Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
503results about How to "Avoid reading" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
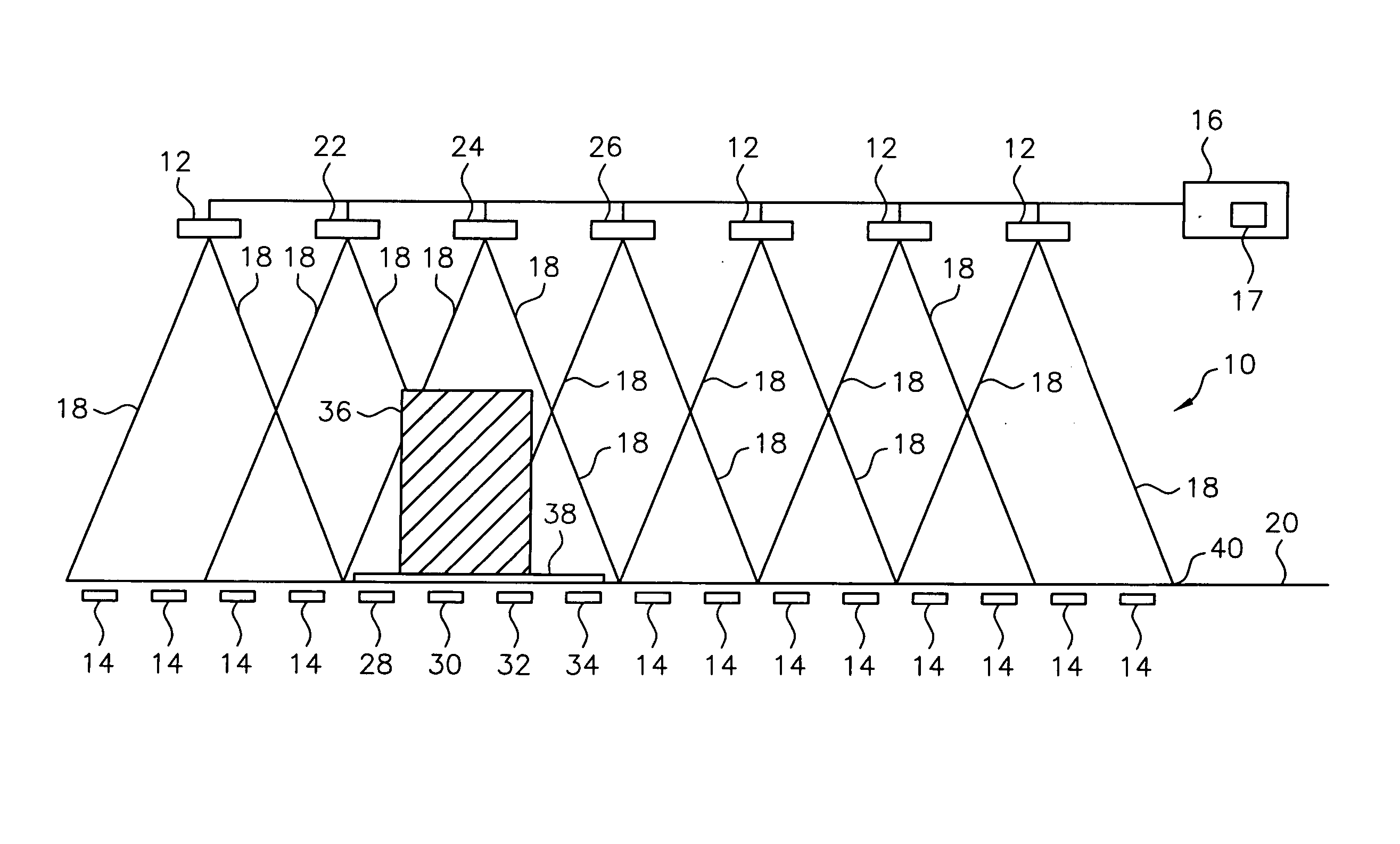
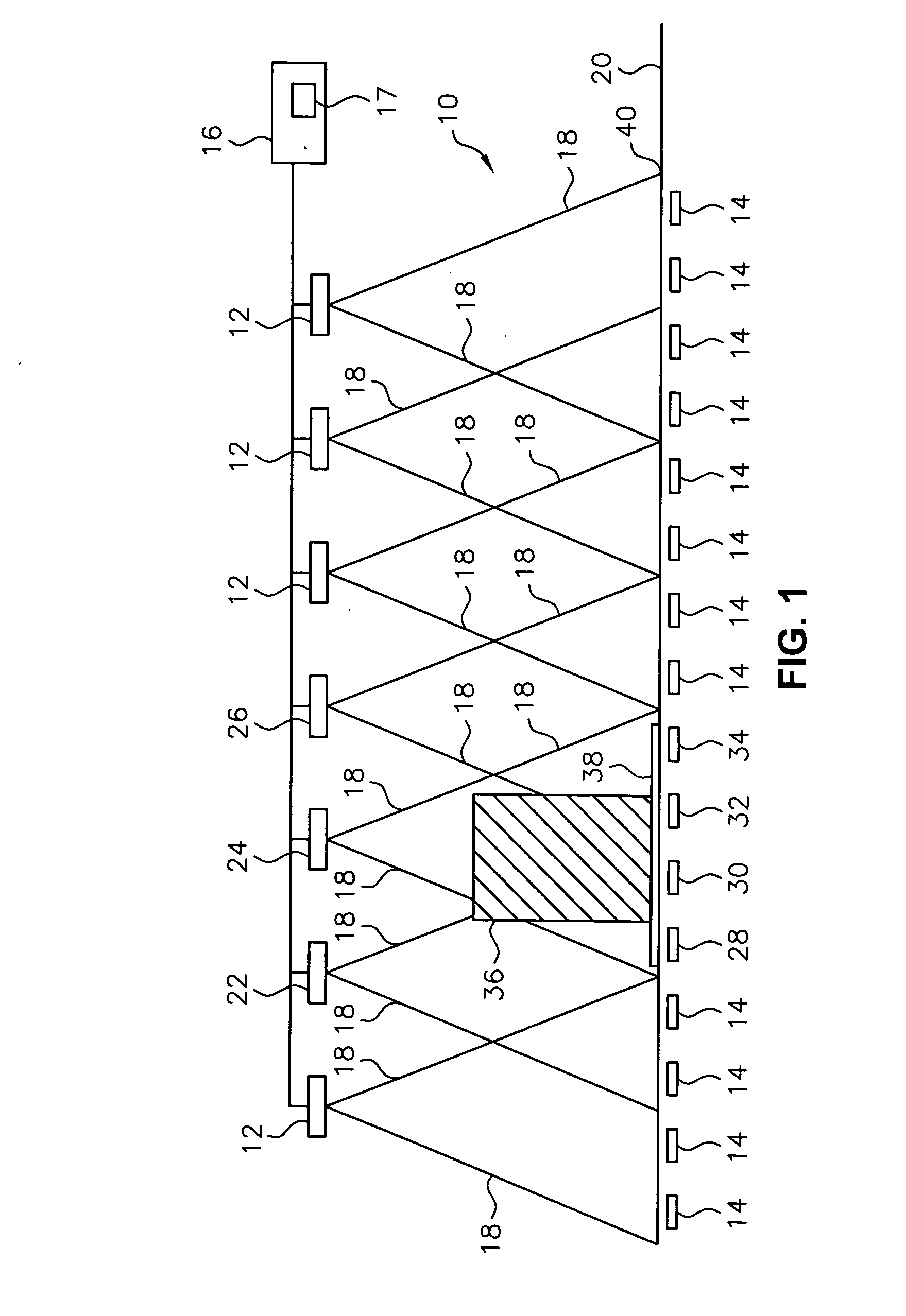
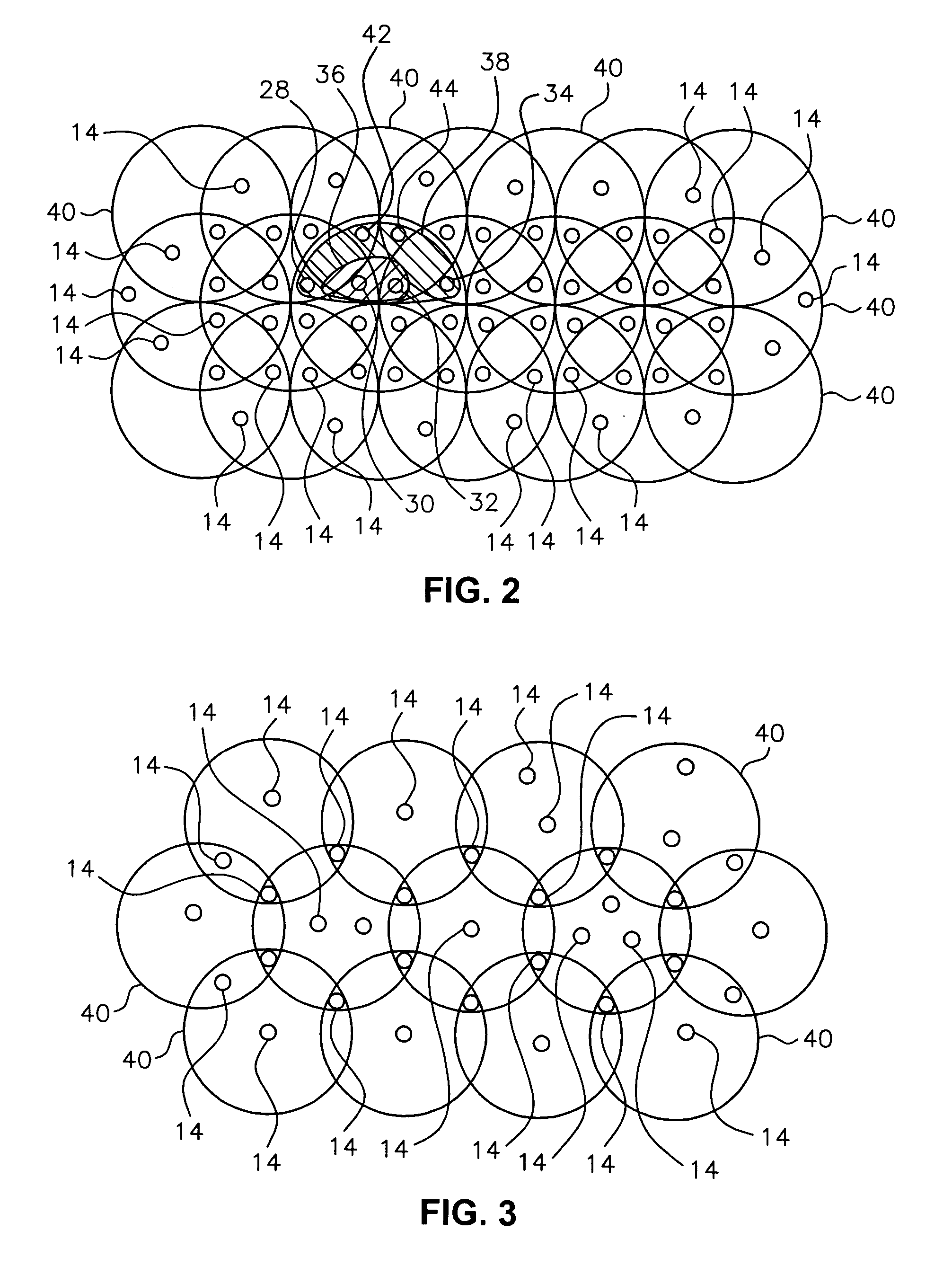
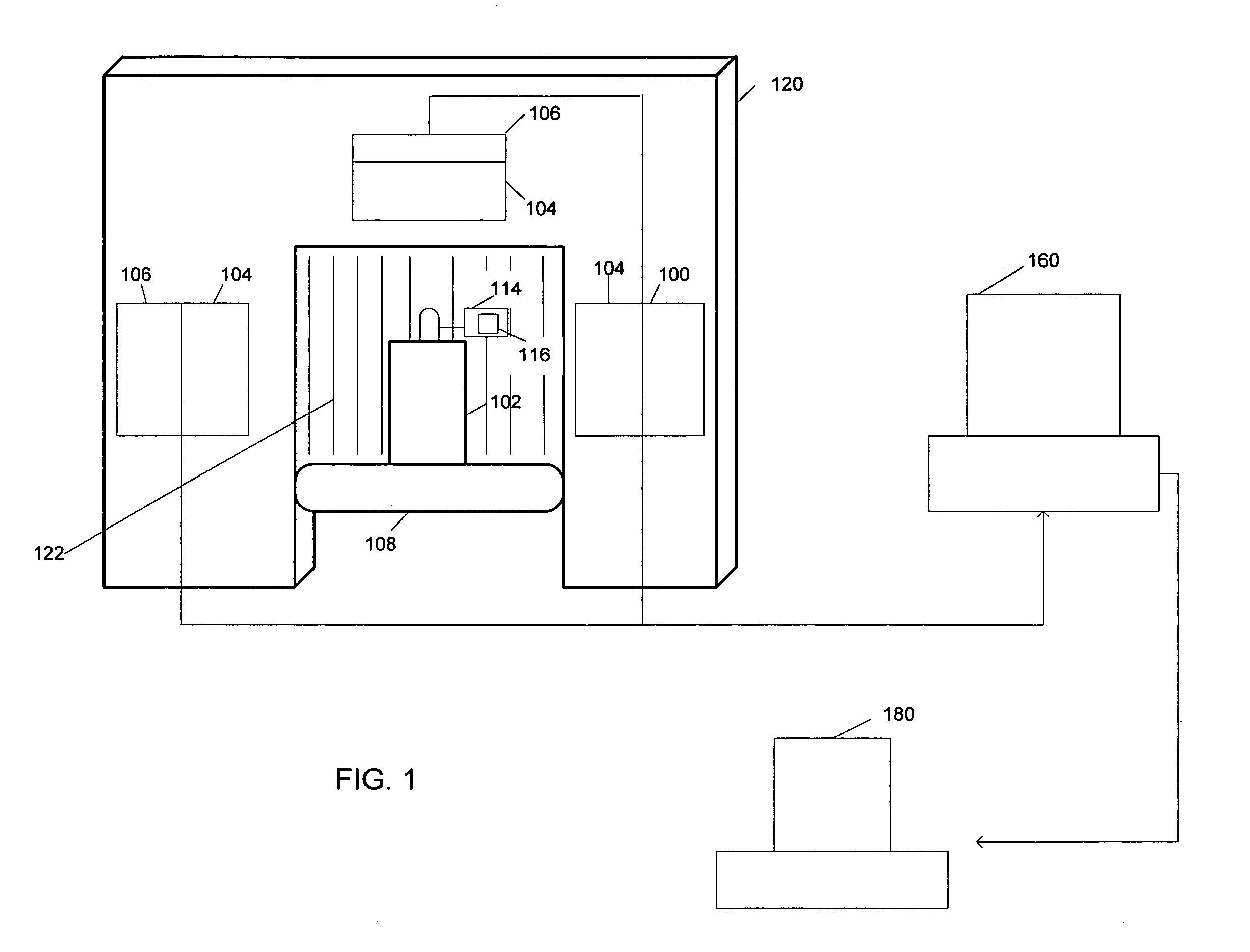
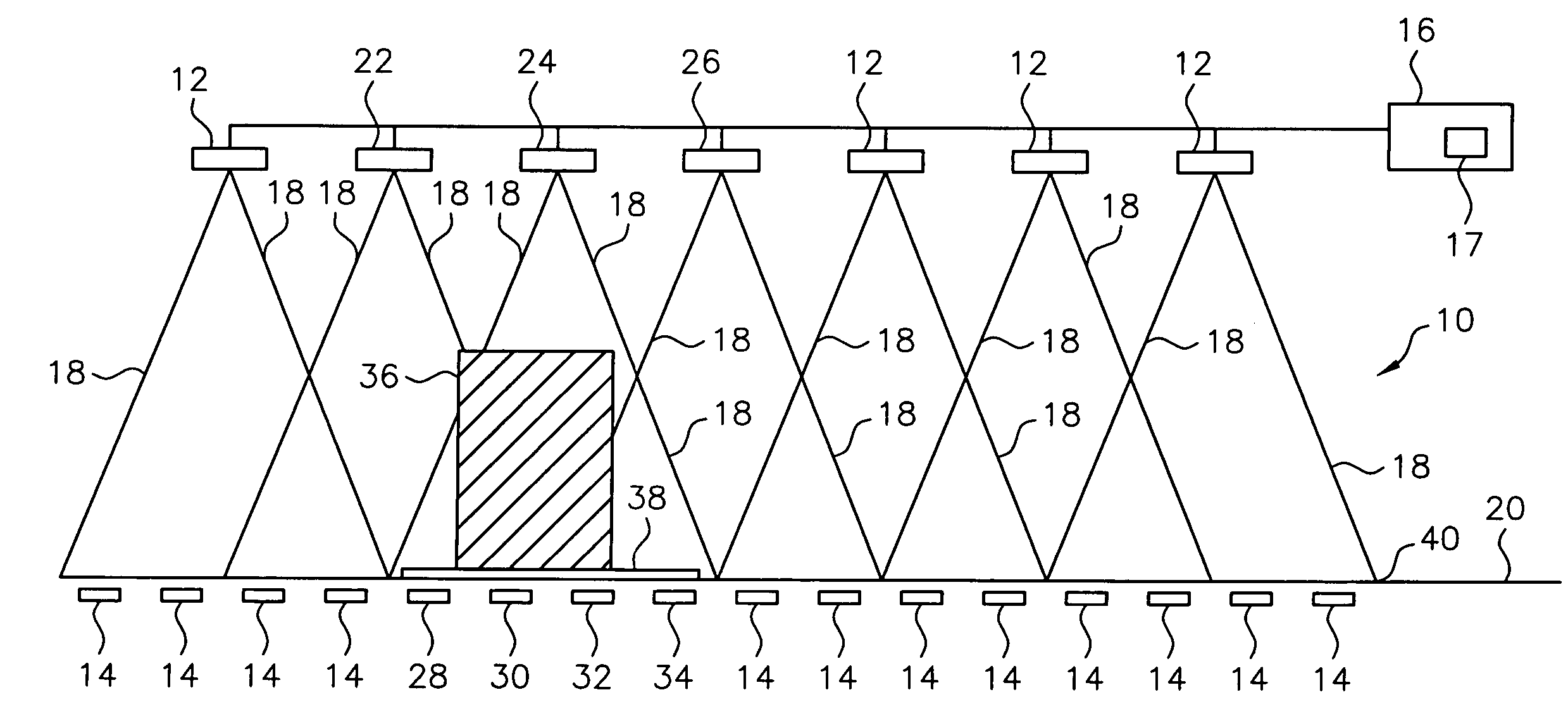
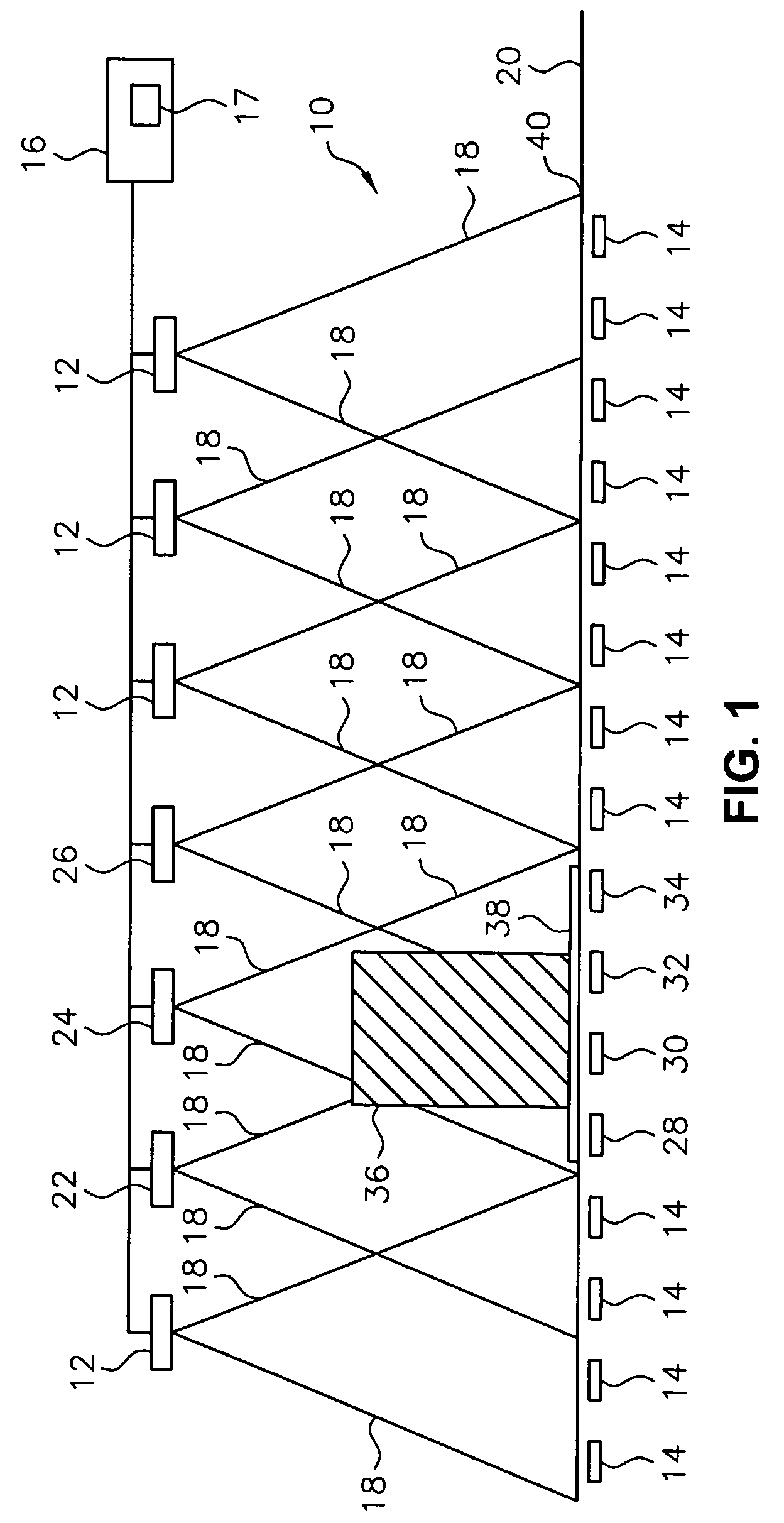
Article identification and tracking using electronic shadows created by RFID tags
InactiveUS20050012613A1Easy to identifyEasy to trackElectric signal transmission systemsMemory record carrier reading problemsElectromagnetic couplingEngineering
A tracking system uses RFID (radio frequency identification) tag technology to facilitate the identification and tracking of items in an environment through a technique known as shadowing. As an object or target moves within a pre-described detection zone with communicating antenna and RFID sensors, the object or target blocks the line of sight between respective antenna and sensors, preventing electromagnetic coupling between the sensor and the antenna and thus casting an electromagnetic shadow along the line of sight. One approach of this invention uses this shadow technique to perform functions such as theft (shrink) deterrence / detection; tracking the motion of objects through an environment by monitoring the shadow; and correlation analysis of people shadows to tagged items (e.g., merchandise, articles) to foster marketing and merchandising effectiveness.
Owner:CHECKPOINT SYST INC
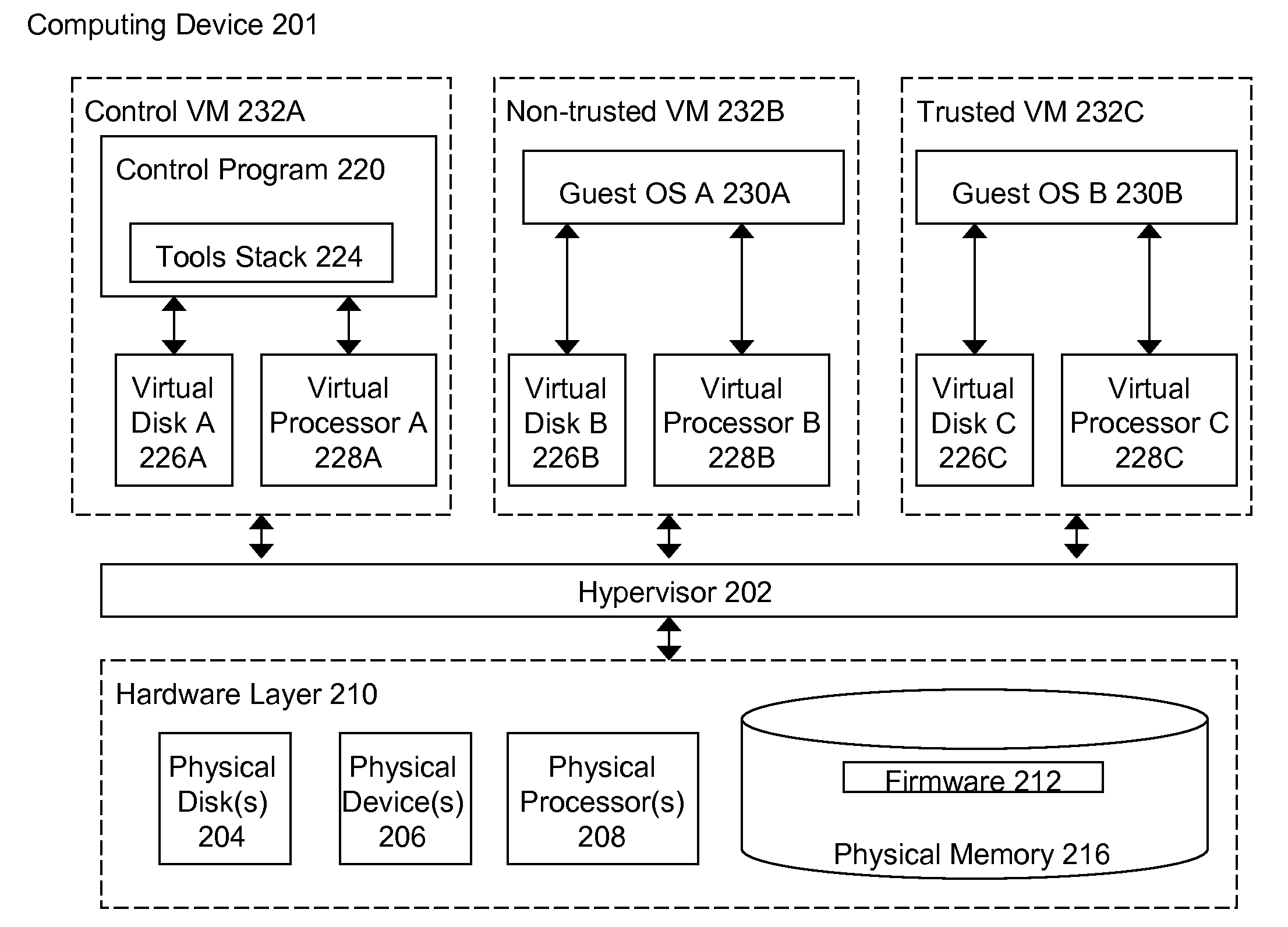
Methods and systems for preventing access to display graphics generated by a trusted virtual machine
ActiveUS20110145916A1Avoid accessAvoid readingDigital data processing detailsUser identity/authority verificationGraphicsSoftware engineering
The methods and systems described herein provide for preventing a non-trusted virtual machine from reading the graphical output of a trusted virtual machine. A graphics manager receives a request from a trusted virtual machine to render graphical data using a graphics processing unit. The graphics manager assigns, to the trusted virtual machine, a secure section of a memory of the graphics processing unit. The graphics manager renders graphics from the trusted virtual machine graphical data to the secure section of the graphics processing unit memory. The graphics manager receives a request from a non-trusted virtual machine to read graphics rendered from the trusted virtual machine graphical data and stored in the secure section of the graphics processing unit memory, and prevents the non-trusted virtual machine from reading the trusted virtual machine rendered graphics stored in the secure section of the graphics processing unit memory.
