Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
19070results about How to "Reduce security risks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
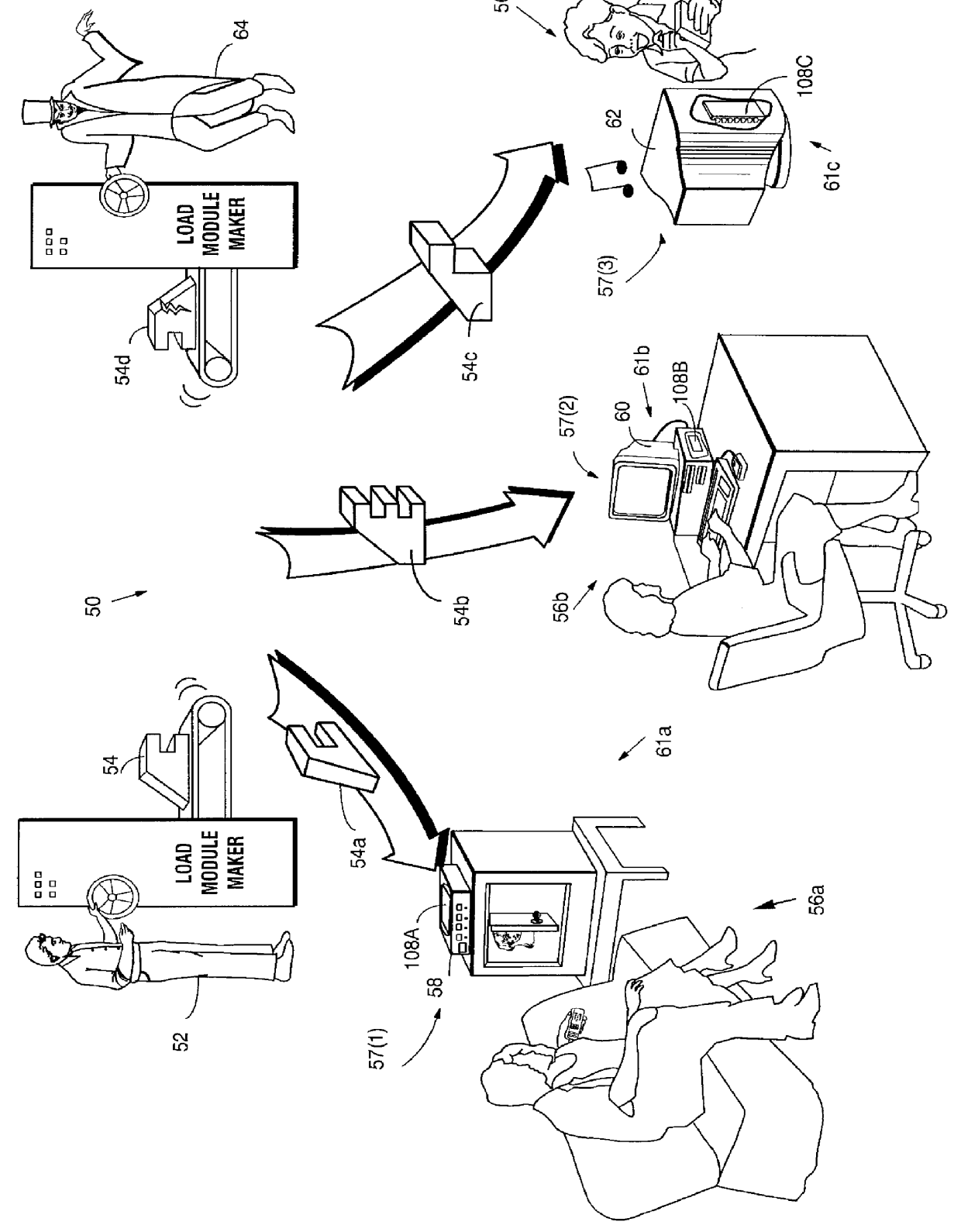
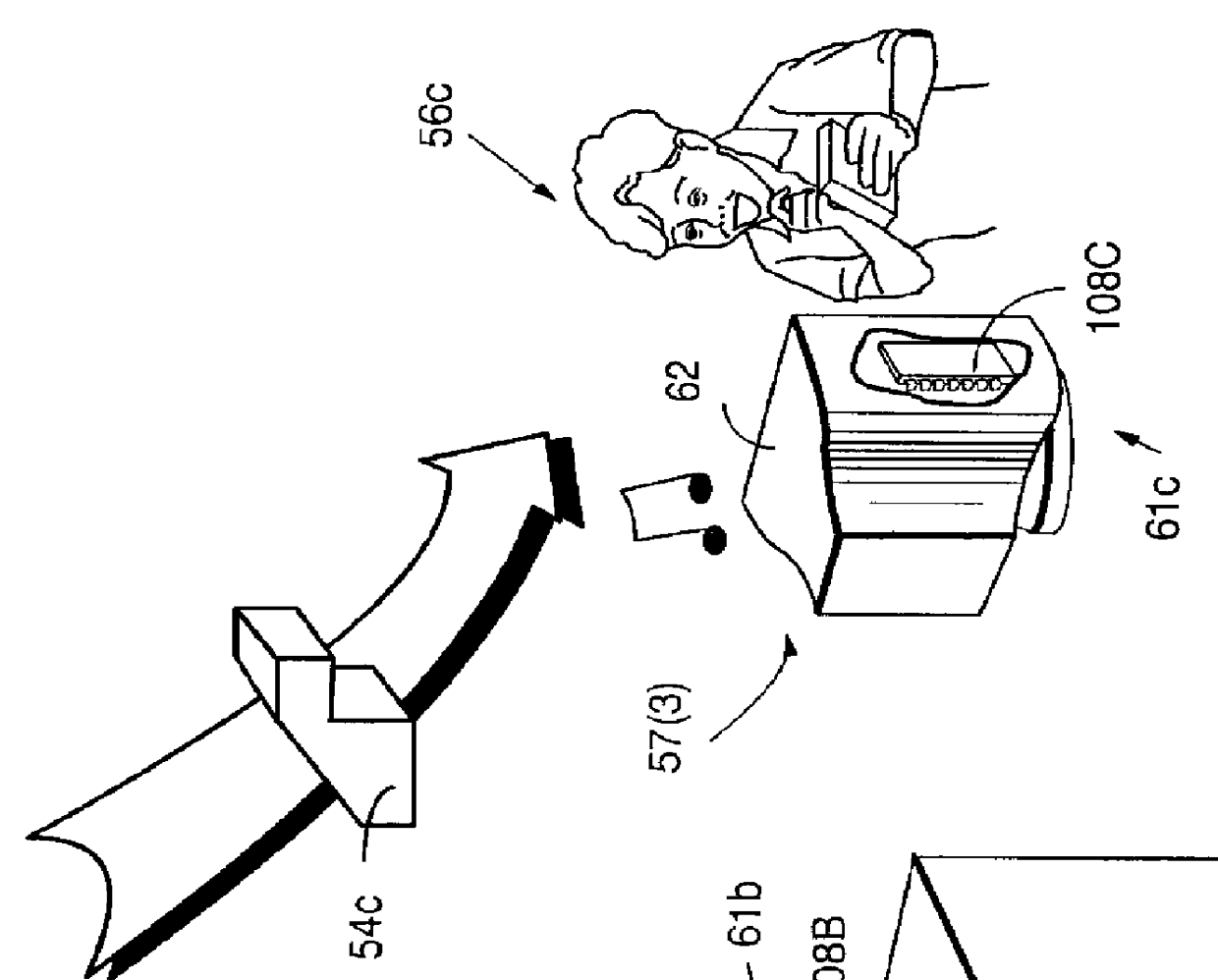
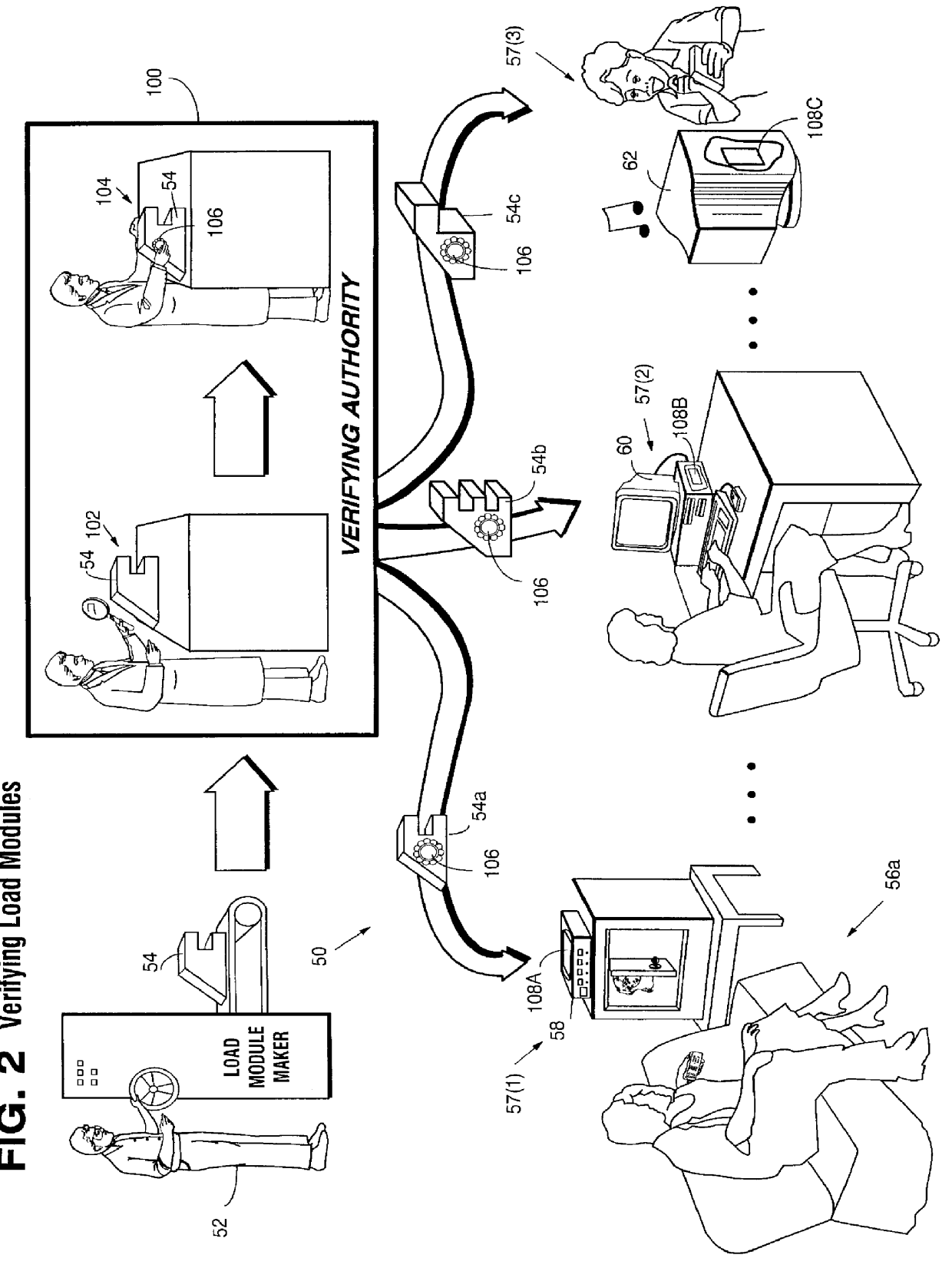
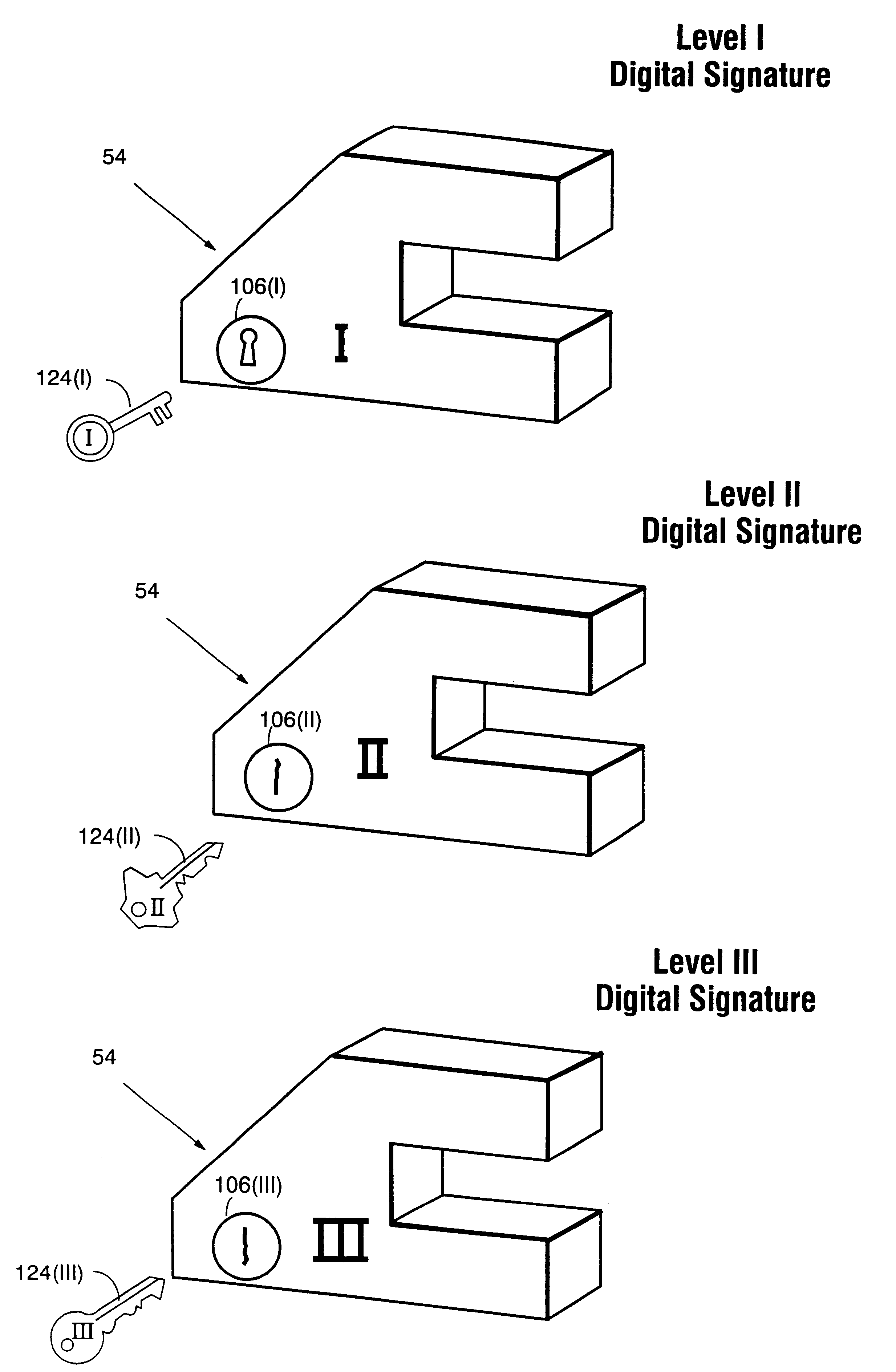
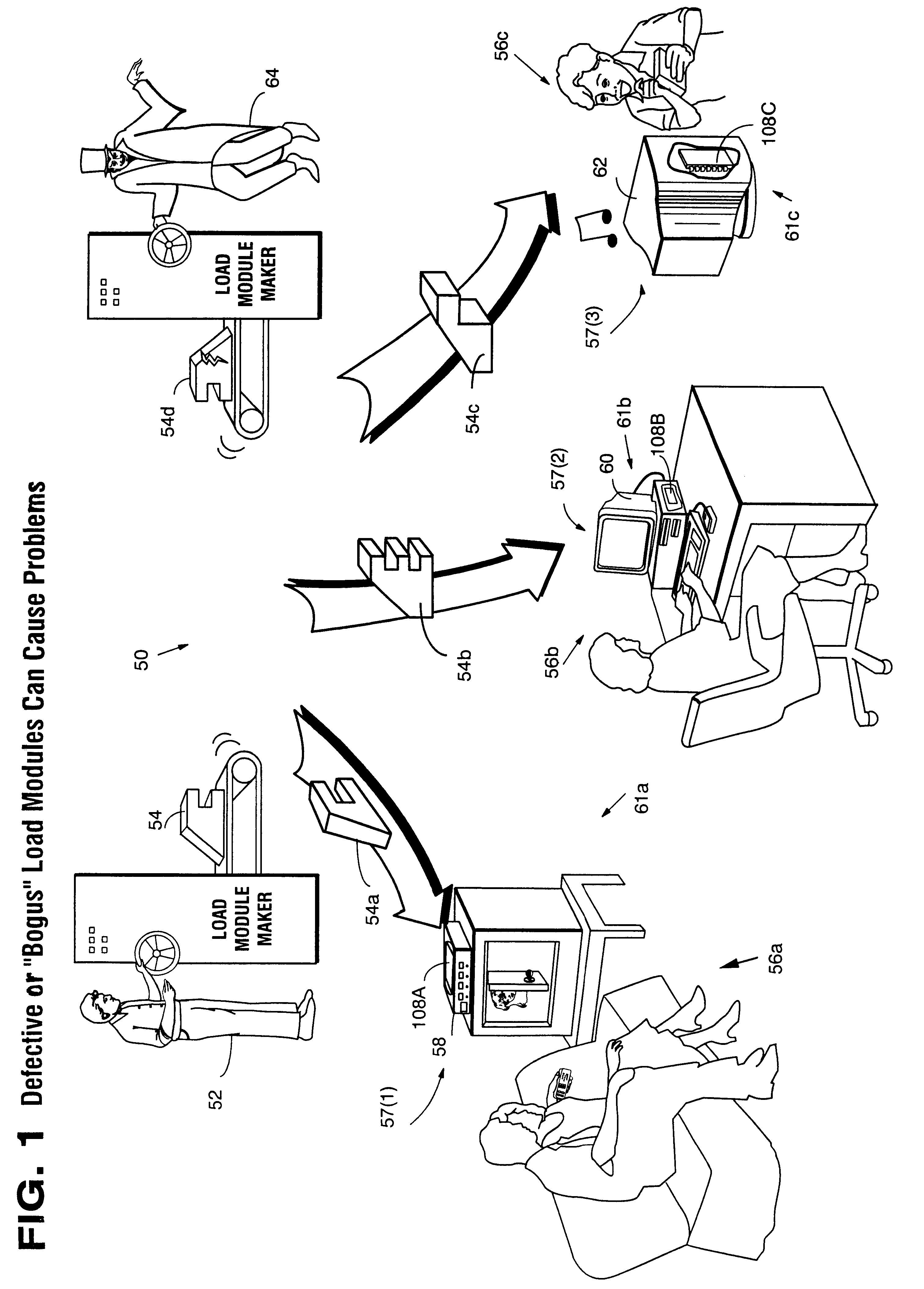
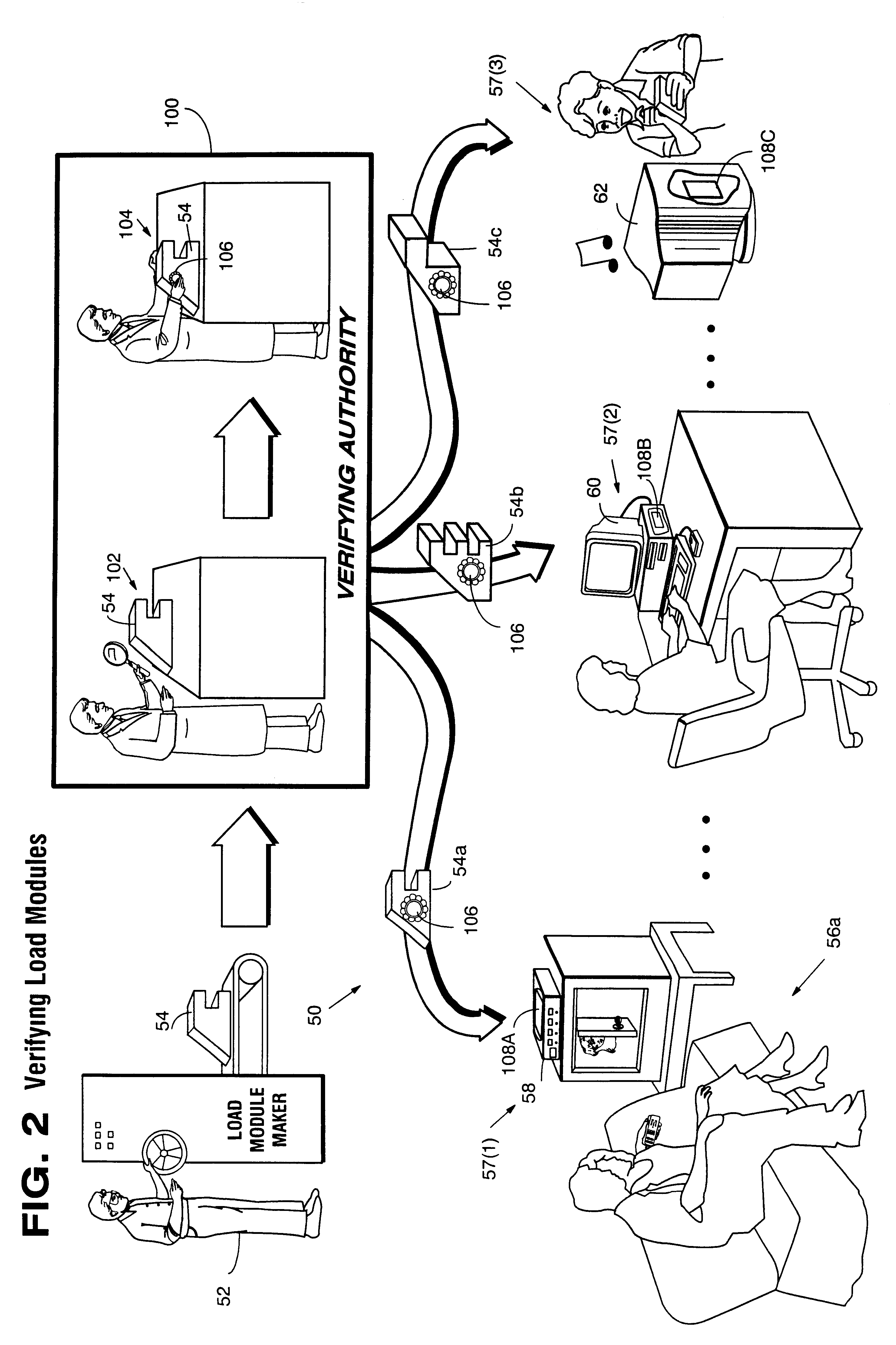
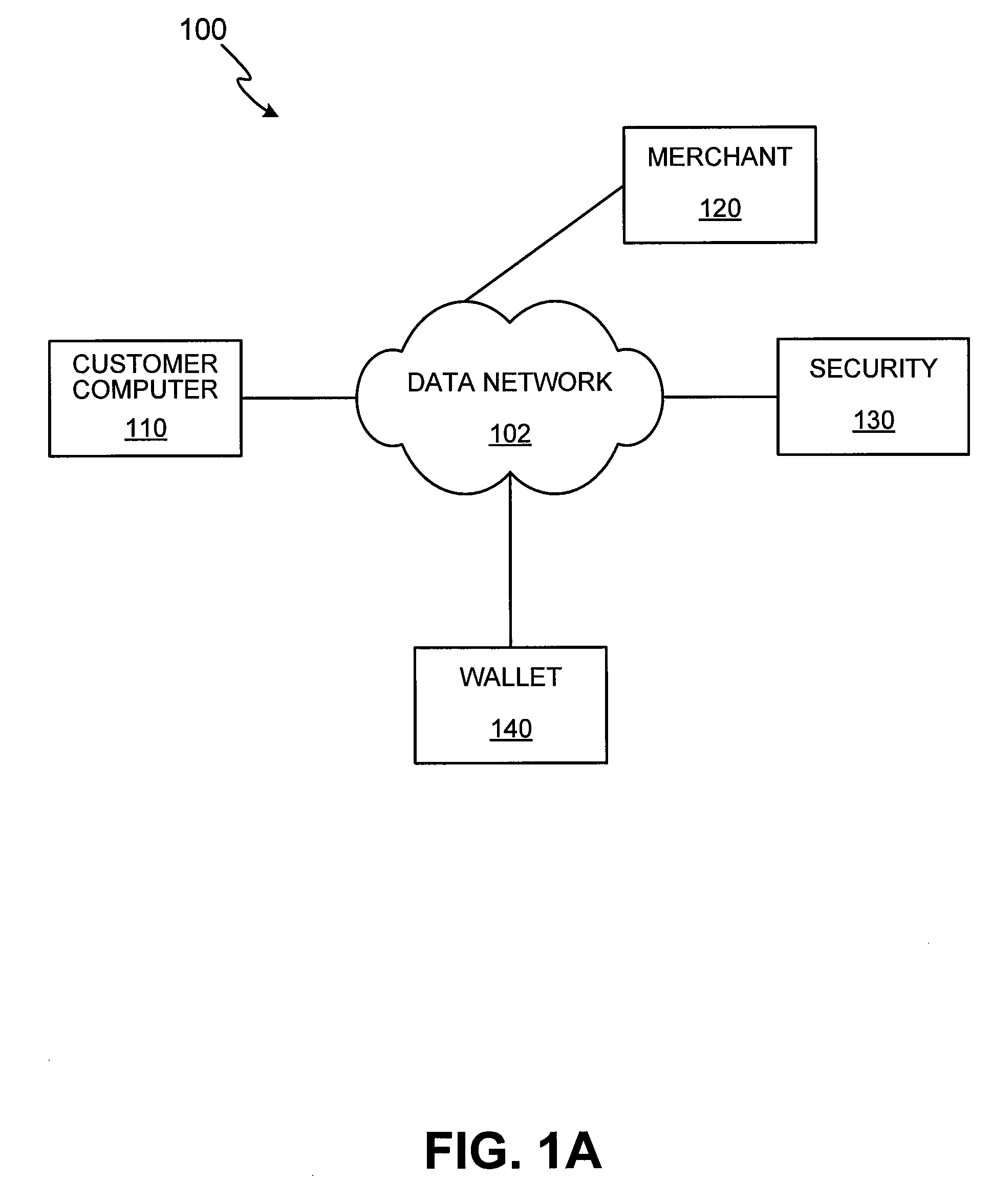
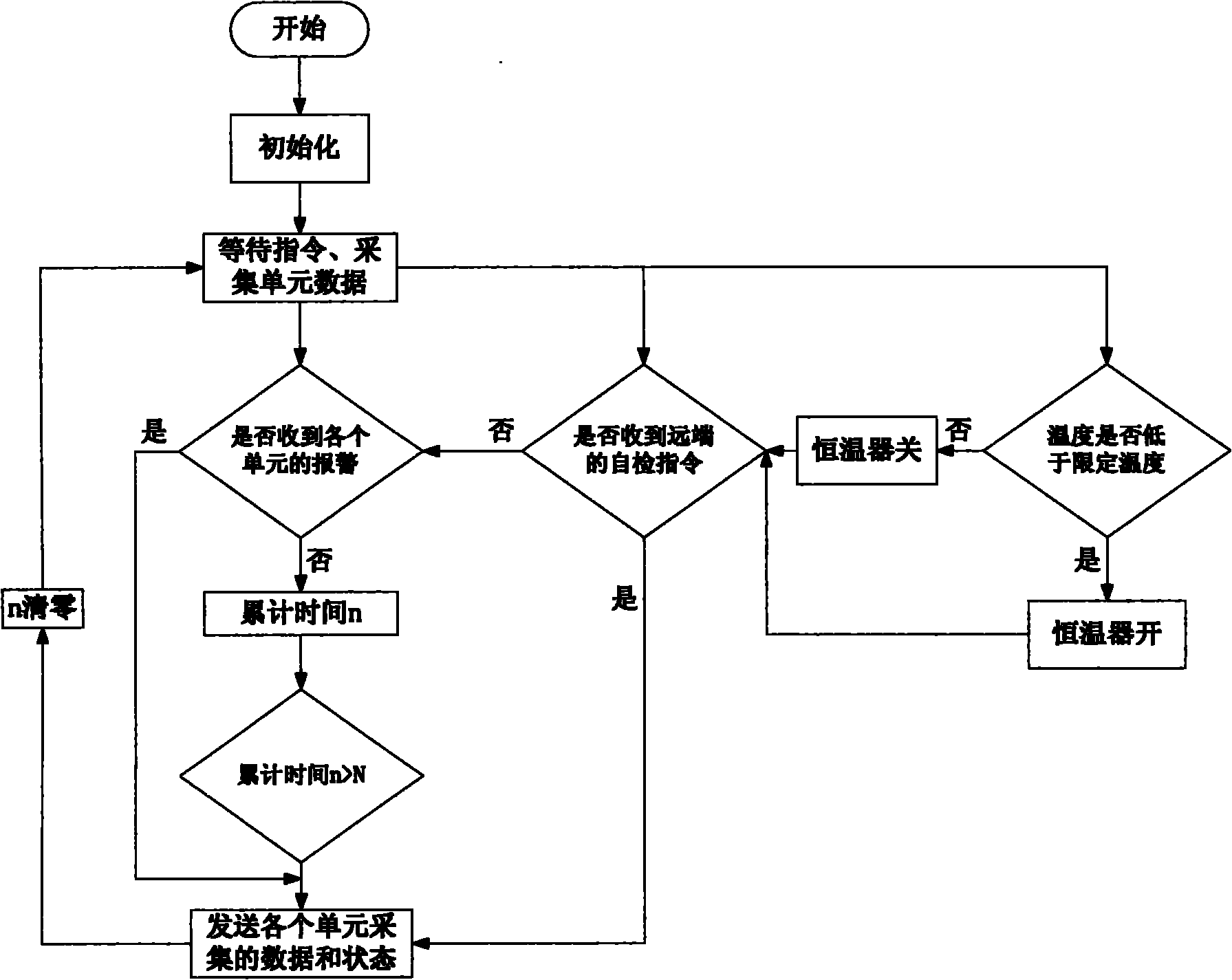
Systems and methods using cryptography to protect secure computing environments
InactiveUS6157721AProtection from disclosureSpeeding up digital signature verificationRecording carrier detailsDigital data processing detailsThird partyTamper resistance
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm compromise, and subsets of multiple digital signatures may be used to reduce the scope of any specific compromise.
