Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
562results about How to "Realize security protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
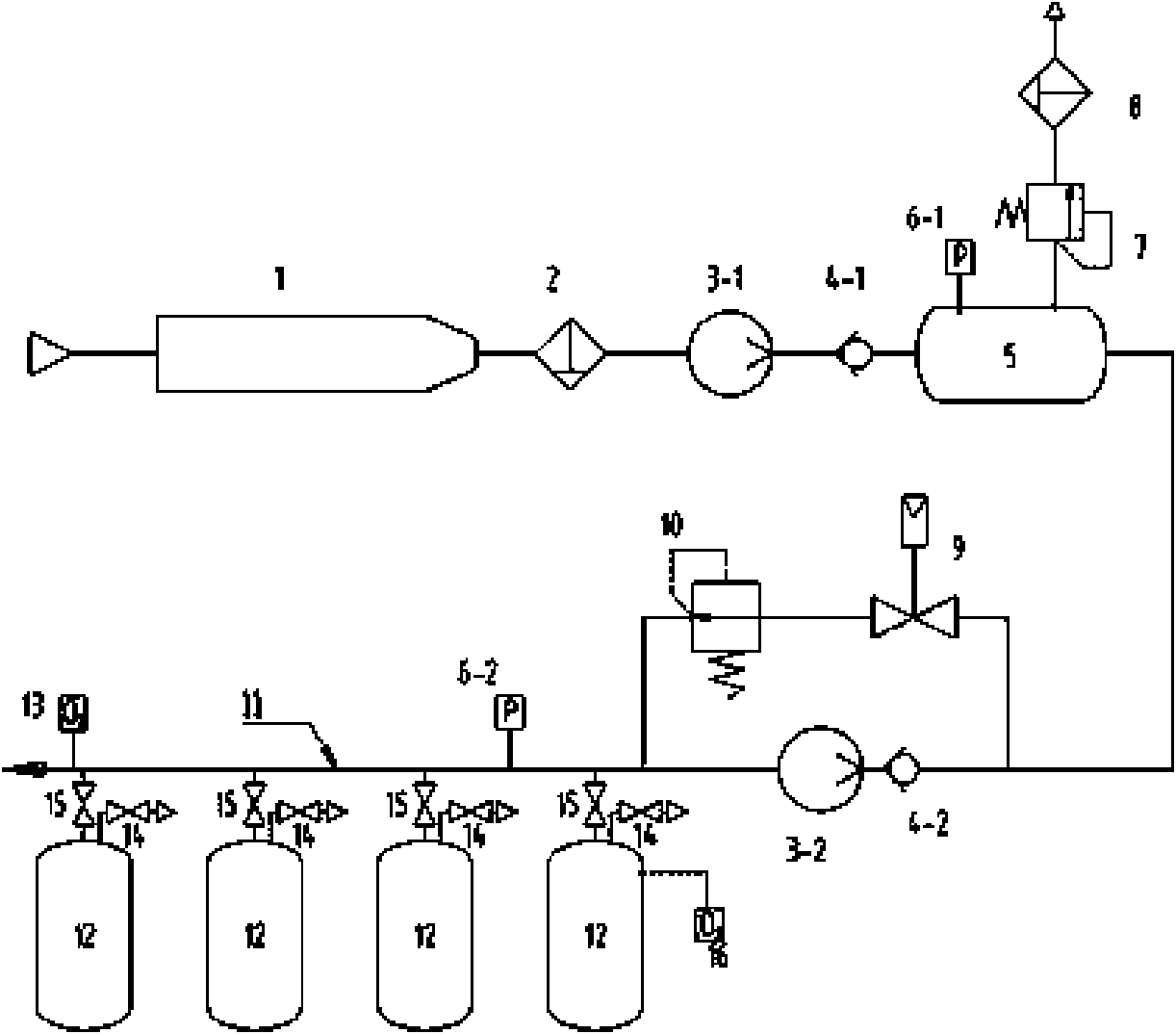
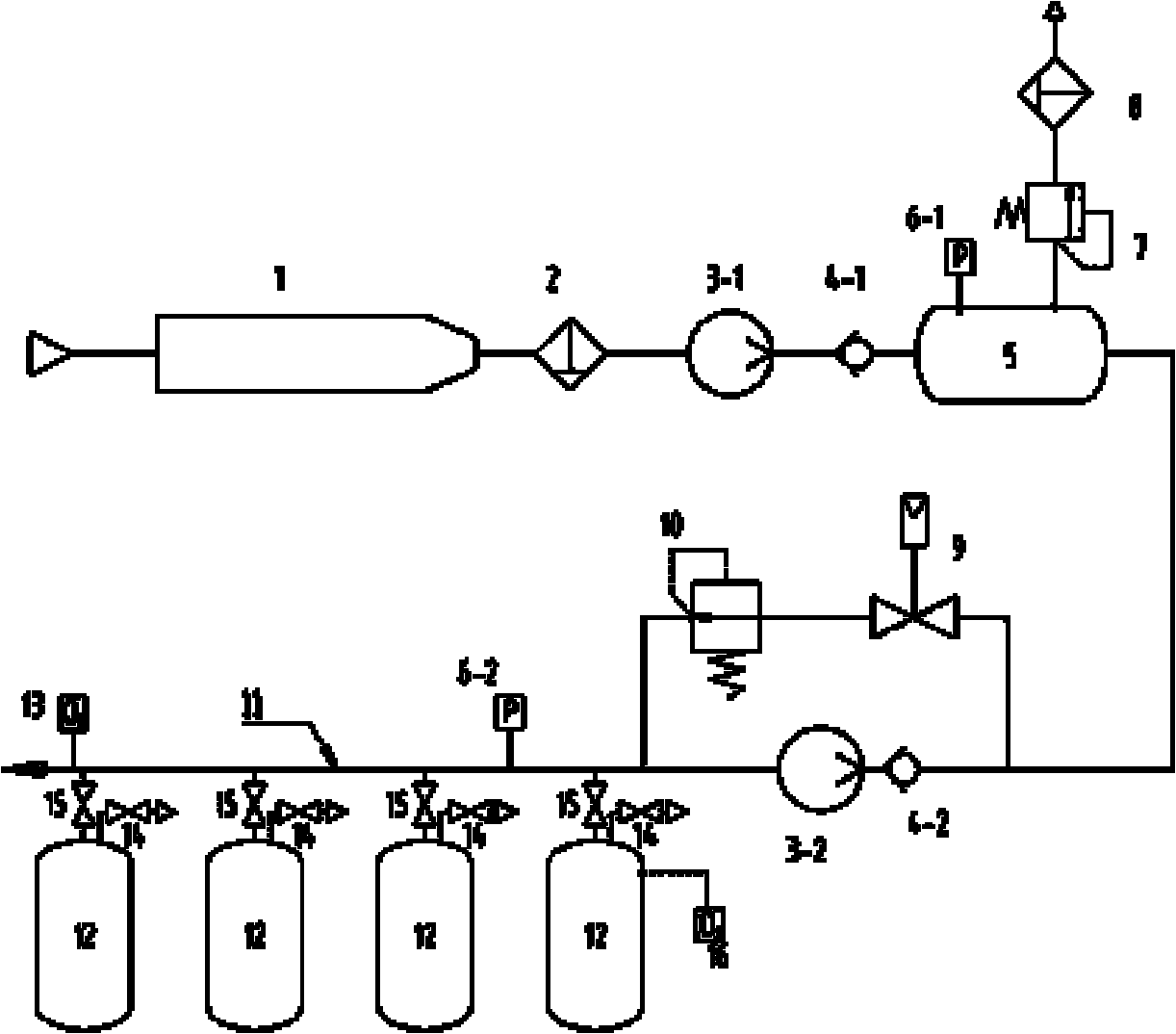
Intrinsically safe inerting protection method and device for oil storage tank
ActiveCN101767697ARealize security protectionImprove real-time performanceLarge containersPipeline systemsEngineeringLimit value
The invention discloses an intrinsically safe inerting protection method and an intrinsically safe inerting protection device for an oil storage tank, relates to a method and a device for active fire and explosion prevention of the oil storage tank, and aims to solve the problem of fire and explosion prevention of the oil storage tank. The method comprises the following steps: a, performing inerting on each oil tank in sequence to ensure that each oil tank achieves an inexplosive condition, namely, the oxygen concentration of gas in the tank is lower than 10 percent; b, detecting the pressure of a pipe network for supplying inert gas to the oil tank, and supplying the inert gas to the pipe network and inputting the inert gas to the oil tank through the pipe network if the pressure is lower than a set lower limit value; c, detecting the pressure of the pipe network for supplying the inert gas to the oil tank, emitting the inert gas in the pipe network if the pressure exceeds a set upper limit value; and d, detecting the oxygen concentration in the pipe network for supplying the inert gas to the oil tank, and repeating the step a if the concentration exceeds the set upper limit value. The device comprises a buffer device, a breathing pipe network, a first pressure transmitter, a second pressure transmitter, an online oxygen analyzer and an electric control device.
Owner:LOGISTICAL ENGINEERING UNIVERSITY OF PLA +1
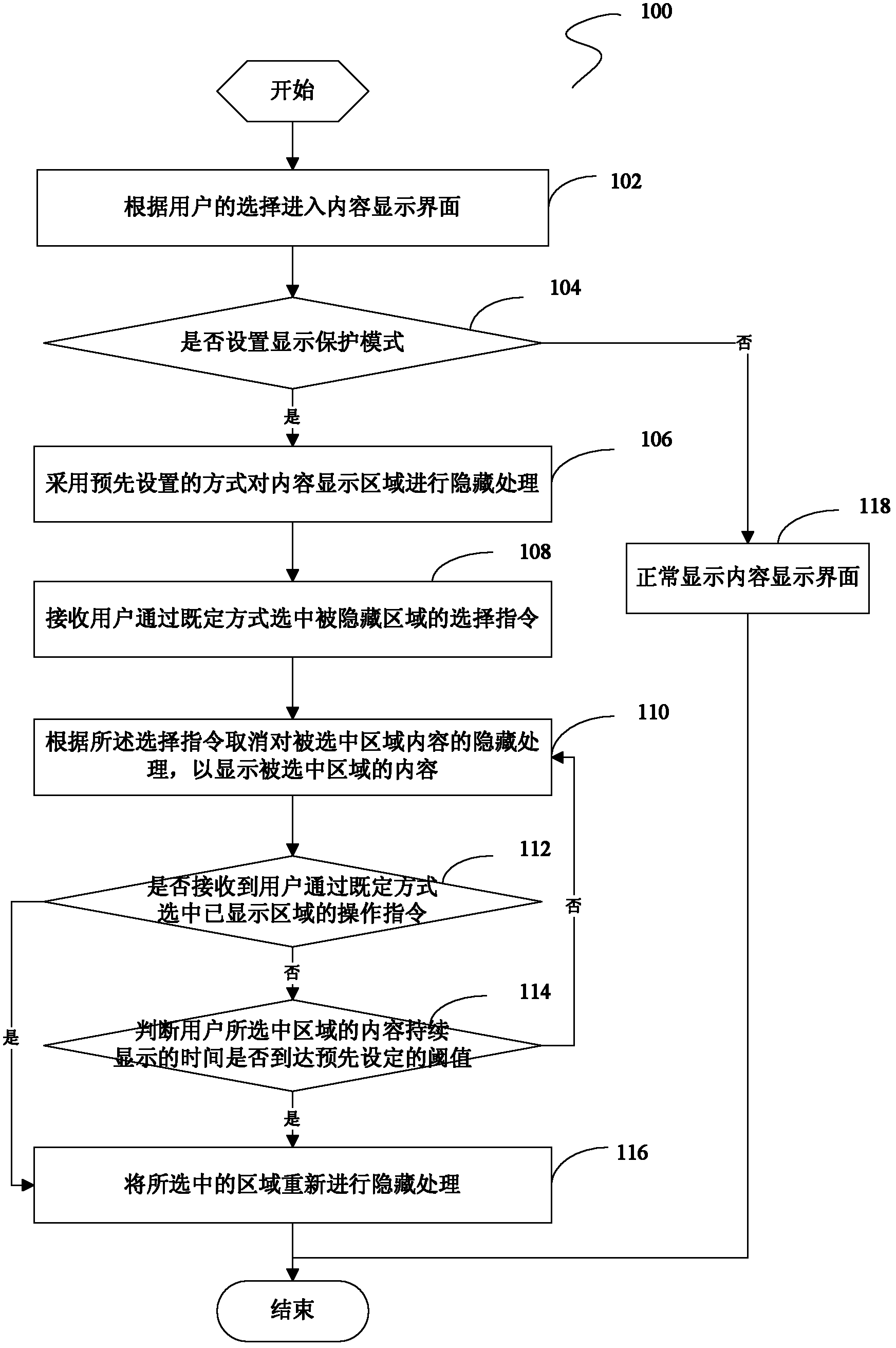
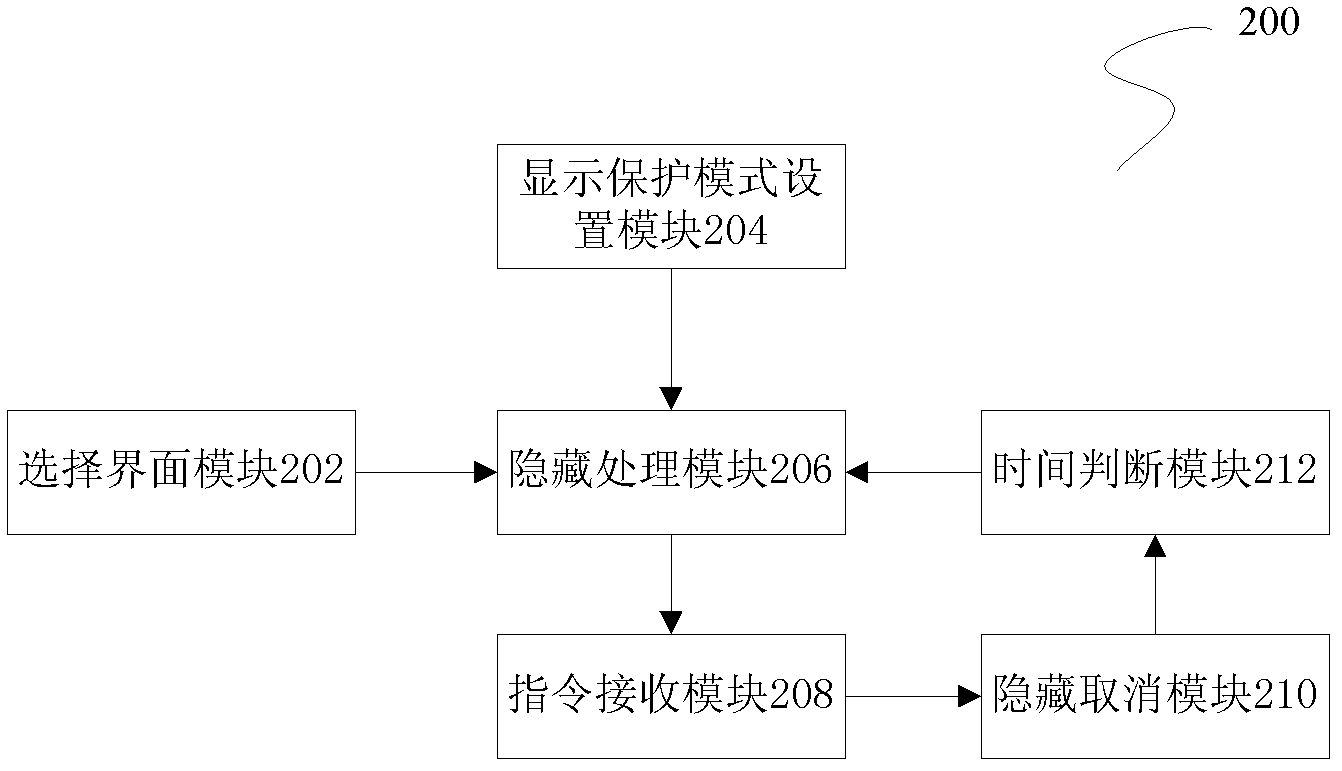
Display method and system for intelligent terminal interface
ActiveCN103186331AEasy to useImprove operating experienceInternal/peripheral component protectionInput/output processes for data processingLarge screenComputer terminal
The invention discloses a display method and system for an intelligent terminal interface. The method comprises the following steps of: entering a content display interface according to the selection of a user; according to a display protection mode set by the interface, carrying out the processing of hiding on a content display area by adopting a pre-setting mode; receiving a selection command of a hidden area selected by the user via a set mode; and cancelling the processing of hiding on content in a selected area according to the selection command so as to display the content of the selected area. According to the display method and system, the user is enabled to use a large screen intelligent terminal to safely read the text content of a message, a mail and the like, the text content can not be easily peeped by others, and safe protection of individual information is realized; and additionally the realization method is relatively simple and can be easily realized on a terminal, the cost of hardware can not be increased, the use of the user is extremely convenient, and the operation experience of the user is promoted.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
