Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
414 results about "Trusted application" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A trusted application is an application developed by a third party that is given trusted status to run as part of Skype for Business Server but that is not a built-in part of the product.
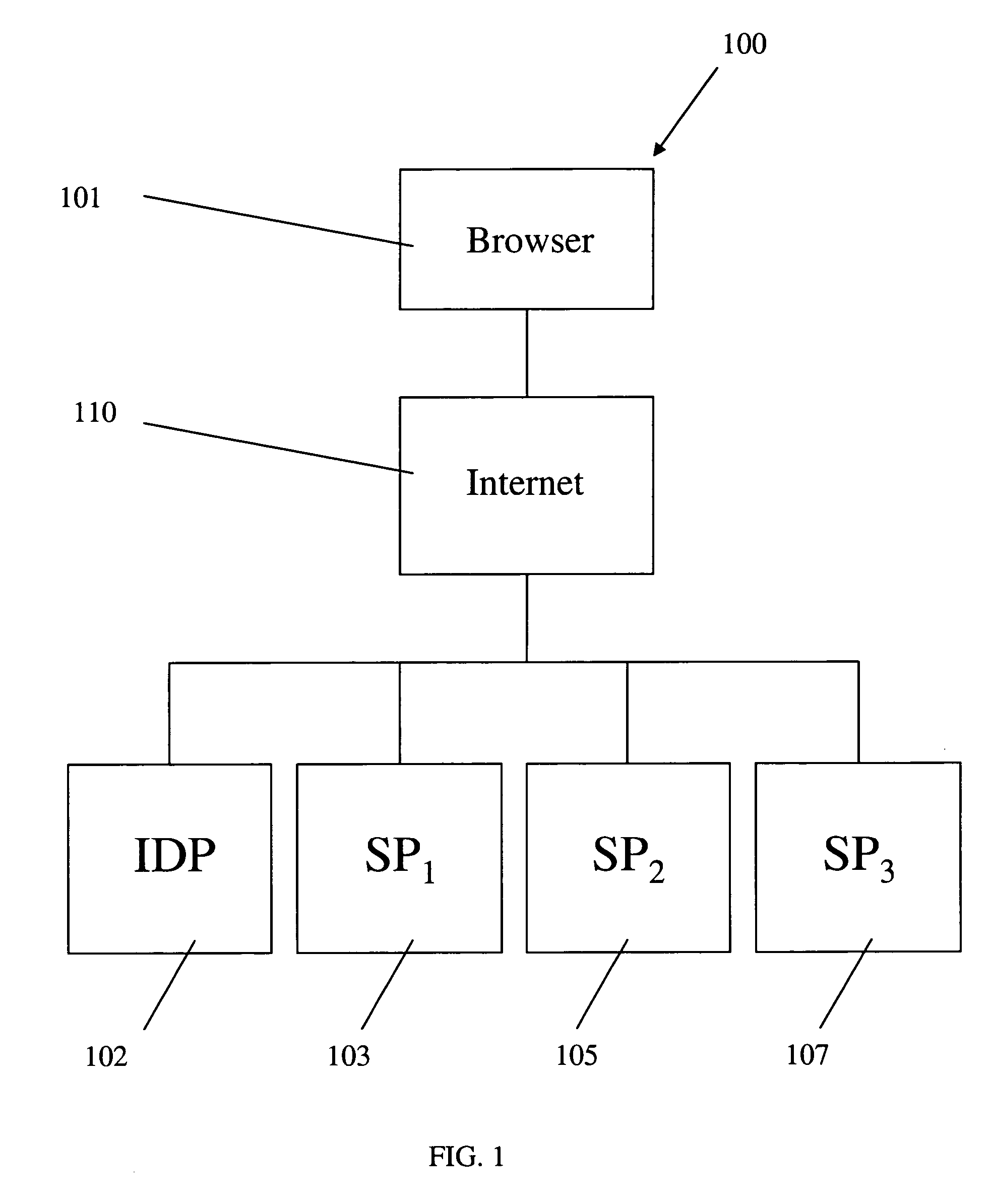
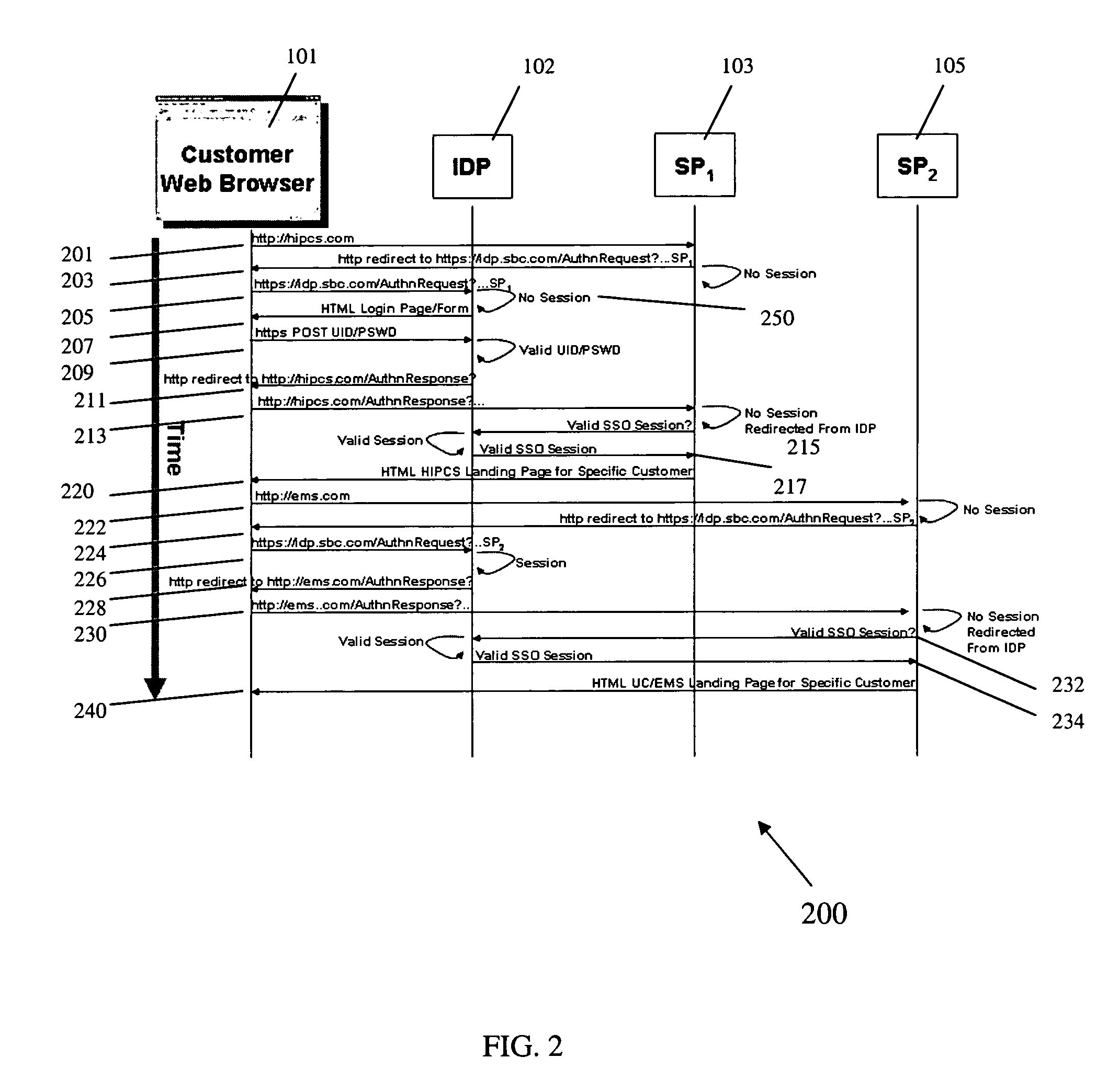
Opt-in linking to a single sign-on account
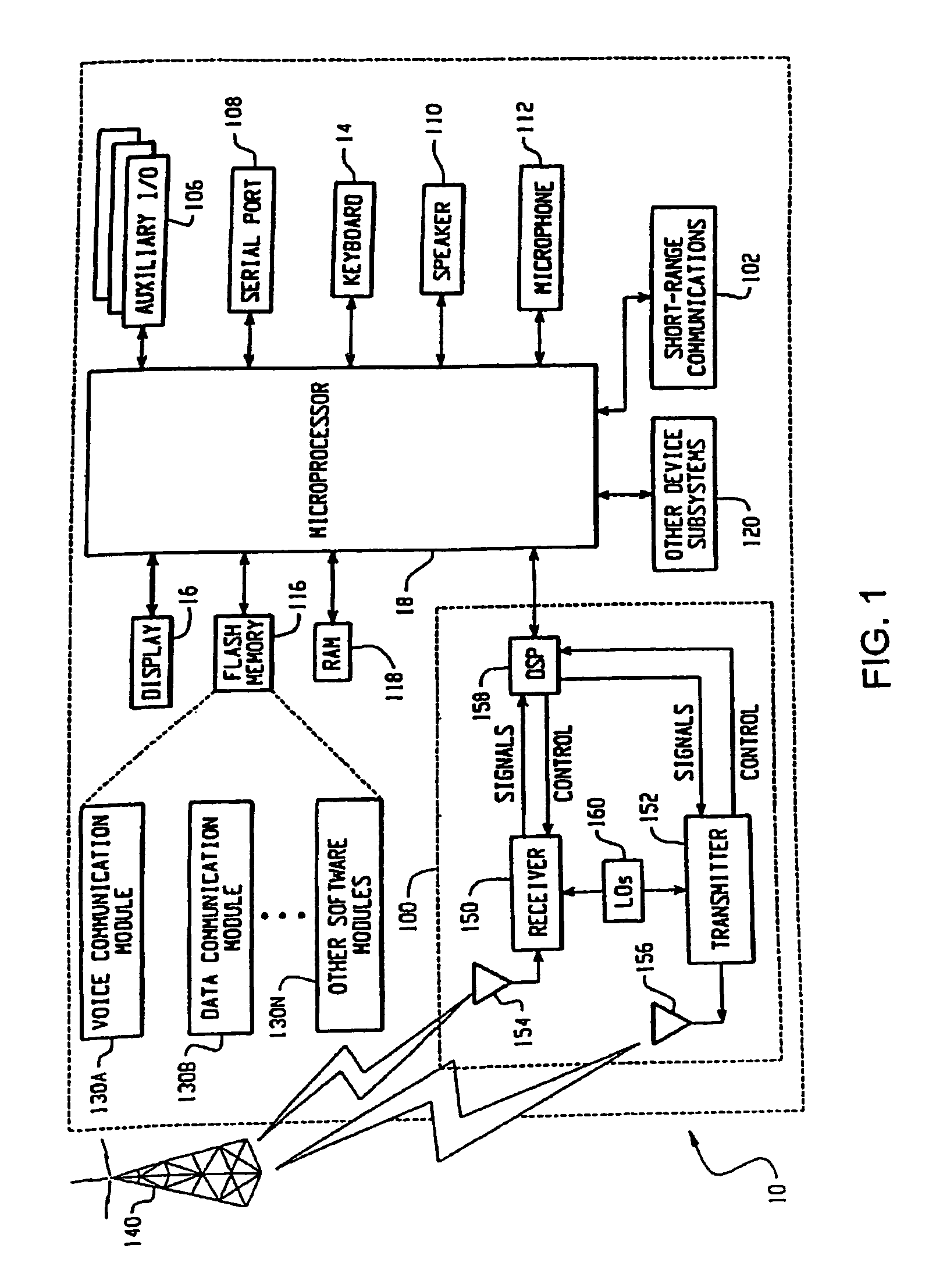
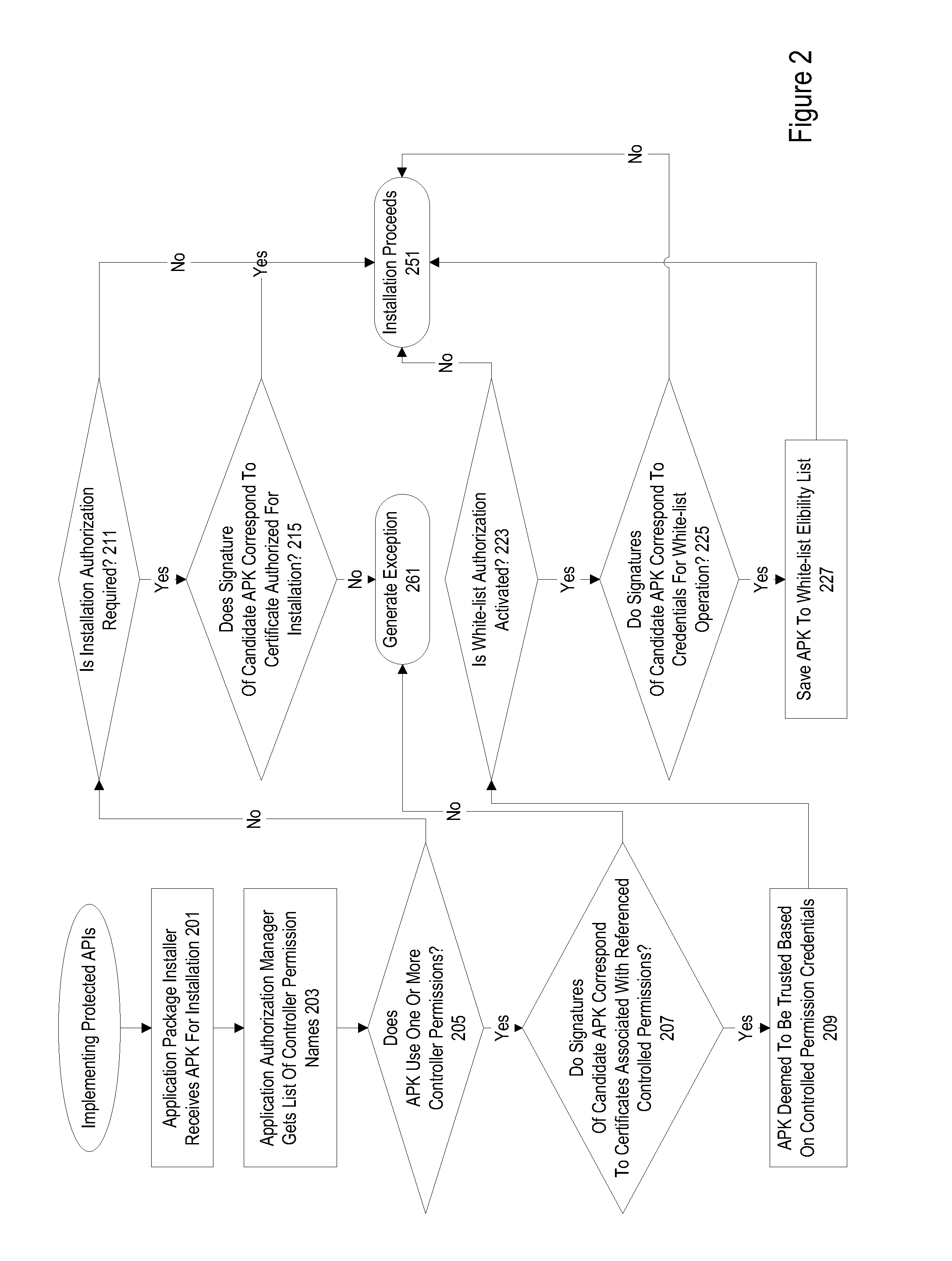
InactiveUS20060218630A1Digital data processing detailsMultiple digital computer combinationsTrusted applicationApplication software
A system and method for providing a portal view of a trusted application to a user over a communication network is discussed. The portal view can be generated from at least one of the services linked to the application according to a trust model in which trust is extended to the application from the user. When the application provides single sign-on capabilities, those services that are linked to the application can then be logged into simultaneously when the user logs into only one of the services. The trusted application is opaque to those services not linked to the application. The portal view provides a means for linking and de-linking services.
Owner:SBC KNOWLEDGE VENTURES LP
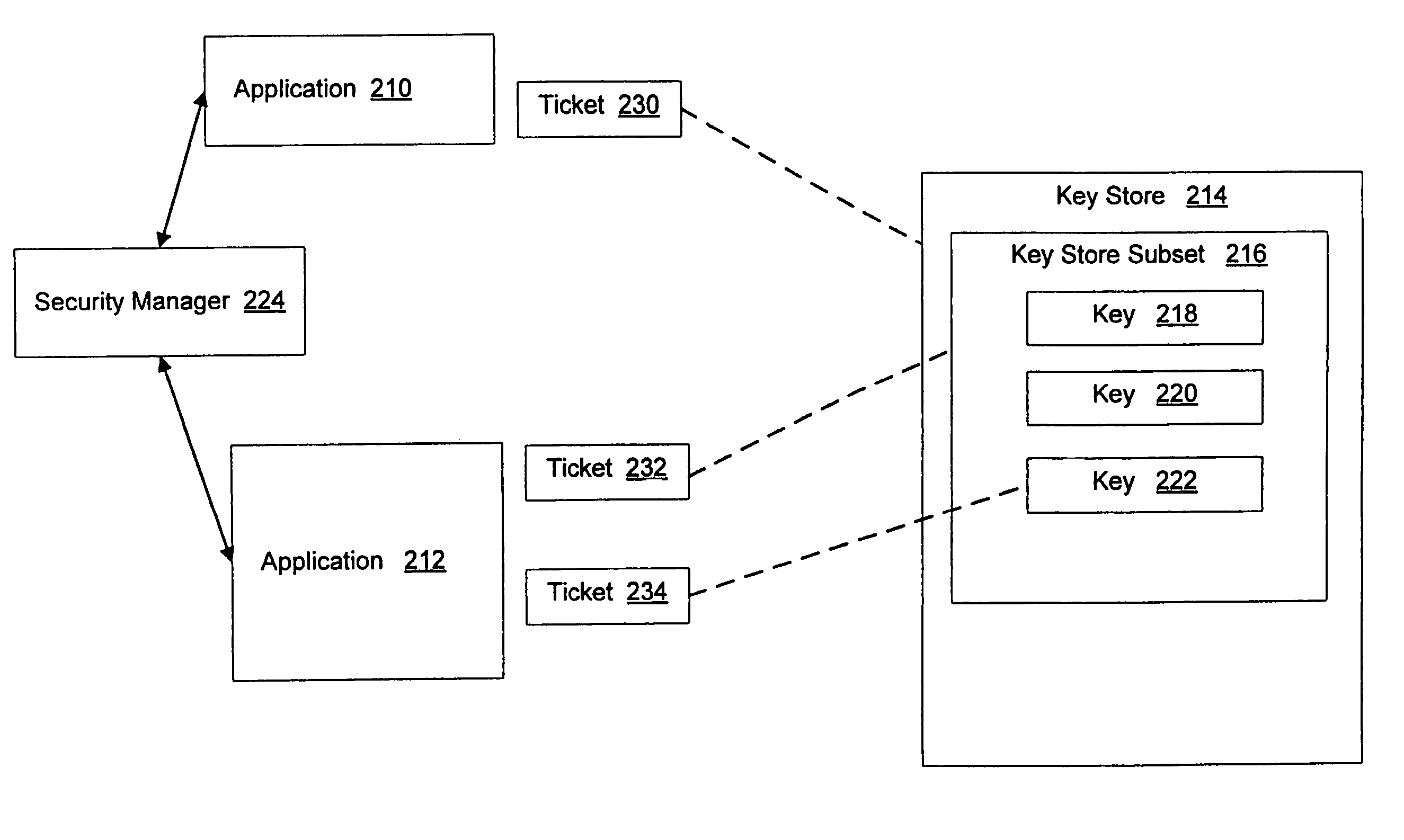
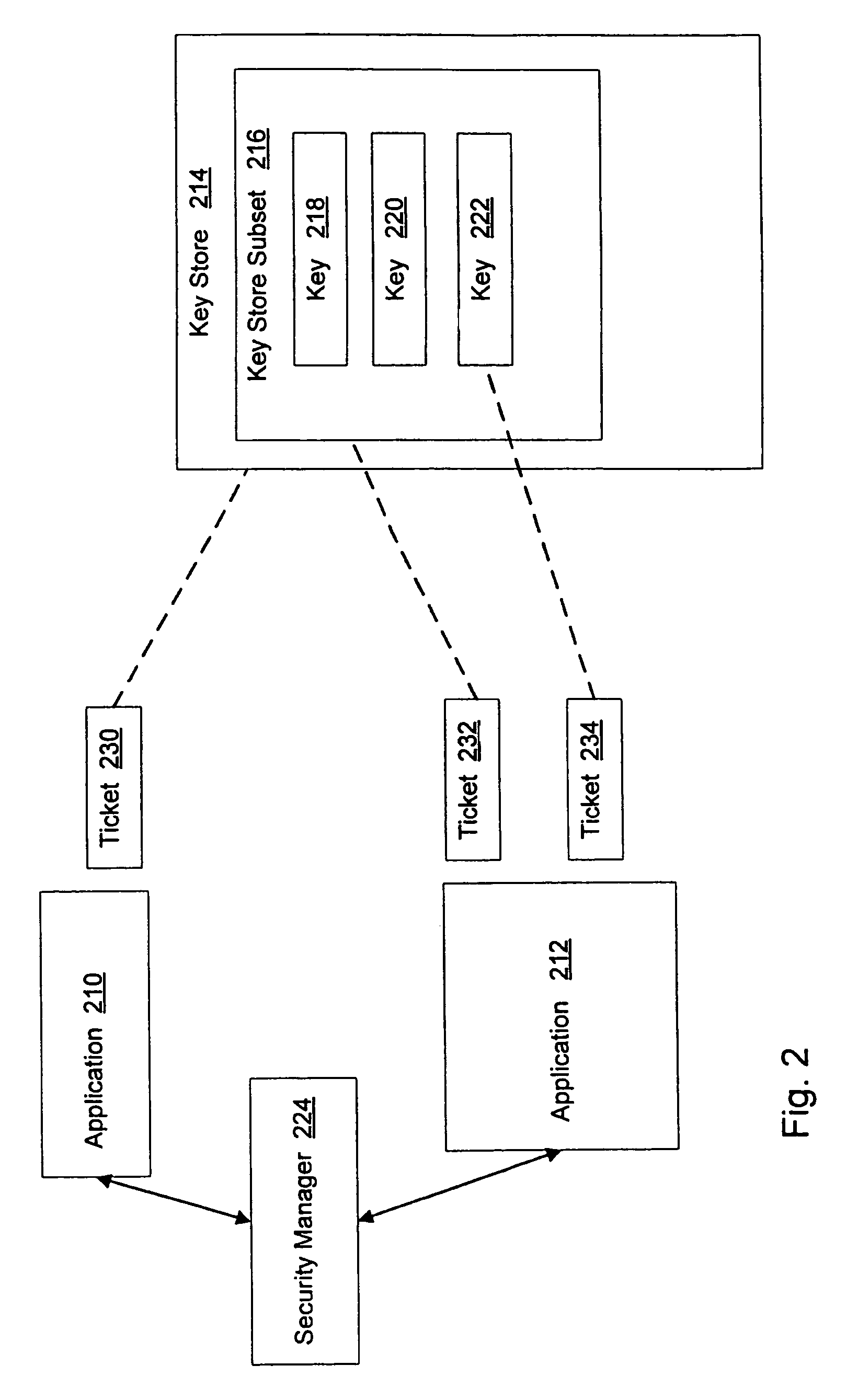
System and method for application authorization
ActiveUS7805755B2Reduced promptingDigital data processing detailsUnauthorized memory use protectionPasswordApplication software
A method and system for authorization of applications executing on a device having a key store. Applications obtain an application-level ticket to permit access to one or more key values located in the key store. Each ticket is securely associated with an application and being generated on the determination that the application is a trusted application. Tickets are potentially associated with one key value in the key store, with a subset of key values in the key store, or with all key values in the key store. Access to key values by an application is possible independently of a user providing a password for each such access.
