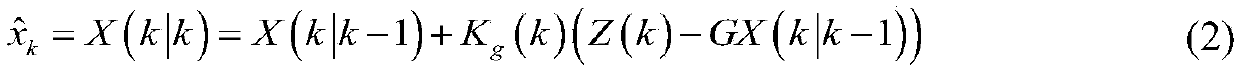Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
287 results about "Injection attacks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
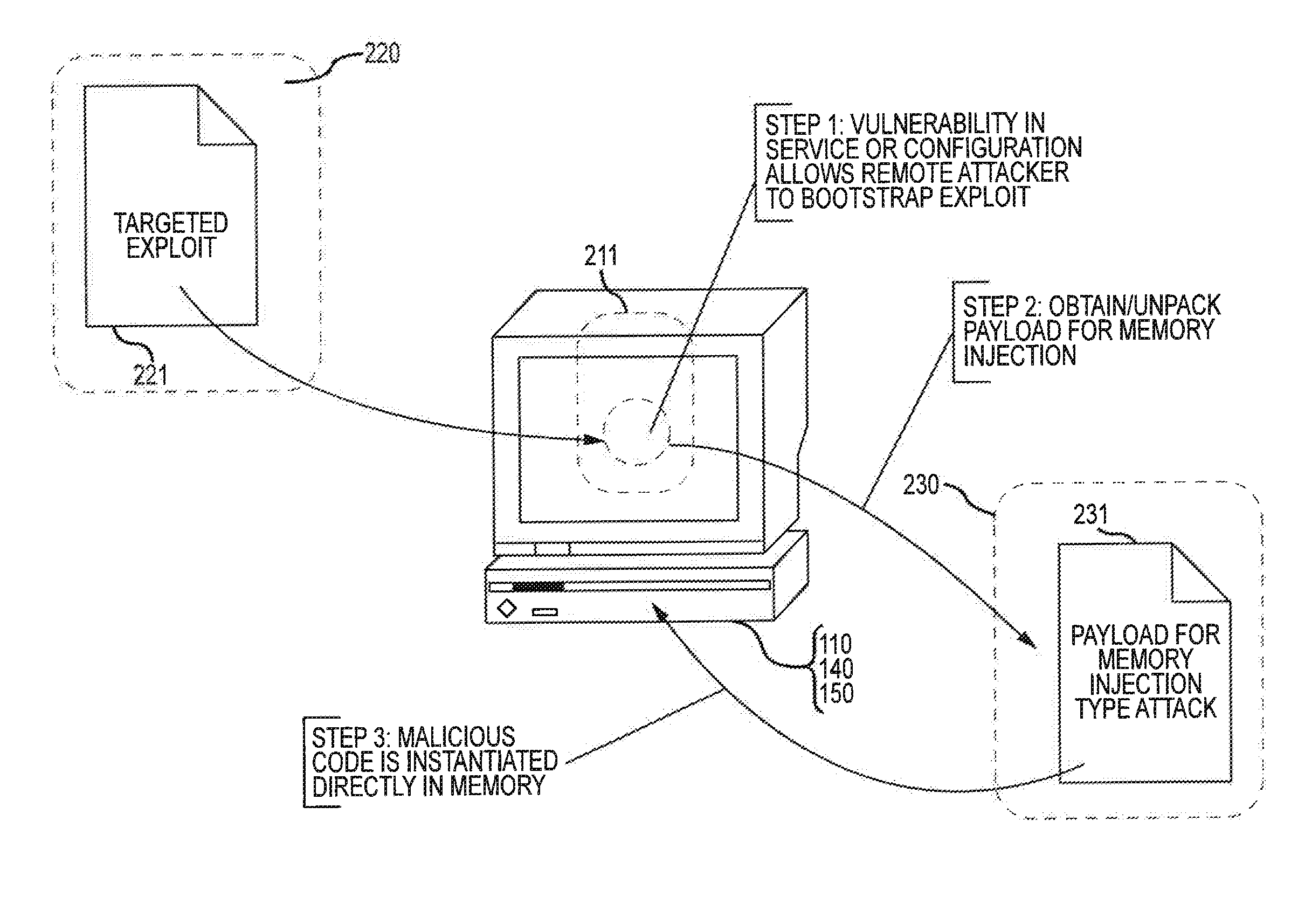
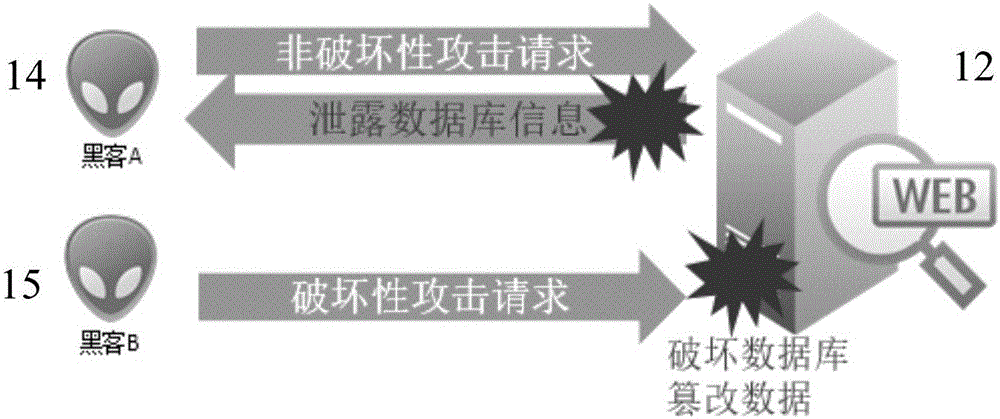
Injection attacks refer to a broad class of attack vectors that allow an attacker to supply untrusted input to a program, which gets processed by an interpreter as part of a command or query which alters the course of execution of that program. Injection attacks are amongst the oldest and most dangerous web application attacks.
Alteration of web documents for protection against web-injection attacks
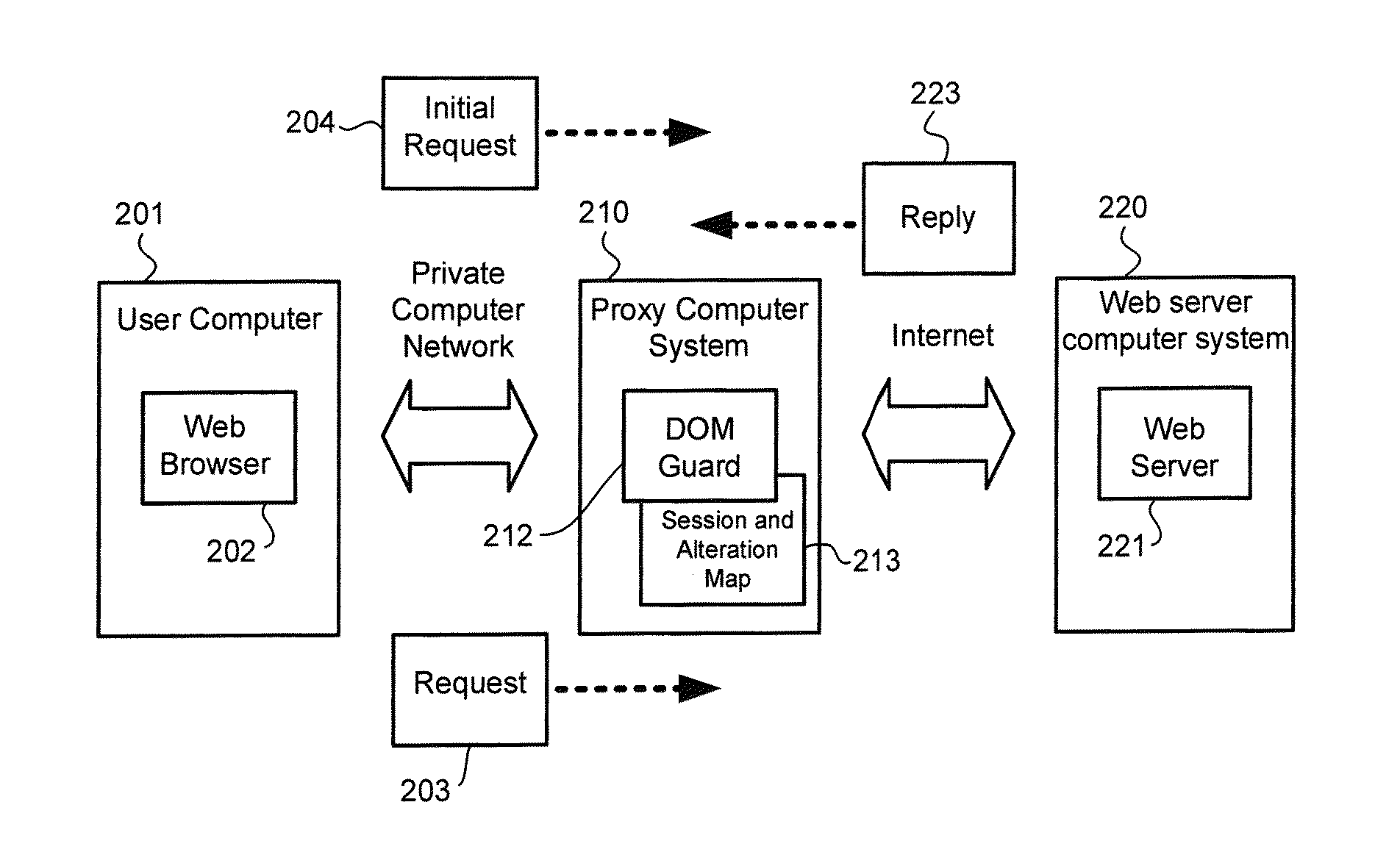
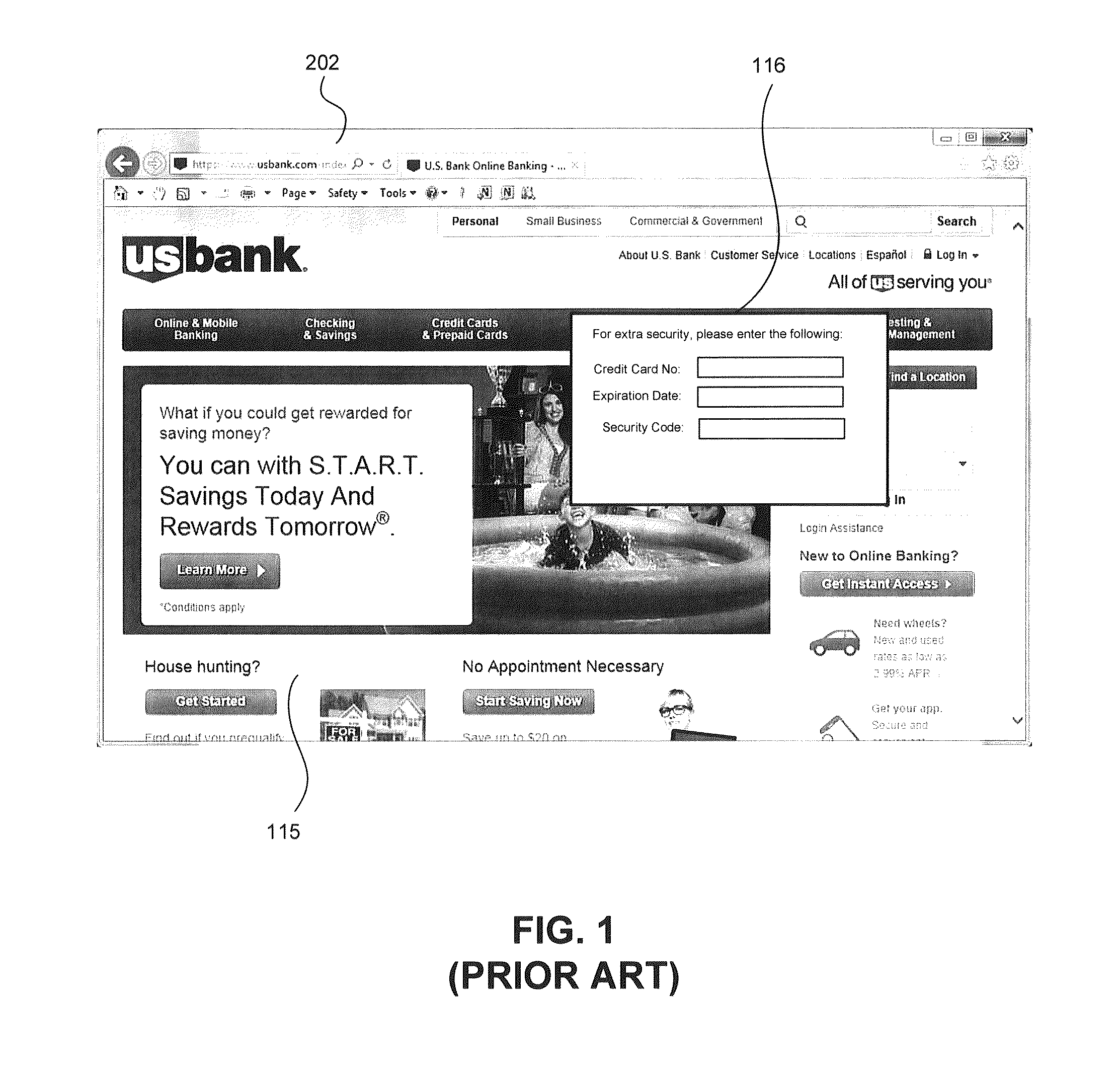
A web document protection module protects web documents against web-injection and other malicious attacks. The web document protection module may be implemented in a user computer, a proxy server computer system, a web server computer system, or other computers. The web document protection module receives a web document, such as a webpage, and alters the web document to change its structure. For example, the web document protection module may obfuscate the web document to make it difficult for malware to find locations in the web document to insert additional program code. The web document protection module provides the obfuscated web document to a web browser for rendering.
Owner:TREND MICRO INC
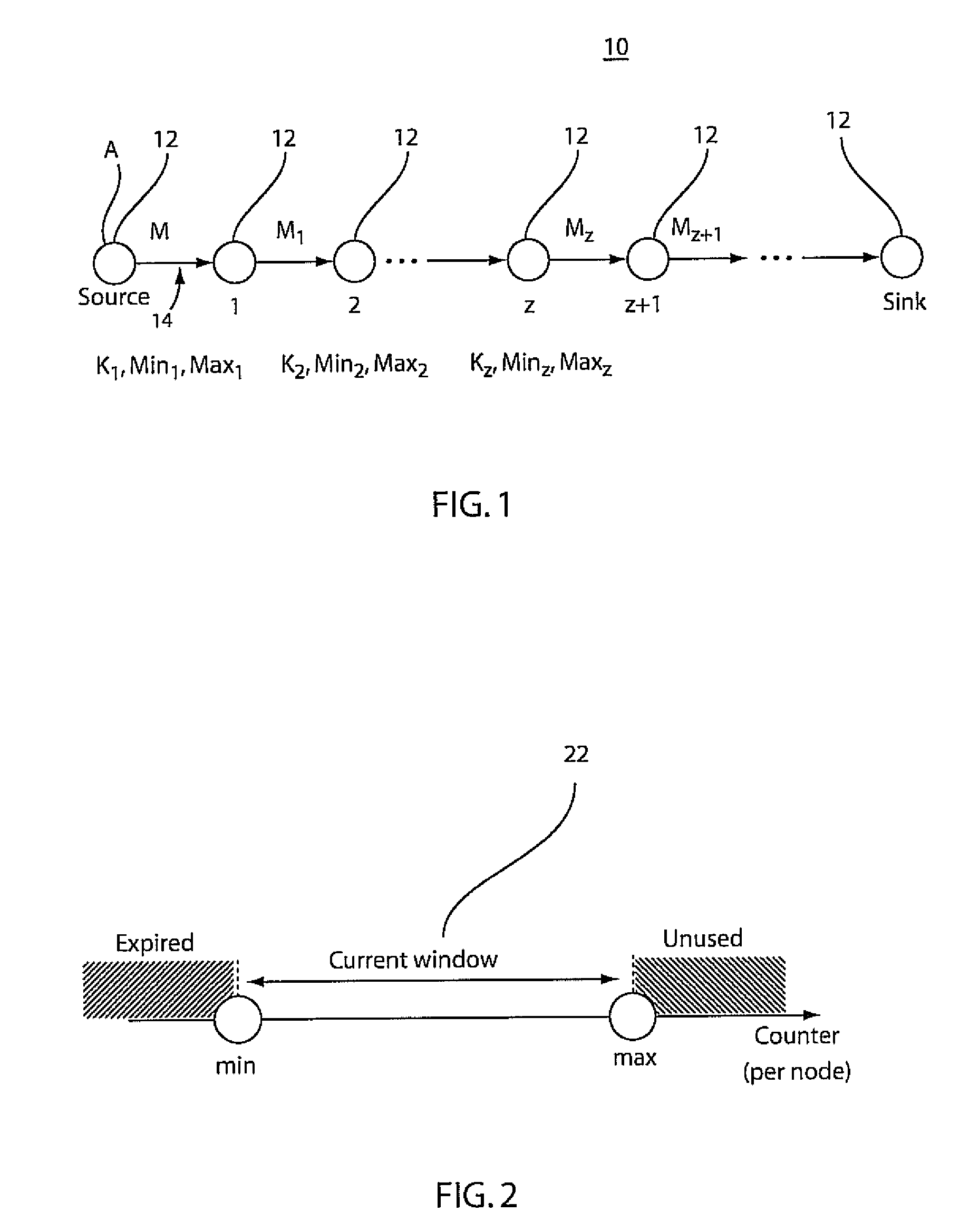
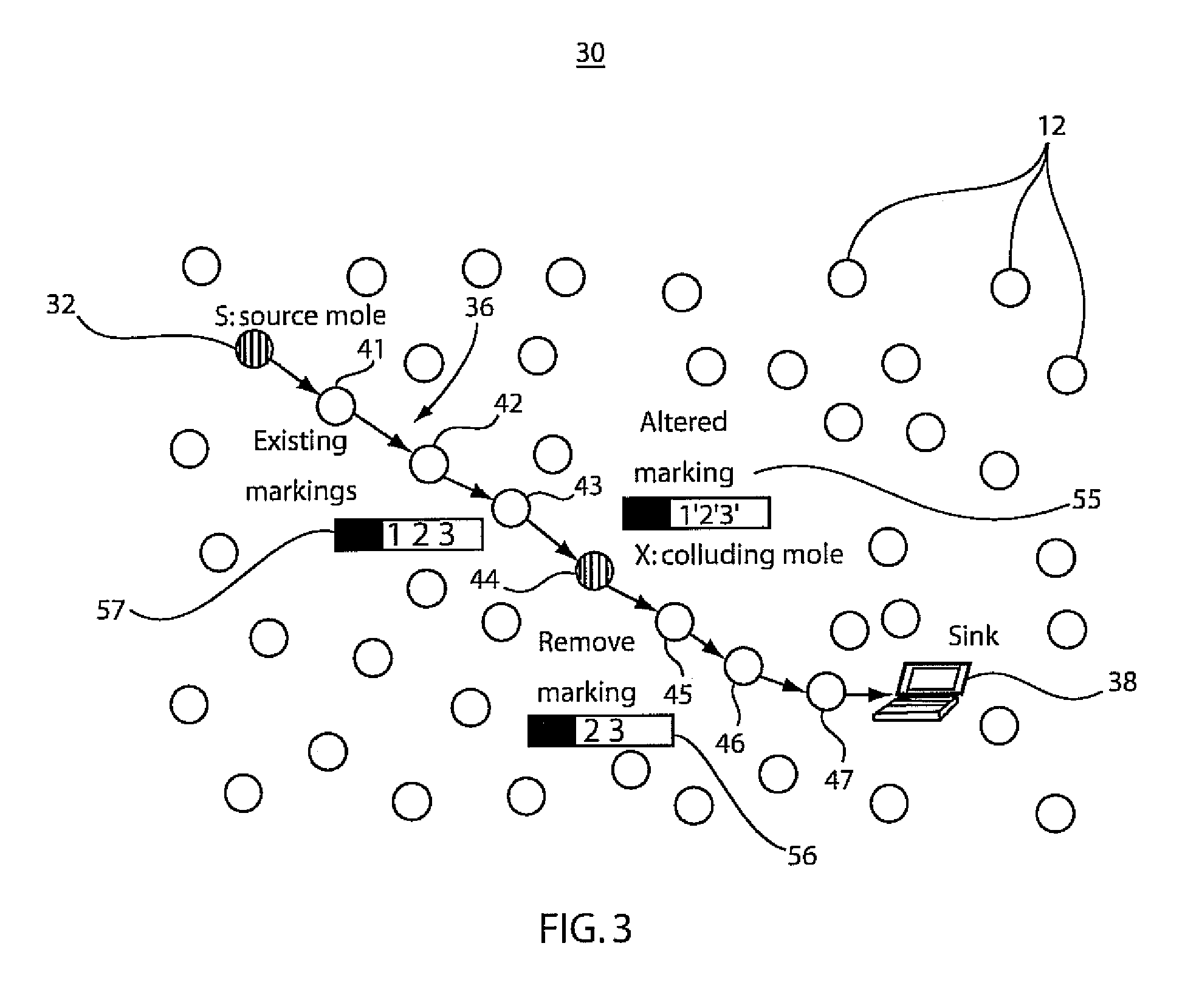
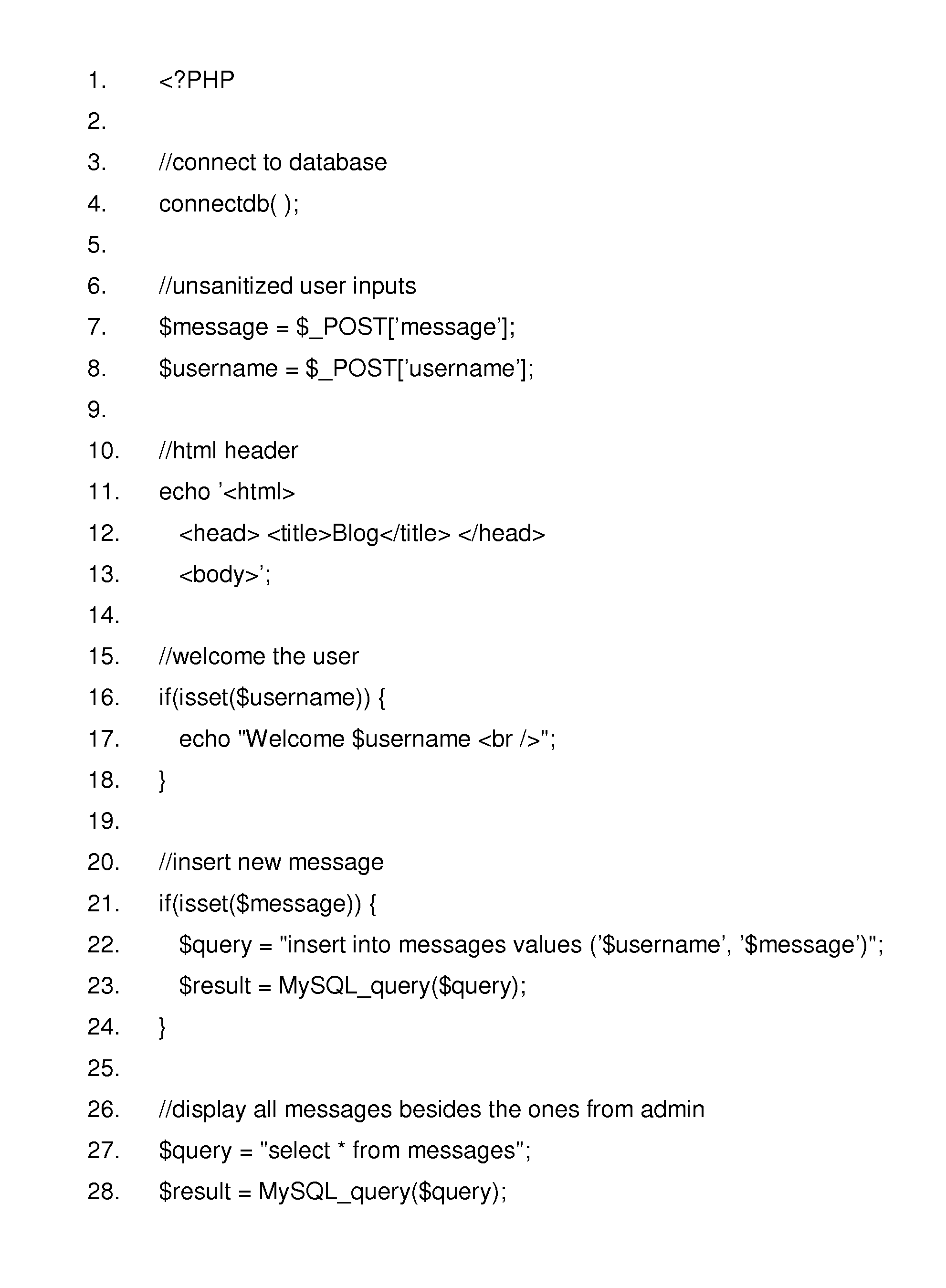
Method and system for resilient packet traceback in wireless mesh and sensor networks
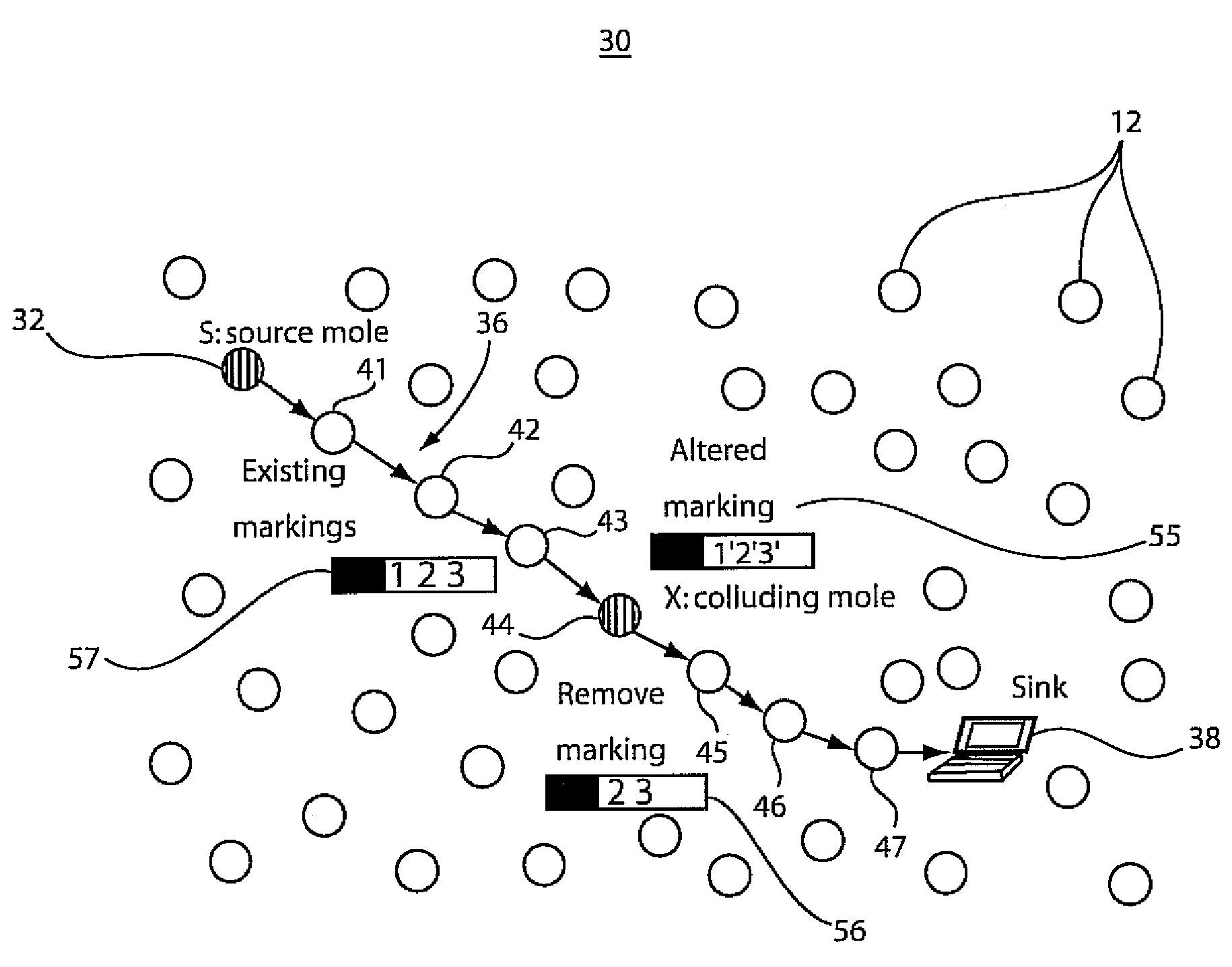
A system and method for packet traceback in a network includes maintaining an identity number (ID) for each node in a network and generating a signature (e.g., a message authentication code (MAC)) using a secret key shared between each node on a forwarding path and a sink. Each forwarding node leaves a mark by appending its ID and a signature in the packet, either in a deterministic manner or with a probability. Upon receiving a packet at the sink, correctness of the signatures included in each packet is verified in the reverse order by which these signatures were appended. A last valid MAC is determined in the forwarding path to determine the locations of compromised nodes that collude in false data injection attacks.
