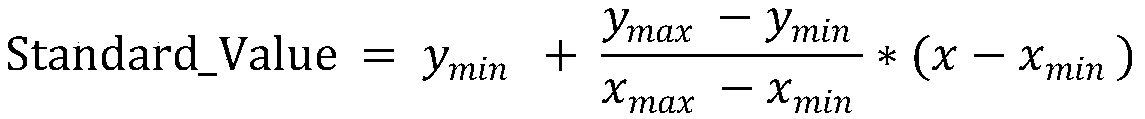Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
297 results about "SQL injection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
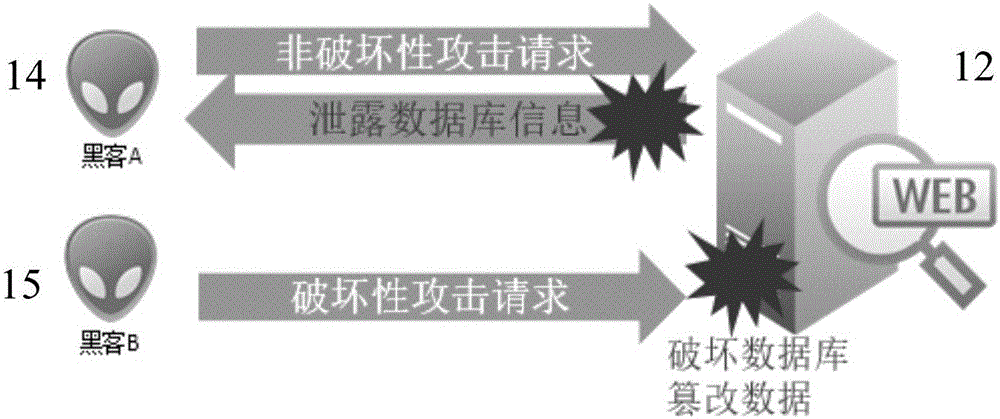
SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). SQL injection must exploit a security vulnerability in an application's software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL database.
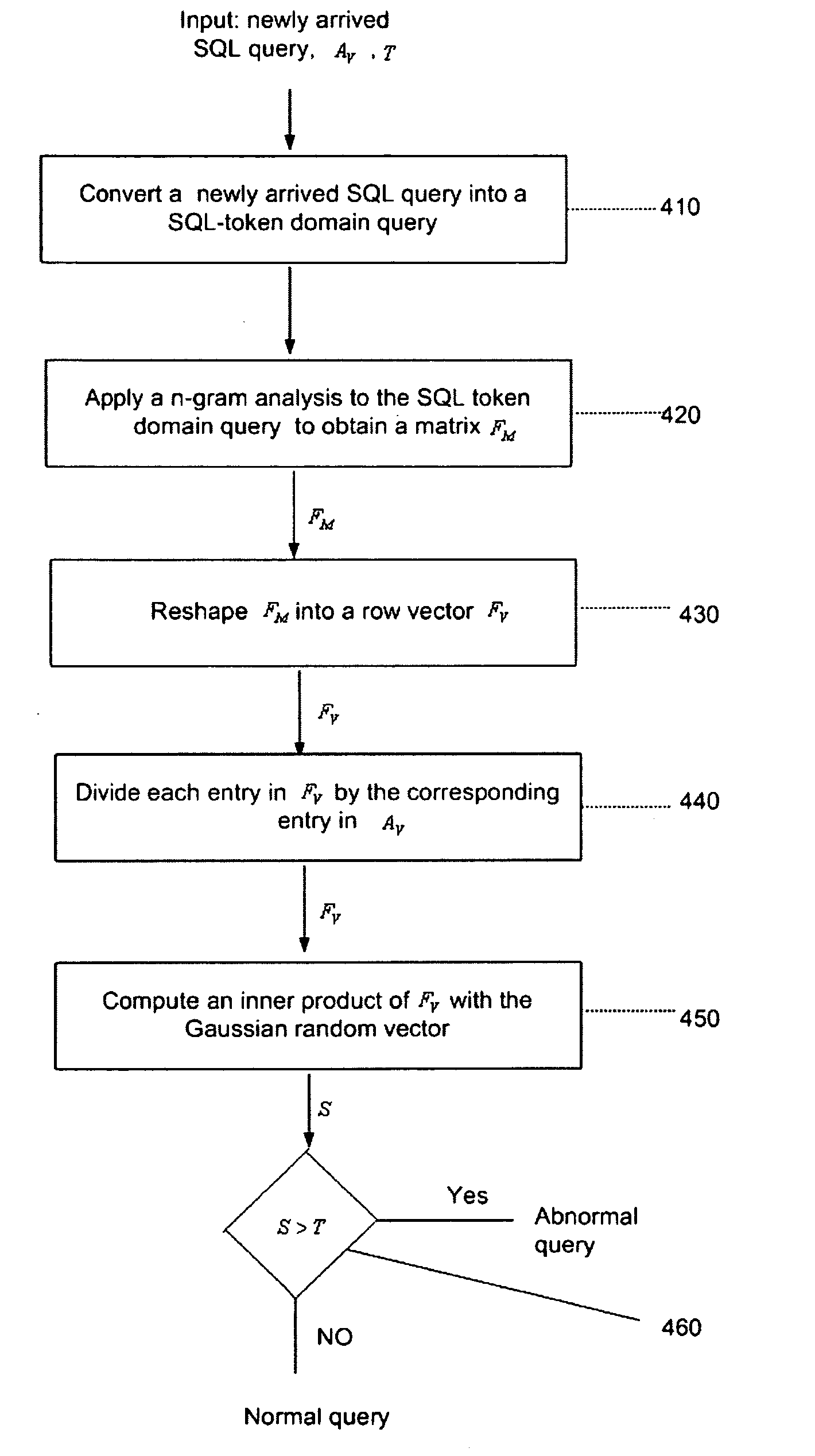
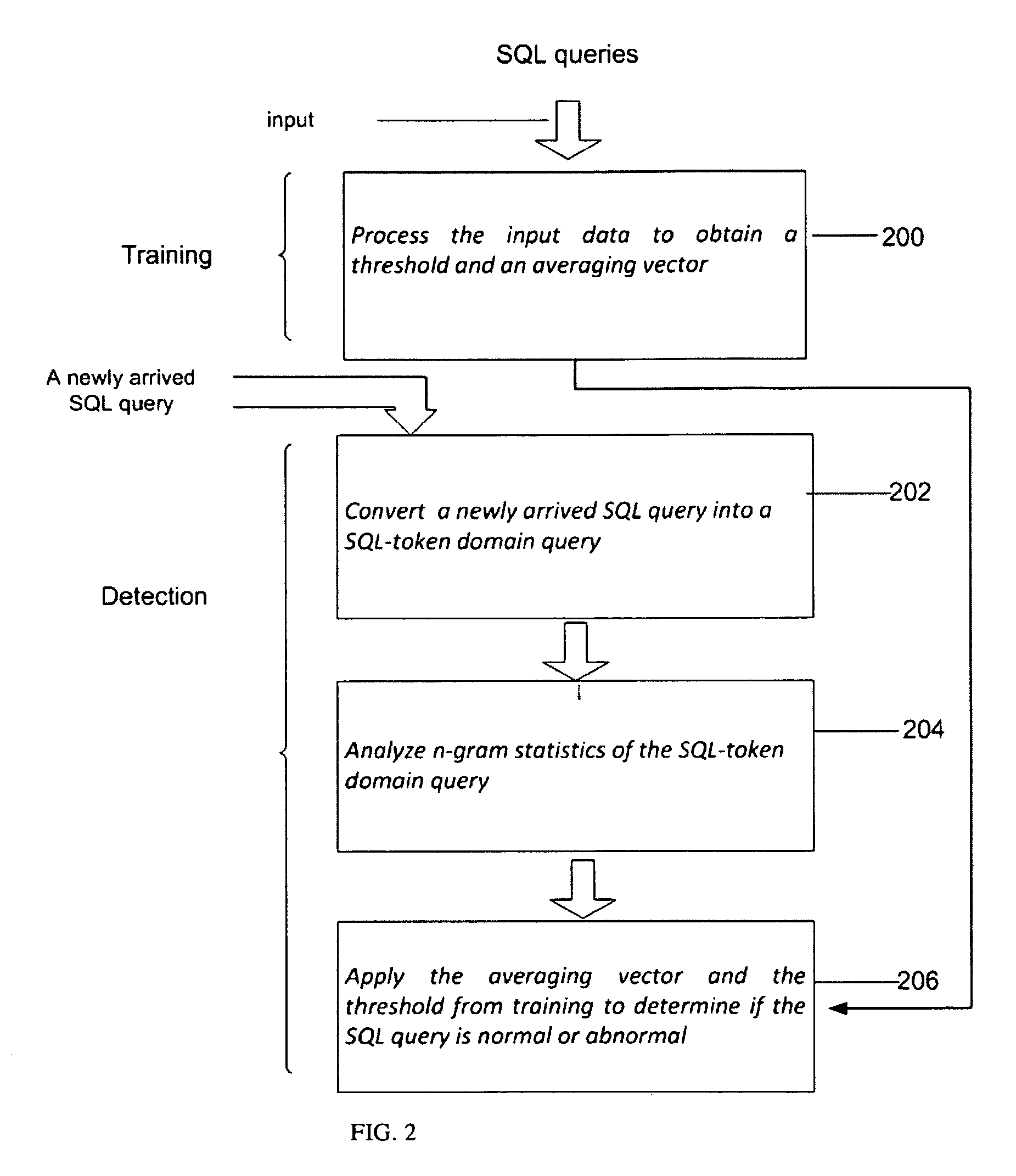
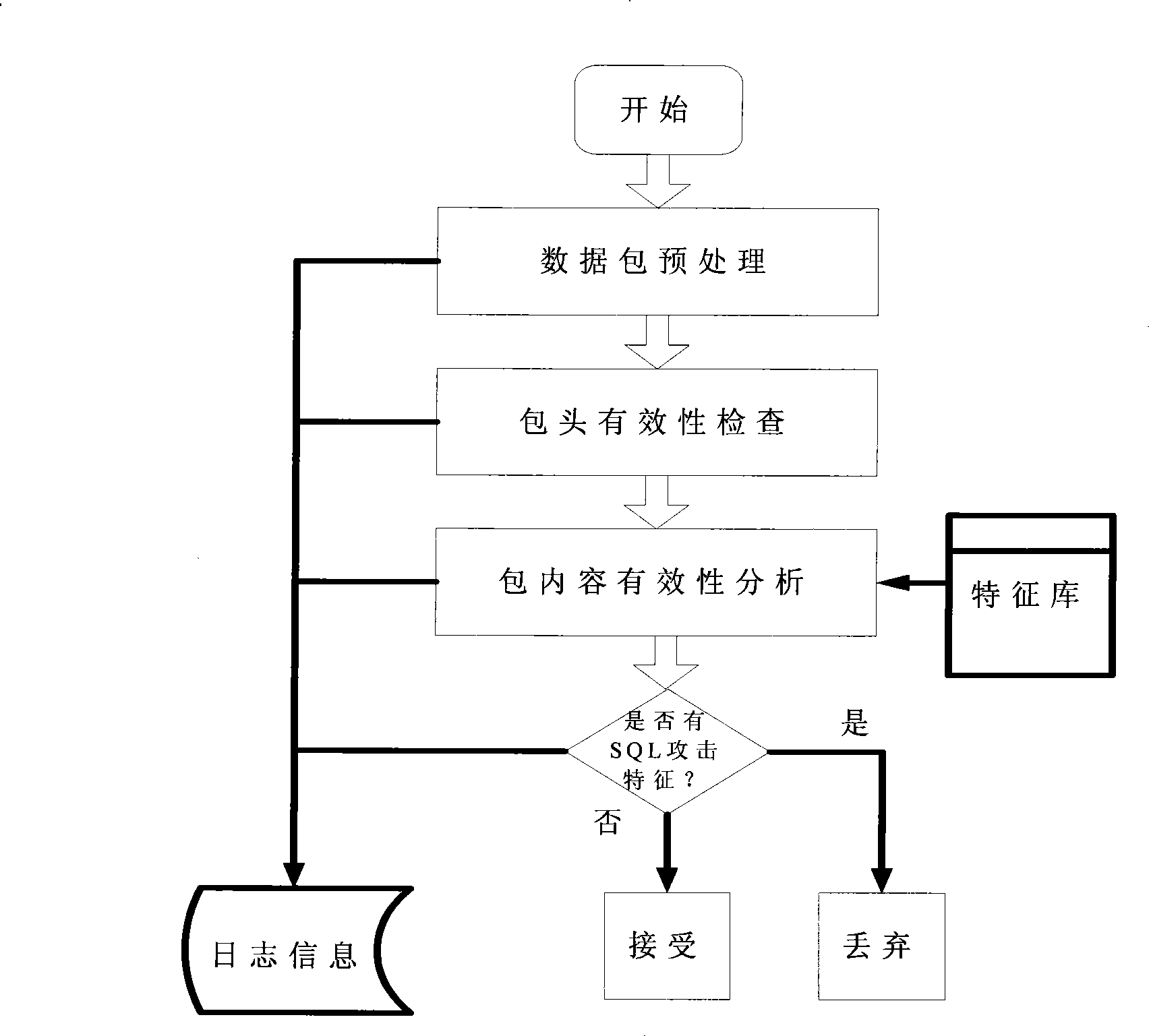
Anomaly-based detection of SQL injection attacks
InactiveUS8225402B1Reduce dimensionalityFailure can not be detectedMemory loss protectionError detection/correctionTraining phaseSQL injection
Owner:AVERBUCH AMIR +2
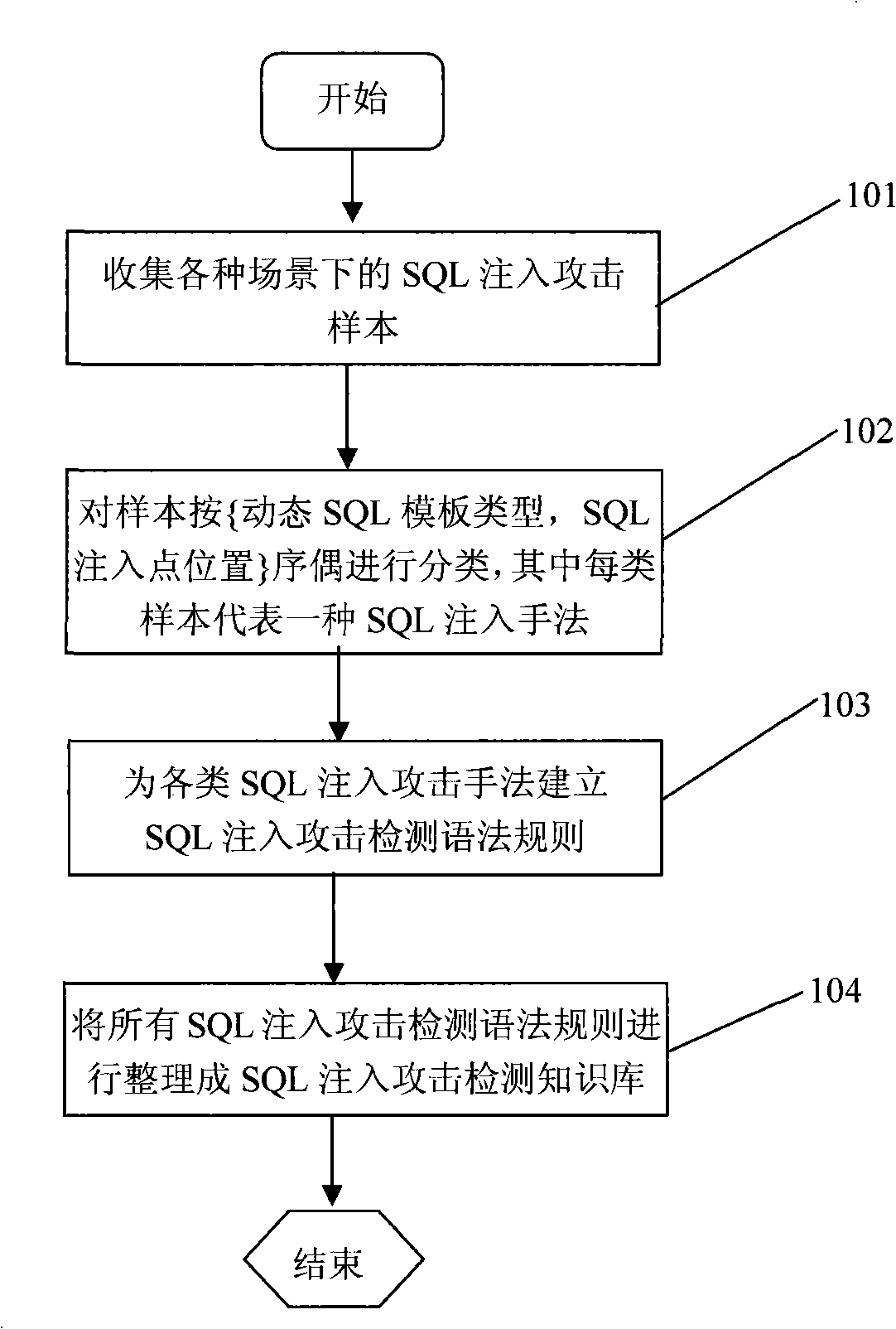
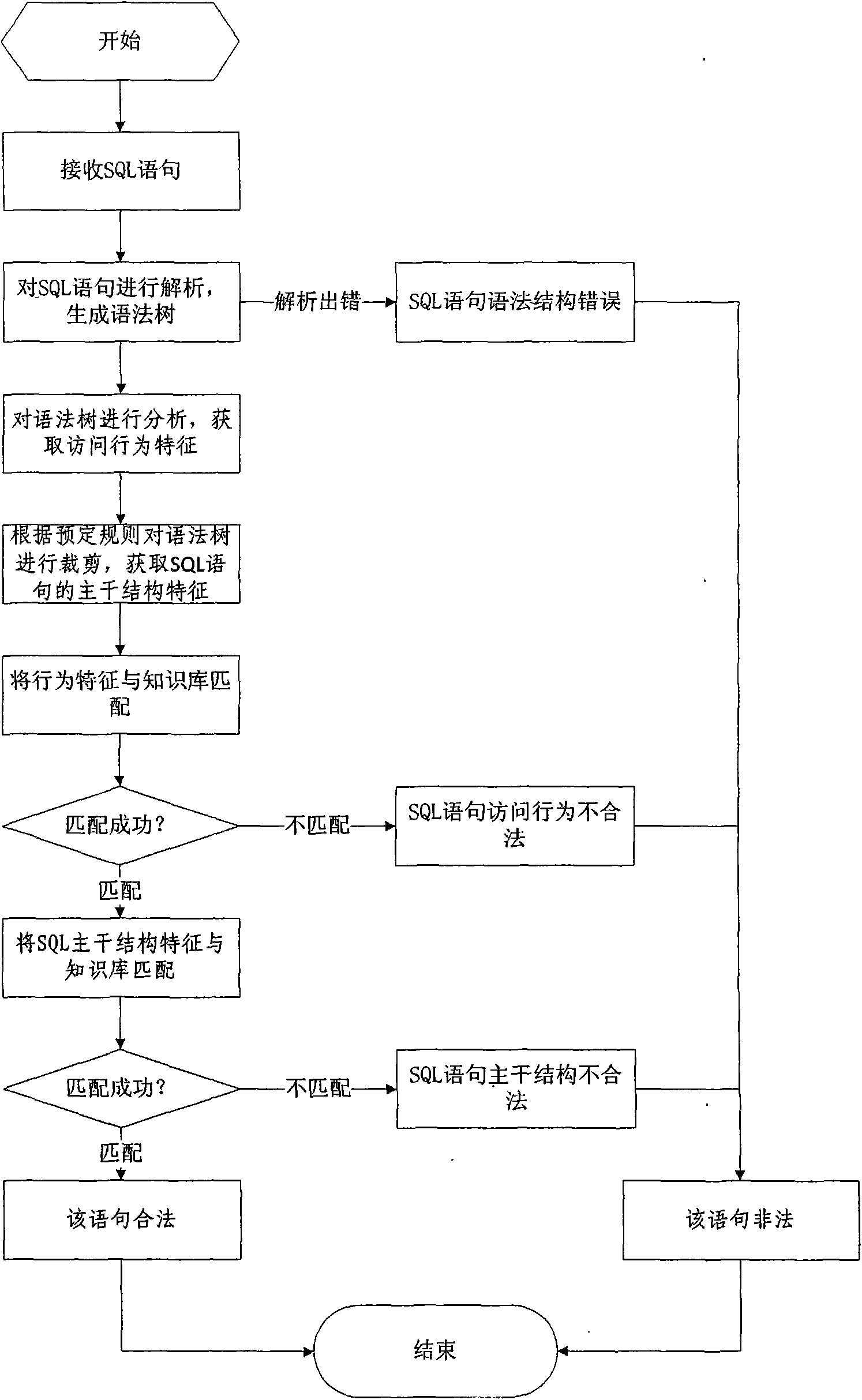
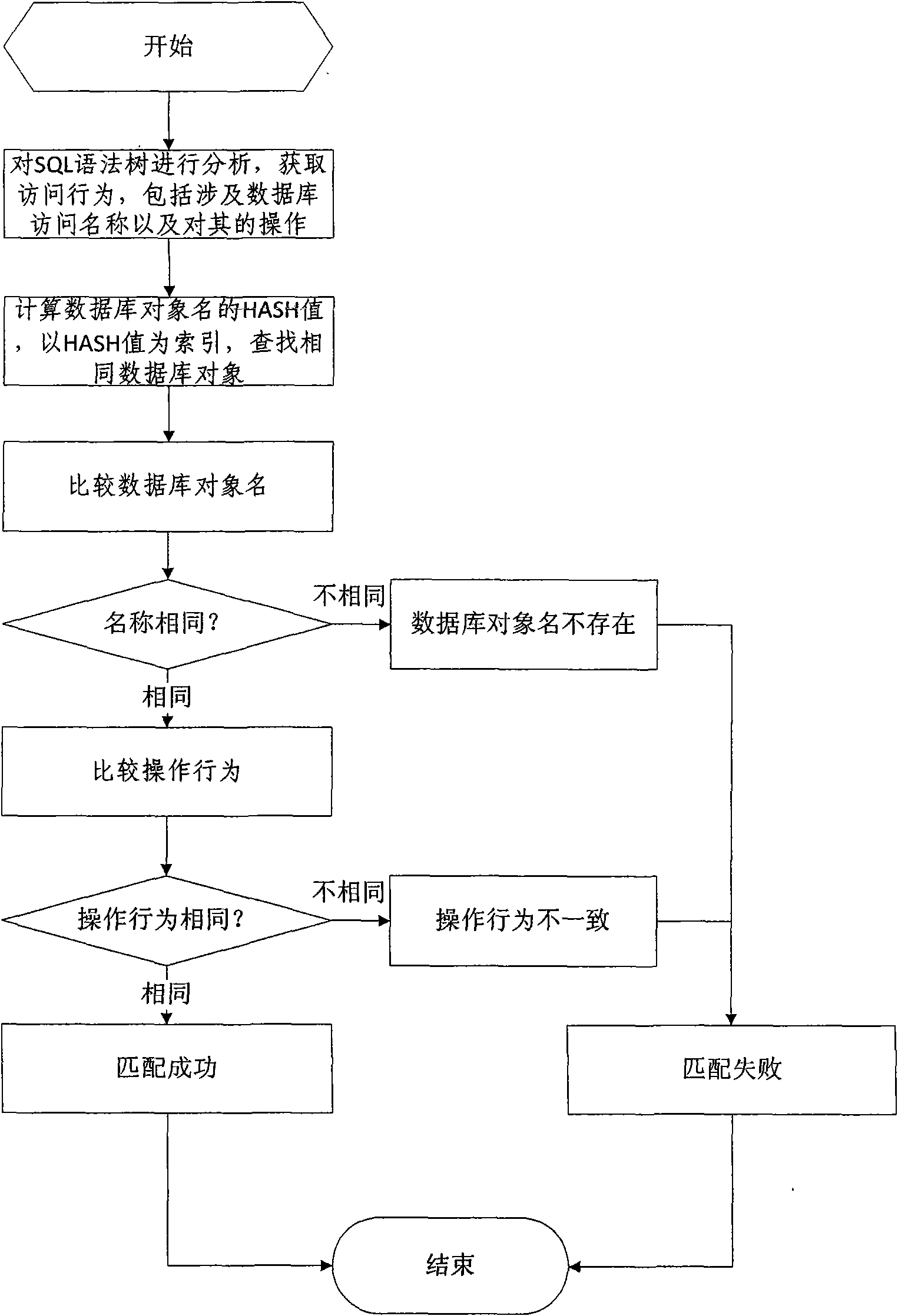
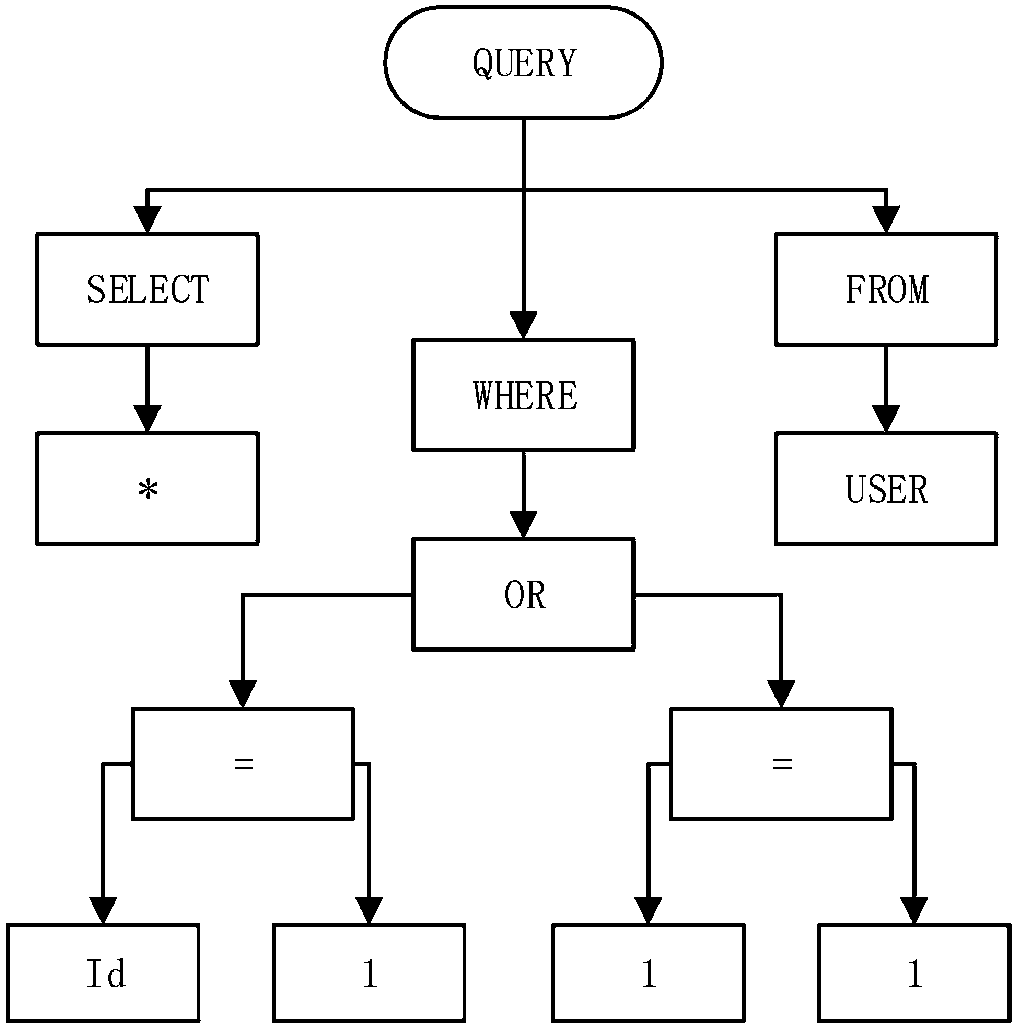
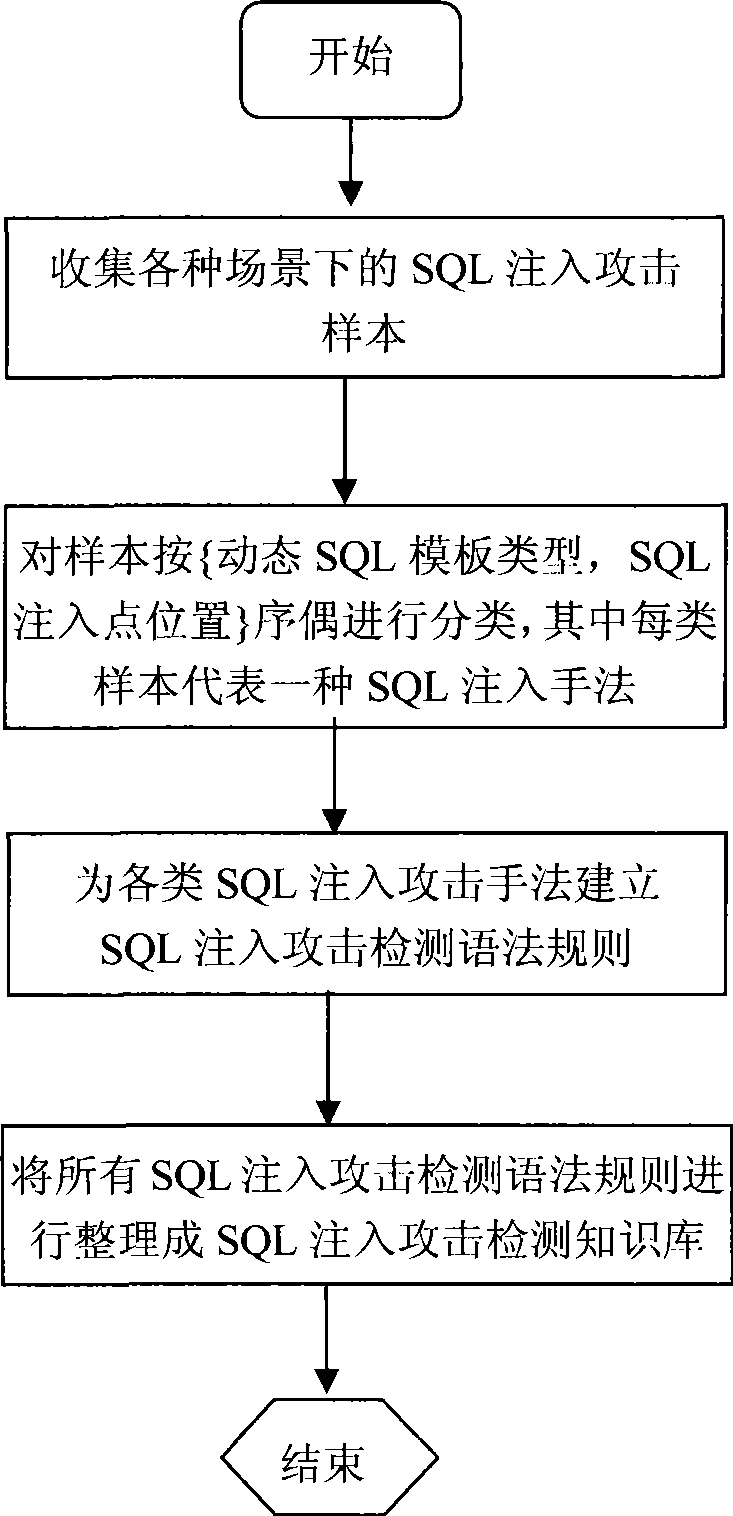
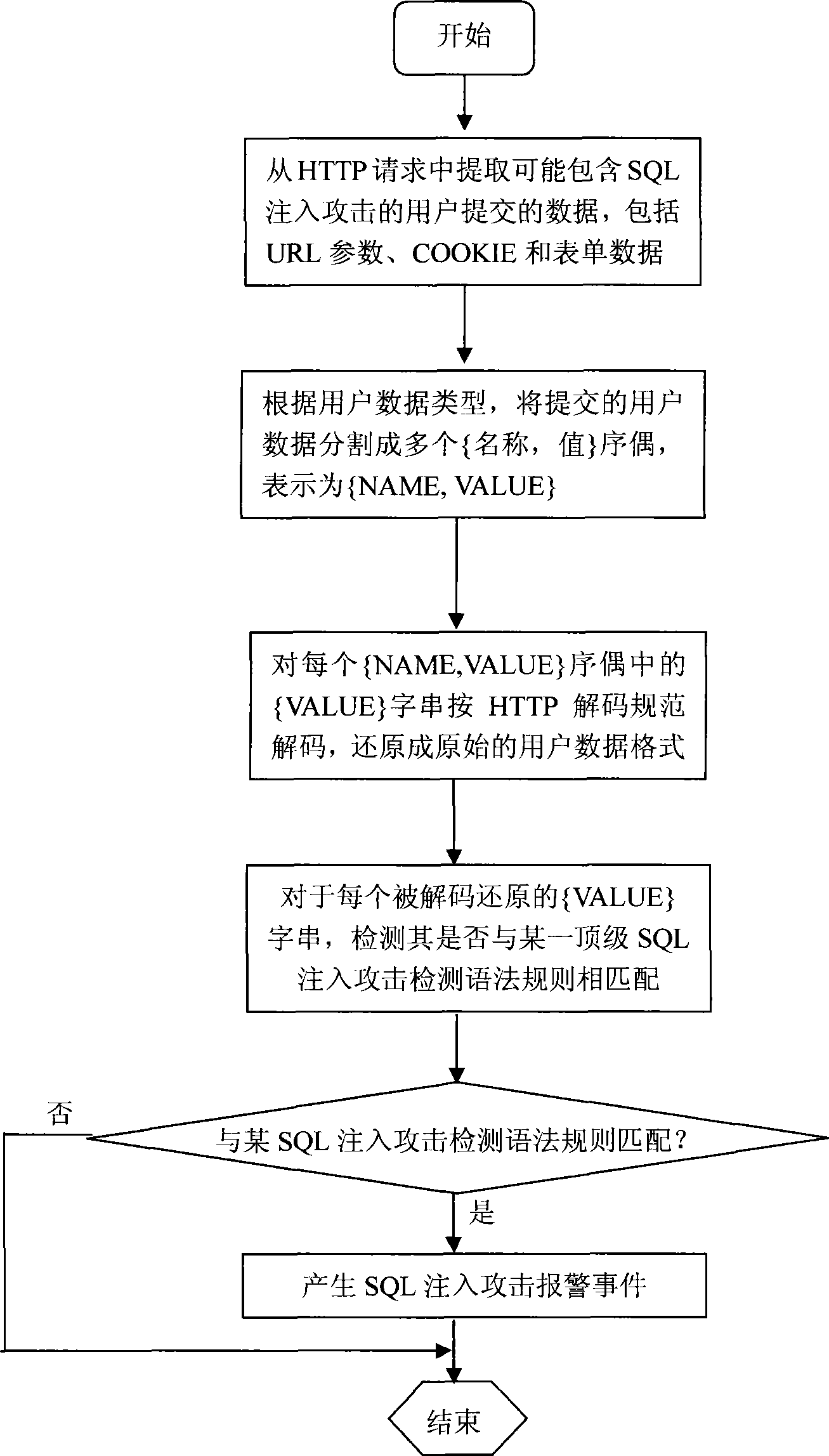
A SQL injection attack detection method and system
InactiveCN101267357AOvercoming difficult extractionOvercome shortcomings such as being easily deceivedUser identity/authority verificationData switching networksSQL injectionUser input
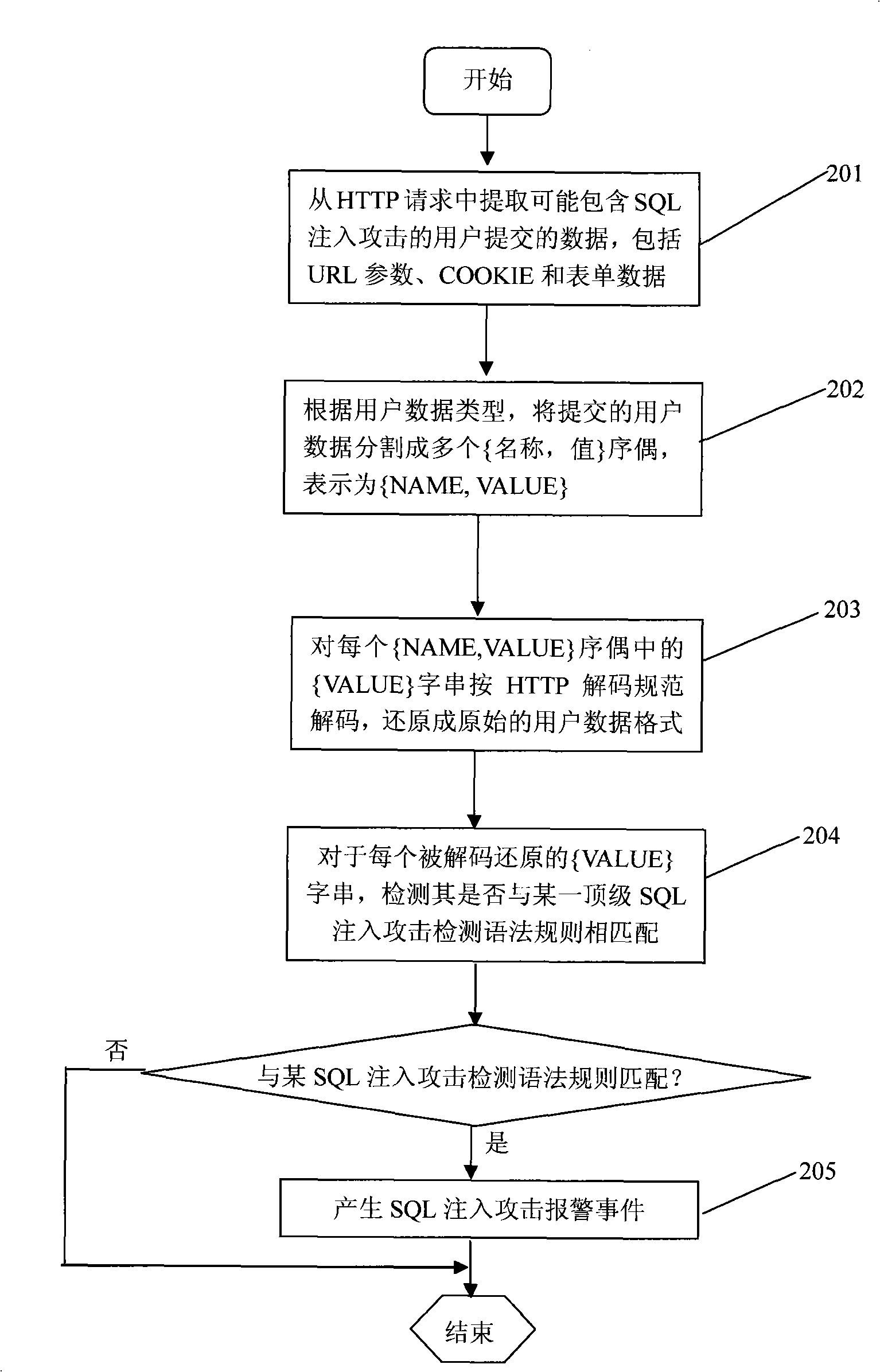
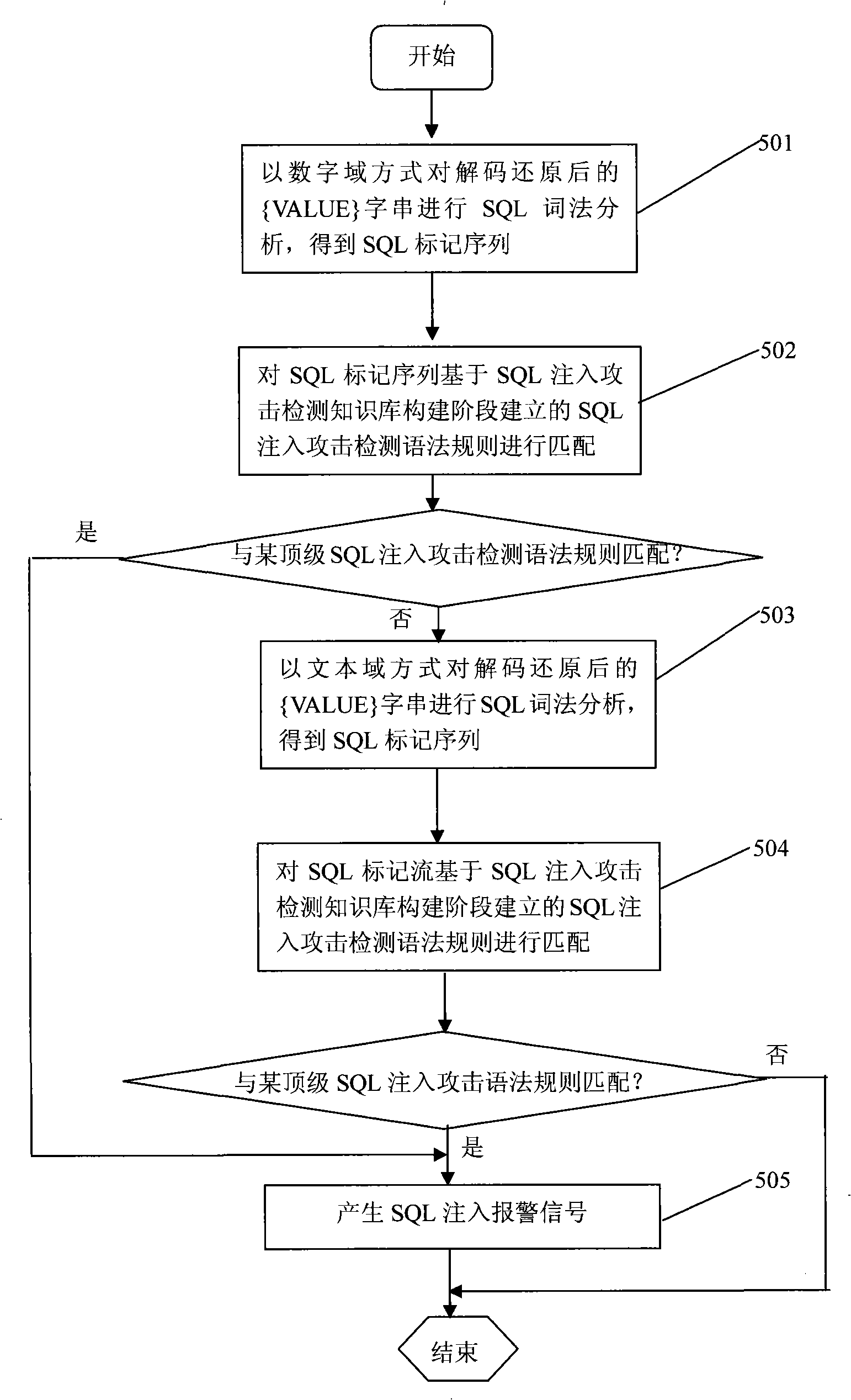
