Secure storage service system and method based on TrustZone technology
A secure storage and service system technology, applied in the field of secure data storage of mobile terminal equipment, can solve problems such as denial of service attacks, sensitive data theft, and insufficient security, and achieve the effects of transparency, isolation, and security improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
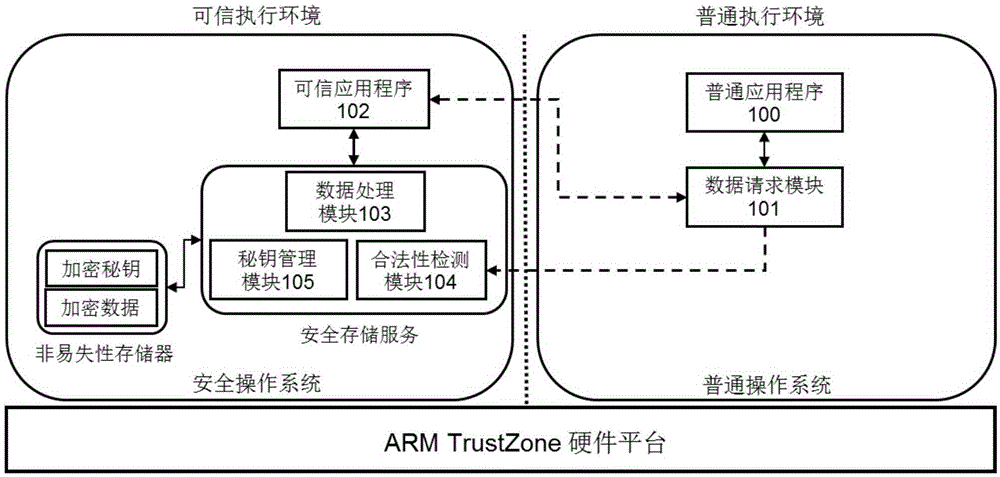
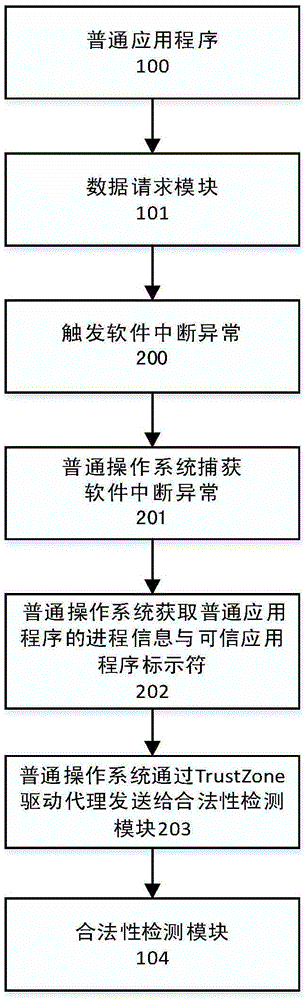
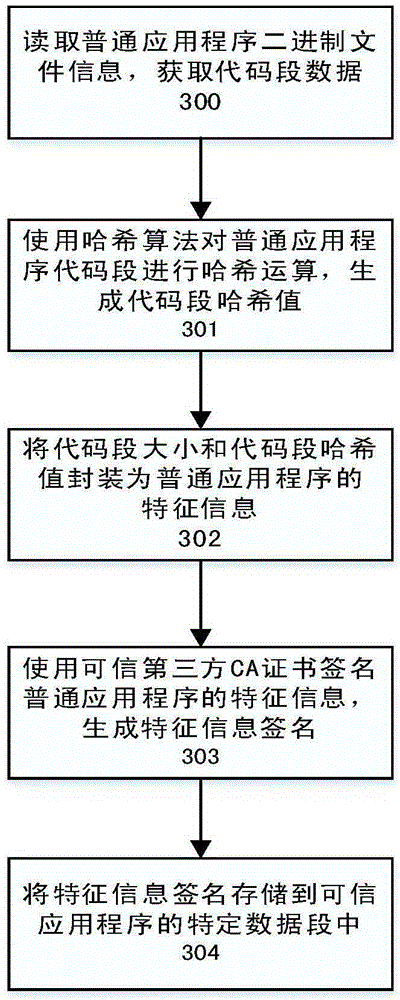
[0036] The present invention utilizes the ARMTrustZone hardware isolation technology and the Trusted Execution Environment (TEE) as the basic platform to effectively provide data security storage services, and common applications and trusted applications on the basic platform call the unified interface provided by the security storage service system Realize the safe storage, safe loading and safe destruction of sensitive data; at the same time, under the premise of ensuring the minimum modification of the operating system, in the trusted execution environment, the common application program that initiates the data safe storage service request is checked for runtime legitimacy and rejected Service requests initiated by illegal common applications or maliciously attacked by legitimate common applications prevent sensitive data from leaking, thereby effectively ensuring data security. Based on this, the secure storage service system and method based on the TrustZone technology of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com