Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
537results about How to "Raise security concerns" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
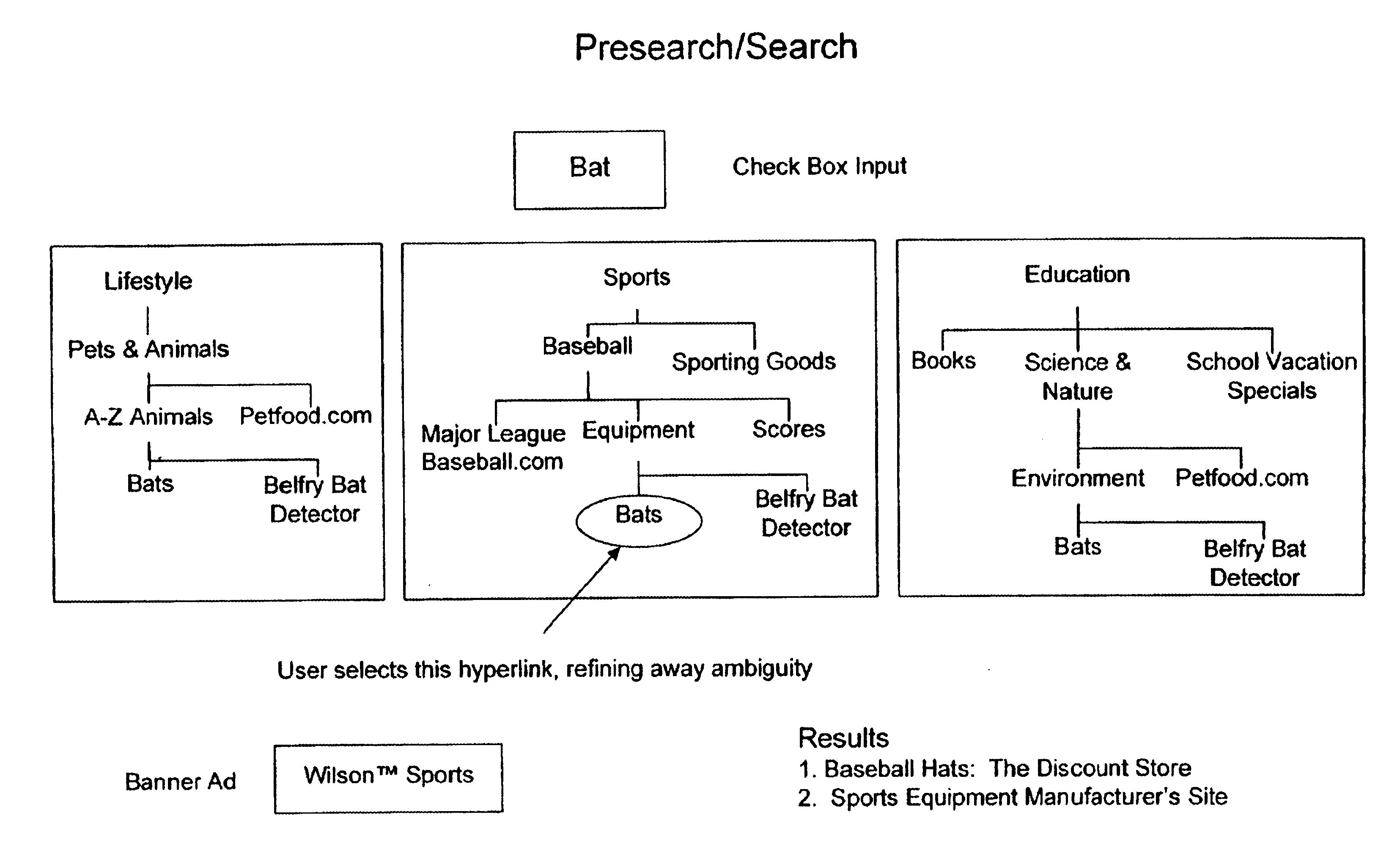
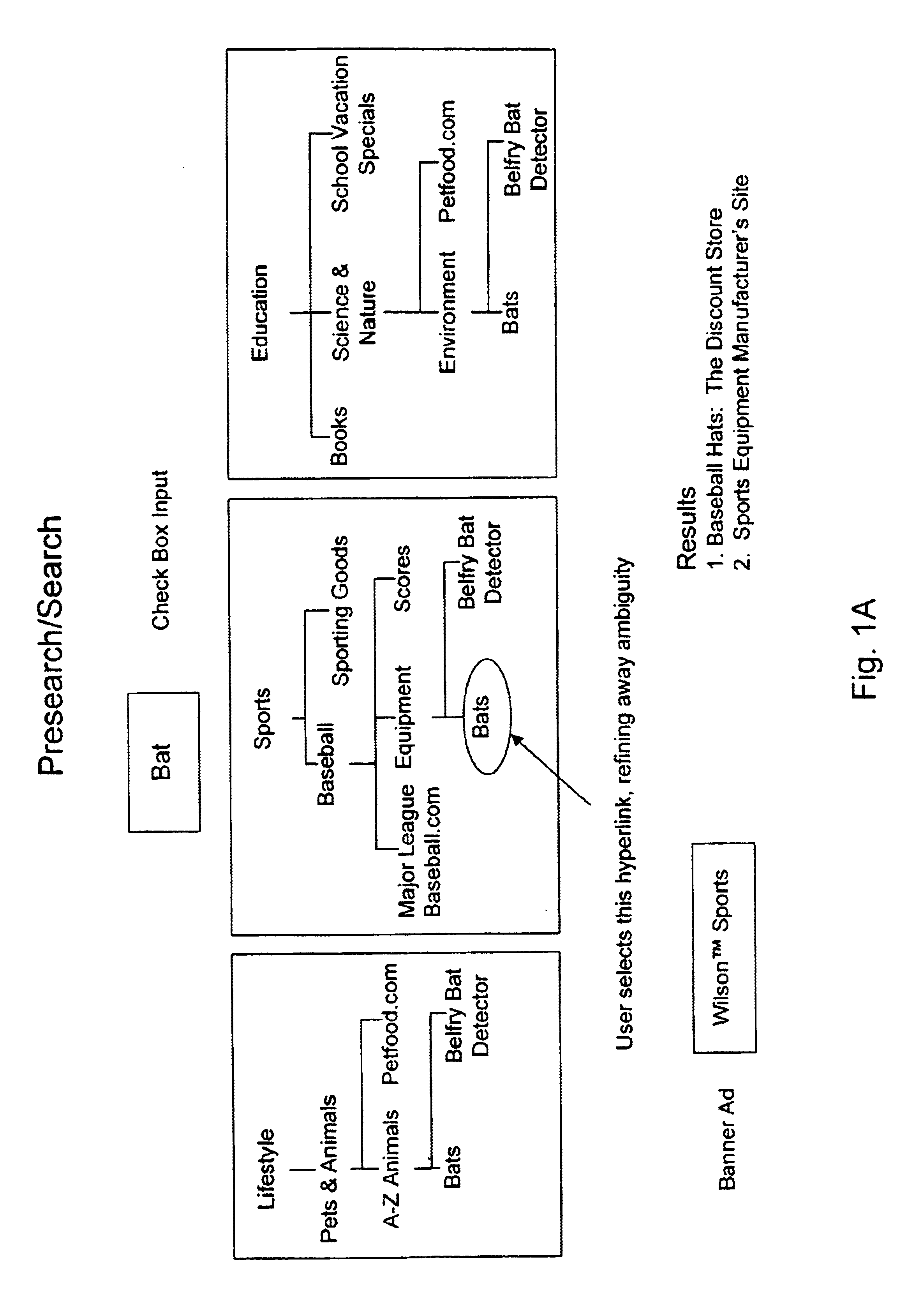
Computer graphic display visualization system and method
InactiveUS6868525B1Improve compactnessIncrease flexibilityDrawing from basic elementsAdvertisementsGraphicsCollaborative filtering
An improved human user computer interface system, providing a graphic representation of a hierarchy populated with naturally classified objects, having included therein at least one associated object having a distinct classification. Preferably, a collaborative filter is employed to define the appropriate associated object. The associated object preferably comprises a sponsored object, generating a subsidy or revenue.
Owner:RELATIVITY DISPLAY LLC
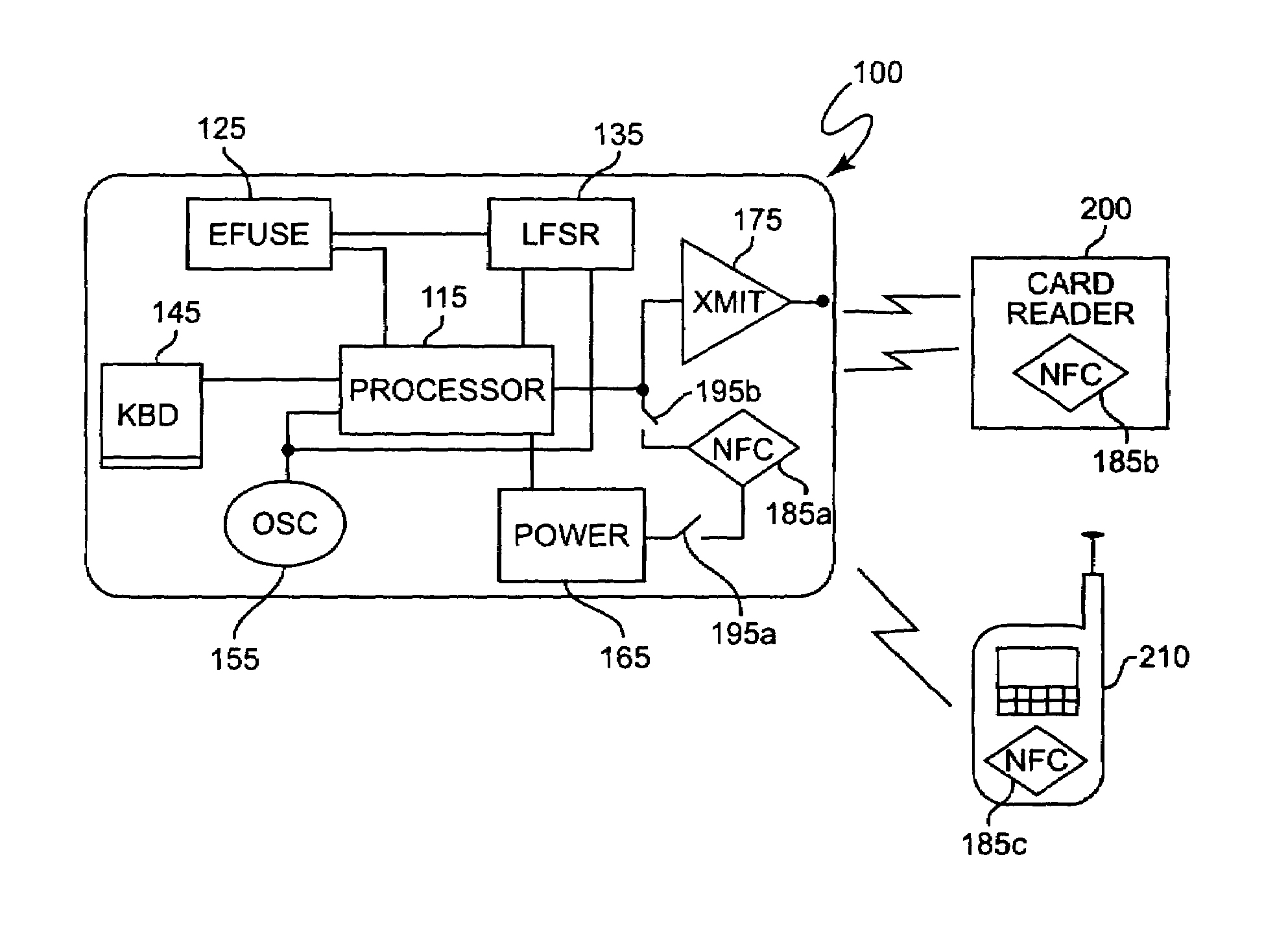
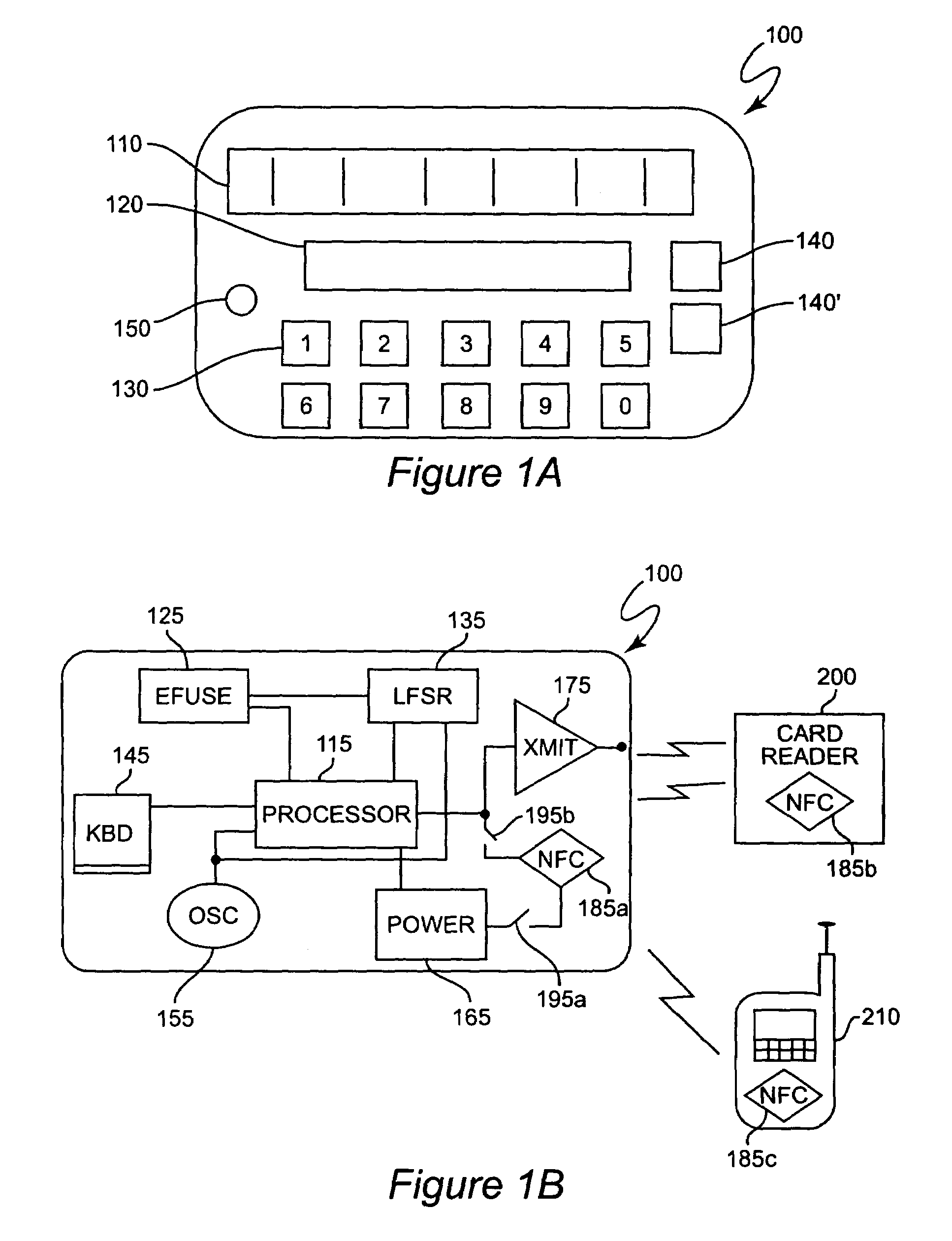
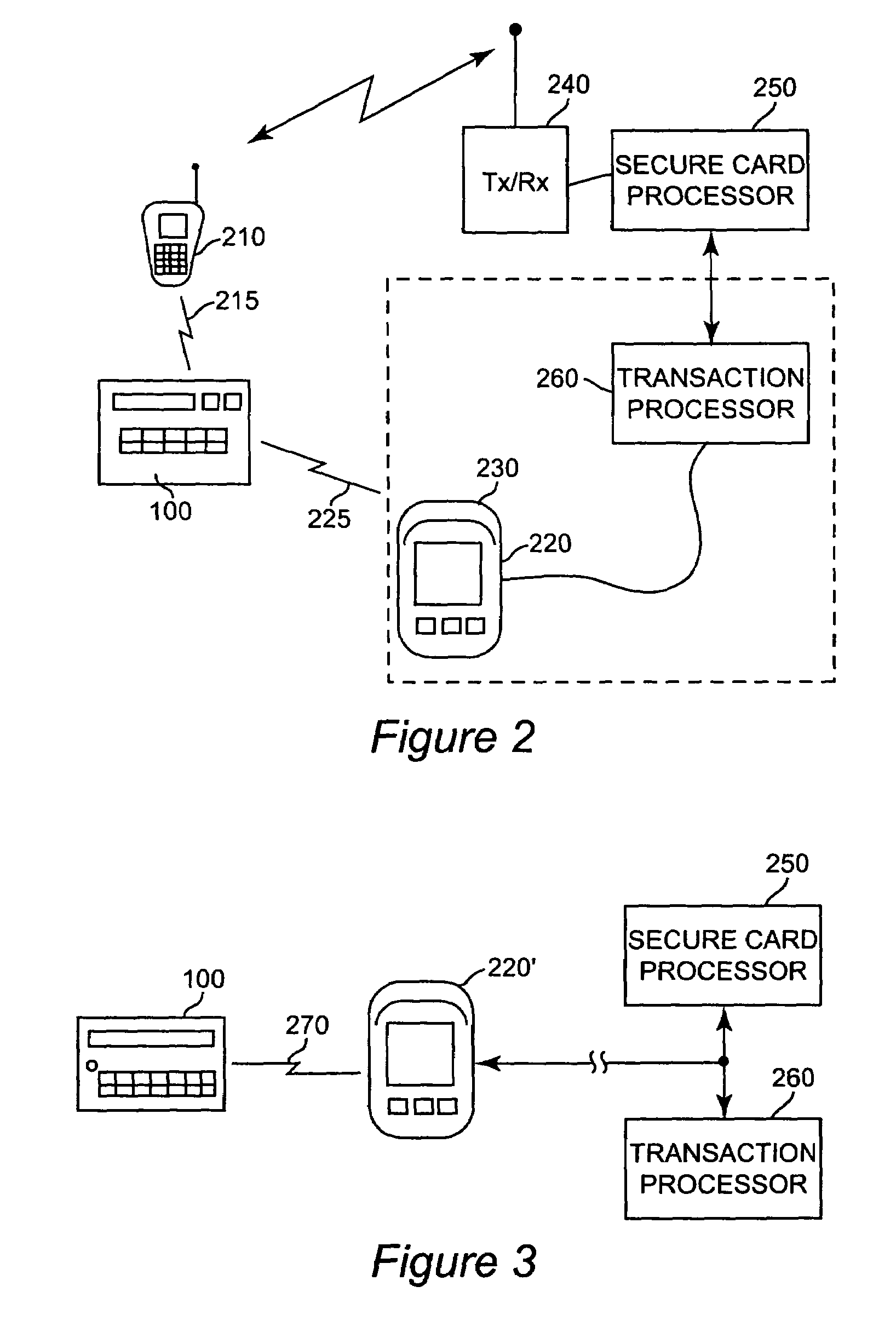
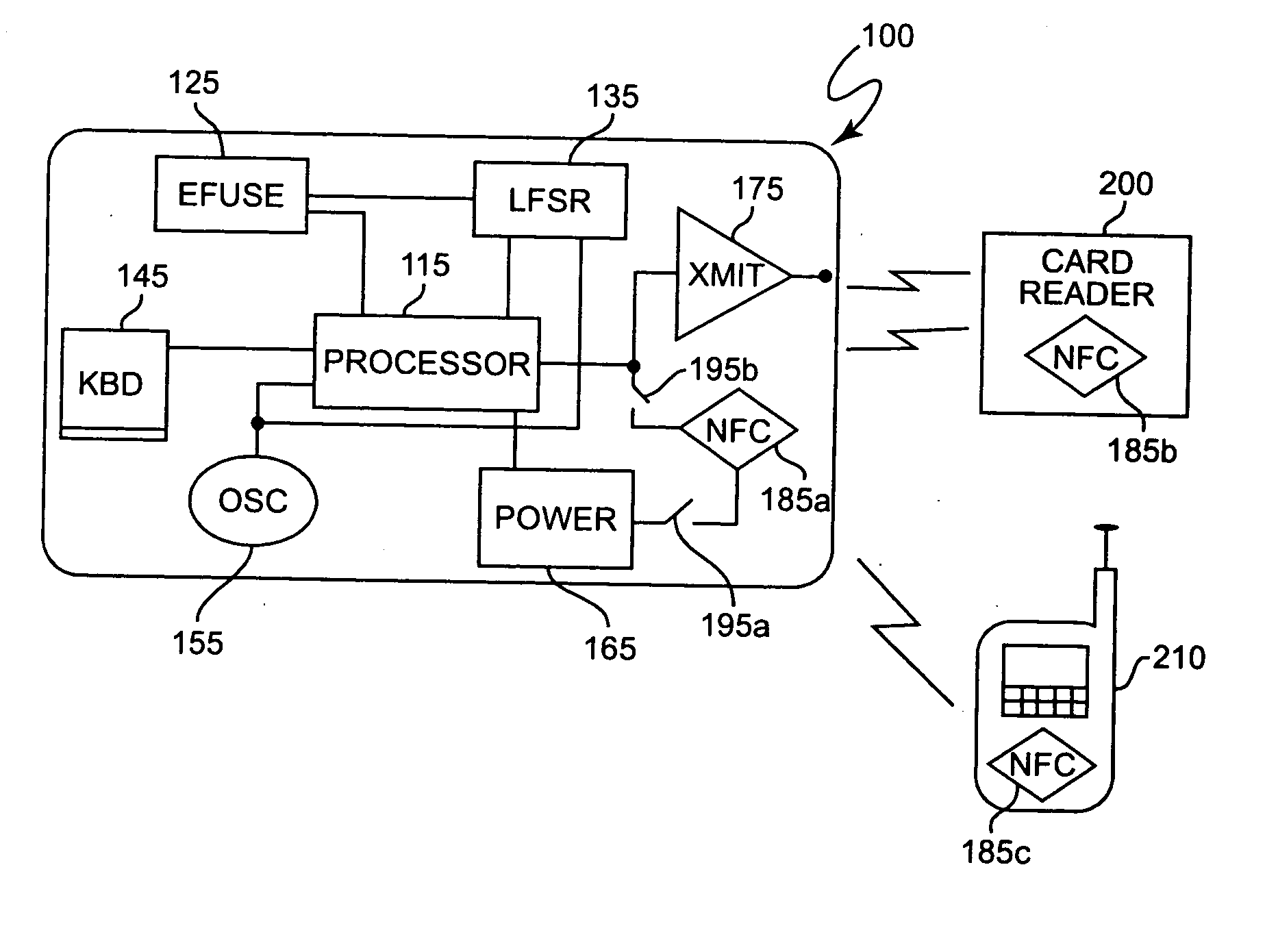
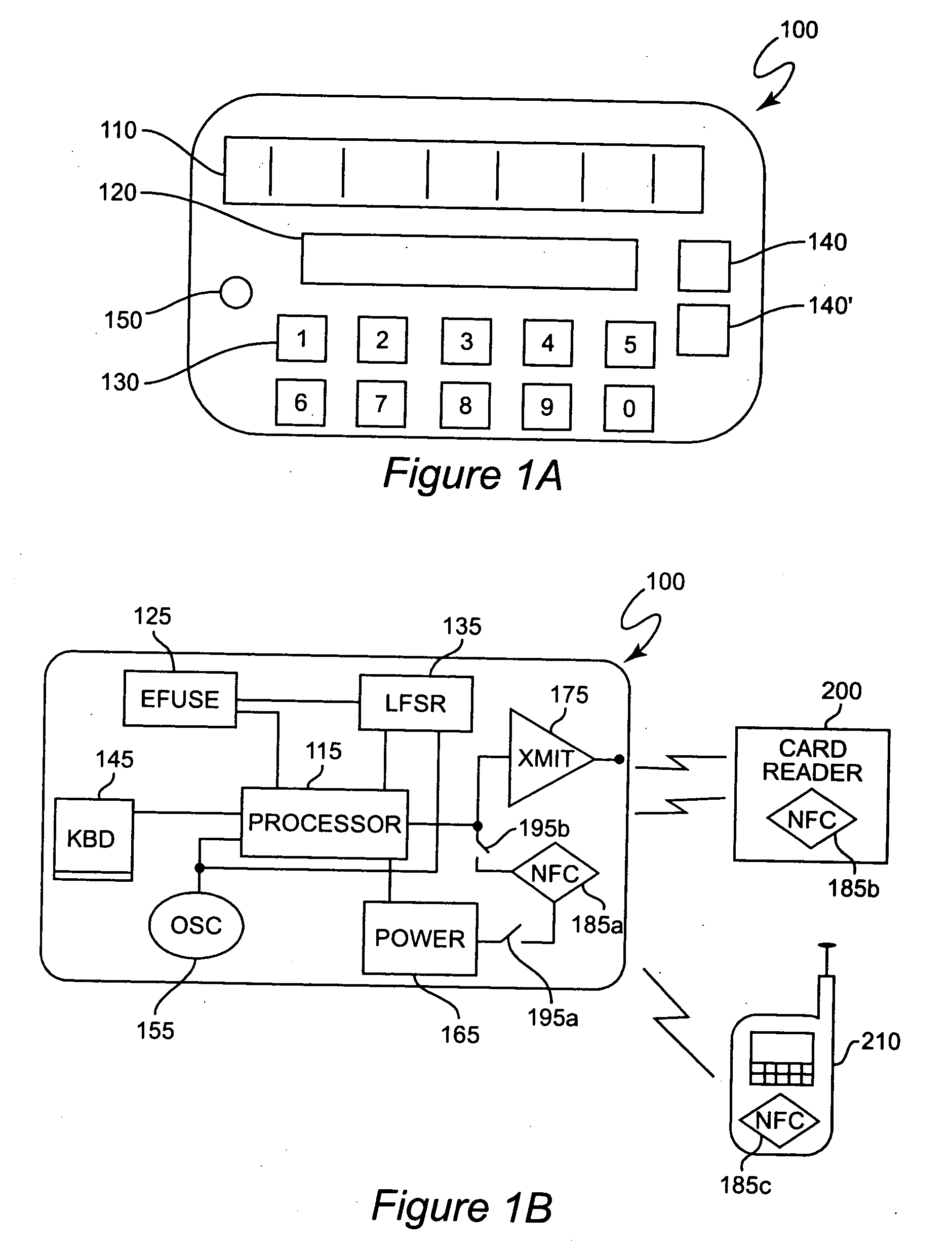
Secure credit card with near field communications
ActiveUS7128274B2Facilitate communicationIncrease speedAcutation objectsMemory record carrier reading problemsComputer hardwareCredit card
A near field communication device included in a secure transaction card provides an addition and / or transitional communication link for communicating secure transaction information. The near field communication device may be selectively engaged or disengaged and, when engaged, either active or passive modes of operation of the near field communication device can be selected. in the active mode, secure transaction information is transmitted upon establishment of a communication link with a complementary near field communication device. In the passive mode, secure transaction information is transmitted upon interrogation from a complementary near field communication device. Secure transaction information is generated and stored for transmission in a memory and at least a portion of the memory is erased or nulled upon transmission or upon expiration of a selected period of time.
