Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
201 results about "Mobile operating system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
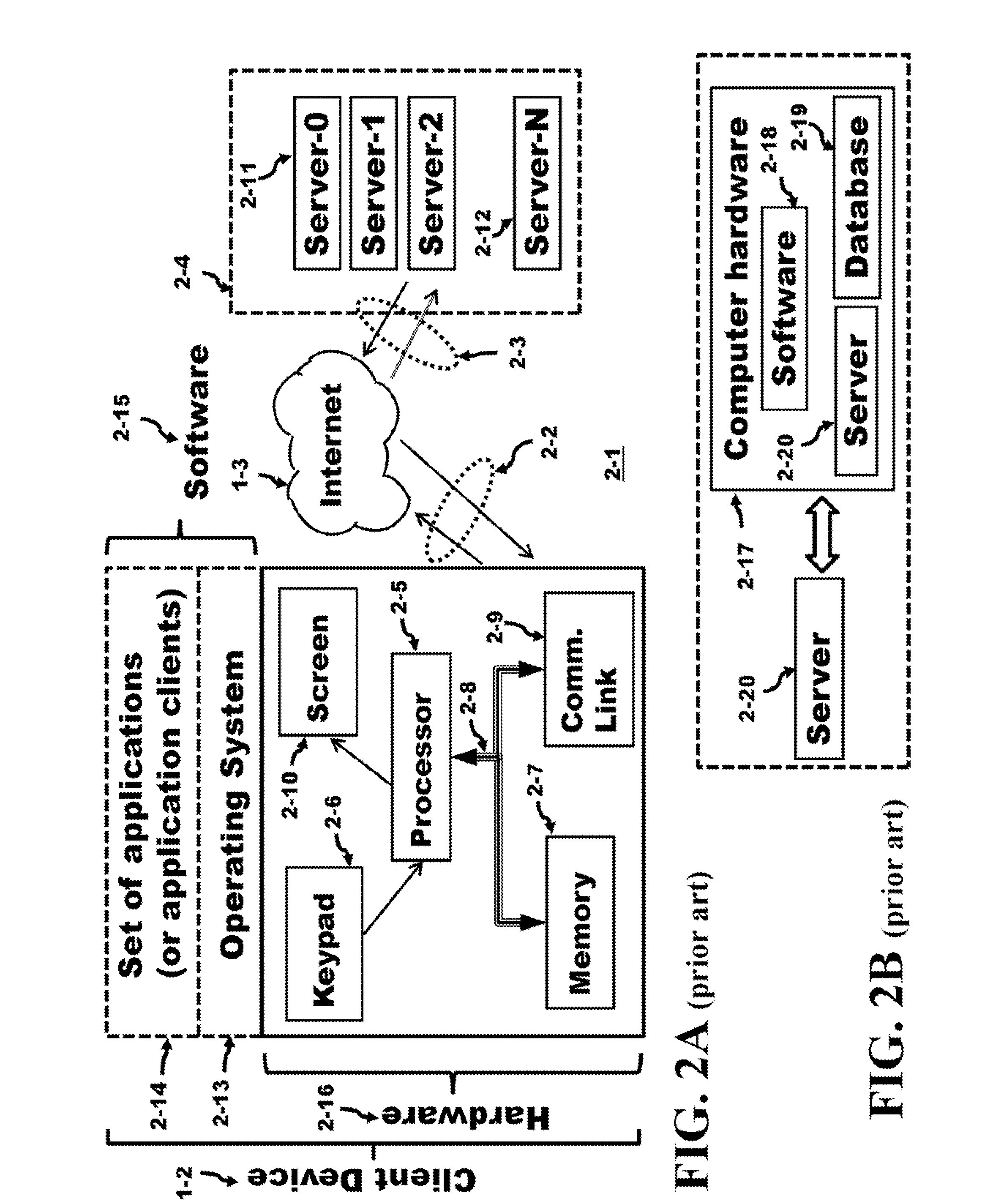
Mobile operating system(or mobile is an operating system for phones, [[tablet computers, [[Smart match ok, or other s. While computers such as typical s are 'mobile', the operating systems usually used on them are not considered mobile ones, as they were originally designed for [[s that historically did not have or need features.
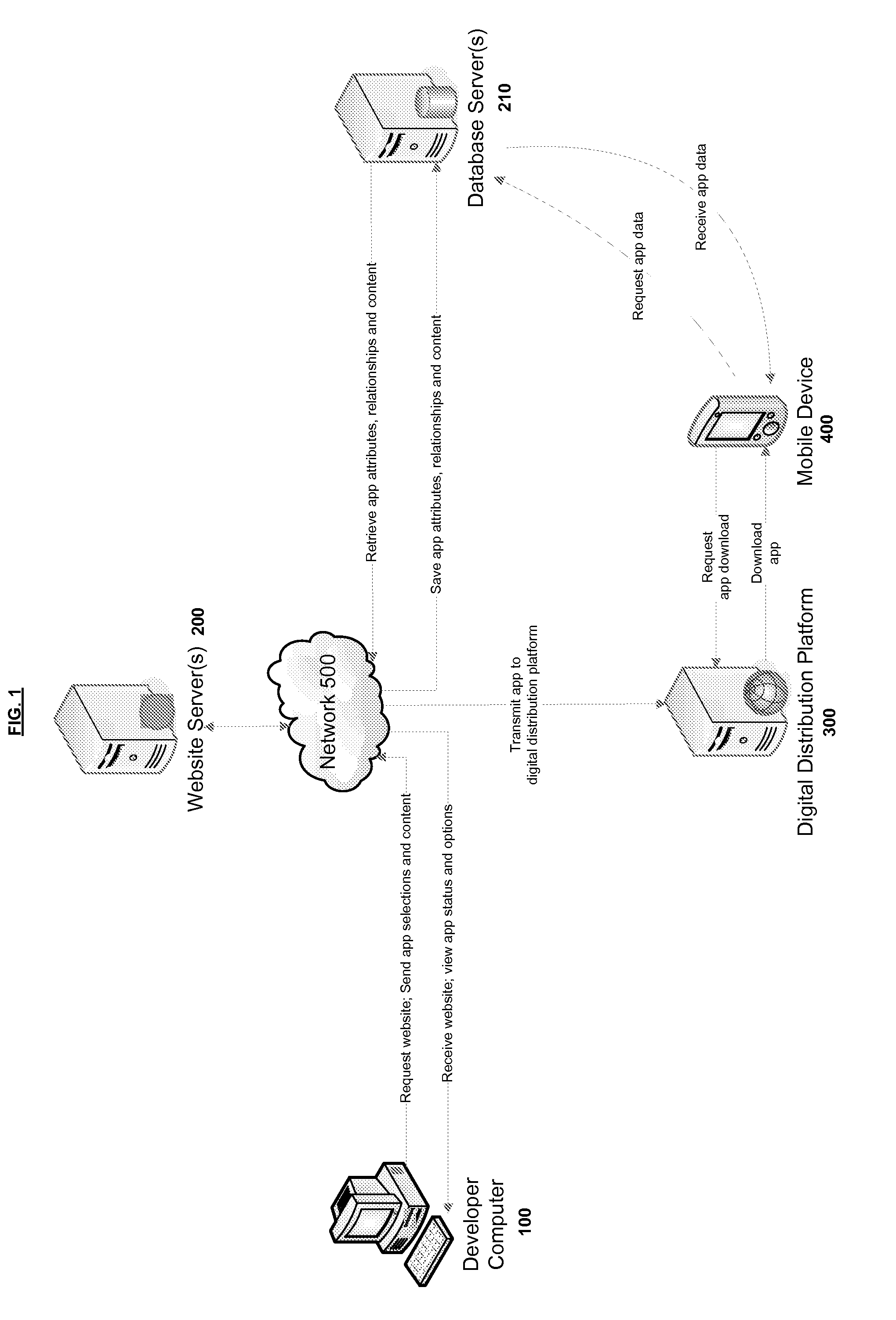
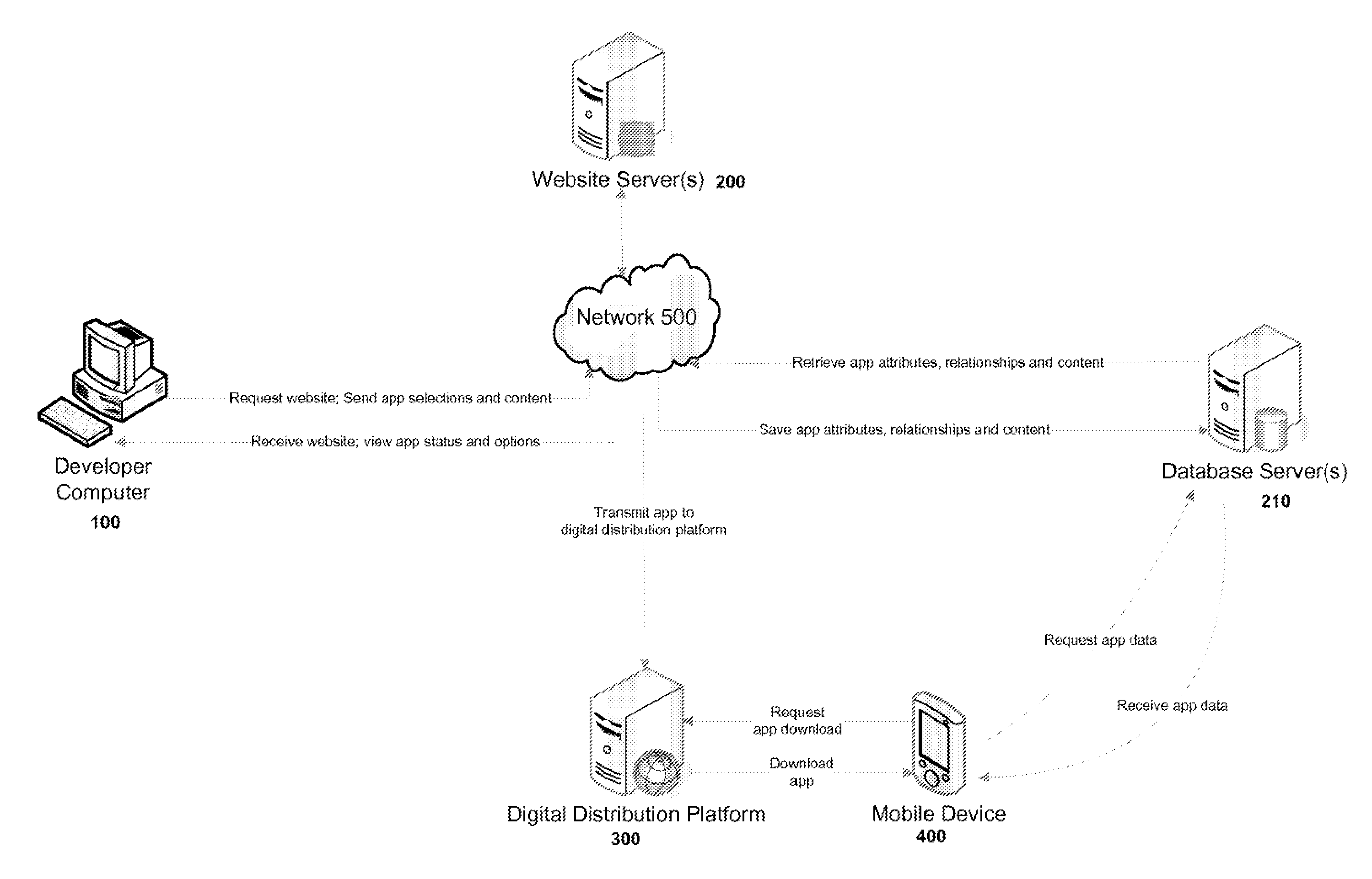
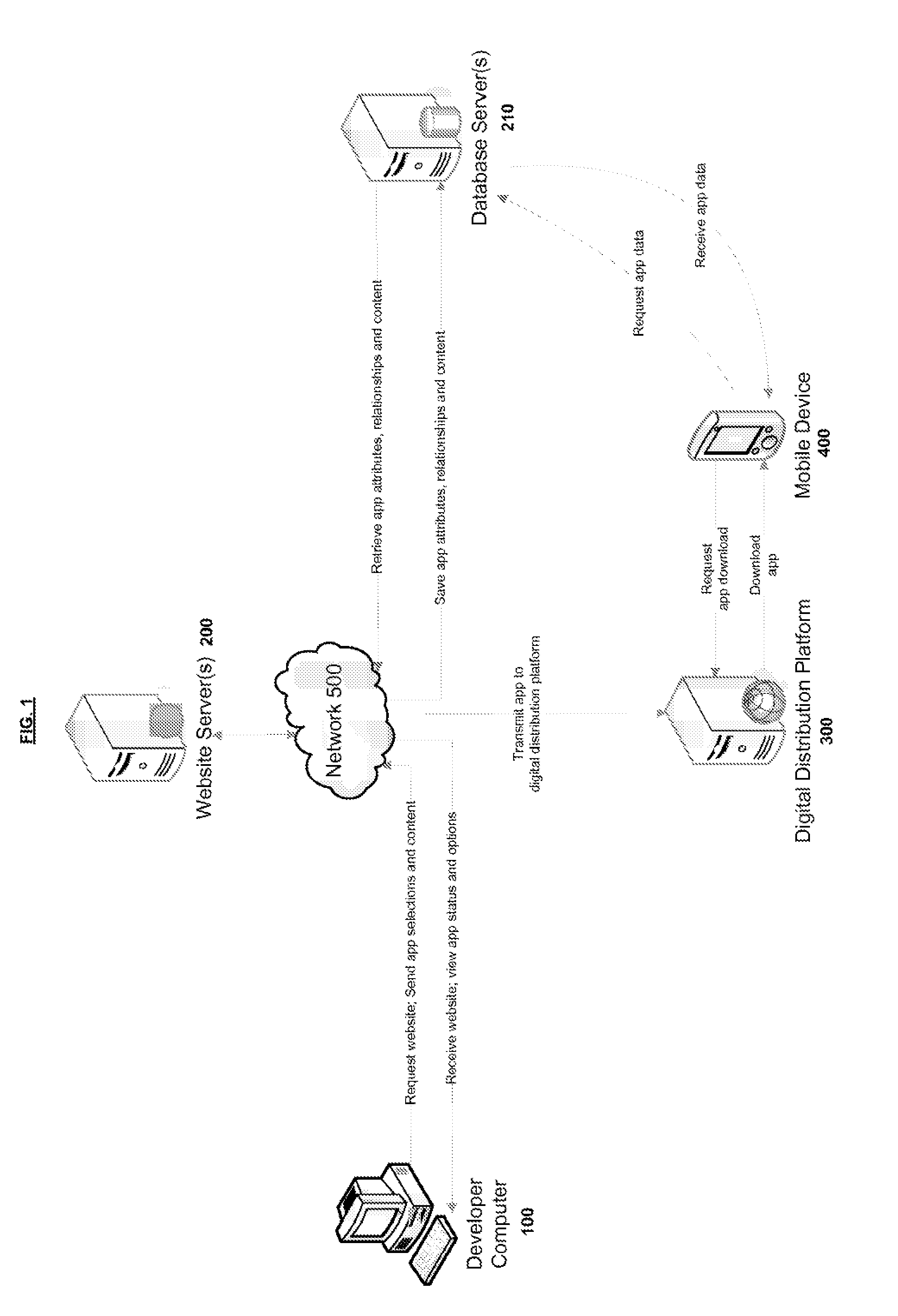
Systems and methods for a mobile application development and development platform
ActiveUS8261231B1High degreeVersion controlMultiple digital computer combinationsApplication softwareInternet based
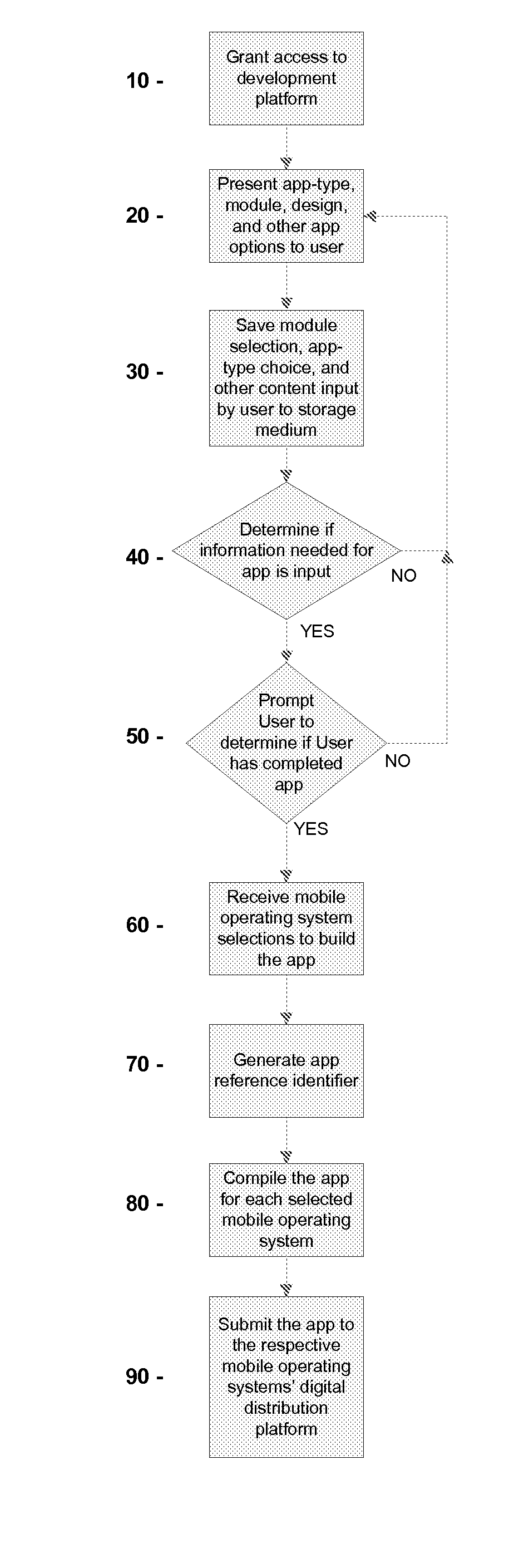
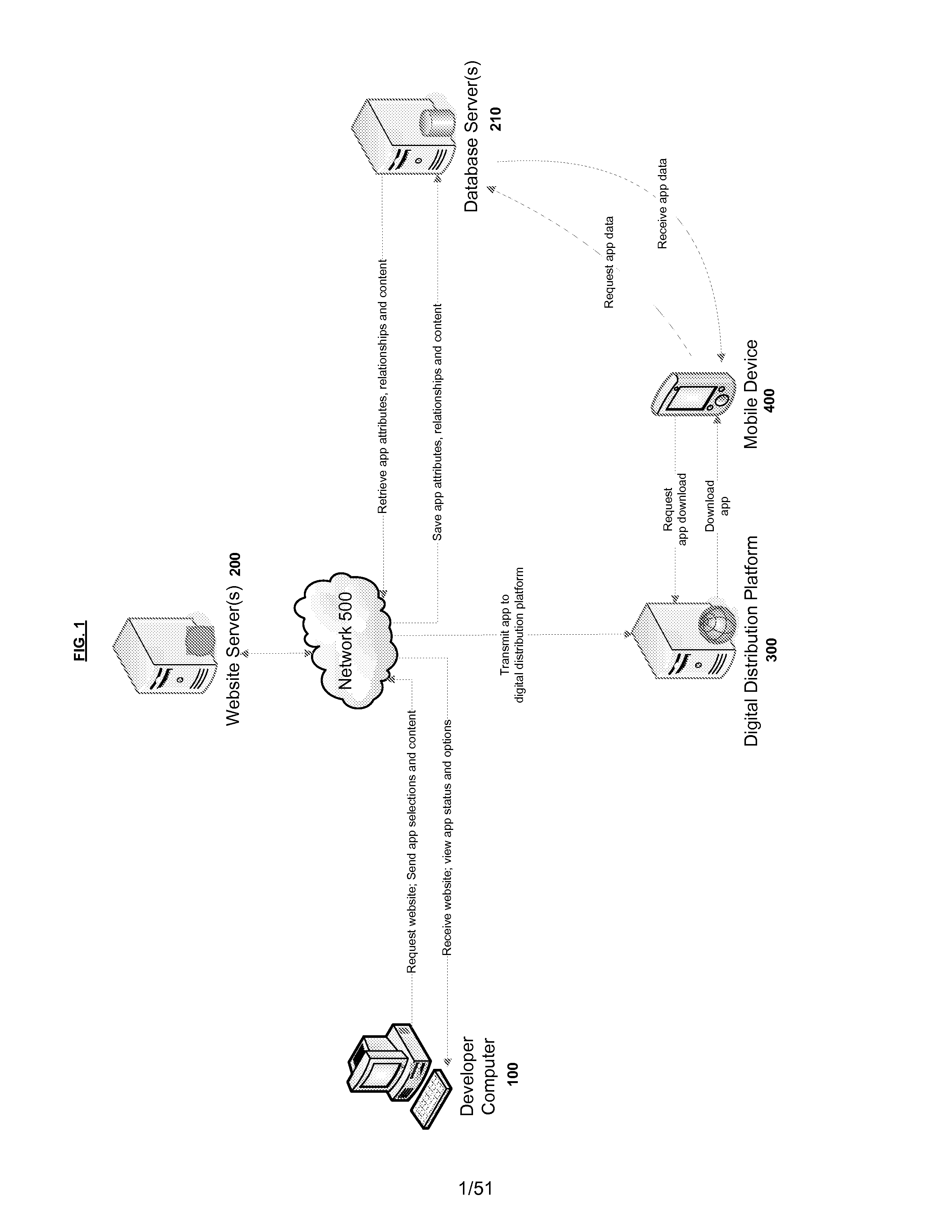
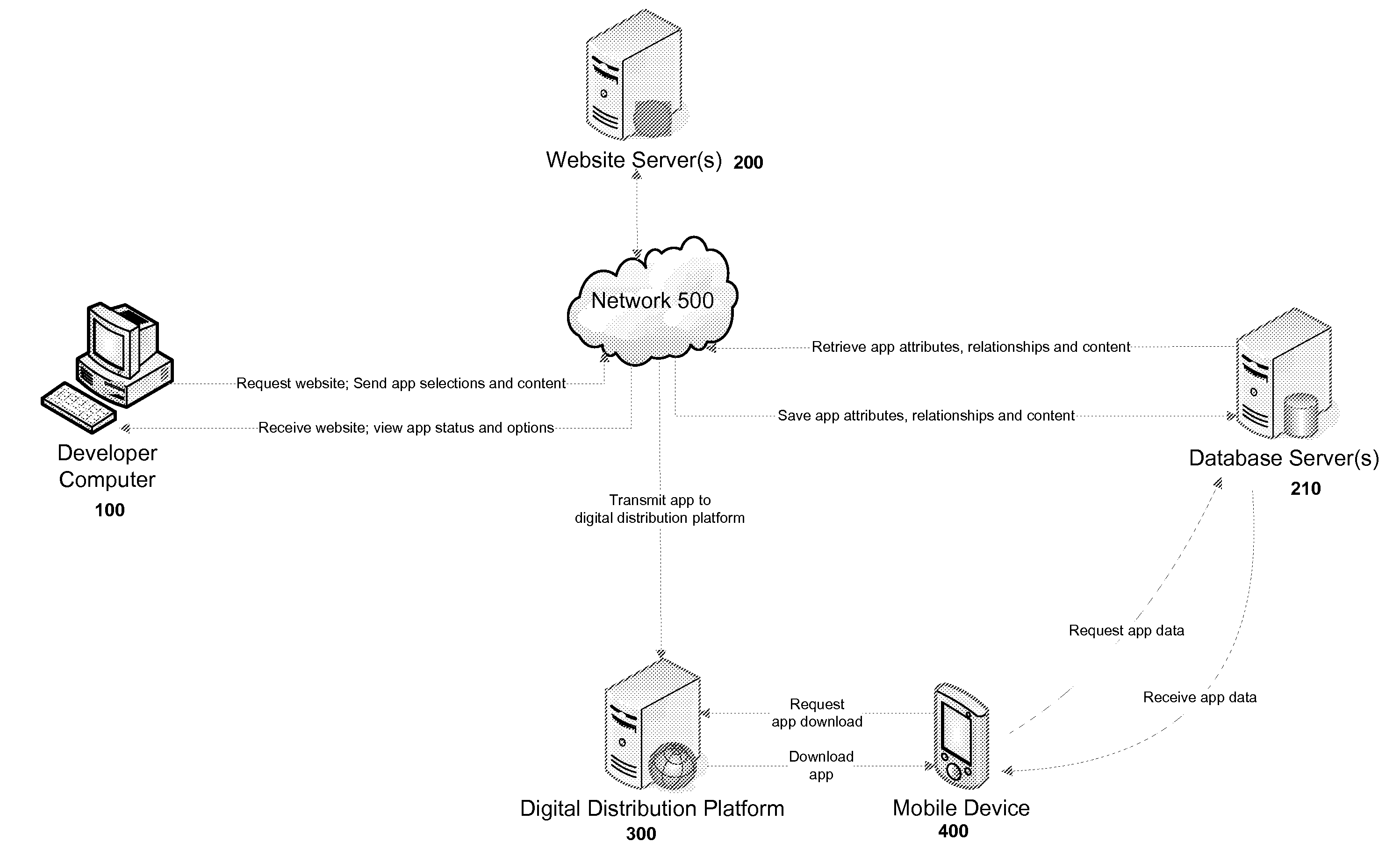
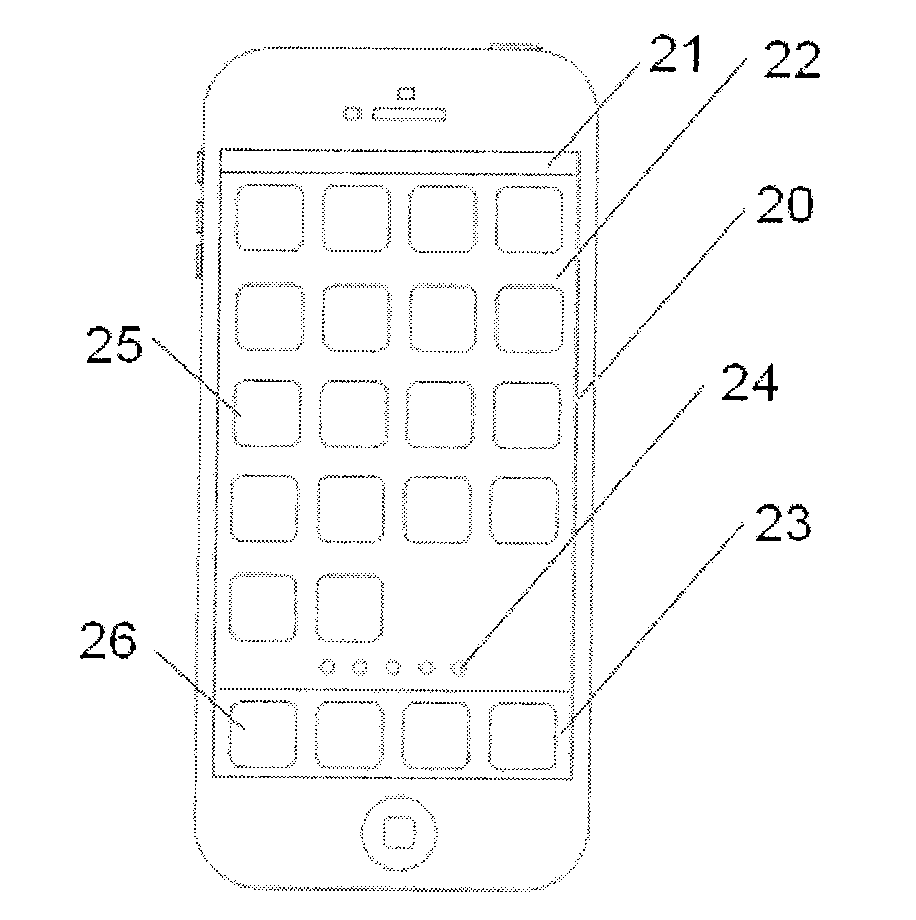
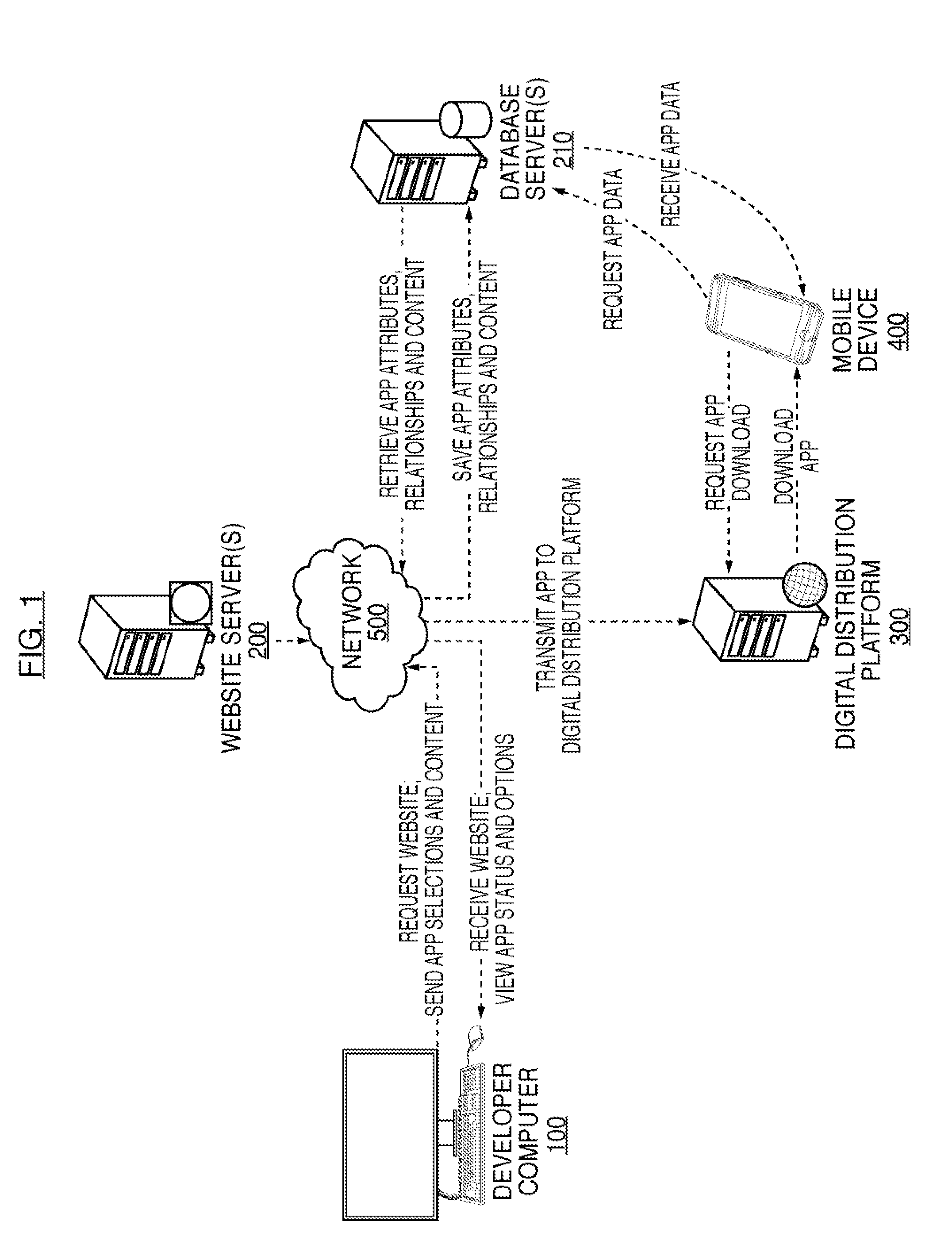
Systems and methods for developing, customizing, and deploying mobile device applications are provided through a mobile application development and deployment platform. Preferably, these systems and methods are implemented in an Internet based environment that allows non-technical users to build sophisticated, highly-customizable cross-platform mobile applications. The platform allows users to select, input, create, customize, and combine various content, design characteristics, and application components, such as modules, some of which utilize features and functionality associated with various mobile devices and mobile operating systems. In certain embodiments, the platform allows users to compile, and generate a configuration file for, the mobile application that can be distributed to end users for execution on various mobile devices and mobile operating systems. When the mobile application is installed on, or executed by the mobile device, the configuration file may enable the retrieval of various data associated with the mobile application.
Owner:MEDIA DIRECT
Systems and methods for a mobile application development and deployment platform
ActiveUS20120260232A1High degreeVersion controlMultiple digital computer combinationsOperational systemApplication software
Systems and methods for developing, customizing, and deploying mobile device applications are provided through a mobile application development and deployment platform. Preferably, these systems and methods are implemented in an Internet based environment that allows non-technical users to build sophisticated, highly-customizable cross-platform mobile applications. The platform allows users to select, input, create, customize, and combine various content, design characteristics, and application components, such as modules, some of which make use of features and functionality associated with various mobile devices and mobile operating systems. In certain embodiments, the platform allows users to compile the mobile application for various mobile operating systems and generates a configuration file for the mobile application that can be distributed to end users for execution on various mobile devices. When the mobile application is installed on, or executed by the mobile device, the configuration file may enable the retrieval of various data associated with the mobile application.
Owner:MEDIA DIRECT
Mobile operation system
