A power system false data injection attack identification method based on generative adversarial network
A false data attack, power system technology, applied in the field of power system operation safety and maintenance, can solve problems such as difficulty in walking, the scale cannot meet the training conditions, and has little practical significance, achieving good industrial practicability and overcoming the effect of sample shortage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] In order to understand the above-mentioned purpose, features and advantages of the present invention more clearly, the technical solution of the present invention will be further described in detail below in combination with the specific implementation forms of the model.
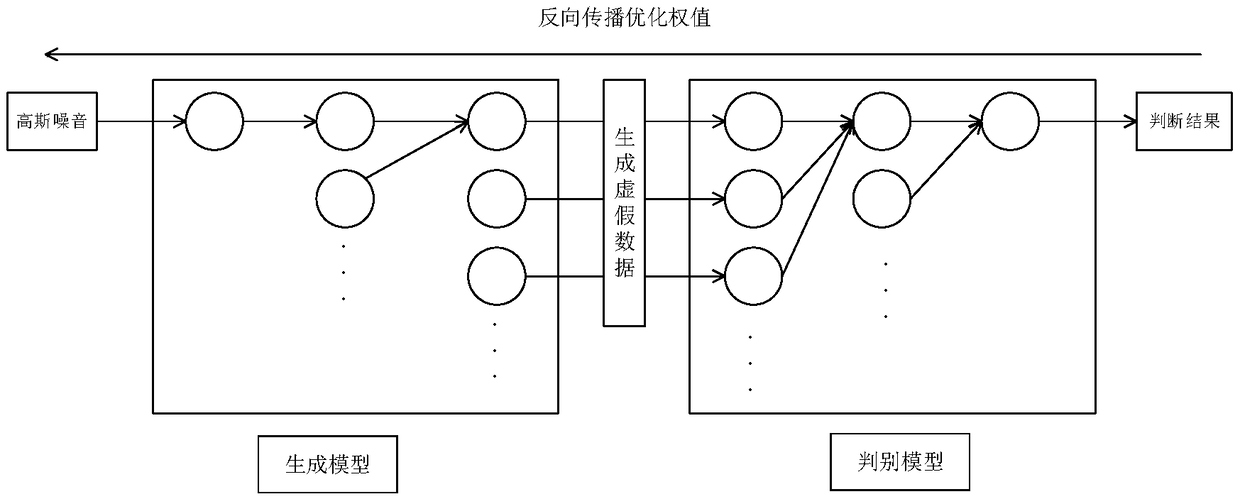
