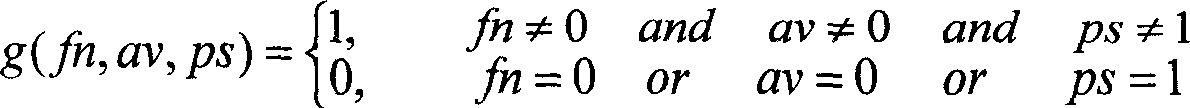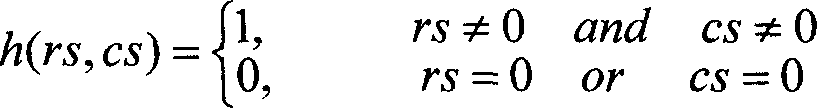Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
504 results about "Security question" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A security question is form of shared secret used as an authenticator. It is commonly used by banks, cable companies and wireless providers as an extra security layer. Financial institutions have used questions to authenticate customers since at least the early 20th century. In a 1906 speech at a meeting of a section of the American Bankers Association, Baltimore banker William M. Hayden described his institution's use of security questions as a supplement to customer signature records. He described the signature cards used in opening new accounts, which had spaces for the customer's birthplace, "residence", mother's maiden name, occupation and age.
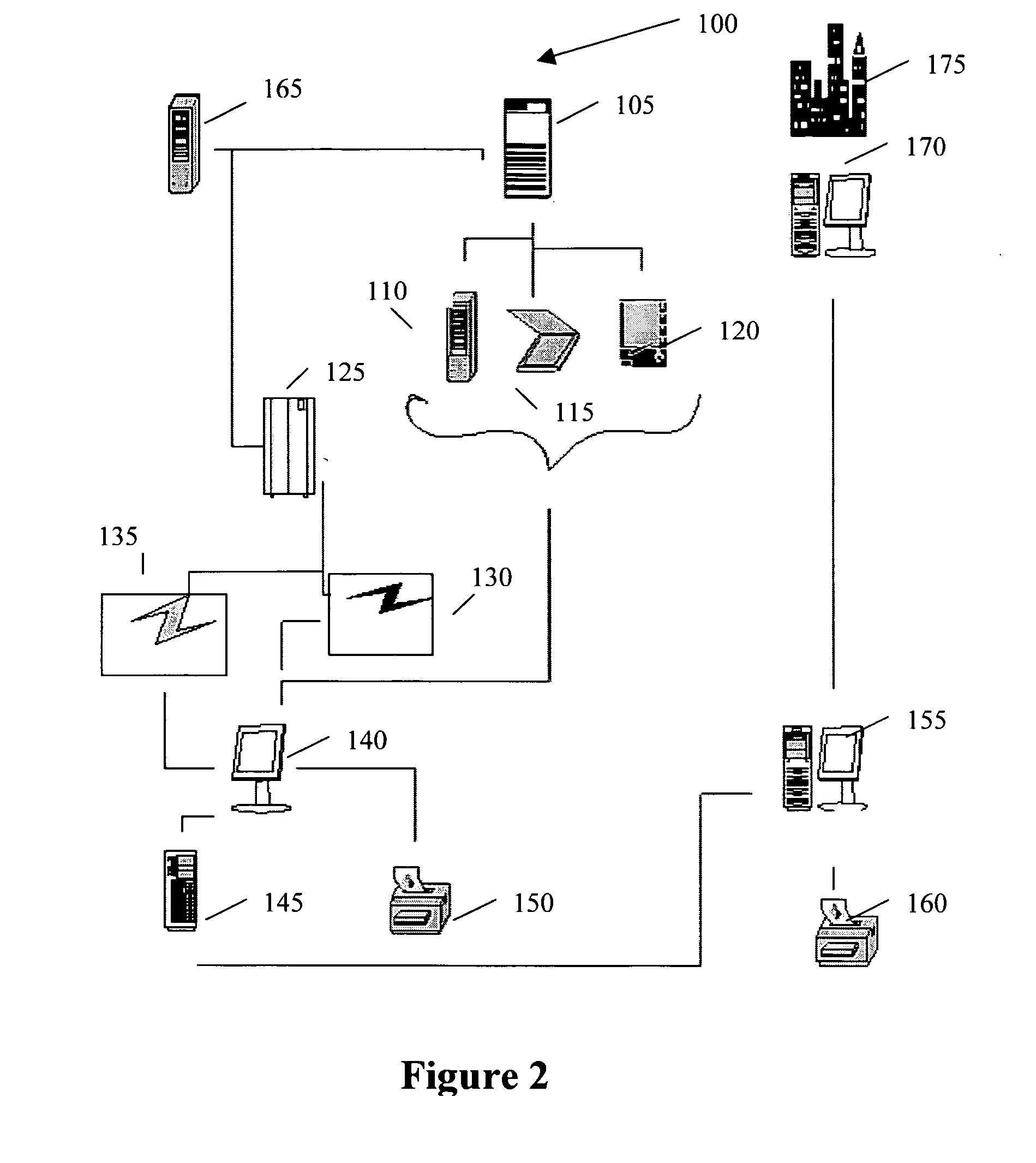
Secure enterprise network
ActiveUS8166554B2Digital data processing detailsDigital computer detailsUser authenticationApplication software
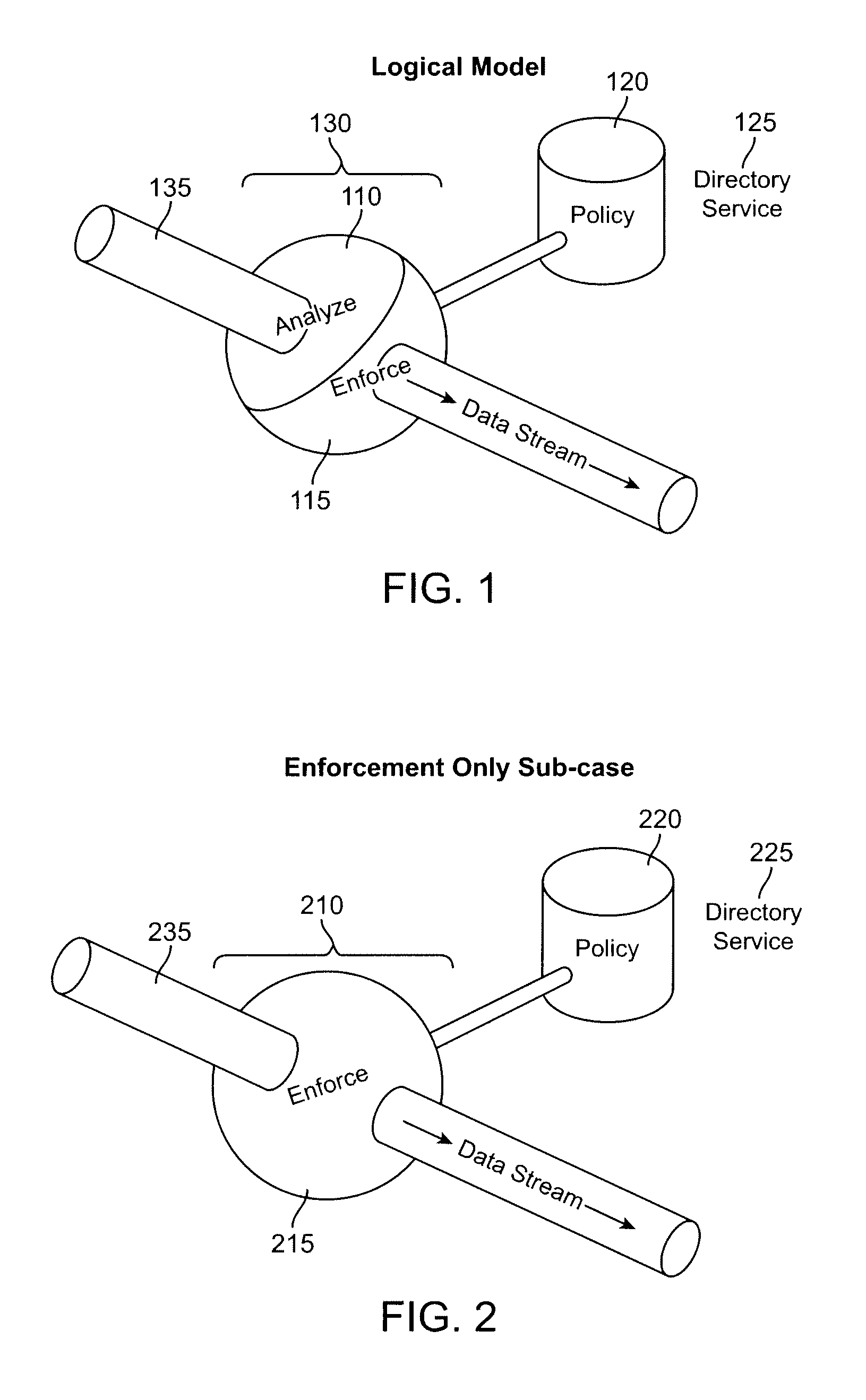
What is proposed is a method of implementing a security system (Packet Sentry) addressing the internal security problem of enterprises having a generalized approach for inferential determination and enforcement of network policy with directory service based group correlation with transparent authentication of the connected customer and the policy enforcement inside the network. The security system enables the network to analyze and enforce policy using any bit or bits in a stream or a packet, conduct Flow Vector analysis on the data traffic, provide Application Monitoring, Normalization and user authentication validation. The system enables the network to implement Group relationship Analysis and correlation using combination of Network inferences and Directory service data resulting in generation of Group norms using statistically significant relationships. These will provide a more secure enterprise environment where data security levels can be enforced and the usage monitored effectively in the infrastructure.
Owner:VMWARE INC
Software safety code analyzer based on static analysis of source code and testing method therefor
InactiveCN101017458AImprove accuracySupport for expansionSoftware testing/debuggingStatic timing analysisStructure analysis
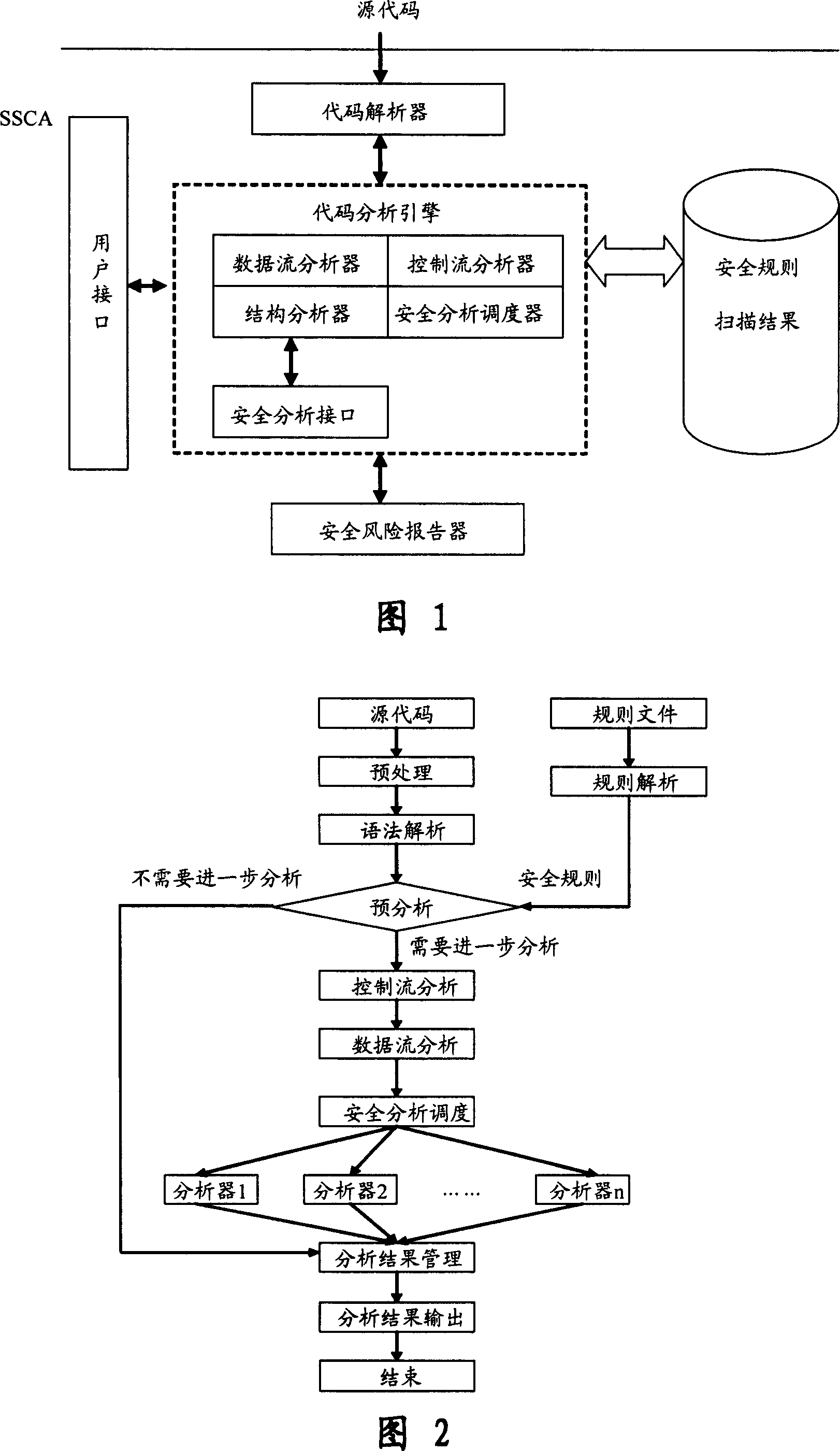
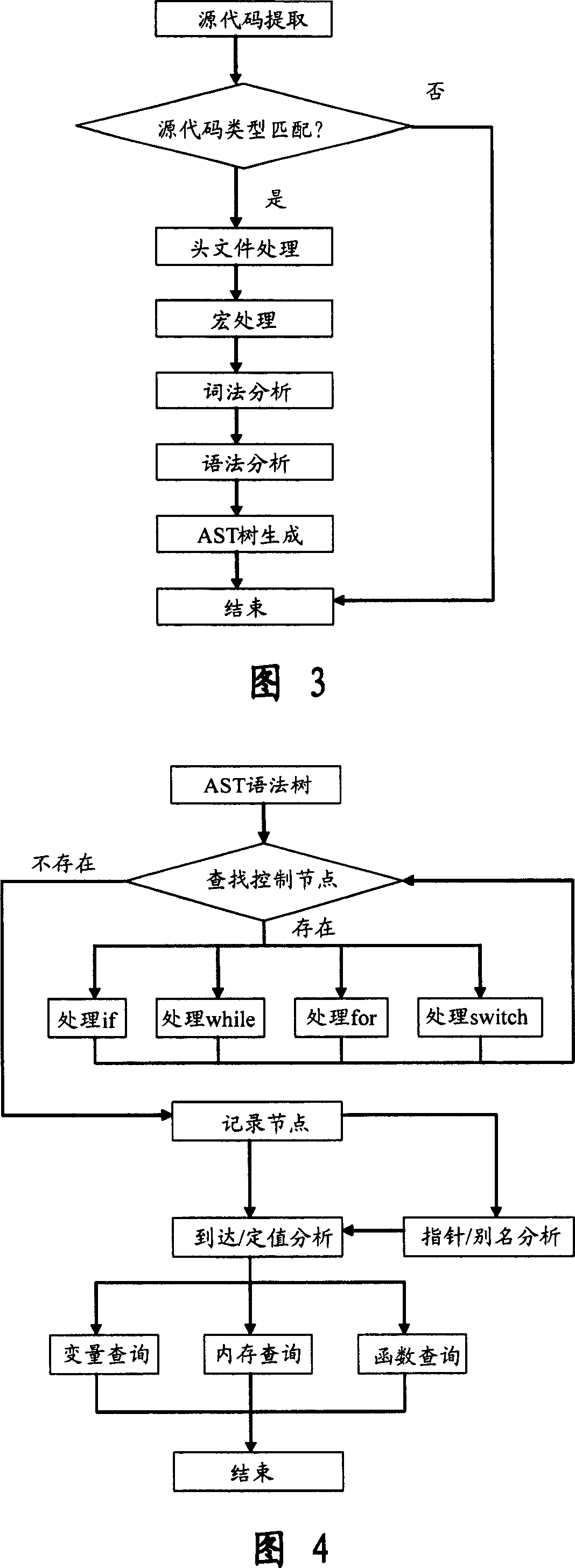
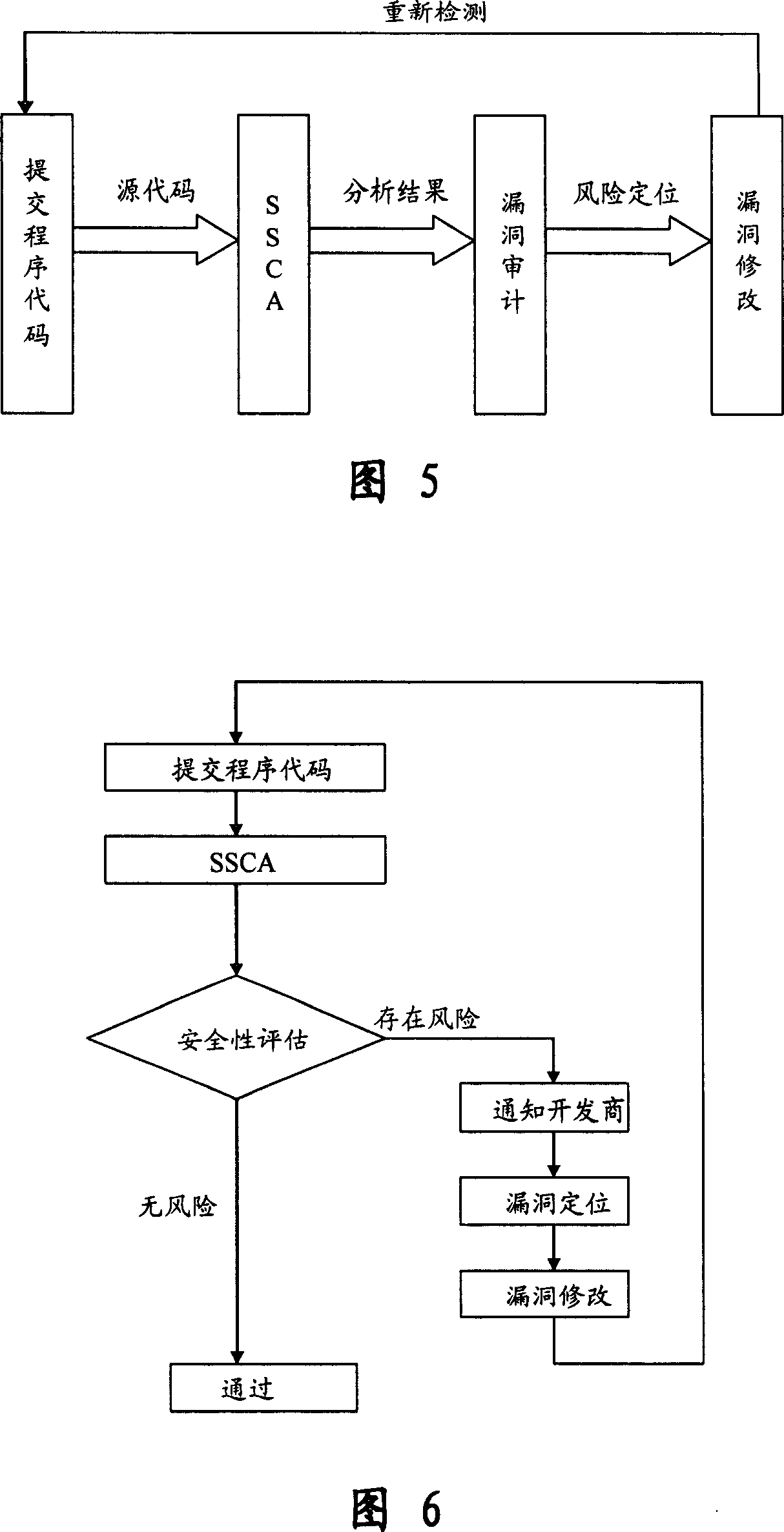
This invention relates to one software analyzer and its test method based on source codes static analysis, wherein the analysis device comprises five function modules of code analysis device, codes analysis engine, safety risk report device, safety rules database and user interface; this invention gets programs safety risk to user according to the source program and grammar and meanings and delivers the safety leak to the user for audit and evaluation.
Owner:深圳北邮网络科技有限公司
Alarm with remote monitor and delay timer
InactiveUS7075429B2Easy to installEasy maintenanceBurglar alarm by openingATM surveillanceFiberEngineering
An alarm apparatus for detecting an intrusion or compromise situation upon critical equipment or private areas. The apparatus detects an unauthorized radio transmitter (like a wireless camera), or the covering of a critical piece of equipment. Fiber optics, solar cells and special radio antennas are used to detect intrusion remotely and a delay timer will allow normal activity to occur, while reducing false alarms. This alarm apparatus will notify an existing system of the intrusion or compromise when limits are exceeded. This alarm apparatus also addresses privacy concerns of wireless cameras and recording devices in areas like changing rooms, bathrooms, or boardrooms. The apparatus addresses security issues for critical devices like smoke alarms and ATM machines.
Owner:MARSHALL CRANBROOK
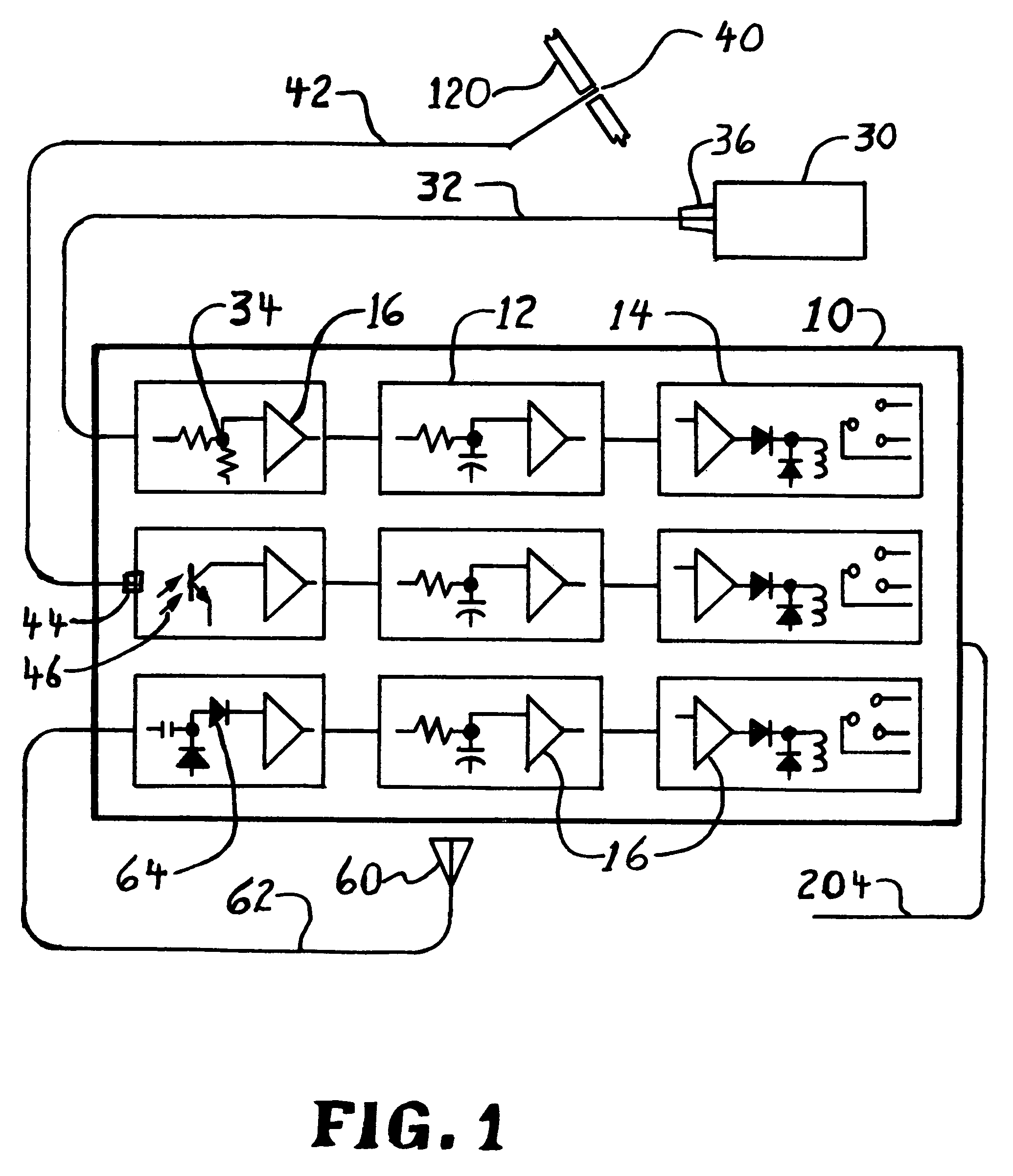
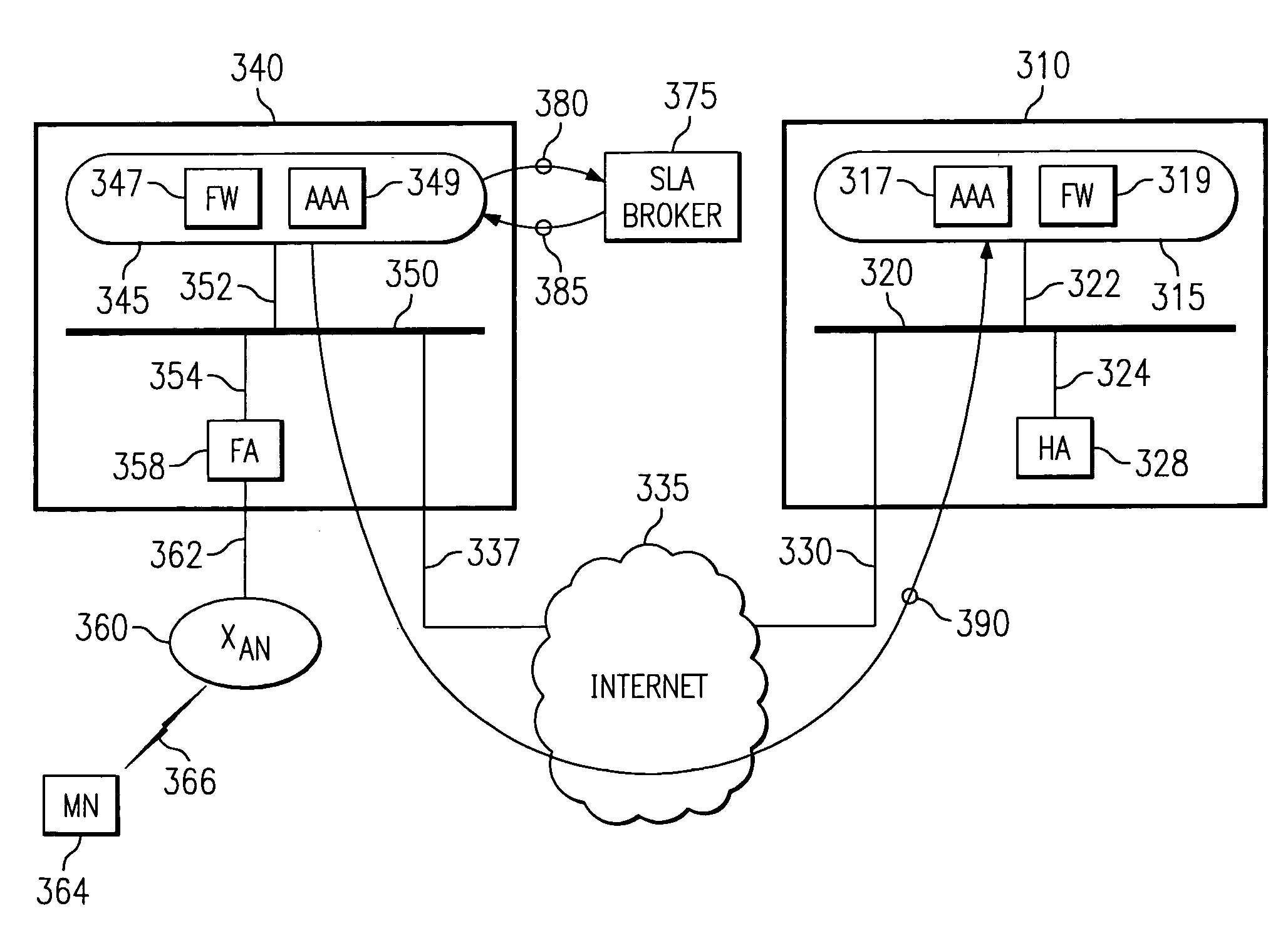
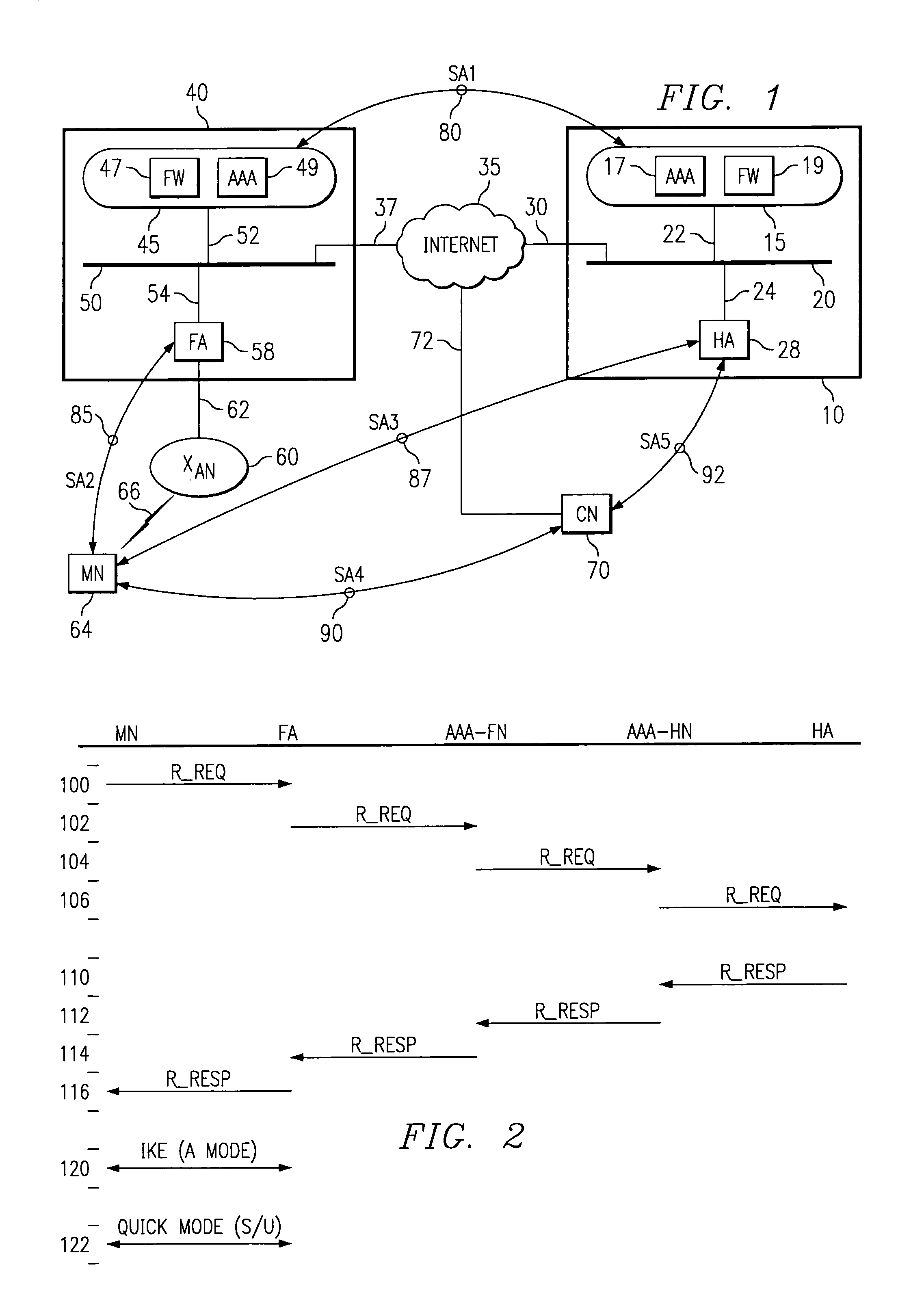
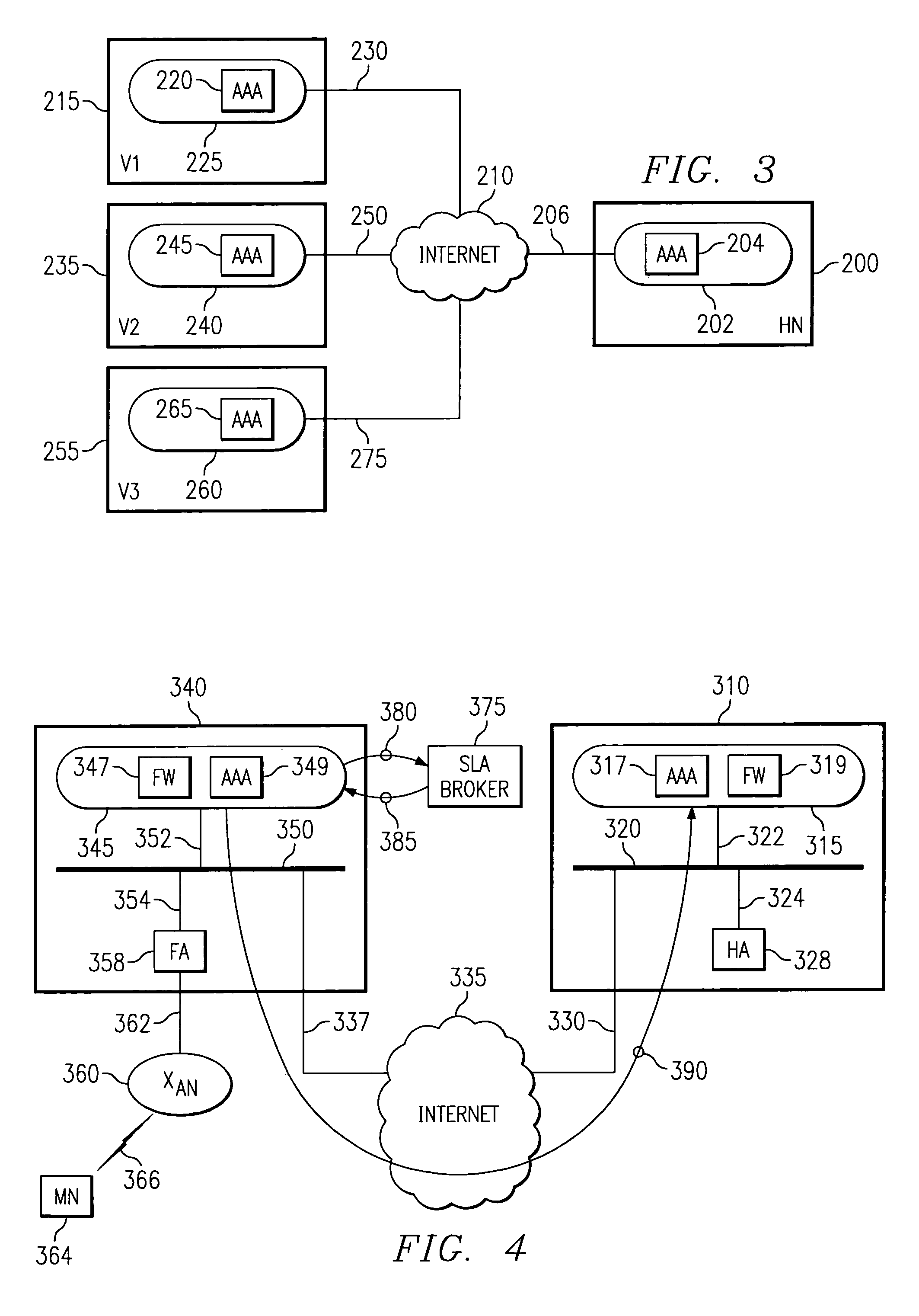
Security framework for an IP mobility system using variable-based security associations and broker redirection
InactiveUS7174018B1Improve securityPromote large-scale roamingWireless network protocolsSecret communicationService-level agreementSecurity association
In an IP-based mobile communications system, the Mobile Node changes its point of attachment to the network while maintaining network connectivity. Security concerns arise in the mobile system because authorized users are subject to the following forms of attack: (1) session stealing where a hostile node hijacks session from mobile node by redirecting packets, (2) spoofing where the identity of an authorized user is utilized in an unauthorized manner to obtain access to the network, and (3) eavesdropping and stealing of data during session with authorized user. No separate secure network exists in the IP-based mobility communications system, and therefore, it is necessary to protect information transmitted in the mobile system from the above-identified security attacks.The present invention improves the security of communications in a IP mobile communications system by creating variable-based Security Associations between various nodes on the system, a Virtual Private Network supported by an Service Level Agreement between various foreign networks and a home network, and an SLA Broker to promote large-scale roaming among different SLAs supported by the SLA Broker or agreements with other SLA Brokers.
