An Internet of Things terminal secure communication method based on a block chain technology
A technology for secure communication of IoT terminals, which is applied in the field of secure communication of IoT terminals based on blockchain technology, can solve problems such as limited resources of IoT devices, unrealized integrity protection of data, and increased central server load, etc. , to achieve the effect of ensuring that it is difficult to tamper with, realize high efficiency, and reduce load
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
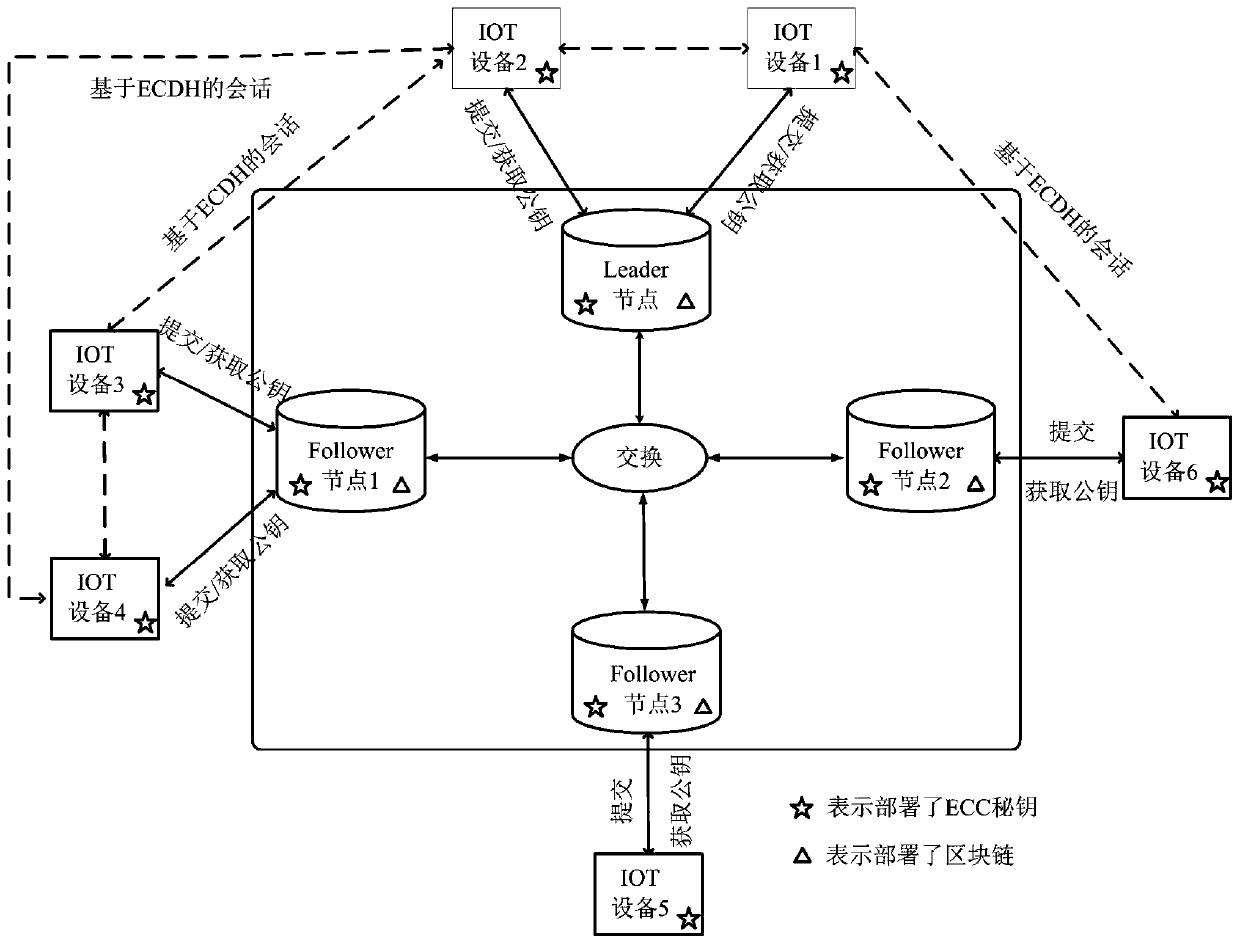
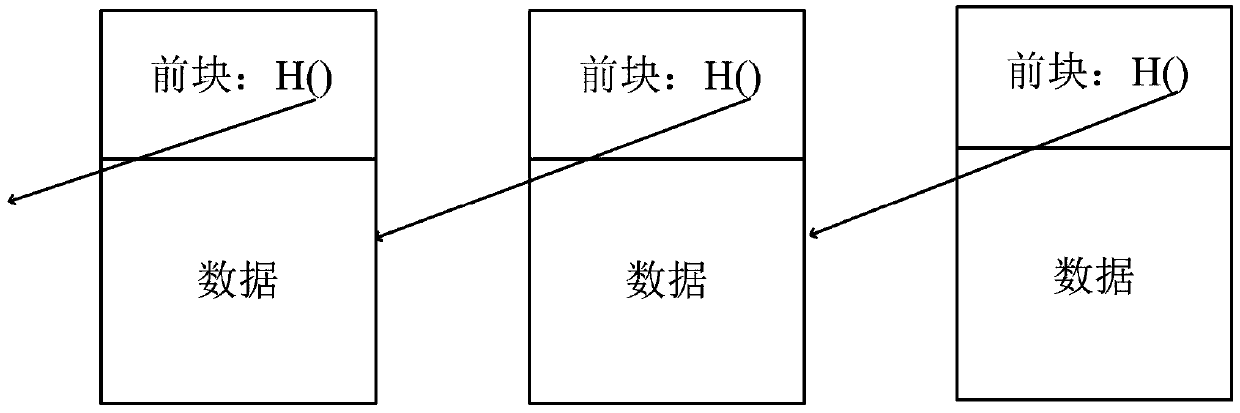
[0057] In order to reduce the load pressure of the service center, realize efficient and safe communication and data transmission between IoT terminal devices, ensure the non-tampering of data, and the convenience of equipment use, based on blockchain technology, a compromise Internet of Things is proposed. A method for secure transmission and storage of information between terminal devices, the security architecture of the system is as follows: figure 2 shown. This solution can solve remote communication and transmission security issues at the same time, and meet practical application requirements such as small load and safe storage. It mainly includes three aspects of work: (1) Starting from the separation of IoT device authorization and inter-device communication, based on asymmetric encryption algorithm and D-H key exchange mechanism, the secure communication of IoT terminal devices is realized; (2) Raft consensus is designed The algorithm meets the strong consistency an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com