Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
674 results about "Electronic memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
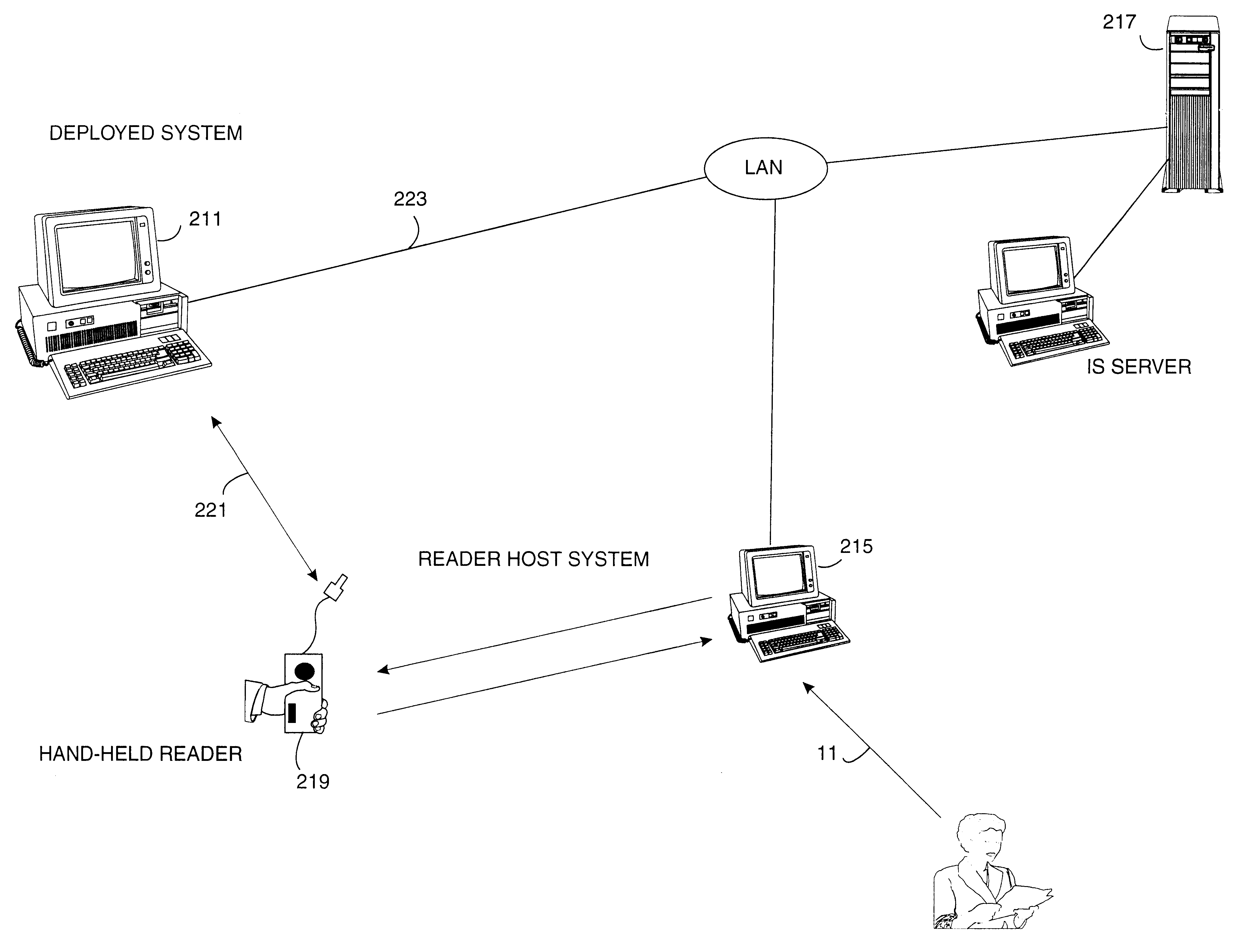
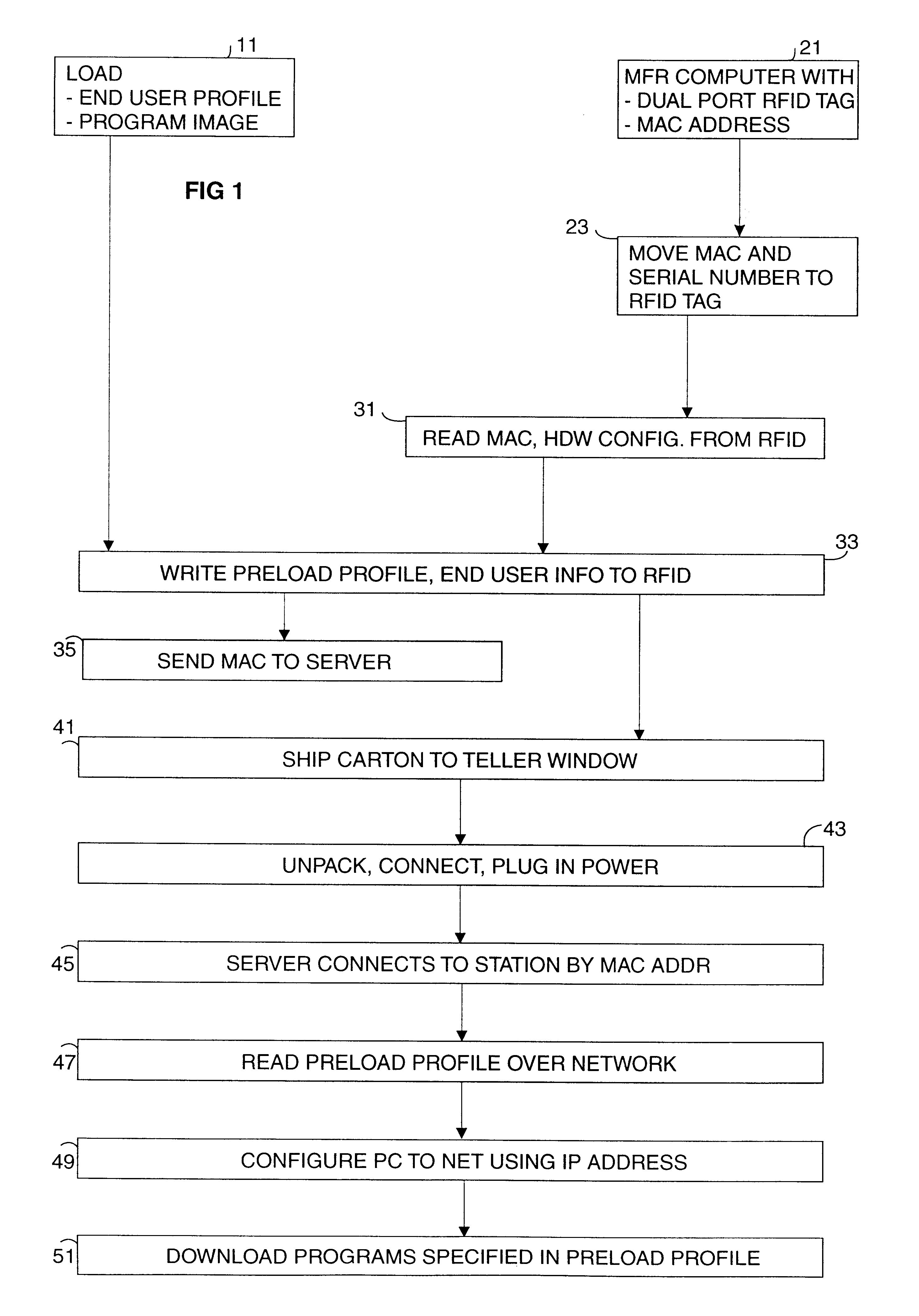
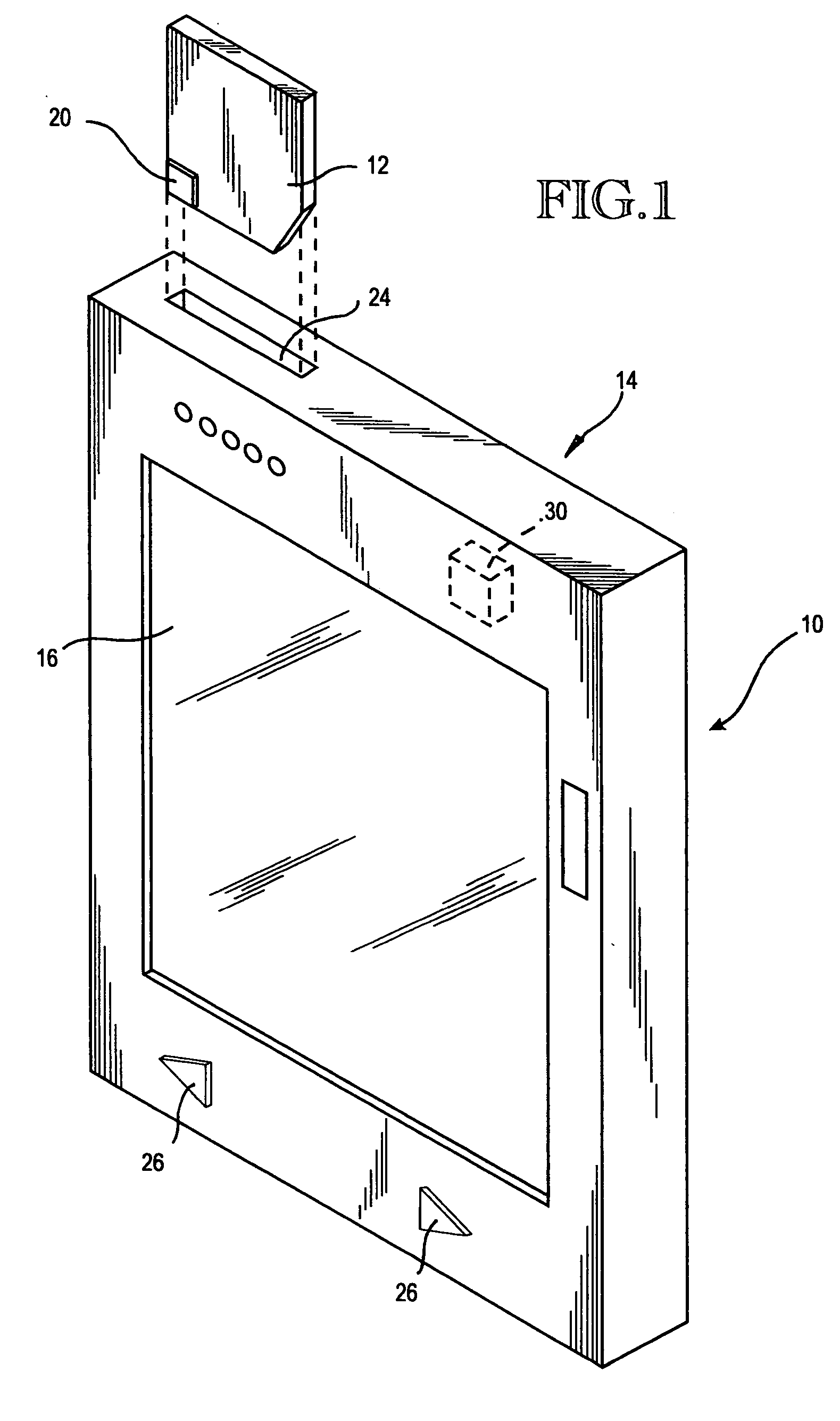
Method and economical direct connected apparatus for deploying and tracking computers
A method of asset control and workstation computer deployment that utilizes a dual port electronic memory identification RFID tag to hold serial number and hardware and software configuration profiles as well as user information. The RFID tag is mapped into the workstation computer memory space and can also be read and written by radio frequency signalling through a wired plug and access flap in a shipping carton. Serial numbers and MAC address is stored on the tag by the manufacturer. User information, workstation profile and software image information is stored onto the tag while the computer is being received for forwarding to the final workstation destination without the need to unpack and power up the computer. The information stored on the tag is used to allow automated system configuration and software downloading to the computer.
Owner:IBM CORP
Process for making and programming and operating a dual-bit multi-level ballistic MONOS memory
A fast low voltage ballistic program, ultra-short channel, ultra-high density, dual-bit multi-level flash memory is described with a two or three polysilicon split gate side wall process. The structure and operation of this invention is enabled by a twin MONOS cell structure having an ultra-short control gate channel of less than 40nm, with ballistic injection which provides high electron injection efficiency and very fast program at low program voltages of 3~5V. The cell structure is realized by (i) placing side wall control gates over a composite of Oxide-Nitride-Oxide (ONO) on both sides of the word gate, and (ii) forming the control gates and bit diffusion by self-alignment and sharing the control gates and bit diffusions between memory cells for high density. Key elements used in this process are: 1) Disposable side wall process to fabricate the ultra short channel and the side wall control gate with or without a step structure, and 2) Self-aligned definition of the control gate over the storage nitride and the bit line diffusion, which also runs in the same direction as the control gate. The features of fast program, low voltage, ultra-high density, dual-bit, multi-level MONOS NVRAM of the present invention include: 1) Electron memory storage in nitride regions within an ONO layer underlying the control gates, 2) high density dual-bit cell in which there are two nitride memory storage elements per cell, 3) high density dual-bit cell can store multi-levels in each of the nitride regions, 4) low current program controlled by the word gate and control gate, 5) fast, low voltage program by ballistic injection utilizing the controllable ultra-short channel MONOS, and 6) side wall control poly gates to program and read multi-levels while masking out memory storage state effects of the unselected adjacent nitride regions and memory cells. The ballistic MONOS memory cell is arranged in the following array: each memory cell contains two nitride regions for one word gate, and ½ a source diffusion and ½ a bit diffusion. Control gates can be defined separately or shared together over the same diffusion. Diffusions are shared between cells and run in parallel to the side wall control gates, and perpendicular to the word line.
Owner:HALO LSI INC
Non-invasive cardiac monitor and methods of using continuously recorded cardiac data
ActiveUS20070255153A1Improve fidelityElectrocardiographyLocal control/monitoringAdhesiveCardiac monitoring
One embodiment of the invention is a cardiac monitor having a housing; a plurality of electrodes within and extending from the housing; a state machine within the housing configured to digitialize and store in memory signals from the plurality of electrodes; a sealing surface and an adhesive on the sealing surface configured to form a watertight perimeter around the plurality of electrodes when the housing is affixed to a mammal. Another embodiment of the invention provides a continuous cardiac monitor having a housing; a surface on the housing adapted to be sealably engaged to a mammal; an adhesive on the surface that is adapted to remain affixed to the mammal for at least 7 days; at least two electrodes within the housing positioned to detect a cardiac information of the mammal while the surface is sealably engaged to the mammal; an electronic memory within the housing wherein, the electronic memory is sized to store at least 24 hours of continuous cardiac information; and wiring within the housing connecting the electronic memory to the electrodes.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
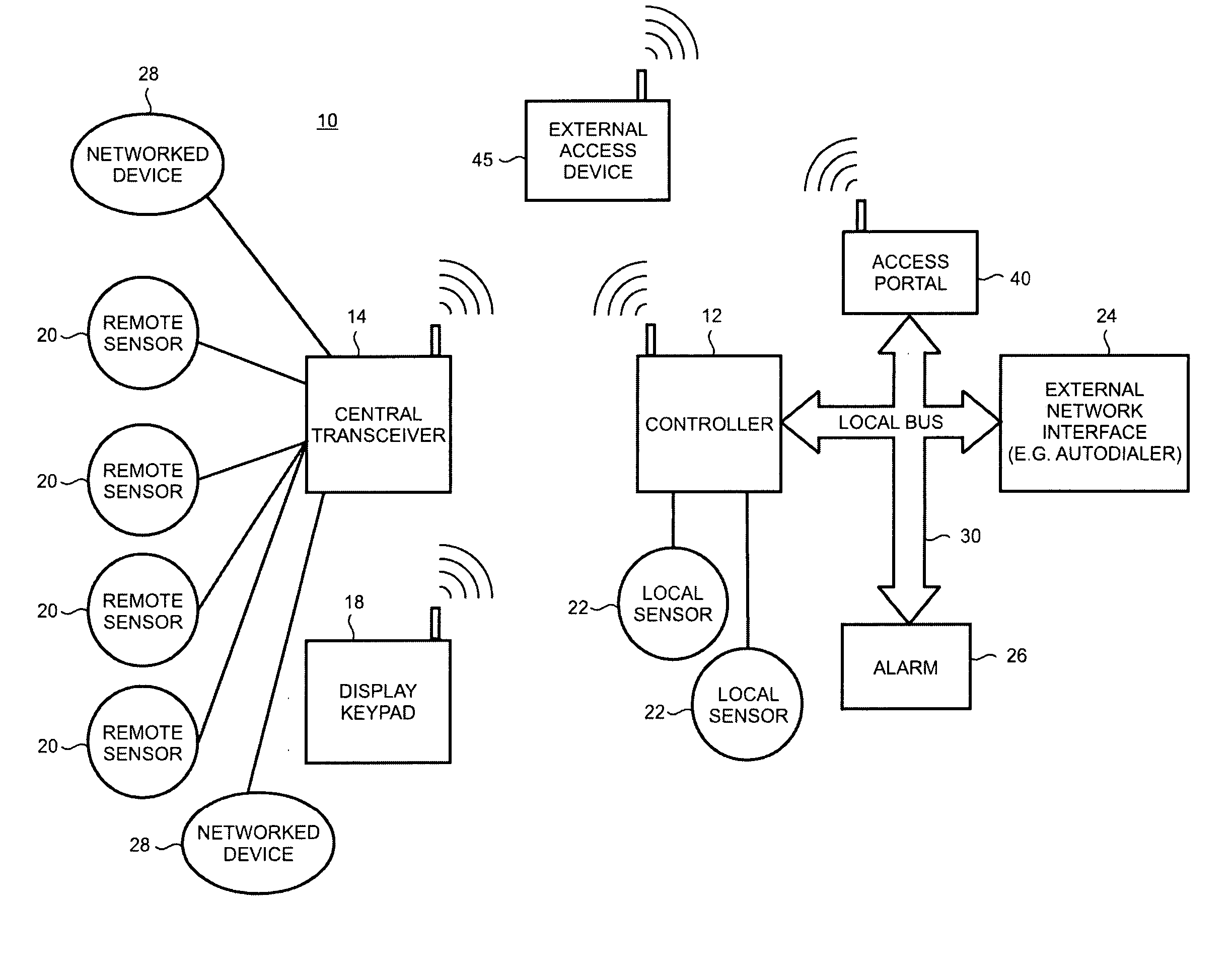
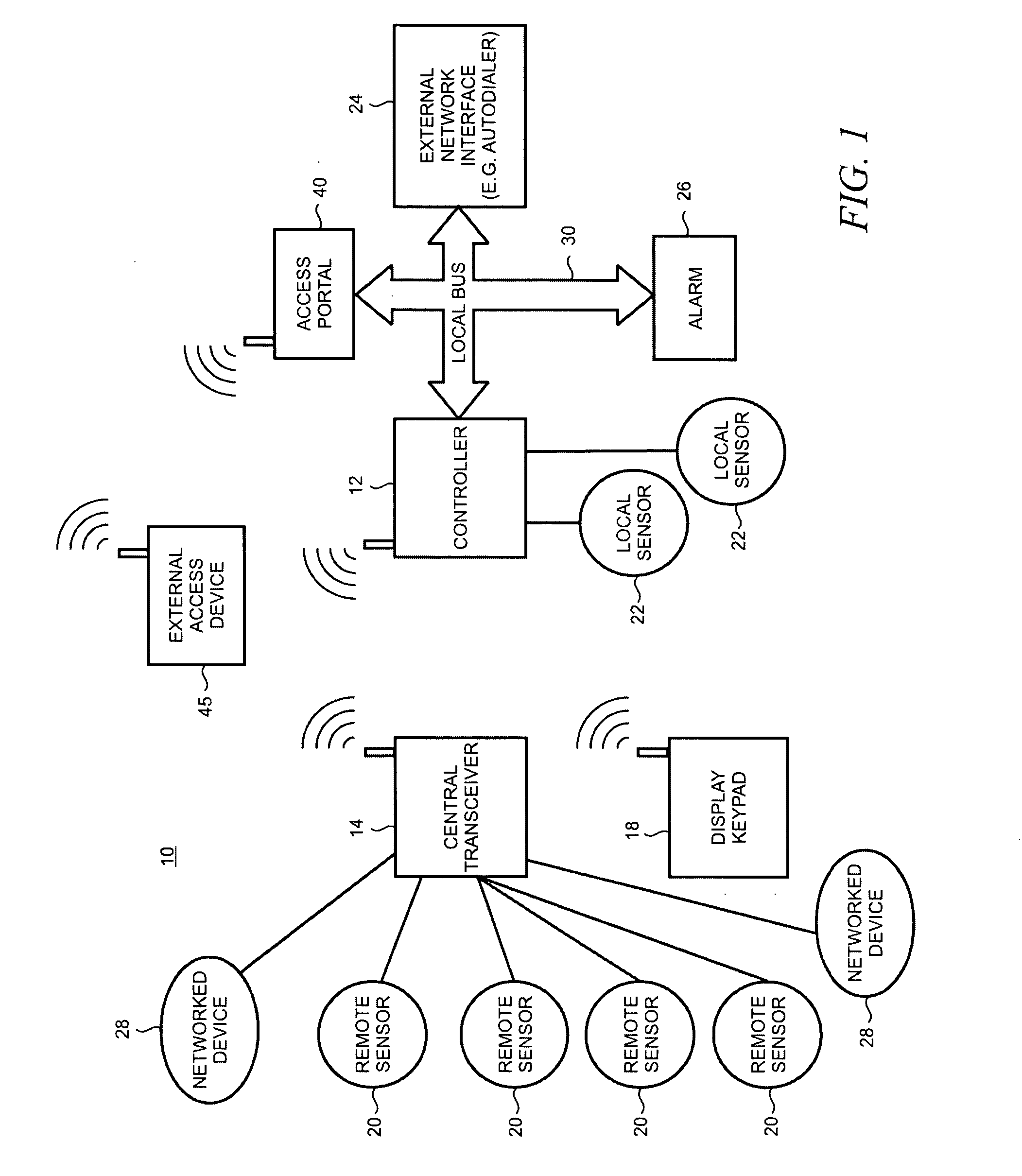
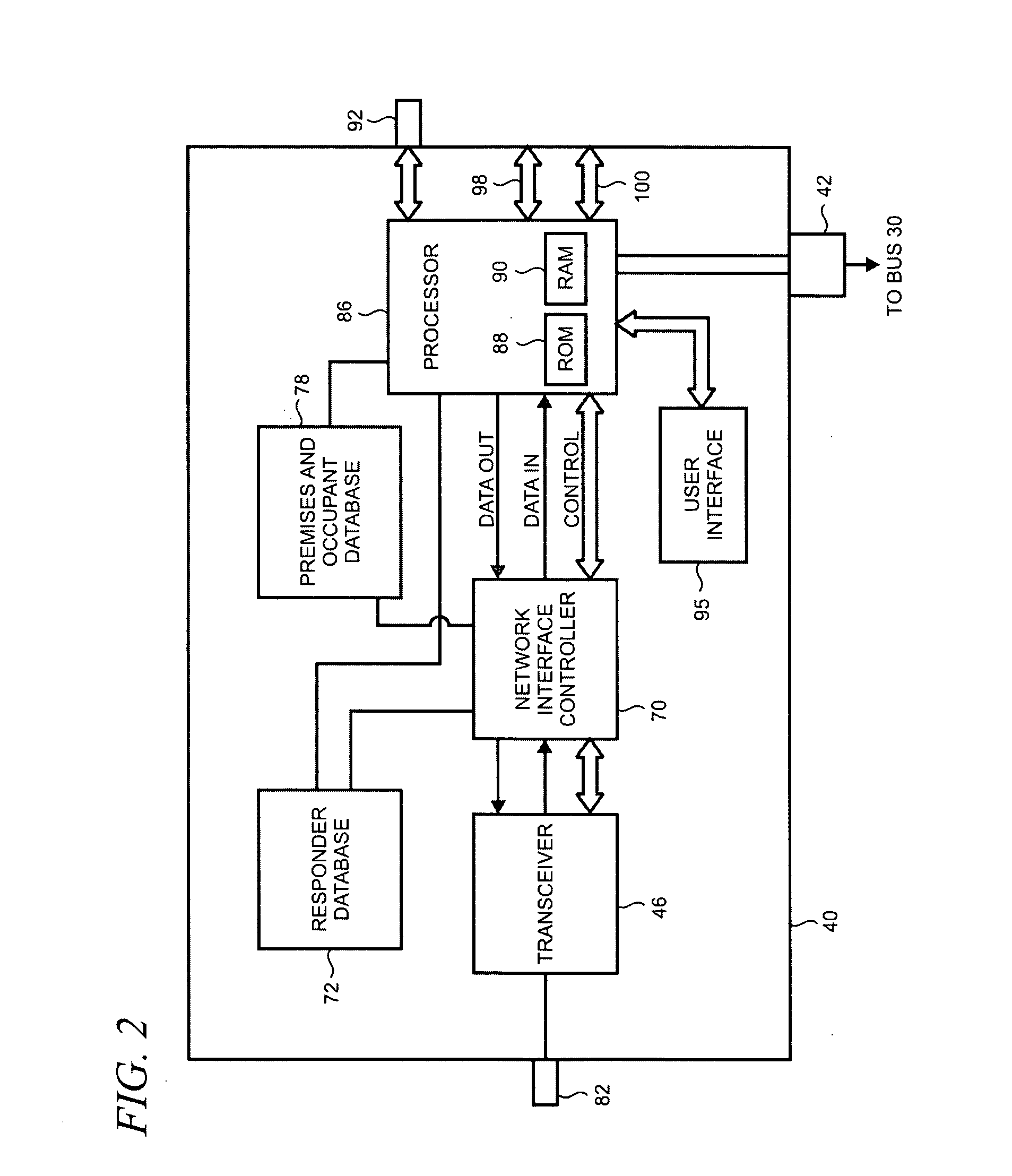
Method and apparatus for providing status information from a security and automation system to an emergency responder
An access portal is provided for establishing communication between an environmental management system used on a premises and an authorized responder equipped with an external access device. In some cases a remote host server is provided for obtaining information from the environmental management system, which in turn can transmit the information to the external access device. The access portal includes a first electronic memory segment configured to store access information associated with at least one authorized responder and a second electronic memory segment configured to store information pertaining to the premises and / or at least one occupant residing in the premises. The access portal also includes a processor for identifying a responder as an authorized responder by comparing identifying information received from the responder through the external access device with the access information stored in the first electronic memory segment. A wireless transceiver is provided for (i) receiving the identifying information and requests from the responder and, (ii) in response to a request, transmitting the premises information stored in the second electronic memory segment and status information obtained from at least one sensor in the environmental management system to an authorized responder.
