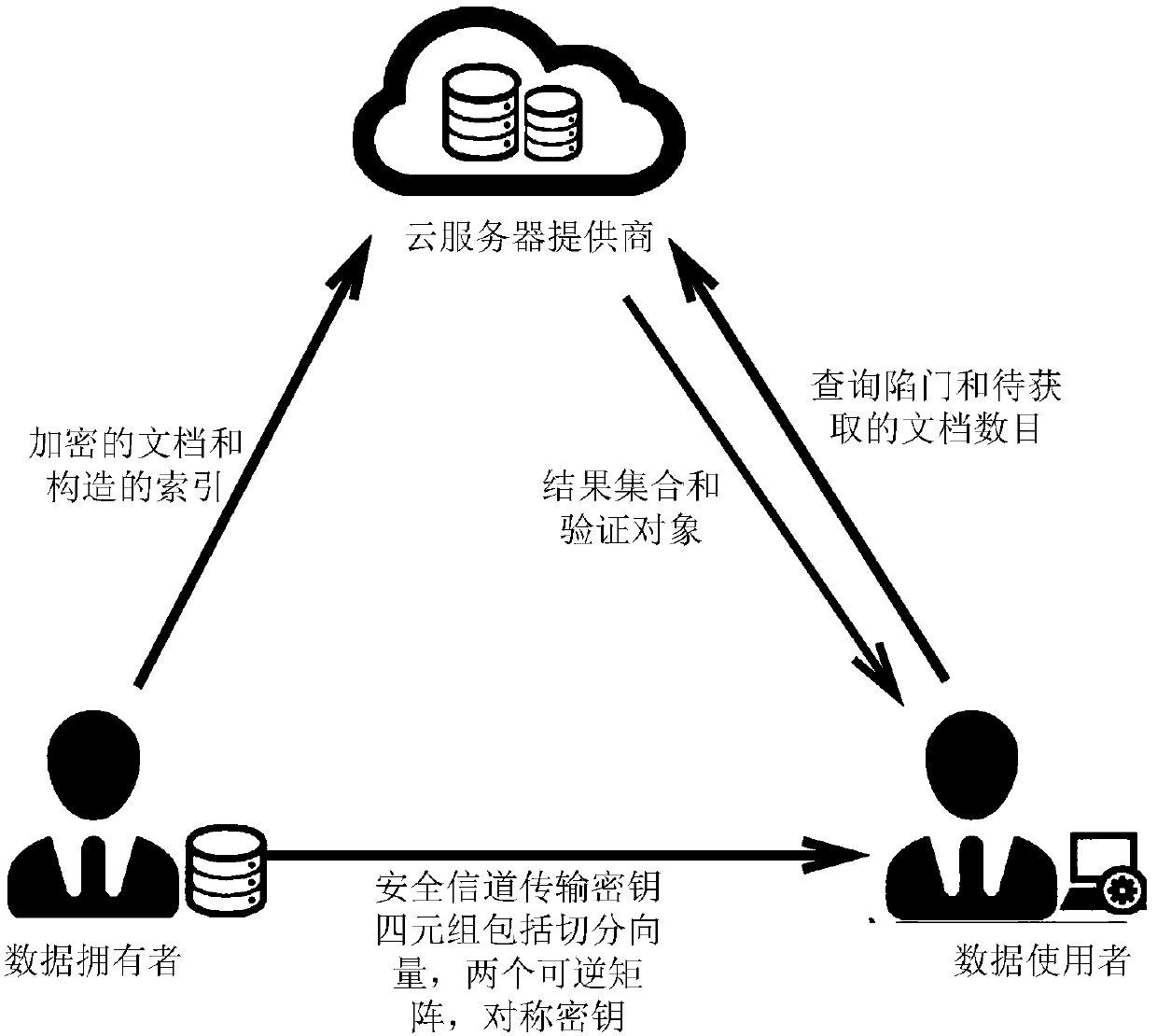
Multi-user supported searchable encryption system and method
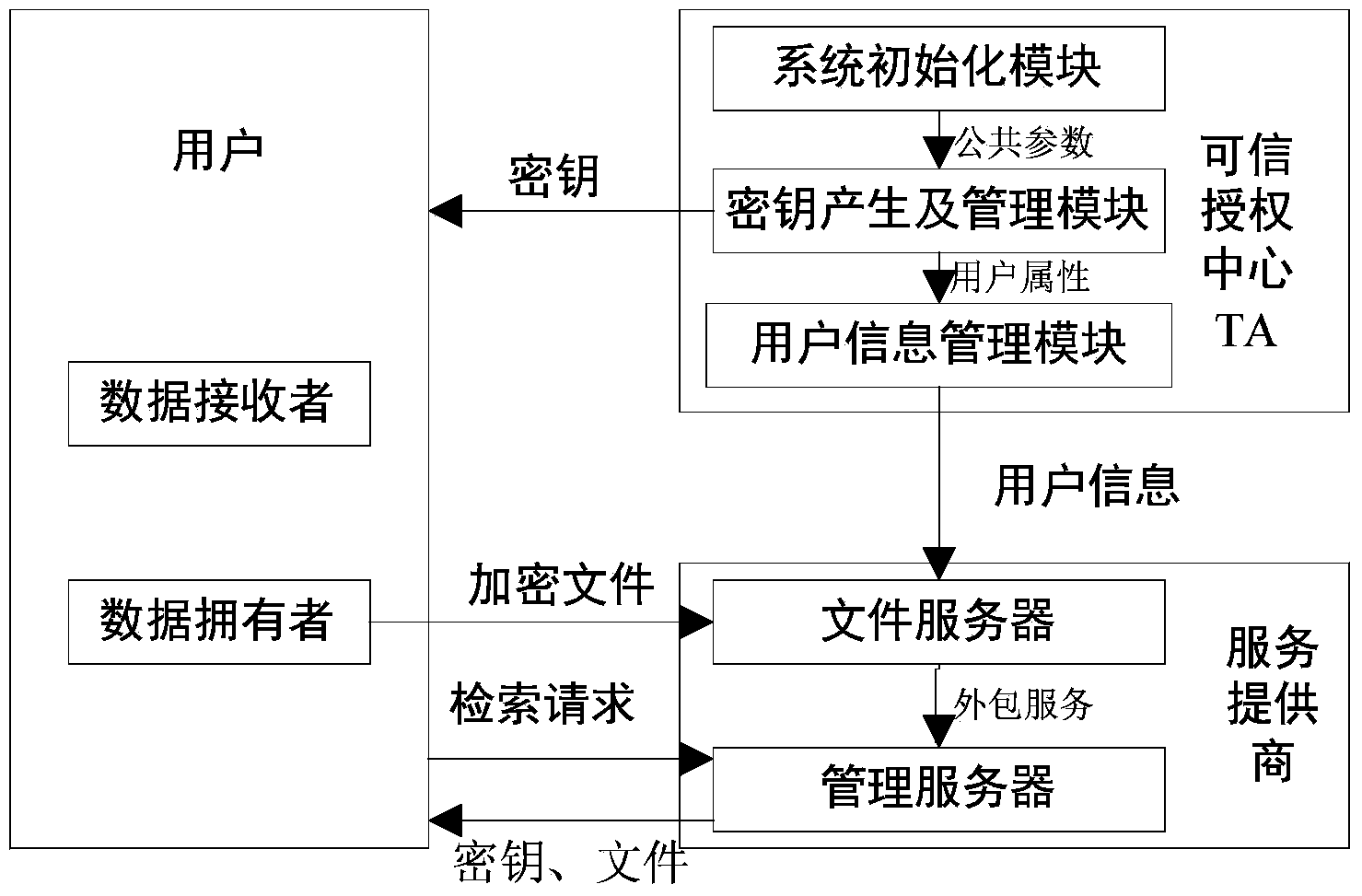
InactiveCN103731432AMeet the actual application needsImprove securityKey distribution for secure communicationSpecial data processing applicationsData providerService provision
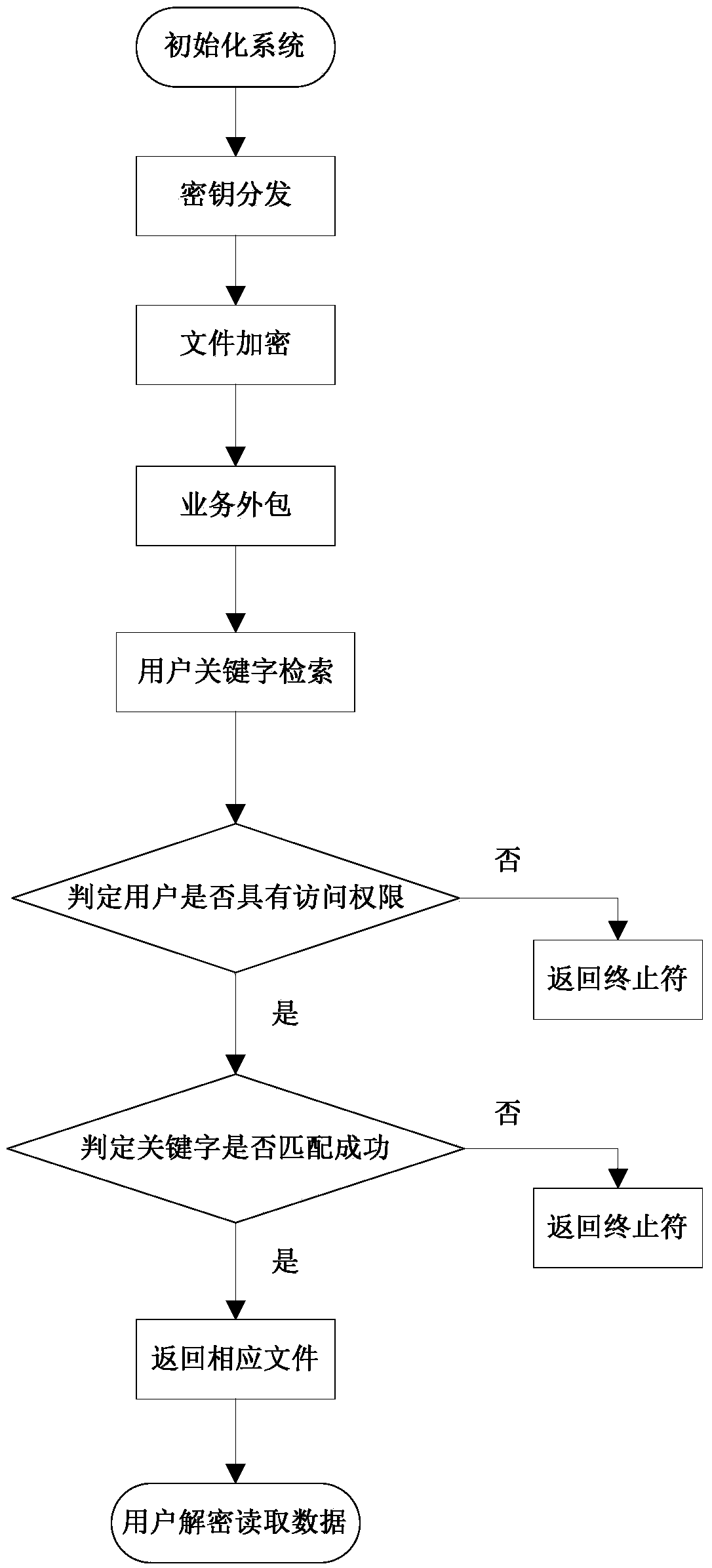
The invention discloses a multi-user supported searchable encryption system and method and accordingly the problem that specific encrypted files cannot be searched accurately in the prior art is mainly solved. The multi-user supported searchable encryption system comprises a credible authorization center TA, service providers and users; the credible authorization center TA is formed by a system initialization module, a secret key generation and management module and a user information management module; the service providers comprise a file server and a management server; the users comprise data providers and data receivers. The multi-user supported searchable encryption method comprises the steps of system initialization, secret key distribution, file encryption, business outsourcing, file retrieval, user decryption and user logout and adding. According to the multi-user supported searchable encryption system and method, the file retrieval time of the users is shortened due to the establishment of a key word index on files, the storage and computational overhead of the users is reduced due to the accurate file retrieval, the file retrieval is accurate, meanwhile the forward and backward security of the files is ensured, and meanwhile the multi-user simultaneous decryption is supported.
Owner:西安电子科技大学昆山创新研究院 +1
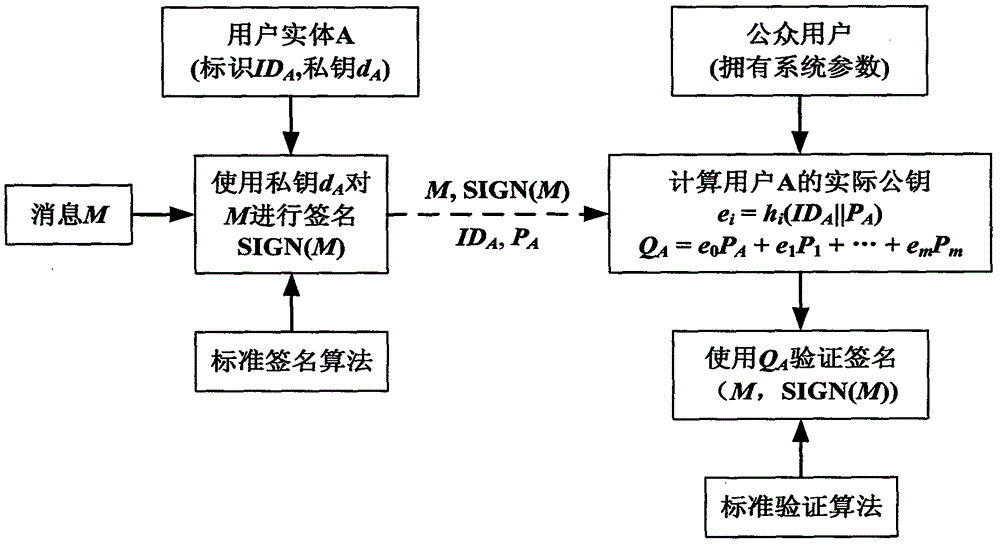
Achievement method of certificate-less public key cryptosystem without bilinear pairing operation
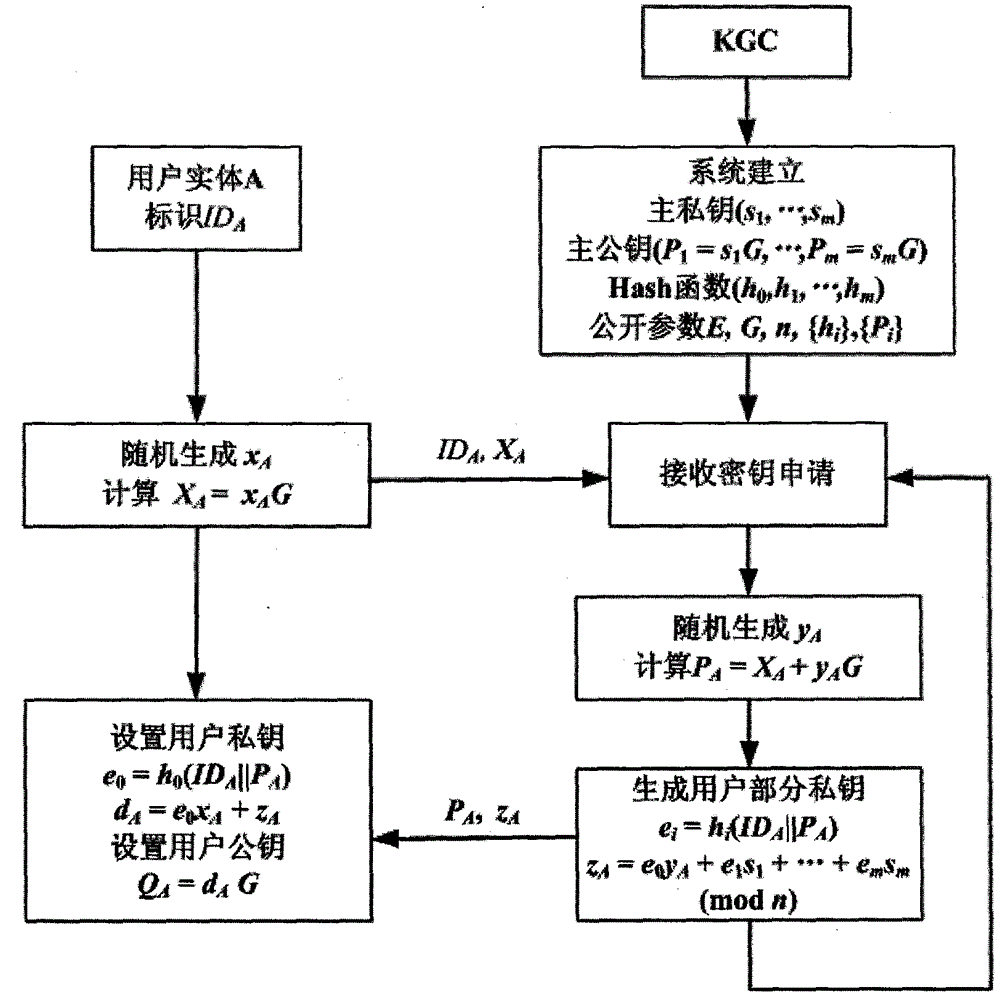
ActiveCN104539423AEfficient managementImprove computing efficiencyPublic key for secure communicationUser identity/authority verificationCommunications securityInformation security
The invention provides an achievement method of a certificate-less public key cryptosystem without bilinear pairing operation and belongs to the field of information safety. The achievement method is used for solving the problems of generation of a secret key of a user, usage and authentication of a public key of the user. According to the achievement method, firstly, a user sets a secret value and calculates a temporary public key, then a secret key generating center generates the other part of the secret key for the user and enables the two parts to be bound, and finally the user synthesizes a his / her actual public and secret key pair. The defect that public key replacement and signature counterfeit possibly exist in a common certificate-less cryptosystem is overcome, the user has complete control right on the secret key, the secret key can be revoked and re-generated, and the signature of the user has non-repudiation. The achievement method adopts a public key cryptographic algorithm of a standard elliptic curve, does not adopt the bilinear pairing operation, is few in occupied resources and high in safety and can operate without the secret key generating center when being applied to signature, authentication and secret key negotiation. By means of the achievement method, identity authentication, communication security and non-repudiation application demands of large-scale systems and low-power-consumption devices can be met.
