Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
256 results about "Process memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Memory is the processes that is used to acquire, retain, and later retrieve information. The memory process involves three domains: encoding, storage, and retrieval.
Shared object memory with object management for multiple virtual machines
InactiveUS20050102670A1Save memoryEasy accessMultiprogramming arrangementsSoftware simulation/interpretation/emulationProcess memoryTerm memory
A shared object memory system that includes a shared object memory for storing encapsulated software objects that are directly accessible by plural object application processes. The shared object memory is distinct from the process memories of the object application processes and does not include an execution model. A shared object memory manager provides management of objects within the shared object memory.
Owner:GEMSTONE SYST
NAND flash module replacement for DRAM module
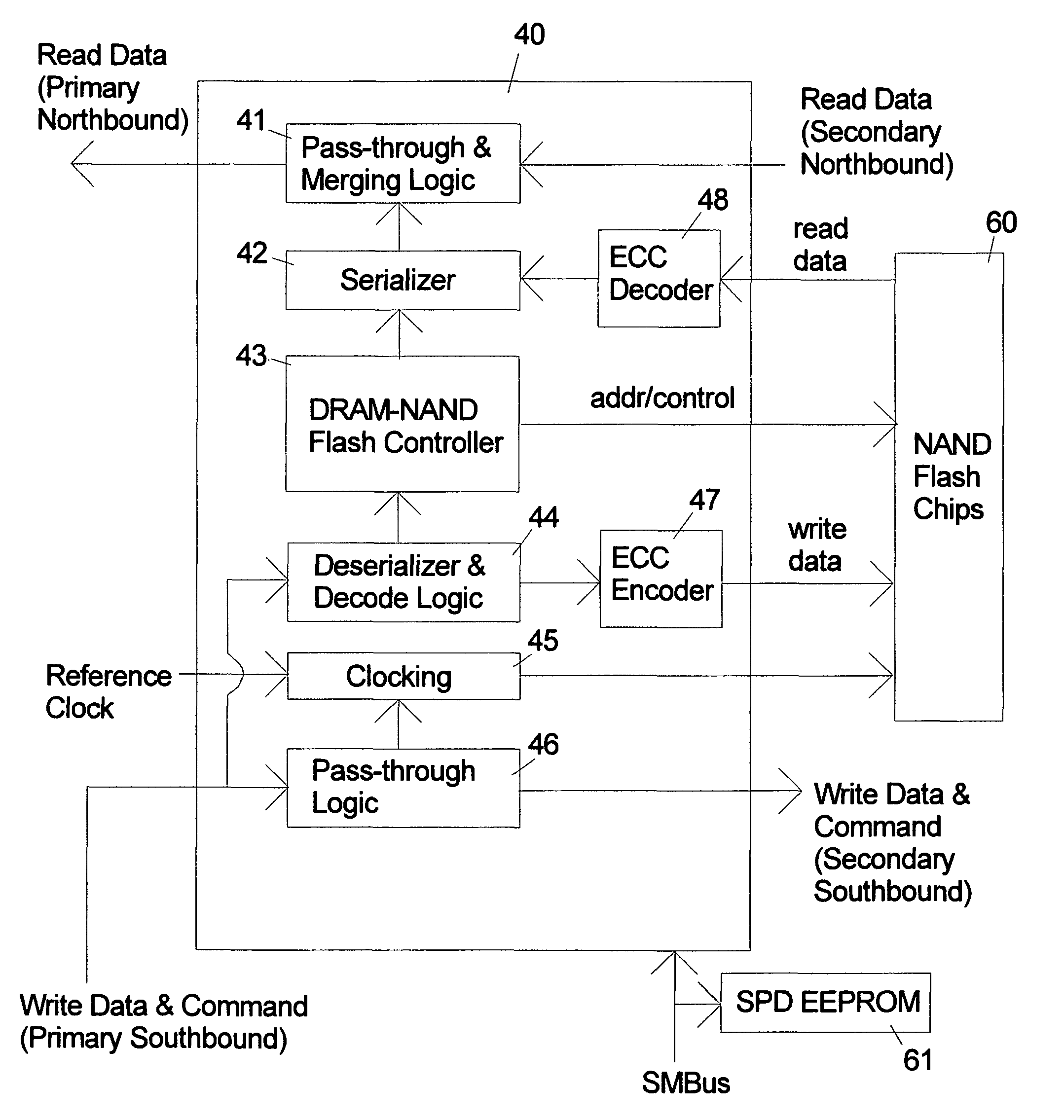
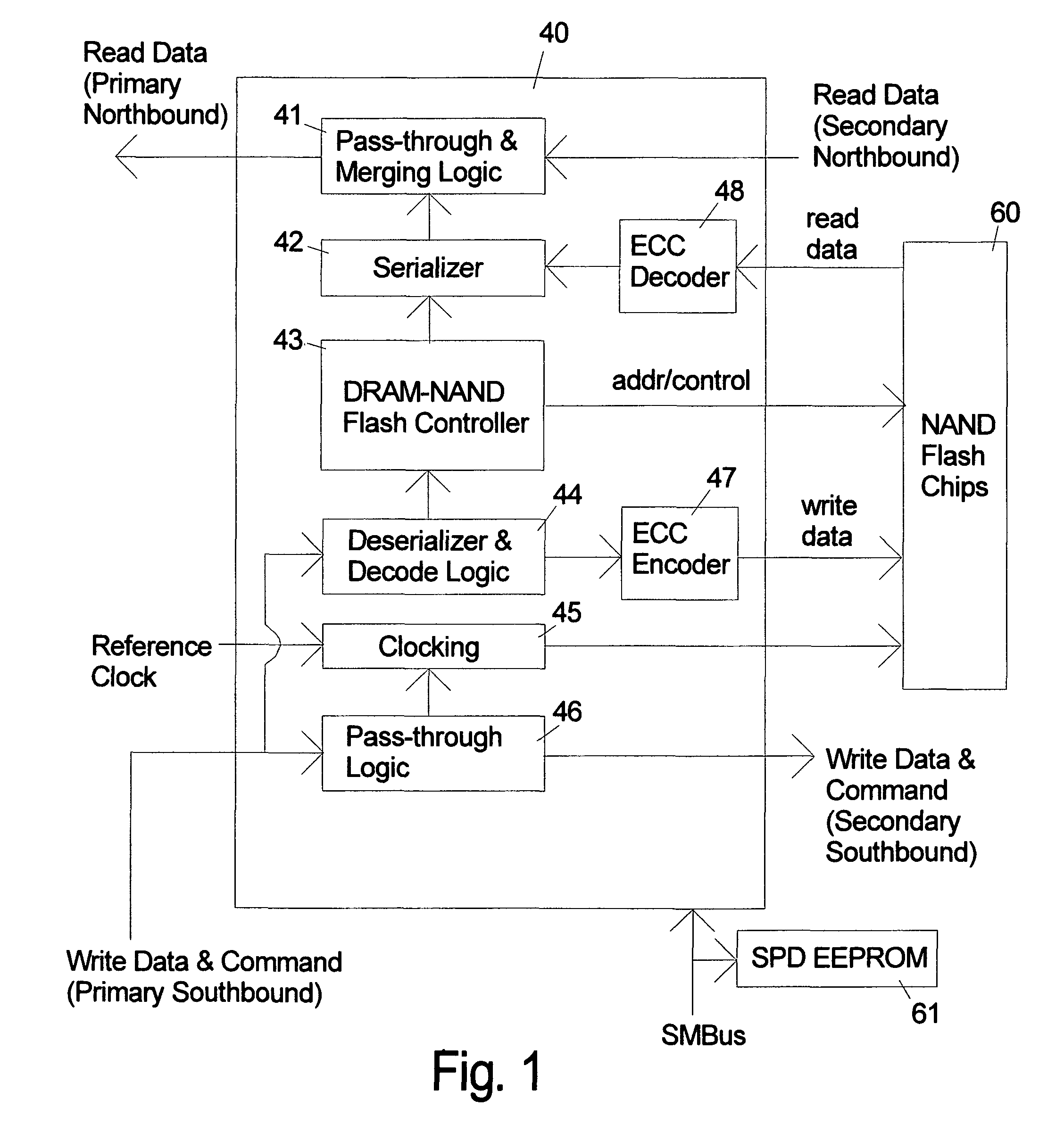
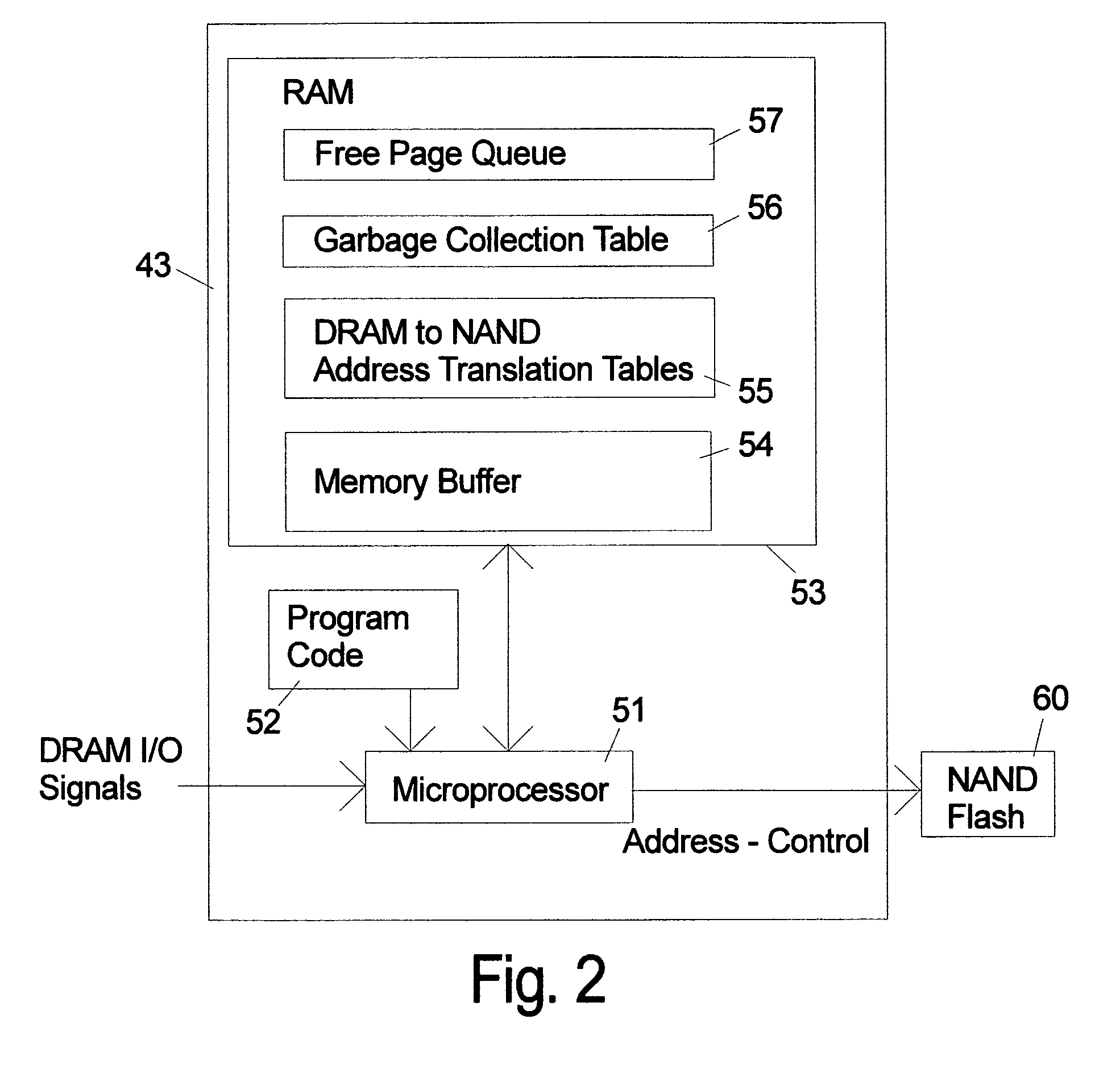
ActiveUS8185685B2Reduce speedMost efficientMemory architecture accessing/allocationMemory adressing/allocation/relocationProcess memoryControl signal
An electronic memory module according to the invention provides non-volatile memory that can be used in place of a DRAM module without battery backup. An embodiment of the invention includes an embedded microprocessor with microcode that translates the FB-DIMM address and control signals from the system into appropriate address and control signals for NAND flash memory. Wear-leveling, bad block management, garbage collection are preferably implemented by microcode executed by the microprocessor. The microprocessor, additional logic, and embedded memory provides the functions of a flash memory controller. The microprocessor memory preferably contains address mapping tables, free page queue, and garbage collection information.
Owner:WESTERN DIGITAL TECH INC
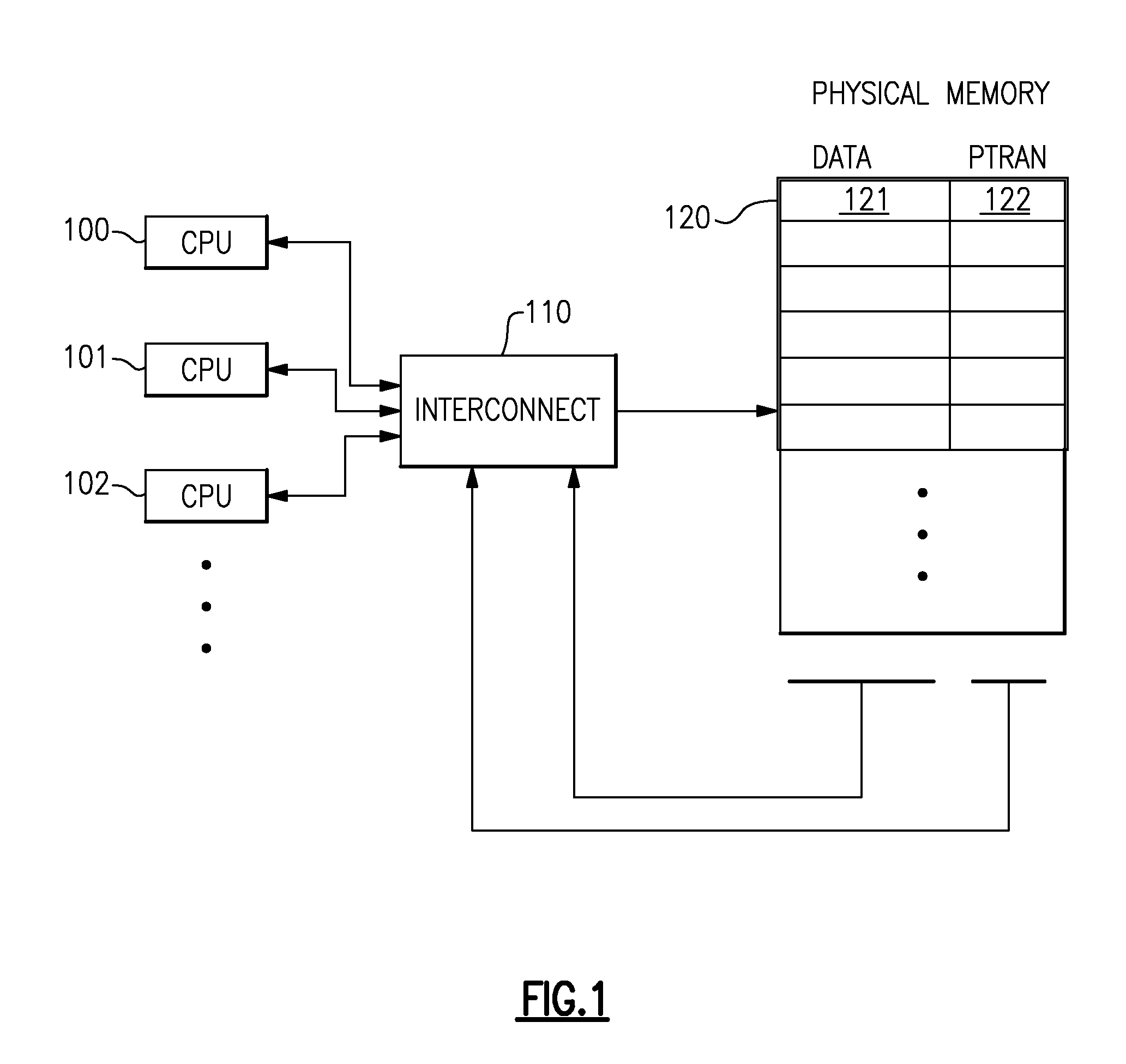