Owner:MARVELL ASIA PTE LTD
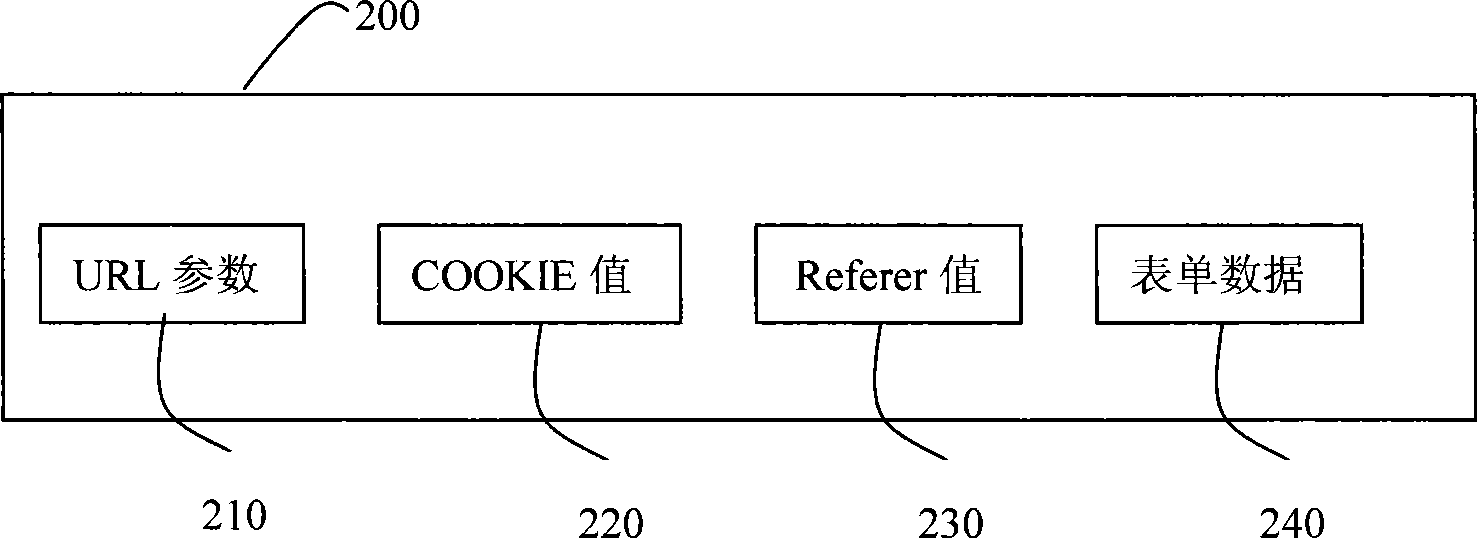
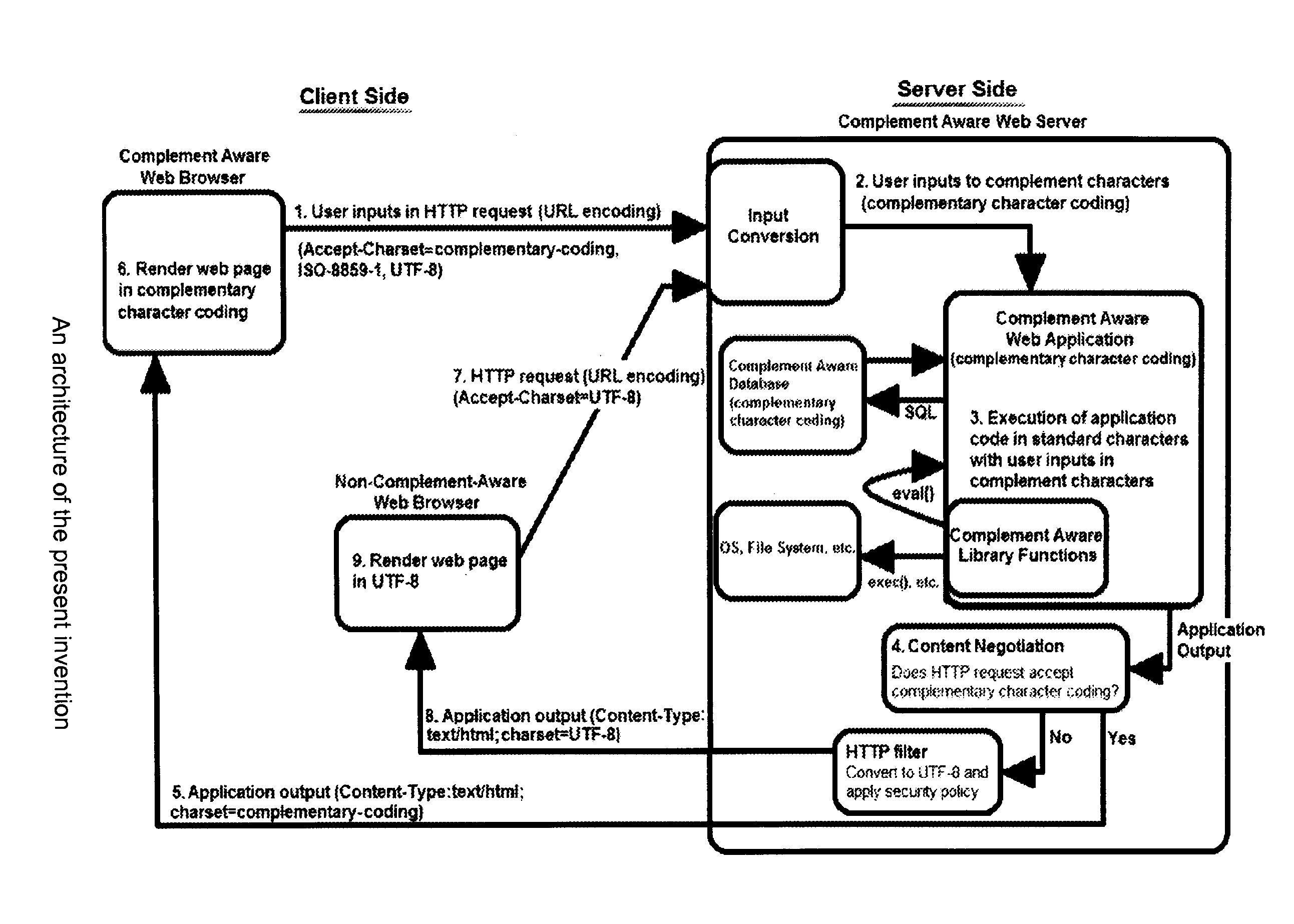
Complementary Character Encoding for Preventing Input Injection in Web Applications
InactiveUS20110252475A1Reduce overheadPreventing executionMemory loss protectionError detection/correctionSQL injectionLexical analysis
Method to prevent the effect of web application injection attacks, such as SQL injection and cross-site scripting (XSS), which are major threats to the security of the Internet. Method using complementary character coding, a new approach to character level dynamic tainting, which allows efficient and precise taint propagation across the boundaries of server components, and also between servers and clients over HTTP. In this approach, each character has two encodings, which can be used to distinguish trusted and untrusted data. Small modifications to the lexical analyzers in components such as the application code interpreter, the database management system, and (optionally) the web browser allow them to become complement aware components, capable of using this alternative character coding scheme to enforce security policies aimed at preventing injection attacks, while continuing to function normally in other respects. This approach overcomes some weaknesses of previous dynamic tainting approaches by offering a precise protection against persistent cross-site scripting attacks, as taint information is maintained when data is passed to a database and later retrieved by the application program. The technique is effective on a group of vulnerable benchmarks and has low overhead.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
Double-layer defense method facing power system false data injection attack
ActiveCN107819785AOptimizationOvert aggressive behaviorData processing applicationsTransmissionInjection attacksData identification
The present invention discloses a double-layer defense method facing a power system false data injection attack, comprising an upper-layer defense policy and a lower-layer defense policy. In the upper-layer defense policy, based on internal defense means of a power system, methods such as bad data identification, injected power detection, and the like are mainly comprised, and injected false datais preliminarily detected, to generate attack space; and in the lower-layer defense policy, based on redundancy measurement defense means, a configuration position of a measurement apparatus is optimized by using a two-person zero-sum game theory according to an attack range that can be defended by the measurement apparatus, to make the measurement apparatus to implement an optimal defense capability on an attack behavior that is not detected by the upper-layer policy. The double-layer defense method facing a power system false data injection attack is used to assist a defender in establishinga power system security defense counterattack system.
Owner:SOUTHEAST UNIV
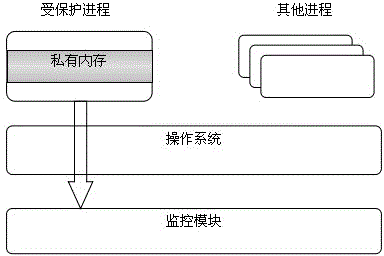
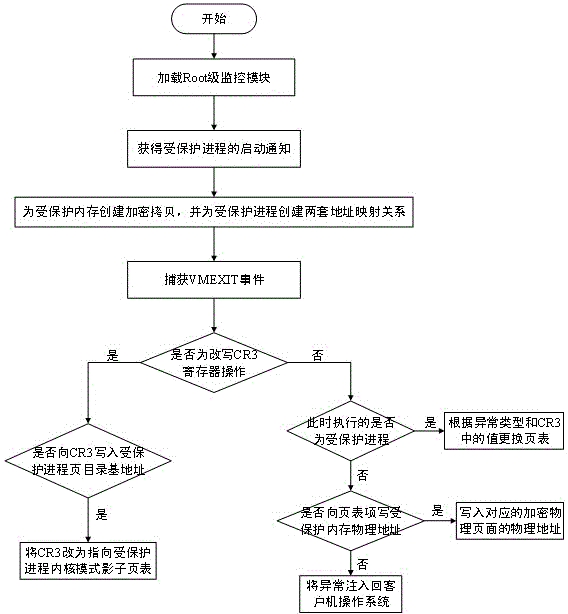
Process memory protecting method based on auxiliary virtualization technology for hardware
InactiveCN103955438AEffective protectionAvoid accessUnauthorized memory use protectionInternal memoryData Execution Prevention
The invention provides a process memory safety protecting method based on auxiliary virtualization for hardware. The method comprises the following steps: 1, loading a process memory monitoring module; step 2, informing the monitoring module during the starting of a protected process; step 3, creating an encrypted copy for a protected internal memory space of the protected process; step 4, realizing internal memory virtualization to a virtual machine system by using a shadow page table mechanism; step 5: acquiring rewritten operation and page fault abnormality of a CR3 register. The process memory safety protecting method provided by the invention has the advantages as follows: the monitoring module working at a Root stage is created to monitor page directories, page tables and modification of a page directory register in all processes so as to prevent any process except the protected process from visiting data in the memory space of the protected process, when the protected process is switched to a core state, a page in a user-mode space is replaced so as to prevent codes in a kernel mode from injection attacks, and a data execution prevention technology is used for setting the page of the data area of the protected process to be non-executable. Therefore, codes in the user mode are prevented from injection attacks.
Owner:NANJING UNIV
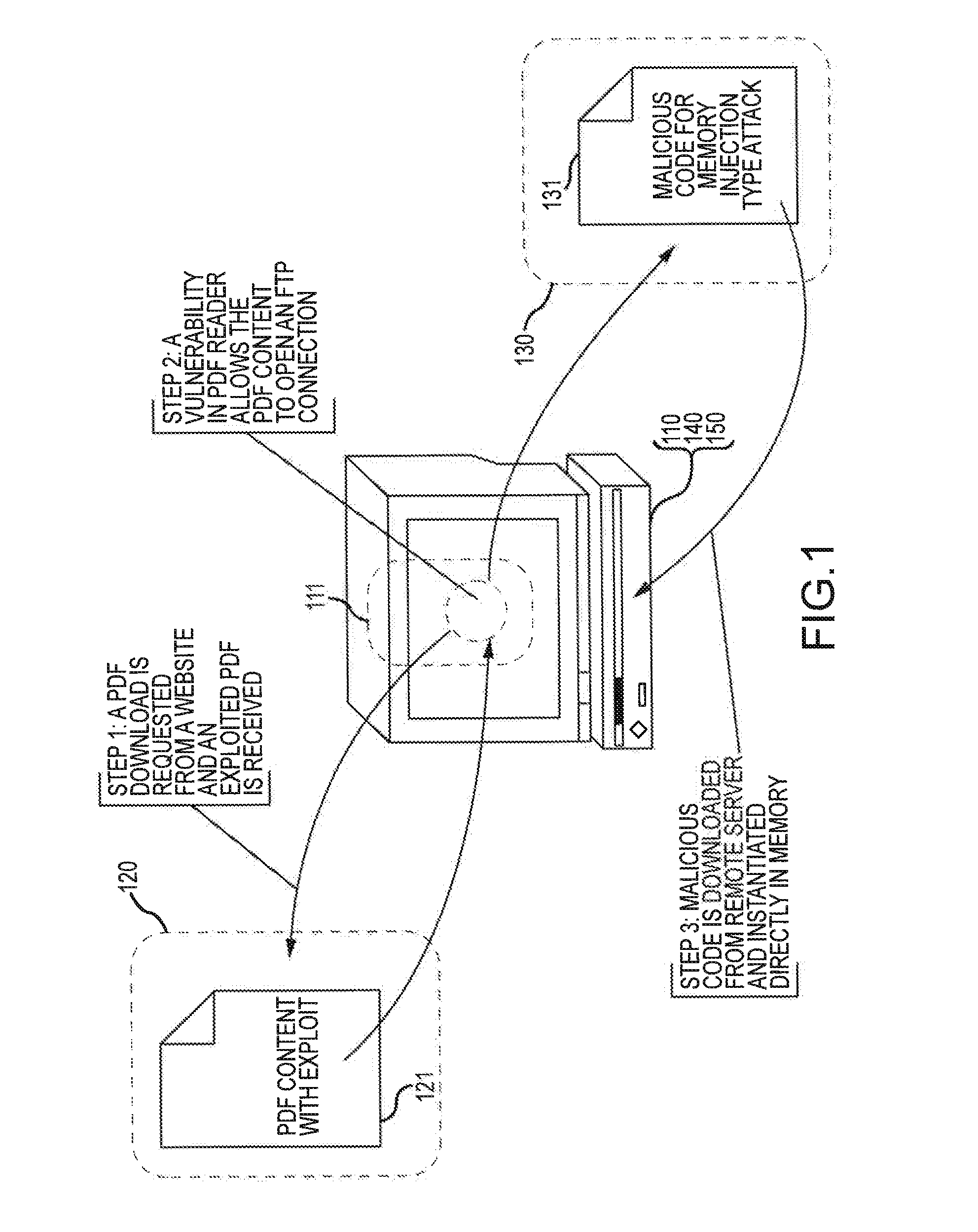
Information security techniques including detection, interdiction and/or mitigation of memory injection attacks
ActiveUS20130290662A1Easy to processUnauthorized memory use protectionPlatform integrity maintainanceComputerized systemInformation security
Methods of detecting malicious code injected into memory of a computer system are disclosed. The memory injection detection methods may include enumerating memory regions of an address space in memory of computer system to create memory region address information. The memory region address information may be compared to loaded module address information to facilitate detection of malicious code memory injection.