Owner:EBAY INC
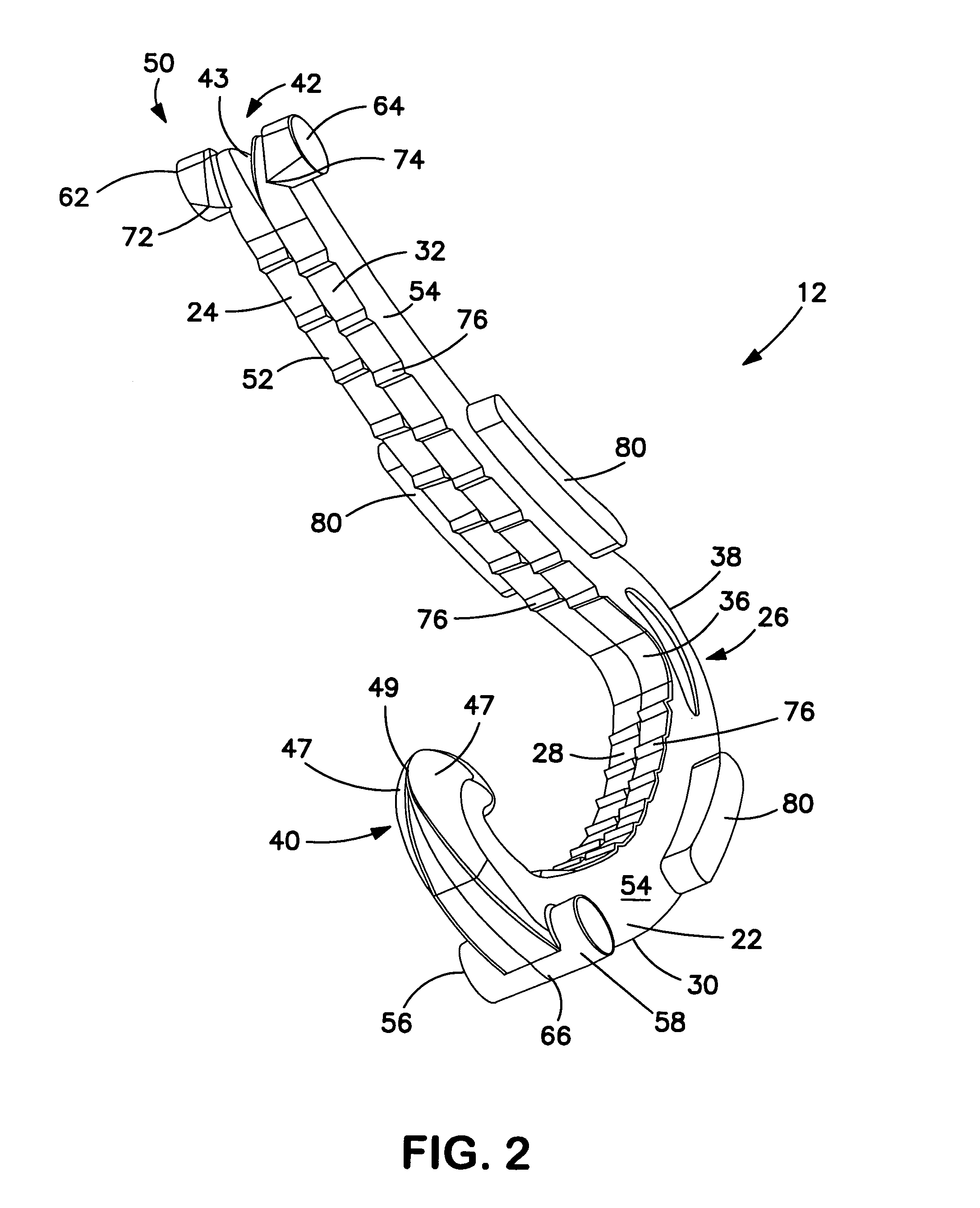
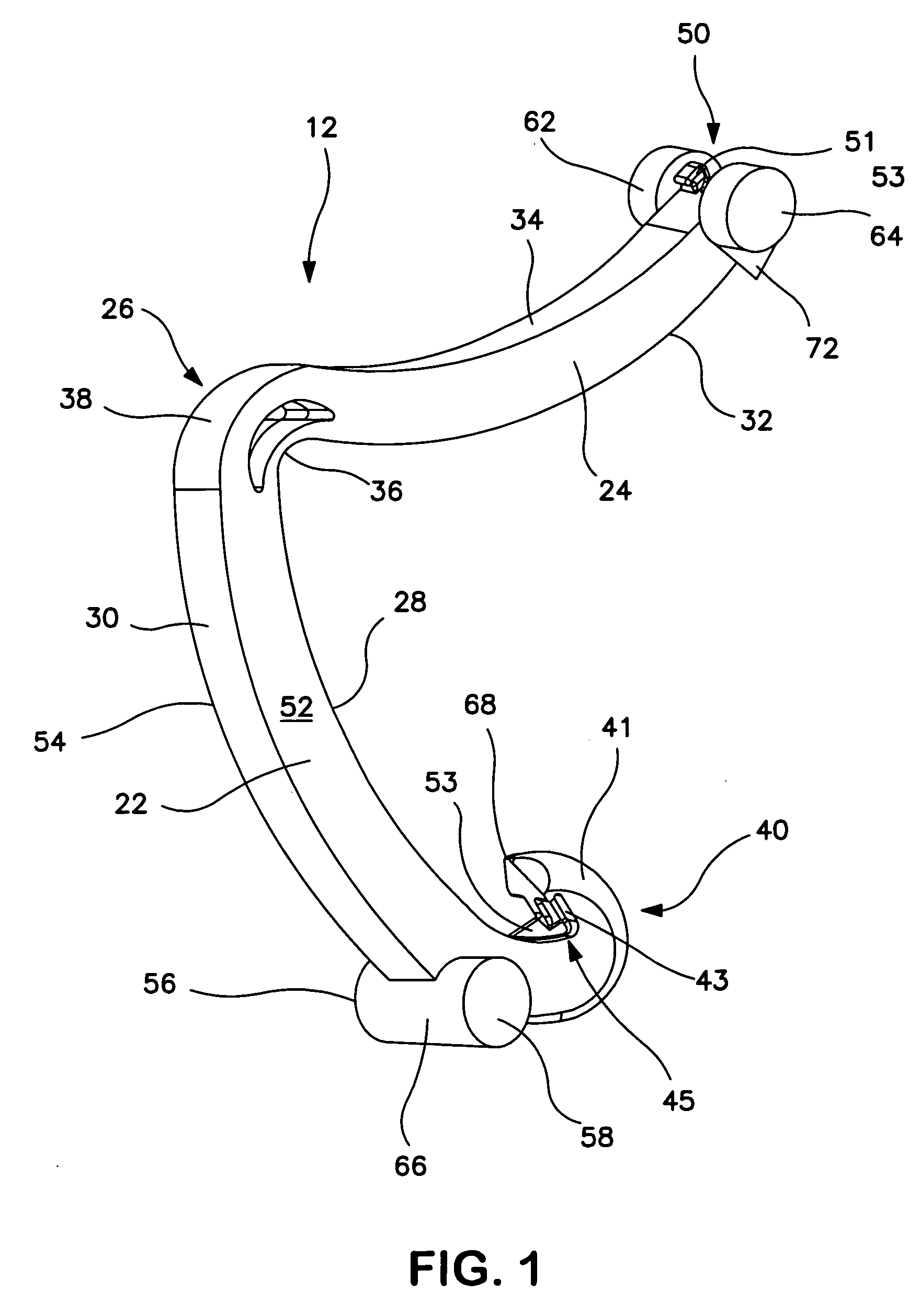
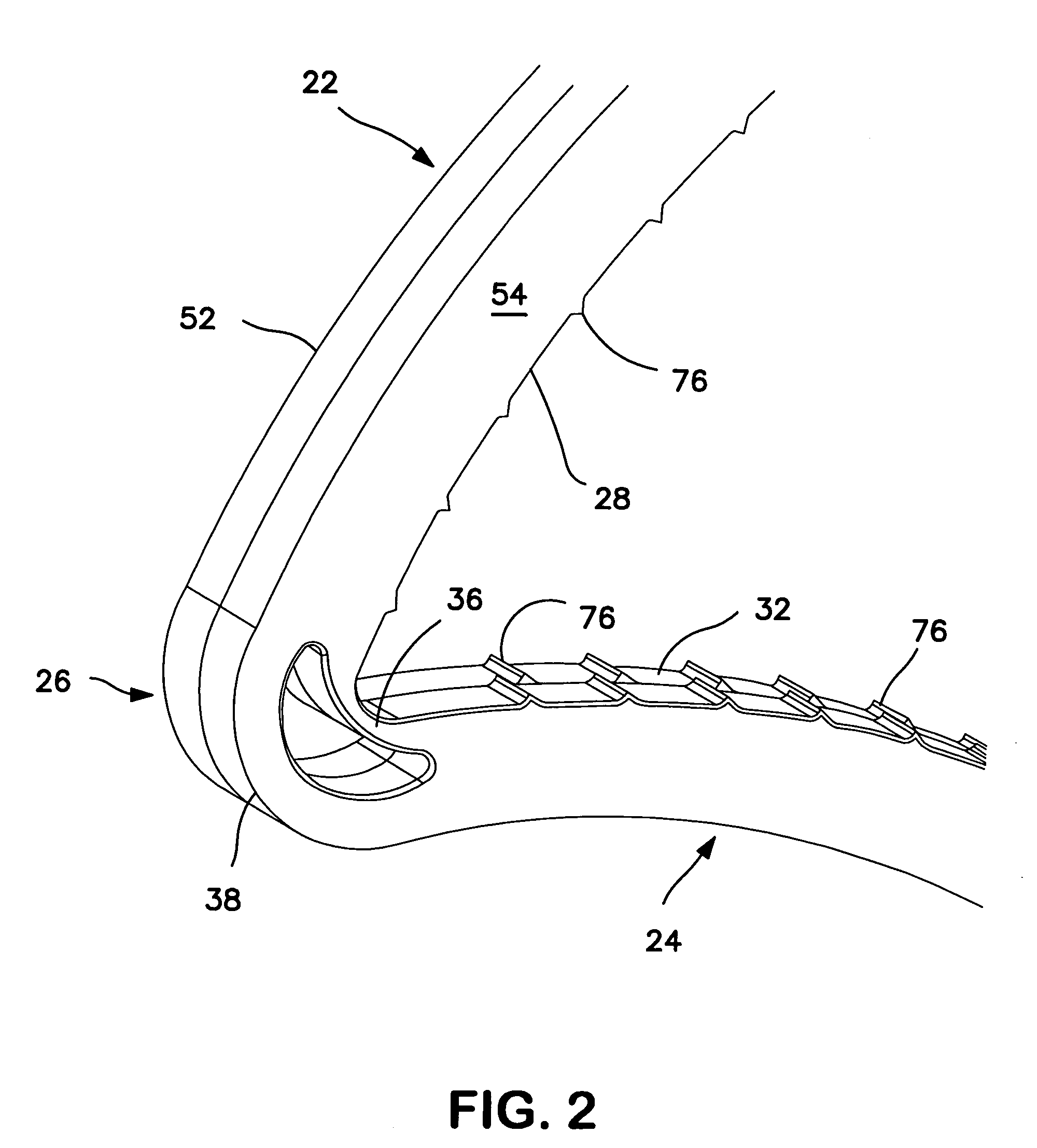
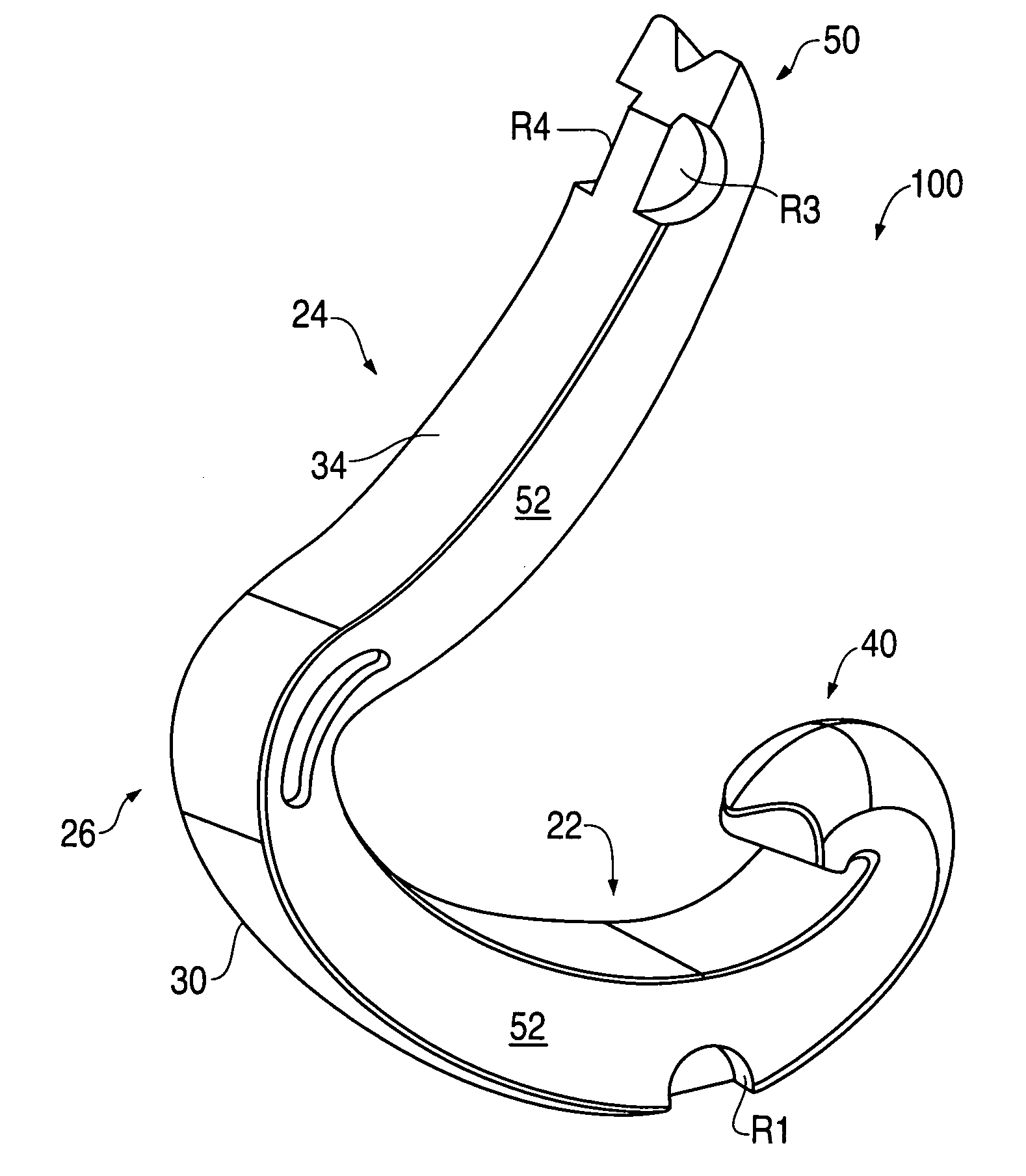
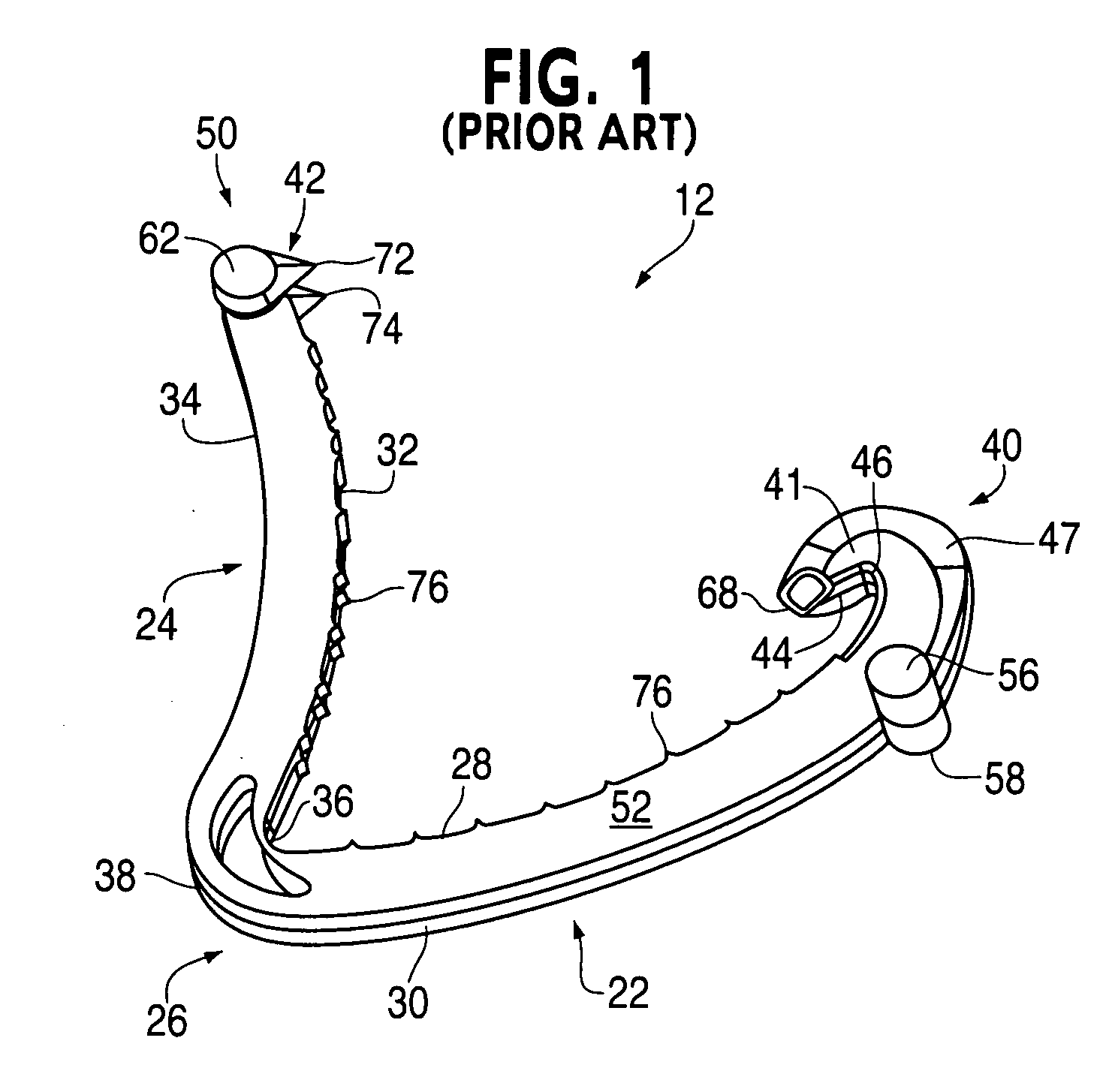
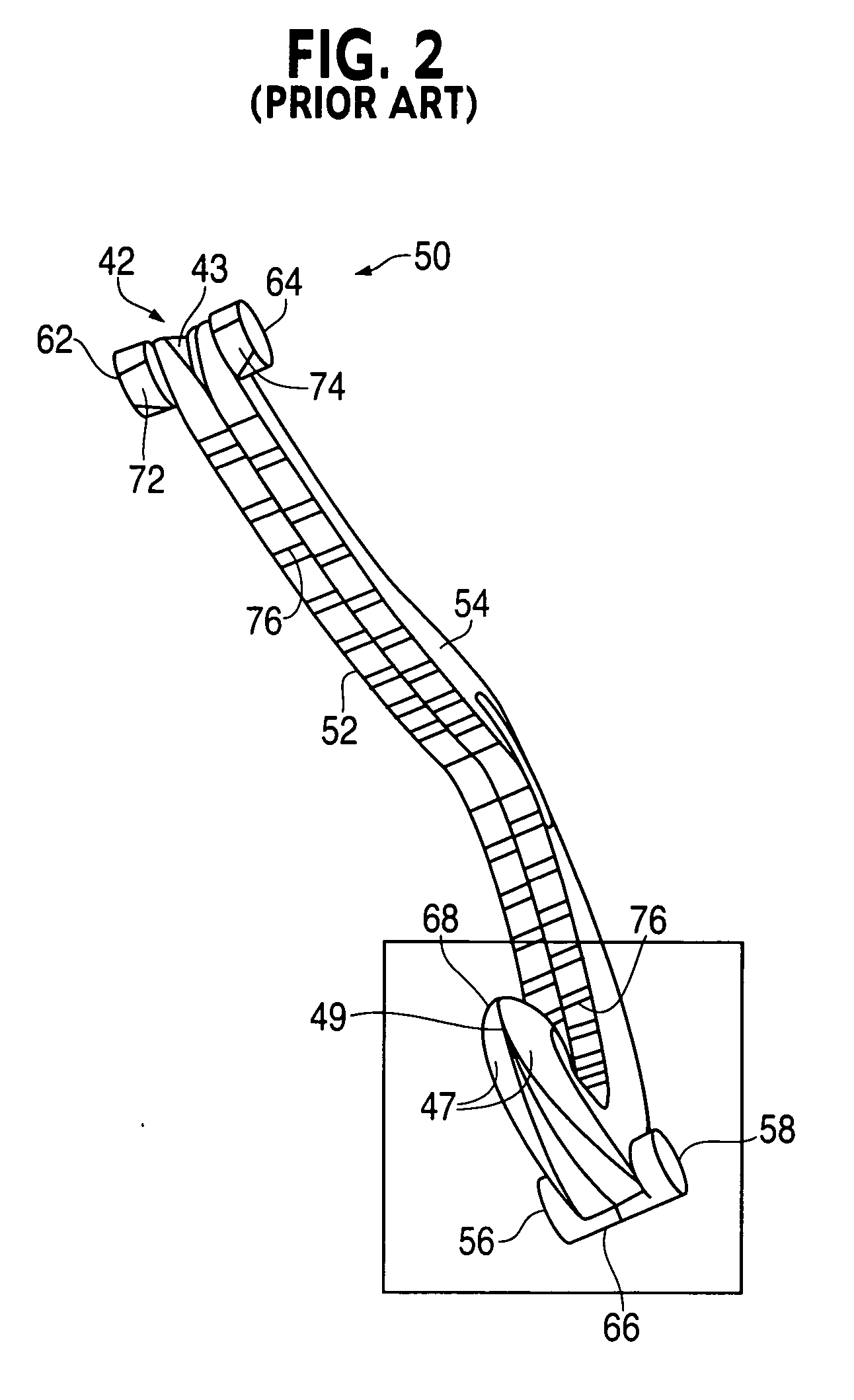
Ligating clip with integral cutting guide
InactiveUS7326223B2Removably lock the clipHigh retention rateCurling devicesHair dryingEngineeringLigating clips
A polymeric, surgical clip having first and second curved legs with each having a pair of opposing side surfaces joined at their proximal ends by a flexible hinge section and movable from an open position to a closed position for clamping a vessel between curved opposing inner surfaces. The first leg terminates at its distal end in a female locking member, and the second leg member terminates in a male locking member complimentary to the female locking member such that when the first and second leg members are moved from an open position to a closed position about the hinge section the male member is lockingly engaged in the female locking member. The clip has at least one cutting guide extending outward from and disposed along at least a portion of the length of at least one of the side surfaces of at least one of the first and second legs. The cutting guide aids in cutting the ligated tissue a safe distance from the clip such that a tissue cuff is formed.
Owner:TECH HLDG CO II
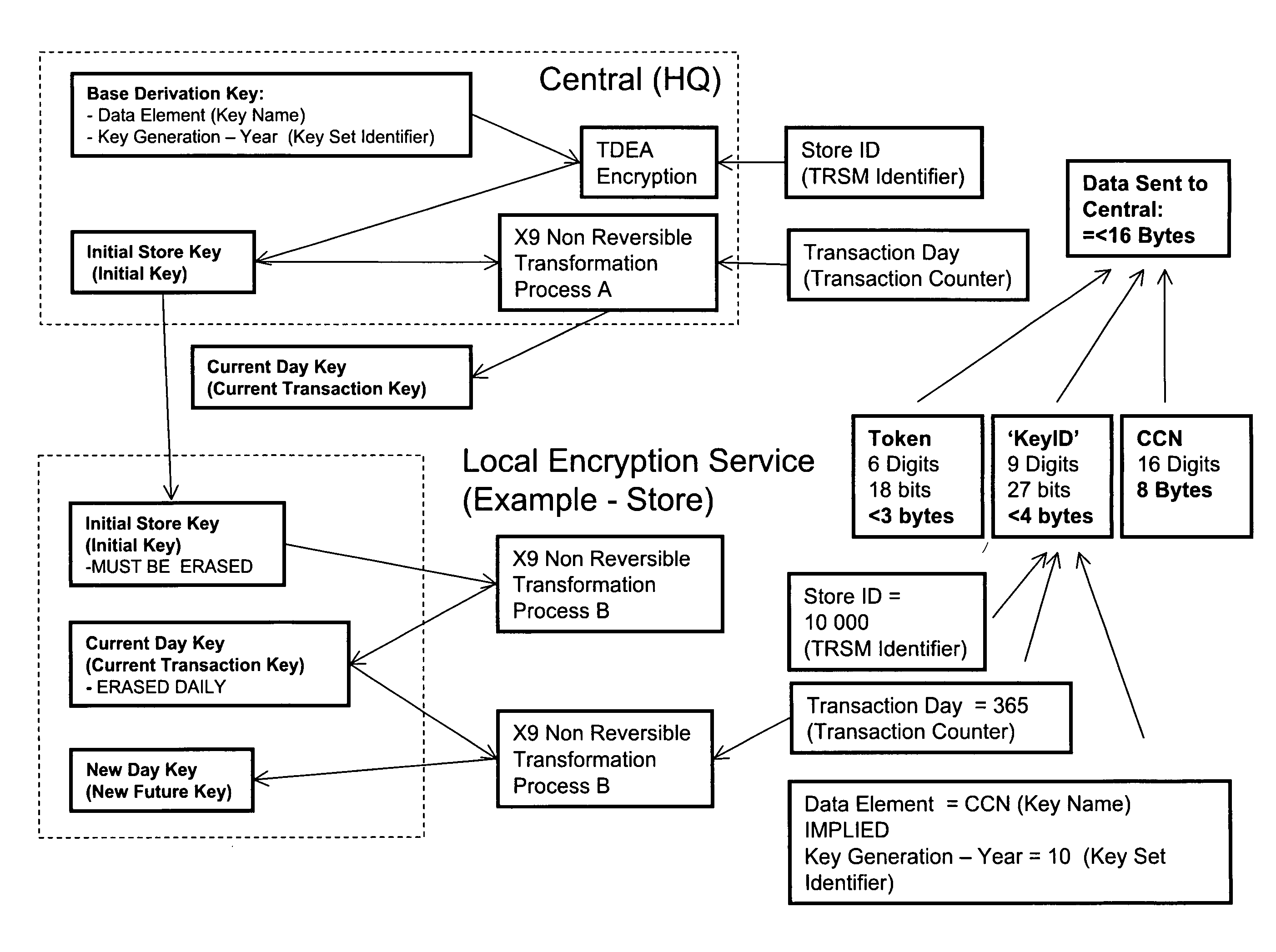
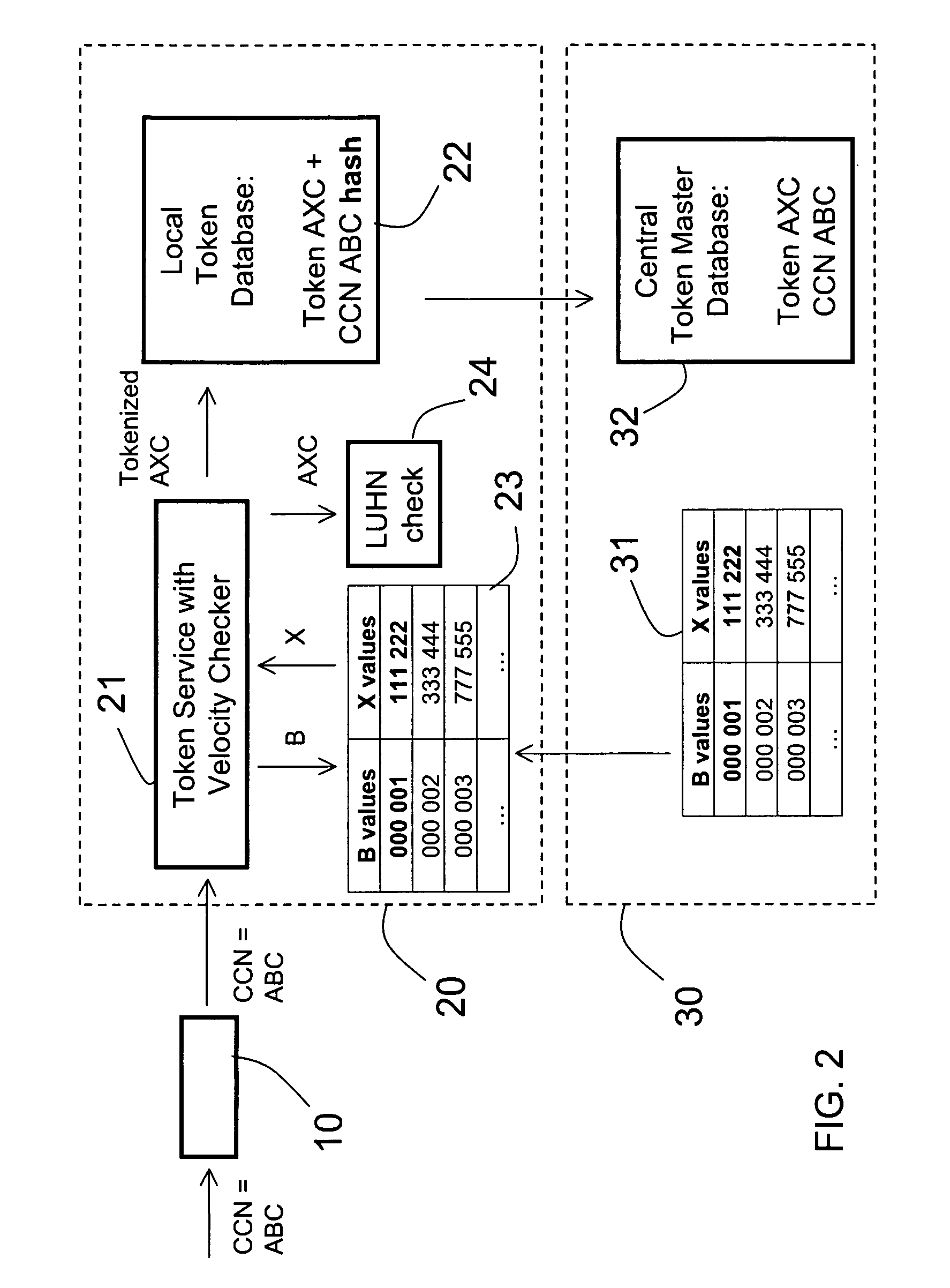
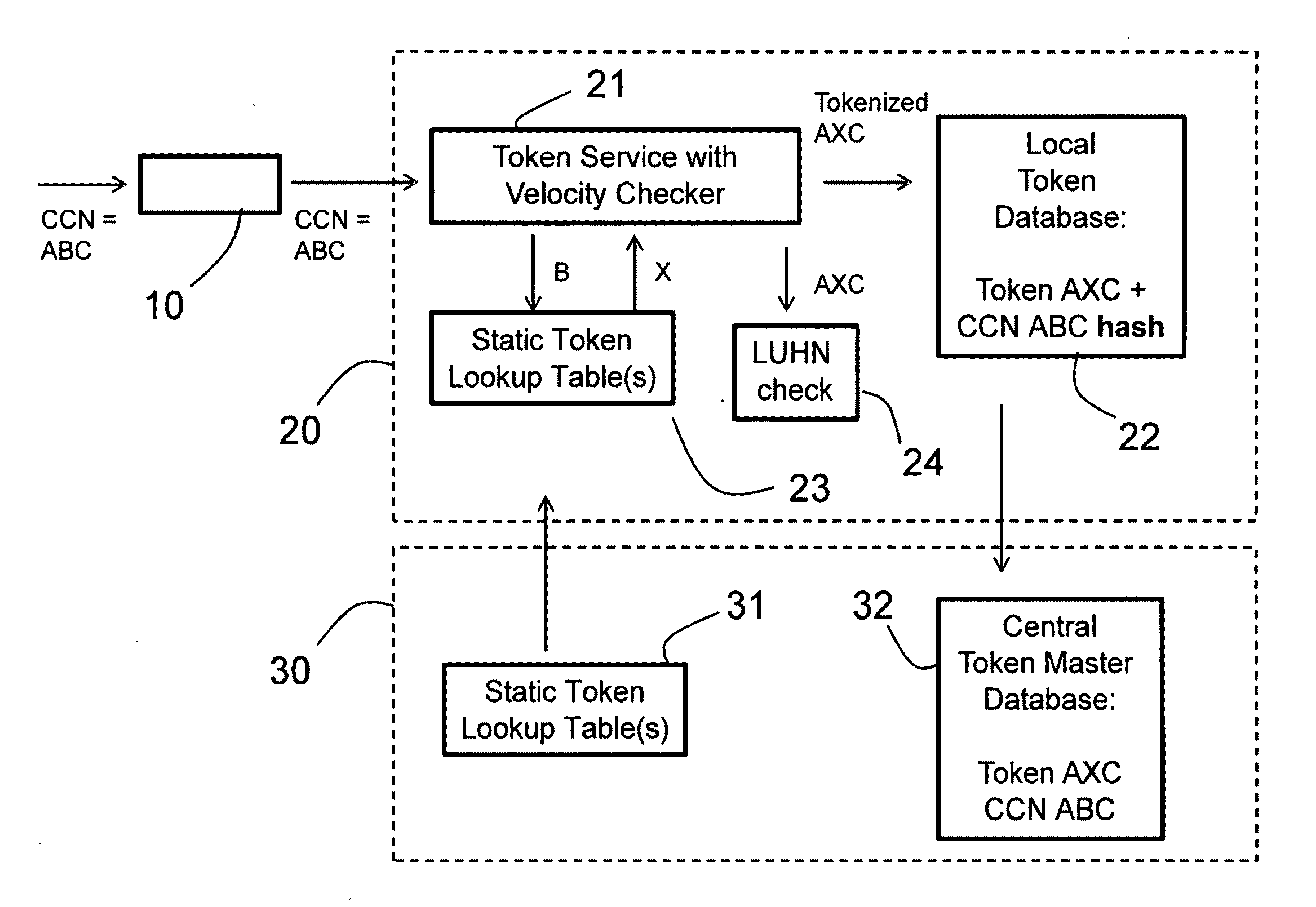
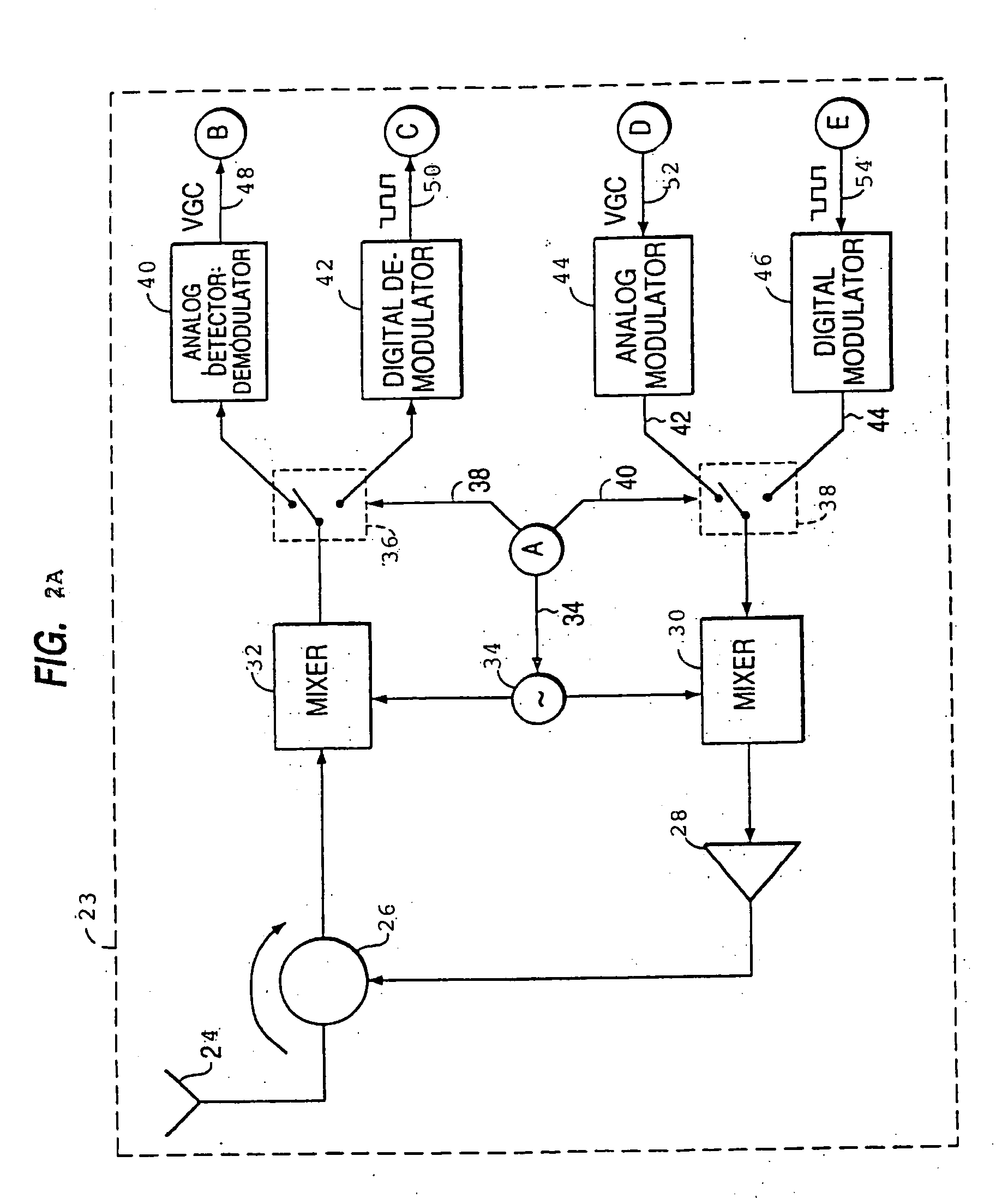
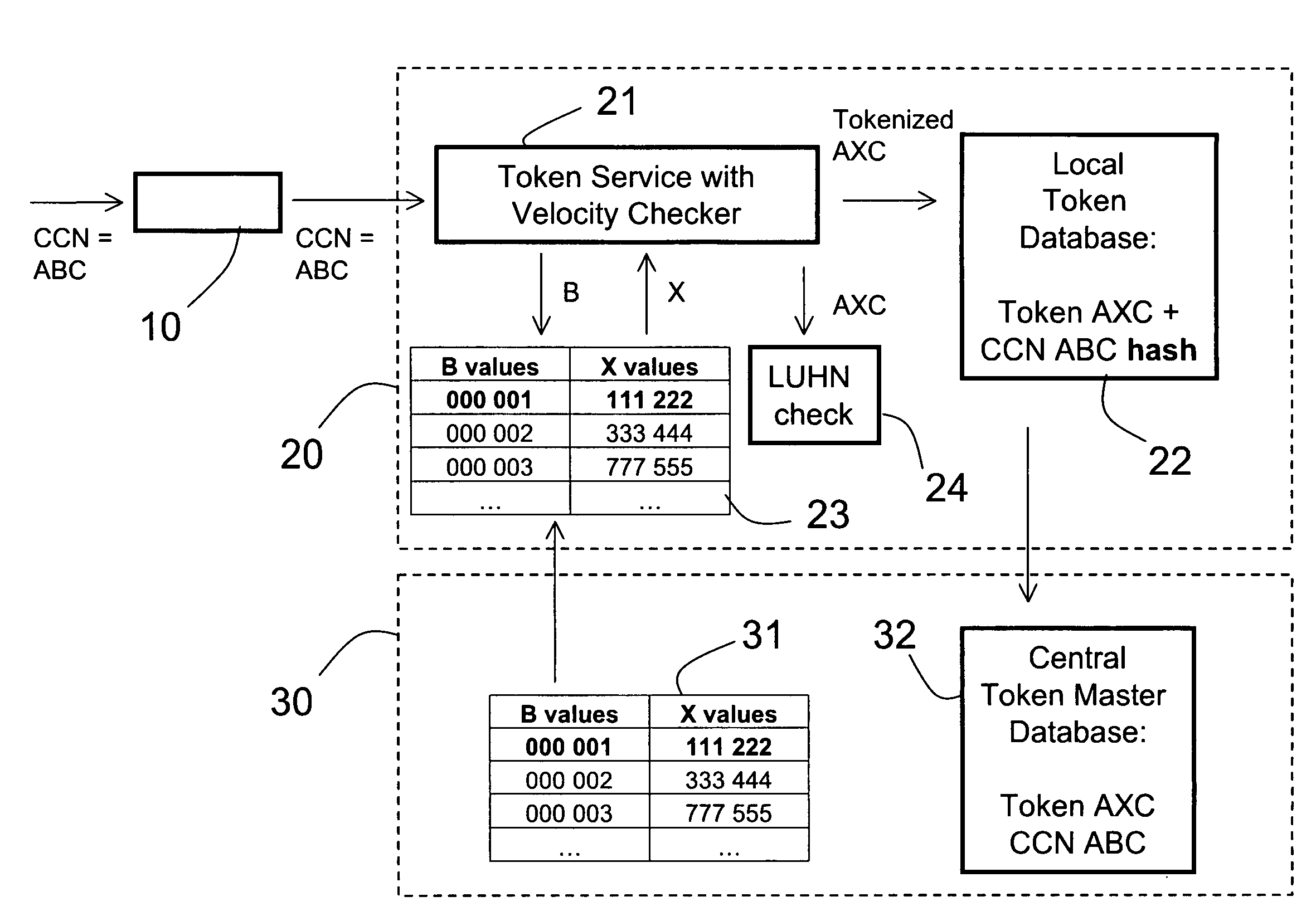
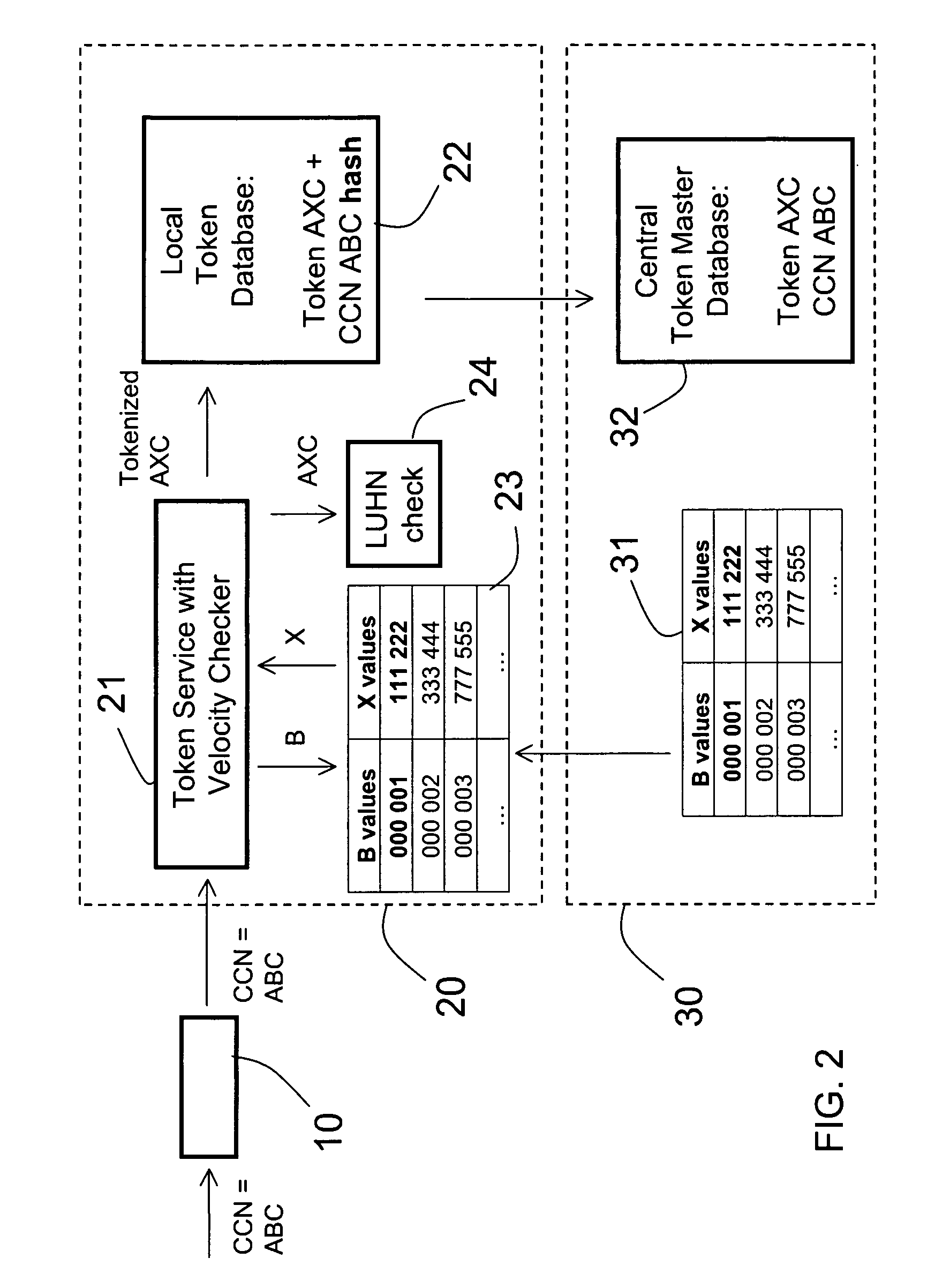
Method and apparatus for tokenization of sensitive sets of characters
ActiveUS8578176B2Reduce demandImprove forecastAcutation objectsUnauthorized memory use protectionComputer networkSafe handling
A method and system for secure handling of sensitive sets of characters in a distributed hierarchical system are disclosed, comprising at least one local server on a lower hierarchic level and at least one central server at a higher hierarchic level. The method comprises the steps: receiving a sensitive set of characters in said local server; replacing a part of said sensitive set of characters with a token to form a tokenized set of characters, said token belonging to a subset of possible tokens assigned to the local server by the central server; transferring at least one of said sensitive set of characters and said tokenized set of characters to the central server; and canceling said sensitive set of characters from said local server within a limited time from said transferring, while maintaining said tokenized set of characters in a local database connected to said local server.
