Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
35 results about "Network integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
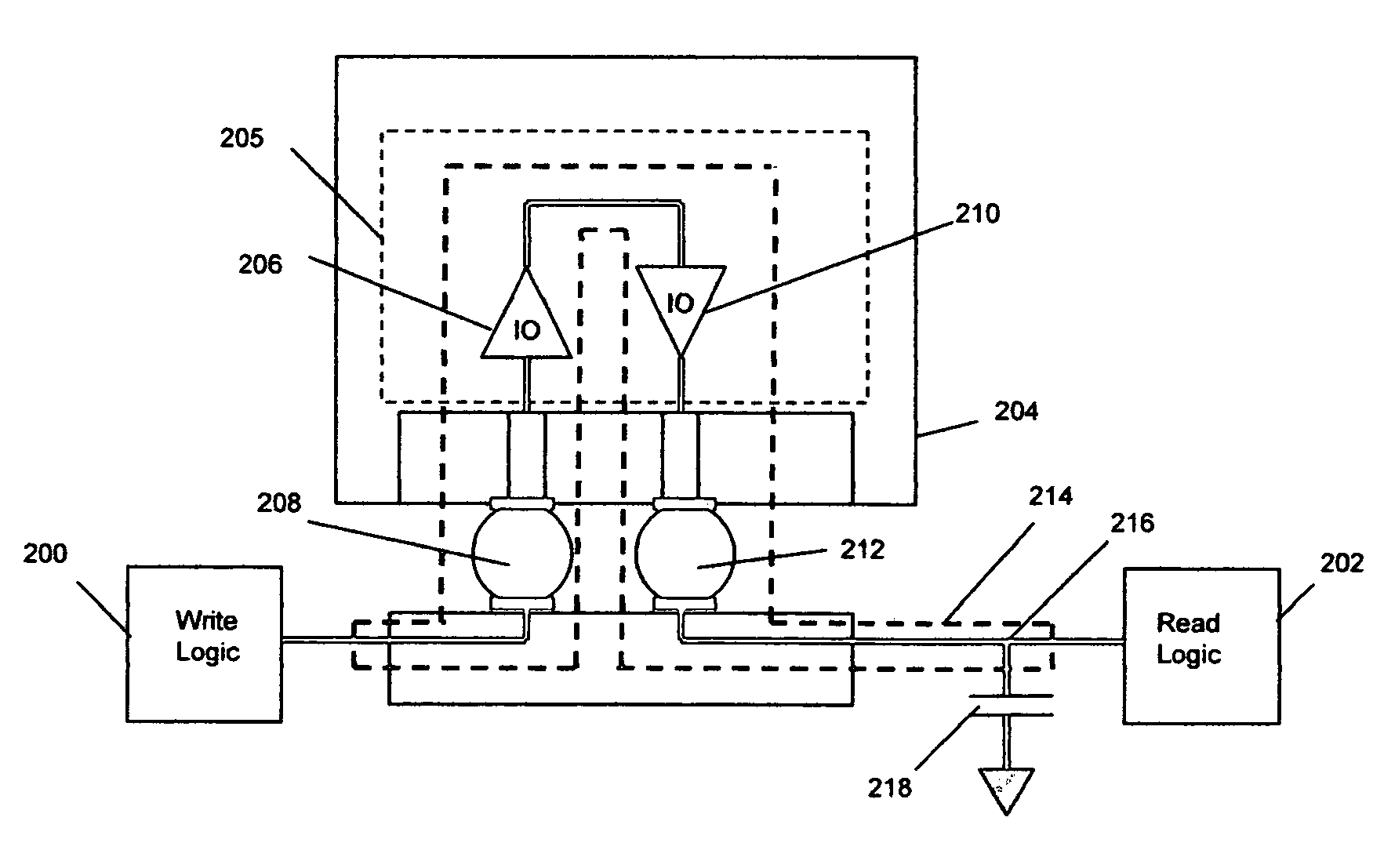
At an enterprise level, however, network integrity refers to the complete network as a whole with network-discoverable resources matching that listed in inventory. Any discrepancies indicate a compromise in network integrity, whether by hardware failure, software failure, network intrusion or otherwise.
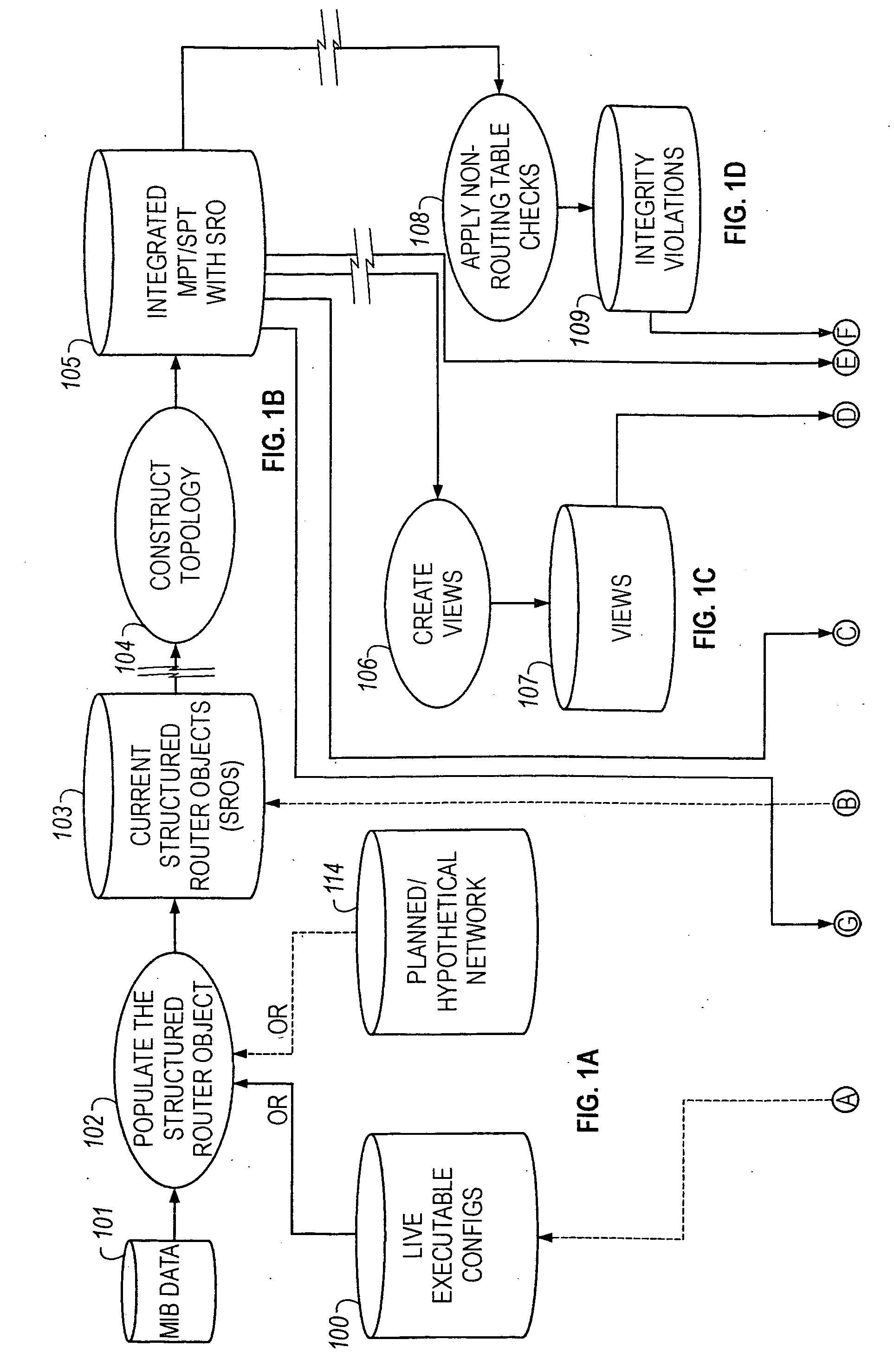
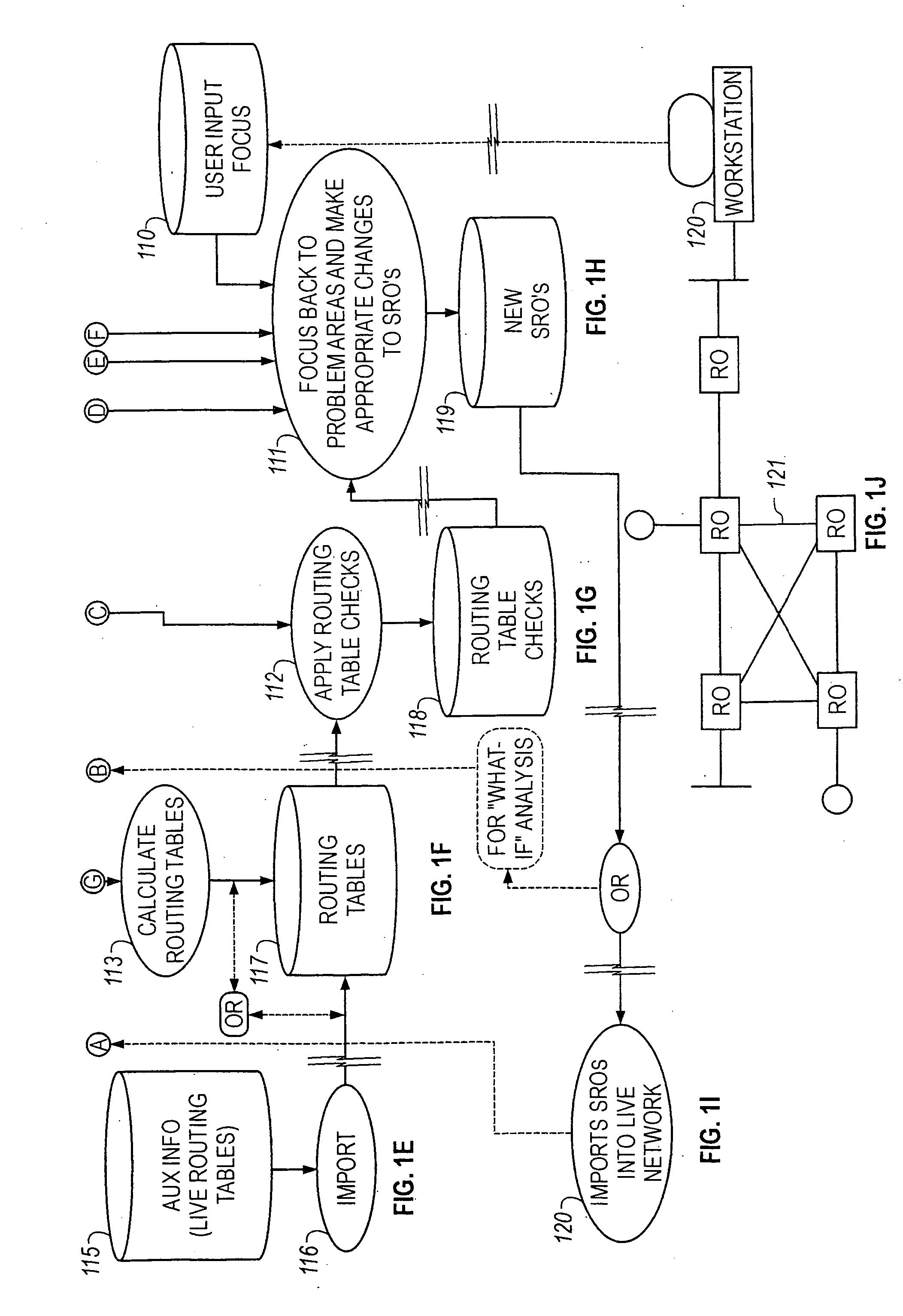
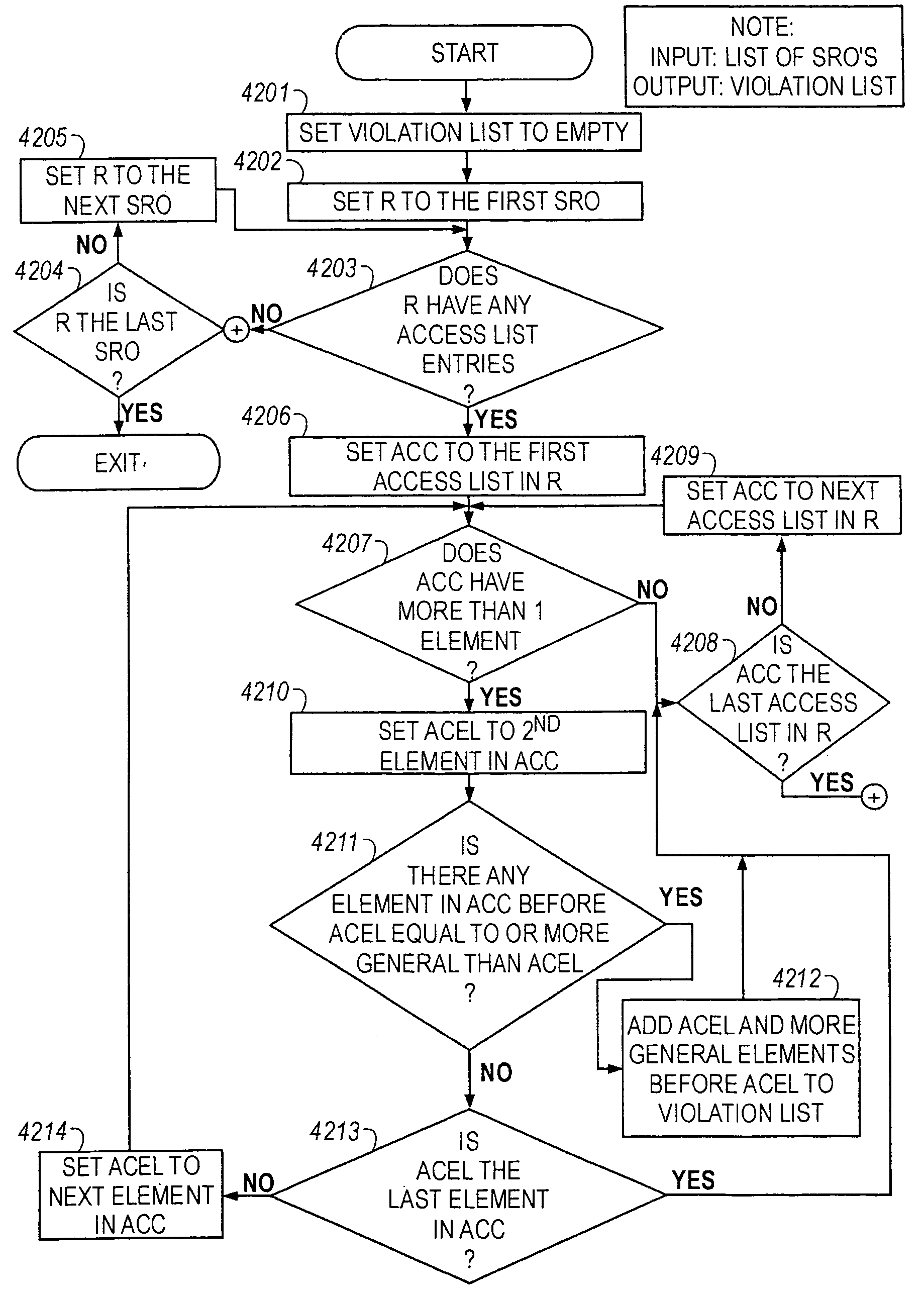
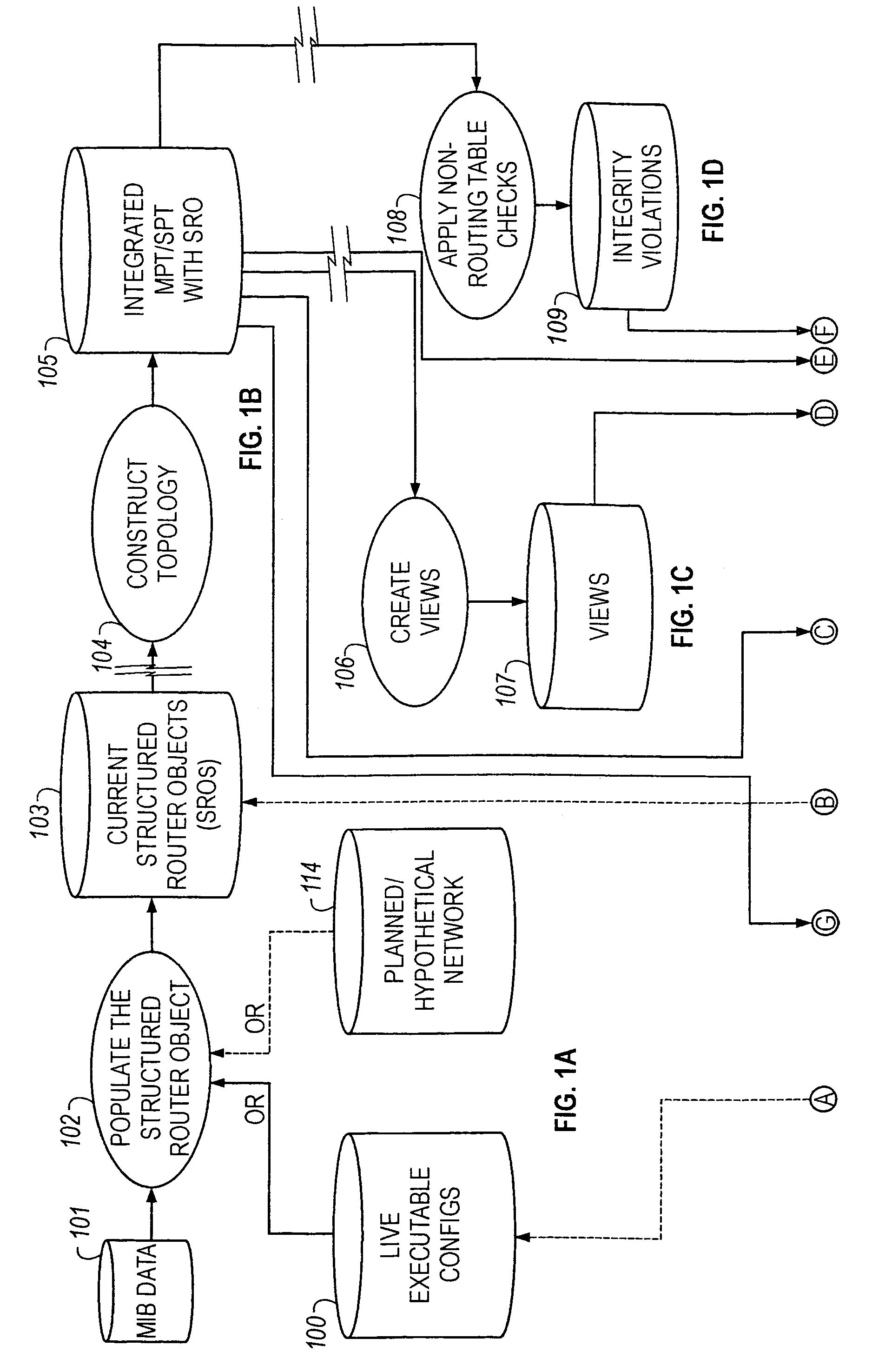
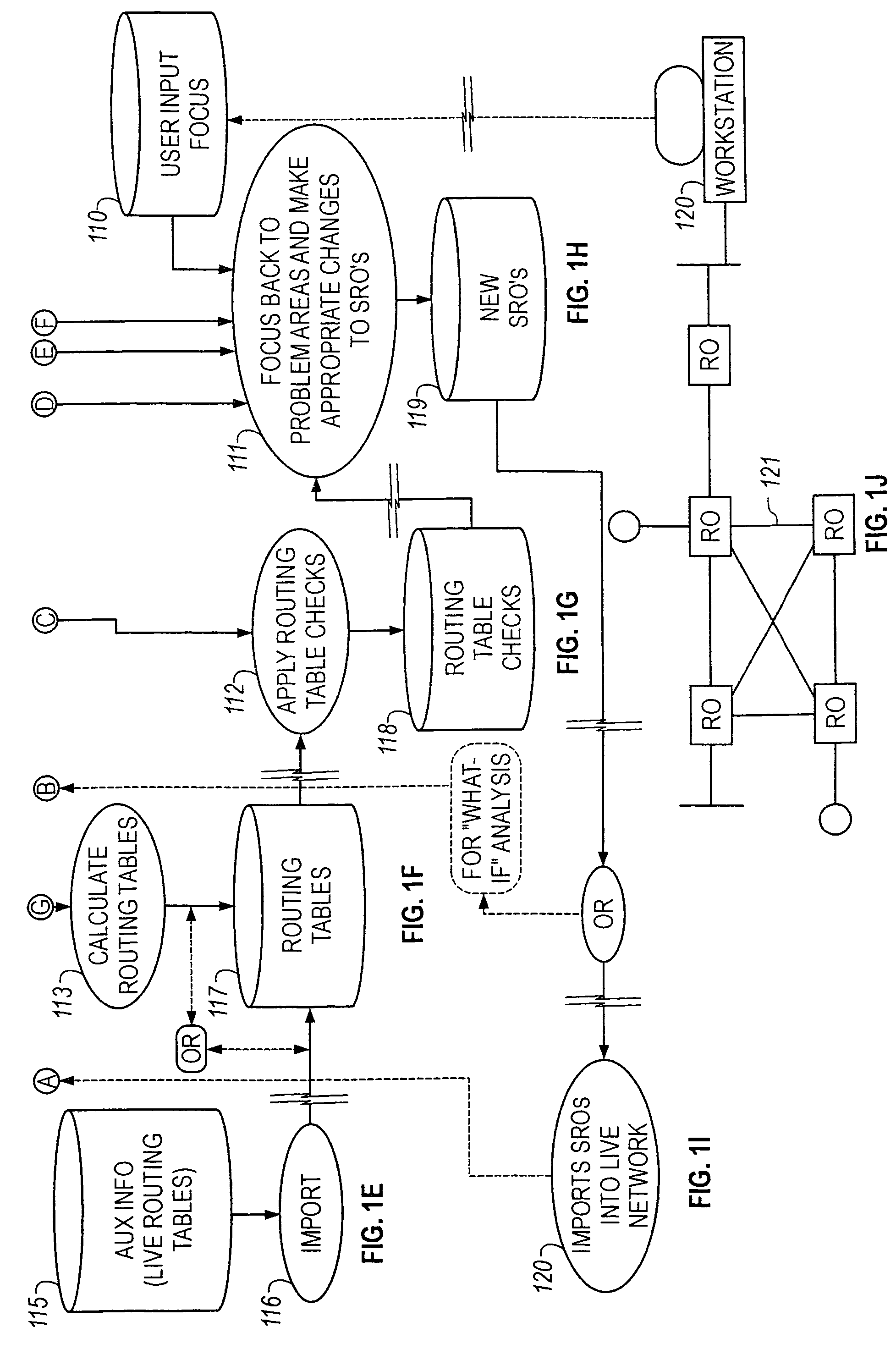
Method of resolving conflicts in access control lists in router by comparing elements in the lists based on subsumption relations
InactiveUS6883034B1Easy networkingEasy to importDigital computer detailsData switching by path configurationNetwork integrityComputer science
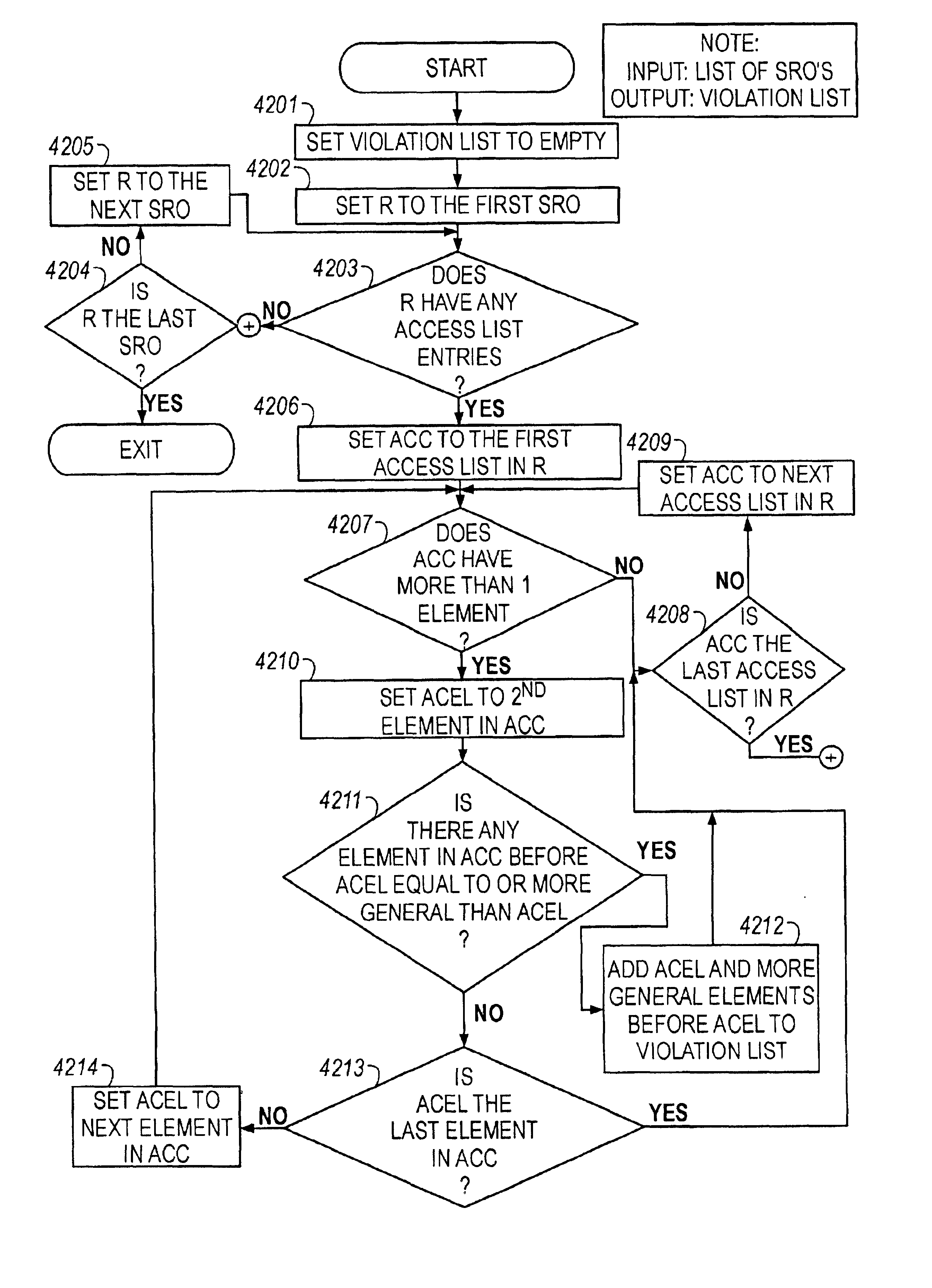
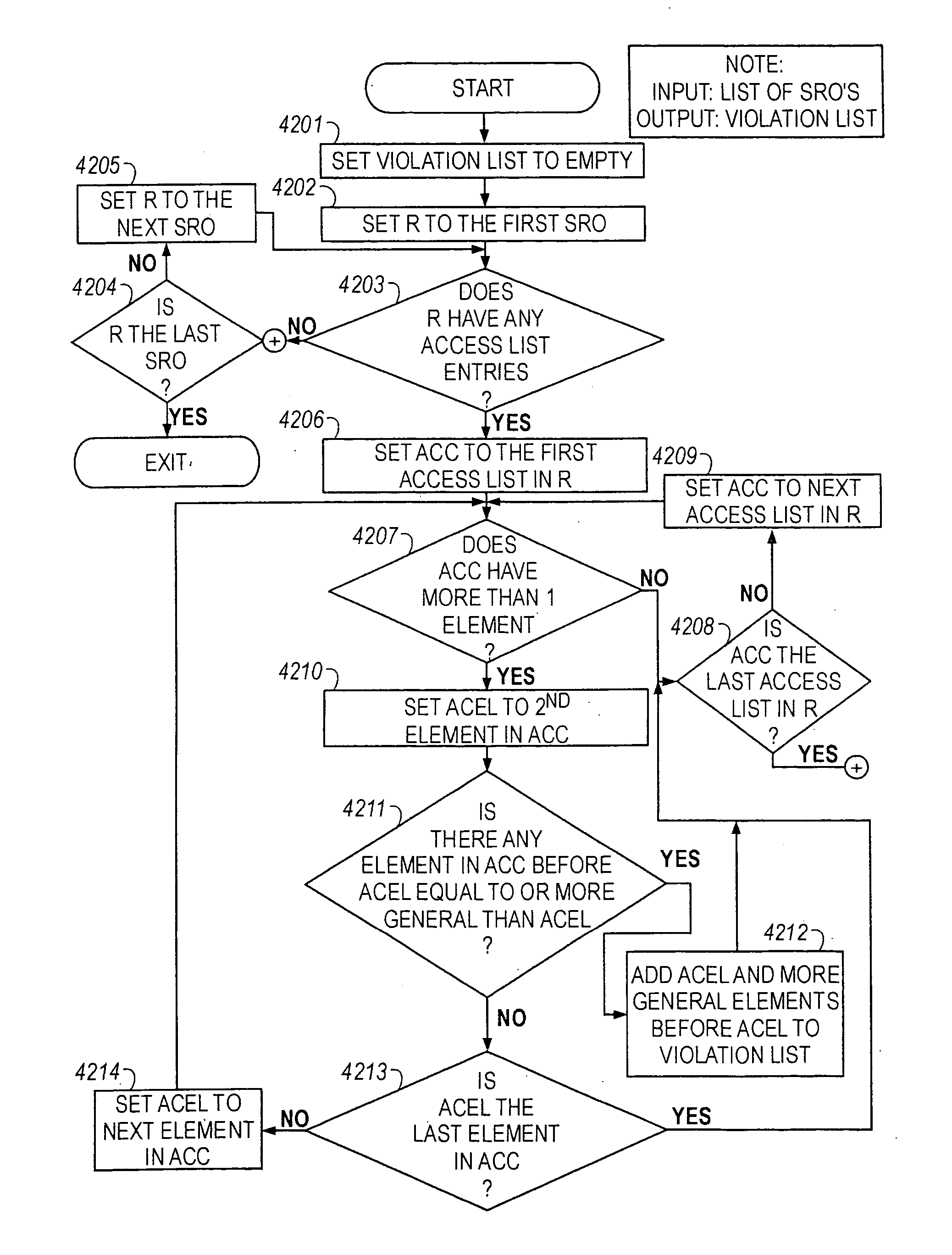
Methods are described for analyzing access list subsumption in routing devices of a computer network and for identifying computer network integrity violations, by producing structured data that includes stored router names and access lists that include elements with address / mask pairs, or patterns used to filter data into and out of a routing device, respectively; determining whether access lists in the structured data include elements in which a first element in the access list has a more general or equal address / mask pair, or pattern, respectively, than a second or subsequent element, or pattern; and storing in electronic memory a report of elements or a list of patterns, respectively, in which a first element or pattern is more general than or equal to a second or subsequent element or pattern.
Owner:CISCO TECH INC
Analyzing an access control list for a router to identify a subsumption relation between elements in the list
