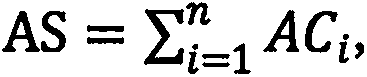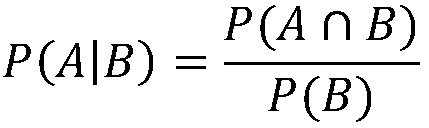Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
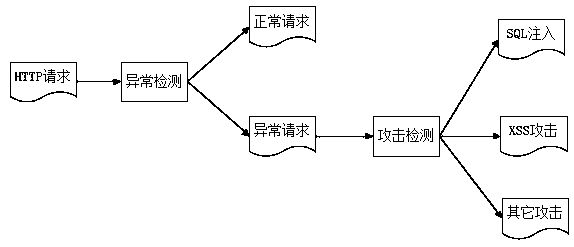
92 results about "Web attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
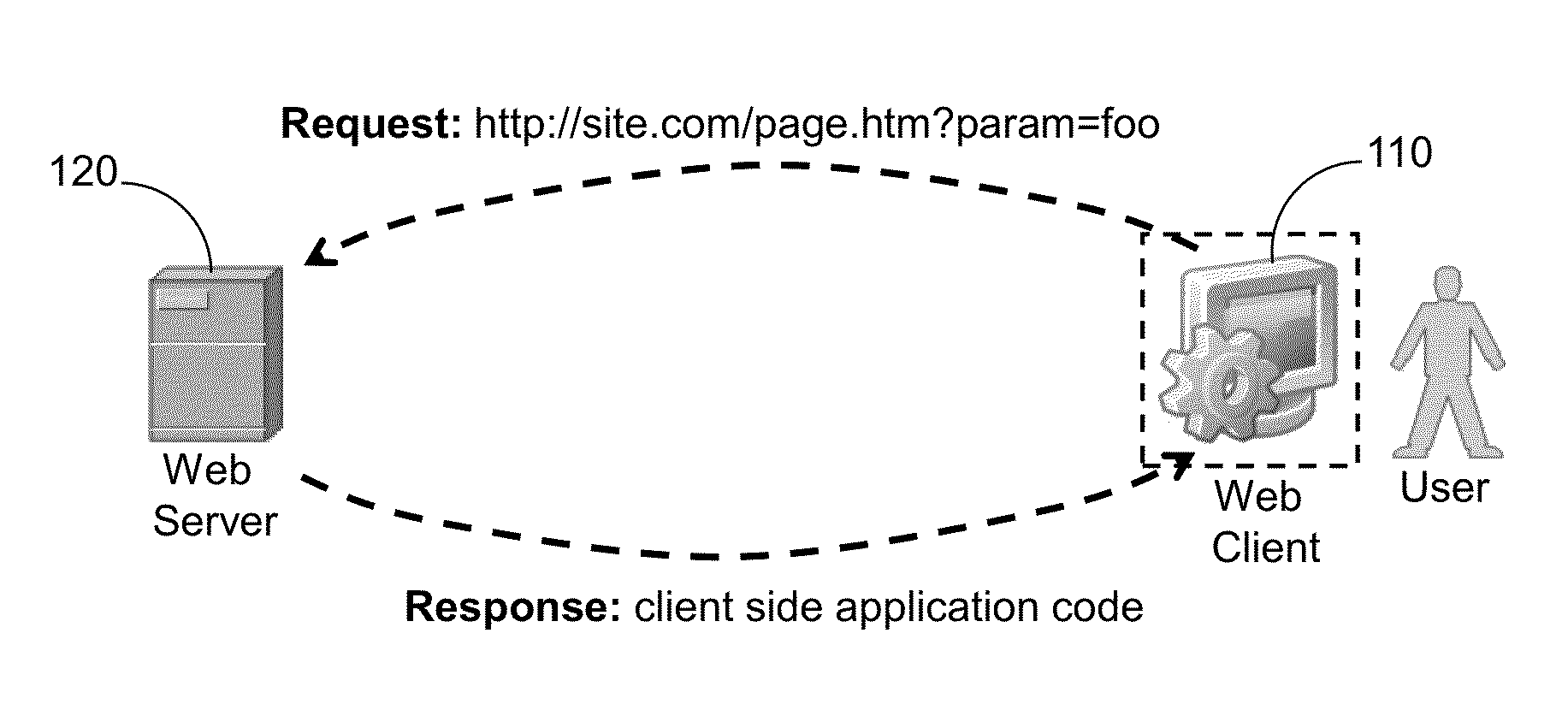
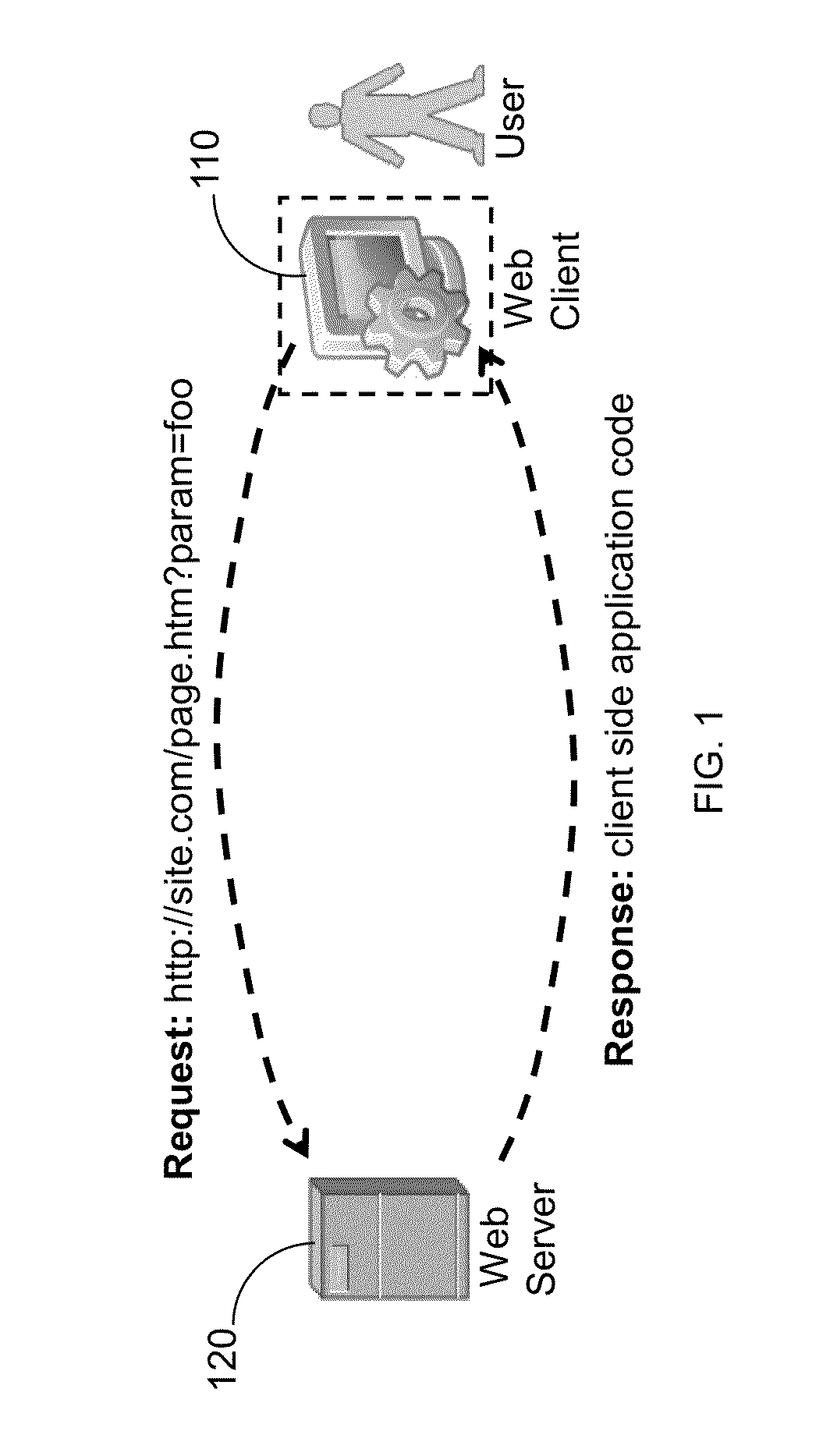
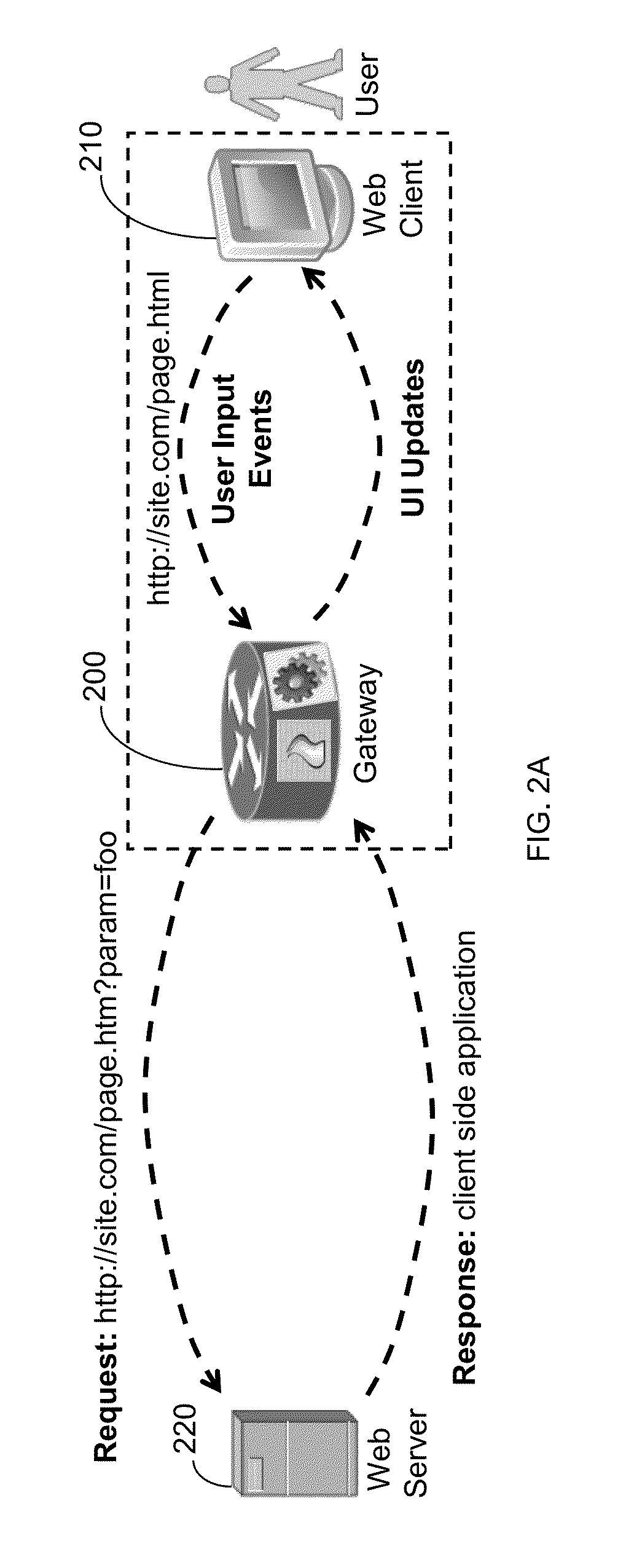
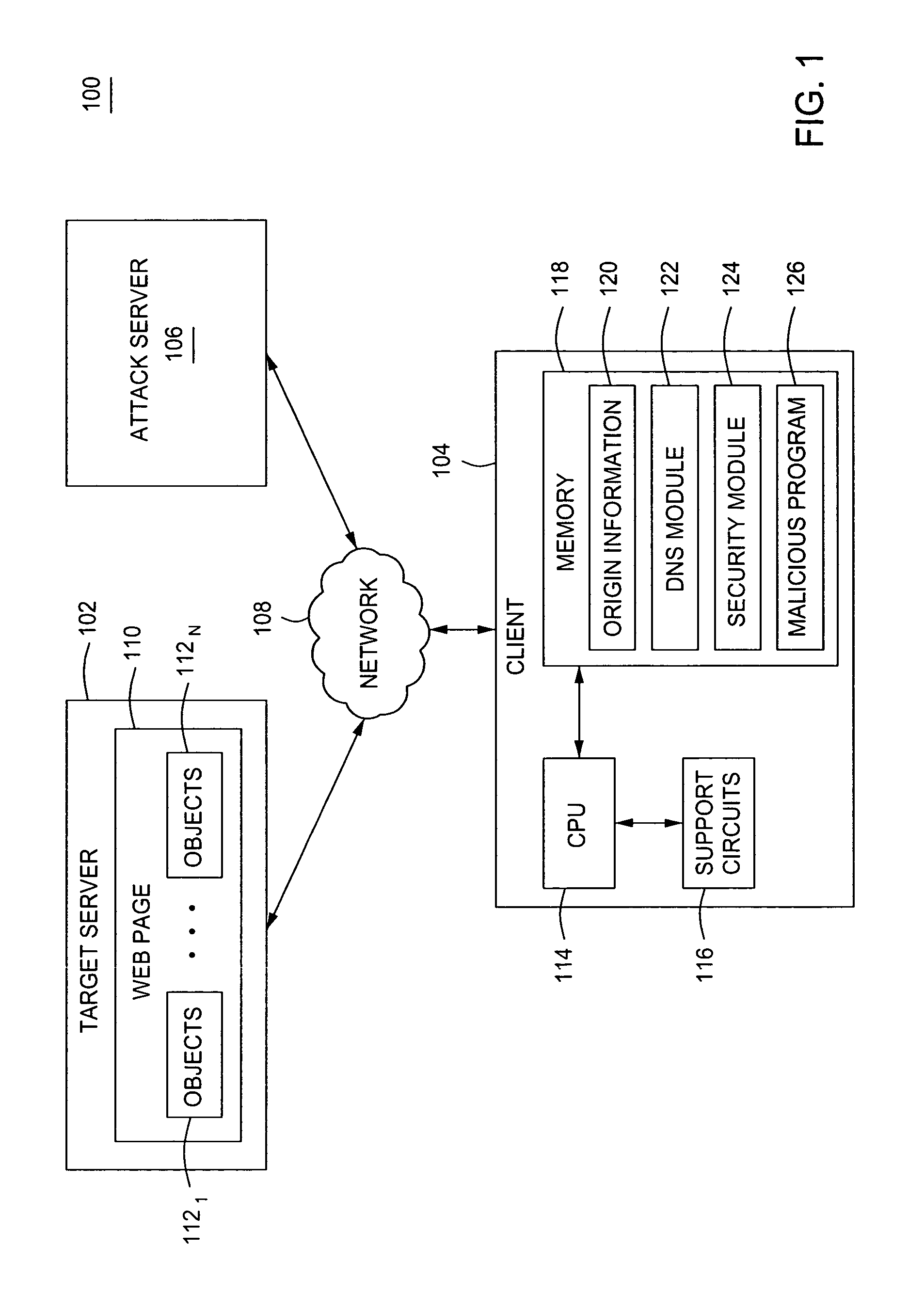
System and method for protecting web clients and web-based applications
ActiveUS8464318B1Digital data processing detailsMultiple digital computer combinationsWeb serviceWeb attack
A method for securing a web client against malicious web attacks, the method is performed by a secure gateway deployed between a web client and a web server. The method comprises receiving a uniform resource locator (URL) request from the web client; sending the URL request to the web server for executing server side web application code responsive to the URL request; receiving client side application code from the web server; executing the client side application code on behalf of the web client; and sending the web client user interface updates rendered responsive to the execution of the client side application code.