Owner:GENERAL INSTR CORP
Method and apparatus for locating and measuring the distance to a target
Embodiments of the invention comprise an apparatus for use with a laser range finder configured to direct a laser beam toward a scene to measure the distance to a target in the scene and having a range finder display for displaying data, including data that is indicative of the distance to a target, wherein the apparatus comprises a protective housing, a camera module in the housing, the camera module including a lens mounted in a front end portion of the housing, and a light path through the lens to image sensor, an image sensor operatively connected to the camera module for receiving images acquired by the camera module, electronic memory for selectively storing data of images from the image sensor, circuitry for controlling the operation of the image sensor and the memory, a camera display in the housing operatively connected to the image sensor for receiving the image data and providing a visual display of the image, and a switch for storing image data in the memory. Other embodiments include a projector in the housing for projecting the data displayed by the second display onto the image sensor to thereby capture the image data of the scene and displayed distance data together.
Owner:ROBERT BOSCH CO LTD
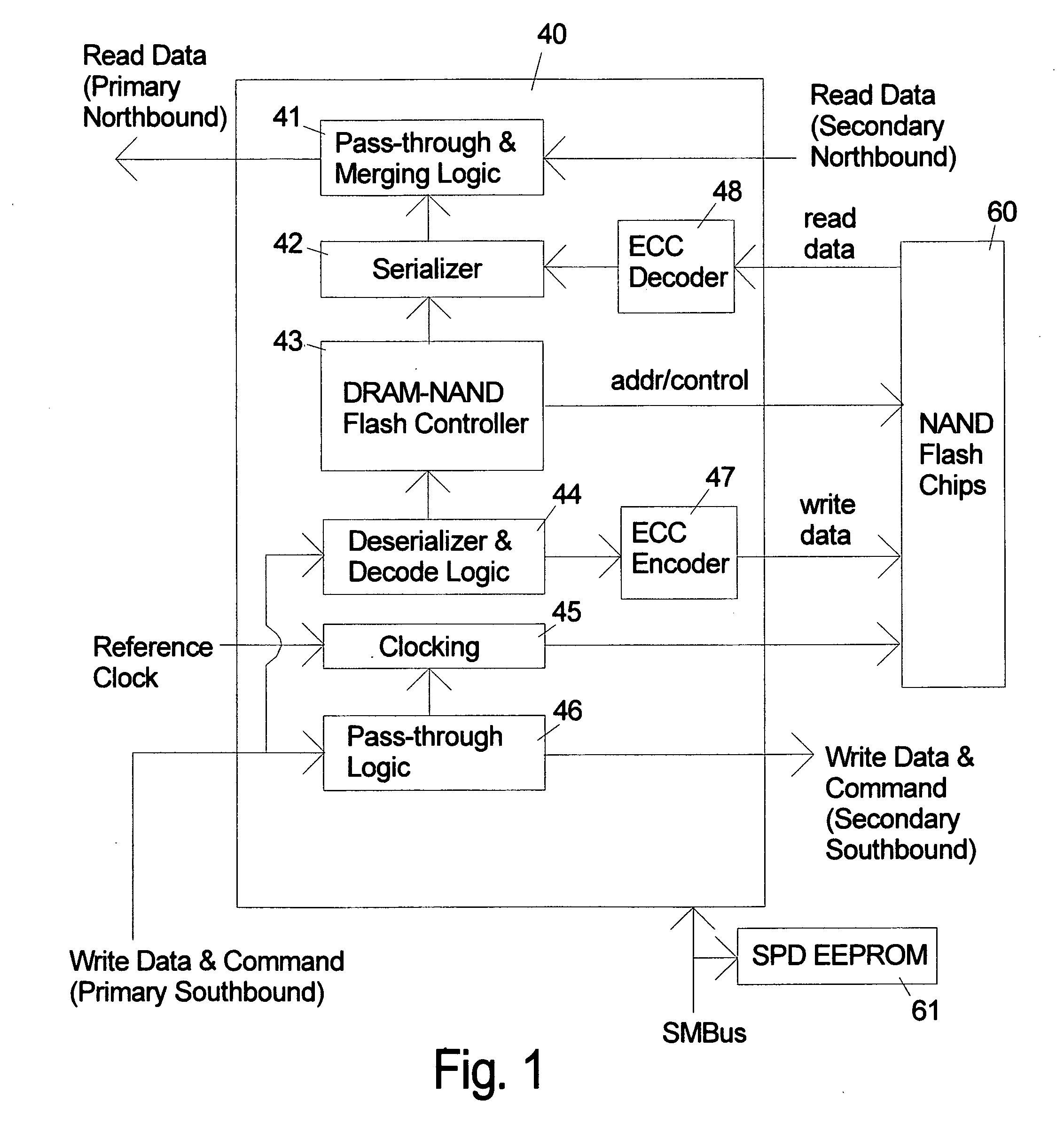
NAND flash module replacement for DRAM module
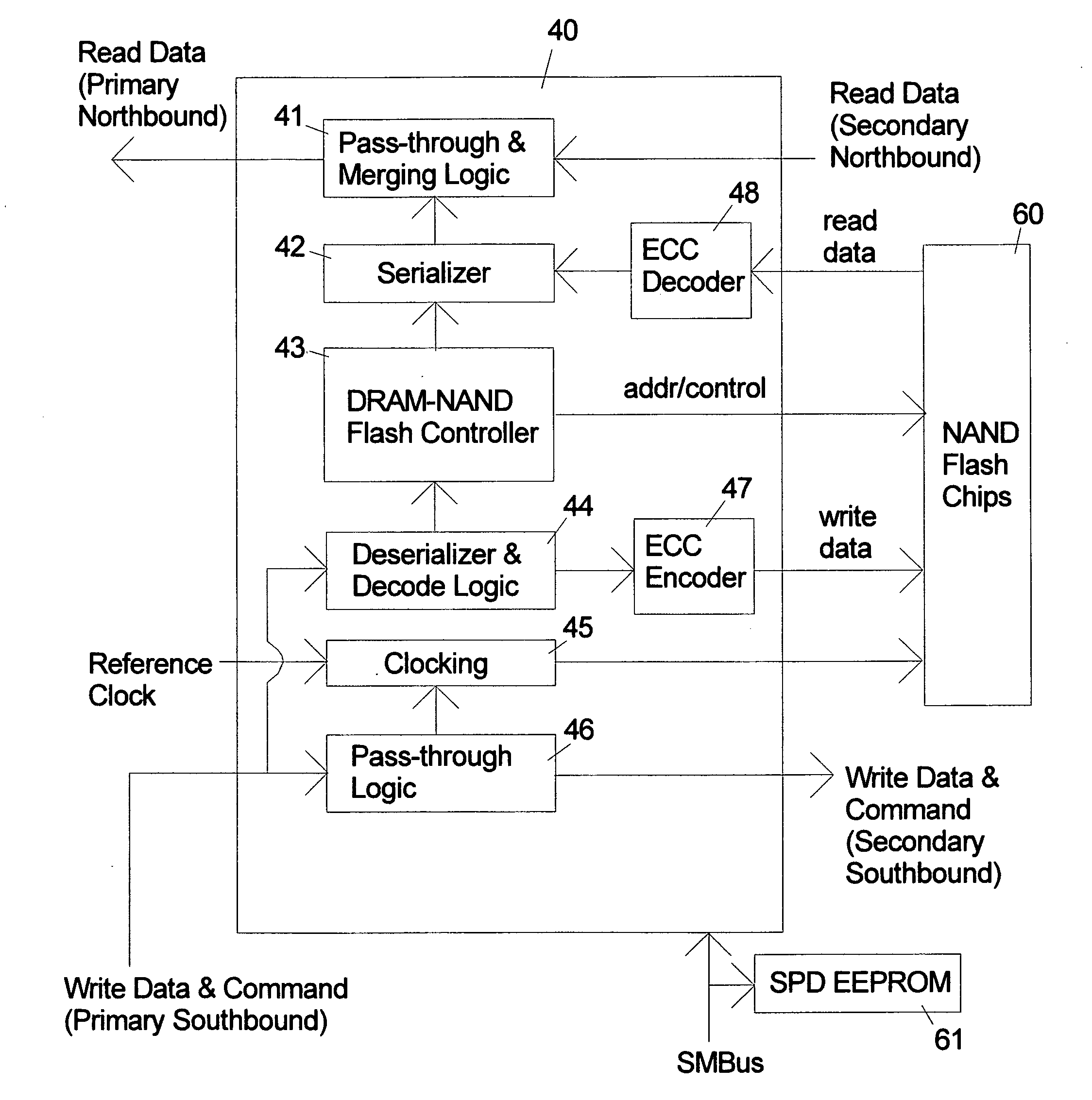
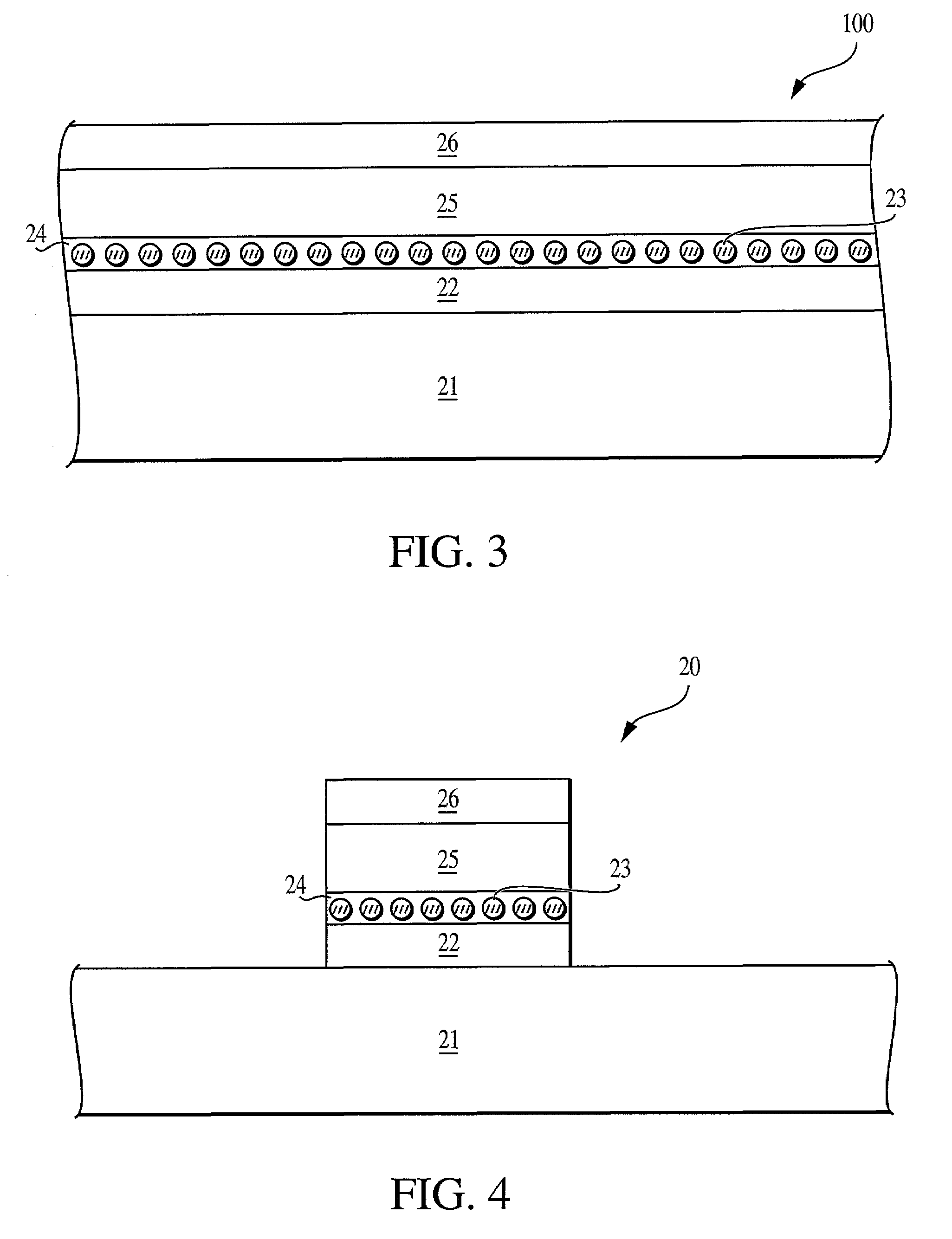
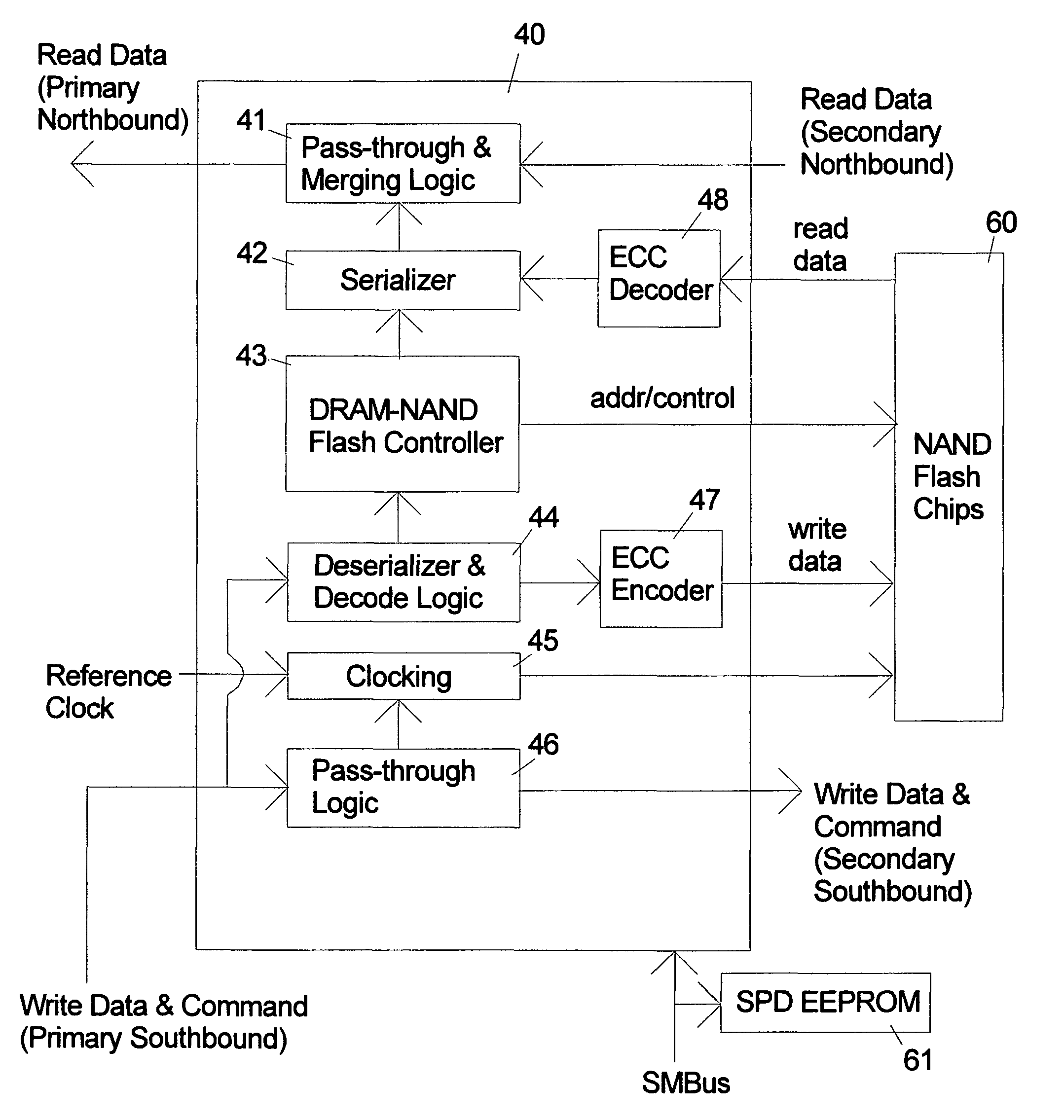
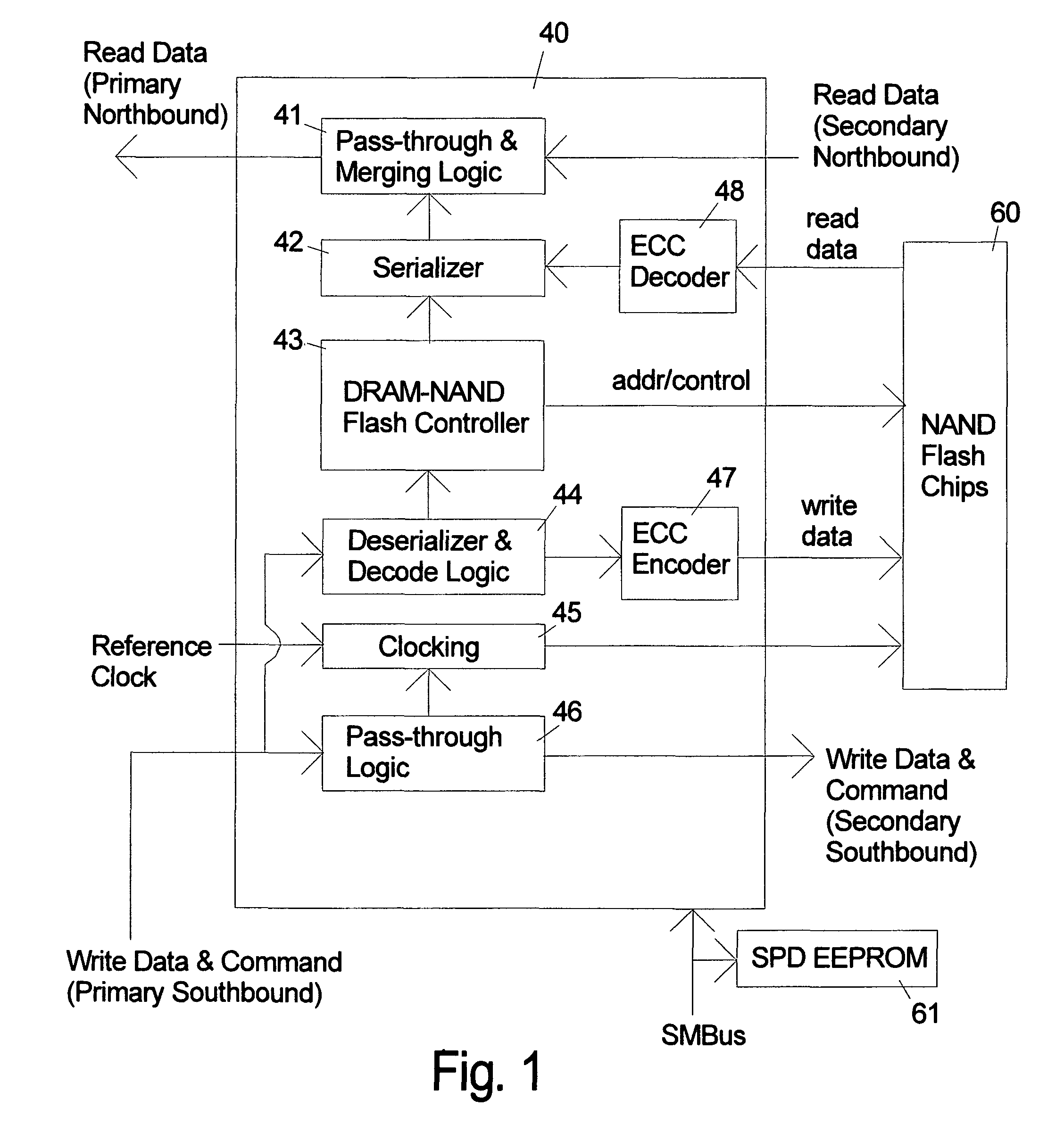
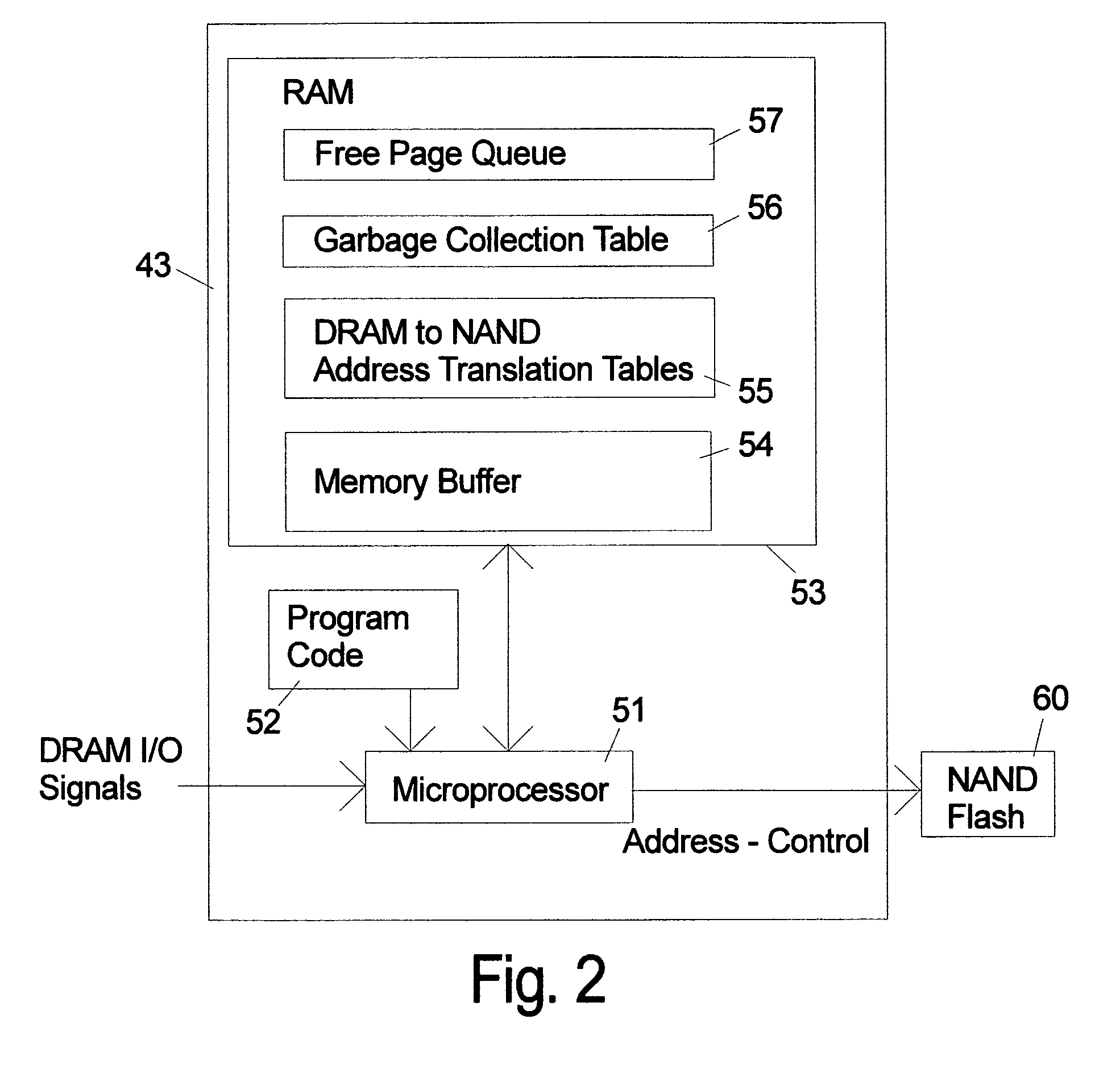
ActiveUS20090157950A1Most efficientAddressing slow performanceMemory architecture accessing/allocationMemory adressing/allocation/relocationControl signalFlash memory controller
An electronic memory module according to the invention provides non-volatile memory that can be used in place of a DRAM module without battery backup. An embodiment of the invention includes an embedded microprocessor with microcode that translates the FB-DIMM address and control signals from the system into appropriate address and control signals for NAND flash memory. Wear-leveling, bad block management, garbage collection are preferably implemented by microcode executed by the microprocessor. The microprocessor, additional logic, and embedded memory provides the functions of a flash memory controller. The microprocessor memory preferably contains address mapping tables, free page queue, and garbage collection information.
Owner:WESTERN DIGITAL TECH INC
Digital controller for surgical handpiece