Owner:CITRIX SYST INC
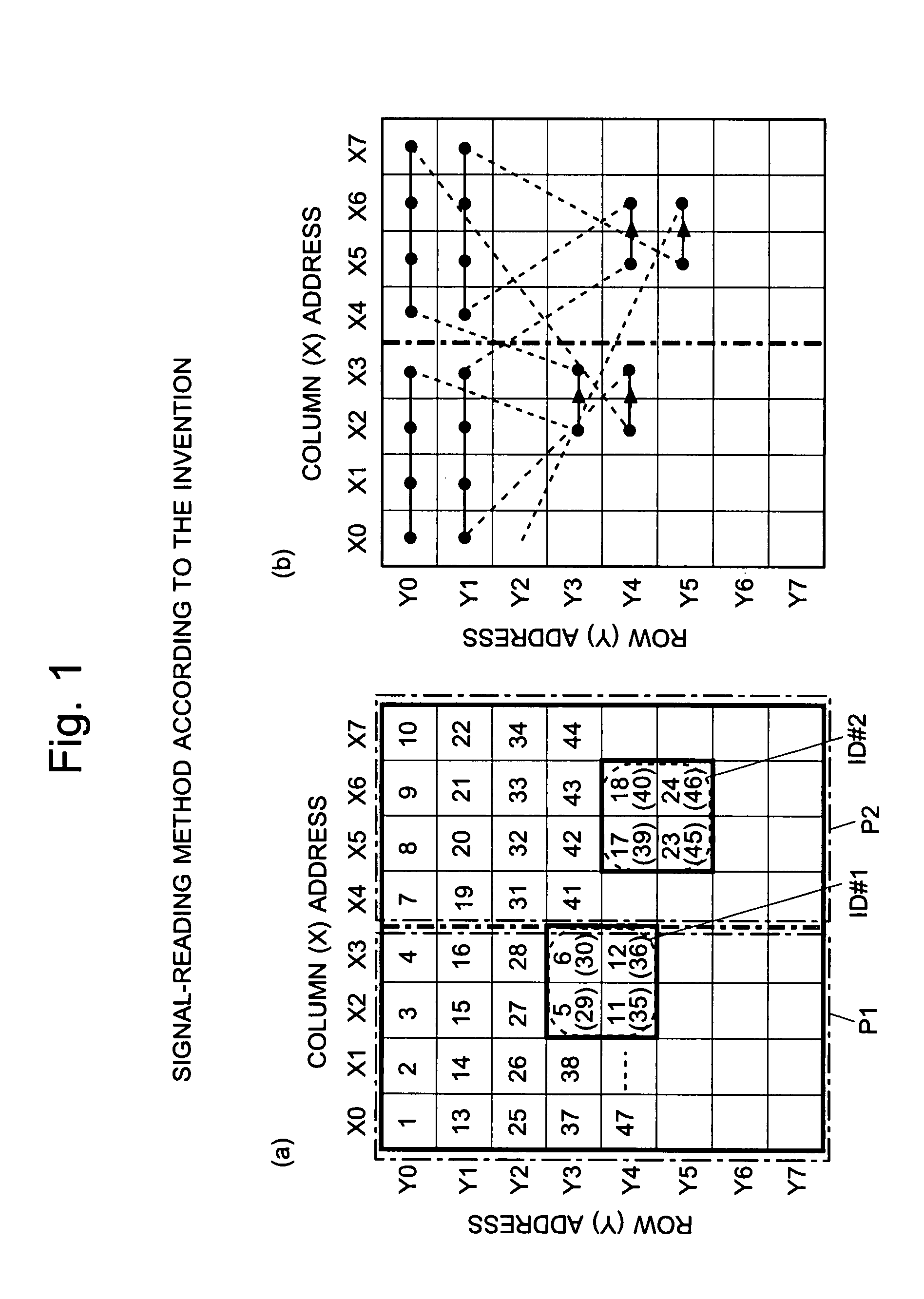
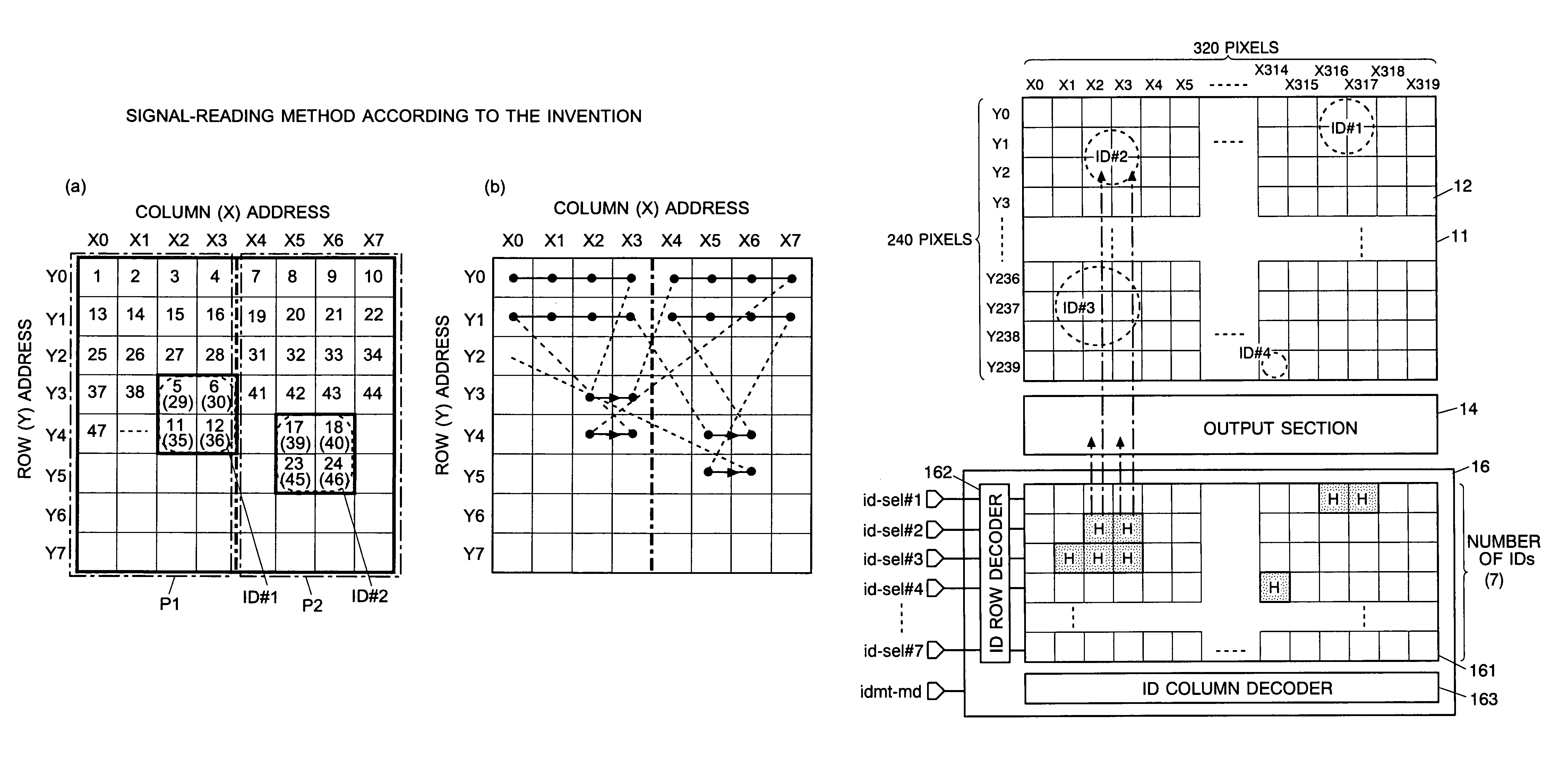
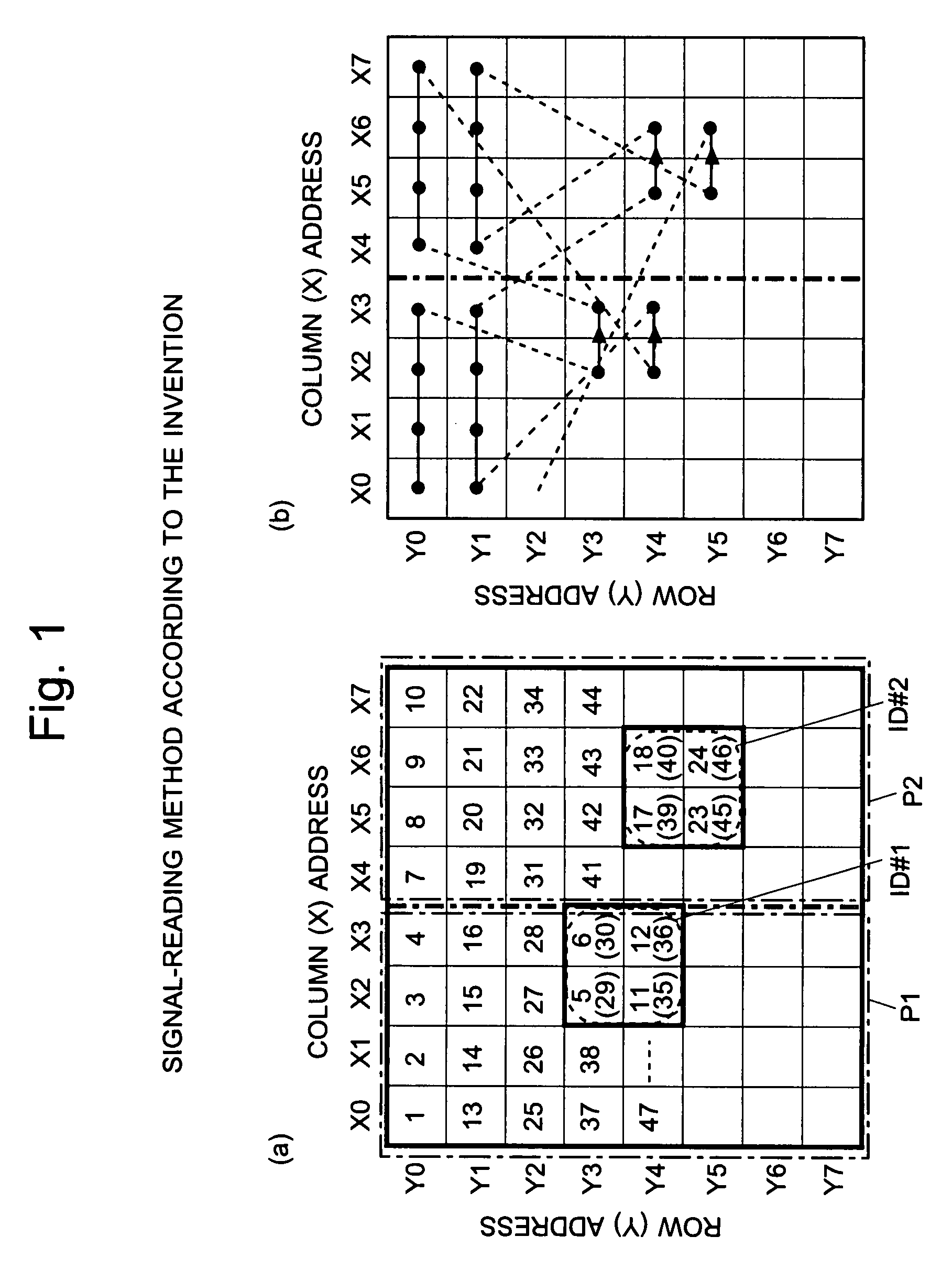
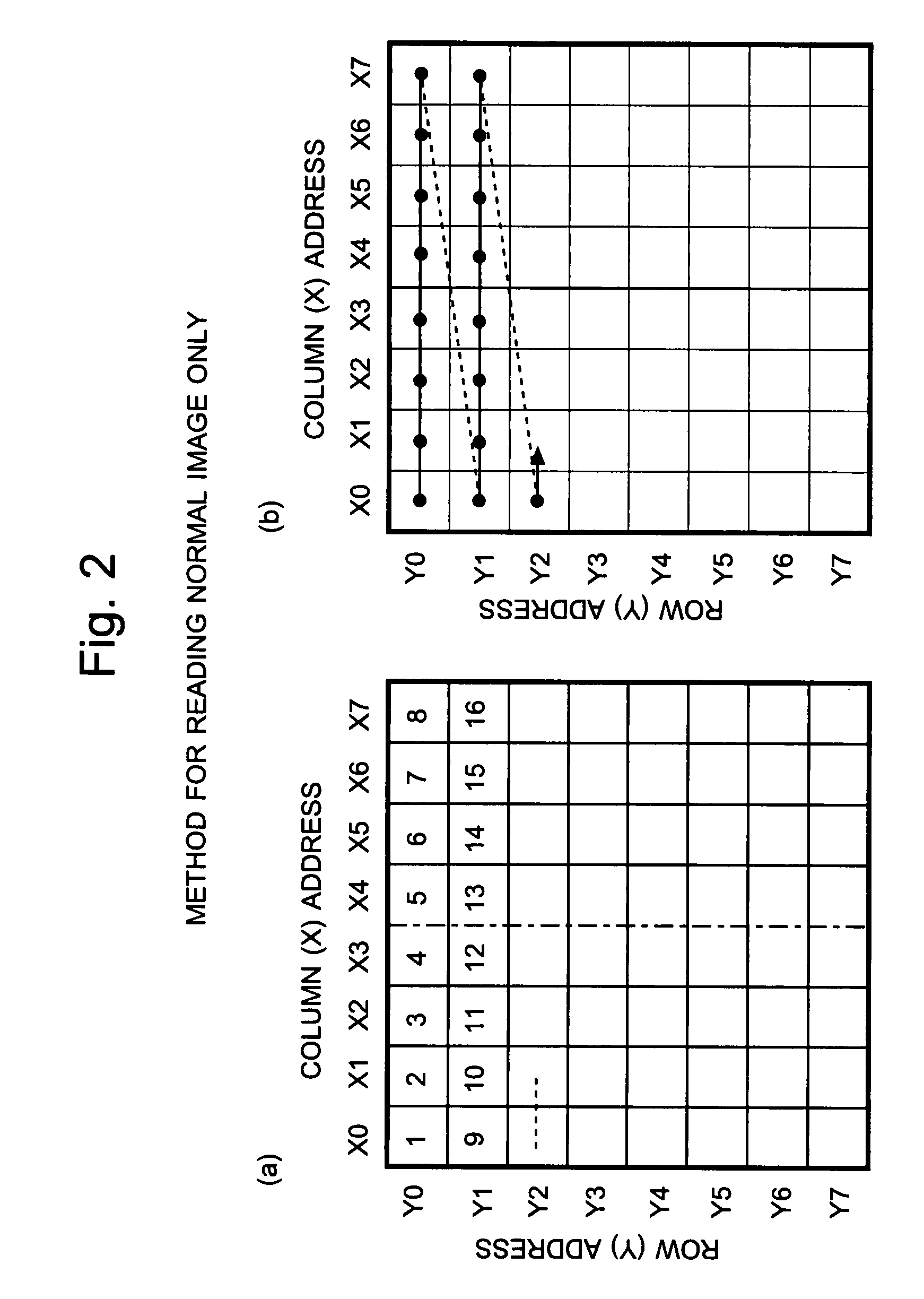
Imaging Device and Method for Reading Signals From Such Device
InactiveUS20080297615A1Small areaIncrease reading speedTelevision system detailsTelevision system scanning detailsImage sensorAudio power amplifier
Each pixel cell (12) of an image sensor (10) is made of a 4-Tr structure, in which only one Tr for resetting a column (X) is so added to an ordinary 3-Tr APS as to reset only an arbitrary pixel selectively, thereby to confine the pixel size. When a pixel signal is to be read, the period, for which the pixel signals composing an ordinary image of one frame are read, is finely divided so that the pixel signals of the pixels receiving an ID light for the period are read out bit by bit and repeatedly. At this time, for only the column being read, an electric current is fed to a read amplifier in the pixel cell (12) or a variable gain amplifier in an output unit (14), thereby to suppress the power consumption. As a result, a lower power consumption and a higher pixel formation can be attained in an image pickup device for picking up an image and for acquiring the ID information of a light beacon existing in the image pickup range.
Owner:JAPAN SCI & TECH CORP +1
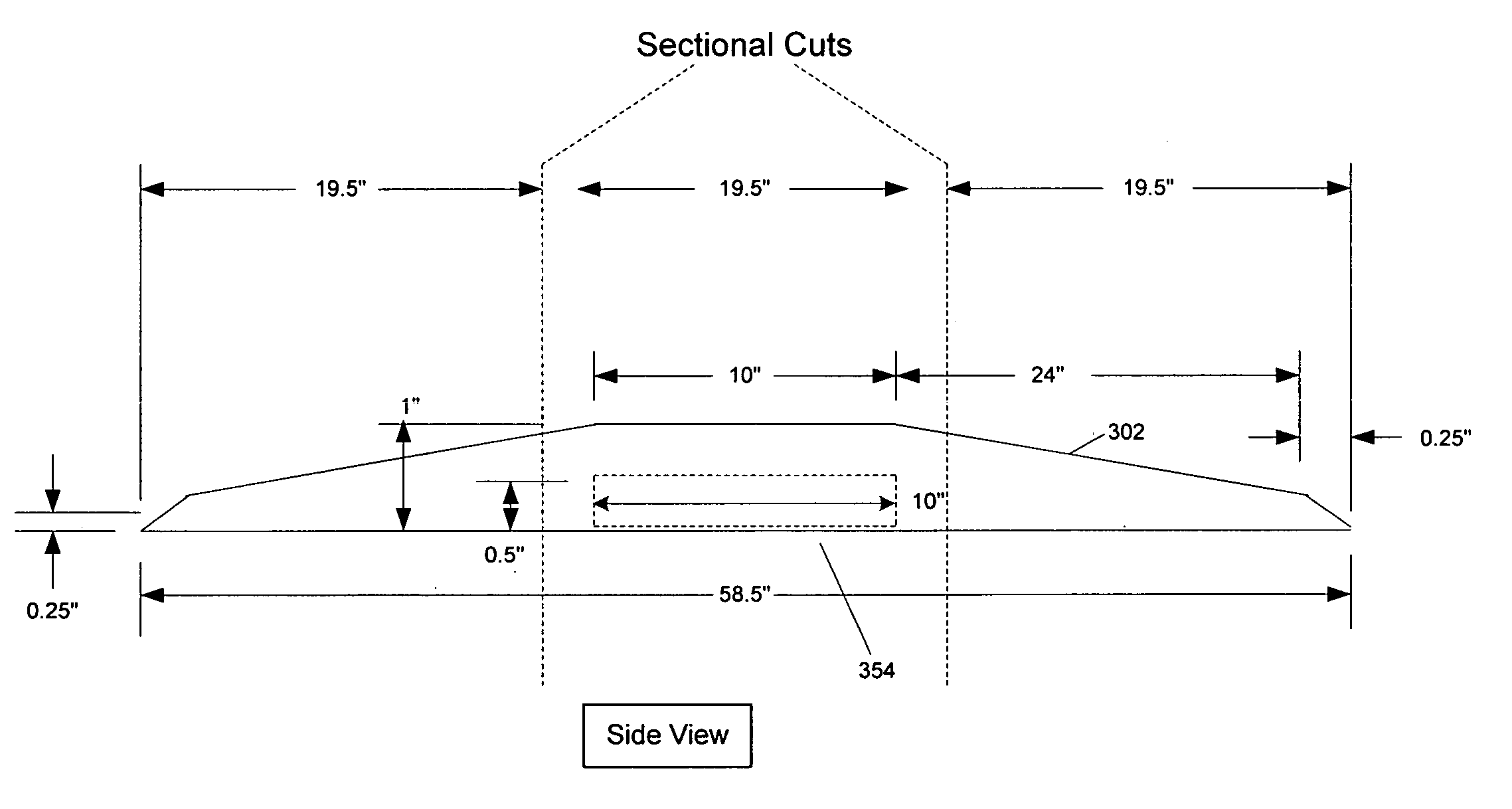
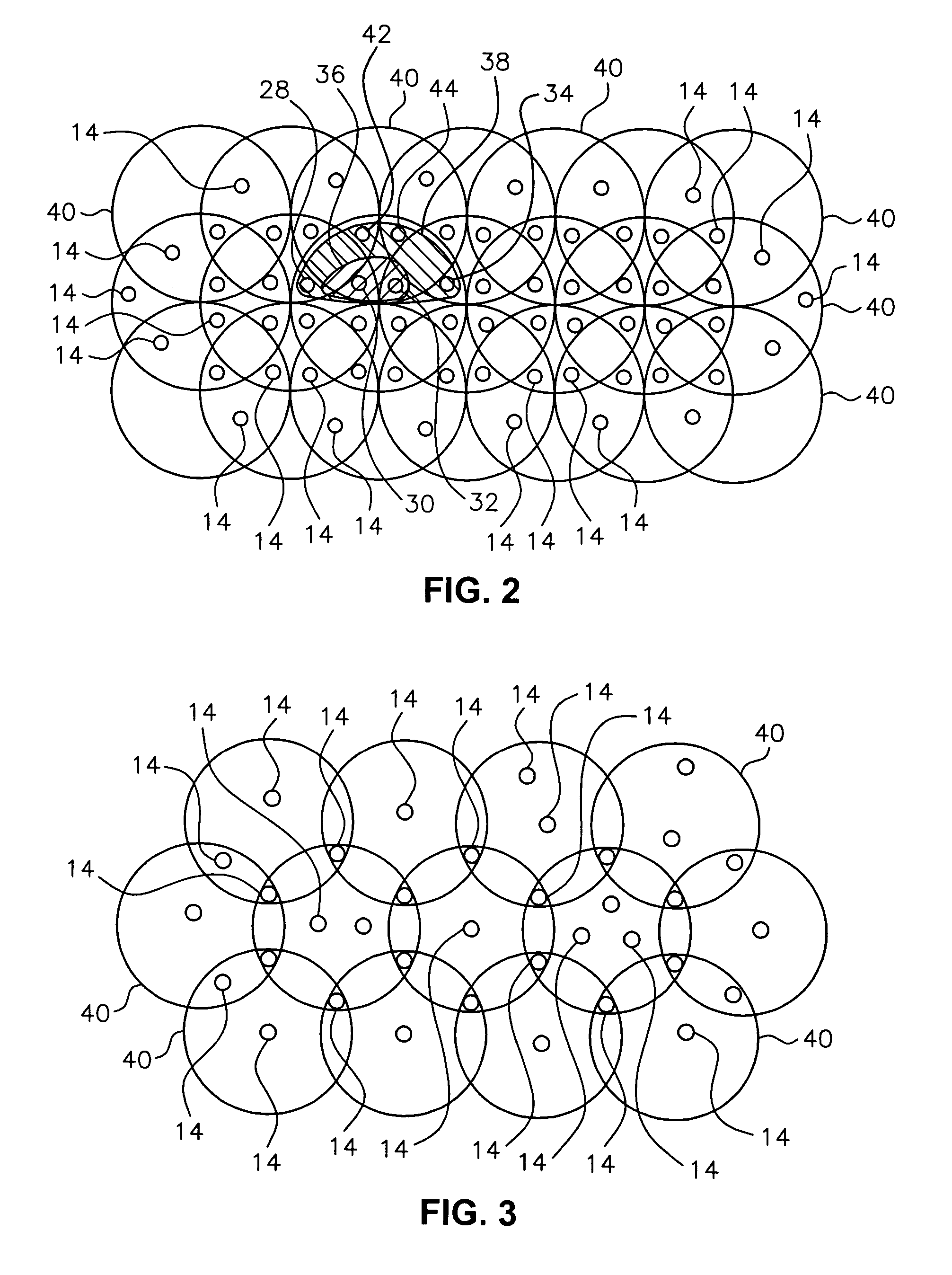
Radio frequency identification for advanced security screening and sortation of baggage
ActiveUS6967579B1Avoid readingMemory record carrier reading problemsBurglar alarm by hand-portable articles removalEnergy absorbingConveyor system
An RFID conveyor system comprises one or more wedges designed to allow an RFID scanner to detect and uniquely identify RFID-tagged baggage as they are conveyed through an antenna array. The RFID conveyor system can also be designed to prevent the reading of previous or subsequent bags by using antennas with highly focused RF read fields in conjunction with RF energy absorbing materials, such as RF curtains, designed to eliminate the identification of any baggage located outside of the “read” area.
Owner:SMARTRAC TECH FLETCHER INC
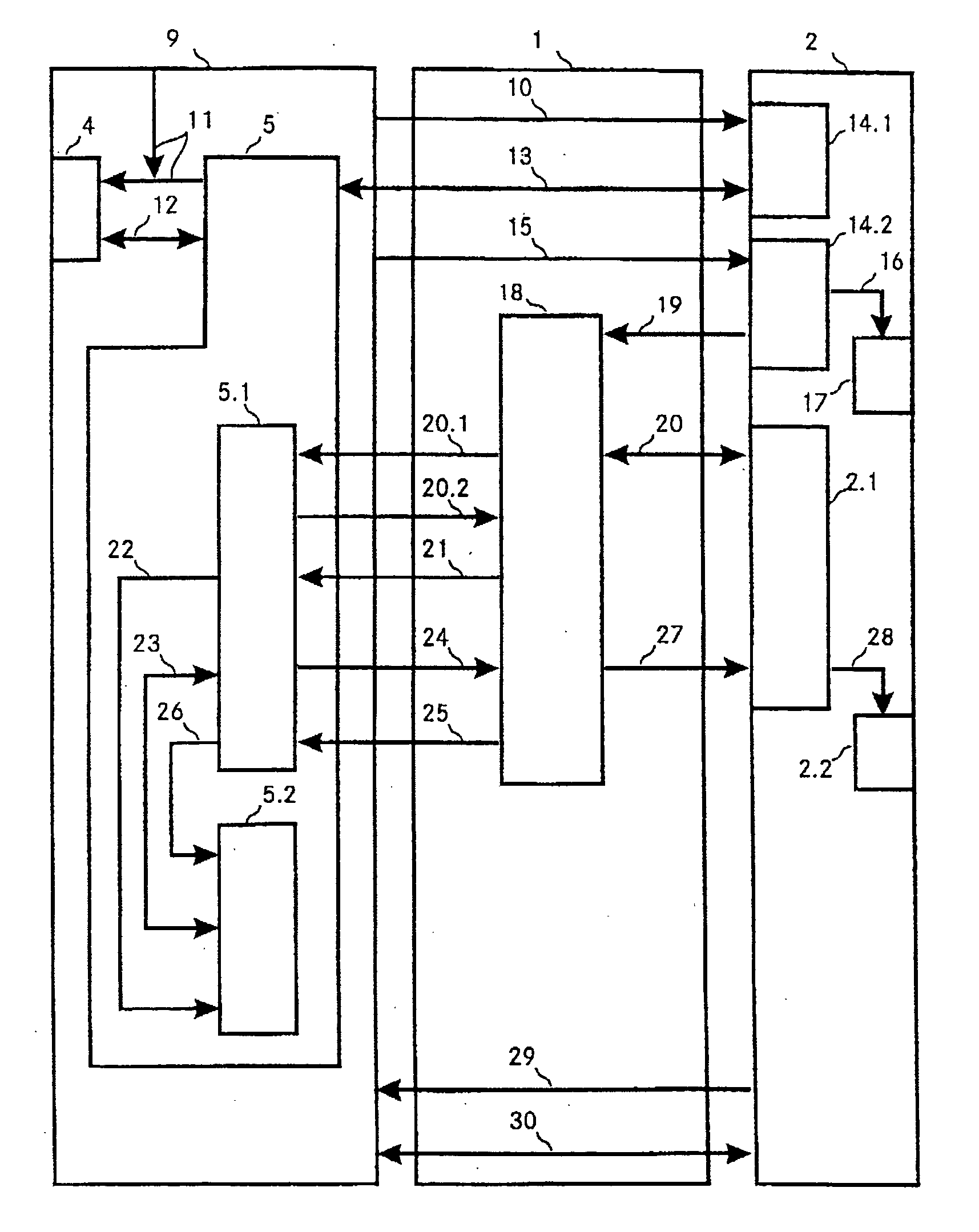
Method, arrangement and secure medium for authentication of a user
InactiveUS20040107367A1Easy to adaptAvoid readingDigital data processing detailsUser identity/authority verificationBiometric dataInternet privacy
When confidential data or areas of an EDP system (2) are accessed by a user (9), the user is granted access only if he registers (16) with the EDP system correctly with a user name and a password and, in addition, can identify himself as having access authorization using an access code (21), to which only he has access, from a database (5.2). The database is stored on a chip card (5), and access to the database has dual protection. Access to the access codes in the database is given only to that user who can correctly authenticate himself (12) to the chip card using biometric data, for example. In addition, the access codes in the database can be accessed only by a program (5.1) which is stored on the chip card and which can be activated only following correct authentication to the chip card by the user and which needs to have correctly authenticated itself (20) directly on the database using an ID incorporated in the program code.
