Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
654results about How to "Reduce false alarms" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
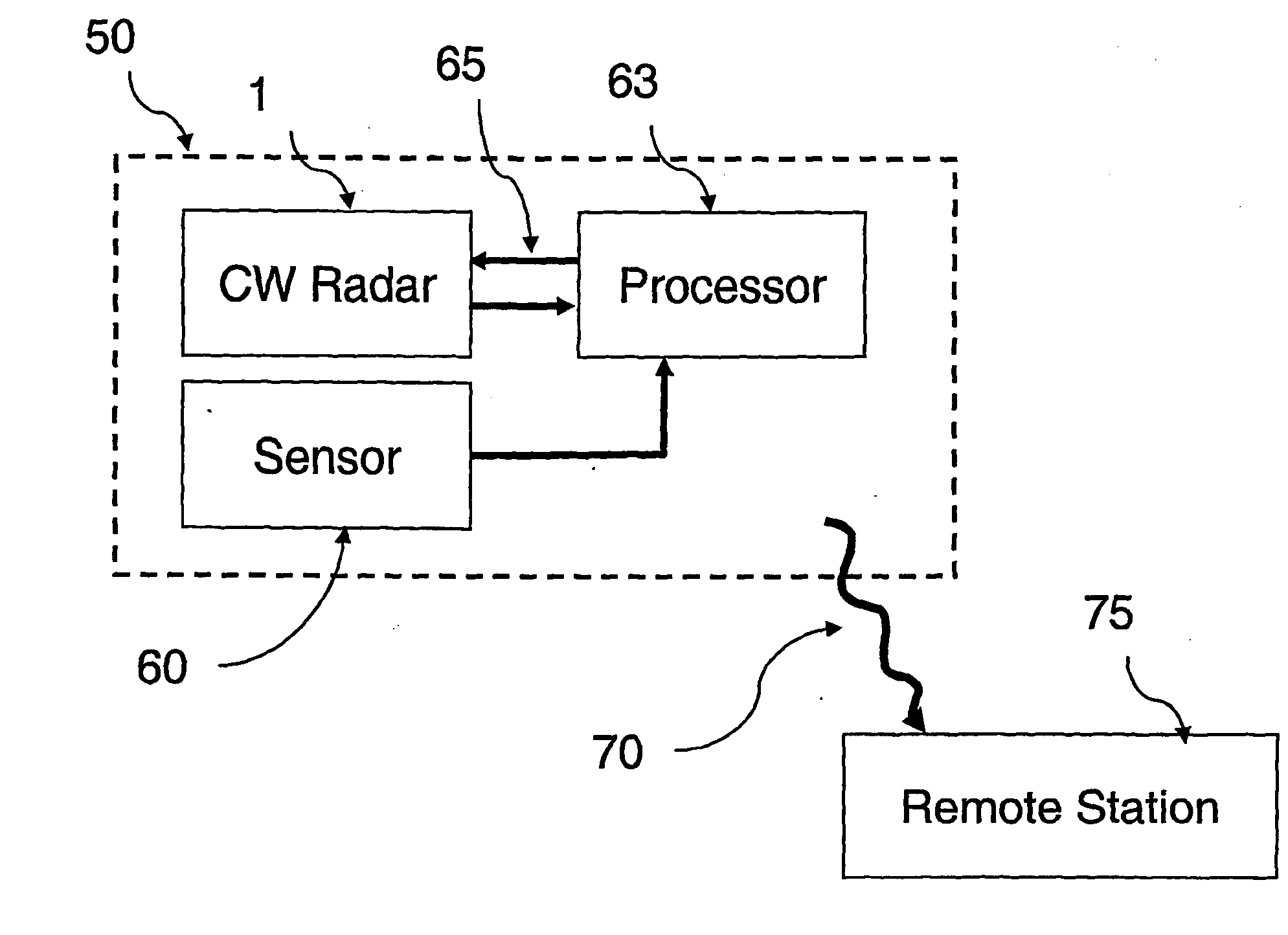
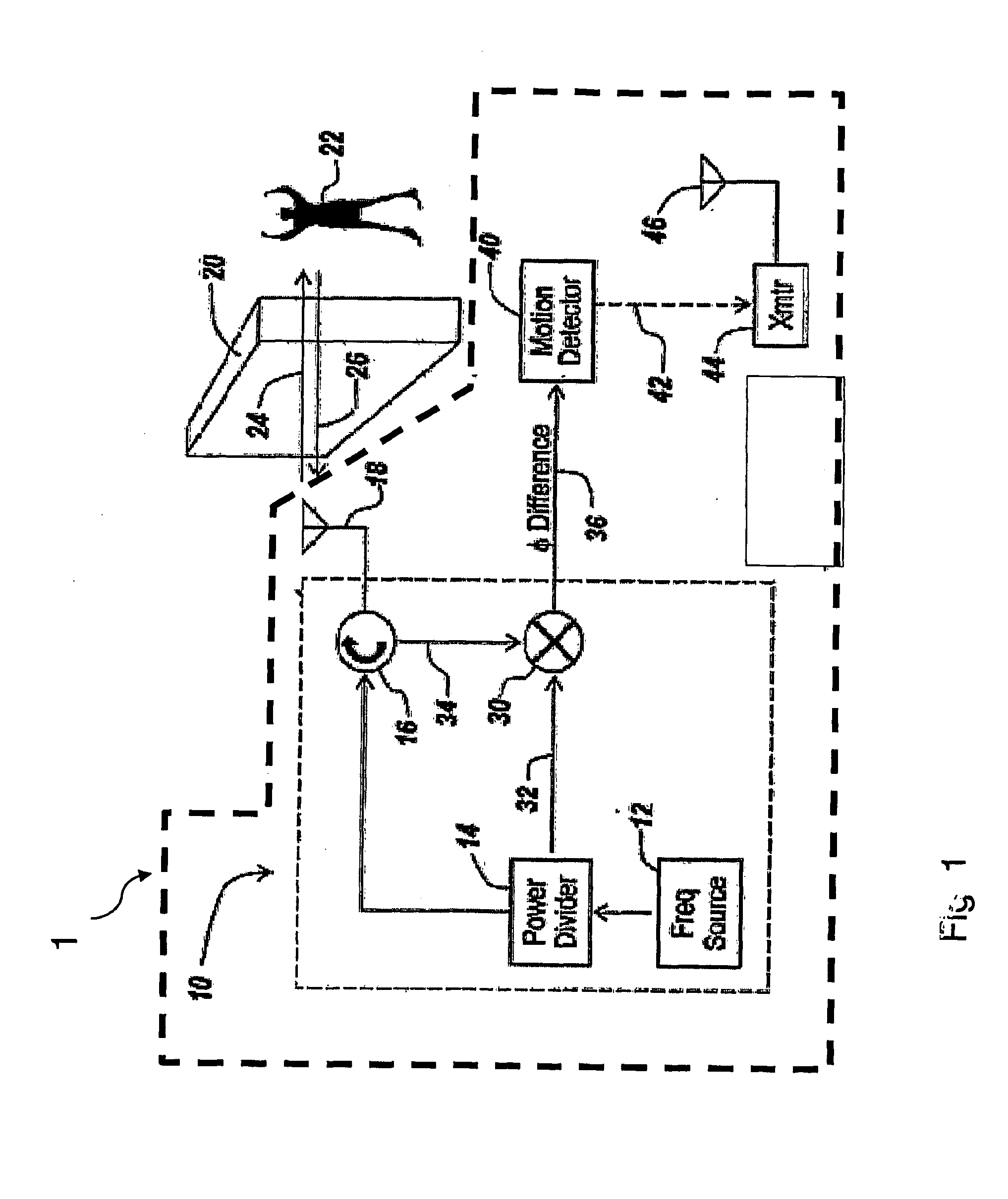
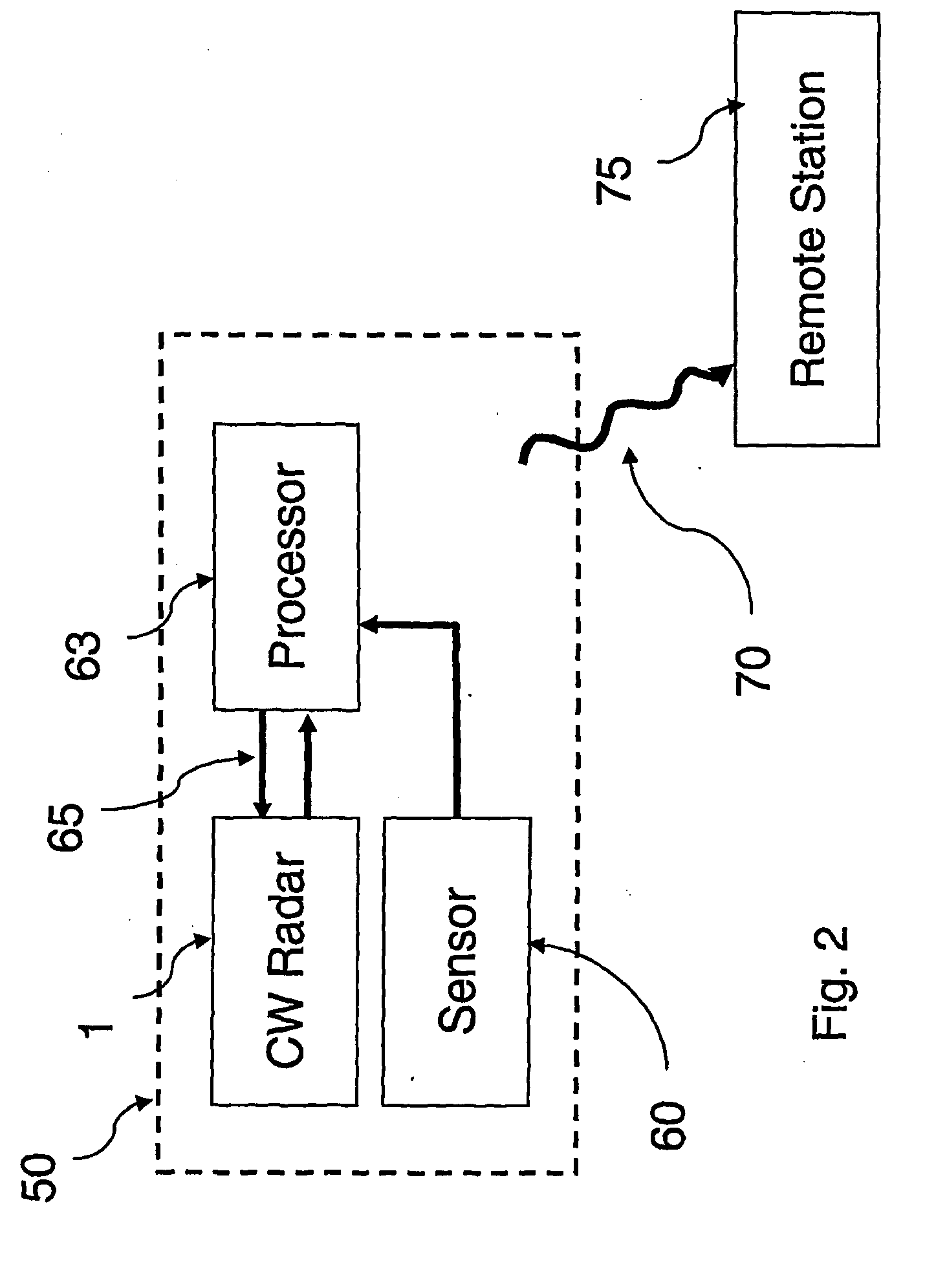
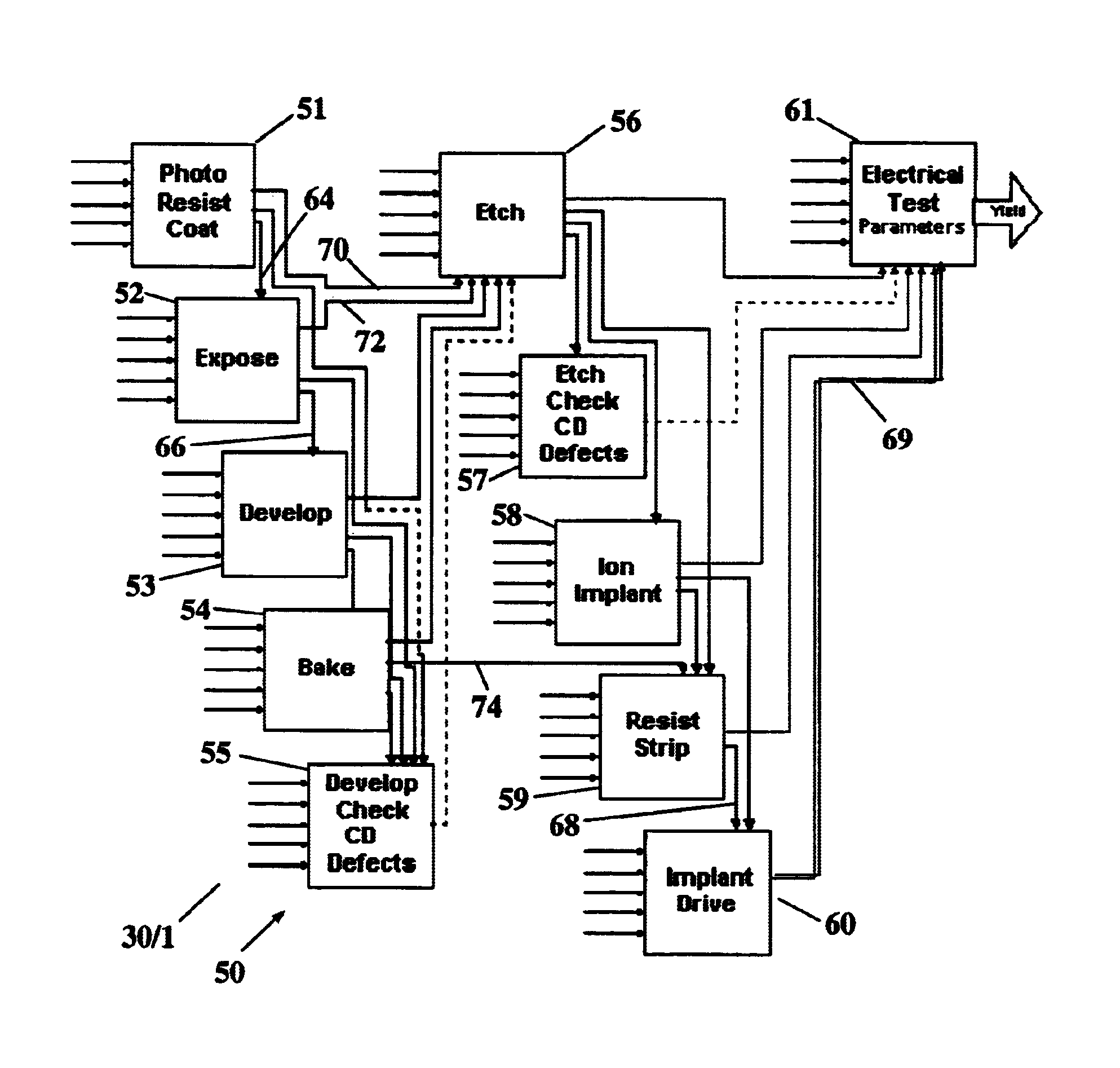
Motion Detection Systems Using CW Radar in Combination With Additional Sensors
ActiveUS20090303100A1Reduce power consumptionImprove discriminationRadio wave reradiation/reflectionRadarFalse alarm
Whether or not the CW radar is utilized for through-the-wall detection, additional one or more sensors are used with the CW radar to confirm the motion detection result or to in fact turn on the CW radar once motion or the physical presence of an individual has been sensed, thereby to provide confirmation of a less-reliable sensor with the use of the more reliable CW radar. Thus, the addition of other sensors provides lower power consumption, lower false alarm rates and better discrimination and classification of moving objects.
