Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
576 results about "Storage security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Storage security is a specialty area of security that is concerned with securing data storage systems and ecosystems and the data that resides on these systems.
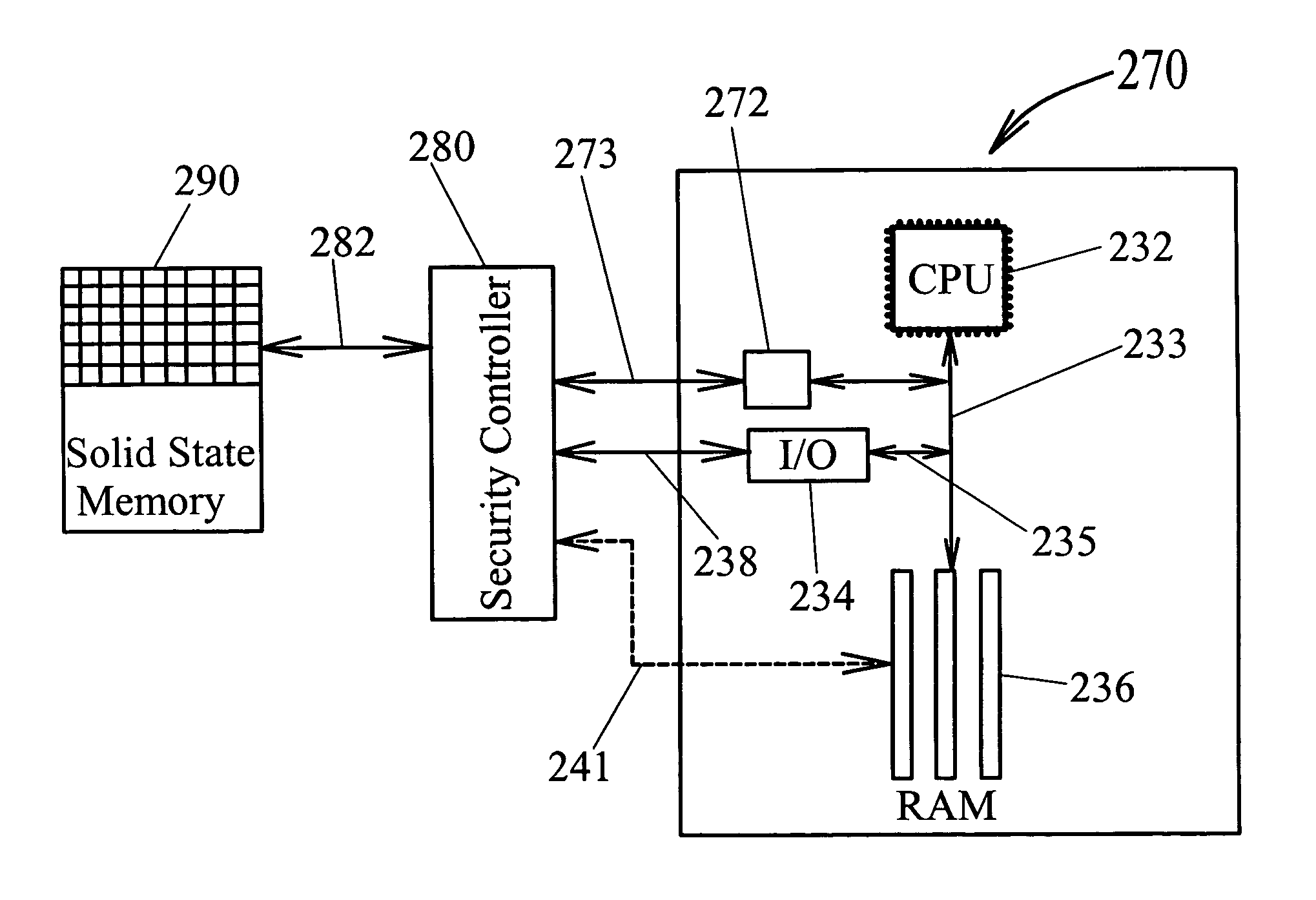
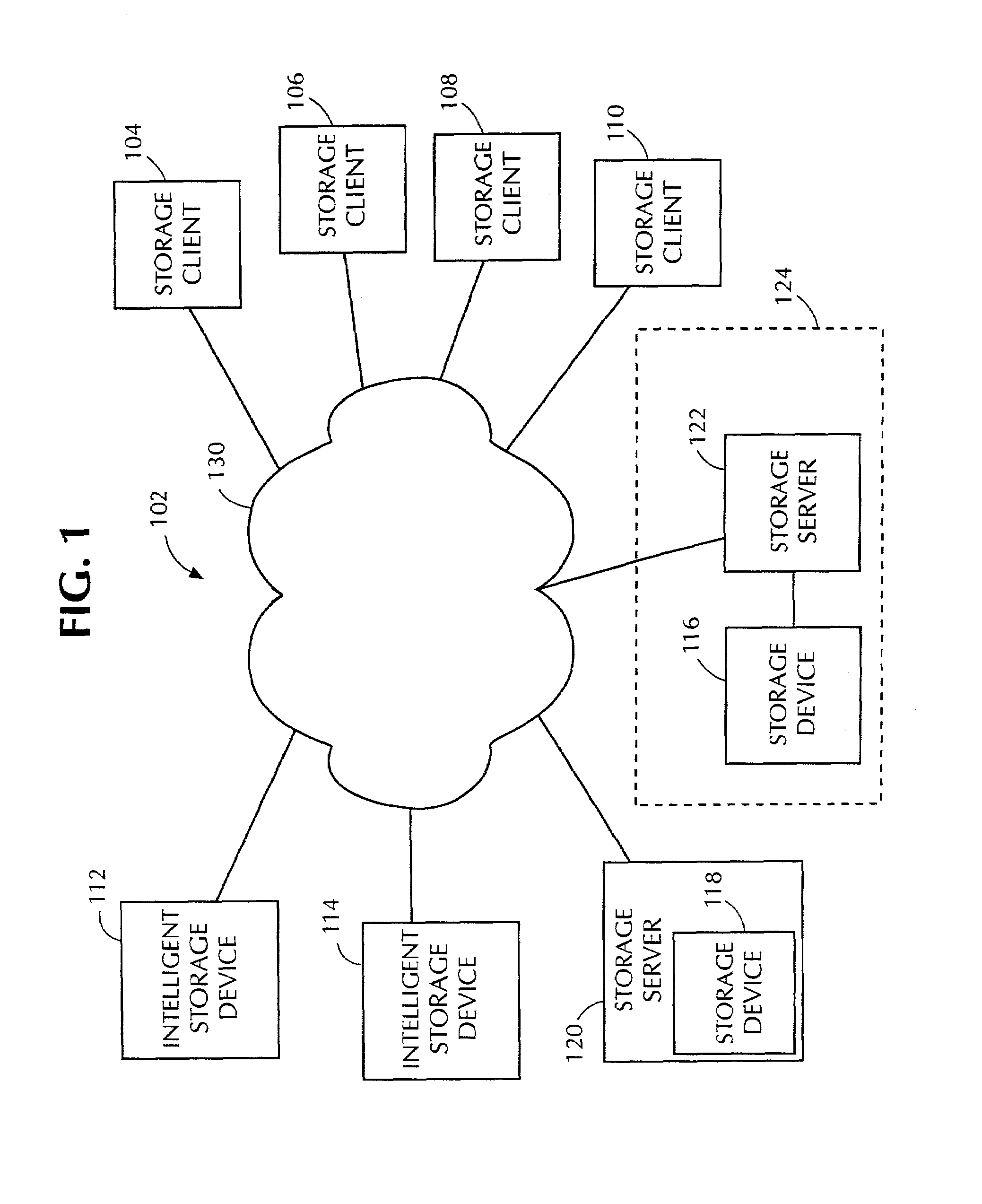
Dynamic associative storage security for long-term memory storage devices
InactiveUS7814554B1Improve protectionSignificant to useDigital data processing detailsUnauthorized memory use protectionStorage securityProgram Thread
A hierarchical folder security system for mapping files into and out of alias directories and / or real directories depending on: 1) the directory of the specific file being accessed, 2) the program thread requesting access to a memory storage device (114), and 3) the type of access request being made (i.e. load, save, run, etc.). For write access requests (i.e. save, modify, paste, delete, cut, move, rename, etc.), security controller (180) determines if the requested folder access address (150a) is associated with the requesting program's folder address (168). If it is, the file is written at absolute address (156b) on disk platter (160) through real folder map (152). If requested address (150a) is not associated with program folder address (168), then an alias directory address is created and the file is written at alias address (156a) through alias folder address map (154).
Owner:RAGNER GARY DEAN
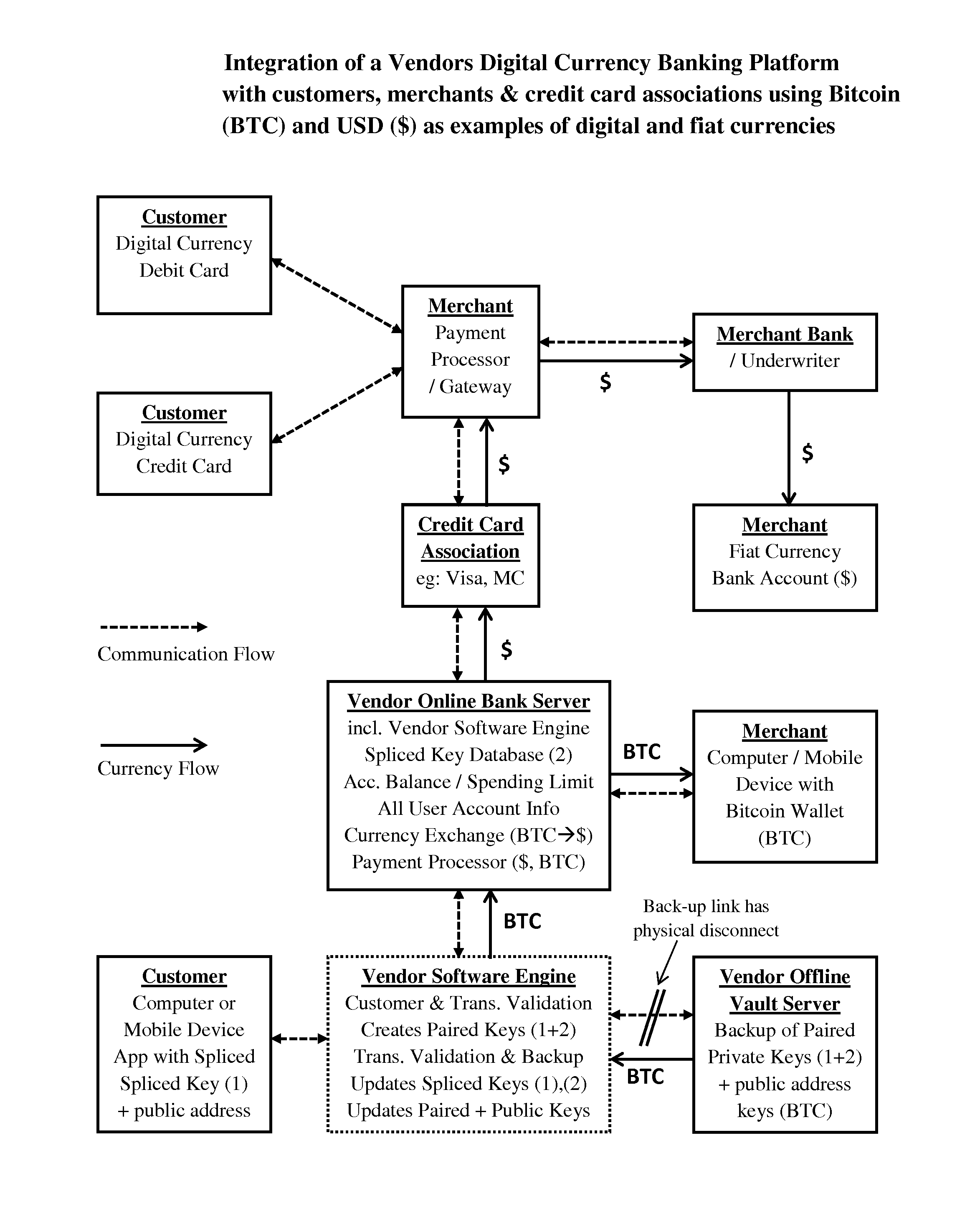
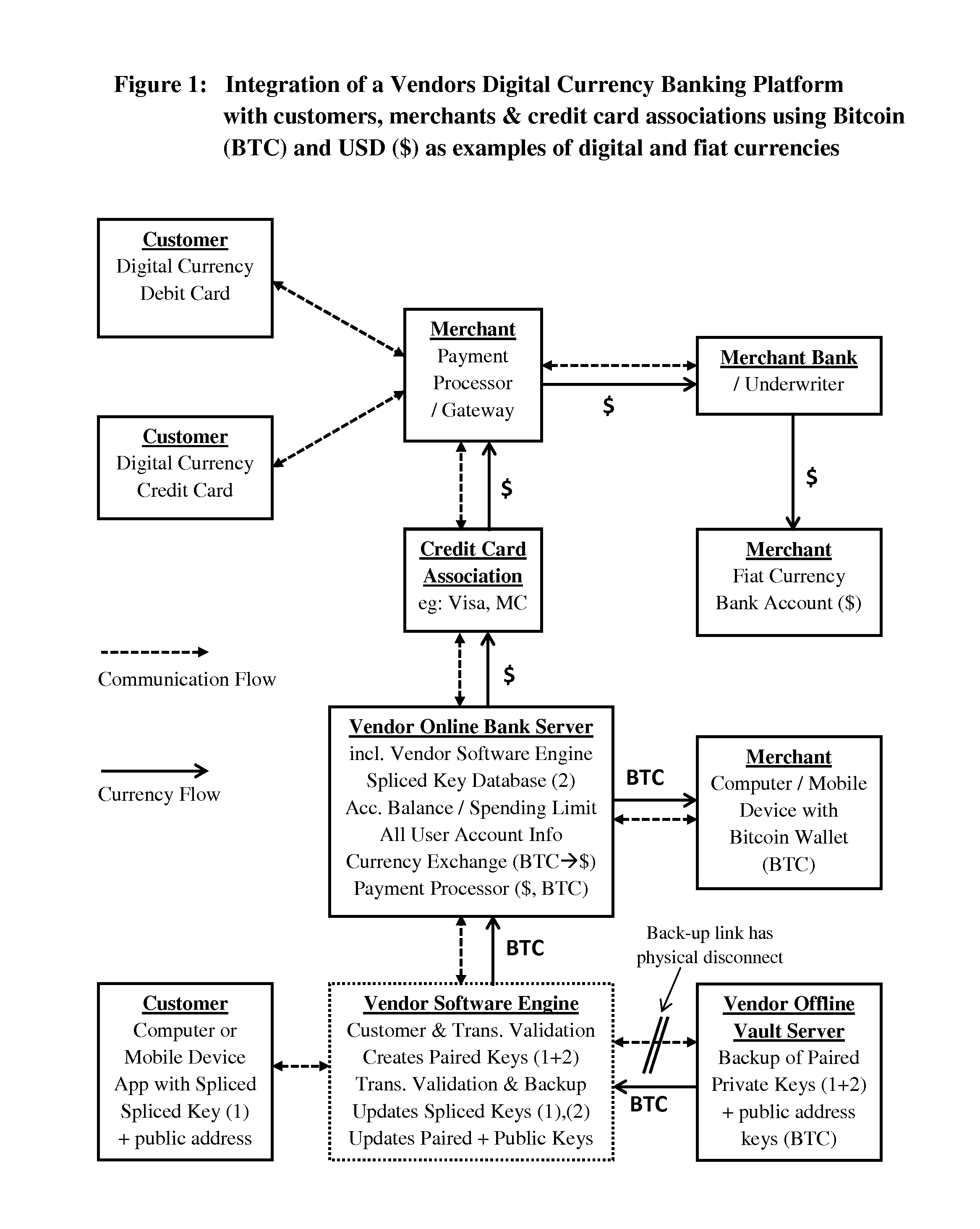
System and method for digital currency storage, payment and credit
InactiveUS20160335628A1Improved credit/debit card security benefitIncreased level securityComputer security arrangementsPayment protocolsDigital currencyStorage security
A system and method for the secure online storage of digital currency or crypto-currency assets, and the secure use of stored online digital currency assets for financial payment transactions and credit lending transactions in either digital currency or fiat currency. The present invention includes various methods for the encryption and secure online storage of a digital currency wallet using spliced / paired design architecture, and various methods for the integration of secure digital currency online wallets with online banking platforms, debit card devices, credit card devices, credit lending networks, merchant payment processors and credit card associations. The present invention also relates to the use of spliced / paired design architecture for non-financial applications that improve the online storage security of other types of data files and document files that are not related to digital currency or financial transactions.
Owner:CRYPTYK INC
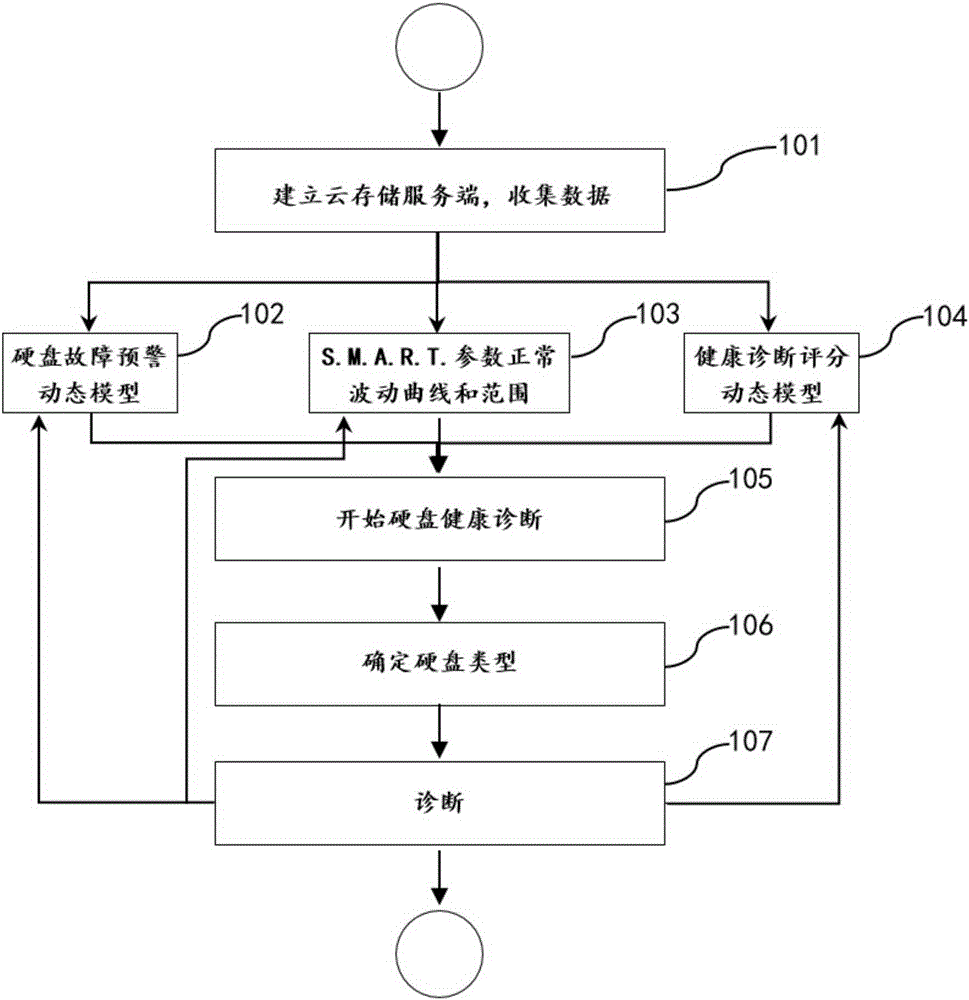
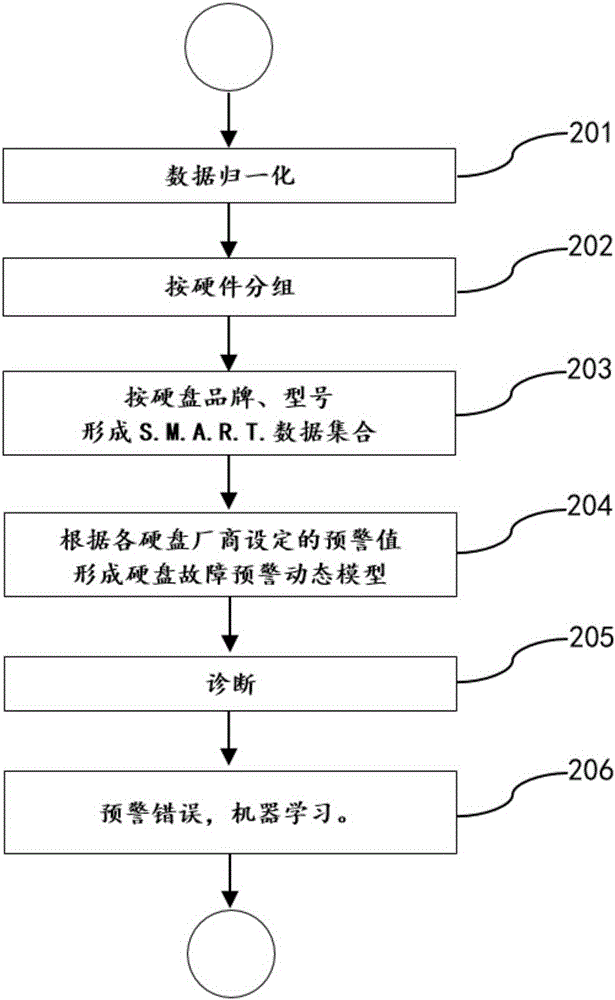
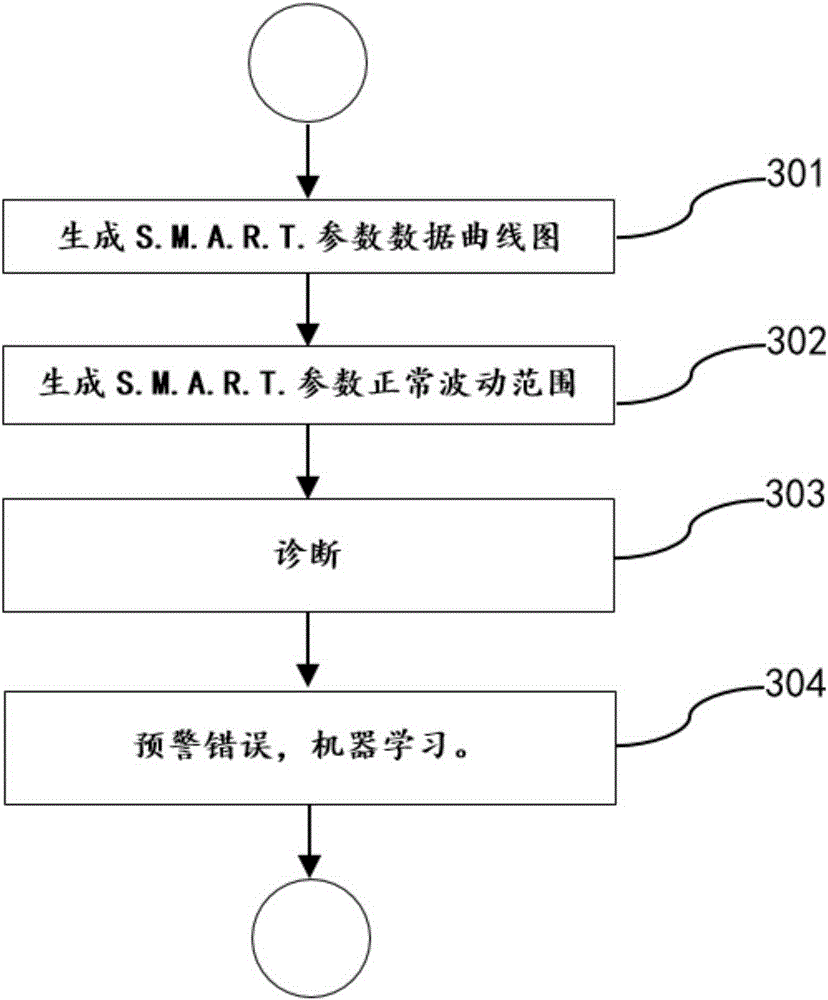
Method and device of dynamically diagnosing hard disk failure based on S.M.A.R.T (Self-Monitoring Analysis and Reporting Technology) data
ActiveCN105260279AImprove accuracyOngoing collection of health-related dataDetecting faulty computer hardwareHardware monitoringStorage securityDynamic models
The invention discloses a method and a device of dynamically diagnosing hard disk failure based on S.M.A.R.T (Self-Monitoring Analysis and Reporting Technology) data and relates to the field of data storage security diagnosis. The method comprises the following steps: 101) establishing a cloud storage server side to continuously collect three types of data; 102) establishing a hard disk failure early-warning dynamic model; 103) establishing S.M.A.R.T parameter normal fluctuation curves and ranges; 104) obtaining a health diagnosis scoring dynamic model through big data analysis. The method and the device of dynamically diagnosing hard disk failure based on S.M.A.R.T data have the following beneficial effects: 1) the cloud storage server side is established to continuously collect data related to health of hard disks; 2) the collected data are organized to establish the hard disk failure early-warning dynamic model, the S.M.A.R.T parameter normal fluctuation curves and ranges and the health diagnosis scoring dynamic model; 3) the correctness of the model is continuously improved through machine learning in hard disk failure diagnosis.