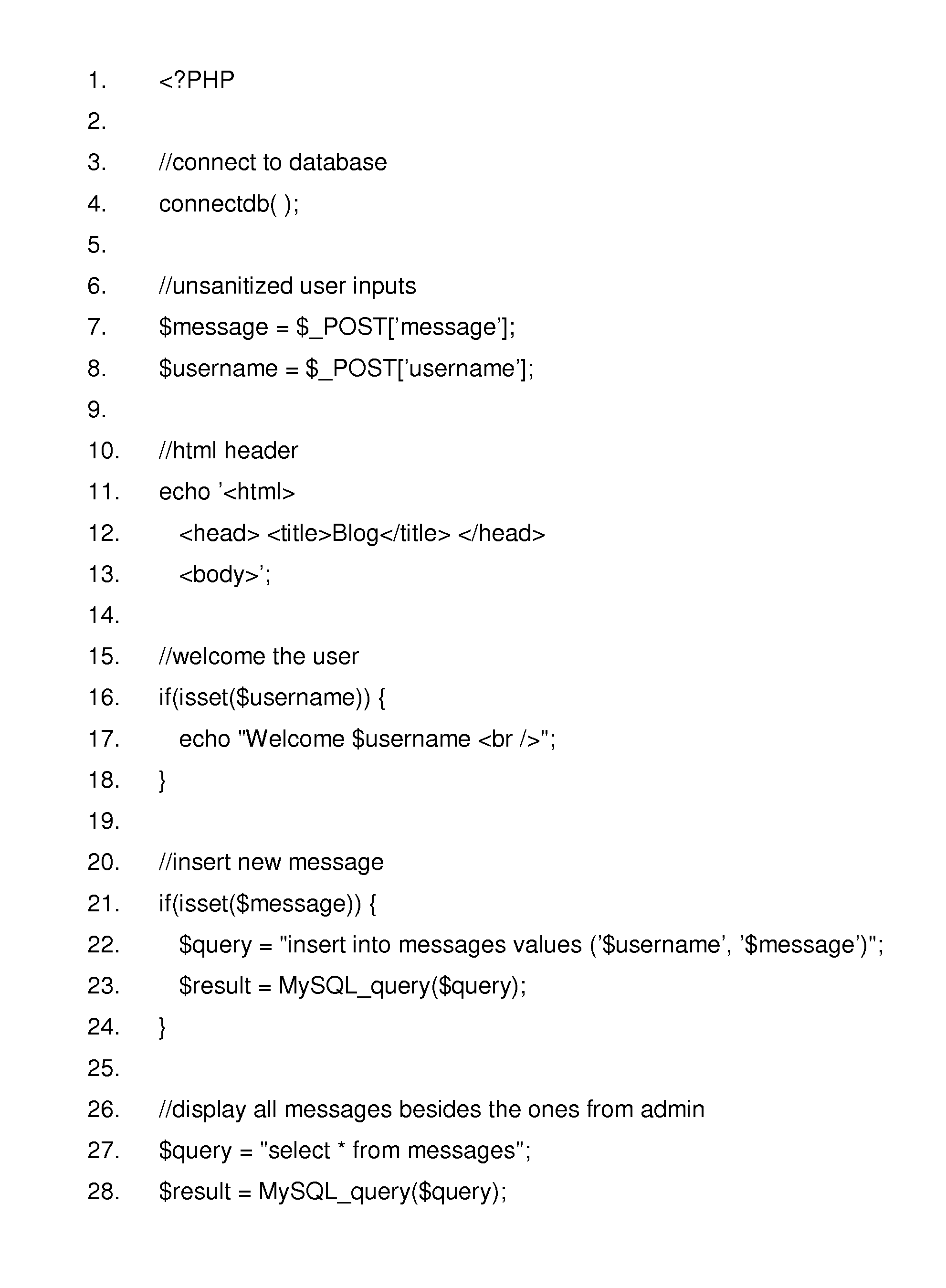
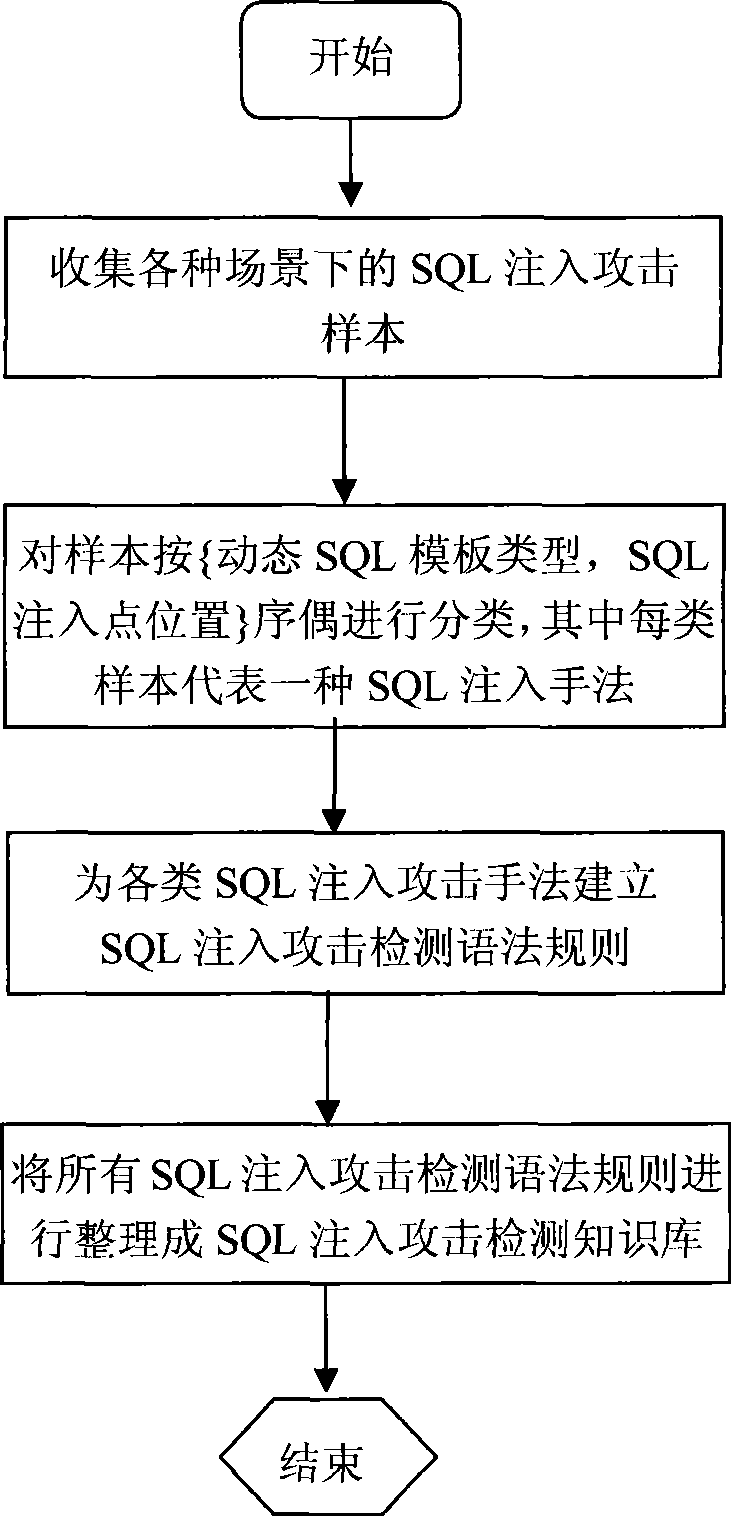
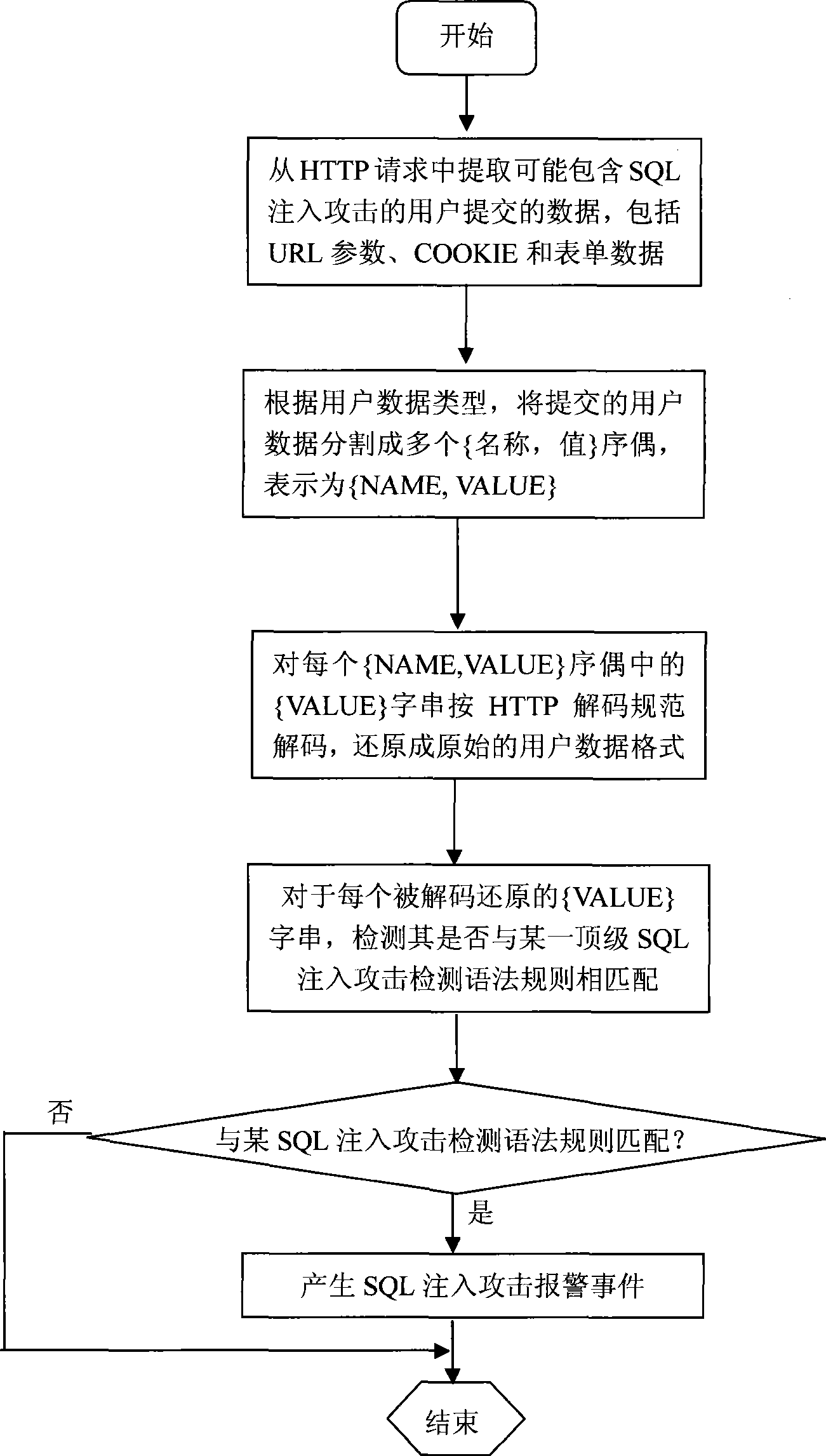
An SQL injection attack detecting method and system are provided, comprising building phase of SQL injection attack detecting knowledge base and detecting phase for real-time SQL injection attack. The build of SQL injection attack detecting knowledge base comprises collection of SQL injection attack sample for sorts of scenes, classification of SQL injection ways, and build of SQL injection attack detecting grammar rules aiming at sorts of SQL injection ways; the detecting phase for real-time SQL injection attack comprises extraction and decoding of user inputting data in HTTP request message and matching of the SQL injection attack detecting grammar rules and so on. This invention defines the SQL injection attack detecting grammar rules by using SQL grammar instead of defining the SQL injection attack detecting grammar rules based on the traditional attack characteristic. The invention overcomes shortcomings of uneasy extraction and inclined fraud of the attach characteristic sign of the SQL injection attack incident, which significantly reduces rate of wrong report and rate of missing report while invading the detecting system for detecting SQL injection attack.
