Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
104 results about "Network Admission Control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Network Admission Control (NAC) refers to Cisco's version of Network Access Control, which restricts access to the network based on identity or security posture. When a network device (switch, router, wireless access point, DHCP server, etc.) is configured for NAC, it can force user or machine authentication prior to granting access to the network. In addition, guest access can be granted to a quarantine area for remediation of any problems that may have caused authentication failure. This is enforced through an inline custom network device, changes to an existing switch or router, or a restricted DHCP class. A typical (non-free) WiFi connection is a form of NAC. The user must present some sort of credentials (or a credit card) before being granted access to the network.
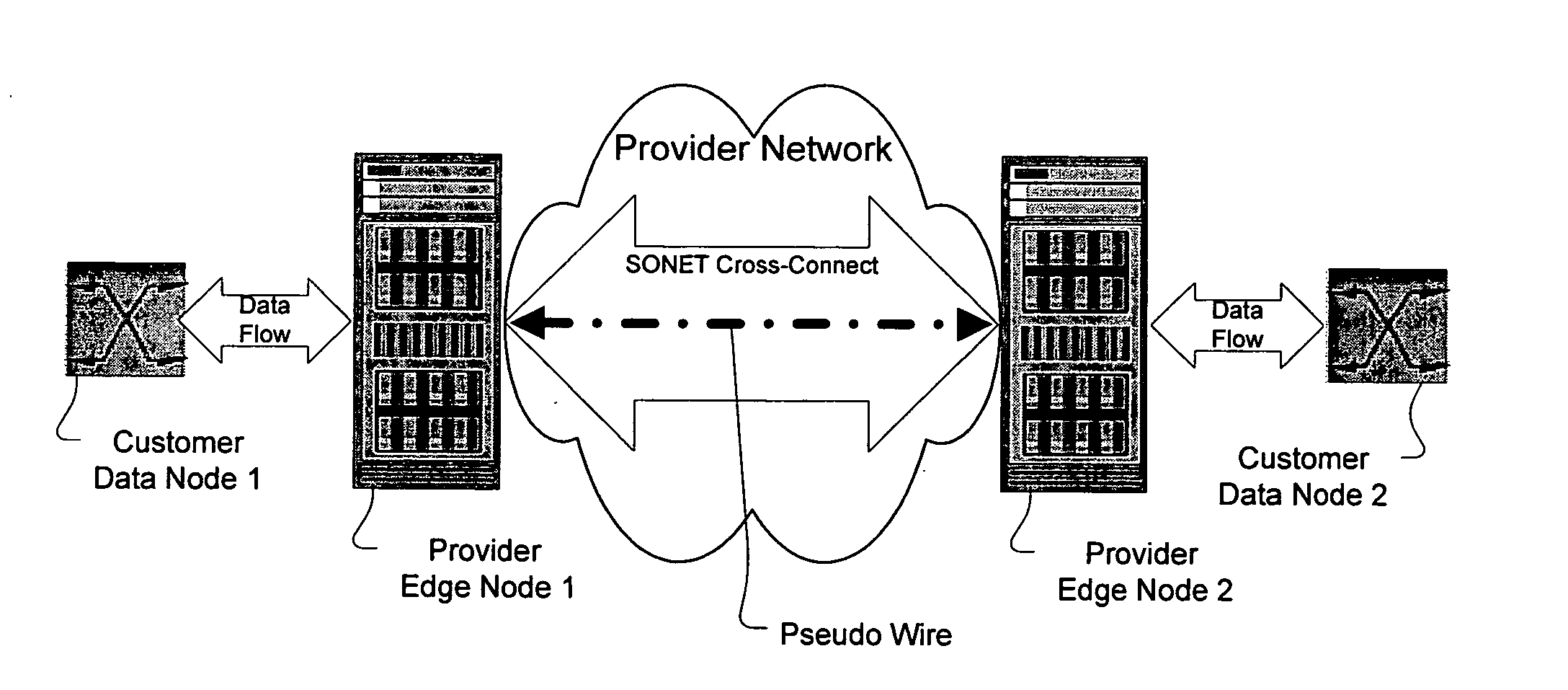
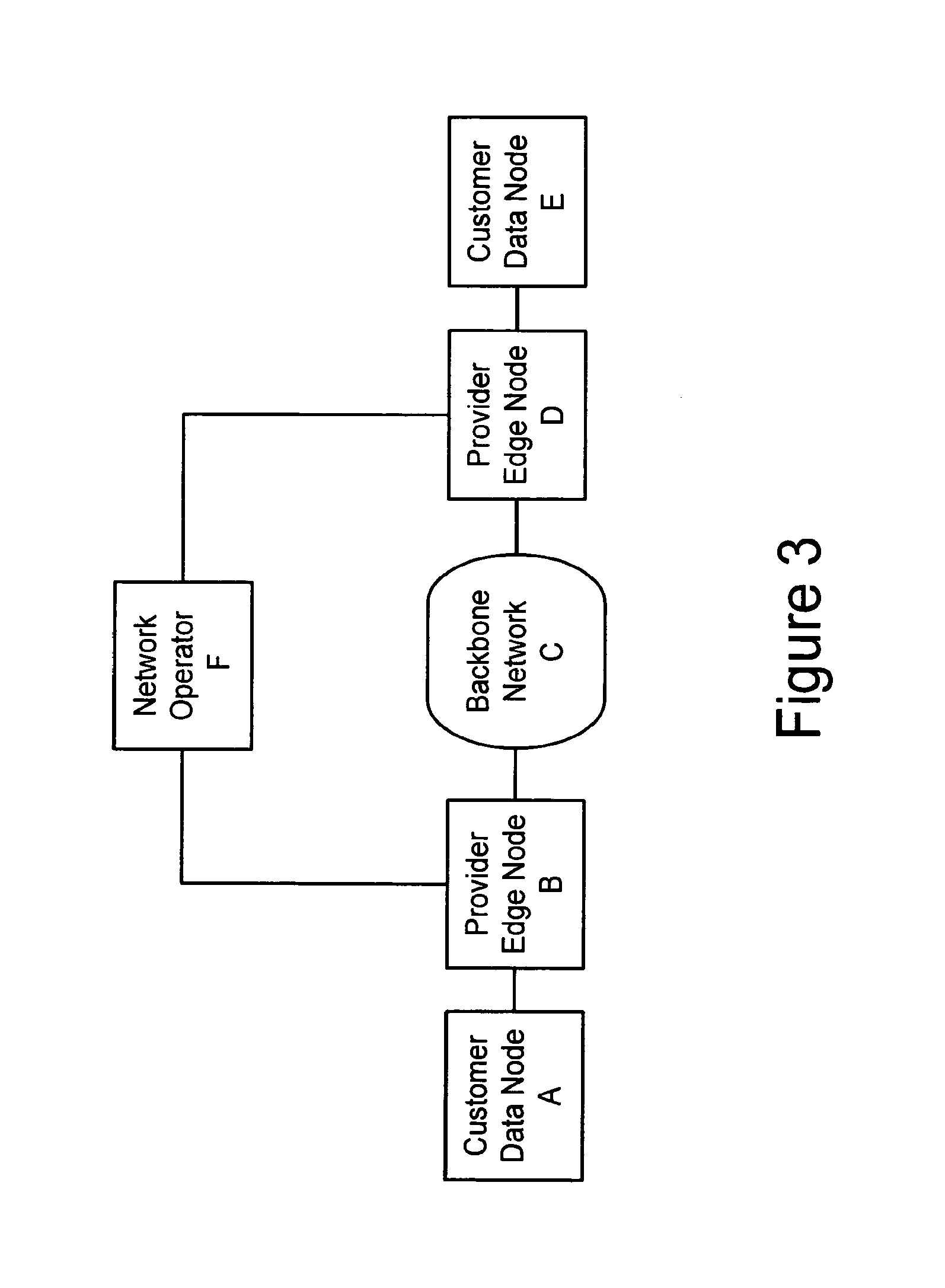
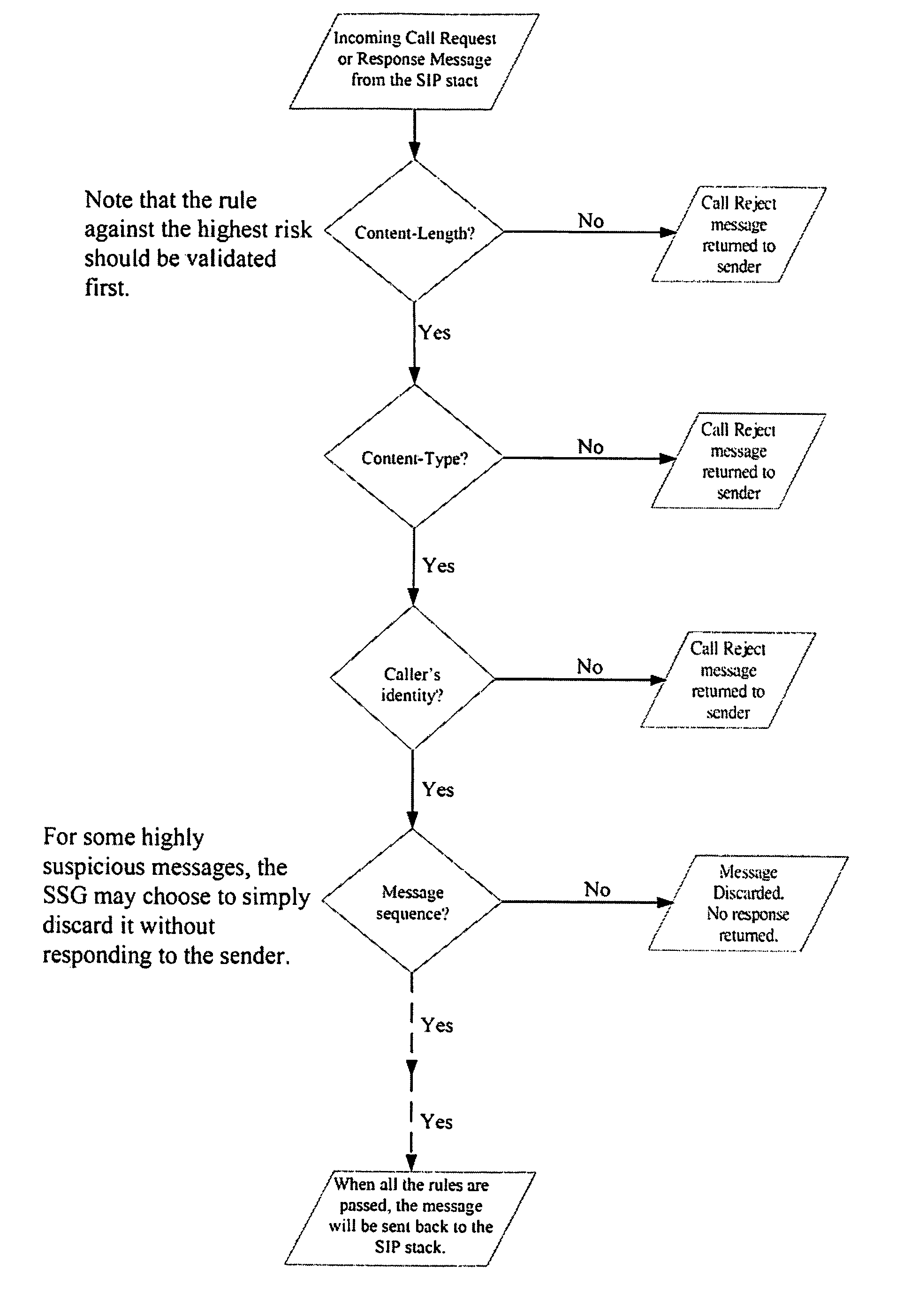
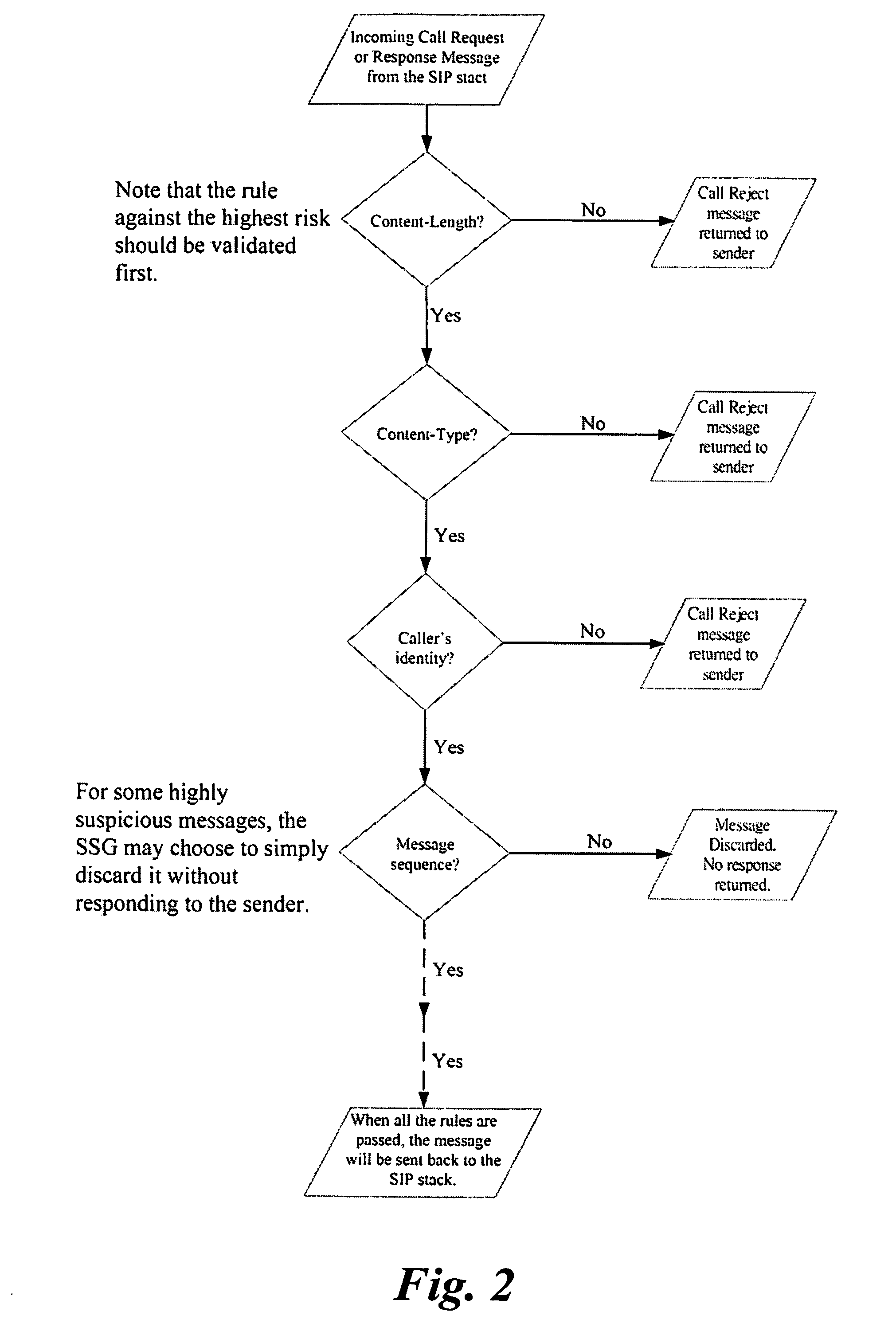
Method and apparatus for performing data flow ingress/egress admission control in a provider network
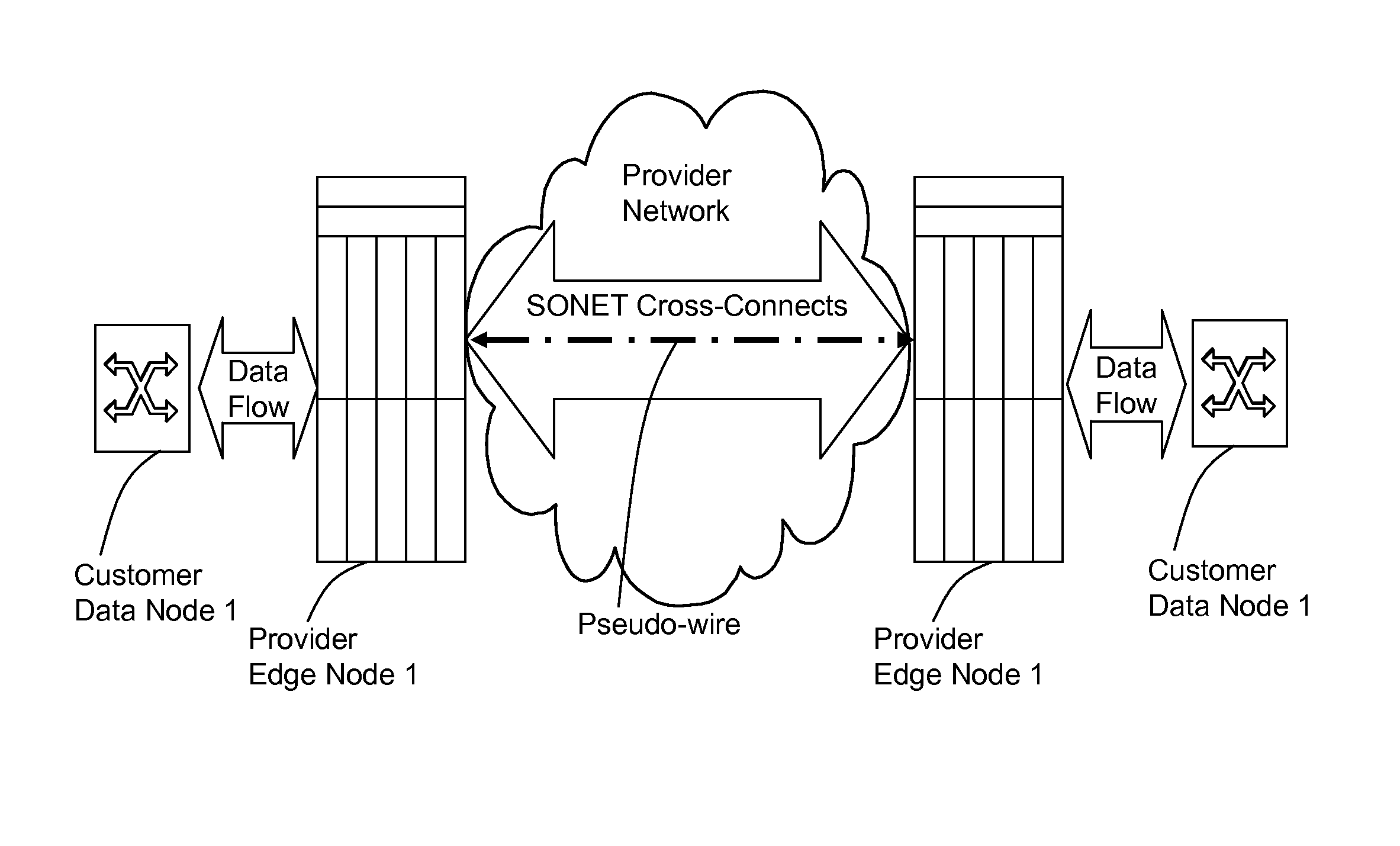
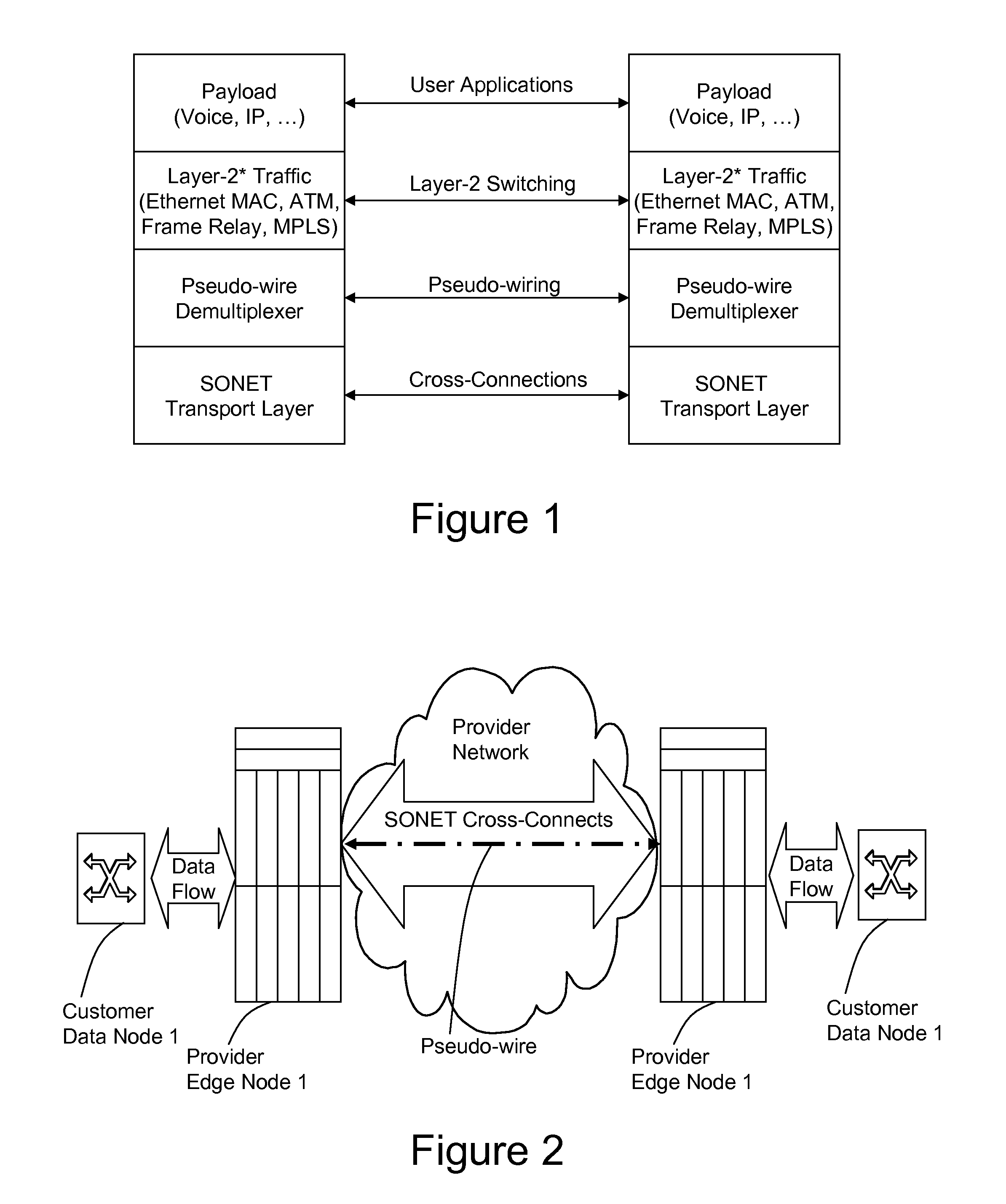
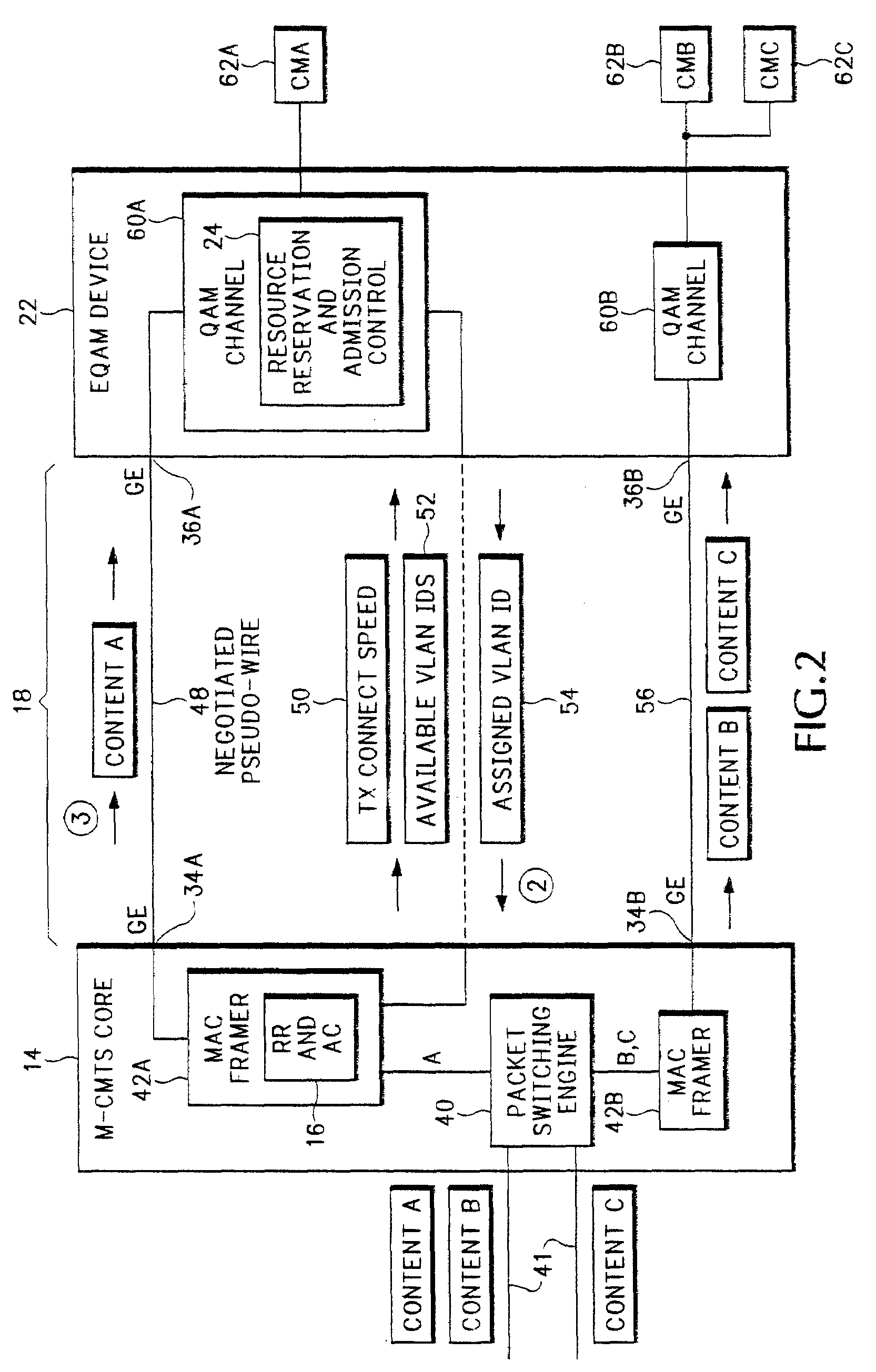
A method, apparatus and network for transporting layer-2 frames, such as Ethernet MAC, ATM AAL5, and Frame Relay, over MPLS, SONET / SDH, or OTN optical transport networks as well as electrical transport networks is disclosed. The method establishes "pseudo-wires" between, for example, routers, Layer-2 packet switches, or SONET / SDH switches. Inter-related ingress and egress resource tables may be used by provider edge nodes to negotiate consistently managed data tunnels across a provider network on behalf of data flowing from / to a diverse base of customer edge nodes. Detailed network resource information particular to each of the data flows is exchanged between provider edge nodes during the creation of pseudo-wires. Admission control algorithms are applied at the ingress and egress points in order to manage the data flows into a provider network and exiting from a provider network to customer equipment. By applying pseudo-wire shuffling and preemption techniques, the providers can make better use of their network resources by admitting more pseudo-wires.
