Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1614results about How to "Avoid security risks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
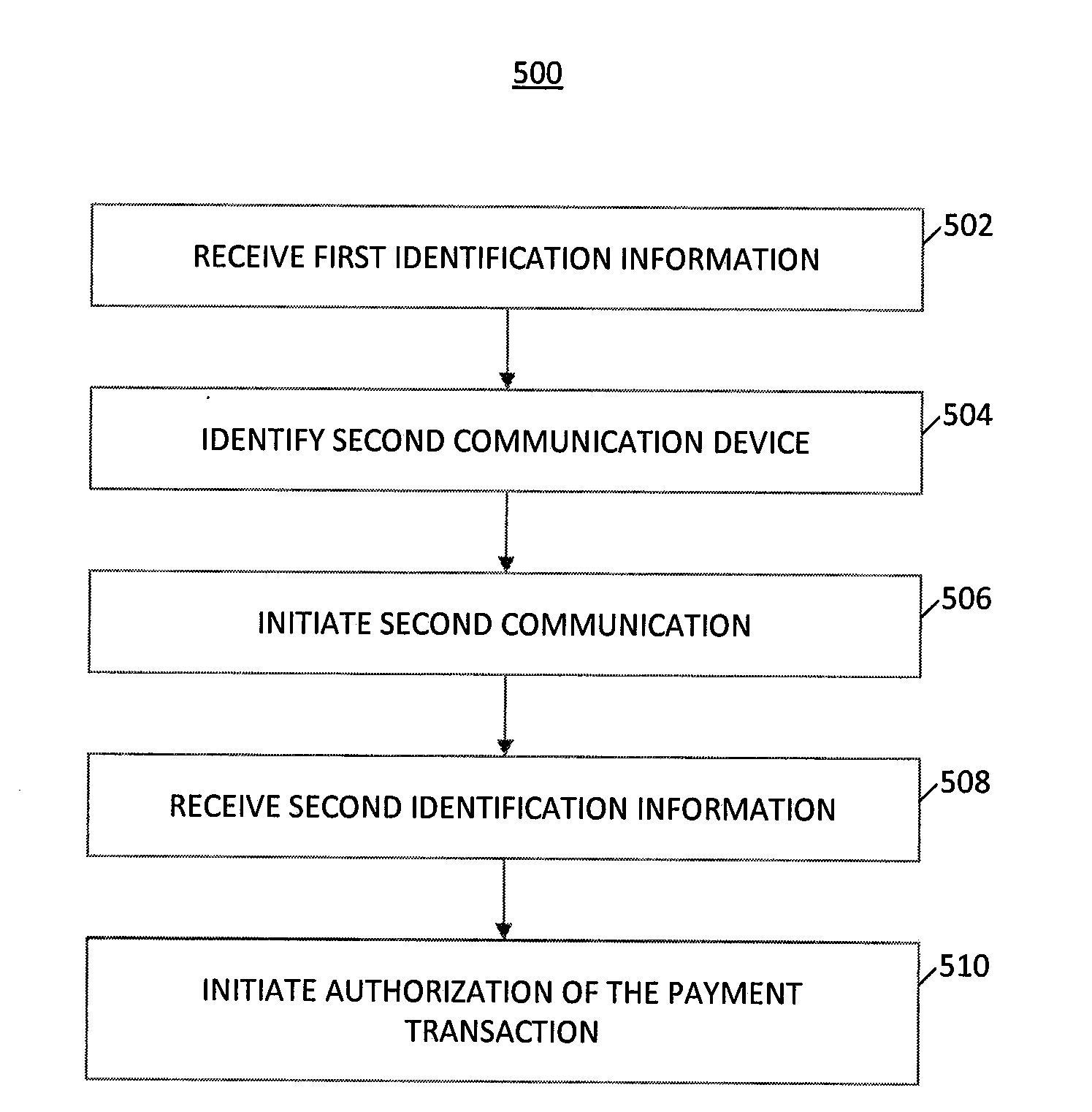
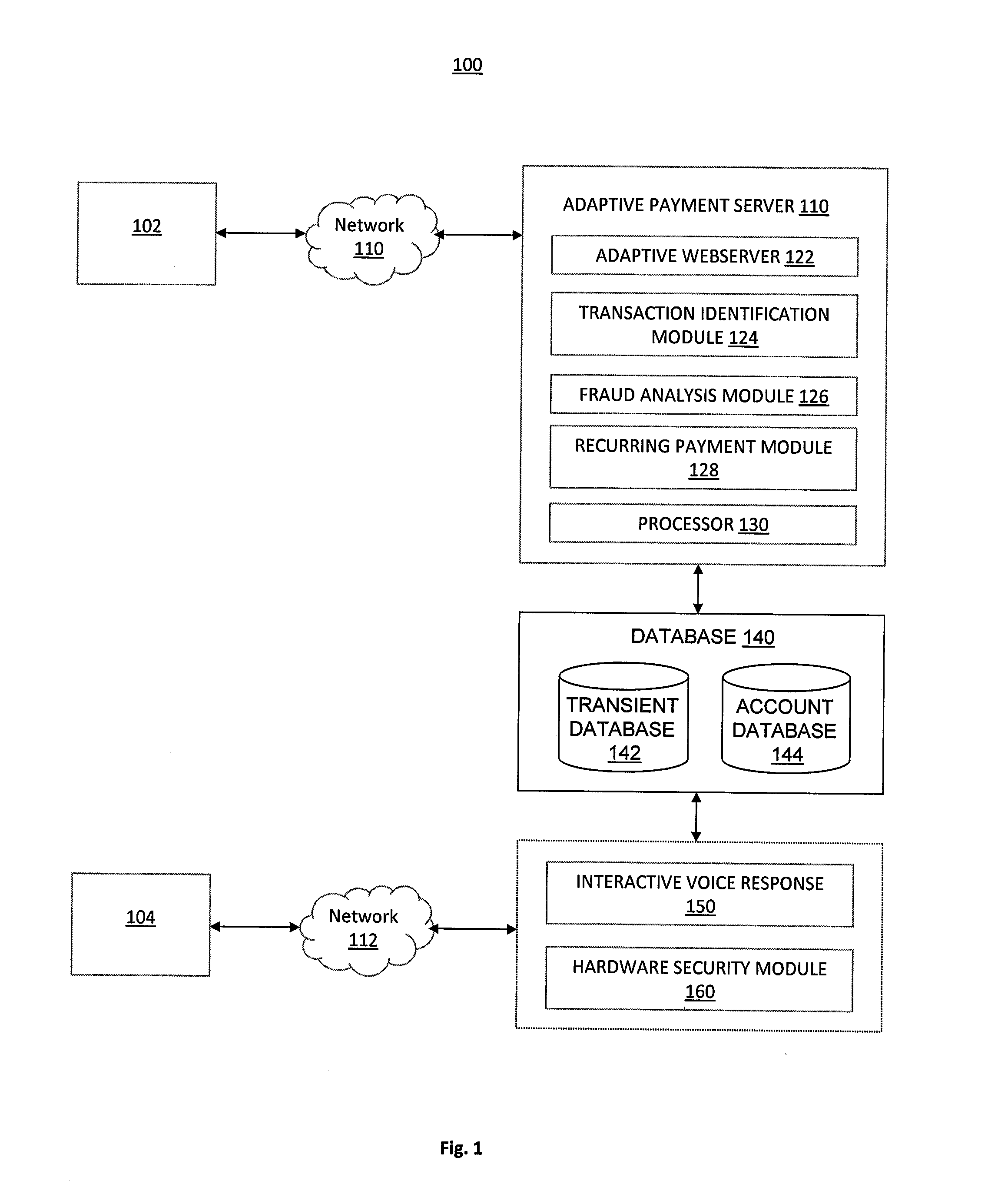
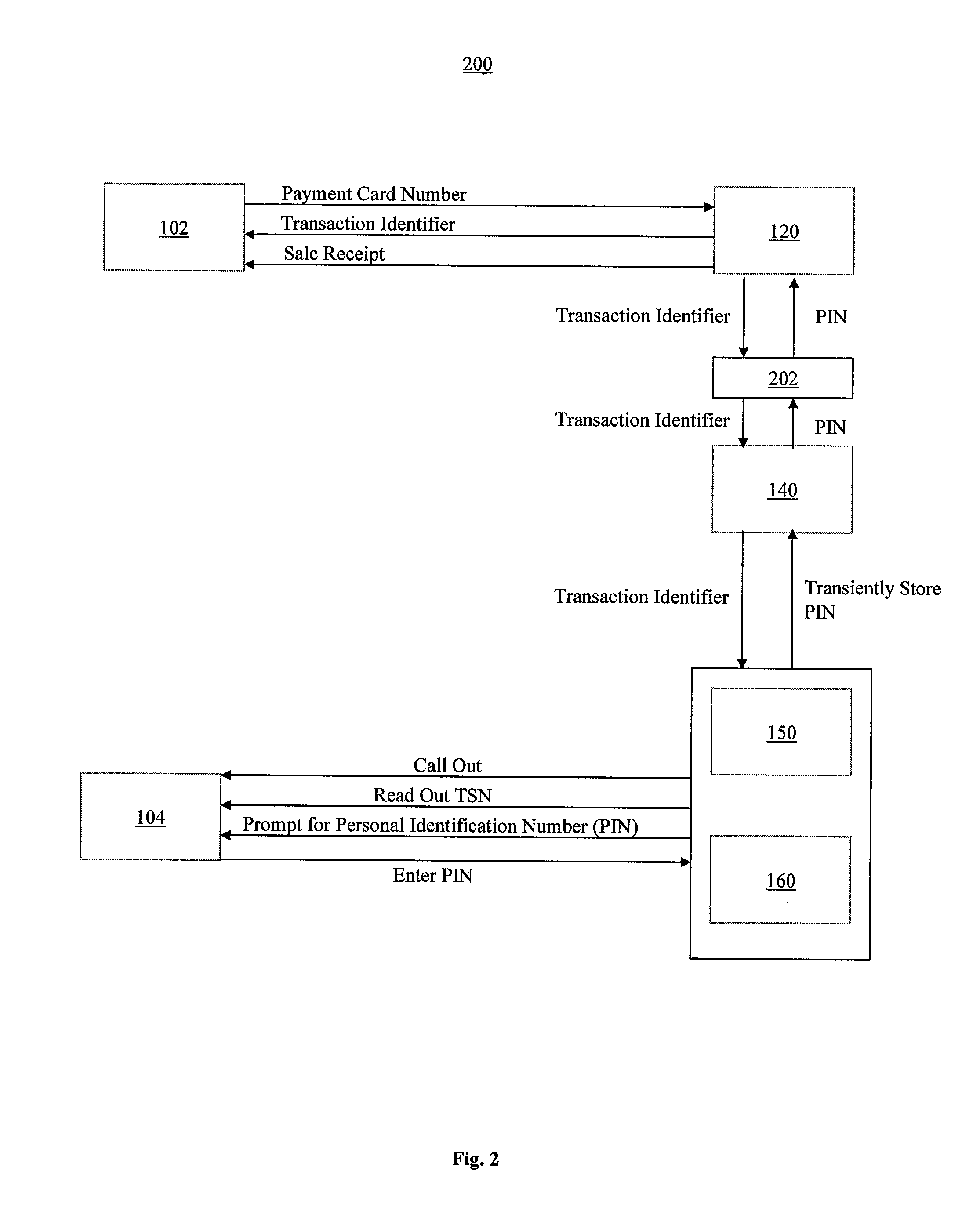
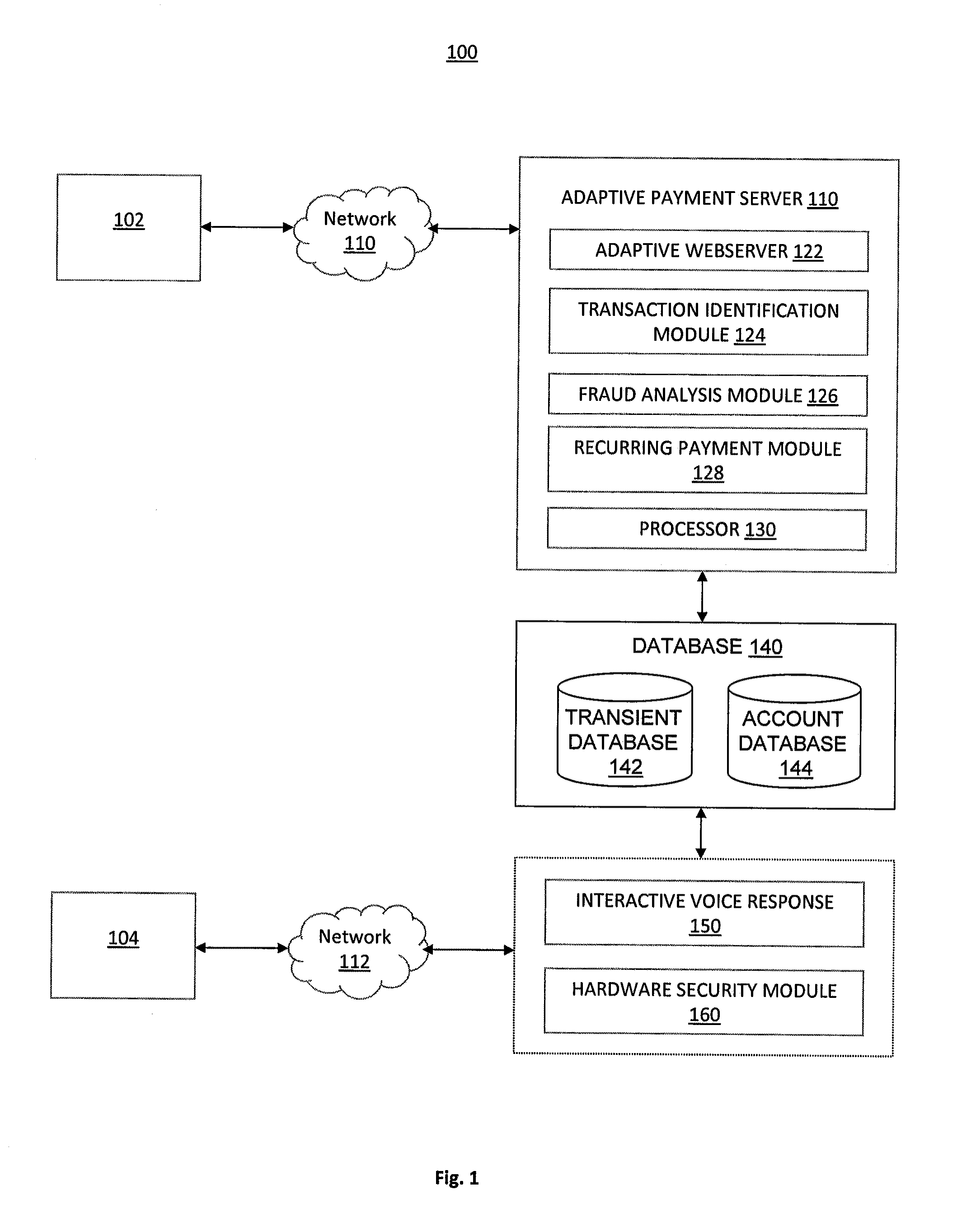
System and Method of Secure Payment Transactions
ActiveUS20100057623A1Facilitate secure payment transactionAuthentication is convenientAcutation objectsFinancePayment transactionCommunication device
A system and method for secure payment transactions is provided. The system may include an adaptive payment server including one or more processors configured to receive a first communication including first identification information from a first communication device on a first communication channel. The adaptive payment server may identify a second communication device based on the first identification information and initiate a second communication to the second communication device on a second communication channel, which may be discrete from the first communication channel. The adaptive payment server may receive second identification information from the second communication device on the second communication channel and authenticate the payment transaction using the first identification information and the second identification information.
