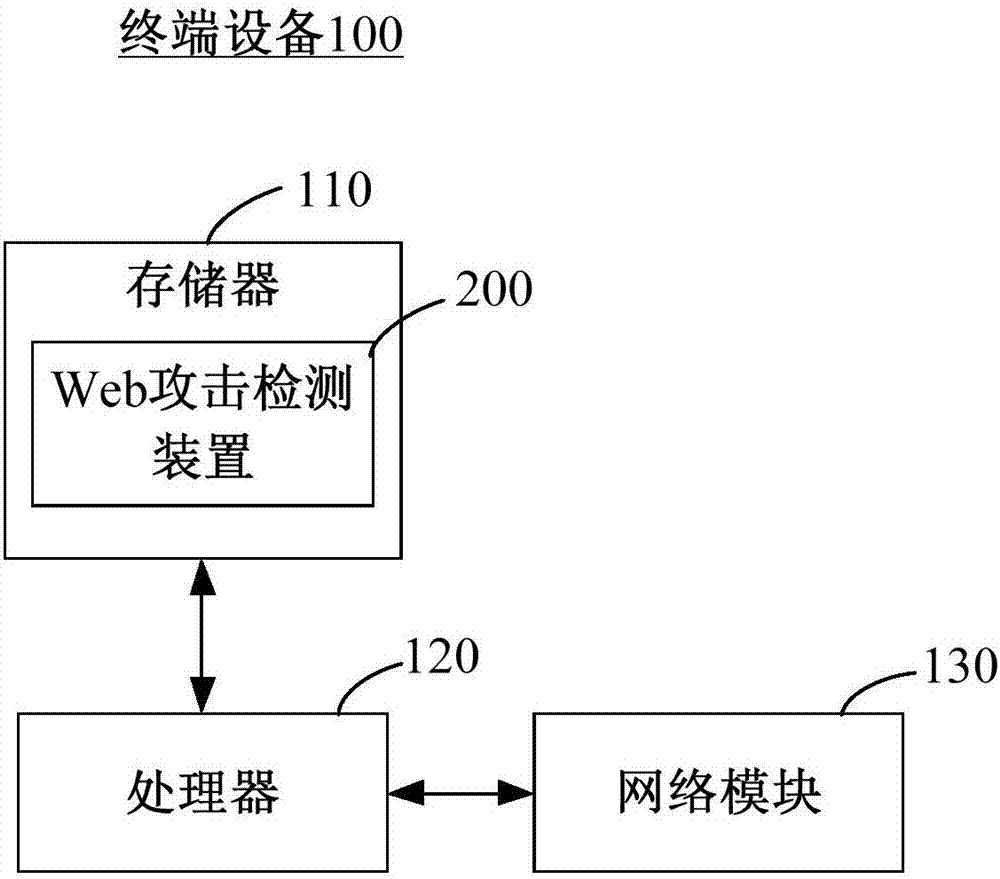
Web attack detection method and Web stack detection device
An attack detection and detection technology, applied in the field of information security, can solve the problems of high false alarm rate, affecting the normal use of users, high labor cost, etc., and achieve the effect of reducing labor cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
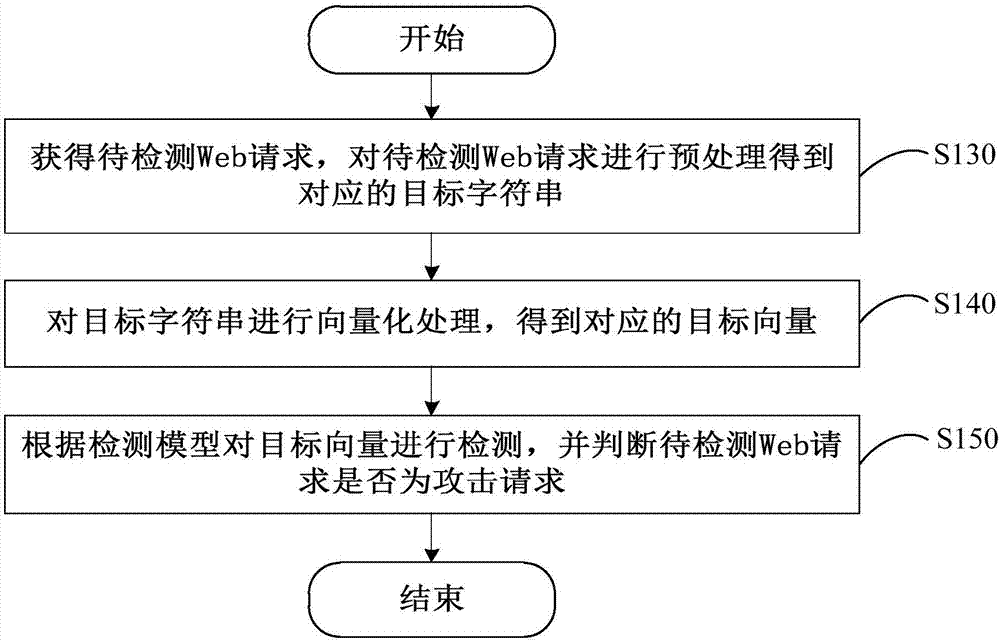
[0035] Please refer to figure 2 , figure 2 It is one of the flow charts of the steps of the Web attack detection method provided in the first embodiment of the present invention. The method is applied to the terminal device 100 . The specific process of the Web attack detection method is described in detail below. The method includes step S130, step S140 and step S150.