Owner:CIENA
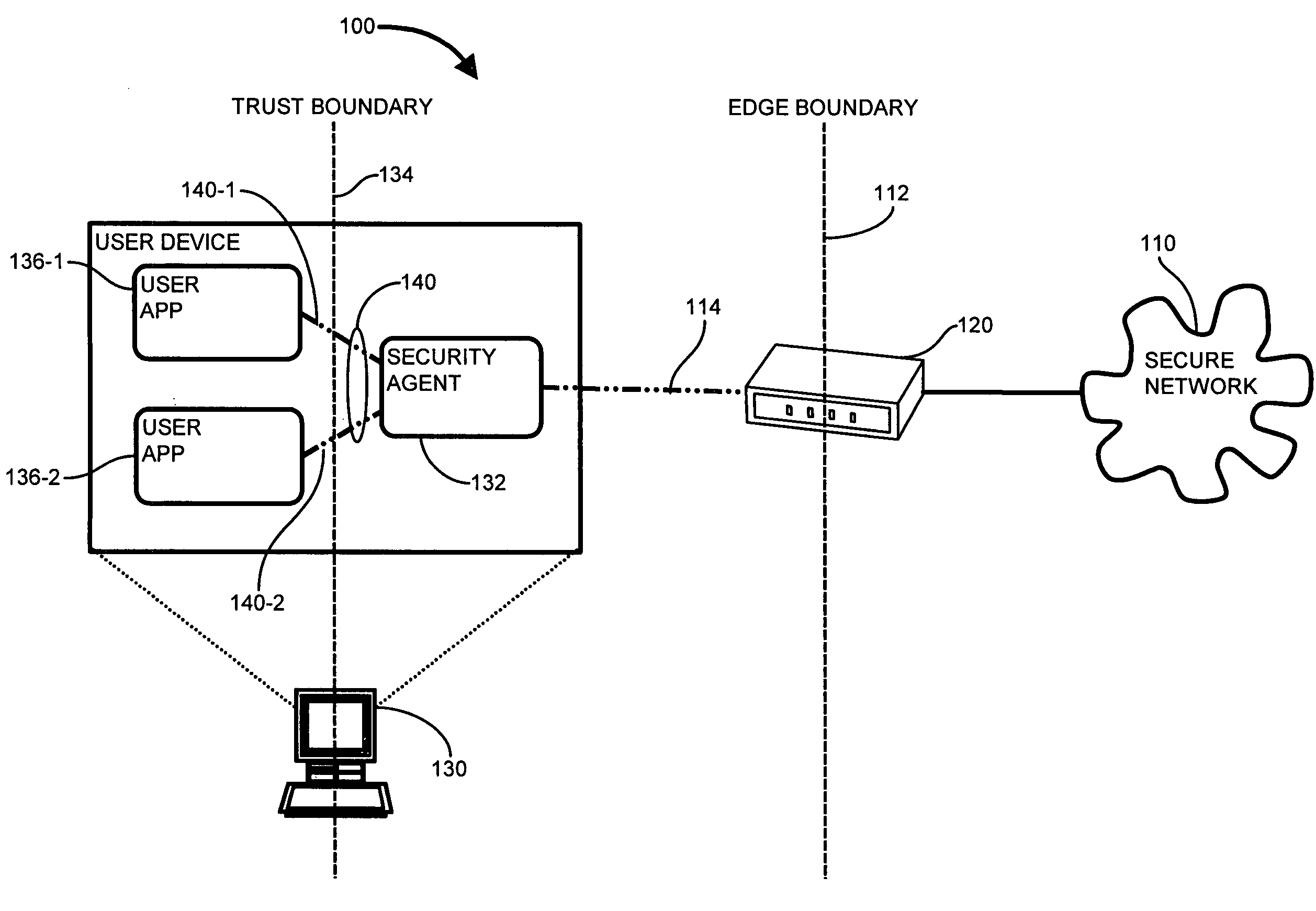
Methods and apparatus for trusted application centric QoS provisioning
ActiveUS7774498B1Increase pointsOvercomes shortcomingMultiple digital computer combinationsProgram controlTraffic capacityUser device
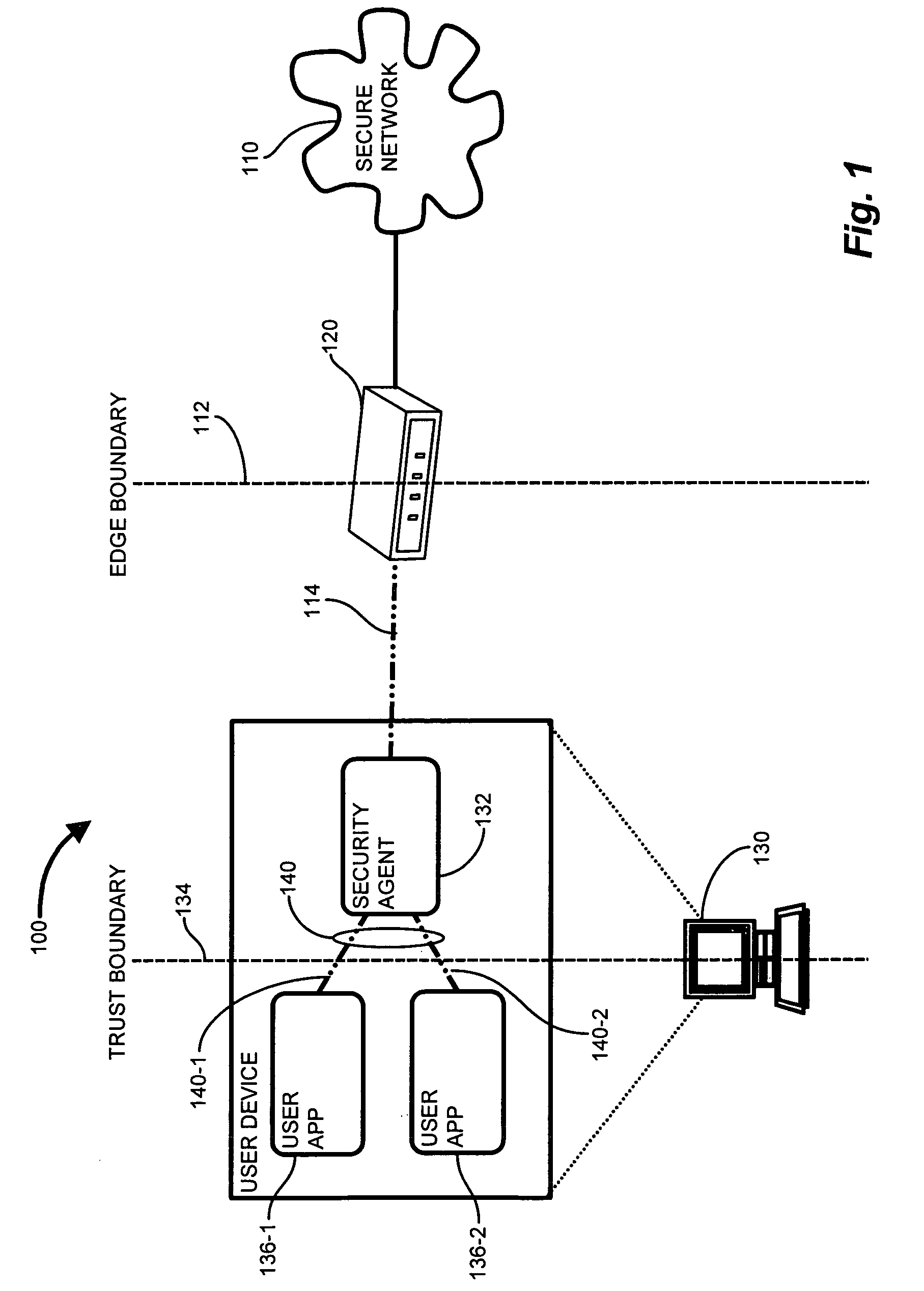
A security agent extends the trust barrier, or trust point, from network gateway nodes to end user devices. A security agent operable to scrutinize network traffic executes on the user device and compares QoS marking attempts with the established QoS marking policy in effect. The security agent examines network traffic attributes deterministic of connection attempts by user processes. Attempts to apply inappropriate or disallowed QoS markings, as dictated by the QoS marking policy, are detected and disallowed. Therefore, only user connections consistent with the QoS marking policy are permitted into the network. Network admission control (NAC) mechanisms ensure that the security agent is the only access point from the user device to the secure network, and the security agent communicates the establishment of the trusted access point to the network gateway, thus ensuring that the network gateway may trust service level designations emanating from the user device executing the security agent.
Owner:CISCO TECH INC
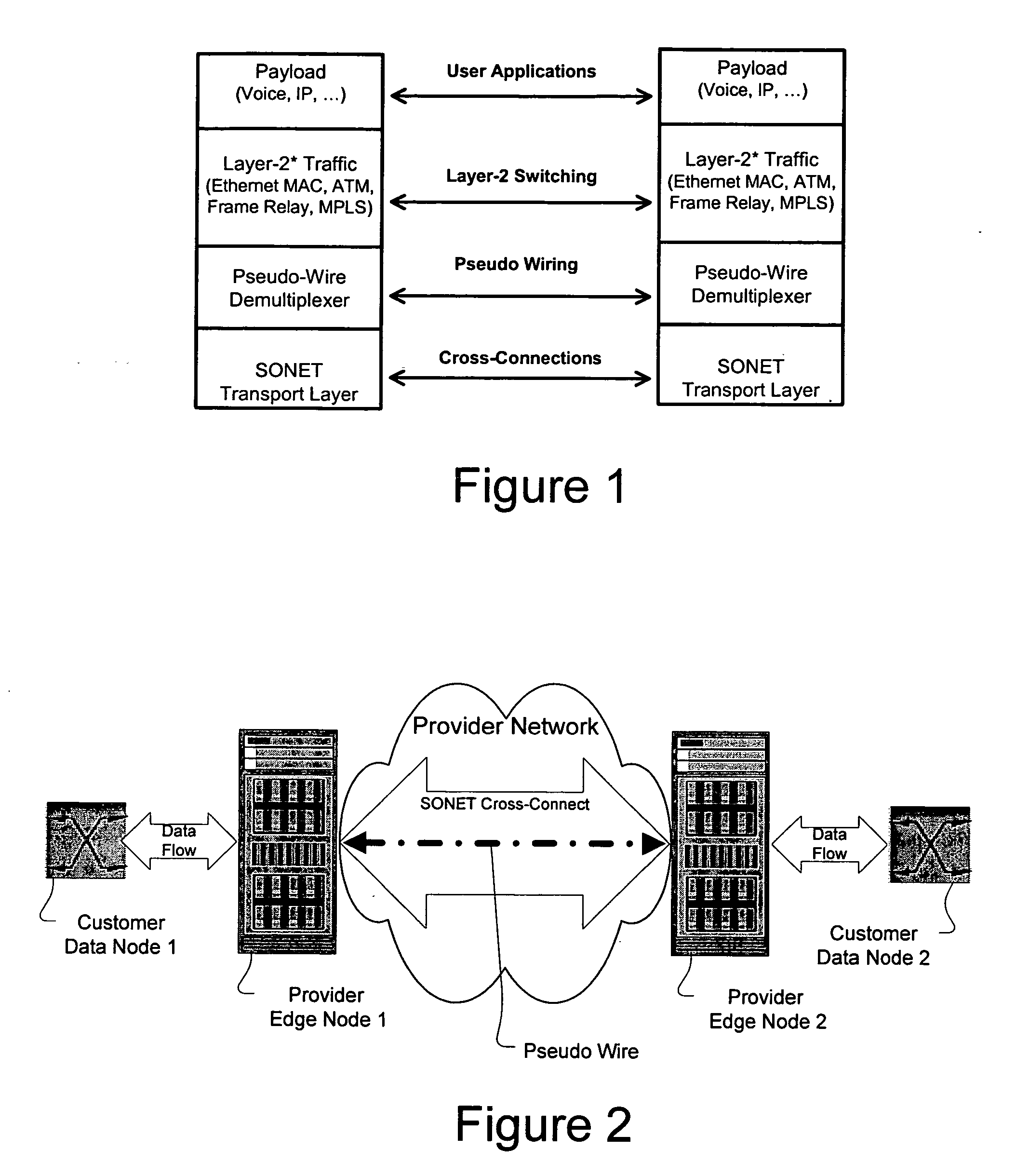
Method and apparatus for performing data flow ingress/egress admission control in a provider network
A method, apparatus and network for transporting layer-2 frames, such as Ethernet MAC, ATM AAL5, and Frame Relay, over MPLS, SONET / SDH, or OTN optical transport networks as well as electrical transport networks is disclosed. The method establishes “pseudo-wires” between, for example, routers, Layer-2 packet switches, or SONET / SDH switches. Inter-related ingress and egress resource tables may be used by provider edge nodes to negotiate consistently managed data tunnels across a provider network on behalf of data flowing from / to a diverse base of customer edge nodes. Detailed network resource information particular to each of the data flows is exchanged between provider edge nodes during the creation of pseudo-wires. Admission control algorithms are applied at the ingress and egress points in order to manage the data flows into a provider network and exiting from a provider network to customer equipment. By applying pseudo-wire shuffling and preemption techniques, the providers can make better use of their network resources by admitting more pseudo-wires.
Owner:CIENA
Method and system for admission control in communication networks, related network and computer program product therefor
ActiveUS20050220019A1Reduce complexityEliminate the effects ofError preventionTransmission systemsNetwork Admission ControlLocal area network
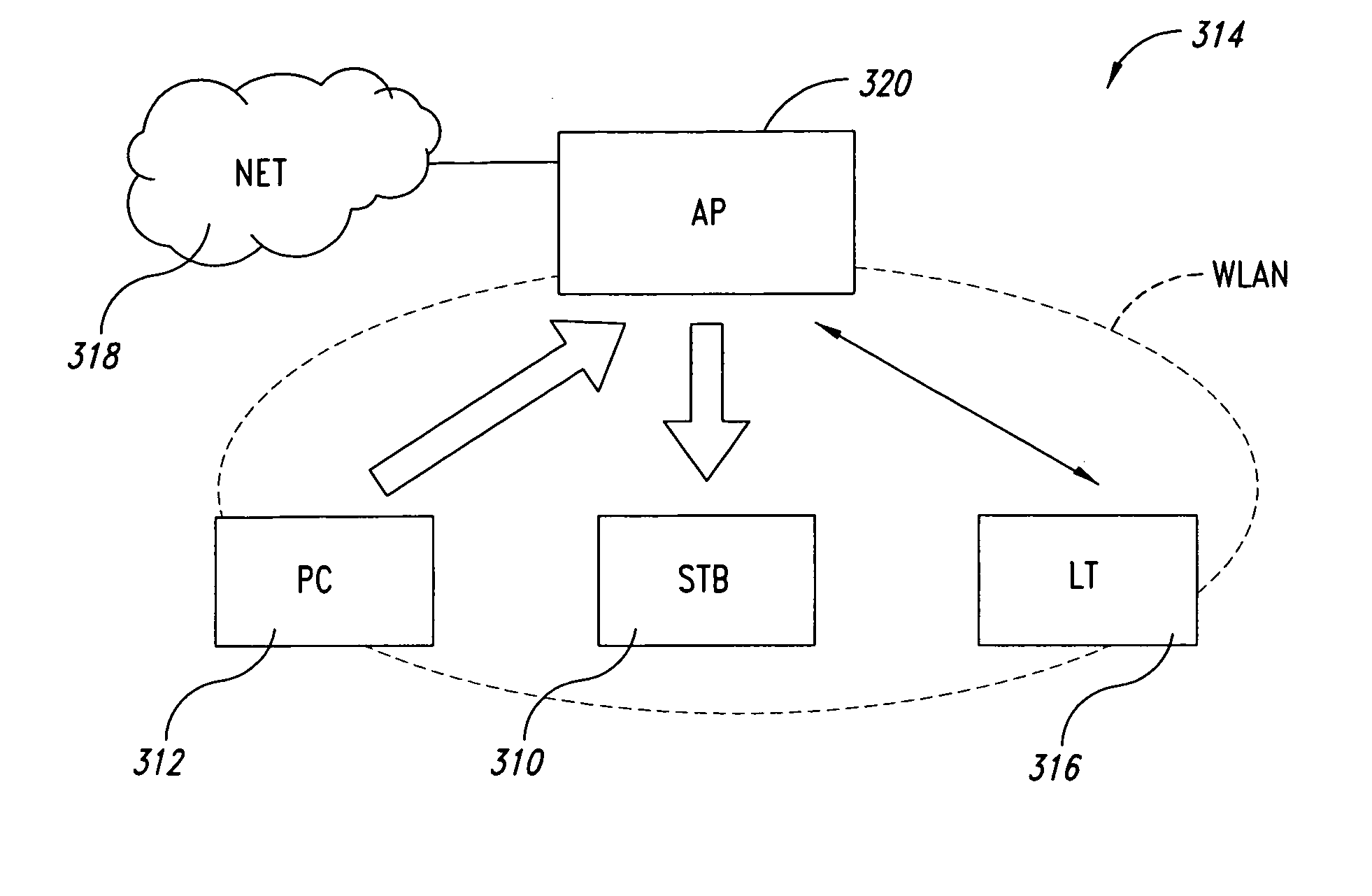
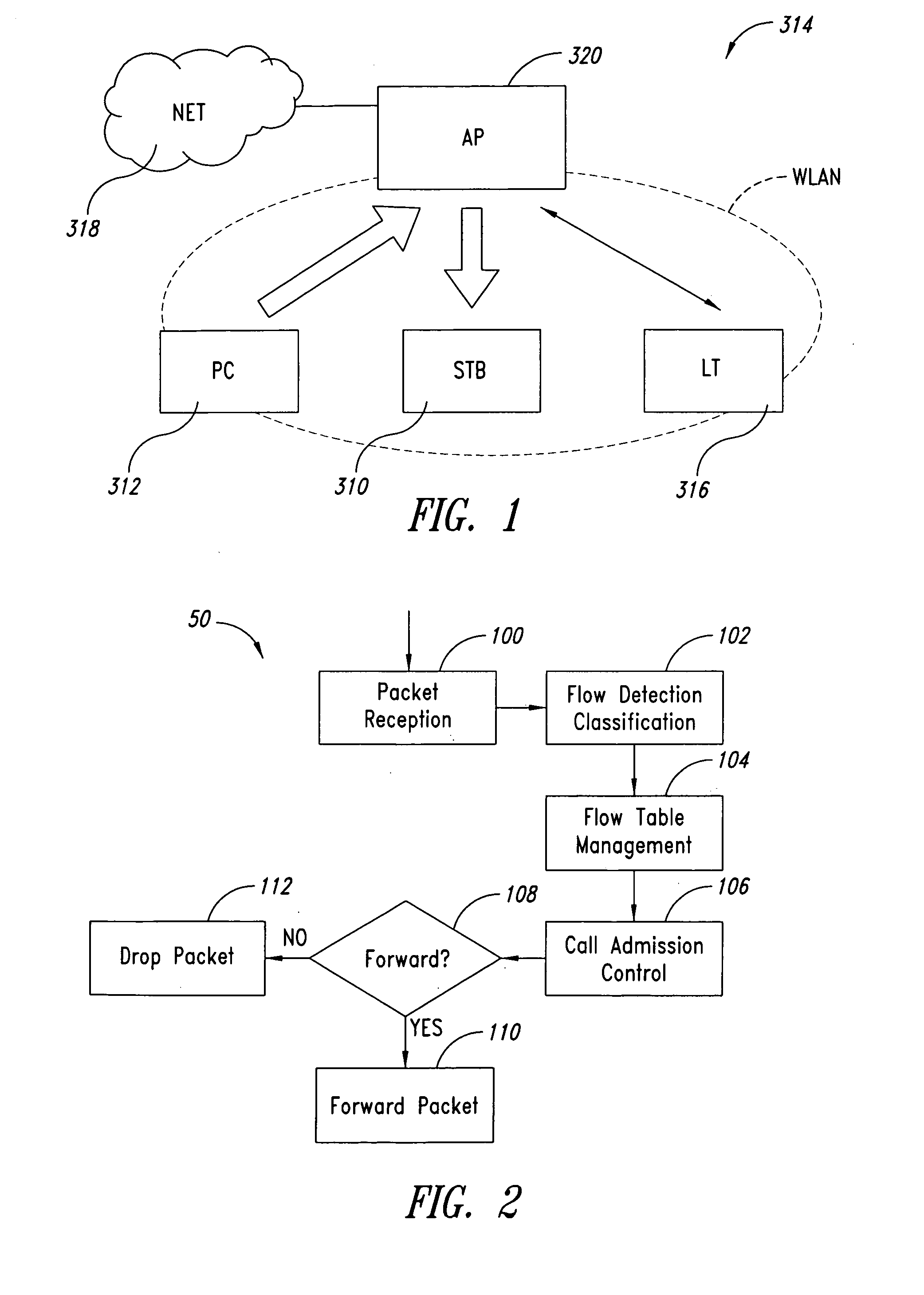
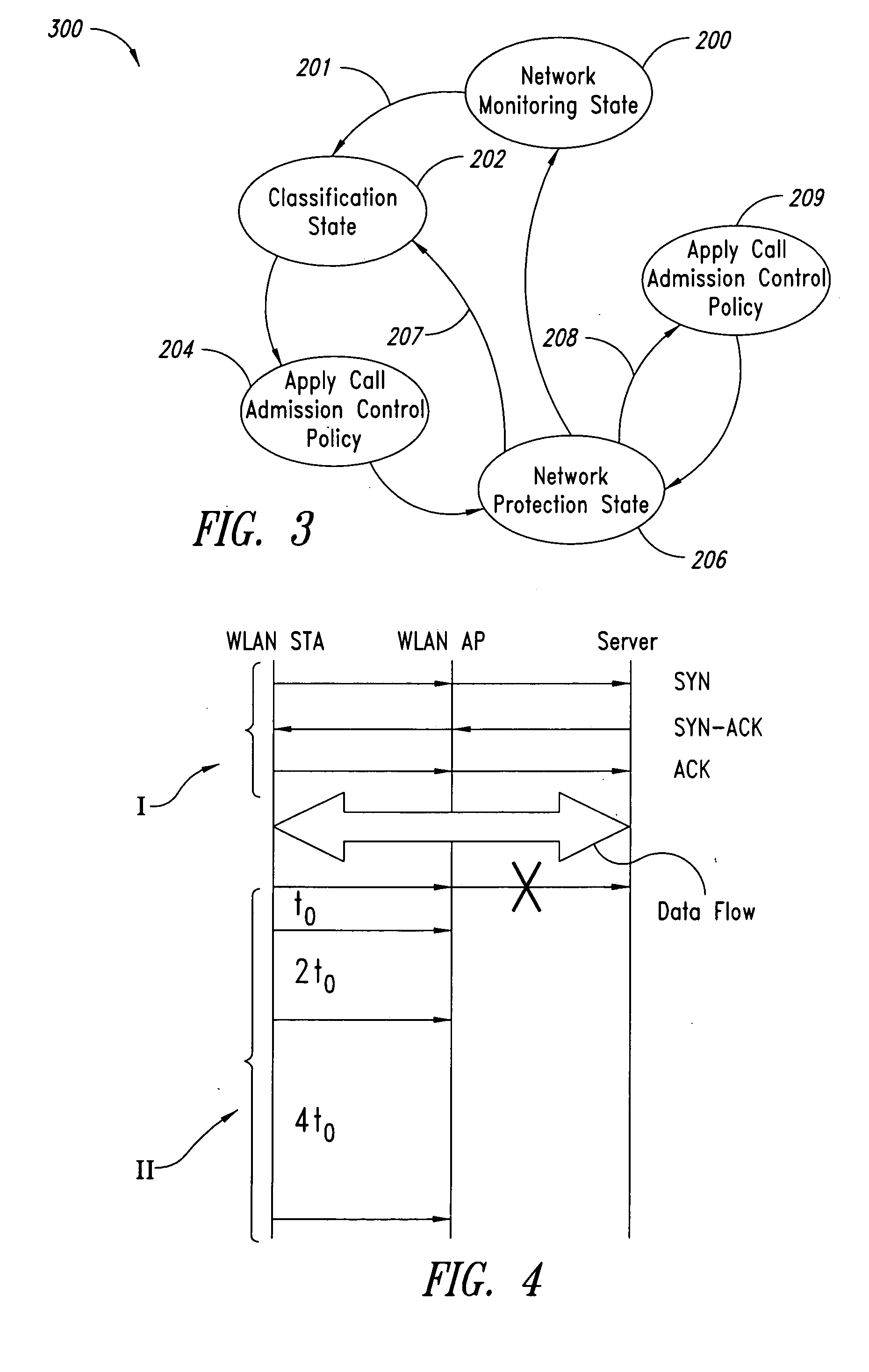
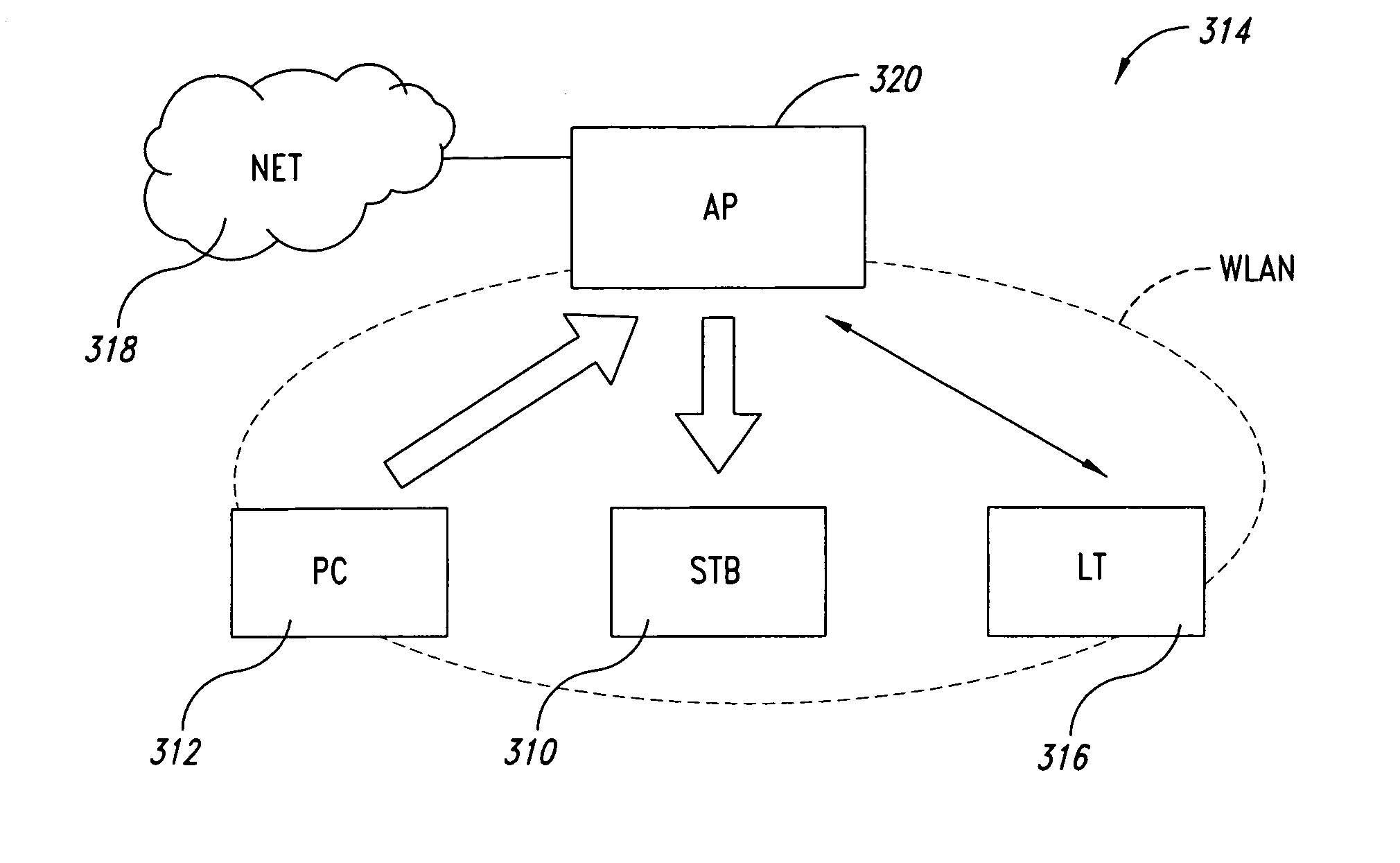
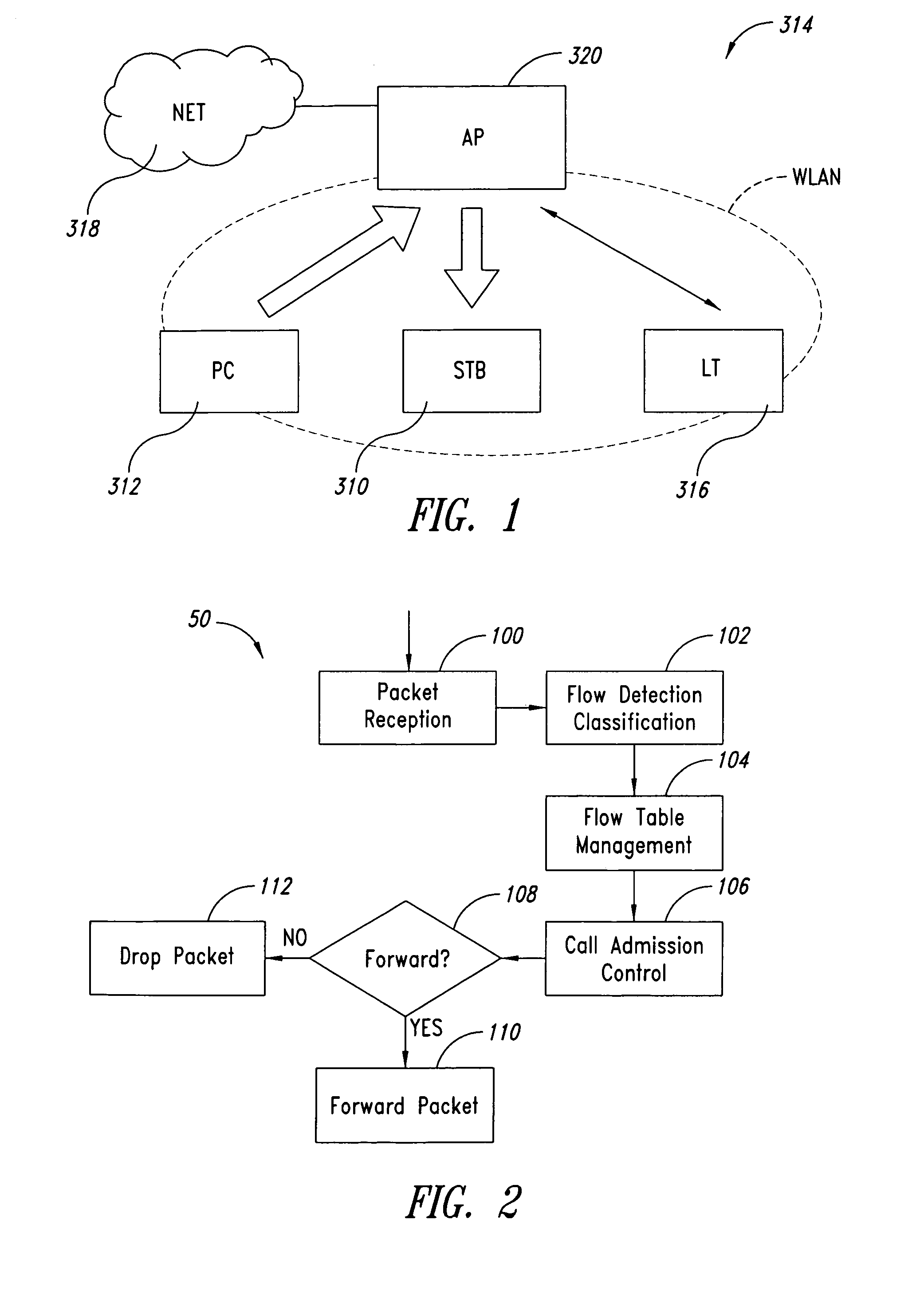
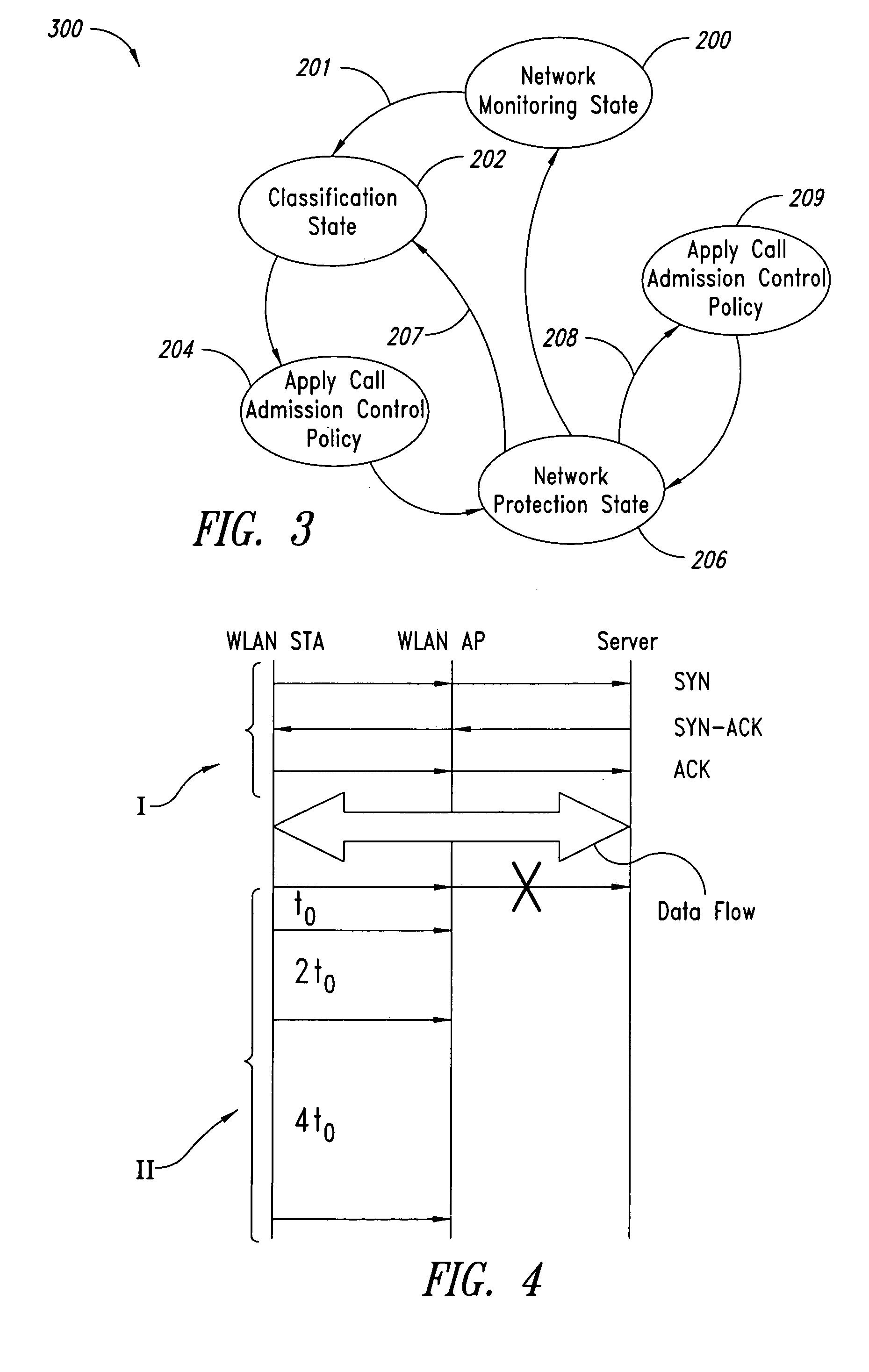
A system for admission control in a wireless local area network adapted to serve a set of stations and manage real time transmission as well as and TCP / IP sessions includes an access point (AP) configured for: when either a new station joins the network or a new TCP / IP session is being initiated, checking if sufficient bandwidth is available in the network for the new traffic flow associated with the new station or TCP / IP session without interfering with any ongoing real time transmission in the network, and in case no sufficient bandwidth is found to be available, whereby said new traffic flow could interfere with said ongoing real time transmission, blocking such new traffic flow.
Owner:STMICROELECTRONICS SRL
Method and system for admission control in communication networks, related network and computer program product therefor
ActiveUS7471629B2Eliminate the effects ofReduce complexityError preventionFrequency-division multiplex detailsTraffic flowCall Admission Control
Owner:STMICROELECTRONICS SRL
