Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
161 results about "Bastion host" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
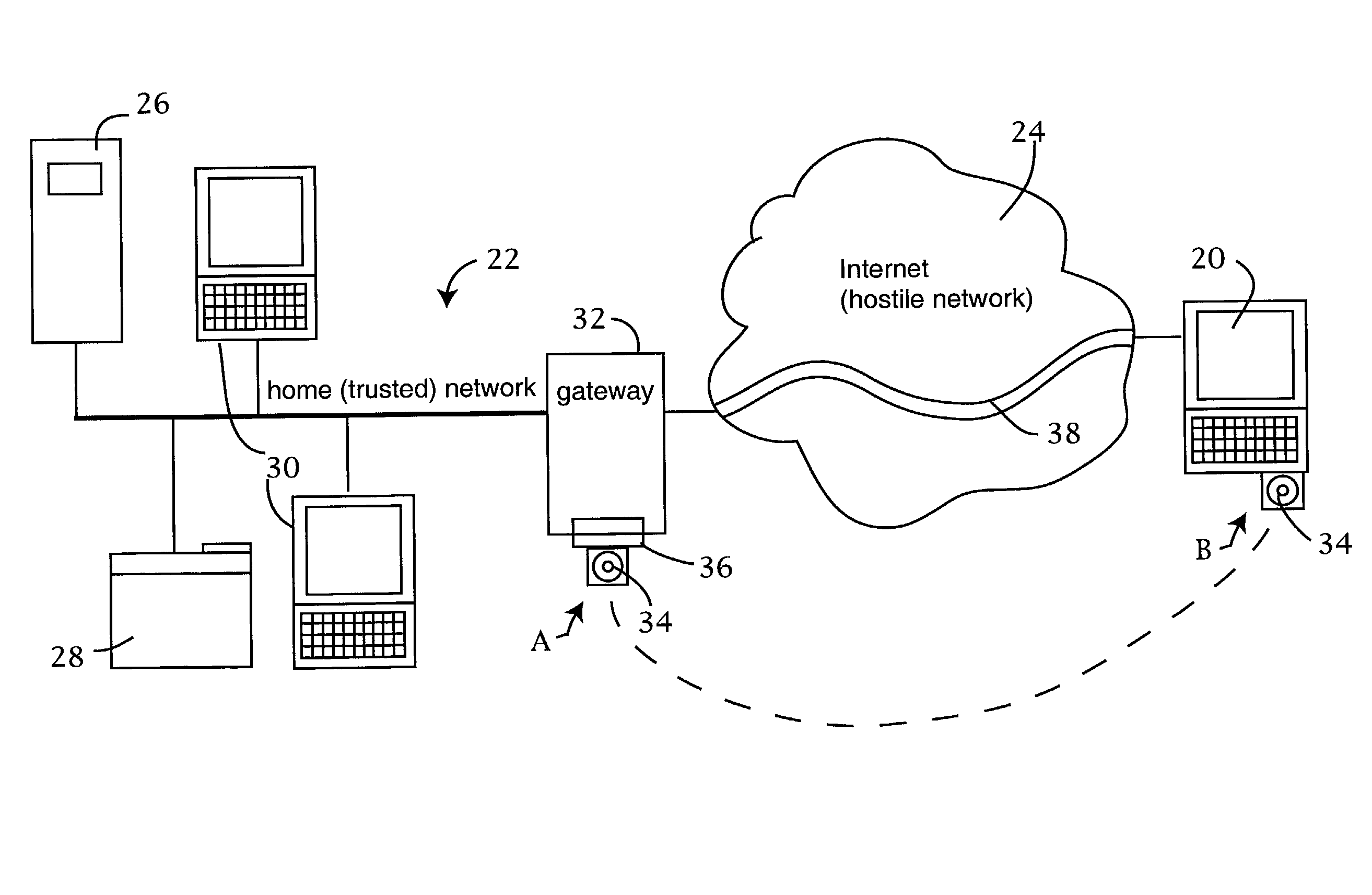
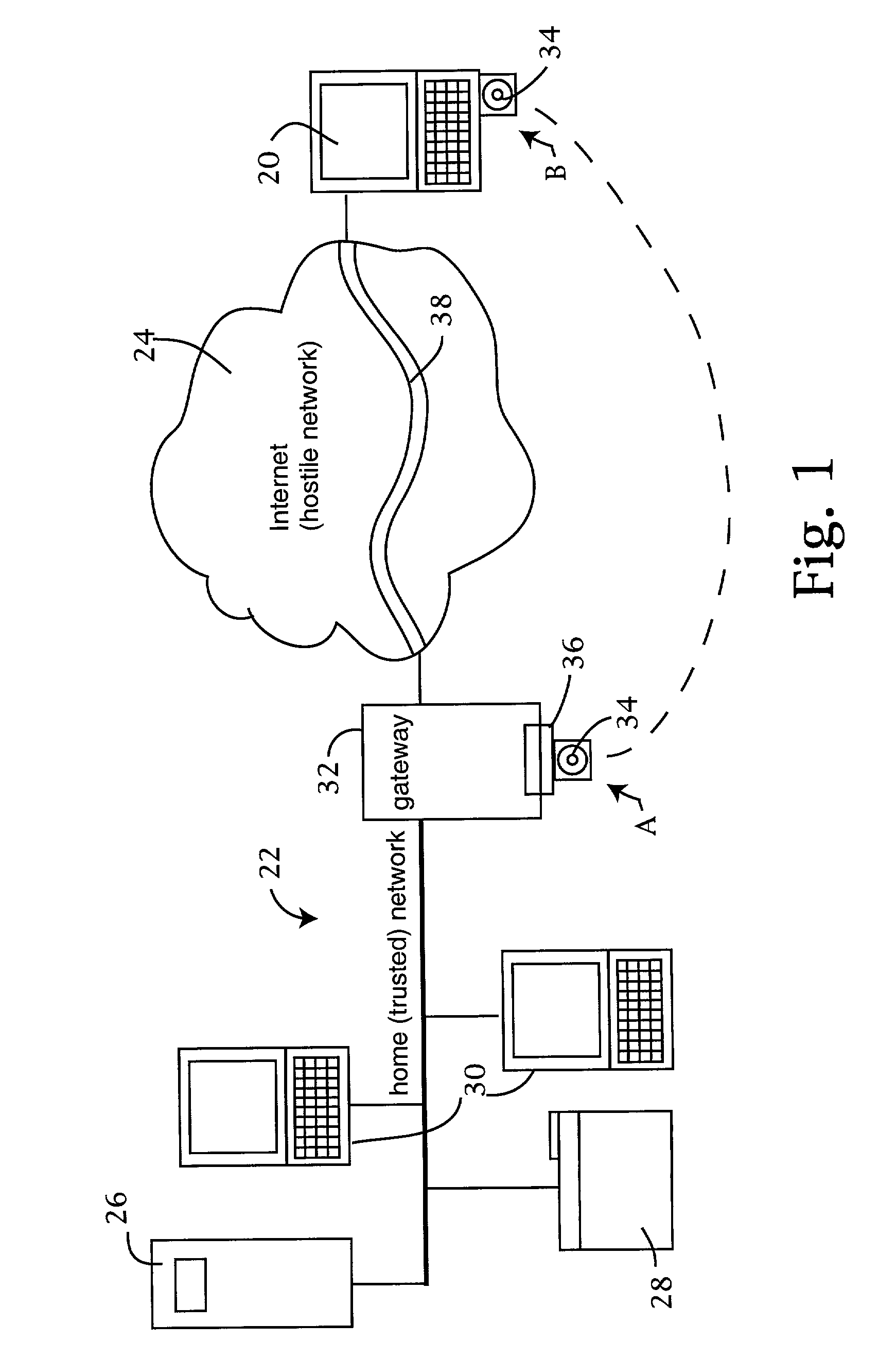
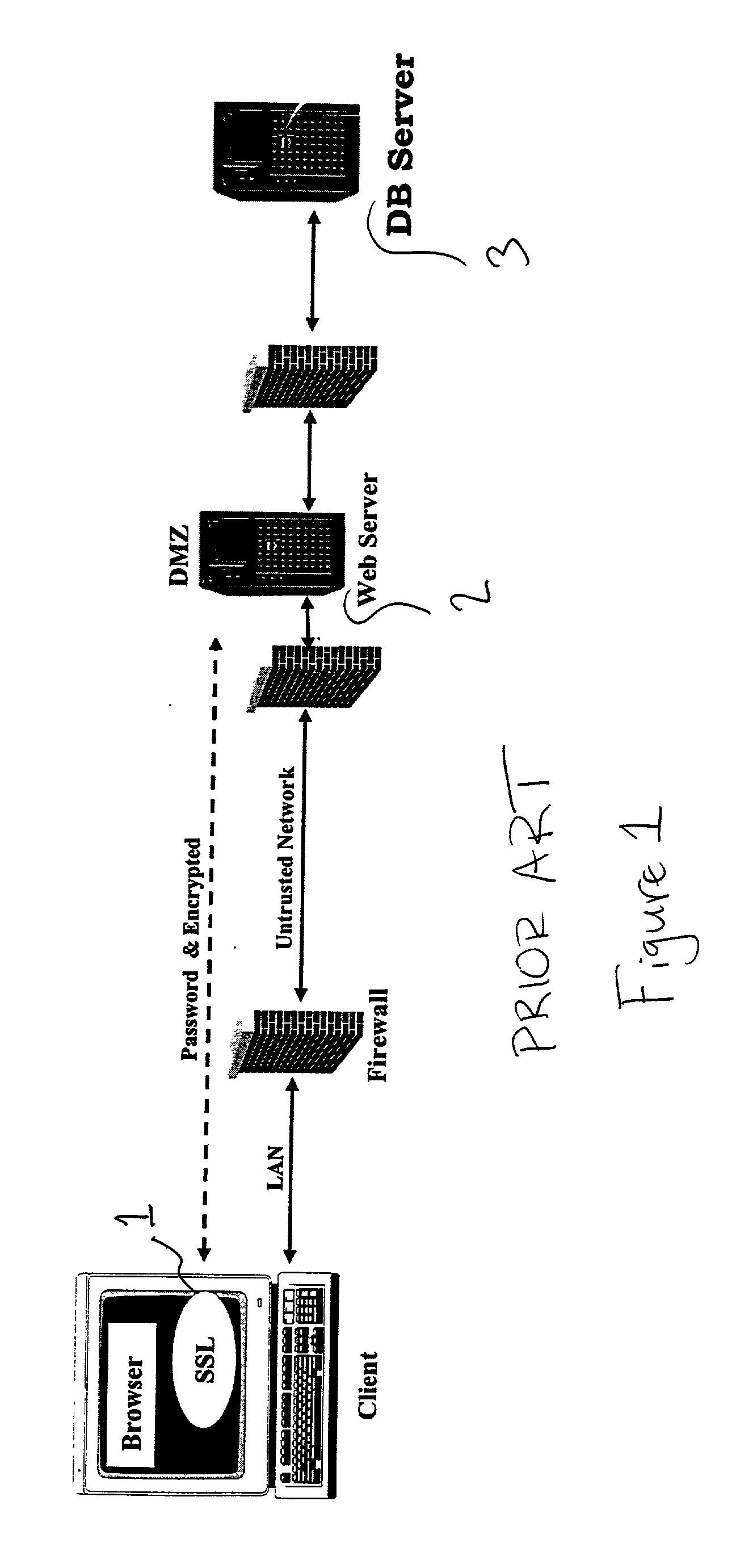
A bastion host is a special-purpose computer on a network specifically designed and configured to withstand attacks. The computer generally hosts a single application, for example a proxy server, and all other services are removed or limited to reduce the threat to the computer. It is hardened in this manner primarily due to its location and purpose, which is either on the outside of a firewall or in a demilitarized zone (DMZ) and usually involves access from untrusted networks or computers.
Computer network security system employing portable storage device
ActiveUS7228438B2Easy to useRaise security concernsUser identity/authority verificationUnauthorized memory use protectionUniform resource locatorClient machine