ActiveCN104063136AExtend battery lifeLarge real display areaDigital data processing detailsSubstation equipmentOperational systemApplication programming interface
A mobile operation system comprises an intelligent dynamic icon, a quick voice assistant, a quick sliding assistant, an intelligent gesture, a full-screen application program interface, a full-domain application program icon interface, a quick full close and an important contact person program. According to the intelligent dynamic icon, icons of application programs in an updating state are automatically displayed on a main interface. By means of the quick voice assistant, the application programs can be directly started through voice without the internet. After the quick sliding assistant slides a regular shape on the main interface, the application programs can be directly started. The application programs can be direction started through the intelligent gesture according to movements of the user. According to the intelligent gesture, when the user takes out a mobile phone from a pocket, the system can be automatically waken up and automatic sliding unlocking can be achieved.
Owner:JIANG HONGMING
Mobile operating system
InactiveCN103309618AThe main interface is cleanThe main interface is beautifulDigital data processing detailsSubstation equipmentHuman–robot interactionChange detection
The invention relates to a mobile operating system which comprises a series of brand-new innovative technologies like intelligent dynamic icon, global icon interface, quick sliding start, quick voice assistant, quick delete assistant, intelligent motion start, an intelligent state change detection, quick complete close, fastback, efficient multi-task interface and global file browsing interface, all aspects of the existing iOS and the existing Android are completely innovated, and a human-computer interaction infrastructure of a mobile operating system of the next generation is established.
Owner:JIANG HONGMING
Systems and methods for a voice- and gesture-controlled mobile application development and deployment platform
ActiveUS20140109046A1High degreeSoftware maintainance/managementSpecific program execution arrangementsOperational systemInternet based
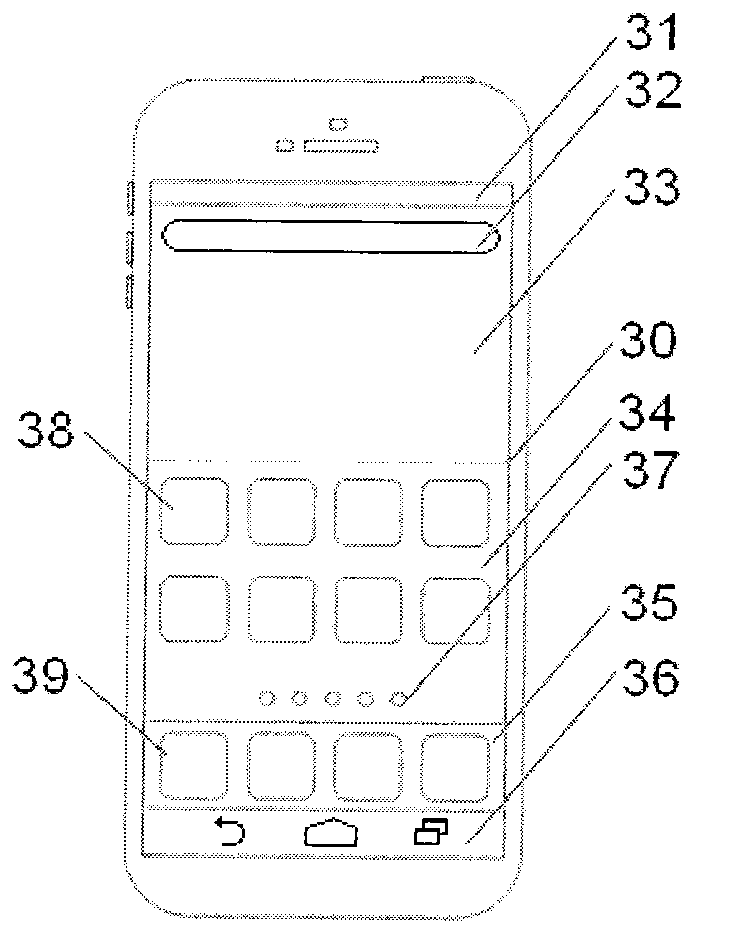
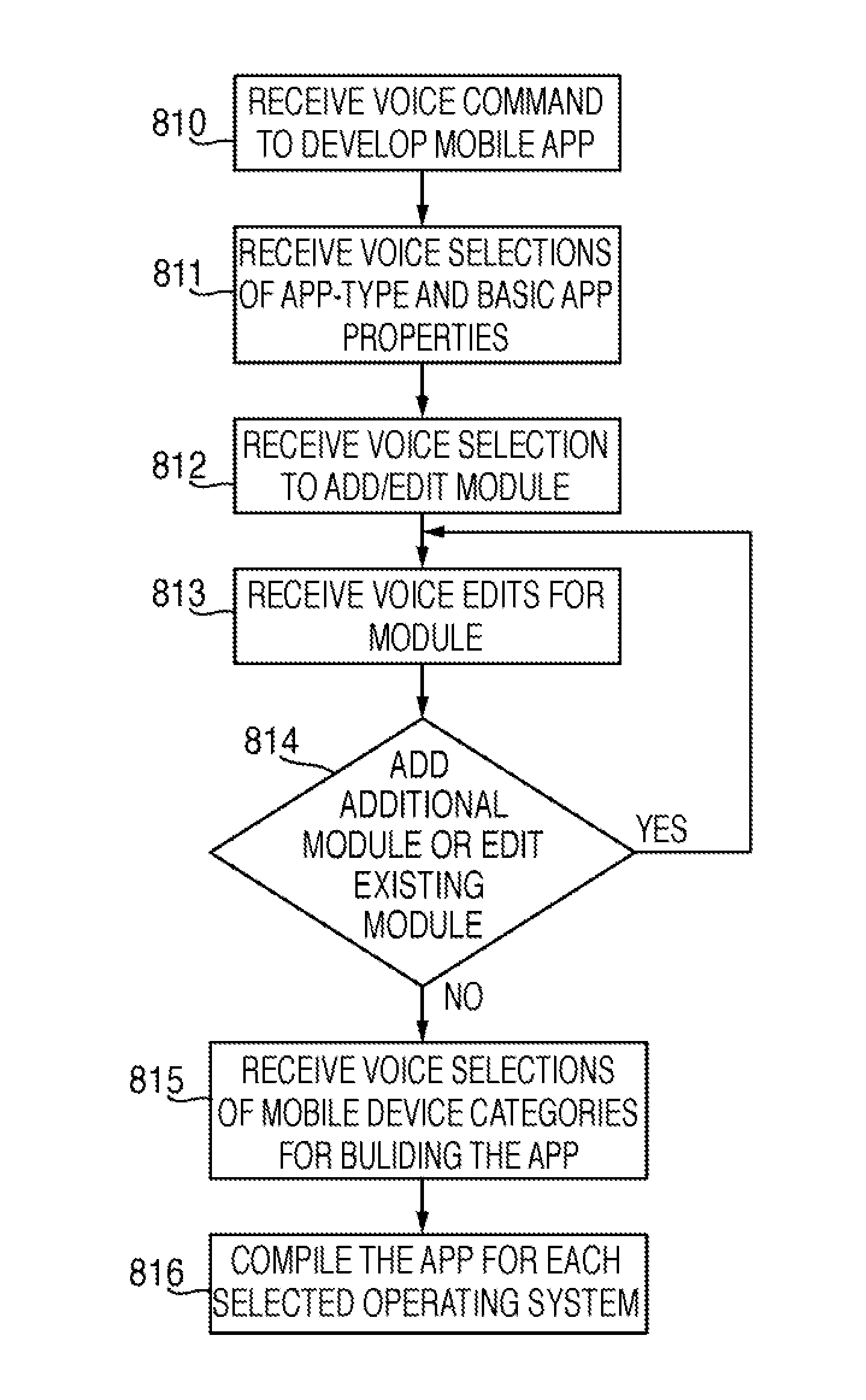
Systems and methods for developing, customizing, and deploying mobile device applications through voice and / or gesture interactions are provided through a mobile application development and deployment platform. Preferably, these systems and methods are implemented in an Internet based environment that allows non-technical users to build sophisticated, highly-customizable cross-platform mobile applications. The platform allows users to use voice and / or gesture interactions to select, input, create, customize, and combine various content, design characteristics, and application components, such as modules, some of which utilize features and functionality associated with various mobile devices and mobile operating systems. In certain embodiments, the platform allows users to compile the mobile application for various mobile operating systems and generates a configuration file for the mobile application that can be distributed to end users for execution on various mobile devices. When the mobile application is installed on, or executed by the mobile device, the configuration file may enable the retrieval of various data associated with the mobile application.