[0036] Step S130, obtaining the Web request to be detected, and performing preprocessing on the Web request to be detected to obtain a corresponding target character string.
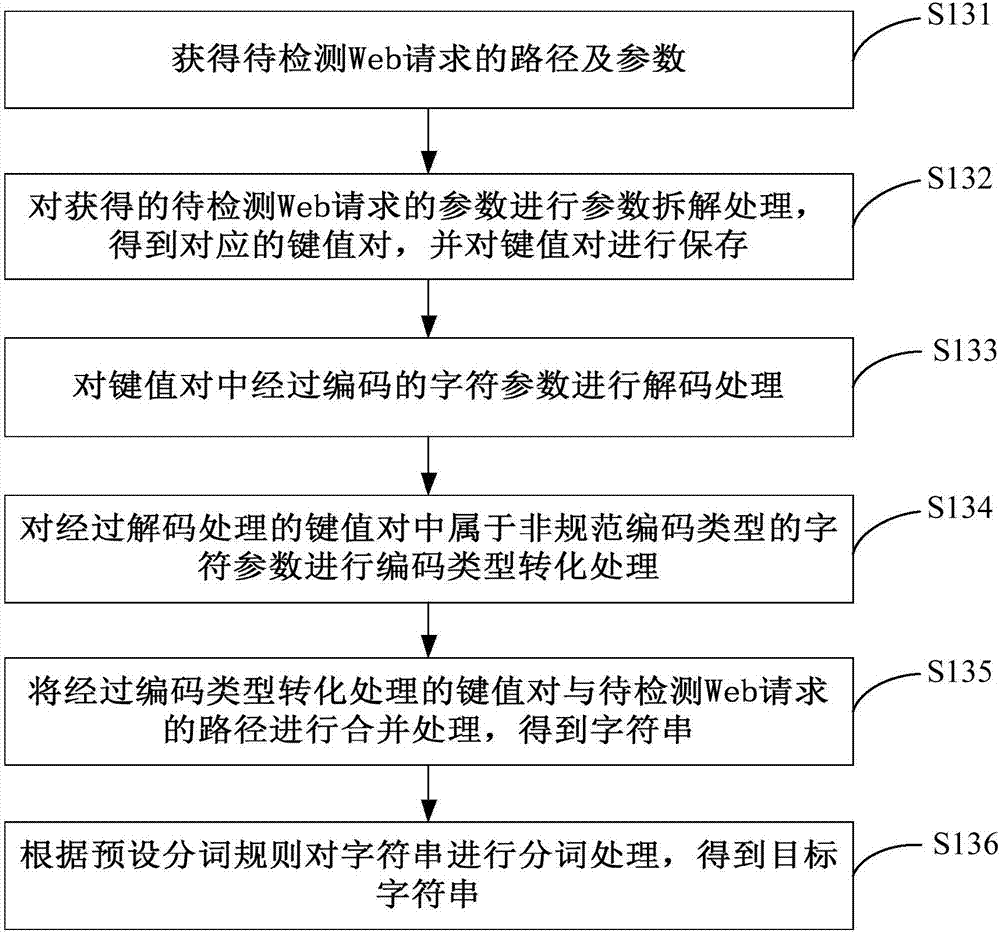
[0037] Please refer to image 3 , image 3 provided by the first embodiment of the present invention figure 2 The sub-step flowchart of step S130 is shown. The step S130 includes: sub-step S131 , sub-step S132 , sub-step S133 , sub-step S134 , sub-step S135 and sub-step S136 .
[0038] Sub-step S131, obtaining the path and parameters of the web request to be detected.
[0039] In this embodiment, when the terminal device 100 ...
no. 2 example
[0088] Please refer to Figure 7 , Figure 7 A block diagram of functional modules of the web attack detection apparatus 200 provided in the second embodiment. The apparatus is applied to the terminal device 100 . The device includes: a preprocessing module 230 , a vectorization processing module 240 and a detection module 250 .
[0089] The preprocessing module 230 is configured to obtain a web request to be detected, and perform preprocessing on the web request to be detected to obtain a corresponding target character string.
[0090] In this embodiment, the preprocessing module 230 is used to execute figure 2 In step S130, for the specific description of the preprocessing module 230, please refer to the description of step S130.
[0091] The vectorization processing module 240 is configured to perform vectorization processing on the target character string to obtain a corresponding target vector.
[0092] In this embodiment, the vectorization processing module 240 is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com