The present disclosure generally pertains to a digital controller for surgical handpieces. The controller is programmable and configurable by software which may be used with a variety of types of handpieces. The controller is equipped with environmental sensors that detect pressure, humidity and temperature, and operational sensors that detect the angle and placement of the rotor of a motor. These sensors provide data used for testing and evaluating the function of the handpiece. A filter program is provided which removes electronic noise from collected data. The controller includes an electronic memory writer and reader to download firmware, control parameters for handpiece operation and read logged data from sensors to determine motor function. The sensor includes a hermetic enclosure constructed from a heat conducting material and that is non-ferromagnetic to allow communication between the trigger and controller.
Owner:INTEGRATED MEDICAL SYST INT INC
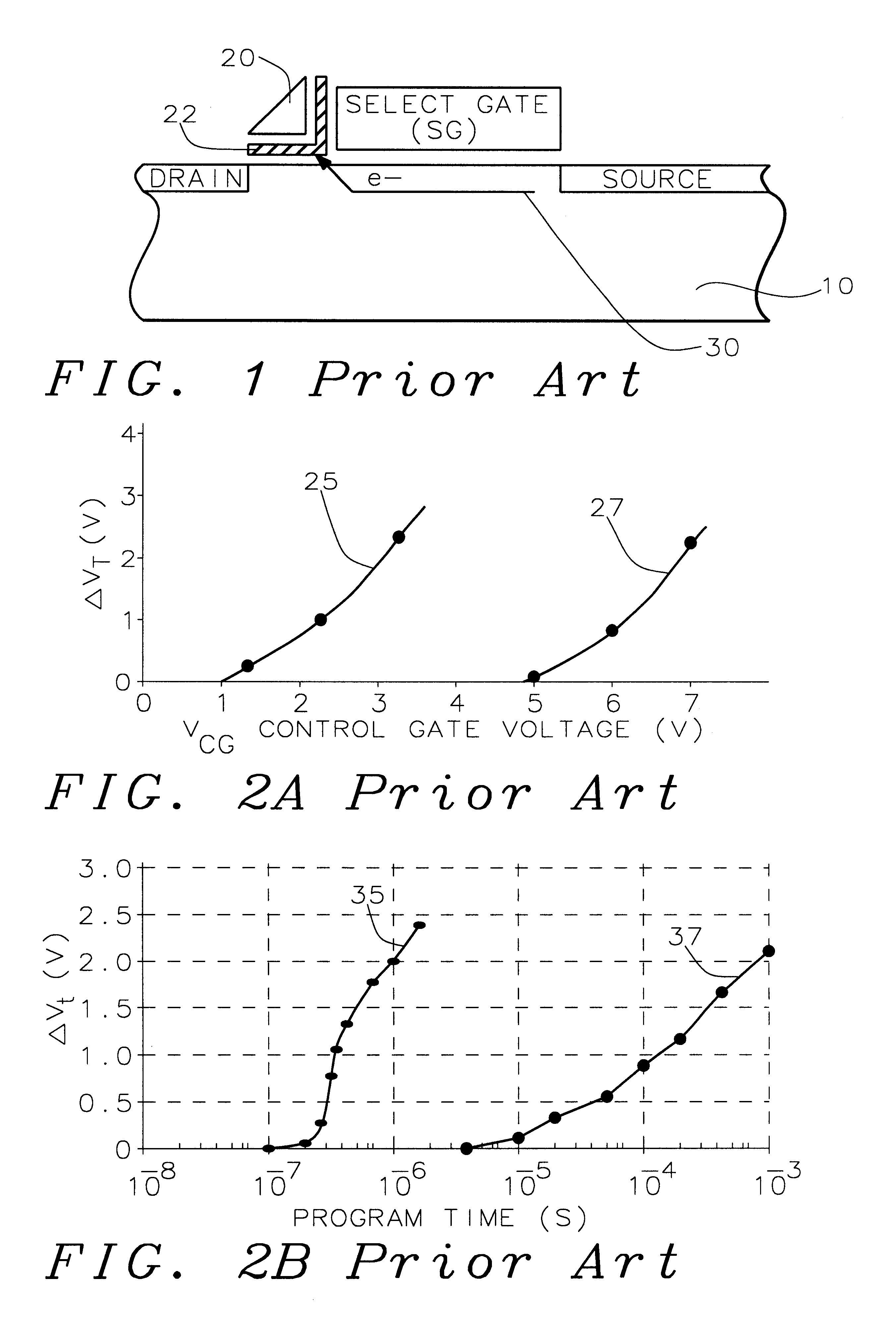
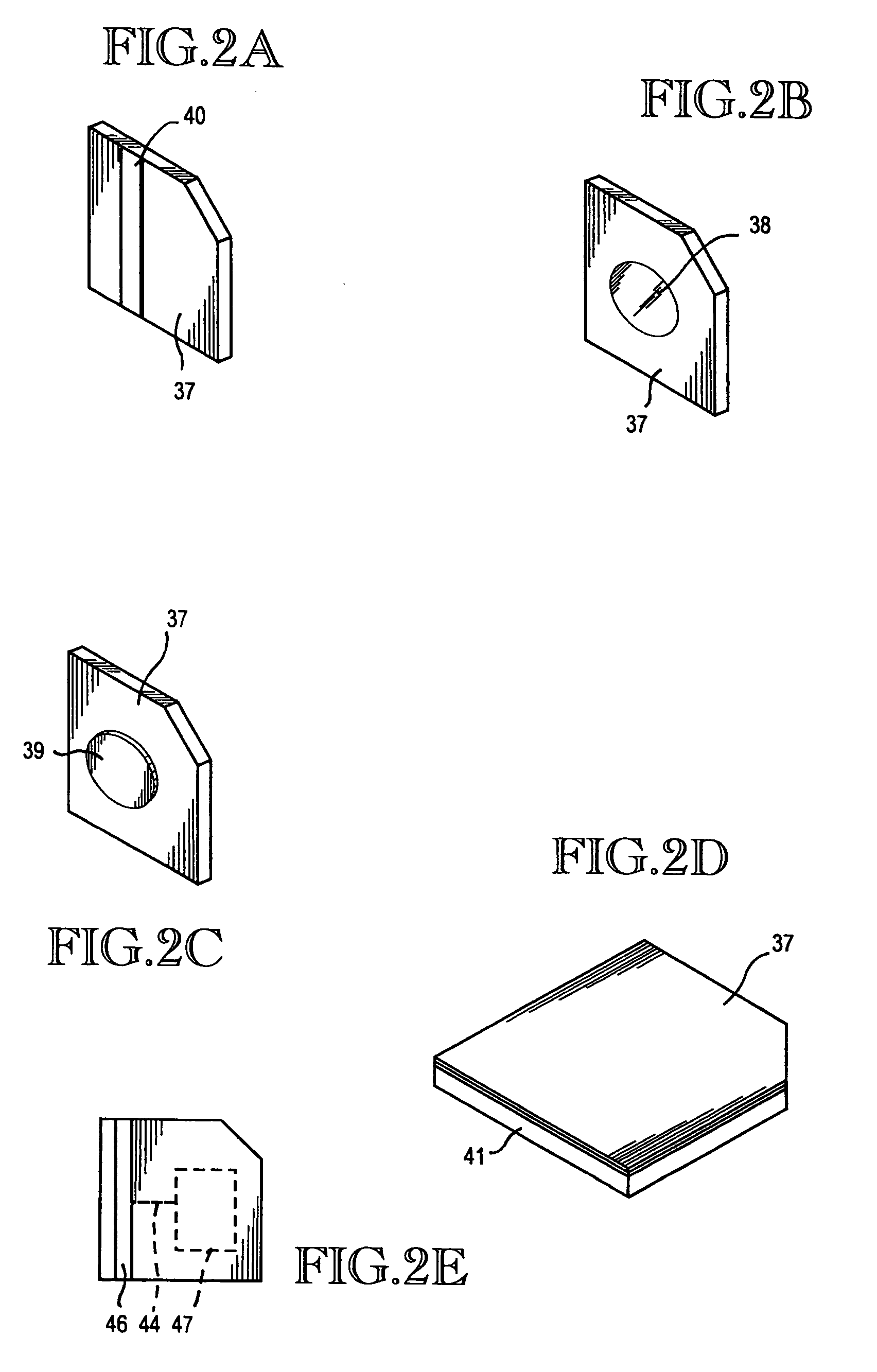
Method of forming a non-volatile electron storage memory and the resulting device
The invention provides a method of forming an electron memory storage device and the resulting device. The device comprises a gate structure which, in form, comprises a first gate insulating layer formed over a semiconductor substrate, a self-forming electron trapping layer of noble metal nano-crystals formed over the first gate insulating layer, a second gate insulating layer formed over the electron trapping layer, a gate electrode formed over the second gate insulating layer, and source and drain regions formed on opposite sides of the gate structure.
Owner:MICRON TECH INC
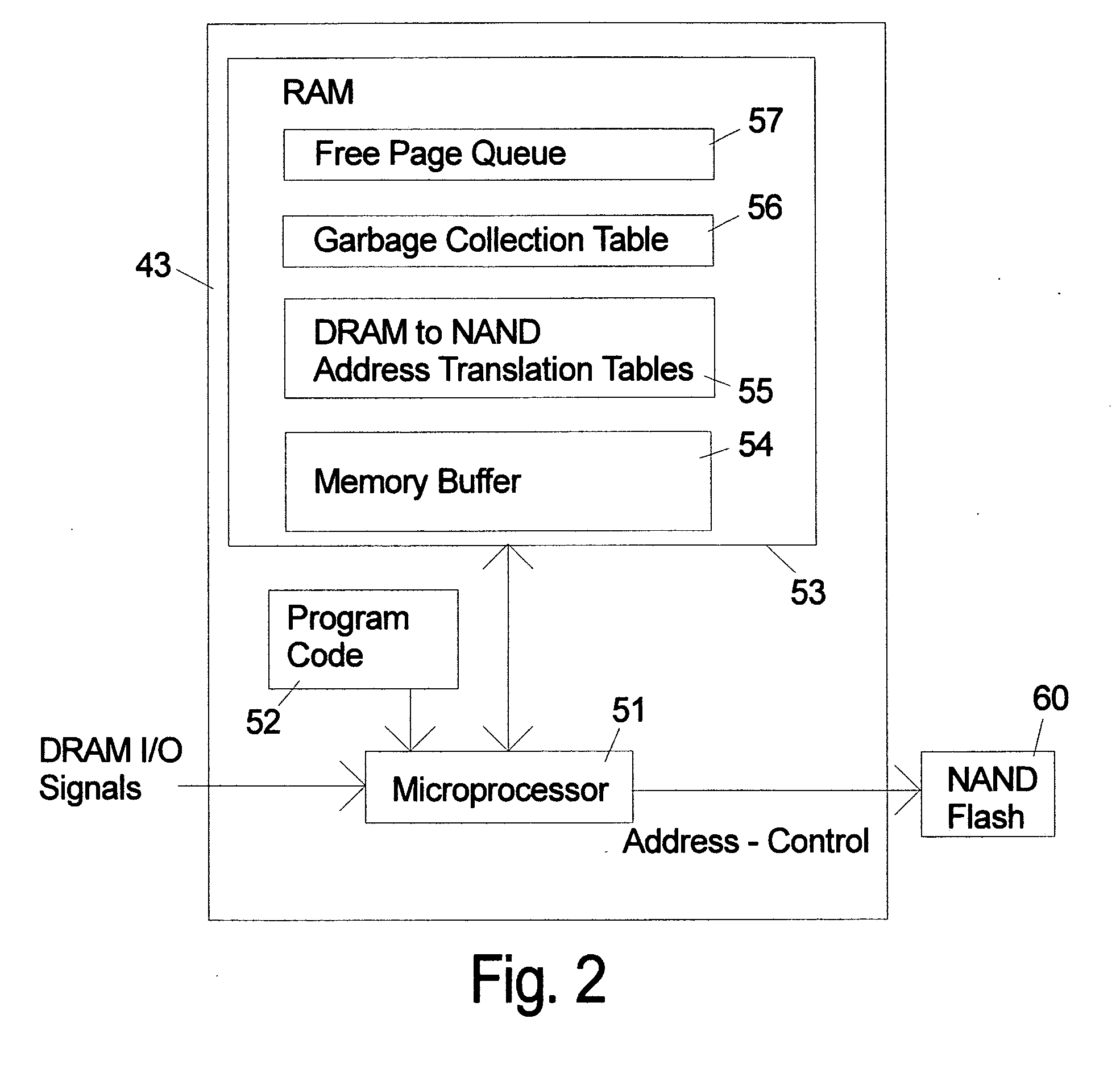
NAND flash module replacement for DRAM module
ActiveUS8185685B2Reduce speedMost efficientMemory architecture accessing/allocationMemory adressing/allocation/relocationProcess memoryControl signal
An electronic memory module according to the invention provides non-volatile memory that can be used in place of a DRAM module without battery backup. An embodiment of the invention includes an embedded microprocessor with microcode that translates the FB-DIMM address and control signals from the system into appropriate address and control signals for NAND flash memory. Wear-leveling, bad block management, garbage collection are preferably implemented by microcode executed by the microprocessor. The microprocessor, additional logic, and embedded memory provides the functions of a flash memory controller. The microprocessor memory preferably contains address mapping tables, free page queue, and garbage collection information.