Owner:IVANTI INC
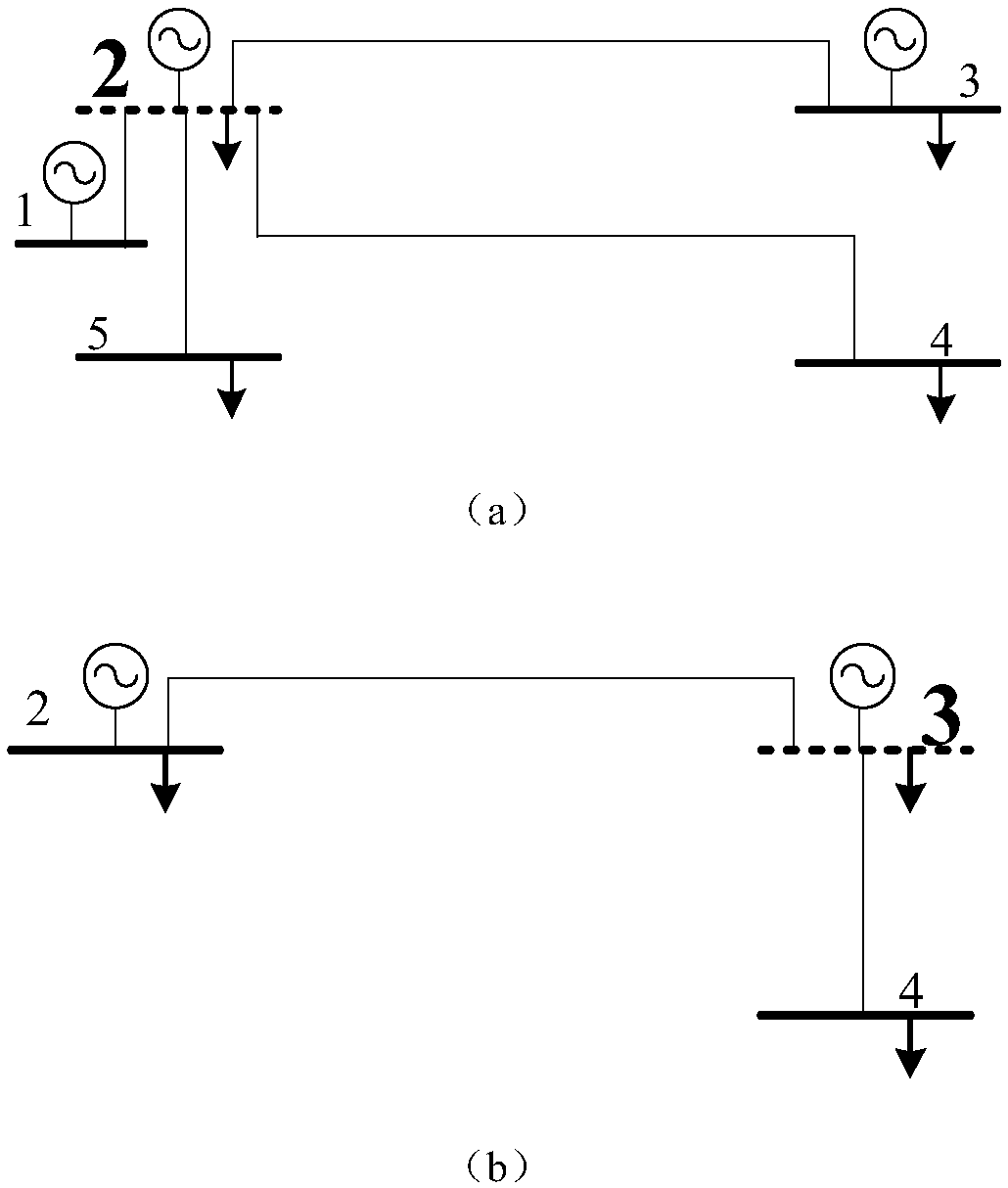
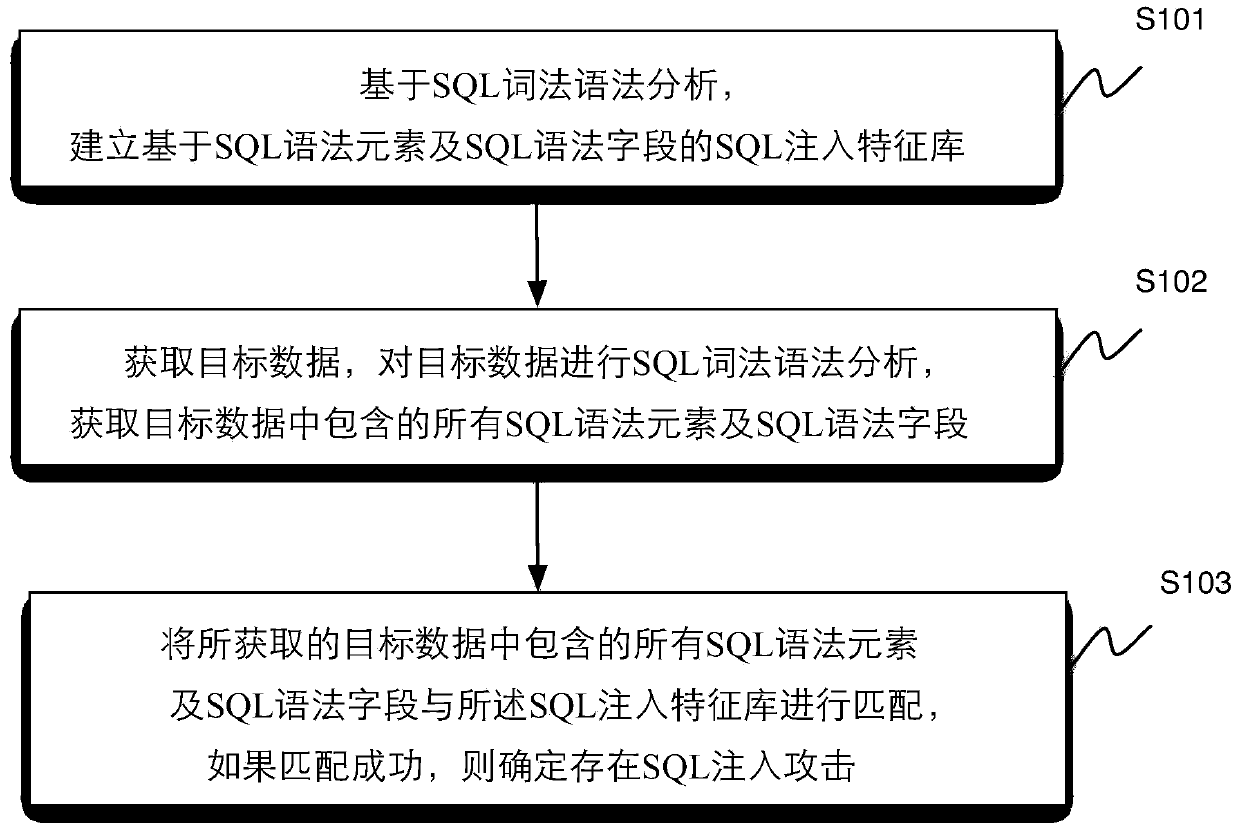
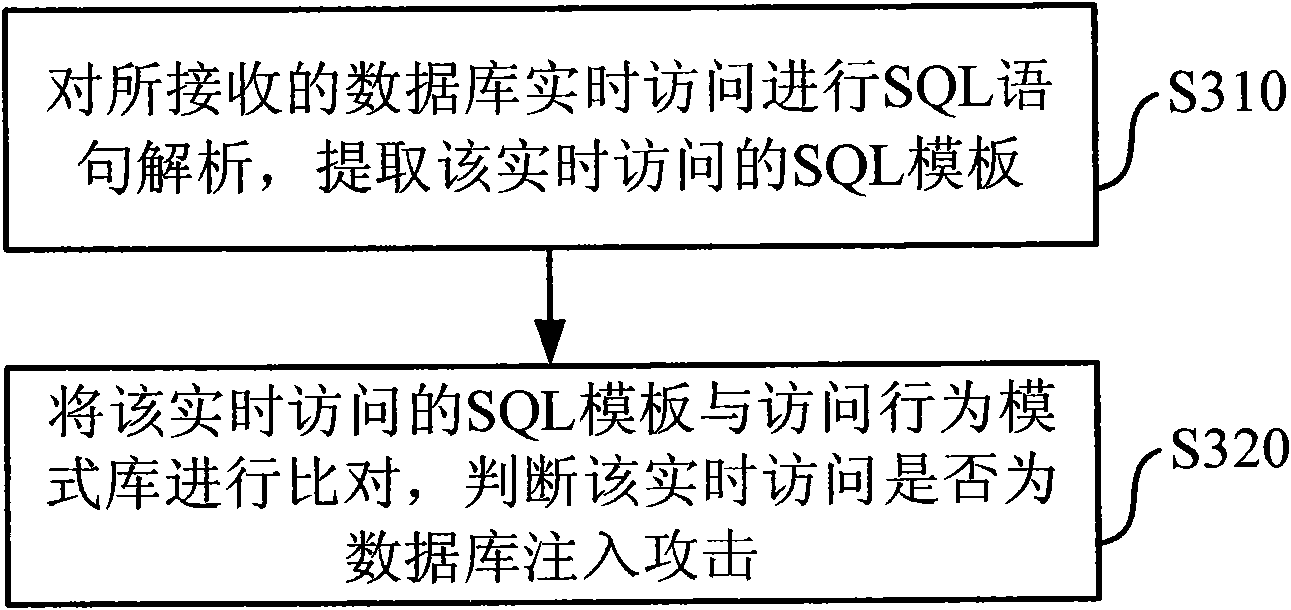
Method and device for identifying SQL injection attacks
ActiveCN103744802AImprove efficiencyReduce false positivesUnauthorized memory use protectionMultiple digital computer combinationsSQL injectionMisinformation
The invention discloses a method and a device for identifying SQL (Structured Query Language) injection attacks, wherein the method comprises the steps of establishing an SQL injection feature library based on SQL syntax elements and SQL syntax fields through SQL lexical and syntactic analysis, obtaining target data, performing the SQL lexical and syntactic analysis on the target data and obtaining all SQL syntax elements and SQL syntax fields included in the target data, next, matching all of the obtained SQL syntax elements and SQL syntax fields included in the target data with the SQL injection feature library, and if matching is successful, determining the existence of the SQL injection attacks. The method and the device are capable of improving the efficiency of identifying SQL injection and reducing misinformation and failures in report.
Owner:BEIJING QIANXIN TECH
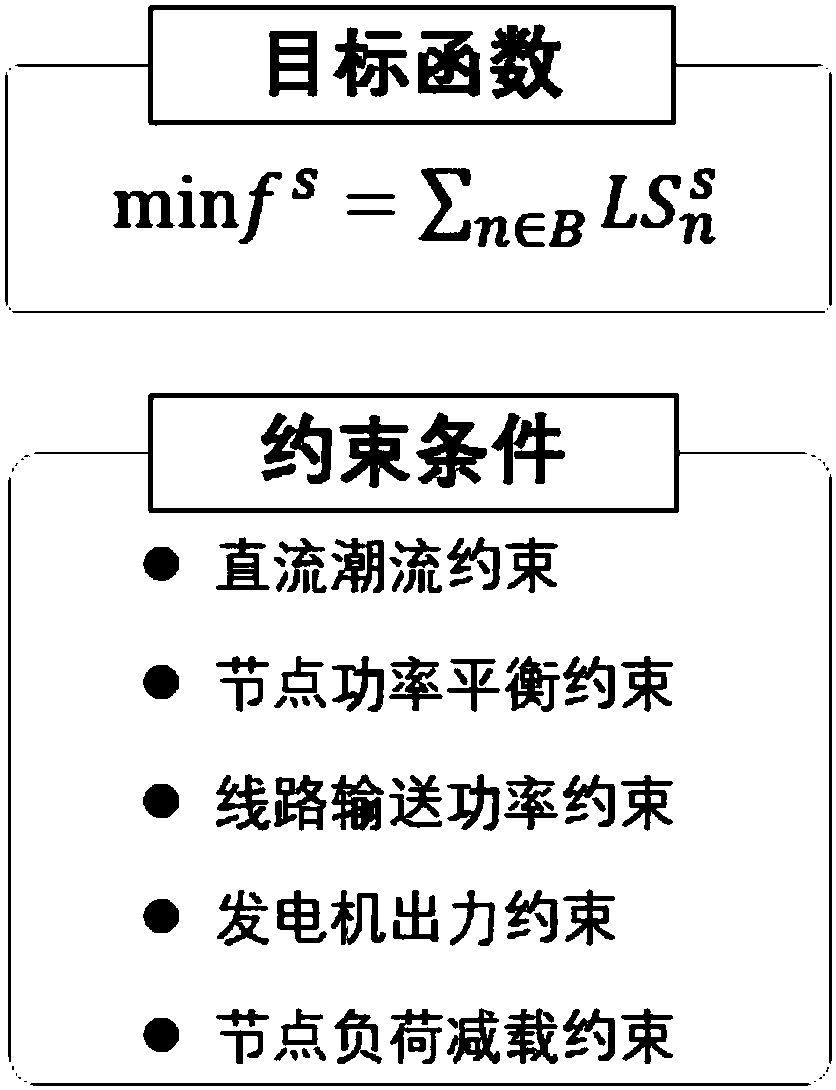
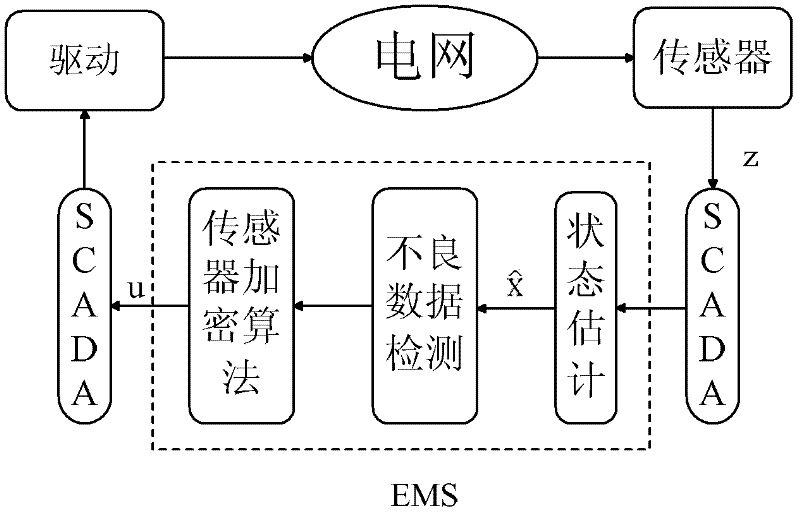
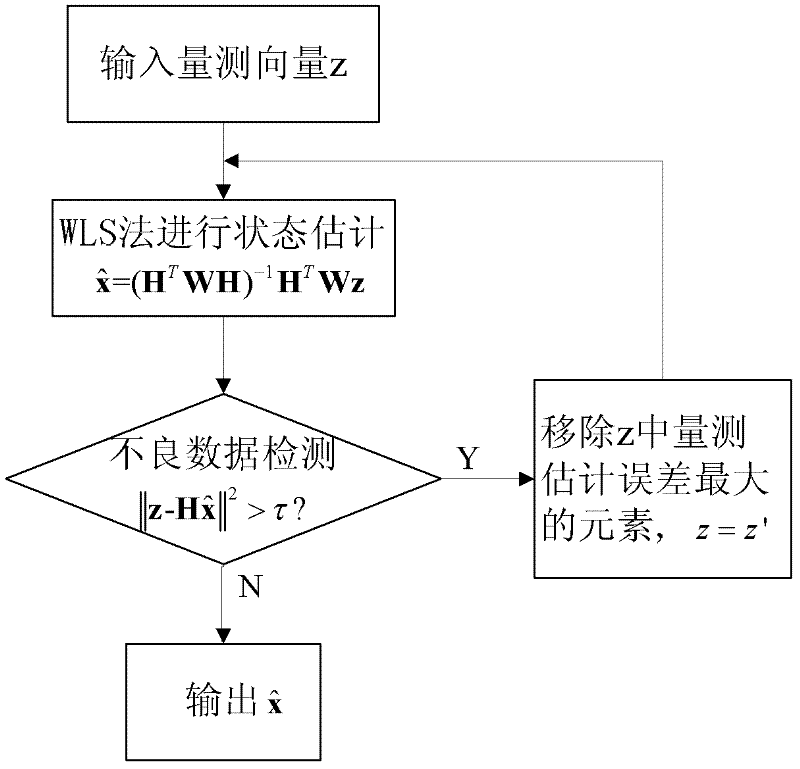
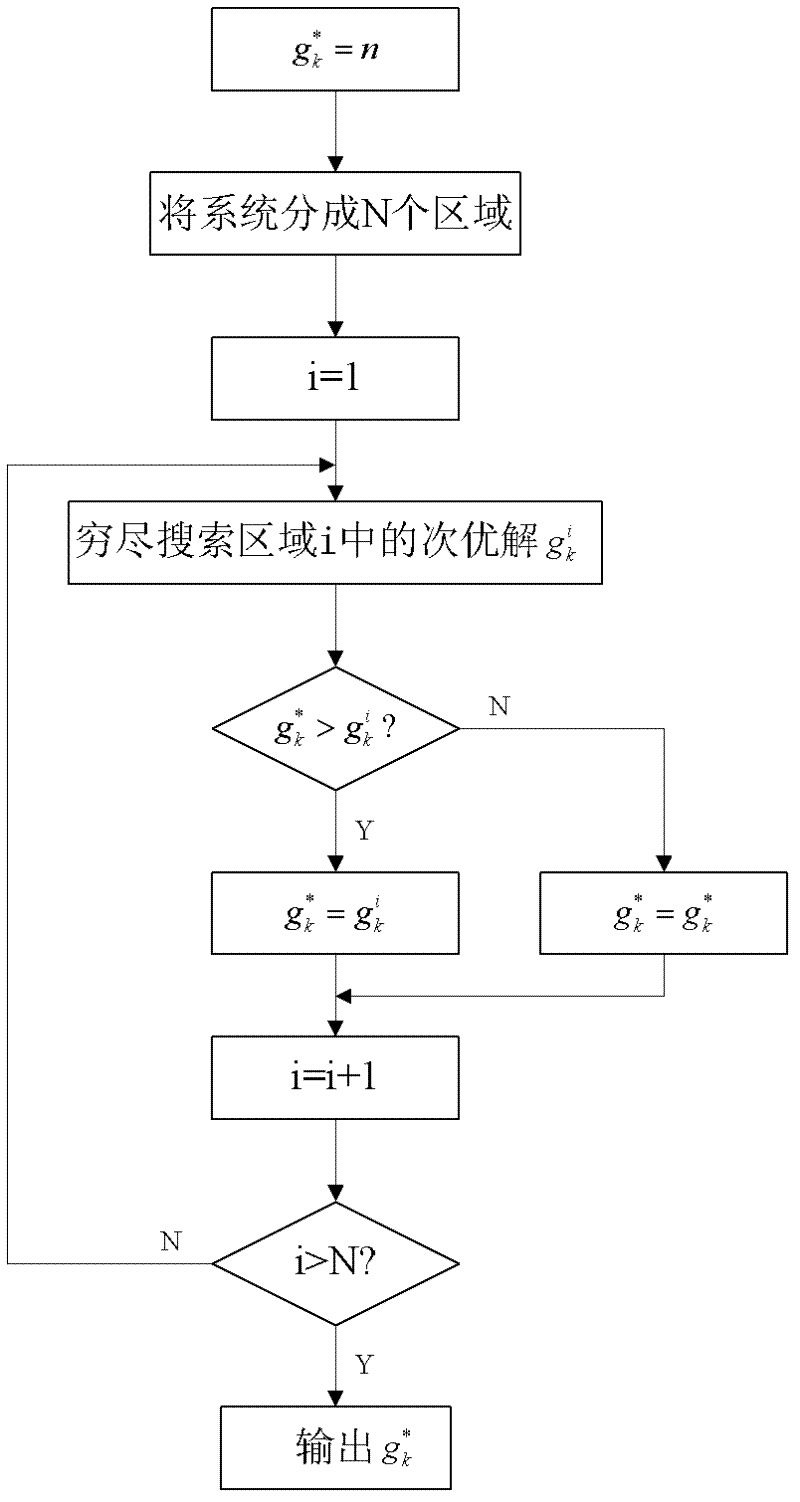
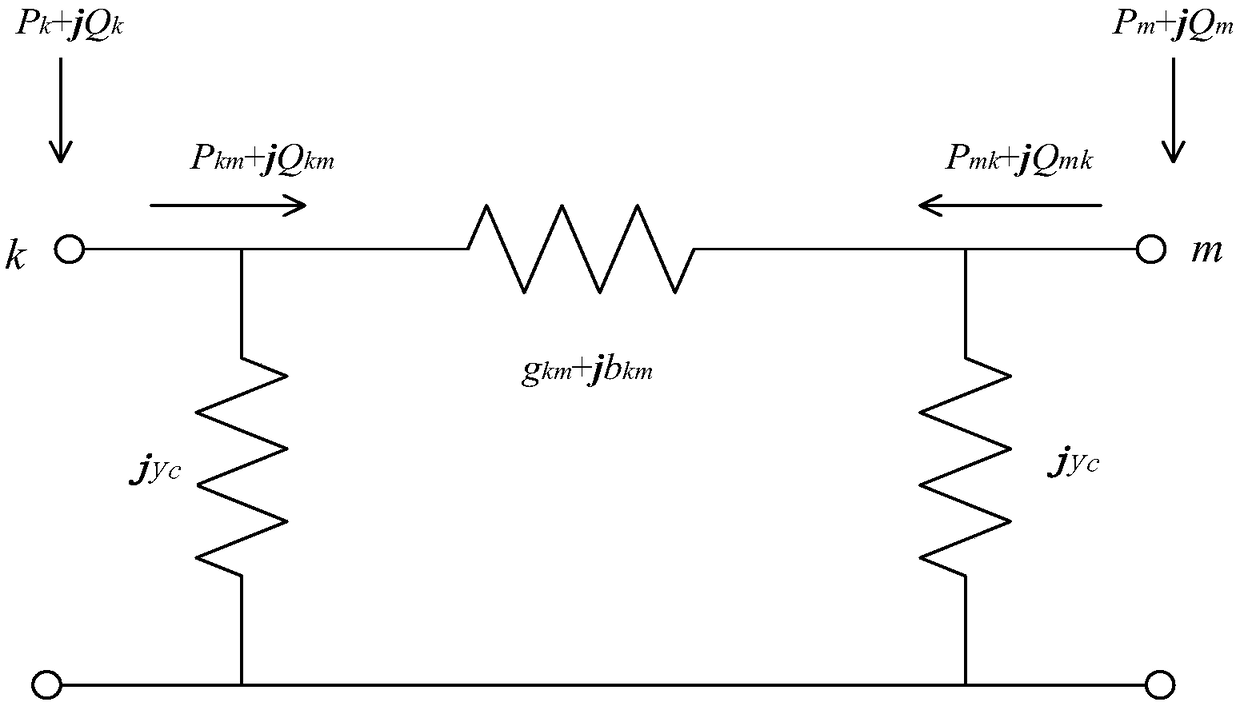
Method for defending false-data injection attack in direct-current state estimation of electrical power system
ActiveCN102522743AImprove accuracySecuring communicationInformation technology support systemComputer scienceInjection attacks
The invention discloses a method for defending false-data injection attacks in the direct-current state estimation of an electrical power system, which belongs to the technical fields of electrical-power system safety and control and comprises the following steps of: estimating the real-time state of a direct-current system by a weighted least square method, and filtering measuring noise and random disturbance; processing a state-estimating result by a maximum standard residual-error detecting method, and detecting and identifying bad data in quantity measurement; and calculating the sensor quantity-measuring combination which is most easily destroyed by the false-data injection attacks by a heuristic algorithm, carrying out encryption protection for a group of sensors, and blocking the false-data injection attacks from occurring from a source. The method can be used for accurately and rapidly defending the false-data injection attacks in the state estimation of the electrical power system, and the state-estimating accuracy and safety of the electrical power system are improved.
Owner:XI AN JIAOTONG UNIV
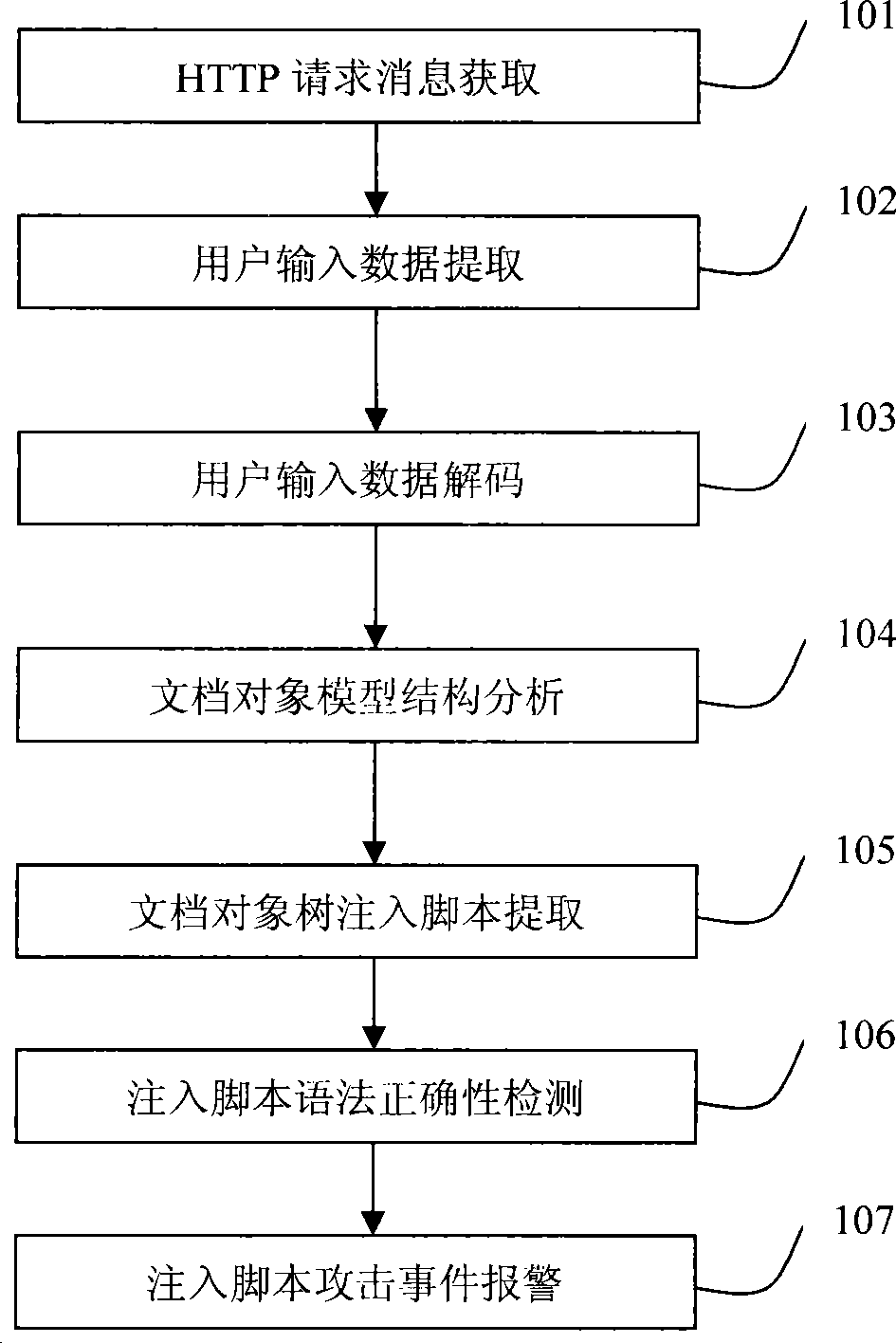
Script injection attack detection method and system
InactiveCN101459548AEasy to detectImprove detection accuracyData switching networksUser inputWeb service
A script injection and attacking detection method and a system belong to the technical field of computing network, wherein the method comprises requesting and obtaining by HTTP, extracting user input data from HTTP request, doing script injection and attacking detection to user input data, and alarming script injection and attacking affairs and the like, wherein script injection and attacking detection step to user input data comprises decoding user input data, analyzing document object model structure, extracting document object model script and detecting script grammar and the like. The script injection and attacking detection system comprises an HTTP requesting and obtaining module, a user inputting data extraction module, a script injection and attacking module and a script injection and attacking alarm module, wherein the script injection and attacking detection module comprises a user input data decoding module, a document object model structure analyzing module, an injection script extracting module and a script grammar detecting module. The script injection and attacking detection method and the system are suitable for applying in Web service security insurance products.