Owner:北京百旺信安科技有限公司 +1
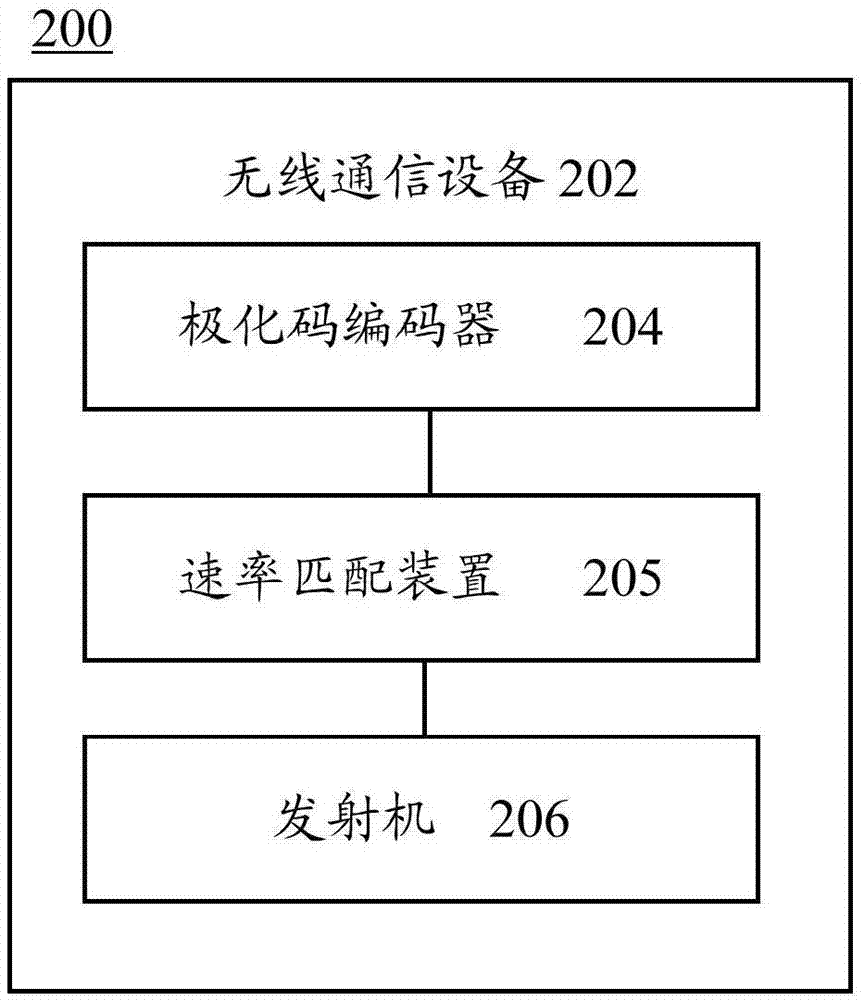
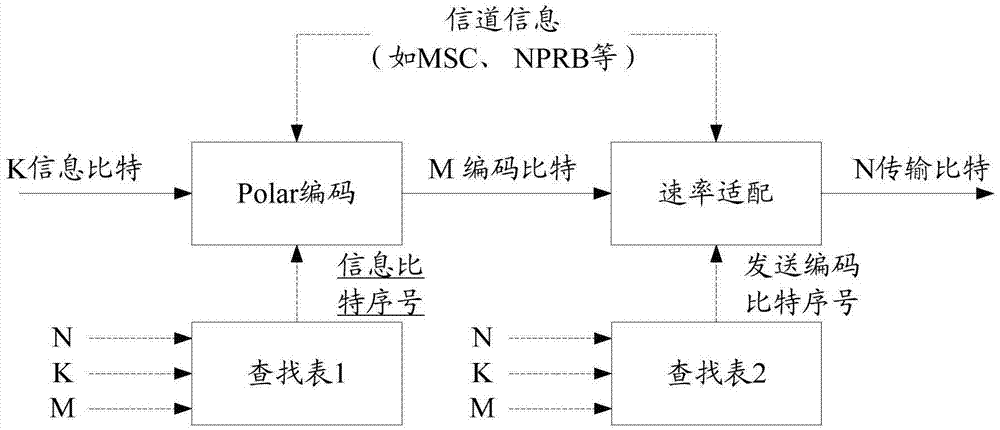
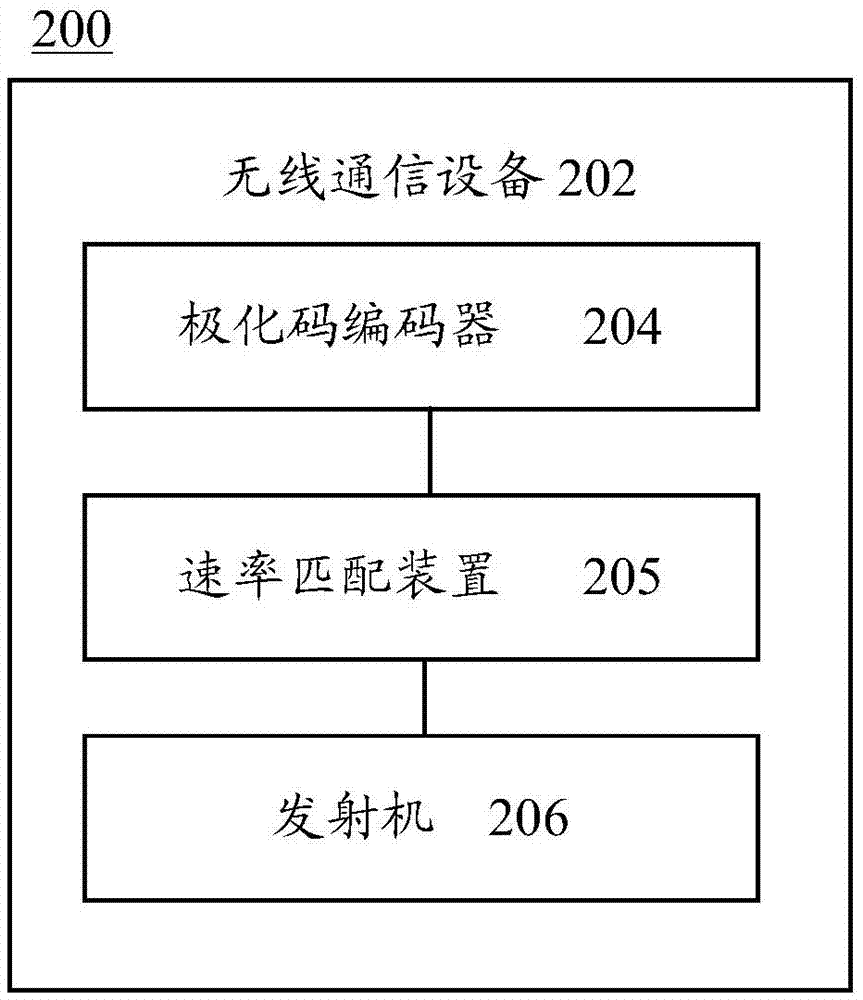
Polarization code processing method and communication device
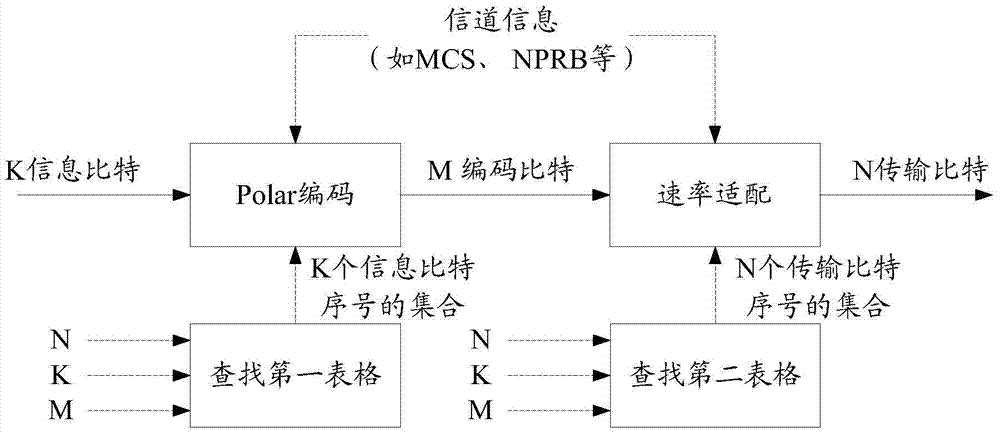
ActiveCN106877973AReduce storage overheadAvoid storage overheadChannel coding adaptationAdaptation strategy characterisationBit numberingCoding block
According to the invention, the information bit number K of a code block to be coded, the transmission bit number N of the code block to be coded during the transmission process in a real channel, and the rate adaption rule of the code block to be coded are determined, the reliability of each bit in M uncoded bits in the code block to be coded is determined by means of the reliability of each bit in N transmission bits, and therefore K information bits can be determined from the M uncoded bits, and the set A formed by sequence numbers of the information bits is used for the coding or decoding process of a Polar code. Thus, the invention can provide a method for coding or decoding the Polar code on line by means of a communication device.
Owner:HUAWEI TECH CO LTD
Efficient verifiable multi-keyword sequencing searchable encryption method supporting preference search and logic search
ActiveCN108388807AEffective pruningNarrow down the search spaceDigital data protectionTransmissionCiphertextCryptogram
The invention discloses an efficient verifiable multi-keyword sequencing searchable encryption method supporting a preference search and a logic search. The encryption method comprises the following steps that a data owner encrypts a document, constructs a cryptogram index based on a document collection, generates summary information of the document by utilizing a secret key and the content of thedocument, and then sends a cryptogram document, an encrypted index and the summary information to a cloud server; a data user shares the information of the secret key, which is generated by the dataowner, generates a query trap door according to a query, and sends an encrypted query trap door and the number K of to-be-obtained documents to the cloud server; the cloud server can execute safe inner product operation after receiving the cryptogram index and the query trap door, searches for K documents most relevant to the query of the user, sequences according to relevant values among the K documents and the query, then generates verification objects, and finally returns the most relevant K documents and the verification objects to the data user, and the data user verifies the correctnessand completeness of a return result through a verification algorithm.
Owner:SOUTH CHINA UNIV OF TECH
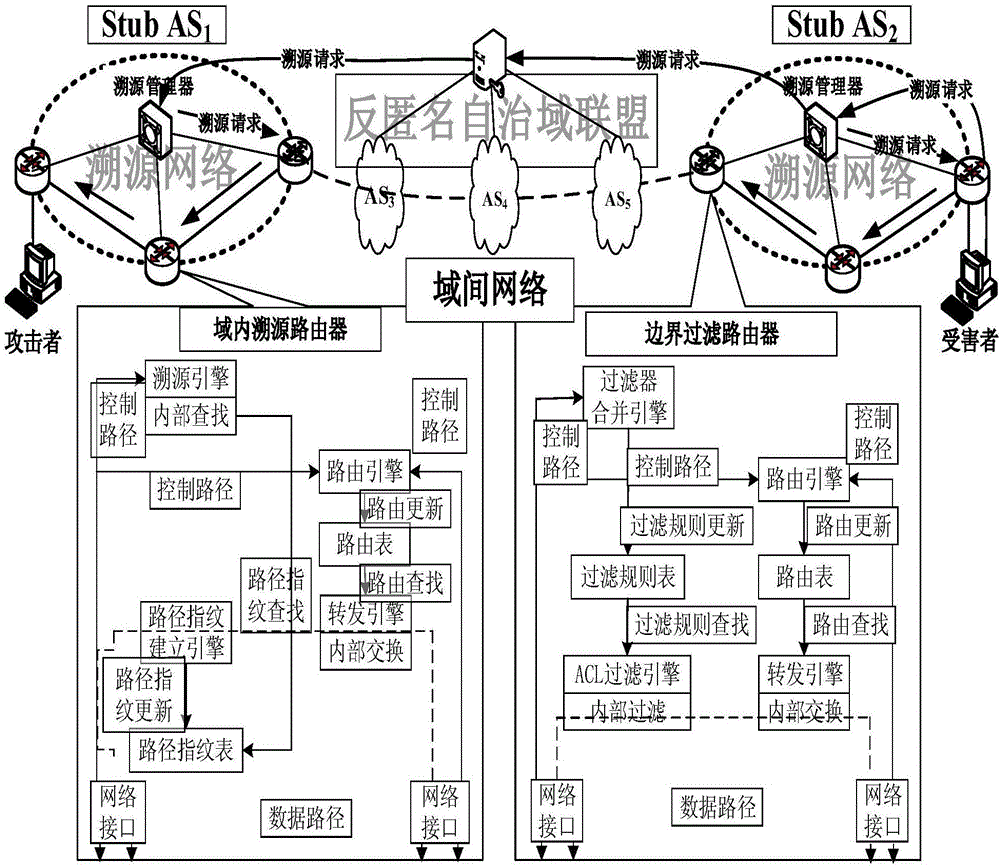
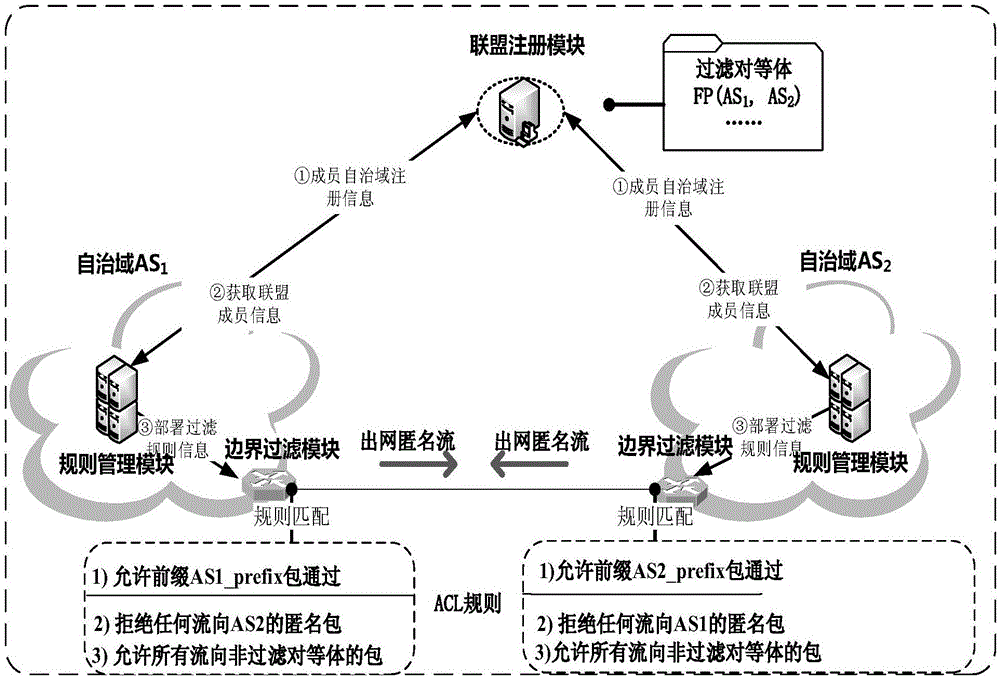
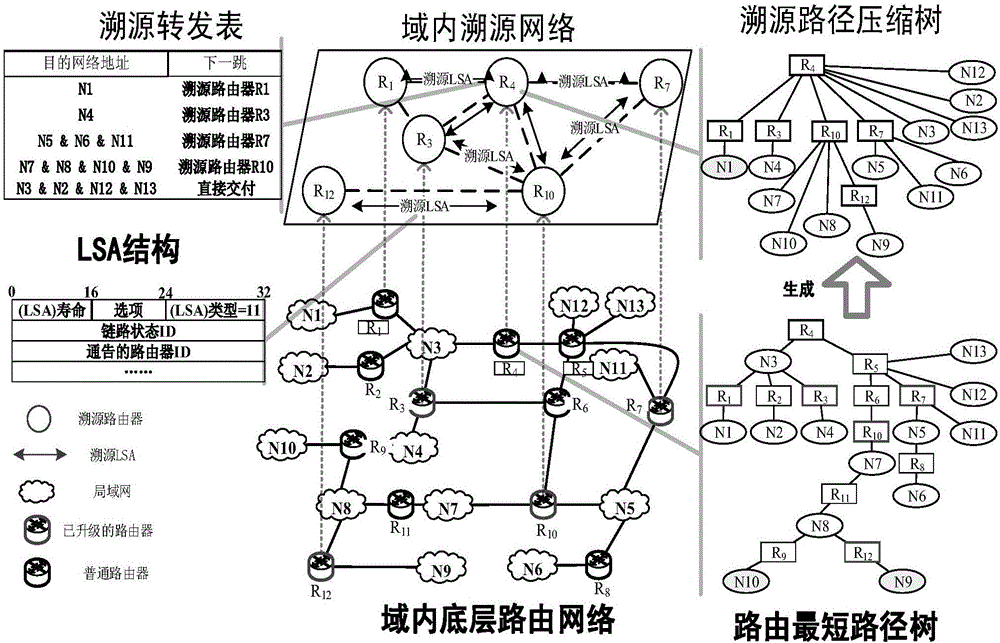
Dynamically extensible and efficient single packet tracing method
The invention discloses a dynamically extensible and efficient single packet tracing method. The method comprises the following steps: in an inter-domain network composed of transit domains, constructing an anti-anonymous union by using all tracing Stub domains, wherein the anti-anonymous union configures ACL filtering rules on boundary routers of the tracing Stub domains, so that all anonymous packets entering the inter-domain network are cleared; constructing a tracing network in the tracing Stub domains, and establishing path fingerprint in the tracing network; and after the occurrence of attack, a network service provider directly locates an attack domain via the source address and an inlet router of the anonymous packet by using the anti-anonymous union, and then reduces an attack path through the extracted path fingerprint. By adoption of the dynamically extensible and efficient single packet tracing method disclosed by the invention, the coupling between autonomous domains is weakened so as to achieve the purpose of phased management and flexible control, and the leakage of the network topology privacy is avoided as well, which is beneficial to the expansion of the scale of the tracing system.