Owner:HUMAN BIOS
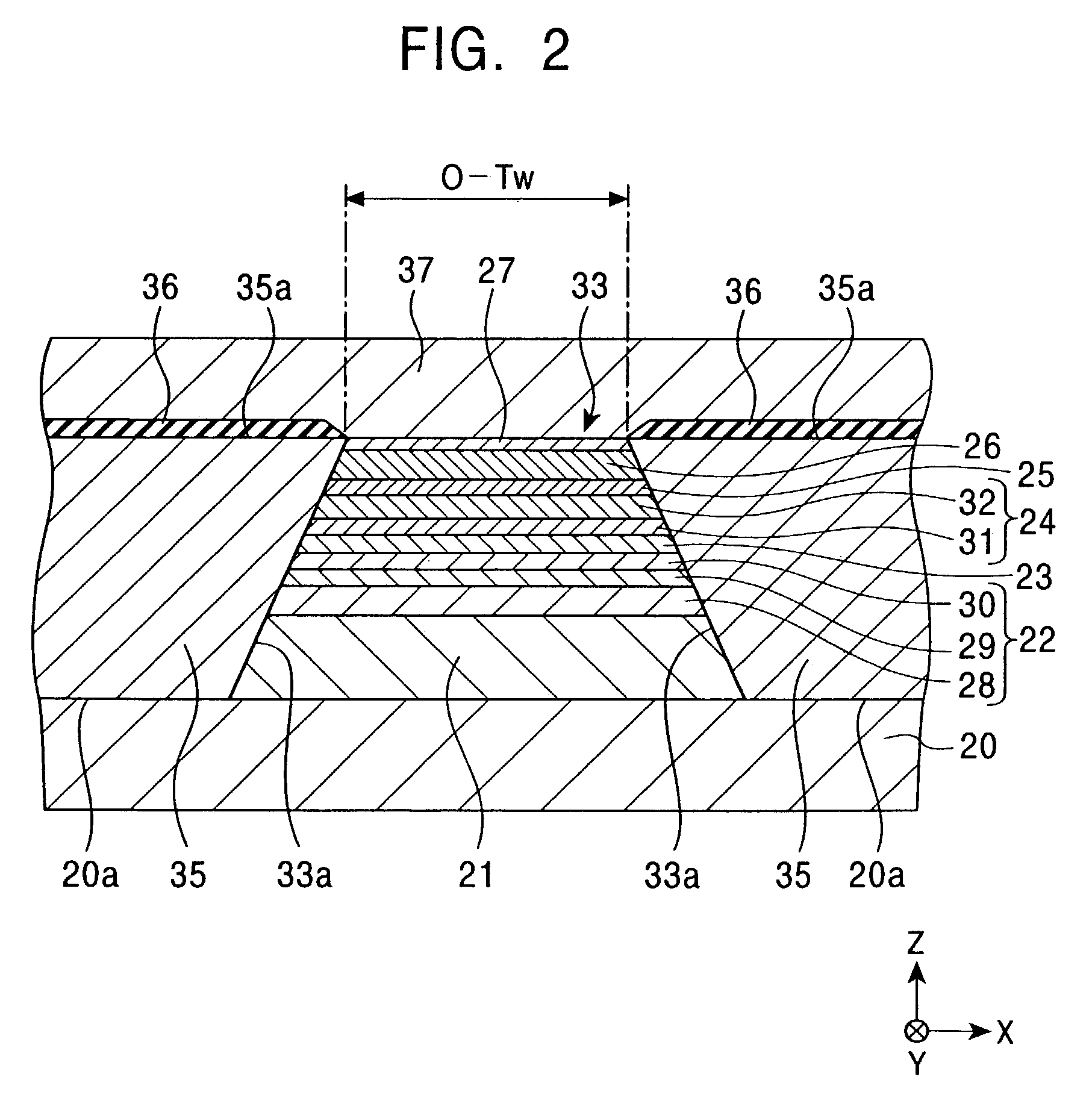
Magnetic sensing element with side shield layers
InactiveUS6980403B2Minimized increaseAvoid readingNanomagnetismMagnetic measurementsComposite filmElectrical and Electronics engineering
A magnetic sensing element of a current-perpendicular-to-plane (CPP) type that minimizes an increase in effective read track width and prevents side reading is provided. The magnetic sensing element includes a composite film, an upper shield layer, a lower shield layer, and side shield layers. The side shield layers are disposed at the two sides of the composite film in the track width direction between the lower shield layer and the upper shield layer.
Owner:TDK CORPARATION
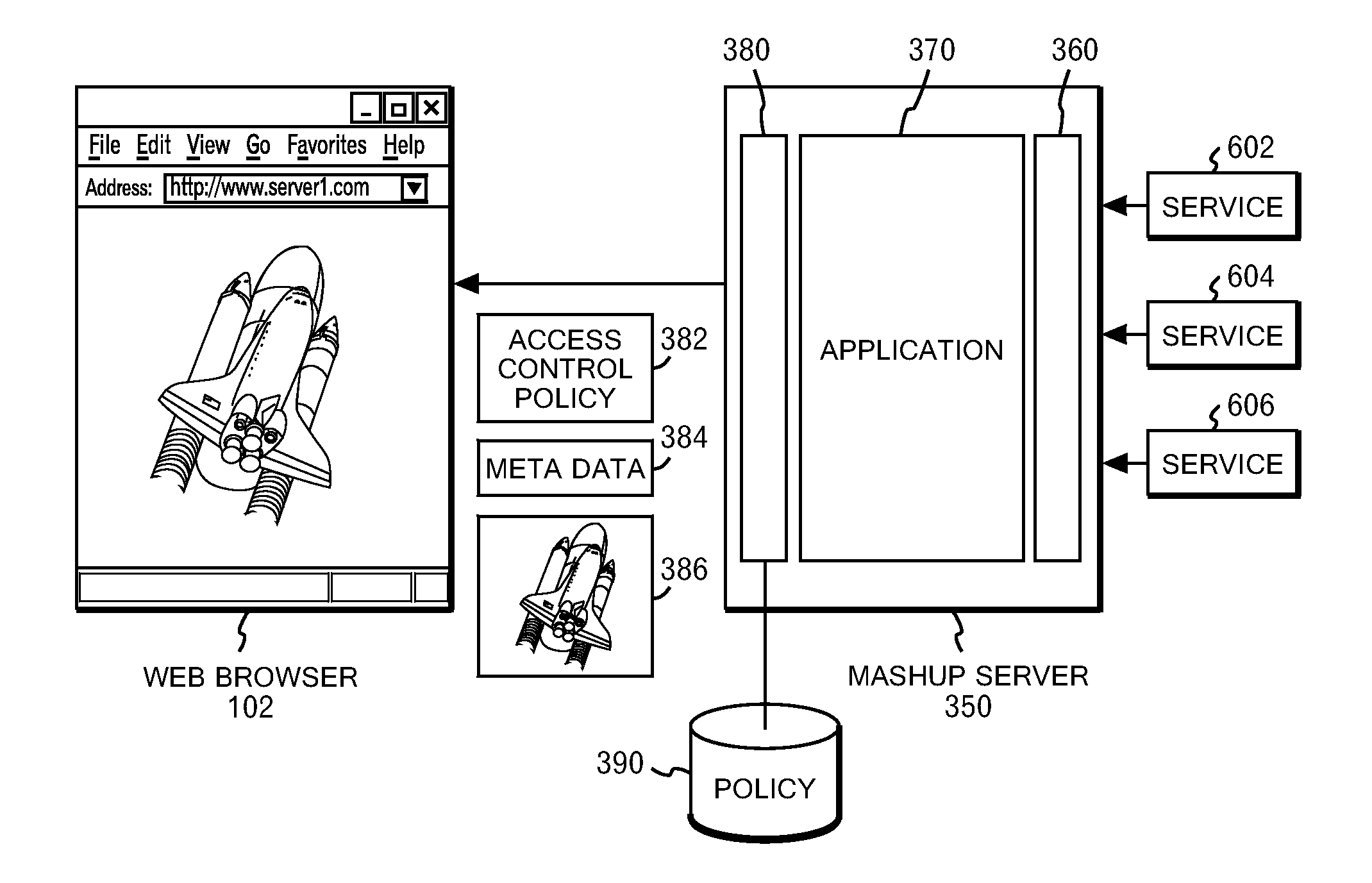
Content processing system, method and program
InactiveUS20080301766A1Prevent harmful processingMinimize changesDigital data protectionTransmissionClient-sideHandling system
Access control for each part in an HTML document constituting a Web page is performed according to the origin of the part in the document. Thereby, a content provided by a malicious user or server is prevented from fraudulently reading and writing other parts in the HTML document. More precisely, on a server side, each content (including a JavaScript program) is automatically provided with a label indicating the domain that is the origin of the content. Thereby, the control of accesses to multiple domains (cross domain access control) can be performed on a client side. Under this configuration, a combination of the contents, metadata and the access control policy is transmitted from the server side to the client side.
Owner:IBM CORP
Article identification and tracking using electronic shadows created by RFID tags
InactiveUS7081818B2Facilitate identification and trackingFoster marketing and merchandising effectivenessElectric signal transmission systemsMemory record carrier reading problemsElectromagnetic couplingCorrelation analysis
A tracking system uses RFID (radio frequency identification) tag technology to facilitate the identification and tracking of items in an environment through a technique known as shadowing. As an object or target moves within a pre-described detection zone with communicating antenna and RFID sensors, the object or target blocks the line of sight between respective antenna and sensors, preventing electromagnetic coupling between the sensor and the antenna and thus casting an electromagnetic shadow along the line of sight. One approach of this invention uses this shadow technique to perform functions such as theft (shrink) deterrence / detection; tracking the motion of objects through an environment by monitoring the shadow; and correlation analysis of people shadows to tagged items (e.g., merchandise, articles) to foster marketing and merchandizing effectiveness.
Owner:CHECKPOINT SYST INC
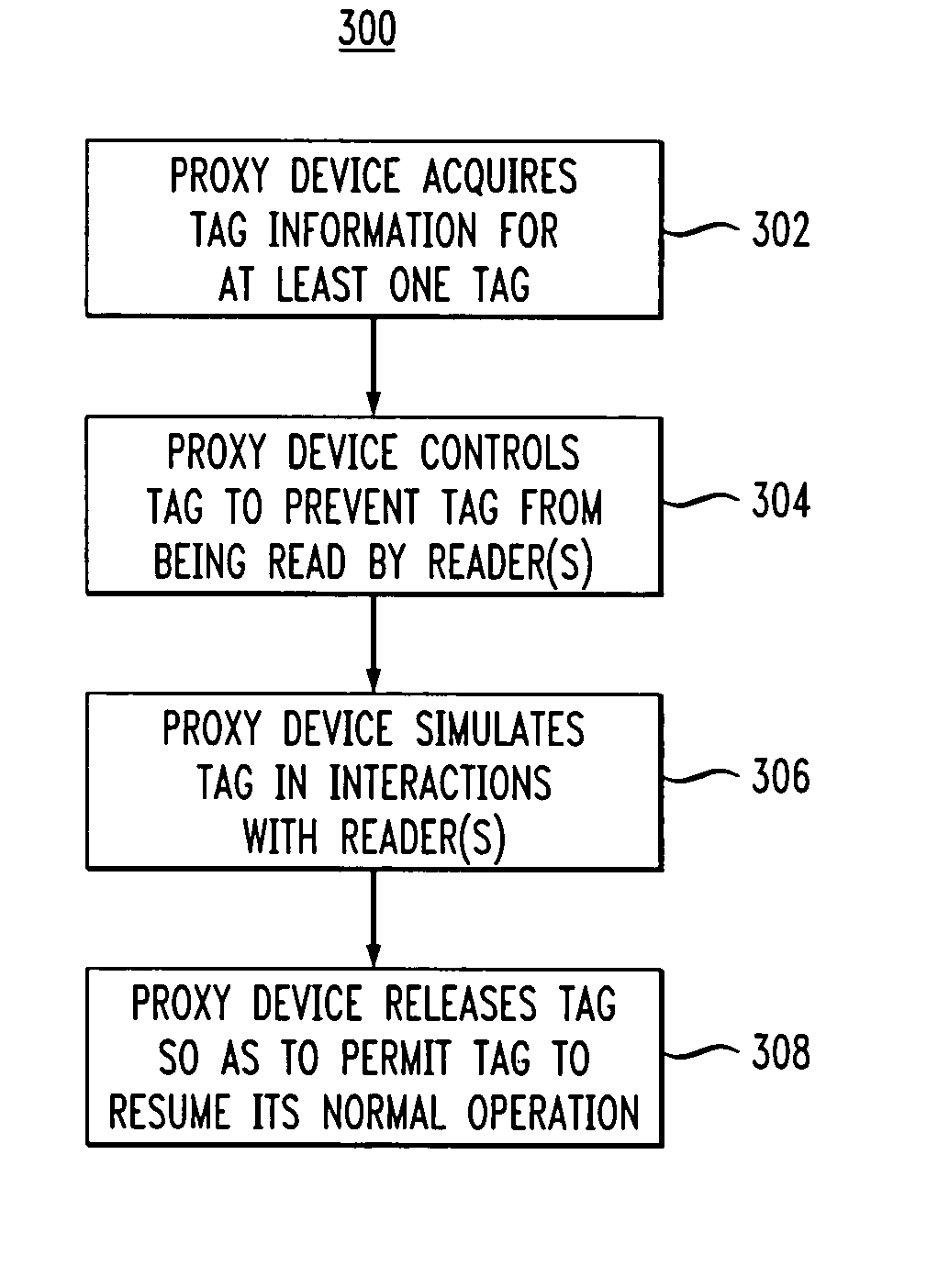
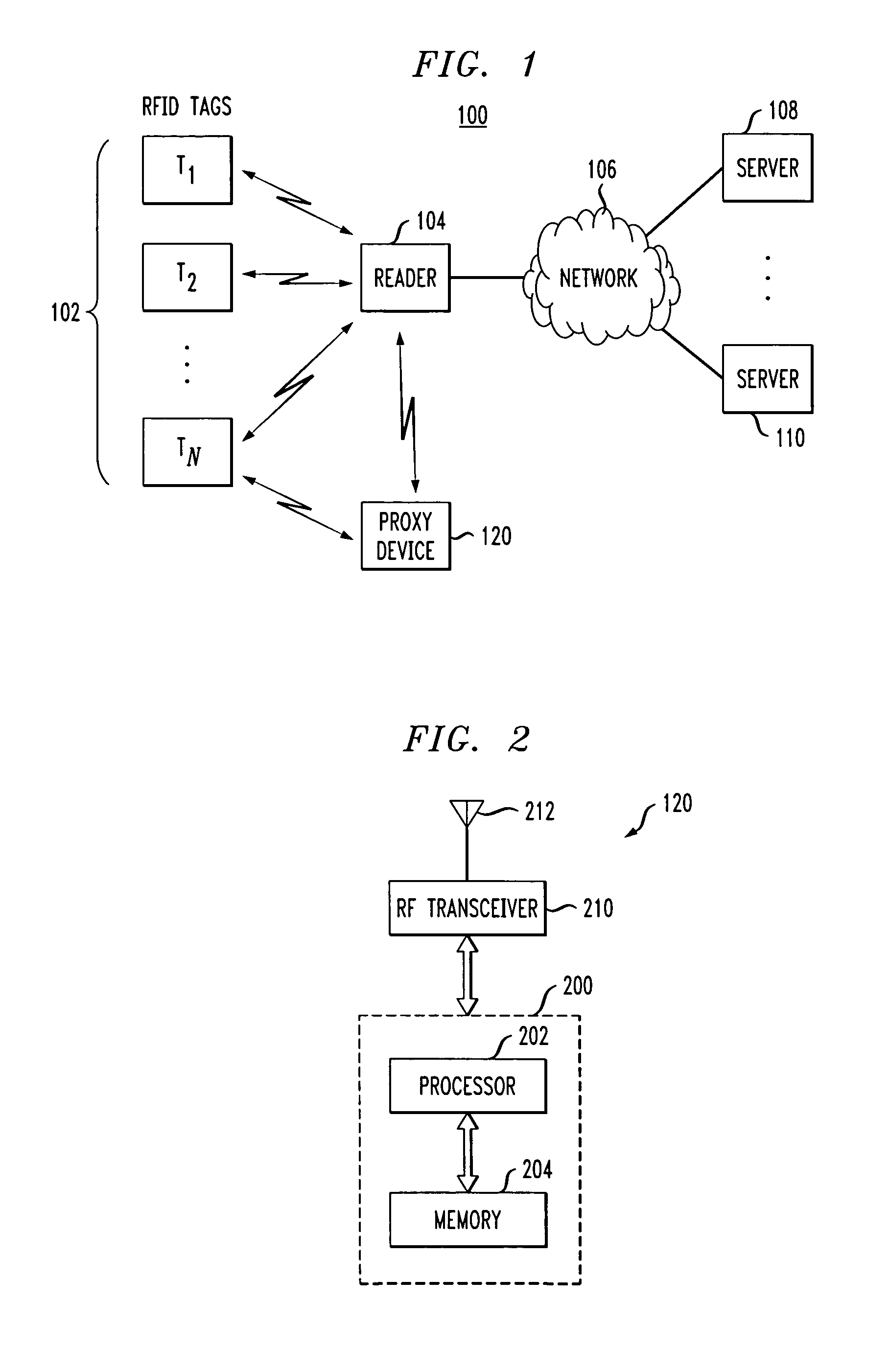
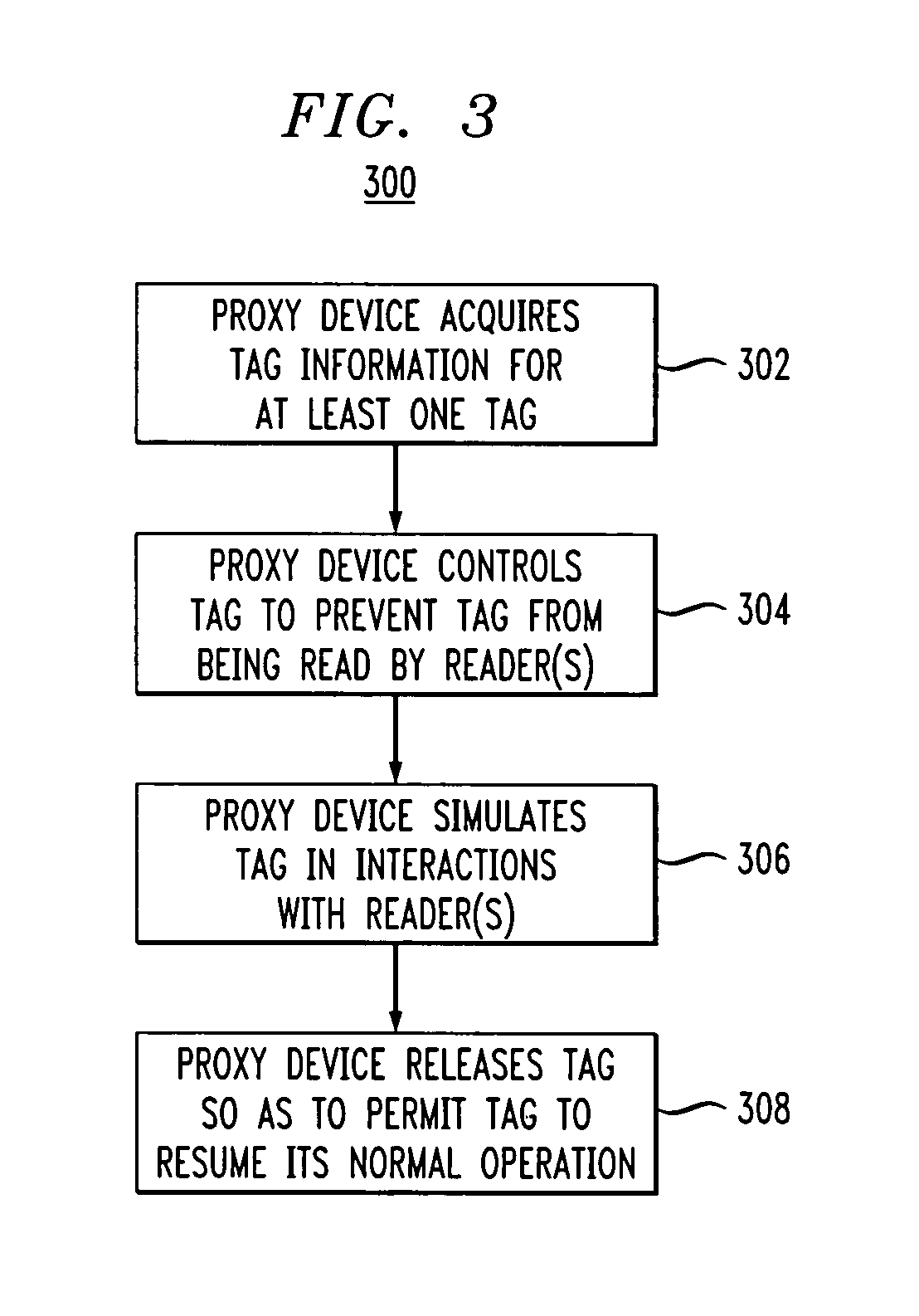
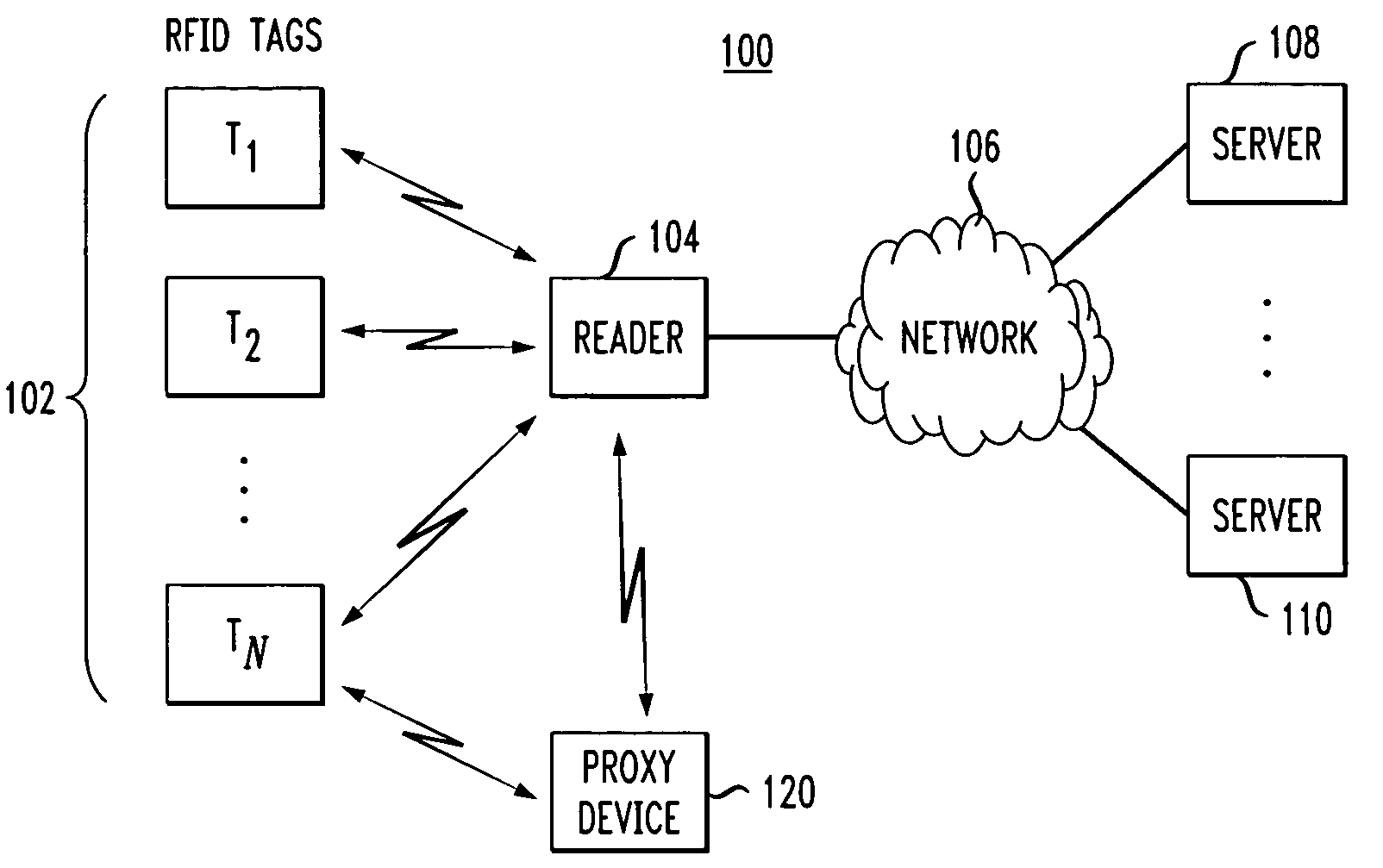
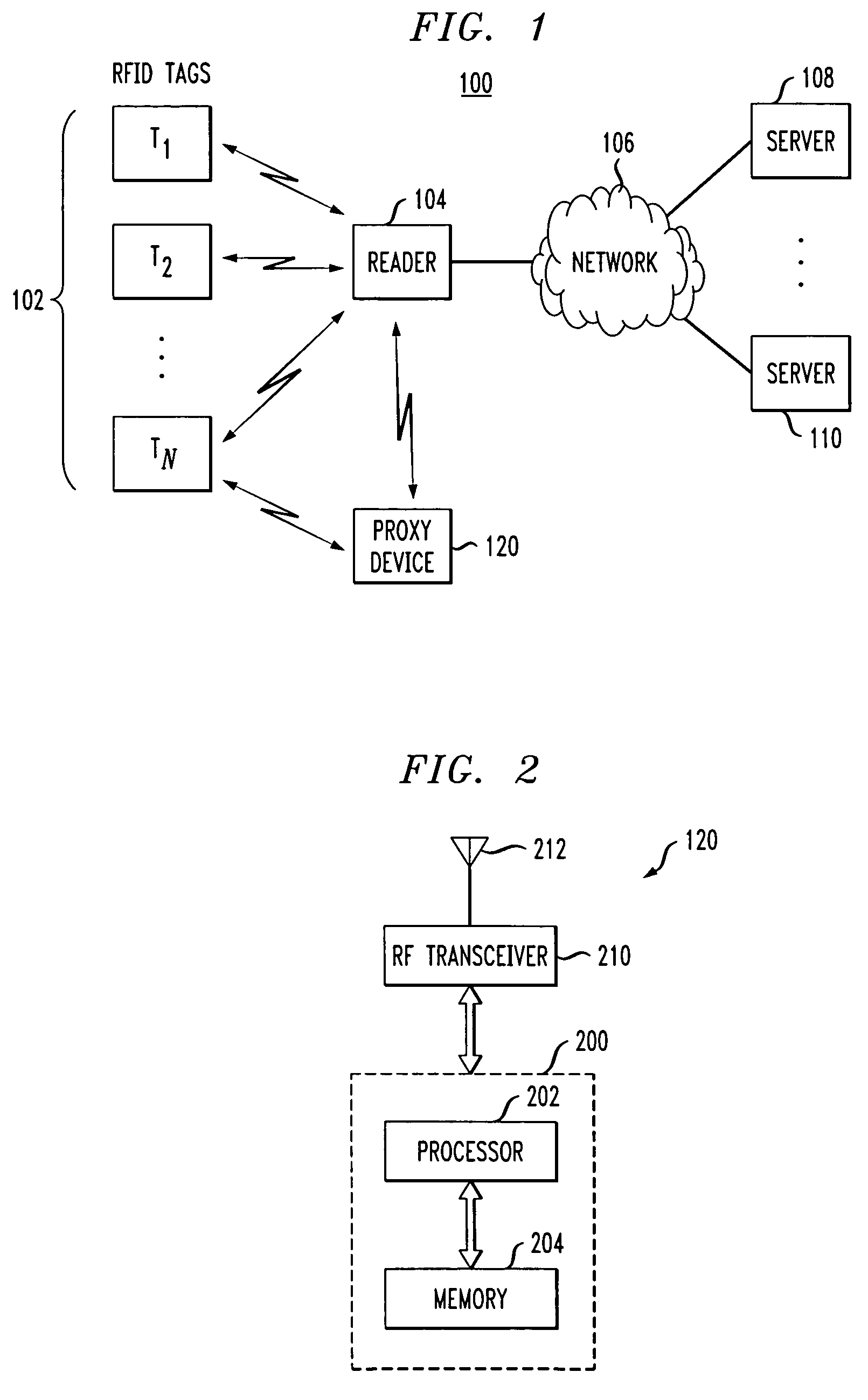
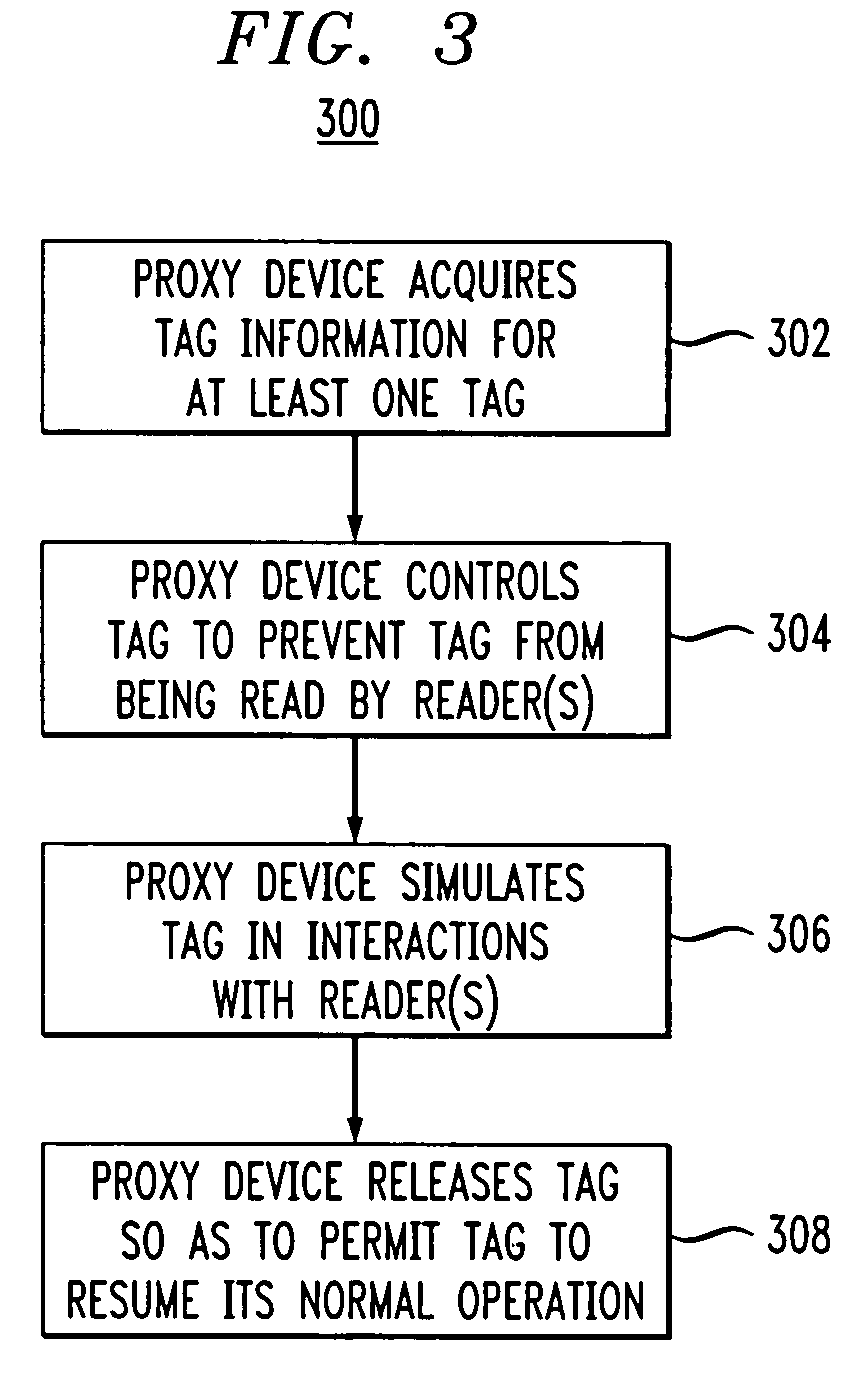
Proxy device for enhanced privacy in an RFID system
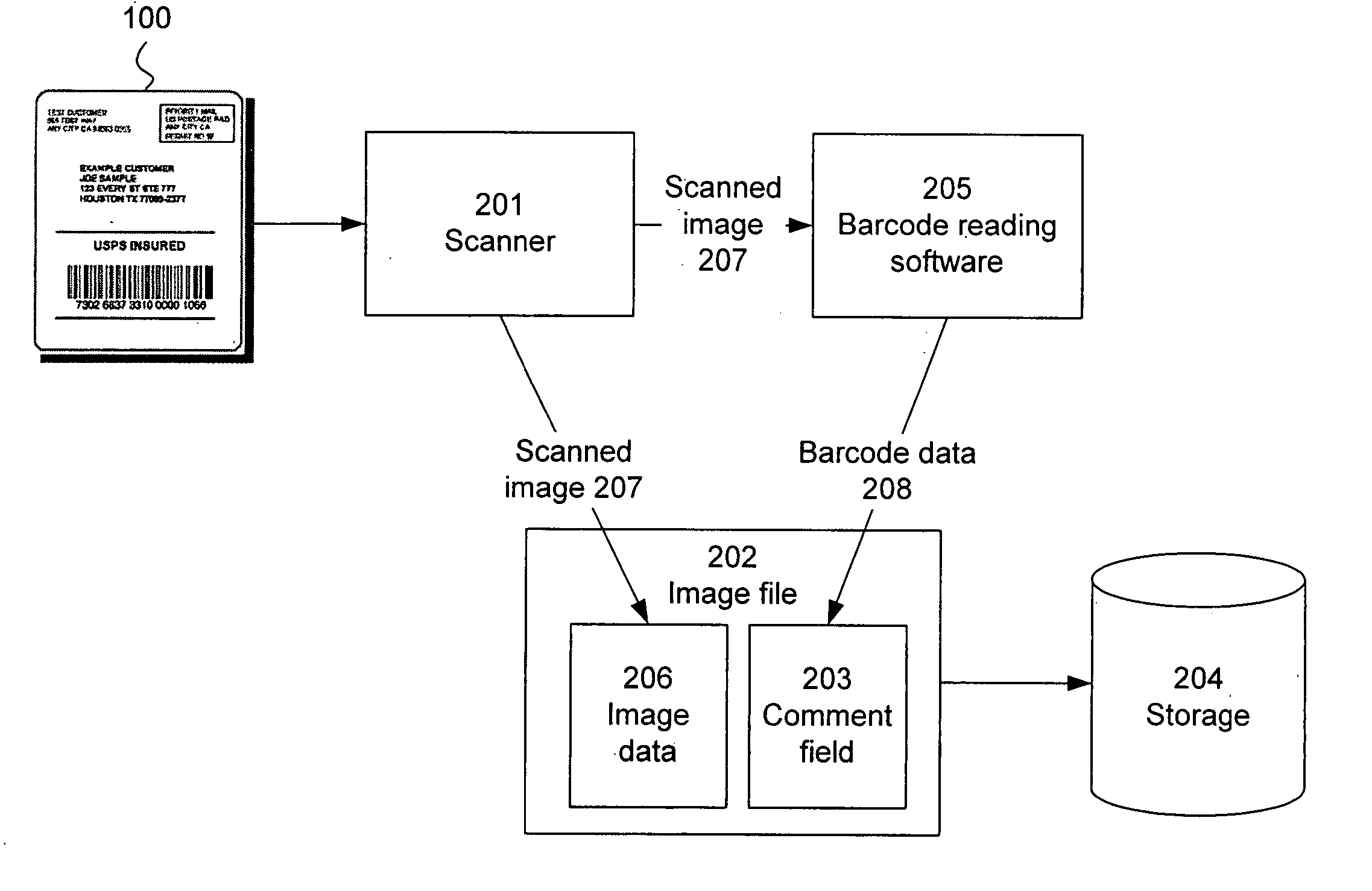
ActiveUS20060033608A1Improve privacyAvoid readingSensing record carriersSubscribers indirect connectionEmbedded systemPrivacy policy
A proxy device is disclosed for use in an RFID system comprising a plurality of RFID devices and at least one reader which communicates with the proxy device and one or more of the RFID devices. The proxy device acquires information characterizing at least a given one of the RFID devices, controls the given RFID device so as to at least partially prevent the given RFID device from being read by the reader, and communicates with the reader in a manner which simulates the given RFID device. This advantageously allows the proxy device to implement privacy policies of arbitrary sophistication on behalf of the given RFID device. The proxy device subsequently releases control of the given RFID device so as to permit the given RFID device to again be read by the reader.