Owner:III HLDG 1
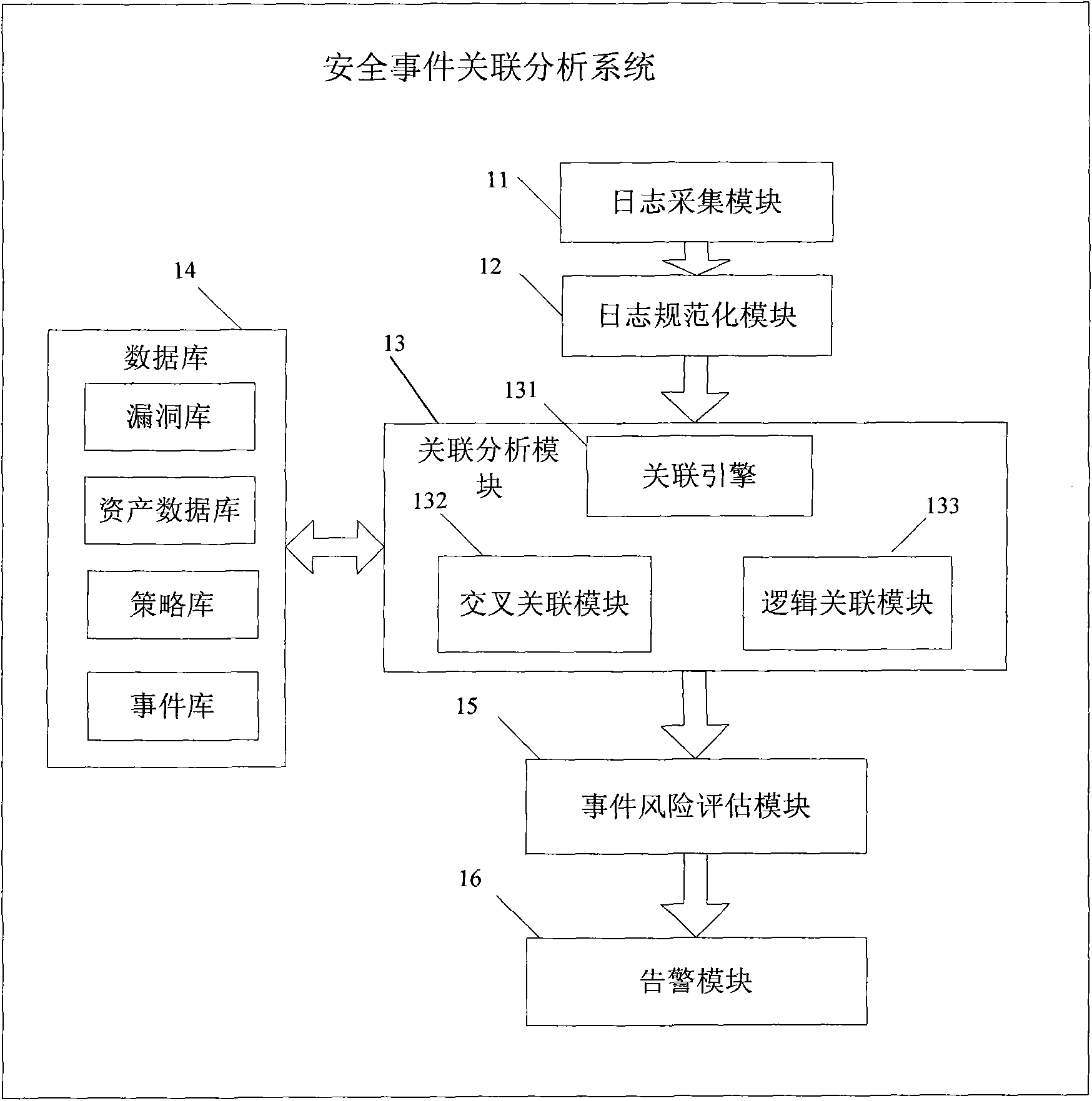
Log correlation analysis system and method
ActiveCN101610174ACalculation speedReduce false alarmsData switching networksEvent correlationCross correlation analysis
The invention provides a log event correlation analysis system and a method, which comprises the steps of: collecting log data, extracting characteristic data of the log data through a preset regular expression, constructing log events with uniform format according to the extracted characteristic data, querying treatment strategies of the log events, implementing cross correlation analysis and event flow logic correlation analysis to the events according to the instruction of strategies, as well as implementing risk evaluation on the log events and automatically responding. The method effectively reduces false-alarm, improves the objectivity of risk evaluation and the warning thereof has higher actual direction on users. The invention also provides a log event correlation analysis system corresponding to the method.
Owner:SHENZHEN Y& D ELECTRONICS CO LTD
Knowledge-engineering protocol-suite
InactiveUS6952688B1Improve efficiencyExtension of timeKnowledge representationSpecial data processing applicationsEnsemble simulationControl communications
A Knowledge-Engineering Protocol-Suite is presented that generally includes methods and systems, apparatus for search-space organizational validation, and appurtenances for use therewith. The protocol-suite includes a search-space organizational validation method for synergistically combining knowledge bases of disparate resolution data-sets, such as by actual or simulated integrating of lower resolution expert-experience based model-like templates to higher resolution empirical data-capture dense quantitative search-spaces. Furthermore, from alternative technological vantages, the suite relates to situations where this synergetic combining is beneficially accomplished, such as in control systems, command control systems, command control communications systems, computational apparatus associated with the aforesaid, and to quantitative modeling and measuring tools used therewith. The protocol-suite also includes facile algorithmic tools for use with the method and a process-modeling computer for use in a distributed asynchronous system of process modeling computers.
Owner:ADA ANALYTICS ISRAEL
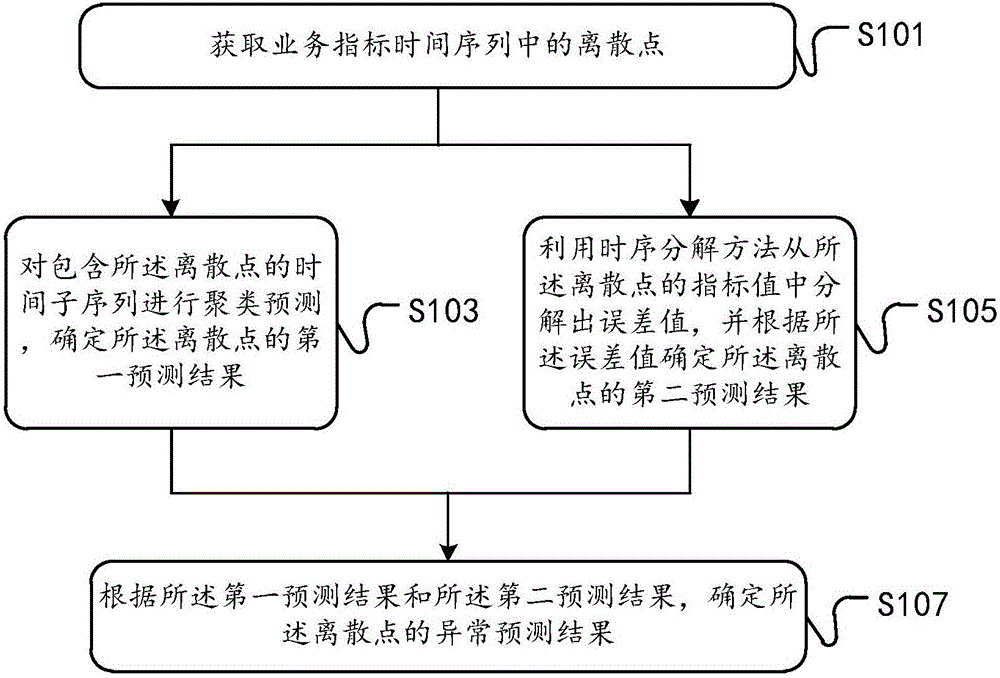
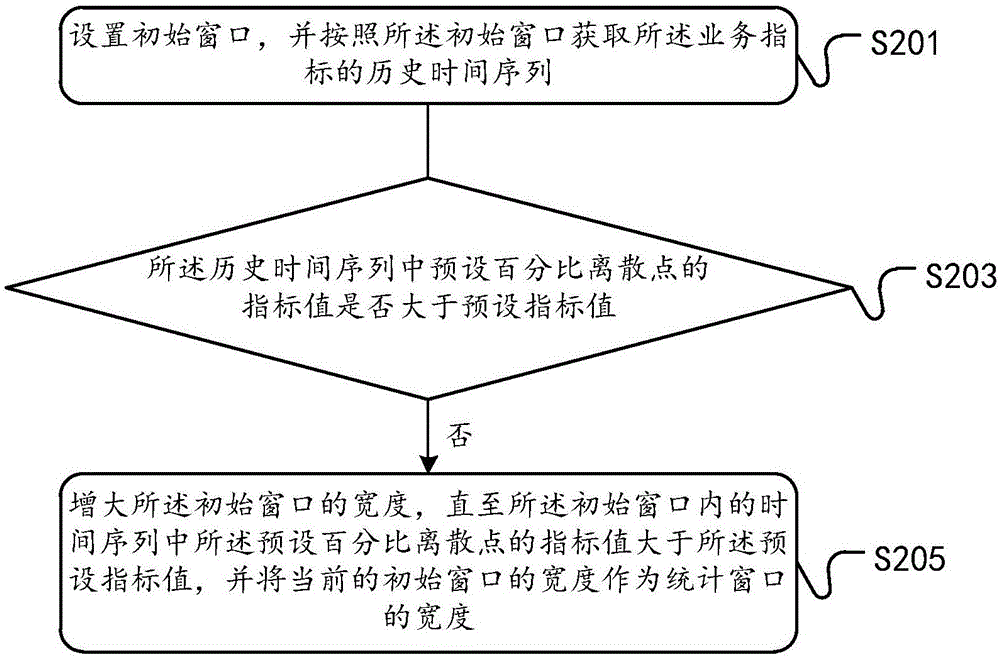
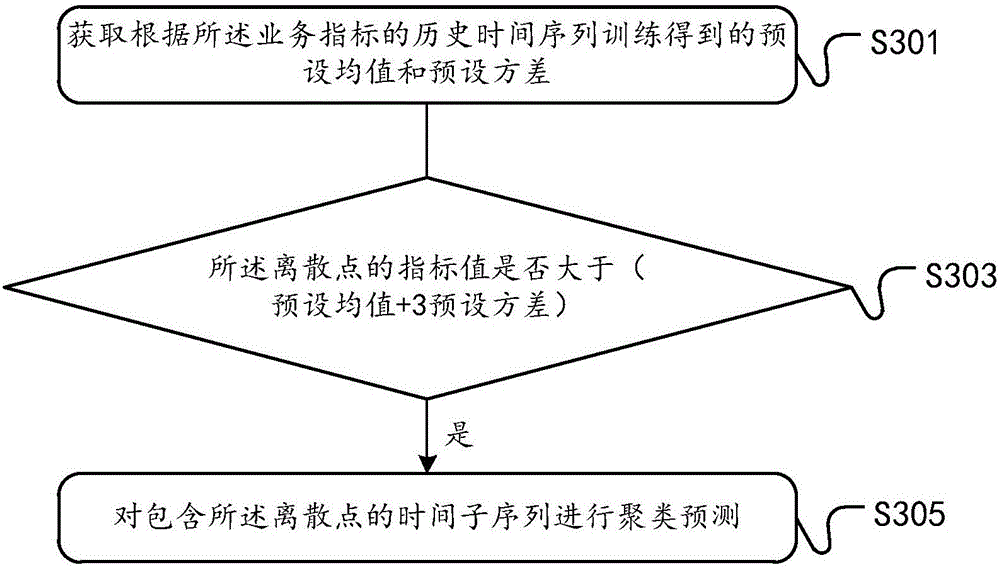
Method and device for detecting abnormal point in time sequence
ActiveCN107528722ADetrendElimination cycleCharacter and pattern recognitionData switching networksAlgorithmDecomposition
The embodiment of the invention discloses a method and device for detecting an abnormal point in a time sequence. The method comprises the following steps: acquiring a discrete point in a business index time sequence; carrying out clustering prediction on a time subsequence comprising the discrete point, and determining a first prediction result of the discrete point; obtaining an error value from an index value of the discrete point through decomposition according to the time sequence decomposition method, and determining a second prediction result of the discrete point according to the error value; and determining an anomaly detection result of the discrete point according to the first prediction result and the second prediction result. The method and device adopting the technical scheme has the advantages that the abnormal point identification accuracy can be improved; and compared with the baseline detection mode in the prior art, the method and device achieves a much lower occurrence rate of abnormal point false alarms.
Owner:ADVANCED NEW TECH CO LTD
Detection method for accidental precursor access
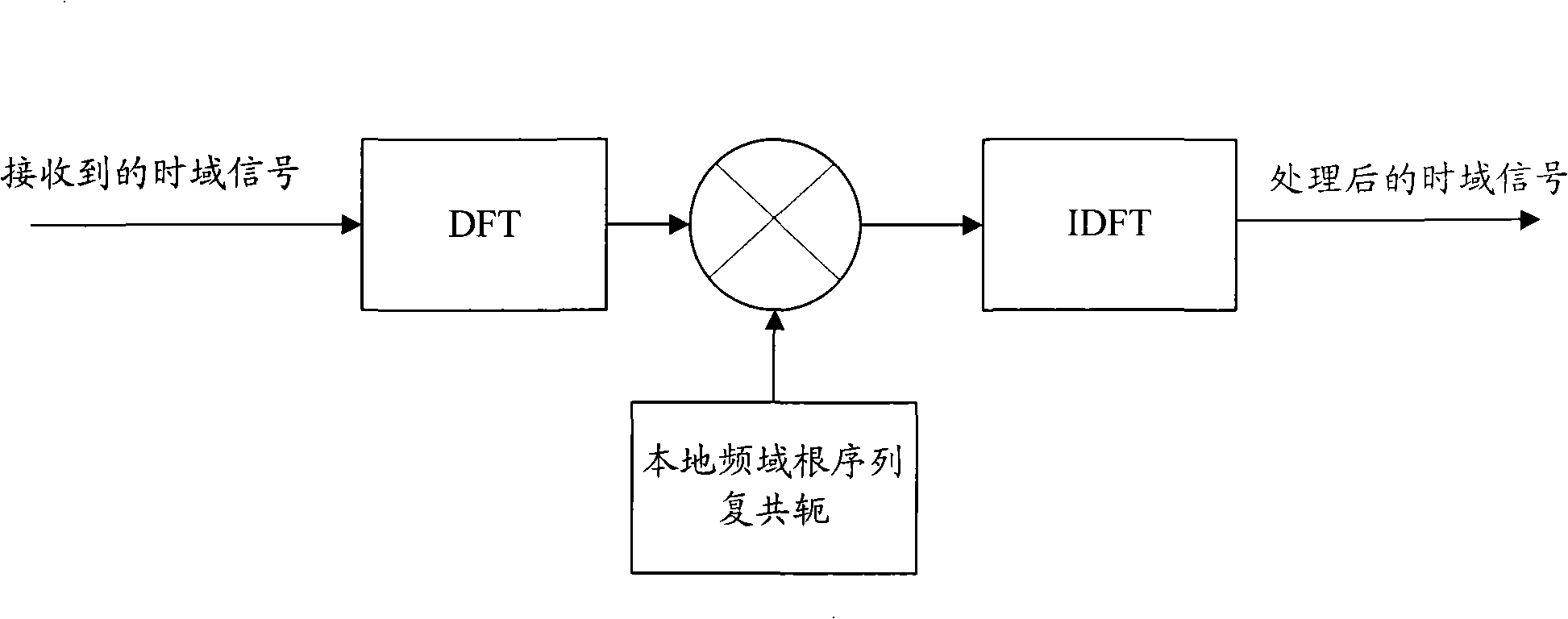
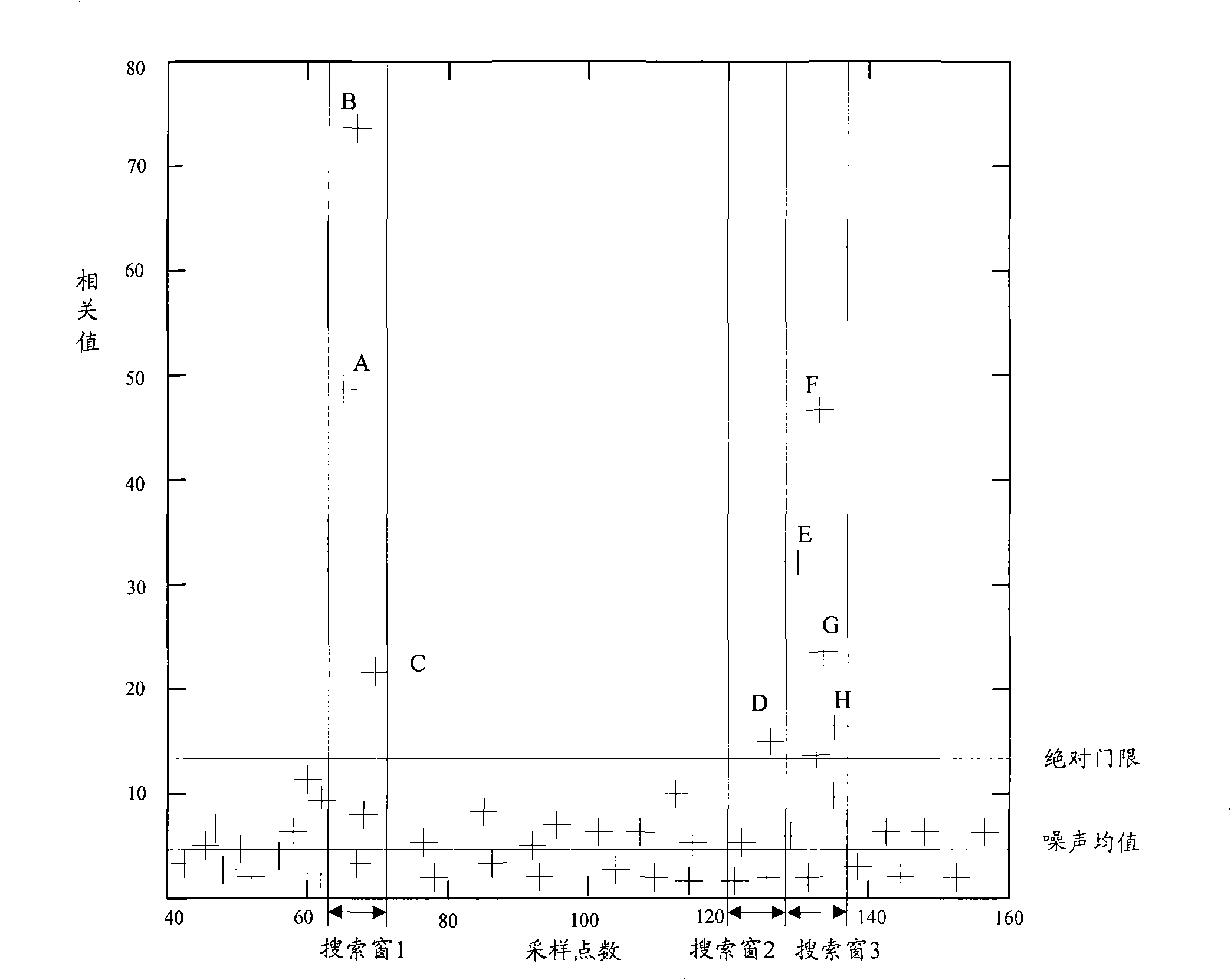
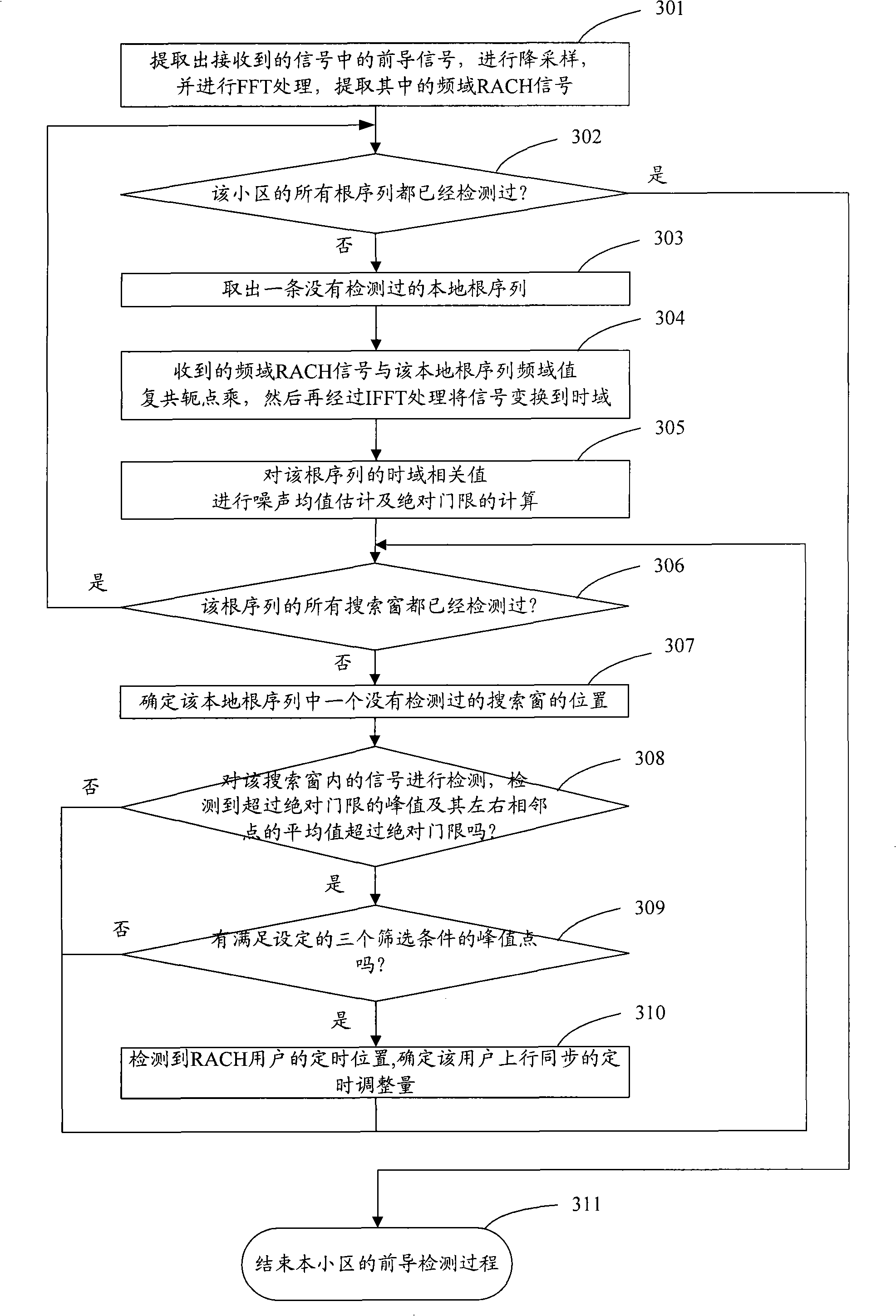
ActiveCN101295999AReduce computationReduce the difficulty of data processingModulated-carrier systemsWireless communicationTime domainAbsolute threshold