Owner:东北大学秦皇岛分校
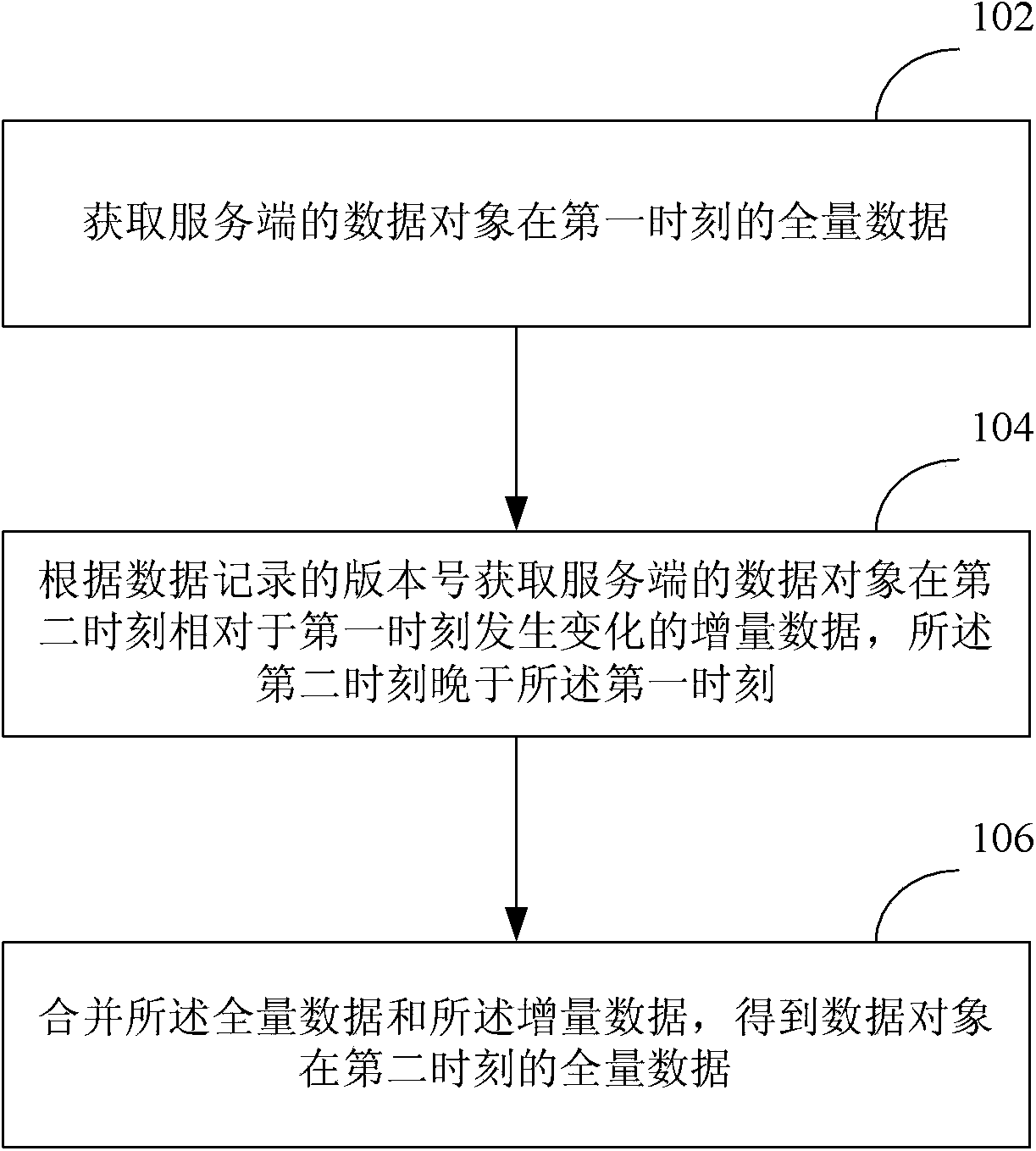
Method and device for client side and server side data synchronization
InactiveCN103678494AReduce complexityReduce the number of interactionsTransmissionSpecial data processing applicationsData synchronizationClient-side
The invention discloses a method and device for client side and server side data synchronization and belongs to the field of database technologies. The method includes the steps that total data of a data object of a server side at a first moment are obtained; according to version numbers of data records, incremental data, changing relative to the first moment, of the data object of the server side at a second moment are obtained, wherein the second moment is later than the first moment; the total data and the incremental data are merged, so that total data of the data object at the second moment are obtained. According to the method and device, the number of times of interaction and the data size of interaction transmission between the client side and the server side can be reduced, and storage consumption of the client side can be reduced.
Owner:BEIJING QIHOO TECH CO LTD +1
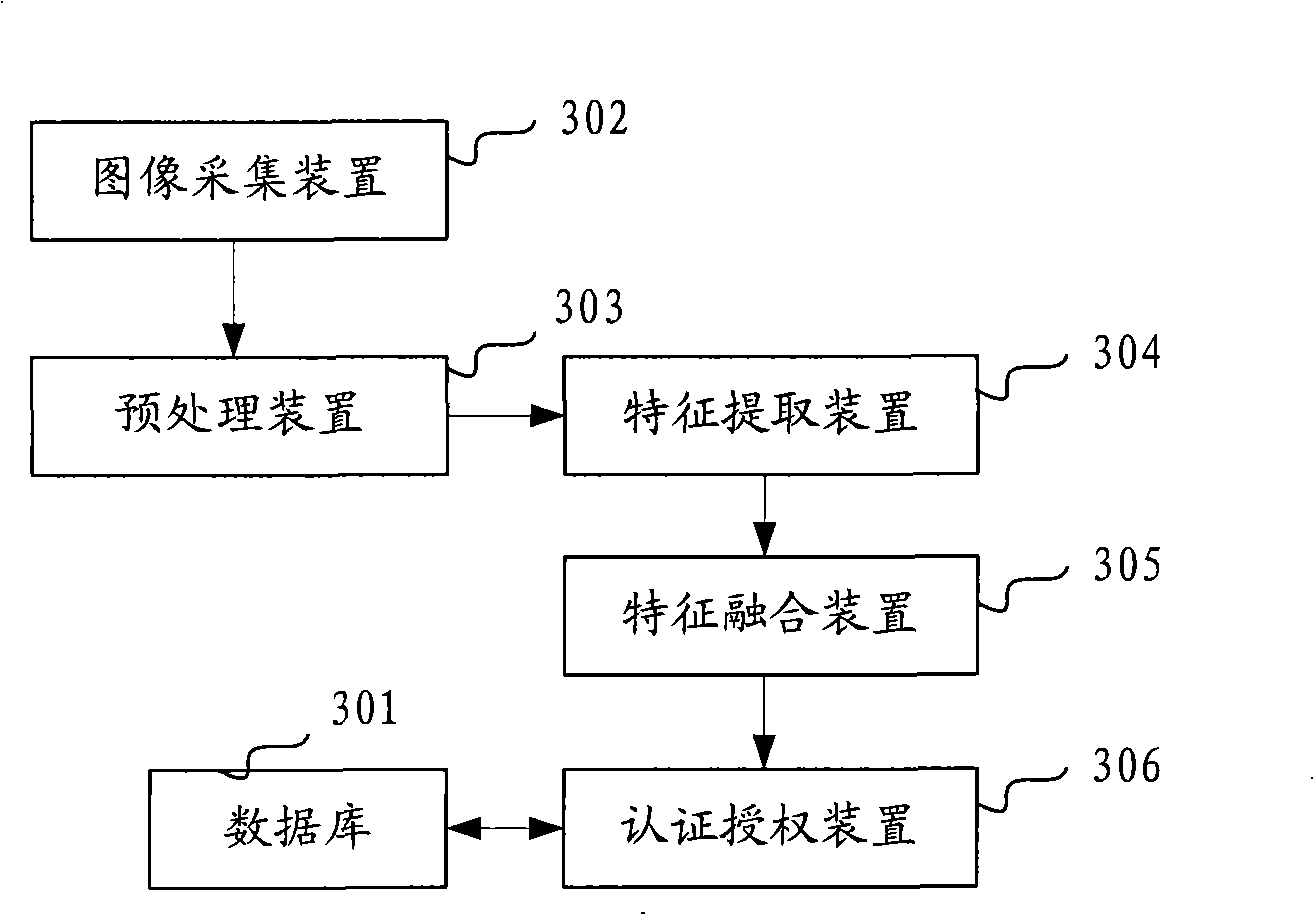
Authentication authorization method and system
InactiveCN101303724AEasy to useImprove securityComplete banking machinesAcutation objectsUser needsPassword
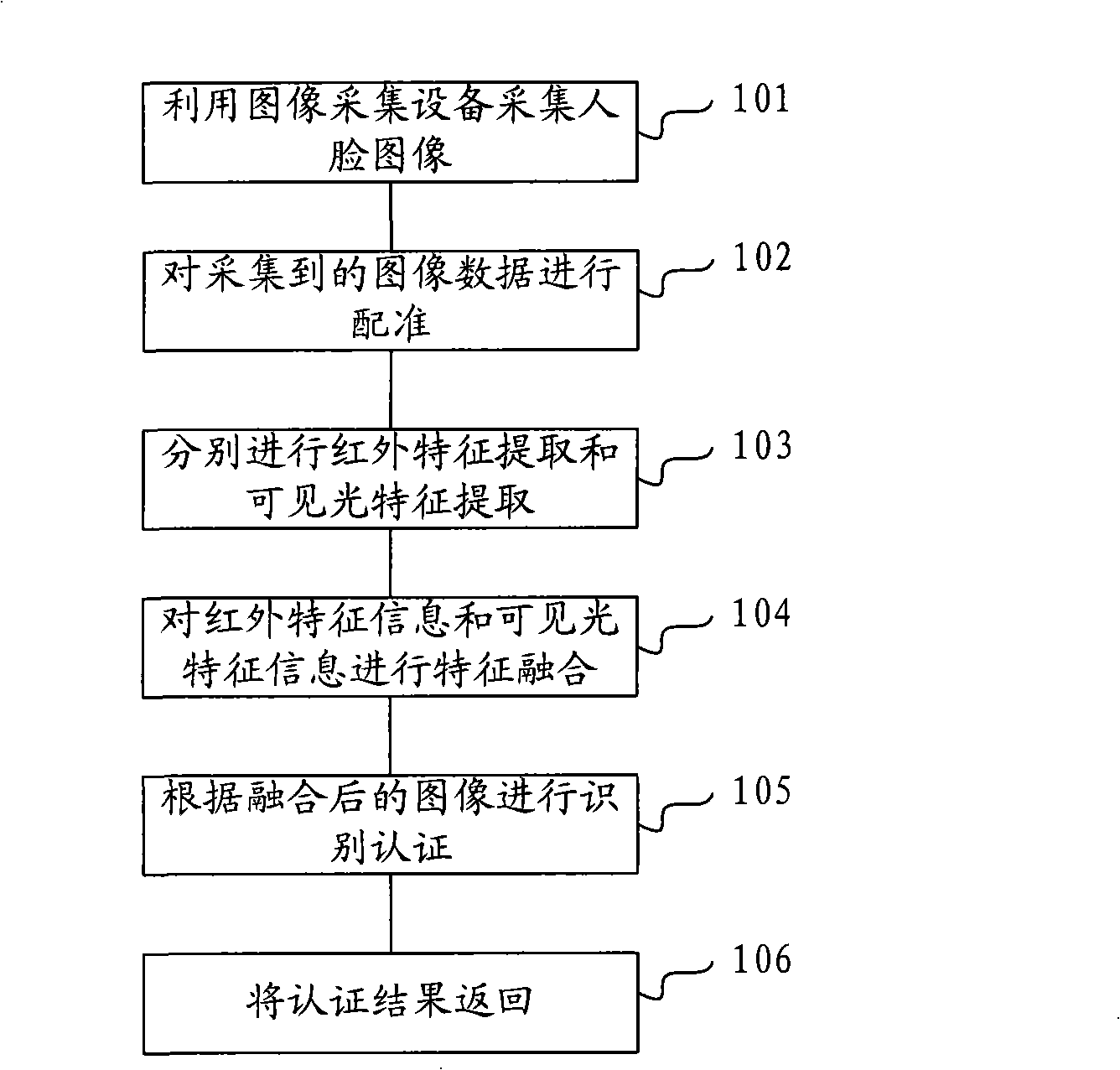
The invention discloses an authentication authorization method and an authentication authorization system and solves the problem that the traditional authentication authorization method is ineffective when the passwords are deciphered or stolen. The method includes: respectively collecting infrared image data and visible light image data on the same image; extracting the infrared characteristic information and the visible light characteristic information; carrying out characteristic integration treatment on the infrared characteristic information and the visible light characteristic information to generate the characteristic information of one image; comparing the image characteristics after being integrated with the pre-memorized image characteristics to carry out authentication authorization. Compared with the traditional password authentication authorization method, the authentication authorization method of the invention based on face identification has high safety and no dangers that the passwords are deciphered or stolen; besides, a user need not to memorize the passwords, thus being more convenient for using. The invention also discloses an authentication authorization system and a terminal system that is matched to be used. The invention can be used in the authentication process of face identification.
Owner:CHINA UNIONPAY
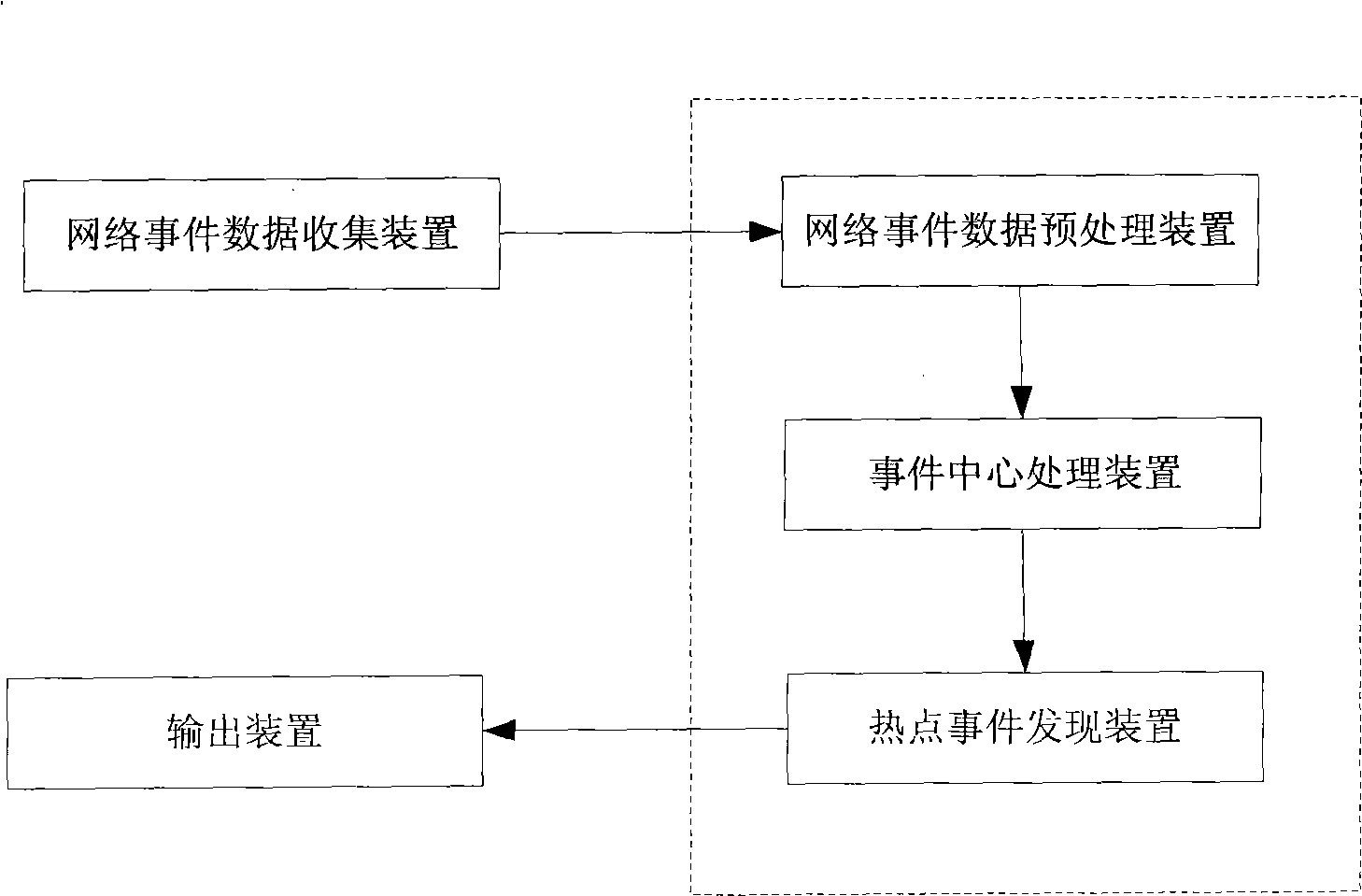
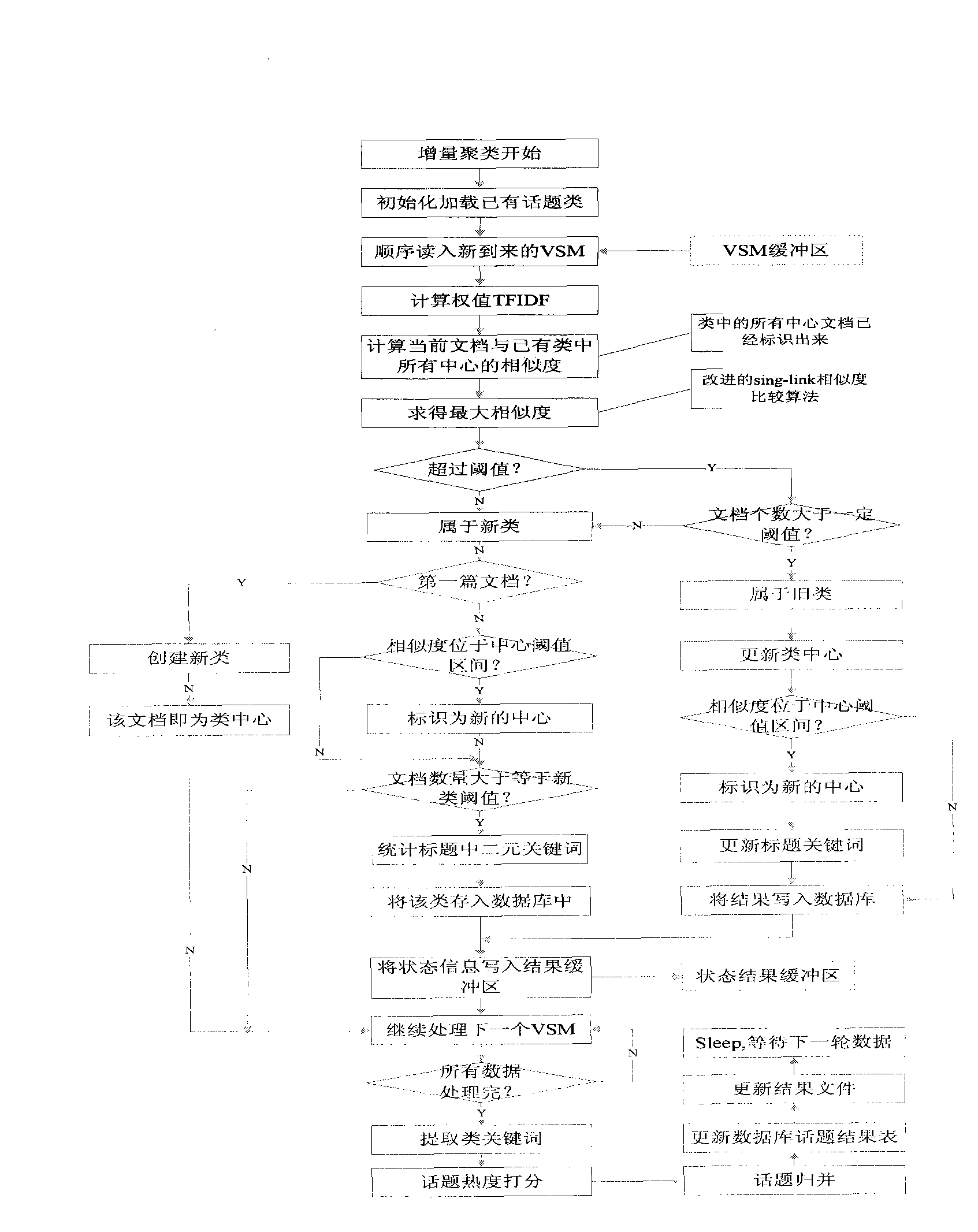
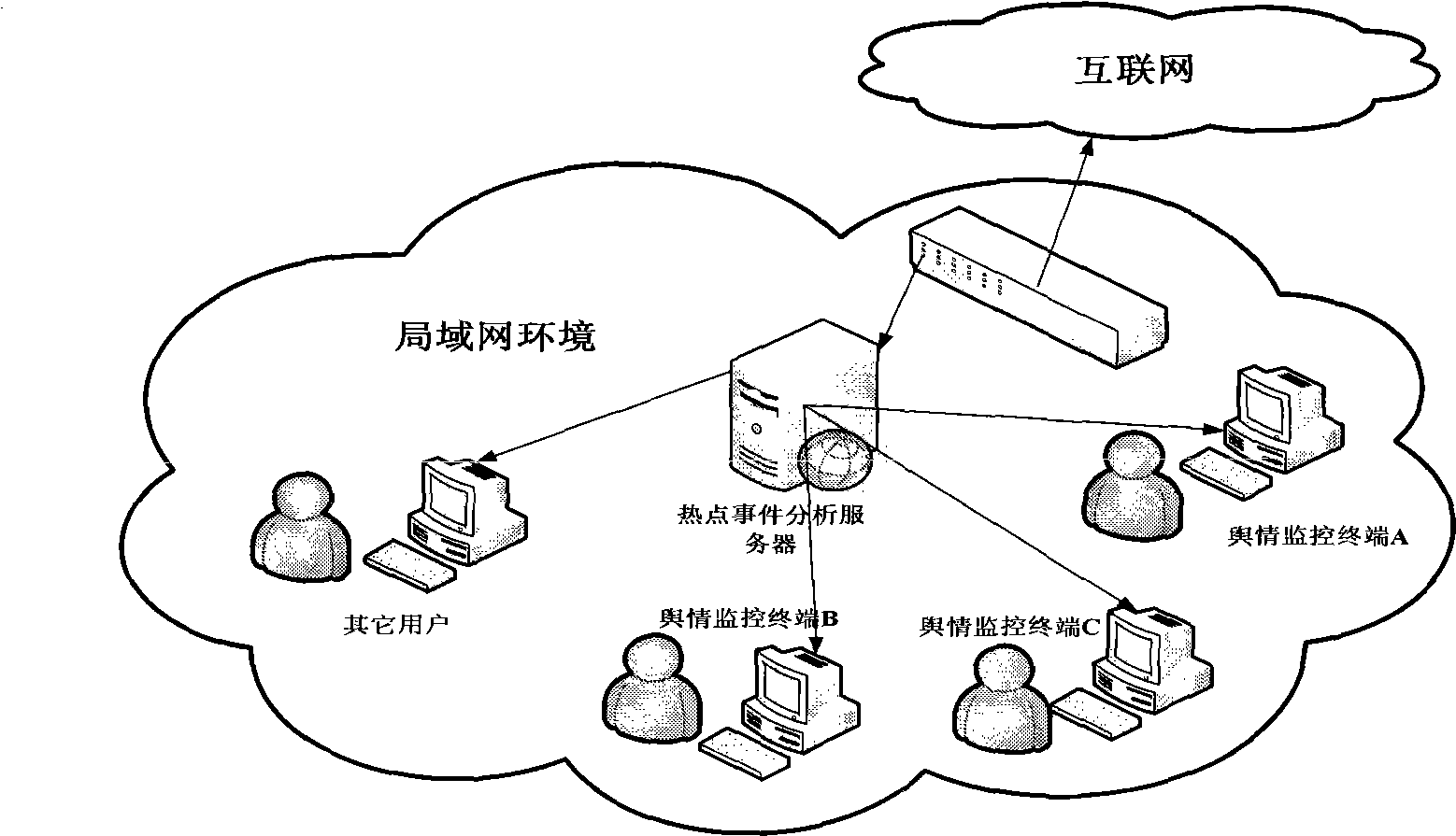
Real-time multi-view network focus event analysis apparatus and analysis method
InactiveCN101488150AUnderstand comprehensivelyReduce calculationSpecial data processing applicationsThe InternetEvent data
The invention provides a real-time multi-view network hotspot event analyzing device and an analyzing method thereof. The analyzing device comprises a network event data collecting device, a network event data preprocessing device, an event central processing device and an output device. The analyzing method comprises a network event information collecting step, a network event spotting step, a network event central initializing step, a network event similarity comparing step, a network event multi-center generating step and a hotspot event outputting step. With the device and the method thereof adopted, hotspot event information currently published on the internet can be real-timely spotted and the developing process of the event can be shown in multi-views to help network management personnel to know the trend of network hotpot events more comprehensively.