Owner:EMC IP HLDG CO LLC +1
Microbial detection and quantification
InactiveUS20060134728A1Increase brightnessGood colorBioreactor/fermenter combinationsBiological substance pretreatmentsMicroorganismCell membrane
A method for semi-quantitatively or quantitatively detecting the presence of a microbe in a sample is provided. The method utilizes a test dye that undergoes a detectable color change in the presence of one or more microbes. For example, in one embodiment, the test dye is a solvatochromic dye (e.g., Reichardt's dye) that responds to differences in polarity between microbe components (e.g., cell membrane, cytoplasm, etc.) and the environment outside the cell. Alternatively, other mechanisms may be wholly or partially responsible for the interaction between the dye and the microbe, such as acid-base reactions, redox reactions, and so forth. Regardless, the color of the test dye may be compared to the color of a control dye, wherein the color of the control dye corresponds to a known microbe concentration.
Owner:KIMBERLY-CLARK WORLDWIDE INC
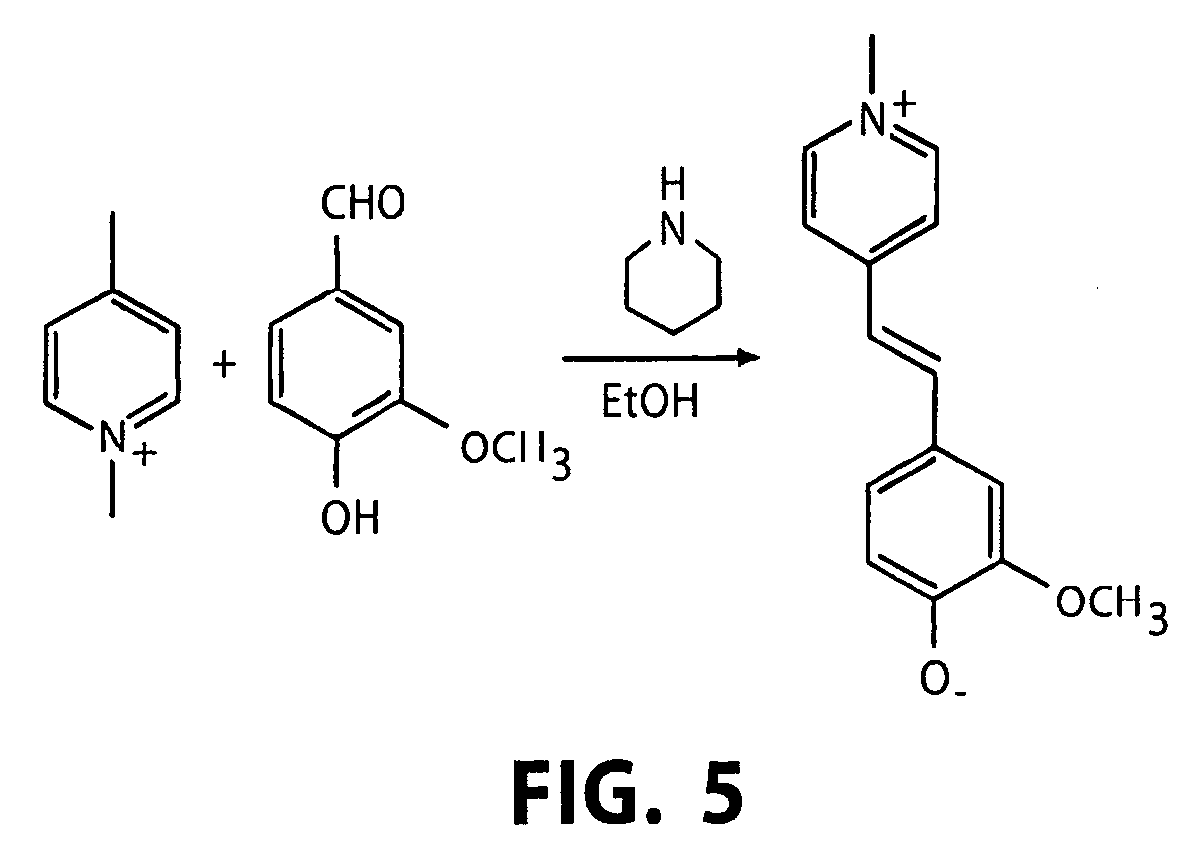
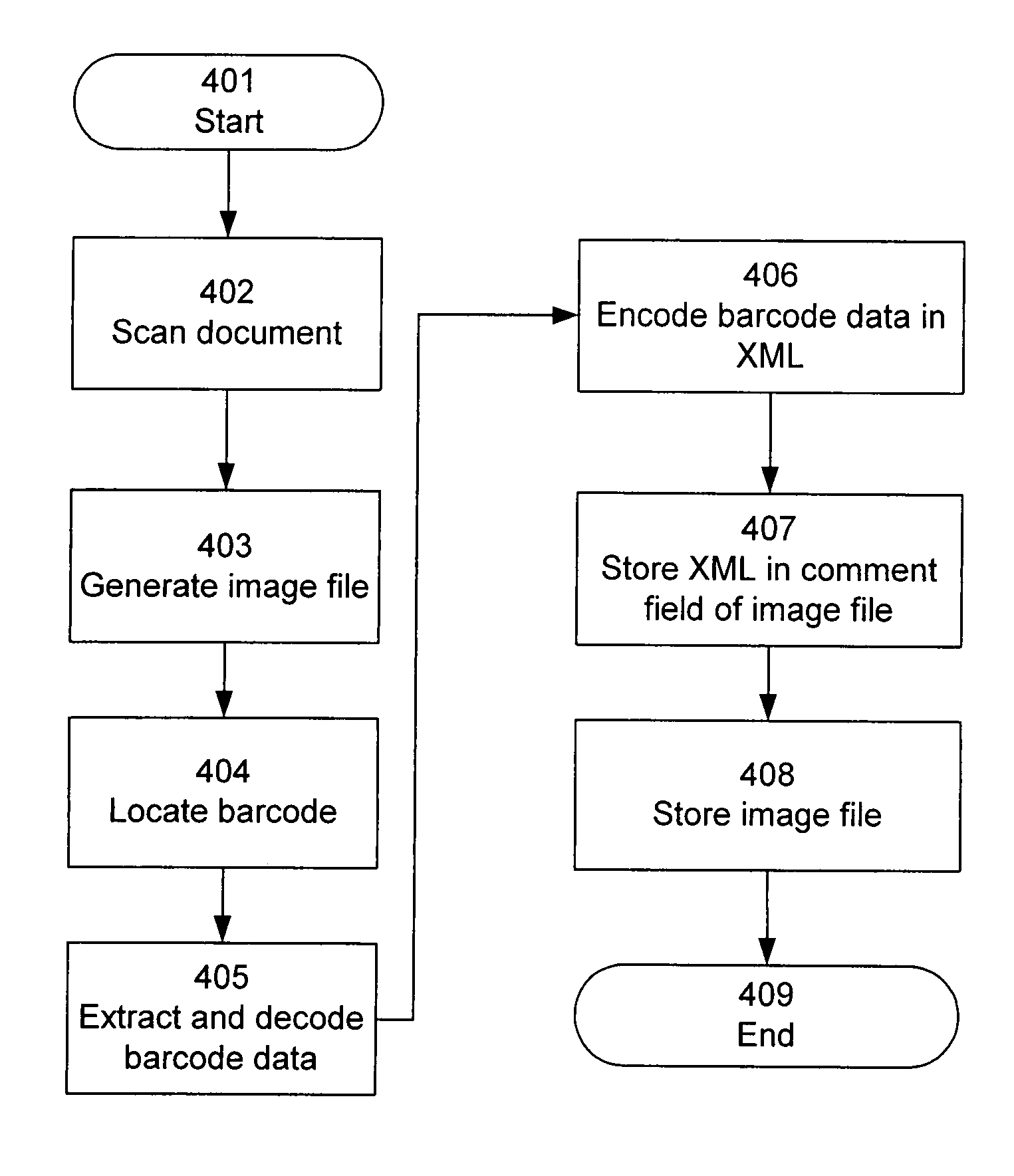
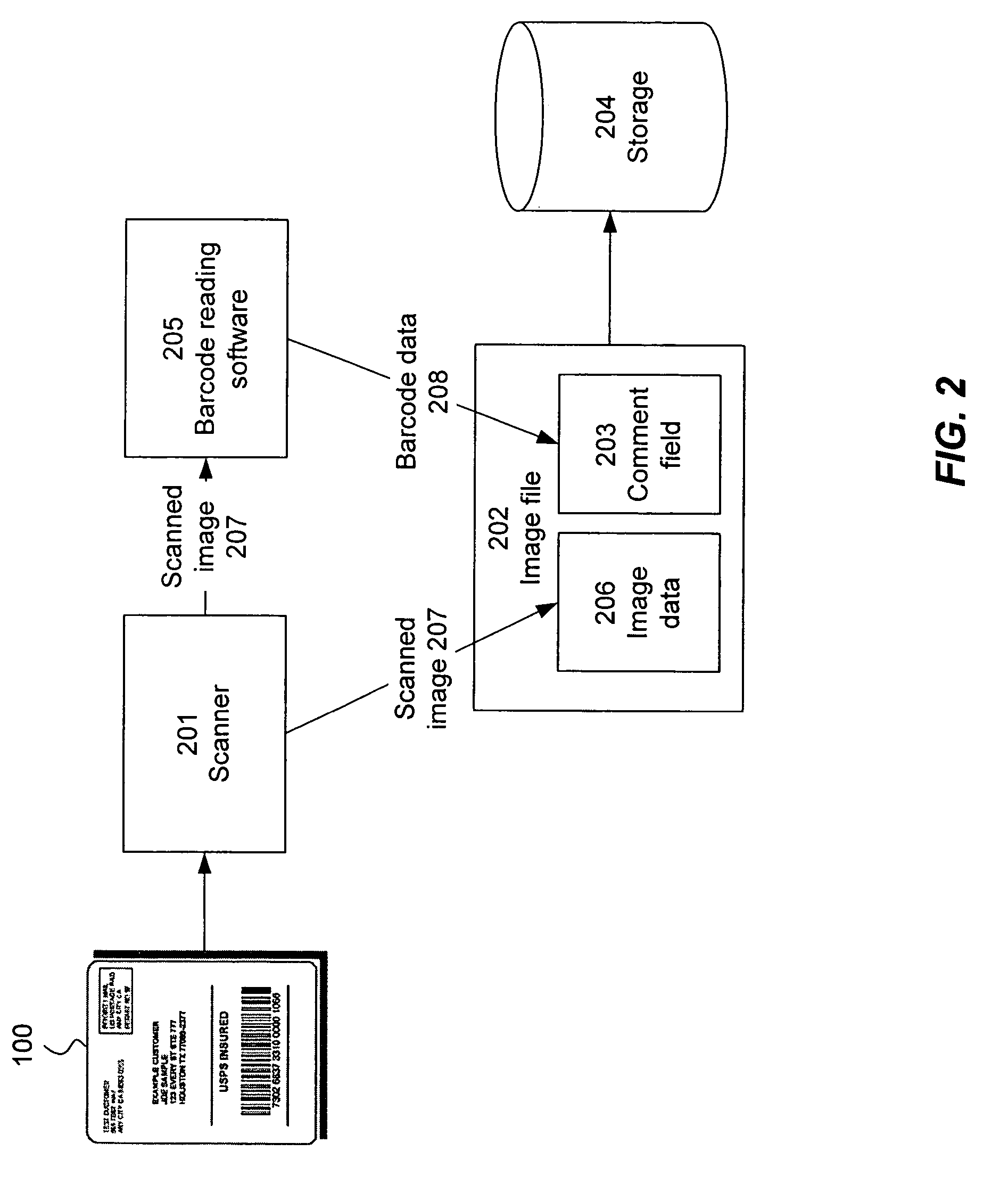
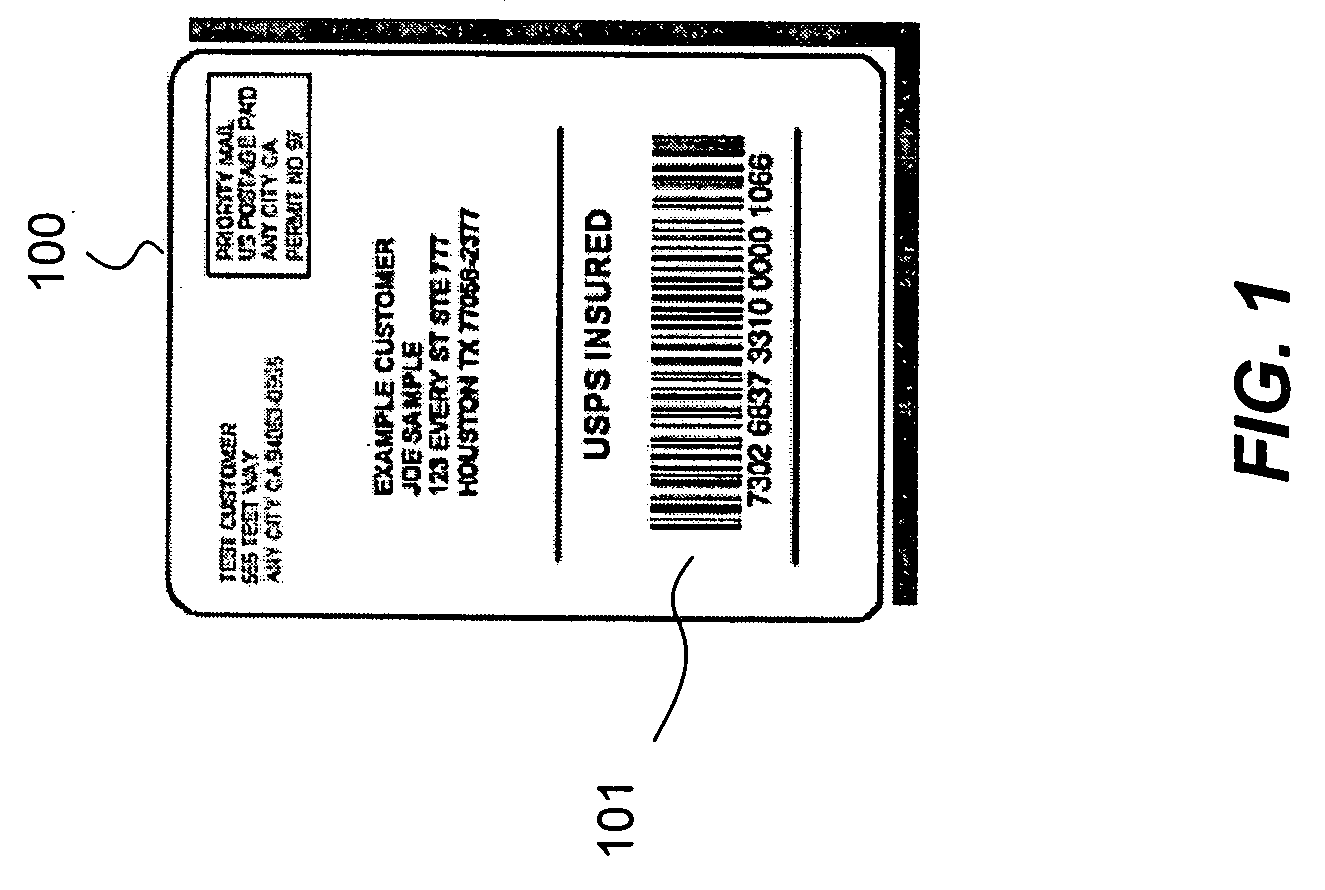
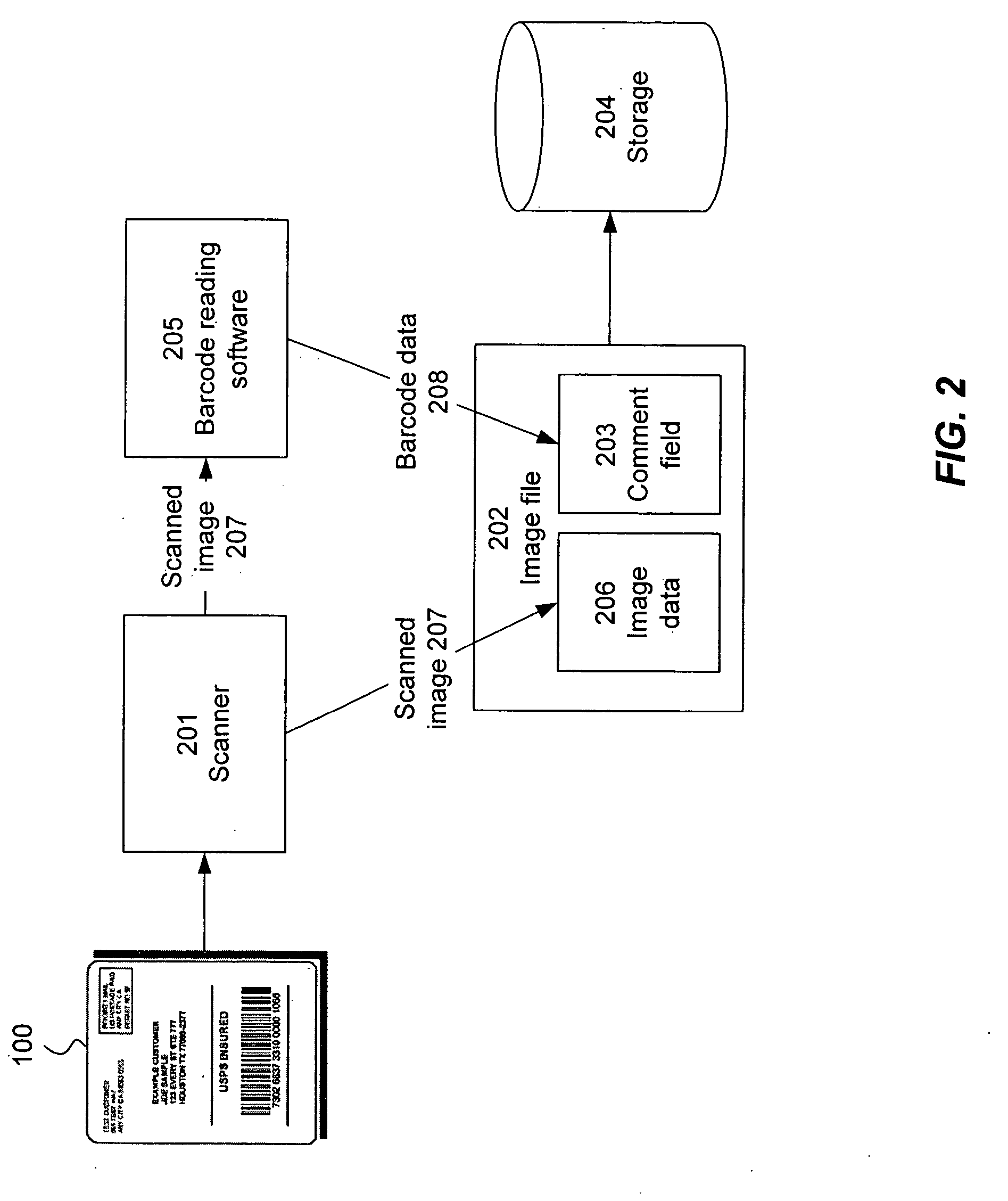
Embedding barcode data in an auxiliary field of an image file
ActiveUS7150399B2Easy accessAvoid the needCharacter and pattern recognitionMetadata still image retrievalProgramming languageImaging analysis
Information decoded from a barcode or other machine-readable code within an image file is stored as character-based data in an auxiliary field, such as a comment field, of the image file. Subsequently, the information can be extracted from the auxiliary field so as to avoid the need to repeat the image analysis and decoding operation. In one aspect, the extracted data is validated to ensure that it is consistent with the machine-readable code.