The invention discloses a method for detecting a random access leader. After a random access channel (RACH) signal is treated with the simplified time domain-related operation, noise mean estimation is carried out to each root sequence; an absolute threshold is then detected according to a signal obtained by the noise estimation and signals in a search window are detected; the signals which exceed the detection threshold are screened and then a timing position can be determined in a fast and accurate way so as to provide reliable uplink timing adjustment information to a mobile terminal, guarantee the accuracy of the uplink synchronization and effectively eliminate the timing error due to the over-sampling and reduce the false alarm in the detection.
Owner:ZTE CORP
Network centric sensor fusion for shipping container security
InactiveUS20070200701A1Maintain container securityReduce false alarmElectric signal transmission systemsDigital data processing detailsEngineeringSensor fusion
A method of monitoring an entrance to a cargo container, comprising the following steps: (a) creating a entry record for each item of cargo loaded into a cargo container; (b) creating an ID record for each RFID tag that enters the cargo container during loading of the items of cargo; and (c) correlating the video and ID records to raise an alarm if an item of cargo is loaded without an authorized RFID tag attached thereto.
Owner:THE BOEING CO
State validation using bi-directional wireless link
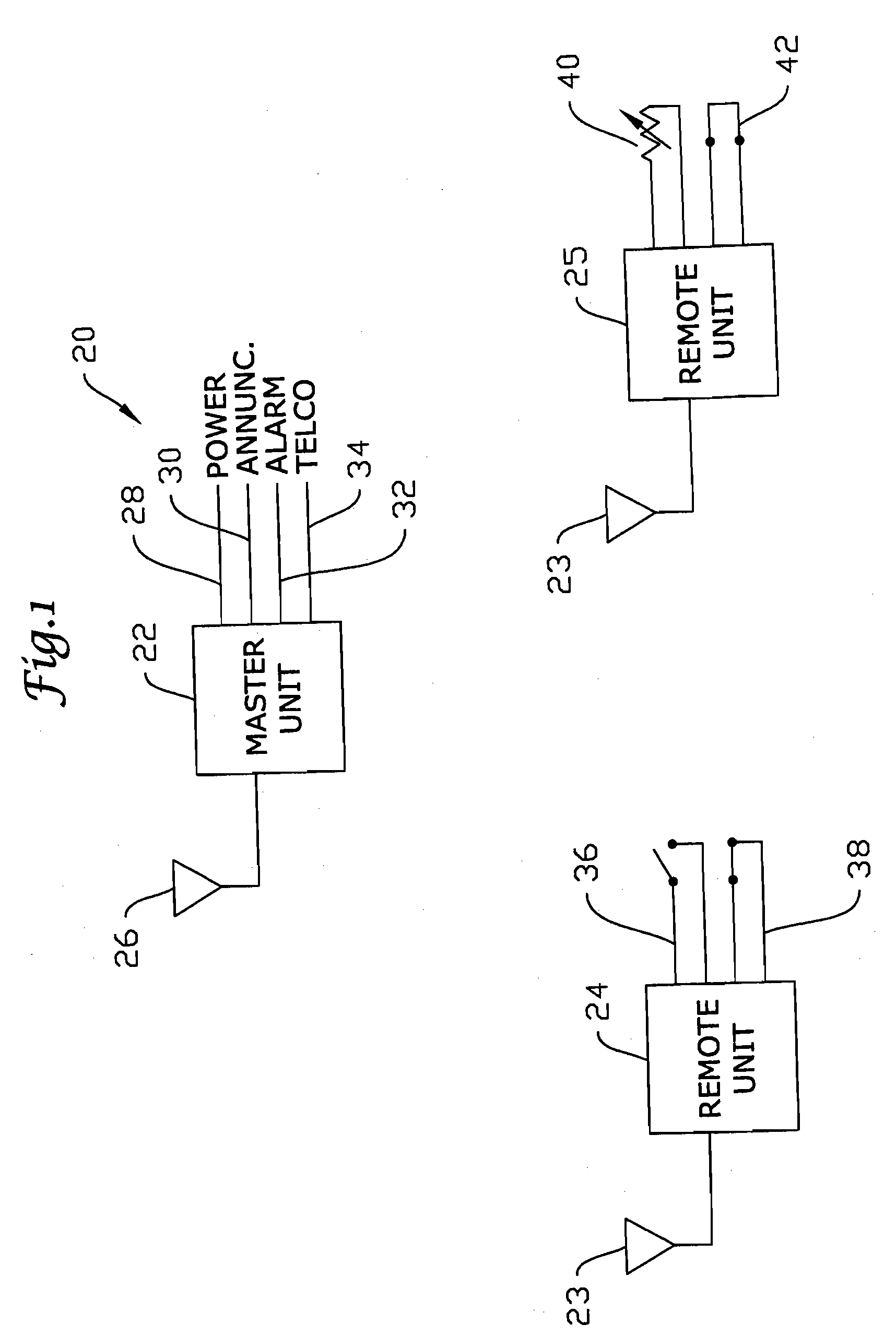
InactiveUS7015789B1Reduce power consumptionReduce false alarmsTelemetry/telecontrol selection arrangementsElectric testing/monitoringControl systemMonitoring and control
Building monitoring and control systems including bi-directional radio frequency links between master and remote units wherein the remote units operate in a low power, non-receiving state a majority of the time is disclosed. The bi-directional capability allows coordinated scheduling which aids in allowing the remote units to transmit data only at periodic time intervals to extend battery life. The bi-directional capabilities also allow for re-read requests for alarm validation and for putting remote units in armed and disarmed states for power conservation.
Owner:HONEYWELL INC
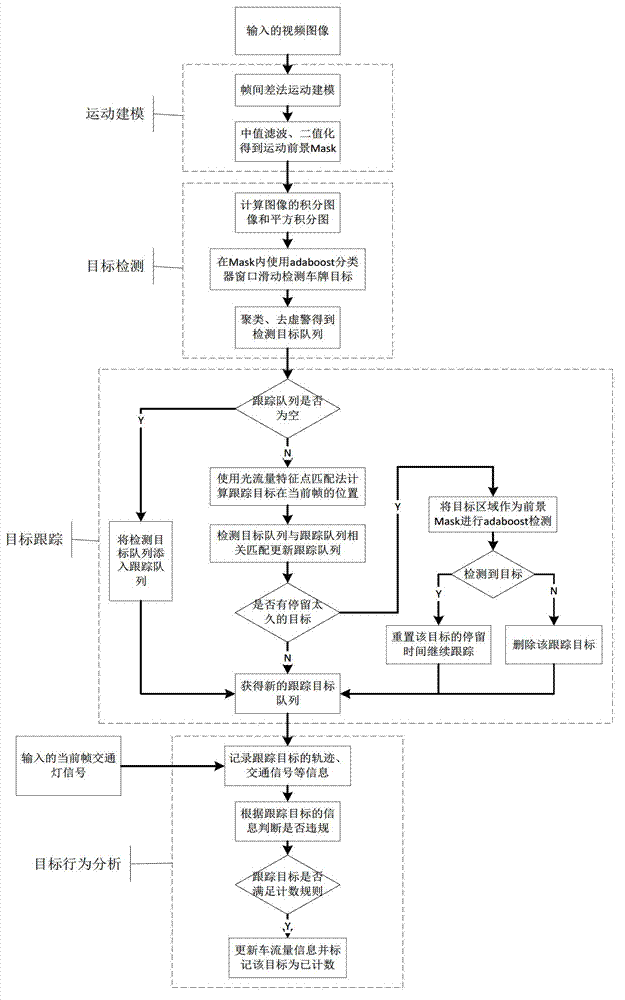
Traffic flow statistic and violation detection method based on surveillance video processing
InactiveCN103116987AReduce computationReduce error rateRoad vehicles traffic controlCharacter and pattern recognitionTraffic volumeTraffic capacity
The invention discloses a traffic flow statistic and violation detection method based on surveillance video processing. The method comprises the steps of obtaining a video source, reading a frame of image, judging if the current frame is a first frame, utilizing difference information of corresponding pixel points of the current frame and the previous frame to update foreground and background images if the current frame is not the first frame, utilizing the foreground and background images to extract an interest area MASK of the current frame, calculating integral images and integrated square images of the current frame, detecting in the interest area MASK of the current frame if a plate number target exists according to the obtained integral images and integrated square images of the current frame and utilizing an Adaboost algorithm, storing position information of the detected plate number target in a list TmpList, judging if the temporary target list TmpList is empty, judging if a tracking target sequence Track-List is empty if the temporary target list TmpList is empty, and adding the detected target in an ObjList into the Track-List if the tracking target sequence Track-List is empty. By means of the method, crossing traffic flow can be counted precisely, and if a vehicle target breaks the rule is judged combining indication of traffic signal lamps.