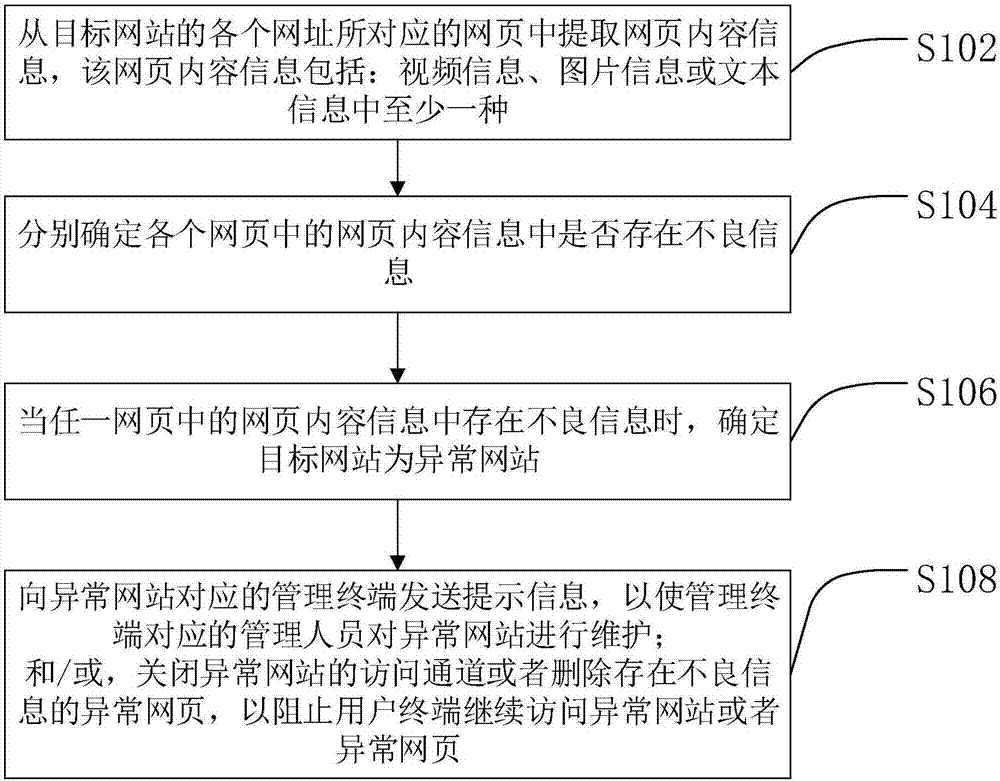
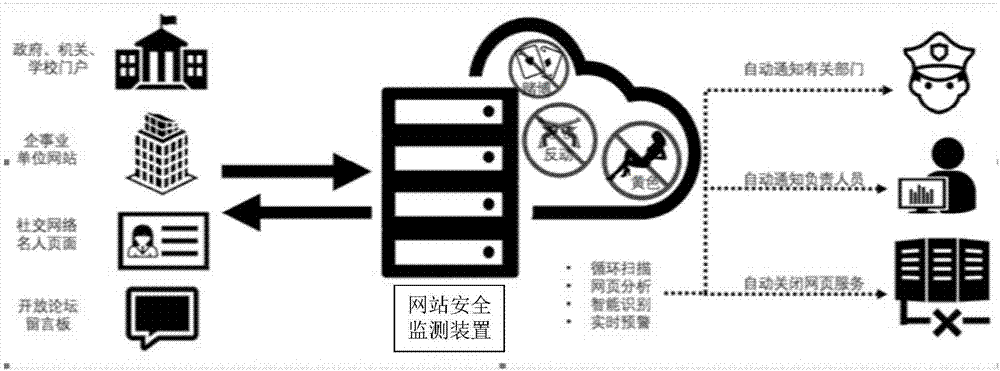
Website security monitoring method and device
The invention provides a website security monitoring method and device. The method comprises the following steps: extracting web page content information from web pages corresponding to each web address of a target website, wherein the web page content information includes at least one of video information, picture information or text information; separately determining whether malicious information exists in the web page content information of each web page; when the malicious information exists in the web page content information in any web page, determining that the target website is an abnormal website; sending prompt information to a management terminal corresponding to the abnormal website to ensure that corresponding managers maintain the abnormal website; and / or, closing an accesschannel of the abnormal website or deleting abnormal web pages with the malicious information to prevent user terminals from continuing to access the abnormal website or web pages. According to the method and device, the web page contents of the target website can be monitored in real time, rapid early warnings can be made when identifying that the malicious information exists in the web page contents, and thus the full range of security protection on the target website can be achieved.
Owner:北京匠数科技有限公司
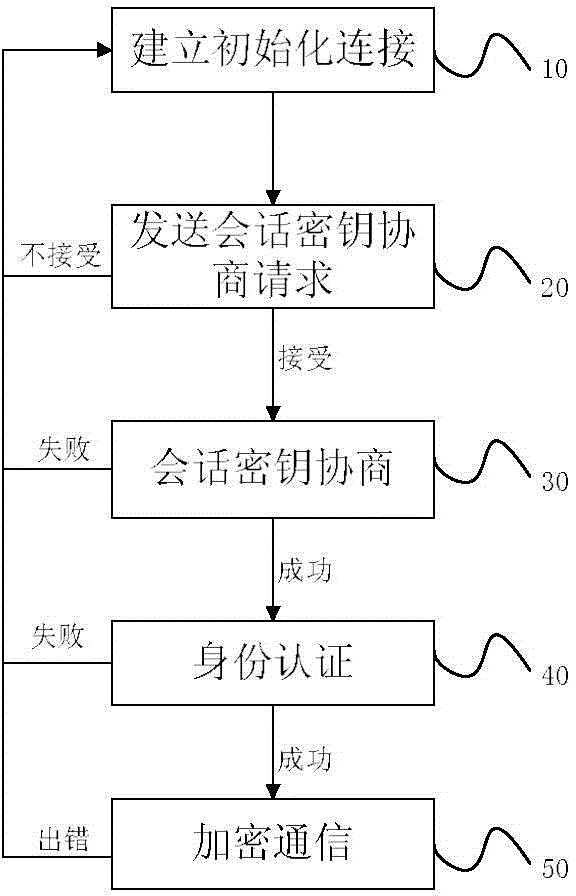
Method of secure communication based on commercial cipher algorithm
ActiveCN104158653APrevent eavesdroppingEnsure safetyKey distribution for secure communicationData transmissionSecure communication
The invention discloses a method of secure communication based on a commercial cipher algorithm. The method comprises the following steps: step 10, initializing connection between a client and a server is established; step 20, the client sends a session key negotiation request; step 30, the client and the server carry out session key negotiation; step 40, the client sends client device information for identity authentication; and step 50, the client and the server communicate in an encrypted way. According to the method of secure communication based on a commercial cipher encryption and decryption technology, key negotiation of a key exchange algorithm, a data encryption algorithm and a data integrity check algorithm is adopted to enable the client and the server to carry out bidirectional authentication and determine the session key, and a secure channel is established to prevent data eavesdropping, tampering and destruction and replay attack insertion in the data transmission process and ensure the security of data transmission. The method of the invention does not rely on a network access mode, can be implemented on any basic network, and can realize end-to-end security protection.