Owner:RPX CLEARINGHOUSE
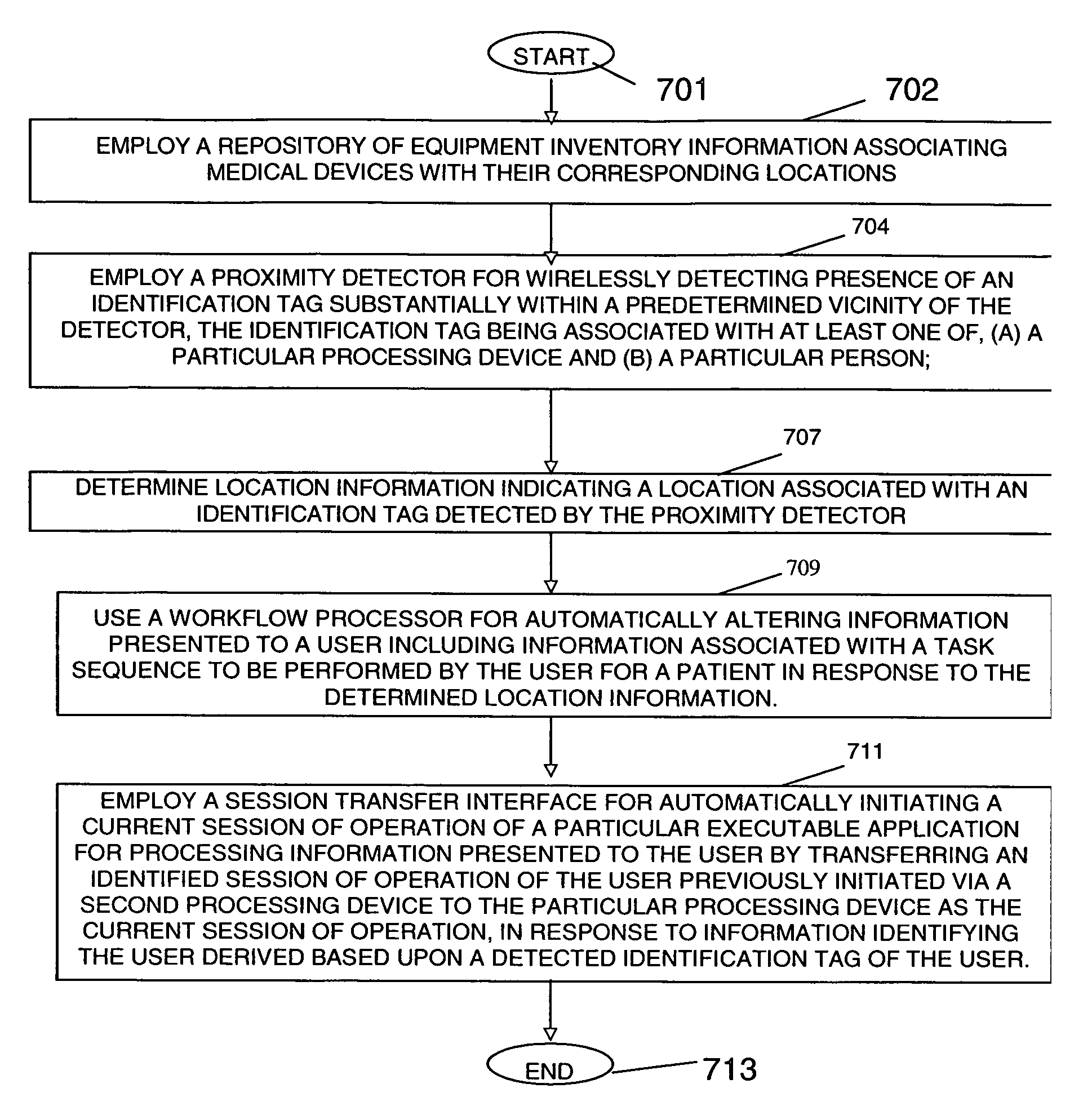
Patient and device location dependent healthcare information processing system
ActiveUS20060288095A1Digital computer detailsHospital data managementInformation processingContext data
A system automatically establishes context information (e.g., determining changes to user interface workflows, screens, menus, and access requirements for devices such as monitors, ventilators, and diagnostic equipment) used by a worker in using healthcare information applications based on patient geographic location (e.g., a room or bed or department). The system addresses the need for a user to sign onto a system with each location change and manually change context information which consumes computer, server and network resources and represent a potential security problem. A healthcare system selects information to be provided to a user in response to received location dependent context data. The system includes a proximity detector for wirelessly detecting presence of an identification tag substantially within a predetermined vicinity of the detector. The identification tag is associated with at least one of, (a) a particular processing device and (b) a particular person. A location detector determines location information indicating a location associated with an identification tag detected by the proximity detector. A workflow processor automatically alters information presented to a user including information associated with a task sequence to be performed by the user for a patient in response to the determined location information.
Owner:CERNER INNOVATION
Method and system for evaluating network safety situation
InactiveCN101436967AEasy to operateImprove securityData switching networksThree levelSecurity solution
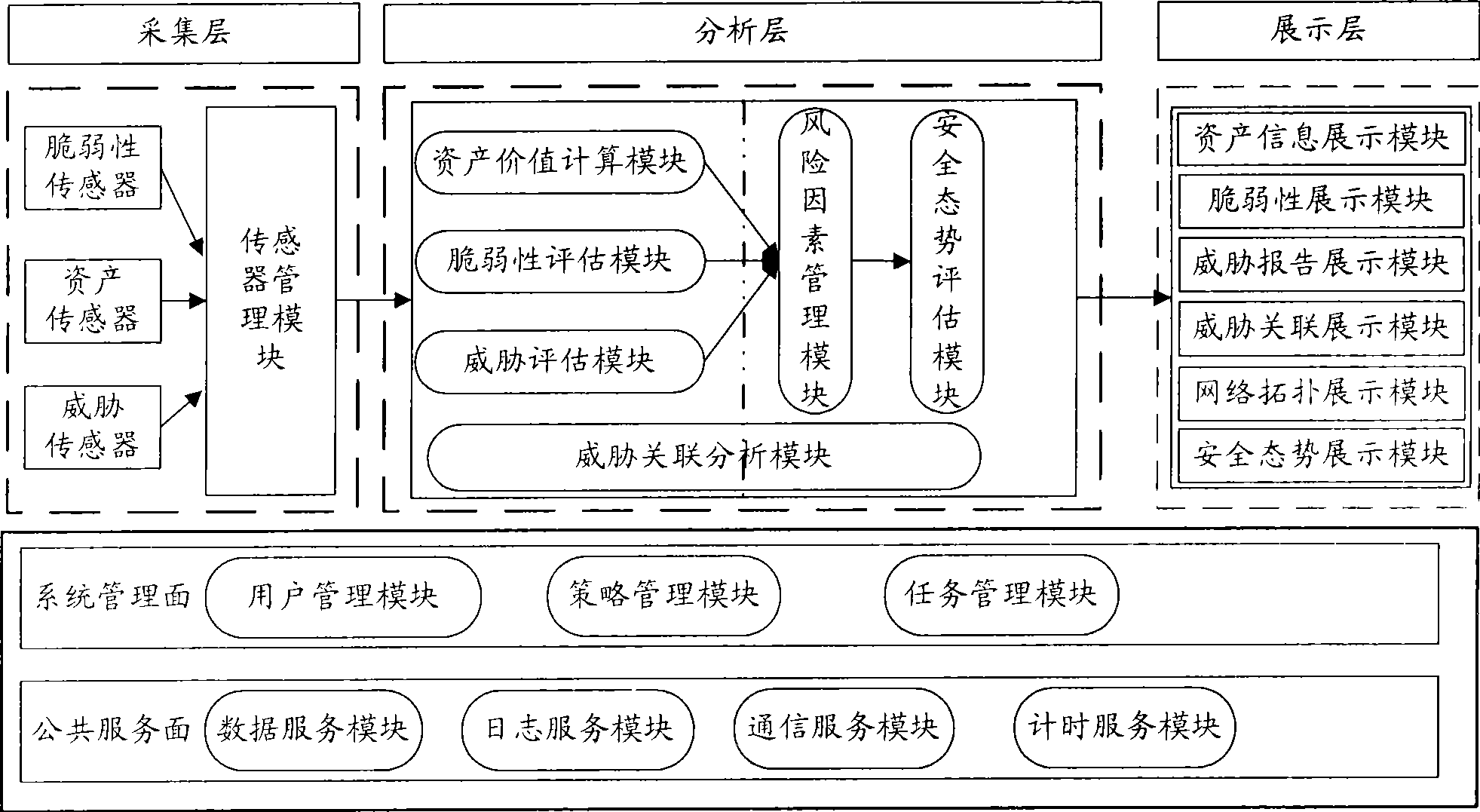
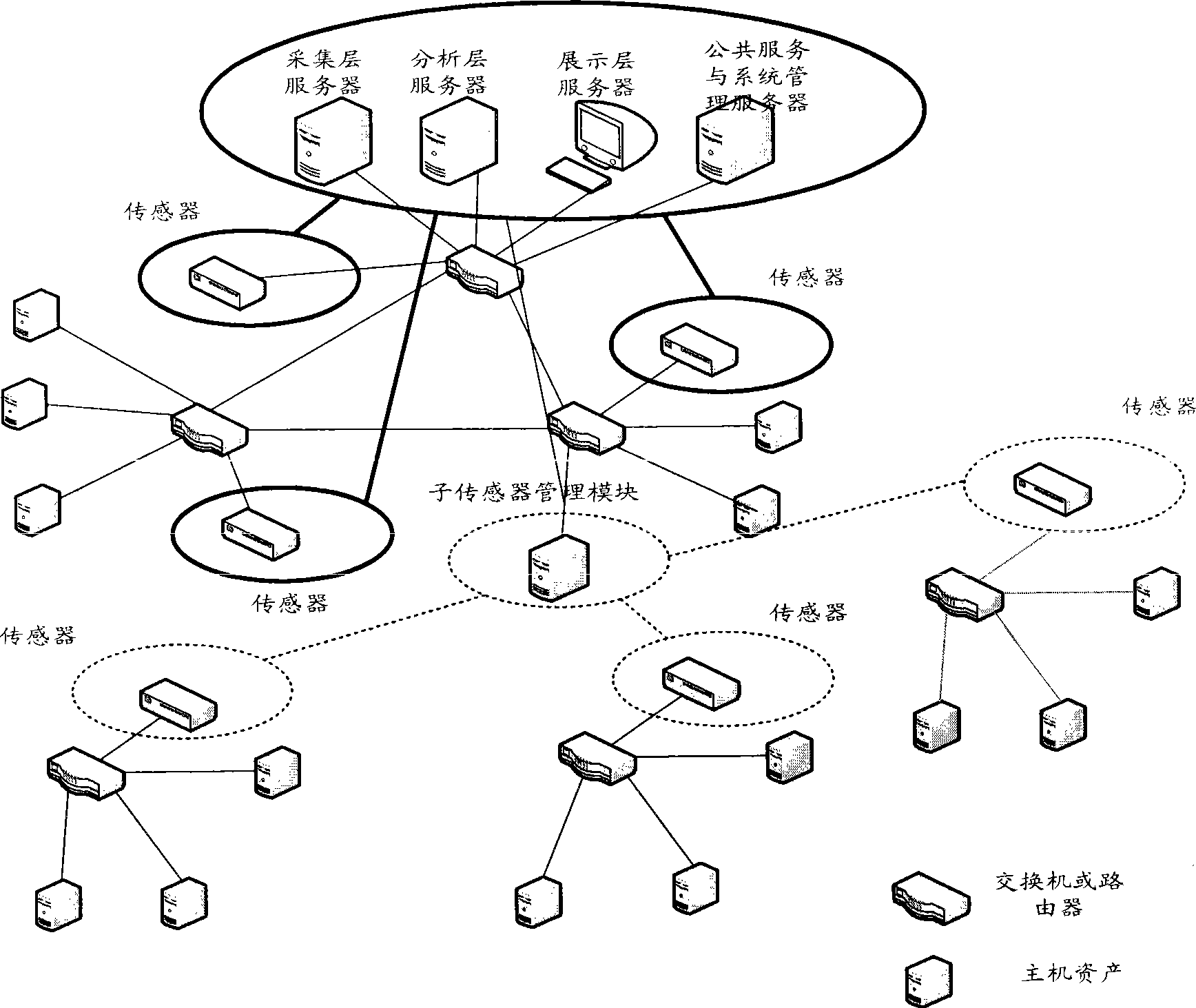
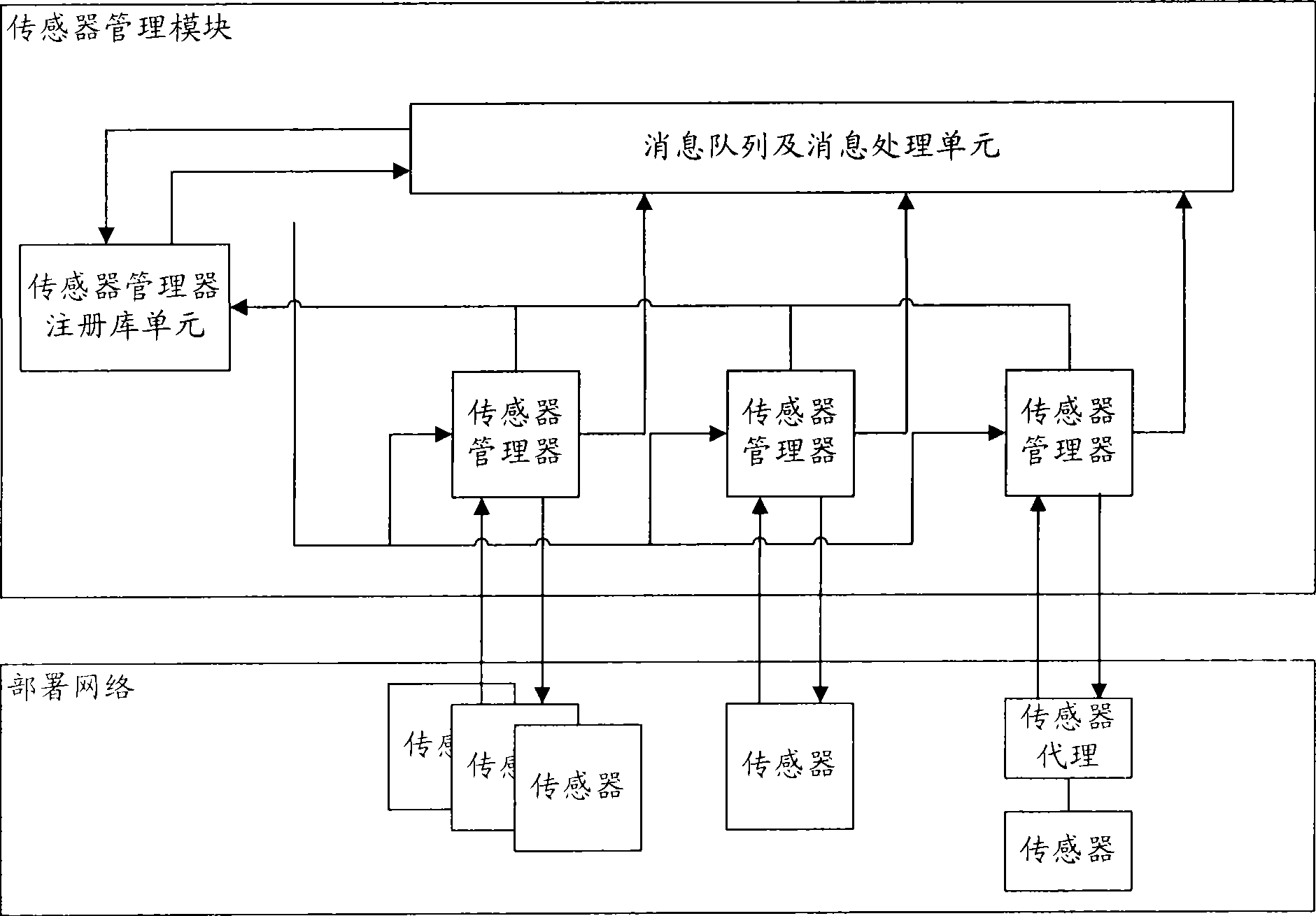
The invention relates to a method for evaluating the security situation of a network and a system thereof. The system has a two-surface three-level framework and is provided with a public service surface and a service management surface for executing uniform coordinated management on each functional module of the system; according to a service logic processing flow, the system is divided into three levels: an acquisition level, an analysis level and an exhibition level for completing four evaluating operations of assets, frangibility, threat and security situation; the invention is based on the characteristic of service operation in the network, combines the prior risk evaluation method, the prior flow and the prior security detection tool and provides a set of a novel dynamic real-time evaluation method. The system can analyze the assets and service of the network and the risk of the whole network and carries out the evaluation of the security situation. The system can provide the security state of the whole network in macroscopy, can deepen to specific service and assets and know the specific security problem, thereby effectively helping network security personnel to analyze the root of the security problem and assisting to provide a security solution proposal and implement a defense measure.