Multiple security layers for time-based network admission control
InactiveUS20100043066A1Reduce energy consumptionOptimize networkDigital data processing detailsUser identity/authority verificationComputer methodsNetwork Access Control
Embodiments of the present invention include a computer method of controlling access to a computer-based network comprising: (i) receiving an indication of an attempt to gain access to a computer-based network; (ii) applying a respective network access control policy to determine whether to allow the attempt to gain access to the computer-based network at each of multiple security layers; and (iii) allowing or blocking the attempt to gain access through the security layer to the computer-based network based on the application of the respective network access control policy at each security layer. Other embodiments include a computer method of controlling access to a computer-based network comprising: (a) scanning a host computer for viruses; (b) temporarily disabling a firewall of the host computer during an audit; and (c) shutting down high risk services running on the host computer.
Owner:NETCLARITY
Call admission control for Wi-Fi
ActiveUS20080146240A1Facilitate seamless mobilityNetwork traffic/resource managementData switching by path configurationWi-FiTelecommunications
Call admission control within a wireless network is implemented using a service controller that manages a set of access points. The call admission control (CAC) function for a given access point determines whether the access point has sufficient unused bandwidth to handle an additional call. The service controller makes this determination by monitoring the access points and evaluating certain probability functions and load conditions. In one embodiment, a determination of whether the access point has sufficient unused bandwidth to handle an additional call is a function of two (2) independent probabilities: (i) a probability of an active session moving to the access point from one or more neighbor access points, and (ii) a probability of an idle mobile device already associated with the access point entering into a new active session by initiating an inbound or outbound call. According to another aspect, the service controller issues and manages “call admission credits” among the set of access points, where a call admission credit value indicates a number of calls that idle mobile devices associated with the access point may initiate from the AP. The call admission credits value is a function of a determined load on the AP, and a mobility probability, which is a probability of an active call moving to the access point from one or more neighbor access points. The call admission credit value for the access point is adjusted as a function of a change of the load or in the mobility probability.
Owner:VALTRUS INNOVATIONS LTD +1
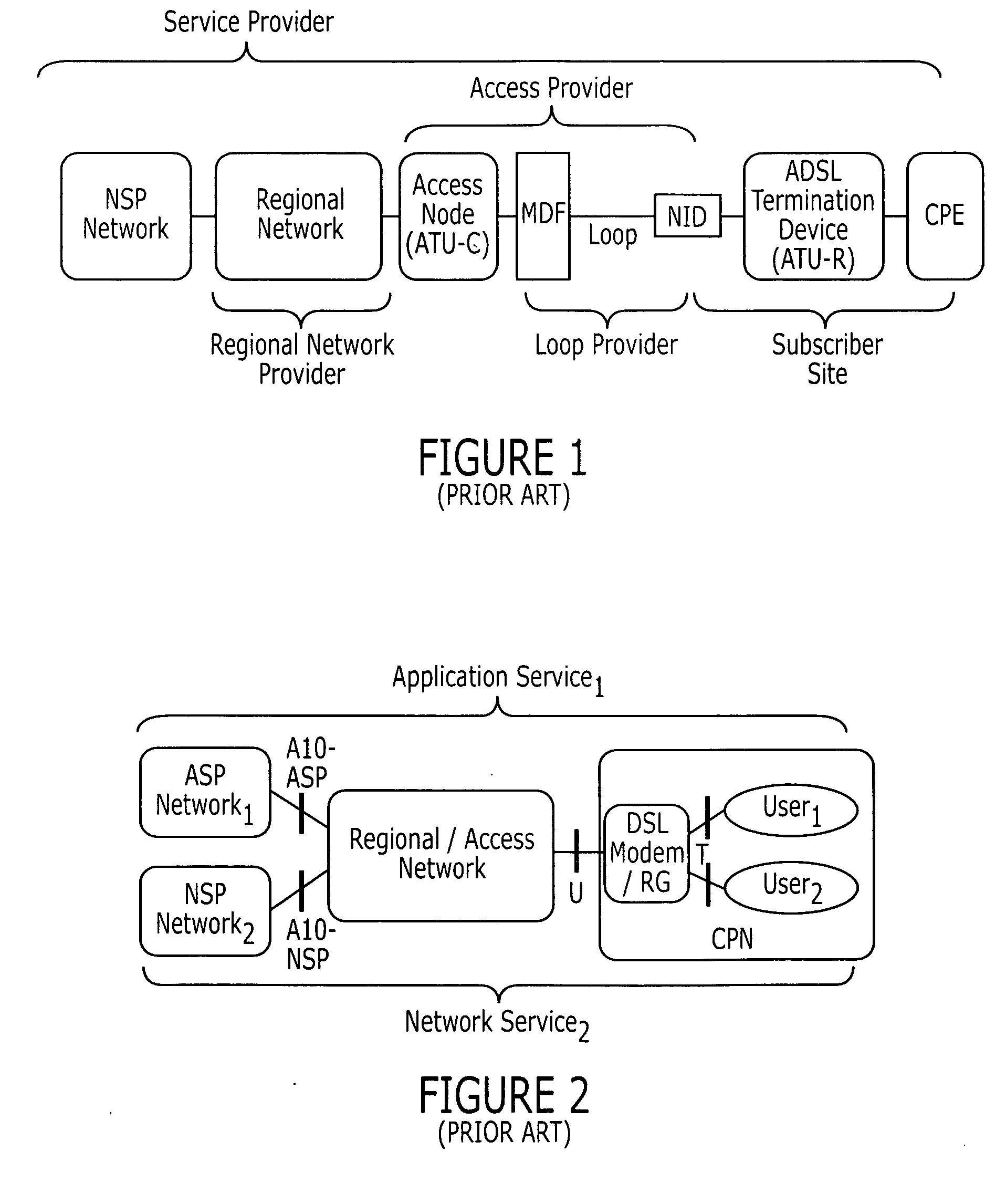
Methods, systems, and computer program products for managing admission control in a regional/access network based on user preferences
ActiveUS20060028980A1Facilitates differentiated end-to-end data transportError preventionFrequency-division multiplex detailsTraffic capacityAccess network
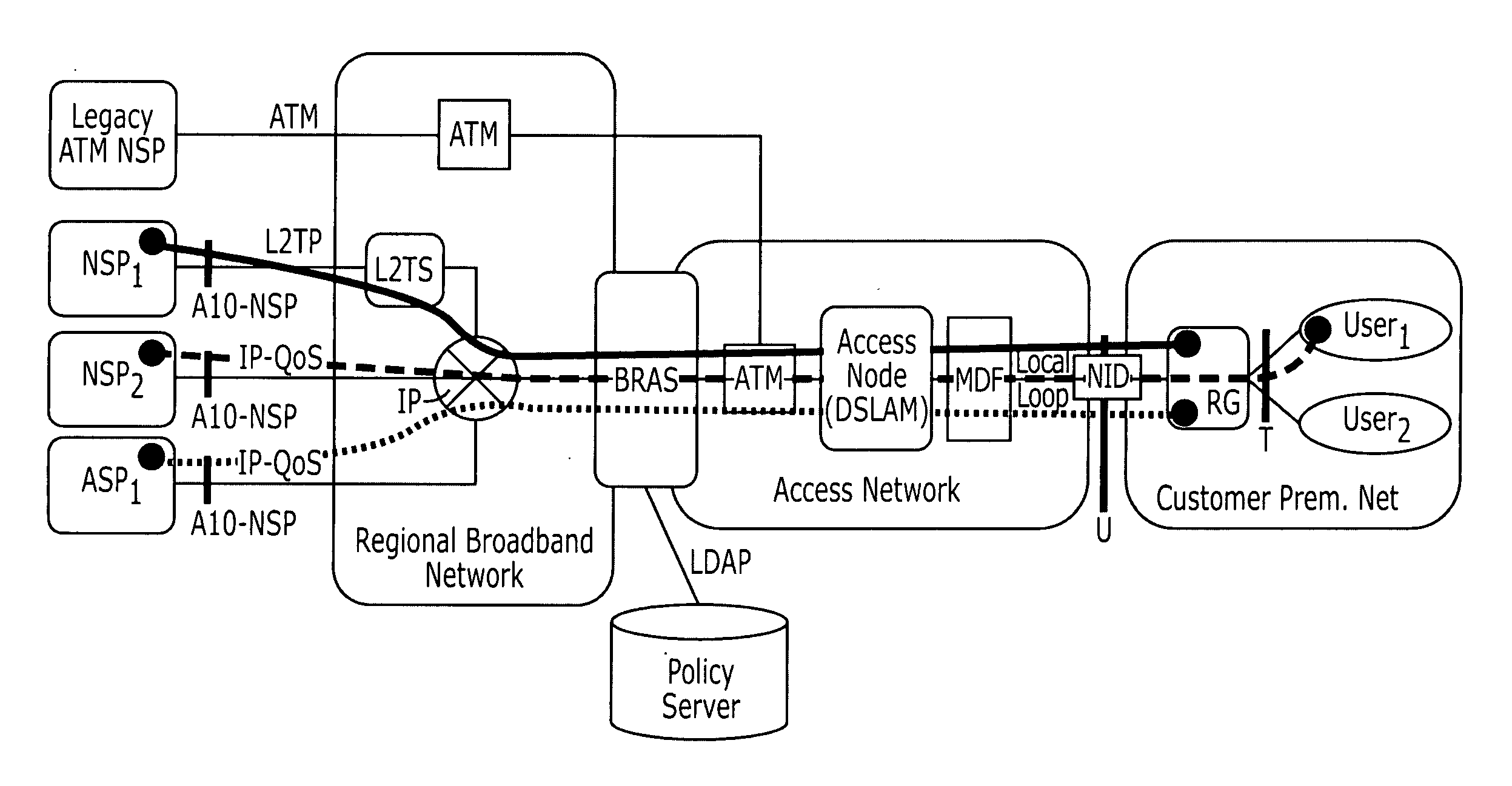
Traffic is admitted to a network that facilitates differentiated end-to-end data transport between a Network Service Provider (NSP) and / or an Application Service Provider (ASP) and a customer Premises Network (CPN) that includes Customer Premises Equipment (CPE) by obtaining from a user of the network policy information associated with services accessed through the network. Communication is established between a node in the network and the NSP and / or the ASP and between the node in the network and the CPN using a resource reservation protocol (RSVP) to request resources for a flow having one of the services associated therewith between the NSP and / or the ASP and the CPN. A determination is made at the node in the network whether to grant or deny access to the RAN to the flow based on the policy associated with the one of the services.