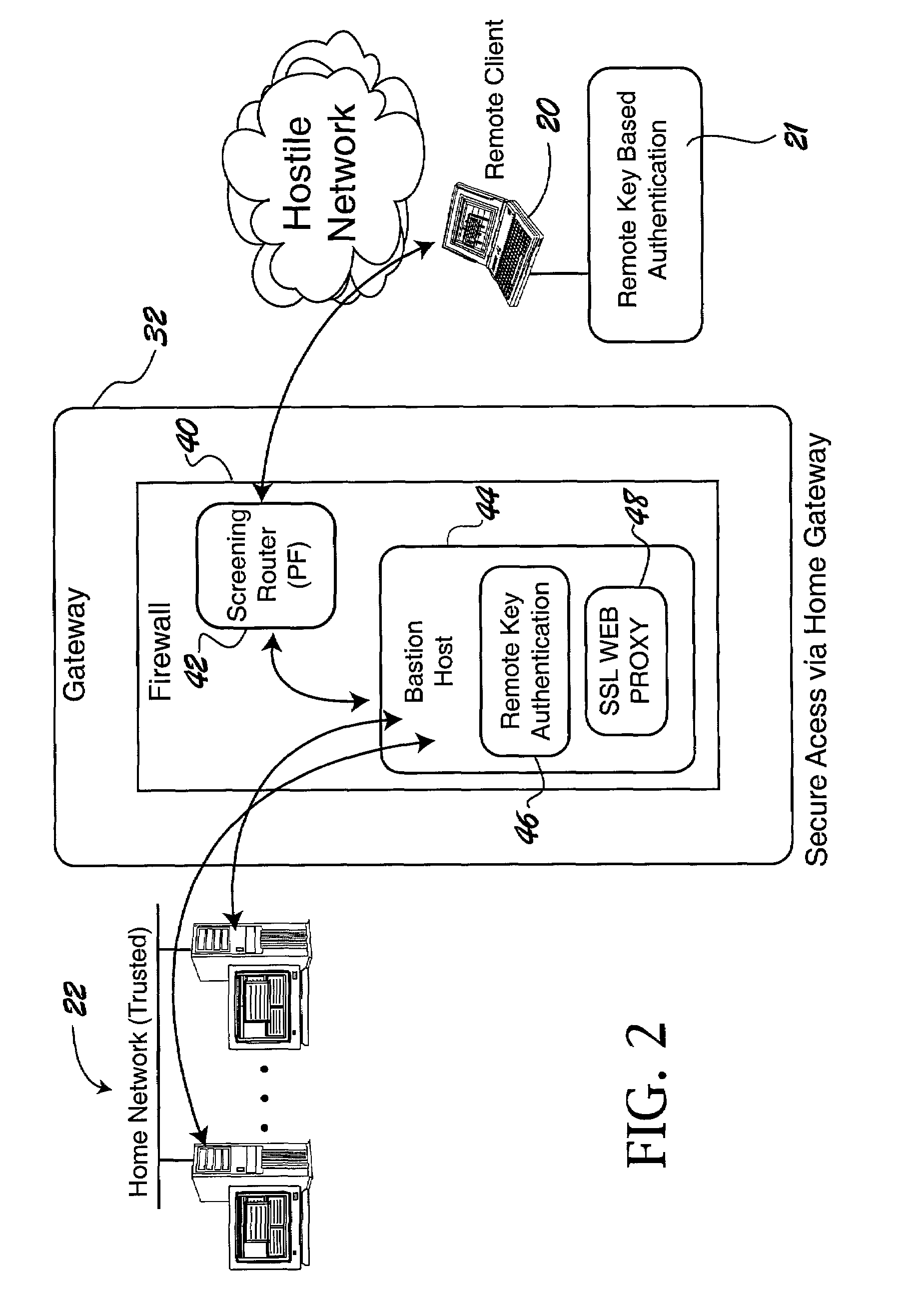
The trusted computer network is protected behind a gateway that includes a bastion host and screening router which blocks all URLs associated with the trusted network. The bastion host includes a remote client authentication mechanism and web proxy component that verifies and translates incoming URL requests from authenticated remote clients. Authentication is performed using one-time passwords that are stored on a portable storage device. The user configures the portable storage device by operating configuration software from the protected side of the gateway. The portable storage device also stores plug-in software to enable the client computer to properly retrieve the one-time password and exchange authentication messages with the bastion host. Further security is obtained by basing the one-time password on an encrypted version of the user's PIN. A symmetric key used to encrypt the PIN is stored in a protected area within the portable storage device.