Owner:BEIJING UNIV OF POSTS & TELECOMM
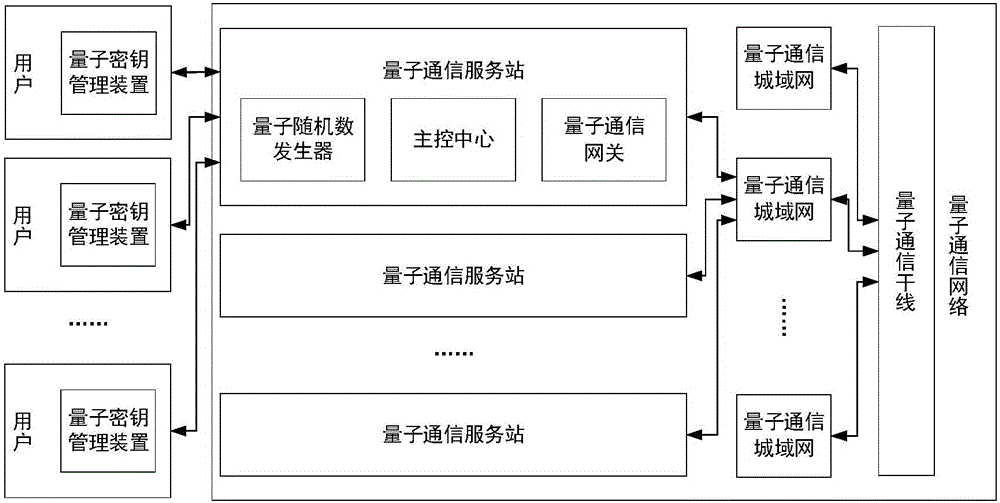
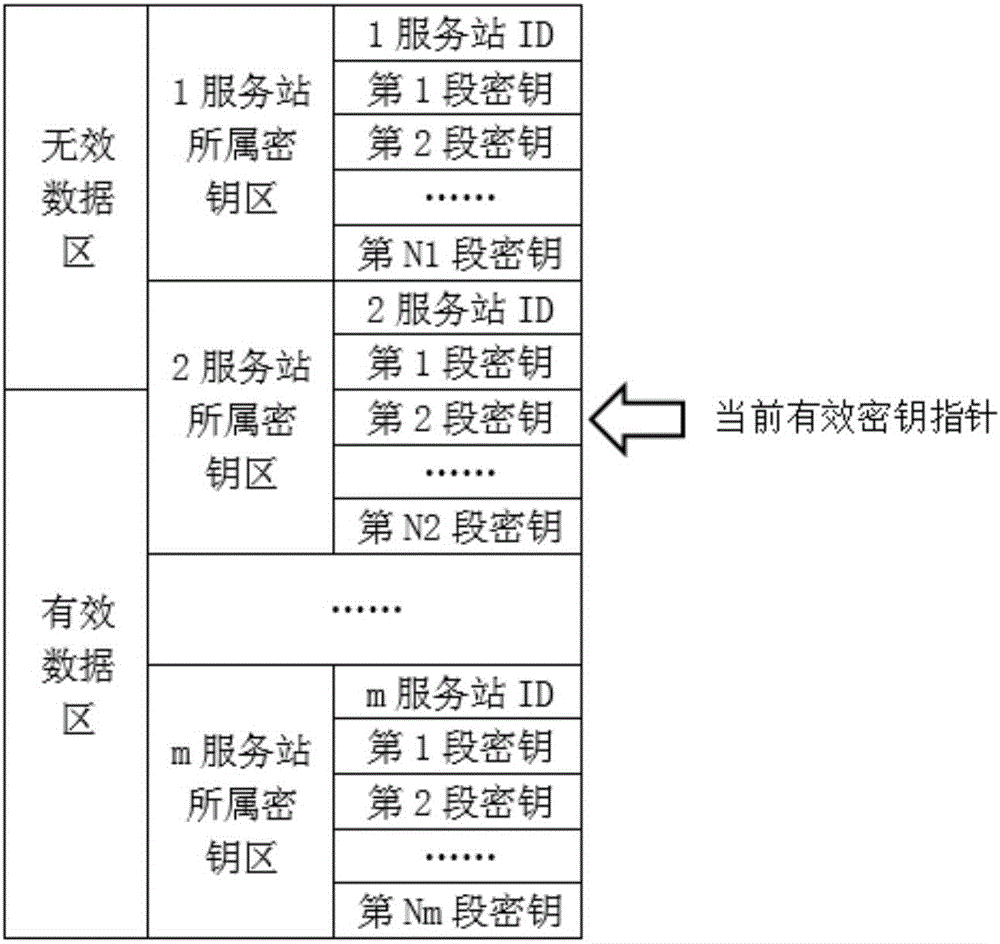
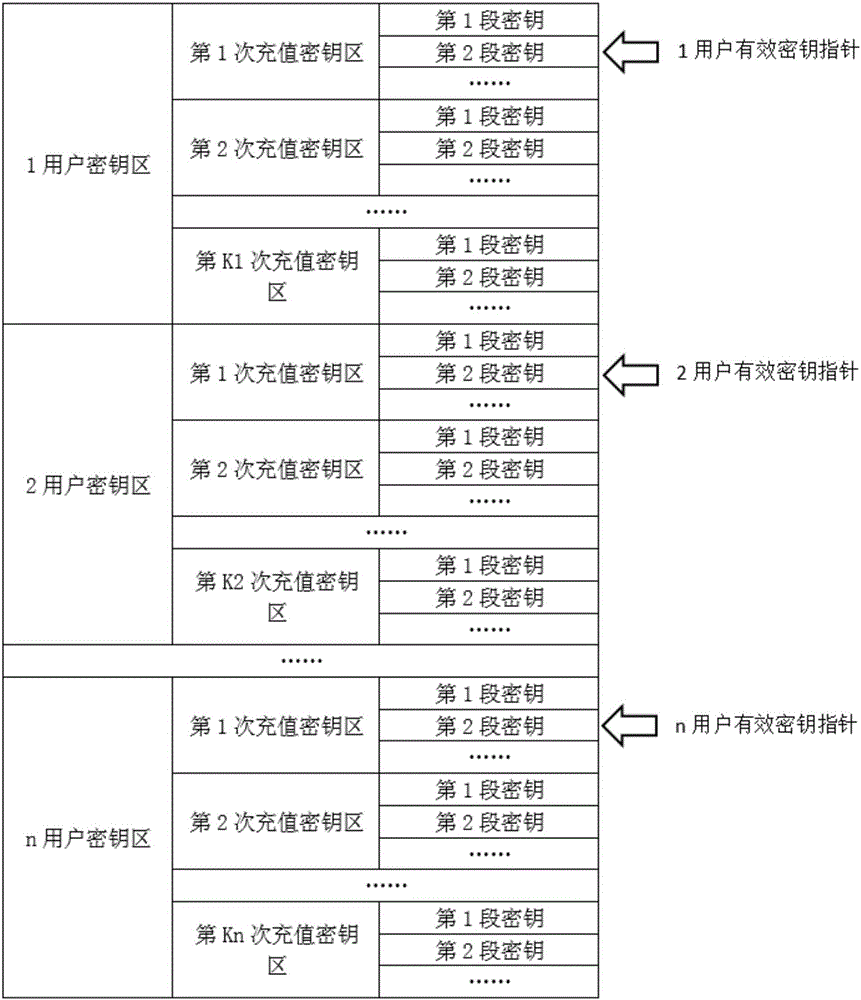
Quantum communication service station, quantum key management device, key configuration network, and key configuration method
ActiveCN106452740AAddress access security issuesAchieve coverageKey distribution for secure communicationSecurity questionKey distribution
The invention discloses a quantum communication service station, a quantum key management device, a key configuration network, and a key configuration method. The key configuration method comprises the following steps: responding to a key distribution request; authenticating a user of the key distribution request; writing a key generated with a true random number into a quantum key management device of the authenticated user. The key configuration method is different from the existing quantum key distribution QKD method in that key distribution of ultra high security is realized by pairing quantum key management devices and service stations at the end of a quantum communication network, the problem about access security at the end of a quantum communication network is solved, and terminal access is not a weak link of a quantum communication scheme. The quantum communication network can completely cover and replace the classic communication network in service.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
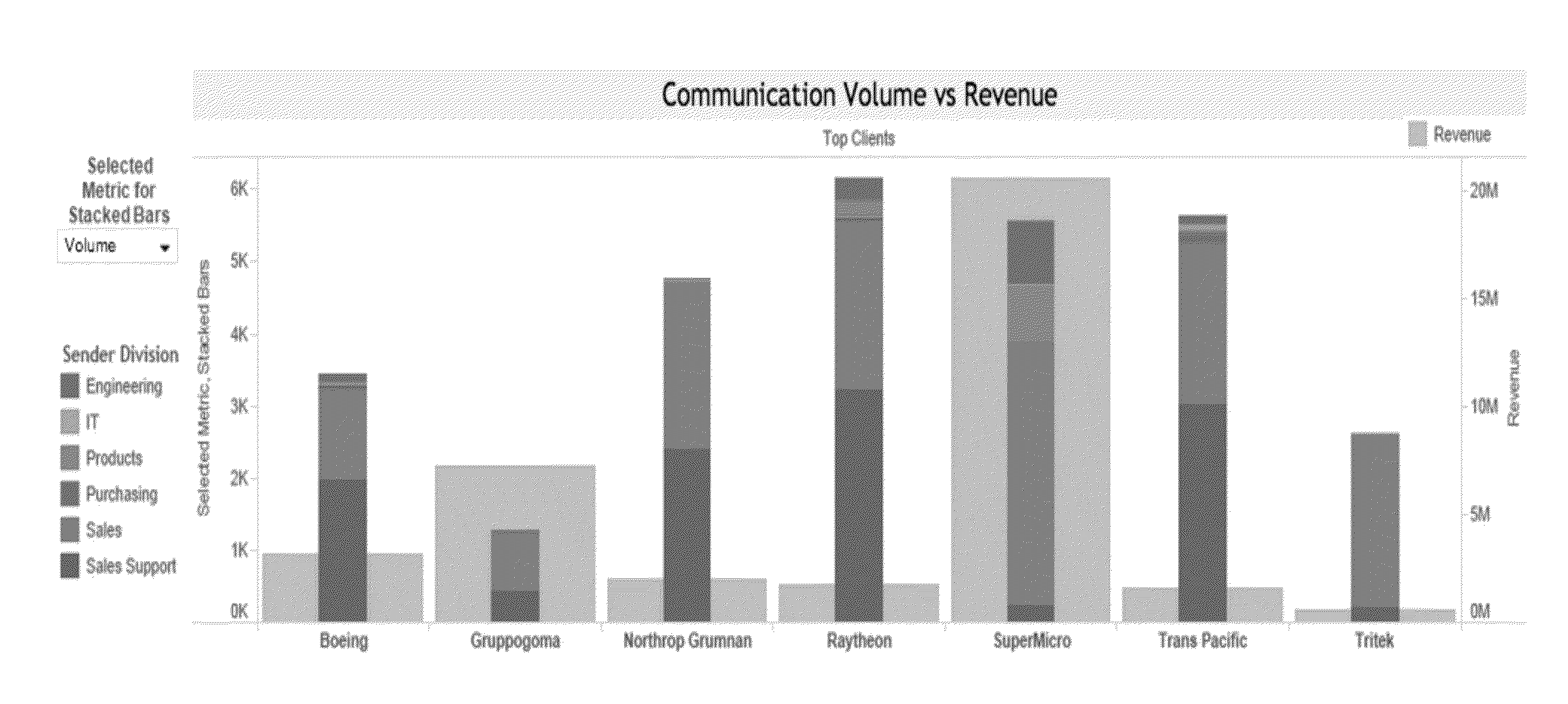
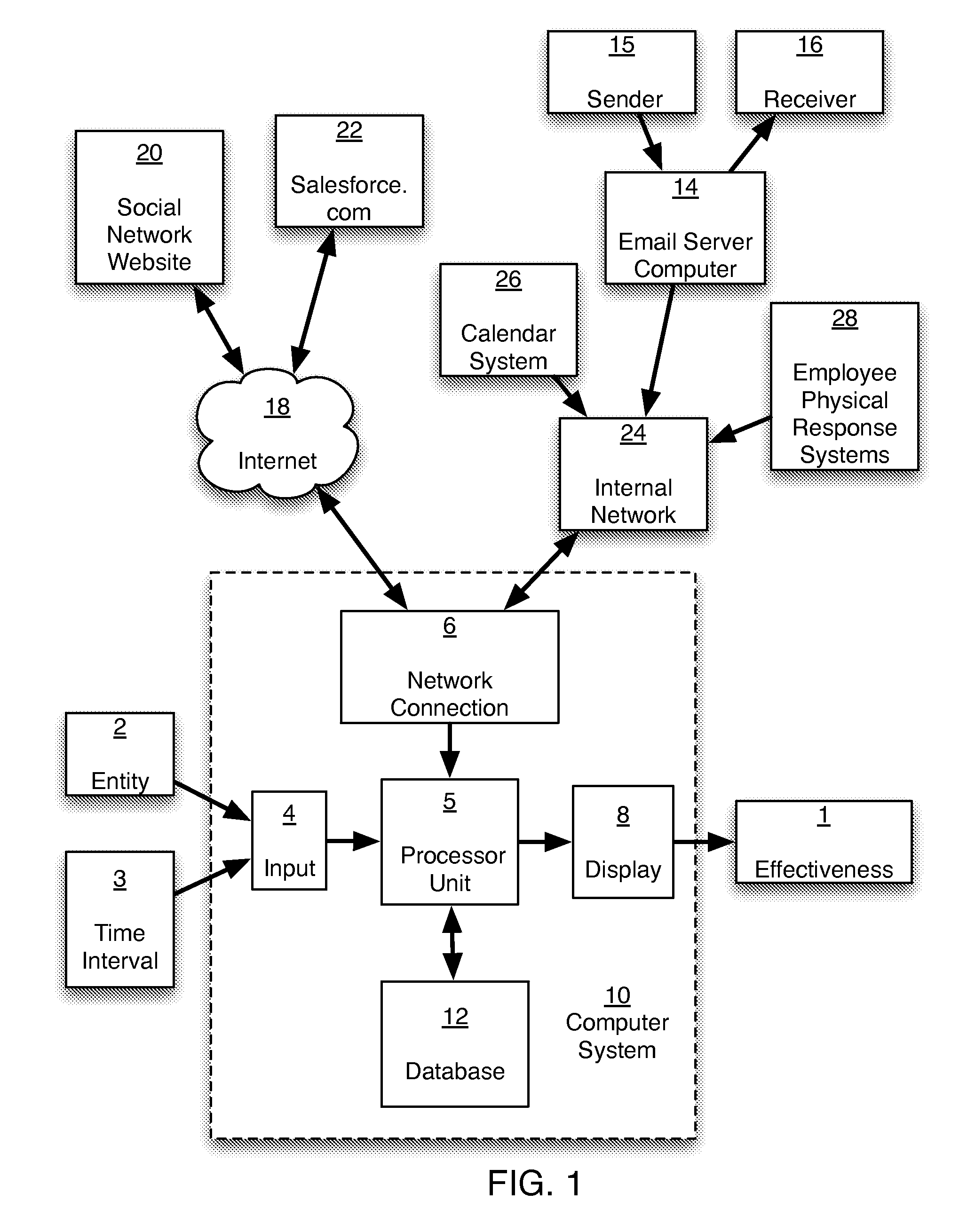
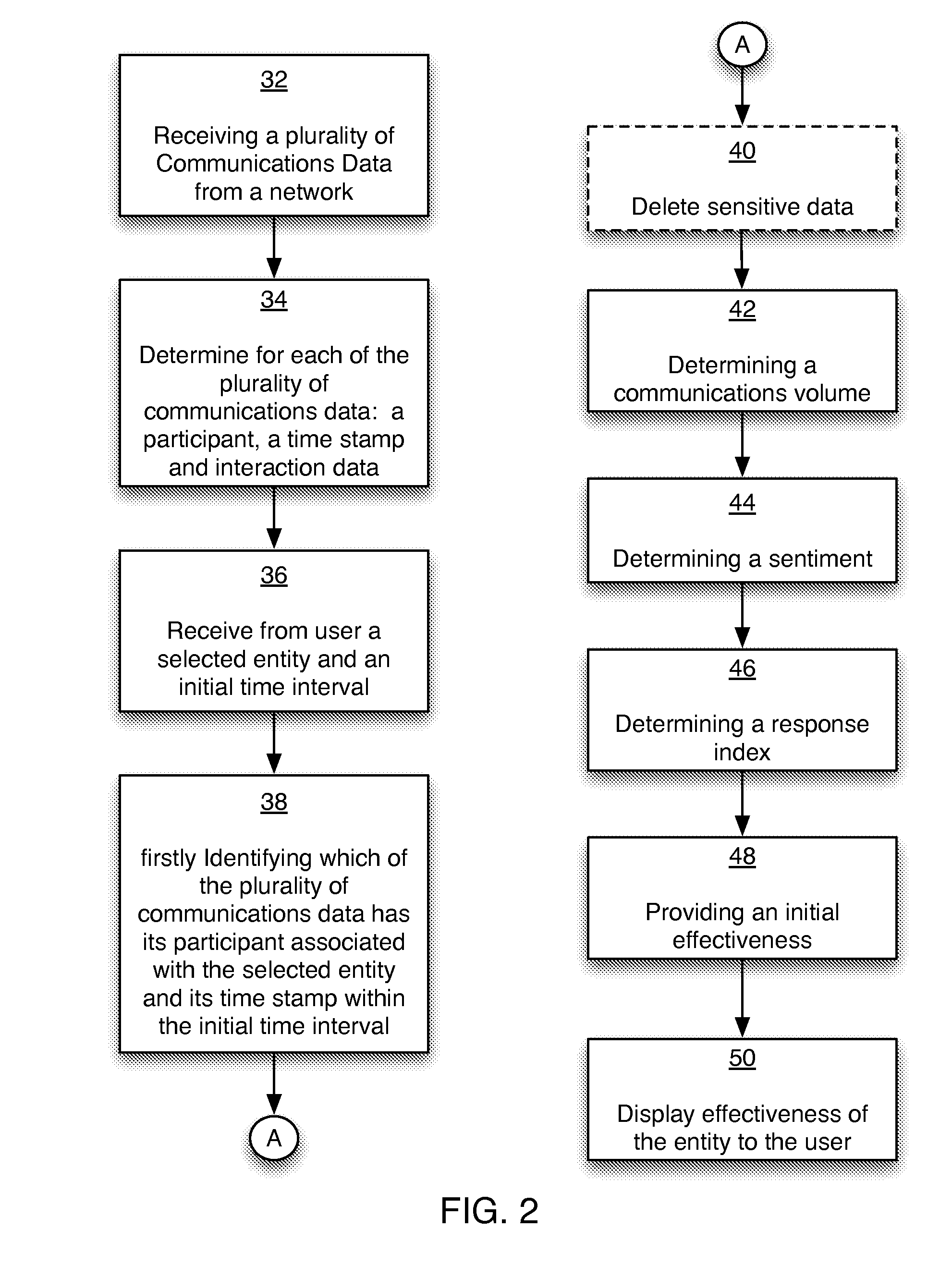
Methods and systems for providing the effectiveness of an entity
InactiveUS20150046233A1Determine effectivenessMonitor relationshipResourcesWorking environmentSecurity question
A computer implemented method and system for providing to a user (a manager) the effectiveness of an entity (employee or group of employees) by analyzing emails, social network data, CRM, calendar data, audio / video data, typing speed, galvanic skin response, etc. The computer method captures, analyzes and displays communication volumes, response times, and sentiment metrics, enabling the user to understand the effectiveness of an entity, optimal use of resources, trends, customer contact, collaboration patterns, security issues, entity turnover, entity health, and ideal work environments.
Owner:THRIVE METRICS
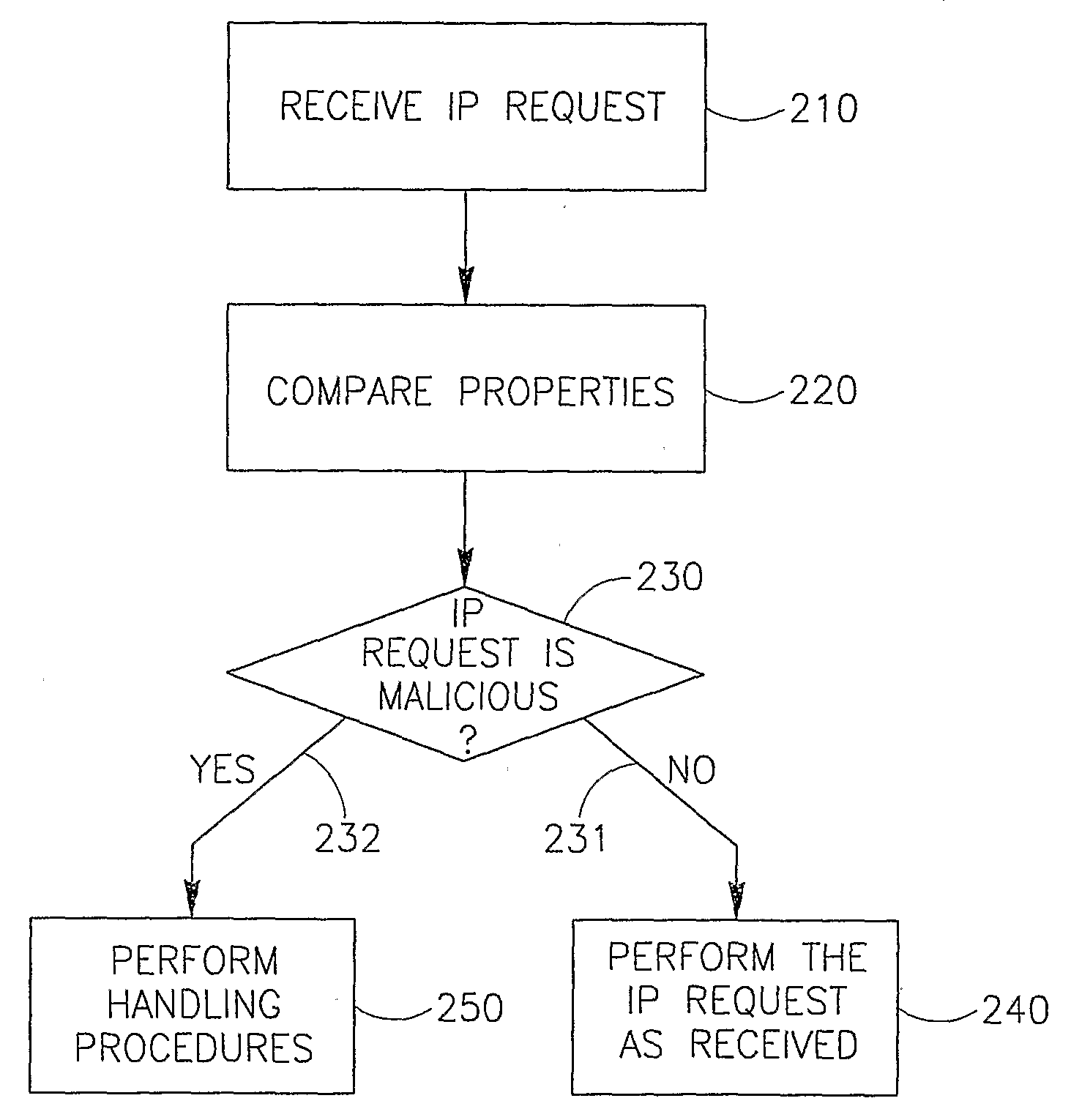
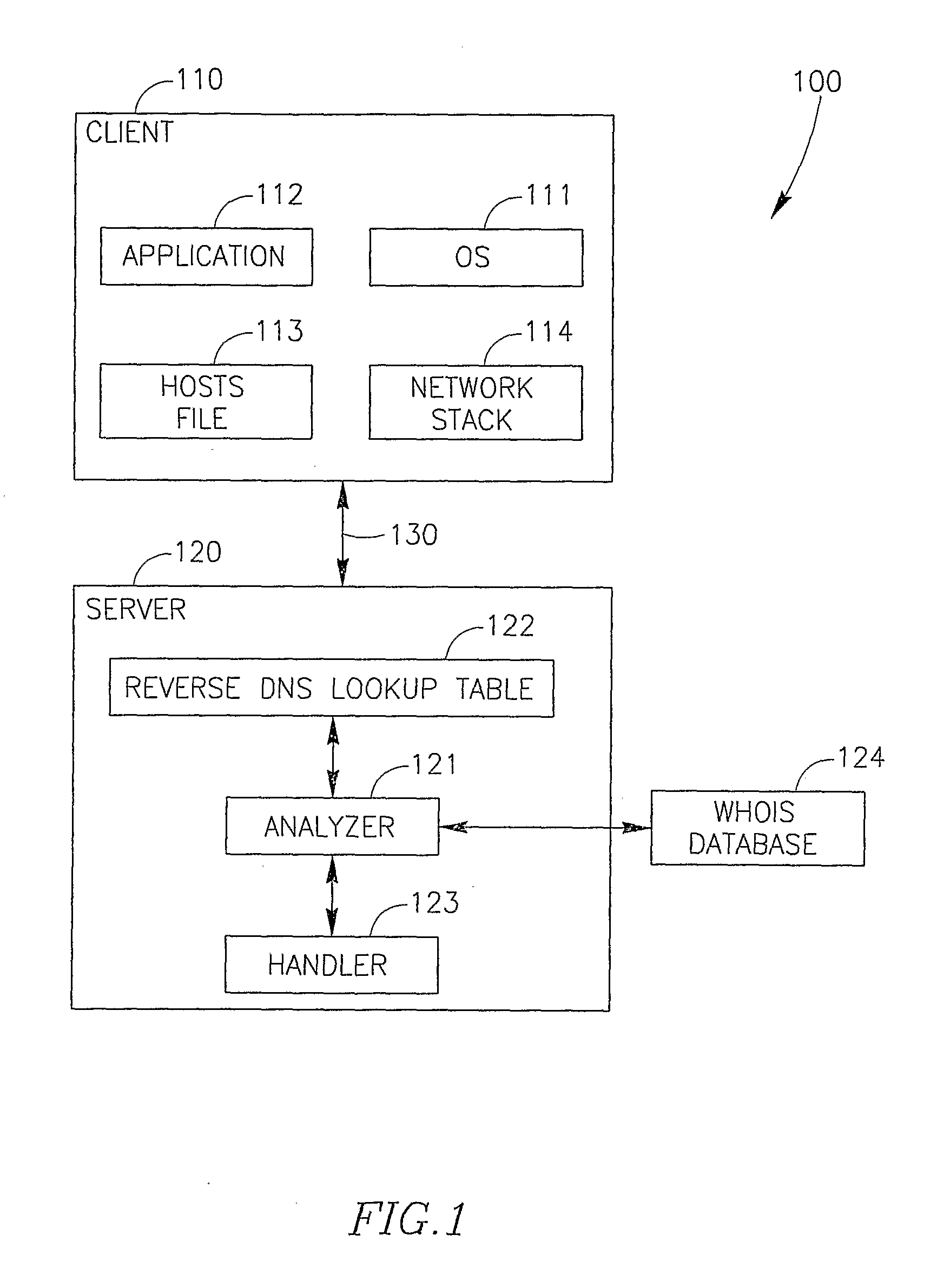
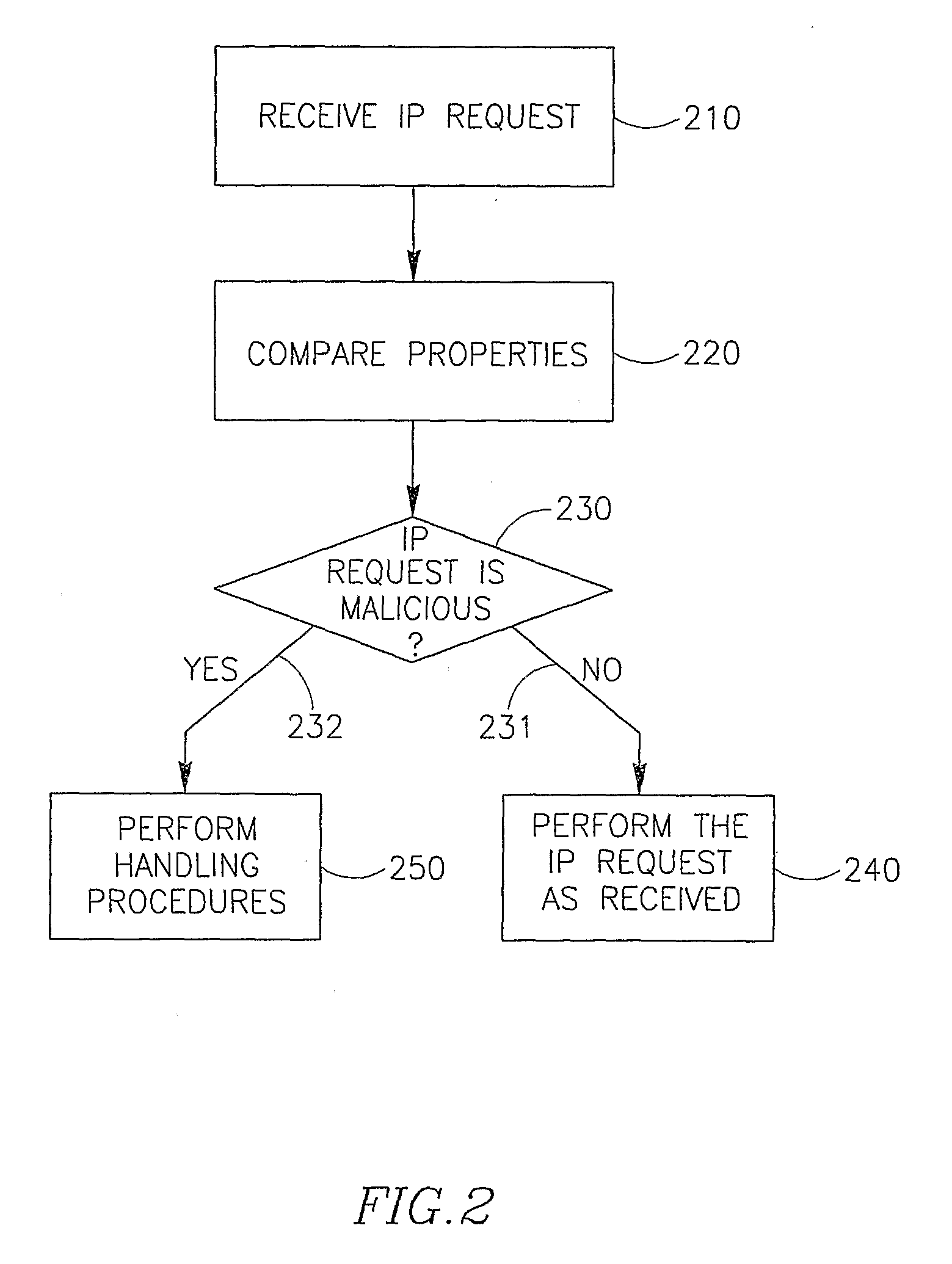
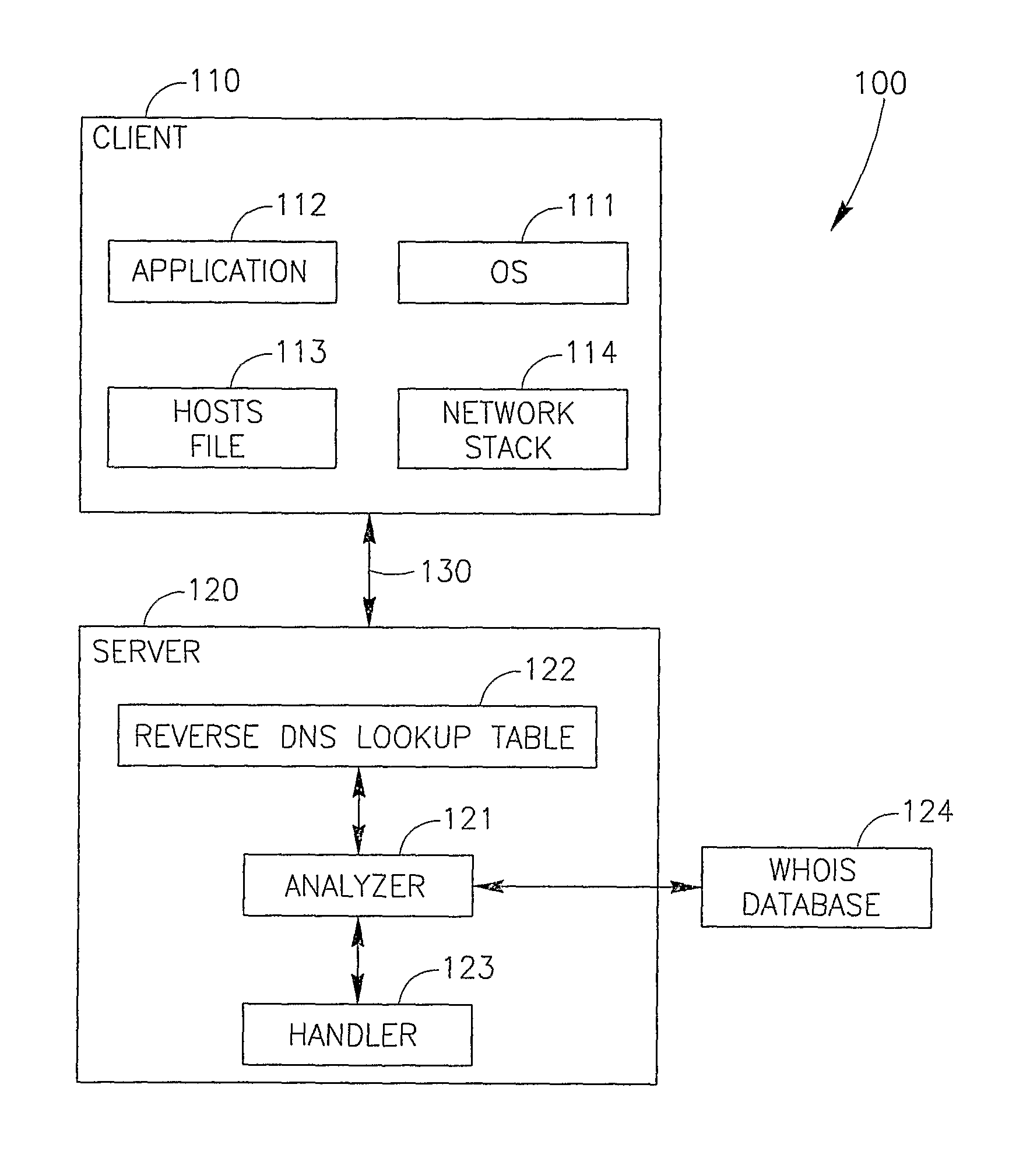
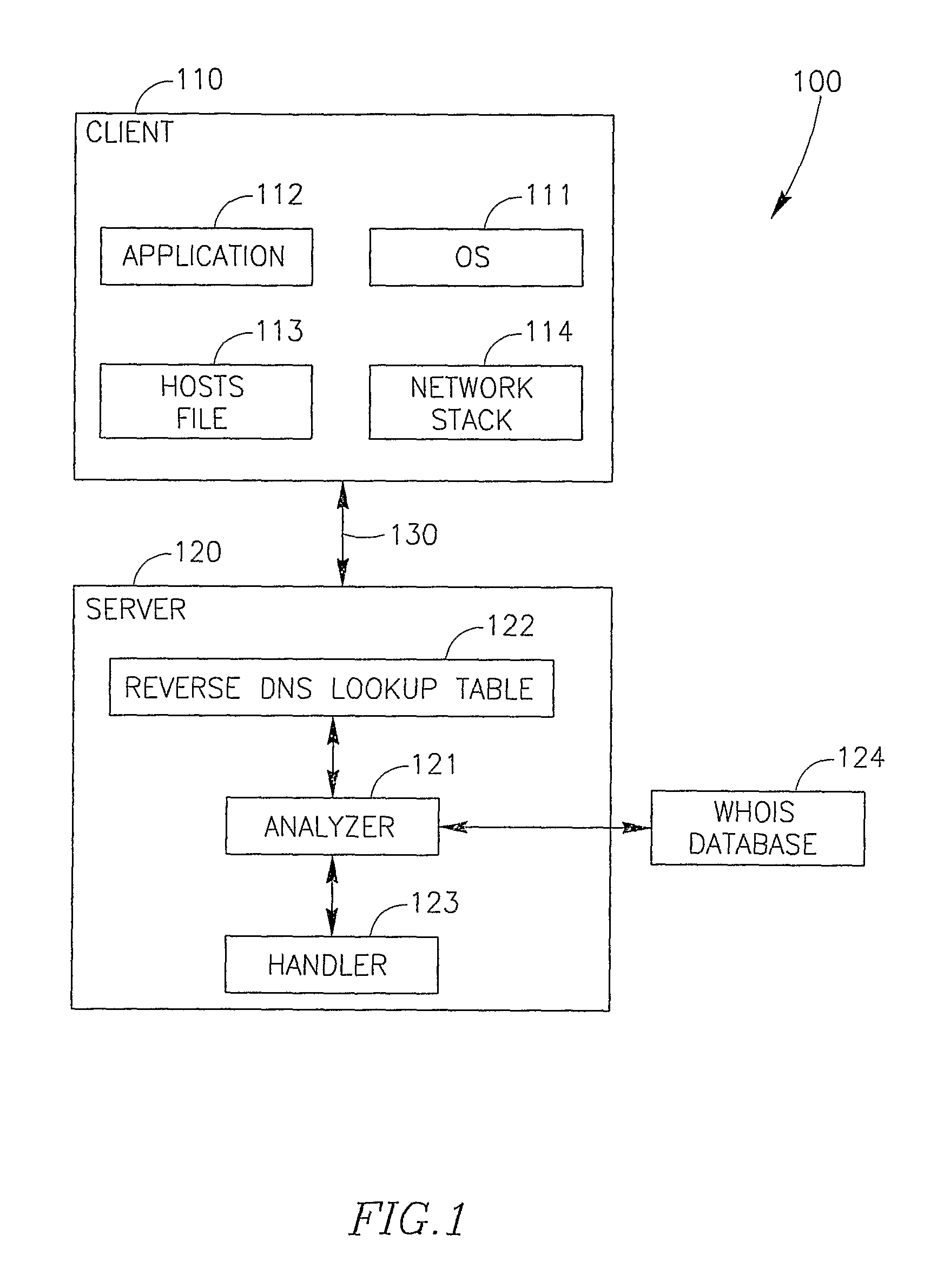
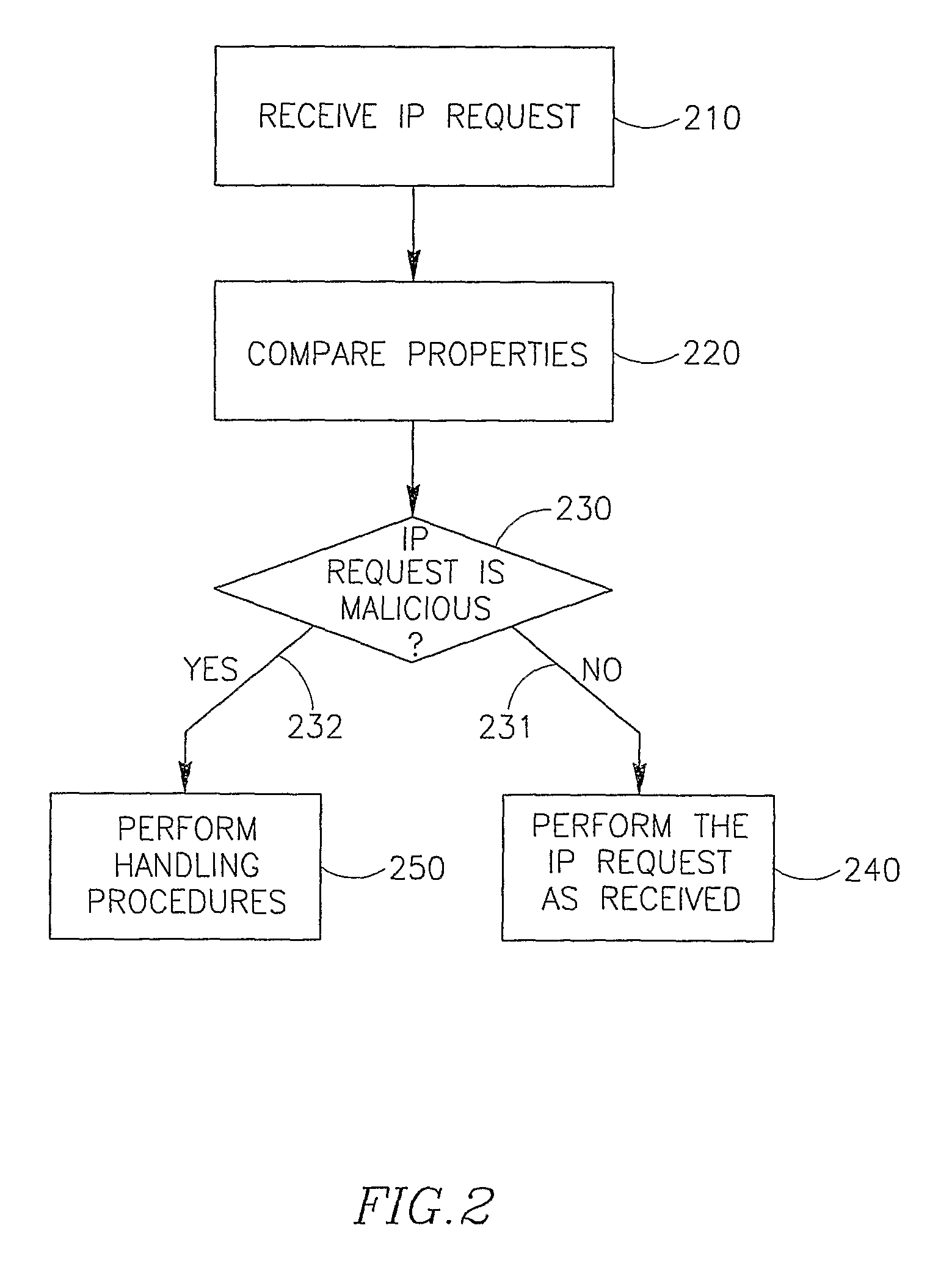
System and Method for Detecting and Mitigating Dns Spoofing Trojans
ActiveUS20080147837A1Avoid connectionMultiple digital computer combinationsTransmissionDomain nameLocation detection
Embodiments of the present invention relate to a method and system for detecting and / or mitigating domain name system (DNS) spoofing Trojan horse (or Trojan) code. Trojan code (sometimes called malware or malicious software) is a common computer security problem. Some Trojans modify the DNS resolution mechanism employed by the infected computer, such that the computer traffic, when browsing the Internet, is routed to a location not intended by the rightful owner of the computer. The present invention can detect this phenomenon from a remote device or location and may take action to mitigate its effects.
Owner:EMC IP HLDG CO LLC
Network intrusion detection with distributed correlation