Owner:INTERTRUST TECH CORP
Systems and methods using cryptography to protect secure computing environments
InactiveUS6292569B1Improve connectivityComputationally orRecording carrier detailsError detection/correctionThird partyTamper resistance
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm.
Owner:INTERTRUST TECH CORP
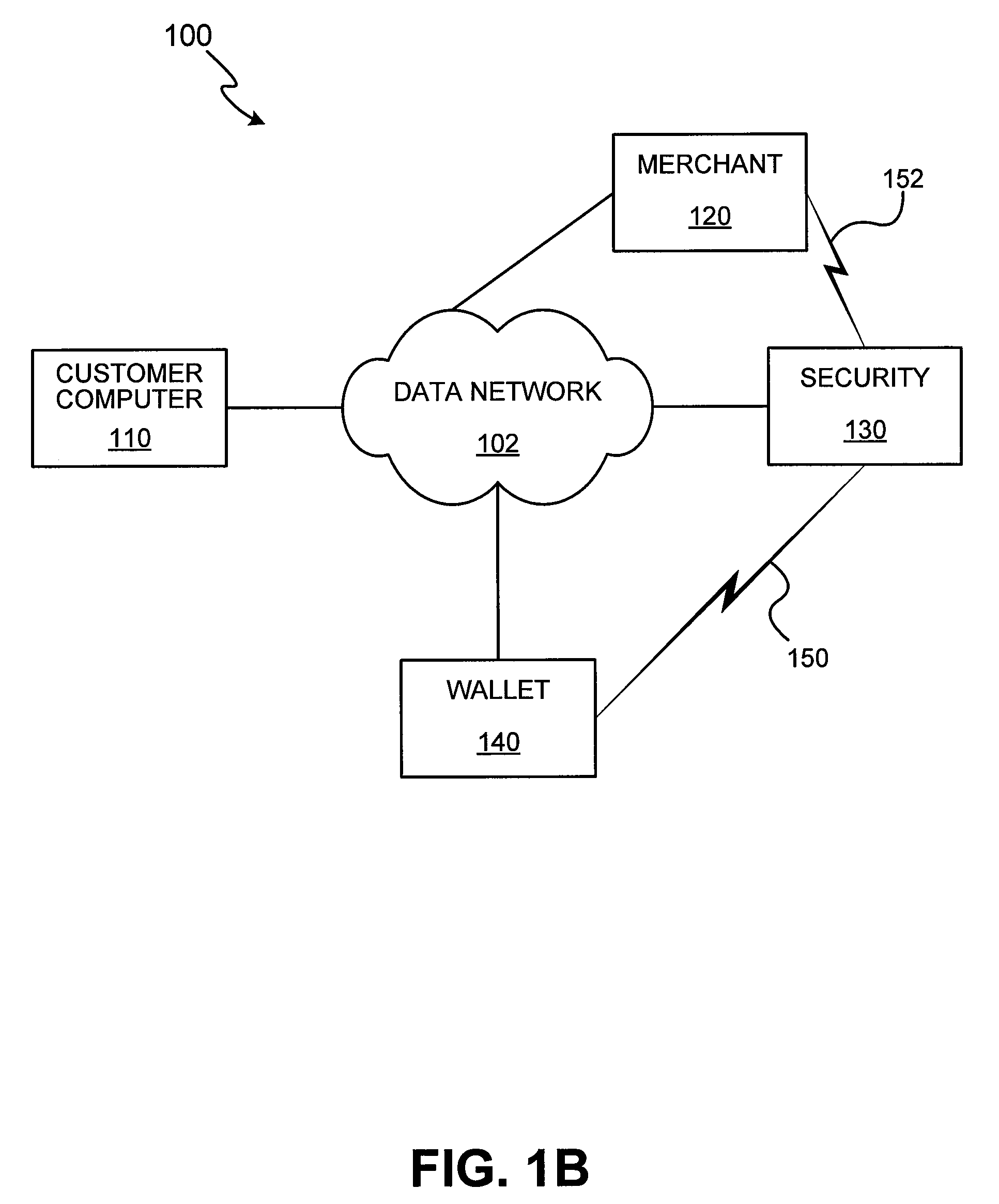
Systems and methods for dynamic protection from electronic attacks
InactiveUS8726379B1Reduce security risksMemory loss protectionError detection/correctionIp addressComputer security
Systems and methods for gathering, classifying, and evaluating real time security intelligence data concerning security threats presented by an IP address, and reporting in real time the degree and character of such security threats.
Owner:NORSE NETWORKS INC
Systems and Methods for Dynamic Protection from Electronic Attacks
InactiveUS20140366132A1Reduce security risksMemory loss protectionError detection/correctionIp addressComputer security
Systems and methods for gathering, classifying, and evaluating real time security intelligence data concerning security threats presented by an IP address, and reporting in real time the degree and character of such security threats.
Owner:NORSE NETWORKS INC
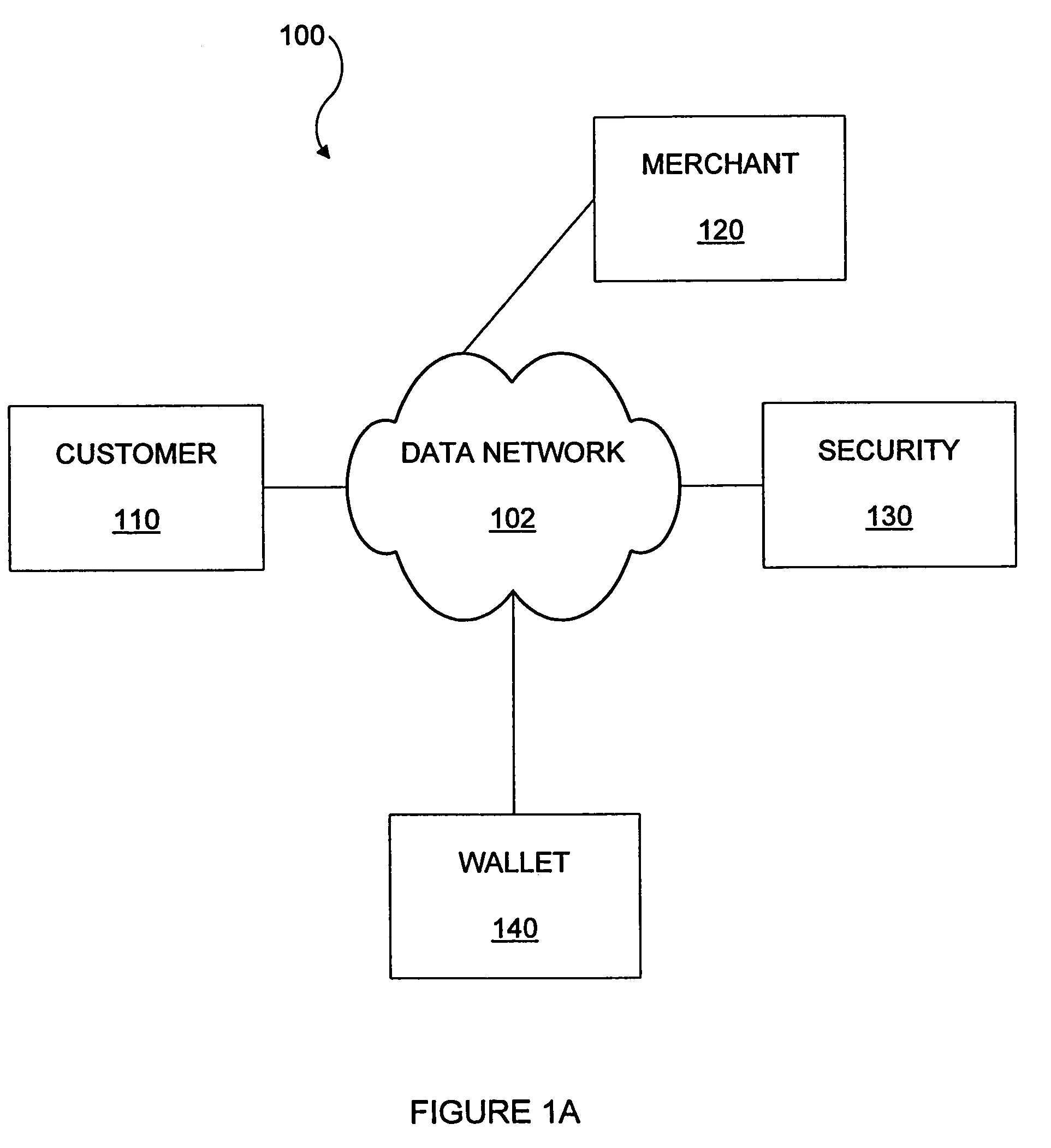
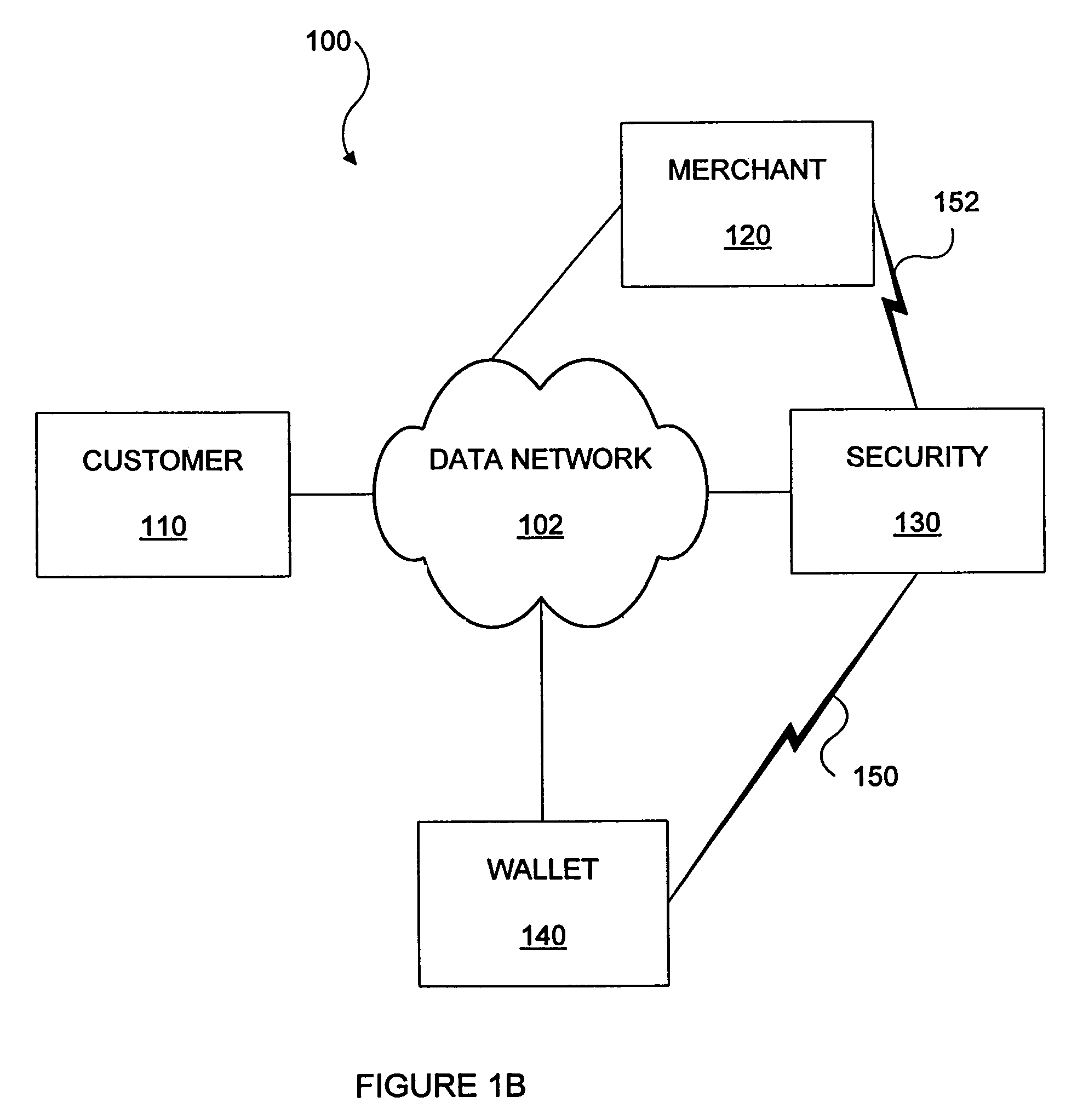
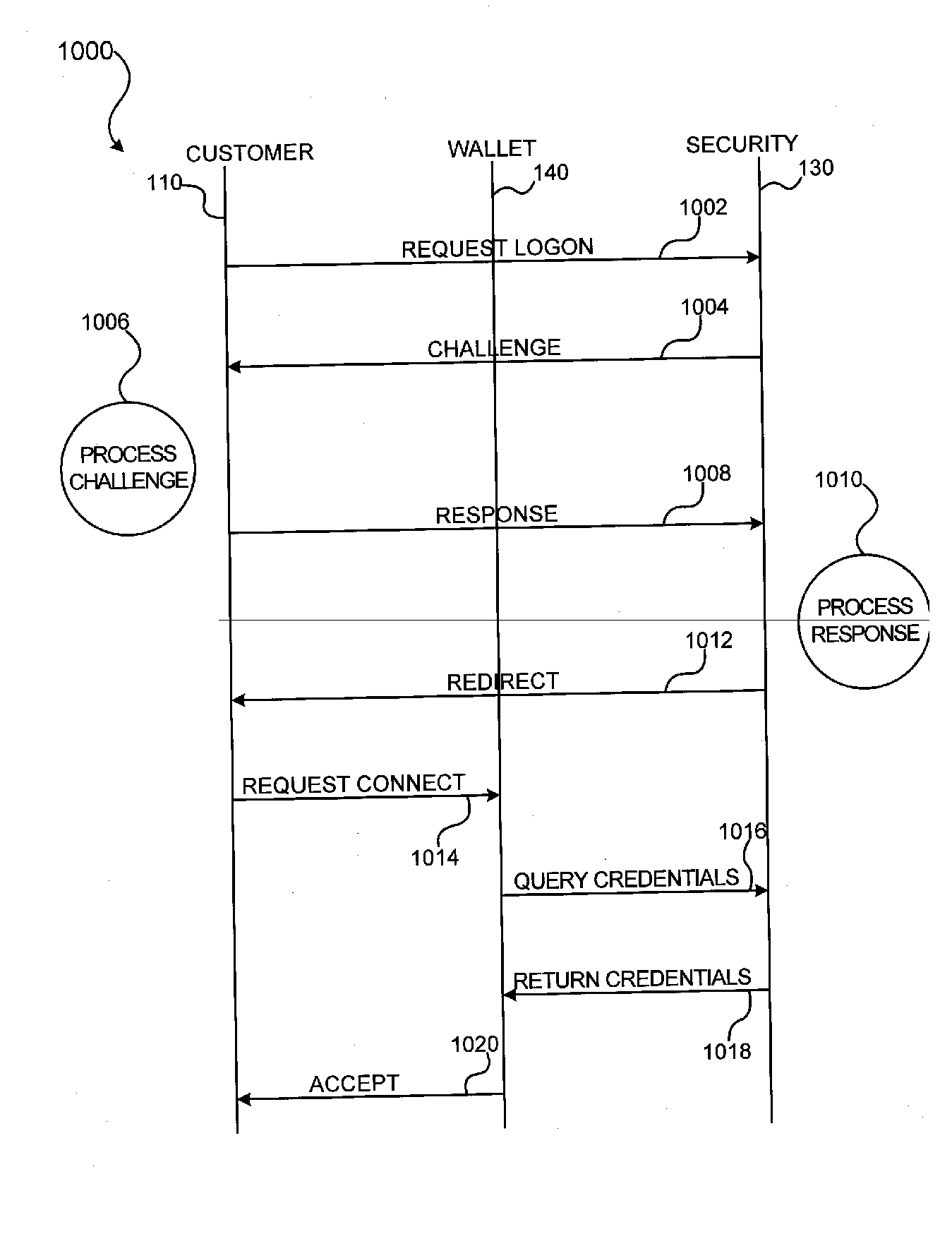
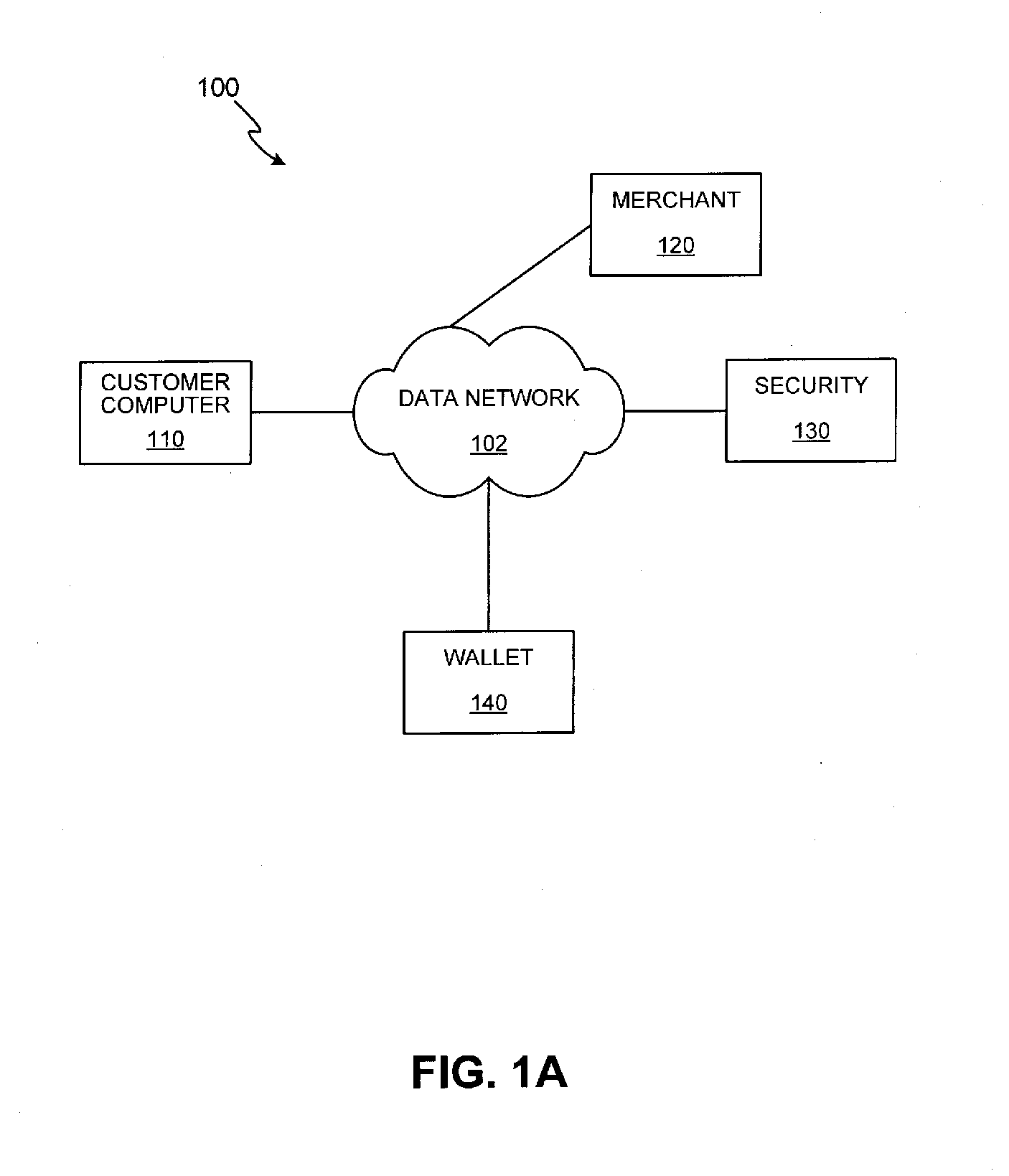
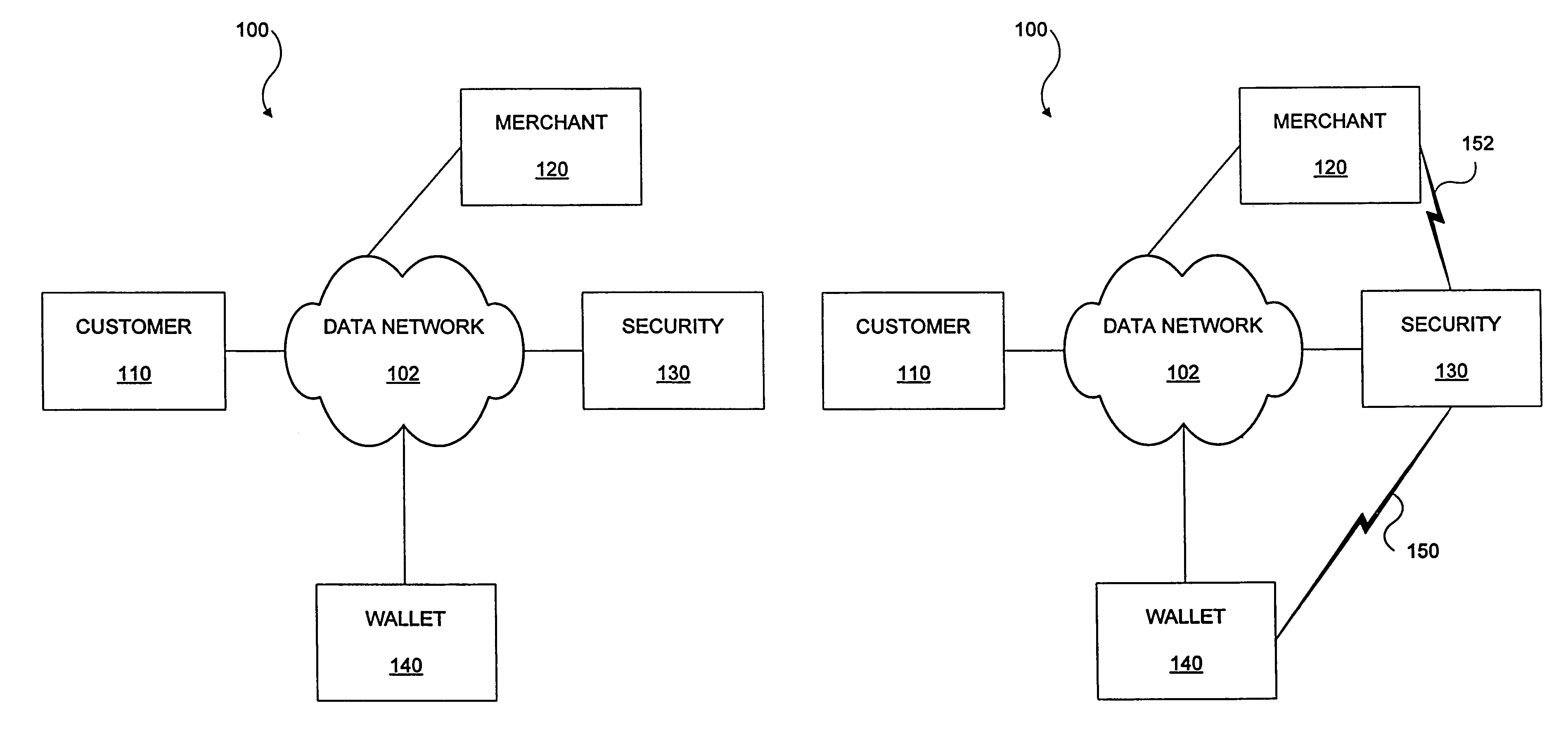
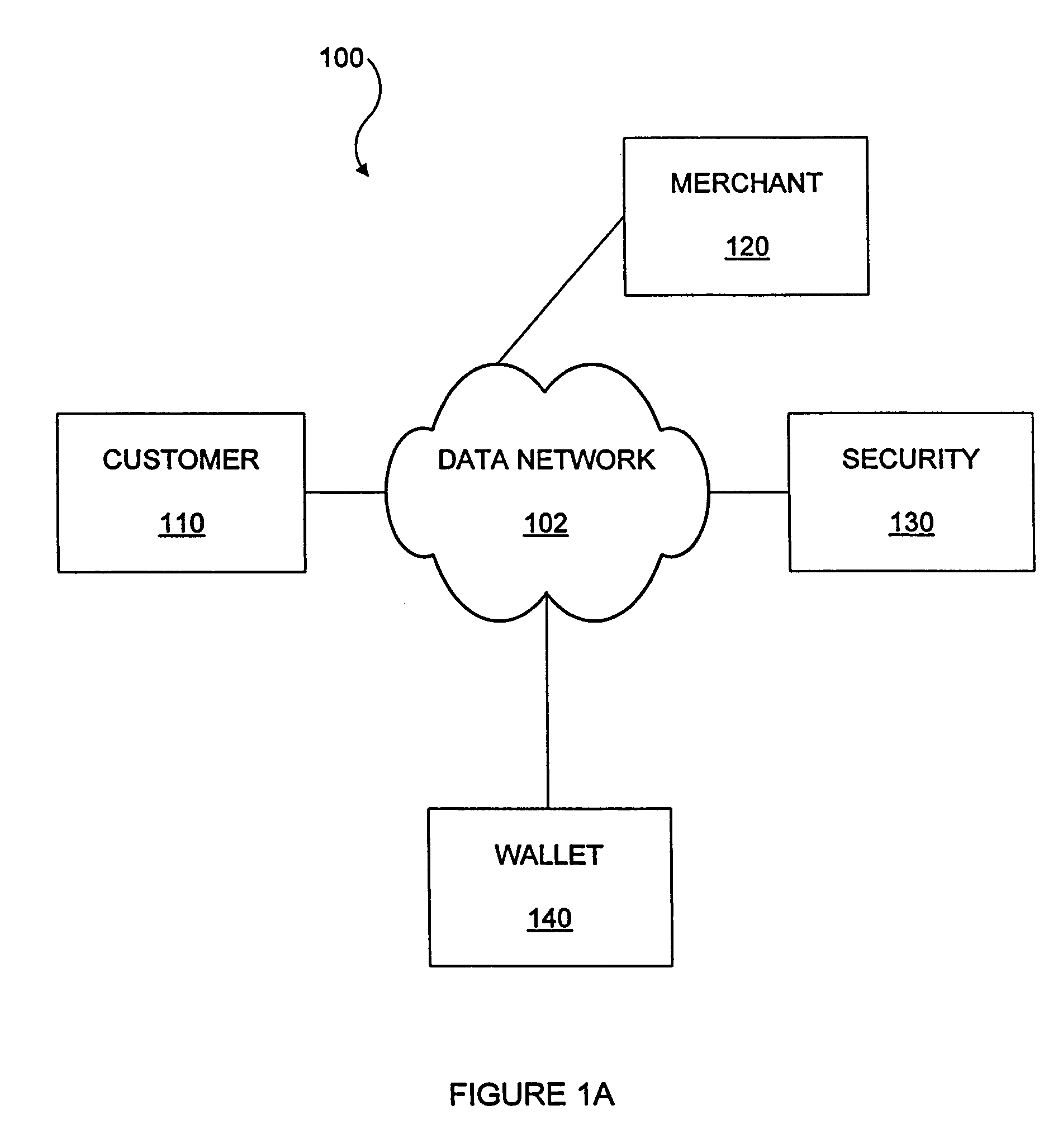
Methods and apparatus for conducting electronic transactions
InactiveUS20090076966A1Enhanced reliability and confidenceReduce security risksComplete banking machinesAcutation objectsAuthorization certificateChallenge response
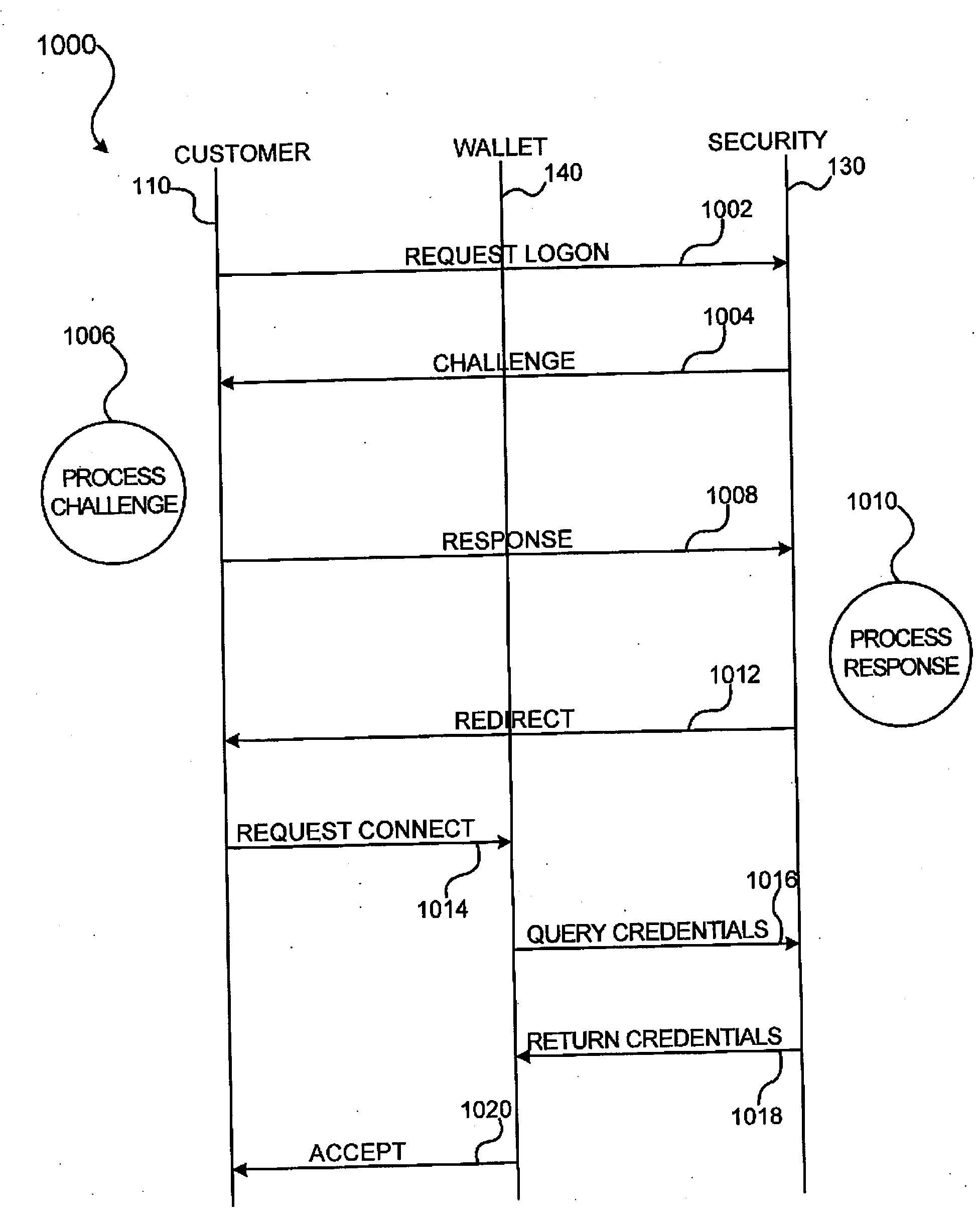
A system and method for facilitating electronic transactions using an intelligent instrument is disclosed. An authorization server enables users to obtain authorization credentials through the use of the intelligent instrument by issuing a challenge to an intelligent token of the intelligent instrument. The intelligent token generates a challenge response and transmits the challenge response to the authorization server, which assembles credentials including a key for the electronic transaction upon validating the response. The authorization server sends the assembled credentials to the intelligent instrument and the intelligent instrument transmits the assembled credentials to the authorization server during a subsequent transaction. The authorization server validates the assembled credentials and provides authorization for the transaction in response to the validating the assembled credentials.
Owner:LIBERTY PEAK VENTURES LLC
Methods and apparatus for conducting electronic transactions
InactiveUS7343351B1Improve reliabilityConfidenceDigital data processing detailsAnalogue secracy/subscription systemsSmart cardE-commerce