Owner:北京华电天益信息科技有限公司
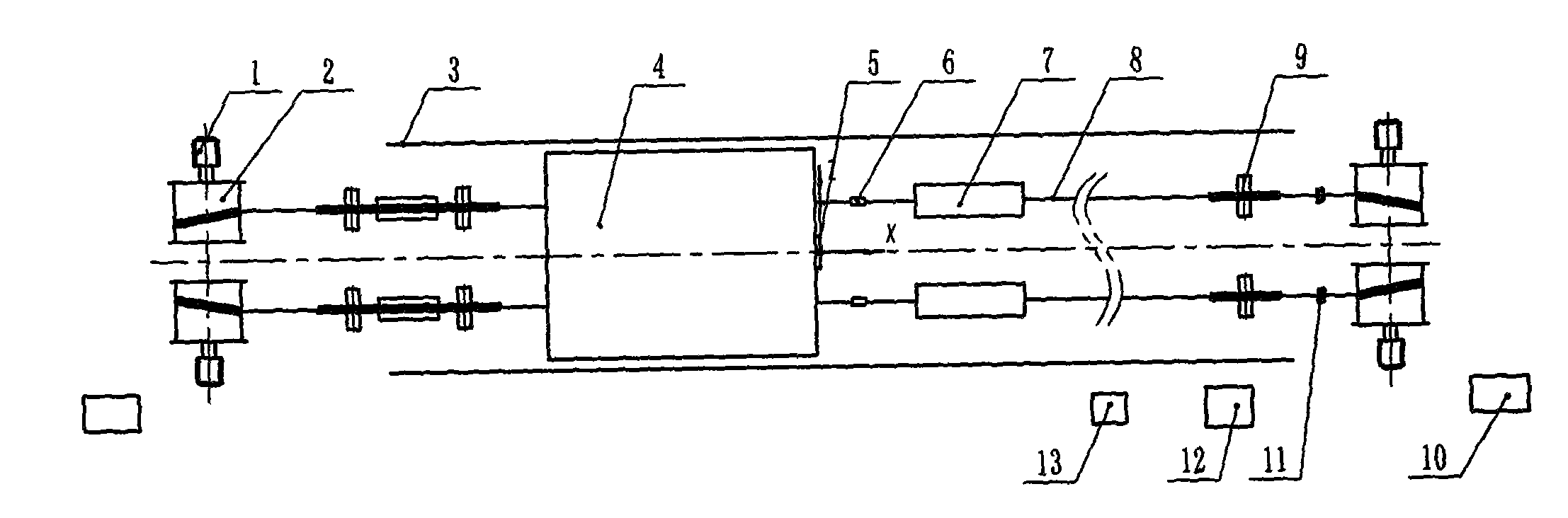
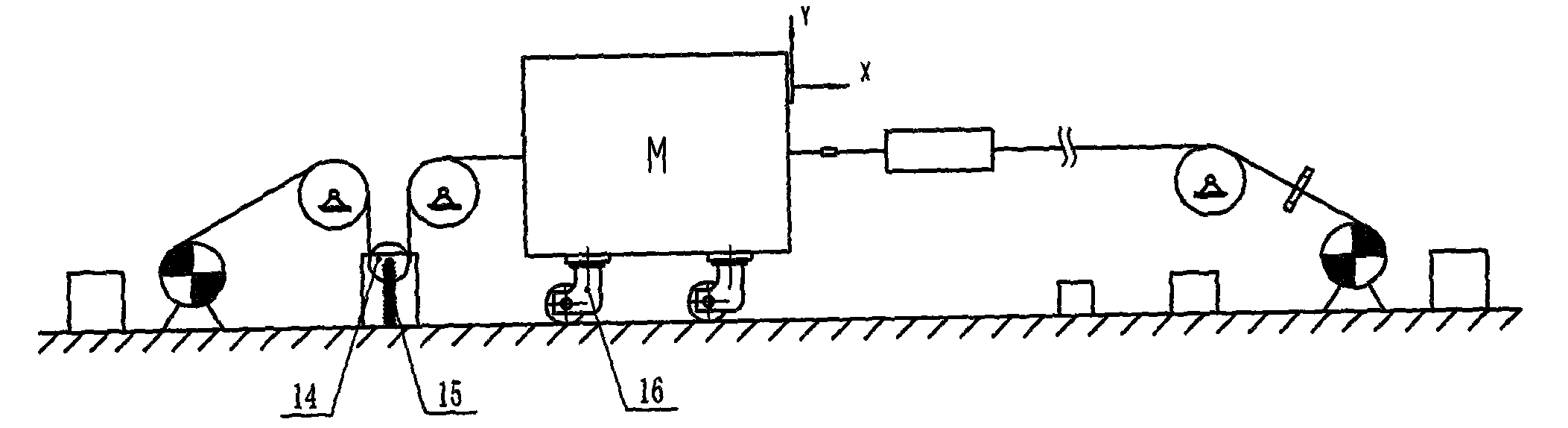
Test stand and method for ultra-deep mine hoisting systems
The invention discloses a test stand and a method for ultra-deep mine hoisting systems. The test stand comprises four variable-frequency motors (1), four hoist drums (2), horizontal guide rails (3), a hoisting container (4), a pose angle sensor (5), tension sensors (6), servo hydraulic cylinders (7), steel wire ropes (8), pulleys (9), a variable-frequency motor controller (10), wire and strand breakage detectors (11) for the steel wire ropes, a servo hydraulic cylinder controller (12), a pose monitoring device (13), a tension wheel (14), a tension spring (15) and universal wheels (16). The four hoist drums (2) correspond to the four variable-frequency motors (1). The test stand and the method have the advantages that vertical hoisting working conditions under actual working conditions can be replaced by motor horizontal dragging modes which can be easily implemented by the motors of the test stands, accordingly, the test stand is simple in operation and easy to maintain, and various functions can be simulated by the aid of the test stand.
Owner:CHINA UNIV OF MINING & TECH
Control system based on cloud computing encryption storage service
InactiveCN102143188ARealize privacy protectionEnsure data synchronizationTransmissionSpecial data processing applicationsData synchronizationThird party
The invention discloses a control system based on cloud computing encryption storage service, comprising a cloud computing processor, a cloud computing storage, a cloud computing user access front end, a cloud computing backstage controller module and a cloud computing third-party access end, wherein, a company or a content provider is connected with the system through a third-party access port; and a mobile terminal is interconnected with the cloud computing encryption through wireless manners of 2G, 3G or WIFI and the like. The movable encryption storage equipment is adopted as the stored mobile terminal, the interactive data is the encryption data, and a decryption secret key is controlled by a user; the data at a client side can not be decrypted by the system side under the non-authorized condition, thus realizing the private protection of users, also realizing the safety protection of the company level, and simultaneously ensuring the data synchronism of the client side and the backstage server when the data is backed up.
Owner:SHANGHAI QINGLONG COMM TECH
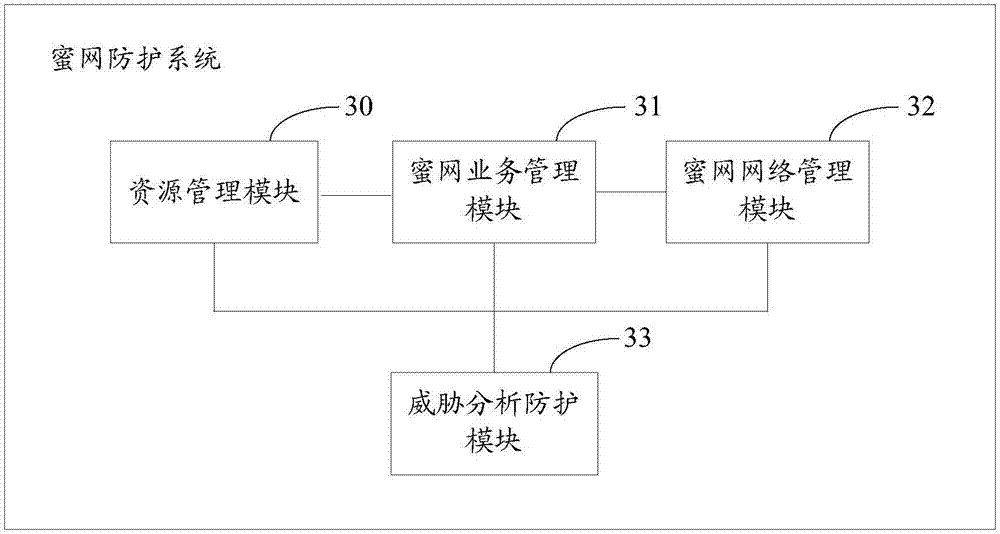
Honeynet protection method and system
ActiveCN107370756AImprove concealmentAchieve consistencyTransmissionAnomaly detectionNetwork overhead
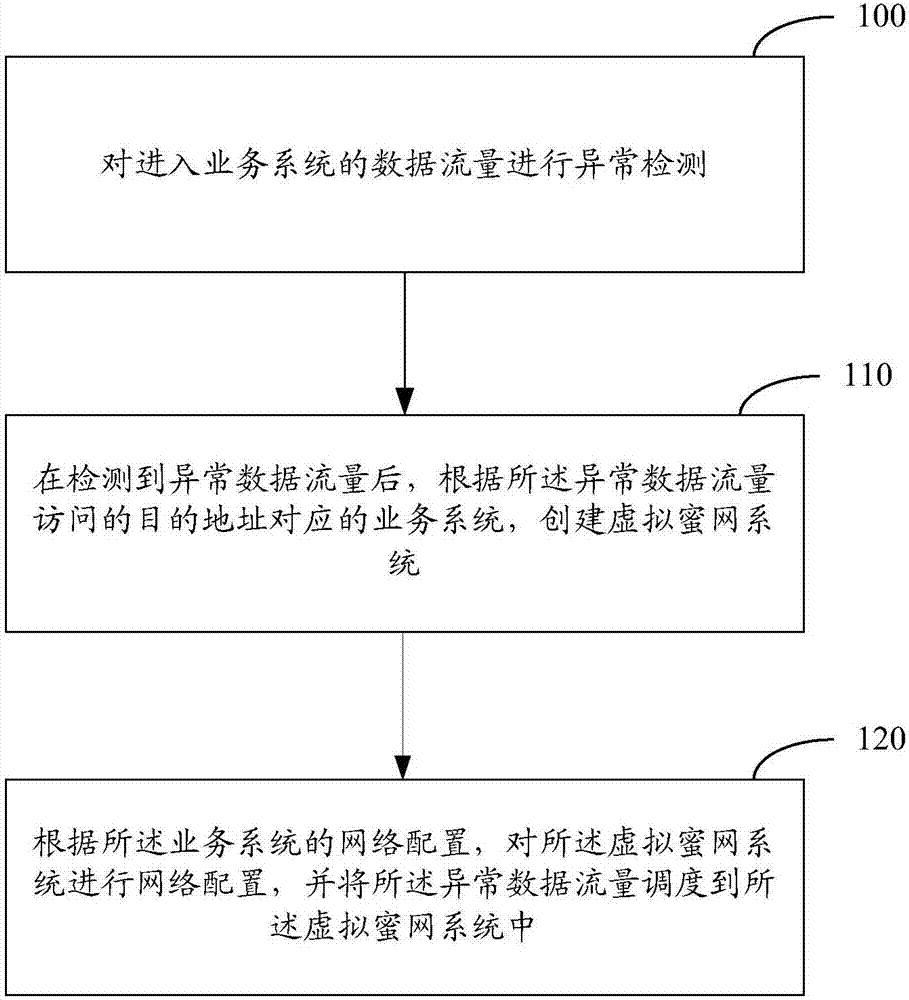
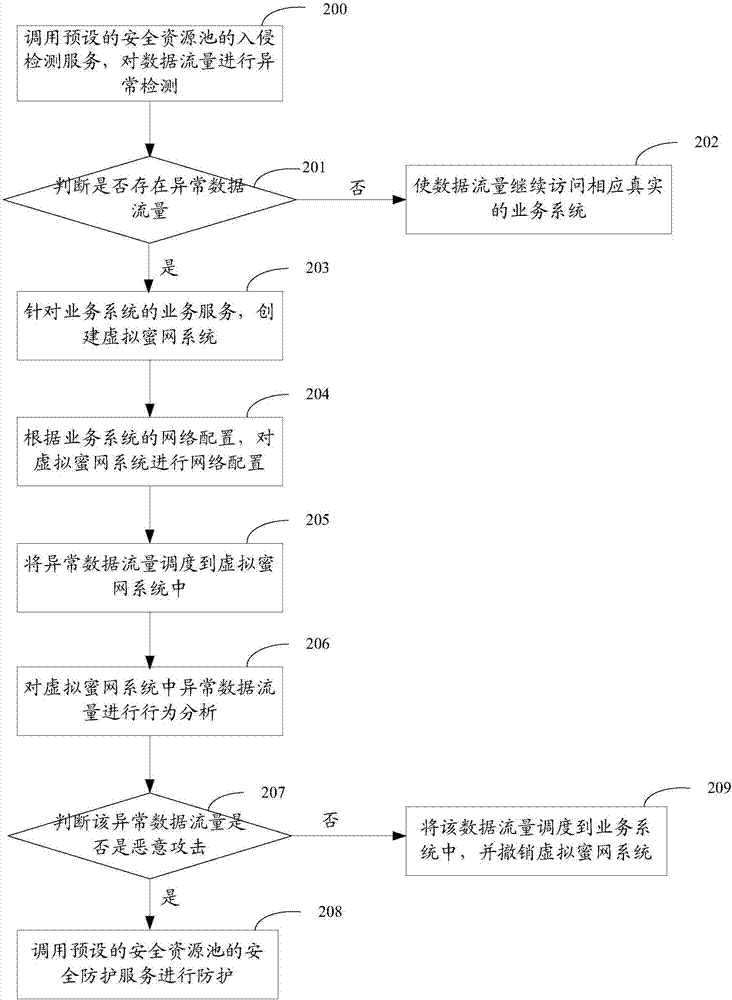