A network security system employing multiple levels of processing to identify security threats. Multiple host machines may each contain an agent that detects possibilities of security threats based on raw data sensed locally at that host. The hosts may share information obtained from local analysis and each host may use information generated at one or more other hosts, in combination with information generated locally, to identify a security concern, indicating with greater certainty that a security threat exists. Based on security concerns generated by multiple hosts, a security threat may be indicated and protective action may be taken.
Owner:MICROSOFT TECH LICENSING LLC
Method for securing a payment transaction over a public network
InactiveUS20060089906A1Reduce the possibilityFinanceBilling/invoicingPayment transactionPublic network
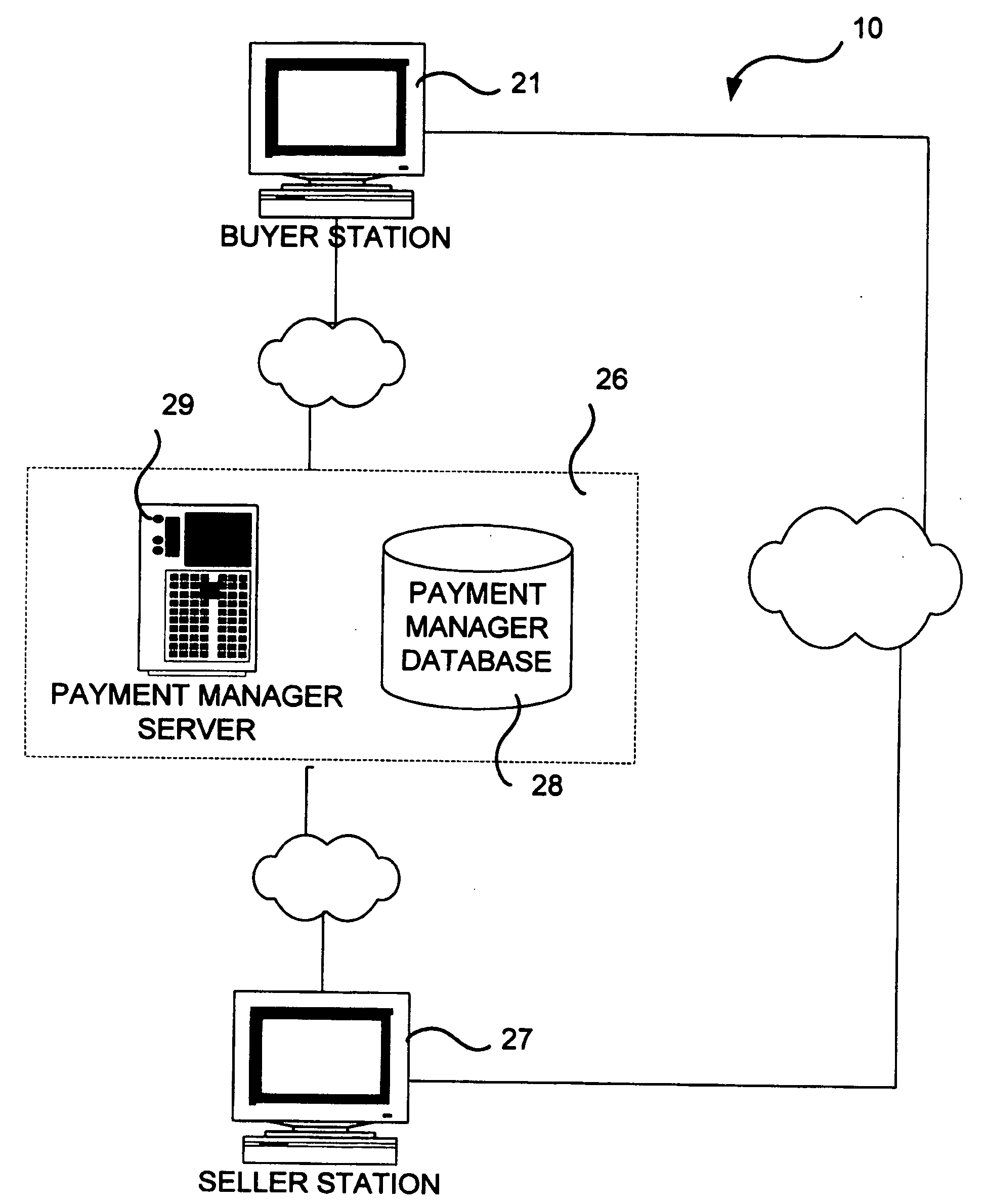
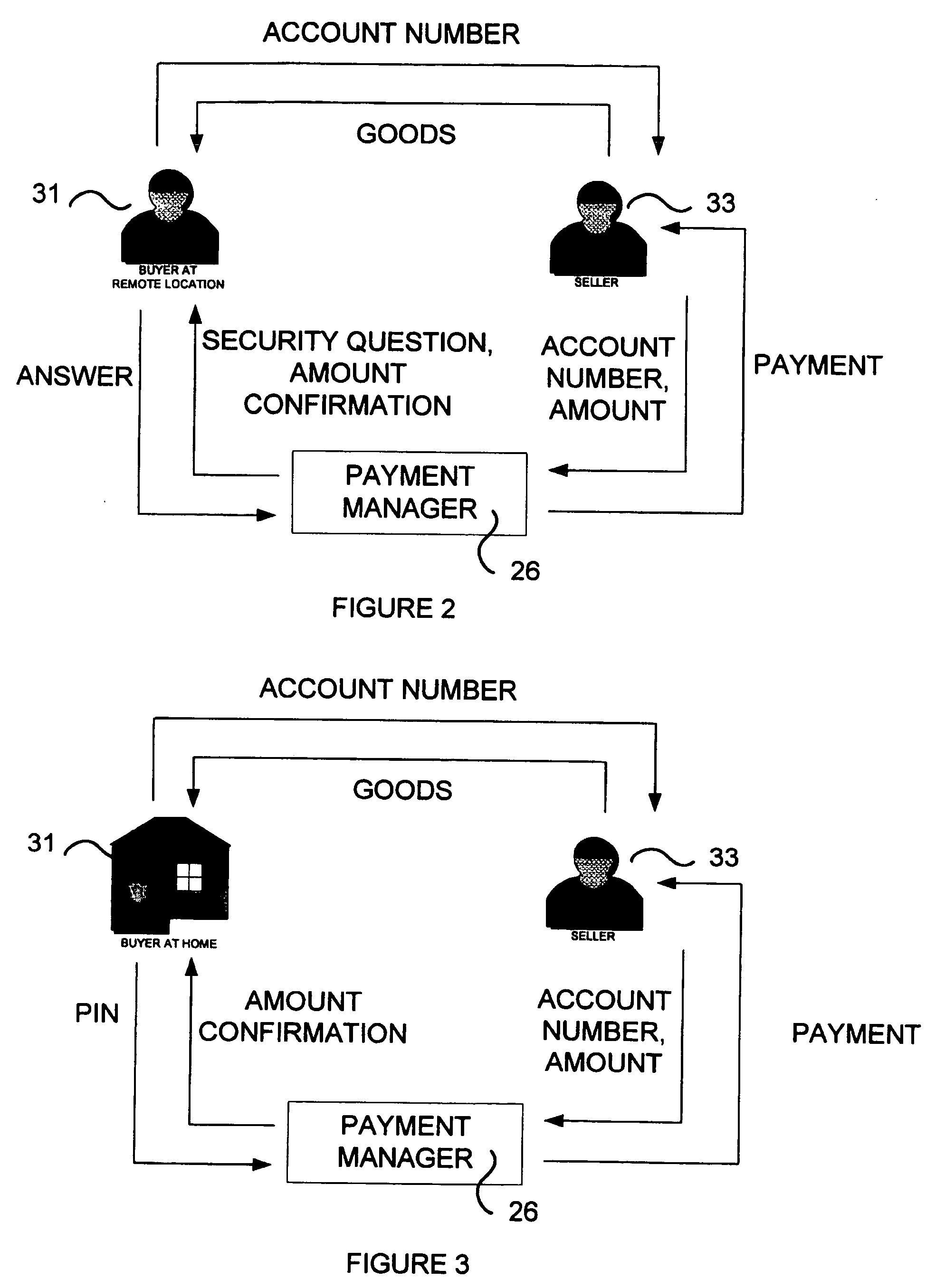
A method for processing a payment transaction between a buyer and a seller over a network using a payment manager is provided. The payment manager manages a plurality of buyer and seller accounts, each account having an account id associated with it. The payment manager receives payment authorization requests for payment transactions, including a payment amount and an identification of a seller. The buyer provides an account id and a location identification to the payment manager, so that the payment manager may determine whether the buyer is communicating over a secure network. If buyer communicates over a secure network, the payment manager requests that the buyer provides a security code to confirm the transaction. If the location identification indicates that the buyer communicates over an insecure network, the payment manager requesting that the buyer answers at least one security question to confirm the transaction. If the confirmation is correct, the payment manager authorizing the payment transaction and sending confirmation to the seller. The security code is used repeatedly for confirmation of all payment transactions for which the location identification indicates that the network is secure, and the security question is repeated randomly for some payment transactions for which the location identification indicates that the network is insecure.
Owner:ROWLEY MICHAEL
Methods and apparatus for secure online access on a client device
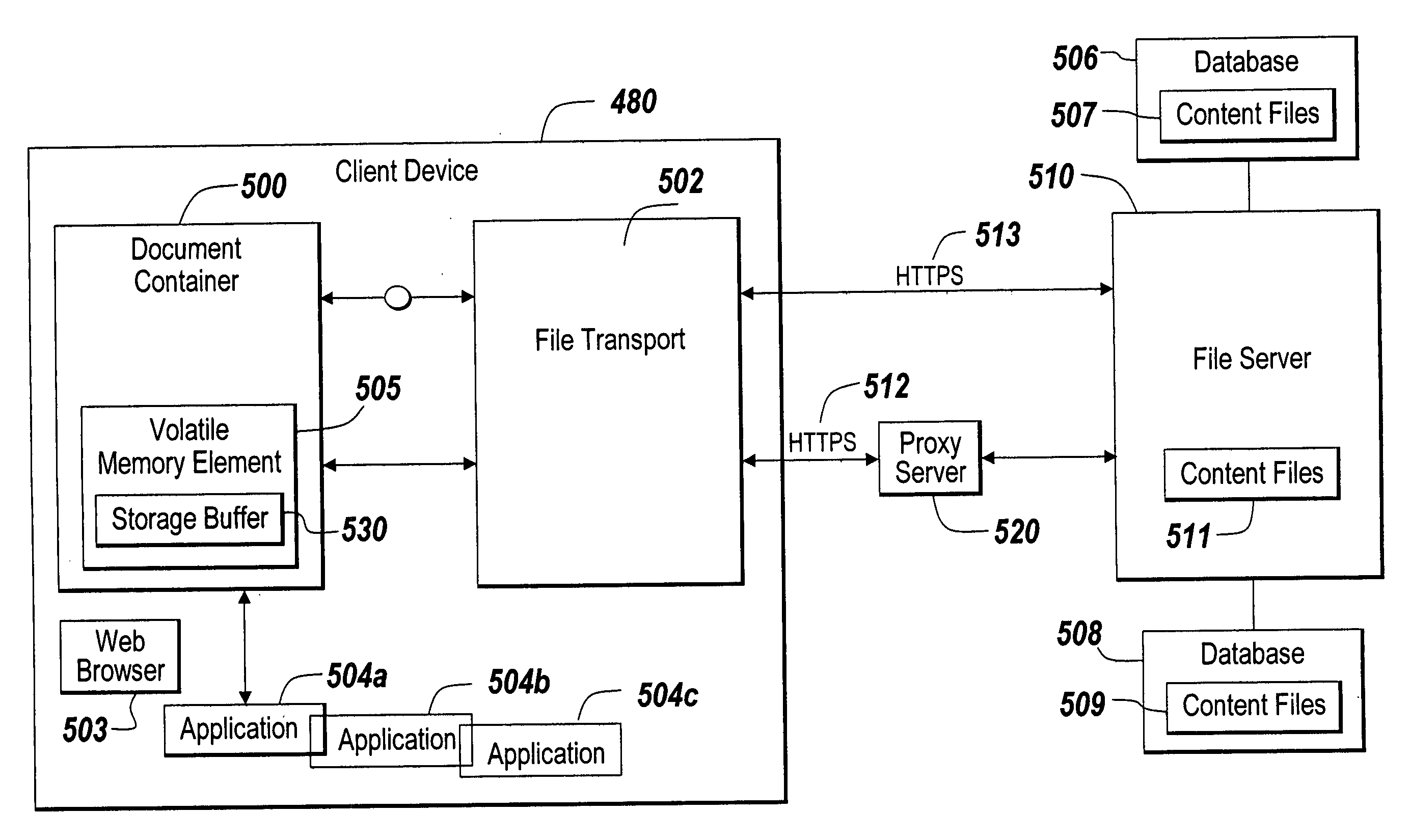
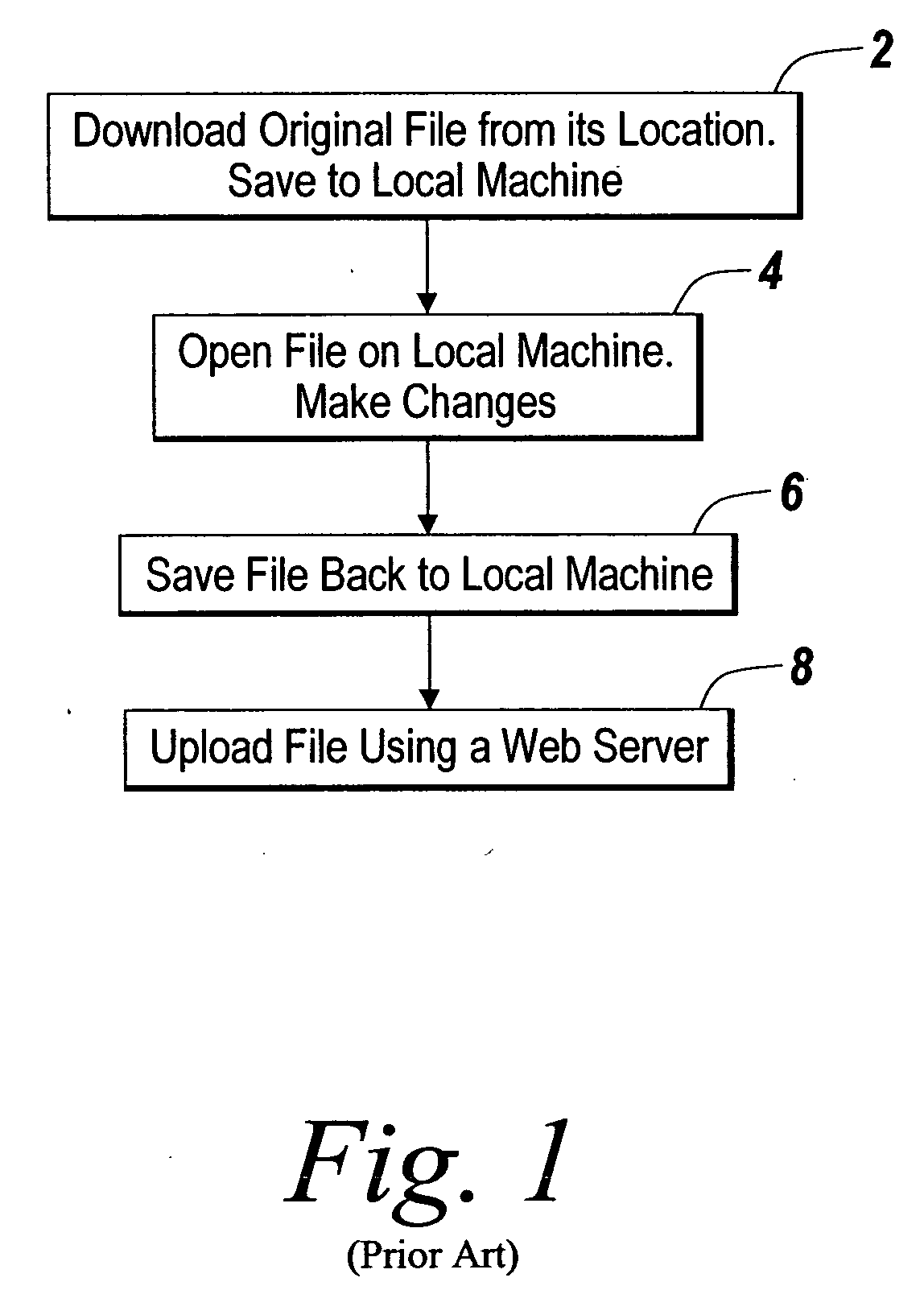
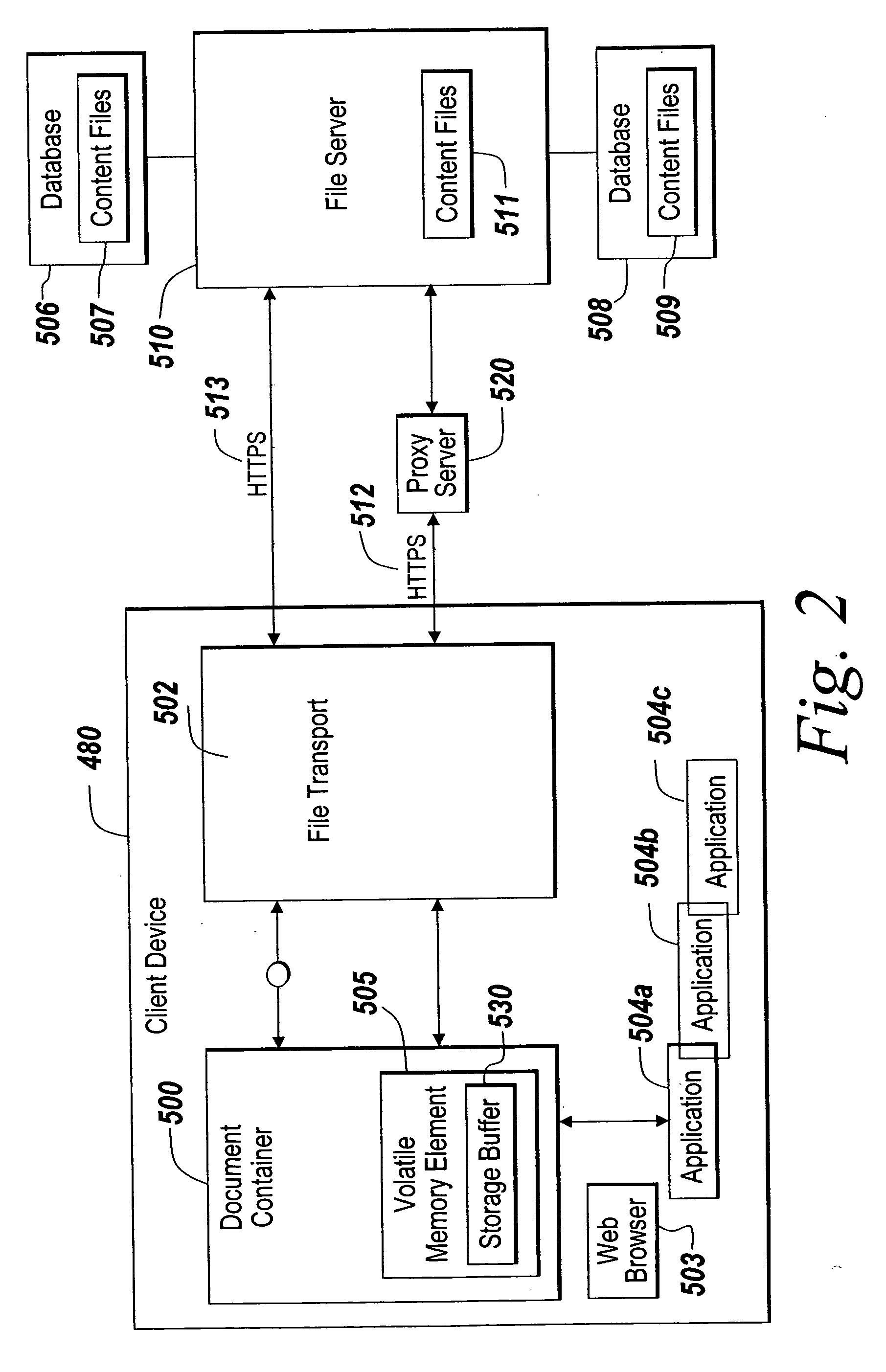
ActiveUS20060047956A1Prevent unwanted disclosure of confidential informationManipulation is limitedComputer security arrangementsSpecial data processing applicationsPaper documentDocument preparation
A method of securely accessing at a client device content from a server without using the non-volatile memory of the client device is disclosed. The bypassing of non-volatile memory lessens the security risk of unauthorized viewing of the server originated content. An transport mechanism is initiated on a client device and creates a document container. Downloaded documents from a server are mapped into the document container and saved within the document container in volatile memory. Substitute menus are generated within the container to replace application menus. User documents are saved directly to the originating server via the substitute menus. The downloaded copies in volatile memory automatically delete when the document container is destroyed thereby reducing security concerns of unauthorized viewing of the content at the client device.