Owner:SOVEREIGN PEAK VENTURES LLC
Arrangement in a data communication system
InactiveUS6578151B1Improve securityEasy maintenanceMultiple digital computer combinationsProgram controlCommunications systemDigital signature
The present invention relates to an arrangement a data communication system, wherein users, managers and / or machines (actors) intercommunicate via ports, especially comprising a Transport Service Access Port (TSAP) comprising port number and Internet Protocol (IP) address, which ports communicate through firewalls by means of firewall classification / logic which is controlled by a bastion host therefor, and in order to resolve security issues related to such network, it is according to the present invention suggested that said bastion host is configured to accept digitally signed configuration messages from one of more distributed operator(s) and / or manager(s), for thereby ensuring intergrity of said configuration messages.
Owner:TELEFON AB LM ERICSSON (PUBL)
Internal control bastion host and security access method of internal network resources
InactiveCN102333090ARealize centralized loginImplement access controlTransmissionAccess methodBastion host
Owner:LIAONING GOETHINK TECH
System for secure communication between domains
InactiveUS20020129239A1Exceeds capabilityEliminate needMultiple digital computer combinationsProgram controlSecure communicationInternet privacy
A method of executing secure communications between first and second domains includes a translating data received from a node of the first domain to a target protocol and transmitting the translated data to a bastion host. The translated data may be filtered by the bastion host to block unauthorized transmissions. The data may then be authenticated and transmitted to a node of the second domain for use in an application. In one embodiment, the first domain is an untrusted domain and the second domain is a trusted domain.
Owner:CLARK PAUL C
Method, device and system for network security auditing
ActiveCN102821161AImprove securityNetworks interconnectionRemote desktopProtocol for Carrying Authentication for Network Access
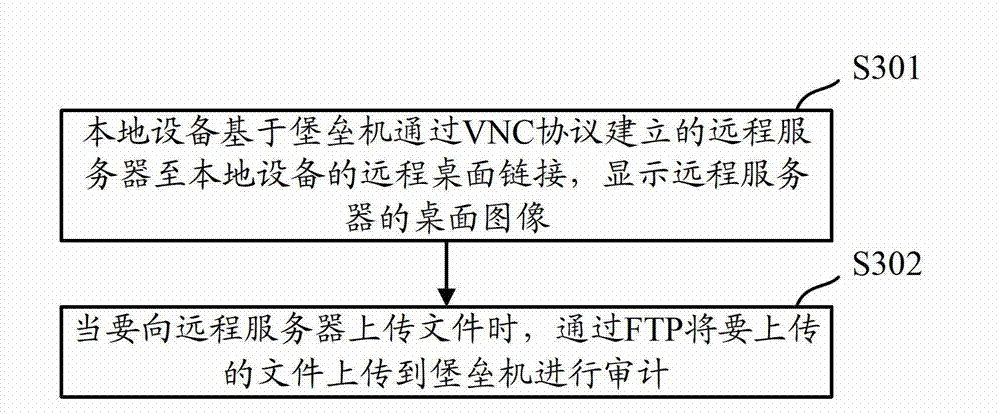
The invention discloses a method, a device and a system for network security auditing. The method, the device and the system are used for solving the problem of poor security of a remote server in the prior art. The method includes that a bastion host sets up a remote desktop link from a remote server to local equipment through the VNC (virtual network computing) protocol, receives a file uploaded by the local equipment through the FTP (file transfer protocol), audits the file according to stored auditing strategies, transmits the file to be stored in the remote server when audit is eligible and abandons the file when the audit is ineligible. In the method, file transmission between the local equipment and the remote server is realized by the aid of the FTP, so that the bastion host can audit the file when receiving the file uploaded by the local equipment through the FTP and can control the file according to the audit results, and security of the remote server is improved.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Remote access reinforced and centralized monitoring system of scheduling data network
InactiveCN108366090AAchieve recordRealize forwardingTransmissionMonitoring systemInteraction interface
The invention discloses a remote access reinforced and centralized monitoring system. The system comprises an operation and maintenance terminal, a bastion host, target equipment and auditor user terminal; the operation and maintenance terminal is connected with the target equipment through the bastion host, the bastion host is further connected with the auditor user terminal; the bastion host comprises an administrator interaction interface, a policy management module, a policy configuration base, a user interaction interface, a data processing module, an application proxy module, an auditorinteraction interface, an auditing module and an auditing log database. Relying on the conception of the bastion host, a unique entrance and a unified interaction interface are constructed between theoperation and maintenance terminal and the target equipment to record the instruction and operation process of the user operation in detail; the session is audited and monitored in a centralized way,the recording, forwarding, callback, monitoring and auditing of the session data are realized, and the behaviors of all maintainers are regulated and controlled.
Owner:ANHUI ELECTRIC POWER FUYANG POWER SUPPLY
Database auditing method based on bridged mode
InactiveCN103475727AImprove data securityTransmissionSpecial data processing applicationsDatabase serverSecurity policy
The invention relates to the technical field of database auditing, in particular to a database auditing method based on a bridged mode. According to the database auditing method, a bastion host establishes the connection of a local device and a remote database server through the bridged mode, meanwhile, the bastion host analyzes an SQL sentence executed by a user according to a security policy, when the SQL sentence belongs to normal database operation, the user can execute the operation continuously, when the SQL sequence comprises high-risk operation fields, the user is forbidden to continue executing, and a prompt is given out. According to the database auditing method based on the bridged mode, the bastion host makes the security policy so as to audit the operation to the remote database server on the local device by an operational user, and the data safety of a remote kernel database is improved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Distributing overlay network ingress information
ActiveUS20130124685A1Multiple digital computer combinationsTransmissionPrivate networkNetwork addressing
Aspects of the present disclosure relate to providing secure access to resources of a private network. For example, a client device may transmit a request identifying the protected resource to an authentication server. The authentication server queries a network address lookup table to identify a network address of the protected resource based on the identifying information of the request. If the network address denotes a network location that is not generally accessible, the authentication server generates a resource record that identifies a bastion host, a port, and a connection method for accessing the protected resource. The resource record and the network address may then be transmitted to the client device. In response, the client device may use the information in the resource record to establish a tunnel connection with the bastion host, and the client device uses the tunnel connection to access the protected resource via the bastion host.
Owner:GOOGLE LLC
Remote command interaction method and bastion host
InactiveCN102045375AEasy to operateSimplify operating proceduresTransmissionComputer scienceOperating system
The embodiment of the invention discloses a remote command interaction method and a bastion host. The method comprises the following steps of: providing a back-stage host list for a user terminal through a browser; receiving back-stage host information which is sent by the user terminal and selected from the back-stage host list; connecting to the back-stage host selected by the user terminal through a safe guide plug-in unit according to the selected back-stage host information and providing the user terminal with an interaction window through the browser, wherein the interaction window is used for interacting a command with the back-stage host; and receiving a command which is input by the user terminal through the interaction window and sending to the back-stage host through the safe guide plug-in unit. The bastion host comprises a list unit, a receiving unit, a connecting unit and a processing unit. The embodiment of the invention provides users with a remote command interaction method based on a B / S (Blower / Server) mode so that the users can more conveniently access a remote host.