Owner:MEDIA DIRECT
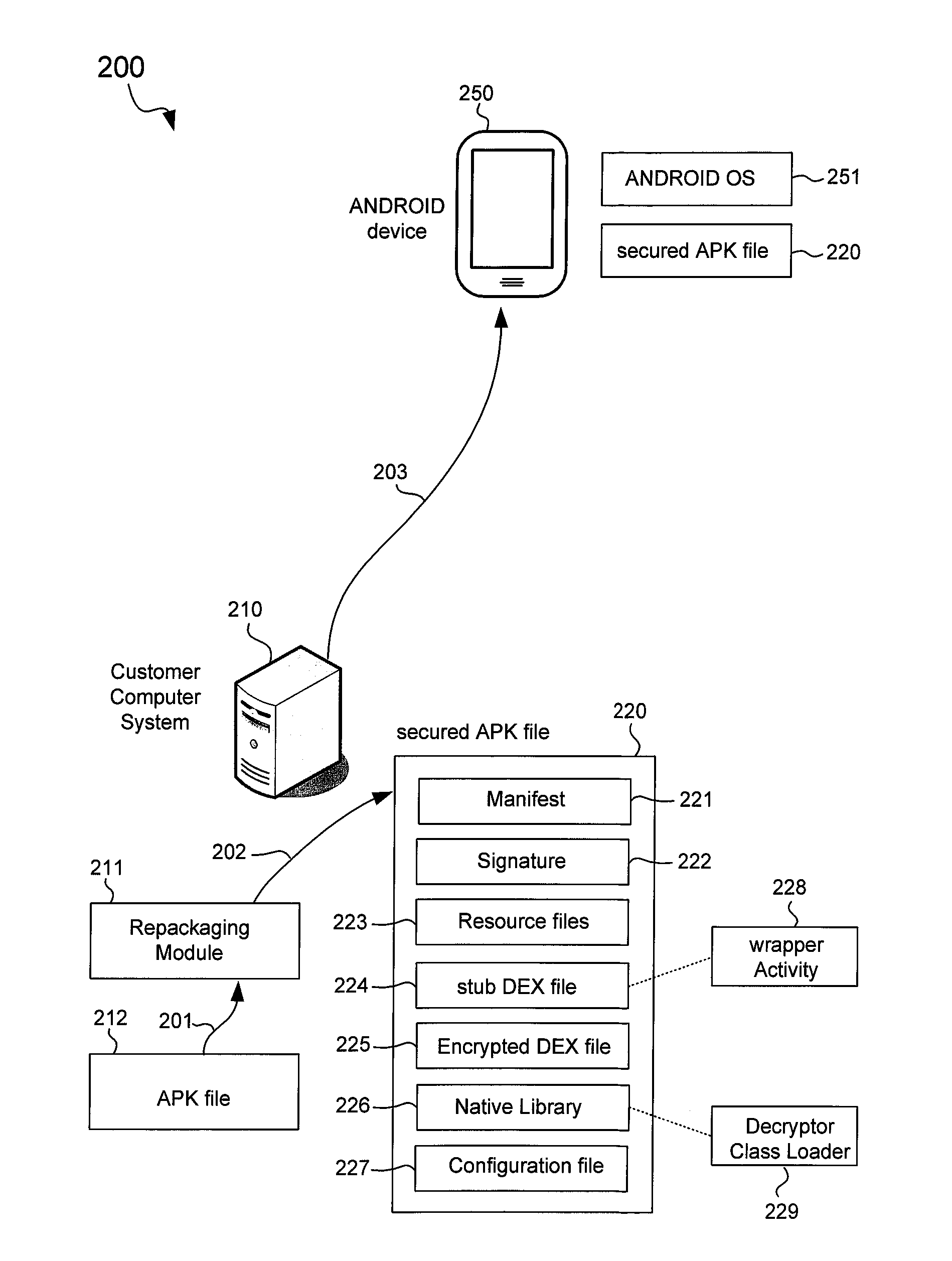
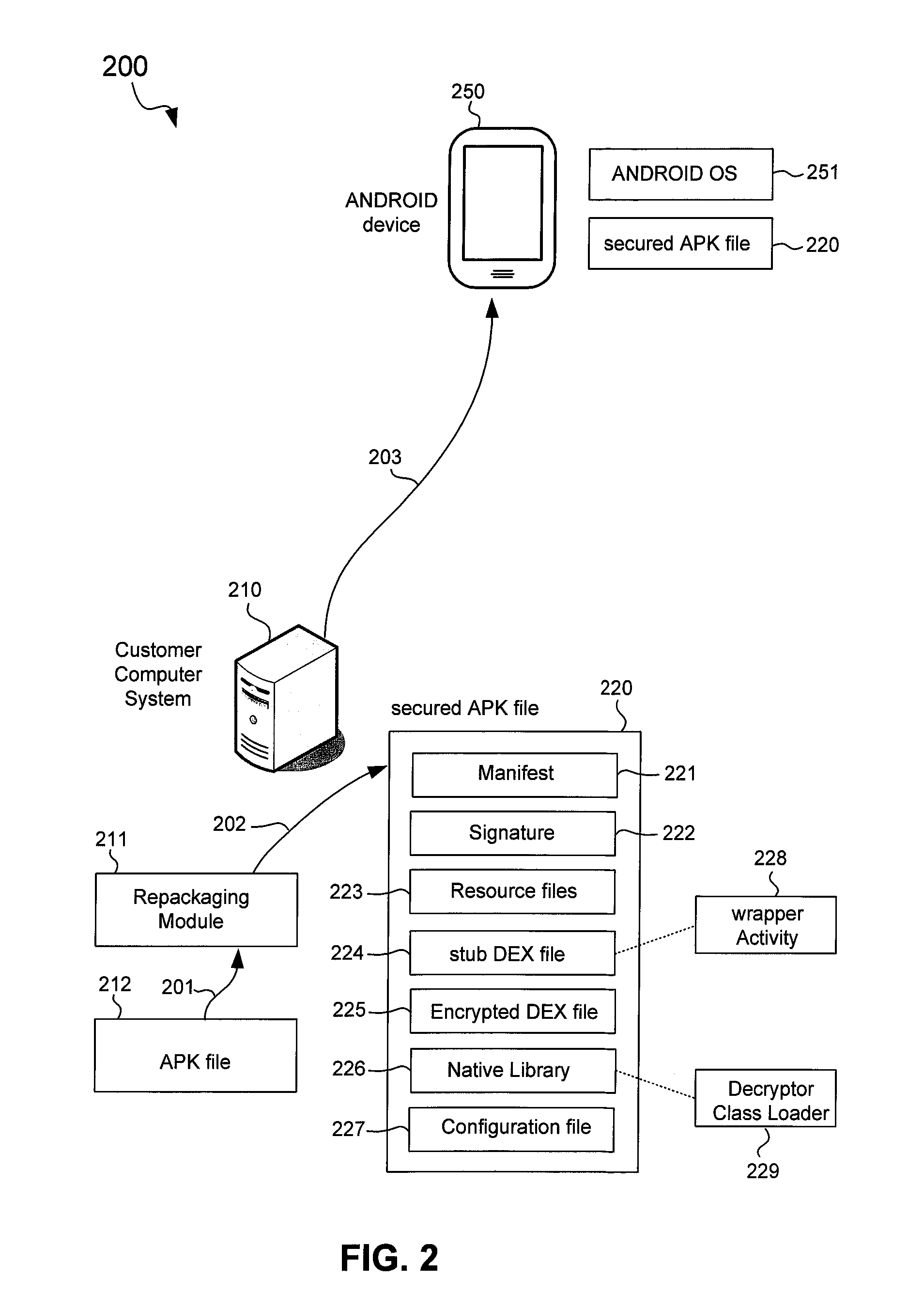
Secured application package files for mobile computing devices
An ANDROID application package (APK) file for an application is repackaged into a secured APK file to protect a Dalvik executable (DEX) file of the application. The DEX file is encrypted to generate an encrypted DEX file that is included in the secured APK file along with a stub DEX file. The secured APK file is received in a mobile computing device where the stub DEX file is started to start a wrapper Activity. The wrapper Activity replaces an APK class loader of a mobile operating system of the mobile computing device with a decryptor class loader. The decryptor class loader decrypts the encrypted DEX file to recover the DEX file, and loads classes of the DEX file into a Dalvik virtual machine. The original Activity of the application is then started to provide the functionality of the application in the mobile computing device.
Owner:TREND MICRO INC
Systems and methods for a mobile business application development and deployment platform
ActiveUS20130247005A1Improve customizabilityHigh degreeVersion controlSpecific program execution arrangementsOperational systemMobile business
Systems and methods for developing, customizing, and deploying mobile device business applications are provided through a mobile application development and deployment platform. Preferably, these systems and methods are implemented in an Internet based environment that allows non-technical users to build highly-customizable cross-platform mobile applications. The platform allows users to select, input, create, customize, and combine various content, design characteristics, database structure, and application components, such as modules, some of which allow an end user to store and access data in an end user database for business applications. In certain embodiments, the platform allows users to compile and generate a configuration file for the mobile application that can be distributed to end users for execution on various mobile devices and mobile operating systems. When the mobile application is installed on, or executed by the mobile device, the configuration file may enable the retrieval of data associated with the mobile application.
Owner:MEDIA DIRECT
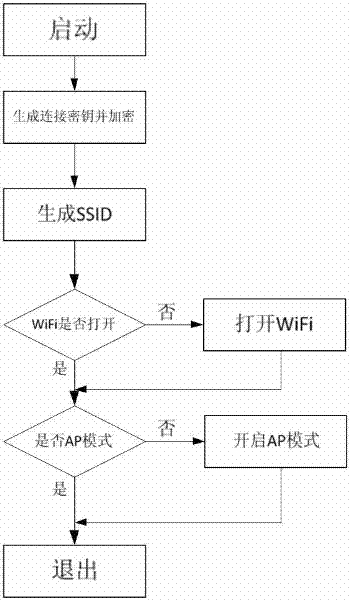
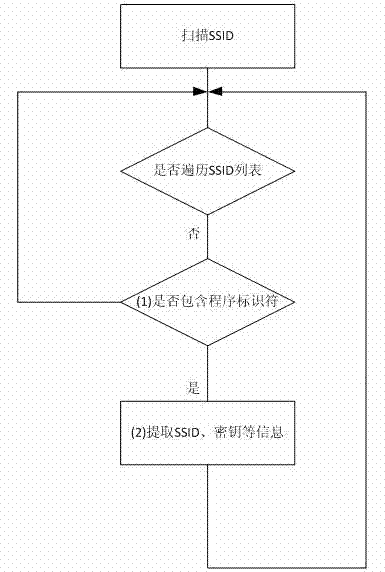
Method for safely building WiFi connection by SSID in application program
The invention belongs to the transmission technical field of wireless network and specifically relates to a method for safely building WiFi connection by SSID in application program. The method uses the open API of mobile operation system, controls and manages WiFi module by program and configures SSID to automatically build WiFi connection by the application program, and exchanges data in safe manner. The method is characterized in that SSID comprises program identifiers and SSID connecting key; the SSID connecting key is encrypted by encrypting program and a process (authorization from user should be acquired after automatically building the WiFi connection, or else, the connection will be removed) is confirmed by the connection to improve the safety.
Owner:FUDAN UNIV
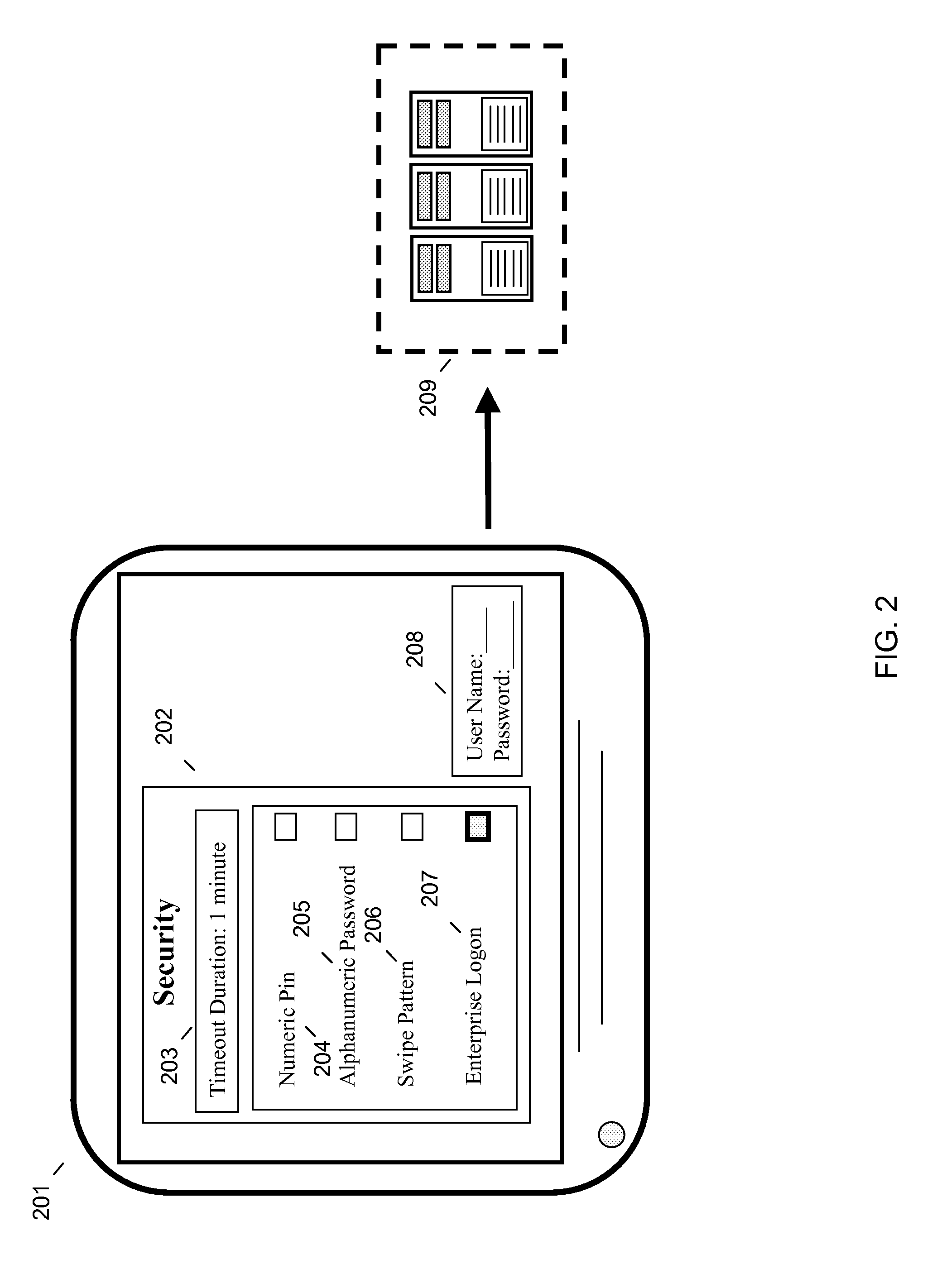
Remote authentication screen locker for a mobile device
InactiveUS20130031619A1Access be denyDigital data processing detailsUser identity/authority verificationComputer hardwareOperational system
Devices, methods and products are described that provide for remote authentication of mobile information handling devices. One aspect provides a method comprising configuring an information handling device operating through a mobile operating system to allow communication with least one remote authentication architecture; denying access to a information handling device of the information handling device responsive to a device lock event; and granting access to the display device responsive to an unlock event comprising entry of logon credentials authenticated at the at least one remote authentication architecture. Other embodiments and aspects are also described herein.