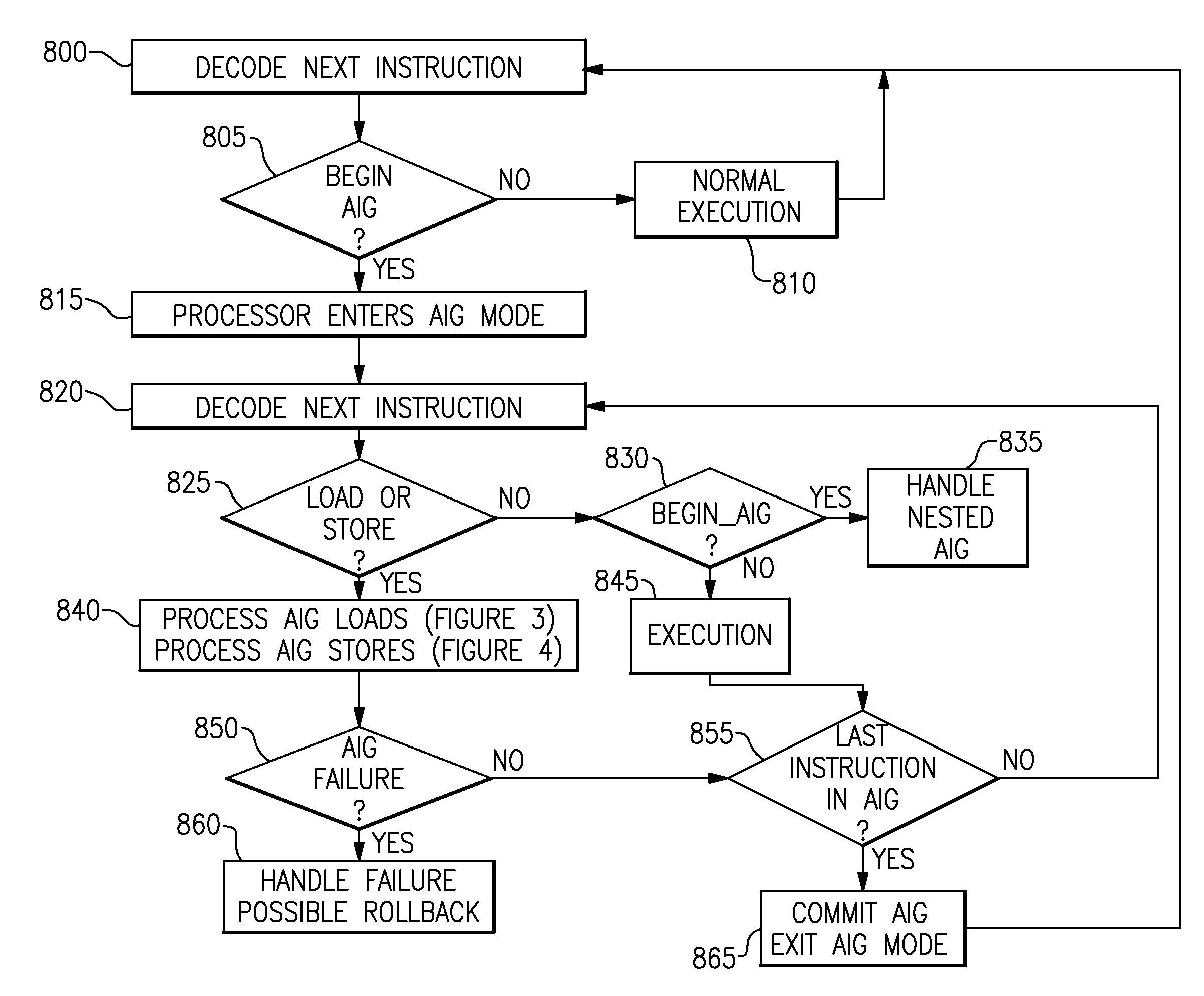
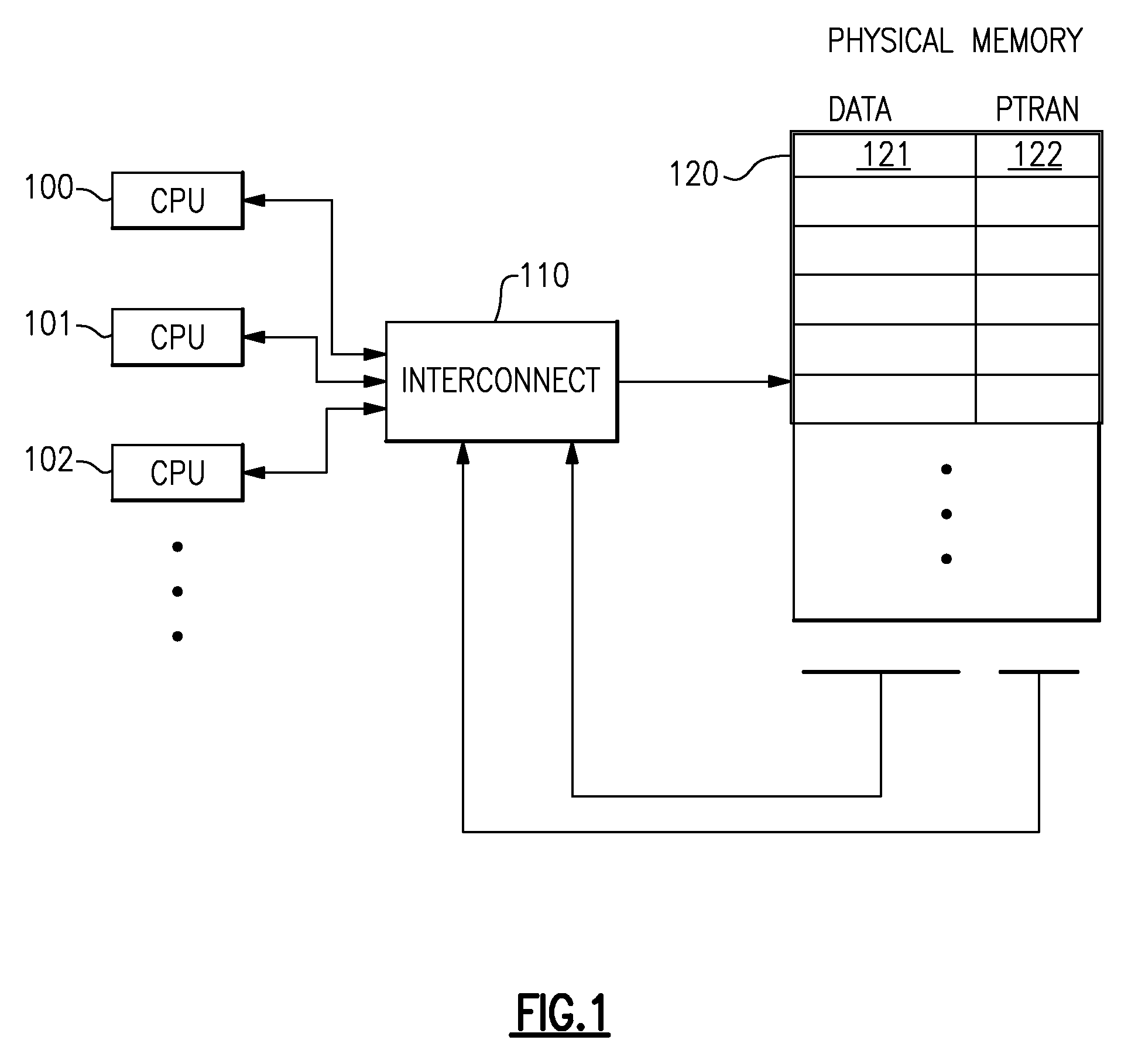
Computing System with Transactional Memory Using Millicode Assists
InactiveUS20080288819A1FasterSolve excessive overheadRuntime instruction translationDigital computer detailsProcess memoryTransactional memory
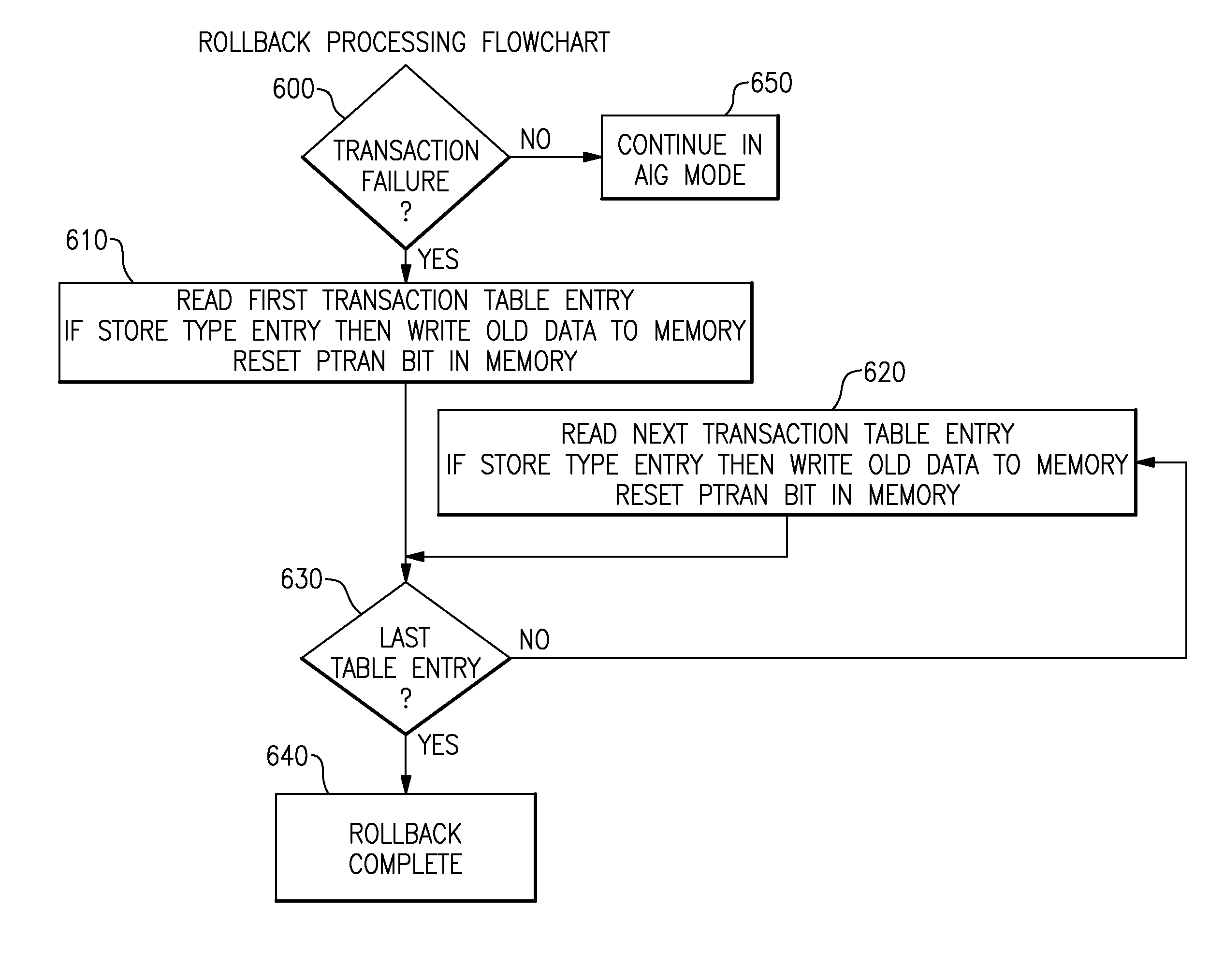
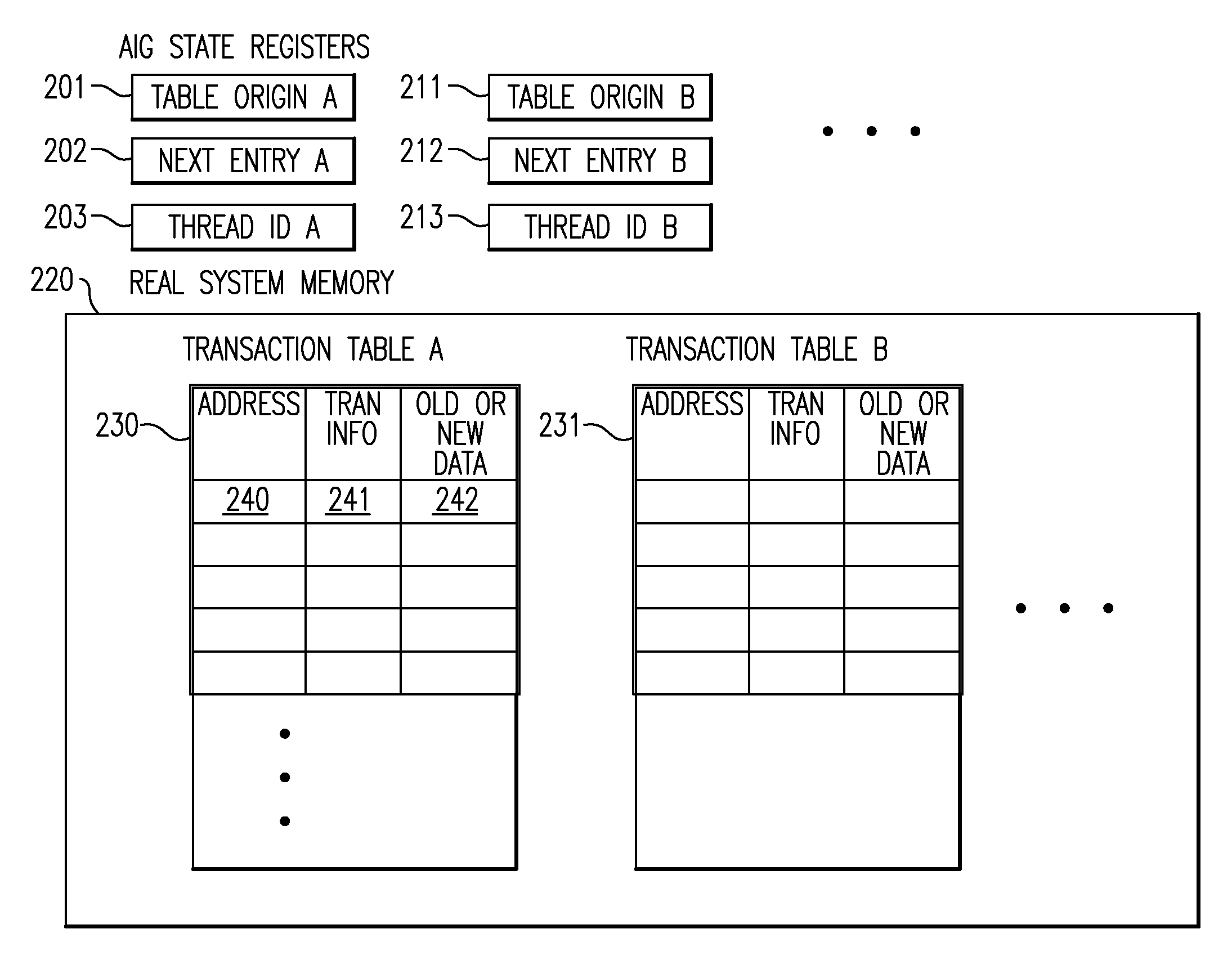
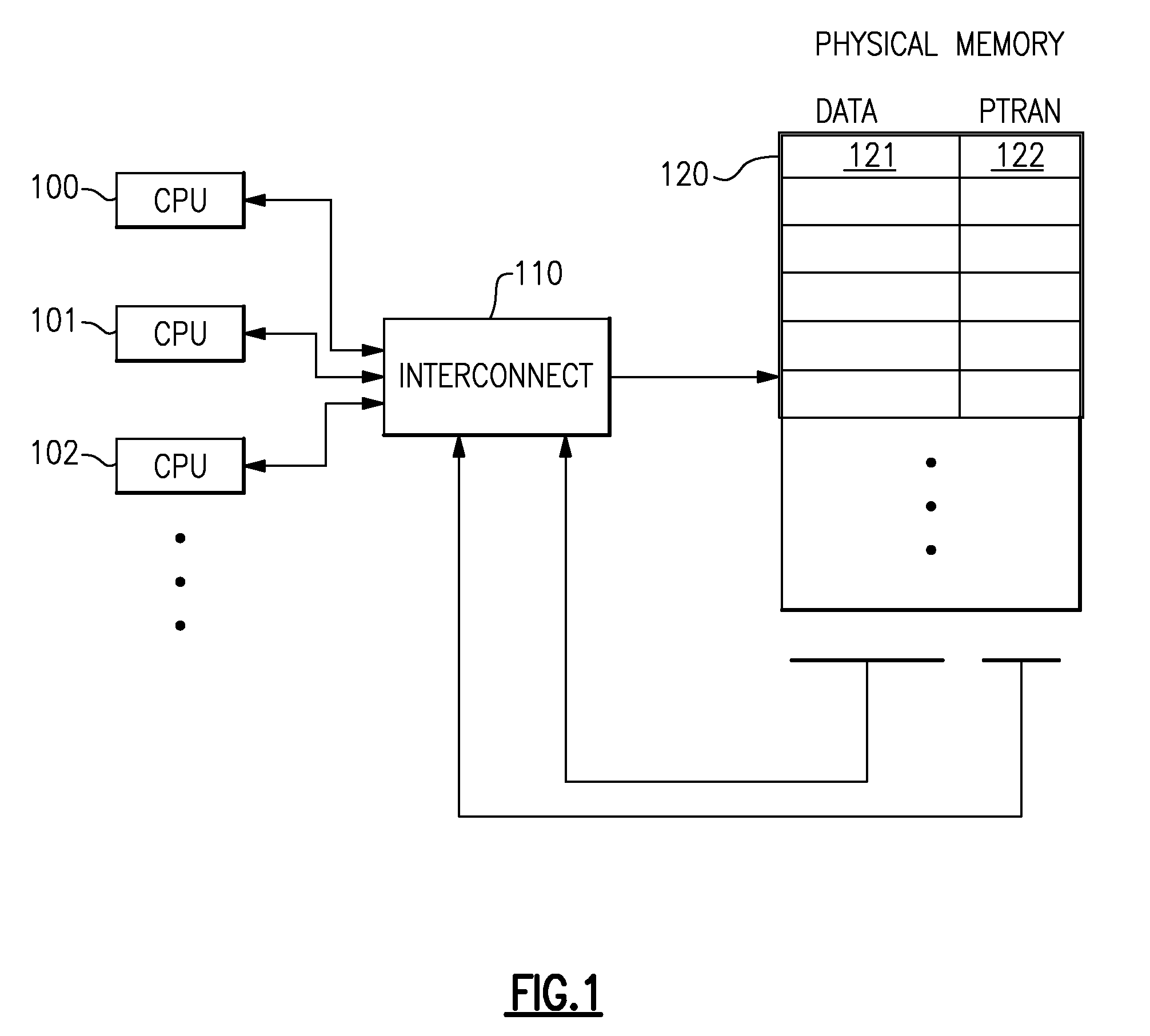
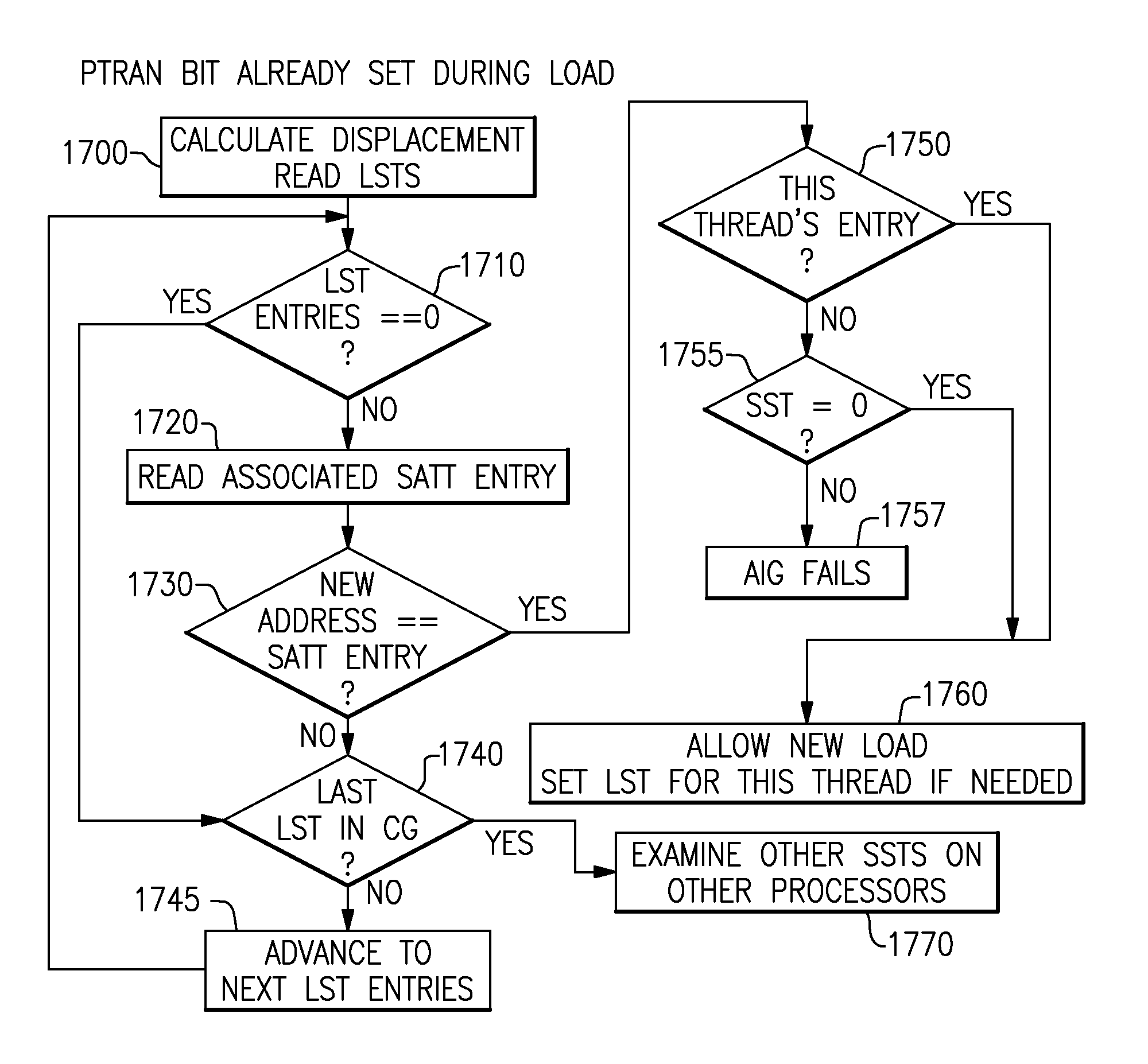
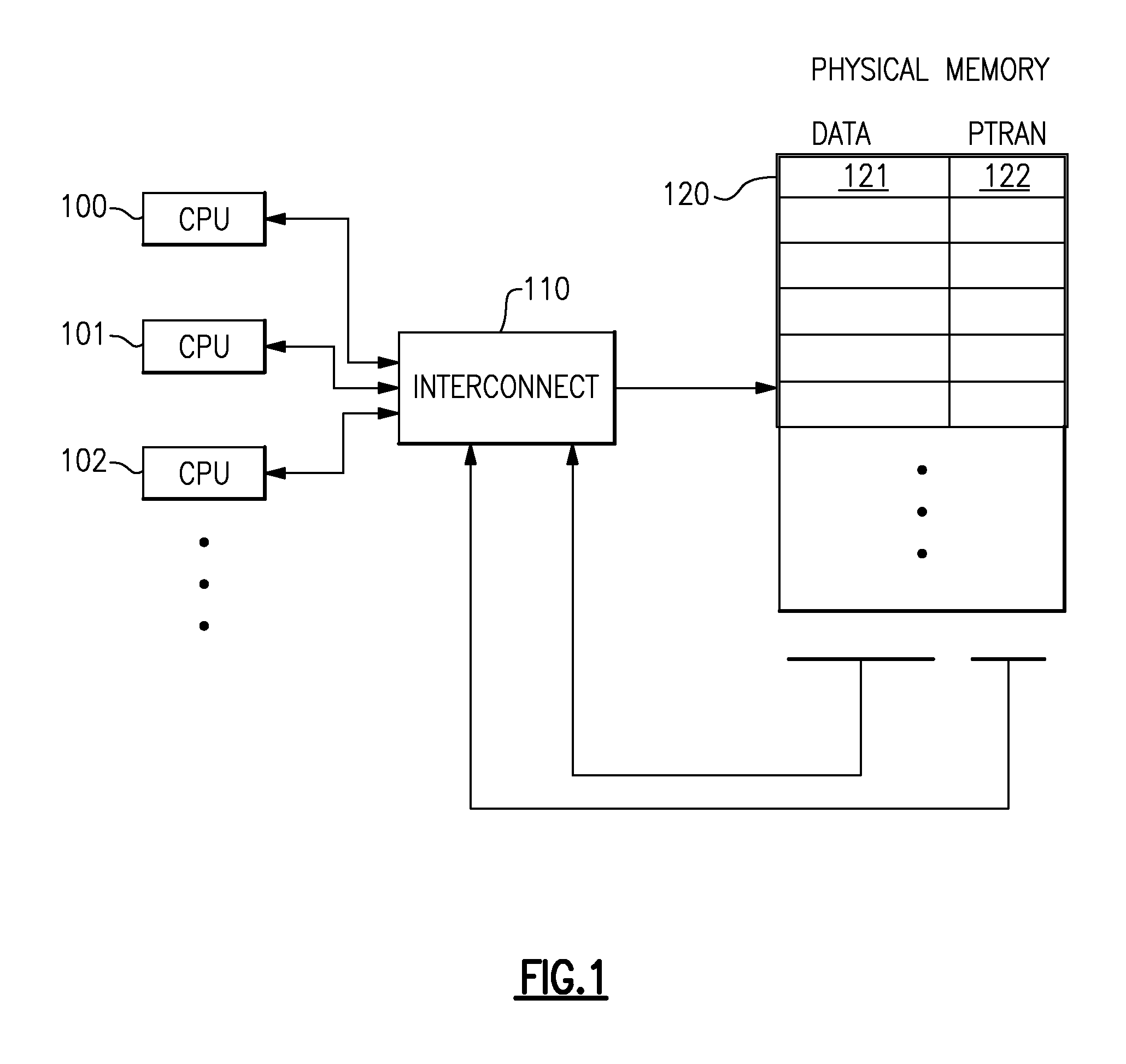
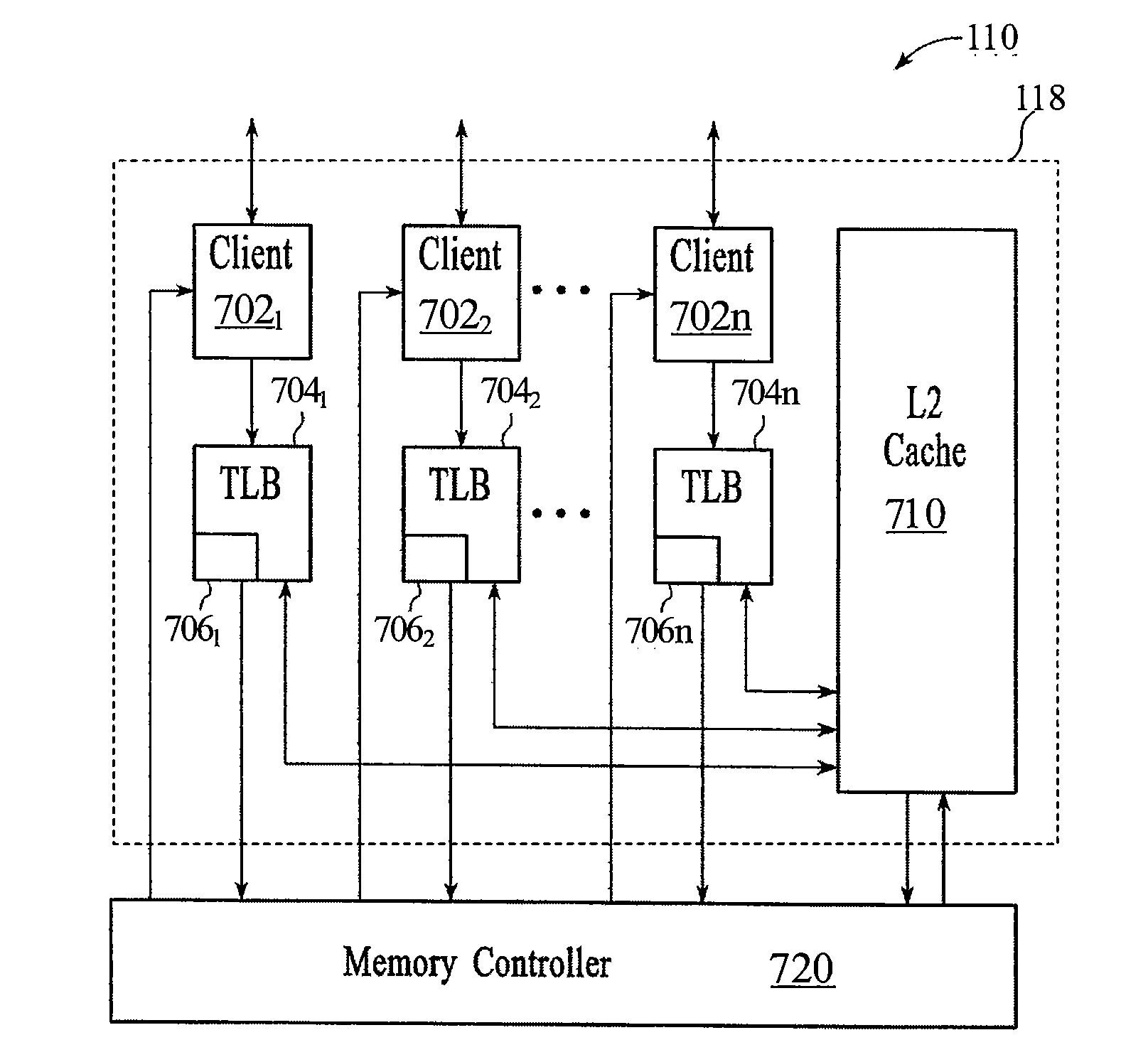
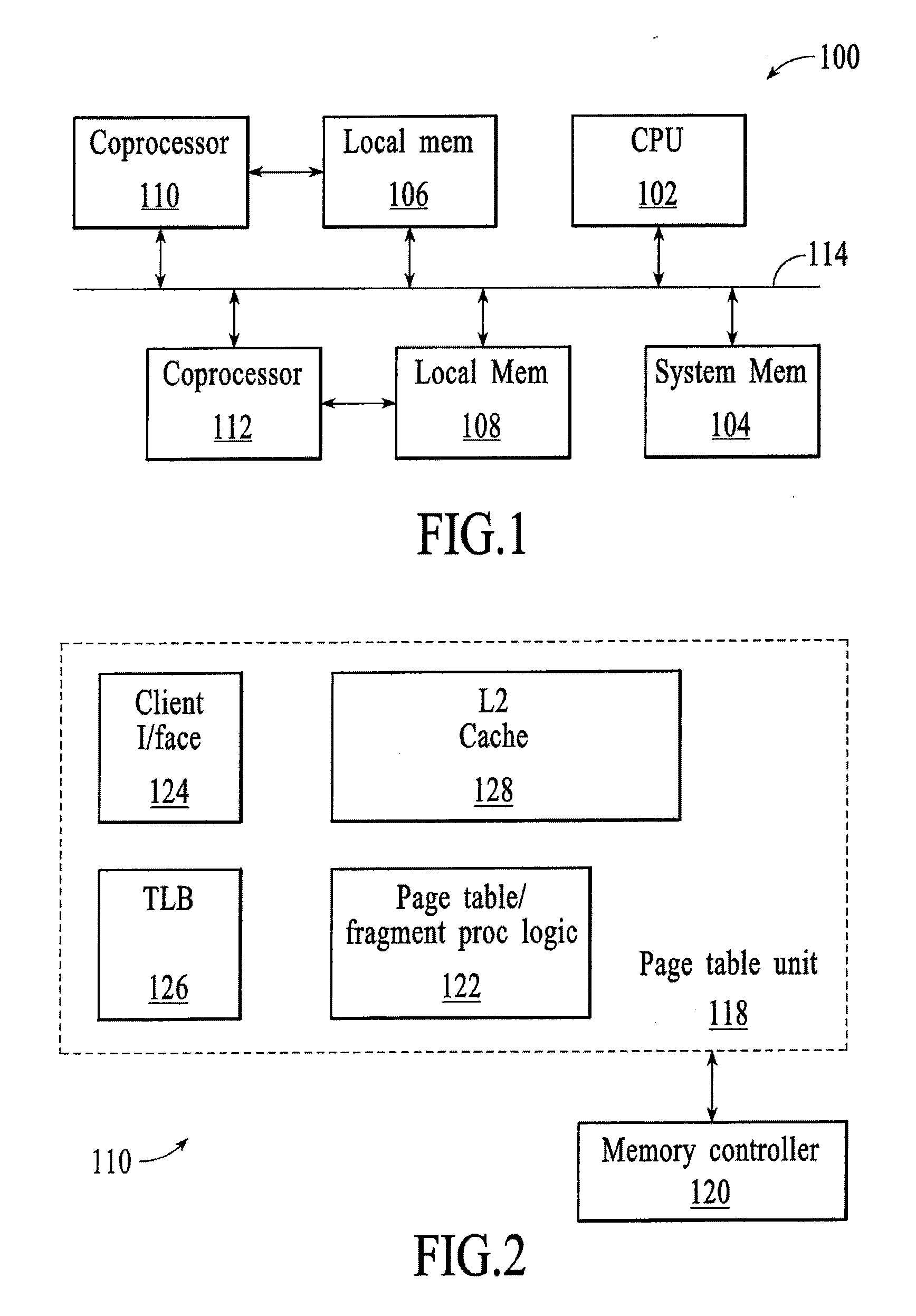
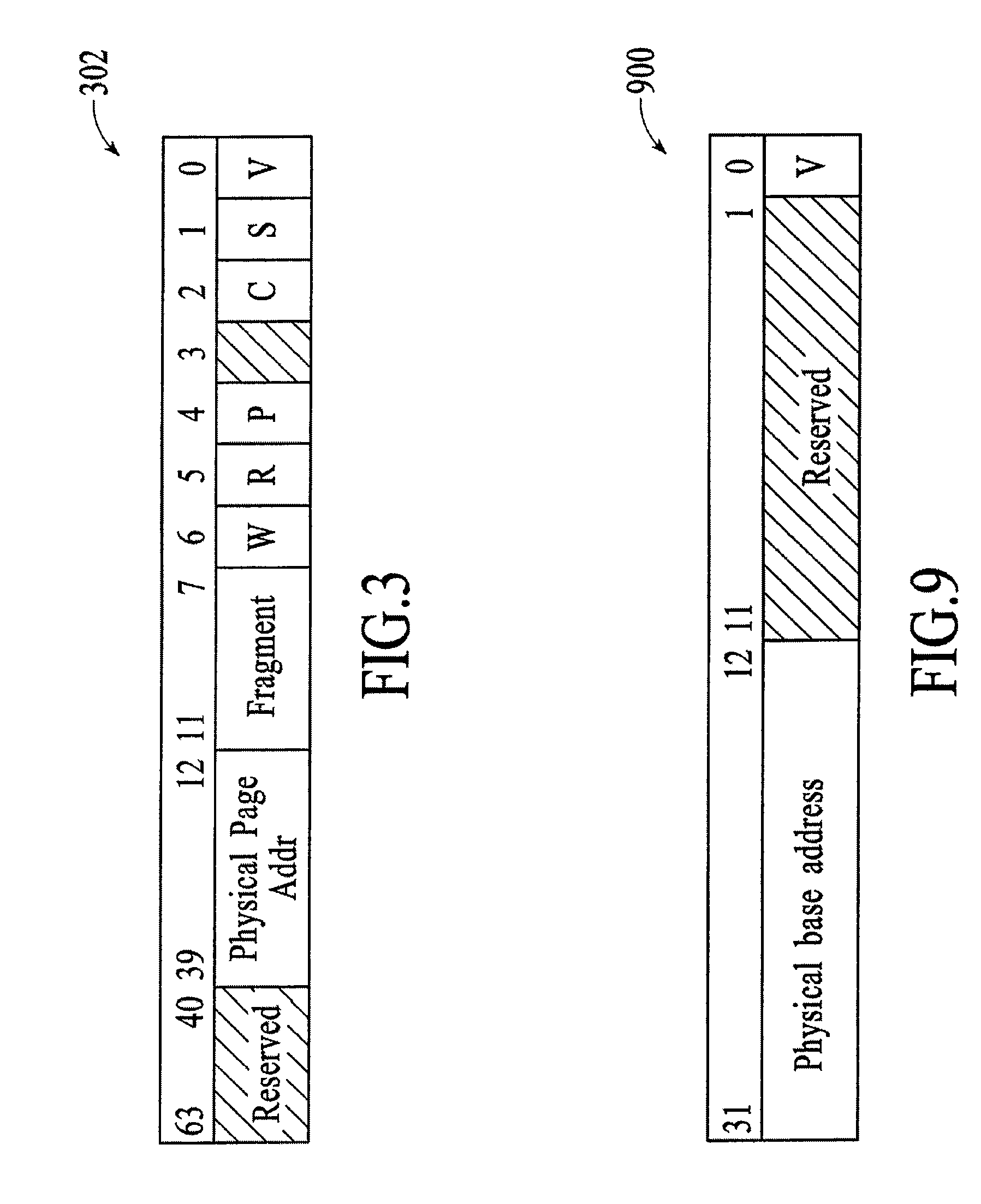
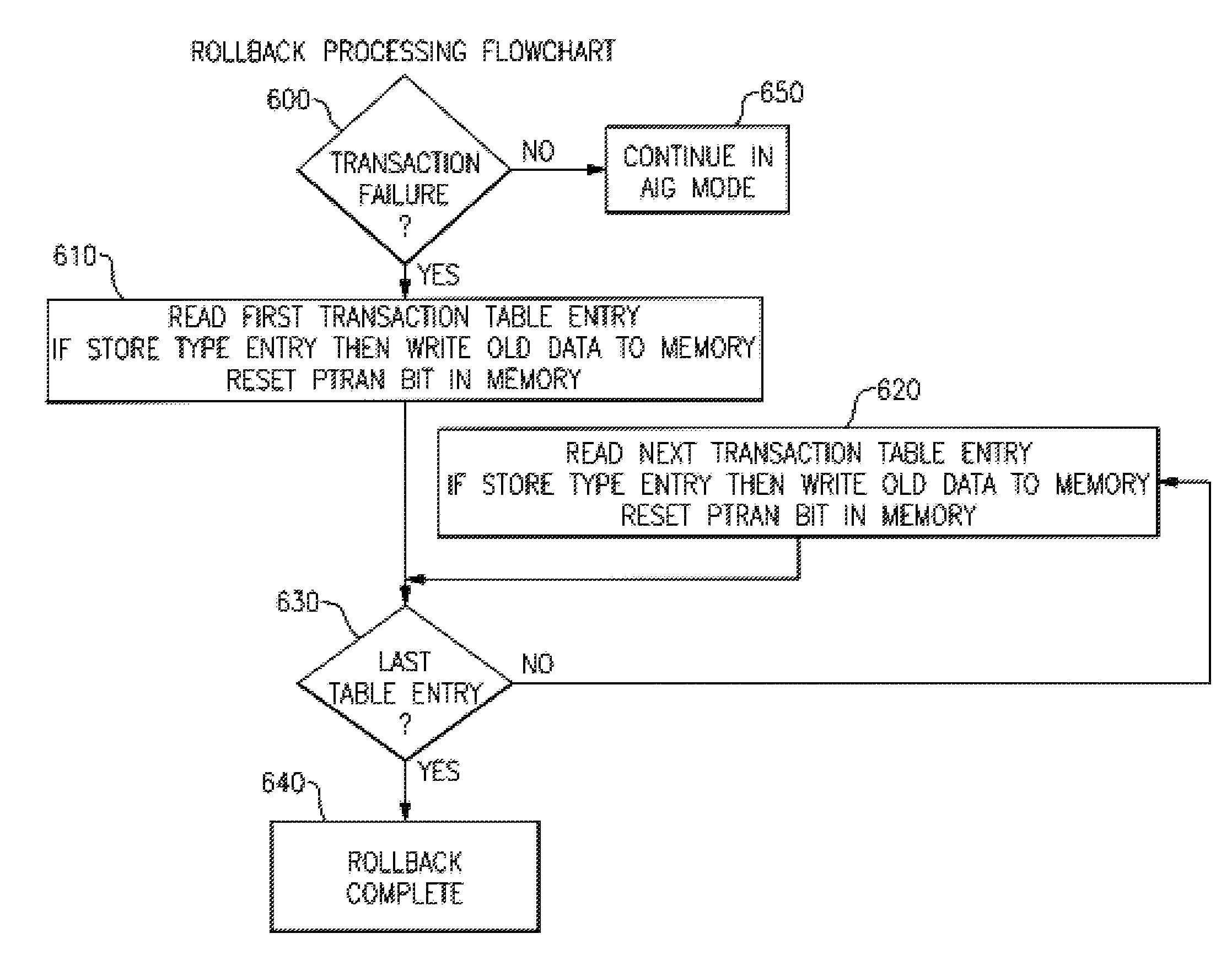
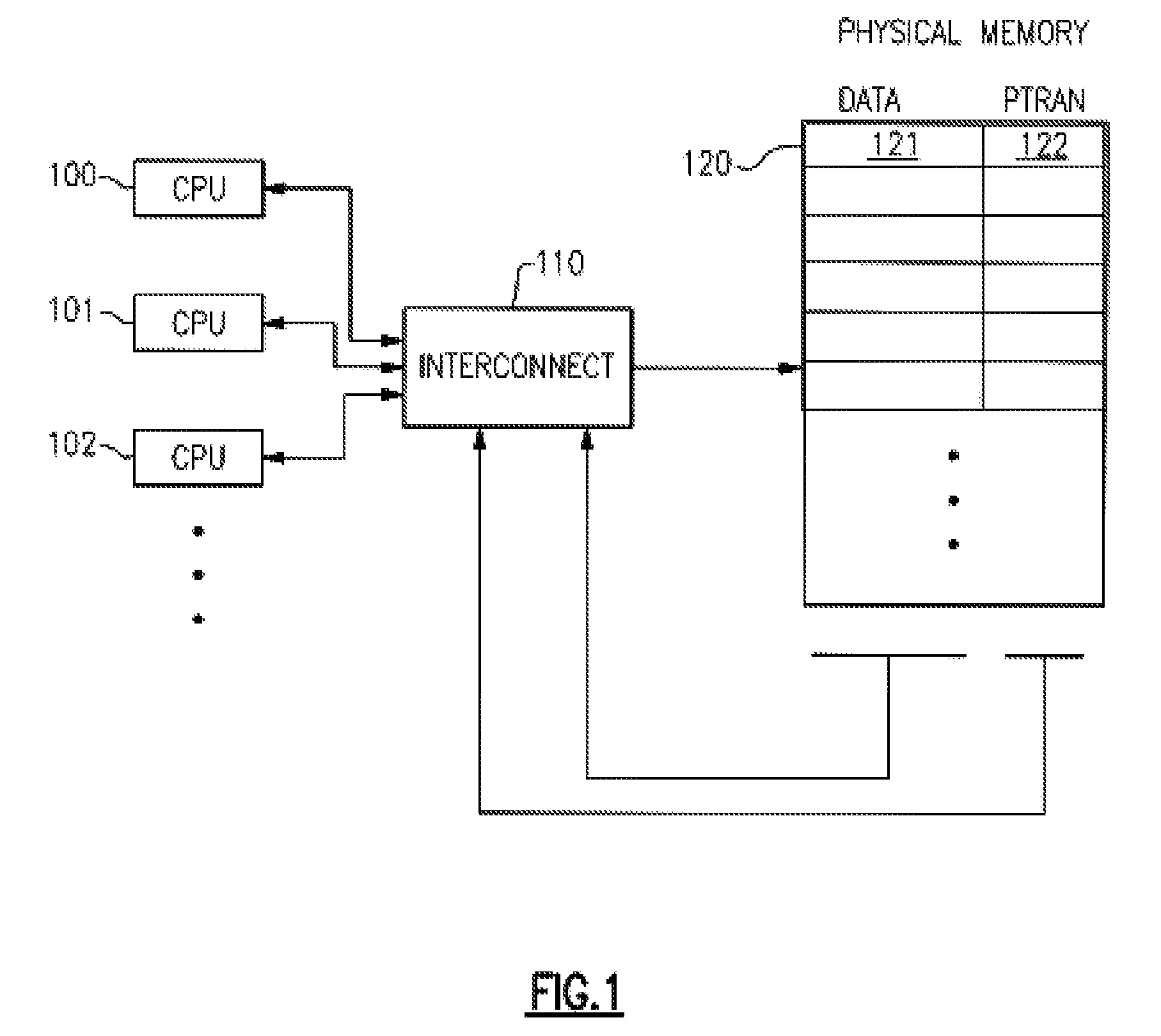
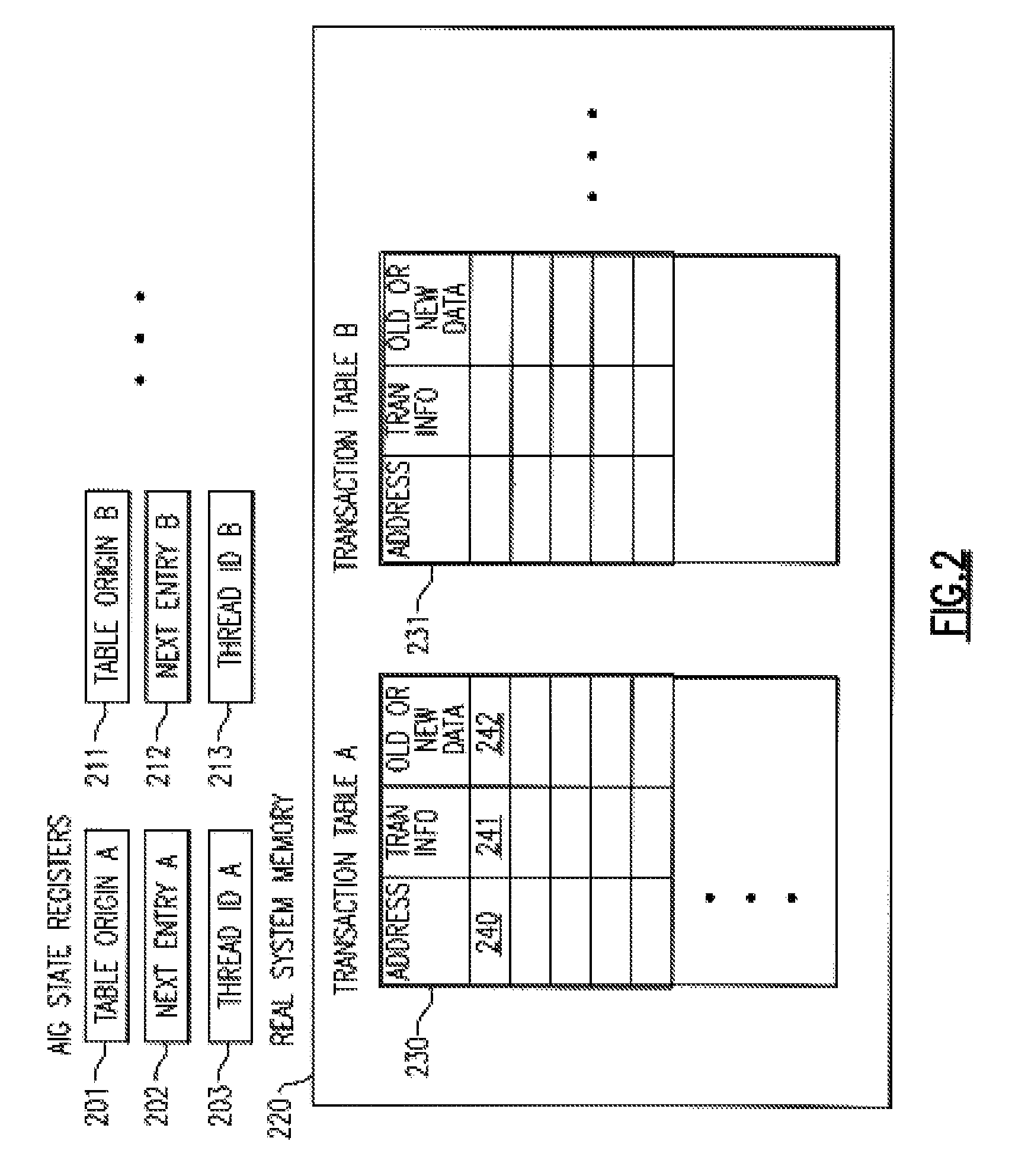
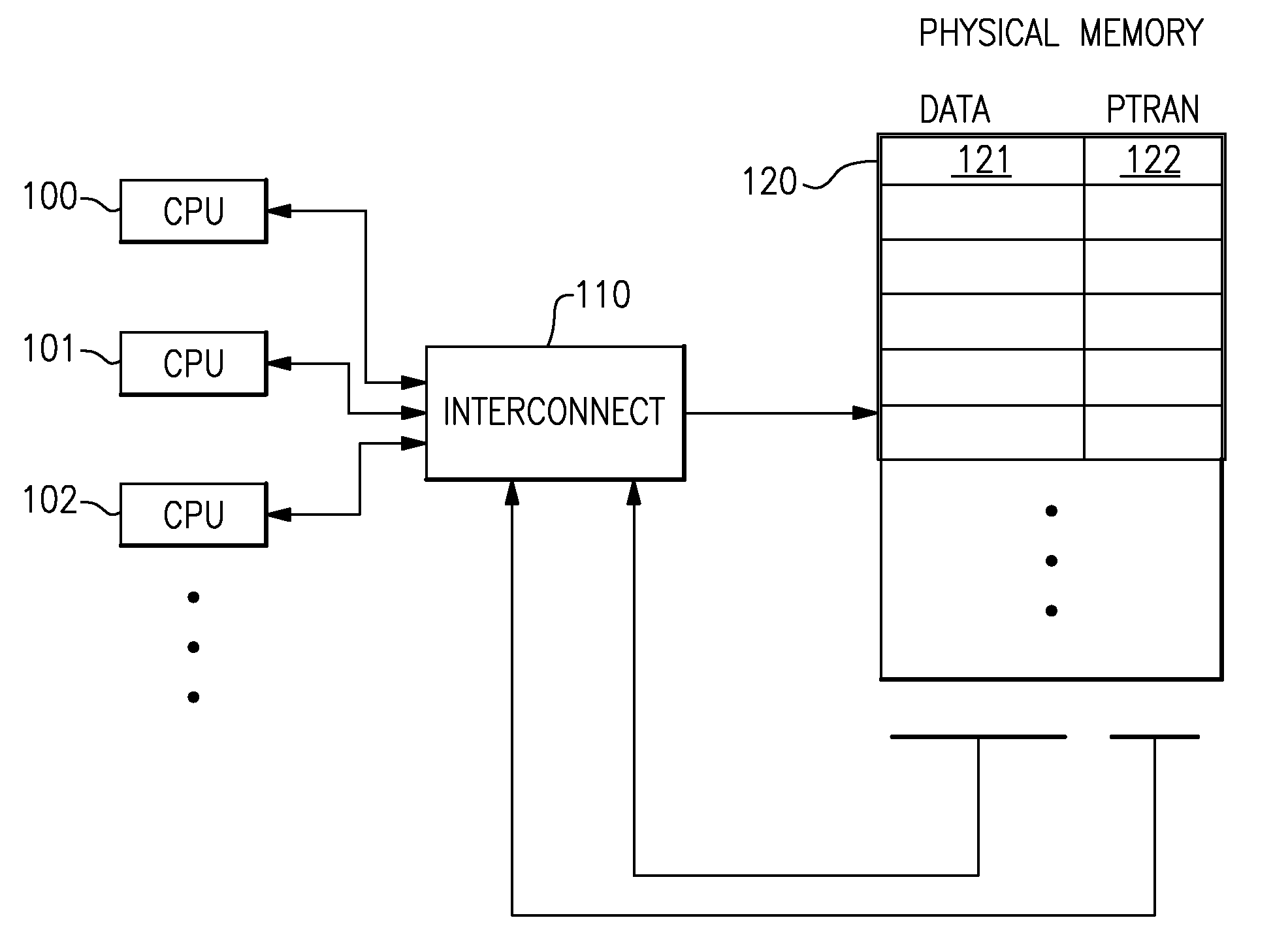
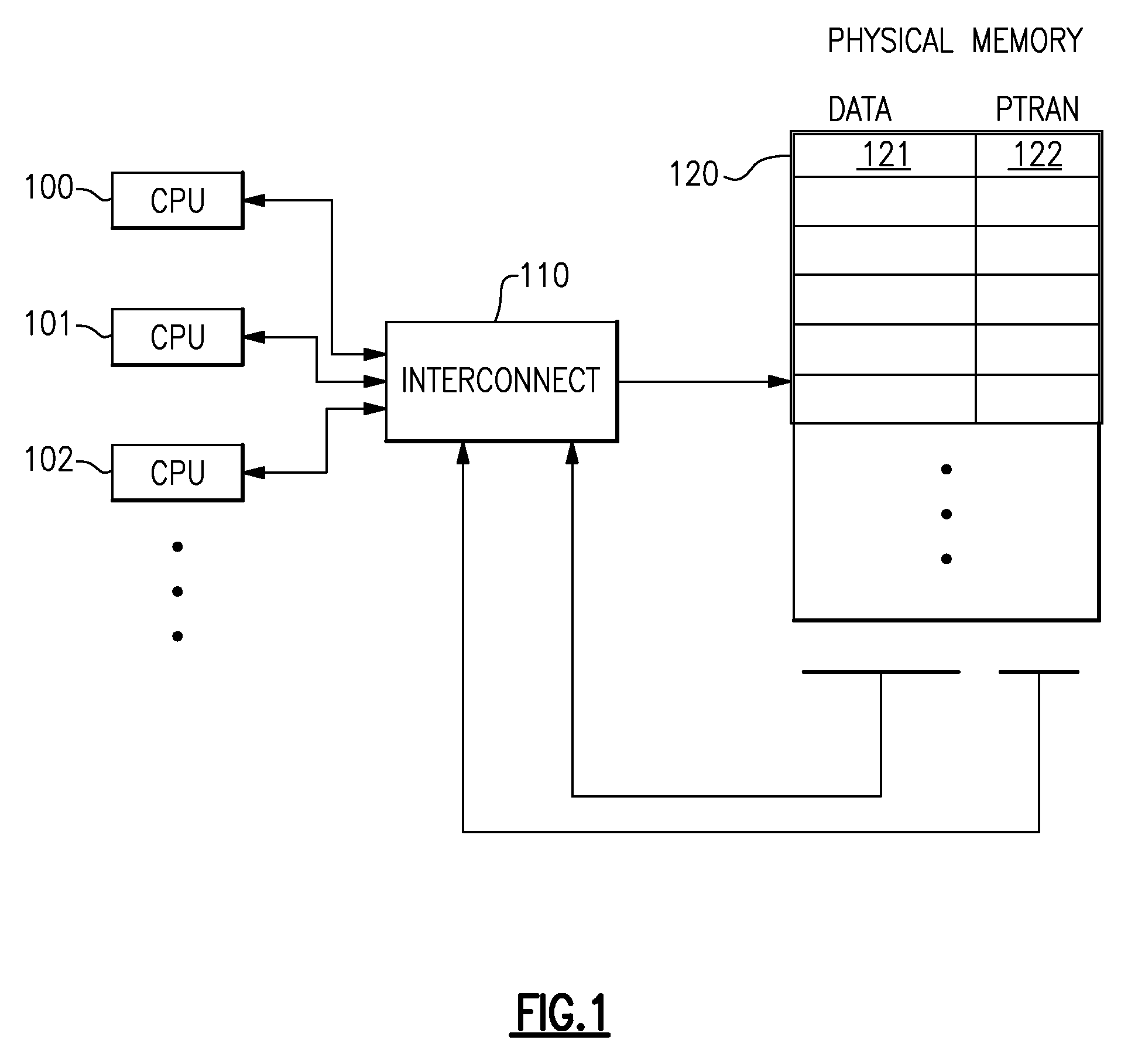
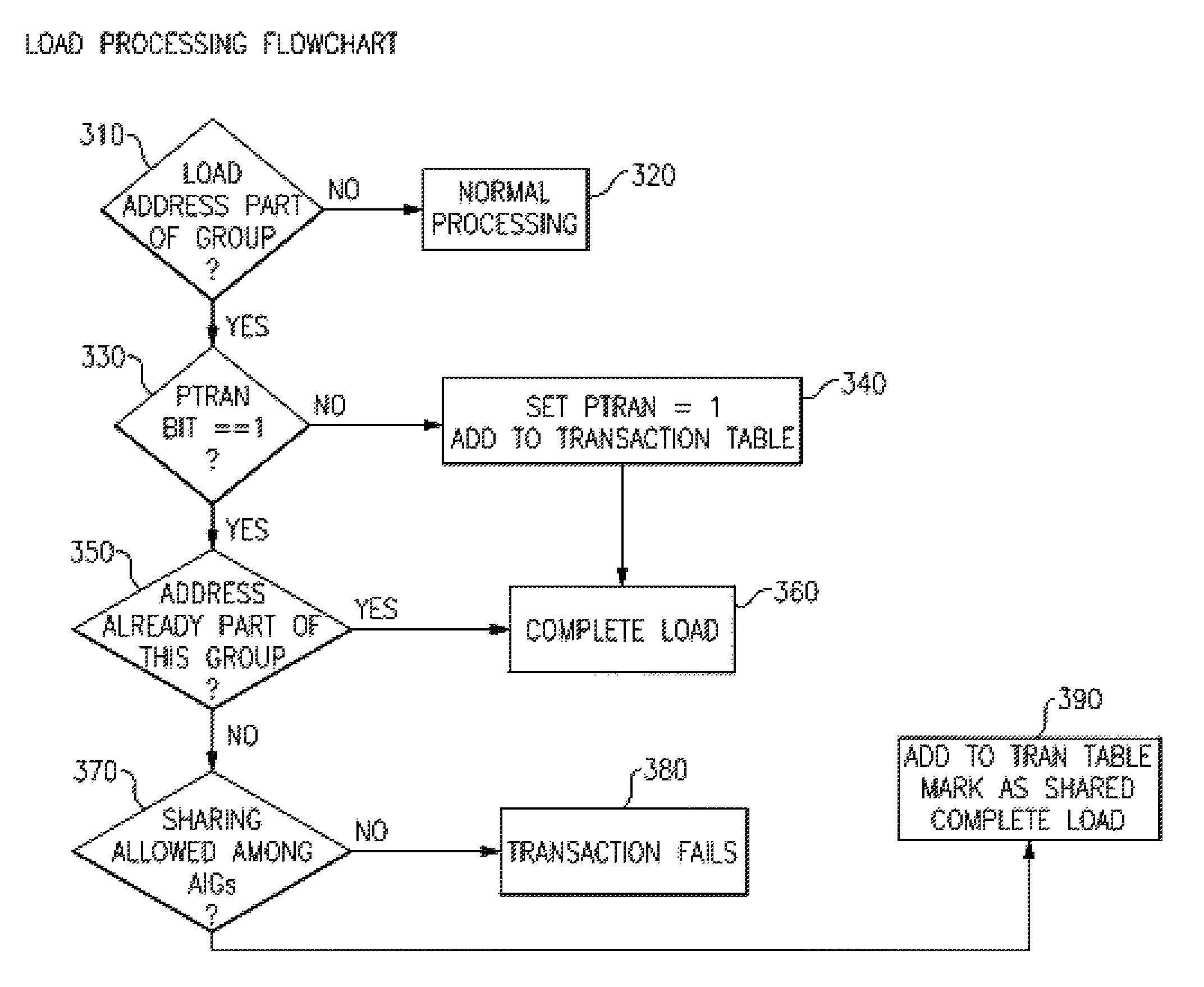
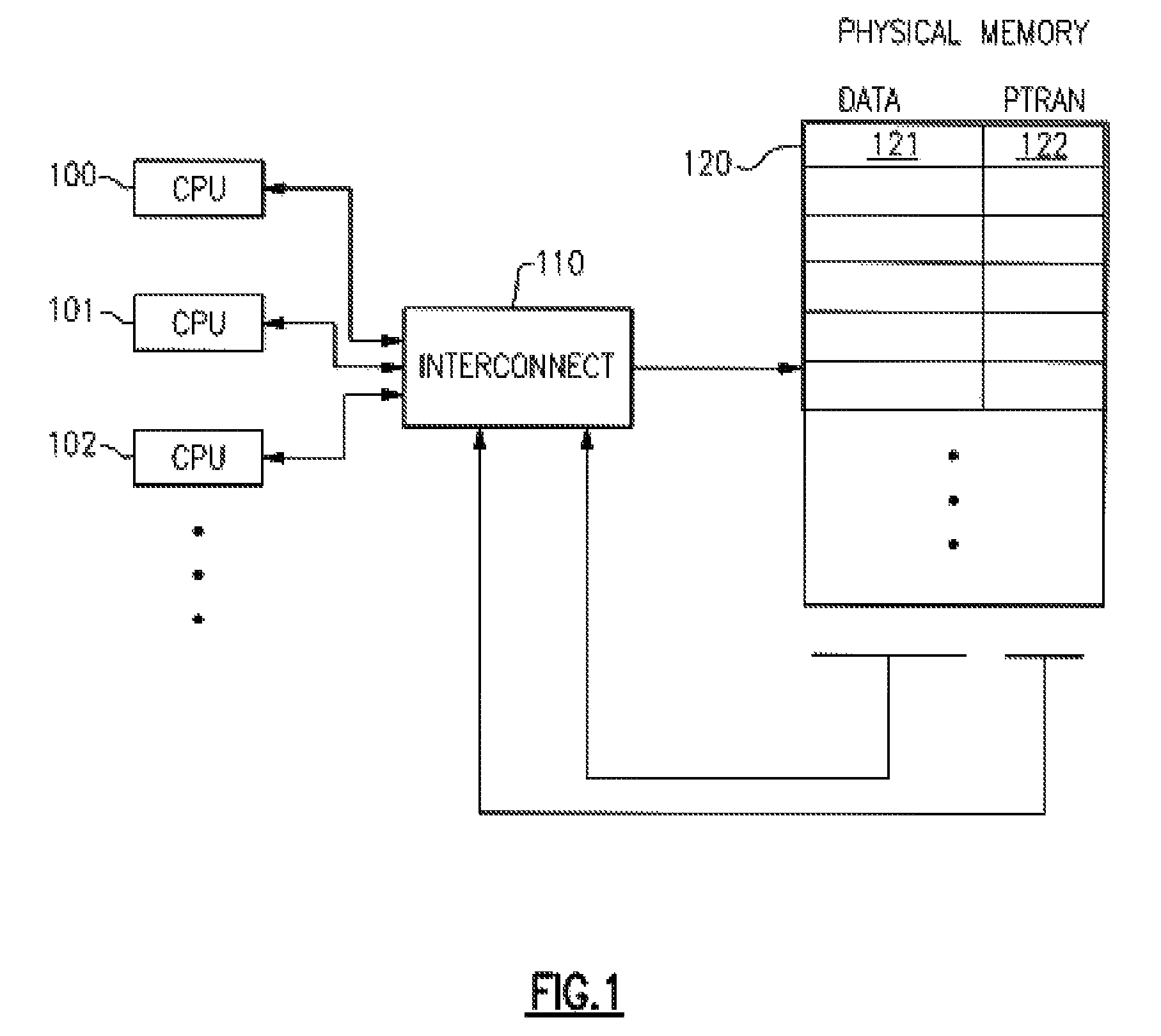
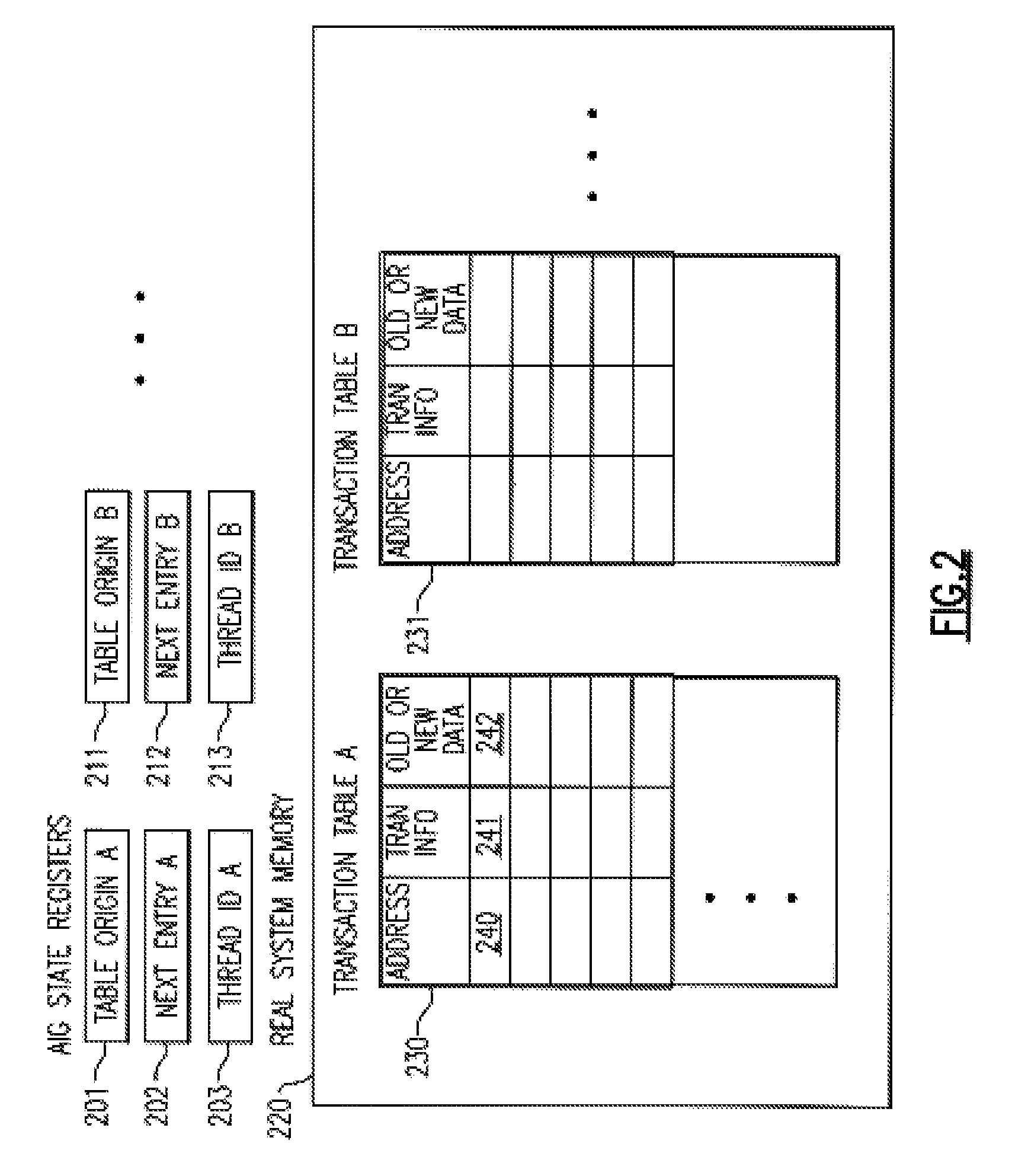
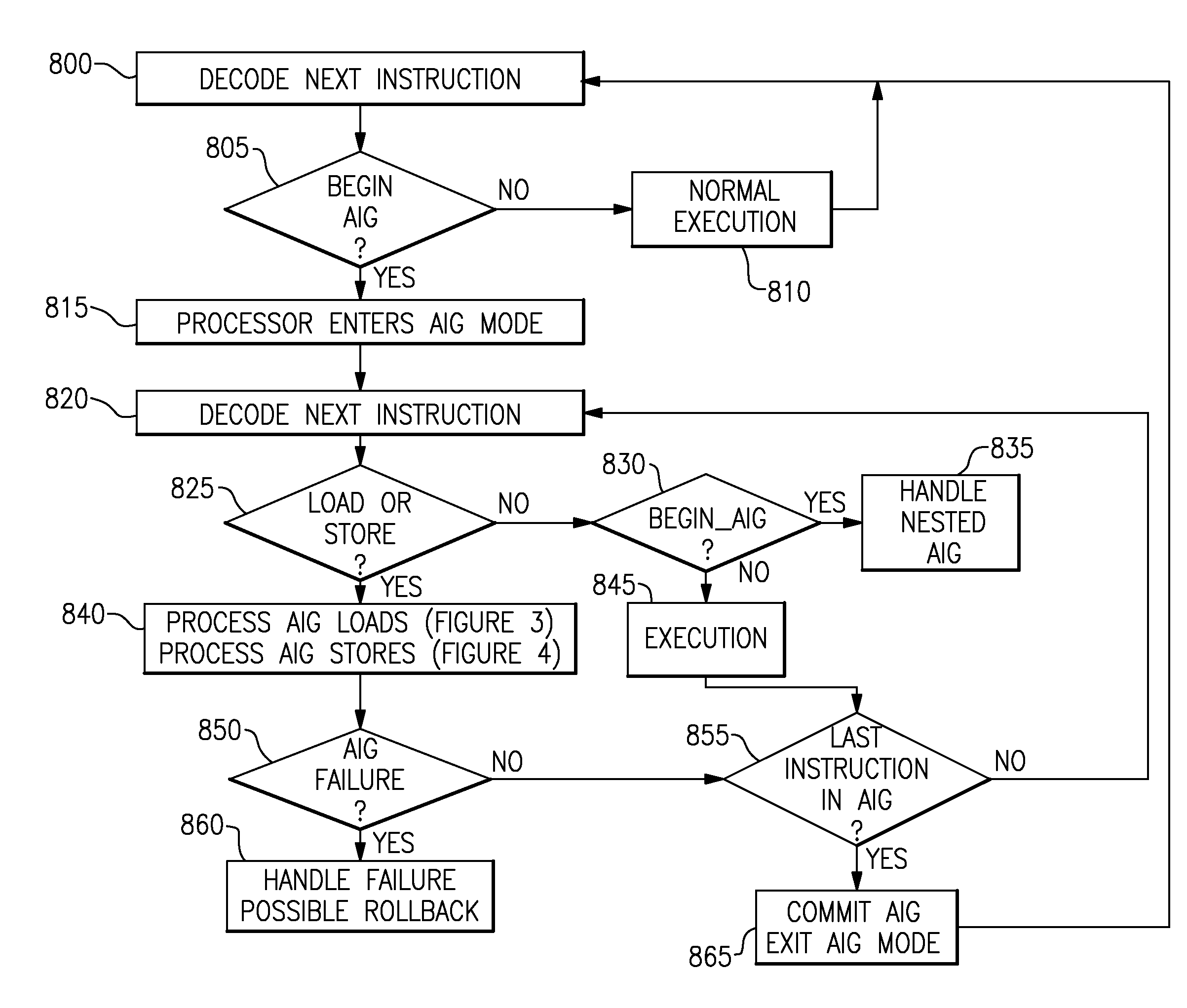
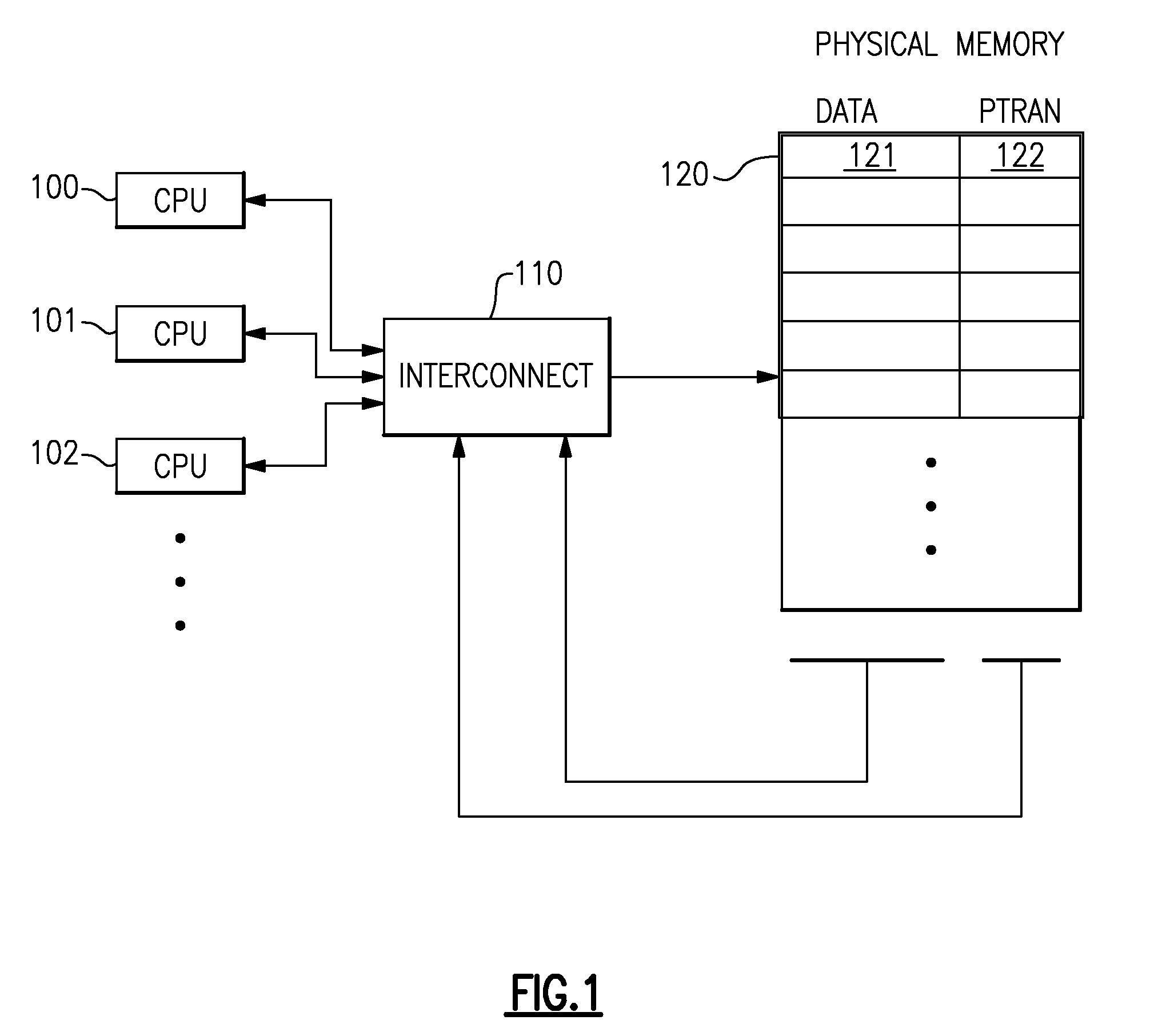
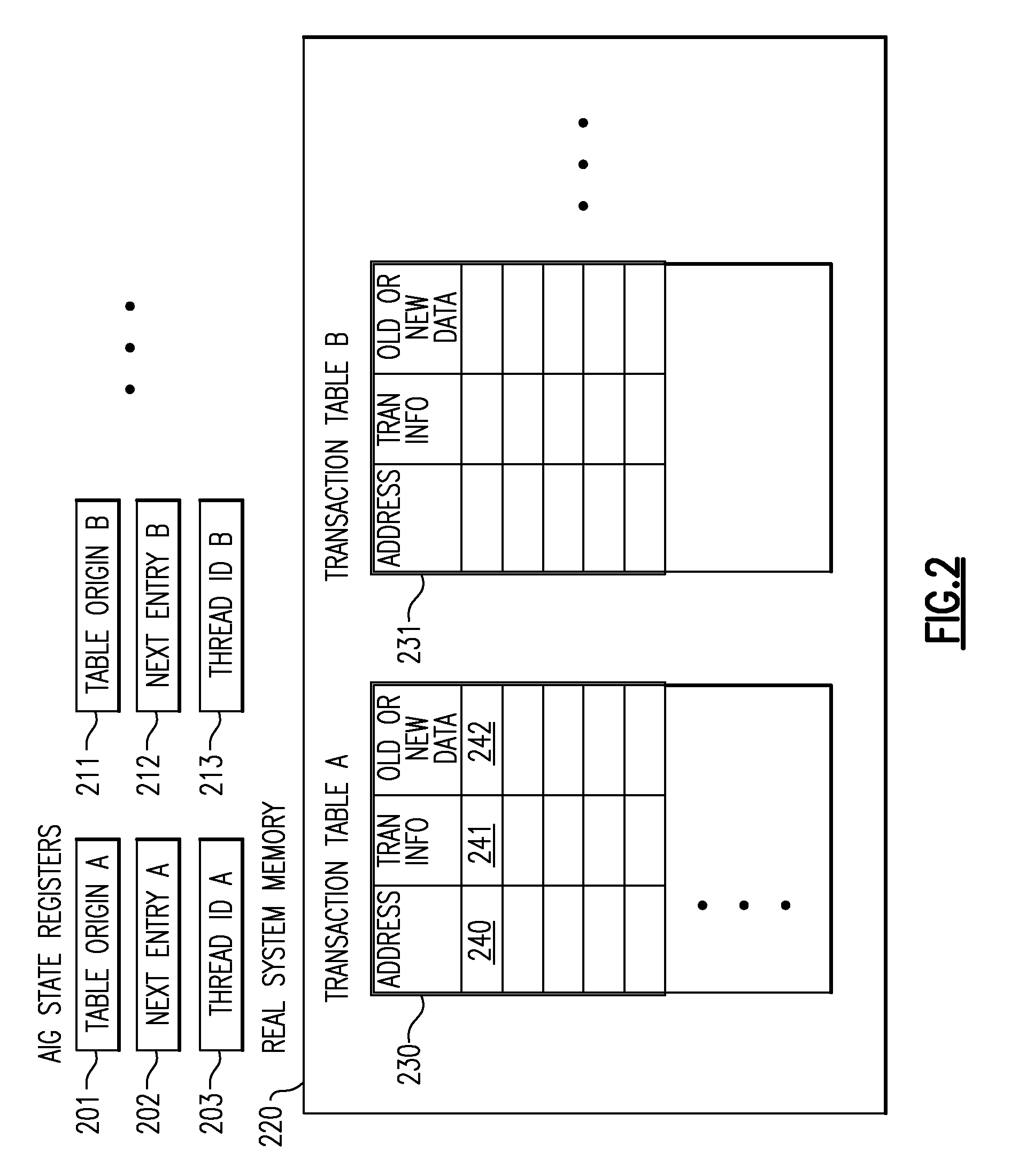
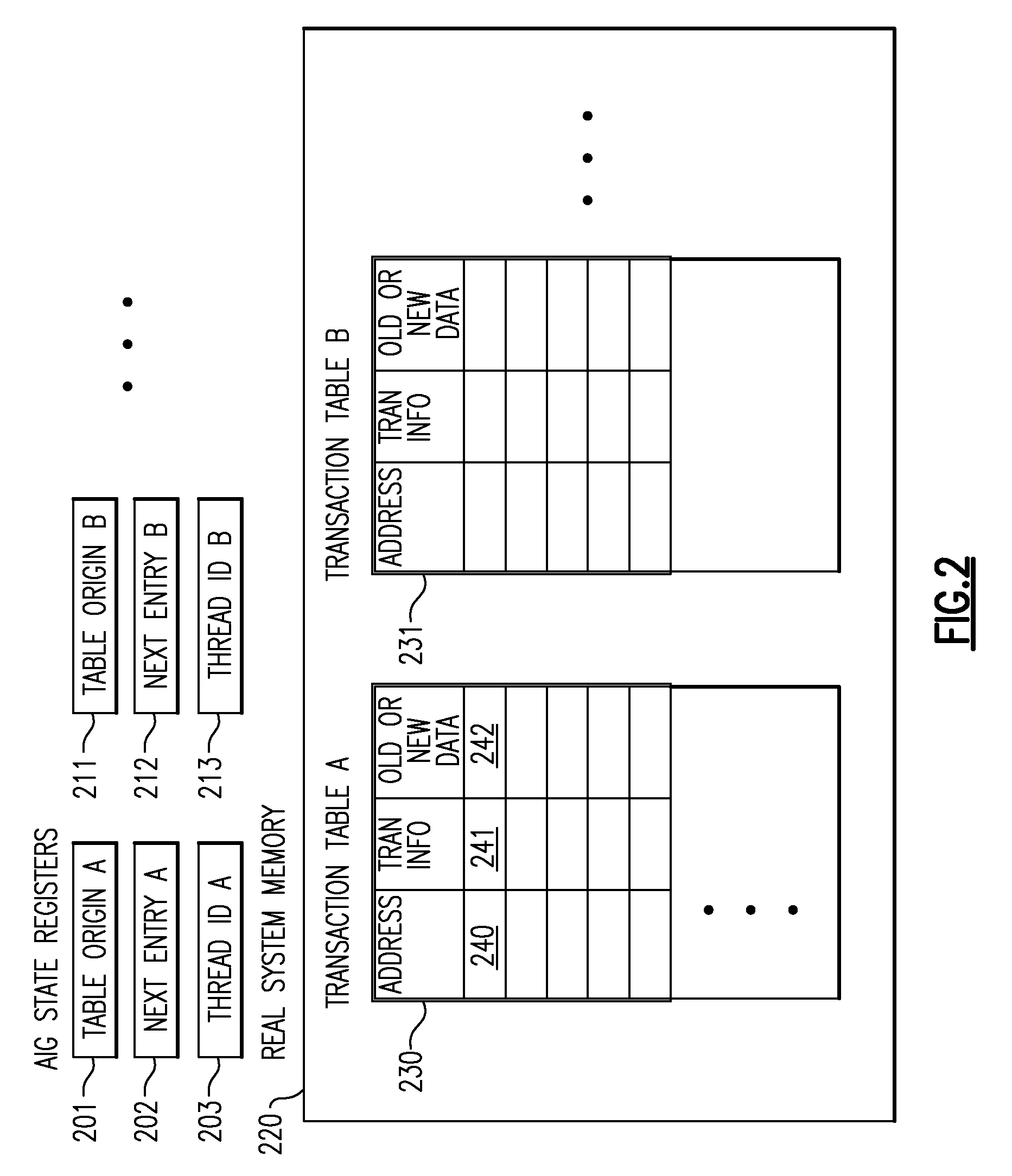
A computing system processes memory transactions for parallel processing of multiple threads of execution with millicode assists. The computing system transactional memory support provides a Transaction Table in memory and a method of fast detection of potential conflicts between multiple transactions. Special instructions may mark the boundaries of a transaction and identify memory locations applicable to a transaction. A ‘private to transaction’ (PTRAN) tag, directly addressable as part of the main data storage memory location, enables a quick detection of potential conflicts with other transactions that are concurrently executing on another thread of said computing system. The tag indicates whether (or not) a data entry in memory is part of a speculative memory state of an uncommitted transaction that is currently active in the system. Program millicode provides transactional memory functions including creating and updating transaction tables, committing transactions and controlling the rollback of transactions which fail.