Owner:HUAZHONG UNIV OF SCI & TECH
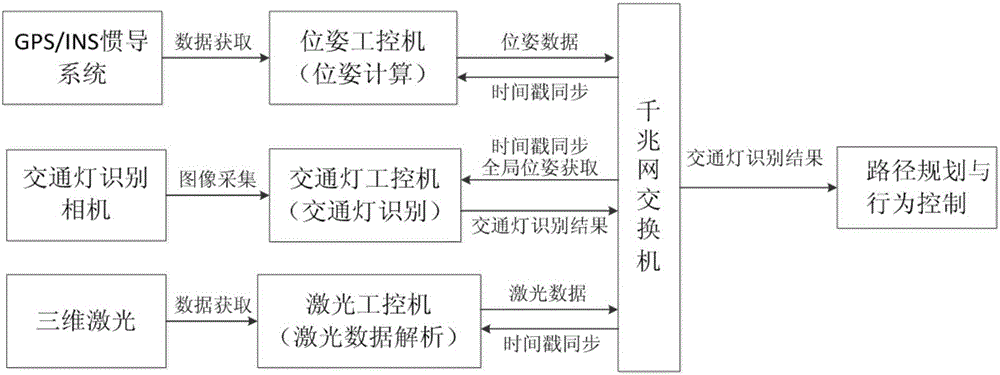
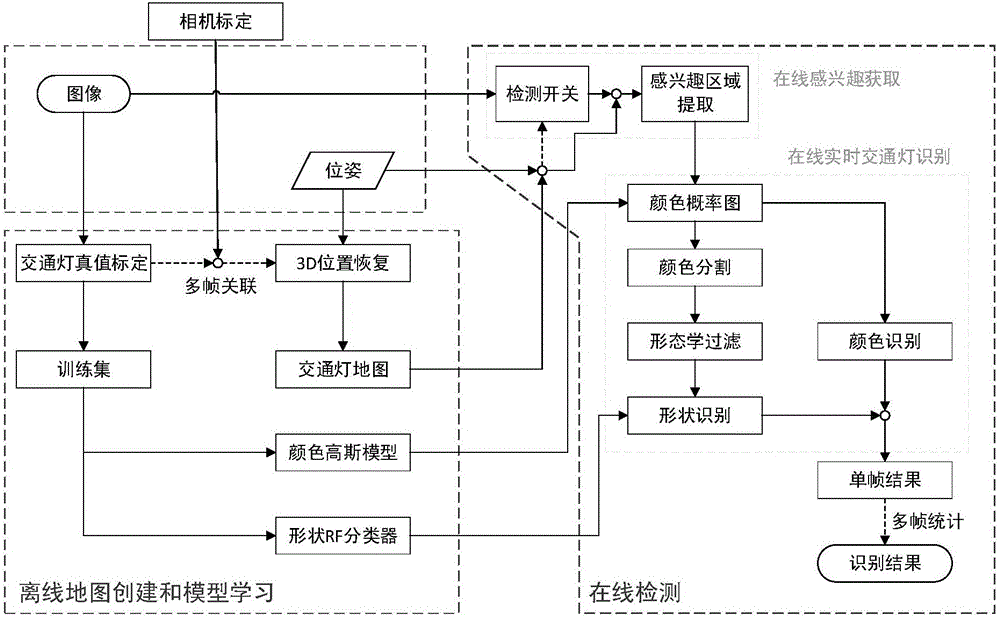
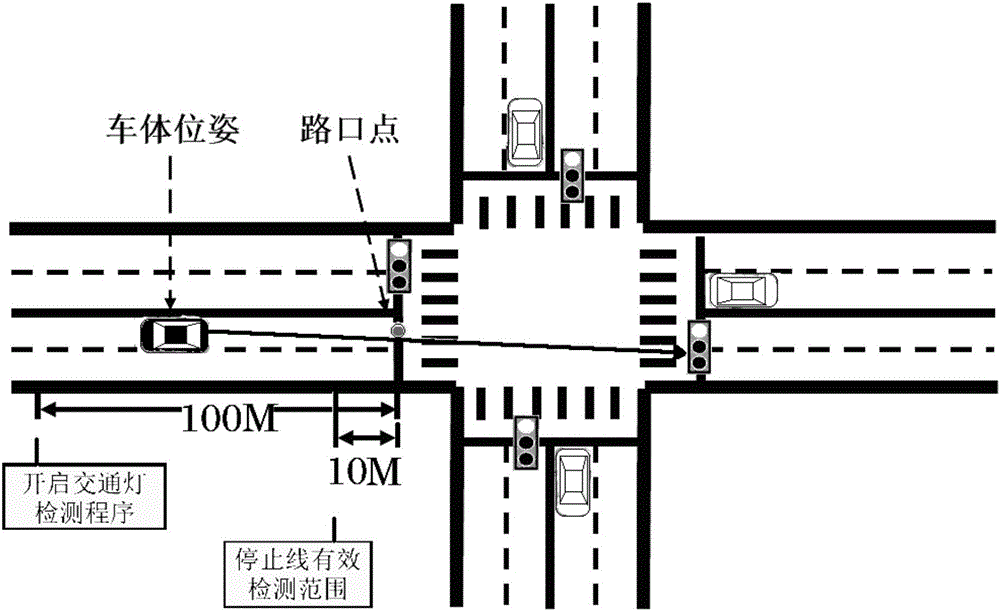
System for real-time identifying urban traffic lights based on single eye vision and GPS integrated navigation system
ActiveCN105930819ARealize identificationRecognition is stable and continuousCharacter and pattern recognitionDistance detectionNavigation system
The invention discloses a system for real-time identifying urban traffic lights based on single eye vision and a GPS integrated navigation system. The system establishes a map of traffic lights in an off-line manner through the methods of interactive image annotation, camera calibration, 3D position recovery, etc., and provides position coordinates and semantic attributes of the traffic lights under the globally positioned GPS coordinate system. Upon online detection, with the established offline map of traffic lights as a prior, an area of interest is determined by solving the substantial scope of the traffic lights in images in combination with the pose position, and the identification of the color segmentation and shapes of the traffic lights are carried out by using form information of the traffic lights in the area of interest. The system is applicable to road conditions and scenarios of different kinds, implements stable and long-distance detection sensing of the traffic lights under various environments. Since the system adopts a low-cost and low-power consumption navigation device, an image acquisition device and a computer platform, the system can be widely applied to the fields of vision navigation of driverless vehicles, vision auxiliary driving of intelligent vehicles, etc.
Owner:XI AN JIAOTONG UNIV
Residual error posterior-based abnormal value online detection and confidence degree assessment method
ActiveCN107092582AImprove accuracyImprove reliabilityComplex mathematical operationsNormal densityState model
The invention discloses a residual error posterior-based abnormal value online detection and confidence degree assessment method. The method comprises the steps of collecting data, establishing time series data, performing linear fitting on the time series data to obtain a linear combination formula of data at a current moment and p pieces of previous data, and predicting a data value of subsequent time; comparing the predicted data value with an actually detected data value to obtain a predicted residual error series; determining a probability density function of the predicted residual error series by adopting a KDE (Kernel Density Estimation) method; performing posterior ratio check on the predicted residual error series, and judging whether the data at the current moment is an abnormal point or not; and by taking the time series data as an input, building an SOM state model, obtaining state series and state transition probability matrixes, defining an abnormal scoring function, and outputting an abnormal score. By comparing the probability that the data is the abnormal point with the probability that the data is a normal point, the abnormal value in the pollutant discharge concentration time series data is identified online, so that the accuracy and reliability of abnormal value judgment are improved.
Owner:JIANGSU FRONTIER ELECTRIC TECH +2
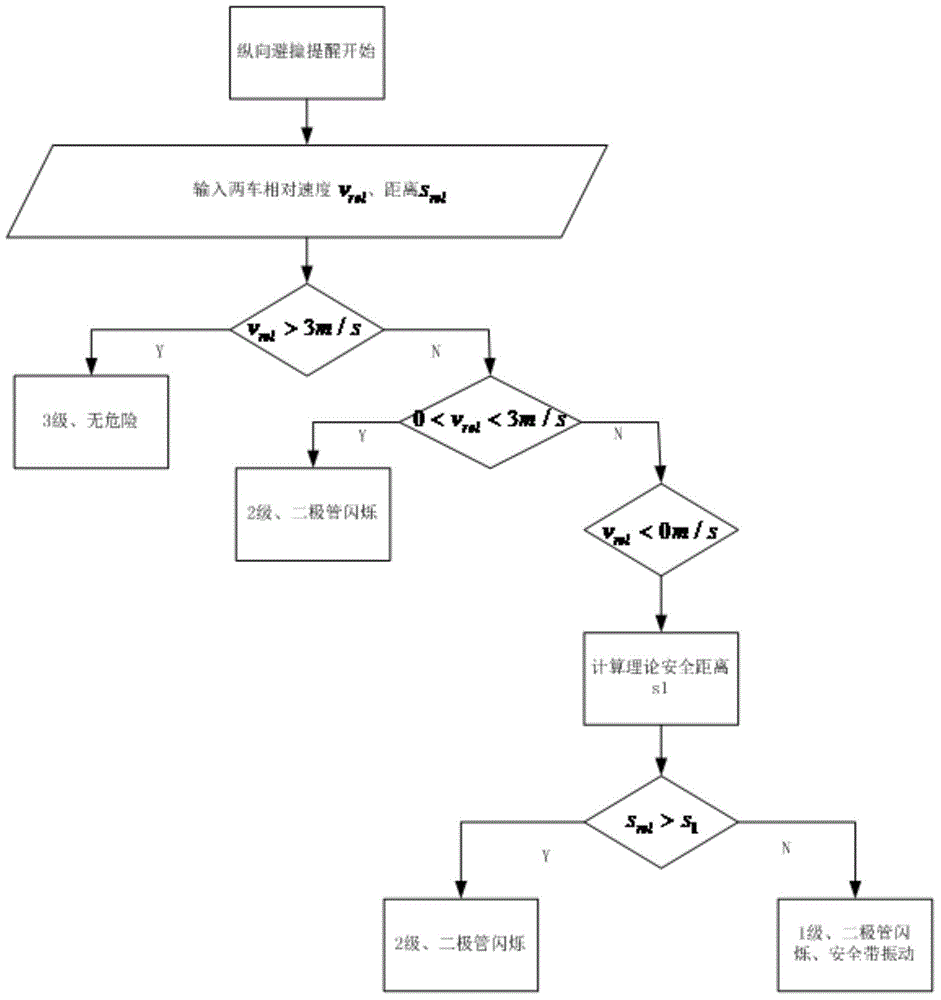
Longitudinal collision avoidance reminding and automatic following integration system and method
The present invention provides a longitudinal collision avoidance reminding and automatic following integration system and a method, and belongs to the vehicle collision avoidance field. The system comprises a collision avoidance mode selection unit, a sensing unit, a central control ECU unit, a reminding unit and an execution unit. The sensing unit obtains the type and number of front barriers, the position of a target vehicle in a lane line, the relative speed and the relative distance of an own vehicle and the front barriers, sends the obtained information to the central control ECU unit, carries out the comprehensive determination of a safe state by a D-S evidence theory, and finally determines the number of the front barriers, the relative distance vrel, the relative speed srel and an acceleration a of the own vehicle and the front target vehicle, thereby reducing the false alarm situations of a vehicle-mounted radar and a vehicle-mounted camera furthest. The central control ECU unit generates an instruction, and the reminding unit and the execution unit execute the correlated actions. The system and method of the present invention enable the false alarm rate to be reduced and the response speed and the comfort level of the drivers to be improved simultaneously, at the same time, satisfy the collision avoidance demands on different road conditions.
Owner:JIANGSU UNIV
An abnormal data detection method and device
ActiveCN109948669AReduce manual dependenceEasy to detectCharacter and pattern recognitionAnomaly detectionFalse alarm
The embodiment of the invention provides an abnormal data detection method and device, and relates to the technical field of data processing, and the method comprises the steps: obtaining to-be-detected data of a target object, traversing each random binary tree in an isolated forest model based on the to-be-detected data of the target object, and determining the position of the target object on each random binary tree; determining an abnormal score of the target object according to the position of the target object on each random binary tree, and then determining an abnormal condition of thetarget object according to the abnormal score of the target object. Due to the fact that the isolated forest model is adopted to detect the abnormal condition of the target object, dependence on manpower is reduced, and the detection process is simplified. When the isolated forest model is trained, the characteristics of the training sample at least comprise the time sequence characteristics of the target object, so that when the isolated forest model detects the abnormal condition of the target object, the influence of the time sequence characteristics of the target object on the abnormal condition is considered, the accuracy of abnormal detection is improved, and false alarms are reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
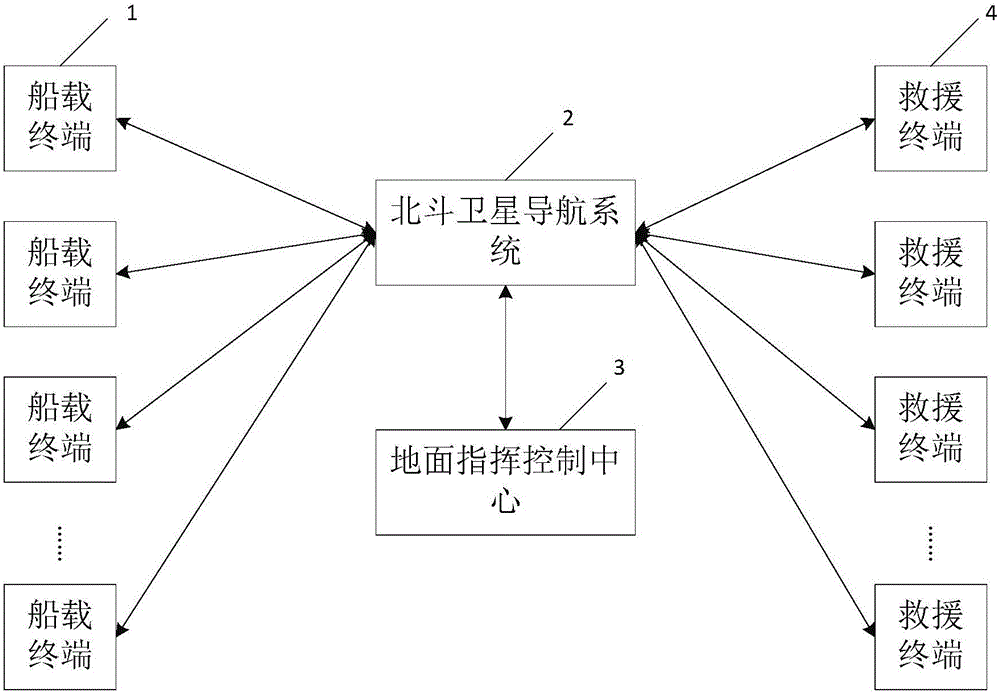
Maritime navigation rescue system based on Beidou satellite
InactiveCN106125099AConfirm authenticityReduce false alarmsTransmission systemsSatellite radio beaconingMaritime navigationCommand and control
The invention relates to a maritime navigation rescue system based on a Beidou satellite. The system utilizes the specific short message communication function of the Beidou satellite navigation system, after a ground command and control center receives a distress message sent by a ship, the short message communication function of the Beidou satellite navigation system can be used for getting in touch with the ship in distress, the authenticity of the distress message is confirmed, and false alarms are greatly reduced. Meanwhile, a ship-mounted terminal of the system is free from restrictions of external factors of distance, weather, sea conditions and the like due to the short message communication function of the Beidou satellite navigation system, and has functions of actively sending position information of the ship in distress at any time and conducting short message communication with the ground command and control center at any time. The ship-mounted terminal is stable and effective, can accurately and timely send distress messages, and is helpful for ground staff to position and track people in distress, and thus the rescue speed is accelerated. Furthermore, compared with existing ships with mutually-independent navigation systems and rescue equipment, the ship-mounted terminal of the system has functions of navigation and rescue at the same time.