Owner:XLY SALVATIONDATA TECHNOLOGY INC
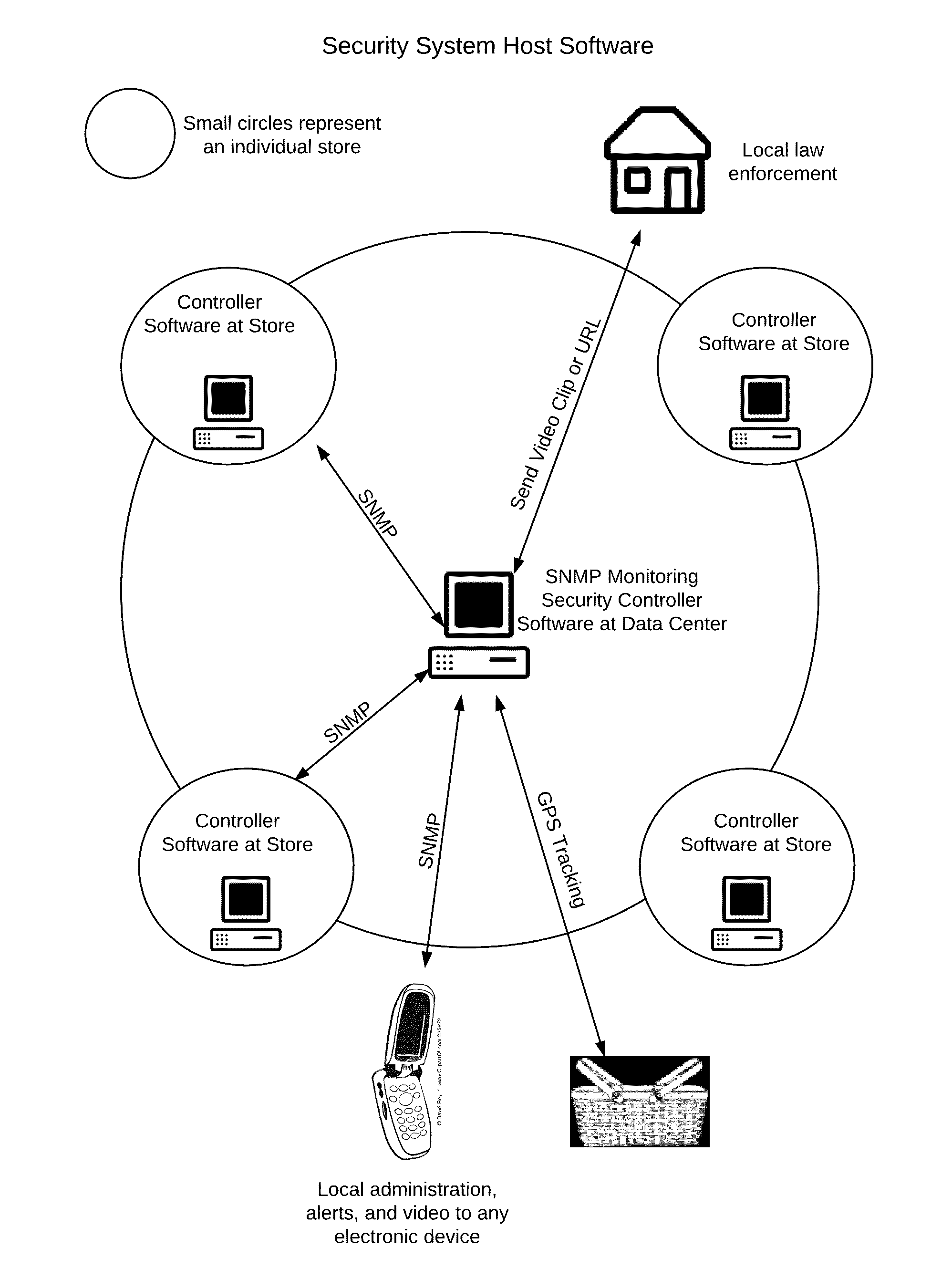
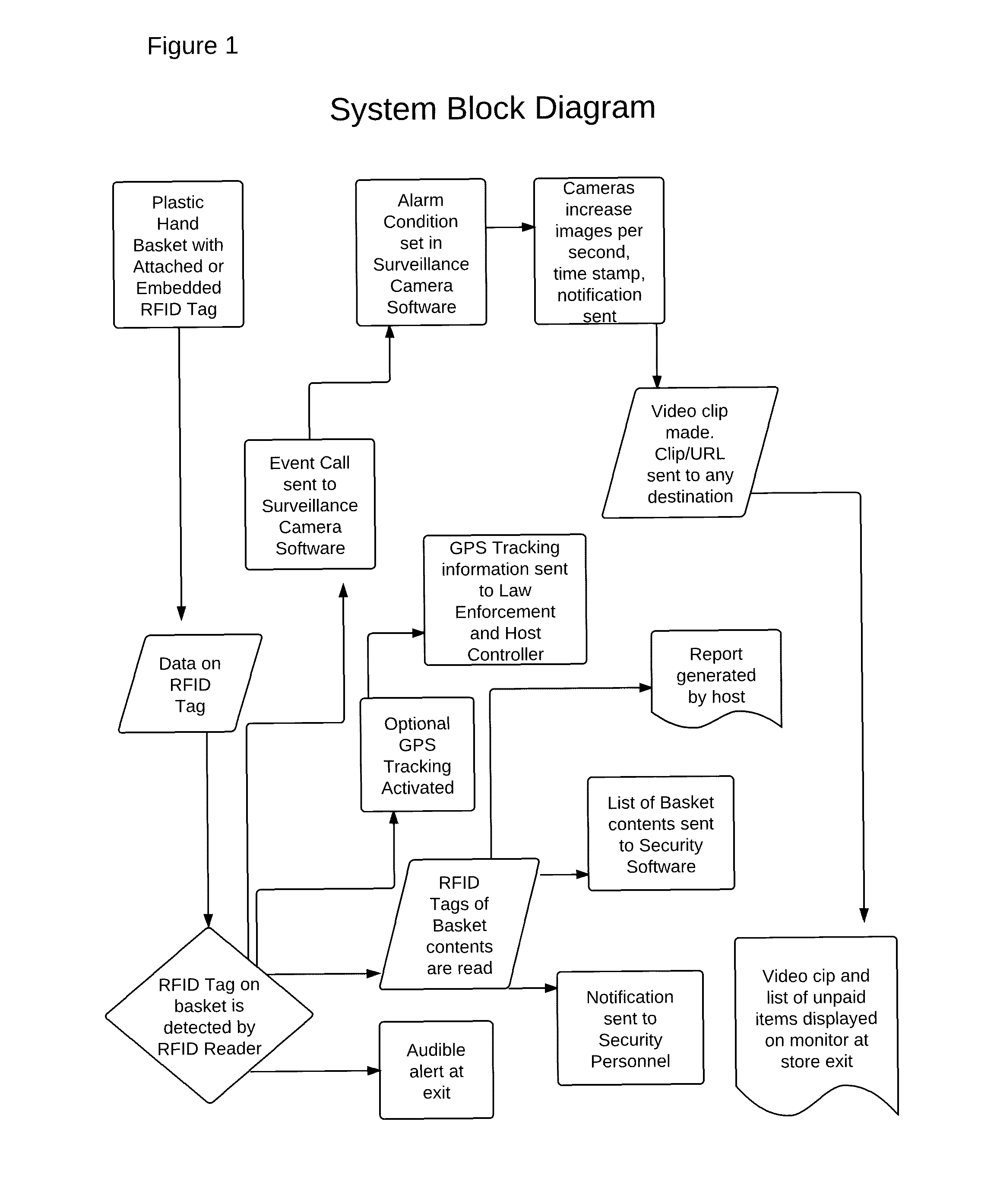
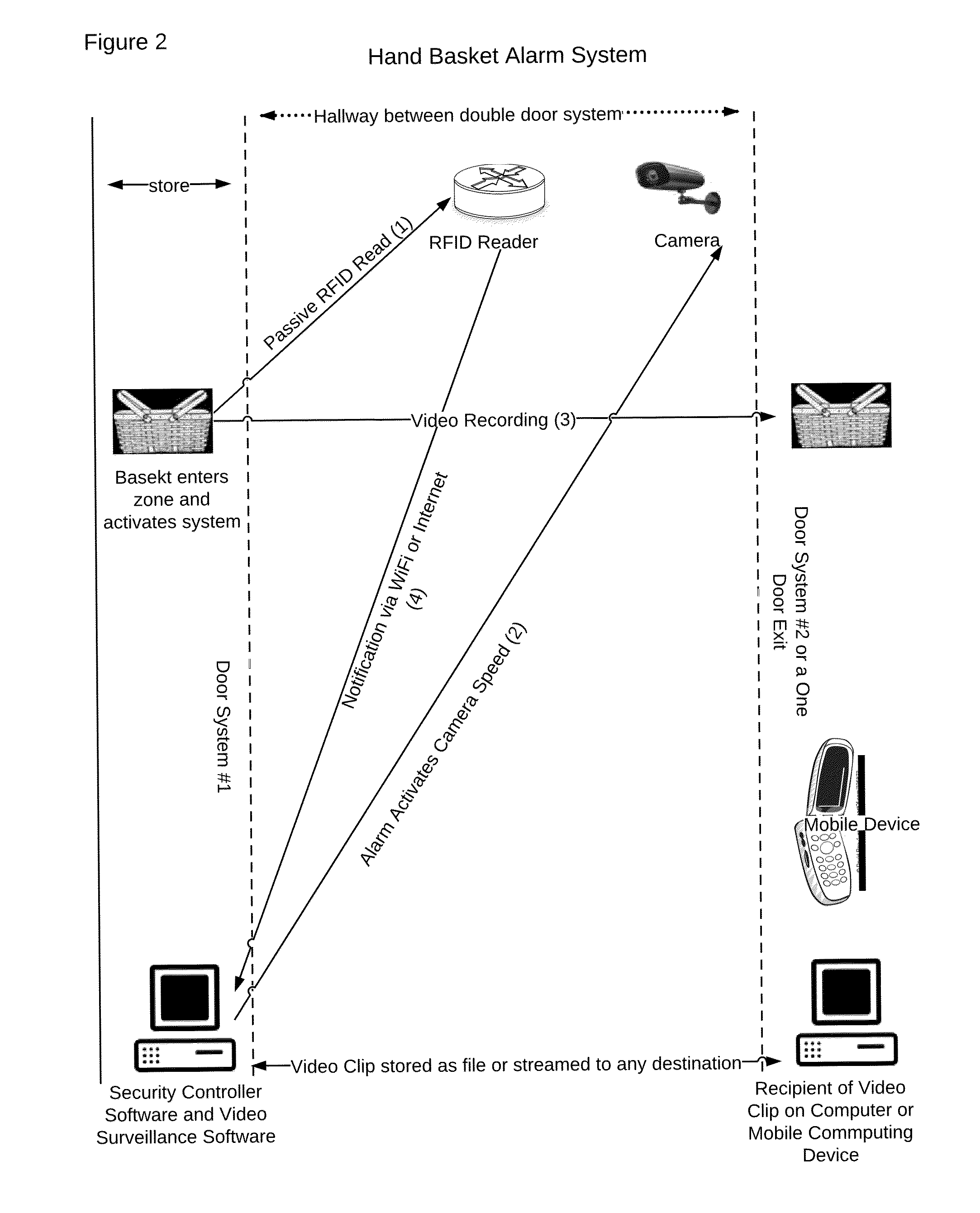
Method and system for hand basket theft detection
A method for using electronic product identification devices to track the location and movement of plastic hand baskets in a food store or other retail store, to sound an audible alarm, to activate an alarm condition in a video surveillance system, alert store security, and send tag information (basket ID and contents thereof) and video clip to store security, and law enforcement if desired this method and system is designed to promote a major deterrence to theft of store items in a portable hand carried basket, and in the case of theft, to provide notification and video clip to security personnel and to any law enforcement office.
Owner:GREEN ROBERT M
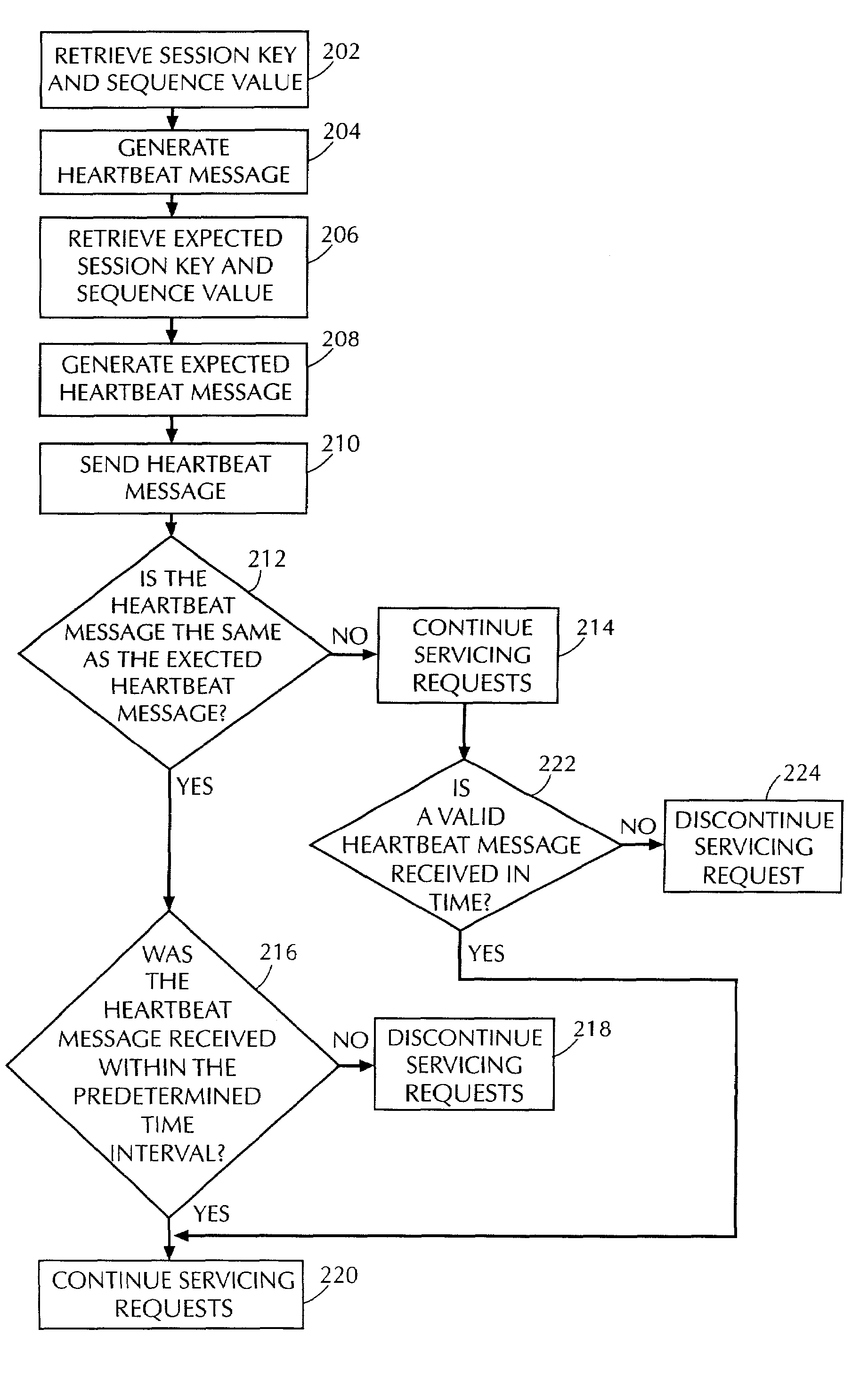
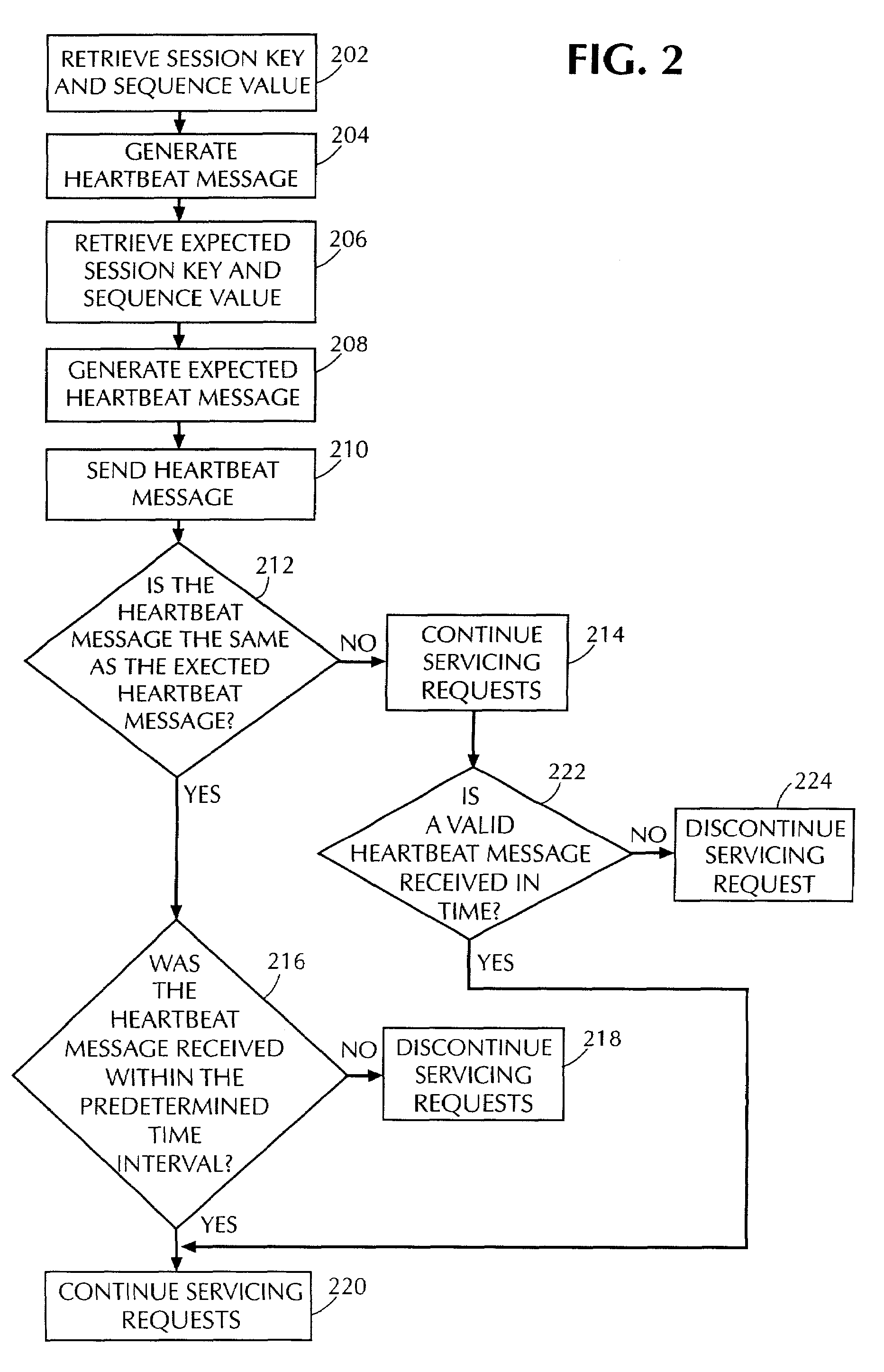
System and method for computer storage security
ActiveUS7093127B2Improve securityDigital data processing detailsUser identity/authority verificationComputer hardwareStorage security
A system and method that improves security of a computer storage system by requiring an initiating computer to periodically reaffirm its identity by transmitting a message to a servicing computer. The message contains a previously established authentication message and a sequence value, established by and known only to the original participants. A message must be received by the servicing computer within a predetermined time interval in order to maintain data communications between the original participants.