Owner:IBM CORP
Multi-processing memory duplication system
InactiveUS7047341B2Reduce computing costIncrease computing speedError detection/correctionMemory systemsProcess memoryParallel computing
Embodiments of the present invention relate to an apparatus including a first processor module, a second processor module, and a bus. The bus is coupled to the first processor module and the second processor module. The bus is configured to transmit both processor related communication and memory related communication. In embodiments, the first processor module includes a first central processing unit and the second processing module includes a second central processing unit. Accordingly, in embodiments of the present invention, a single bus can be used to communicate between processors and memories. The present invention is useful for real time duplication of memory, high speed duplication of memory, and / or a coherency check of memory between a first processing module and a second processing module.
Owner:LG ERICSSON
Multistream processing memory-and barrier-synchronization method and apparatus
ActiveUS7437521B1Memory architecture accessing/allocationProgram synchronisationFile synchronizationProcess memory
A method and apparatus to provide specifiable ordering between and among vector and scalar operations within a single streaming processor (SSP) via a local synchronization (Lsync) instruction that operates within a relaxed memory consistency model. Various aspects of that relaxed memory consistency model are described. Further, a combined memory synchronization and barrier synchronization (Msync) for a multistreaming processor (MSP) system is described. Also, a global synchronization (Gsync) instruction provides synchronization even outside a single MSP system is described. Advantageously, the pipeline or queue of pending memory requests does not need to be drained before the synchronization operation, nor is it required to refrain from determining addresses for and inserting subsequent memory accesses into the pipeline.