Owner:BELLSOUTH INTPROP COR
Method and apparatus for network-based admission control using path-coupled quality of service signaling
ActiveUS20070008882A1Improved admission controlImproved of medium path routingError preventionTransmission systemsAccess networkNetwork control
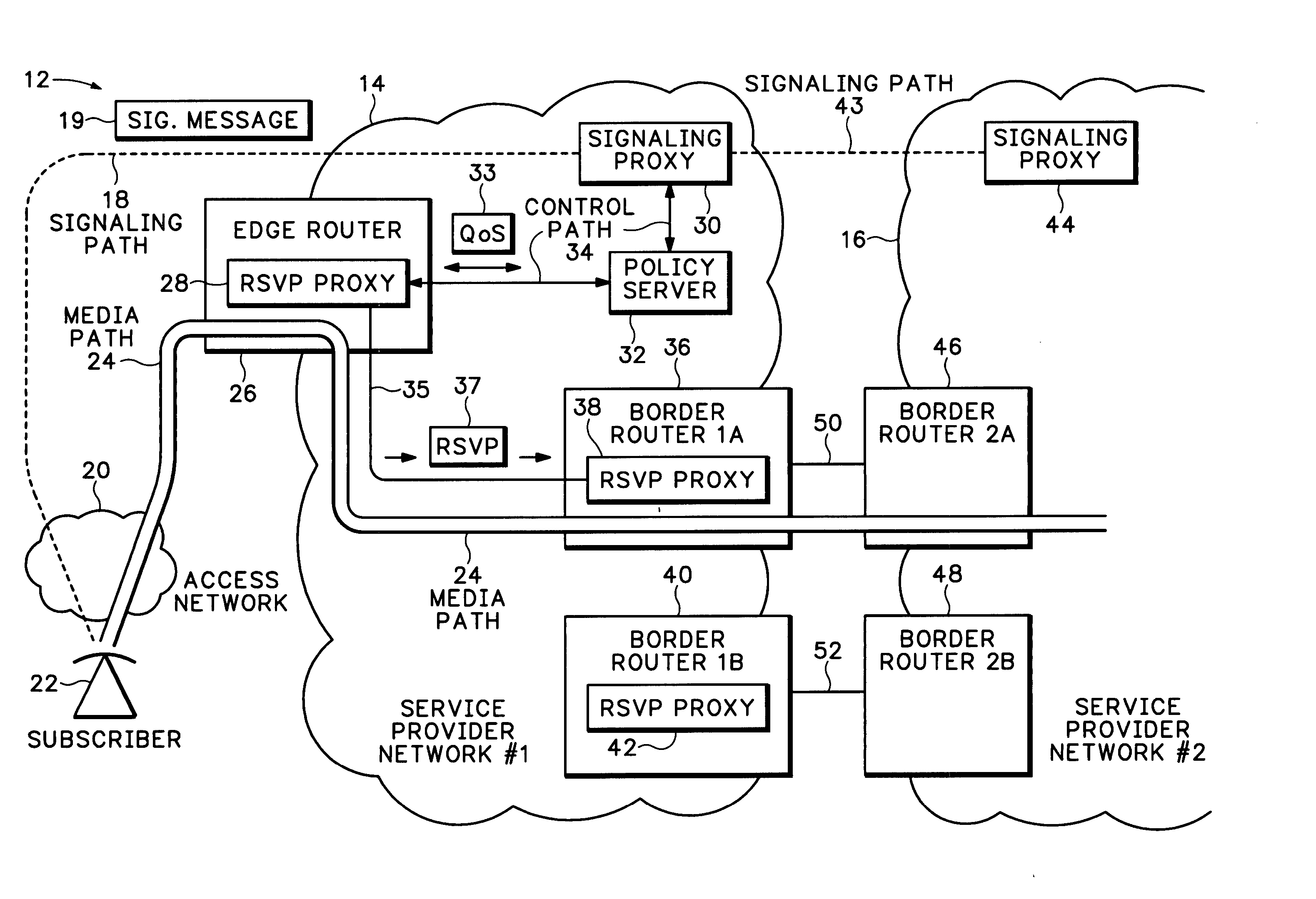
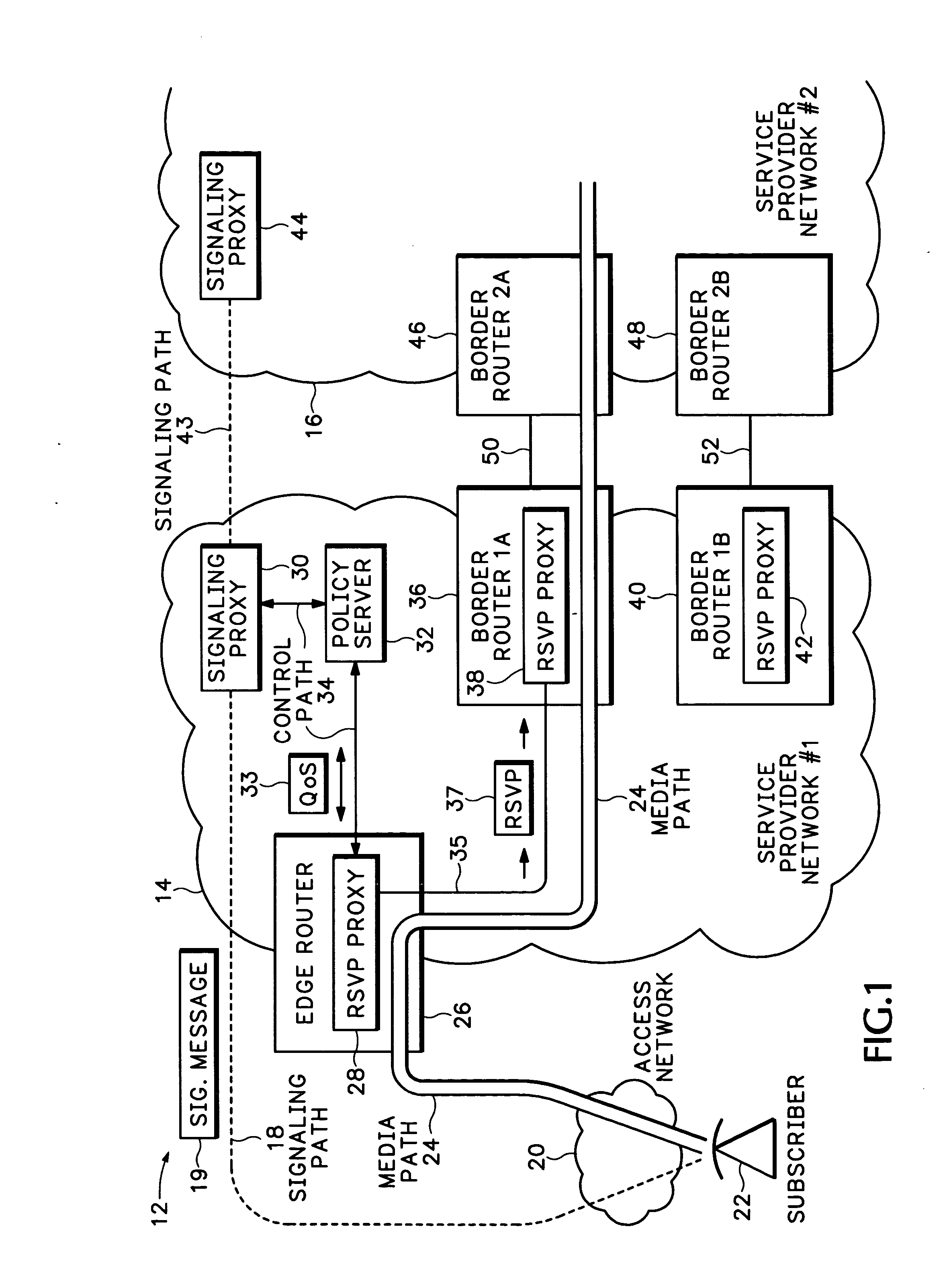
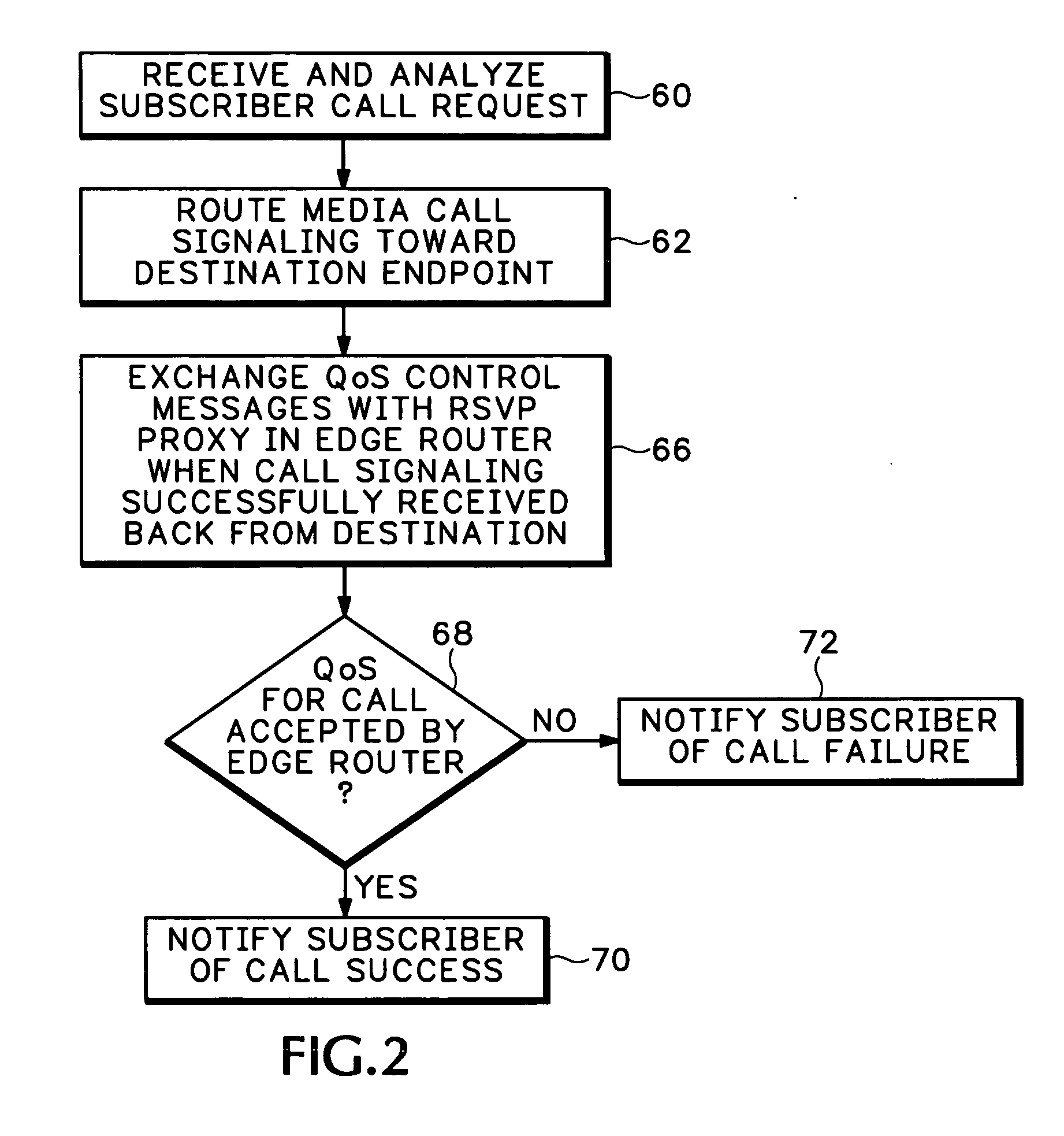
A Resource ReSerVation Protocol (RSVP) proxy is used in combination with a signaling proxy to provide improved admission control, Quality of Service (QoS) reservation, and media path routing. This avoids entangling call signaling with media plane functions as required with Session Border Controllers (SBCs). A QoS access network control scheme, such as Packet Cable Multi-Media (PCMM) and / or Dynamic Quality of Service (DQoS), is conventionally used to set up QoS and other flow states on an access network. However, the gate parameters established during this access operation are also provided to an RSVP proxy in an edge router. The gate parameters trigger the RSVP proxy to attempt to establish a QoS reservation over the packet network toward a media flow destination. If admission control for the QoS reservation is successful, the edge router permits the signaling proxy to complete the media call.
Owner:CISCO TECH INC
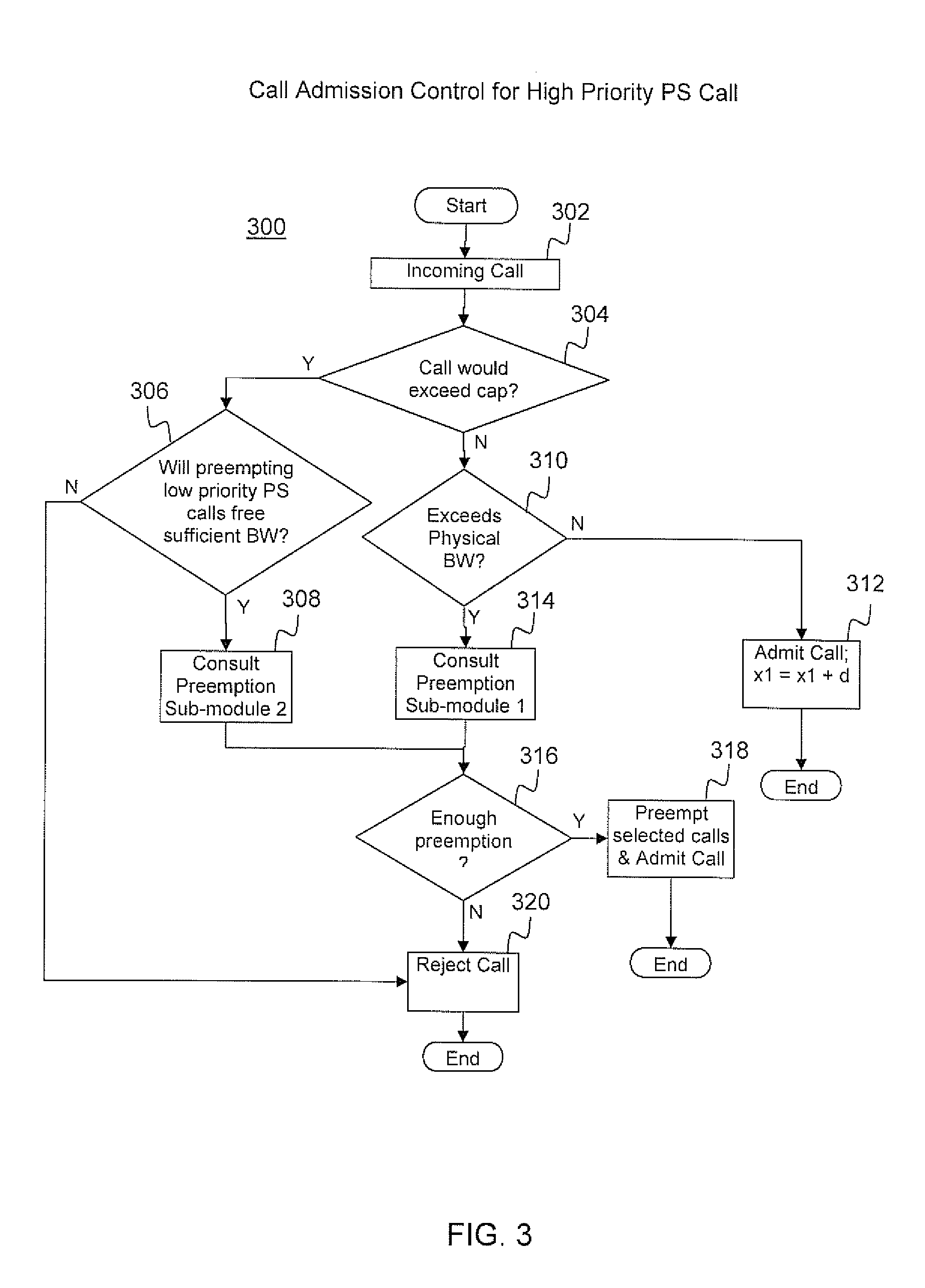
Admission control for shared LTE network
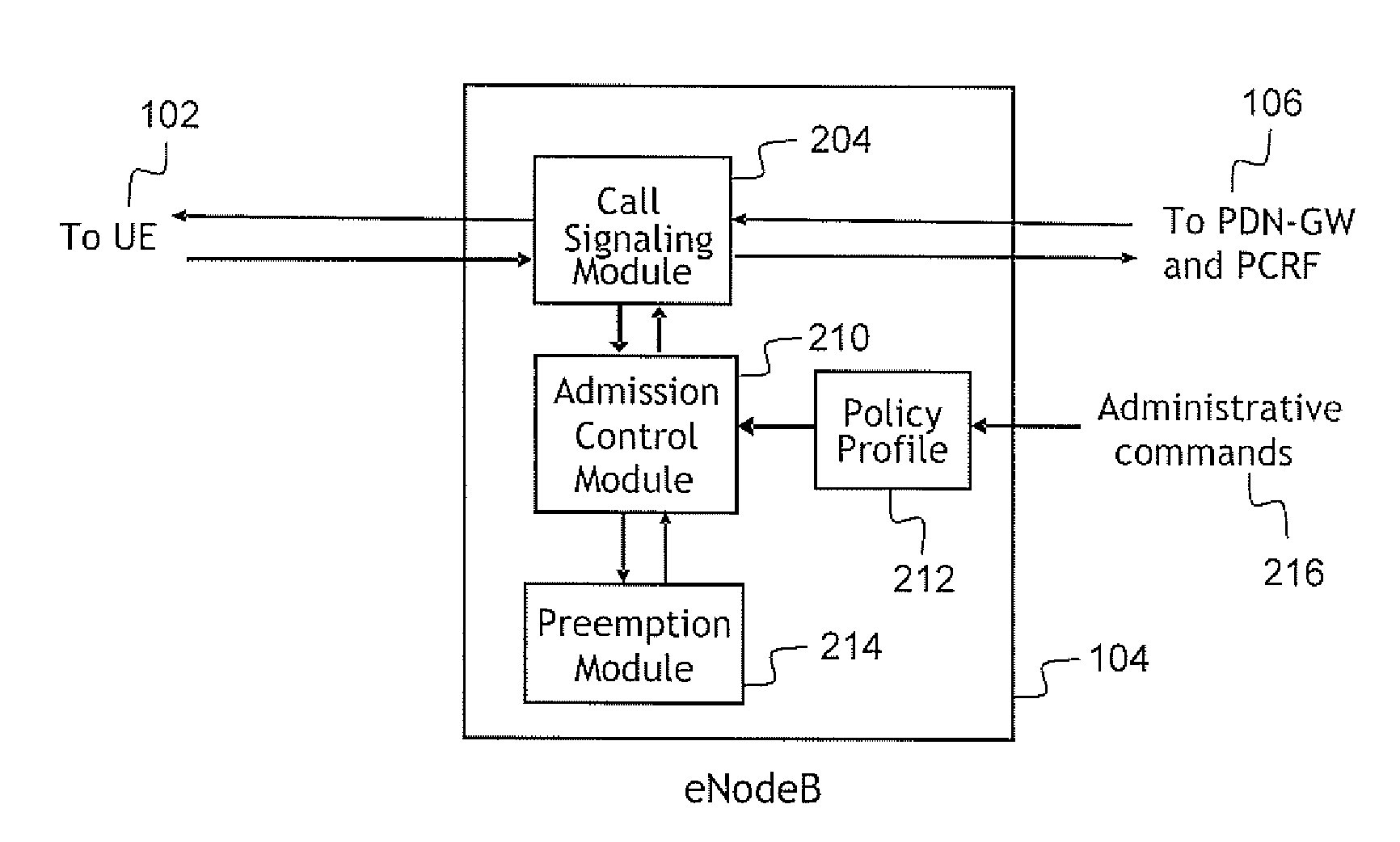
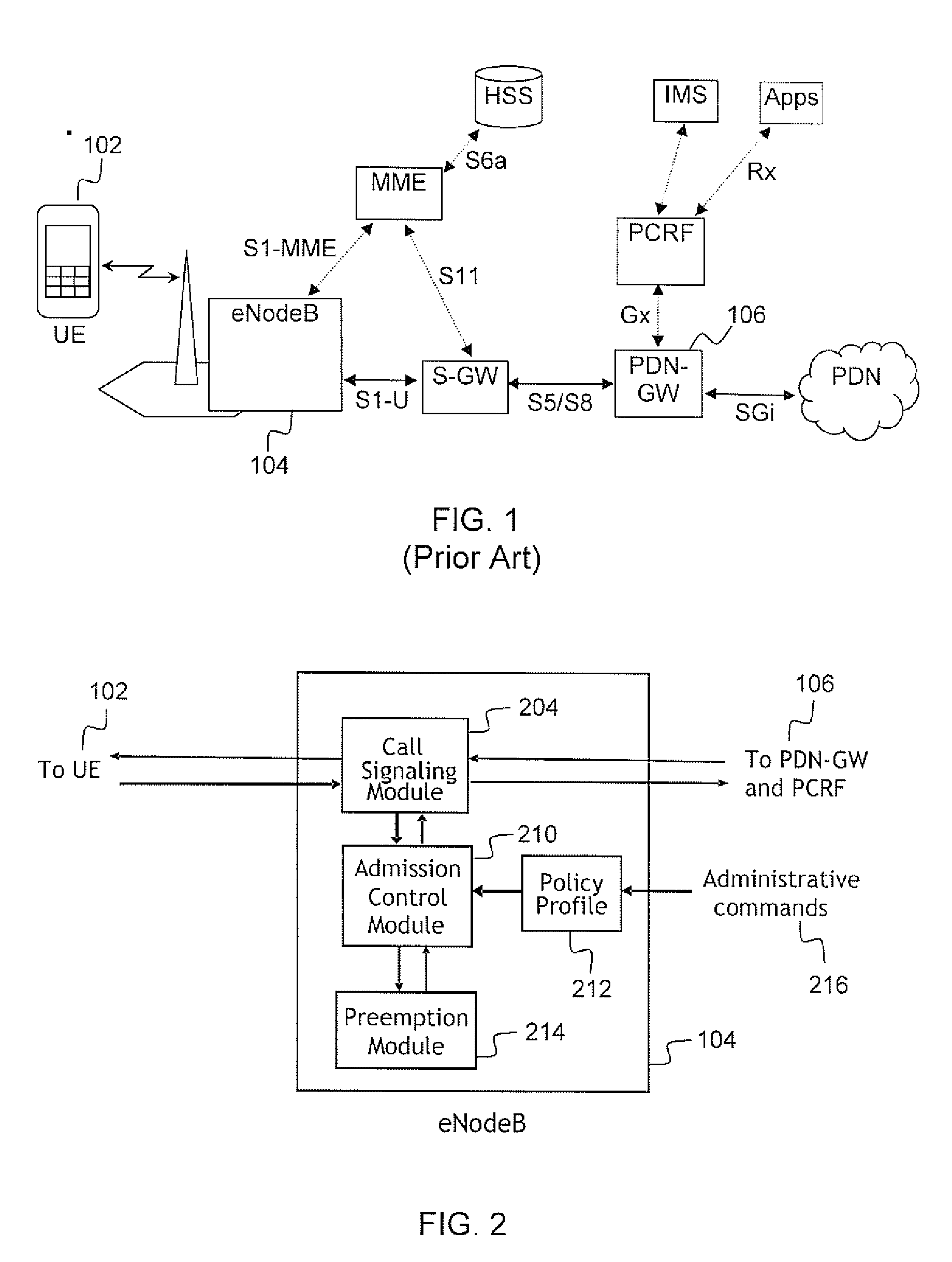
Embodiments of the present invention are directed to providing a method and system for call admission control for a Long Term Evolution (LTE) network shared between a plurality of user classes, such as, for example, a public safety user class and a consumer user class. An admission control module oversees the call admission process based on a specified policy profile. When there are insufficient resources in the network to support an incoming call, the admission control module will consult with a preemption module to determine whether, by preemption of lower priority calls, enough resources can be recovered to support the incoming call.
Owner:ALCATEL LUCENT SAS
Distributed admission control
InactiveUS20020049062A1Eliminate errorsNetwork traffic/resource managementUnauthorised/fraudulent call preventionCommunications systemRadio networks
A mobile communications system has a radio network controller and a Node B coupled to the radio network controller, the Node B being operable to control a plurality of its Node B internal resources for admission control. Admission control is moved from a controlling radio network controller (CRNC) to the Node B so as to avoid possible errors relating to fragmentation that occur in systems in which the CRNC controls admission. To support network related requirements, such as reserving capacity for high priority calls and incoming handovers, the CRNC informs the Node B about the reservations that shall be applied, and the Node B configures the admission control algorithm in accordance with the reservations.
Owner:TELEFON AB LM ERICSSON (PUBL)
Network invitation to enter controlling method and network invitation to enter controlling system
ActiveCN101068183AImprove convenienceEnsure safetyUser identity/authority verificationNetworks interconnectionControl systemClient-side
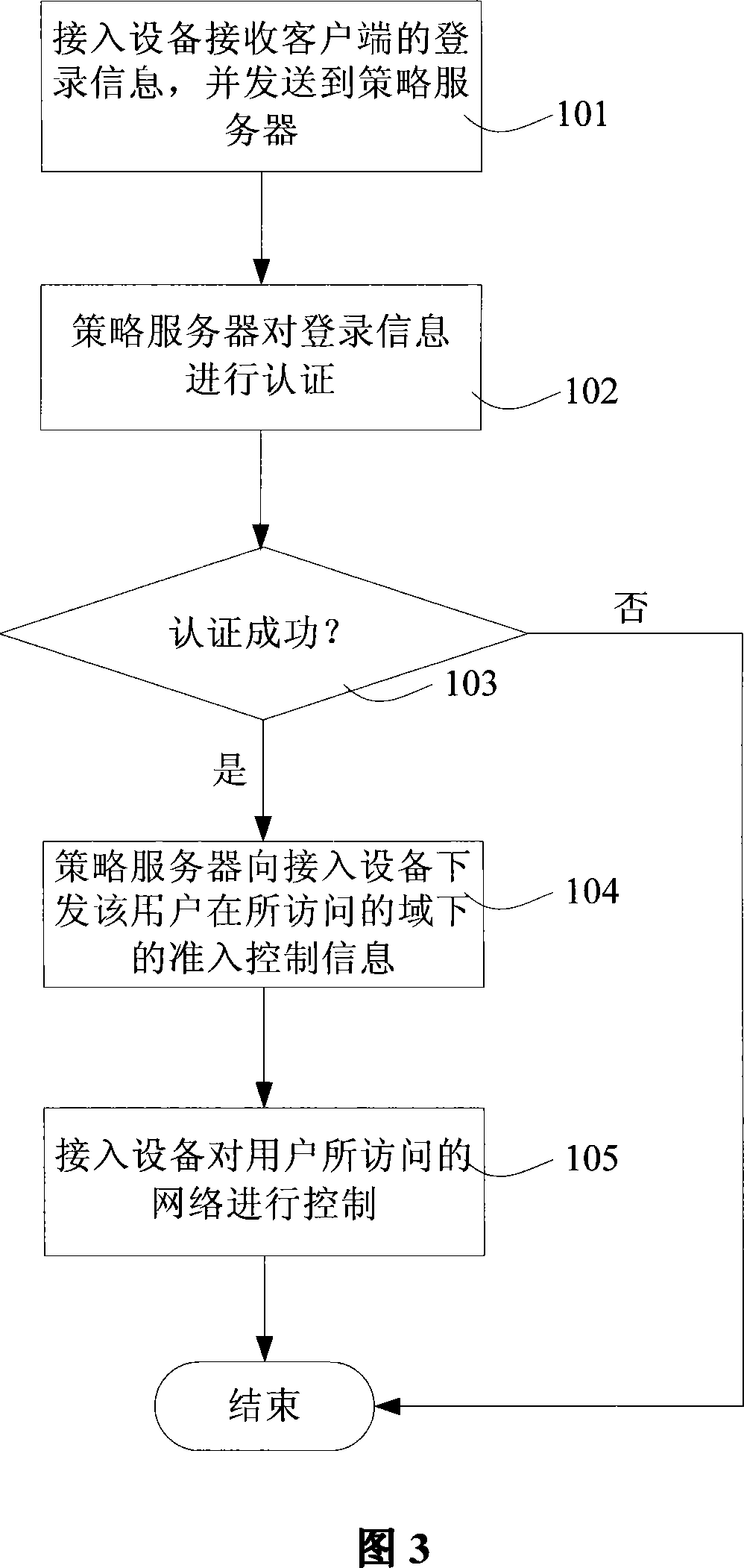
A method for controlling access of network includes receiving login information of client end by access device and sending said information to policy server, carrying out certification on login information by policy server, down-sending access control information of user under domain to be called to access device by policy server for using access device to control network to be called by user if certification is successful. The system used for realizing said method is also disclosed.