The invention relates to the field of network security, and especially relates to a Honeynet protection method and system. The method includes the following steps: detecting whether the data traffic entering a business system is abnormal; after detecting abnormal data traffic, creating a virtual Honeynet system according to a business system corresponding to a destination address accessed by the abnormal data traffic; and carrying out network configuration on the virtual Honeynet system according to the network configuration of the business system, and scheduling the abnormal data flow to the virtual Honeynet system. The virtual Honeynet system consistent with the business service of the business system is created, and network configuration is carried out on the virtual Honeynet system. The consistency between the virtual Honeynet system and the business system in business logic and network configuration is ensured, the virtual Honeynet system is more concealed, and attack seduction and forensic analysis are more concealed and less detectable to attackers. Moreover, the deployment is relatively simple, and the method and the system can be quickly deployed to an SDN (Software Defined Network) to achieve security protection without increasing the overhead of the business network.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
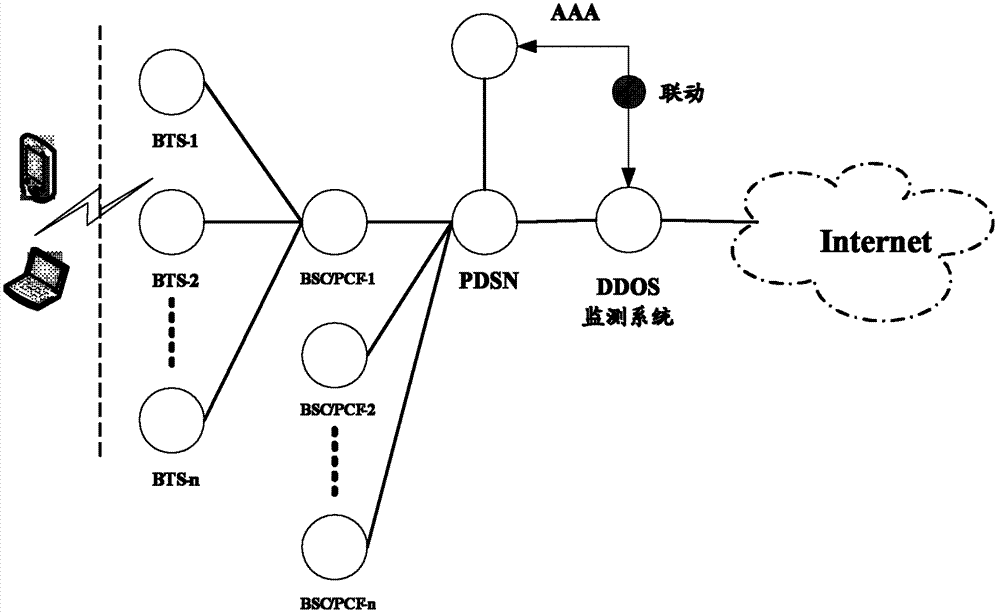
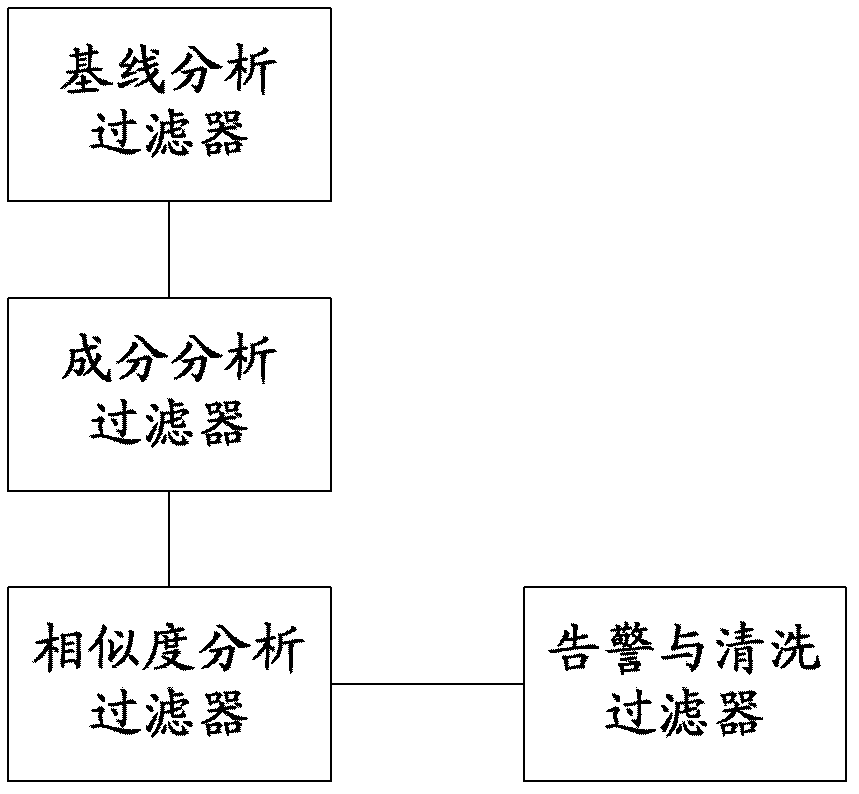
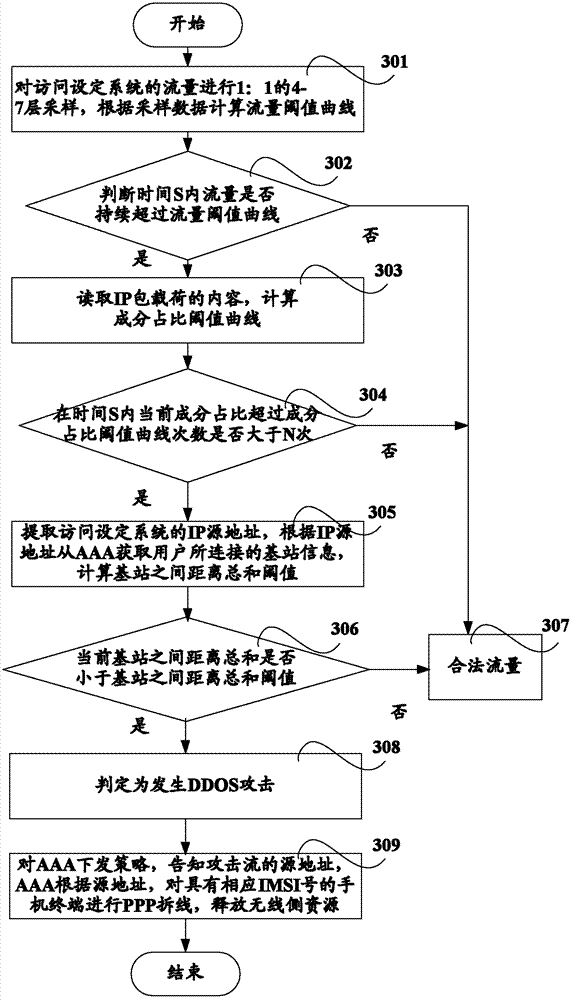
Method and system for monitoring DDOS (distributed denial of service) attacks in small flow
ActiveCN102821081AMake up for the inability to detect low-rate DDoS attacksHigh false positive rateData switching networksSimilarity analysisProtocol Application
The invention discloses a method and a system for monitoring DDOS (distributed denial of service) attacks in small flow, solves the problems that the existing DDOS attack detection technology is high in cost, complex to implement and high in misjudgment rate, cannot respond to DDOS attacks aiming at an application layer and the like, and provides the monitoring scheme of an integrated DPI (dots per inch) technology. A baseline analysis, component analysis and similarity analysis method is used to establish a normal use model, characteristics are accurately matched to detect the attacks in small flow and the application layer attacks, deployment at one point of an operator network and complete coverage of the operator network are achieved, and detection accuracy is increased.
Owner:CHINA TELECOM CORP LTD
Speed controlling method for running of combined train
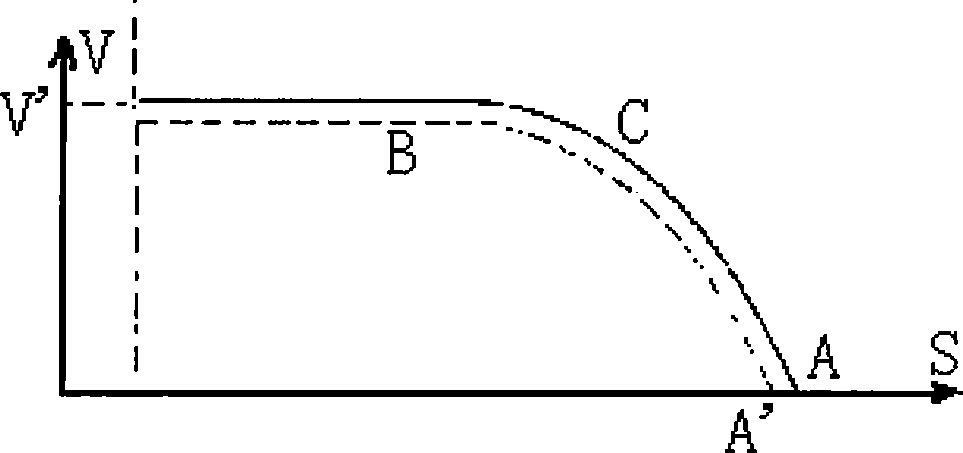
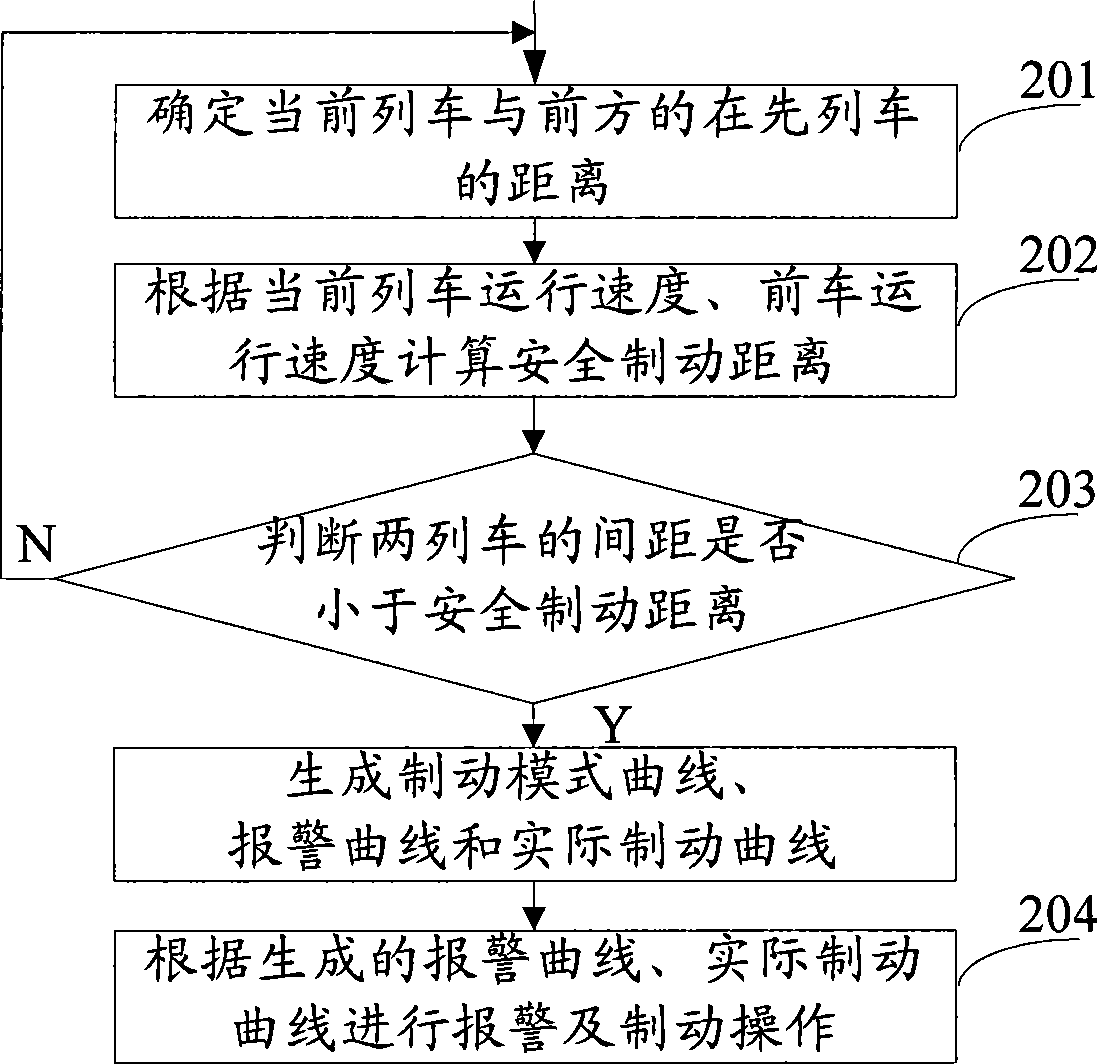
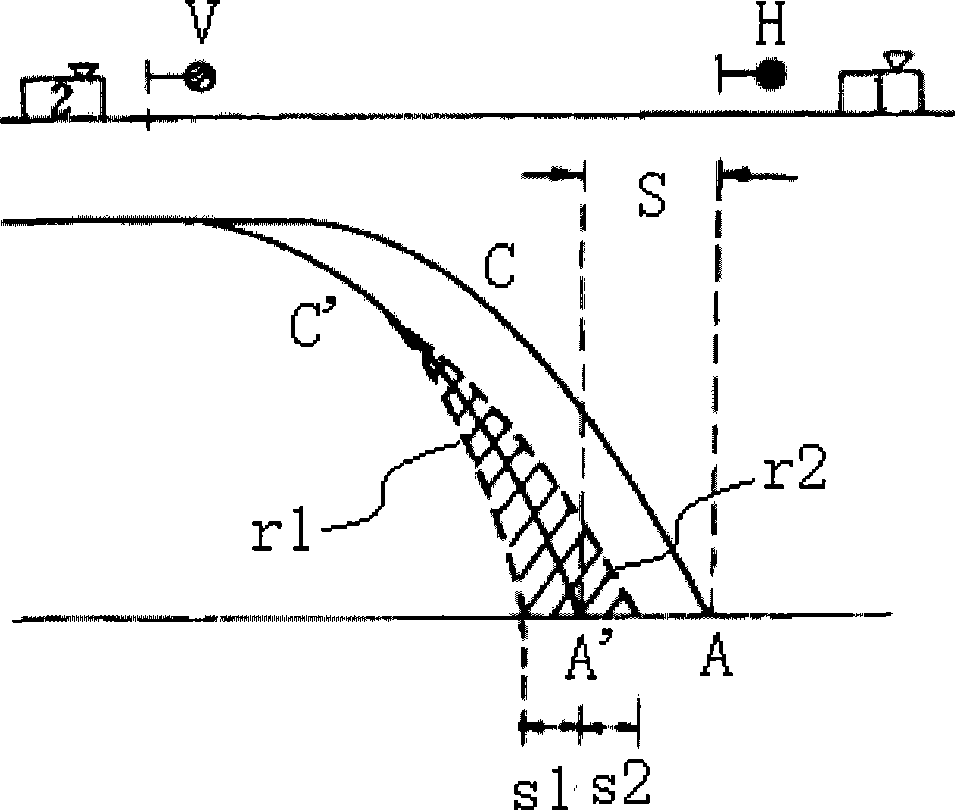
ActiveCN101480962ARealize security protectionImprove transportation efficiencyRailway signalling and safetyControl theoryBraking distance
The invention provides a running speed control method of a combined train. The method comprises following steps: A, the present distance between the train and an object is confirmed; B. the present safe braking distance between the train and the object is calculated; C, when the present distance between the train and the object is judged to be smaller than the safe stopping distance, a braking mode curve is generated to perform braking. By adopting the method, the speed of the combined train can be controlled in real time on a whole rail way, and the signaling security of the transportation of the train can be improved.