Owner:BEIJING VENUS INFORMATION TECH
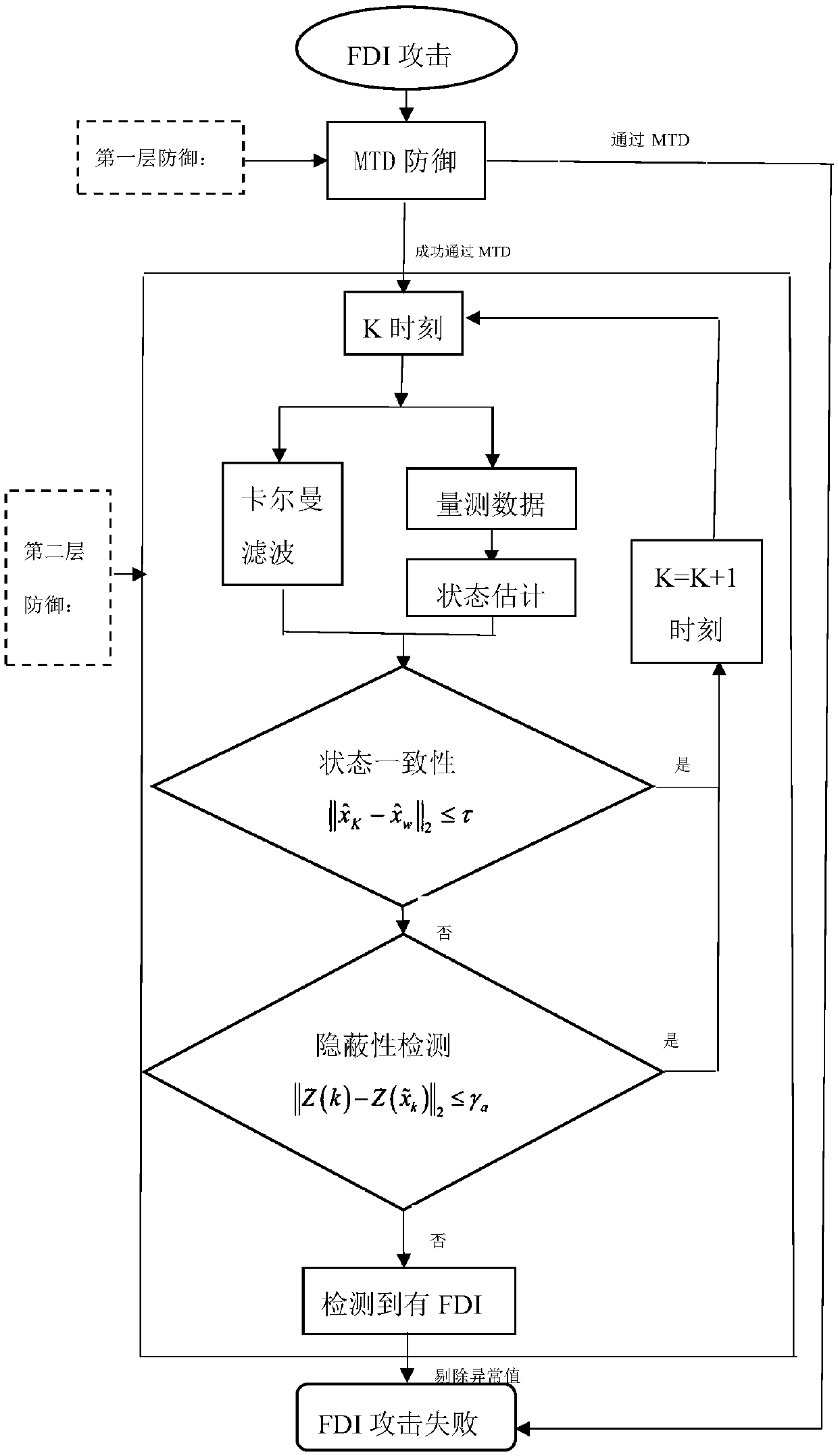
A two-layer defense method against spurious data injection attack in power system
ActiveCN108989330ADefense against injection attacksTransmissionInformation technology support systemEstimation methodsElectric power system
The invention discloses a two-layer defense method for false data injection attack in a power system, comprising a two-layer defense strategy. The first layer adopts moving target defense to defend the false data injection attack from the source, and the second layer adopts Kalman filter state estimation method to eliminate the false data injection attack after moving target defense. The inventionadopts a double-layer defense strategy, which makes up for the deficiency of using only the moving target defense, so as to maintain the normal operation of the electric power system.
Owner:GUANGDONG UNIV OF TECH
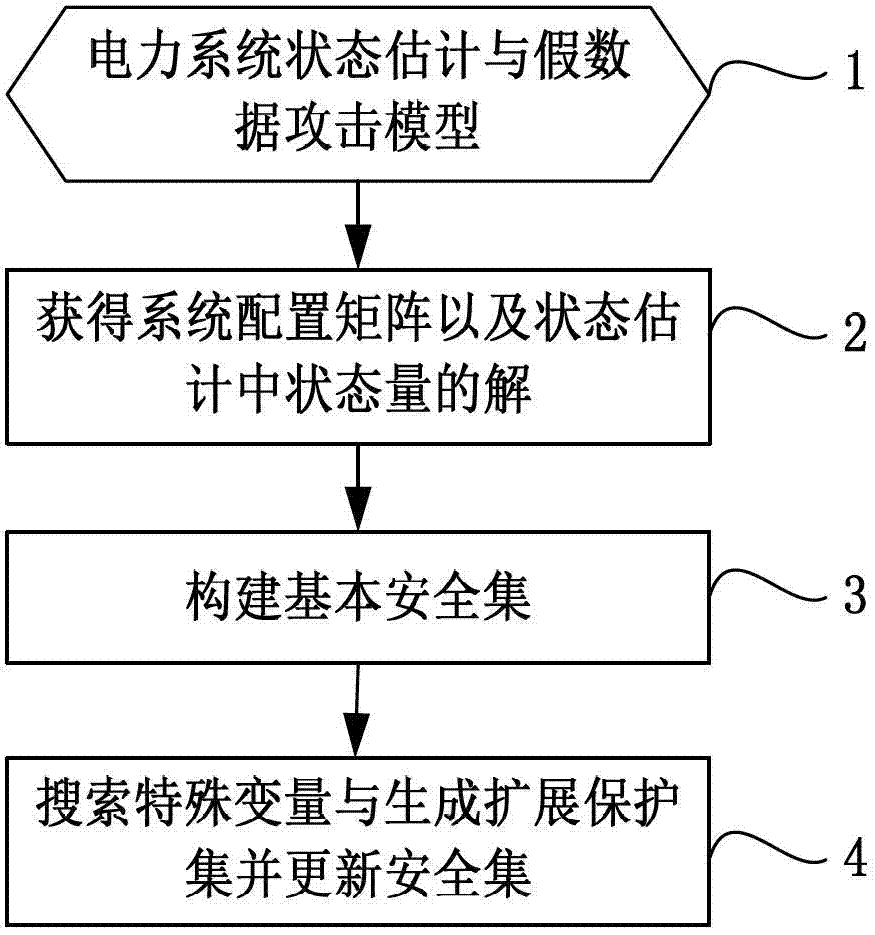
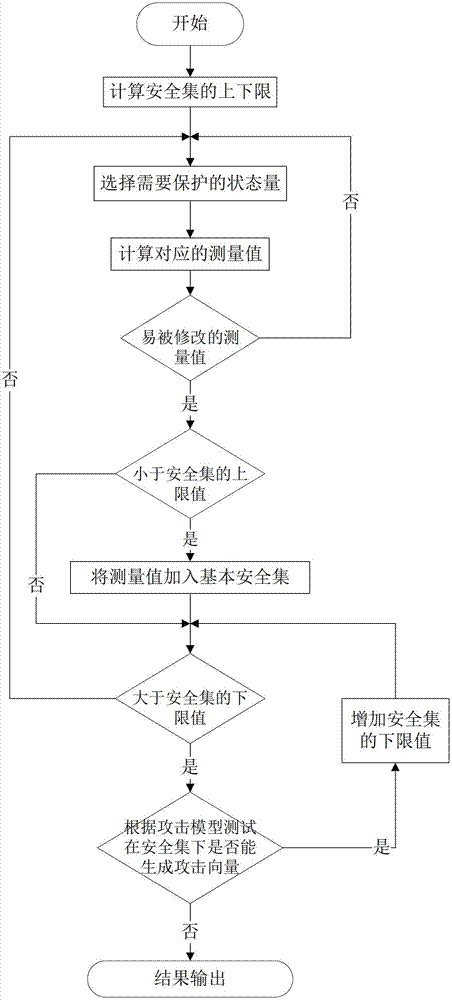
Defense method of false data injection attack of power state estimation system
The invention discloses a defense method of false data injection attack of a power state estimation system, belonging to the field of intelligent power grid and information safety. The method comprises the following steps of: firstly establishing a power system state estimating model and a false data attack model; subsequently calculating a system configuration matrix so as to obtain the solution of the state quantity of the power system state estimating model; further establishing the safety set of the system; and updating the safety set when the power system is changed in structure. The method is based on a protection set and by arranging an expansion protection set, the false data injection attack can be defended even a network structure is changed, thereby ensuring the security of the power system.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
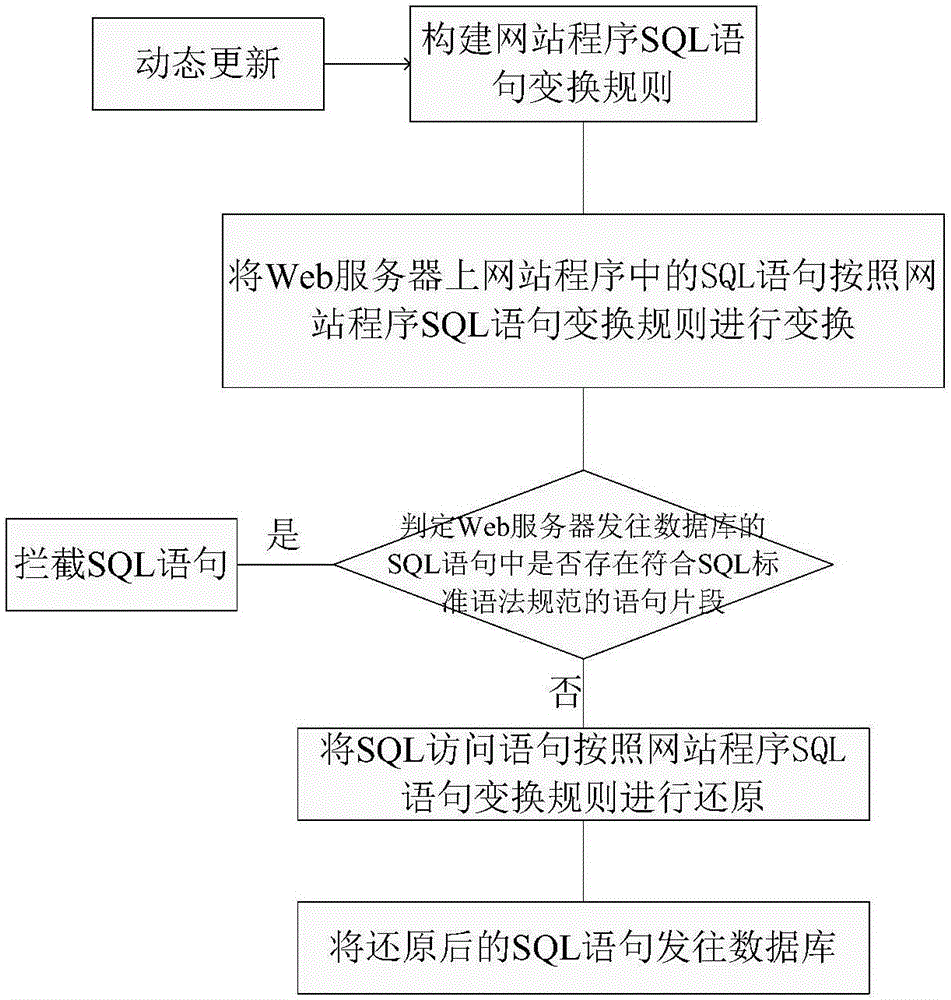
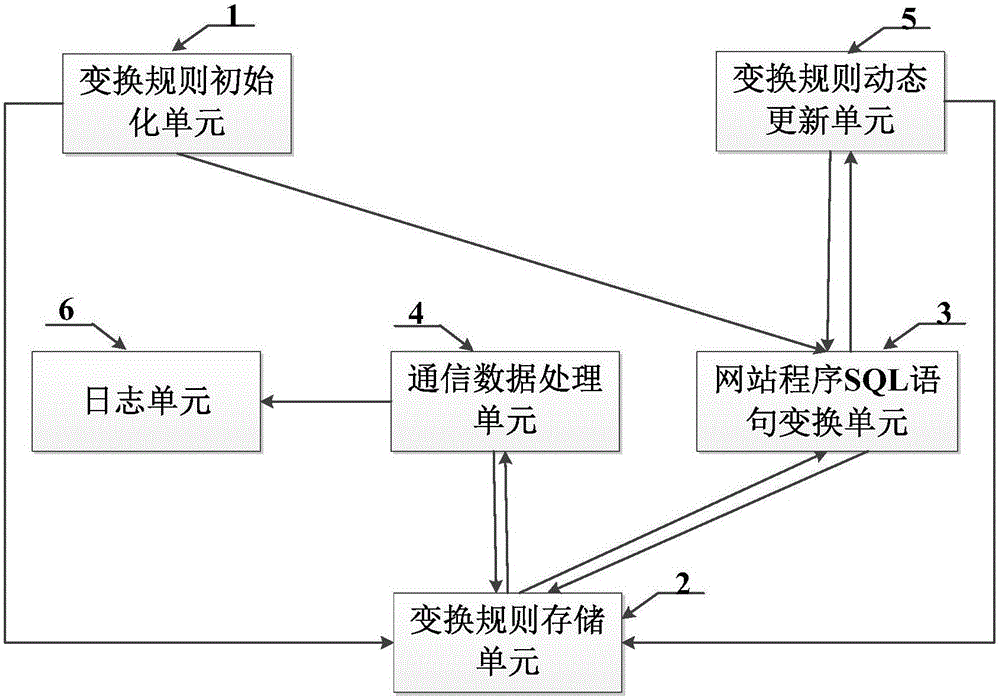
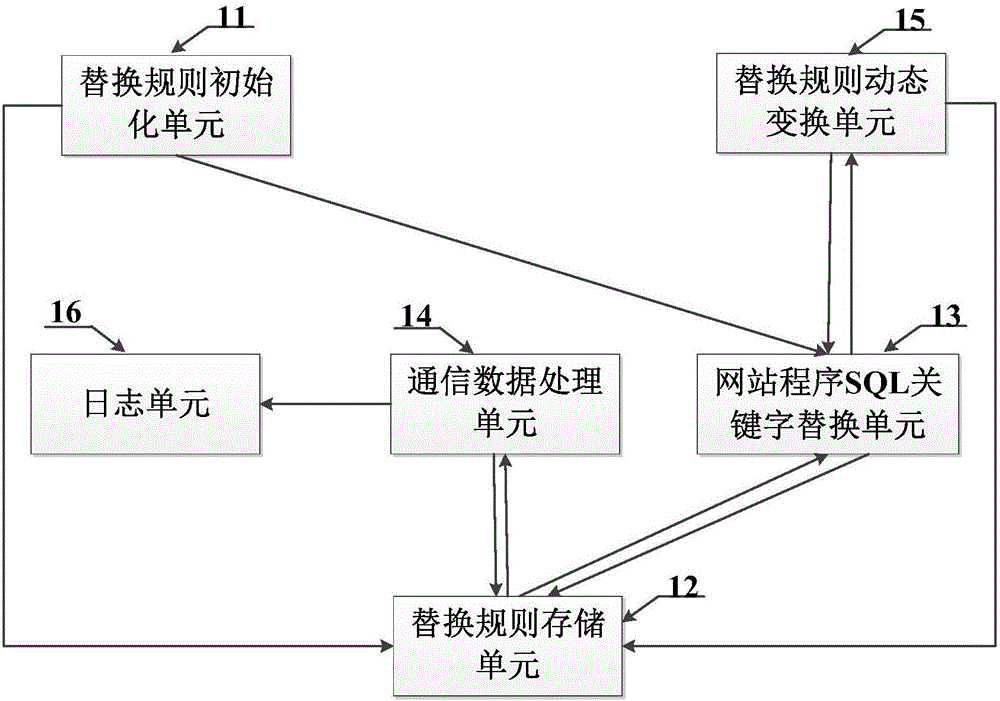
SQL (structured query language) injection attack defensive system and defensive method based on grammar transformation
ActiveCN106355094AReduce development and maintenance costsReduce false alarm ratePlatform integrity maintainanceWeb serviceSQL injection
The invention provides an SQL (structured query language) injection attack defensive system and method based on grammar transformation. The SQL statement transformation rule of website program is built; SQL statements in the website program on a Web server are subjected to initialization transformation operation; whether attack statements are injected into SQL access statements sent to a database by the Web server or not is judged; the SQL statement transformation rule of the website program is dynamically transformed, so that the effective defense on the SQL injection attack is realized. The SQL injection attack defensive system and method based on grammar transformation do not depend on rules; the vicious SQL injection attack is precisely recognized on the basis of statement transformation and grammatical analysis; the false alarm rate and the missing report rate are extremely low; the system and the method are applicable to various types of Web servers and database systems; the SQL injection attack behavior can be effectively defensed; the safety protection on the Web server and a background database is obviously improved.