A system and method for conducting electronic commerce are disclosed. In various embodiments, the electronic transaction is a purchase transaction. A user is provided with an intelligent token, such as a smartcard containing a digital certificate. The intelligent token suitably authenticates with a server on a network that conducts all or portions of the transaction on behalf of the user. In various embodiments a wallet server interacts with a security server to provide enhanced reliability and confidence in the transaction. In various embodiments, the wallet server includes a toolbar. In various embodiments, the digital wallet pre-fills forms. Forms may be pre-filled using an auto-remember component.
Owner:LIBERTY PEAK VENTURES LLC
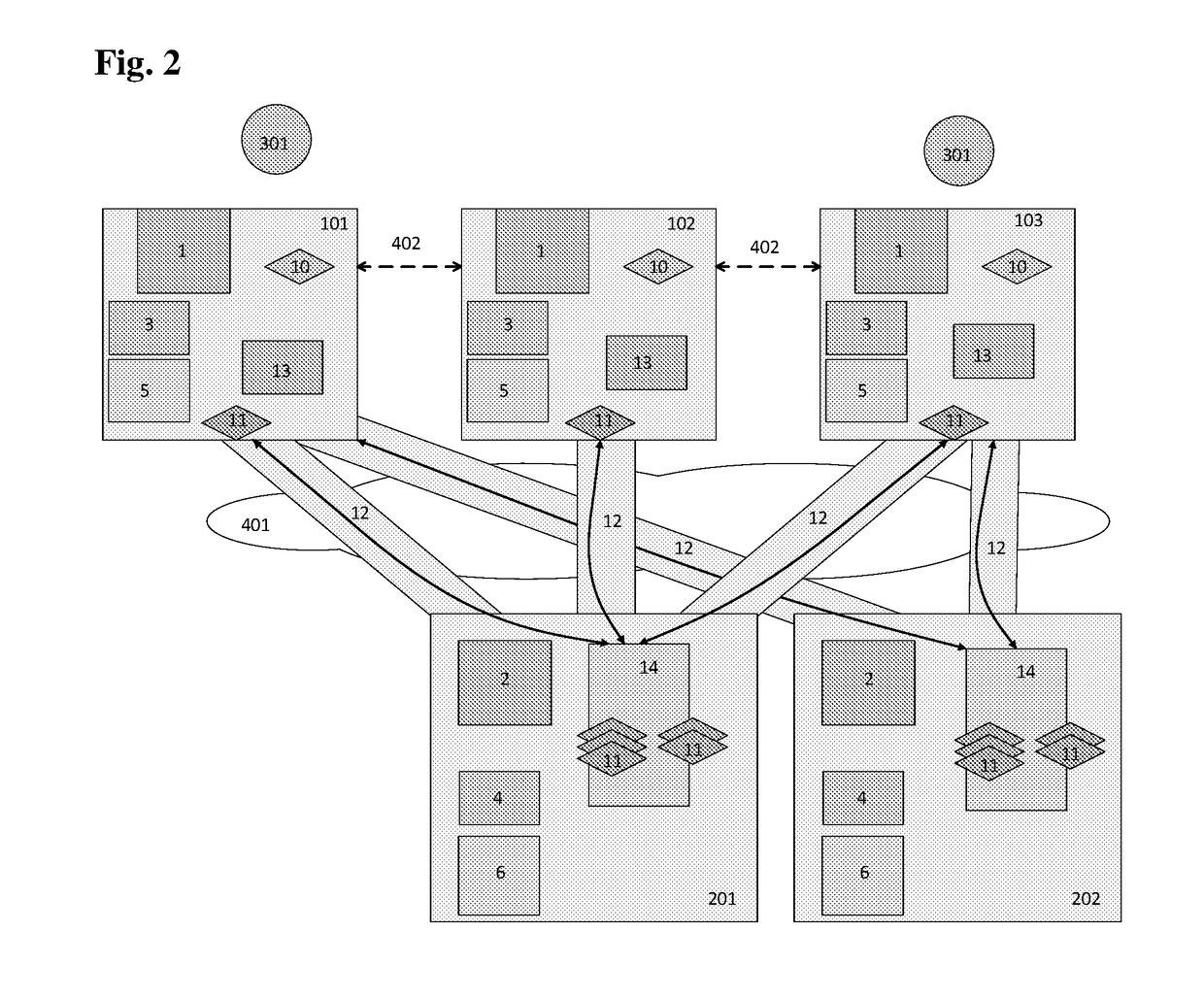
Method for mapping at least two authentication devices to a user account using an authentication server
ActiveUS20180198614A1Improve securityReduce security risksSynchronising transmission/receiving encryption devicesUser identity/authority verificationSecure communicationAuthentication server
The invention provides a method for mapping at least two authentication devices to a user account using an authentication server, where each authentication device connects to the authentication server using a secured communication channel; their mapping to the user account is recorded on the authentication server, and, when a transfer of data between the authentication devices mapped to the user account occurs, the data is passed over from the first authentication device to the authentication server using a secured communication channel and from the authentication server to another authentication device mapped to the account of said user using a secured communication channel, where the aforesaid secured communication channel is created by the second authentication device. This procedure allows the use of a single personal local authentication factor for multiple authentication devices and increases the security of authentication of devices with authentication servers.
Owner:ADUCID
Method and apparatus for efficiently initializing mobile wireless devices
InactiveUS6980660B1Efficient administrationEliminating inflexibilityKey distribution for secure communicationDigital data processing detailsSecure communicationUnique identifier
A method and system for enabling wireless devices distributed throughout an enterprise to be efficiently initialized for secure communications. The method and system utilize well known public key cryptography and machine unique identifiers to establish a secure channel and initialize the wireless devices.
Owner:IBM CORP
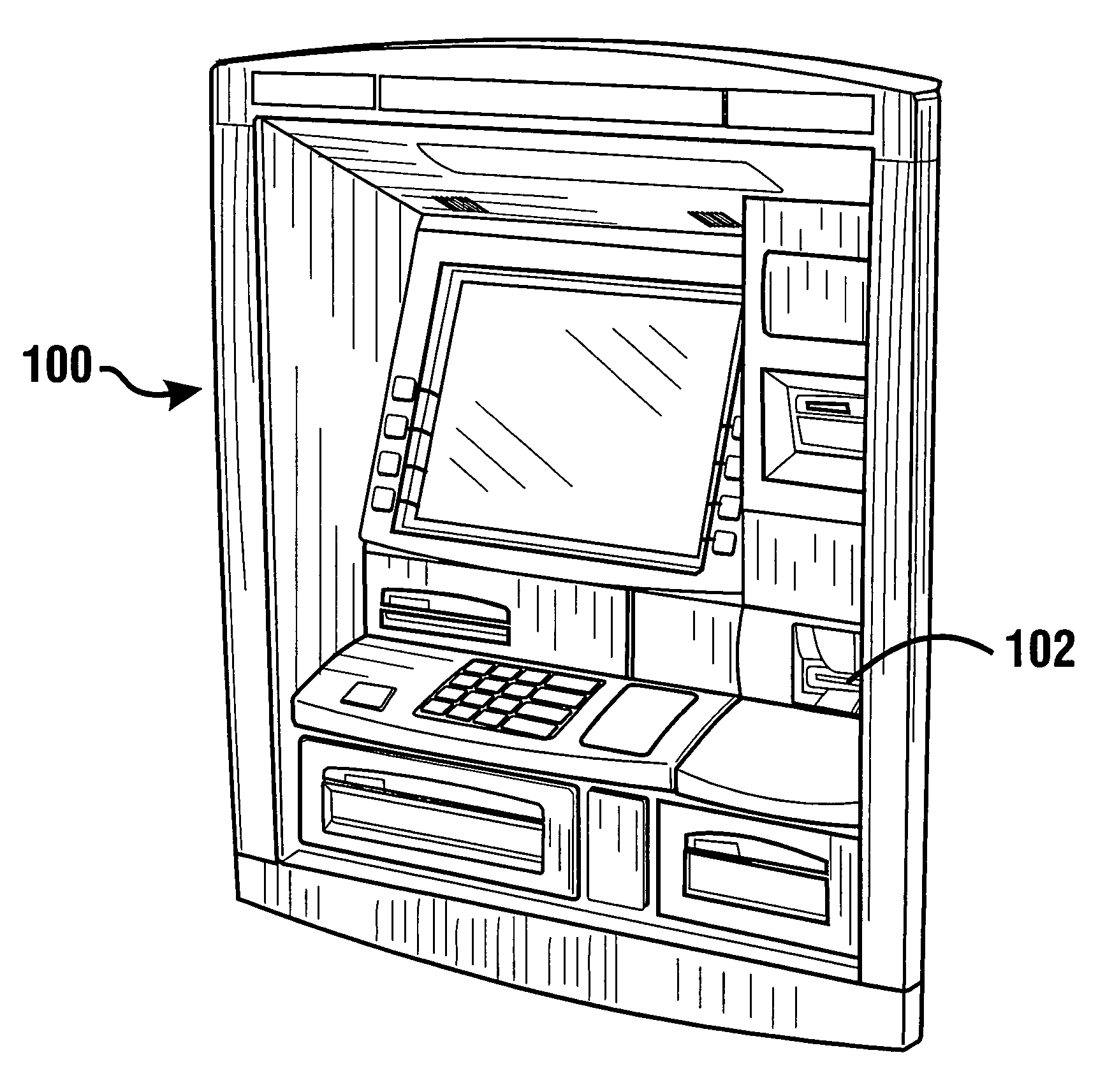
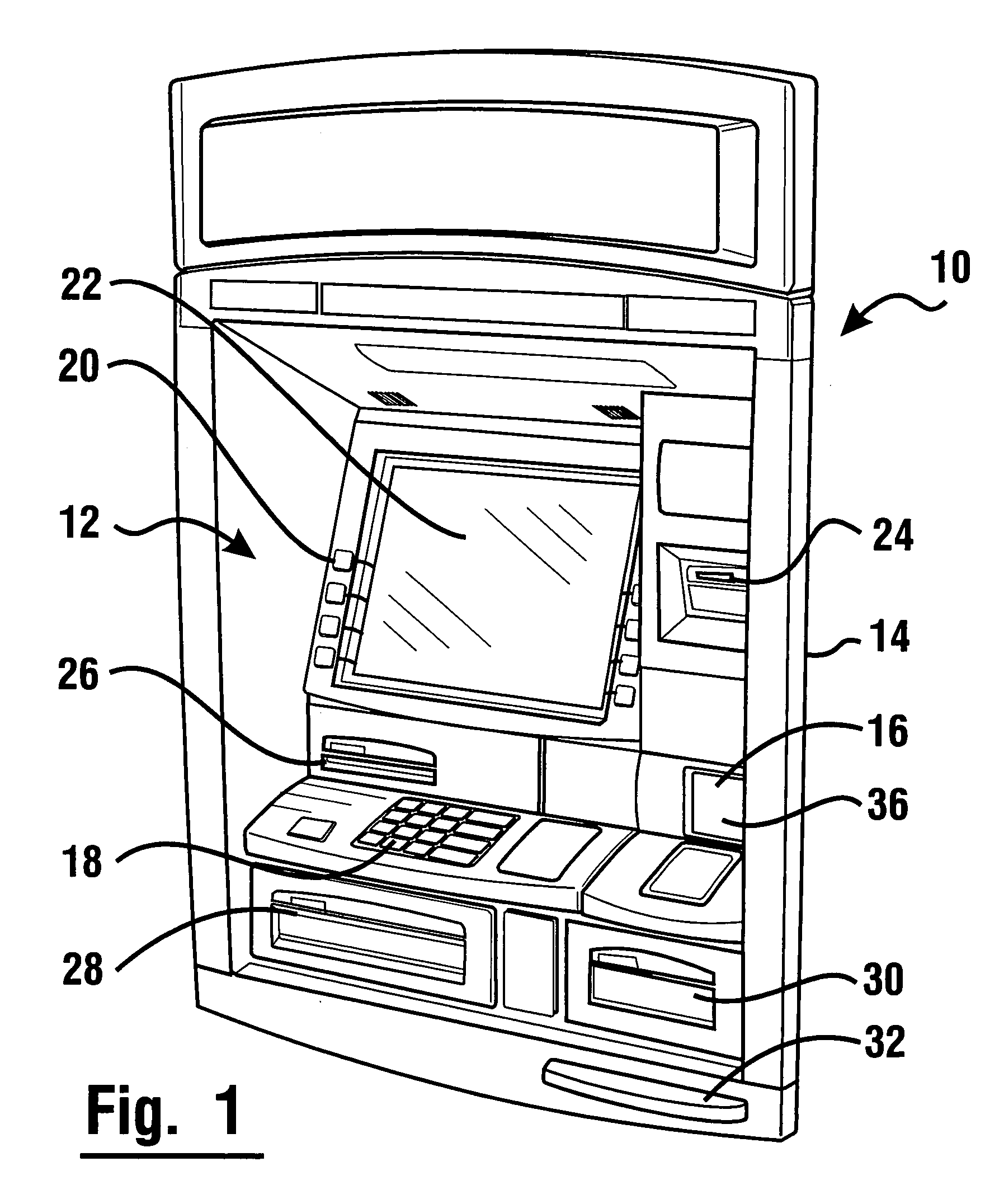
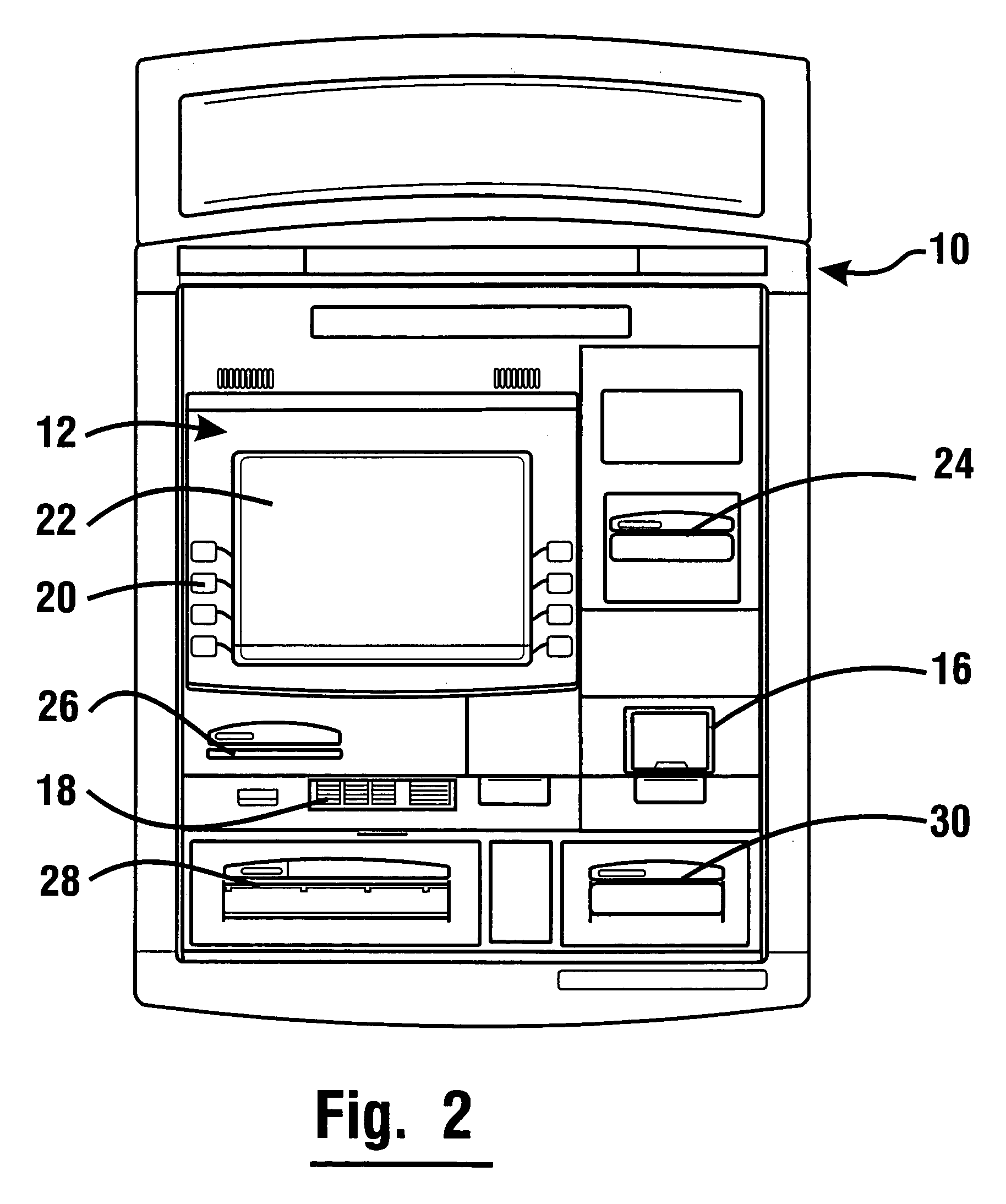
Currency dispensing ATM with RFID card reader
InactiveUS7004385B1Reduces security riskEnhanced machine reliabilityComplete banking machinesFinanceATM cardMagnetic stripe card
An ATM with a currency dispenser includes a contactless card reader. The card reader can read data from an RFID tag of a customer's ATM card. An ATM RFID card reader can be located so as to provide additional space for another transaction component or can be used in conjunction with a magnetic stripe or other reader. Currency dispensing is enabled responsive to tag data. A housing is adapted to prevent interception of radio signals. The ATM is able to prevent dispensing of currency in situations where unauthorized detection of signals is sensed.