Owner:CRSC RESEARCH & DESIGN INSTITUTE GROUP CO LTD +1
Key configuration method, device and system
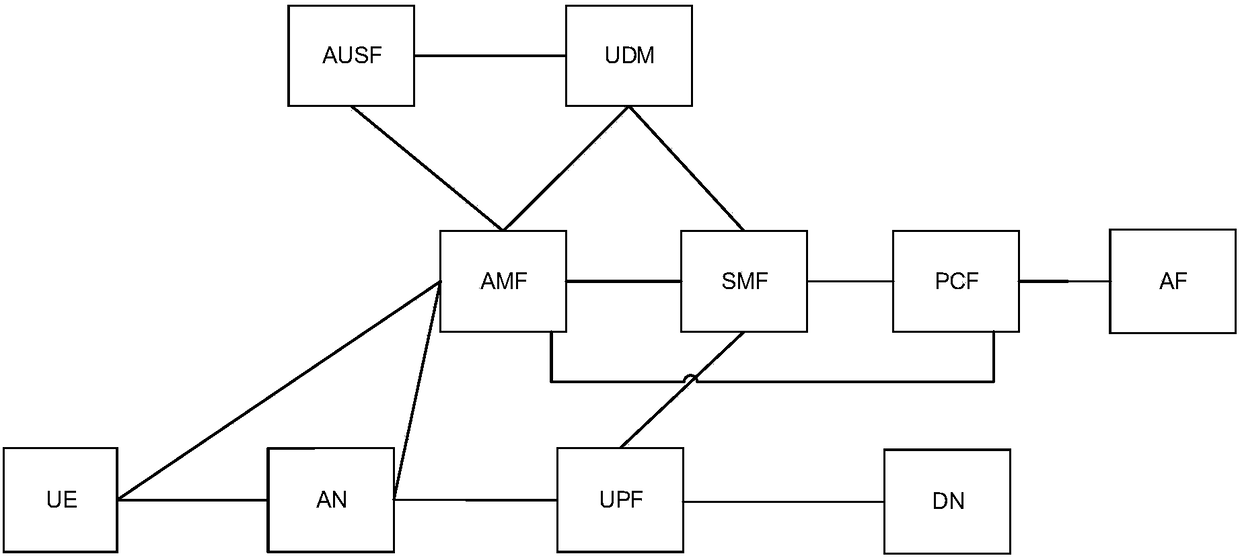
ActiveCN108810884ARealize security protectionImprove securityKey distribution for secure communicationMultiple keys/algorithms usageProtection mechanismData transmission
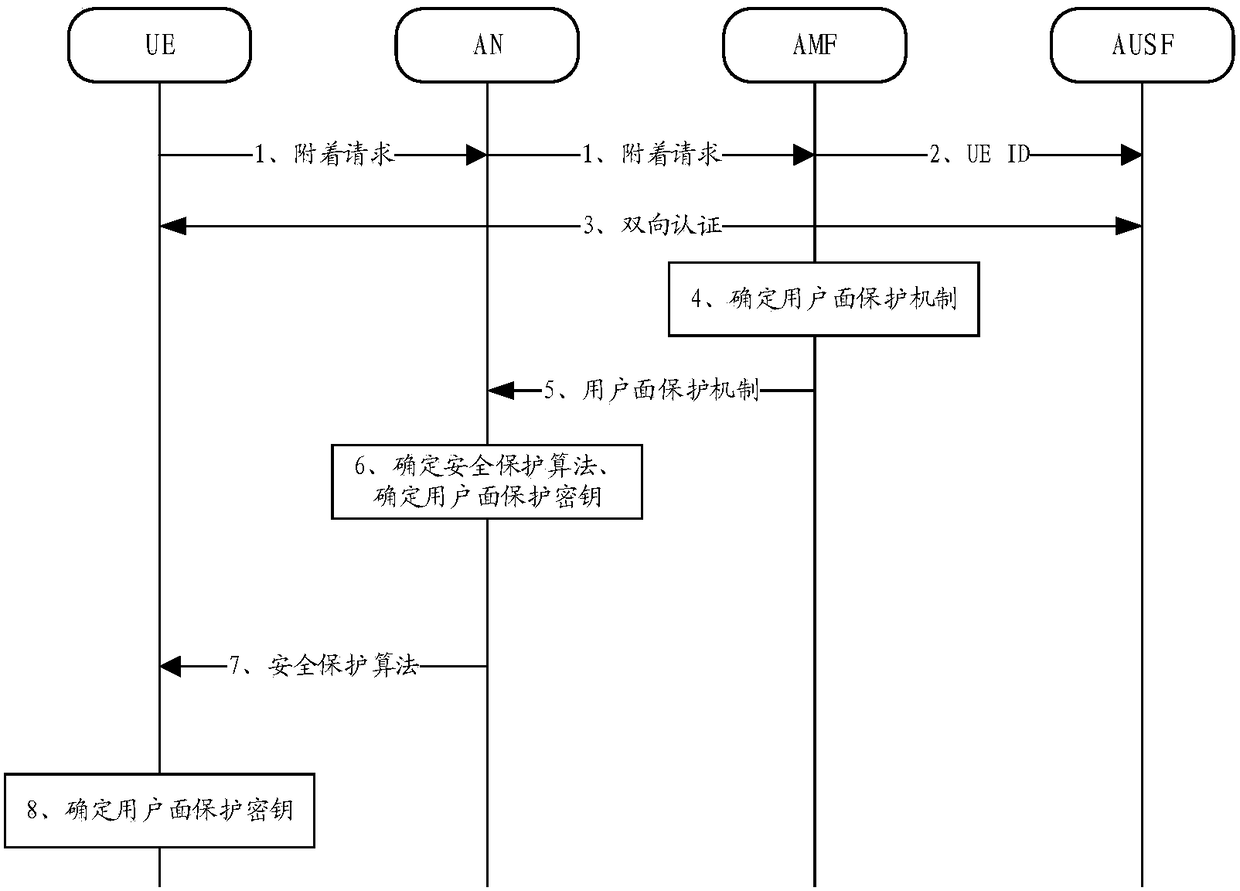
The embodiment of the invention provides a key configuration method, a device and a system, and the method comprises the following steps: a strategy function network element receives a request of communication between user equipment and network equipment; based on the request, and UE registration information, subscribed service data and service security demands, the strategy function network element determines a user plane protection mechanism; when the network equipment is CN equipment, the strategy function network element sends the user plane protection mechanism to an algorithm network element; the algorithm network element determines a security protection algorithm based on the user plane protection mechanism, generates a first user plane protection key based on the security protection algorithm, sends the first user plane protection key to the CN equipment and sends the security protection algorithm to the user equipment, and the user equipment generate a second user plane protection key based on the security protection algorithm. By implementation of the key configuration method, the device and the system provided by the embodiment of the invention, the user equipment and the network equipment can respectively complete configuration of the user plane protection key in the 5G communication, security of user plane data transmission is improved, and network security protection is realized.
Owner:HUAWEI TECH CO LTD
Integrated multifunctional parking braking system and control method thereof
InactiveCN104442900AAutomate implementationReduce volumeRailway hydrostatic brakesRailway hydrodynamic brakesFiltrationEngineering
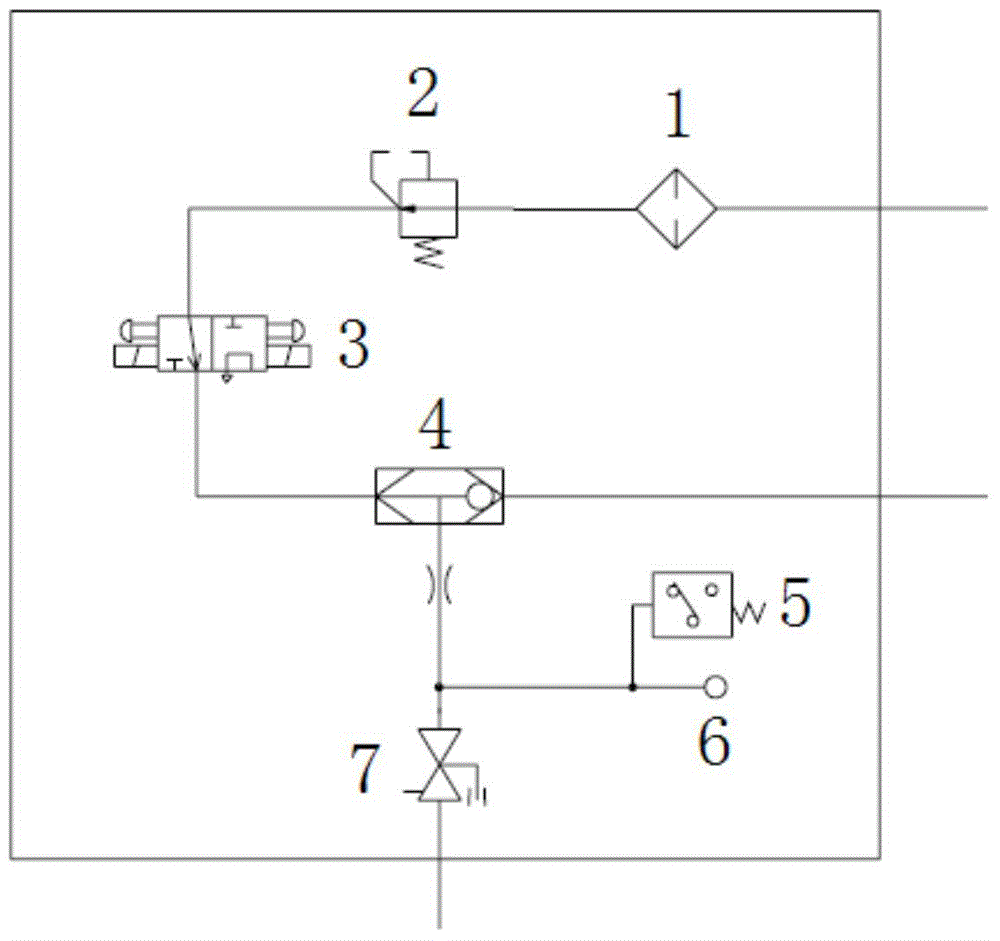
The invention discloses an integrated multifunctional parking braking system and a control method thereof. A first bi-directional valve, a dust filtration check valve, a pressure reducing valve, a parking braking electromagnetic valve, a second bi-directional valve, an electric interlocking cock and an outlet in the system are connected in sequence. The first bi-directional valve is connected with a first air source and a second air source. A parking braking air cylinder is arranged between the dust filtration check valve and the pressure reducing valve. The second bi-directional valve is connected with a comparison outlet. A first pressure switch and a second pressure switch are arranged between the electric interlocking cock and the outlet. The integrated multifunctional parking braking system and the control method thereof have the advantages that the original parking braking function is reserved, meanwhile, the function of the double air sources from a total air pipe and a train pipe (or other external air sources) is achieved, and it can be guaranteed that parking braking can be automatically implemented when total air does not exist; meanwhile, the functions of parking braking status display, mechanical display or digital display, manual release and the like can be achieved; an air board integration mode is adopted, the size is small, the integration degree is high, and rapid installation or maintenance is facilitated.