Owner:PROTEGRITY CORP
Reduced closure force ligating clip
InactiveUS20060217749A1Removably lock the clipFacilitate closure and lockingWound clampsLigating clipsEngineering
Owner:TELEFLEX MEDICAL INC
Ligating clip with integral interlocking latch mechanism
ActiveUS7316696B2High retention rateInterference minimizationCurling devicesIntravenous devicesDetentEngineering
A polymeric, surgical clip having first and second curved legs joined at their proximal ends by a flexible hinge section and movable from an open position to a closed position for clamping a vessel between curved opposing inner surfaces. The first leg terminates at its distal end in a female locking member comprising a resilient inwardly turned hook having a recess in the mouth of the hook, and the second leg member terminates in a male locking member complimentary to the female locking member and comprising a detent such that when the first and second leg members are moved from an open position to a closed position about the hinge section the hook member will deflect about the distal end of the second leg member thereby engulfing the male locking member in the mouth of the hook and matingly engaging the detent in the recess thereof, thus securely locking the clip in the closed position. The locking feature provides greater closure security to the clip when clamping large diameter or uncompressible tissue.
Owner:TELEFLEX MEDICAL INC
Non-snag polymer ligating clip
InactiveUS20070118161A1Removably lock the clipInterference minimizationWound clampsCoronary Artery BypassesLigating clips
A polymeric, surgical clip having first and second curved legs with each having a pair of opposing side surfaces joined at their proximal ends by a flexible hinge section and movable from an open position to a closed position for clamping a vessel between curved opposing inner surfaces. The first leg terminates at its distal end in a female locking member, and the second leg member terminates in a male locking member complimentary to the female locking member such that when the first and second leg members are moved from an open position to a closed position about the hinge section the male member is lockingly engaged in the female locking member. The clip is provided with low profile boss-like elements on the legs thereof to reduce the risk of snagging a suture during coronary artery bypass graft surgery.
Owner:TELEFLEX MEDICAL INC
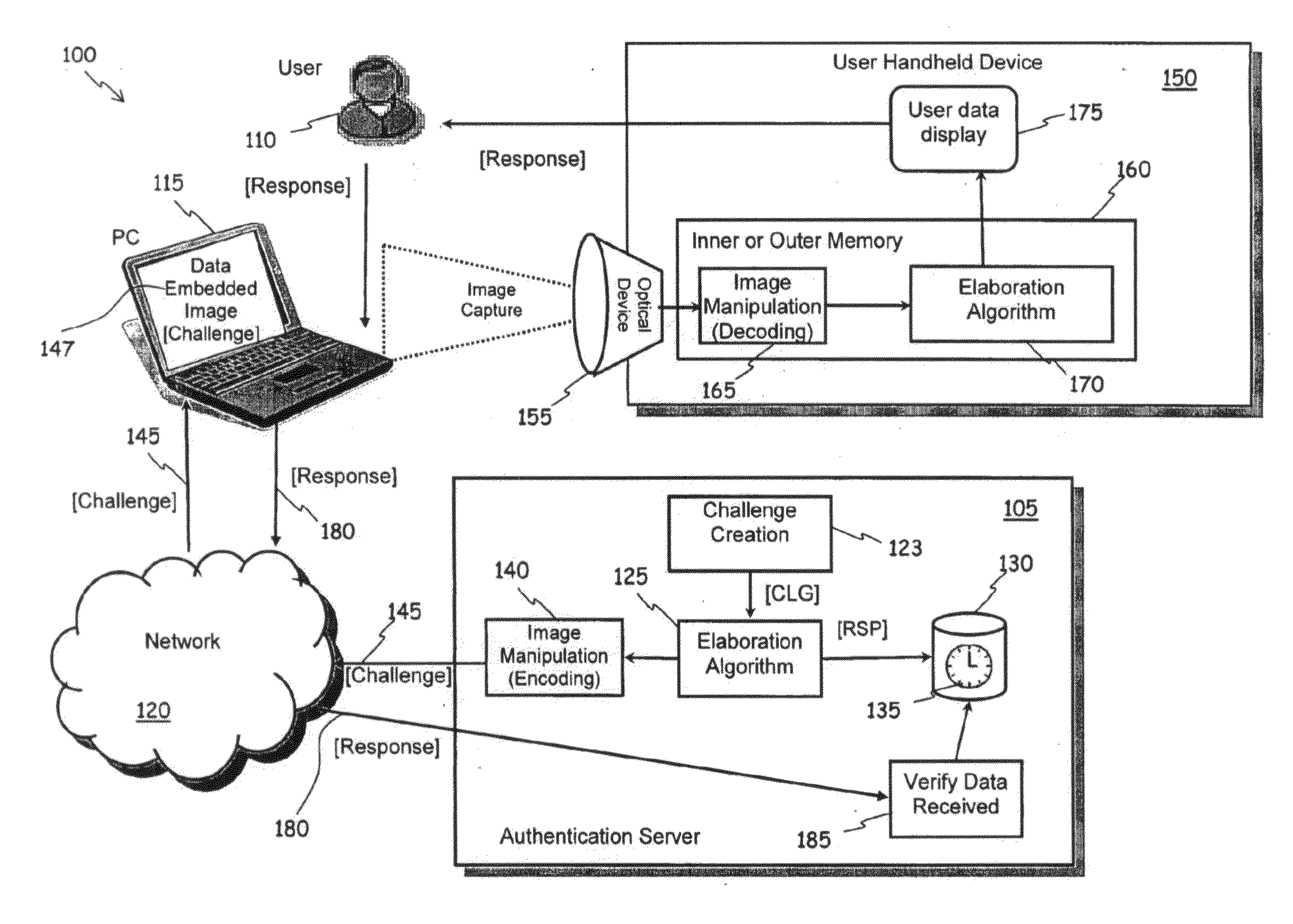
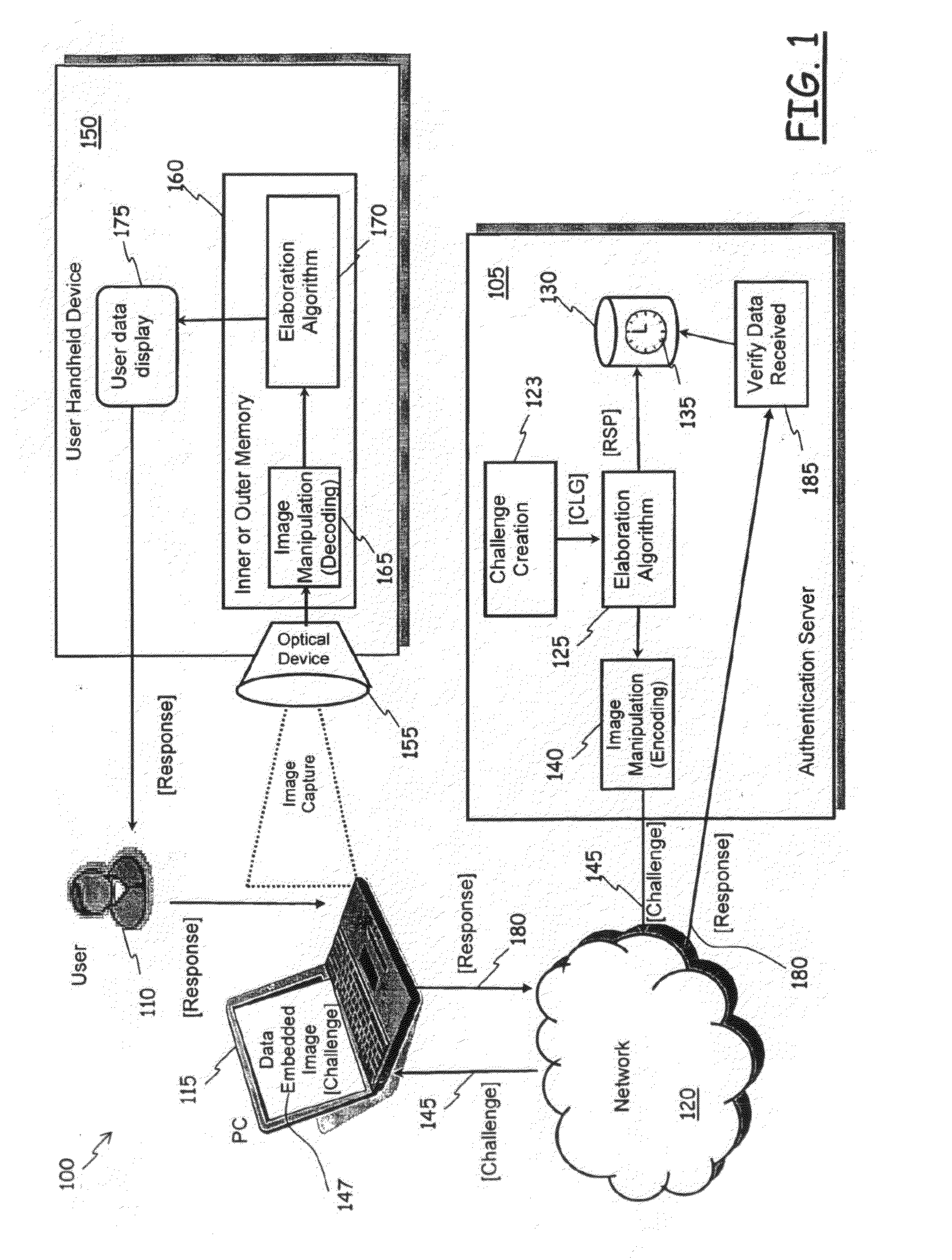
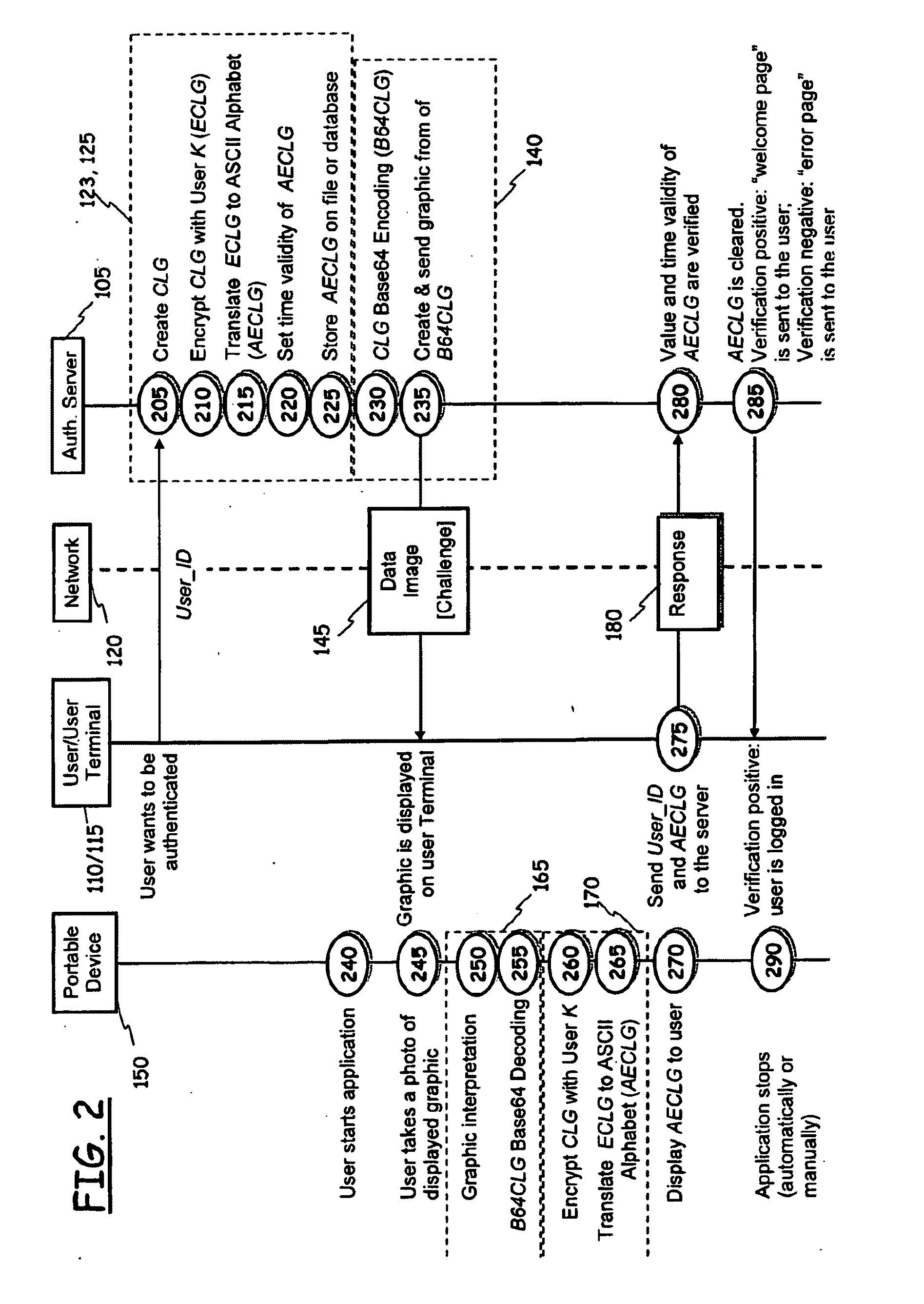
Method of Authentication of Users in Data Processing Systems
ActiveUS20100275010A1Raise security concernsLow implementation costDigital data processing detailsUser identity/authority verificationData processing systemUser device
A method of authentication of users in a data processing system is provided. The method includes a “Challenge” univocally associated with a user to be authenticated; processing the “Challenge” to generate an expected answer code, to be compared with an answer code that the user has to provide for authentication; encoding the generated “Challenge” for obtaining an image displayable through a display device; sending the image containing the “Challenge” to the user; displaying the image containing the “Challenge”; through a user device provided with an image-capturing device, optically capturing the displayed image; through the user device, processing the captured image for extracting from the captured image the “Challenge”, and subsequently processing the obtained “Challenge” for generating the answer code; receiving the answer code from the user and comparing it to the expected answer code; and, in case of positive comparison, authenticating the user. One among the actions of generating a “Challenge” and an expected answer code, and the action of processing the captured image that generates the answer code exploit secret information univocally associated with the user.
Owner:TELECOM ITALIA SPA
Auto-injector
ActiveUS7442185B2Reduce riskPreventing accidental misfiringAutomatic syringesInfusion needlesAutosamplerBiomedical engineering
A device for auto-injection of a dose of medicament, comprises a housing arranged to contain a medicament container therein and a contact part intended to be applied against an injection site, a needle cover surrounding a needle arranged to the medicament container and extending at least the length of the needle, spring elements for, upon activation, pushing the needle past the end of the cover as well as operating the medicament container to supply the dose of medicament, first locking elements for locking the spring elements in a pressurized state, first activating elements for, upon manual operation, releasing the spring elements for injection. There is a second locking element capable of locking the first activating element and a second activating element, capable of releasing the second locking element when the contact part is exposed to pressure.
Owner:SHL MEDICAL AG
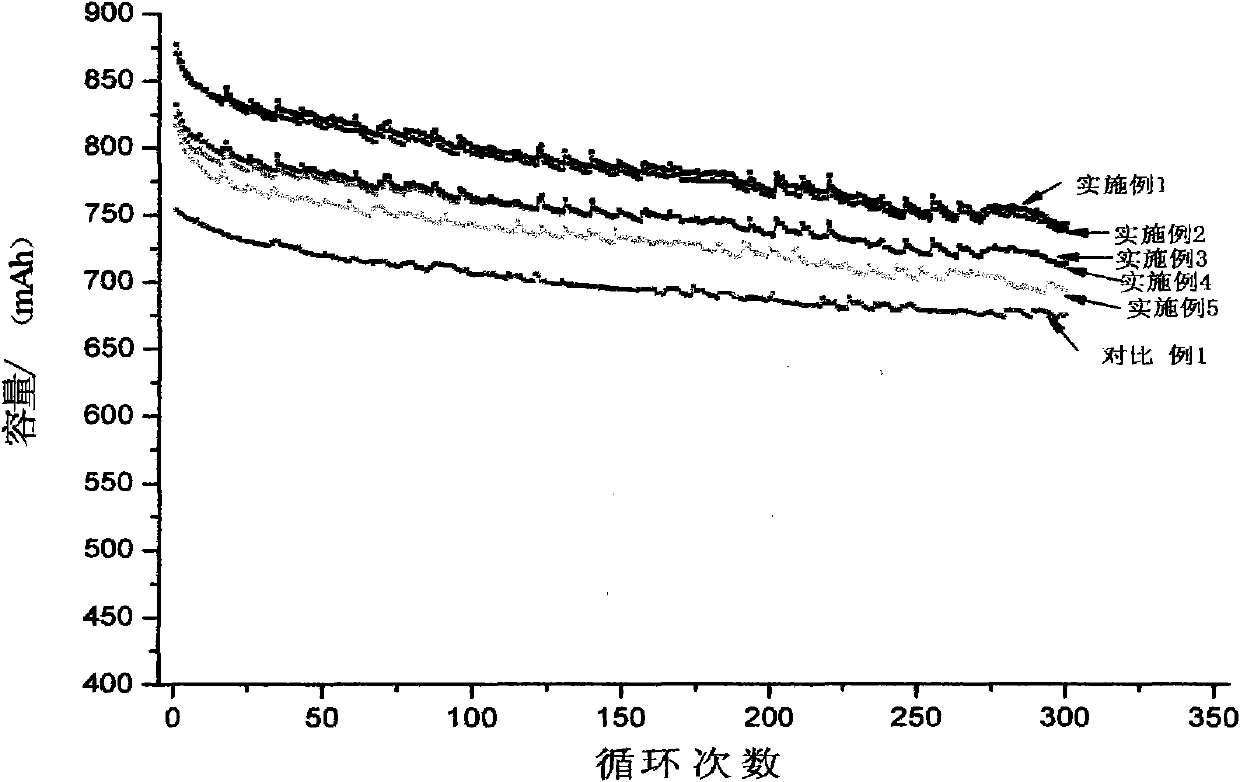
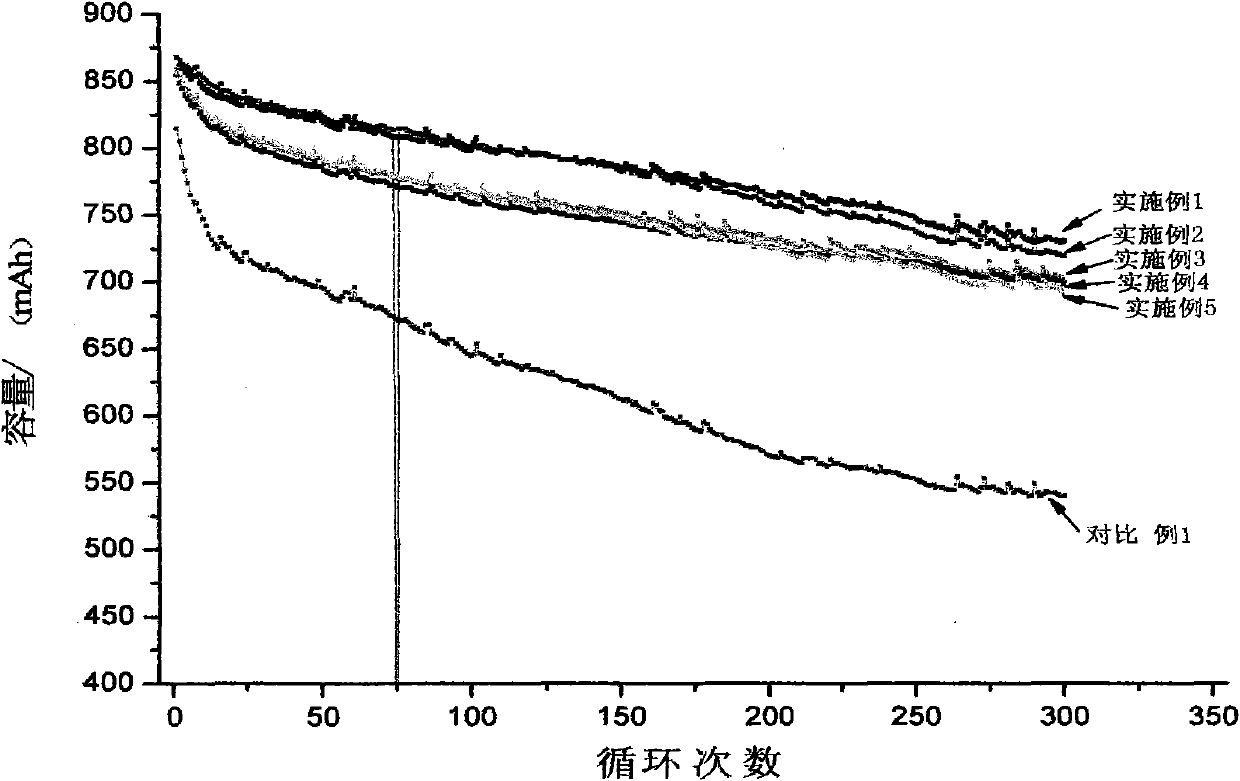
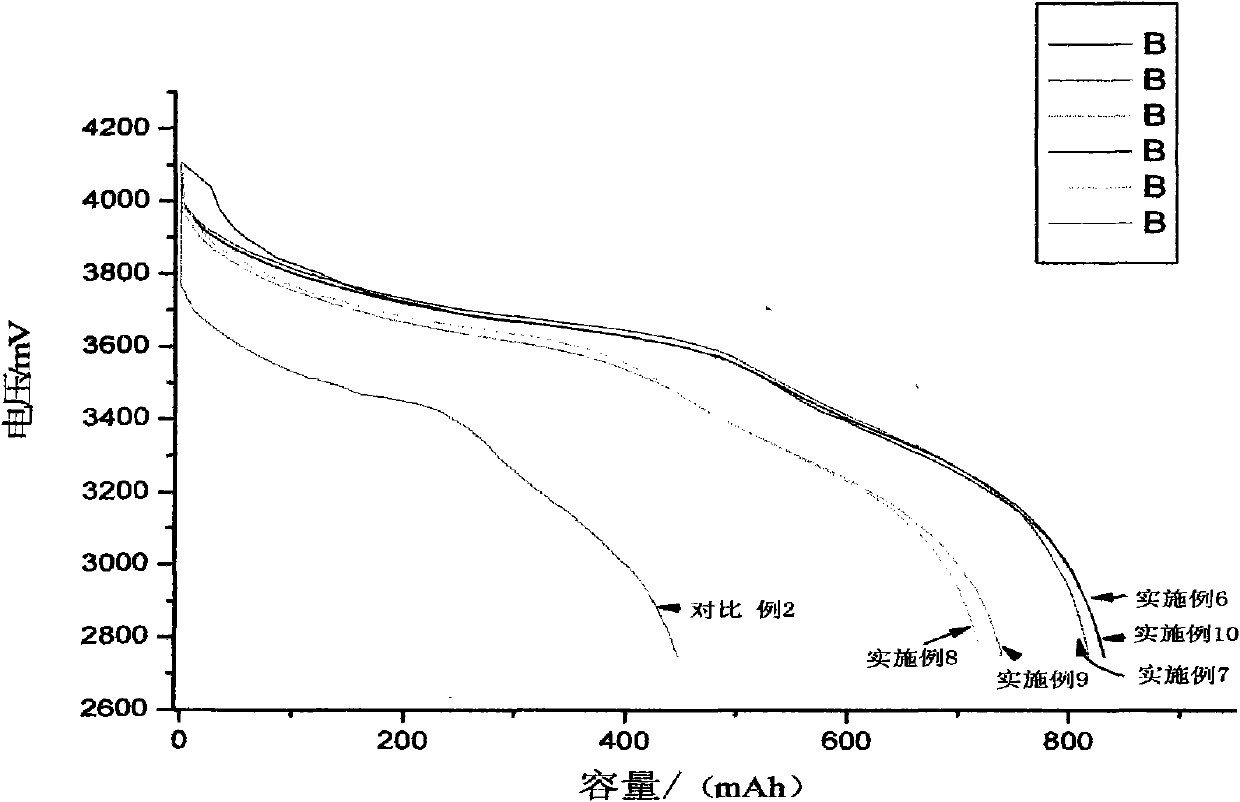
High-capacity lithium-ion electrolyte, battery and preparation method of battery
ActiveCN101771167AIncrease capacityLow costFinal product manufactureCell electrodesElectrolytic agentPhysical chemistry
The invention relates to a high-capacity lithium-ion electrolyte, a battery and a preparation method of a battery, in particular to the high-capacity lithium-ion electrolyte and the battery using the high-capacity lithium-ion electrolyte and the preparation method of the battery. The electrolyte disclosed by the invention comprises lithium salt and non-aqueous organic solvent, and also consists of the following components in weight percent in terms of the total weight of the electrolyte: 0.5-7% of film-forming additive, 0-15% of flame-retardant additive, 2-10% of antiovefill additive, 0.01-2% of stabilizer and 0.01-1% of wetting agent; the electrolyte can enable the anode with high Ni content to work stably, and reduce the battery cost; the high-capacity lithium-ion battery can perform high ratio capacity and excellent safety and high temperature property and cyclic life fully due to the addition and synergetic functions of various functional additives.
Owner:JIUJIANG TINCI ADVANCED MATERIALS CO LTD
Secure credit card with near field communications
ActiveUS20060213972A1Reduces acceptabilityErroneous rejectionAcutation objectsMemory record carrier reading problemsComputer hardwareCredit card
A near field communication device included in a secure transaction card provides an addition and / or transitional communication link for communicating secure transaction information. The near field communication device may be selectively engaged or disengaged and, when engaged, either active or passive modes of operation of the near field communication device can be selected. in the active mode, secure transaction information is transmitted upon establishment of a communication link with a complementary near field communication device. In the passive mode, secure transaction information is transmitted upon interrogation from a complementary near field communication device. Secure transaction information is generated and stored for transmission in a memory and at least a portion of the memory is erased or nulled upon transmission or upon expiration of a selected period of time.