Owner:MALIKIE INNOVATIONS LTD
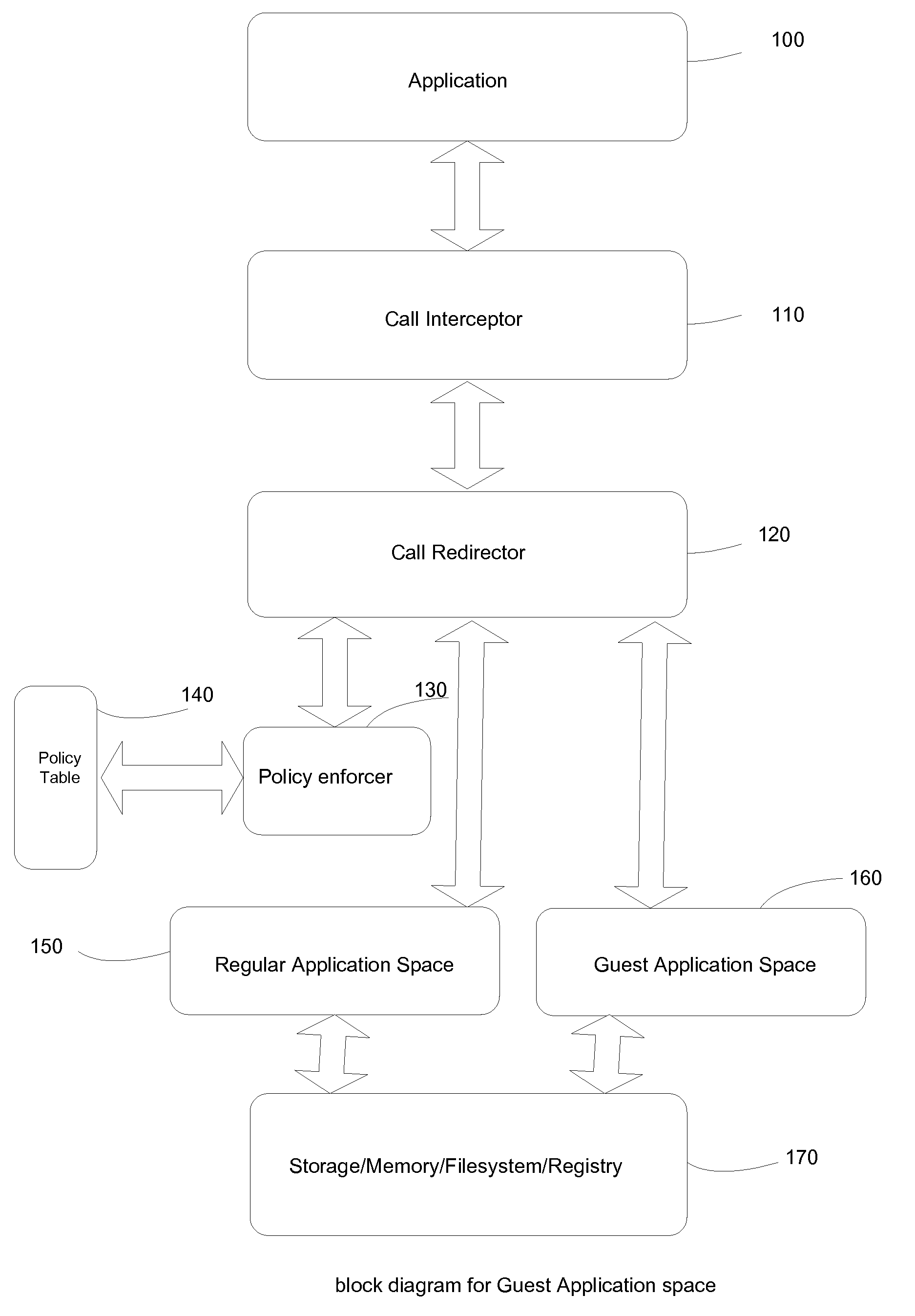
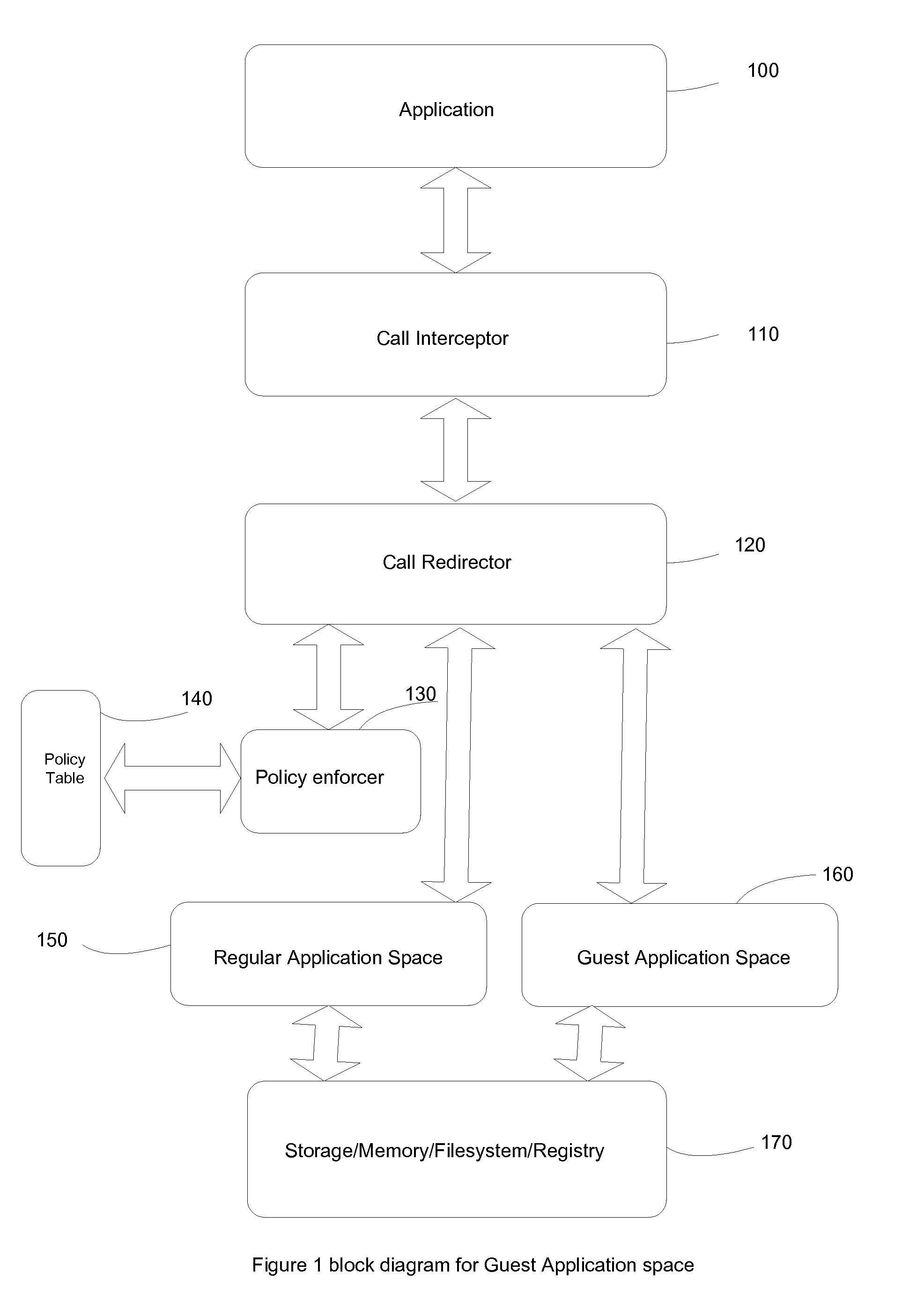
Safe and secure program execution framework with guest application space
InactiveUS20100175104A1Increase workspaceCreate efficientlyMemory loss protectionError detection/correctionComputer usersData information
A system and method is provided here that allow computer user to create a temporary guest running space for application without switching user environment. This unique method allows user to run trusted applications in regular running space while keeping a separate working space for applications that uses or visit non trusted data sources.Proposed method provides a safe execution environment while application running in guest space can't temper or alter data information stored in regular running space. A set of policy rules dictates how information will be exchanged between applications running in two separate working spaces transparently.The proposed system also make sure program files can't be altered or modified without proper need and suspicious call to modify program files or alter execution environment is blocked.
Owner:KHALID ATM SHAFIQUL
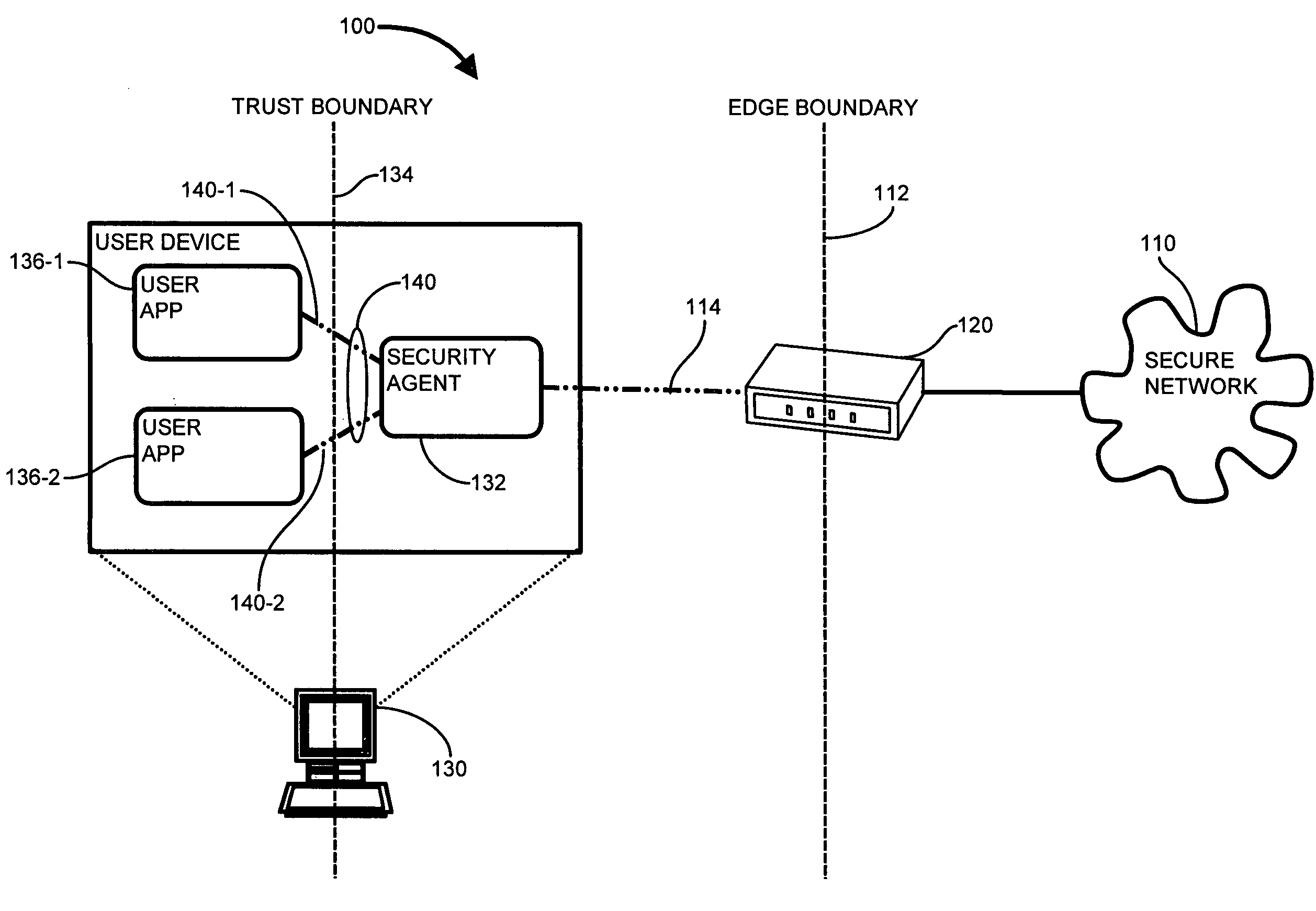
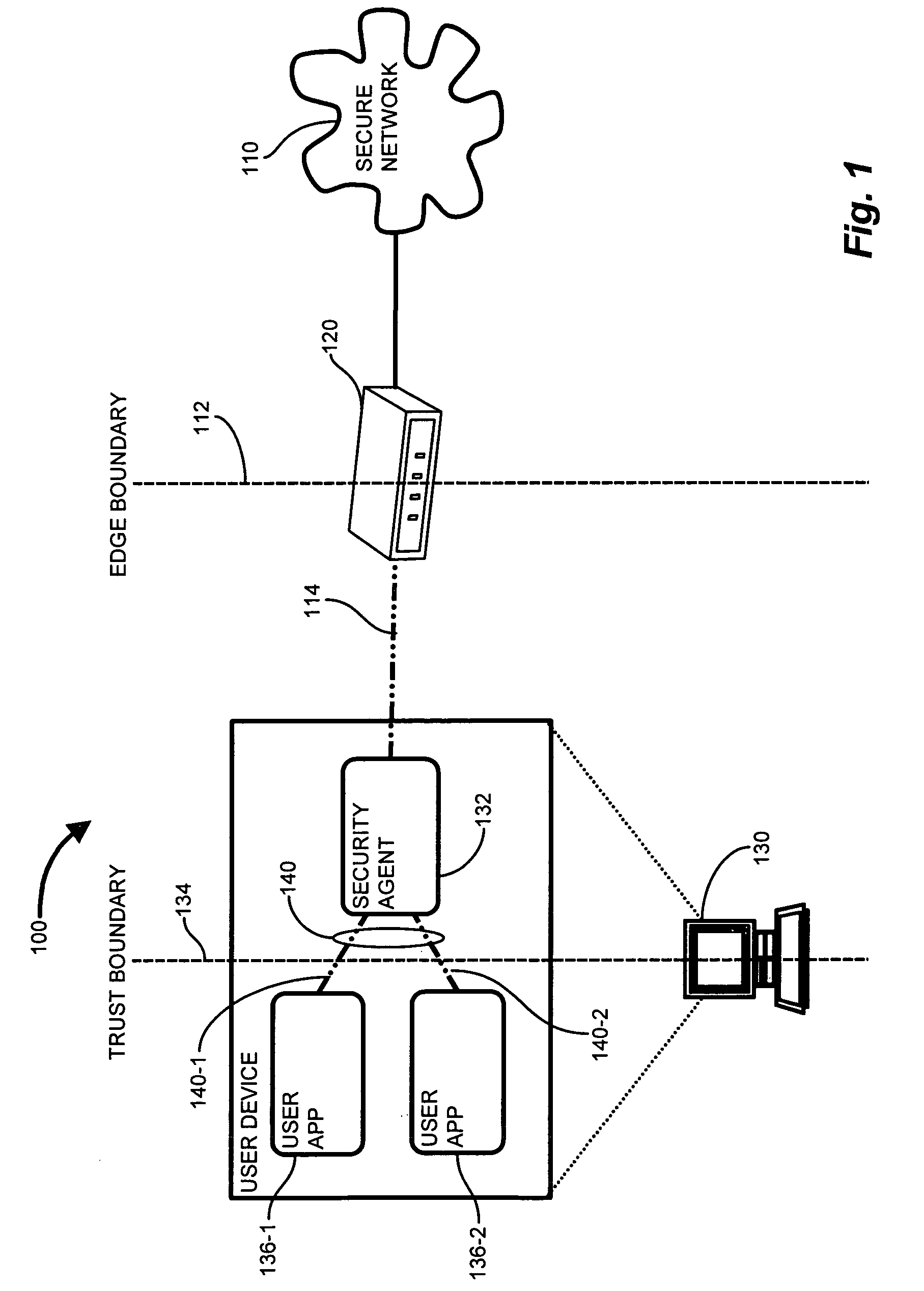
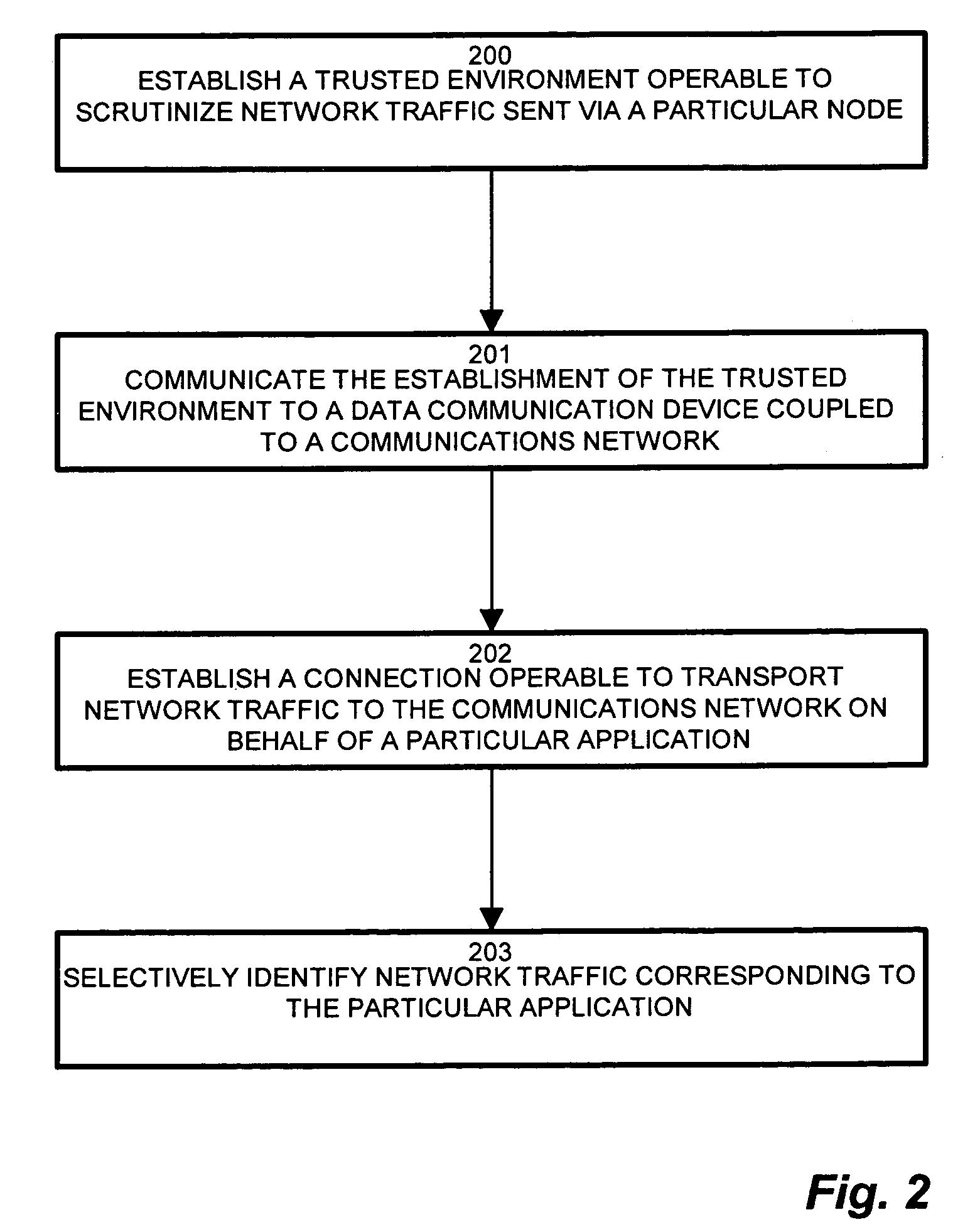
Methods and apparatus for trusted application centric QoS provisioning
ActiveUS7774498B1Increase pointsOvercomes shortcomingMultiple digital computer combinationsProgram controlTraffic capacityUser device
A security agent extends the trust barrier, or trust point, from network gateway nodes to end user devices. A security agent operable to scrutinize network traffic executes on the user device and compares QoS marking attempts with the established QoS marking policy in effect. The security agent examines network traffic attributes deterministic of connection attempts by user processes. Attempts to apply inappropriate or disallowed QoS markings, as dictated by the QoS marking policy, are detected and disallowed. Therefore, only user connections consistent with the QoS marking policy are permitted into the network. Network admission control (NAC) mechanisms ensure that the security agent is the only access point from the user device to the secure network, and the security agent communicates the establishment of the trusted access point to the network gateway, thus ensuring that the network gateway may trust service level designations emanating from the user device executing the security agent.
Owner:CISCO TECH INC
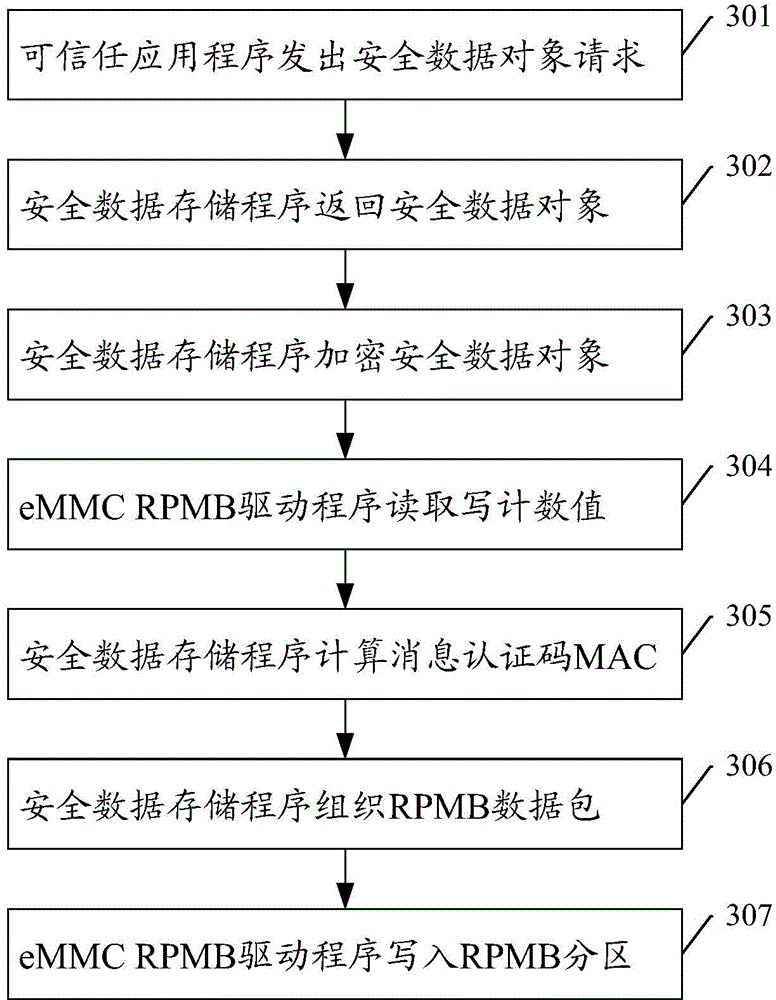
