Machine learning-based SQL injection detection method, and database security system
A technology of machine learning and detection methods, applied in computer security devices, electrical digital data processing, special data processing applications, etc., can solve problems affecting the normal operation of Web services, normal HTTP request interception, labor-intensive analysis, etc., and achieve background information The effect of low dependence, lower false alarm rate, and good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] In order to make the object, technical solution and advantages of the present invention more clear, the present invention will be further described in detail below in conjunction with the examples. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
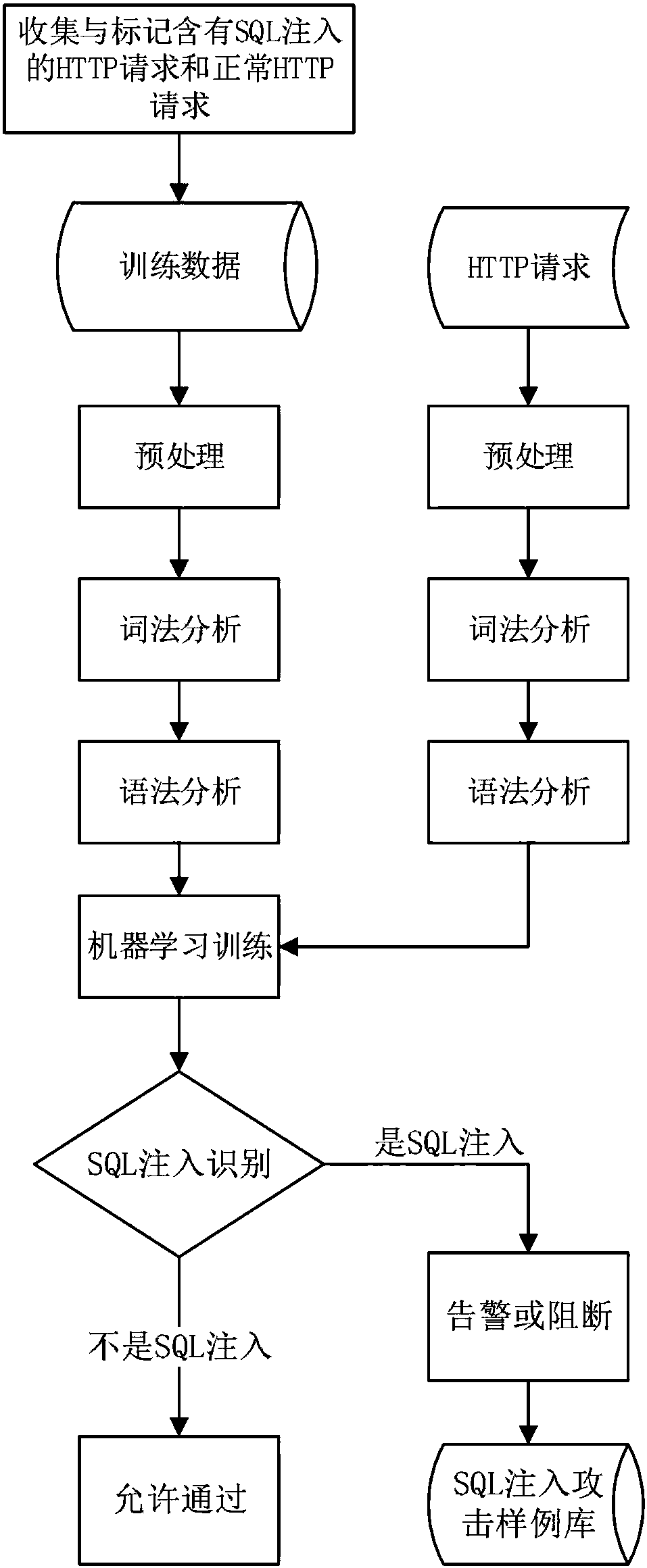
[0037] The invention uses a machine learning algorithm to train a detection model and deploys the model between a Web client and a server to classify HTTP requests and judge whether they contain SQL injection attacks.