Owner:北京卫达信息技术有限公司
Detection method for injection attack of database and system
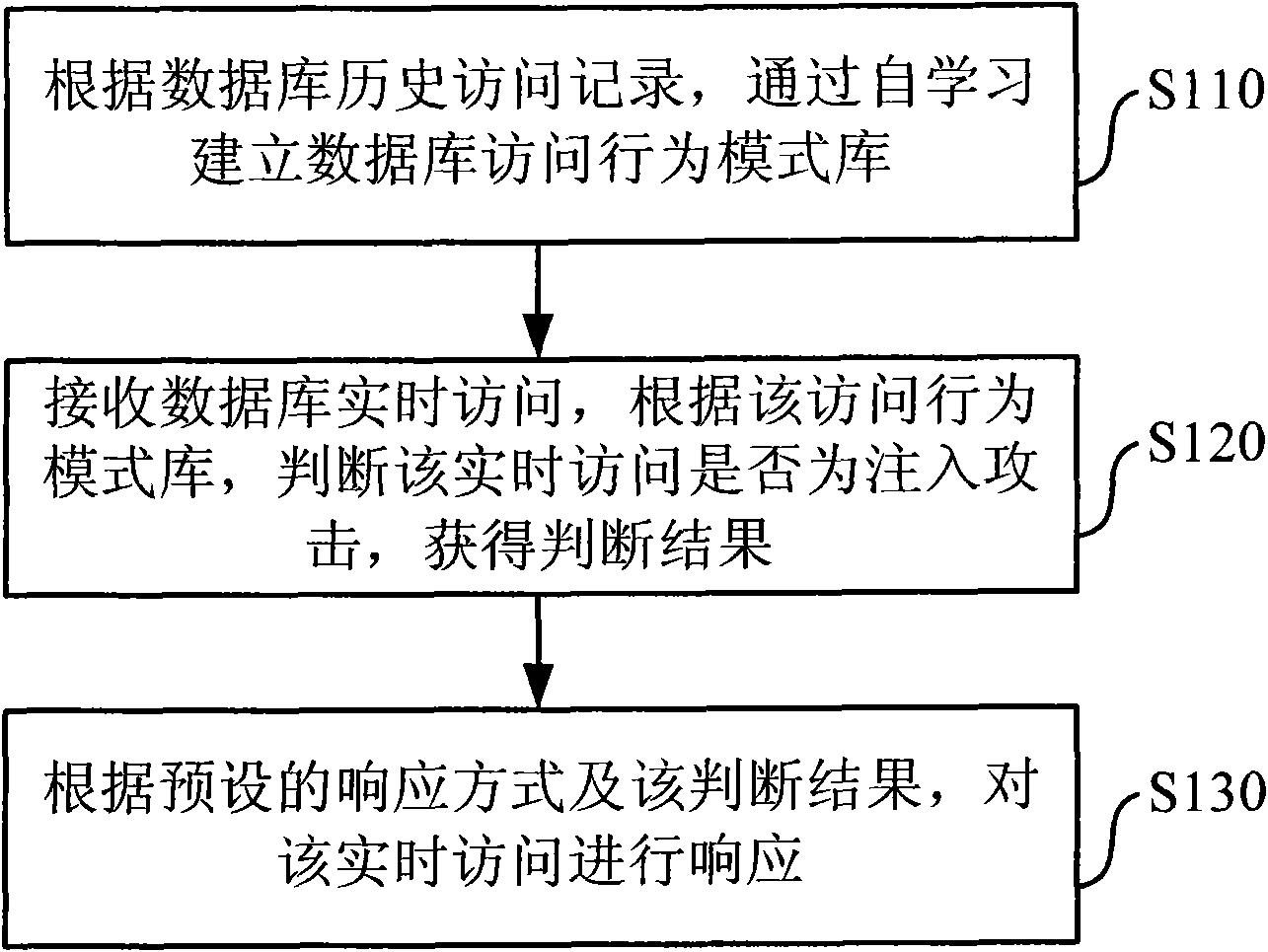
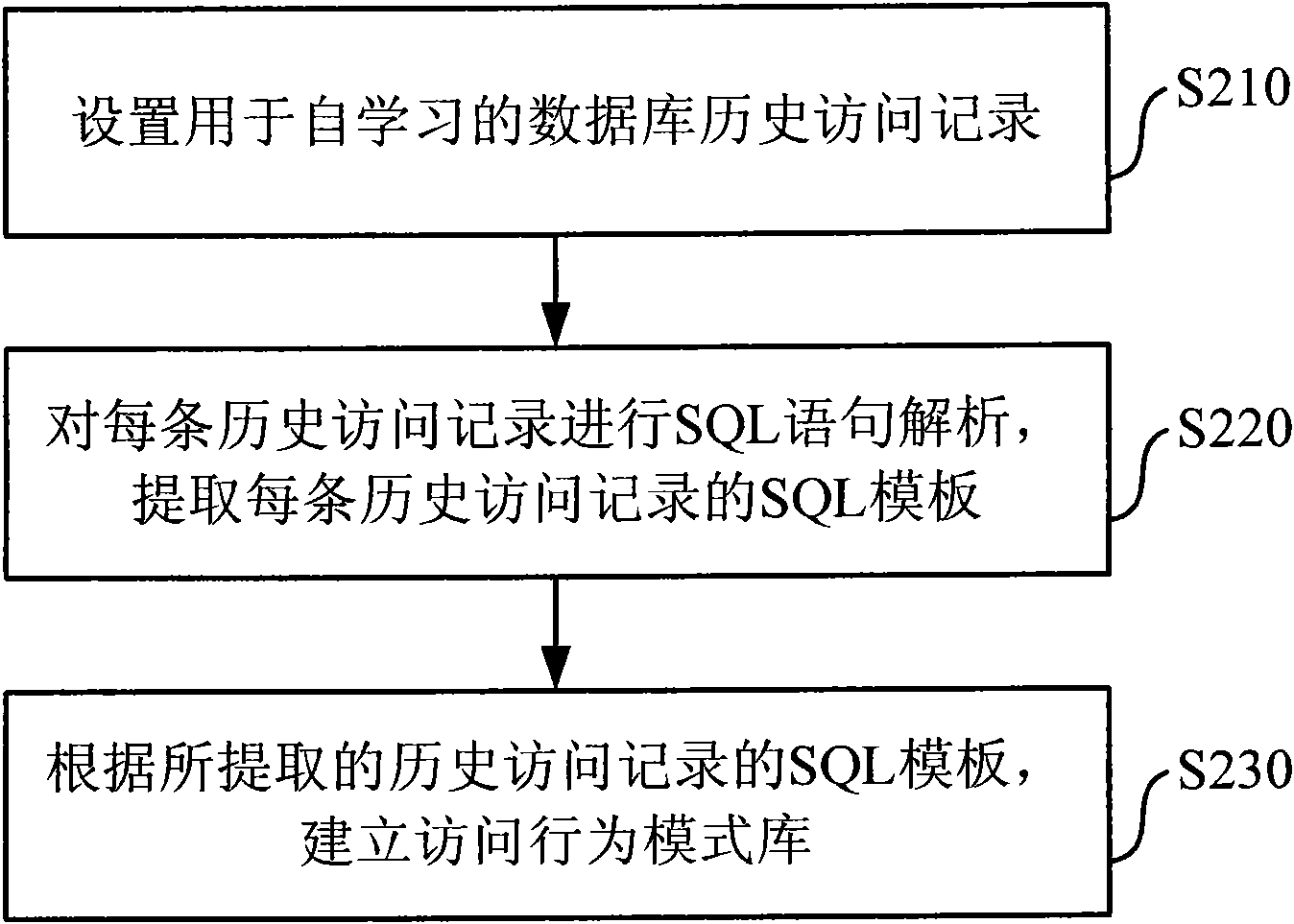
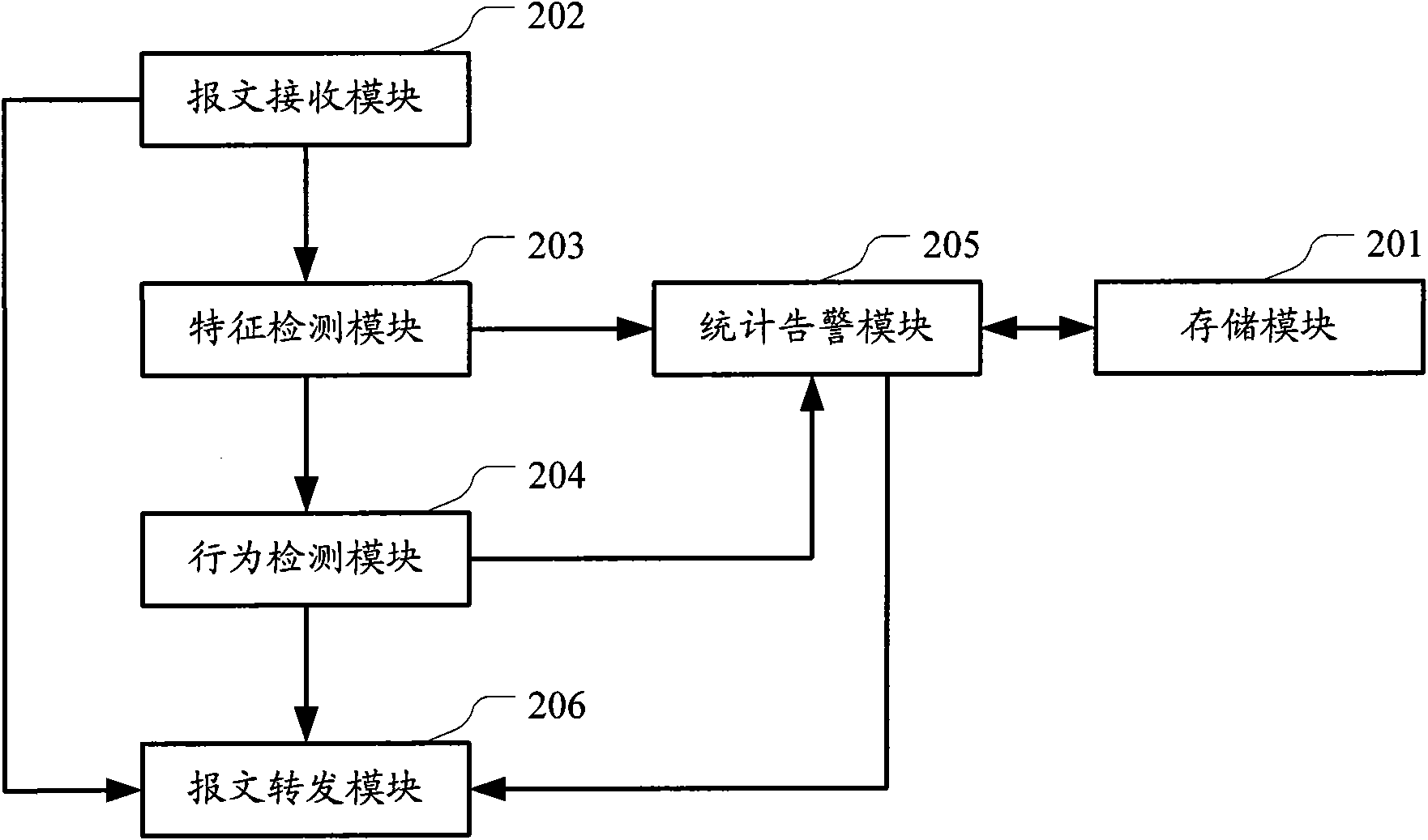
InactiveCN101901219AProtection securityReduce workloadPlatform integrity maintainanceSpecial data processing applicationsDatabase serverBehaviour pattern
The invention discloses a detection method for the injection attack of a database and a system, detecting the access activities of a database in real time. The method comprises the following steps of: solely leaning through the history access record of the database and establishing an access activity pattern library of the database; receiving the real-time access of the database, judging whether the real-time access is injection attack or not according to the access activity pattern library and acquiring a judging result; and responding the real-time access according to the judging result and the preset response mode. Compared with the prior art, the invention can automatically recognize normal database access and injection attack and blocks the injection attack so as to protect the safety of a database server.
Owner:BEIJING VENUS INFORMATION TECH +1
Method and device for detecting structured query language injection attack
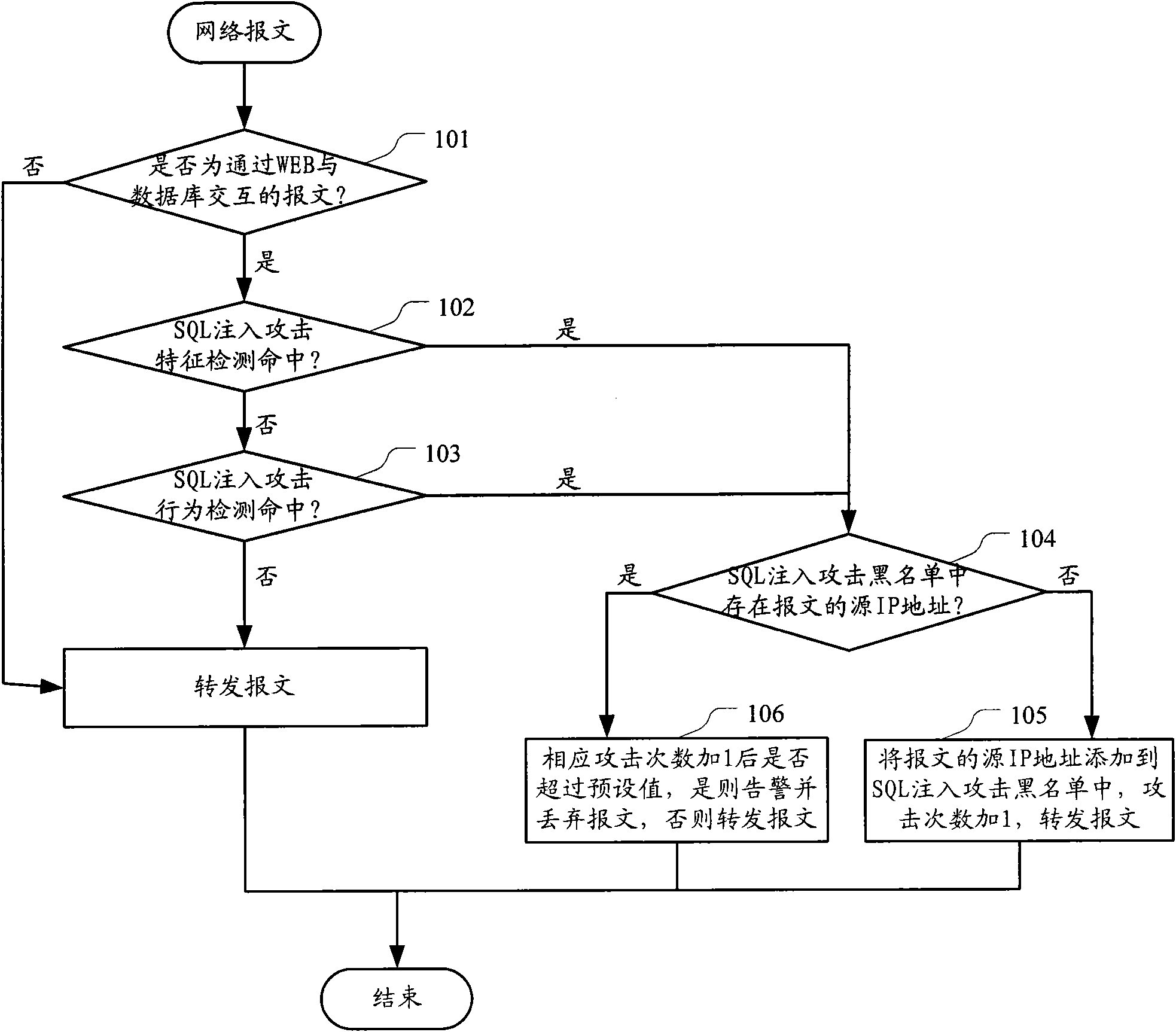
InactiveCN101594266AReduce false positives of attacksData switching networksSpecial data processing applicationsSQL injectionIp address
The invention discloses a method and a device for detecting a structured query language SQL injection attack. The method comprises the following steps: firstly detecting a received message based on SQL injection attack characteristics, and then detecting the received message based on SQL injection attack behaviors; counting the attack frequency of a source IP address of each hit message; alarming the IP address of which the attack frequency exceeds a preset value. The technical proposal of the invention greatly reduces the conditions of attack omission.
Owner:NEW H3C TECH CO LTD
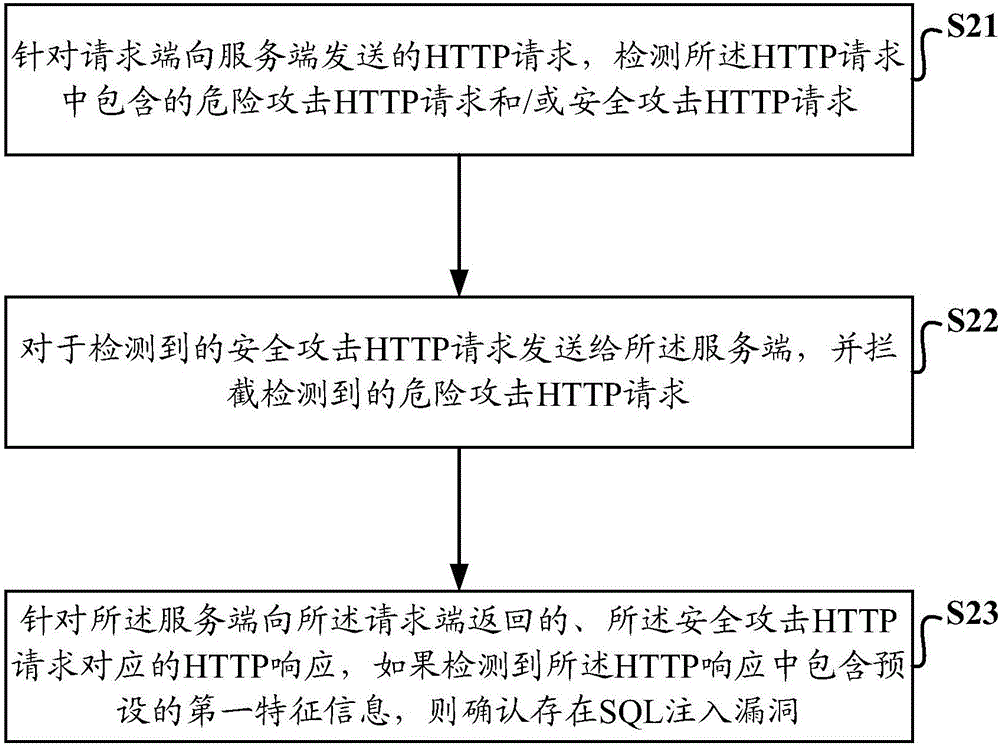
Detection method and detection system for SQL injection attack
The invention discloses a detection method and a detection system for SQL (Structured Query Language) injection attack. The detection method and the detection system are used for increasing the accuracy of vulnerability detection for SQL injection attack and assisting the website in finding the true SQL injection vulnerability. The detection method for SQL injection attack comprises the following steps of: detecting a dangerous attack HTTP (Hyper Text Transfer Protocol) request and / or safe attack HTTP request contained in an HTTP request, for the HTTP request sent to a server by a request terminal; sending the detected safe attack HTTP request to the server and intercepting the detected dangerous attack HTTP request; for an HTTP response corresponding to the HTTP request containing the safe attack HTTP request returned to the request terminal by the server, confirming the existence of the SQL injection vulnerability if detecting the preset first feature information contained in the HTTP response.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
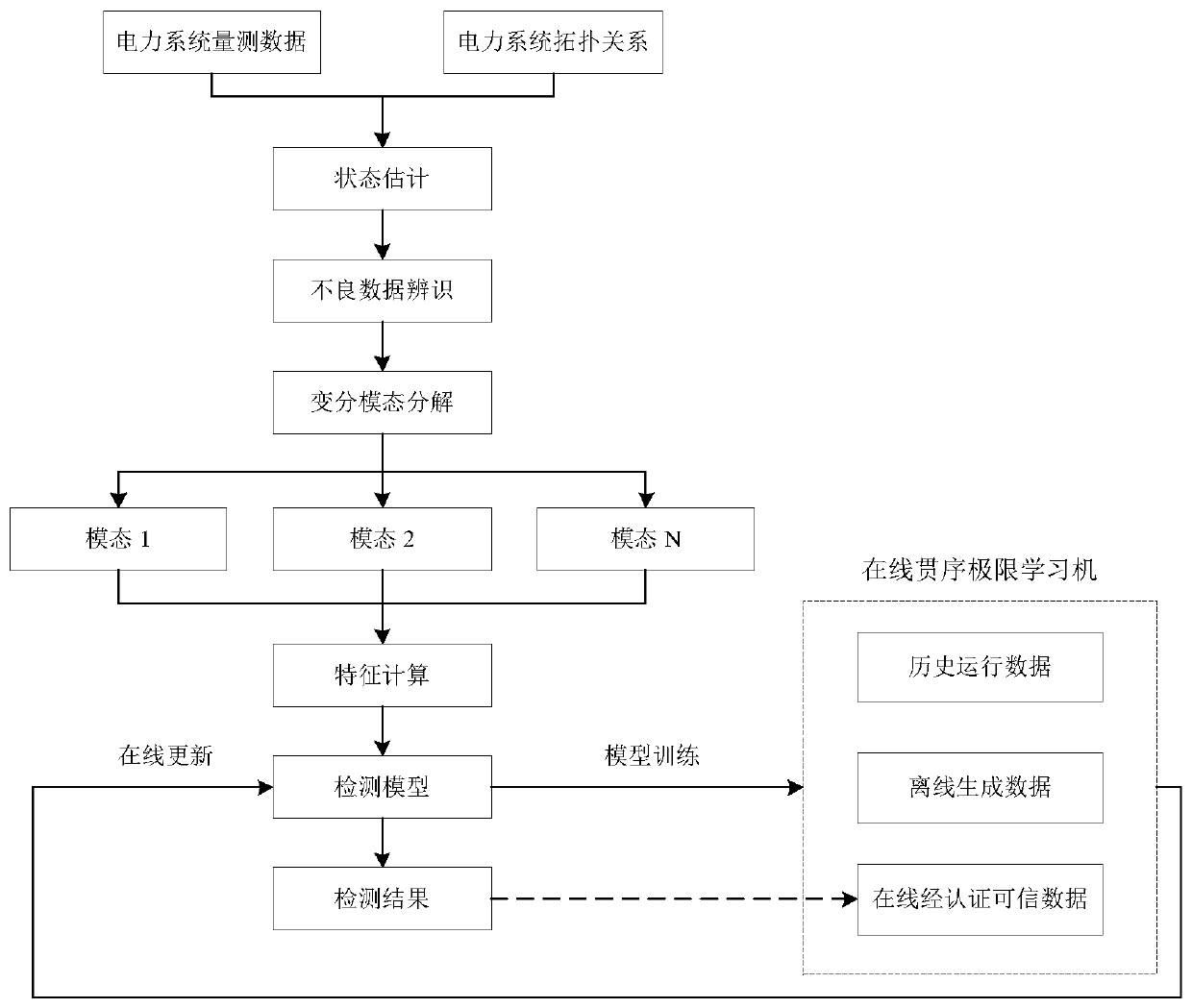
Intelligent power grid false data injection attack detection method
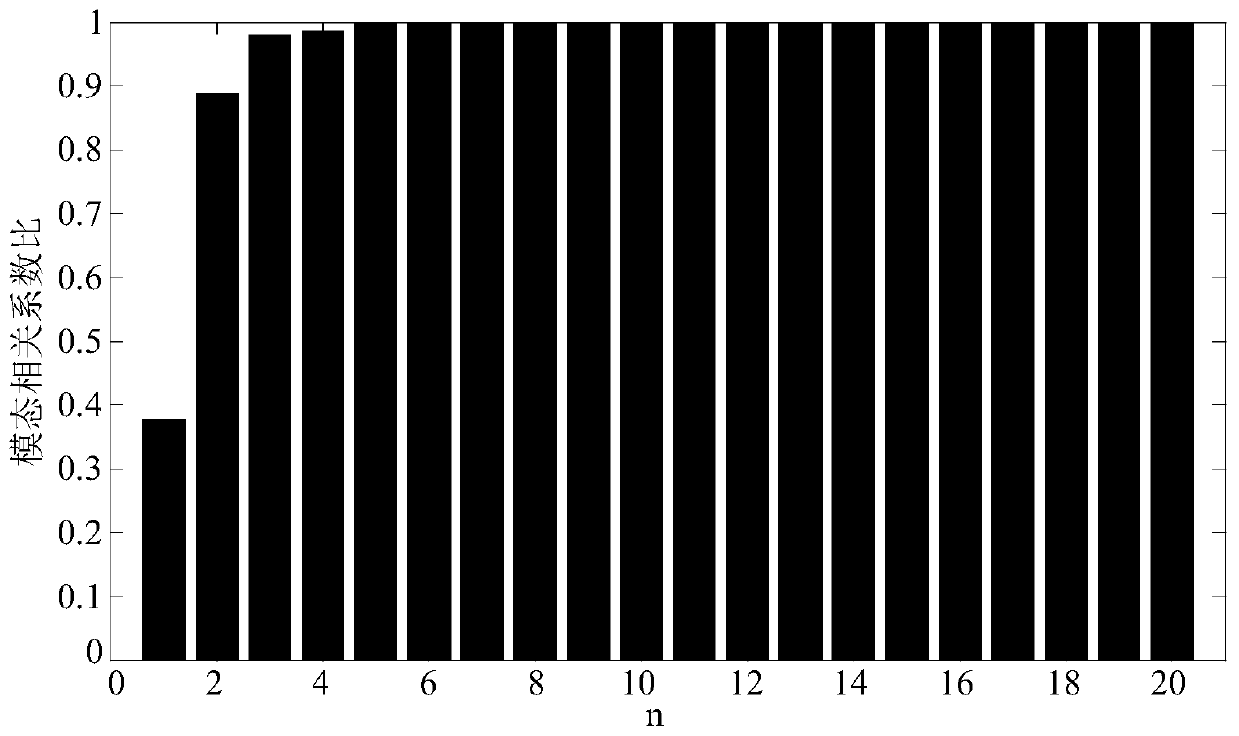
ActiveCN110035090AObvious regularityImprove performanceCharacter and pattern recognitionMachine learningFeature setData segment
The invention discloses an intelligent power grid false data injection attack detection method which combines a variational mode decomposition technology and a machine learning technology. The detection method is added behind a power system state estimation part, and comprises the following steps: firstly, decomposing a system state time sequence into a set of a plurality of sub-sequences with different center frequencies by using a variational mode decomposition technology; secondly, in order to compress redundant data to facilitate model training, expressing data segment characteristics by using characteristic quantities based on statistical indexes; and finally, constructing a false data injection attack detector under the smart power grid by taking the calculated feature set as a training set of an online sequential extreme learning machine. In the process, the credible authenticated data can be used as an extended training set to continuously optimize the performance of the detector with the online learning capability. The invention aims to establish an efficient and accurate false data injection attack detection method for the smart power grid to ensure safe control and stable operation of a power system.