Owner:北京紫光通信科技集团有限公司
Resource reservation and admission control for IP network
ActiveUS7701951B2Error preventionTransmission systemsModem deviceNetworked Transport of RTCM via Internet Protocol
Owner:CISCO TECH INC
System and method for IEEE 802.11 network admission control
ActiveUS20050083838A1Error preventionTransmission systemsReal-time computingNetwork Admission Control
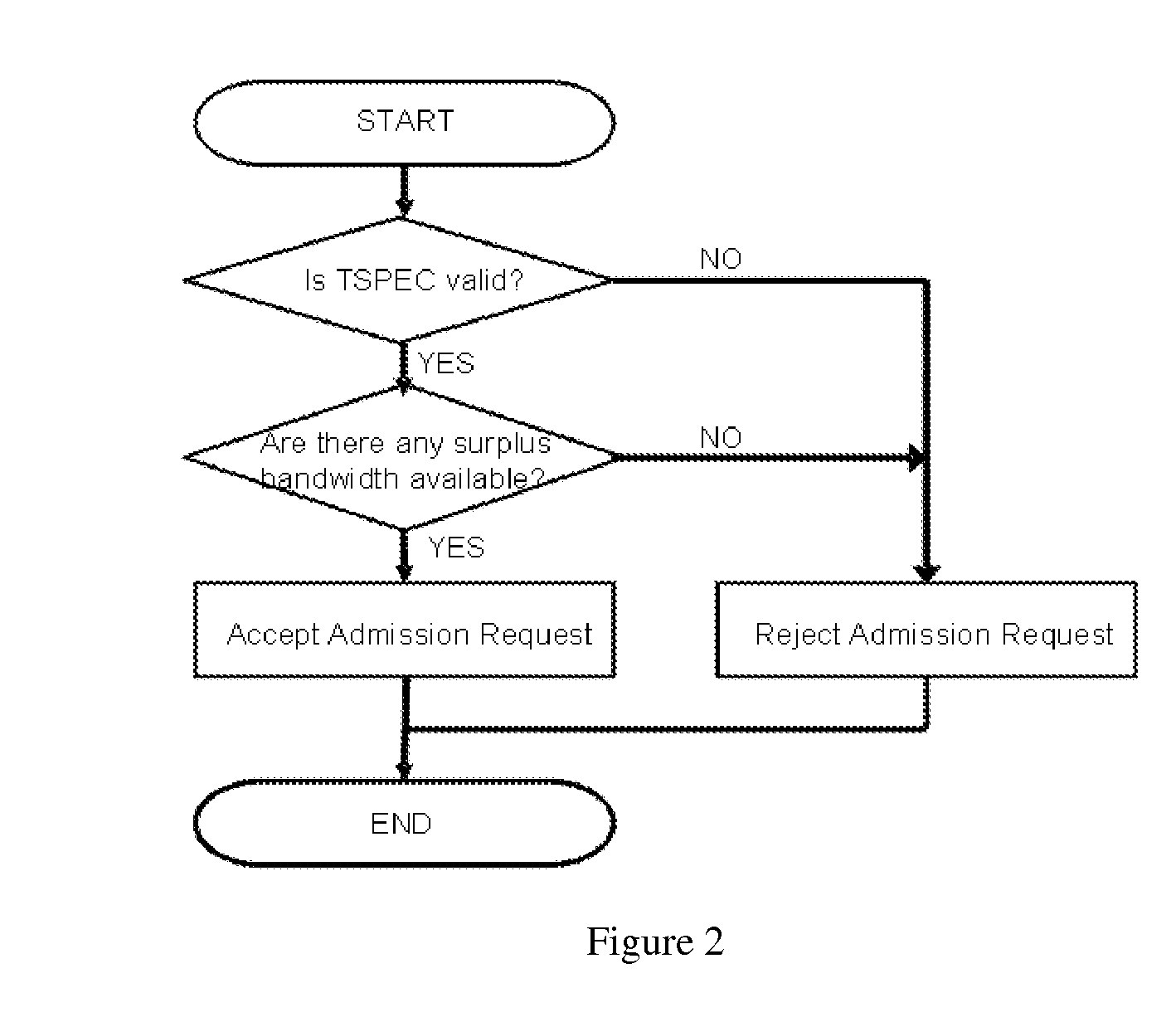
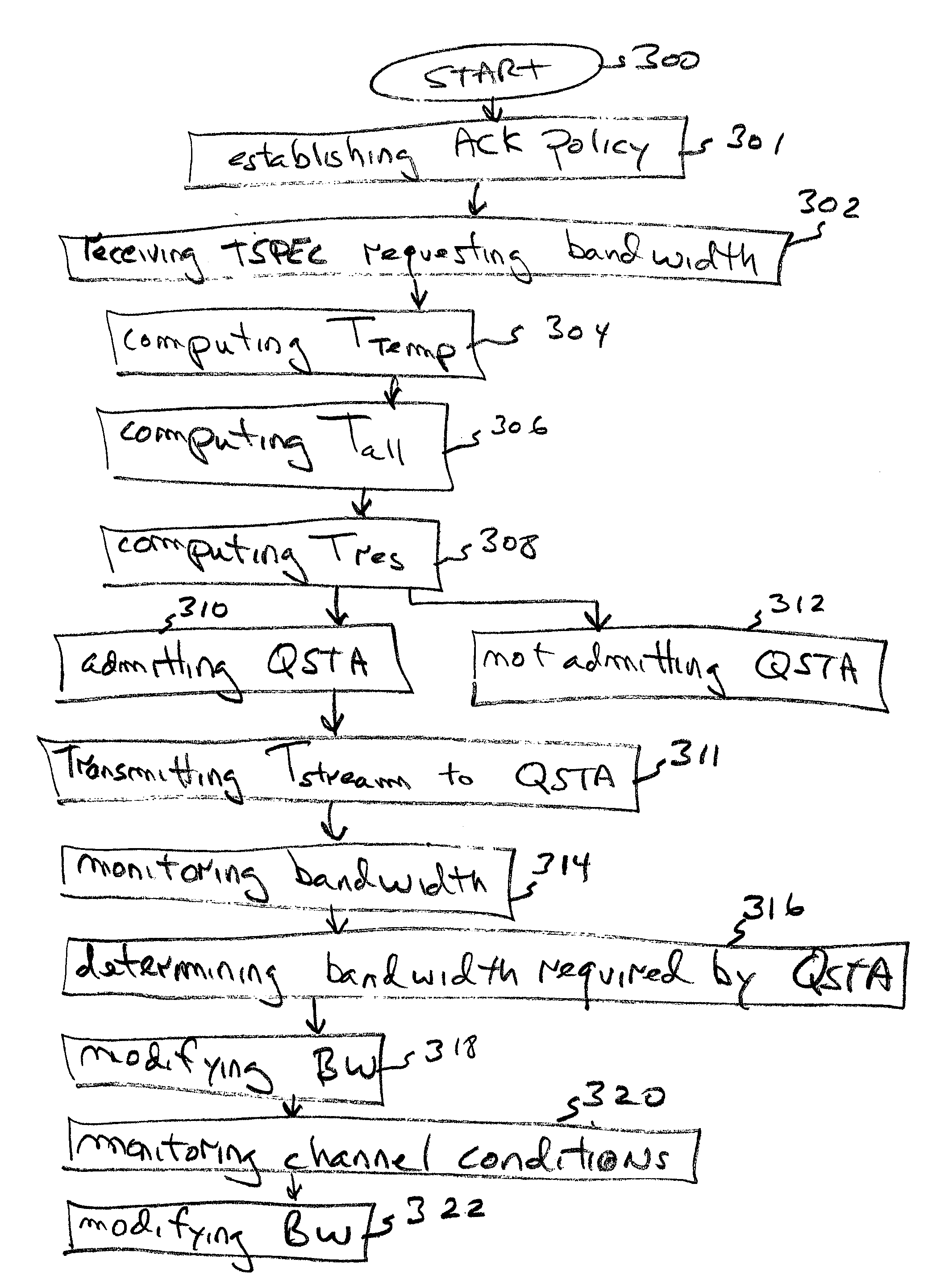
A system and method are provided for periodic stream admission control in an IEEE 802.11 network. The method comprises: at an access point (AP), receiving a transmit specification, including a requested bandwidth, from a quality of service station (QSTA); computing Ttemp, the time equivalent to the requested bandwidth; computing Tall, the time already allocated; and, computing Tres, the total time available. If Ttemp+Tall<Tres, then the QSTA is admitted. If Ttemp+Tall>Tres, the QSTA is not admitted. Some aspects of the method further comprise: monitoring the bandwidth of the admitted QSTA. In another aspect, the method: determines the bandwidth required by the admitted QSTA; and, modifies the bandwidth of the admitted QSTA in response to the determined QSTA requirements. In one aspect, the method: monitors channel conditions; and, modifies the bandwidth of the admitted QSTA in response to the channel conditions.
Owner:SHARP KK
Methods, systems, and computer program products for managing admission control in a regional/access network based on implicit protocol detection
InactiveUS20060028982A1Facilitates differentiated end-to-end data transportError preventionTransmission systemsTraffic capacityAccess network
Traffic may be admitted to a network that facilitates differentiated end-to-end data transport between a Network Service Provider (NSP) and / or an Application Service Provider (ASP) and a customer Premises Network (CPN) that includes Customer Premises Equipment (CPE) by establishing a flow between the ASP and / or NSP and the CPE. A node in the RAN snoops the flow to determine a protocol associated with the flow. A determination is made at the node in the network whether sufficient network element resources are available in the network for the flow based on the protocol associated with the flow and / or whether an administrative policy criterion exists for the flow. A determination is made at the node in the network whether to grant or deny access to the network to the flow based on the determination of whether sufficient network element resources are available in the network for the flow and / or whether an admininistrative policy criterion exists for the flow.
Owner:BELLSOUTH INTPROP COR
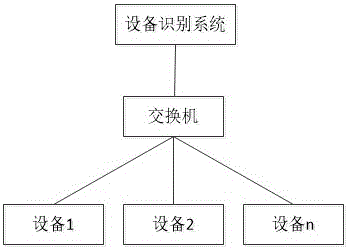
Equipment identification system based on equipment fingerprint
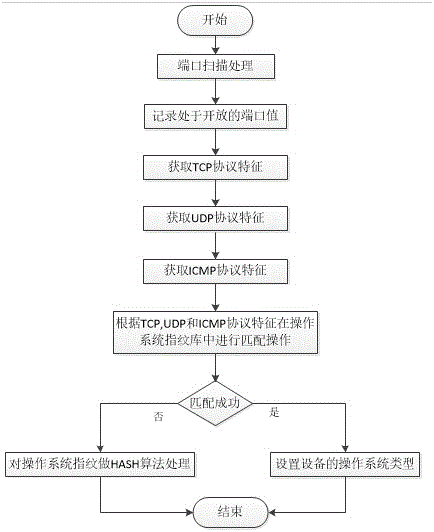
The invention belongs to the field of network admission control technology, and particularly relates to an equipment identification system based on an equipment fingerprint, wherein the equipment fingerprint information comprises hardware information, operating system information and application service information of the equipment. The system comprises the components of an equipment fingerprint database, an equipment discovery module, an equipment fingerprint acquisition module, an equipment fingerprint processing module, an equipment fingerprint matching module and an artificial identification module. The equipment fingerprint information comprises the MAC OUI hardware information and the operating system information of the equipment and the application service information in a port list. The formats of the fingerprint database comprise MAC OUI, operating system information, port list and equipment type. The equipment fingerprint acquisition module comprises operating system fingerprint information and port fingerprint information. The equipment identification system has advantages of performing network admission control on network equipment through the equipment type, making different security strategies on different kinds of equipment, preventing equipment counterfeiting, and ensuring high safety of enterprise network.
Owner:BEIJING VRV SOFTWARE CO LTD
Terminal-based network access control system
ActiveCN102594814APerformance is not affectedSimple configuration and maintenanceTransmissionControl systemSecure state
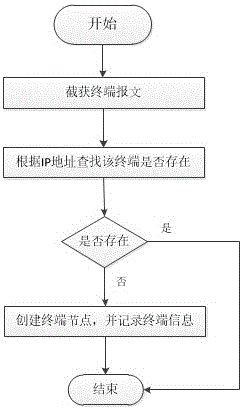
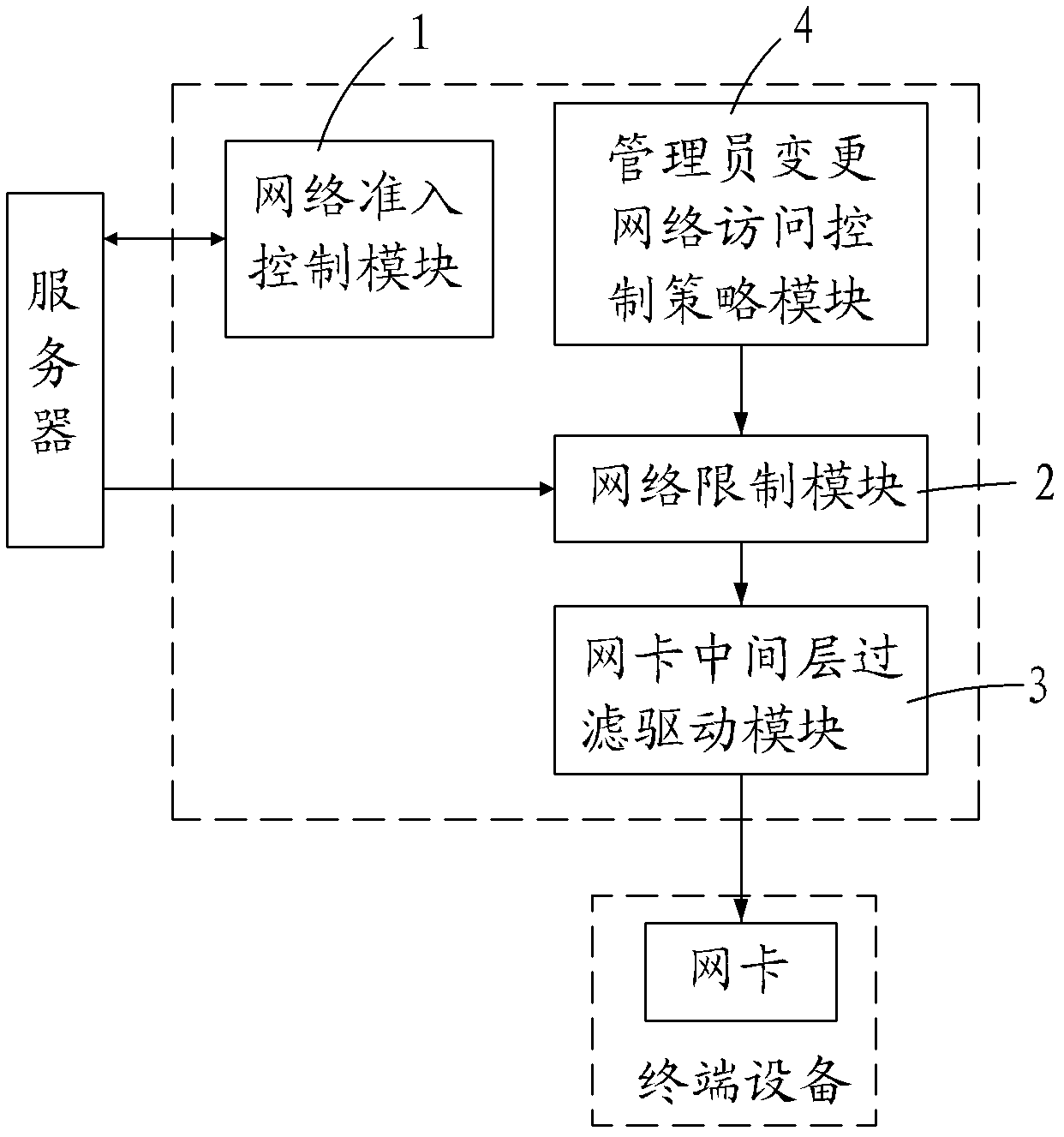
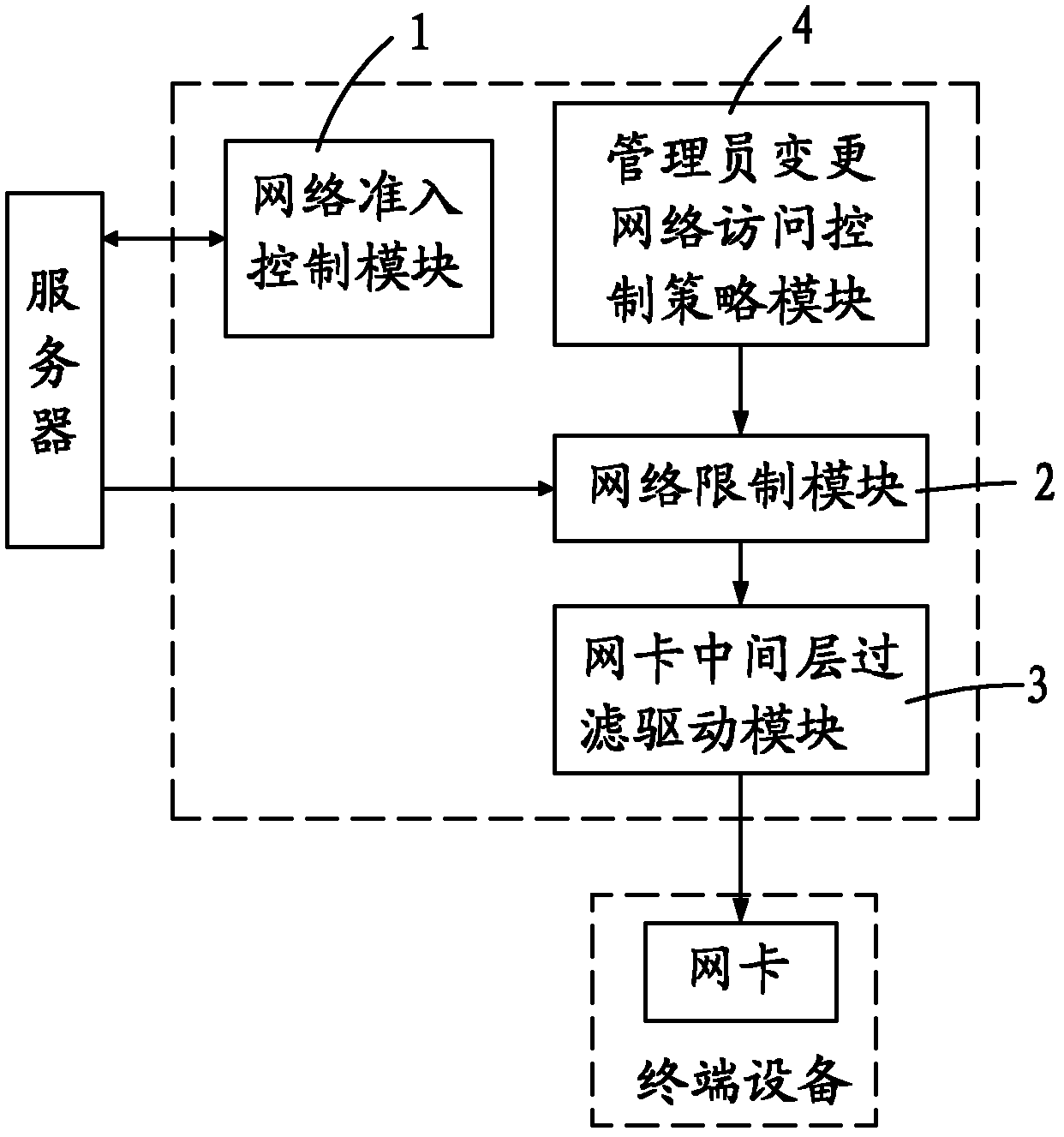
The invention provides a terminal-based network access control system. The terminal-based network access control system comprises a network access control module, a network limit module and a network card middle layer filtering driving module, wherein the network access control module performs network authentication according to the identity of a user to determine whether to allow terminal equipment used by the user to connect a network; the network limit module is used for analyzing a network access control policy transmitted by a server, converting the network access control policy into an access control list and distributing the access control list to the network card middle layer filtering driving module; and the network card middle layer filtering driving module is used for filtering data frames received by a network card of the terminal equipment to intercept network access action forbidden in the network access control policy. By the system, network access actions to a computer can be limited at a terminal, and different computers or users can only access to appointed networks. Under the condition that the safety state of the user is changed, the user can be isolated in an appointed network area, and influence to others is prevented.
Owner:FUJIAN CENTM INFORMATION
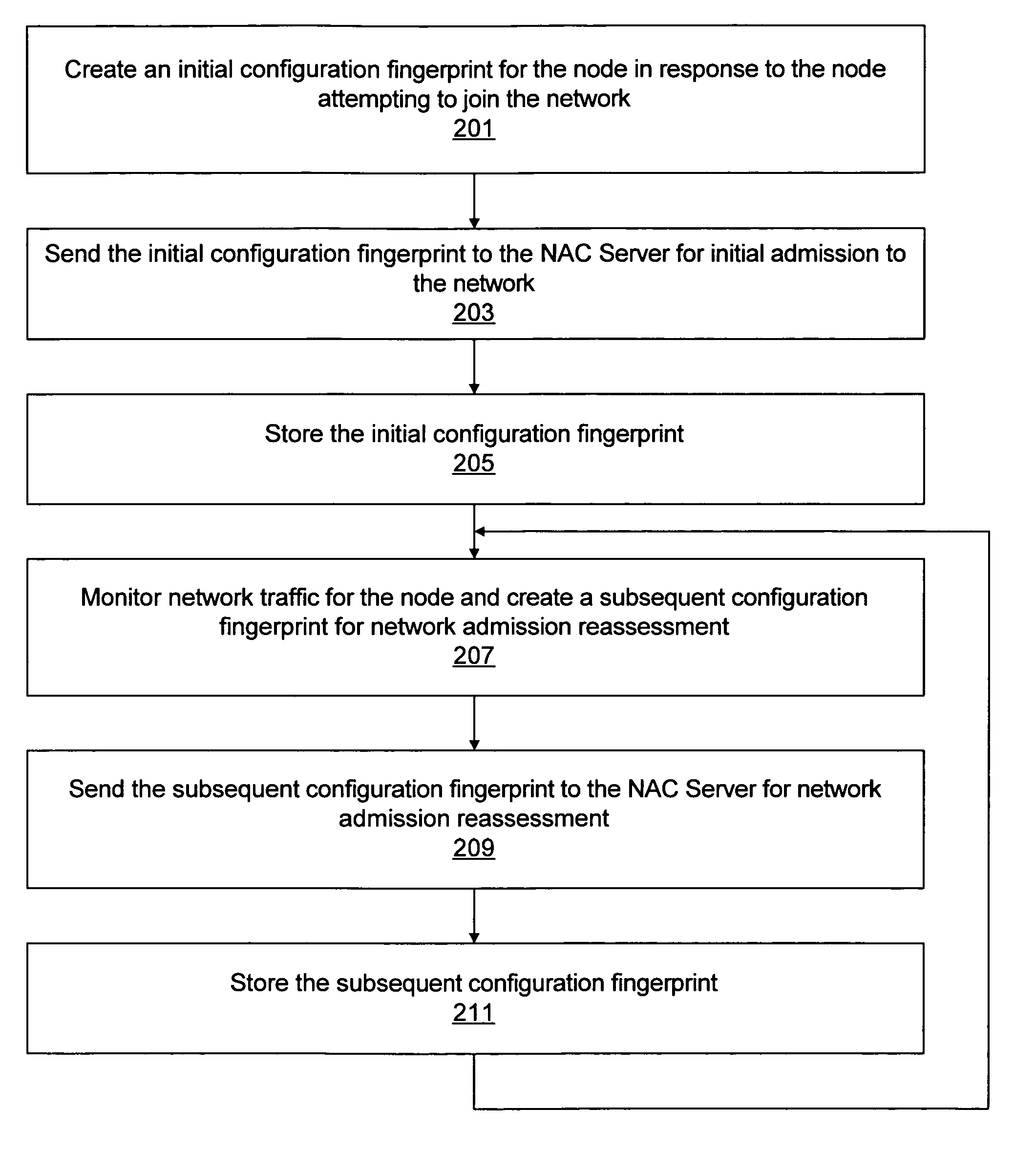
System analyzing configuration fingerprints of network nodes for granting network access and detecting security threat
ActiveUS7506056B2Digital computer detailsComputer security arrangementsSystems analysisDistributed computing
Various embodiments of a method for detecting a trend in a computer network comprising a plurality of nodes are described. According to one embodiment of the method, network admission control is performed for each node in the network. One or more configuration fingerprints may be created for each node in response to the network admission control for the node, e.g., where the configuration fingerprints for a given node identify selected aspects of the configuration of the node. The method further comprises detecting a trend based on at least a subset of the configuration fingerprints for the nodes. For example, the configuration fingerprints may be analyzed in order to detect trends that indicate security threats.