Owner:WESTERN DIGITAL TECH INC
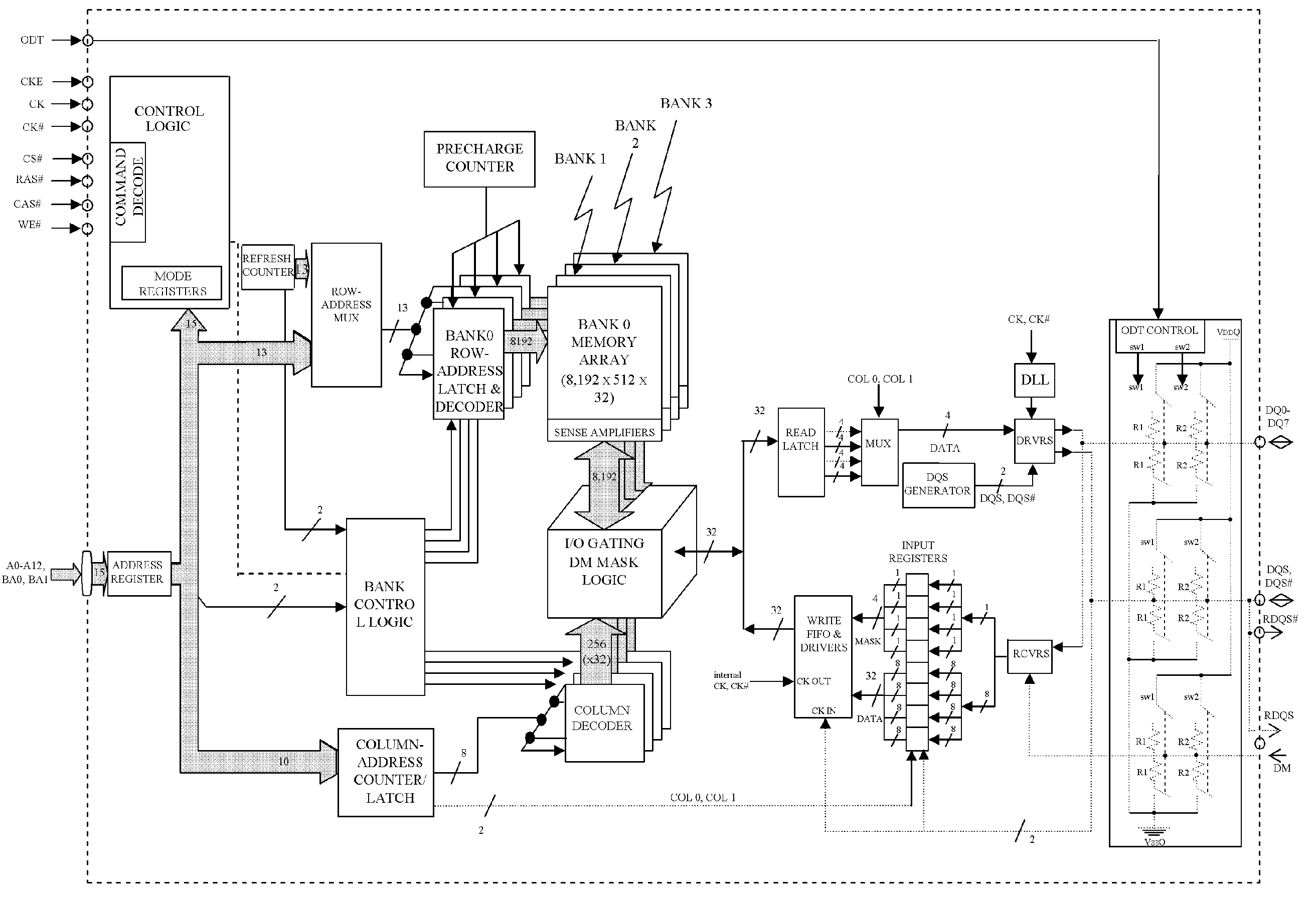
Posted precharge and multiple open-page ram architecture
InactiveUS20050078506A1Operational delayLower performance requirementsDigital storageElectronic memory
A method and architecture that overcomes the problem of latency-caused performance degradation of electronic memory systems. The method involves a “Posted Precharge,” by which an external command for Precharge is given as early as possible, such as immediately following a Read command. The execution of the Precharge is delayed by a precharge counter until all Read / Write commands are completed. By posting a precharge command on a bus at the first available opportunity, multiple pages can be open on the same bank of a memory device. As a result, access latencies are significantly reduced and efficiency of bus in electronic memory systems is significantly improved.
Owner:DATASECURE
Methods and systems for risk mining and for generating entity risk profiles
A computer implemented method for mining risks includes providing a set of risk-indicating patterns on a computing device; querying a corpus using the computing device to identify a set of potential risks by using a risk-identification-algorithm based, at least in part, on the set of risk-indicating patterns associated with the corpus; comparing the set of potential risks with the risk-indicating patterns to obtain a set of prerequisite risks; generating a signal representative of the set of prerequisite risks; storing the signal representative of the set of prerequisite risks in an electronic memory; and aggregating potential risks linked to an entity to an entity risk profile (ERP). A computing device or system for mining risks includes an electronic memory; and a risk-identification-algorithm based, at least in part, on the set of risk-indicating patterns associated with a corpus stored in the electronic memory.
Owner:REFINITIV US ORG LLC
Stacked printed circuit board memory module and method of augmenting memory therein
InactiveUS6418034B1Coupling device connectionsElectrically conductive connectionsEngineeringPrinted circuit board
A stacked printed circuit board memory module in which a plurality of daughter circuit boards can be stacked onto a primary circuit board. The primary board and each of the plurality of daughter boards have electronic memory ICs mounted on the respective surfaces. The primary board and each of the daughter boards have mounted connectors so that the boards can be electronically and mechanically interconnected with another board.
Owner:MICRON TECH INC
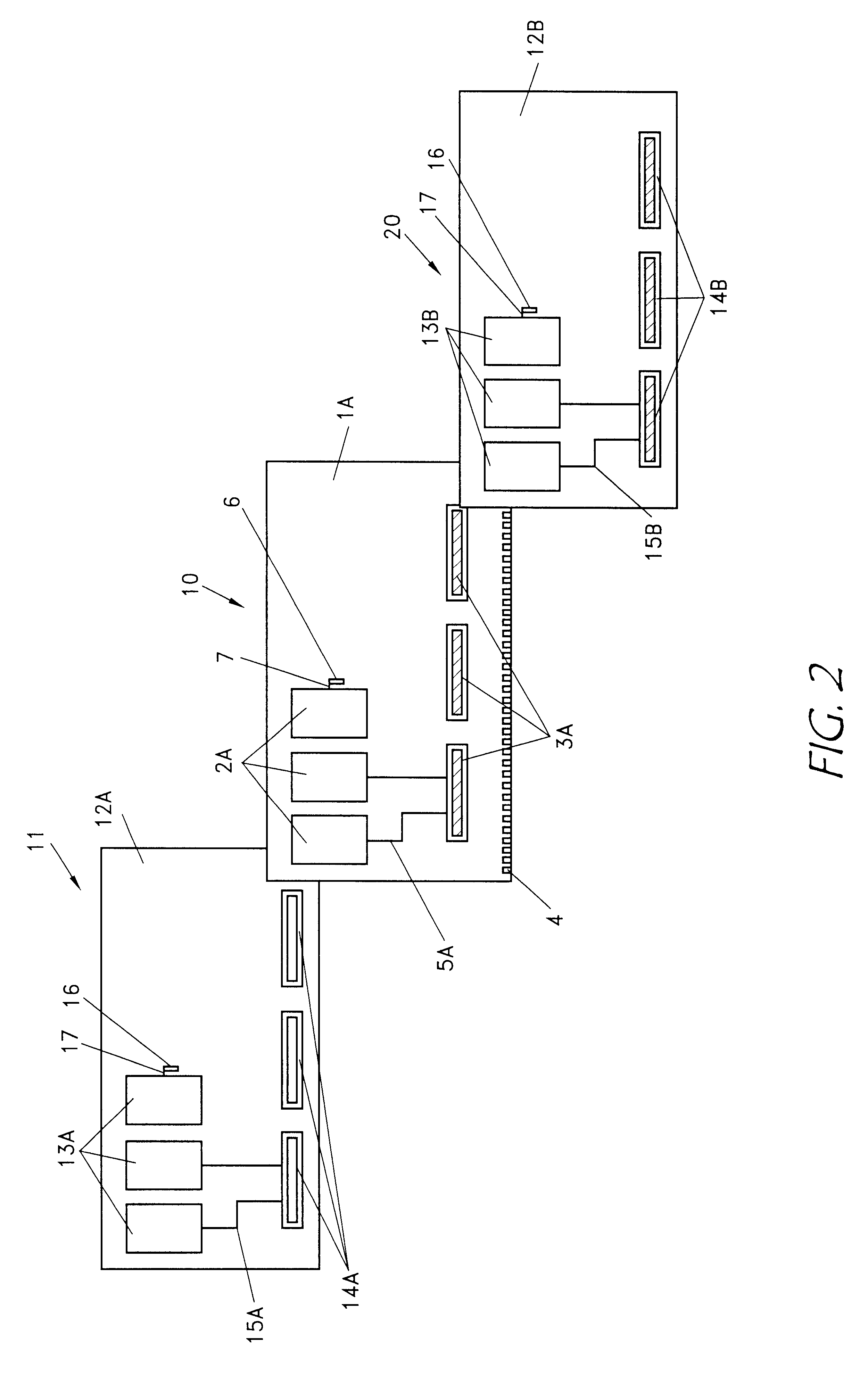
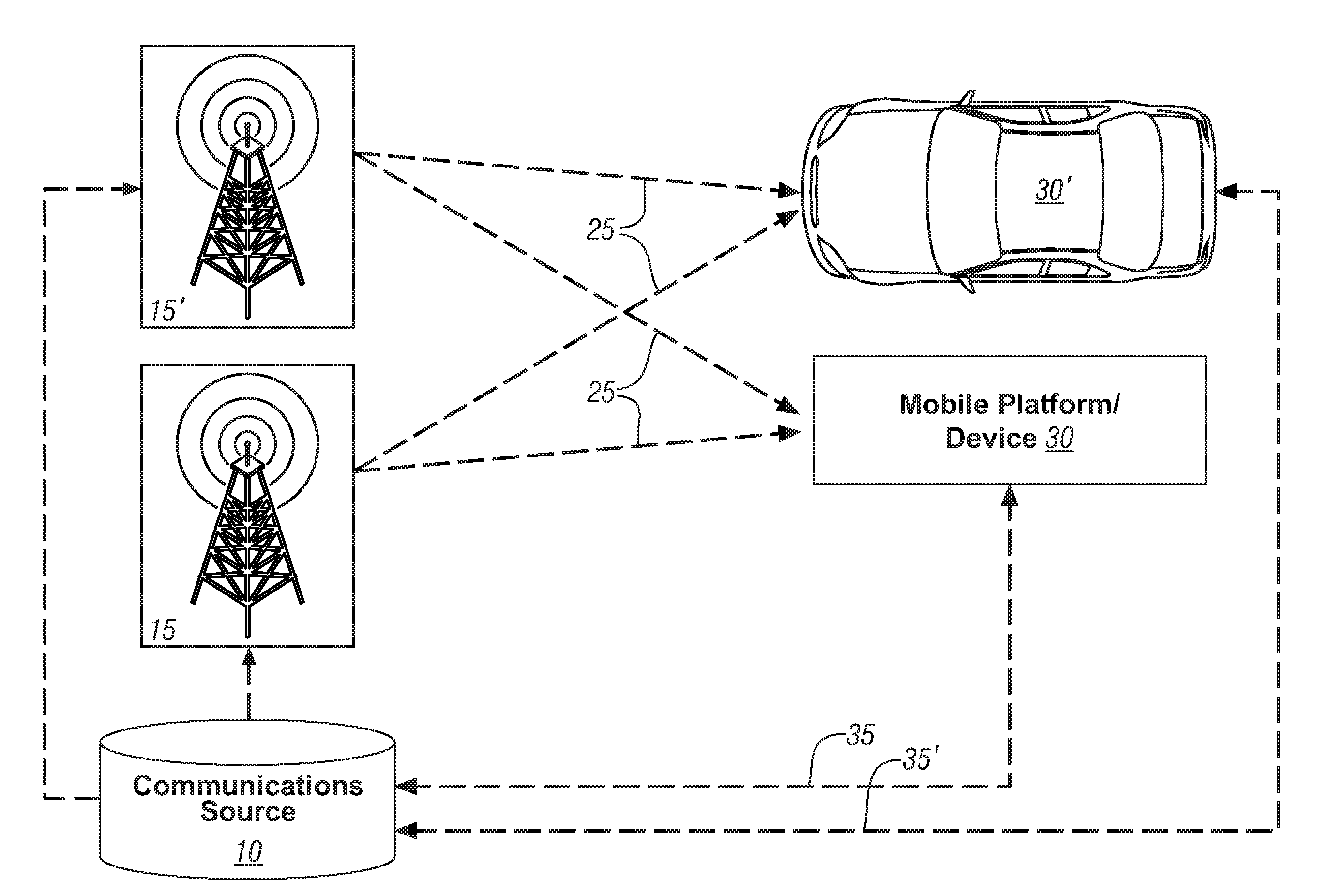
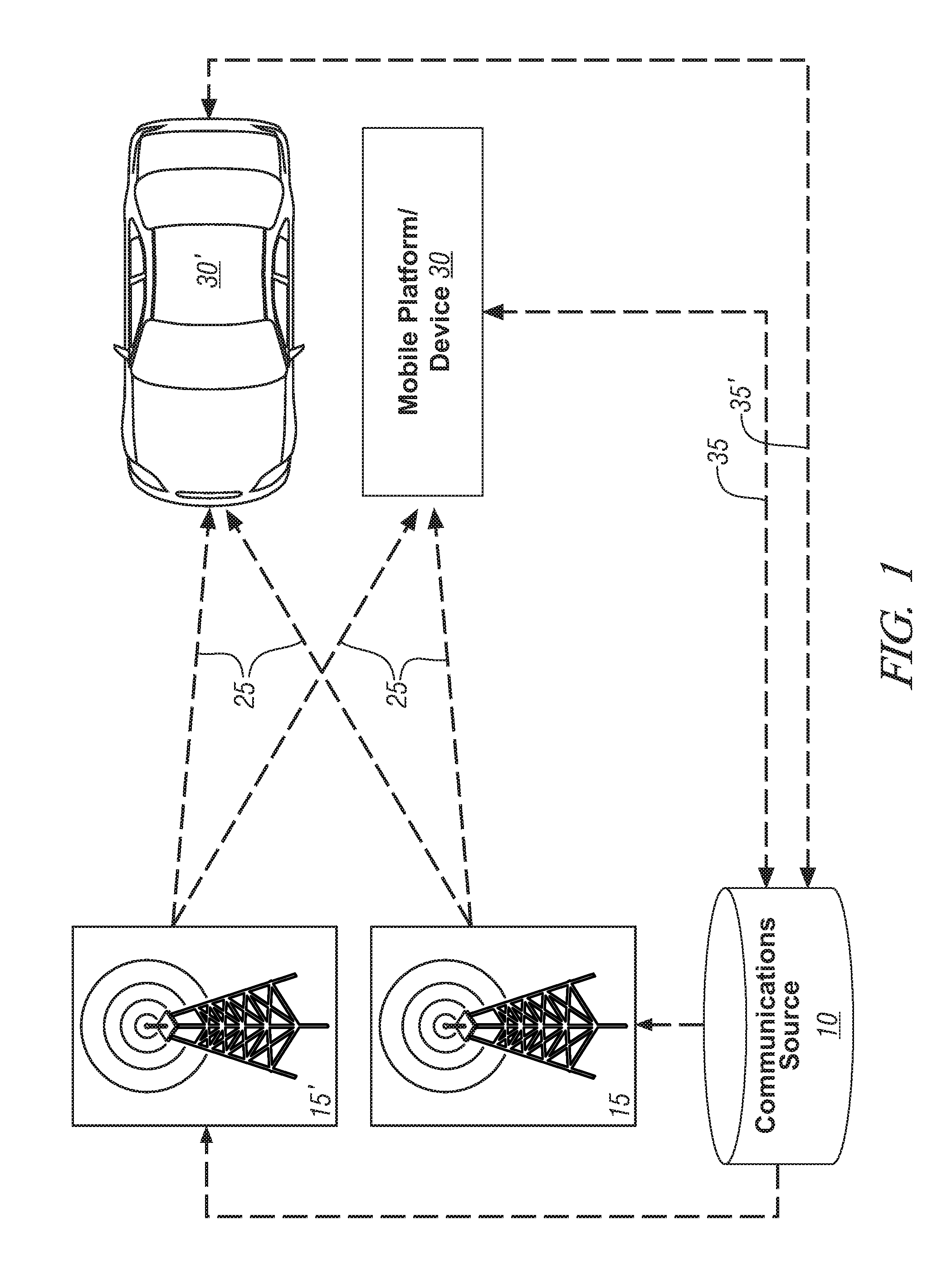
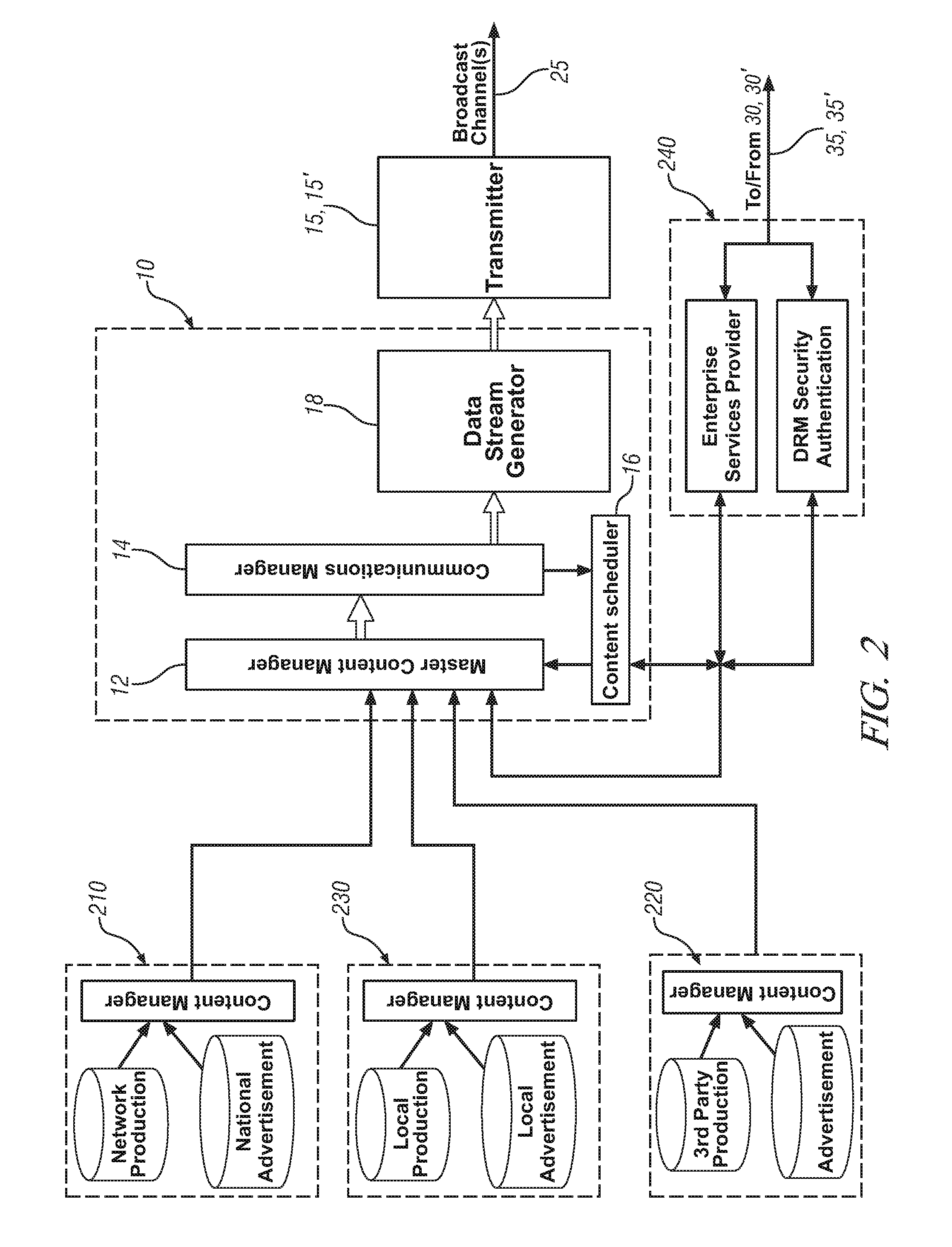
Method and system for communicating information to a user of a mobile platform via broadcast services
ActiveUS20080032721A1Radio/inductive link selection arrangementsWireless commuication servicesHuman–machine interfaceTransceiver
A mobile platform is equipped with a transceiver to receive a broadcast message and to execute two-way wireless communications. The mobile platform is also equipped with an electronic memory storage device, a processor, and a human-machine interface. A first message is formed at the communications source, broadcasted, and received at the mobile platform by way of the transceiver. A portion of the first message is selectively cached in the electronic memory storage device and selectively communicated to the human-machine interface. A second message is formed and wirelessly communicated between the communications source and the mobile platform by way of the two-way wireless communications device.
Owner:GM GLOBAL TECH OPERATIONS LLC
Security for mobile communications device
A mobile communications device for communicating with a wireless network, including an electronic storage having data stored thereon, a processor connected to the storage for accessing the data, a communications sub-system connected to the processor for exchanging signals with the wireless network and with the processor, a user input interface connected to send user input signals to the processor in response to user action, and a security module associated with the processor for detecting a trigger condition and automatically taking a security action if a bypass user action is not detected after detection of the trigger condition.
