Vehicle system and virtual key authentication method thereof
An authentication method and a technology to be authenticated, applied in the field of car rental, can solve the problems of high cost, easy cracking of physical keys, and low efficiency, so as to avoid potential safety hazards, improve leasing efficiency, and ensure property safety.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
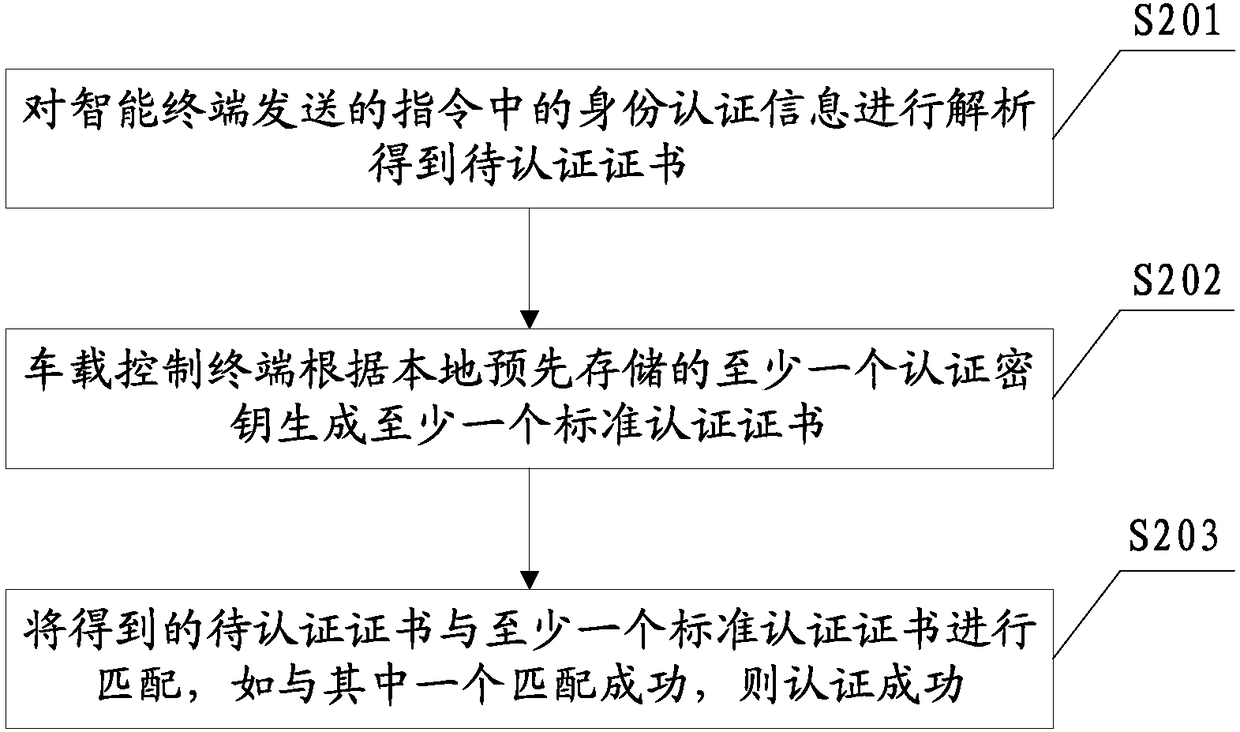
[0056] The car rental system in this embodiment involves a car rental platform, a vehicle-mounted control terminal installed on a car to be rented, and an intelligent terminal as a virtual key for the car. It should be understood that the car rental platform architecture in this embodiment can be various communication architectures that can realize functions such as car rental account management, timing, billing, and fee deduction, and details will not be described here. The vehicle-mounted control terminal can be installed anywhere in the car in theory, as long as it can reliably establish a communication connection with the smart terminal to realize information interaction. At the rear of the car, it can even be installed outside the car; the vehicle-mounted control terminal can be a variety of terminals that can communicate with smart terminals and have computing and authentication processing functions; and the vehicle-mounted control terminal can control the door switch. T...
Embodiment 2
[0106] This embodiment provides a car rental system, see Figure 5 As shown, it includes: a car rental platform 1, a taxi 2, and an intelligent terminal 3 as a car virtual key. The connection relationship between the three is shown in Embodiment 1, and will not be repeated here. Wherein, the taxi 2 is provided with a vehicle-mounted control terminal 21, see Image 6 As shown, the vehicle control terminal 21 in this embodiment includes:
[0107] The storage module 211 is used to store the authentication key; the storage module 211 of the vehicle-mounted control terminal 21 can store the same authentication key as that on the car rental platform 1, that is, all the authentication keys are stored, and a vehicle corresponds to For all authentication keys, this setting method has good versatility, and the user can find any car under the car rental platform for identity authentication. In this embodiment, the car rental platform can also differentiate and manage each rental vehicl...
Embodiment 3
[0126] In this embodiment, the smart terminal (that is, the virtual key) is used as an example to illustrate the mobile phone. After the smart terminal obtains the identity authentication information from the car rental platform, it sends the vehicle-mounted smart terminal for authentication control along with the unlock command or door lock command. The details are as follows.
[0127] The user's mobile phone (or tablet) is used as a virtual key. After the user places an order to rent a car on the car rental client or website on the mobile phone, the car rental platform sends the user's mobile phone the identity authentication information required to open and close the car lock at the scheduled car rental time. The identity authentication information may be an encrypted message sequence, which includes validity period information of the identity authentication information.
[0128] A vehicle-mounted control terminal is installed on the vehicle to be rented. The vehicle-mounted...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com