Owner:HALLAK RENEN
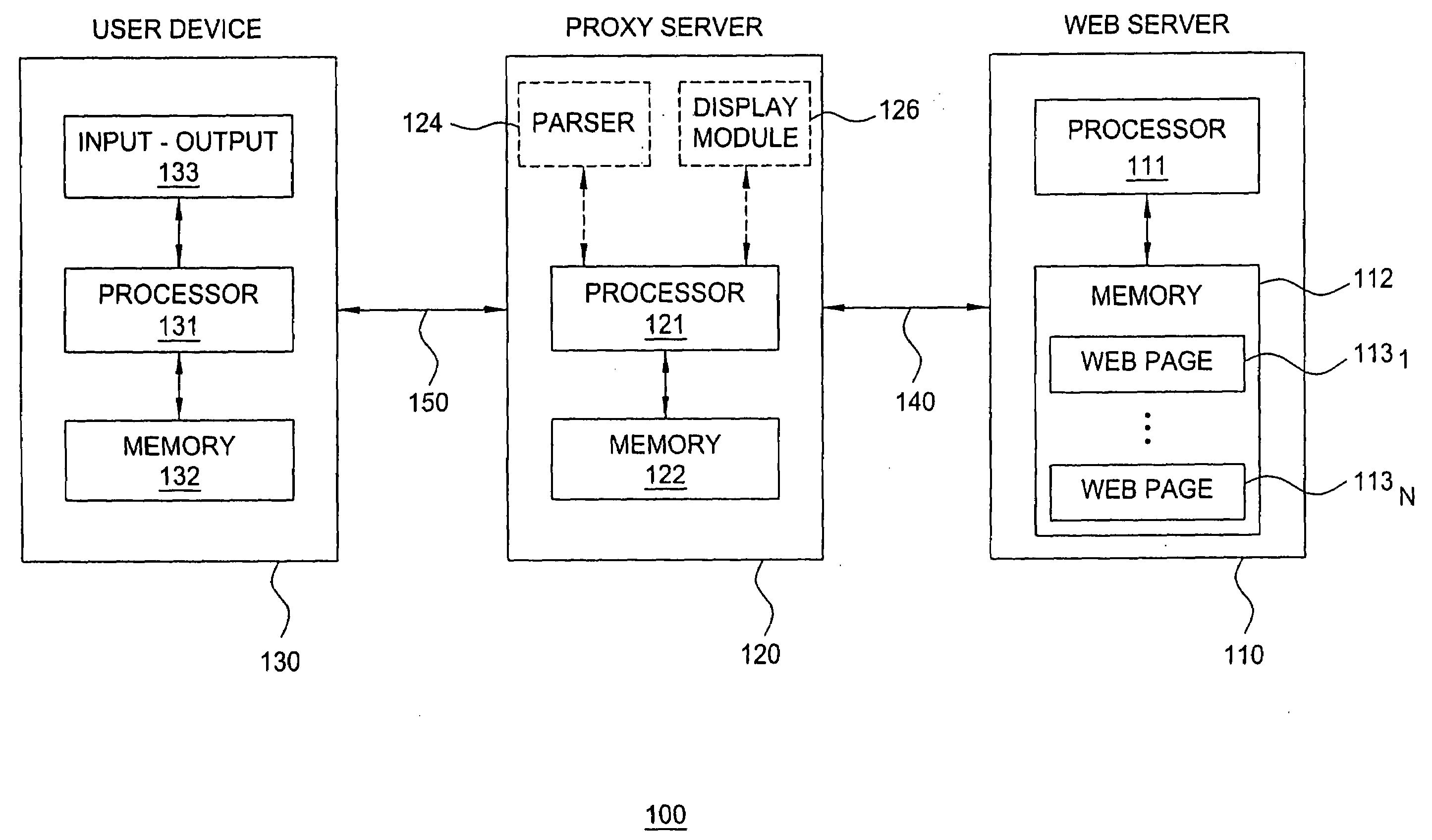
Method and apparatus for secure web browsing
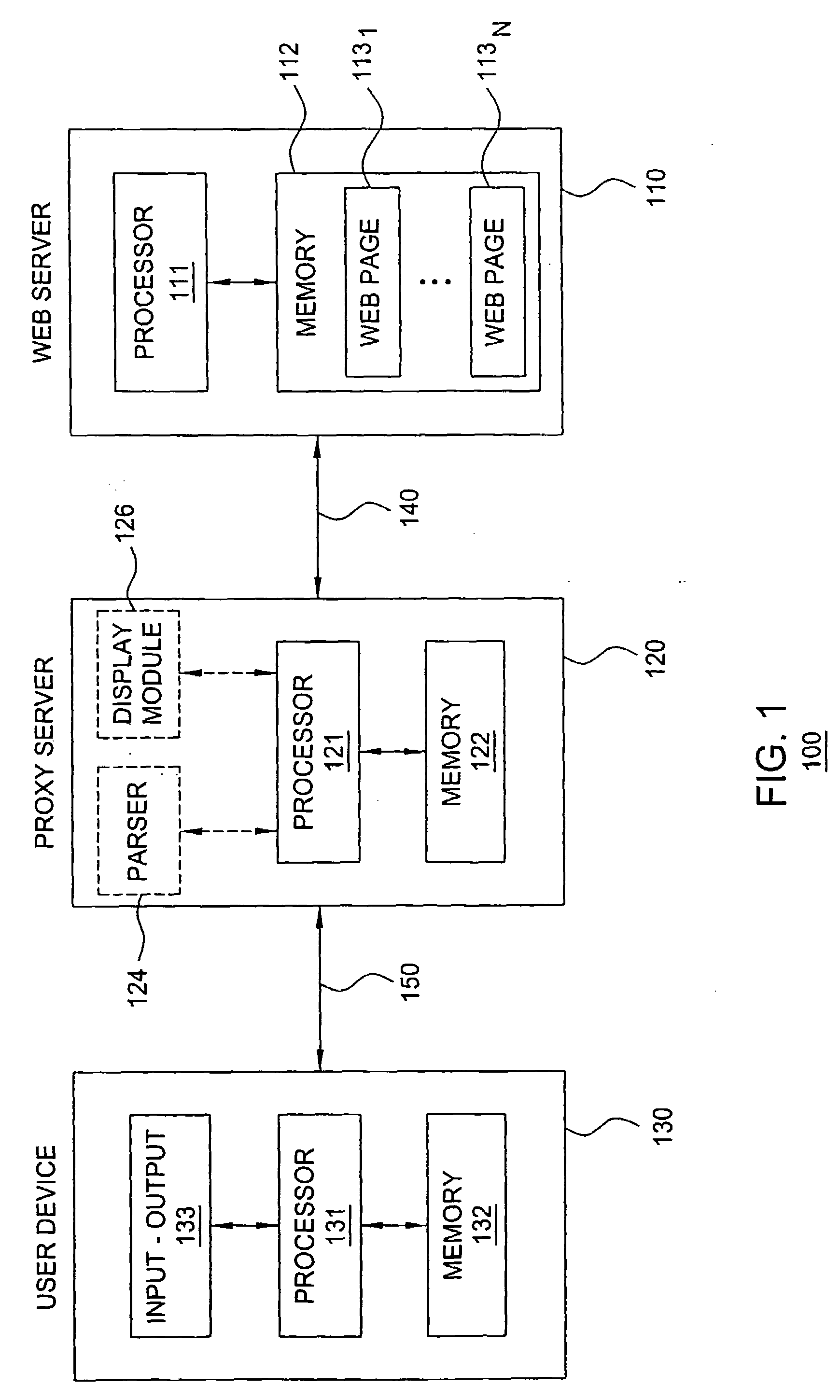
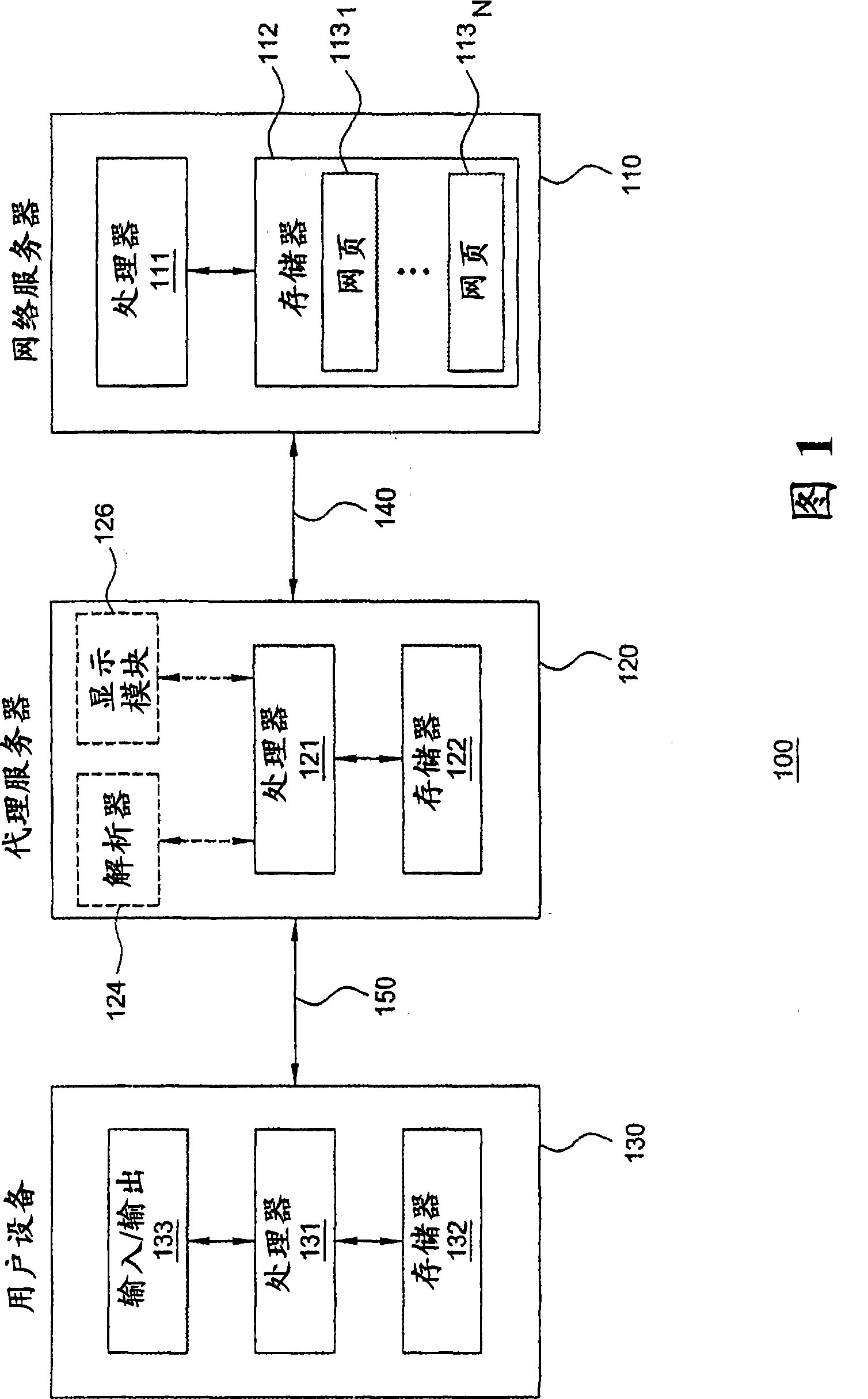
InactiveUS20080229427A1Digital data processing detailsAnalogue secracy/subscription systemsUser deviceWeb service
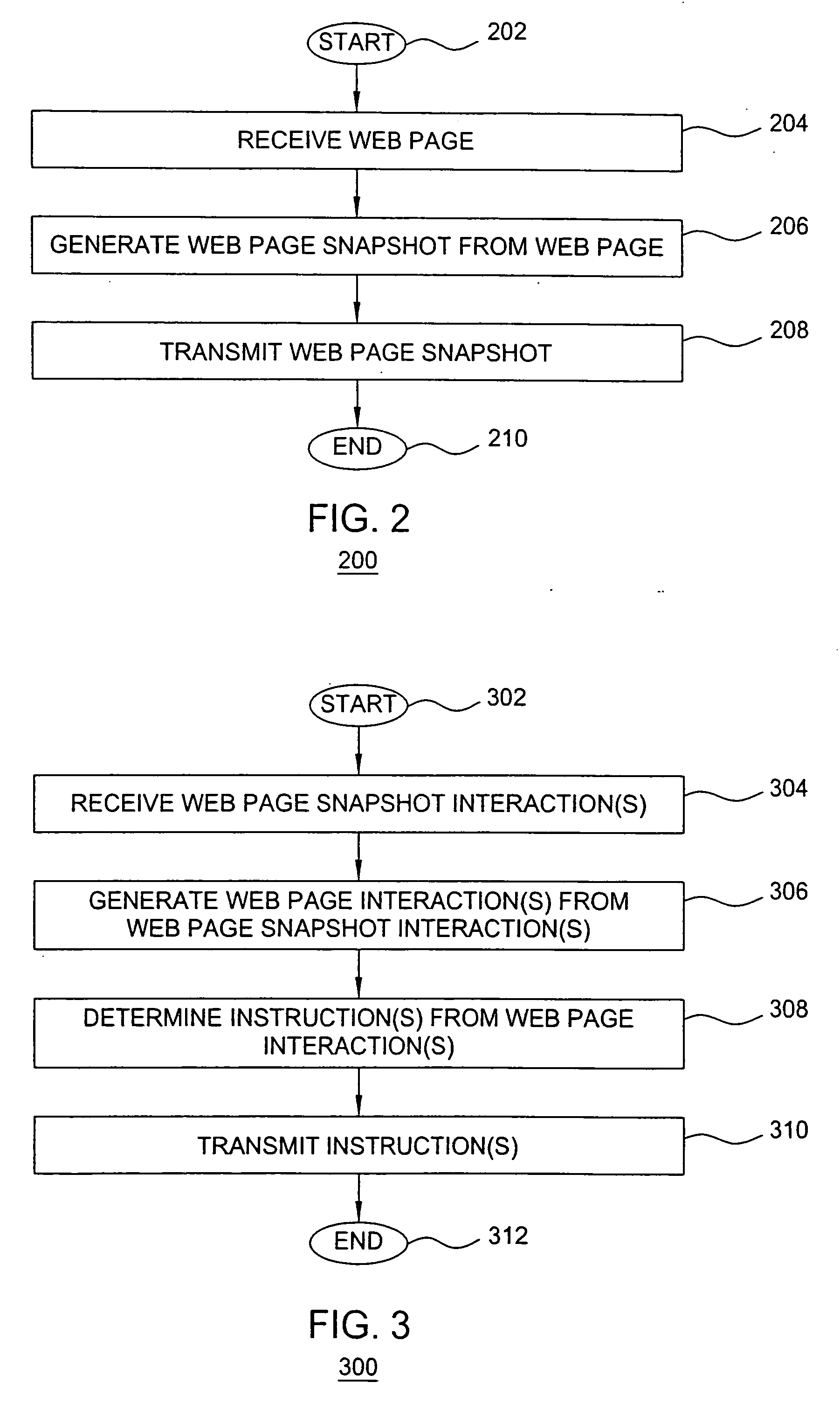
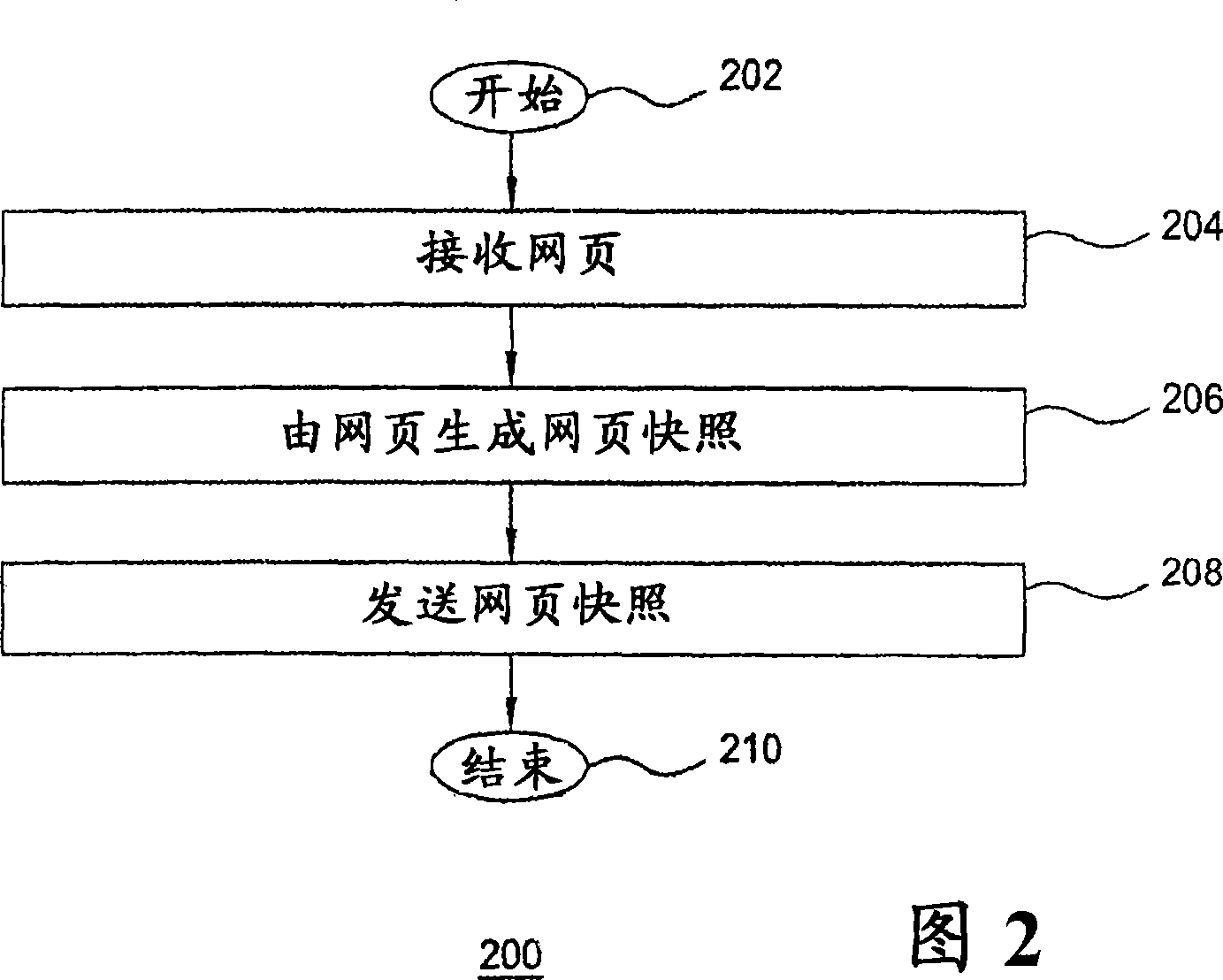
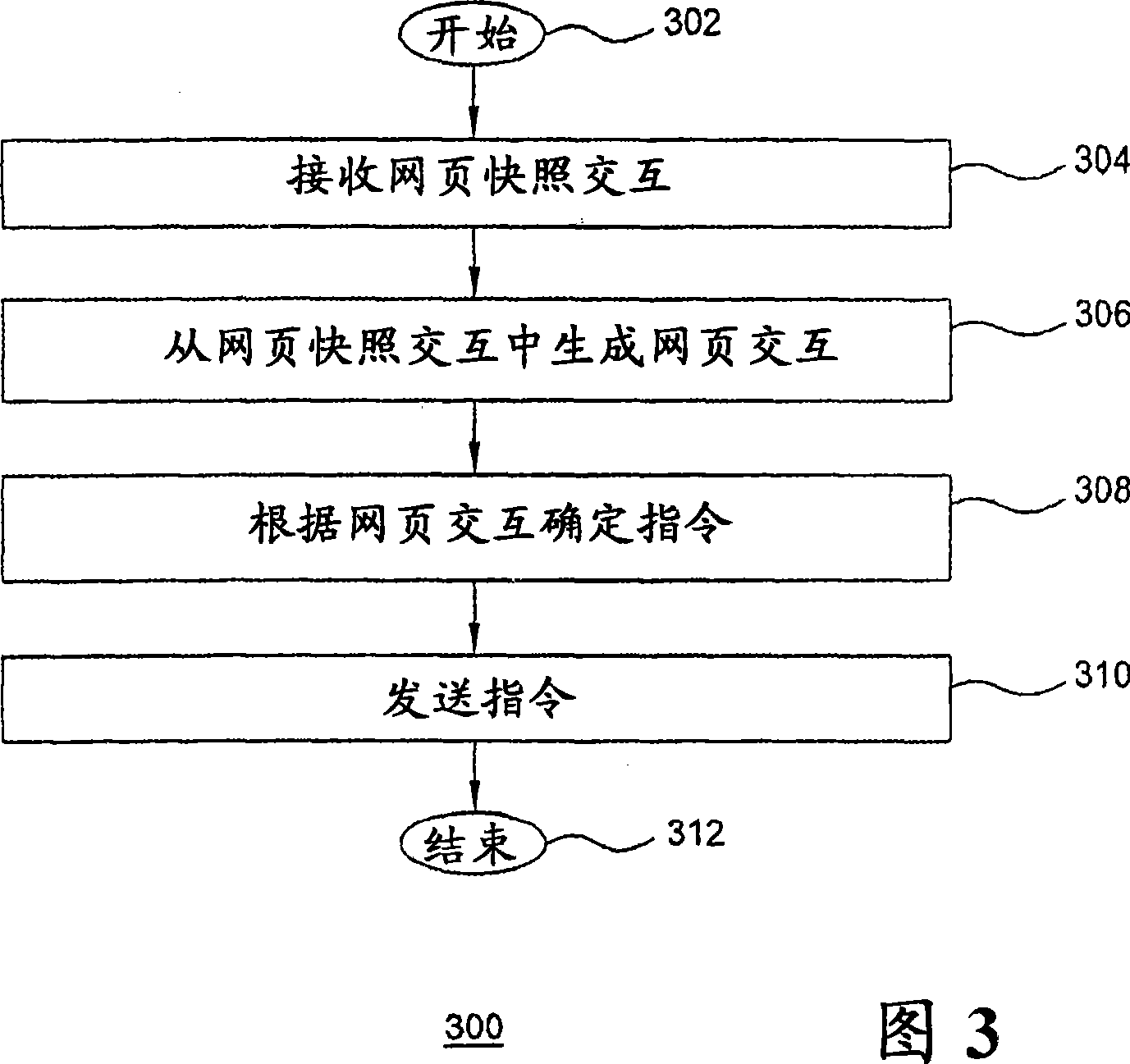
The invention includes a method and apparatus for protecting a user device from web attacks using a proxy server. In one embodiment, a method includes receiving a web page comprising web page content and code, generating an image-based representation of the web page that includes the web page content and excludes the code, and propagating the image-based representation of the web page toward the user device. In one embodiment, a method includes receiving an interaction with an image-based representation of a web page, generating a web page interaction from the interaction with the image-based representation of the web page, implementing the web page interaction, generating an instruction using the implemented web page interaction, and propagating the instruction toward a web server.
Owner:LUCENT TECH INC
Multi-mode Web application protection method based on Mshield machine learning
InactiveCN107404473ALow technical requirementsEfficient and more secure protection capabilitiesCharacter and pattern recognitionTransmissionData warehouseData set
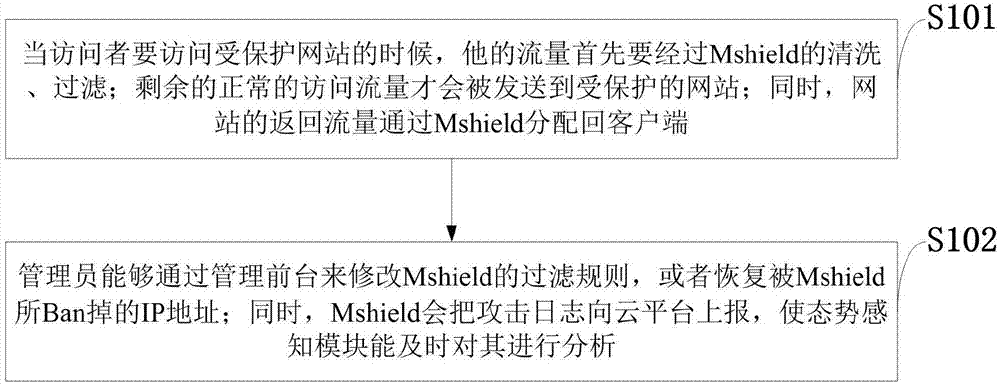
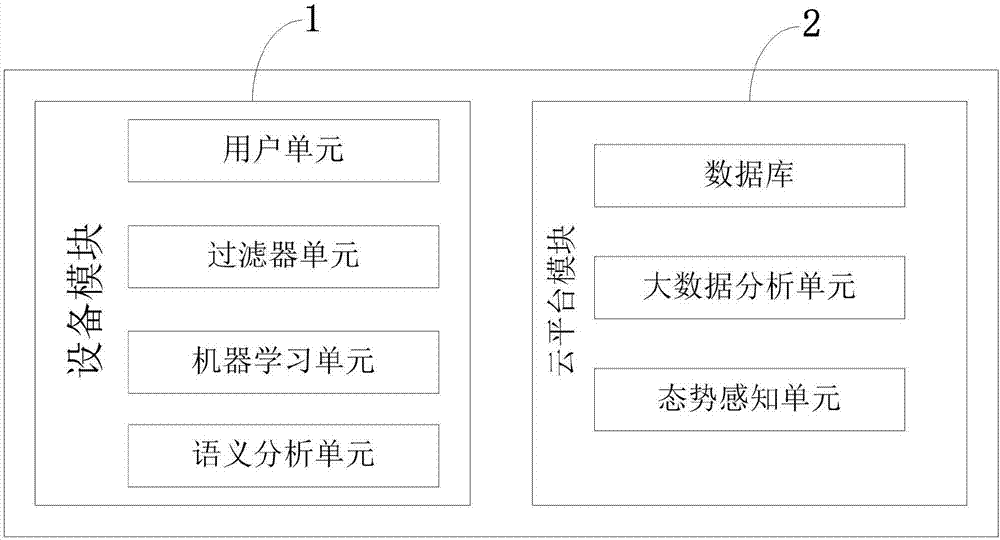
The invention belongs to the technical field of the Web application protection, and discloses a multi-mode Web application protection method based on Mshield machine learning. The method comprises the following steps: extracting features through a semantic analysis unit, transmitting to a machine learning unit to recognize, and applying a random forest algorithm and a logic regression algorithm; effectively distinguishing hostile attack from a normal access request, and immediately intercepting the attack, wherein the Mshield cloud platform screens logs reported by the device everyday and them summarizes to place in a database as the iteration and a data set for improving the algorithm effect; performing deduction according to the past security posture, predicting the possible attack event and an application easy to be attacked in future. By acquiring the features of mega attack load data, through the training and the generalization of a machine learning model, the Mshield is more efficient and safer protection capacity in the face of the current even the unknown Web attack in future in comparison with the traditional WAF.