Owner:CITRIX SYST INC
Arrangement in a data communication system
InactiveUS6578151B1Improve securityEasy maintenanceMultiple digital computer combinationsProgram controlCommunications systemDigital signature
The present invention relates to an arrangement a data communication system, wherein users, managers and / or machines (actors) intercommunicate via ports, especially comprising a Transport Service Access Port (TSAP) comprising port number and Internet Protocol (IP) address, which ports communicate through firewalls by means of firewall classification / logic which is controlled by a bastion host therefor, and in order to resolve security issues related to such network, it is according to the present invention suggested that said bastion host is configured to accept digitally signed configuration messages from one of more distributed operator(s) and / or manager(s), for thereby ensuring intergrity of said configuration messages.
Owner:TELEFON AB LM ERICSSON (PUBL)
Apparatus system and method for validating users based on fuzzy logic
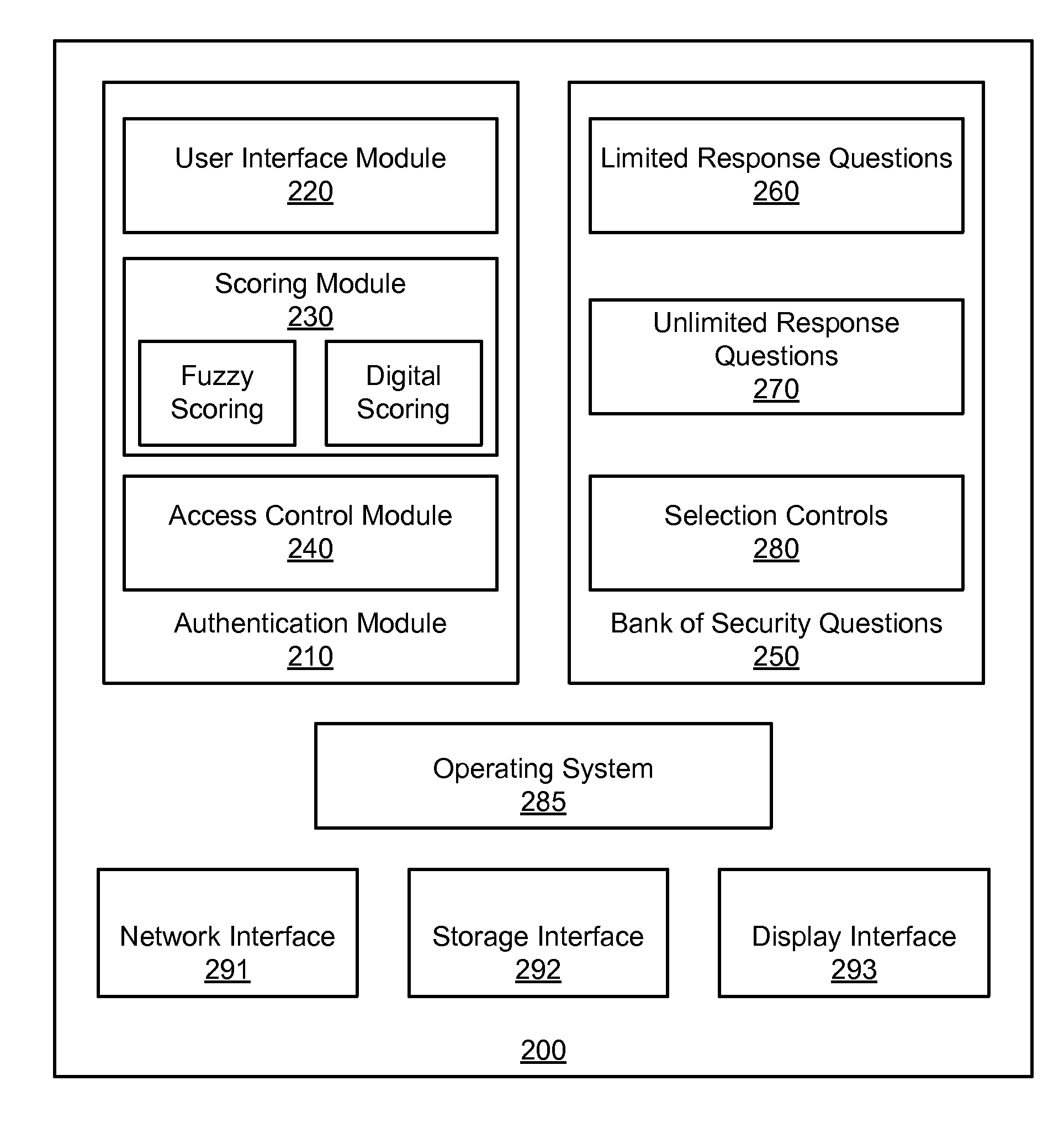
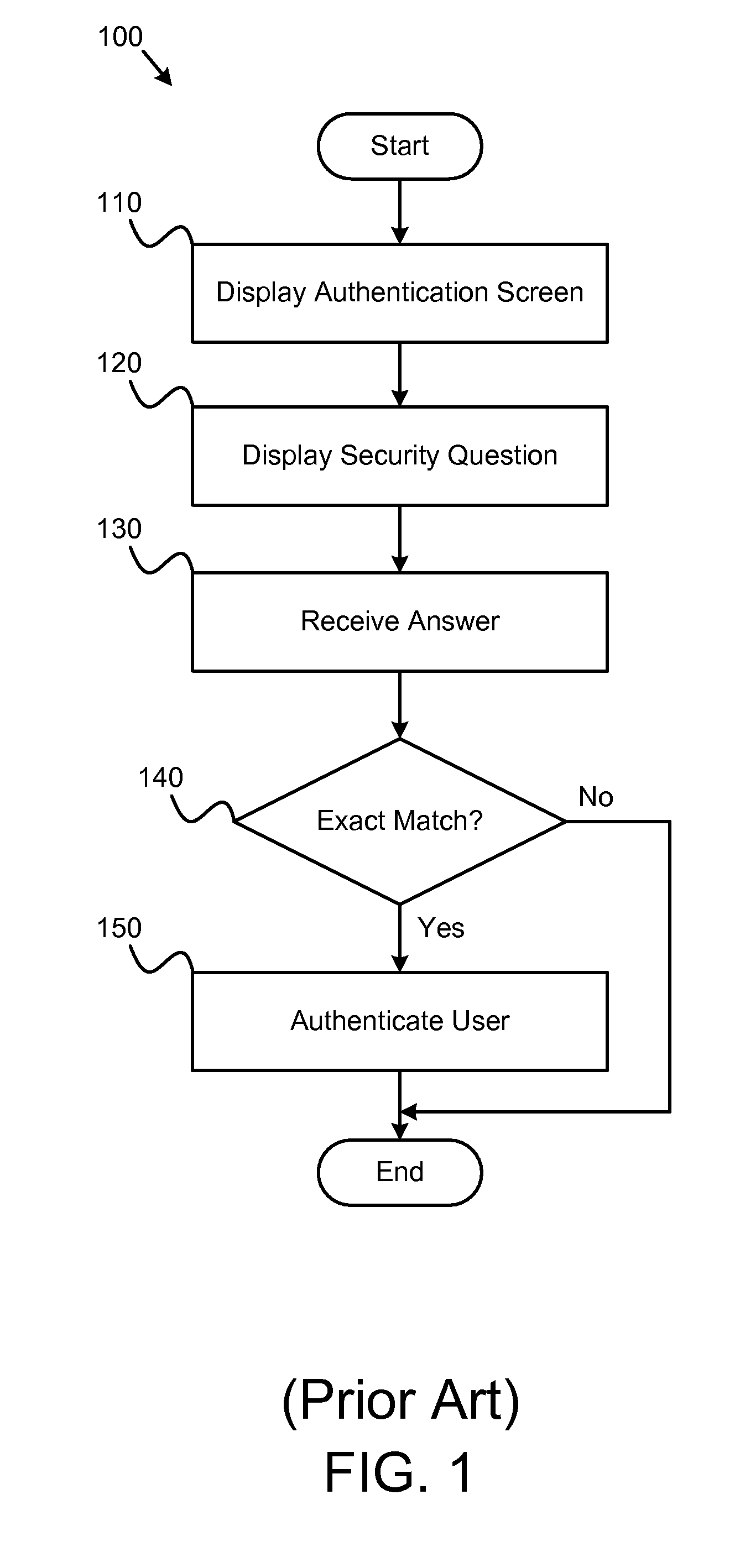
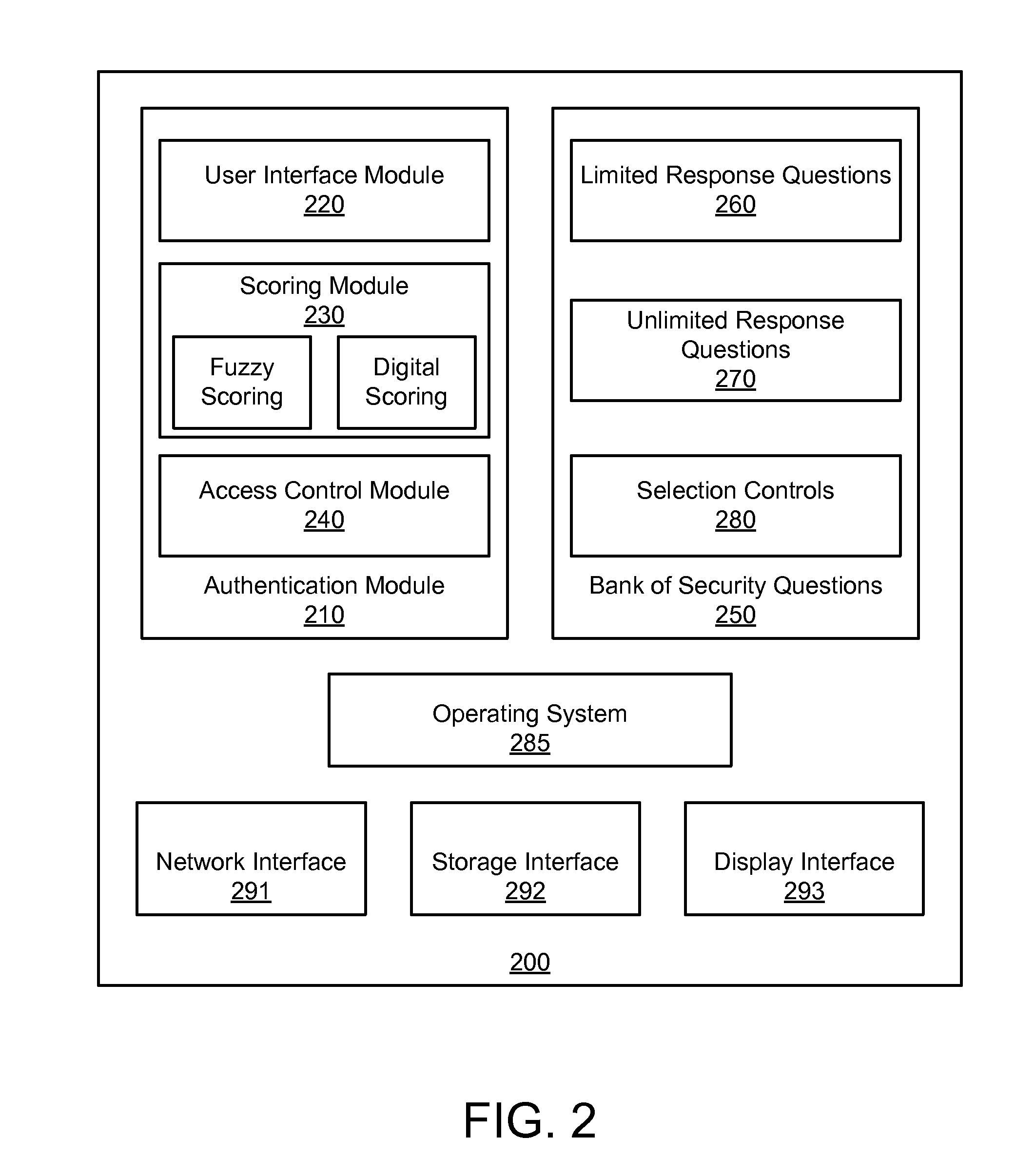
InactiveUS20090089876A1Valid conversionDigital data processing detailsUnauthorized memory use protectionPasswordTheoretical computer science
An apparatus, system, and method are disclosed for validating users based on fuzzy logic. An interface with security questions is presented to a user who requires authentication. A typical scenario is authentication for password recovery. The interface comprises security questions for the user to answer. The security questions may be limited or unlimited response questions. The answers to the security questions are either scored using fuzzy logic, which may attribute a value between “1” and “0” based on similarity with the original, correct answer; or scored using digital logic. When fuzzy logic scoring is used, a similarity score is computed for each answer. The similarity score is compared against a similarity score threshold to either grant or deny access. An average similarity score is also computed for all answers and compared against an average similarity score threshold to either grant or deny access.
Owner:LENOVO (SINGAPORE) PTE LTD
Voice remote command and control of a mapping security system
InactiveUS20050206513A1Frequency-division multiplex detailsTime-division multiplexTime informationCommand and control
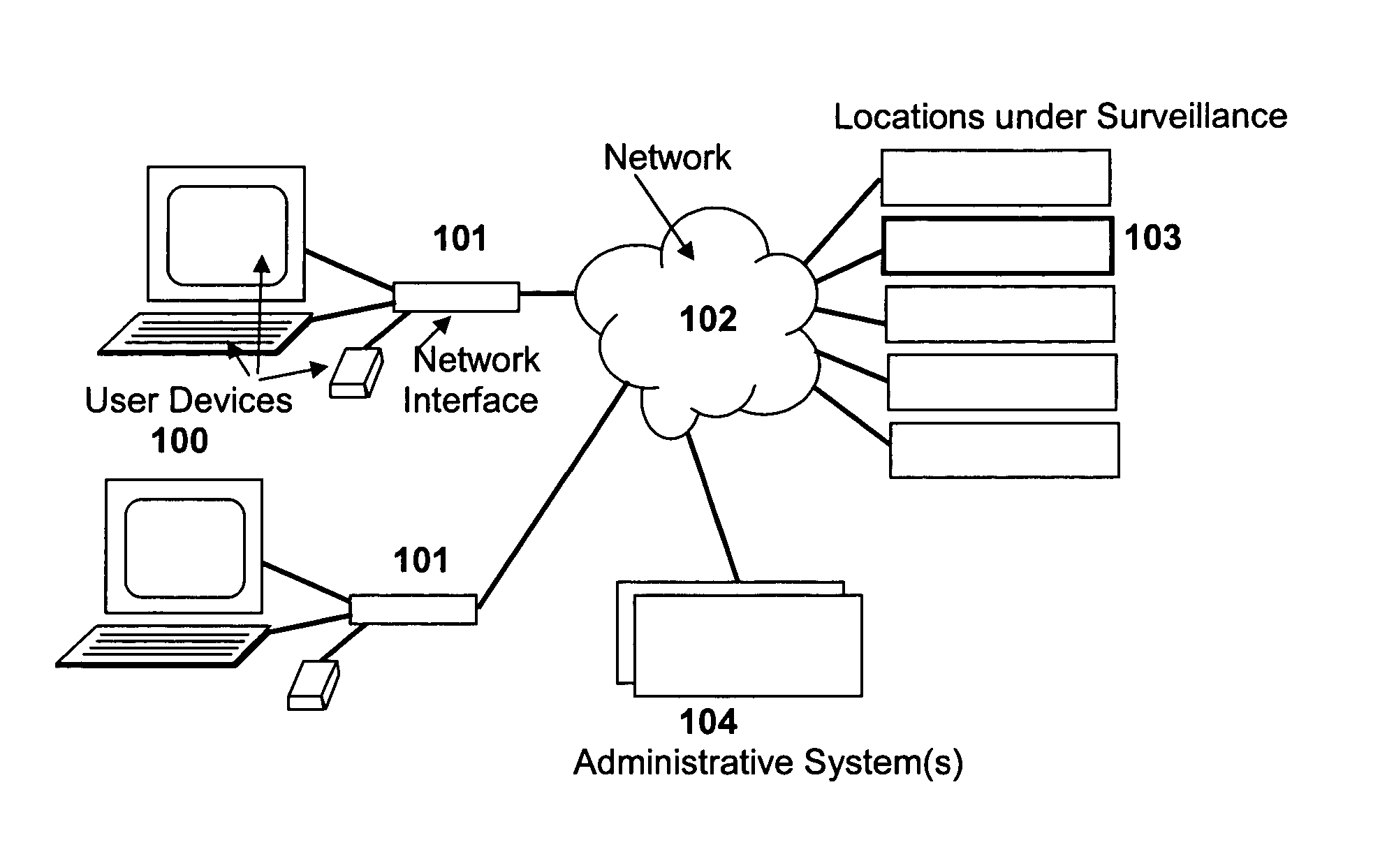
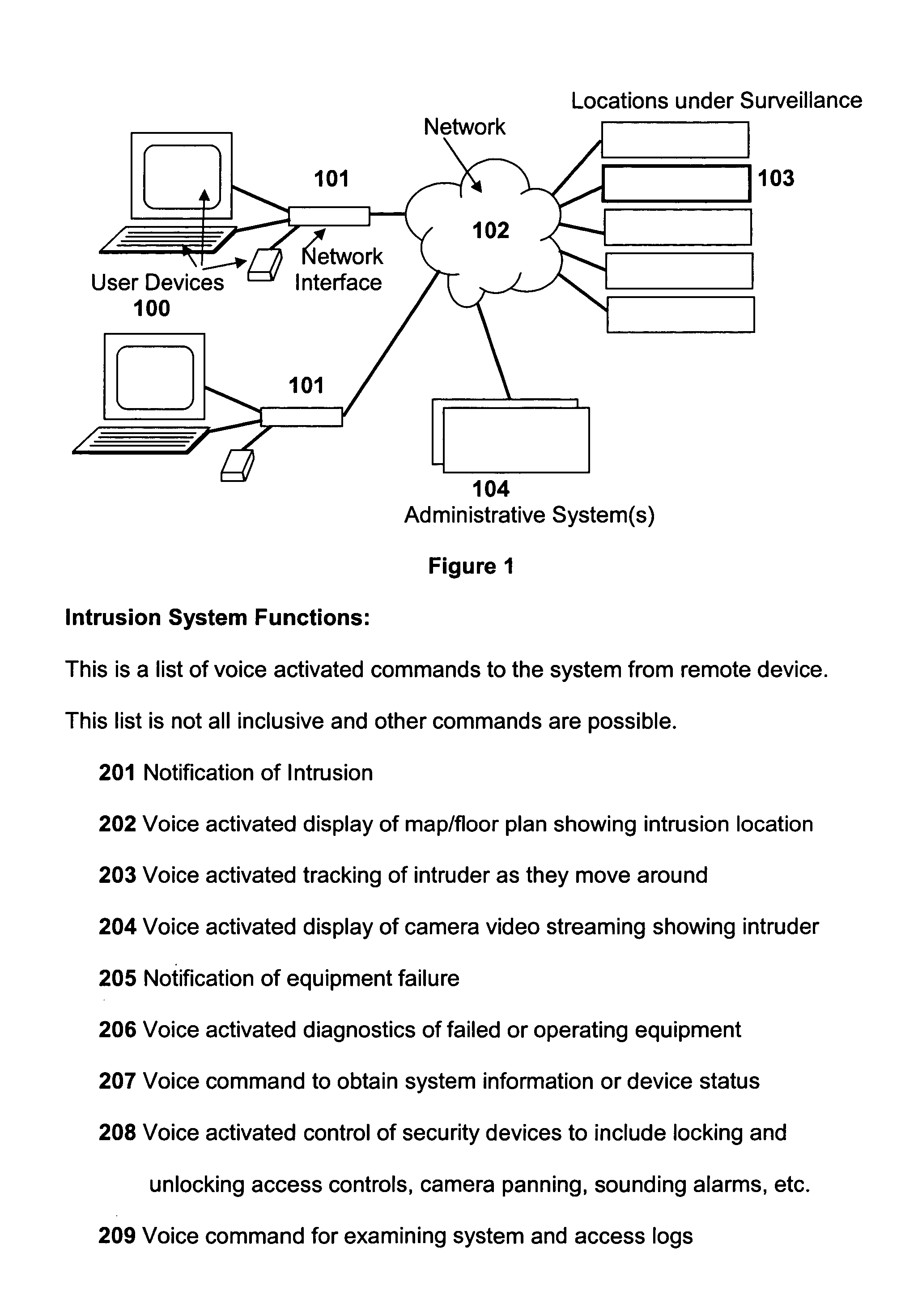
An invention that enables the use of human speech to remotely access, interrogate, control and obtain real time information from security devices in a facility or location. Wireless, or other network connectivity, mobile devices are used as the voice recognition system. These devices interface to a management system located at the facility or location under surveillance. The user is able to view the mobile display device and command the system using human voice. The system supports detecting and tracking security intrusions, controlling the security devices at the location, requesting changes to the display, obtaining status information of the system or any device, and communicating to others that may be accessing the system jointly. The invention also uses hierarchical maps to quickly identify security problems within an enterprise. The system uses real-time altered icons or element pictures that identify the status of that element at a quick glance. The organized use of hierarchical maps to quickly traverse to and identify particular security problems to include intrusions, alarms, failures, pending failures, etc. Intruder movement is also automatically tracked on or between maps.
Owner:FALLON KENNETH T
System and method for sharing items in a computer system
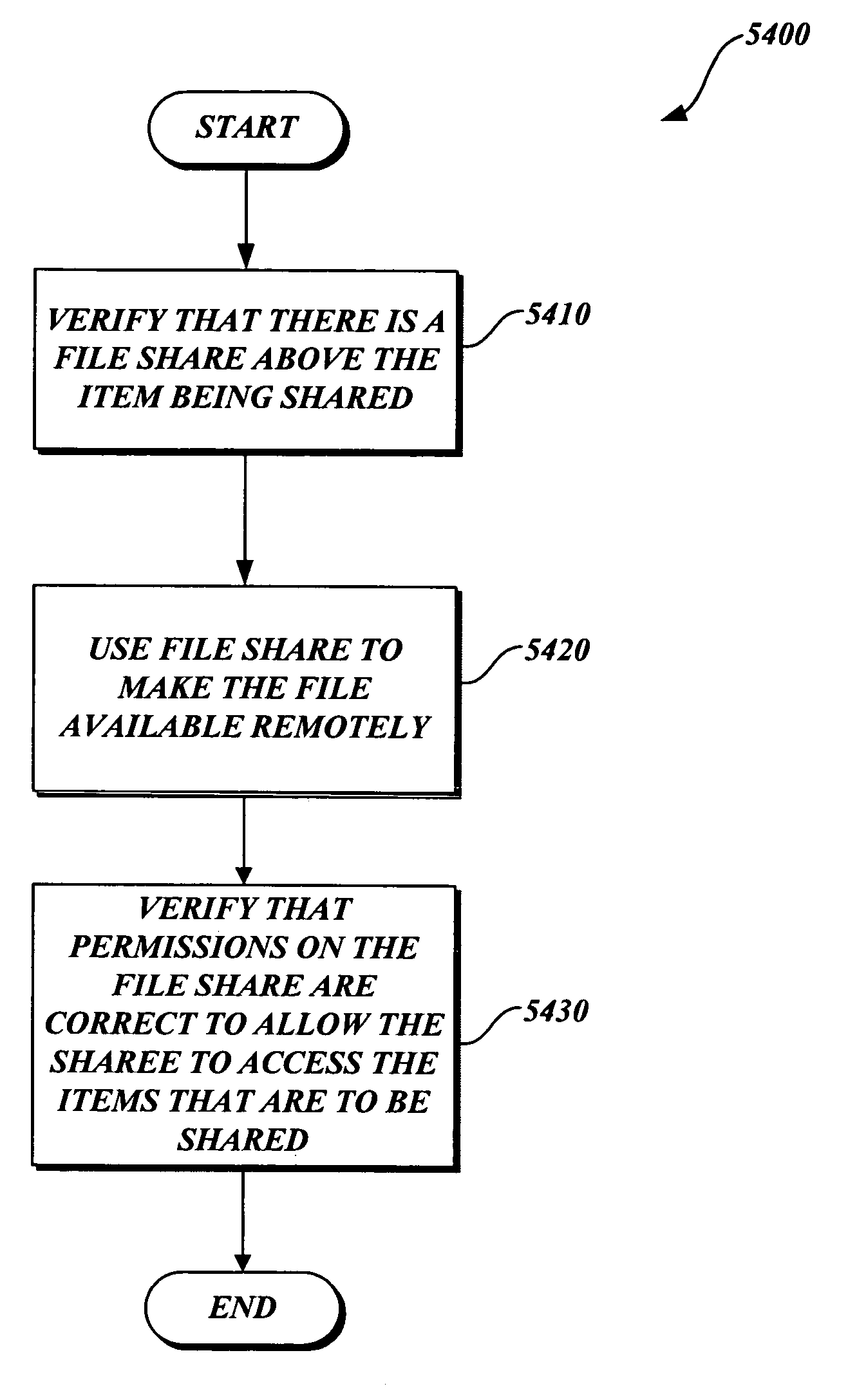
InactiveUS7536386B2Easy to shareDigital data information retrievalData processing applicationsIndividual itemComputerized system
A system and method for sharing items. A sharer may choose to share individual items, such as documents, contacts, and e-mails. To begin the sharing process, a user selects the items that are to be shared. The user then selects the sharees who the items are to be shared with, and the permissions that are to be assigned to the sharees. When items are to be shared, they are left in place on the sharer's machine, while the system ensures that the permissions are set, and any security issues are handled so that the sharees are able to access the items. In addition, the details of the sharing transactions may be tracked and recorded for later review. The sharer may also have the system send a link to the sharee for directly accessing the shared items from the sharer's machine. The sharee may also be able to query the sharer's machine to see what the sharer has shared out with the sharee.
Owner:MICROSOFT TECH LICENSING LLC
System, apparatus and method for screening personnel
ActiveUS20060087439A1Programme controlElectric signal transmission systemsMilitary installationEngineering
Apparatus and techniques are provided for screening personnel at secured installations like airports, courthouses, police stations, secured administrative buildings, military installations and other installations requiring heightened security. The apparatus and the system integrate state of the art available technologies in biometric identification, metal detection, document identification, and body scan apparatus. All technologies are integrated to provide reliable, efficient and economic solution to security problems. A corresponding method of screening is provided.
Owner:TOLLIVER CHARLIE L
Database security auditing method
InactiveCN104484474APreventive actionsDiscover usability in timePlatform integrity maintainanceSpecial data processing applicationsSQL injectionNetwork Communication Protocols
The invention relates to a database security auditing method which comprises the following steps: acquiring database network communication data; parsing a database network communication protocol; carrying out self-learning digging on audit rules; detecting database risk event invasion; evaluating database user permissions; tracking the three-layer correlation of a primary user. The database security auditing method can be used for auditing and monitoring a database in real time, so that the automatic assessment, audit, protection and invasion detection operation can be realized; the method can be used for preventing, recording and tracking the complete database operation behavior so as to help an administrator to find out the internal safety problems of unauthorized use, privilege abuse, permission theft and the like of the database in time; furthermore, after the method is used, the outside attacks such as SQL (structured query language) injection and the like can be avoided.