Owner:CRAY
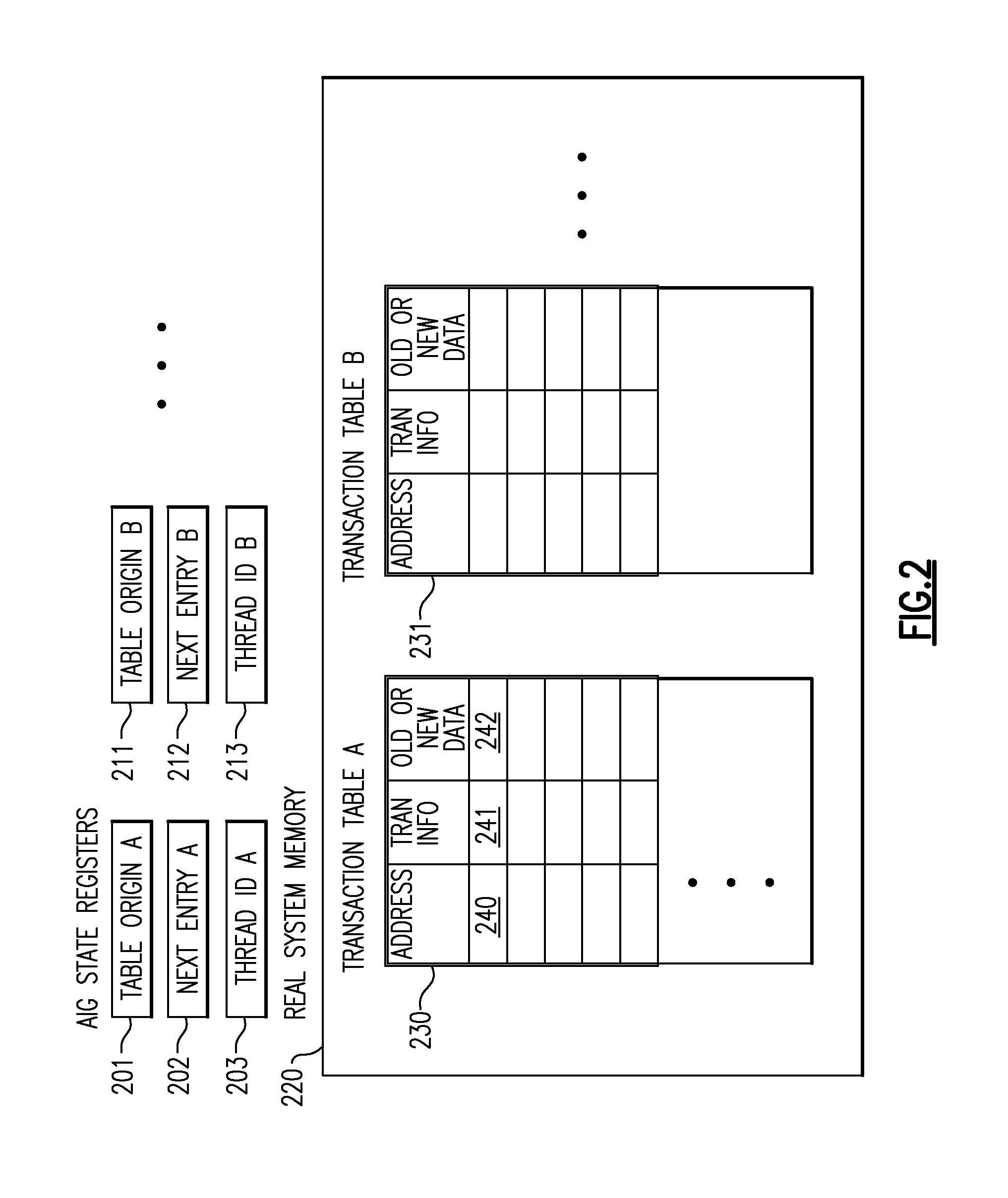
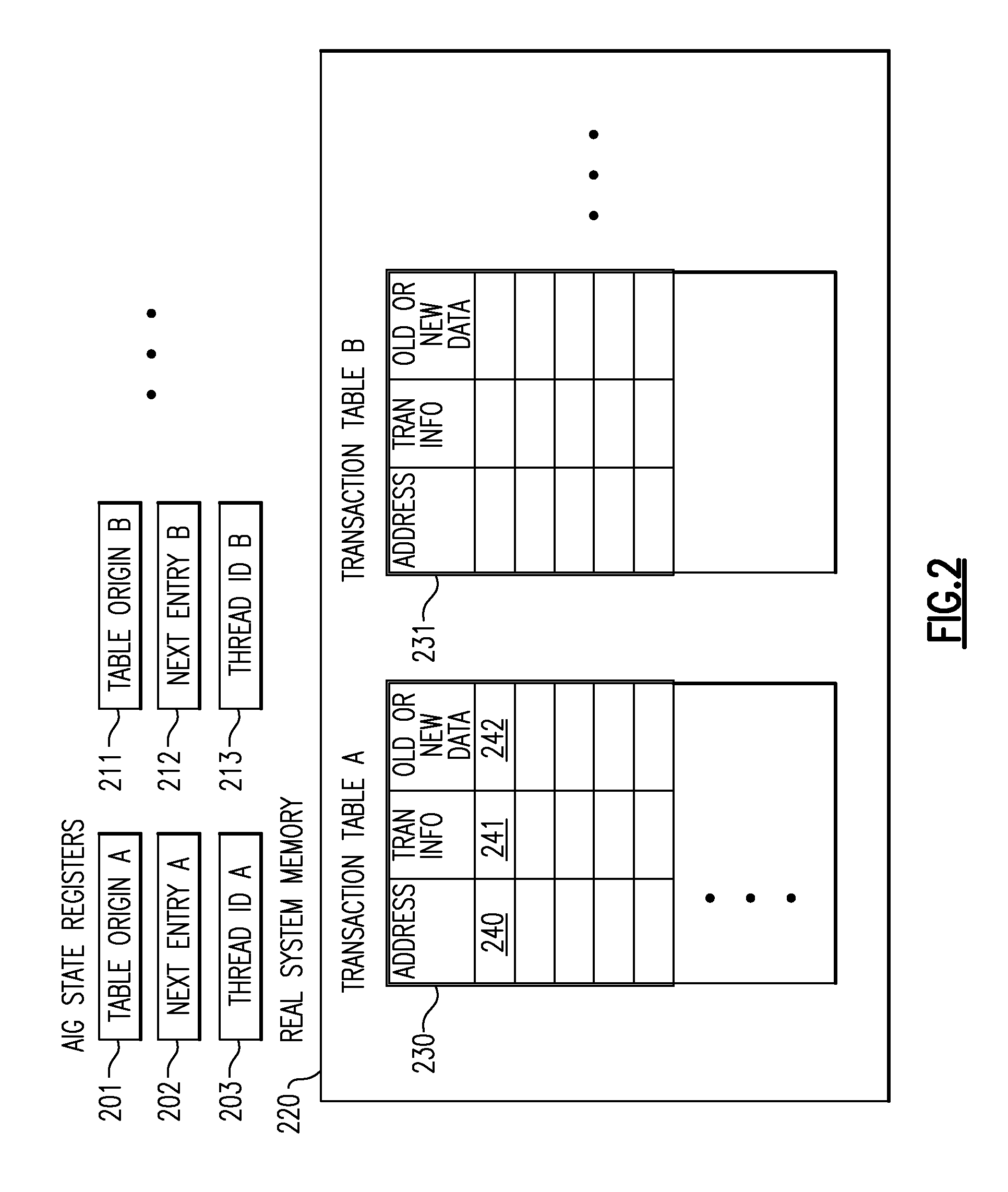
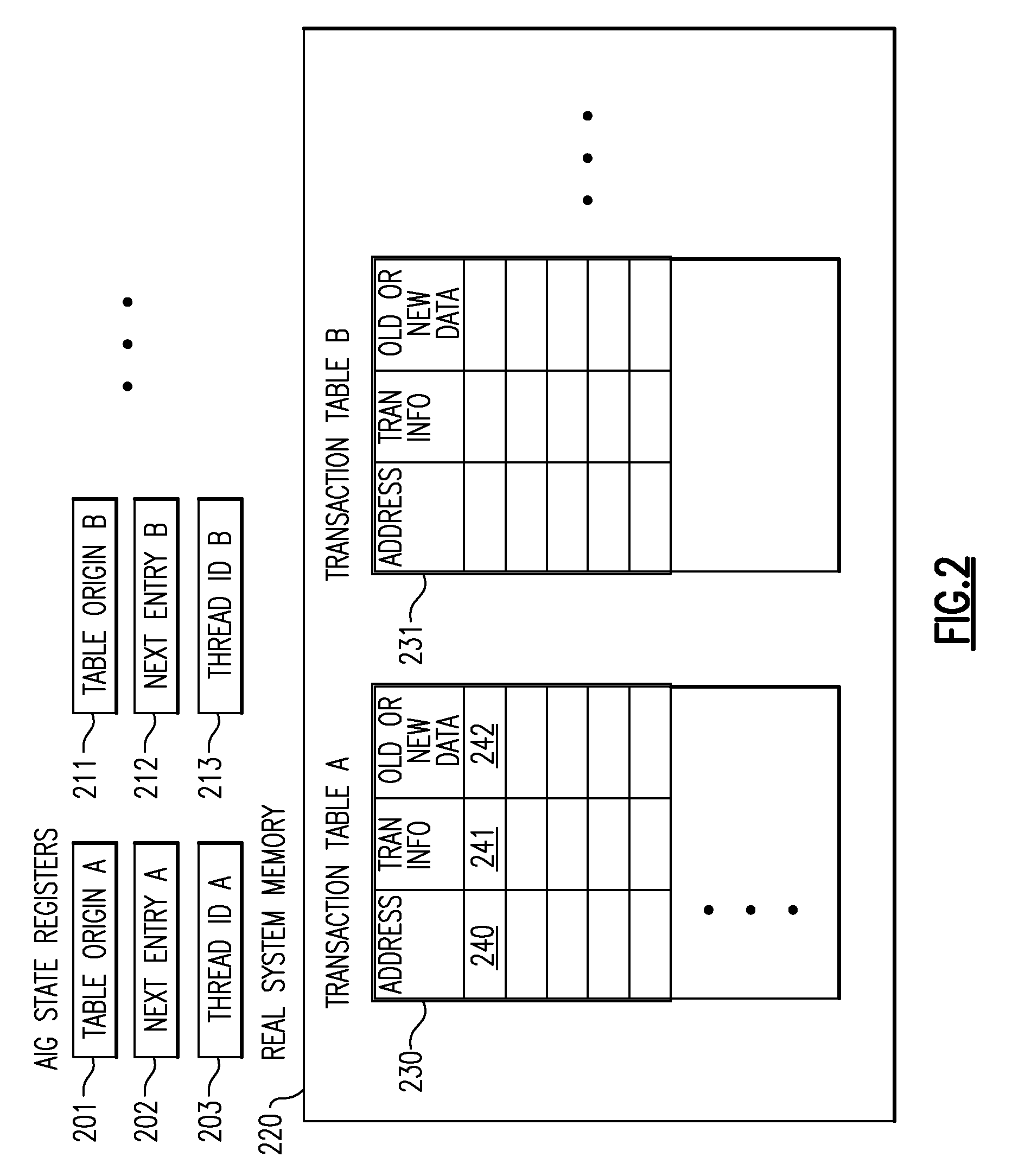
Transactional Memory System Which Employs Thread Assists Using Address History Tables
A computing system uses specialized “Set Associative Transaction Tables” and additional “Summary Transaction Tables” to speed the processing of common transactional memory conflict cases and those which employ assist threads using an Address History Table and processes memory transactions with a Transaction Table in memory for parallel processing of multiple threads of execution by support of which an application need not be aware. Special instructions may mark the boundaries of a transaction and identify memory locations applicable to a transaction. A ‘private to transaction’ (PTRAN) tag, directly addressable as part of the main data storage memory location, enables a quick detection of potential conflicts with other transactions that are concurrently executing on another thread of said computing system. The tag indicates whether (or not) a data entry in memory is part of a speculative memory state of an uncommitted transaction that is currently active in the system.
Owner:IBM CORP
Transactional Memory Computing System with Support for Chained Transactions
ActiveUS20090113443A1Program synchronisationError detection/correctionProcess memoryTransactional memory
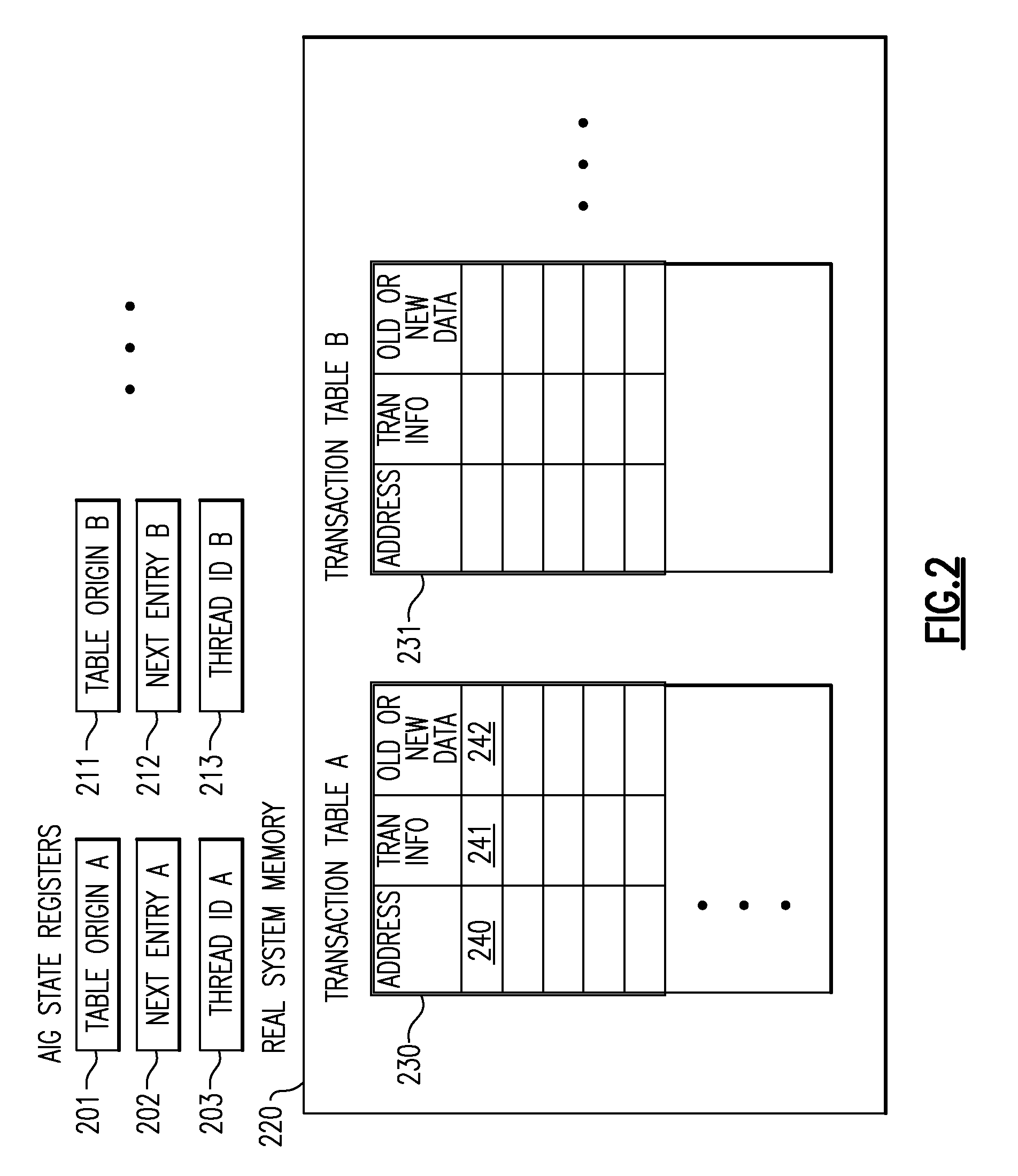
A computing system processes memory transactions for parallel processing of multiple threads of execution provides execution of multiple atomic instruction groups (AIGs) on multiple systems to support a single large transaction that requires operations on multiple threads of execution and / or on multiple systems connected by a network. The support provides a Transaction Table in memory and fast detection of potential conflicts between multiple transactions. Special instructions may mark the boundaries of a transaction and identify memory locations applicable to a transaction. A ‘private to transaction’ (PTRAN) tag, directly addressable as part of the main data storage memory location, enables a quick detection of potential conflicts with other transactions that are concurrently executing on another thread. The tag indicates whether (or not) a data entry in memory is part of a speculative memory state of an uncommitted transaction that is currently active in the system.
Owner:IBM CORP
Data processing system, data processing method, and program
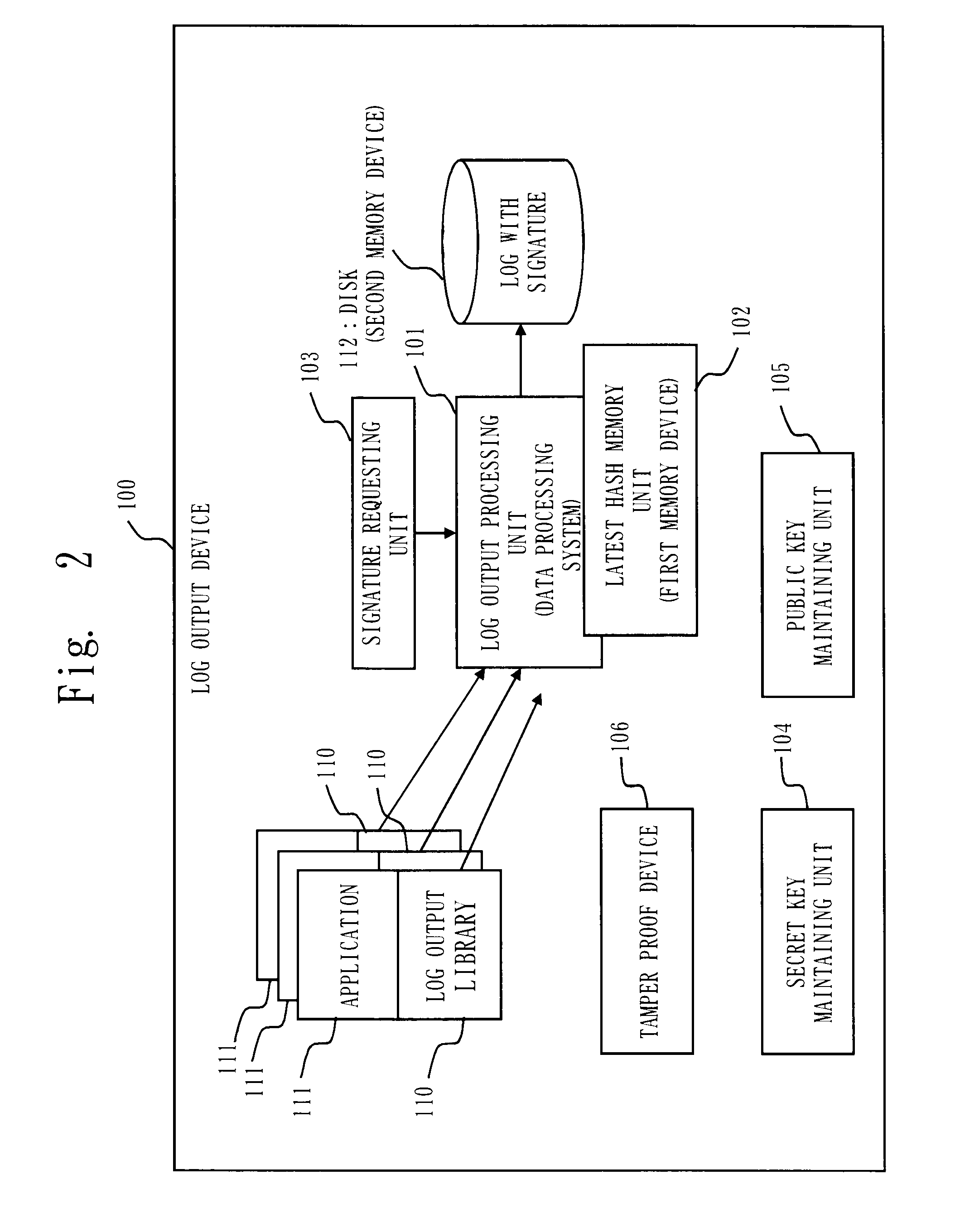
InactiveUS20090328218A1Reduce loadPrevent undetectable tamperingMemory loss protectionError detection/correctionData processing systemProcess memory
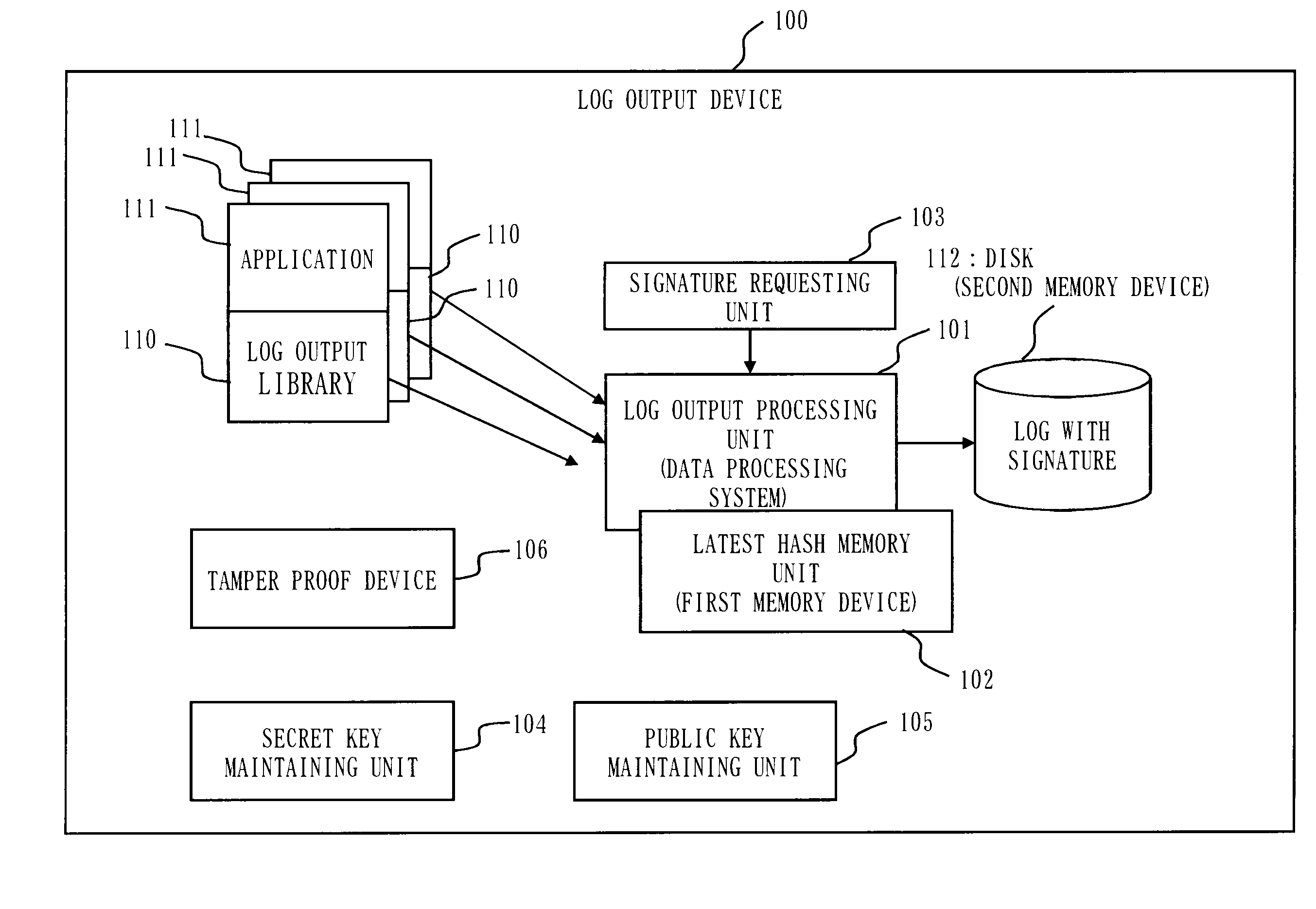
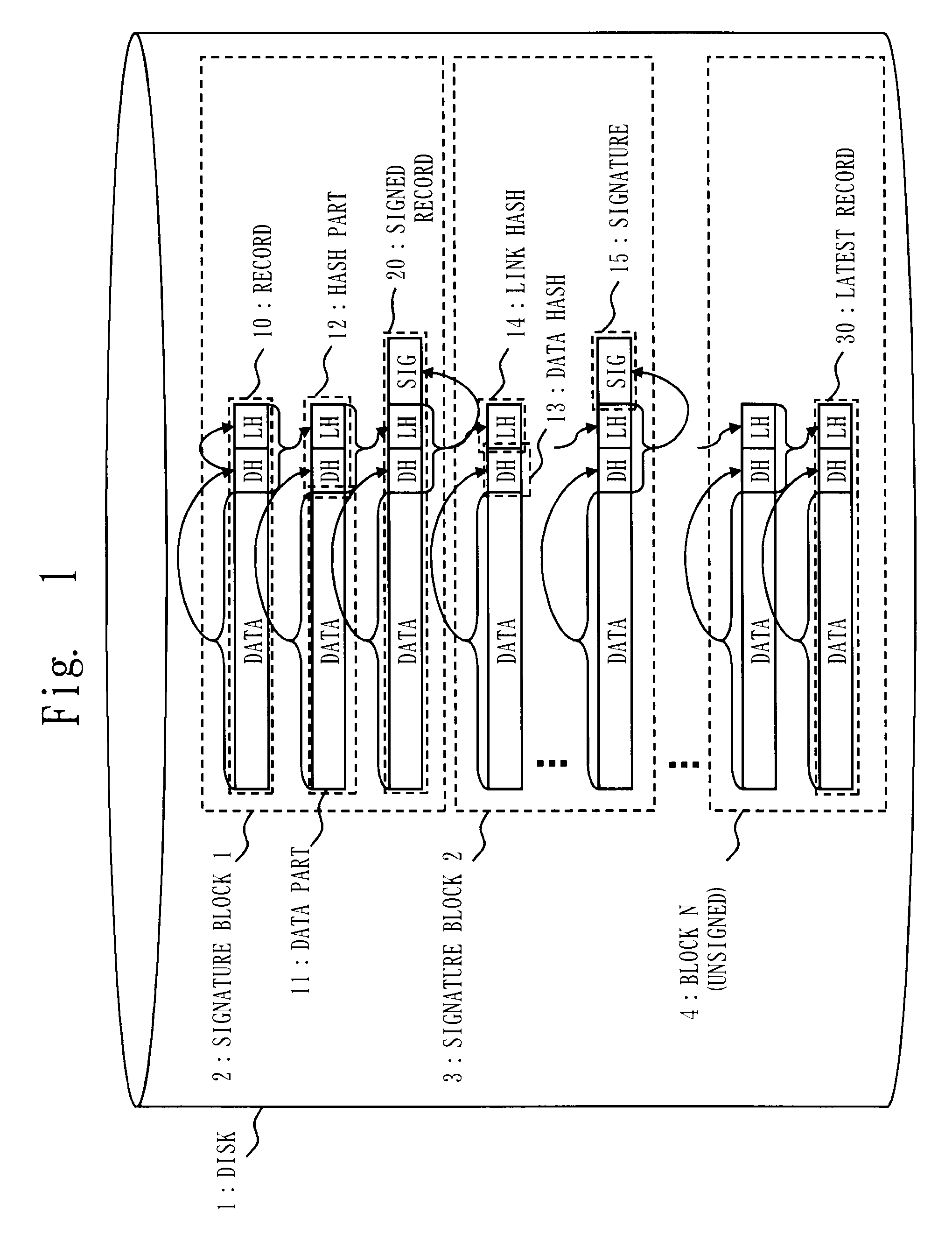
A log output device and a program are provided, which append a signature to a log, prevent an undetectable tampering (alteration, insertion, deletion, etc.), and are able to narrow tampered position if tampered. The log output device forms a log record including a data part and a hash part, and outputs to a disk; the hash part is formed by combining a hash of the data part (data hash) and a hash of the hash part of the previous record (link hash); a signature is appended to only a part of records of a hash chain; when outputting the record to the disk, a copy of the hash part of the record is maintained on a process memory; when outputting next record, the hash part of the latest record on the disk and the hash part maintained on the process memory are compared; if they are matched, the record on the disk is determined as not being tampered, and if mismatched, the record is determined as tampered.
Owner:MITSUBISHI ELECTRIC CORP
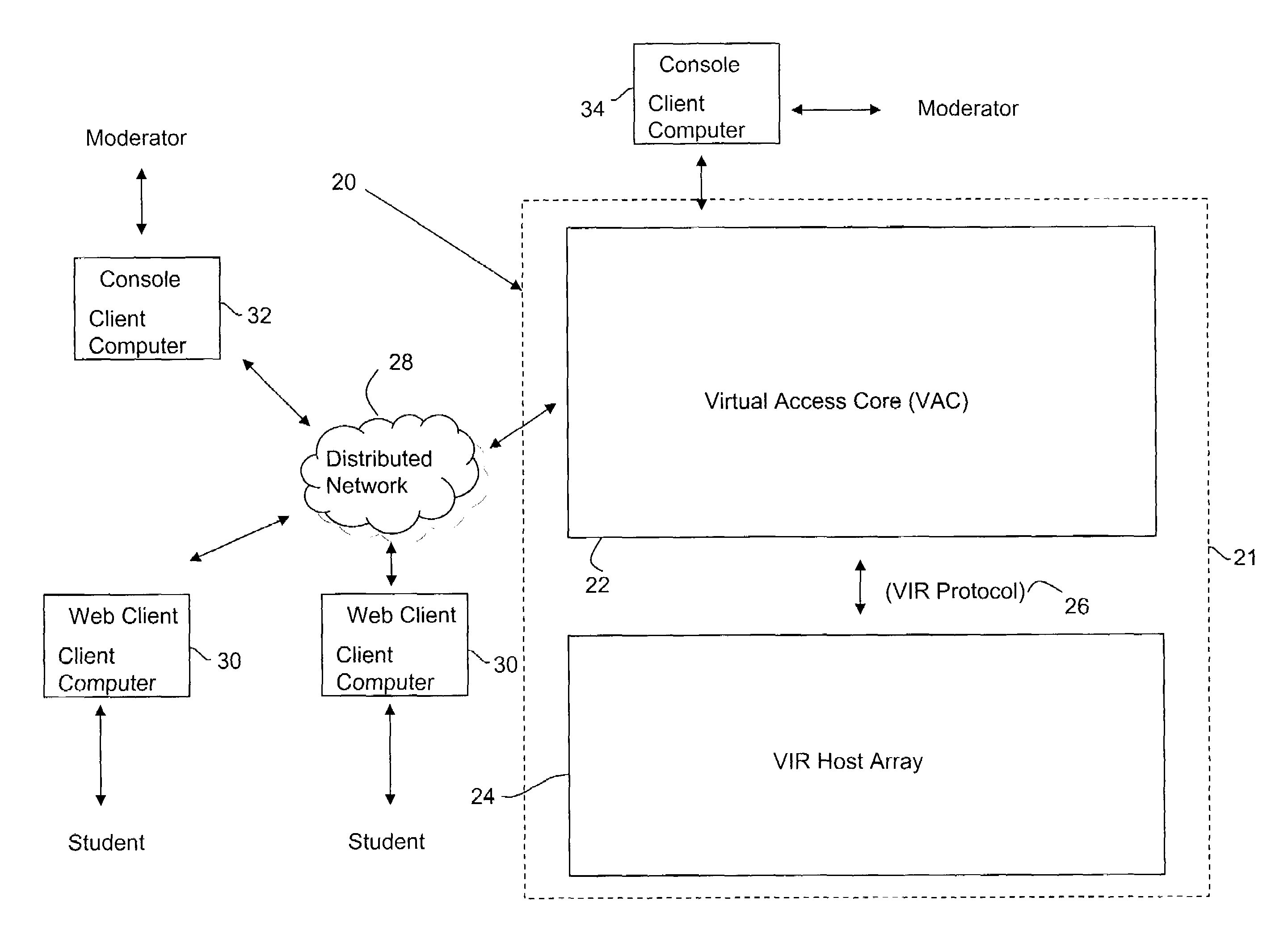
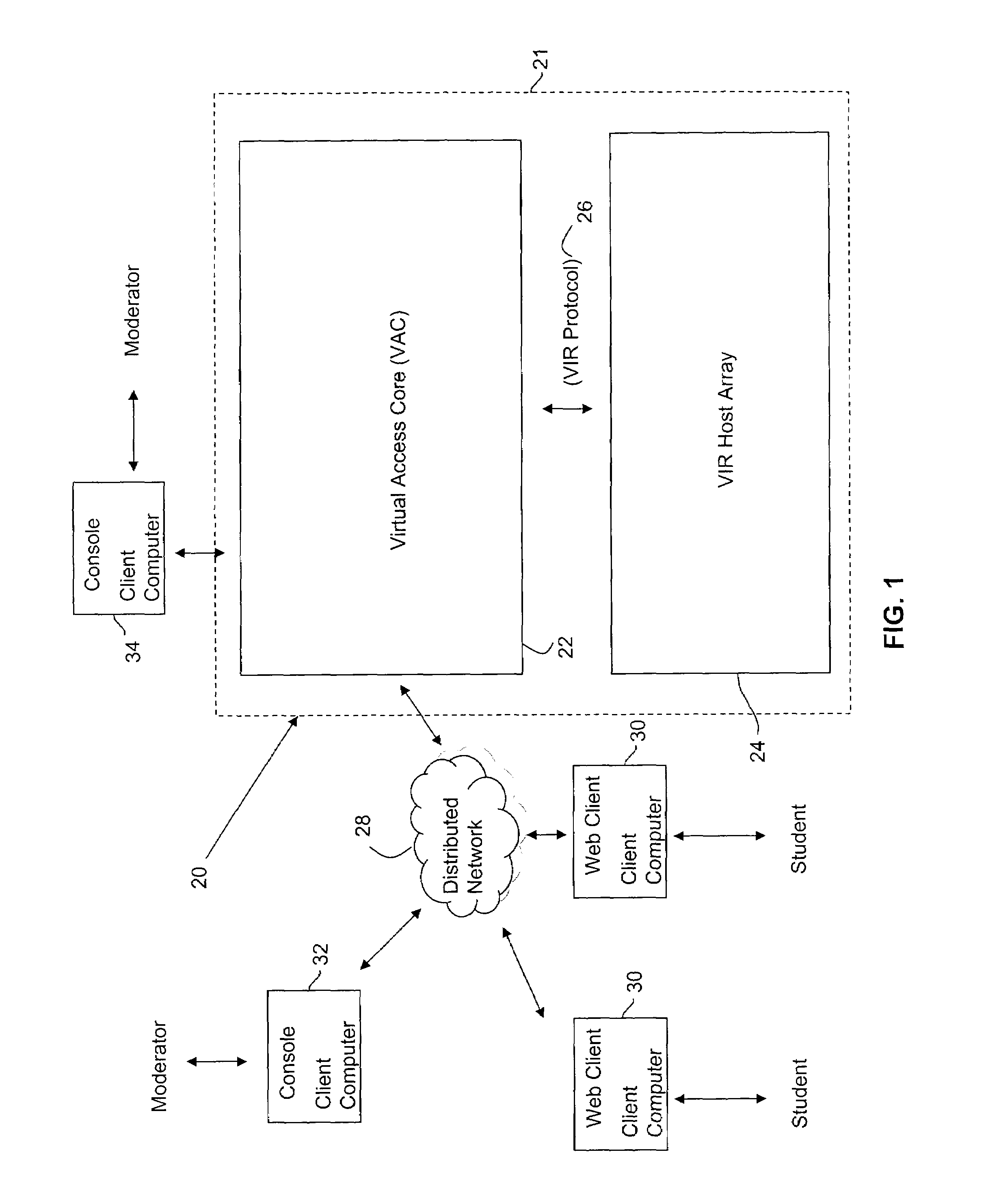
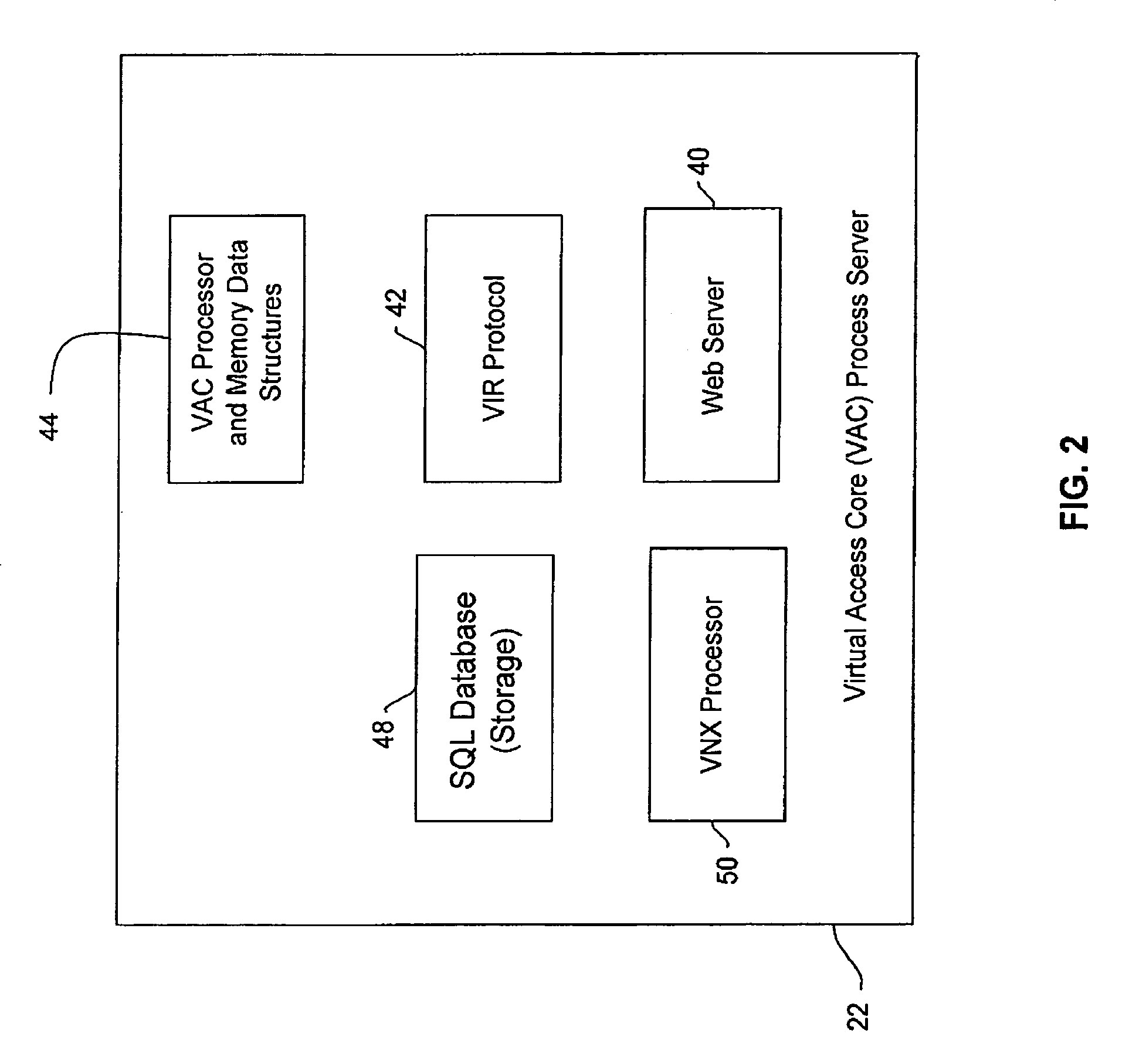
Method and system for accessing and managing virtual machines
A Virtual Access Core (VAC) manages and controls access to virtual machines. A Virtual Instruction Routine (VIR) protocol is used by all components of the system to pass instructions and information about a Virtual Session. The VAC issues commands in the VIR protocol language causing virtual machines to start and stop. A VIR host that hosts virtual machines responds to VAC commands. Web clients access the system via links, which a web server uses to send access requests to the VAC. The VAC responds by searching through process memory and database tables for information about free slots on a plurality of VIR hosts grouped into a Host Array. When one or more free slots have been identified, the VAC issues VIR Protocol commands instruction one or more VIR Hosts to load and start specific virtual machines in Specific Slots.