Owner:CRRC ZIYANG CO LTD
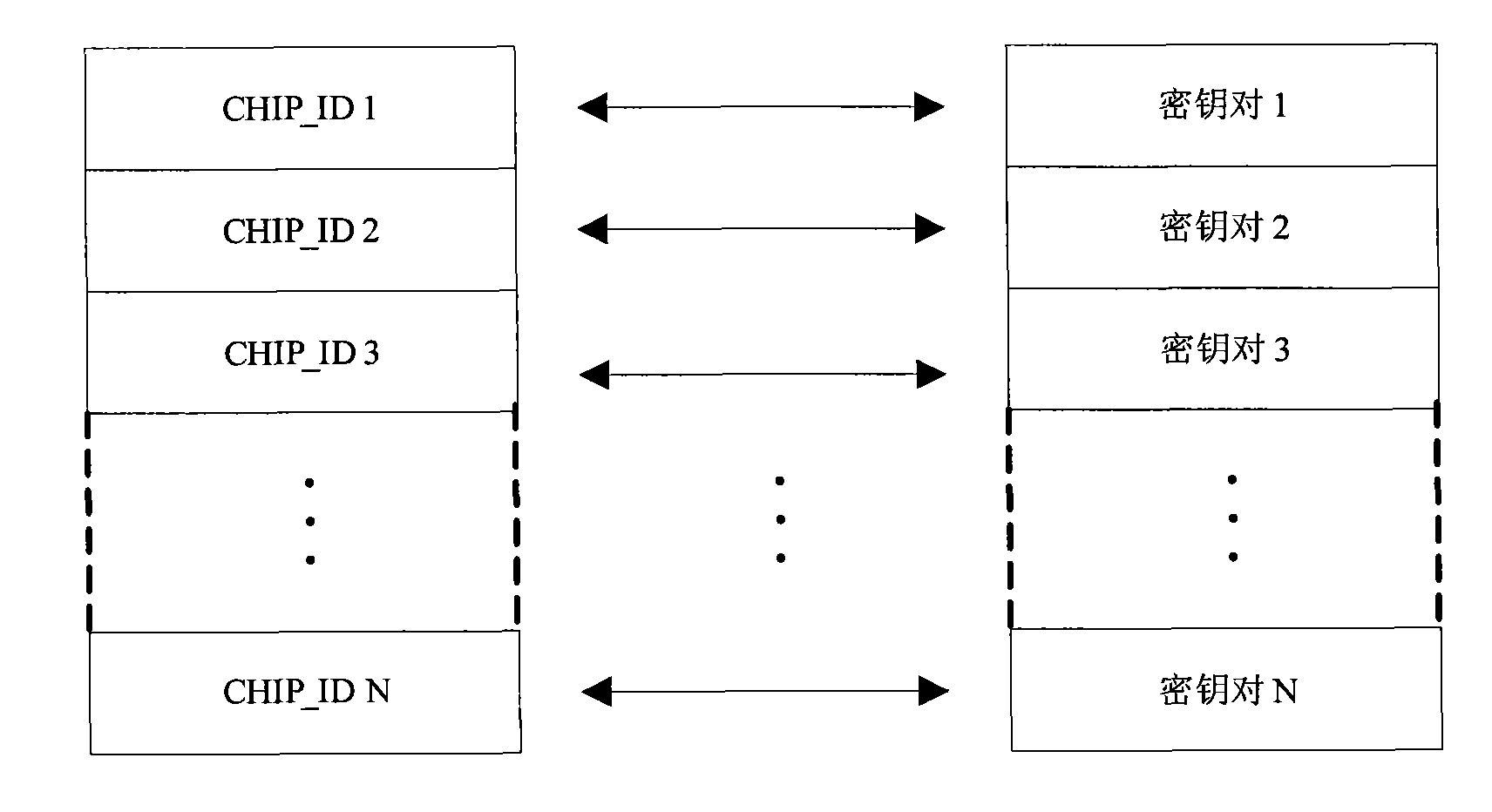
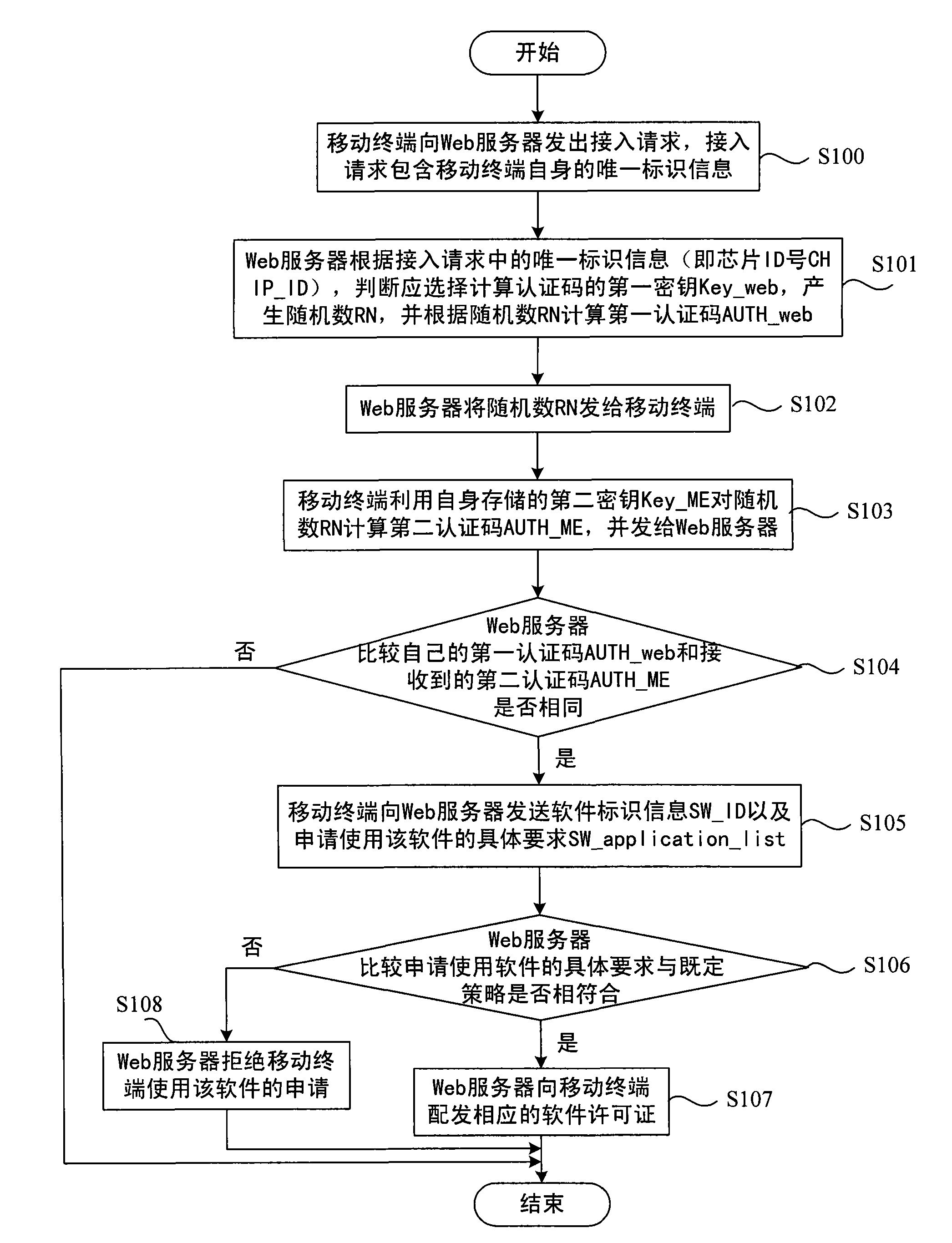
Web server-based method for downloading software license of mobile terminal
InactiveCN101541002AImplement software security protectionRealize security protectionTransmissionSecurity arrangementSoftware licenseWeb server
The invention relates to a Web server-based method for downloading a software license of a mobile terminal, which realizes the authentication and protection of software of the mobile terminal. The method comprises a technical proposal that: through comparison of an authentication code calculated by the mobile terminal and an authentication code calculated by the Web server in the Web server, whether the authentication can be obtained is determined. After the software of the mobile terminal passes the authentication, the corresponding software license is dispensed according to the specific requirement of the applied and used software. The method is applied to the field of mobile communication.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
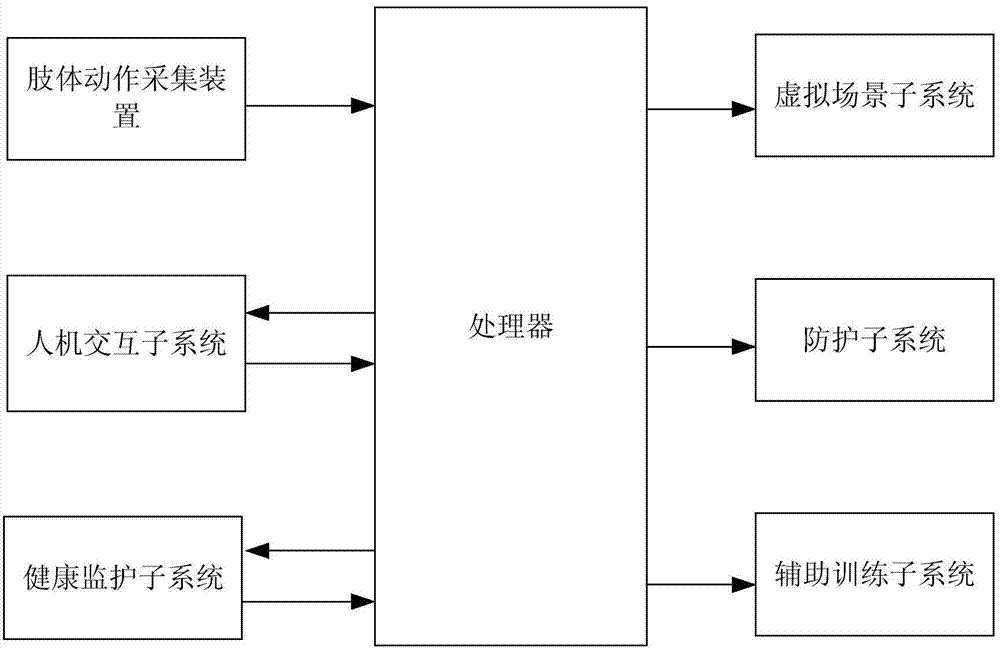
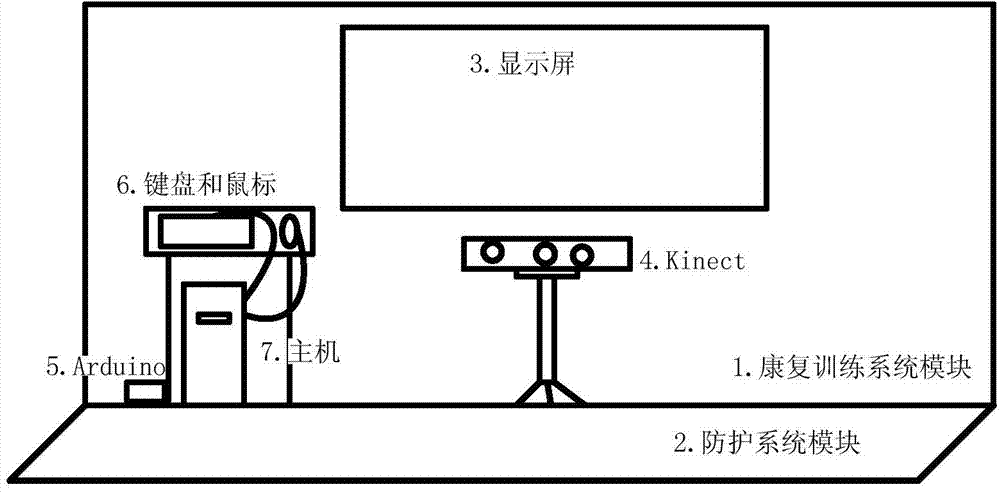
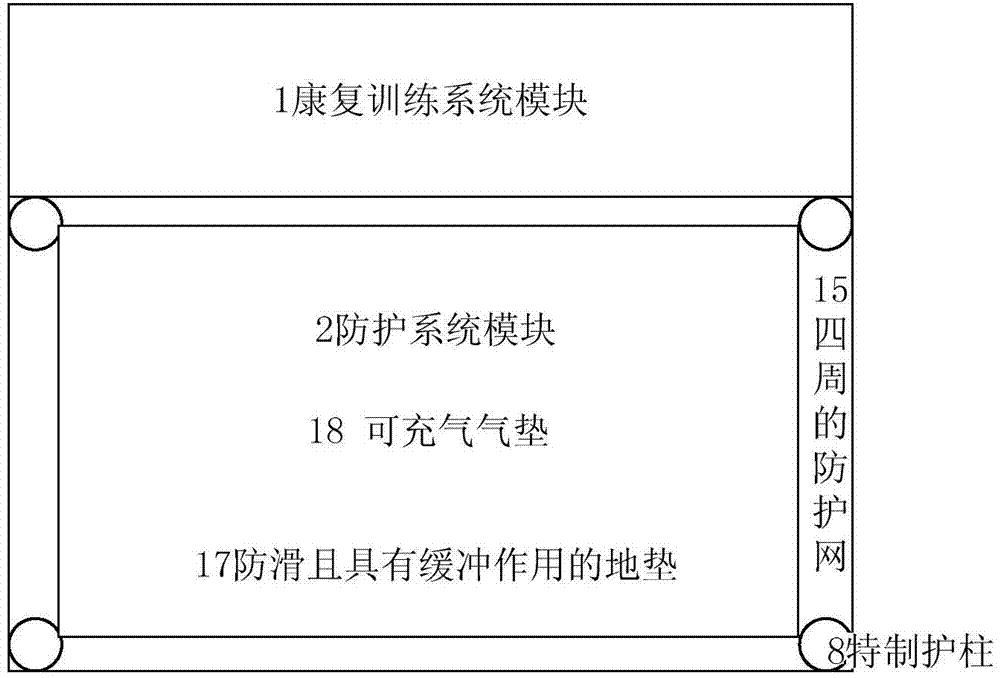
Elderly people rehabilitation and monitoring system based on interaction of virtual reality and body movement
InactiveCN104258539AAvoid tediumRealize security protectionInput/output for user-computer interactionGymnastic exercisingFalls in older adultsPhysical exercise
The invention discloses an elderly people rehabilitation and monitoring system based on interaction of virtual reality and body motions. The elderly people rehabilitation and monitoring system based on interaction of the virtual reality and the body motions comprises a virtual scene subsystem, a body motion collecting device, a human-computer interaction subsystem, a health supervision subsystem, a processor, a protection subsystem and a training aiding subsystem. According to the elderly people rehabilitation and monitoring system based on interaction of the virtual reality and the body motions, for the demand of elderly people for body motion training, the purposes of exercise and rehabilitation training of elderly people are achieved through action games by organically combining the virtual reality technology, the motion recognition technology, a rehabilitation training device and a training aiding device; in addition, warning and health monitoring are achieved when elderly people tumble or an accident happens to elderly people; during exercise and rehabilitation training of elderly people, the boringness of training is avoided, and safety protection of elderly people is achieved.