Owner:SHENZHEN UNIV
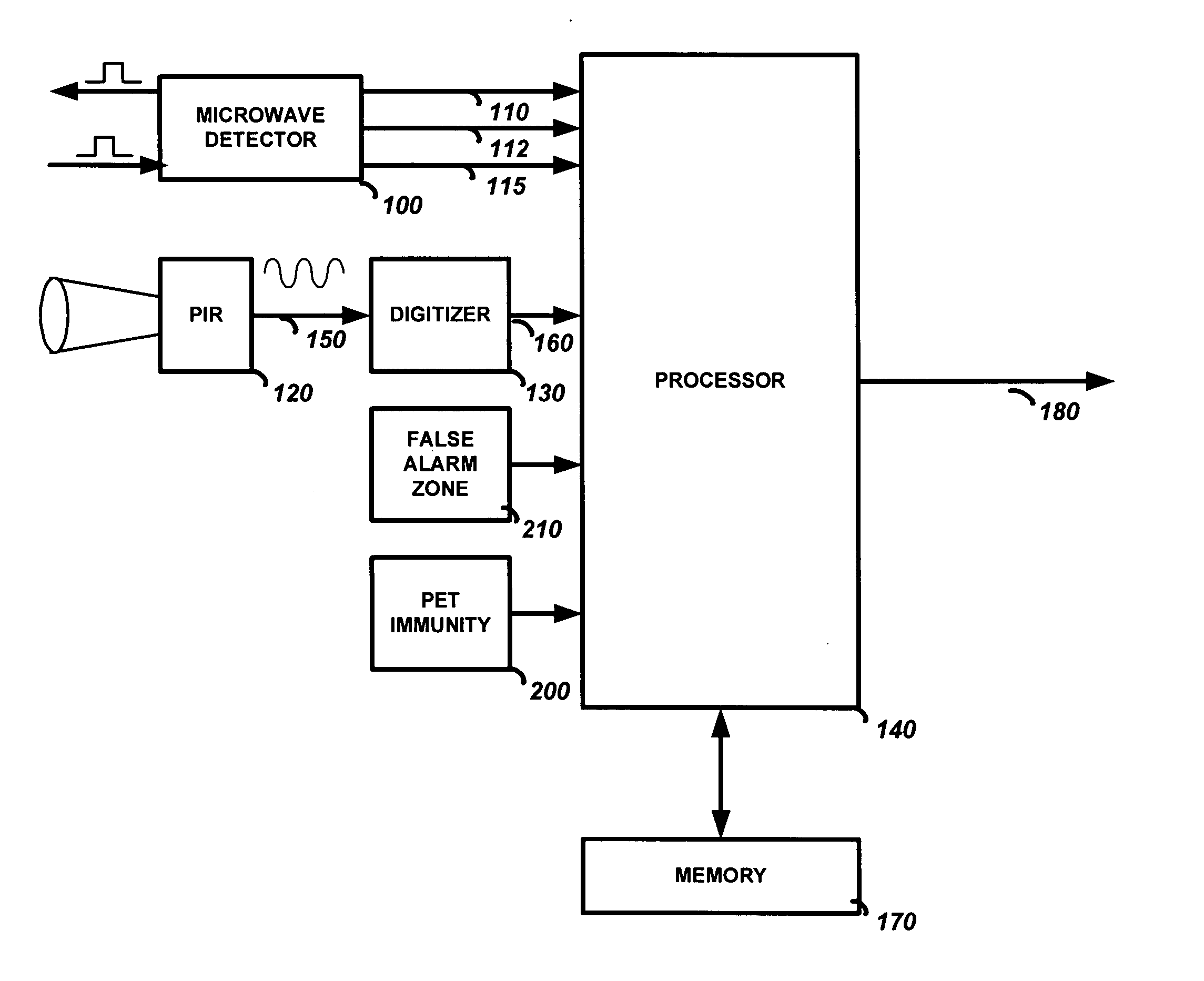
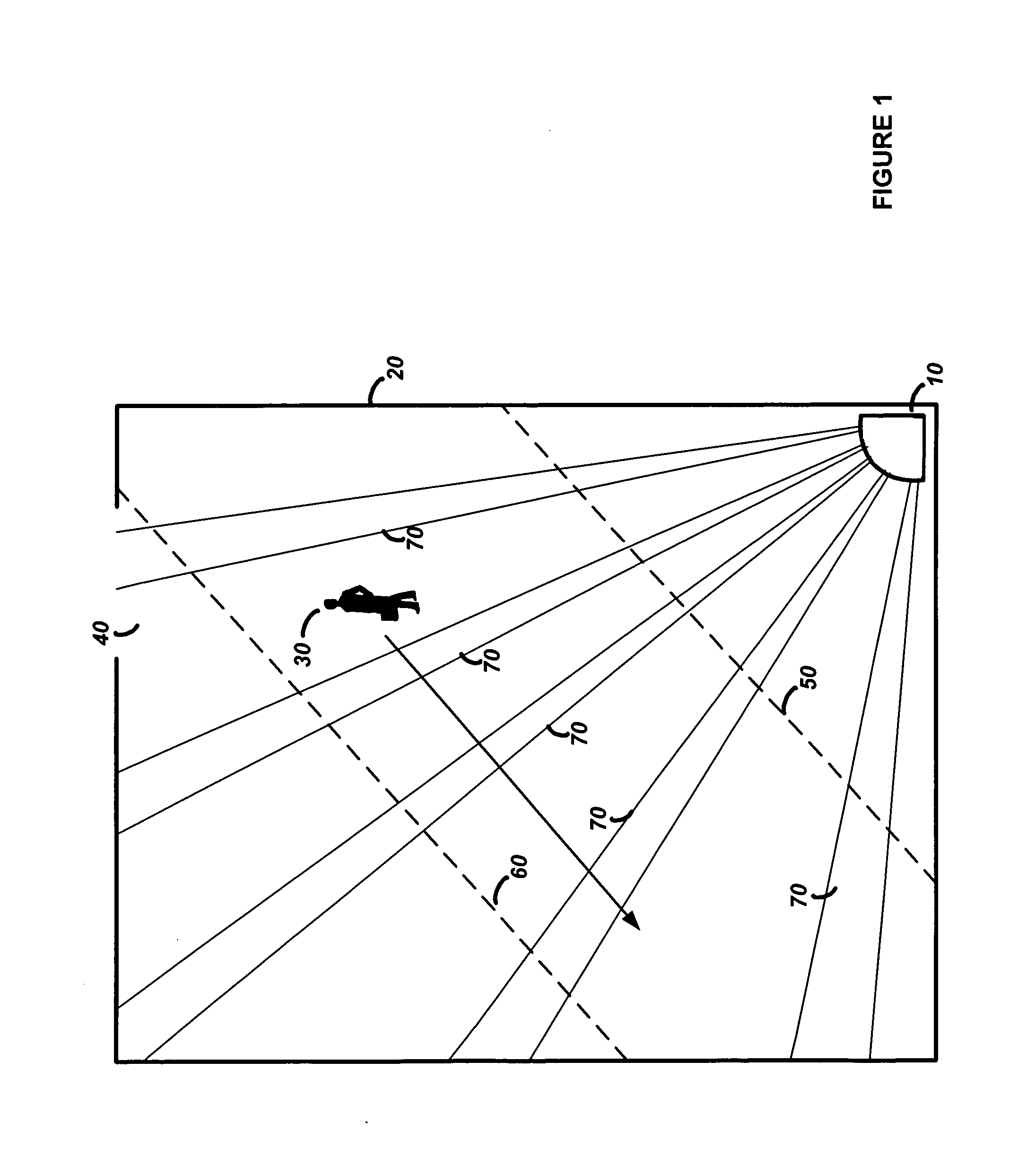
Dual technology sensor device with range gated sensitivity
InactiveUS20070176765A1Improve performanceDecreased false alarmBurglar alarm short radiation actuationInformation processingRange gate
A method and device for detecting an intruder in a region with increased performance and decreased false alarms. The security device has a microwave sensor and a PIR sensor operatively coupled to a processor. To increase the performance of the security device the device determines distance information of an object in the region with the microwave sensor, processes the distance information to adapt a frequency response of the PIR sensor to provide a frequency adapted PIR signal, and determines if the object is an intruder by using the frequency adapted PIR signal.
Owner:HONEYWELL INT INC
Methods and systems for identifying the crossing of a virtual barrier
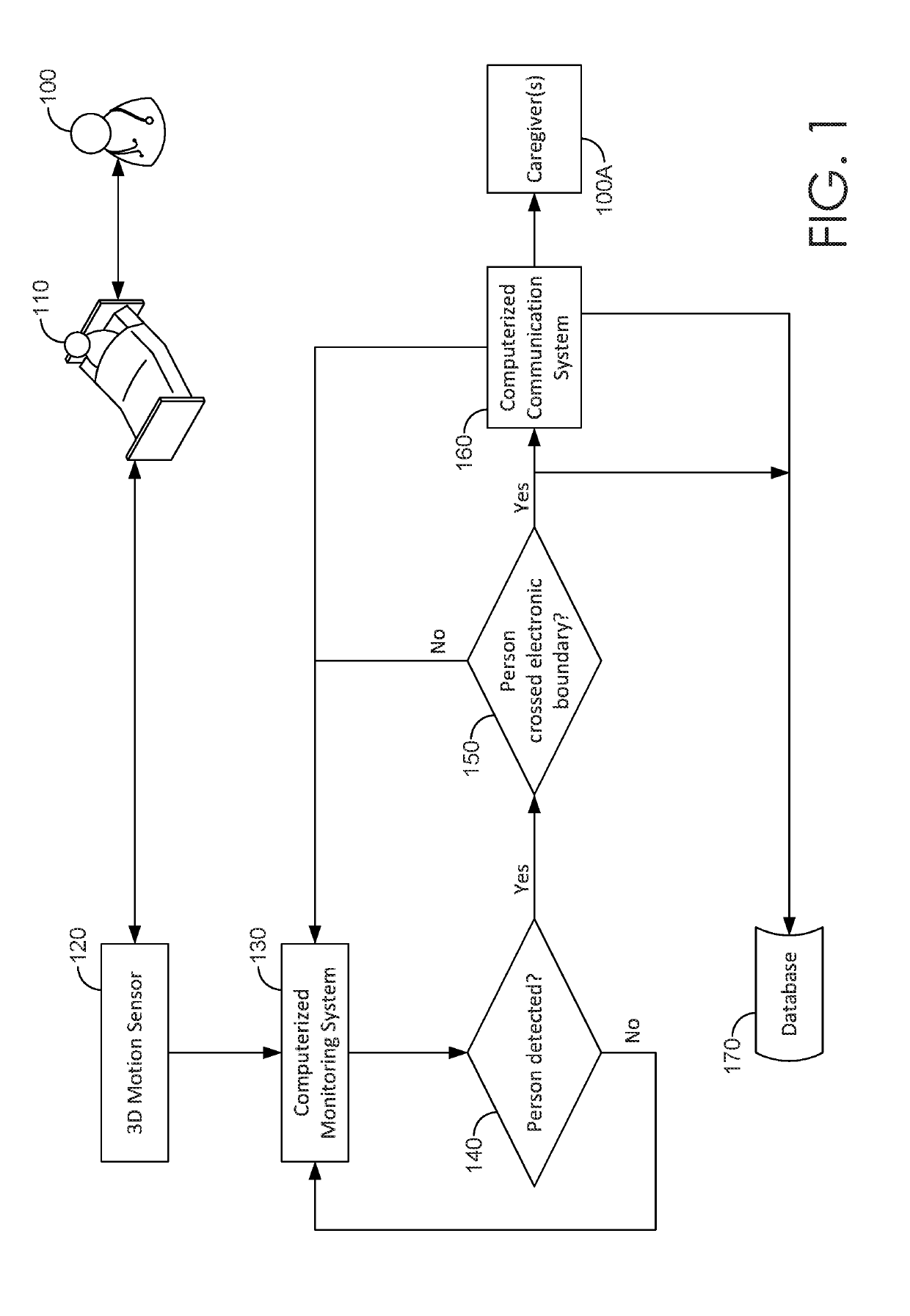
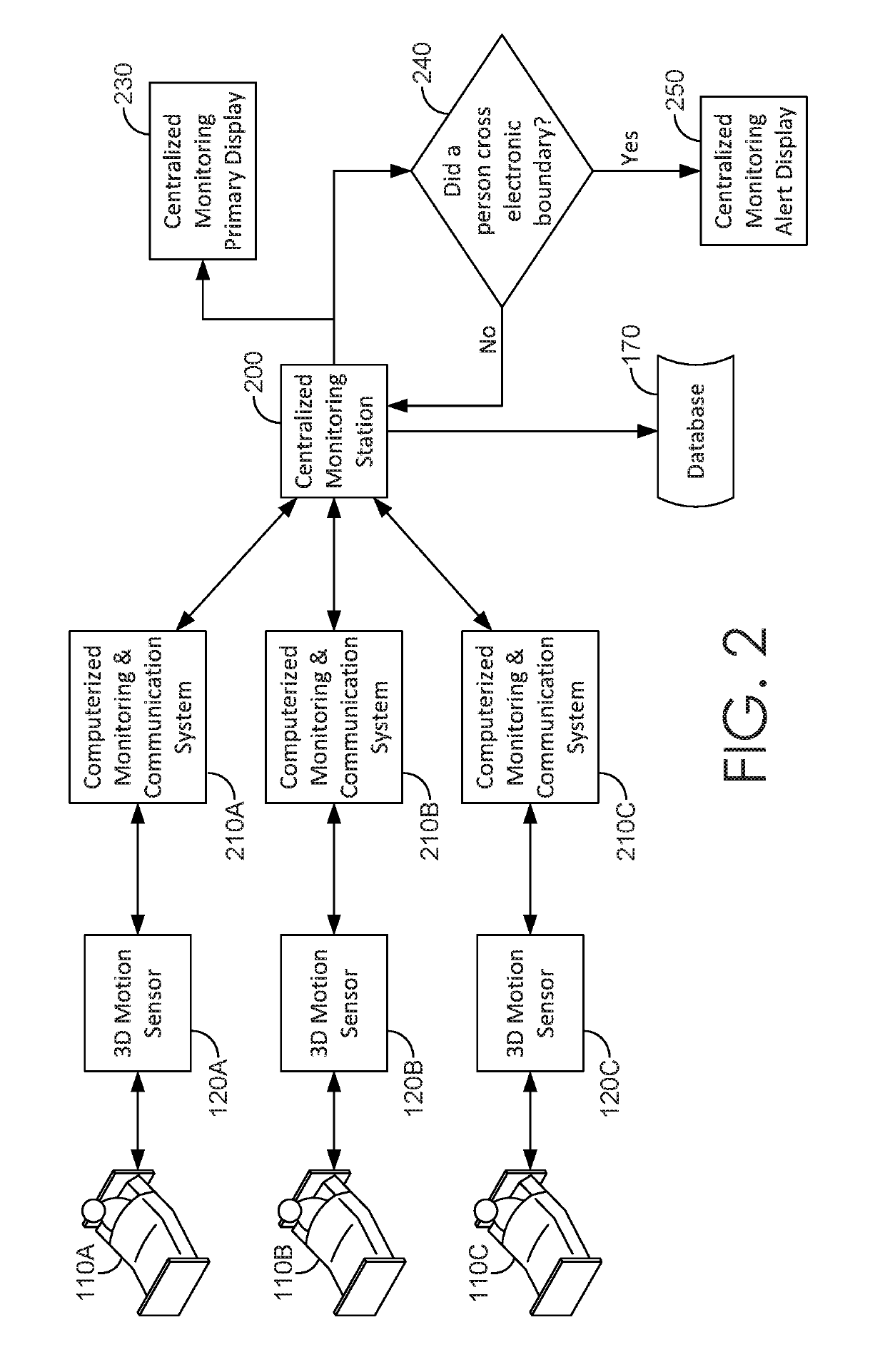
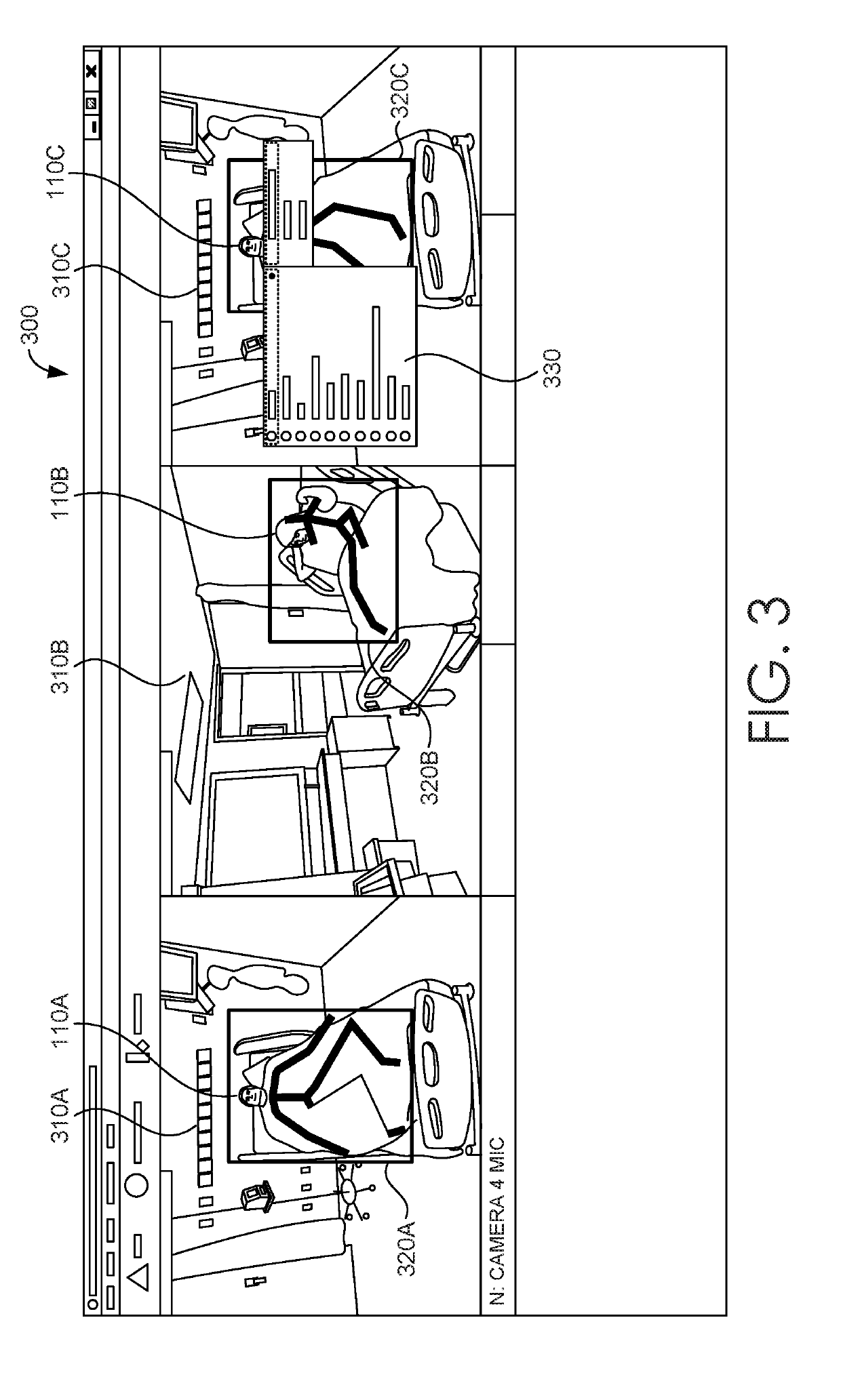
ActiveUS20190205630A1Function increaseLess memory capacityImage enhancementImage analysisCaregiver person3d image
Owner:CERNER INNOVATION
System for real-time intrusion detection of SQL injection WEB attacks
ActiveCN101370008AReduce false alarmsHigh detection rateData switching networksSQL injectionWeb attack
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Illegal parking detection method based on image texture
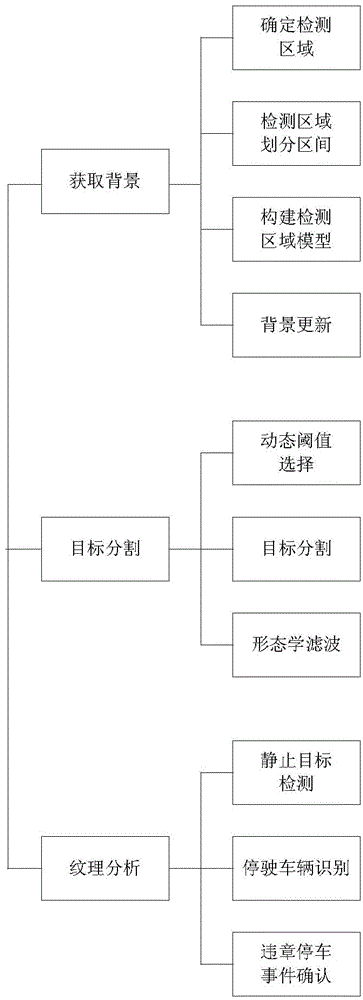
ActiveCN104376554AImplement updateFast updateImage enhancementImage analysisFalse alarmCo-occurrence matrix
The invention discloses an illegal parking detection method based on image texture. The method sequentially includes the following steps of obtaining the background, segmenting targets and analyzing the texture. The background obtaining is mainly achieved through the regional division of a determined detection area and a detection area, the establishment of a detection area model and the background renewing. The target segmenting is mainly achieved through the dynamic threshold value selection, the target segmentation and the morphology filtering. By means of the target segmentation method where dynamic threshold values are adopted, moving targets can be more accurately obtained through segmentation; meanwhile, the noise interference generated in the segmentation process can be effectively eliminated through the opening operation in the morphology filtering; the texture analyzing is mainly achieved through the static target detection, the running and parked vehicle recognition and the illegal parking event conforming; whether static objects appear or not is judged by analyzing the process during which the image gray value reaches the steady state; meanwhile, the false alarm existing in the process is eliminated through the entropy of an image gray level co-occurrence matrix.