Owner:LENOVO (SINGAPORE) PTE LTD
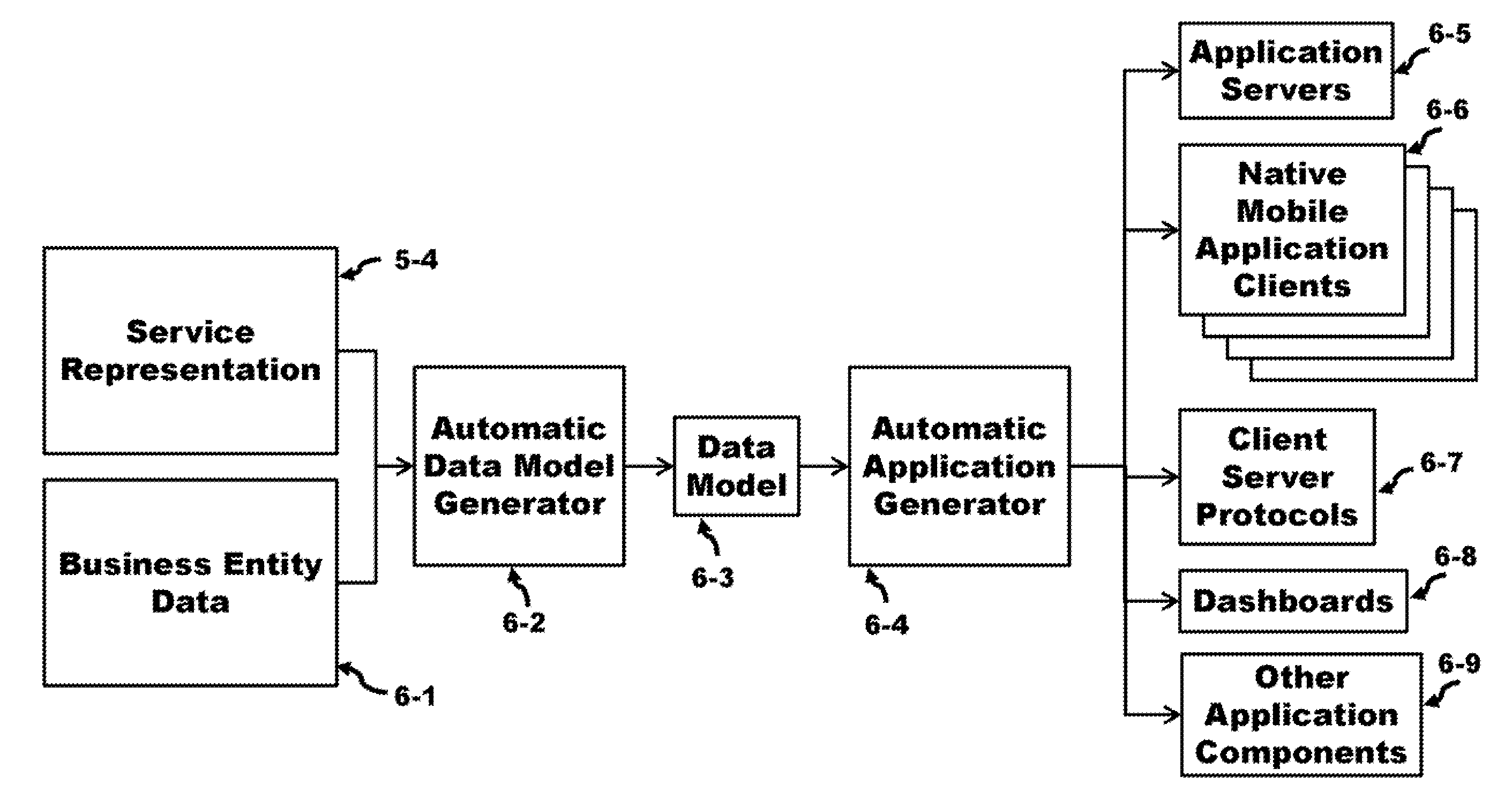
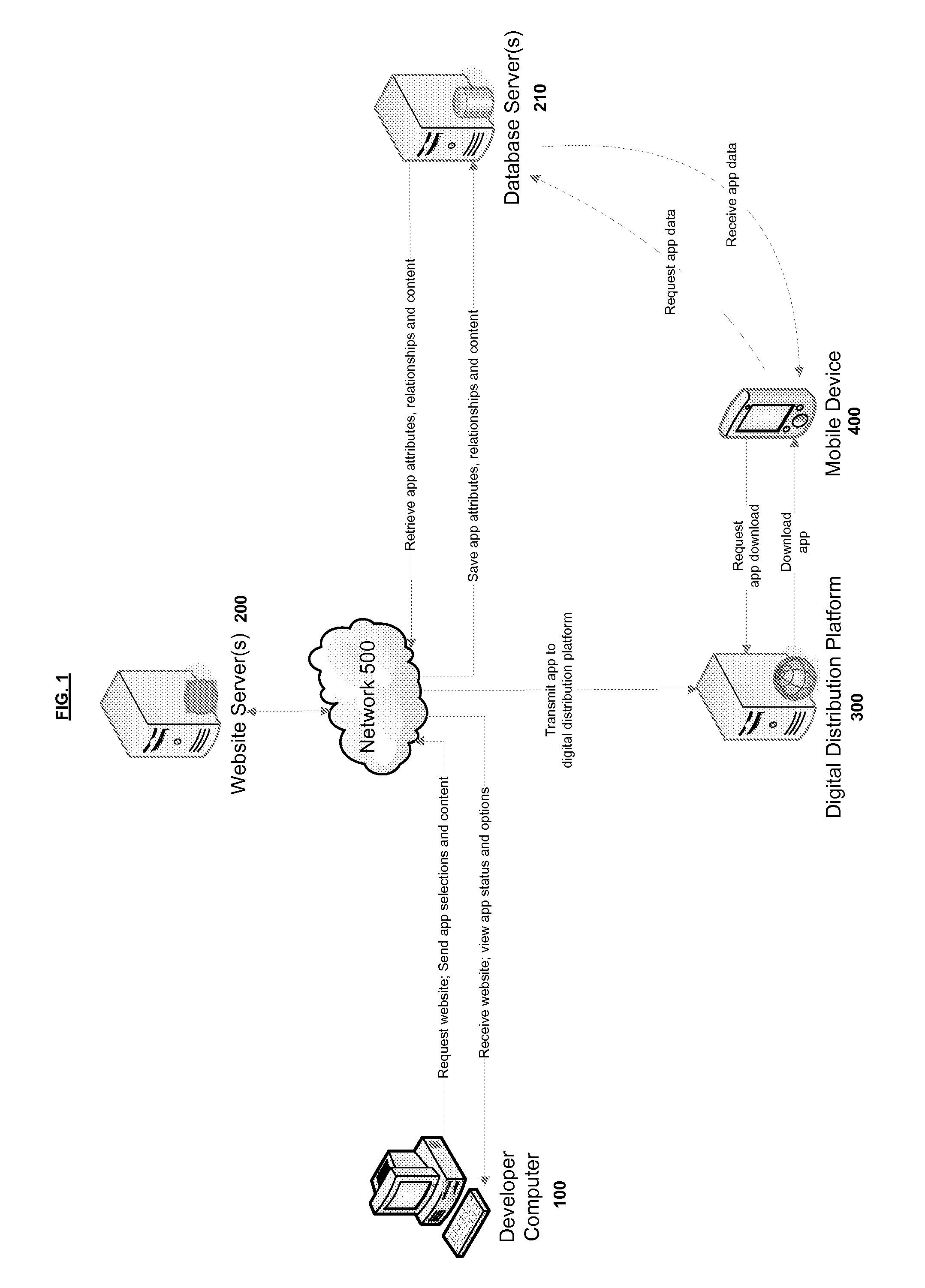
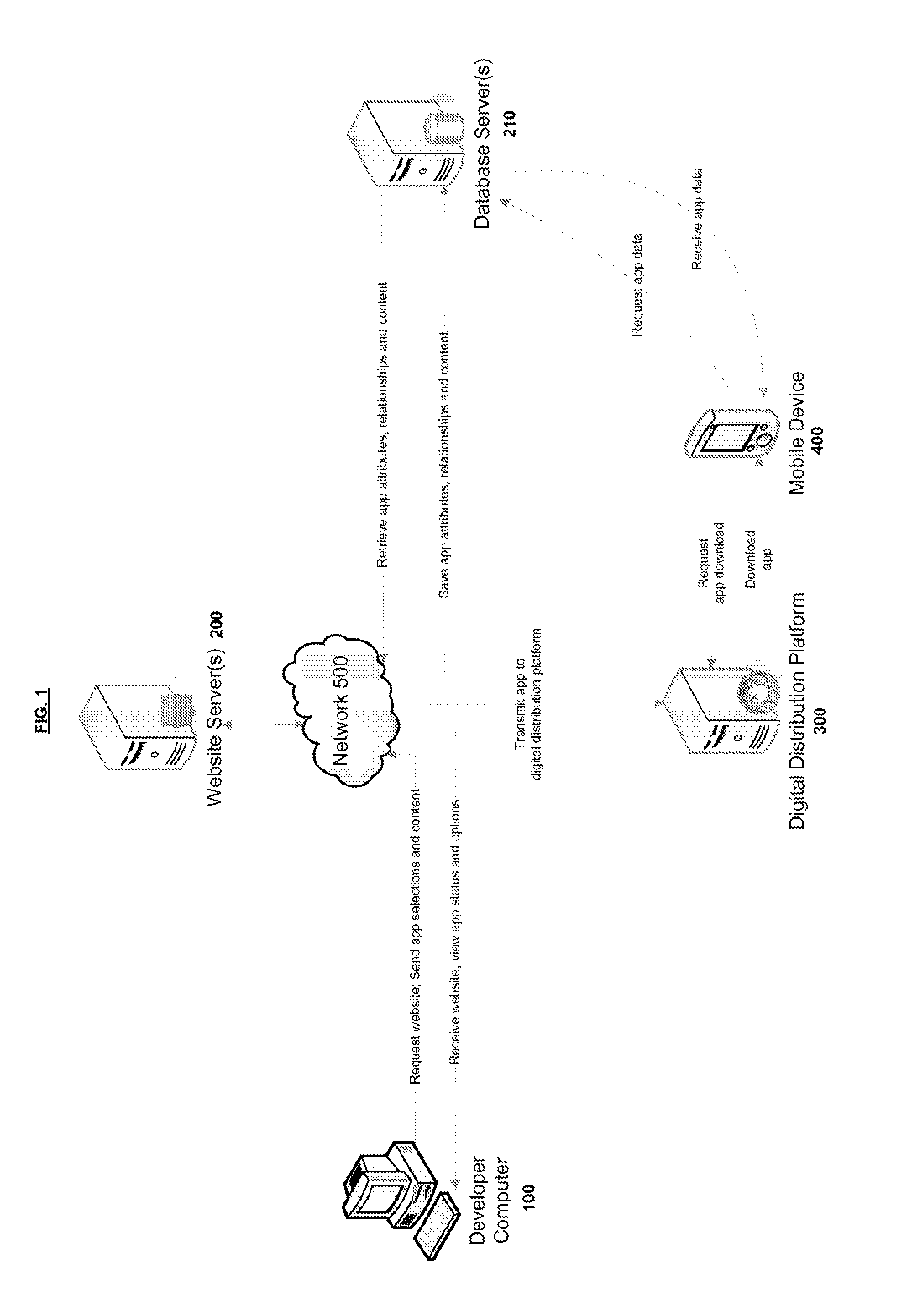
Method for Single Workflow for Multi-Platform Mobile Application Creation and Delivery
ActiveUS20140280476A1Component with highService provisioningMobile application execution environmentsMulti platformApplication software
A high-level functionality generates a Data Model which is used to automatically generate Applications comprising Application Clients, Application Servers, Client-Server Protocols, Dashboards and other components. These Applications are derived for different mobile and non-mobile's Operating Systems. This functionality uses Services, Service Representation, Application Flow, Rules, and Presentation Attributes. The input for the automation is a very high-level, “service” level “language,” from which all parts are automatically generated. The output of the automation also includes a way to validate the correctness of the generated Applications. The generated Dashboard provide a Business Entity with functionality to continuously update the generated Data Model based on the Services and Business Entity data, and from the updated Data Model automatically generate updated versions of the Application. The functionality may be a graphical representation, a set of forms, a set of policies, or a set of values associated to a set of pre-defined parameters.
Owner:GADGET SOFTWARE INC
Systems and methods for a mobile application development and deployment platform
ActiveUS20130205276A1High degreeVersion controlMultiple digital computer combinationsOperational systemApplication software
Systems and methods for developing, customizing, and deploying mobile device applications are provided through a mobile application development and deployment platform. Preferably, these systems and methods are implemented in an Internet based environment that allows non-technical users to build sophisticated, highly-customizable cross-platform mobile applications. The platform allows users to select, input, create, customize, and combine various content, design characteristics, and application components, such as modules, some of which utilize features and functionality associated with various mobile devices and mobile operating systems. In certain embodiments, the platform allows users to compile, and generate a configuration file for, the mobile application that can be distributed to end users for execution on various mobile devices and mobile operating systems. When the mobile application is installed on, or executed by the mobile device, the configuration file may enable the retrieval of various data associated with the mobile application.
Owner:MEDIA DIRECT
Systems and methods for a mobile business application development and deployment platform
ActiveUS8978006B2High degreeVersion controlProgram loading/initiatingOperational systemMobile business
Systems and methods for developing, customizing, and deploying mobile device business applications are provided through a mobile application development and deployment platform. Preferably, these systems and methods are implemented in an Internet based environment that allows non-technical users to build highly-customizable cross-platform mobile applications. The platform allows users to select, input, create, customize, and combine various content, design characteristics, database structure, and application components, such as modules, some of which allow an end user to store and access data in an end user database for business applications. In certain embodiments, the platform allows users to compile and generate a configuration file for the mobile application that can be distributed to end users for execution on various mobile devices and mobile operating systems. When the mobile application is installed on, or executed by the mobile device, the configuration file may enable the retrieval of data associated with the mobile application.
Owner:MEDIA DIRECT
Malware detection method and malware detection system of mobile operating system
ActiveCN103839005ARealize detectionEfficient detectionPlatform integrity maintainanceOperational systemSoftware engineering
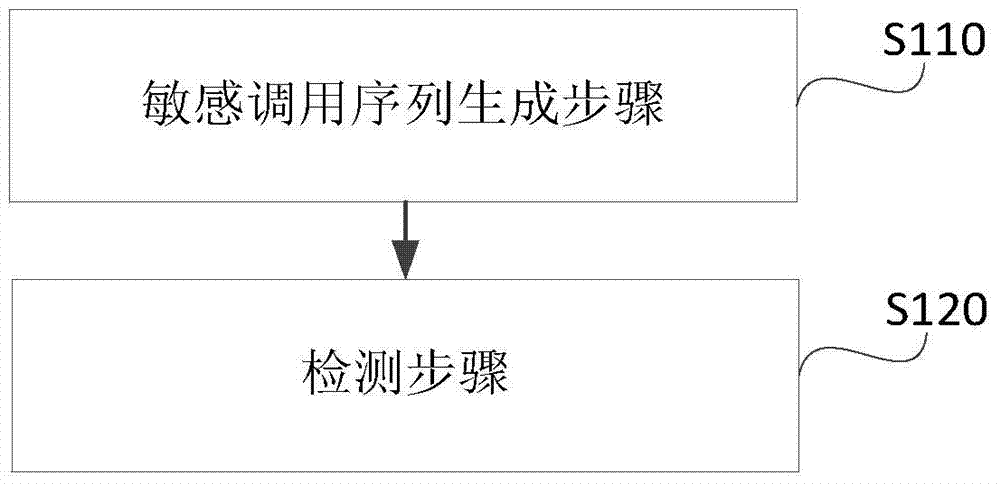
The invention provides a malware detection method of a mobile android operating system. The method includes the sensitive calling sequence generation step and the detection step, wherein in the sensitive calling sequence generation step, code analysis is performed on software for at least one entry function in software, and a sensitive system calling sequence is generated; in the detection step, the sensitive system calling sequence is matched according to a predefined malware feature library, and a malware detection result is obtained. According to the characteristic that current malware is achieved mainly depending on system calling, system calling used by the malware is effectively detected, thus, the problem existing in the detection technology in the prior art can be effectively solved, the essential behavior of the malware can be detected, and the detection efficiency of the malware is improved.
Owner:BEIJING ZHIGU RUI TUO TECH
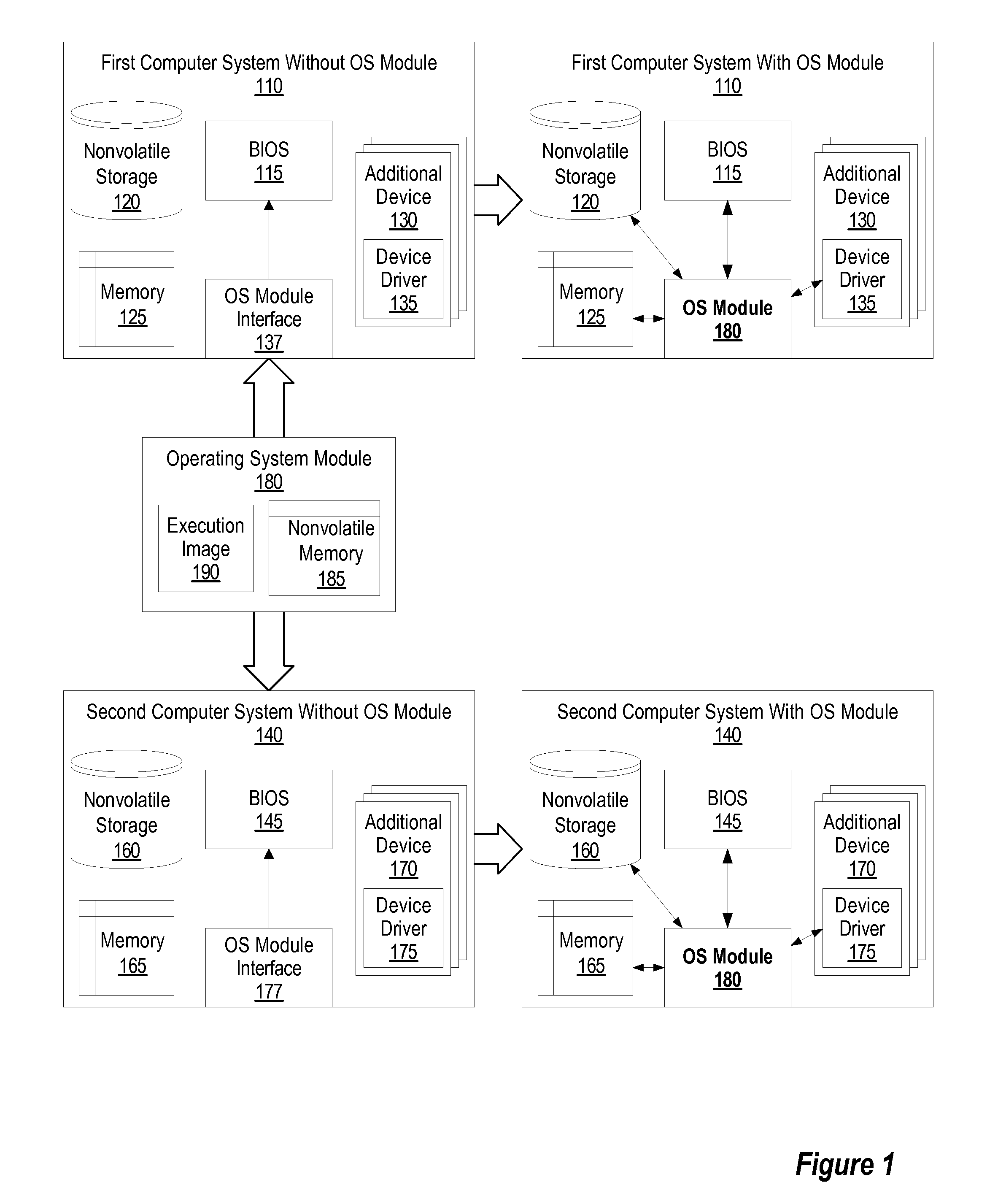
System and method for portable running operating system
ActiveUS20050038932A1Digital computer detailsComponent plug-in assemblagesOperational systemEngineering
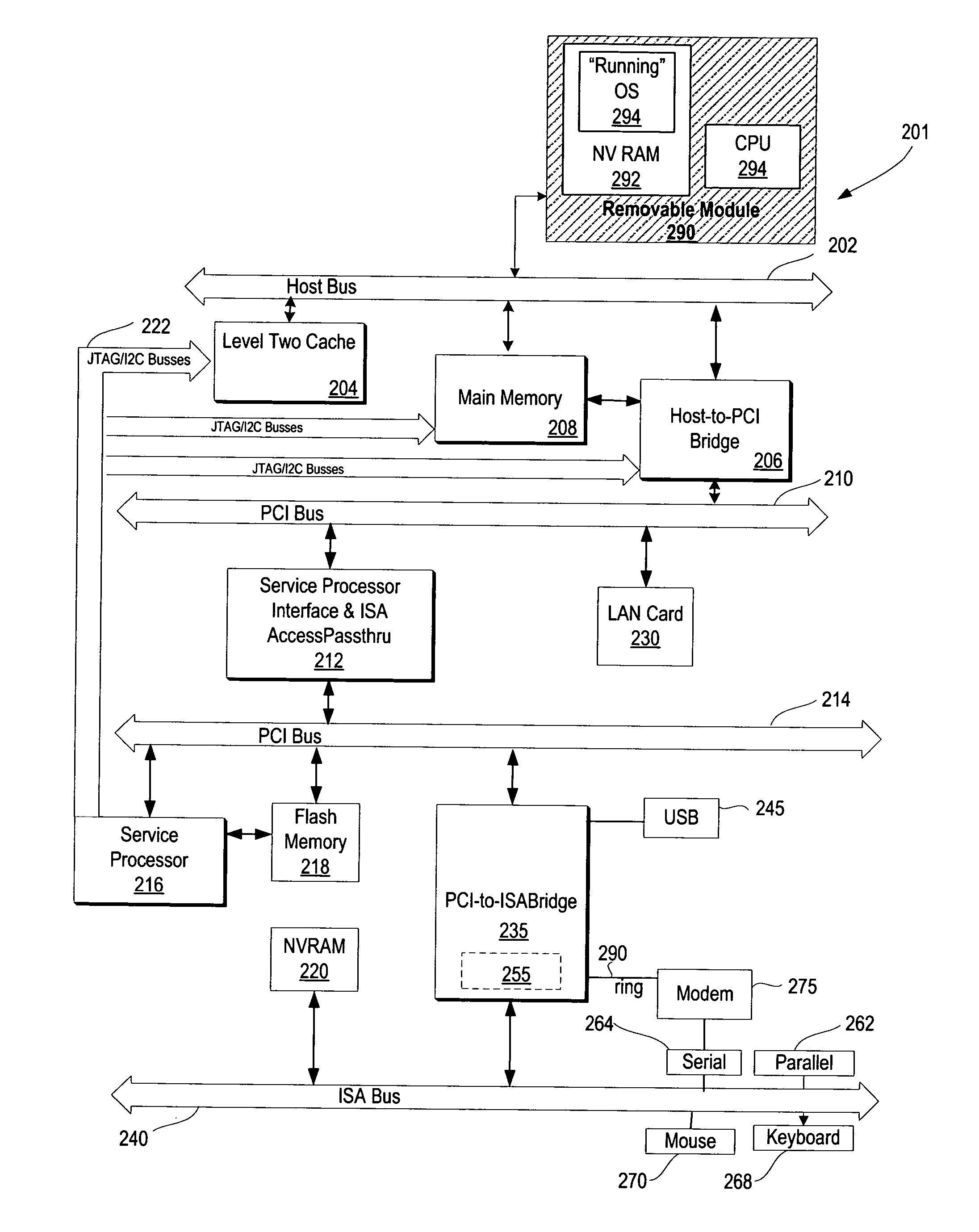
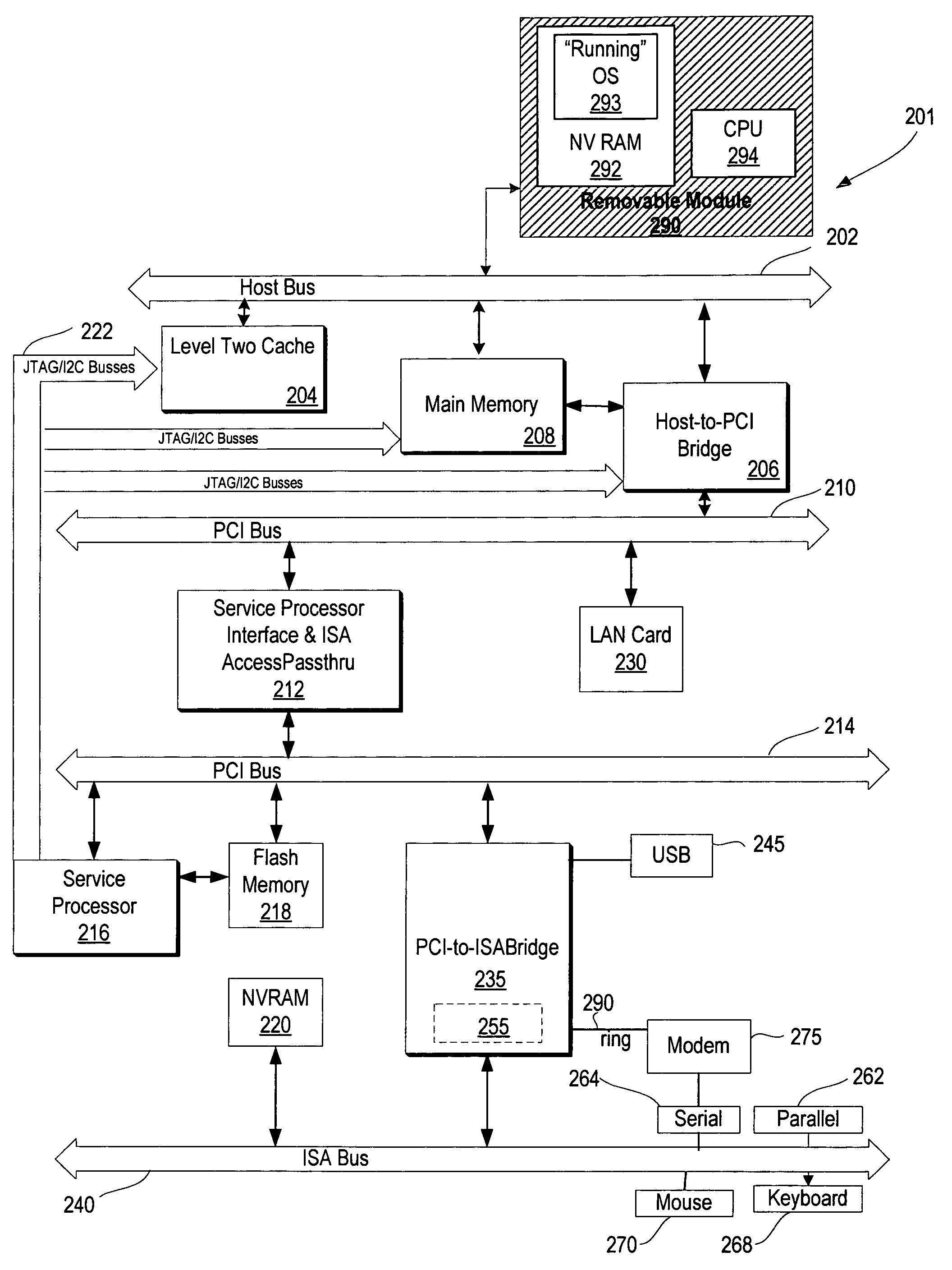
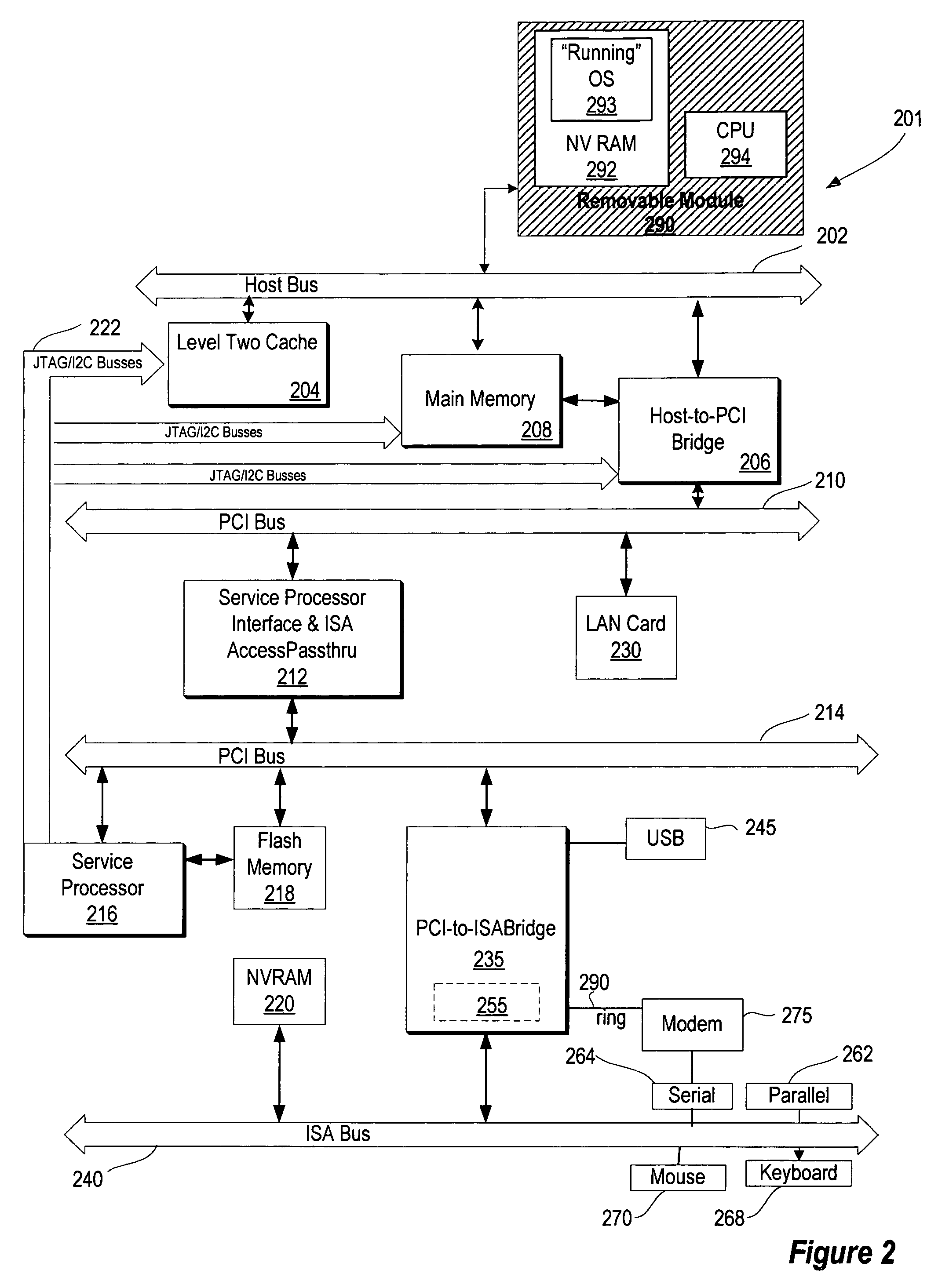
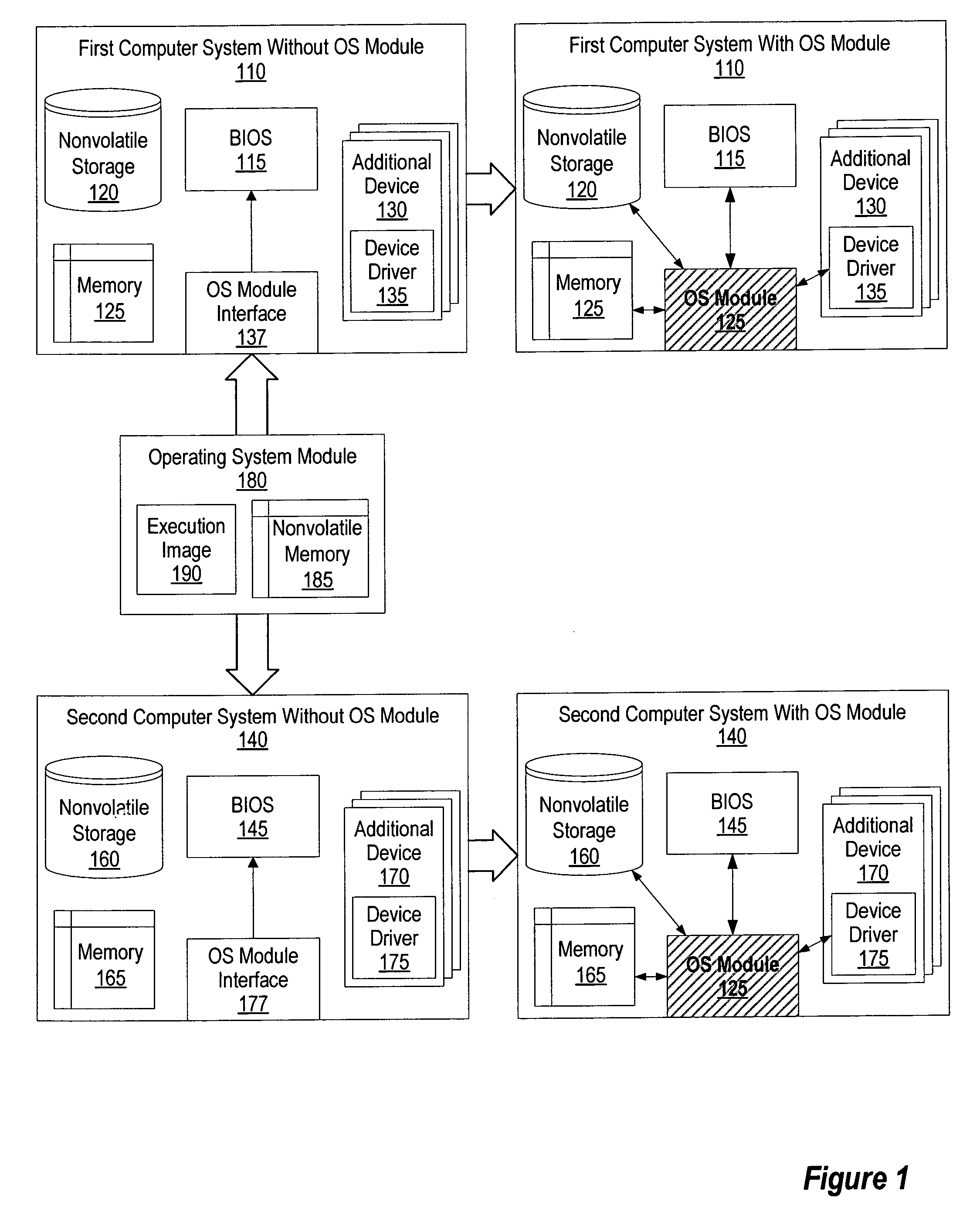