Owner:FALCONSTOR
Electronic medical record management method and system
InactiveCN106934243AGuaranteed originalityGuarantee authenticitySpecial data processing applicationsPatient-specific dataMedical recordStorage security
The present invention provides an electronic medical record management method and system. According to the method and system provided by the present invention, the block chain idea is used in the electronic medical record system, the time chain based distributed database is used to keep patient historical medical record information original, and the source for each record can be traced. The method and system provided by the present invention have the following beneficial effects that: 1. medical record information and medical record operation information are ensured to be original and authentic; 2. data storage security of medical record information and medical record operation information is ensured; 3. personal privacy of the patient can be ensured not to be exposed; and 4. rapid sharing of medical record information and medical record operation information is realized.
Owner:北京医拍智能科技有限公司
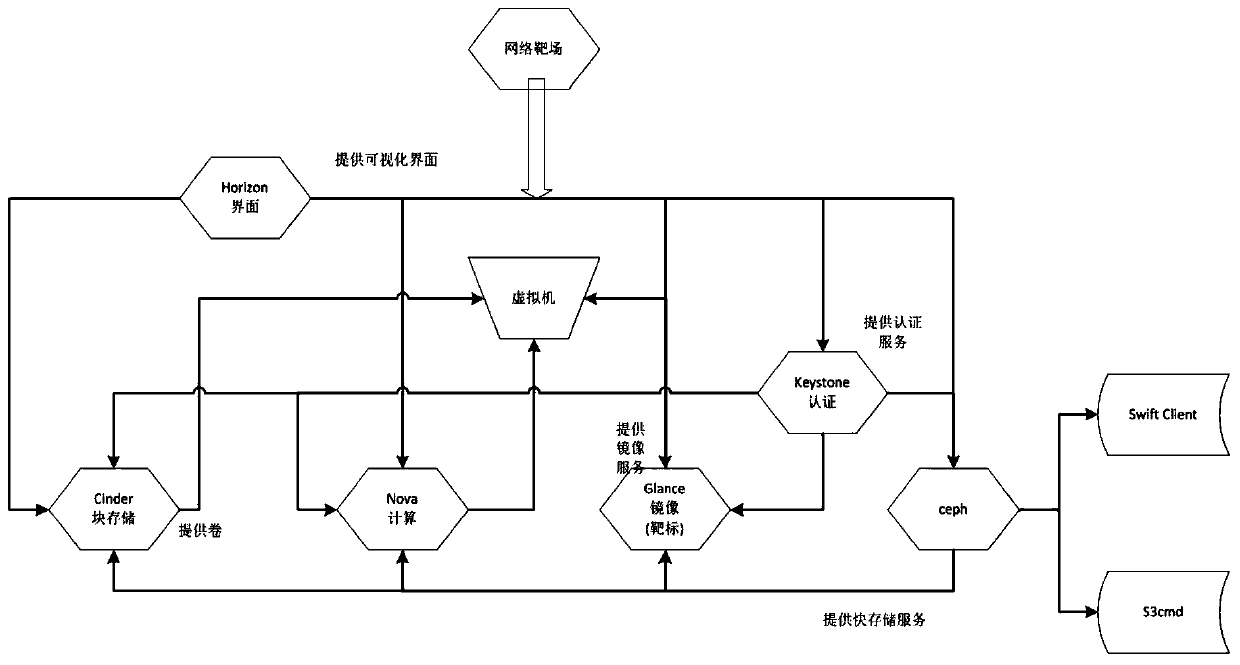
Ceph-based network target range rear-end storage system design method
PendingCN110750334AImprove deployment efficiencyImprove storage securityInput/output to record carriersSoftware simulation/interpretation/emulationStorage securityIncremental backup
The invention relates to a Ceph-based network target range rear-end storage system design method, and relates to the technical field of information security. The invention provides a construction method of a network target range rear-end storage system under a cloud architecture in order to solve the problems existing in an existing network target range rear-end storage system. According to the method, the Ceph is combined with the OpenStack, the Ceph is used as Nova in the OpenStack; an identity authentication service Keystone of the OpenStack is bound with a Ceph object gateway at a storagerear end of a Glance, Cinder native component, and secondary development of management application is carried out based on a Ceph gateway module. The method can effectively improve the deployment efficiency and the storage security of the network target range. Therefore, the functions of second-speed starting of the virtual machine, real-time migration of the virtual machine, data fragmentation storage, data full backup, data incremental backup and the like in the network target range are achieved.
Owner:BEIJING INST OF COMP TECH & APPL
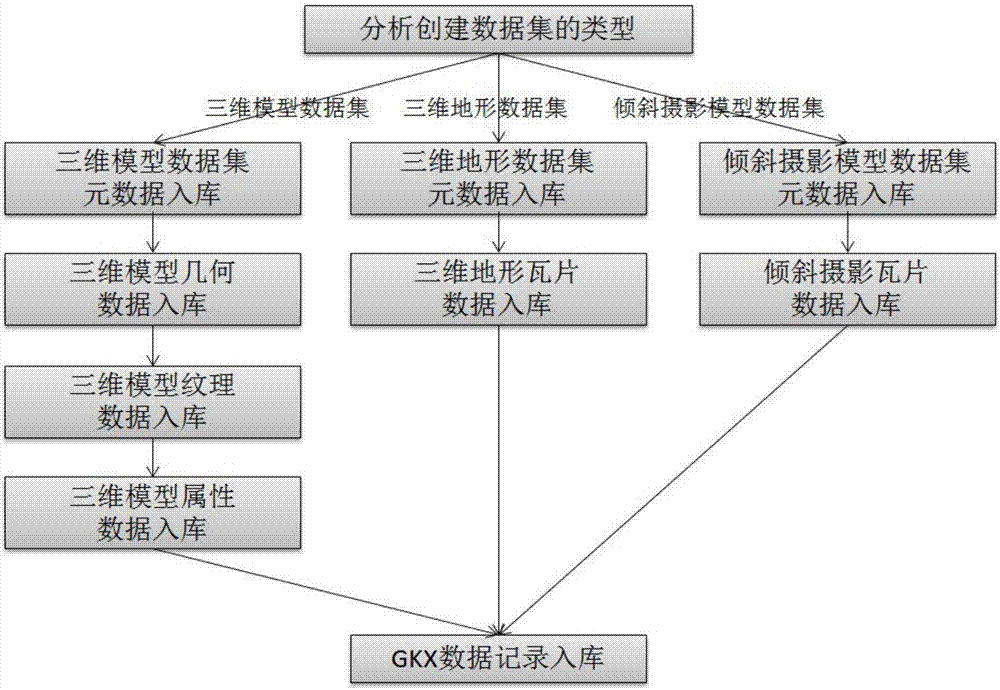
Creating and visiting method for GKF three-dimensional space database
ActiveCN107402958AEasy to storeIncrease demandSpecial data processing applications3D modellingStorage securityRelational database
The invention discloses a creating and visiting method for a GKF three-dimensional space database, and belongs to the field of three-dimensional digital cities and three-dimensional geographic information systems. For meeting requirements of storage and rapid visiting of data of a three-dimensional model, a three-dimensional topography and an inclined camera shooting model, the creating and visiting method for the GKF three-dimensional space database on the basis of NoSQL thinking and a memory mapping technology is provided, and the storage safety and the rapid visiting efficiency of the data of the three-dimensional model, the three-dimensional topography and the inclined camera shooting model are improved. Characteristics of mass, binary fluidization, capability of not requiring transaction awareness in visiting and the like of the three-dimensional model, the three-dimensional topography and the inclined camera shooting model are considered, compared with a three-dimensional space database stored based on a relational database, the creating and visiting method for the GKF three-dimensional space database conforms to features of the data of the three-dimensional model, the three-dimensional topography and the inclined camera shooting model, and is more compact in utilization of storage space, better in safety and higher in data access efficiency.
Owner:CHONGQING SURVEY INST
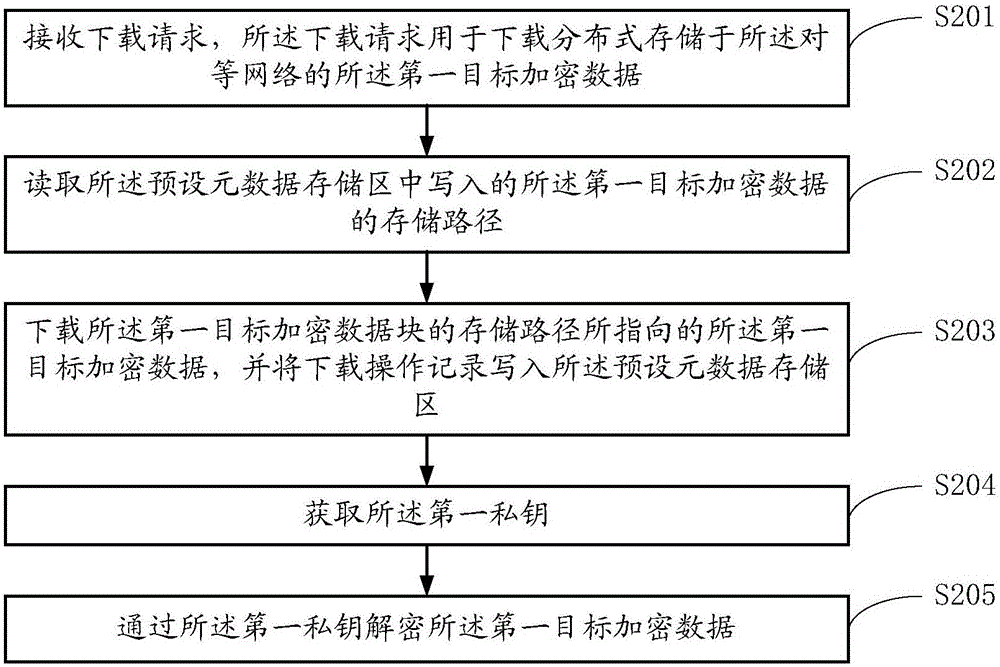
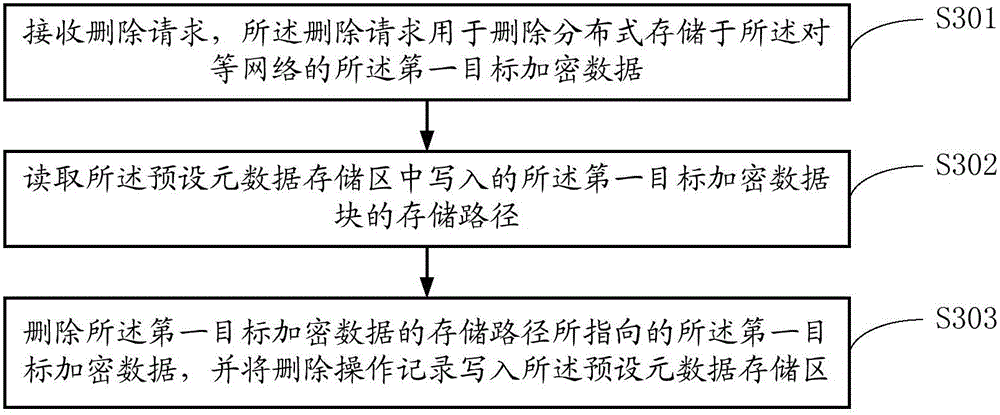
Distributed cloud data management method and system based on peer-to-peer network
ActiveCN106612285AKeep storage safeIncrease storage spaceTransmissionCloud data managementStorage security
The invention belongs to the technical field of electronics, and provides a distributed cloud data management method and system based on a peer-to-peer network. The peer-to-peer network comprises a plurality of user nodes, and each user node in the peer-to-peer network can encrypt data via a private key of a user of the node and then upload the data to the peer-to-peer network to store the encrypted data to other user nodes of the peer-to-peer network in a distributed manner. By encrypting data and storing the data to the user nodes of the peer-to-peer network in the distributed manner, mass data can be stored, so that the storage security of data is effectively guaranteed while the existing storage space is expanded.
Owner:TCL CORPORATION
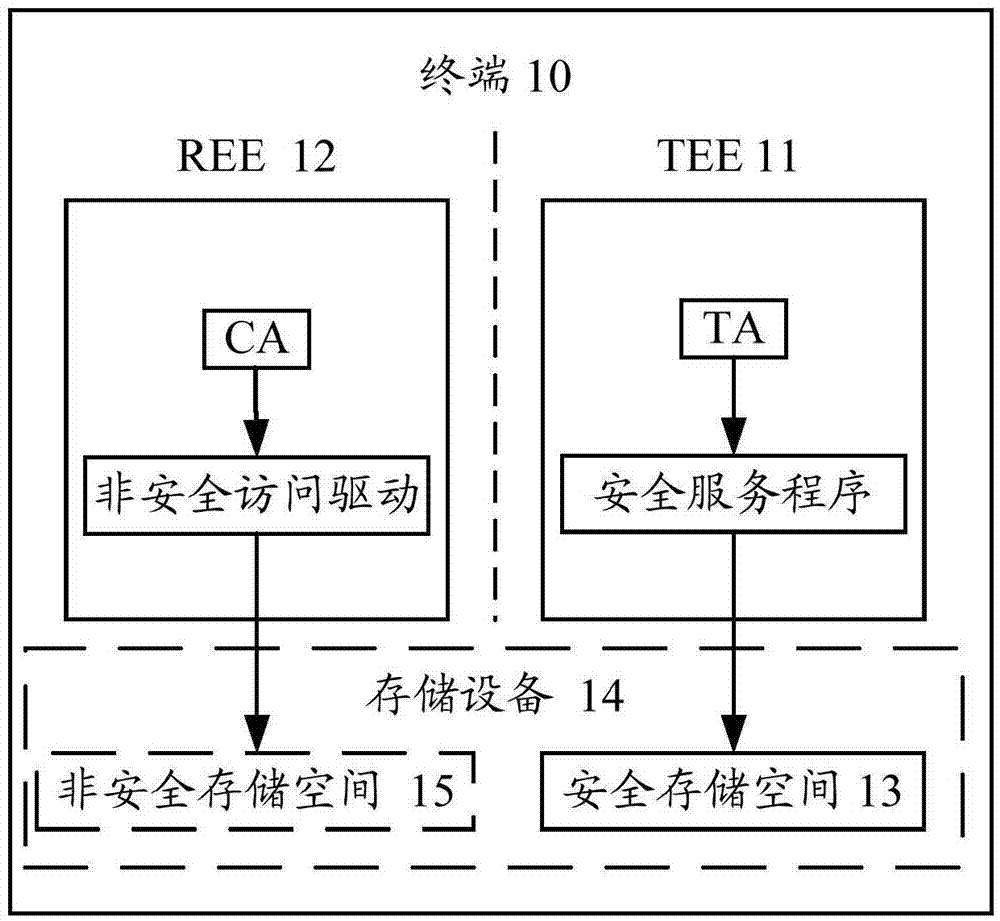
Method and apparatus for accessing storage space
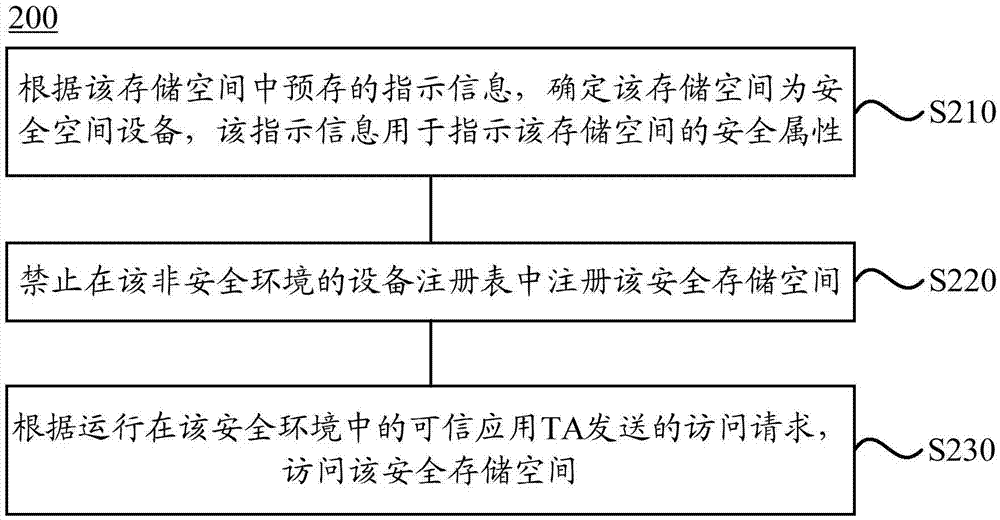
ActiveCN105447406APrevent leakageAvoid destructionDigital data protectionInternal/peripheral component protectionStorage securityComputer terminal
The present invention discloses a method and apparatus for accessing a storage space, so as to improve the storage security of private data on a terminal. The method is applied to the terminal configured with the storage space, and a running environment of an operating system of the terminal comprises a secure environment and an insecure environment. The method comprises: according to indication information pre-stored in a storage space, determining that the storage space is a secure storage space, wherein the indication information is used for indicating a secure attribute of the storage space; prohibiting registering the secure storage space in a device registry in an insecure environment; and accessing the secure storage space according to an access request sent by a trusted application TA running in a secure environment. The apparatus comprises a determining module, a registration module, and an access module. The determining module, the registration module, and the access module are used for carrying out the method described above.