Owner:COSCO SHIPPING TECH CO LTD
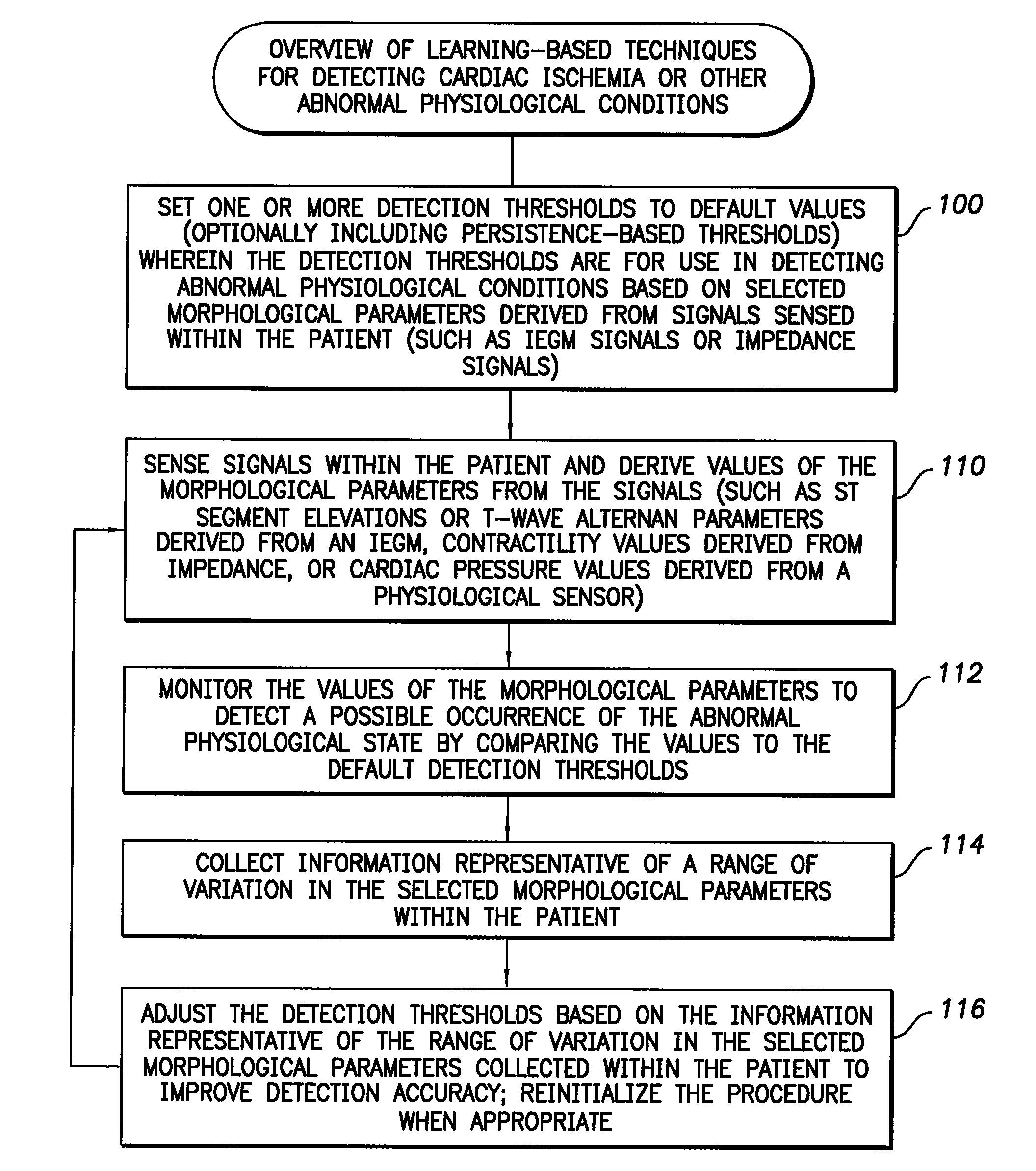
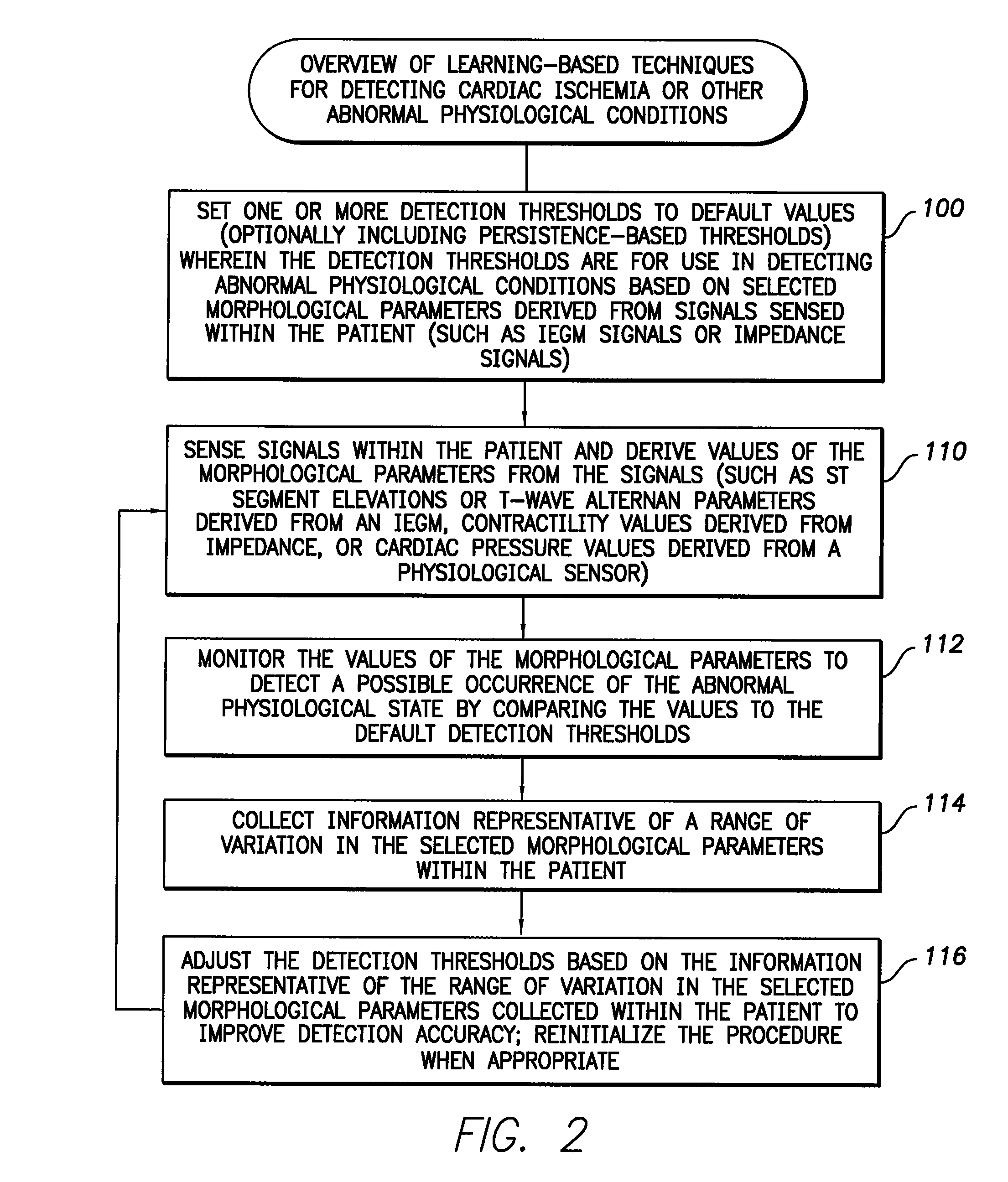
System and method for adaptively adjusting cardiac ischemia detection thresholds and other detection thresholds used by an implantable medical device
InactiveUS7769436B1Simple technologyFacilitate warningElectrotherapyElectrocardiographyCardiac pacemaker electrodeSelf adaptive
Techniques are described for adaptively adjusting detection thresholds for use in detecting cardiac ischemia and other abnormal physiological conditions based on morphological parameters derived from intracardiac electrogram (IEGM) signals, impedance measurements, or other signals. In one example, where ST segment elevation is used to detect cardiac ischemia, default detection thresholds are determined in advance from an examination of variations in ST segment elevations occurring within a population of patients. Thereafter, an individual pacemaker or other implantable medical device uses the default thresholds during an initial learning period to detect ischemia within the patient in which the device is implanted. During the initial learning period, the pacemaker also collects data representative of the range of variation in ST segment elevations occurring within the patient. The pacemaker then adaptively adjusts the thresholds based on the range of variation so as to improve detection specificity within the patient.
Owner:PACESETTER INC
Auto-tuning program analysis tools using machine learning
InactiveUS20160182558A1Reduce false alarmsMachine learning is facilitatedMemory loss protectionError detection/correctionLearning machineFeature set
Machine learning (ML) significantly reduces false alarms generated by an automated analysis tool performing static security analysis. Using either user-supplied or system-generated annotation of particular findings, a “hypothesis” is generated about how to classify other static analysis findings. The hypothesis is implemented as a machine learning classifier. To generate the classifier, a set of features are abstracted from a typical witness, and the system compares feature sets against one another to determine a set of weights for the classifier. The initial hypothesis is then validated against a second set of findings, and the classifier is adjusted as necessary based on how close it fits the new data. Once the approach converges on a final classifier, it is used to filter remaining findings in the report.
Owner:IBM CORP
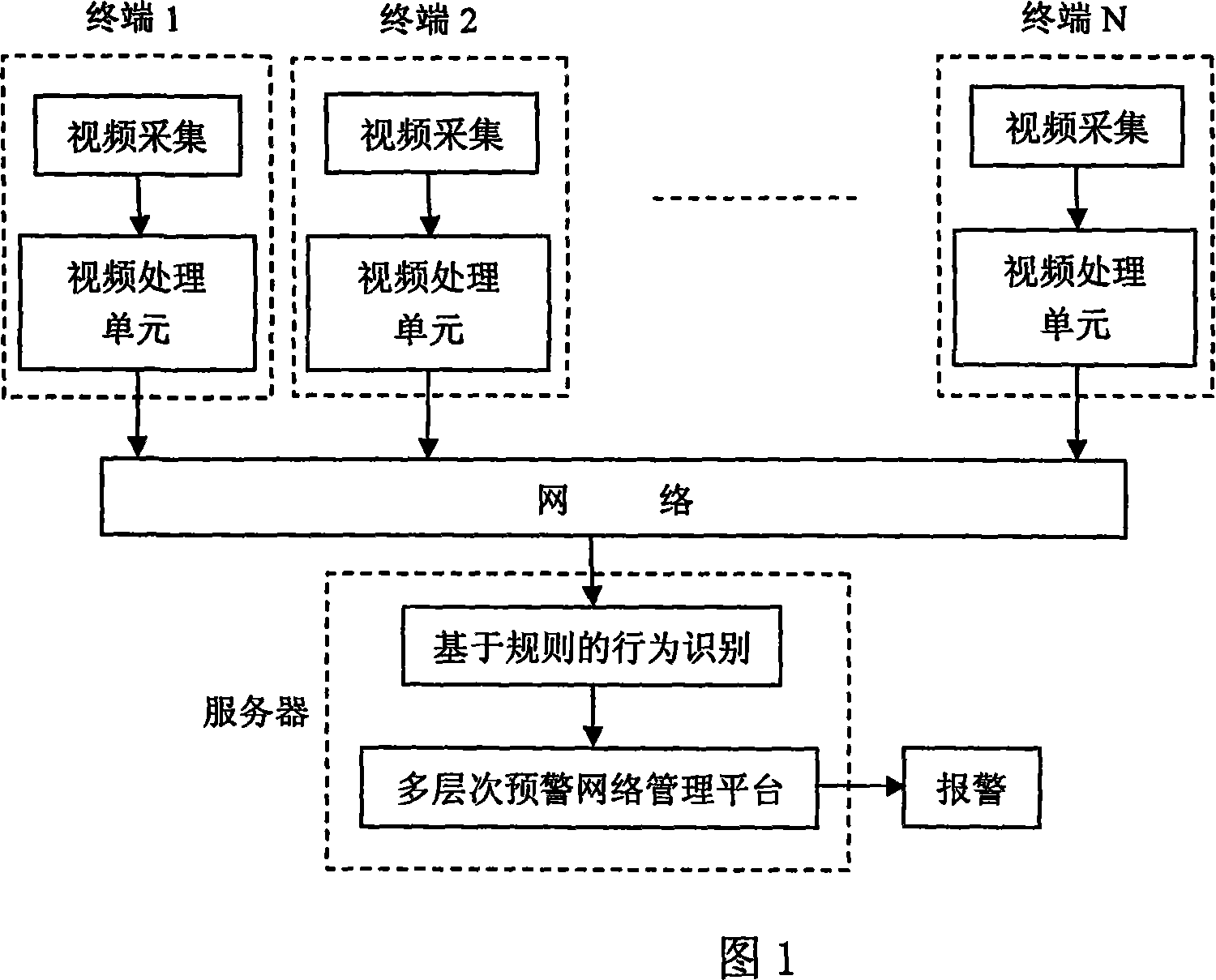
Multi-layer real time forewarning system based on the intelligent video monitoring
InactiveCN101055662AGreat practicabilityReduce false alarmsBurglar alarmVideo monitoringEarly warning system
The invention relates to an intelligent early warning system, especially a multiple layered real-time early warning system based on target detection, positioning, class recognition of intelligent video analysis and based on network management. The system comprises five portions: a video collecting unit, a video processing unit, an action recognition module based on a rule, a network management platform and an alarming module. The method comprises: 1, a user appointing an early warning rule for every vidicon on the network management platform, realizing a multiple layered real-time early warning mechanism; 2, in the video processing unit, dividing a video sequence into three paths, wherein a path is used for coding and compressing, a path is used for scene analysis, and a path is used for background modeling, the video processing unit has encoding and compressing functions, can obtain a traget track after video analysis; 3, transmitting the traget track via a network to the action recognition module, and performing action recognition according to the rule defined by the user.
Owner:BEIJING HUIDA TONGYE TECH +2
State validation using bi-directional wireless link
InactiveUS20060152335A1Reduce power consumptionReduce false alarmsTelemetry/telecontrol selection arrangementsElectric testing/monitoringControl systemEngineering
Building monitoring and control systems including bi-directional radio frequency links between master and remote units wherein the remote units operate in a low power, non-receiving state a majority of the time is disclosed. The bi-directional capability allows coordinated scheduling which aids in allowing the remote units to transmit data only at periodic time intervals to extend battery life. The bi-directional capabilities also allow for re-read requests for alarm validation and for putting remote units in armed and disarmed states for power conservation.