Owner:RICOH KK
Biometric authentication device, system and method of biometric authentication
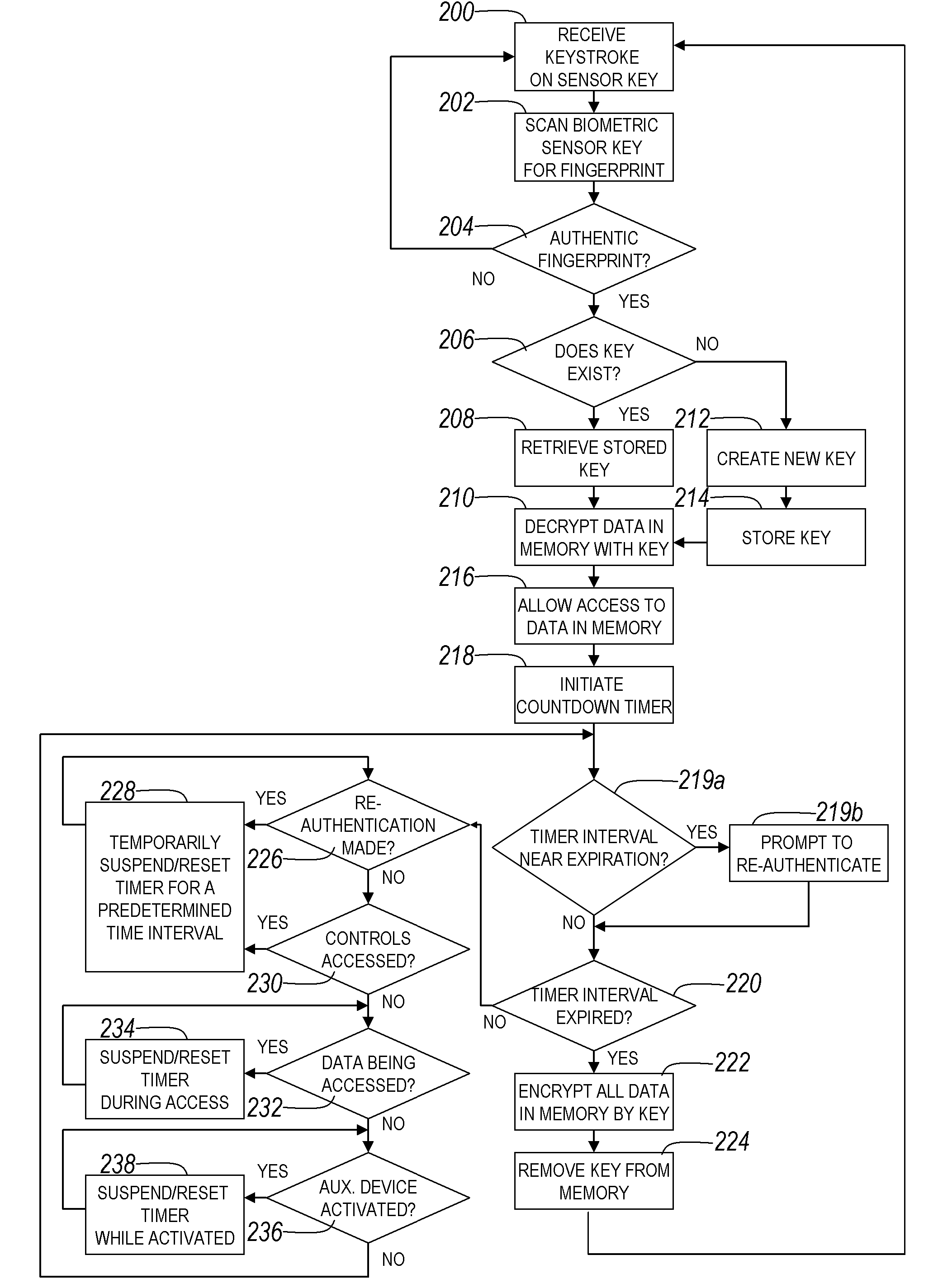
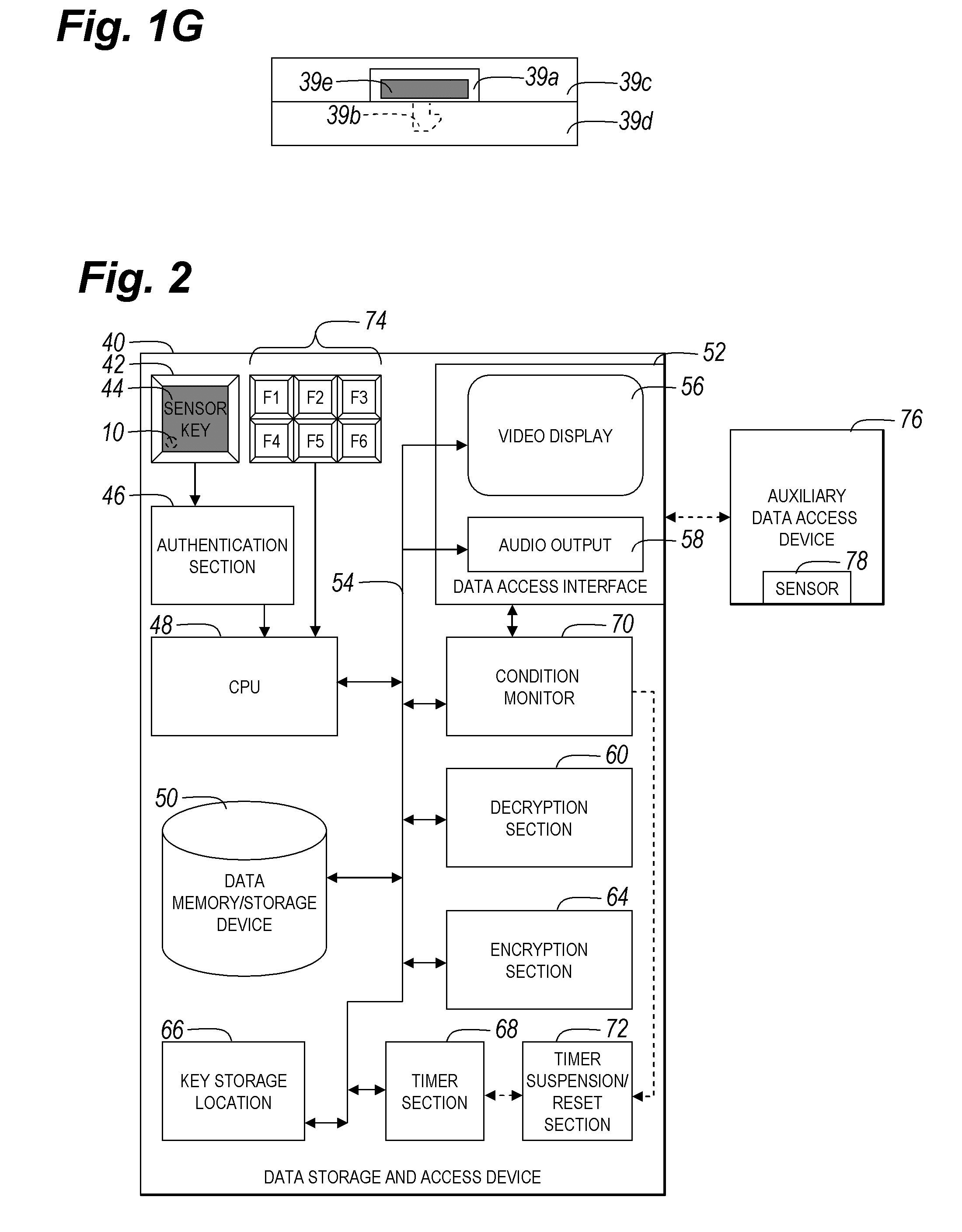
InactiveUS20090037742A1Minimal interferenceAvoid readingUser identity/authority verificationComputer security arrangementsData accessPartial verification
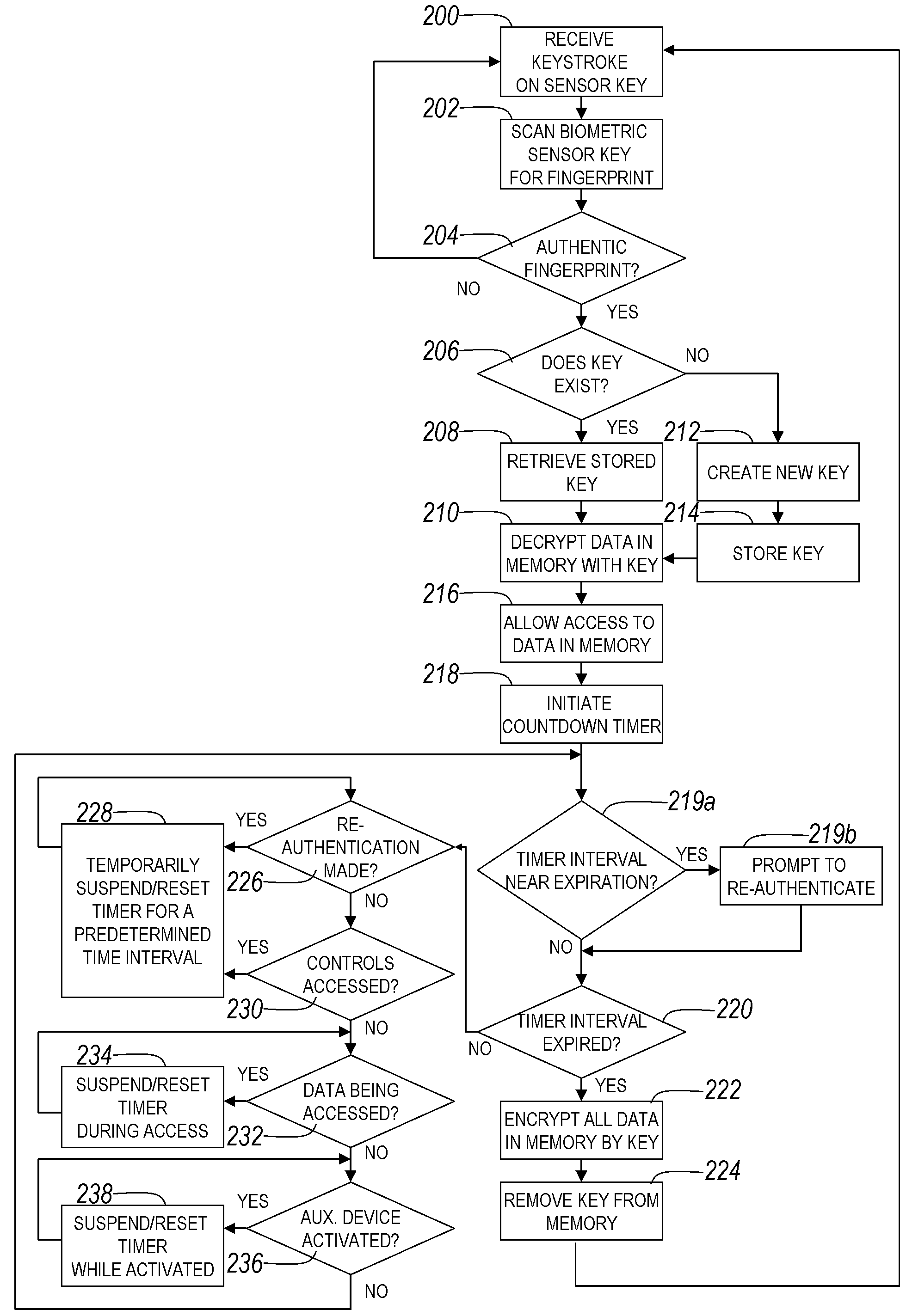
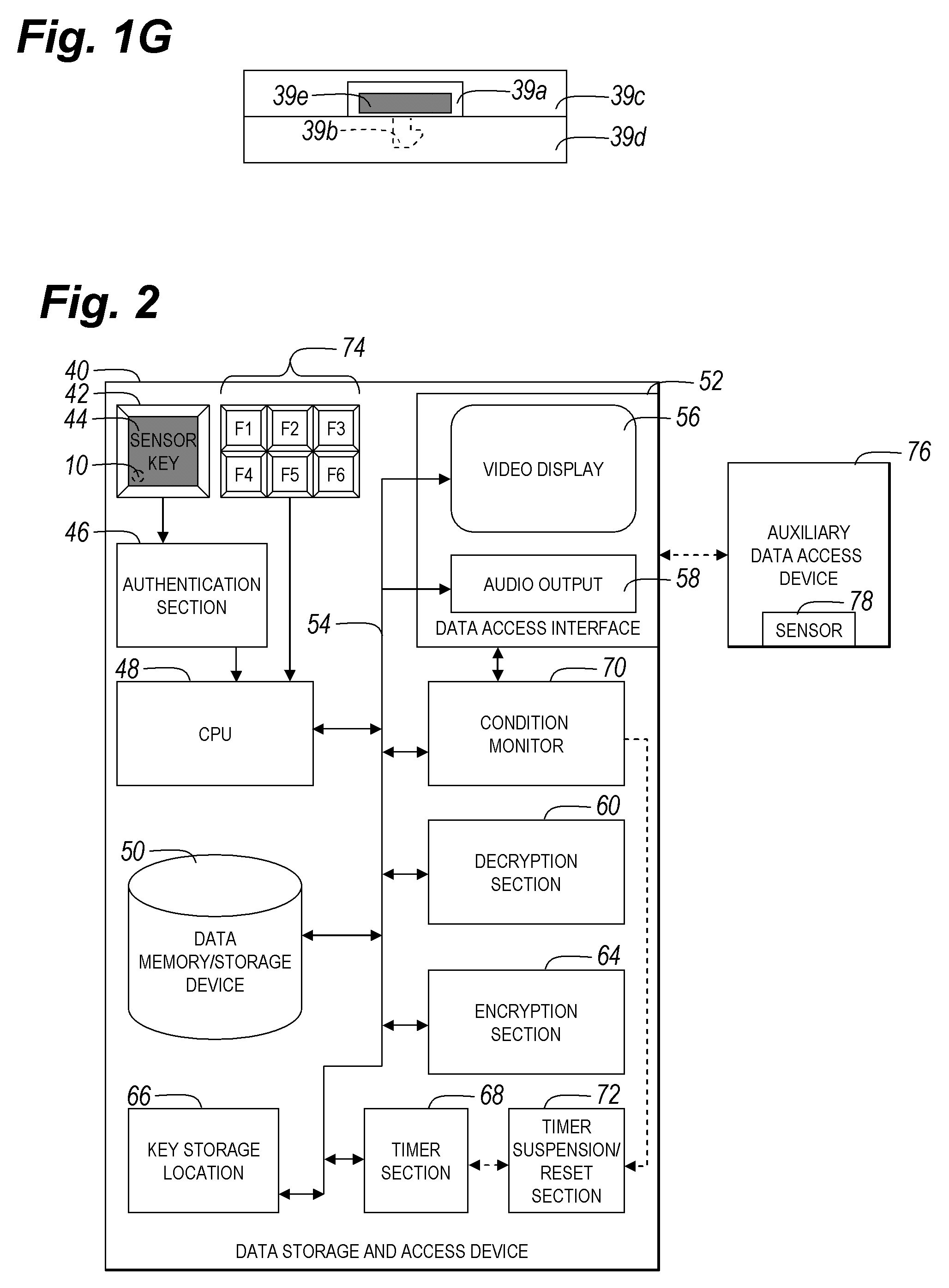
A biometric sensor device, a portable electronic device including an actuatable biometric input device, and method of biometric authentication that includes an input device that generates a signal or completes a circuit when actuated, and a biometric reader that reads a biometric of a user when the user actuates the input device to generate the signal or complete the circuit. An authentication section authenticates the biometric read on the biometric reader to generate one of a data access allowance function based on authentication of the biometric input to the actuatable biometric input device and a data access prevention function based on non-authentication of the biometric input to the actuatable biometric input device. The data access allowance function permits data to be accessed at the data access interface, and the data access prevention function prevents reading and / or access to data anywhere on the data storage and access device.
Owner:IBM CORP
Proxy device for enhanced privacy in an RFID system
ActiveUS7920050B2Improve privacyAvoid readingSensing record carriersSubscribers indirect connectionEmbedded systemPrivacy policy
Owner:EMC IP HLDG CO LLC +1
Embedding barcode data in an auxiliary field of an image file
ActiveUS20050274807A1Less memory-intensiveLess processorCharacter and pattern recognitionMetadata still image retrievalAlgorithmImaging analysis
Information decoded from a barcode or other machine-readable code within an image file is stored as character-based data in an auxiliary field, such as a comment field, of the image file. Subsequently, the information can be extracted from the auxiliary field so as to avoid the need to repeat the image analysis and decoding operation. In one aspect, the extracted data is validated to ensure that it is consistent with the machine-readable code.
Owner:RICOH KK
Open registry for identity of things
ActiveUS20160358186A1Avoid readingMultiple keys/algorithms usageCryptography processingThird partyRegistry data
An identity system for the Internet of Things (IOT) that enables users and machines to identify, authenticate and interact with products and collectibles without relying on a third-party-controlled authentication service. The system includes wireless tamperproof tags coupled to products and an open registry database where a chain of ownership of the items is able to be stored. The open registry enables public access to the item identity and data combined with item registration anonymity.
Owner:CHRONICLED INC
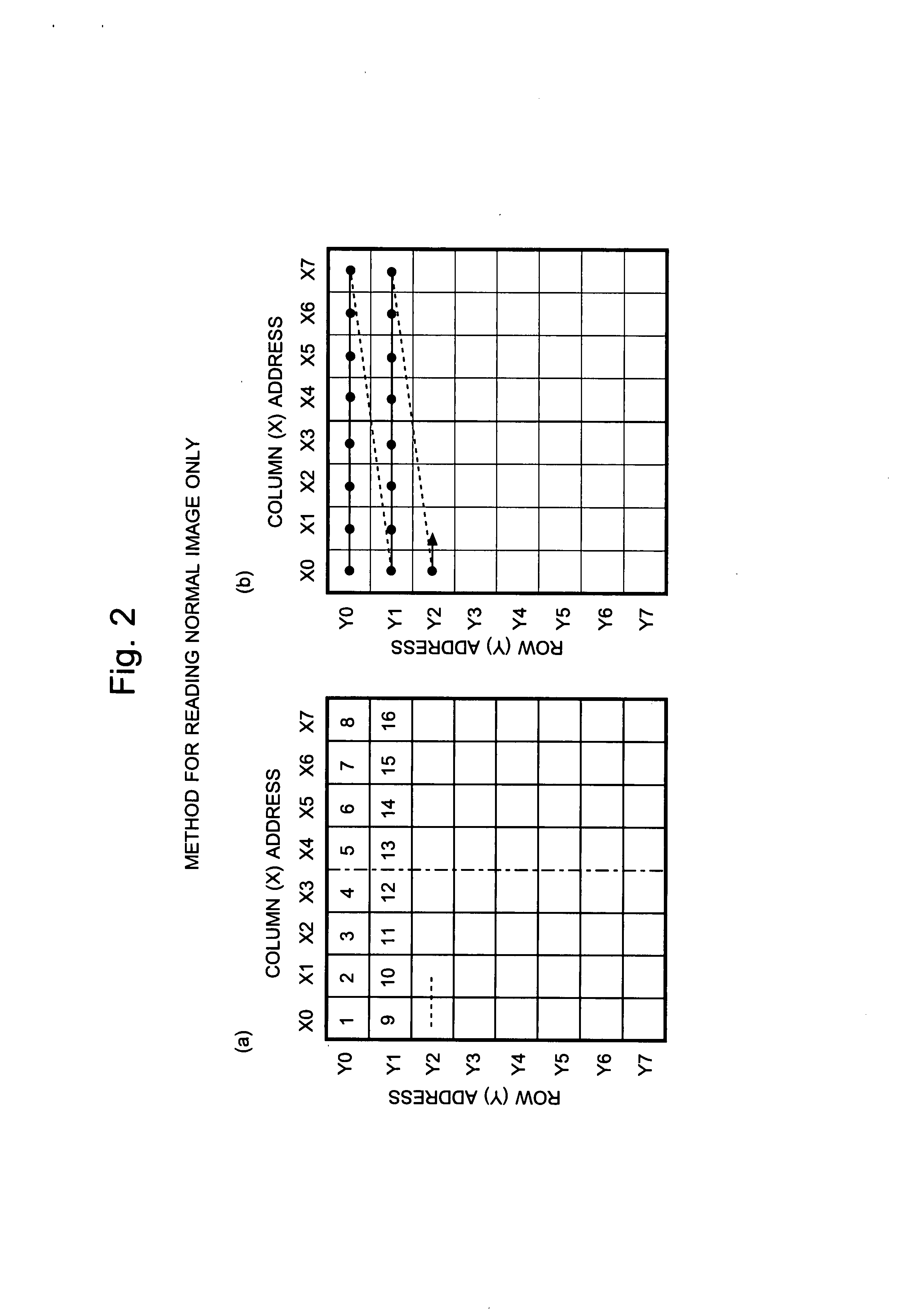
Imaging device and method for reading signals from such device
InactiveUS7728893B2Reduce the numberImprove reading speedTelevision system detailsTelevision system scanning detailsAudio power amplifierVariable-gain amplifier
Each pixel cell (12) of an image sensor (10) is made of a 4-Tr structure, in which only one Tr for resetting a column (X) is so added to an ordinary 3-Tr APS as to reset only an arbitrary pixel selectively, thereby to confine the pixel size. When a pixel signal is to be read, the period, for which the pixel signals composing an ordinary image of one frame are read, is finely divided so that the pixel signals of the pixels receiving an ID light for the period are read out bit by bit and repeatedly. At this time, for only the column being read, an electric current is fed to a read amplifier in the pixel cell (12) or a variable gain amplifier in an output unit (14), thereby to suppress the power consumption. As a result, a lower power consumption and a higher pixel formation can be attained in an image pickup device for picking up an image and for acquiring the ID information of a light beacon existing in the image pickup range.
Owner:JAPAN SCI & TECH CORP +1
Methods and compositions for analyte detection
ActiveUS7932099B2Avoid readingBioreactor/fermenter combinationsBiological substance pretreatmentsAnalyteInfectious agent
The present invention is directed to methods and apparatus for detection of one or more analytes. Analytes include agents or components of infectious agents such as pathogenic virus, as well as enzymes, proteins and biomarkers.
Owner:NEXUS DX
Directory read inhibitor for optical storage media
InactiveUS6838144B2Low costChange is minimalLayered productsPhotomechanical apparatusOptical reflectionTime function
Systems and methods are described for inhibiting the readability of an optical media due to changes in a pseudo-reflective material that composes the optical media after the optical media has been exposed to air for a predetermined time. An optical media includes a data encoded component. At least a fraction of the data encoded component transforms from a substantially optically reflective state to a substantially optically non-reflective state as at-least-in-part a function of time from an initializing event. The systems and methods provide advantages because of low cost, limited content lifetime, avoidance of rental returns and minimum changes to existing manufacturing processes.
Owner:FLEXPLAY TECH INC
Open registry for identity of things including social record feature
An identity system for the Internet of Things (IOT) that enables users and machines to identify, authenticate and interact with products and collectibles without relying on a third-party-controlled authentication service. The system includes wireless tamperproof tags coupled to products and an open registry database where a chain of ownership of the items is able to be stored. The open registry enables public access to the item identity and data combined with item registration anonymity.
Owner:CHRONICLED INC
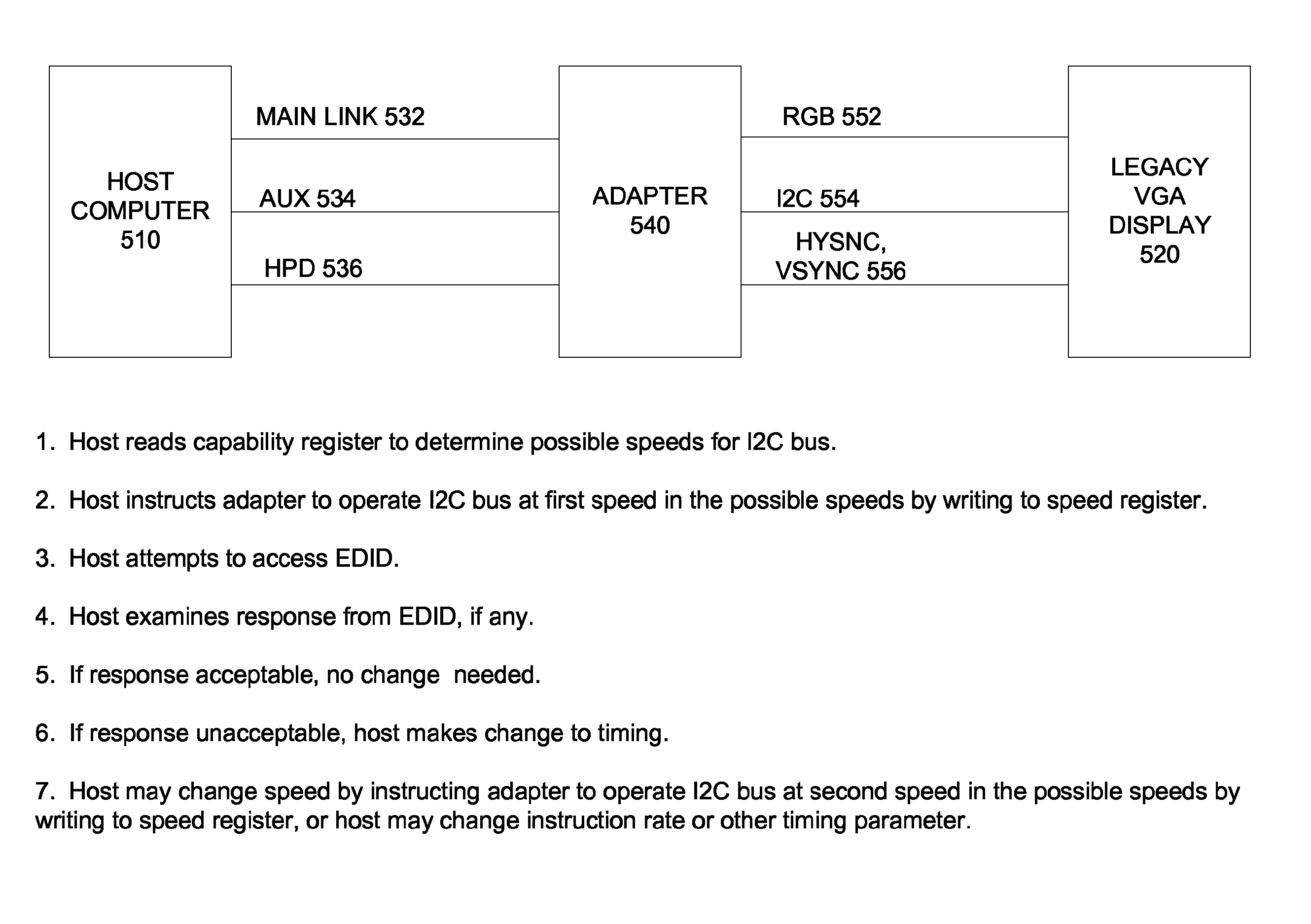
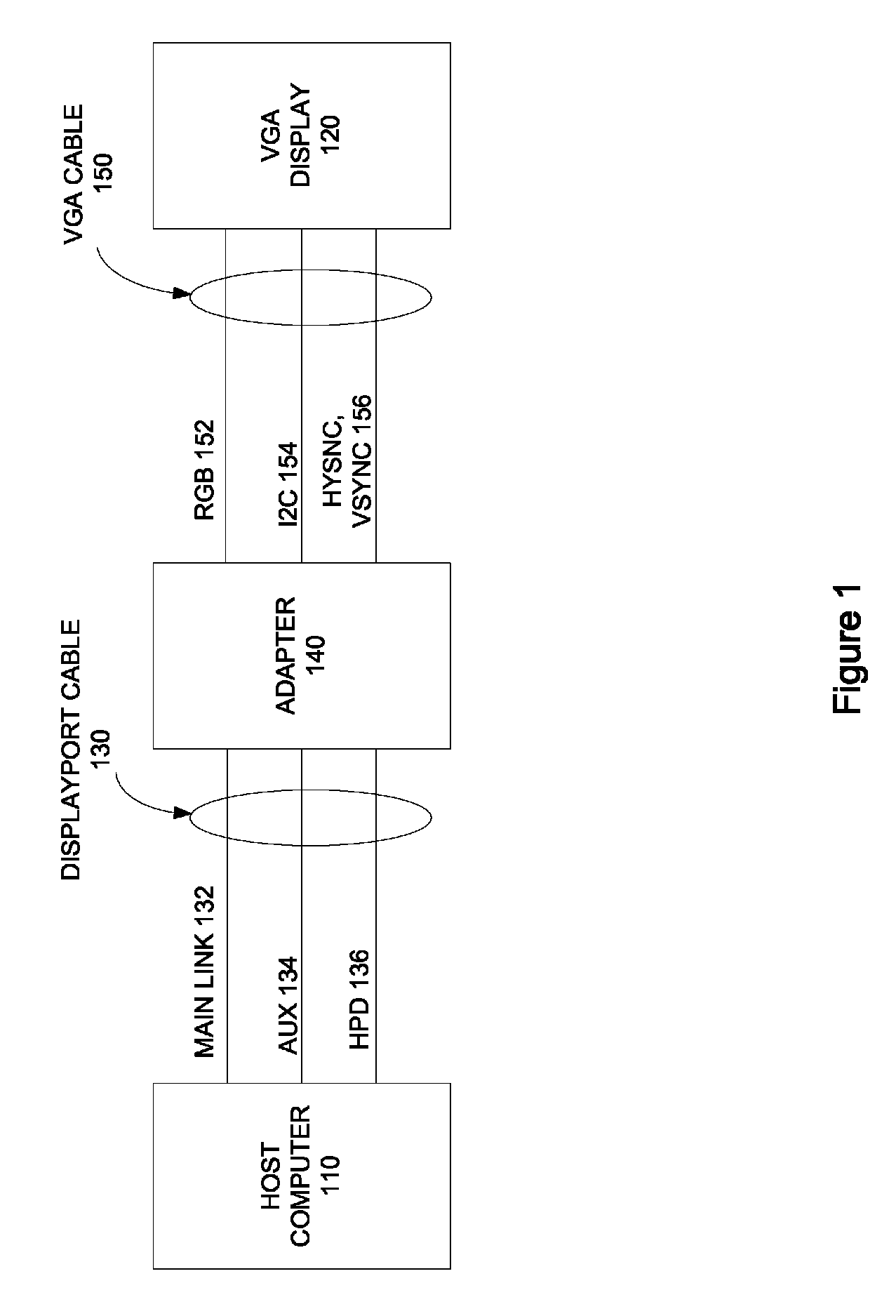
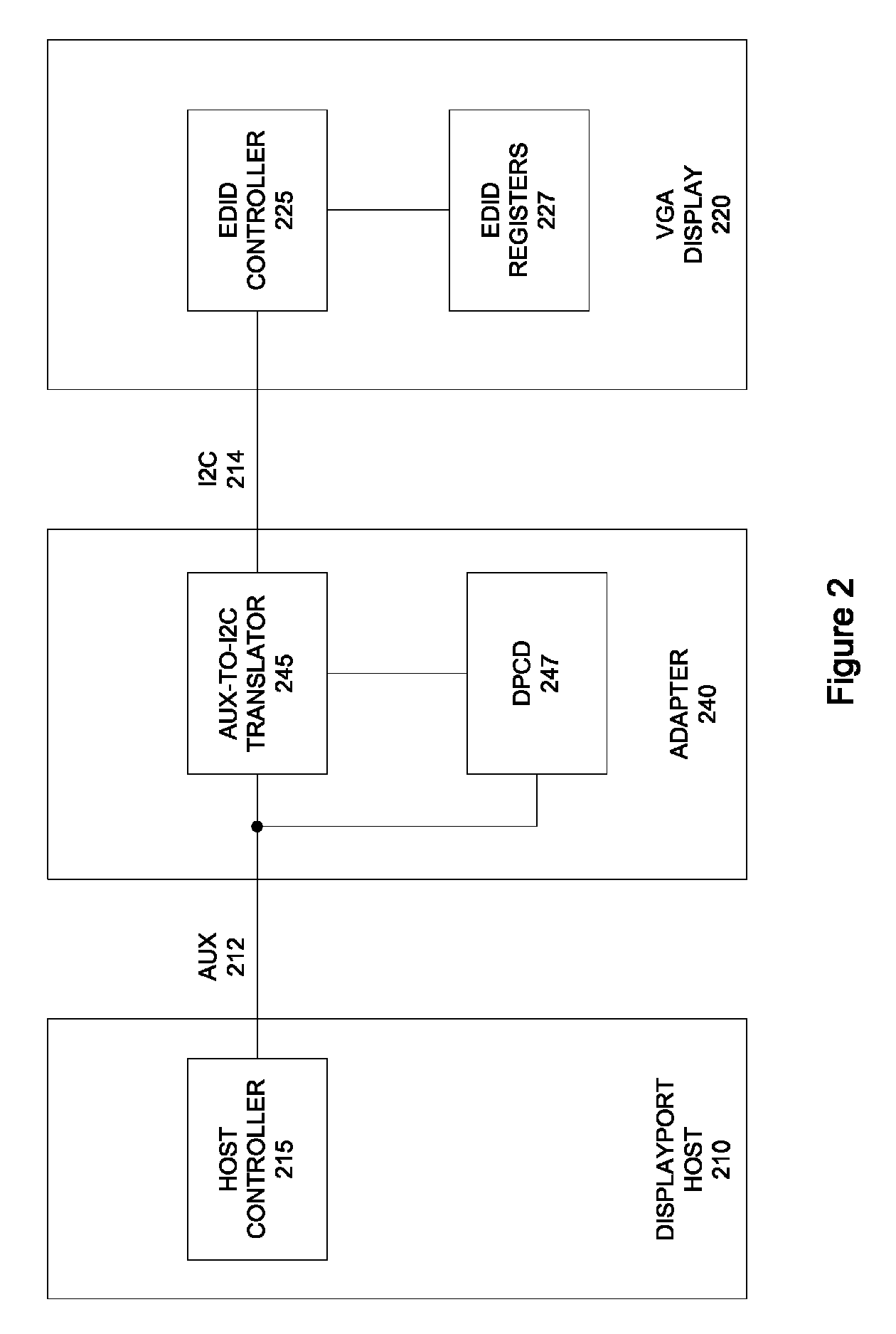
Displayport I2C speed control
ActiveUS7899941B2Simple systemAvoid readingInput/output processes for data processingData conversionProcessor registerControl data
Circuits, methods, and apparatus that allow a DisplayPort compatible host device to control data transactions over an I2C bus when communicating with a legacy monitor. One example includes an adapter having a compatibility register that may have a number of locations, where at least some of the locations correspond to I2C bus speeds. Values stored at these locations can indicate whether the adapter is compatible or incompatible with the corresponding I2C bus speed. Another example includes an adapter having a speed register that may have a number of locations, where at least some of the locations correspond to I2C bus speeds. A defined value written to one of these locations dictates the corresponding I2C bus speed.