Owner:YANSHAN UNIV
Security chip design method based on control flow detection and resistant to error injection attack
InactiveCN103345445AReduce overheadAvoid detecting blind spotsSoftware testing/debuggingControl flowLexical analysis
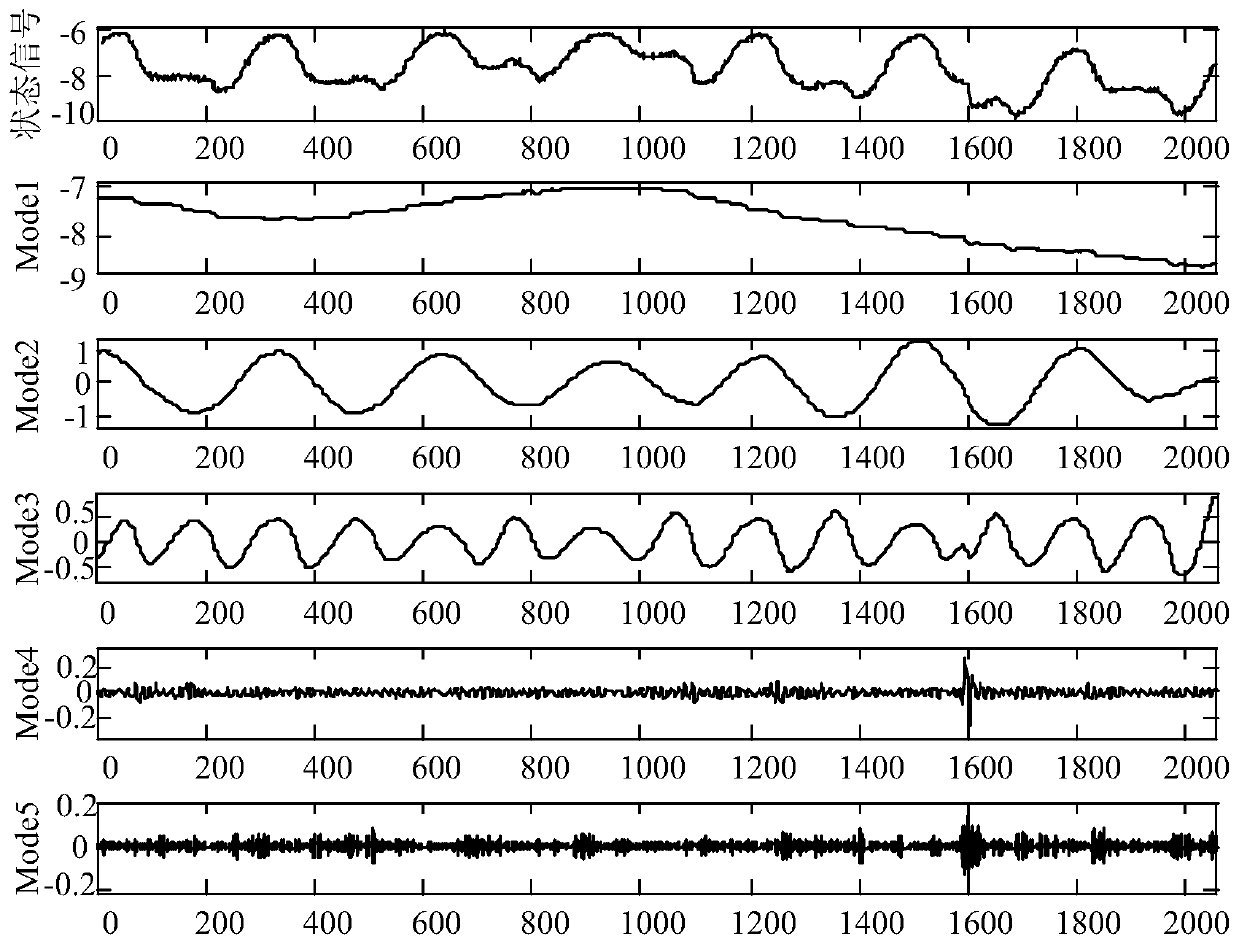
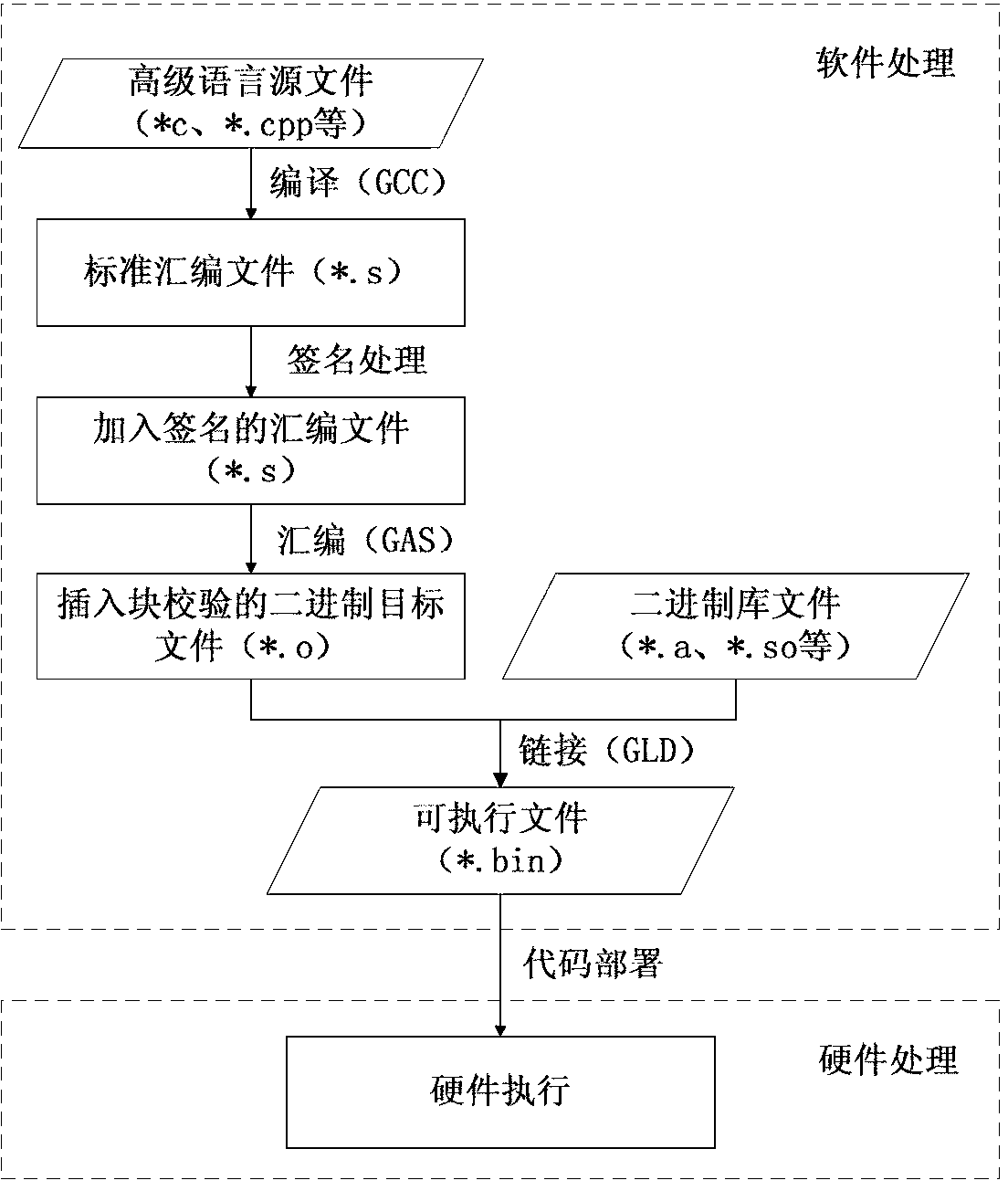
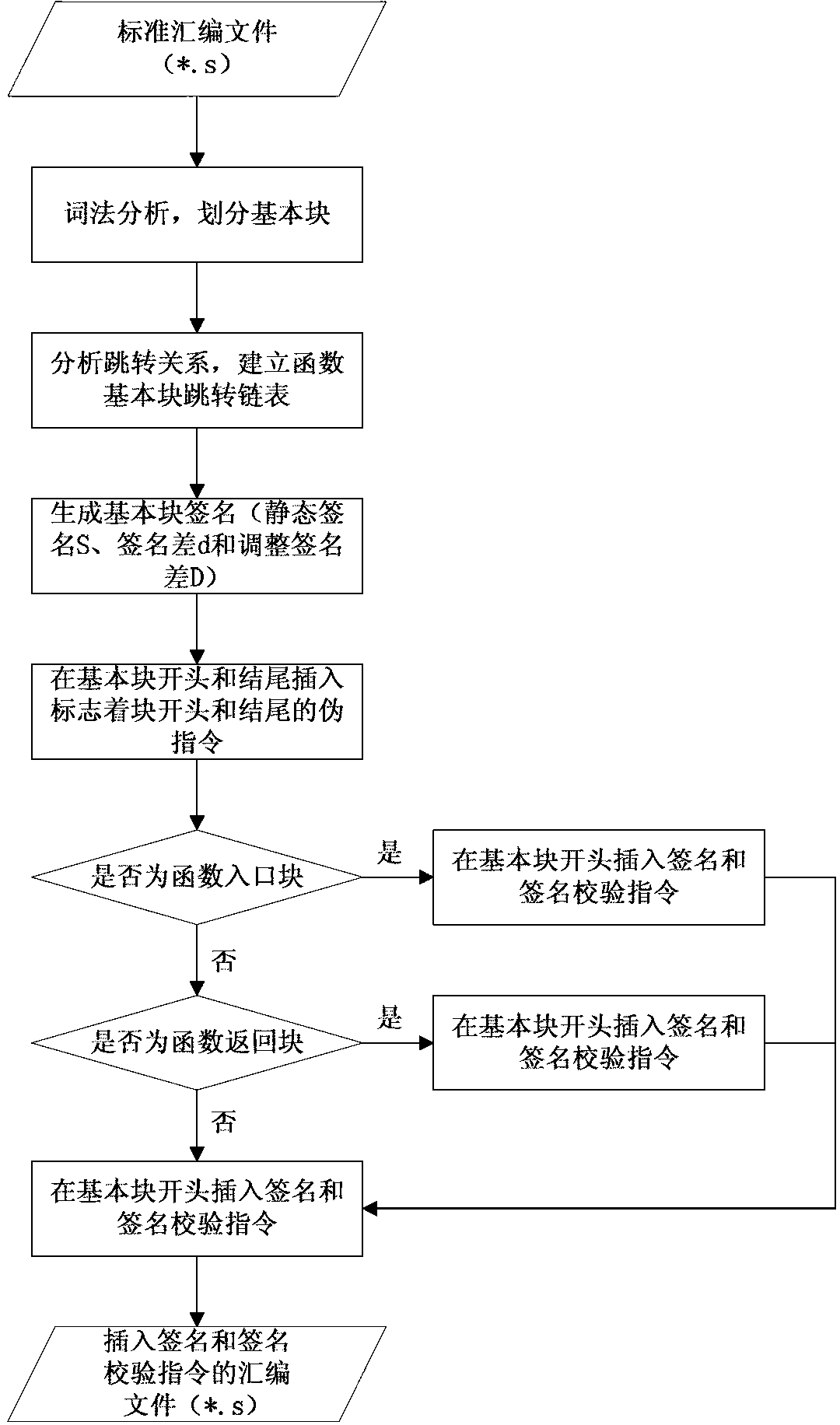
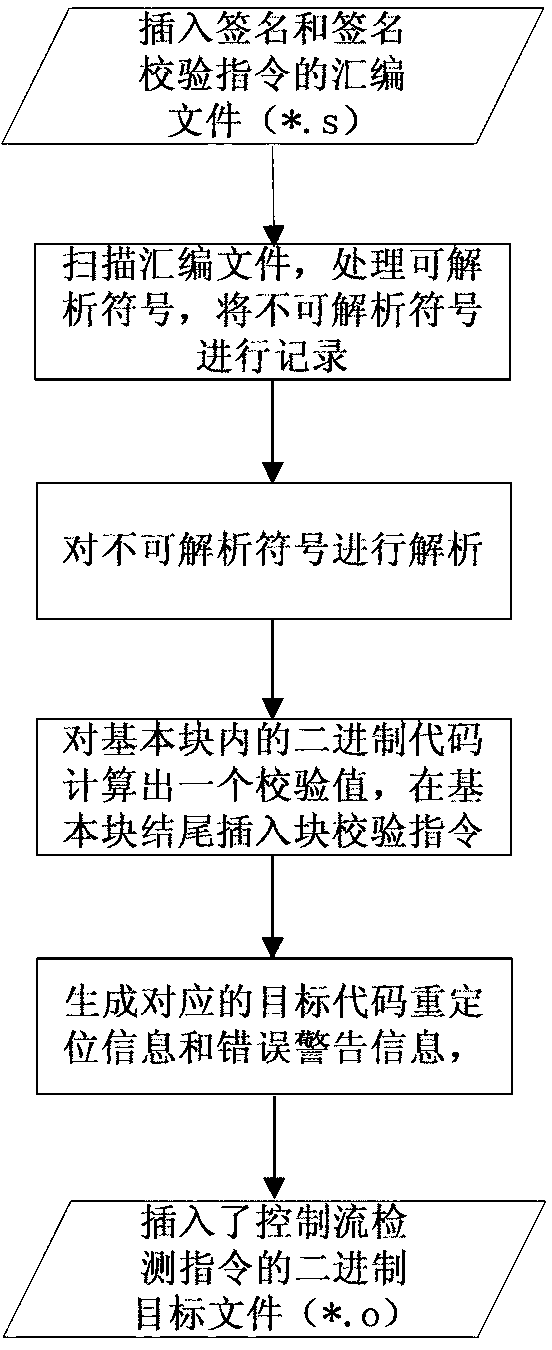
The invention relates to a security chip design method based on control flow detection and resistant to error injection attack. The security chip design method comprises a first step of compiling a standard assembling file which supports a security chip, a second step of dividing the standard assembling file into basic blocks by means of lexical analysis, a third step of generating basic block signature values and forming an assembling file with a control flow detection instruction, a fourth step of translating the assembling file into a target file, generating basic block checking values and inserting basic block checking instructions, and a fifth step of generating an executable file from the target file and a database file link and executing the executable file on hardware. The security chip design method based on control flow detection and resistant to error injection attack can effectively detect skip errors among the basic blocks and inside each basic block and non-skip errors of a command sequence, has the self checking function on the control flow detection instruction which is newly added, and is simple in implementation and low in redundancy code cost by the adoption of the mode of combination of software and hardware.
Owner:HUAZHONG UNIV OF SCI & TECH
Method of detecting power grid false data injection attack based on nonlinear measurement equation
InactiveCN107016236AApply onlineImprove detection accuracyDigital data protectionSpecial data processing applicationsElectric power systemPower grid
The invention relates to the technical field of power grid data security, and is a method of detecting the power grid false data injection attack based on the nonlinear measurement equation. The method comprises the steps that in the first step, power grid data are obtained; in the second step, correlation analyses are performed on the states and measuration of the system; in the third step, innovation vectors are computed; in the fourth step, the detection and location of the false data are conducted; in the fifth step, the updates on the false data are carried out; in the sixth step, the estimations of the states are carried out. According to the method of detecting the power grid false data injection attack based on the nonlinear measurement equation, through the analyses of the correlation between states and measuration of the power grid system, the false data injection attacks which cannot be detected by traditional methods based on the measurement residuals are effectively detected, and the detection accuracy is improved; different from the multiple iterative detections in the traditional methods, the method can detect all the attacked measuration at one time, effectively saves on the computation time, and is suitable for the online applications of power grid; the method can locate specific malicious injection data and utilizes the measured predicted values to update the measuration containing fake data, and ensures that the state estimations can be rerun to obtain the system accurate running status.
Owner:新疆电力建设调试所有限责任公司 +2
Method and device for detecting SQL (Structured Query Language) injection attack
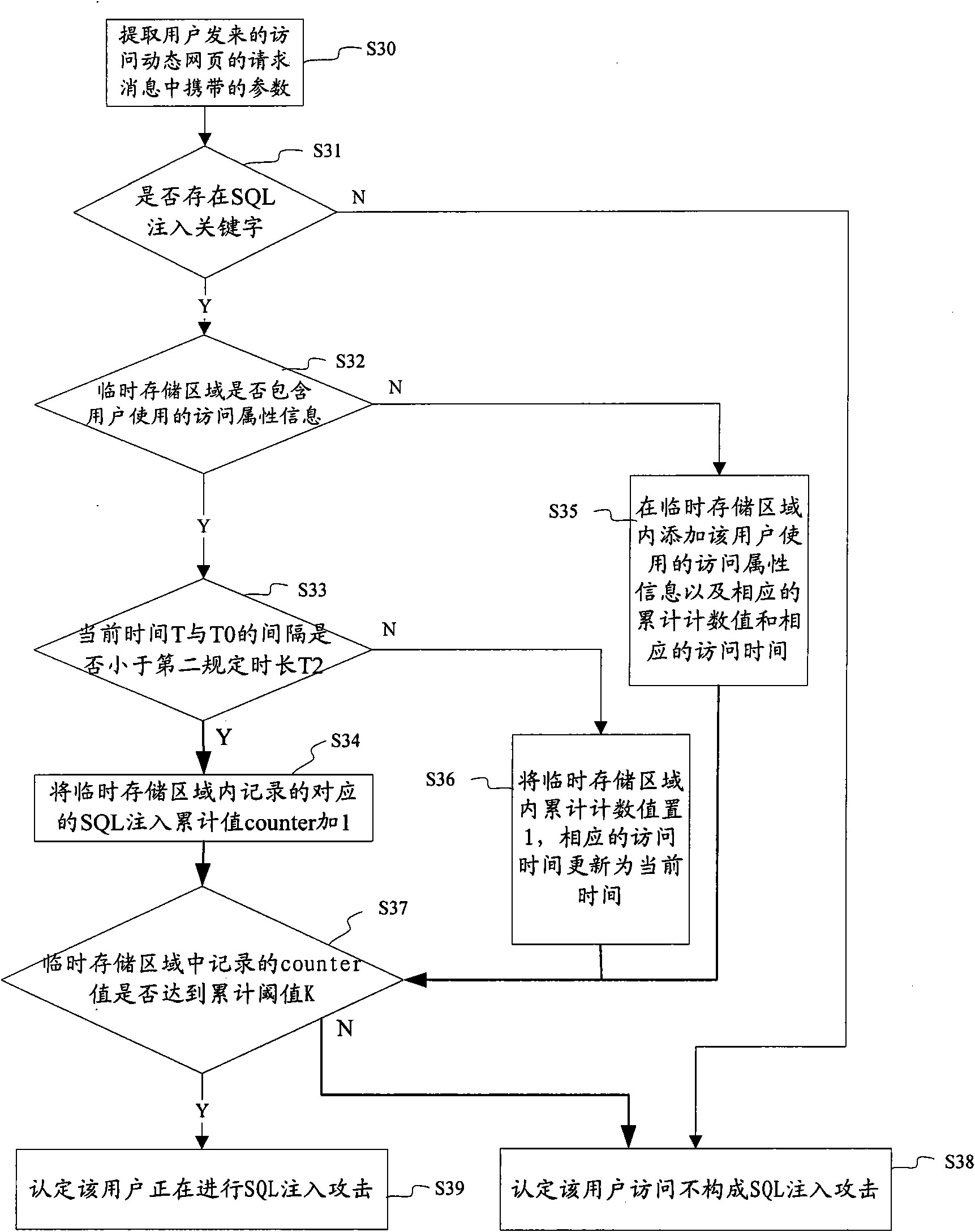
ActiveCN102045319AAvoid defectsSolve the problem of high false positive ratePlatform integrity maintainanceTransmissionSQL injectionUniform resource locator
The invention discloses a method for detecting an SQL (Structured Query Language) injection attack. The method comprises the following steps of: detecting whether a user sends universal resource locator (URL) request messages of a prescribed number of times, which carry SQL injection keywords and are used for requesting to access a related website with the same access attribute information in prescribed time duration or not; if so, affirming that the user is carrying out an SQL injection attack on the website at the moment; and if not, affirming that the user does not carry out the SQL injection attack on the website. The embodiment of the invention also discloses an SQL injection attack detection device. The method and the device for detecting the SQL injection attack provided by the embodiment of the invention effectively overcome the defects of the traditional SQL detection mechanisms on the basis of the behavioral characteristics of the SQL injection attack of malicious personnel and solve the problem of high false alarm rate in the traditional SQL injection attack detection method.
Owner:CHINA MOBILE GROUP SHANDONG
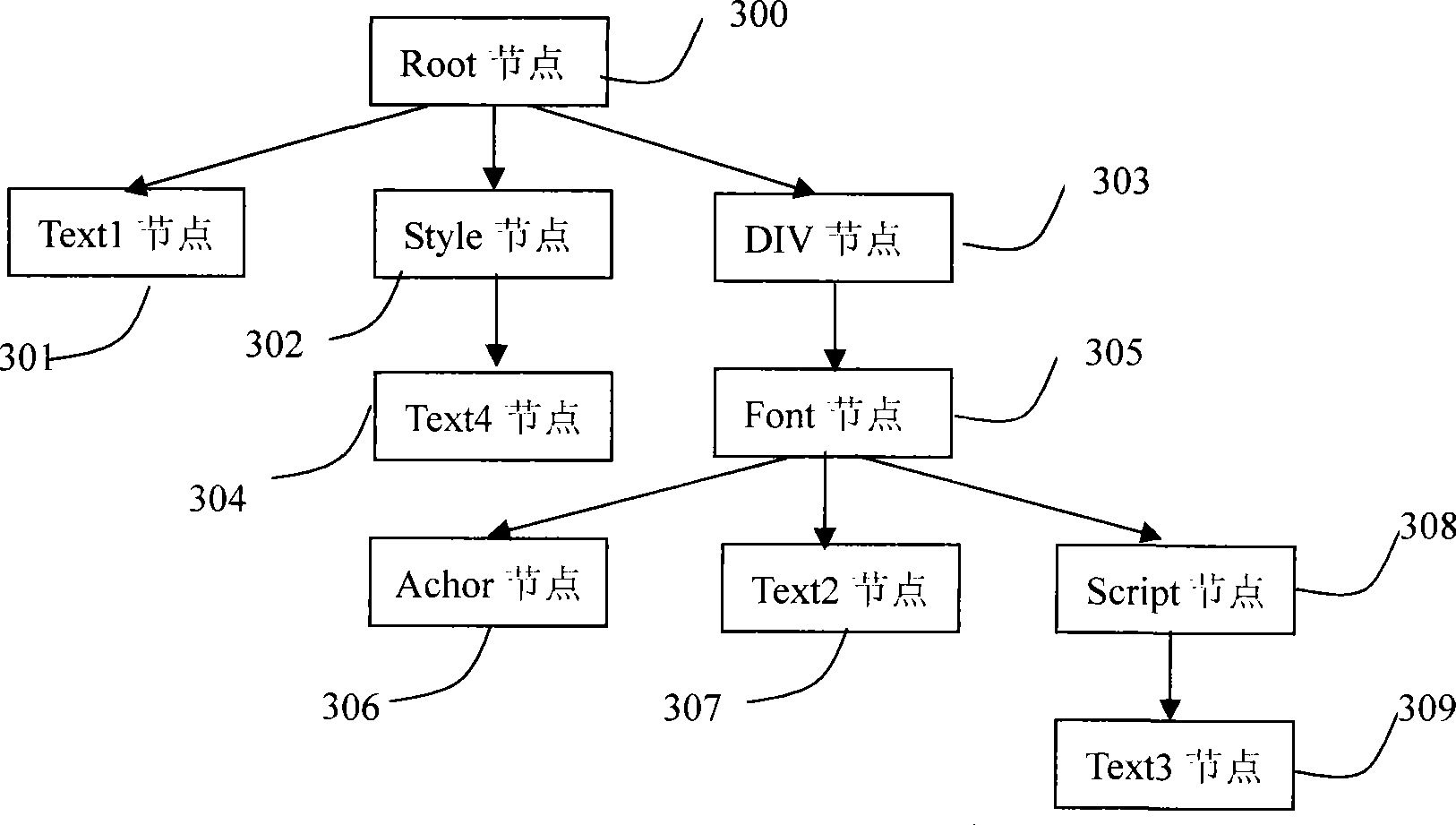
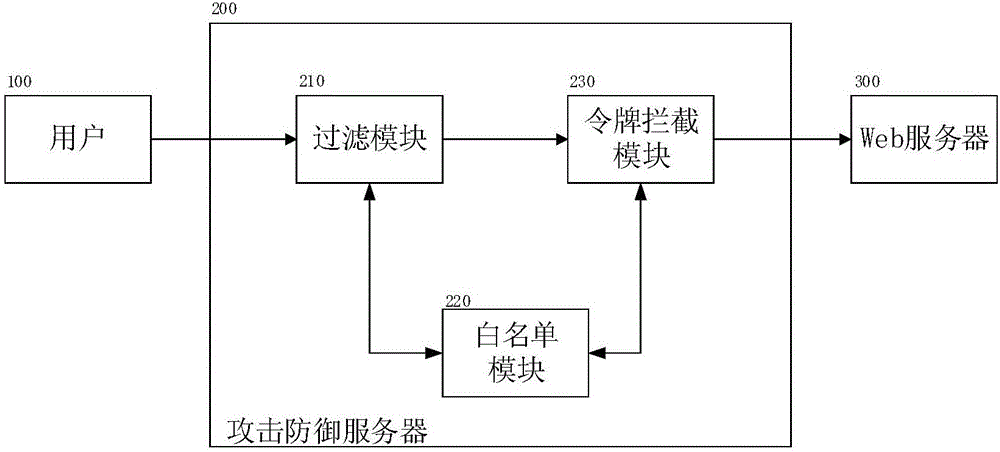
XSS and CSRF based Web attack defense system and method
InactiveCN106790007AImprove recognition accuracyHigh precisionTransmissionExtensibilityHTML scripting
The invention discloses an XSS and CSRF based Web attack defense system and method, and relates to the field of network security. The system comprises a filtering module, a white list module and a token interception module. The method comprises the following steps: (1) the filtering module filters user input by using the following four manners: verifying the validity of the user input, processing special characters, performing cookie anti-theft and performing recursive purification on sensitive words; (2) for HTML script injection, the white list module uses an HTML parsing library to traverse all nodes so as to obtain original label attributes of the data therein, and reconstructs an HTML element tree through labels in the white list module to prevent HTML script injection attacks fundamentally; and (3) the token interception module intercepts HTTP requests not satisfying the requirements through a Token verification function. The XSS and CSRF based Web attack defense system disclosed by the invention has the characteristics of high accuracy, low false alarm rate and expandability.