Owner:EBAY INC
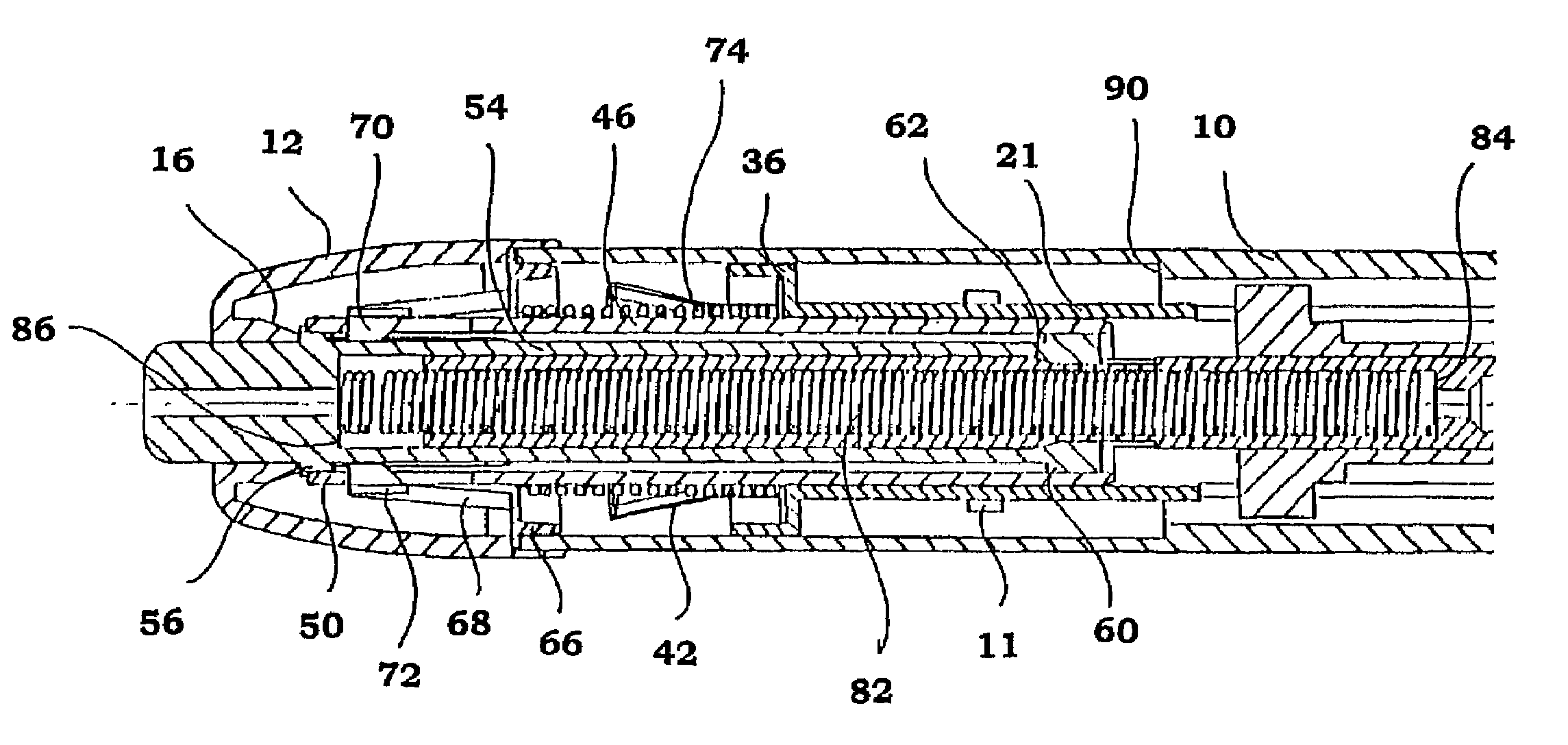
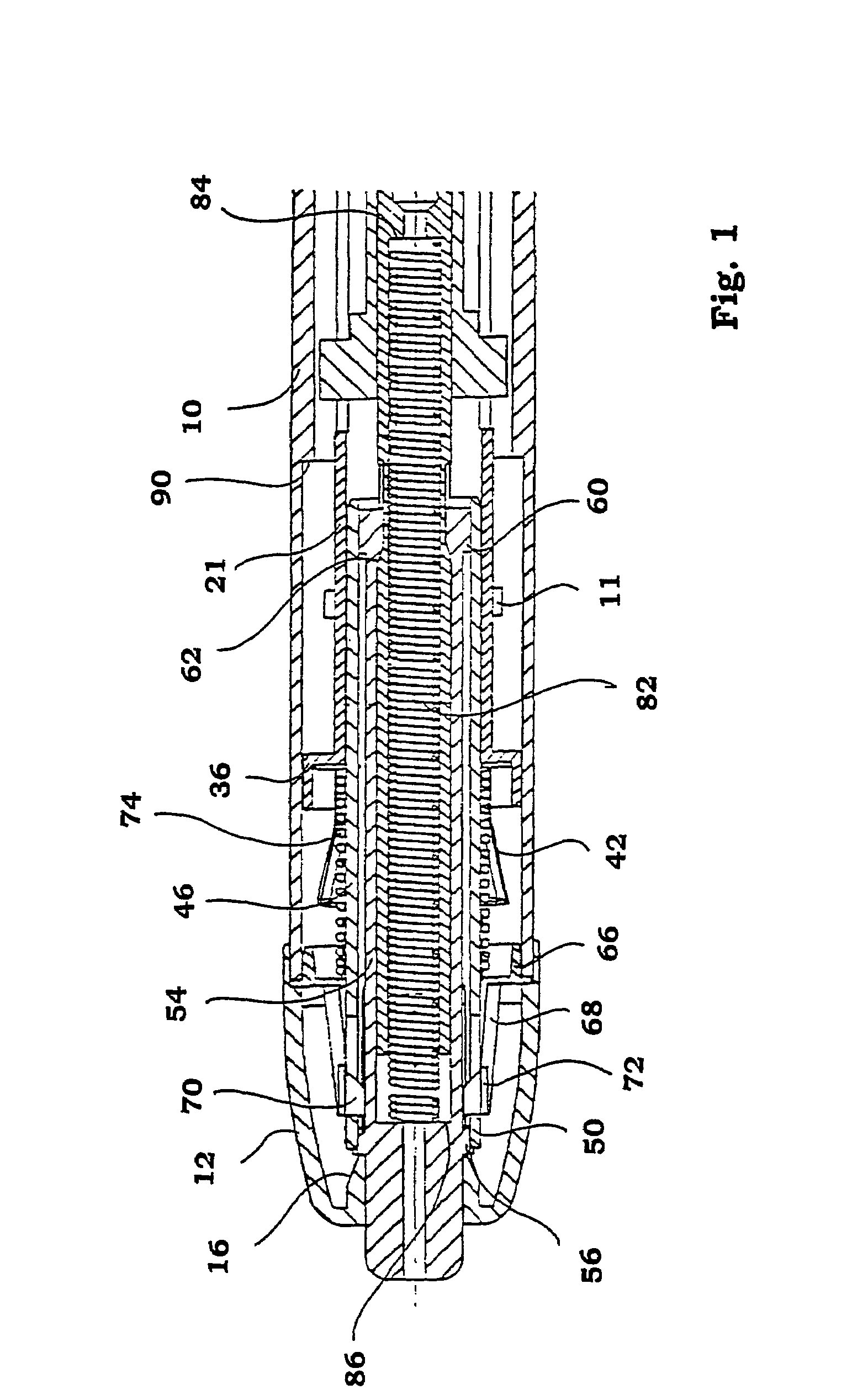
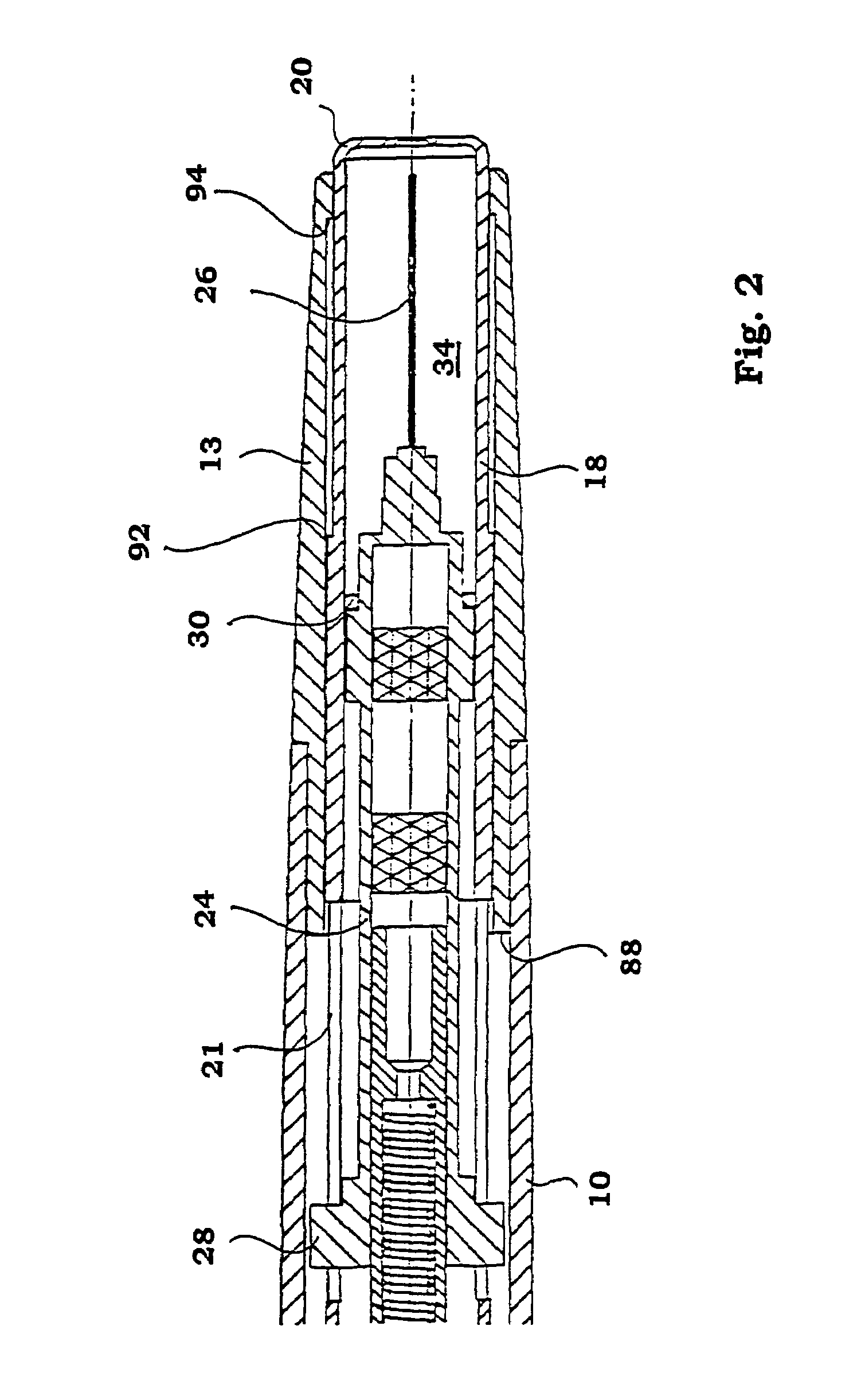
Injection device for administering a vaccine
InactiveUS7670314B2Simple and inexpensive to prepareSimple and inexpensive to and operateAmpoule syringesAutomatic syringesMedication injectionInjection device
A manually-powered injection device that self-administers a painless injection. The injection device provides a method for substantially painless injections of vaccine and other medication into a patient that does not require the use of an anesthetic, that does not require the medical personnel to spend a substantial amount of time performing the injection procedure, that is relatively simple and inexpensive to perform and operate, and that provides a relatively high degree of safety for both the medical personnel and for the patient. The injection needle can have an outside diameter greater than 0.10 mm and less than about 0.38 mm. The vaccine or other medicament can be injected painlessly through the needle and into the patient at a substantially constant volumetric flow rate of about 0.05 μL / s to about 50 μL / s, typically over a 3- to 5-minute period of time. The injection device is configured for easy handling, and is manually powered by the use of the hand or fingers of the medical technician, patient or other person.
Owner:CHILDRENS HOSPITAL MEDICAL CENT CINCINNATI
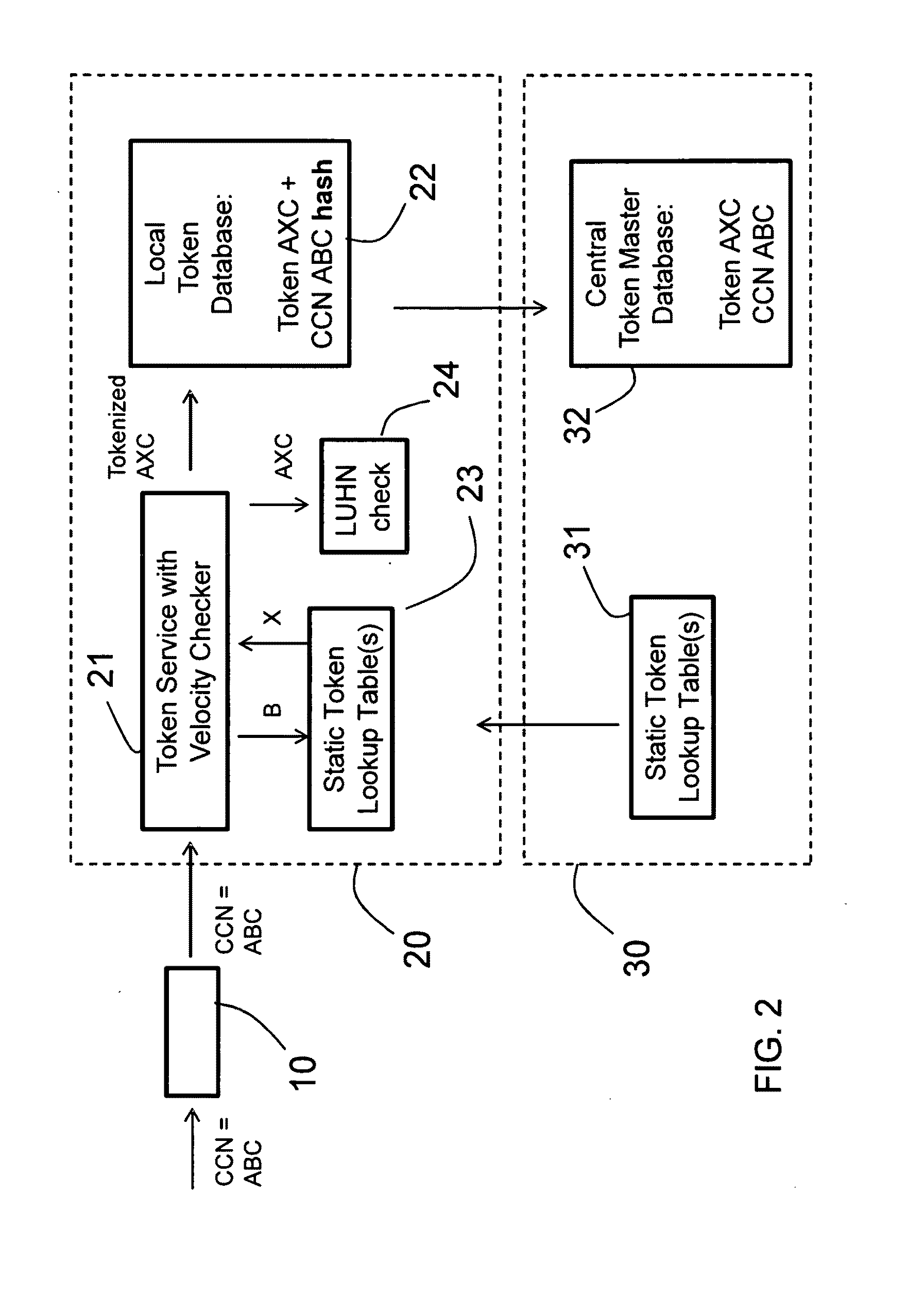
System and method for distributed tokenization using several substitution steps
ActiveUS20110213807A1Reduce disadvantagesReduce problemsAcutation objectsDigital data processing detailsCredit cardSocial Security number
A method for distributed tokenization of sensitive strings of characters, such as social security numbers, credit card numbers and the like, in a local server is disclosed. The method comprises the steps of receiving from a central server at least one, and preferably at least two, static token lookup tables, and receiving a sensitive string of characters. In a first tokenization step, a first substring of characters is substituted with a corresponding first token from the token lookup table(s) to form a first tokenized string of characters, wherein the first substring of characters is a substring of the sensitive string of characters. Thereafter, in a second step of tokenization, a second substring of characters is substituted with a corresponding second token from the token lookup table(s) to form a second tokenized string of characters, wherein the second substring of characters is a substring of the first tokenized string of characters. Optionally, one or more additional tokenization steps is / are used.
Owner:PROTEGRITY CORP
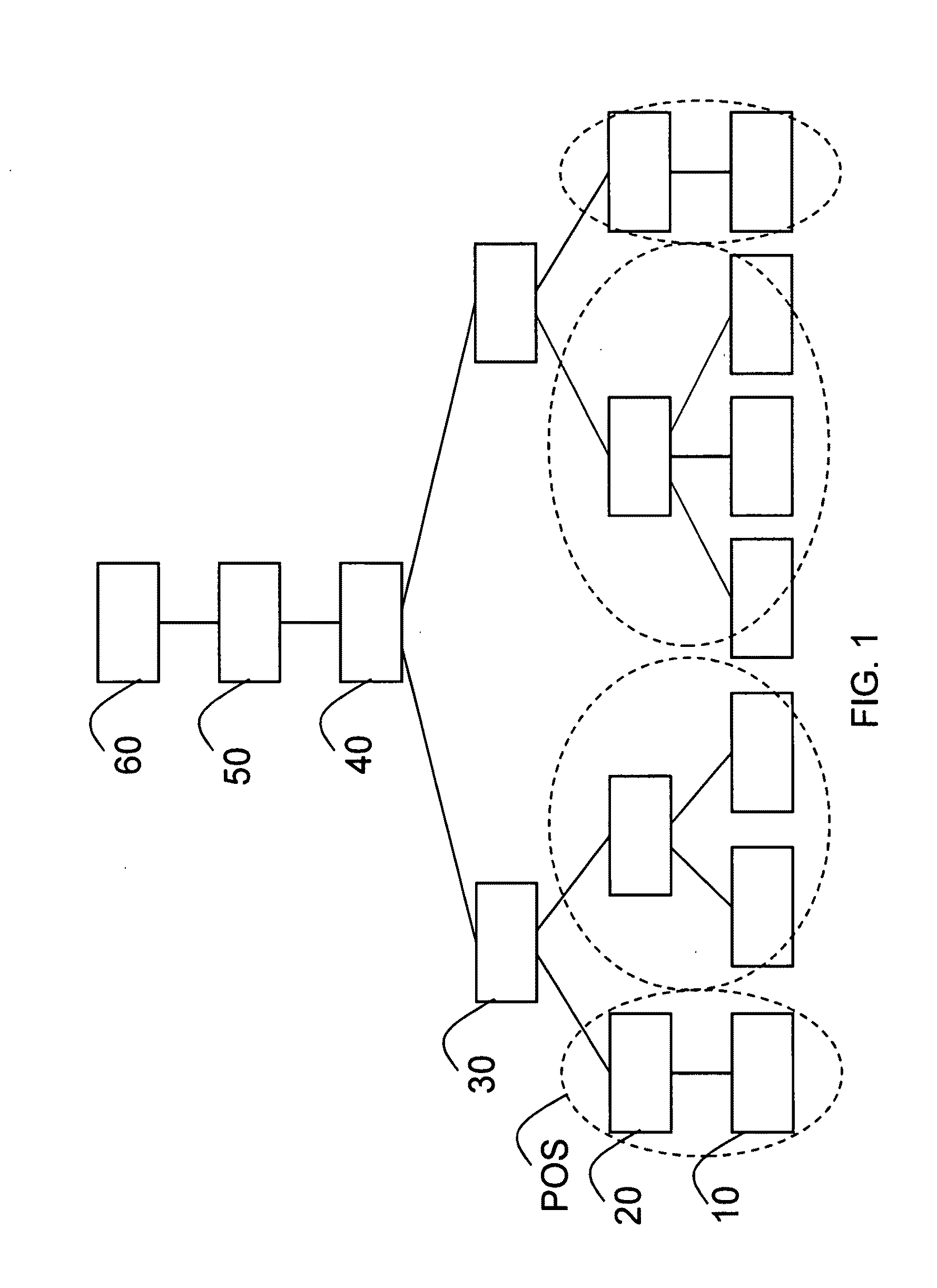
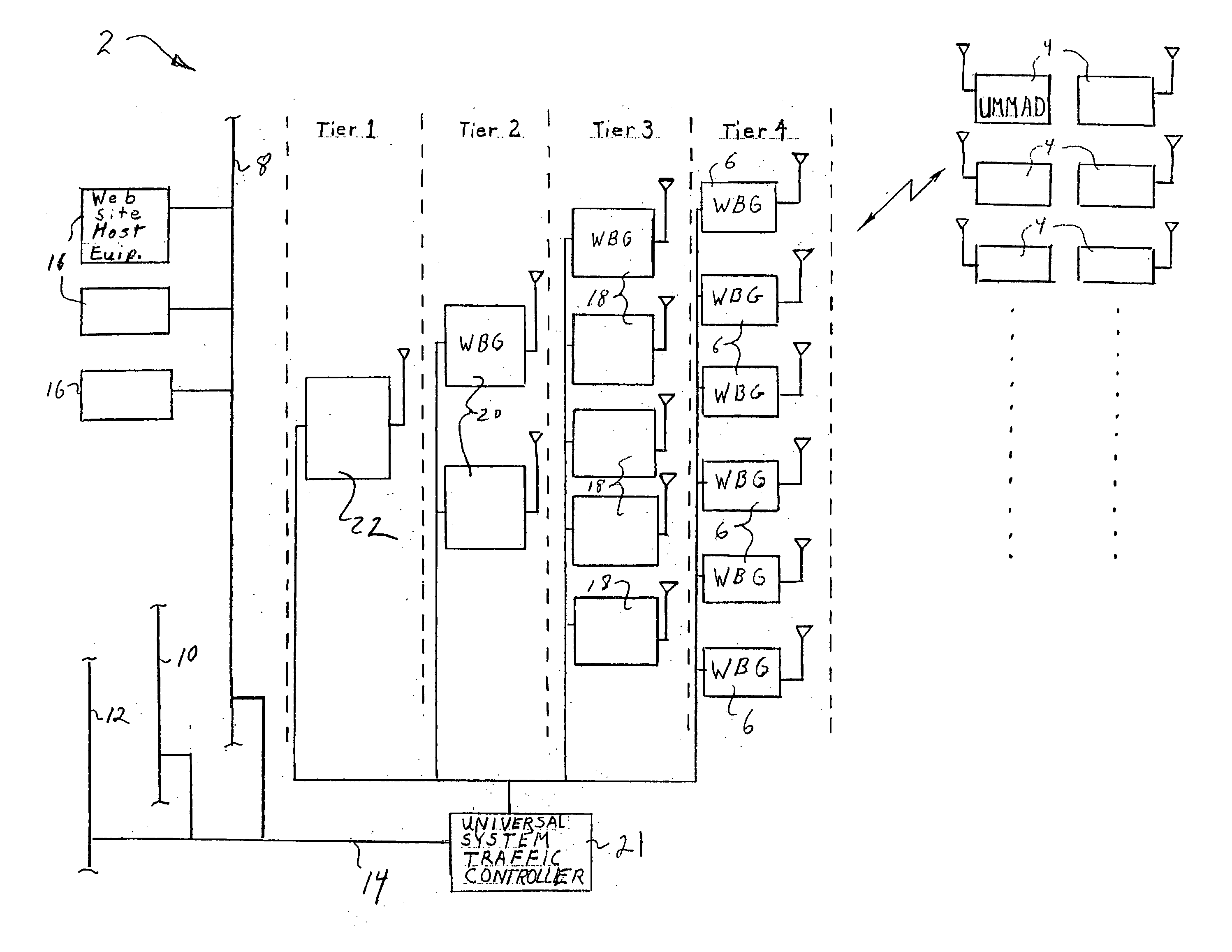
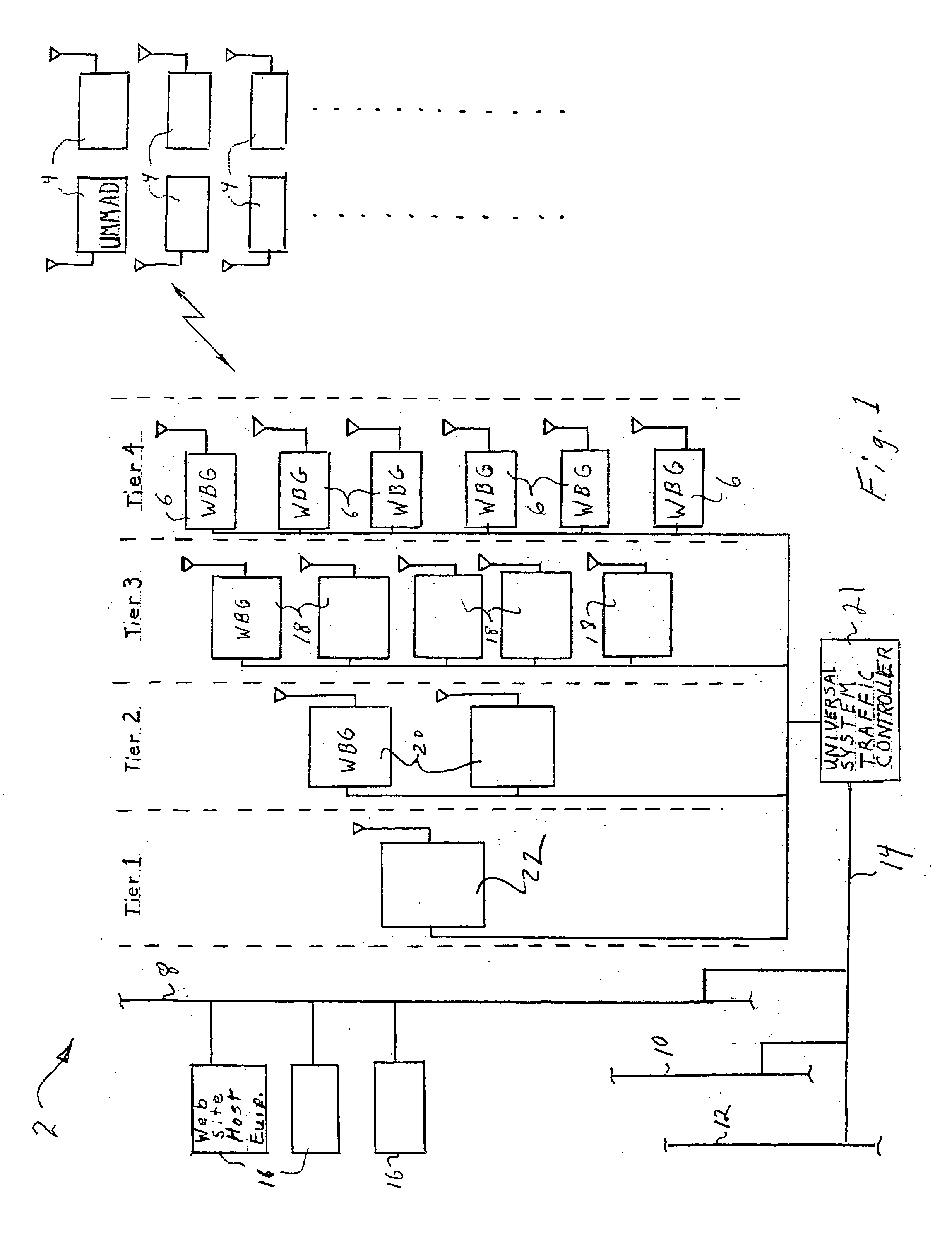
Tiered wireless, multi-modal access system and method
InactiveUS20050159164A1Facilitate easeEasy accessNetwork traffic/resource managementUnauthorised/fraudulent call preventionTelecommunications linkCommunication link
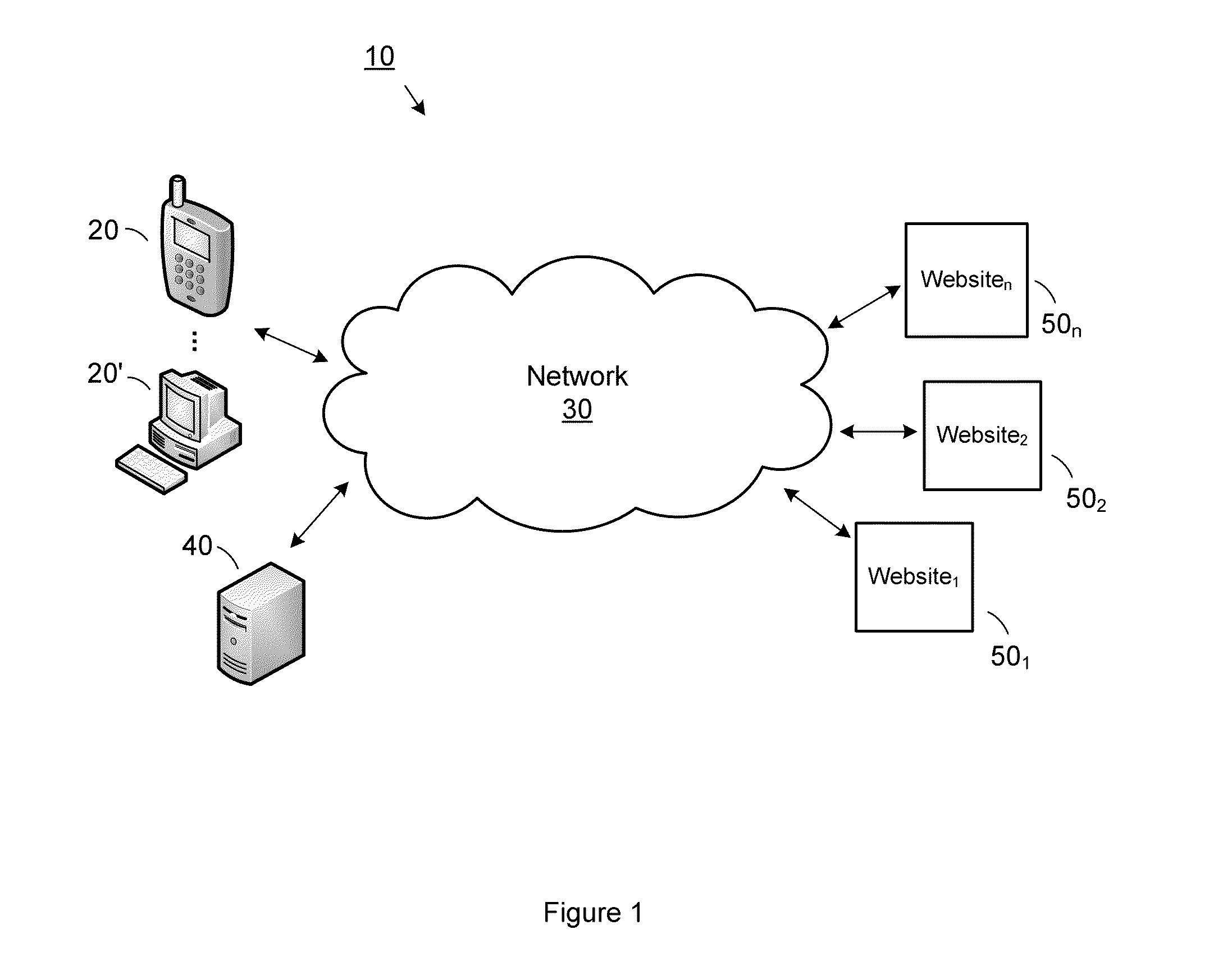
A wireless, multi-modal access device and system adapted to integrate a number of communications networks operating in differing communication modes to facilitate transfer of communication links during a communication session to promote efficient use of the communication networks. The system includes a plurality of Universal Multi-Modal Access Devices UMMAD that are capable of operating at different frequencies and different protocols (TDMA, AMPS, CDMA, GSM, PCS etc) to communicate with any one of a number of Wide Bandwidth Gateways (WBG), which are each capable of communication using one or more of the protocols. The communication links may be switched from one WBG to another or from one protocol to another during a communication session to continue the session under the control of a Universal System Traffic Controller. Numerous other applications of the UMMADs for unique identification and e-commerce are disclosed.
Owner:MOBILE DATA OFF LOADING
Method and apparatus for tokenization of sensitive sets of characters
ActiveUS20090249082A1Simple methodSafe handlingAcutation objectsUnauthorized memory use protectionComputer networkServer allocation
A method and system for secure handling of sensitive sets of characters in a distributed hierarchical system are disclosed, comprising at least one local server on a lower hierarchic level and at least one central server at a higher hierarchic level. The method comprises the steps: receiving a sensitive set of characters in said local server; replacing a part of said sensitive set of characters with a token to form a tokenized set of characters, said token belonging to a subset of possible tokens assigned to the local server by the central server; transferring at least one of said sensitive set of characters and said tokenized set of characters to the central server; and canceling said sensitive set of characters from said local server within a limited time from said transferring, while maintaining said tokenized set of characters in a local database connected to said local server.