A method and system for providing a running image of an operating system on a removable operating system module to multiple computer systems. The removable operating system module includes a memory unit for storing the running image of the operating system. Upon insertion of the module into a computer system, a BIOS loads the operating system from the removable operating system module and initiates the execution of the operating system. In response to a request by the user, the BIOS may resume or restart the operating system. The operating system may also discover any available local and remote devices, resume any available previously running applications, and perform tasks requested by the applications and the user. In response to a user's removal request, the state of the operating system is saved on the module and the removable operating system module is removed from the computer system.
Owner:GOOGLE LLC
Device and method for JavaScript native interface calling conducted by crossing mobile operating system platform
ActiveCN104461575AImprove development efficiencyImprove experienceSpecific program execution arrangementsComputer terminalData exchange
The invention discloses a device and method for JavaScript native interface calling conducted by crossing a mobile operating system platform. The device comprises a forward system and a reverse system, wherein the forward system is used for transferring data exchange carriers of web script programs to a native interface of a mobile terminal, and the reverse system is used for transferring the data exchange carriers returned by the native interface of the mobile terminal to the web script programs in the mode that local services are executed synchronously or asynchronously. The forward system comprises a unified interface calling module, a calling prompt module, a kernel encapsulation class module and a plug-in management module. The reverse system comprises a call-back module and a call-back server module.
Owner:北京华电万通科技有限公司
Root-permission-free safe virtual mobile application program running environment system, method and application
InactiveCN106897611ARun program securityPrevent movementPlatform integrity maintainanceOperational systemAccess time
The invention discloses a root-permission-free safe virtual mobile application program running environment system, method and application. A user opens a virtual running environment control program and selects a target mobile application program; a container process loads the target application program; a hook is arranged in the container process, and communication and interface calling of the target application program and an operation system is dynamically intercepted through the hook method; a proxy service agents target application program and operation system interaction according to a request for intercepting communication and interface calling; a safety module analyzes the target application program and operation system interaction, and dynamic permission control over the interaction is achieved through the proxy service; a log module records all system access time and contents, and bases are provided for further safety analysis. The system is a safe virtual environment which can directly run in an existing Android system and support and protect running of target mobile programs, the running cost is low, root permission does not need to be obtained, the existing Android system does not need to be modified, and compatibility and applicability are high.
Owner:JIN GUANG +1
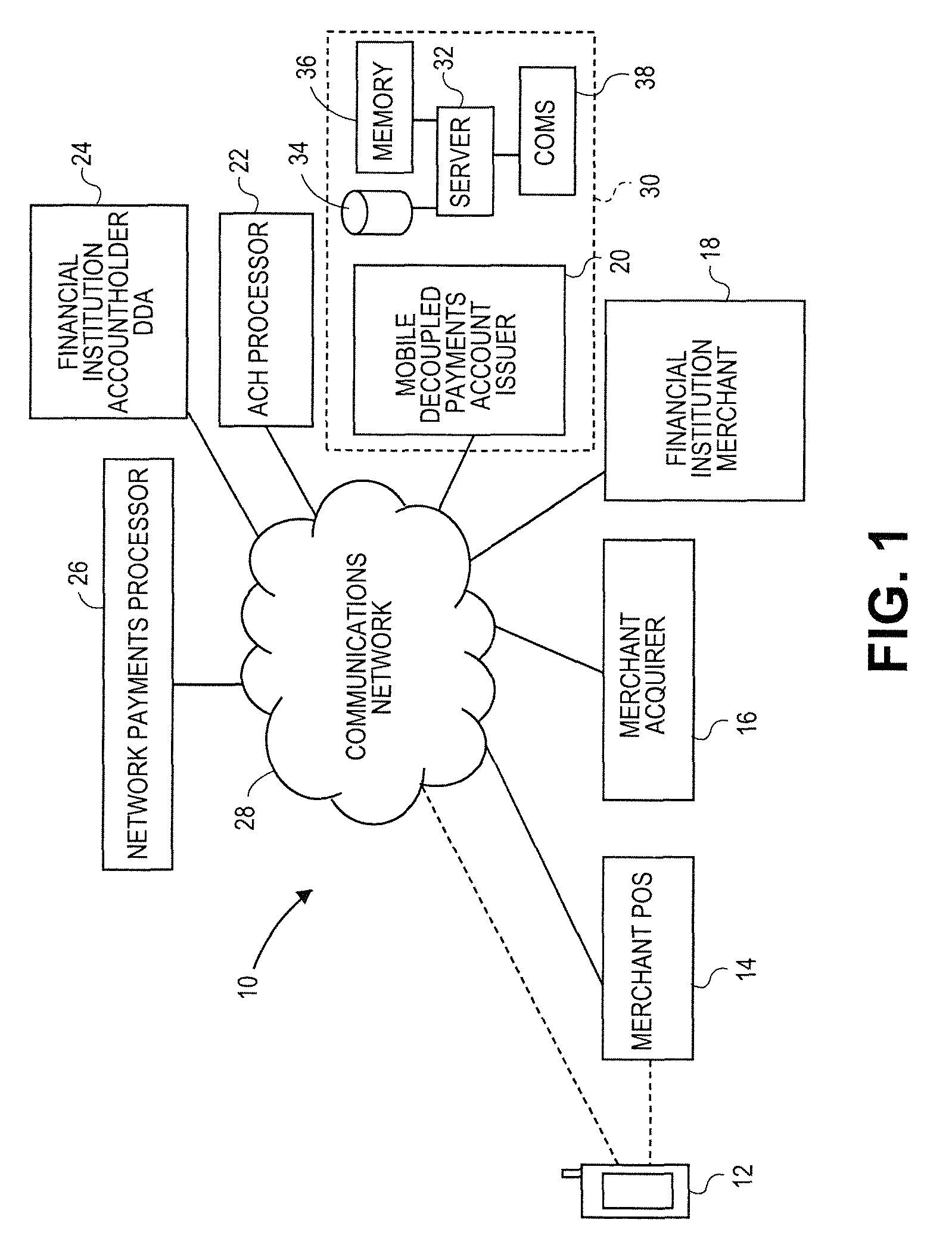
Mobile payment systems and methods
A method includes providing a first payment account that is issued by a first financial institution and enables an accountholder thereof to make payments at merchants via a closed-loop payments network corresponding to the first financial institution and mobile person-to-person payments using the payment account. The method includes enabling a second payment account that is issued by a second financial institution to be electronically linked to the first payment account and used as a source of funds. The method includes providing a mobile operating system and enabling a plurality of merchant-specific payment accounts to be associated with a mobile communications device having the operating system. The method includes determining whether a merchant-specific payment account that is accepted only by a particular merchant is available to the accountholder via the mobile communications device and receiving a fee when the first payment account is used for a purchase.
Owner:GOFIGURE PAYMENTS
System and method for loading, executing, and adapting a portable running operation system from a removable module to multiple computer systems
ActiveUS7032053B2Digital computer detailsComponent plug-in assemblagesOperational systemComputerized system
A method and system for providing a running image of an operating system on a removable operating system module to multiple computer systems. The removable operating system module includes a memory unit for storing the running image of the operating system. Upon insertion of the module into a computer system, a BIOS loads the operating system from the removable operating system module and initiates the execution of the operating system. In response to a request by the user, the BIOS may resume or restart the operating system. The operating system may also discover any available local and remote devices, resume any available previously running applications, and perform tasks requested by the applications and the user. In response to a user's removal request, the state of the operating system is saved on the module and the removable operating system module is removed from the computer system.