Owner:HONEYWELL INT INC
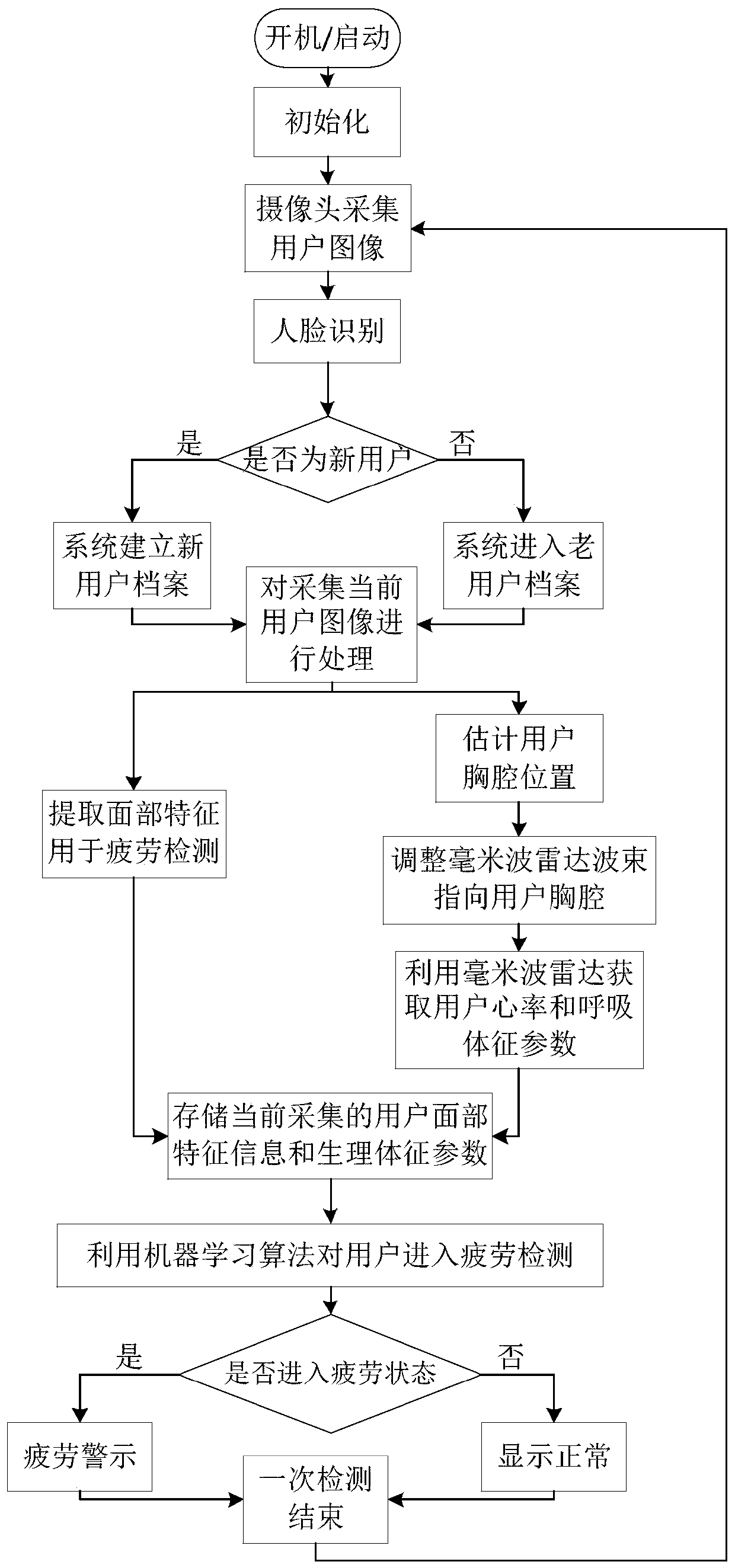
Multi-sensor fusion type fatigue monitoring device system and monitoring method thereof
InactiveCN111166357AImprove accuracyReduce false alarmsDiagnostic recording/measuringSensorsPattern recognitionDriver/operator
The invention provides a multi-sensor fusion type fatigue monitoring device system and a monitoring method thereof. A camera collects facial features of a monitored driver, and a millimeter-wave radaris used for collecting physiological sign parameters of the monitored driver; a signal processing module judges whether the driver is in a fatigue state through combination of the current physiological sign parameters and facial features of the driver, historical storage data and medical guidance data by virtue of a machine learning algorithm, acquires a judgment result and outputs the judgment result to a warning display module; a data storage module stores identity information of a monitored object, data, collected in the past, of the monitored object and medically accepted universal indexes; and the warning display module displays whether the monitored object is in the fatigue state at present and is capable of giving an alert. The multi-sensor fusion type fatigue monitoring device system can be used for recognizing each monitored object, so that the influence caused by individual sign differences to a detection result is reduced; and by utilizing multi-information fusion detection, the accuracy of the detection result is improved, and false-alarm phenomena are reduced.
Owner:四川宇然智荟科技有限公司
Airfield runway foreign object detection system
InactiveCN101852869AReduce the impactWill not affect normal operationOptical detectionEnvironment effectControl system
The invention relates to an airfield runway foreign object detection system which comprises laser scanning devices, imaging devices, an alarm device, a display device, a control system, and the like, wherein multiple groups of the laser scanning devices and the imaging devices corresponding to the laser scanning devices are provided as well as arrayed and arranged at both sides of an airfield runway; and laser scanning and imaging signals are transmitted to the control system and the display device through transmission lines. In the airfield runway foreign object detection system, the characteristic of high precision of laser is utilized, thus smaller foreign objects on the airfield runway can be detected, and the physical coordinate positions of the smaller foreign objects can be determined; and the imaging devices are used for providing visual and visible image information for staff so as to be convenient for confirming and processing alarm targets for the staff. The system can be used for monitoring the airfield runway around the clock for 24 hours without being influenced by environment, thereby false alarms are reduced. Meanwhile, the system can automatically carry out detection during the period of a regular flight without influencing the normal operations of the airport.
Owner:CIVIL AVIATION UNIV OF CHINA
Range-extended target adaptive detection method under inverse Gaussian texture complex Gaussian clutter
InactiveCN105425230AHigh precisionReduce false alarmsRadio wave reradiation/reflectionWideband radarHypothesis model
The present invention belongs to the technical field of radar target detection and discloses a range-extended target adaptive detection method under inverse Gaussian texture complex Gaussian clutter for the target detection under a wideband radar system. The method comprises a step of establishing the binary hypothesis model of radar target detection, a step of using a spherically invariant vector process model to construct an inverse Gaussian texture complex Gaussian clutter signal, a step of using a generalized likelihood ratio to obtain a range-extended target adaptive detector under the inverse Gaussian texture complex Gaussian clutter, a step of determining the detection threshold of the adaptive detector, a step of obtaining radar echo data and determining the detection statistic amount of the radar echo data according to the adaptive detector, and a step of judging whether the radar echo data has a range-extended target according to the detection statistic amount and the detection threshold, and if the detection statistic amount is larger than the detection threshold, determining that the radar echo data has the range-extended target, otherwise, determining that the radar echo data has no range-extended target.
Owner:XIDIAN UNIV
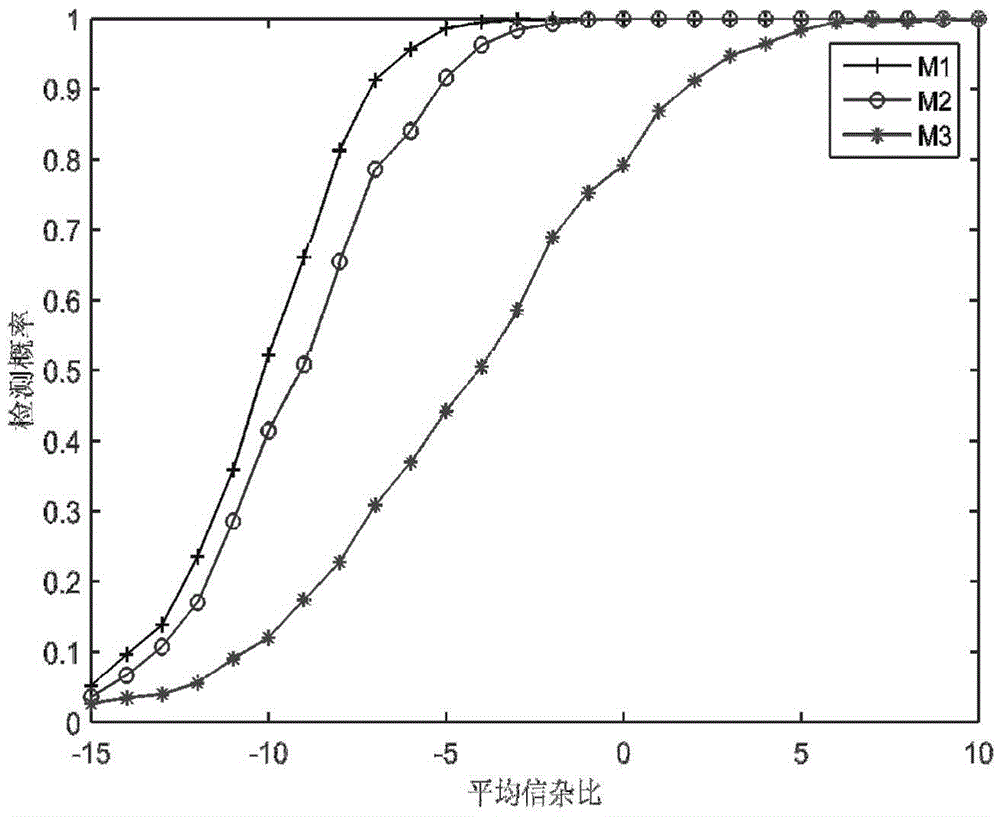
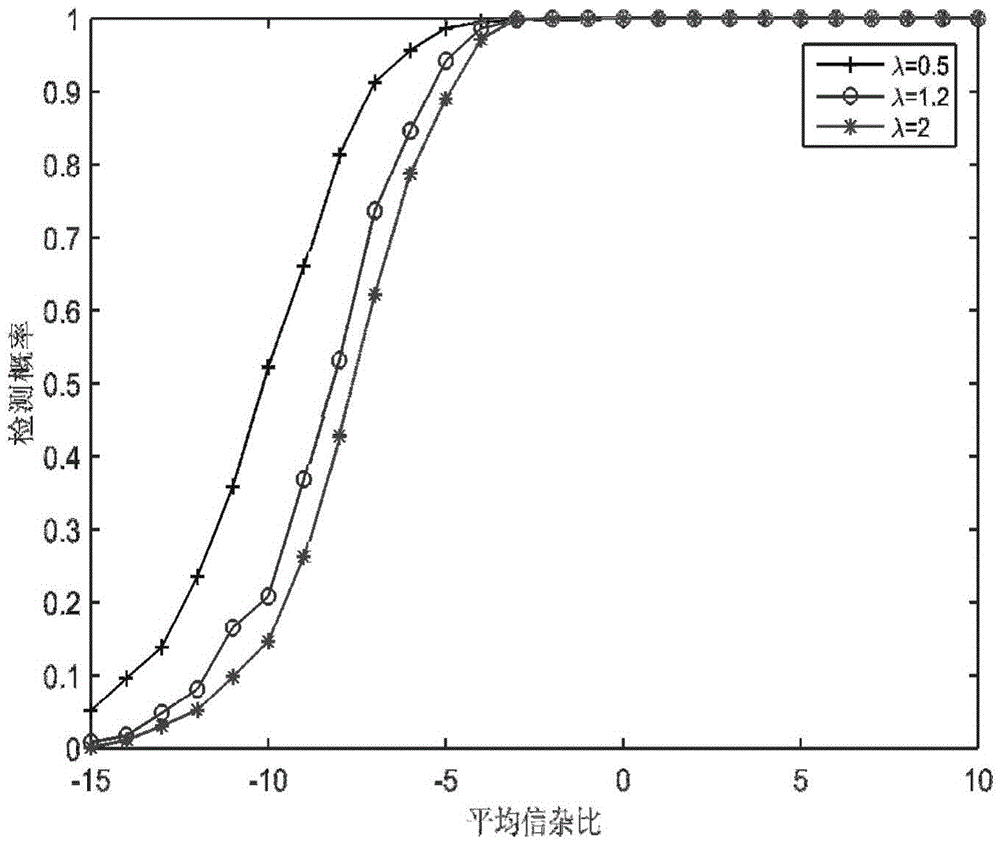
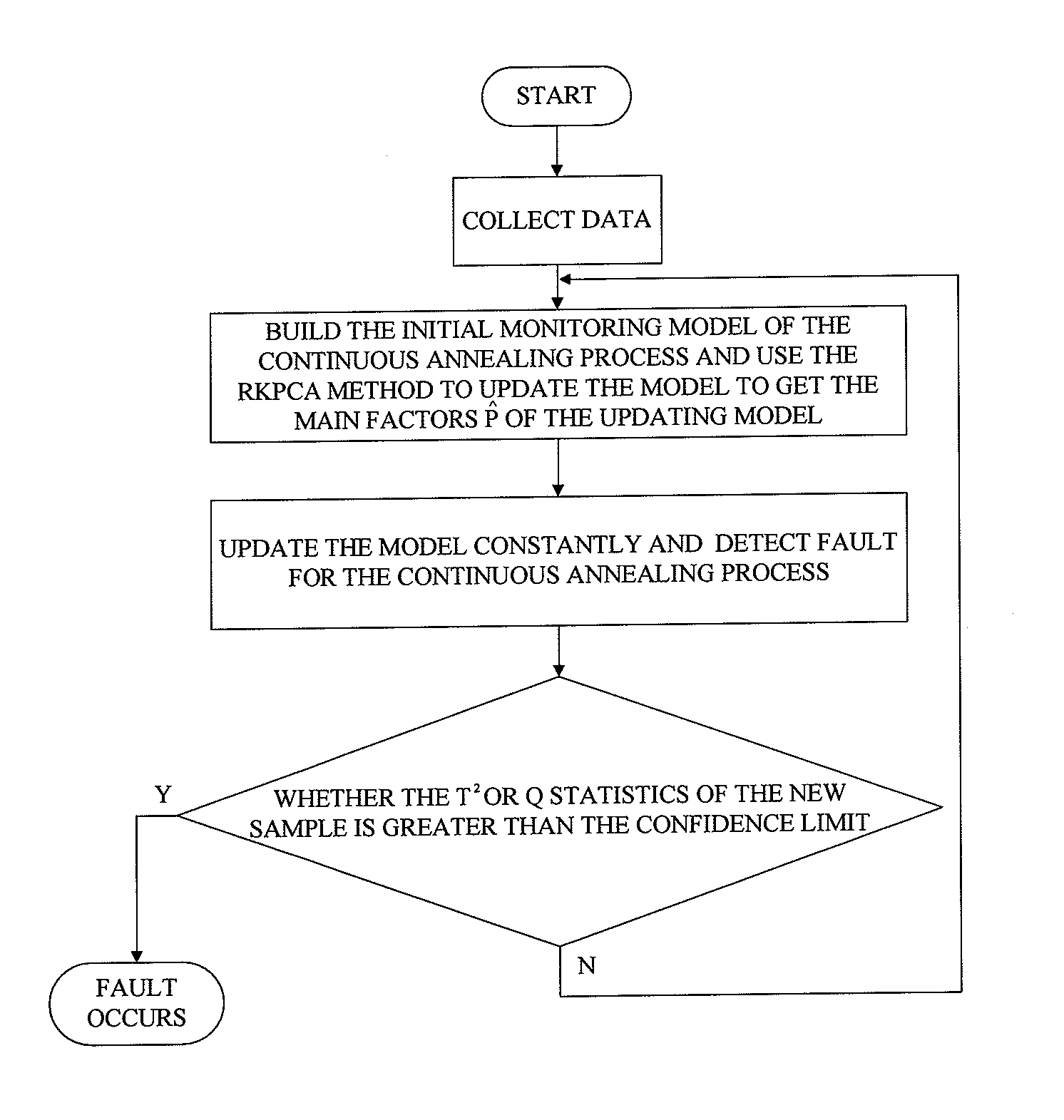
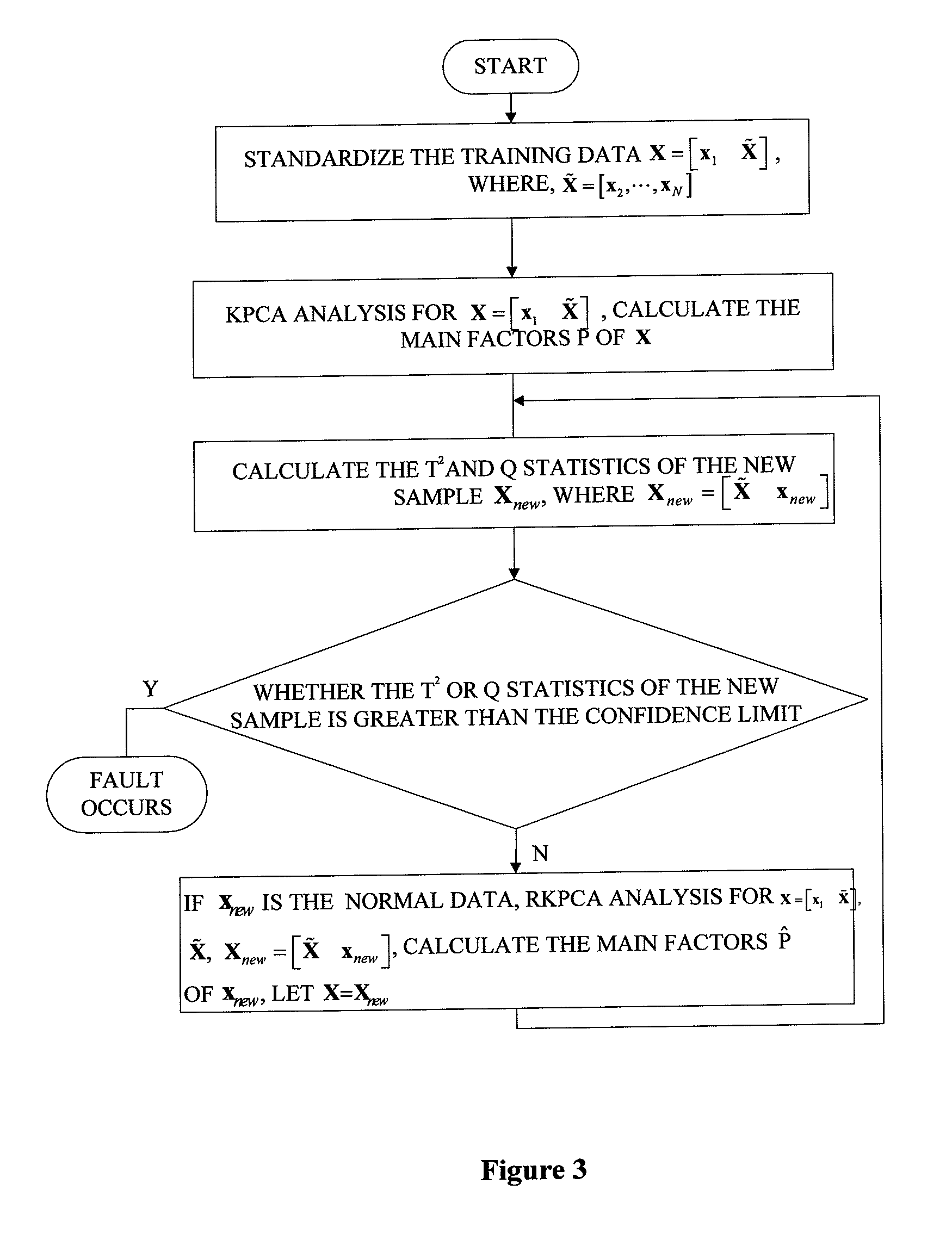
Continuous annealing process fault detection method based on recursive kernel principal component analysis
ActiveUS20130035910A1Reduce false alarm rateImprove accuracyTesting/monitoring control systemsComputation using non-denominational number representationKernel principal component analysisAlgorithm
A fault detection method in a continuous annealing process based on a recursive kernel principal component analysis (RKPCA) is disclosed. The method includes: collecting data of the continuous annealing process including roll speed, current and tension of an entry loop (ELP); building a model using the RKPCA and updating the model, and calculating the eigenvectors {circumflex over (p)}. In the fault detection of the continuous annealing process, when the T2 statistic and SPE statistic are greater than their confidence limit, a fault is identified; on the contrary, the whole process is normal. The method mainly solves the nonlinear and time-varying problems of data, updates the model and calculates recursively the eigenvalues and eigenvectors of the training data covariance by the RKPCA. The results show that the method can not only greatly reduce false alarms, but also improve the accuracy of fault detection.