Owner:PROTEGRITY CORP
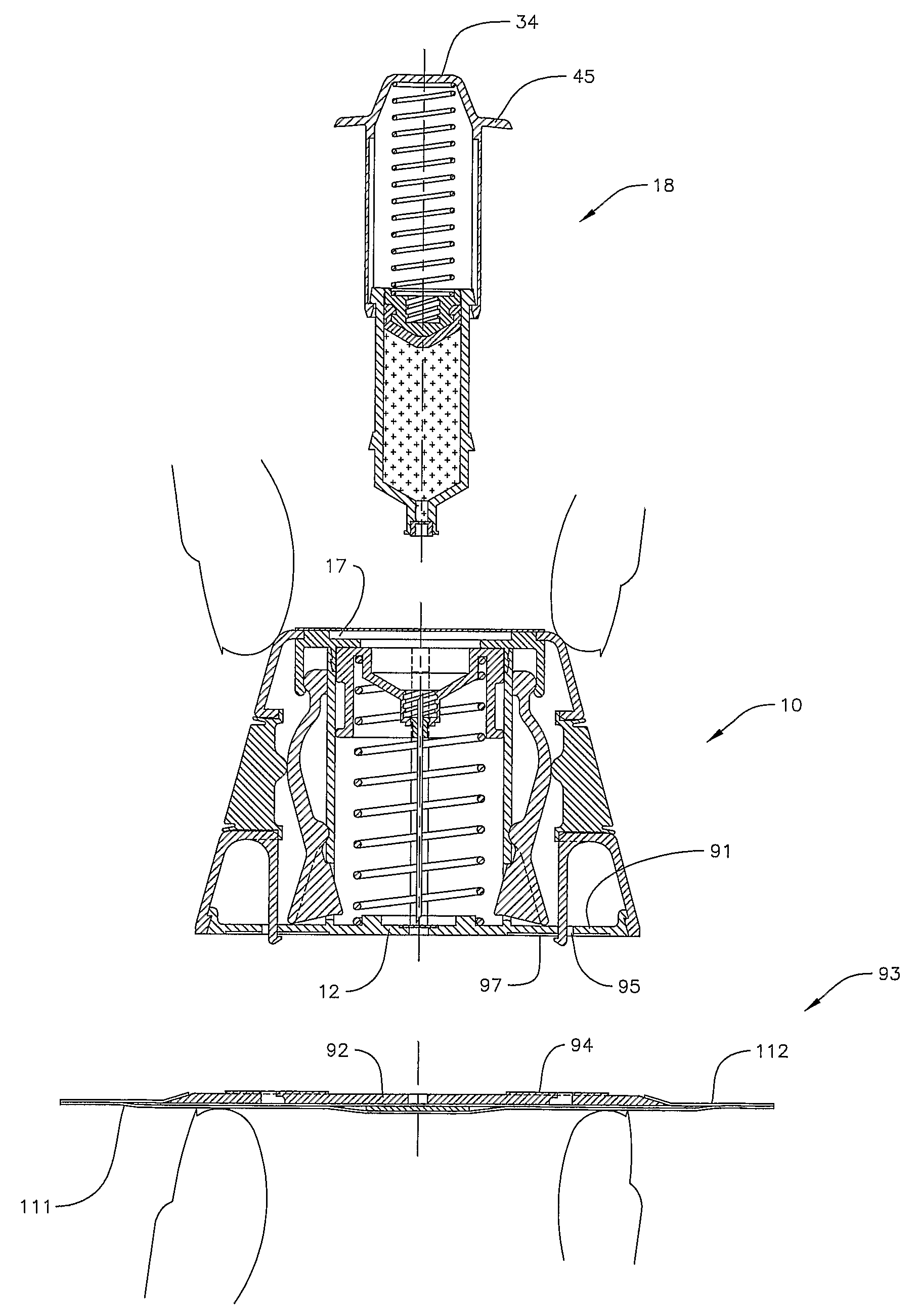
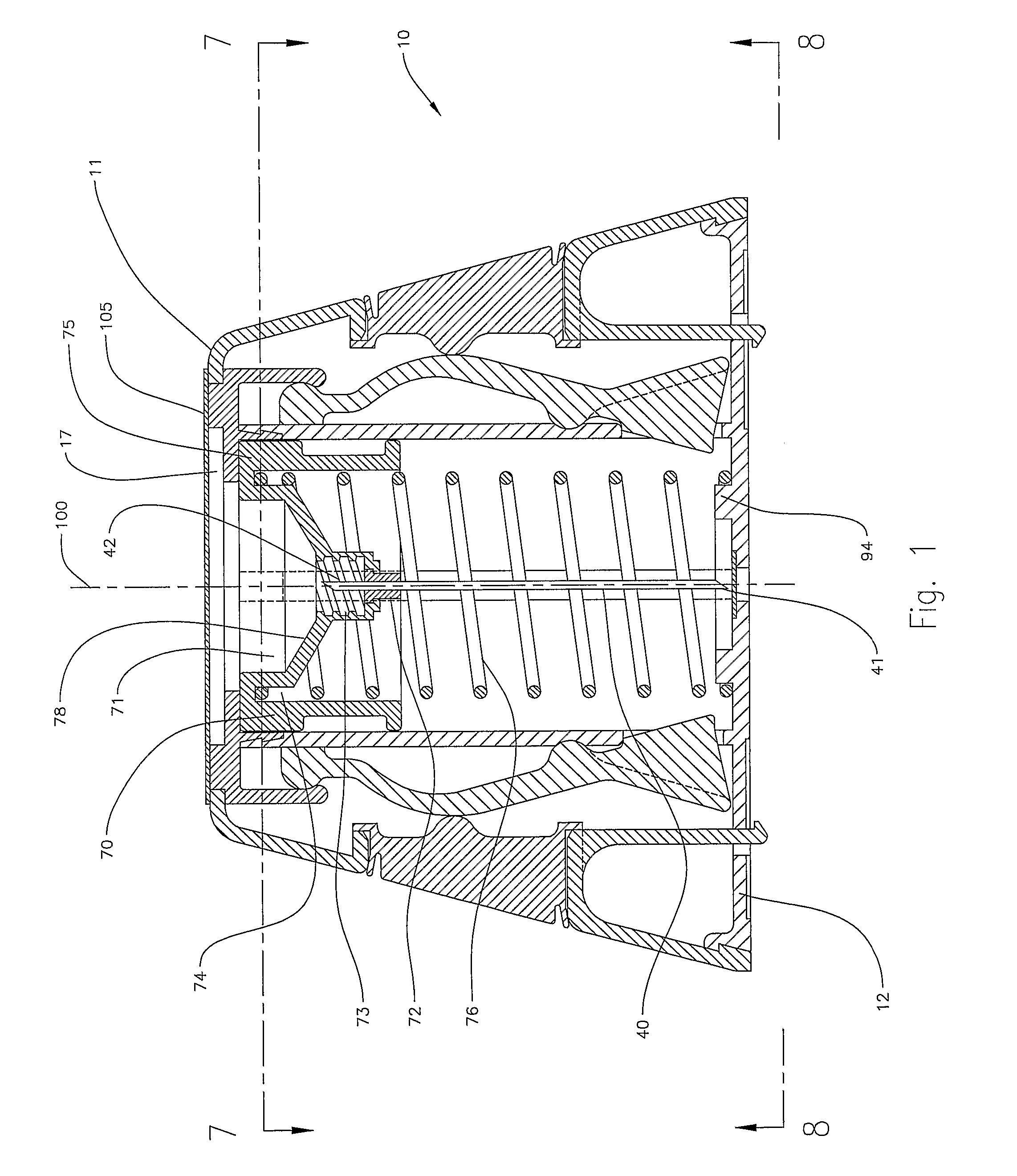
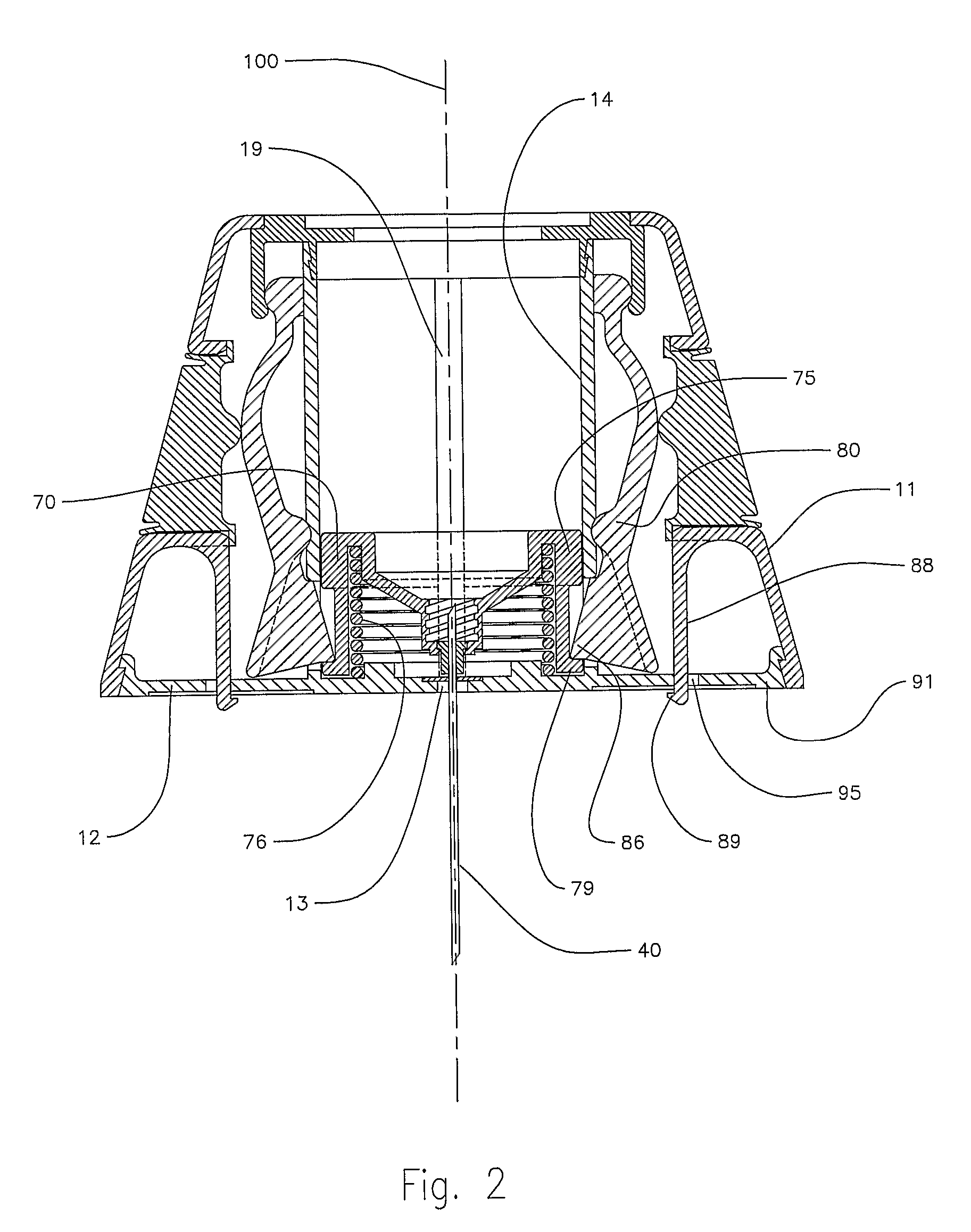
Retraction means for transcutaneous device
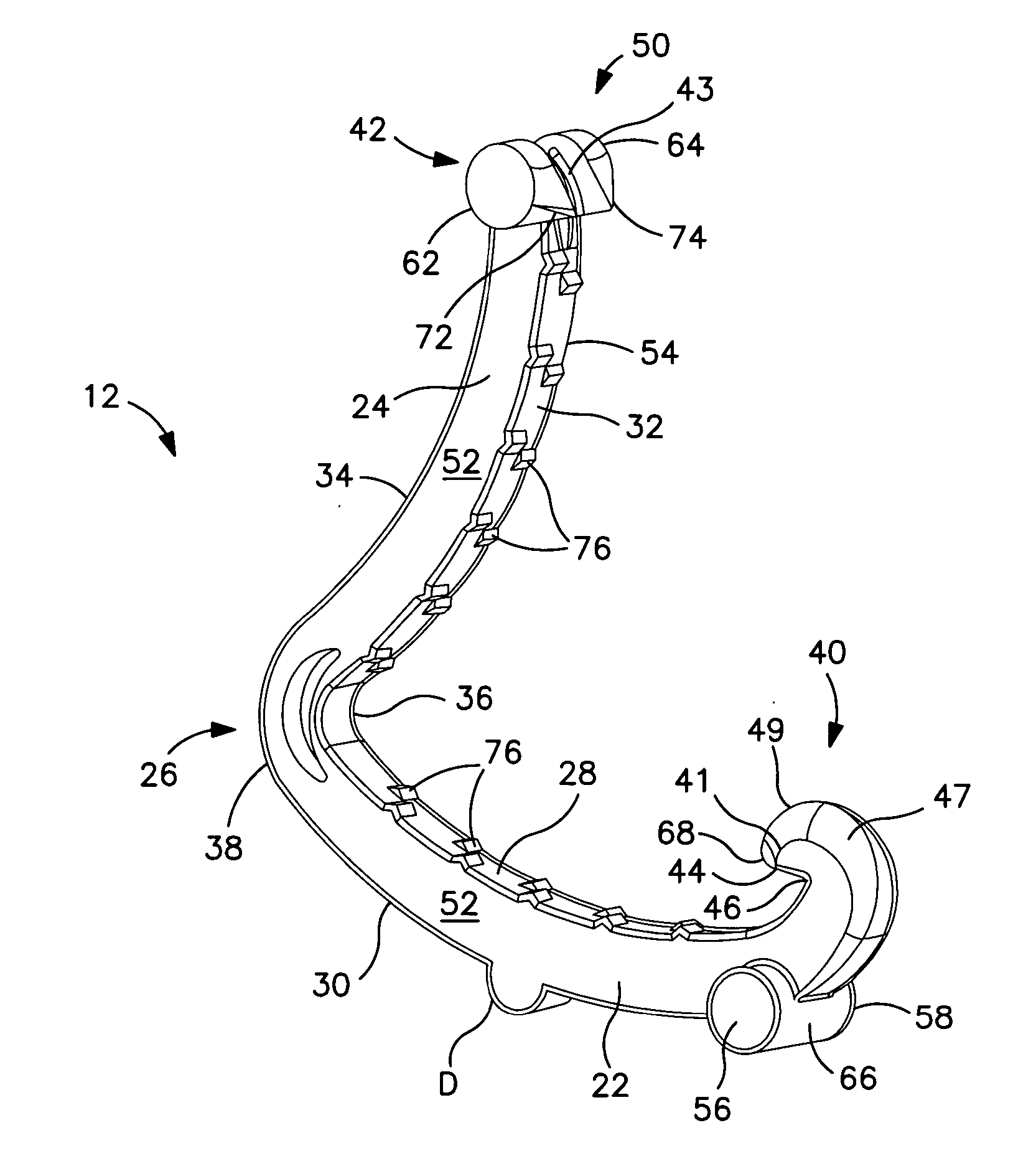
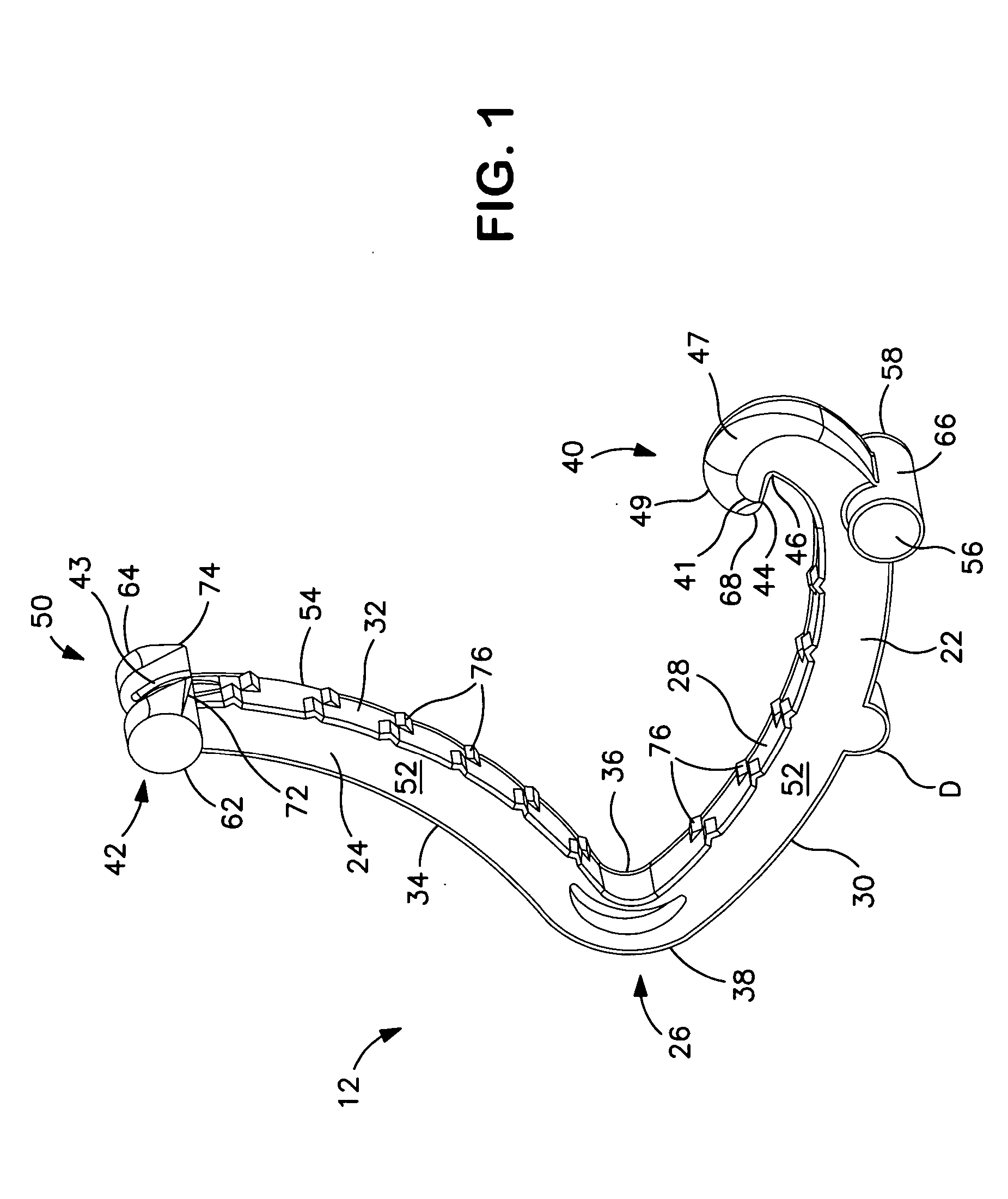
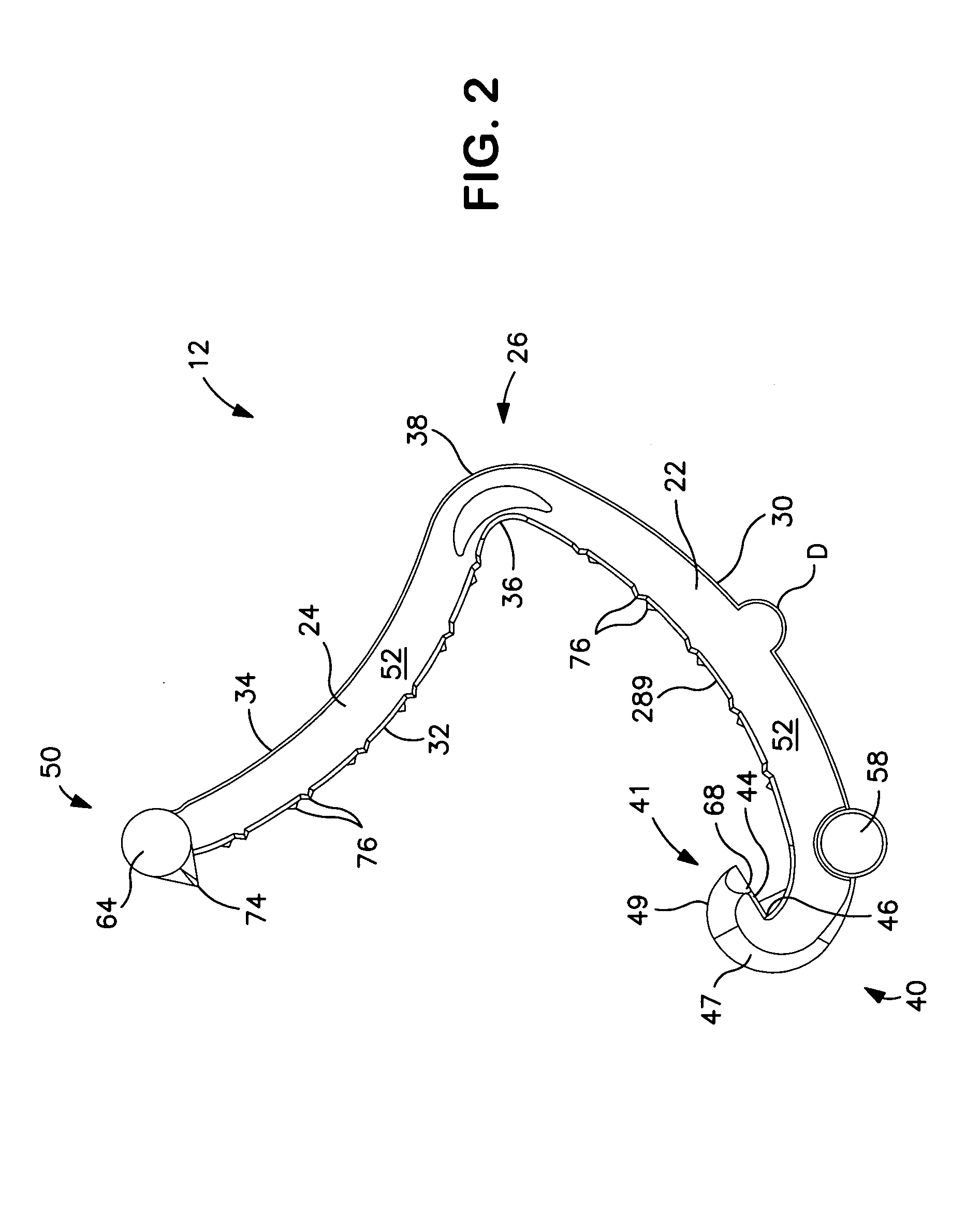
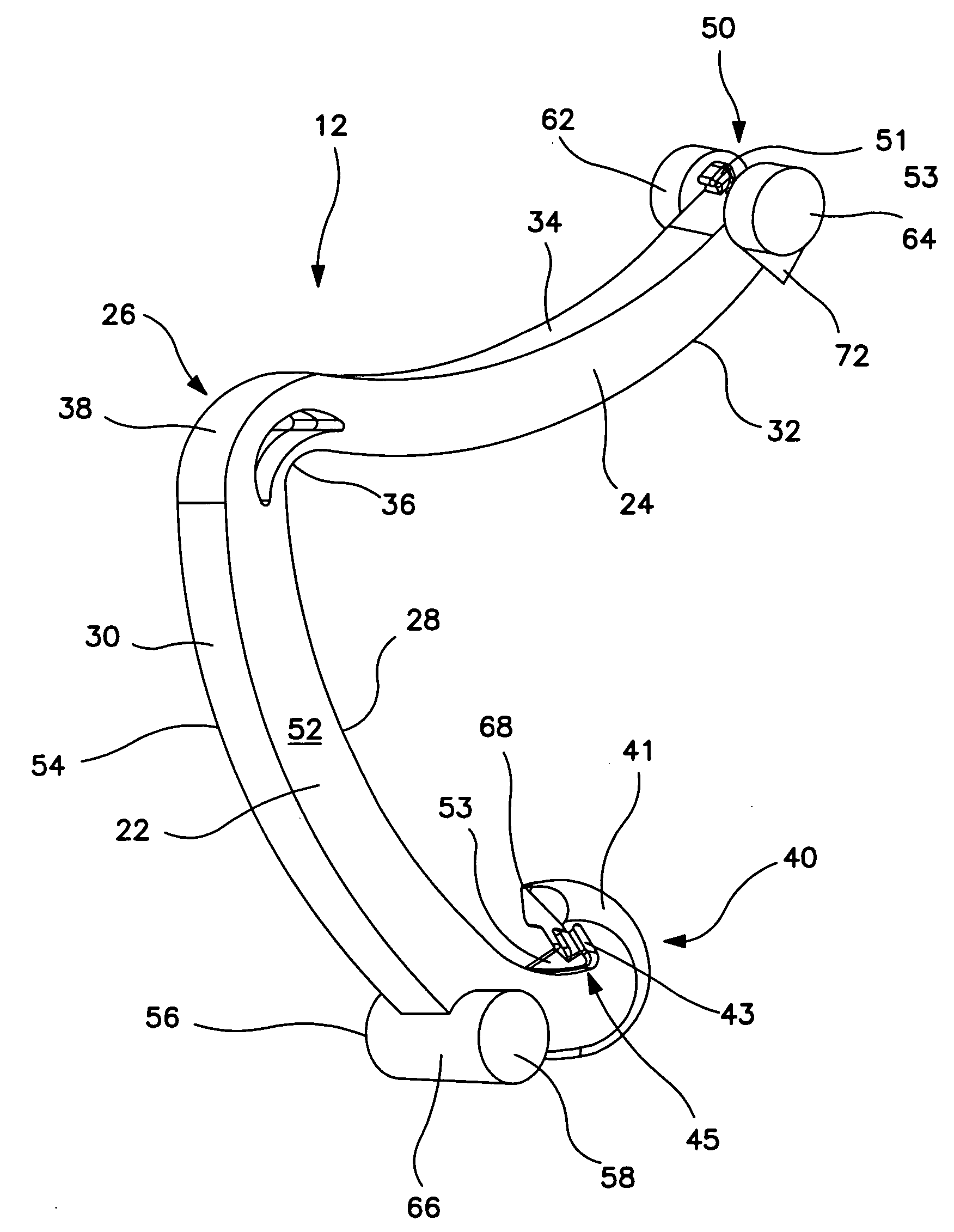
InactiveUS7955297B2Easy to useRaise security concernsInfusion syringesMedical devicesIntermediate stateMedical device
The invention provides a transcutaneous medical device (502, 250, 150, 600) comprising a lower surface adapted for application towards the skin of a subject, attaching means (571, 272, 161) for securing the lower surface relative to the skin, and a transcutaneous device (530, 182, 213, 651) adapted to penetrate the skin of the subject. The transcutaneous device is mounted for movement between an extended position in which the transcutaneous device projects relative to the lower surface and a retracted position in which the transcutaneous device is retracted relative to the lower surface. The medical device further comprises release means (550, 275, 162) which can be operated from a first state through an intermediate state to a second state, whereby operation of the release means from the first to the intermediate state causes the transcutaneous device to be moved from the extended position to the retracted position, and operation of the release means from the intermediate to the second state causes release of the attaching means.
Owner:NOVO NORDISK AS
Methods for Single Signon (SSO) Using Decentralized Password and Credential Management
ActiveUS20130166918A1Information be quite largeImprove safetyUser identity/authority verificationComputer security arrangementsDistributed serversEnd to end security
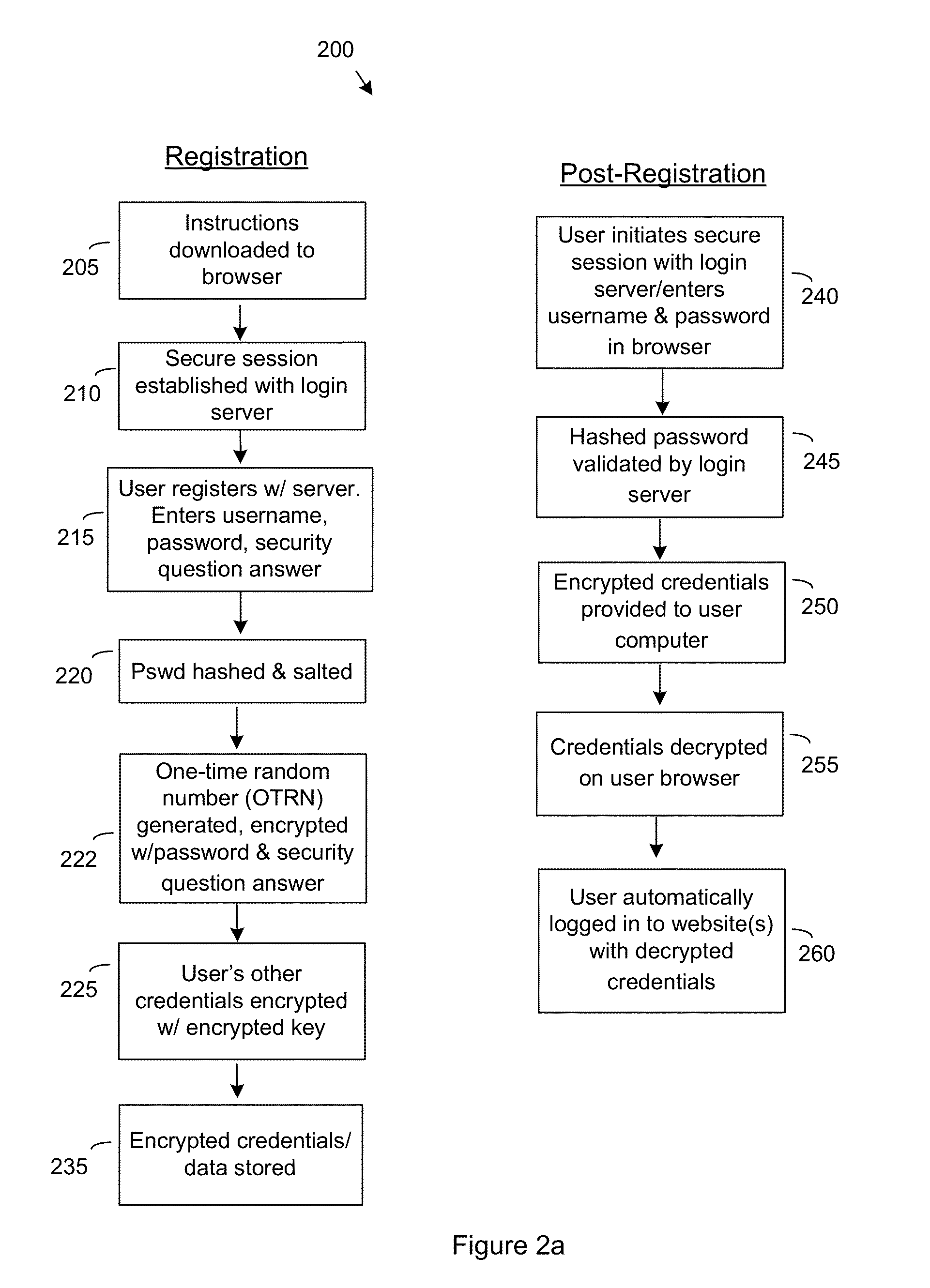
A method for single sign-on (SSO) that provides decentralized credential management using end-to-end security. Credential (and other personal user information) management is decentralized in that encryption is performed locally on the user's computer. The user's encrypted credentials may be stored by the login server and / or a plurality of distributed servers / databases (such as a cloud). The login server never has access to the user's credentials or other personal information. When the user wants to use single sign-on, he enters his password into his browser and the browser submits the encrypted / hashed password to the login server for validation. Upon validation, the browser receives the user's encrypted credentials. The credentials are decrypted by the browser and provided to relevant websites to automatically log the user in.