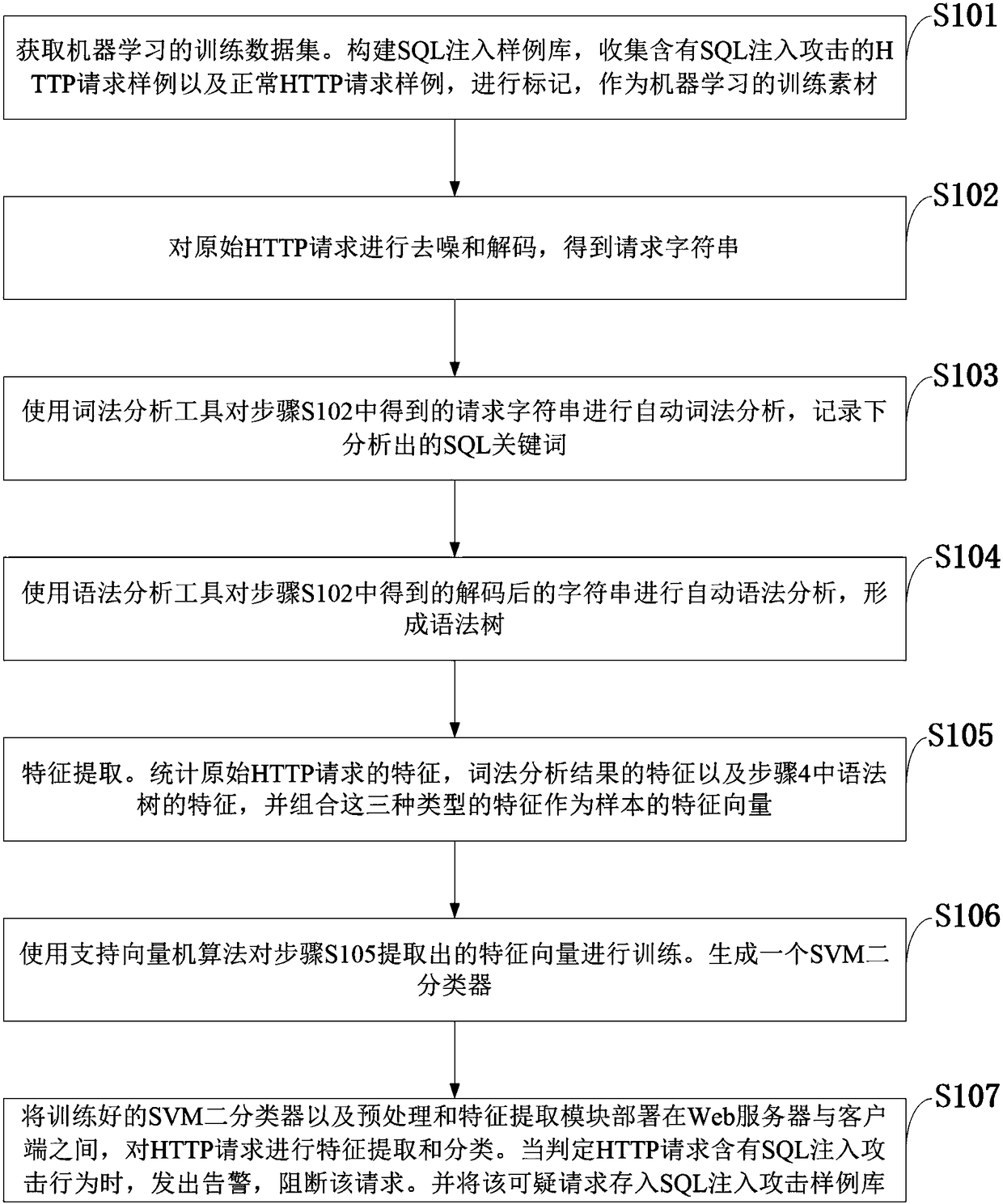
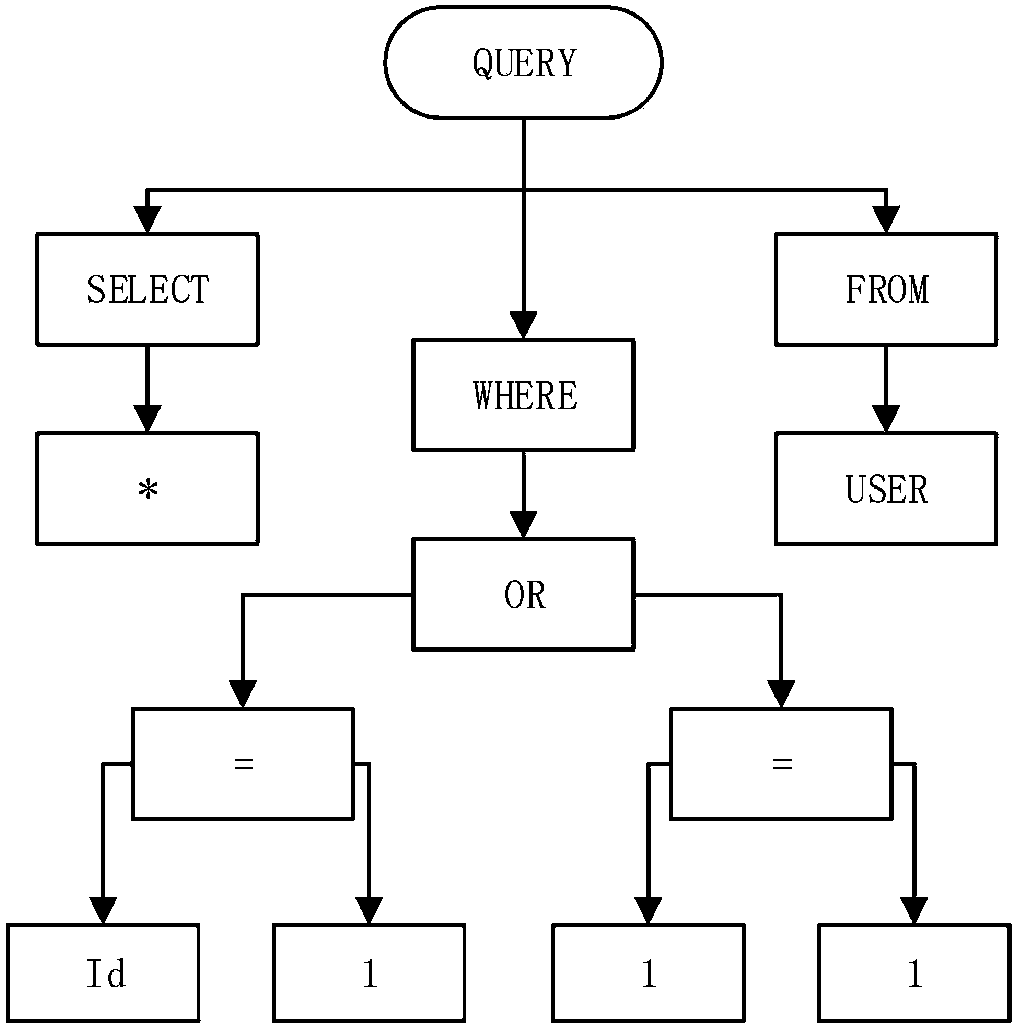
[0038] like figure 1 As shown, the machine learning-based SQL injection detection method provided by the embodiment of the present invention includes the following steps:
[0039]S101: Acquire a training data set for machine learning. Build a SQL injection sample library, collect HTTP request samples containing SQL injection attacks and normal HTTP request samples, and mark them as training materials for ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com