Owner:DIEBOLD SELF SERVICE SYST DIV OF DIEBOLD NIXDORF INC
Methods and apparatus for conducting electronic transactions using biometrics
InactiveUS20050187883A1Improve reliabilityConfidenceDigital data processing detailsAnalogue secracy/subscription systemsBiometricsComputer science
A system and method for facilitating electronic transactions using a biometric are disclosed. The system for facilitating electronic transactions using a biometric comprises a smartcard-reader transaction system. The method comprises determining if a transaction violates an established rule, such as a preset spending limit. The method also comprises notifying a user to proffer a biometric sample in order to verify the identity of said user, and detecting a proffered biometric at a sensor to obtain a proffered biometric sample. The method additionally comprises verifying the proffered biometric sample and authorizing a transaction to continue upon verification of the proffered biometric sample.
Owner:LIBERTY PEAK VENTURES LLC
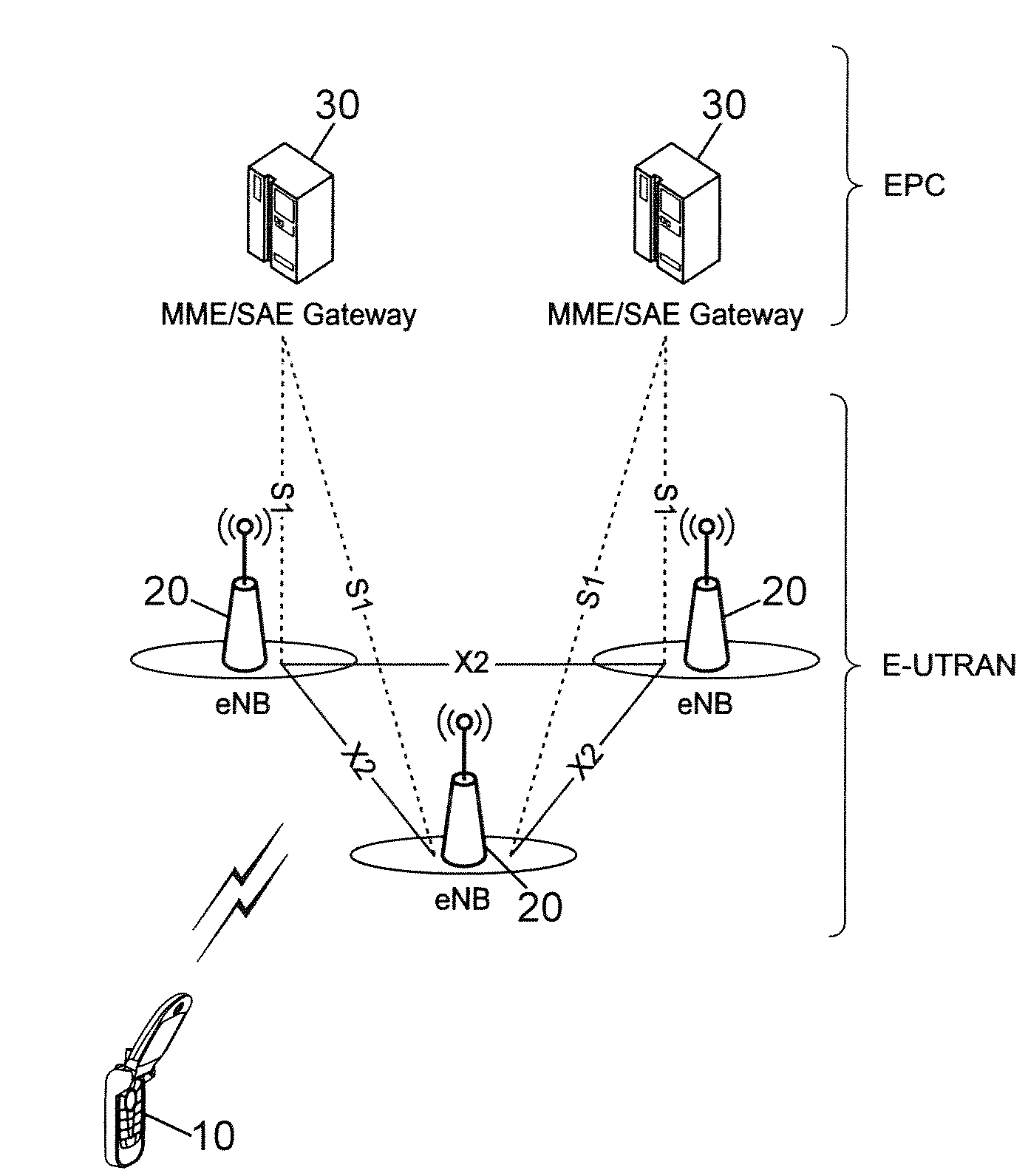
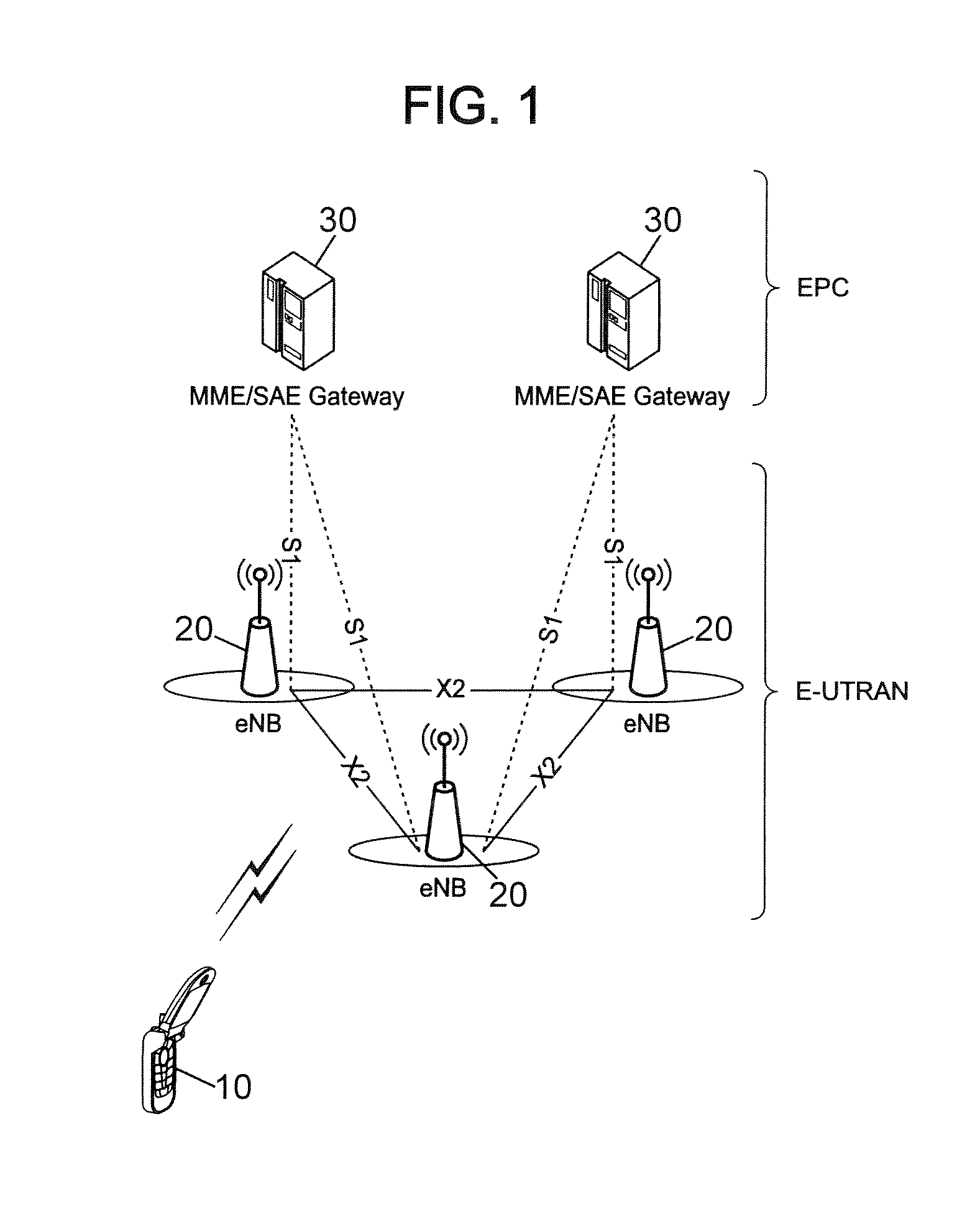
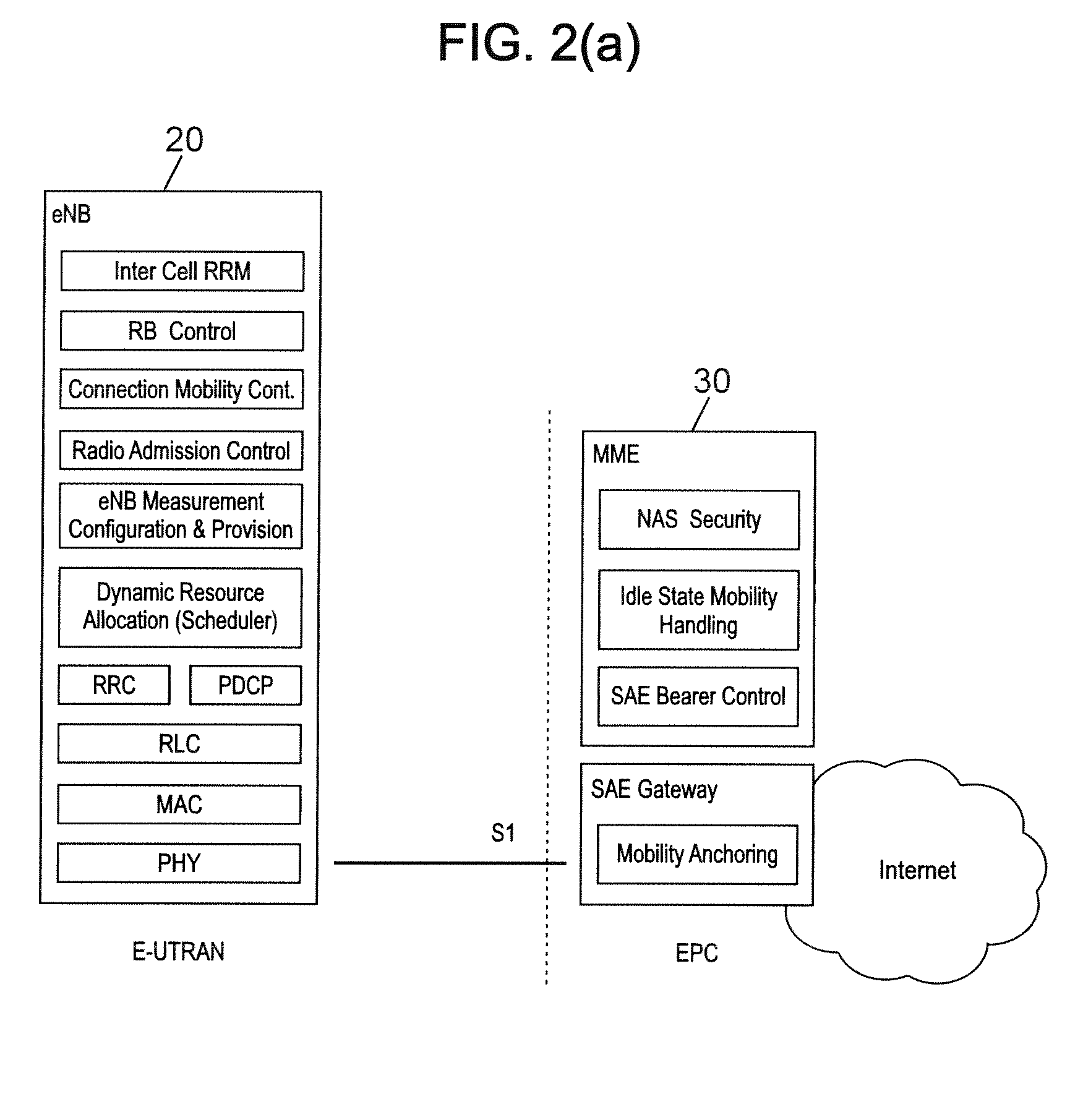
Handover method with link failure recovery, wireless device and base station for implementing such method
ActiveUS20090061878A1Reduce probabilityReduce security risksNetwork traffic/resource managementTransmission systemsTelecommunications linkCommunication link
For each target cell determined by a handover decision process, a first message is transmitted from a source base station (20S) to a target base station (20T) servicing that target cell. The first message includes an identifier of a wireless device (10) having a communication link with the source base station and information for obtaining authentication data for this wireless device. The authentication data depends on a secret key available to the wireless device and the source base station and on an identity of the target cell. Upon failure of the communication link, a cell is selected at the wireless device, which transmits to that cell a reestablishment request message including its identifier and authentication data depending on the secret key and on an identity of the selected cell. If the selected cell is a target cell serviced by a target base station that received a first message, conformity of the authentication data included in the reestablishment request message with the authentication data obtained from this first message is verified to authorize transfer of the communication link to the selected cell.
Owner:VIVO MOBILE COMM CO LTD
Method and System for Inspecting a Surface Area for Material Defects
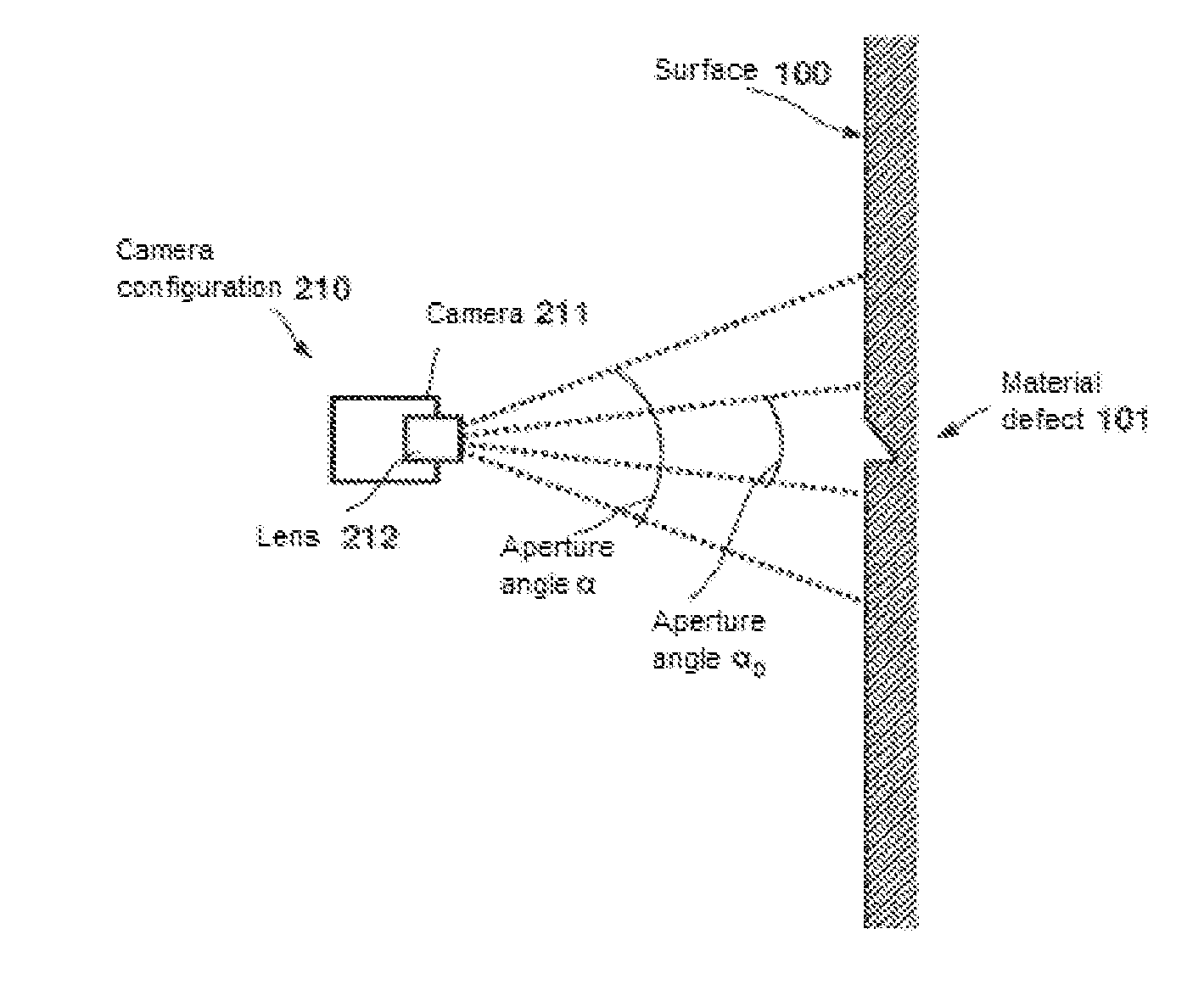
ActiveUS20140168420A1Reduce associated effortReduce security risksPicture taking arrangementsColor television detailsMaterial defectEngineering
A camera assembly arranged on an unmanned and autonomously navigating aerial vehicle is employed to inspect a surface area of for material defects. The vehicle is automatically flown to the surface area from a launch site, wherein it can fly around obstacles using automatic obstacle detection and avoidance methods. A relative position of the aerial vehicle with respect to the surface area with the aid of a position sensor is continuously measured and a sequence of images of the surface area is recorded. Between the individual images, the aerial vehicle is moved along a flight path overlapping image details of the surface area. The images of the sequence are composed into an overall image of the surface area to allow for the surface area to be inspected for defects and the location of defects to be ascertained on the basis of the overall image.
Owner:EADS DEUT GMBH
Network appliance for dynamic protection from risky network activities
InactiveUS20160044054A1Efficient solutionLighten the taskMemory loss protectionError detection/correctionNetwork activityDistributed computing
Electronic appliances, computer-implemented systems, non-transitory media, and methods are provided to identify risky network activities using intelligent algorithms. The appliances, systems, media, and methods enable rapid detection of risky activities.
Owner:NORSE NETWORKS INC
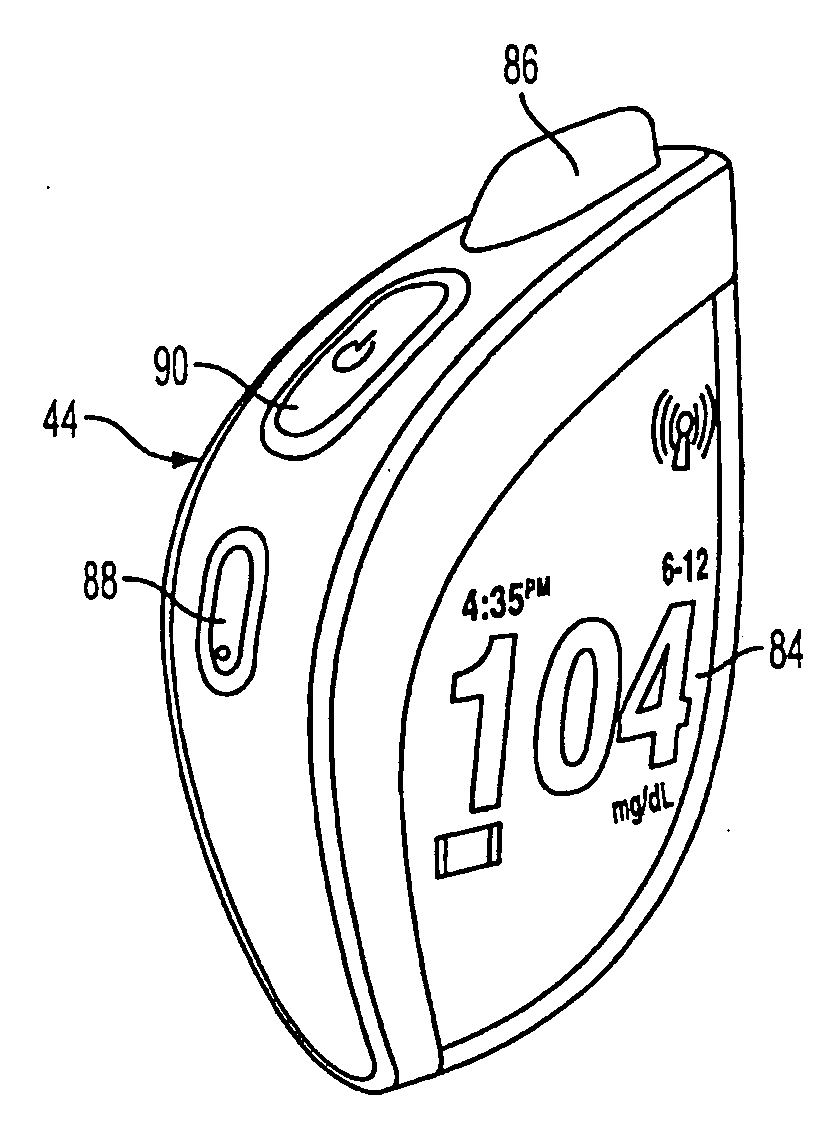
System and Methods for Improved Diabetes Data Management and Use Employing Wireless Connectivity Between Patients and Healthcare Providers and Repository of Diabetes Management Information
ActiveUS20100069730A1Shorten development timeExtended service lifePhysical therapies and activitiesDrug and medicationsDiseaseInformation repository
Methods, devices and a system for disease management are provided that employ diagnostic testing devices (e.g., blood glucose meters) and medication delivery devices (e.g., insulin delivery devices) for providing data to a repository in real-time and automatically. Repository data can be analyzed to determine such information as actual test strip use, patient health parameters to outside prescribed ranges, testing and medication delivery compliance, patient profiles or stakeholders to receive promotional items or incentives, and so on. Connected meters and medication delivery devices and repository data analysis are also employed to associate a diagnostic test to a mealtime based on timing of a therapeutic intervention performed by an individual.