Owner:WUHAN HONGXU INFORMATION TECH
Complementary character encoding for preventing input injection in web applications
InactiveUS8615804B2Appropriate treatmentImprove efficiencyMemory loss protectionError detection/correctionSQL injectionLexical analysis
Method to prevent the effect of web application injection attacks, such as SQL injection and cross-site scripting (XSS), which are major threats to the security of the Internet. Method using complementary character coding, a new approach to character level dynamic tainting, which allows efficient and precise taint propagation across the boundaries of server components, and also between servers and clients over HTTP. In this approach, each character has two encodings, which can be used to distinguish trusted and untrusted data. Small modifications to the lexical analyzers in components such as the application code interpreter, the database management system, and (optionally) the web browser allow them to become complement aware components, capable of using this alternative character coding scheme to enforce security policies aimed at preventing injection attacks, while continuing to function normally in other respects. This approach overcomes some weaknesses of previous dynamic tainting approaches by offering a precise protection against persistent cross-site scripting attacks, as taint information is maintained when data is passed to a database and later retrieved by the application program. The technique is effective on a group of vulnerable benchmarks and has low overhead.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
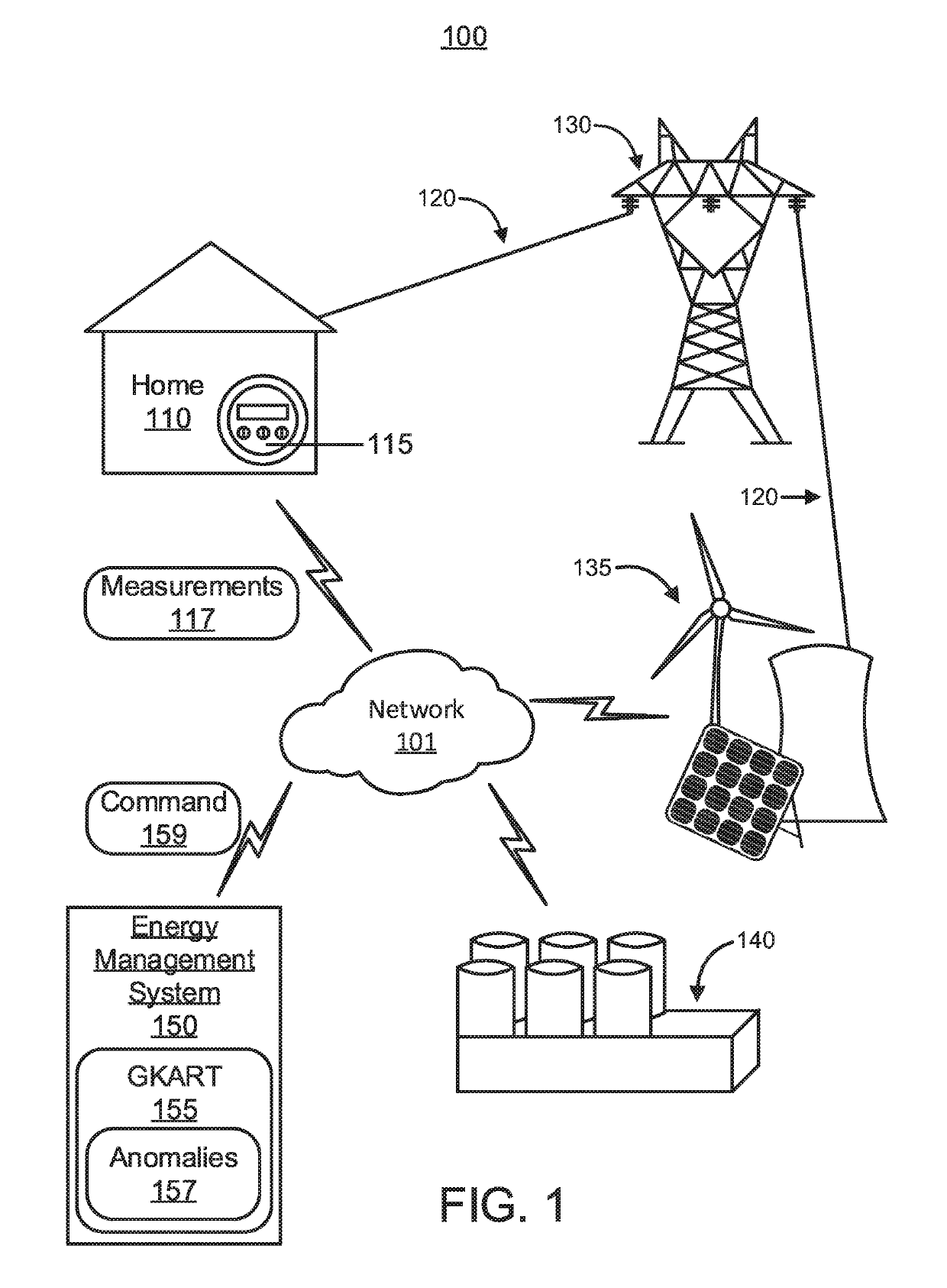
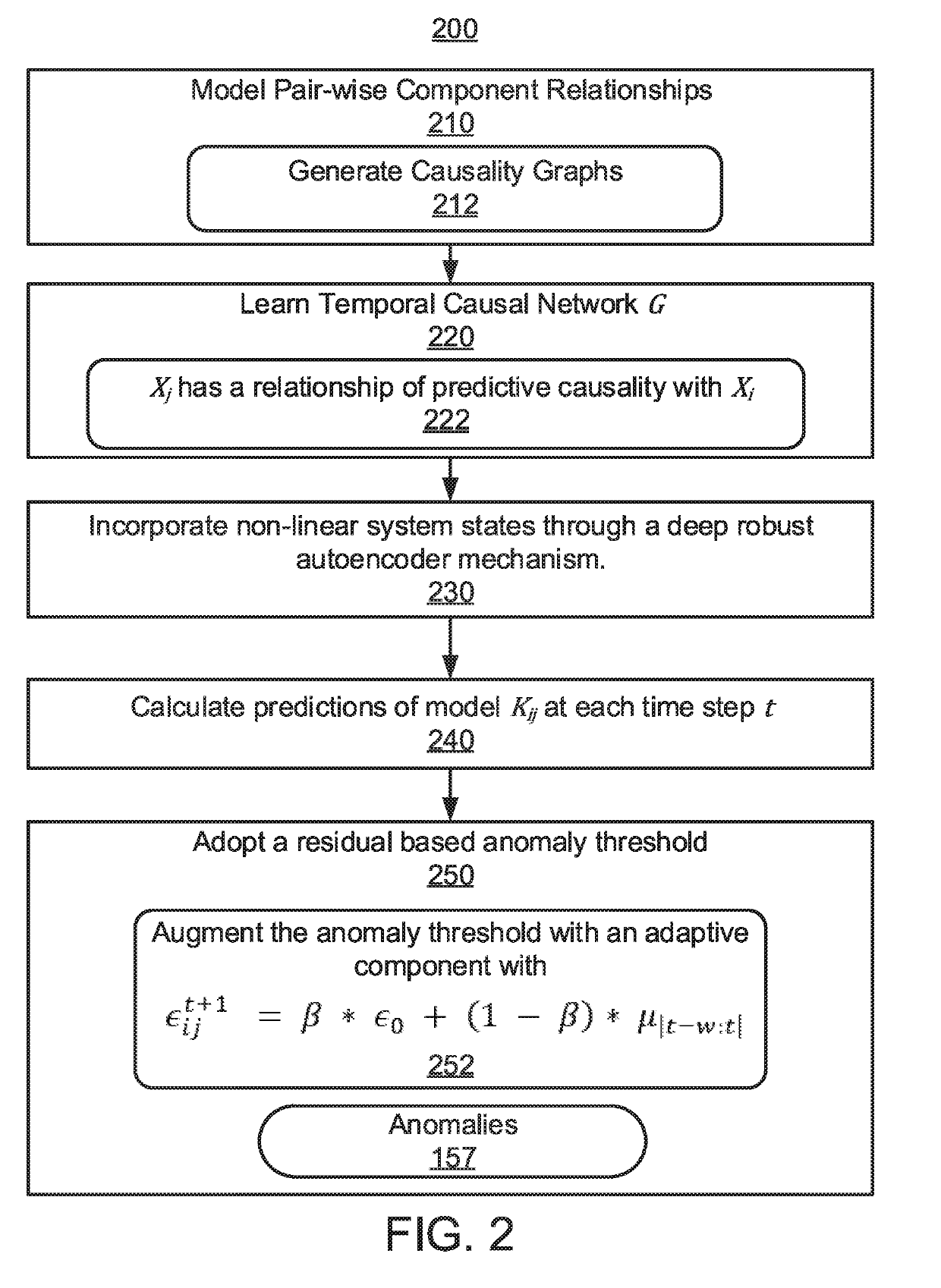
Detection of false data injection attacks in power systems using multiplex invariant networks and domain knowledge
ActiveUS20190113549A1Data processing applicationsCharacter and pattern recognitionAnomaly detectionElectric power system
A computer-implemented method, system, and computer program product are provided for anomaly detection in a power system. The method includes receiving, by a processor-device, a plurality of measurements from a plurality of meters throughout the power system. The method also includes generating, by the processor-device, temporal causal networks based on pair-wise relationships between the plurality of measurements from the plurality of meters over time. The method additionally includes determining, by the processor-device, invariant relationships for the plurality of meters between the temporal causal networks. The method further includes predicting, by the processor-device, an anomaly from the invariant relationships for the plurality of meters with a residual anomaly threshold. The method also includes disabling one of the plurality of meters that originated the anomaly.
Owner:NEC CORP
Injection attack detection method based on gating cycle unit and attention mechanism
ActiveCN110414219AImprove detection success rateEasy to detectPlatform integrity maintainanceSpecial data processing applicationsAlgorithmThe Internet
The invention discloses an injection attack detection method based on a gating loop unit and an attention mechanism, and the method is characterized in that the method comprises the following steps: step 1, extracting a statement related to a database in the Internet as a sample; preprocessing each sample, and obtaining a category label of each sample; step 2, inputting a result after sample preprocessing into an injection attack detection model, and predicting a category label corresponding to the result; wherein the injection attack detection model comprises an activation layer, a gating cycle unit layer, an attention mechanism layer and an output layer which are connected in sequence; step 3, training an injection attack detection model based on the sample data; and step 4, for a to-be-detected statement, preprocessing the to-be-detected statement, and inputting a preprocessing result into the trained injection attack detection model to obtain a category label of the to-be-detectedstatement, thereby judging whether the to-be-detected statement is an injection attack statement or not. The method is high in accuracy.
Owner:长沙市智为信息技术有限公司
False data injection attack method based on imprecise mathematical model
InactiveCN108196448AReduce computing costReduce residualAdaptive controlControl systemMathematical model
The invention provides a false data injection attack method based on an imprecise mathematical model, which can successfully destroy the performance of a control system without being detected by a detector. Sensor readings and control commands are stolen from network channels; imprecise mathematical model parameters for a controlled object are recognized; a false data attack sequence is designed according to the recognized imprecise mathematical model parameters and the sensor readings and control commands; the false data attack sequence is injected into the sensor readings to form false sensor readings; the false sensor readings are transmitted to a controller; the controller detects whether a system is abnormal according to the false sensor readings; control commands are generated according to the false sensor readings and transmitted to the controlled object. The false data injection attack method based on the imprecise mathematical model is applicable to testing the defense effectof a control system for false data injection attacks, and a test means is provided for the design of defense methods.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Method for testing the security of an electronic device against an attack, and electronic device implementing countermeasures
ActiveUS20140075203A1Digital data processing detailsUnauthorized memory use protectionComputer networkChinese remainder theorem
A method of testing security of an electronic device against a combination of a side-channel attack and a fault-injection attack implemented during a method of cryptographic processing that includes: delivering a message signature based on a secret parameter and implementing a recombination of at least two intermediate values according to the Chinese remainder theorem; and verifying the signature on the basis of at least one public exponent. The method of testing includes: transmitting a plurality of messages to be signed by said electronic device; disturbing each message, including modifying the message by inserting an identical error for each message, before executing a step of determining one of the intermediate values; and analyzing physical measurements, obtained during the step of verifying the signature as a function of the message to be signed, the identical error for each message, and an assumption of a value of part of the secret parameter.
Owner:IDEMIA FRANCE
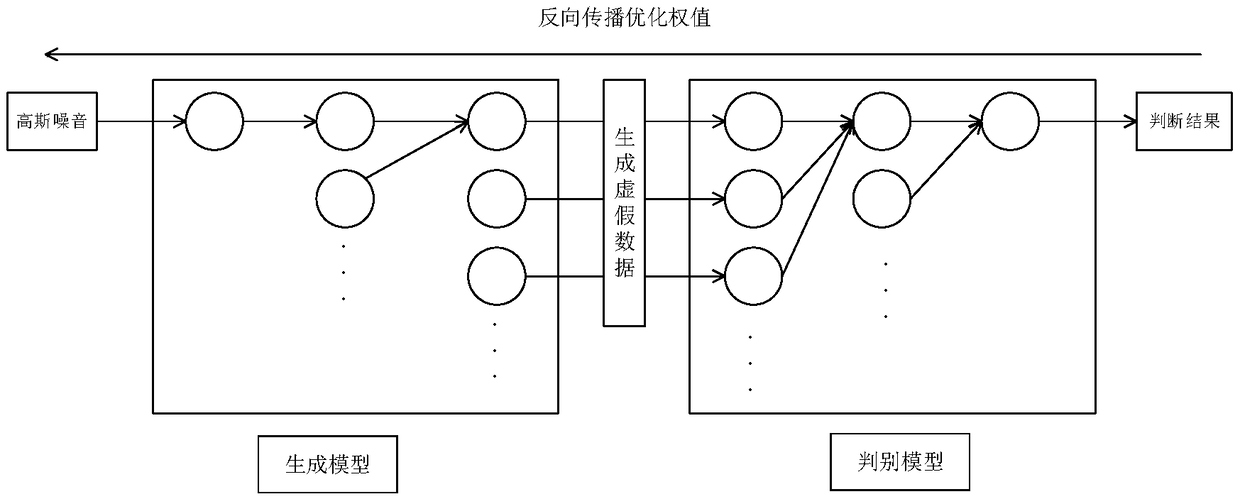
A power system false data injection attack identification method based on generative adversarial network
ActiveCN109165504ASolve the problem of not being able to detect data containing FDAAHigh industrial applicabilityPlatform integrity maintainanceNeural architecturesHypothesisElectric power system