Owner:CA TECH INC
Call admission control of shared-access resources through a call-handling server
ActiveUS20060116128A1Low costAmount of logic added to the SIP proxy is minimal and straightforwardNetwork traffic/resource managementWireless network protocolsSession Initiation ProtocolThe Internet
A method and an apparatus are disclosed that enable call admission control for telecommunications terminals that use shared-access resources, without relying on an implementation at every access point to provide those resources. In particular, in accordance with the illustrative embodiment of the present invention, a first wireless terminal calls a second terminal by transmitting a traffic stream description that specifies the nature of the call to an intermediary call-handling server, such as a Session Initiation Protocol (SIP) proxy server. The SIP proxy determines from the Internet Protocol address of the calling terminal that the terminal uses a shared-access resource—in this case, a wireless shared-communications channel—and makes a request to a channel utilization manager to admit the call. Subsequently, the SIP proxy receives a message from the channel utilization manager that indicates whether the call has been admitted.
Owner:AVAYA INC
Providing connection admission control in a communications network
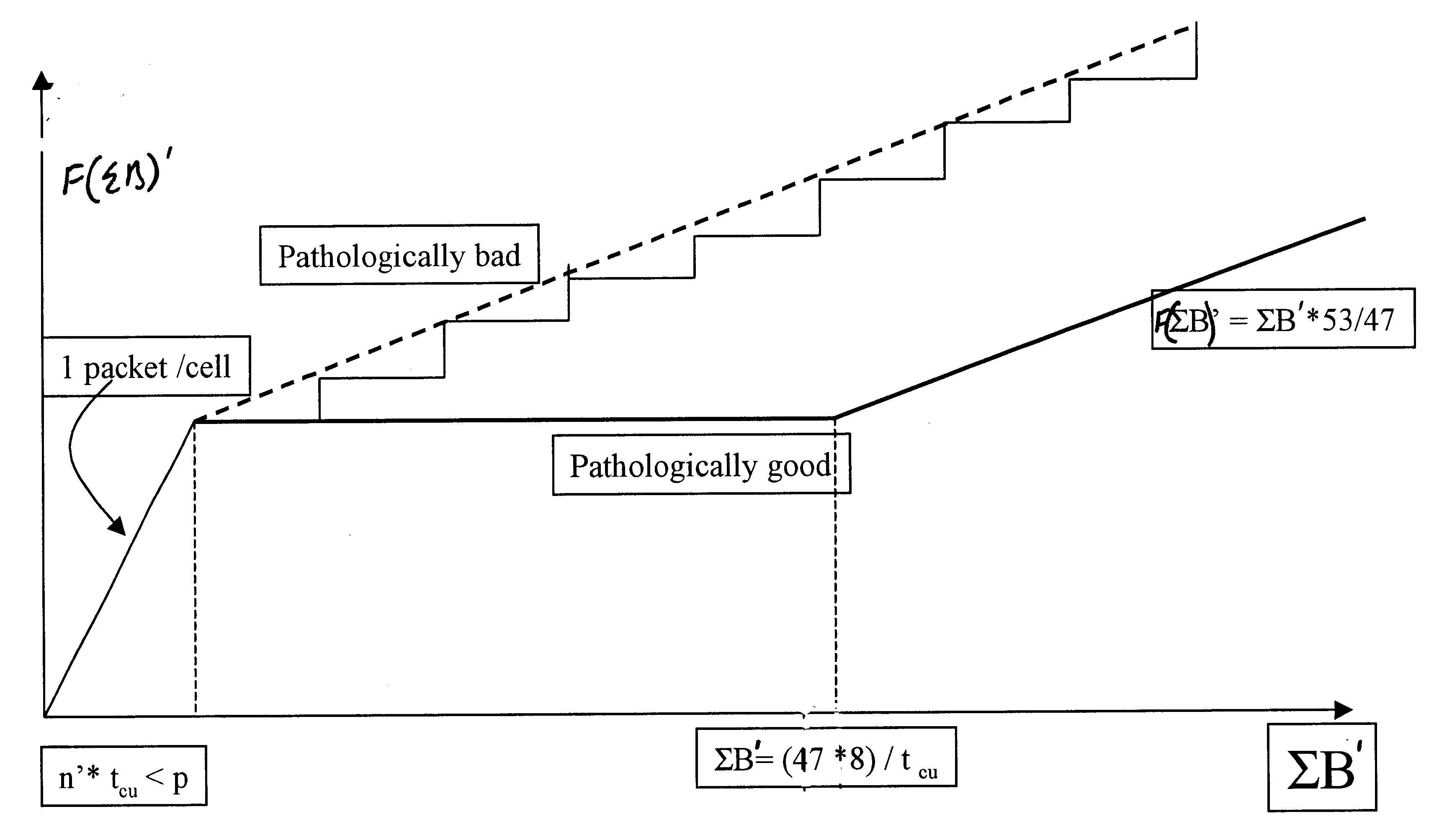
Connection admission control to an ATM network from a plurality of sources sharing a common virtual channel connection in which information packets are carried in cells is effected by determining whether that connection requires the transmission of a single packet per cell, partially filled cells containing more than one packet or fully filled cells. Where a single packet is to be transmitted per cell, the bandwidth requirement is calculated via a first algorithm. Where fully filled cells are to be transmitted, the bandwidth requirement is calculated via a second algorithm. Where partially filled cells containing more than one packet are to be transmitted the bandwidth requirement is calculated via an interpolation between the two algorithms. This provides a more accurate measure of equivalent bandwidth and thus facilitates efficient use of network resources.
Owner:NORTEL NETWORKS LTD
Admission control system and admission control method in load supporting interface of communication network
ActiveCN1874319AImprove business qualityPulse modulation television signal transmissionError preventionTransceiverTraffic flow
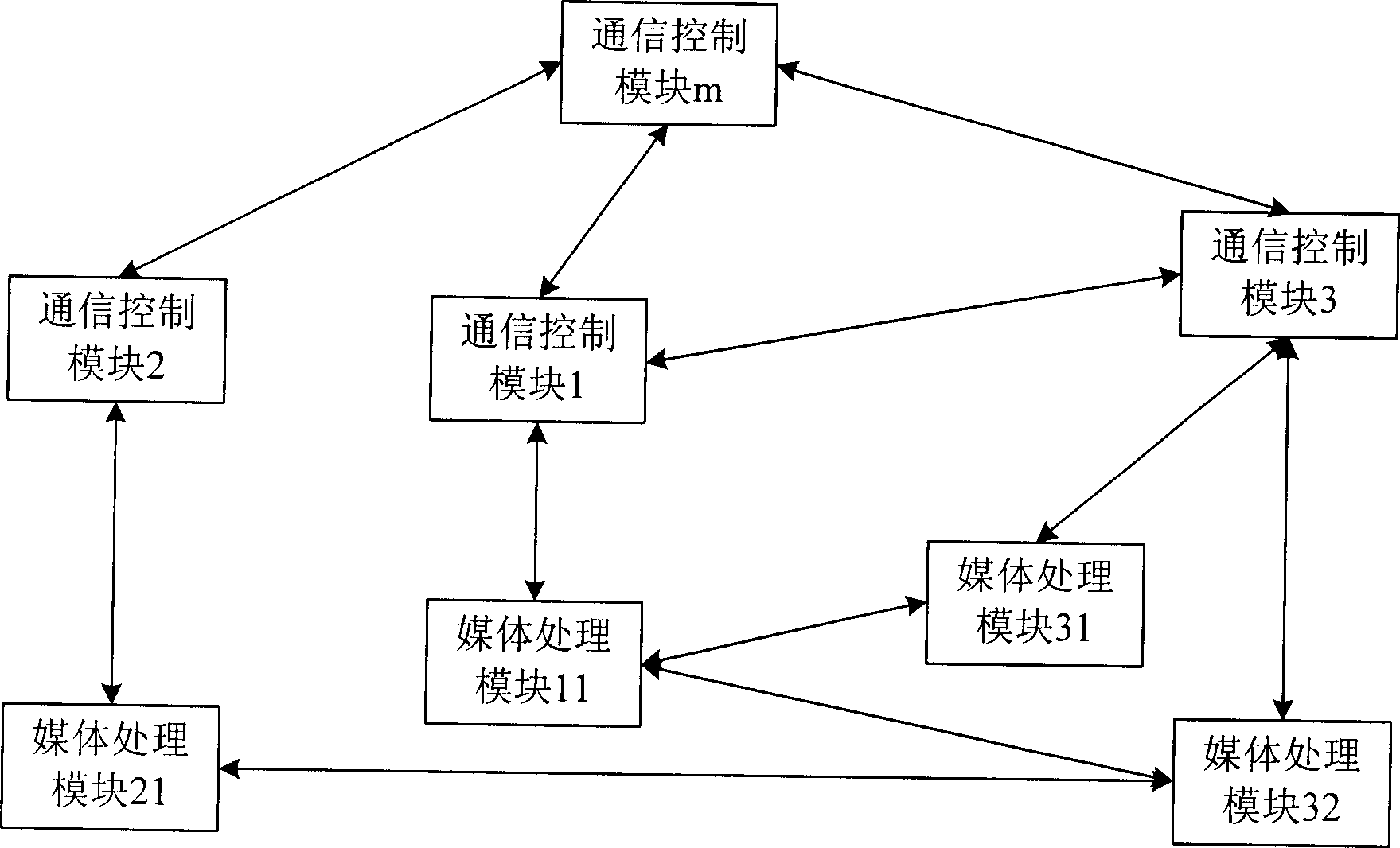
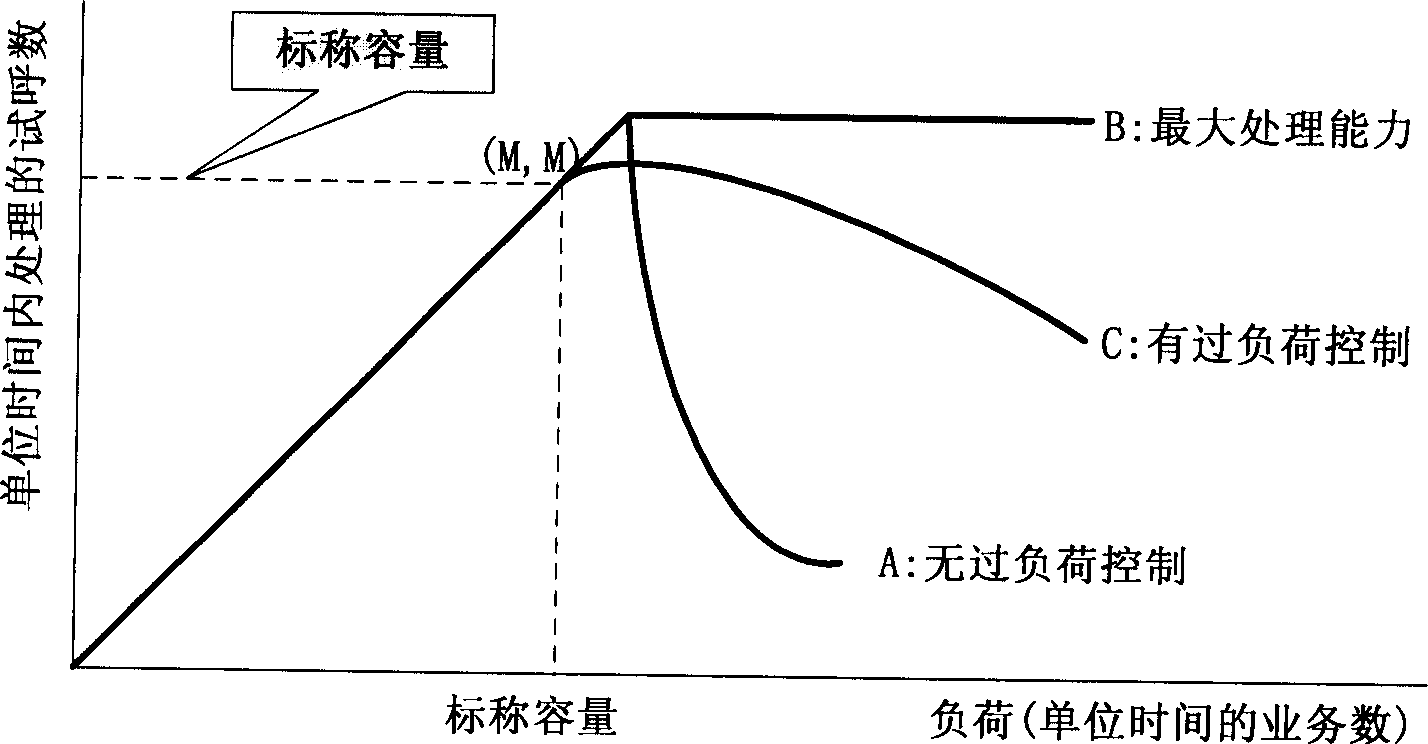
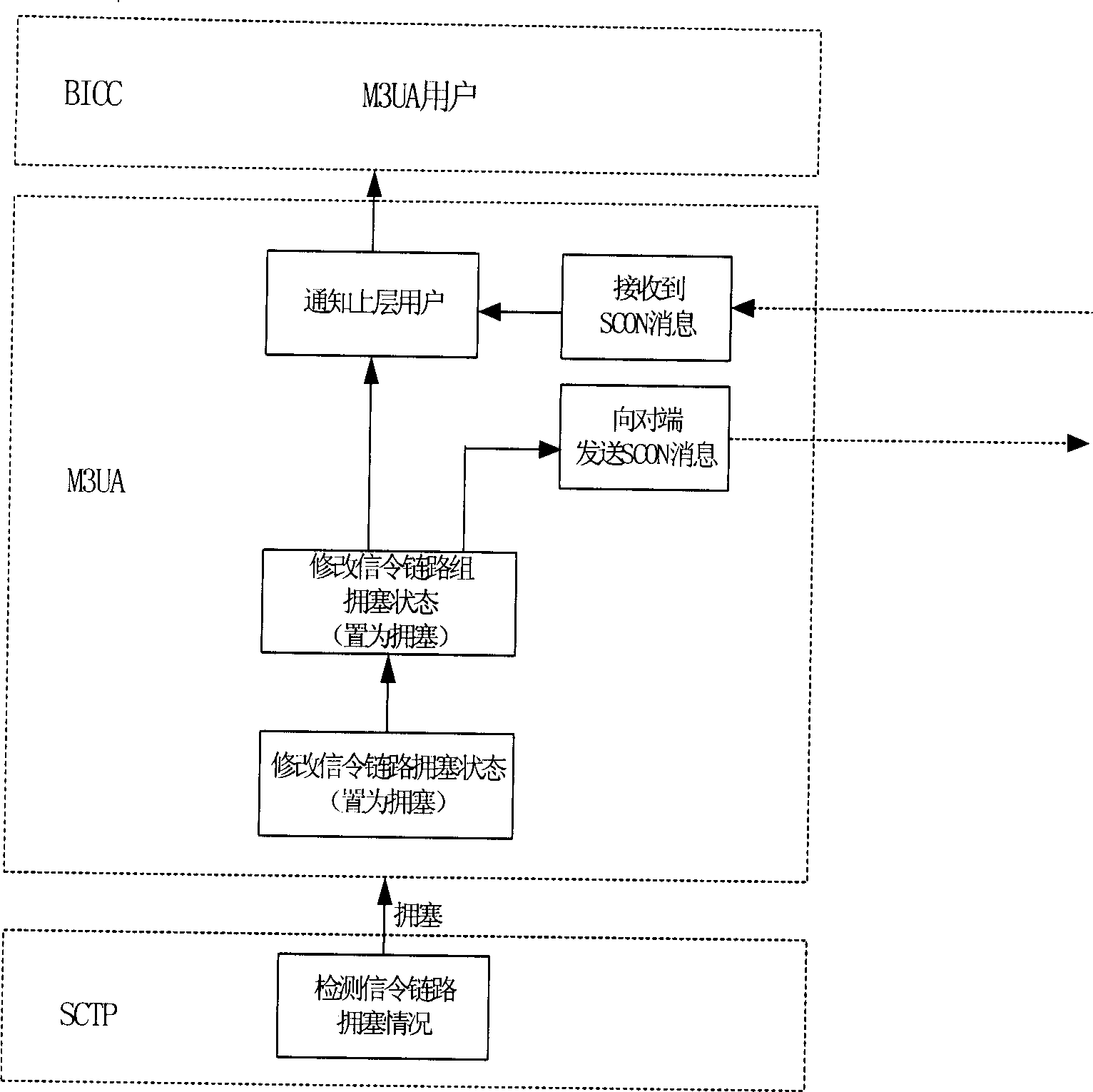
The system thereof comprises a communication control module and one or more multi media processing modules connected to the said communication control module through management control interface. The multi media processing module comprises a packet transceiver and a congestion detection module. The communication module comprises a congestion state management module and a calibration operation module. The method thereof includes: determining the traffic flow direction required by the communication service; accessing the congestion management module to get the congestion state information about the traffic flow; in term of predetermined strategy and congestion level information, executing, admitting or refusing the operation of communication service.
Owner:CHINA MOBILE COMM GRP CO LTD
Intranet security unified management platform and management method of management platform
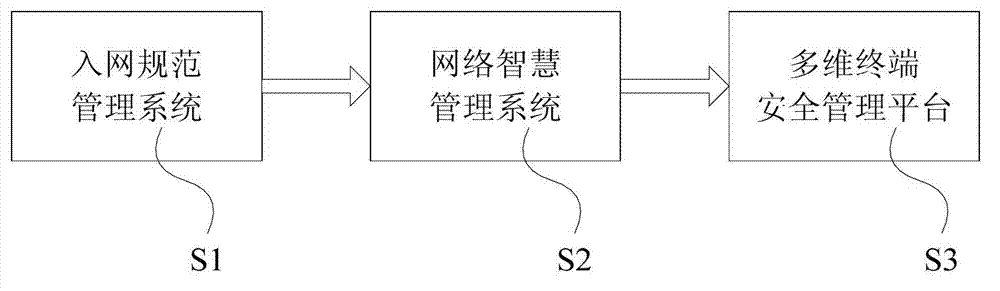
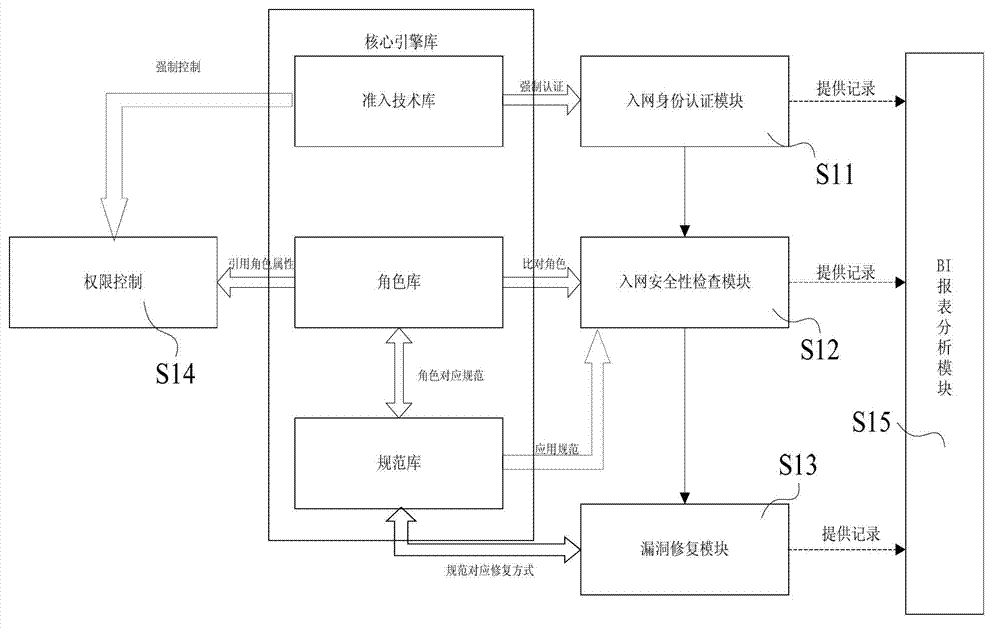
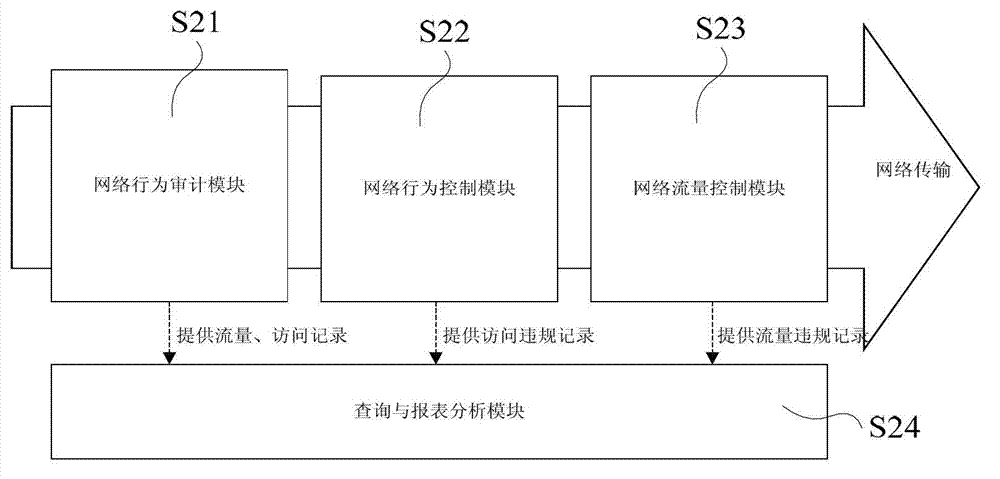
ActiveCN103179130AImplement access controlAvoid simultaneous access to the networkNetworks interconnectionWeb authenticationMulti dimensional
The invention discloses an intranet security unified management platform and a management method of the management platform. The intranet security unified management platform comprises an admission standard management system, an intelligent network management system and a multi-dimensional terminal security management platform. The management method comprises the steps of: carrying out feature identification on a terminal accessing to a network; carrying out query according to a feature of the terminal, taking an admission role; carrying out standard examination on the role to access the network according to the role authority; carrying out monitoring and irregularity response on security configuration and operation behaviors after the terminal accesses the network; carrying out monitoring and irregularity response on flow condition of the network; and carrying out statistics and BI (Business Intelligence) analysis on various kinds of events. According to the intranet security unified management platform and the management method of the management platform, admission control is realized through switching of an isolation region, the transmission of all data of a device in the isolation region is controlled through the management platform, the standard restriction is realized through a WEB authentication page on which the an access device is forced to access the management platform, and thus the non-client end admission control is realized, and the defect that a plurality of devices under a single port are simultaneously accessed to the network or simultaneously isolated is avoided.