Owner:NANJING DUNLEI NETWORK TECH CO LTD
System and method for monitoring data in a client environment
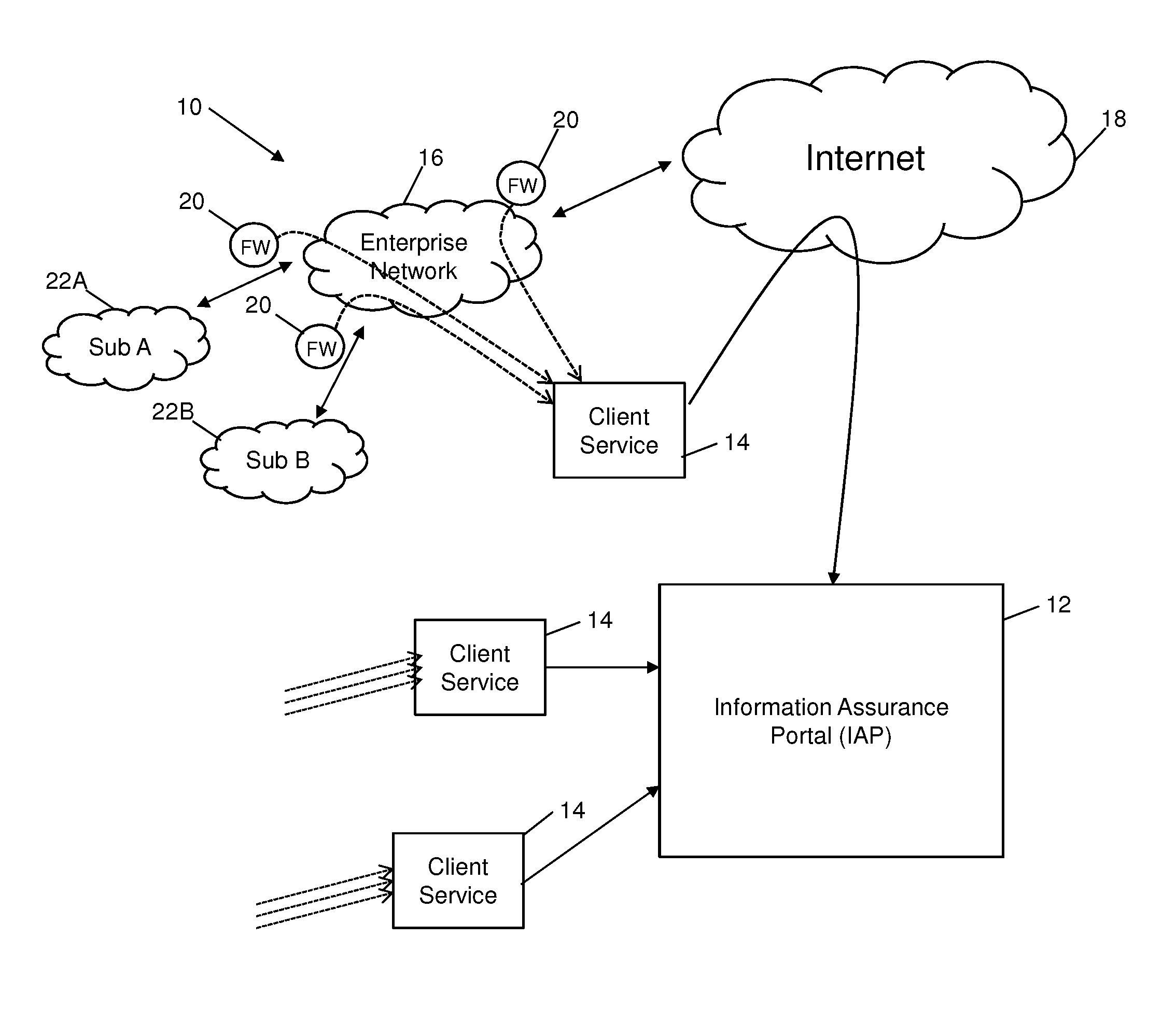
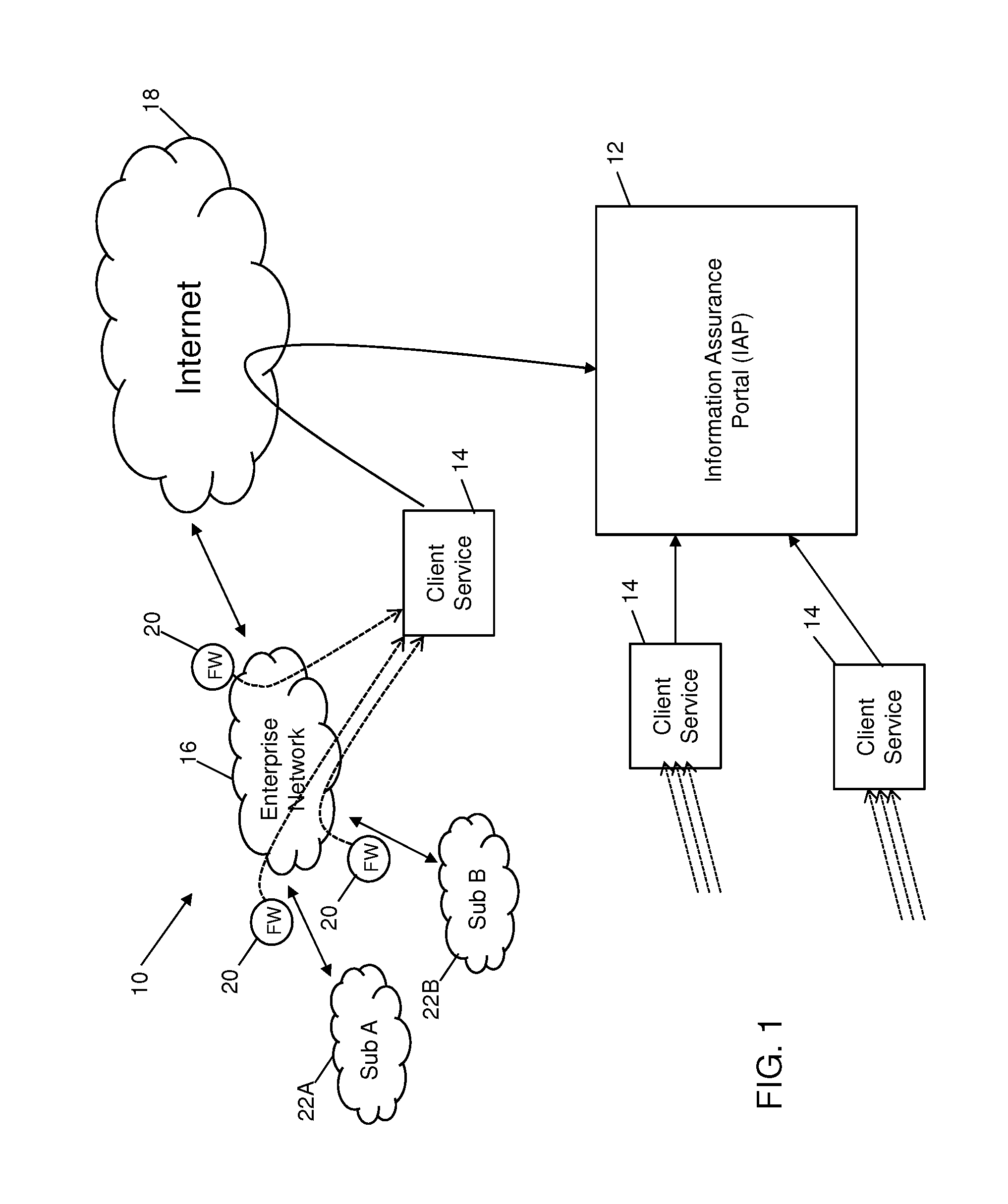
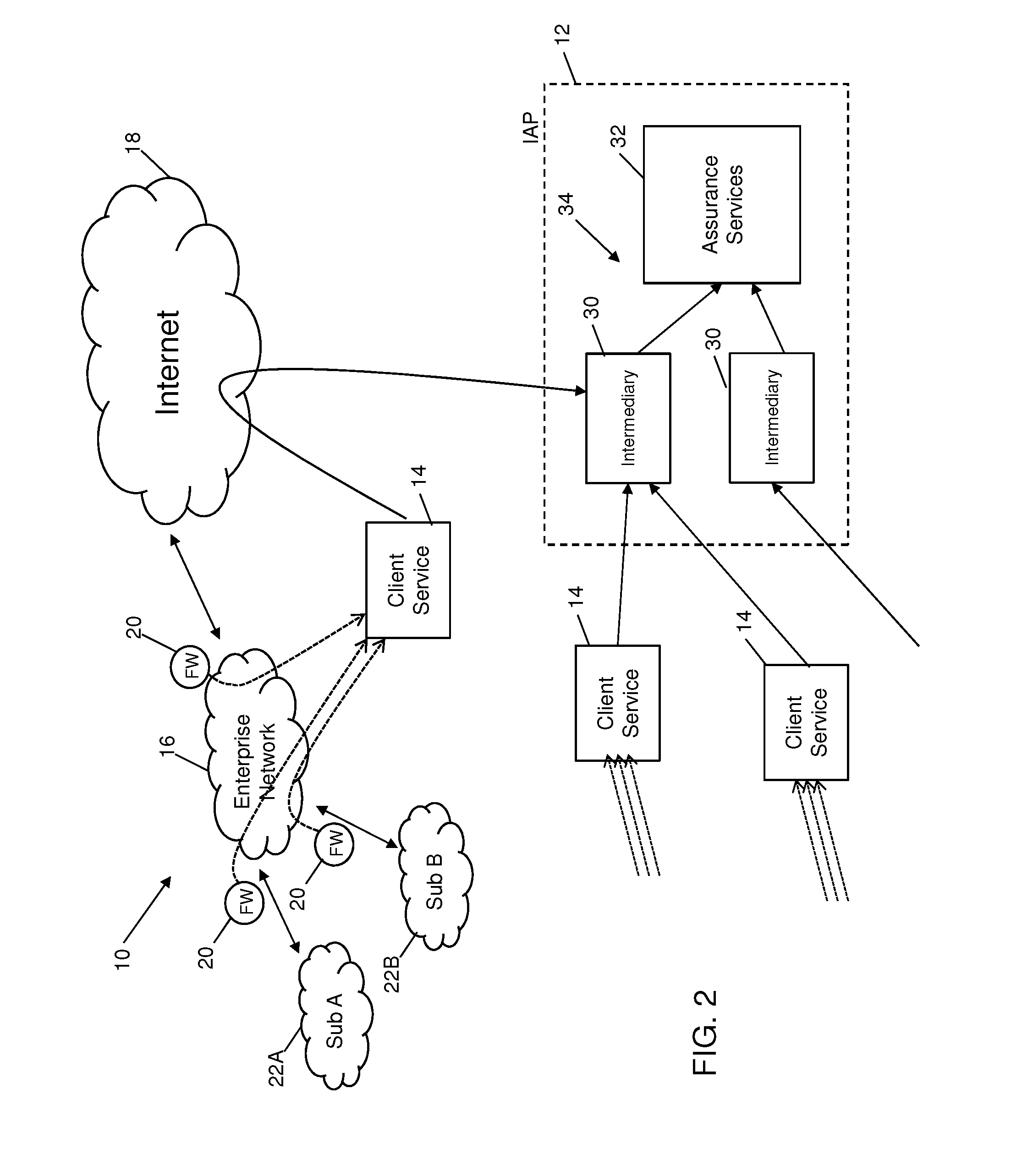
InactiveUS20150347751A1Memory loss protectionError detection/correctionCloud baseInformation assurance
Systems and methods are provided which enable client environments, such as corporate and government enterprises, to adopt an integrated, strategic approach to governance, risk and compliance. The systems described herein provide a “cloud-based” information security service that provides such enterprises with round-the-clock visibility into security issues and risks across the enterprise. An advanced security information and event management system, also referred to as an information assurance portal (IAP), is described, which enables client customers to select various services such as threat and vulnerability management, asset classification and tracking, and business threat and risk assessments through a software-as-a-service portal.
Owner:SECCURIS INC
Securely hosting workloads in virtual computing environments
ActiveUS20100275241A1Poor resource utilizationImprove resource utilizationSpecific access rightsDigital data processing detailsSecurity questionWorkload
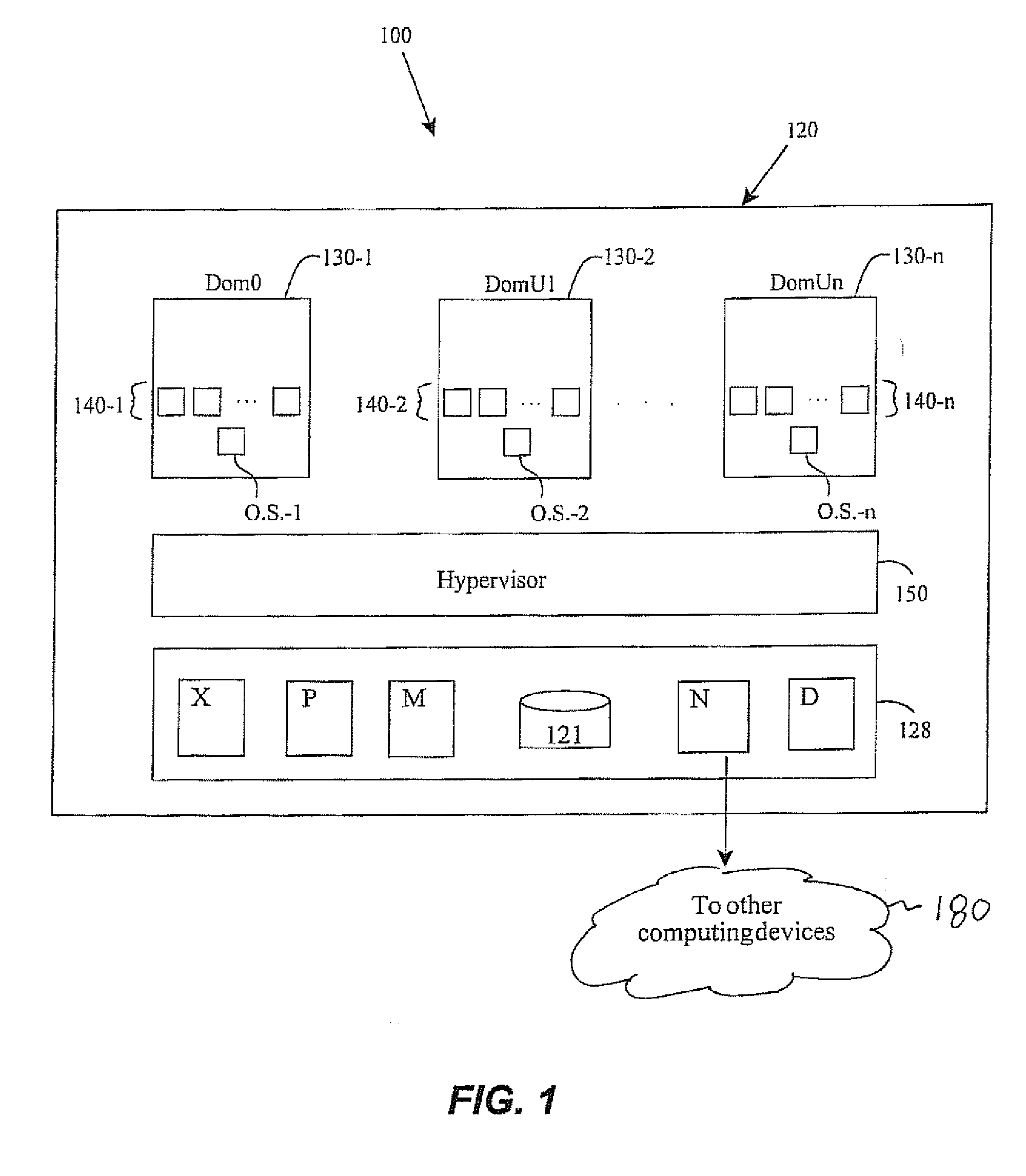
Methods and apparatus involve securely hosting workloads. Broadly, computing workloads are classified according to security concerns and those with common concerns are deployed together on common hardware platforms. In one instance, security tags are bi-modally attached or not to workloads meeting a predetermined security threshold. Those with tags are deployed on a common machine while those without tags are deployed on other machines. Tags may be embedded in meta data of open virtual machine formats (OVF). Considerations for re-booting computing devices are also contemplated as are multiplexing workloads. Computer program products are further disclosed.
Owner:SUSE LLC
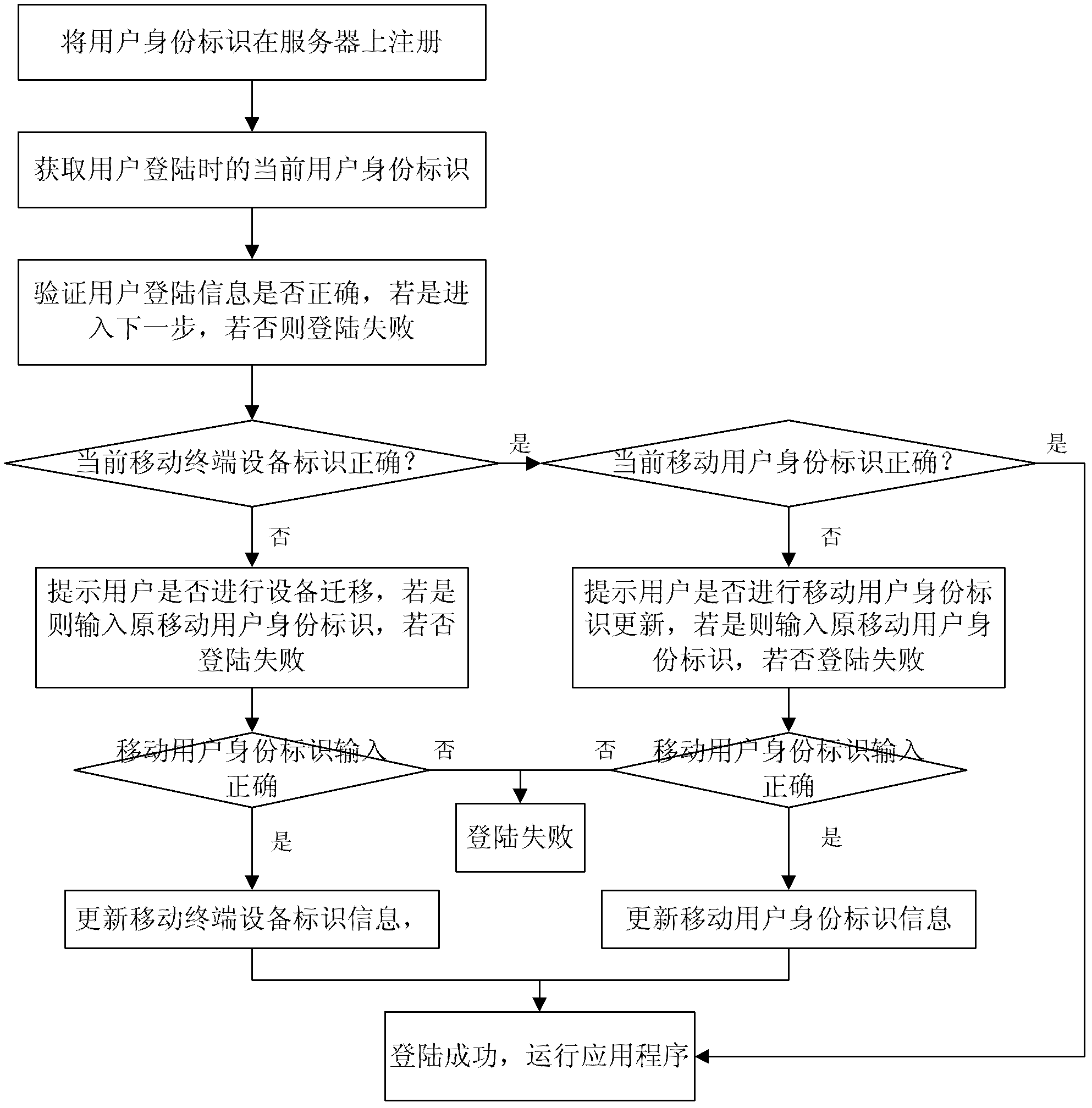
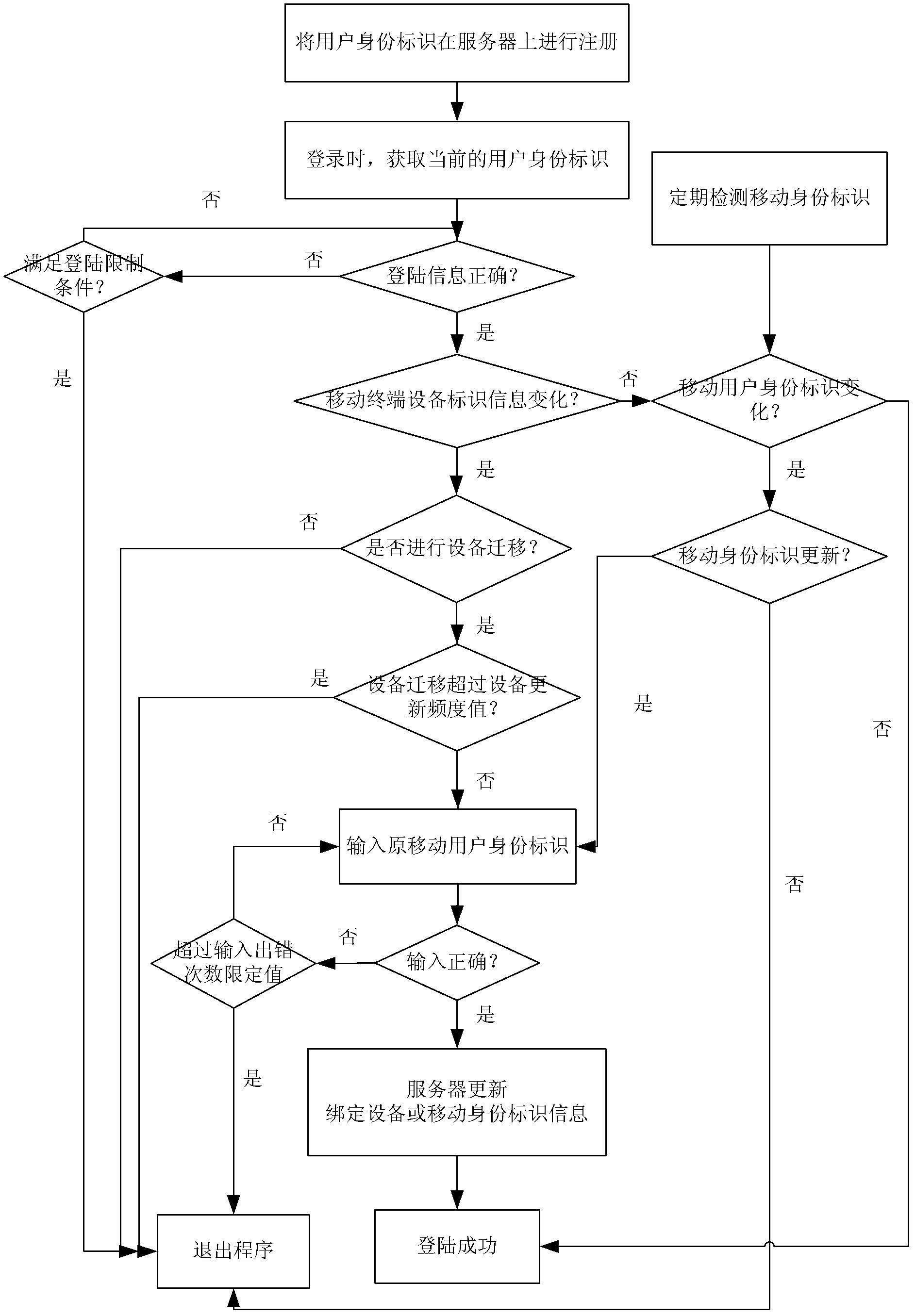
Security protection method and security protection system for mobile terminal application
ActiveCN103188668AImprove securityImprove convenienceSecurity arrangementTerminal equipmentApplication security
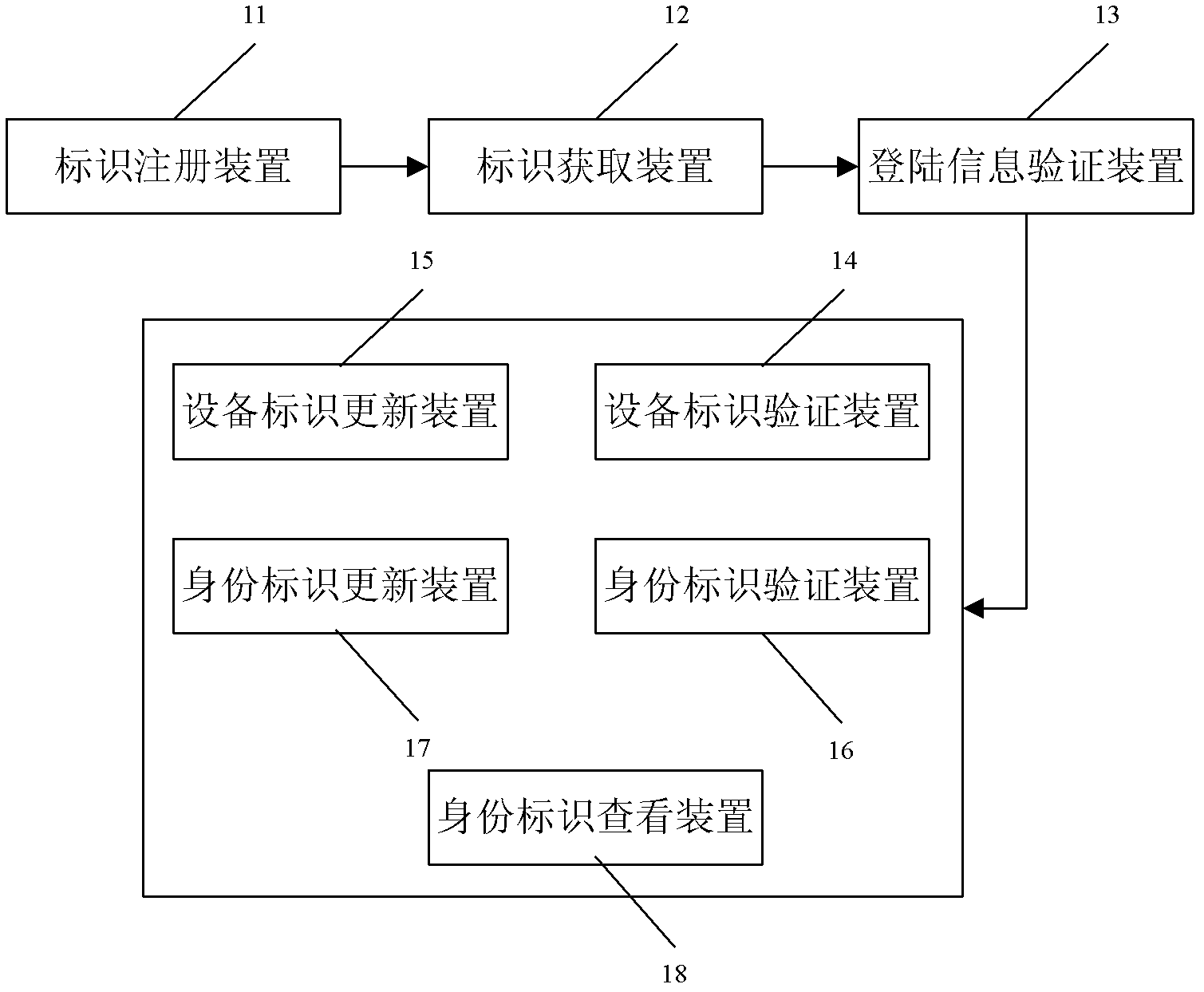
The invention discloses a security protection method and a security protection system for a mobile terminal application, and belongs to the field of terminal application security protection. The method comprises the steps that a mobile terminal equipment identity, a mobile subscriber identity and subscriber login information are sent to a server for registration during a registration course, and bound to form a subscriber identity; login information, the mobile terminal equipment identity and the mobile subscriber identity in the current subscriber identity are compared with the original subscriber identity in the server sequentially during a login course to determine information required to be updated; and updating is performed by authentication of the original mobile subscriber identity finally. According to the method and the system, a mobile terminal equipment information binding method is adopted, so that the security problems due to the fact that terminal equipment is updated, an SIM (Subscriber Identity Module) card number is replaced or the subscriber login information is stolen under the condition of single registration of a subscriber are solved, and the security and conveniences of the terminal application are improved.