Owner:APPLE INC
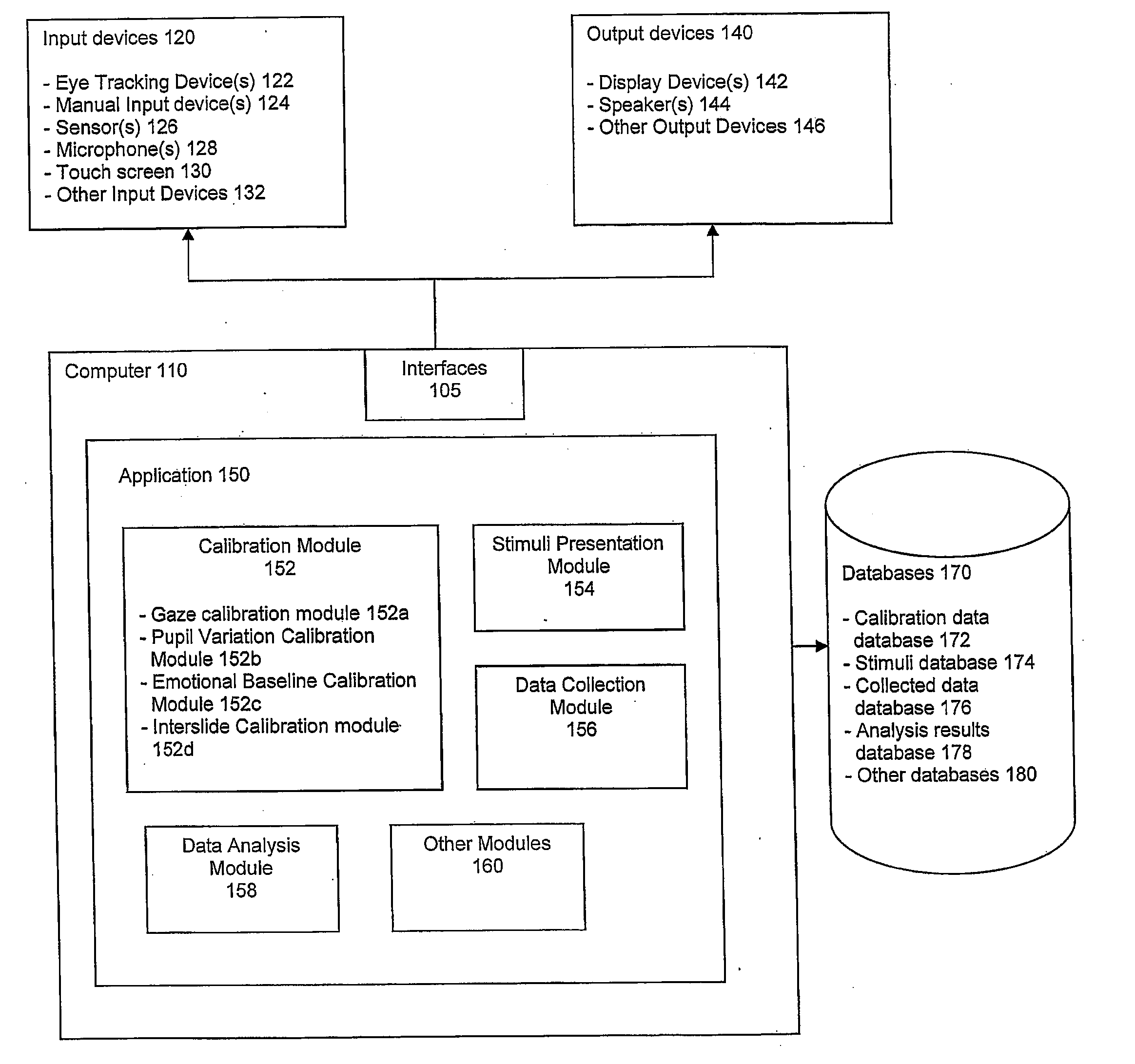
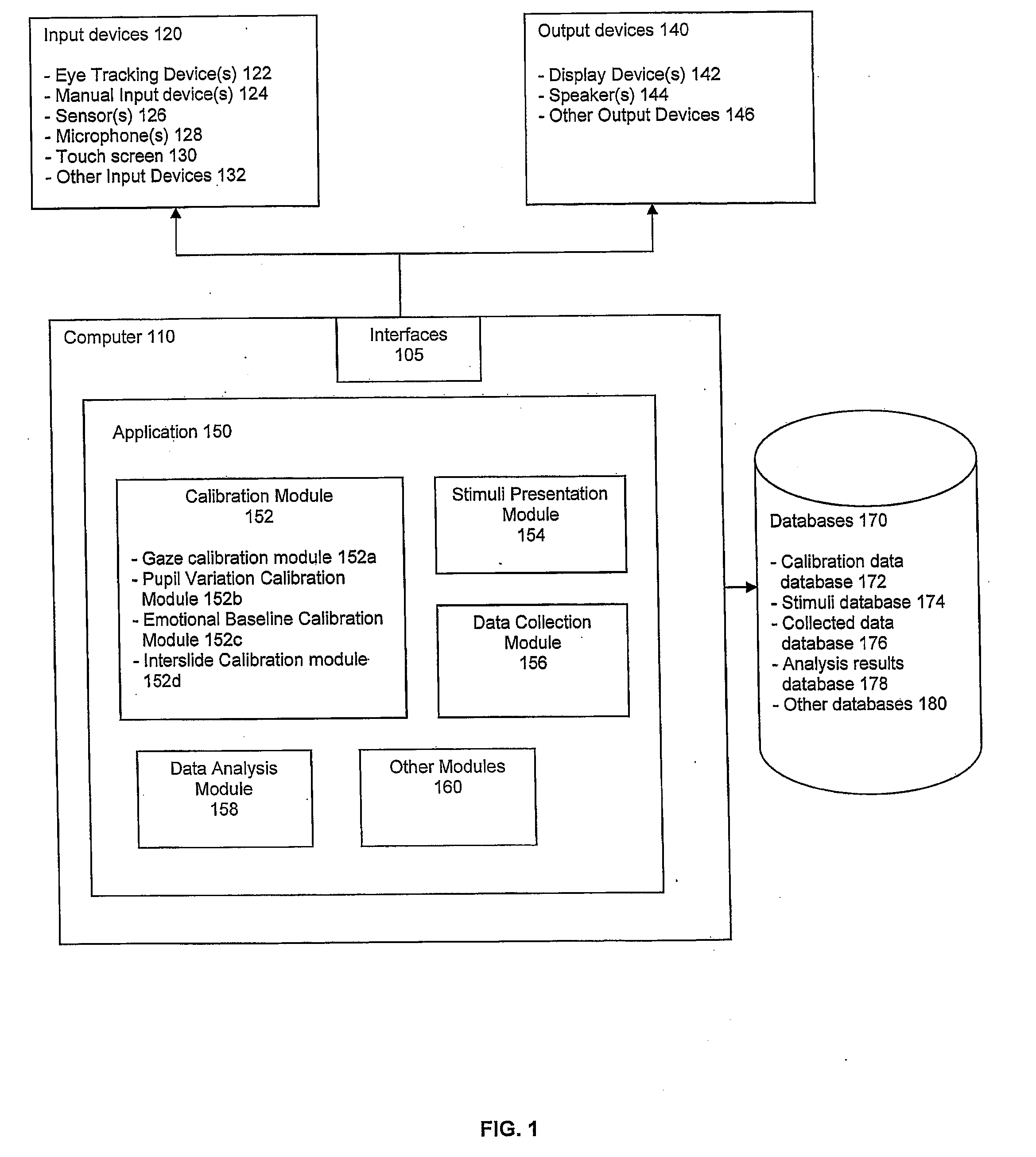
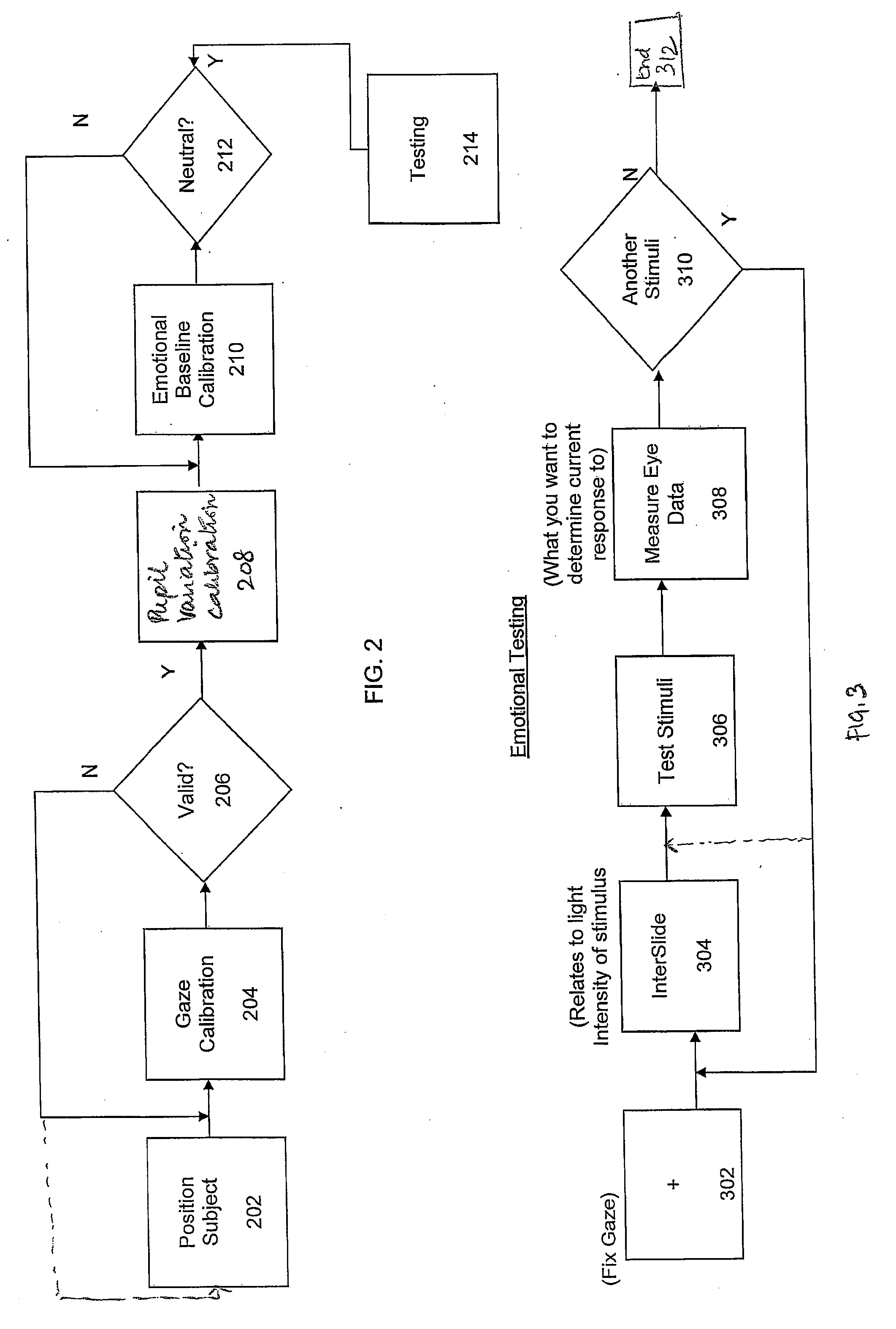
System and method for calibrating and normalizing eye data in emotional testing
InactiveUS20100010370A1Normalize gaze dataAvoid readingAcquiring/recognising eyesEye diagnosticsComputer scienceStandardization
A system and method is provided for calibrating and normalizing eye data of one or more subjects prior to and / or during emotional testing of the subjects. In particular, initially performing one or more calibration or normalization operations prior to an emotional test of a subject may result in accurate evaluations of emotional responses based on measurements of eye data. Additionally, further calibration or normalization performed during the emotional test may be used to refine the initial calibration or normalization, further increasing the accuracy of the evaluated emotional responses.
Owner:IMOTIONS - EYE TRACKING APS
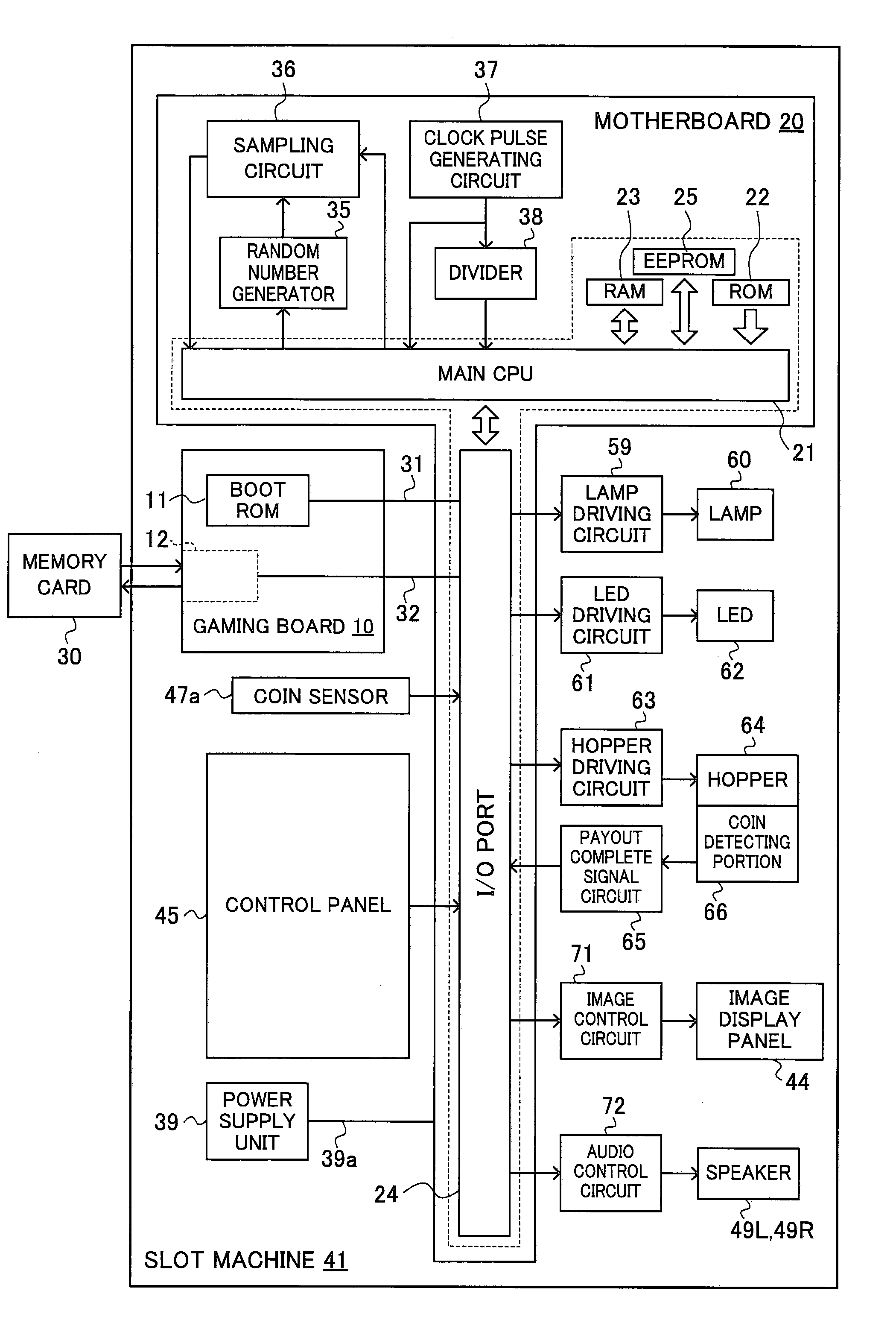
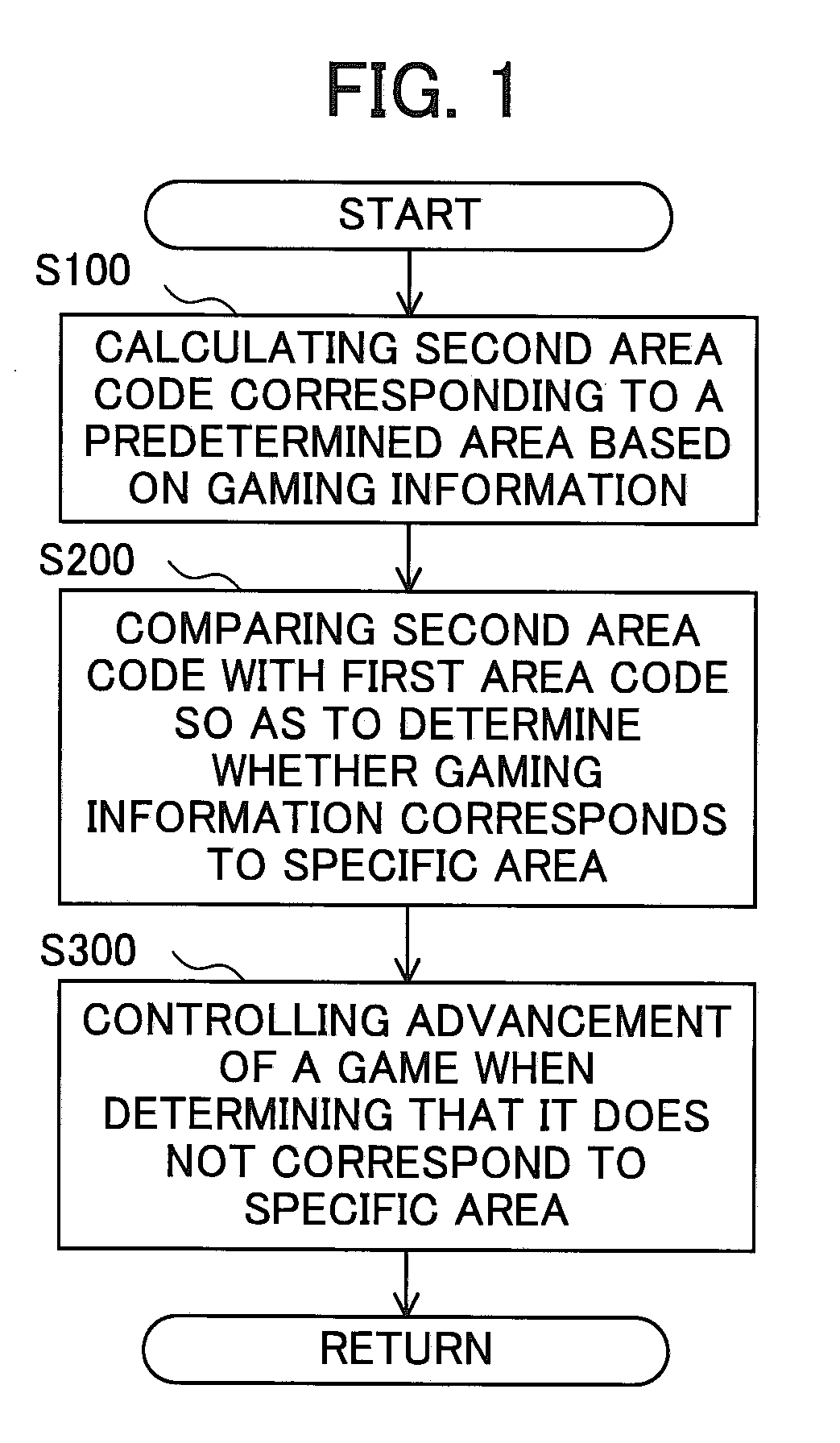
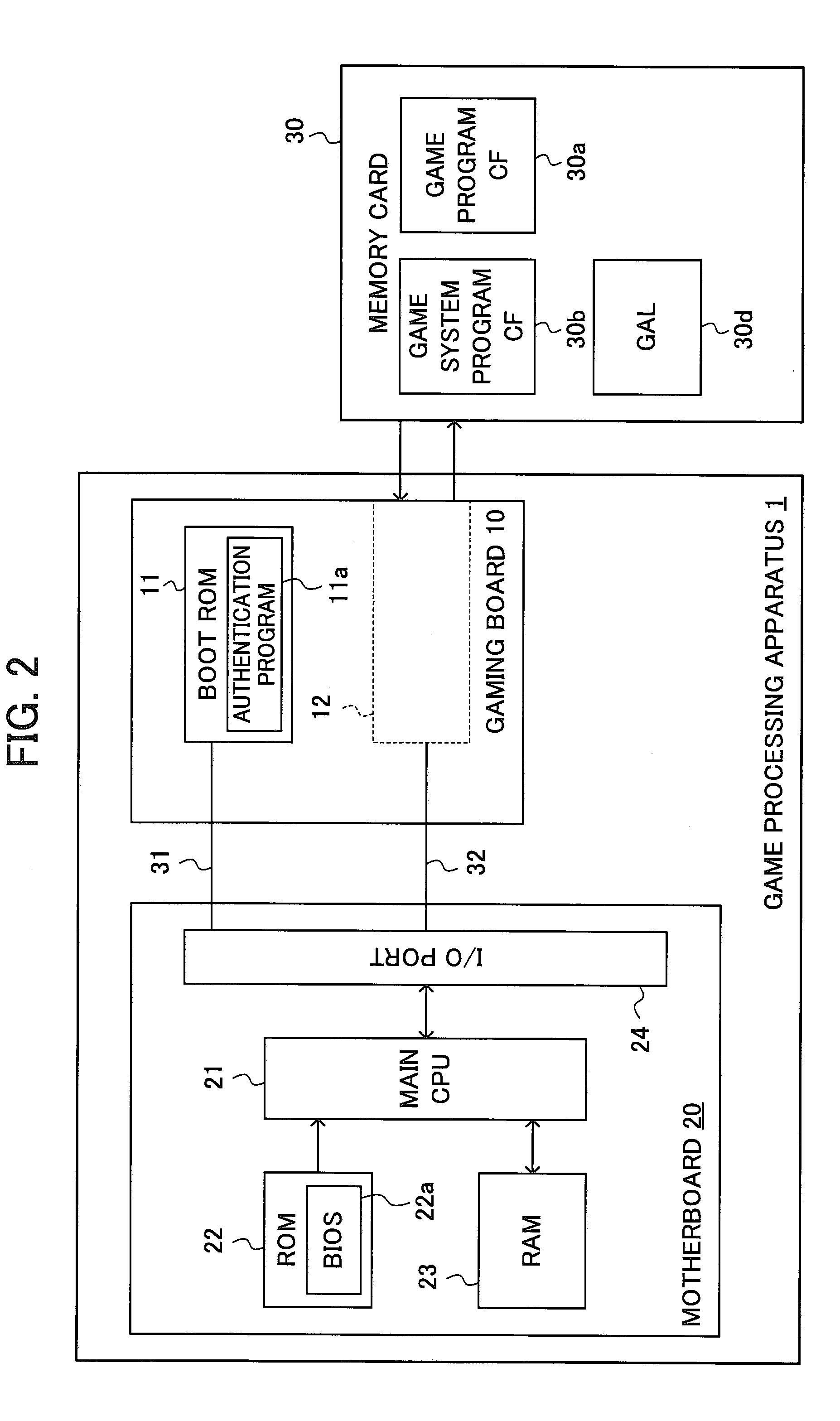
Game Processing Apparatus For Performing Area Authentication Of Gaming Information
ActiveUS20090005177A1Improve securityEasy maintenanceComputer security arrangementsApparatus for meter-controlled dispensingComputer hardwareAuthentication
A game processing apparatus is provided, which includes a first memory, a second memory, and a controller. The first memory stores gaming information including information related to gaming rules corresponding to an area. The second memory stores a predetermined first area code representing a specific area. The controller is configured with logic to: (a) calculate a second area code corresponding to the area according to the gaming information; (b) compare the second area code with the first area code so as to determine whether the gaming information matches the specific area; and (c) when the controller determines a mismatching, restrict a start of a game.