Owner:GOOGLE LLC
System and method for manufacturing and updating insertable portable operating system module
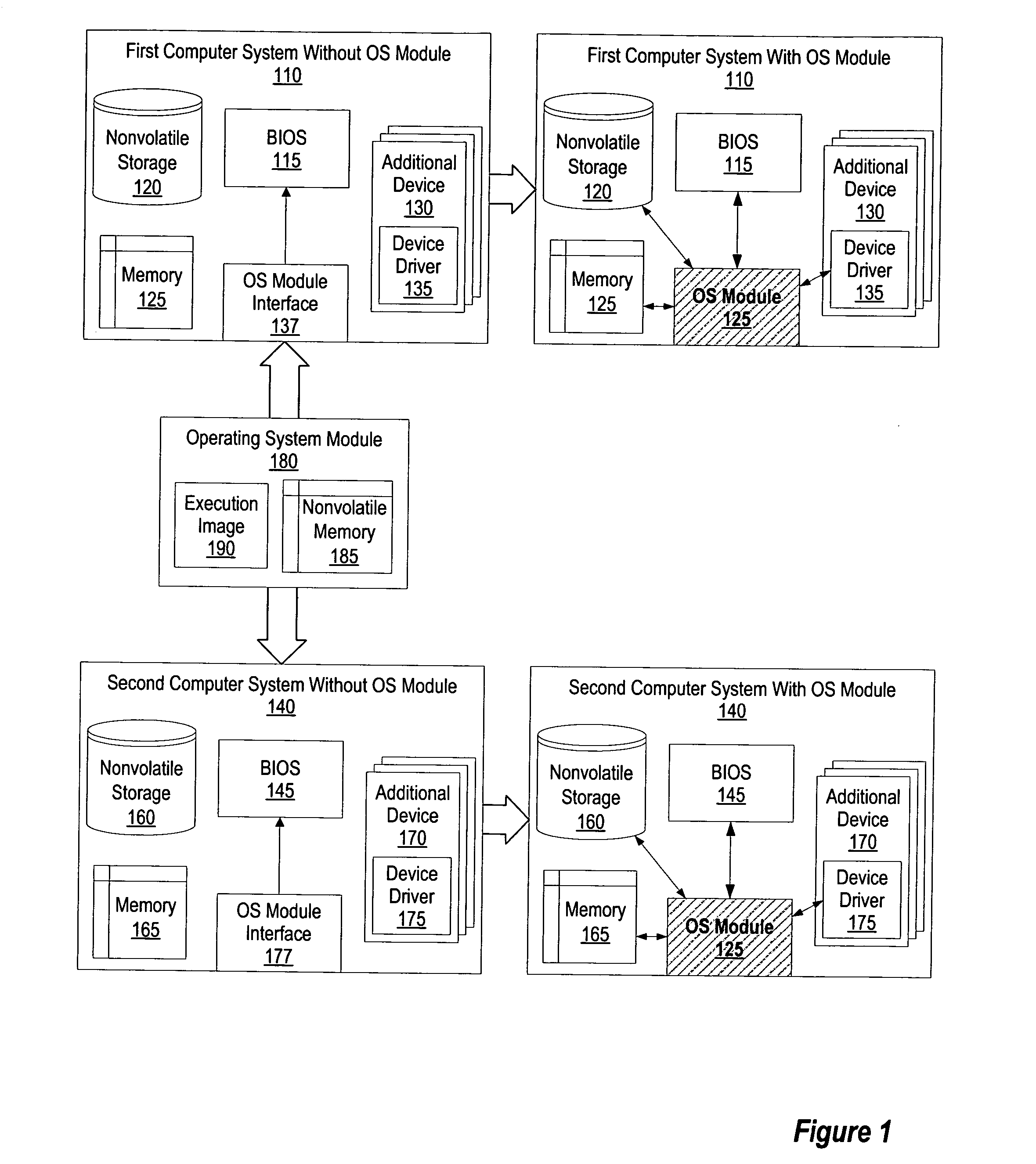
ActiveUS20050038960A1Program control using stored programsDigital data processing detailsOperational systemOperating system
Owner:GOOGLE LLC
Unmanned vehicle civil communications systems and methods
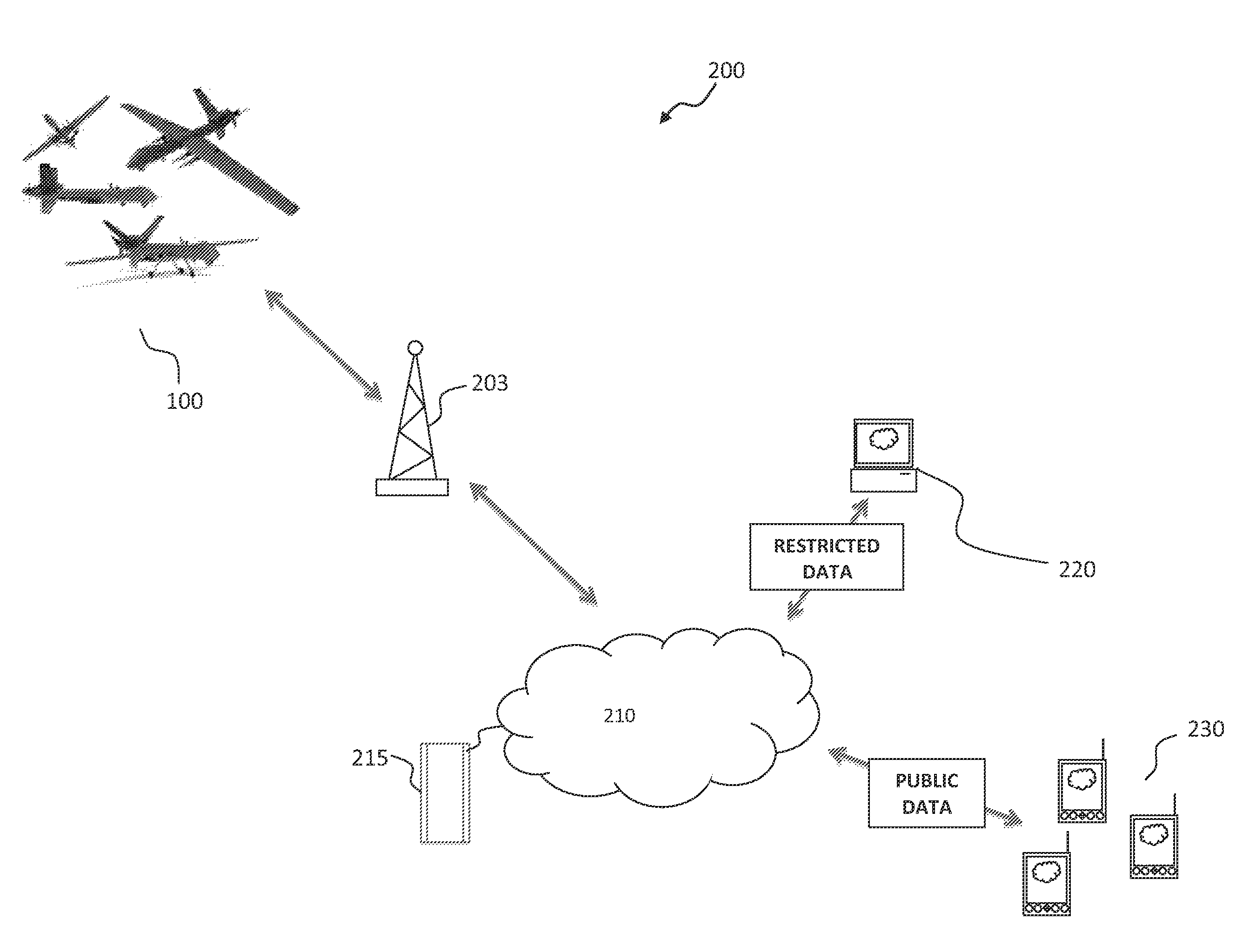
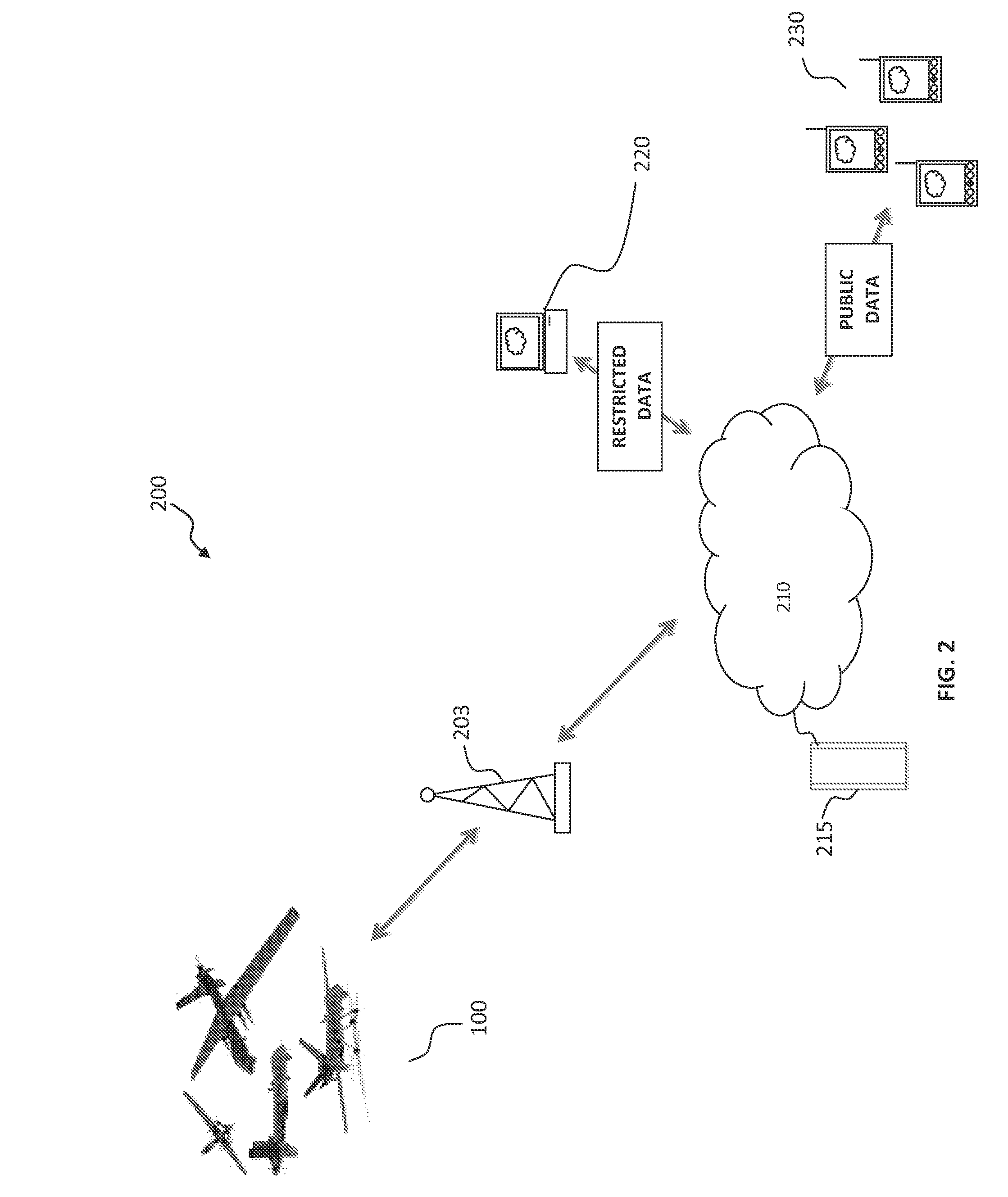
A mass notification push application and a civic-communication application combined into one with the primary purpose of allowing up-to-the-minute UAV aerial imagery as selected by drone ground-based commanders to be automatically transmitted to subscribed end-users via the current OS mobile operating systems for smartphones, iPads, laptops, and web-enabled devices in a manner comprised of separate technologies such as voice (voice to text, voice recognition), video stills (embedded with personalized iconographic identifiers), and with a secondary purpose of allowing the notified recipients to engage others by allowing the retransmitting of received messages along with (or without) registered user annotations so as to create a civil communications hub for wider, real-time dissemination of ongoing situational awareness data.
Owner:VERNA IP HLDG
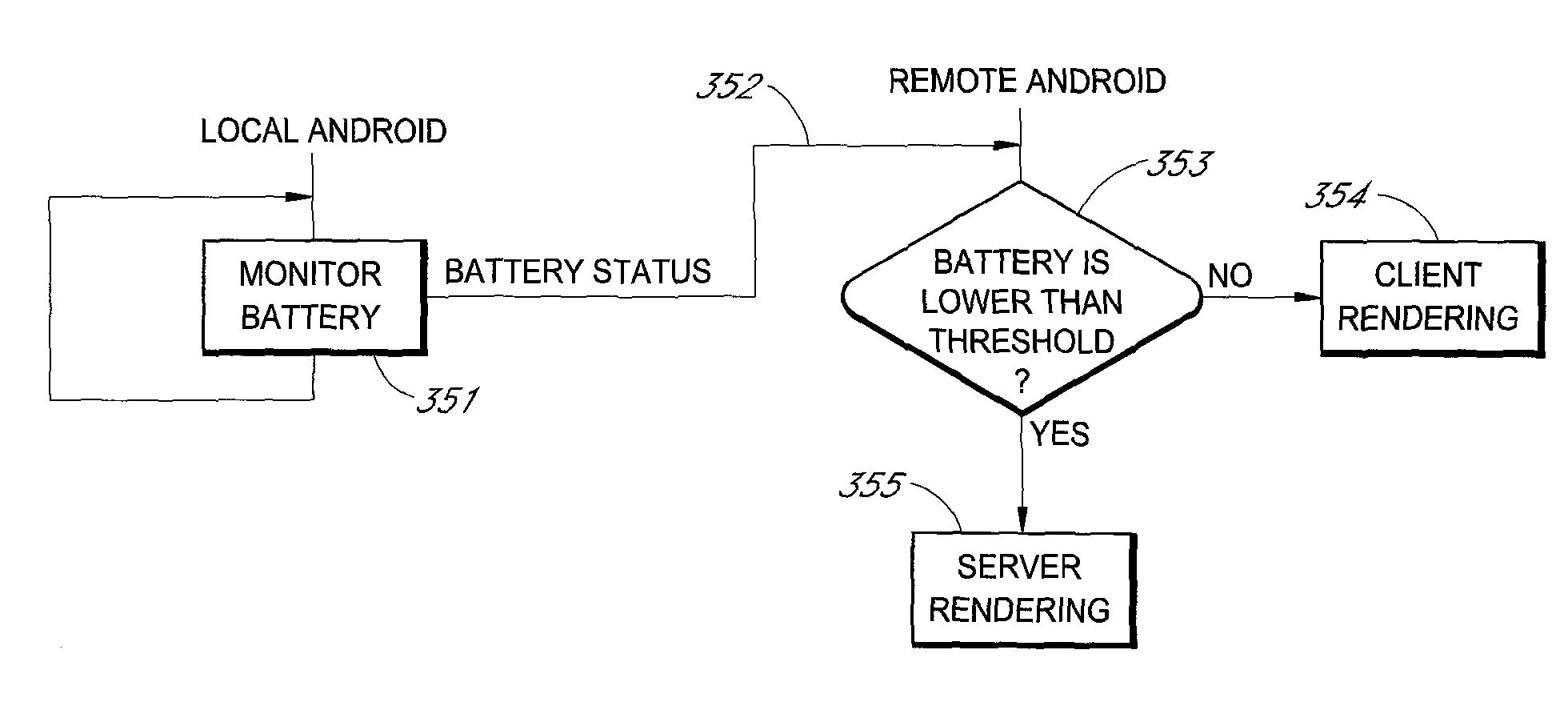
Client-side rendering for virtual mobile infrastructure
A virtual mobile infrastructure performs client-side rendering by intercepting and redirecting screen data for generating a screen image of a remote mobile operating system from a server computer to a mobile client device. The mobile client device receives the screen data and generates the final screen image of the remote mobile operating system. The screen data include drawing application programming interface (API) calls to generate surfaces for applications running on the remote mobile operating system and data for compositing the surfaces together. The mobile client device makes the drawing API calls to generate the surfaces and generates the final screen image of the remote mobile operating system by compositing the surfaces in accordance with the compositing data.
Owner:TREND MICRO INC
Mobile payment systems and methods
A method includes providing a first payment account that is issued by a first financial institution and enables an accountholder thereof to make payments at merchants via a closed-loop payments network corresponding to the first financial institution and mobile person-to-person payments using the payment account. The method includes enabling a second payment account that is issued by a second financial institution to be electronically linked to the first payment account and used as a source of funds. The method includes providing a mobile operating system and enabling a plurality of merchant-specific payment accounts to be associated with a mobile communications device having the operating system. The method includes determining whether a merchant-specific payment account that is accepted only by a particular merchant is available to the accountholder via the mobile communications device and receiving a fee when the first payment account is used for a purchase.