Owner:HUAWEI TECH CO LTD
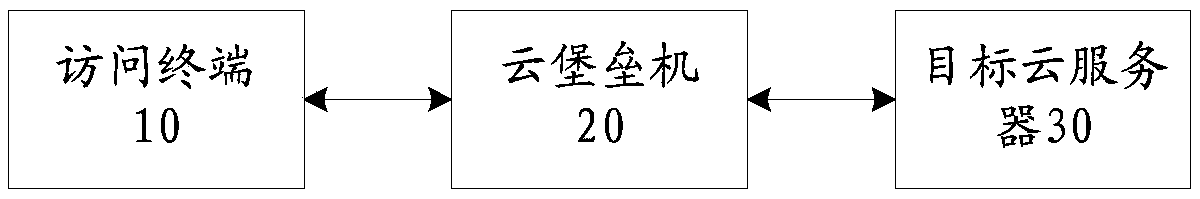
Remote login method, device and system
The invention discloses a remote login method, a device and a system. The system comprises an access terminal used for determining a target cloud server to be logged in; a cloud bastion host which isconnected with the access terminal, wherein a key pair of the target cloud server is stored in the cloud bastion host, the key pair comprises a public key and a private key corresponding to the publickey, and the cloud bastion host is used for performing signature by using the private key in the key pair; and the target cloud server which is connected with the cloud bastion host, stores a publickey of the key pair, and is used for performing signature verification on the signature by using the public key of the key pair, and establishes communication with the cloud bastion host under the condition that the signature verification is passed. The technical problem that in the prior art, the login credential of the cloud server is manually set by an administrator, and consequently the password strength is low is solved.
Owner:ALIBABA GRP HLDG LTD
Cache password-based network equipment security access system and working method thereof
ActiveCN110719276AEnhance and ensure securityEnhancing and Ensuring ConsistencyTransmissionServer logPassword
The invention discloses a cache password-based network equipment security access system and method. The system is provided with a bastion host server, an AAA server, a log analysis server, a client and managed network equipment, wherein the structures of the bastion host server and the AAA server are respectively improved. The system is innovatively characterized in that a bastion host server caches an account and a password of a client user and forwards the account and the password to an AAA server for authentication; and the traditional local storage and local authentication mode of accountpassword and authority setting of the network equipment is replaced. The cache password is transmitted in an encrypted manner. The managed network equipment only allows the user to access after passing the authentication of the cache password, so that the security and reliability of the login account password of the network equipment can be enhanced and ensured. The AAA server realizes centralizedmanagement of local authentication information dispersed in numerous network devices. The user management authority is finely divided, and the user behavior is limited in a legal management control range, so that the security of the network equipment is ensured.
Owner:BEIJING WANGRUIDA TECH CO LTD
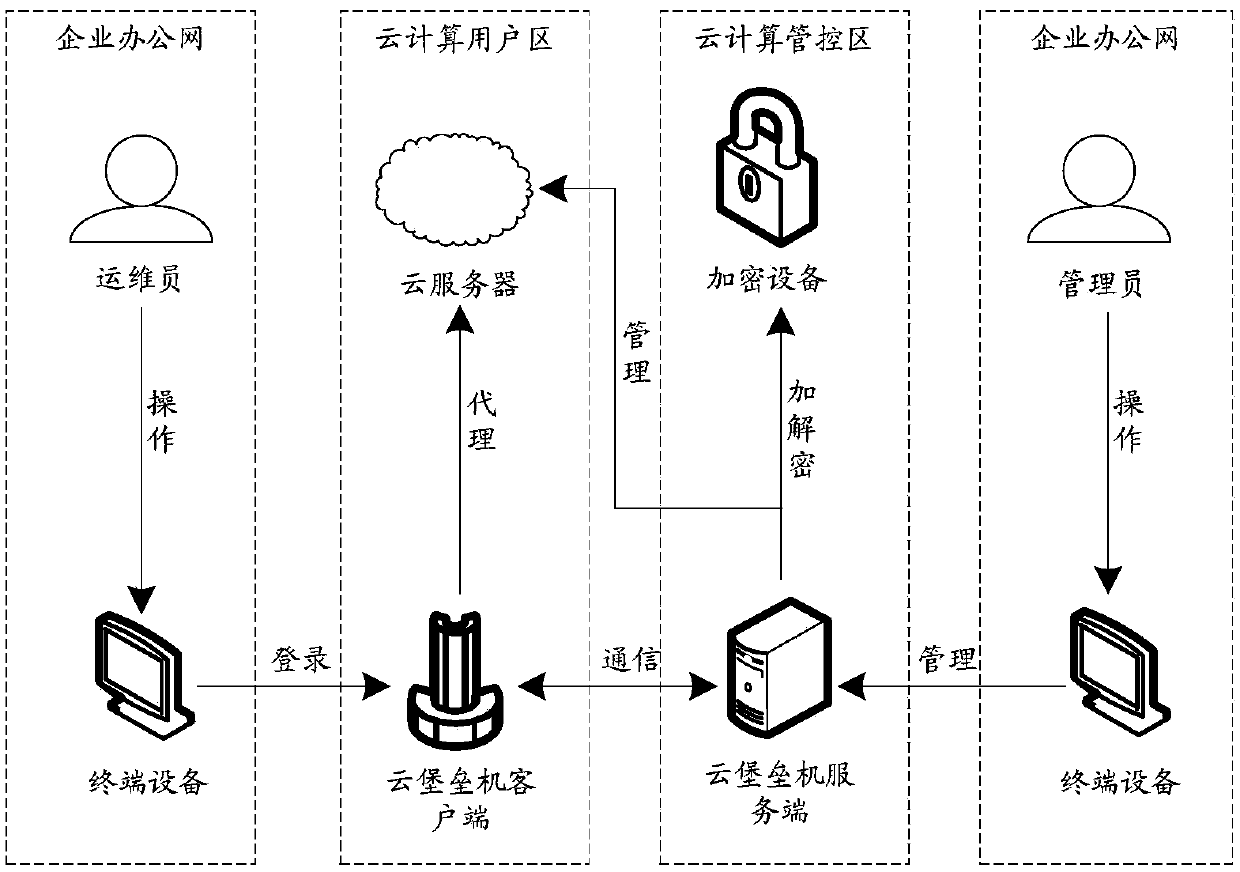
Virtual desktop-based operation and maintenance management method
InactiveCN103188336AAchieve physical isolationEasy to operateTransmissionMaintenance managementEngineering
The invention provides a virtual desktop-based operation and maintenance management method which can reduce the harm caused by misoperation during operation and maintenance and can be used for managing the operation and maintenance personnel in a centralized way. The method comprises the following steps of: (1) enabling the operation and maintenance personnel to log in an operation and maintenance management system by using a browser / server (B / S) mode at an operation and maintenance terminal, and entering the virtual desktop provided by a bastion host; (2) looking over equipment and tools which are needed to be maintained on the virtual desktop; (3) after the operation and maintenance tool corresponding to the operation is selected, automatically establishing the corresponding interlinkage between the operation and maintenance tool and the maintained server according to the configuration of a system administrator; and (4) carrying out maintenance operation by connecting the server on the virtual desktop by the operation personnel. According to the virtual desktop-based operation and maintenance management method, the harm caused by misoperation during operation and maintenance can be alleviated, the operation and maintenance personnel can be managed in a centralized way, the operation of the operation and maintenance personnel is simple by technologies such as the virtual desktop, and single sign-on, and the maintenance process of the server is controllable and auditable by the technologies such as access control and audit for the operation and maintenance.
Owner:BEIJING GUOLUAN INFORMATION TECH
Maintenance auditing method and device
The embodiment of the invention provides a maintenance auditing method and device. The method and the device are applied to a virtualized bastion host. Multiple virtual bastion hosts are installed onthe bastion host. The method comprises steps of acquiring a maintenance operation request sent by a client; according to a preset corresponding relation between indication information and the virtualbastion hosts, determining a target virtual bastion host represented target indication information from multiple virtual bastion hosts; and through the target virtual bastion host, auditing the maintenance operation that the client requests for auditing. One bastion host comprises multiple virtual bastion hosts, so one bastion host is enabled to audit multiple tenants simultaneously, demand for the bastion hosts is reduced and cost of maintenance auditing is reduced.