Owner:HUAWEI TECH CO LTD
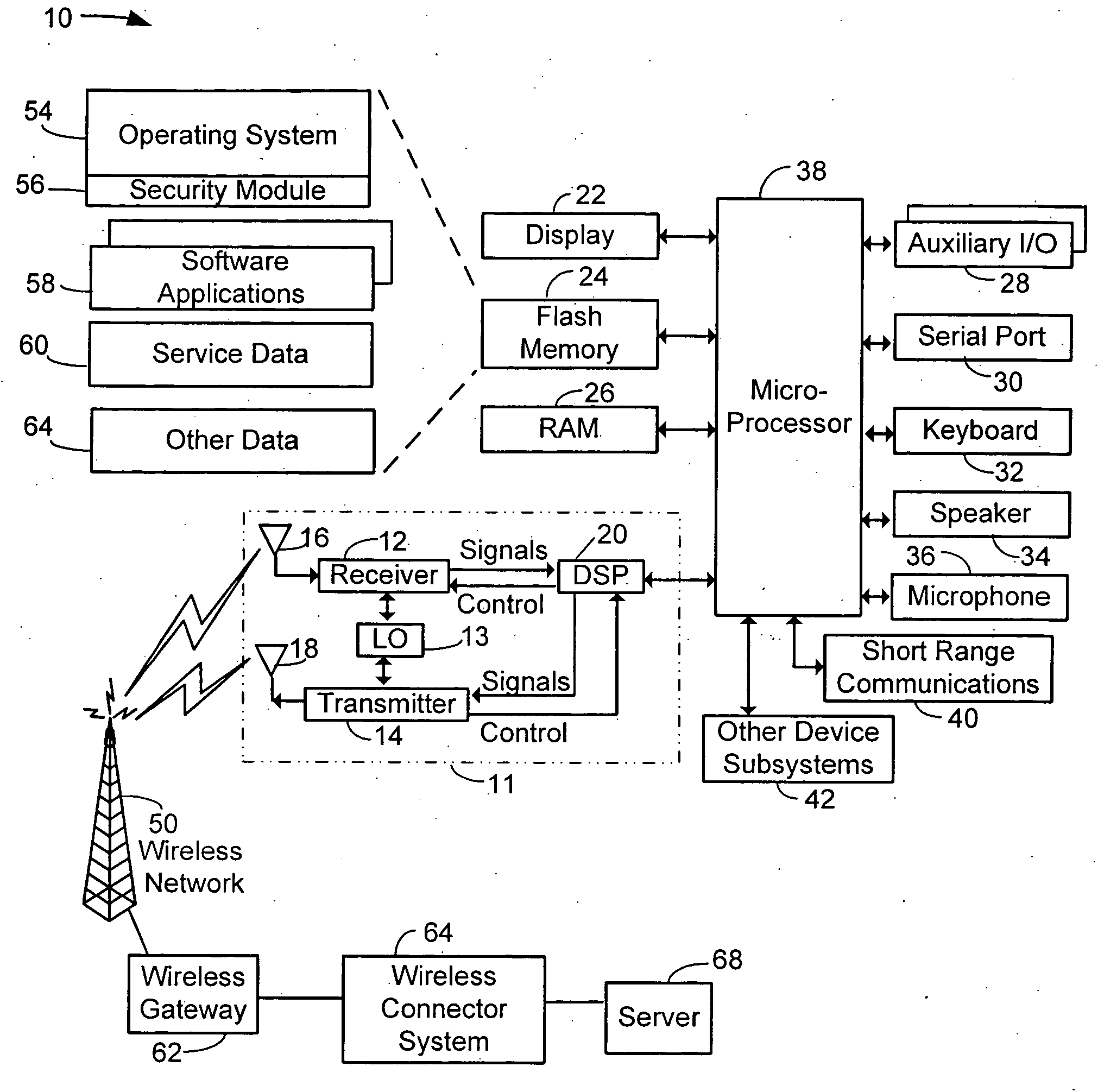
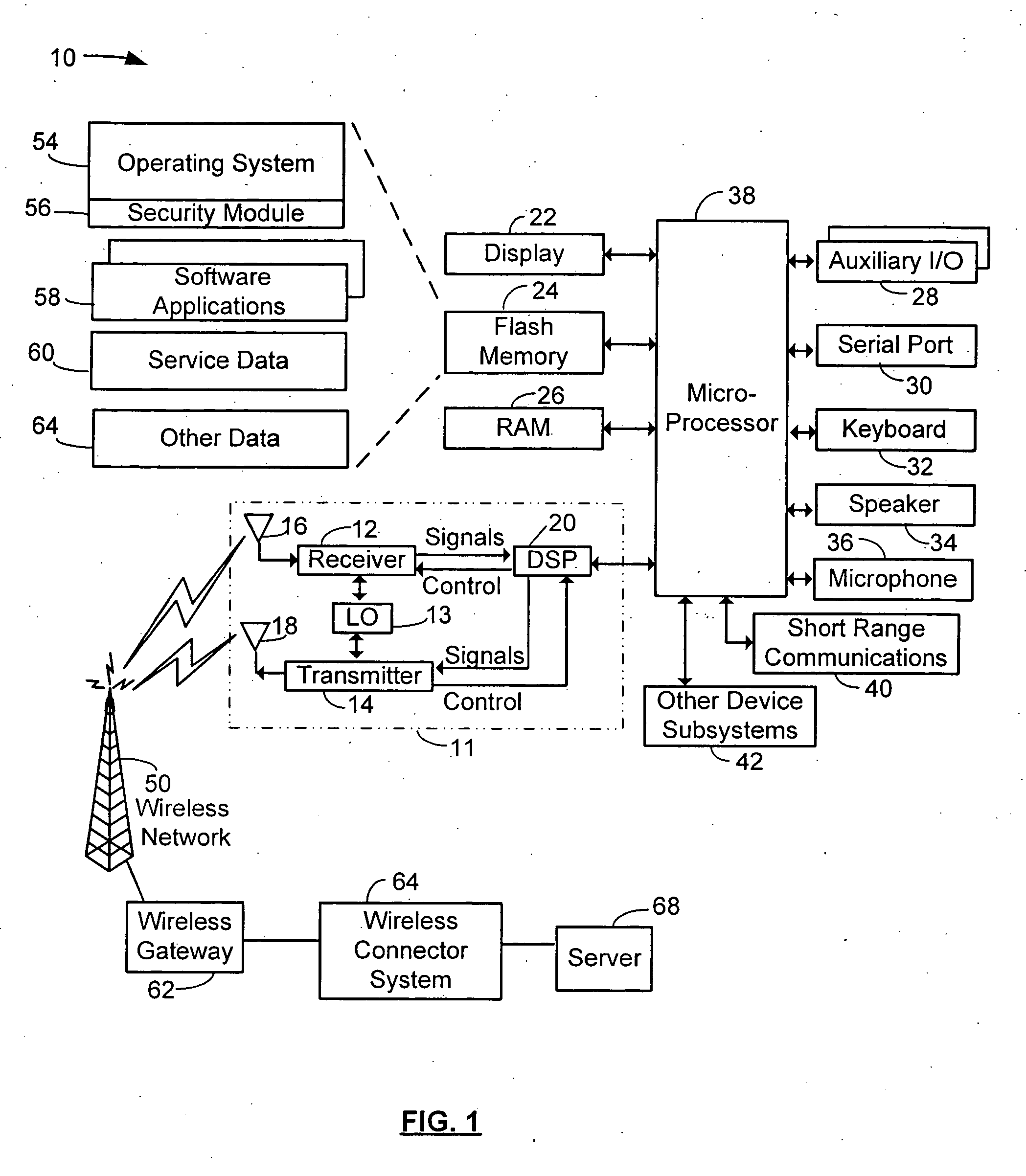
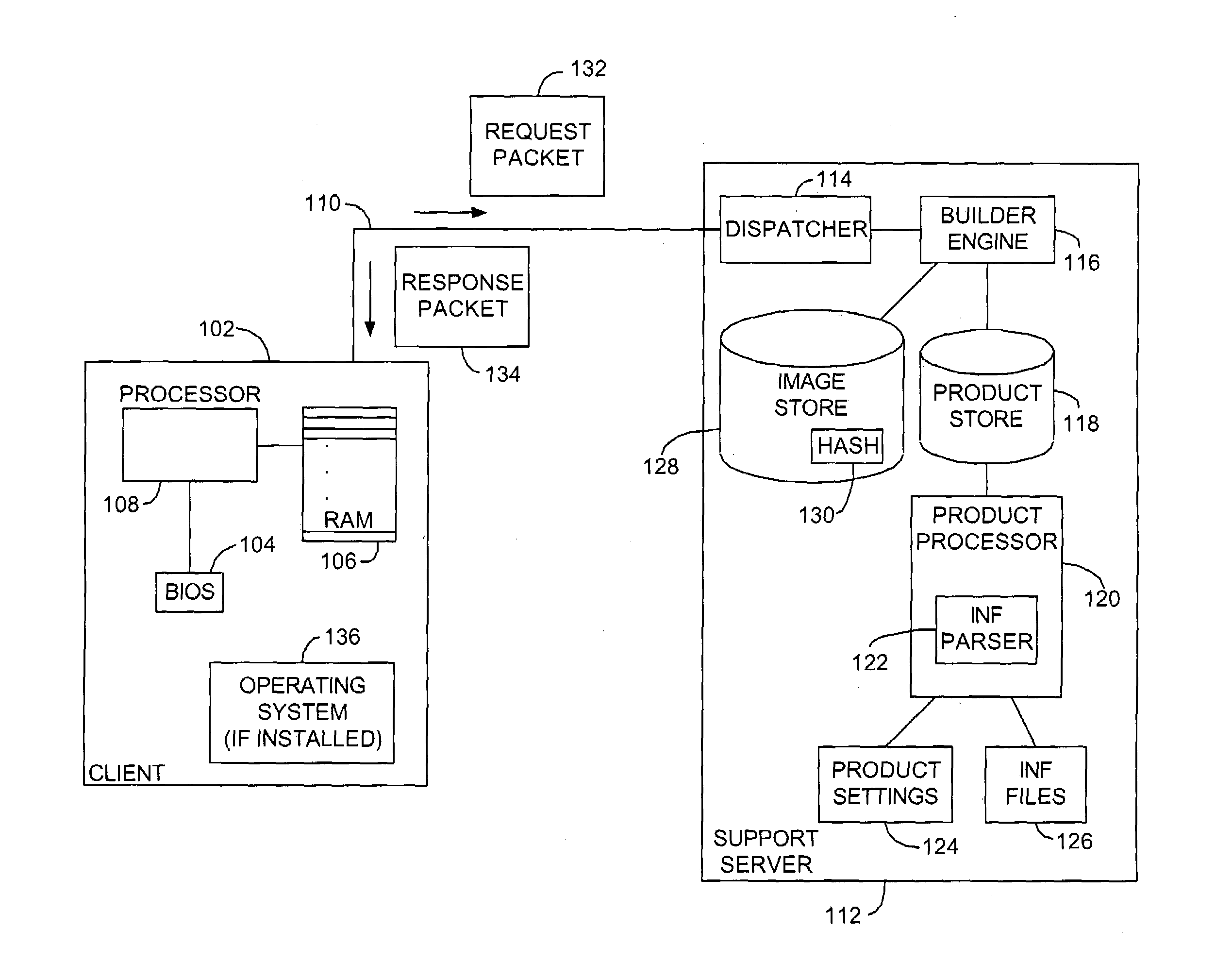
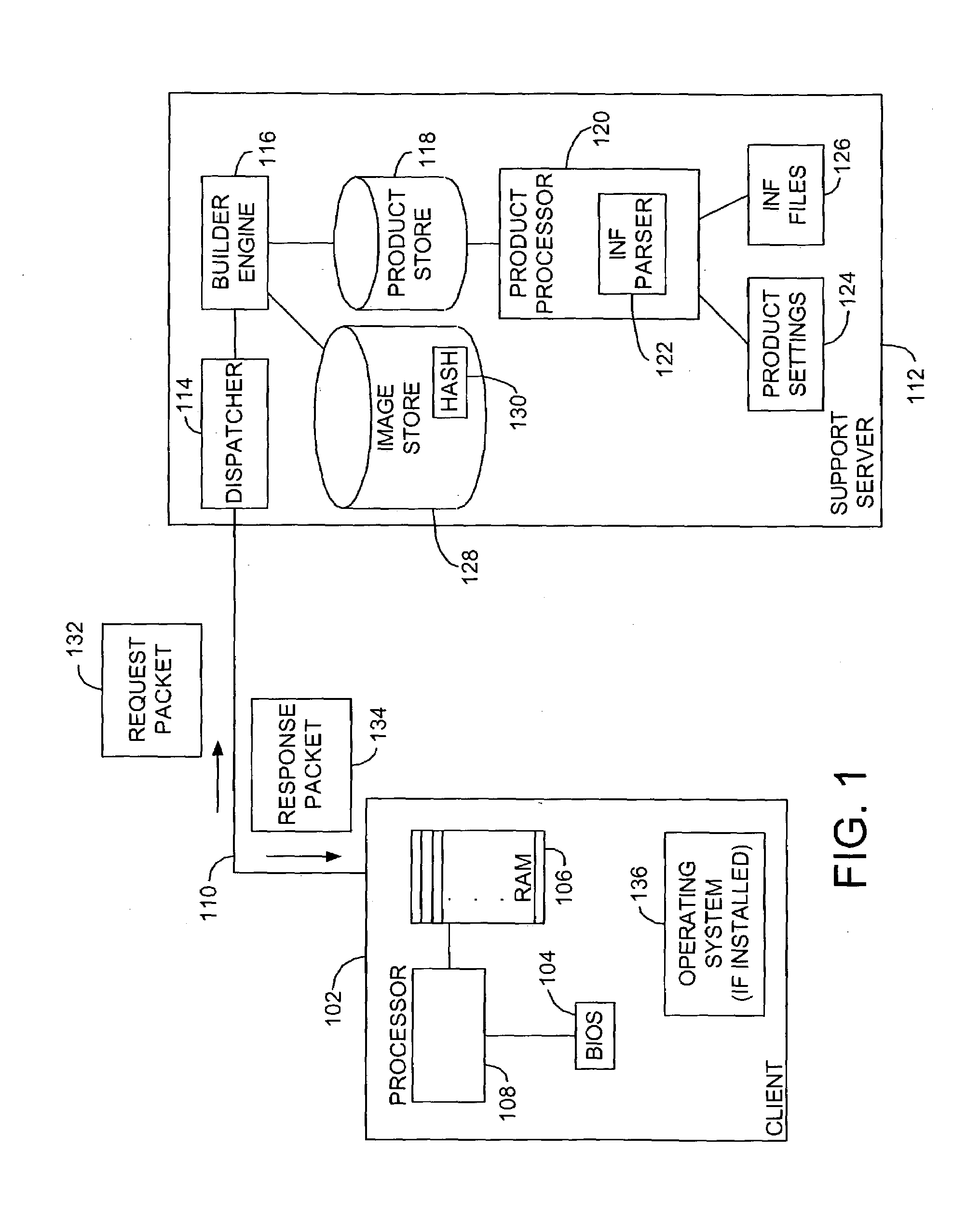
System and method for custom installation of an operating system on a remote client
A platform for remotely installing an operating system on a client machine includes a builder engine, for instance running on a support server. The builder engine may interrogate a remote client, for instance a diskless thin client or a machine having a disk but malfunctioning, and receive a machine state image from that machine. The builder engine may then assemble a customized image or kernel of an operating system such as Microsoft Windows™ for transmission to the client. A file system may be initialized in electronic memory, or otherwise and the machine may commence operation, without having executed an operating system setup process. In embodiments, the client machine may then link to a complete image of an operating system to reinstall a comprehensive version of that system, or perform other tasks.