Owner:GOFIGURE PAYMENTS
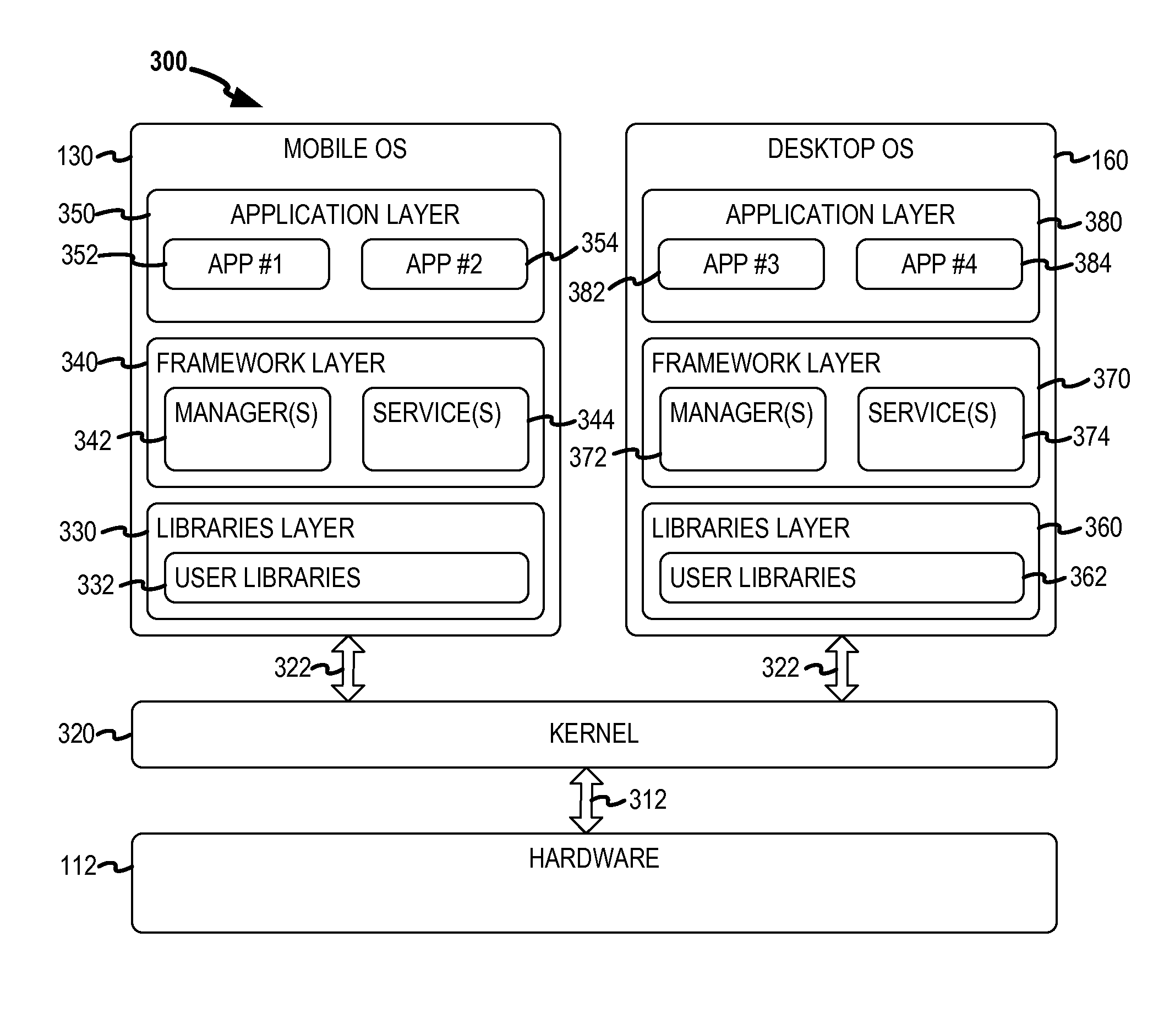
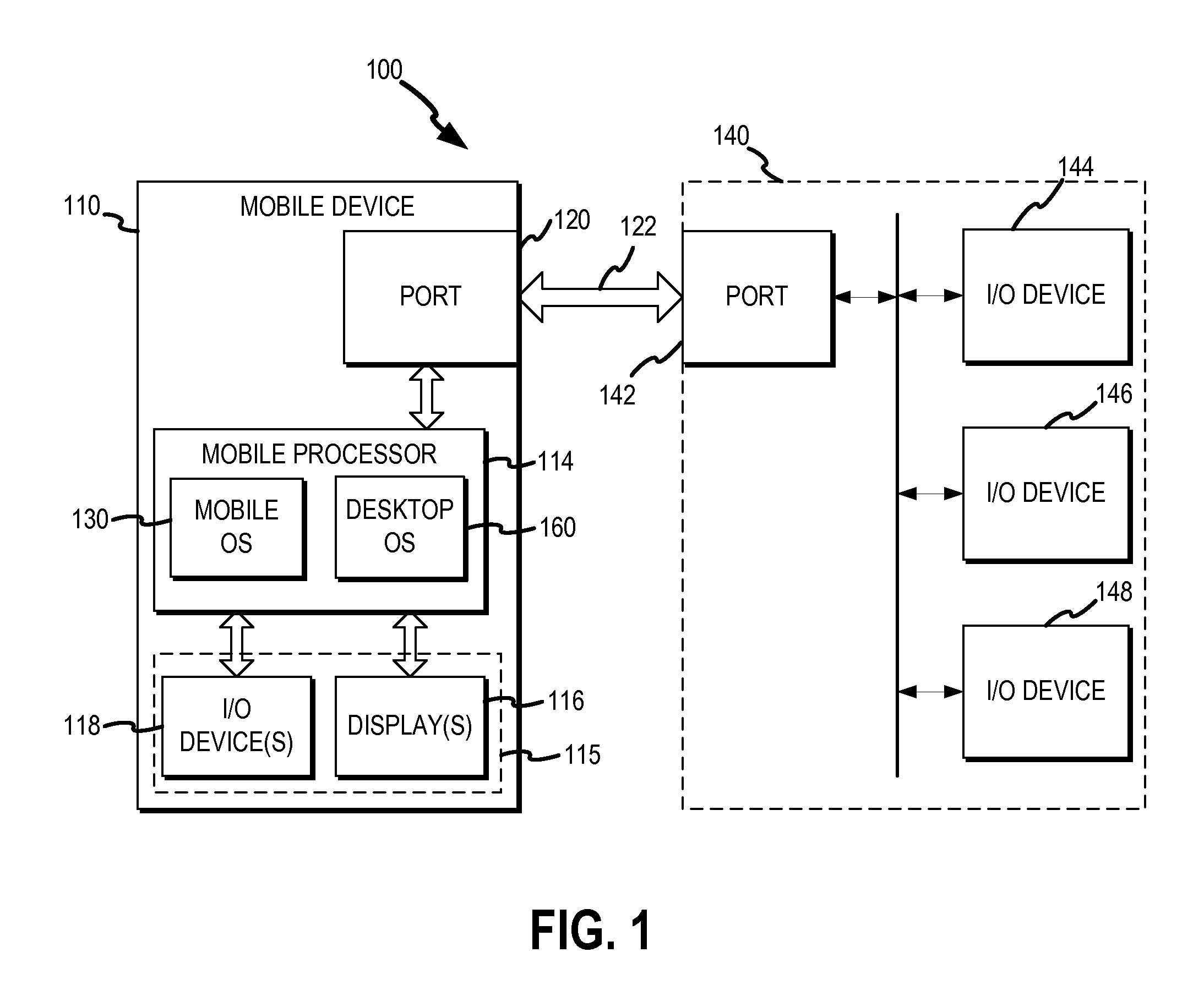
Cross-environment redirection
Cross-environment rendering and user interaction support provide a seamless computing experience in a multi-operating system computing environment. The multi-operating system computing environment may include a mobile operating system and a desktop operating system running concurrently and independently on a mobile computing device. Full user interaction support is provided for redirected and / or mirrored applications that are rendered using an extended graphics context. An extended input queue handles input events from virtual input devices for remotely displayed applications. Remotely displayed applications are mapped to separate motion spaces within the input queue. The mobile computing device may be a smartphone running the Android mobile operating system and a full desktop Linux distribution on a modified Android kernel.
Owner:Z124 MAPLES SERVICES
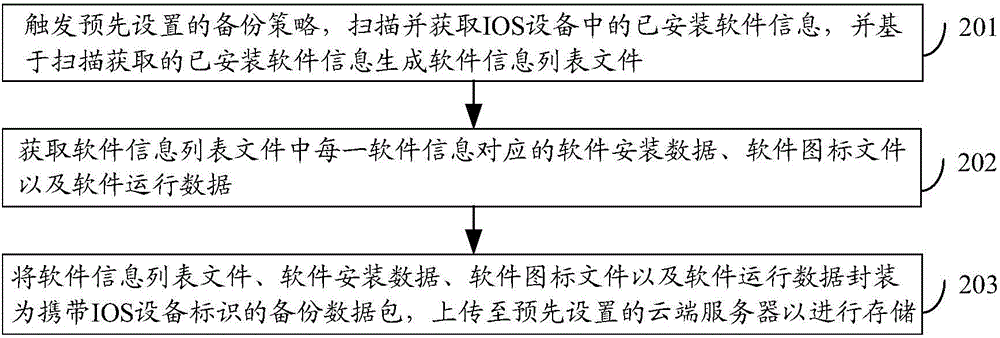
Data recovery method as well as data backup method, device and system based on mobile operating system
InactiveCN104866389ABackup in real timeTroubleshoot technical issues with high backup costsSpecial data processing applicationsRedundant operation error correctionRecovery methodCommunication interface
The invention discloses a data recovery method as well as a data backup method, device and system based on a mobile operating system. The data backup method comprises the following steps: after a preset backup strategy is triggered, information of software installed in the mobile operating system is scanned and acquired, and a software information list file is generated according to the scanned and acquired information of the installed software; software backup data corresponding to each piece of software information in the software information list file are acquired; the software information list file and the software backup data are encapsulated into a backup data packet carrying a device identification of the mobile operating system, a wireless communication interface used for data transmission is called, and the backup data packet is uploaded through a wireless communication network to a preset cloud server for storage. With application of the invention, the backup cost can be reduced, and the resource utilization rate can be increased.
Owner:BEIJING QIHOO TECH CO LTD +1
System and method for securing a portable processing module
InactiveUS7308584B2Volume/mass flow measurementUser identity/authority verificationOperational systemTime delays
A method and system for securing a removable module. Upon removal of the removable module from a computer system, the removable module is locked. The removable module may be locked by setting the removable operating system module to auto lock, by pressing a lock button on the removable module, or by setting a time delay, where the time delay determines the time after which the removable module locks after removing the removable module from the computer system. Upon reinsertion of the removable module, a user attempting to use the removable module is first authenticated. The user may be authenticated by the user entering a password and the system comparing the password to a list of authenticated passwords, by scanning the user's fingerprints using a fingerprints scanner or the user's retina using a retina scanner and comparing the image to a list of authenticated image signatures.
Owner:GOOGLE LLC
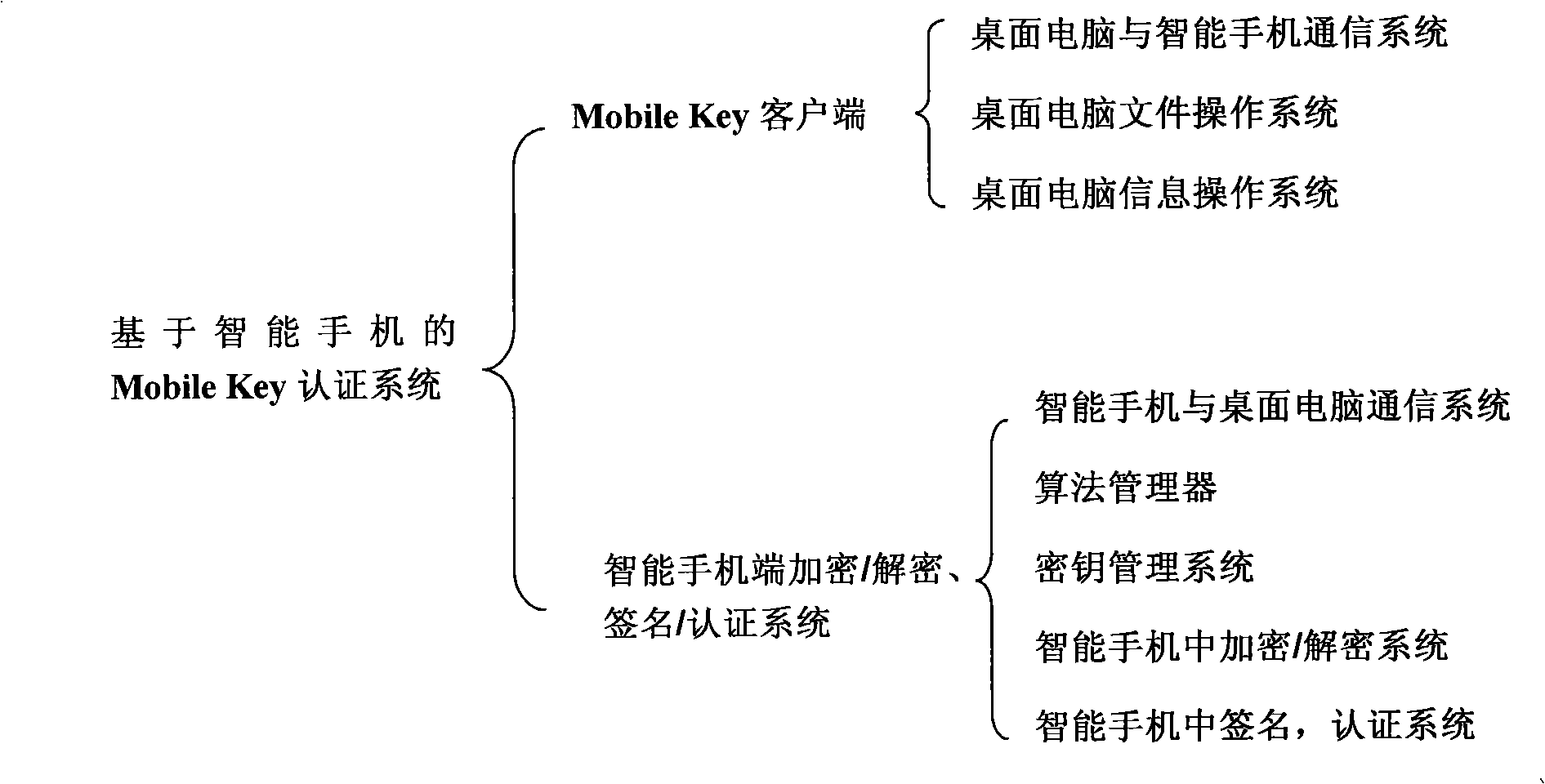
Mobile authentication system based on intelligent mobile phone
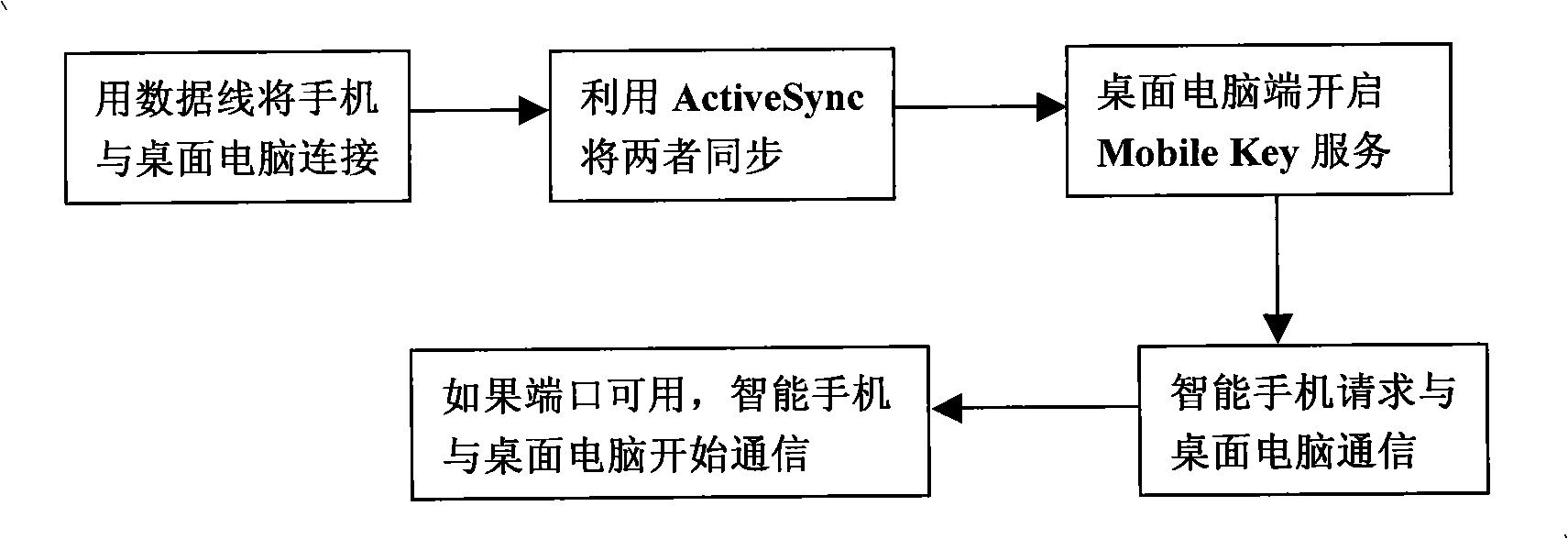
InactiveCN101304569AStrong computing powerHigh speedUser identity/authority verificationRadio/inductive link selection arrangementsOperational systemMobile authentication
The invention discloses a system combined with smartphones of carrying out digital signature and certification, file encryption and decryption by utilizing mobile key technology, which saves user keys or certificates on the smartphones and also carries out the processes of signature / certification, encryption / decryption on the smartphones. The invention mainly uses a smartphone of Windows mobile operating system, a desktop computer software module and a smartphone software module. Firstly, a mobile key client is designed and realized on the desktop computer, including file encryption and decryption files, office signature, and certification Plug-ins. Then, a security system of mathematical manipulation of digital signature, certification, file encryption / decryption, etc. is designed and realized on the smartphone. Beside the inherent advantages of a USB key of convenient use, high security, etc., the invention also has multiple advantages that the USB Key does not have, such as, rapid arithmetic speed, long key support, supporting the processing of overlarge files, good sharing performance, high security and better expandability.
Owner:SUN YAT SEN UNIV
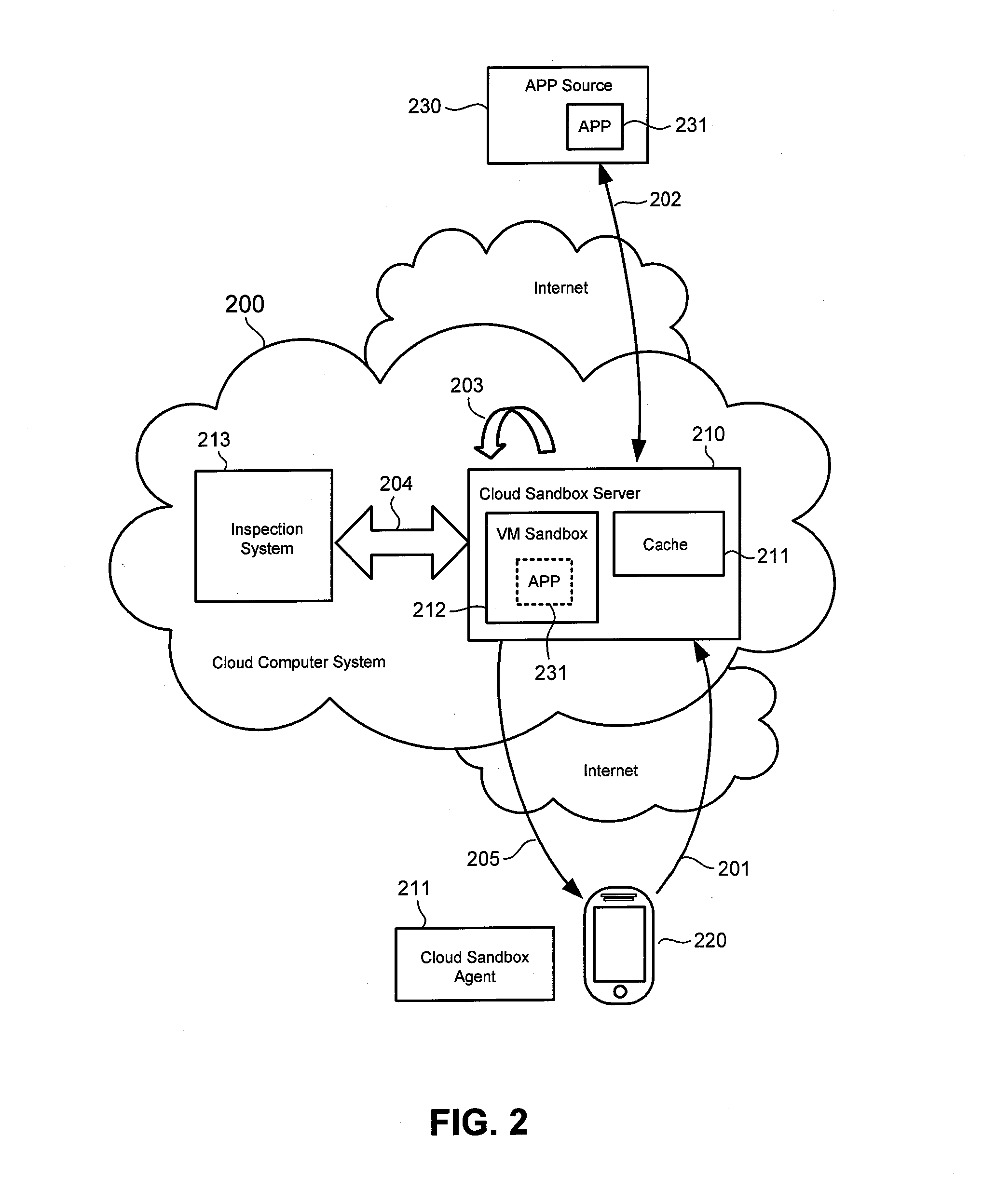
In-the-cloud sandbox for inspecting mobile applications for malicious content
ActiveUS8966632B1Memory loss protectionError detection/correctionTablet computerApplication software
A low resource mobile device, such as a smart phone or a tablet running a mobile operating system, requests a cloud computer system to inspect a mobile application for malicious content. The cloud computer system downloads the mobile application from a mobile application source, and installs the mobile application in a virtual machine sandbox. The cloud computer system inspects the mobile application for malicious content while the mobile application executes in the virtual machines sandbox. The result of the inspection is sent to the user in accordance with a setting that may be indicated in a cloud sandbox agent running on the mobile device.