Owner:NEW H3C SECURITY TECH CO LTD
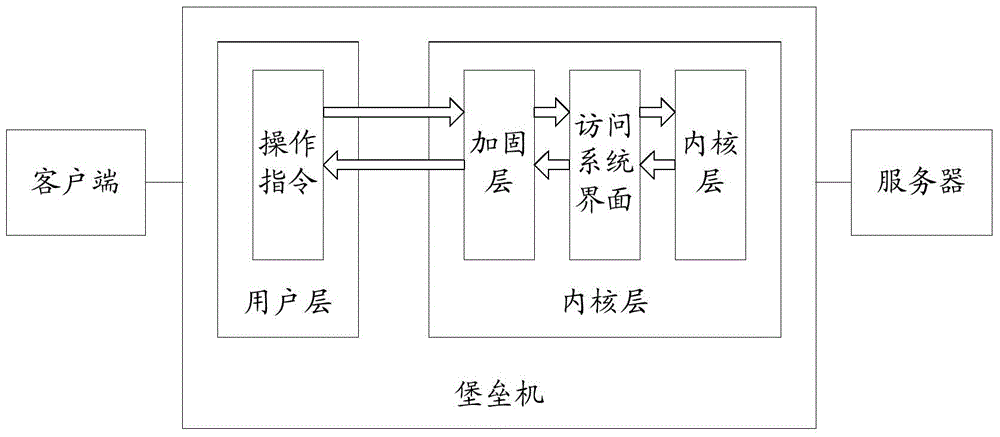
Bastion host
PendingCN111586032ASolve the problem of ambiguous identityConstrain and Monitor BehaviorTransmissionInternet privacyEngineering
The invention discloses a bastion host. The bastion host serves as an operation and maintenance operation gateway of a data center. An identity account, a server account and a matching relationship between the identity account and the server account are arranged in the bastion host; each server account has respective operation authority, the bastion host establishes connection between the terminaland the server according to the operation authority, and the terminal operates the server to form an operation log to be stored in the bastion host. The bastion host has the advantages that the bastion host confirms the identity of the person twice: the responsible person applying for entering belongs to a set of persons allowed to enter, and the person applying for entering is the person. Thus,the problem of fuzzy identity is solved, and if the problem is found, people can be directly traced back. Identity authentication, access control, authority control and operation auditing can be carried out on the terminal entering the server at the equipment and host layers, and behaviors of workers are restrained and monitored.
Owner:ZHEJIANG QIZHI TECH CO LTD
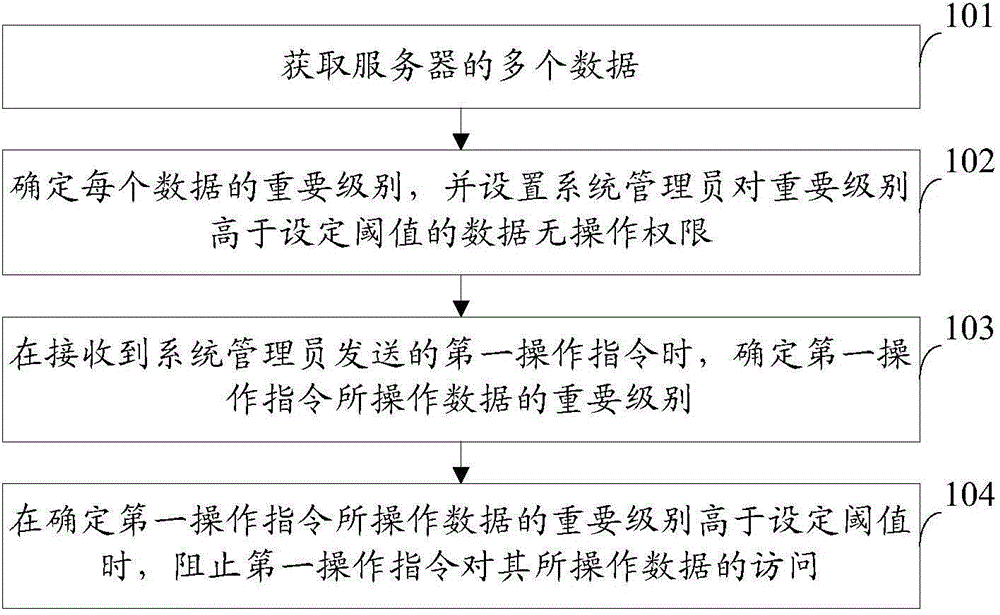
Data protection method and safety bastion host
The invention provides a data protection method and a safety bastion host which is connected in series to a path between a client terminal and a server. The method comprises the following steps: acquiring a plurality of data of a server; determining the importance level of each datum, and setting up no operation privilege of a system administrator to data with higher importance level than the set threshold; determining the importance level of data operated by a first operation instruction sent by the system administrator when the first operation instruction is received; and preventing the first operation instruction from access to the data operated by the first operation instruction when the importance level of the data operated by the first operation instruction is higher than the set threshold. According to the scheme, attacking server data by a hacker through acquiring the privilege of the system administrator is avoided through setting no operation privilege of the system administrator to the data with higher importance level than the set threshold, thereby improving the safety performance of the server data.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
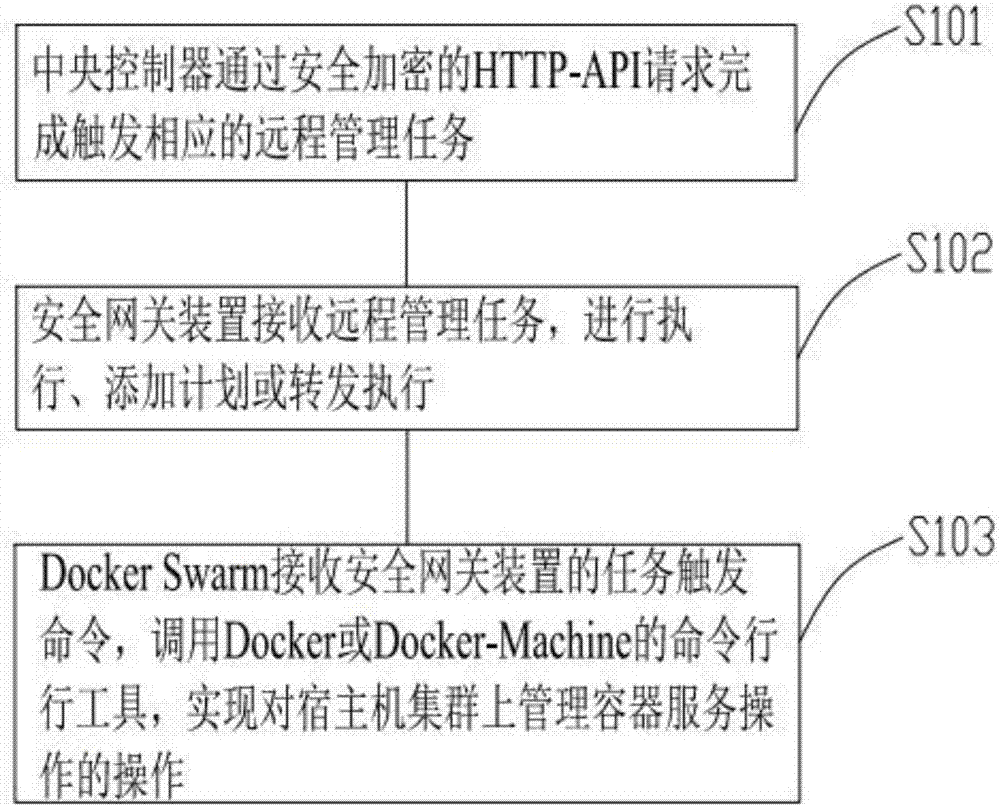
Method and system for realizing remote project system supervision based on Docker, and device
InactiveCN107247648AReduce procurement costsIncrease purchase costHardware monitoringProgram loading/initiatingComputer clusterProgram planning
The invention discloses a method and a system for realizing remote project system supervision based on Docker, and a device, and relates to the technical field of devices or methods used to execute special programs. The method comprises the following steps: a central controller completing to trigger a corresponding remote management task through a secure encrypted HTTP-API request; a security gateway device receiving a remote management task, executing the task, adding plans or transferring and executing; Docker Swarm receiving a task trigger command of the security gateway device, calling a command line tool of the Docker or Docker-Machine, to realize operation of container management on a host computer cluster. The method saves cost for an enterprise to buy bastion hosts and network management system purchase cost, and improves supervision degree of an enterprise on project system operation states. In addition, a management means for project system automatic operation and maintenance is also enhanced, and workload of operation and maintenance staffs is reduced.