Owner:MTS HLDG
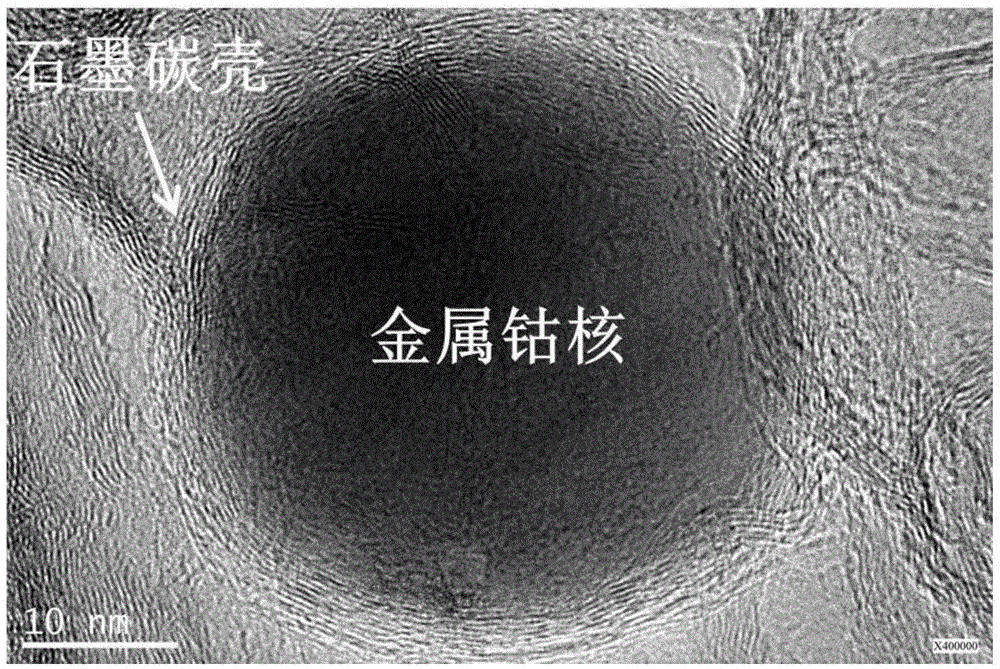
Method for preparing non-metallic element doped carbon coated metal nanoparticle magnetic composite
ActiveCN105478755AGood dispersionHigh purityTransportation and packagingMetal-working apparatusDispersityCyanamide compound
The invention discloses a method for preparing a non-metallic element doped carbon coated metal nanoparticle magnetic composite. The method comprises the steps that water-soluble metal divalent salt, a cyanamide compound and a nitrogen or boron or sulfur containing non-metallic compound are added into a methanol solution to be mixed, dissolved, dried and ground, and obtained homogeneous-phase powder is subjected to roasting pyrolysis under the protection of inert gas; and a pyrolysis product is subjected to acid pickling, washing, drying and grinding, and a target product is obtained. According to the whole preparing process of the method, metal ion reduction, metal nanoparticle coating and doping of nitrogen / boron / sulfur and other non-metallic elements are achieved in one step. The composite prepared through the method is high in degree of graphitization, good in dispersity between particles and high in purity, and the preparing method has the advantages that the cost is low, the process is simple, and large-quantity synthesis can be easily achieved.
Owner:合肥庐阳科技创新集团有限公司
User-oriented cloud storage data integrity protection method
InactiveCN105320899ASave storage spaceAvoid Lost Security RisksDigital data protectionData integrityOriginal data
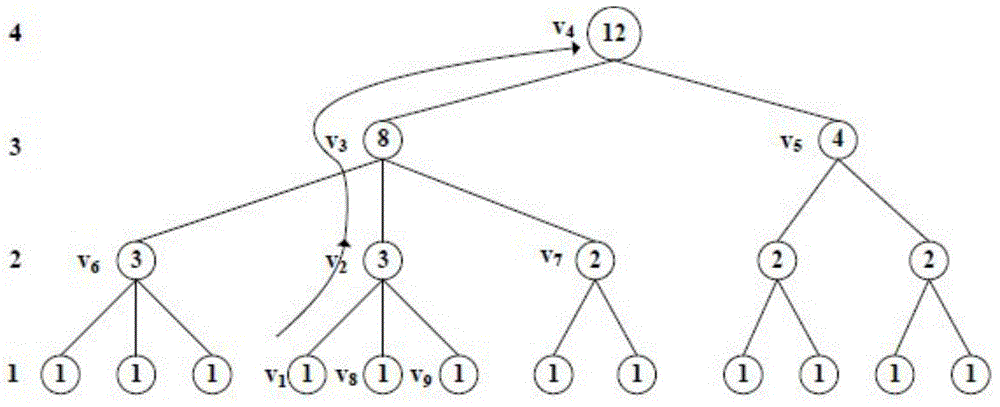
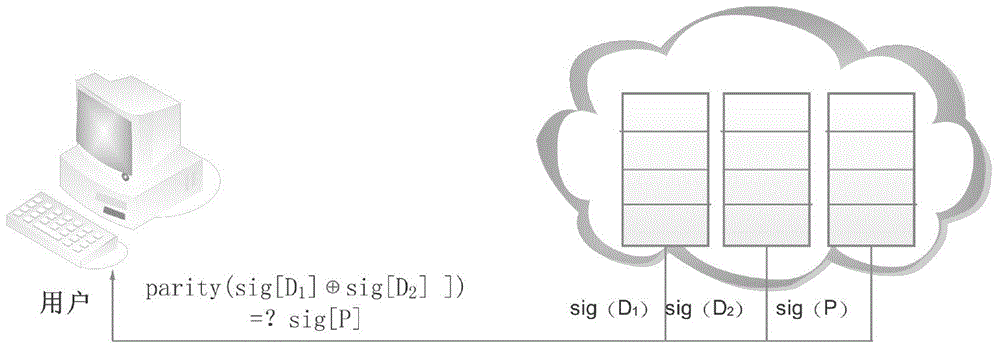
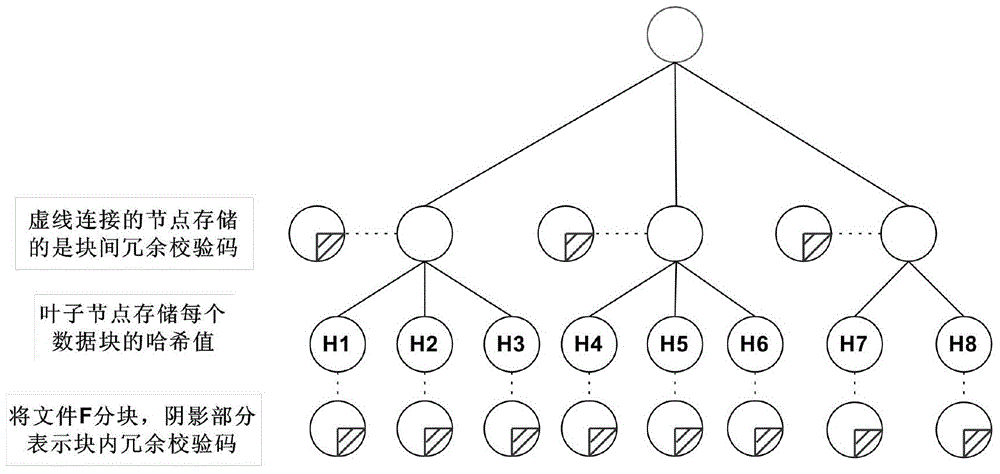
The invention discloses a user-oriented cloud storage data integrity protection method. The method includes the steps of 1, uploading, wherein a user side segments and numbers a file to generate intra-block redundancy check codes, the hash value of each file block is calculated and saved as a range-based 2-3 tree, the hash values are linked into one value and signed with private keys, and inter-block redundancy check codes are generated and encrypted with stream substitution secret keys; 2, verification, wherein a cloud management node sends a verification request to a corresponding cloud storage server, corresponding original data and algebraic signatures of the inter-block redundancy check codes corresponding to the original data are calculated and returned to the user side for data integrity verification, and the step 3 is executed if data destruction is found; 3, recovery, wherein the user side acquires all the file blocks on corresponding branch trees from a cloud side according to tree information and performs error recovery on the file blocks through erasure codes of the file blocks. According to the method, integrity verification and recovery are performed on the dynamic data stored in the cloud side from the user perspective.
Owner:PEKING UNIV
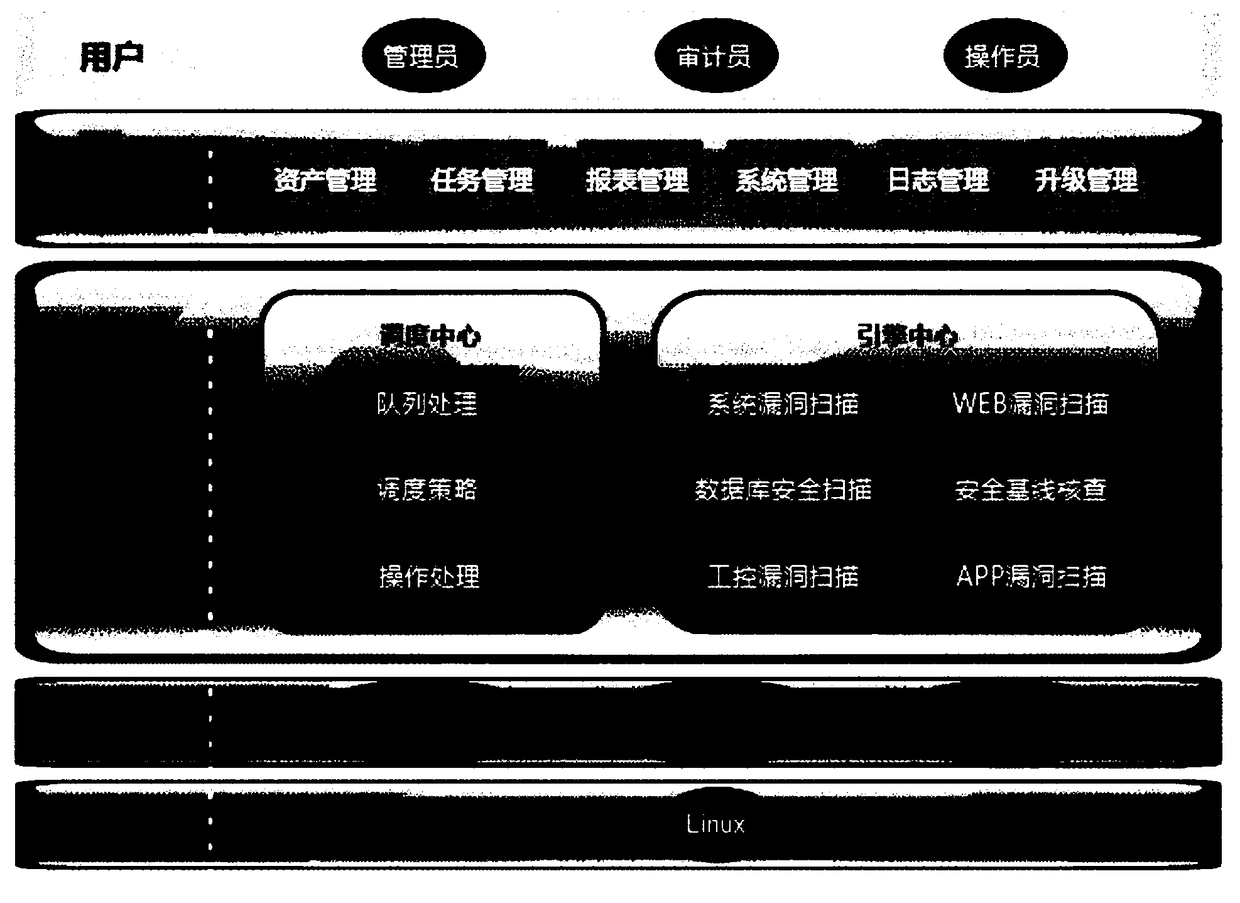
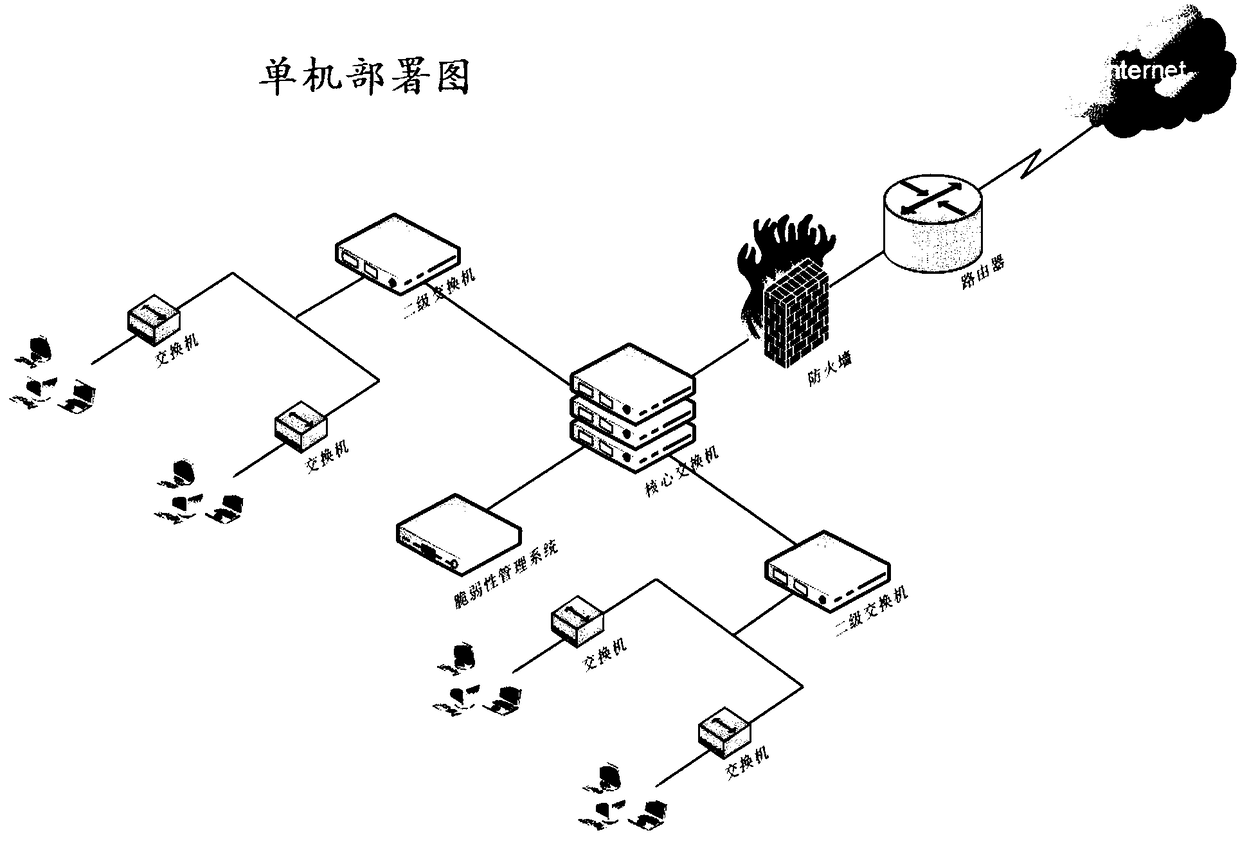
Vulnerability management system based on multi-engine vulnerability scanning association analysis
ActiveCN108737425AMeet safety construction requirementsEfficient and accurate executionTransmissionVulnerability managementOperational system
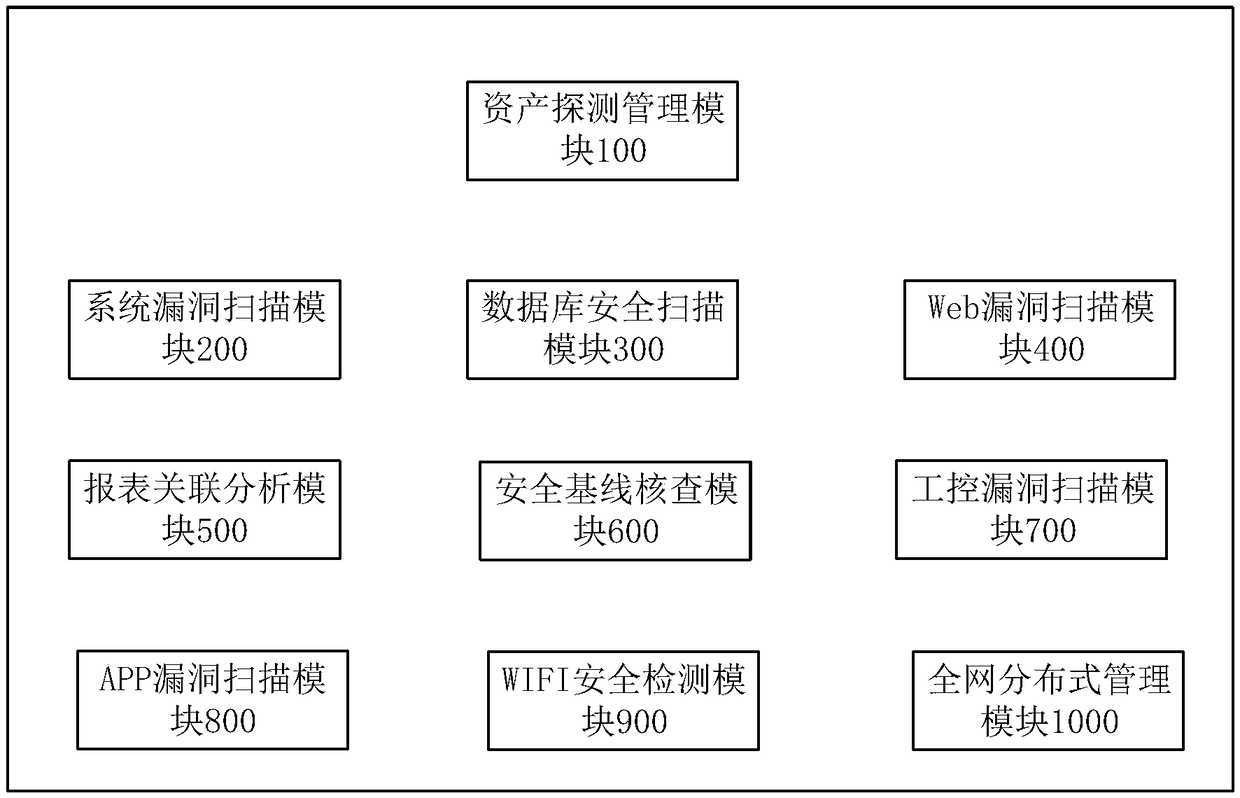
The invention provides a vulnerability management system based on multi-engine vulnerability scanning association analysis. The vulnerability management system comprises: an asset detection managementmodule used for detecting asset information in a scanning network; a system vulnerability scanning module used for performing vulnerability scanning and analysis on a network device, an operating system, application service and a database according to the asset information, and supporting intelligent service identification; a Web vulnerability scanning module used for automatically parsing data according to the asset information, scanning the data, verifying a discovered WEB vulnerability, and recording a test data packet discovered by vulnerability scanning; a database security scanning module; a security baseline verification module; an industrial control vulnerability scanning module; an APP vulnerability scanning module; a WIFI security detection module; a report association analysismodule; and a whole-network distributed management module. The vulnerability management system provided by the invention can perform association analysis on a detection result and a compliance libraryof information security level protection to generate a level protection evaluation report that meets the specification requirements, and the security requirements of different customers are comprehensively met.