Owner:汇智金合(北京)科技有限公司
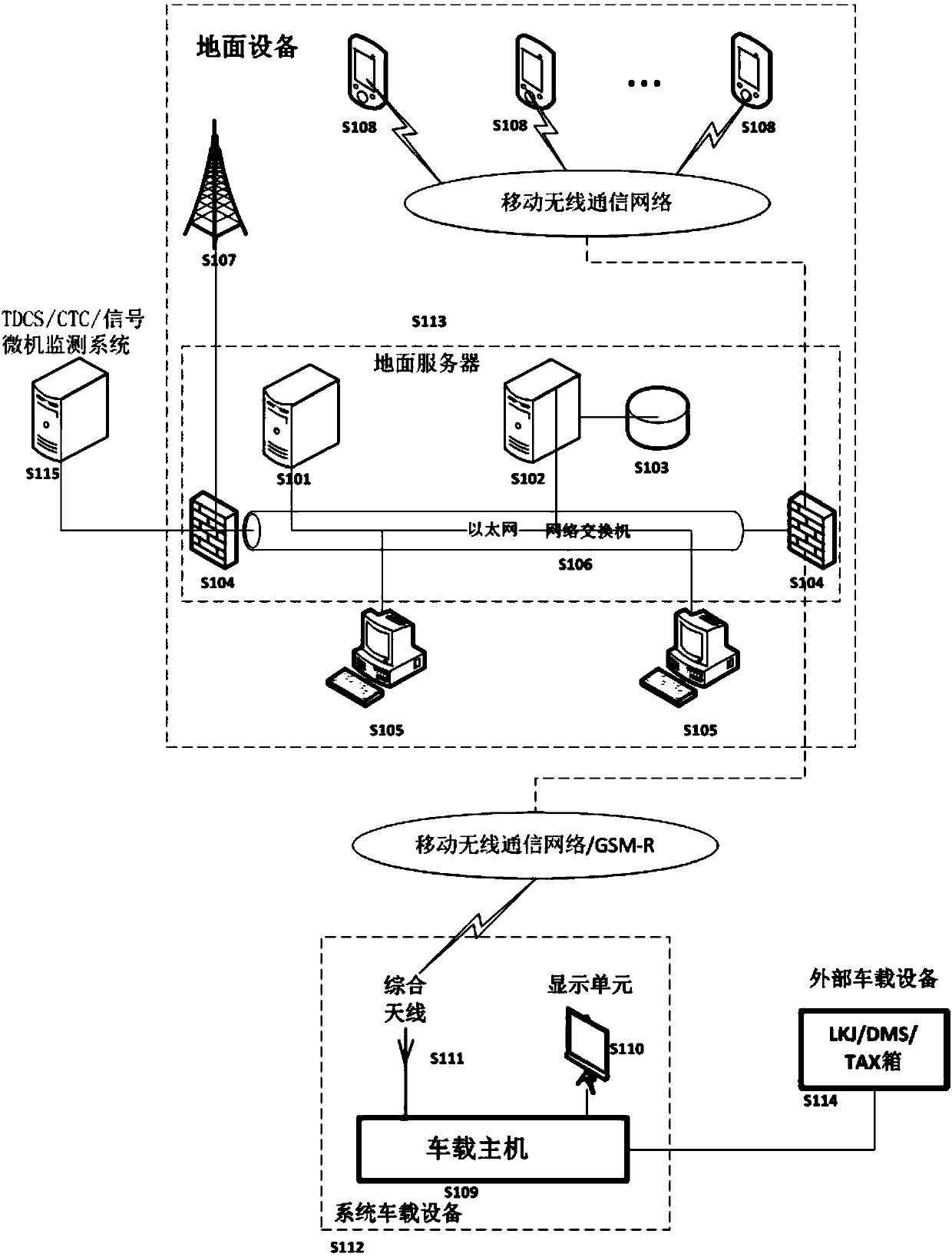
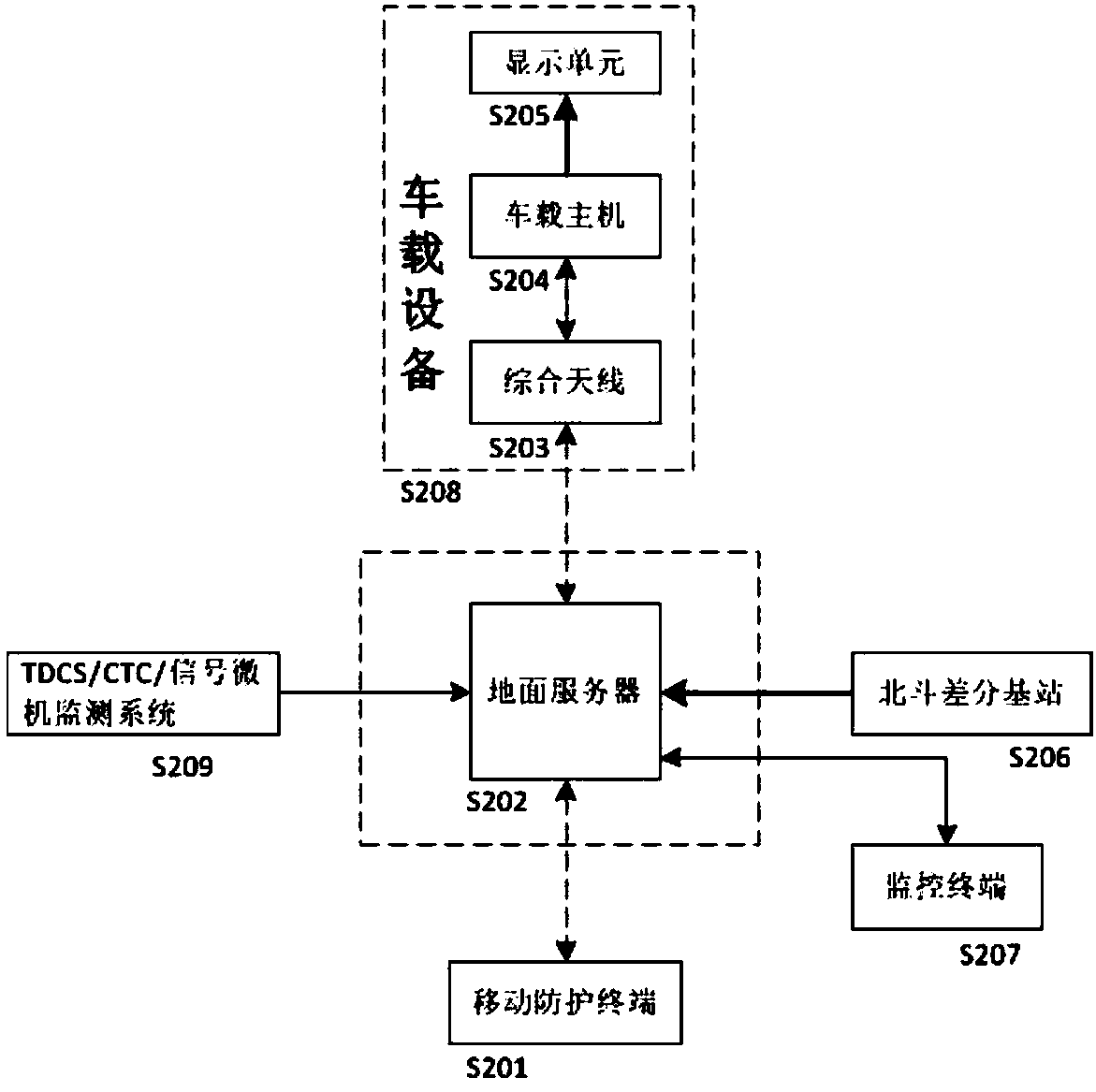
Vehicle-ground integrated operation safety protection system and method
PendingCN110435718ASolve the problem of personal safety protectionRealize security protectionRailway signalling and safetyIntegrated operationsYard
The invention relates to a vehicle-ground integrated operation safety protection system and method. In the process that on-site operators carry out operation on a railway, accurate position information of the operators is obtained through satellite differential positioning, train operation information is obtained through external vehicle-mounted equipment, signal state information of a station yard is obtained through an interface for connection with an external TDCS, comprehensive operation processing is carried out by combining the accurate position information of the operators, the train operation information and the signal state information of the station yard and basic data, then operation safety protection information is output and transmitted to the on-site operators and the systemvehicle-mounted equipment through mobile wireless communication network / GSM-R network, and the on-site operators stop operation and get off for avoidance in time when receiving early warning information or alarm information. The system has the following advantages that accurate positioning of the on-site operators, automatic identification and alarm of collision between an on-site operation area and an approach train route, vehicle-ground integrated linkage protection and remote operation assistance are realized, and personal safety protection under single-person or multi-person operation on site is effectively achieved.
Owner:HENAN LANXIN TECH
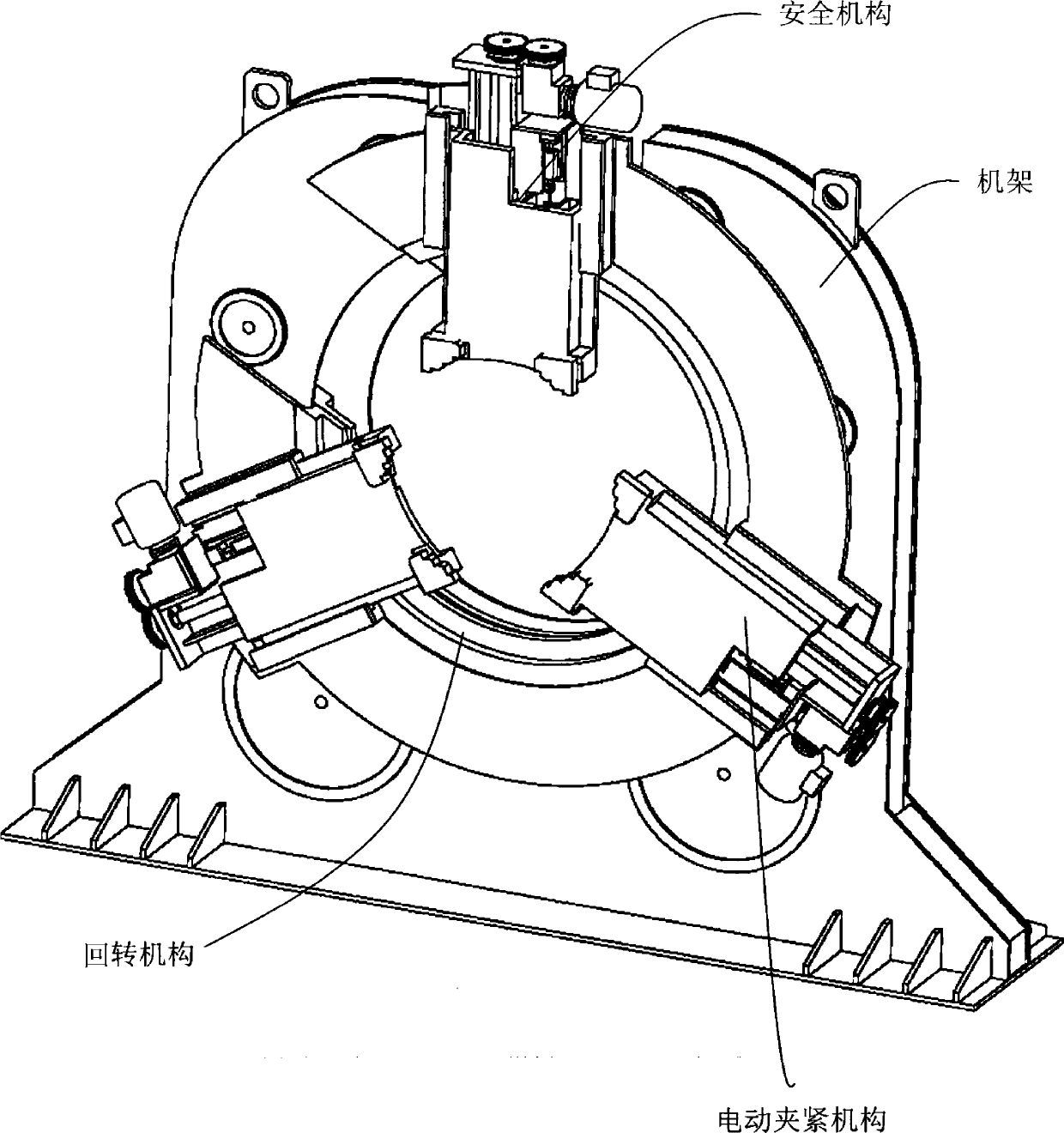
Alignment clamp with top opening and 360-degree rotation function
InactiveCN103801889AMeet structural requirementsSmooth transmissionWelding/cutting auxillary devicesAuxillary welding devicesRotation functionGravity center
The invention discloses an alignment clamp with a top opening and the 360-degree rotation function. The alignment clamp with the top opening and the 360-degree rotation function is a clamping and turnover device for welding a weld assembly which is of a long-box-shaped steel structure, can achieve rapid clamping and high-accuracy and 360-degree continuous rotation of the weld assembly of the long-box-shaped steel structure, and can stop at any position. When the center of gravity of the weld assembly of the long-box-shaped steel structure and the alignment clamp with the top opening and the 360-degree rotation function do not share the same axis, the center of gravity of the weld assembly of the long-box-shaped steel structure can coincide with the center of rotation by adjusting the positions of three sliding plates. The alignment clamp with the top opening and the 360-degree rotation function comprises a rack, a rotation mechanism, an electric clamping mechanism and a safety mechanism.
