Method for detecting and classifying all-network flow abnormity on line
A network traffic and abnormal technology, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems of immediate identification, unable to meet the actual needs of network security management, etc., achieve low storage overhead, meet real-time detection and classification network Exceptional, low-time-complexity effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
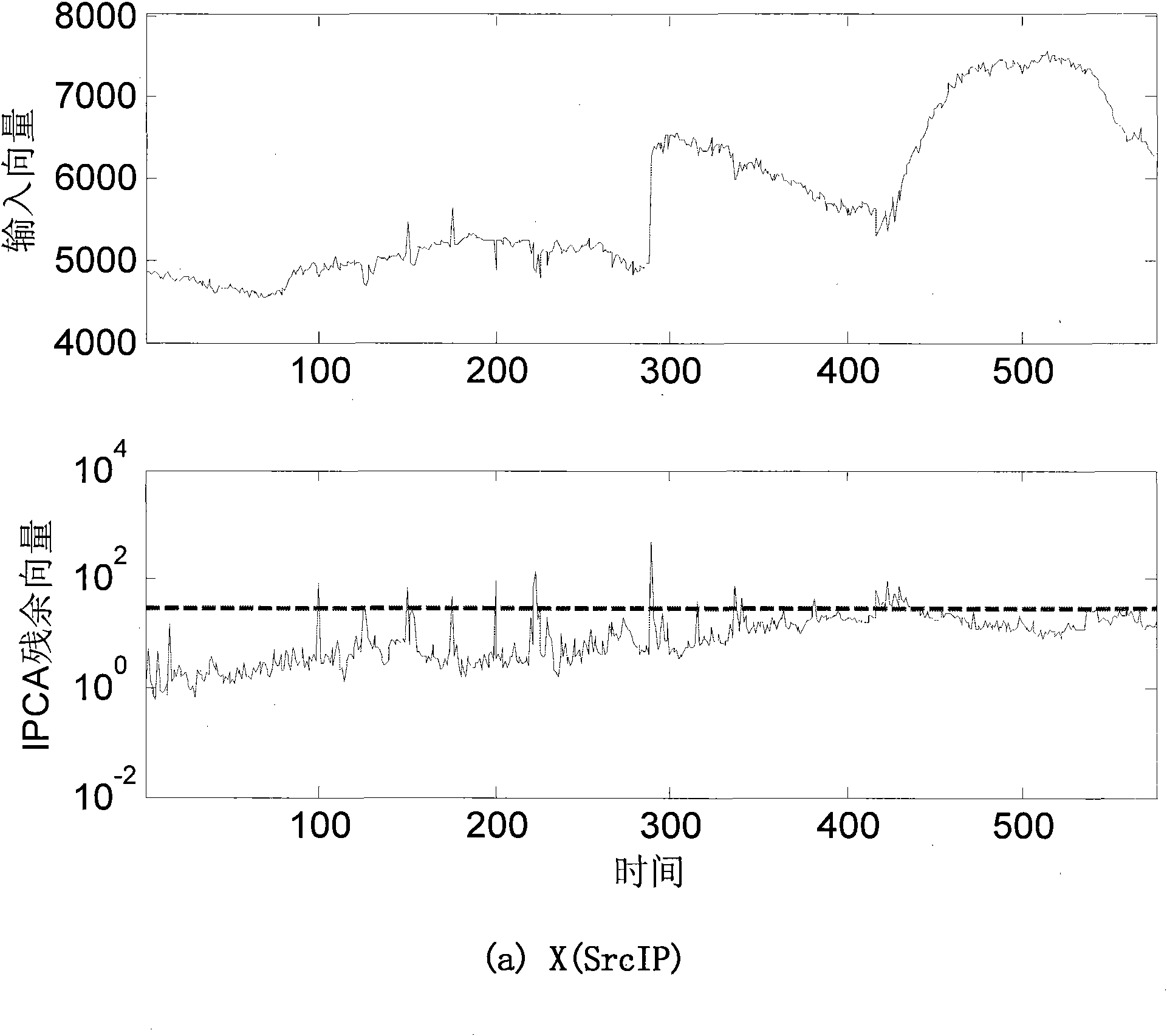
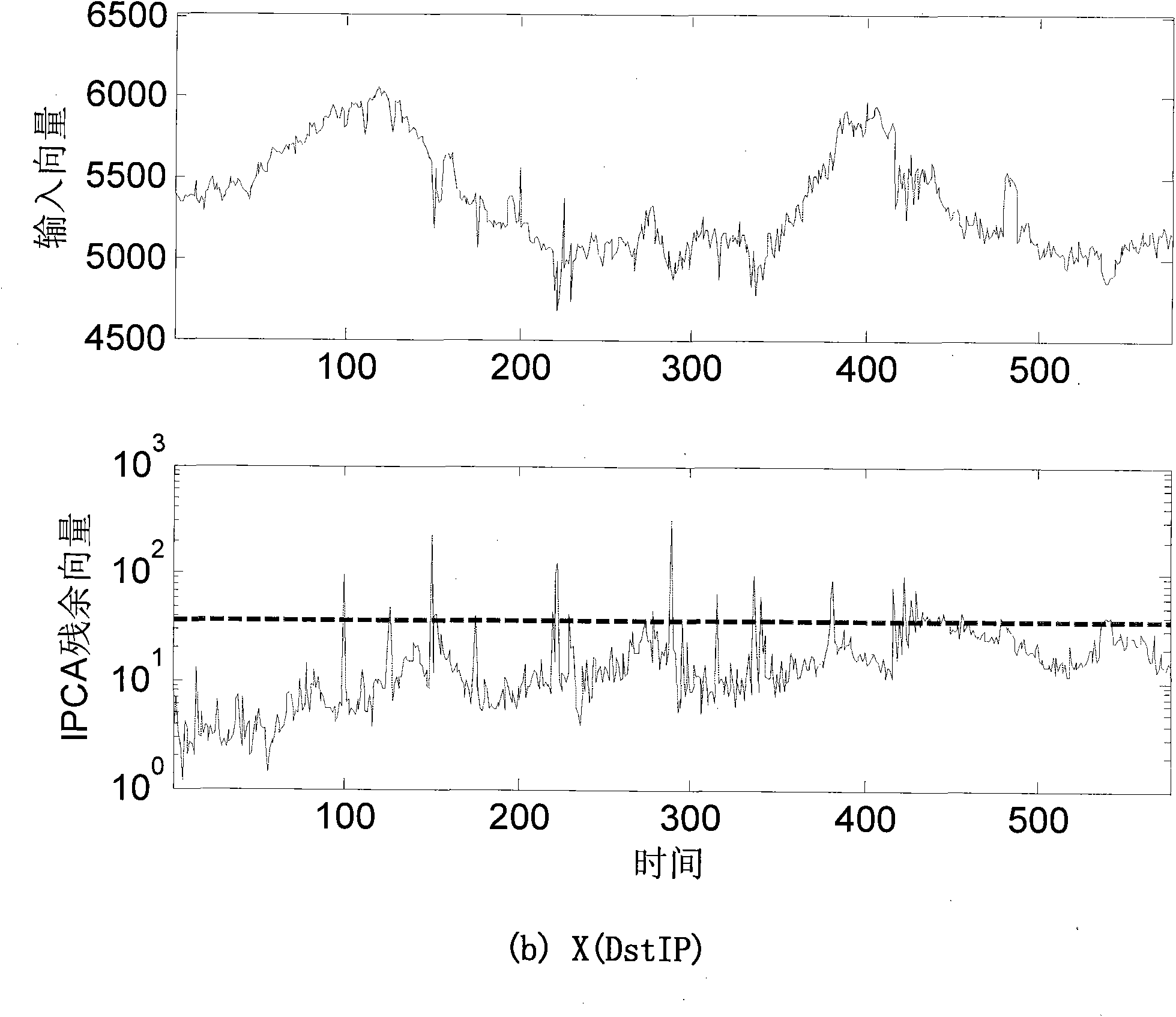