Owner:HUAWEI TECH CO LTD
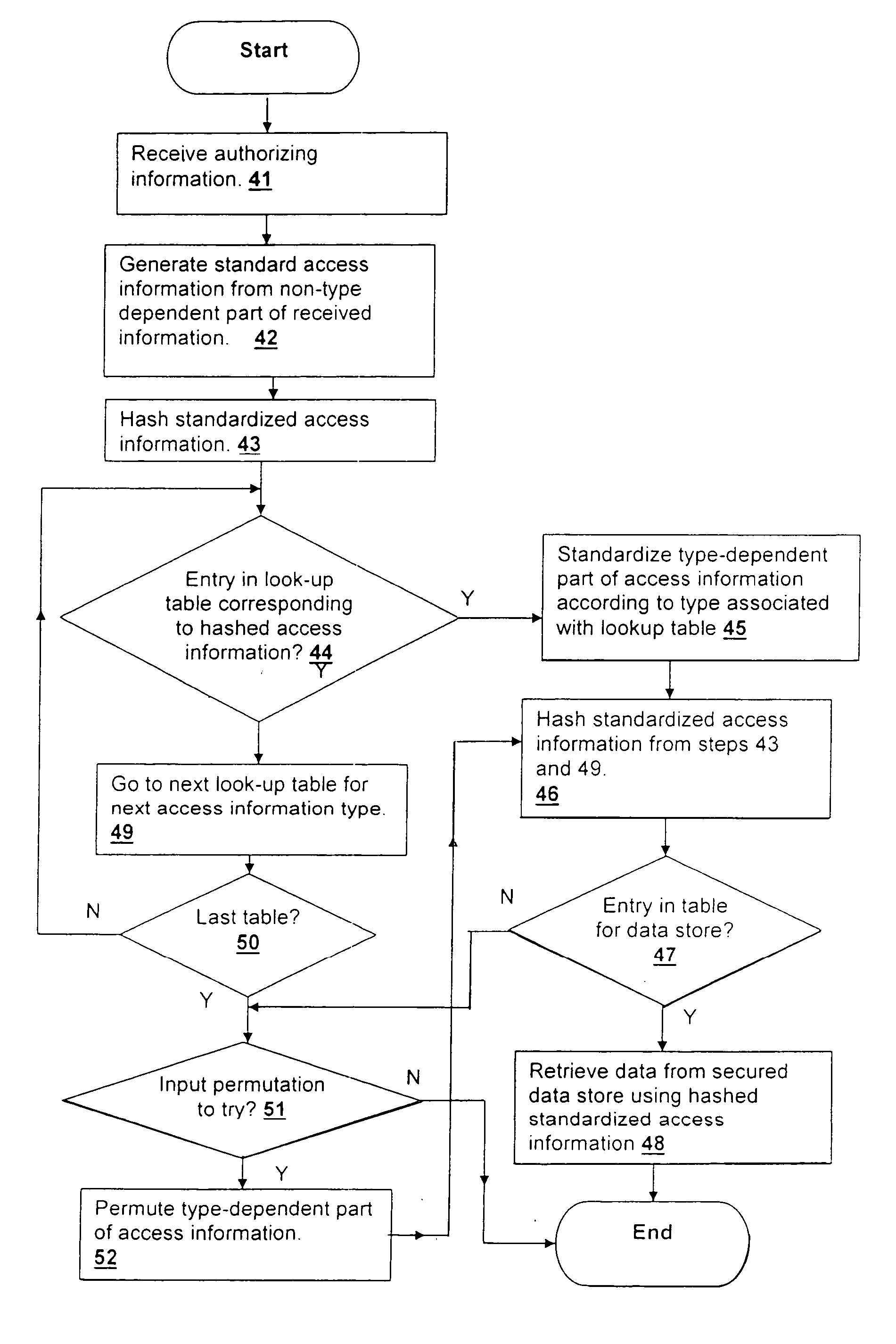
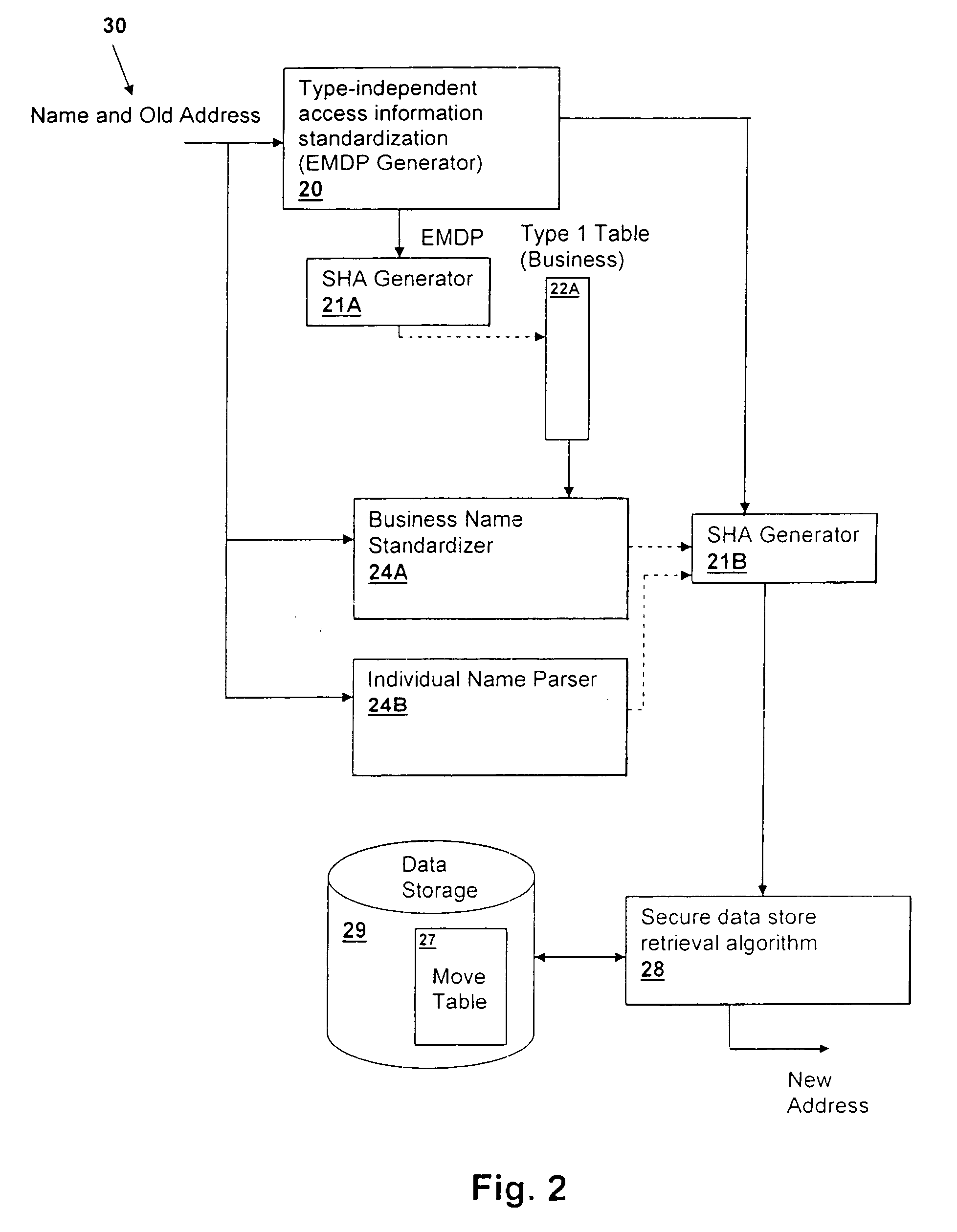
Method and system for efficientyly retrieving secured data by securely pre-processing provided access information
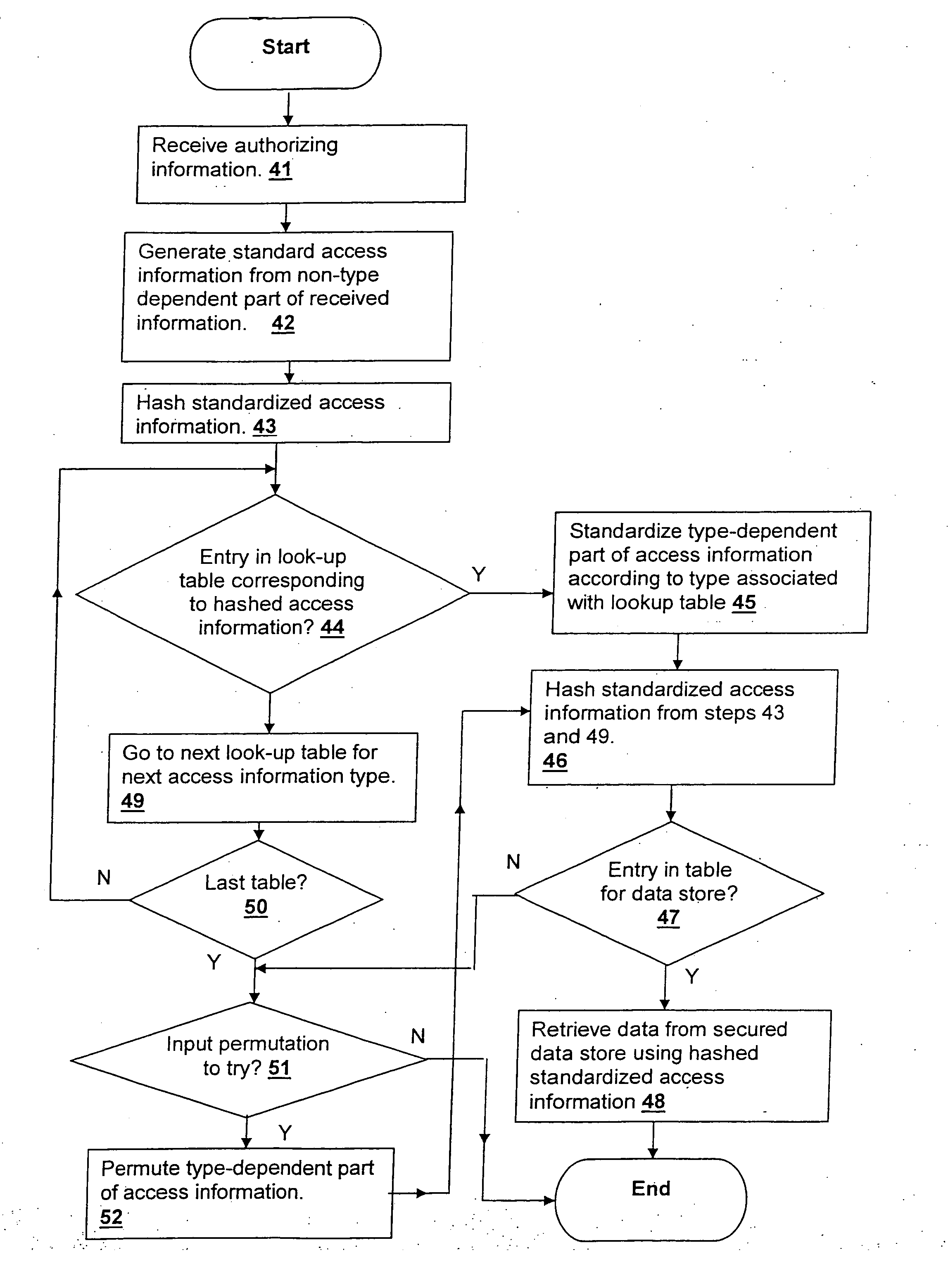
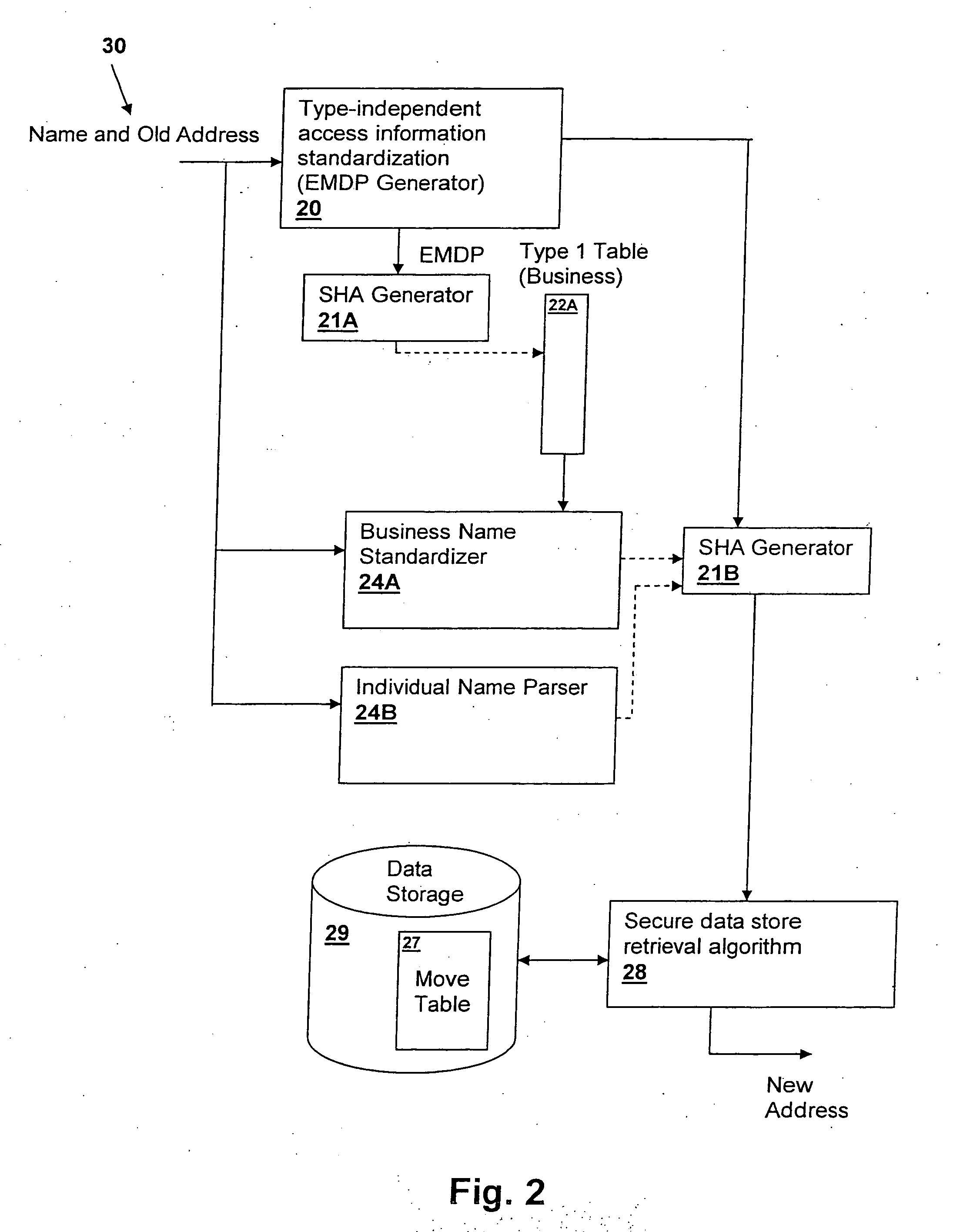
InactiveUS20060031213A1Data processing applicationsDigital data information retrievalInformation typeStorage security
A method and system for efficiently retrieving secured data by securely pre-processing provided access information, provides data store security based on only a single piece of access information, which is generally public, such as the proper name of a business or individual that is used to retrieve mailing address information. The access information is hashed for access to a secured data store and efficient access and low data storage for permutations of input access information are provided by verifying the presence of an entry for the hashed access information in a look-up table. If an entry is found, the data store is accessed using the hashed access information, but if an entry is not found, another look-up table corresponding to another information type may be tried or the input access information permuted and retried.
Owner:US POSTAL SERVICE
Method and system for accessing cloud storage data by user
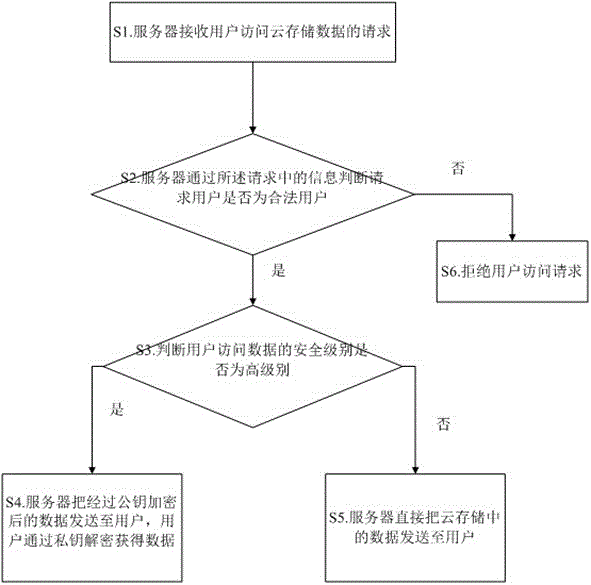
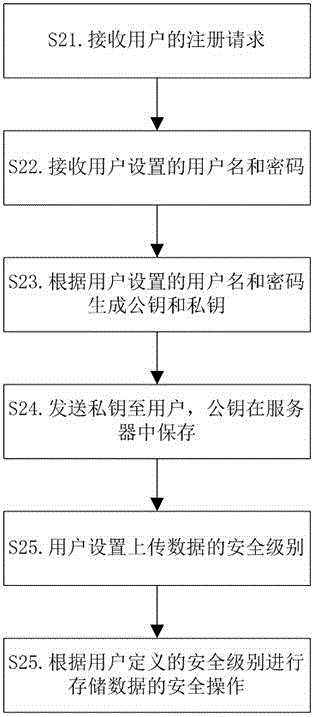
InactiveCN106027552AAchieve securityImplement storage securityTransmissionStorage securityData information
The invention relates to a method and system for accessing cloud storage data by a user. Specifically, the method comprises the steps that a server receives a request of the user for accessing the cloud storage data; the server judges whether the request user is a legal user or not through the request; a security level of user access data is further judged through the requested data information if the request user is the legal user; the server sends data encrypted by a public key to the user if it is judged that the security level is a high level selected by the user; the user decrypts the data through a private key to obtain the data; the server directly sends the data in the cloud storage to the user if it is judged that the security level is not the high level selected by the user; and an access request is refused if the server judges that the request user is an illegal user. According to the method and the system, the security level of the cloud data is set by the user; different data storage and encryption operations are carried out for different security levels; and through identification of user information, the user authentication security is realized; and the storage security of important data is realized.
Owner:中经汇通电子商务有限公司
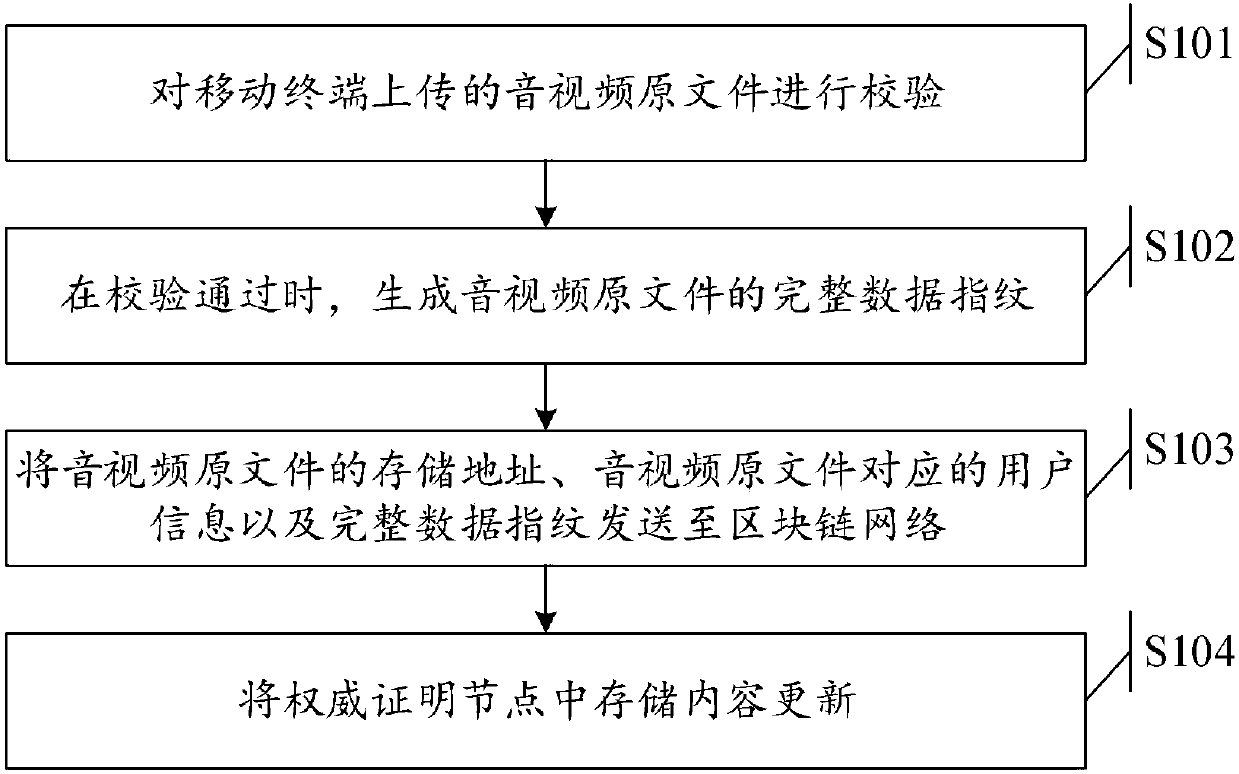
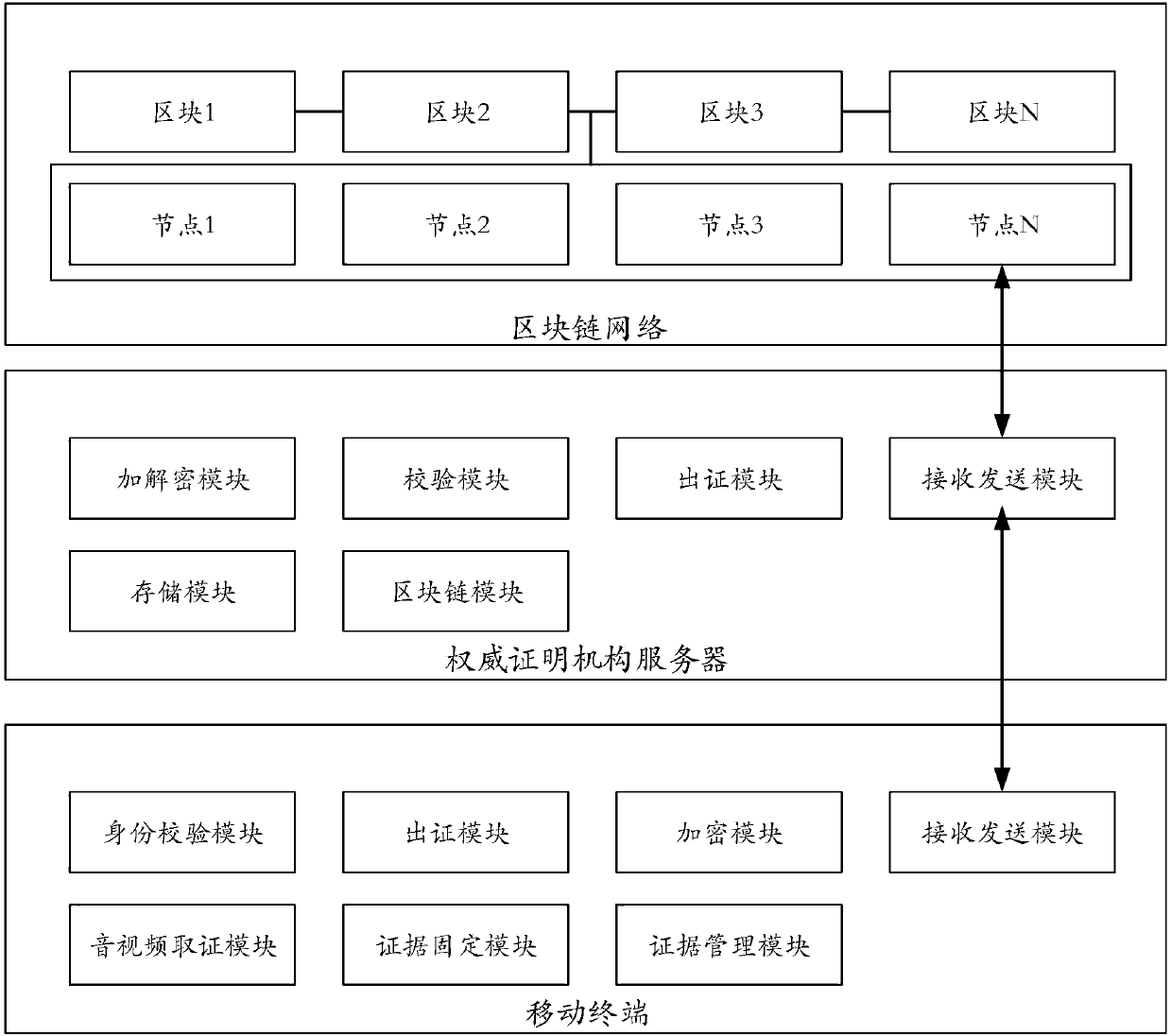
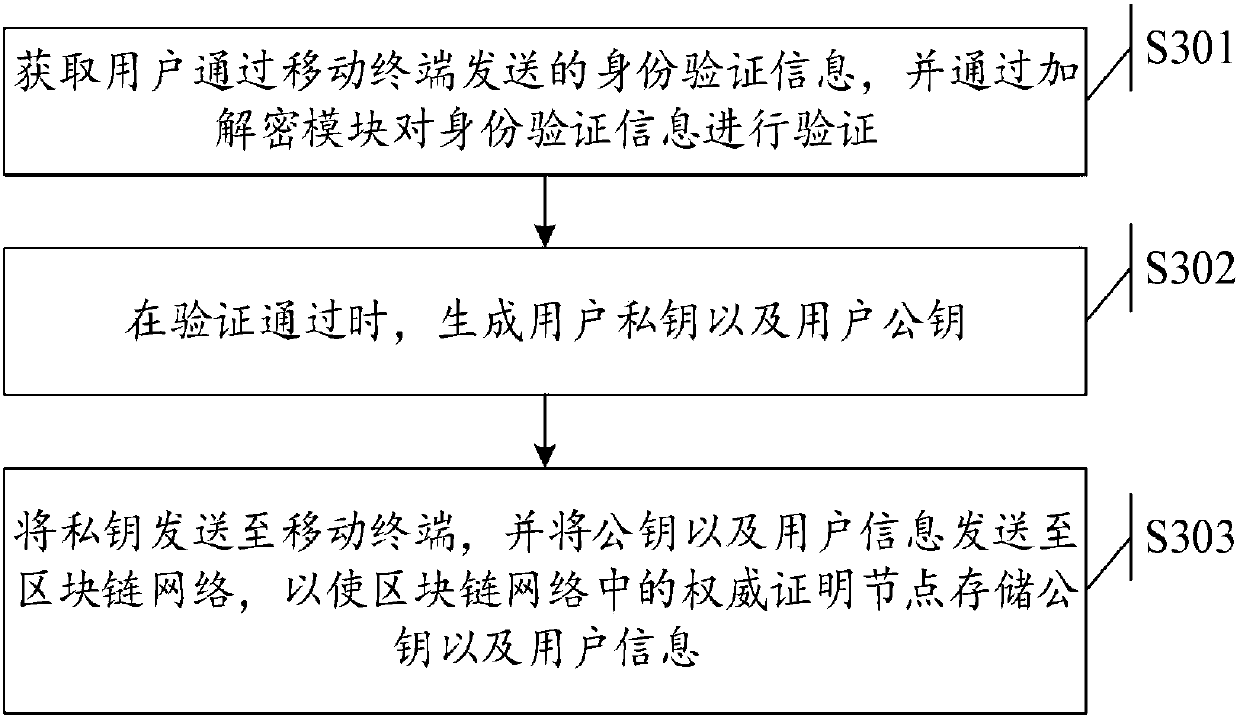
Audio and video evidence preservation method and system
InactiveCN107948736AImprove securityImprove immutabilityTelevision system detailsColor television detailsComputer hardwareComplete data
The invention discloses an audio and video evidence preservation method and system. The method comprises the following steps: verifying an audio and video original file uploaded by a mobile terminal;when the verification passes, generating a complete data fingerprint of the audio and video original file, sending a storage address of the audio and video original file, user information corresponding to the audio and video original file and the complete data fingerprint to a block chain network, and updating storage contents in an authoritative certification node. By adoption of the method, theformation time of the audio and video files and the instantaneity, directness, authenticity, reliability and storage security of recorded contents can be proved, therefore the audio and videos recorded by mobile terminals become credible judicial evidence.