Owner:HARBIN ENG UNIV
Apparatus and Method for Read Optimized Bulk Data Storage
ActiveUS20110010330A1Reliable handlingAvoid overheadDigital data information retrievalDigital data processing detailsData warehouseData store
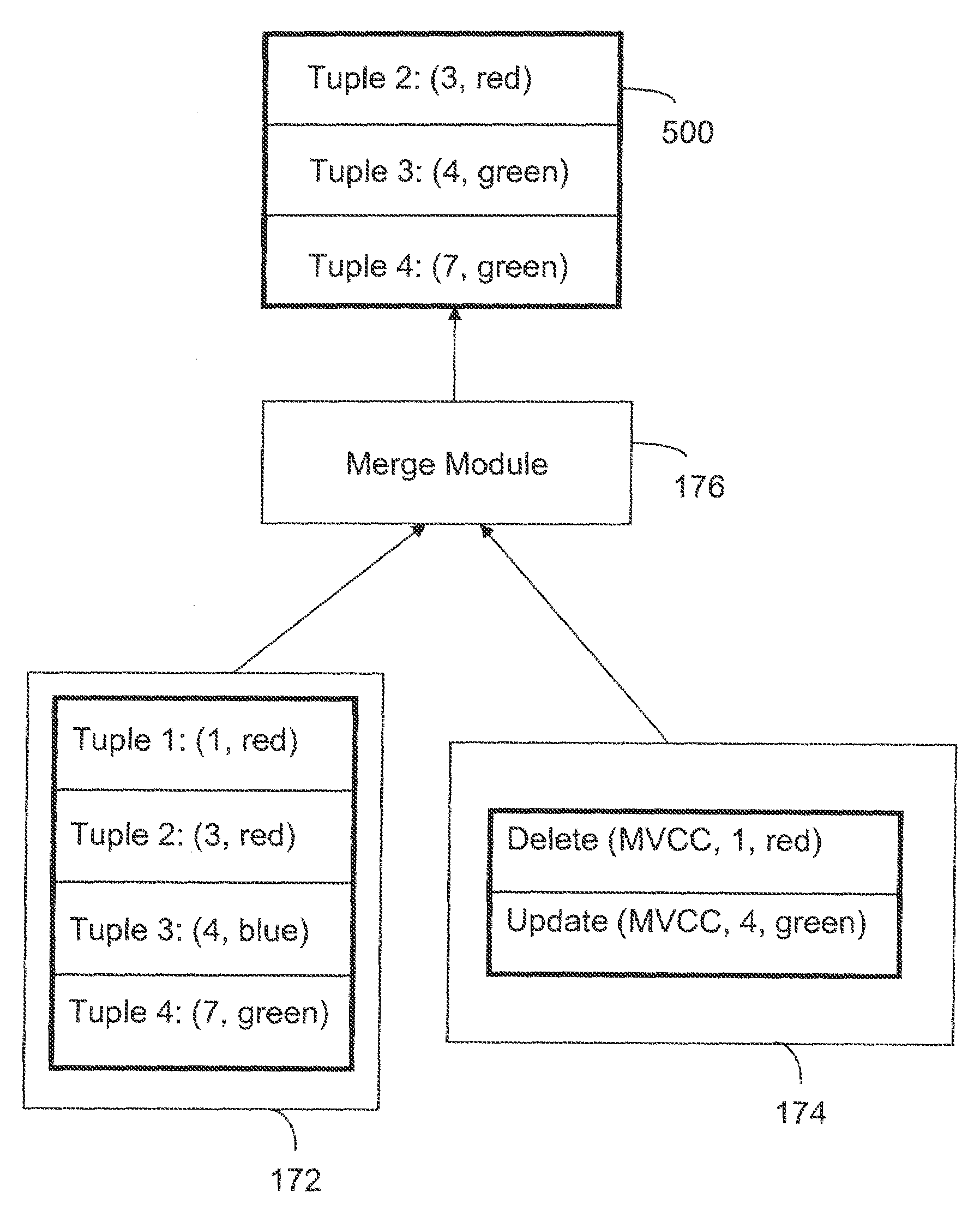
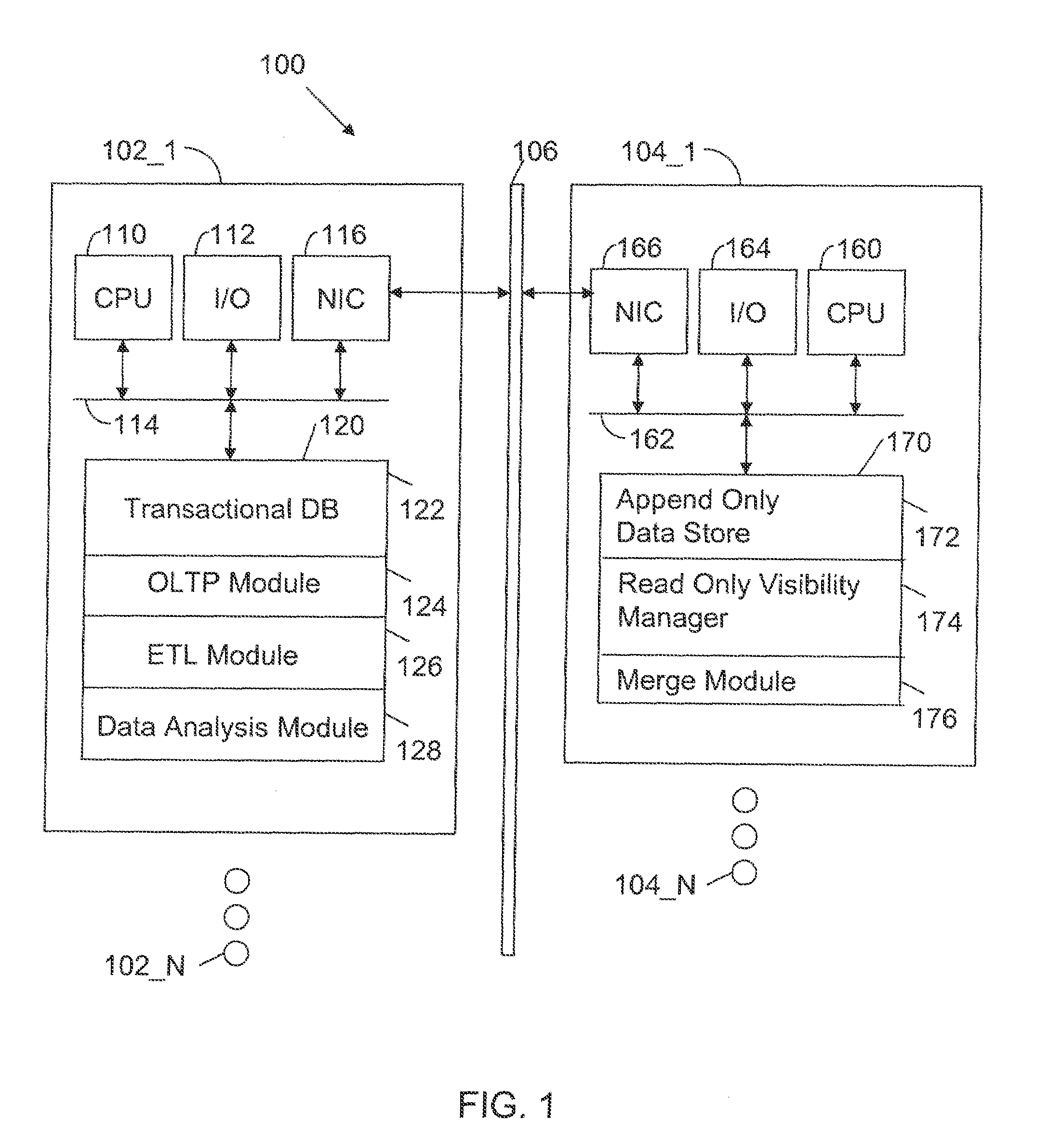
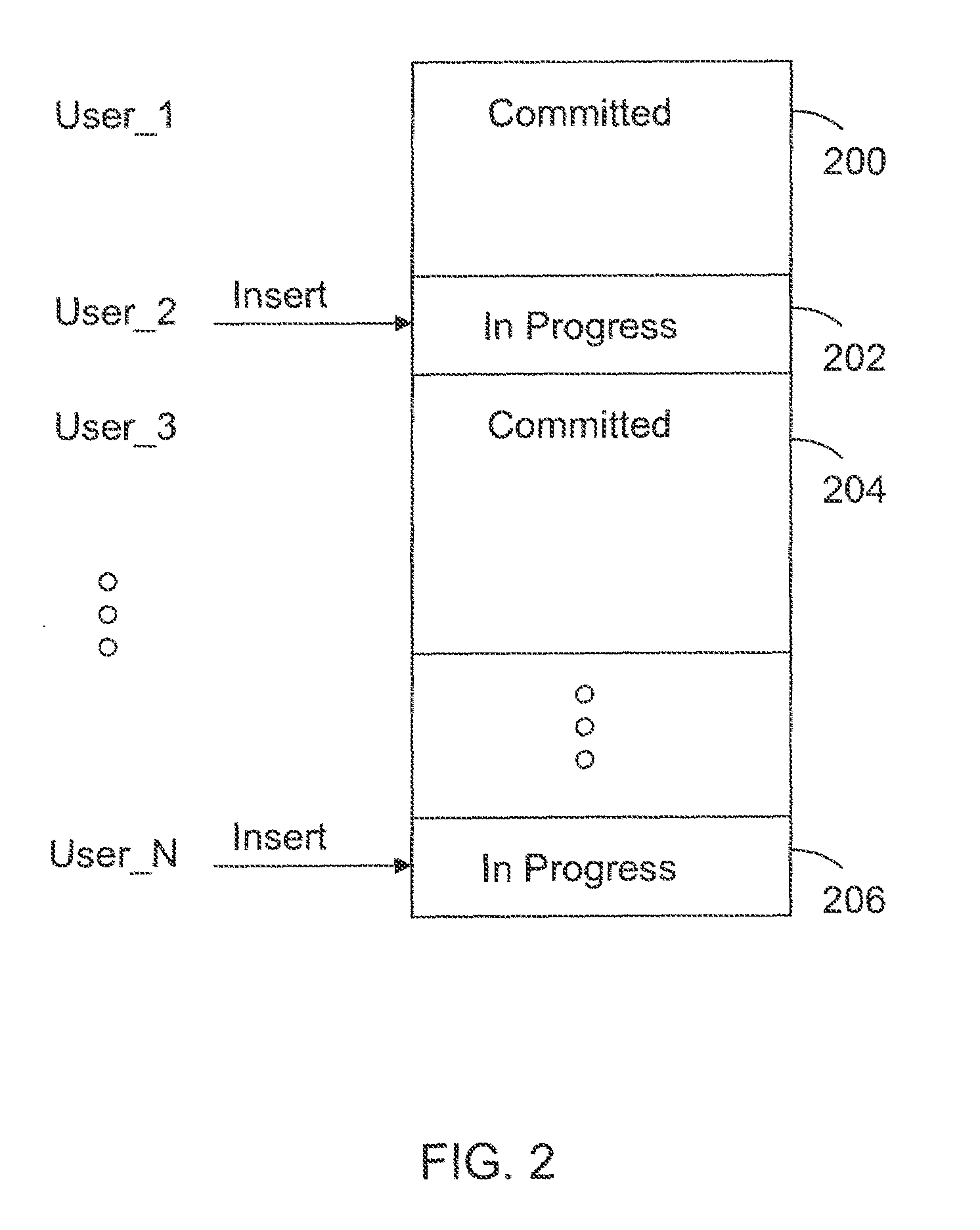
A computer readable storage medium includes executable instructions to store load data in new rows of an append only table within a data warehouse, without updating or deleting existing rows in the append only table. The new rows are added in a database transaction that guarantees that the distributed reads and writes of all transactions are processed reliably and that the transactions obey snapshot isolation rules. Data changes associated with the load data are maintained in a separate update table. Data from the append only table is merged with data changes from the update table to supply read data.