Owner:方正国际软件(北京)有限公司
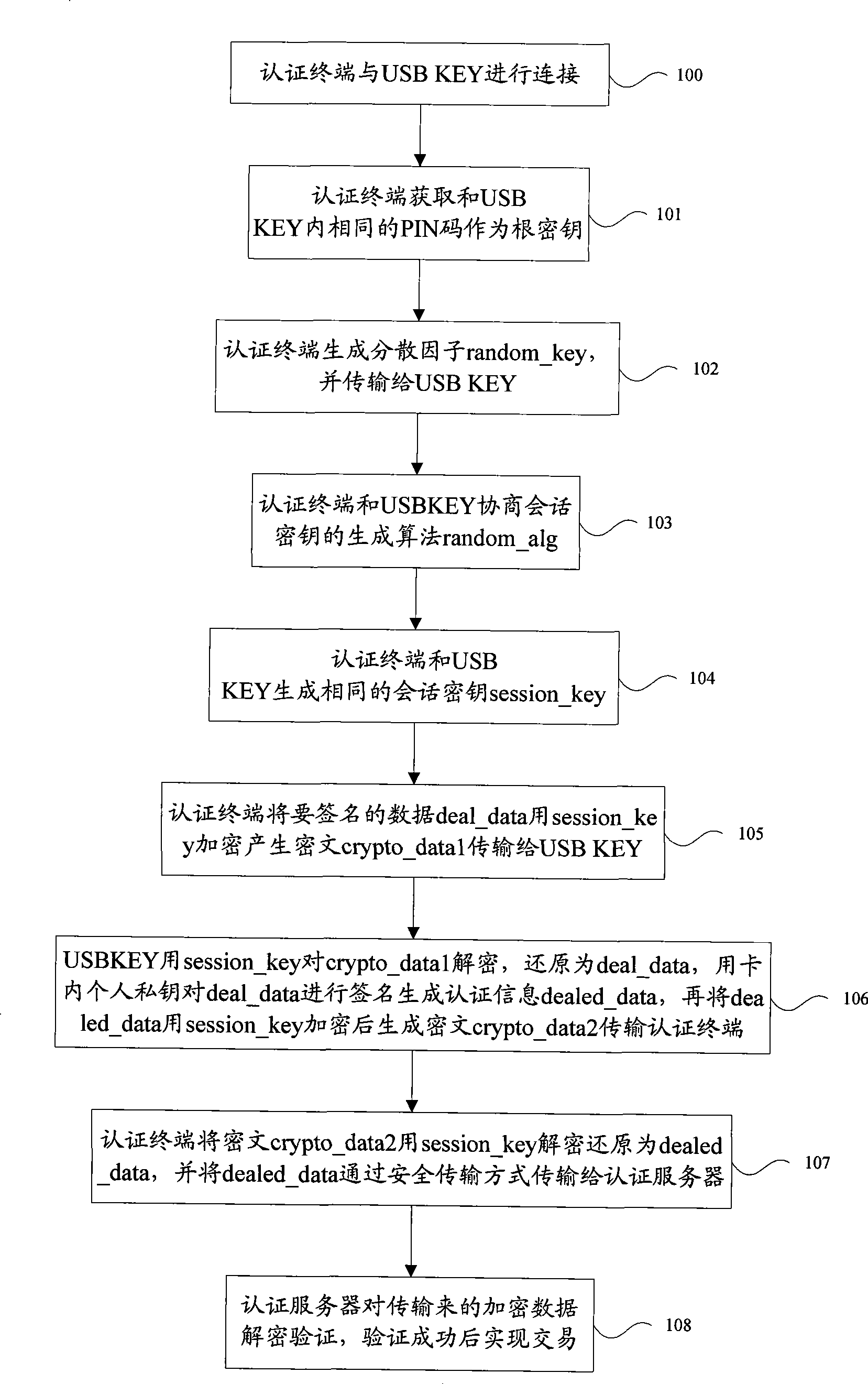
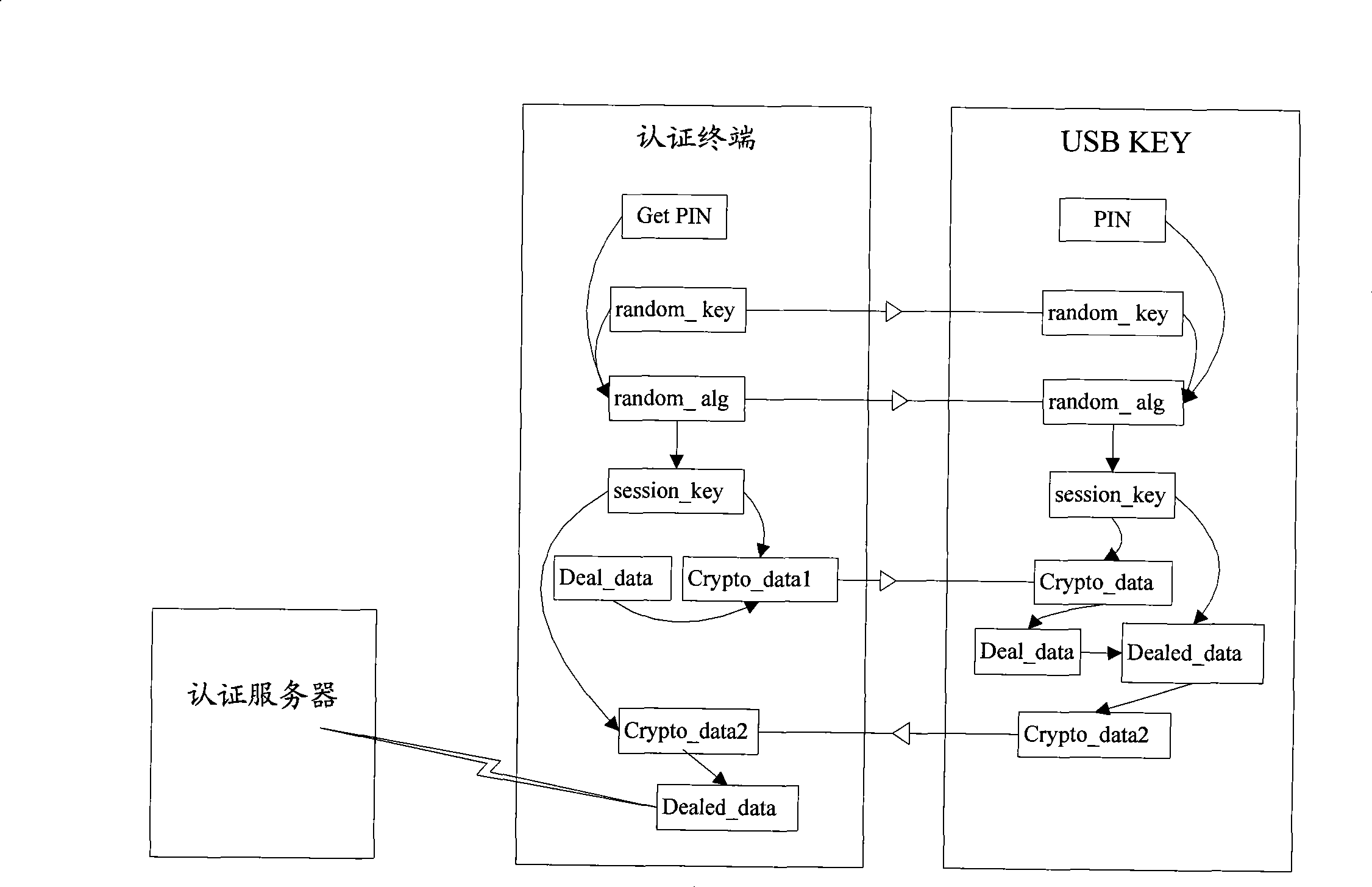
Method and system for implementing authentication and data safe transmission
InactiveCN101483654AEnable secure interactionsEnsure safetyTransmissionSecurity arrangementSecure transmissionPassword
The invention discloses an authentication and safe transmission of data realizing method. A terminal safety device and an authentication terminal after being connected negotiates to have a same data to be used as a root key, and at the same time negotiates to have a same dispersion factor and a same algorithm, the negotiated root key and dispersion factor generate a same session key used as a symmetrical key by using the algorithm, and then, safety authentication and data encryption and decryption can be performed and safety data interaction between the two ends can be realized. The invention also discloses a system for realizing authentication and safe transmission of data, and the system comprises a terminal safety device, an authentication terminal and an authentication server. According to the invention, randomness of the session key for data encryption transmission can be assured, even though a session key is decrypted, the safety of the whole system can be assured, and at the same time, atom manipulation for safety authentication and safe transmission of data can be realized for avoiding that in the current authentication process, once a password is verified by the terminal safety device, limits of authority are totally released and potential safety hazard is generated, therefore, authentication safety is improved greatly.
Owner:BEIJING HUADA ZHIBAO ELECTRONICS SYST
Method, device and system of id based wireless multi-hop network authentication access
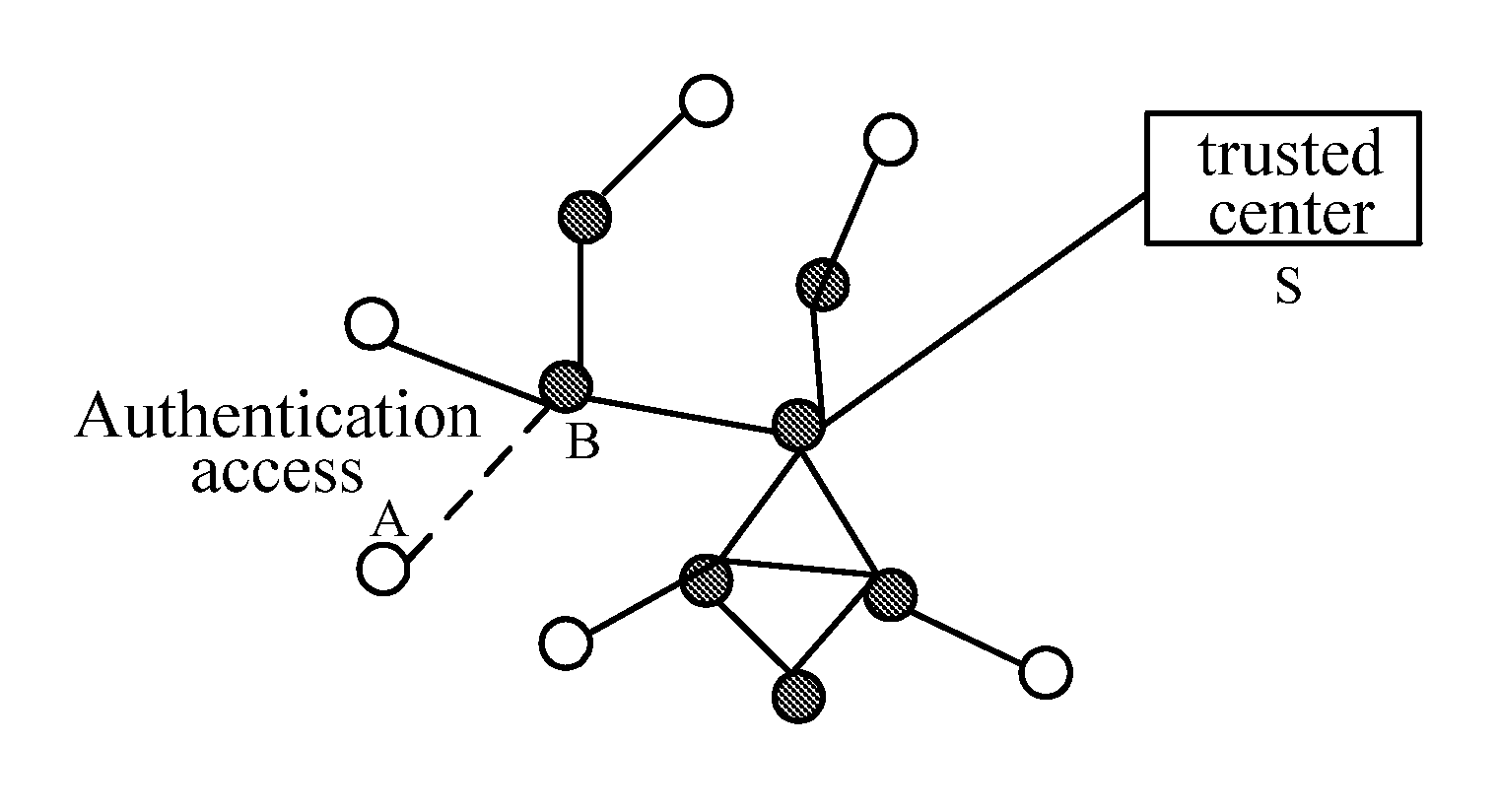
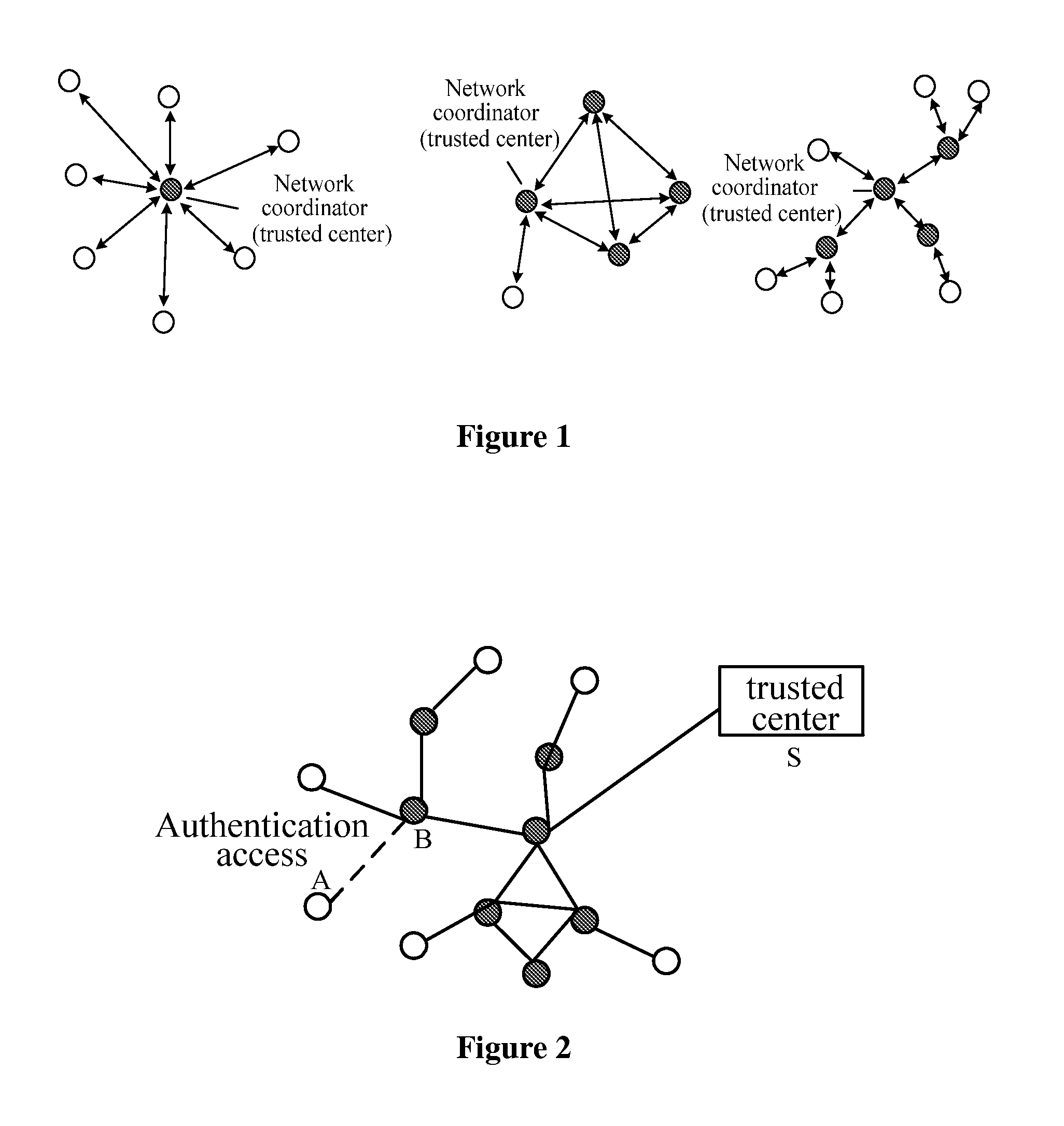
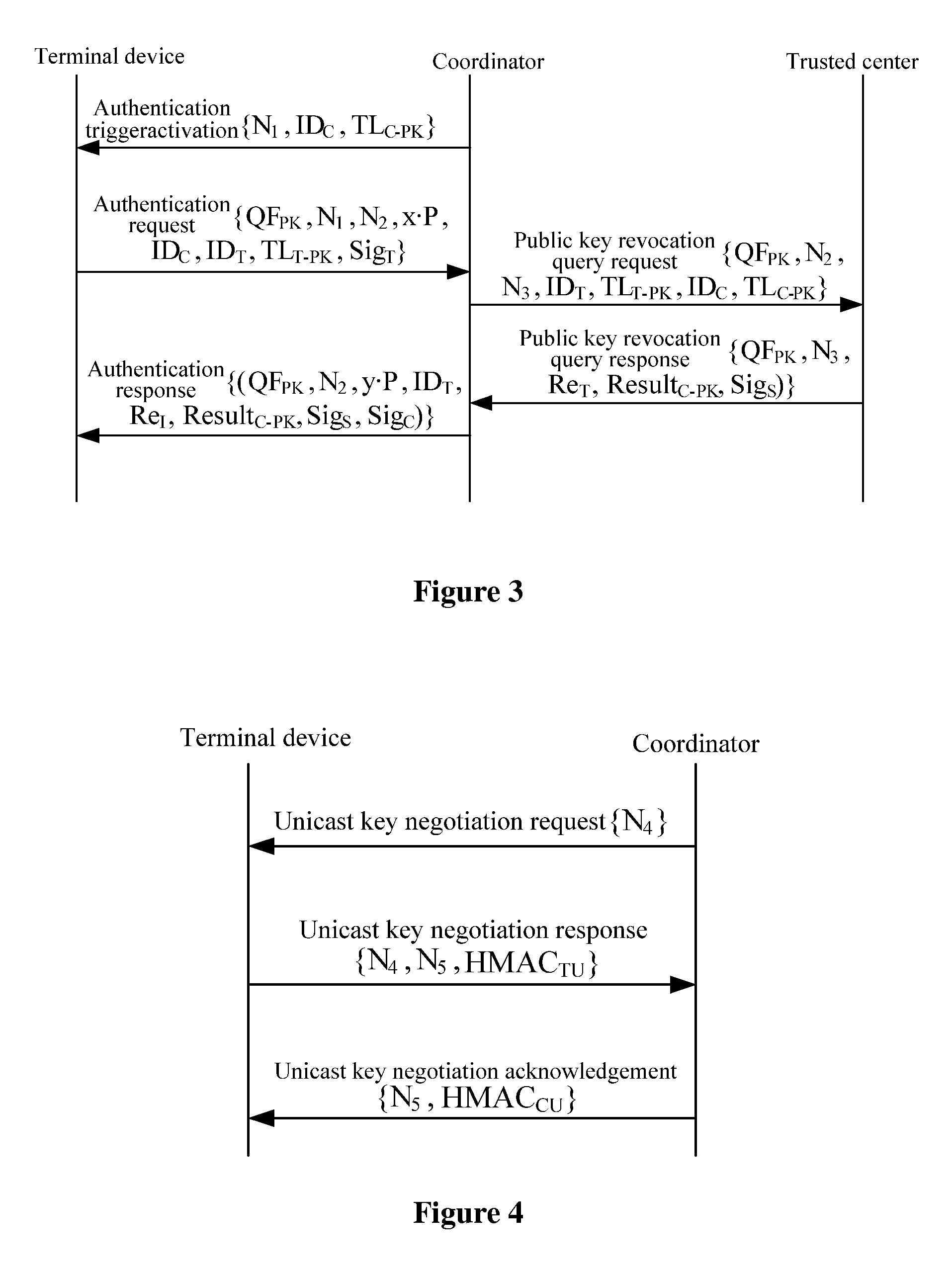
InactiveUS20100293378A1Improve access securityImprove access performanceUser identity/authority verificationNetwork topologiesCommunications securityPrivate network
A method, device and system of ID based wireless multi-hop network authentication access are provided, which are used for security application protocol when the WAPI frame method (TePA, Triple-Element and Peer Authentication based access control method) is applied over the specific network including the wireless LAN, wireless WAN and wireless private network. The method includes the following steps: defining non-controlled port and controlled port; the coordinator broadcasts the beacon frame, the terminal device sends the connection request command; the coordinator and the terminal device perform the authentication procedure; the coordinator opens the controlled port and sends the connection response command at the same time if the authentication is successful; the terminal device receives the connection response command and opens the controlled port in order to access the network. The method of the present invention solves the technical problem of the presence of the security trouble in the present wireless multi-hop network authentication access method, improves the security and performance of accessing the wireless multi-hop network from the terminal device, and ensures the communication safety between the terminal device and the coordinator.
Owner:CHINA IWNCOMM
Method and device for repairing cheap-copy application programs
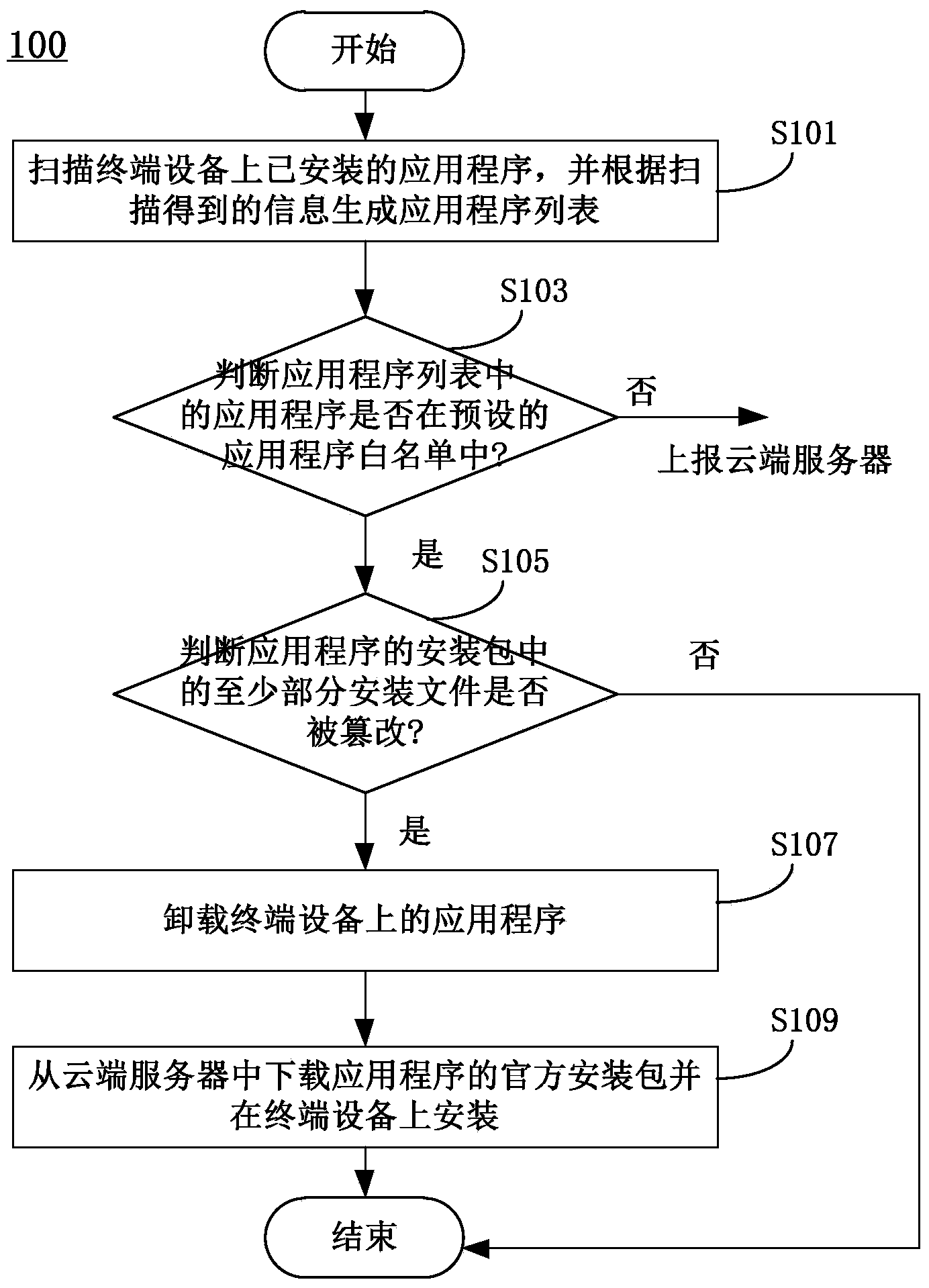
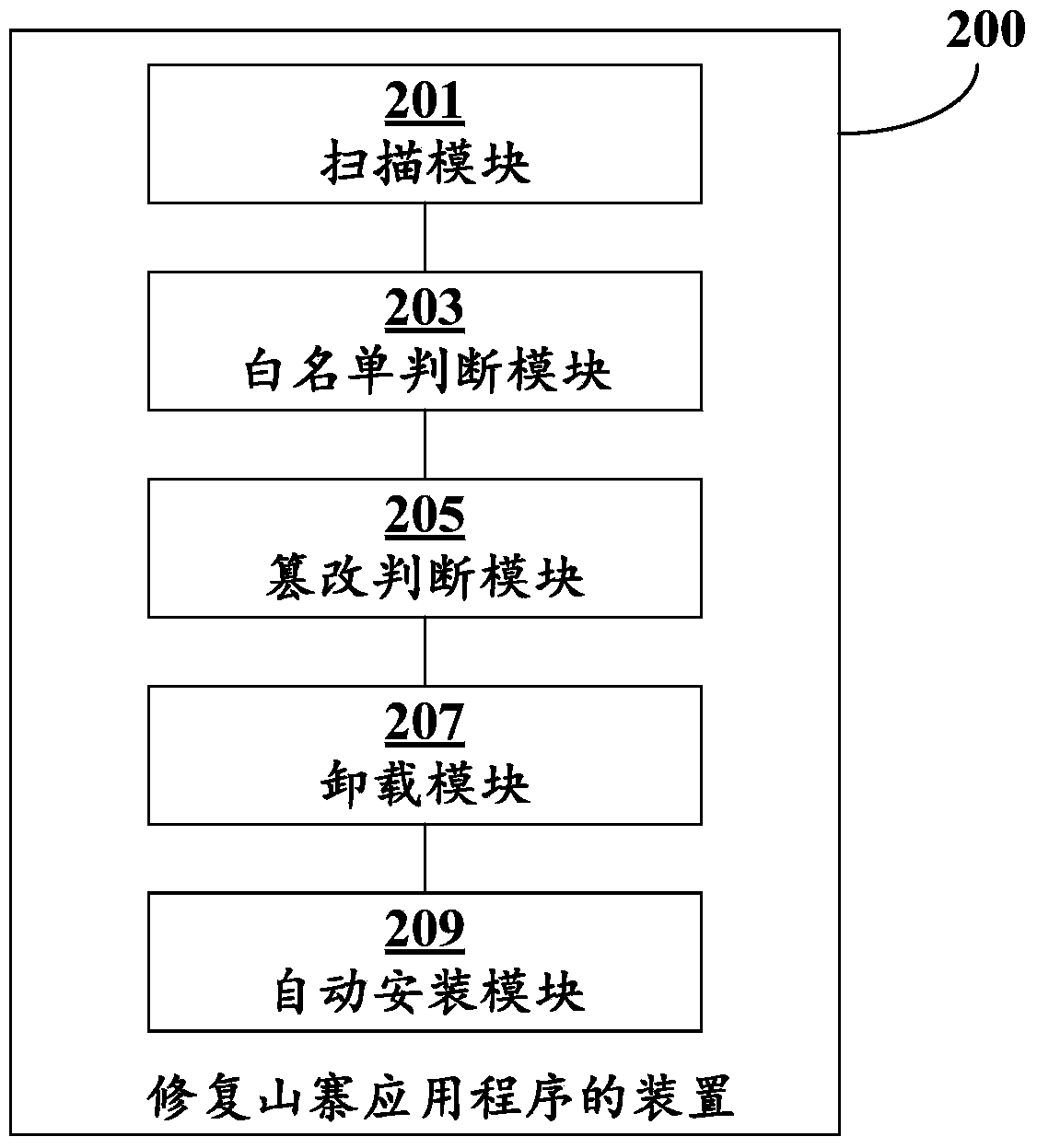
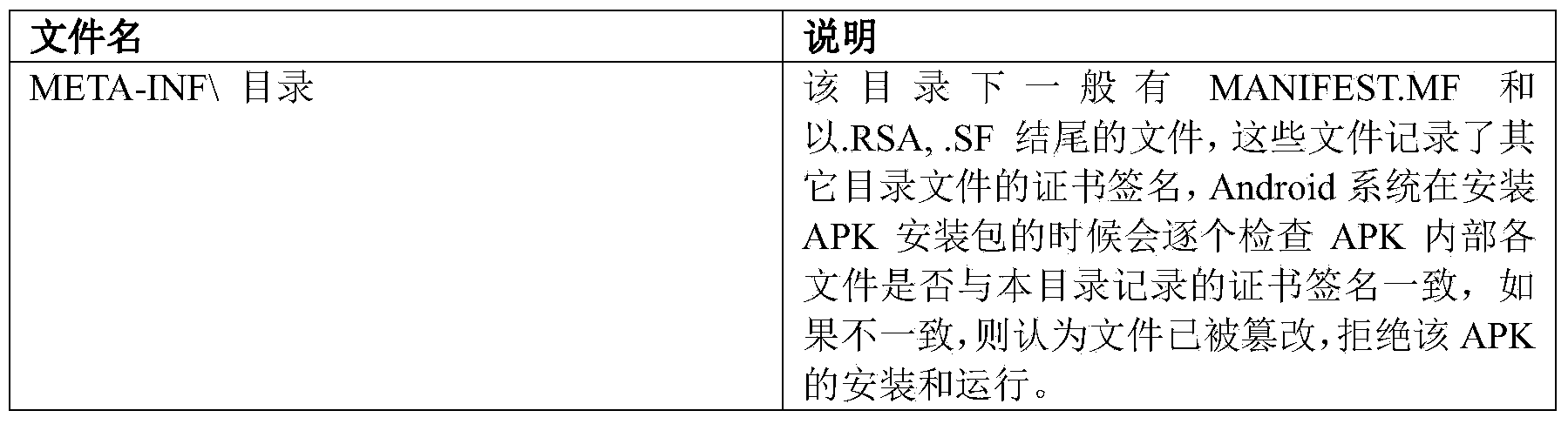
InactiveCN103679029AAvoid security issuesImprove securityPlatform integrity maintainanceProgram loading/initiatingOperational systemTerminal equipment
The invention discloses a method and device for repairing cheap-copy application programs. The method comprises the steps that the application programs installed on a terminal device are scanned and an application program list is generated according to information obtained through scanning; whether the application programs in the application program list exist in a preset application program white list or not is judged; if the application programs exist in the preset application program white list, whether at least parts of files in installation packages of the application programs are tampered or not is judged; if the parts of files in the installation packages of the application programs are tampered, the application programs on the terminal device are unloaded; official installation packages of the application programs are downloaded from a cloud-side server and are installed on the terminal device. By means of the method and device, a user can be helped to replace the cheap-copy application programs on the terminal device by the application programs in the official version, safety problems brought by malicious codes in the cheap-copy application programs are effectively avoided and the safety of an operation system of the terminal device is improved.