InactiveUS20050102423A1Easy to importDigital computer detailsData switching networksNetwork integrityWorld Wide Web
Methods are described for analyzing access list subsumption in routing devices of a computer network and for identifying computer network integrity violations, by producing structured data that includes stored router names and access lists that include elements with address / mask pairs, or patterns used to filter data into and out of a routing device, respectively; determining whether access lists in the structured data include elements in which a first element in the access list has a more general or equal address / mask pair, or pattern, respectively, than a second or subsequent element, or pattern; and storing in electronic memory a report of elements or a list of patterns, respectively, in which a first element or pattern is more general than or equal to a second or subsequent element or pattern.
Owner:CISCO TECH INC
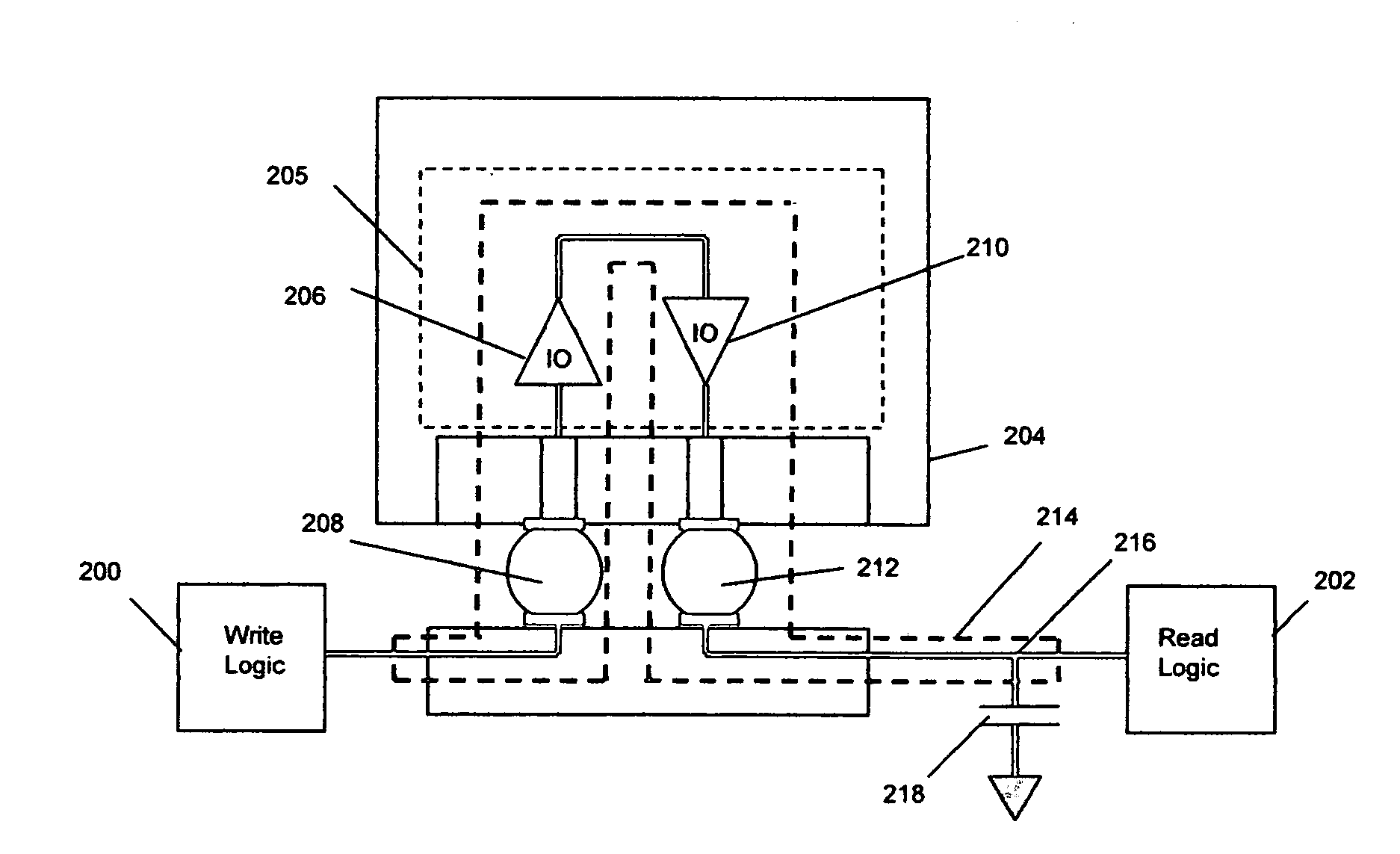
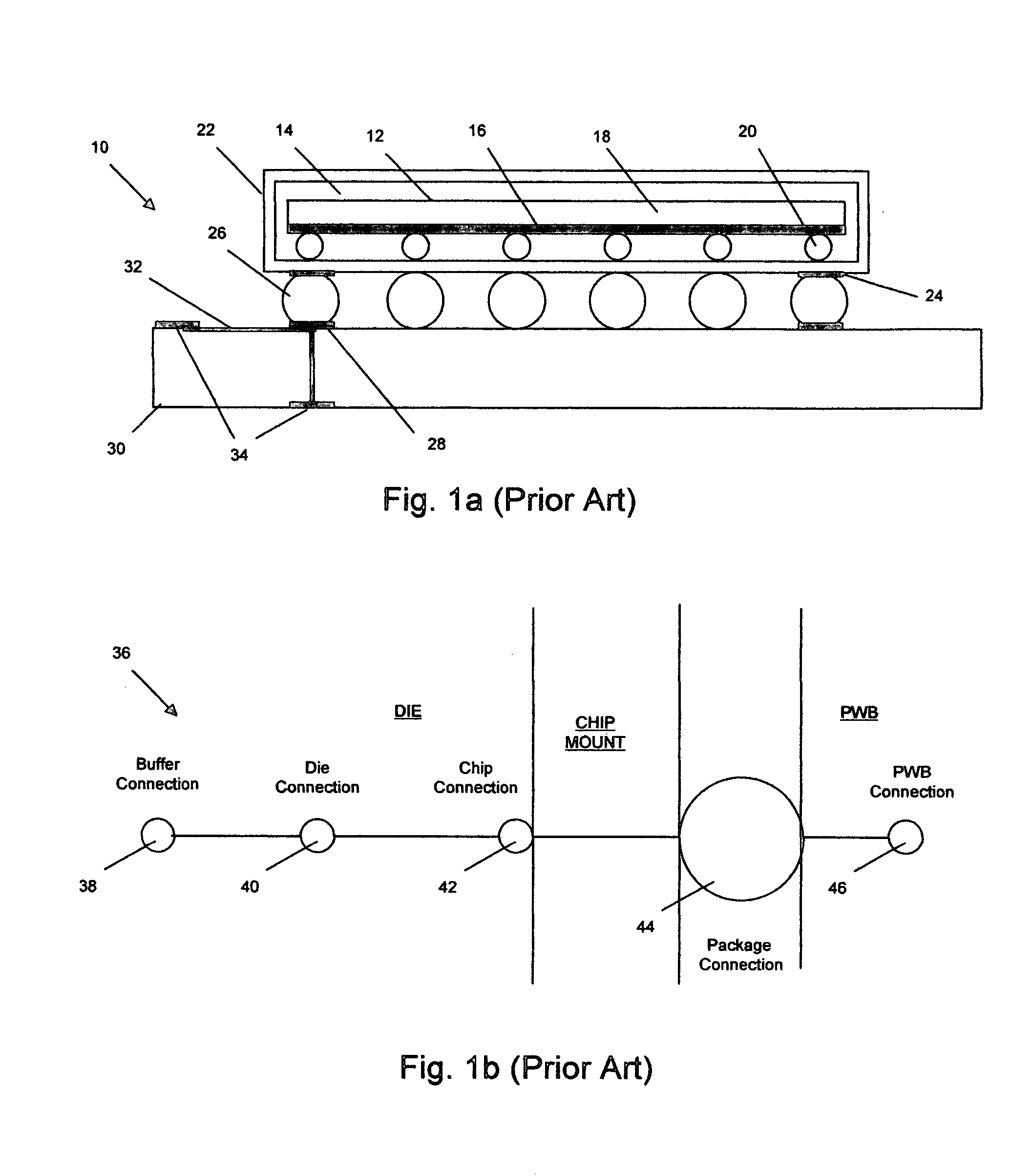
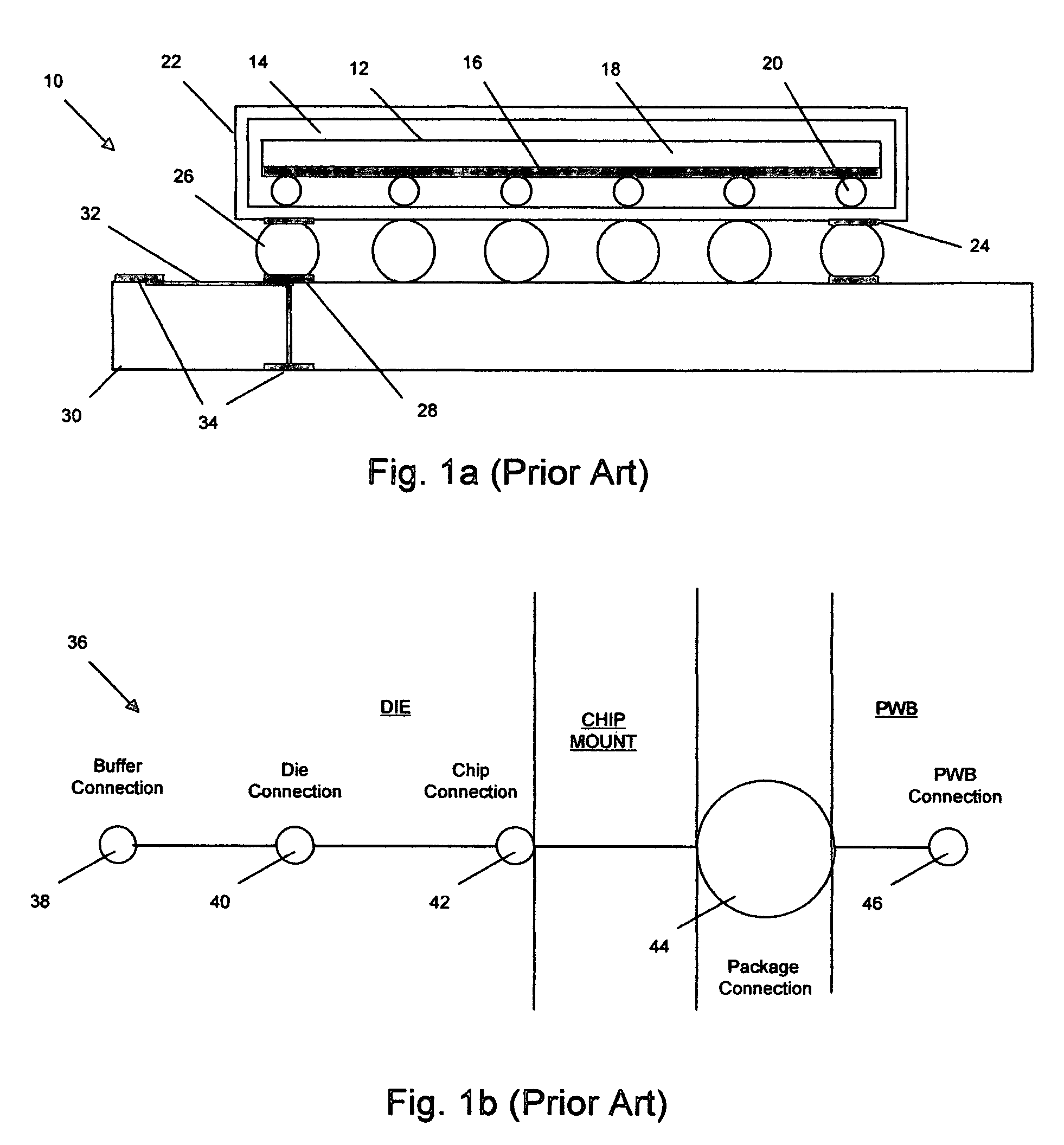
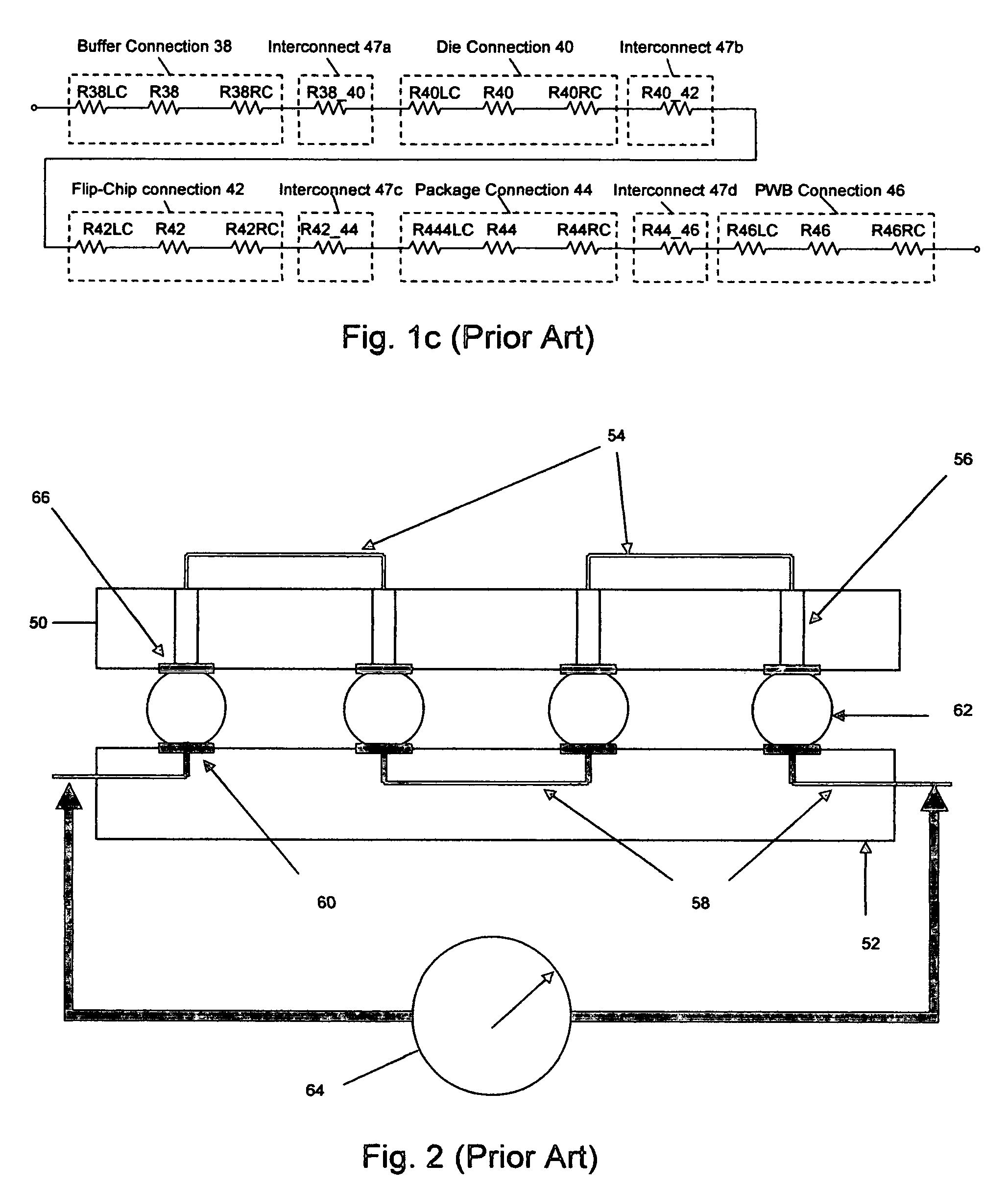
Method and circuit for the detection of solder-joint failures in a digital electronic package
InactiveUS20060194353A1Well formedSemiconductor/solid-state device testing/measurementElectric connection testingMicrocontrollerNetwork integrity
The solder-joint integrity of digital electronic packages, such as FPGAs or microcontrollers that have internally connected input / output buffers, is evaluated by applying a time-varying voltage through one or more solder-joint networks to charge a charge-storage component. Each network includes an I / O buffer on the die in the package and a solder-joint connection, typically one or more such connections inside the package and between the package and a board. The time constant for charging the component is proportional to the resistance of the solder-joint network, hence the voltage across the charge-storage component is a measurement of the integrity of the solder-joint network.