Owner:EMBECTA CORP
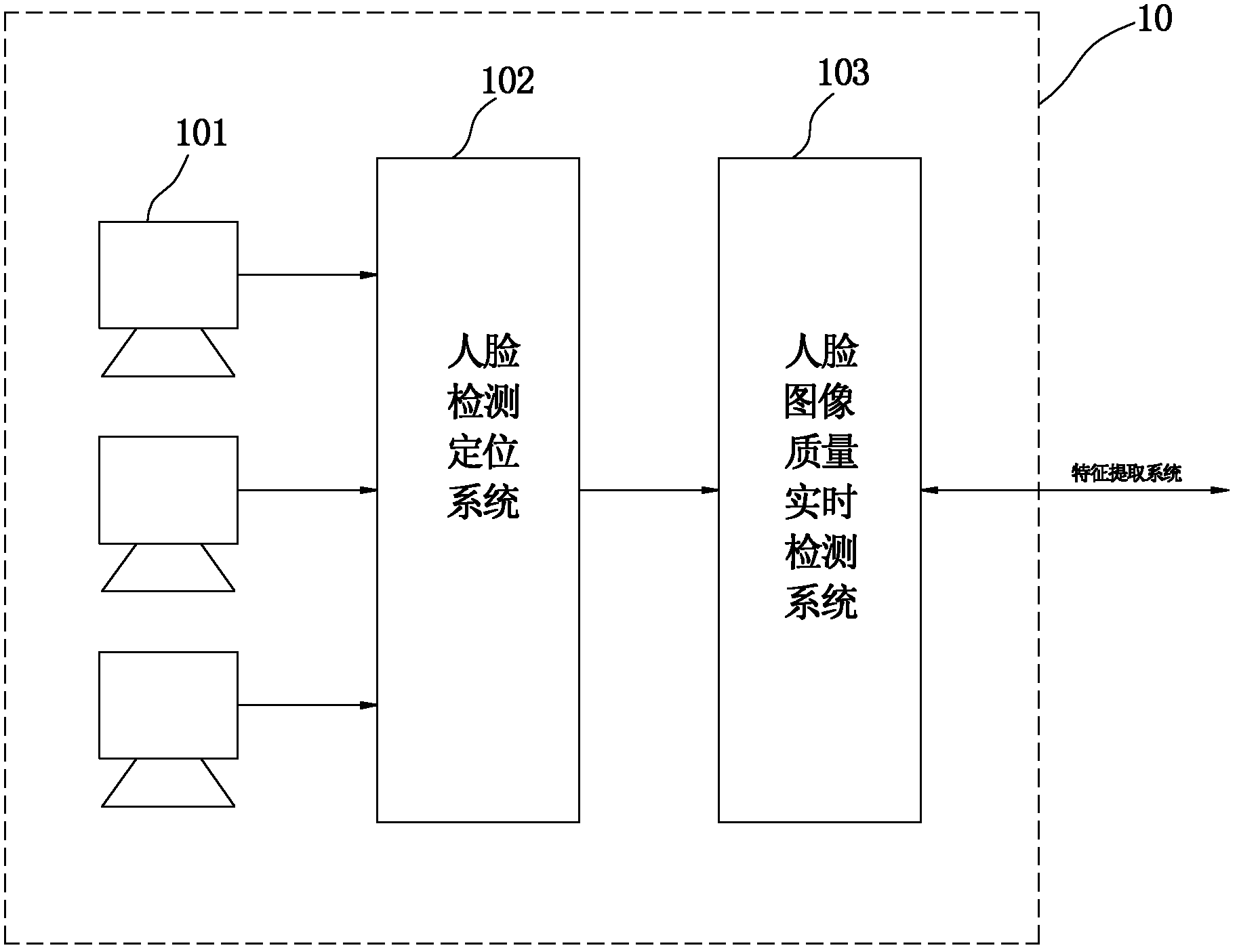
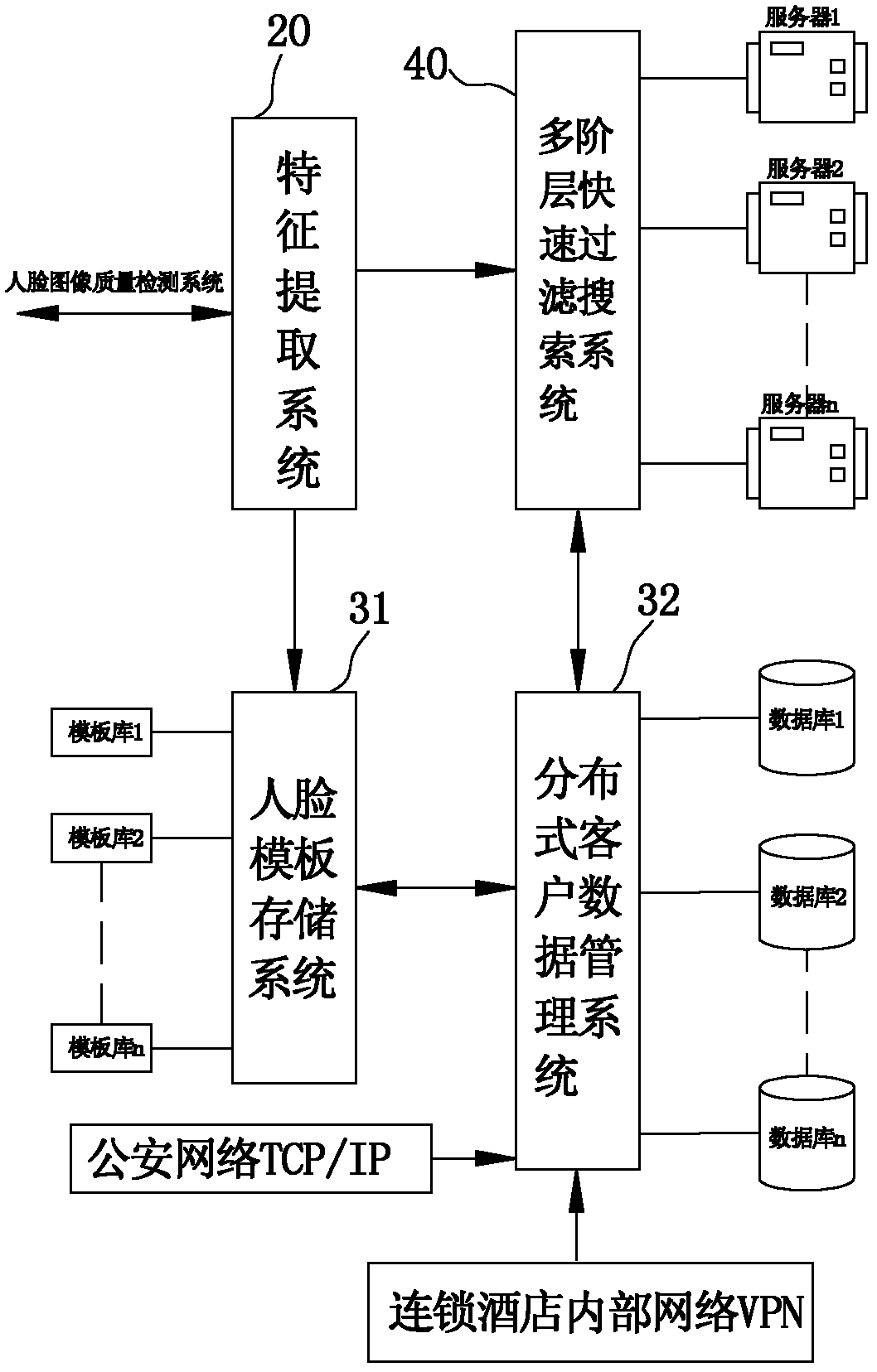
Intelligent safety monitoring system and method based on multilevel filtering face recognition
InactiveCN102201061AImprove recognition accuracyImprove search efficiencyCharacter and pattern recognitionSpecial data processing applicationsFace detectionPattern recognition
The invention discloses a method based on multilevel filtering face recognition. The method comprises the following steps of: collecting a face image of a detected man through an image collection system on a user terminal; automatically detecting and partitioning an exact position of a face from the collected face image by a face detection and positioning system, and performing intelligent indication and image quality real-time monitoring on a face image collection process through an automatic and real-time face image quality detection system; extracting characteristic points from the face image of the user terminal according to an image quality detection threshold value, and generating corresponding target face templates; and performing real-time comparison on a face to be recognized which is detected by a client and a known face database based on a multilevel filter searching algorithm through a background server, finding out the face template having the highest matching score, judging according to a preset threshold value of the system and determining identity information of the shot man in real time. The invention also provides an intelligent identity recognition and safety monitoring system based on a multilevel face filtering and searching technology with high reliability and flexibility.
Owner:CHANGZHOU RUICHI ELECTRONICS TECH
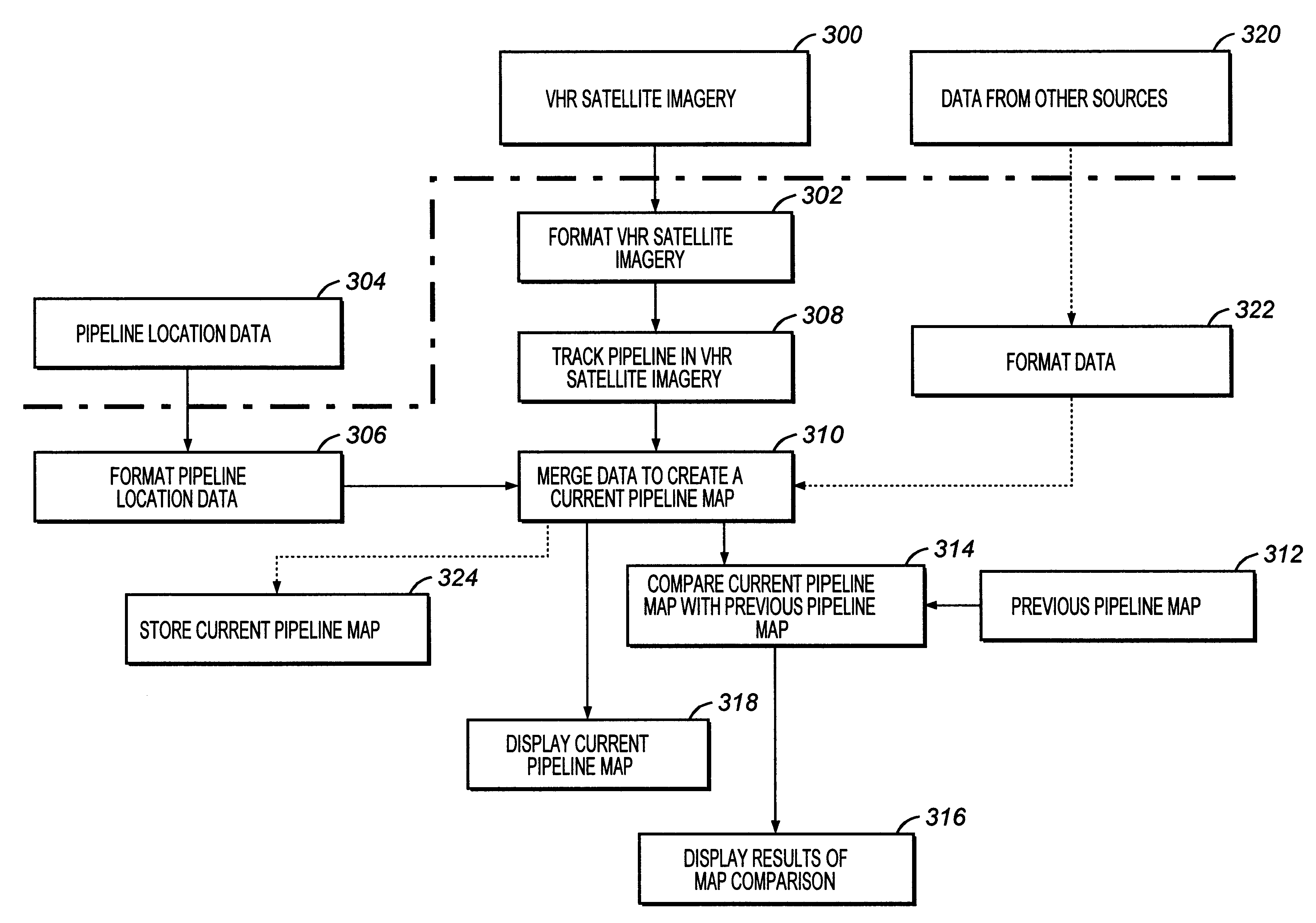
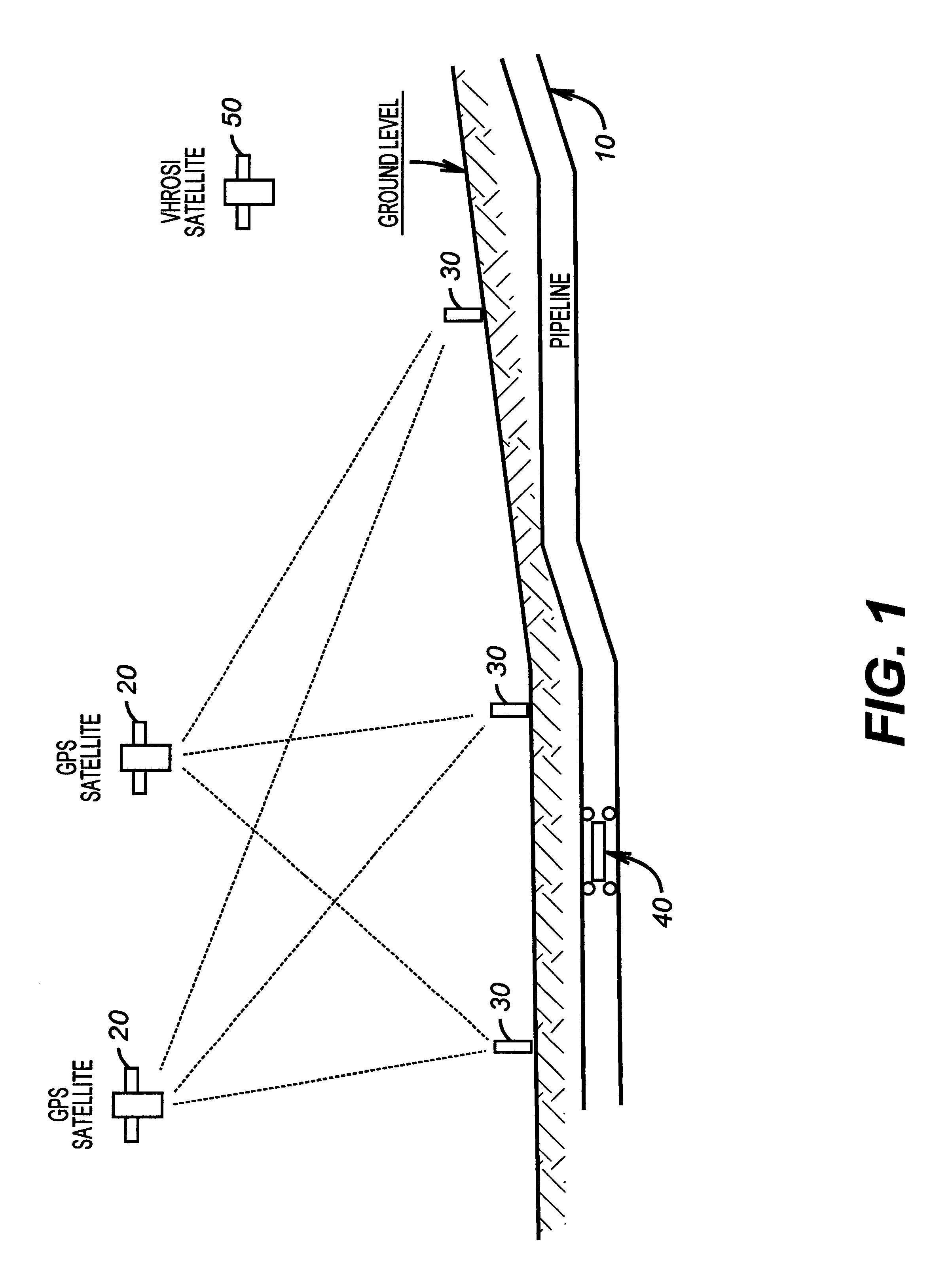
Mapping system for the integration and graphical display of pipeline information that enables automated pipeline surveillance
InactiveUS6243483B1Reduce security risksLow costPosition fixationCharacter and pattern recognitionGraphicsSatellite data
Pipeline data and satellite data are used to provide surveillance for a pipeline. The satellite data is integrated with the pipeline data to produce a current pipeline map. The current pipeline map is then compared with a previous pipeline map to determine whether the route of the pipeline or a surrounding environment of the pipeline has changed. The satellite data includes very high resolution (VHR) satellite imagery and the pipeline data includes location data that is a series of global positioning system (GPS) coordinates.
Owner:PII NORTH AMERICA
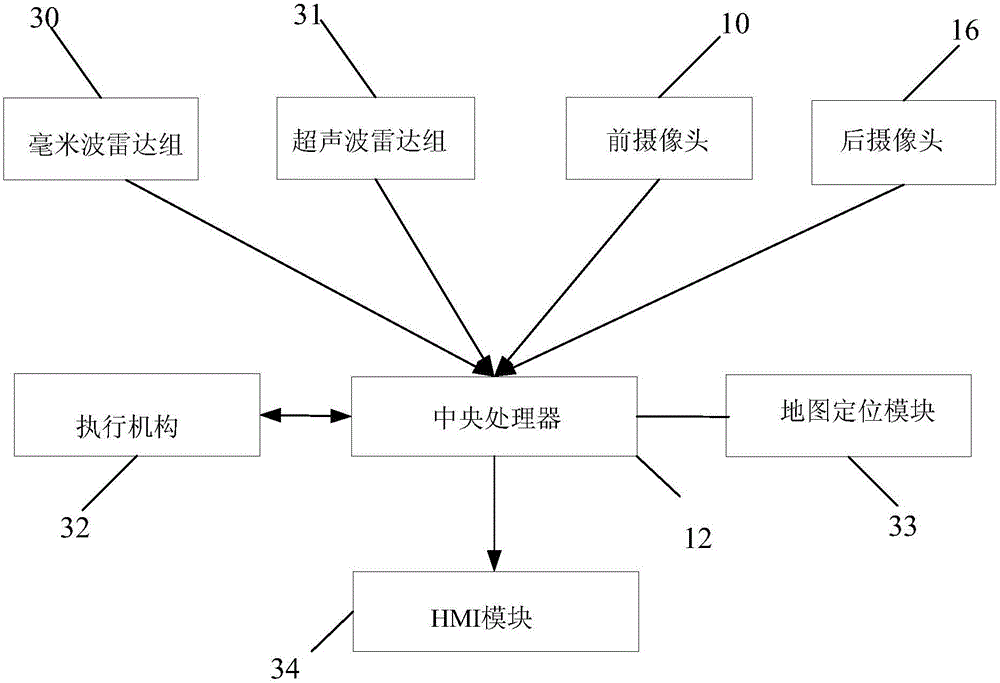
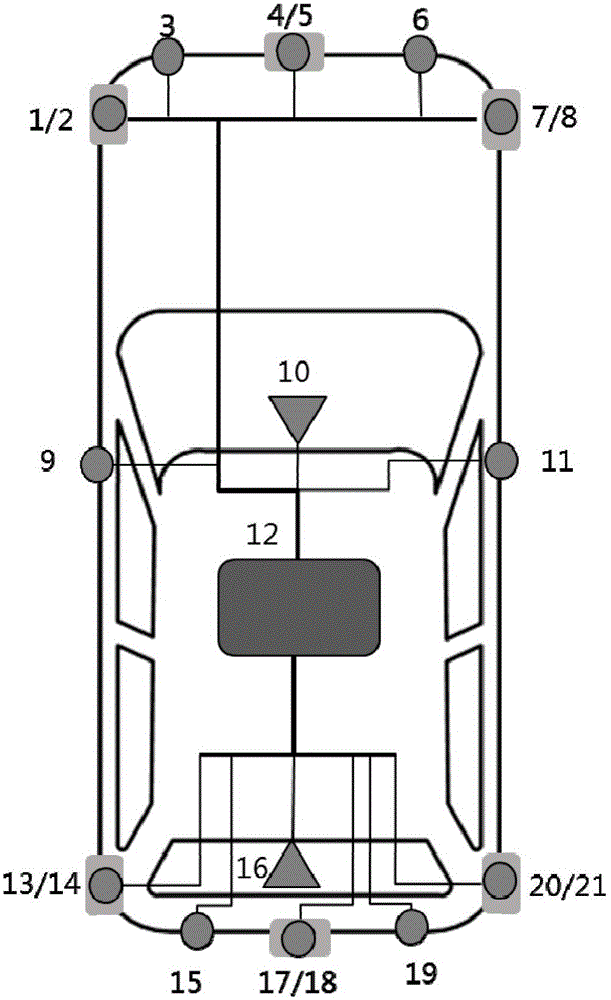
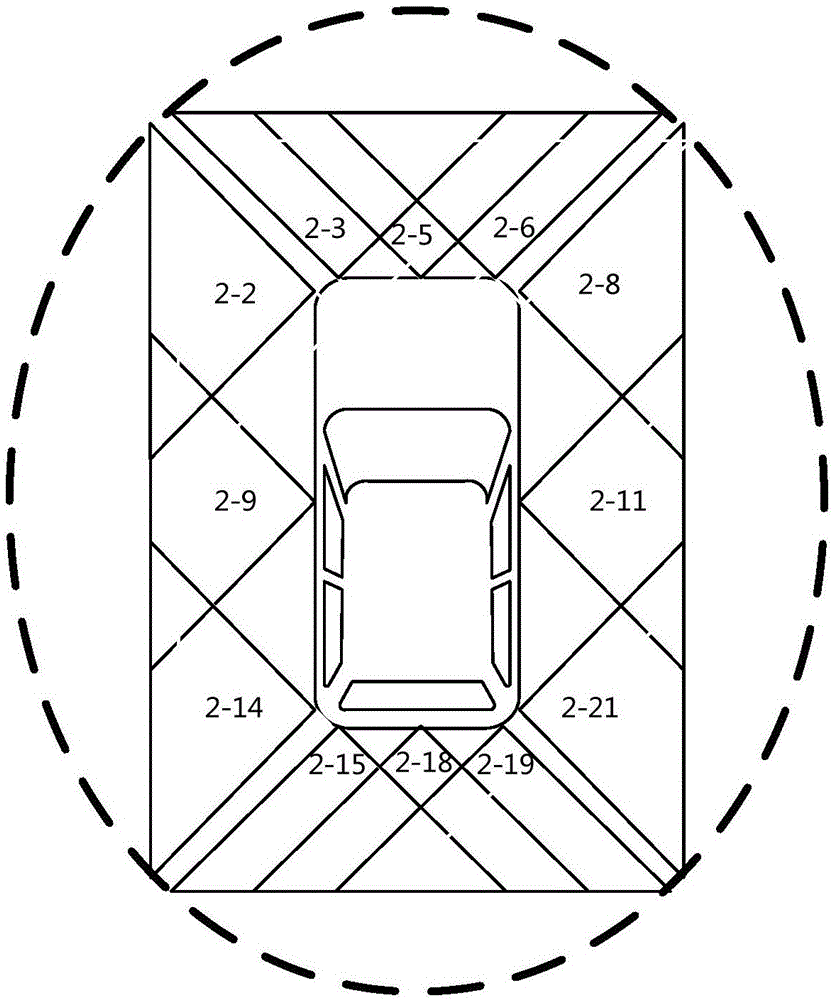
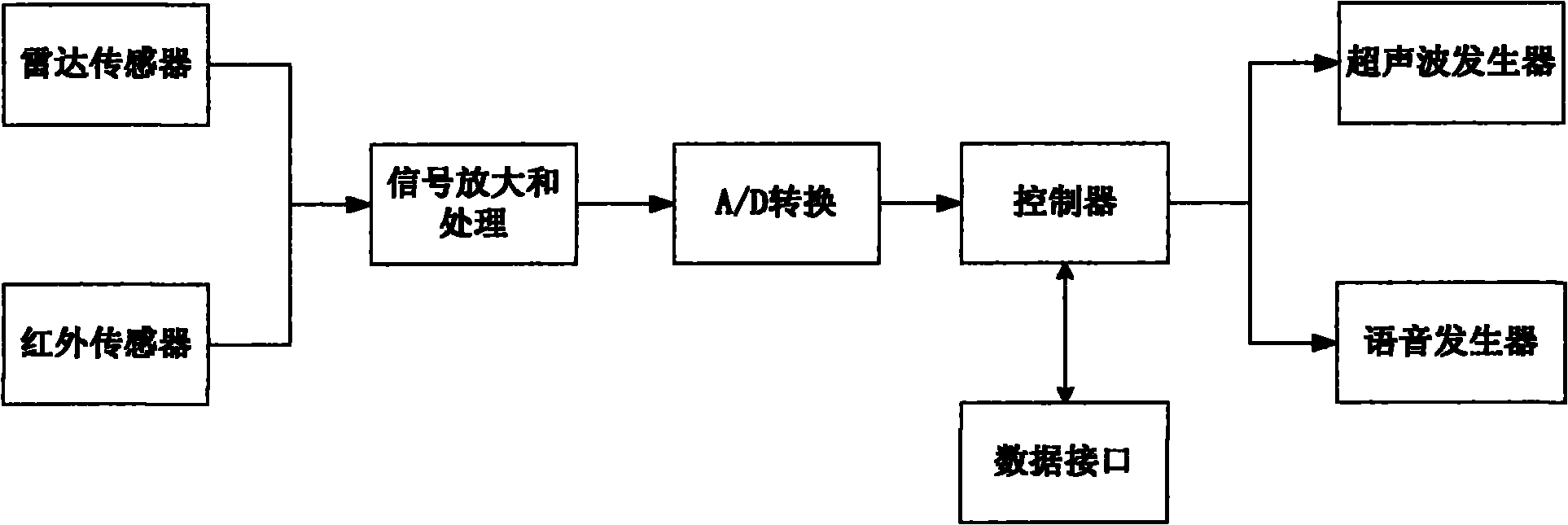
Sensor module of automatic driving system, automatic driving system and automatic driving method
ActiveCN106708040AImprove situational awarenessImprove reliabilityPosition/course control in two dimensionsAutomotive engineeringRadar
The invention discloses a sensor module of an automatic driving system, an automatic driving system and an automatic driving method. The sensor module comprises a front camera, a rear camera, a millimeter-wave radar group and an ultrasonic-wave radar group, and is characterized in that the front camera is used for recognizing lane lines, traffic marking lines, traffic signs and obstacles in front of a vehicle; the rear camera is used for recognizing lane lines and obstacles in rear of the vehicle; the millimeter-wave radar group comprises a plurality of short-range millimeter-wave radars and one or more middle-range millimeter-wave radars, the short-range millimeter-wave radars can cover all areas around the vehicle within 360 degrees and are used for detecting obstacles within the coverage scope and judging the position and the speed of the obstacles, and the middle-range millimeter-wave radars are used for detecting obstacles in front of the vehicle and judging the position and the speed of the obstacles; and the ultrasonic-wave radar group comprises a plurality of ultrasonic-wave radars, can cover all areas around the vehicle within 360 degrees and are used for detecting obstacles. The sensor module disclosed by the invention improves the reliability of the automatic driving system and reduces the security risk.