Owner:BEIJING VENUS INFORMATION TECH
Complementary Character Encoding for Preventing Input Injection in Web Applications
InactiveUS20110252475A1Reduce overheadPreventing executionMemory loss protectionError detection/correctionSQL injectionLexical analysis
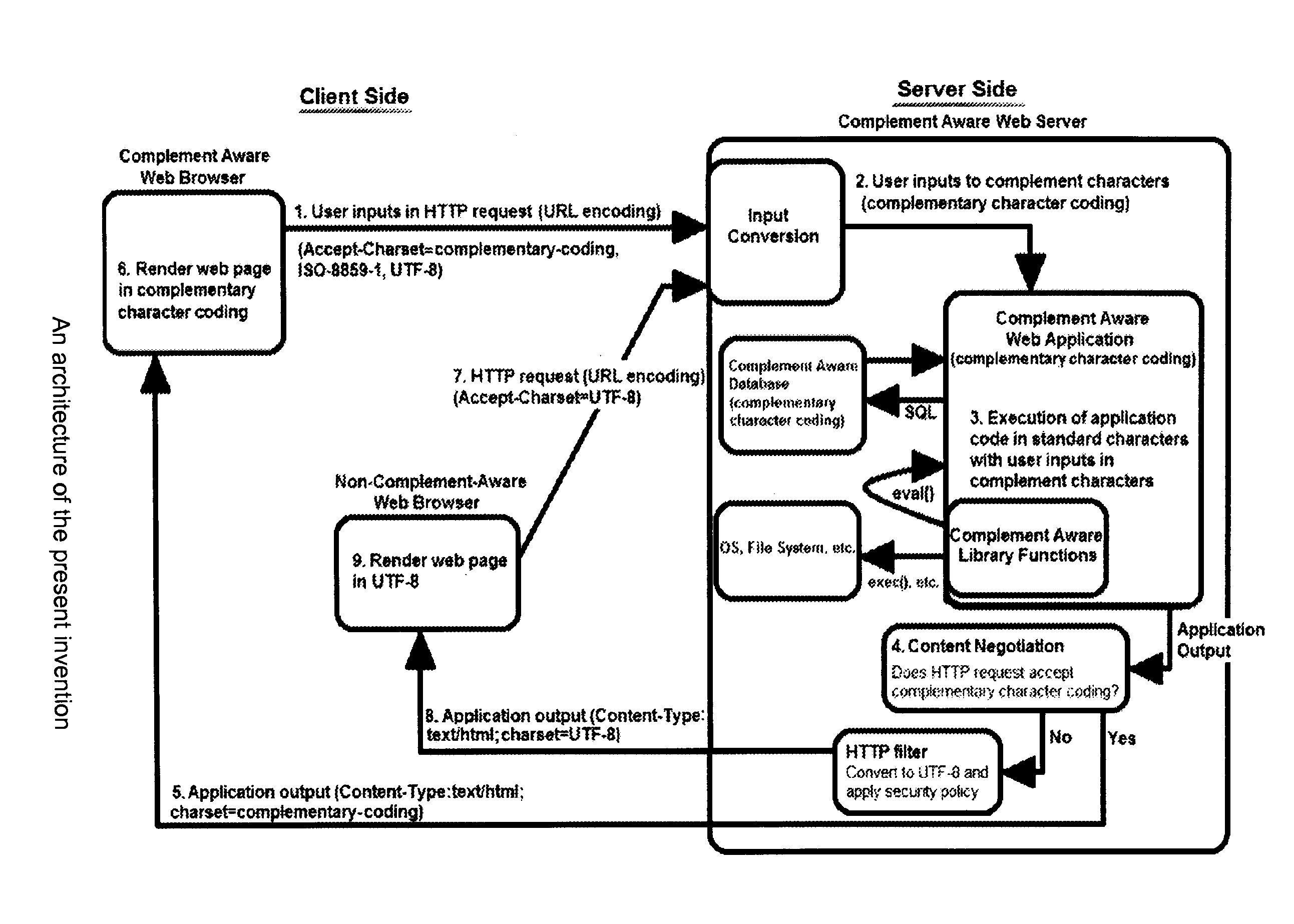
Method to prevent the effect of web application injection attacks, such as SQL injection and cross-site scripting (XSS), which are major threats to the security of the Internet. Method using complementary character coding, a new approach to character level dynamic tainting, which allows efficient and precise taint propagation across the boundaries of server components, and also between servers and clients over HTTP. In this approach, each character has two encodings, which can be used to distinguish trusted and untrusted data. Small modifications to the lexical analyzers in components such as the application code interpreter, the database management system, and (optionally) the web browser allow them to become complement aware components, capable of using this alternative character coding scheme to enforce security policies aimed at preventing injection attacks, while continuing to function normally in other respects. This approach overcomes some weaknesses of previous dynamic tainting approaches by offering a precise protection against persistent cross-site scripting attacks, as taint information is maintained when data is passed to a database and later retrieved by the application program. The technique is effective on a group of vulnerable benchmarks and has low overhead.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
Database SQL infusion protecting method based on self-learning
InactiveCN101609493AOvercome false negativesOvercome the False Positive FlawComputing modelsDigital data protectionLearning basedSQL injection
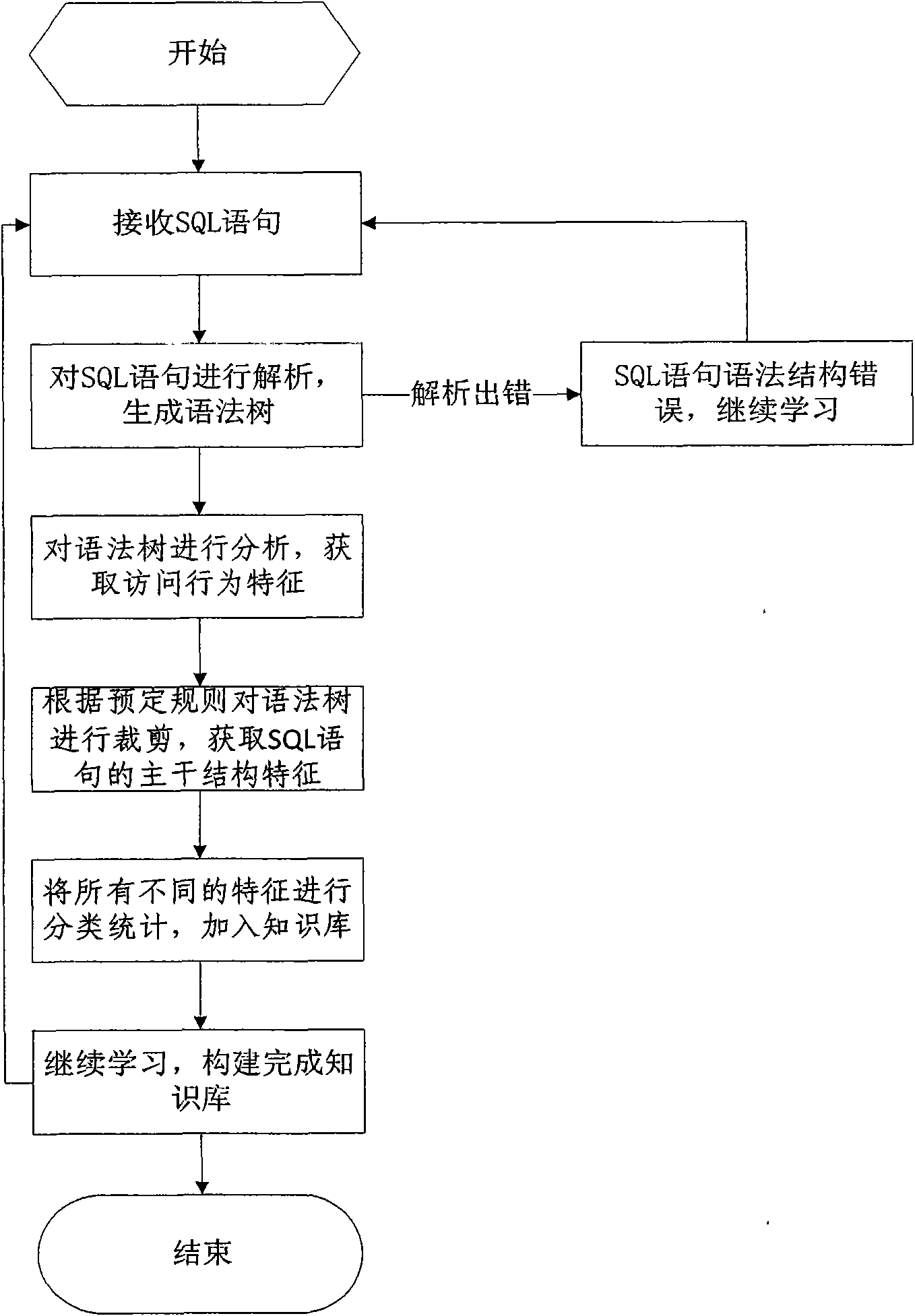
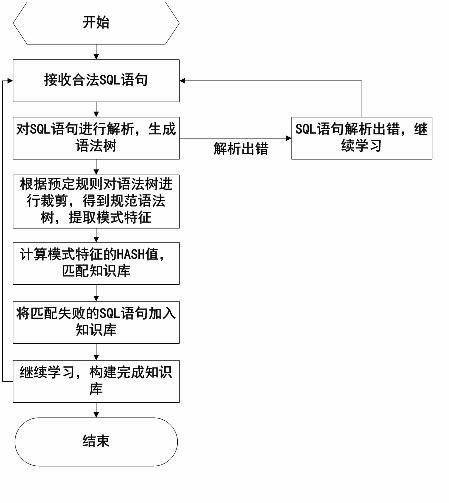
The invention discloses a database SQL infusion protecting method based on self-learning, comprising a learning phase and a filtering phase. The learning phase works in safe environment. At the moment, all SQL sentences are legitimate SQL sentences generated by an application system. A knowledge model (knowledge base) of the legitimate SQL sentences can be constituted by analyzing the sentences as well as analyzing and summarizing the characteristics of the sentences on the basis of sentence analysis results. The filtering phase works in real environment. At the moment, all SQL sentences are assumed to be possibly illegitimate SQL sentences. The sentences undergo pattern matching with the knowledge base established in the safe environment. If the matching is successful, the sentences are legitimate SQL sentences, otherwise, the sentences are illegitimate SQL sentences. The database SQL infusion protecting method has the advantage that an SQL infusion protecting system based on learning the legitimate SQL sentences can greatly reduce the false report rate and missing report rate which are caused by traditional SQL infusion protection, and the defending capability of the whole system can be improved.
Owner:STATE GRID ELECTRIC POWER RES INST +1
Database security auditing method
InactiveCN104484474APreventive actionsDiscover usability in timePlatform integrity maintainanceSpecial data processing applicationsSQL injectionNetwork Communication Protocols
The invention relates to a database security auditing method which comprises the following steps: acquiring database network communication data; parsing a database network communication protocol; carrying out self-learning digging on audit rules; detecting database risk event invasion; evaluating database user permissions; tracking the three-layer correlation of a primary user. The database security auditing method can be used for auditing and monitoring a database in real time, so that the automatic assessment, audit, protection and invasion detection operation can be realized; the method can be used for preventing, recording and tracking the complete database operation behavior so as to help an administrator to find out the internal safety problems of unauthorized use, privilege abuse, permission theft and the like of the database in time; furthermore, after the method is used, the outside attacks such as SQL (structured query language) injection and the like can be avoided.
Owner:NANJING DUNLEI NETWORK TECH CO LTD
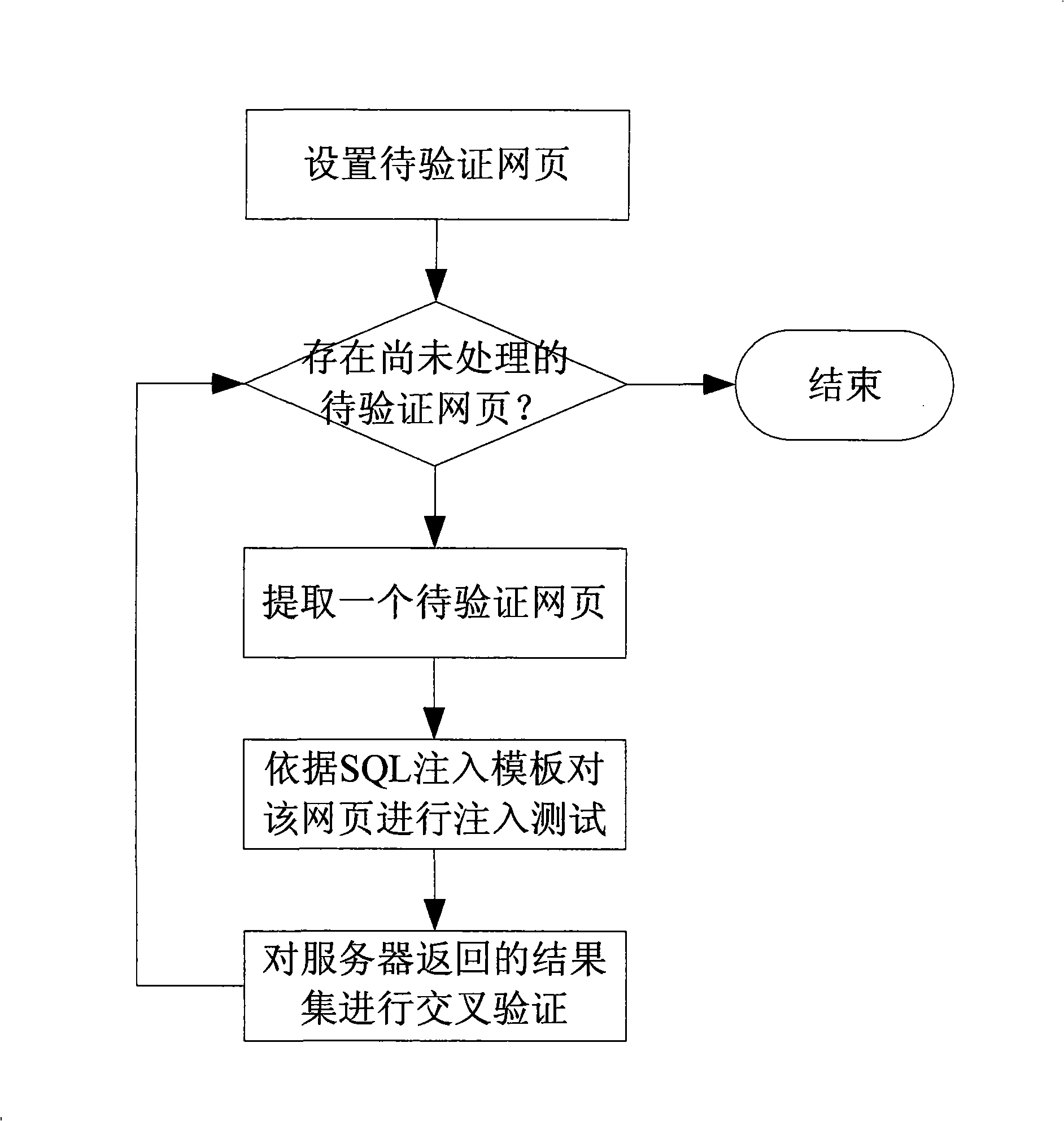
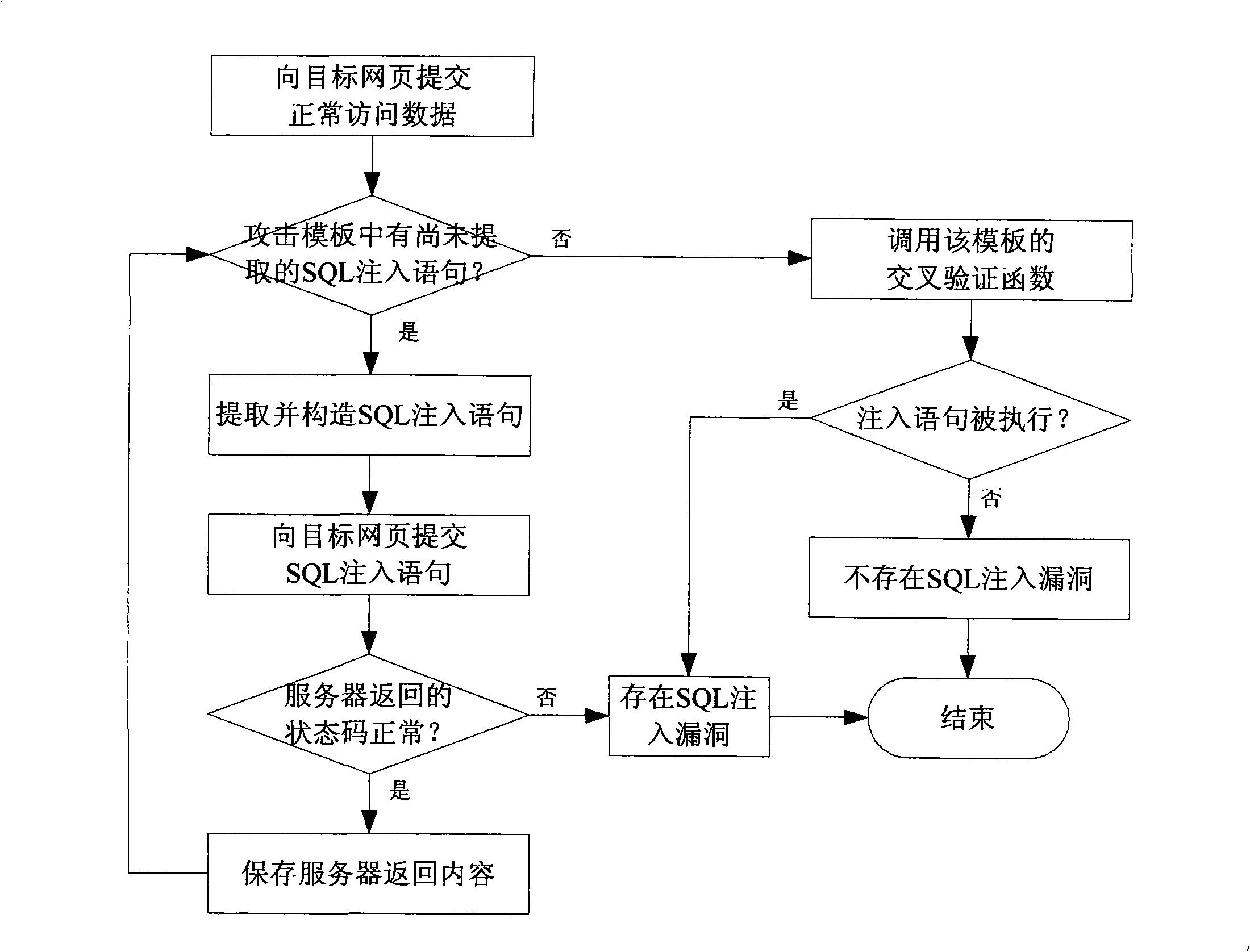
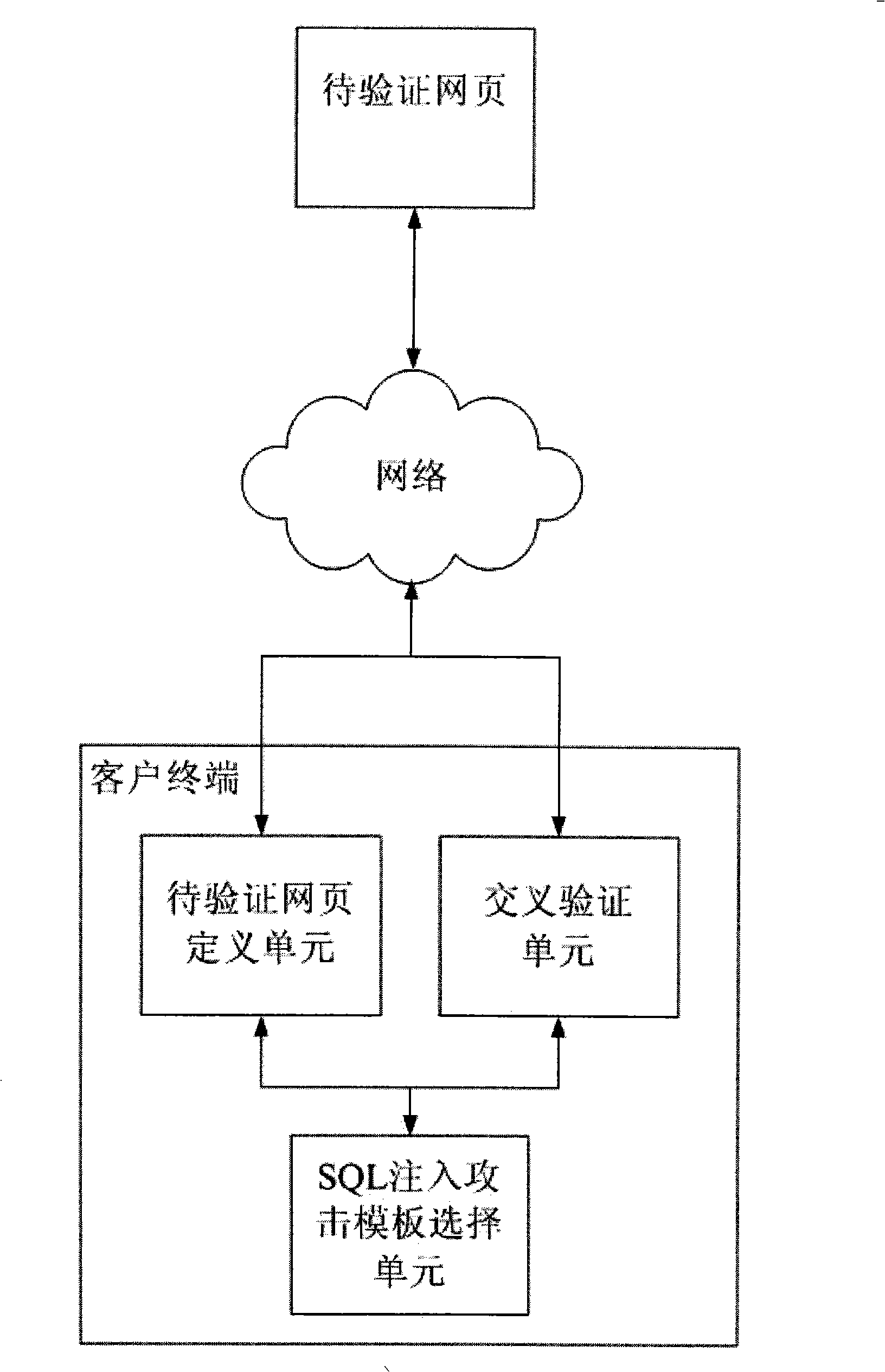
Detection method and system for SQL injection loophole
The invention discloses a key technique-SQL injection vulnerability detection technique of a host vulnerability scanning system as one important product for network security. The SQL injection vulnerability detection technique is characterized by submitting normal access request data and different types of SQL injection data to a server, receiving results returned by the server, then cross-comparing the returned results of different requests, and further determining exists of SQL injection vulnerabilities from the processing of submitted data by the server according to the compared results. To-be-certified website addresses are defined by means of website crawler, browser plug-in and manual input. One or a plurality of attacking templates of four different types of attacking templates can be selected to detect exists of SQL injection vulnerabilities on the to-be-certified websites. And the exists of SQL injection vulnerabilities during processing the user-submitted data by the server can be judged through cross-comparing the returned results of the normal access requests and SQL injection statements, under the condition that the server shields error information.