Owner:RIDGETOP GROUP
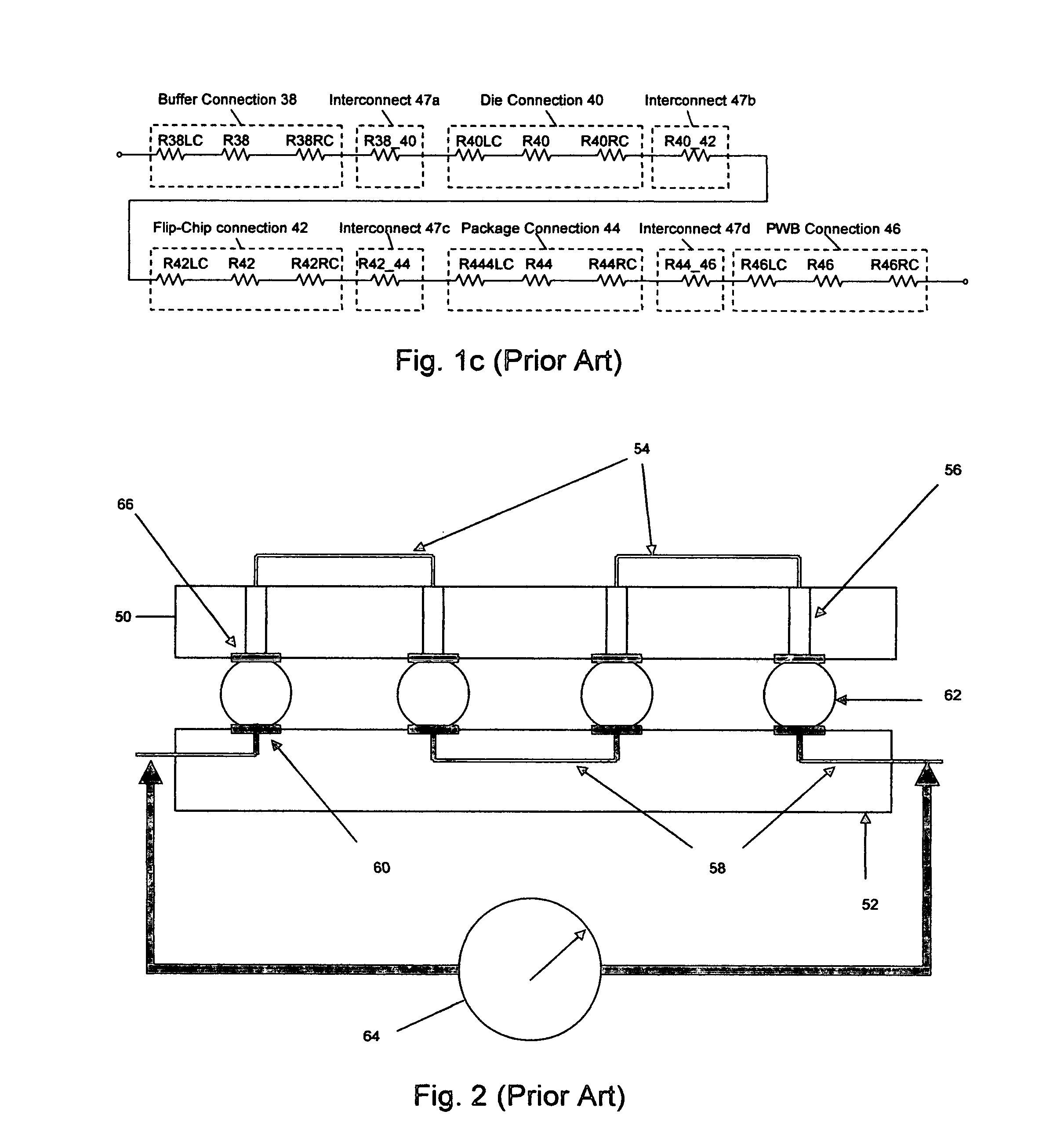
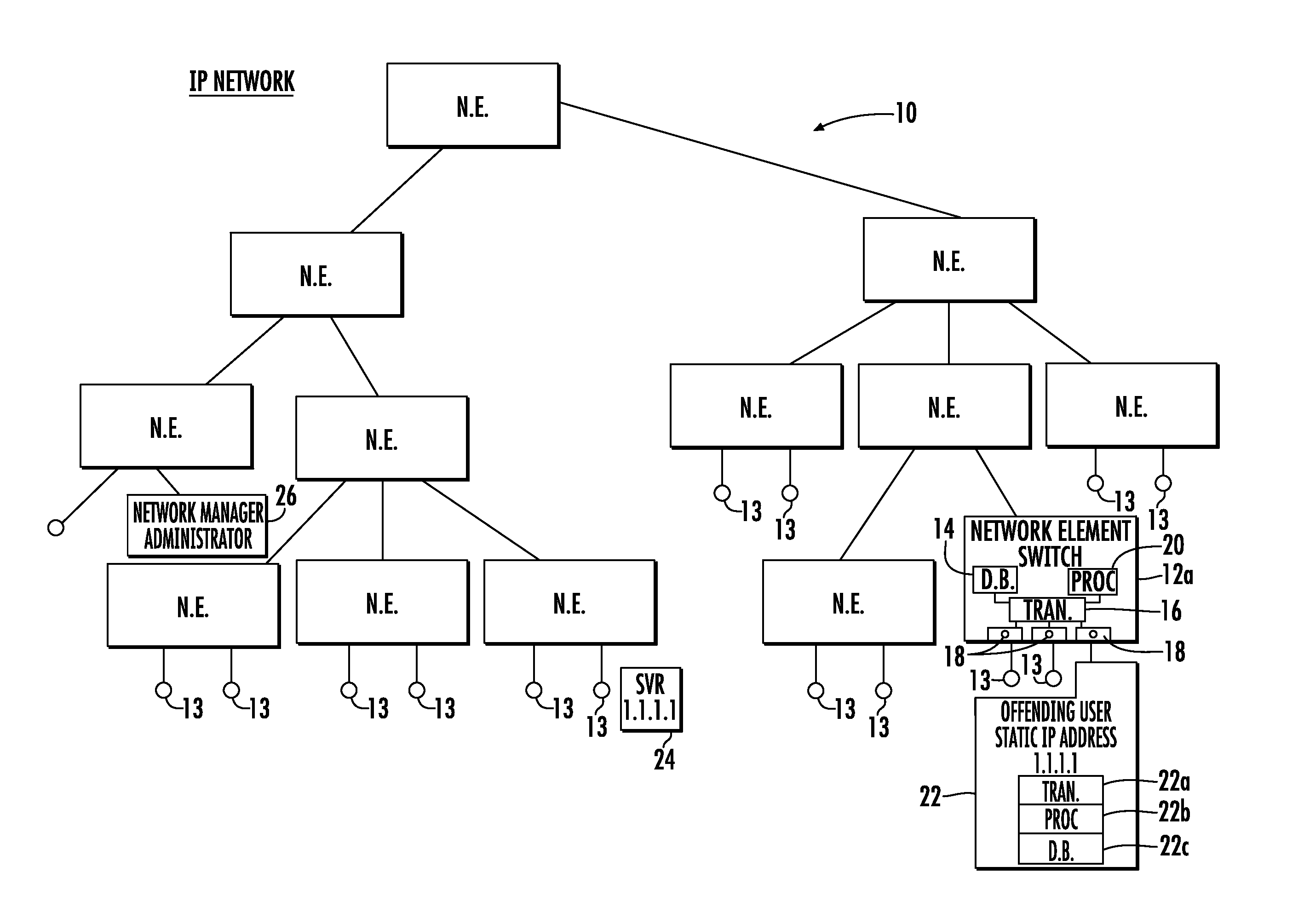
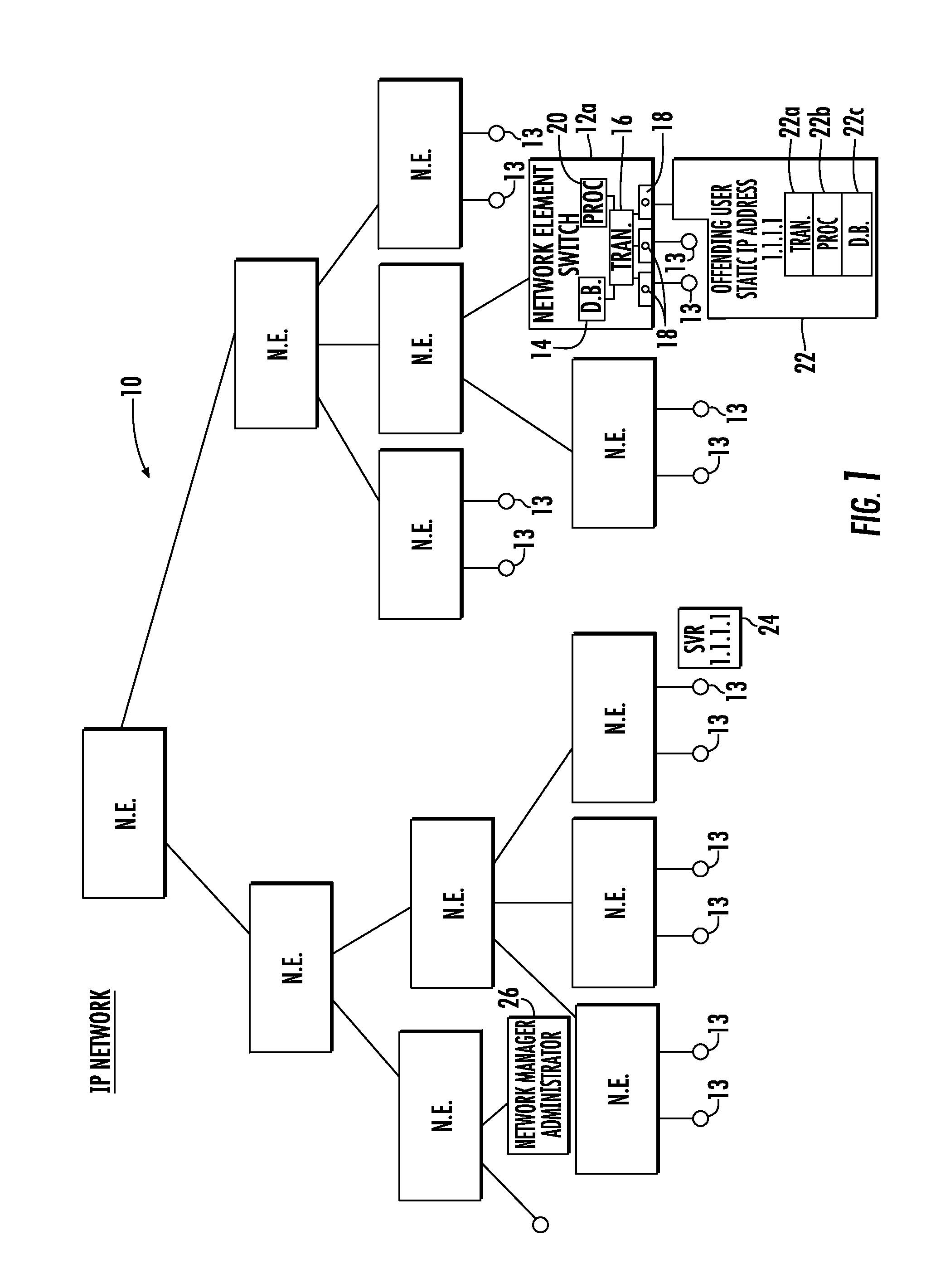
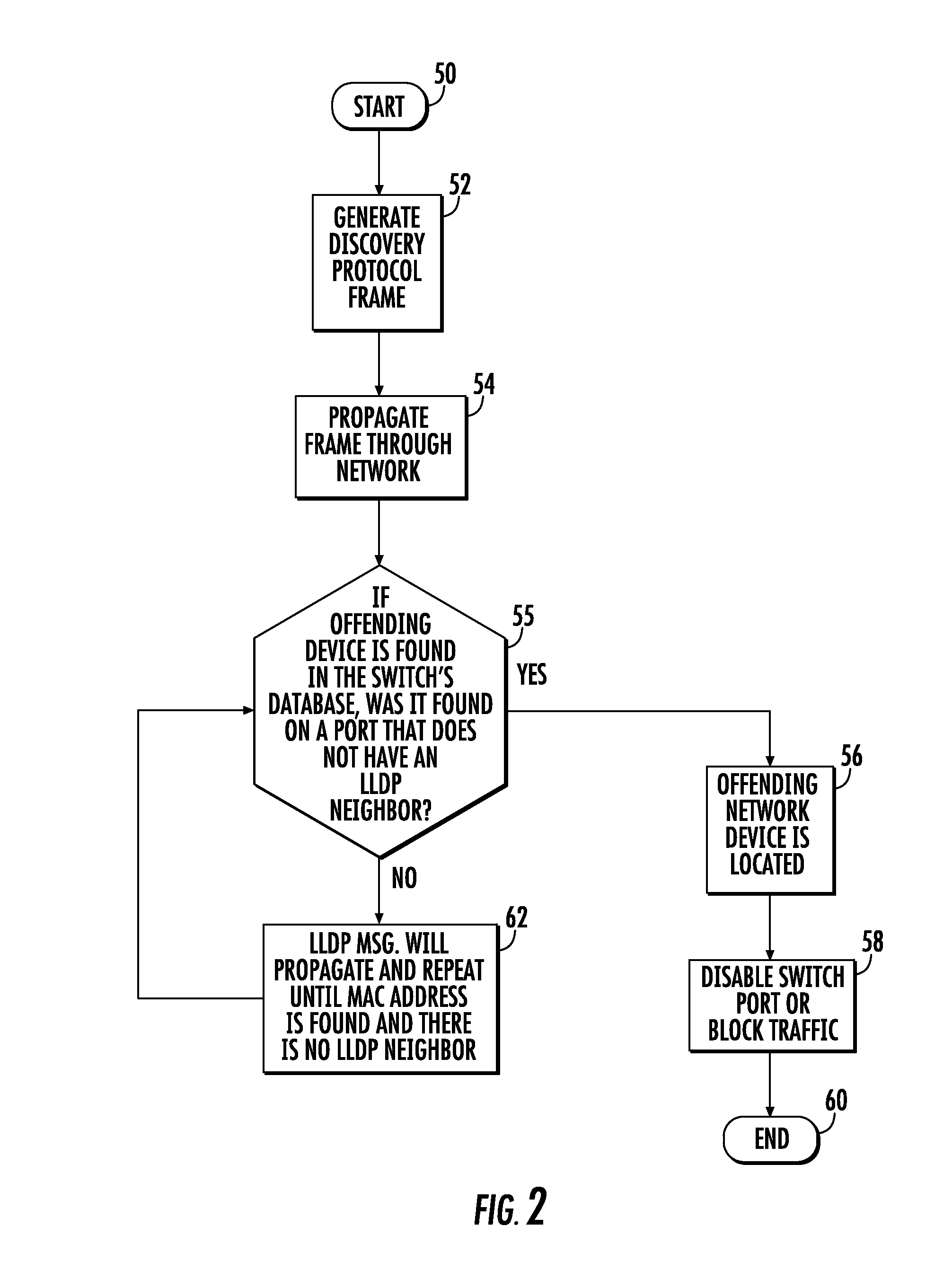
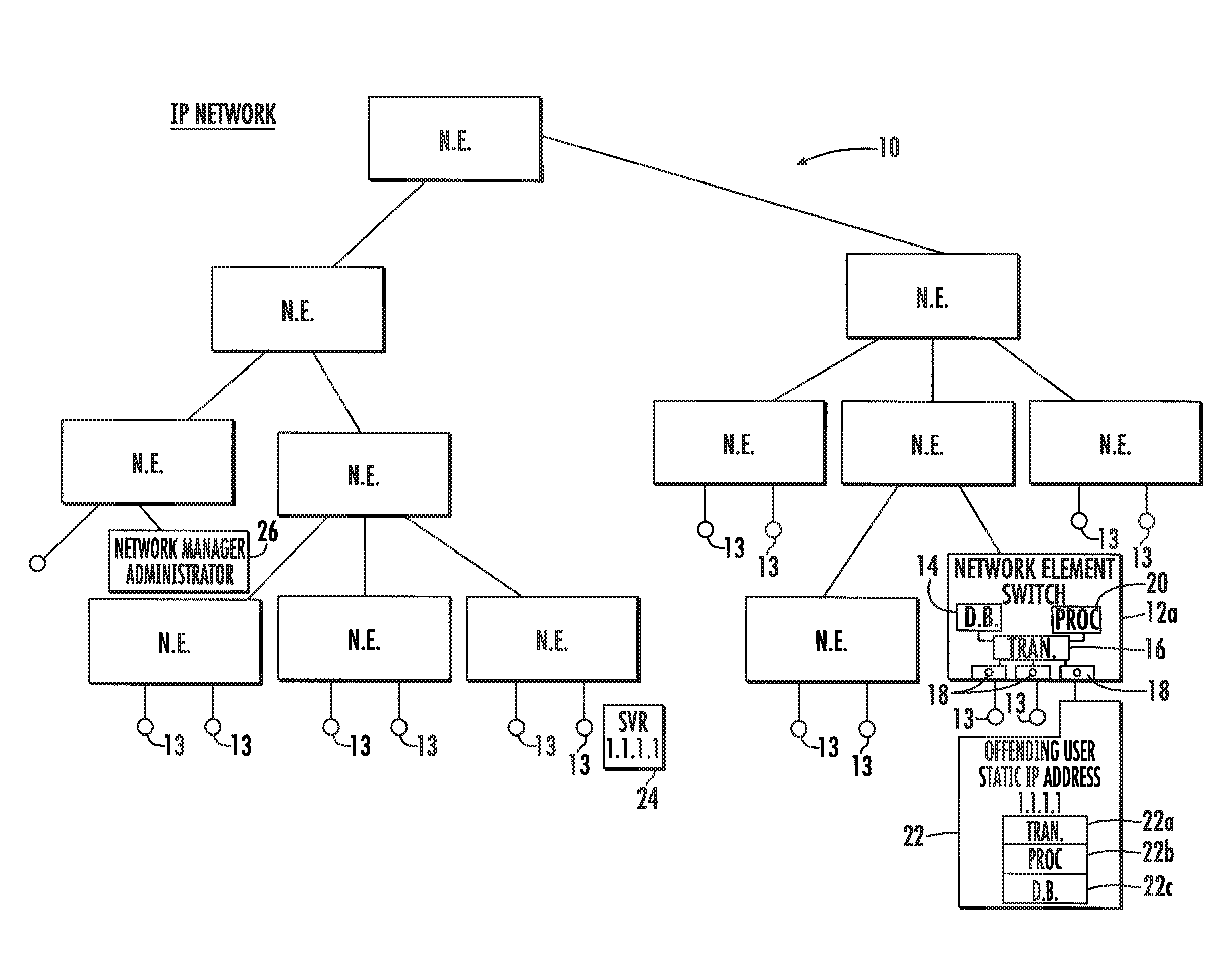
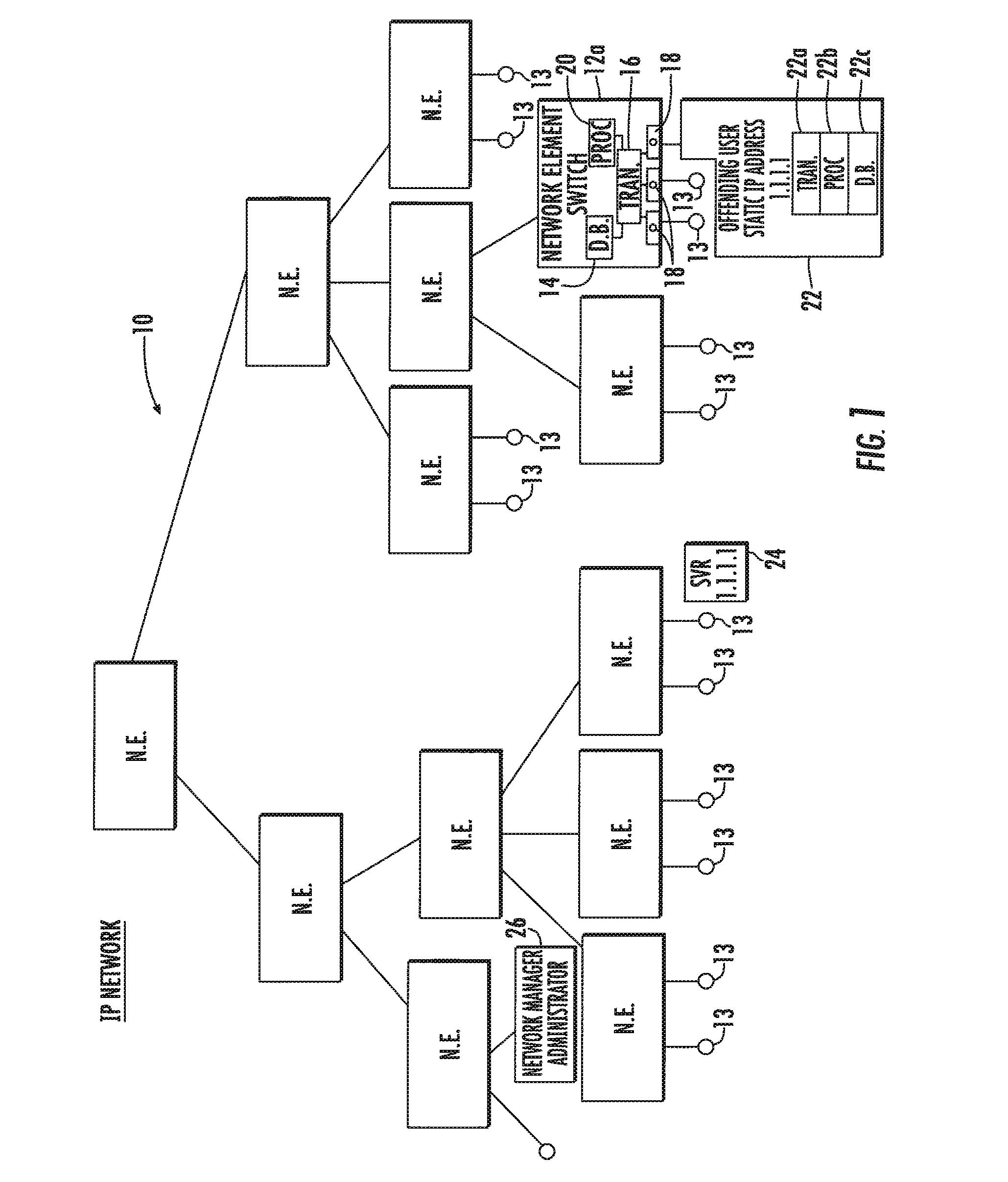
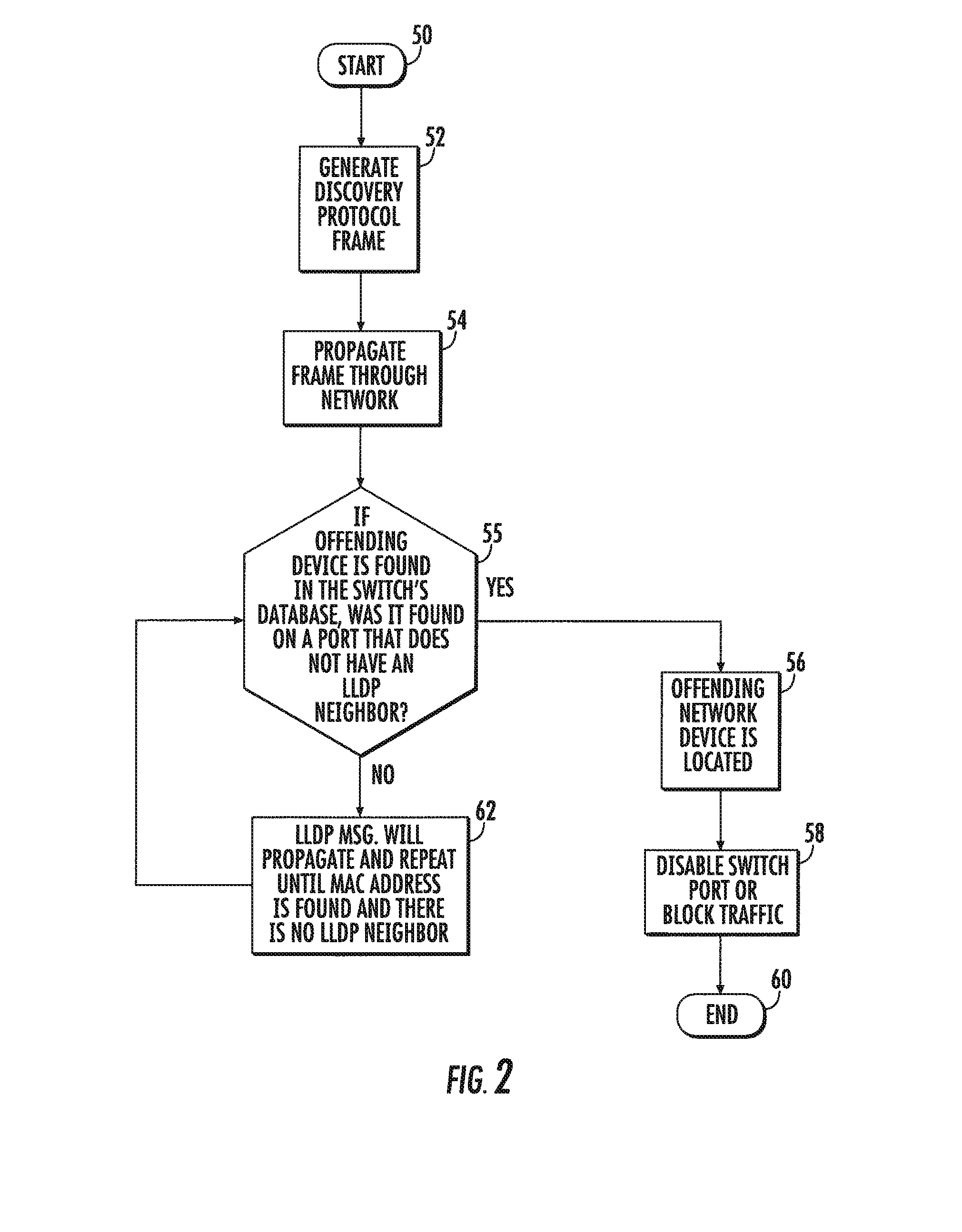
System and method for locating offending network device and maintaining network integrity
A system and method detects within an IP network an offending network device that has been adversely affecting the IP network performance. A discovery protocol frame is propagated to successive network switches and is formed as a field having a query for inquiring within each network switch to which the frame is propagated whether the network switch has a database entry regarding the MAC address and switch port for the offending network device to locate the offending network device. This discovery protocol frame includes a command for any network switch that has the offending network device connected thereto to disable the switch port to which the offending network device is connected or block all data traffic from the MAC address of the offending network device.