Owner:UNIVERSAL ENTERTAINMENT CORP
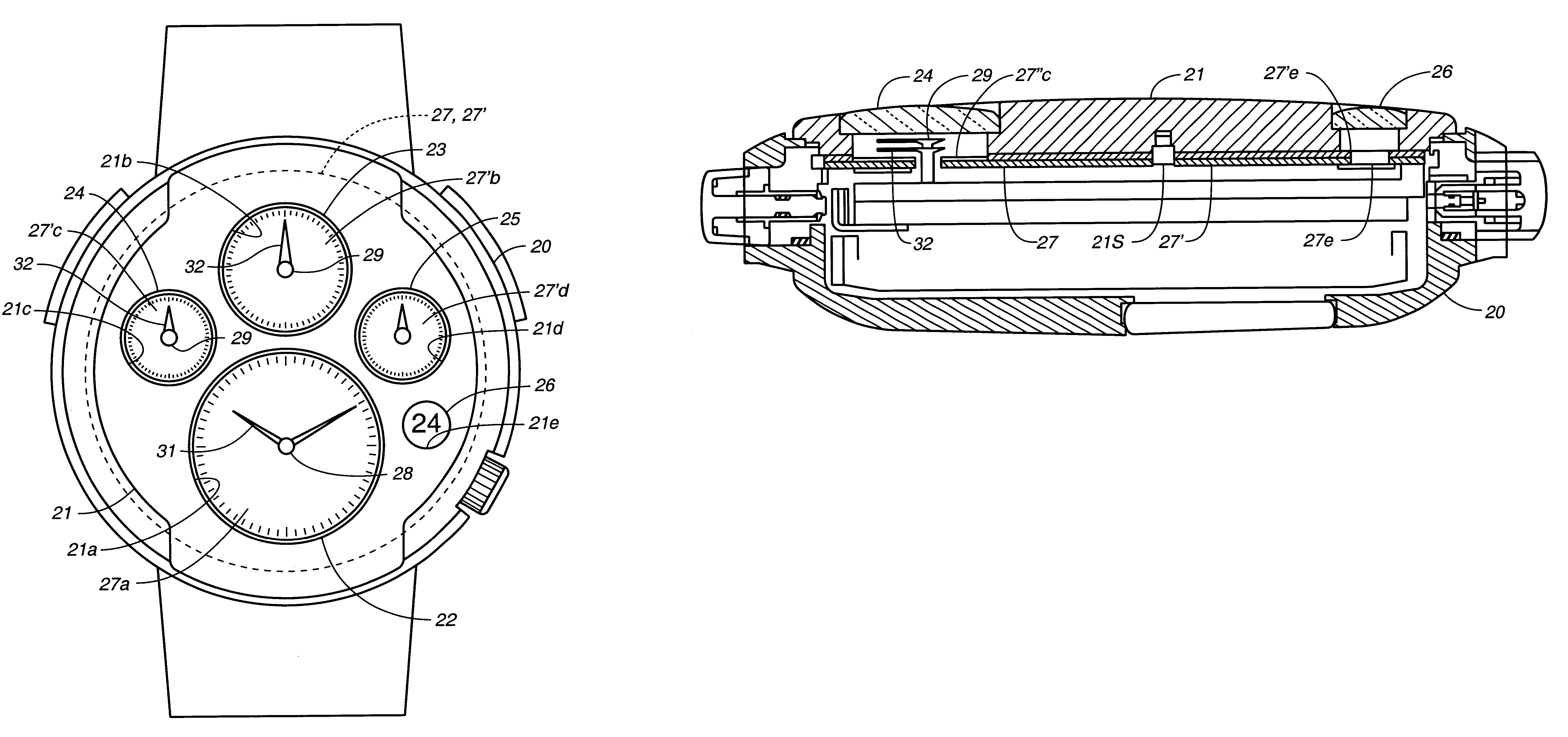
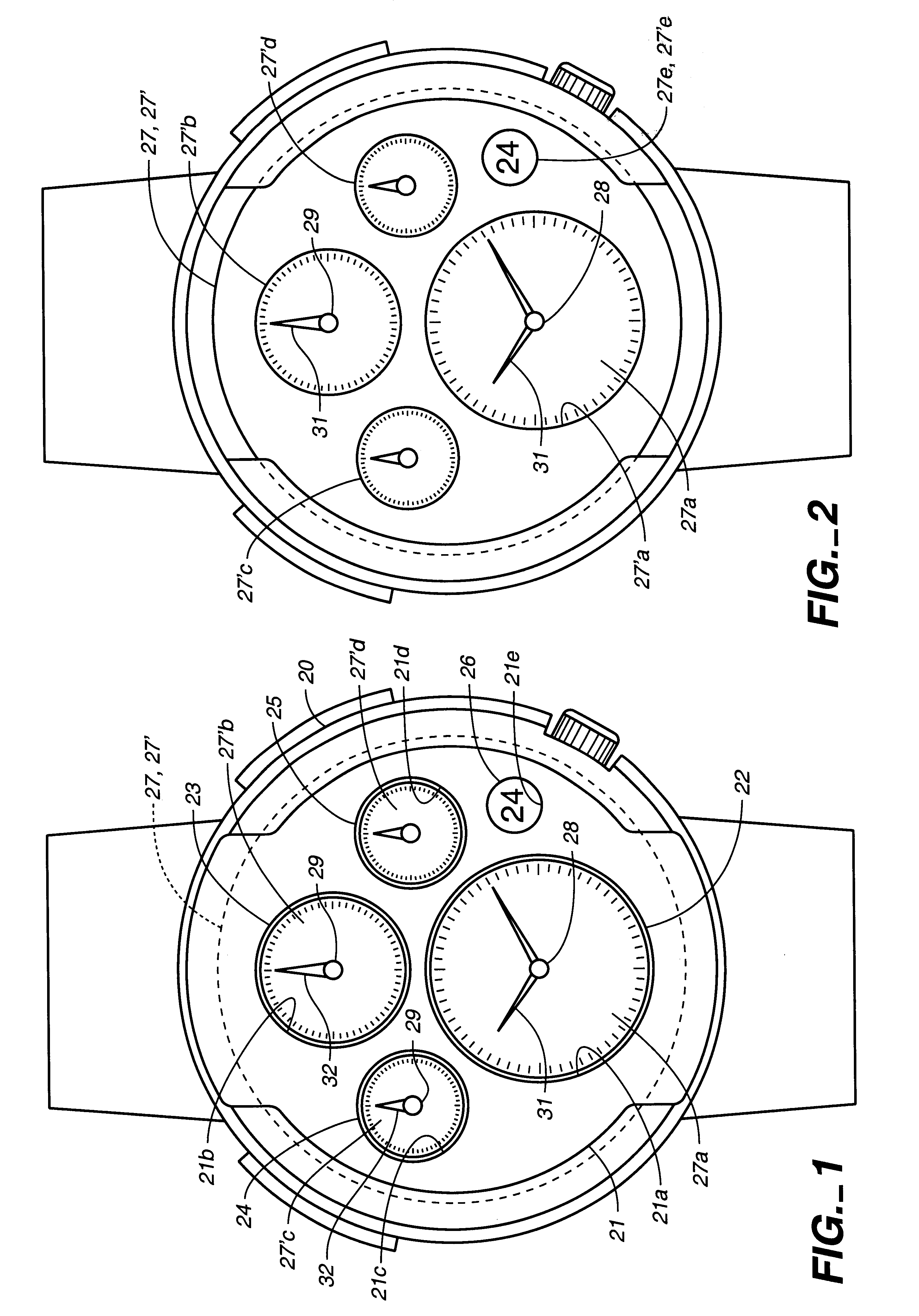
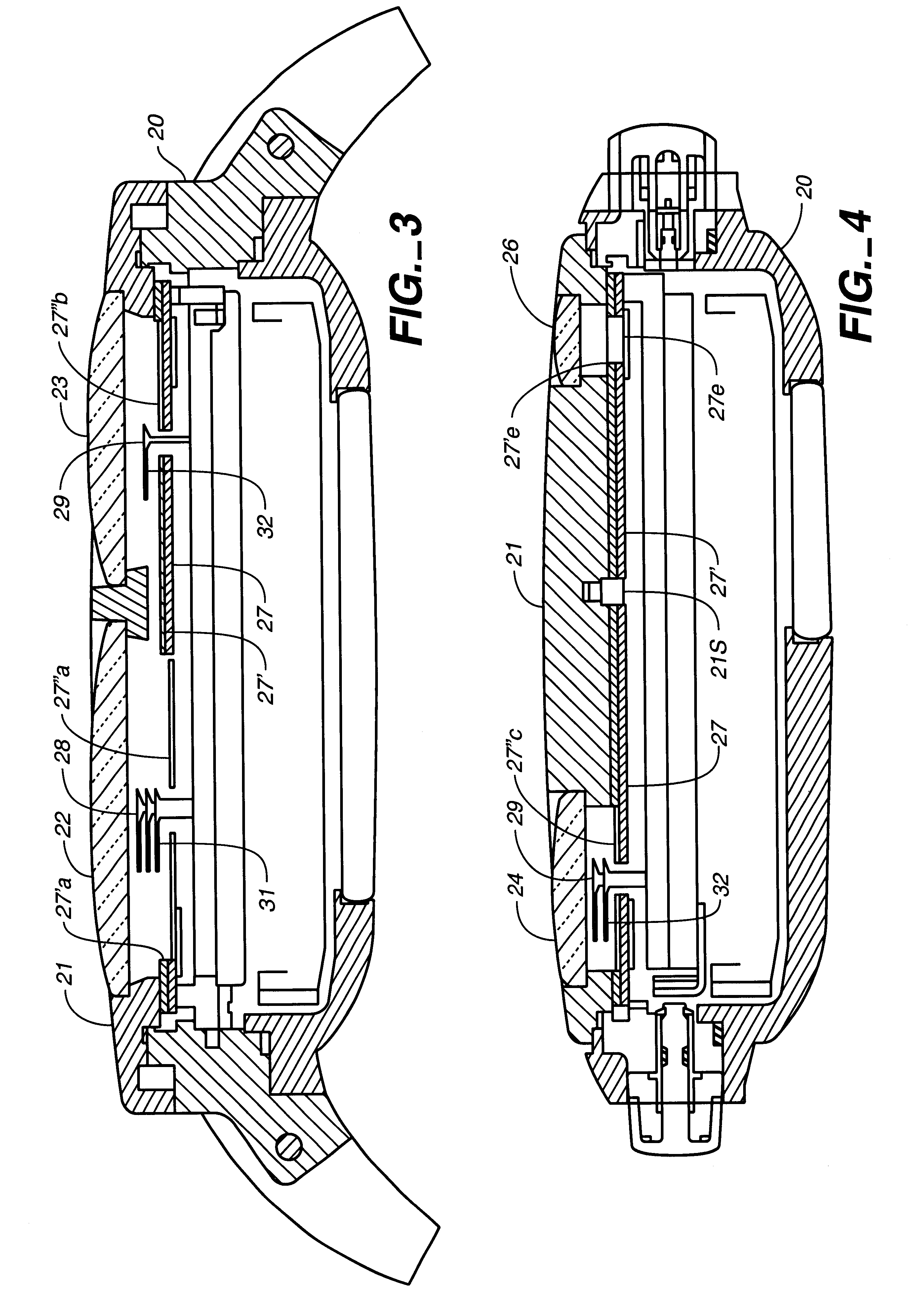
Timepiece
InactiveUS6275450B1Strengthen the strength of attachmentShorten the fit lengthVisual indicationElectric indicationEngineeringTime of day
Owner:SEIKO EPSON CORP
Biometric authentication device, system and method of biometric authentication
ActiveUS20090037743A1Easy to customizeMinimal interferenceUser identity/authority verificationComputer security arrangementsData accessPartial verification
A biometric sensor device, a portable electronic device including an actuatable biometric input device, and method of biometric authentication that includes an input device that generates a signal or completes a circuit when actuated, and a biometric reader that reads a biometric of a user when the user actuates the input device to generate the signal or complete the circuit. An authentication section authenticates the biometric read on the biometric reader to generate one of a data access allowance function based on authentication of the biometric input to the actuatable biometric input device and a data access prevention function based on non-authentication of the biometric input to the actuatable biometric input device. The data access allowance function permits data to be accessed at the data access interface, and the data access prevention function prevents reading and / or access to data anywhere on the data storage and access device.
Owner:IBM CORP
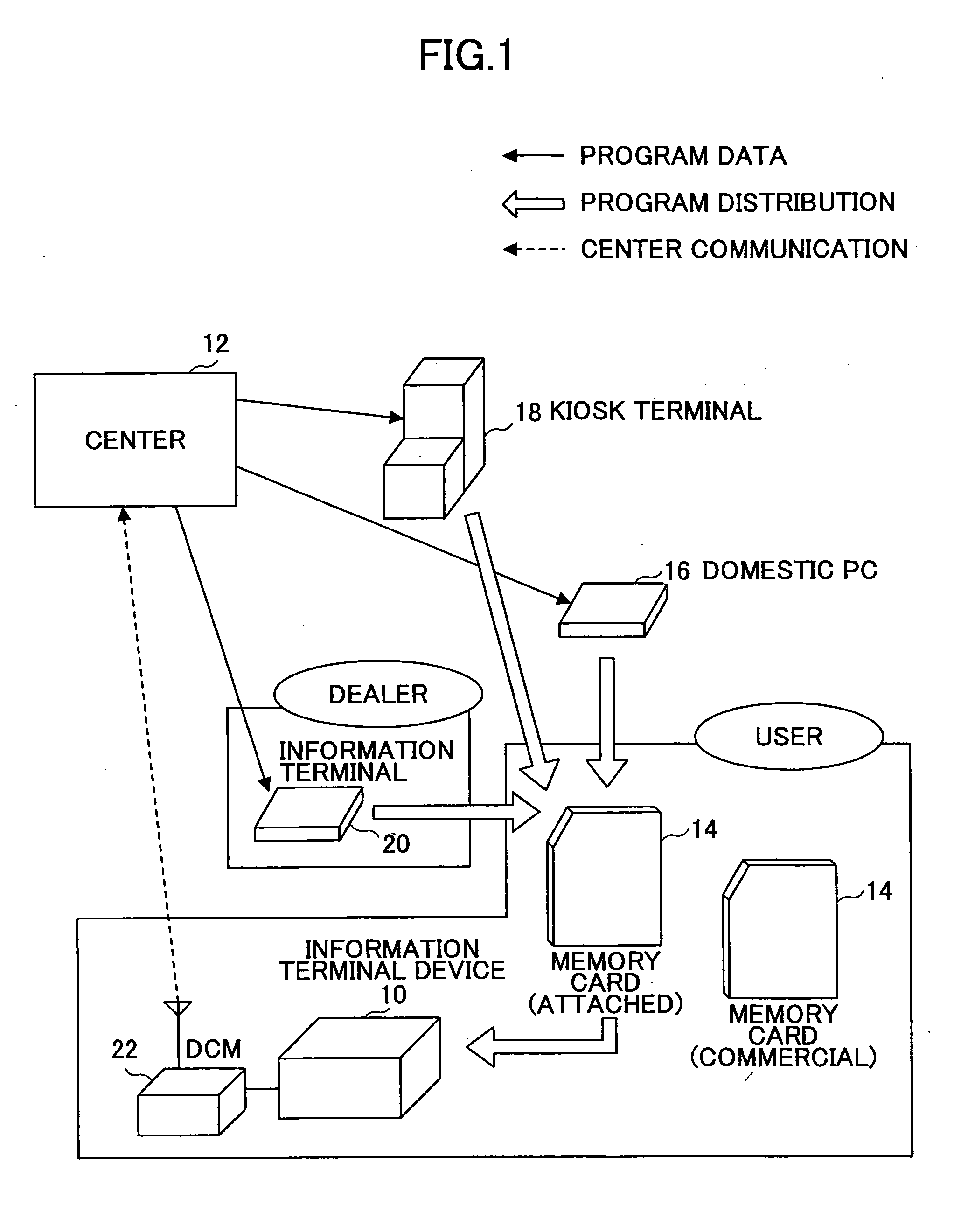
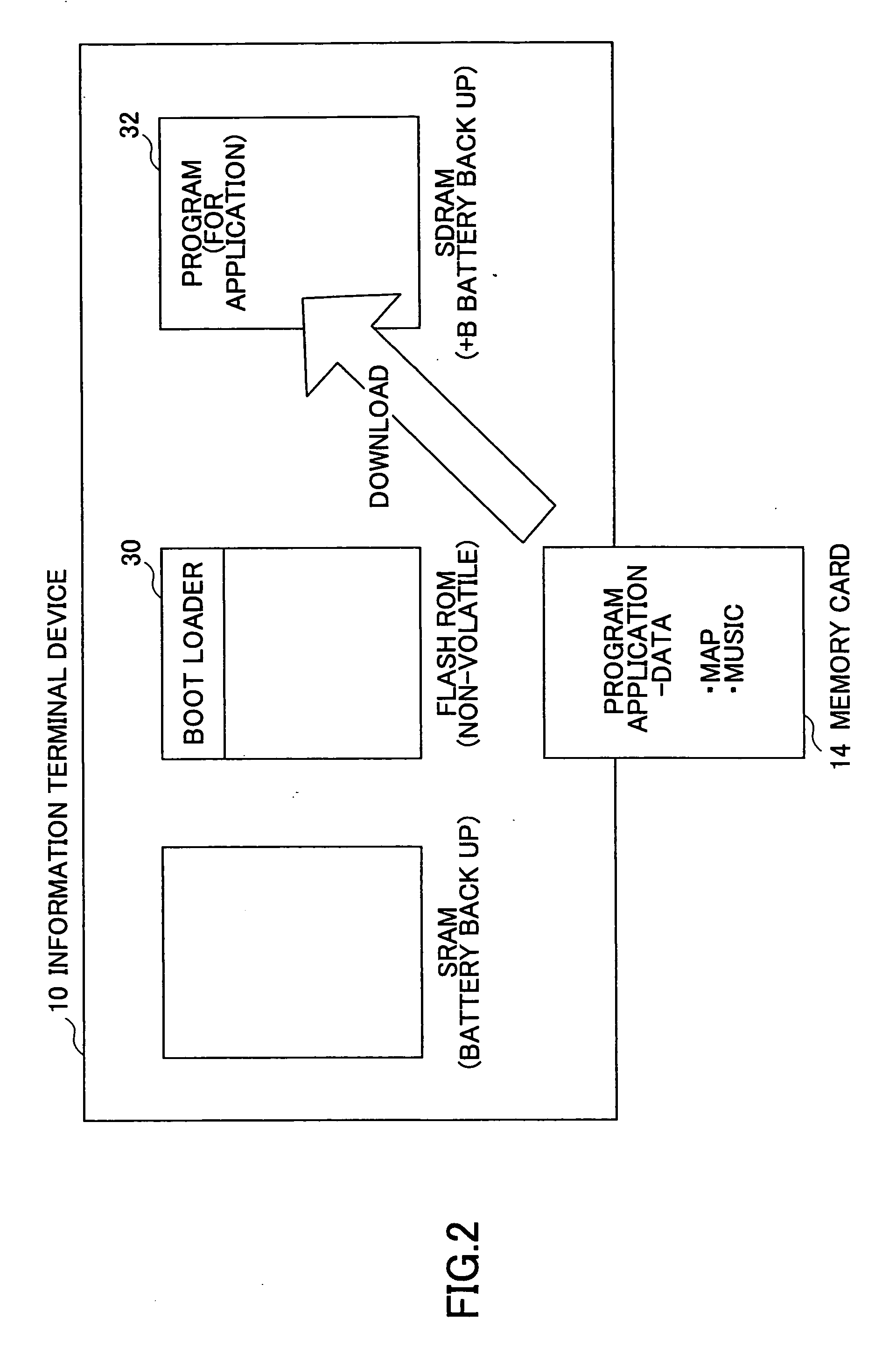
Information terminal deice and operation control method thereof
InactiveUS20060031826A1Hinders provisionStored informationProgram control using stored programsDigital data processing detailsTerminal equipmentInformation device
The present invention is directed to an information terminal device. A memory card 14 stores a serial number MID of the memory card 14 and a MID register program for registering the serial number MID in the information terminal device 10. At starting the information terminal device 10, the MID register program is downloaded from the installed memory card 14 and the serial number MID stored in the memory card 14 is stored in a non-volatile flash ROM 30 in accordance with the program. Then, the MID register program is cleared out of the memory card 14 and the MID register program on a SDRAM 32 downloaded to the information terminal device 10 is made invalid. Such processing prevents the serial number of the memory card 14 from being thereafter stored in the other information terminal device 10.
Owner:PANASONIC CORP +1
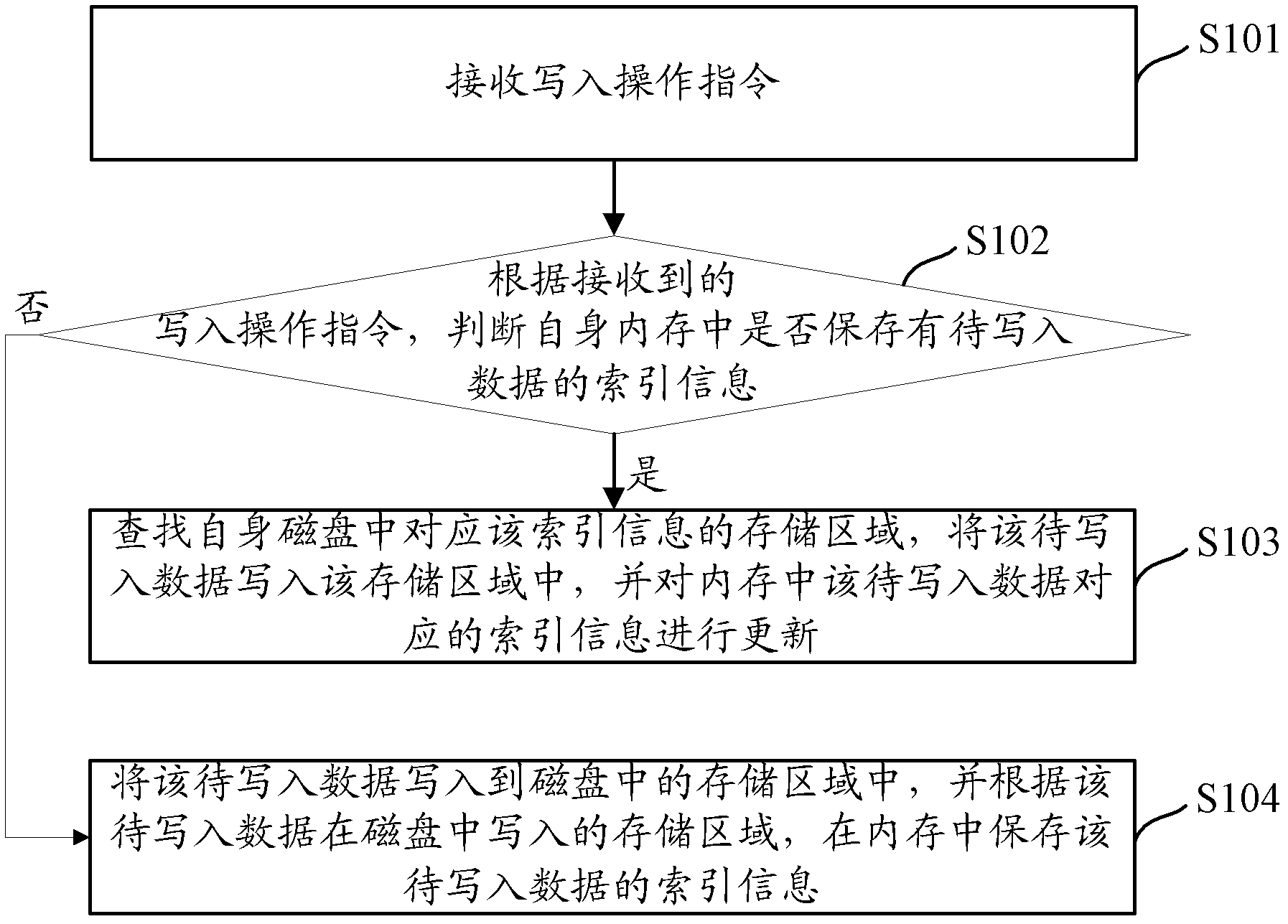
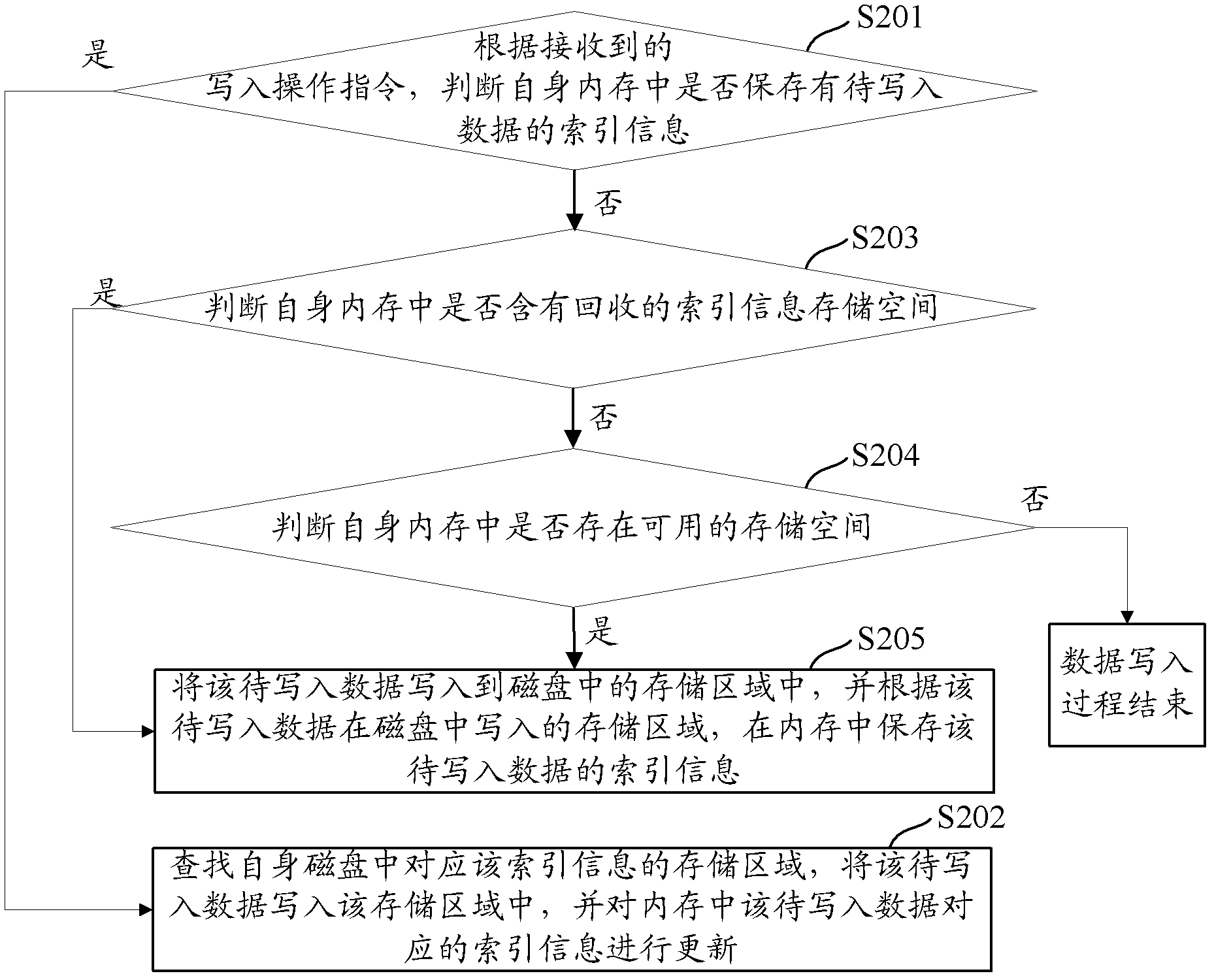
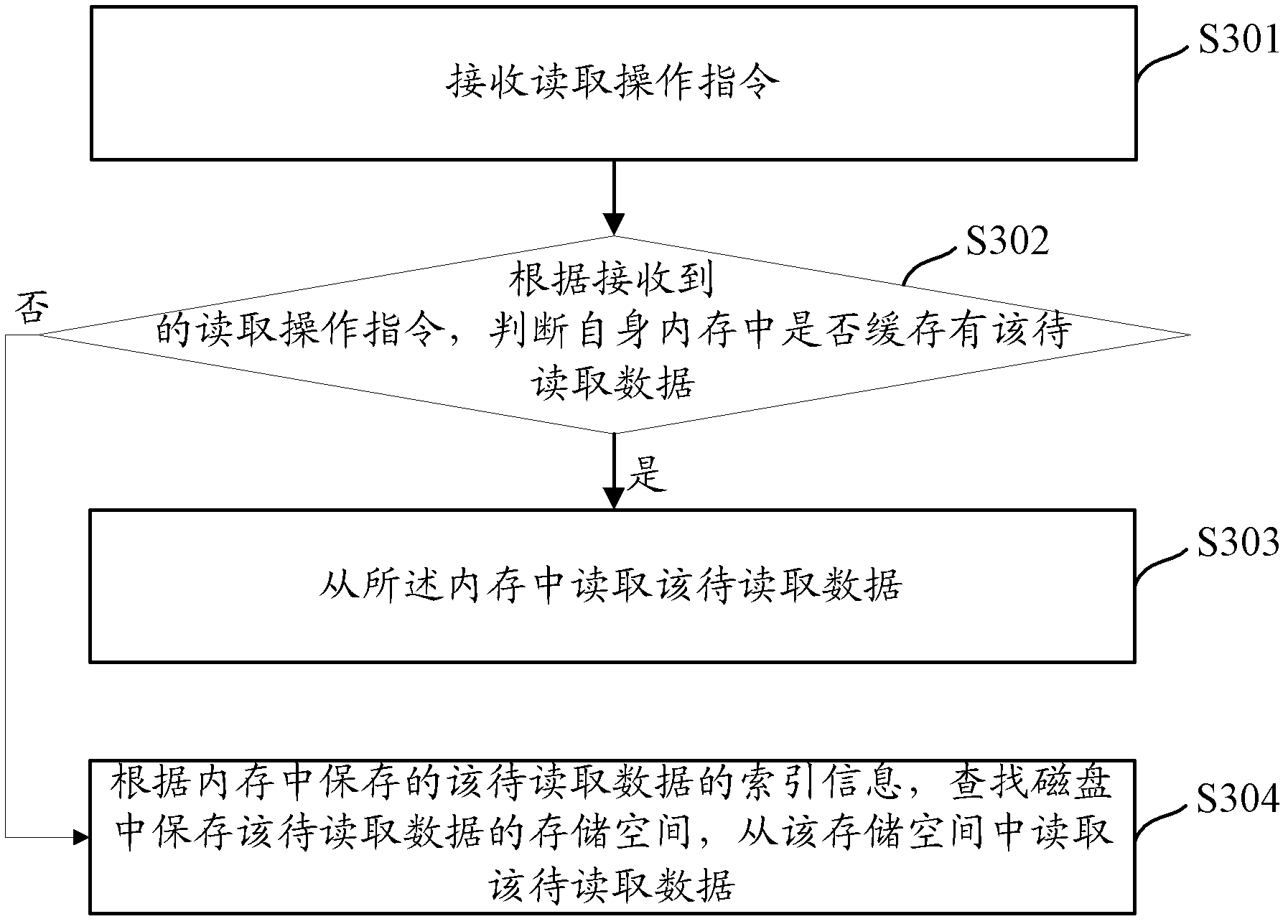
Data writing and reading method and device in distributed caching system
ActiveCN102843396AAchieve readAvoid writingInput/output to record carriersDigital data information retrievalInternal memoryComputer architecture
The invention discloses data writing and reading method and device in a distributed caching system. According to the distributed caching system, the indexing information of the data is stored in an internal memory, and the data information is stored in a hard disk; and when the writing and reading of the data are carried out, corresponding operation be performed on the hard disk through the indexing information stored in the internal memory. According to the method and device provided by the embodiment of the invention, the data is written and read in combination of the internal memory and the hard disk, and the internal memory is only used for storing indexing information; the reading and writing of the data are carried out in combination of the internal memory and the hard disk, so that the problem that all data is stored into the internal memory can be avoided, and the requirements on caching of a large number of data can be met; and furthermore, the data read-write efficiency can be improved by reading and writing the data in the combination of the internal memory and the hard disk, so the reliability of the system can be improved.