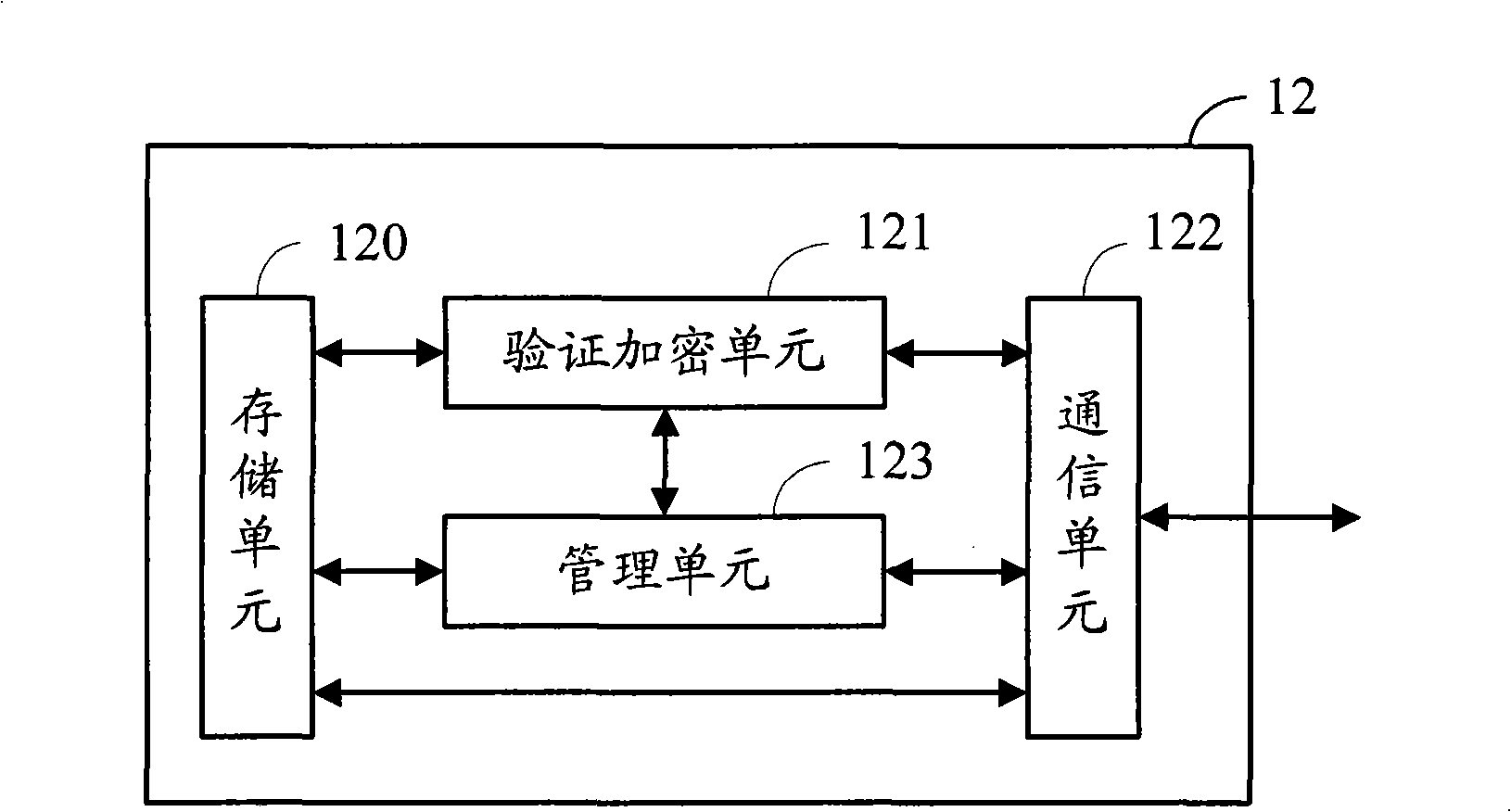
Security data storage method and system
ActiveCN104392188AEnsure safetyAvoid readingDigitally marking record carriersInternal/peripheral component protectionApplication softwareData store
Owner:SAMSUNG ELECTRONICS CHINA R&D CENT +1
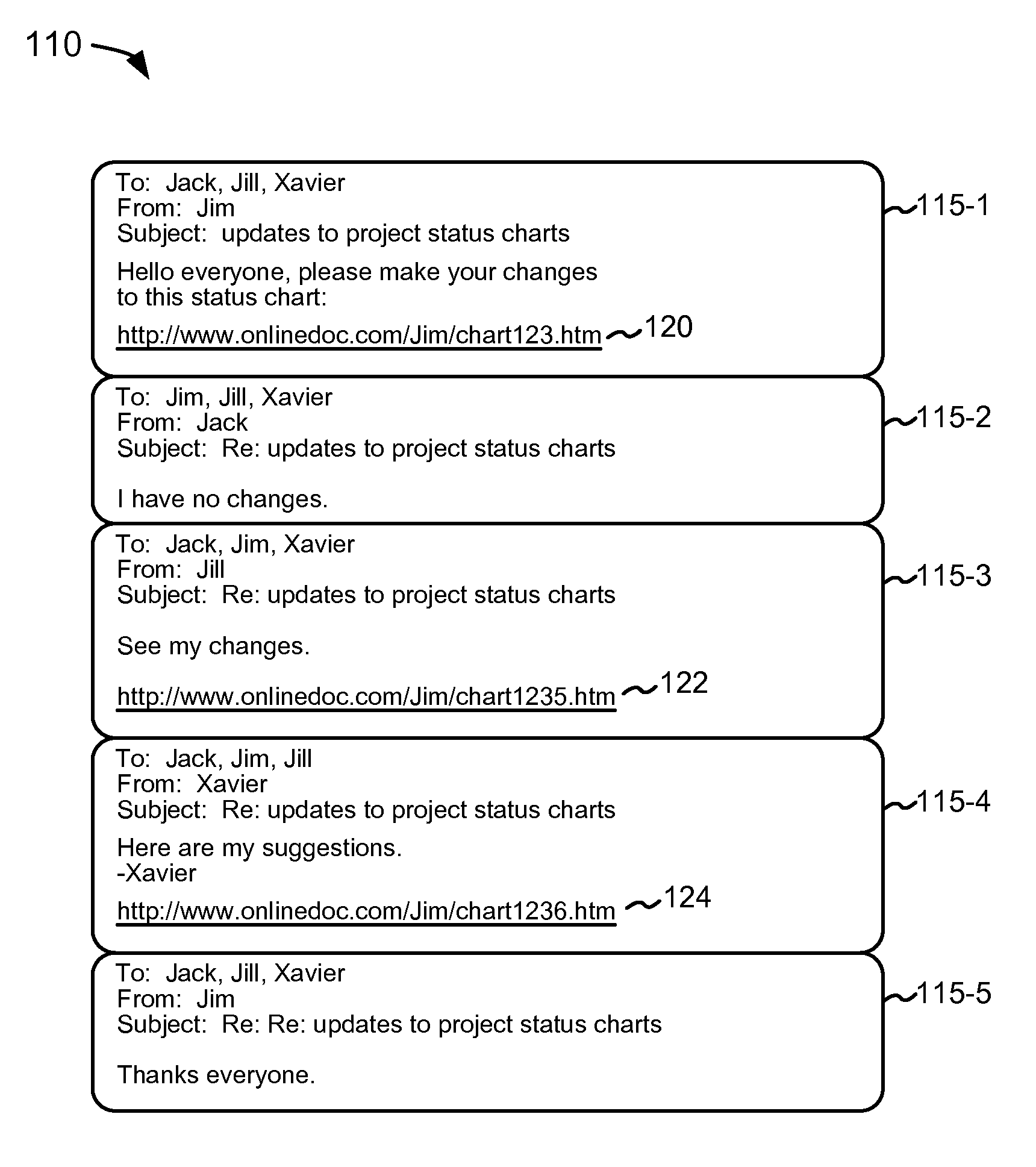
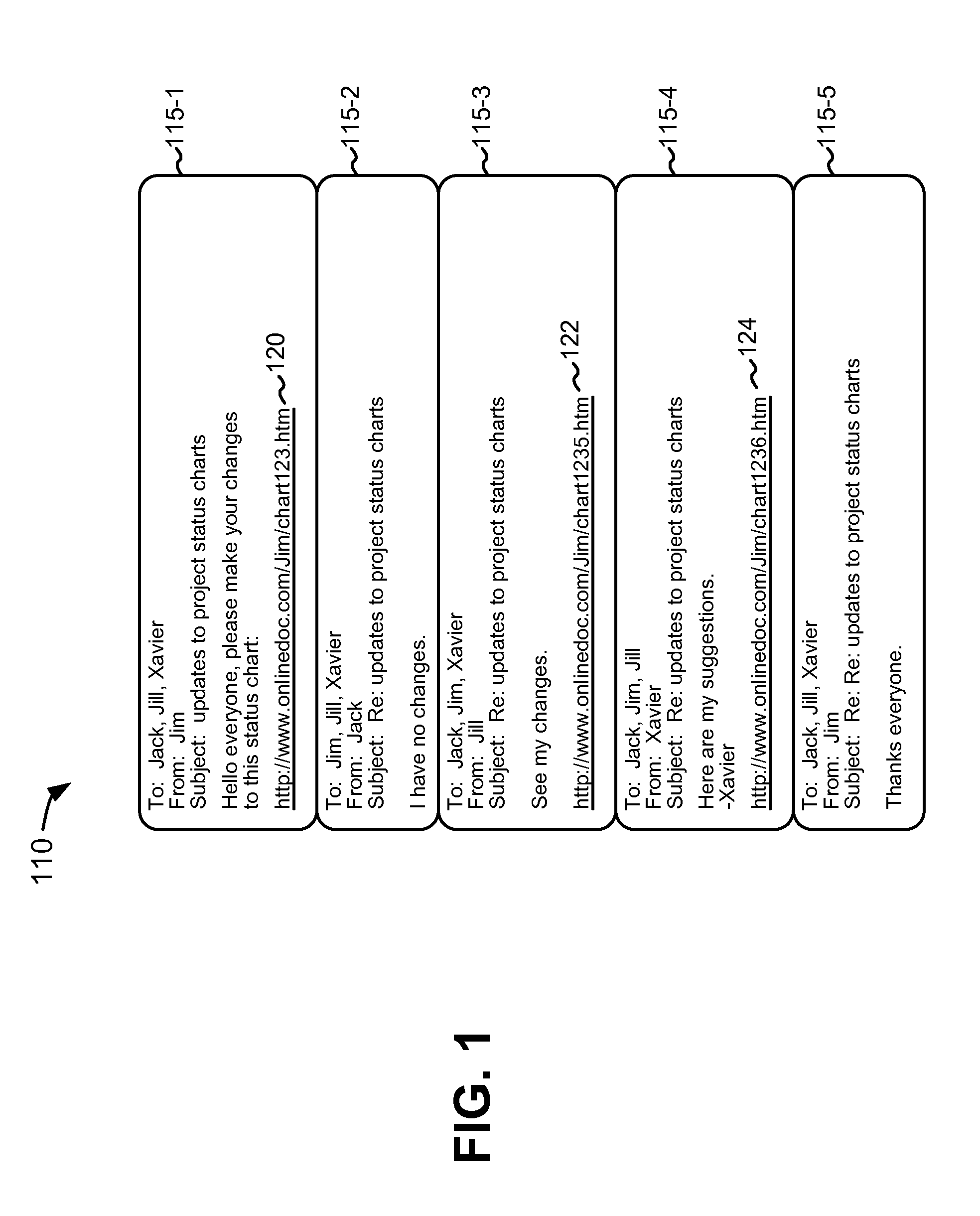
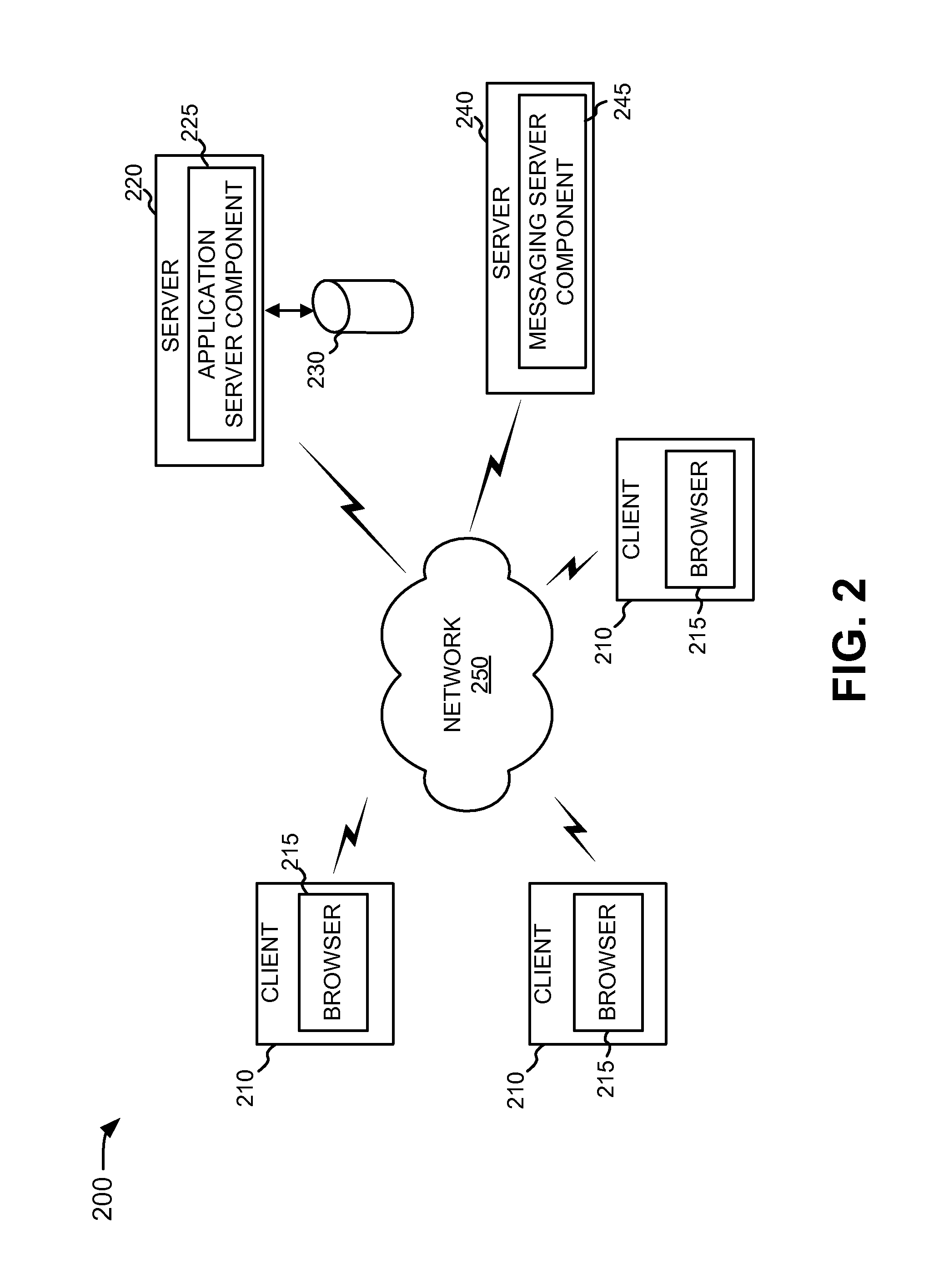
Collaborative workflow through messaging conversations
ActiveUS8108464B1Promote generationTo offer comfortNatural language data processingMultiple digital computer combinationsApplication serverApplication software
A networked application and email application were described herein that provide for an intuitive system by which users can participate in collaborative workflow relating to a network document. In one implementation, a system includes a messaging server component to provide messaging services and an application server component to provide a networked application. The application server component interacts with the messaging server component in response to a user command to initiate collaboration on the network document. The interaction with the messaging server component includes providing a link that refers to a version of the network document as created or edited by the user.
Owner:GOOGLE LLC
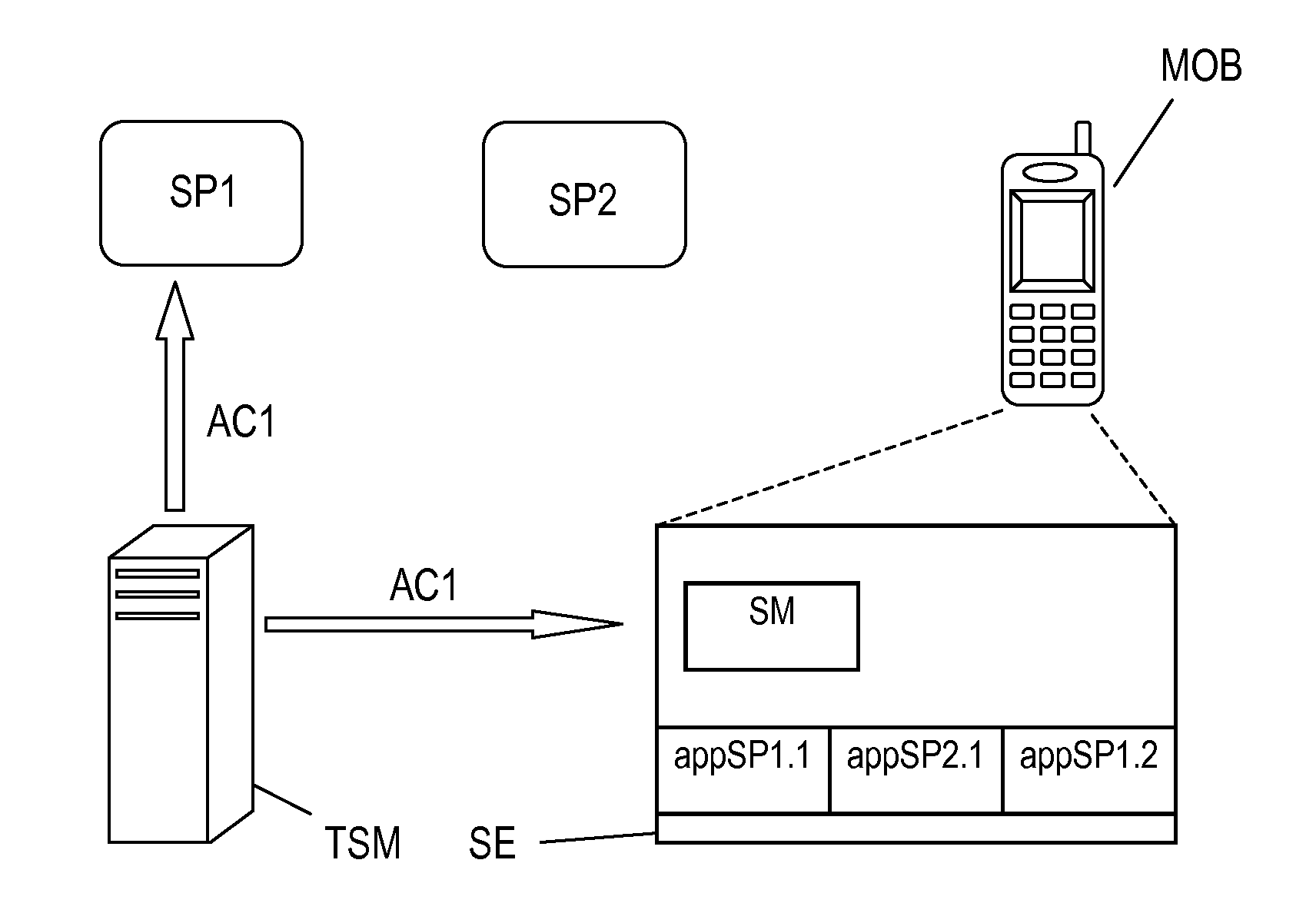
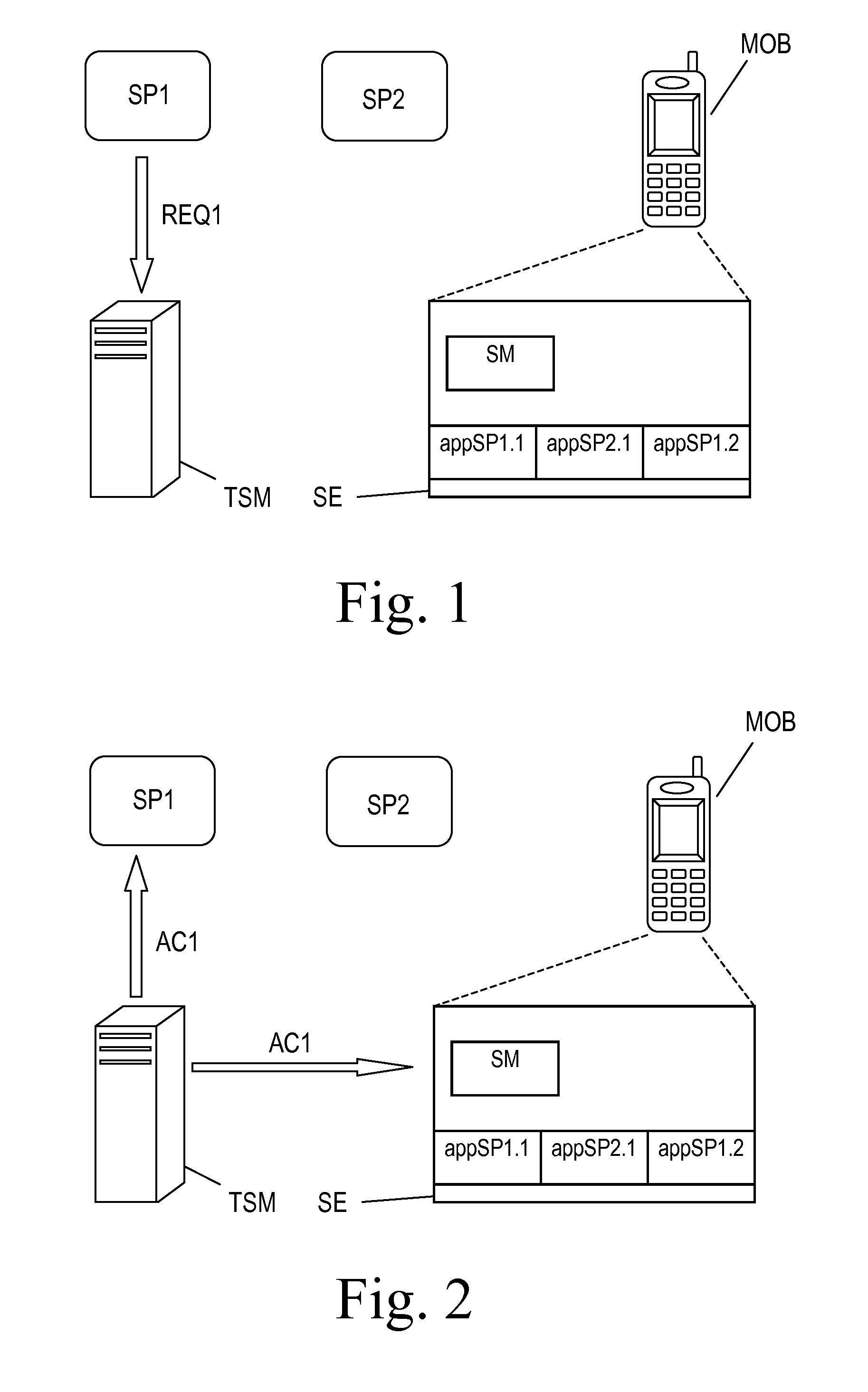
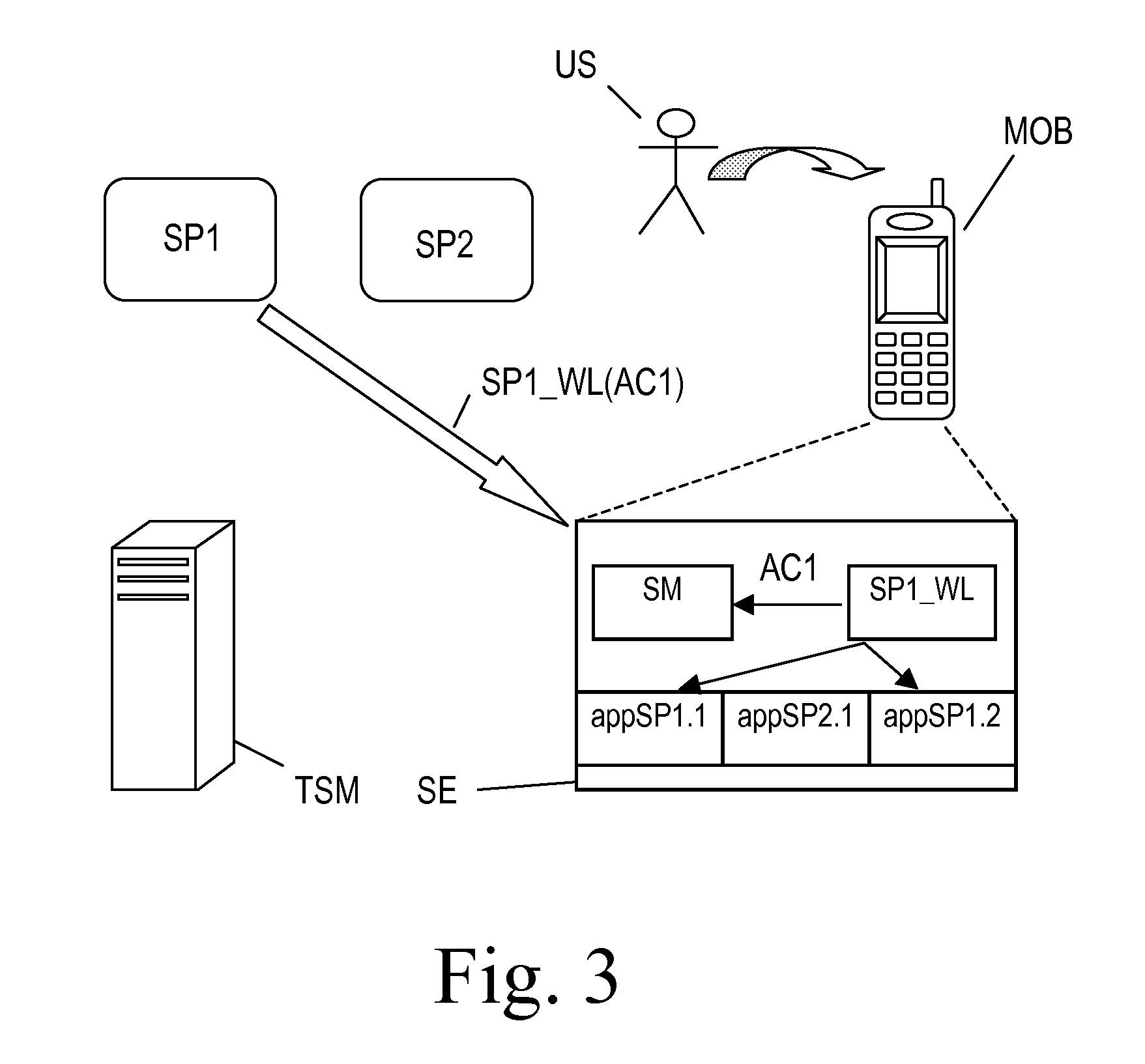
Method, system, trusted service manager, service provider and memory element for managing access rights for trusted applications
ActiveUS20100205432A1Digital data protectionPayment architectureService provisionPayment service provider
A method for granting trusted applications (SP1_WL) of a Service Provider (SP1, SP2) access to applications (appSP1.1, appSP1.2; appSP2.1) of that Service Provider (SP1, SP2) that have been stored in a secure element (SE) comprises: the Service Provider (SP1, SP2) transmits a request (REQ1) for granting access to its applications to a Trusted Service Manager (TSM); the Trusted Service Manager (TSM) generates an access right code (AC1) and transmits it to both the Service Provider (SP1, SP2) and a service manager (SM) in the secure element (SE); the Service Provider (SP1, SP2) generates the trusted application (SP1_WL), provides it with the access right code (AC1) and sends it to the secure element (SE); the trusted application (SP1_WL) connects to the service manager (SM) with the access right code (AC1) whereupon the service manager (SM) grants the wallet (SP1_WL) access to the applications (appSP1.1, appSP1.2; appSP2.1).