Owner:北京凌云信安科技有限公司
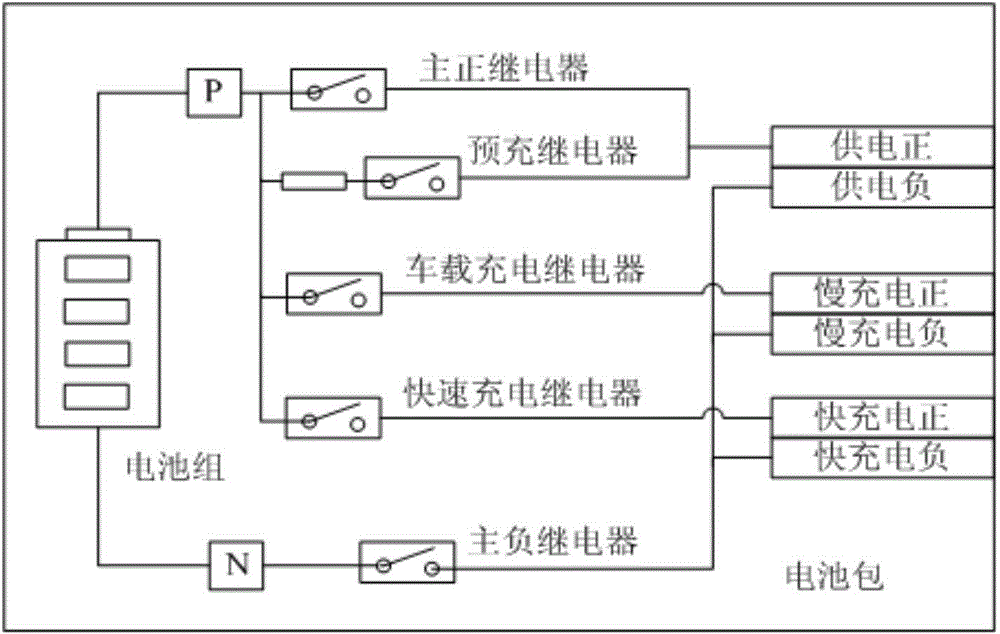
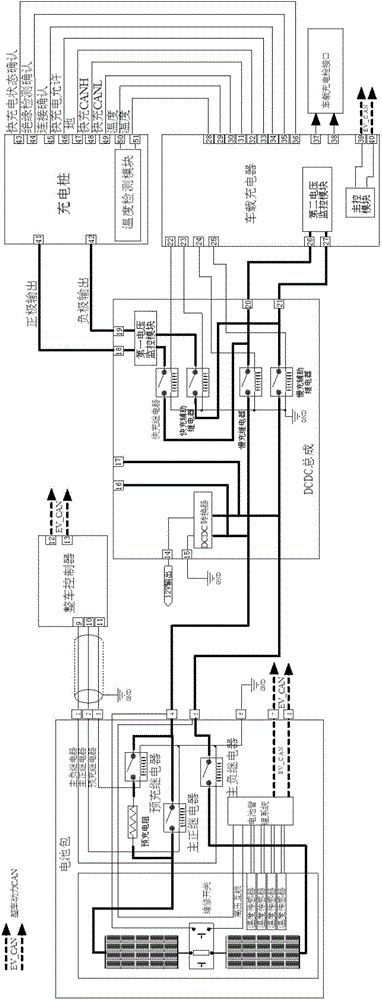
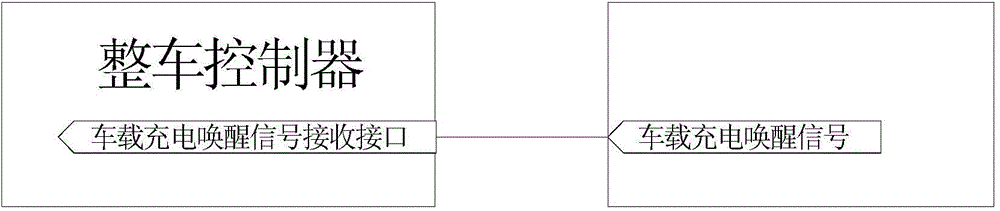
Electromobile charging system and charging control method
ActiveCN104600815AAchieve closureAvoid safety hazardsBatteries circuit arrangementsCharging stationsCharge controlEngineering
The invention provides an electromobile charging system which comprises a battery pack, a main positive relay, a main negative relay, an electromobile controller, a quick-charging relay, a quick-charging auxiliary relay, a slow-charging relay, a slow-charging auxiliary relay and an electromobile-mounted charger. Normally-open contacts of the quick-charging relay and the slow-charging relay are in series connection, and normally-open contacts of the quick-charging auxiliary relay and the slow-charging auxiliary relay are in series connection. The invention further provides a control method adopting the electromobile charging system for quick charging and slow charging. By the electromobile charging system and the charging control method, charging safety of an electromobile can be improved.
Owner:ANHUI JIANGHUAI AUTOMOBILE GRP CORP LTD
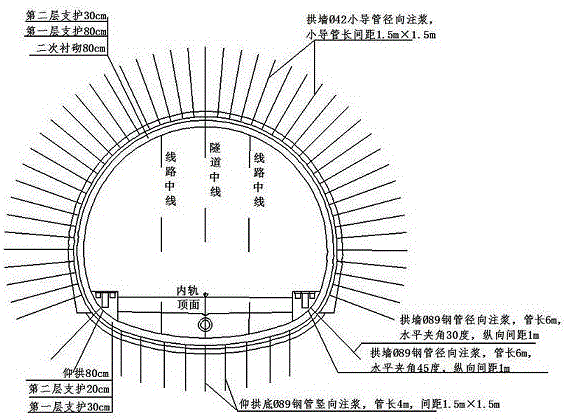
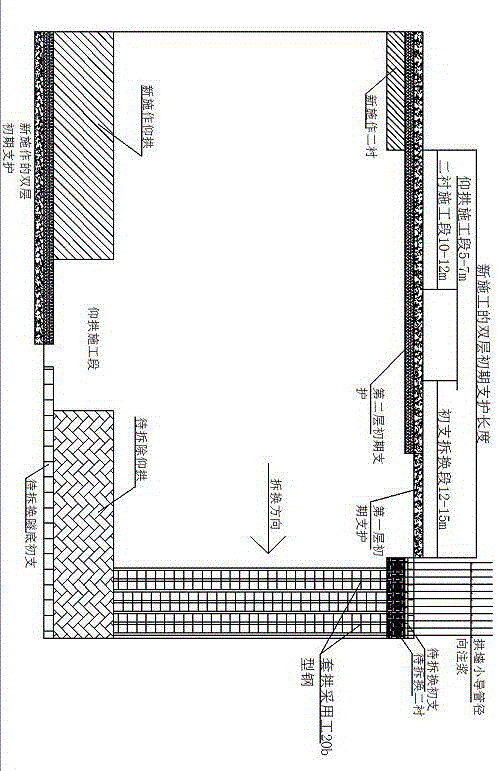
Construction method for soft rock deformation tunnel lining support dismantling-replacing arch
InactiveCN105781571AGuaranteed carrying capacityGuaranteed integrityUnderground chambersTunnel liningEngineeringLarge deformation
The invention provides a construction method for a soft rock deformation tunnel lining support dismantling-replacing arch. One-time whole section integral dismantling and replacing of a lining support is achieved. The construction method has the advantages that before dismantling and replacing, a lining which loses bearing capacity is subjected to grouting reinforcement treatment first, then a temporary cover arch is additionally arranged outside for reinforcement, and afterwards, the lining support is dismantled step by step, so that potential safety hazards caused by dismantling or removing of a temporary platform frame are avoided, and some security risks are avoided effectively. According to the construction method, the construction difficult problem of soft rock large deformation occurs during construction of a tunnel in special and complex geology is solved. Through the created novel construction method, the construction difficult problem of second lining cracking deformation needing remediation due to weak surrounding rock large deformation is solved. Through the construction method, safe, fast and economic treatment and remediation of the lining support and arch replacing construction are achieved, and the tunnel structure stability and construction safety are ensured effectively.
Owner:CCCC SECOND HIGHWAY ENG CO LTD
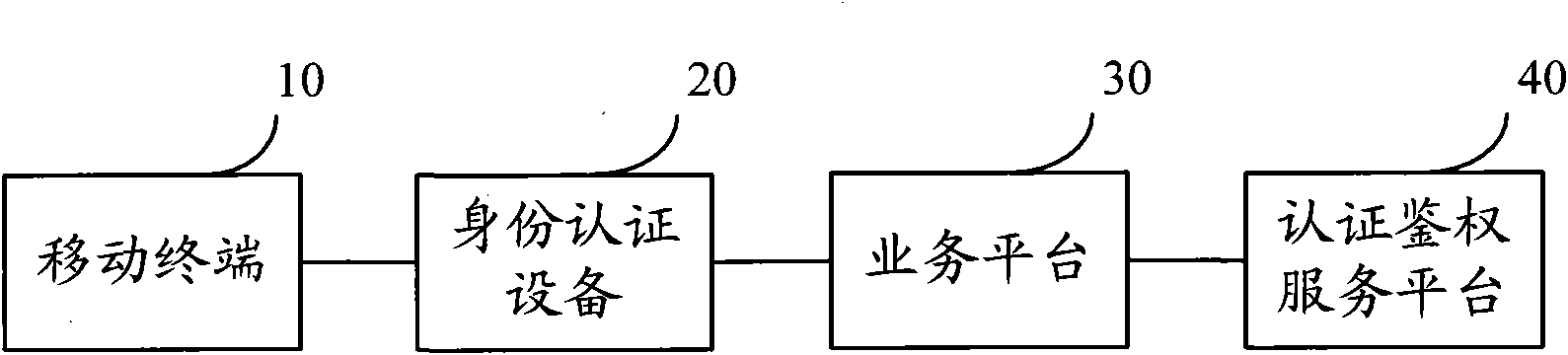
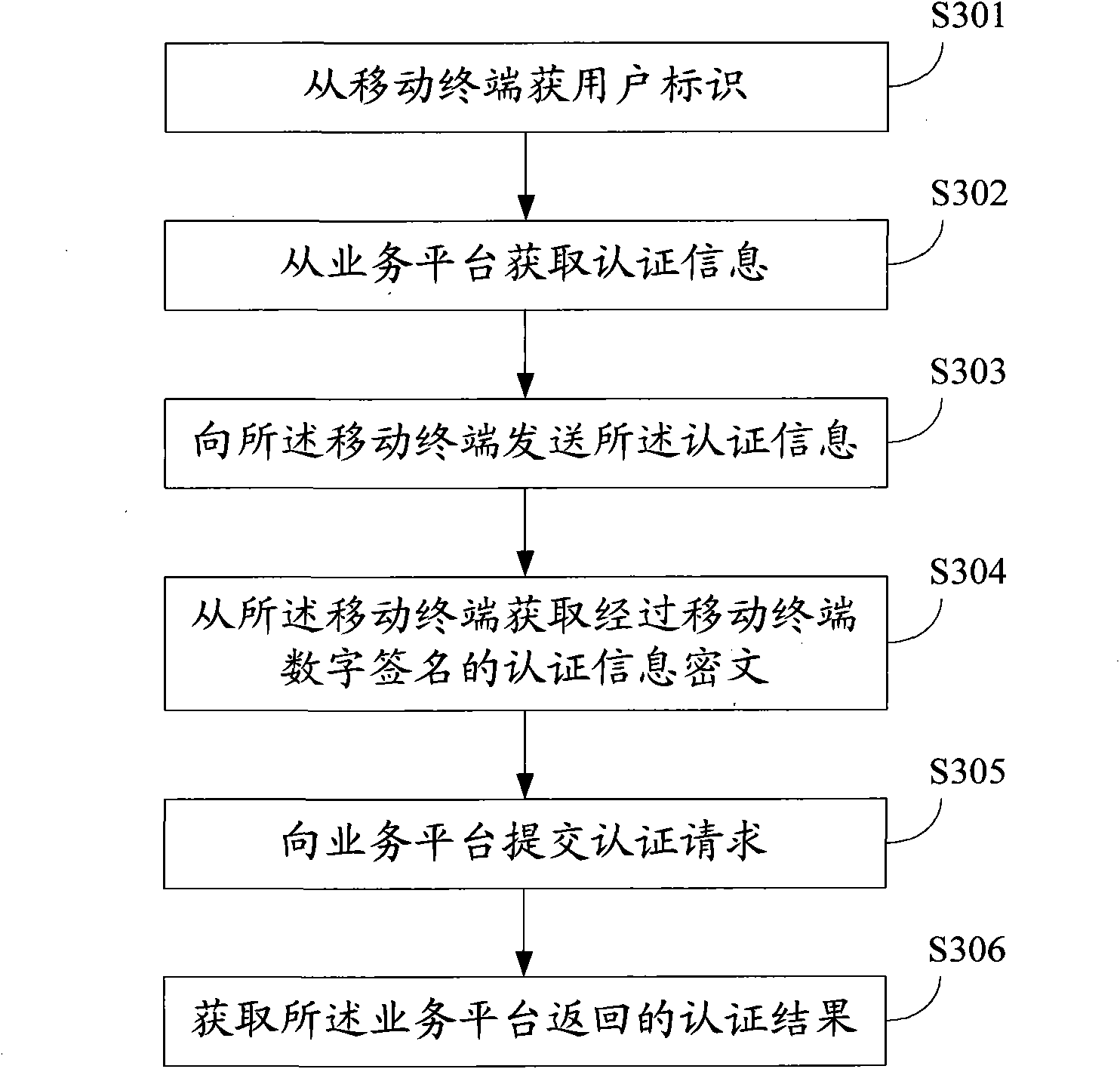
Identity authentication method, device and system
InactiveCN101778380AAchieve authenticationAvoid security risksUser identity/authority verificationSecurity arrangementCiphertextSerial code
The embodiment of the invention provides an identity authentication method, which comprises the steps of acquiring a user identification from a mobile terminal; acquiring identification information including an authentication serial number and authentication time from a service platform; sending the identification information to the mobile terminal; acquiring authentication information cipher text digitally signed via the mobile terminal form the mobile terminal; submitting an authentication request including the user identification, the authentication information and the authentication information cipher text to the service platform; and acquiring authentication results returned by the service platform. Accordingly, the embodiment of the invention also discloses an identity authentication device and an identity authentication system. With the invention, the user identity is authenticated, and various safety risks and losses brought by fake or alternative identity and the like are avoided.