Owner:CHONGQING CHANGAN AUTOMOBILE CO LTD
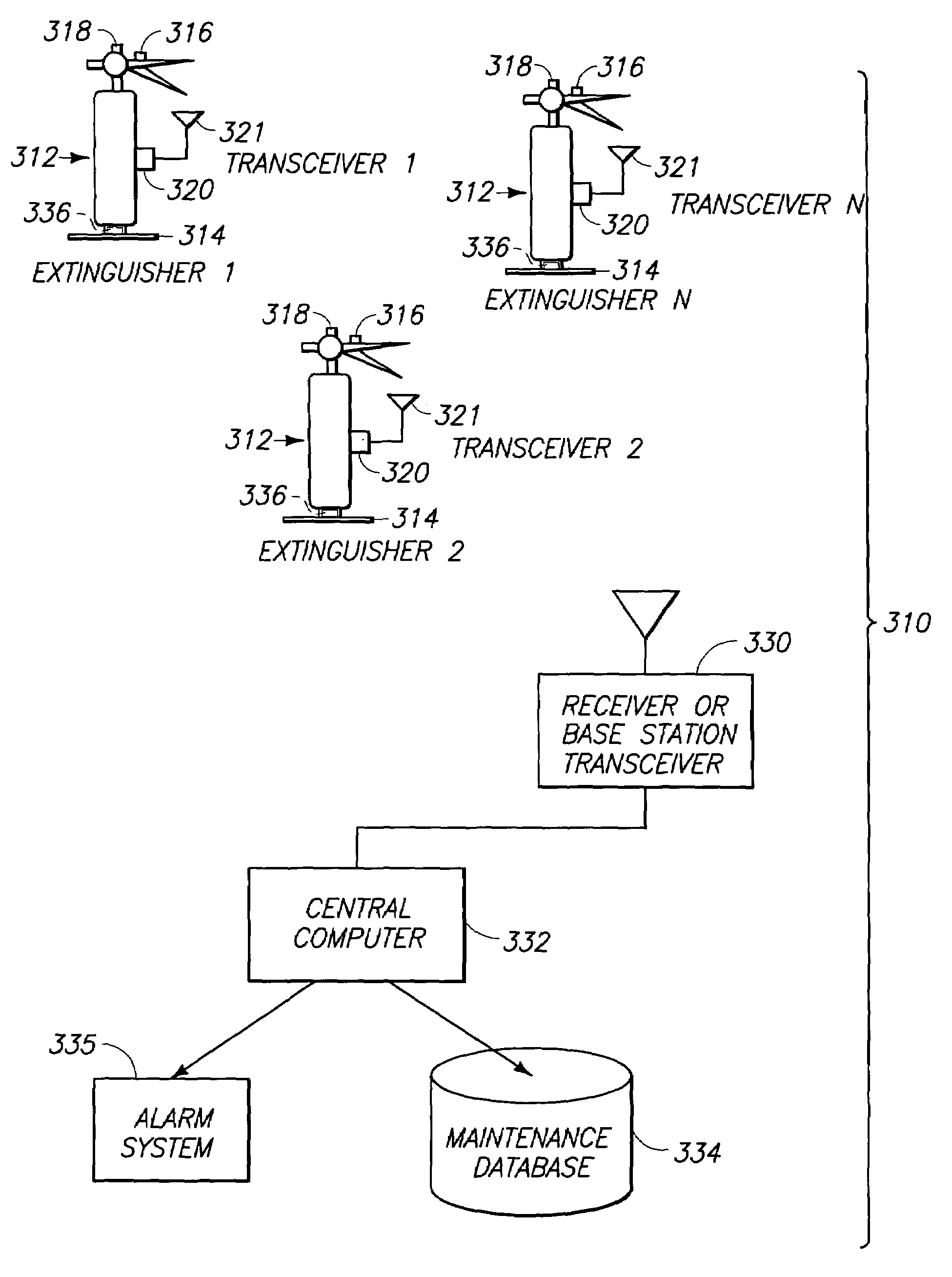
Radio frequency security system, method for a building facility or the like, and apparatus and methods for remotely monitoring the status of fire extinguishers
InactiveUS7081815B2Reduce security risksFrequency-division multiplex detailsTime-division multiplexFire extinguisherEngineering
A system for remotely monitoring the status of one or more fire extinguishers includes means for sensing at least one parameter of each of the fire extinguishers; means for selectively transmitting the sensed parameters along with information identifying the fire extinguishers from which the parameters were sensed; and means for receiving the sensed parameters and identifying information for the fire extinguisher or extinguishers at a common location. Other systems and methods for remotely monitoring the status of multiple fire extinguishers are also provided.
Owner:BATTELLE MEMORIAL INST
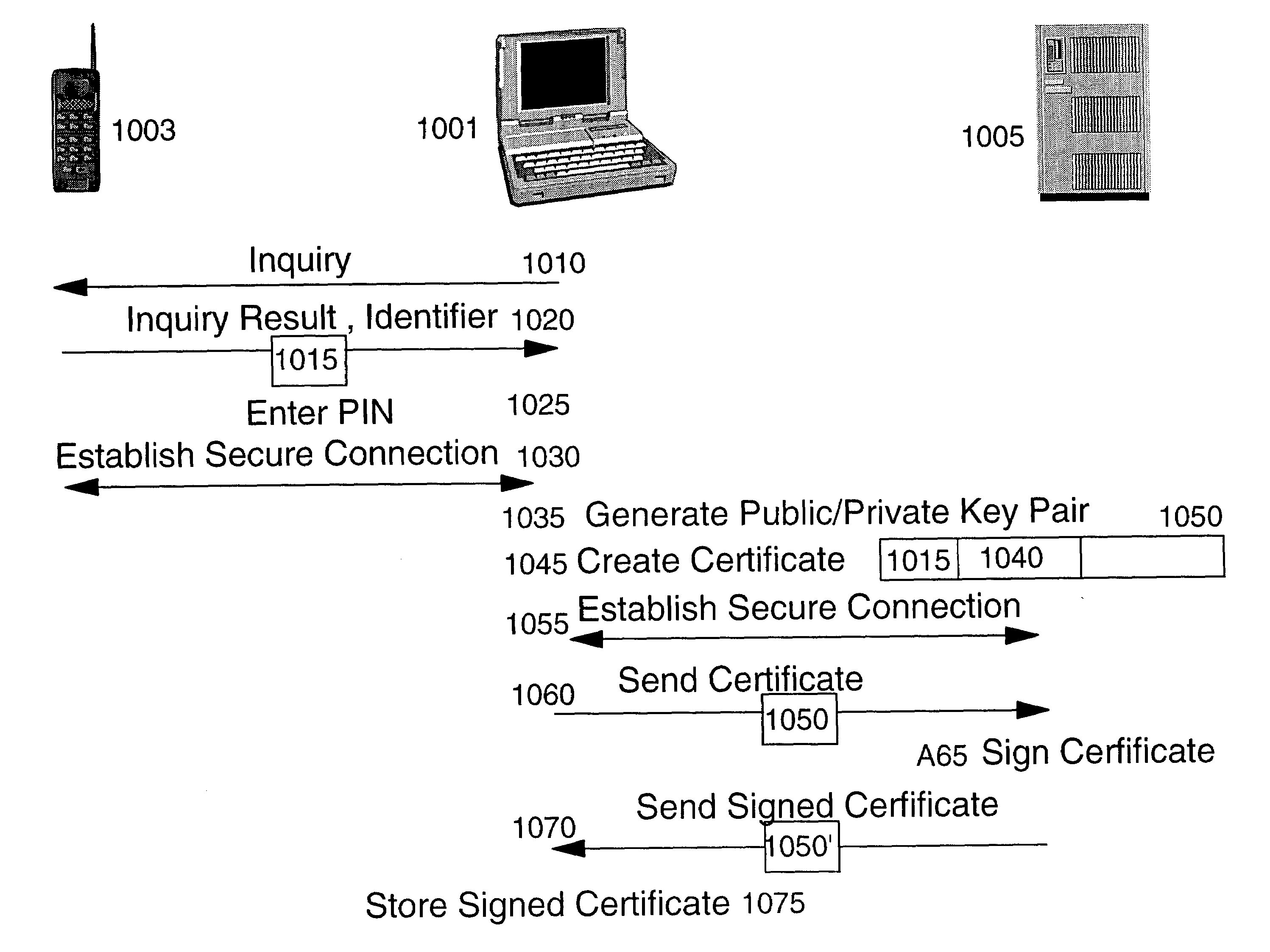
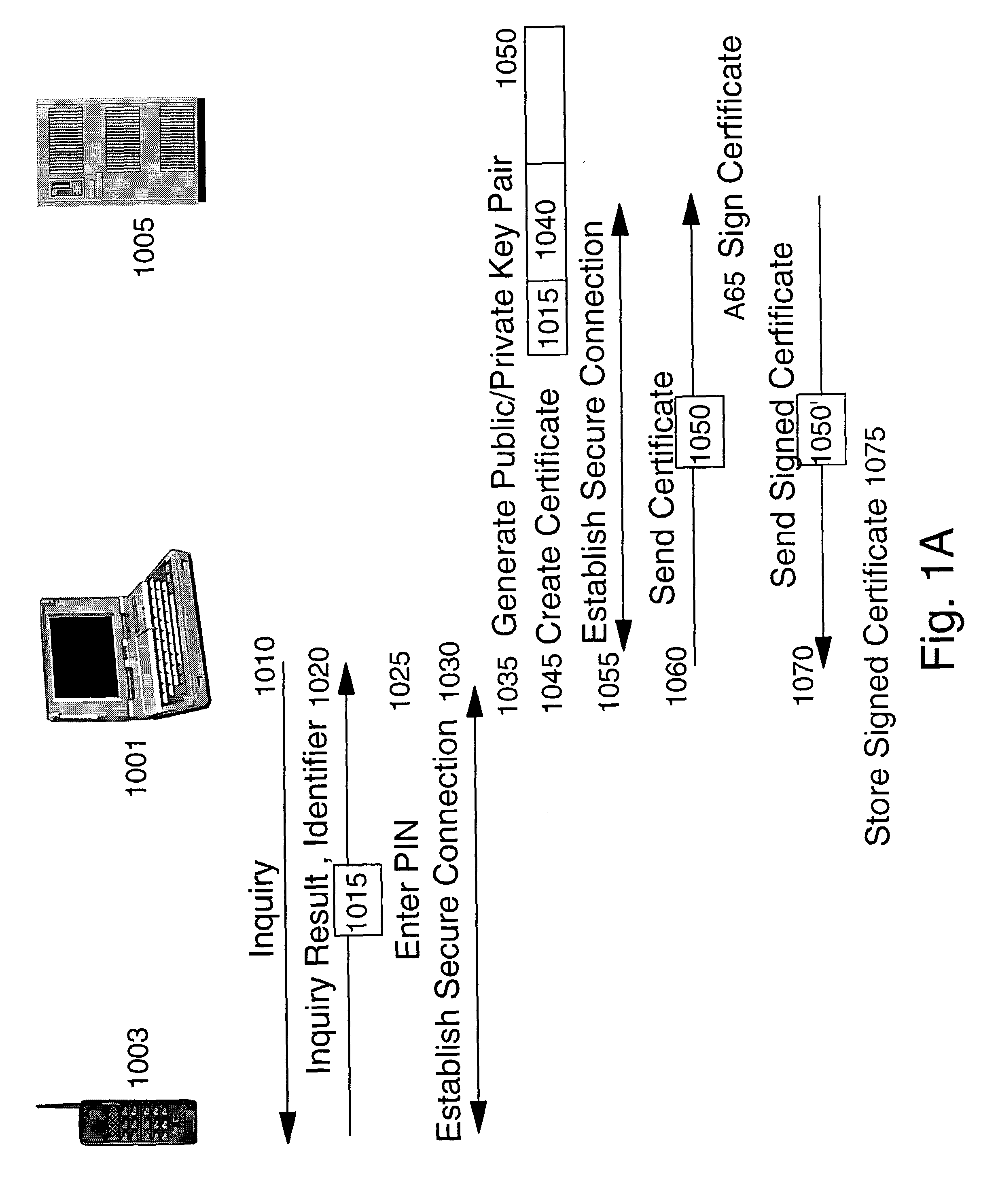
Methods and apparatus for conducting electronic transactions
InactiveUS7953671B2Enhanced reliability and confidenceReduce security risksComplete banking machinesAcutation objectsChallenge responseAuthorization
A system and method for facilitating electronic transactions using an intelligent instrument is disclosed. An authorization server enables users to obtain authorization credentials through the use of the intelligent instrument by issuing a challenge to an intelligent token of the intelligent instrument. The intelligent token generates a challenge response and transmits the challenge response to the authorization server, which assembles credentials including a key for the electronic transaction upon validating the response. The authorization server sends the assembled credentials to the intelligent instrument and the intelligent instrument transmits the assembled credentials to the authorization server during a subsequent transaction. The authorization server validates the assembled credentials and provides authorization for the transaction in response to the validating the assembled credentials.
Owner:LIBERTY PEAK VENTURES LLC
Method for quick-speed preparing aerogel by hydro-thermal synthesis at low cost
InactiveCN101456569AReduce surface tensionIntegrity guaranteedSilicaAlkali metal silicatesReaction temperatureHydrothermal synthesis
The invention discloses a method for preparing aerogel materials by combining hydrothermal synthesis technology and sol-gel technology. The prepared aerogel comprises one or more of alumina aerogel, silica aerogel, zirconia aerogel and titania aerogel. The method comprises the following steps: mixing a reactant and a structure-directing agent according to certain proportion, and adding a pH value control agent to adjust the pH value; sealing hydrothermal reaction equipment, heating the mixture to be between 50 and 280 DEG C, making the mixture stand for 0 to 72 hours, raising the temperature to be between 60 and 300 DEG C, and continuously reacting for 0.1 to 72 hours; and cooling gel, taking out the gel, drying the gel and obtaining the aerogel. Compared with the prior art, the method has low reaction temperature and pressure, small equipment investment and simple and controllable technology, reduces potential safety hazards, greatly improves the preparation speed of the aerogel, saves the production cost, and is favorable to realize commercial mass production.
Owner:纳诺科技有限公司 +1
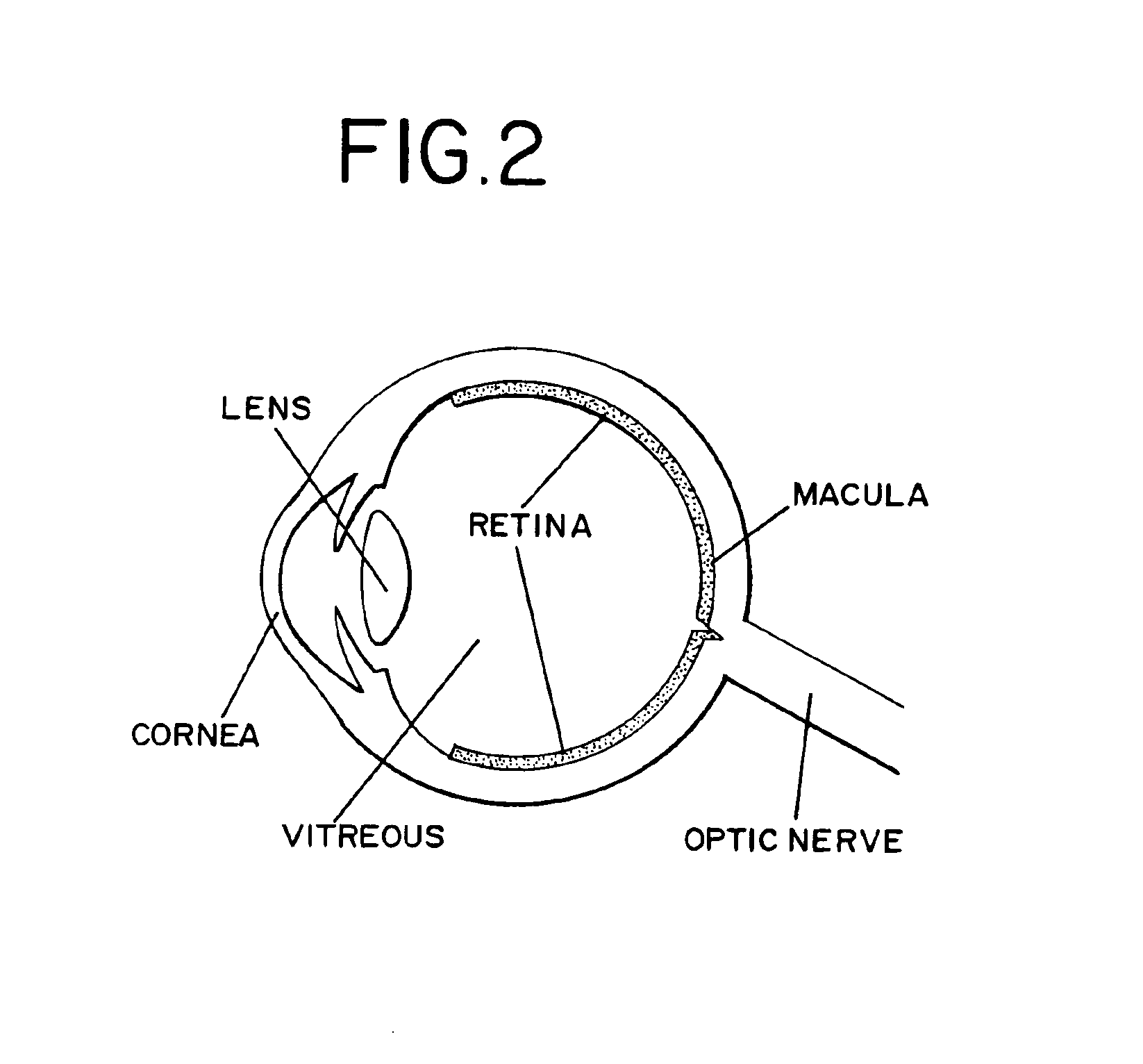
Method of radiation delivery to the eye
InactiveUS6875165B2Optimal balance of powerOptimal balance of penetrationDiagnosticsSurgeryOcular operationRadical radiotherapy
A surgical device for localized delivery of beta radiation in surgical procedures, particularly ophthalmic procedures. Preferred surgical devices include a cannula with a beta radiotherapy emitting material at the distal end of the cannula. The surgical device is particularly suitable for use in the treatment of treat Age Related Macular Degeneration (AMD).
Owner:RETINALABS COM
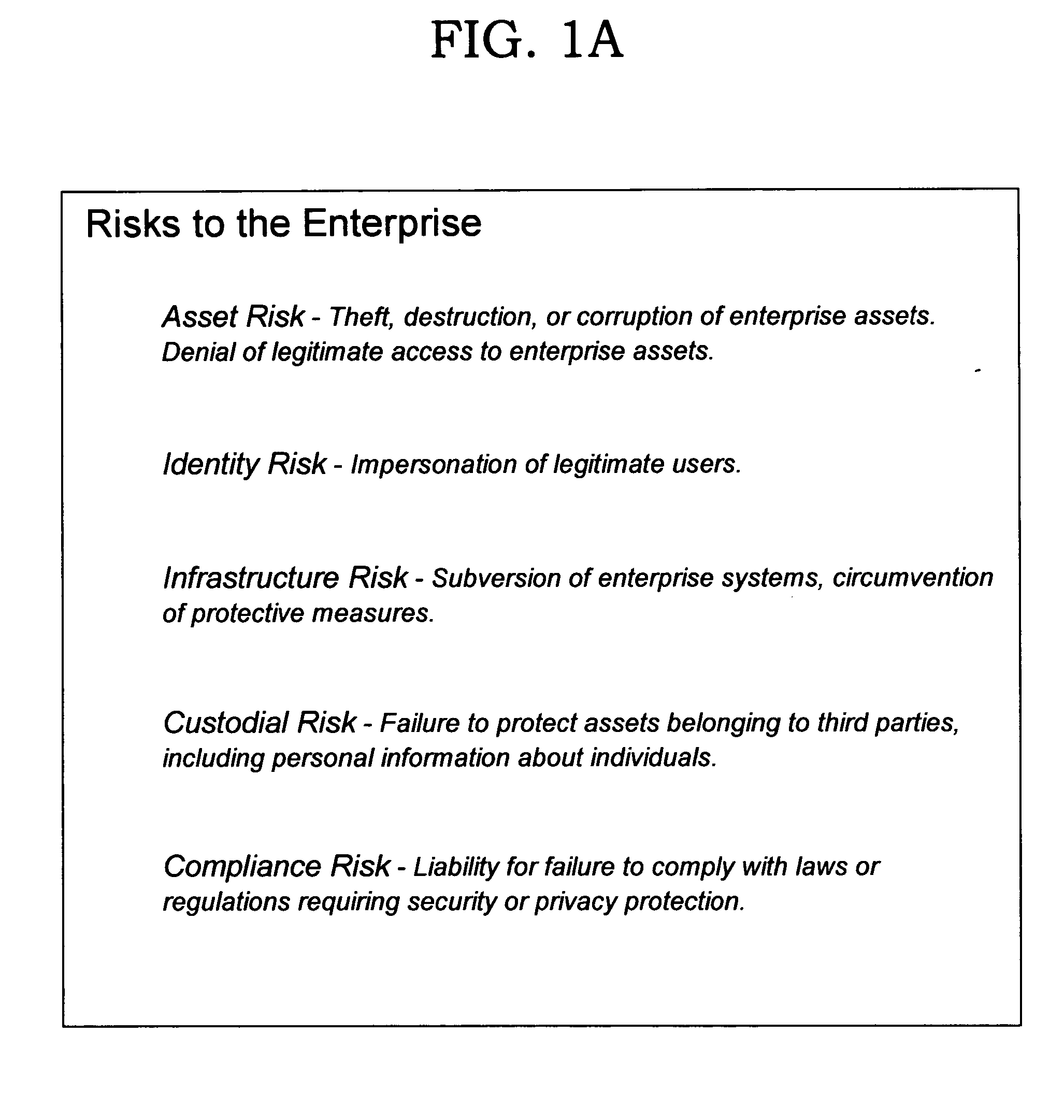
Deriving security and privacy solutions to mitigate risk
InactiveUS20050080720A1Reduce security risksFinanceSpecial data processing applicationsSecurity solutionDecision maker
Techniques are disclosed for systematically assessing an enterprise's security risks in view of a set of security patterns. Each pattern that is applicable to the enterprise's operation is then considered against the backdrop of a set of common attributes that are used, in turn, to further distinguish each pattern from a risk and security solution perspective. Using the disclosed techniques, specific security risks can be identified and appropriate security products can be selected to address those risks in a systematic manner, thereby assisting information technology decision makers across a wide variety of enterprises in deriving security solutions. These security solutions will typically be more effective and efficient from a functional perspective, as well as being more cost-effective, than security solutions created using prior art ad hoc approaches. The disclosed techniques may also be leveraged to create a requirements list for function to be included in a security product.