Owner:北京赢点科技有限公司
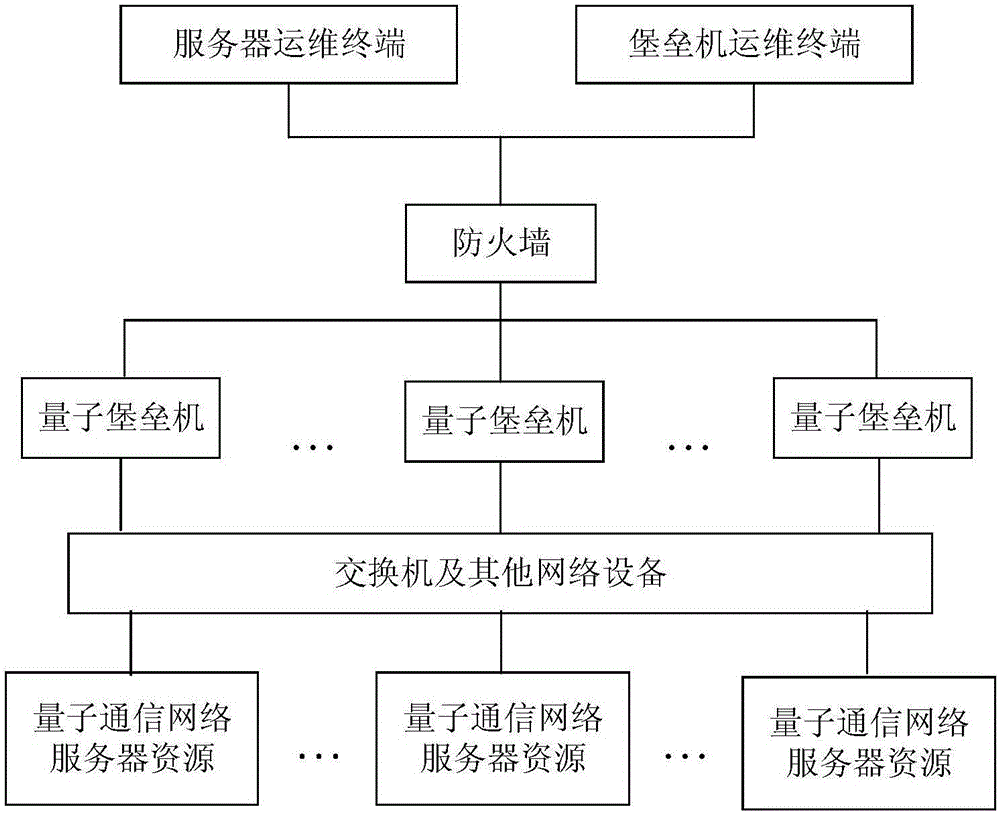
Auditing system and auditing method based on quantum bastion host and quantum bastion host system
ActiveCN106789029AImprove securityEnsure safetyKey distribution for secure communicationStorage securityCiphertext
The invention discloses an auditing system and an auditing method based on a quantum bastion host and a quantum bastion host system, wherein the auditing method based on the quantum bastion host comprises the following steps: responding to an authentication request of an operation and maintenance terminal and performing authentication; after passing authentication, auditing the operation and maintenance operation of the operation and maintenance terminal, generating an audit record, and sending the audit record to a security encryption device in the form of hardware, so as to generate an audit file and anti-tampering identification information in the security encryption device and perform encryption to generate a storage ciphertext; and receiving and storing the storage ciphertext from the security encryption device. According to the method provided by the invention, the audit file is encrypted and stored by virtue of special hardware equipment, a secret key used for encryption is a quantum random number secret key with true randomness, and the issuing of the quantum random number key depends on a quantum communication network and special hardware equipment to ensure that the security of the key is extremely high, so that the storage security of the audit file in the quantum bastion host is guaranteed.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
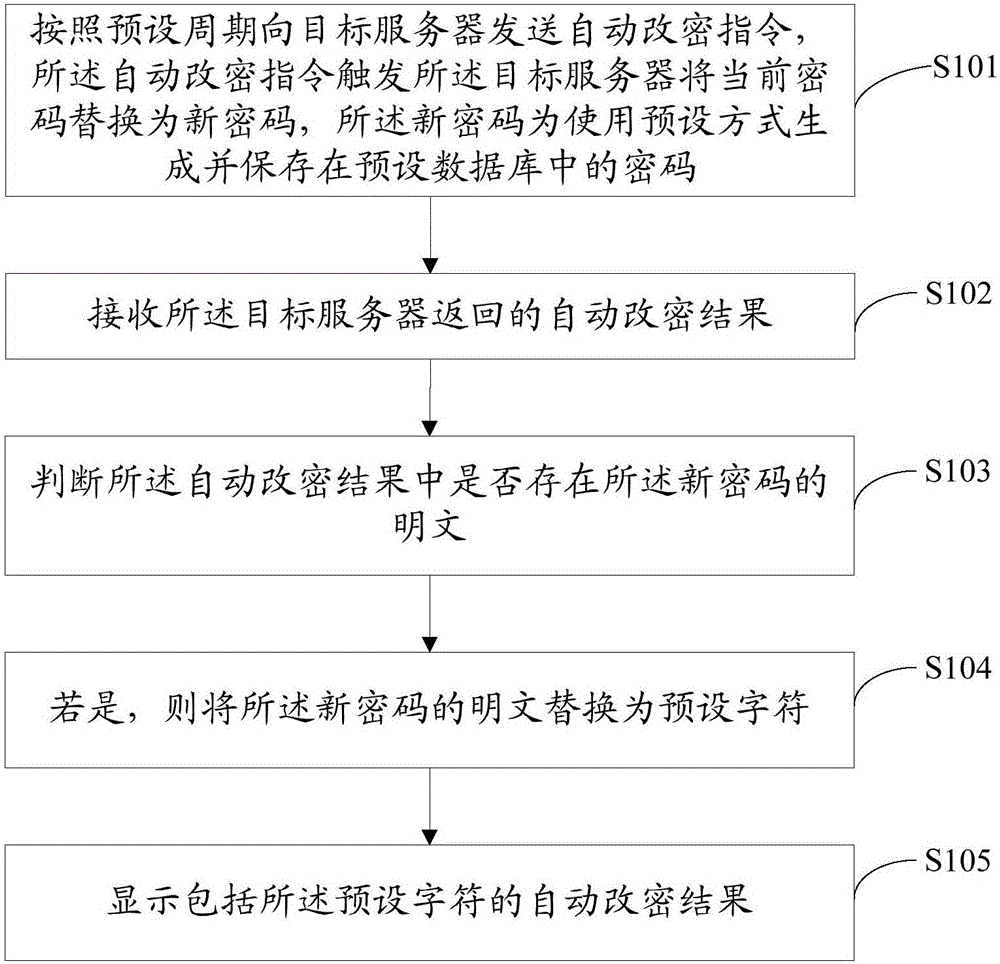
Automatic password change method and apparatus, and bastion host
Owner:ZHEJIANG QIZHI TECH CO LTD
Data interaction method and device, bastion host and computer readable storage medium
ActiveCN110324338AImprove securityThe data interaction process is orderlyTransmissionInteraction deviceComputer terminal
The invention relates to the field of financial science and technology and discloses a data interaction method. The method comprises the following steps: an operation request sent by a terminal is received, a target bastion host verifies the operation request; wherein if the terminal receives the operation request, the terminal determines a first operation attribute of the operation request and atarget server corresponding to the operation request, and when the bastion host corresponding to the operation request is determined to be a target bastion host based on the first operation attribute,the terminal sends the operation request to the target bastion host; if the verification is passed, the target bastion host sends the operation request to a target server; and when an execution result returned by the target server based on the operation request is received, the target bastion host sends the execution result to the terminal. The invention further discloses a data interaction device, a bastion host and a computer readable storage medium. According to the invention, the security of data interaction can be effectively improved, and the data interaction process is orderly.