Owner:卓望数码技术(深圳)有限公司
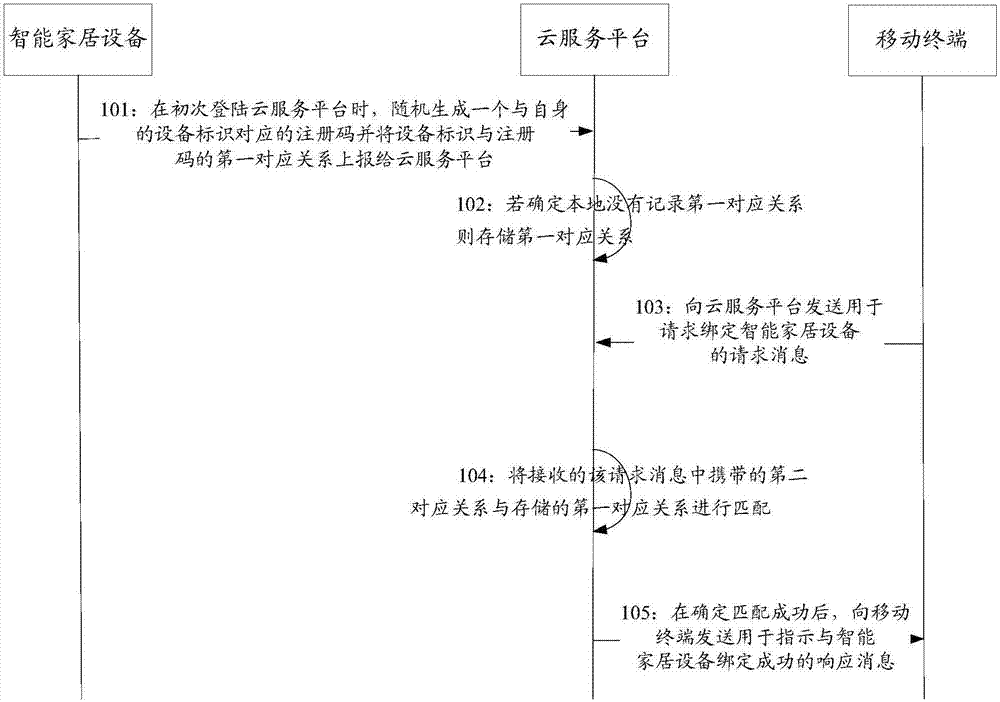
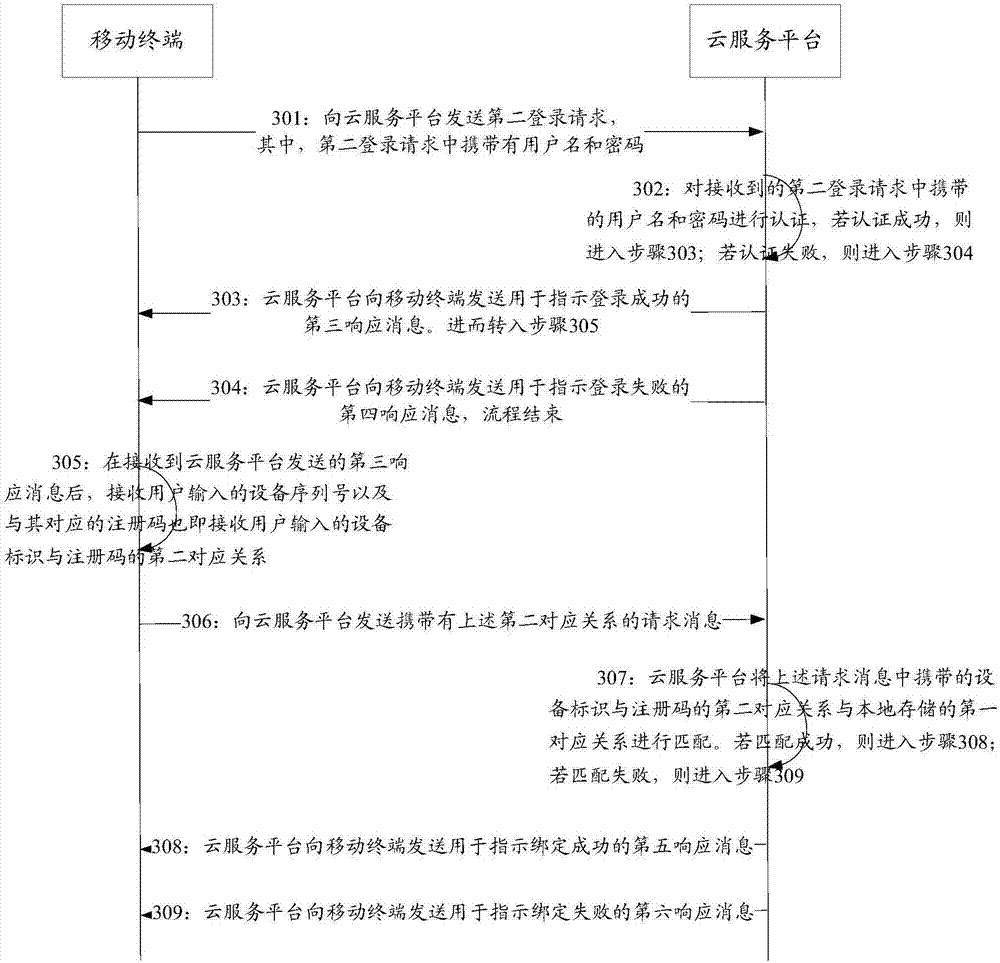
System, method and device for equipment binding
The invention relates to the technical field of the internet, in particular relates to a system, method and device for equipment binding, and is used for solving the problem that the security when intelligent home equipment is bound with a mobile terminal is relatively low in the prior art. The method for equipment binding provided in the embodiment of the invention comprises the steps that: a cloud service platform receives the first corresponding relationship of an equipment identifier and a registration code sent by the intelligent home equipment, wherein the registration code is randomly generated when the intelligent home equipment logs in the cloud service platform for the first time; if the fact that the first corresponding relationship is not recorded locally is determined, the first corresponding relationship is stored; after a request message used for requesting for binding the intelligent home equipment sent by the mobile terminal is received, the second corresponding relationship of the equipment identifier and the registration code carried in the request message is matched with the stored first corresponding relationship; and, if matching is successful, a response message used for indicating that binding with the intelligent home equipment is successful is sent to the mobile terminal.
Owner:ZHEJIANG DAHUA TECH CO LTD
Method for reinforcing search engine result safety
InactiveCN101059818AGuarantee authenticityAvoid security risksPlatform integrity maintainanceSpecial data processing applicationsWeb siteSafety index
The invention relates to a method for improving the result safety of search engine, comprising that first processing basic safety evaluation on the webpage collected by a search engine, according to two kinds of list information as pre-collected safe website and malice website, processing an integral safety evaluation on the search result, leading a safety index into the result display, and processing different treatments on different result items according to the levels of the safety index, to make user differ the risk degrees of different results. The method can improve the safety of search engine in complex internet condition, to avoid user to enter into malice website effectively and avoid benefit loss.
Owner:申屠浩
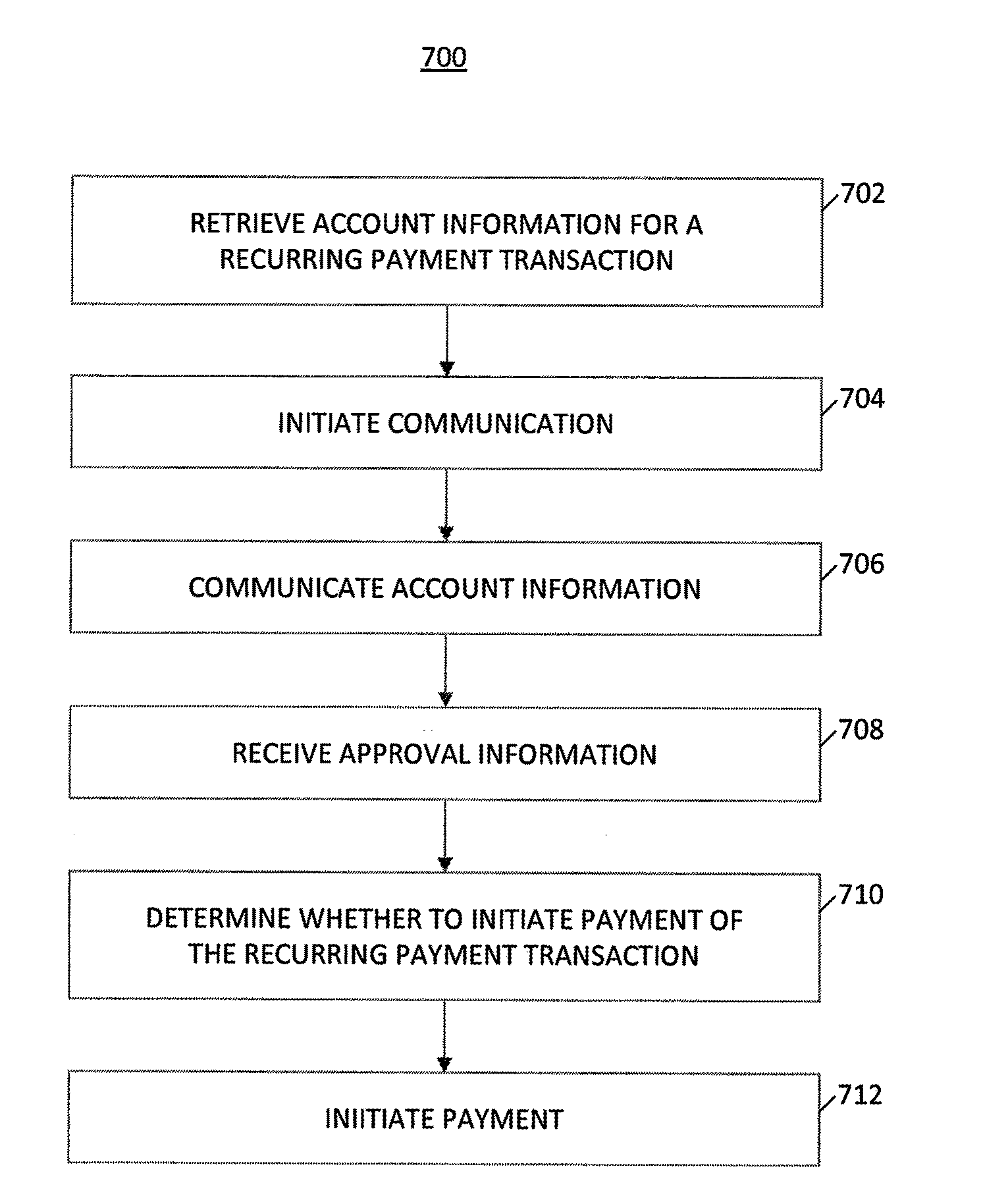
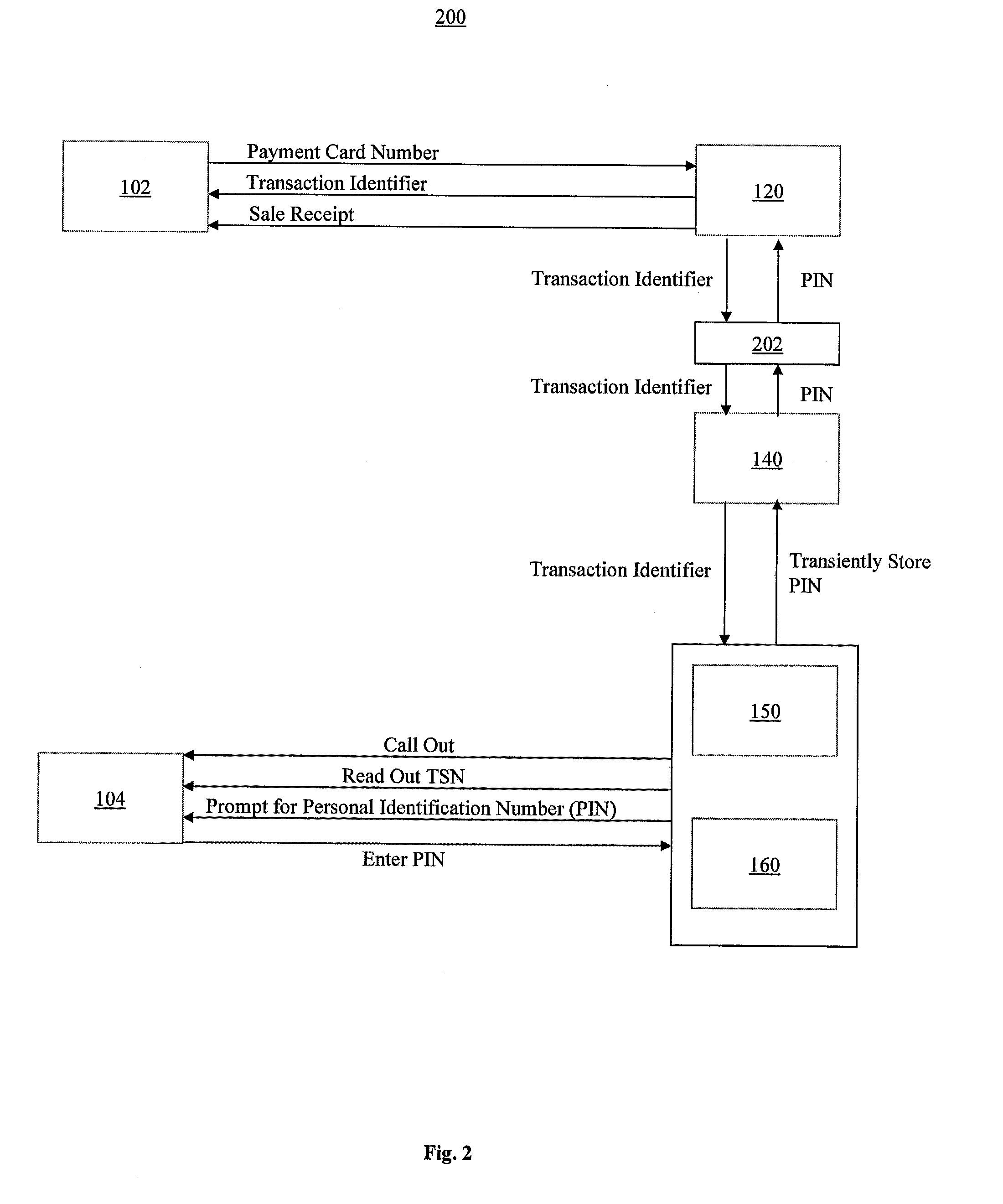
System and Method of Recurring Payment Transactions
InactiveUS20100057616A1Facilitate secure payment transactionAuthentication is convenientAcutation objectsFinanceInternet privacyPayment transaction
A system and method for a recurring payment transaction is provided. A system of authenticating a recurring payment transaction may include an adaptive payment server that includes one or more processors configured to retrieve account information, which may include a payment date and an identification of a communication device of a payor. The adaptive payment server may initiate a communication to the communication device on or before the payment date and communicate at least a portion of the account information to the communication device. The adaptive payment server may receive, from the communication device, approval information and determine whether to initiate payment of the recurring payment transaction using the approval information. The adaptive payment server may initiate payment of the recurring payment transaction based on the determination.