Owner:MICROSOFT TECH LICENSING LLC
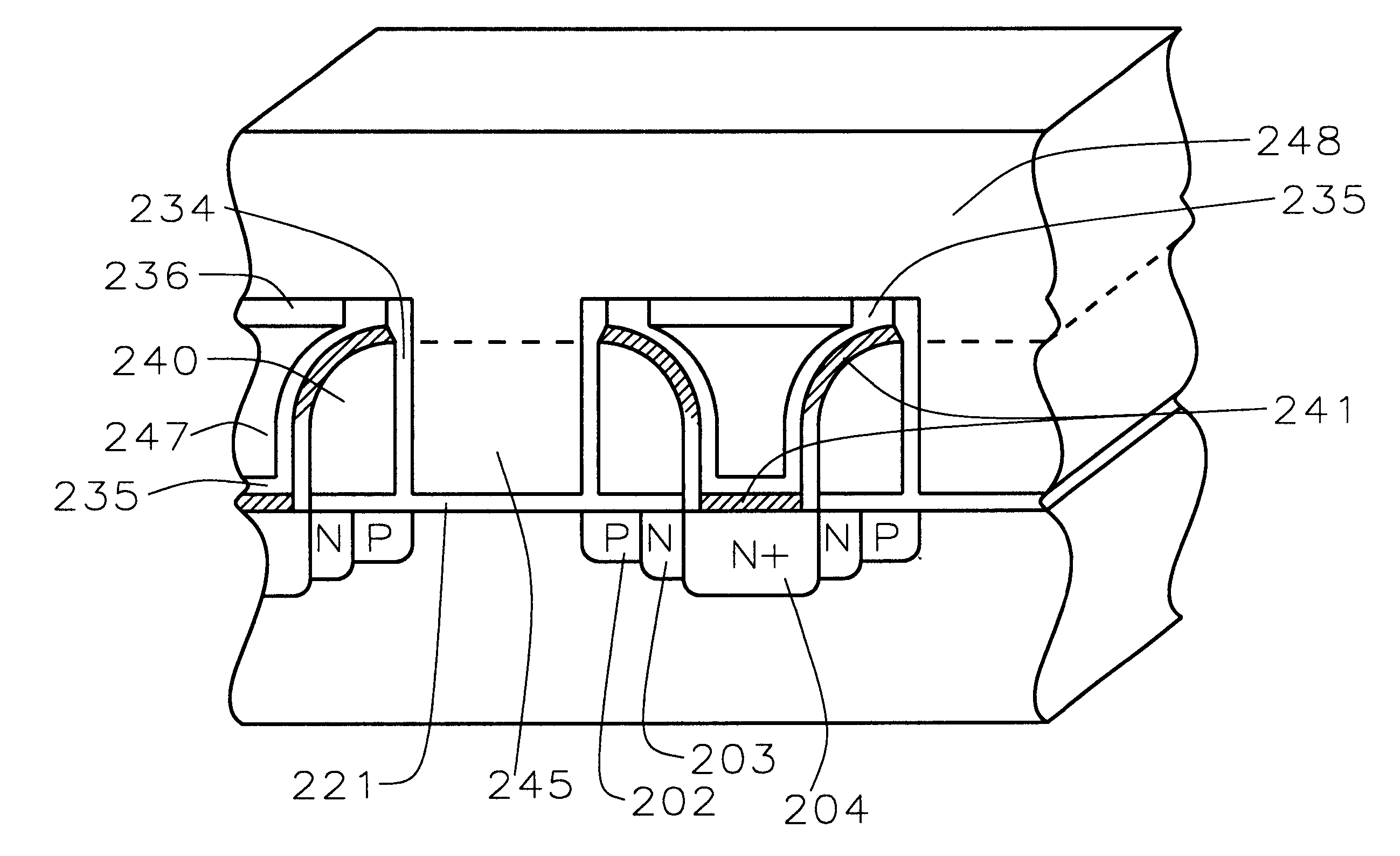
Damascene architecture electronics storage and method for making same
InactiveUS20040029345A1Easy to integrateImproved floating gate-control gate capacitanceSemiconductor/solid-state device manufacturingSemiconductor devicesEngineeringElectronics
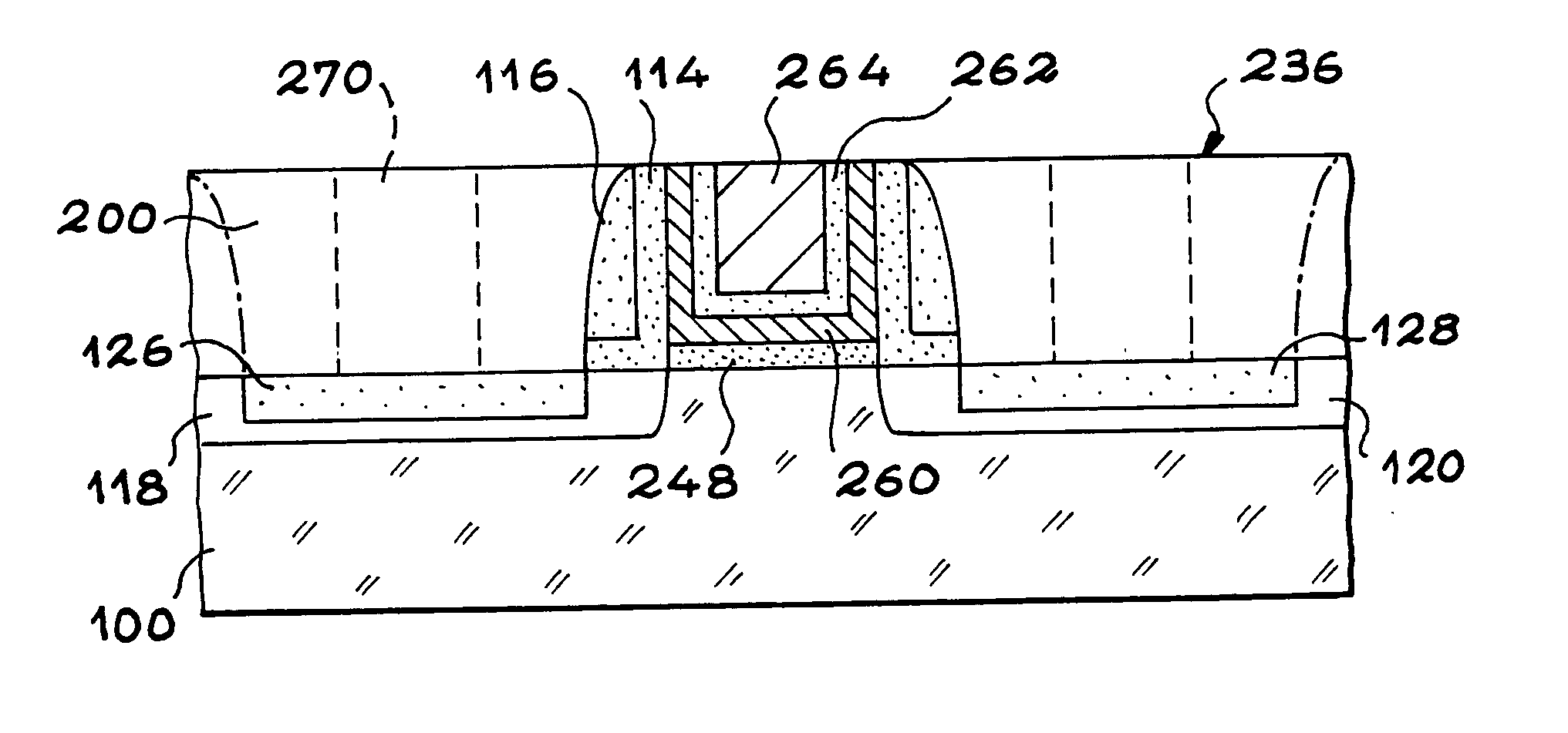
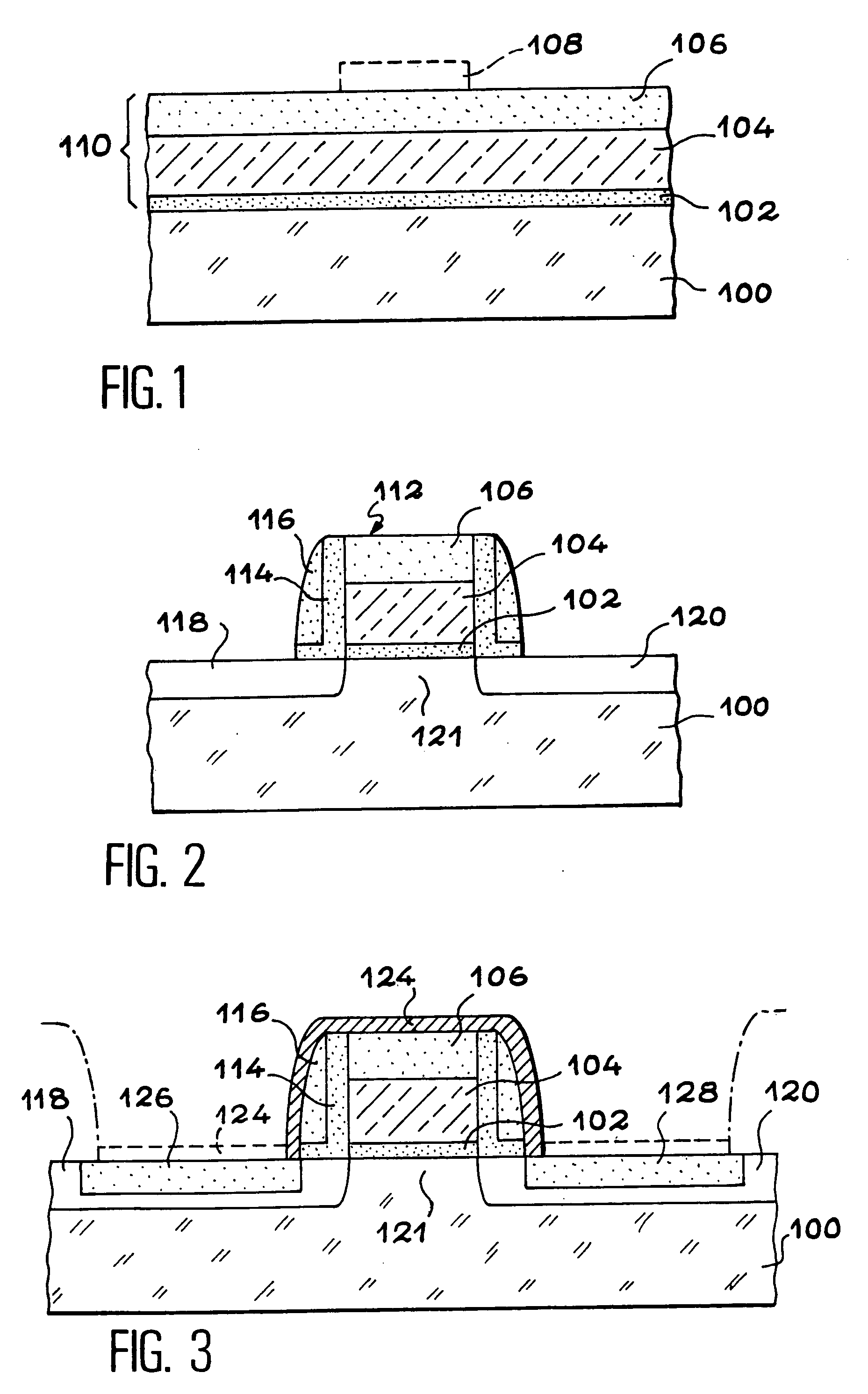
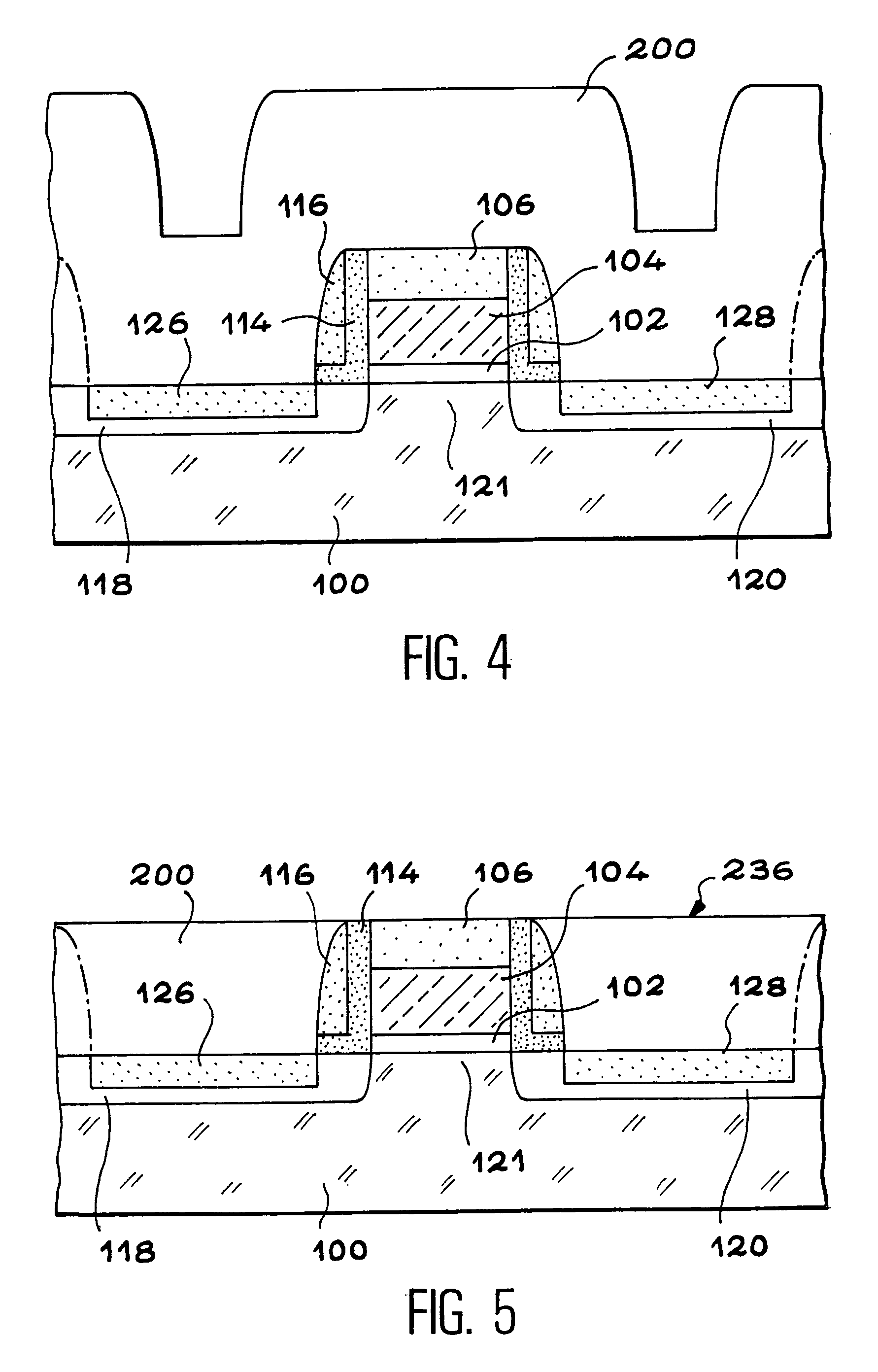
An electronic memory having a source (118) and a drain (120) comprising on a substrate (100) a floating gate (260) and a control gate (264). According to the invention, the floating gate (260) has a substantially U-shaped cross-section defining a space within which the control gate (264) is arranged.
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES +1
Methods and systems for risk mining and for generating entity risk profiles and for predicting behavior of security
A computer implemented method for mining risks includes providing a set of risk-indicating patterns on a computing device; querying a corpus using the computing device to identify a set of potential risks by using a risk-identification-algorithm based, at least in part, on the set of risk-indicating patterns associated with the corpus; comparing the set of potential risks with the risk-indicating patterns to obtain a set of prerequisite risks; generating a signal representative of the set of prerequisite risks; storing the signal representative of the set of prerequisite risks in an electronic memory; aggregating potential risks linked to an entity to an entity risk profile (ERP); and predicting a movement in a security associated with an entity.
Owner:REFINITIV US ORG LLC
Wireless gateway supporting a plurality of networks
In accordance with various aspects of the disclosure, systems and methods are illustrated for an apparatus comprising a modem component, a wireless communications component, at least one processor, and at least one tangible electronic memory storing data and numerous computer-executable modules to enable wireless hotspots with multiple network identifiers. Examples of at least some of the computer-executable modules includes, but is not limited to an input module, network identifier module, session management module, network management module, automatic location management module, authentication module, bandwidth negotiation module, billing interface module, and activity-based location module.
Owner:COMCAST CABLE COMM LLC
Wireless Gateway Supporting A Plurality of Networks
ActiveUS20110044304A1Telephonic communicationWireless network protocolsSession managementModem device
In accordance with various aspects of the disclosure, systems and methods are illustrated for an apparatus comprising a modem component, a wireless communications component, at least one processor, and at least one tangible electronic memory storing data and numerous computer-executable modules to enable wireless hotspots with multiple network identifiers. Examples of at least some of the computer-executable modules includes, but is not limited to an input module, network identifier module, session management module, network management module, automatic location management module, authentication module, bandwidth negotiation module, billing interface module, and activity-based location module.
Owner:COMCAST CABLE COMM LLC
Stand-alone system for storing books in electronic memory
InactiveUS20050228821A1Coin-freed apparatus detailsInternal/peripheral component protectionDisplay deviceMemory cards
The system includes a memory card, such as flash memory, containing information which would otherwise be published in conventional book form, such as a textbook, wherein the information on the card is in read-only form and further includes security elements, which prevent unauthorized access to the book content in the card. The system also includes a display device for receiving the memory card, reading the information in the memory card and displaying the information, wherein the display device is a stand-alone system, incapable of being connected to a network or other system so as to prevent transfer or copying of information from the display device. The system further includes a vending machine for dispensing the memory cards in response to a selection by the customer / user, the memory cards including security elements.
Owner:GOLD CHARLES D
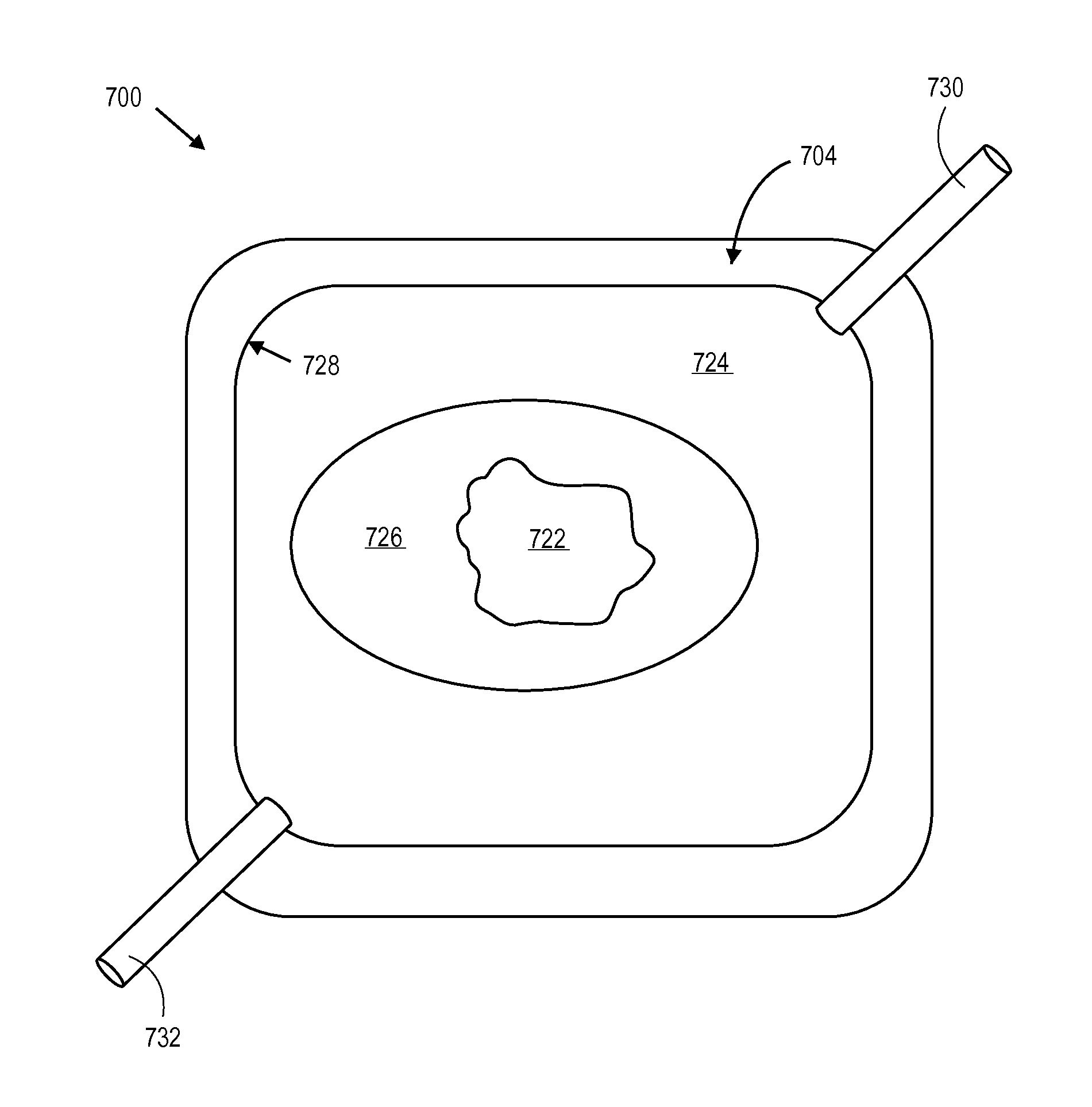
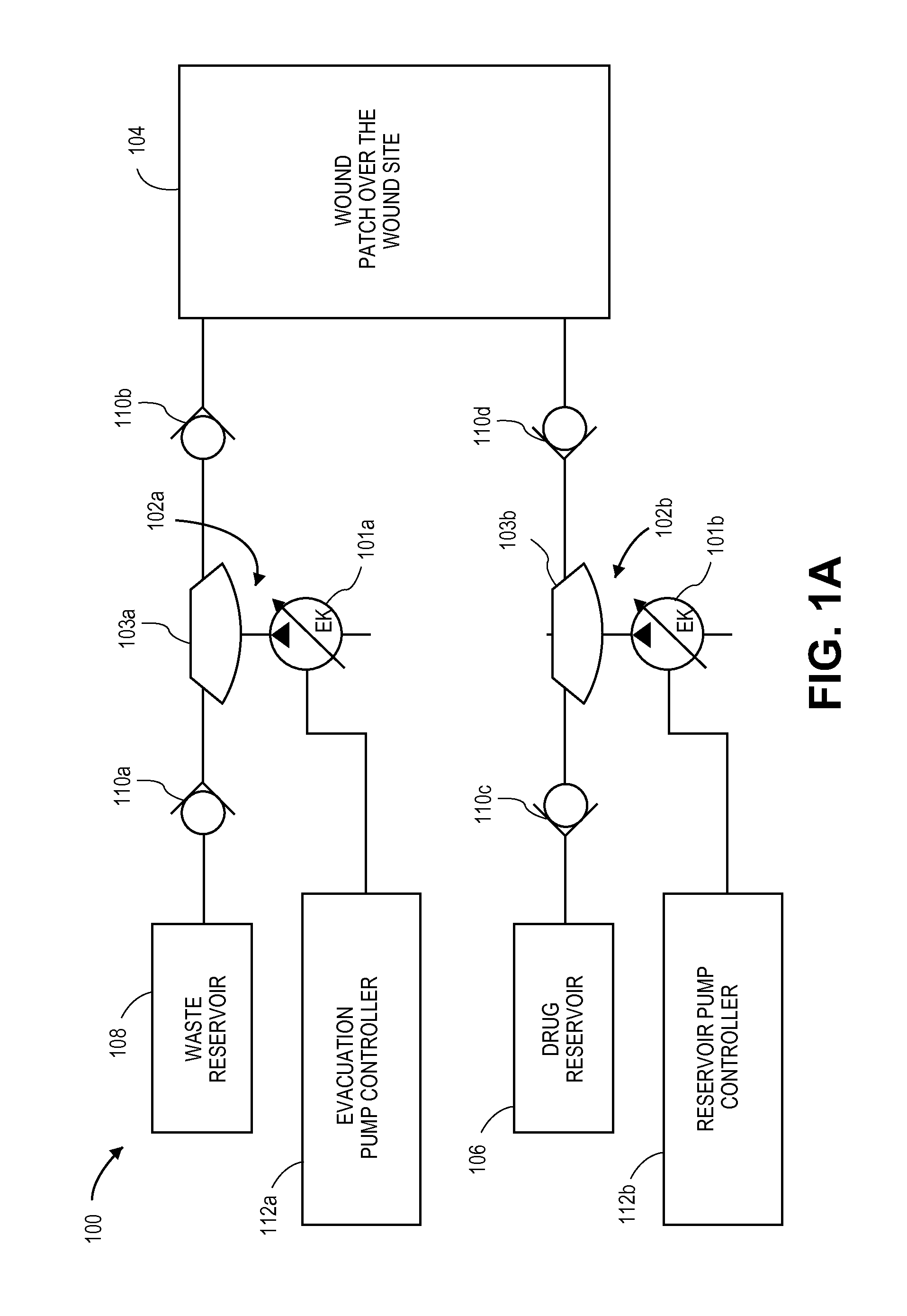
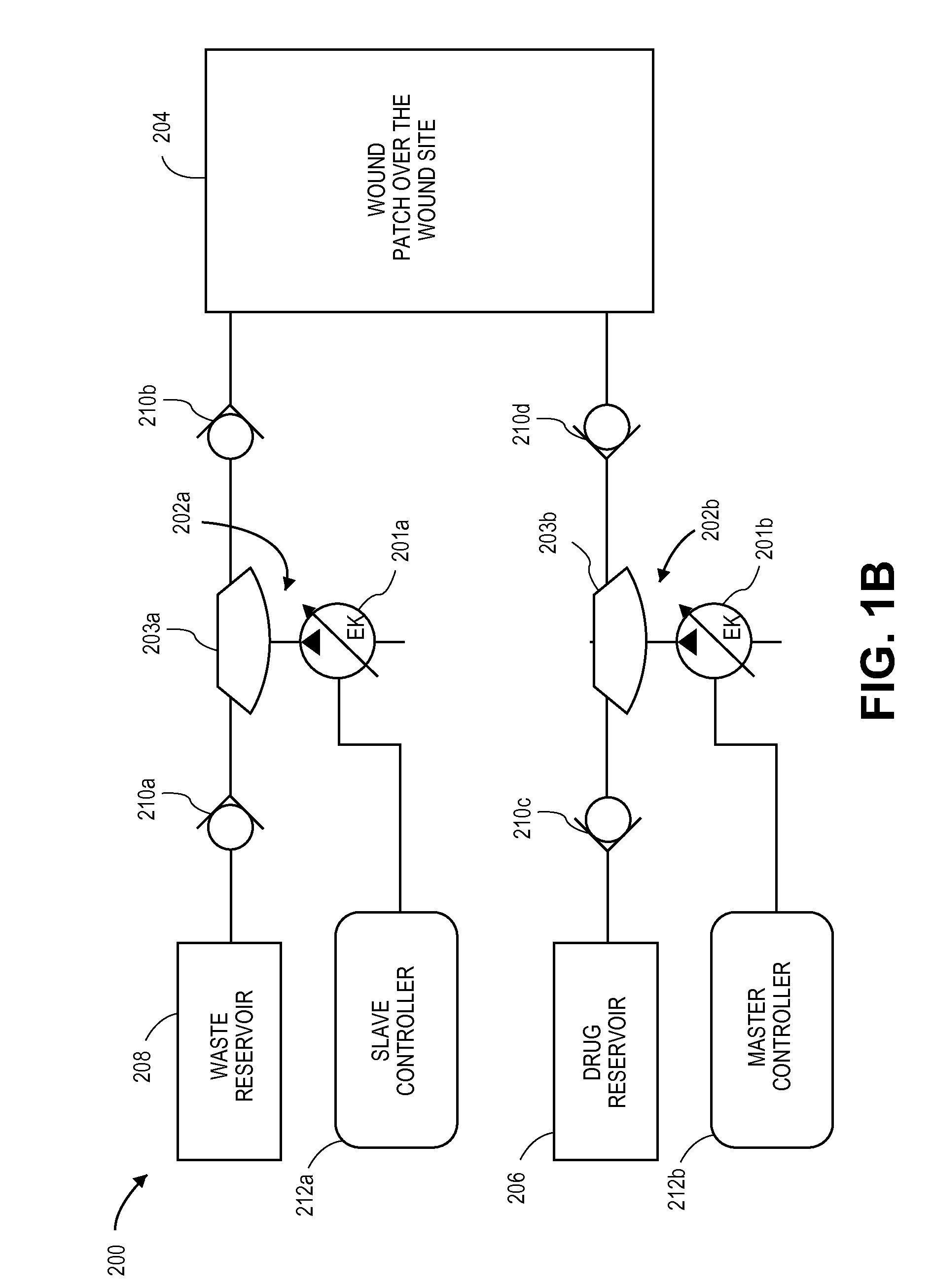
Electrokinetic pump based wound treatment system and methods
A wound treatment system includes a patch, first and second fluid reservoirs, an electrokinetic pump assembly, and a controller. The patch is configured to enclose a wound area and includes an inlet and an outlet. The first fluid reservoir is fluidically connected to the inlet and the second fluid reservoir is fluidically connected to the outlet. The electrokinetic pump assembly is configured to pump a first treatment fluid from the first fluid reservoir into the patch through the inlet and to pump fluid from the patch through the outlet and into the second fluid reservoir. The controller is configured to operate the electrokinetic pump assembly and to include an electronic memory containing computer readable instructions for operating the electrokinetic pump assembly to perform a wound therapy protocol in the wound area.