Owner:NORTHEASTERN UNIV +3
Home-based care system based on body feeling network and control method thereof
ActiveCN106875629AOvercoming False Positive Technical BoundariesReduce false alarmsAlarmsTotal factory controlEngineeringEmergency medicine
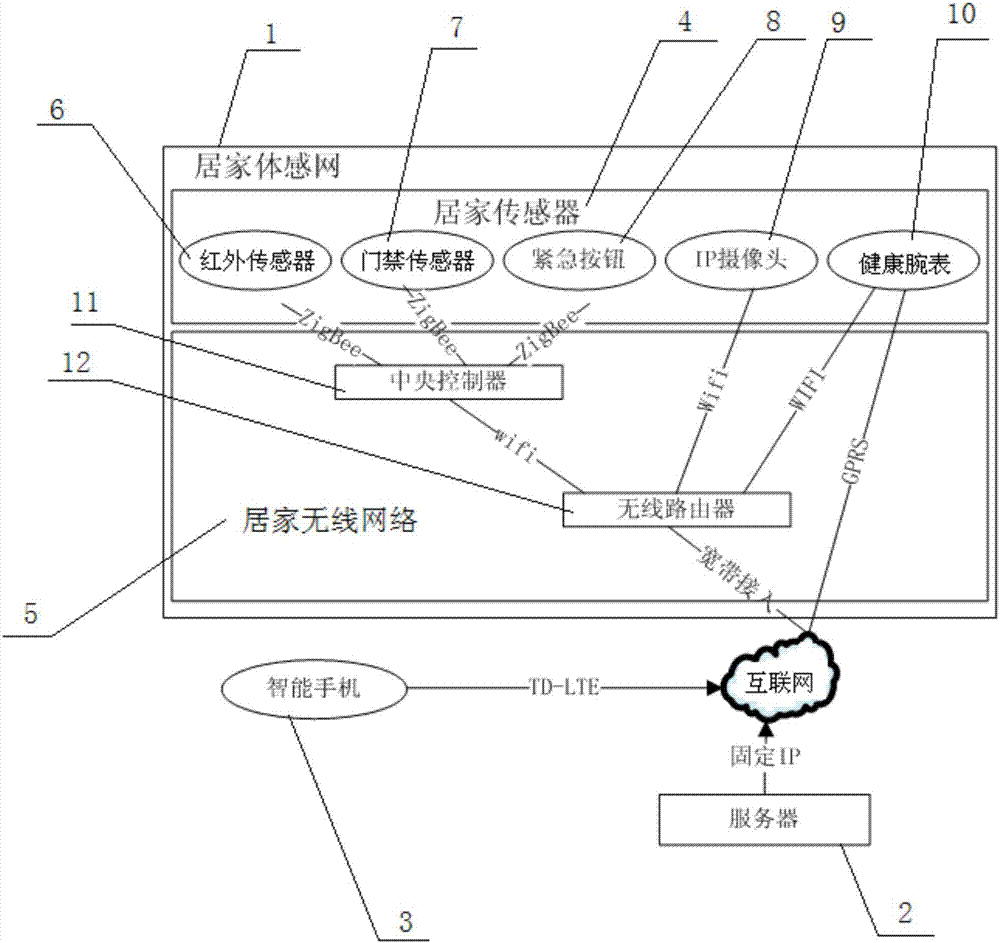
A home-based care system based on a body feeling network and a control method thereof belong to the intelligent household service system technology field. A household body feeling network, a server and an intelligent mobile phone are included. The household body feeling network comprises a household sensor and a household wireless network. The household sensor comprises an infrared sensor, an access control sensor, an emergent button, an IP camera and a healthy watch. The household wireless network comprises a central controller and a wireless router. In the invention, a body feeling network environment is created in a family; through a plurality of sensors, a state of a senior citizen wearing the healthy watch is analyzed so that false alarm conditions are greatly reduced; according to an individual, alarm threshold correction is performed and a false alarm technology boundary of a single sensor is overcome; and a healthy and safe informatization monitoring system is provided for the home-based senior citizen. A remote monitoring informatization platform of children is erected so that a platform used for monitoring health of the senior citizen, monitoring household safety and communicating with the senior citizen is provided for the children.
Owner:CHANGCHUN WHY E SCI & TECH
Ship target detection method based on coastline data and spectral analysis
ActiveCN105303526AEfficient removalReduce false alarmsImage enhancementImage analysisFrequency spectrumSatellite image
The invention provides a ship target detection method based on coastline data and spectral analysis. The invention relates to the ship target detection method. According to the invention, the problems that noise cannot be effectively removed and the detection of a ship target in a large-size satellite image consumes a lot of computing resources and time in the prior art are solved. The invention provides the ship target detection method based on coastline data and spectral analysis The method comprises the steps that an image with background ocean image data is formed, wherein the image is masked; the image without cloud noise is acquired; a binary image is acquired, and a seed point or a seed region is detected in the binary image; according to the detected seed point or seed region, region growing is carried out to acquire a ship body region; and through the area and the length-width ratio feature of the ship body region, screening is carried out to acquire a ship target detection result in the high-resolution satellite image. The method provided by the invention is applied to the field of ship target detection.
Owner:HARBIN INST OF TECH
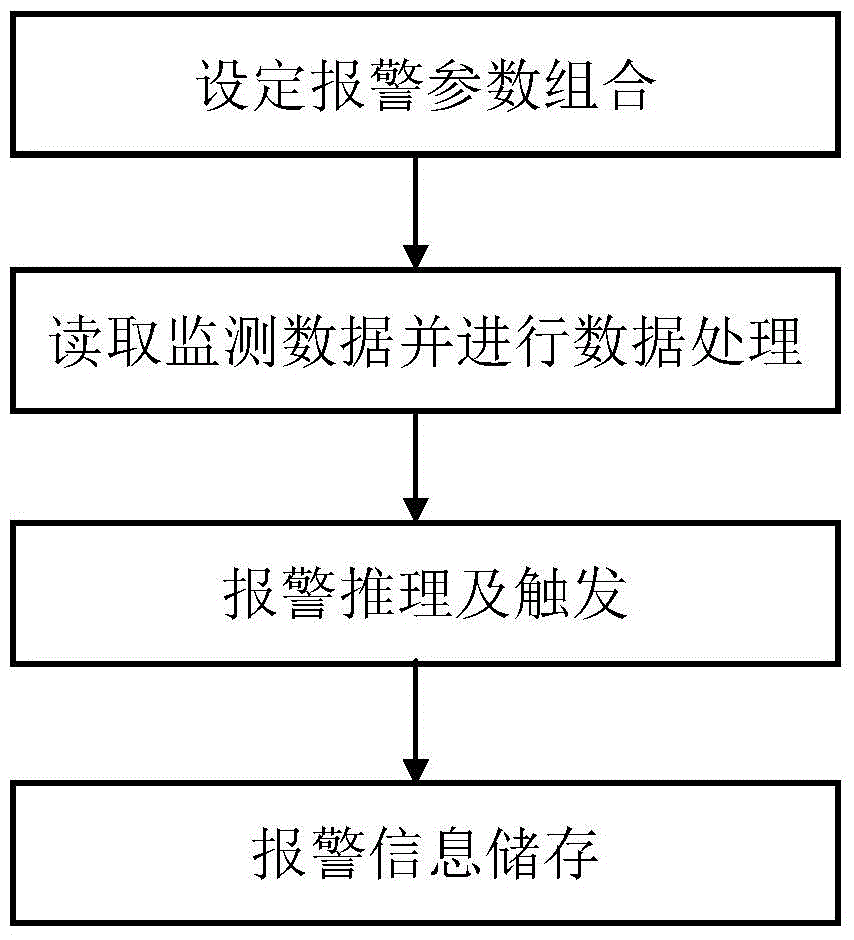
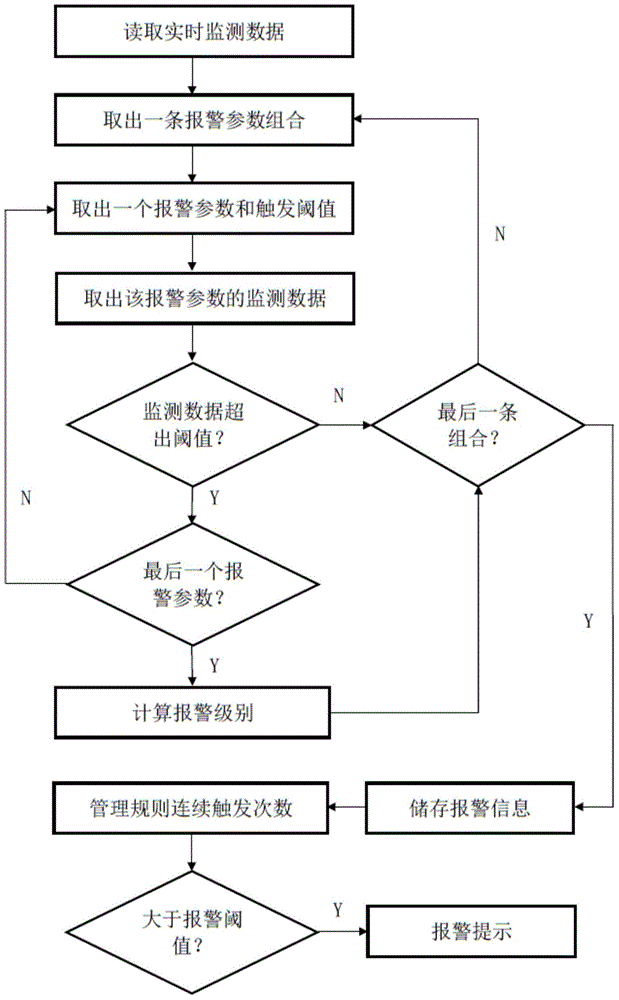
Combined alarming method for on-line monitoring system for rotary machinery
ActiveCN104880247AFlexible settingsMultiple alarm parameters are set and the combination is flexibleSubsonic/sonic/ultrasonic wave measurementMonitoring systemAcousto-optics
The invention discloses a combined alarming method for an on-line monitoring system for rotary machinery. The method includes the following steps: selecting multiple parameters from vibration parameters and rate of change parameters of the vibration parameters, making the multiple parameters serve as monitored objects, and successively setting multiple alarming parameter combinations; reading basic monitor data in a database, and obtaining monitor values of the corresponding vibration parameters and the rates of change of the vibration parameters; successively reading the alarming parameter combinations from an alarming rule list, comparing the monitor values with corresponding trigger threshold values, triggering the alarming parameter combinations if all the monitor values exceed the trigger threshold values, and calculating the alarming level and the continuous trigger frequency of the alarming parameter combinations; and giving an acousto-optic alarm if the continuous trigger frequency of one alarming parameter combination is greater than a continuous alarming threshold value. Through adoption of the method, the alarming accuracy and the alarming efficiency are improved, false alarming is minimized, people can know the danger level, and then on-site workers can conveniently cope with the danger in time.
Owner:HUAZHONG UNIV OF SCI & TECH
Laser-vision linked night invasion detection device
InactiveCN101976489AImprove anti-interference abilityHigh sensitivityBurglar alarmAnti invasionLaser detection
The invention discloses a laser-vision linked night invasion detection device, which realizes the detection and identification of invasion events by laser detection and active vision technology at night. The invention relates to invasion detection technology in security protection, in particular to optoelectronic and visual information processing technology-based invasion detection. The technical problems needing to be solved are to detect and identify the invasion events of pedestrians or vehicles in an environment with poor light at night, and prevent false alarms. In the device, a modulated laser beam is used as a detection light source and is matched with a photoelectric signal collector, a photoelectric signal amplifier and a photoelectric signal processor to form a front-end unit; and a camera provided with active illumination and an embedded image processor are used as a rear-end response processing unit. When the invasion events occur in a detection area, a laser photoelectric signal is interrupted to trigger an active vision system so as to realize linkage and improve the reliability of the invasion detection. The laser-vision linked night invasion detection device can be used for anti-invasion security detection around residential areas, storerooms, airports and other important places.
Owner:李原
Perimeter alarming method and system for implementing orientation of composite type complete optical fiber
InactiveCN101303788AImprove alarm accuracyImprove anti-disturbance abilitySubsonic/sonic/ultrasonic wave measurementUsing wave/particle radiation meansMonitoring systemEngineering
The embodiment of the invention provides a method and a system for realizing composite entire optical fiber localizable perimeter alarm. An auxiliary optical fiber micro vibration sensor is arranged on a monitor optical cable provided with a precise positioning sensor; whether a disturbance signal exists is judged by the precise positioning sensor and the auxiliary optical fiber micro vibration sensor together, namely, whether people invade is judged; if the judgment is confirmed, an alarming signal is sent out, thus effectively improving the anti-interference capacity of the system, lowering effect caused by outside environmental factors like temperature and stress, and the like, reducing false alert rate and missing report rate, and improving the alarming precision of the monitoring system.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com