Owner:TREND MICRO INC
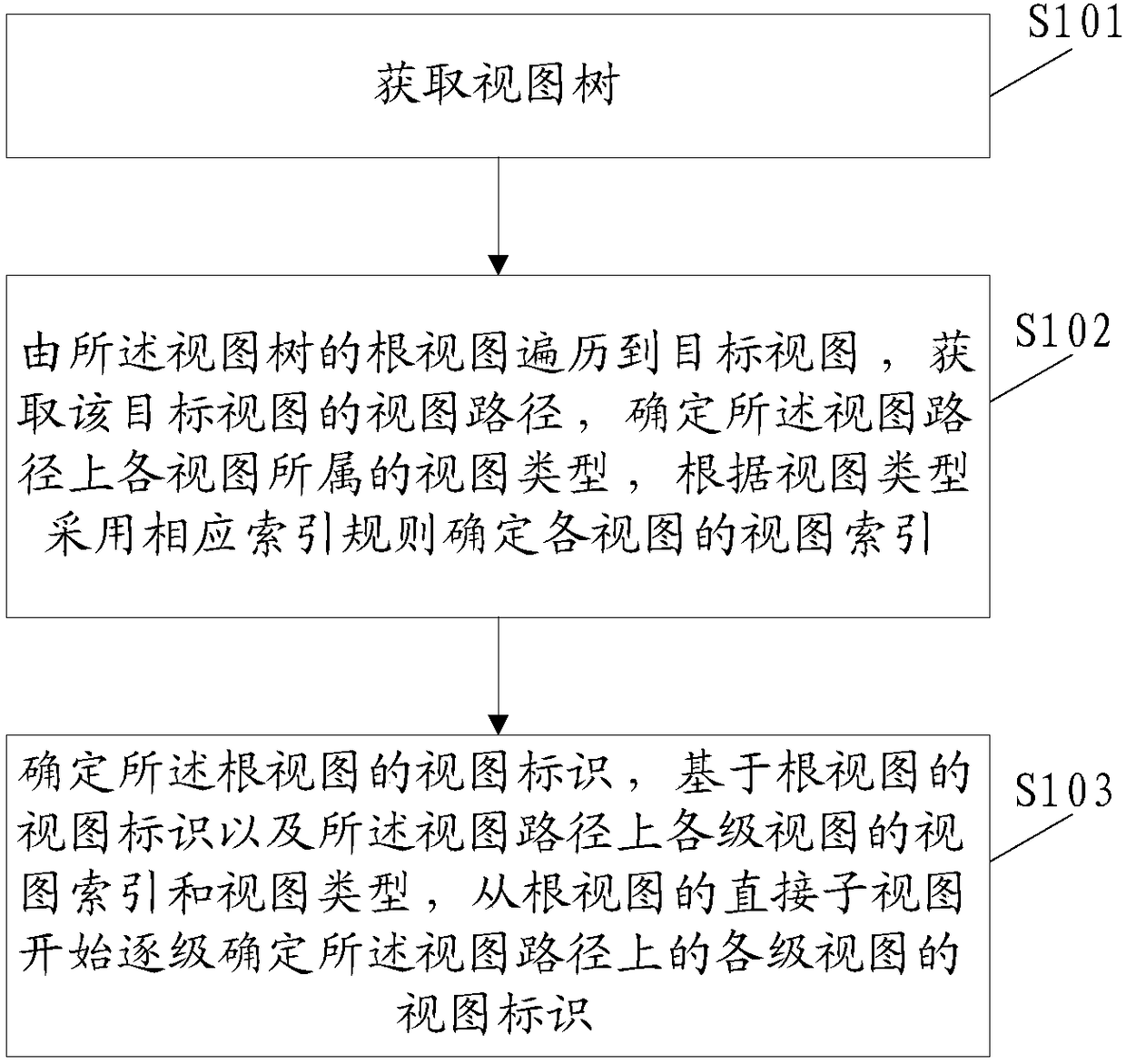
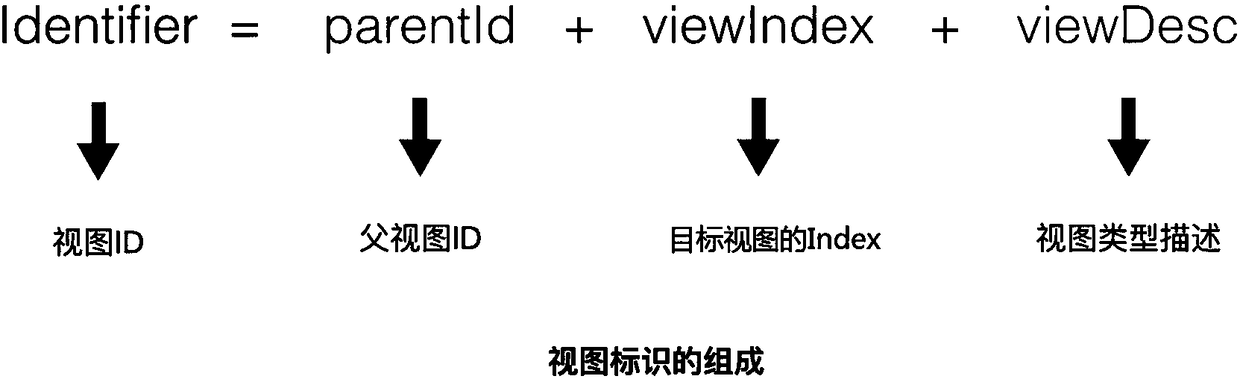
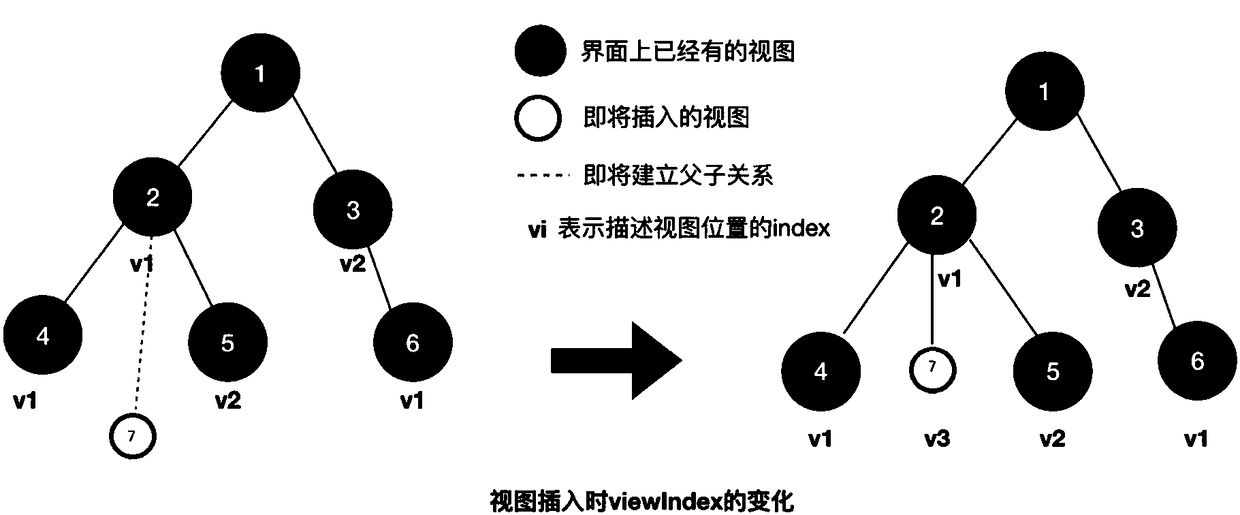
Identification method and device used for interface view
ActiveCN108345485ASolve the problem that the interface view cannot be uniquely identifiedExecution for user interfacesOperational systemComputer graphics (images)
The application discloses an identification method used for an interface view. The method includes: acquiring a view tree; carrying out traversal from a root view of the view tree to a target view, acquiring a view path of the target view, determining a view type to which each view on the view path belongs, and adopting corresponding index rules according to the view types to determine a view index of each view; and determining a view identifier of the root view, and starting from a direct sub-view of the root view to determine a view identifier of the view of each level on the view path levelby level on the basis of the view identifier of the root view and the view index and the view type of the view of each level on the view path. Therefore, the problem that interface views cannot be uniquely identified on different terminals based on the same mobile operating system is solved.
Owner:KOUBEI SHANGHAI INFORMATION TECH CO LTD
Method of starting applications installed on a mobile operating system in a multi-window mode and device using the same
ActiveUS20140365933A1Optimal operational efficiencyImprove convenienceProgram loading/initiatingExecution for user interfacesOperational systemMultiple applications
A method and a device of starting applications installed on a mobile operating system (OS) is performed by a mobile device for the mobile OS to flag any application installed on the mobile OS as a windowed application and display the application under a multi-window mode when the application is started. When multiple applications are simultaneously started, the mobile OS sequentially determines if each application is a windowed application. If positive, the application is displayed under the multi-window mode, and the size and location of the displayed window frame with the application running thereon are adjustable, rendering higher operational efficiency and convenience of software applications installed on a mobile OS.
Owner:INSYDE SOFTWARE
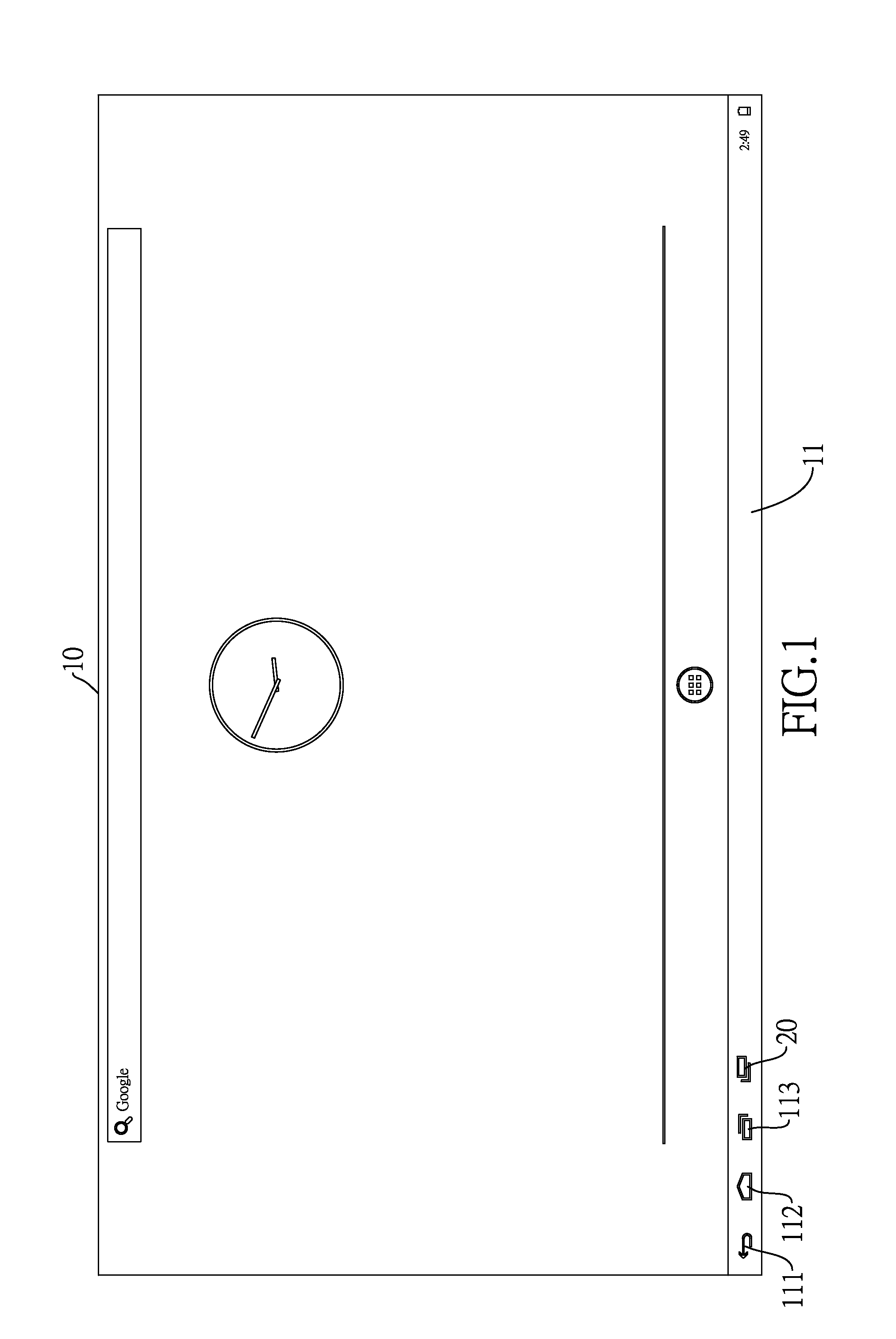
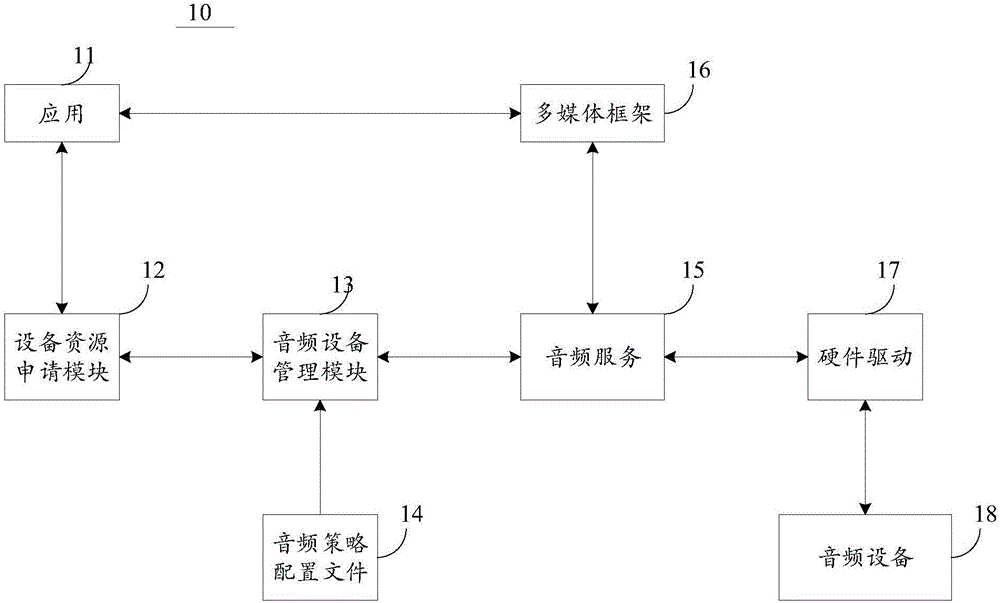
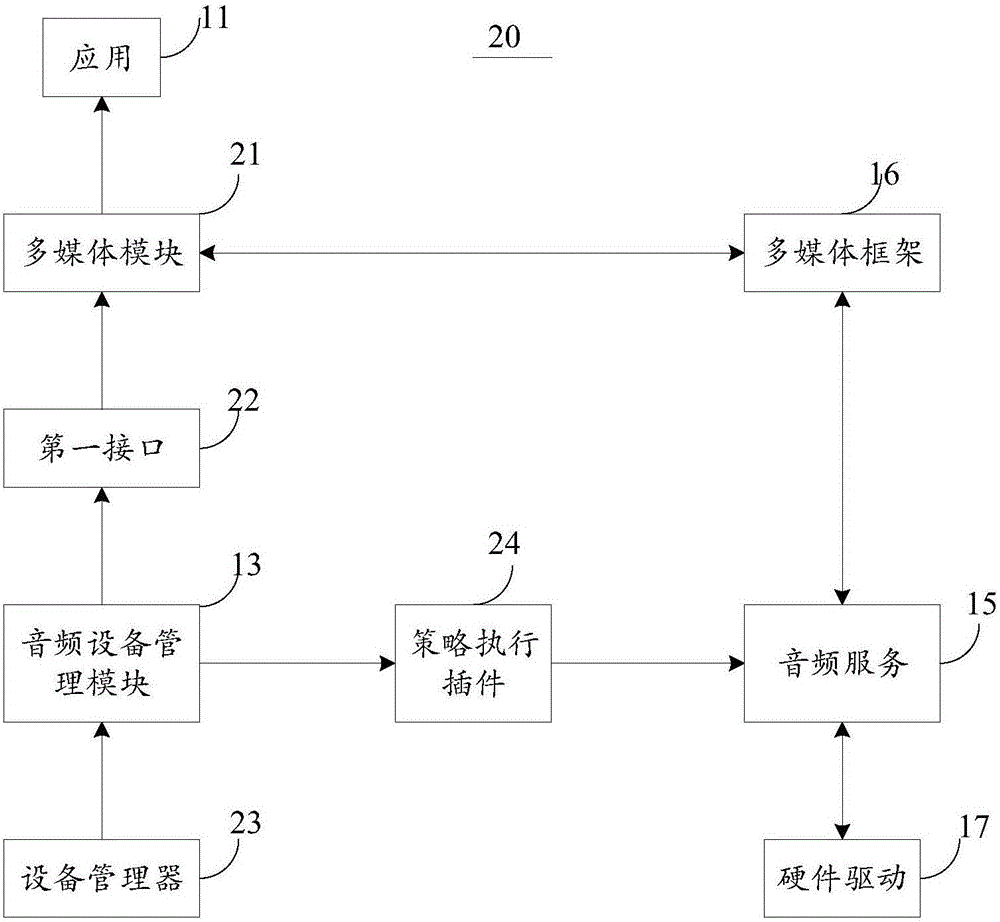
Audio device control method and system of terminal and mobile terminal
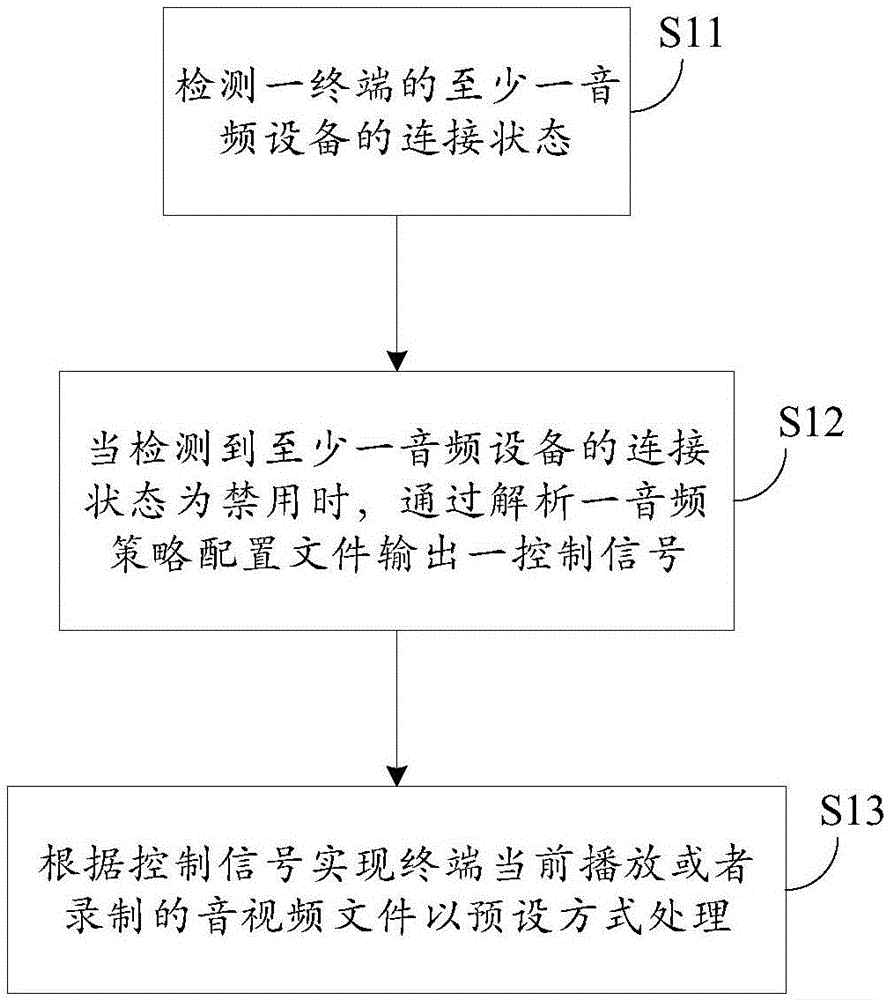
ActiveCN106445448APrevent leakageAvoid consumptionSound input/outputComputer hardwareMobile operating system
The invention discloses an audio device control method and system of a terminal and the mobile terminal, and relates to a mobile terminal technology. The audio device control method of the terminal comprises the steps of detecting a connection state of at least one audio device of the terminal; when it is detected that the connection state of the at least one audio device is forbidden, outputting a control signal by analyzing an audio policy configuration file; and processing an audio-video file currently played or recorded by the terminal according to the control signal in a preset way. According to the method, a customization demand of an application when the audio device is pulled out is met through an open hardware manager of a mobile operation system, and the application does not need to pay attention to the connection state and the type of the audio device.
Owner:PRANUS BEIJING TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com