Owner:NACON CONSULTING
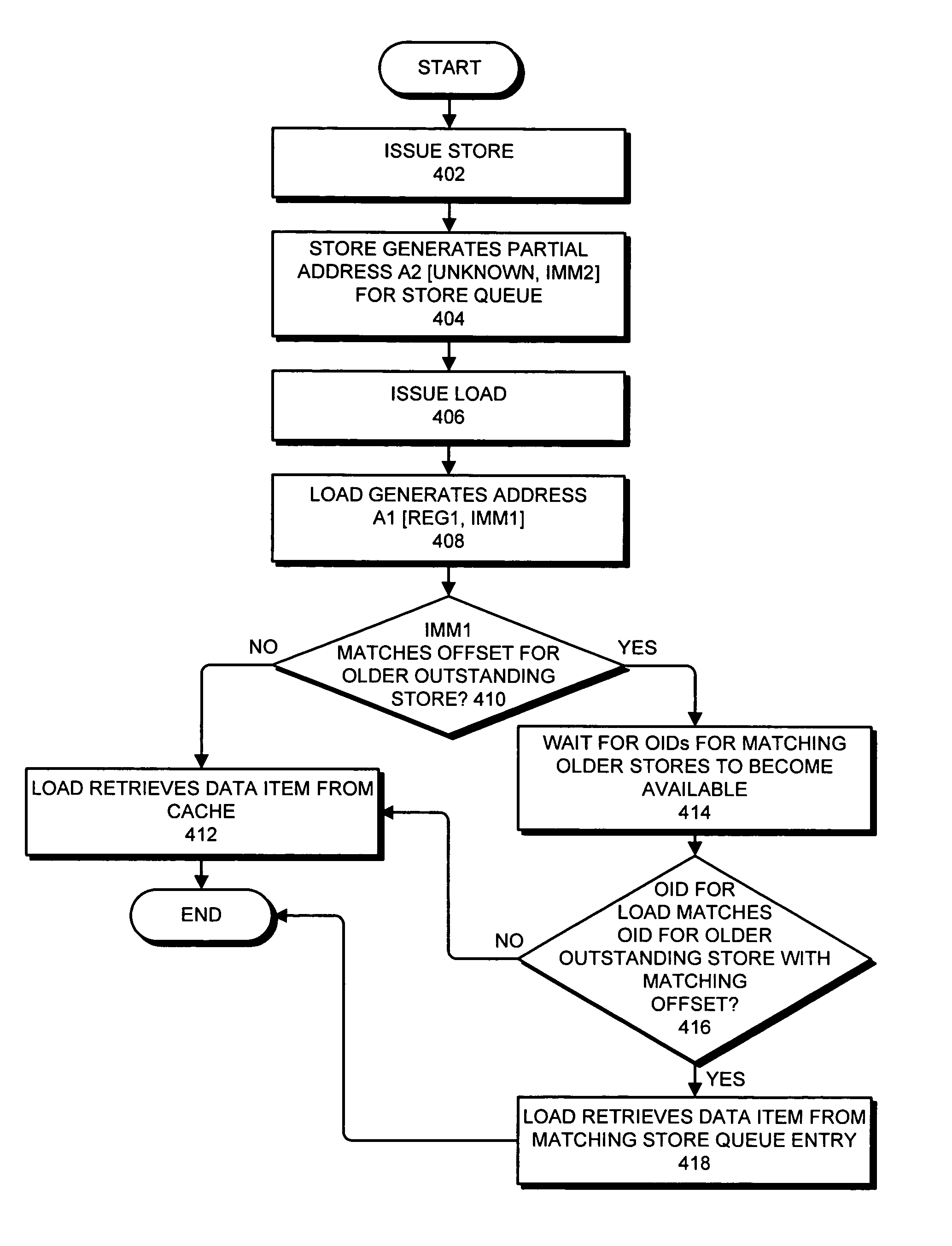
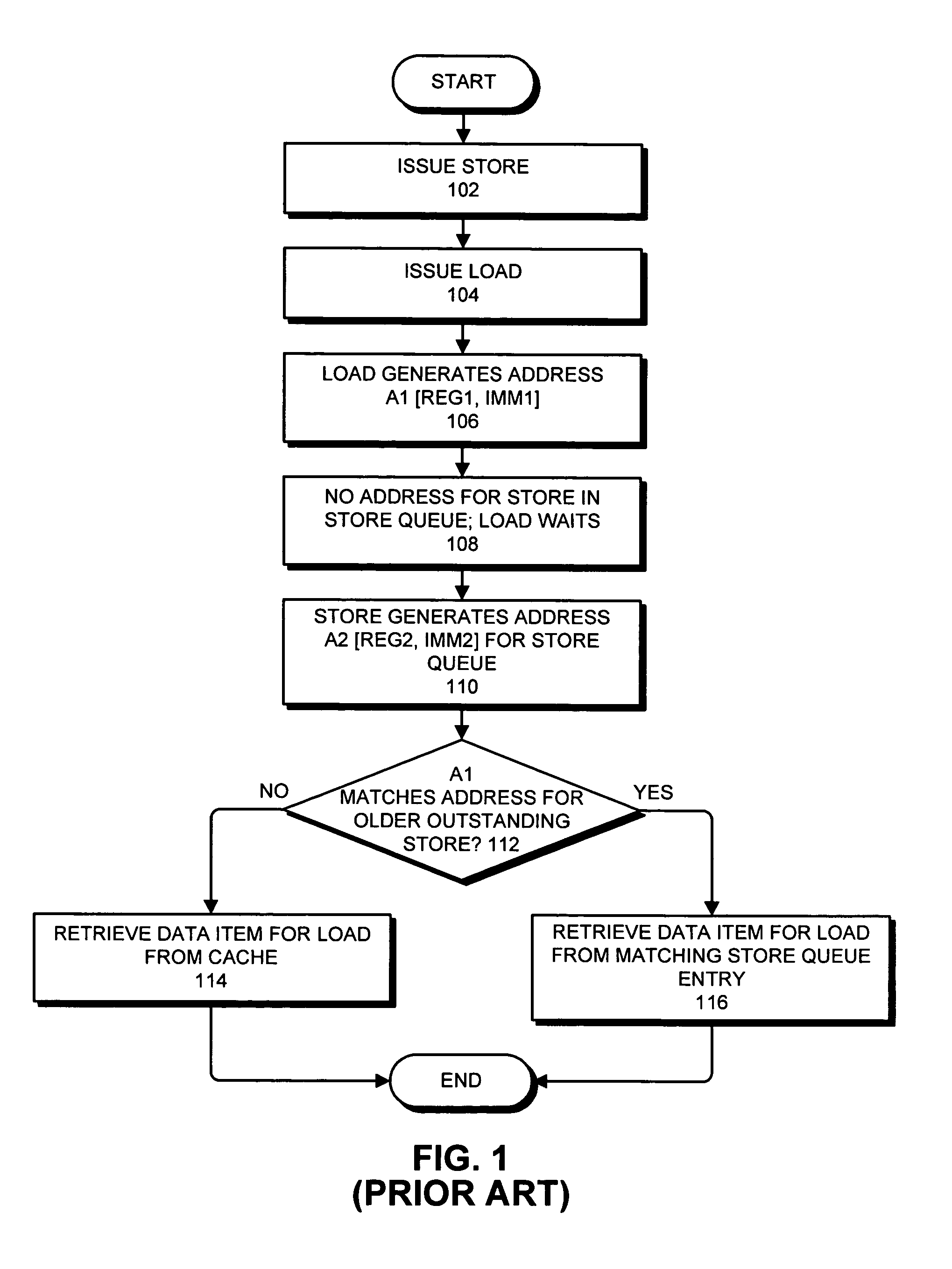
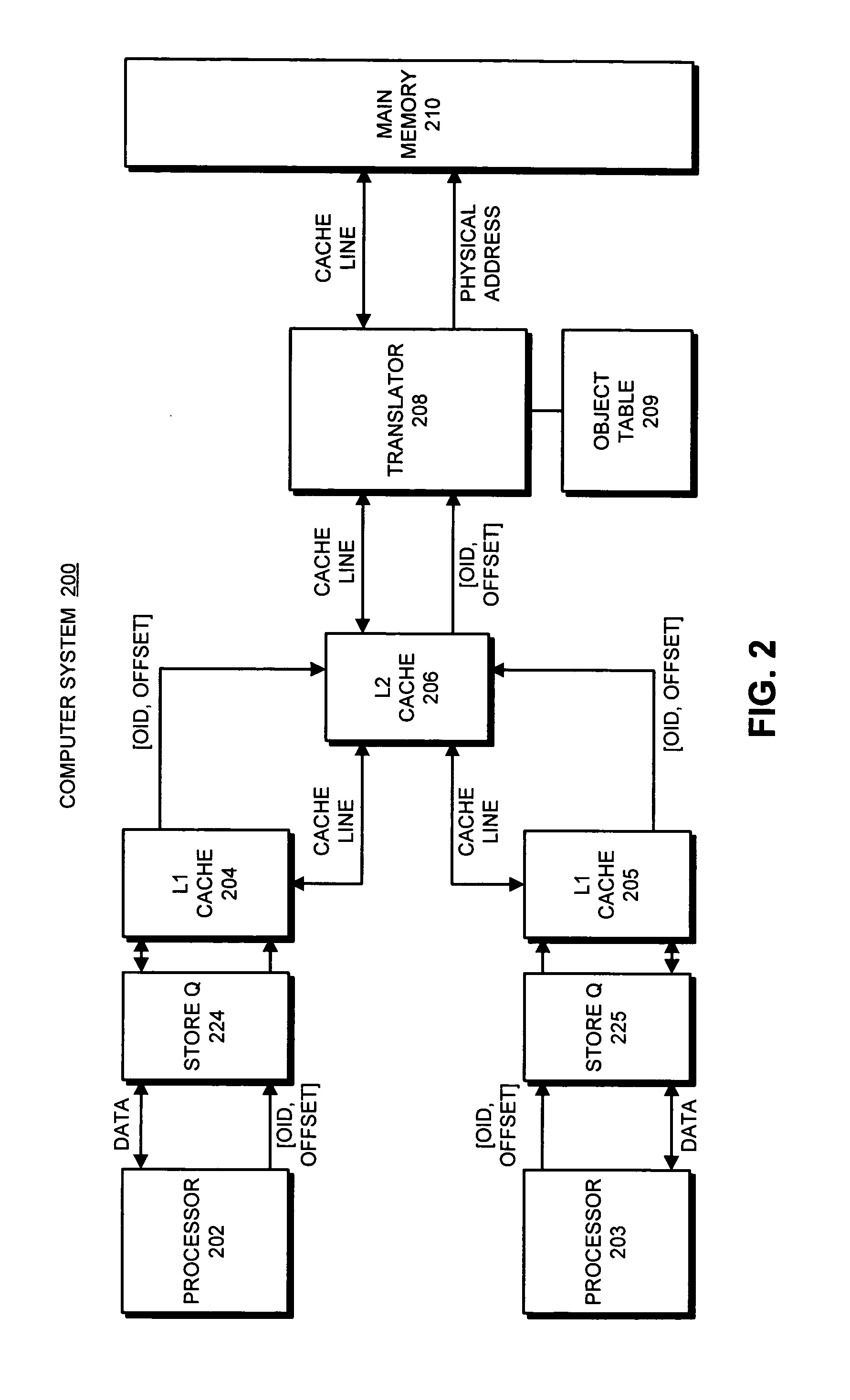
Detecting raw hazards in an object-addressed memory hierarchy by comparing an object identifier and offset for a load instruction to object identifiers and offsets in a store queue
One embodiment of the present invention provides a system that processes memory-access instructions in an object-addressed memory hierarchy. During operation, the system receives a load instruction to be executed, wherein the load instruction loads a data item from an object, and wherein the load instruction specifies an object identifier (OID) for the object and an offset for the data item within the object. Next, the system compares the OID and the offset for the data item against OIDs and offsets for outstanding store instructions in a store queue. If the offset for the data item does not match any of the offsets for the outstanding store instructions in the store queue, and hence no read-after-write (RAW) hazard exists, the system performs a cache access to retrieve the data item for the load instruction.
Owner:ORACLE INT CORP
Transactional memory system which employs thread assists using address history tables
A computing system uses specialized “Set Associative Transaction Tables” and additional “Summary Transaction Tables” to speed the processing of common transactional memory conflict cases and those which employ assist threads using an Address History Table and processes memory transactions with a Transaction Table in memory for parallel processing of multiple threads of execution by support of which an application need not be aware. Special instructions may mark the boundaries of a transaction and identify memory locations applicable to a transaction. A ‘private to transaction’ (PTRAN) tag, directly addressable as part of the main data storage memory location, enables a quick detection of potential conflicts with other transactions that are concurrently executing on another thread of said computing system. The tag indicates whether (or not) a data entry in memory is part of a speculative memory state of an uncommitted transaction that is currently active in the system.
Owner:INT BUSINESS MASCH CORP
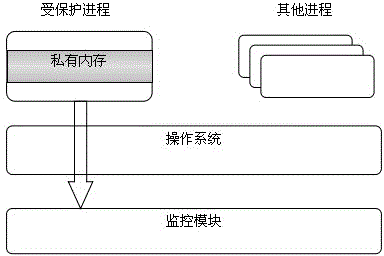
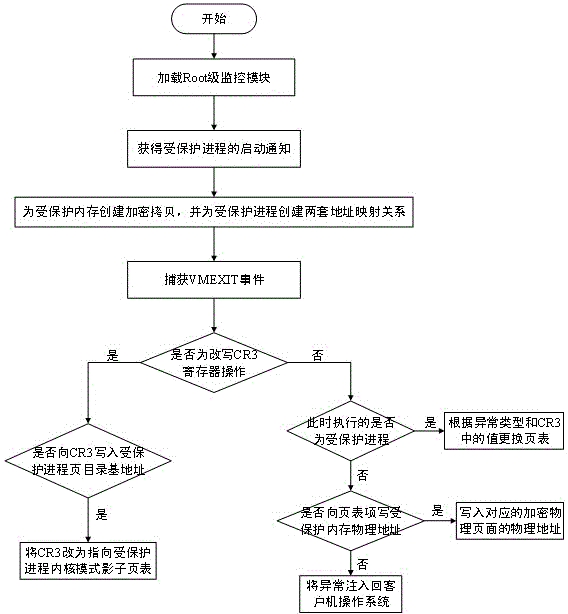
Process memory protecting method based on auxiliary virtualization technology for hardware
InactiveCN103955438AEffective protectionAvoid accessUnauthorized memory use protectionInternal memoryData Execution Prevention
The invention provides a process memory safety protecting method based on auxiliary virtualization for hardware. The method comprises the following steps: 1, loading a process memory monitoring module; step 2, informing the monitoring module during the starting of a protected process; step 3, creating an encrypted copy for a protected internal memory space of the protected process; step 4, realizing internal memory virtualization to a virtual machine system by using a shadow page table mechanism; step 5: acquiring rewritten operation and page fault abnormality of a CR3 register. The process memory safety protecting method provided by the invention has the advantages as follows: the monitoring module working at a Root stage is created to monitor page directories, page tables and modification of a page directory register in all processes so as to prevent any process except the protected process from visiting data in the memory space of the protected process, when the protected process is switched to a core state, a page in a user-mode space is replaced so as to prevent codes in a kernel mode from injection attacks, and a data execution prevention technology is used for setting the page of the data area of the protected process to be non-executable. Therefore, codes in the user mode are prevented from injection attacks.
Owner:NANJING UNIV
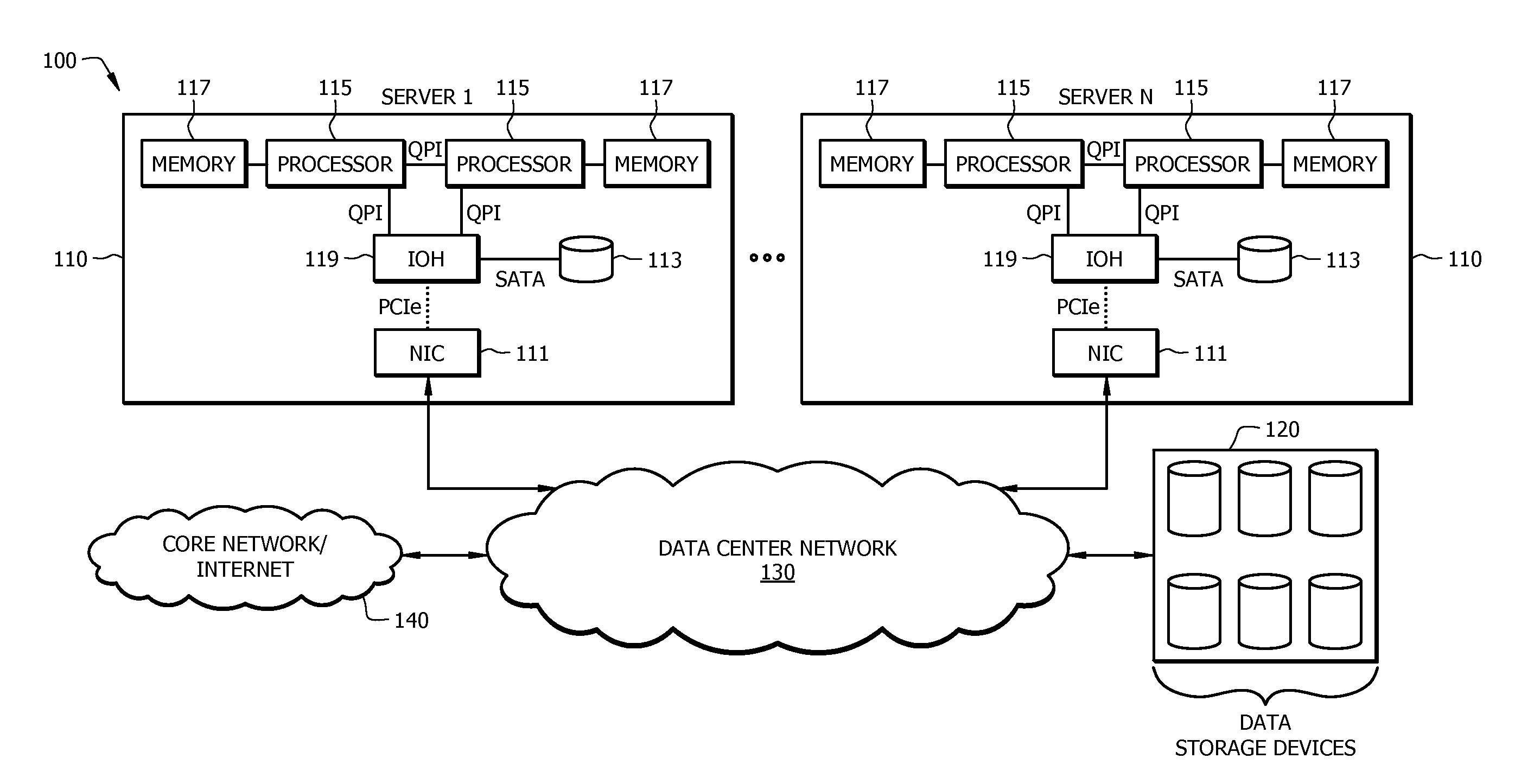
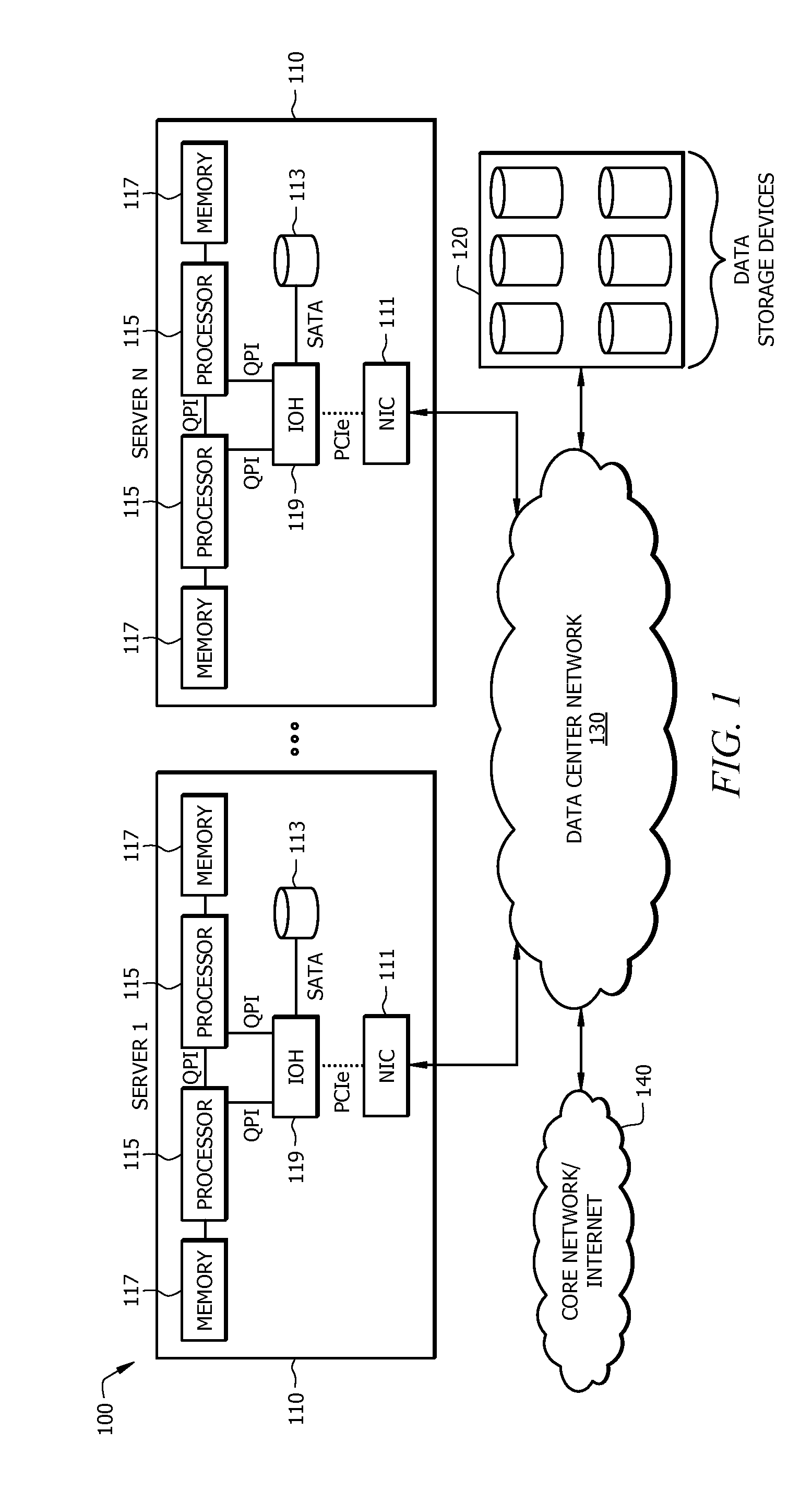
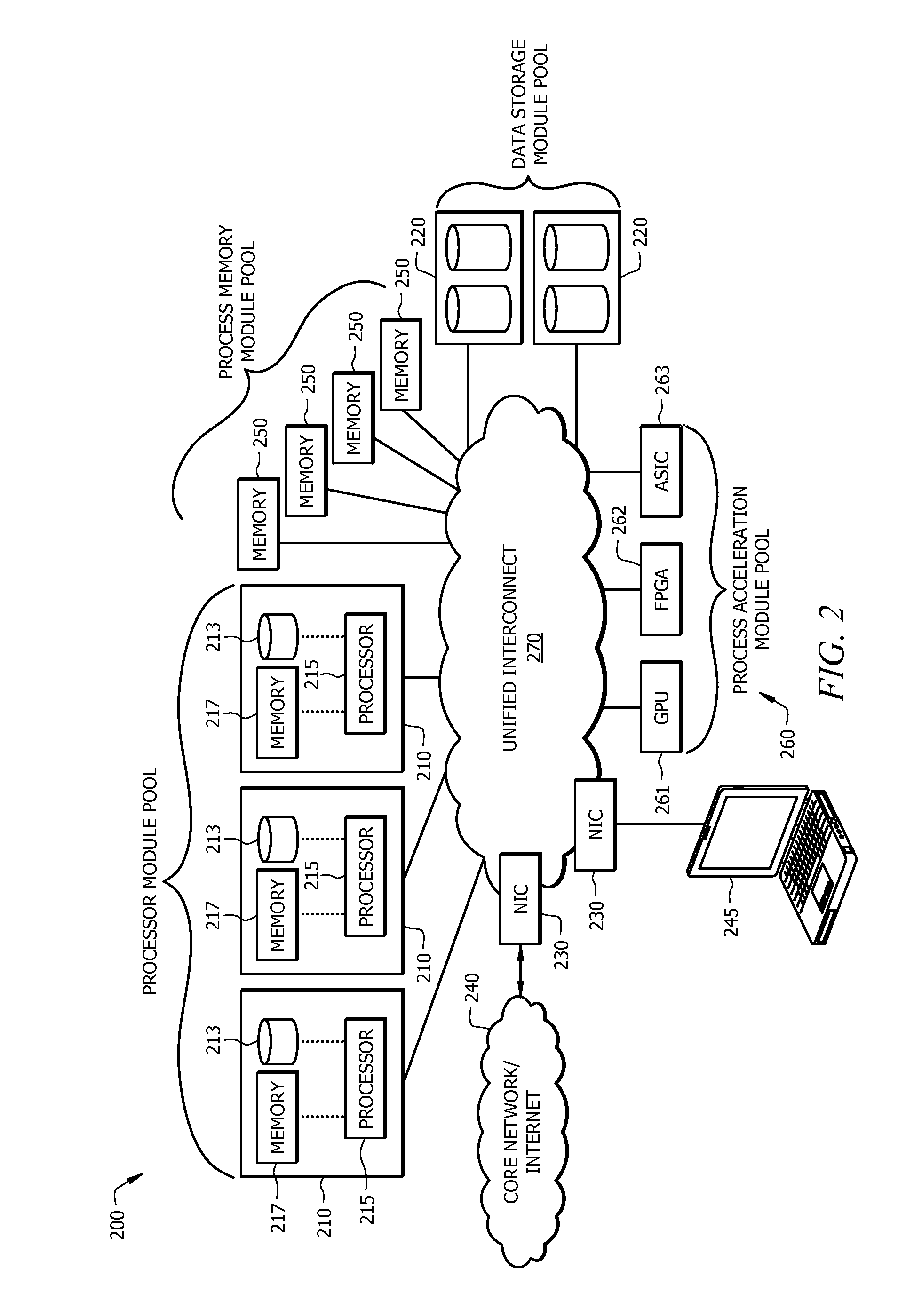
Disaggregated Server Architecture for Data Centers
ActiveUS20140280687A1Digital computer detailsElectric digital data processingResource poolProcess memory
A system comprising a unified interconnect network, a plurality of process memory modules, and a plurality of processor modules configured to share access to the memory modules via the unified interconnect network. Also disclosed is a method comprising communicating data between a plurality of processor modules and a plurality of shared resource pools via a unified interconnect network, wherein the communications comprise a protocol that is common to all resource pools, and wherein each resource pool comprises a plurality of resource modules each configured to perform a common function. Also disclosed is an apparatus comprising a network interface controller (NIC) module configured to receive data from a plurality of processor modules via a unified interconnect network, and provide core network connectivity to the processor modules.
Owner:FUTUREWEI TECH INC
Virtual memory fragment aware cache
ActiveUS20070073996A1Improve cache hit ratioMemory architecture accessing/allocationMemory systemsVirtual memoryMemory address
The present invention is directed to a method, computer program product, and system for processing memory access requests. The method includes the following features. First, page table entries of a page table are organized into at least one fragment that maps logical memory to at least one of logical memory or physical memory. The at least one fragment has a fragment size and an alignment boundary. Then, a subset of the page table entries stored in one of a plurality of cache banks is accessed to determine a mapping between a first logical memory address and at least one of a second logical memory address or a physical memory address. Each cache bank is configured to store at least one page table entry corresponding to a fragment of a predetermined set of fragment sizes and a predetermined alignment boundary.
Owner:ATI TECH INC
Computing System with Optimized Support for Transactional Memory
InactiveUS20080288727A1FasterSolve excessive overheadDigital data processing detailsSpecial data processing applicationsProcess memoryTransactional memory
A computing system processes memory transactions for parallel processing of multiple threads of execution by support of which an application need not be aware. The computing system transactional memory support provides a Transaction Table in memory and a method of fast detection, of potential conflicts between multiple transactions. Special instructions may mark the boundaries of a transaction and identify memory locations applicable to a transaction. A ‘private to transaction’ (PTRAN) tag, directly addressable as part of the main data storage memory location, enables a quick detection of potential conflicts with other transactions that are concurrently executing on another thread of said computing system. The tag indicates whether (or not) a data entry in memory is part of a speculative memory state of an uncommitted transaction that is currently active in the system.