Owner:TELEFLEX LIFE SCI PTE LTD
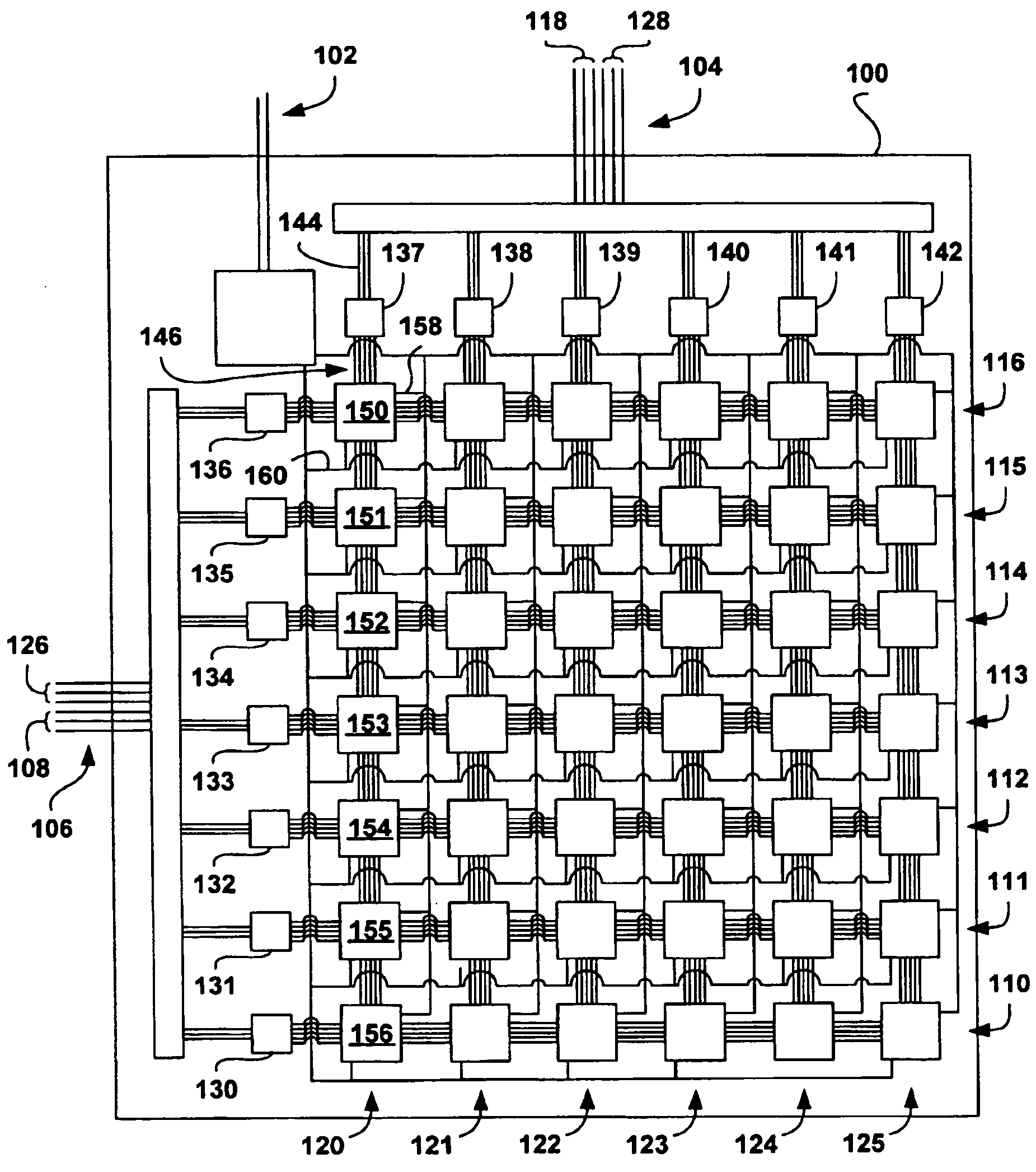
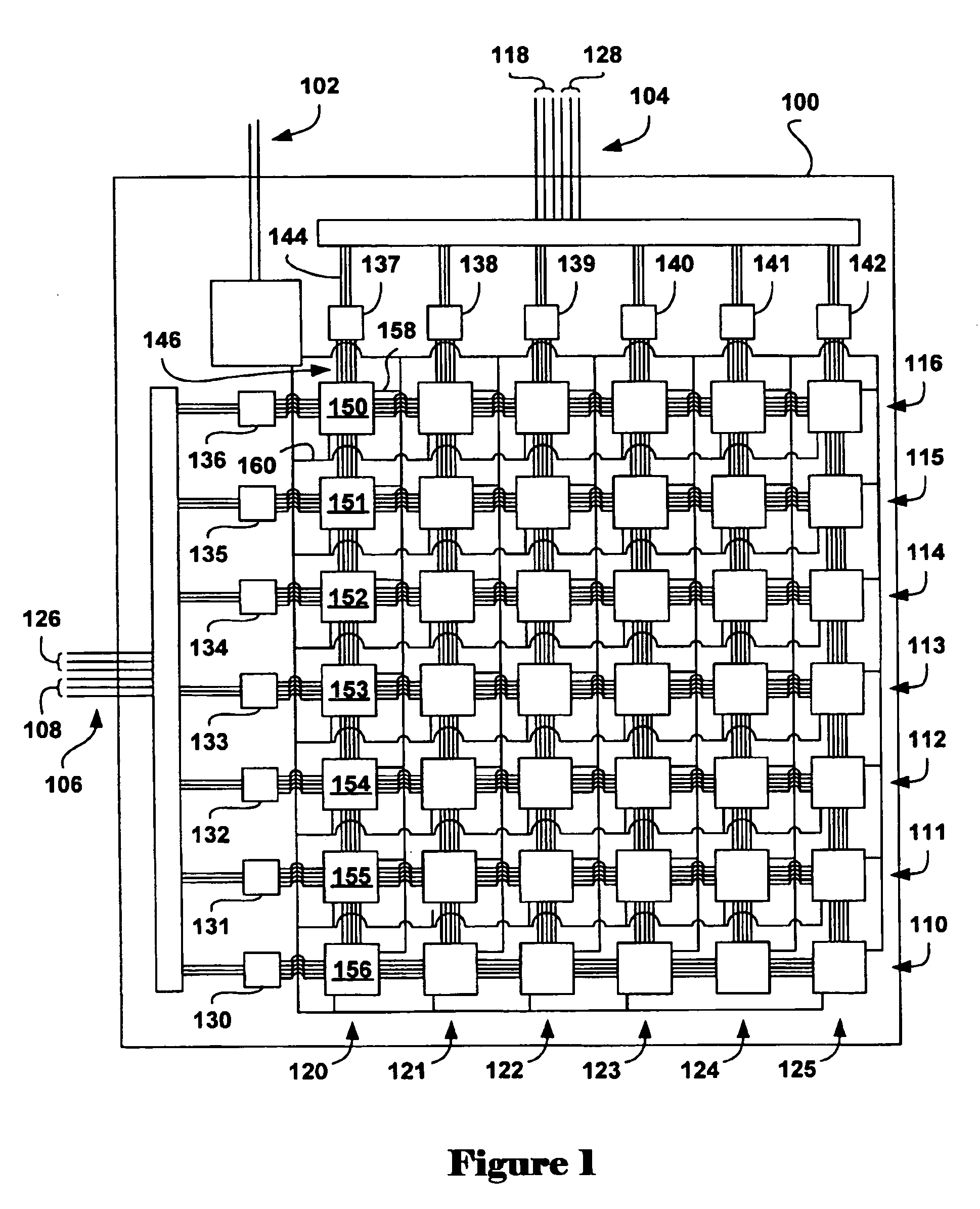
Defect-tolerant and fault-tolerant circuit interconnections
ActiveUS20050055387A1Increase currentHigh voltageNanoinformaticsCode conversionFault toleranceElectricity
Methods for increasing defect tolerance and fault tolerance in systems containing interconnected components, in which a signal level is classified as belonging to one of a plurality of different, distinguishable classes based on one or more thresholds separating the signal-level classes, and defect-and-fault tolerant systems embodying the methods. An electronic-device embodiment including an array of nanowire crossbars, the nanoscale memory elements within the nanowire crossbars addressed through conventional microelectronic address lines, and a method embodiment for providing fault-tolerant interconnection interfaces with electrically distinguishable signal levels are described. In the described embodiment, in order to interconnect microelectronic address lines with the nanowire crossbars within the electronic memory, an address encoding technique is employed to generate a number of redundant, parity-check address lines to supplement a minimally required set of address signal lines needed to access the nanoscale memory elements.
Owner:VALTRUS INNOVATIONS LTD +1
Techniques for directory server integration
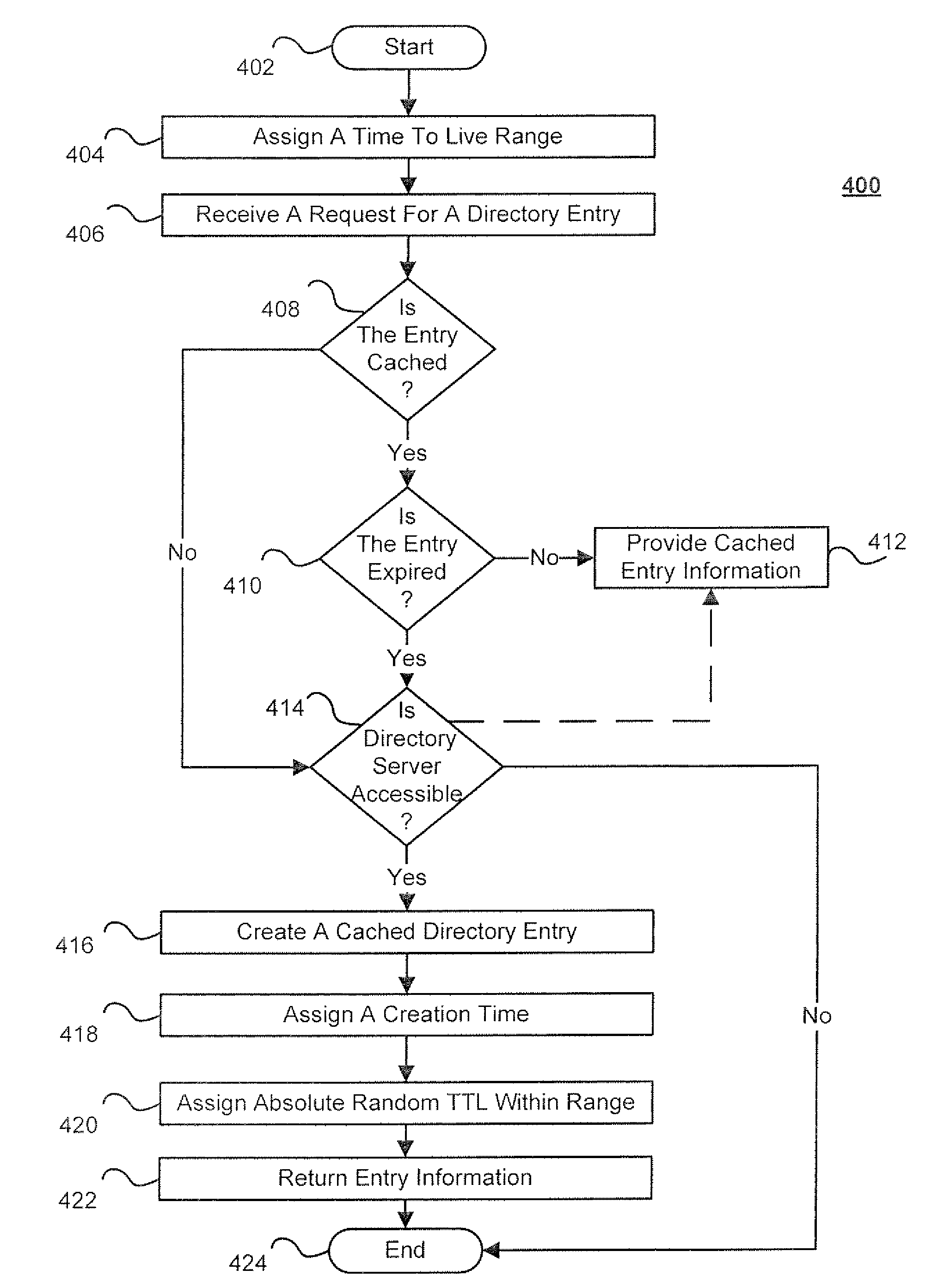
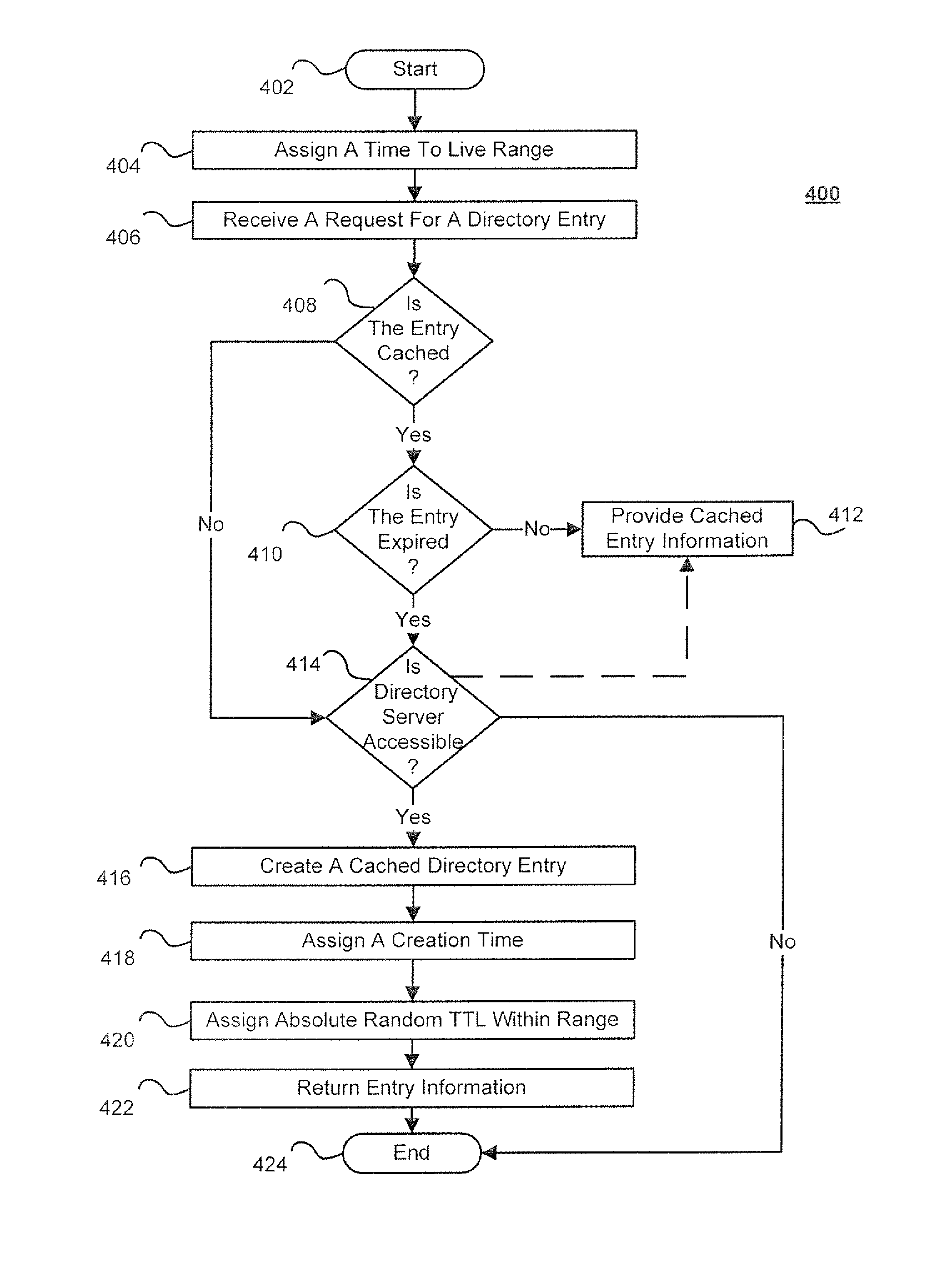
ActiveUS8209491B2Reduce the amount requiredSpecial data processing applicationsMemory systemsExpiration TimeTime range
Techniques for directory server integration are disclosed. In one particular exemplary embodiment, the techniques may be realized as a method for directory server integration comprising setting one or more parameters determining a range of permissible expiration times for a plurality of cached directory entries, creating, in electronic storage, a cached directory entry from a directory server, assigning a creation time to the cached directory entry, and assigning at least one random value to the cached directory entry, the random value determining an expiration time for the cached directory entry within the range of permissible expiration times, wherein randomizing the expiration time for the cached directory entry among the range of permissible expiration times for a plurality of cached directory entries reduces an amount of synchronization required between cache memory and the directory server at a point in time.