Owner:法信公证云(厦门)科技有限公司
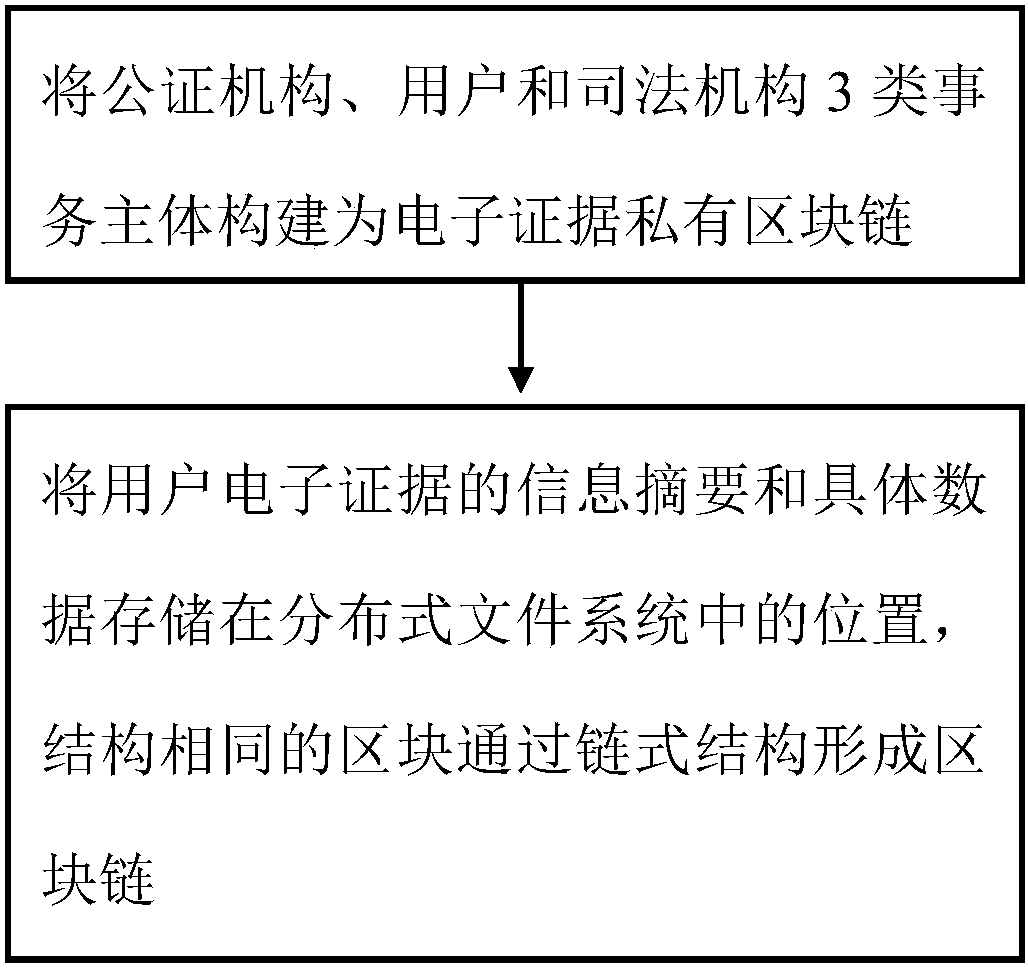
Decentralized storage security implementation method
ActiveCN108429759ASafe for secure storageSafe to useEncryption apparatus with shift registers/memoriesUser identity/authority verificationStorage securityChain structure
The invention provides a decentralized storage security implementation method. The method comprises the following steps: building an electronic evidence private block chain by three types of affair main bodies, namely a notary organization, a user organization and a judicial organ; and storing information abstracts and specific data of electronic evidences of users into positions in a distributedtype file system, and forming a block chain by blocks of same structures through chain structures. The invention provides the decentralized storage security implementation method, which effectively implements secure storage and effective use of the electronic evidences of the users.
Owner:CHENGDU RES INST OF UESTC
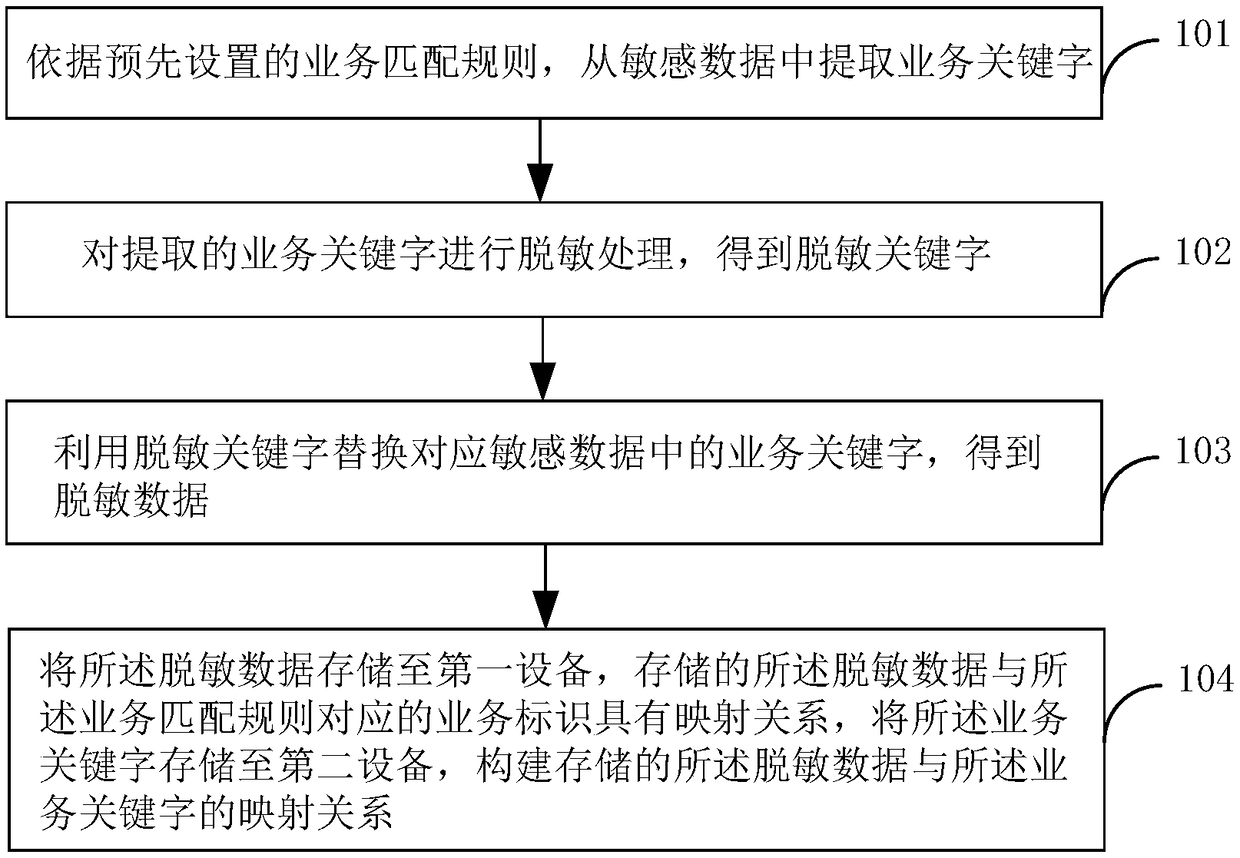
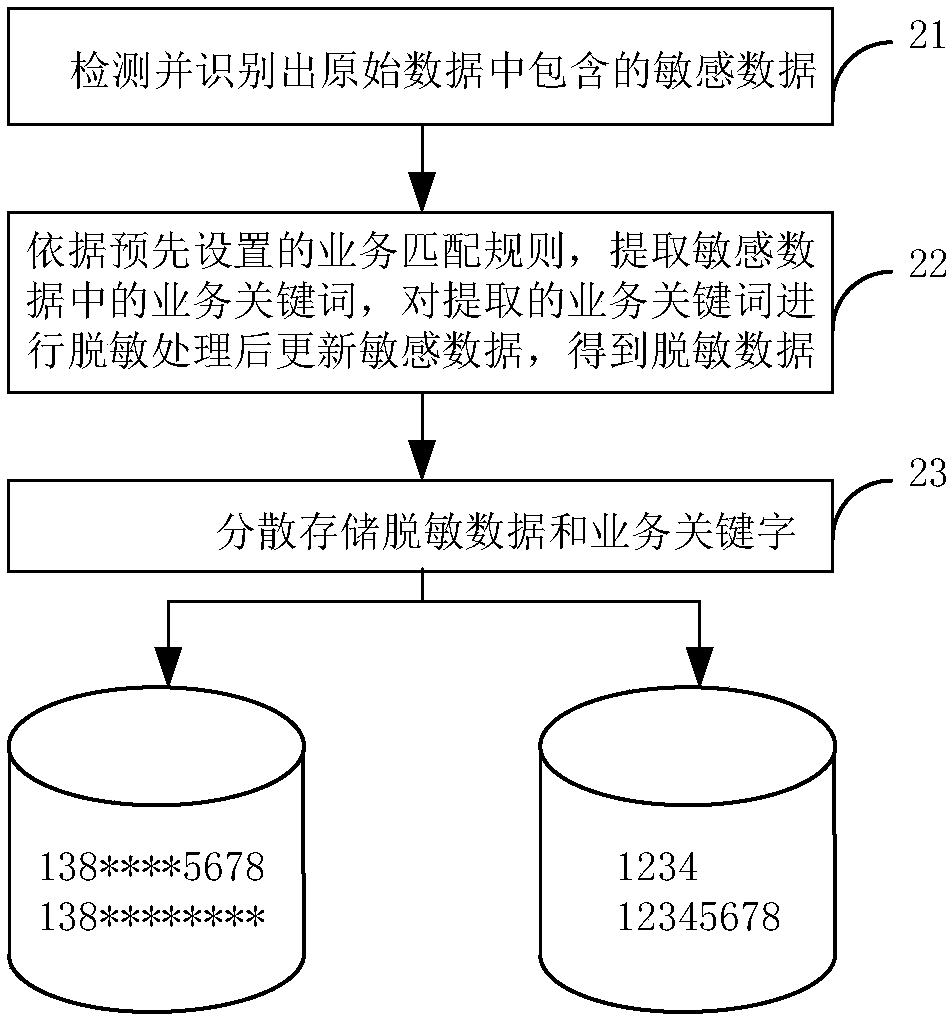
Sensitive data storage method, device and system
InactiveCN108289095AImprove storage securityMetadata multimedia retrievalTransmissionStorage securityMatch rule
The application provides a sensitive data storage method, device and system capable of improving the storage security of sensitive data. The method includes: extracting a service keyword from the sensitive data according to a preset service matching rule; desensitizing the extracted service keyword to obtain a desensitized keyword; replacing the service keyword in the corresponding sensitive databy the desensitized keyword to obtain desensitized data; storing the desensitized data in a first device, wherein the stored desensitized data has a mapping relationship with a service identifier corresponding to the service matching rule, and storing the service keyword in a second device and constructing a mapping relationship between the stored desensitized data and the service keyword.
Owner:诚壹泰合(北京)科技有限公司
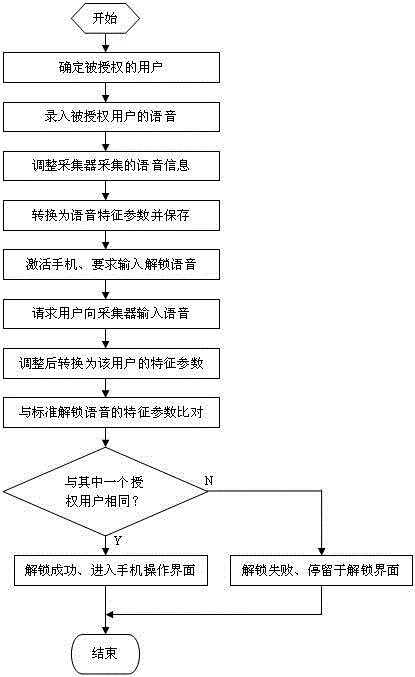
Mobile phone unlocking method based on voice recognition
InactiveCN102752453AImprove securityImprove reliabilitySubstation equipmentKey pressingStorage security
The invention discloses a mobile phone unlocking method based on voice recognition, and the method comprises following steps of recording and storing standard unlocking voice; requiring the unlocking voice when requesting the user to actuate the mobile phone; inputting the voice and converting the voice into voice characteristic parameters; and comparing the voice characteristic parameters of the request user with the standard voice characteristic parameters, and enabling successful unlocking if the voice characteristic parameters are identical to the voice characteristic parameters of one authorized user. Due to the adoption of the method, the problem that the unlocking password is easy to decipher or to peer can be overcome, the collected voice information is finally converted to the voice characteristic parameters after being corrected and adjusted, so that the accuracy of the characteristic parameter calculation result is improved, and the reliability of the voice unlocking is further improved; the information content is compared with the voice characteristic parameters, the unlocking can be completed when the inputted voice characteristic parameters completely conform to the standard unlocking voice, the unlocking voice is not easy to decode, the storage security of the private data of the mobile phone is high, and the stored private data of the mobile phone is not easy to leak; and in the unlocking process, the keystroke operation is not needed, so that convenience in use can be realized.
Owner:CHENGDU CK SCI & TECH
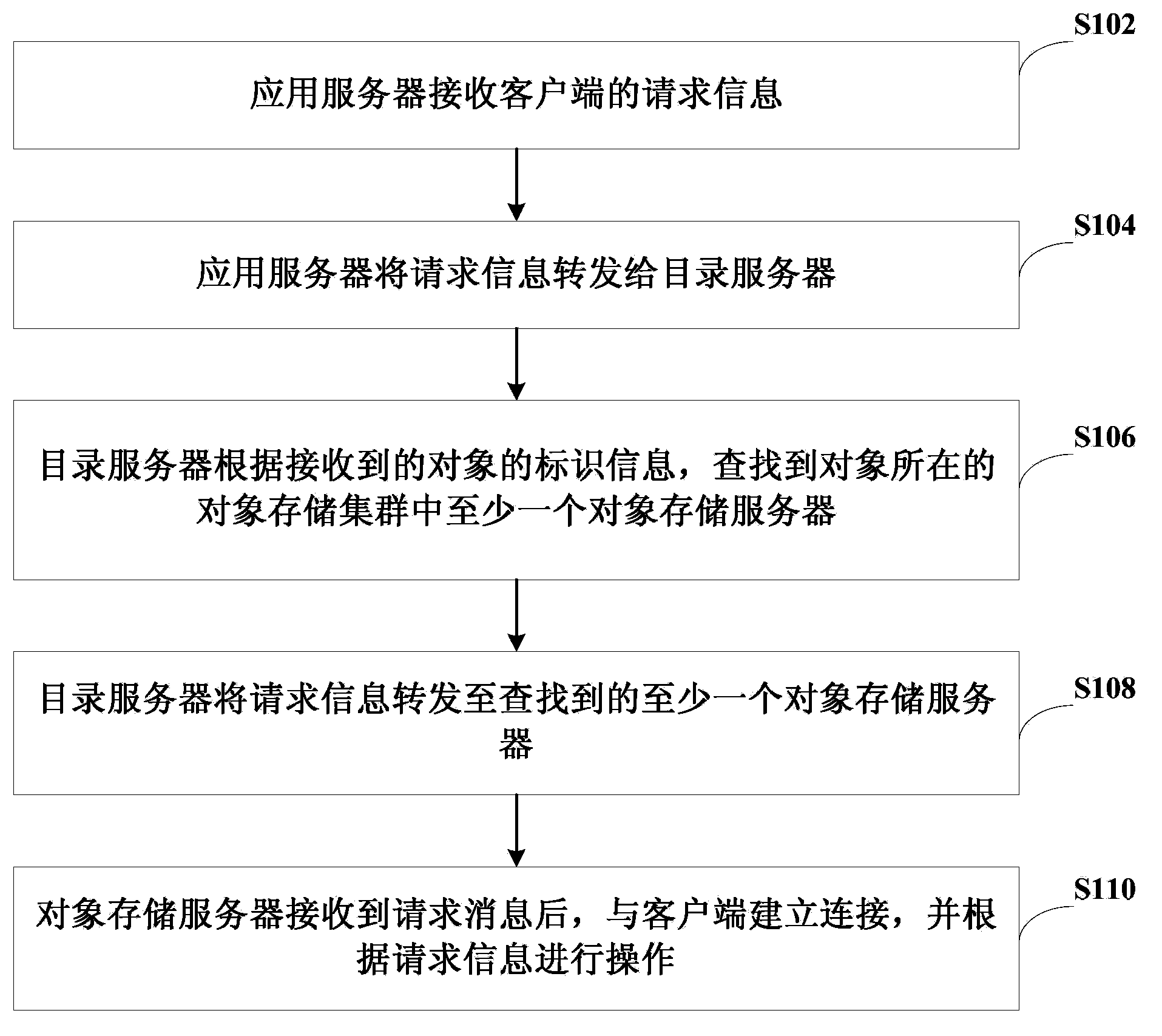
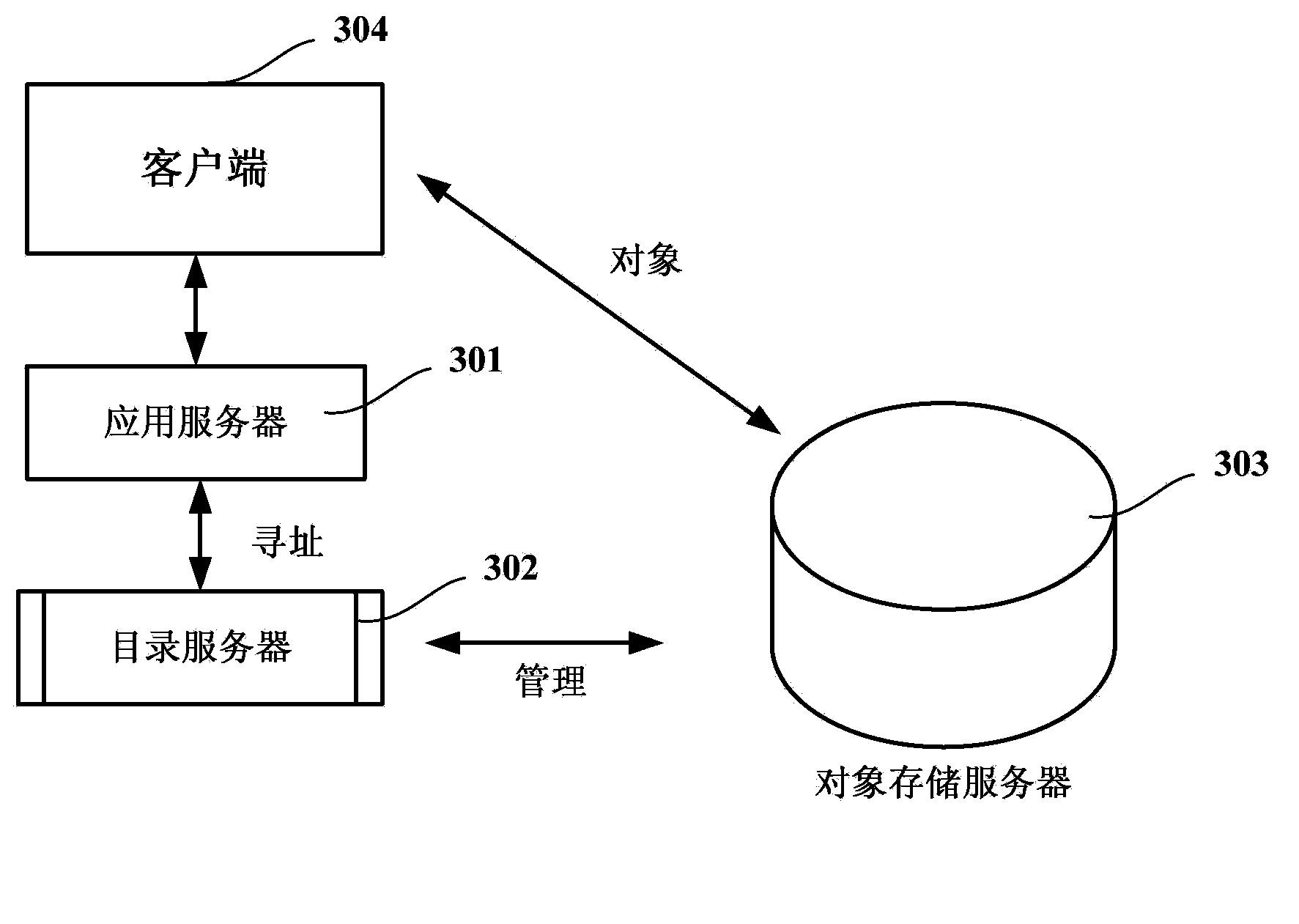
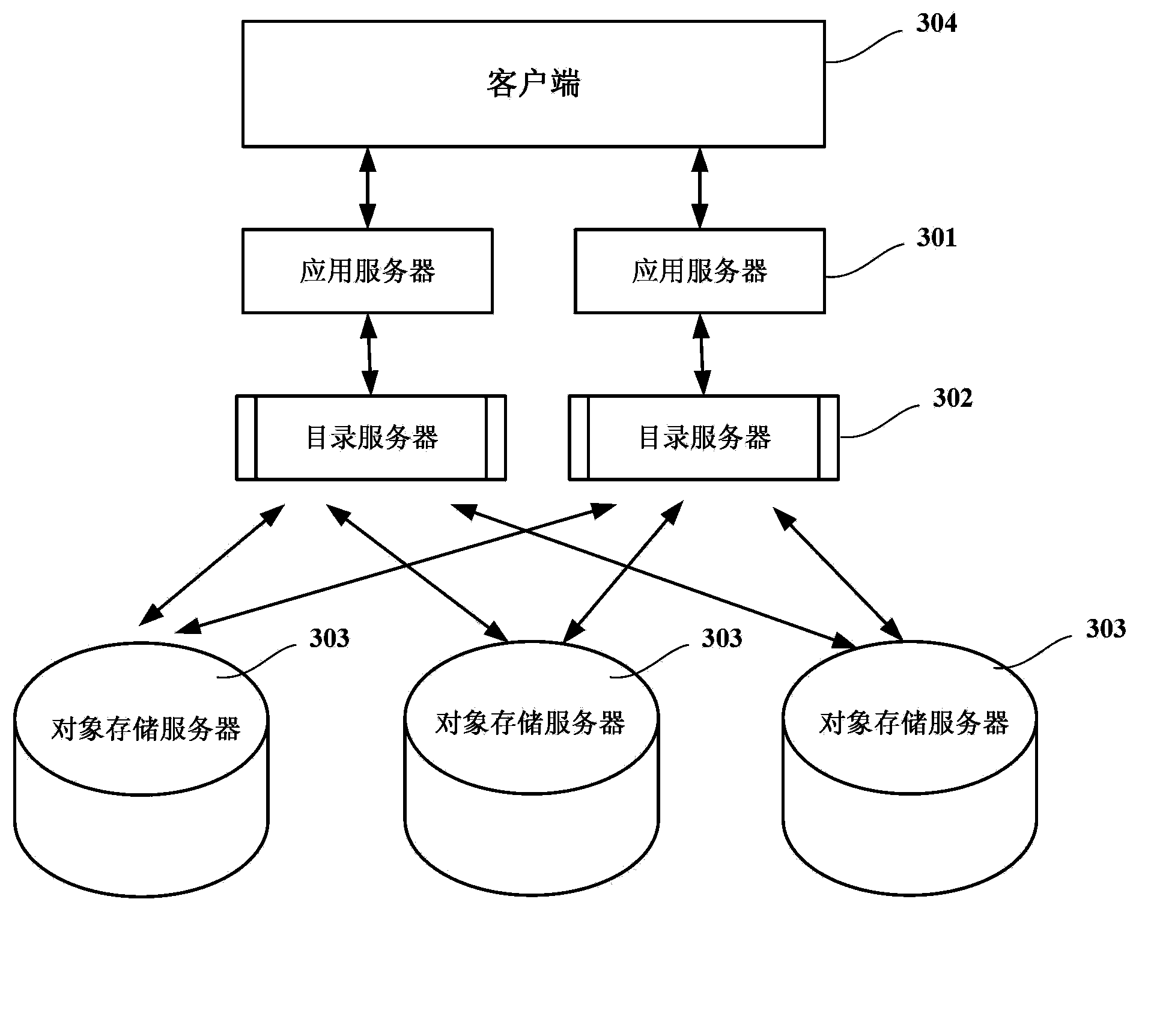
Distributed object processing method and system
The invention provides a distributed object processing method and system. The method comprises: an application server receiving request information of a client, the request information comprising the identification information of an object; the application server forwarding the request information to a directory server; the directory server, according to the identification information of the object of the received request information, finding at least one object storage server in the object storage cluster where the object is in; the directory server forwarding the request information to the found at least one object storage server; and the object storage server, establishing connection with the client after receiving the request information, and carrying out operation according to the request information. Through such an architecture based on distributed object storage, large-scale unstructured data storage needed by a network disc server can be provided, and at the same time, through storage of multiple duplicates of the object, the storage security of the object is guaranteed.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
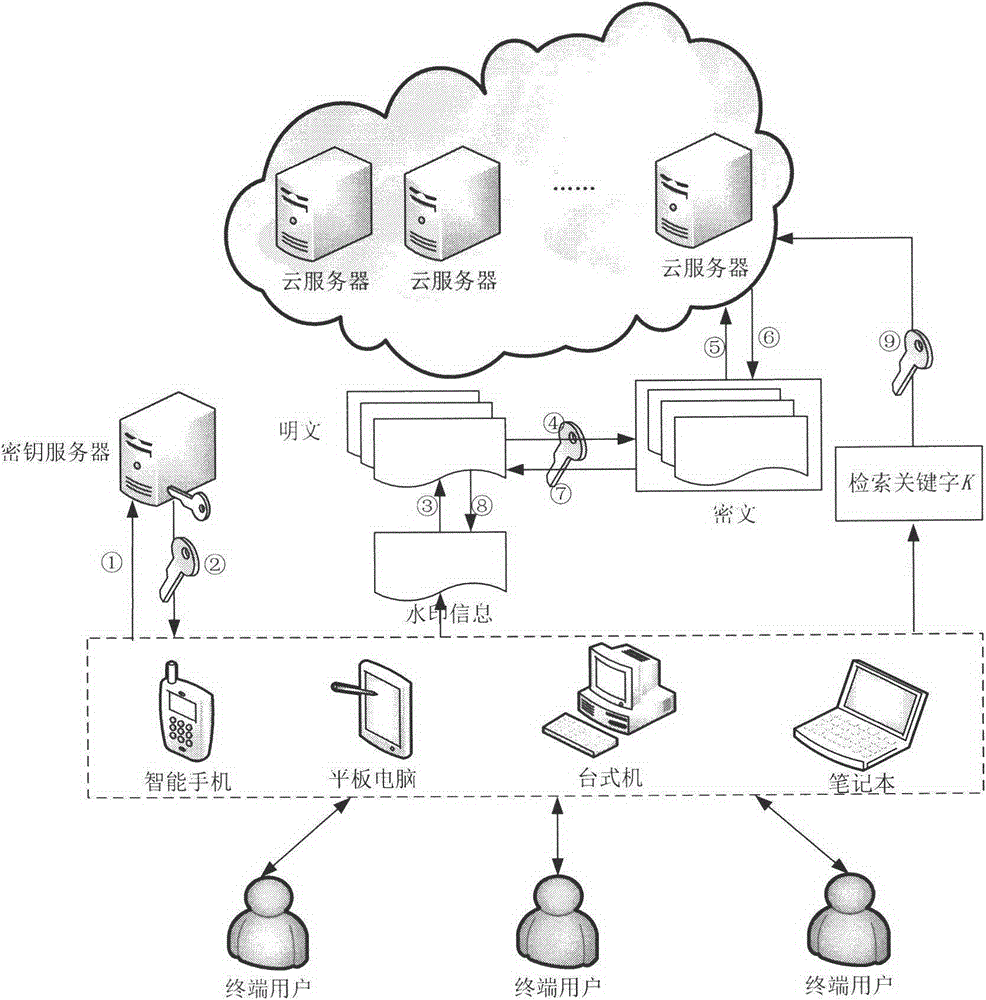
Cloud data security protection method adopting fully homomorphic encryption technology and multiple digital watermarking technology
InactiveCN105323209AEnsure transmission securityEnsure storage securityTransmissionThird partyStorage security
The present invention discloses a cloud data security protection method adopting a fully homomorphic encryption technology and a multiple digital watermarking technology. The cloud data security protection method is characterized in that in a cloud computing environment, a trusted third-party organization distributes a key to a user, after the user stores the key, a fully homomorphic encryption scheme is adopted to encrypt to-be-uploaded data at a user side, then the encrypted data is uploaded to a cloud side, thereby ensuring transmission security and storage security of data; in addition, when the user searches for data, direct search for ciphertext can be performed after a search keyword is encrypted, thereby improving search efficiency; and moreover, before the data is uploaded to the cloud side, a fragile watermarking and a robust watermarking are respectively embedded into the to-be-uploaded data, the purpose of embedding of the fragile watermarking is to prevent illegal modification of the data, so as to achieve authentication for integrity of the data, and the purpose of embedding of the robust watermarking is to protect copyright of the data, so as to achieve authentication for copyright of the data.