Owner:BEIJING VENUS INFORMATION TECH
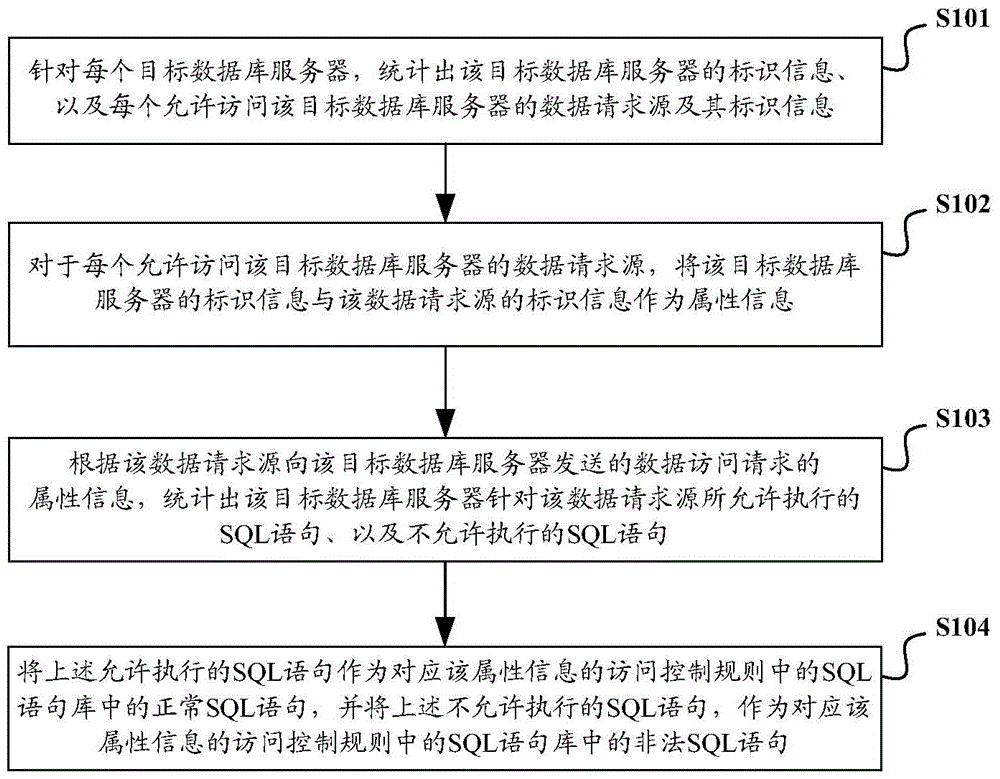
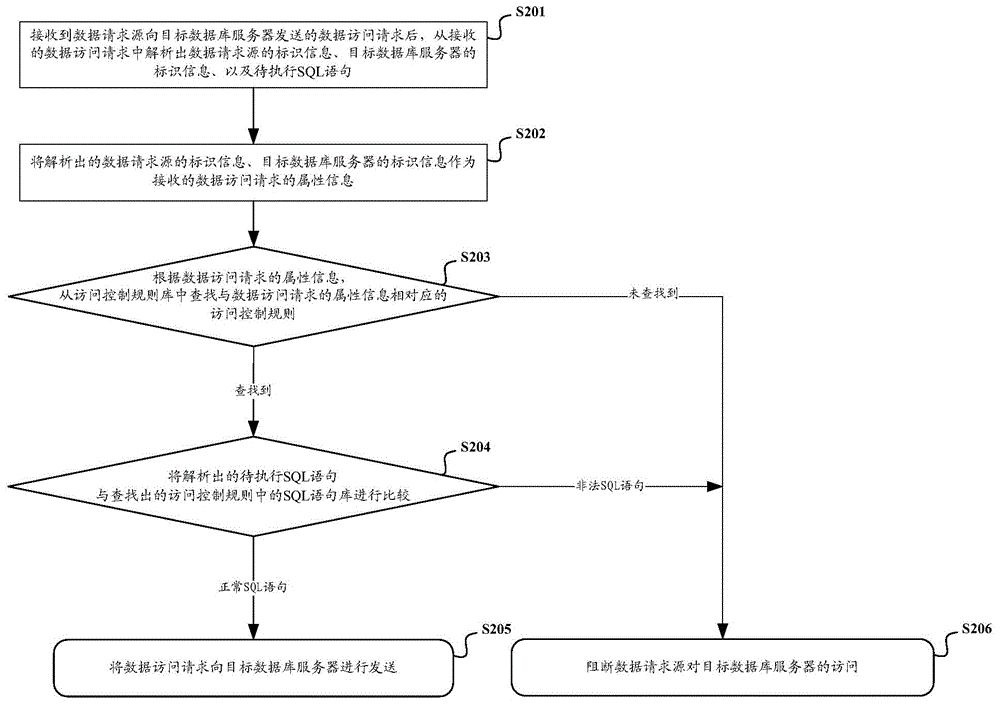
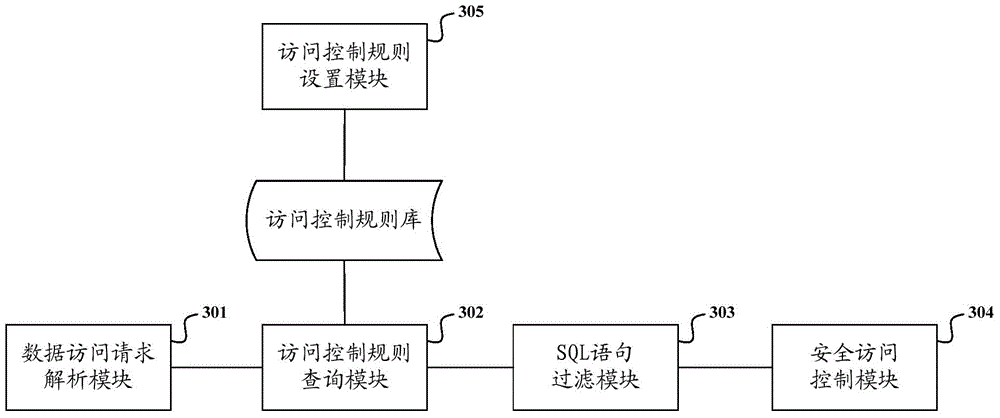
Database security access control method and system
InactiveCN104008349AHigh strengthDigital data protectionSpecial data processing applicationsSQL injectionDatabase server
The invention discloses a database security access control method and system. The method comprises the steps of: analyzing a to-be-executed SQL (Structured Query Language) statement in a data access request sent from a data request source to a target database server and analyzing label information of the data request source and label information of the target database server to serve as attribute information of the data access request; comparing the to-be-executed SQL statement with an SQL statement library in an access control rule after the access control rule corresponding to the attribute information is found in the access control rule library based on the attribute information; if the comparison result is that the to-be-executed SQL statement is an illegal SQL statement in the SQL statement library, interdicting the access of the data request source to the target database server. By the application of the database security access control method and system, SQL injection attacks can be prevented, and security control intensity of a database system is enhanced.
Owner:STATE GRID CORP OF CHINA +3
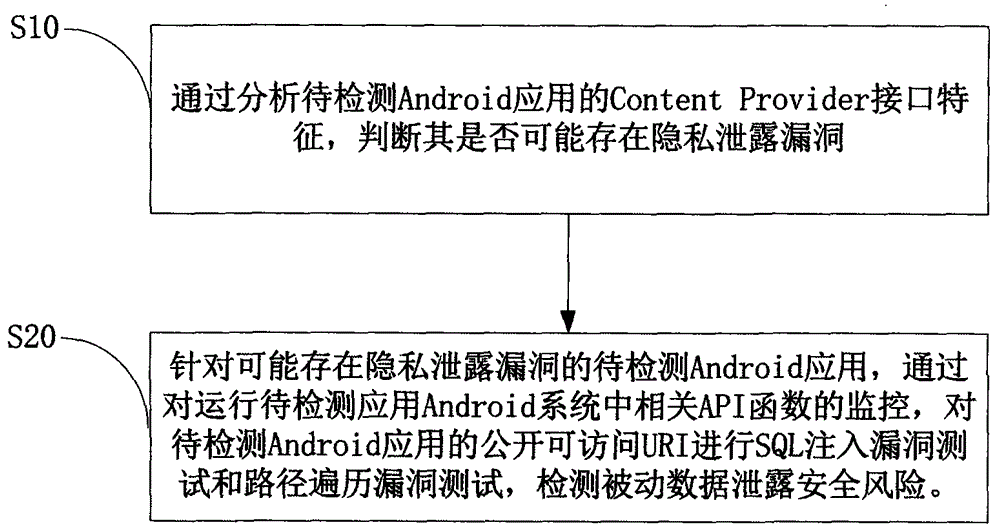
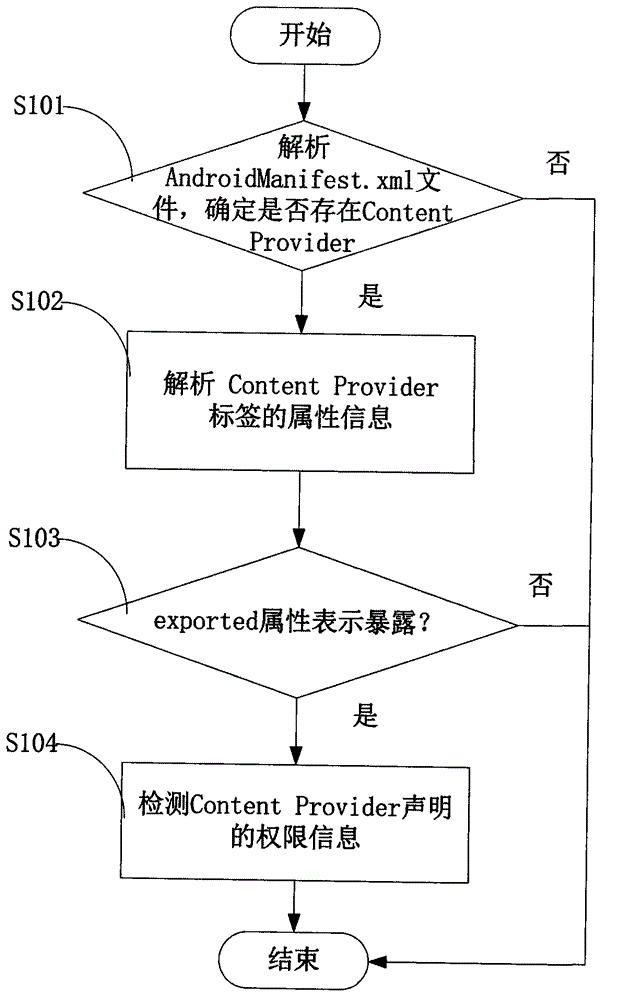
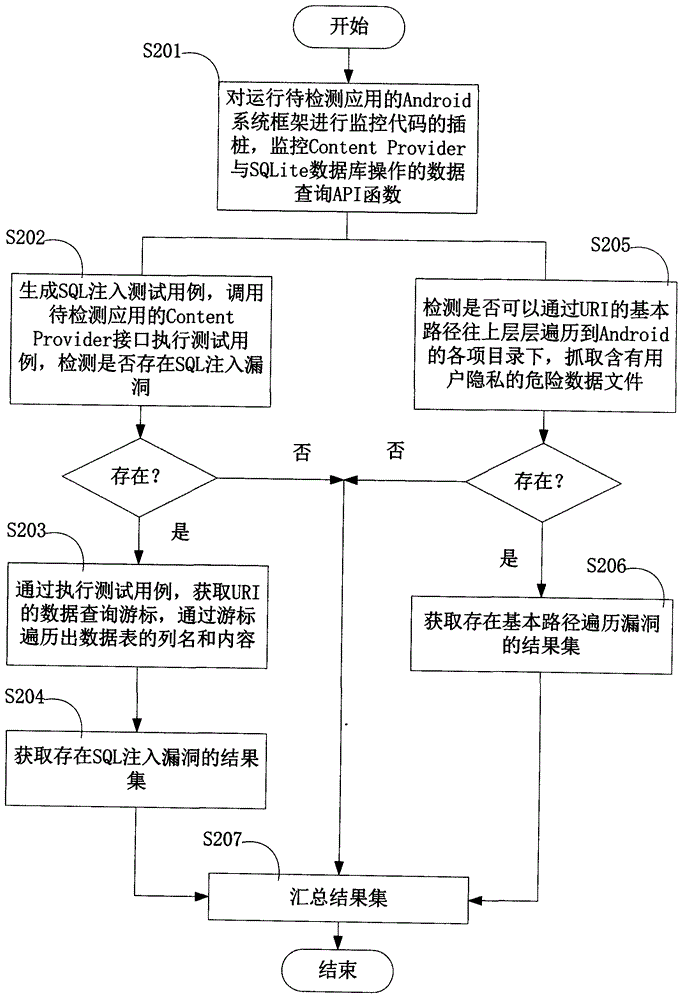
Android application vulnerability detection method and Android application vulnerability detection system
InactiveCN103984900AAvoid false positivesEfficient discoveryPlatform integrity maintainanceSQL injectionUniform resource identifier
The invention provides an Android application vulnerability detection method which comprises the following steps: 1, judging whether a privacy leakage vulnerability possibly exists or not by virtue of analyzing Content Provider interface characteristics of a to-be-detected Android application; 2, if the privacy leakage vulnerability possibly exists, performing an SQL (Structured Query Lanaguge) injection vulnerability test and a path traversal vulnerability test on a public accessible URI (Uniform Resource Identifier) of the to-be-detected Android application which possibly has the privacy leakage vulnerability by virtue of monitoring a related API (Application Program Interface) function in an Android system, and then detecting passive data leakage safety risks. The invention also provides an Android application vulnerability detection system. The method and the system can be used for rapidly discovering privacy leakage and data pollution vulnerabilities possibly existing in the Android application, avoiding misdeclaration, and providing a powerful support for discovering the privacy leakage and data pollution vulnerabilities in the Android application on a large scale.
Owner:南京赛宁信息技术有限公司 +1
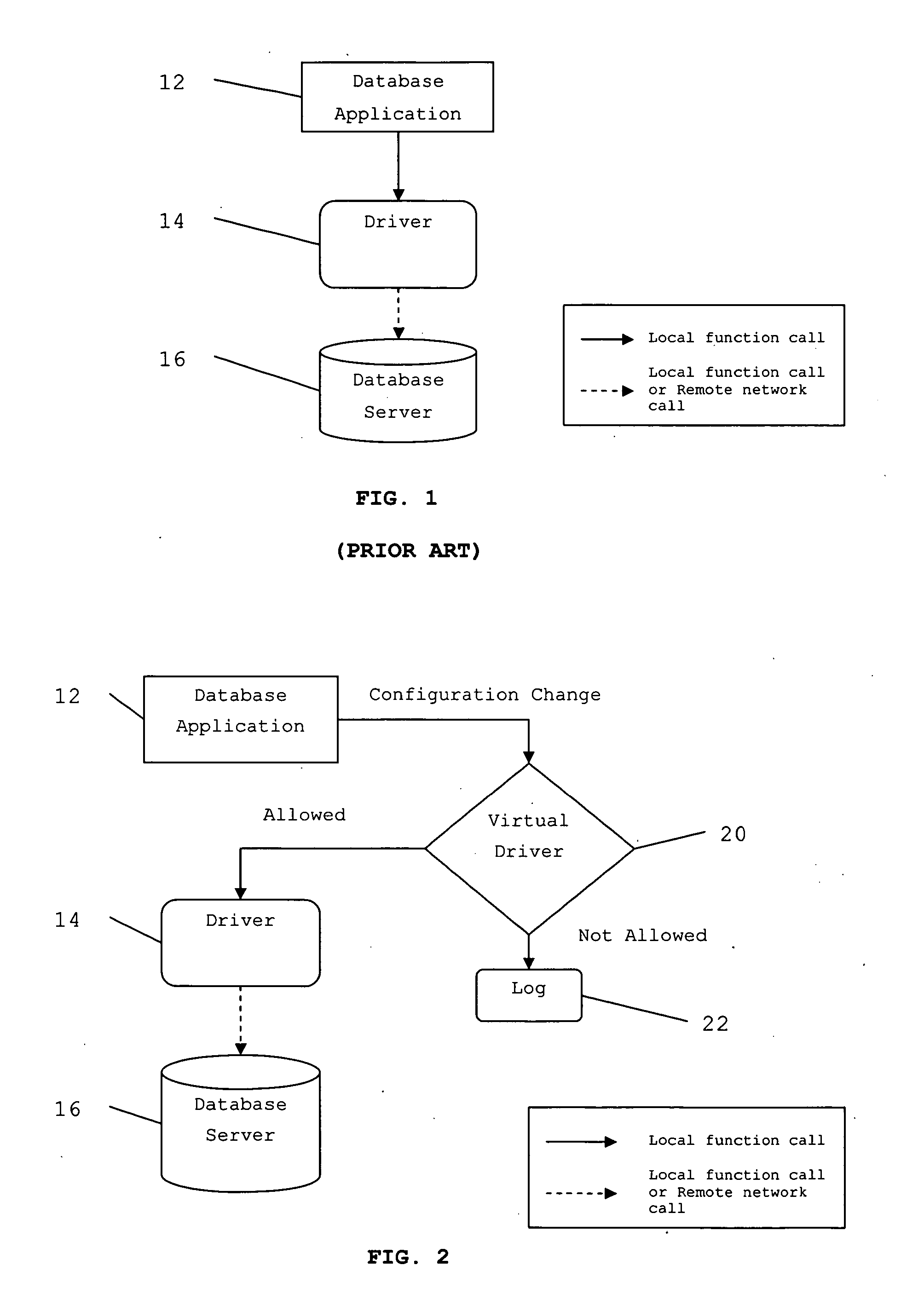
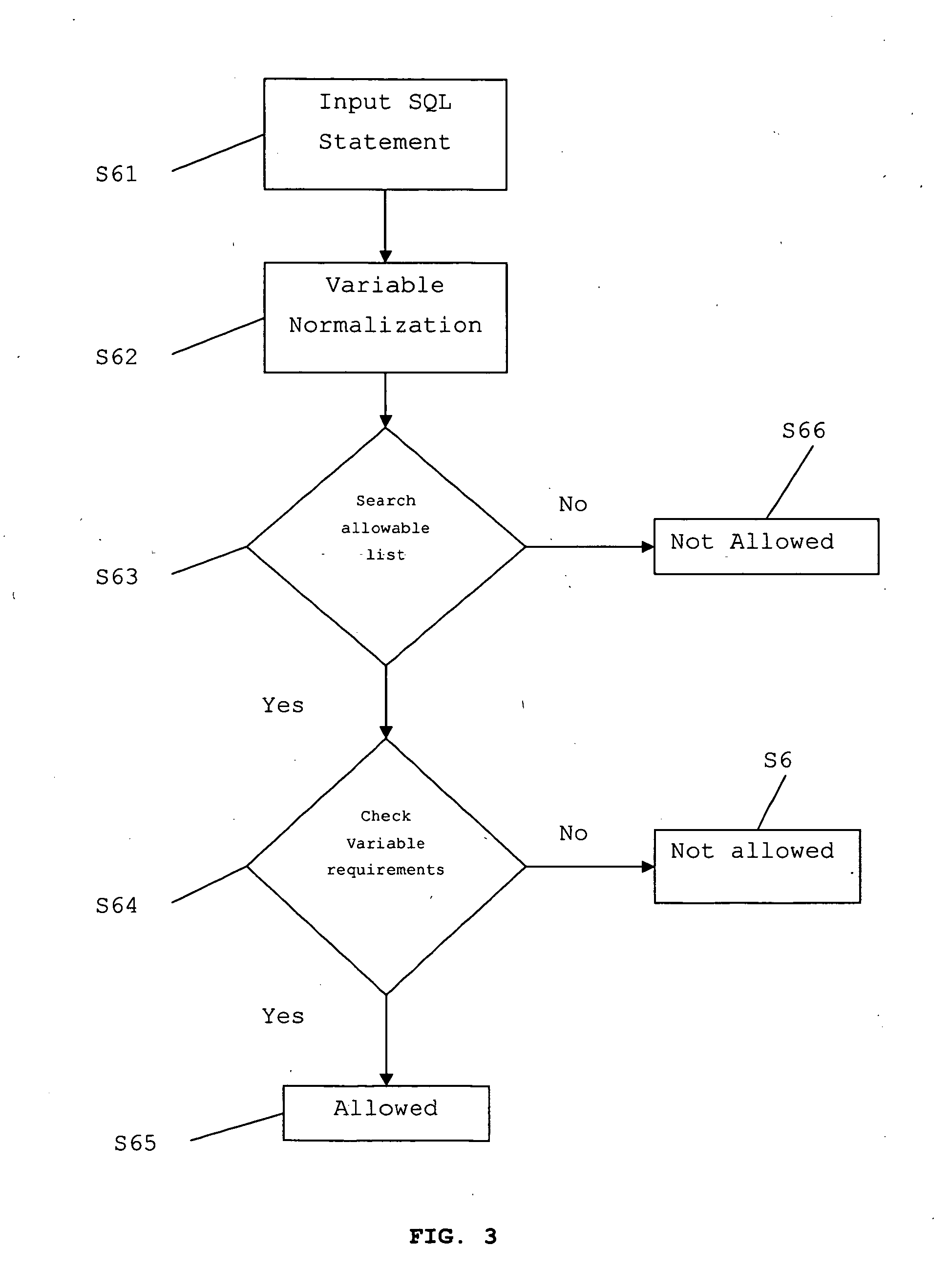
SQL injection protection by variable normalization
InactiveUS20060212438A1Digital data information retrievalSpecial data processing applicationsSQL injectionQuery language
The invention provides a method for determining allowability of a structured query language (SQL) statement, the method comprising the steps of normalizing the SQL statement, and comparing the normalized SQL statement with a predetermined set of allowable statements.