Owner:NXP BV
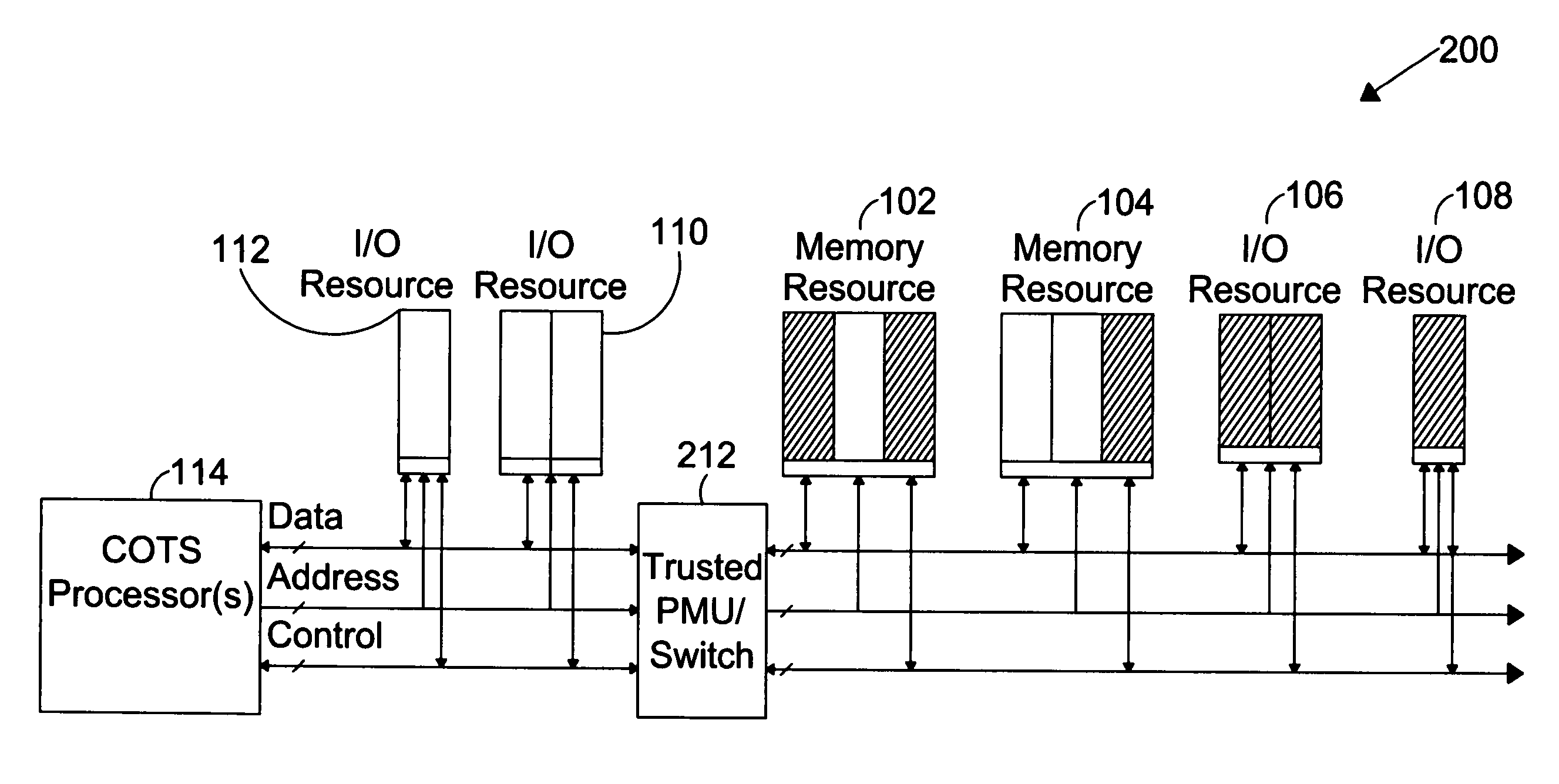
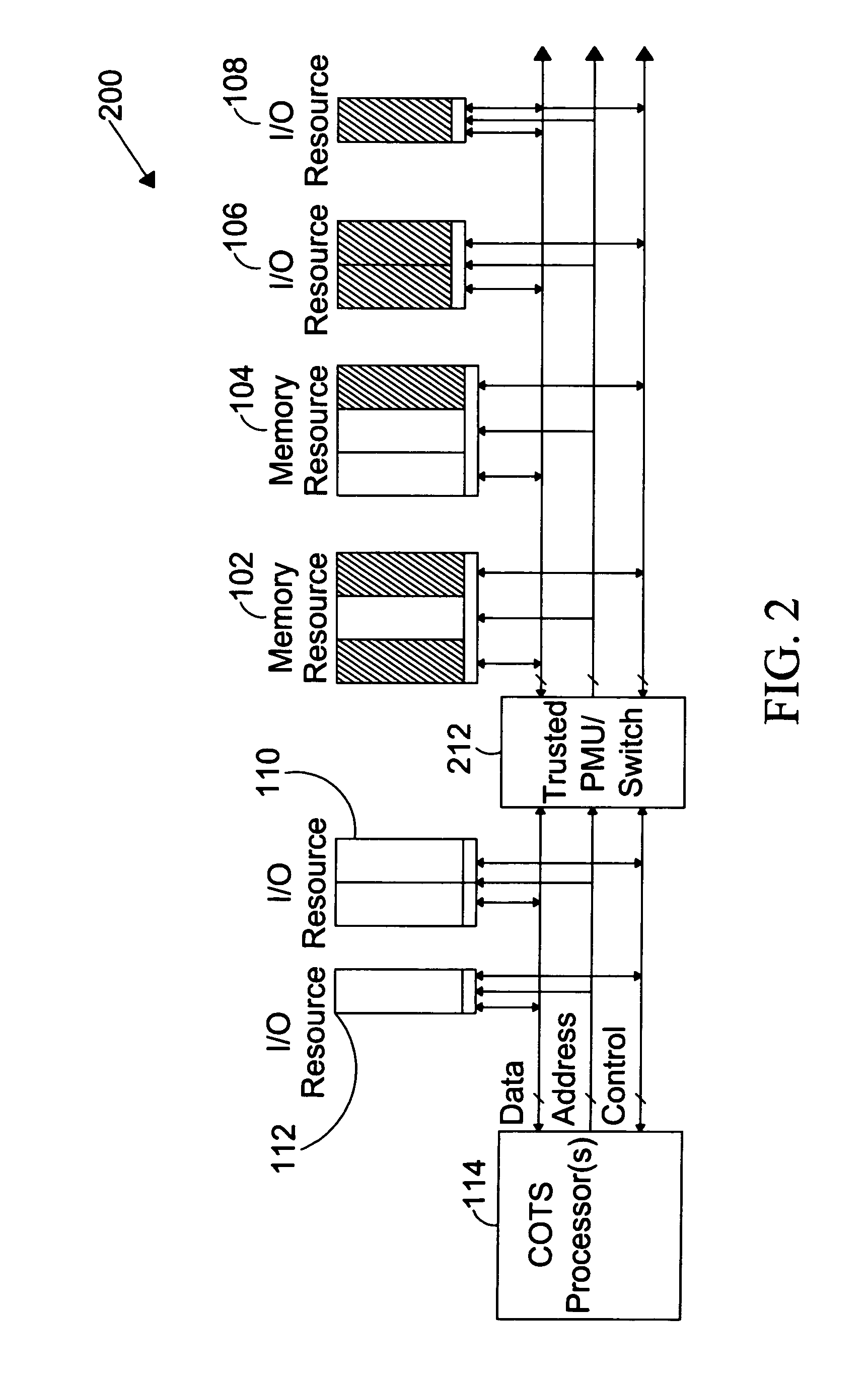
System for providing secure and trusted computing environments
ActiveUS7716720B1Provide partEnvironment safetyDigital data processing detailsUser identity/authority verificationTrusted ComputingComputer module
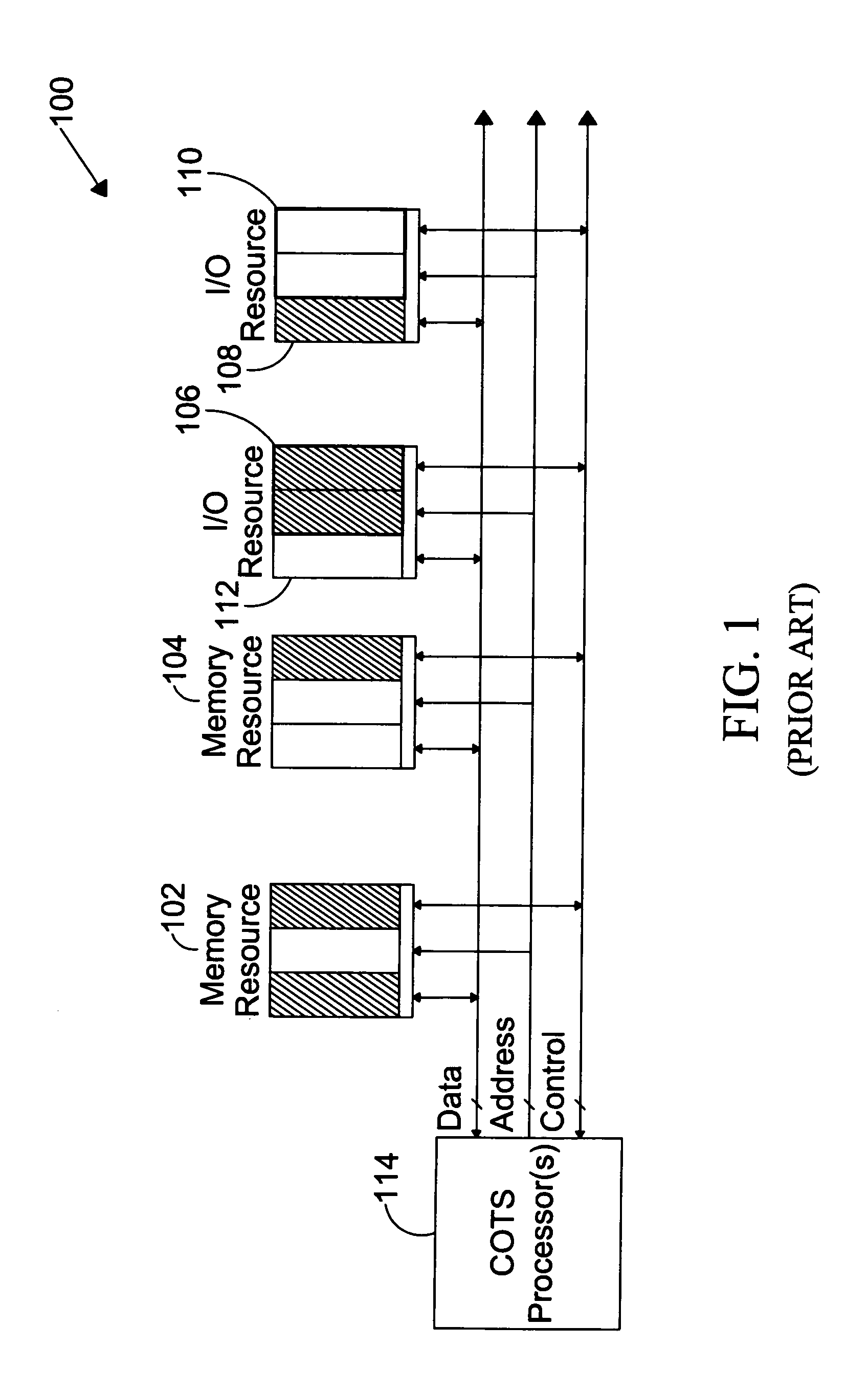
The present invention is directed to a system for providing a trusted environment for untrusted computing systems. The system may include a HAC subsystem managing shared resources and a trusted bus switch for controlling a COTS processor to access the shared resources. The shared resources such as memory and several I / O resources reside on the trusted side of the trusted bus switch. Alternatively, the system may include a SCM as an add-on module to an untrusted host environment. Only authenticated applications including COTS OS execute on the SCM while untrusted applications execute on the untrusted host environment. The SCM may control secure resource access from the untrusted host through a plug-in module interface. All secure resources may be maintained on the trusted side of the plug-in module interface.
Owner:ROCKWELL COLLINS INC
Methods and Systems for Forcing an Application to Store Data in a Secure Storage Location
ActiveUS20110277013A1User identity/authority verificationPlatform integrity maintainanceClient-sideClient machine
The present application is directed to methods and systems for redirecting write requests issued by trusted applications to a secure storage. Upon redirecting the write requests, the data included in those requests can be stored in the secure storage area of a client computer. In some embodiments, the methods and systems can include determining whether an application issuing the request is a trusted application that requires data to be stored in a secure storage repository. Upon making this determination, a filter driver can identify a secure storage area on a client computer and can redirect the write request to this secure storage. In other embodiments, the filter driver may deny requests of trusted applications to write to unsecure storage areas.
Owner:CITRIX SYST INC
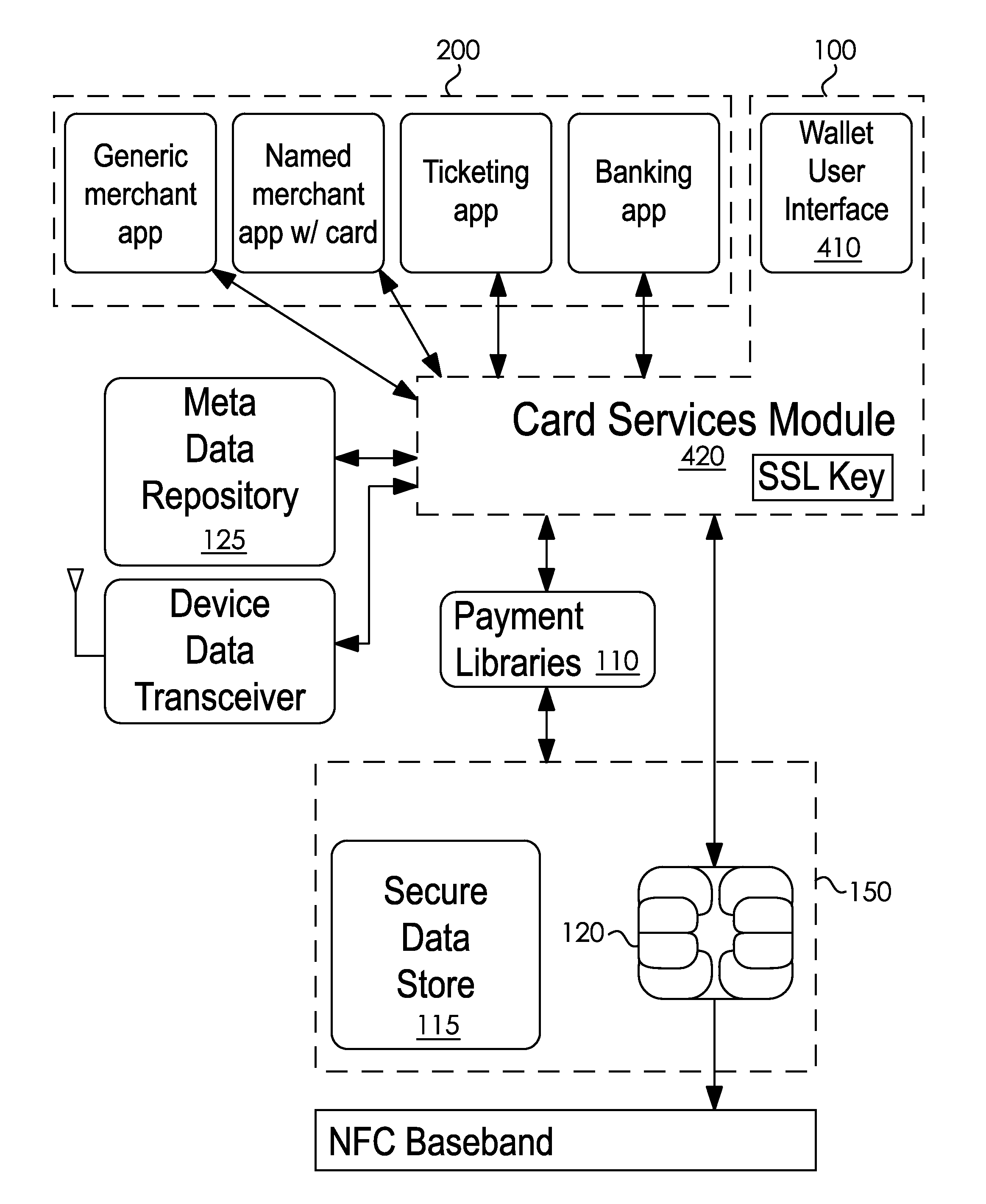
System and Method for Providing Secure Data Communication Functionality to a Variety of Applications on a Portable Communication Device
ActiveUS20120124658A1Digital data processing detailsMultiple digital computer combinationsApplication programming interfaceComputer module
A system for providing an application associated with a portable communication device the ability to communicate via a secure element. The system has a digital identifier and digital token operably associated with the application; a card services module that provides an application programming interface to the secure element; and a secure data table associated with the card services module. The secure data table includes a list of trusted applications each identifiable by paired digital identifier and token. The card services module [includes] compares the identifier and the token with each of the identifier-token pairs in the table until a match indicates the application is trusted. The card services module issues commands to the secure element based on an action requested by a trusted application in conjunction with the presentation of the digital token. A method of providing an application with the ability to communicate via secure element is also disclosed.
Owner:T I S
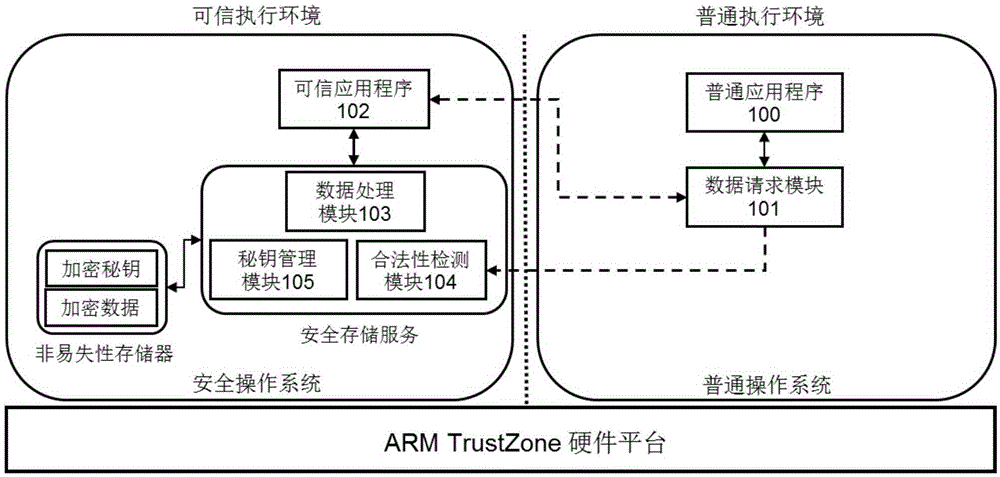
Secure storage service system and method based on TrustZone technology
InactiveCN105260663AEnsure safetyGuaranteed isolationDigital data protectionTerminal equipmentComputer terminal
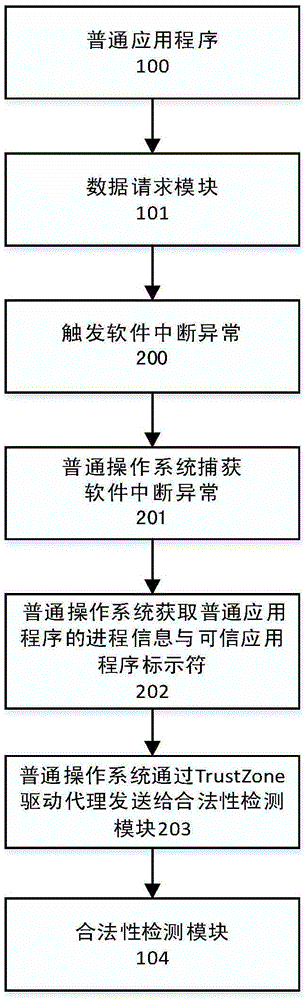
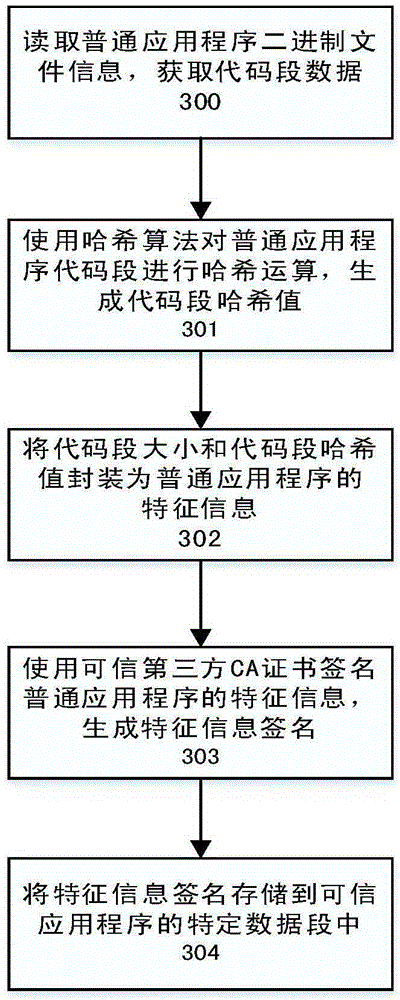
The invention relates to a secure storage service system and method based on a TrustZone technology. The secure storage service system comprises a data request module, a common application program, a secure storage service and a trusted application program; the data request module is responsible for packaging and transferring a secure storage service request of data between the common application program and the trusted application program, and providing a unified service request interface for data storage, data loading and data destruction for the common application program; and the secure storage service comprises a legality detection module, a data processing module and a secrete key management module. The secure storage service system and method disclosed by the invention aim to provide the unified data secure storage interface for the application programs on terminal equipment supporting the TrustZone technology; therefore, the secure storage problem of sensitive data of the application programs can be solved; and furthermore, the development convenience of the application programs is ensured.
Owner:INST OF INFORMATION ENG CAS
Method and system for logging on third party server through instant communication software
ActiveCN101350717AEasy to operateImprove user experienceData switching networksSecuring communicationAuthorization certificateThird party
The present invention discloses a method of logging on a third party server through instant communication software. In the method, when the user logs on the instant communication IM server through a single-point logging-on SSI server, the client acquires the authority certificate information of the user to log on the third party server from the SSI server, according to the operating command of the user, and then transmits the login request information with the authority certificate information to the third party server; the authority certificate information is encrypted by a first secret key corresponding to the third party server; the third party server deciphers the authority certificate information in the login request information according to the first secret key; the user logs on after the identity of the user is confirmed at the client. The user can log on the IM server through the client, and can visit all the mutually trusting application systems only by inputting the name and the password of the user once. Therefore, the method simplifies the operating processes of the user, and improves the experience of the user to certain extent.
Owner:CHINA MOBILE COMM GRP CO LTD +1
System for providing secure and trusted computing environments through a secure computing module
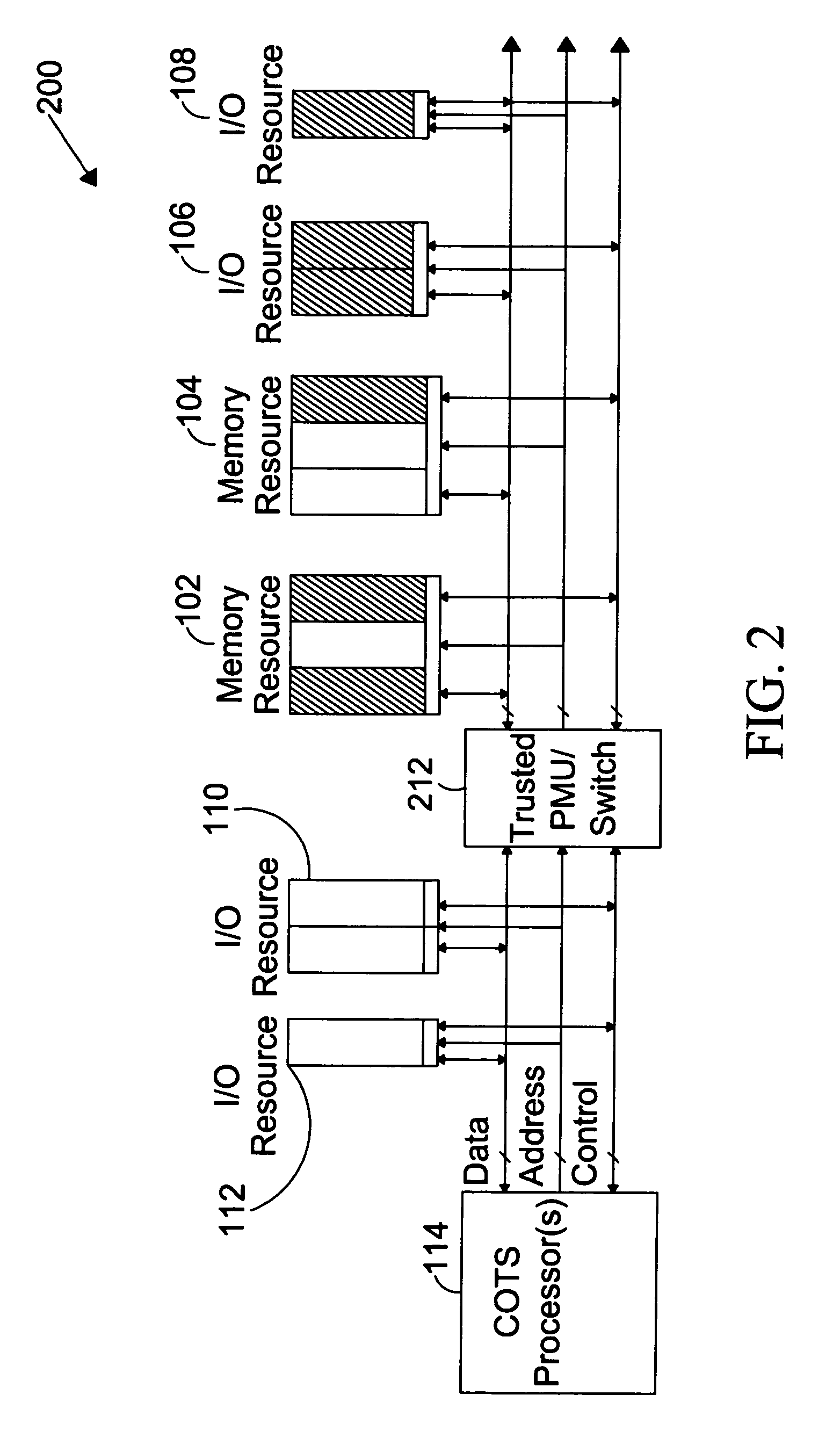
ActiveUS7734933B1Provide partUnauthorized memory use protectionHardware monitoringTrusted ComputingHosting environment
The present invention is directed to a system for providing a trusted environment for untrusted computing systems. The system may include a HAC subsystem managing shared resources and a trusted bus switch for controlling a COTS processor to access the shared resources. The shared resources such as memory and several I / O resources reside on the trusted side of the trusted bus switch. Alternatively, the system may include a SCM as an add-on module to an untrusted host environment. Only authenticated applications including COTS OS execute on the SCM while untrusted applications execute on the untrusted host environment. The SCM may control secure resource access from the untrusted host through a plug-in module interface. All secure resources may be maintained on the trusted side of the plug-in module interface.