Owner:ADTRAN
Method and circuit for the detection of solder-joint failures in a digital electronic package
InactiveUS7501832B2Semiconductor/solid-state device testing/measurementElectric connection testingMicrocontrollerEngineering
The solder-joint integrity of digital electronic packages, such as FPGAs or microcontrollers that have internally connected input / output buffers, is evaluated by applying a time-varying voltage through one or more solder-joint networks to charge a charge-storage component. Each network includes an I / O buffer on the die in the package and a solder-joint connection, typically one or more such connections inside the package and between the package and a board. The time constant for charging the component is proportional to the resistance of the solder-joint network, hence the voltage across the charge-storage component is a measurement of the integrity of the solder-joint network.
Owner:RIDGETOP GROUP
On device policy enforcement to secure open platform via network and open network
ActiveUS20110197257A1User identity/authority verificationSpecial data processing applicationsOpen platformNetwork integrity
Embodiments of the invention provide methods and systems for using policy enforcement for securing open devices and networks. The method includes accessing, by a policy enforcer, a plurality of policies configured to enforce network integrity and monitoring programs and / or services running on a device. The method further includes based on at least one of the plurality of policies, comparing the programs and / or services running on the device against the programs and / or services allowed by the at least one of the plurality of policies, and based on the comparison, determining that the device is running at least one program and / or service disallowed by the at least one policy. Further, the method includes in response, prohibiting access of the device to the network.
Owner:ORACLE INT CORP
Data flow-based deterministic network integrity fault detection method
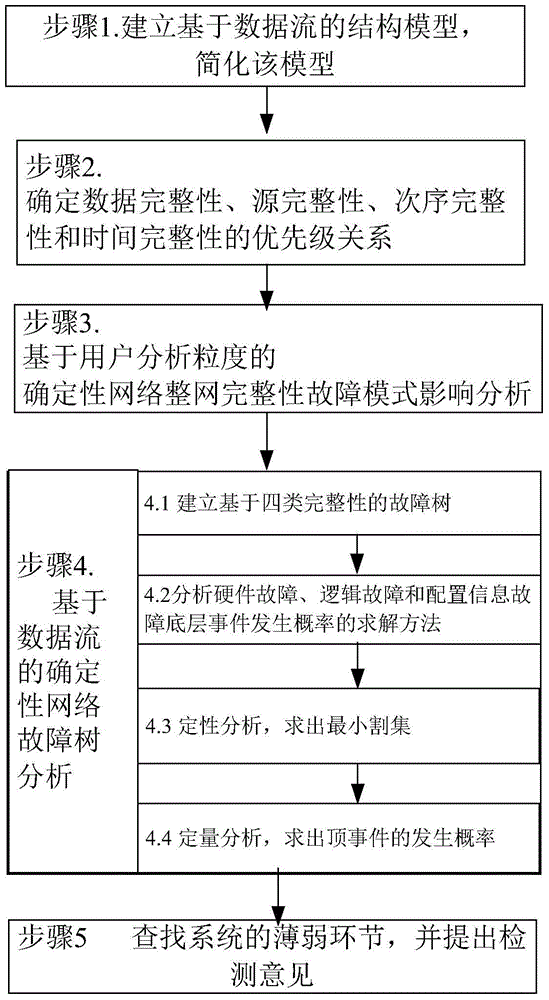
The invention relates to a data flow-based deterministic network integrity fault detection method. The method includes the steps of: according to a topological structure of a whole deterministic network, establishing a data flow-based triad model; by determining a priority relation of data integrity, source integrity, order integrity and time integrity, analyzing granularity required by a user, and aiming at hardware faults, logic faults and configuration information faults, making a fault mode analysis; on this basis, performing fault tree analysis, proposing a measurable and computational bottom event probability acquisition method, and performing qualitative and quantitative calculation; and finally completing fault detection. Aiming at the problem that a conventional fault detection method serial-parallel model cannot complete fault positioning in practical engineering, the problems of deterministic network data accuracy and integrity fault detection are solved. A method having engineering value is provided for integrity research of deterministic networks such as an aviation airborne network, an industrial control network and a military communication network.
Owner:PLA SECOND ARTILLERY ENGINEERING UNIVERSITY
Novel method and system of Network Integrity via Digital Authorization (NIDA) for enhanced internet security
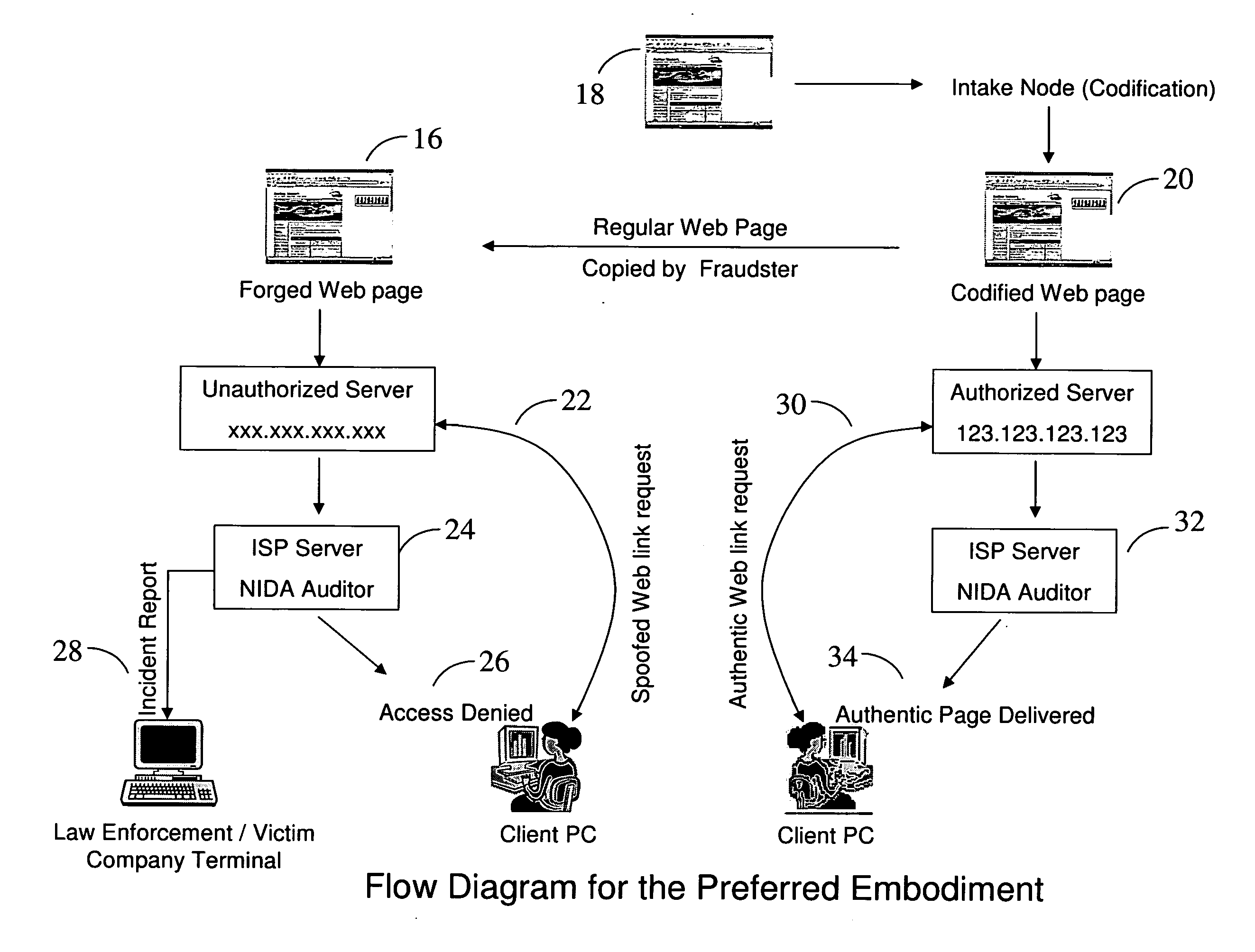
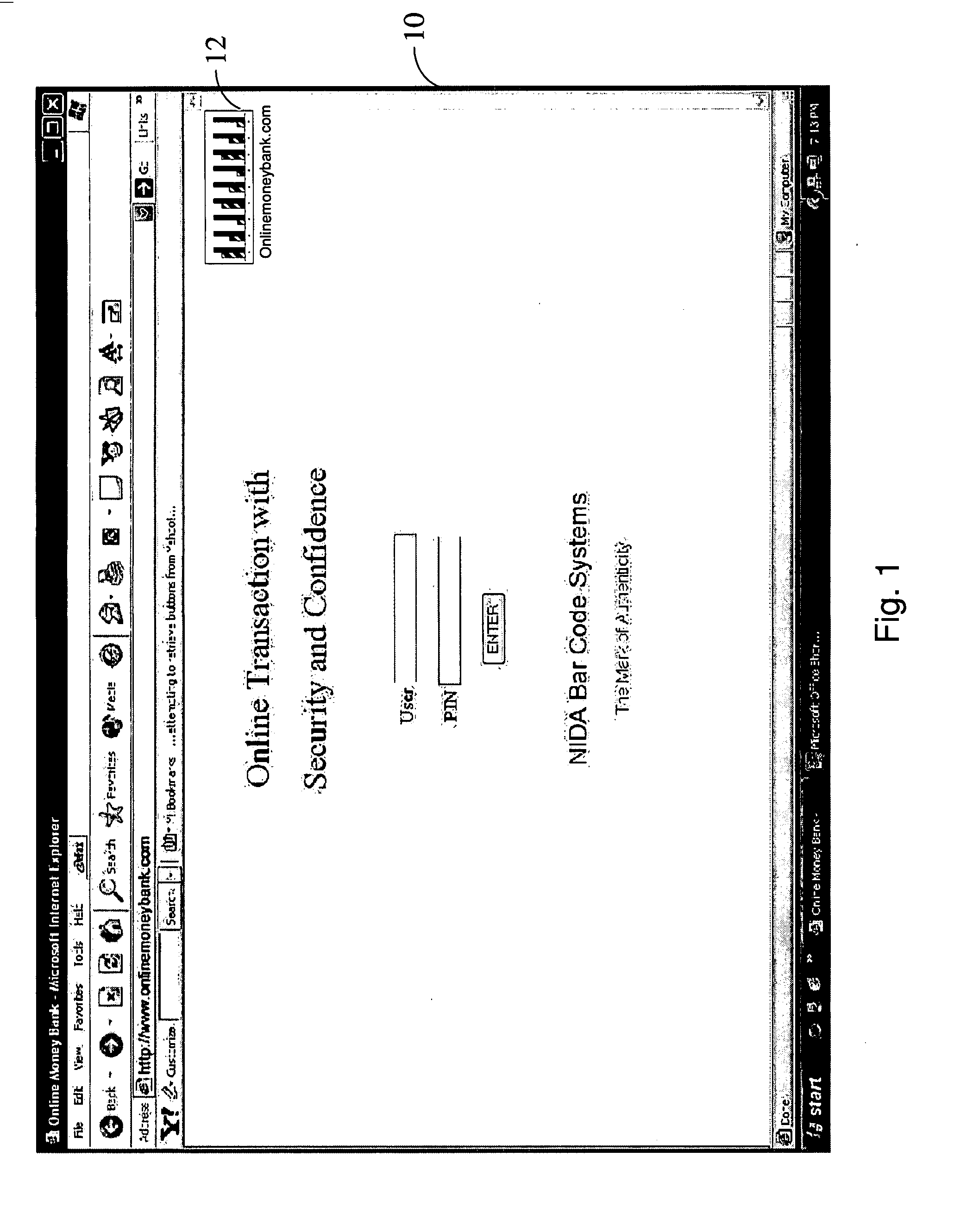
InactiveUS20080066163A1Quicker method of authenticationMemory loss protectionDigital data processing detailsGraphicsThe Internet