Owner:SHAHBAZI MAJID +1
System and method of subscription identity authentication utilizing multiple factors
ActiveUS7340042B2Low costRaise security concernsAutomatic call-answering/message-recording/conversation-recordingSpeech recognitionSpeech verificationSpeech sound
Owner:CSIDENTITY CORP
Security server system
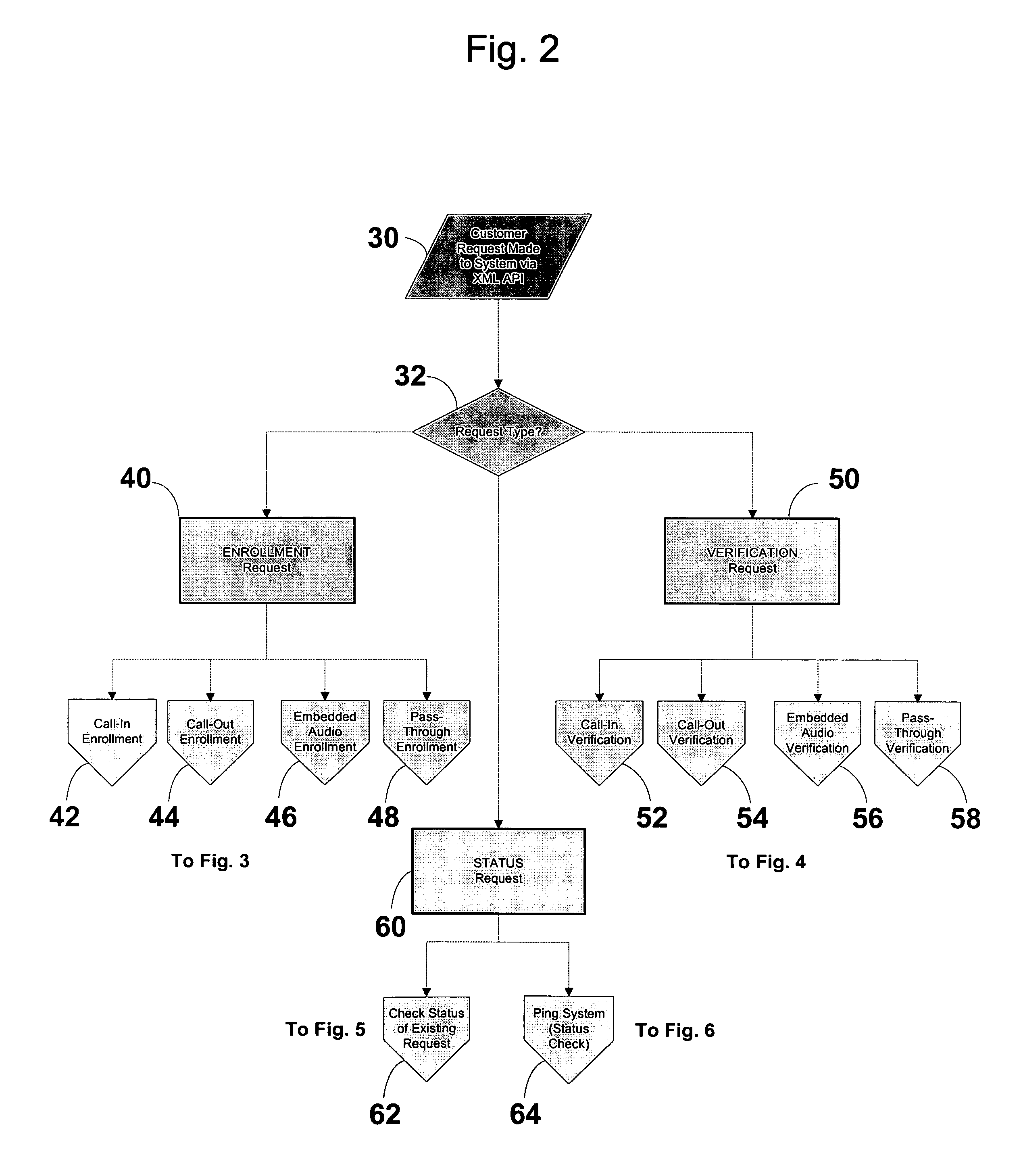
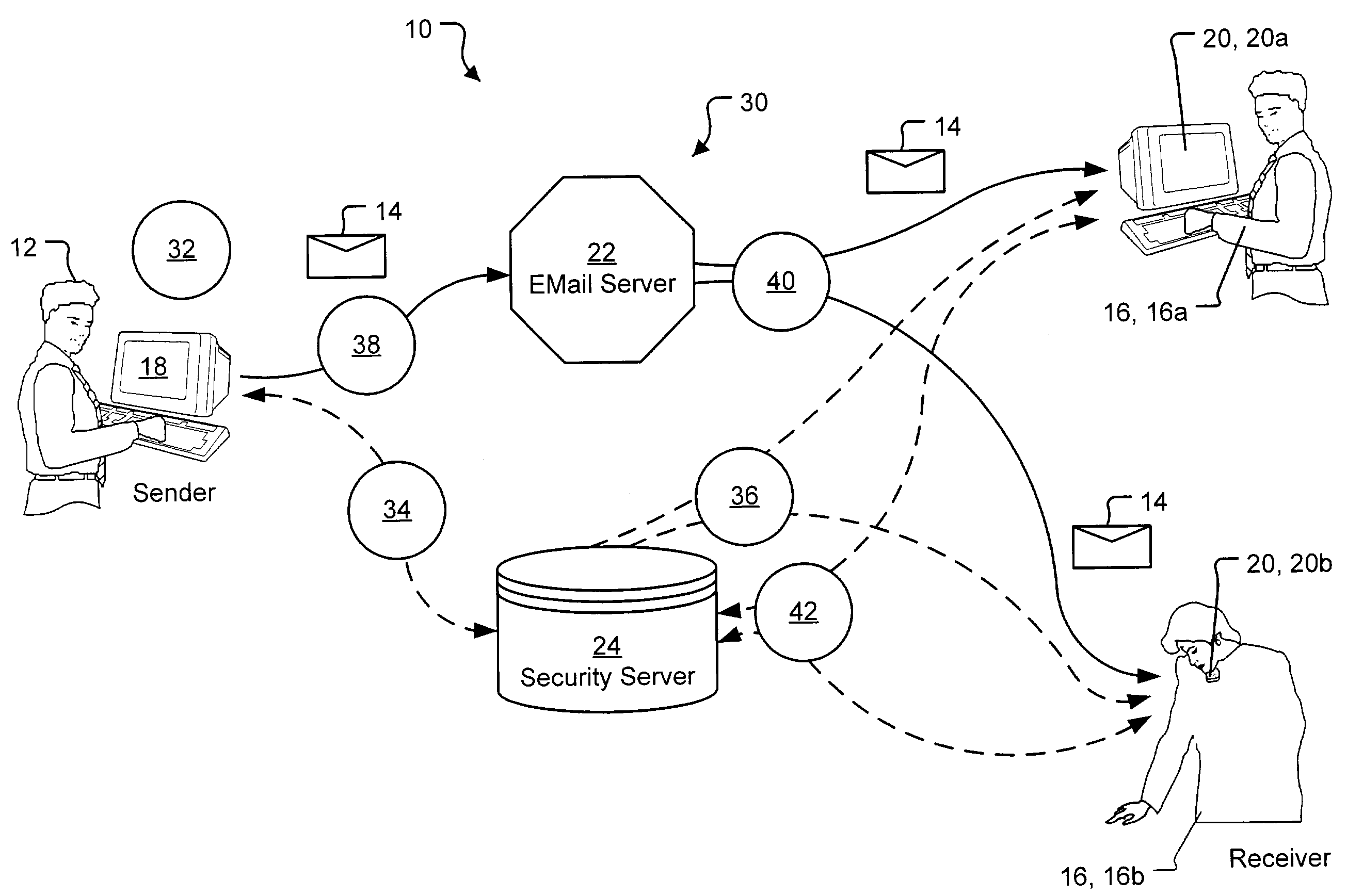
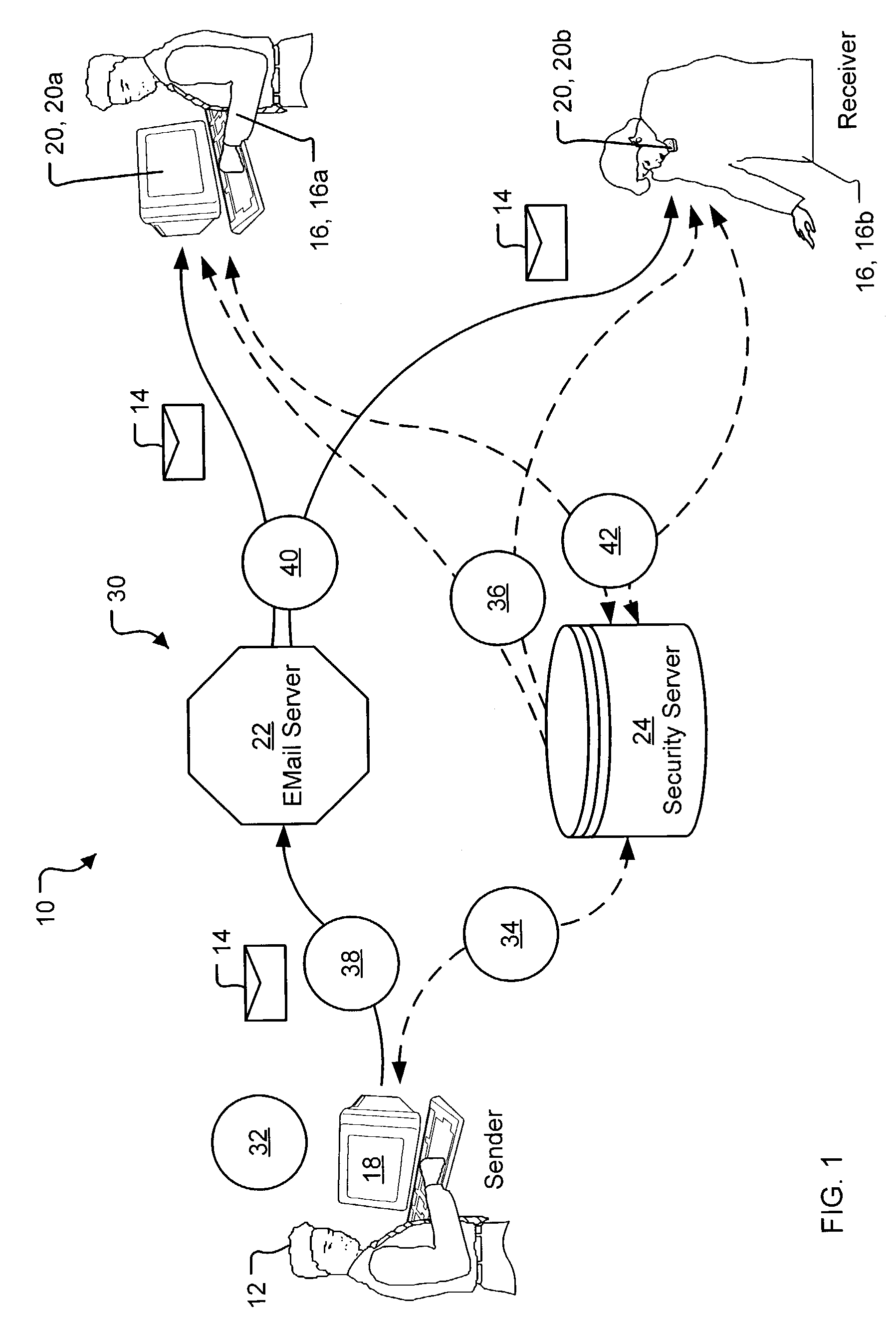
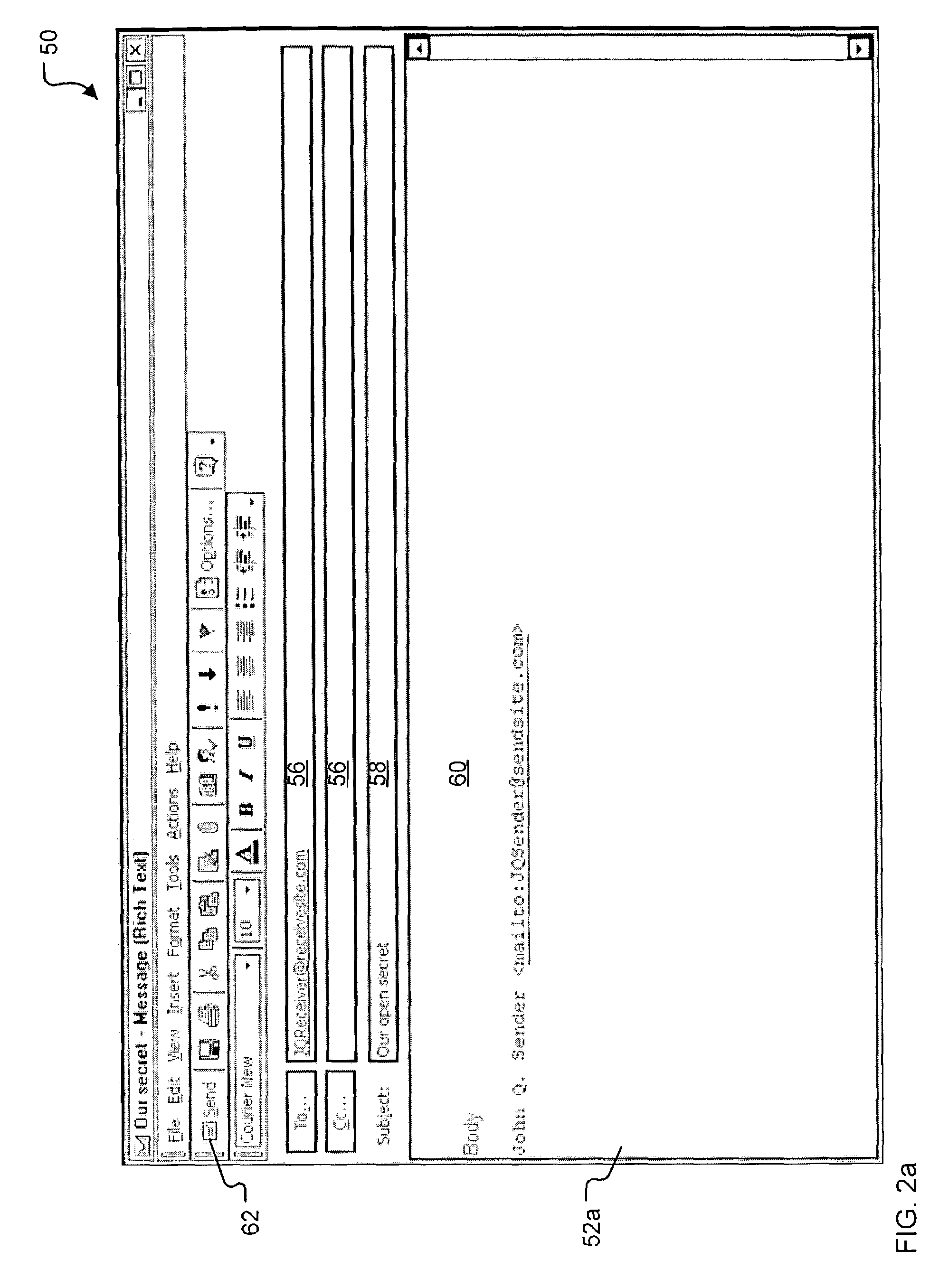
InactiveUS7325127B2Raise security concernsHigh degreeData switching networksSecuring communicationKey serverMessage Title
A security server system and method permitting participants acting as the source or destinations for a message or a conversation with multiple messages to securely communicate the messages. The messages have a message header and a message content. A message router connects the participants via a network and delivers the message between the participants based on the message header. A key server creates, stores, and releases conversation keys that the participants use to protect the message content of the message.
Owner:PROOFPOINT INC
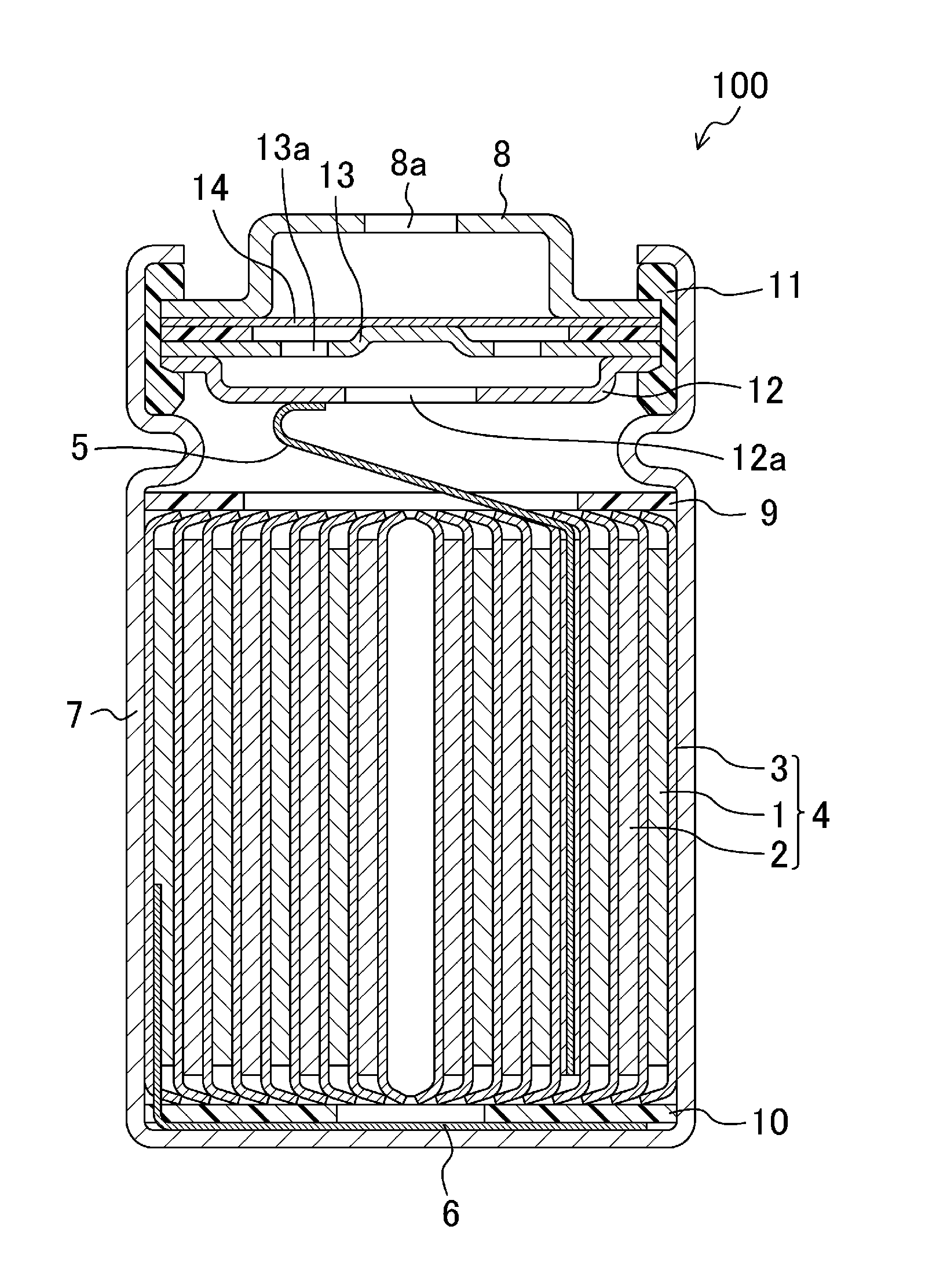
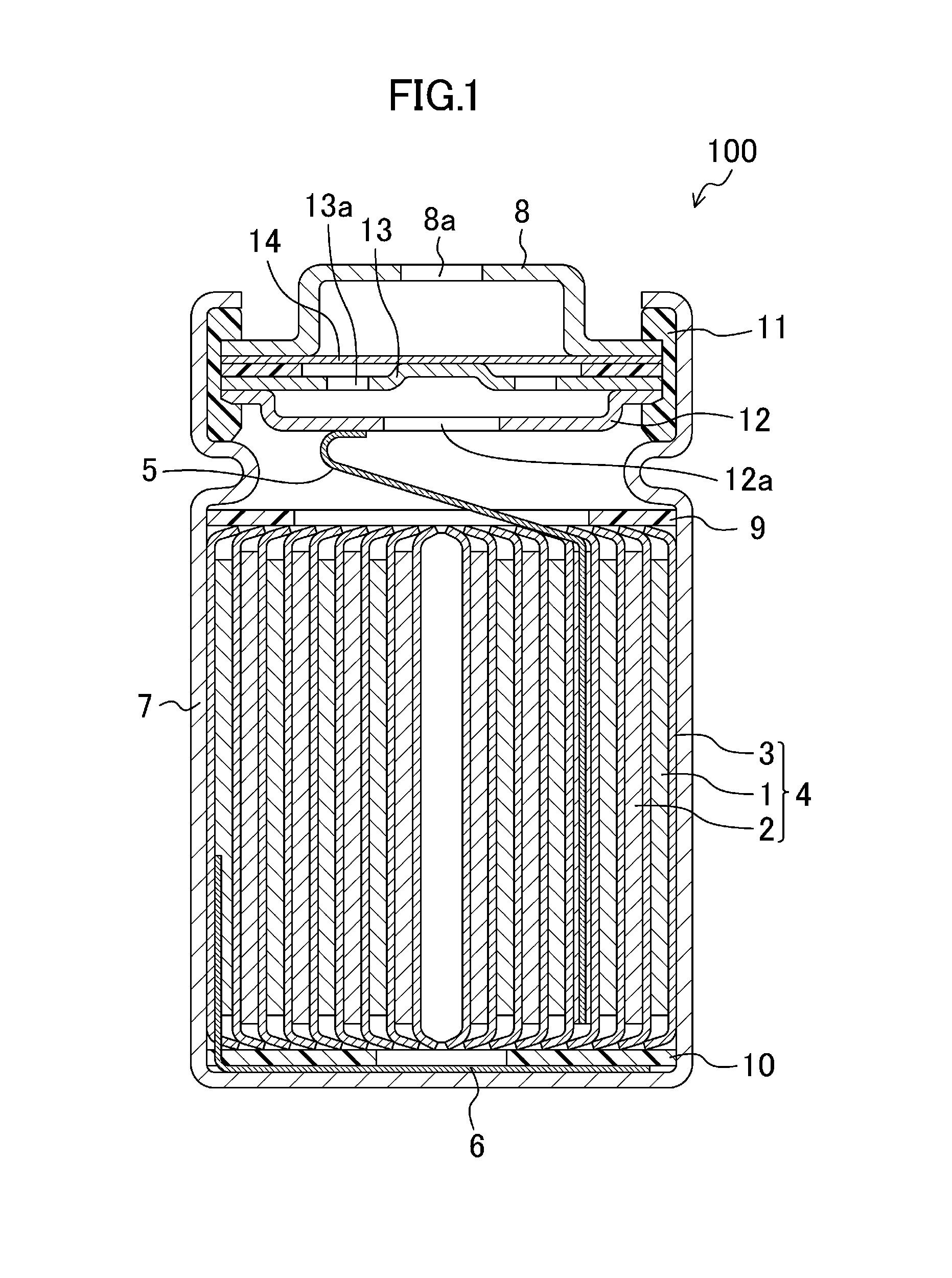
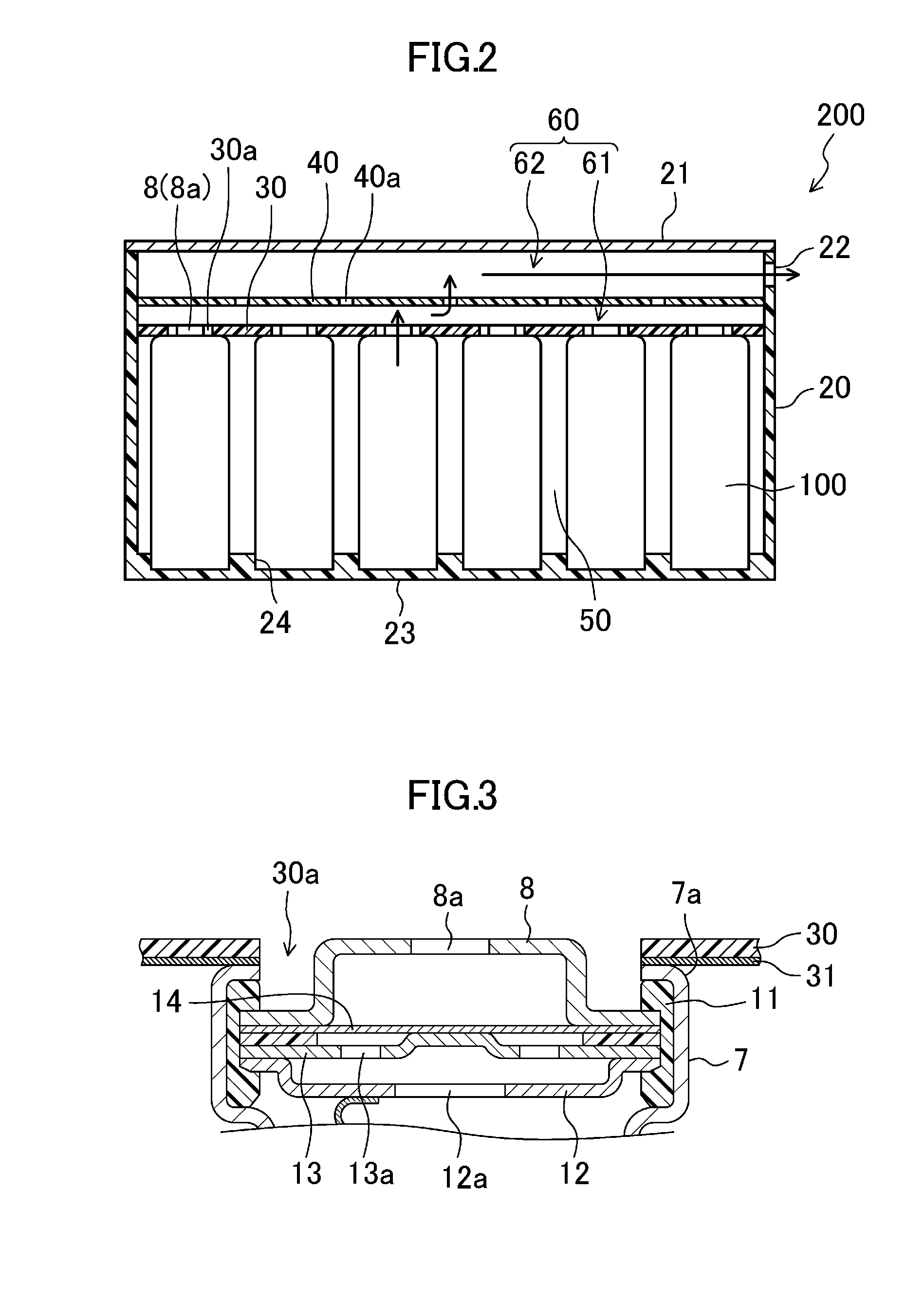
Battery module
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
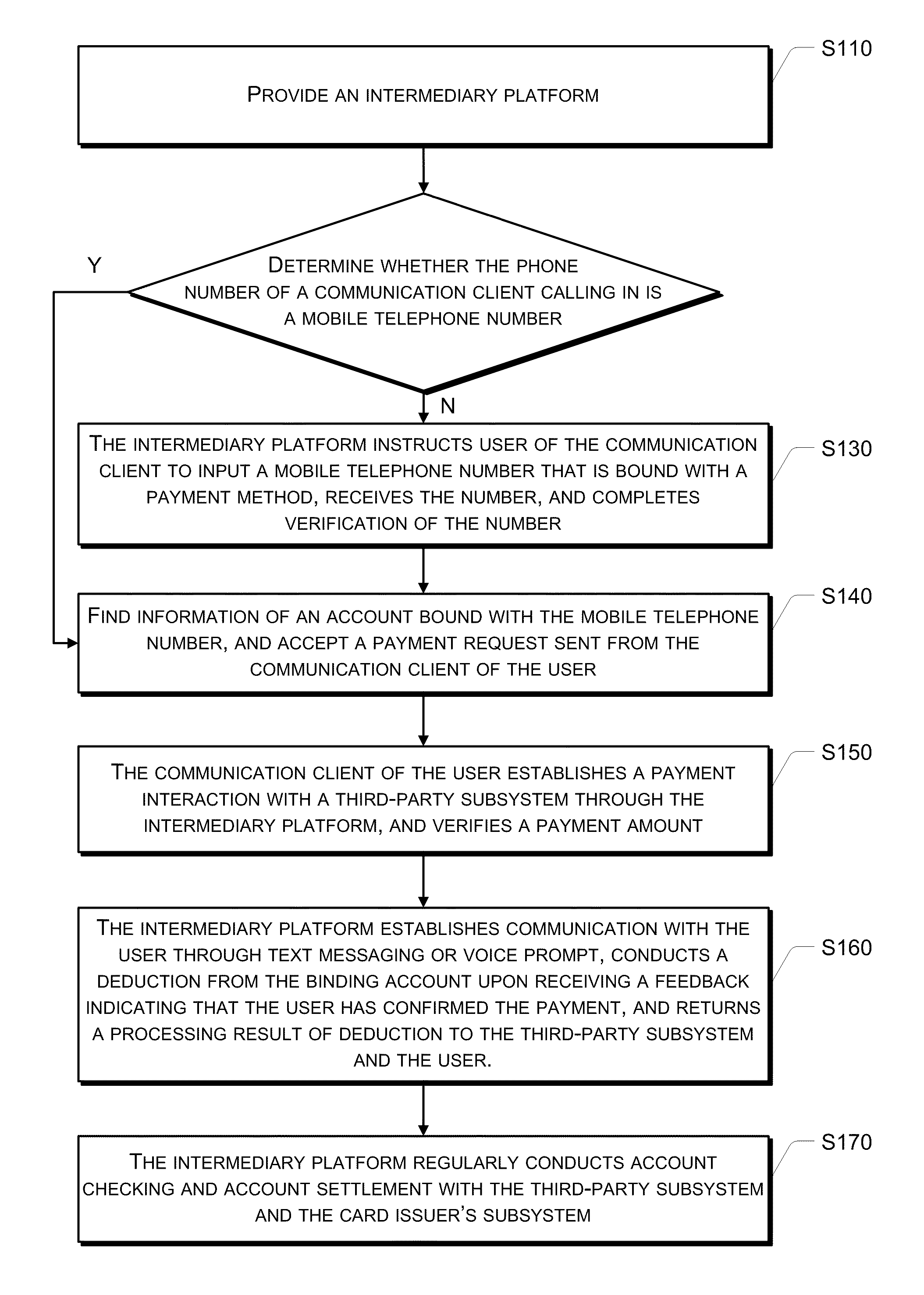
Making Payment Using Communication Client
InactiveUS20100153249A1Convenient and highly secure and low-cost wayBusiness applicationMetering/charging/biilling arrangementsUnauthorised/fraudulent call preventionMobile telephonyClient-side
Disclosed are a method and a system for making a payment to a third party using a communication client such as a mobile phone. The payment is made through an intermediary platform adapted for establishing communication between the communication client and the third-party subsystem. The intermediary platform receives a call-in request from the communication client, determines whether the communication client has a mobile telephone number, and further determines whether the mobile telephone number has a payment account bound therewith. If affirmative, the intermediary platform accepts a payment request from the communication client, and makes a deduction from the payment account in order to complete the payment. The intermediary platform may also be used to make a payment to the third-party through a network client such as a PC.
Owner:ALIBABA GRP HLDG LTD
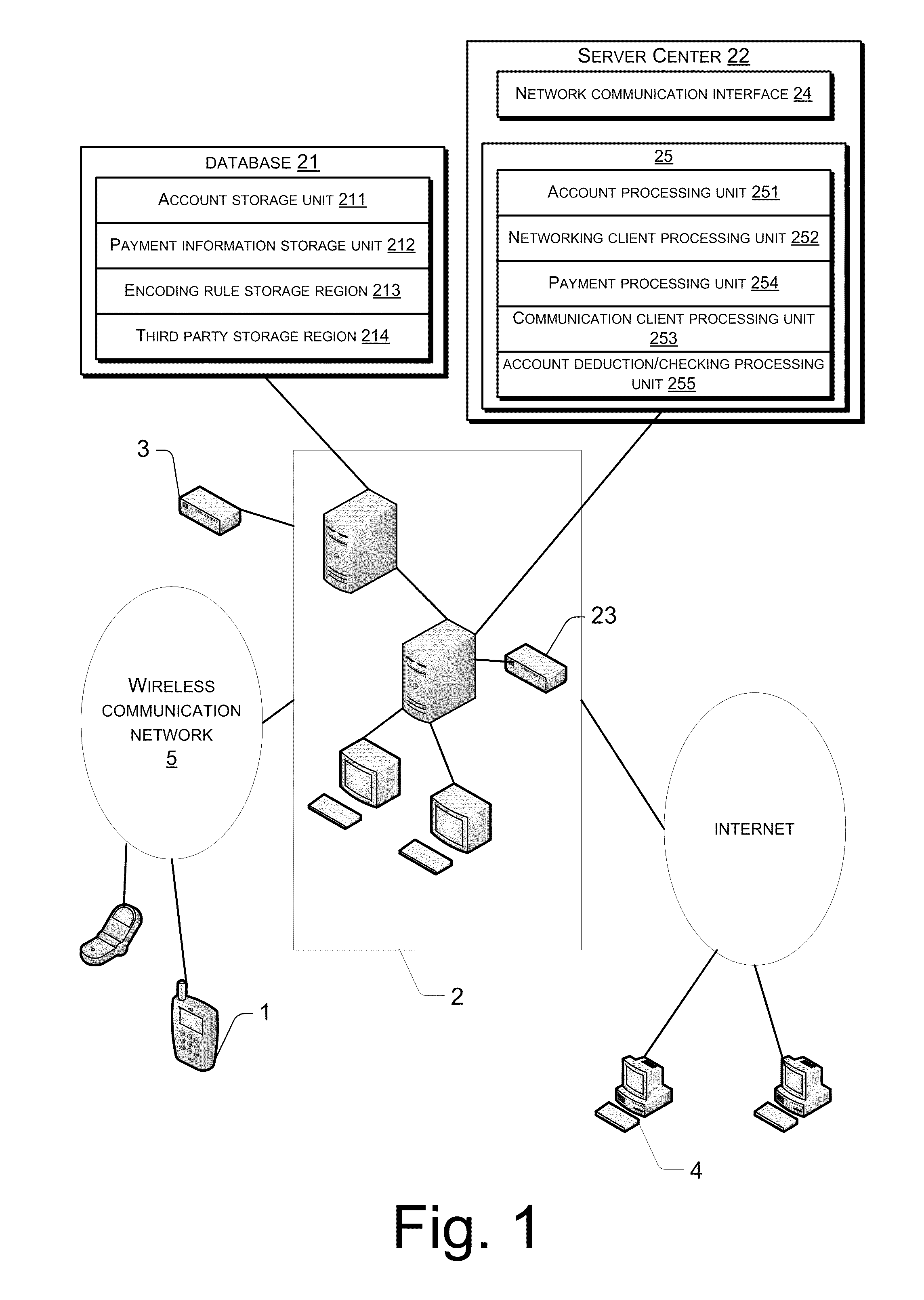
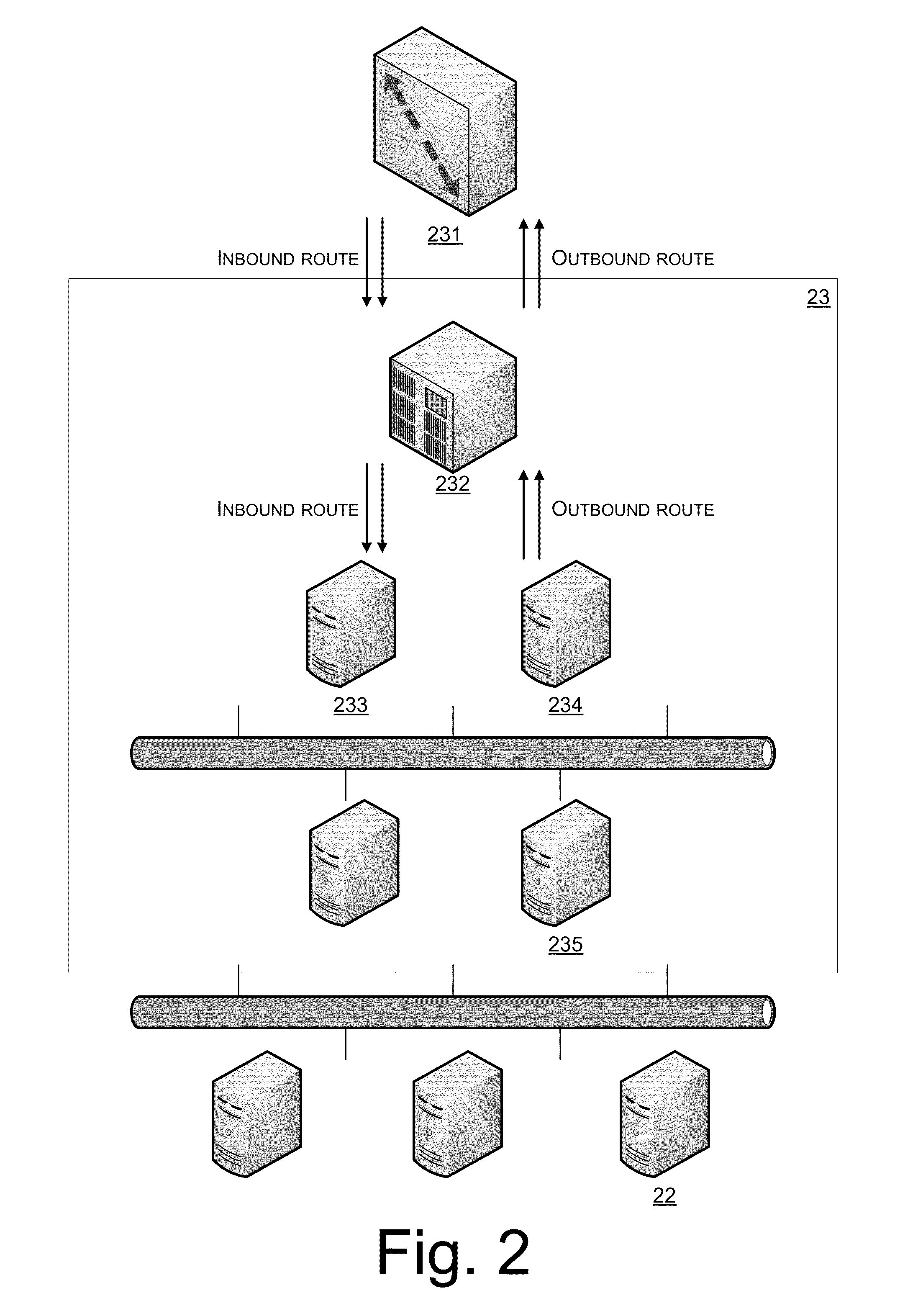
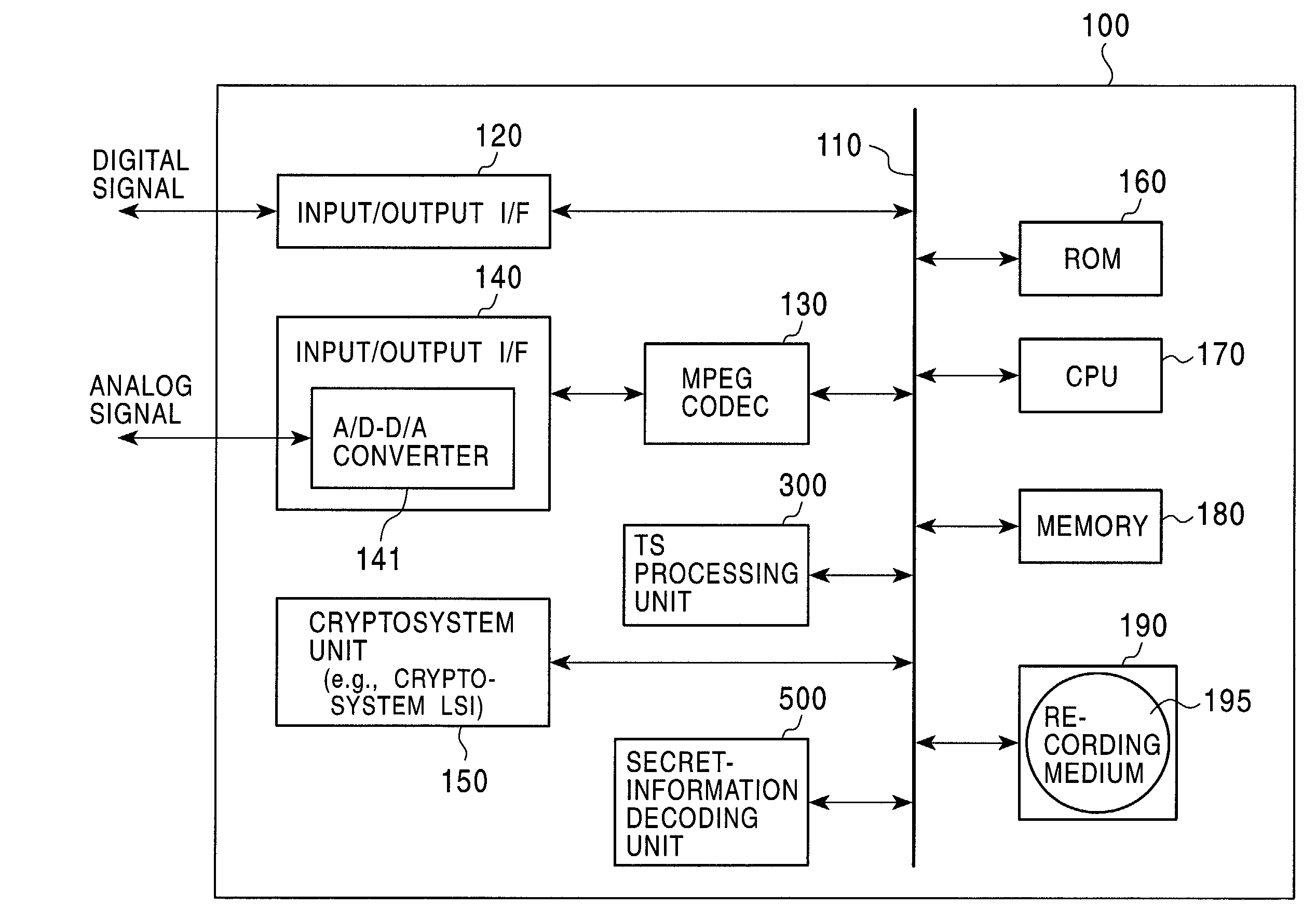
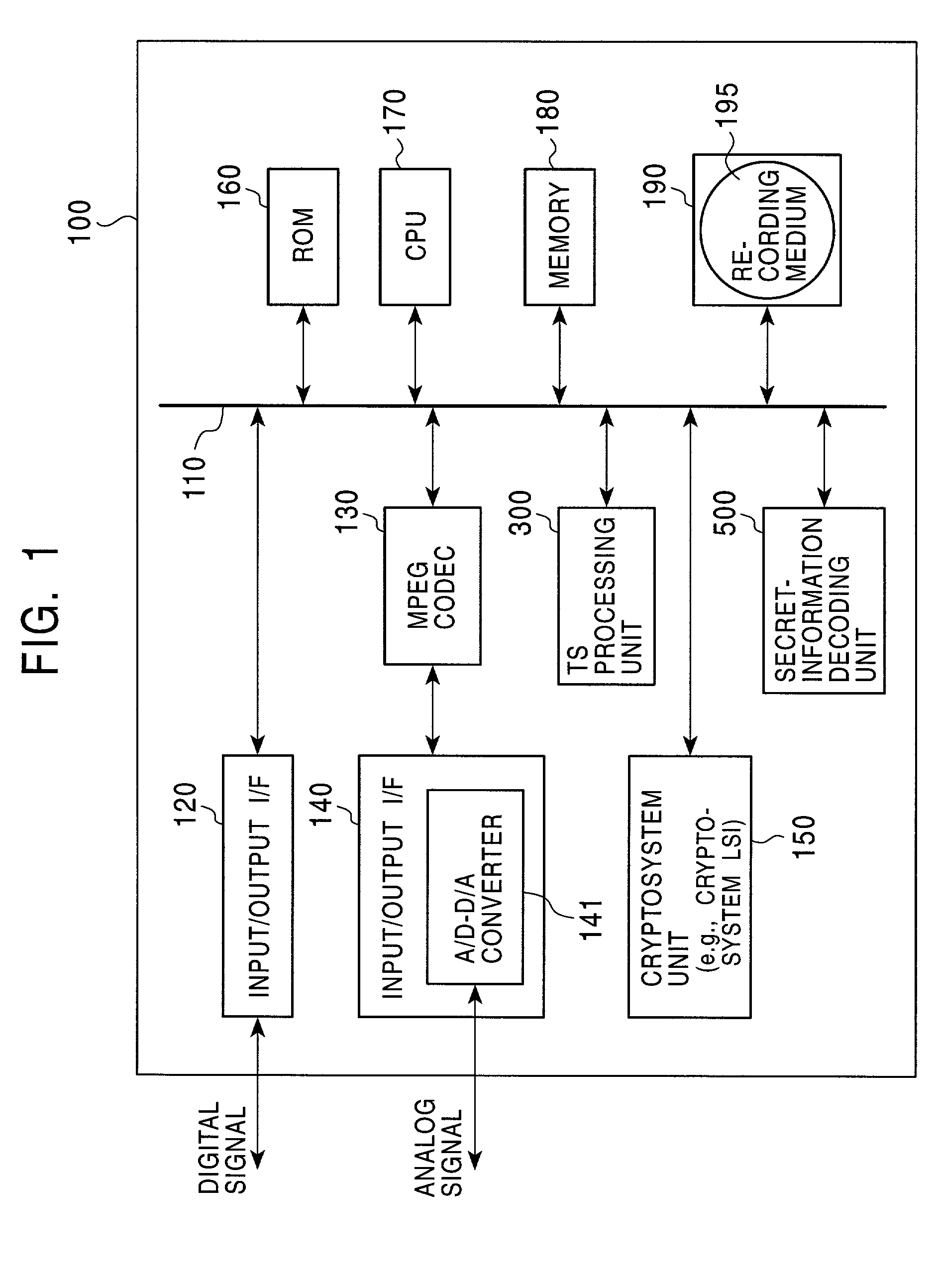
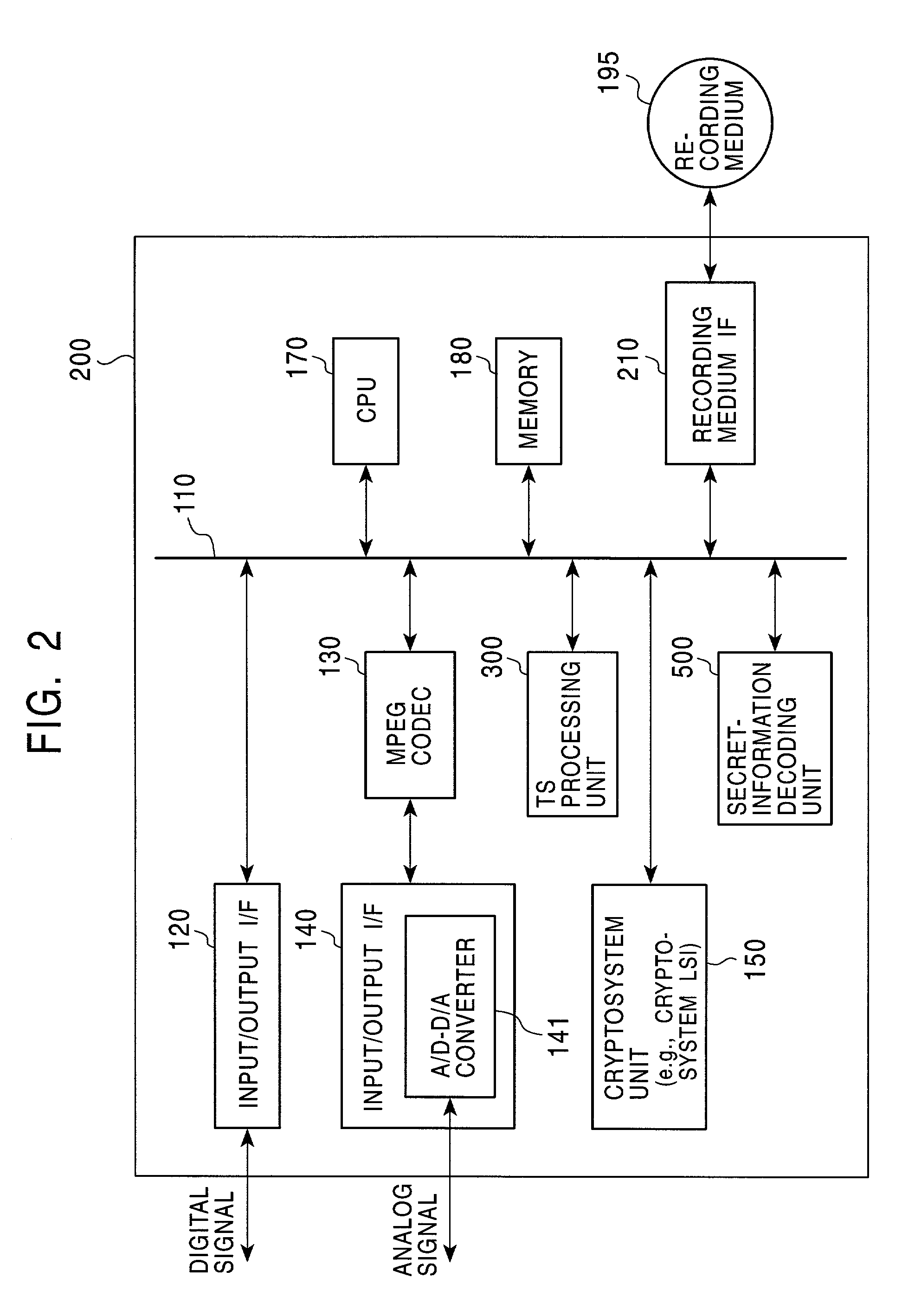
Information recording device, information playback device, information recording method, information playback method, and information recording medium and program providing medium used therewith
InactiveUS7319752B2Raise security concernsUnauthorized useTelevision system detailsKey distribution for secure communicationComputer hardwareCryptosystem
An information recording / playback device stores beforehand, on a recording medium, secret information in which a writing / reading method thereof cannot be analyzed and which can be read only by a special reading method. The secret information is applied to a key for content encryption or decryption when performing recording or playback of contents on the recording medium, such as music data and image data. The secret information is, for example, a stamper ID. By using the stamper ID as secret information, and a master key and a media key which are distributed in a tree-structure key-distribution system, a content-cryptosystem key is generated. Accordingly, each content is allowed to be used in only an appropriate device in which the special reading method for the secret information can be executed and to which the key is distributed by the tree-structure key-distribution system.