Owner:NG MING SUM SAM
Attack prevention system based on structured query language (SQL)
ActiveCN101448007AImprove accuracyNo false positivesData switching networksSpecial data processing applicationsFeature extractionApplication server
The invention provides a modified misuse-type structured query language (hereinafter referred as to SQL) attack defense system which is based on application system services and an SQL-injected characteristic extraction malicious attack behavior characteristic library and combined with the SQL request of the characteristic library to a user to carry out strict test and block the SQL request with the attack characteristics according to test results, so as to provide the security protection for the database and the corresponding audit record. The invention can be flexibly allocated to boundary defense devices, application servers, database servers and various security audit software, and the SQL attack behavior characteristic library can be updated at any time when the application environment is changed and a new attack type or normal behavior pattern appears.
Owner:CHINA ELECTRIC POWER RES INST +2
Method and device for identifying SQL injection attacks
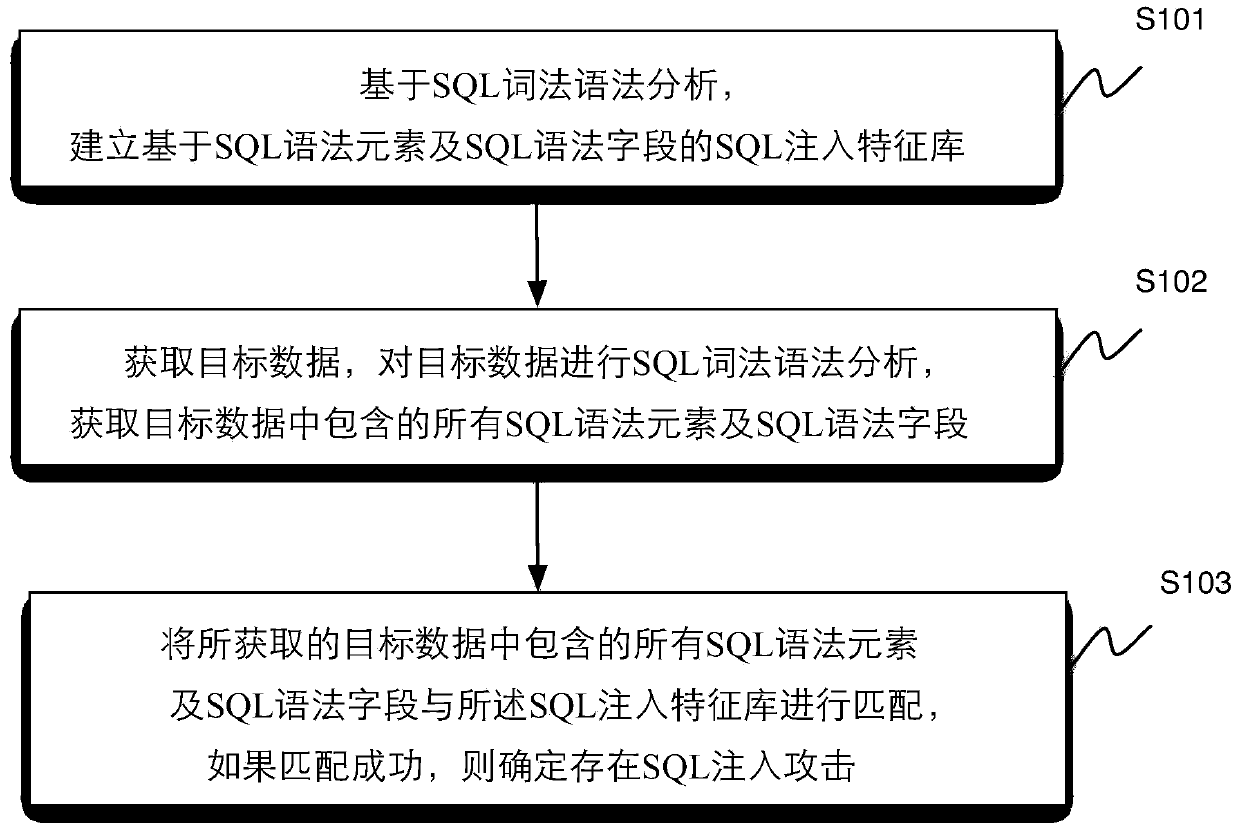
ActiveCN103744802AImprove efficiencyReduce false positivesUnauthorized memory use protectionMultiple digital computer combinationsSQL injectionMisinformation
The invention discloses a method and a device for identifying SQL (Structured Query Language) injection attacks, wherein the method comprises the steps of establishing an SQL injection feature library based on SQL syntax elements and SQL syntax fields through SQL lexical and syntactic analysis, obtaining target data, performing the SQL lexical and syntactic analysis on the target data and obtaining all SQL syntax elements and SQL syntax fields included in the target data, next, matching all of the obtained SQL syntax elements and SQL syntax fields included in the target data with the SQL injection feature library, and if matching is successful, determining the existence of the SQL injection attacks. The method and the device are capable of improving the efficiency of identifying SQL injection and reducing misinformation and failures in report.
Owner:BEIJING QIANXIN TECH
Website data tampering preventing method based on network isolation structure
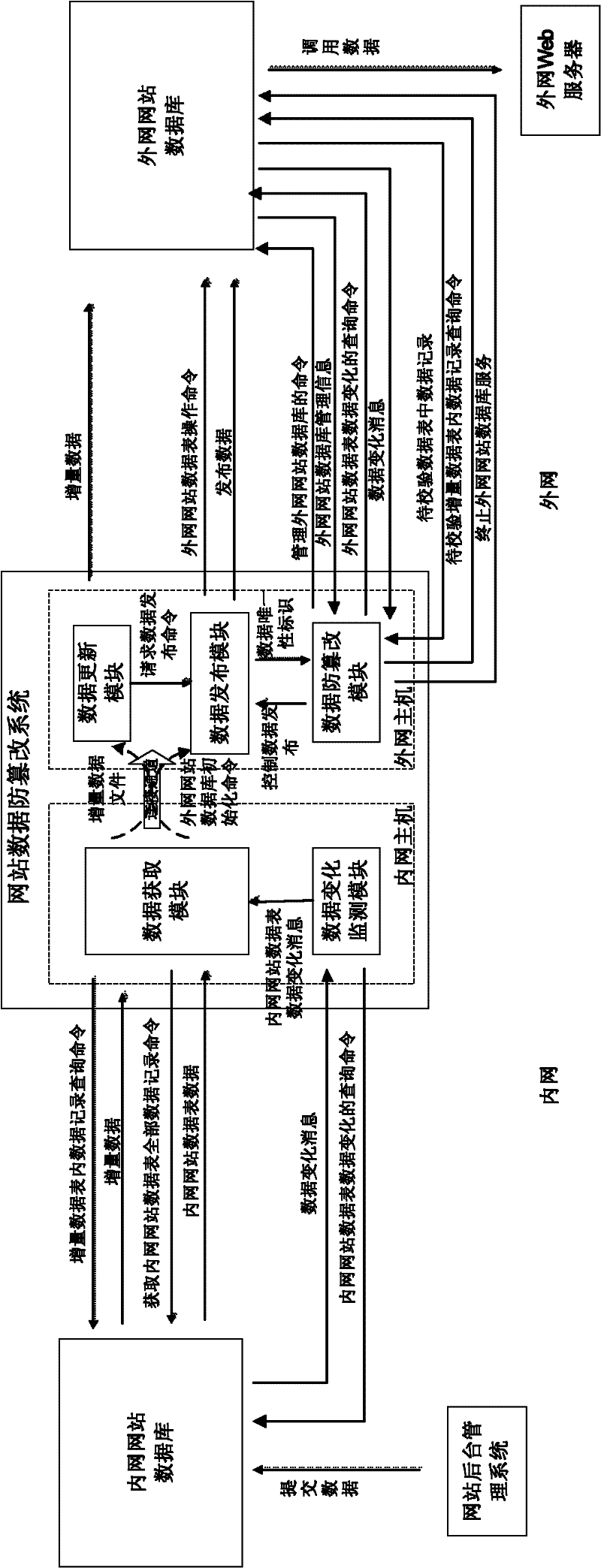
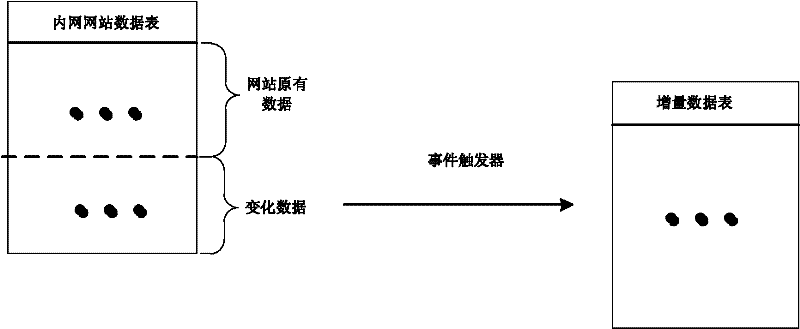
ActiveCN102609645AEnsure safetyPlatform integrity maintainanceSpecial data processing applicationsWeb siteSQL injection
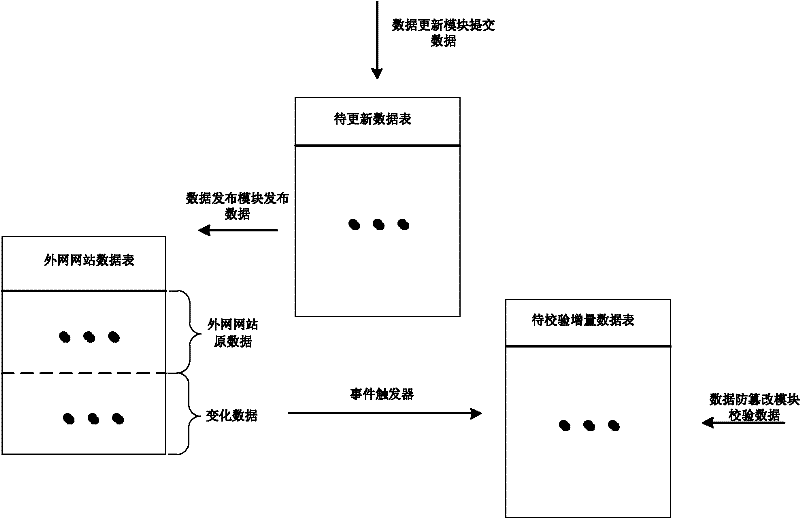
A website data tampering preventing method based on a network isolation structure belongs to the technical field of network safety. The website data tampering preventing method includes: disposing a database server storing website data to the high-safety-level network, publishing the content in a database to a database server of the low-safety-level network connected with the internet unidirectionally and protecting the website data in the low-safety-level network. Therefore, a website data tampering preventing system consisting of an intranet mainframe and an outer net mainframe which are connected to each other is built, in the outer net mainframe, a data updating module submits incremental data to a data sheet to be updated, and a data publishing module publishes the incremental data to an outer net website data sheet. A data tampering preventing module inquires system configuration and data variation in an incremental data sheet to be checked at regular time, starts corresponding operation when detecting data variation and ensures operations of the outer net website data sheet to be authorized. By the aid of the website data tampering preventing method based on the network isolation structure, attacks to the database, such as SQL (structured query language) injection and the like, can be effectively avoided and data safety of the website database is guaranteed.
Owner:北京中关村银行股份有限公司
Injection point extracting method in SQL (Structured Query Language) injection vulnerability detection
InactiveCN102831345AIncrease the analysis processSolve the problem of false positivesComputer security arrangementsSoftware testing/debuggingFiltrationSQL injection
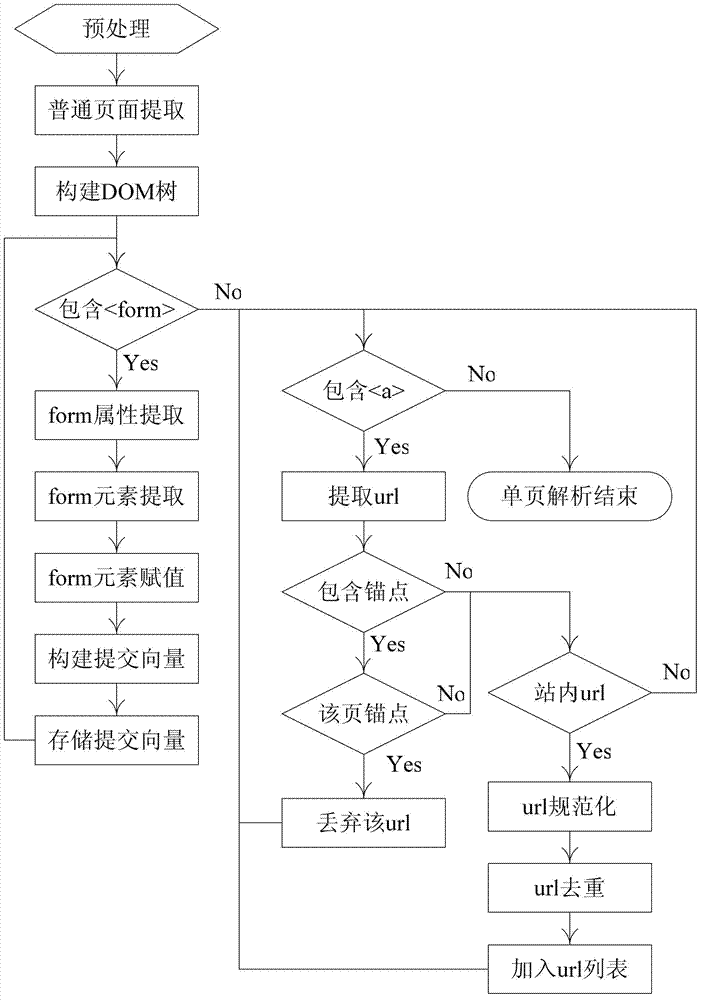
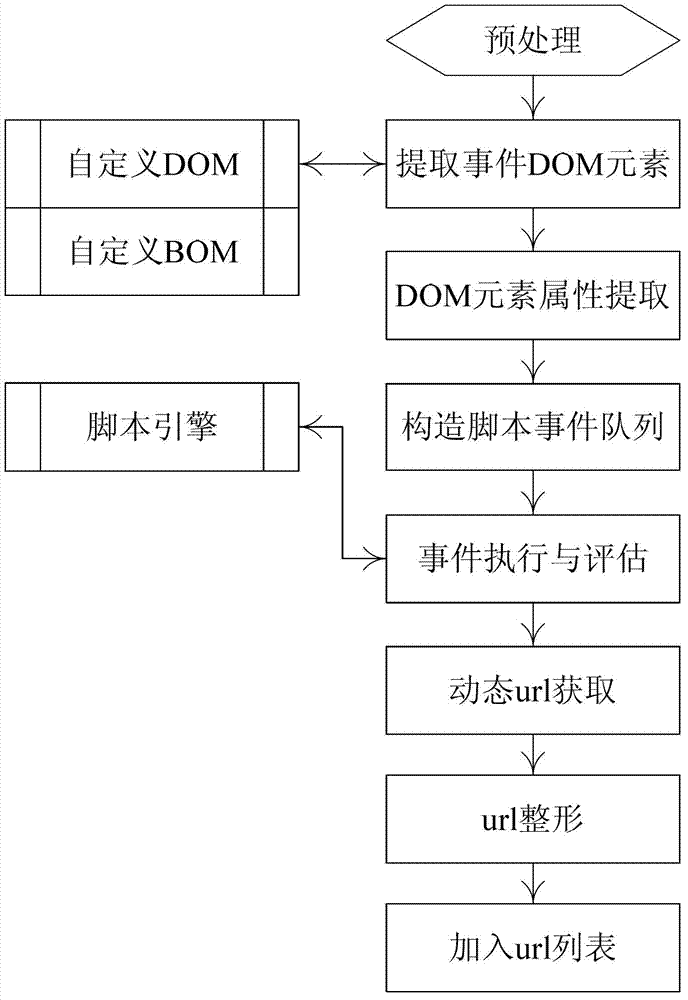
The invention discloses an injection point extracting method in SQL (Structured Query Language) injection vulnerability detection, which is used for solving the technical problem of poor accuracy of the traditional method in the SQL injection vulnerability detection under a Web environment. According to the technical scheme, the injection point extracting method comprises the steps of: firstly, preprocessing a downloaded webpage, dividing the webpage into a simple webpage and a complex webpage, extracting a data injection point of the simple webpage, extracting a data injection point of the complex webpage, extracting a test case through constructing the test case, analyzing service response, and establishing a decision rule of an SQL injection vulnerability. According to the invention, starting from obtaining the data injection points of a Web application system, through constructing the targeted test case, the used test case is used for carrying out character string, numerical value, annotation and delay testing according to the types and the parameter compositions of the data injection points, thus the test of the injection vulnerability caused by simple filtration of URL (Uniform Resource Locator) parameters and table submitted data is effectively dealt; and through analysis response, the established decision rule of the SQL injection vulnerability is improved in testing accuracy.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Method for detecting SQL (structured query language) injection vulnerability
InactiveCN102185930AReduce false alarm rateImprove accuracyTransmissionSpecial data processing applicationsUser inputSQL injection
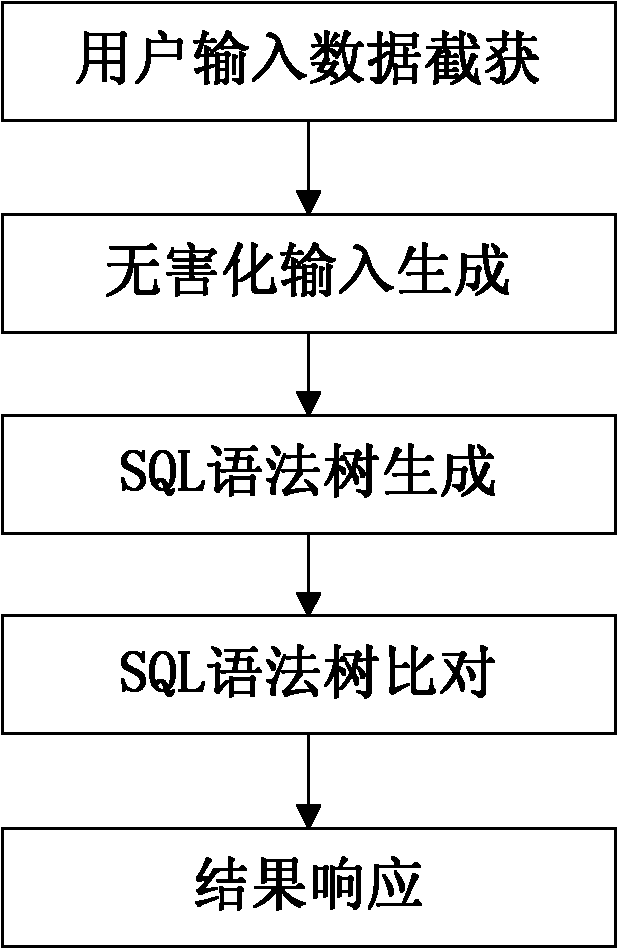
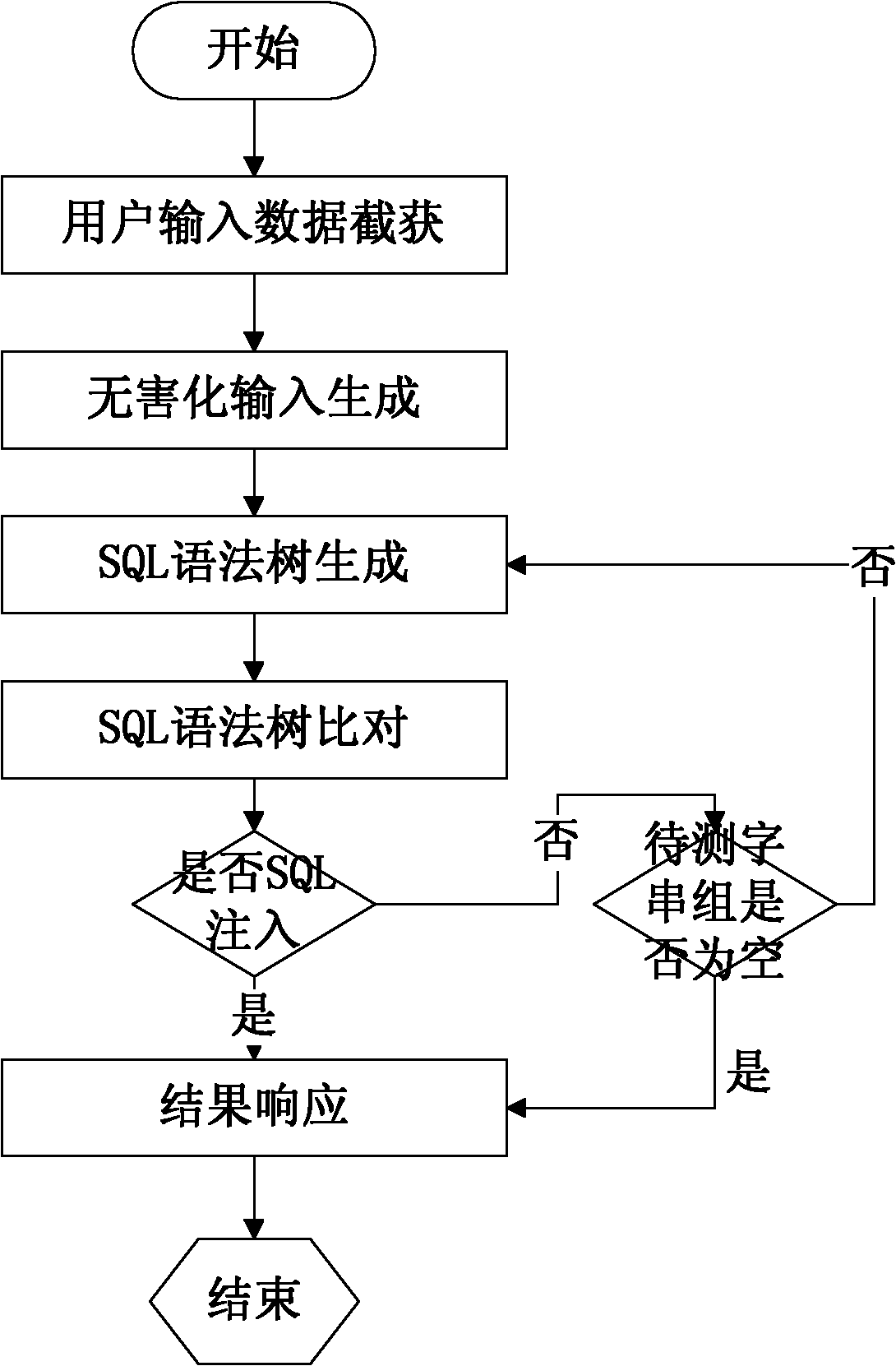
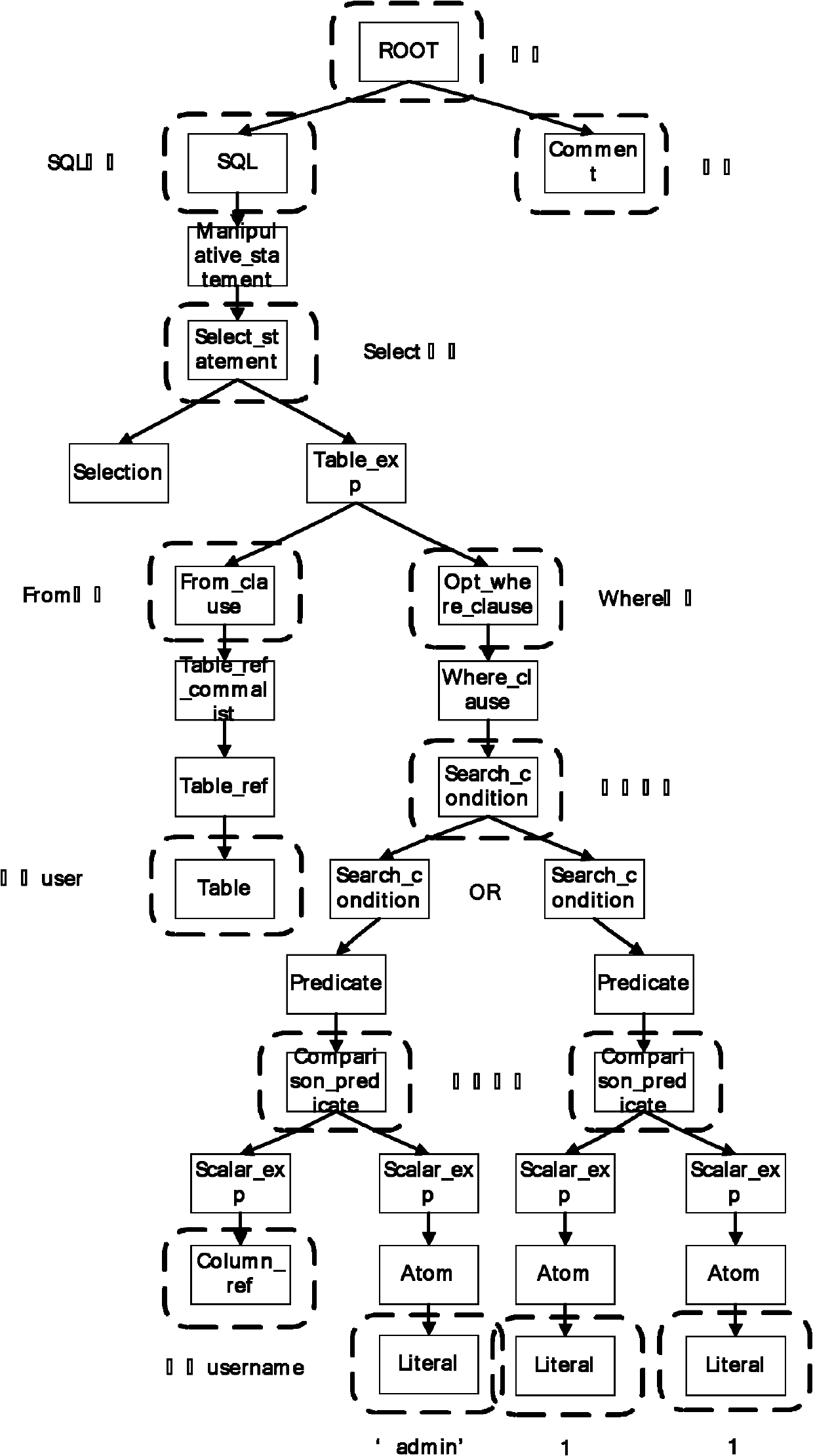
The invention relates to a method for detecting SQL (structured query language) injection vulnerability, comprising the following steps: 1, capturing user input data; 2, generating harmless input; 3, carrying out SQL lexical analysis and syntactic analysis to generate SQL syntax trees, wherein the SQL syntax trees comprise a syntax tree based on user input word strings and a syntax tree based on harmless word strings; 4, comparing the two SQL syntax trees, and if the two SQL syntax trees are same, considering a group of testing word strings to pass a test; and 5, responding the result, if a user attempting to carry out SQL injection is found out, blocking an HTTP (hyper text transport protocol) package, and otherwise, releasing the HTTP package. In the method, analyzed objects are input by the user directly or indirectly, thus maximally restoring the real intentions of the user and reducing the rate of false alarm; and meanwhile, based on the analysis of the SQL syntax trees, the SQL injection can be blocked fundamentally, thereby improving the accuracy rate of the detection.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
System for real-time intrusion detection of SQL injection WEB attacks
ActiveCN101370008AReduce false alarmsHigh detection rateData switching networksSQL injectionWeb attack
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Malicious script static detection method based on SVM (support vector machine)
InactiveCN103577755AImprove the ability to resist evasionReduce false alarm ratePlatform integrity maintainanceAcquired characteristicSorting algorithm
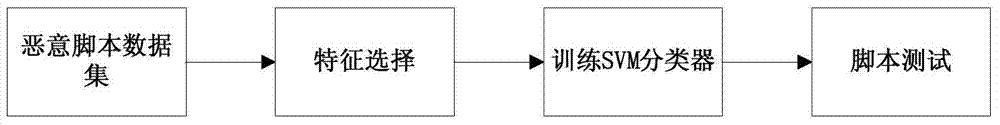
A malicious script detection method based on an SVM (support vector machine) comprises the following steps: 1), crawling a webpage from the Internet, and acquiring the webpage link; 2), acquiring Java script content corresponding to the link; 3), analyzing web intrusion such as SQL (structured query language) injection and the like based on the script to obtain characteristics relative to the intrusion, performing characteristic extraction on acquired script content according to the intrusion characteristics, and transforming every script into a characteristic-based characteristic vector; and 4), acquiring an optimal classification model of the SVM according to a sort algorithm, classifying the acquired characteristic vectors by the model, and judging whether the script is a malicious script so as to perform related follow-up processing.