Owner:JIANGSU BOZHI SOFTWARE TECH CO LTD
System and method for realizing security storage and access control of data
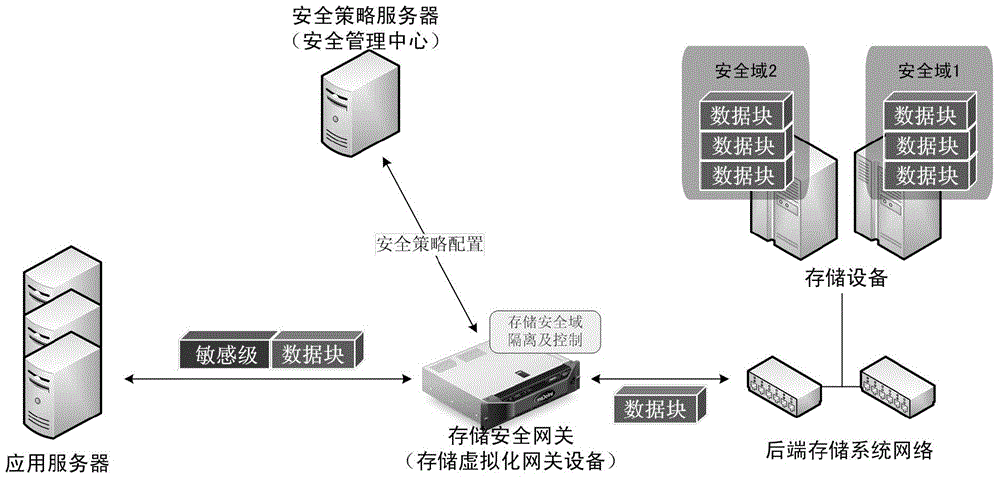
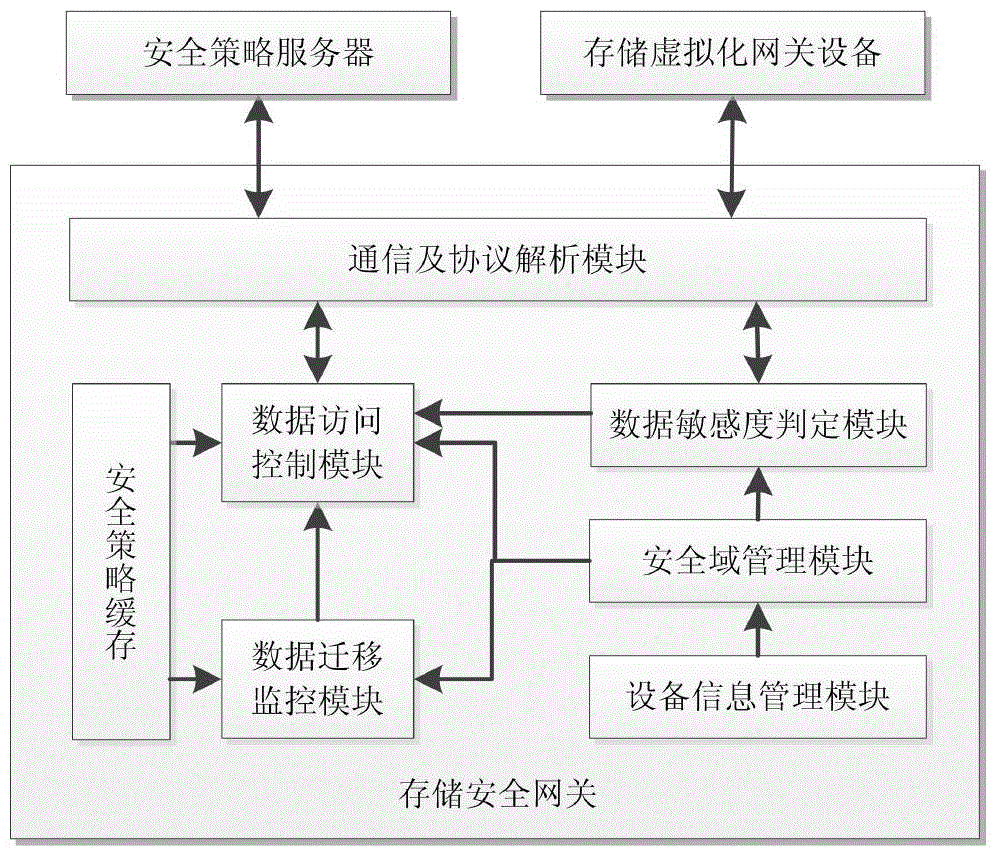
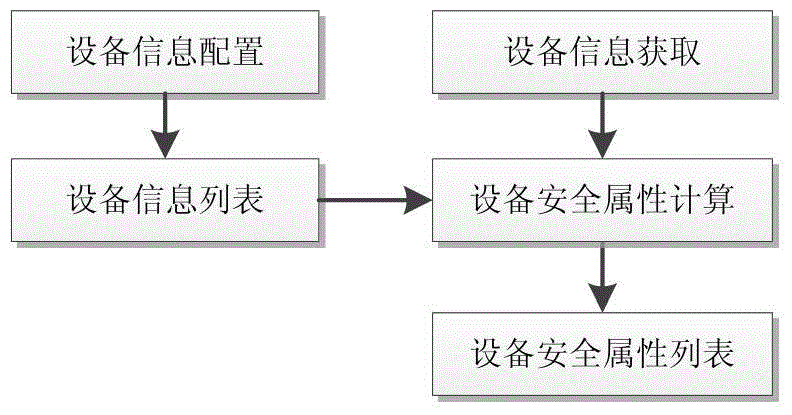
ActiveCN104660578AMeet the need for protectionHigh security requirementsTransmissionStorage securitySecurity domain
The invention discloses a system and method for realizing the security storage and the access control of data. The system comprises an application server, a storage security gateway, a security strategy server and a backend storage system, wherein the storage security gateway is additionally arranged between the application server and the backend storage system so as to realize the partition, the isolation and the access control of data security domains. The storage security gateway and a storage virtualization gateway can synergistically work, and data can be stored in the manner of the security domains on an actual physical medium by utilizing a virtualization technique. When a data access request arrives at the storage virtualization gateway, the storage virtualization gateway can invoke the functions of the storage security gateway so as to realize the isolation and the access control of the data security domains. Because all data requests for access to the backend storage system can be processed by the storage security gateway, security control is guaranteed to be performed on the single path of data without being bypassed. In addition, security control is realized at the bottom layer of data access, so that attack means to data by upper application layers can be effectively avoided.
Owner:董唯元
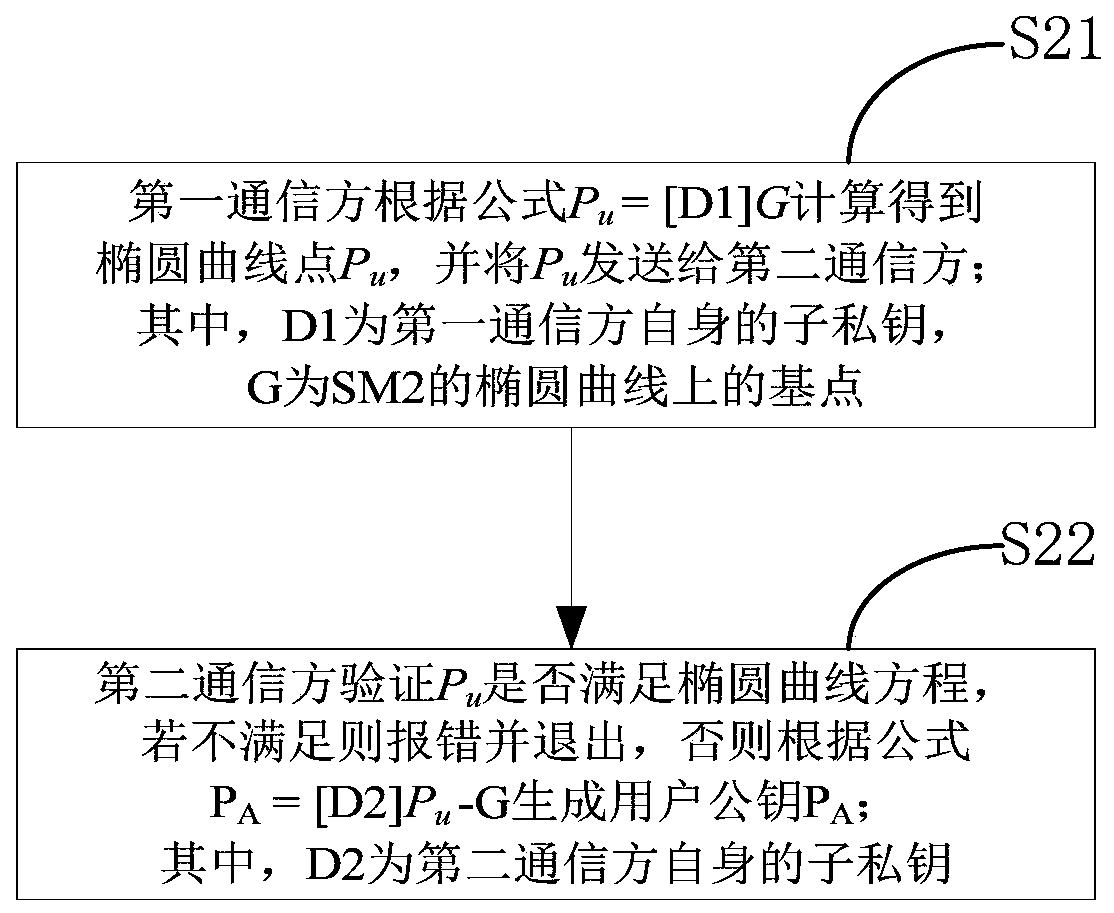
SM2-based two-party collaborative signature method and decryption method
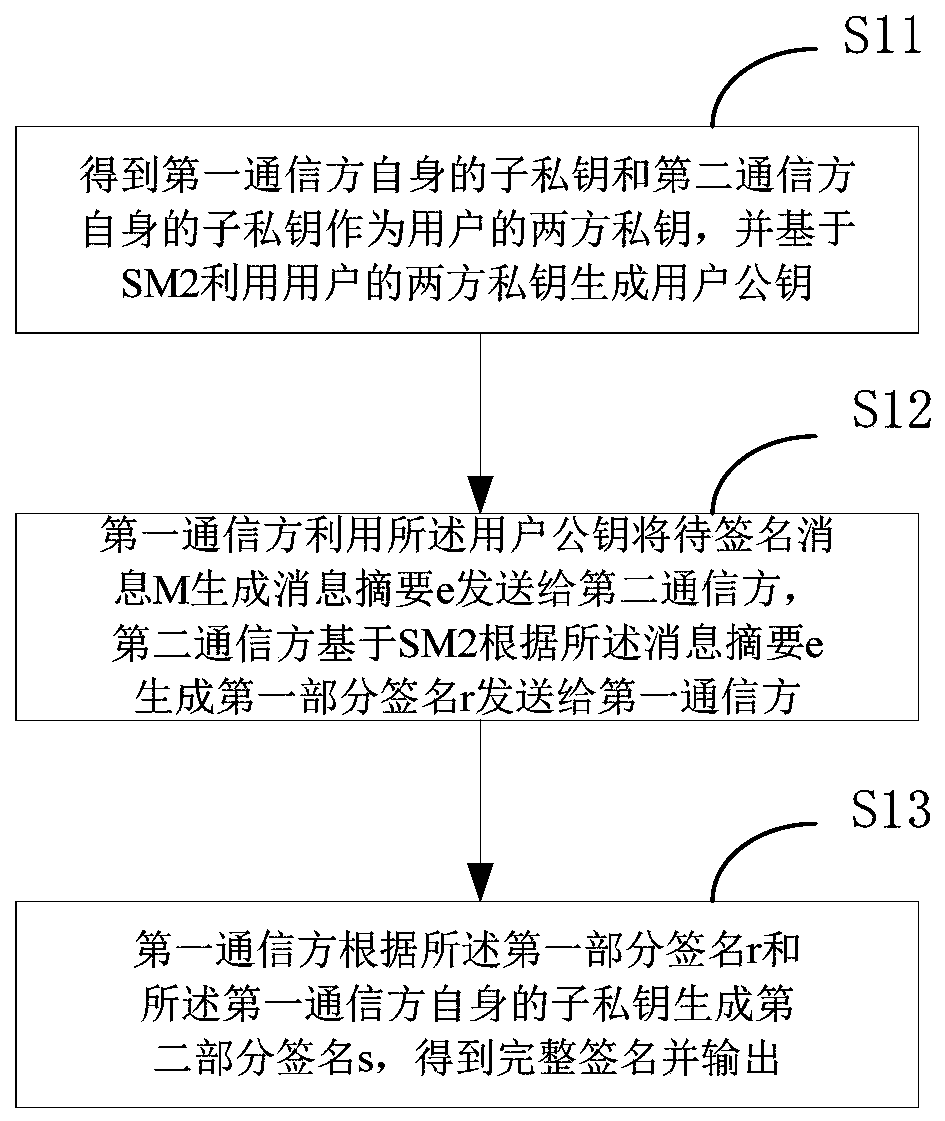
ActiveCN111314089AAddress storage securityEnhanced interactionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesStorage securityInternet privacy
The invention relates to an SM2-based two-party collaborative signature method and decryption method, and belongs to the technical field of digital signature and decryption. The collaborative signature method comprises the following steps: obtaining a sub-private key of a first communication party and a sub-private key of a second communication party as two-party private keys of a user, and generating a user public key by using the two-party private keys of the user based on SM2; the first communication party uses the user public key to generate a message digest e from a to-be-signed message Mand sends the message digest e to the second communication party, and the second communication party generates a first part signature r according to the message digest e based on SM2 and sends the first part signature r to the first communication party; and the first communication party generates a second part signature s according to the first part signature r and a sub private key of the firstcommunication party, and obtains and outputs a complete signature. Meanwhile, the invention relates to a two-party decryption method based on SM2. According to the embodiment of the invention, the problem that the storage security and the use security of the secret key in the prior art have great hidden dangers is solved.
Owner:DATA COMM SCI & TECH RES INST +1
Smart security supervision system
InactiveCN109639797AImprove storage securityImprove robustnessParticular environment based servicesNetwork topologiesMonitoring statusStorage security
The invention is applicable to the technical field of smart security, and provides a smart security supervision system, comprising: a cloud server; a plurality of edge servers that communicate with the cloud server through a first network; a plurality of access devices connected to the edge server; and a plurality of detecting terminals connected to the access devices, wherein the access devices are configured to report the current monitoring data acquired by the detecting terminals to the edge servers by using the second network communication; the edge servers are configured to receive and store the current monitoring data, determine whether the monitoring data exceeds a preset threshold based n the monitoring data, and if so, report the current monitoring data and a first warning messageto the cloud server. The system enhances the storage security of the monitoring data by adding edge servers to analyze and store the monitoring data, so that the data analysis is completed on the local edge server, and the system can still operate normally locally in the case of network delay and network failure with enhanced reliability and good robustness.