A novel method for online authentication of an authorized website is described to prevent the circulation of forged web pages on the World Wide Web. The novel feature of the instant invention is encryption-independent method of securing online transactions by authenticating the server to the client and client to the server. In the instant invention the approach is deployed in curbing the menace of spoofed websites on the World Wide Web by allowing the delivery of only those web pages that are authentic and hosted on an authorized remote server. The method comprises of a graphic representation of the identity of the authorized remote server on the visible portion of the web page served by that remote server. Such graphic representation is capable of being scanned, read and allowed access, only if resolved to the identity of the authorized remote server every time that web page is requested by another authorized computer connected to the Internet.
Owner:RAHEMAN FAZAL
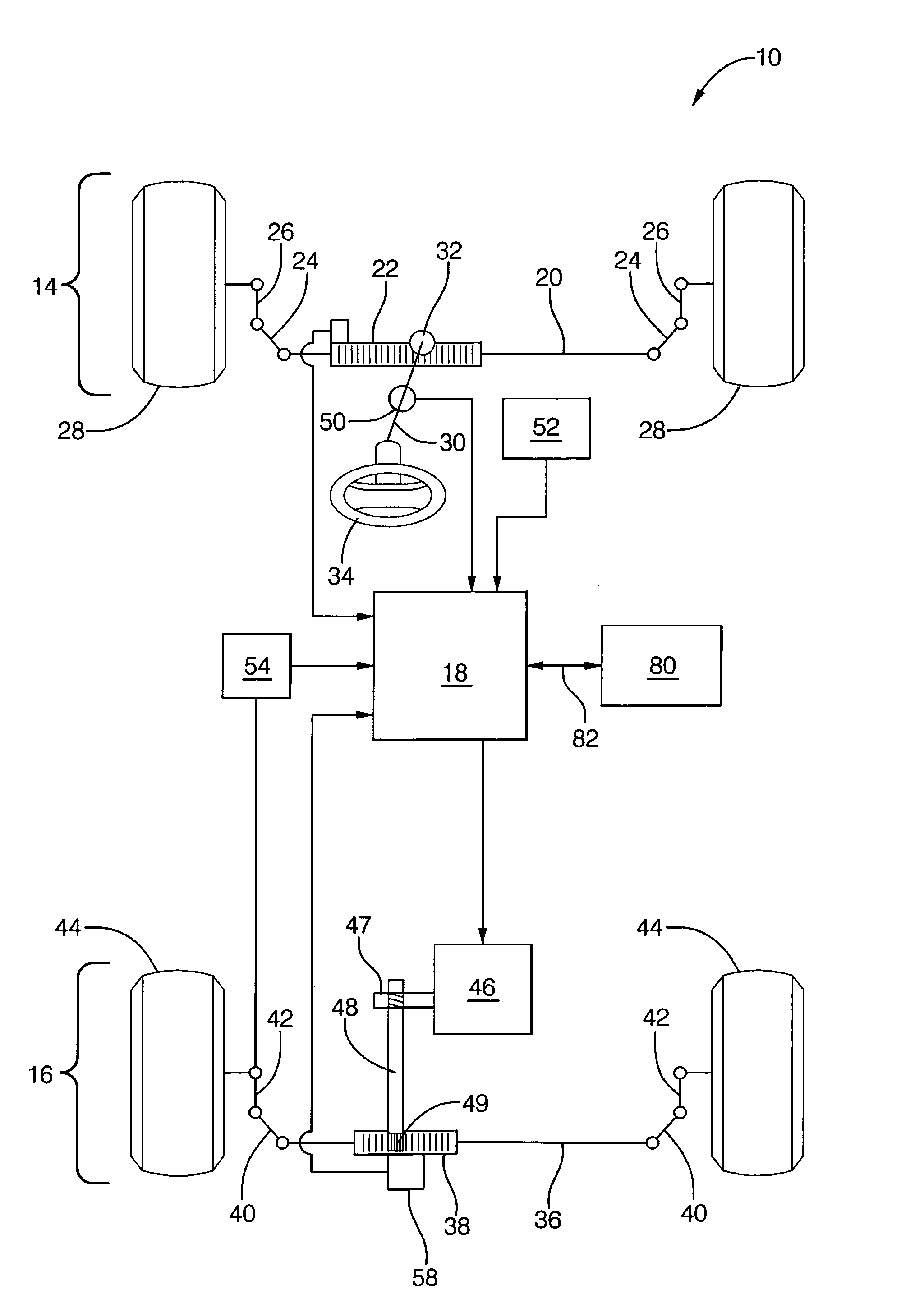
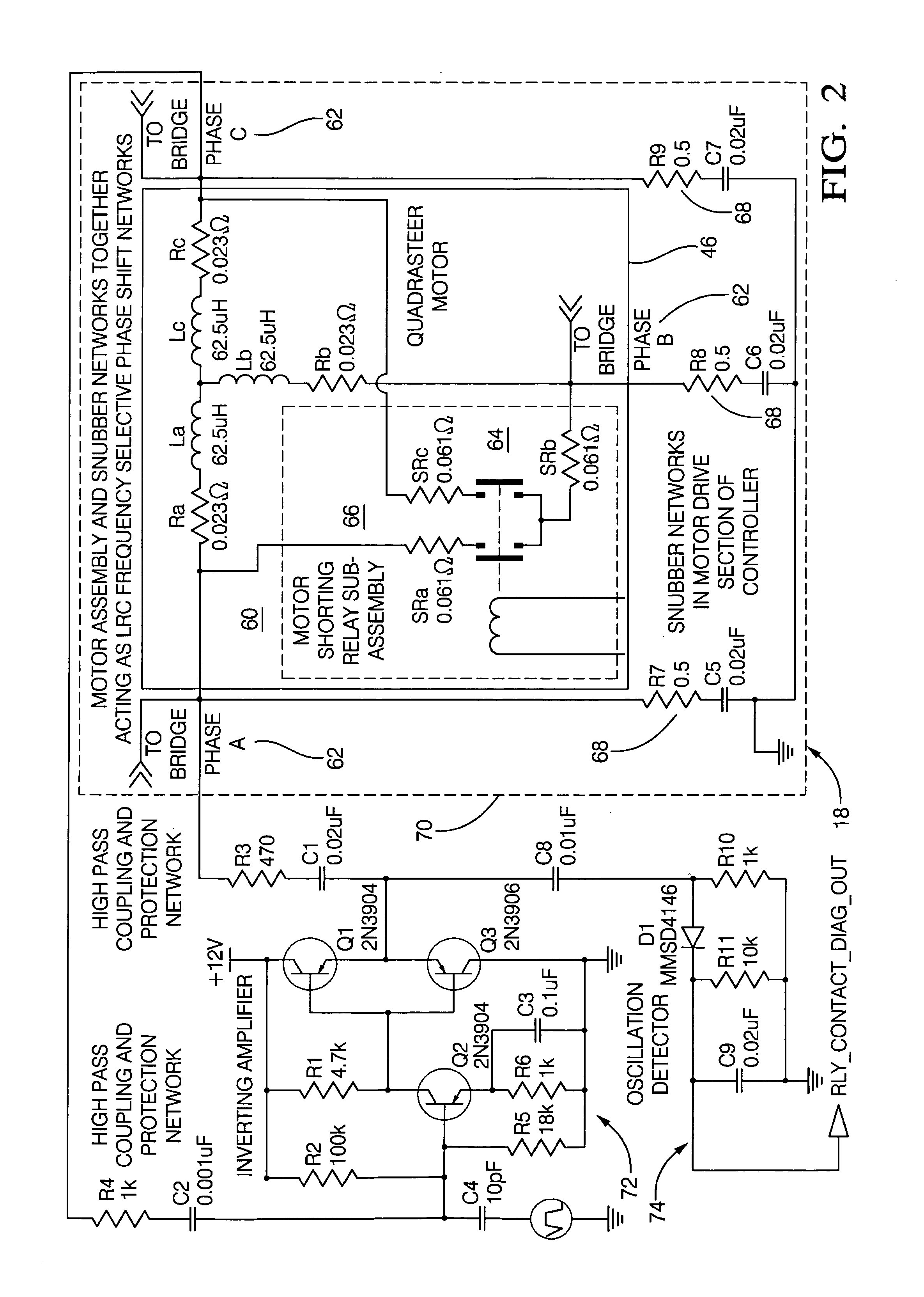
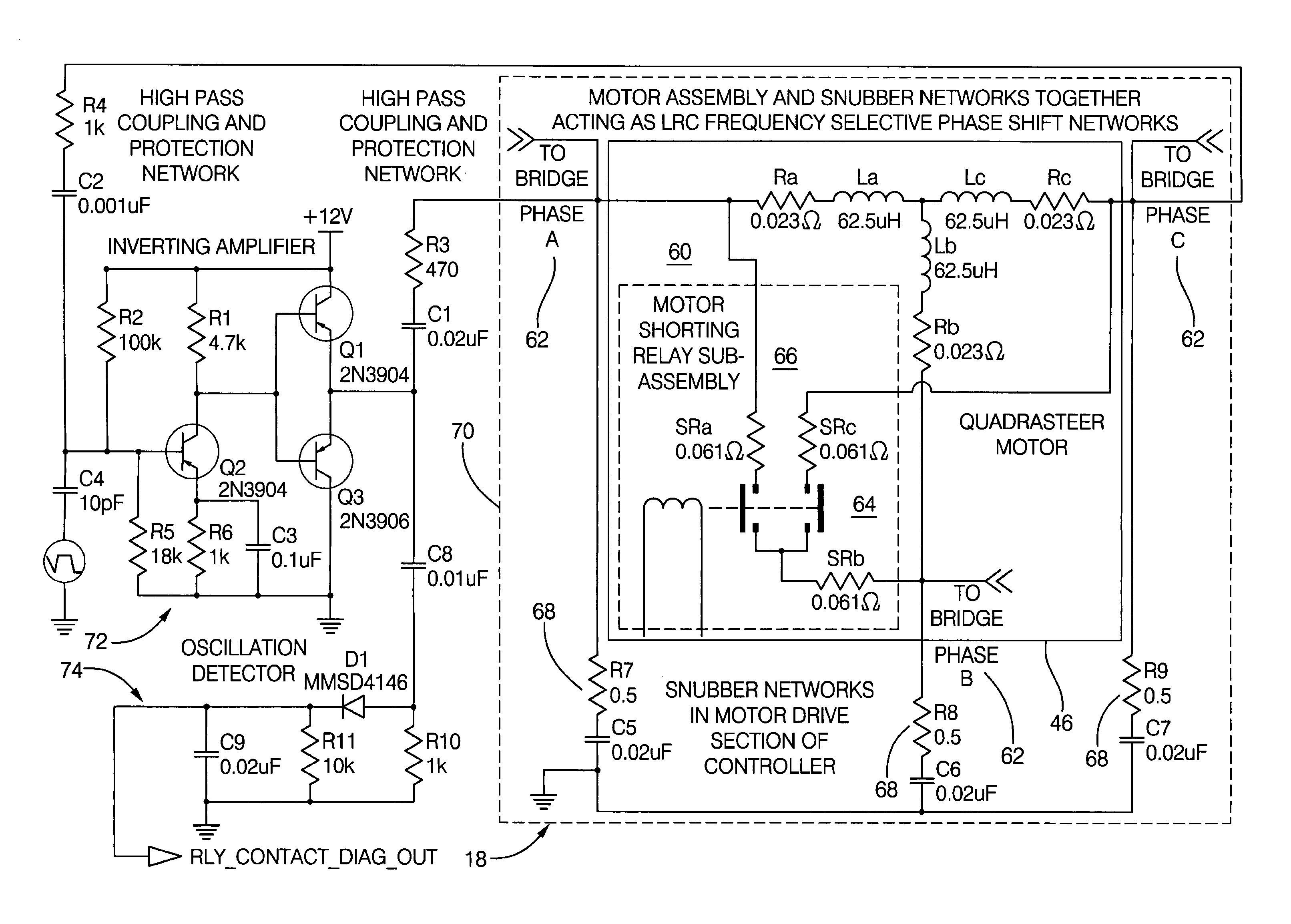
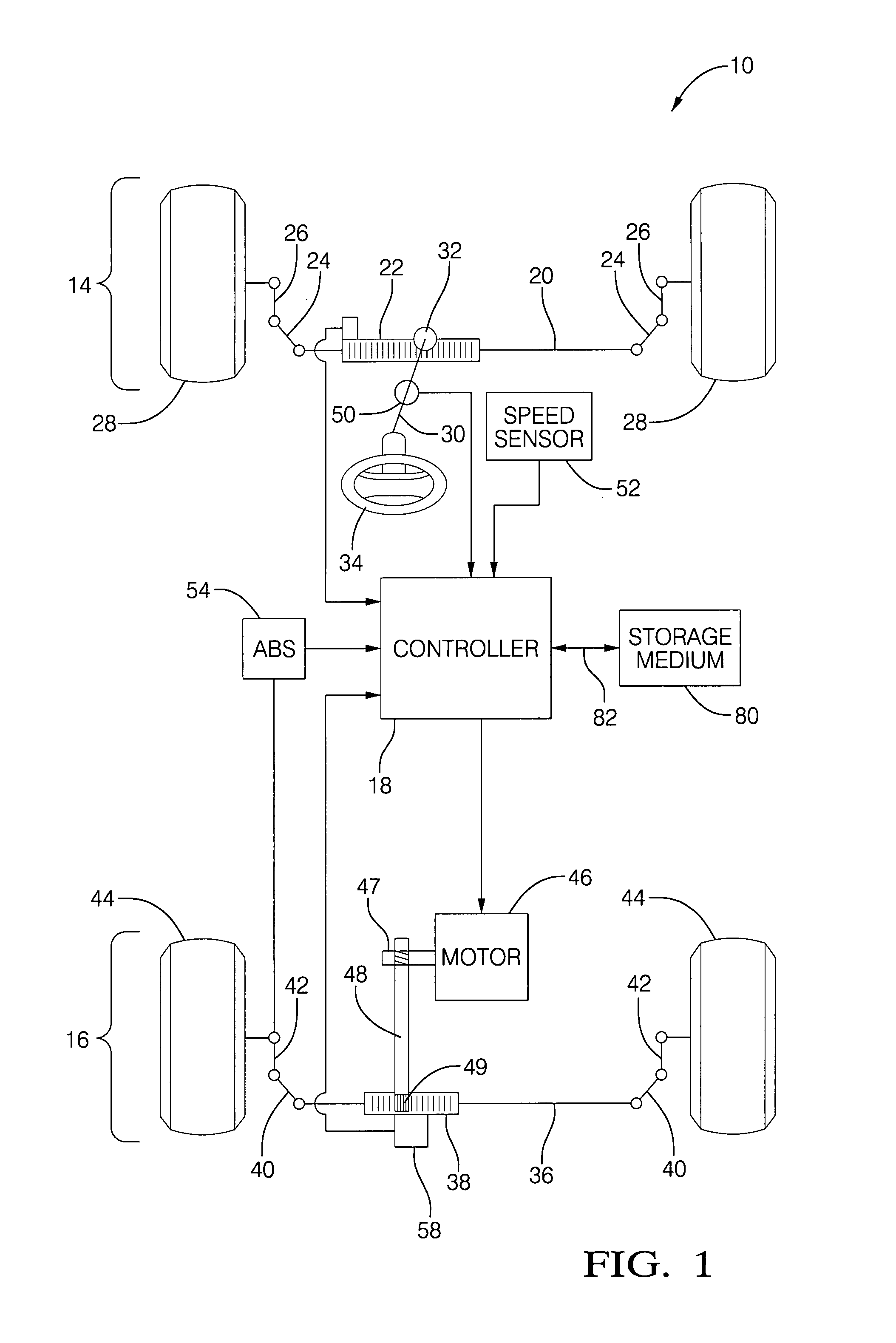
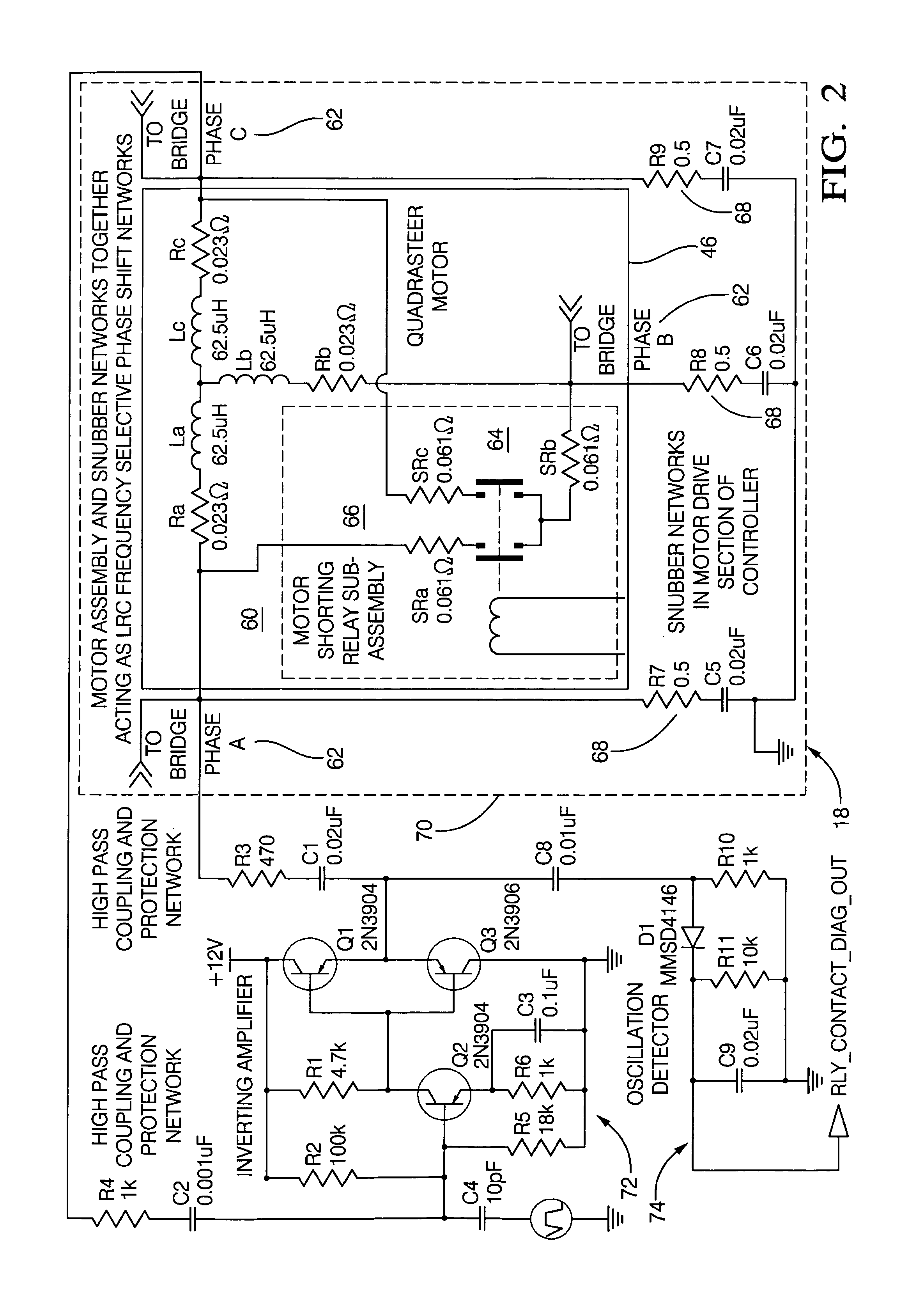
Method and apparatus for diagnosing motor damping network integrity
InactiveUS20060271336A1Electric devicesResistance/reactance/impedenceDetector circuitsNetwork detector
An apparatus for diagnosing motor damping network integrity, the motor damping network configured for selective short-circuiting of the windings of a motor in a motor control system. The apparatus includes a motor controller with a motor drive portion thereof electrically isolated from the windings of the motor. A resonant network is based on the windings of the motor, the damping network, and a remaining non-isolated portion of the controller. An amplifier circuit applies an excitation signal to the resonant network. A detector circuit detects a response of the resonant network based on the excitation signal. A state of the damping network is determined based on the response.
Owner:STEERING SOLUTIONS IP HLDG +1
System and method for locating offending network device and maintaining network integrity
A system and method detects within an IP network an offending network device that has been adversely affecting the IP network performance. A discovery protocol frame is propagated to successive network switches and is formed as a field having a query for inquiring within each network switch to which the frame is propagated whether the network switch has a database entry regarding the MAC address and switch port for the offending network device to locate the offending network device. This discovery protocol frame includes a command for any network switch that has the offending network device connected thereto to disable the switch port to which the offending network device is connected or block all data traffic from the MAC address of the offending network device.
Owner:ADTRAN
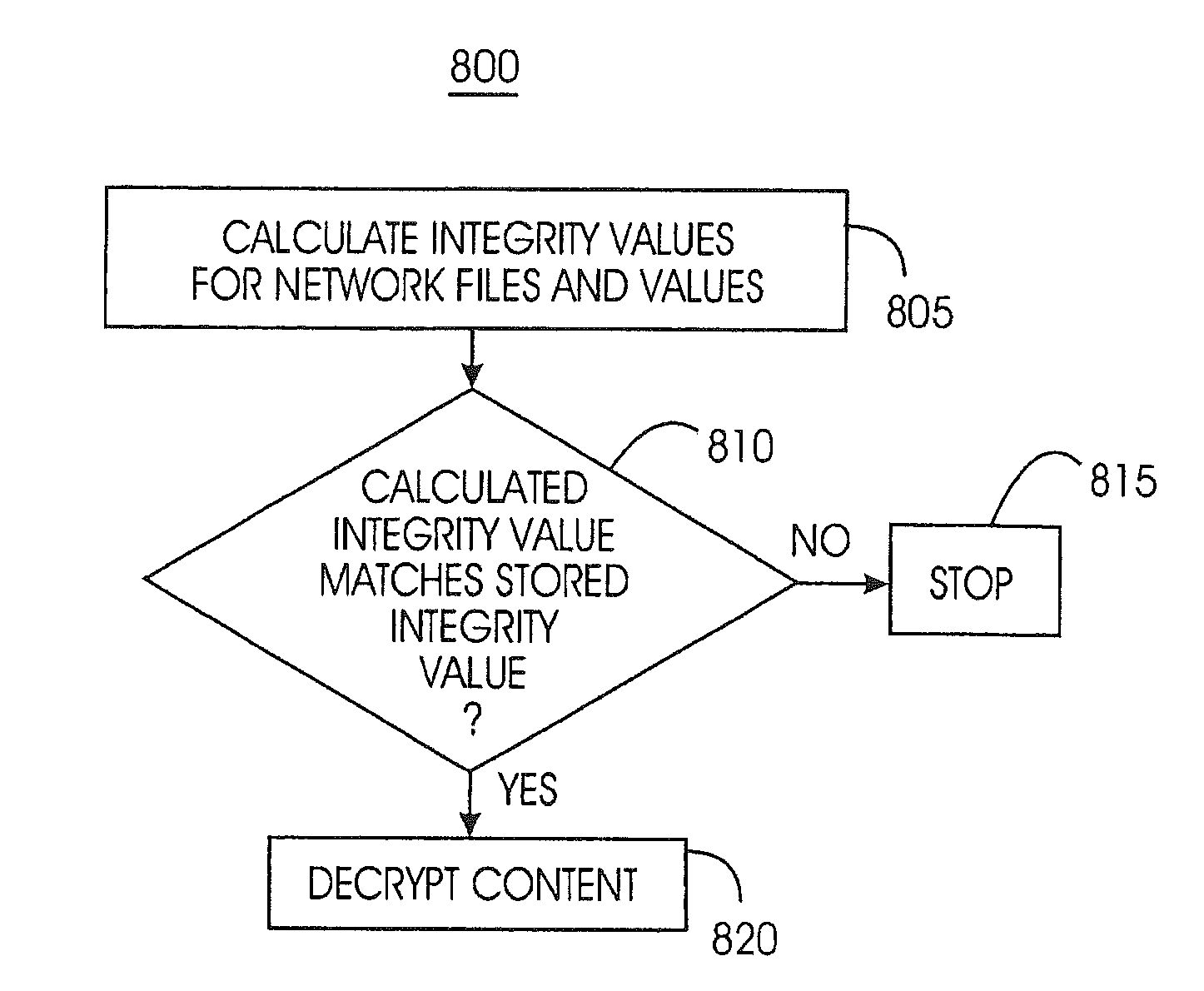
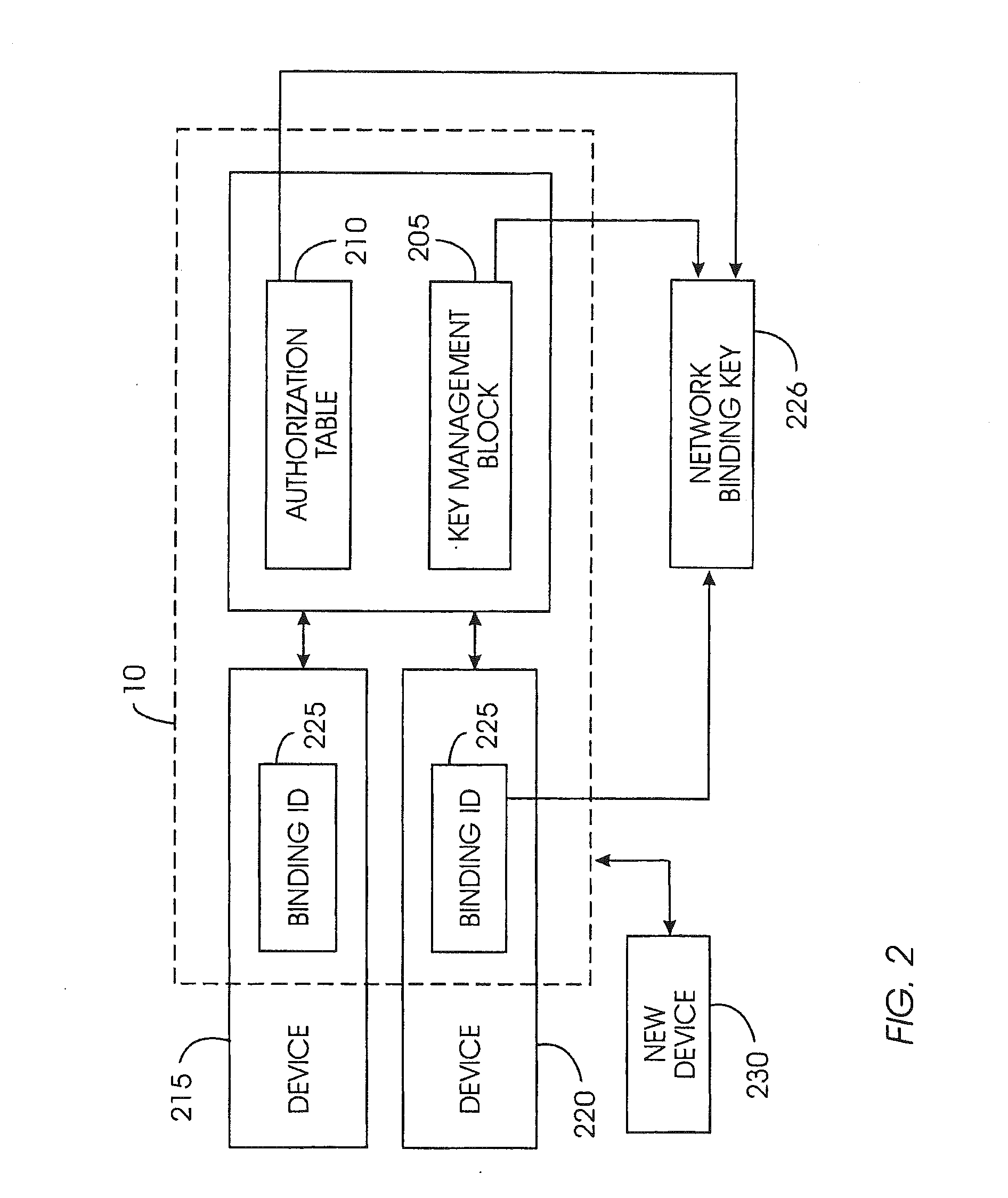
Network integrity maintenance
InactiveUS20110238983A1Minimize storageDoubling sizeKey distribution for secure communicationComputer hardwareWeb service
A device removal system securely removes an item of content or a device from a content-protected home network. An authorization table maintains a list of devices in the content-protected home network in addition to removed devices. The authorization table also maintains a list of deleted content. Through management of various cryptographic keys and techniques, devices and content will not play on a content-protected home network after they have been removed. A secret network ID reduces the possibility of unauthorized playing of content on the content-protected home network. A web server may join the content-protected home network as a device, providing backup for the secret network ID. Otherwise, the device manufacturer will provide the secret network ID in case of a device failure. Storing a verification value in each device ensures integrity of critical cryptographic values. This verification value is compared to network values to ensure network values have not been corrupted.