Owner:GOPIVOTAL
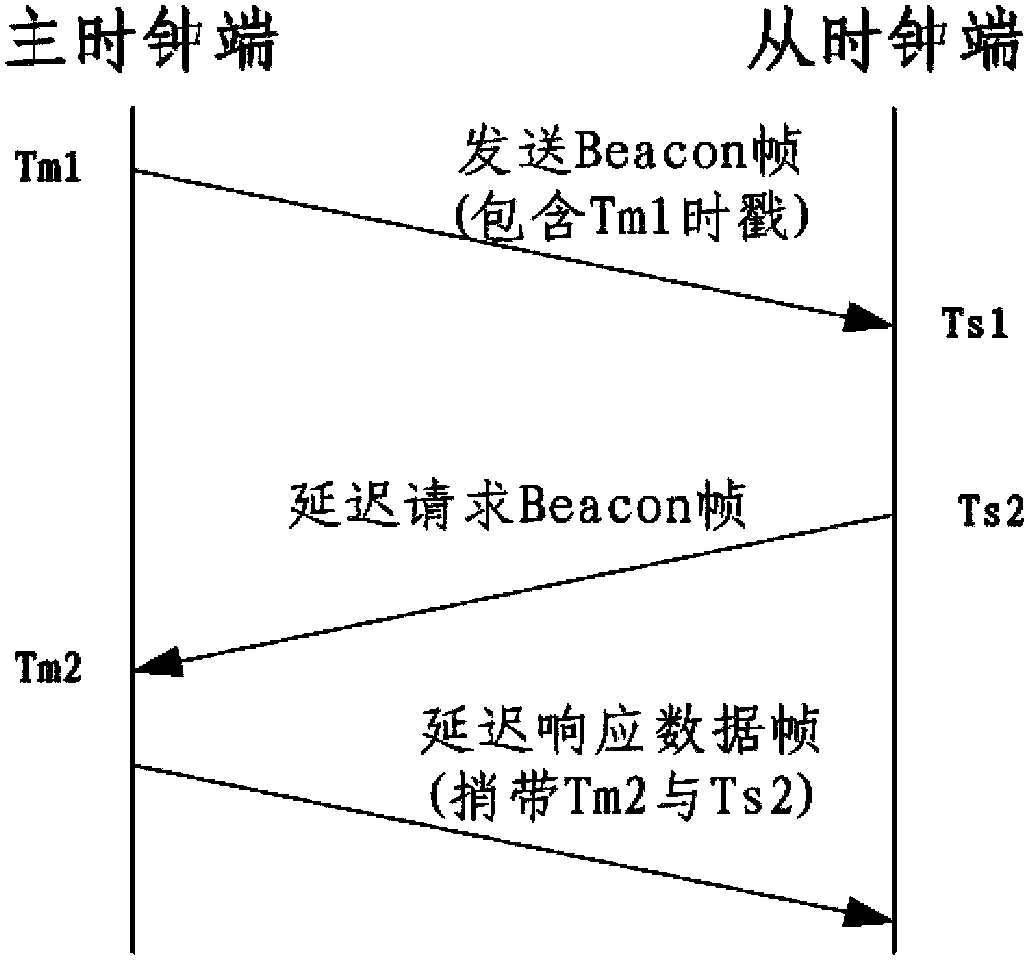
Method for precisely synchronizing time of industrial wireless network on basis of prediction and compensation
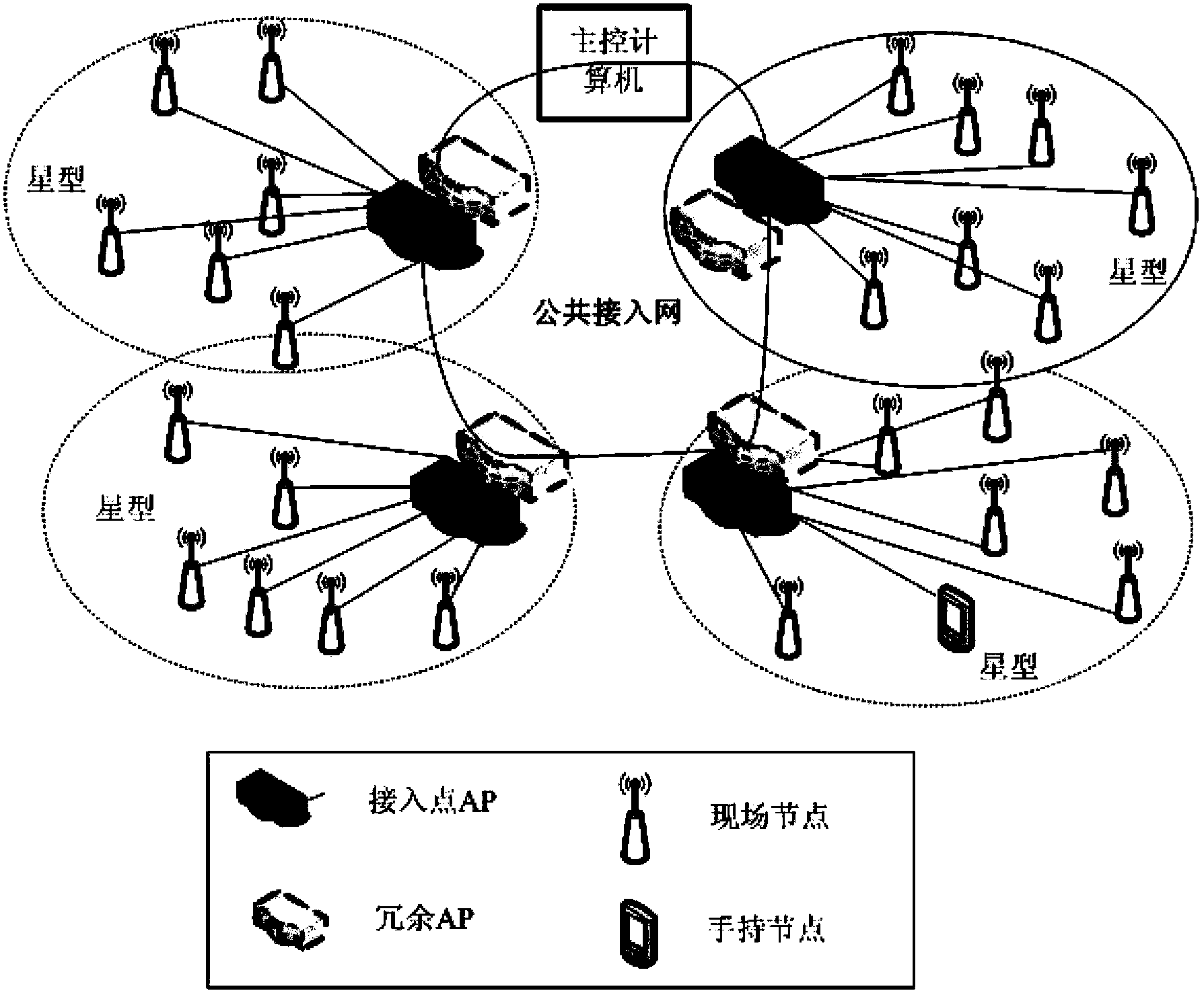
The invention relates to technologies for industrial wireless networks, in particular to a method for precisely synchronizing time of an industrial wireless network on the basis of prediction and compensation. The method includes constructing the factory-automation-oriented industrial wireless network into a star network on the basis of an IEEE (institute of electrical and electronics engineers) 802.11 single-hop basic service set (BBS) structure; setting a master clock and slave clocks according to types and functions of nodes in the industrial wireless network; enabling a master clock side and slave clock sides to interact with one another via two-way timestamp information and computing a time deviation value of a current synchronizing cycle; predicting a time deviation value of a next synchronizing cycle by the aid of the time deviation value of the current synchronizing cycle; compensating clock drift by the aid of the predicted time deviation value of the next synchronizing cycle and correcting the clocks. The method has the advantages that the method is implemented on the premise that application requirements of factory automation are sufficiently considered, so that high time synchronization precision can be realized by the aid of few wireless communication resources, and purposes of high precision, high efficiency, low expenditure and easiness in implementation can be achieved.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
Method used for processing polarization code and communication device
ActiveCN106899379AImprove coding efficiencySave spaceCode conversionChannel coding adaptationComputer scienceSerial code
The embodiment of the invention discloses a method used for processing a polarization code and a communication device. The method comprises the steps of obtaining a first serial number set of M uncoded bits corresponding to the number M of target coded bits based on preset first mapping relationship information and the number M of the target coded bits, wherein the first mapping relationship information is used for indicating a one-to-one correspondence relationship between the number of the multiple coded bits and the serial number set of the multiple uncoded bits, the M uncoded bits comprise K information bits, and the M target coded bits are obtained after the M uncoded bits are subjected to polarization coding; and selecting K serial numbers from the first serial number set of the M uncoded bits according to a preset first selecting rule to serve as a serial number set of the K information bits. In the embodiment, the corresponding relationship between the length 2n of the coded bits and the serial number set of the uncoded bits can only be included, so the storage space is greatly reduced, and the coding and decoding efficiency of the polarization code is improved.
Owner:HUAWEI TECH CO LTD
Method and system for carrying out multi-dimensional regional inquiry on distribution type sequence table
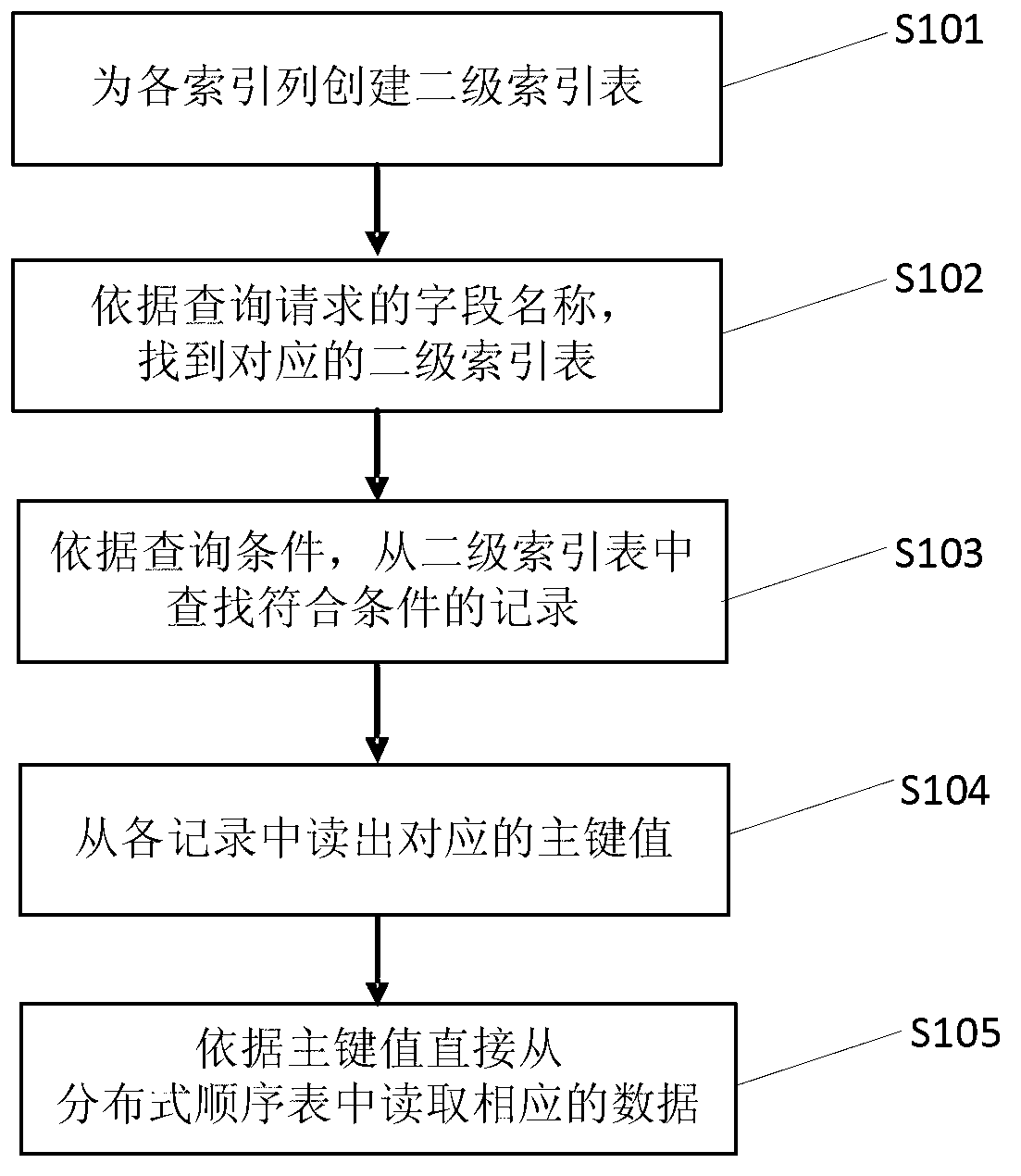
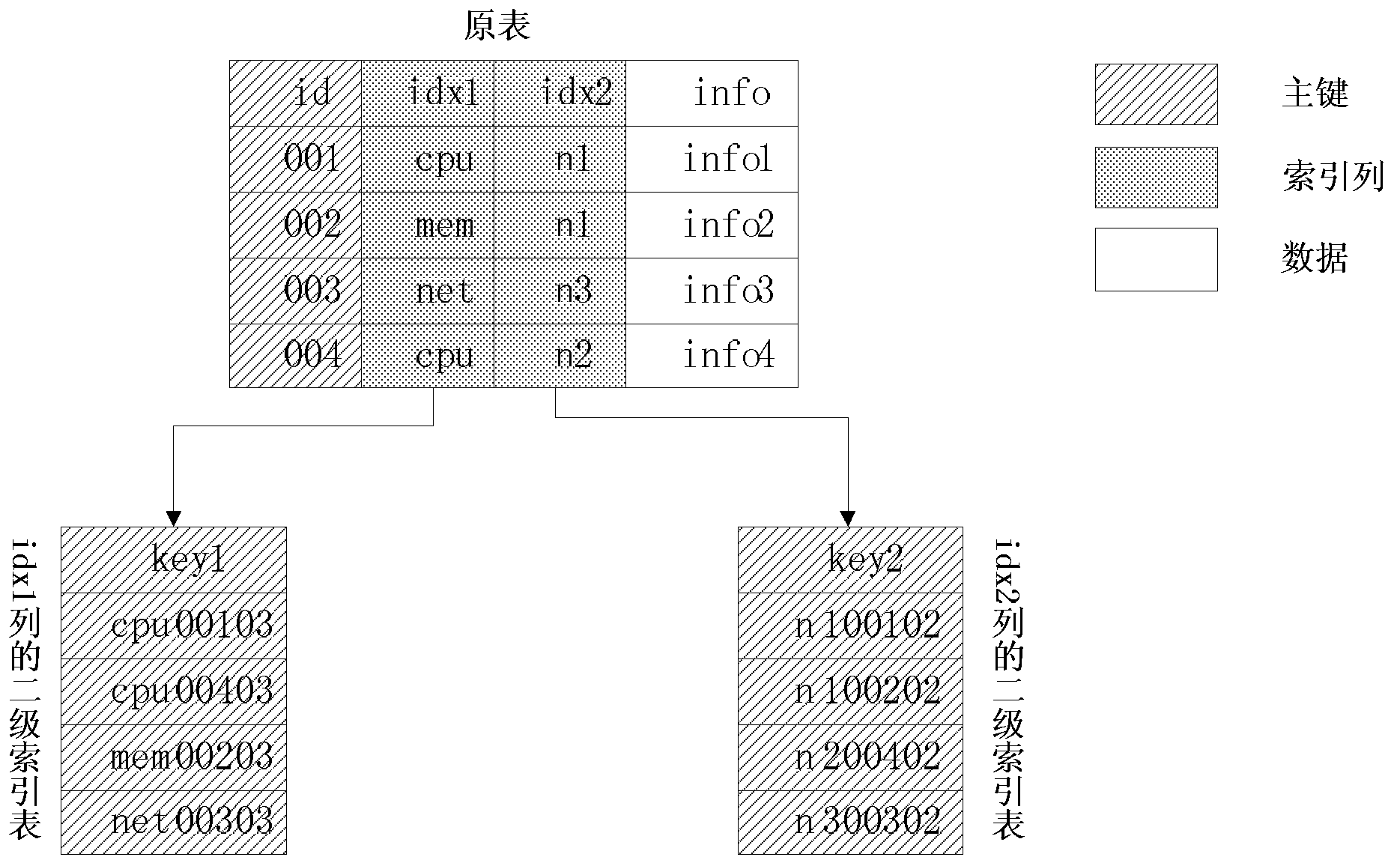
ActiveCN103020204AImprove query speedImprove performanceSpecial data processing applicationsDependabilityData mining
The invention discloses a method and a system for carrying out multi-dimensional regional inquiry on a distribution type sequence table. The method comprises the following steps of: respectively establishing a sheet of corresponding secondary index table for each index list of the distribution type sequence table, and the principal linkage of the corresponding secondary index table of each index list is a combination value of an index list value, the principal linkage of the distribution type sequence table, and the length of the index list value; and when a regional inquiry request is received, according to the field name of the inquiry request, searching a corresponding secondary index table of the field name from each secondary index table, according to the field value of the inquiry request, searching a record position corresponding to the field value of the inquiry request from a corresponding secondary index table, and directly reading corresponding data from the record position of the distribution type sequence table. According to the method and the system, a multi-dimensional regional inquiry speed can be greatly accelerated, and the requirements on high performance, low storage cost and high reliability can be met at the same time.