Owner:IBM CORP
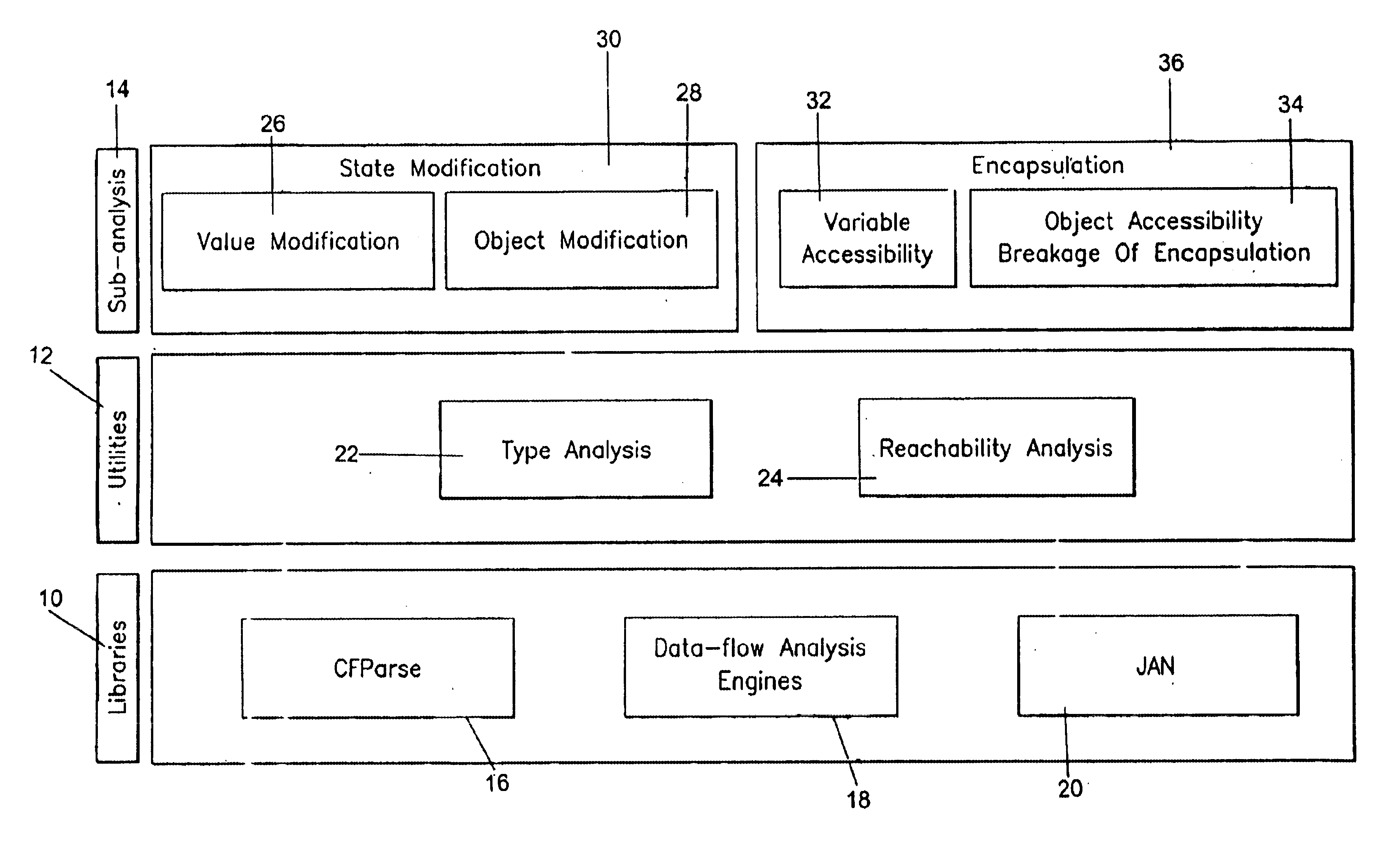
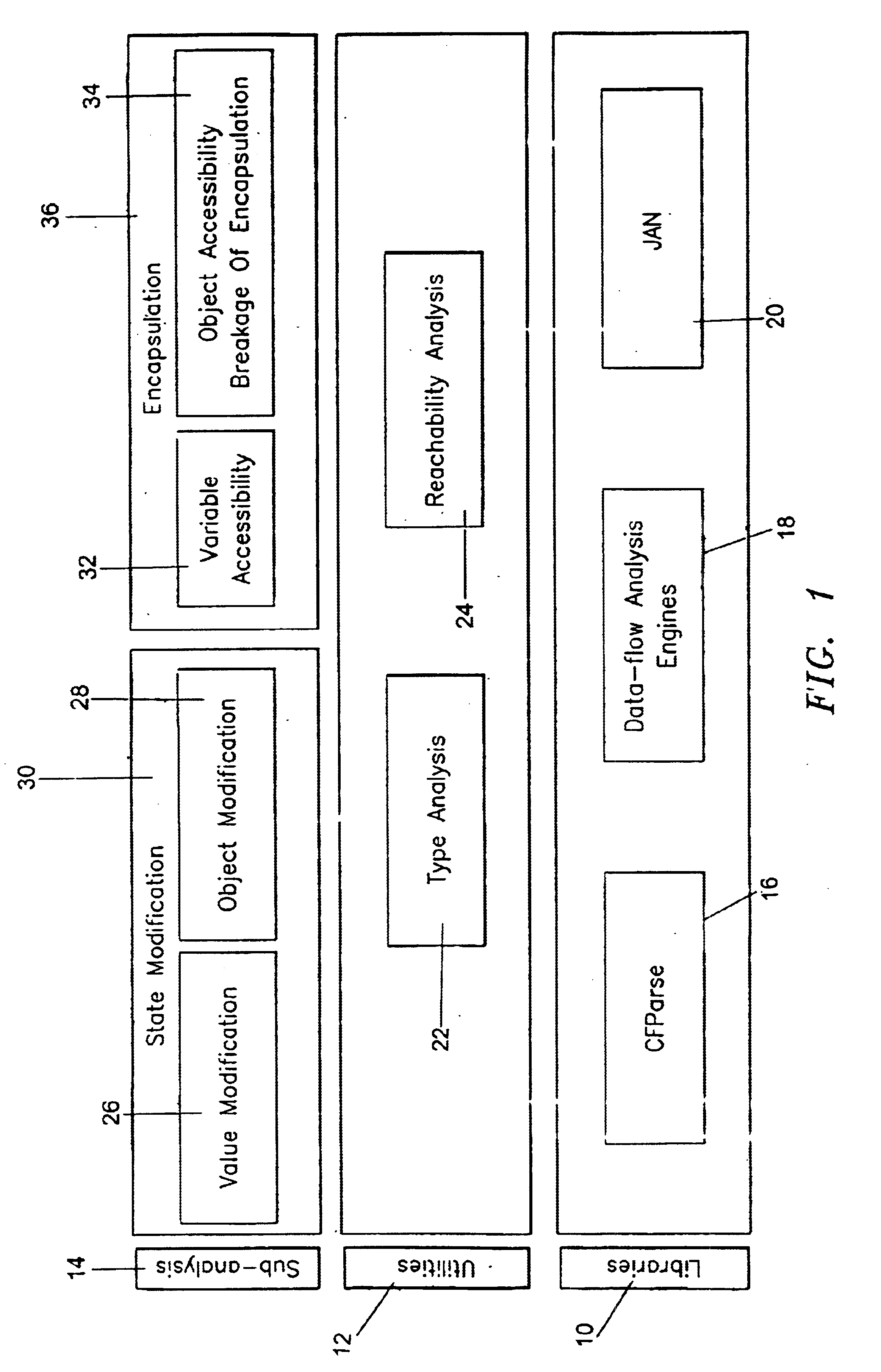
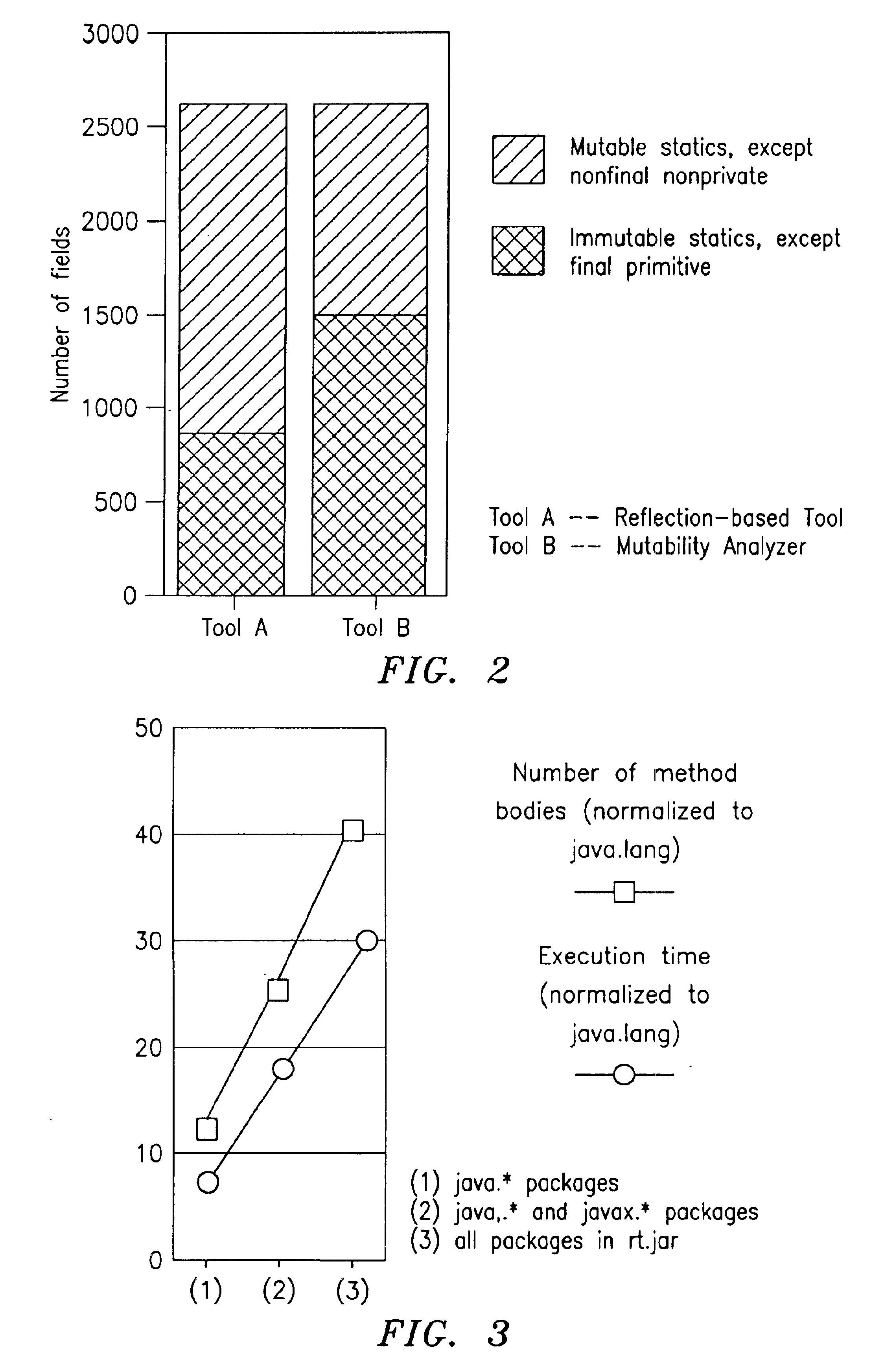
Mutability analysis in Java
InactiveUS6925638B1Reduce security risksEnsure maintenanceSoftware engineeringSpecific program execution arrangementsExtensibilityHuman language
A system and method for detecting the mutability of fields and classes in an arbitrary program component written in an object oriented programming language is disclosed. A variable is considered to be mutable if a new value is stored into it, as well as if any of its reachable variables are mutable. The system and method uses a static analysis algorithm which can be applied to any software component rather than whole programs. The analysis classifies fields and classes as either mutable or immutable. In order to facilitate open-world analysis, the algorithm identifies situations that expose variables to potential modification by code outside the component, as well as situations where variables are modified by the analyzed code. An implementation of the analysis is presented which focuses on detecting mutability of class variables, so as to avoid isolation problems. The implementation incorporates intra- and inter-procedural data-flow analyses and is shown to be highly scalable. Experimental results demonstrate the effectiveness of the algorithms.
Owner:IBM CORP
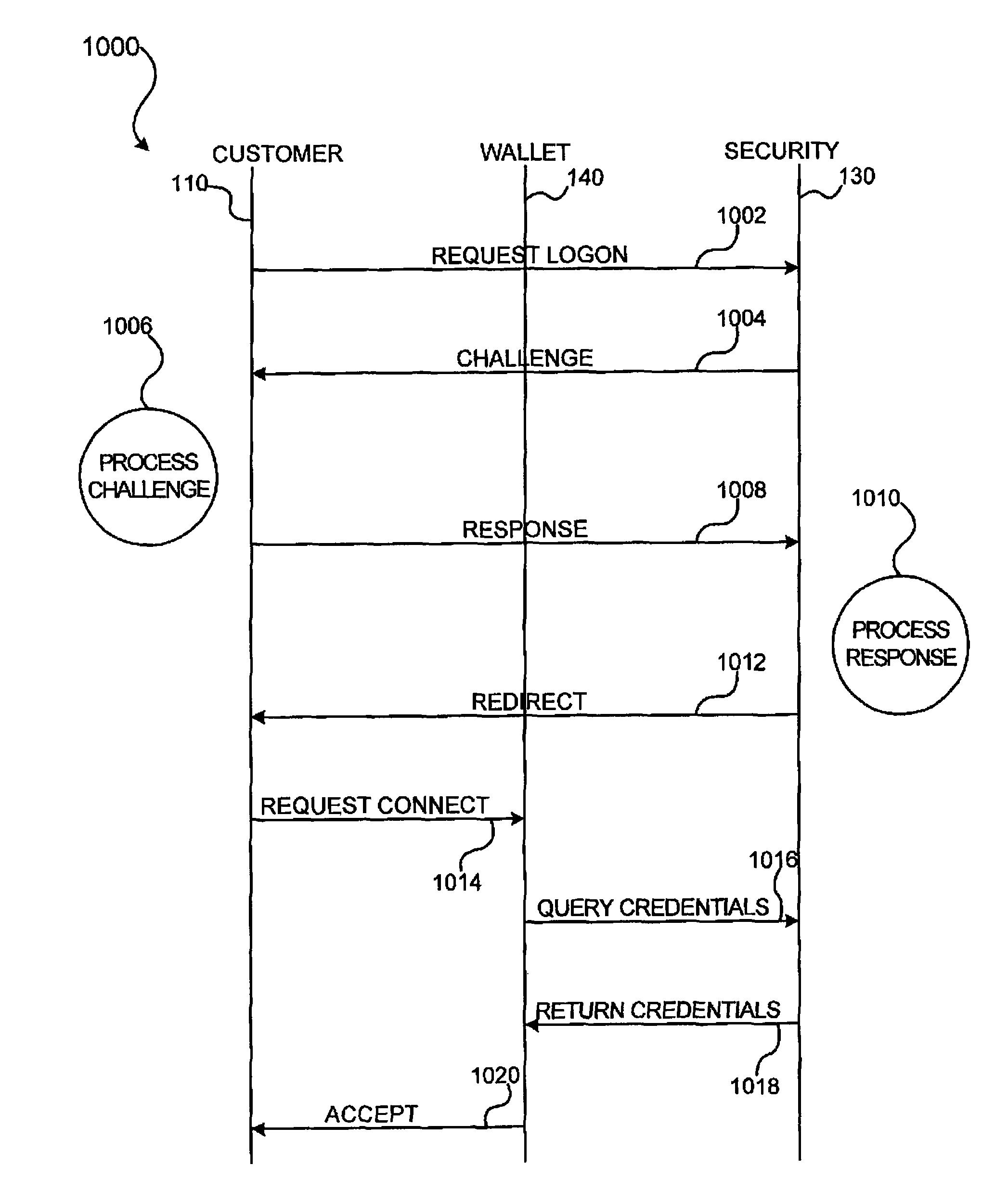
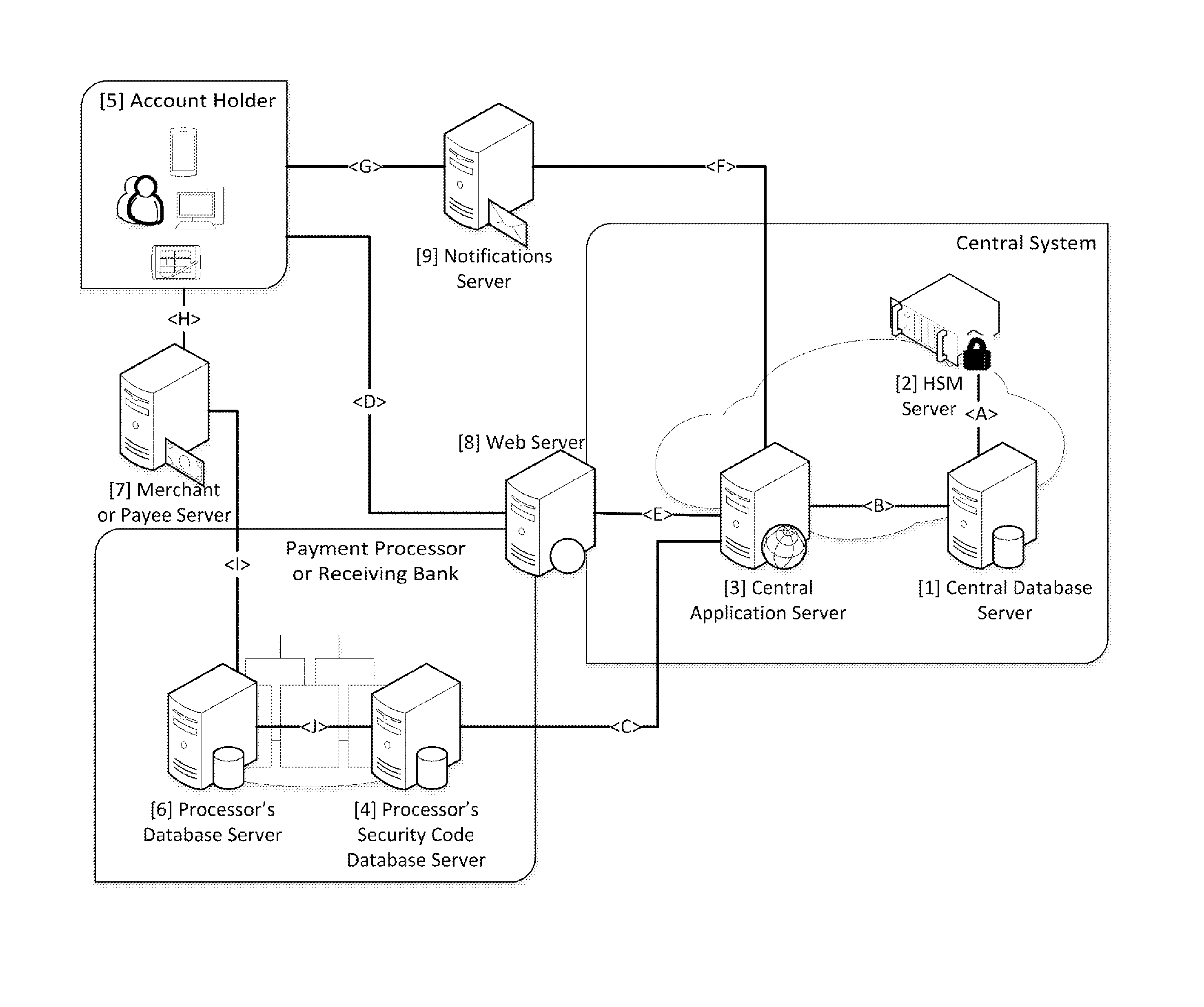
Security for electronic transactions and user authentication
InactiveUS20170004506A1Increase randomnessImprove user securityCryptography processingProtocol authorisationUser authenticationPayment transaction
System and method for generating, disseminating, controlling, and processing limited-life security codes used to authenticate users, particularly for electronic financial transactions, such as payment transactions or interacting with automated teller machines and the like. Providing a user with a single security code usable across multiple accounts or other secured systems is contemplated, each security code having a limited lifetime (e.g., one day). In a particular example of the present invention, a plurality of similarly situated users (each needing authenticated access to a plurality of accounts or other secured systems using the security code) are each assigned a set or group of respective security codes. In a preferred example, each security code is a random number from a random number generator. The respective security codes for each user correspond to a respective security code validity period of limited duration. Thus, a table or matrix that associates the plurality of users with the respective sets of randomly selected security codes (each having their respective validity periods) is generated, and that matrix is provided to the respective entities (such as banks, payment processors, computer networks generally, etc.) to which each user requires secured access. In parallel, at least a current security code (for example, for the current validity period) is provided to each user, and this is how the respective entities being accessed can track which code from which user is currently valid.
Owner:TENDER ARMOR LLC
Method and apparatus for L3-aware switching in an ethernet passive optical network
InactiveUS20050243837A1Avoid forwardingReduce security risksMultiplex system selection arrangementsData switching by path configurationIp addressMedia access control
One embodiment of the present invention provides a system that performs layer 3 (L3) aware switching in an Ethernet passive optical network (EPON) which includes a central node and at least one remote node. During operation, the system maintains a set of mapping information which indicates a correspondence relationship between a logical link identifier of a remote node, a medium access control (MAC) address for a subscriber coupled to the remote node, and an IP address for the subscriber. Upon receiving a packet which contains an IP address, the system selectively attaches a proper logical link identifier to the packet based on the mapping information and the IP address contained in the packet, thereby allowing only one proper remote node to receive the packet.
Owner:AVAGO TECH INT SALES PTE LTD
Driver Identification System and Methods
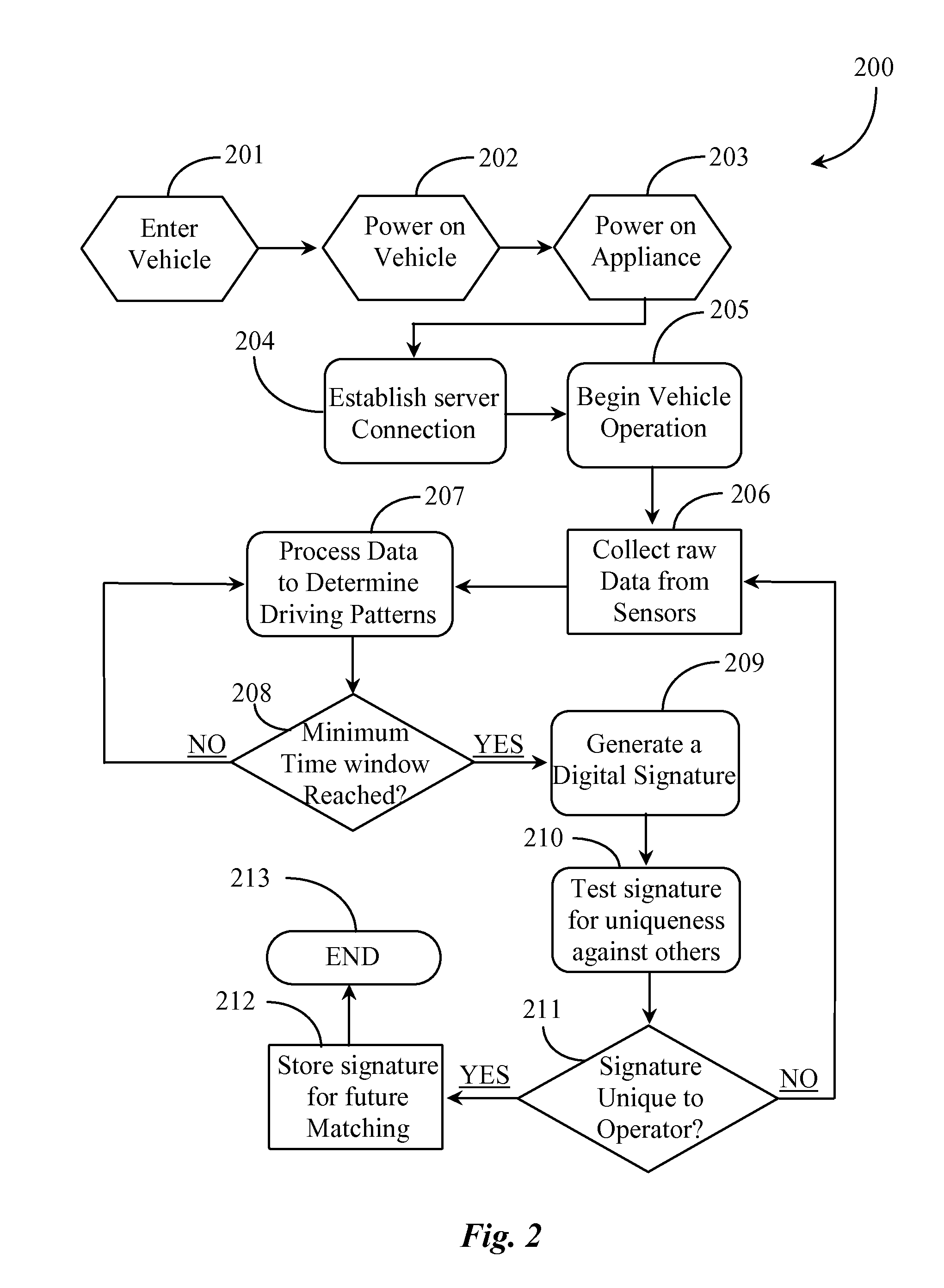
ActiveUS20120226421A1Improve securityReliable informationFinanceRegistering/indicating working of vehiclesAnalysis dataDriver/operator
A system for developing a digital signature identifying a specific person operating a vehicle uses a computerized appliance and software or firmware executing from a non-transitory medium on the computerized appliance and providing a first function collecting raw data regarding vehicle operation from sensors implemented in the vehicle during operation by the specific person, a second function analyzing the raw data and identifying at least one pattern of behavior associated with the specific person; and a third function developing a digital signature from the analyzed data for that specific person.
Owner:AUTOMATIC LABS
Methods and apparatus for secure online access on a client device
ActiveUS20060047956A1Prevent unwanted disclosure of confidential informationManipulation is limitedComputer security arrangementsSpecial data processing applicationsPaper documentDocument preparation
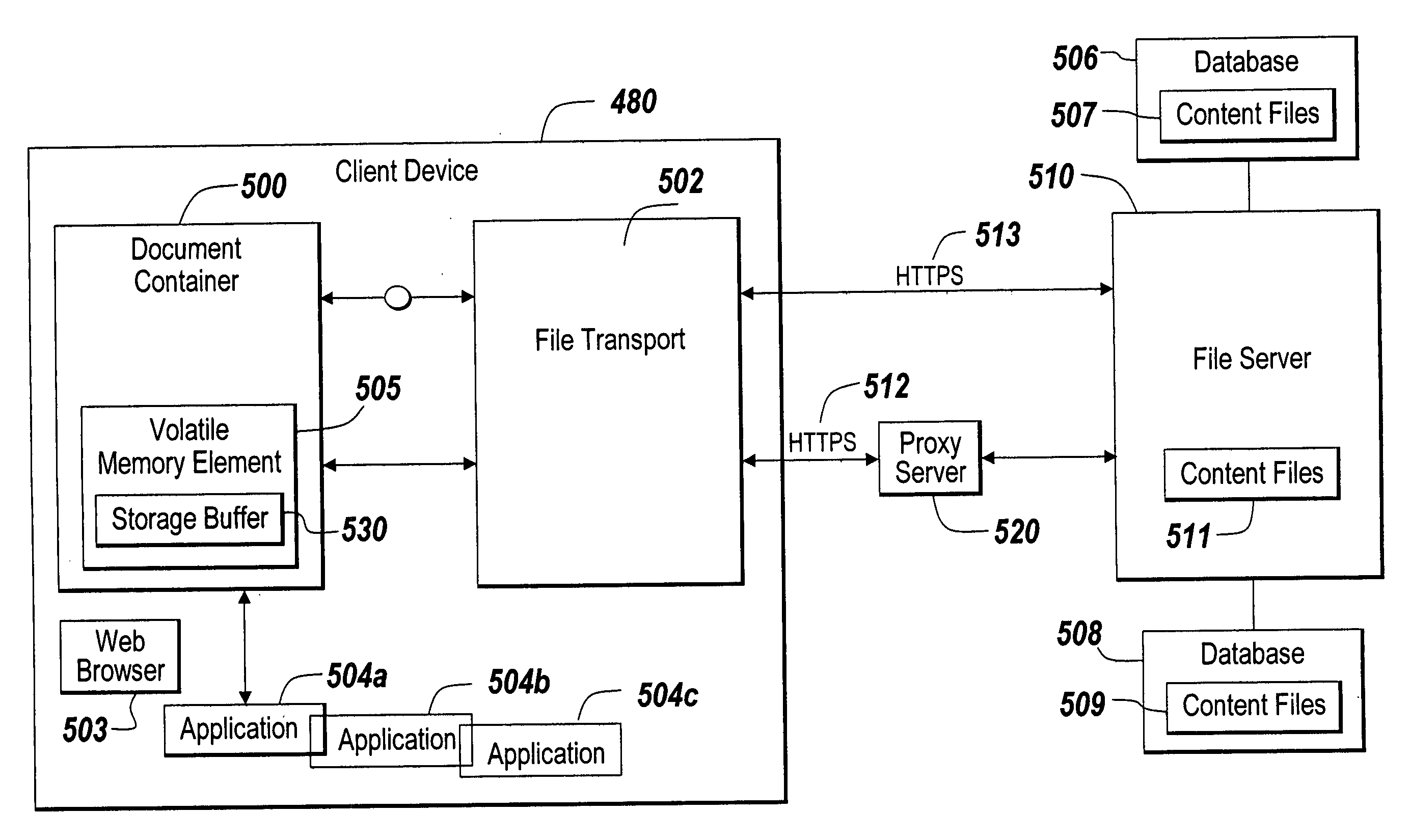
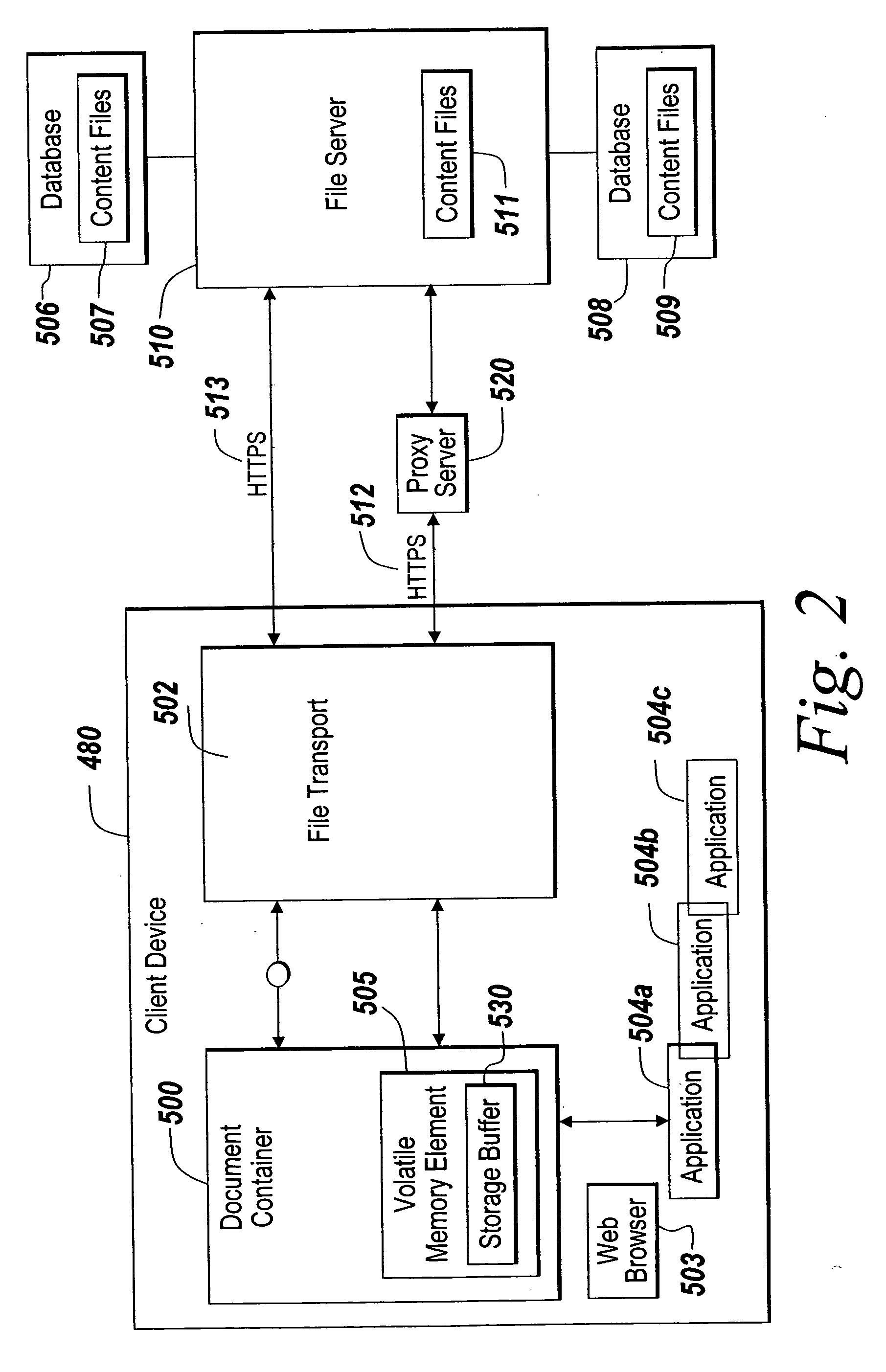
A method of securely accessing at a client device content from a server without using the non-volatile memory of the client device is disclosed. The bypassing of non-volatile memory lessens the security risk of unauthorized viewing of the server originated content. An transport mechanism is initiated on a client device and creates a document container. Downloaded documents from a server are mapped into the document container and saved within the document container in volatile memory. Substitute menus are generated within the container to replace application menus. User documents are saved directly to the originating server via the substitute menus. The downloaded copies in volatile memory automatically delete when the document container is destroyed thereby reducing security concerns of unauthorized viewing of the content at the client device.