Owner:INT BUSINESS MASCH CORP
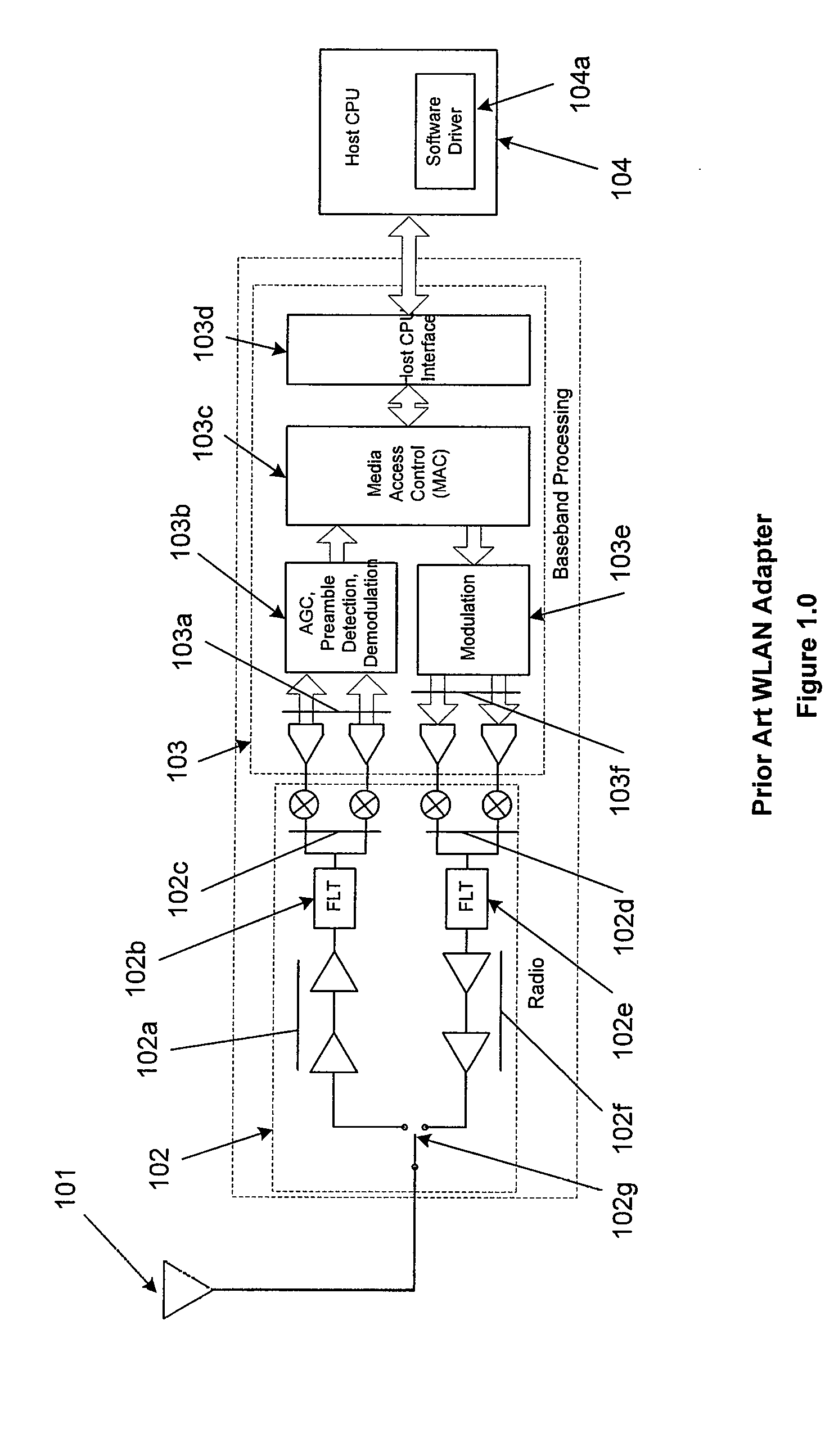
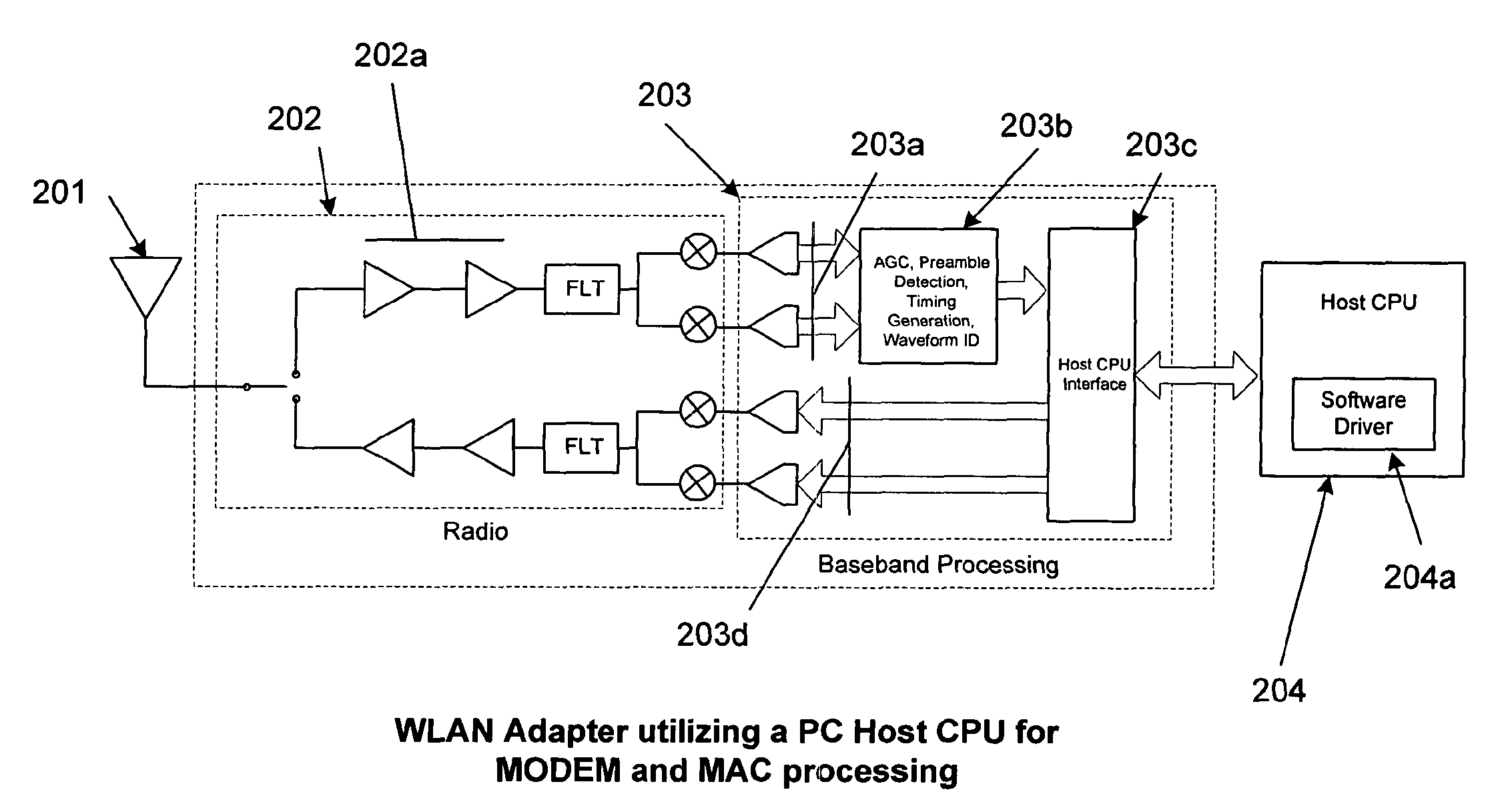
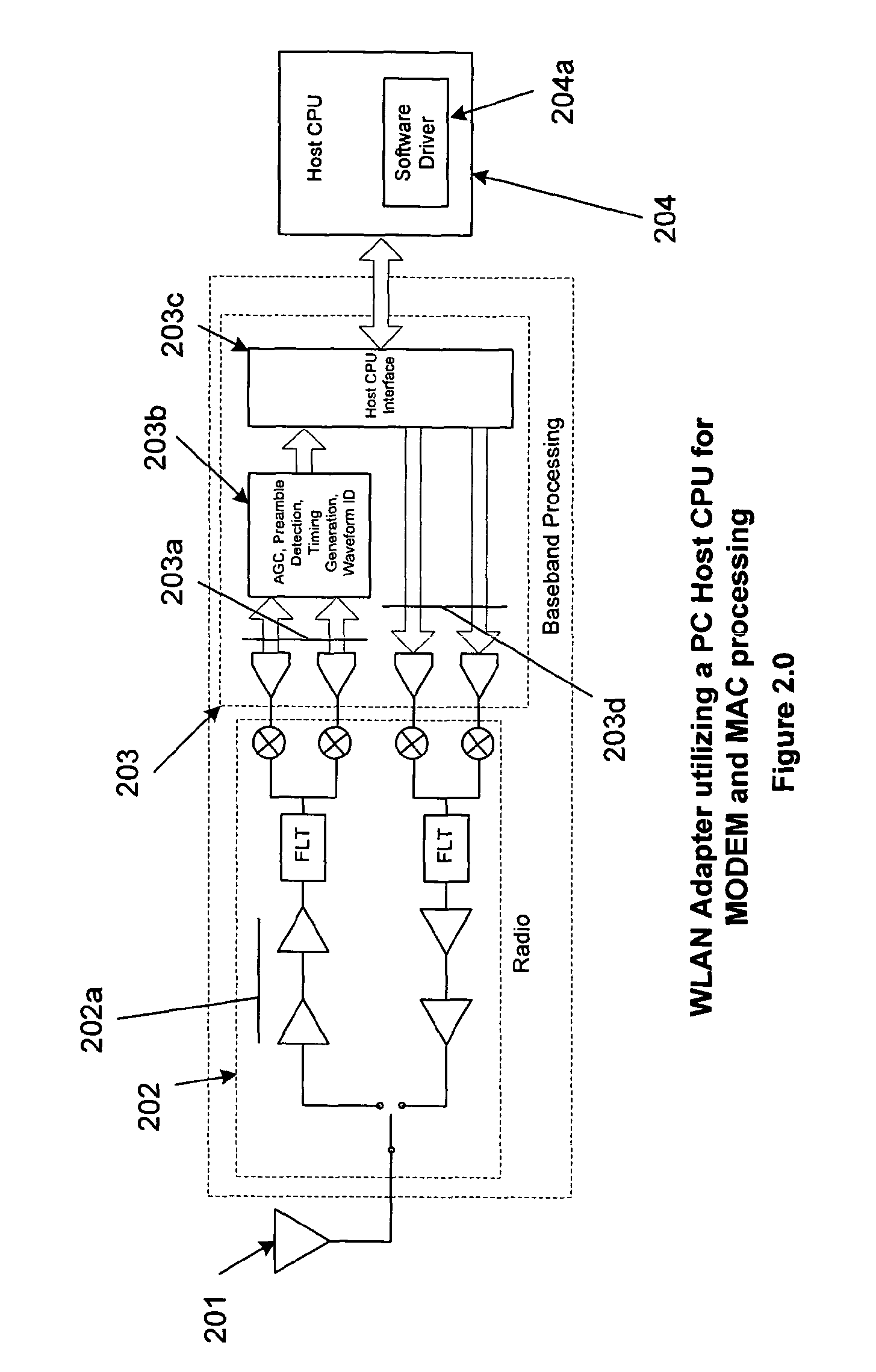
Method for Mitigating Adverse Processor Loading in a Personal Computer Implementation of a Wireless Local Area Network Adapter
ActiveUS20080019277A1Low costMinimizing processing loadEnergy efficient ICTError preventionInternet trafficPeak value
A personal computer's (PC) microprocessor is used to provide both the physical layer (PHY) and media access control (MAC) processing functions required to implement a wireless local area network (WLAN) adapter. This technique uses the polling mechanism associated with the power save (PS) functionality of WLAN protocol to relieve networking stress on the host processing system. It does this while maintaining networking integrity and packet delivery. The WLAN protocol polling mechanism is used to briefly inhibit the transfer of packets from the WLAN access point (AP) during peak periods of network traffic and / or host processor loading. Because the modulation, demodulation, and MAC functions, typically implemented in dedicated hardware on existing adapters are implemented in software running on the host PC microprocessor, other host system processes and applications can interfere with these time critical functions. Conversely, latency introduced by WLAN specific processing tasks during peak periods of network traffic may cause unacceptable delays to the other processes and applications requiring microprocessor attention. In addition to its primary stated purpose of allowing WLAN mobile stations to save power, this technique will use power save polling as a method for controlling delivery of network packets when the host is heavily loaded or when peak interrupt latencies make reliable packet delivery difficult or impossible.
Owner:GLOBESPANVIRATA +1
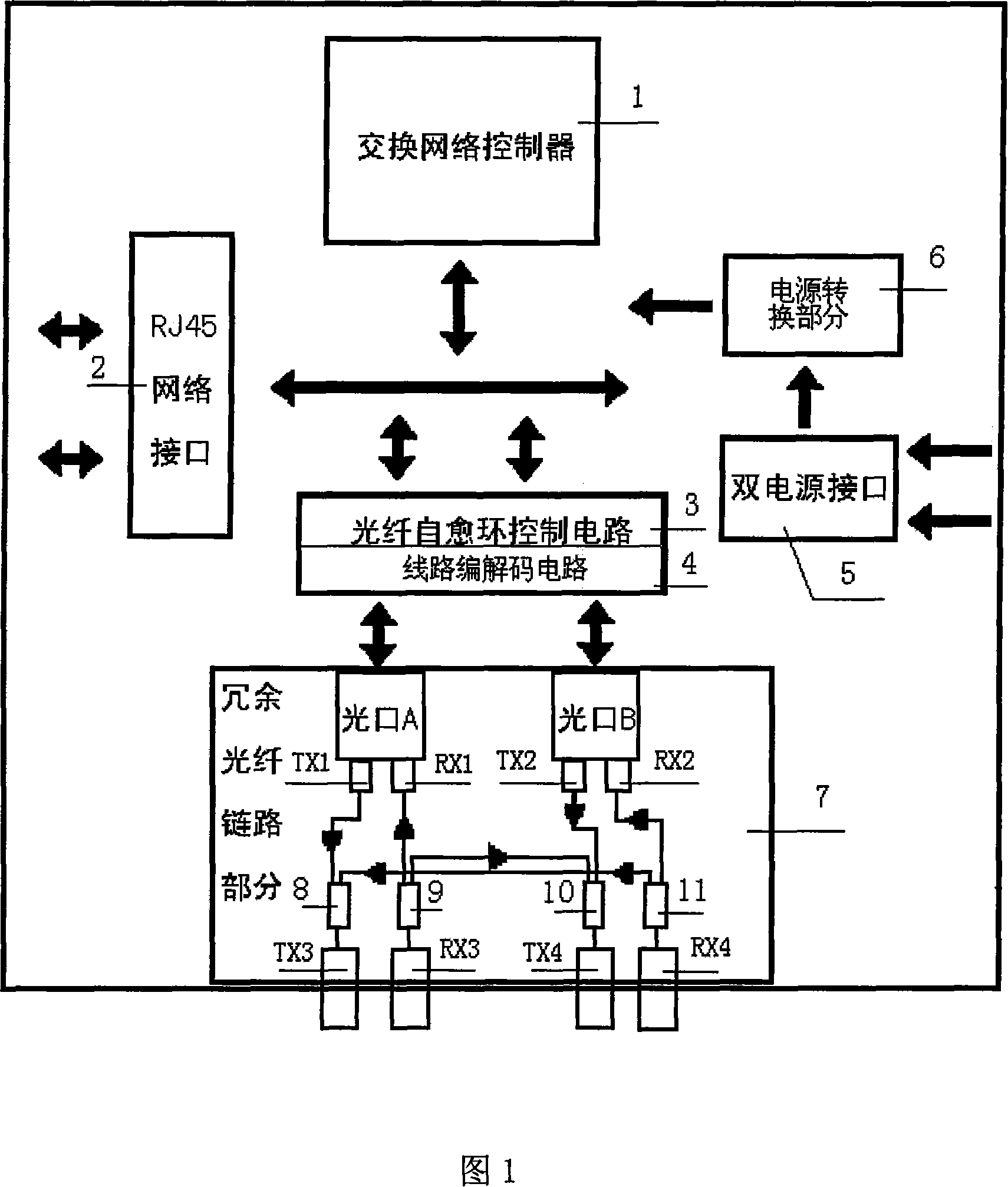
Industry Ethernet switchboard especially used for communication of wind power generation plant
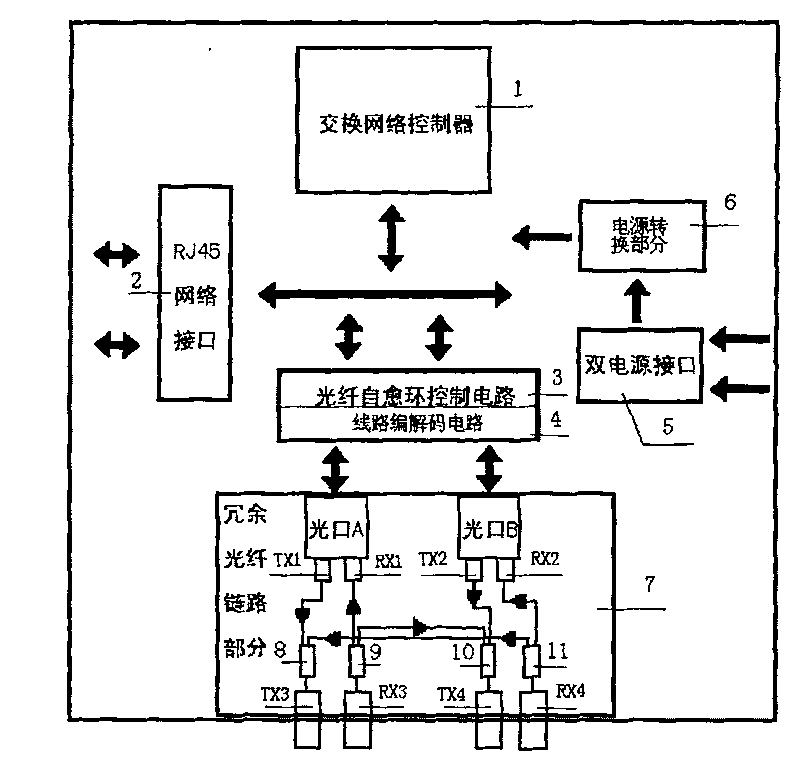
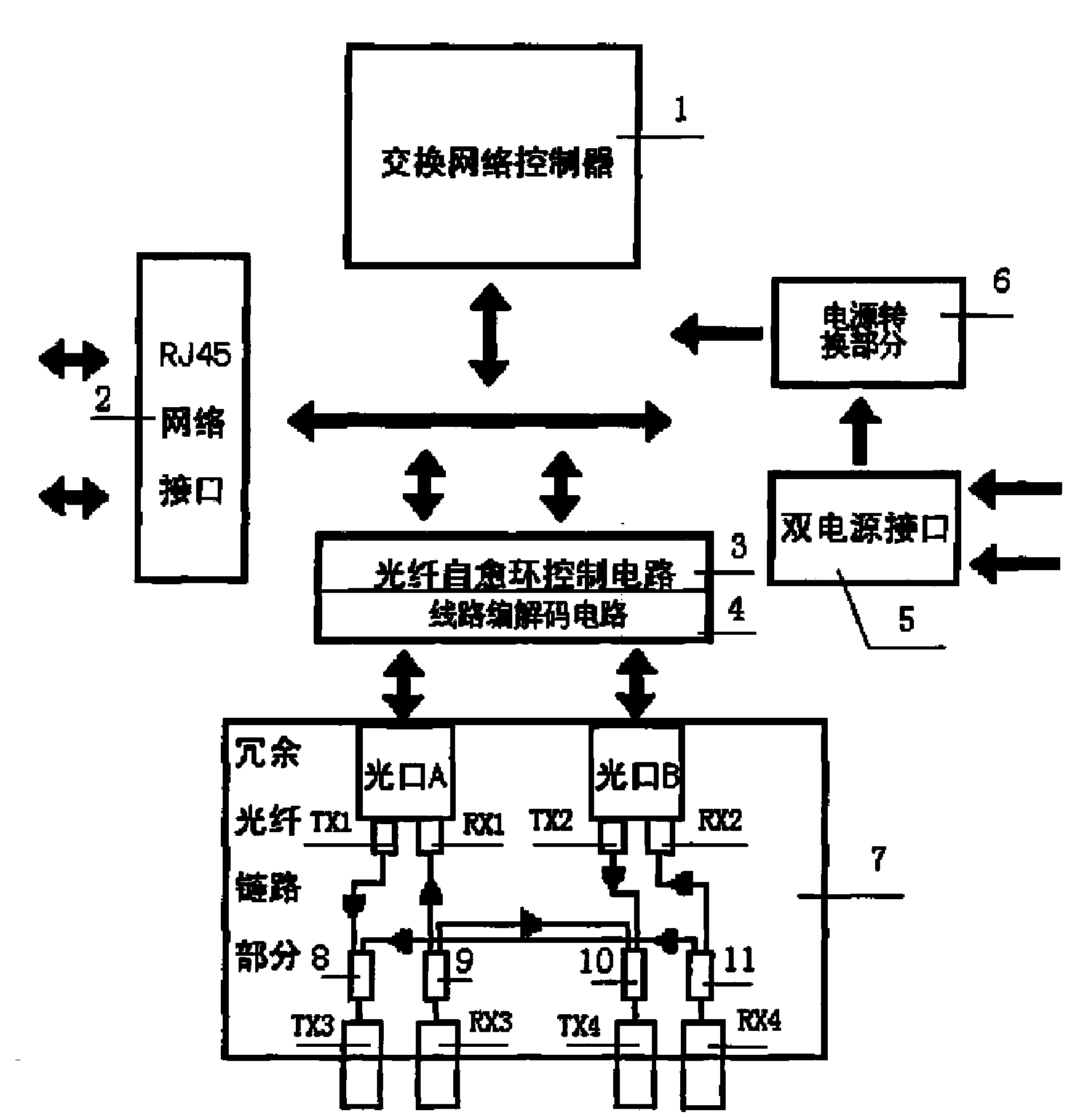
ActiveCN101155434ASolve real-timeSolving a major problem in data communicationsMultiplex system selection arrangementsTime-division multiplexIndustrial EthernetElectricity
An Ethernet switching system special for wind power field communication comprises a switching network controller (1), a network interface (2), an electrical source switching part (6), a double electrical source interface (5), a wiring coding / decoding circuit (4), the wiring coding / decoding circuit (4) connects with the switching network controller (1), the switching network controller (1) separately connects with the electrical source switching part (6) and the network interface (2), the electrical source switching part (6) connects with the double electrical source interface (5), it is characterized in that it also comprise redundant optical fiber chain circuit part (7). The present invention overcomes the shortcomings of the prior Ethernet switching system anti-interfering ability poor, and short communication distance etc. The present invention network can still ensure the optical fiber network integrality and connectivity equipment internal optical redundant chain circuit technique after the equipment power-down, to resolve the wind power plant a big difficult in data communication.
Owner:WUHAN ZHIDE COMM TECH
Method and system of controlling communications delivery to a user
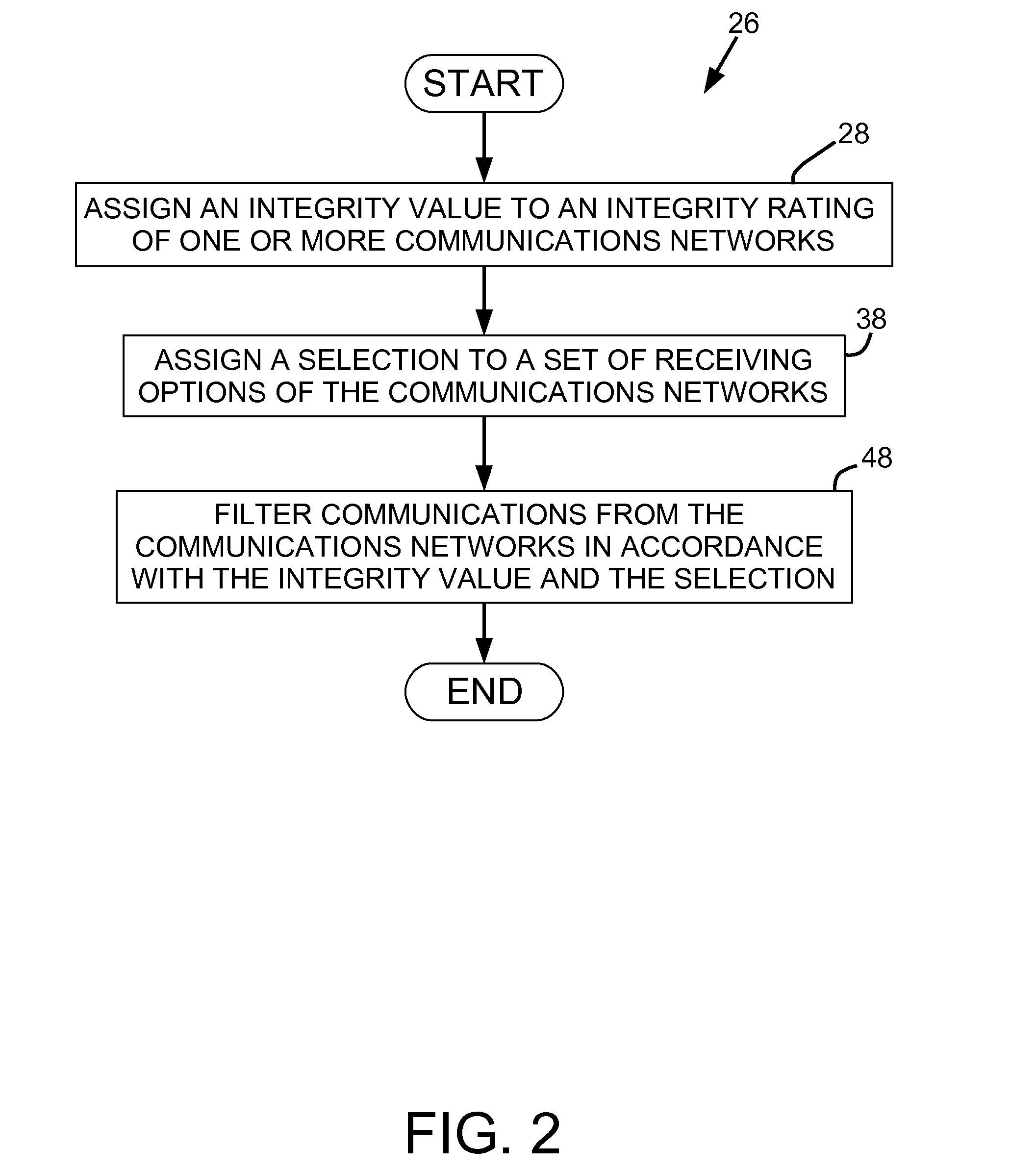
InactiveUS20090024735A1Reduce the valueDigital computer detailsData switching networksNetwork integrityAddress space
A method of controlling communications delivery to a user includes generating an internet protocol address space of internet protocol addresses for each of one or more communications networks operable to transmit marketing communications for delivery to the user; assigning an integrity value to an integrity rating associated with each communications network; assigning a user controllable selection to a set of receiving options associated with the communications networks; and filtering communications received from the communications networks in accordance with respective integrity values and the selection.The method may be performed by a program including computer executable instructions embodied in a signal bearing medium.A system includes a network integrity rating component; an options selection component; a database; and a filter for filtering communications.