Owner:ZHEJIANG UNIV OF TECH
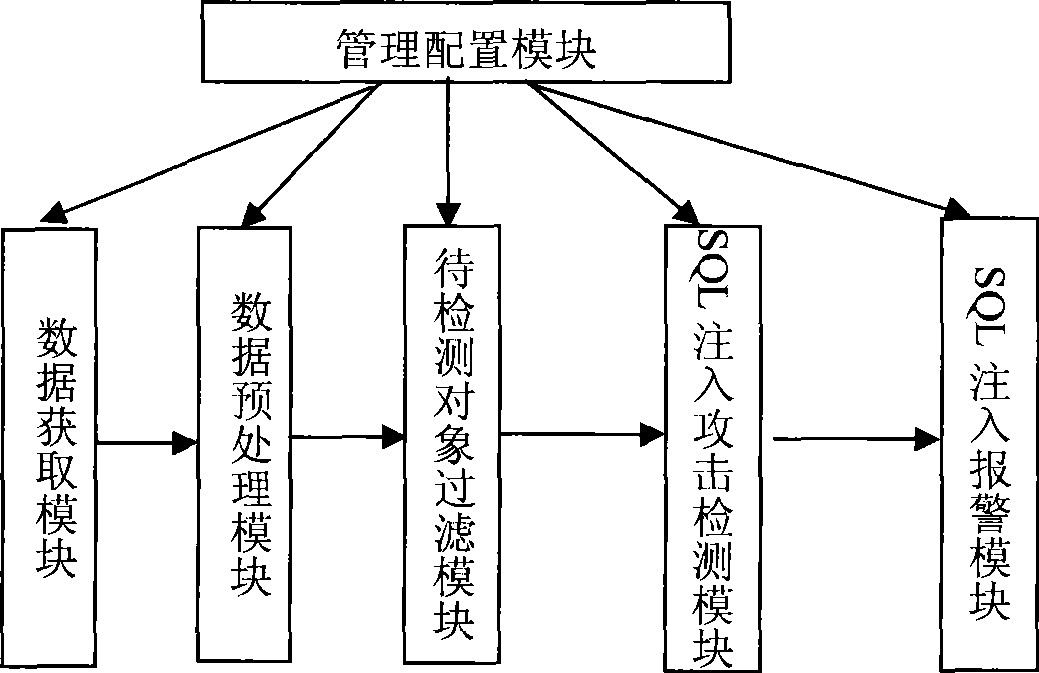
SQL injection attack detection system supporting multiple database types
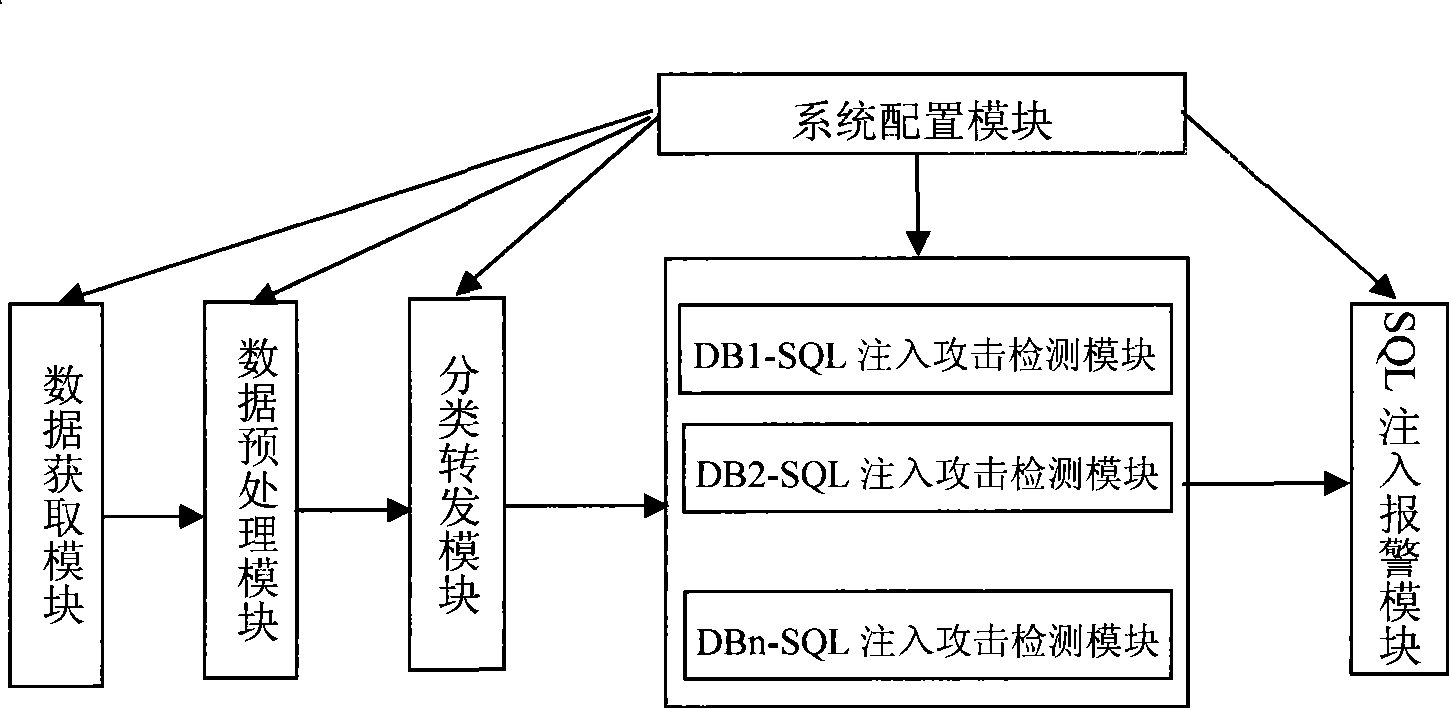
InactiveCN101388763AOvercoming difficult extractionOvercome shortcomings such as being easily deceivedData switching networksSecuring communicationSQL injectionData acquisition
The invention relates to an SQL injection attack detecting system which supports multiple types of databases, which comprises a data acquisition module, a data preprocessing module, SQL injection attack detecting modules, an SQL injection alarming module and a classification transferring module. The system may comprise a plurality of the SQL injection attack detecting modules, and each of the SQL injection attack detecting modules respectively creates SQL injection attack detecting grammar rules based on the expanded SQL grammar of the data base types which are related with the SQL injection attack detecting modules, each of the SQL injection attack detecting modules is bound with the destination address of a certain Web application server, thereby the SQL injection attack detection of all to-be detected objects which have the same determination address is realized. The system fully considers the differences of the SQL grammar of various types of the databases, classifies the to-be detected objects according to the destination address of the Web application server, and detects the objects by the SQL injection attack detecting module which supports the SQL grammar expansion of the specific types of the databases, and greatly reduces the under-reporting problems in the SQL injection attack detecting modules.
Owner:BEIJING VENUS INFORMATION TECH
Mixed structured query language (SQL) injection protection method
InactiveCN102682047AResolve identifiabilitySolve the contradiction between high false positive rateSpecial data processing applicationsSQL injectionPattern matching
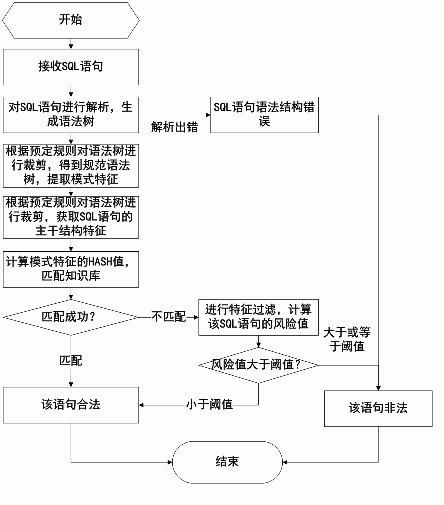
The invention discloses a mixed structured query language (SQL) injection protection method, which combines a static mode matching technology and a dynamic characteristic filtering technology. The method comprises the following steps of: automatically learning all legal SQL sentences of a service system in security environment, and constructing a knowledge base; and matching the SQL sentences with the knowledge base by using a mode matching algorithm in real-time working environment, and if matching succeeds, determining that the SQL sentences are legal. The SQL sentences which are unsuccessfully matched are not immediately determined to be illegal, deep characteristic check is performed by using a characteristic filtering algorithm based on a value-at-risk, and the truly illegal SQL sentences are identified. A mode matching method and a characteristic filtering method are matched and combined with each other, so a good effect is achieved, and a conflict between accuracy rate and mis-alarm rate caused by the conventional injection protection method can be well solved.
Owner:STATE GRID ELECTRIC POWER RES INST
SQL (structured query language) injection attack defensive system and defensive method based on grammar transformation
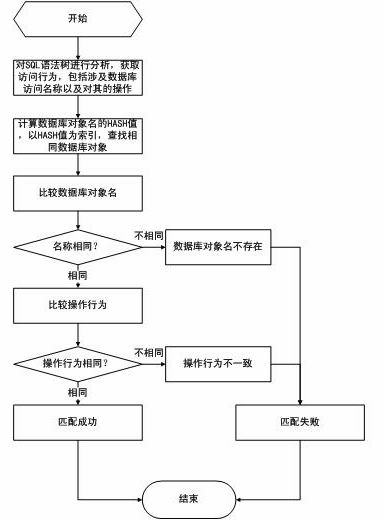
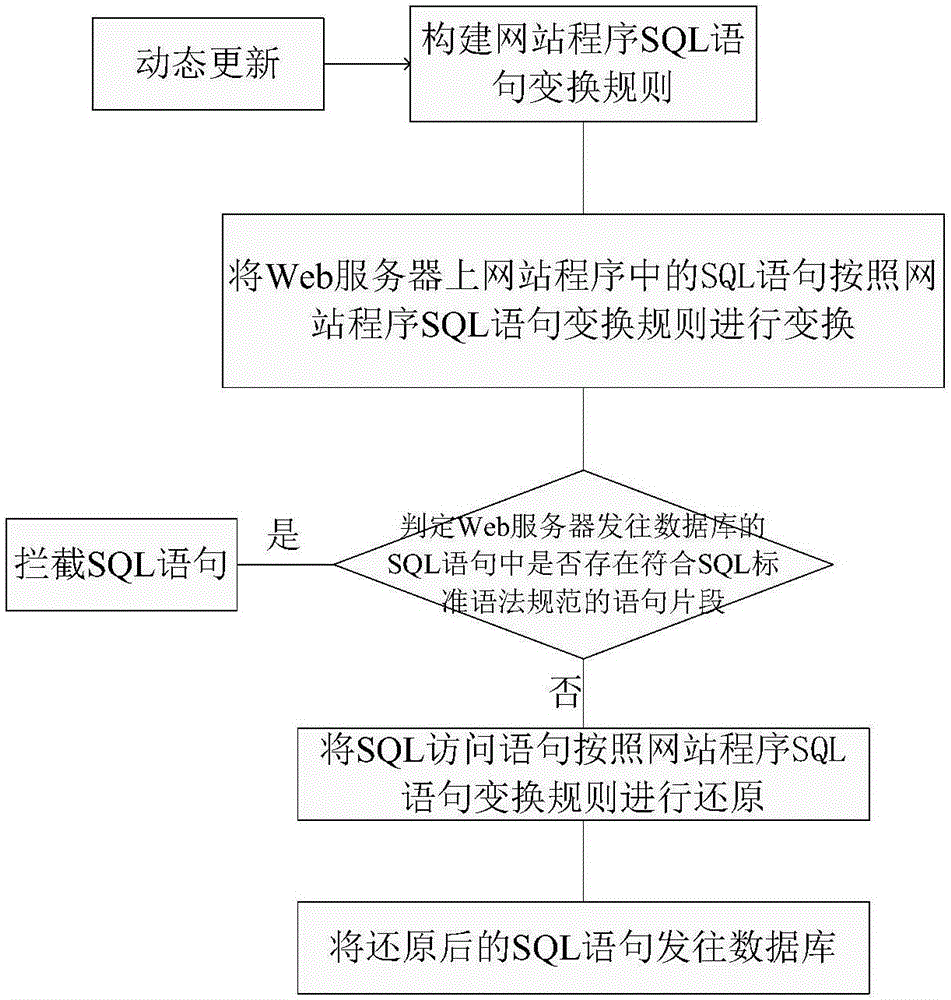
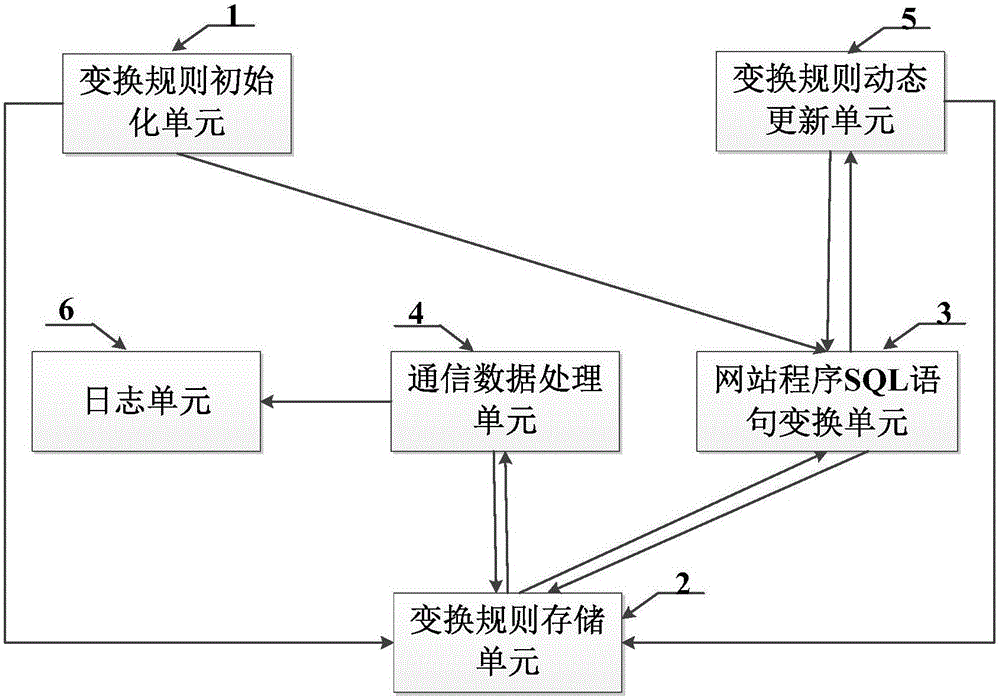
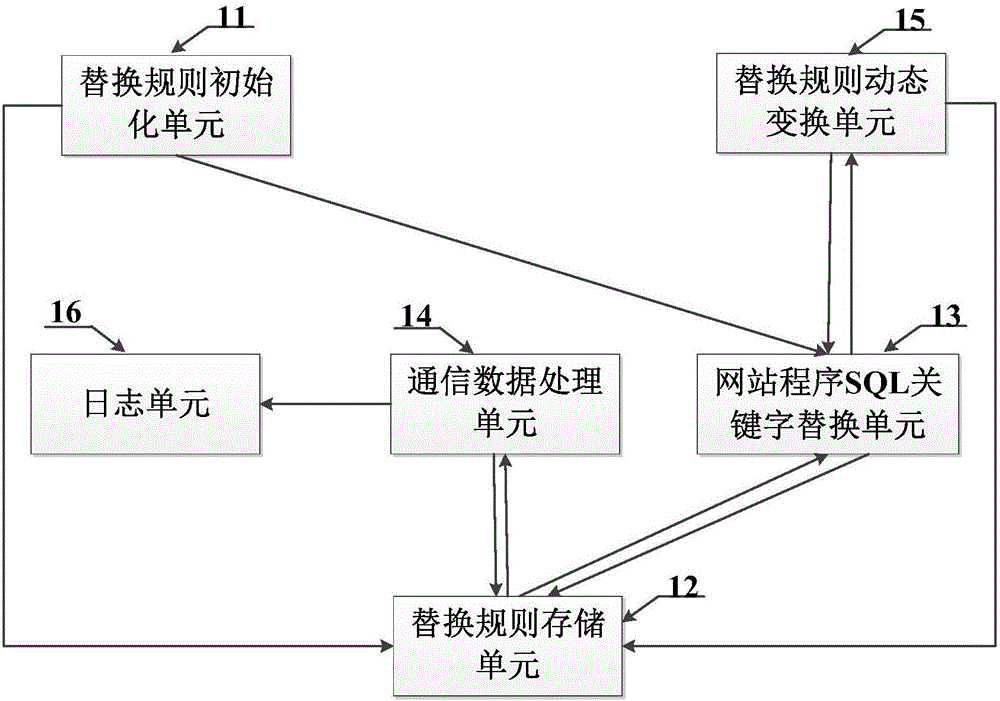
ActiveCN106355094AReduce development and maintenance costsReduce false alarm ratePlatform integrity maintainanceWeb serviceSQL injection
The invention provides an SQL (structured query language) injection attack defensive system and method based on grammar transformation. The SQL statement transformation rule of website program is built; SQL statements in the website program on a Web server are subjected to initialization transformation operation; whether attack statements are injected into SQL access statements sent to a database by the Web server or not is judged; the SQL statement transformation rule of the website program is dynamically transformed, so that the effective defense on the SQL injection attack is realized. The SQL injection attack defensive system and method based on grammar transformation do not depend on rules; the vicious SQL injection attack is precisely recognized on the basis of statement transformation and grammatical analysis; the false alarm rate and the missing report rate are extremely low; the system and the method are applicable to various types of Web servers and database systems; the SQL injection attack behavior can be effectively defensed; the safety protection on the Web server and a background database is obviously improved.