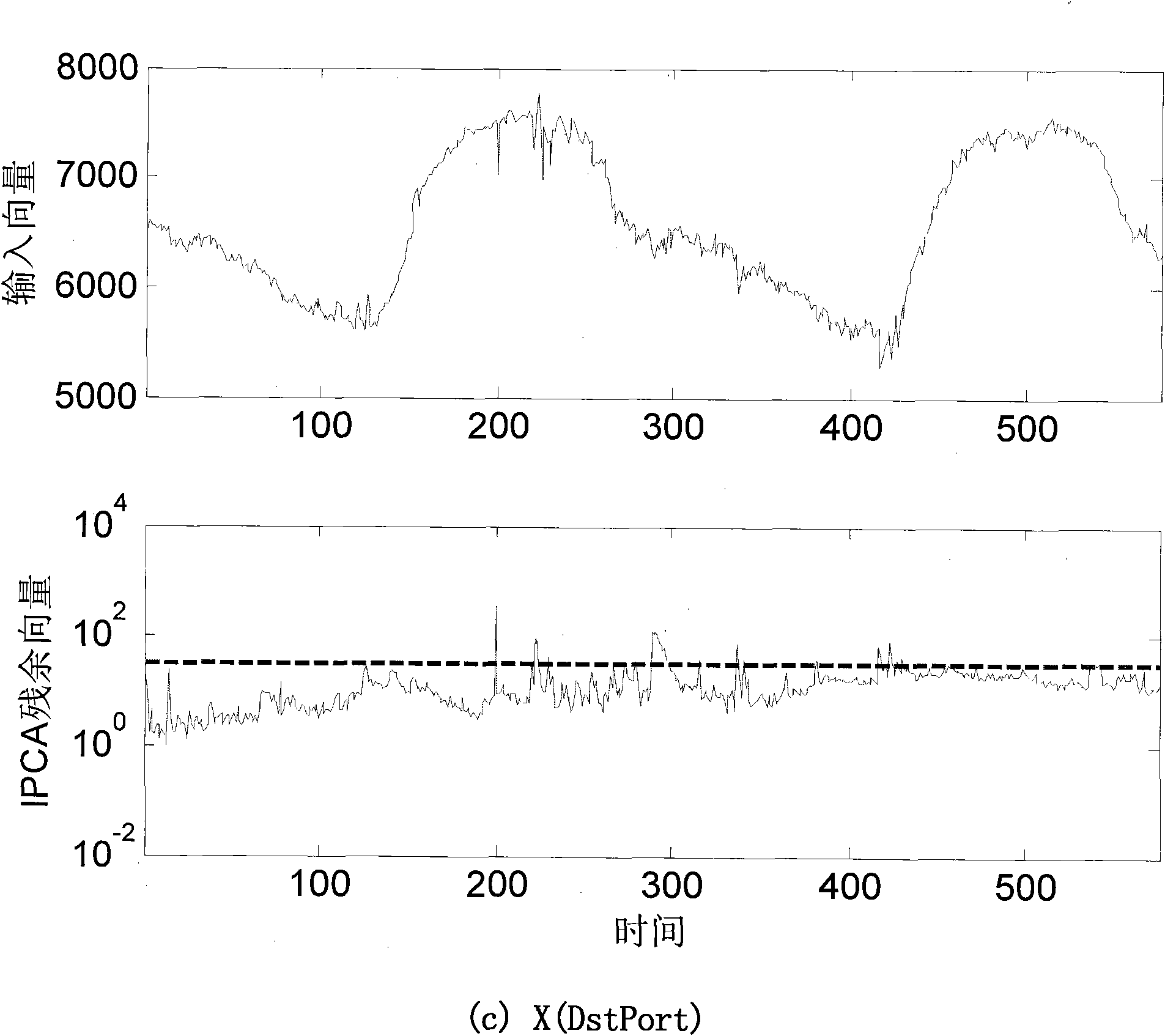
[0033] Such as Picture 1-1 , Figure 1-2 , Figure 1-3 , diagram 2-1 , Figure 2-2 , image 3 As shown, the online detection and classification method of the whole network traffic anomaly of the present invention comprises the following steps:
[0034] The first step is to collect NetFlow traffic:
[0035] After the NetFlow traffic collector is used to receive the NetFlow data packets sent from the border router, the collector will analyze the data packets and aggregate the data flow to form a variety of data suitable for statistical analysis, and then transmit them to the central console through the network for storage. into the database;
[0036] The second step is to construct a flow matrix measured by the entropy of flow characteristics:
[0037]Based on the original NetFlow flow data stored in the central console database, according to the routing information of the border gateway protocol, a traffic matrix measured by the entropy of different flow characteristics...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com