Owner:IBM CORP
Hardware enforced virtual sequentiality
InactiveUS6981110B1Improve performanceData switching by path configurationMultiple digital computer combinationsProcess memoryProcessing element
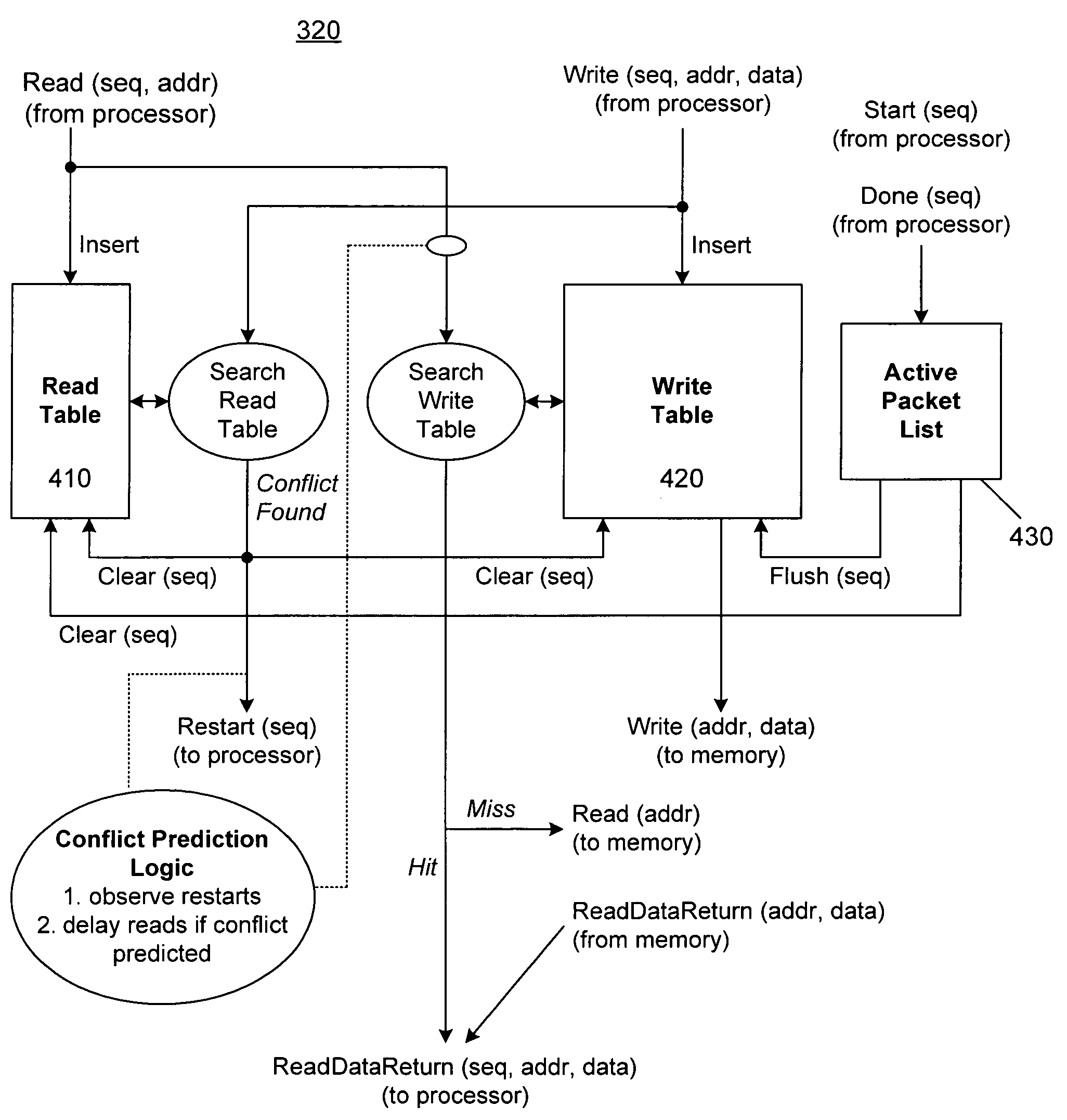
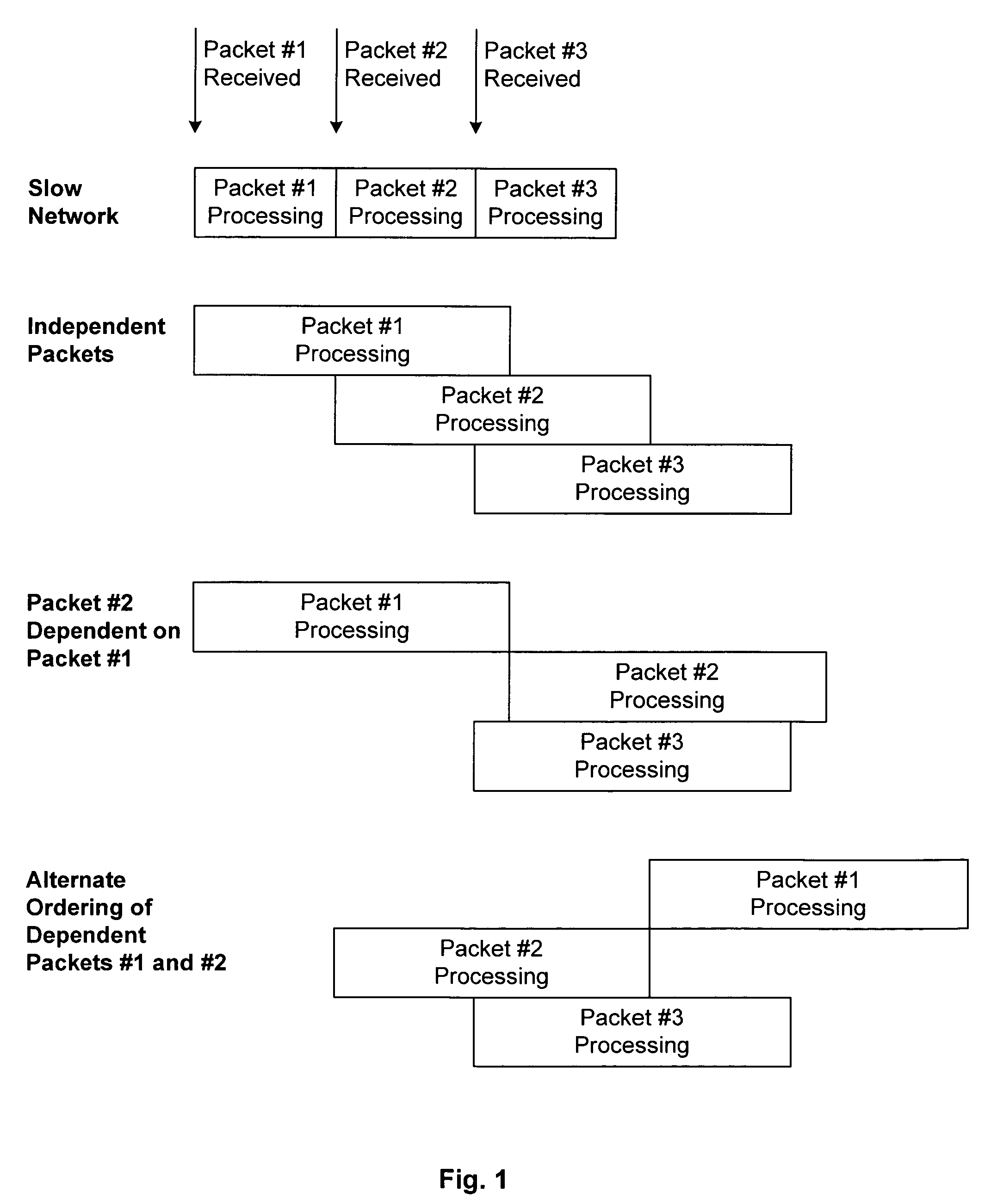
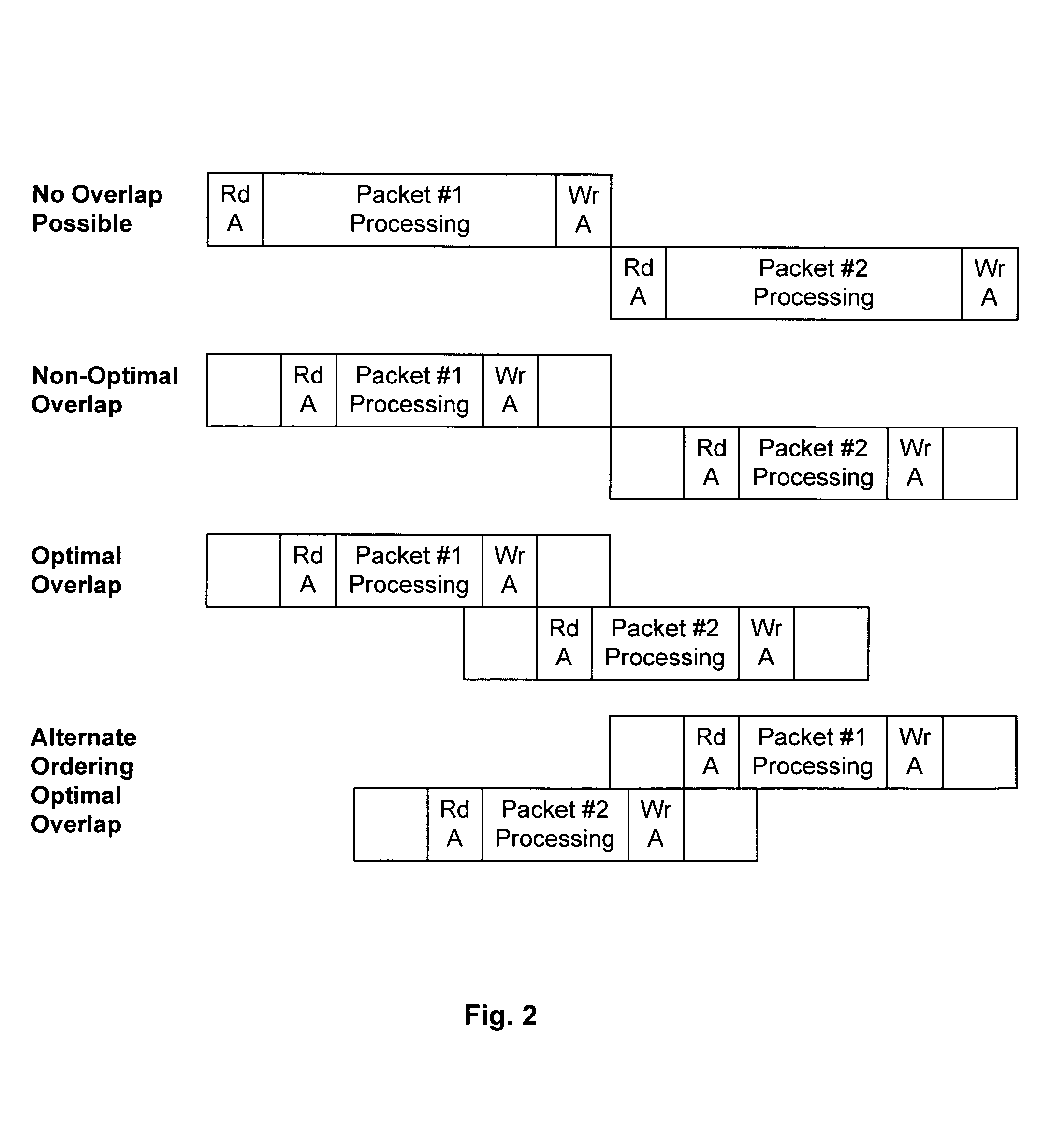
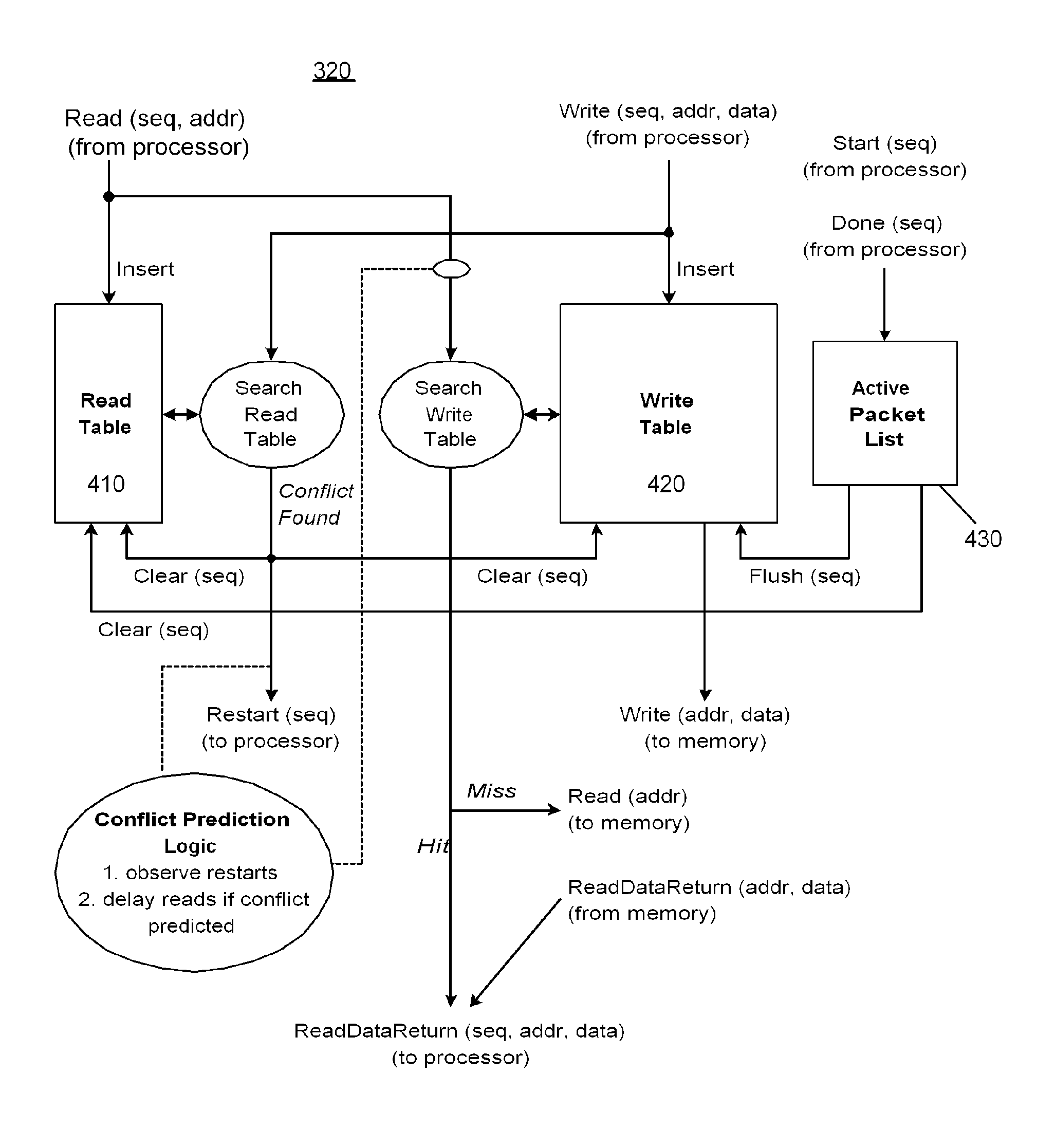
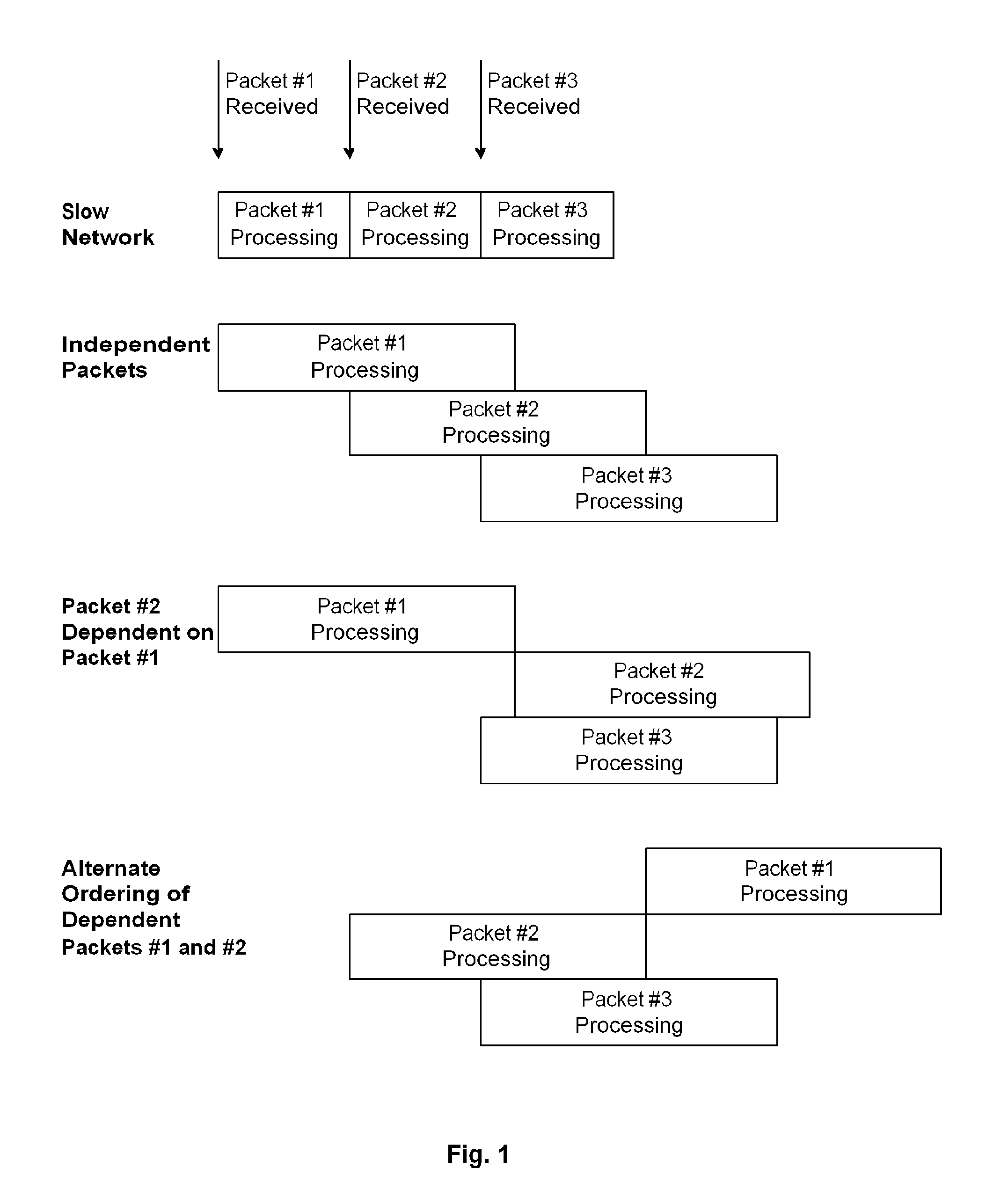
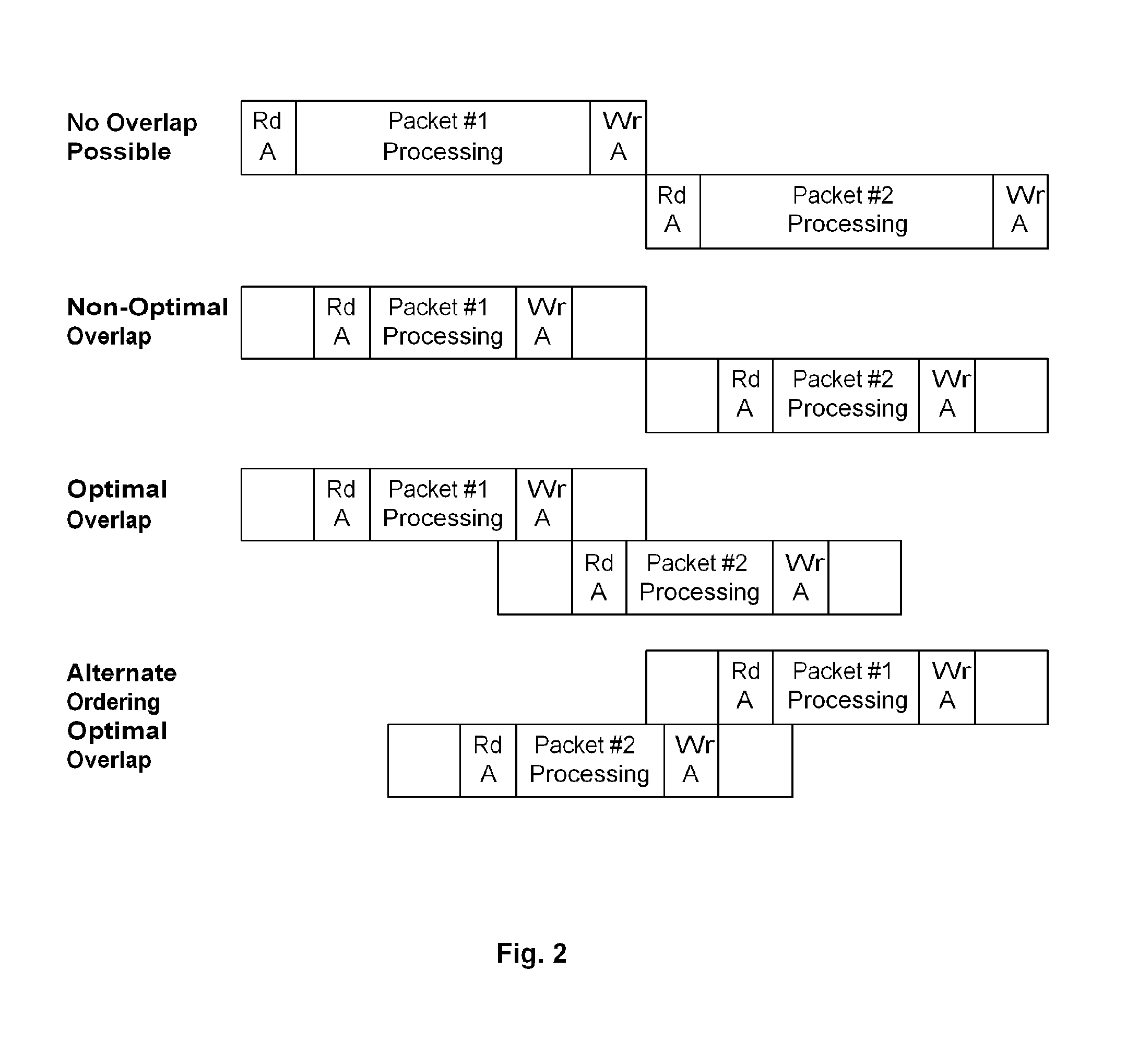
A mechanism processes memory reads and writes in a packet processor. Each memory access has an associated sequence number and information is maintained allowing the detection of memory conflicts. The mechanism is placed between a processing element and a memory system such that write data is buffered and both reads and writes are recorded. When a memory conflict is detected, based on a strict or alternate ordering model, a restart signal is generated and the entries for the associated sequence number are flushed. When the work associated with a sequence number has completed, a signal is made so that associated write data can be sent to the memory system and the entries for that sequence number can be flushed.
Owner:F POSZAT HU
Process memory collection method and apparatus
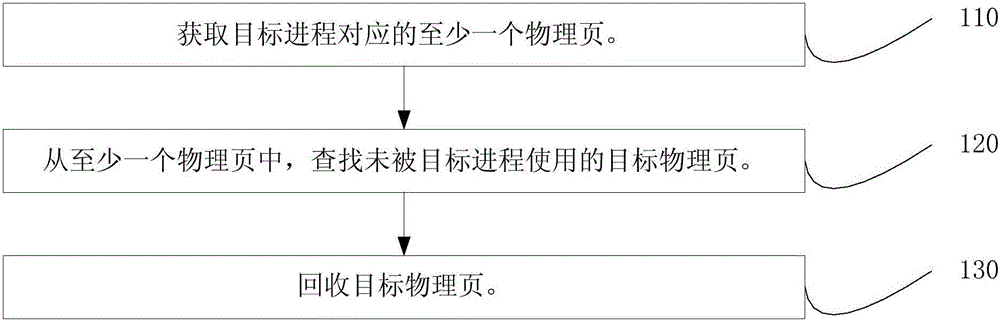
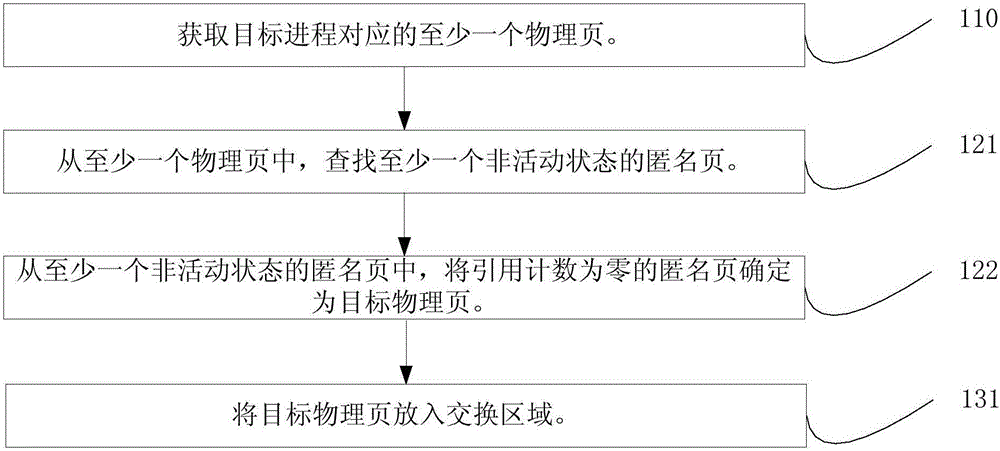
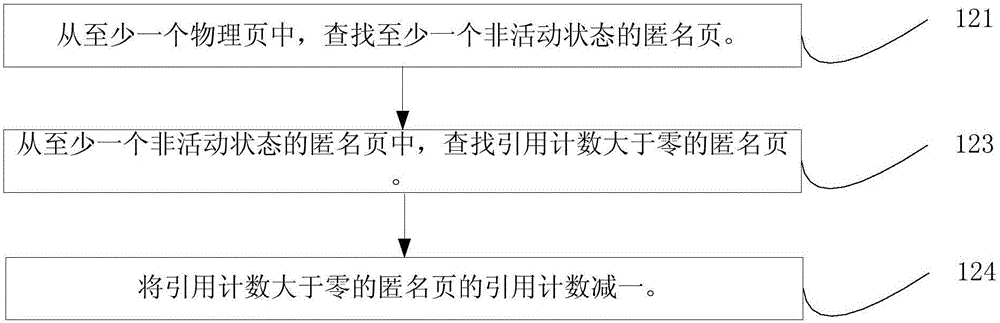
ActiveCN105159777AAchieve recyclingShort timeResource allocationMemory adressing/allocation/relocationRecovery methodComputer hardware
The invention discloses a process memory recovery method and apparatus. The method comprises: obtaining at least one physical page corresponding to a target process; looking for the target physical page which is not used by the target process from the at least one physical page; and recovering the target physical page. According to the process memory recovery method and apparatus, the physical pages corresponding to the target process are looked for, the target physical page which is not used by the target process is found from the physical pages, and the target physical page is recovered. A whole system-oriented memory recovery mode, a mode for directly killing the process or the like is provided in the prior art. According to the process memory recovery method and apparatus, the target physical page which is not used by the target process can be recovered, so that the recovery of the target physical page is realized while the operation of the target process is not influenced, the time consumption is reduced, and the resource utilization rate is increased.
Owner:THUNDERSOFT
Transactional Memory System with Fast Processing of Common Conflicts
ActiveUS20080288726A1Fast executionDigital data processing detailsMemory adressing/allocation/relocationProcess memoryTransactional memory
A computing system processes memory transactions for parallel processing of multiple threads of execution by support of which an application need not be aware. The computing system transactional memory support provides a Transaction Table in memory and performs fast detection of potential conflicts between multiple transactions. Special instructions may mark the boundaries of a transaction and identify memory locations applicable to a transaction. A ‘private to transaction’ (PTRAN) tag, enables a quick detection of potential conflicts with other transactions that are concurrently executing on another thread of said computing system. The tag indicates whether (or not) a data entry in memory is part of a speculative memory state of an uncommitted transaction that is currently active in the system. A transaction program employs a plurality of Set Associative Transaction Tables, one for each microprocessor, and Load and Store Summary Tables in memory for fast processing of common conflict.
Owner:IBM CORP
Method and device for adjusting priority of application process memory release
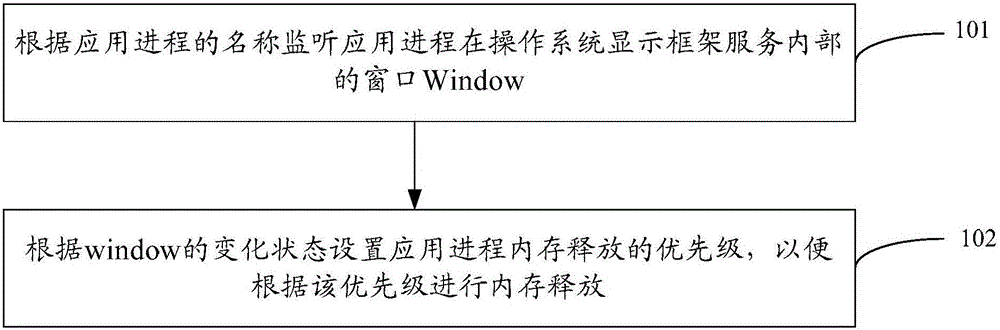
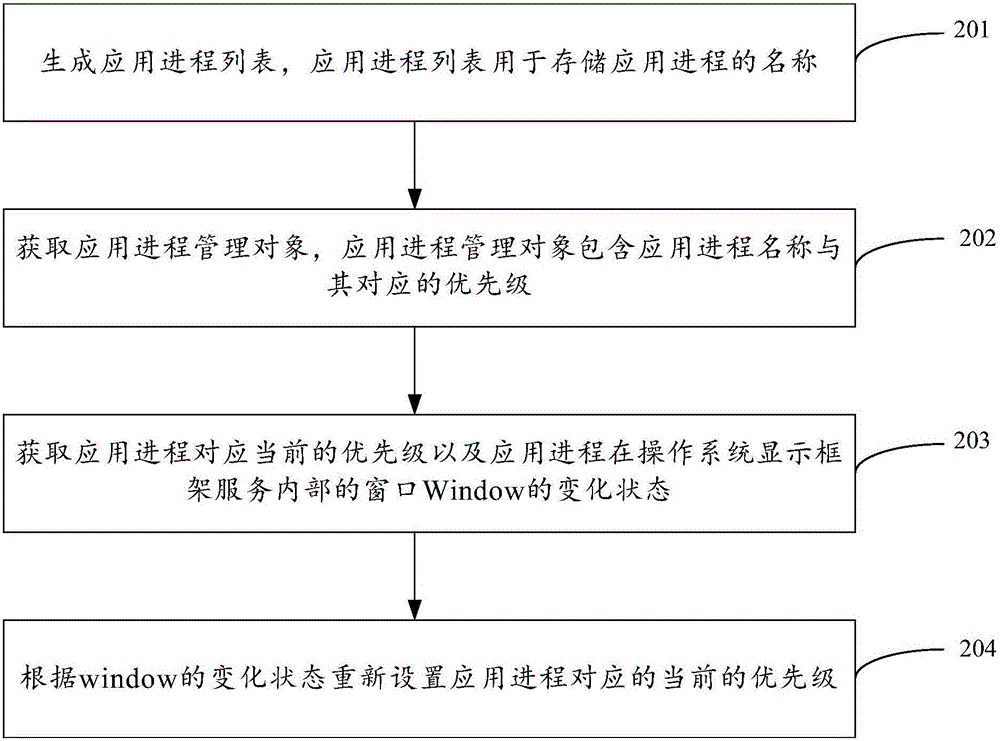
ActiveCN105138402APriority raised or loweredProgram initiation/switchingOperational systemProcess memory
The embodiment of the invention provides a method and device for adjusting the priority of application process memory release, and relates to the technical field of embedded computer software. The priority of the application process memory release of a non-activity interface can be adjusted. The method includes the steps that a window of an application process in a display frame service of an operating system is monitored according to the name of the application process, and the application process is a non-activity interface application process; the priority of the application process is set according to the change state of the window so that memory release can be conducted in accordance with the priority of the application process. The method and device are used for adjusting the priority.