Owner:ROCKWELL COLLINS INC
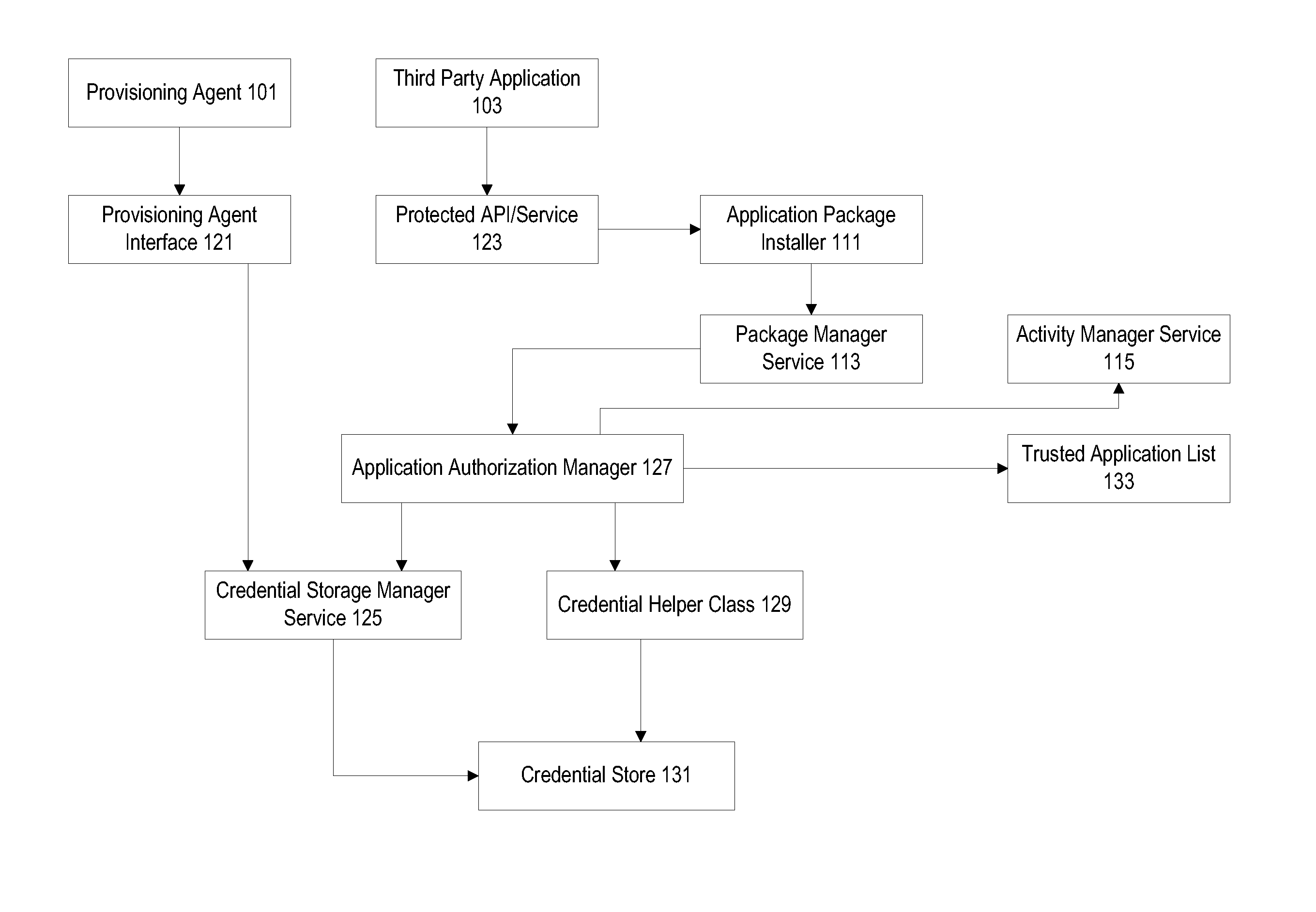
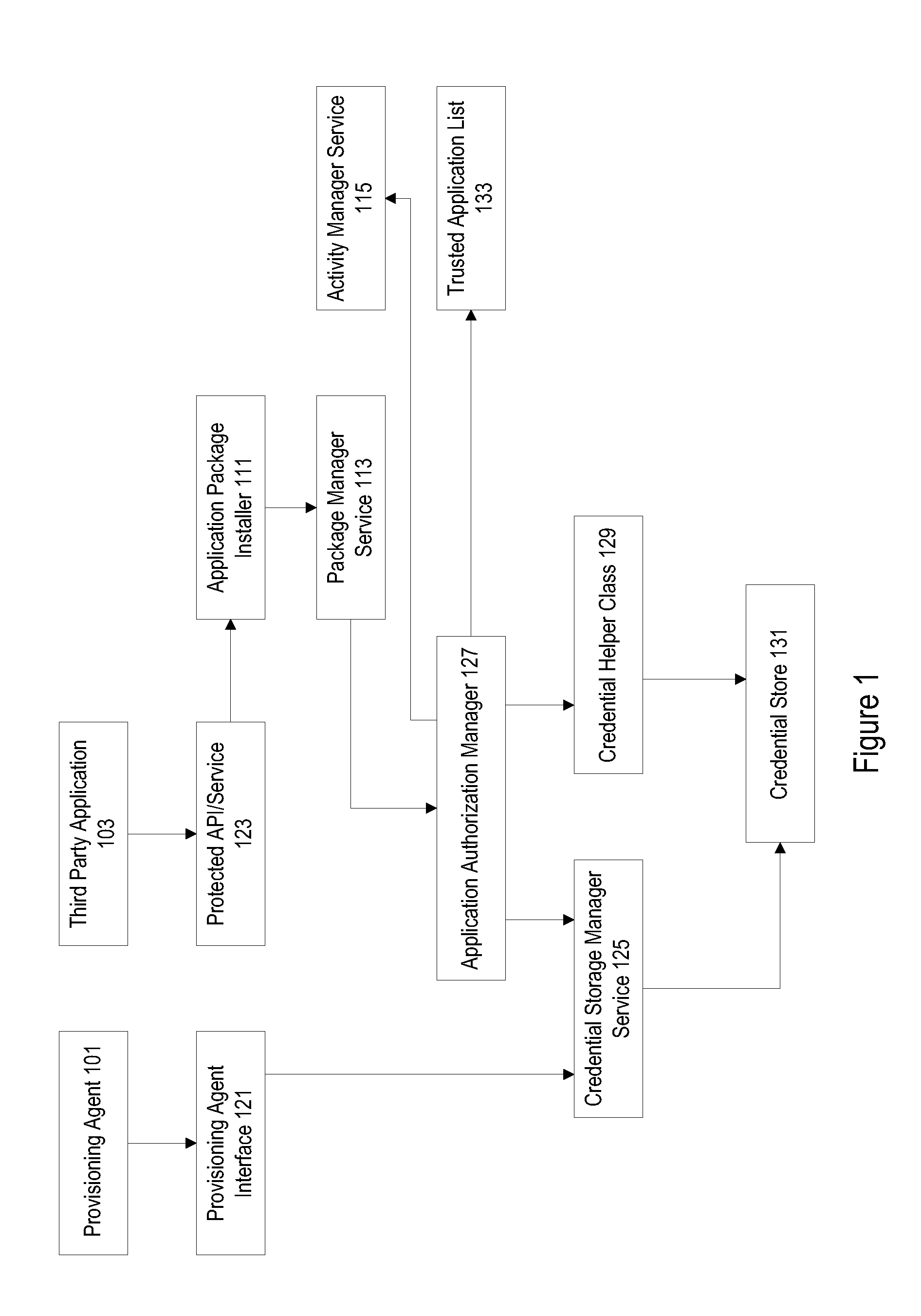
Protected application programming interfaces
ActiveUS20130160147A1Digital data processing detailsAnalogue secracy/subscription systemsApplication programming interfaceSecurity domain
Mechanisms are provided to allow particular parties and applications access to protected application programming interfaces (APIs) without the use of security domains. Trusted parties and applications may have access to protected APIs while unfrosted parties and applications may be restricted to a more limited set of APIs. Public keys associated with individual applications that are used to enforce licensing policies can be repurposed for use in a verification process to prevent unauthorized access to APIs. A credential storage manager can be used to maintain permission and certificate information. An application authorization manager may access credential storage and maintain trusted application information.
Owner:DELL PROD LP
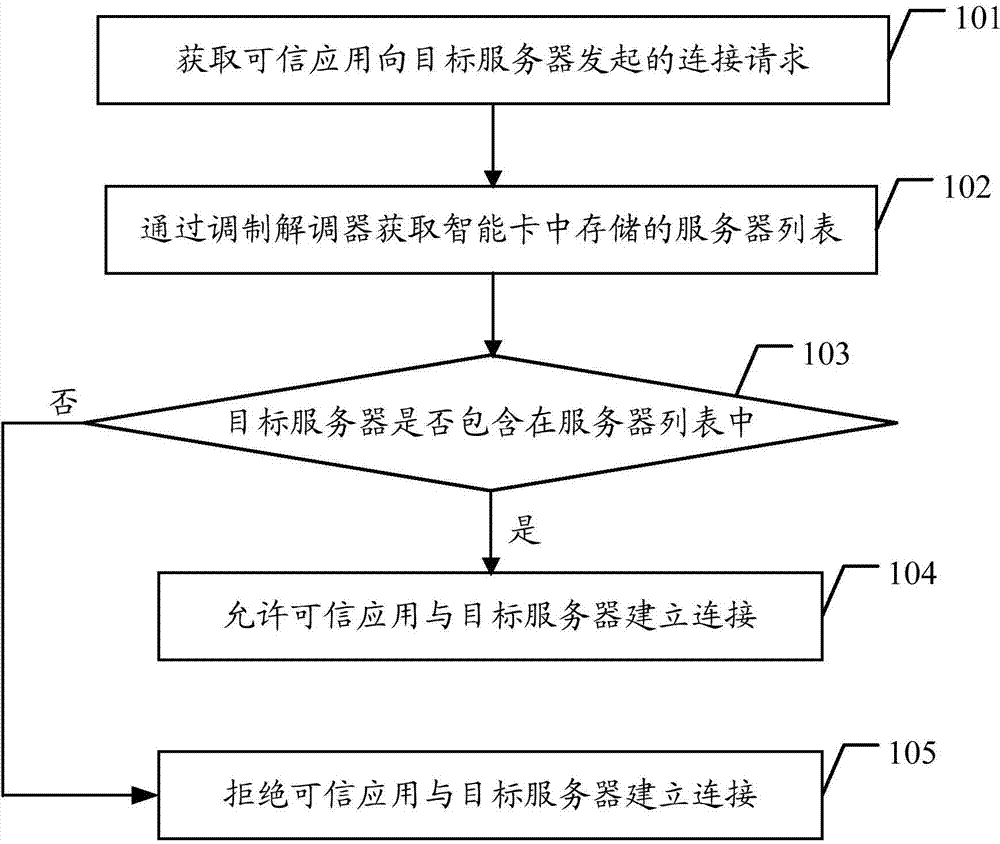
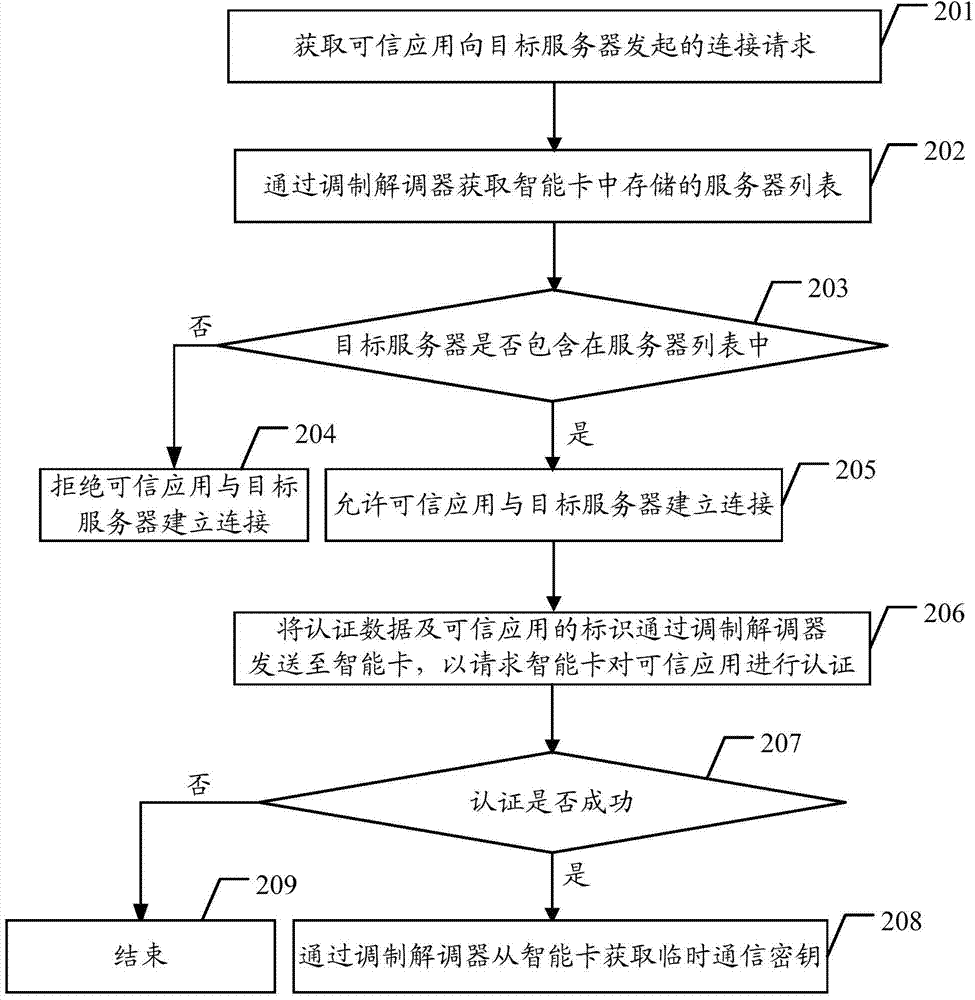
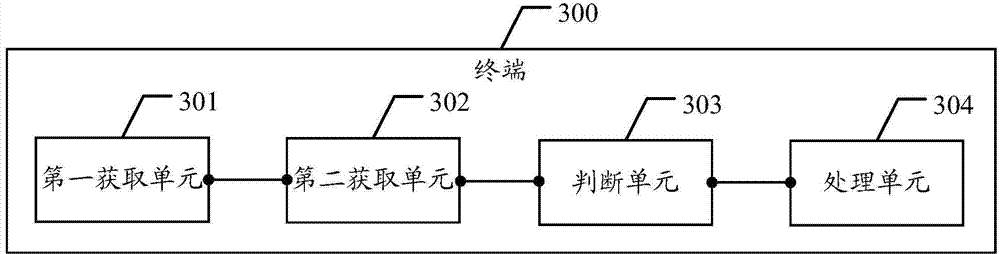
Method, system and terminal capable of improving safety of trusted execution environment
ActiveCN104125216AImprove securityPrevent tamperingUser identity/authority verificationModem deviceSmart card
The embodiment of the invention discloses a method, a system and a terminal capable of improving the safety of a trusted execution environment. The method comprises the following steps of: acquiring the connection request initiated by a trusted application to a target server, the connection request containing the identification of the target server; acquiring a server list stored in a smart card through a modulator-demodulator; judging whether the target sever is contained in the server list according to the identification of the target server; if so, then allowing the trusted application to establish connection with the target server, or else, then refusing the trusted application to establish connection with the target server. The embodiment of the invention is capable of improving the safety of the TEE through the smart card.
Owner:HUAWEI TECH CO LTD
System and method for managing access to protected content by untrusted applications
InactiveUS20050262568A1Data taking preventionDigital data processing detailsInternet privacyFile system
There is provided a communication device, and a method thereof, for managing access to protected content. The communication device comprises an application (302), a trusted file system service (316), a trusted agent (318) and a trusted content renderer (320). The application (302) requests performance of an action for the protected content (306). The trusted file system service (316) identifies the protected content (306) to the application (302). The trusted agent (318) identifies rights associated with the protected content (306) to the application (302). The trusted content renderer (320) performs the action in response to determining that the application (302) is an untrusted application having sufficient rights to perform the action.
Owner:MOTOROLA INC
Method of enabling a multitasking computing device to conserve resources
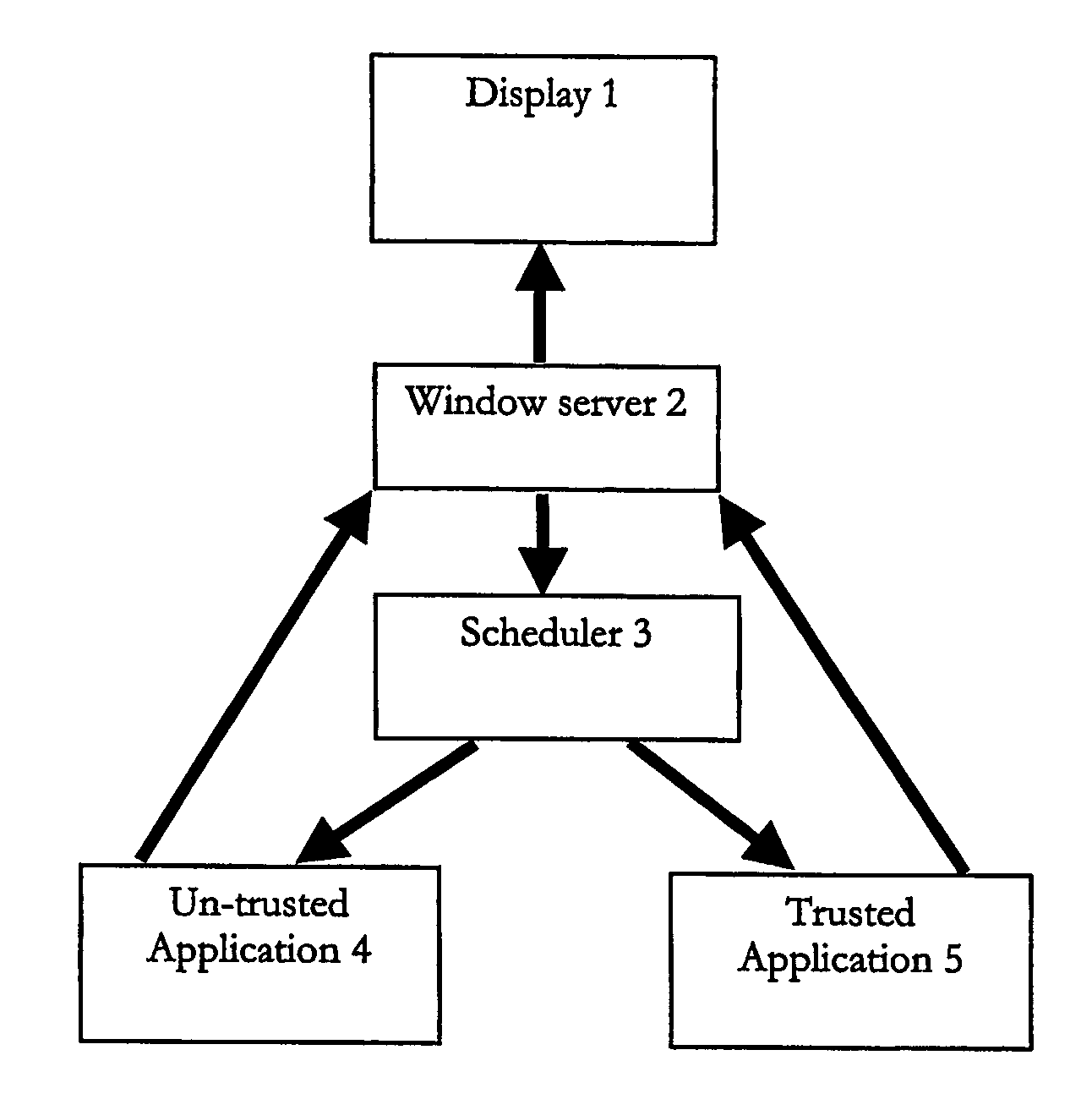
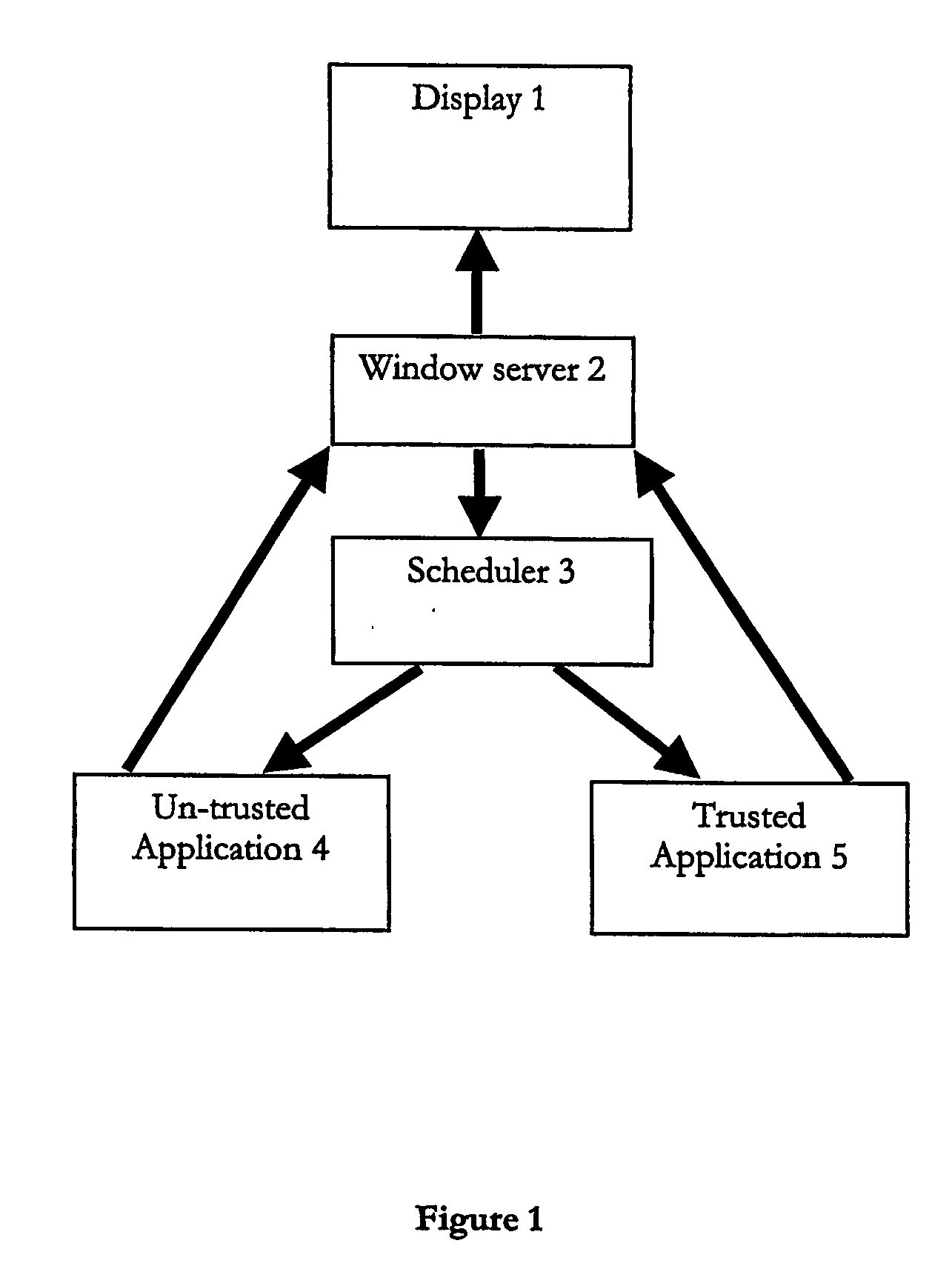
InactiveUS20070038763A1Save system resourcesPreserve system resources (CPU, power)Energy efficient ICTResource allocationTrusted applicationMany-task computing
A multitasking battery operated computing device preserves battery power by determining if an untrusted application is in the background or foreground and preventing an untrusted application that is in the background from running. A window server component may be used to determine if an untrusted application is in the background or foreground; for applications in the background, it can send a control signal to the scheduler or interrupt handler that in effect prevents the untrusted application from running, e.g. being given any services or consuming any resources.
Owner:UIQ TECH
Communication device, program and recording media
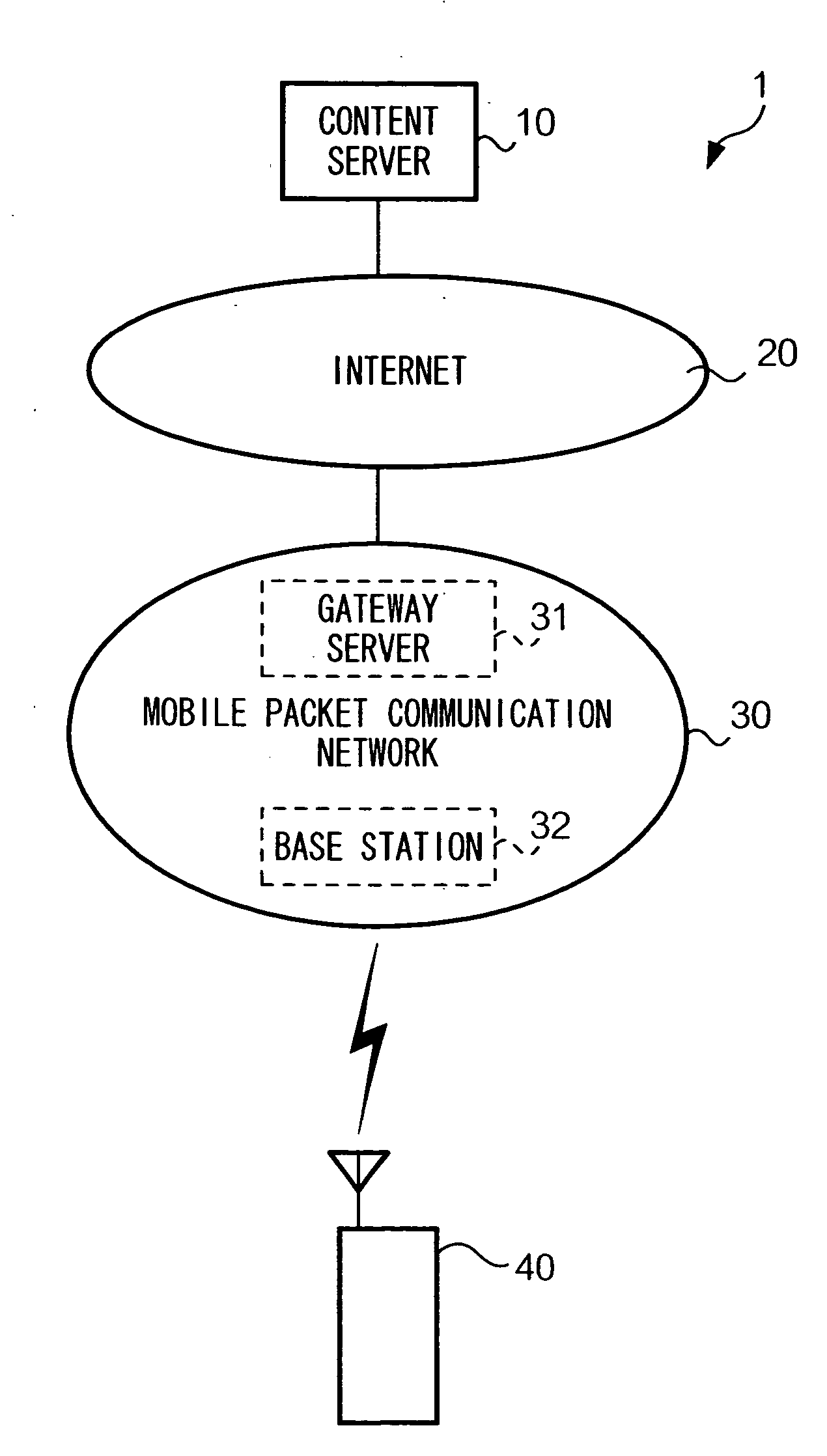
InactiveUS20040142682A1Network traffic/resource managementSubstation equipmentComputer hardwareApplication software
A mobile phone receives a program and identification information of a trusted application for the program, specifies data to be used in executing the program, generates a type of object by selecting either an imperfect encapsulated object or a perfect encapsulated object to be generated on the basis of the identification information of a trusted application, and uses the data by using only the generated object when the program is executed.