Owner:MTS HLDG
Long-distance authorizing system and method
ActiveCN1741104AAvoid security risksImproved business authorization efficiencyAdvertisingDisplay meansComputer terminalAuthorization
The present invention provides a long-distance authorization system and its method. Said system includes several counter terminals for executing service processing and utilizing service server to give out service authorization request message to at least an authorization supervisor; at least one authorization supervisor terminal for receiving service authorization request repeated by service server, making authorization processing and forming authorization result message; and service server for receiving every service authorization request message given out by each of several counter terminals, repeating said service authorization request message to at least one authorization supervisor terminal, and receiving authorization result message given out by at least one authorization supervisor terminal and repeating said result message to said counter terminal.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
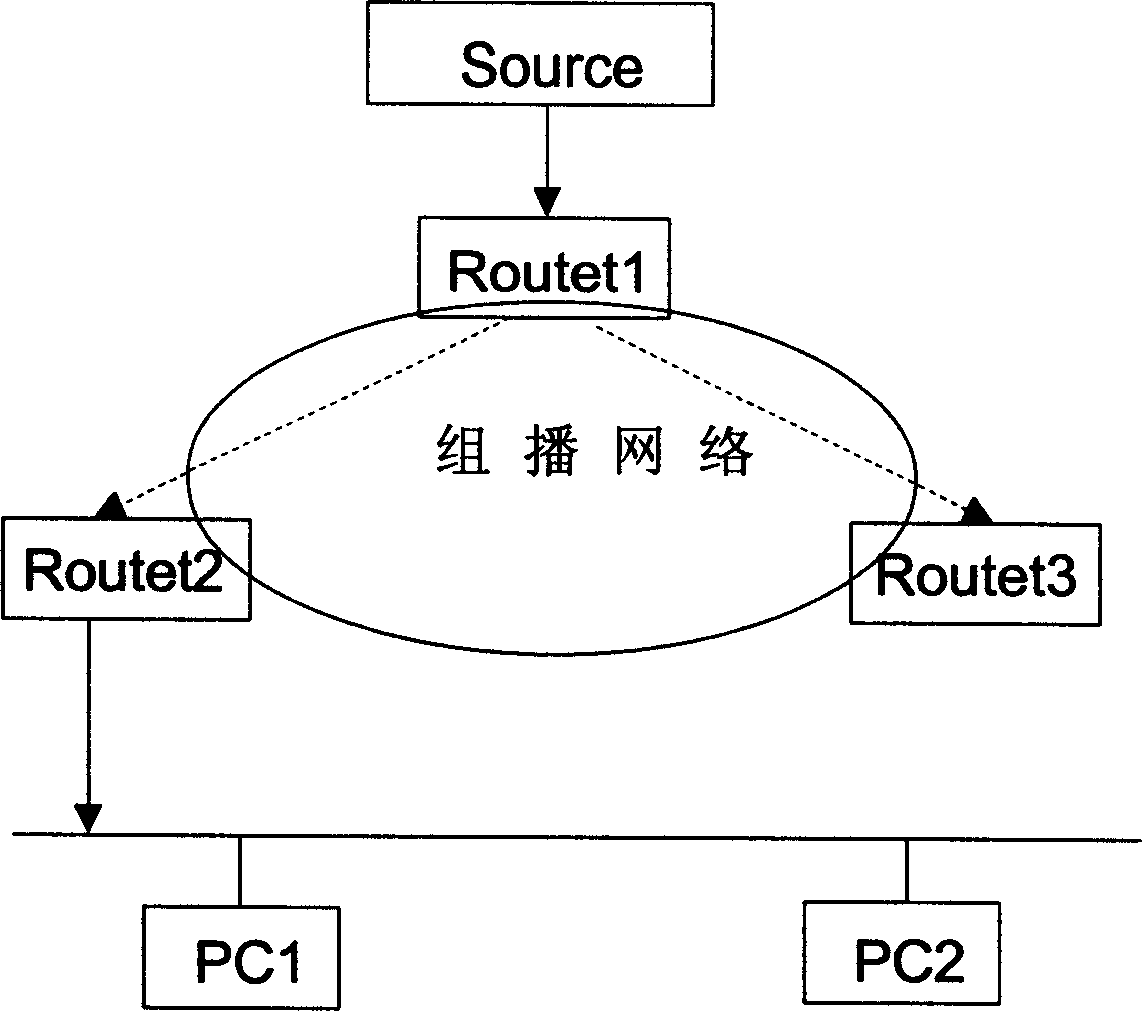
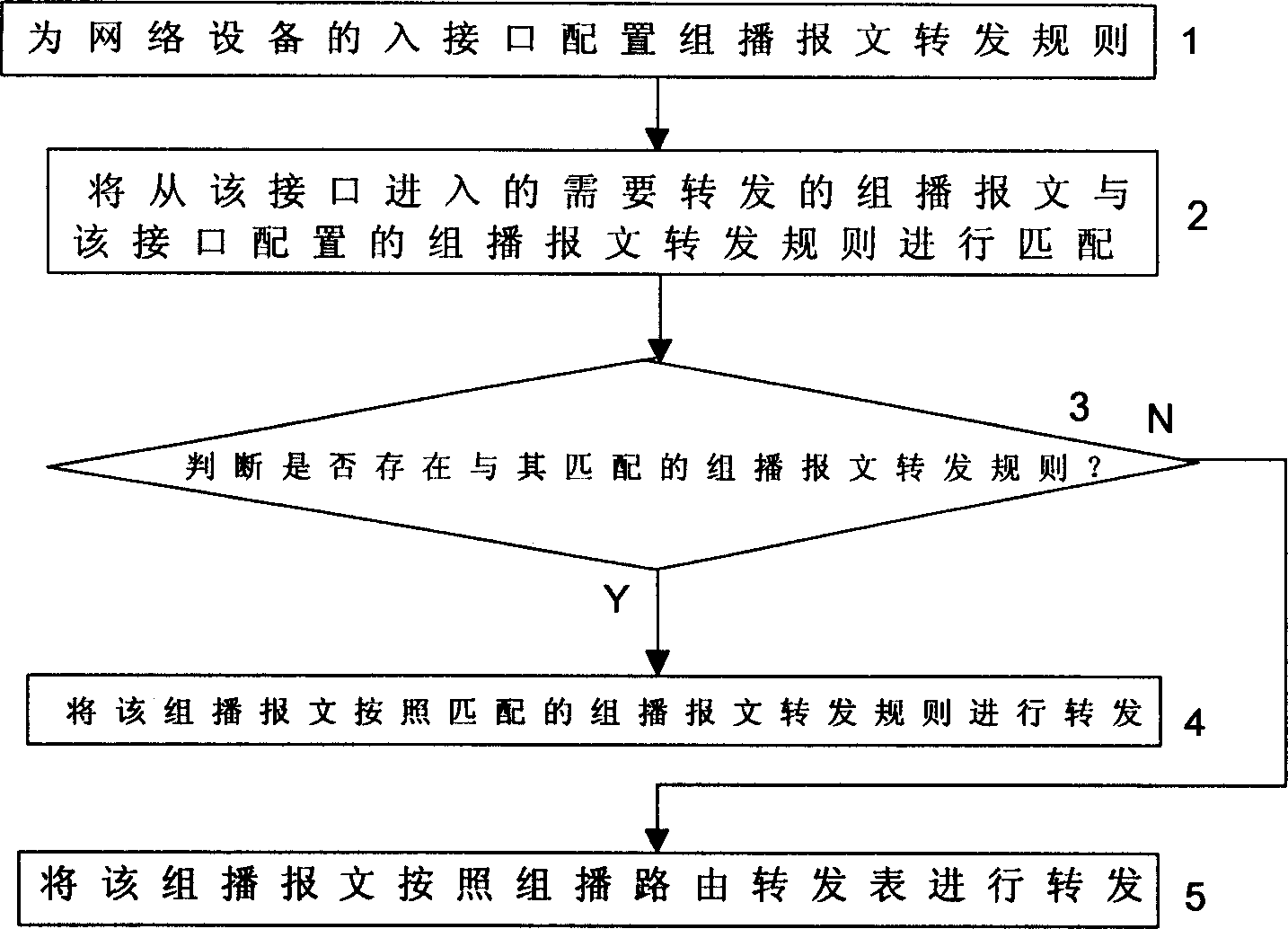
Repeating method for multi-broadcast message in network communication
InactiveCN1474563AAvoid efficiency lossEasy to useSpecial service provision for substationStore-and-forward switching systemsMulticast networkNetwork communication
This invention relates to a forward method for multicast messages in network communications which arranges transfer matching conditions at the interface of a network equipment needed in forwarding multicast messages, the condition stipulates a rule to transfer multicast messages, then multicast messages necessary to be forwarded enter into the network from the said interface to match with transfer matched conditions and to forward the said multicast messages based on the matched result, avoiding the security risk resulted from applying broadcast mode in the link layer and efficiency loss resulted from receiving large quantity of idle multicast messages.
Owner:HUAWEI TECH CO LTD
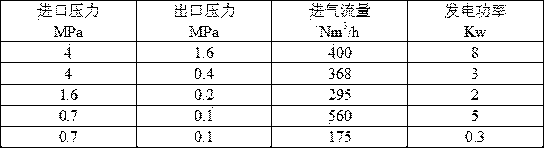
A pressure energy-recycling generation device for a natural gas pipe network
InactiveCN104213939AReduce wasteEnable recyclingMachines/enginesSafety/regulatory devicesElectricitySolenoid valve
The invention provides a pressure energy-recycling generation device for a natural gas pipe network. The device can efficiently transform the pressure energy in the natural gas pipe network into electricity, thereby realizing recycling. The operation state of the generation device can be automatically real-time monitored by combining a PLC and a solenoid valve, a pressure transmitter, a leakage detector and a sealing machine pry. The device can automatically forewarn and interlock to shut off when conditions like excess pressure and gas leakage occur, so the device has superior security and stability. The device can produce outstanding economic benefit, and has important meaning to reducing resource waste and accelerating establishment of resource-saving and environmentally friendly society.
Owner:JIANGSU AEROSPACE HEWLETT ENVIRONMENTAL PROTECTION TECH
Safety early warning method and device for online reservation taxis, storage medium and server
InactiveCN108961669AImprove securityEnsure safetyClosed circuit television systemsAlarmsVideo imageComputer science
The invention relates to a safety early warning method and device for online reservation taxis, a storage medium and a server. The safety early warning method comprises the steps of obtaining video images shot by a camera when a passenger takes an online reservation taxi, wherein the camera is installed in the online reservation taxi; identifying the video images to determine state information ofa driver; determining the danger level at least according to the state information of the driver; and sending an early warning prompt according to the danger level. According to the technical scheme of the invention, the safety of the online reservation taxi can be improved, safety risks are avoided, and the safety of passengers is effectively guaranteed.
Owner:SHANGHAI XIAOYI TECH CO LTD
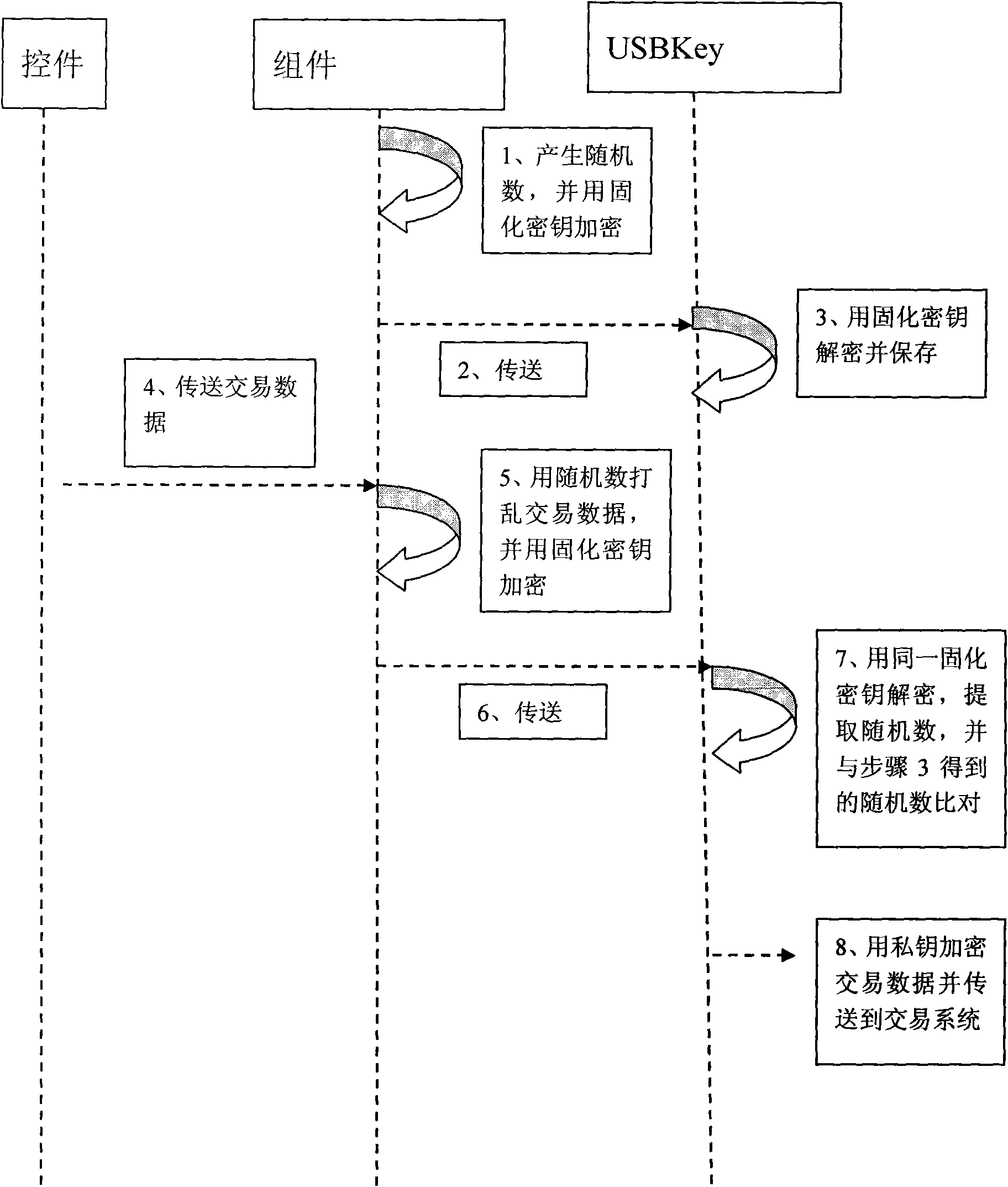
Method and system based on USBKey online banking trade information authentication
The invention discloses a method based on USBKey online banking trade information authentication; when being used for the first time, system software is automatically mounted into an operating systemand a solidifying key is mounted simultaneously; when a user finishes pressing a trade fingerprint to confirm the trade, application software generates a random number and uses the solidifying key toencrypt and transmit to a USBKey; meanwhile, the application software uses the random number to implement inserting and upsetting on the received trade data and uses the solidifying key to encrypt andtransmit to the USBKey; the USBKey uses the shared solidifying key to decrypt to obtain one random number and a string of trade data upset by the random number, uses the shared key to take out the random number inserted into the trade data and compares the random number with the random number obtained by directly deciphering, and the random number is confirmed to be true and valid if the resultsare the same. The invention can guarantee the trade information to be safely transferred in the network links by establishing a data truth authentication system, stop the trade information from beingmaliciously altered and protect the user trade to be safely and validly executed.