Owner:HISENSE
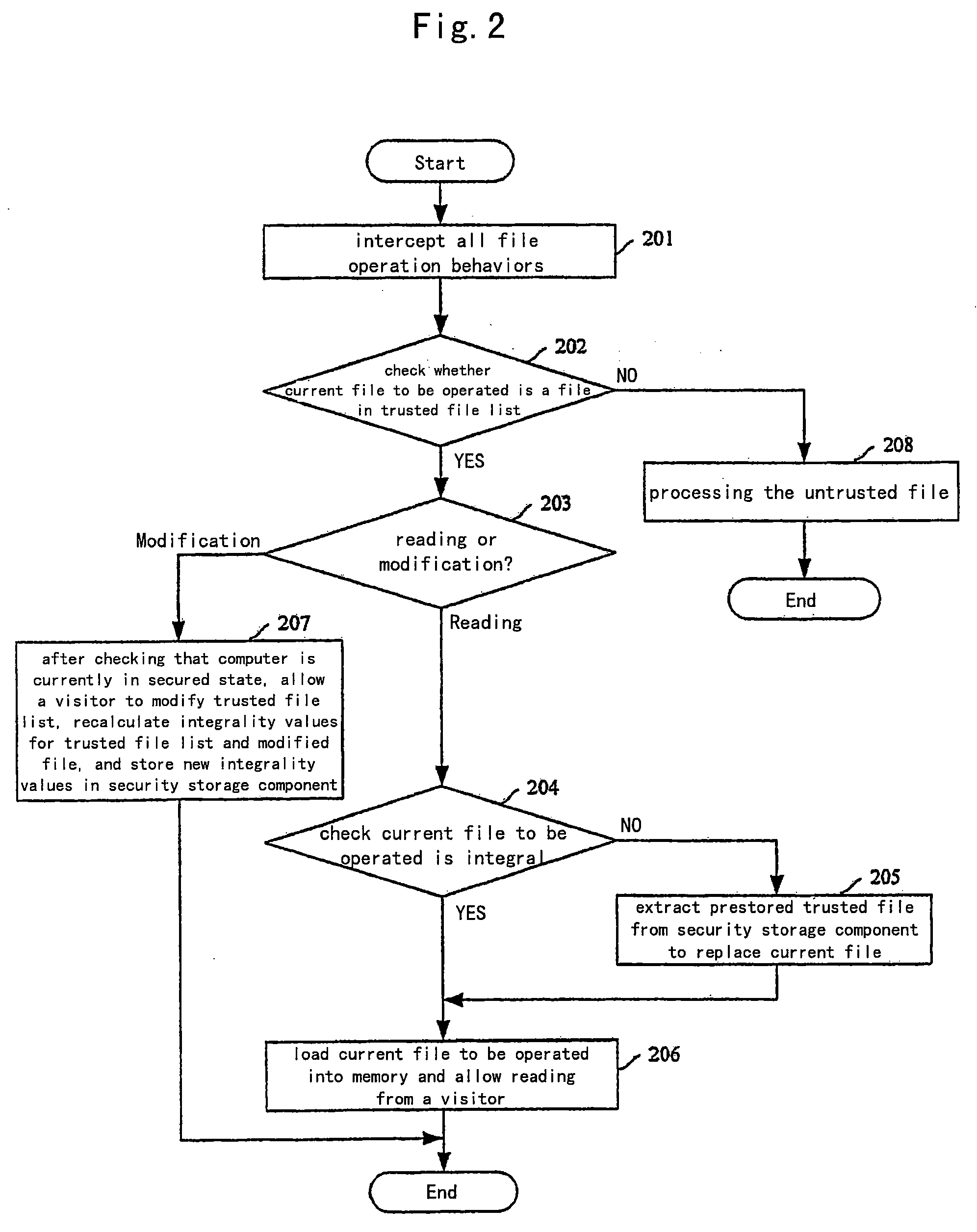
Method for establishing a trusted running environment in the computer
InactiveUS20090288161A1Broaden applicationLow implementation costMemory loss protectionError detection/correctionOperational systemProcess memory
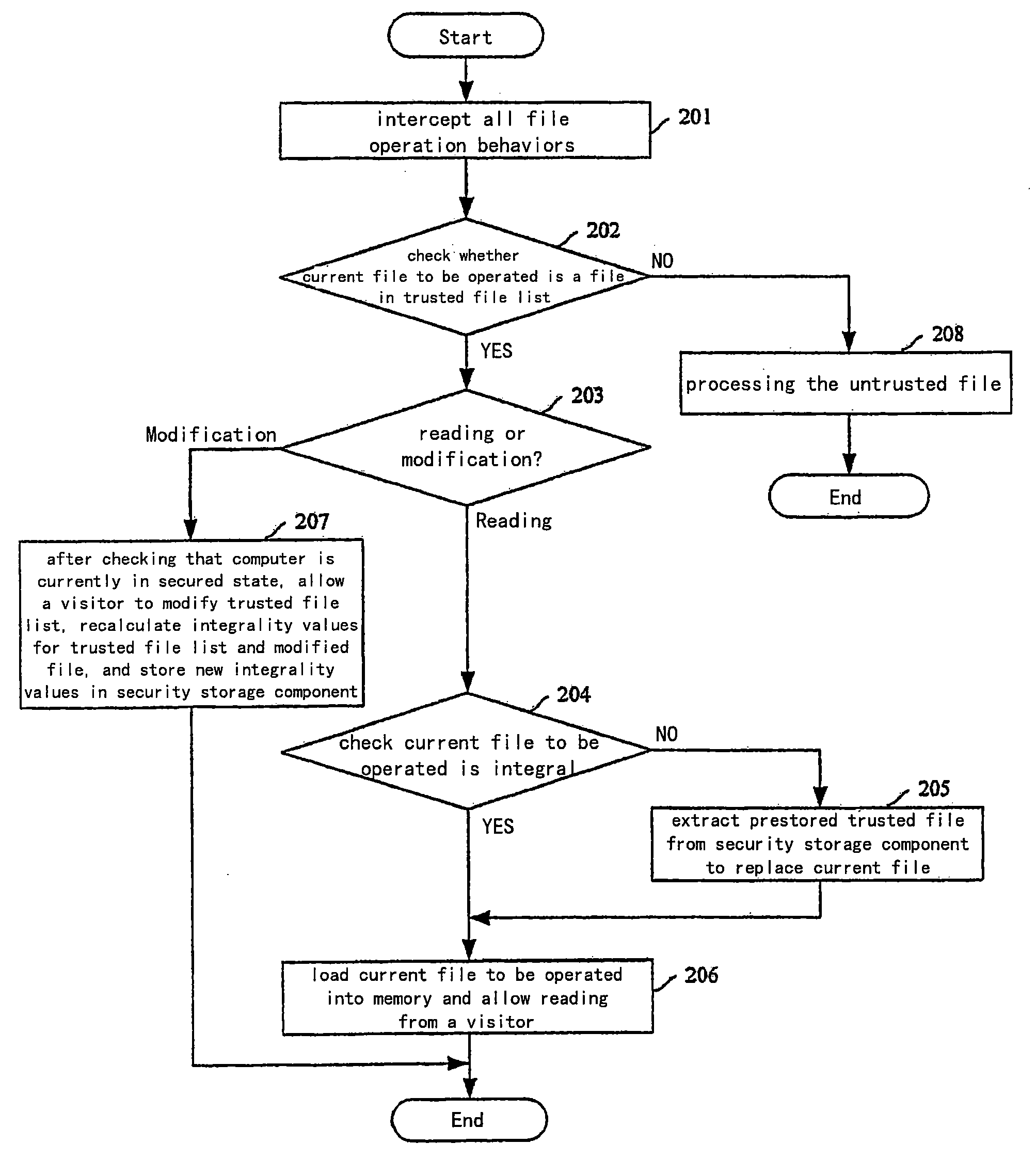
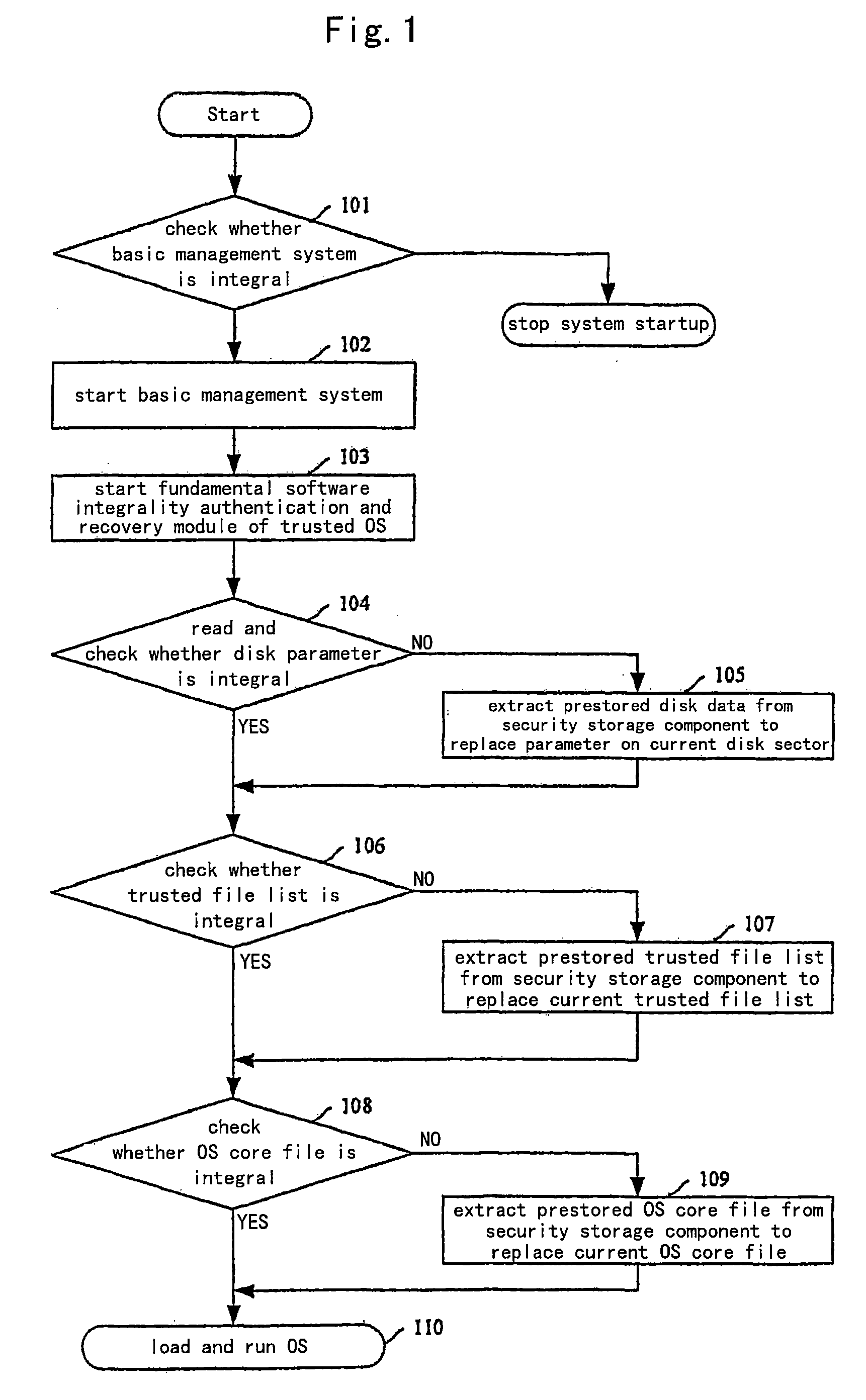
The present invention discloses a method for establishing a trusted running environment in a computer. A trusted file authentication module and a trusted process memory code authentication module are preset in operation system (OS) of the computer and a secured OS is loaded and run. The trusted file authentication module intercepts all file operation behaviors, checks whether current file to be operated is a trusted file or not, and processes the file according to its operation type if it is trusted, otherwise processes the file after its eligibility is verified; the trusted process memory code authentication module authenticates on timing whether the running state and the integrality for all process code are normal or not; if any process is abnormal, giving an alarm, saving field data run by the process and closing down the process; otherwise continuing to run normally. With this invention, the security for the running environment in the computer can be ensured whether the attack from known or unknown virus exists or not, and this facilitates application and reduces implementation cost.
Owner:LENOVO (BEIJING) CO LTD
Computing system with optimized support for transactional memory
InactiveUS8321637B2Fast executionFaster transactional memory systemDigital data processing detailsSpecial data processing applicationsProcess memoryApplication software
A computing system processes memory transactions for parallel processing of multiple threads of execution by support of which an application need not be aware. The computing system transactional memory support provides a Transaction Table in memory and a method of fast detection, of potential conflicts between multiple transactions. Special instructions may mark the boundaries of a transaction and identify memory locations applicable to a transaction. A ‘private to transaction’ (PTRAN) tag, directly addressable as part of the main data storage memory location, enables a quick detection of potential conflicts with other transactions that are concurrently executing on another thread of said computing system. The tag indicates whether (or not) a data entry in memory is part of a speculative memory state of an uncommitted transaction that is currently active in the system.
Owner:INT BUSINESS MASCH CORP
Transactional memory computing system with support for chained transactions
ActiveUS8095741B2Error detection/correctionMultiprogramming arrangementsProcess memoryPotential conflict
A computing system processes memory transactions for parallel processing of multiple threads of execution provides execution of multiple atomic instruction groups (AIGs) on multiple systems to support a single large transaction that requires operations on multiple threads of execution and / or on multiple systems connected by a network. The support provides a Transaction Table in memory and fast detection of potential conflicts between multiple transactions. Special instructions may mark the boundaries of a transaction and identify memory locations applicable to a transaction. A ‘private to transaction’ (PTRAN) tag, directly addressable as part of the main data storage memory location, enables a quick detection of potential conflicts with other transactions that are concurrently executing on another thread. The tag indicates whether (or not) a data entry in memory is part of a speculative memory state of an uncommitted transaction that is currently active in the system.
Owner:IBM CORP
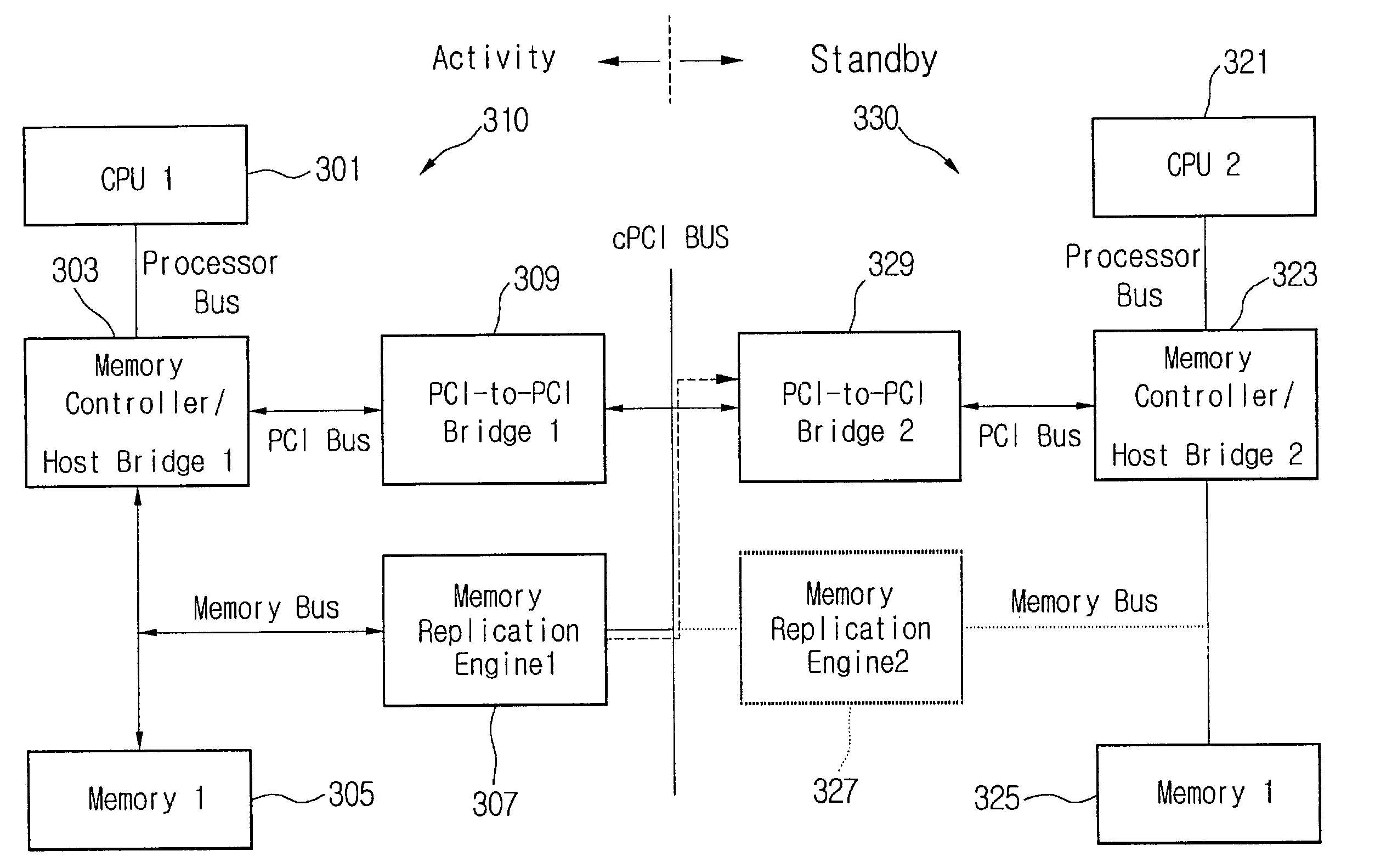
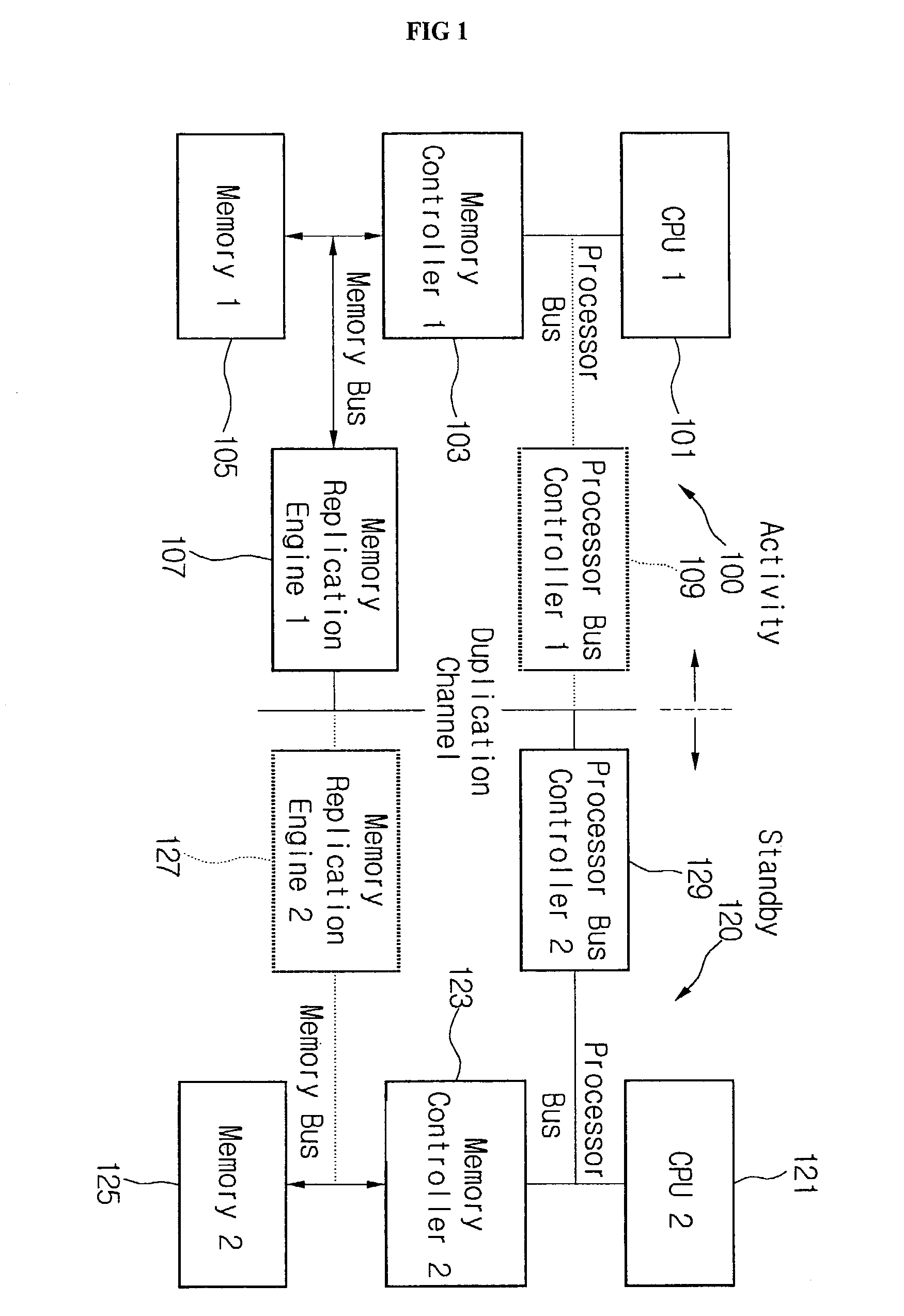
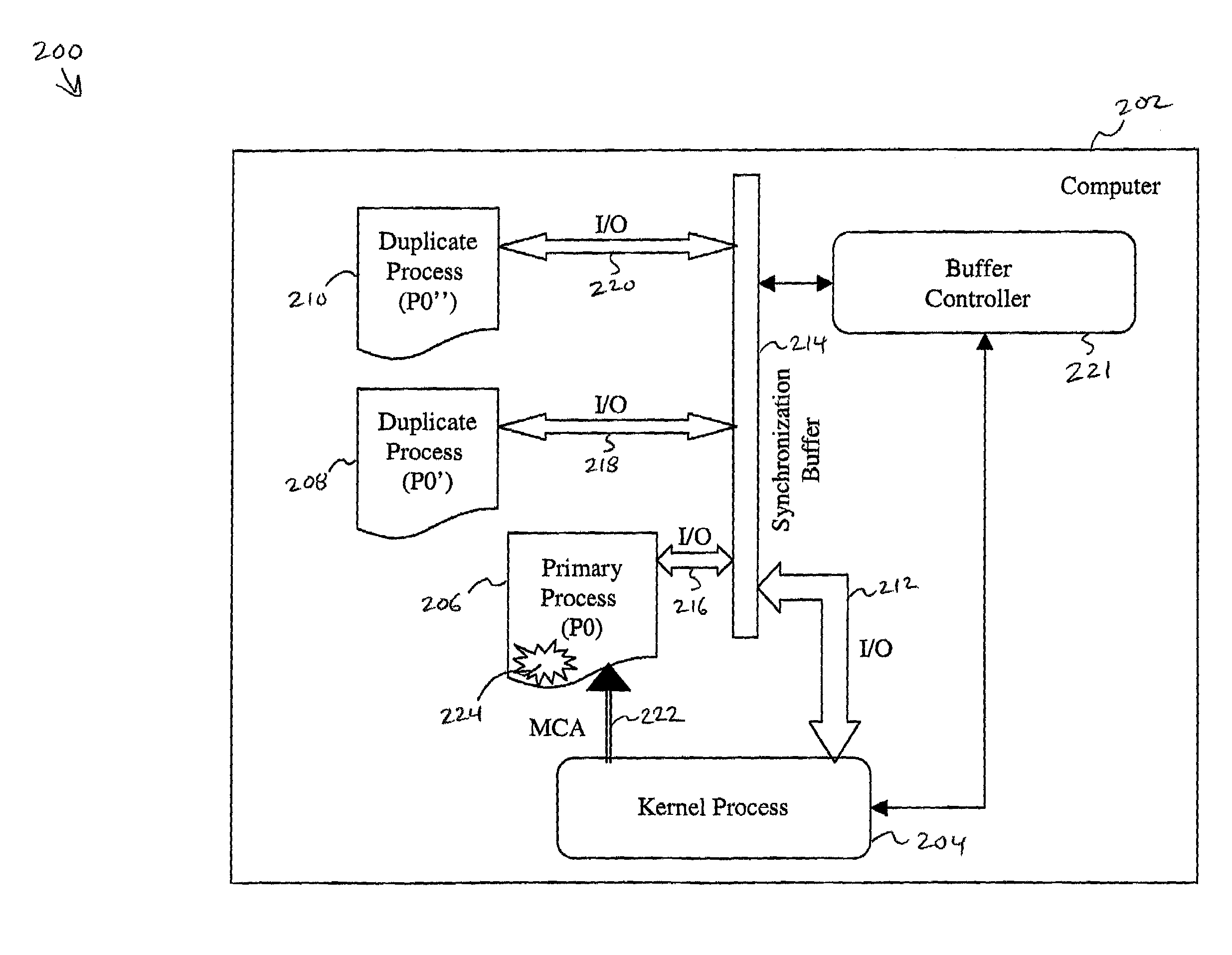
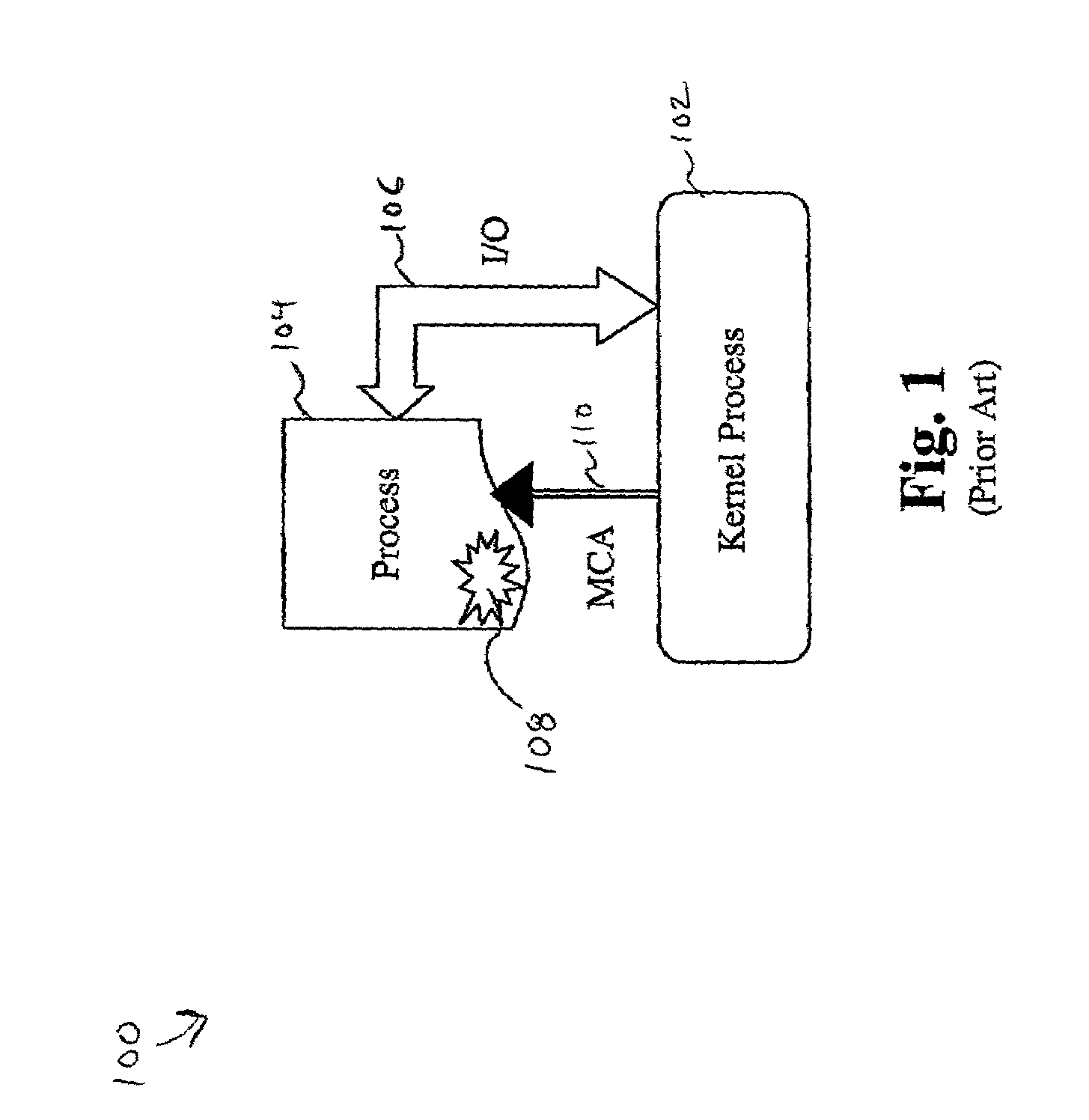
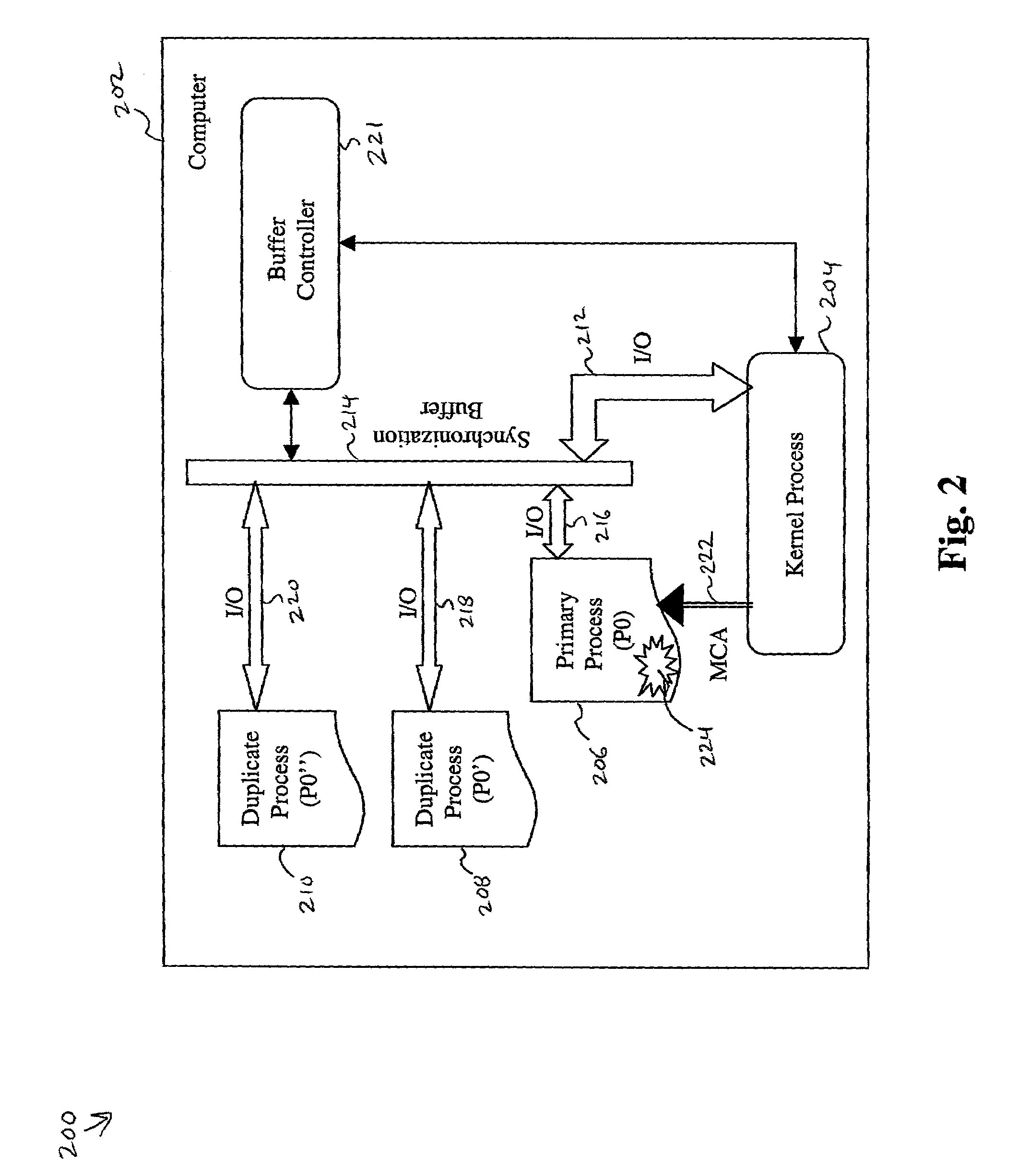
System and method for memory failure recovery using lockstep processes
A system and method for memory failure recovery is disclosed. The method discloses the steps of maintaining a predetermined number of duplicate and primary processes; keeping the processes in synchronization; managing the processes so that a single process image is presented to an external environment; detecting a computer system exception which affects one of the processes; and terminating the affected process. The system discloses, a primary process memory space which hosts a primary process; a duplicate process memory space which hosts a duplicate process corresponding to the primary process; a synchronization buffer which keeps the duplicate process in synchronization with the primary process; a processor which generates an exception signal in response to detection of a memory failure condition which affects the primary process; and an operating system which receives the exception signal, terminates the affected primary process, and maintains a predetermined number of primary and duplicate processes.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Transactional memory system with fast processing of common conflicts
ActiveUS8095750B2Digital data processing detailsSpecial data processing applicationsProcess memoryApplication software
A computing system processes memory transactions for parallel processing of multiple threads of execution by support of which an application need not be aware. The computing system transactional memory support provides a Transaction Table in memory and performs fast detection of potential conflicts between multiple transactions. Special instructions may mark the boundaries of a transaction and identify memory locations applicable to a transaction. A ‘private to transaction’ (PTRAN) tag, enables a quick detection of potential conflicts with other transactions that are concurrently executing on another thread of said computing system. The tag indicates whether (or not) a data entry in memory is part of a speculative memory state of an uncommitted transaction that is currently active in the system. A transaction program employs a plurality of Set Associative Transaction Tables, one for each microprocessor, and Load and Store Summary Tables in memory for fast processing of common conflict.
Owner:INT BUSINESS MASCH CORP
Packet processor memory interface
InactiveUS7107402B1Improve performanceData switching by path configurationMultiple digital computer combinationsProcess memoryMemory interface
A mechanism processes memory reads and writes in a packet processor. Each memory access has an associated sequence number and information is maintained allowing the detection of memory conflicts. The mechanism is placed between a processing element and a memory system such that write data is buffered and both reads and writes are recorded. When a memory conflict is detected, based on a strict or alternate ordering model, a restart signal is generated and the entries for the associated sequence number are flushed. When the work associated with a sequence number has completed, a signal is made so that associated write data can be sent to the memory system and the entries for that sequence number can be flushed.
Owner:F POSZAT HU
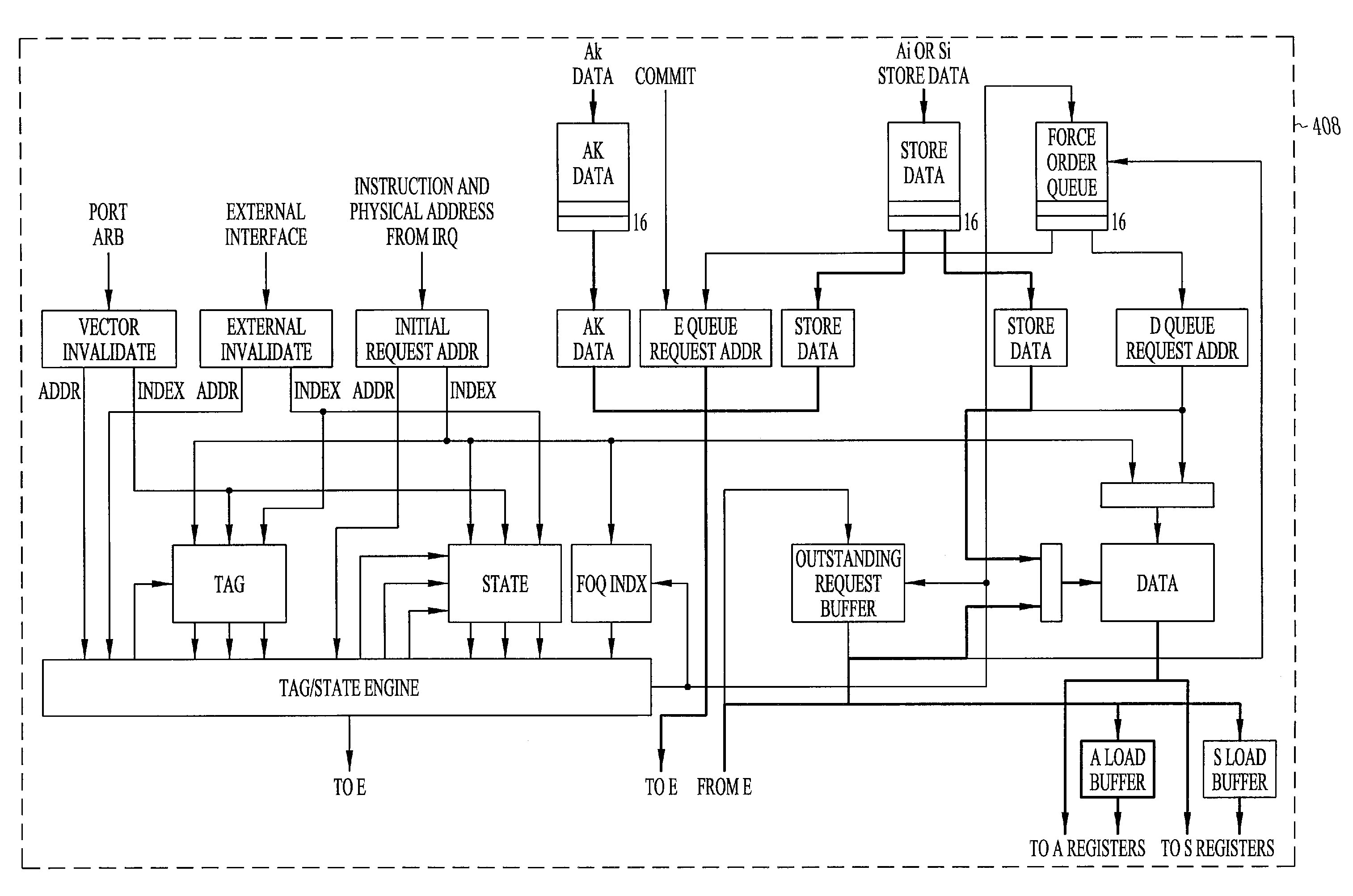
System and method for processing memory instructions using a forced order queue
A novel system and method for processing memory instructions. One embodiment of the invention provides a method for processing a memory instruction. In this embodiment, the method includes obtaining a memory request; storing the memory request in an Initial Request Queue (IRQ); and processing the memory request from the IRQ by a cache controller, wherein processing includes: identifying a type of the memory request, and processing the memory request in both a local cache and an Force Order Queue (FOQ), wherein processing includes determining if a portion of an address associated with the memory request matches one or more partial addresses in the FOQ and, if the memory request misses in the cache and the address does not match one or more partial addresses in the FOQ, adding the memory request to the FOQ and allocating a cache line in the local cache corresponding to the local cache miss.