Owner:北京卫达信息技术有限公司
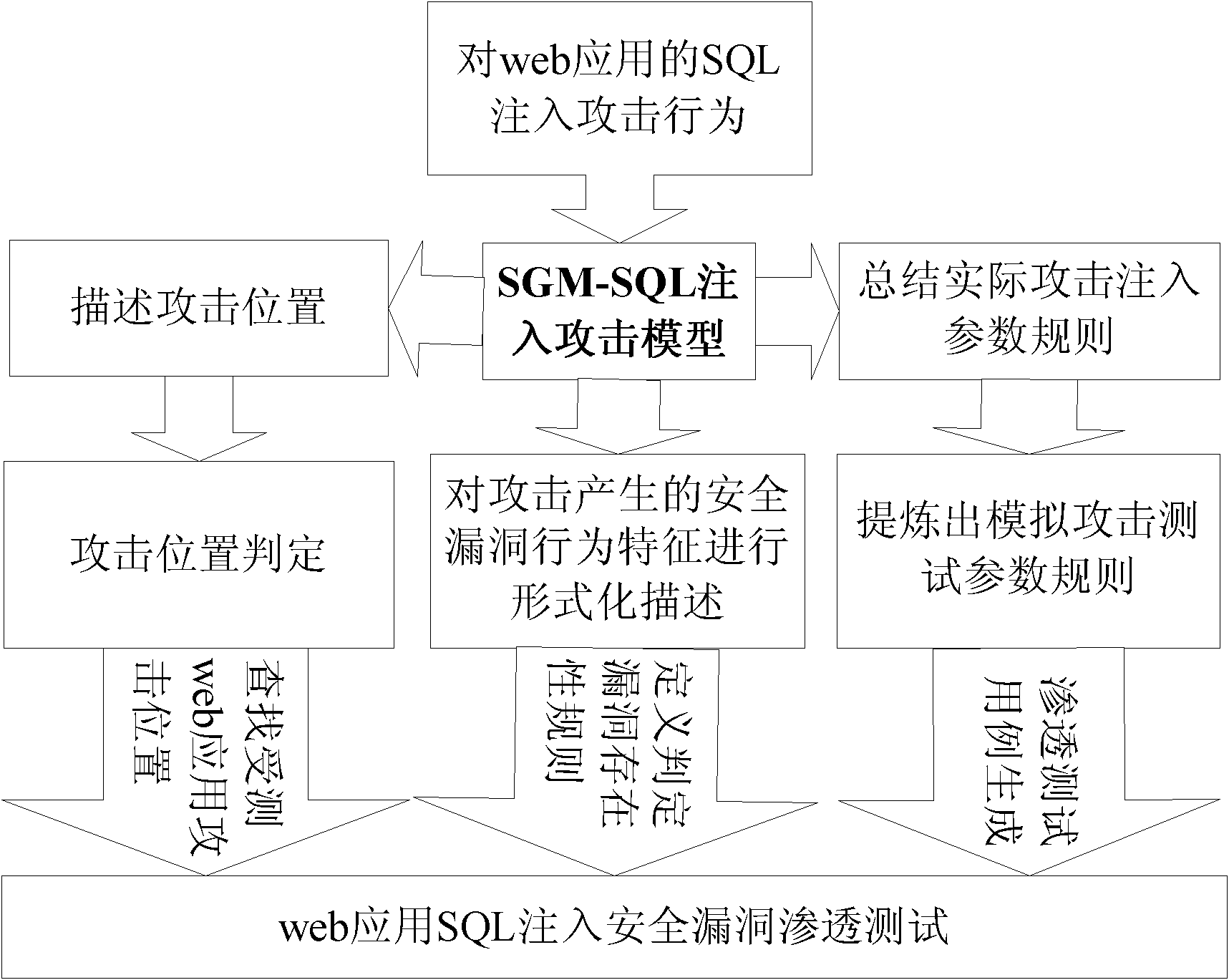
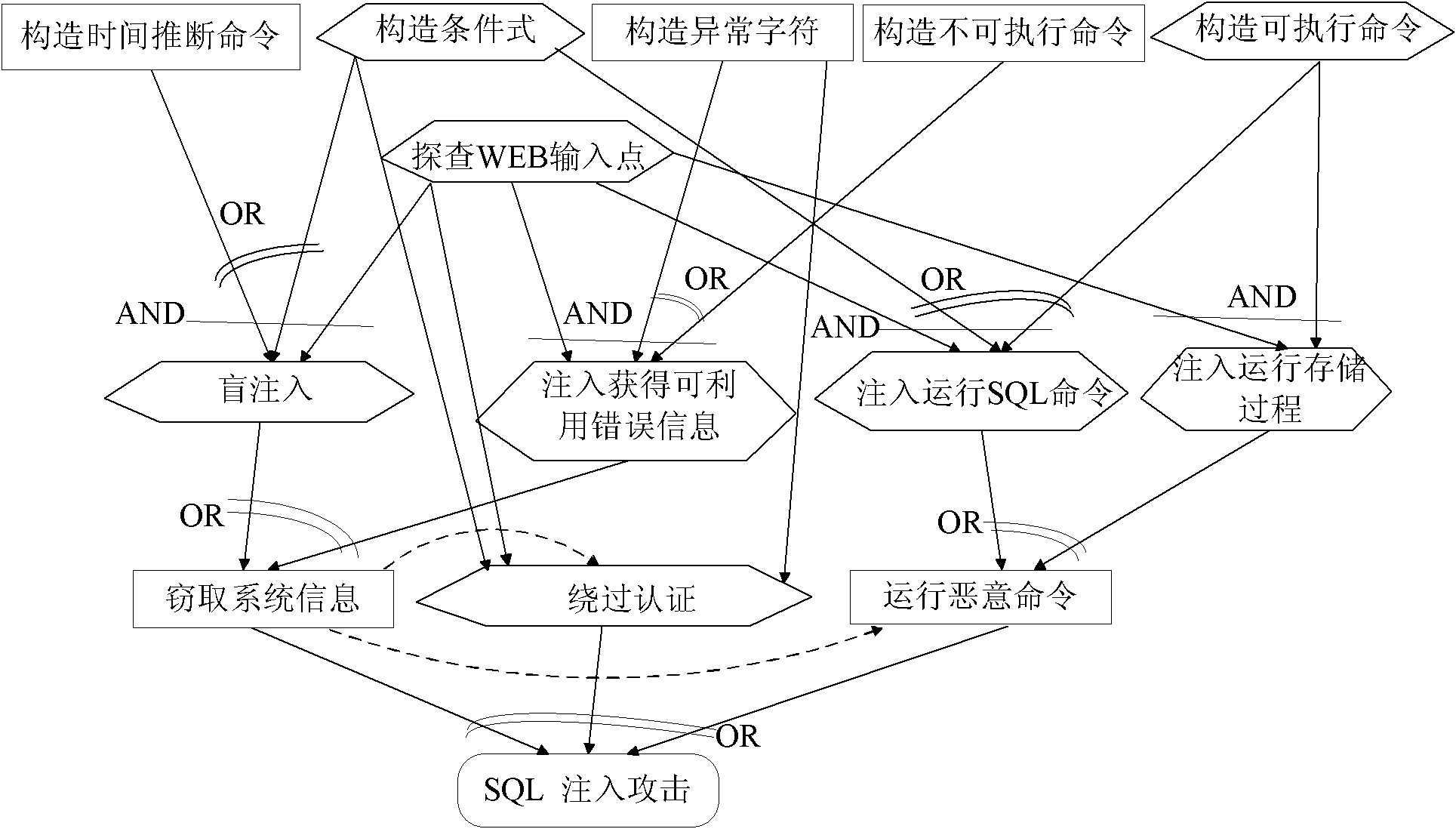
Method for driving web application penetration testing by applying SGM-SQL (sage grant management-structured query language) injection model
InactiveCN102136051AImprove accuracyMake up for the shortcomings of low accuracySoftware testing/debuggingPlatform integrity maintainanceAttack modelRDF query language
The invention relates to a method for driving web application penetration testing by applying an SGM-SQL (sage grant management-structured query language) injection model, in the method, a web application penetration test framework driven by an SGM-SQL injection attack model is defined; by defining the SGM-SQL injection attack model in the framework and guiding the definition of a formalized definition set of SQL injection safety loopholes and a formalized description system of penetration test cases thereof, the accurate criterion for judging existence of the safety loopholes and the orderedcomplete test cases are further provided for the penetrating testing, and an SQL injection safety loophole penetration test algorithm driven by the SGM-SQL injection attack model is accordingly provided, thereby improving the accuracy of the web application SQL injection safety loophole penetration testing. Practices prove that the method is credible, systematic and complete, and can be applied in the field of the web application safety loophole penetration testing.
Owner:NANKAI UNIV +1
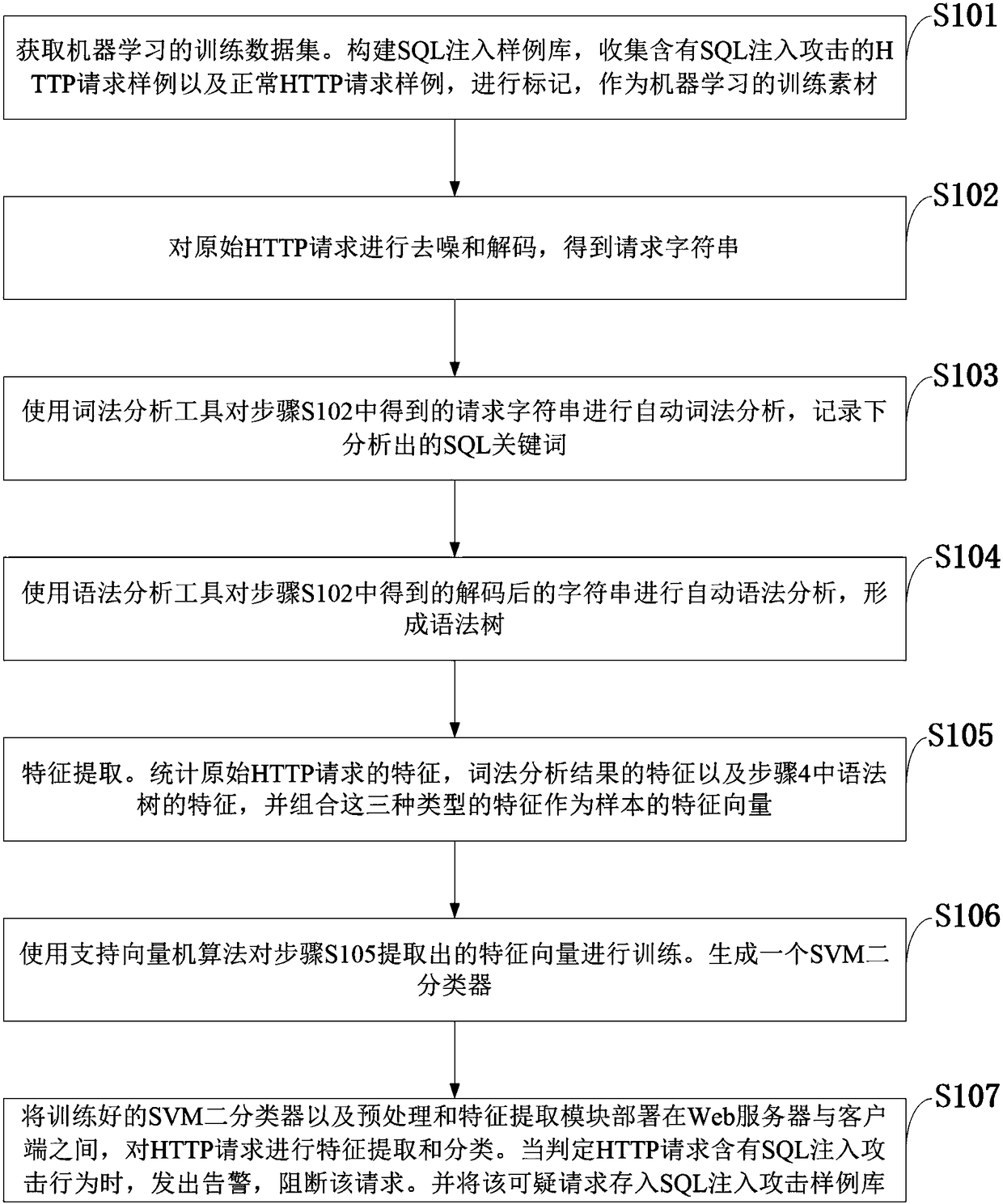
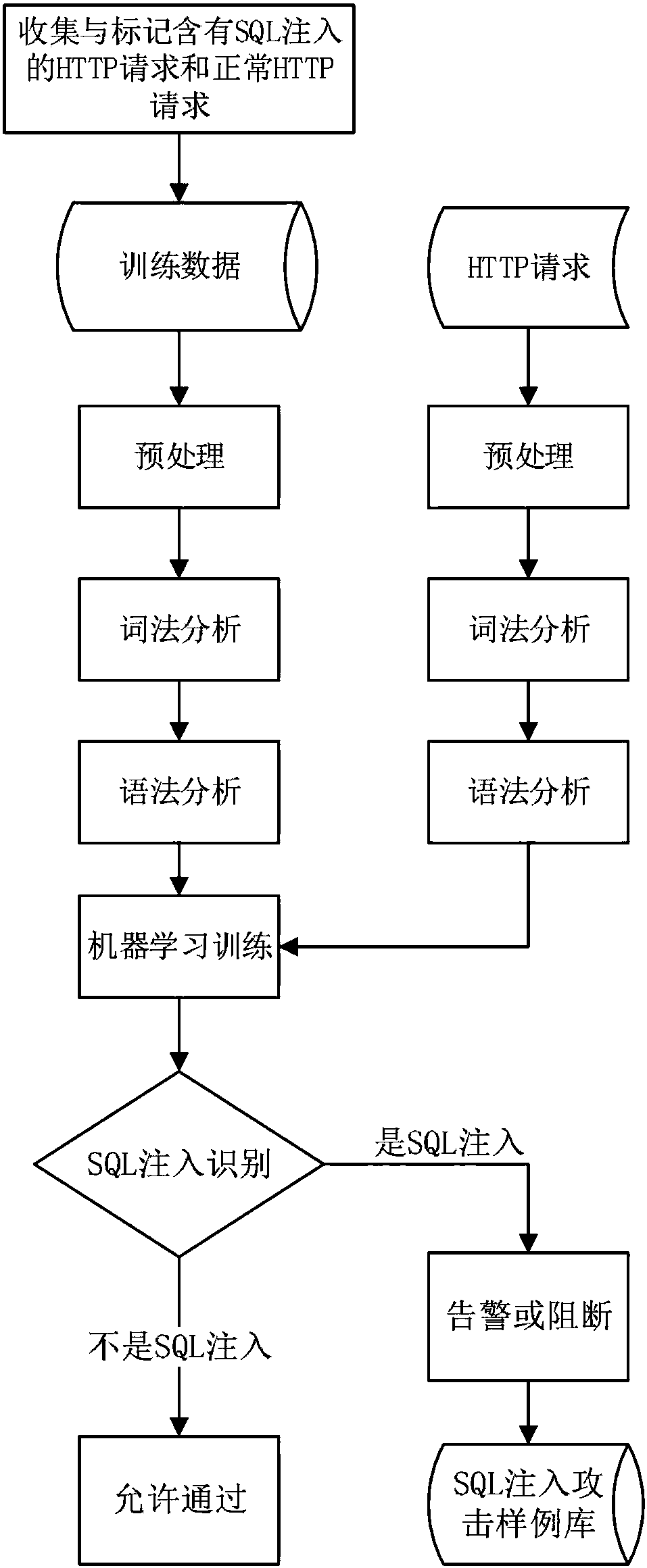
Machine learning-based SQL injection detection method, and database security system
InactiveCN108549814AReduce dependenceImprove recognition accuracyPlatform integrity maintainanceSpecial data processing applicationsWeb serviceSQL injection
The invention discloses a machine learning-based SQL injection detection method, and a database security system, and belongs to the technical field of network security. The machine learning-based SQLinjection detection method comprises the steps of extracting parameters from HTTP requests, generating a grammar tree of a sample through lexical analysis and grammatical analysis, extracting featuresof the grammar tree and a URL, and performing training by adopting a machine learning algorithm of a support vector machine; and deploying a trained classification model between a Web service and a client, classifying the HTTP requests in a production environment, when it is judged that the HTTP requests comprise SQL injection attacks, giving a warning and blocking the requests, and finally storing the requests in an SQL injection attack sample library. According to the method, the dependency on background information is low, so that the HTTP requests received by the Web service only need tobe obtained; the deployment difficulty is low, so that the classification model can be deployed between a Web server and the client to serve as a flow filter; the method has high accuracy; the methodhas a continuous learning capability; and the method has high expansibility.
Owner:XIDIAN UNIV
SQL injection attack detection system suitable for high speed LAN environment
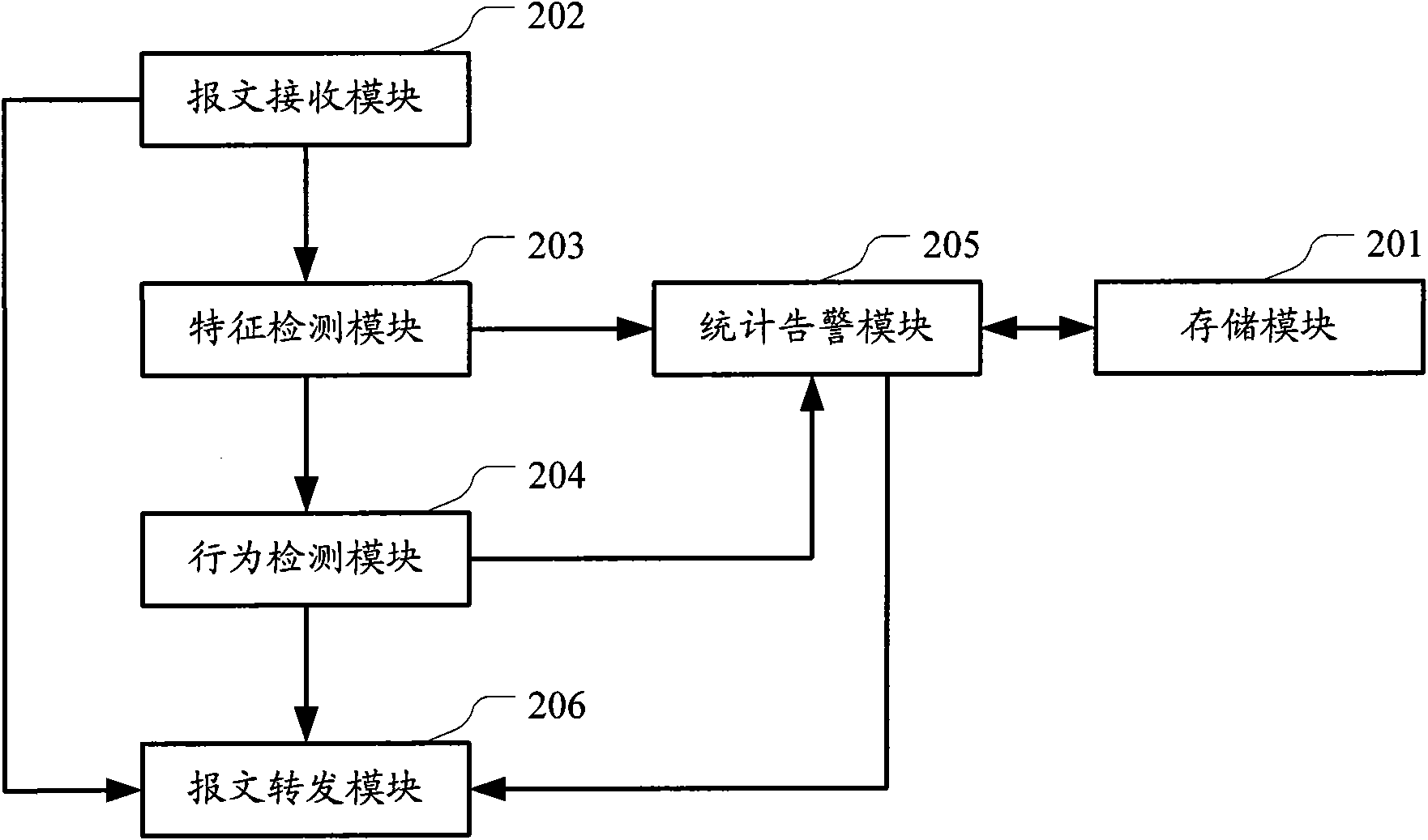
InactiveCN101425937AReduce false alarm rateRelieve stressData switching by path configurationNetwork packetSQL injection
SQL injection attack detection system adapting to high speed LAN environment comprises data acquisition module, data pretreatment module, filter module for object to be detected, SQL injection attack detection module and SQL injection alarming module. The data acquisition module acquires network data pack related with HTTP service from protected network; data pretreatment module resolves operation and establishes object to be detected and transmits to the filter module for object to be detected based on TCP stream reassembly and HTTp protocol; the filter module for object to be detected matches URL of every object to be detected according to filtering rule sequence established, and performs designated processing action of matched filtering rule. The Web object type of HTTP request is divided into static Web type and dynamic Web type; static Web type HTTP requests during real time SQL injection attack detection is filtered out, which largely relieves processing pressure for SQL injection attack detection module, reduces rate of false alarm.
Owner:BEIJING VENUS INFORMATION TECH
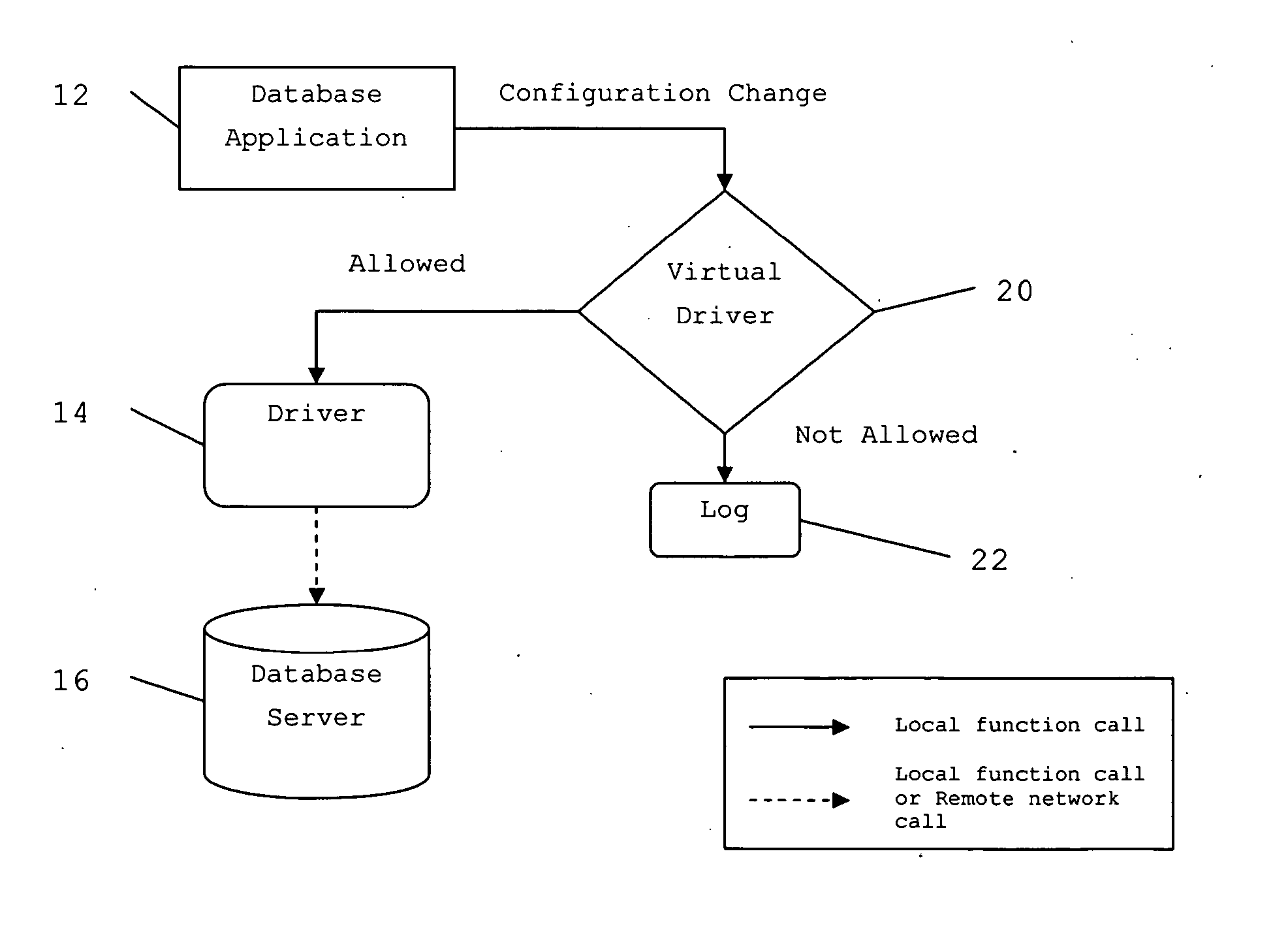
Method and system for SQL injection and defense
The invention provides an SQL injection and defense method aiming at a data base, which comprises the following steps: (a), receiving SQL statements accessing a data base and sent out by an application system; (b), performing the injection judging and checking to the SQL statements; if the SQL statements are SQL injection, intercepting the SQL injection, recording the mistake, and returning the abnormal information to the application system; if the SQL statements are not the SQL injection, querying an operational interface specification of the corresponding data base required to be accessed by the SQL statements, and splicing SQL statements conform to the data base operational interface specification; (c), sending the specified SQL statements spliced in the step (b) to a corresponding data base to perform data base operation; (d), returning the queried result to the application system. According to the invention, a data base agent server is arranged as per the method provided by the invention, an operation and maintenance method is used for rejecting access permission of any other application system except the data base agent server to the data base, thereby preventing the SQL injection.