Owner:ZHEJIANG WELLCOM TECH
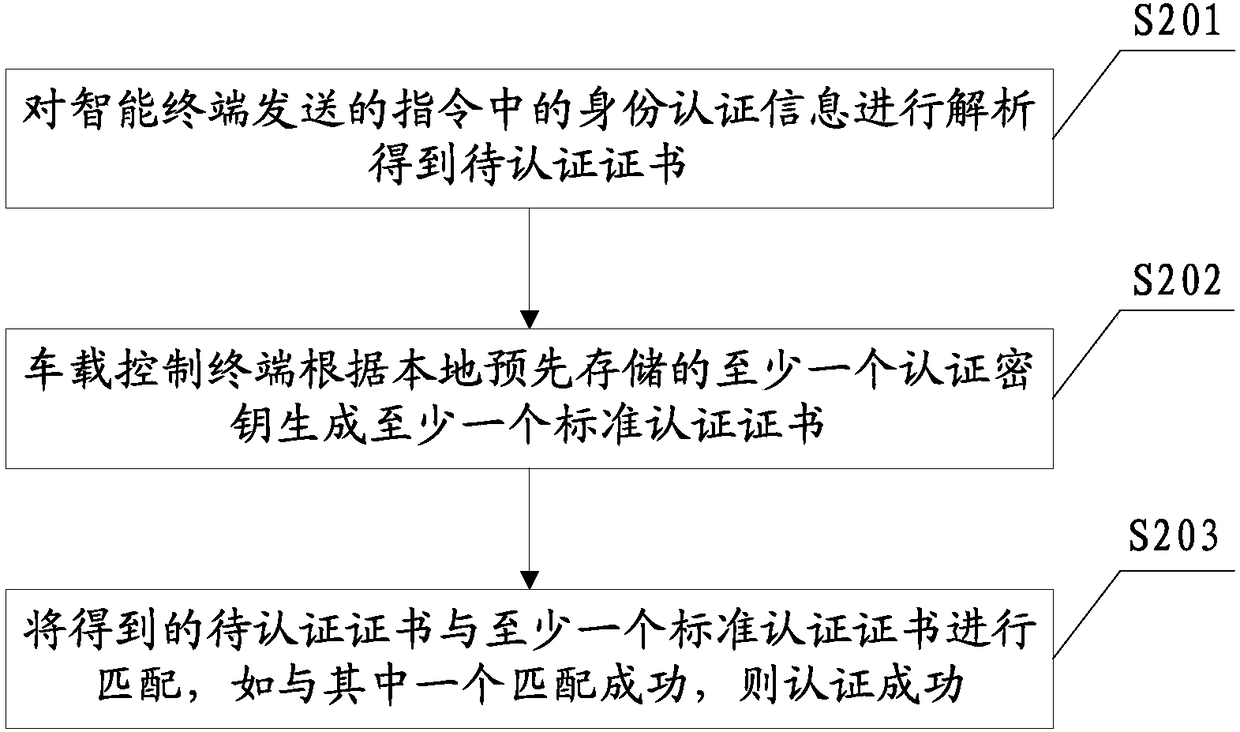
Vehicle system and virtual key authentication method thereof
InactiveCN108665337AImprove leasing efficiency andConducive to developmentIndividual entry/exit registersBuying/selling/leasing transactionsAuthentication informationComputer science
The invention provides a vehicle system and a virtual key authentication method thereof. As a vehicle virtual key, an intelligent terminal can register and order in a vehicle rental platform. After receiving the order request of the intelligent terminal, the vehicle rental platform generates identity authentication information according to a corresponding authentication key and sends the identityauthentication information to the intelligent terminal. The intelligent terminal transmits an instruction including identity authentication information to a vehicle-mounted control terminal on a vehicle, the vehicle-mounted control terminal performs authentication processing on the identity authentication information according to a pre-stored authentication key, and when authentication is successful, the intelligent terminal is allowed to control the vehicle. A user can directly use the intelligent terminal to interact with the vehicle rental platform and the vehicle-mounted control terminal on the vehicle, authentication is completed to achieve vehicle rental, improving rental efficiency, and avoiding various security risks caused by an entity key being cracked in the vehicle rental process; and the authentication key is only stored on the vehicle rental platform and the vehicle-mounted control terminal in the whole process, further ensuring the security of the key system.
Owner:CHONGQING WIRELESS OASIS COMM TECHCO
Control method for implementing coordinated operation of multiple vehicle groups of hydraulic heavy duty truck
InactiveCN103217978ACoordinated controlEasy to correctPosition/course control in two dimensionsArea networkSteering angle
The invention relates to a control method for implementing coordinated operation of multiple vehicle groups of a hydraulic heavy duty truck, which can be used for implementing unmanned automatic driving of a roadway trackless wheel-type hydraulic heavy duty truck. Positions between vehicle bodies and a roadway are determined by applying an ultrasonic distance measurement principle; various information of the truck, which is measured by ultrasonic distance measurement sensors, is transmitted to a central processor; information of the truck relative to the roadway, such as a vehicle body speed, a steering angle, a traveling track and a path, is calculated by the processor according to a set program; the position information is uploaded to a CAN (Controller Area Network) bus system for being called by a next truck; a next truck processor downloads posture information of a previous truck from a CAN bus; according to the posture information of the previous truck, the processor operates geometrical parameters required for tracking the movement track of the previous truck according to a control program so as to determine the movement track of the next truck and fulfill the aim that the next trunk automatically tracks the previous truck, thereby implementing steering control of the split heavy duty transportation truck.
Owner:YANSHAN UNIV
Super high-rise core tube horizontal direction and vertical direction synchronous construction top formwork system and construction method
InactiveCN106869489AReduce productionReduce consumptionForms/shuttering/falseworksForm treatmentSupporting systemControl system
The invention discloses a super high-rise core tube horizontal direction and vertical direction synchronous construction top formwork system which comprises a truss platform system, a hanger enclosure system, a supporting system, a formwork system and a hydraulic control system. The formwork system is an aluminum alloy formwork system. The aluminum alloy formwork system comprises vertical wall formworks and horizontal formworks. Each vertical wall formwork comprises a plurality of aluminum alloy standard unit plates spliced transversely, and C-shaped aluminum alloy grooves located in the aluminum alloy standard unit plates. Each horizontal formwork is formed by splicing a plurality of aluminum alloy bulk slicing plates. The horizontal formworks on the different layers are formed by splicing the aluminum alloy bulk slicing plates different in quantity. The horizontal formworks are connected with the vertical wall formworks through the C-shaped aluminum alloy grooves. According to the super high-rise core tube horizontal direction and vertical direction synchronous construction top formwork system provided by the invention, synchronous construction of horizontal structures and vertical structures of a core tube is achieved.
Owner:NO 1 CONSTR ENG CO LTD OF CHINA CONSTR THIRD ENG BUREAU CO LTD
Vehicle safety control system and method for lane line detection temporary loss in automatic drive
InactiveCN106681318AImprove the ability to deal with special working conditionsAvoid security risksPosition/course control in two dimensionsVehiclesDriver/operatorImaging processing
The invention discloses a vehicle safety control system and method for lane line detection temporary loss in automatic drive, and the system comprises an automatic drive decision-making module, an image processing module, a light controller, an execution mechanism, an HMI module and a camera, wherein the image processing module, the light controller, the execution mechanism and the HMI module are respectively connected with the automatic drive decision-making module, and the camera is connected with the image processing module. The image processing module carries out the processing of an image, and carries out the detection of a lane line. The automatic drive decision-making module carries out the planning of a driving path of a vehicle based on the lane line, and controls the running of the vehicle. When the image processing module cannot detect the lane line, the automatic drive decision-making module obtains a passable region of a road according to a historical track of the vehicle and the information detected by a radar group, and controls the vehicle to reduce the speed and run in the passable region, and the light controller turns on an emergency light, and the HMI module continuously reminds a driver of taking charge of the vehicle. When the lane line cannot be detected in a short time, the system can guarantee that the vehicle is in a safety state, and guarantees the safety of the driver.
Owner:CHONGQING CHANGAN AUTOMOBILE CO LTD
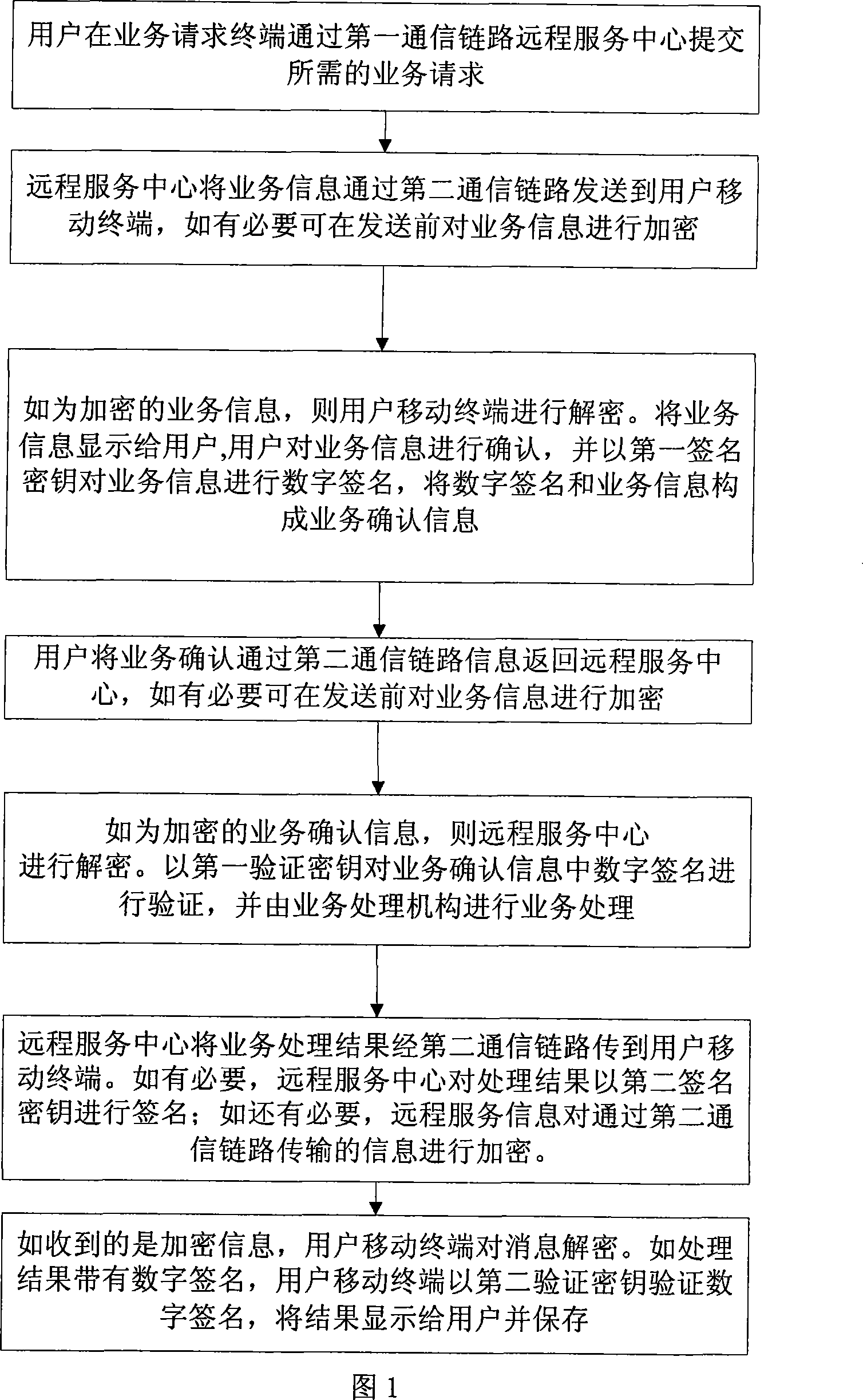
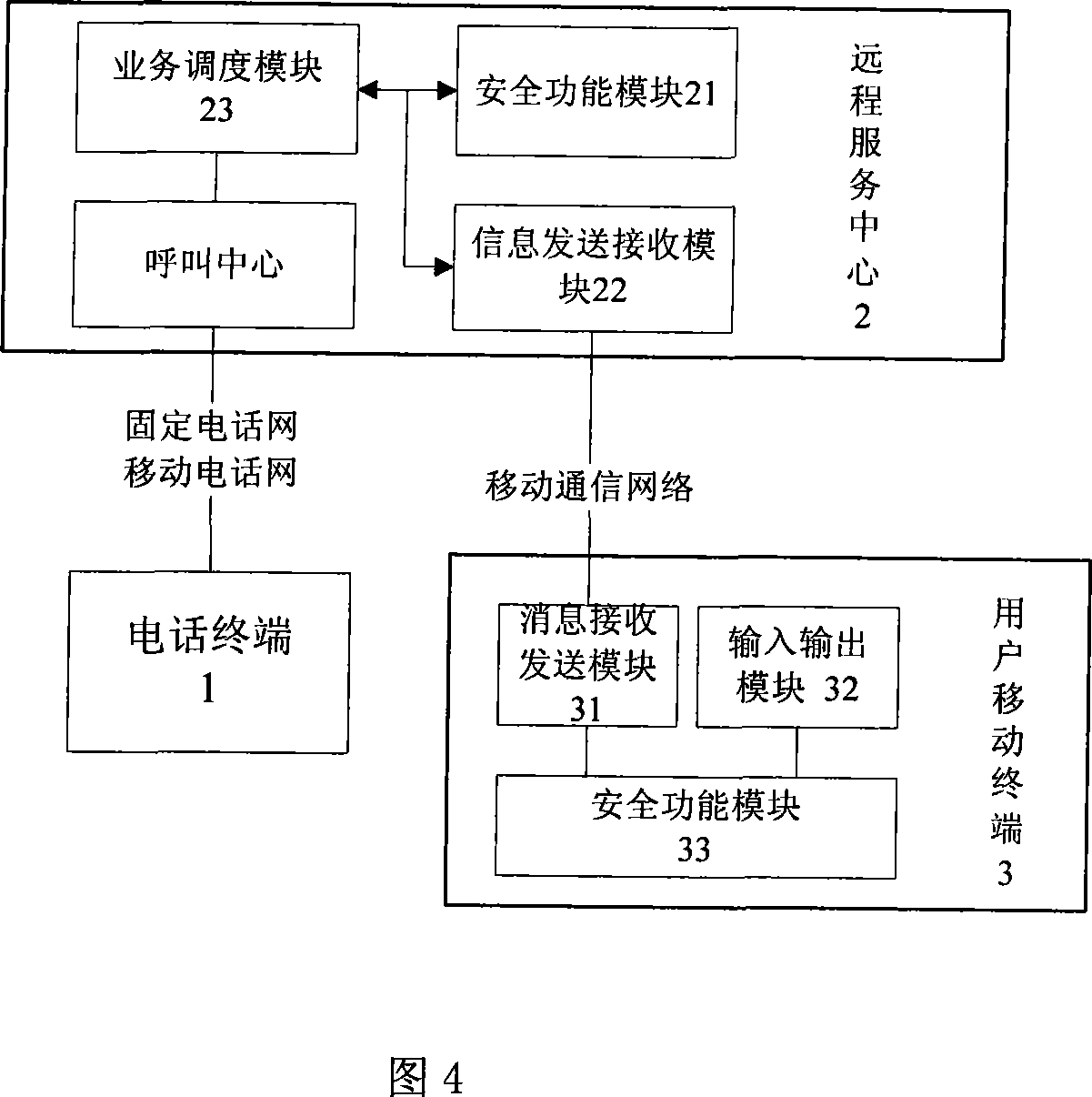
Trusted remote service method and system
ActiveCN101242271AAvoid security risksGuarantee authenticityUser identity/authority verificationRadio/inductive link selection arrangementsTelecommunicationsTelecommunications link
The invention discloses a trusted teleservice method and a system thereof. The system comprises an operation request terminal, an teleservice center and a subscriber mobile terminal. The subscriber submits a required operation to the teleservice center by a first communication link at the operation request terminal; the teleservice center sends an operation request information generated from an operation request submitted by the subscriber to the subscriber mobile terminal by a second communication link for authenticating, and the operation information returns to the teleservice through the second communication link after signed on and confirmed by the subscriber mobile terminal; the teleservice center complete the operation after the digital signature is authenticated in an acknowledge information, sets a digital signature to an operation treating result to form a result information which is sent to the subscriber mobile terminal by the second communication link; and the subscriber authenticates and stores the received result information. The invention is secure, has a simple operation, and is especially used in electronic trade and bank financial transaction.