Owner:WEBANK (CHINA)
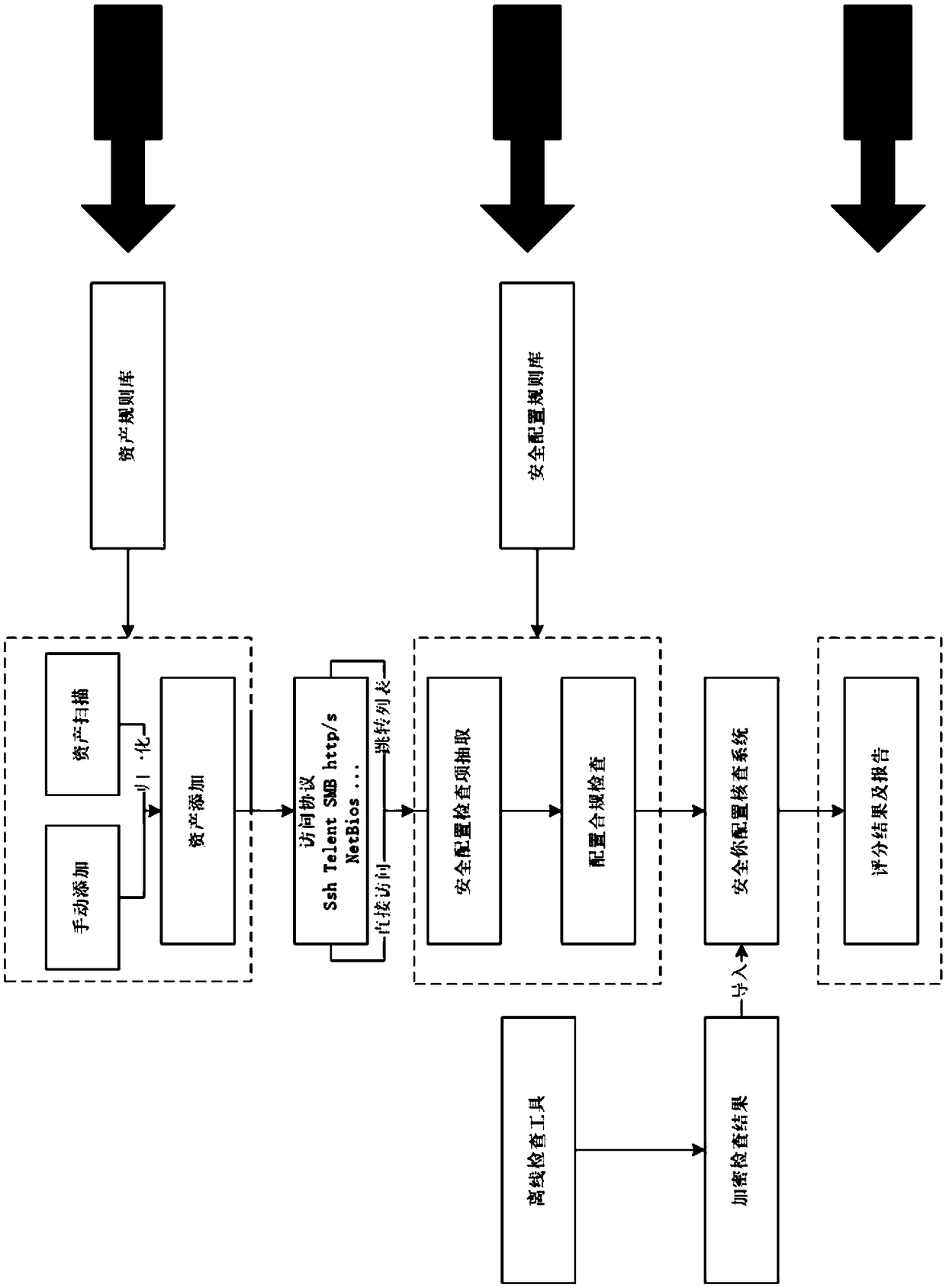
Security configuration checking system
The invention discloses a security configuration checking system. In a remote checking process, an access mode of target equipment, a login user name and a login password need to be output; remote check can be achieved only when a check target and a tool can be reached by an IP and the check target opens related service and ports; for the remote check, a plurality of sets of equipment can be simultaneously checked through the appointed concurrent access quantity; for the remote check which the IP cannot reach directly, property information and login information of skip intermediate equipment can be set through some intermediate equipment such as bastion host skip and through a skip table function; target equipment is accessed after skip; when a dynamic password is needed, corresponding intermediate equipment or the bastion host can be mutually logged in to form activity conversation through a share conversation function, a system can be connected to the intermediate equipment or the bastion host through the conversation to access the target equipment to collect security configuration to perform security configuration base line check, and finally a configuration check result is output.
Owner:信联科技(南京)有限公司
Service authority opening method and device, storage medium and electronic device
ActiveCN109670297AImprove experienceAvoid manual configurationDatabase management systemsDigital data authenticationBastion hostComputer engineering
The invention relates to the field of computers, and provides a service authority opening method and device, a computer readable storage medium and an electronic device, and the method comprises the steps of obtaining authority application information sent by a user, the authority application information comprising one or more pieces of information related to the service authority; automatically generating field information corresponding to the authority application information according to the authority application information; sending the field information to a bastion host system through apreset interface; and receiving prompt information returned by the bastion host system through the preset interface. According to the present invention, on one hand, manual configuration of operationand maintenance personnel can be avoided, the pressure of the operation and maintenance personnel is reduced, the labor cost of operation and maintenance is reduced, and the operation and maintenanceefficiency is improved; on the other hand, the opening accuracy is greatly improved compared with the opening accuracy of manual configuration, and the user experience is further improved.
Owner:TAIKANG LIFE INSURANCE CO LTD
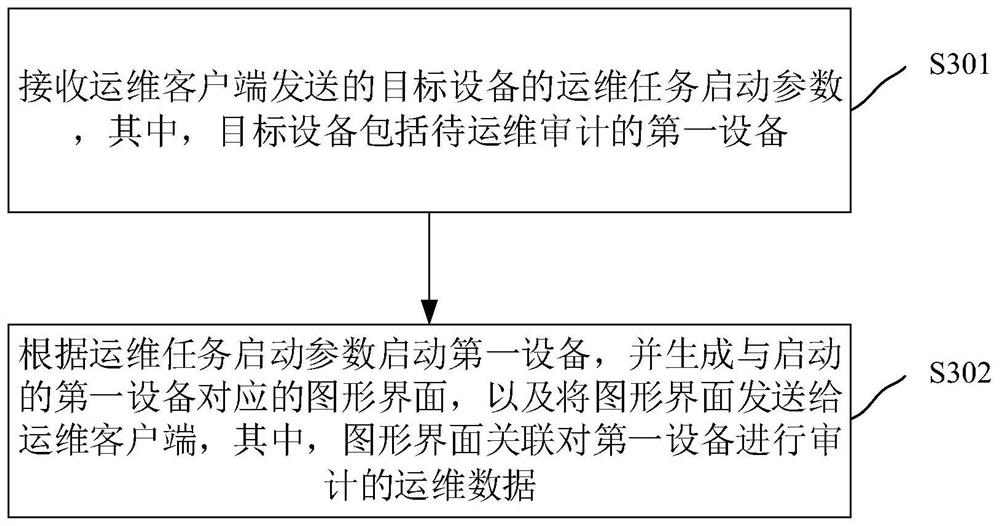
Bastion host, operation and maintenance auditing method, electronic equipment and storage medium
The invention relates to a bastion host, an operation and maintenance auditing method, electronic equipment and a storage medium. The bastion host comprises a protocol proxy service module and a graphical interface service module, and the protocol proxy service module is coupled with the graphical interface service module; the protocol proxy service module is used for receiving operation and maintenance task starting parameters, sent by an operation and maintenance client, of target equipment, and the target equipment comprises first equipment to be subjected to operation and maintenance auditing; and the graphical interface service module is used for starting the first equipment according to the operation and maintenance task starting parameters, generating a graphical interface corresponding to the started first equipment and sending the graphical interface to the operation and maintenance client through the protocol agent service module, and the graphical interface is associated with operation and maintenance data for auditing the first equipment. According to the invention, the problem of low security of operation and maintenance auditing in related technologies is solved, and the security of operation and maintenance auditing is improved.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Private key management method and apparatus for bastion host
ActiveCN107181589ADoes not compromise securityImprove securityKey distribution for secure communicationPasswordCiphertext
The invention provides a private key management method and apparatus for a bastion host. The private key management method for a bastion host includes the steps: when the bastion host is started, acquiring a first private key parameter in a bastion host process file, wherein the first private key parameter includes a first sharing key decryption password; acquiring a second private key parameter from a private key management platform, wherein the second private key parameter includes a second sharing key decryption password, a cryptograph private key and a private key encryption algorithm; according to the sharing key algorithm, calculating the first sharing key decryption password and the second sharing key decryption password, and obtaining the decryption key; and according to the private key encryption algorithm and the decryption key, decrypting the cryptograph private key, and obtaining a bastion host private key. The private key management method for a bastion host can improve storage safety of the bastion host private key.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
Data processing method, device and system and storage medium
InactiveCN107229864ASafe handlingPlatform integrity maintainanceTransmissionData processing systemData provider
Owner:UCLOUD TECH CO LTD
Account configuration method, device and system of cloud equipment and data processing method
ActiveCN110730153ASolving the configuration is more cumbersome and complicatedData switching networksCloud resourcesBastion host
The invention discloses an account configuration method, device and system of cloud equipment and a data processing method. The method comprises: acquiring a sub-account corresponding to a currently logged primary account, wherein the primary account has the authority of accessing cloud resources, and the sub-account has the authority of part or all of the primary account; and importing the sub-account into a target cloud device so as to log in the target cloud device through the sub-account to perform operation and maintenance on the target cloud device, the cloud resource including the target cloud device. The technical problem that the account configuration of the bastion host is tedious and complex due to the fact that the account of the bastion host needs to be built by the existing bastion host is solved.