Owner:BEIJING QIHOO TECH CO LTD +1
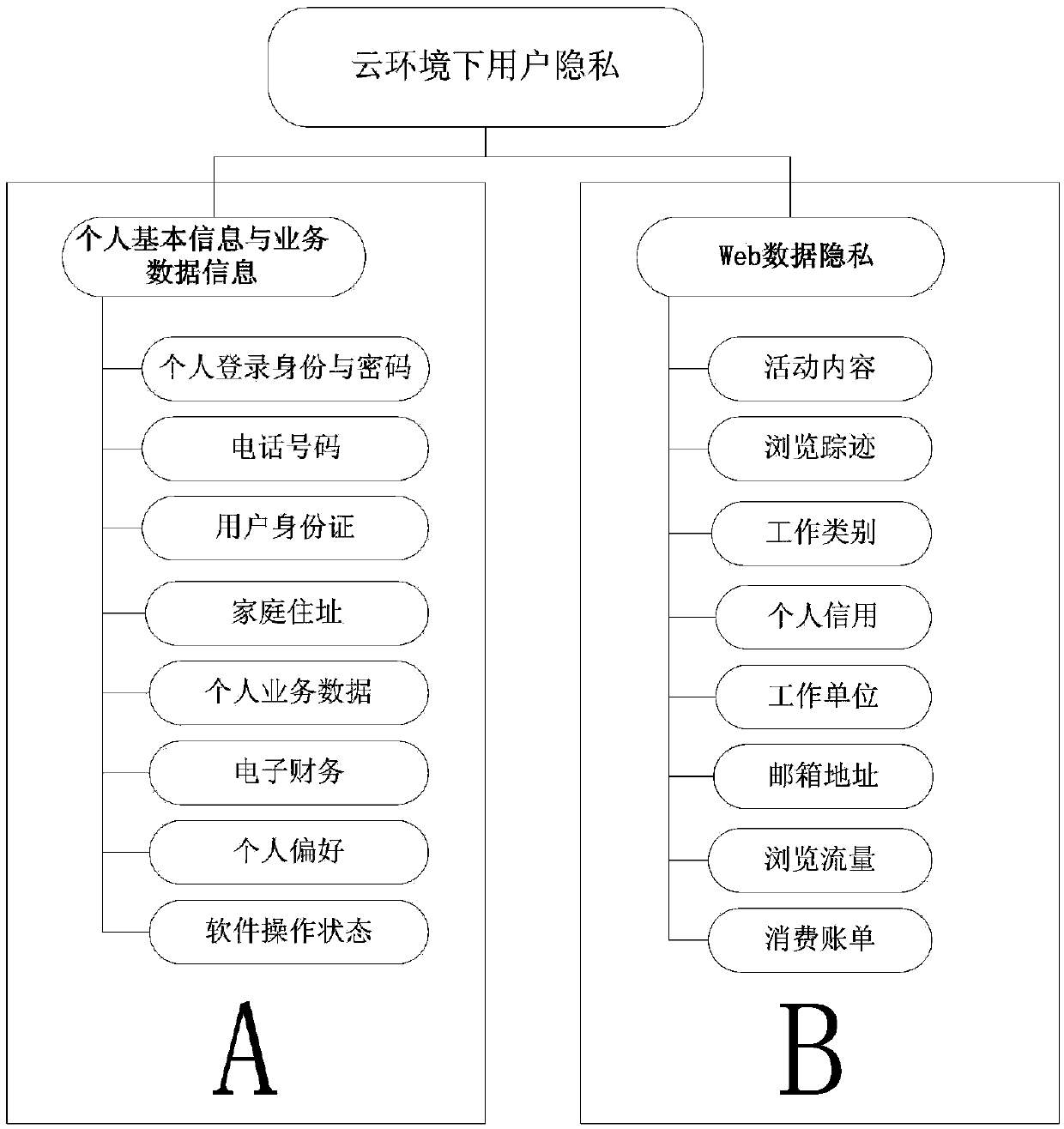
User privacy protection method based on attribute and homomorphism mixed encryption under cloud environment
ActiveCN104079574AGuaranteed fair accessEnsure safetyTransmissionAttribute-based encryptionInternet privacy
The invention provides a user privacy protection method based on attribute and homomorphism mixed encryption under a cloud environment. The method is mainly used for solving the safety problem of user privacy under the cloud environment. Firstly, a user sends the information of the user to a cloud service provider, and the cloud service provider clarifies the user privacy. Secondly, the user adopts different encryption modes for different types, namely a homomorphism encryption mode and an encryption mode based on the attribute. It is guaranteed that important privacy information is more difficult to be leaked out and stolen through the homomorphism encryption mode for the user, and the user can conduct operation on the privacy information of the user. Through the encryption mode based on the attribute, it is guaranteed that certain network resources can be shared with other users. Finally, the user downloads and decodes cryptograph. Through the mixed encryption mode, safety of the user data privacy is further guaranteed. Meanwhile, the user can operate important service data of the user conveniently. Moreover, coding efficiency and decoding efficiency are further improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Dynamic security question compromise checking based on incoming social network postings
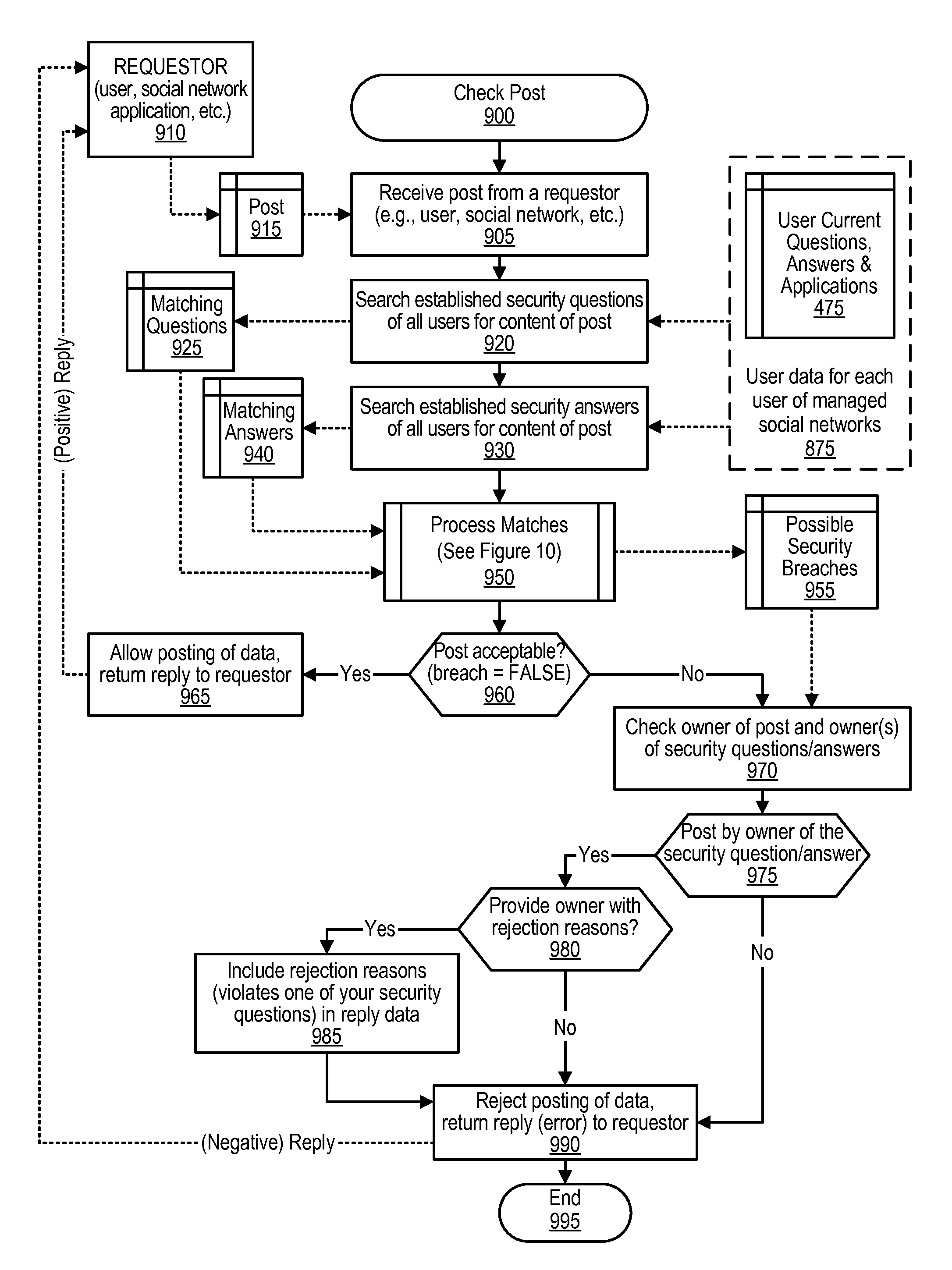
ActiveUS8856945B2Digital data processing detailsAnalogue secracy/subscription systemsInternet privacySecurity question
An approach is provided to secure security questions by checking posts directed at a social network. In the approach, requested post is received from one of the social network users. The content of the requested post is compared to previously established security questions and corresponding security answers, either established by the user or by another user. The requested post is allowed when the comparison reveals that the content does not compromise one of the previously established security questions and corresponding security answers. However, the requested post is rejected if the comparison reveals that the content compromises one of the previously established security questions and corresponding security answers.
Owner:INT BUSINESS MASCH CORP
Rf-id product tracking system with privacy enhancement
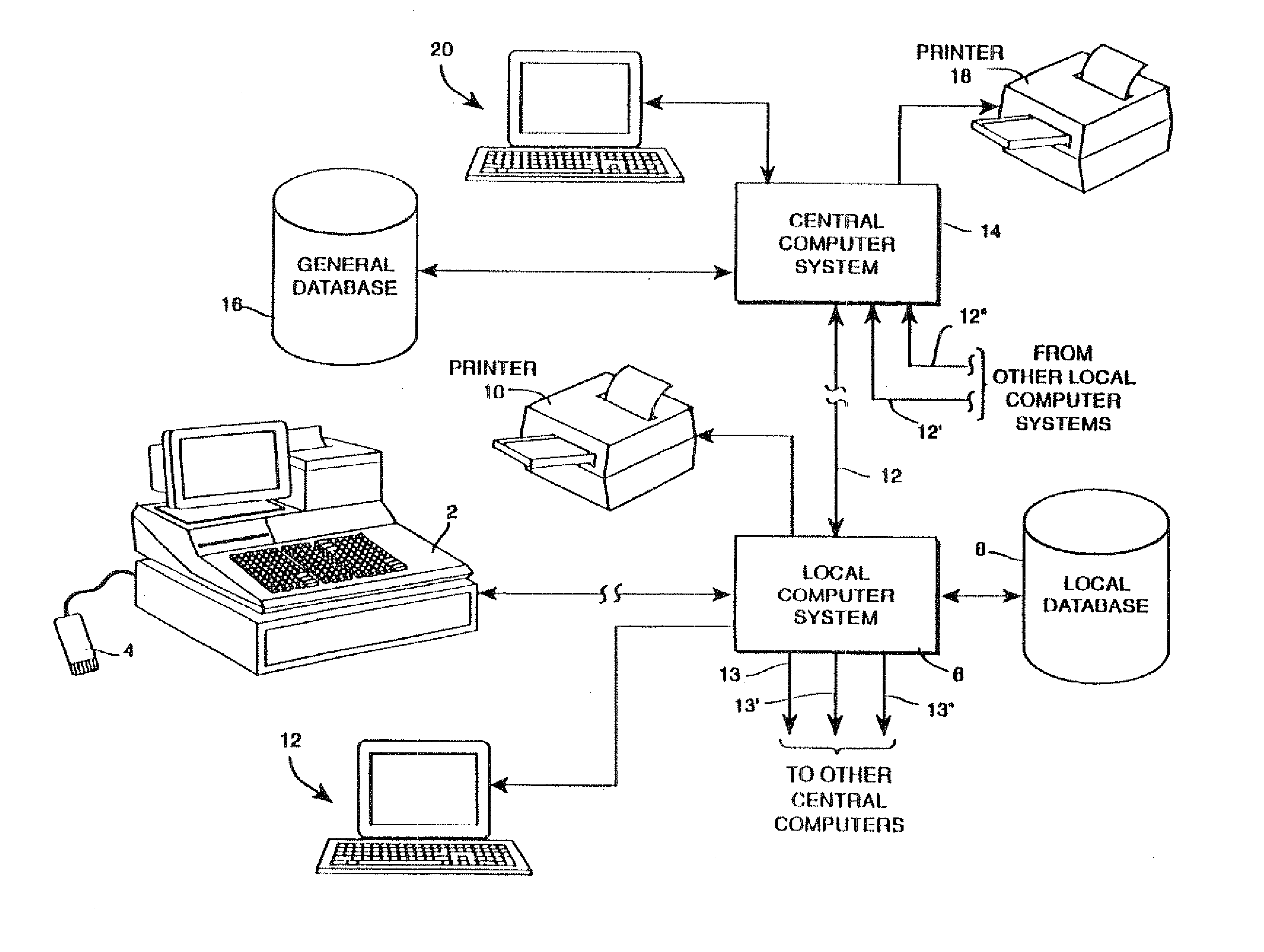
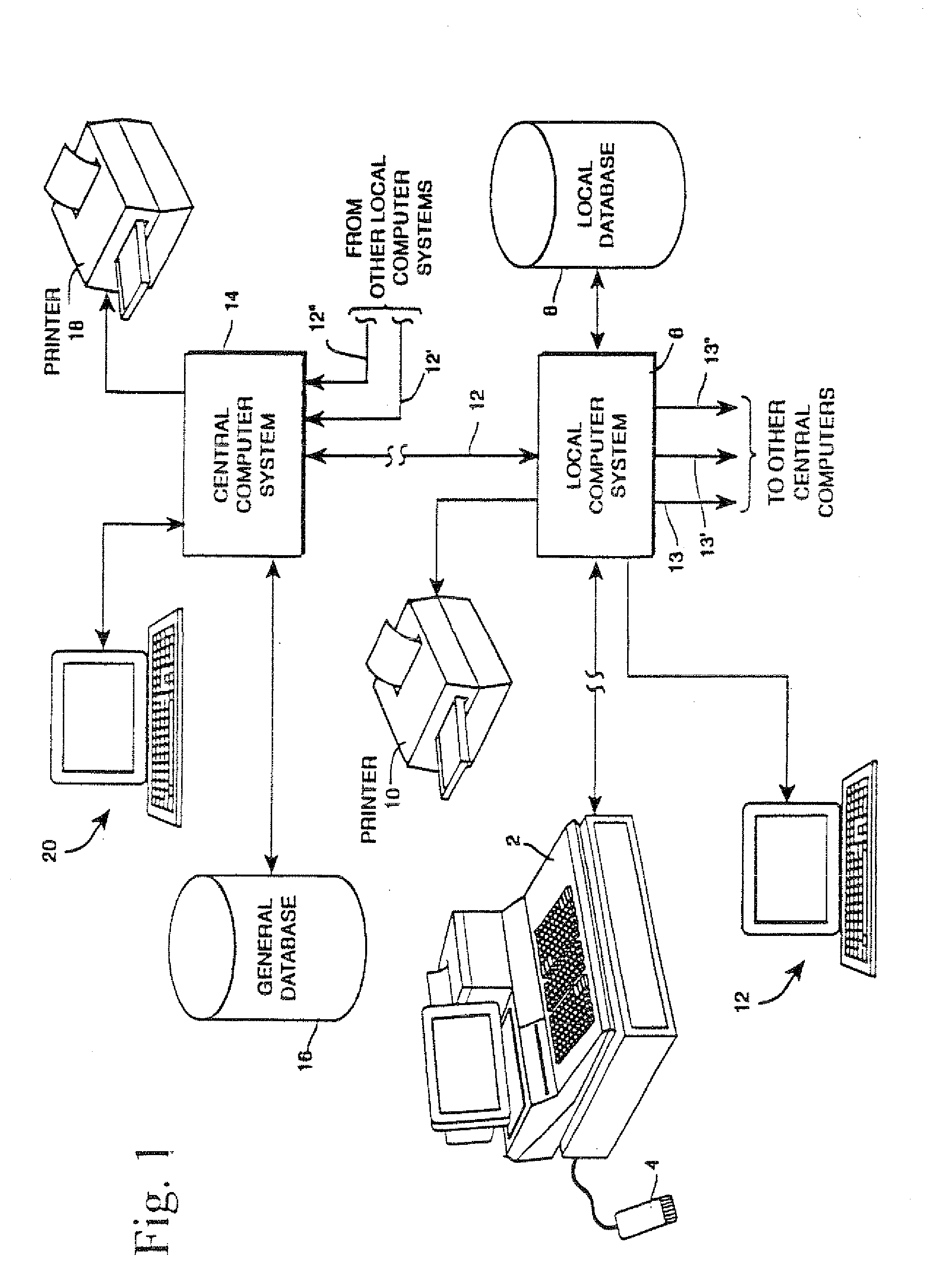
ActiveUS20110029397A1Easy to useEliminating, orLogisticsPoint-of-sale network systemsIdentification deviceSecurity question
Owner:E2INTERACTIVE INC D B A E2INTERACTIVE
Active network safety loophole detector
InactiveCN1694454AImprove confidentialityReduce trafficData switching networksExtensibilityAnalysis data
This invention discloses an active network safety leakage detector composed of three control modules of a detect agent, a data center and an analysis control stand, among which, the detection agent collection system matches the information and upwards it to the data center, the analysis control stand analyzes information stored in the data center to identify the host leakage by the OVAL leakage definition and carry out the associate analysis of attack / leakage by the predicate logic theory to find out the safety problem brought with the leakage combination to display potential attack paths in sight.
Owner:XI AN JIAOTONG UNIV
System and method applied to transaction platform for realizing grading safety processing of financial information
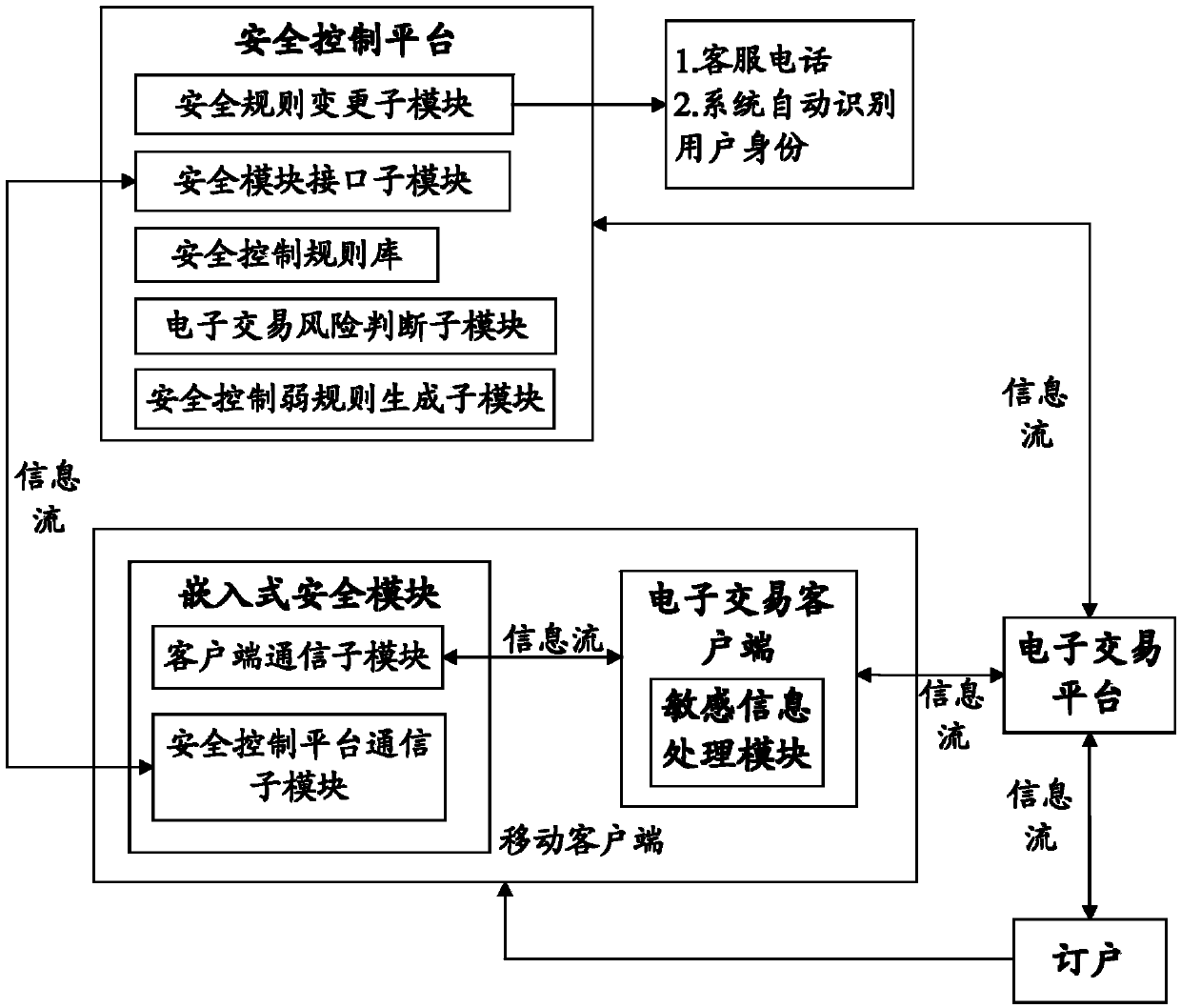
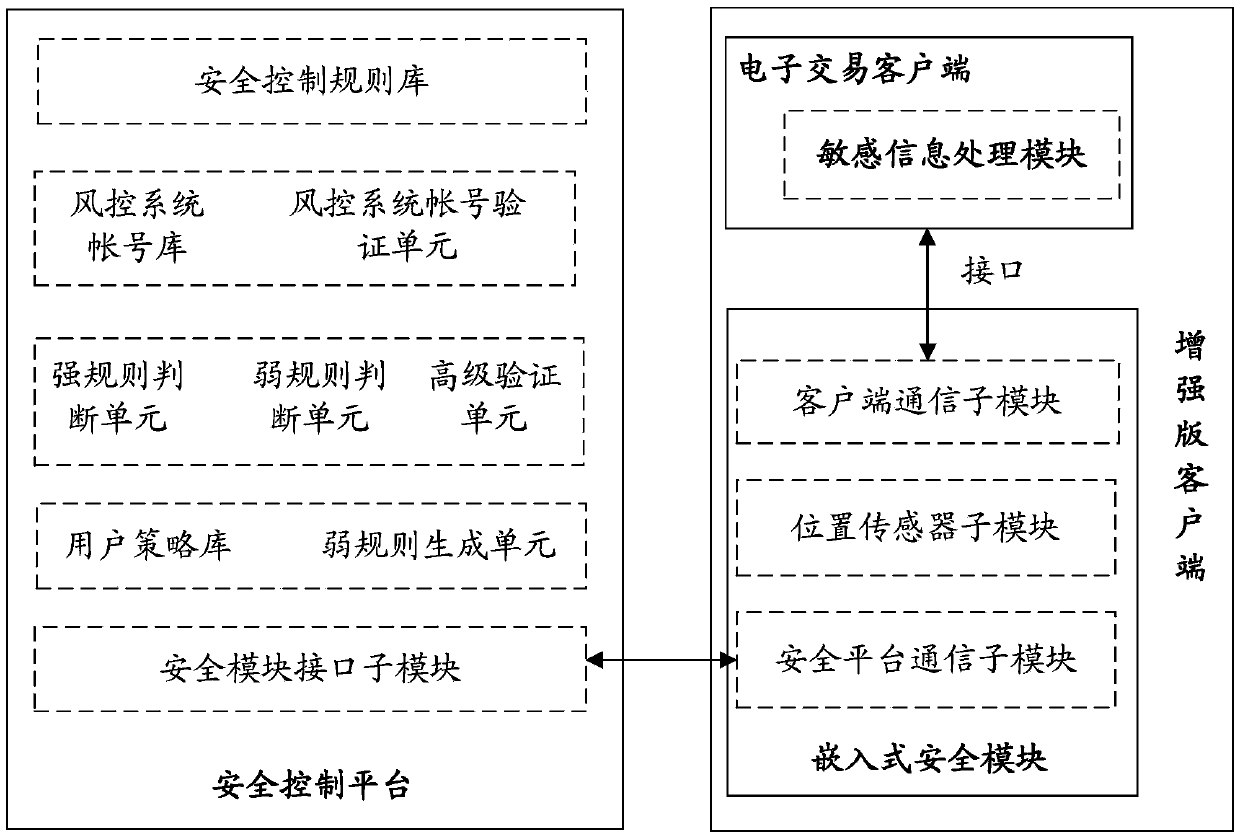
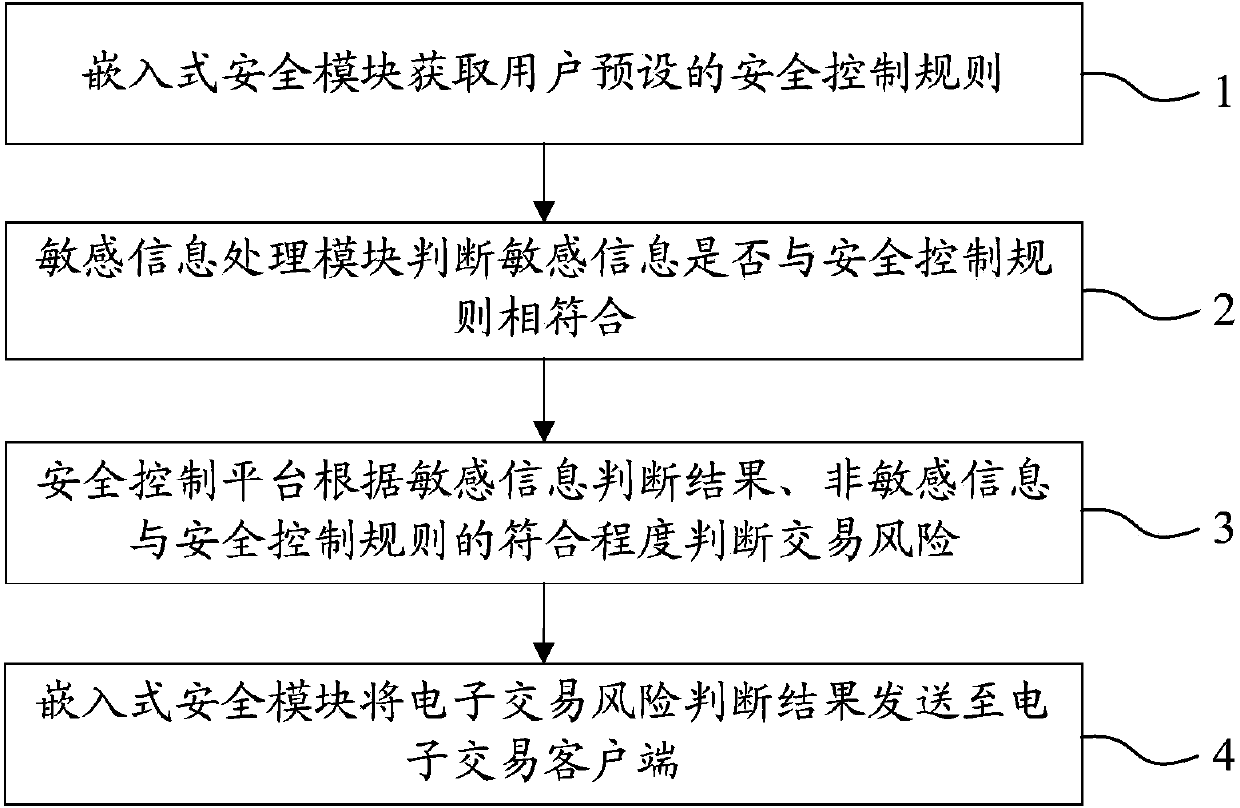
InactiveCN103745345AImprove securityDoes not compromise security by designPoint-of-sale network systemsProtocol authorisationInformation processingEmbedded security
The invention relates to a system applied to a transaction platform for realizing the grading safety processing of financial information. The system comprises an embedded safety control module for acquiring a safety control rule preset by a user, a sensitive information processing module for judging the coincidence degree of the sensitive information in electronic transaction information of the user and the safety control rule and a safety control platform for judging the risk of the electronic transaction and performing identity verification on the user for which the safety rule needs to be altered. The invention also relates to a method applied to the transaction platform for realizing the grading safety processing of the financial information. According to the system, adopting such a structure, and the method applied to the transaction platform to realize grading safety processing of the financial information, the financial information of the user can be divided into the sensitive information and insensitive information, the sensitive information processing module and an electronic transaction client end are integrally packaged, the user information safety is further ensured by grading processing, loss caused by the problem of account unsafety is reduced and the system and method have a wide application range.
Owner:COEUSYS
System and method for detecting and mitigating DNS spoofing trojans
Embodiments of the present invention relate to a method and system for detecting and / or mitigating domain name system (DNS) spoofing Trojan horse (or Trojan) code. Trojan code (sometimes called malware or malicious software) is a common computer security problem. Some Trojans modify the DNS resolution mechanism employed by the infected computer, such that the computer traffic, when browsing the Internet, is routed to a location not intended by the rightful owner of the computer. The present invention can detect this phenomenon from a remote device or location and may take action to mitigate its effects.
Owner:EMC IP HLDG CO LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com