Owner:NTT DOCOMO INC
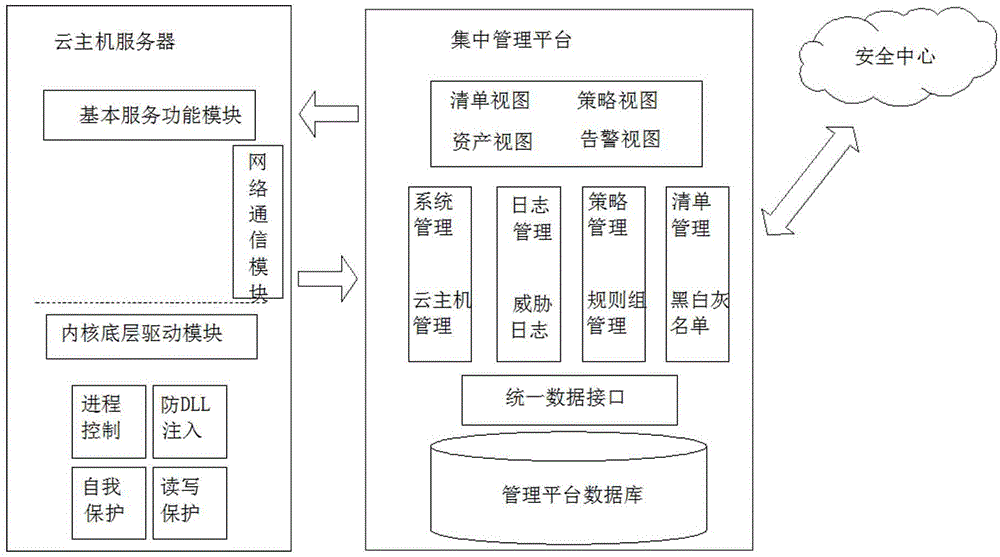
White list based realization method for active defense of cloud host
ActiveCN105138901APrecise managementStop runningPlatform integrity maintainanceMalwareZero-day attack
The invention discloses a white list based realization method for active defense of a cloud host. The method involves a centralized management platform of a server and a client, and the client is mounted on each cloud host needed to be protected. The specific realization process is as follows: all binary files in the protected cloud host are scanned through server software; a cloud security center identifies out trust ratings of the scanned files and adds a graded file list library into a white list library, a black list library and a gray list library separately; and at the client, only trusted application programs in a white list are allowed to run for preventing loading of a dynamic-link library file in a kernel. Compared with the prior art, the white list based realization method for active defense of the cloud host can completely prevent potential unwanted application programs and codes and prevent advanced threats, is free of feature code update, and can consistently enable known good software, prevent known or unknown bad software, correctly manage new software and effectively prevent unknown malicious software and zero-day attacks.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
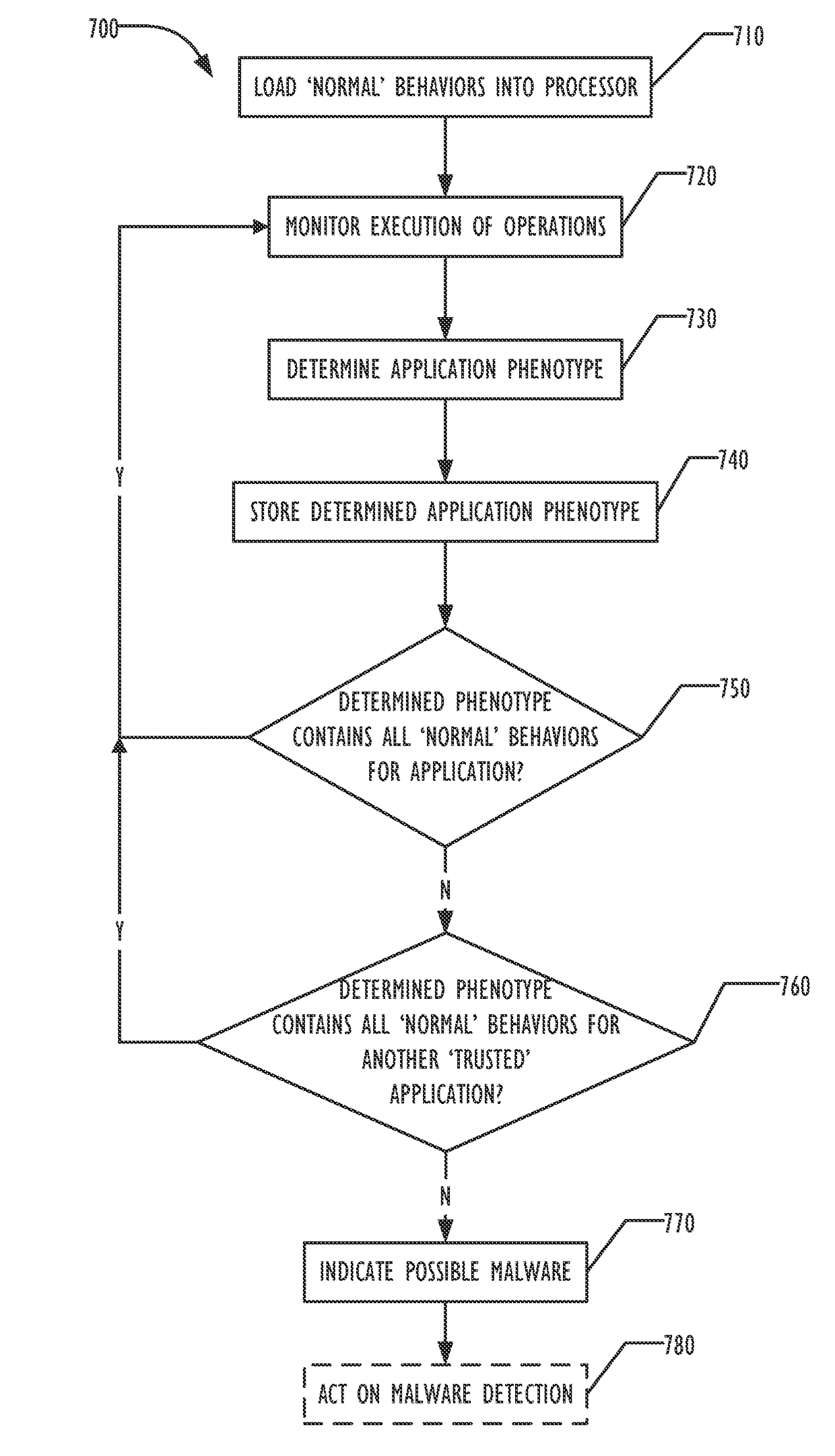
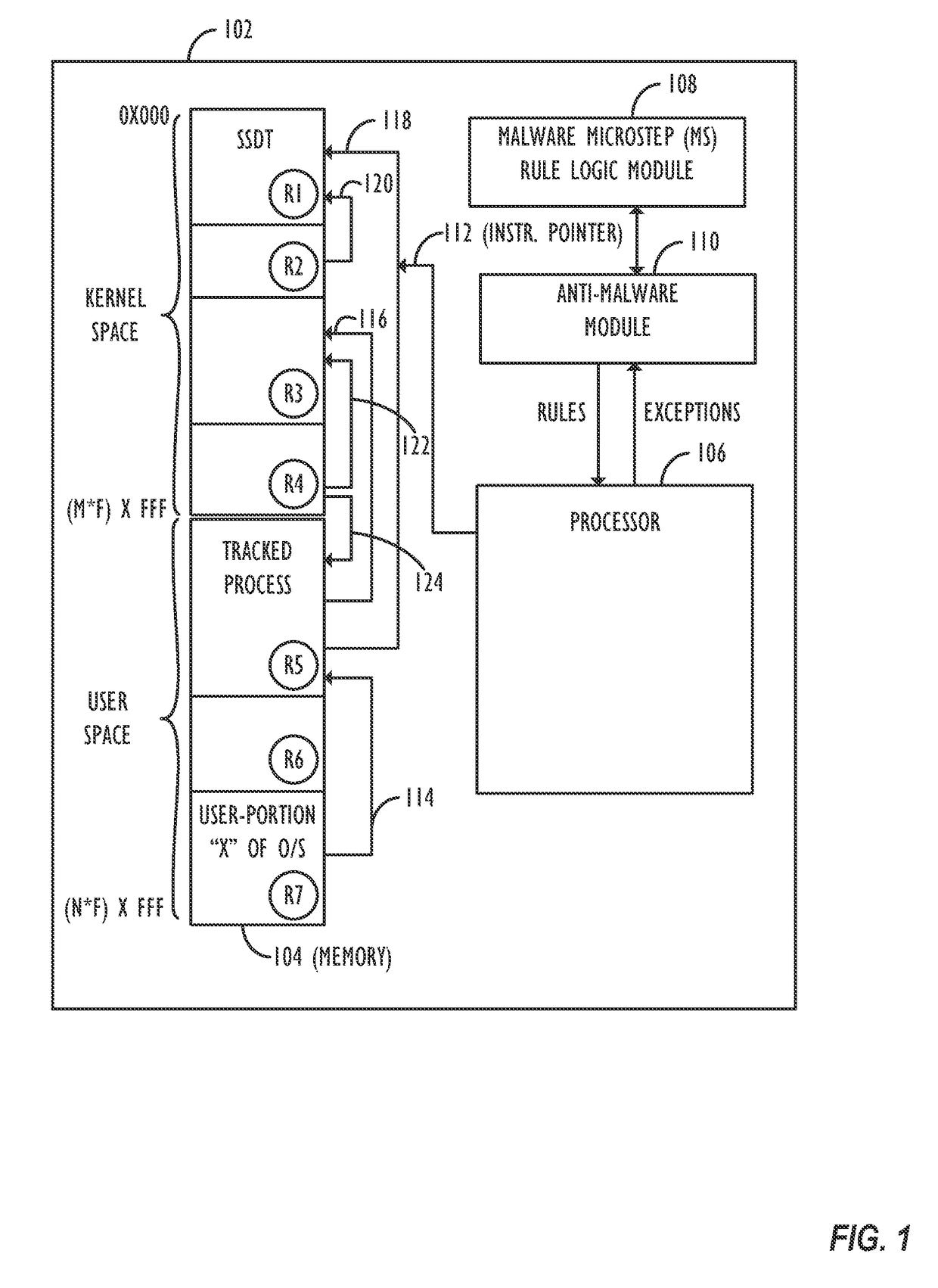
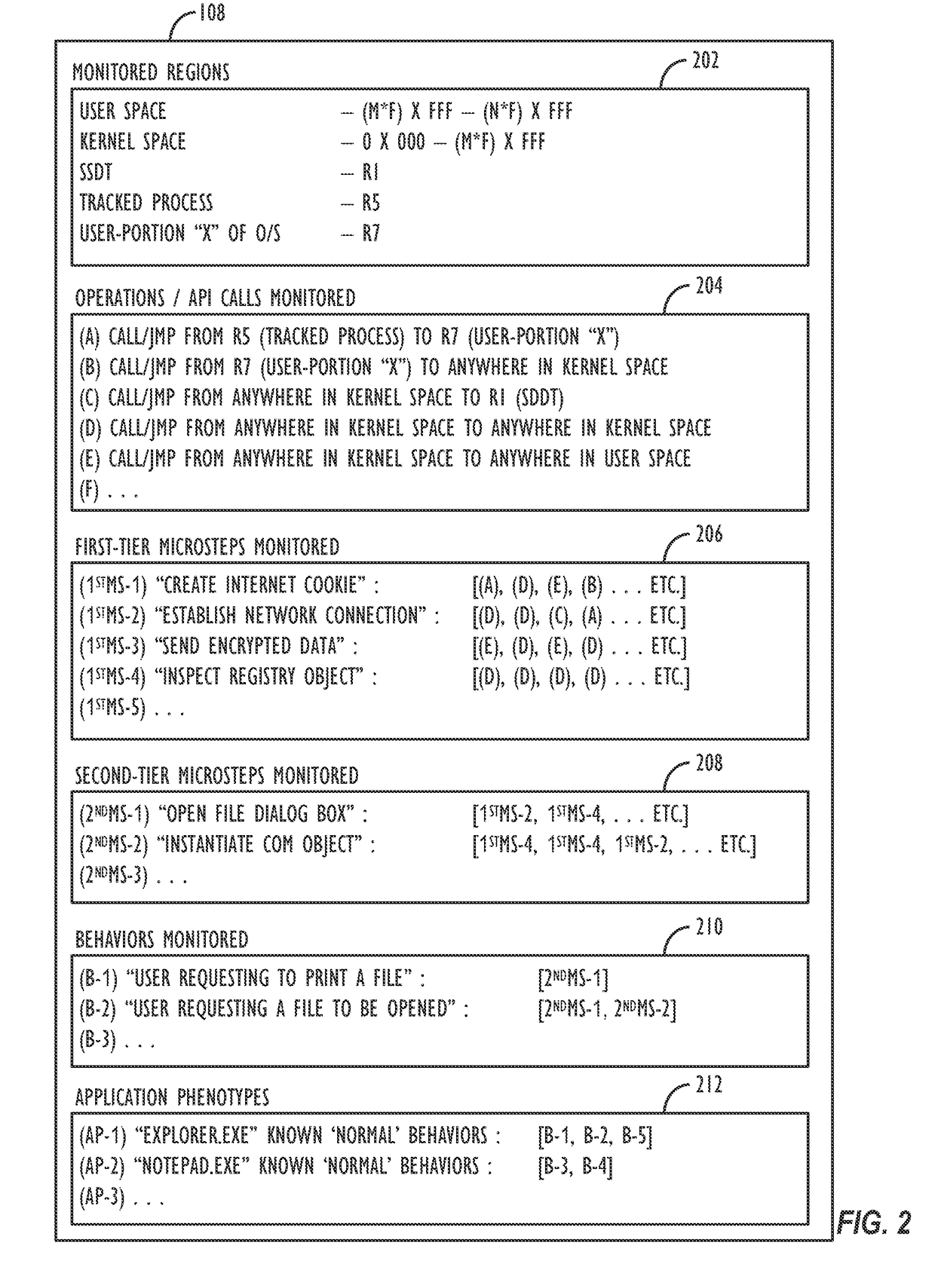
Application phenotyping
ActiveUS20170093897A1Digital data information retrievalComputer security arrangementsUser deviceInternet privacy
A collection of techniques is disclosed to allow for the detection of malware that leverages pattern recognition and machine learning to effectively provide “content-less” malware detection, i.e., detecting a process as being an ‘anomaly’ not based on its particular content, but instead based on comparisons of its behavior to known (and characterized) ‘trusted’ application behaviors, i.e., the trusted applications' “phenotypes” and / or the phenotypes of known malware applications. By analyzing the patterns of normal behavior performed by trusted applications as well as malware applications, one can build a set of sophisticated, content-agnostic behavioral models (i.e., “application phenotypes”)—and later compare the processes executed on a user device to the stored behavioral models to determine whether the actual measured behavior reflects a “good” application, or if it differs from the stored behavioral models to a sufficient degree and with a sufficient degree of confidence, thus indicating a potentially malicious application or behavior.
Owner:MCAFEE LLC
Digitalized campus cloud platform
InactiveCN104240035ARealize digital managementFacilitate resource sharingResourcesInformation resourceUser authentication
The invention discloses a digitalized campus cloud platform. The digitalized campus cloud platform comprises an office system (1), a single-sign-on system (2), a user authentication system (3), an SQL (structured query language) database (4), e-commerce (7), a digital library (5) and a comprehensive educational management system (6). The office system is used for office automation, the single-sign-on system is used for users to sign on the cloud platform through a desktop and access trusted application systems by once sign, the user authentication system is used for unified authentication and authority management of users, the SQL database is used for storing digitalized information and recording and managing all data, the e-commerce is used for payment related to student admission, registration and graduation procedures, the digital library comprises intelligent retrieval and information storage, and the comprehensive educational management system comprises a scientific research system, a plant asset management system, a human resource management system, a financial management system and a foreign affairs management system. Campus digitalized management is realized, information resources of campuses are shared, and management efficiency and decision-making level are improved.
Owner:CHONGQING WENRUN SCI & TECH CO LTD
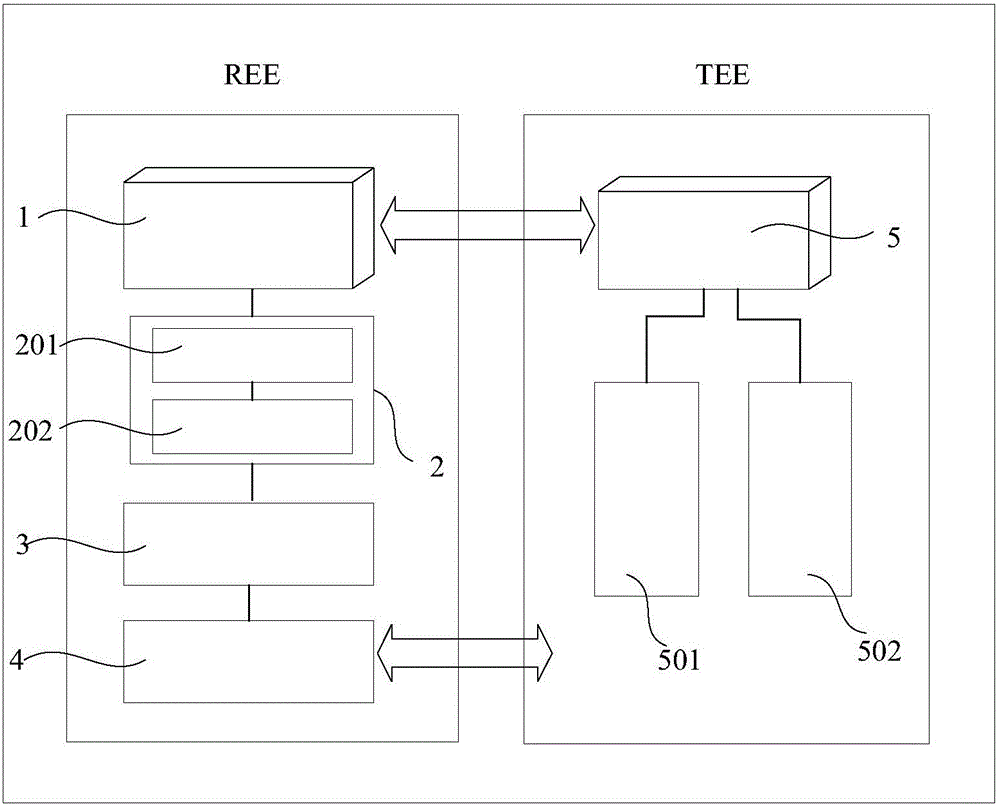
Personalized and cryptographically secure access control in trusted execution environment
ActiveUS20200034528A1Reduce eliminateCommunication securityUser identity/authority verificationDigital data protectionOperational systemFile system
An access control system includes a processor configured to provide a trusted execution environment isolated from a rich execution environment. A rich OS operates in the rich execution environment while a trusted OS operates in the trusted execution environment. An access monitoring module operates within the kernel of the rich OS and a trusted application operates in the trusted OS. The access monitoring module intercepts file requests directed at the file systems of the rich OS, and forwards the file requests to the trusted application. The trusted application then evaluates whether the file request is permitted and provides the access monitoring module with a response. The access monitoring module forwards the request to the file system only if the trusted application approves the request.