Owner:ALIBABA GRP HLDG LTD
IP address acquiring method and IP address acquiring device
ActiveCN104811507ASolve the problem that the source IP address of the external network terminal cannot be obtainedNetworks interconnectionTerminal serverIp address
The invention discloses an IP address acquiring method and an IP address acquiring device. The method comprises the following steps: an SSO control acquires an intranet destination address which an extranet terminal is to access when monitoring that the extranet terminal is connected with a VPN server by a VPN control and accesses an intranet through the VPN server; the SSO control establishes connection with a character bastion host which is connected with the intranet corresponding to the intranet destination address; and the source IP address of the extranet terminal is forwarded to the intranet through the character bastion host. By adopting the scheme provided by an embodiment of the invention, the intranet can acquire the source IP address of the extranet terminal when an extranet terminal server accesses the intranet.
Owner:CHINA MOBILE GRP HENAN CO LTD
Automatic configuration management method and device based on bastion host
ActiveCN109889381ARealize centralized managementImplement automatic backupData switching networksUser inputOperating system
The invention discloses an automatic configuration management method and device based on a bastion host, and the method comprises the steps: providing an automatic operation and maintenance entrance through a front-end management interface, collecting user input, and constructing an operation and maintenance task request according to an operation and maintenance task; the Thrift service receives the task request sent by the front end and analyzes the task request, and an Ansile interface is called; the Ansile receives the calling of the Thrift service and logs in the target host through the SSH to execute the operation and maintenance task, and a task result returns the Thrift service in a JSON format; the Thrift returns a task result after the Ansile execution to the front-end managementinterface in a JSON format; and displaying the task result by a front-end management interface.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
Access control device, method, computer program product and computer readable medium
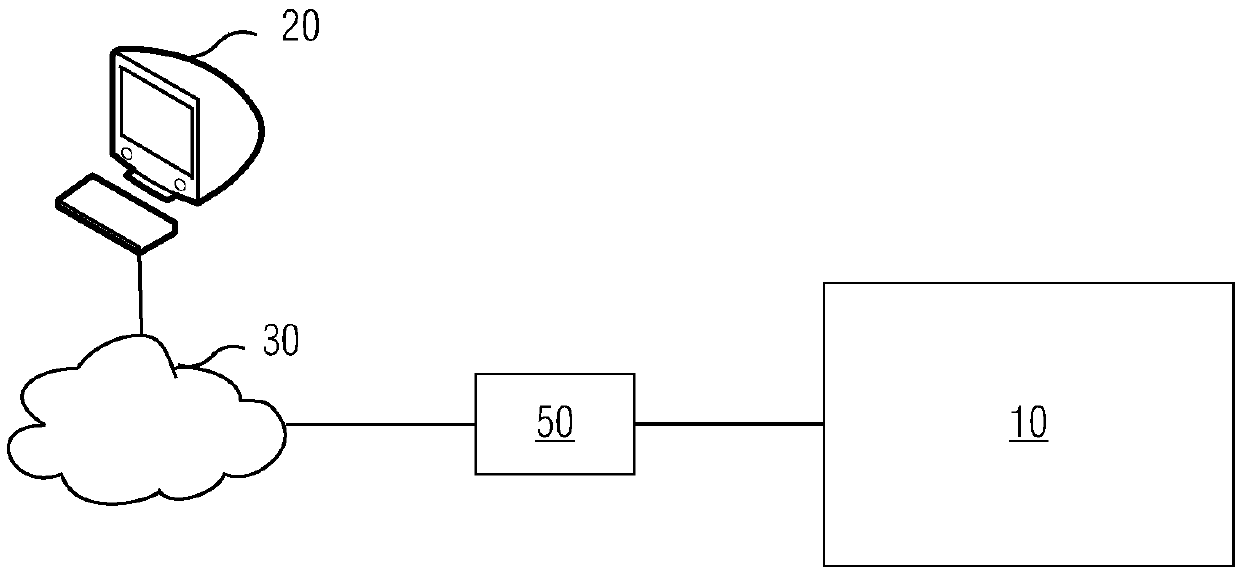
The invention relates to the technical field of industrial safety, in particular to access control device and method, which can provide effective safety protection in the remote access process of a system. An access control device (50) comprises a front-end firewall (501), a first network port (51) is provided to be connected with a remote computer (20); a bastion host (502) connected with the front-end firewall (501); a rear-end firewall (503) connected with the bastion host (502) and provides a second network port (52) to be connected with the system (10); and a back-end firewall (503) which scans resources allowed to be remotely accessed in the system (10) through the second network port (52) and determines the resources which can be remotely accessed by a computer (20) from the resources; and the bastion host (502) provides information that the computer (20) can remotely access resources to the computer (20) through the front-end firewall (501) via the first network port (51). The invention has the advantages of safety and simplicity in use and plug-and-play performance.
Owner:SIEMENS AG
Financial security integrated management and control platform
InactiveCN106385431AHave superiorityChange the status of information islandsDigital data protectionAlarmsIsolated systemIslanding
The invention relates to a financial security integrated management and control platform, which comprises a front-end bastion host and a background bastion host, and is characterized in that the front-end bastion host is connected to a plurality of front-end switches, each front-end switch is connected to a monitoring device and an application module, a core switch is connected between the background bastion host and the front-end bastion host, the front-end bastion host is connected with each front-end subsystem through a data bus, and the front-end subsystem comprises a server cluster, a financial service system and a television wall monitoring service system. The financial security integrated management and control platform makes full use of existing security resources, and can connect built scattered and isolated system equipment to the platform in an integrated manner to perform centralized management and control, thereby completely changing an information island condition of traditional security technical prevention, and achieving the purposes of active prevention and in-process control for security events.
Owner:四川泰尔科技有限公司
Report automatic generation method and device, computer equipment and storage medium
PendingCN111666743AImprove accuracyImprove efficiencyNatural language data processingWebsite content managementData displaySoftware engineering
The invention discloses an automatic report generation method and device, computer equipment and a storage medium, a report configuration file is generated by responding to a first user operation, andthe report configuration file comprises a custom script address and a task type; generating a custom script through Zabbix according to the custom script address, and collecting target report data from the target terminal by adopting the custom script; performing data processing on the target report data, and displaying the target report data after data processing in a report page; after a task triggering instruction is received, collecting target report data after data processing from the report page through a Puppter; and analyzing and extracting the target report data after data processingto generate a data report. By combining a Zabbix custom script and a Puppter automatic collection technology, the limitation that a target terminal database cannot be accessed due to the existence ofa bastion host is broken through, the accuracy and efficiency of data collection are improved, the state of a data collection process can be monitored, and the error-tolerant rate of the collection process is improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com