Owner:北京东方国信科技股份有限公司
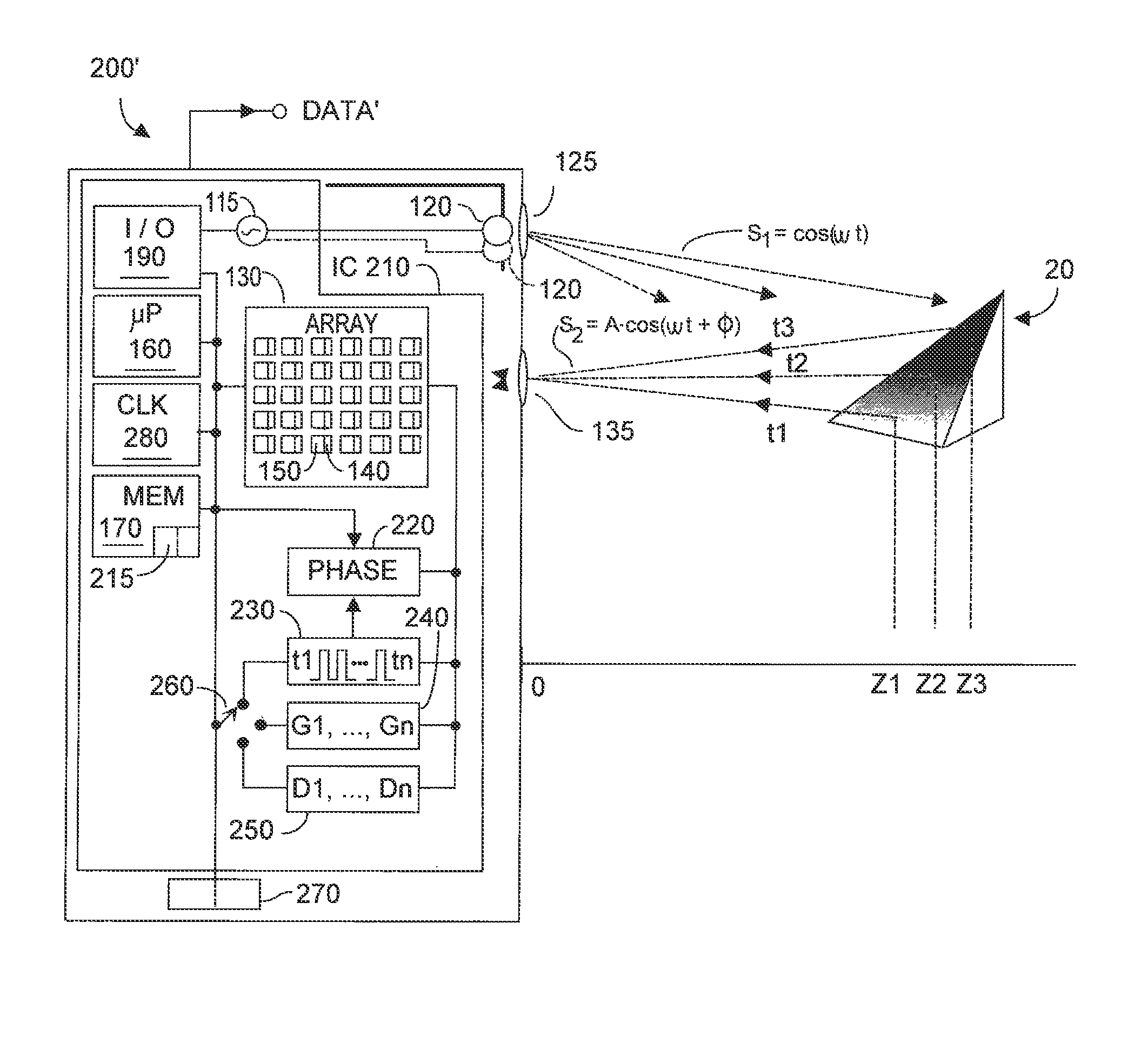
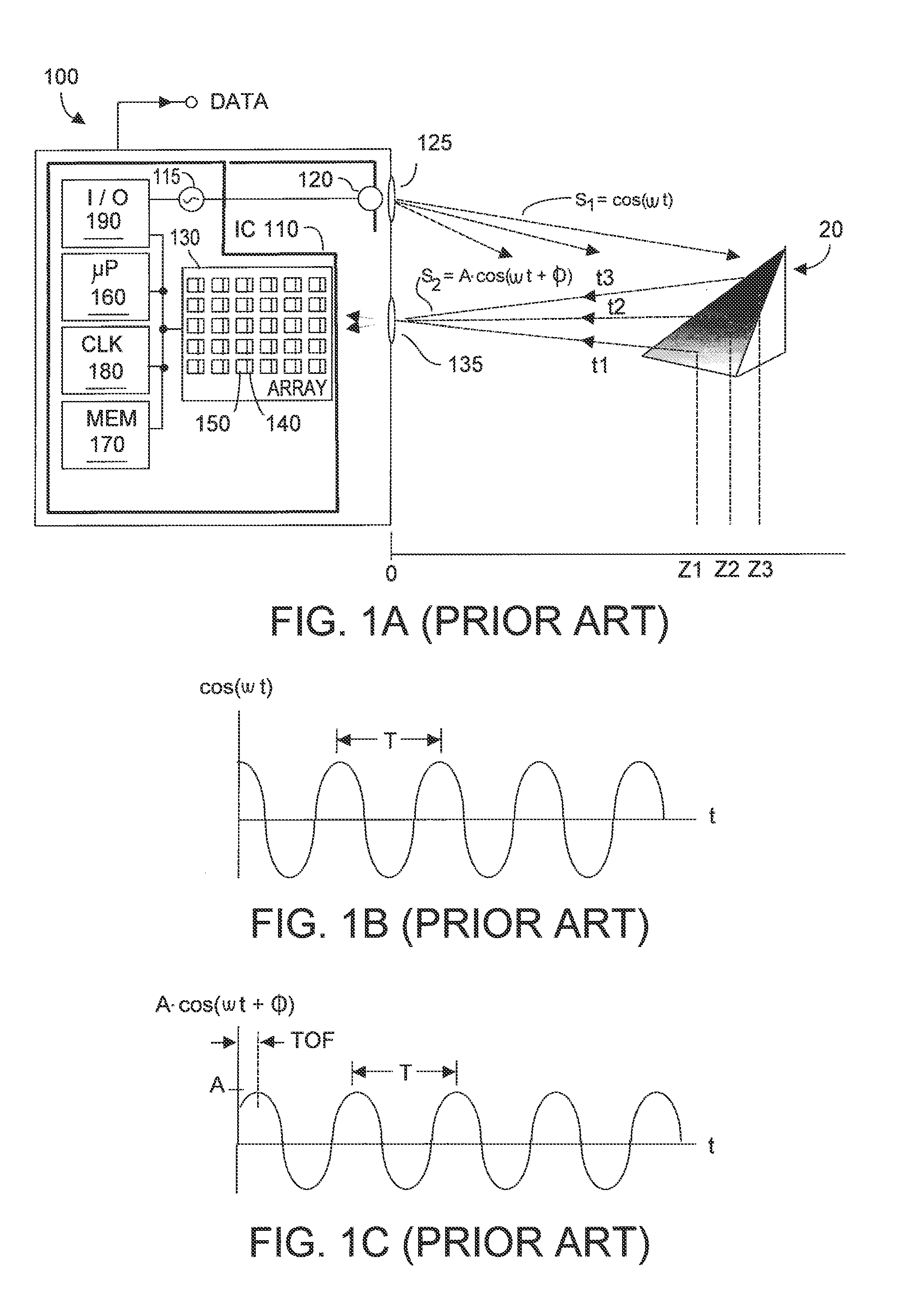
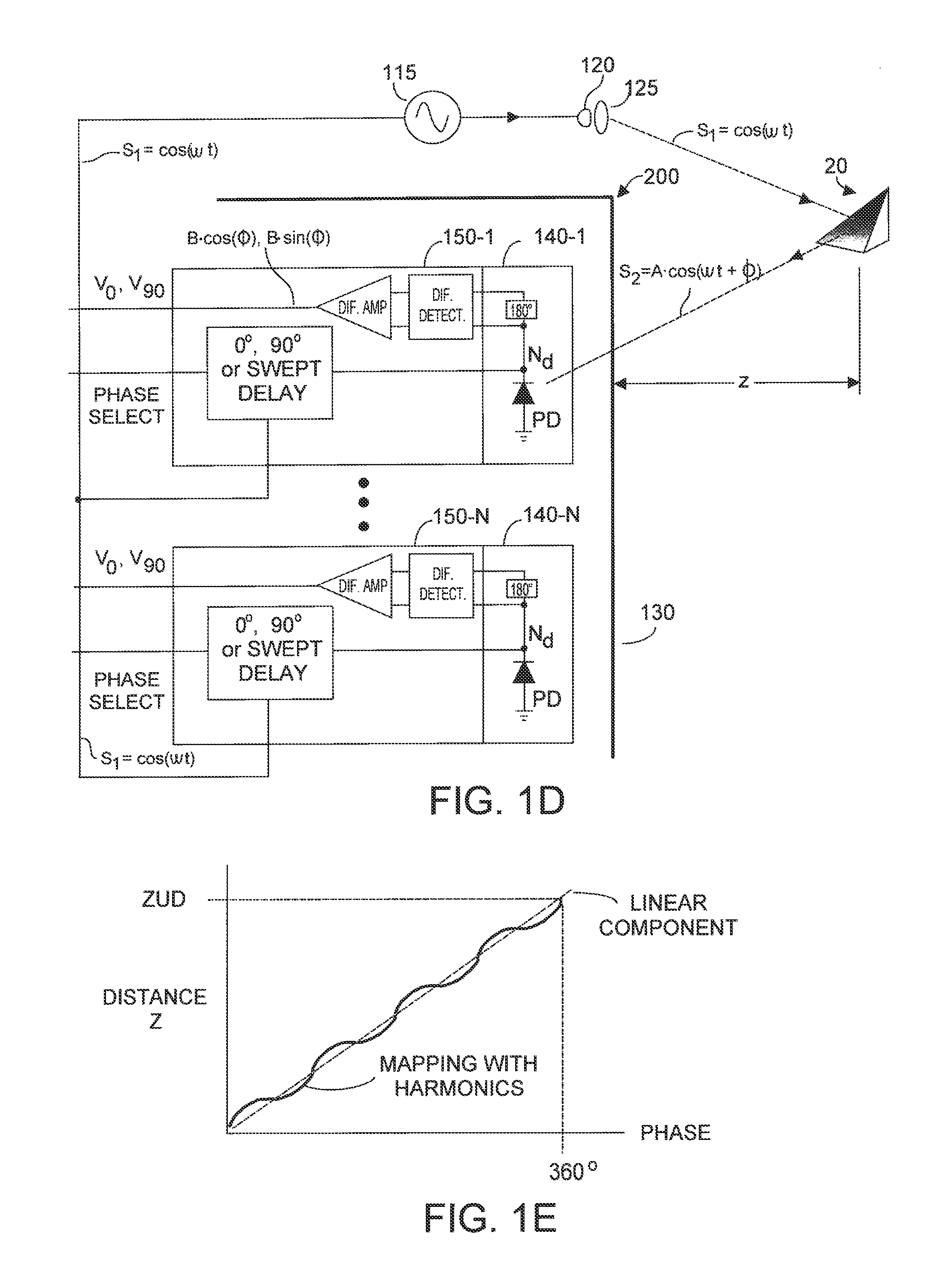
Method and system for multi-phase dynamic calibration of three-dimensional (3D) sensors in a time-of-flight system
ActiveUS8587771B2Low efficiencyDynamically calibratedOptical rangefindersMaterial analysis by optical meansHigher order harmonicsEngineering
Owner:MICROSOFT TECH LICENSING LLC
Method and Apparatus for Allocating A Dynamic Data Structure
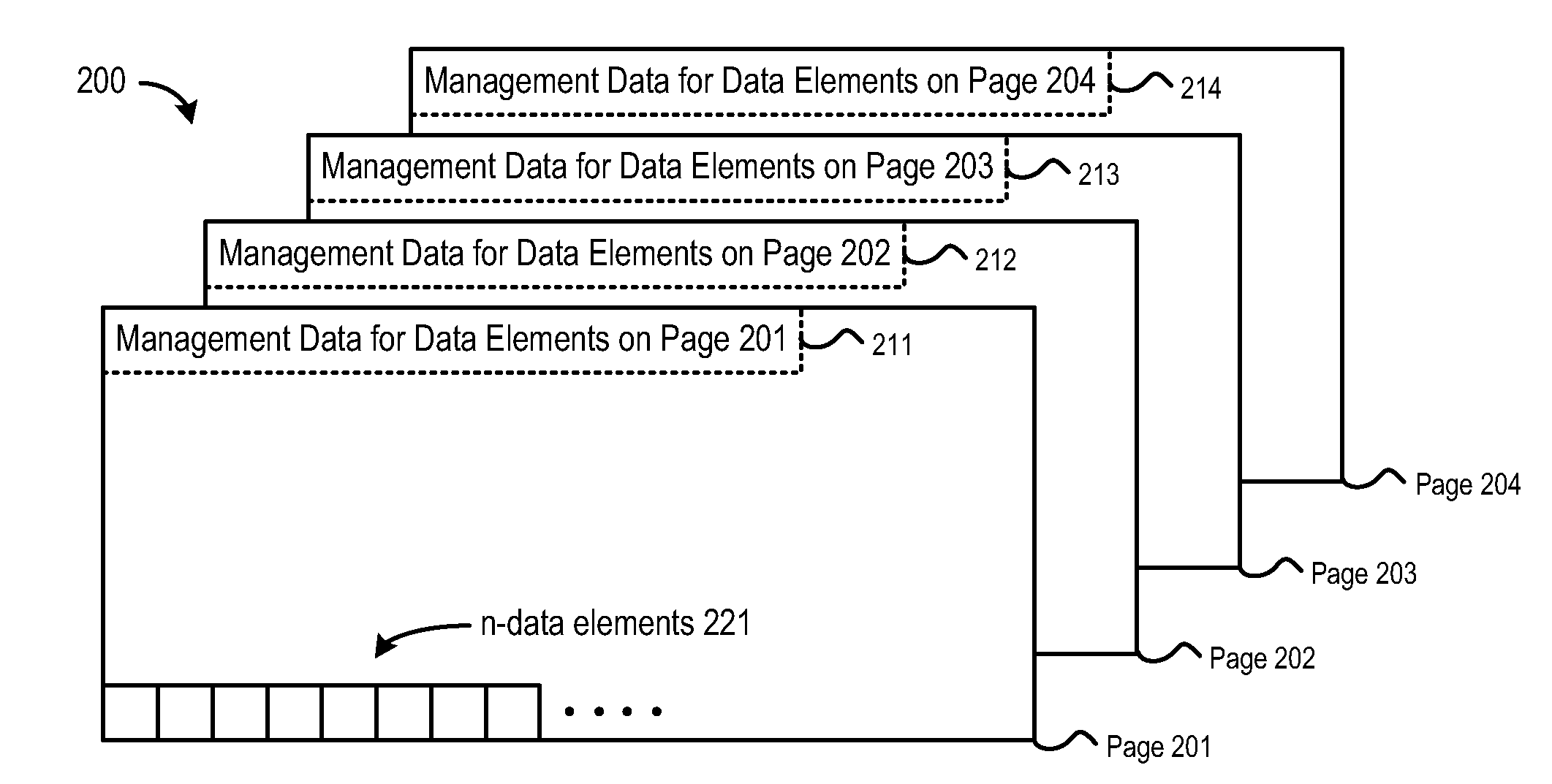
InactiveUS20080148002A1Efficient storageAllocation is fastMemory architecture accessing/allocationMemory adressing/allocation/relocationDynamic dataData element
A method, system and program are provided for allocating a data structure to memory by selecting a page of memory having a free entry, allocating the free entry for exclusive storage of a data element in the data structure, and then updating control information on the selected page with management data specifying that the free entry is allocated. In a selected embodiment, the page of memory is part of a heap of memory pages which is organized so that a page, having at least one free entry and fewer free entries than any other page in the heap, is located at the top of the heap. This allows allocations to proceed first with pages having fewer free entries, thereby promoting pages having all free entries.