Owner:陕西海基业高科技实业有限公司
Hydraulic fabricated crossing structure
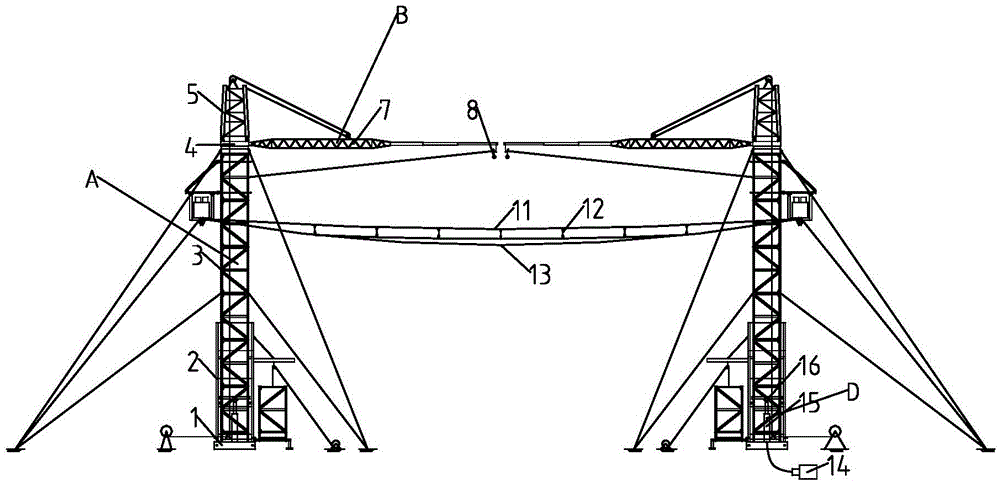
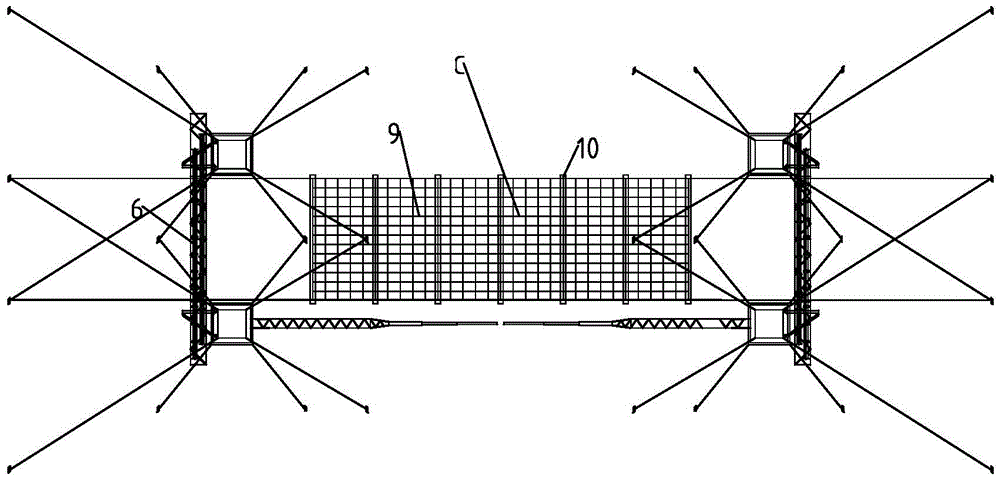
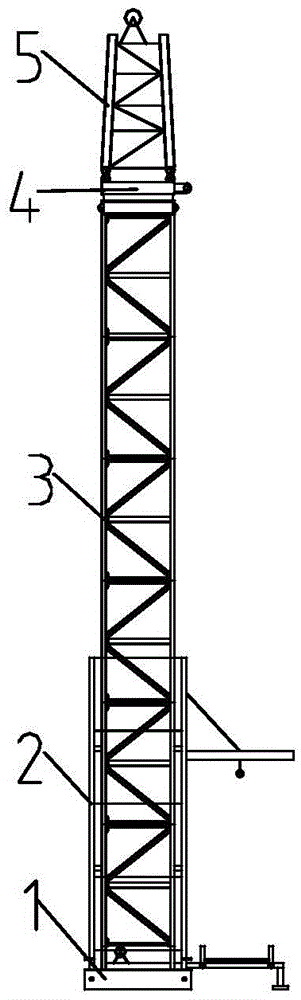
ActiveCN105529648ARealize self-elevating and self-descendingImprove impact resistanceApparatus for overhead lines/cablesSafety netEngineering
The invention discloses a hydraulic fabricated crossing structure, which comprises a structure body, a safety net device, rotating arm mechanisms and hydraulic jacking mechanisms, wherein the structure body comprises a plurality of upright posts and beam components; the safety net device comprises a carrying rope, a circulating rope, a safety net, insulating stay bars and sling members; each rotating arm mechanism comprises a rotating arm and a magnetic docking device; and each hydraulic jacking mechanism comprises an oil station, an oil cylinder and a jacking platform. Stabilization of the structure body is achieved through stay wires; each upright post is stabilized by upper and lower layers of stay wires; four stay wires are unevenly distributed on each layer; the upper layer of stay wires are located at the lower parts of rotary assemblies of the upright posts; and the lower layer of stay wires are located close to the center positions of the waists of the upright posts. According to the hydraulic fabricated crossing structure, the shock resistance of the crossing structure is improved by the measures of optimizing the overall structure of the crossing structure, adopting a high-strength steel material, adding a buffer force reliever, reasonably arranging the stay wires and the like; meanwhile, lightweight, fabricated and automatic design is carried out; and the 'hydraulic fabricated crossing structure' can meet the requirements of field construction.
Owner:STATE GRID CORP OF CHINA +2
Authentication method, authentication device and system applied to intelligent terminal
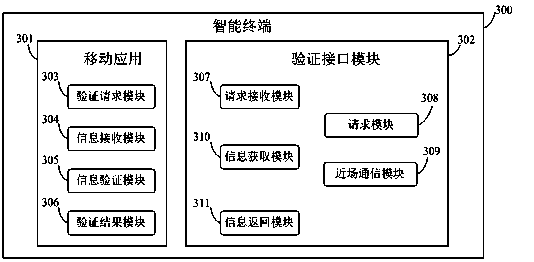
InactiveCN104301110AImprove securityImprove efficiencyUser identity/authority verificationAuthenticationNear field communication
The invention provides an authentication method, an authentication device and a system applied to an intelligent terminal. The method includes the steps that an applied account number is bound with a public key of the authentication device which is carried along with a user; the intelligent terminal receives the verification request of at least one application, and the verification request requests that the signing message sent back by the authentication device is used for conducting verification; based on the verification request, the near-field communication function is used for sending the verification request message to the authentication device near the intelligent terminal by a certain distance; the authentication device uses a private key preset in the authentication device and a designated cryptographic algorithm to conduct signing on the verification message, and the signed verification request message is sent back to the application; the public key, bound in advance, of the authentication device and the designated cryptographic algorithm are used for verifying the verification request signing message which is sent back, and a verification result is obtained. By means of the authentication method, the authentication device and the system applied to the intelligent terminal, the problems of inadequate safety, complex operation and high cost in the application verification process in the prior art can be solved.
Owner:刘文清
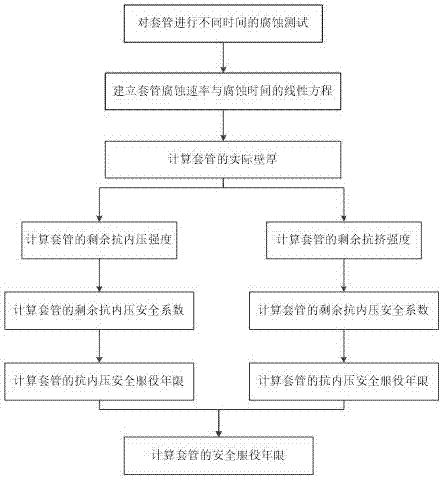
Method for predicting corrosion lifetime of casing pipe
ActiveCN107290270AAccurate lifeAvoid security risksWeather/light/corrosion resistanceSafety coefficientCorrosion
The invention discloses a method for predicting a corrosion lifetime of a casing pipe, which belongs to the field of corrosion protection of oil and gas well. The method is characterized by comprising the following steps: firstly performing corrosion test for casing pipe steel under a simulation working condition by utilizing a high-temperature high-pressure kettle, obtaining a uniform corrosion rate value, then obtaining an actual wall thickness of the casing pipe, and respectively solving remaining internal pressure strength and remaining collapse resisting strength of the casing pipe by utilizing the actual wall thickness of the casing pipe; and then calculating a remaining internal pressure resisting safety coefficient and a remaining collapse resisting strength safety coefficient of the casing pipe, respectively calculating an internal pressure resisting safety service lifetime and a collapse resisting safety service lifetime of the casing pipe according to a given internal pressure resisting safety coefficient threshold value and a collapse resisting safety threshold value, and finally obtaining a safety service lifetime of the casing pipe. The method has the advantages that the lifetime of the casing pipe can be reasonably predicted, and the safety risk caused by the corrosion of the oil and gas well casing pipe can be reduced or avoided.
Owner:SOUTHWEST PETROLEUM UNIV
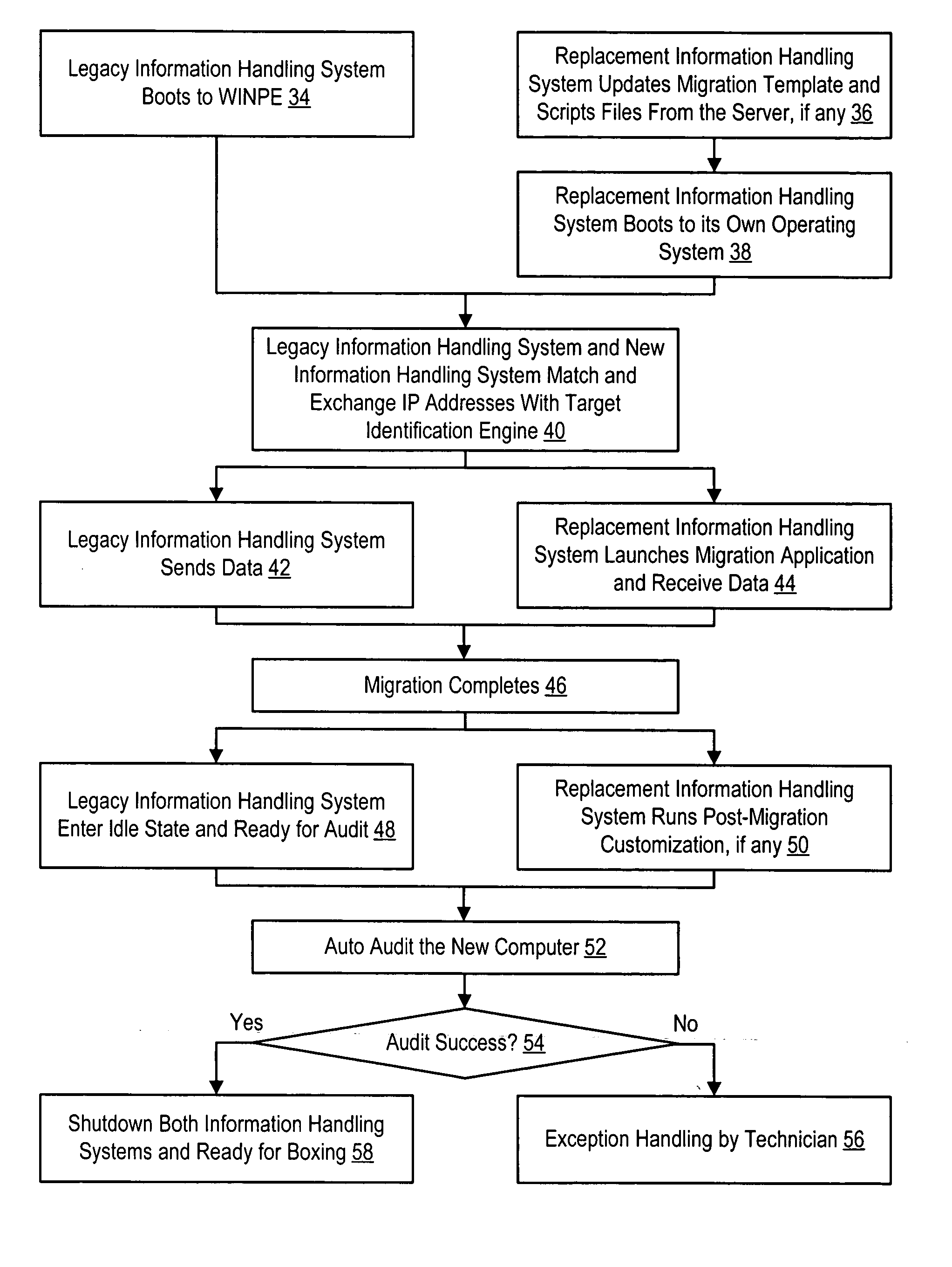
System and method for migration to manufactured information handling systems
InactiveUS20060129769A1Reduce disadvantagesReduce problemsMemory loss protectionProgram controlInformation processingOperational system
Data migration directly from legacy to replacement information handling systems is managed over a set of one or more switches. The legacy information handling system boots with a manufacturing operating system provided from a data migration information handling system server and runs a data migration application also provided from the server. Running the data migration application over the manufacturing operating system avoids password protection of the legacy information handling system. A pair of target storage device keys interface with a legacy and associated replacement system to aid in location of the replacement system on the network for direct system-to-system data transfer.