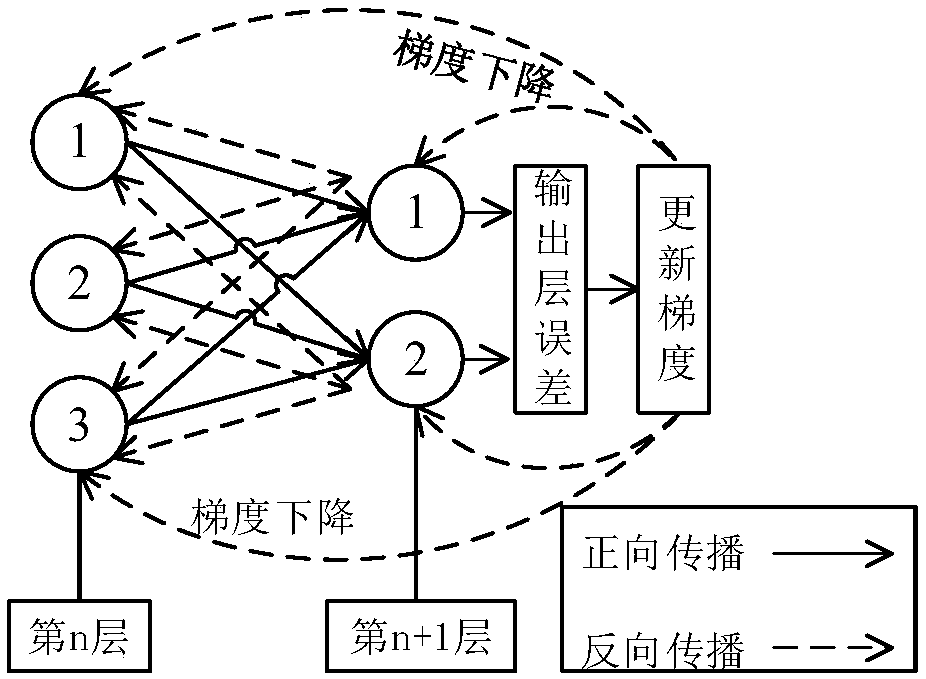
[0061] A method for identifying false data attacks in a power system based on an adversarial generative network, comprising the following steps:
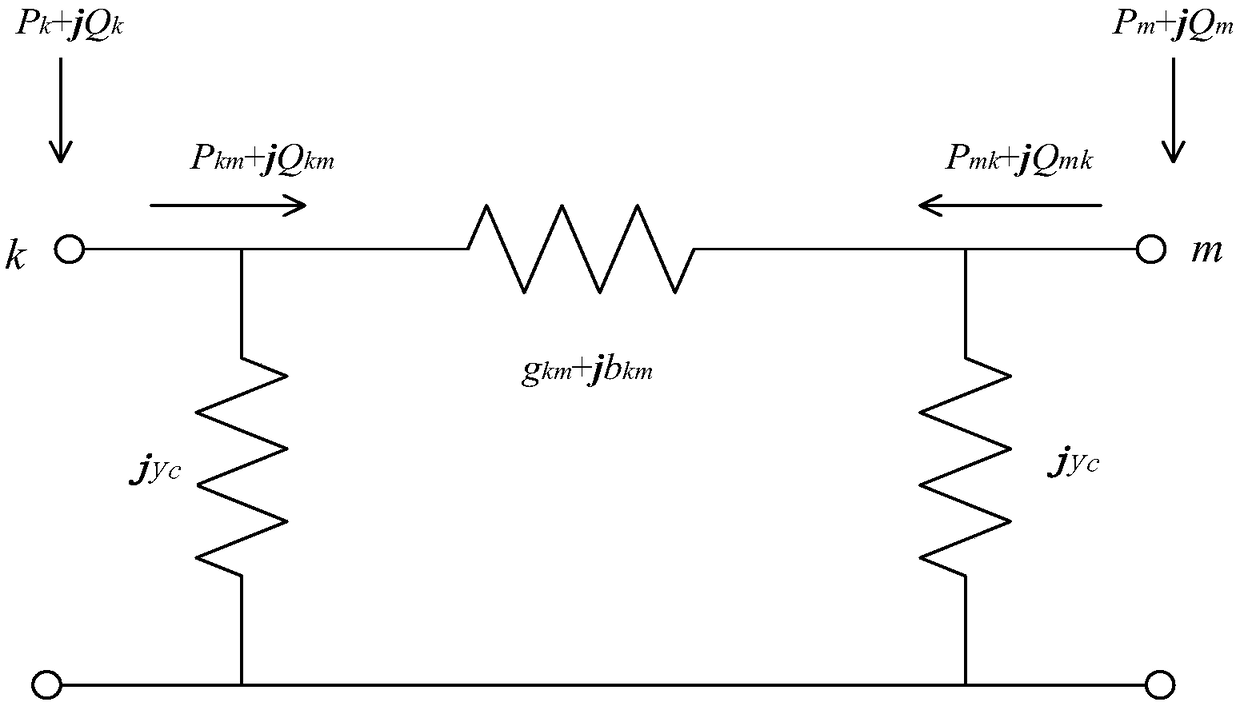
[0062] Step 1. Establish a linear state estimation model, take the state quantity of the power system as an uncertain set, and model it with the telemetry, Jacobian matrix and noise in the power system; by minimizing the noise, the estimated state quantity can be solved and the estimated state can be inversely deduced The estimated quantity corresponding to the quantity is measured; the difference between the estimated quantity measurement and the real quantity measurement is obtained to obtain the residual quantity measurement; the residual quantity measur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com