Owner:BEIJING 58 INFORMATION TECH
Method and device for detecting structured query language injection attack
InactiveCN101594266AReduce false positives of attacksData switching networksSpecial data processing applicationsSQL injectionIp address
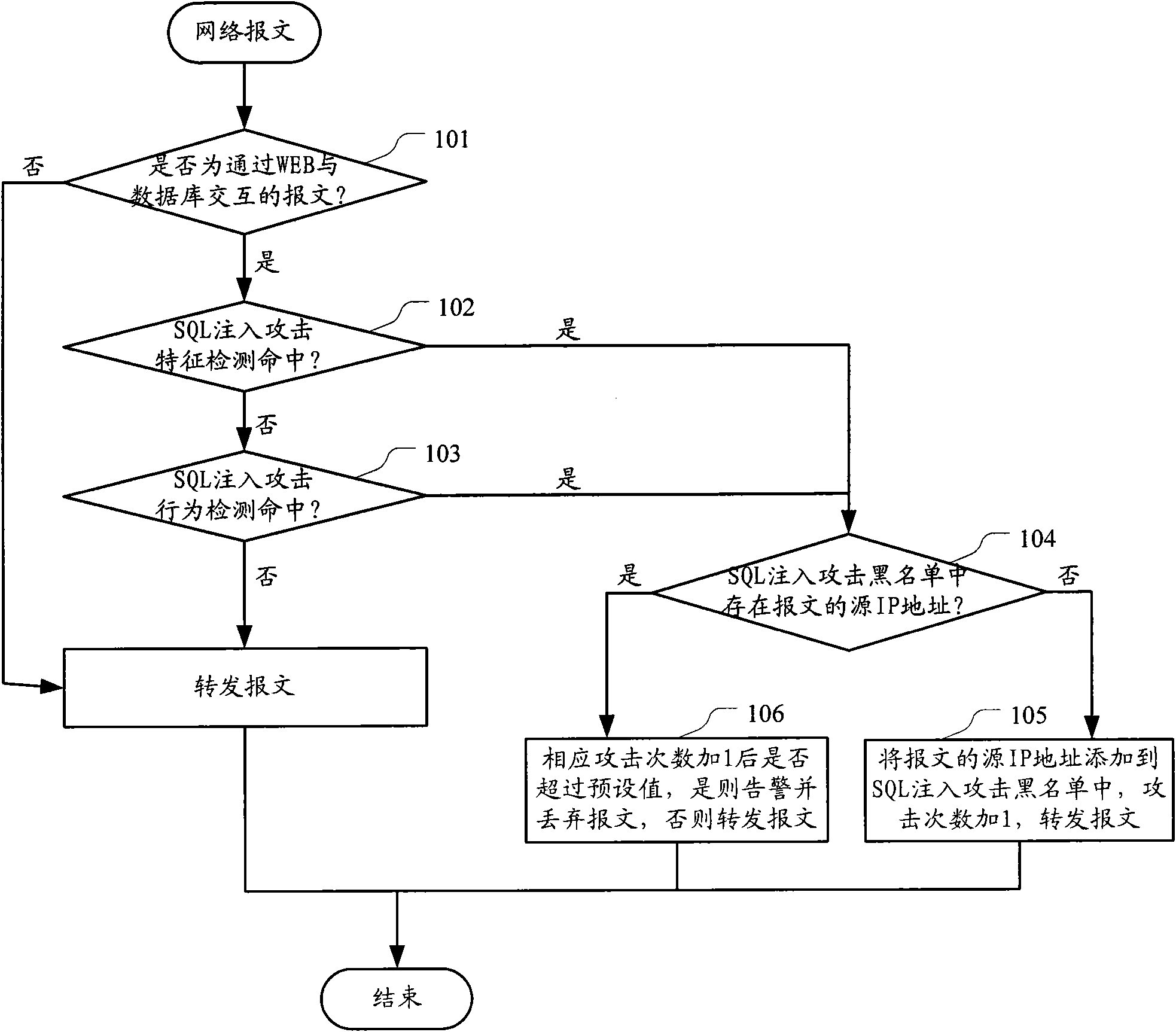
The invention discloses a method and a device for detecting a structured query language SQL injection attack. The method comprises the following steps: firstly detecting a received message based on SQL injection attack characteristics, and then detecting the received message based on SQL injection attack behaviors; counting the attack frequency of a source IP address of each hit message; alarming the IP address of which the attack frequency exceeds a preset value. The technical proposal of the invention greatly reduces the conditions of attack omission.
Owner:NEW H3C TECH CO LTD
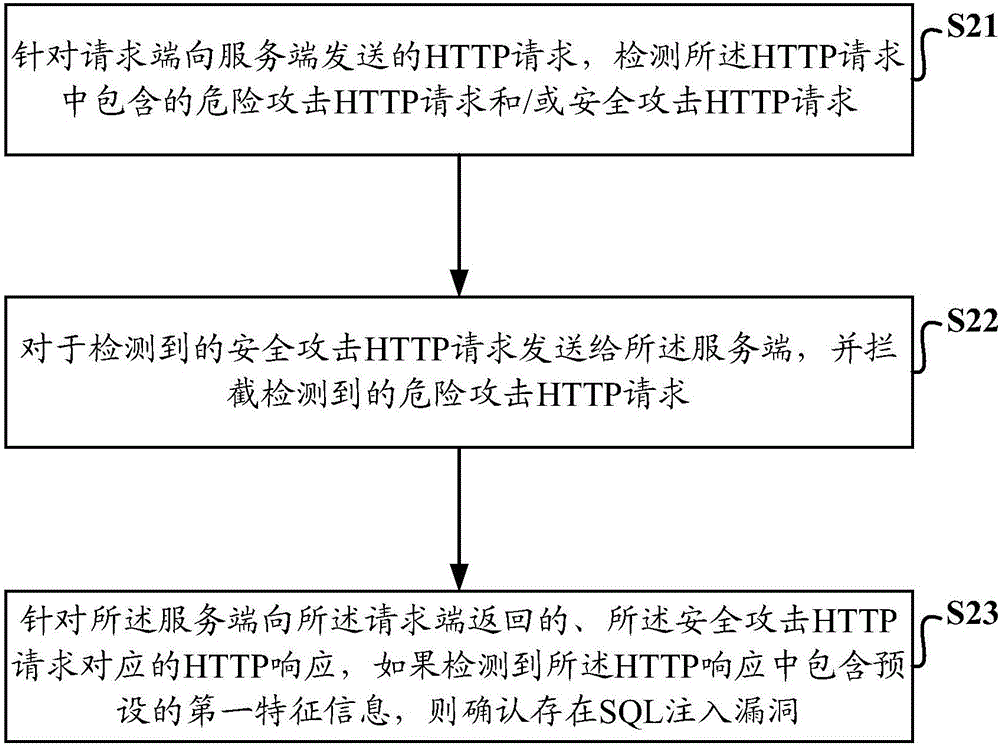
Detection method and detection system for SQL injection attack
The invention discloses a detection method and a detection system for SQL (Structured Query Language) injection attack. The detection method and the detection system are used for increasing the accuracy of vulnerability detection for SQL injection attack and assisting the website in finding the true SQL injection vulnerability. The detection method for SQL injection attack comprises the following steps of: detecting a dangerous attack HTTP (Hyper Text Transfer Protocol) request and / or safe attack HTTP request contained in an HTTP request, for the HTTP request sent to a server by a request terminal; sending the detected safe attack HTTP request to the server and intercepting the detected dangerous attack HTTP request; for an HTTP response corresponding to the HTTP request containing the safe attack HTTP request returned to the request terminal by the server, confirming the existence of the SQL injection vulnerability if detecting the preset first feature information contained in the HTTP response.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
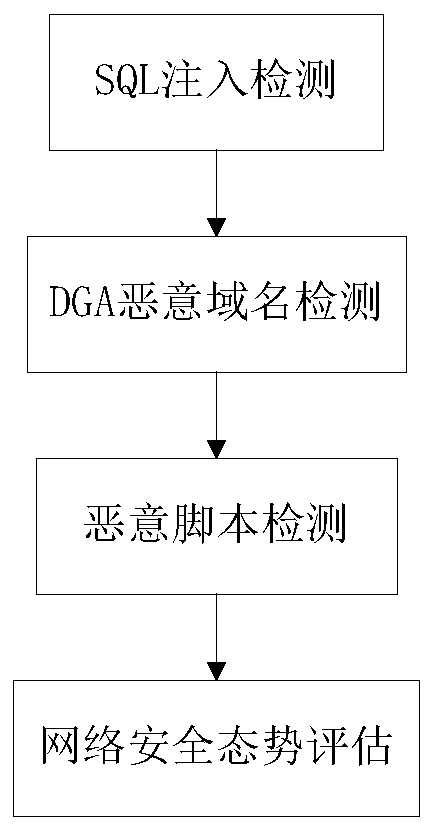
Network security situation analysis method and system
The invention relates to a network security situation analysis method and system, and the method comprises the steps: A, carrying out the SQL injection detection: obtaining a corresponding word vectoraccording to the condition whether a part with an SQL injection attack exists in a domain name, and building a model for detecting the SQL injection attack; B, DGA malicious domain name detection: extracting feature vectors in a domain name to obtain a training model, and performing cross validation on the training model to obtain precision and recall rate; C, detecting malicious scripts: detecting whether a malicious code exists in the webpage script or not through a training model; D, assessing network security situation: assessing the total situation value of all the hosts according to thesecurity level; E, predicting network security situation: outputting prediction results through an LSTM layer and a Bi-LSTM layer and three fully connected layers. The accuracy of network security situation analysis can be obviously improved, different types of network security can be tested and analyzed from multiple angles, and the comprehensiveness of network security situation analysis and prediction is effectively improved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
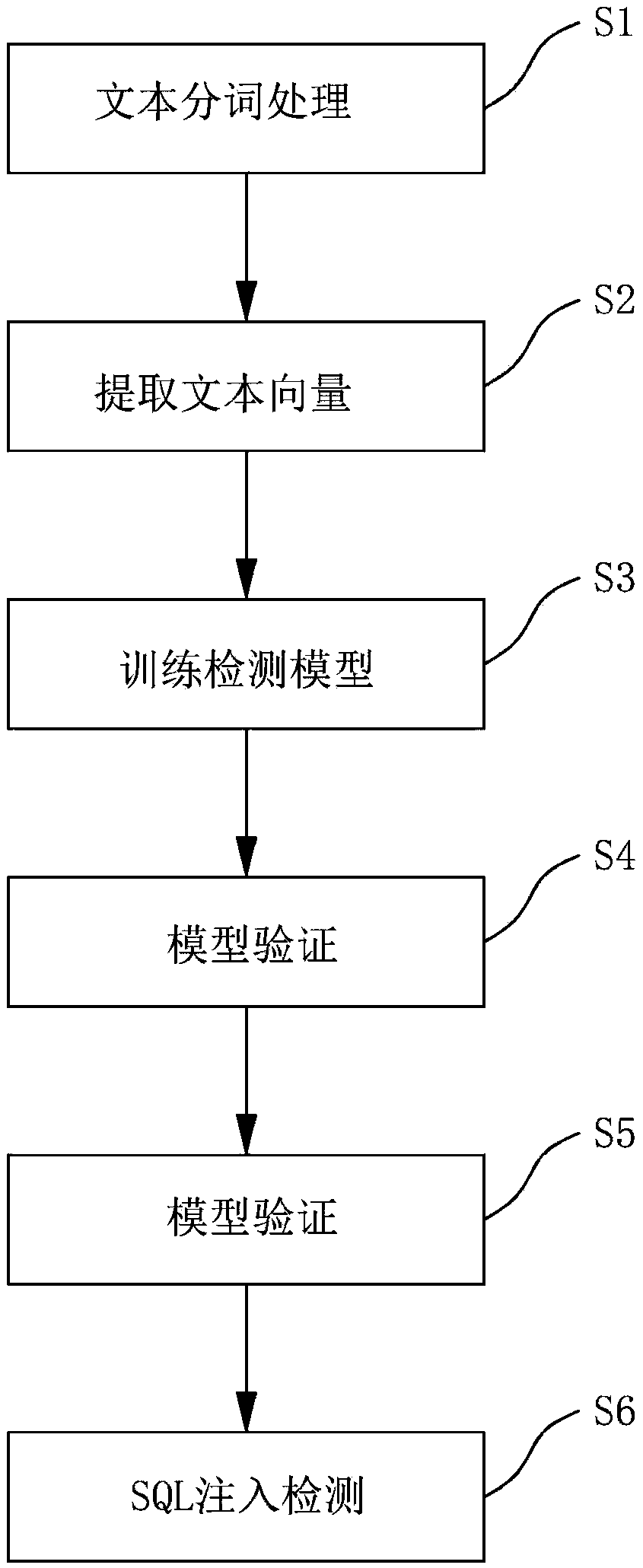
SQL injection detection method based on convolution neural network algorithm
ActiveCN109413028AReduce the impactImprove recognition rateNatural language data processingNeural architecturesActivation functionAlgorithm
The invention discloses a SQL injection detection method based on a convolution neural network algorithm. The method comprises the following steps: step one, performing text word-segmentation processing; step two, extracting a text vector: performing vocabulary model training on a training sample after the word segmentation processing by using a CBOW algorithm in a Word2Vec tool, converting the text data into the text vector; step three, training a detection model: designing a convolution neural network structure; selecting a convolution layer, a pooling layer and an activation function as parameters; inputting the text vector extracted from the step 2 into the convolution neural network to perform model training to obtain a detection model; step four, performing SQL injection detection: inputting the to-be-detected SQL injection instance into the detection model of the step three, or abandoning the data packet. Through the SQL injection detection method disclosed by the invention, the feature vector of an attack sample is extracted through the own characteristics of the CNN algorithm, the false alarm rate of the loophole detection is reduced, and a recognition rate for the variation attack is improved.
Owner:厦门市德道优升教育服务有限公司
Method and device for detecting SQL (Structured Query Language) injection attack
ActiveCN102045319AAvoid defectsSolve the problem of high false positive ratePlatform integrity maintainanceTransmissionSQL injectionUniform resource locator
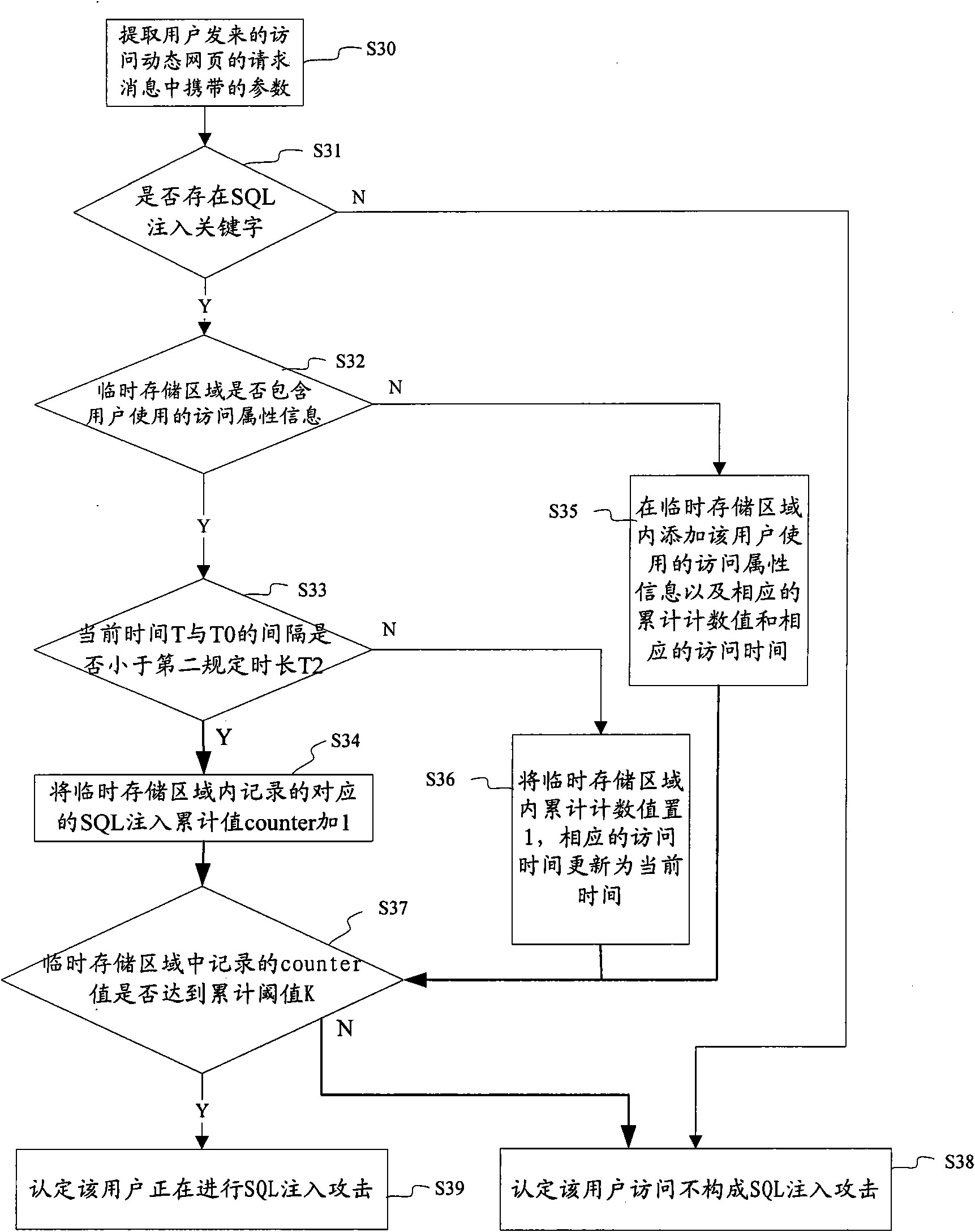
The invention discloses a method for detecting an SQL (Structured Query Language) injection attack. The method comprises the following steps of: detecting whether a user sends universal resource locator (URL) request messages of a prescribed number of times, which carry SQL injection keywords and are used for requesting to access a related website with the same access attribute information in prescribed time duration or not; if so, affirming that the user is carrying out an SQL injection attack on the website at the moment; and if not, affirming that the user does not carry out the SQL injection attack on the website. The embodiment of the invention also discloses an SQL injection attack detection device. The method and the device for detecting the SQL injection attack provided by the embodiment of the invention effectively overcome the defects of the traditional SQL detection mechanisms on the basis of the behavioral characteristics of the SQL injection attack of malicious personnel and solve the problem of high false alarm rate in the traditional SQL injection attack detection method.
Owner:CHINA MOBILE GROUP SHANDONG
Complementary character encoding for preventing input injection in web applications
InactiveUS8615804B2Appropriate treatmentImprove efficiencyMemory loss protectionError detection/correctionSQL injectionLexical analysis
Method to prevent the effect of web application injection attacks, such as SQL injection and cross-site scripting (XSS), which are major threats to the security of the Internet. Method using complementary character coding, a new approach to character level dynamic tainting, which allows efficient and precise taint propagation across the boundaries of server components, and also between servers and clients over HTTP. In this approach, each character has two encodings, which can be used to distinguish trusted and untrusted data. Small modifications to the lexical analyzers in components such as the application code interpreter, the database management system, and (optionally) the web browser allow them to become complement aware components, capable of using this alternative character coding scheme to enforce security policies aimed at preventing injection attacks, while continuing to function normally in other respects. This approach overcomes some weaknesses of previous dynamic tainting approaches by offering a precise protection against persistent cross-site scripting attacks, as taint information is maintained when data is passed to a database and later retrieved by the application program. The technique is effective on a group of vulnerable benchmarks and has low overhead.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
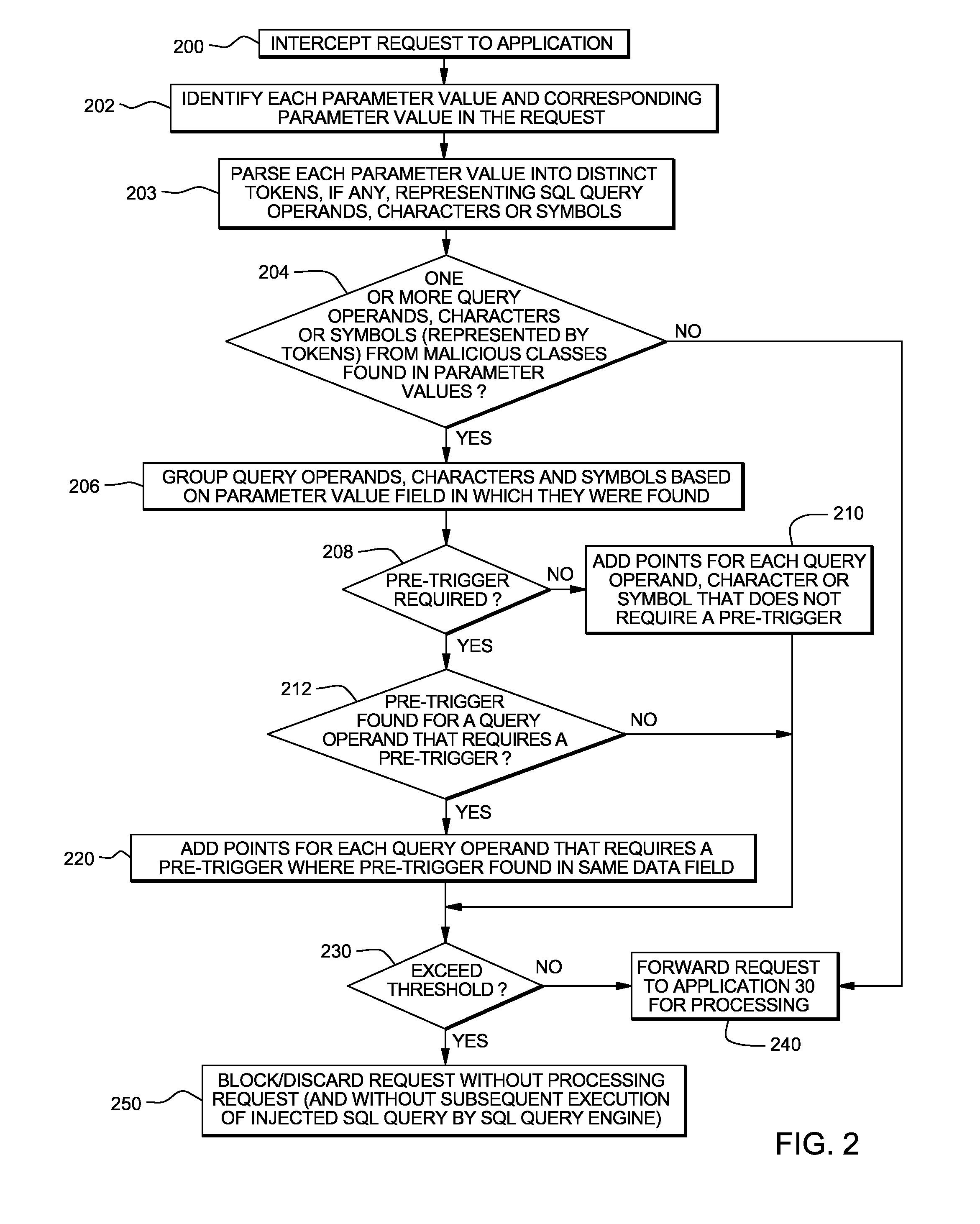
System, method and program product for detecting SQL queries injected into data fields of requests made to applications
InactiveUS20090150374A1Digital data processing detailsComputer security arrangementsSQL injectionData field
System, method and program product for detecting a malicious SQL query in a parameter value field of a request. The parameter value field is searched for query operands, characters and / or symbols and combinations of query operands, characters and / or symbols indicative of malicious SQL injection. A respective score assigned to each of the query operands, characters and / or symbols or combinations of query operands, characters and / or symbols found in the parameter value field is added to yield a total score for at least two of the query operands, characters and / or symbols or combinations of query operands, characters and / or symbols found in the parameter value field. Responsive to the total score exceeding a threshold, the request is blocked.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com