Owner:HANGZHOU INFOGO TECH
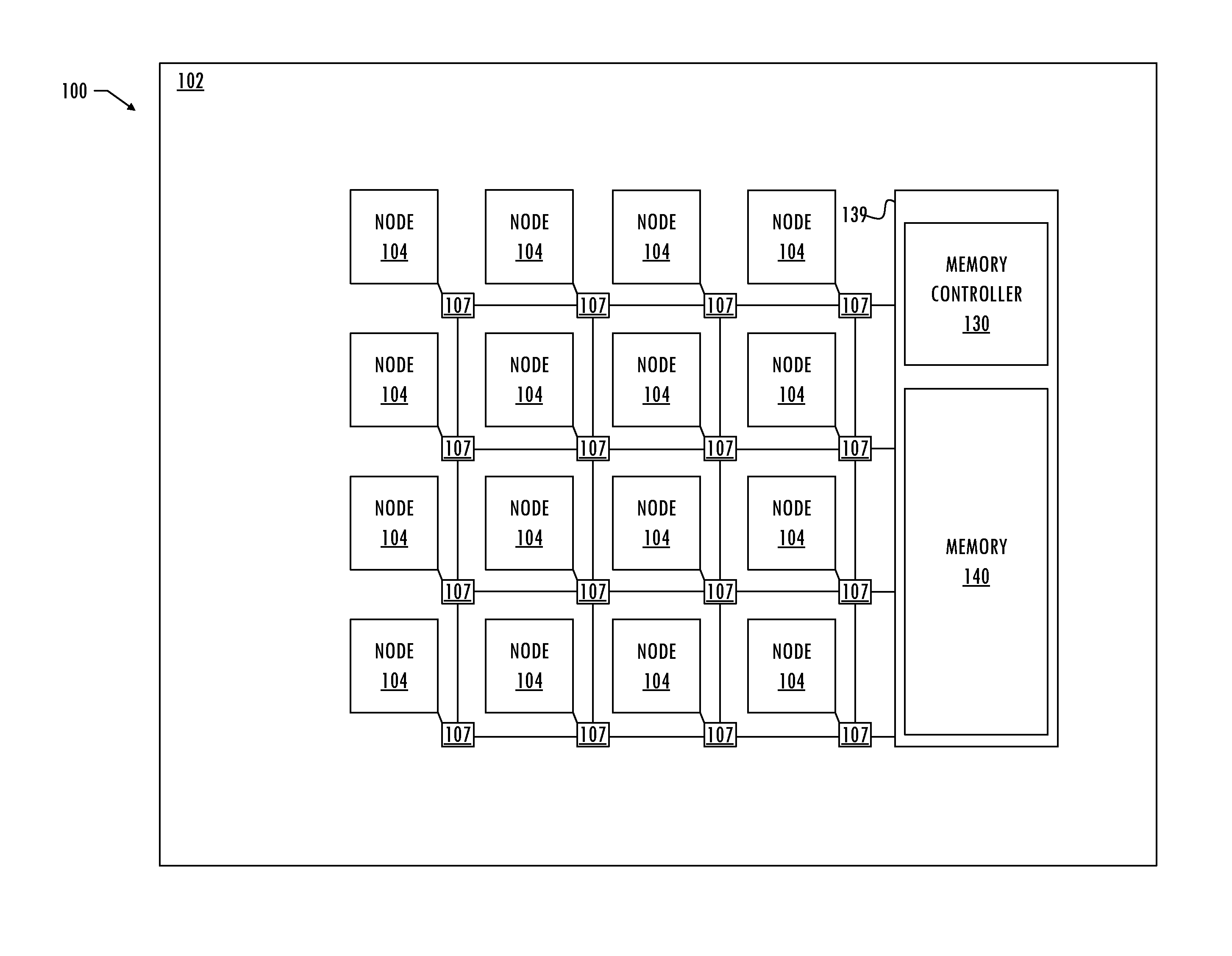
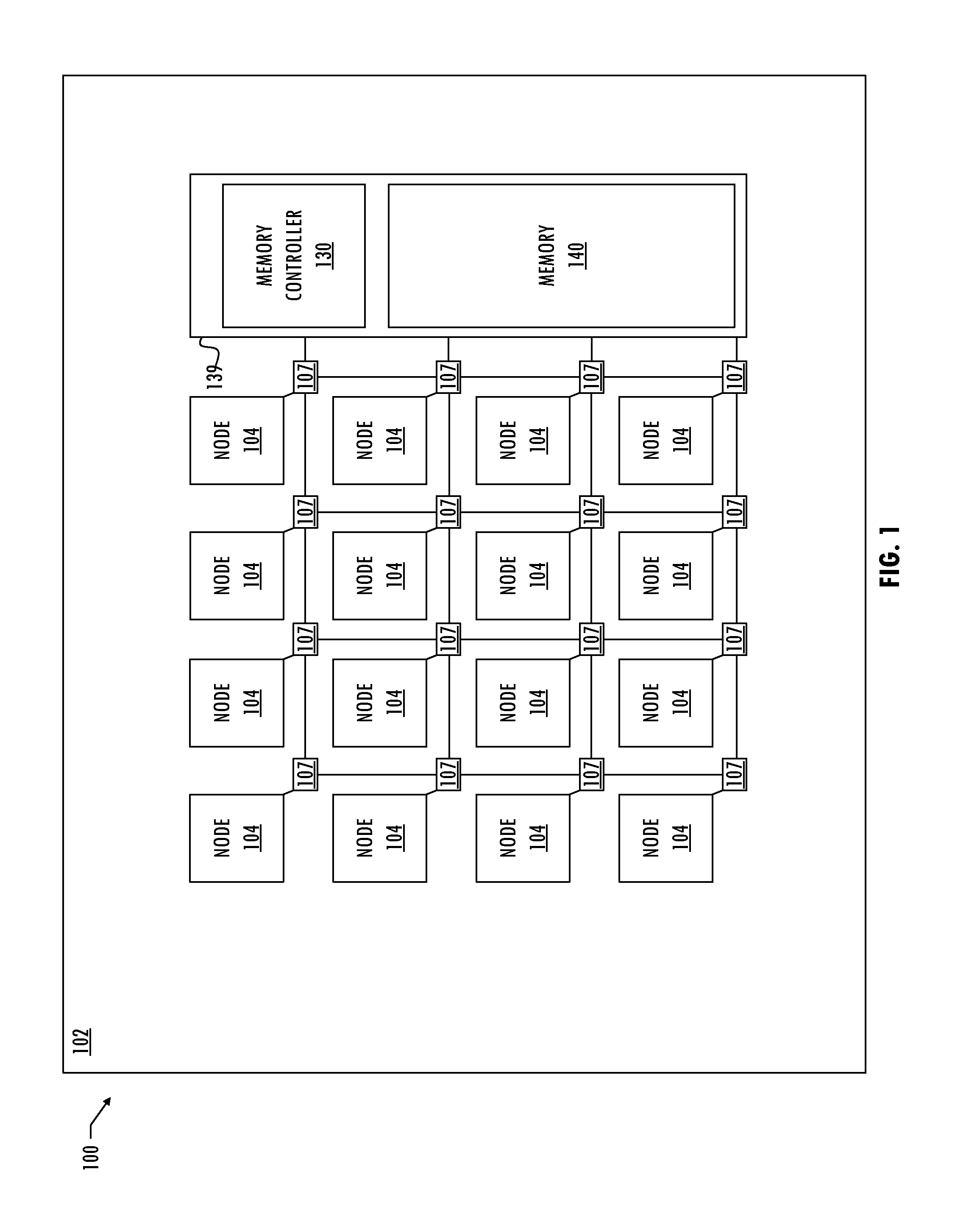
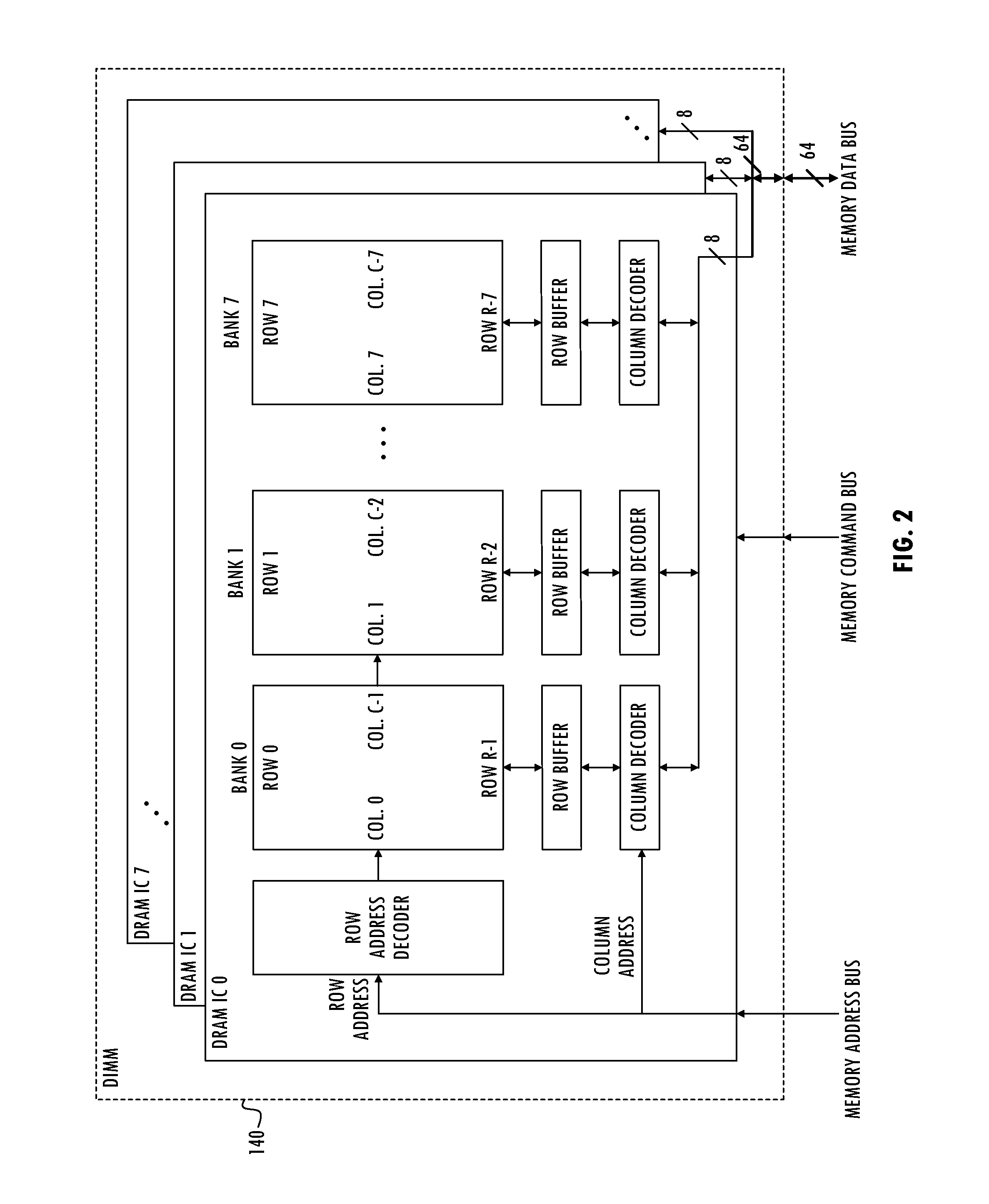
Source-Side Resource Request Network Admission Control
A technique for source-side memory request network admission control includes adjusting, by a first node, a rate of injection of memory requests by the first node into a network coupled to a memory system. The adjusting is based on an injection policy for the first node and memory request efficiency indicators. The method may include injecting memory requests by the first node into the network coupled to the memory system. The injecting has the rate of injection. The technique includes adjusting the rate of injection by the first node. The first node adjusts the rate of injection according to an injection policy for the first node and memory request efficiency indicators. The injection policy may be based on an injection rate limit for the first node. The injection policy for the first node may be based on an injection rate limit per memory channel for the first node. The technique may include determining the memory request efficiency indicators based on comparisons of target addresses of the memory requests to addresses of recent memory requests of the first node.
Owner:ADVANCED MICRO DEVICES INC
Method for providing performance cues for a server-based software application
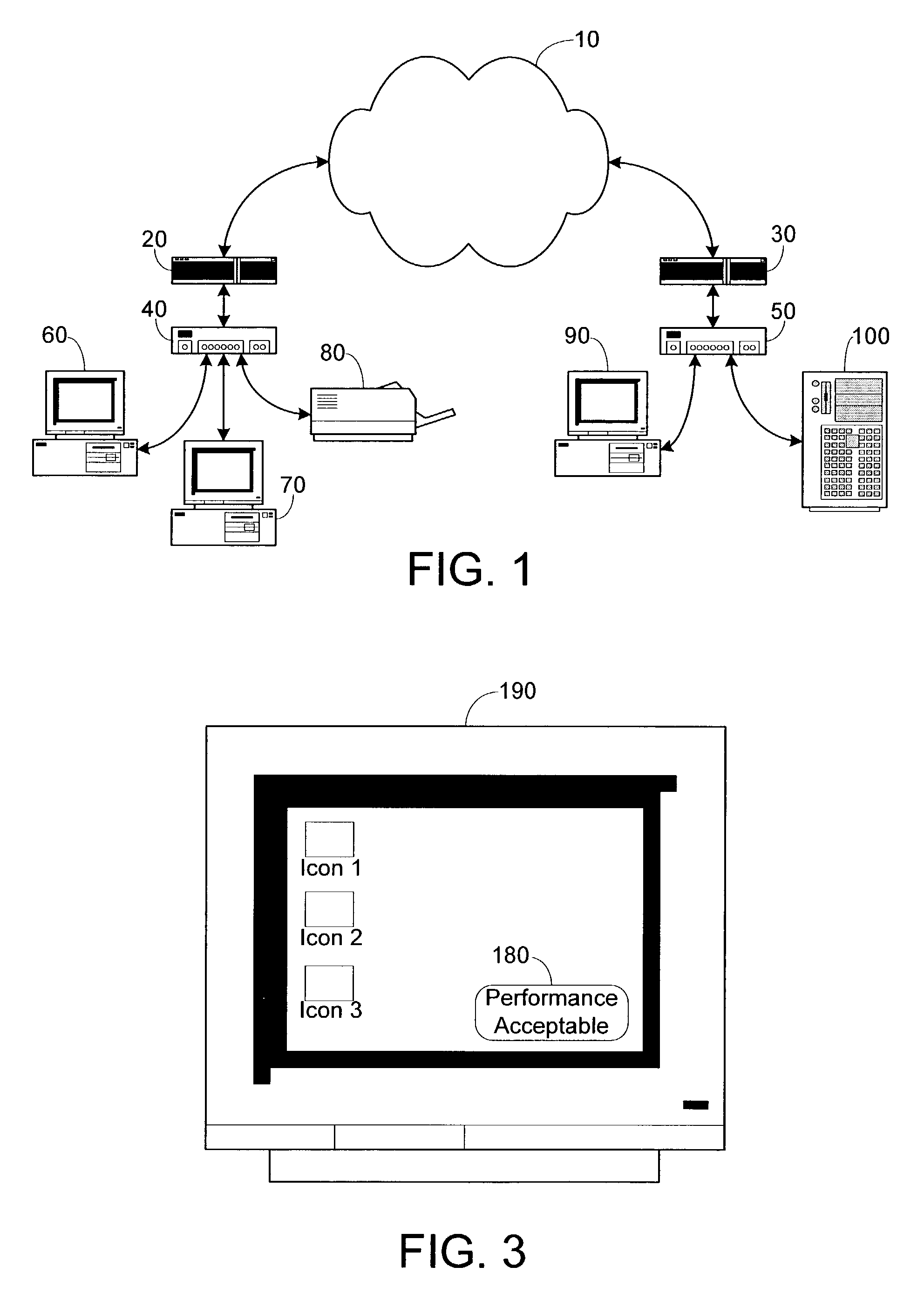
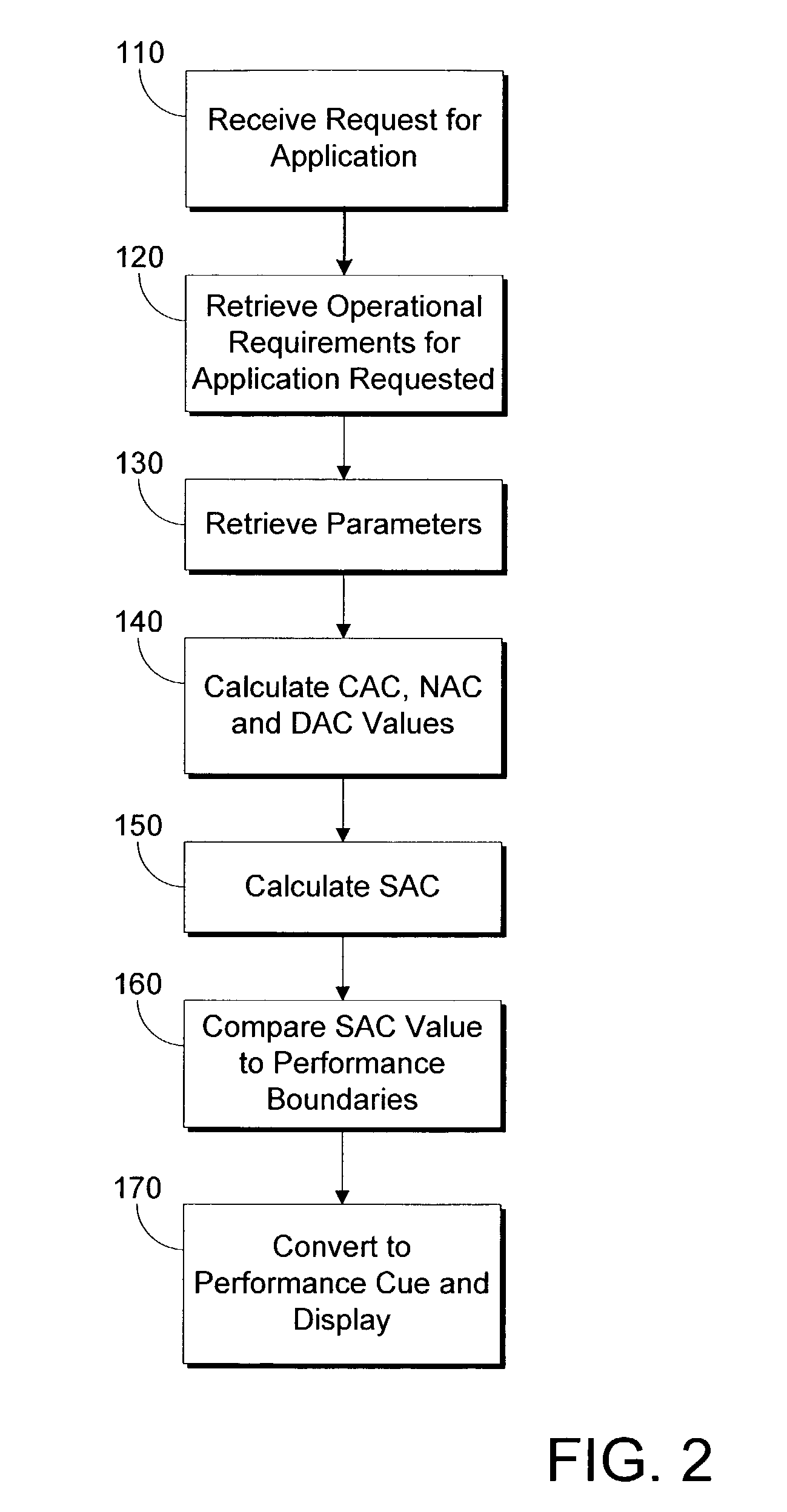
ActiveUS7433970B1Multiple digital computer combinationsTransmissionApplication softwareOperational requirements
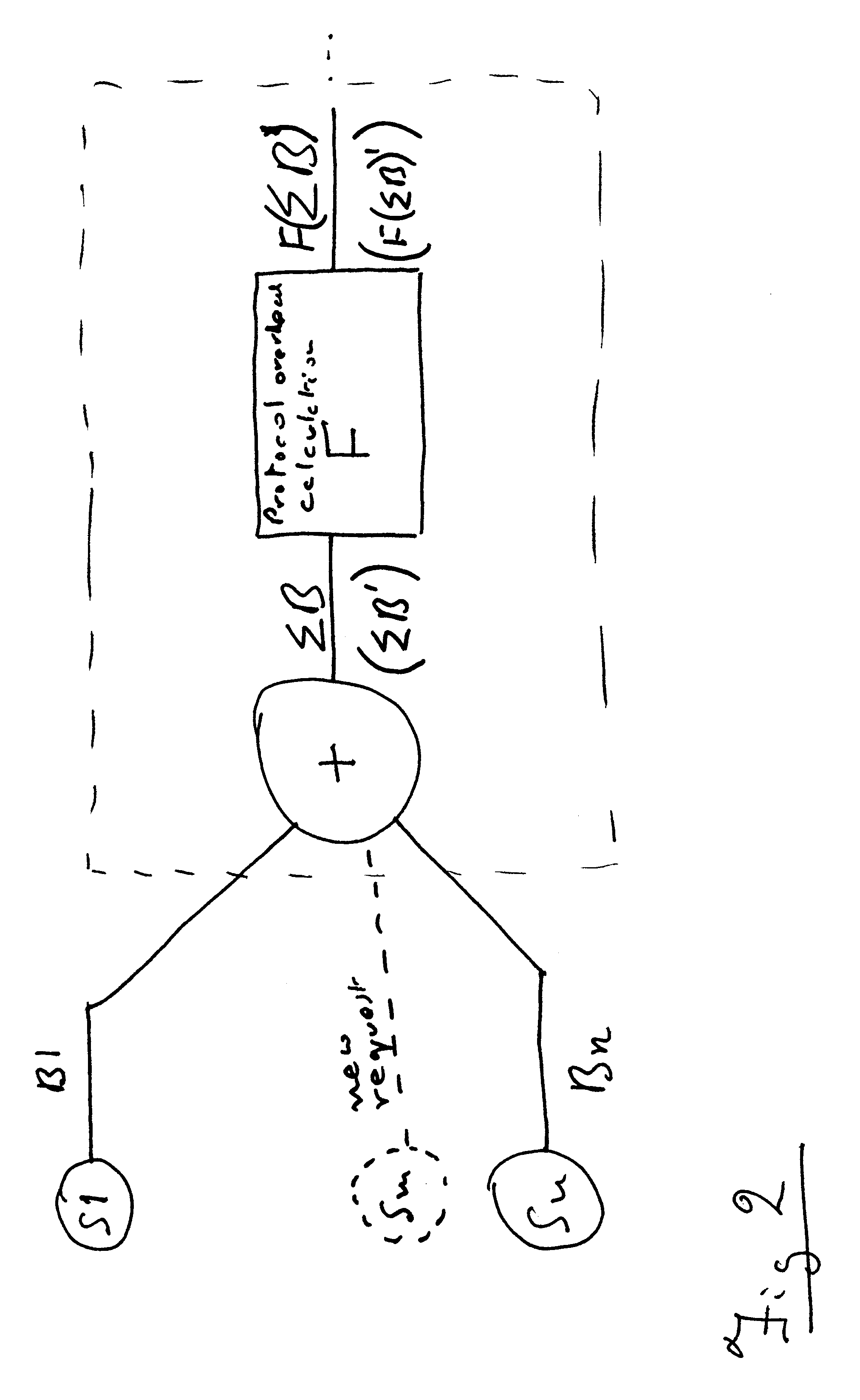
The present invention provides a method for determining whether a server-based application will execute in an acceptable manner and thereafter providing this information to a user. After receiving a request for service relating to a particular application, the method retrieves the operational requirements for the application, which include the service admission control, content admission control, network admission control, and data admission control formula and the performance boundaries. Next, the values of the parameters required to evaluate the operational requirements are retrieved. The values of content admission control, network admission control, and data admission control are then calculated and used in the service admission control formula to determine the service admission control value for the application. Thereafter, the service admission control value is compared to the application's performance boundaries to determine the manner in which application will execute. Finally, a performance cue that corresponds to the relative manner in which the application will execute is displayed for the user.
Owner:T MOBILE INNOVATIONS LLC
Method and apparatus for policy and admission control in packet-based communication systems
ActiveUS7428216B2Reduce dependenceReduce complexityError preventionTransmission systemsCommunications systemByte
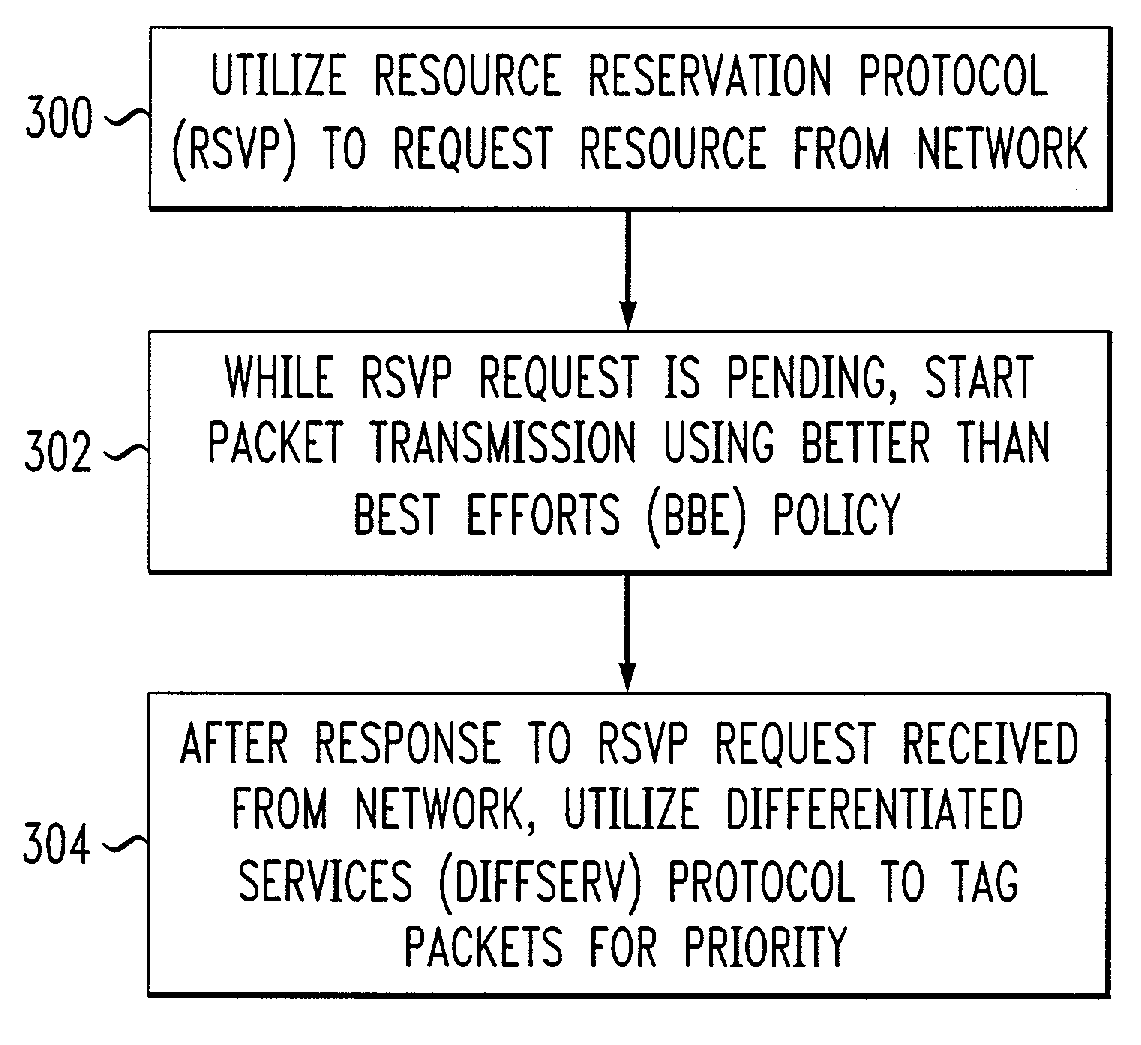
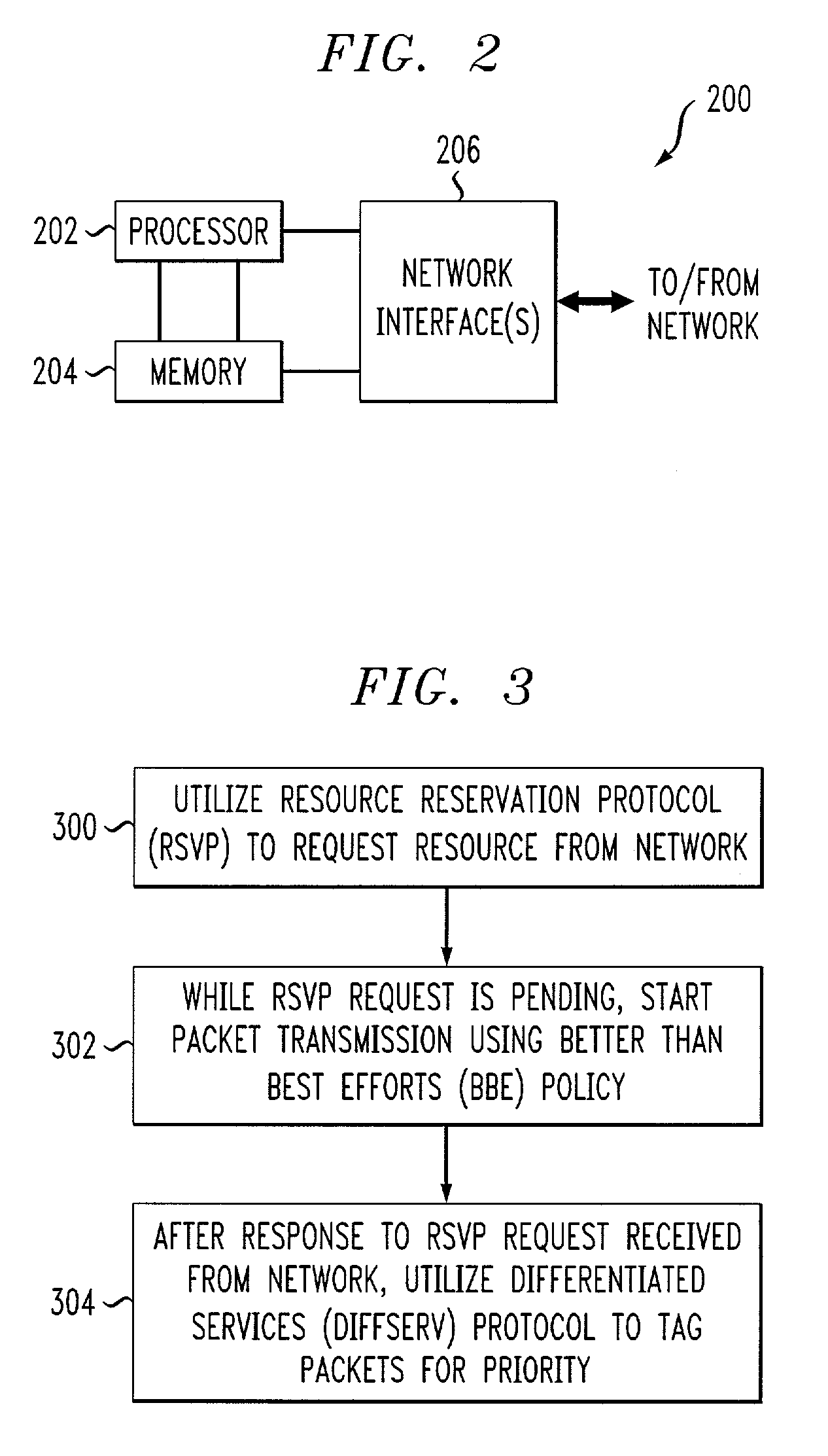
Techniques are disclosed for establishing packet-based communication between first and second endpoints over a network, in a manner which reduces the latency and complexity associated with call setup. In accordance with one aspect of the invention, a resource is requested from the network utilizing a first protocol, and while the request is pending, transmission of packets at a first priority level is commenced. After a response is received from the network granting access to the requested resource, a tagging mechanism is utilized to identify particular packets for transmission at a second priority level higher than the first priority level. In an illustrative embodiment, the first protocol is the Resource Reservation Protocol (RSVP), the first priority level corresponds to a Better than Best Effort (BBE) policy, and the second, higher priority level corresponds to an Expedited Forwarding (EF) policy. These policy levels may be implemented for a given packet by setting a Type of Service (TOS) byte in a header of the given packet to a value specifying the corresponding policy.