Owner:ZDST COMM TECH CO LTD
Distributed storage-based object storage method
ActiveCN106506668AImprove reliabilityImprove usabilityUser identity/authority verificationSpecial data processing applicationsStorage securityAuthentication server
The present invention discloses a distributed storage-based object storage method. The method comprises the steps of building an authentication server by using a distributed storage technology, and completing secure authentication of a user end and a server end; and then optimizing a background IO model for recording fragmented logs so as to improve object storage security. Compared with the prior art, the distributed storage-based object storage method ensures data storage security and the security of a storage cluster, and improves the reliability, availability, security and practicability of the distributed storage cluster.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
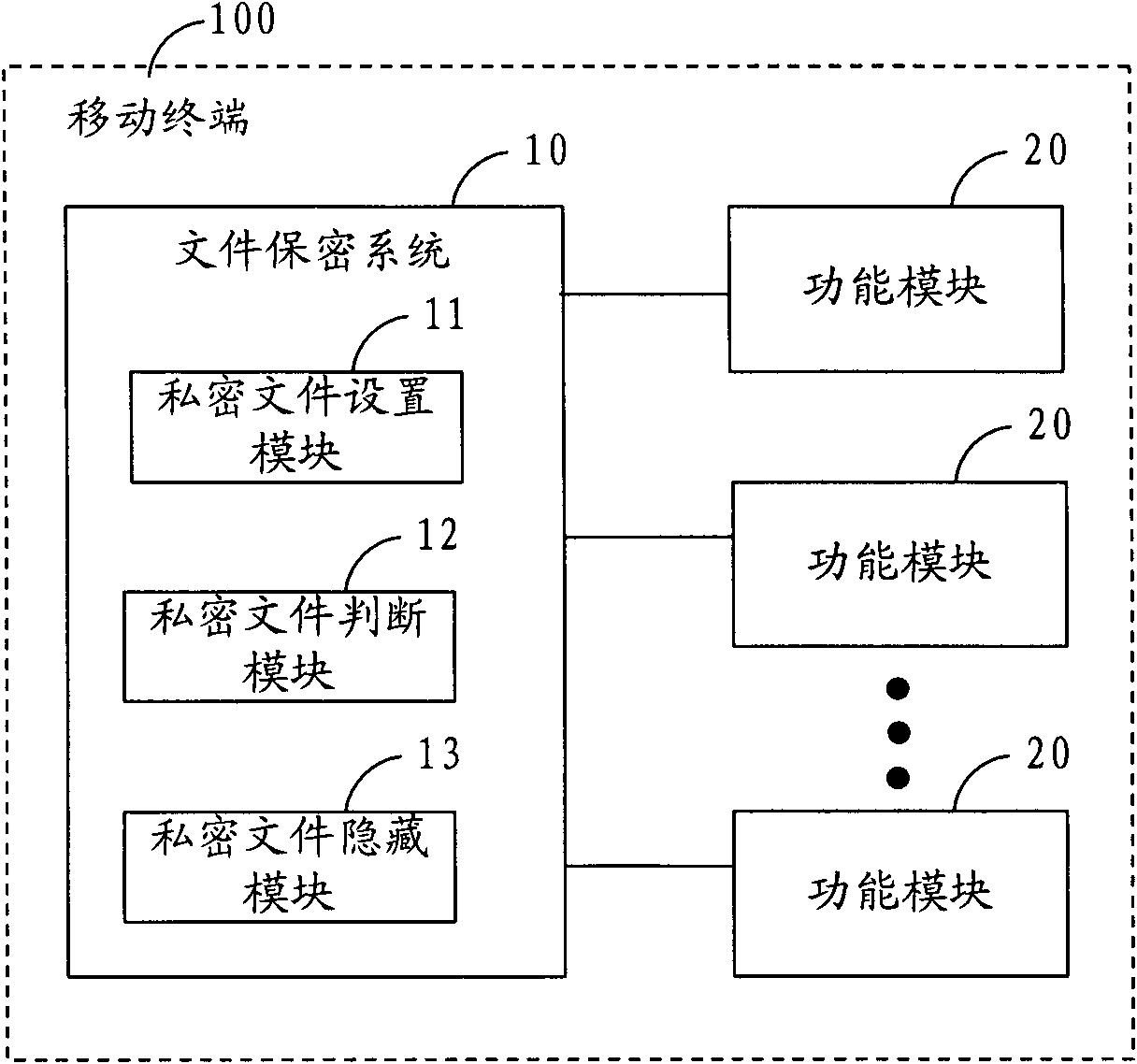
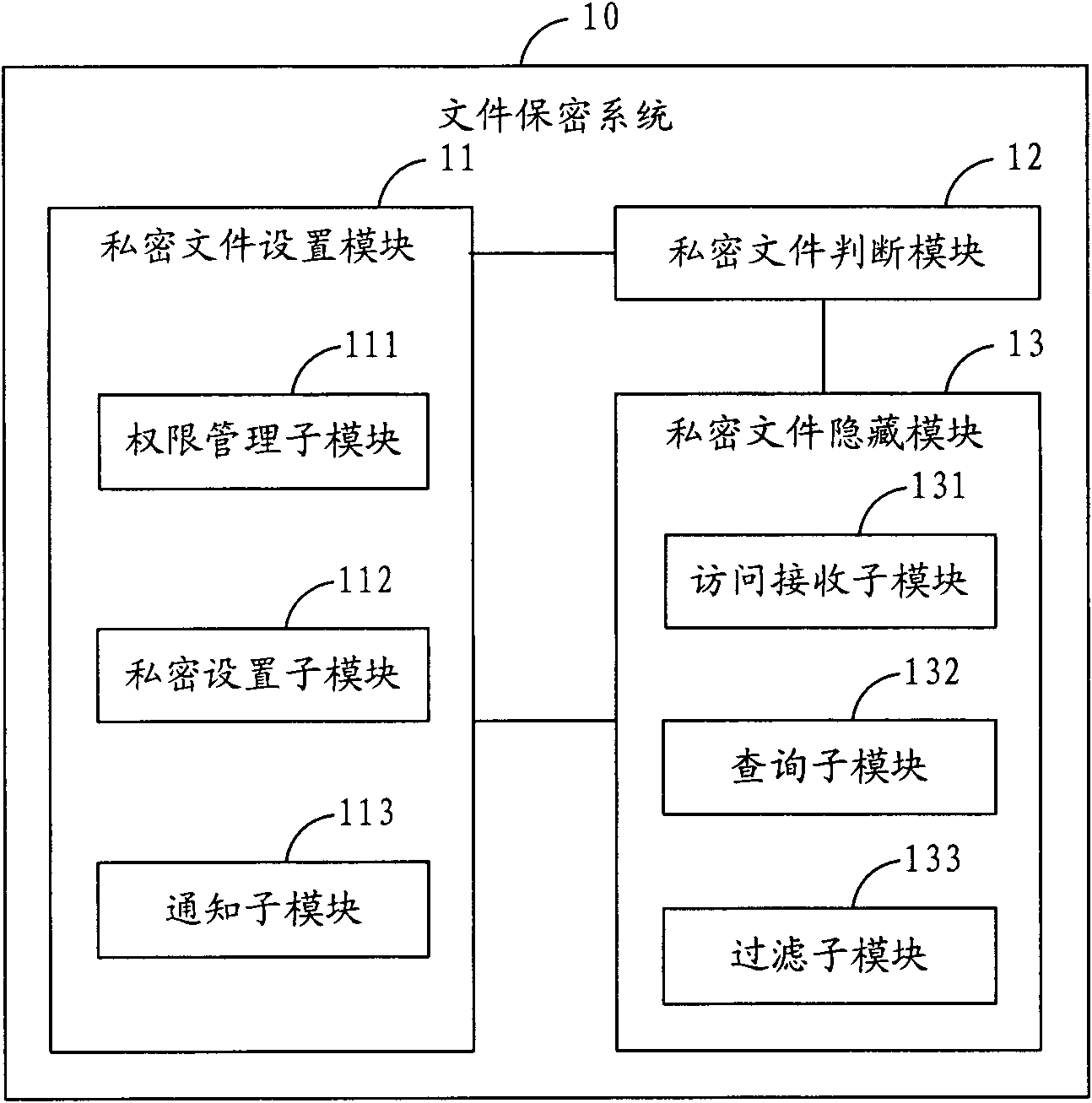
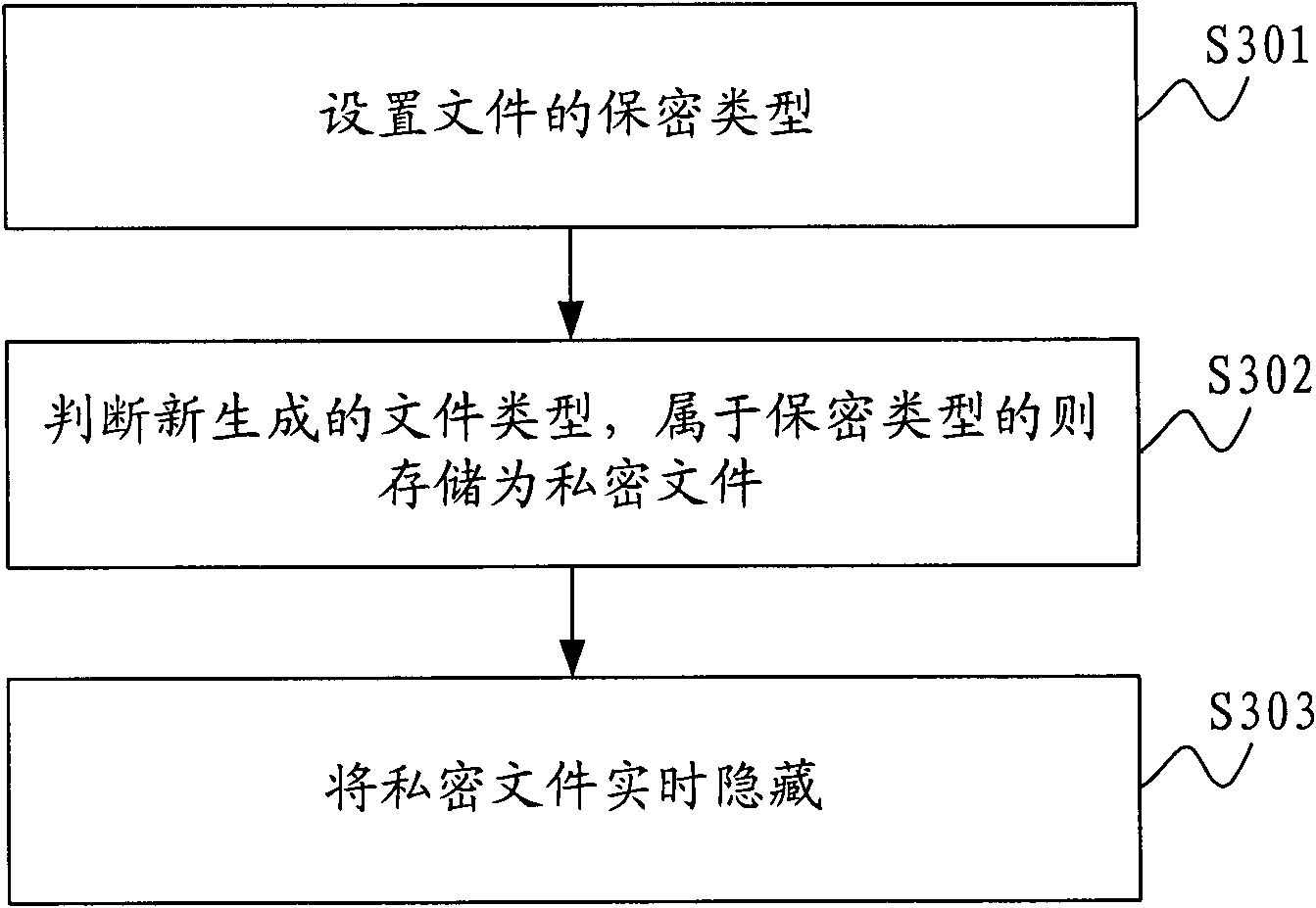
File security method, system and mobile terminal
InactiveCN101951443APrevent unauthorized accessPrevent operabilitySubstation equipmentStorage securityComputer terminal
The invention is applied in the technical field of communication, and provides a file security method, a file security system and a mobile terminal. The file security system comprises a private file setting module, a private file judgment module and a private file hiding module, wherein the private file setting module is used for setting the security types of files; the private file judgment module is used for judging the types of newly-generated files and storing the newly-generated files as private files if the newly-generated files belong to the security types; and the private file hiding module hides the private files in real time. Therefore, the method and the system can hide in real time the private files, such as photos, videos, diaries and the like, newly generated by the mobile terminal to prevent the private files from being illegally accessed and operated by other users and effectively protect the storage security of the private files of a user.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method and system for efficiently retrieving secured data by securely pre-processing provided access information
InactiveUS20040049682A1Data processing applicationsDigital data information retrievalInformation typeStorage security
A method and system for efficiently retrieving secured data by securely pre-processing provided access information, provides data store security based on only a single piece of access information, which is generally public, such as the proper name of a business or individual that is used to retrieve mailing address information. The access information is hashed for access to a secured data store and efficient access and low data storage for permutations of input access information are provided by verifying the presence of an entry for the hashed access information in a look-up table. If an entry is found, the data store is accessed using the hashed access information, but if an entry is not found, another look-up table corresponding to another information type may be tried or the input access information permuted and retried.
Owner:US POSTAL SERVICE
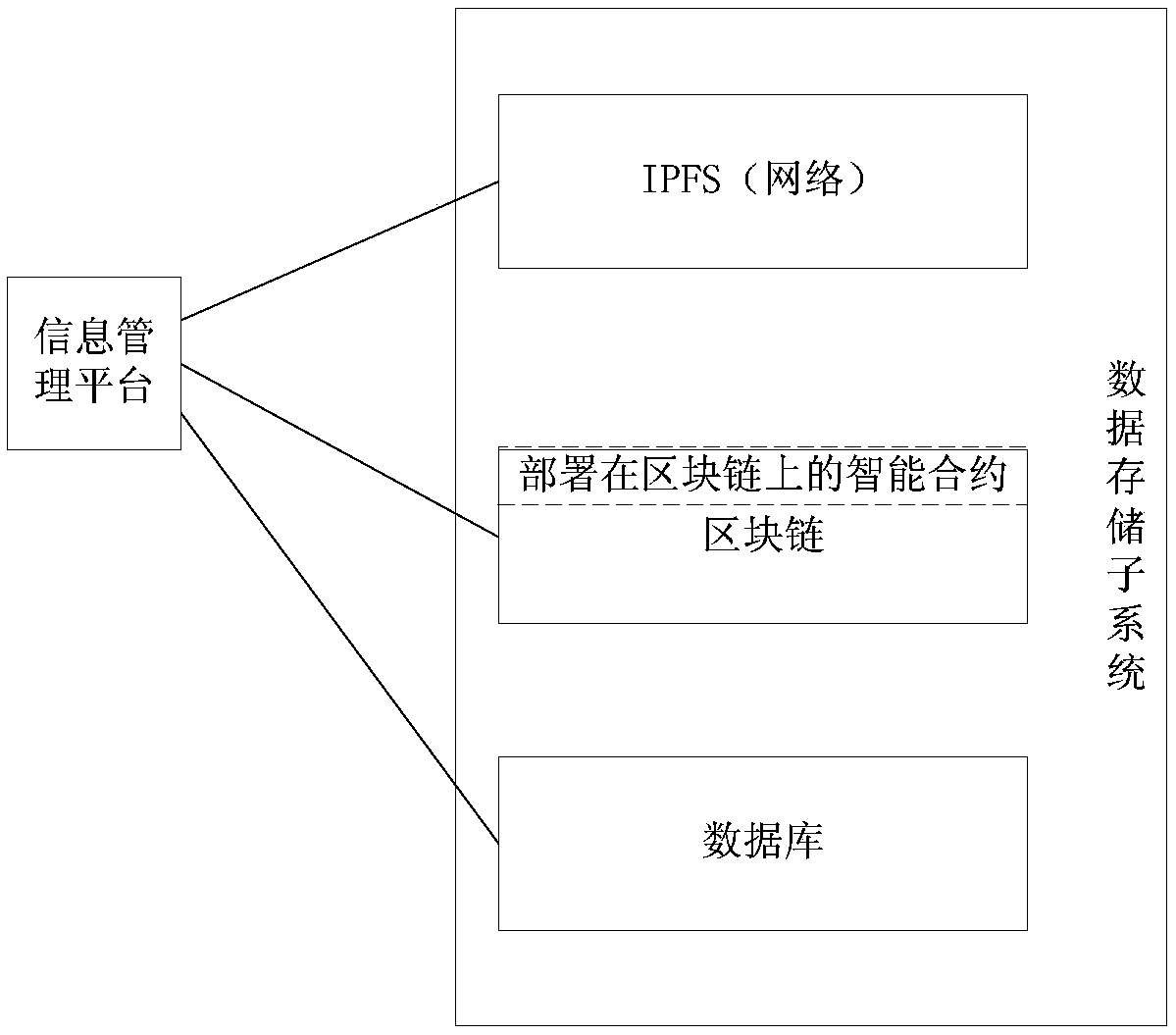
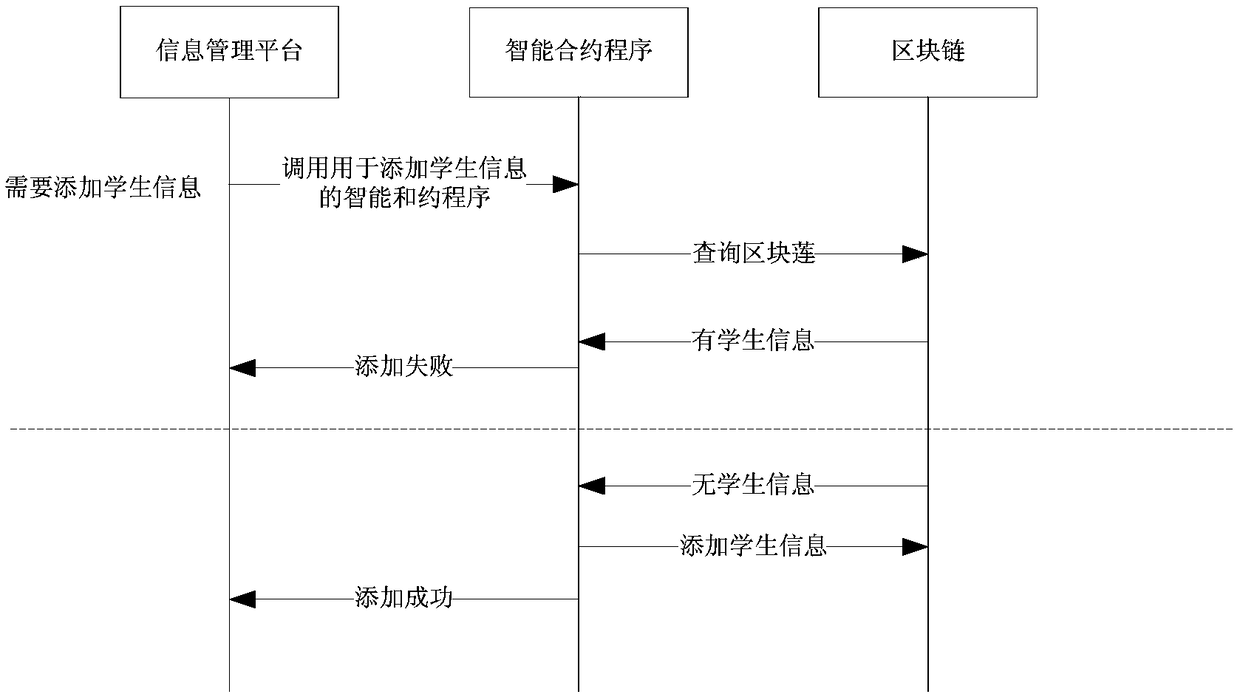
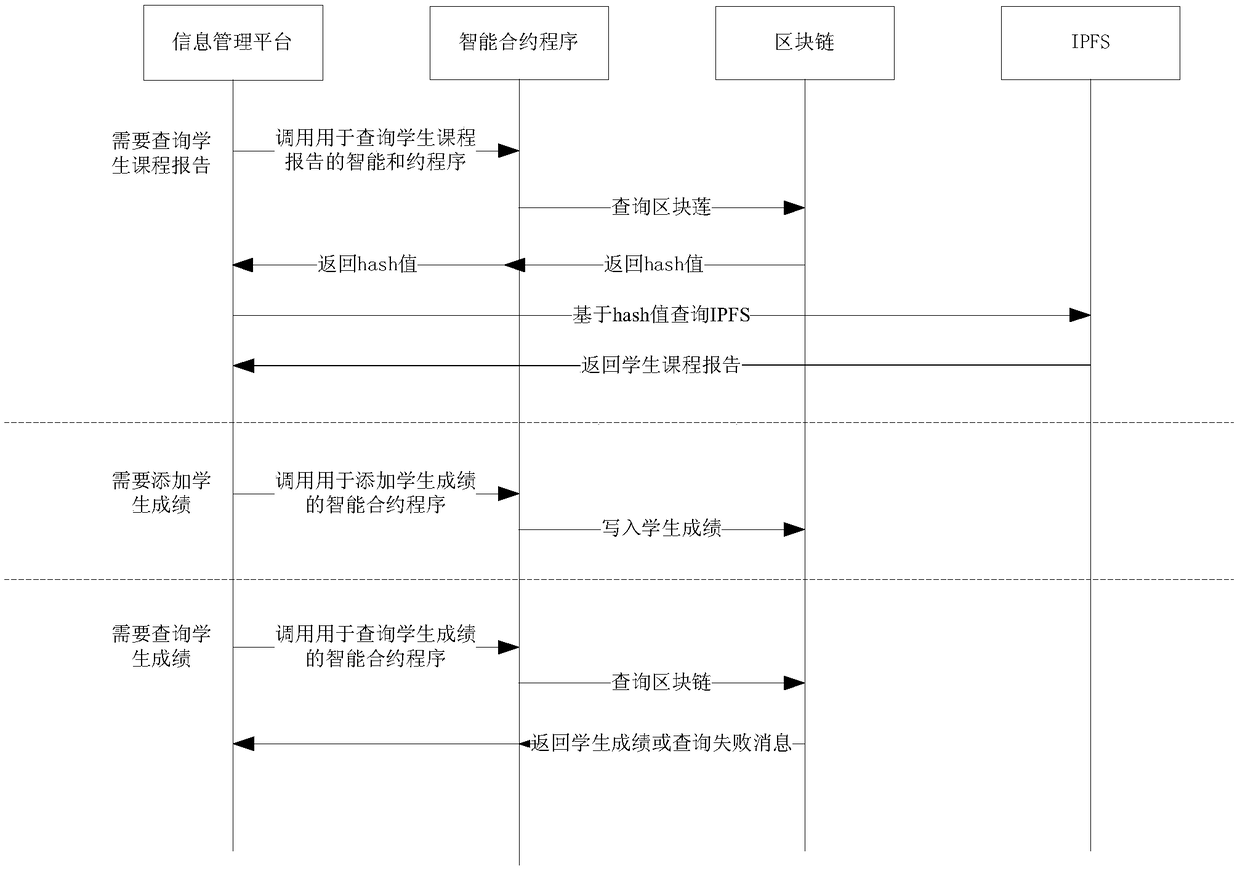
Block chain and interplanetary file system-based information management method and platform
InactiveCN108734029ASolve tampered withAddress lack of credibilityData processing applicationsDigital data protectionStorage securityFile system
The invention provides a block chain and IPFS-based information management method, which is applied to an information management platform. The method comprises the steps of creating a platform accountand a block chain account during registration in the information management platform; during login of the information management platform through the platform account, unlocking the block chain account; during information management, if a target storage position of to-be-managed information is a block chain, performing block chain-based management operation on the to-be-managed information by utilizing the block chain account; and if the target storage position of the to-be-managed information is an IPFS, performing IPFS-based management operation on the to-be-managed information, and performing block chain-based management operation a hash value corresponding to the to-be-managed information returned by the IPFS through utilizing the block chain account. According to the method, the problem that real information is tampered can be effectively solved, so that the data storage security is ensured.