Owner:XIDIAN UNIV
System for real-time intrusion detection of SQL injection WEB attacks
ActiveCN101370008AReduce false alarmsHigh detection rateData switching networksSQL injectionWeb attack
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Web attack protection method
ActiveCN104361283AThe protection time is advancedQuick defensePlatform integrity maintainanceTraffic capacityUniform resource identifier
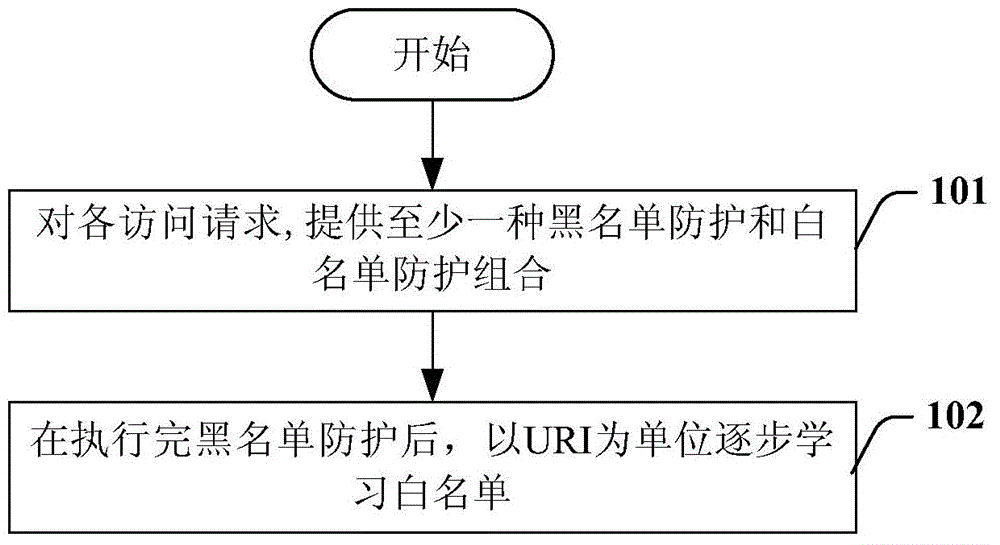
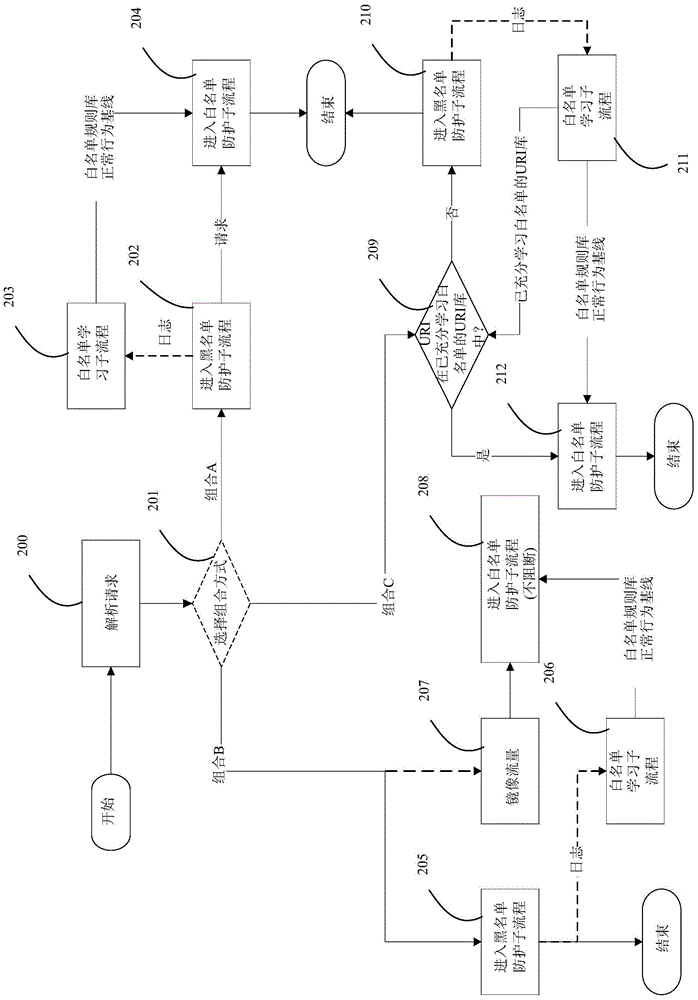
The invention relates to a Web attack protection method, which comprises the following steps that for each access request, at least one of the following protection combinations is provided: A, a blacklist protection sub flow process is firstly executed, and then, a white list protection sub flow process is executed; B, the blacklist protection sub flow process is executed, and meanwhile, the white list protection sub flow process is executed for the mirror flow rate of the access request; C, whether a URI (uniform resource identifier) of the access request is in a URI library sufficiently learning the white list or not is judged, if so, the white process protection sub flow process is executed on the access request, and if not, the blacklist protection sub flow process is executed for the access request, wherein in each combination, after the execution of the blacklist protection sub flow process on the access request for each access request, the white list learning sub flow process is executed, and the white list is learned by using the URI in the access request as the unit.
Owner:CHINANETCENT TECH
Web attack detection method and device
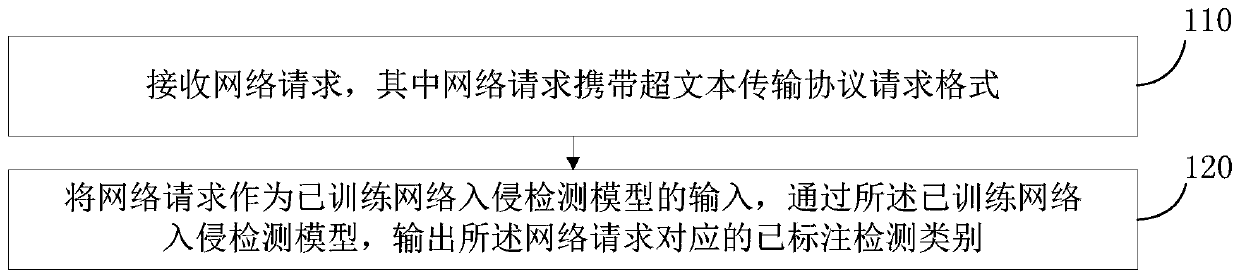
ActiveCN111371806AImprove accuracyAccurate attackNeural architecturesTransmissionFeature extractionEngineering
The embodiment of the invention provides a Web attack detection method and device, and the method comprises the steps: receiving a network Web request which carries a hypertext transfer protocol request format; taking the Web request as the input of a trained Web intrusion detection model; a Web intrusion detection model is trained; outputting a marked detection category corresponding to the Web request; wherein the trained Web intrusion detection model is obtained by training a sample set based on a Web log text; according to the to-be-trained Web intrusion detection model, a sample set of aWeb log text is used as input of the to-be-trained Web intrusion detection model; local features and high-order implicit features of data are extracted through the CNN network layer on the basis of Web log texts, sequence information between contexts in the Web log texts is extracted through the GRU network layer on the basis of the local features and the high-order implicit features, and the sequence information is classified through the full connection layer.
Owner:BEIJING UNIV OF POSTS & TELECOMM
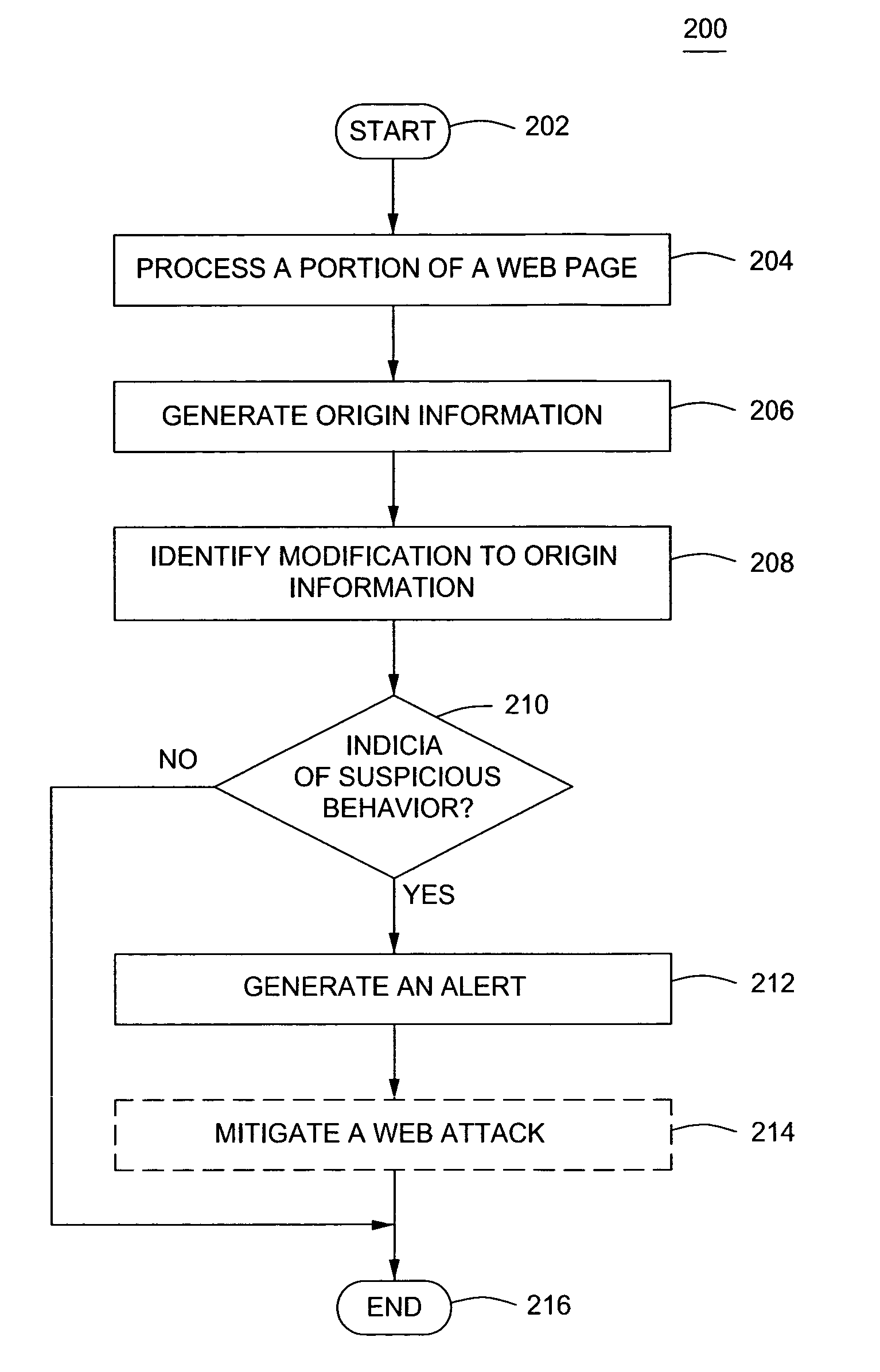
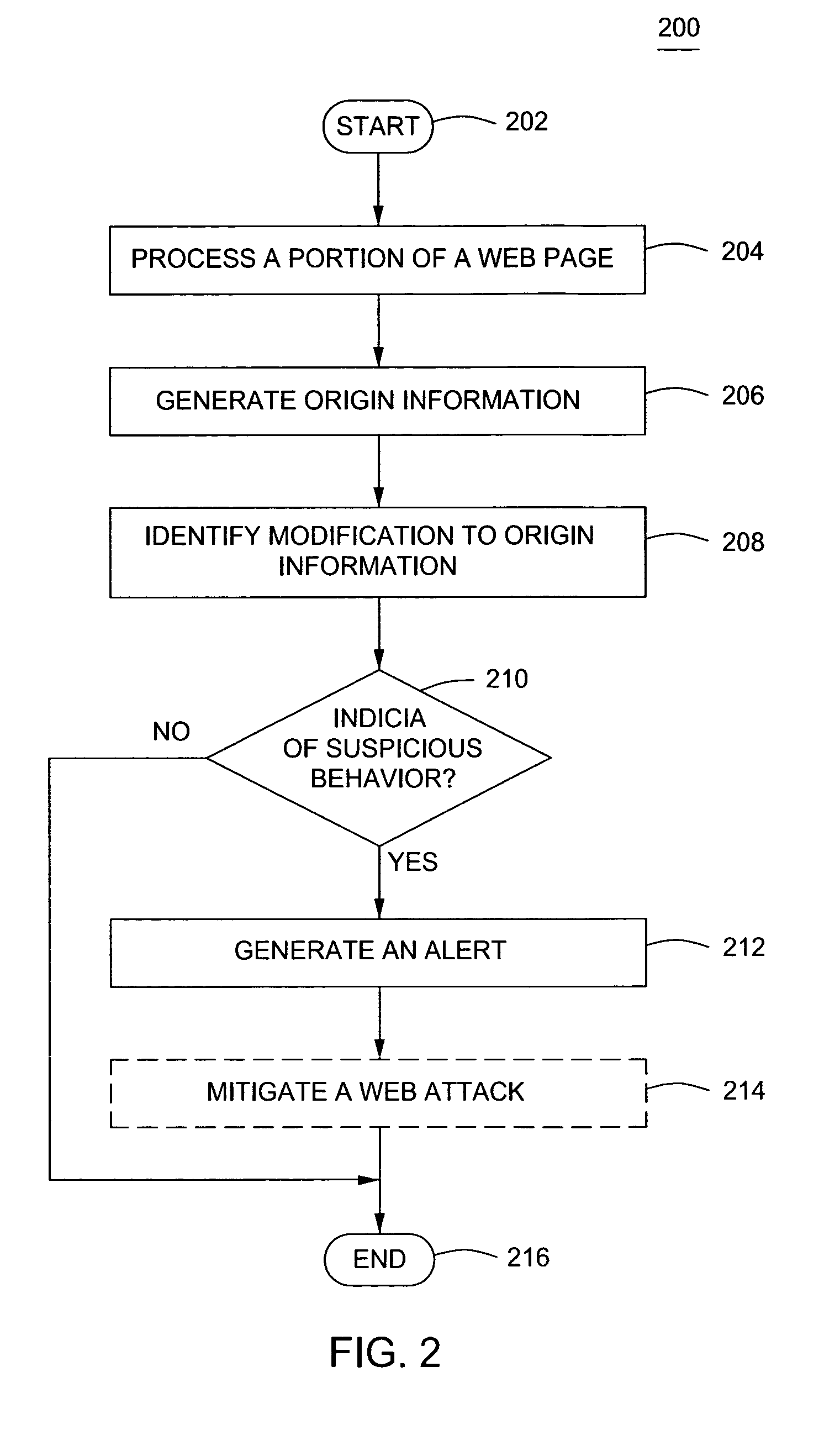
Method and apparatus for identifying web attacks
A method and apparatus for identifying web attacks is described. In one embodiment, a method of securing a computer comprises generating origin information for a portion of a web page and identifying a modification in the origin information. The identified modification is used to determine an indicia of suspicious behavior at a computer.
Owner:CA TECH INC
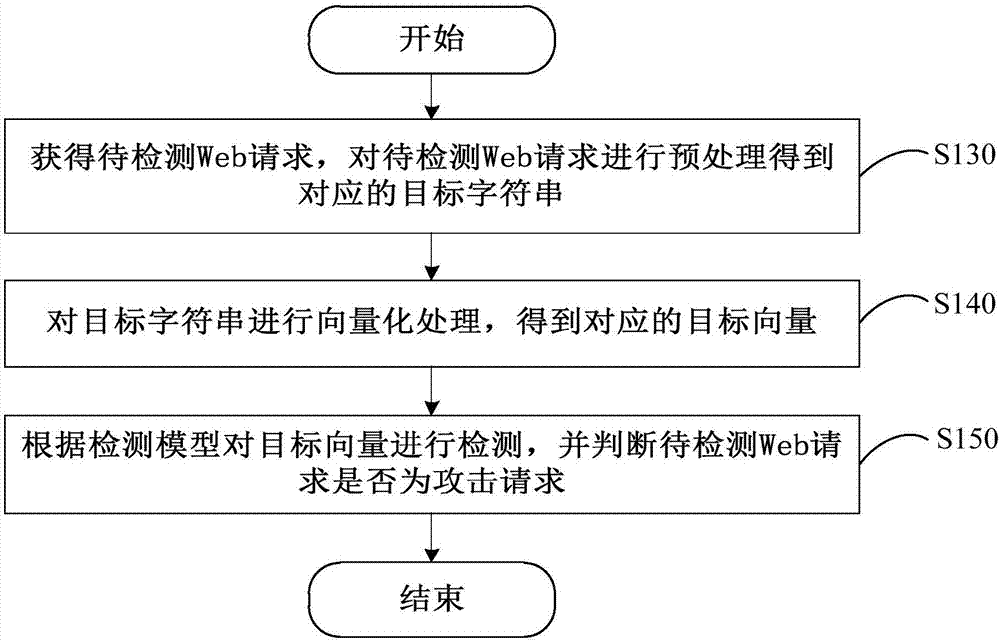
Web attack detection method and Web stack detection device
ActiveCN107346388ATimely detectionEfficient detectionPlatform integrity maintainanceWeb attackData mining
The invention provides a Web attack detection method and a Web attack detection device. The method comprises the following steps: acquiring a to-be-detected Web request, and pretreating the to-be-detected Web request to acquire a corresponding target character string; carrying out vectorization treatment on the target character string to acquire a corresponding target vector; and detecting the target vector according to a detection model, and judging whether a to-be-detected Web request is an attack request or not. Therefore, the attack request and even a novel unknown attack can be timely and effectively detected. Meanwhile, after building of the detection model is completed, manual intervention is not needed, and detection rules do not need to be established, so that labor cost is reduced.
Owner:四川无声信息技术有限公司 +1
Method, device and system for defending against Web attacks
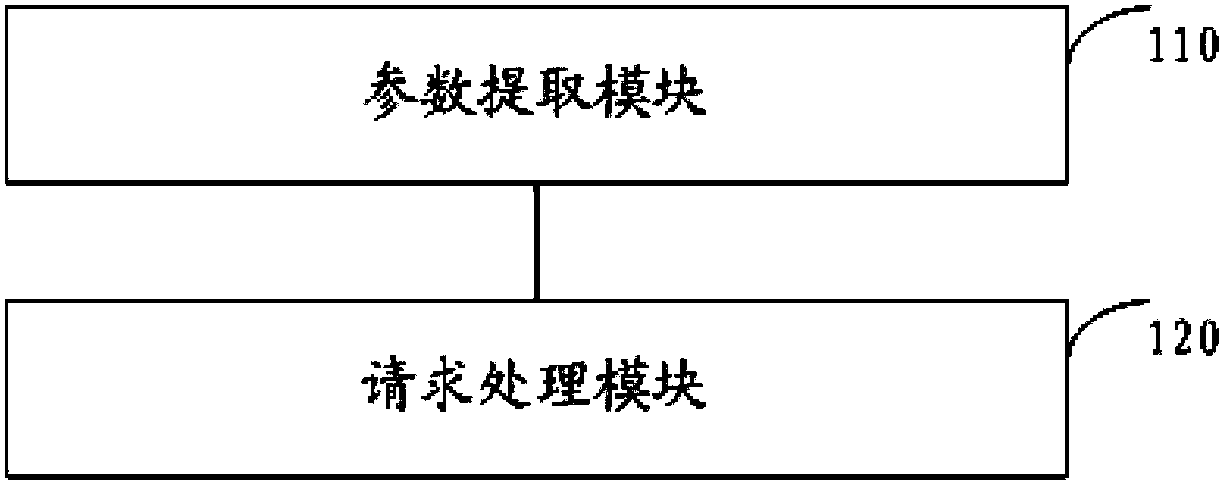
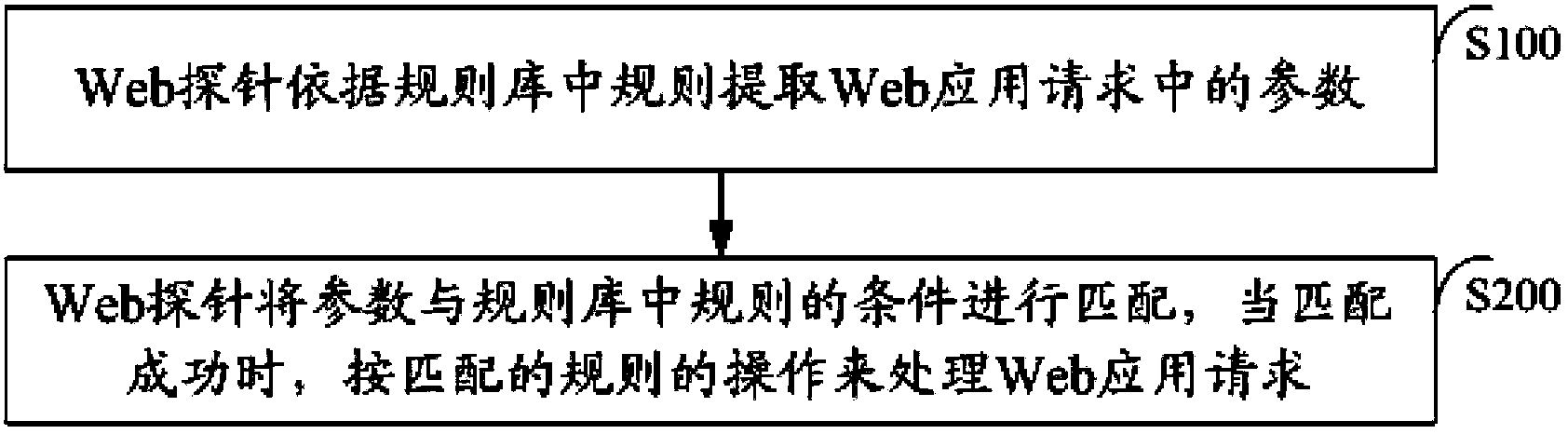
ActiveCN103491060ASimplify the development processPromote expansionTransmissionComputer moduleWeb attack
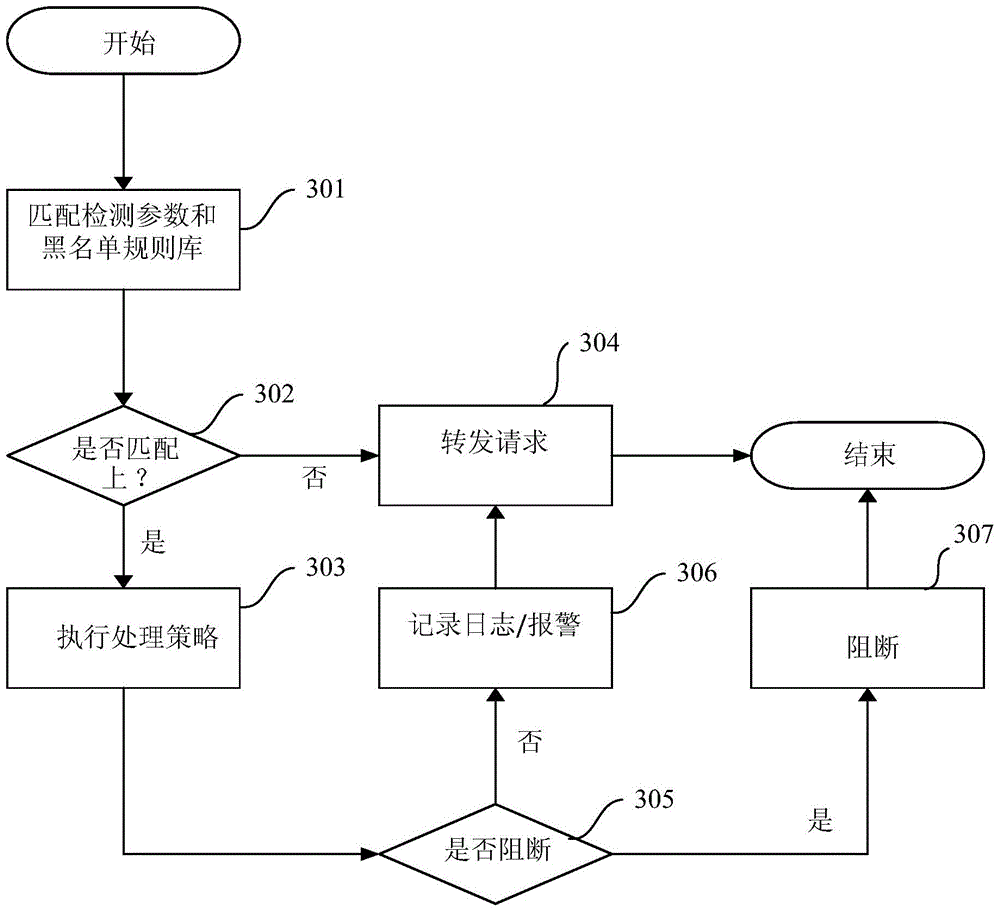
The invention discloses a method, device and system for defending against Web attacks. The device comprises Web probes embedded in the device. Each probe comprises a parameter extraction module and a request processing module, wherein the parameter extraction module is used for extracting parameters in Web application requests according to rules in a rule base, and the request processing module is used for enabling the parameters to be matched with conditions in the rule base. When matching succeeds, the Web application requests are processed according to the matching rules. The method, device and system for defending against the Web attacks can carry out special defense against the Web attacks.