Owner:SONY CORP
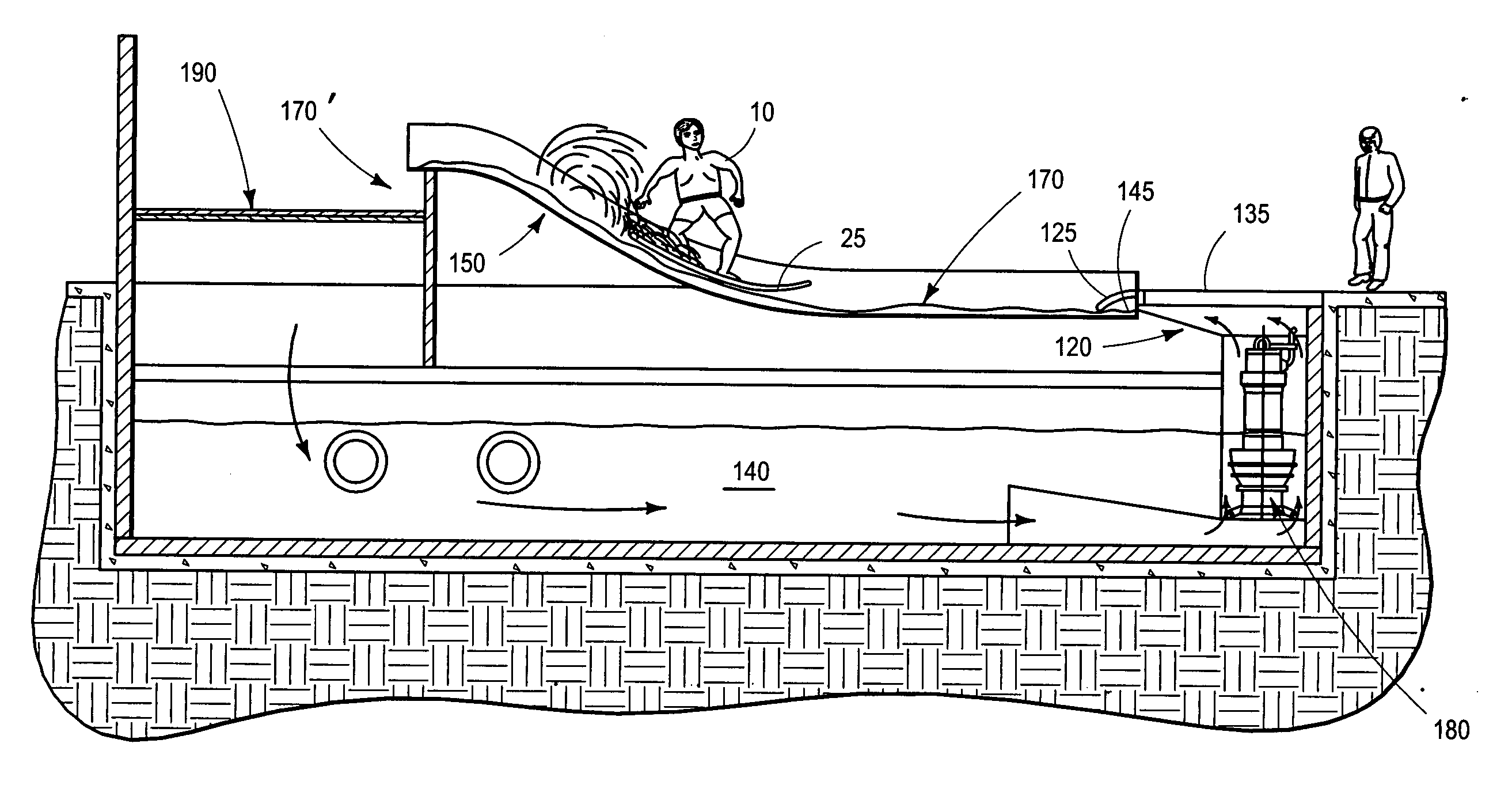
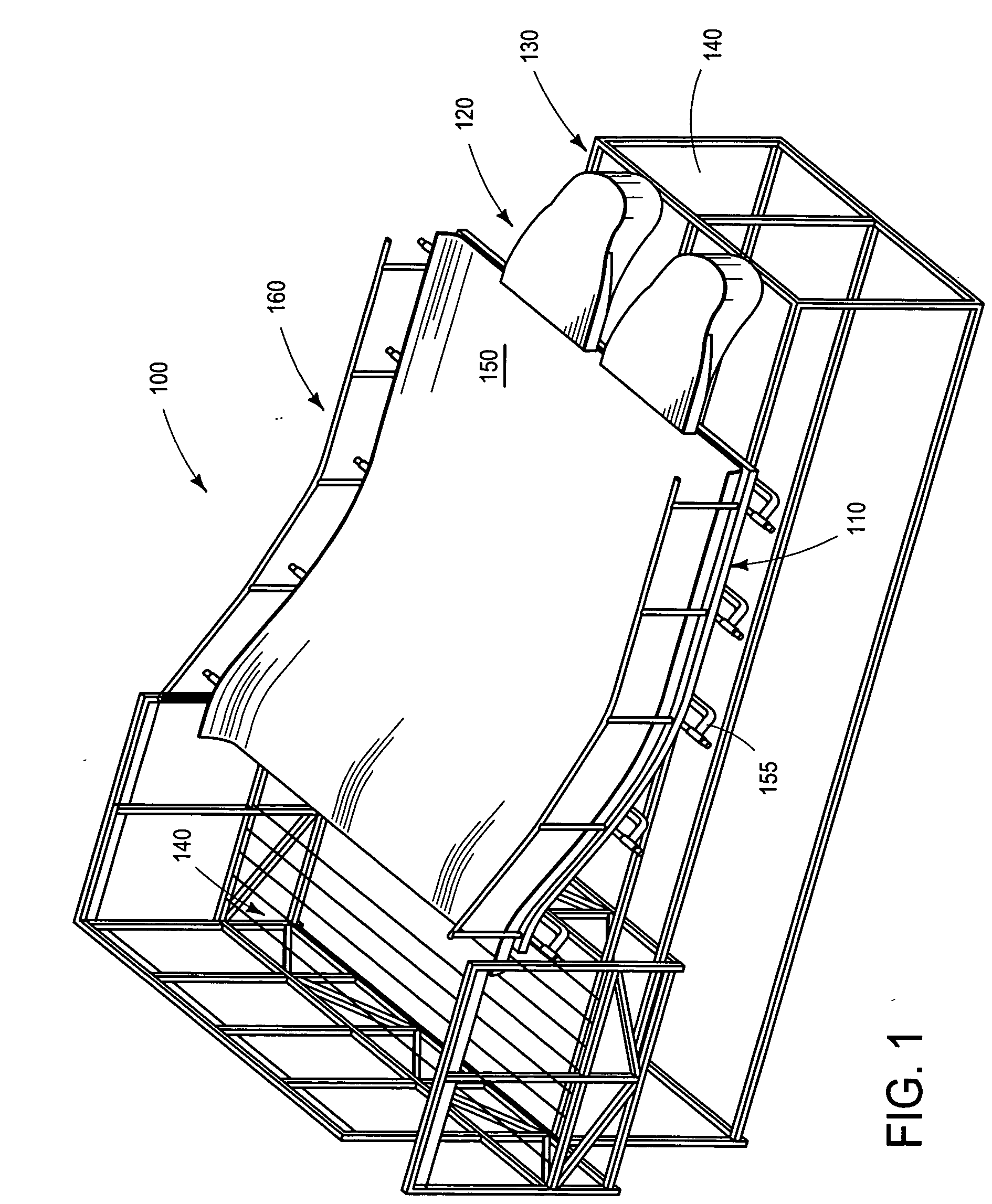
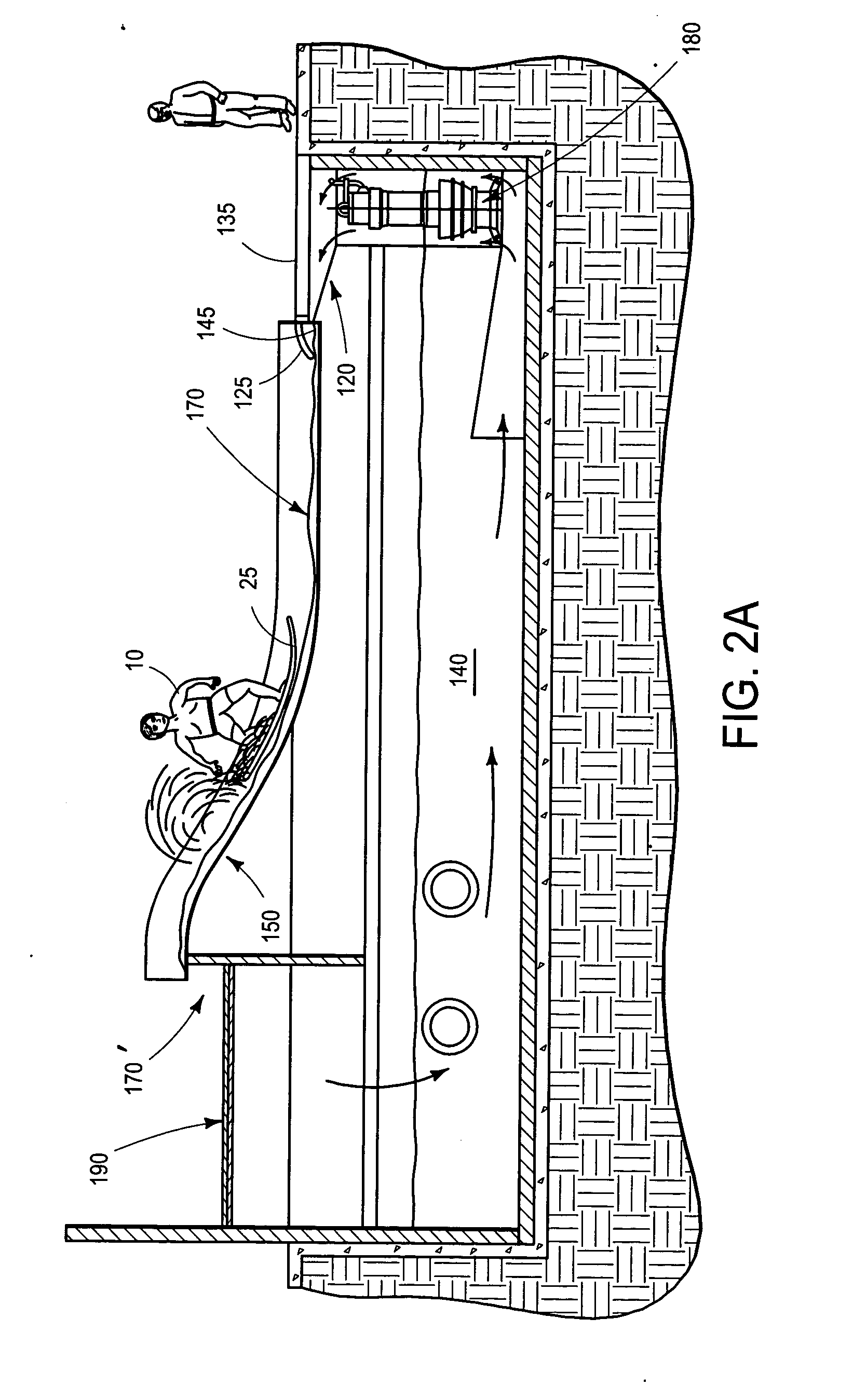
Contoured variably tensionable soft membrane ride surface for ride attraction
InactiveUS20050148398A1SaferRaise security concernsSki bindingsLayered productsBraced frameWater flow
A ride surface for water ride attractions and the like is provided. The ride surface is fabricated from a reinforced membrane material tensioned over a supporting framework. The tensioned membrane ride surface serves the dual role of providing structural support for water flow and riders thereon while at the same time providing an impact safe surface that is non-injurious to riders who may fall thereon. The tensioned membrane can be adjusted actively and / or passively in order to accommodate different and varied ride experiences. Optionally, the shape of the membrane ride surface can be changed either dynamically or passively by special tensioning techniques and / or by using auxiliary support structures such as air bladders, pressure / suction, foam supports or / or the like.
Owner:WHITEWATER WEST INDS
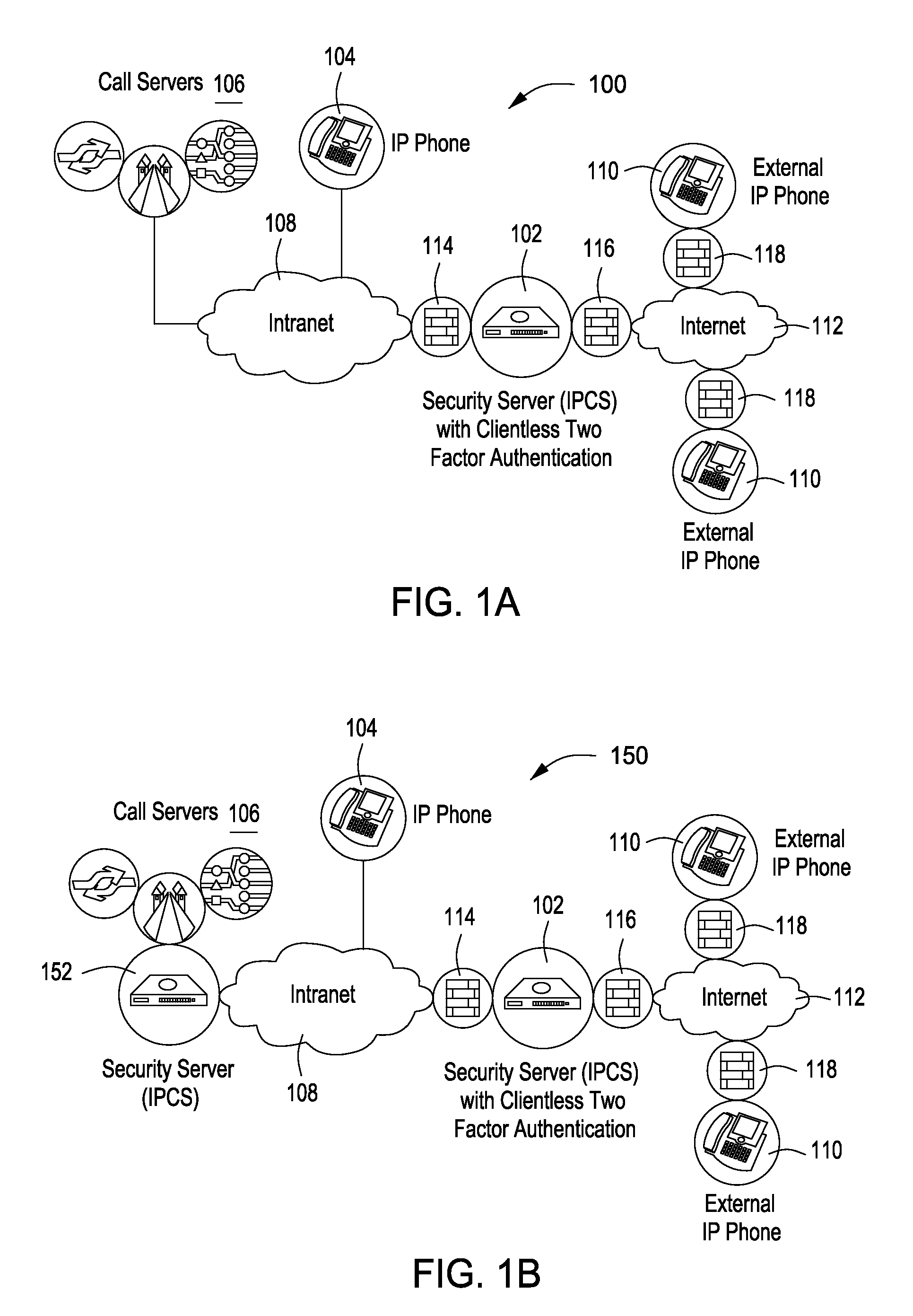
Computer network security system employing portable storage device
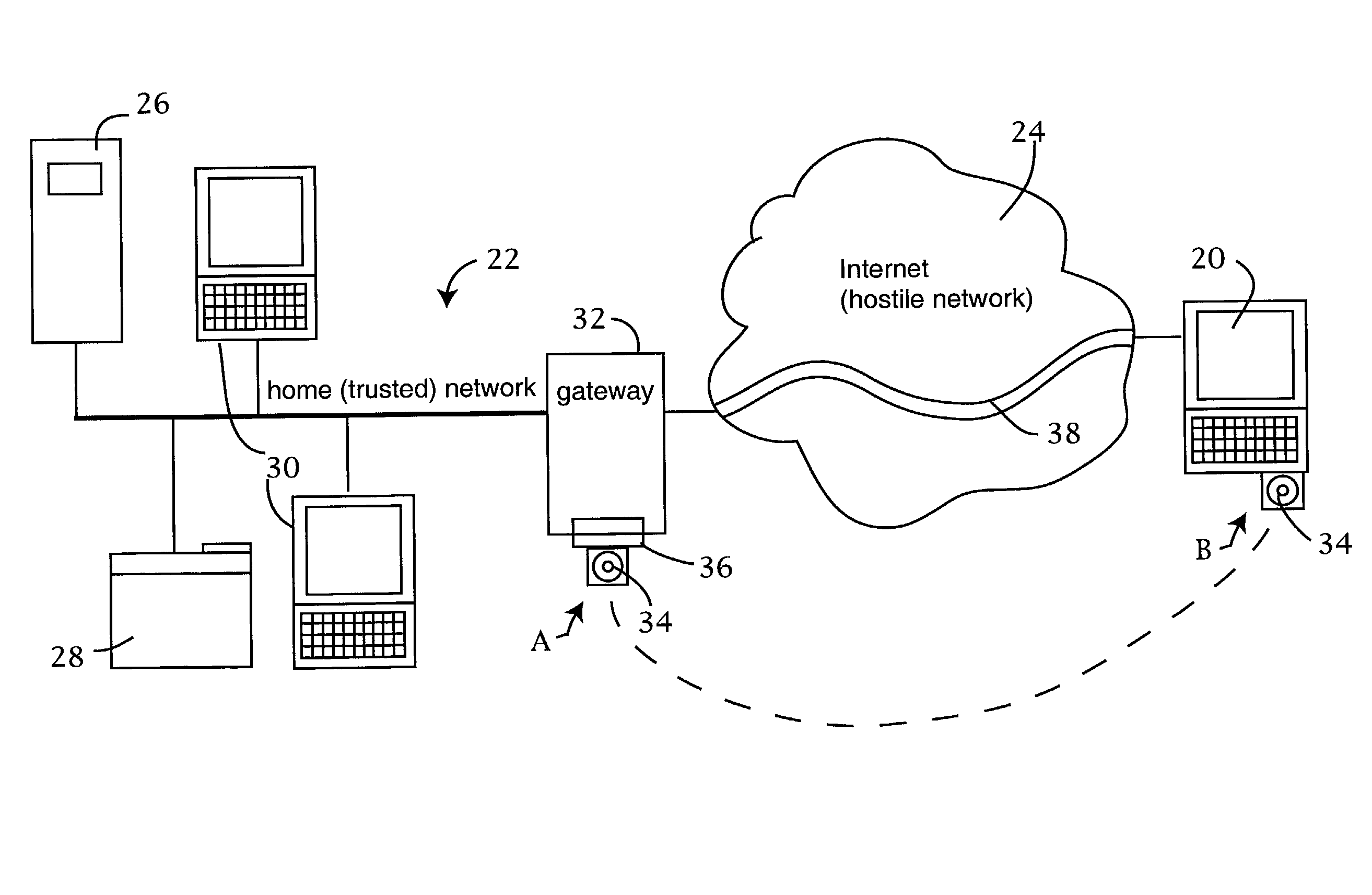
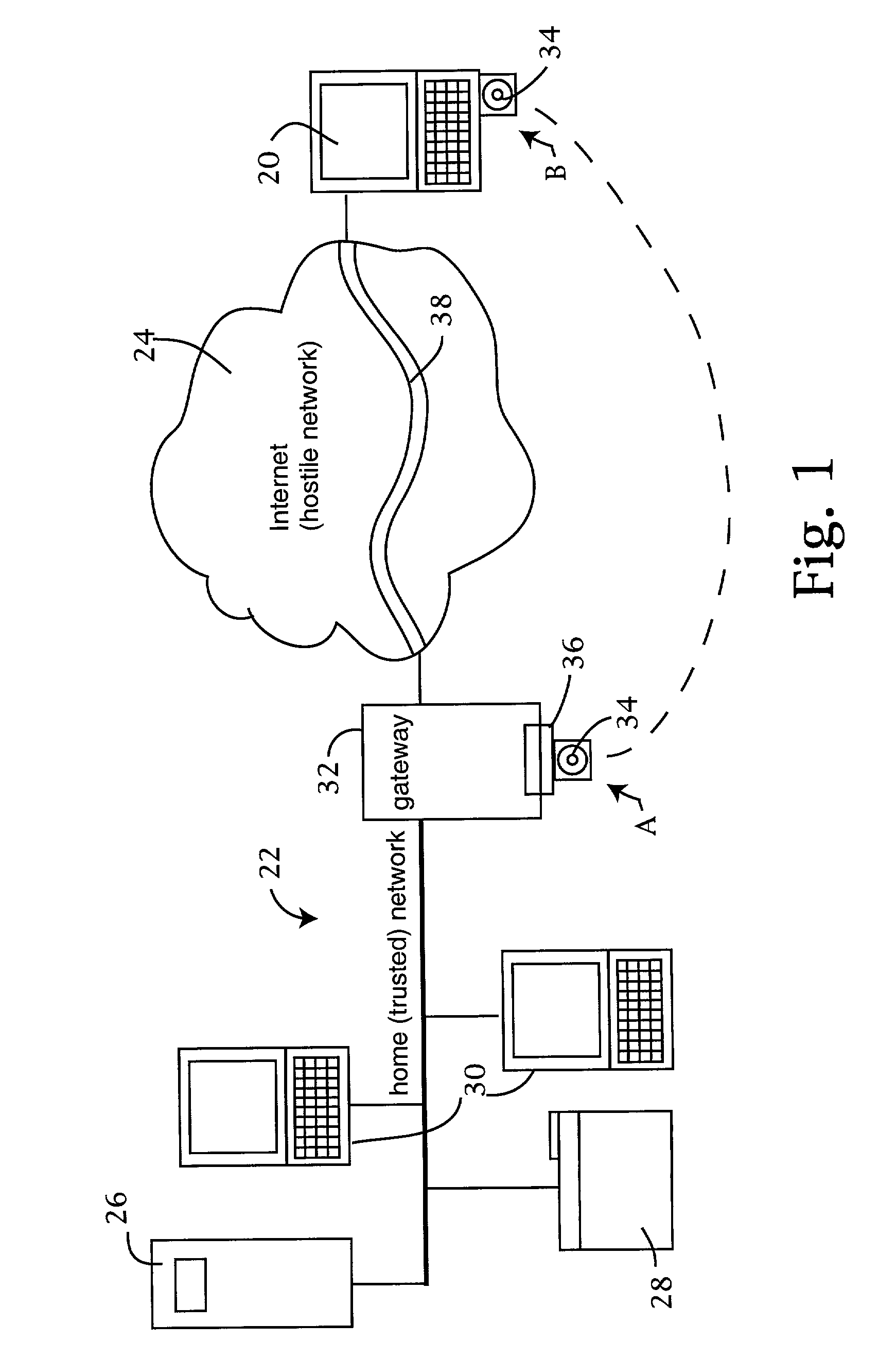
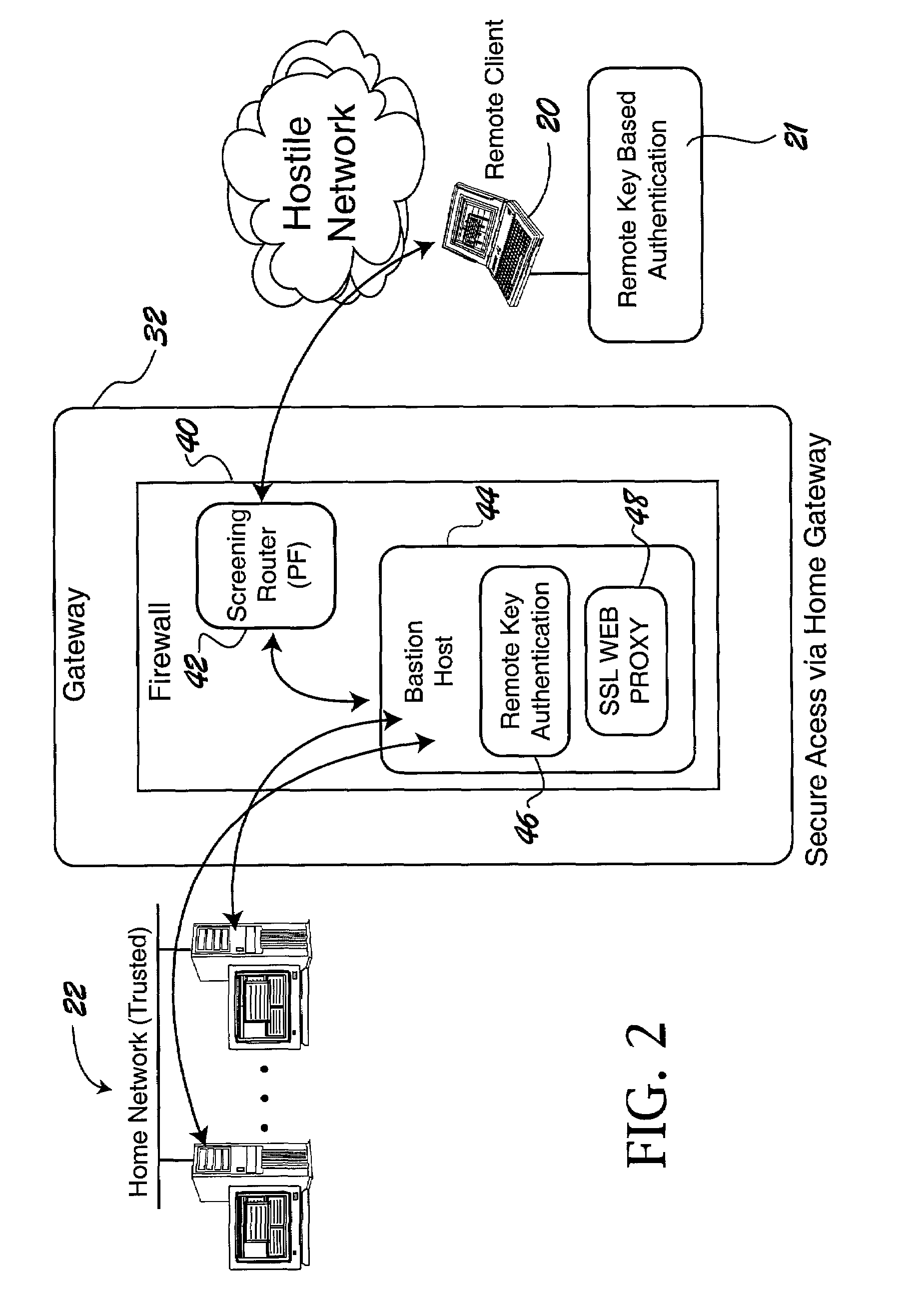
ActiveUS7228438B2Easy to useRaise security concernsUser identity/authority verificationUnauthorized memory use protectionUniform resource locatorClient machine
The trusted computer network is protected behind a gateway that includes a bastion host and screening router which blocks all URLs associated with the trusted network. The bastion host includes a remote client authentication mechanism and web proxy component that verifies and translates incoming URL requests from authenticated remote clients. Authentication is performed using one-time passwords that are stored on a portable storage device. The user configures the portable storage device by operating configuration software from the protected side of the gateway. The portable storage device also stores plug-in software to enable the client computer to properly retrieve the one-time password and exchange authentication messages with the bastion host. Further security is obtained by basing the one-time password on an encrypted version of the user's PIN. A symmetric key used to encrypt the PIN is stored in a protected area within the portable storage device.