Owner:PEDDEMORS MICHAEL G
Method for Mitigating Adverse Processor Loading in a Personal Computer Implementation of a Wireless Local Area Network Adapter
InactiveUS20100208612A1Low costLoad minimizationEnergy efficient ICTError preventionPeak valueHandling system
A personal computer's (PC) microprocessor is used to provide both the physical layer (PHY) and media access control (MAC) processing functions required to implement a wireless local area network (WLAN) adapter. This technique uses the polling mechanism associated with the power save (PS) functionality of WLAN protocol to relieve networking stress on the host processing system. It does this while maintaining networking integrity and packet delivery. The WLAN protocol polling mechanism is used to briefly inhibit the transfer of packets from the WLAN access point (AP) during peak periods of network traffic and / or host processor loading. Because the modulation, demodulation, and MAC functions, typically implemented in dedicated hardware on existing adapters are implemented in software running on the host PC microprocessor, other host system processes and applications can interfere with these time critical functions. Conversely, latency introduced by WLAN specific processing tasks during peak periods of network traffic may cause unacceptable delays to the other processes and applications requiring microprocessor attention. In addition to its primary stated purpose of allowing WLAN mobile stations to save power, this technique will use power save polling as a method for controlling delivery of network packets when the host is heavily loaded or when peak interrupt latencies make reliable packet delivery difficult or impossible.
Owner:INTELLECTUAL VENTURES I LLC
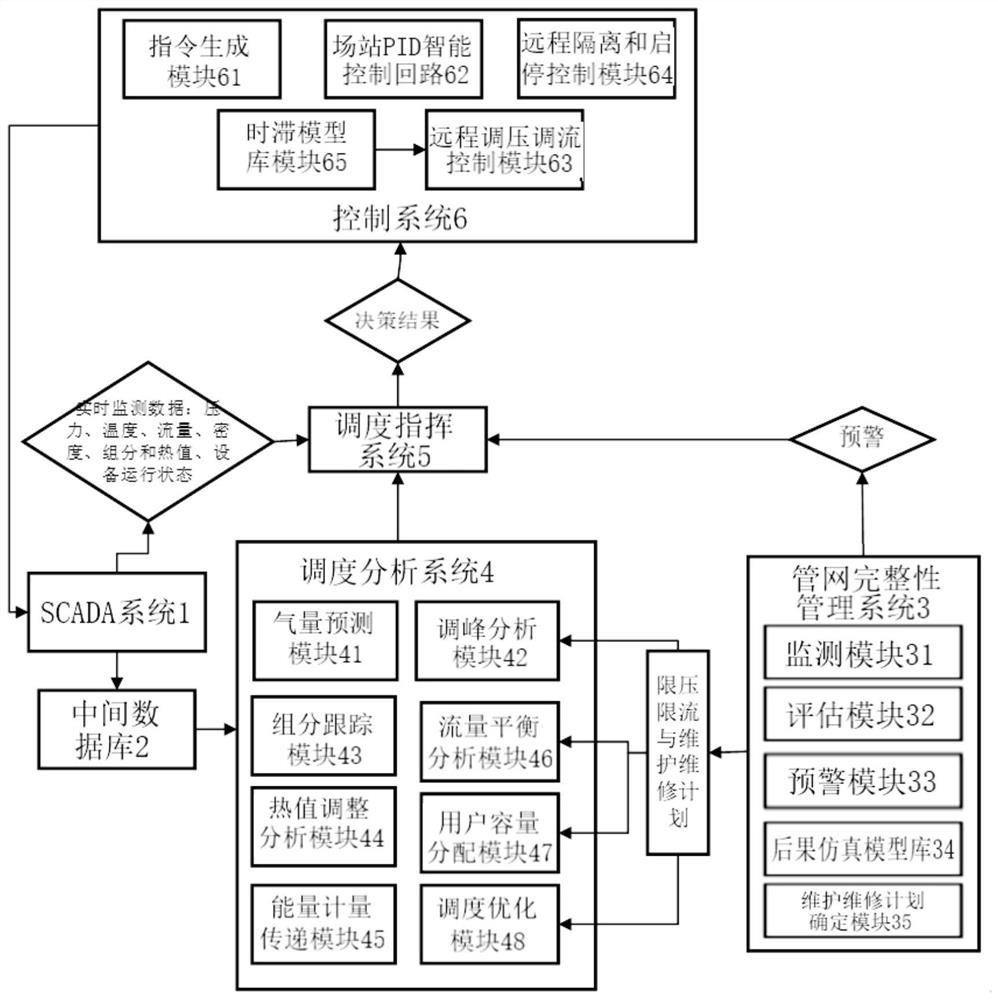
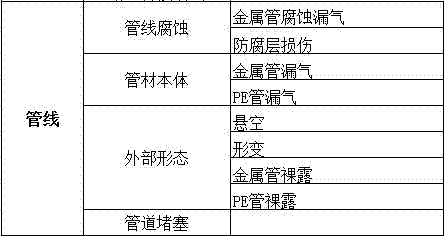
Intelligent high-order scheduling and operation and maintenance system and method for gas transmission pipe network
PendingCN113723834AFully adapt to independent and open operationCompletely adapted to the needsForecastingPipeline systemsEngineeringData bank
The invention relates to an intelligent high-order scheduling and operation and maintenance system and method for a gas transmission pipe network. The system is characterized in that the system comprises: an SCADA systemused for collecting the operation parameter data of the gas transmission pipe network in real time; an intermediate database used for storing the operation parameter data of the gas transmission pipe network and the historical gas consumption data of the user in real time; a pipe network integrity management system used for determining limited pressure and limited flow of field station equipment and gas pipelines in the gas transmission pipe network in real time and performing online early warning on abnormal data; a scheduling analysis system for obtaining a scheduling auxiliary analysis result of the gas transmission pipe network; a dispatching command system used for determining a decision result; and a control system used for generating an instruction according to the determined decision result so as to control each station device of the gas transmission pipe network to work. The system and the method can be widely applied to the technical field of operation scheduling of natural gas long-distance pipelines and gas transmission pipe networks.
Owner:CNOOC GAS & POWER GRP
Method and apparatus for diagnosing motor damping network integrity
An apparatus for diagnosing motor damping network integrity, the motor damping network configured for selective short-circuiting of the windings of a motor in a motor control system. The apparatus includes a motor controller with a motor drive portion thereof electrically isolated from the windings of the motor. A resonant network is based on the windings of the motor, the damping network, and a remaining non-isolated portion of the controller. An amplifier circuit applies an excitation signal to the resonant network. A detector circuit detects a response of the resonant network based on the excitation signal. A state of the damping network is determined based on the response.
Owner:STEERING SOLUTIONS IP HLDG +1
Analyzing an access control list for a router to identify a subsumption relation between elements in the list
InactiveUS7484004B2Easy to importDigital computer detailsData switching by path configurationNetwork integrityWorld Wide Web
Methods are described for analyzing access list subsumption in routing devices of a computer network and for identifying computer network integrity violations, by producing structured data that includes stored router names and access lists that include elements with address / mask pairs, or patterns used to filter data into and out of a routing device, respectively; determining whether access lists in the structured data include elements in which a first element in the access list has a more general or equal address / mask pair, or pattern, respectively, than a second or subsequent element, or pattern; and storing in electronic memory a report of elements or a list of patterns, respectively, in which a first element or pattern is more general than or equal to a second or subsequent element or pattern.
Owner:CISCO TECH INC
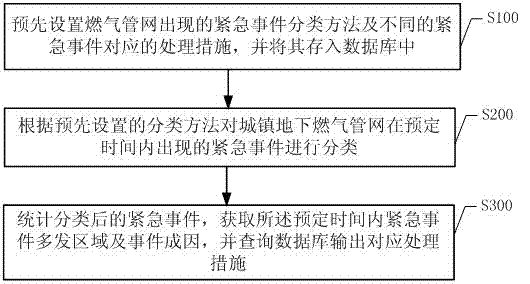
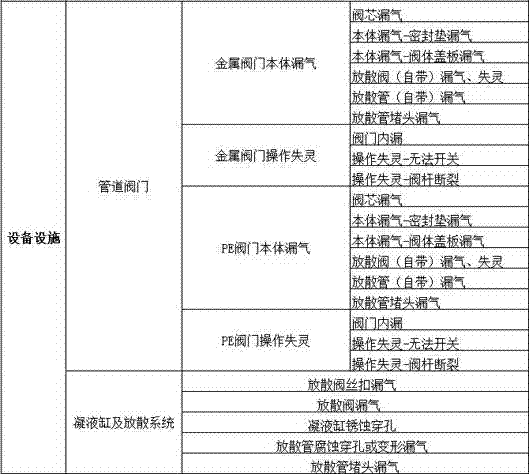
Emergency analyzing method and system based on gas pipe network integrity system
InactiveCN104732343AReduce accidentsImprove the efficiency of finding incident-prone areasResourcesStatistical classificationClassification methods
The invention discloses an emergency analyzing method and a system based on a gas pipe network integrity system, wherein the emergency analyzing method comprises the steps that the classification method of the emergencies occurring in the gas pipe network and corresponding treating measures of different emergencies are pre-set and are stored in a database; classification is conducted on the emergencies occurring in an urban underground gas pipe network in a pre-set time according to the preset classification method; statistics is conducted on the classified emergencies, the emergency-prone areas and emergency causes in the pre-set time are acquired, and corresponding treating measures are output by querying the database. According to the emergency analyzing method and the system based on the gas pipe network integrity system, reasonable statistical classification is conducted aiming at the underground gas pipe network emergencies when the the recovery work is finished, the efficiency of an enterprise to find the emergency-prone areas in the underground gas pipe network is improved, the possibility that emergencies occur in the underground gas pipe network is decreased to the maximum extent, and convenience is provided for the enterprise to prevent emergencies in the underground gas pipe network from occurring.
Owner:SHENZHEN GAS CORP
System and method for maintaining network integrity for incrementally training machine learning models at edge devices of a peer to peer network
PendingUS20210256421A1Avoid skewUser identity/authority verificationCharacter and pattern recognitionAlgorithmEngineering
A method and a system for maintaining network integrity for incrementally training machine learning (ML) models at edge devices is provided. The method includes registering, by a certifying node, one or more edge devices with a peer to peer network. Upon registration, an incrementally updated ML model is received from a first registered device at the certifying node. The certifying node accepts the incrementally updated ML model if a contribution of the first edge device is within a predetermined threshold, and else rejects the updated ML model if the contribution is beyond the predetermined threshold. Limiting the contribution by each edge device enables prevention of skew by any of the edge devices at the certifying node. Upon accepting the updated ML model, the certifying node certifies the updated ML model and transfers the certified ML model to one or more other edge devices in the peer to peer network.
Owner:SUNDARESAN SUBASH MR
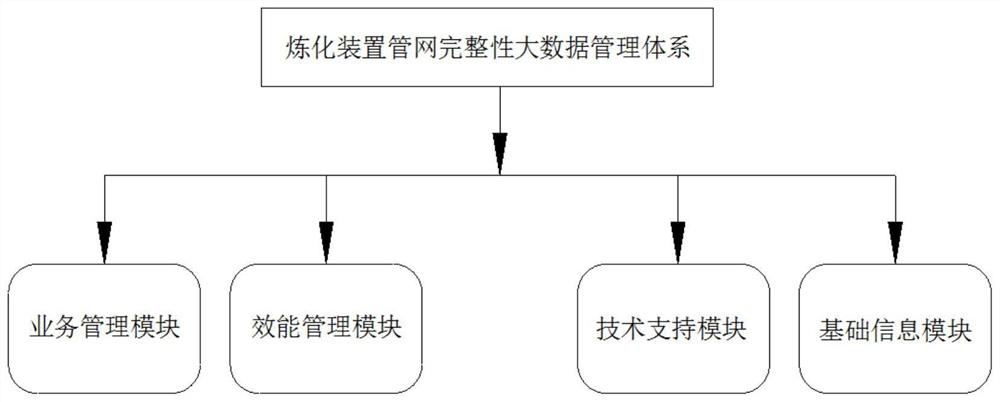
Refining device pipe network integrity big data management system
InactiveCN114117699AImprove integrity management measuresGeometric CADForecastingCluster algorithmEngineering
The invention relates to a refining device pipe network integrity big data management system. Comprising the following construction steps: step 1, construction of a big data management system of a refinery device pipe network integrity management system, step 2, design of an improved whale algorithm, and step 3, determination of a K-MAX clustering algorithm. 4, optimizing a K-MAX clustering algorithm based on the improved whale algorithm; and step 5, marking abnormal data of refinery device pipe network integrity management. By means of the constructed refining device integrity big data management system, abnormal data can be accurately found, then the defects existing in refining device pipe network integrity management can be found, and therefore the refining device pipe network integrity management system can be improved in time.
Owner:LIAONING UNIVERSITY OF PETROLEUM AND CHEMICAL TECHNOLOGY
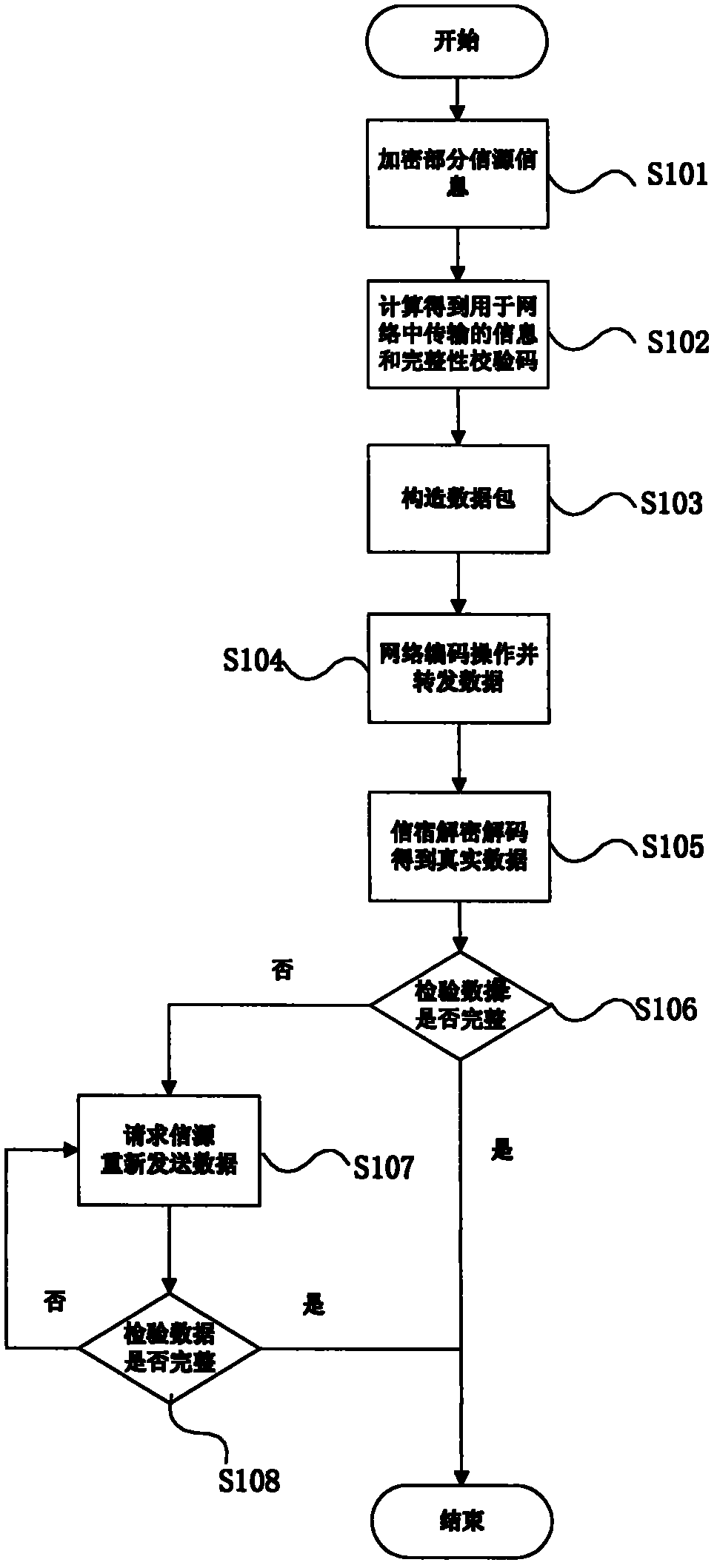
Secure network coding method for optical networks based on source information encryption
ActiveCN102427399AImprove confidentialityImprove integrityError preventionSecuring communicationNetwork codeNetwork integrity
The invention relates to a secure network coding method for optical networks based on source information encryption. The secure network coding method specifically comprises the steps of: realizing network security by using a method of encrypting information of an information source; and realizing a network integrity check function by using a method of integrity check codes. During source information encryption, the security function of the network can be realized as long as a small part of the information is encrypted, thereby quantity of information needed to be encrypted is indirectly reduced. A check function in the optical networks is realized by the methods of destination integrity check and source retransmission.
Owner:BEIJING UNIV OF POSTS & TELECOMM
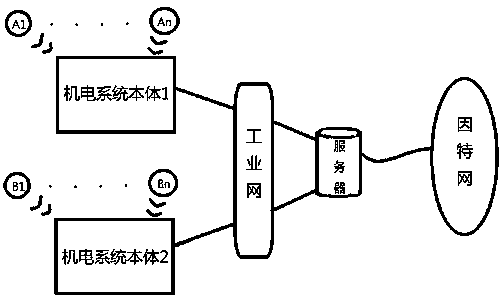
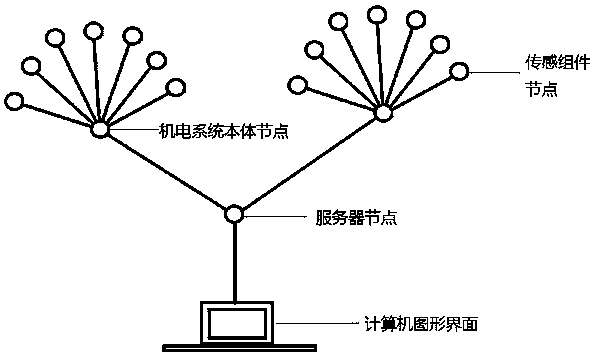
Evaluation and verification system for data monitoring quality of high-power electromechanical equipment
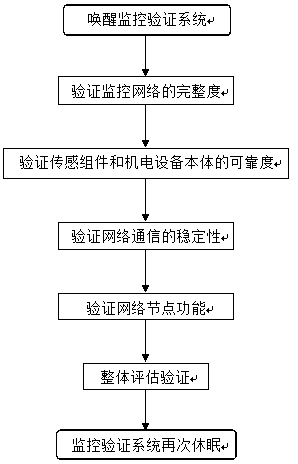
InactiveCN109284930AOngoing access to monitoring qualityContinuously obtain assessment conclusions of monitoring qualityResourcesData switching networksComputer moduleGeolocation
The invention provides an evaluation system for data monitoring quality of high-power electromechanical equipment. The evaluation and verification system is embedded in the monitoring system and is ina dormant state in a non-evaluation verification state, characterized in that: includes a monitoring network integrity evaluation module. The module obtains the evaluation data of the integrity of the monitoring network by confirming whether the geographic position and network position of the sensor components in the monitoring network, the electromechanical system body are true, and whether thegeographic position and network position match each other, and the evaluation data is reflected in the network node topology diagram preset by the graphical interface.