Owner:BEIJING FEINNO COMM TECH
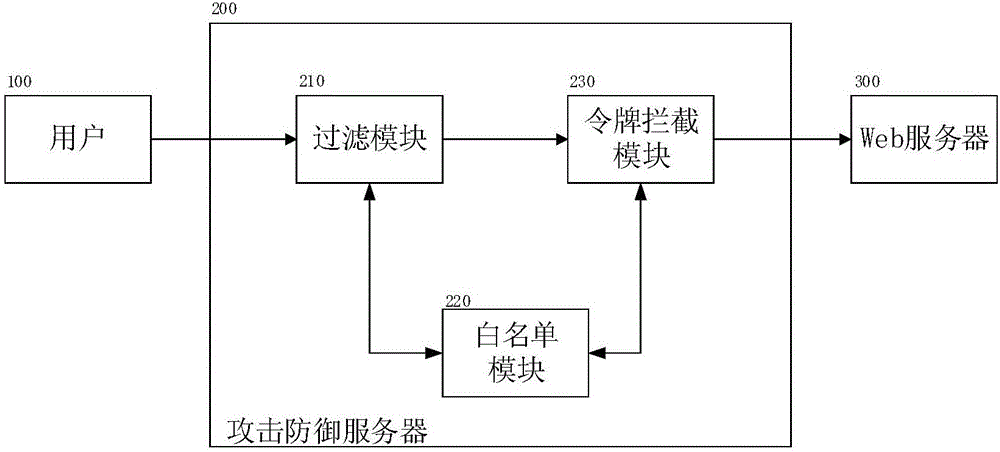
XSS and CSRF based Web attack defense system and method
InactiveCN106790007AImprove recognition accuracyHigh precisionTransmissionExtensibilityHTML scripting
The invention discloses an XSS and CSRF based Web attack defense system and method, and relates to the field of network security. The system comprises a filtering module, a white list module and a token interception module. The method comprises the following steps: (1) the filtering module filters user input by using the following four manners: verifying the validity of the user input, processing special characters, performing cookie anti-theft and performing recursive purification on sensitive words; (2) for HTML script injection, the white list module uses an HTML parsing library to traverse all nodes so as to obtain original label attributes of the data therein, and reconstructs an HTML element tree through labels in the white list module to prevent HTML script injection attacks fundamentally; and (3) the token interception module intercepts HTTP requests not satisfying the requirements through a Token verification function. The XSS and CSRF based Web attack defense system disclosed by the invention has the characteristics of high accuracy, low false alarm rate and expandability.
Owner:WUHAN HONGXU INFORMATION TECH
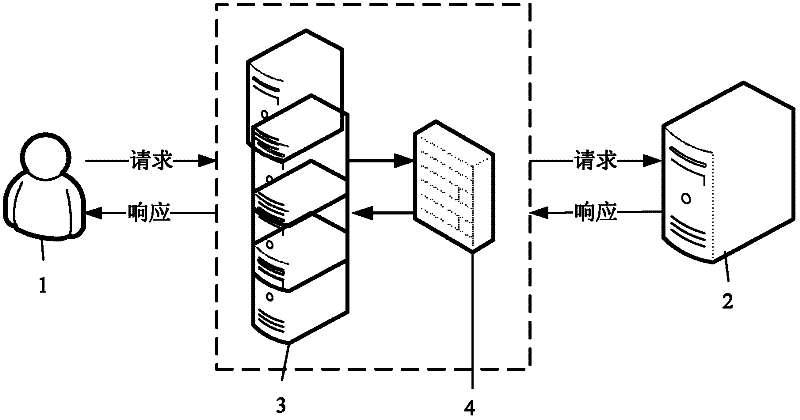
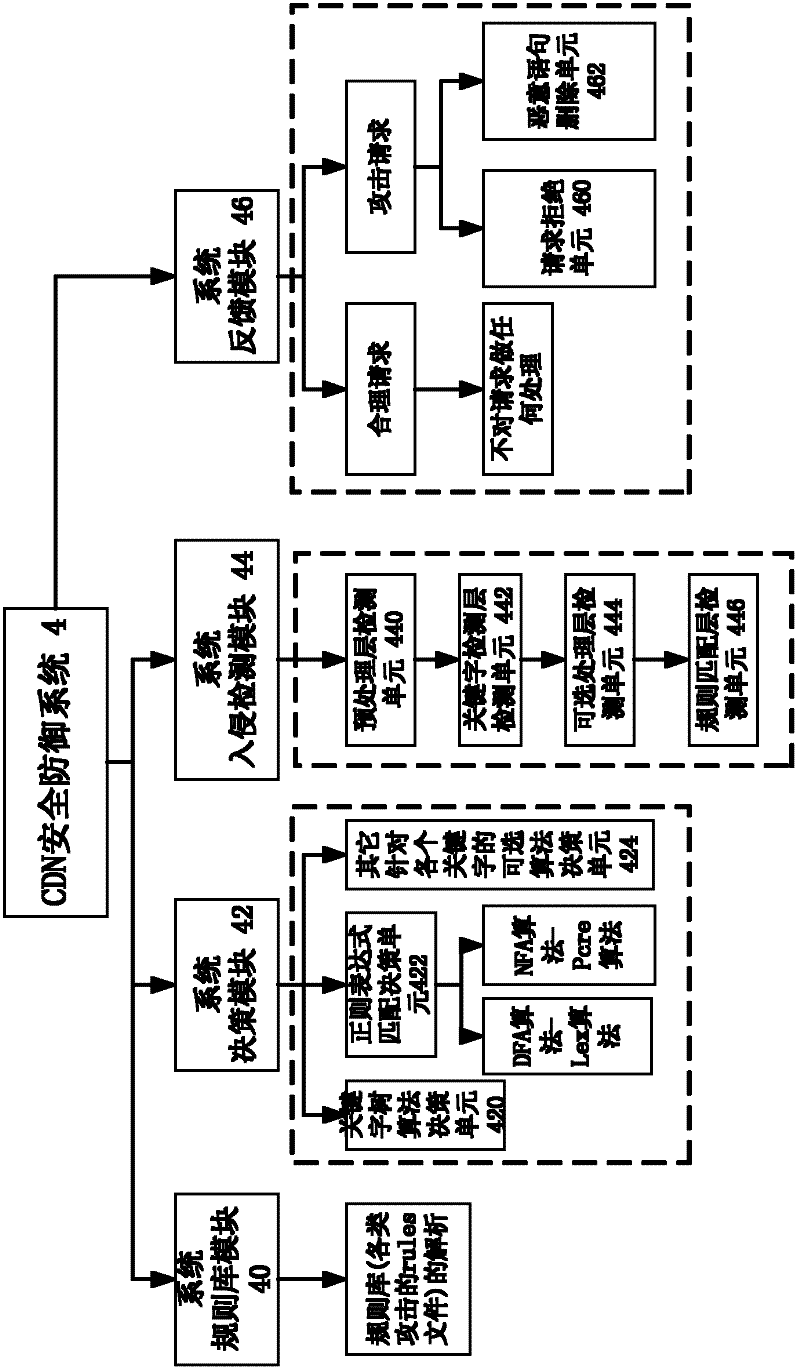
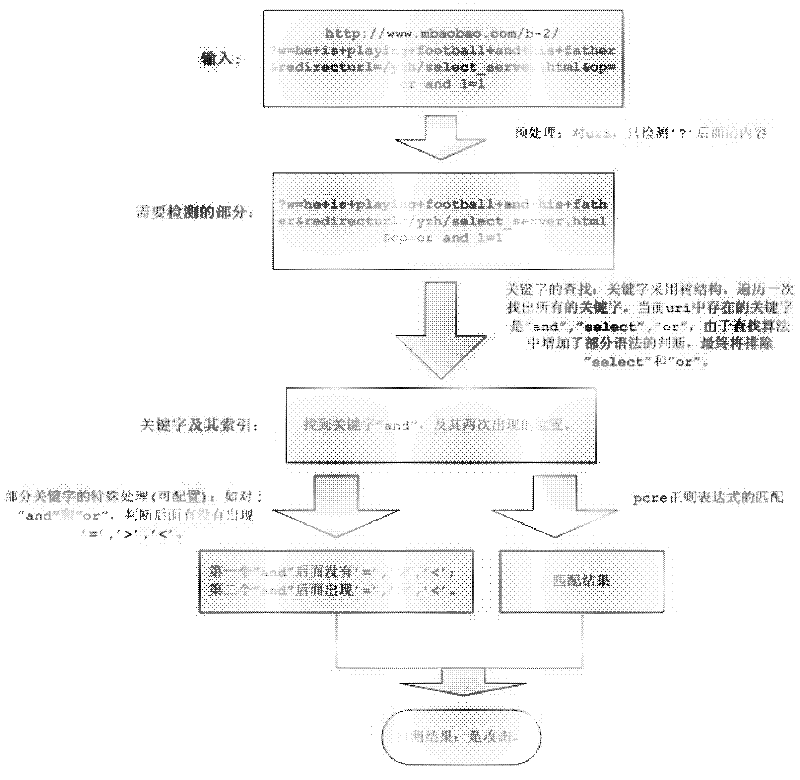
Security defense system based on network acceleration equipment
The invention discloses a security defense system based on network accelerating equipment. The system aims to effectively protect various web sites purchasing network accelerating service. The technical scheme provided by the invention is that: the system comprises a system rule base module, a system decision module, a system intrusion detection module and a system feedback module, wherein the system rule base module initializes rule base files aiming at web attack; the system decision module registers a decision algorithm required by security detection; the system intrusion detection module receives a request from a web application program client, performs content detection and verification on the request according to the decision algorithm in the system decision module so as to guarantee the security of the request, and then transmits a detection result to the system feedback module; and if the request meets the security requirement, the system feedback module allows the request to directly access the next flow after security defense, and if the request cannot meet the security requirement, the system feedback module adopts corresponding defending measures.
Owner:CHINANETCENT TECH
Web intrusion detection technology based on machine learning
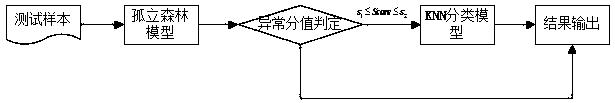
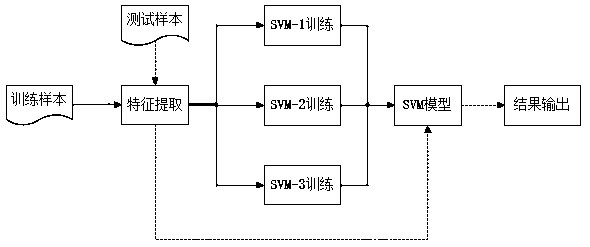
The invention discloses a Web intrusion detection method based on machine learning. The method mainly comprises the following steps of step 1, collecting data as a learning sample of anomaly detectionand attack detection; step 2, training an anomaly detection model, determining the random sampling number, the number of isolated trees, a K value and a threshold value needing to be set for secondary detection, training an attack detection model, and determining hyper-parameters C and g of three SVM models by using SQL injection and XSS as research objects; and collecting data of an HTTP requestin real time, carrying out anomaly detection and attack detection on the HTTP request, and recognizing an abnormal request and a corresponding attack behavior. Experiments show that the research method provided by the invention is effective, and compared with an existing method, the intrusion detection can be carried out on a Web attack rapidly and effectively.
Owner:SICHUAN UNIV
System and a method for calculating a website risk index based on a mass Web log
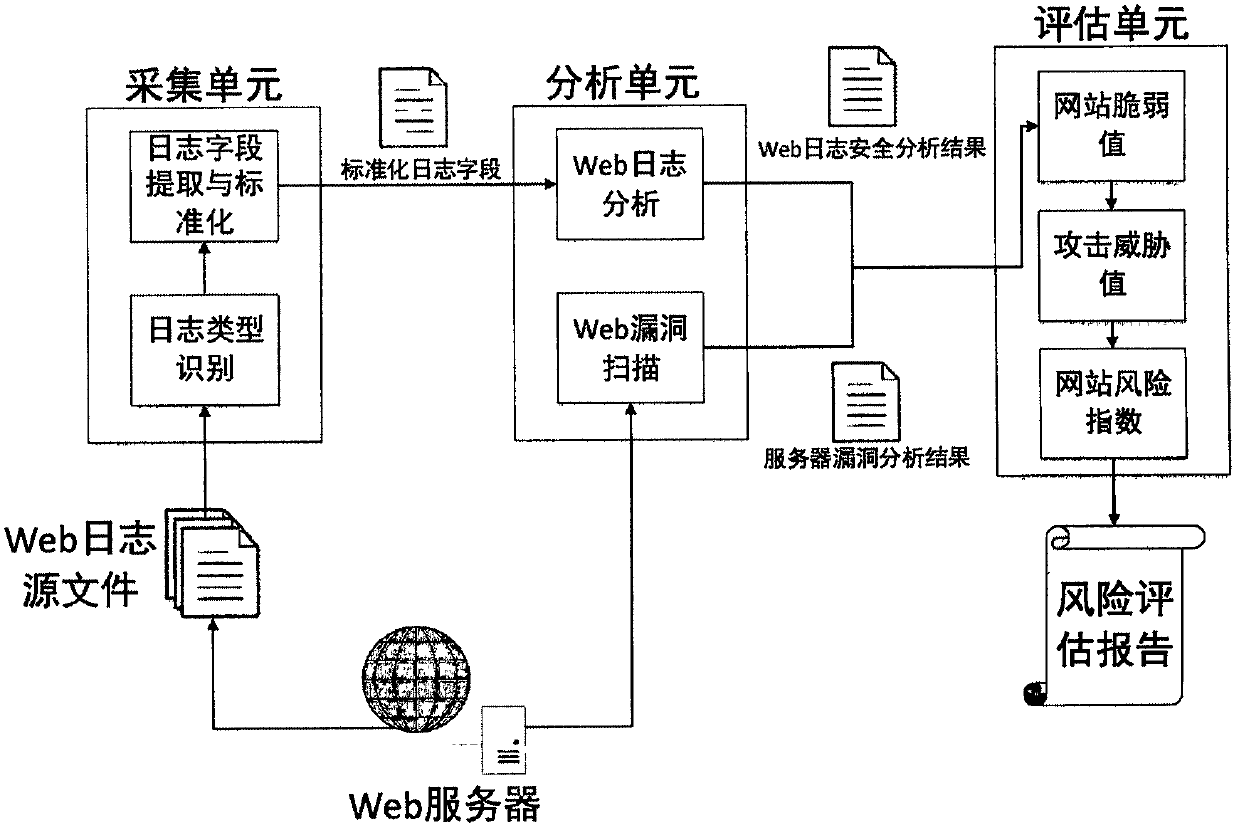
InactiveCN109257329AImplement risk assessmentRisk assessment is easyTransmissionInformation analysisWeb service
The invention relates to a website risk index calculation method based on a massive Web log, comprising a collection unit supporting the massive Web log, a safety information analysis unit and a website risk assessment unit arranged on a Web server; the collection unit, the analysis unit and the evaluation unit are sequentially connected. The collecting unit monitors the log file in real time, extracts the Web log generated in real time according to a certain time interval, and pretreats the generated fields. The invention is based on massive Web log analysis, can catch Web attack events in real time, combines the CVSS value with the vulnerability of the website and the harm degree of the attack, carries out the website risk assessment, and ensures the accuracy, real-time and predictability of the assessment index.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY
Method and device for detecting abnormal flow, and method and device for defending against Web attack
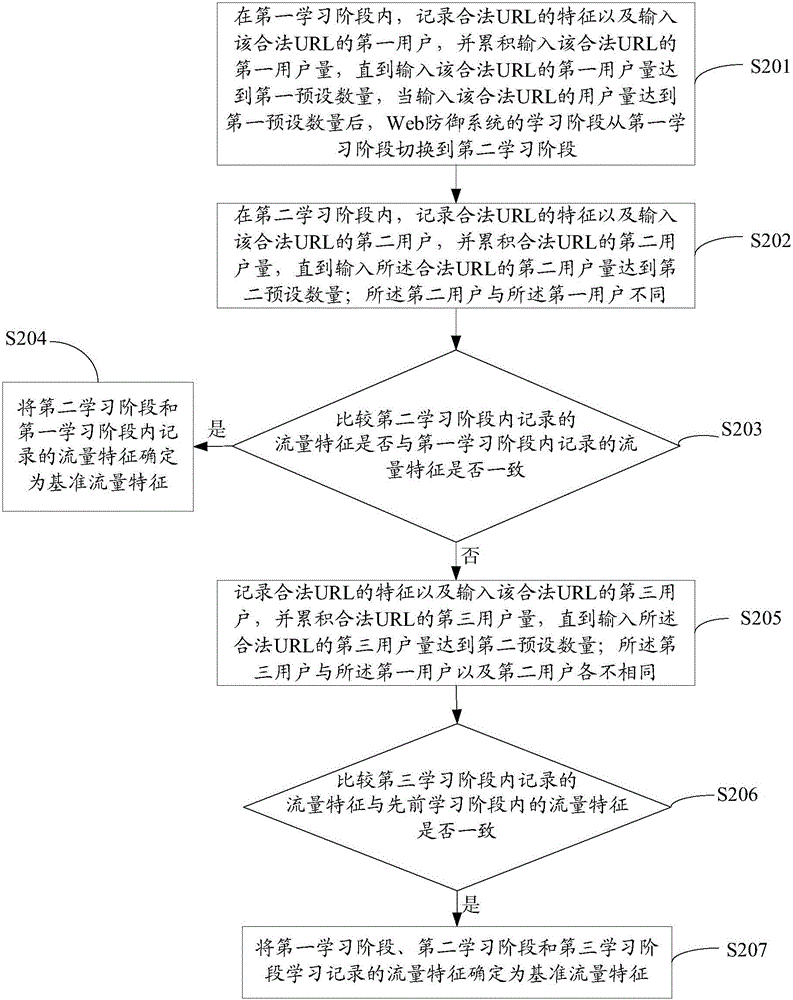
ActiveCN104994091AThere will be no missed detectionCope wellTransmissionWeb attackUniform resource locator
The invention provides a method and a device for detecting abnormal flow. The method comprises the following steps of obtaining reference flow characteristics of a website, wherein the reference flow characteristics comprise URL (Uniform Resource Locator) characteristics constructed by a legal URL; extracting to-be-detected flow characteristics from received to-be-detected flow; matching the to-be-detected flow characteristics and the reference flow characteristics to determine whether characteristics which are unmatched with the reference flow characteristics exist in the to-be-detected flow characteristics; and when the characteristics which are unmatched with the reference flow characteristics exist in the to-be-detected flow characteristics, analyzing the characteristics which are unmatched with the reference flow characteristics to determine whether the to-be-detected flow is abnormal flow. According to the method provided by the invention, a 0day loophole can be coped with well to help to improve network security. The invention also provides a method and device for defending against a Web attack.