Owner:IBM CORP
Method for storing IOT time series data related to geographical location information
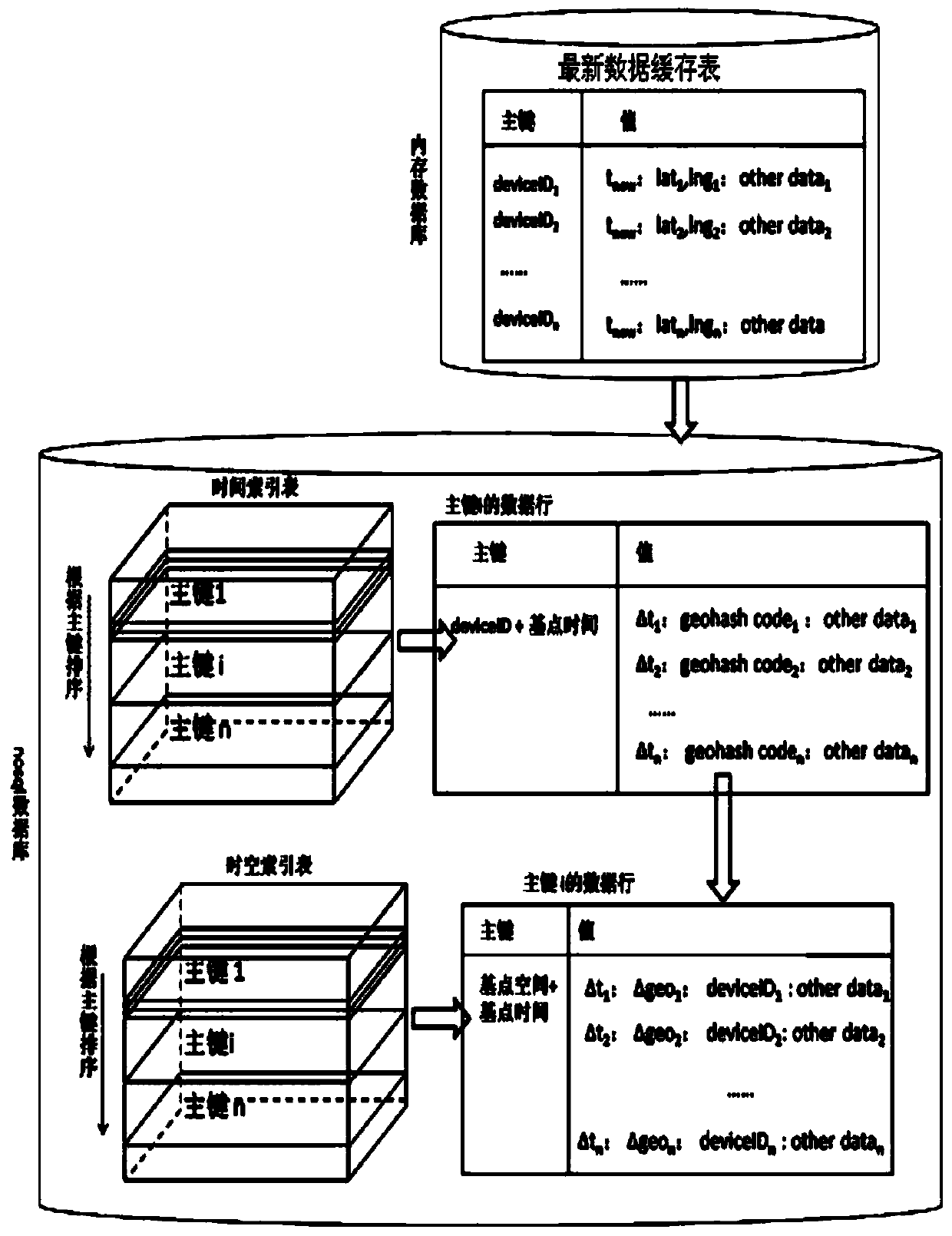
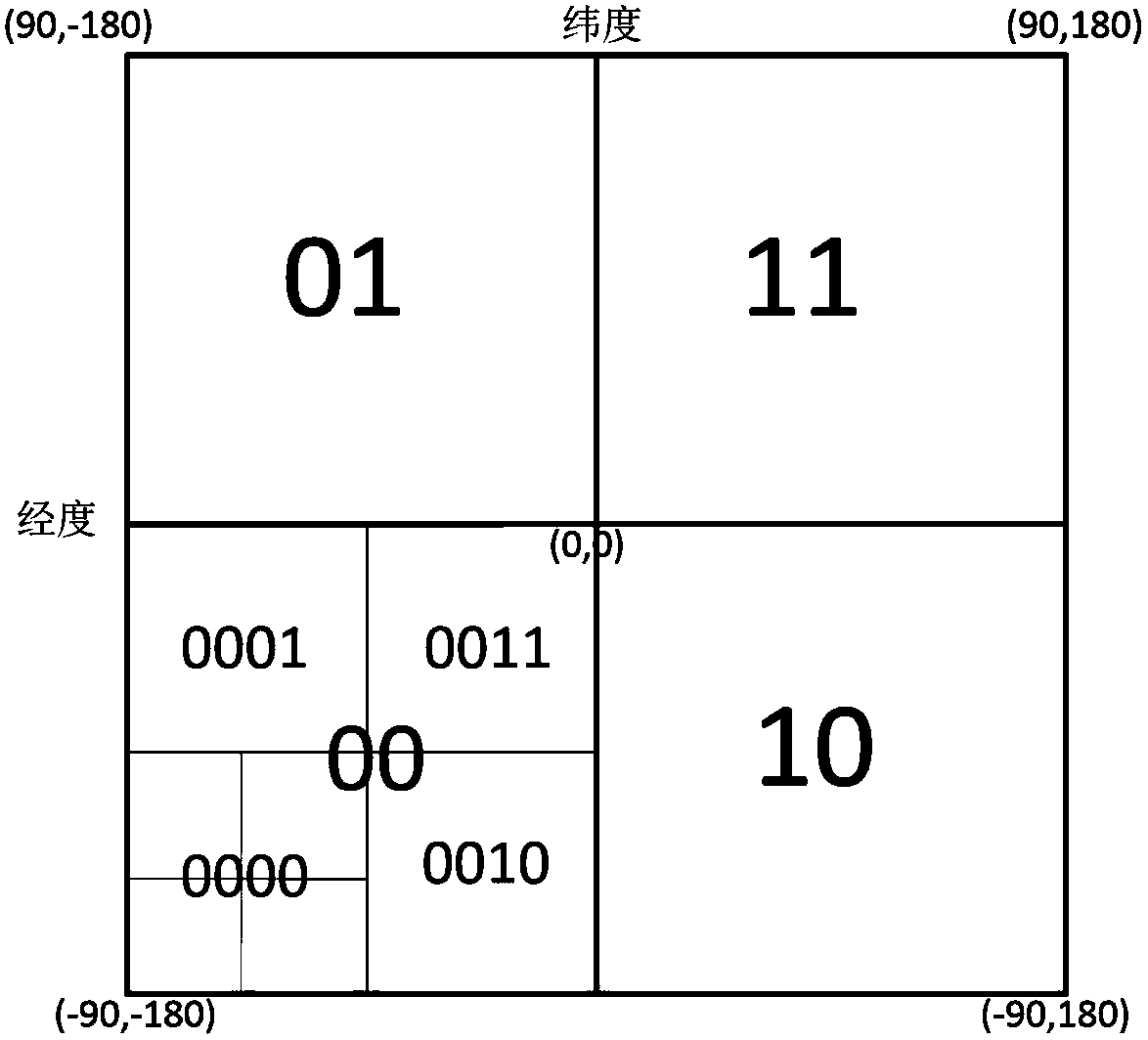
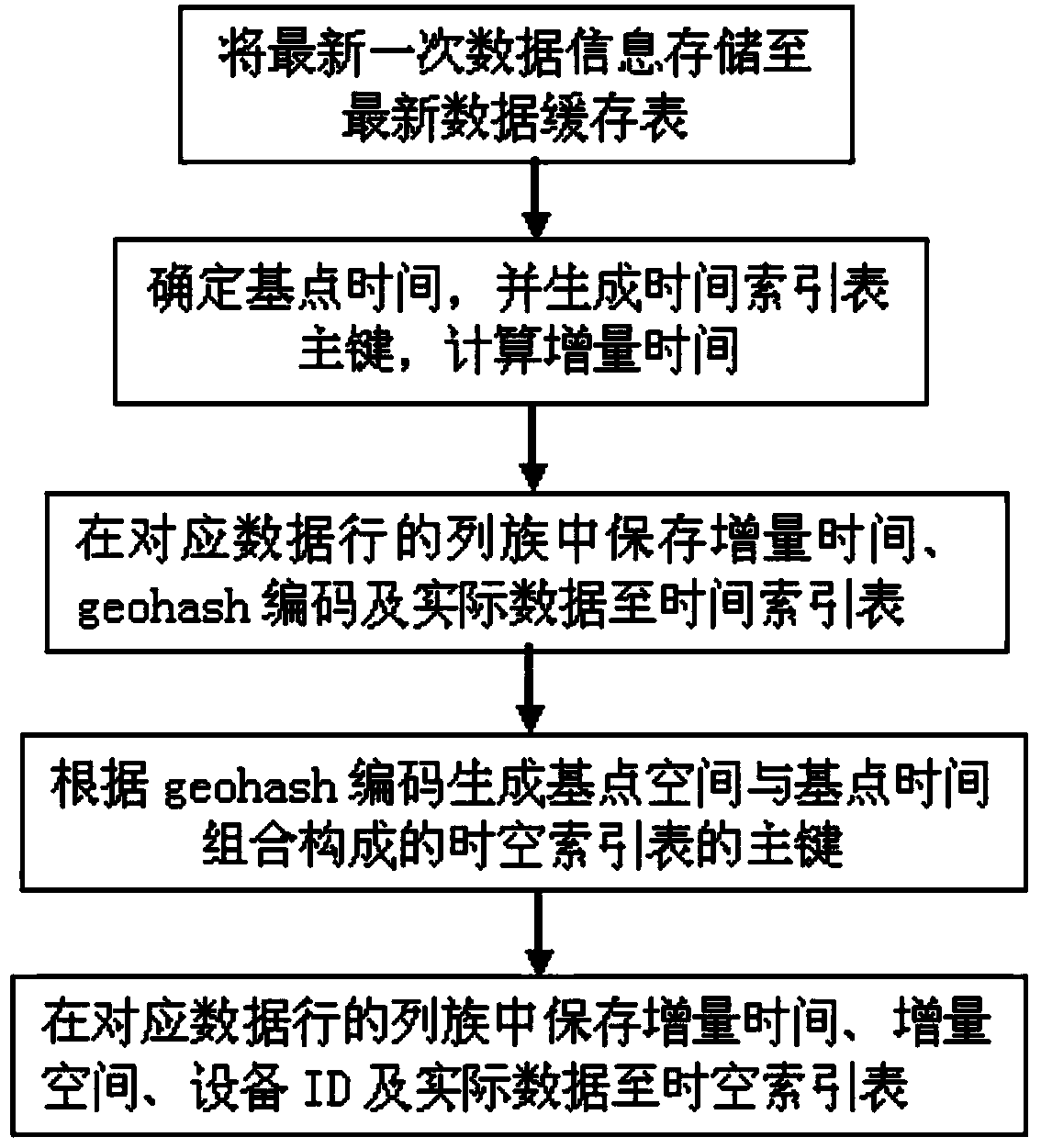
ActiveCN104008212AQuick searchSmall footprintSpecial data processing applicationsGeographic siteSystem requirements
The invention provides a method for storing IOT time series data related to geographical location information, and belongs to the field of computer big data storage. The method includes the steps that (1) latest data information is stored to a latest data cache table; (2) base point time is determined, and a time index table major key is generated; (3) increment time, geohash codes and actual data are stored to a time index table in a column family of a corresponding data row; (4) a space-time index table major key which is formed by base point space and base point time in a combined mode is generated according to the geohash codes; (5) increment time, increment space, equipment IDs and actual data are stored to a space-time index table in a column family of a corresponding data row; (6) data information is inquired. By means of the method, the IOT time series data related to the geographical location information can be stored and inquired quickly, and the mass IOT time series data management system requirement related to the geographical location information can be effectively met.
Owner:CHONGQING INST OF GREEN & INTELLIGENT TECH CHINESE ACADEMY OF SCI
Optimizing method for storing virtual machine mirror images based on CAS (content addressable storage)
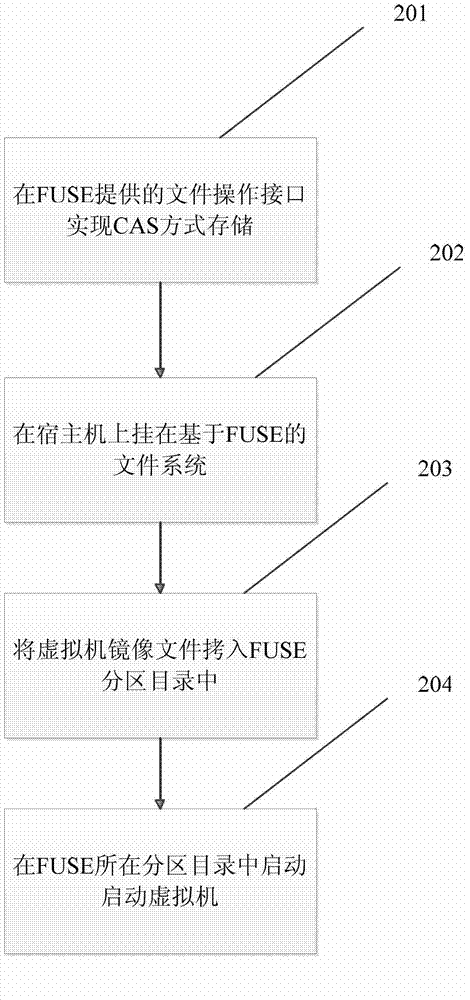
InactiveCN103034684AI/O performance is not affected muchReduce storage overheadProgram loading/initiatingSoftware simulation/interpretation/emulationComputer moduleSystem call
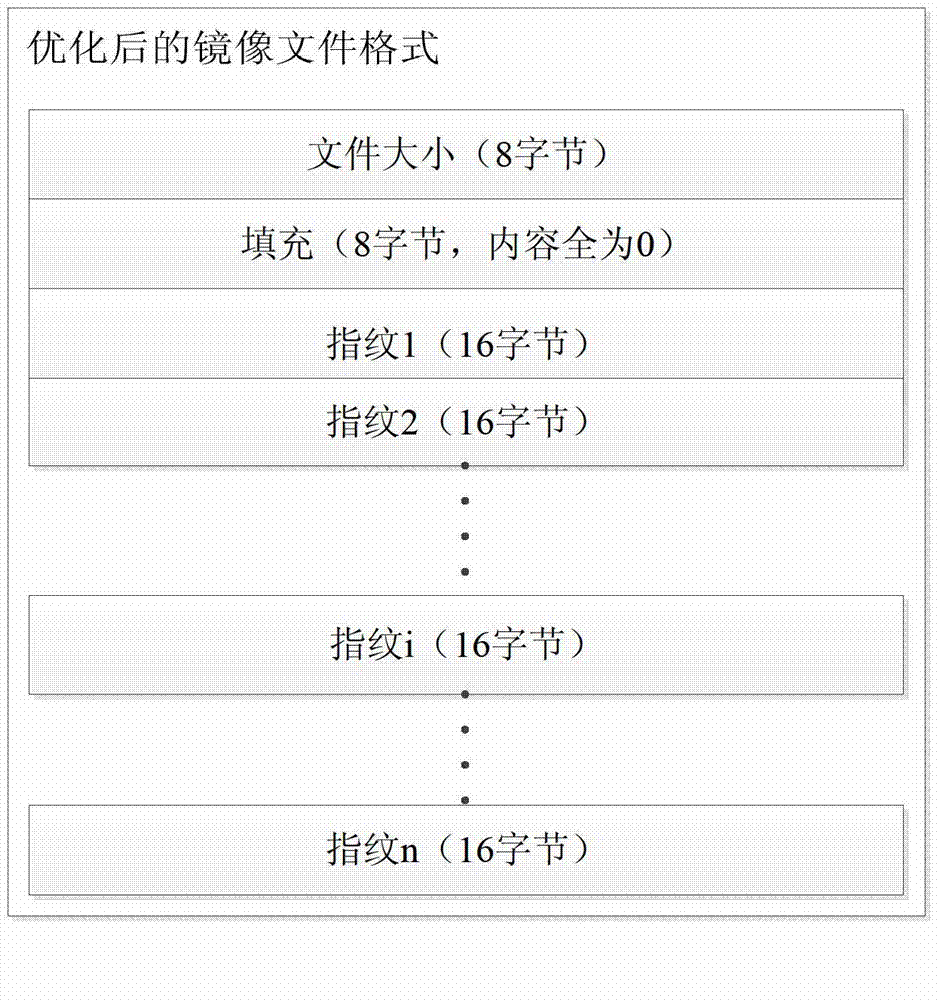
The invention relates to an optimizing method for storing virtual machine mirror images based on CAS (content addressable storage). The method specifically comprises the following steps of adopting a CAS method to divide a virtual machine mirror image file into blocks, calculating fingerprint sequences, and judging the repetitive data through the fingerprint sequences. Only one data block is reserved for the data blocks with the same content, and the number of corresponding share times is stored in each block file. The original file is actually stored with the finger sequences (as shown in Figure 3), and the data part is stored in a shared storage system. To ensure the transparent storage of a virtual machine monitor and the portability of the shared storage system, the operation process of the virtual machine mirror images is packaged into the realizing process of a corresponding system calling and response interface by a FUSE (filesystem in user space)-based framework, so as to service a FUSE inner module to obtain an I / O (input / output) request generated by an upper-layer user operating a virtual machine, and convert the direct storage of the virtual machine mirror image files into the storage based on the CAS method. The method for eliminating the repetitive data based on the CAS has the advantages that the occupation amount of disks of the vertical machine mirror images is reduced by more than 50%, and the application prospect is wide for the current states of the large-scale application of the existing virtual machine.
Owner:BEIHANG UNIV
Query optimization method based on join index in data warehouse
ActiveCN104866608AReduce storage overhead and maintenance costsGood performanceMulti-dimensional databasesSpecial data processing applicationsQuery optimizationMemory address
The invention relates to a query optimization method based on a join index in a data warehouse. The method comprises the following steps: creating a fact table foreign key join index based on a dimension table surrogate key; creating a join index update strategy; when a predicate condition exists on a dimension table, making a predicate judgment after direct access to dimension table record through the join index, and performing calculation through a dynamic bitmap join index by reference to a bitmap join index to generate a join bitmap index; when the selection rate on the dimension table is very low, further compressing a dimension table bitmap in order to raise the cache level of dimension table bitmap calculation; and calculating simple memory address access by only using an array-bitmap data structure with a reference bitmap join index calculation method based on co-processor memory calculation. Through adoption of the query optimization method, the calculation performance of the bitmap index can be effectively increased. Moreover, the query optimization method can be combined with high-performance co-processors such as GPU and Intel Xeon Phi TM to accelerate the index calculation performance, and can be widely applied to the field of data warehouses.
Owner:RENMIN UNIVERSITY OF CHINA
Consistency maintenance device for multi-kernel processor and consistency interaction method
InactiveCN102346714AReduce storage overheadImprove memory access efficiencyMemory adressing/allocation/relocationLinear growthData access
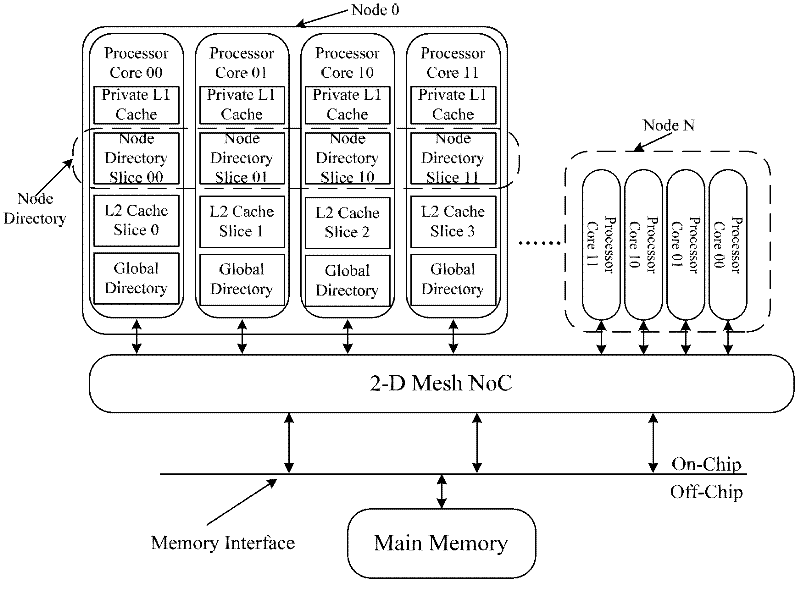
The invention discloses a consistency maintenance device for a multi-kernel processor and a consistency interaction method, mainly solving the technical problem of large directory access delay in a consistency interaction process for processing read-miss and write-miss by a Cache consistency protocol of the traditional multi-kernel processor. According to the invention, all kernels of the multi-kernel processor are divided into a plurality nodes in parallel relation, wherein each node comprises a plurality of kernels. When the read-miss and the write-miss occur, effective data transcription nodes closest to the kernels undergoing the read-miss and the write-miss are directly predicted and accessed according to node predication Cache, and a directory updating step is put off and is not performed until data access is finished, so that directory access delay is completely concealed and the access efficiency is increased; a double-layer directory structure is beneficial to conversion of directory storage expense from exponential increase into linear increase, so that better expandability is achieved; and because the node is taken as a unit for performing coarse-grained predication, the storage expense for information predication is saved compared with that for fine-grained prediction in which the kernel is taken as a unit.