Owner:AVAYA INC
Security gatekeeper for a packetized voice communication network
Admission control means for controlling admission of traffic into a voice communication network, the admission control means comprises means for examining a call control message of a call control dialogue when admission of said traffic into said voice communication network is requested, the admission control means admit a traffic into said voice communication network only if the call control message accompanying the traffic admission request satisfies a pre-determined admission criterion.
Owner:HONG KONG APPLIED SCI & TECH RES INST
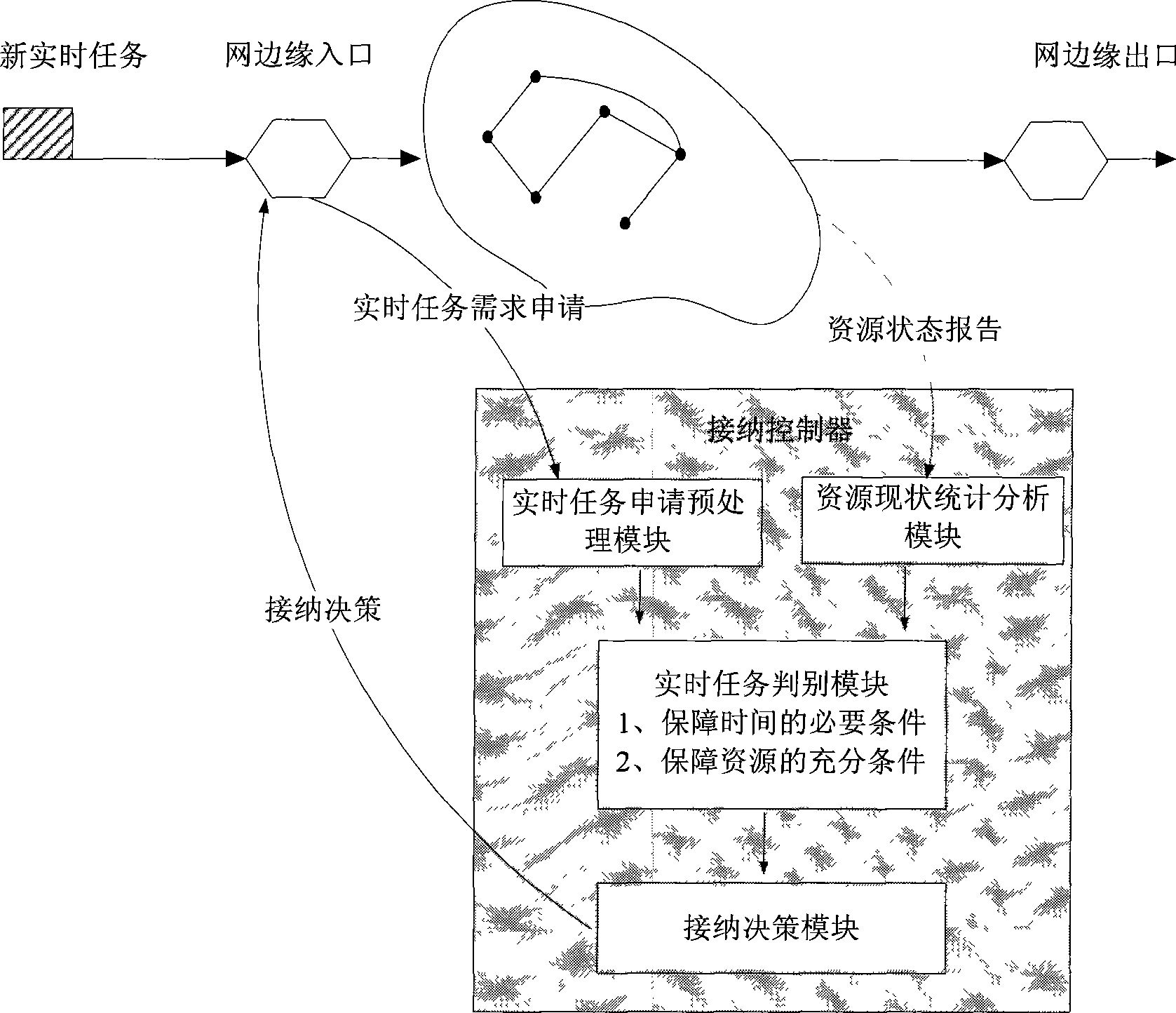
Real-time task admission control method of shared resource network
InactiveCN101431467AMeet real-time requirementsNetworks interconnectionStatistical analysisTime limit
The invention discloses a control method for real time task admission for shared resource network. The invention is to provide a control method for network admitting real time task so that the admission is not only performed but satisfy the demand for time limit. The technical scheme: first establishing real time task admission controller for network composed of resource status statistical analysis module, real time task application pretreatment module, real time judging module and admission and decision-making module. The resource status statistical analysis module gathers, calculates and analyzes the network resource status; the real time task application pretreatment module pretreats the real time task application; the real time task judging module judges necessary and sufficient condition of executable task; if several window time periods satisfies necessary and sufficient condition, then window time period of maximum executable probability is selected; the admission and decision-making module makes decision for real time task and forms notice for admission or not. The invention can performs network admission control for real time task.
Owner:NAT UNIV OF DEFENSE TECH
Network access control system
InactiveCN104660523AEasy to implementReduce procurement costsUser identity/authority verificationData switching networksAccess controlNetwork Admission Control
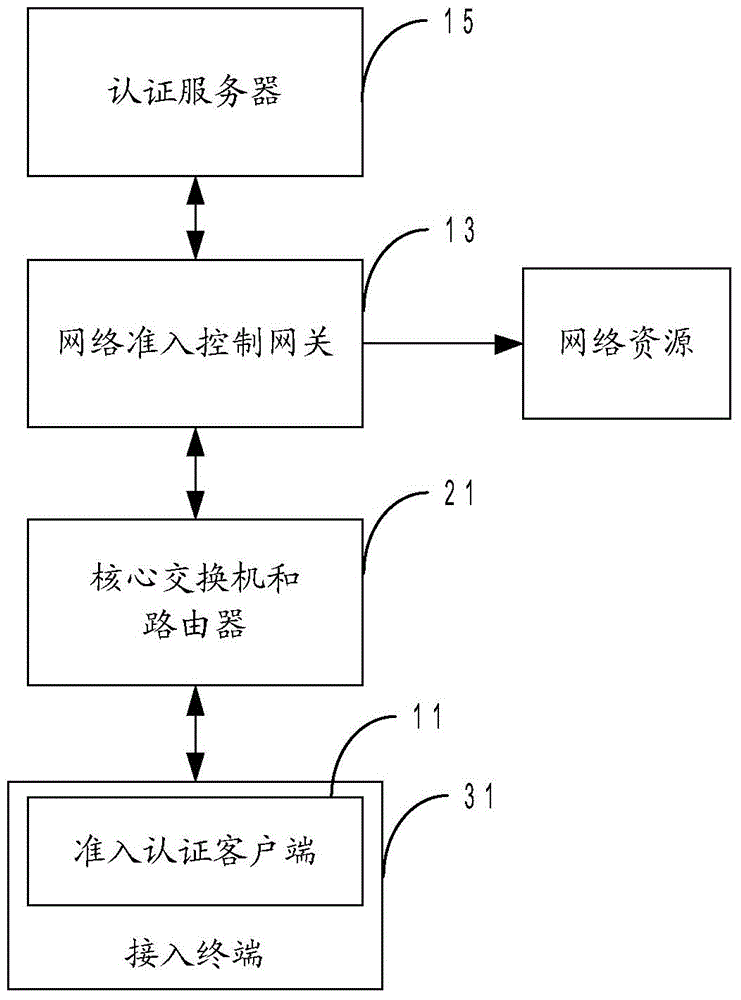
The invention is applicable to the field of network security, and provides a network access control system. The network access control system comprises an access authentication client, a network access control gateway and an authentication server, wherein the access authentication client is arranged at an access terminal and is used for authenticating network resource access of the access terminal; the network access control gateway is accessed to a node on a key path in which the access terminal accesses network resources, and is used for initiating authentication to the access terminal of accessing the network resources and controlling the network resource access of the access terminal according to an authentication state of the access terminal; the authentication server is used for issuing a security policy to the access authentication client, checking an identity of the access authentication client and a checking state of the security policy, and issuing a corresponding network resource access control instruction to the network access control gateway. According to the network access control system, network access control is realized by adopting a gateway manner, and a user does not need to completely replace network equipment such as all access layer network switches; the network access control system is simple to implement, and low in purchasing and implementing costs.
Owner:GUIZHOU POWER GRID CO LTD ZUNYI POWER SUPPLY BUREAU
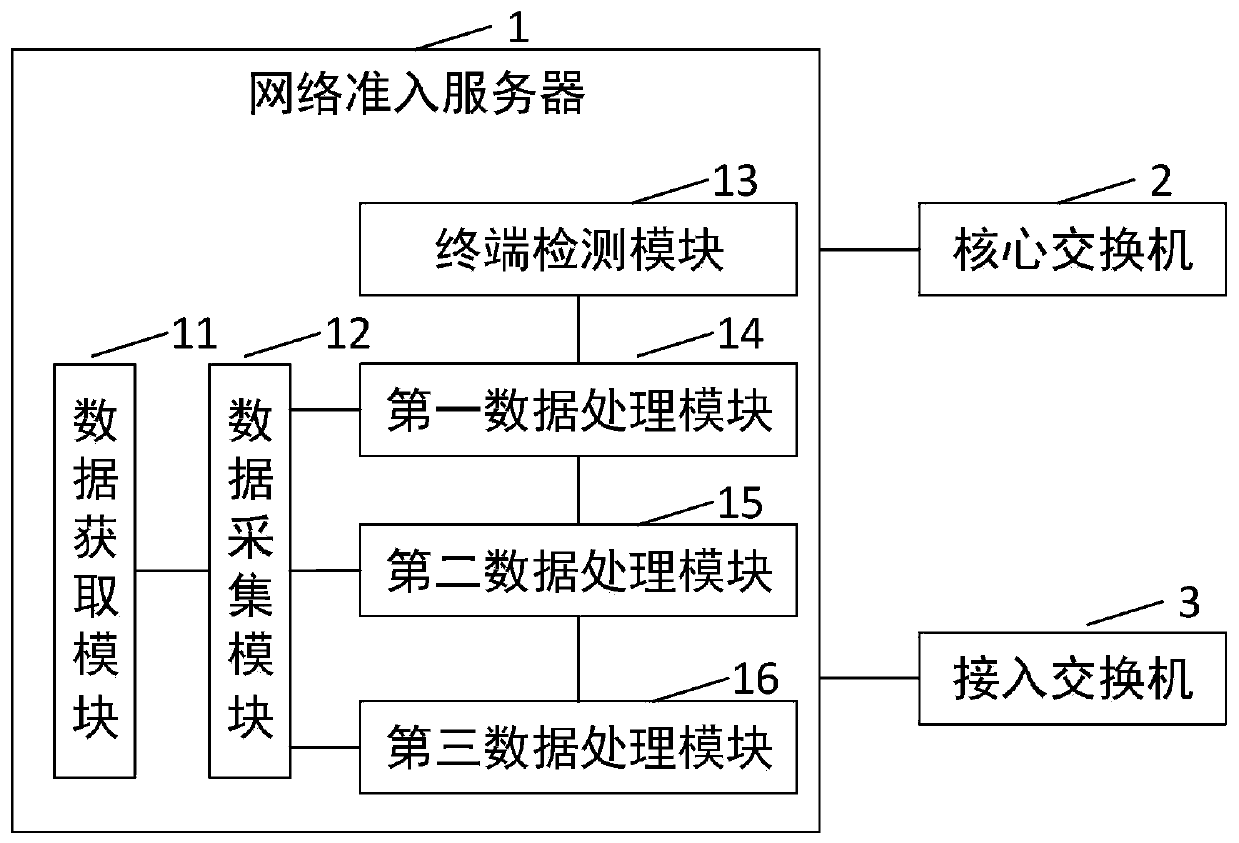
Network admission control method and system
ActiveCN110493195AImplement access controlGain accessTransmissionComputer terminalNetwork security policy
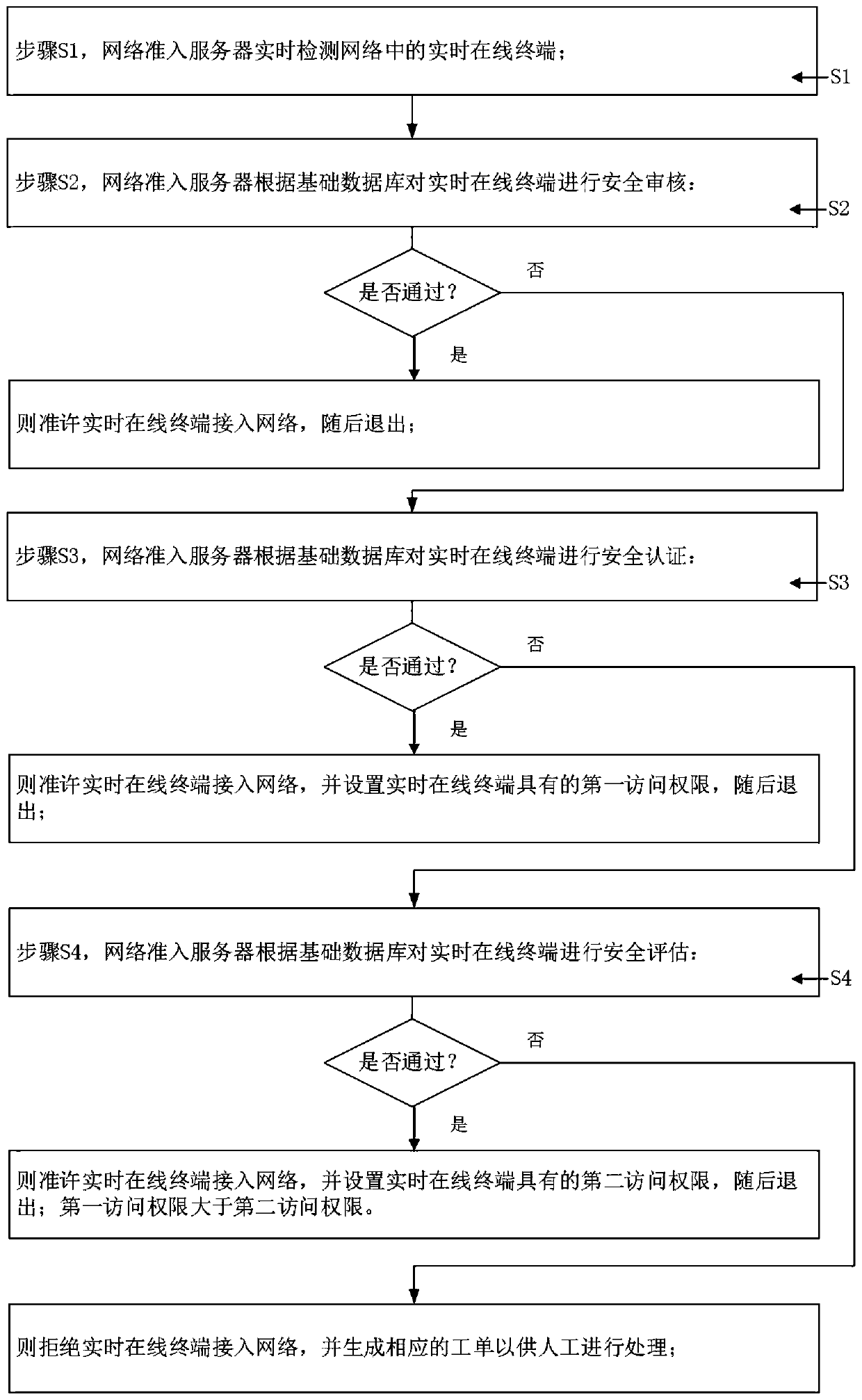
The invention provides a network admission control method and system, and relates to the technical field of network security, and the method comprises the steps: detecting a real-time online terminalin a network; performing security auditing on the real-time online terminal according to a basic database; if the real-time online terminal passes the security auditing, permitting the real-time online terminal to access the network; if the real-time online terminal does not pass the security audit, performing security authentication on the real-time online terminal according to the basic data if the real-time online terminal passes the security authentication, permitting the real-time online terminal to access the network, and setting a first access permission; if the real-time online terminal does not pass the security authentication, performing security evaluation on the real-time online terminal according to the basic data if the real-time online terminal passes the securityevaluation, permitting the real-time online terminal to access the network, and setting a second access permission; and if the real-time online terminal does not pass the security assessment, refusingthe real-time online terminal to enter the network. According to the invention, multiple verification is carried out on the authenticity of the user identity and the terminal risk, network admissioncontrol and access permission acquisition are realized, and the network security is improved.
Owner:上海文化广播影视集团有限公司 +1
A network switching method and apparatus based on network load control
InactiveCN103596230AGuaranteed rateImprove experienceWireless communicationIp addressComputer terminal
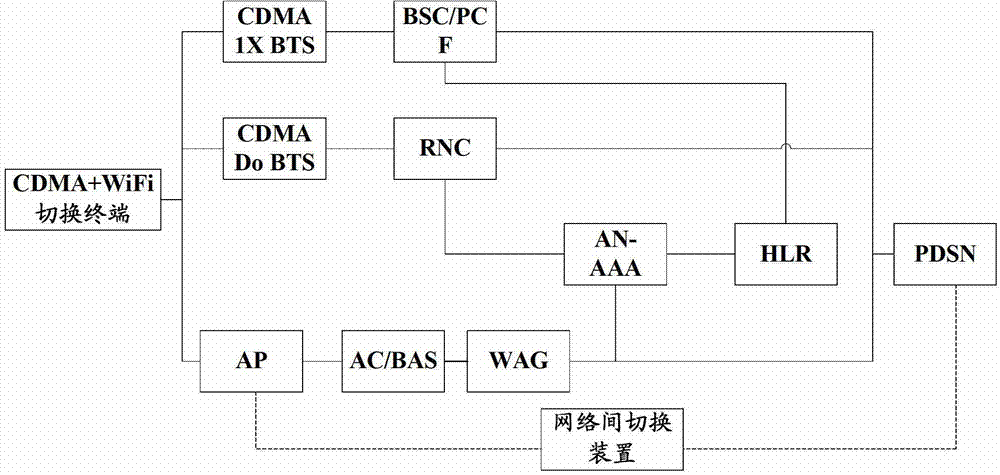
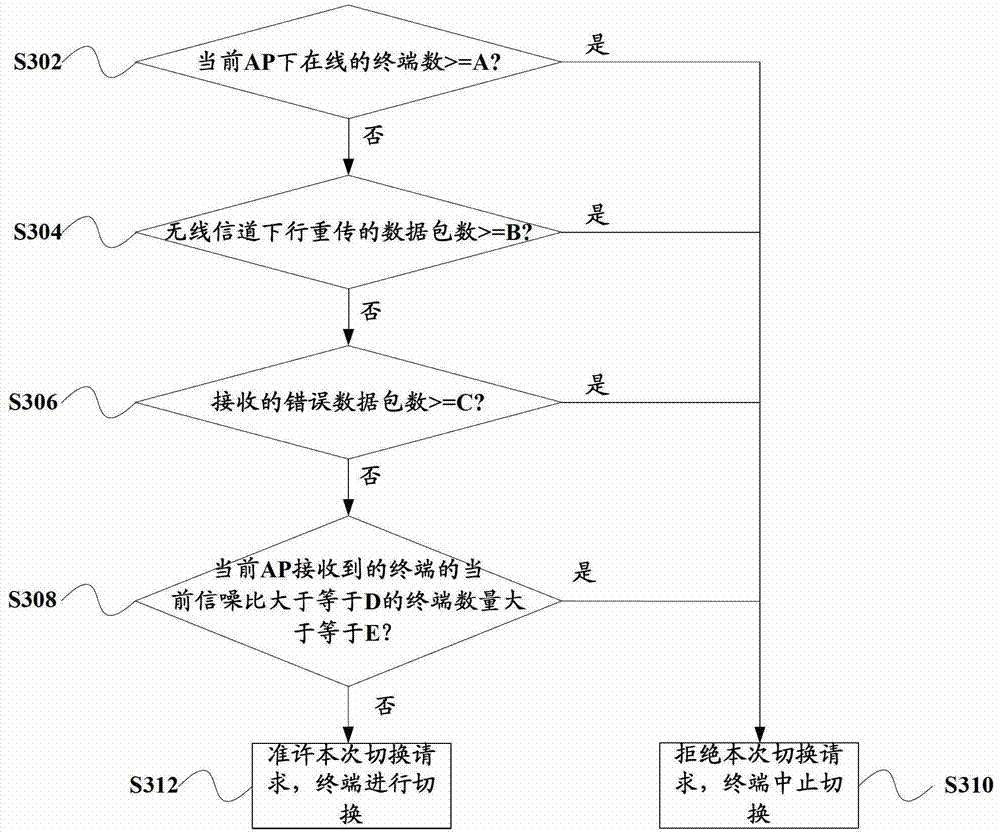
The embodiment of the invention discloses a network switching method and apparatus based on network load control. The method comprises initiating a request for measuring the load of a target access point AP through a mobile broadband network by a receiving terminal, wherein the request comprises the MAC address of the target AP; querying and obtaining the IP address of the target AP according to the MAC address of the target AP; transmitting the request to the target AP on the basis of the IP address of the target AP; receiving a measured result fed by the target AP, comparing the measured result and a set parameter threshold, and determining whether to execute the switch from the mobile broadband network to a wireless broadband network; and if network switching is determined, transmitting switching indication to a terminal in order that the terminal achieves the switch from the mobile broadband network to the wireless broadband network. The network switching apparatus is still capable of effectively maintaining the user rate in the mobile broadband network after switched to the wireless broadband network so as to further guarantee good user experience.
Owner:CHINA TELECOM CORP LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com