Owner:NEUSOFT CORP
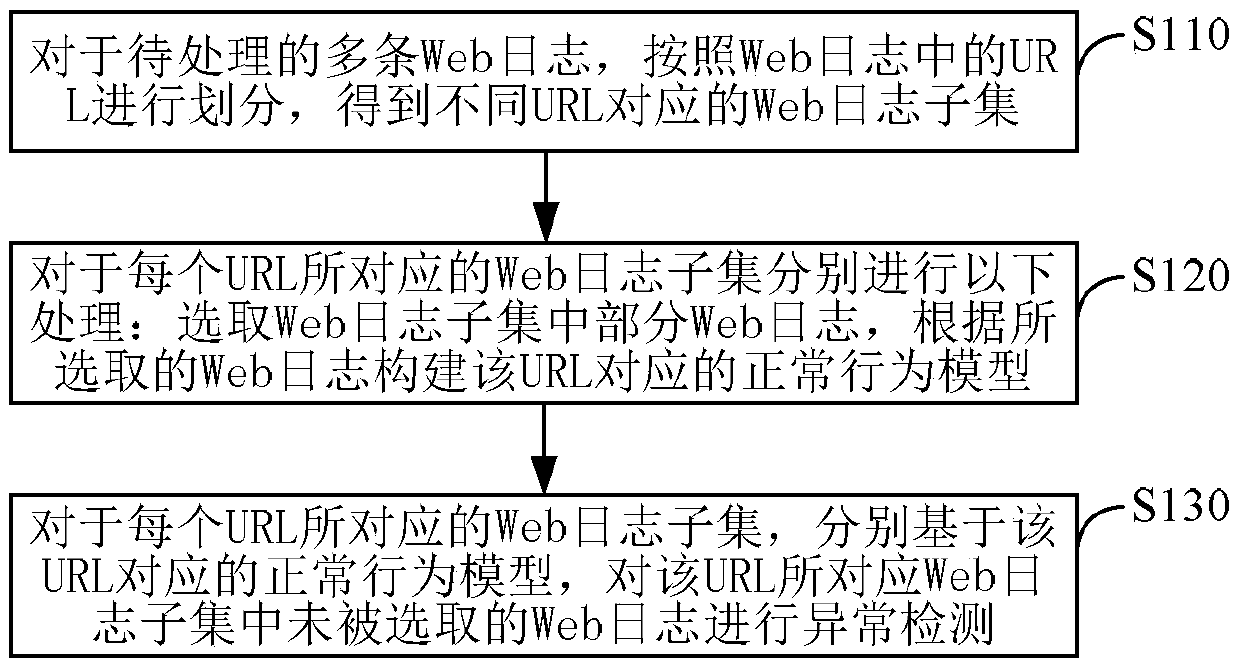
Detecting method and device of Web attack
The invention discloses a detecting method and device of a Web attack. The detecting method of the Web attack comprises the steps of dividing multiple to-be-processed Web logs according to a URL (Uniform Resource Locator) in each Web log to obtain Web log subsets which correspond to different URLs; carrying out the following processing respectively for the Web log subset which corresponds to each URL, including, selecting partial Web logs in each Web log subset, wherein the proportion of the selected Web logs in each Web log subset is less than or equal to a preset proportion upper limit, and establishing a normal behavior model corresponding to the URL based on the selected Web logs; and, for the Web log subset corresponding to each URL, carrying out abnormality detection for the unselected Web logs in the Web log subset which corresponds to the URL respectively based on the normal behavior model corresponding to the URL. According to the detecting method and device of the Web attack, attack detection and evidence collection after the attack can be carried out for the Web attack which is not discovered by applying a firewall.
Owner:CHINA ELECTRONICS STANDARDIZATION INST
Method and device for intercepting web attacks, and customer premise equipment
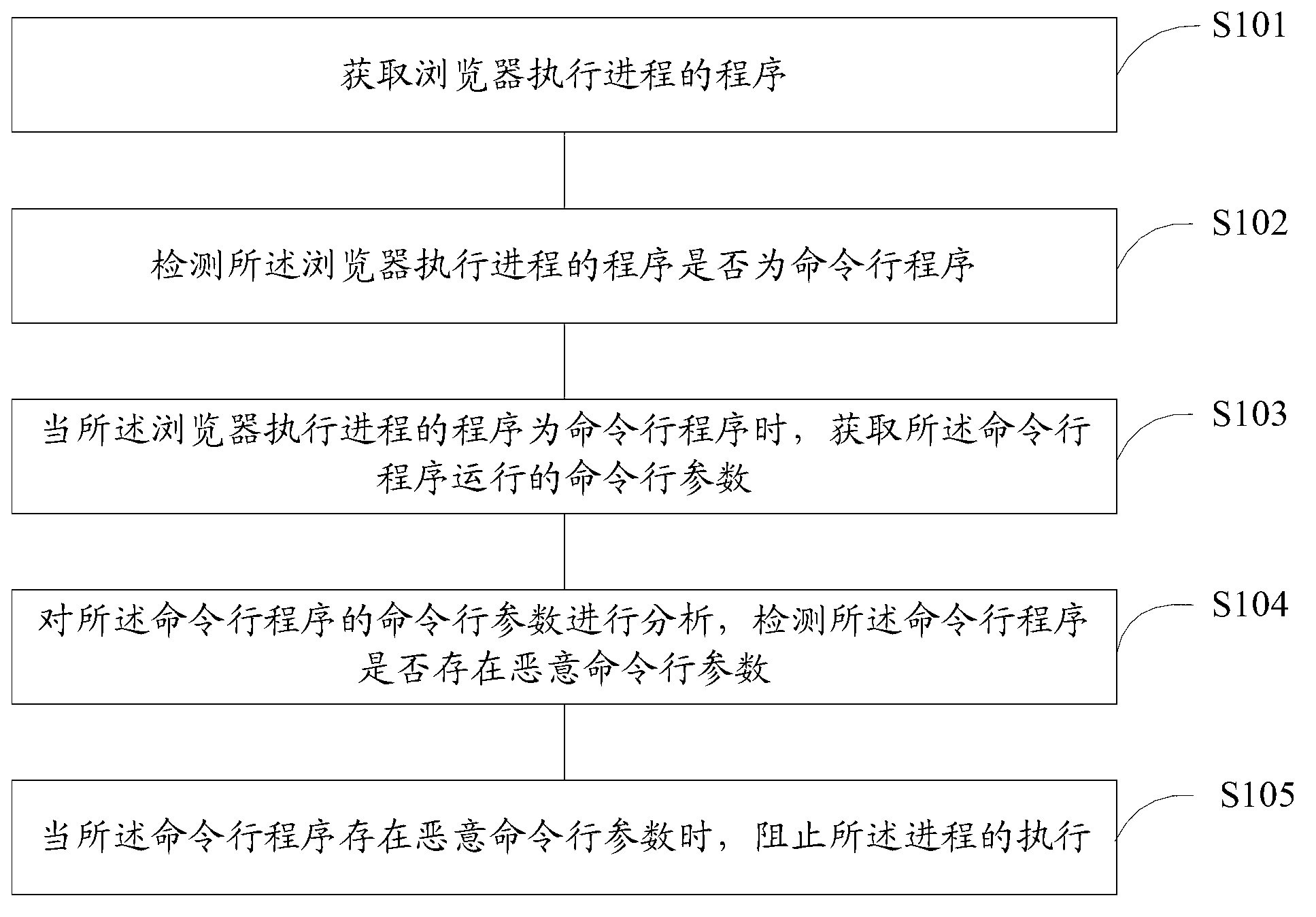
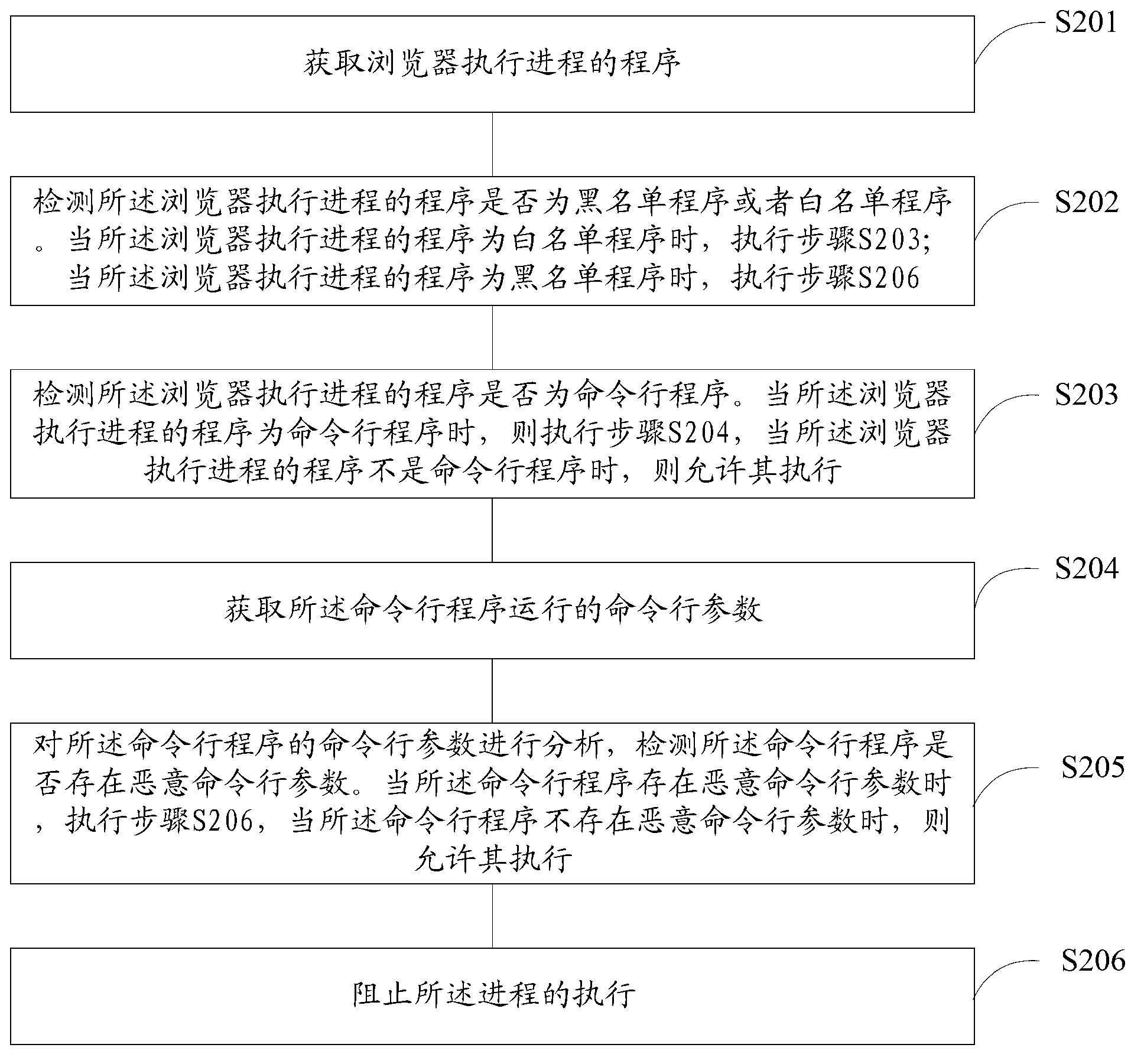
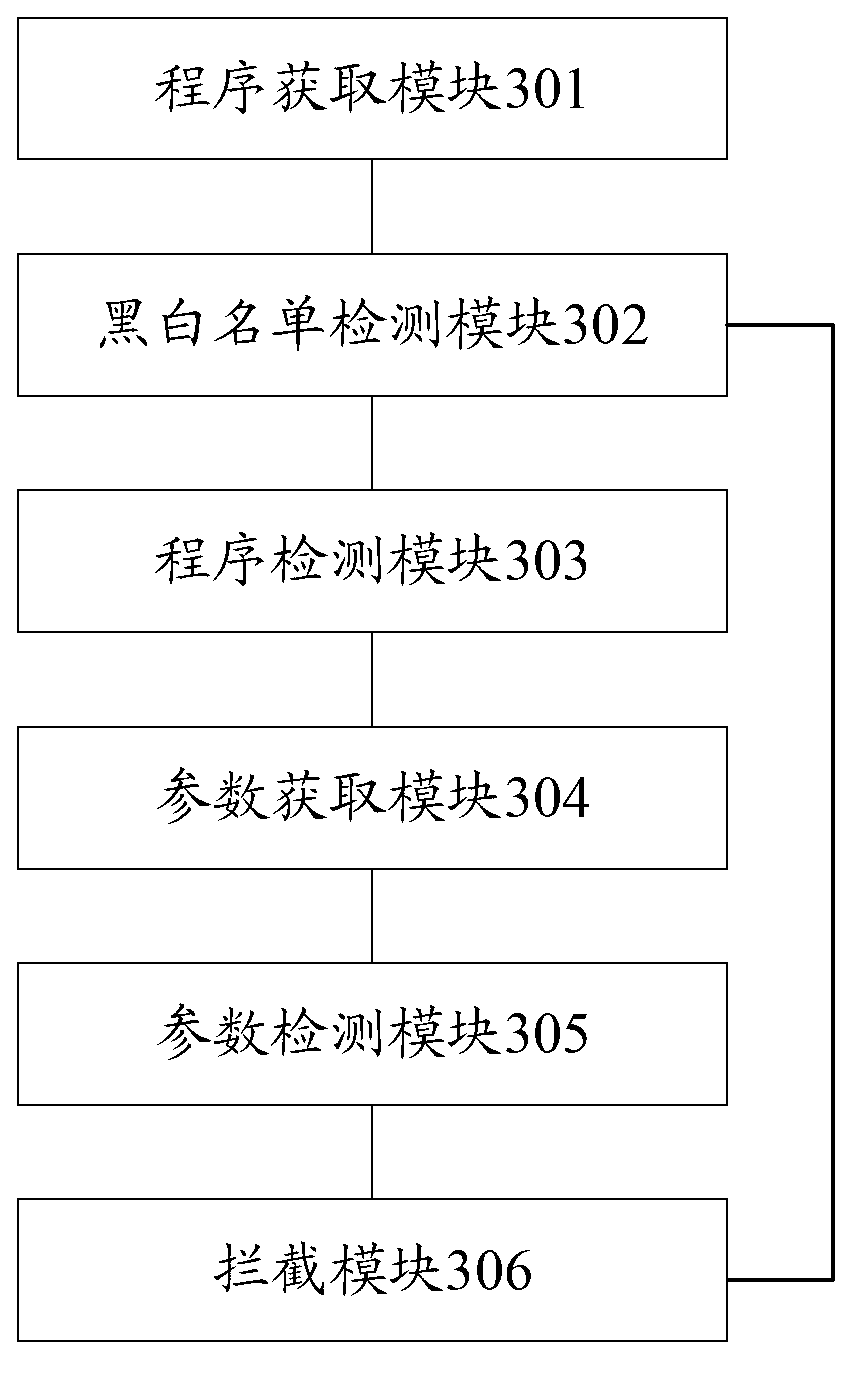
The invention discloses a method and a device for intercepting web attacks, and customer premise equipment, solving the problem that the web attacks come round intercept of black and white lists through an action command running program, and finally a rogue program is successfully carried out, wherein the method comprises the following steps: obtaining a program of a browser execution process; detecting whether the program of the browser execution process is the command running program; when the program of the browser execution process is the command running program, obtaining a command running parameter of the command running program; analyzing the command running parameter of the command running program, detecting whether a malicious command running parameter exists in the command running program; and when the malicious command running parameter exists in the command running program, preventing execution of the process. According to the method and the device, the security of browsing a webpage is improved, and a hostile attack of the webpage can be more effectively intercepted.
Owner:BEIJING QIHOO TECH CO LTD +1
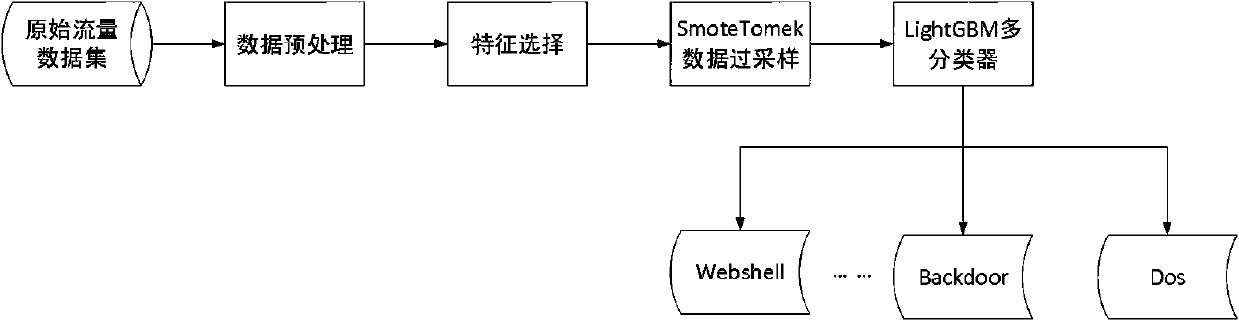
Web anomaly detection method and system based on SMOTETomek and LightGBM
InactiveCN110138786ASolve the imbalanceSolve training difficultiesDigital data information retrievalTransmissionData setAnomaly detection
The invention relates to a Web anomaly detection method and system based on SMOTETomek and LightGBM, and the method comprises the steps: firstly, collecting a mirror image flow PCAP packet from a switch, extracting network flow characteristics, then cleaning redundant data of a training data set, carrying out missing value processing, processing character type flow characteristics, and employing min-max method to normalize the data; then, calculating the flow feature importance based on the GBDT algorithm of the Gini coefficient; carrying out feature selection, carrying out oversampling on afew classes by combining an SMOTE algorithm and a Tomek Links algorithm, training a classifier through a LightGBM algorithm to detect abnormal flow , and finally, carrying out response and feedback processing on a detection result. According to the invention, unknown Web attacks can be detected, and the detection rate and the detection precision on few types of Web attacks are high.
Owner:FUZHOU UNIV
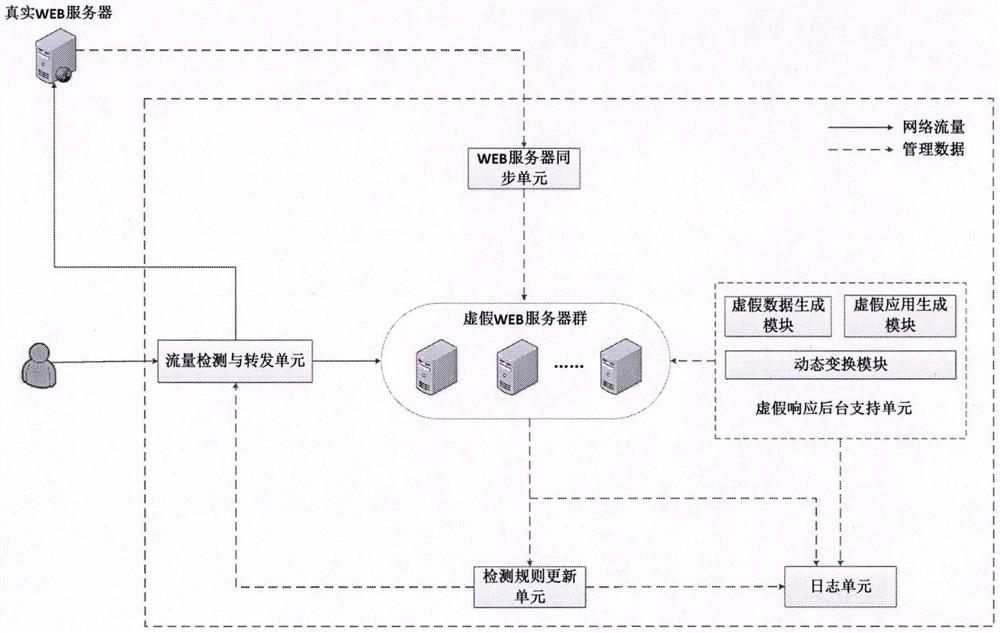
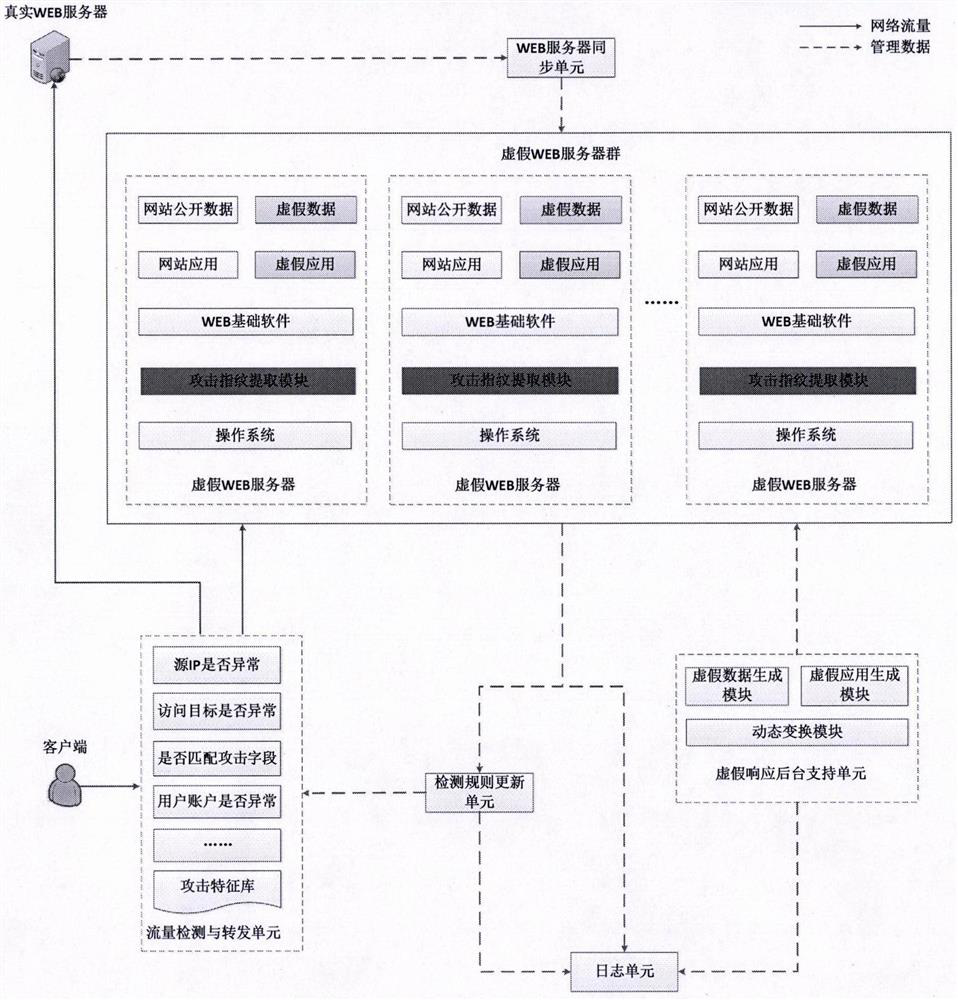
WEB dynamic adaptive defense system and defense method based on false response
The invention provides a WEB dynamic adaptive defense system and defense method based on false response. Based on the concept of moving target defense, a plurality of false WEB servers capable of being dynamically transformed is constructed around a protected WEB server, false sensitive data, false applications, false vulnerabilities and the like are constructed on the false WEB servers, and cheating hackers attack the false WEB servers. When a known attack or a suspicious behavior is identified, the known attack or the suspicious behavior is introduced into the false WEB server, and an attacker enters the false environment and then executes a subsequent attack action in the false environment until the attack is finished, so that multiple attempt attacks of the attacker are effectively defended, and meanwhile, the method has a relatively good defending capability on an unknown WEB attack. Besides, by continuously observing attack behaviors in a false environment, WEB attack features can be automatically extracted, attack detection rules are dynamically and adaptively adjusted, and the dynamic adaptive capacity of a defense system is improved.