Owner:CRAY
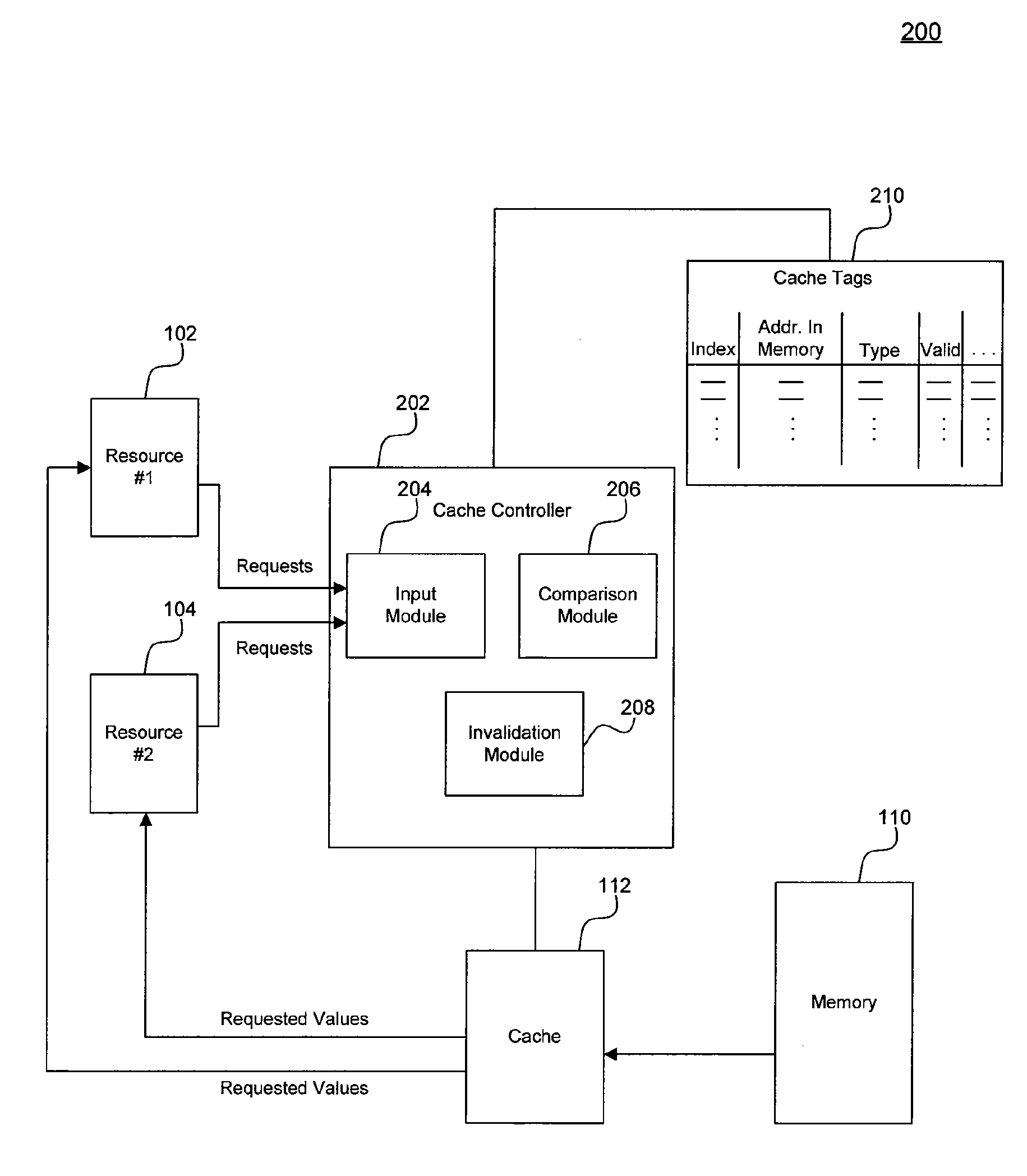
Dynamically Partitionable Cache
Methods and systems for dynamically partitioning a cache and maintaining cache coherency are provided. In an embodiment, a system for processing memory requests includes a cache and a cache controller configured to compare a memory address and a type of a received memory request to a memory address and a type, respectively, corresponding to a cache line of the cache to determine whether the memory request hits on the cache line. In another embodiment, a method for processing fetch memory requests includes receiving a memory request and determining if the memory request hits on a cache line of a cache by determining if a memory address and a type of the memory request match a memory address and a type, respectively, corresponding to a cache line of the cache.
Owner:ADVANCED MICRO DEVICES INC
Apparatus and method for simultaneous multi-thread processing
InactiveUS20050022192A1Reduce memory collisionReduce collisionResource allocationMemory adressing/allocation/relocationProcess memoryParallel computing
A method and apparatus for data processing including a microprocessor for simultaneously processing a plurality of processes, where a process memory is assigned to one or more processes, the processes include corresponding threads of that are assigned to corresponding thread memories that are independent from the process memory, and have access to the process memory.
Owner:SAMSUNG ELECTRONICS CO LTD
Memory device wear-leveling techniques
InactiveUS20110161553A1Memory architecture accessing/allocationMemory adressing/allocation/relocationProcess memoryLogical block addressing
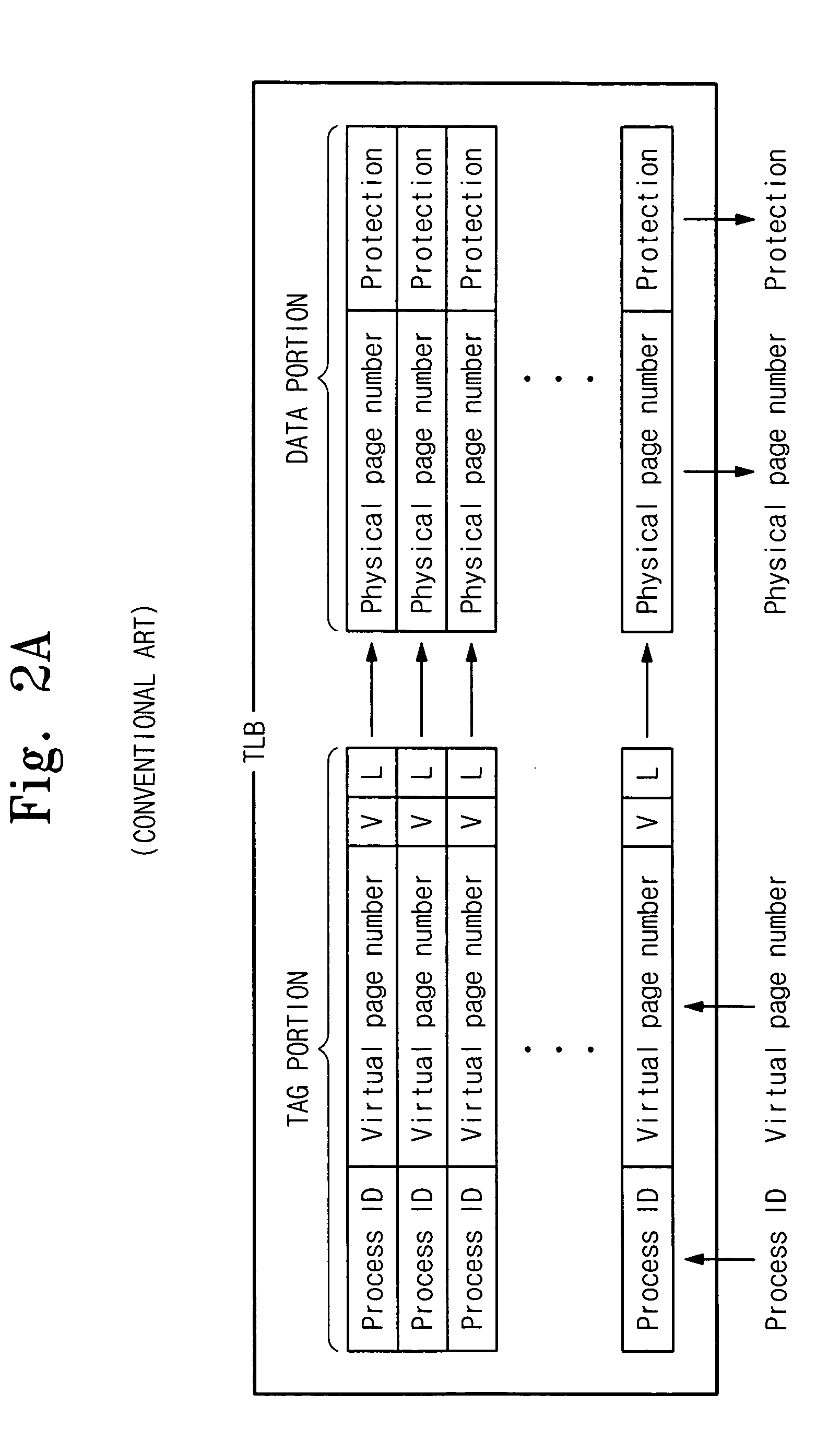
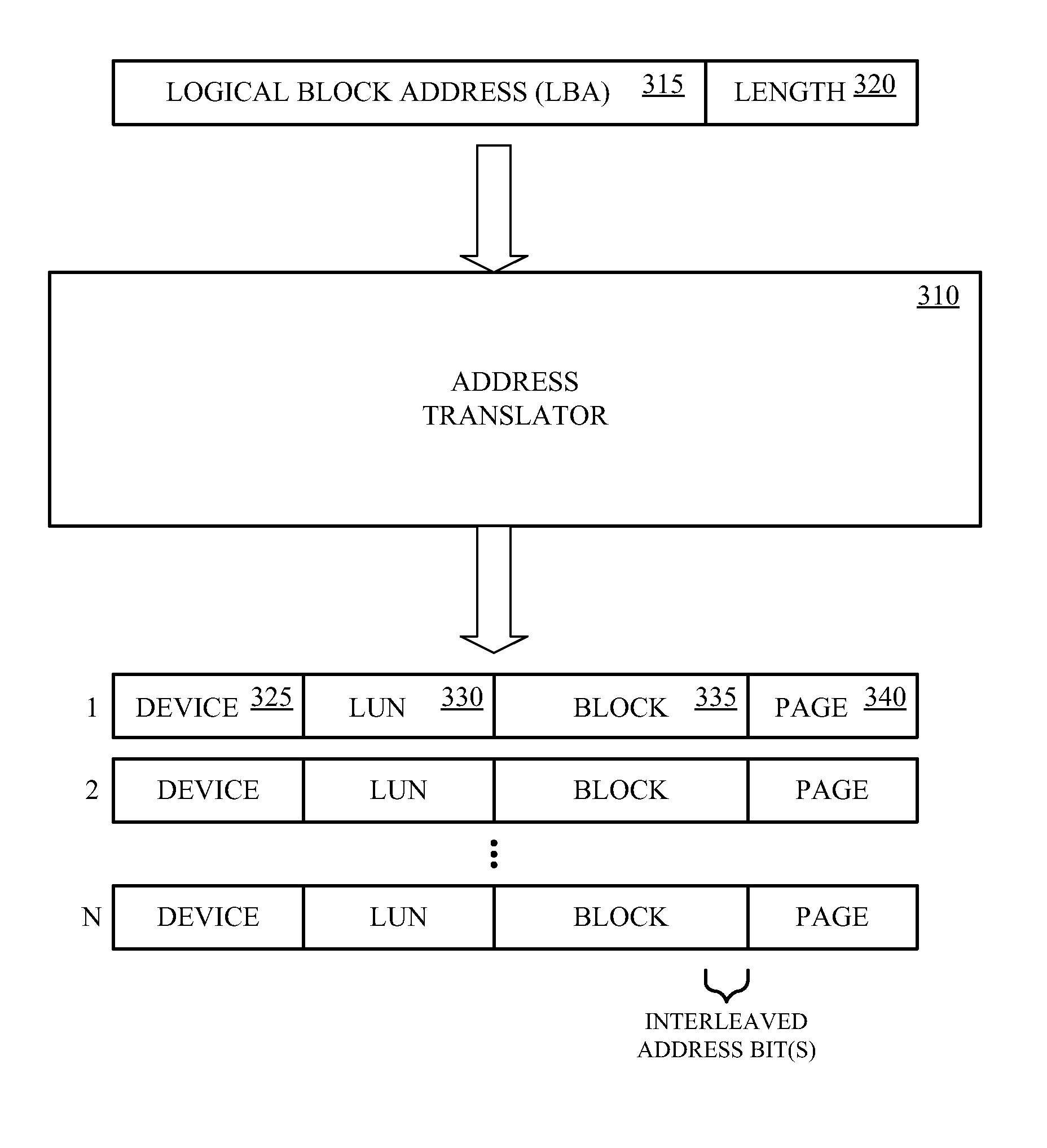
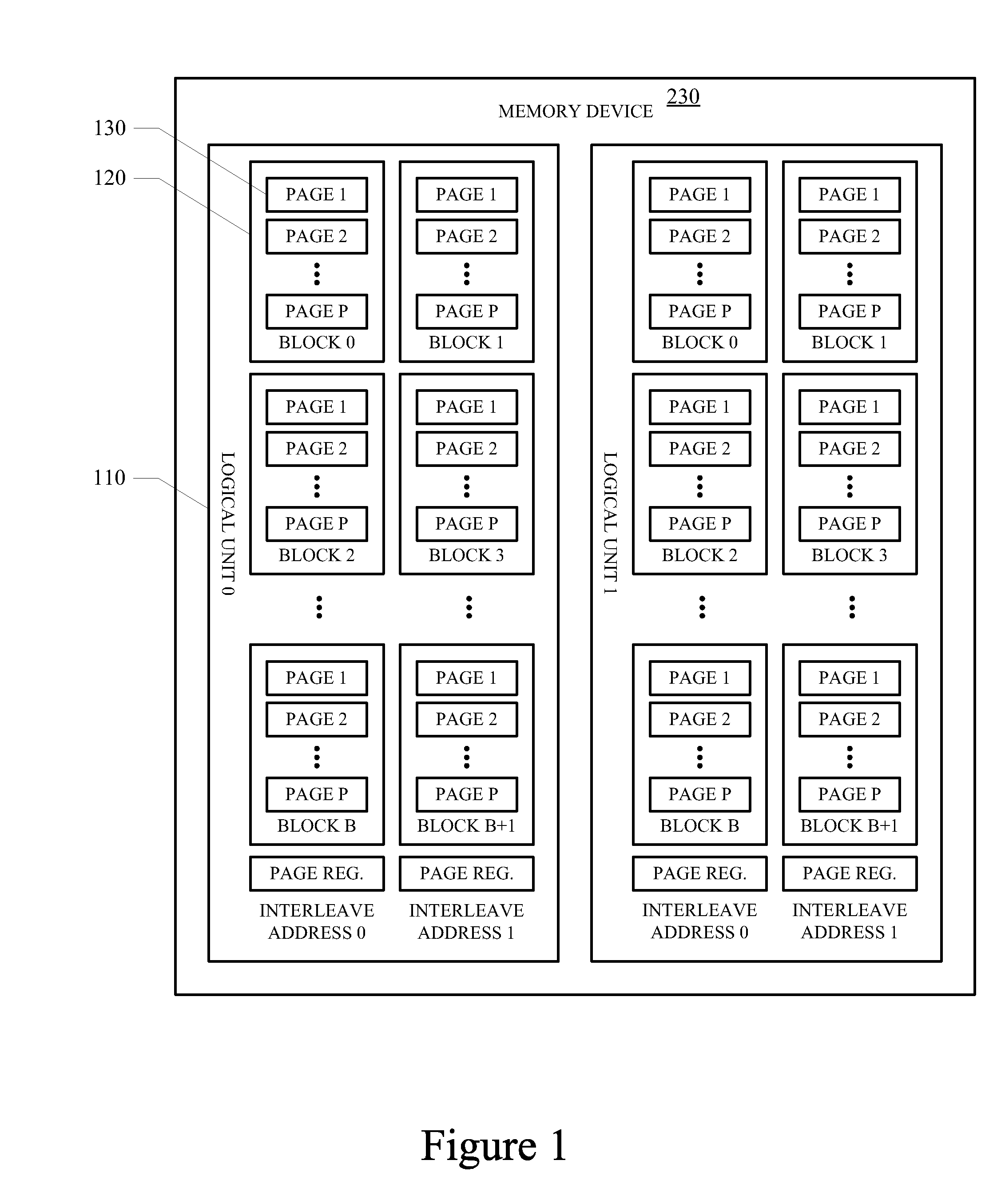
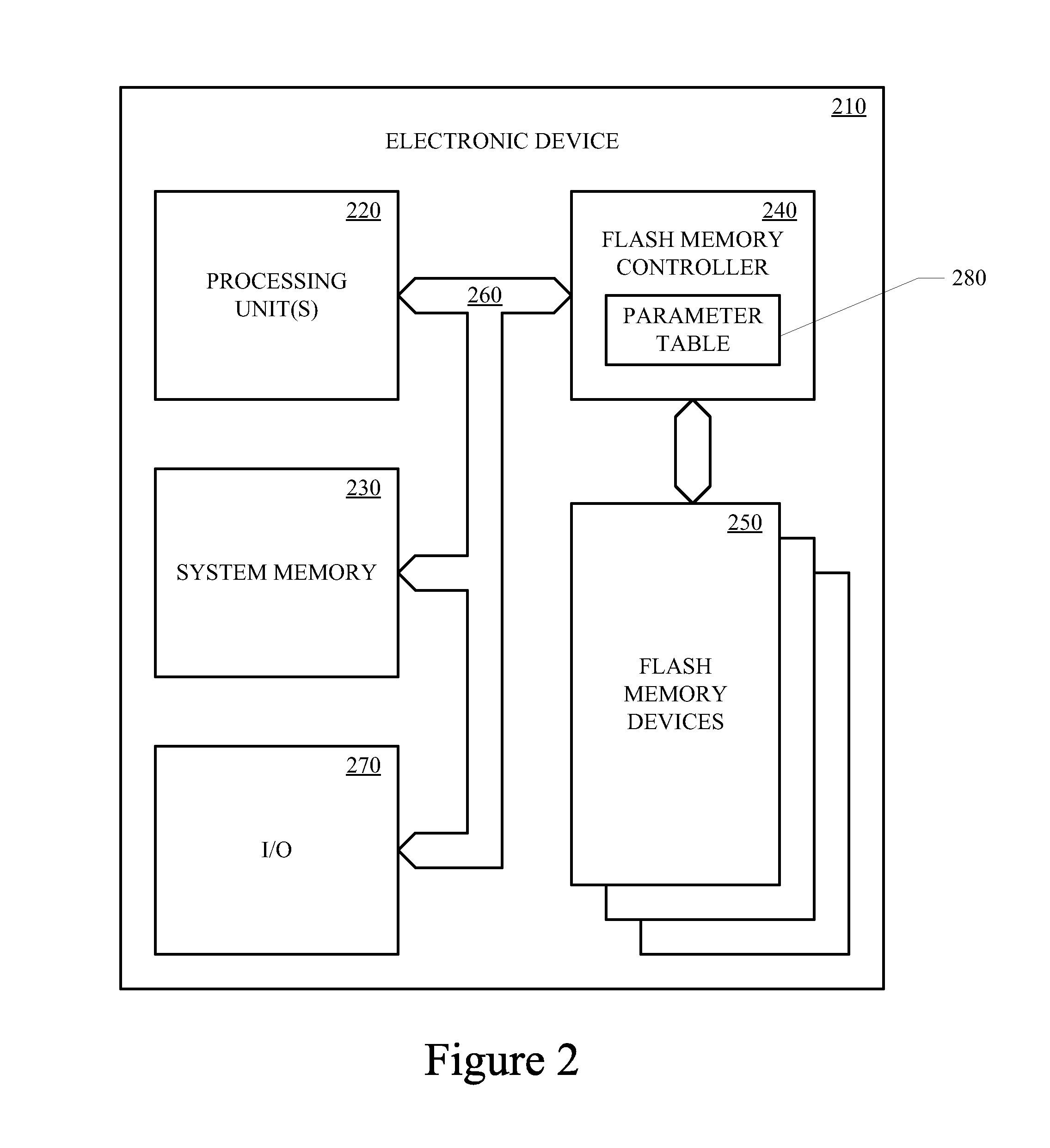
The wear-leveling techniques include discovering a persistent state of one or more memory devices, or building and caching persistent state parameters for each logical unit of a given memory device if a persistent state is not discovered for a given memory device. The techniques may also include processing memory access commands utilizing the cached persistent state parameters. When processing memory access commands, the logical block address and length parameter of a logical address of a command may be translated to a plurality of physical addresses for accessing one or more memory devices, each physical address includes a device address, a logical unit address, a block address, and a page address, wherein the block address includes one or more interleaved address bits.
Owner:NVIDIA CORP
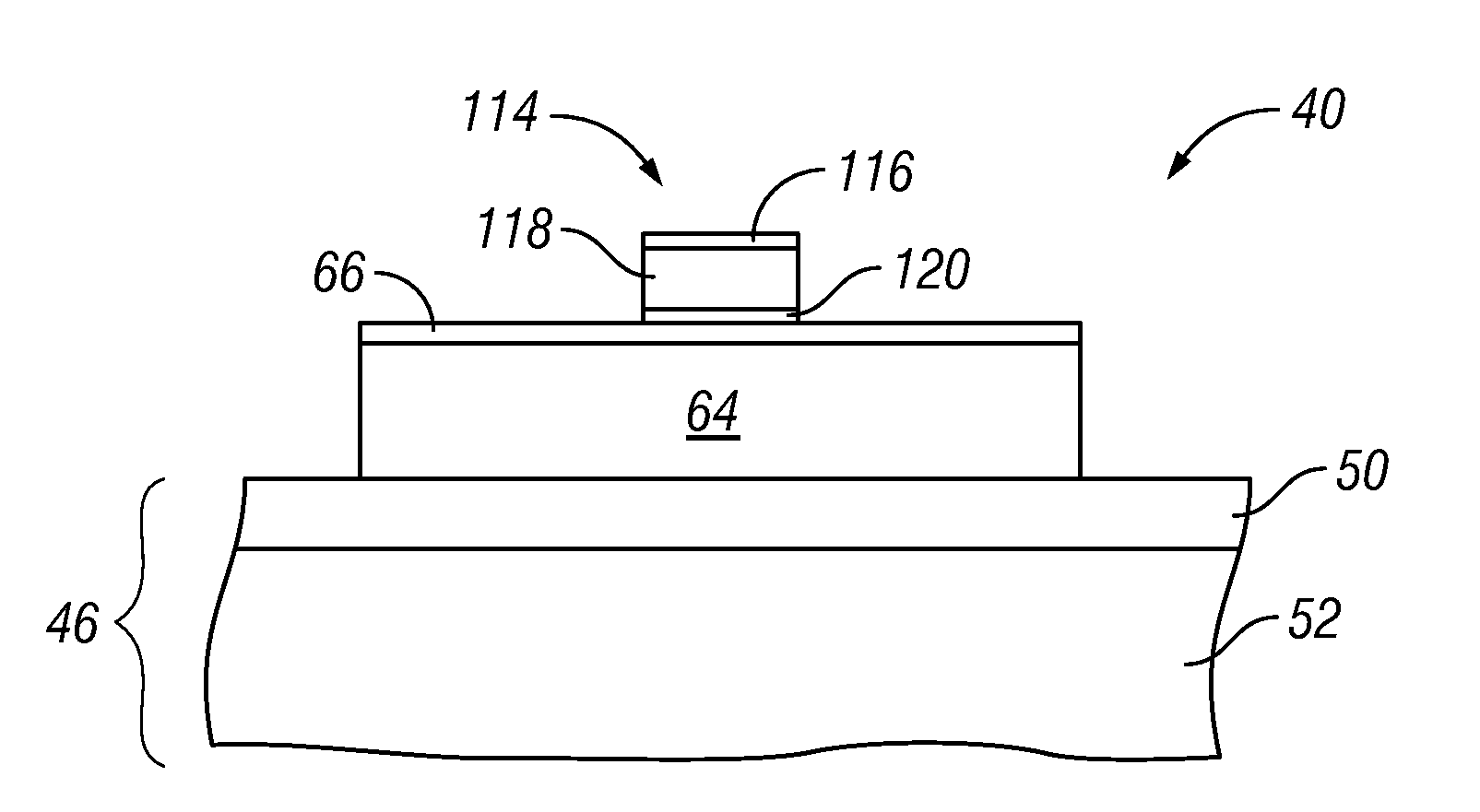
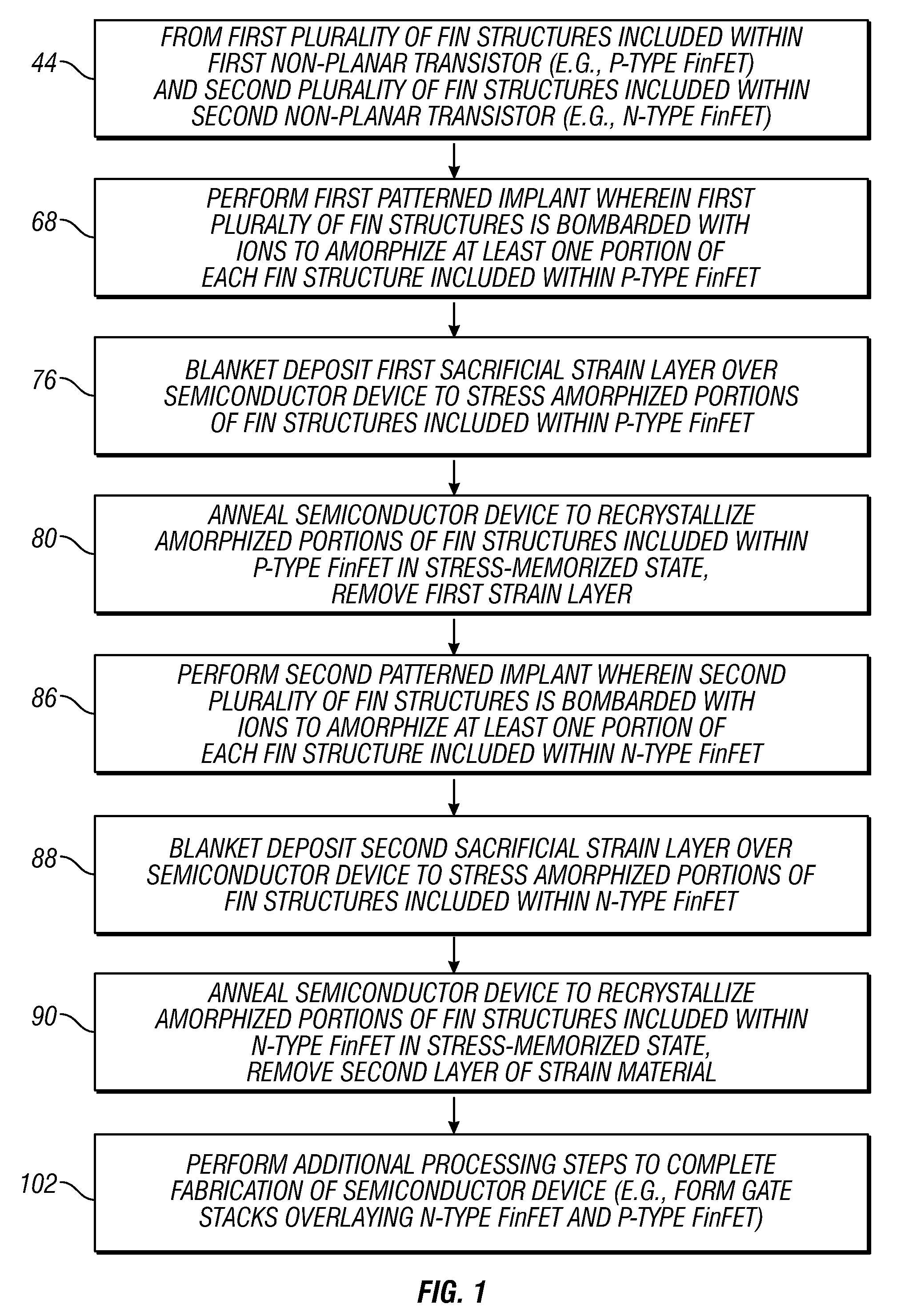
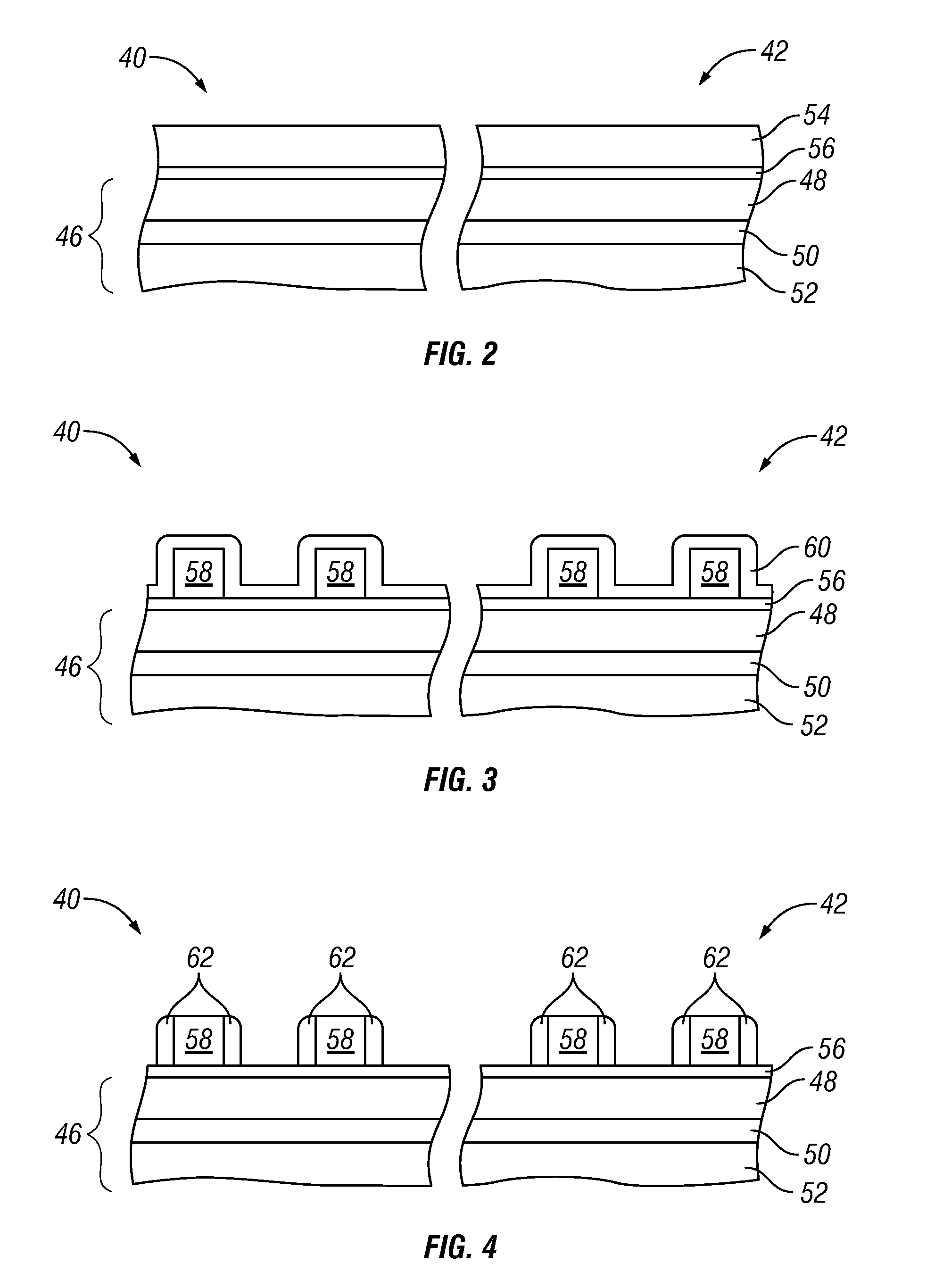
Methods for fabricating non-planar semiconductor devices having stress memory
InactiveUS20110027978A1Semiconductor/solid-state device manufacturingSemiconductor devicesPower semiconductor deviceProcess memory
Embodiments of a method are provided for fabricating a non-planar semiconductor device including a substrate having a plurality of raised crystalline structures formed thereon. In one embodiment, the method includes the steps of amorphorizing a portion of each raised crystalline structure included within the plurality of raised crystalline structures, forming a sacrificial strain layer over the plurality of raised crystalline structures to apply stress to the amorphized portion of each raised crystalline structure, annealing the non-planar semiconductor device to recrystallize the amorphized portion of each raised crystalline structure in a stress-memorized state, and removing the sacrificial strain layer.
Owner:ALSEPHINA INNOVATIONS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com