Owner:CITRIX SYST INC
Comprehensive measuring and controlling device of high voltage pole tower
InactiveCN101989767AReduce pollutionReduce power consumptionCircuit arrangementsIndication of weather conditions using multiple variablesGeneral Packet Radio ServiceSmart grid
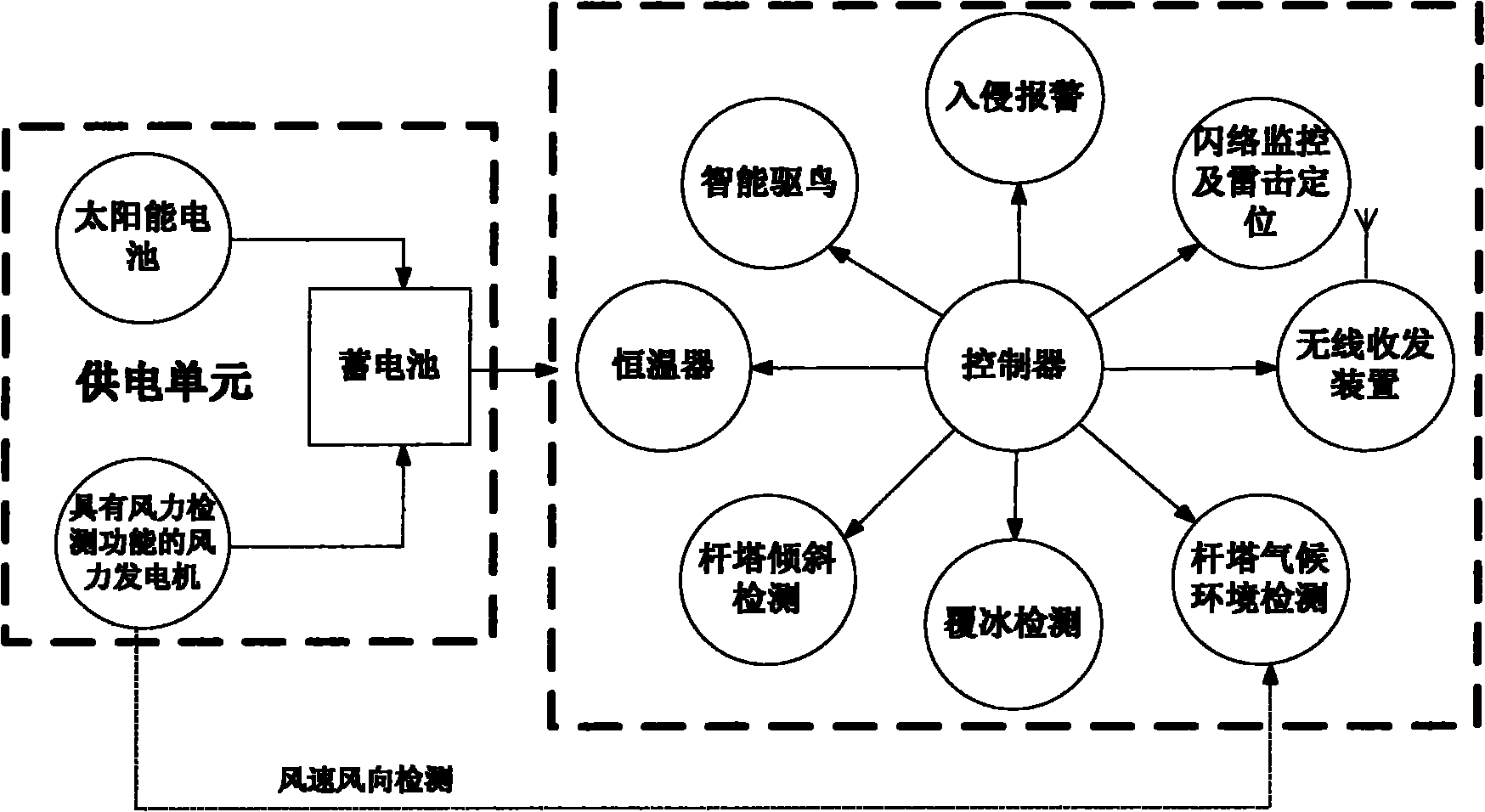
The invention relates to a comprehensive measuring and controlling device of a high voltage pole tower, mainly comprising a power supply unit, an intelligent bird driving unit, a flashover and lightning stroke location detection unit, a pole tower inclination detection unit, a pole tower meteorological environment detection unit, a pole tower intrusion alarm unit, an transmission line icing parameter detection unit, a central controller, a wireless transceiving device and a thermostat, wherein the power supply unit comprises two parts which are a solar battery and a wind turbine, the wind turbine also fulfills the functions of wind speed and wind direction detection and is an important component part of the pole tower meteorological environment detection unit, the power supply unit stores collected electric quantity into a storage battery through a collection circuit and supplies the power to the device, and the wireless transceiving device sends information collected in situ to a distant monitor center through a GPRS (General Packet Radio Service) or a wireless local network. The invention can fulfill the functions of intelligent bird driving, flashover and lightning stroke location, pole tower inclination detection, meteorological environment detection, intrusion alarm, icing parameter detection and the like and has strong environment adaptability because the wind power and the solar power generation accord with the environment self-powered requirement, thereby enhancing the maintenance free performance of a system. The device is an important component part of an intelligent power grid, accords with the requirement of intelligent power grid establishment of a national power grid and has higher practical value and wide application prospect.
Owner:中电国科技术有限公司 +1
Methods and apparatus for conducting electronic transactions
InactiveUS7801827B2Enhanced reliability and confidenceReduce security risksDigital data processing detailsUnauthorized memory use protectionSmart cardE-commerce
A system and method for conducting electronic commerce are disclosed. In various embodiments, the electronic transaction is a purchase transaction. A user is provided with an intelligent token, such as a smartcard containing a digital certificate. The intelligent token suitably authenticates with a server on a network that conducts all or portions of the transaction on behalf of the user. In various embodiments a wallet server interacts with a security server to provide enhanced reliability and confidence in the transaction. In various embodiments, the wallet server includes a toolbar. In various embodiments, the digital wallet pre-fills forms. Forms may be pre-filled using an auto-remember component.
Owner:LIBERTY PEAK VENTURES LLC
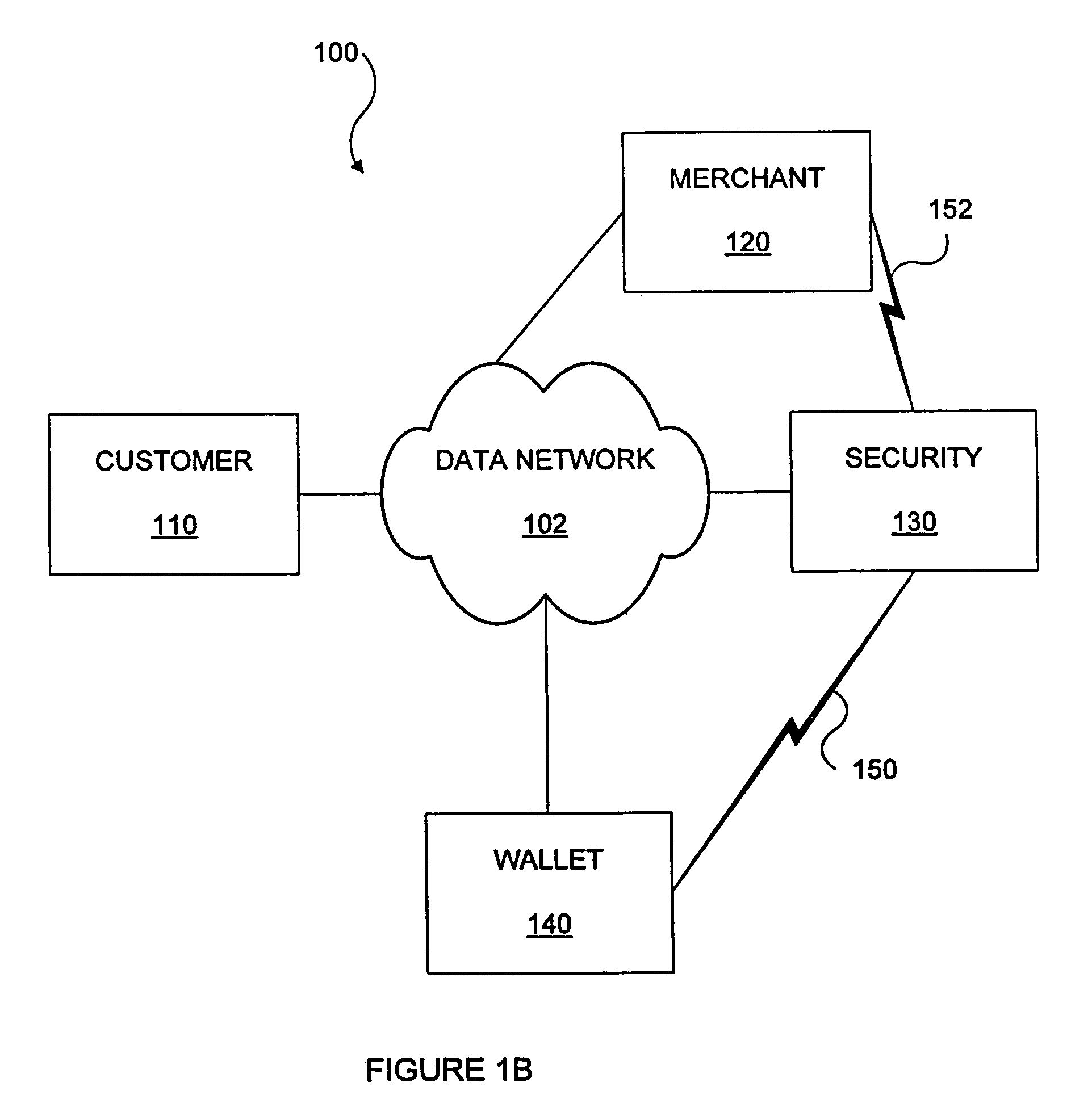
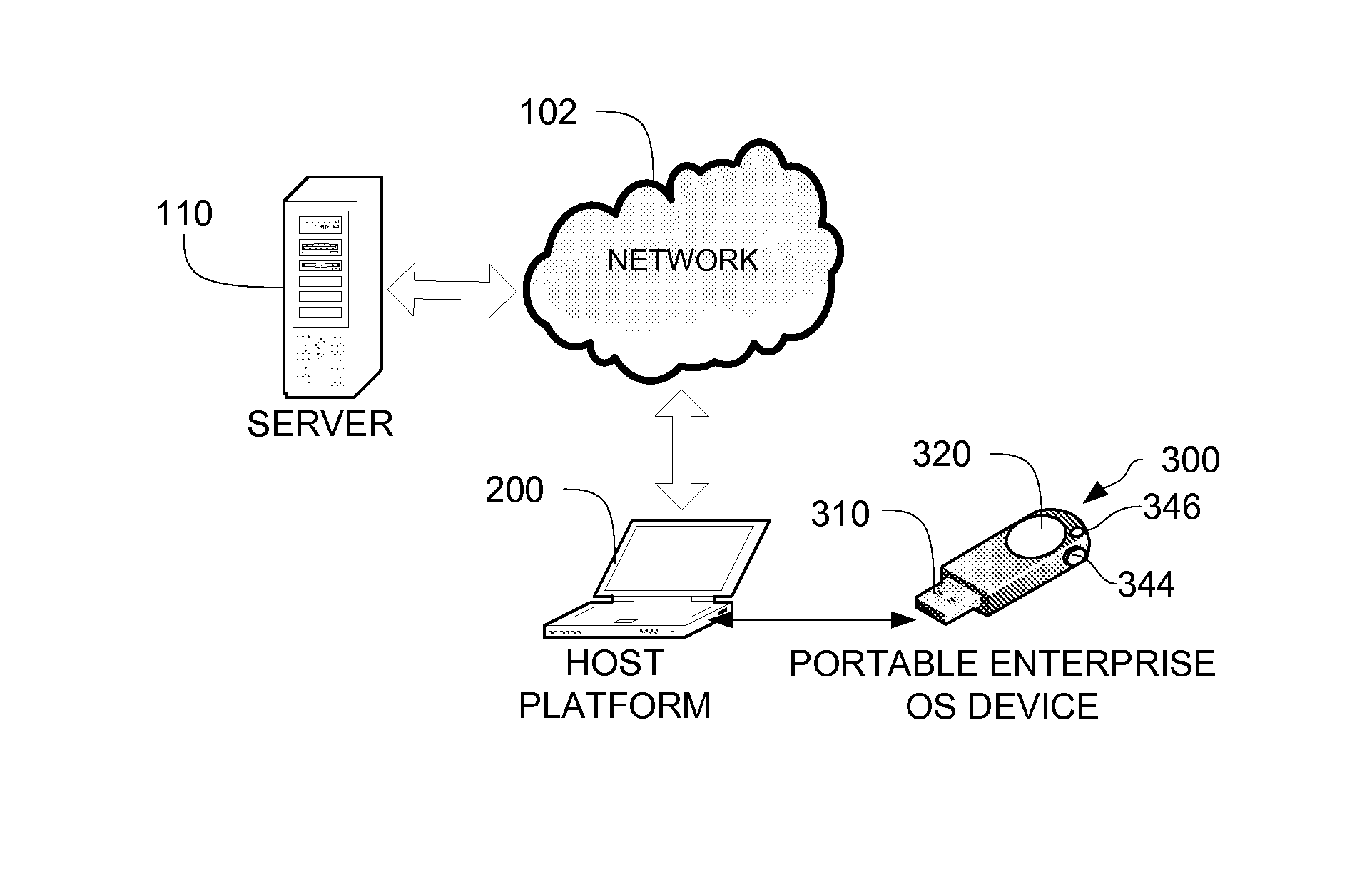
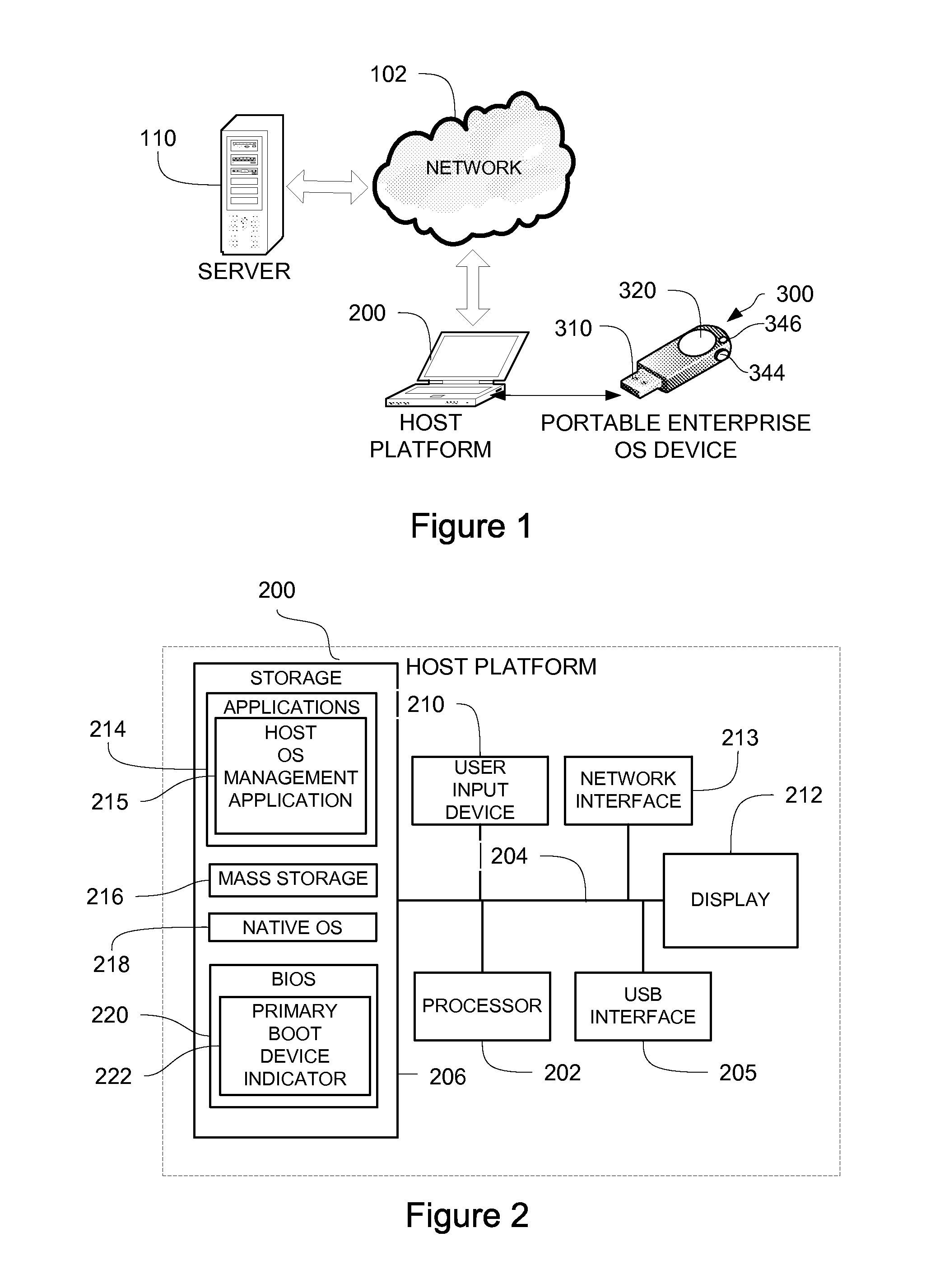
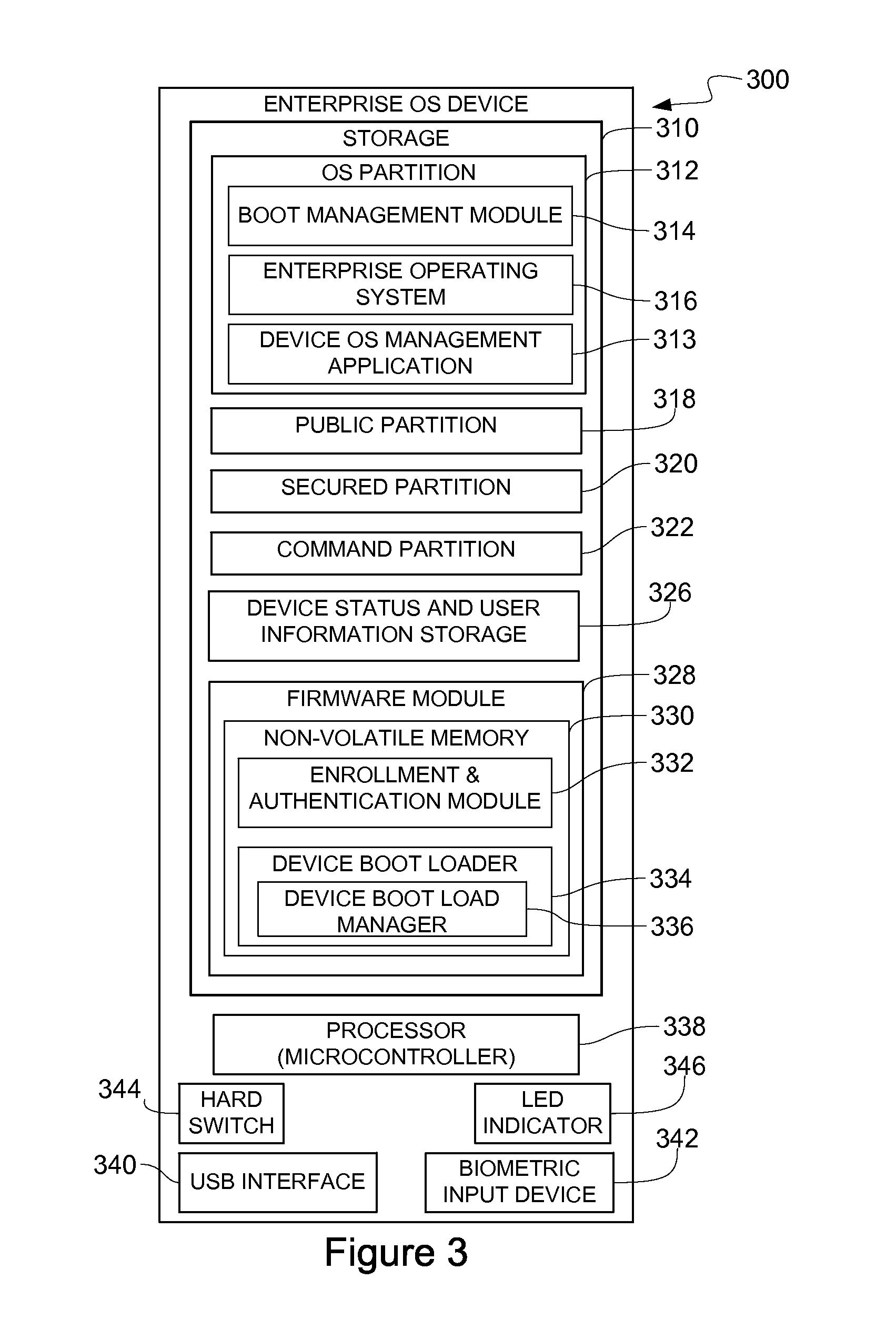
Portable, secure enterprise platforms
InactiveUS20140101426A1Improve securityPrevent unauthorized accessDigital computer detailsDigital data authenticationProgram managementComputer module
A portable, secure enterprise computing platform is provided by a device having a storage or memory, including a firmware module, a processor and an interface for interfacing with a host platform. The interface may be a USB interface and the device may have the form factor of a USB thumb drive. The storage may include a public partition, secure partition, operating system partition and command partition. A boot load manager in the firmware module causes the processor to load an operating system on the operating system partition and selectively enables access to the operating system by the host platform. The operating system partition may be formatted as a CDFS device such that the host platform recognizes the device as a bootable CD drive. The device provides for secure booting to the operating system partition by the host platform, without risk of corruption or malware from the host platform. A user may select from multiple operating systems. Multiple devices may be managed by a policy management application, which may assign groups of users and applications to one or more devices across an enterprise.
Owner:MSI SECURITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com