Owner:张长河
Method and apparatus for secure web browsing
Owner:LUCENT TECH INC
Web attack identification method and device
InactiveCN107644162AReduce false negative rateReduce time wastedPlatform integrity maintainancePattern recognitionValue set
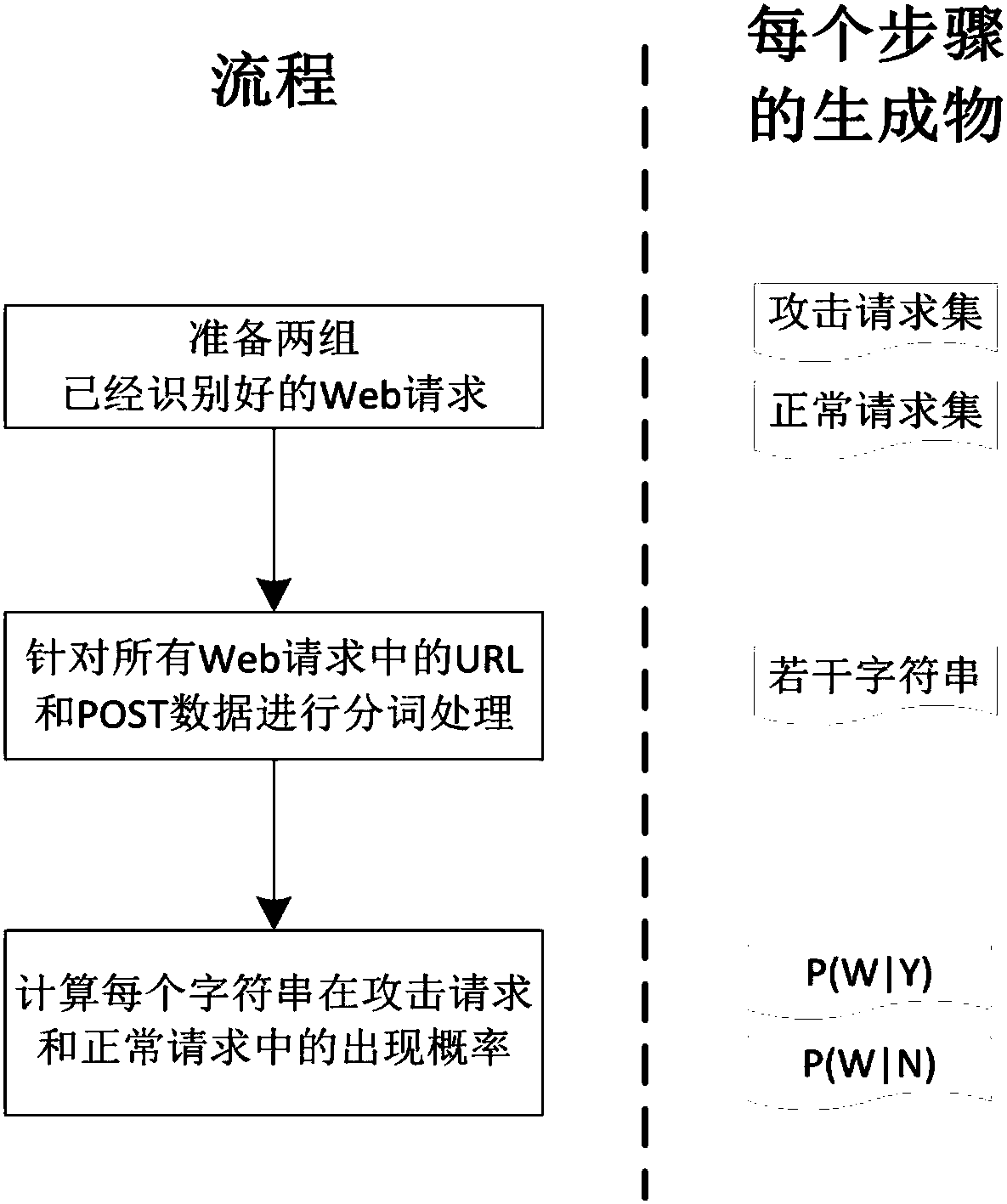
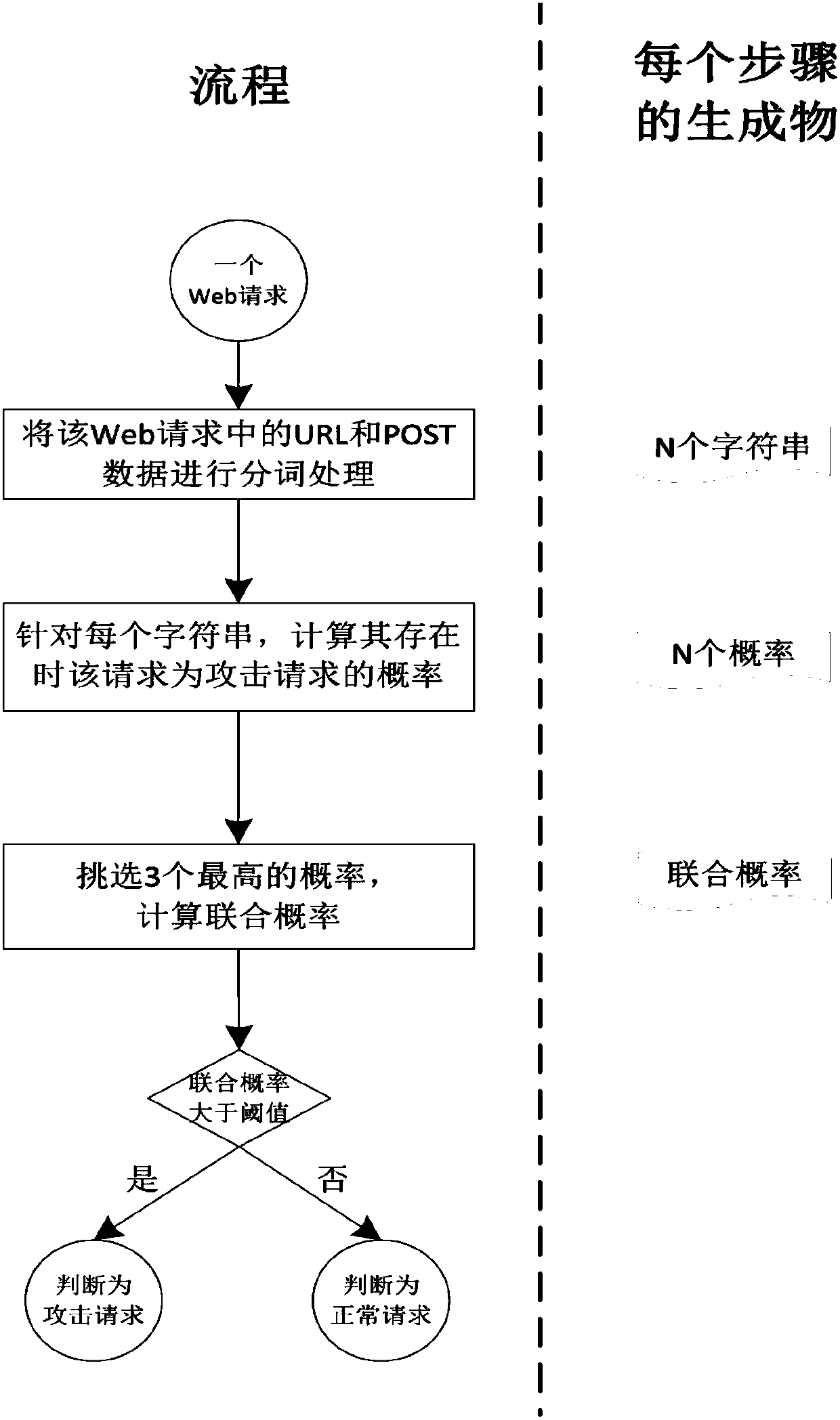
The invention discloses a Web attack identification method and device. The method comprises: 1) carrying out word segmentation processing on URL and POST data of each Web request in a Web normal-request set and a Web attack-request set to obtain a plurality of character strings; 2) for each character string, respectively calculating an occurrence probability of the character string in the Web normal-request set and an occurrence probability thereof in the Web attack-request set; 3) carrying out word segmentation processing on URL and POST data in a to-be-identified Web request to obtain N character strings, and for each character string in the N character strings, calculating a probability that the character string enables the to-be-identified Web request to be identified as an attack request; and 4) selecting a plurality of highest probabilities, calculating a joint probability that the to-be-identified Web request is the attack request, judging that the to-be-identified Web request is the attack request if the joint probability is greater than a threshold value set in advance, and otherwise, judging that the to-be-identified Web request is a normal request.
Owner:北京知道未来信息技术有限公司
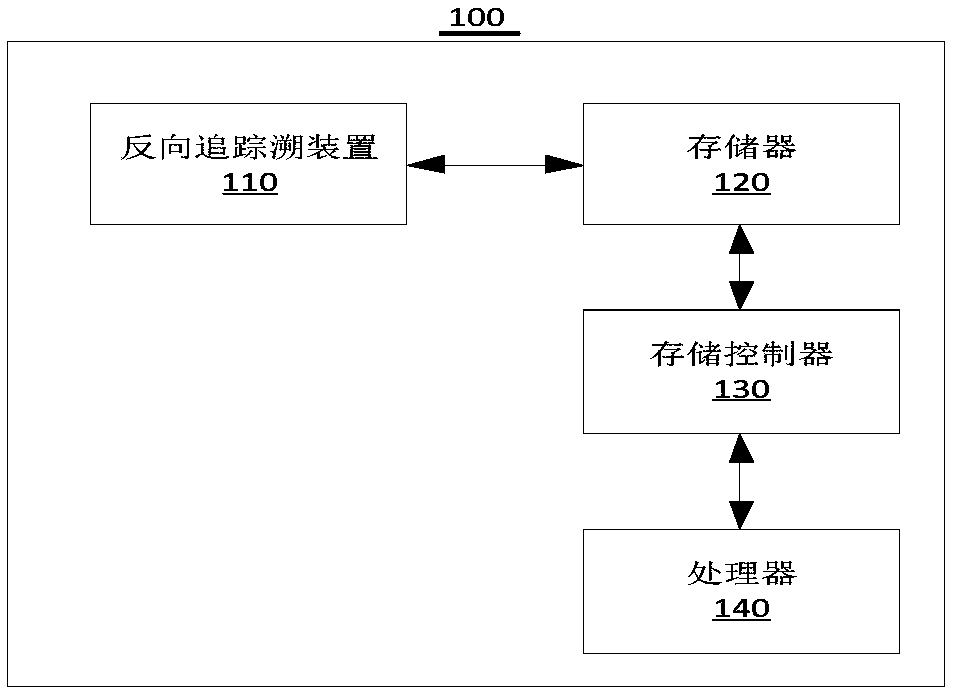
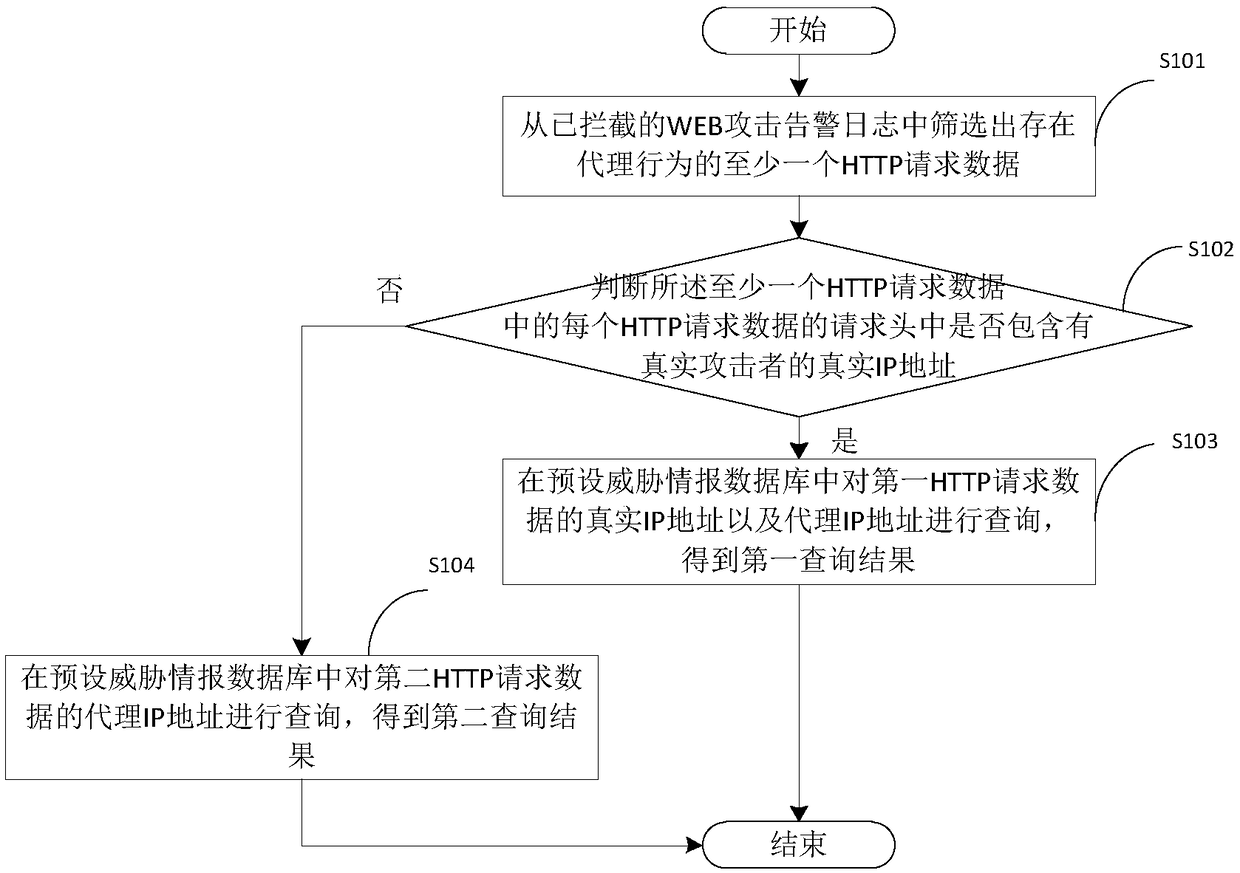
Reverse tracing method and device of proxy host
The invention relates to a reverse tracing method and device of a proxy host, belonging to the technical field of network security. The method comprises the steps of screening out at least one piece of HTTP request data with a proxy behavior from intercepted WEB attack warning logs; determining whether a request head of each piece of HTTP request data of the at least one HTTP request data comprises a real IP address of a real attacker; and if first HTTP request data comprising the real IP address of the real attacker exists in the at least one HTTP request data, searching a preset threat intelligence database for the real IP address and a proxy IP address of the first HTTP request data, so as to obtain a first query result. The method determines the IP address of the real attack source andcompletes tracing work rapidly and effectively, and helps network security protection equipment better identify proxy attack behaviors.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Security protection method and DPMA protection model
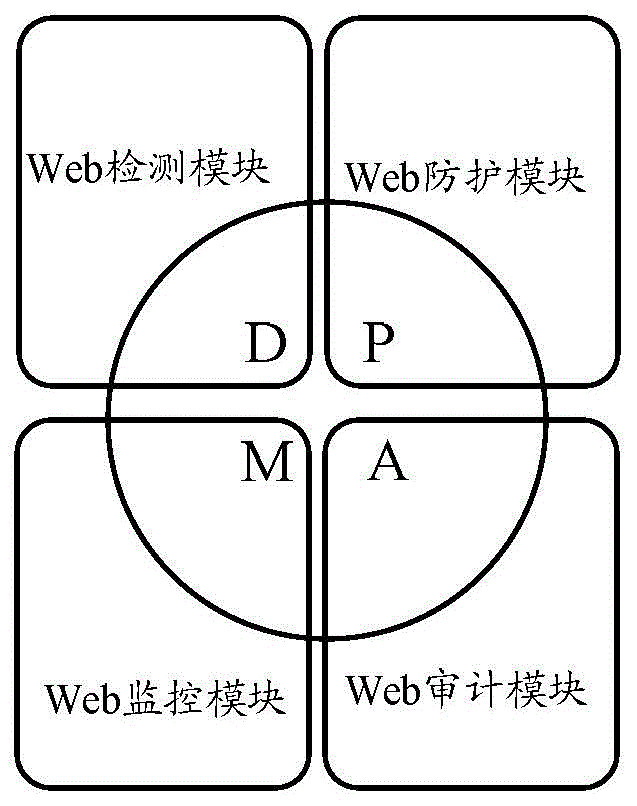
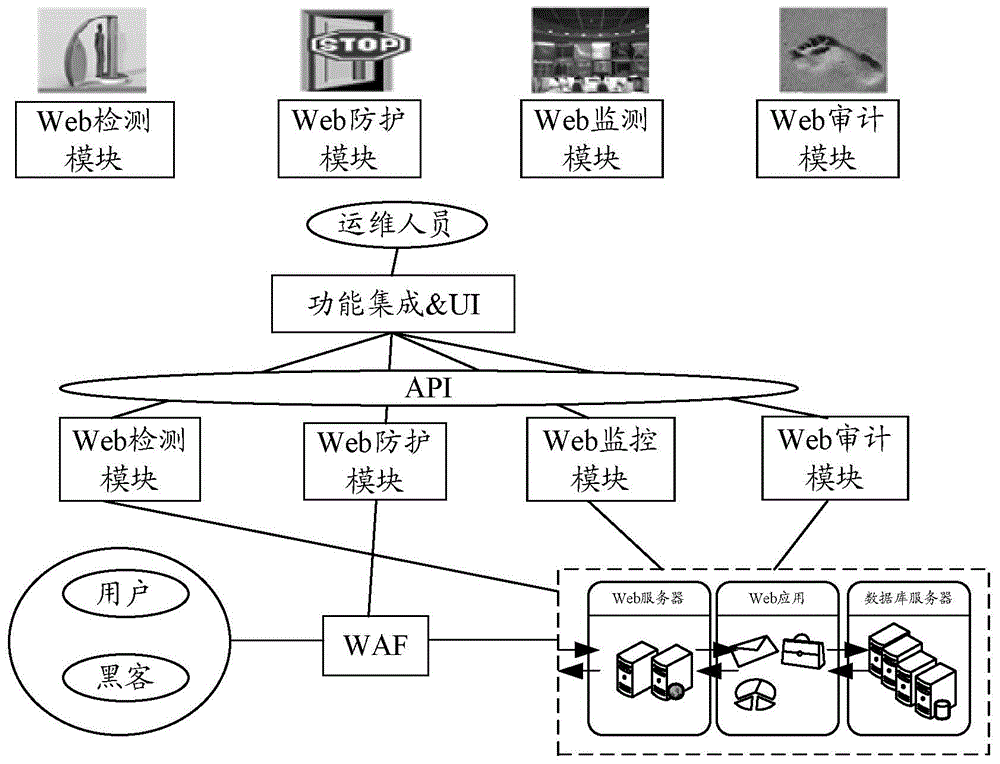
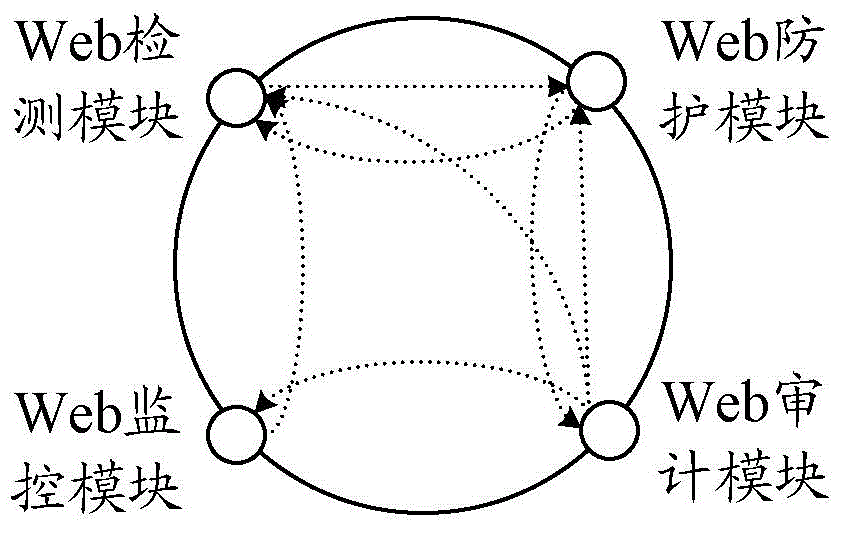
ActiveCN105871775ARealize security protectionImprove securityTransmissionWeb attackComputer security
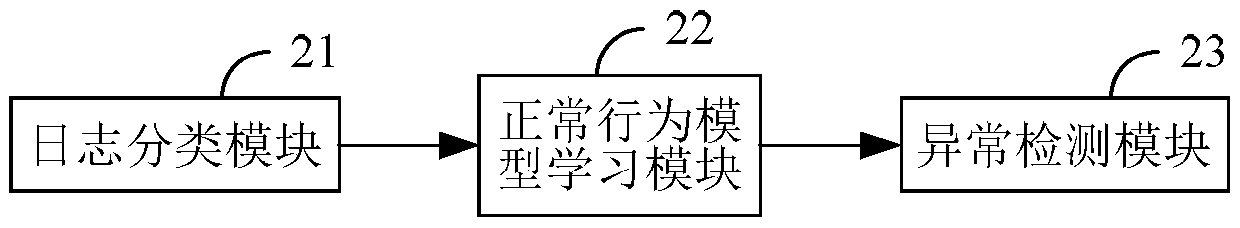
The invention discloses a security protection method. The method comprises: a DPMA protection model obtains protection information about a web attack event, wherein the DPMA protection model comprises a web detection module, a web protection module, a web monitoring module, and a web auditing module; and the DPMA protection model conducts linked actions according to the protection information about the web attack event to achieve security protection of a web application, wherein the linked actions include interactions between the web detection module, the web protection module, the web monitoring module, and the web auditing module by means of the protection information about the web attack event. The invention also discloses a DPMA protection model.