Owner:BICDROID
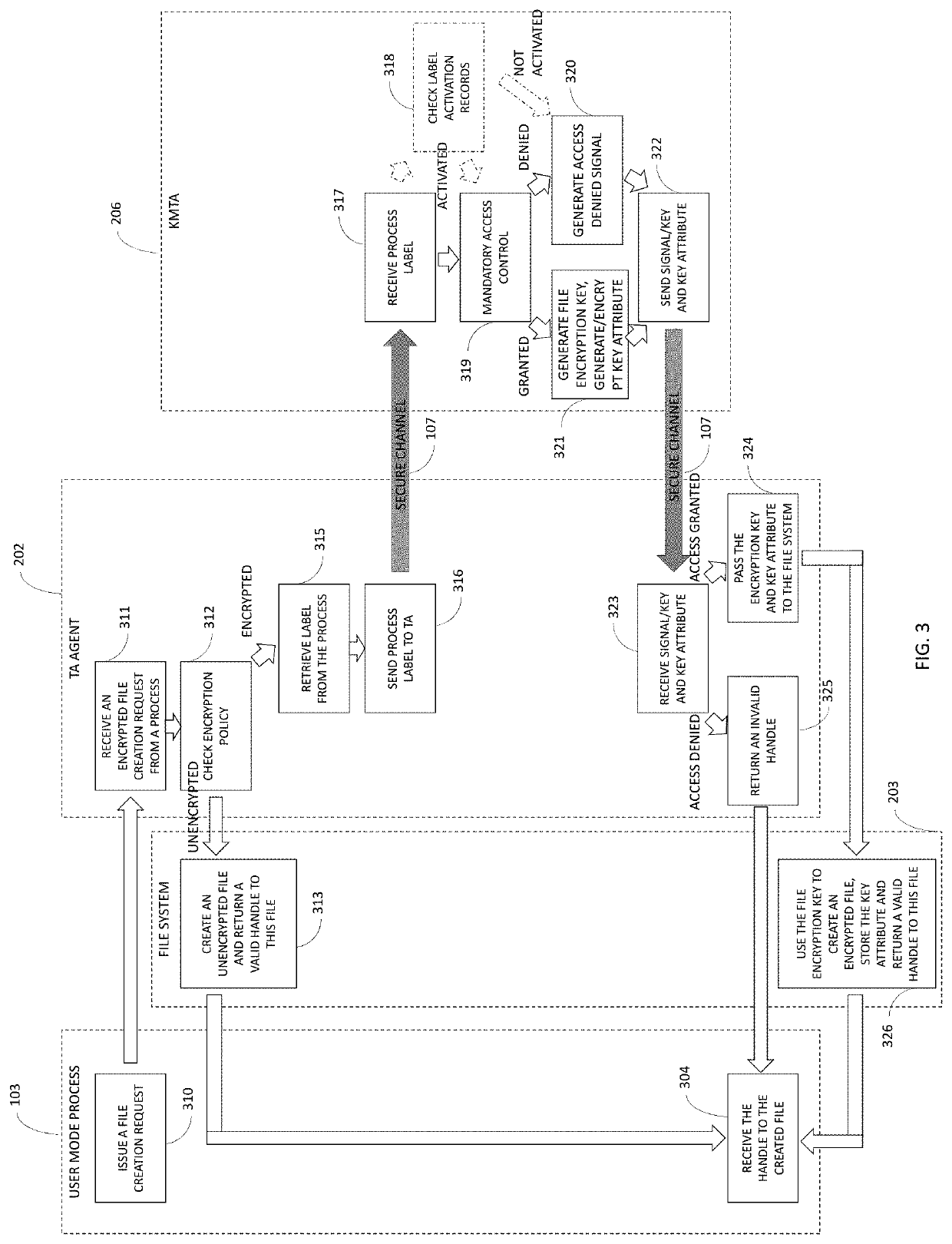
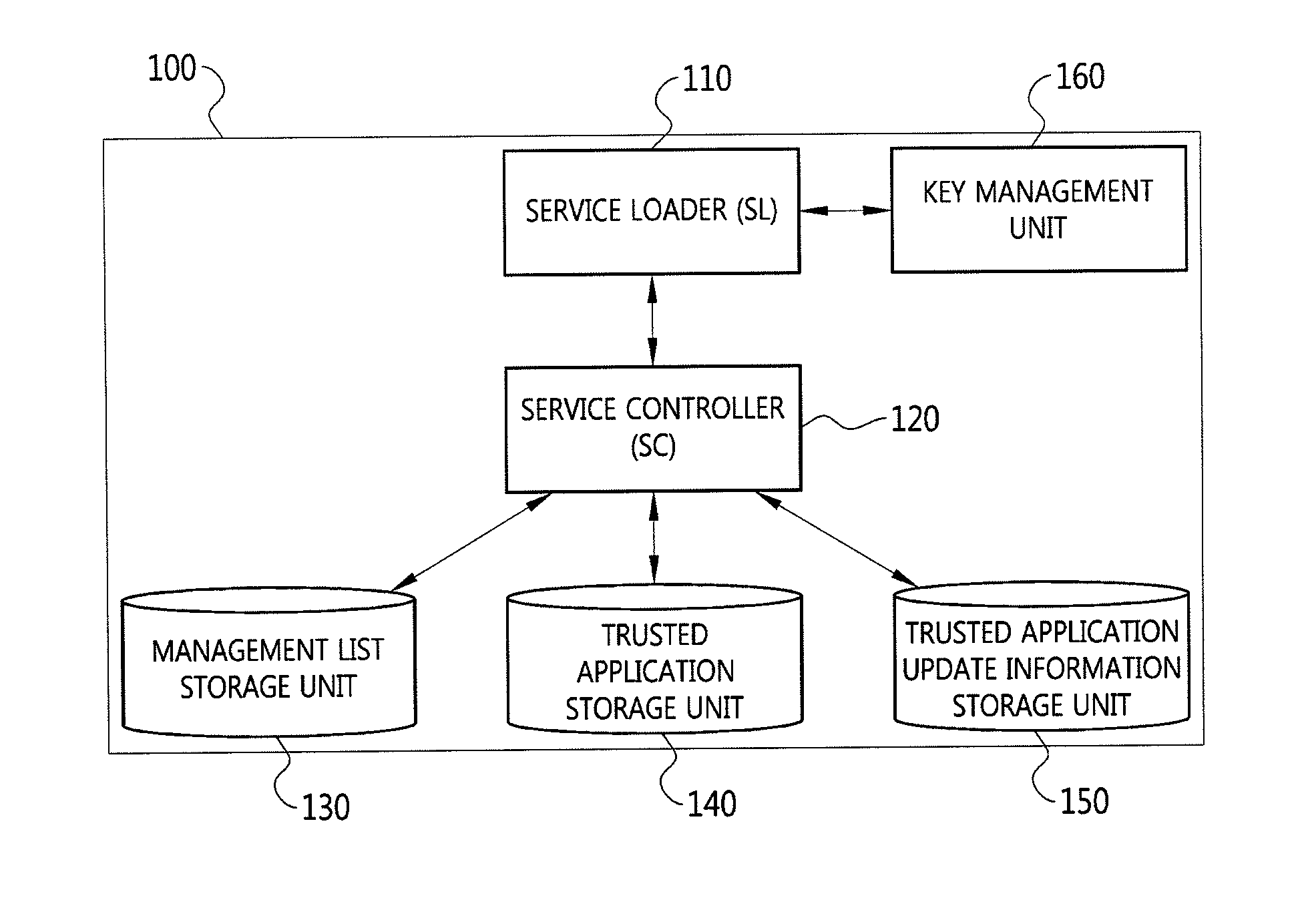
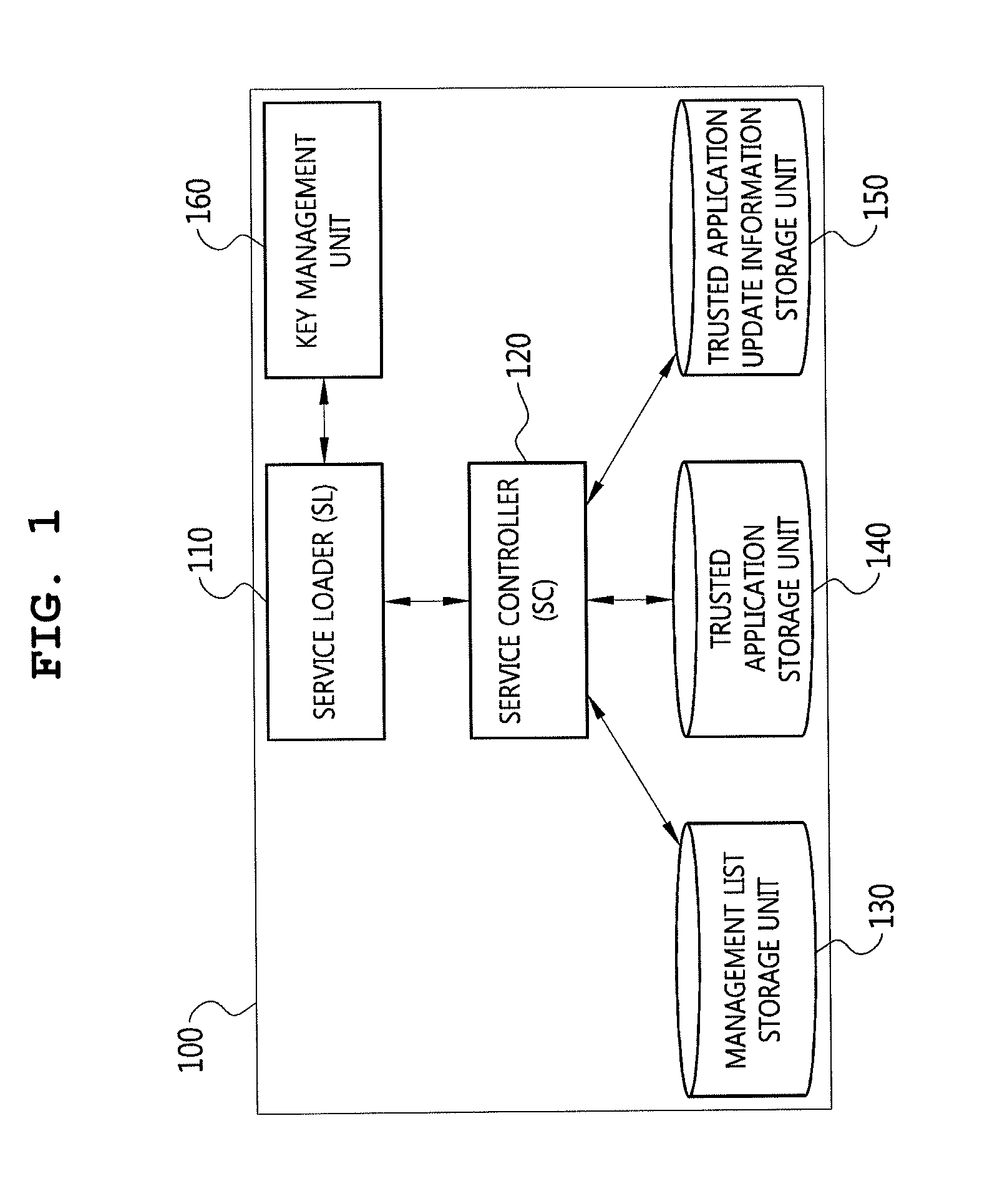
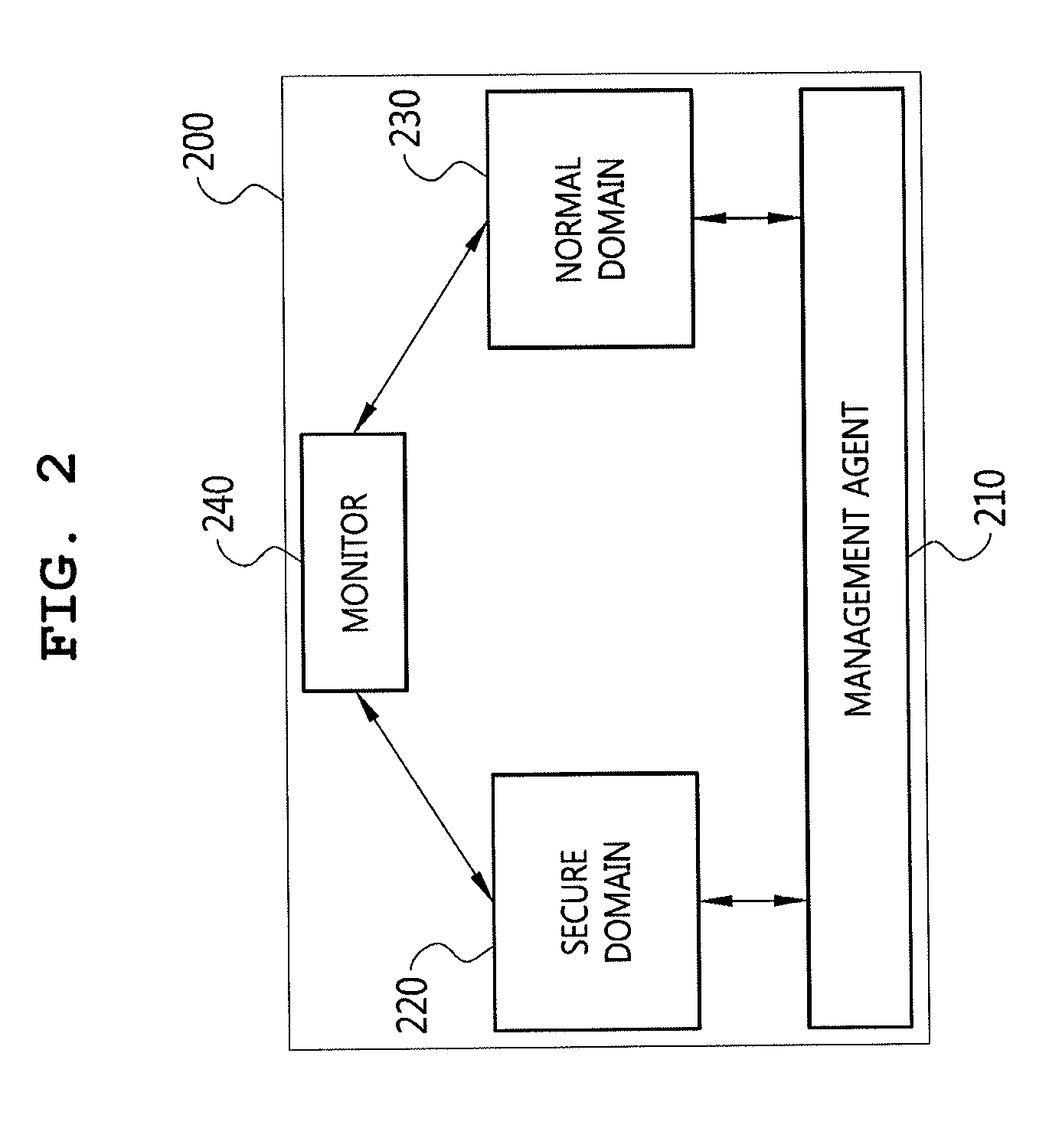
Method for interworking with trustzone between normal domain and secure domain, and management method of trusted application download, management server, device and system using it
ActiveUS20140245013A1Simple procedureResolve mismatchKey distribution for secure communicationDigital data processing detailsApplication softwareAuthentication
The present invention provides a trusted application download management, authentication, and execution method and system. A trusted application download management server according to the present invention includes a service loader, which accesses a device equipped with a trusted platform and establishes a data communication channel, and a service controller which controls the delegation of a download authority for a trusted application and allows the trusted application to be downloaded to the device when a trusted application download is requested by the device, thus totally managing the download of the trusted applications and allowing the trusted application to be securely downloaded.
Owner:SK PLANET CO LTD
Executing Trusted Applications with Reduced Trusted Computing Base
ActiveUS20110154500A1Digital data processing detailsAnalogue secracy/subscription systemsTrusted ComputingApplication software
A system for executing trusted applications with a reduced trusted computing base. In one embodiment, the system includes a processor to dynamically instantiate an application protection module in response to a request by a program to be executed under a trusted mode. The system further includes memory to store the program which is capable of interacting with a remote service for security verification. In one embodiment, the application protection module includes a processor-measured application protection service (P-MAPS) operable to measure and to provide protection to the application.
Owner:INTEL CORP
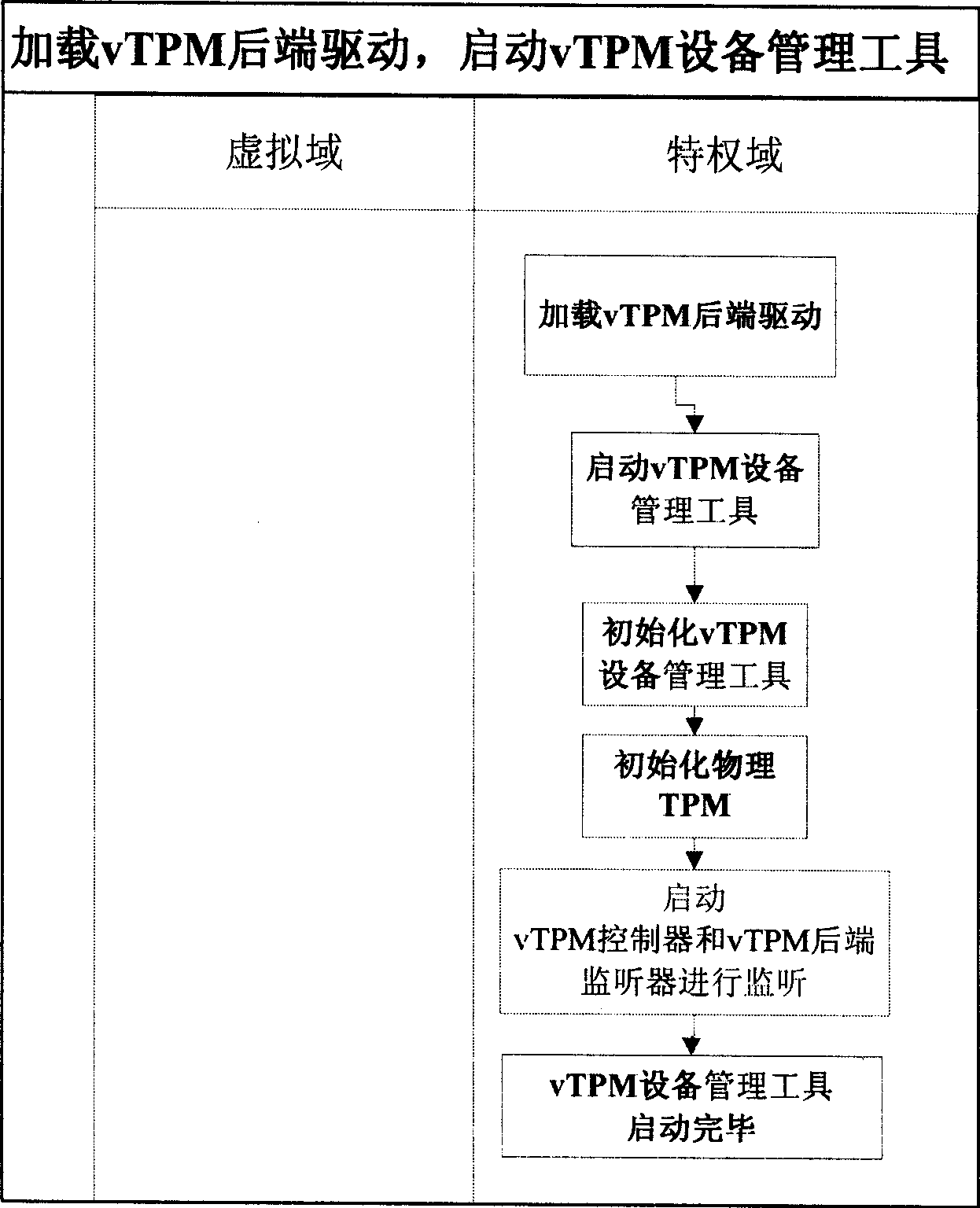
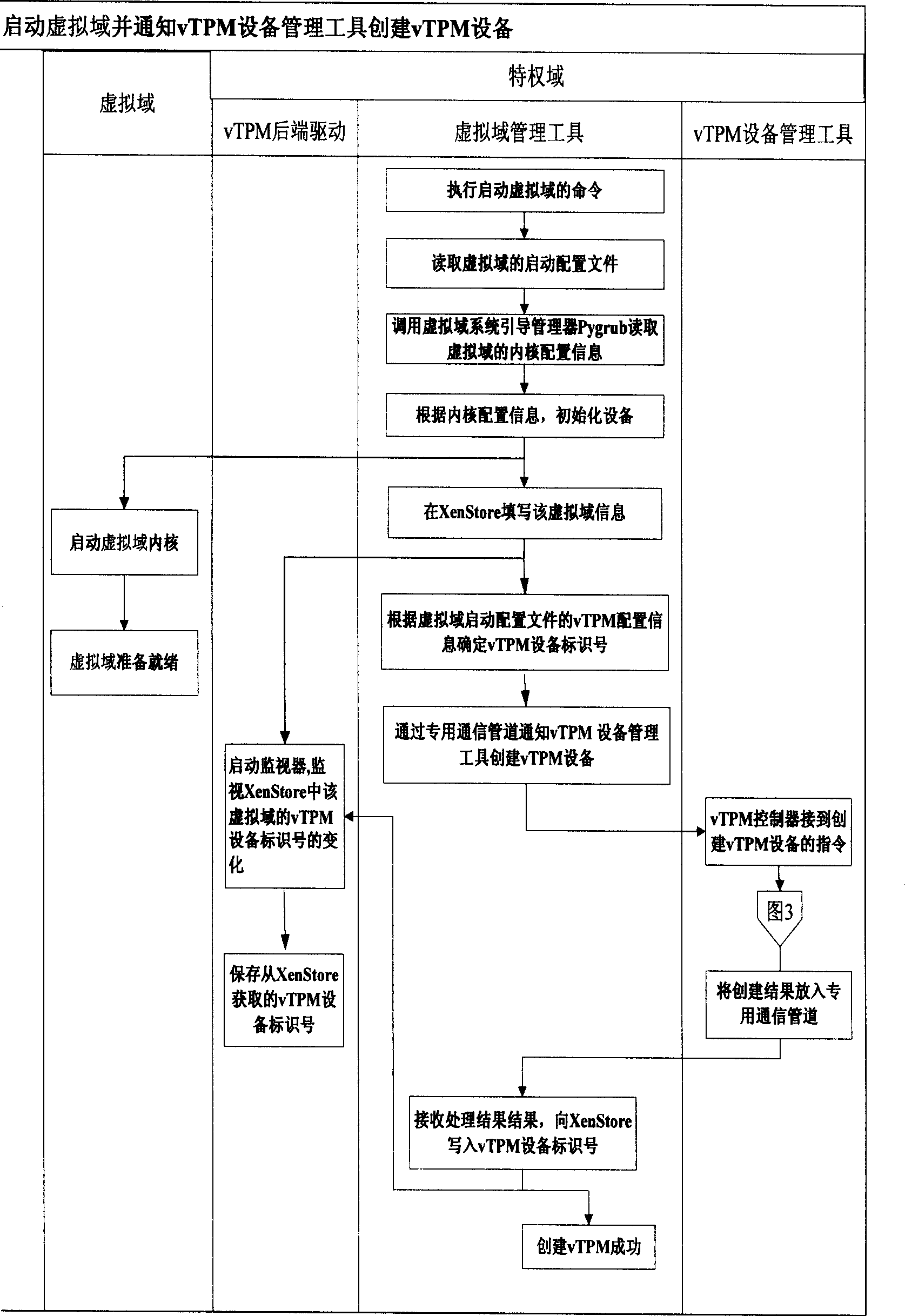
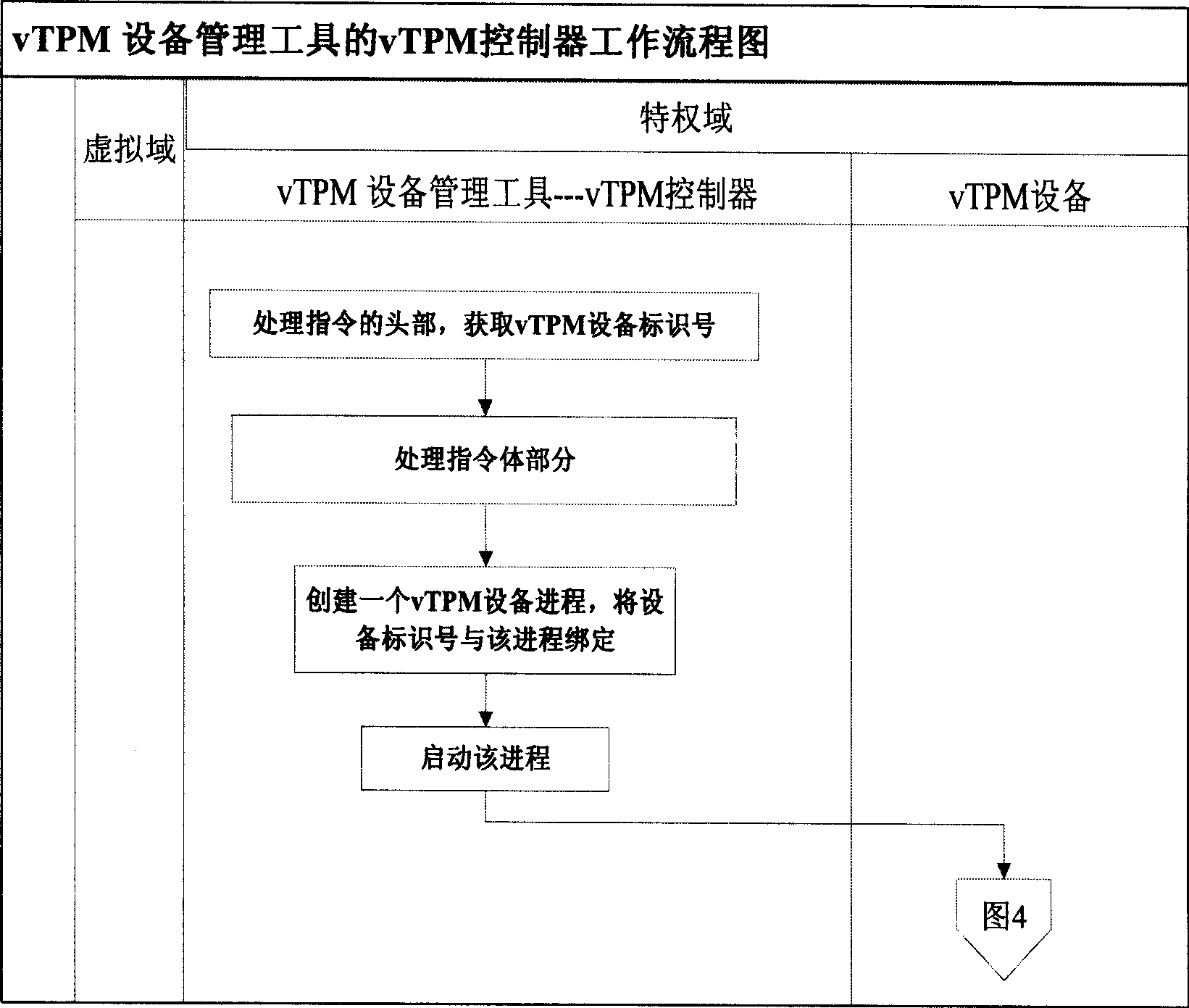
Implementing method for dynamically transparent virtual credible platform module
InactiveCN101488174ARealize the bindingAvoid delayPlatform integrity maintainanceProgram loading/initiatingManagement toolTrusted Platform Module
Owner:BEIJING JIAOTONG UNIV
System and method for trusted application security authentication
ActiveCN105978917AImprove securityTransmissionSecurity arrangementSecurity authenticationMobile device
The present invention proposes a system and method for trusted application security authentication, relating to the technical field of mobile device security and used for improving the security of user data. The system comprises a client application, a security manager, a TEE client API and a trusted application, wherein the client application operates in a rich execution environment and processes a process and / or data irrelevant to security in the client application, and makes a request for invoking the TEE client API to the security manager when running to a process and / or data relevant to security; the security manager monitors authorization states of the client application, and conducts hierarchical authorization on the request for invoking the TEE client API made by the client application according to different authorization states; and the trusted application operates in a trusted application environment, and processes the process and / or data relevant to security in the request of the client application after conducting security authentication on the client application. The system and method provided by the present invention is used for improving the security of user data.
Owner:HENGBAO
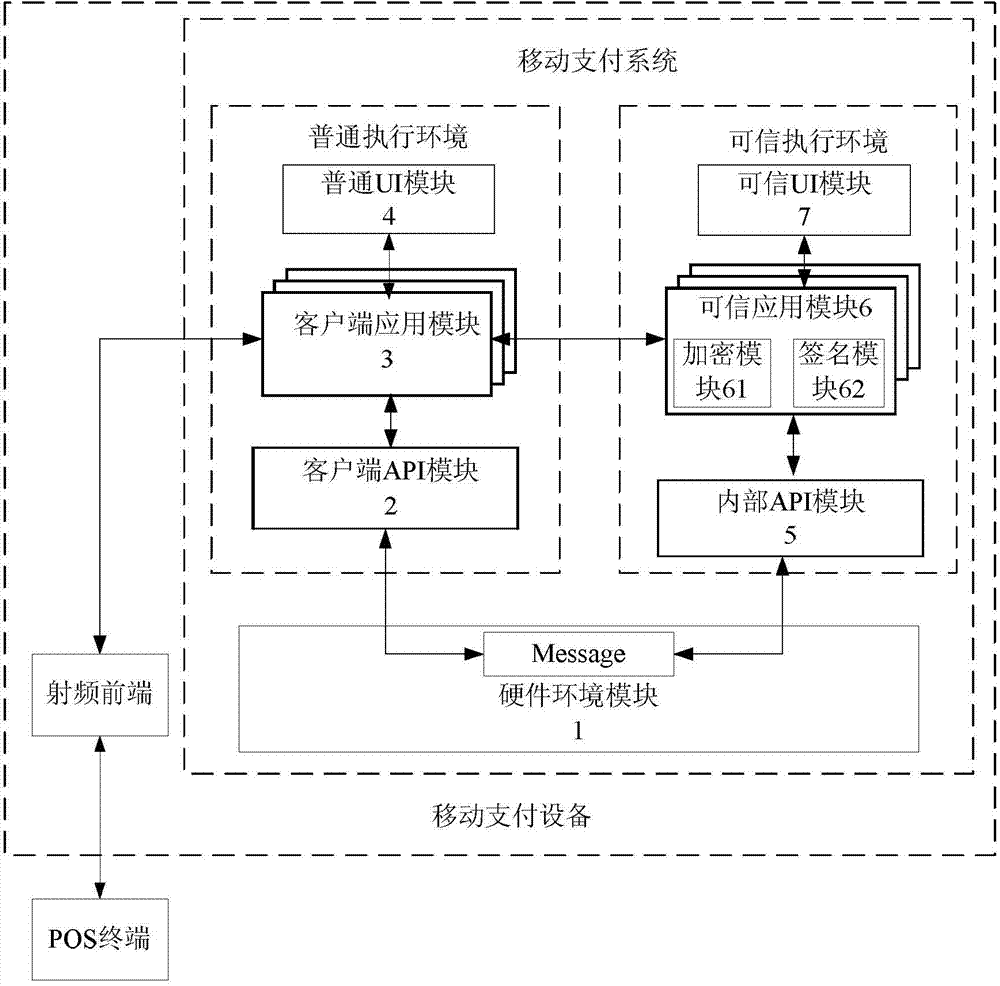
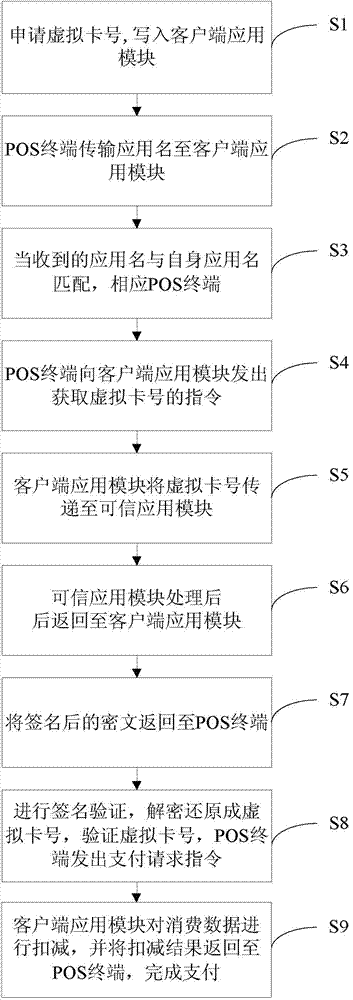
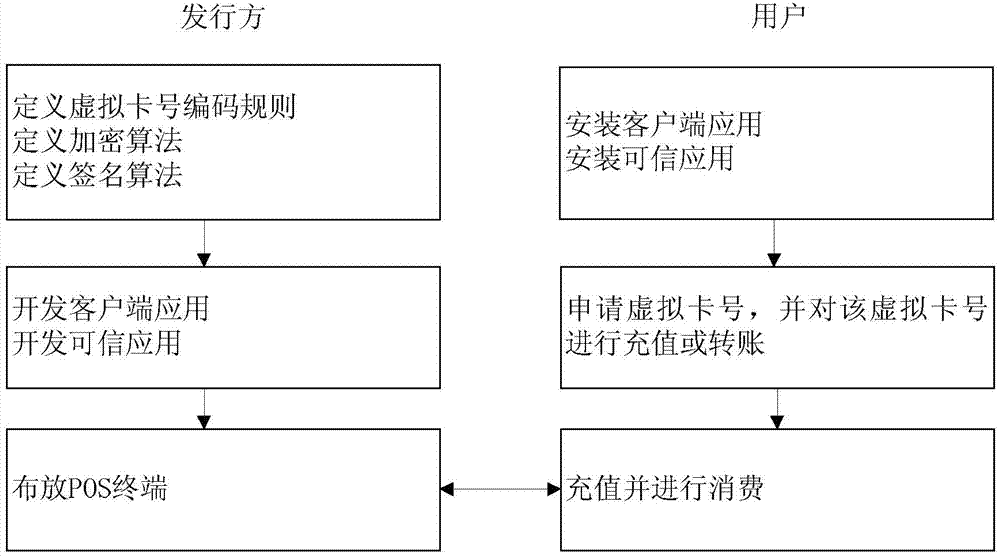
Mobile payment system and method based on trusted execution environment
InactiveCN103942678AUnlimitedSpeed up the issuance processPoint-of-sale network systemsProtocol authorisationClient-sideTrusted application
The invention discloses a mobile payment system and method based on a trusted execution environment, and relates to the technical field of mobile payment. According to the mobile payment system, a hardware environment module, a client terminal application module and a trusted application module are connected in a pairwise mode. The mobile payment method includes the steps that a virtual card number of the client terminal application module is transmitted to the trusted application module to be processed, then the virtual card number is returned to the client terminal application module, and afterwards the virtual card number is transmitted to a POS front end for conducting verification and consumption. The mobile payment system and method based on the trusted execution environment are suitable for near field mobile payment equipment, and the security is high.