Owner:HUNAN INST OF METROLOGY & TEST
Node power control method, device, device and storage medium
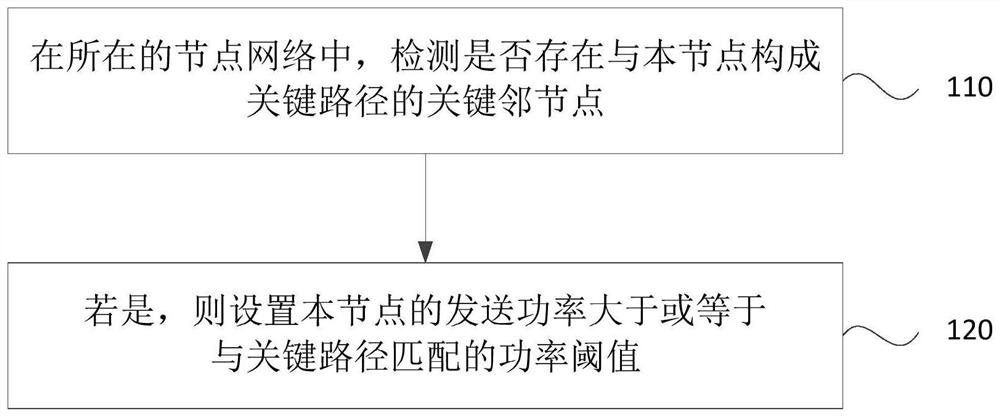
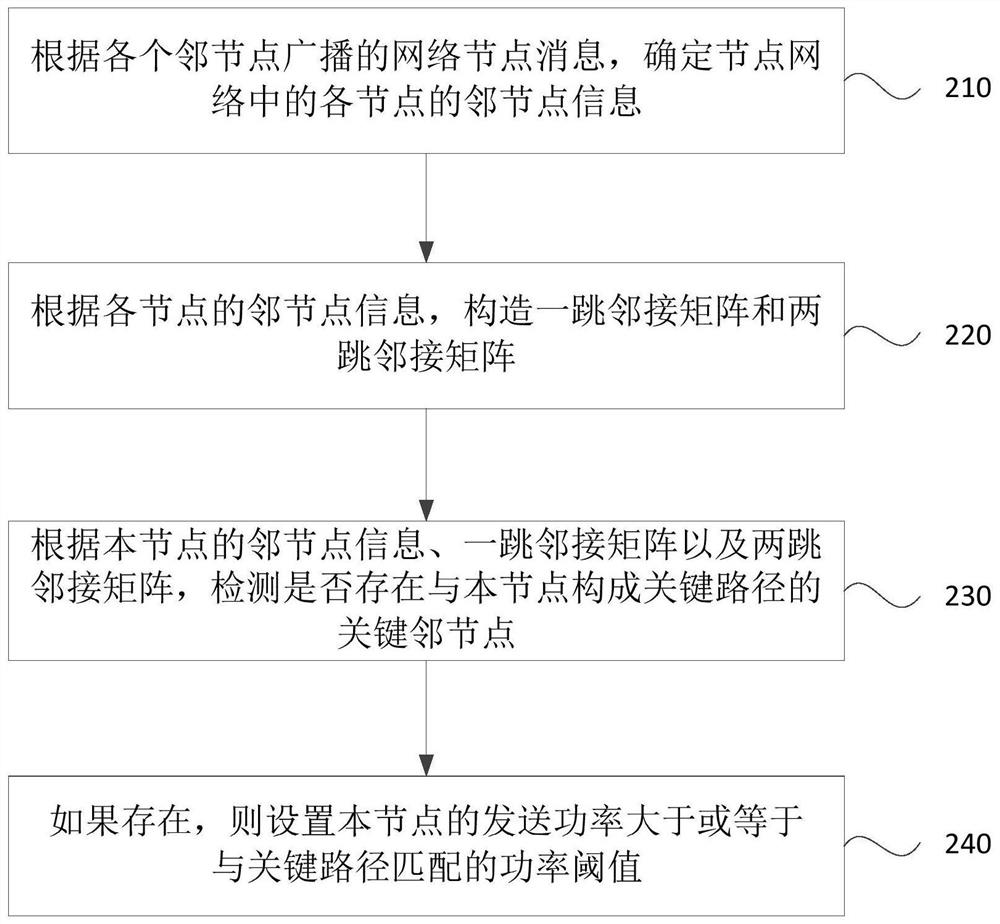
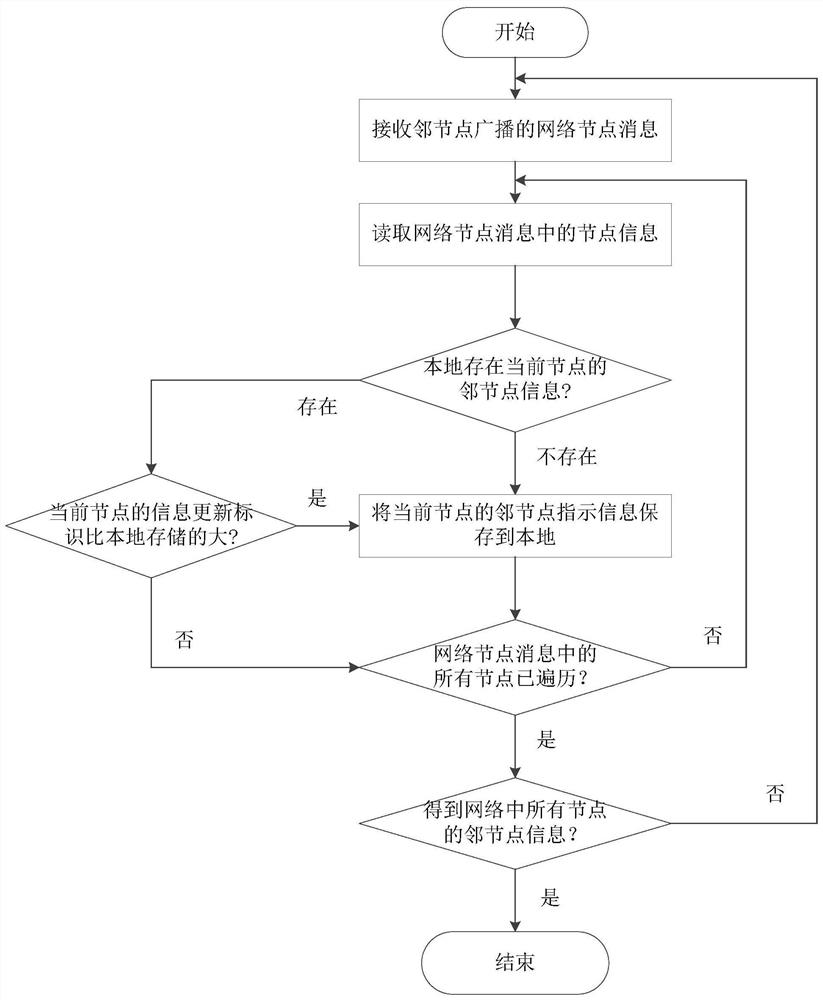
ActiveCN112672394BTroubleshoot splitting into subnetsReduce splitPower managementNetwork topologiesPathPingTransmitted power
The embodiment of the invention discloses a node power control method, device, equipment and storage medium. The method includes: in the node network where it is located, detecting whether there is a key neighboring node forming a critical path with the current node; wherein, when the critical path is disconnected, the node network can be divided into two independent subnets; If yes, set the sending power of the current node to be greater than or equal to the power threshold matching the critical path. The technical solutions of the embodiments of the present invention enable nodes to identify critical paths in the network, and ensure the connection status of the critical paths through power control strategies, reduce the probability of the network splitting into multiple subnets, and ensure the integrity of the network.
Owner:MORNINGCORE HLDG CO LTD
Industry Ethernet switchboard especially used for communication of wind power generation plant
ActiveCN101155434BSolve real-timeSolving a major problem in data communicationsMultiplex system selection arrangementsTime-division multiplexIndustrial EthernetElectricity
An Ethernet switching system special for wind power field communication comprises a switching network controller (1), a network interface (2), an electrical source switching part (6), a double electrical source interface (5), a wiring coding / decoding circuit (4), the wiring coding / decoding circuit (4) connects with the switching network controller (1), the switching network controller (1) separately connects with the electrical source switching part (6) and the network interface (2), the electrical source switching part (6) connects with the double electrical source interface (5), it is characterized in that it also comprise redundant optical fiber chain circuit part (7). The present invention overcomes the shortcomings of the prior Ethernet switching system anti-interfering ability poor,and short communication distance etc. The present invention network can still ensure the optical fiber network integrality and connectivity equipment internal optical redundant chain circuit techniqueafter the equipment power-down, to resolve the wind power plant a big difficult in data communication.
Owner:WUHAN ZHIDE COMM TECH
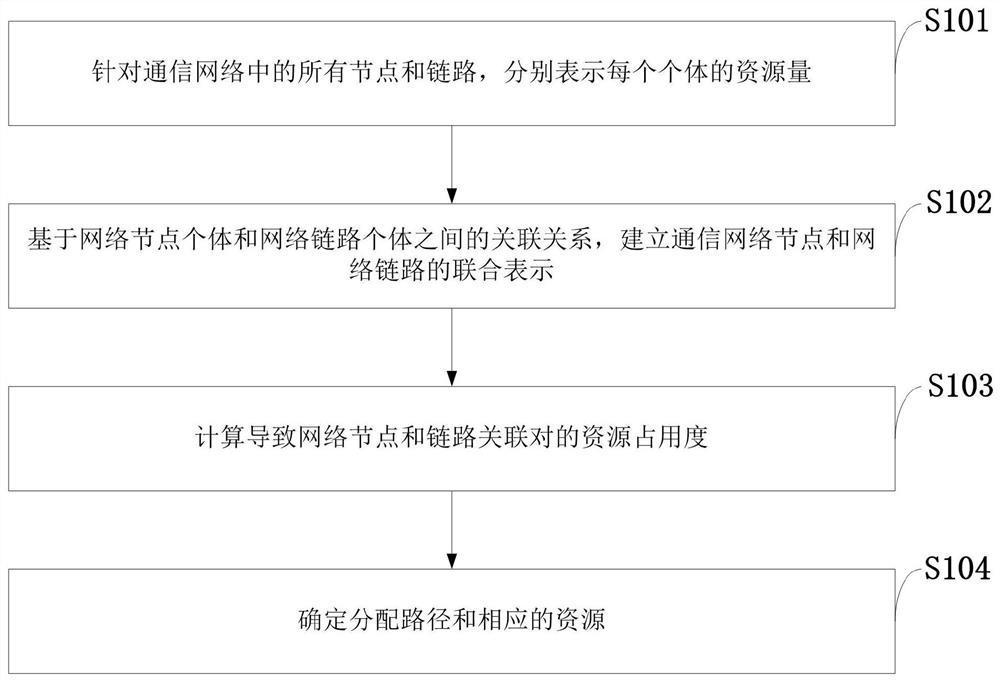
A Joint Resource Allocation Method for Network Node Links with Minimized Resource Occupancy
ActiveCN108174446BAvoid Greedy OccupationGuaranteed performanceWireless communicationResource assignmentNetwork link
The invention belongs to the technical field of wireless communication, and discloses a method for jointly allocating resources of network nodes and links with minimum resource occupancy. For all nodes and links in the communication network, the resource amount of each individual is respectively represented; based on the network node The association relationship between individuals and network link individuals establishes the joint representation of communication network nodes and network links; calculates the resource occupancy of associated pairs of network nodes and links: determines the allocation path and corresponding resources. Compared with the commonly used allocation algorithm for a single service requirement, the present invention selects a link with abundant resources to form a path and allocate resources, avoids greedy occupation of resources by services, reserves sufficient resources for subsequent services, and ensures the integrity of the network as a whole. Performance: Compared with the commonly used network resource overall performance maximization analysis algorithm, the present invention can be specifically formed as a specific resource allocation result of a single service.
Owner:XIDIAN UNIV
Field bus router of solar power generation communication
InactiveCN103457863ASolve the bandwidthSolve real-timeRing-type electromagnetic networksFibre transmissionPower stationSupply management
A field bus router of solar power generation communication comprises a route protocol conversion module (1), an input module (2), a protocol transforming module (6), a power supply management module (5) and a route selecting module (4), wherein the route selecting module (4) is connected with the route protocol conversion module (1) which is respectively connected with the protocol transforming module (6) and the input module (2), and the protocol transforming module (6) is connected with the power supply management module (5). The field bus router is characterized by further comprising a signal transmission module (7). The field bus router overcomes the defects that a conventional field bus router is poor in interference-resistant ability, short in communication distance and the like. According to the field bus router, after equipment is powered off, a network can still achieve signal transmission guaranteeing optical network integrity and communication in the equipment, and the problem in signal communication in a solar power plant is solved.
Owner:KUNSHAN AODELU AUTOMATION TECH
Refining device pipe network integrity management level intelligent evaluation method
InactiveCN114065624AMaster the actual levelGood nonlinear approximation capabilityDesign optimisation/simulationControl engineeringIndex system
The invention relates to a refining device pipe network integrity management level intelligent evaluation method. The method comprises the following steps of 1, construction of a refinery device pipe network integrity management system, 2, determination of a refinery device pipe network integrity management evaluation index system, and 3, design of an intelligent algorithm. The fuzzy ultra-wavelet neural network optimized by using the constructed intelligent algorithm can determine the refinery device pipe network integrity management level, and has high evaluation precision and evaluation efficiency. According to the model, the intelligence of the refinery device pipe network integrity management level evaluation can be improved, and the actual condition of the refinery device pipe network integrity management level can be accurately obtained, so that favorable theoretical support is provided for perfecting a refinery device pipe network integrity management system.
Owner:LIAONING UNIVERSITY OF PETROLEUM AND CHEMICAL TECHNOLOGY
Intelligent prediction method for corrosion rate of oil and gas pipeline
PendingCN114066267AImprove adaptabilityImprove evaluation accuracyArtificial lifeResourcesIndex systemEvaluation data
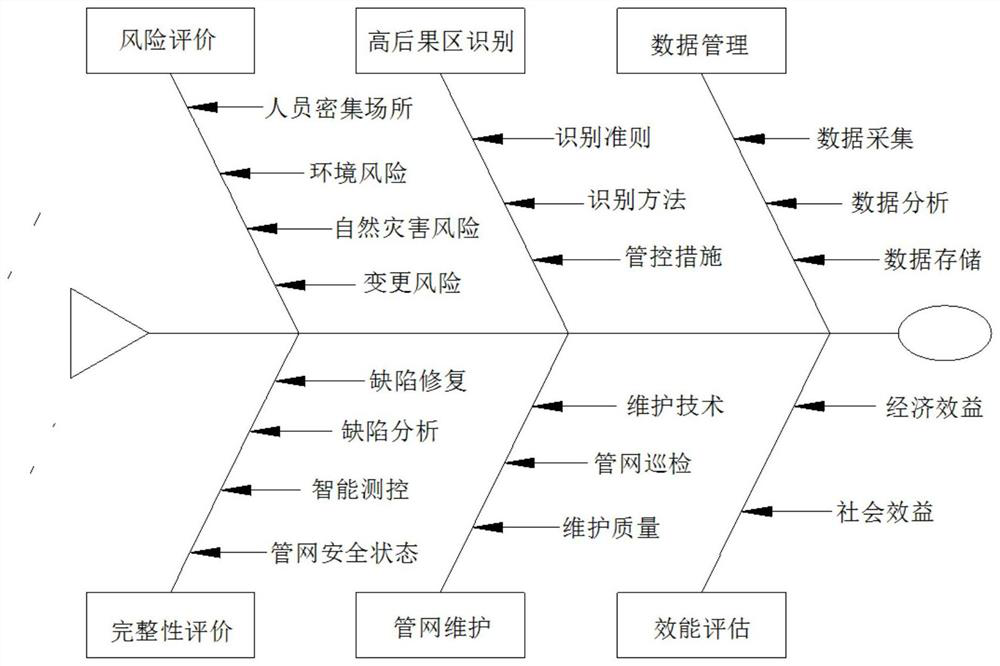
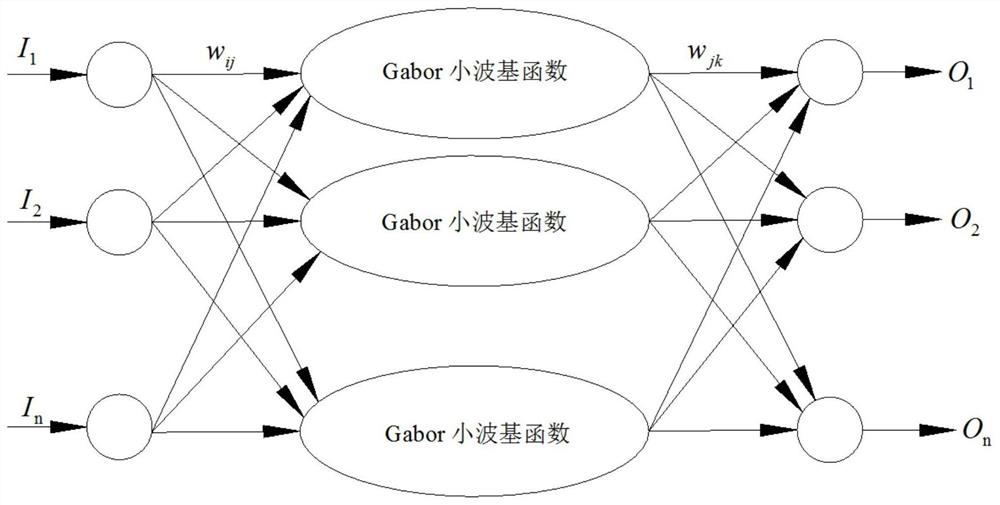
The invention relates to an intelligent method for evaluating the integrity of an oil-gas pipe network. The method comprises the following construction steps: step 1, collecting integrity evaluation data of the oil-gas pipe network; step 2, constructing an oil-gas pipe network integrity evaluation index system; step 3, designing an improved chicken flock algorithm; step 4, designing a Gabor wavelet neural network; step 5, optimizing parameters of the Gabor wavelet neural network by using an improved chicken flock algorithm; and step 6, testing a test sample by using the trained optimal pipe network integrity evaluation model. By means of the intelligent evaluation method for the integrity of the oil-gas pipe network, the integrity level of the oil-gas pipe network can be efficiently and accurately evaluated, a favorable theoretical basis is provided for maintenance of the oil-gas pipe network, and the safety and reliability of the oil-gas pipe network can be ensured.
Owner:LIAONING UNIVERSITY OF PETROLEUM AND CHEMICAL TECHNOLOGY
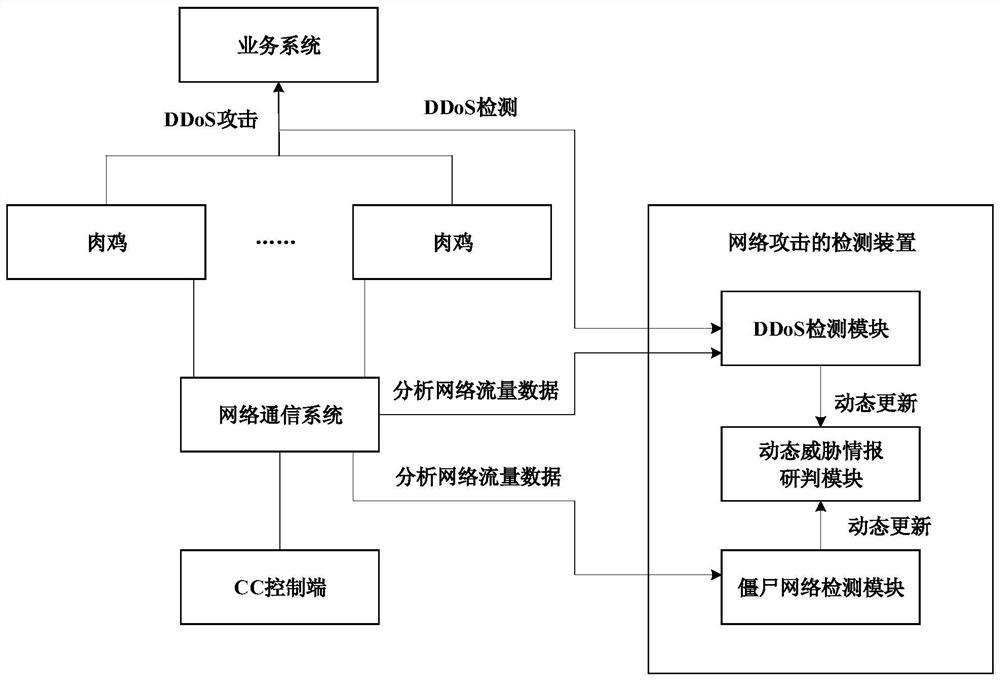
Network attack detection method, device and computer-readable storage medium
ActiveCN112769734BRealize dynamic updateImprove detection accuracySecuring communicationInternet trafficAttack
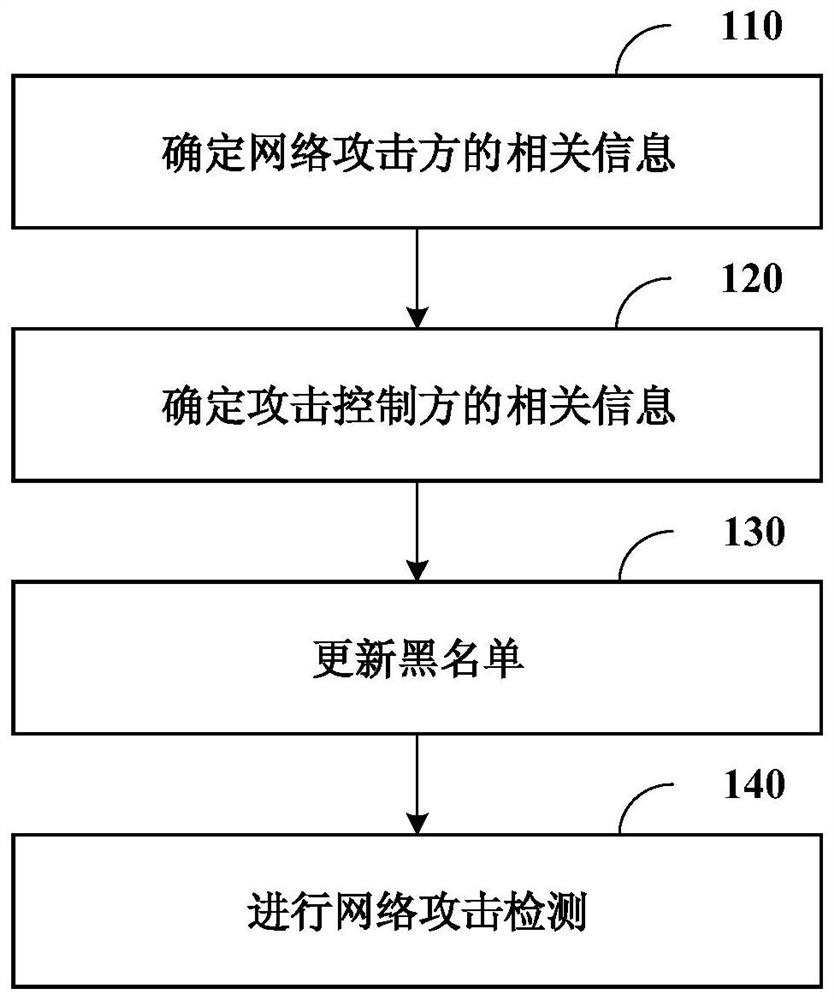
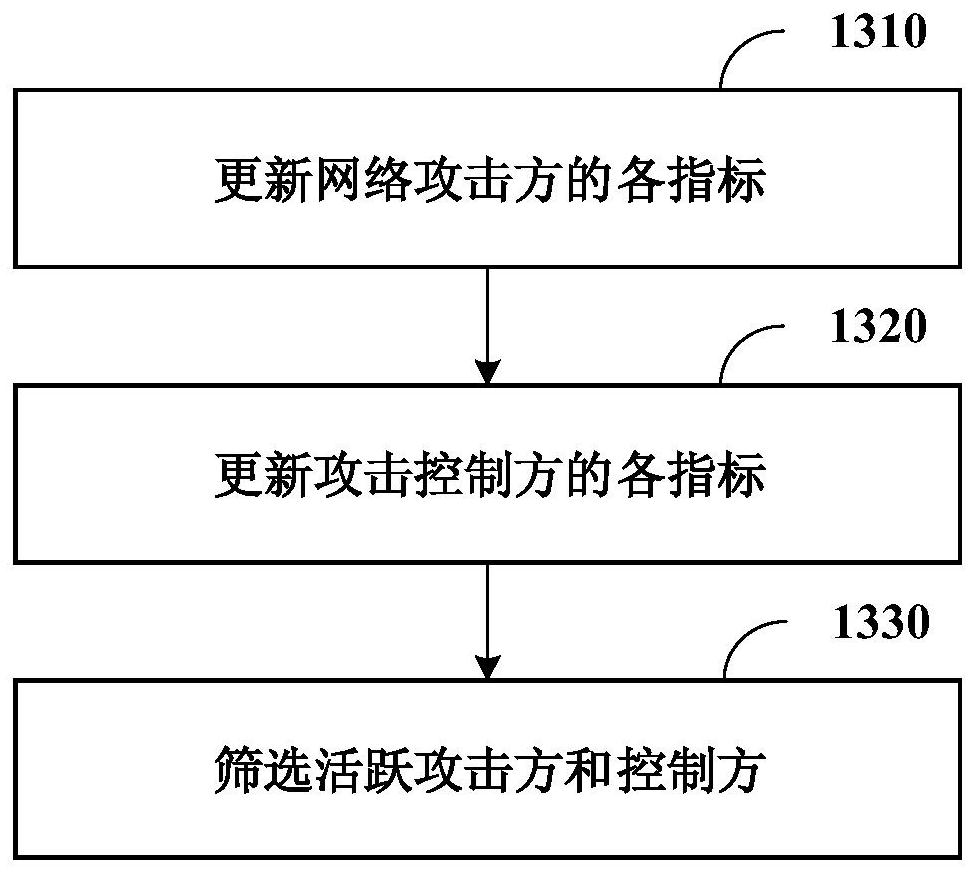
The present disclosure relates to a network attack detection method, device and computer-readable storage medium, and relates to the technical field of network integrity. The method includes: determining the relevant information of the network attacker according to the network attack detection result and the network flow information related to the network attack; determining the relevant information of the attack controller according to the relevant network flow information of the network attacker; Related information and information about the attack controller, screen out the active network attackers and active attack controllers in the blacklist to update the blacklist; perform network attack detection according to the updated blacklist.
Owner:CHINA TELECOM CORP LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com