Owner:CHINA MOBILE COMM GRP CO LTD
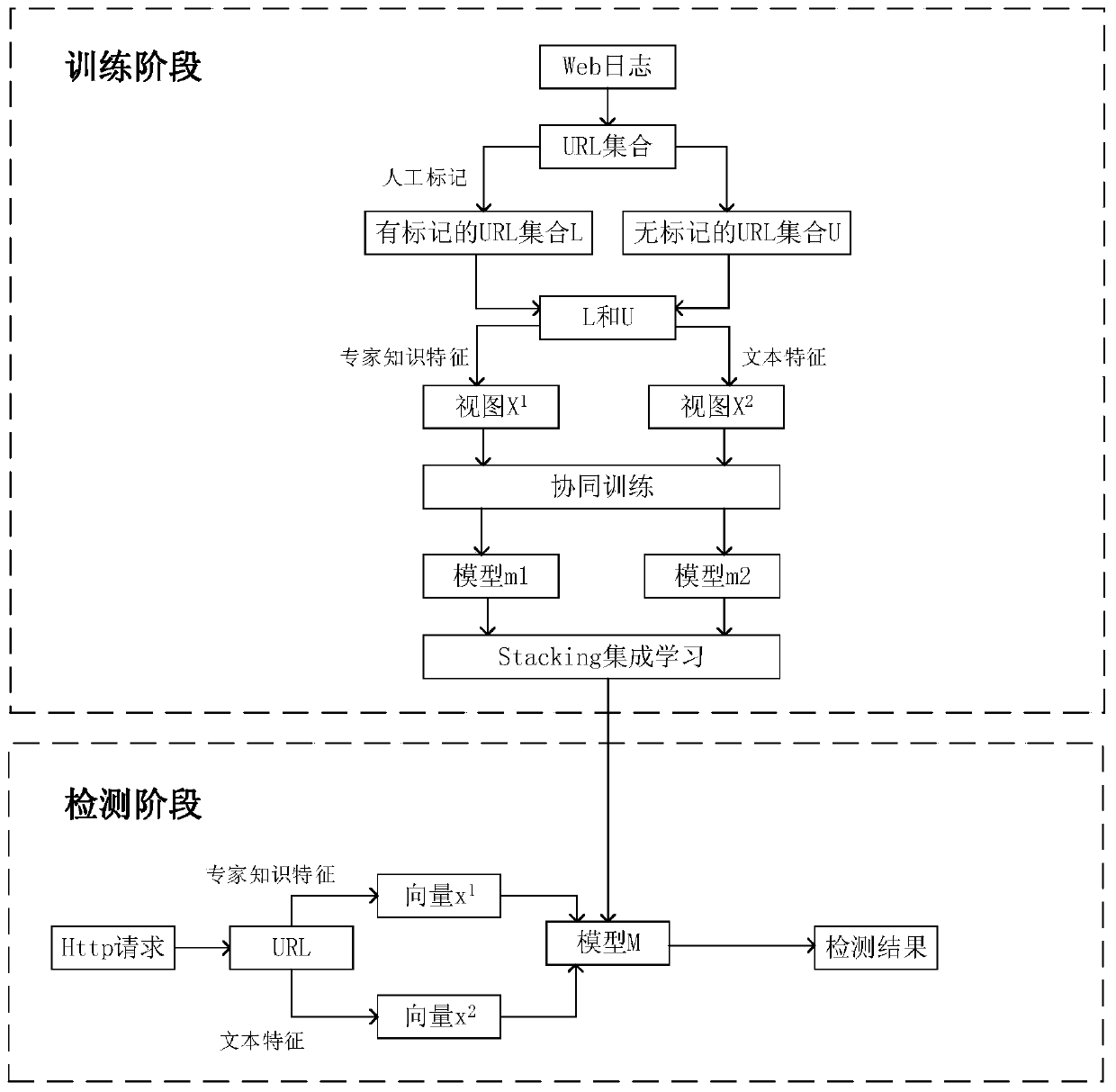
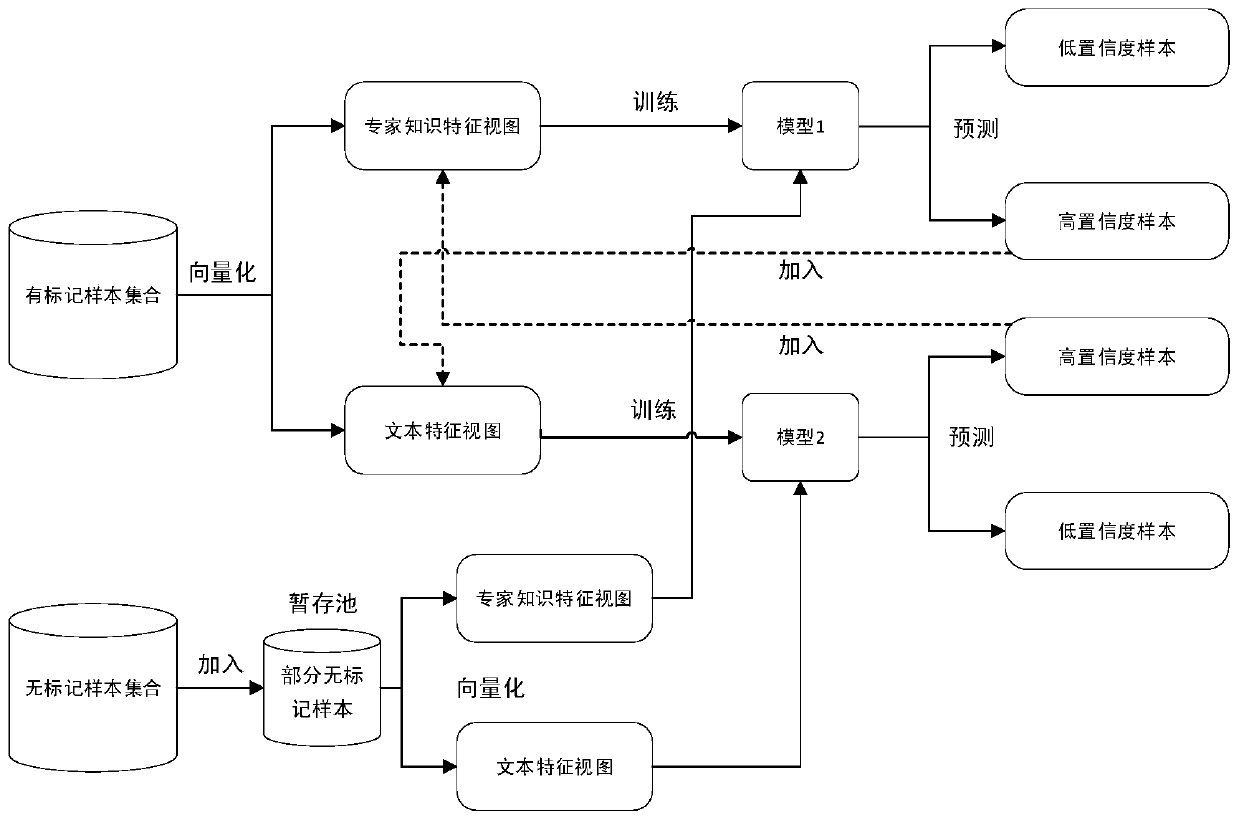
A Web attack detection method based on collaborative training
The invention provides a Web attack detection method based on collaborative training. The problem that a Web attack detection model is difficult to train due to lack of most URL tags is solved. According to the method, a part of marked URLs and a large number of unmarked URLs can be used for carrying out model training; firstly, samples are vectorized through expert knowledge characteristics and text characteristics to obtain two independent views, then the views are used for collaborative training to obtain two attack detection models, and finally, the two models are combined through integrated learning to be used for detecting Web attacks. According to the method, the workload of manual data marking can be reduced, and the cost of Web attack detection can be reduced.
Owner:HANGZHOU NORMAL UNIVERSITY
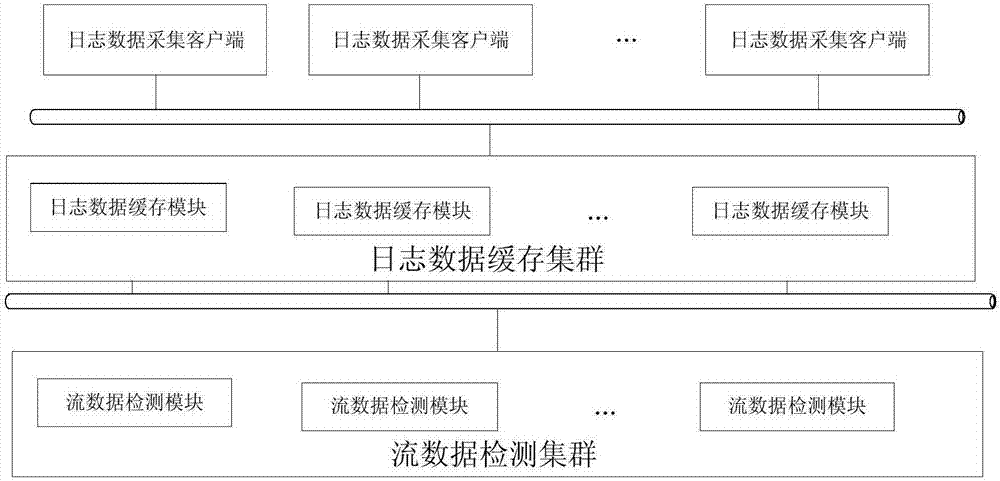
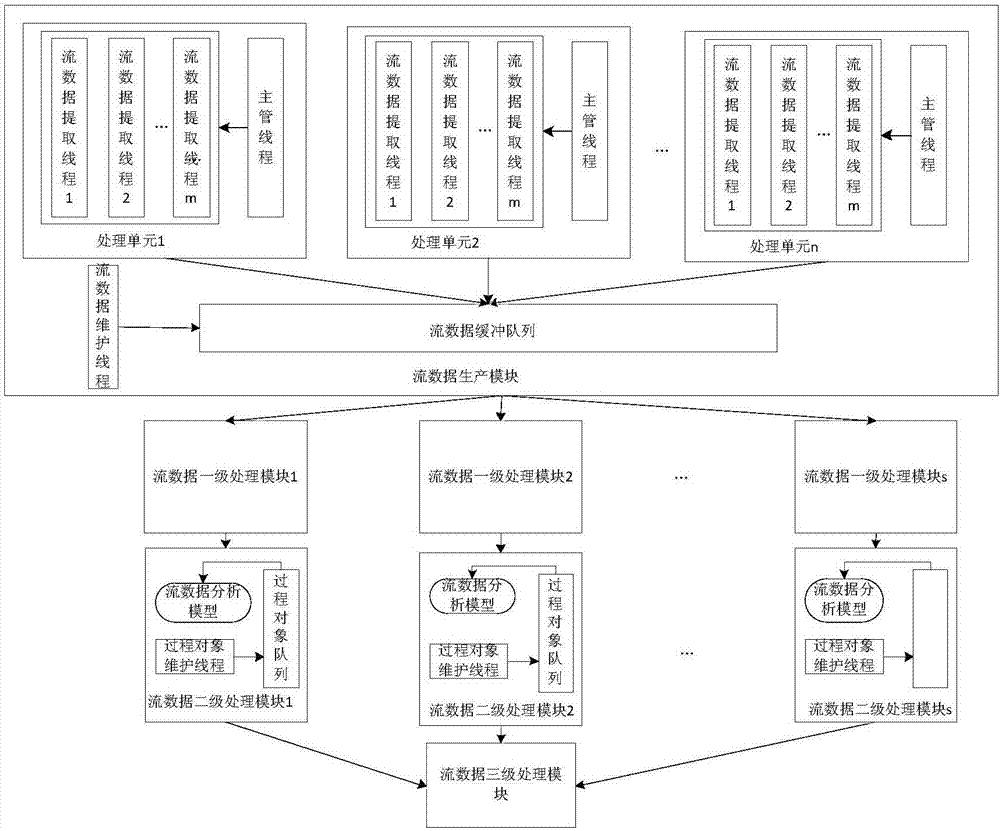
Stream data analysis based Web attack real-time and online detection system
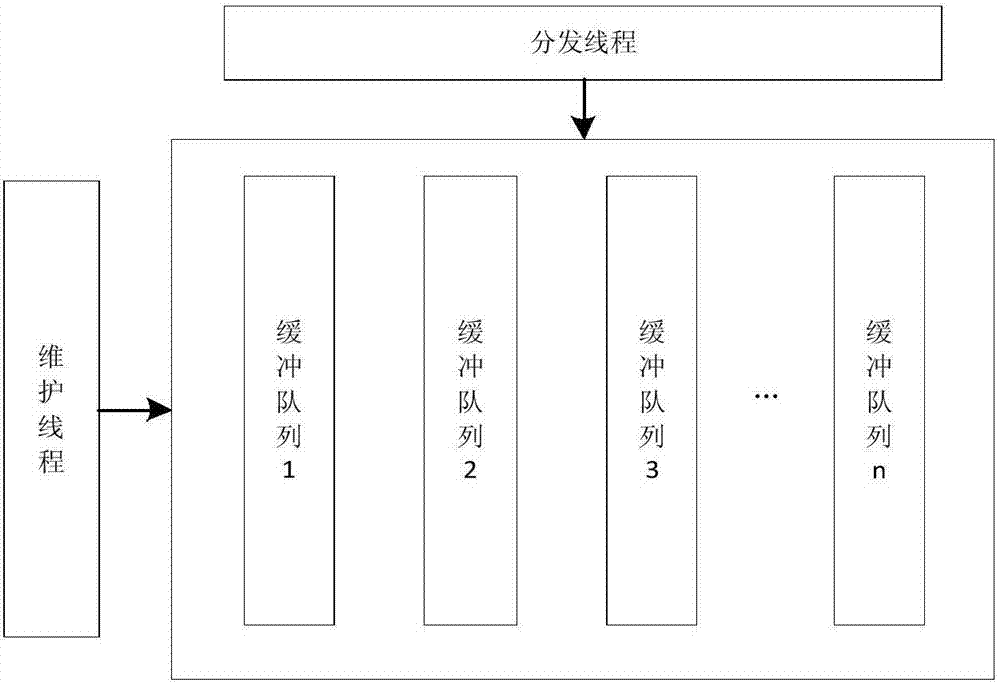
The invention discloses a stream data analysis based Web attack real-time and online detection system. The stream data analysis based Web attack real-time and online detection system comprises a log data acquisition client, a log data buffering cluster and a stream data detecting cluster. The technical effects are that: as multiple buffering queues are adopted for online and real-time acquisition of application logs of an information system, a hacker can be prevented from deleting log data after attacking; as a cluster frame design is adopted and the whole safe log data processing process is composed of the log data buffering cluster and the stream data detecting cluster, load balancing and single-point fault solution can be realized and the data processing real-time performance and reliability are improved; as the dynamic time window based stream data analysis method is adopted, the time window threshold can be adjusted dynamically based on different scenes, and the data fusion accuracy is improved.
Owner:STATE GRID CORP OF CHINA +2
Method and device for monitoring network attack
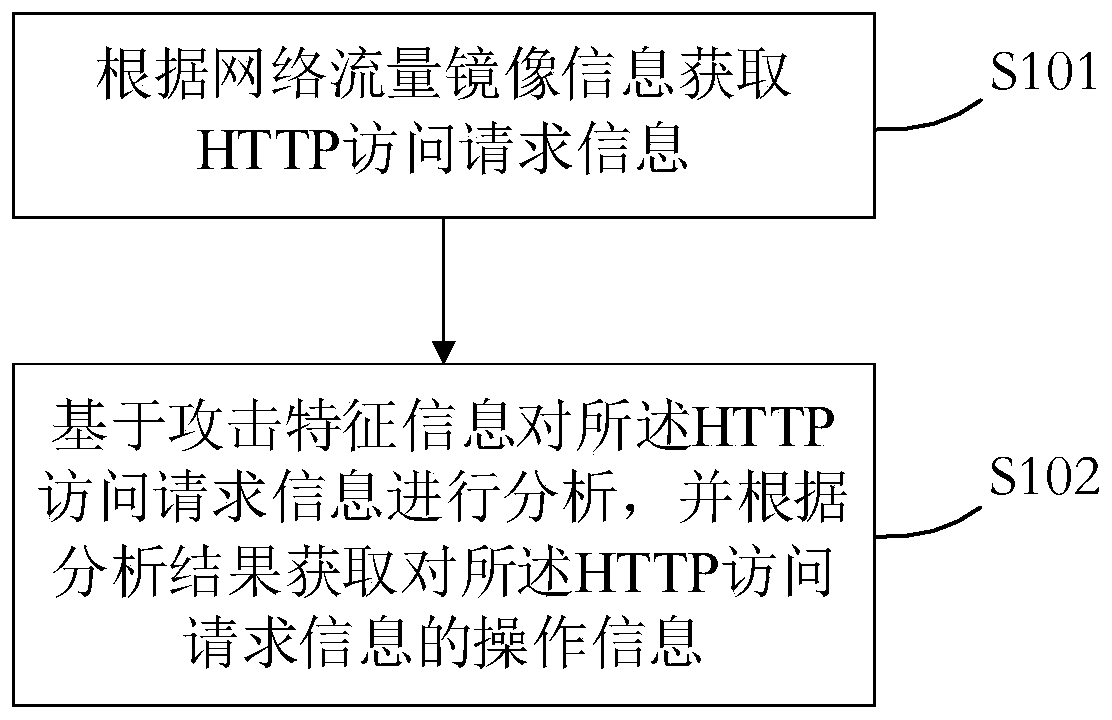
InactiveCN110225062AA lot of content can be detectedImprove accuracyTransmissionWeb attackNetwork attack
The invention provides a method and a device for monitoring a network attack. The method comprises the following steps: acquiring HTTP access request information according to network flow mirror imageinformation; and analyzing the HTTP access request information based on the attack feature information, and obtaining operation information of the HTTP access request information according to an analysis result. Firstly, the HTTP application information extracted from the network flow mirror image information is very complete, more detectable contents can be detected, and the detection accuracy is improved. Secondly, the timeliness of detection is improved, and real-time detection can be carried out when WEB attacks occur. Thirdly, the system can judge whether the WEB attack is successful ornot according to the response content of the server, timely block and early warn the WEB attack, and prevent the situation from deteriorating. And meanwhile, the management cost is reduced.
Owner:北京微步在线科技有限公司
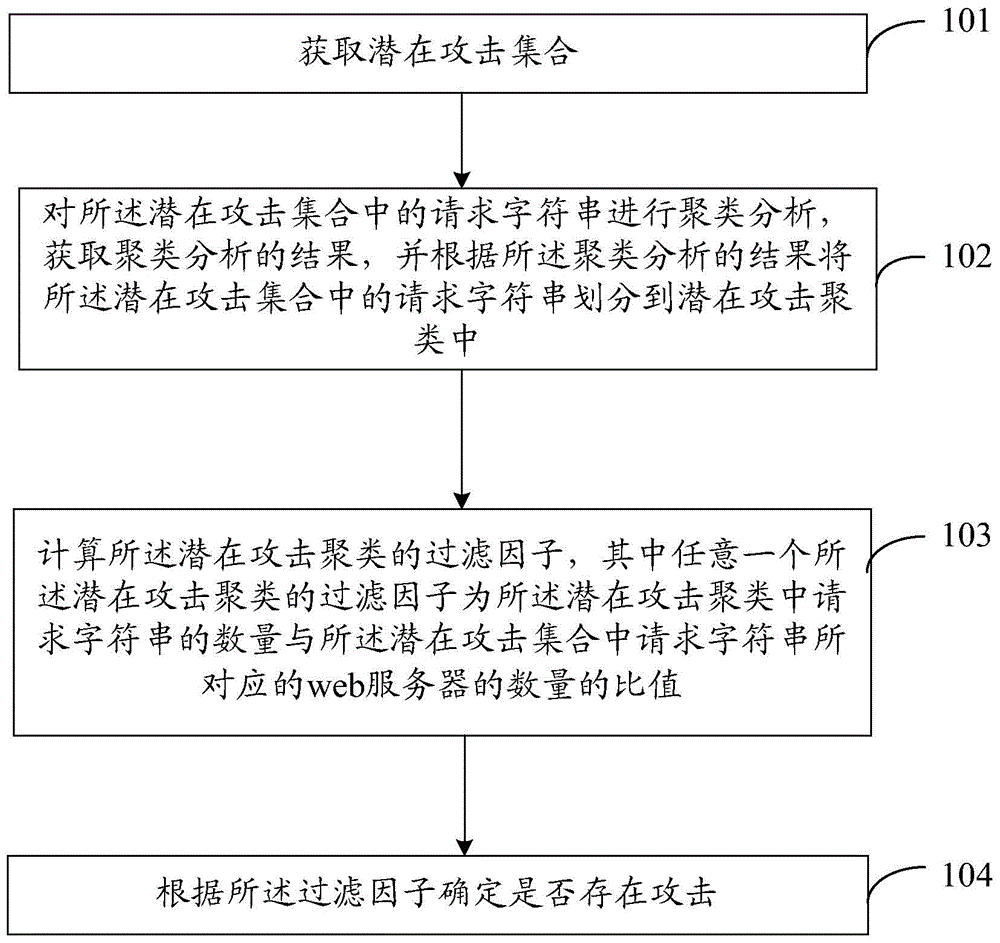
Detection method and device of attack for Web server group
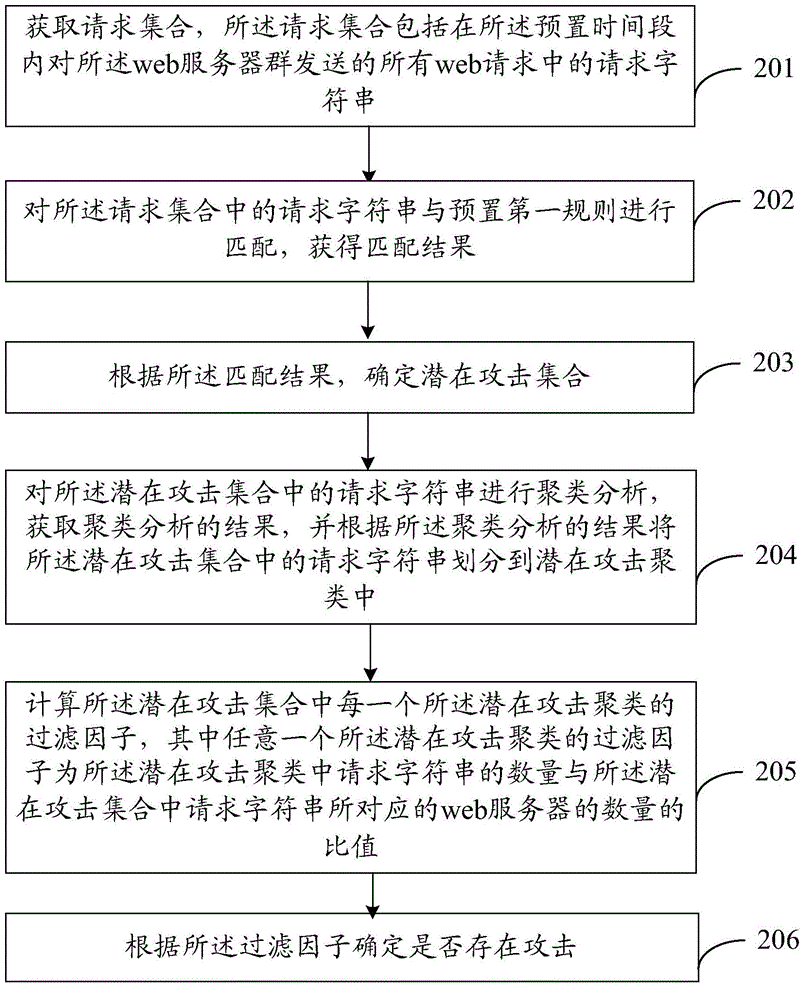
Embodiments of the invention disclose detection method and device of an attack for a Web server group, and the method and device are used to respond to a rapidly changing Web attack. The method comprises obtaining a potential attack set which is determined according to request character strings of Web requests sent to the Web server group in a preset period, performing cluster analysis on the request character strings, diving the request character strings to potential attack clusters according to a result of the cluster analysis, calculating a filtering factor, which is a ratio of the number of request character strings in the potential attach clusters to the number of Web servers corresponding to the request character strings, lurked in each potential attack cluster, and determining whether an attack exists according to the filtering factor. The rapidly changing Web attack can be responded.