Owner:SOVEREIGN PEAK VENTURES LLC
Method and system for the authentication of a user of a data processing system
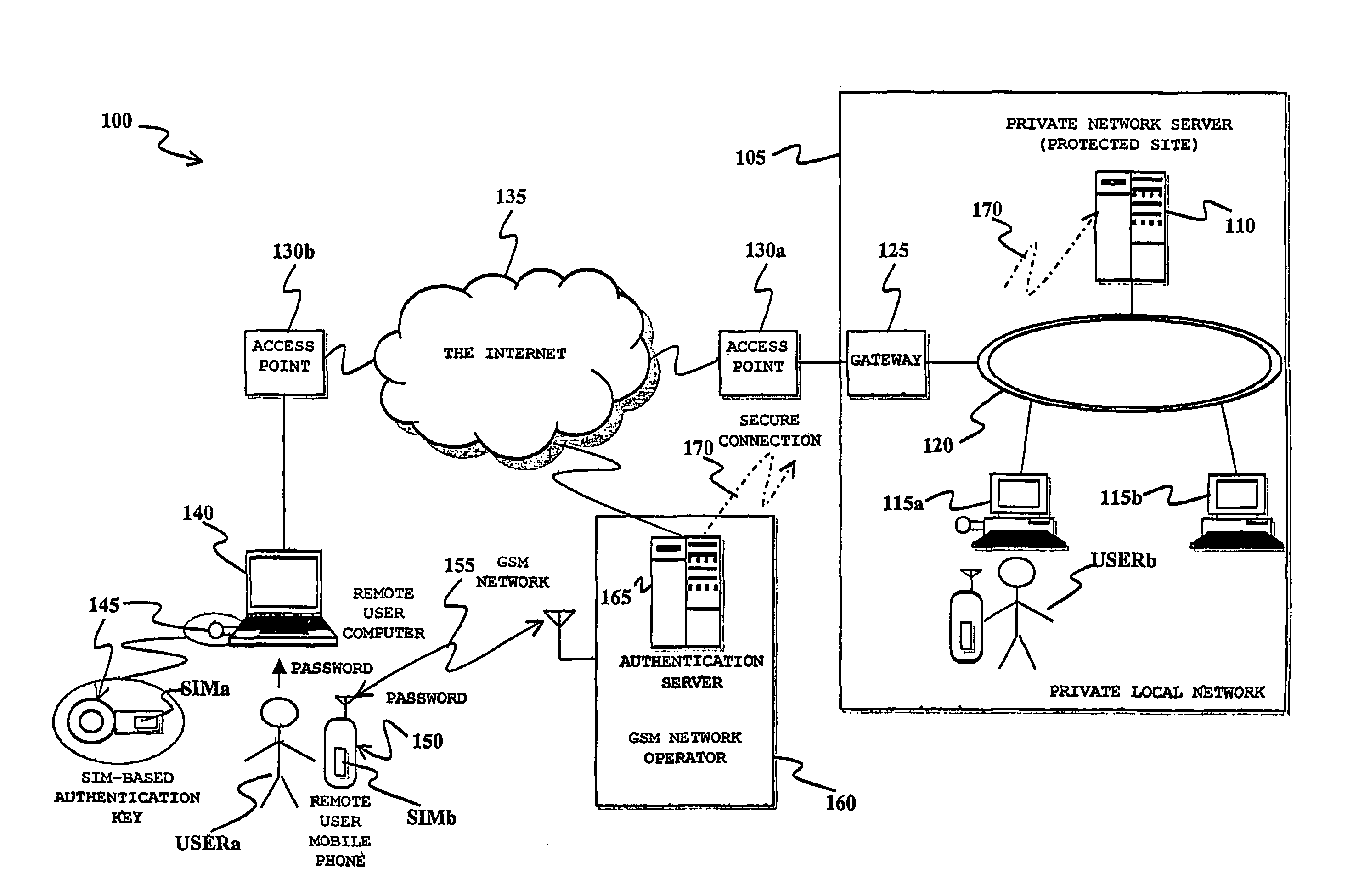
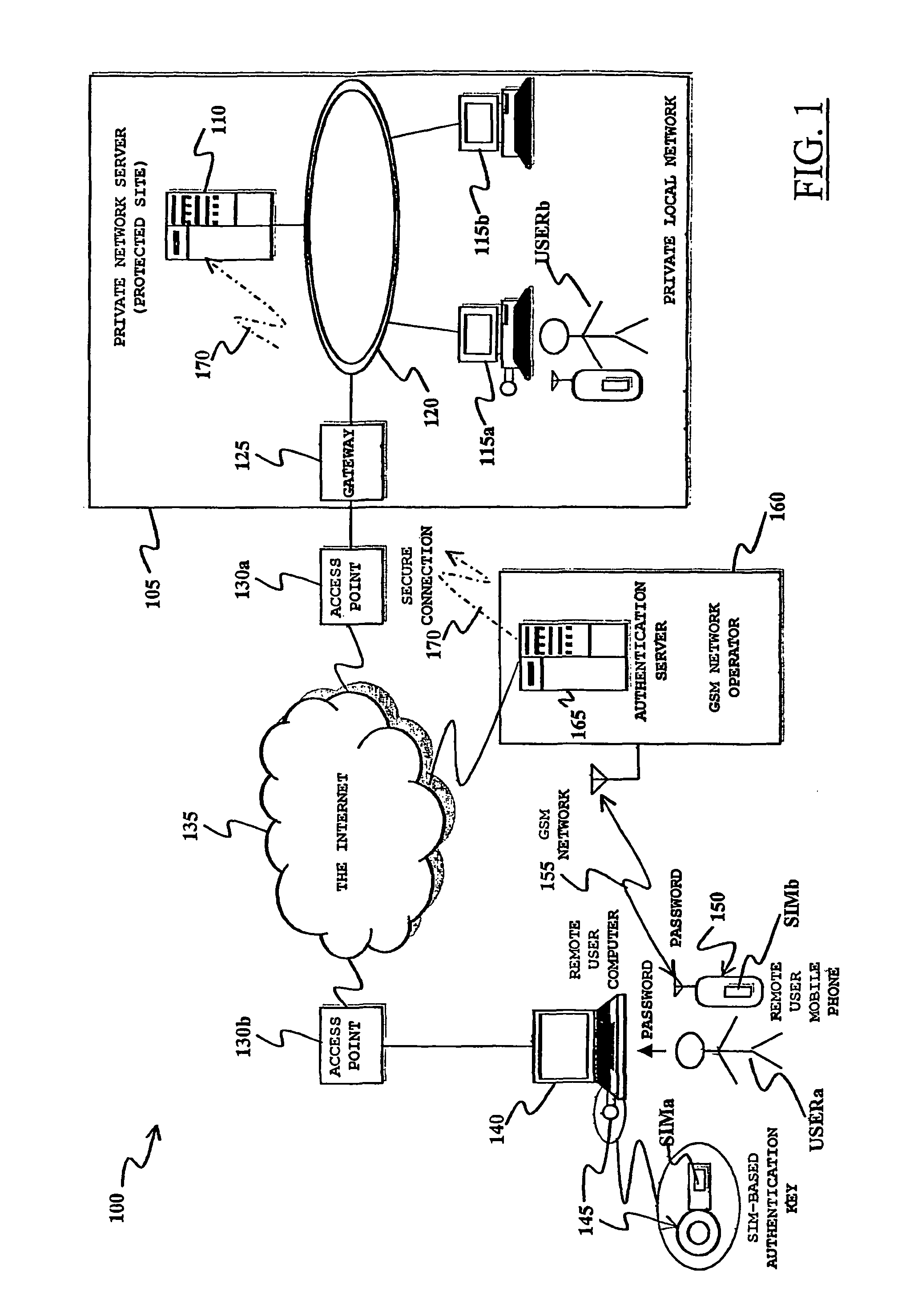
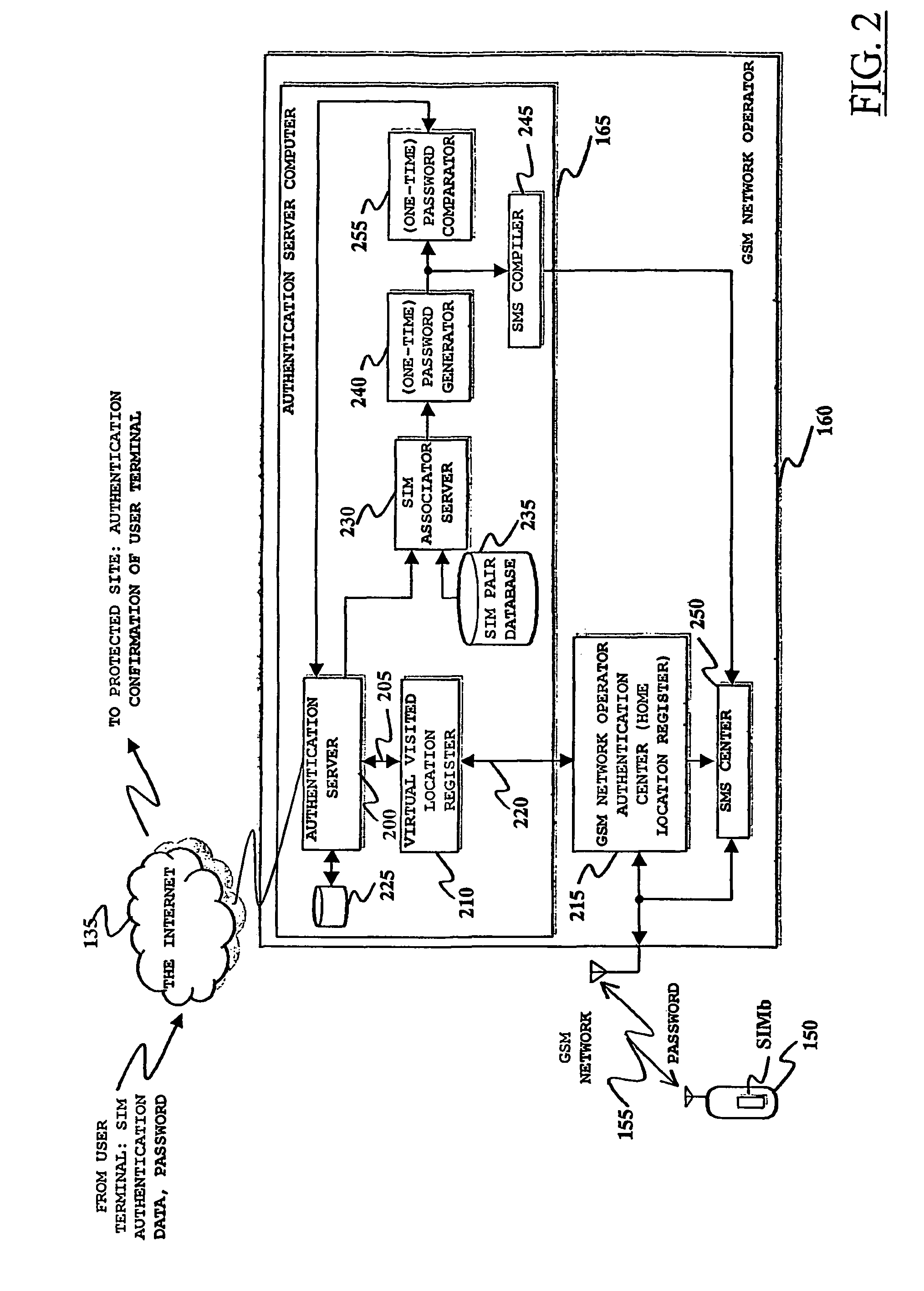
ActiveUS8166524B2Improve securityRaise security concernsElectric signal transmission systemsDigital data processing detailsData processing systemComputer module
A method of authenticating a user's data processing terminal for granting the data processing terminal access to selected services provided by a data processing system. The method includes performing a first, SIM-based authentication of the user's data processing terminal at an authentication data processing server in the data processing system, by operatively associating with the user's data processing terminal a first subscriber identity module issued to the data processing terminal user, for example, of a type adopted in mobile communication networks for authenticating mobile communication terminals. The authentication of the user's data processing terminal in the data processing system is conditioned to a second authentication, based on identification information provided to the user at a mobile communication terminal through a mobile communication network to which the mobile communication terminal is connected, e.g. in the form of an SMS message.
Owner:TELECOM ITALIA SPA
Male luer lock connector for medical fluid lines
InactiveUS6843513B2Raise security concernsEasy to makeEngine sealsSurgeryMechanical engineeringMedical treatment
A male luer lock connector for medical fluid lines comprising an elongated tubular body having an end portion with external luer cone and an internally threaded bushing mounted so that it can turn and slide on a portion with a cylindrical external surface of the tubular body. Cooperating formations disposed between the portion with cylindrical external surface of the tubular body and the bushing are provided to produce during use a perceptible click when the bushing draws near to a fully advanced position of engagement with a female luer lock connector.
Owner:IND BORLA
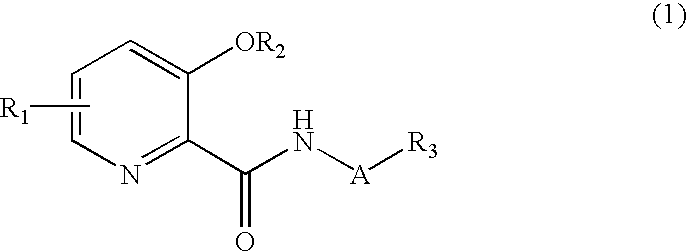
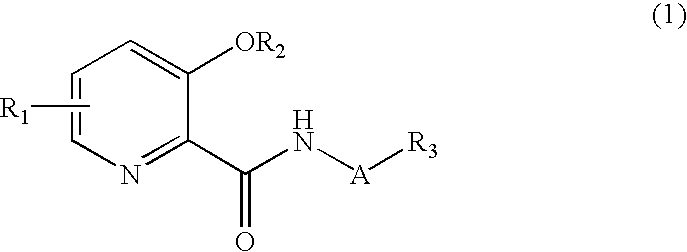
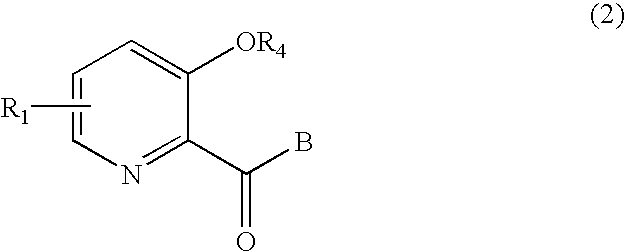
Picolinamide derivative and harmful organism control agent comprising said picolinamide derivative as active component
Disclosed are novel compounds useful for the control of harmful organisms, harmful organism control agents using the same, and processes for producing the novel compounds. The useful novel compounds according to the present invention include compounds represented by formula (1). The compounds represented by formula (1) have potent activity against harmful organisms, and do not have phytotoxicity against agricultural and gardening plants, as objects to which the compounds of the present invention are applied for preventive and exterminating purposes, and human beings and beastswherein A represents a bond or an optionally substituted alkylene chain; R1 represents one or more groups, which may be the same or different, selected from the group consisting of a hydrogen atom, alkoxy, and haloalkoxy; R2 represents a hydrogen atom, benzyl, alkyl or alkanoyl, in which the groups other than the hydrogen atom may be substituted; and R3 represents a hydrogen atom, cycloalkyl, cycloalkenyl, aryl or a heterocyclic group, in which the groups other than the hydrogen atom may be substituted, excluding the case where R1 represents a hydrogen atom, A represents a bond or a methylene chain, and R3 represent phenyl or cyclohexyl, and the case where A represents an alkylene chain and R3 represents a hydrogen atom.
Owner:MEIJI SEIKA KAISHA LTD
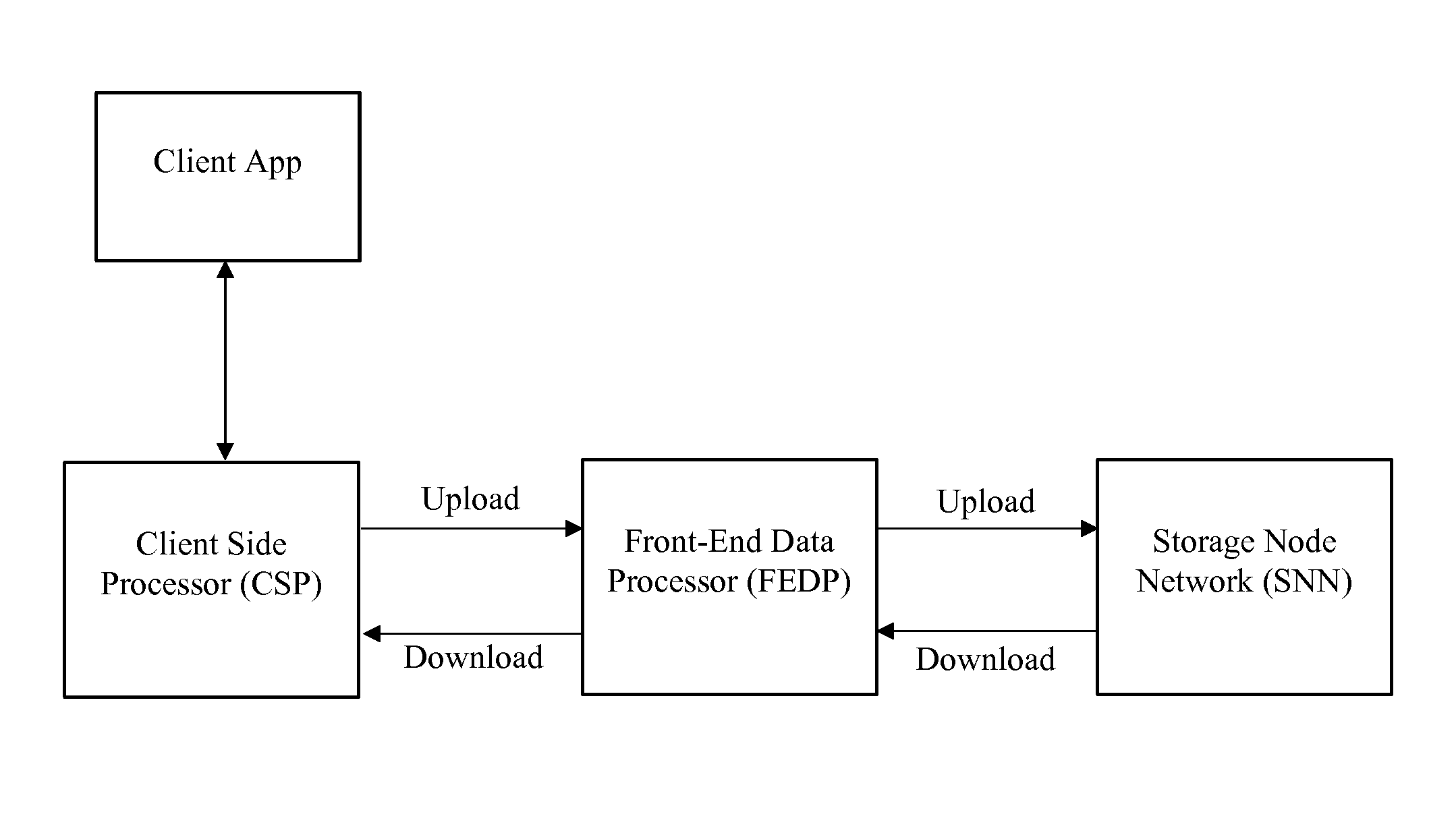
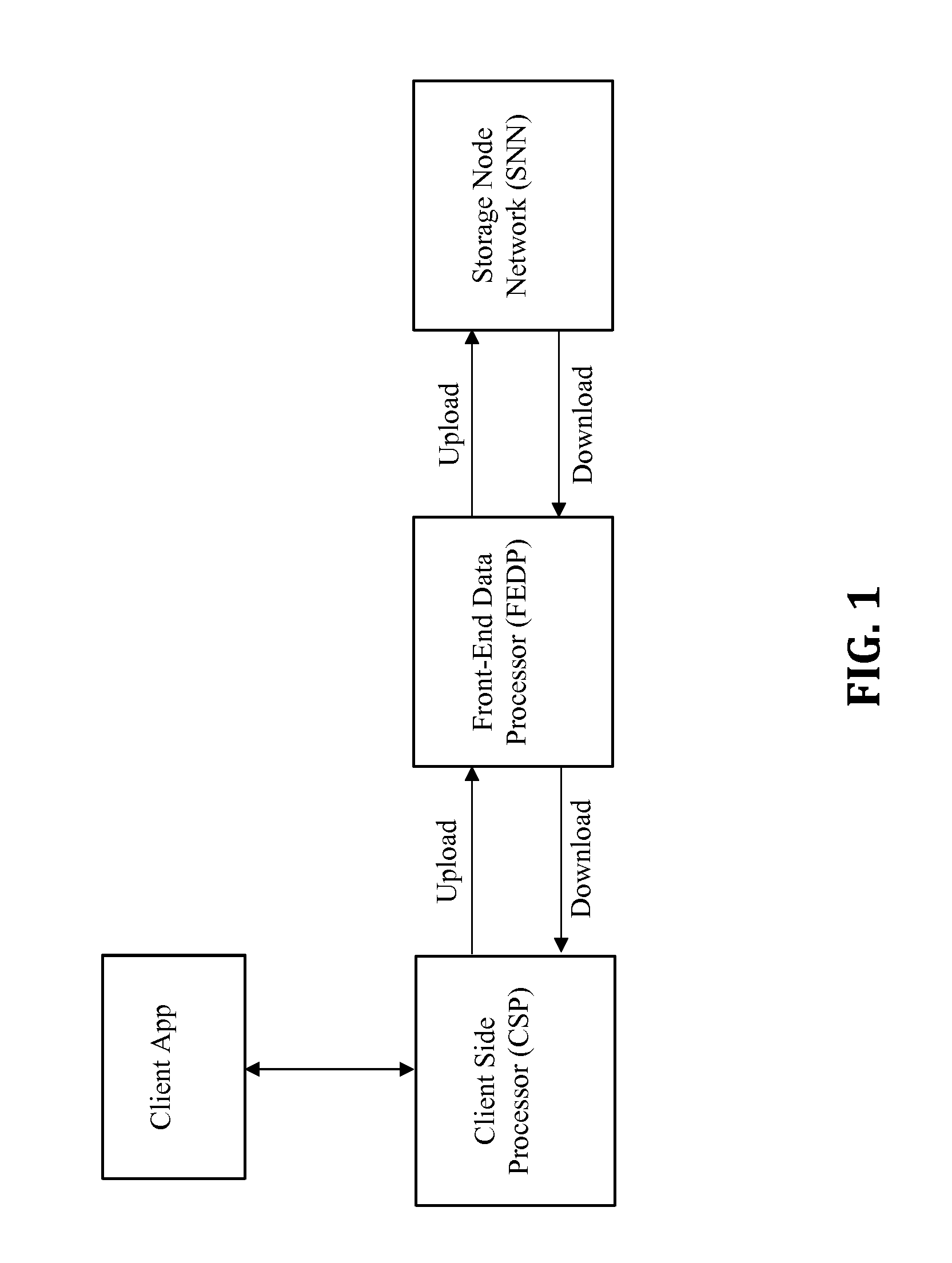
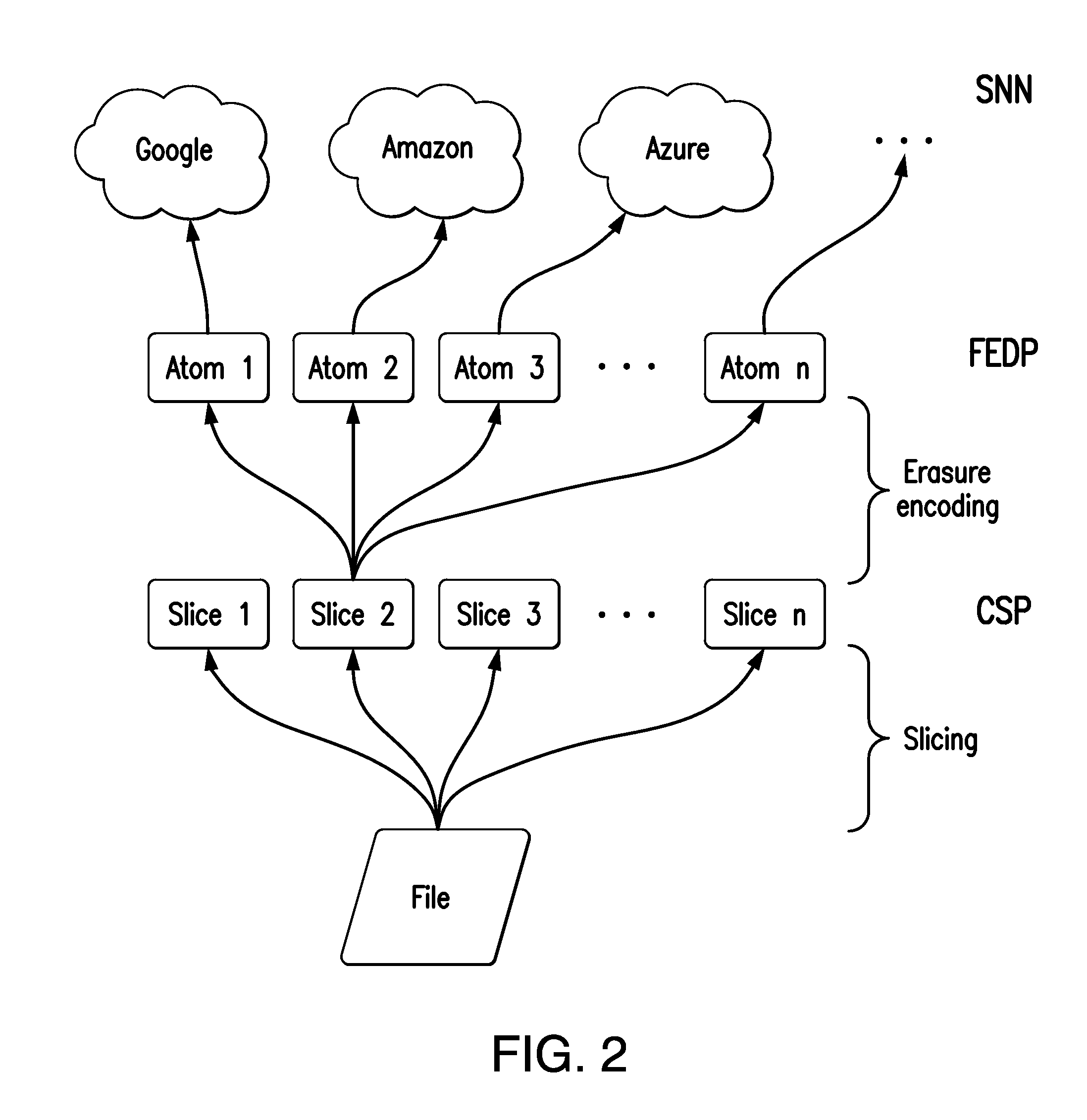
Distributed secure data storage and transmission of streaming media content
InactiveUS20170048021A1Increase safetyHigh degree of safetyError preventionCode conversionDistributed securityMedia content
Disclosed is a method for the distributed storage and distribution of data. Original data is divided into fragments and erasure encoding is performed on it. The divided fragments are dispersedly stored on a plurality of storage mediums, preferably that are geographically remote from one another. When access to the data is requested, the fragments are transmitted through a network and reconstructed into the original data. In certain embodiments, the original data is media content which is steamed to a user from the distributed storage.
Owner:DATOMIA RES LABS OU
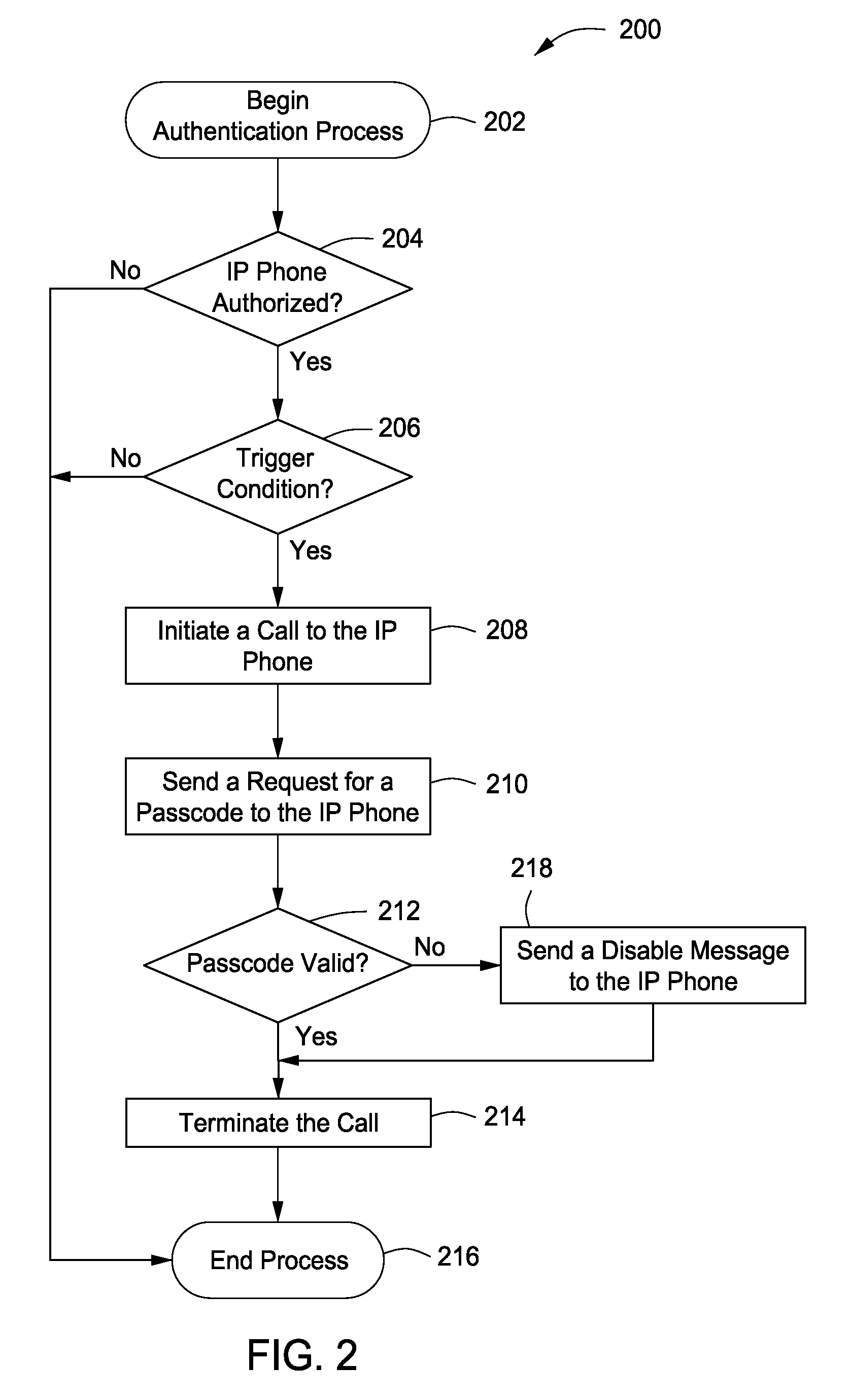
System, method and apparatus for authenticating and protecting an IP user-end device
ActiveUS20100107230A1Raise security concernsInterconnection arrangementsUnauthorised/fraudulent call preventionInternet privacyAttack
A system, method and apparatus authenticates and protects an Internet Protocol (IP) user-end device by providing a client-based security software resident on the IP user-end device, authenticating the IP user-end device using the client-based security software and a network security node communicably coupled to the IP user-end device, authenticating a user of the IP user-end device whenever a trigger condition occurs using an in-band channel between the client-based security software and the network security node, and protecting the IP user-end device by: (a) screening incoming IP traffic to the IP user-end device using the client-based security software, and (b) detecting an attack or a threat involving the IP user-end device using the network security node.
Owner:AVAYA INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com