Owner:陈萍
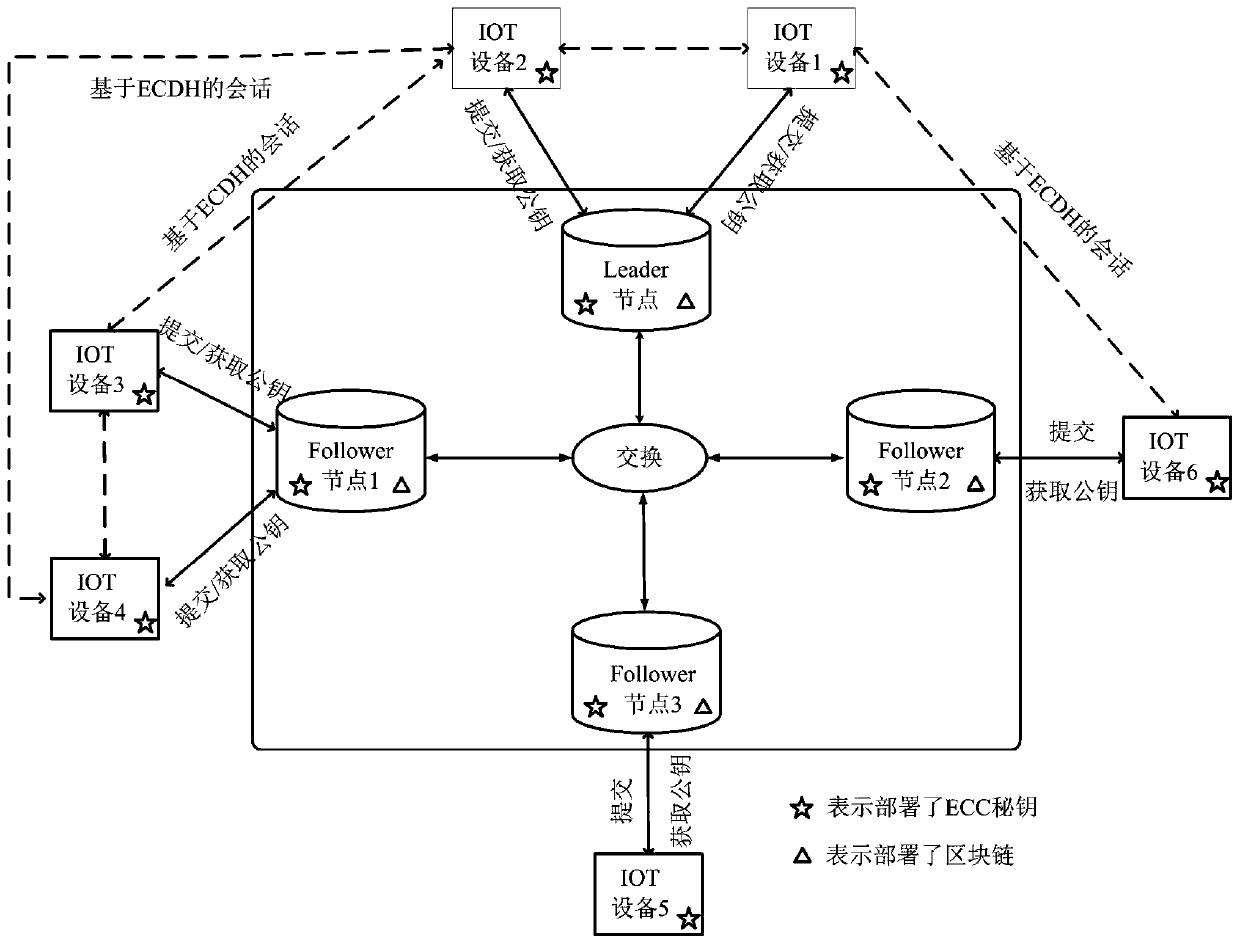
An Internet of Things terminal secure communication method based on a block chain technology
InactiveCN109728898ARealize automatic encrypted communicationAchieve efficiencyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesTamper resistanceSecure communication
The invention discloses an Internet of Things terminal secure communication method based on a block chain technology. The Internet of Things terminal secure communication method comprises the steps that an Internet of Things communication server generates a key; Each IoT device generates a key generation parameter and generates a respective private key; And the two communication parties calculaterespective public keys, obtain the secret keys of the Internet of Things communication server, submit the respective public keys to the Internet of Things communication server for storage, obtain thepublic keys of the communication parties through the Internet of Things communication server, calculate the communication secret key of the current communication and carry out secure communication through the communication secret key of the current communication. According to the invention, automatic encryption communication between the IoT device and the service center and between the IoT deviceand the IoT device is realized; The load capacity of the service center is reduced, and the high efficiency of data communication is realized; And finally, reliable storage of the IoT equipment publickey and other data based on the block chain is realized, the storage integrity and tamper resistance are ensured, and the requirement of storage security is met.
Owner:HUNAN NORMAL UNIVERSITY
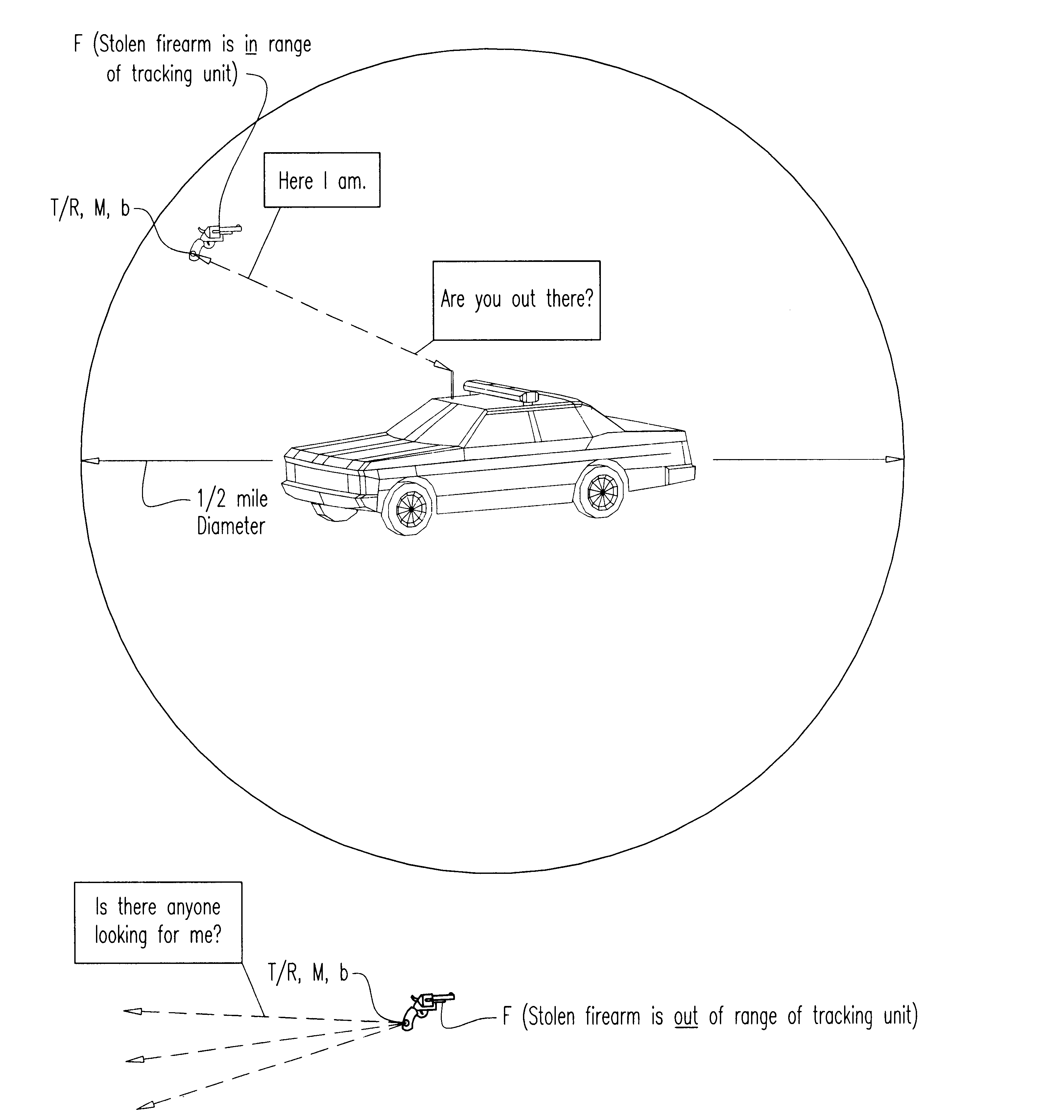
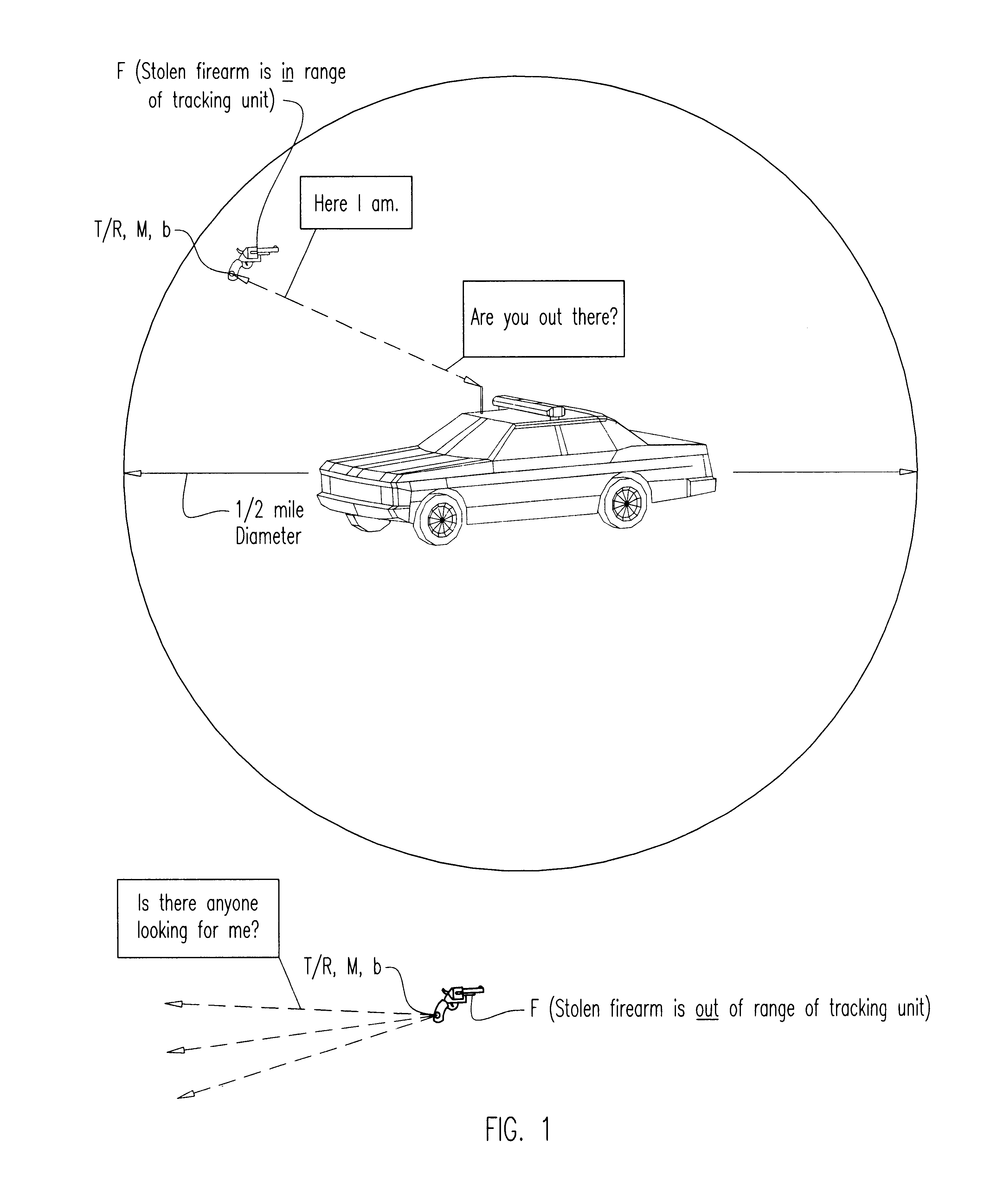
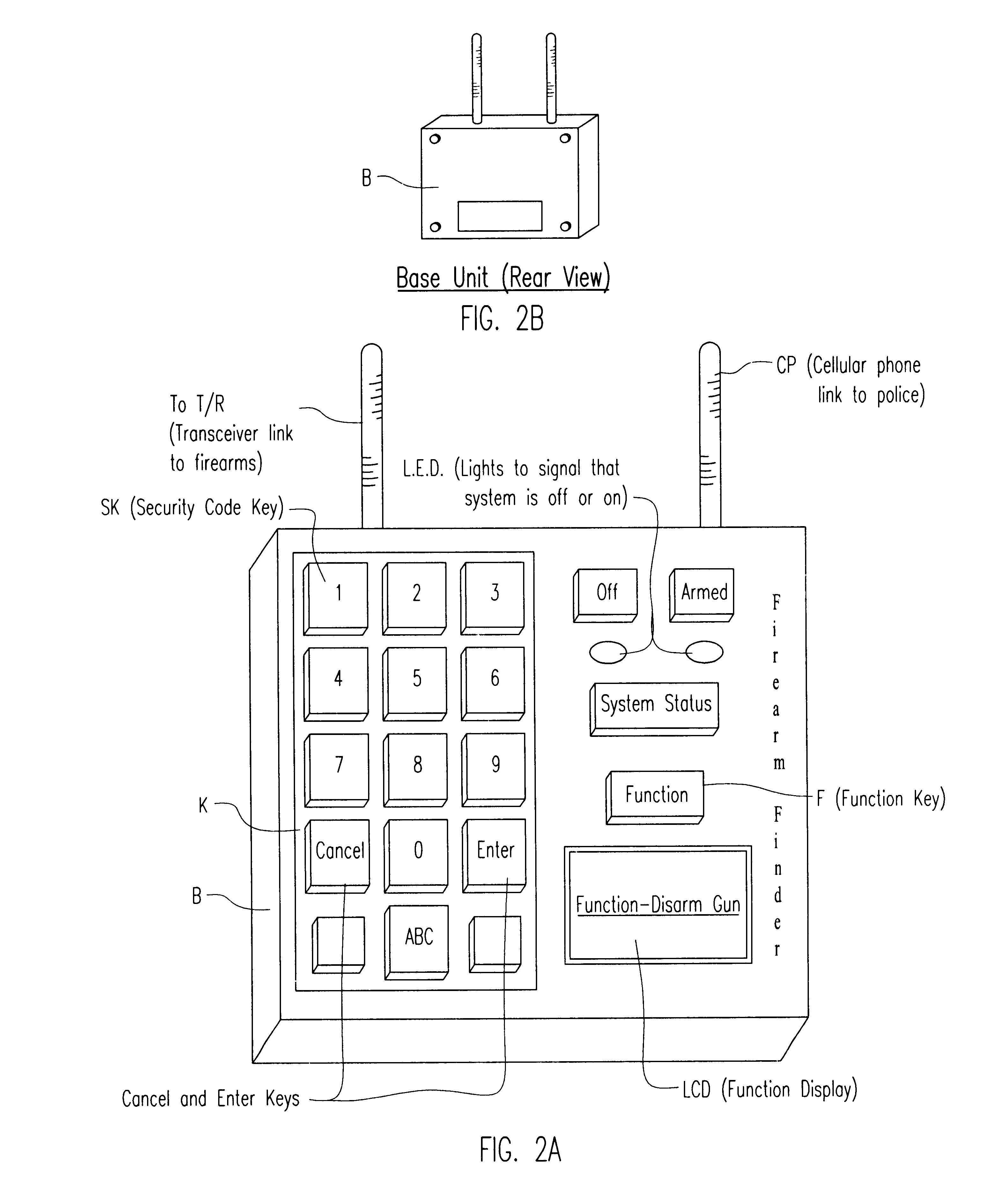
System and method for improving the security of storage of firearms and other objects, and for aiding the recovery of such if removed from storage
A novel technique and system for improved monitoring of the storage security of firearms (and other objects) and, through a microprocessor radio-controlled transceiver embedded within the firearm, enabling detection of theft or removal, and then radio-tracking of the stolen firearm by police or others with continual identification of that firearm, and also with the further feature of providing automatic warning to schools or other public buildings or locations of the intrusion in their vicinity of a bearer carrying the stolen firearm.
Owner:MUISE CHRISTOPHER RUSSELL +2
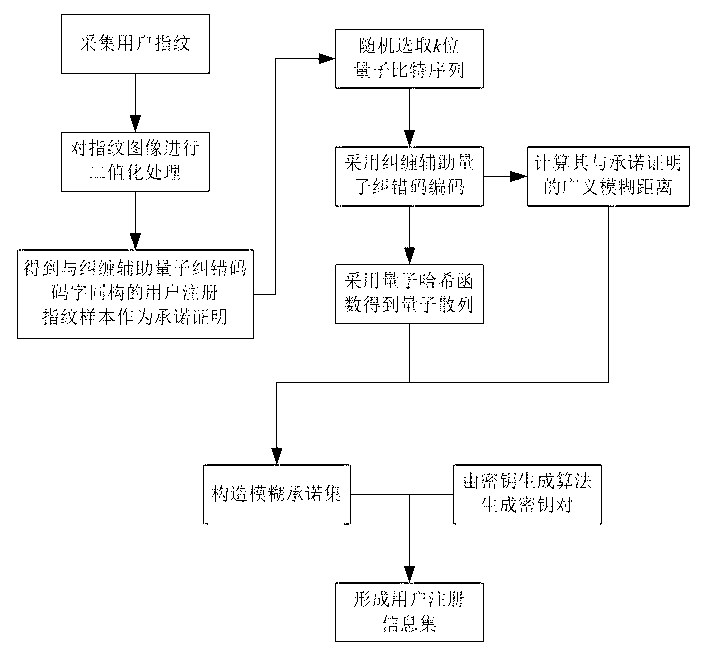
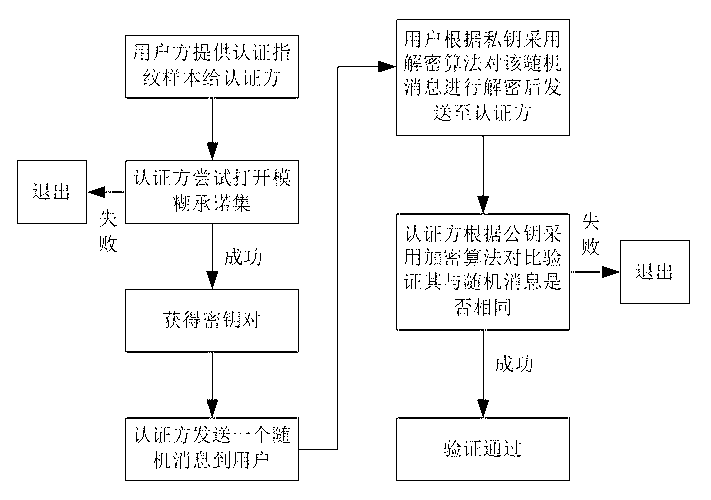
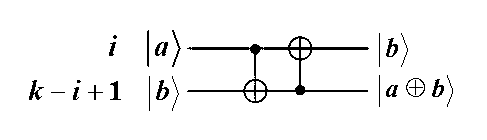
Biometric fingerprint authentication method based on quantum fuzzy commitment
InactiveCN102750529AStrengthen privacy and security protectionObvious superiorityCharacter and pattern recognitionStorage securityBiometric data
The invention discloses a biometric fingerprint authentication method based on a quantum fuzzy commitment, which comprises a registration phase and an authentication phase. The registration phase comprises the following steps of: firstly, constructing a fuzzy commitment set to produce code words required for the commitment phase by using a quantum error correcting code space without self-dual constraint, and applying a noise addition transformation used for fuzzy proving to the code word; and then, constructing a quantum hash algorithm, and mixing, diffusing and encrypting a random quantum sequence so as to realize the security of using one key at one time in the sense of information theory. The authentication phase comprises the following step of opening the fuzzy commitment set by using a quantum fuzzy commitment to obtain random information for decrypting keys Messa. A new quantum fuzzy commitment system is constructed by combing the quantum hash algorithm on the basis of entangling assistant quantum error correcting codes. Compared with other similar fingerprint authentication methods, the biometric fingerprint authentication method based on a quantum fuzzy commitment has prominent advantages in the aspects of storage security and authentication security of biometric data, and the quantum biometric performance and the security of biological template information storage and transmission can be increased.
Owner:NANJING UNIV OF POSTS & TELECOMM
Attribute-based encryption access control system of cloud storage digit library, and access control method thereof
ActiveCN105681355AAchieve integrationSolve the repeatabilityTransmissionStorage securitySecure authentication
The invention discloses an attribute-based encryption access control system of a cloud storage digit library, and an access control method thereof. The access control system comprises five entities: an authority center, a key distribution center, a cloud server, an uploading center, and an access user. The access control method comprise the steps of: system initialization, uploading center encryption and accessing a digit library. In the access control system, the uploading center uploads book data in categories according to corresponding attributes of books, so that the system realizes data integration, and effectively solves the problems of digital resource repeated construction and low sharing degree; in the access control method, the attribute-based encryption technology is introduced, which guarantees data storage security on one hand, and realizes user access control on the other hand. Accordingly, the method realizes user safety certificate and fine grit access control.
Owner:XIDIAN UNIV
Method for protecting copyright of video content
ActiveCN101350918AWith copyright protectionWide applicabilityPulse modulation television signal transmissionStorage securityDigital content
The invention relates to a copyright protection method of video content, which belongs to the technical field of copyright protection. A play module uses the RTSP protocol of the video program to acquire a SDP document and sends the requests for examining the play authority to a DRM Agent. The DRM Agent searches RO locally and implements integrality validation; if the RO is not found or the DRM Agent fails the validation, new RO should be purchased with RI; if the DRM Agent passes the validation, the video content key is acquired from the RO and the content of the selected video program is decoded and then the playing module decodes, plays and stops the program. By upgrading the usage limits in the RO and the RO status word in time, the RO security is effectively enhanced. The invention has the advantages that an SIM card is introduced to ensure the storage security of the RO and the purchased digital content authority could be also used after user replaces the mobile terminal equipment; in this way, the invention could be widely used and suitable to the consumption habits of users.
Owner:TSINGHUA UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com