Owner:ZTE CORP
Display device and electronic apparatus
InactiveUS20060262054A1Ensure visibilityReduce power consumptionCathode-ray tube indicatorsInput/output processes for data processingDriver circuitVisibility
Outside light is received using a light sensor, and in accordance with the outside light intensity, each of a first display mode which expresses multiple gray scales and a second display-y mode which expresses a gray scale smaller in number than that in the first display mode is switched and used. The switching is controlled by a display controller based on data of the outside light intensity. Accordingly, the visibility can be ensured in a wide range of situations, from under a fluorescent lamp in a dark place or inside, to under sunlight outside. In the second display mode, frequencies of a start pulse and a clock pulse to be inputted to a source signal line driver circuit are reduced and a driving voltage is decreased by the display controller; accordingly, a frame period can be longer than that in the first display mode and power consumption can be reduced.
Owner:SEMICON ENERGY LAB CO LTD
Portable device for caching RFID tag and method thereof
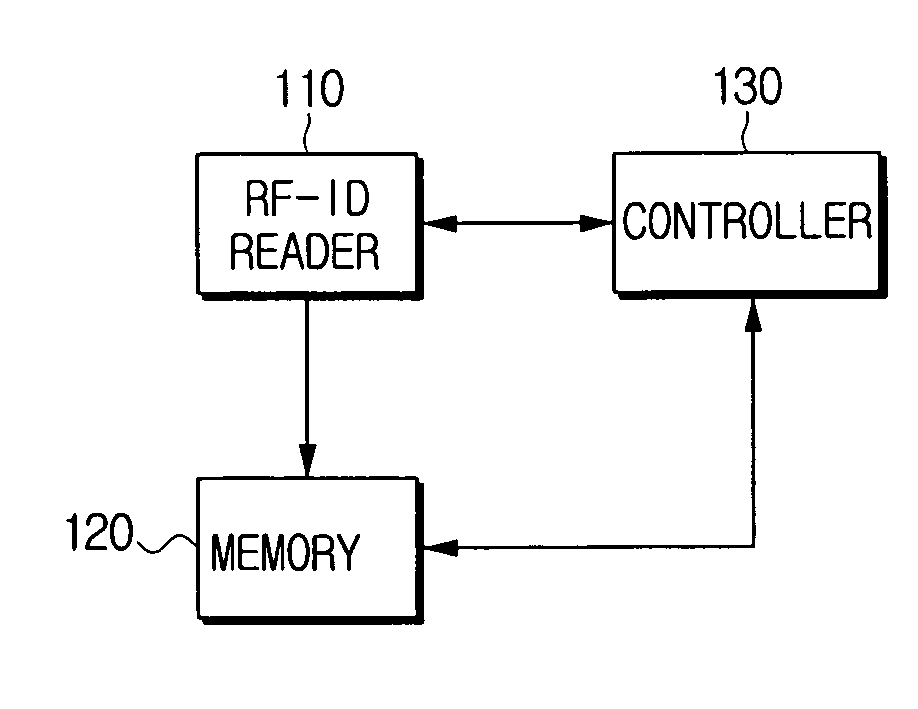
ActiveUS20060202803A1Avoid readingShorten the timeProgramme controlElectric signal transmission systemsComputer hardwarePower consumption
A portable device includes an RFID reader for detecting a tag information of an RFID tag, a memory for storing the tag information detected by the RFID reader, and a controller. When a read command for the RFID tag is input and the tag information is valid, the controller controls the RFID reader to retrieve the tag information of the memory. If the tag information is invalid, the controller controls the RFID reader to re-read the RFID tag. The controller can determine whether the tag information is valid using the time and location. Because unnecessary operation can be omitted to read tags, power consumption is reduced and tag information check time is shortened.
Owner:SAMSUNG ELECTRONICS CO LTD
Quickly turning-on of mobile telephone
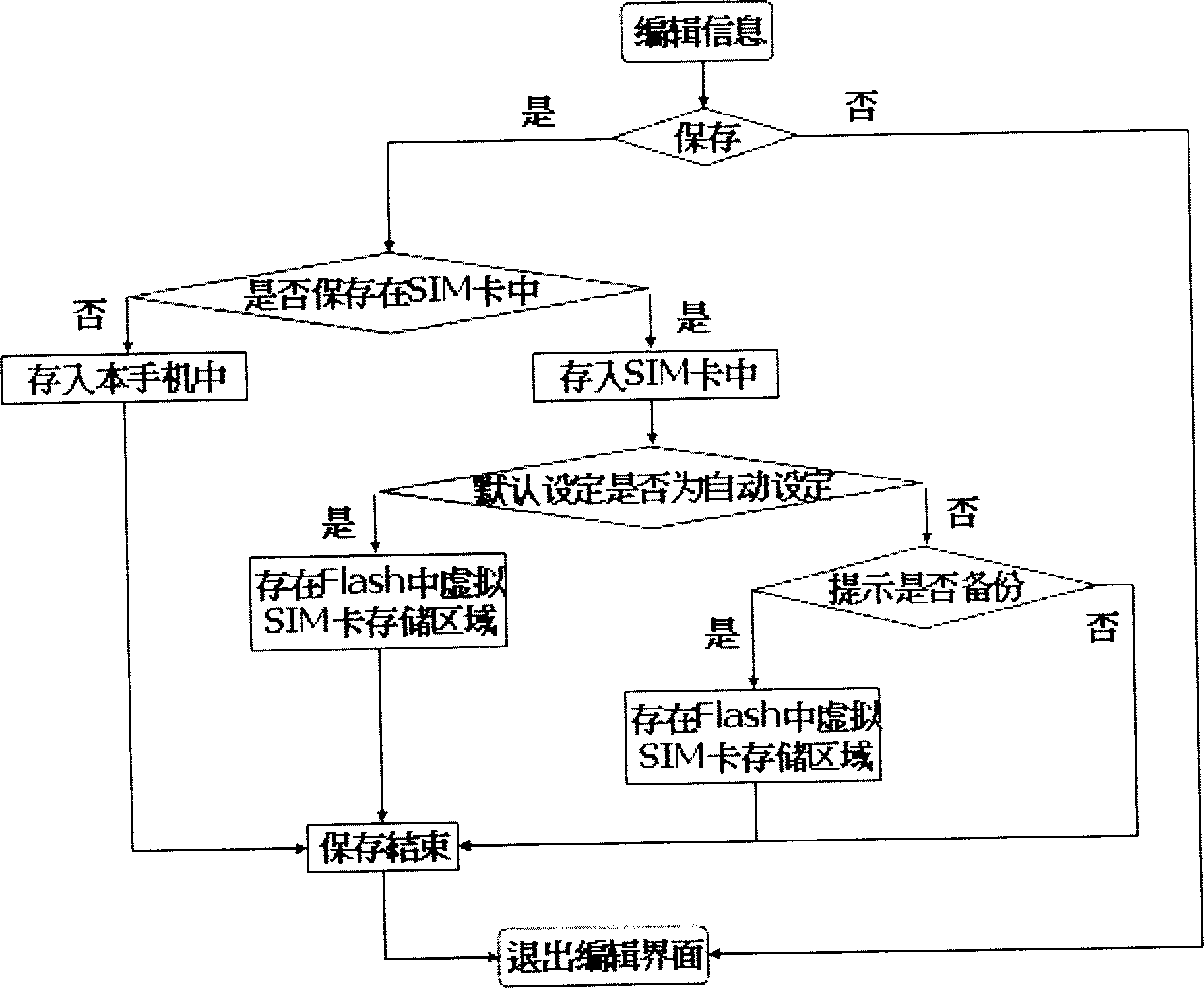
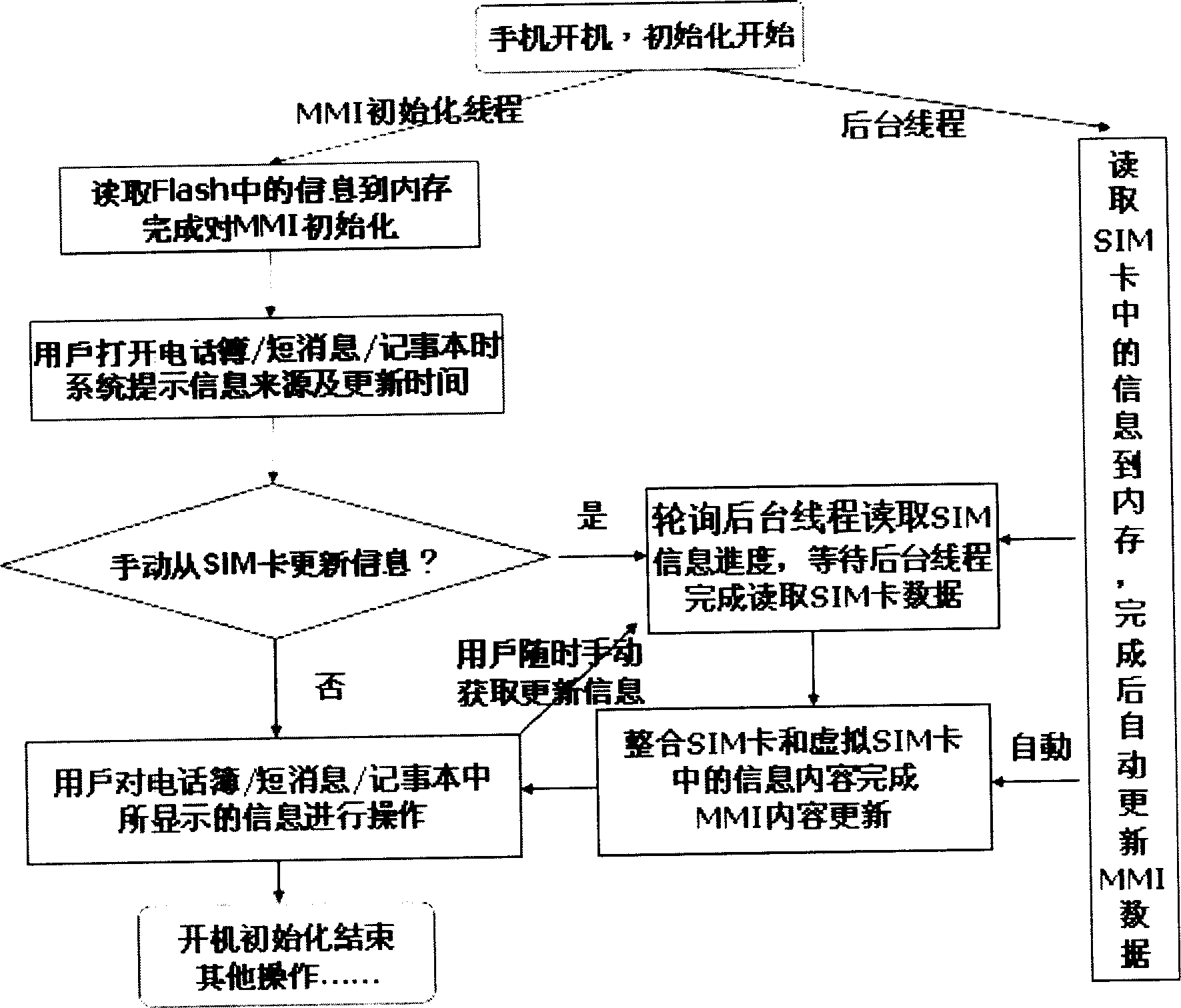
InactiveCN1856138AEasy to completeAvoid readingSubstation equipmentProgram loading/initiatingStart timeMobile phone
A method to achieve the quick starting of the mobile, cuts a free space to be storage space of the virtual SIM card in the flash part of the mobile phone, backups the initialization read information needing by starting in the flash of the mobile phone, in order to achieve the quick completion of the starting initialization. The invention can short the starting time of the mobile phone, the user can use the telephone book or demand the saving short message and colorful short message immediately.
Owner:YINGHUADA (SHANGHAI) ELECTRONIC CO LTD
Image-reading apparatus
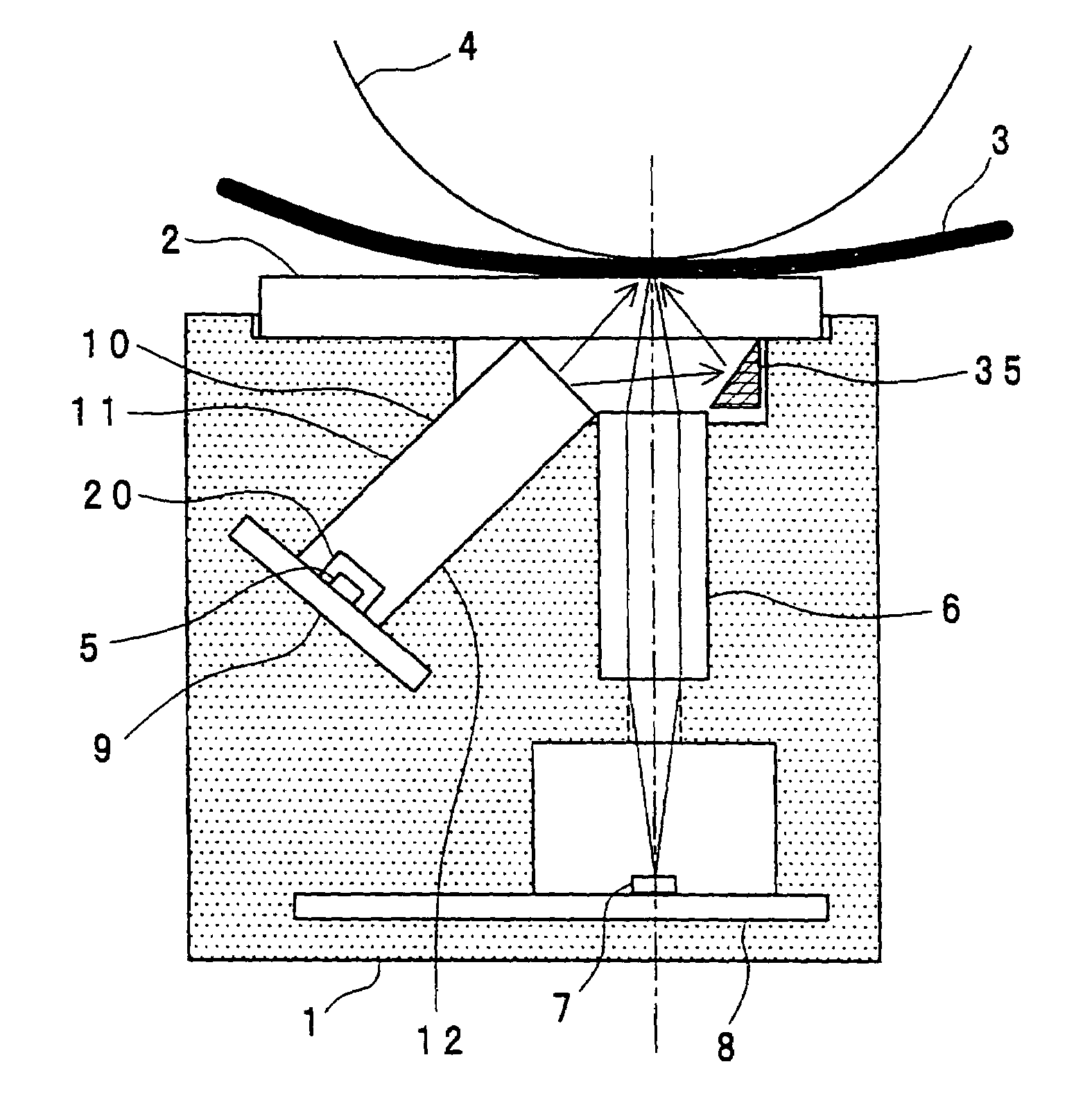
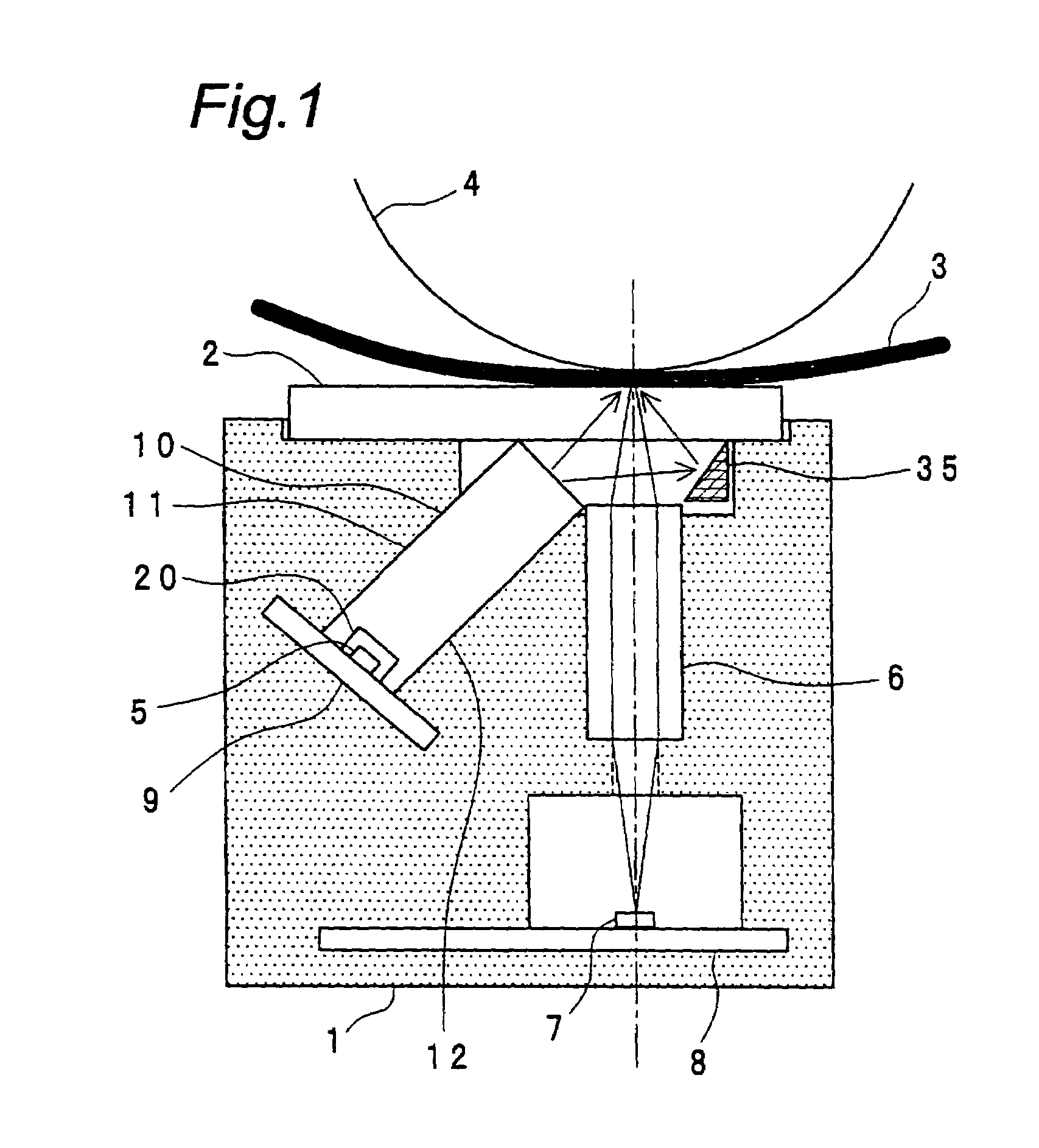
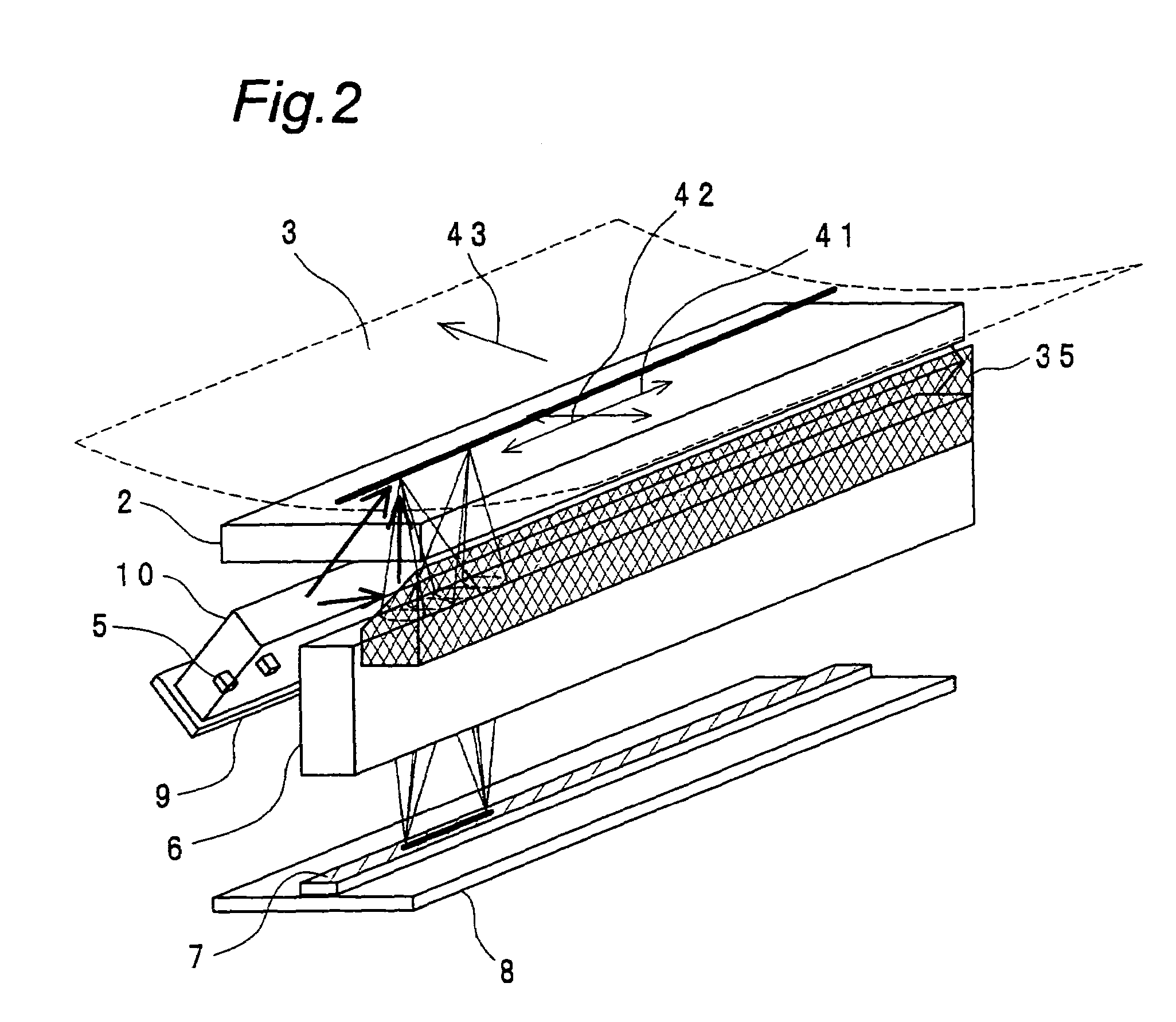
InactiveUS7085023B2Increase light intensityAvoid readingBeam/ray focussing/reflecting arrangementsSolid-state devicesLight guideLuminous flux
There is provided such a shape of a light-guiding body that can guide light emitted from a LED while reflecting such light under conditions which satisfy total reflection as much as possible within the light-guiding body, to thereby improve the light intensity on the surface of a document in the shorter axial direction (i.e., the sub-scanning direction), and also, the light-guiding body has such an optimized shape of a light-incoming face that makes it possible to control the angle of light fluxes in the longer axial direction (i.e., the main scanning direction) to thereby illuminate the surface of the document with light having an uniform intensity distribution. Further, a reflecting member is provided at a position opposite the light outgoing face of the light-guiding body so as to improve the efficiency of illuminating an objective image-reading region on the surface of the document.
Owner:MITSUBISHI ELECTRIC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com