Owner:DELL PROD LP
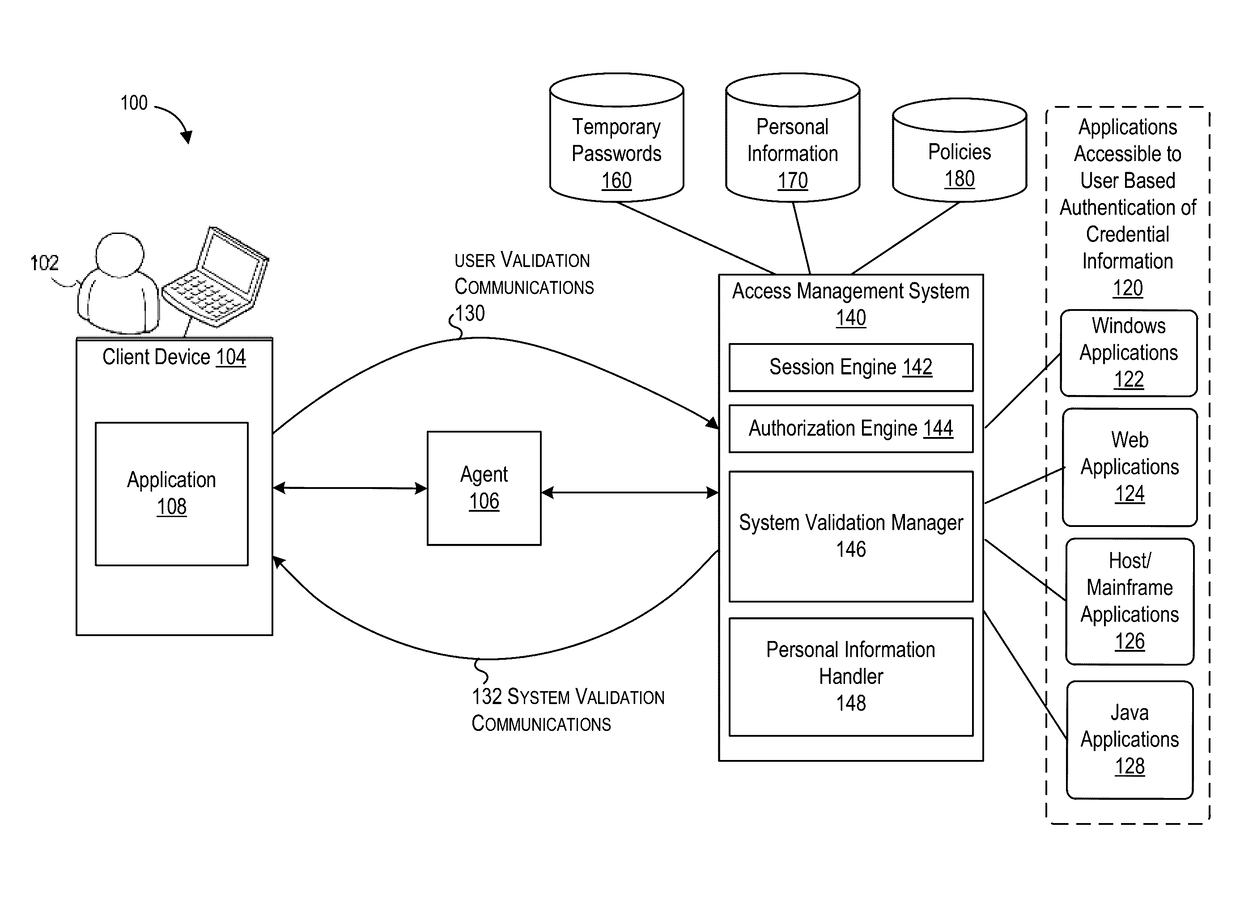
End user initiated access server authenticity check
ActiveUS20170118202A1Prevent safety riskAvoid security risksComputer security arrangementsTransmissionClient-sideWeb access management
Techniques are disclosed for enabling a user to validate the authenticity of a computing system (e.g., an access management system) such as one which controls access to one or more resources. A user can determine the authenticity of an access management system before the user provides credential information to the access management system. A user can be presented at a client system with an interface to request authentication of an access management system. The access management system may provide the user at the client system with temporary access information to submit back to the access management system. The access management system may provide recent personal information to the user at the client system to verify the access management system. Upon verification of the personal information, the access management system may prompt the user for credential information to establish a session.
Owner:ORACLE INT CORP
Automatic closed loop joint debugging method for telecontrol equipment and regulation and control main station of intelligent substation
ActiveCN105978152AImprove operational reliabilityGuaranteed uptimeCircuit arrangementsInformation technology support systemSmart substationPrimary station
The invention relates to an automatic closed loop joint debugging method for telecontrol equipment and a regulation and control main station of an intelligent substation. According to the automatic closed loop joint debugging method, The correctly-debugged SCD configuration files from the monitoring background of the substation and the EXCEL model files issued by the regulation and control main station are taken as the standard basis data source; data source simulation generation software based on the existing IEC61850 protocol is adopted for simulating the operations of sending the telemetry and telecontrol data of the substation to the telecontrol equipment, obtaining messages which are sent to the regulation and control center from the telecontrol equipment, performing analyzing, comparing and the like on the messages, and realizing telemetry and telecontrol automatic closed loop joint debugging; and meanwhile, the software automatically simulates the operations of sending down the telecontrol instruction from the regulation and control center to the telecontrol equipment, obtaining the telecontrol data which is sent down to the substation from the telecontrol equipment, performing analyzing, comparing and the like on the messages, and realizing telecontrol automatic closed loop joint debugging. According to the automatic closed loop joint debugging method, the purpose of joint debugging of the telecontrol equipment and the regulation and control main station can be fulfilled without requiring power failure of primary and secondary equipment; the accuracy can achieve 100%; the time saving rate can reach greater than 95%; and therefore, the working efficiency is greatly improved, and the reliable and safe operation of the power grid can be ensured.
Owner:STATE GRID FUJIAN ELECTRIC POWER CO LTD +3
Low-altitude flight target warning system and low-altitude flight target warning method based on Beidou satellite navigation system
ActiveCN104851322AEnsure safetyAchieving a decision support roleSatellite radio beaconingAircraft navigation/guiding aidsTerrainSafety monitoring
The invention provides a comprehensive flight safety warning system and a comprehensive flight safety warning method, which can be used for performing safety monitoring and command guide on a low-altitude flight target, performing threat comprehensive estimation and real-time warning, based on a Beidou satellite navigation system. By adopting the Beidou satellite navigation system, not only can three-dimensional positioning information of a flight target be provided, but also the flight parameters can be transmitted, so that a good technical supporting platform is provided for realizing comprehensive warning application. On the premise of comprehensively analyzing various security threats, real-time safety warning is realized on the low-altitude flight target; for direct safety threat warning, not only is most-concerned course front height warning in the flight track reflected, but also terrain perception, threat estimation and safety warning are performed at the left and the right sides of the flight object through a barrier warning method, so that the barrier perception and warning system around the flight target is perfected. Through the realization of the barrier warning method, a safe navigation track is planned, and the safety of the whole flight pipeline is further ensured.
Owner:XIAN SHANNON SOFTWARE TECH CO LTD
Android system-based intelligent POS security system, starting method and data management control method
ActiveCN105957276AImprove securityAvoid the risk of obtaining key dataCash registersInternal/peripheral component protectionInternal memoryPayment
The present invention relates to an Android system-based intelligent POS security system, a starting method and a data management control method. The system comprises an application CPU and a security CPU connected with the application CPU, the application CPU is also connected with a communication module, a display screen and an internal memory, and the security CPU is also connected with a touch screen, a contact IC card reader, a non-contact IC card reader, a magnetic card reader and a physical security circuit. According to the present invention, the transaction sensitive information, such as the bank encryption / decryption secret keys, the user ciphers, the account data, etc., is protected effectively, the contact of the sensitive data and an Android system is isolated effectively, at the same time, a signature verification mechanisms is provided to protect the integrity and the legality of the Android system and the APP programs effectively, thereby guaranteeing the payment security of the Android system-based intelligent POS.
Owner:FUJIAN NEWLAND PAYMENT TECH
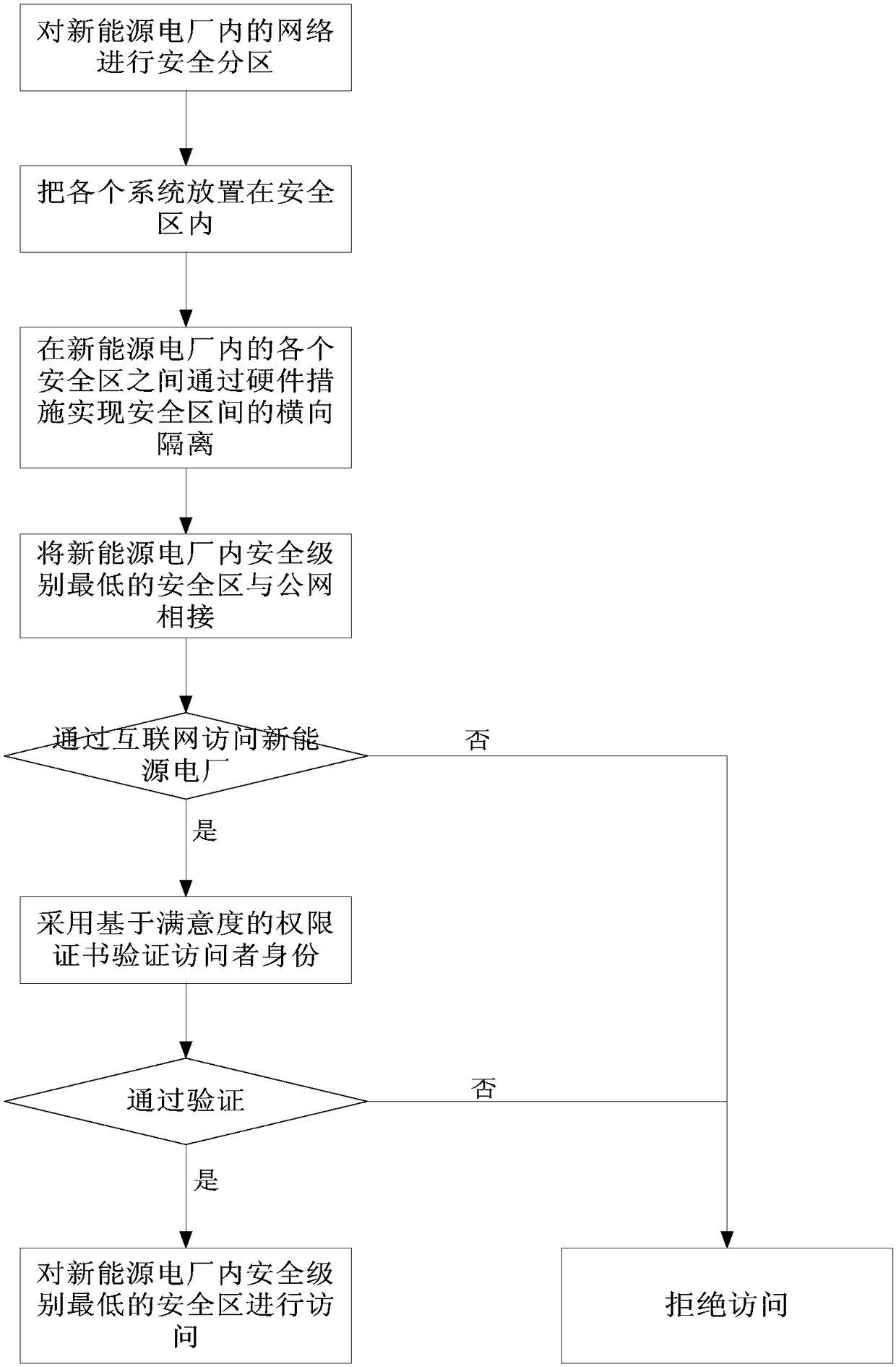
Public network safety access method for new energy power plant
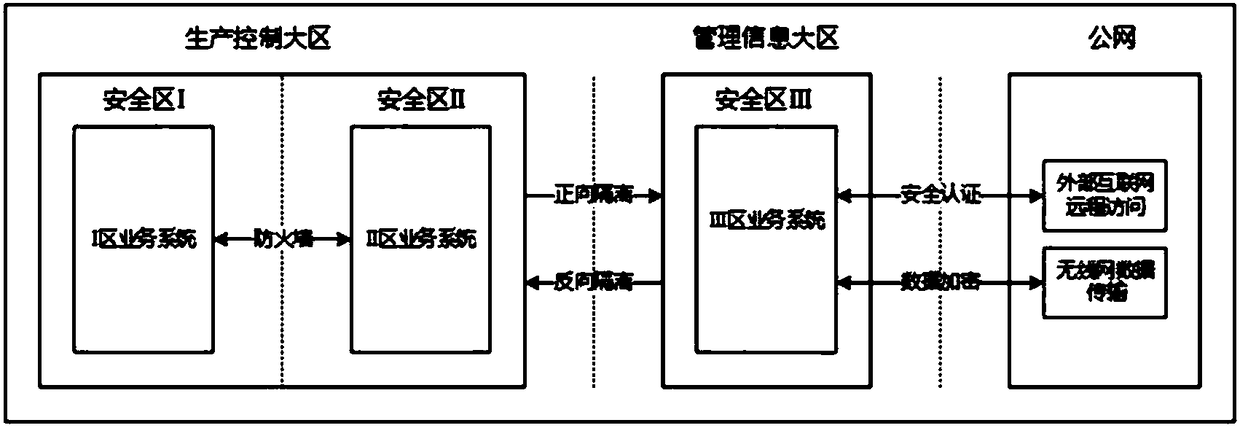
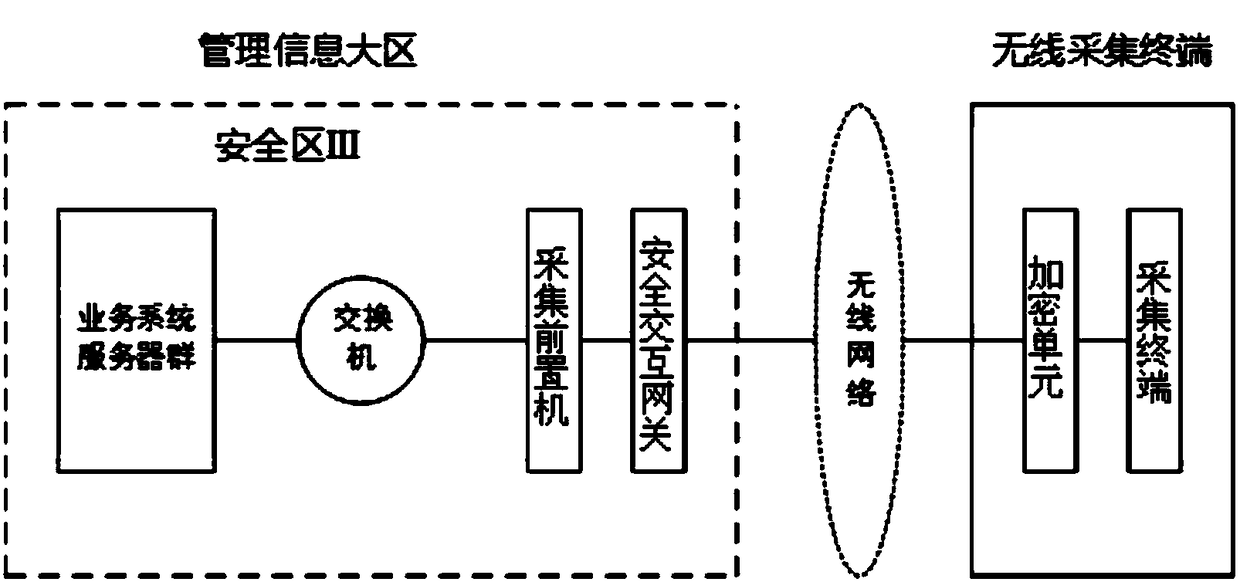
InactiveCN108063751AAvoid security risksIncrease aggressivenessCircuit arrangementsUser identity/authority verificationAccess methodNew energy
The invention discloses a public network safety access method for a new energy power plant, which comprises the following steps of: carrying out safety partitioning on a network in the new energy power plant, and placing each service system in safety regions; carrying out transverse separation between each safety region by a hardware measure; connecting the safety region with the lowest safety level in the new energy power plant with a public network; and when accessing the new energy power plant by the internet, verifying a user identity by an authority certificate based on satisfaction, andpassing verification, carrying out access on the safety region with the lowest safety level in the new energy power plant. By the public network safety access method disclosed by the invention, not only is a safety risk from the public network, which an internal network system of the new energy power plant directly faces, avoided, but also the ability of preventing a public network attack is greatly improved.
Owner:STATE GRID NINGXIA ELECTRIC POWER +1
Method for reversely cloning subscriber identity module, device and system
InactiveCN101938742AAvoid security risksReduce security risksKey distribution for secure communicationSecurity arrangementData transmissionInternational mobile subscriber identity
The embodiment of the invention discloses a method for reversely cloning a subscriber identity module. The method comprises the following steps of: updating a root key K by user equipment by transmitting a new root key K or calculating parameters of the new root key K; receiving updating confirmation information transmitted by the user equipment after updating the root key K; and updating the root key K stored by an authentication center per se to ensure that another subscriber identity module / universal subscriber identity module (SIM / USIM) card which has the same international mobile subscriber identity (IMSI) as the user equipment cannot be authenticated through the old root key K and the authentication center so as not to be accessed to a network. The method fulfils the aim of reducing the safety risk brought by cloning. The embodiment of the invention also discloses a data transmission device and a data transmission system.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com