Owner:XI AN JIAOTONG UNIV
Light-weight authentication key negotiation method based on implicit certificate
ActiveCN106411528ACalculation speedReduce the probability of collisionKey distribution for secure communicationPublic key for secure communicationClient-sideSecure channel
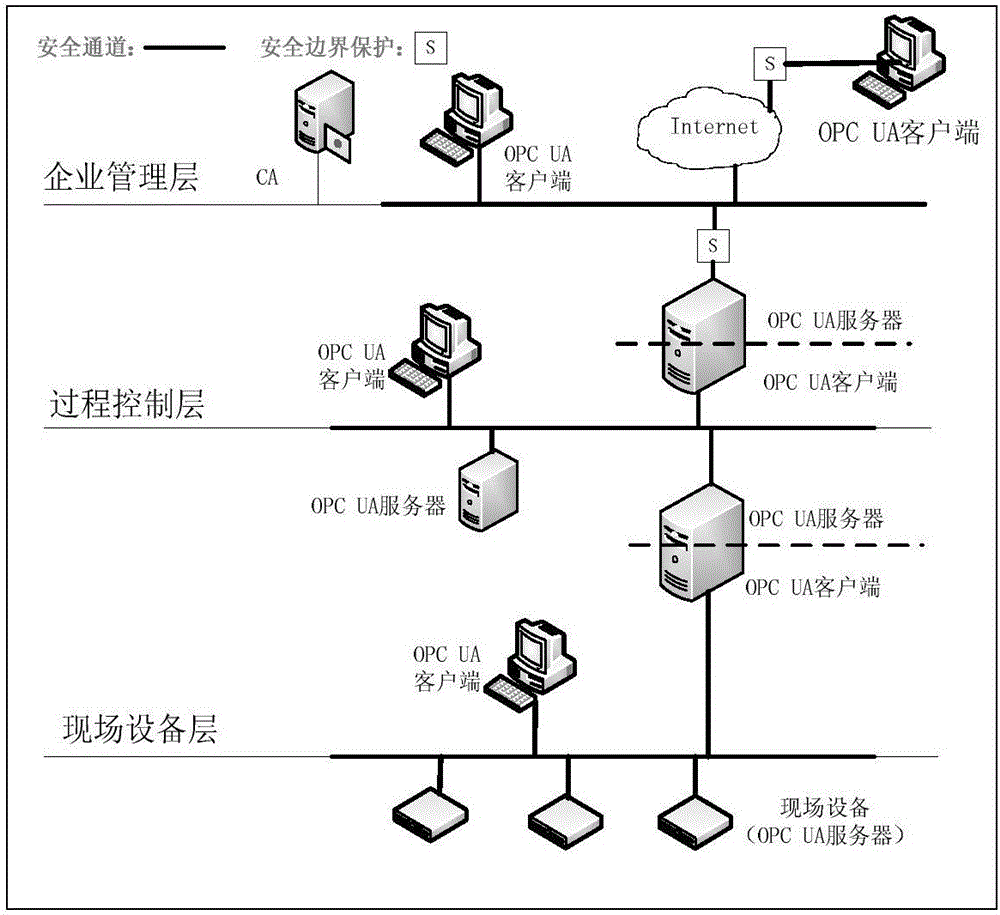
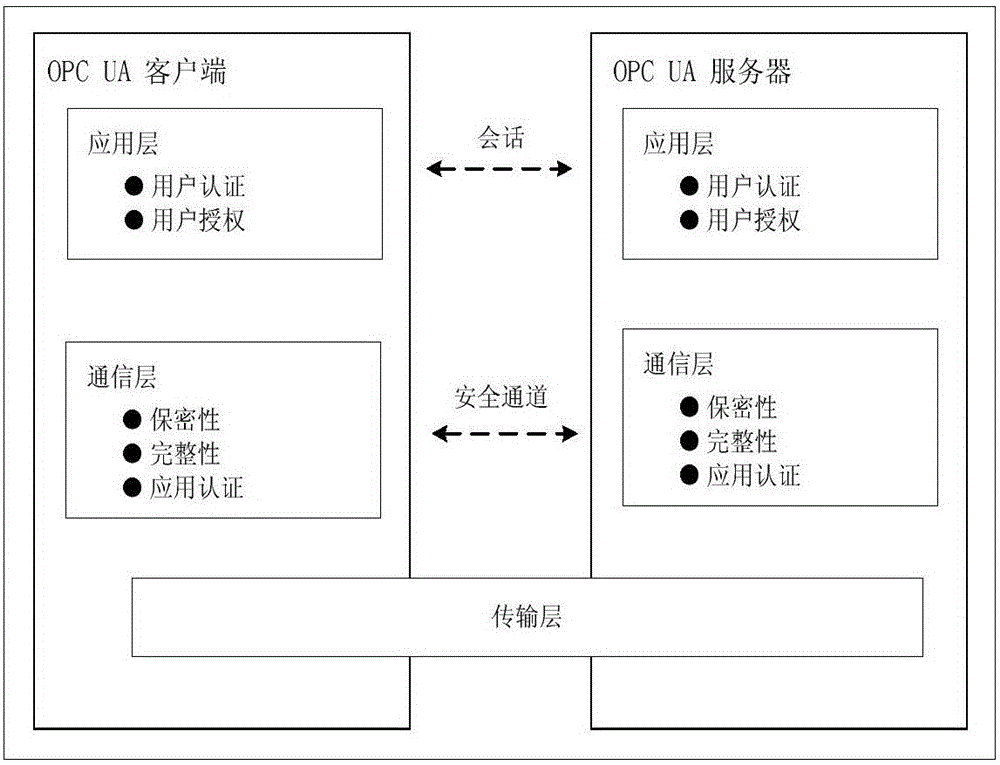
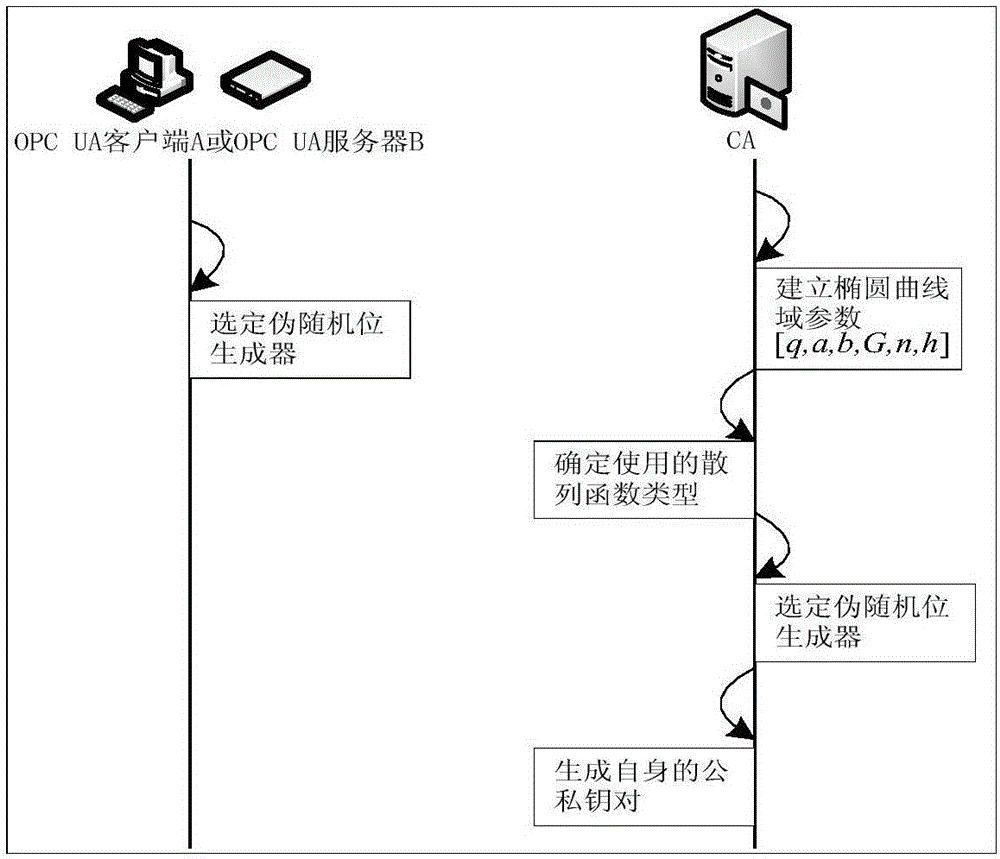
The invention relates to a light-weight authentication key negotiation method based on an implicit certificate, and belongs to the technical field of identity authentication. The method is used for establishing a secure channel between an OPC UA server and an OPC UA client and generating of a session key. Three entities, a credible certification authority (CA), the OPC UA client A and the OPC UA server B, are involved in an authentication key negotiation process. The OPC UA server B and the OPC UA client A acquire the own implicit certificates after the CA completes identity registration. Then the OPC UA server B and the OPC UA client A complete bidirectional authentication and key negotiation between the entities by using a light-weight algorithm. According to the method provided by the invention, the light-weight authentication key negotiation method based on the implicit certificate is provided aiming at the problem that an existing OPC UA security mechanism is not applicable to a resource-constrained communication environment. The method provided by the invention can be efficiently and safely applicable to an industrial network with a large amount of resource-constrained embedded OPC UA equipment.
Owner:KYLAND TECH CO LTD
Blockchain structure for intelligent mobile terminal, generation method and transaction verification method
ActiveCN107612973AReduce storage overheadReduce the proportionUser identity/authority verificationBlockchainOperating system
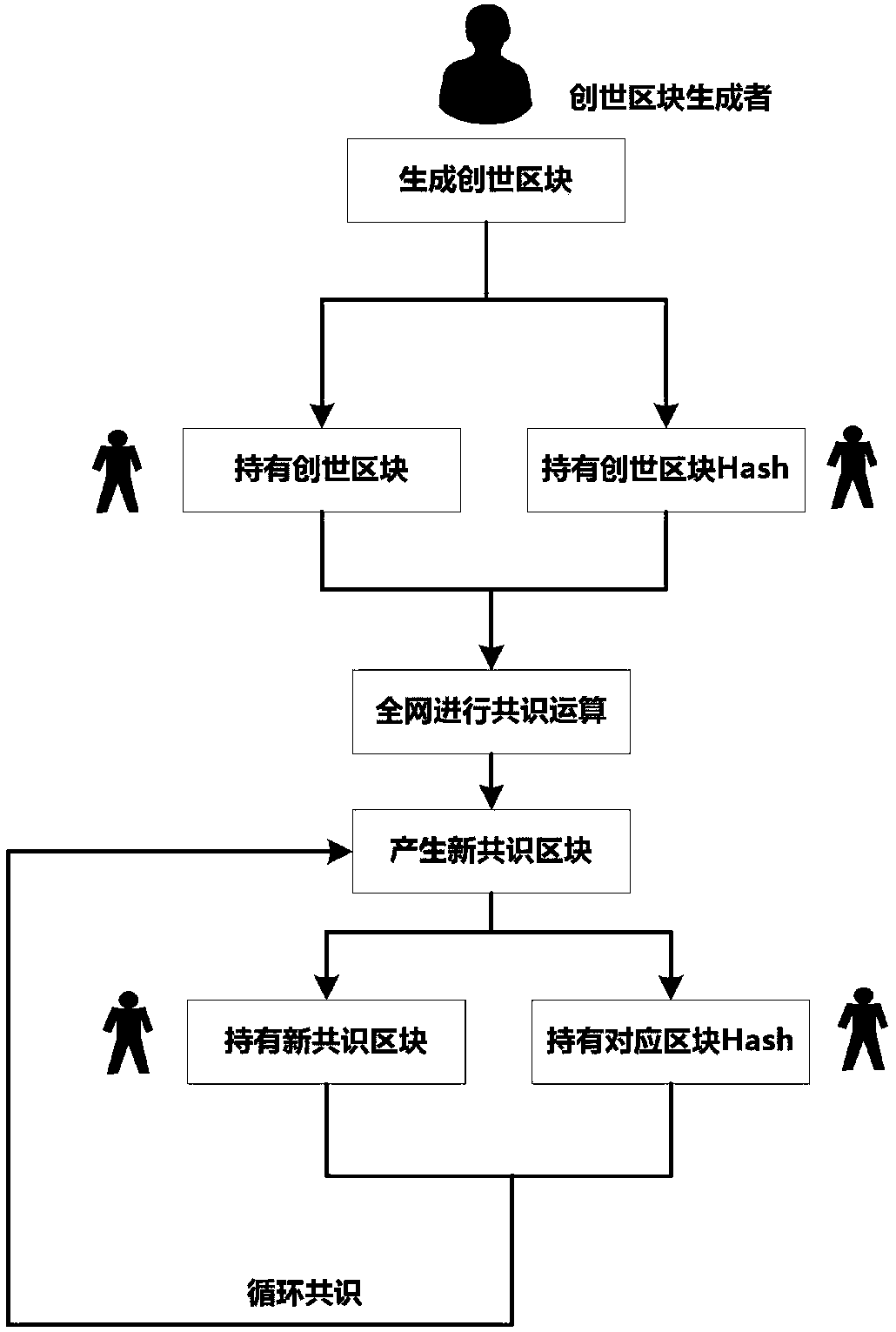
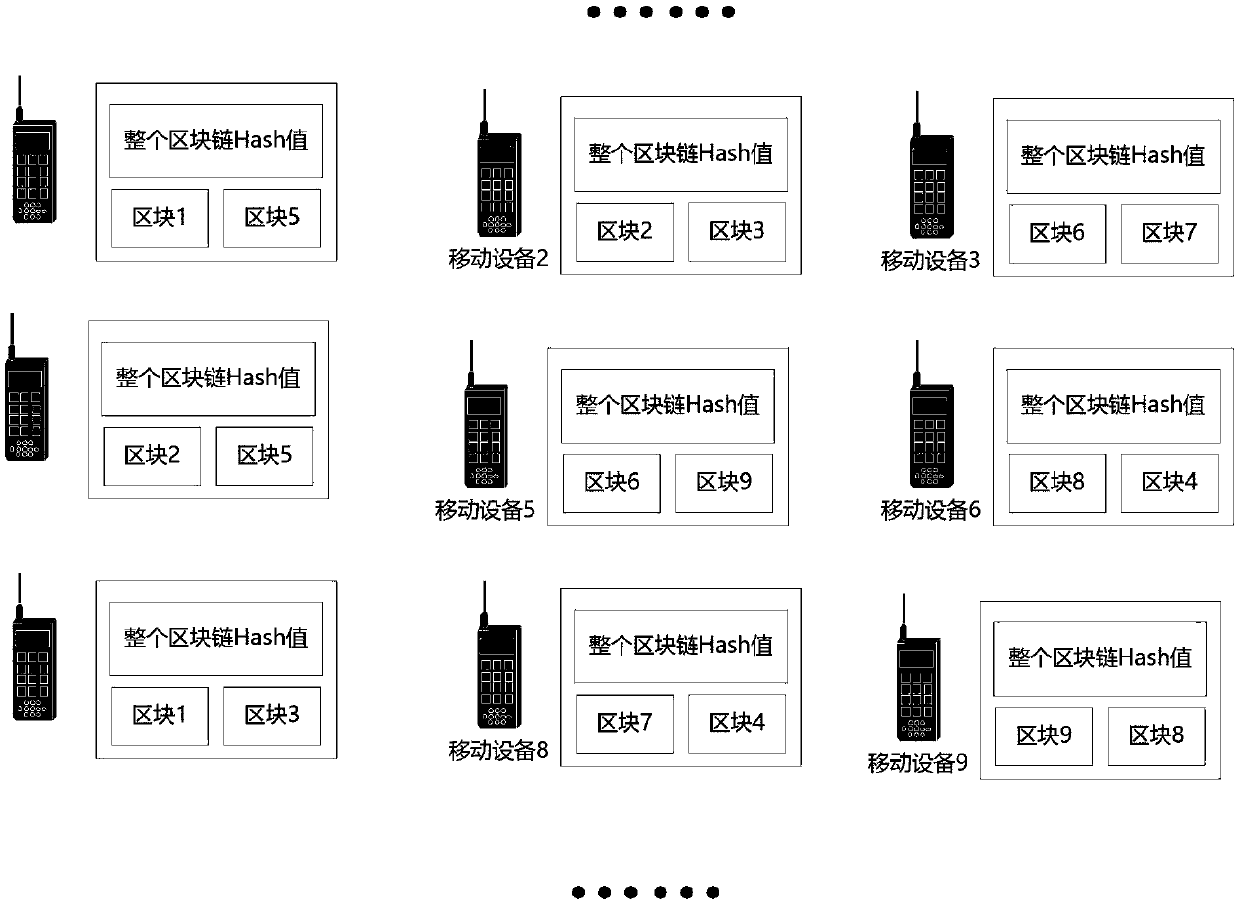
The invention discloses a blockchain structure for an intelligent mobile terminal, a generation method and a transaction verification method. The generation method comprises the following steps: firstof all, a genesis block generator generates a genesis block, and transmits the genesis block or a Hash value to a P2P network via a given rule, such that more than half of nodes in the whole networkhold the genesis block, and the other half of the nodes hold the Hash value of the block; the nodes perform consensus operation on the basis of this and achieve a new consensus; and through continuously performing cyclic consensus, the blockchain structure in which parts of the nodes store parts of blocks of the blockchain is finally obtained. The blockchain structure for the intelligent mobile terminal, the generation method and the transaction verification method have the characteristics that the storage space occupation is small and all consensus mechanisms are compatible.
Owner:JINAN UNIVERSITY
Multi-user multi-keyword sorting searchable encryption system supporting any language query
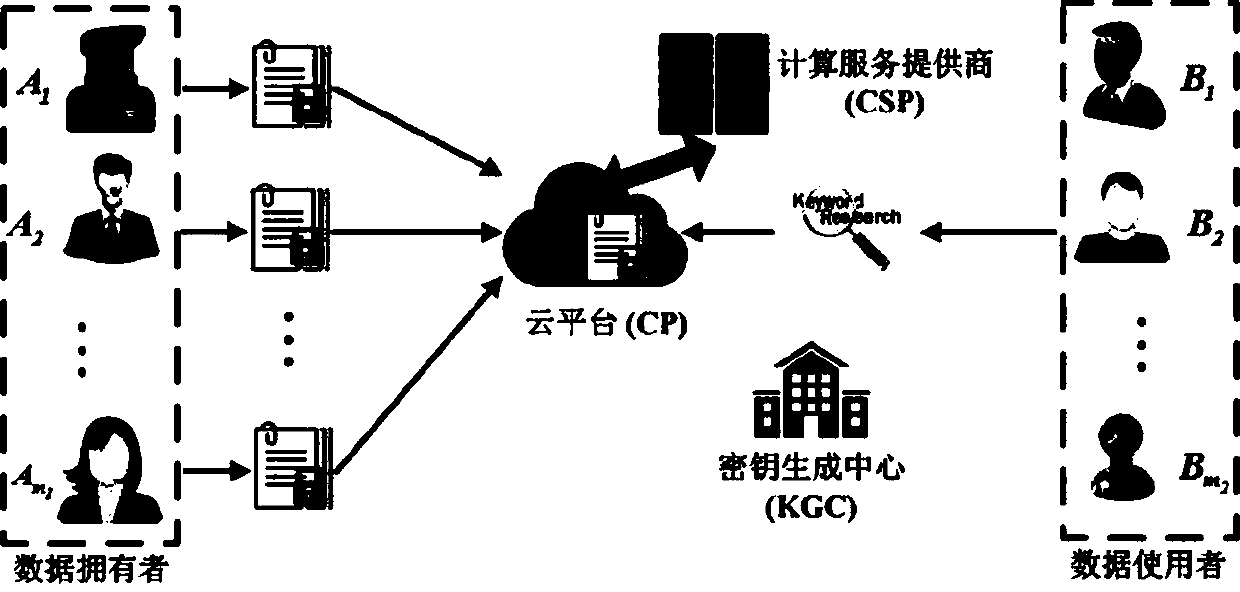
ActiveCN107491497AAdd arbitrarilyReduce storage overheadKey distribution for secure communicationUnstructured textual data retrievalEngineeringServer
The invention relates to a multi-user multi-keyword sorting searchable encryption system supporting any language query. A key generation center generates a key for each entity in the system; a cloud platform stores a document of a user in an encrypted form and makes a response to a data retrieval request of the user; a computing service provider provides an online computing server for online computing; a data owner encrypts keywords and the document, and sends the encrypted keywords and document to the cloud platform for performing storage; and the user generates a keyword trap door and initiates the data retrieval request to the cloud platform. According to the multi-user multi-keyword sorting searchable encryption system supporting any language query, provided by the invention, the storage overhead is small; any language is supported; flexible authorization mechanism and time-based user cancellation mechanism are realized; data of multiple data owners is searched at the same time; flexible keyword weight and preference score setting is realized; and user privacy is protected.
Owner:FUZHOU UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com