Owner:WUHAN TIANYU INFORMATION IND
Method, system and apparatus for carrying out safety authentication on application programs
ActiveCN105095696AEnsure safetyImprove securityDigital data protectionProgram/content distribution protectionSoftware engineeringApplication procedure
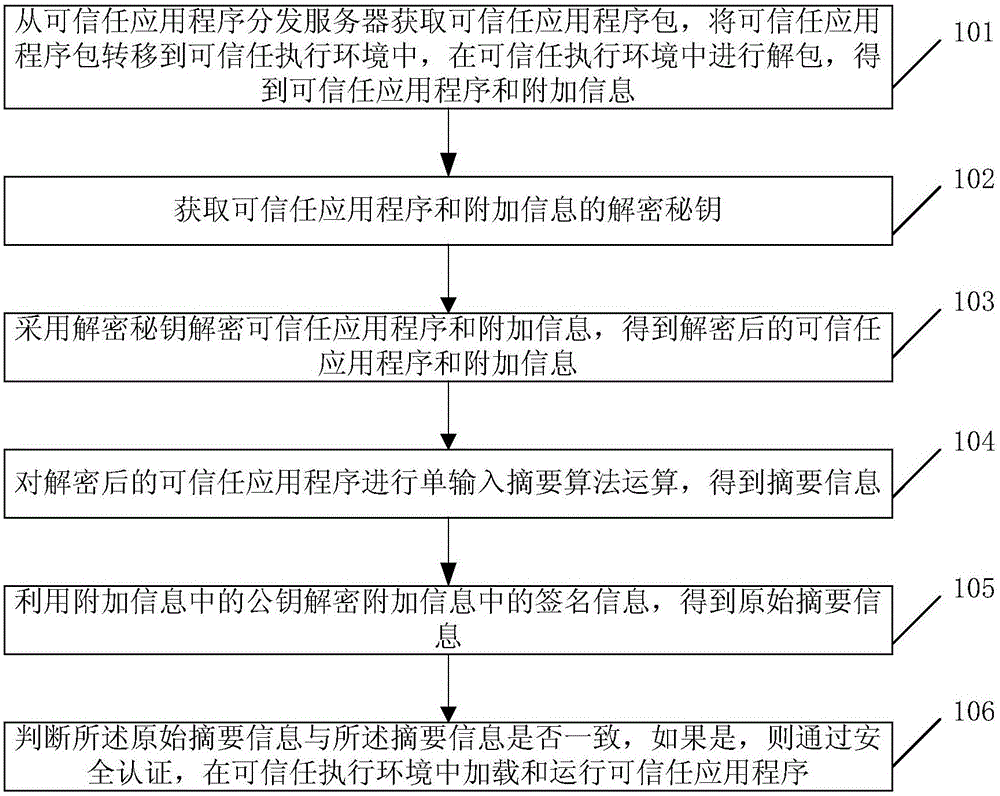
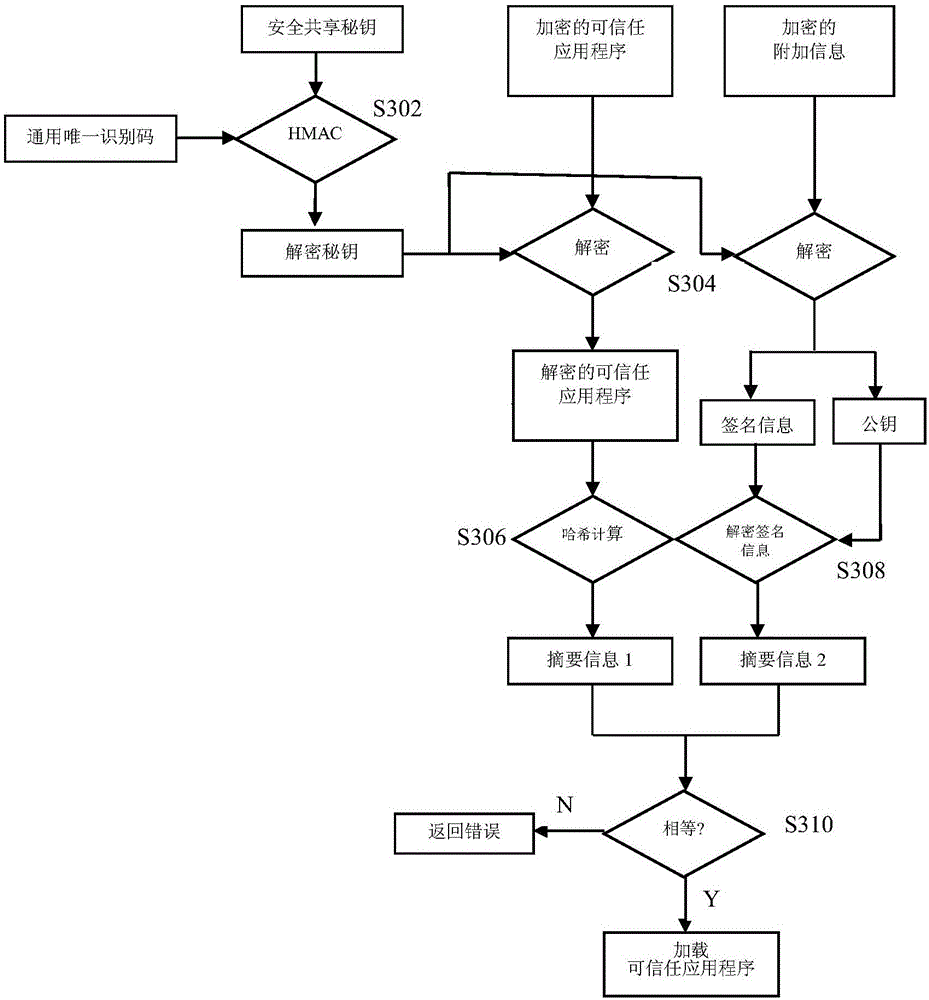
The invention discloses a method, system and apparatus for carrying out safety authentication on application programs. The method comprises acquiring a trusted application package from a distribution server of trusted application programs, transferring the trusted application package to a trusted execution environment, unpacking the trusted application package in the execution environment to obtain a trusted application program and additional information; acquiring decrypting keys of the trusted application program and the additional information; decrypting the trusted application program and the additional information using the decrypting keys to obtain decrypted trusted application program and additional information; carrying out single-input message digest algorithms on the decrypted trusted application program and additional information to obtain summary information; decrypting the additional information using a public key of the additional information to obtain original summary information; determining whether the original summary information is the same as the summary information, completing safety authentication, loading and operating the trusted application program in the trusted execution environment if the original summary information is the same as the summary information By adopting the method, the system and the apparatus, the security of authentication can be raised.
Owner:SAMSUNG ELECTRONICS CHINA R&D CENT +1
Application program starting method, list configuring method, terminal and server
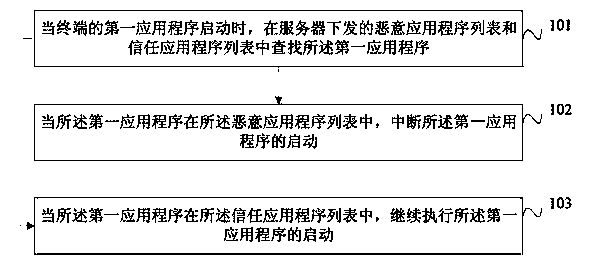
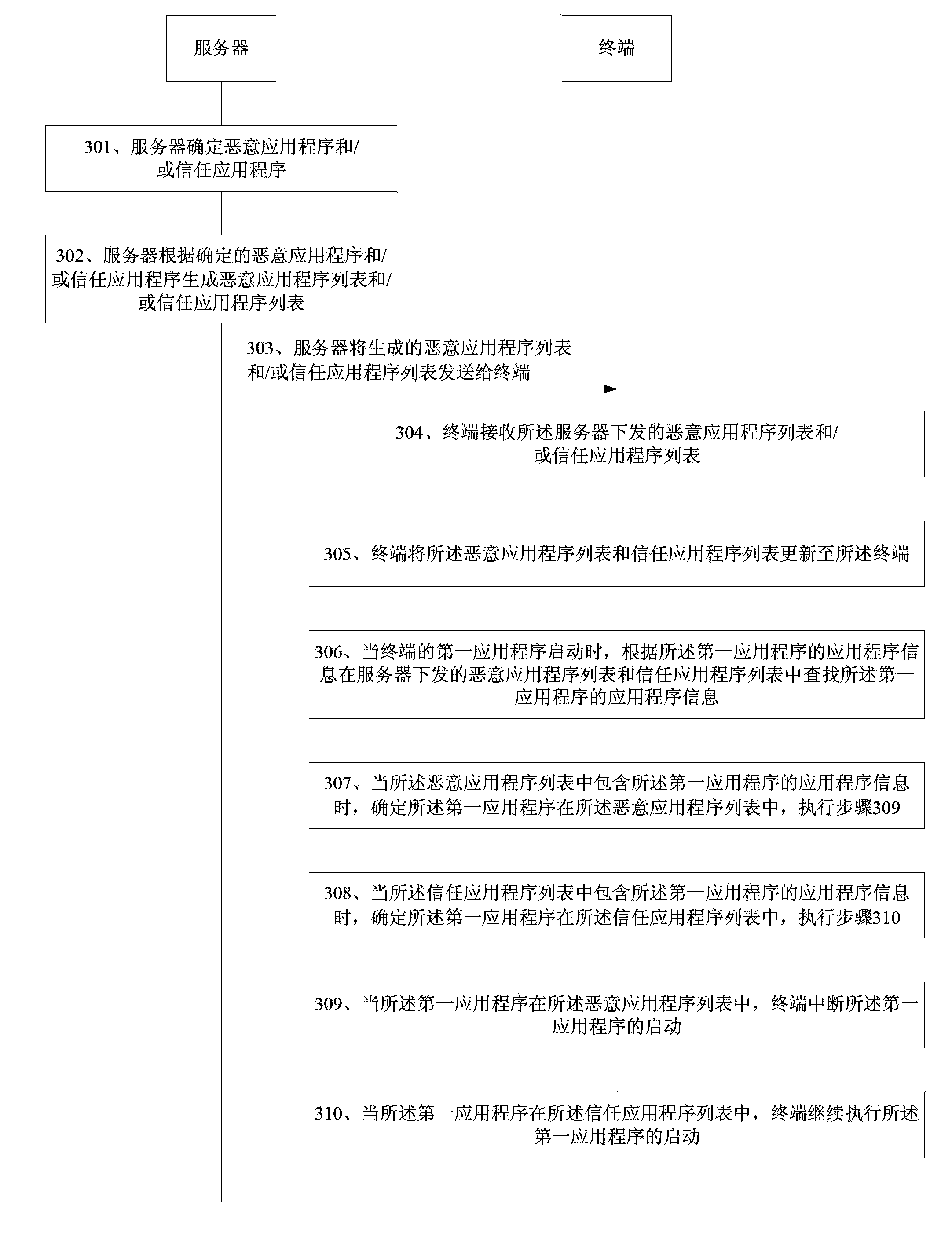
ActiveCN103425926AImprove accuracySimplify the inquiry processComputer security arrangementsComputer terminalApplication software
The invention discloses an application program starting method, a list configuring method, a terminal and a server, and belongs to the field of mobile terminals. The application program starting method includes when a first application program of the terminal is started, searching the first application program in a malicious application program list and a trusted application program list both issued by the server; when the first application program is in the malicious application program list, interrupting starting of the first application program; when the first application program is in the trusted application program list, continuing to execute starting of the first application program. The list configuring method includes determining malicious application programs and / or trusted application programs, generating the malicious application program list and / or the trusted application program list according to the determined malicious application programs and / or the trusted application programs, and sending the generated malicious application program list and / or the trusted application program list to the terminal. The process of inquiring by pop-up frames is simplified, and accuracy of determining of the malicious application programs is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Evidence-based application security
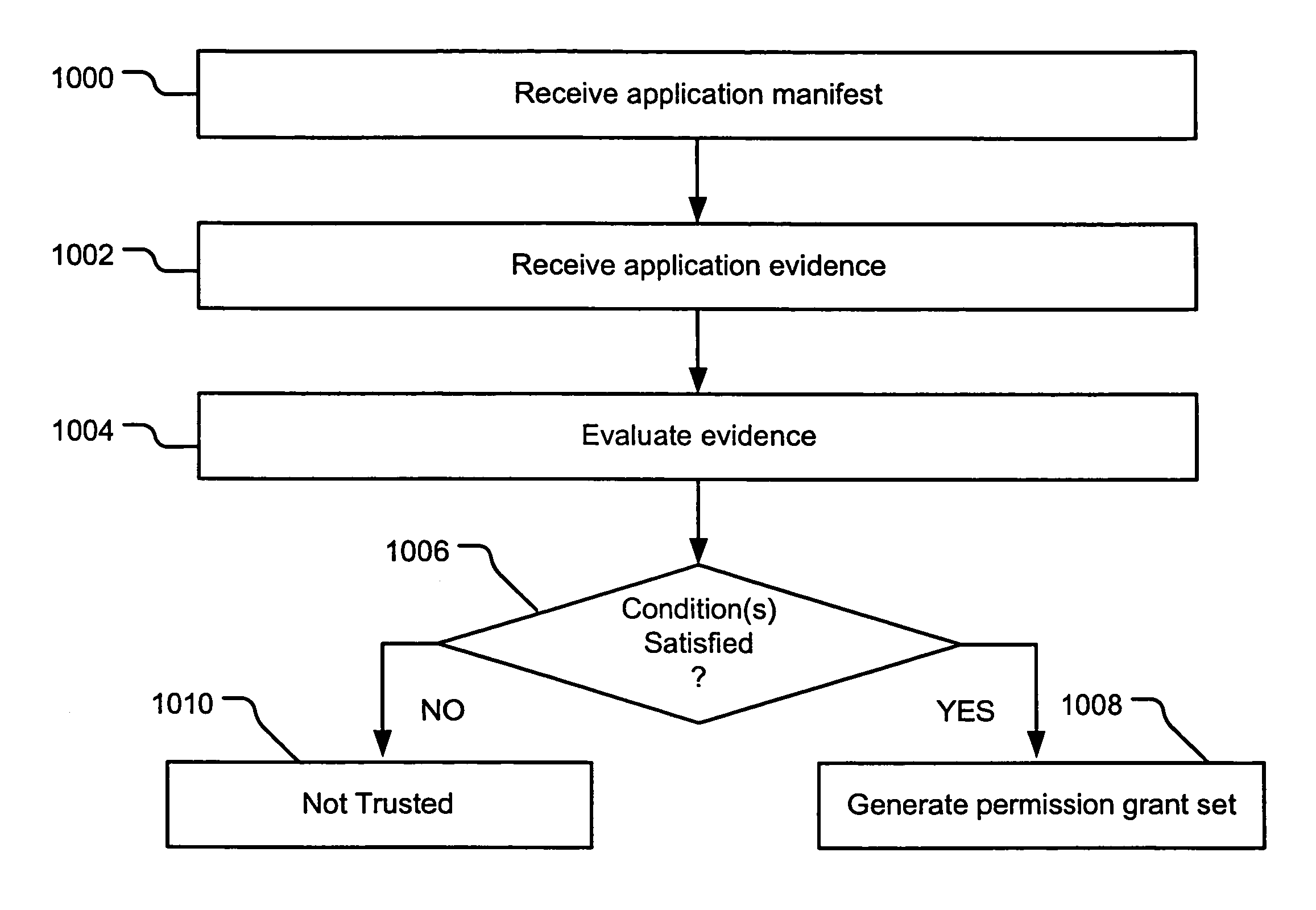
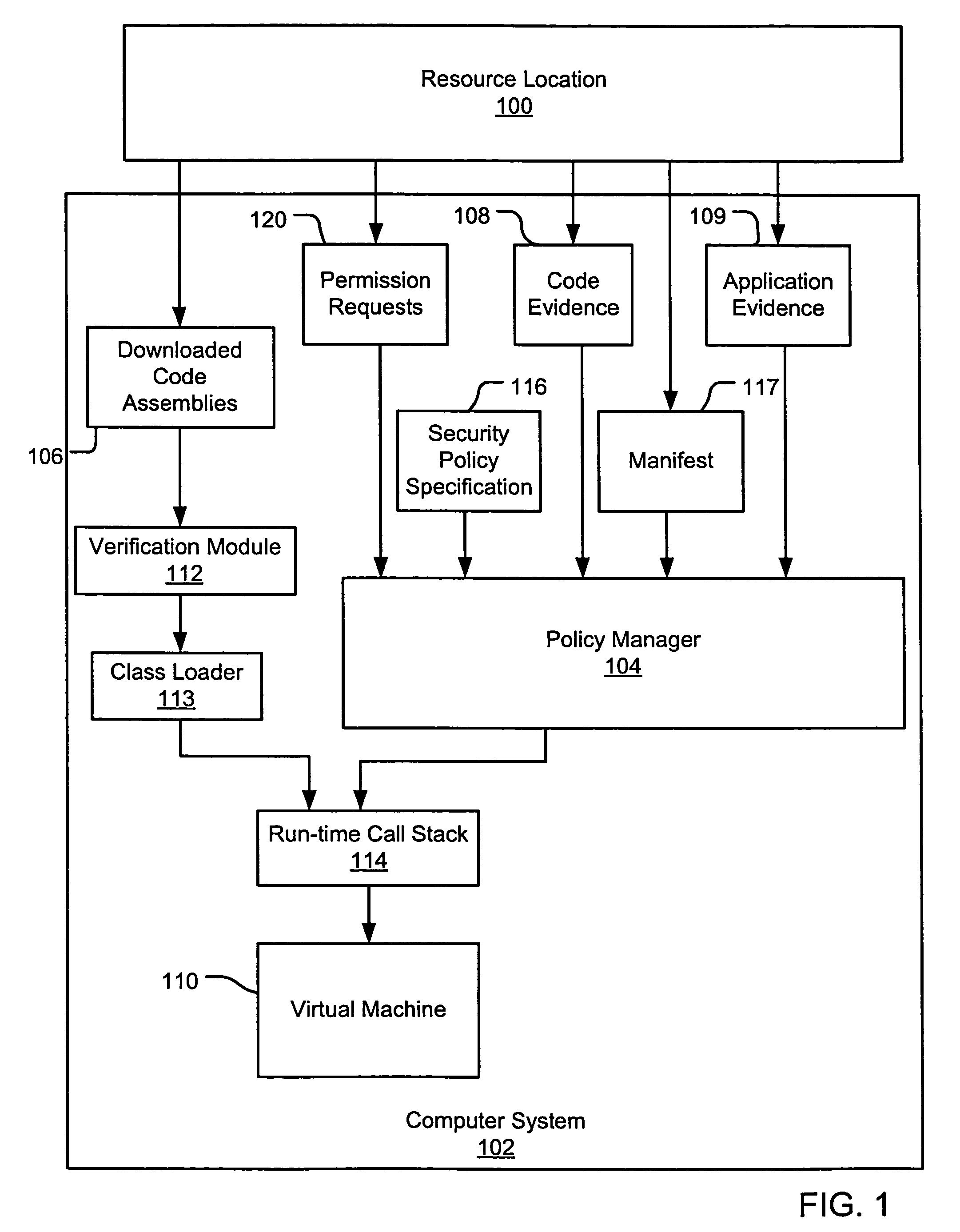
InactiveUS7669238B2Memory loss protectionDigital data processing detailsComputerized systemApplication software
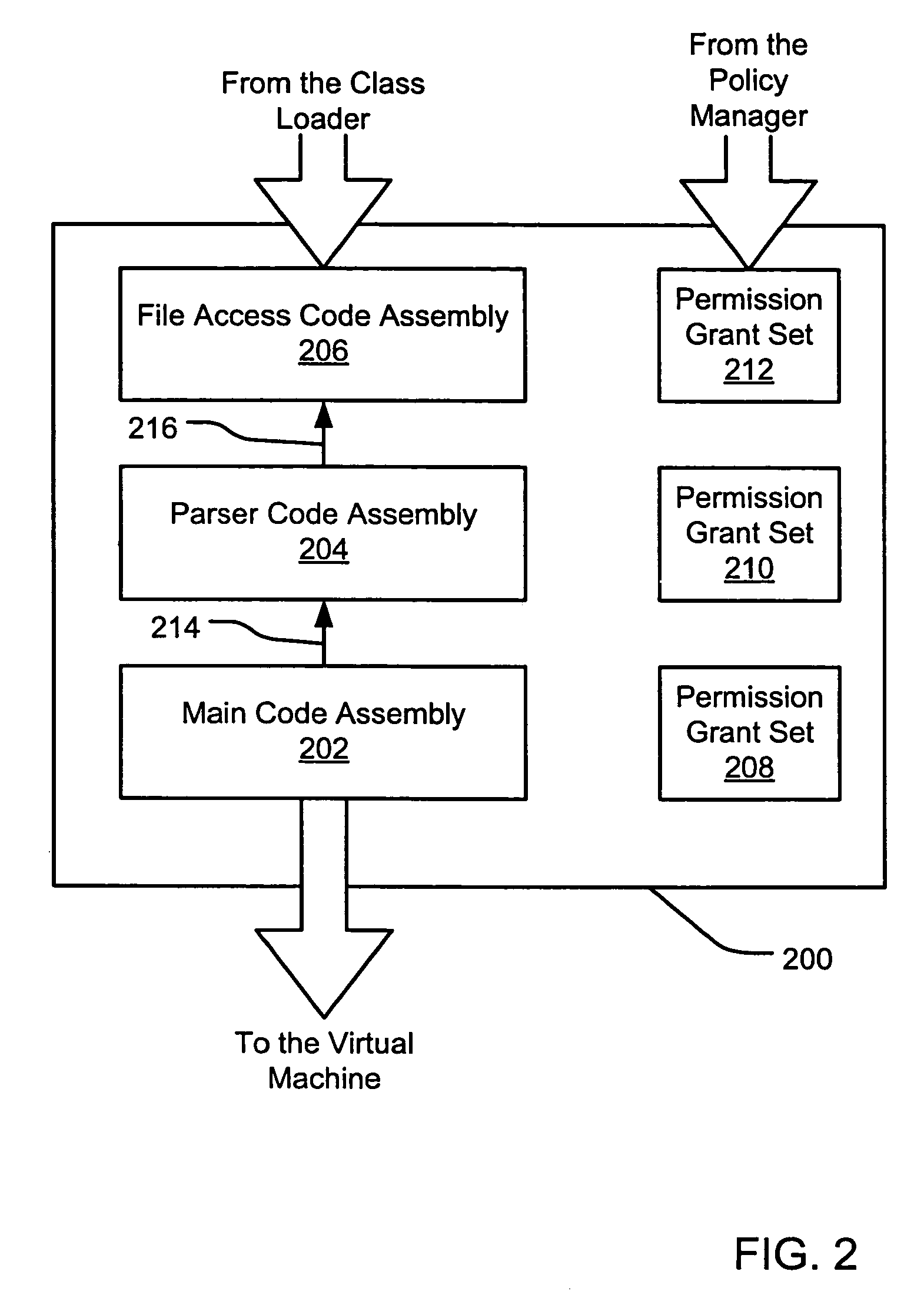
Evidence-based application security may be implemented at the application and / or application group levels. A manifest may be provided defining at least one trust condition for the application or application group. A policy manager evaluates application evidence (e.g., an XrML license) for an application or group of applications relative to the manifest. The application is only granted permissions on the computer system if the application evidence indicates that the application is trusted. Similarly, a group of applications are only granted permissions on the computer system if the evidence indicates that the group of applications is trusted. If the application evidence satisfies the at least one trust condition defined by the manifest, the policy manager generates a permission grant set for each code assembly that is a member of the at least one application. Evidence may be further evaluated for code assemblies that are members of the trusted application or application group.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com