Owner:HUAWEI TECH CO LTD +1
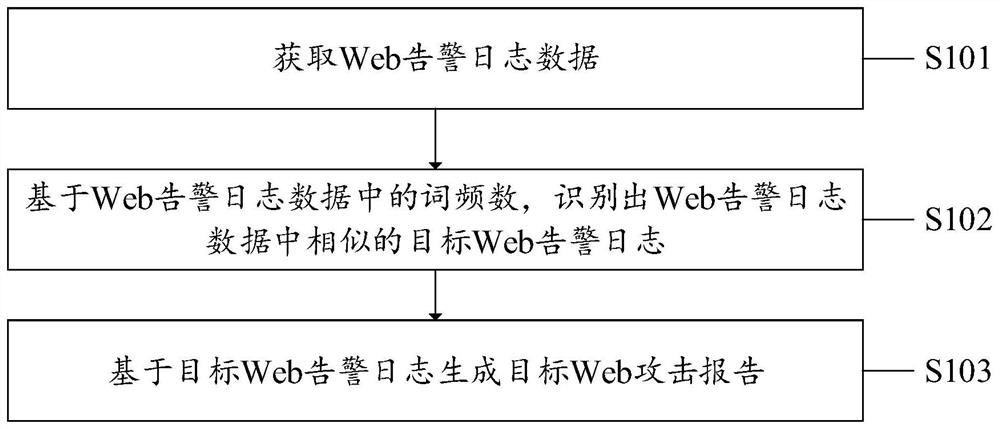
Web attack report generation method, device and equipment and computer medium
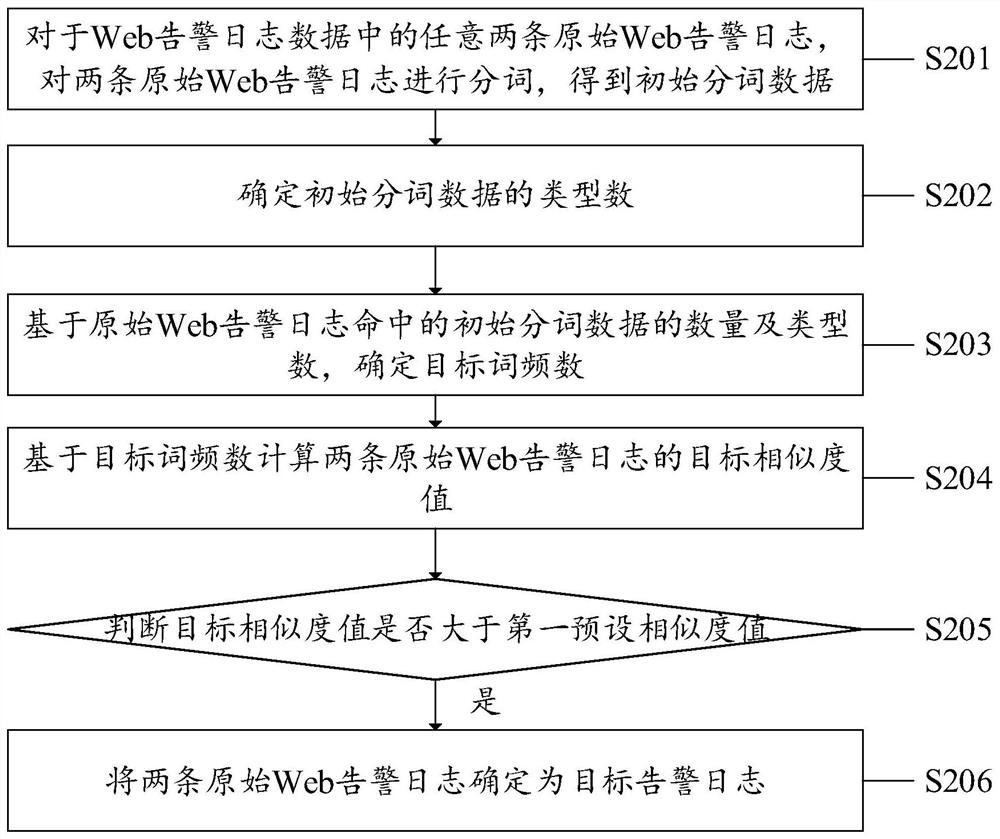
PendingCN111985192AImprove efficiencyImprove accuracyNatural language data processingEngineeringWeb attack
The invention discloses a Web attack report generation method, device and equipment and a medium. The method comprises the steps of obtaining Web alarm log data; based on the word frequency number inthe Web alarm log data, identifying similar target Web alarm logs in the Web alarm log data; and generating a target Web attack report based on the target Web alarm log. In the invention, the similartarget Web alarm logs are identified based on the word frequency number in the Web alarm log data; since the similar target Web alarm logs reflect Web attack characteristics, when the target Web attack report is generated based on the target Web alarm logs, the Web attack characteristics can be reflected by means of the target Web attack report, and compared with manual generation of the Web attack report, the efficiency and accuracy are high, and the applicability is good. According to the Web attack report generation device and equipment and the computer readable storage medium provided by the invention, the corresponding technical problems are also solved.
Owner:杭州安恒信息安全技术有限公司
Web attack protection method and system based on SQL injection
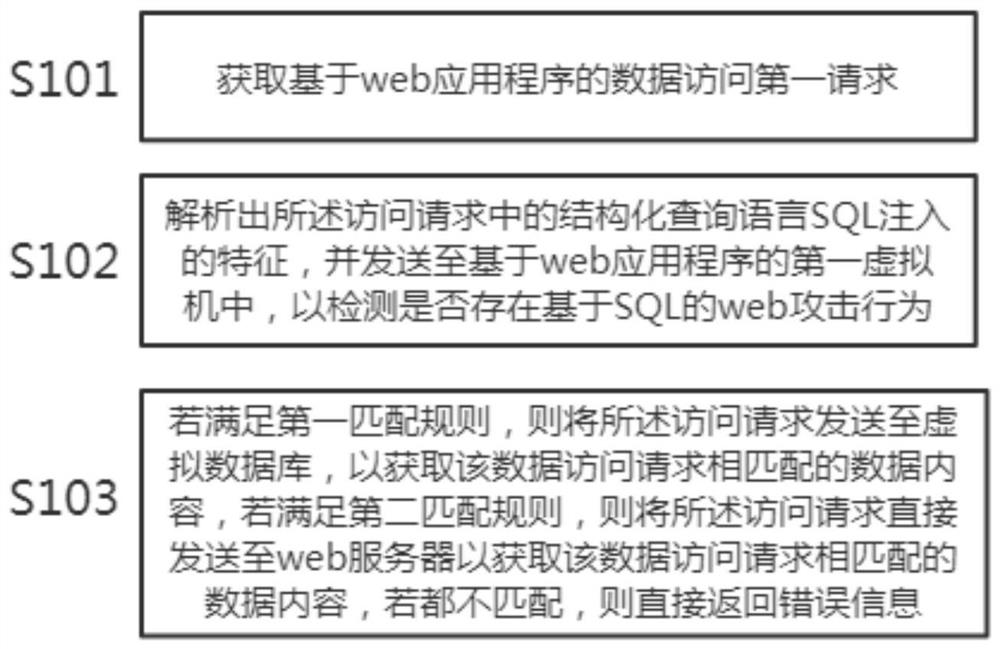
InactiveCN113190839AEffective protectionImprove securityPlatform integrity maintainanceSpecial data processing applicationsSQL injectionData access
The invention provides a web attack protection method based on SQL injection. The method comprises the following steps: acquiring a first data access request based on a web application program; analyzing a structured query language (SQL) injection feature in the access request, and sending the SQL injection feature to a first virtual machine based on a web application program to detect whether a SQL-based web attack behavior exists or not; if a first matching rule is met, sending the access request to a virtual database to obtain data content matched with the data access request; if a second matching rule is met, sending the access request directly to a web server to obtain data content matched with the data access request; and if the data content is not matched with the data access request, returning error information directly. Through the first detection at the web application program end and the second detection of content return, vulnerabilities existing in SQL injection are effectively protected, and the network security in the Internet data interaction process is effectively improved.
Owner:GUIZHOU POWER GRID CO LTD
HTTP session exception detection method and detection system
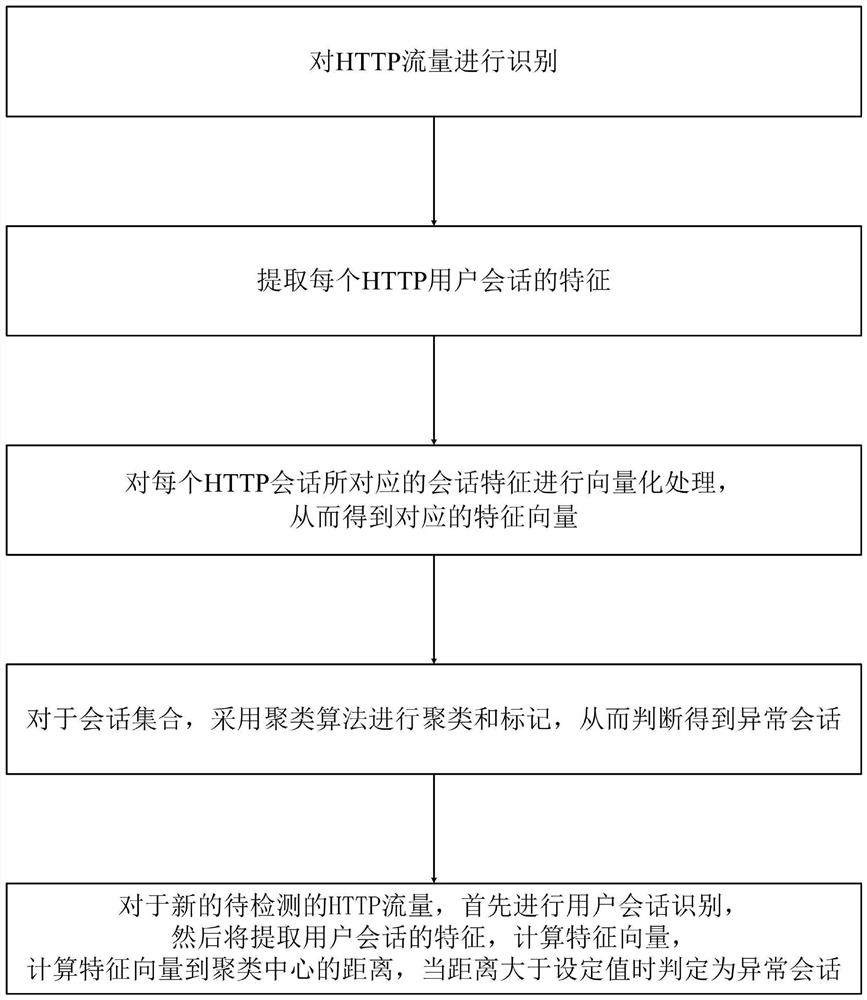
ActiveCN112565270AImprove reliabilityImprove accuracyTransmissionText database queryingCluster algorithmAnomaly detection
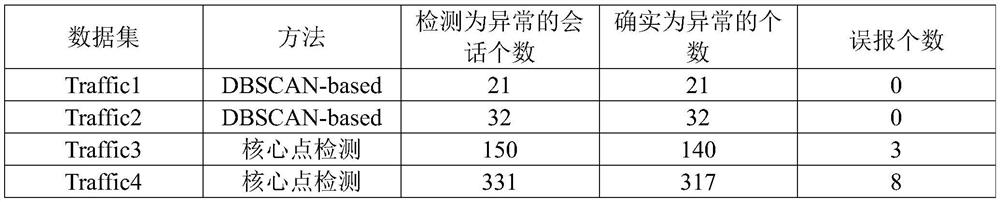
The invention discloses an HTTP session exception detection method. The method comprises the following steps: identifying HTTP traffic; extracting features of each HTTP user session; performing vectorization processing on the session feature corresponding to each HTTP session to obtain a feature vector; and clustering and marking the session set by adopting a clustering algorithm, and judging to obtain an abnormal session. The invention also provides a detection system for realizing the HTTP session exception detection method. According to the method, efficient clustering and core point storage are carried out by utilizing a clustering algorithm under the condition of not needing label data according to the user sessions divided by the HTTP traffic, the session exception in the HTTP traffic is discovered by calculating the distance between the HTTP session to be tested and the core point by utilizing the stored core point, and then the Web attack is discovered; and the method solves alarge number of problems in the prior art, and is high in reliability, good in practicability and high in accuracy.
Owner:STATE GRID HUNAN ELECTRIC POWER +2
Method and device for determing WEB attack result, electronic device and readable storage medium
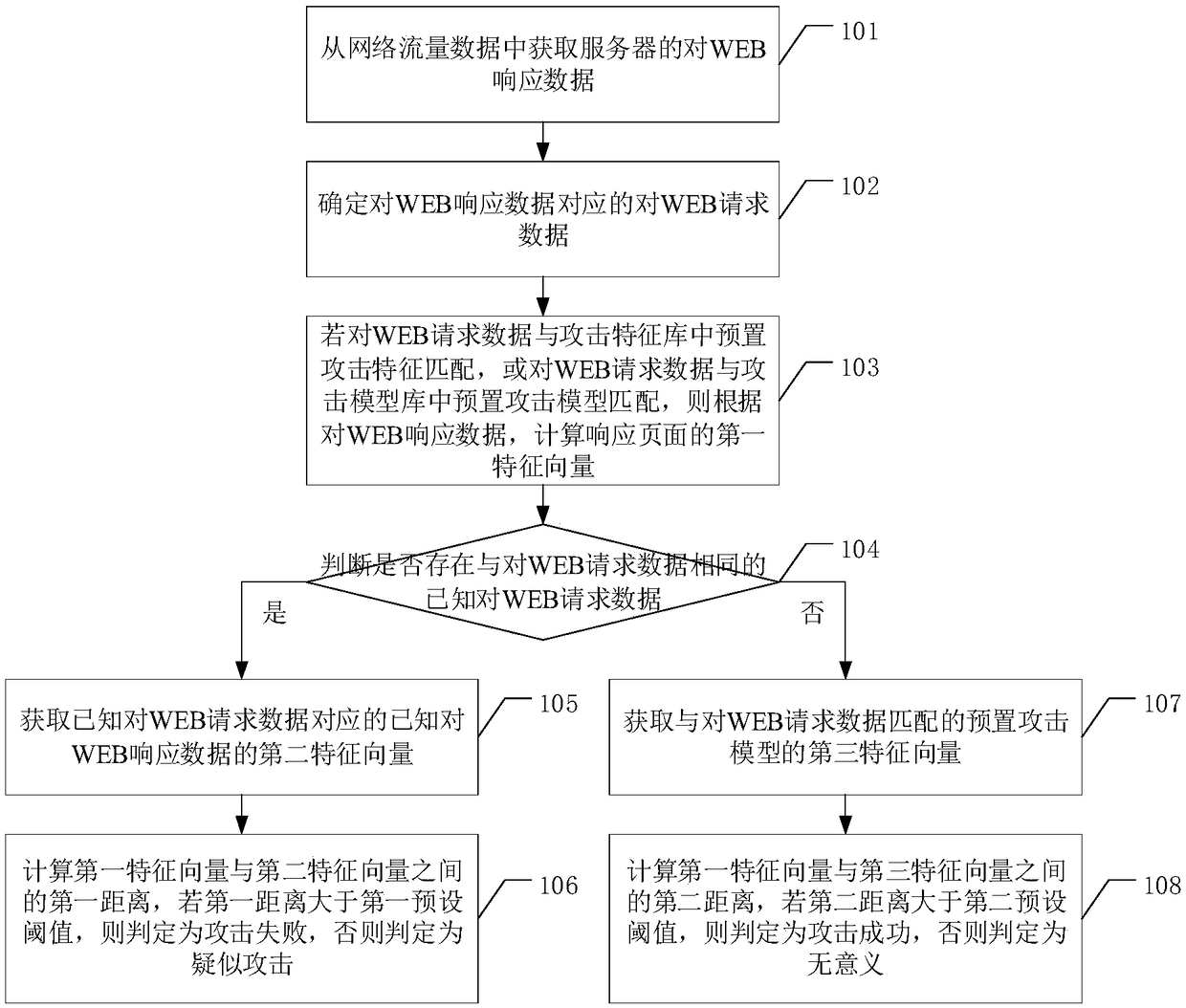
The embodiment of the invention discloses a method and device for determining a WEB attack result, and an electronic device and a readable storage medium. The attack result of the WEB request data corresponding to the WEB response data is determined by calculating the similarity between a response page corresponding to the WEB response data and a normal response page, and an attacked response page, respectively. Therefore, the technical problem that the existing detection systems usually only detect whether a WEB attack has occurred and cannot determine the result and the impact of the attacksis solved.
Owner:EASTCOMPEACE TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
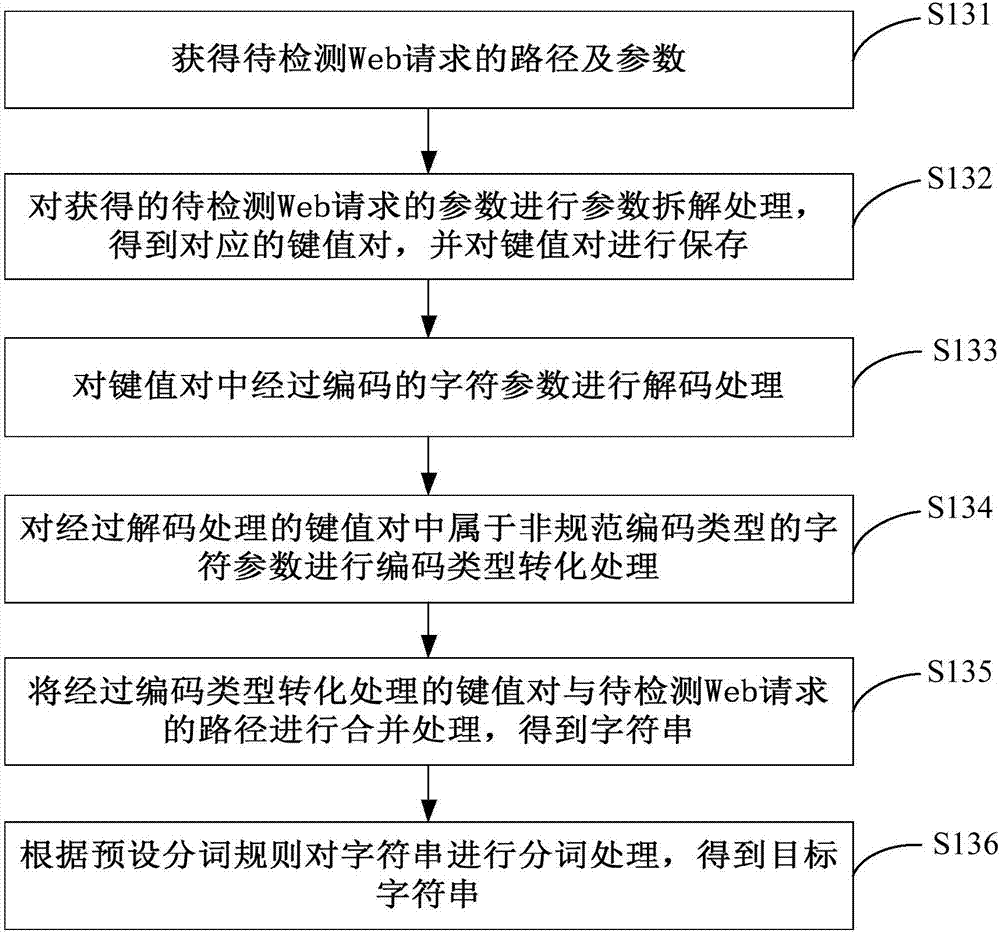
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com