The invention discloses a power system false data injection attack (FDIA) identification method based on a generative adversarial network. The method comprises the following steps of: 1, obtaining residual error measurement, estimating quantity and real quantity measurement by pre-processing based on state estimation, and reserving the residual error measurement and real quantity measurement as detected data of FDIA; 2, detecting and filtering bad data base on a two-norm threshold value for residual error measurement; 3, discriminating whether that FDIA exist or not by using a discriminant model based on the generative adversarial network; 4, generating positioning residual data by a generation model base on the generative adversarial network, detecting the positioning residual data by a two-norm threshold value to locate the problem data and filter the problem data. The invention simplifies the too strong hypothesis condition in the traditional method, the model training does not depend on the large-scale FDIA abnormal data sample, and the practical requirement of the industry for the detection of the measurement data containing FDIA is met.
Owner:GUANGXI UNIV
Method and apparatus for detecting structured query language injection attack
ActiveCN105160252AImprove detection efficiencyReduce matching timePlatform integrity maintainanceSpecial data processing applicationsSQL injectionTheoretical computer science
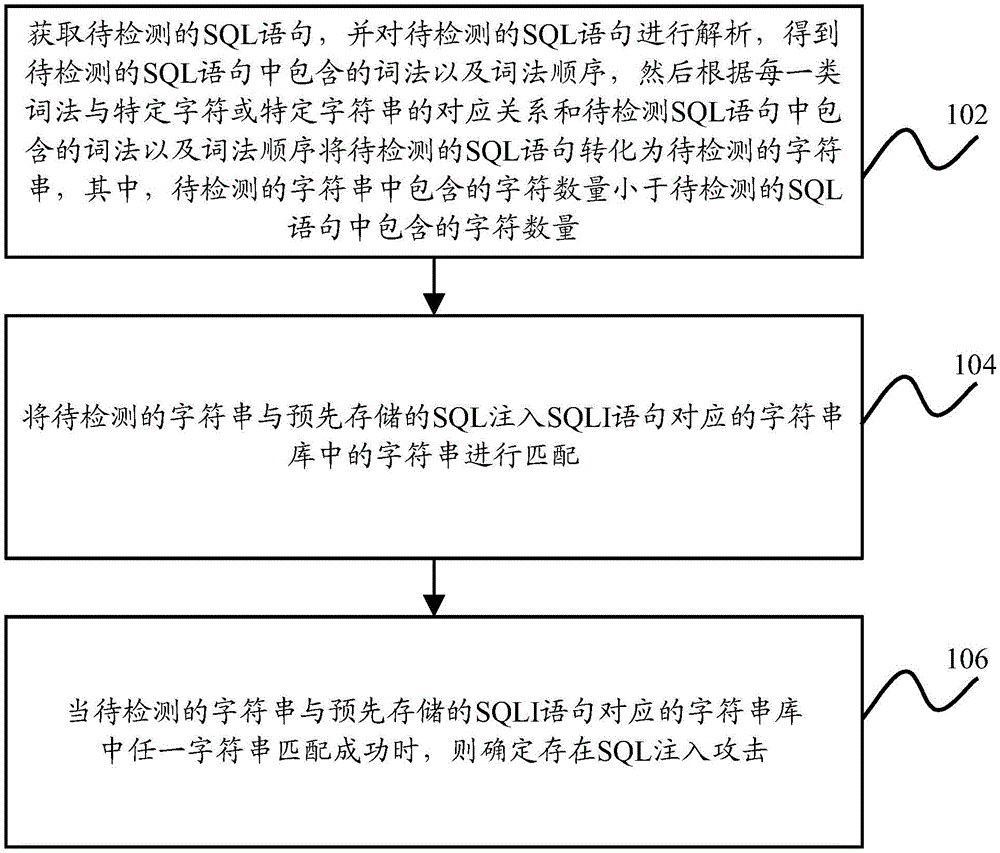
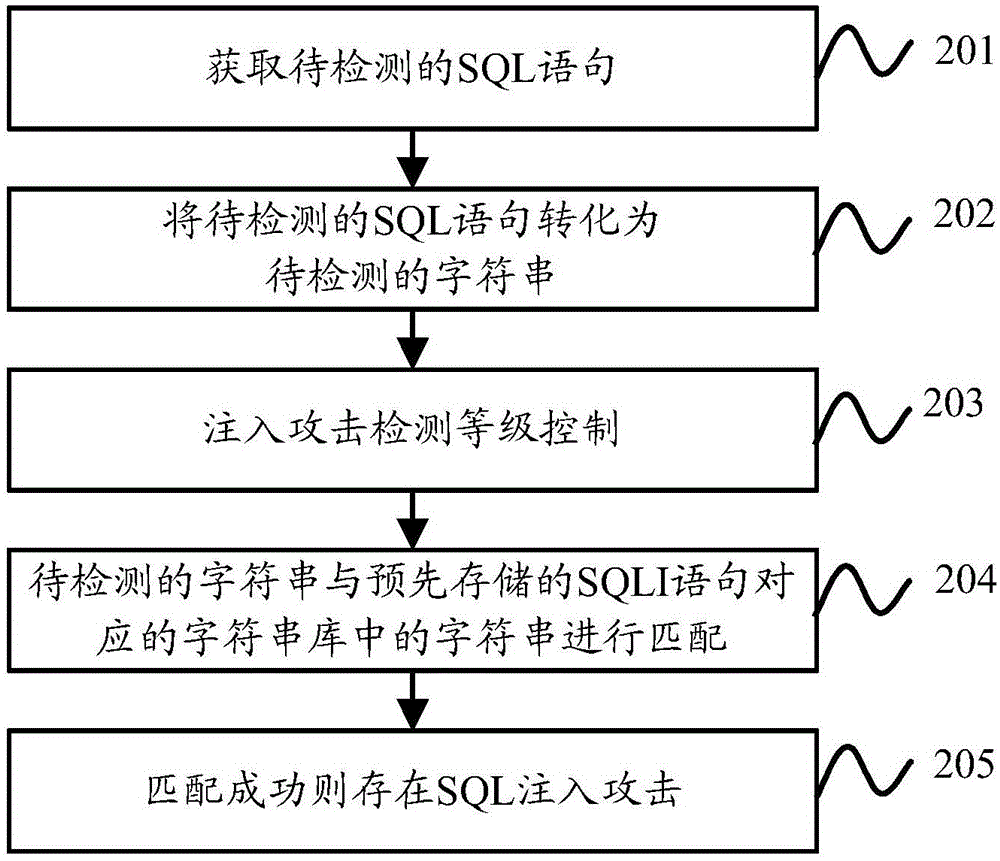
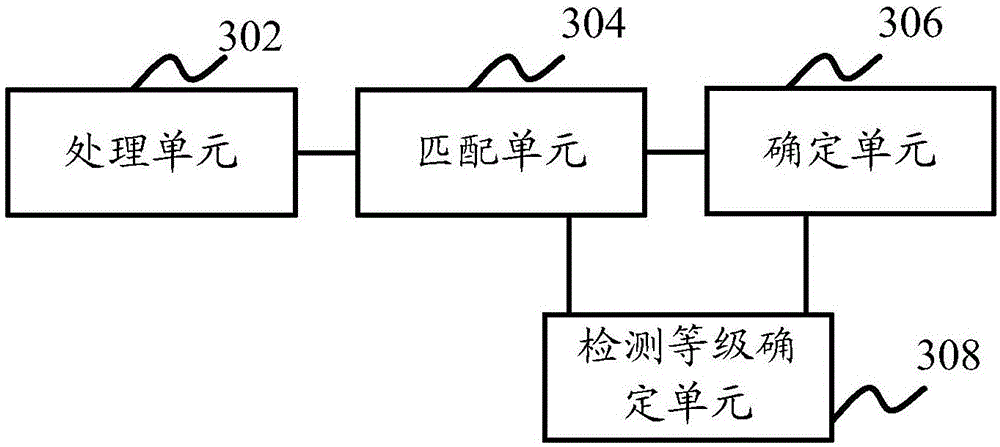
The invention discloses a method and an apparatus for detecting structured query language (SQL) injection attack. The method and the apparatus for detecting the SQL injection attack are used for improving the detection efficiency of the SQL injection attack and reducing the false and missing alarm rate. The method for detecting the SQL injection attack comprises the steps: acquiring a to-be-detected SQL statement, analyzing the to-be-detected SQL statement to obtain morphologies and a morphology sequence contained in the to-be-detected SQL statement, and transforming the to-be-detected SQL statement into a to-be-detected character string according to a corresponding relation between each morphology and a specified character or a specified character string as well as the morphologies and the morphology sequence contained in the to-be-detected SQL statement; matching the to-be-detected character string with the character string in a character string library corresponding to a prestored SQL injection (SQLI) statement; and determining that the SQL injection attack exists when the to-be-detected character string is matched with any character string in the character string library corresponding to the prestored SQLI statement.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Aware-data-based wireless sensor network abnormity type discriminating method
ActiveCN106878995AReduce energy consumptionImprove adaptabilityNetwork topologiesSecurity arrangementLine sensorDensity based
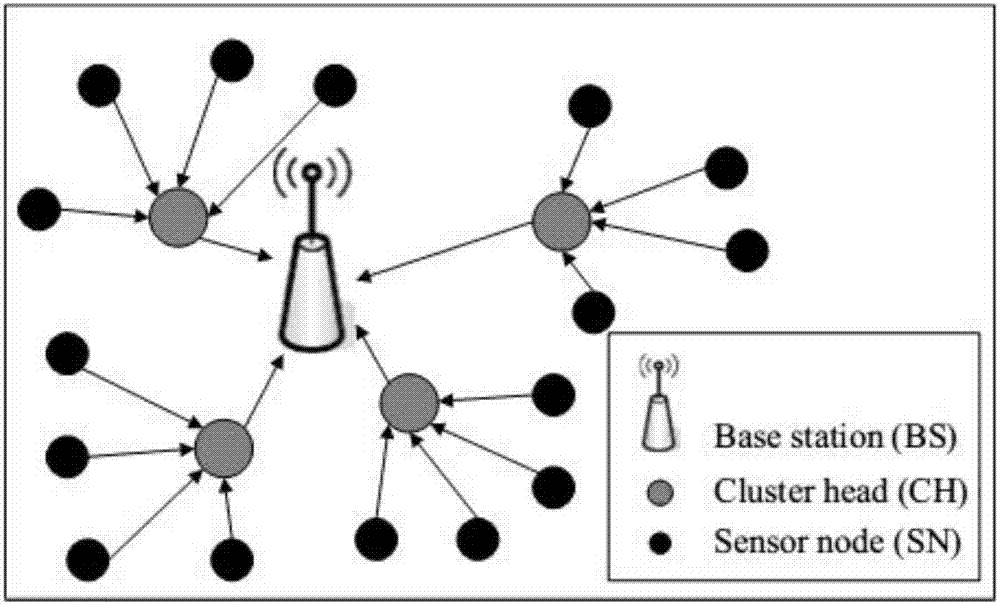
The invention provides an aware-data-based wireless sensor network abnormity type discriminating method, which relates to the security field of wireless sensor network information. According to the method of the invention, the wireless sensor network nodes collect a group of aware data every a fixed interval and transmit the data to a base station. In a normal time period, the detection characteristic set generated by the base station is used as a training set and the training set is normalized with the column mean value and the column variance unchanged. The training set undergoes dimension reduction through a main component analyzing method and the characteristic vector matrix and the column mean value vector are kept. The clustering of the training set is divided into normal clustering and abnormal clustering through a density-based competitive clustering algorithm. When new detection characteristics arise, based on the normalization of the column mean value and the column variance and through the dimension reduction of the characteristic vector matrix and the column mean value vector, it is possible to detect whether the network is abnormal or not according to the gains of the normal clustering and the abnormal clustering the network is divided into. The deployment of the method is simple and is low in cost. Despite that, the method can detect network protocol attacks and malicious data injection attacks, and can reduce the energy of the nodes.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Apparatus and method for preventing falsification of client screen
ActiveUS20130055386A1Prevent forgeryMemory loss protectionError detection/correctionNetwork generationWeb service
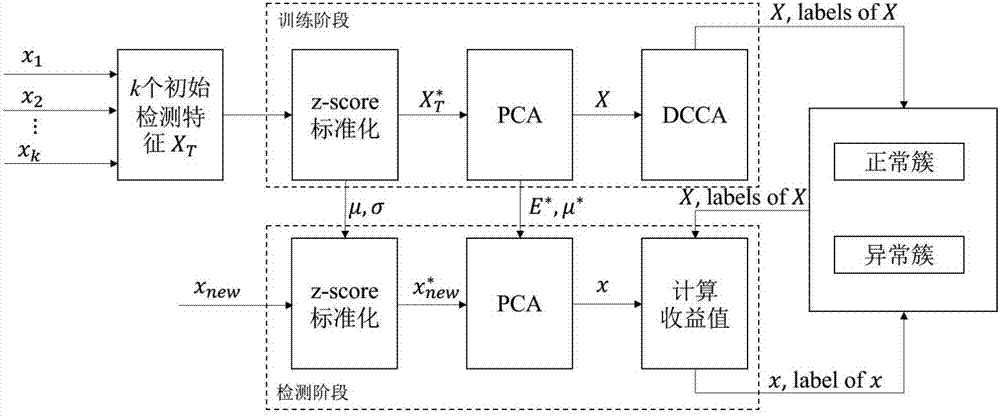
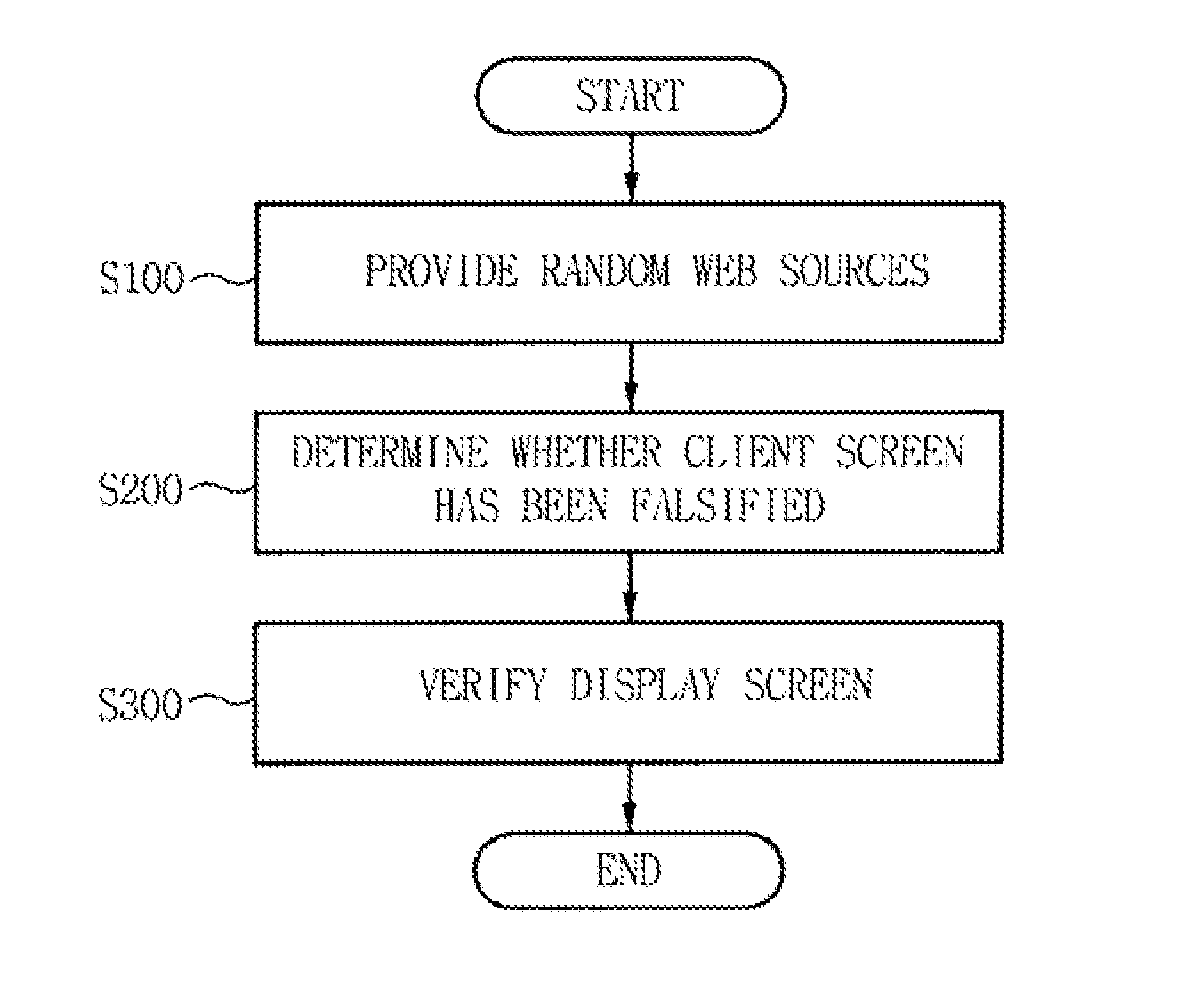
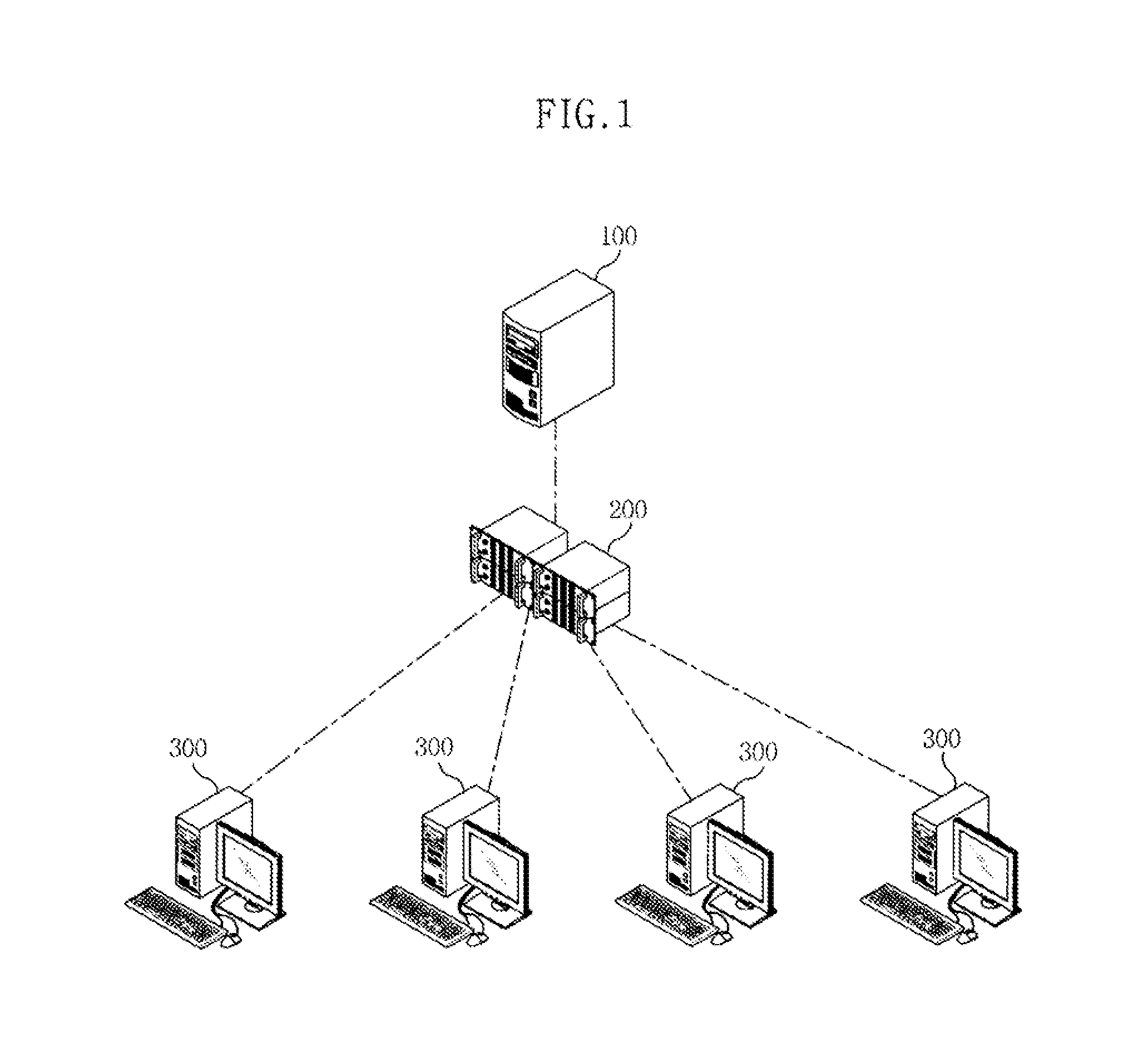
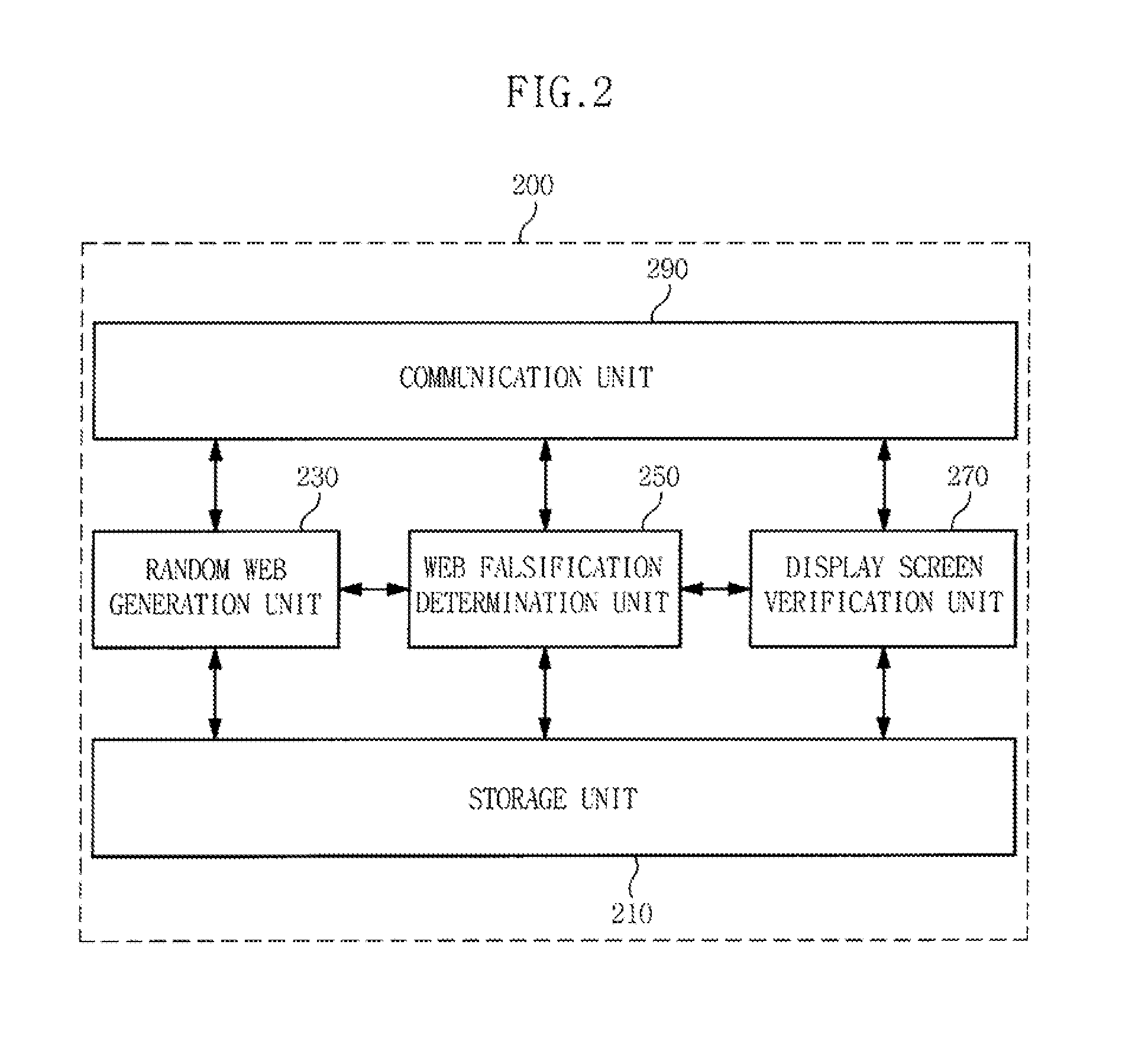
An apparatus and method for preventing falsification of a client screen is provided, in which a web server dynamically generates URIs and provides them to clients, thus preventing the falsification of client screens due to a web injection attack or a memory hacking attack. The apparatus includes a random web generation unit for converting an identical web page into random URIs that are randomly generated, at a request of a plurality of clients, generating different random web sources, and providing the different random web sources to the respective clients. A web falsification determination unit compares display web source eigenvalues respectively generated by the clients with respect to any one of the random web sources with a generative web source eigenvalue for the one of the random web sources, thus determining whether screens corresponding to the random web sources displayed on the respective clients have been falsified.
Owner:ELECTRONICS & TELECOMM RES INST
Structured query language (SQL) injection attack detection method and device
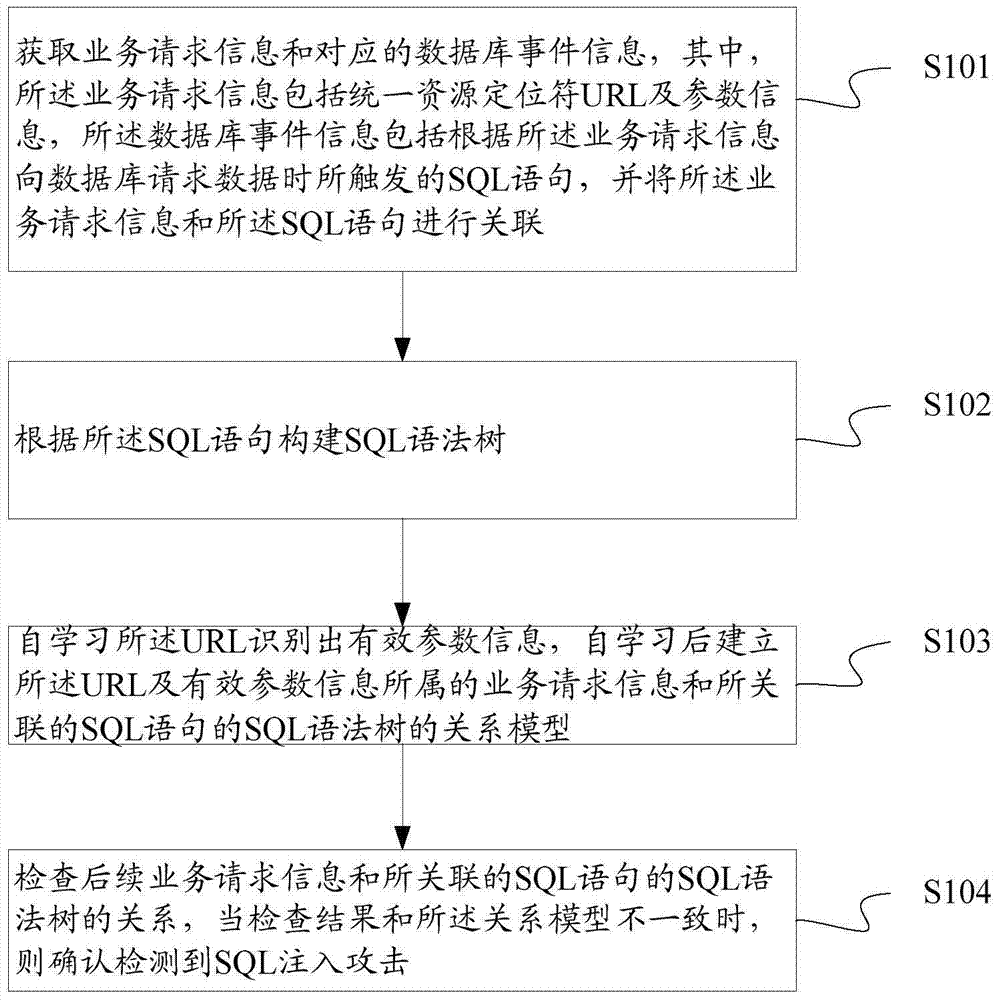
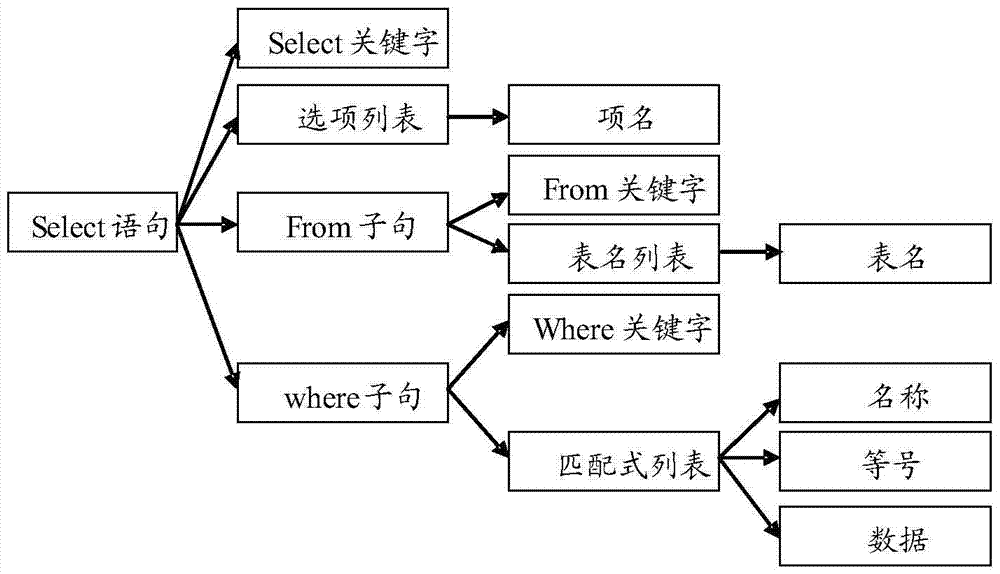
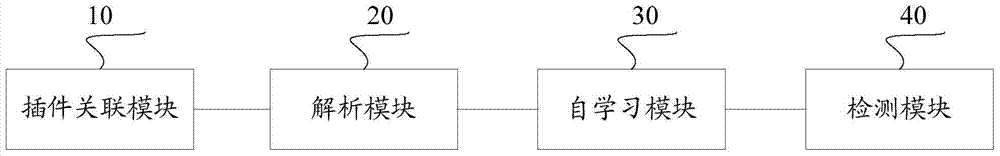
InactiveCN106991322AEnsure business access securityPlatform integrity maintainanceSoftware simulation/interpretation/emulationRelational modelSQL injection
The invention discloses a structured query language (SQL) injection attack detection method and device. The SQL injection attack detection device comprises a plug-in association module, an analysis module, a self-learning module and a detection module. Based on a webpage application system server of a Java virtual machine environment, URL and parameter information in business request information of a client are associated with a triggered SQL statement, syntax analysis is carried out on the SQL statement to construct an SQL syntax tree through self-learning of the URL to identify effective parameter information, after the self-learning process, a relation model of the business request information which the URL and the effective parameter information belong to, and the SQL syntax tree of the associated SQL statement is established, the relation model is taken as the inspection reference, the relationship between the subsequent business request information and the SQL syntax tree of the associated SQL statement is inspected by being compared with the reference, if the inspection result is not consistent, it is determined that an SQL injection attack is detected, business access is rejected, and therefore the SQL injection attack can be detected accurately, and the business access safety of the network application is guaranteed.
Owner:BEIJING VENUS INFORMATION SECURITY TECH +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com