Owner:CA TECH INC
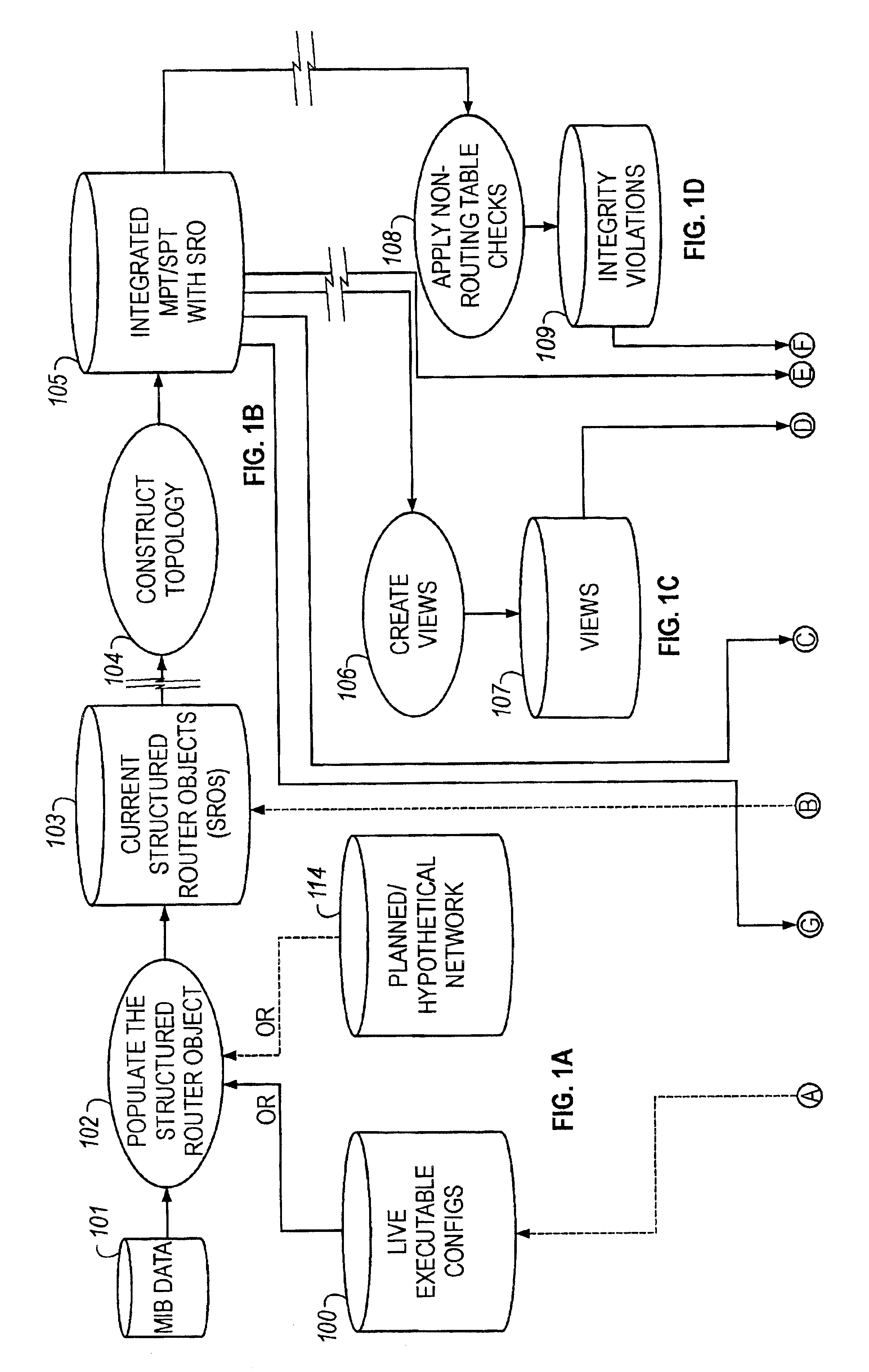
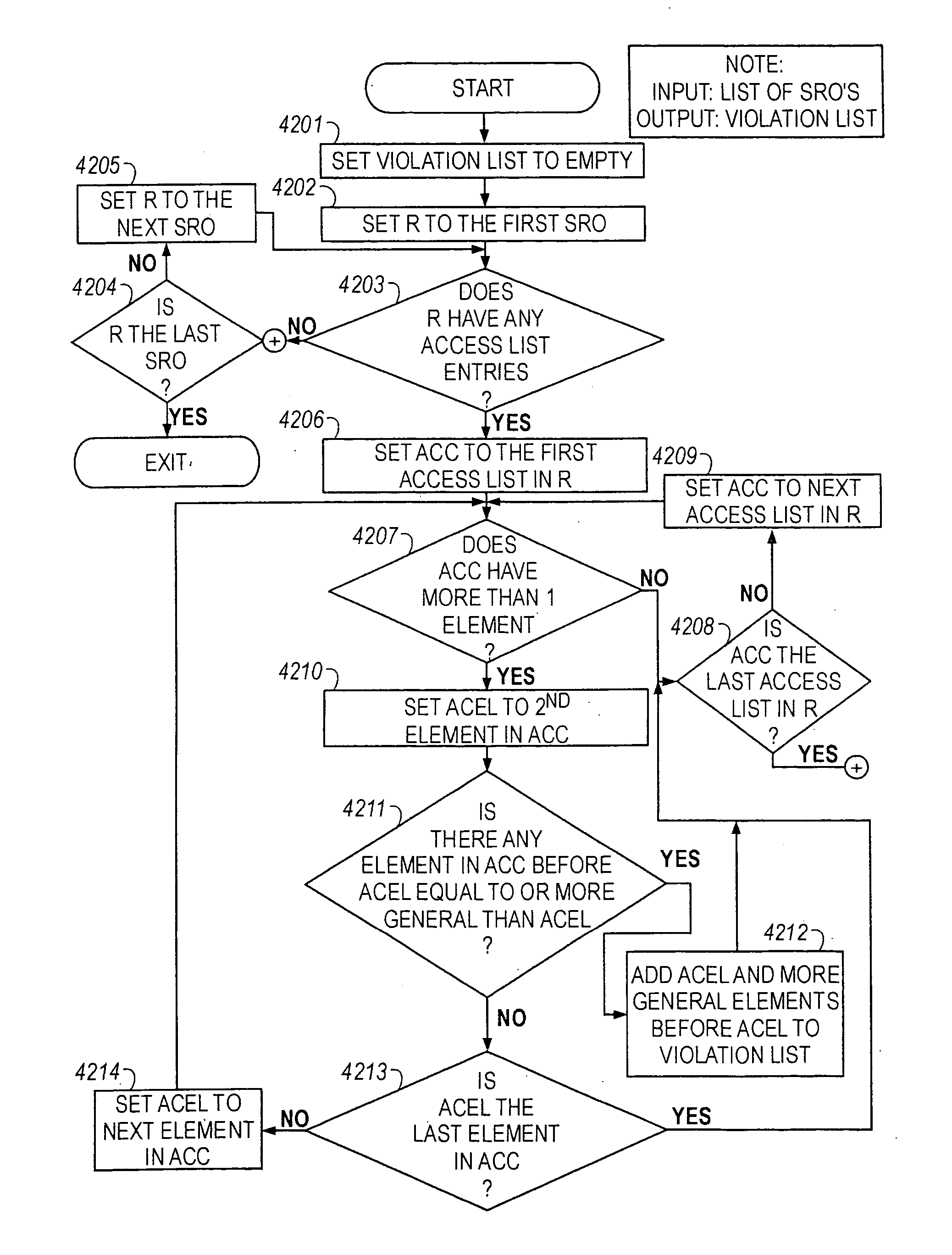
Method of resolving conflicts in access control lists in router by comparing elements in the lists based on subsumption relations
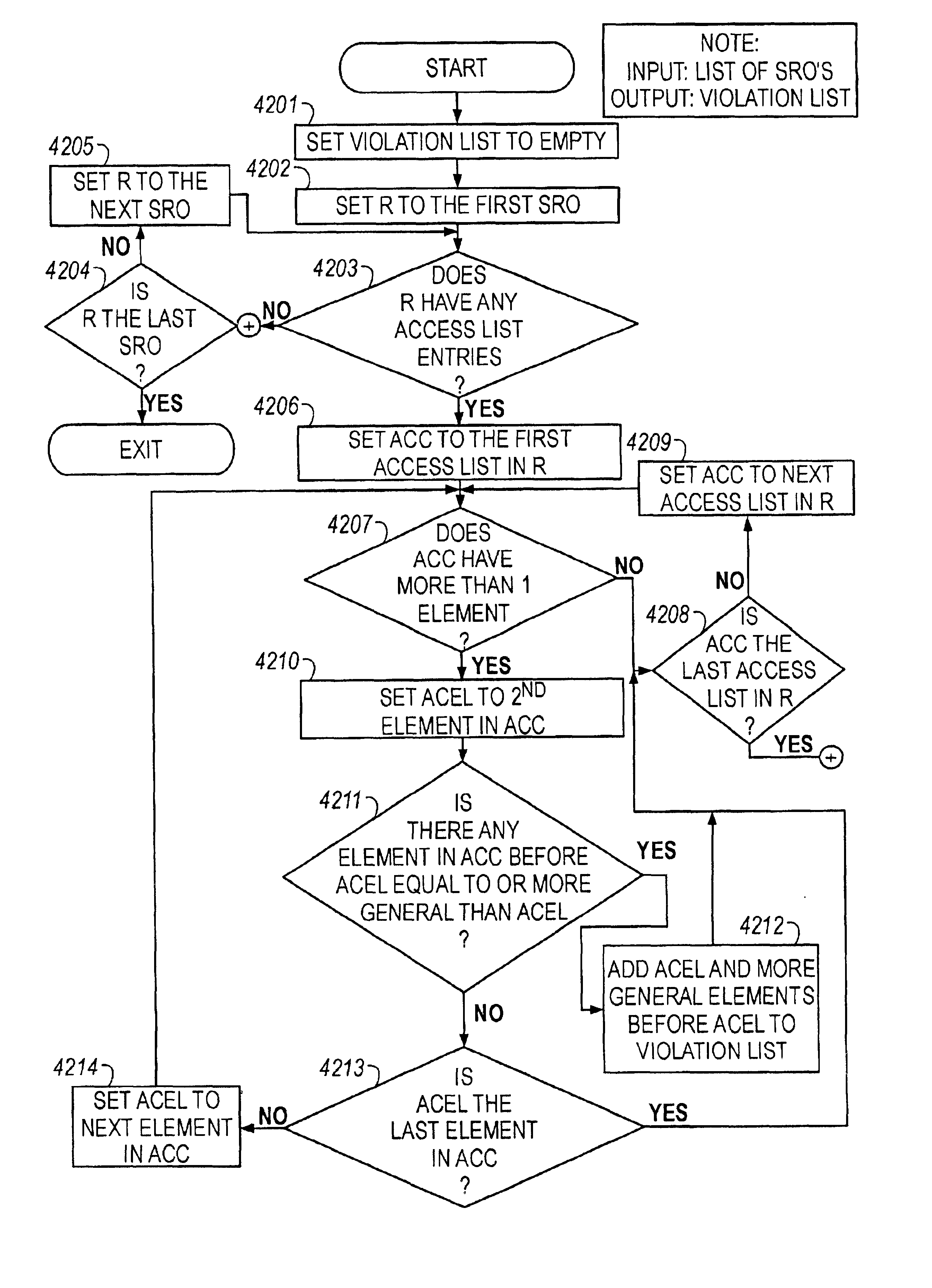
InactiveUS6883034B1Easy networkingEasy to importDigital computer detailsData switching by path configurationNetwork integrityComputer science
Methods are described for analyzing access list subsumption in routing devices of a computer network and for identifying computer network integrity violations, by producing structured data that includes stored router names and access lists that include elements with address / mask pairs, or patterns used to filter data into and out of a routing device, respectively; determining whether access lists in the structured data include elements in which a first element in the access list has a more general or equal address / mask pair, or pattern, respectively, than a second or subsequent element, or pattern; and storing in electronic memory a report of elements or a list of patterns, respectively, in which a first element or pattern is more general than or equal to a second or subsequent element or pattern.
Owner:CISCO TECH INC
Network linking methods and apparatus
Some portions of the present disclosure relate to processing audio signals for network linking. One claim recites an apparatus including: electronic memory for buffering data representing an audio signal; and an electronic processor. The electronic processor is programmed for: analyzing the data representing an audio signal to extract identifying data therefrom; controlling communication of the identifying data to a remote device over a network, in which the remote device uses the identifying data as an index to identify a pointer from among a plurality of pointers, the plurality of pointers each identifying a remote computer or resource on the network; and controlling use of a pointer identified by the index and received from the remote device over the network. Of course, other claims and combinations are provided too.
Owner:DIGIMARC CORP
Method for accessing a secure storage, secure storage and system comprising the secure storage
InactiveUS20130145455A1Reduce complexityFree secure storageDigital data processing detailsUnauthorized memory use protectionMobile deviceComputer security
It is described a method for accessing a secure storage of a mobile device, the method comprising: providing a generic interface for accessing the secure storage; accessing the secure storage using the generic interface by a first application of the mobile device; accessing the secure storage using the generic interface by a second application of the mobile device. Further, a corresponding secure electronic storage and a system is described.
Owner:NXP BV
Analyzing an access control list for a router to identify a subsumption relation between elements in the list
InactiveUS20050102423A1Easy to importDigital computer detailsData switching networksNetwork integrityWorld Wide Web
Methods are described for analyzing access list subsumption in routing devices of a computer network and for identifying computer network integrity violations, by producing structured data that includes stored router names and access lists that include elements with address / mask pairs, or patterns used to filter data into and out of a routing device, respectively; determining whether access lists in the structured data include elements in which a first element in the access list has a more general or equal address / mask pair, or pattern, respectively, than a second or subsequent element, or pattern; and storing in electronic memory a report of elements or a list of patterns, respectively, in which a first element or pattern is more general than or equal to a second or subsequent element or pattern.
Owner:CISCO TECH INC
Digital video system for assembling video sequences
InactiveUS20050206751A1Enjoyable experienceTelevision system detailsColor signal processing circuitsDigital videoDisplay device
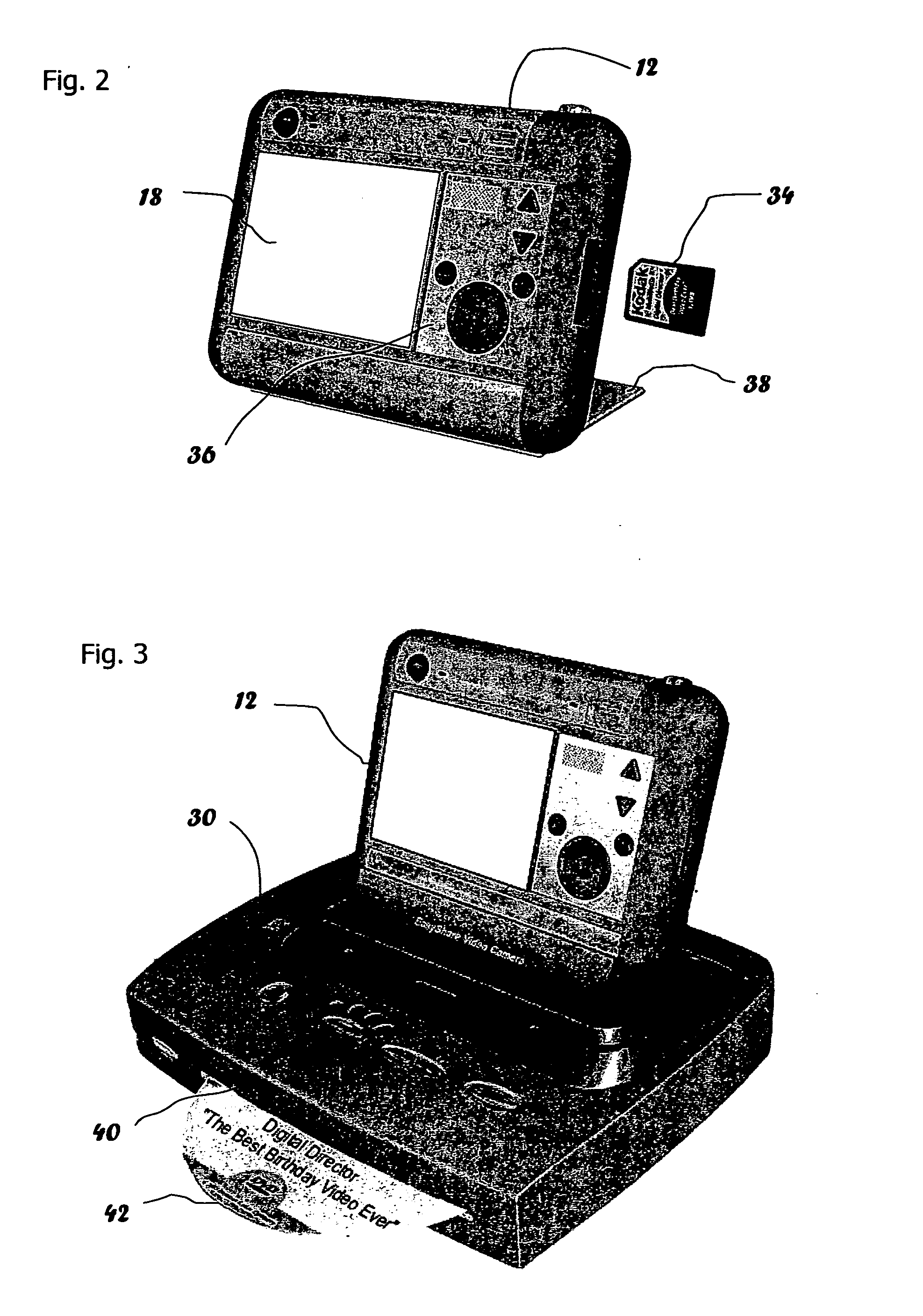
An image processing system (10) obtains image sequences and assembles a presentation therefrom. The system has a camera (12) for capturing image sequences, a random-access electronic memory (16) for temporary storage of the image sequences, an input reader for accepting pre-programmed instructions from a first storage medium, a control panel with a display (18) for viewing image sequences (64) and presenting pre-programmed instructions to the operator and an operator interface for accepting responses to the pre-programmed instructions. A control logic processor (20) executes pre-programmed instructions and arranges the presentation from the captured image sequences stored in random-access electronic memory (16), according to operator responses. An output writer records the presentation onto a storage medium.
Owner:EASTMAN KODAK CO
Techniques for directory server integration
ActiveUS20110264865A1Reduce the amount requiredSpecial data processing applicationsMemory systemsTime rangeExpiration Time
Techniques for directory server integration are disclosed. In one particular exemplary embodiment, the techniques may be realized as a method for directory server integration comprising setting one or more parameters determining a range of permissible expiration times for a plurality of cached directory entries, creating, in electronic storage, a cached directory entry from a directory server, assigning a creation time to the cached directory entry, and assigning at least one random value to the cached directory entry, the random value determining an expiration time for the cached directory entry within the range of permissible expiration times, wherein randomizing the expiration time for the cached directory entry among the range of permissible expiration times for a plurality of cached directory entries reduces an amount of synchronization required between cache memory and the directory server at a point in time.
Owner:CA TECH INC
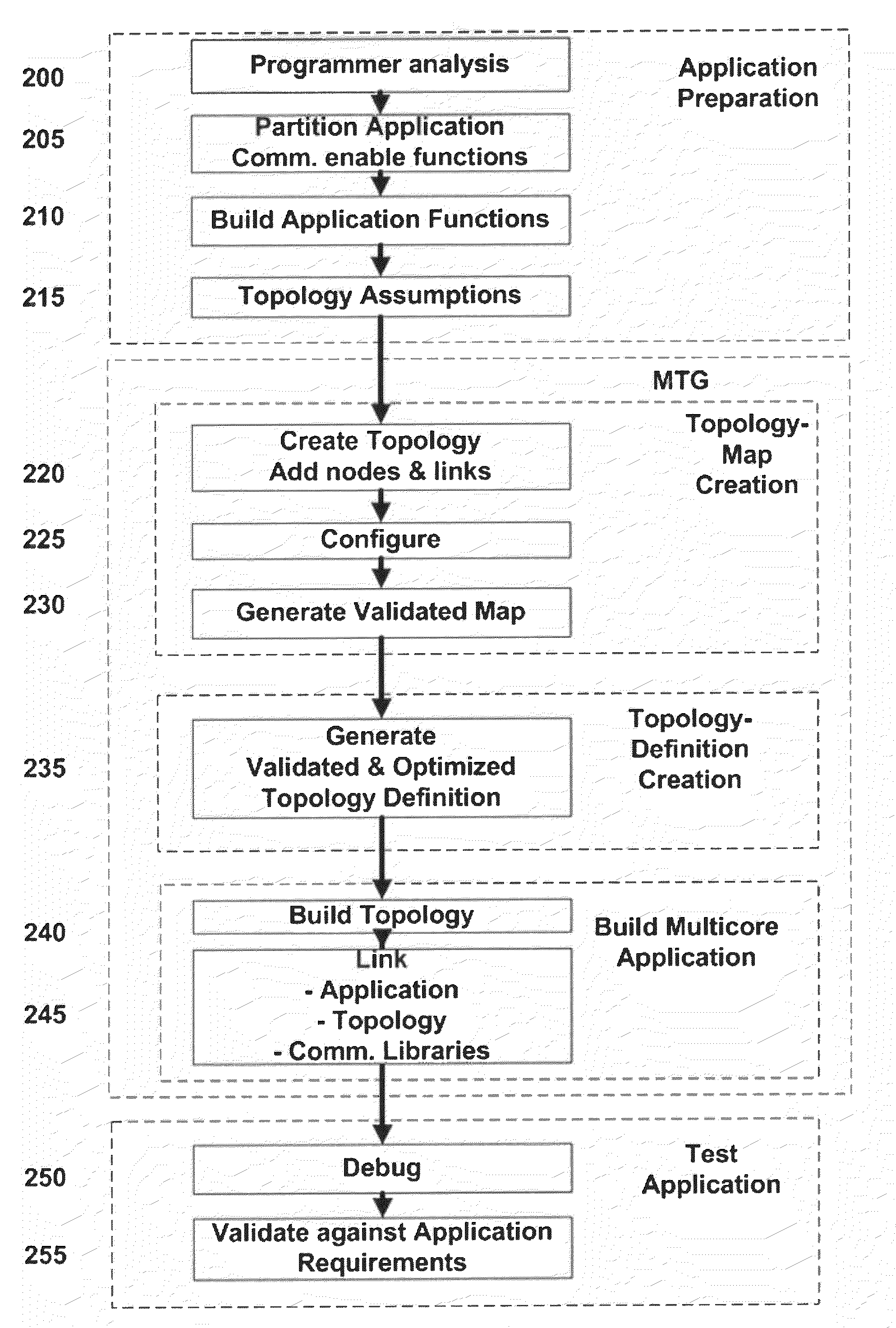
Apparatus & associated methodology of generating a multi-core communications topology
ActiveUS20100235847A1Multiprogramming arrangementsInput/output processes for data processingParallel computingDocument handling
An apparatus and associated method of generating a multi-core communication topology. The topology corresponding to a predetermined number of cores of a multi-core computer, is generated with an application programming device. A number of nodes are described for mapping to the predetermined number of available cores of the multi-core communication topology. Properties of each of the number of nodes are specified. Communication between each of the nodes of the multi-core communication topology is specified using a dedicated multi-core communication library of an electronic memory of the application programming device. A validated output file is generated for the multi-core topology at the application programming device. The output file to is processed to generate a multi-core communication capable executable application program interface (API) for the multi-core computer.
Owner:POLYCORE SOFTWARE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com