Owner:TANGSHAN KAIYUAN ROBOT SYST
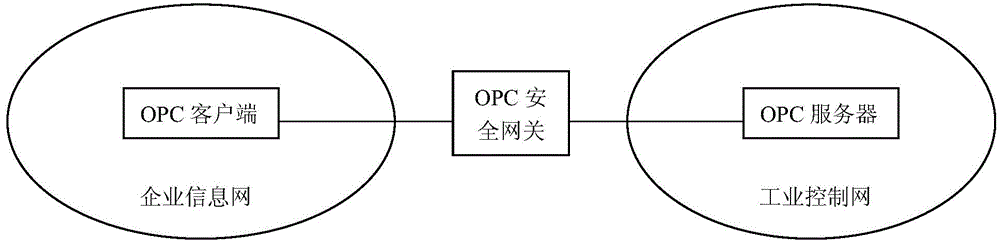
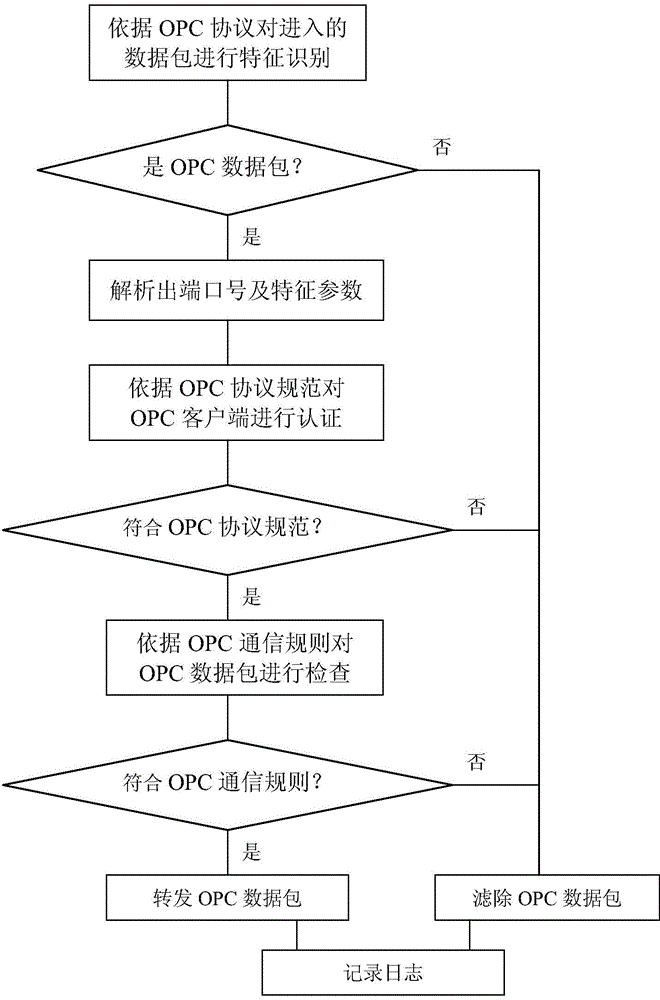
Method for filtering OPC security gateway data packets
InactiveCN104660593ARealize security protectionImprove the protective effectTransmissionNetwork linkNetwork packet
The invention discloses a method for filtering OPC security gateway data packets. The method is used for solving the technical problem of poor security protection of the existing industrial control system. The invention adopts the technical scheme as follows: the method for filtering the OPC security gateway data packets comprises the steps of arranging an OPC security gateway on a network link between an enterprise information network and an industrial control network, checking OPC data packets which pass through the OPC security gateway and carrying out security certification on an OPC client terminal, checking whether communication between the OPC client terminal and an OPC server accords with the security policy by using an OPC communication rule, processing the communication between a primary OPC client terminal and the OPC server according to a security checking rule when the OPC security gateway forwards the data packets and prohibiting the OPC data packets which violate the security rule from entering the industrial control system. According to the method for filtering the OPC security gateway data packets, the security of the industrial control system is protected by arranging the OPC security gateway; the vicious OPC communication operations and the data packets are filtered; the security protection capability of the industrial control system is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
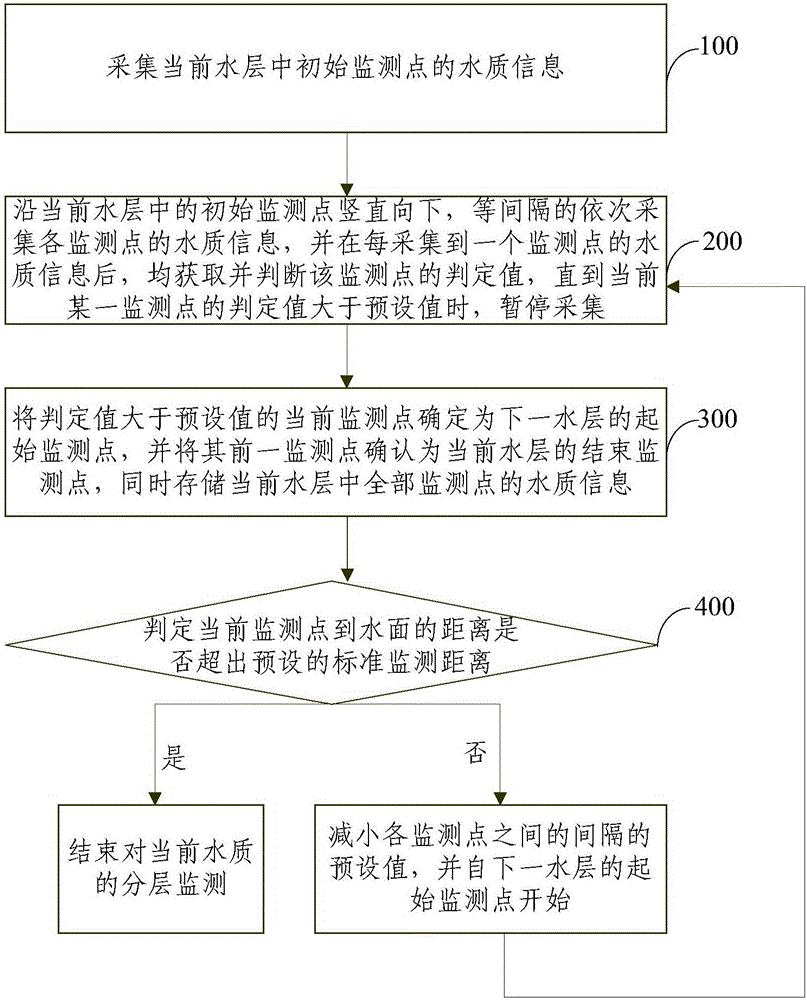
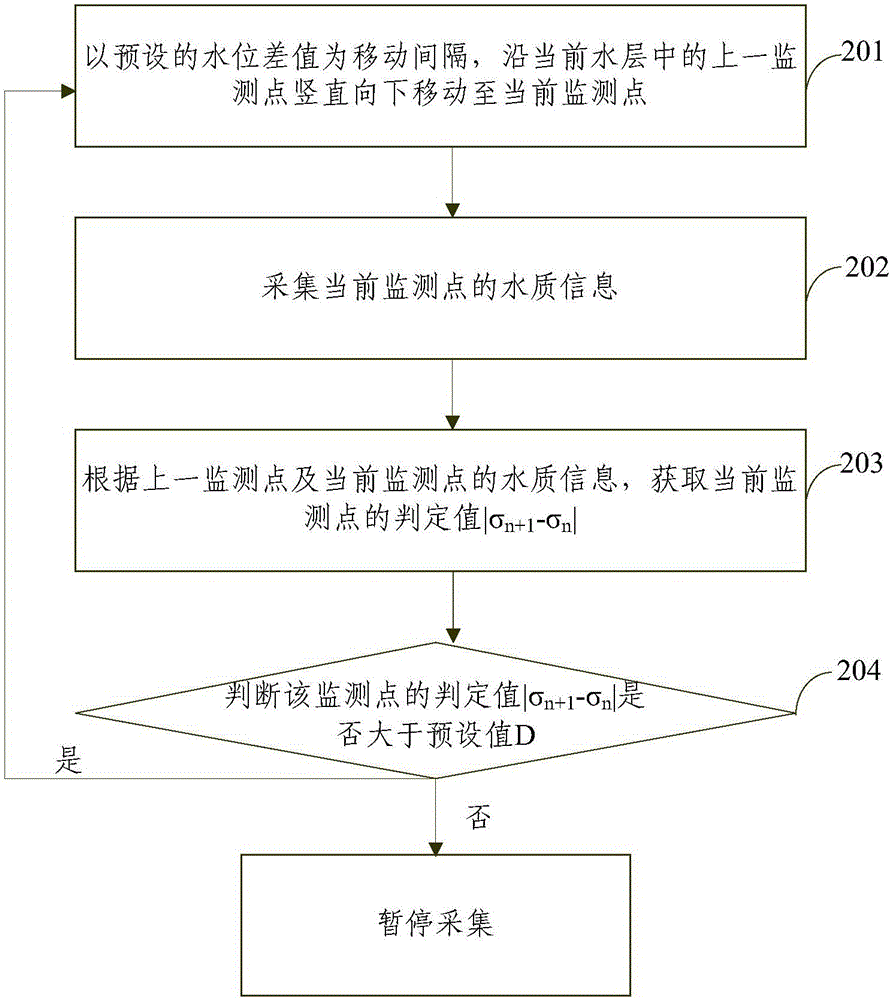
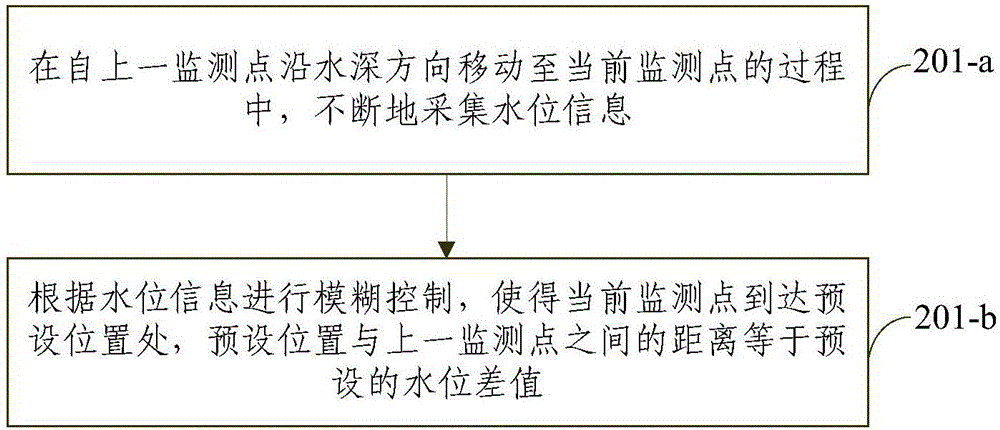
Three-dimensional layered water quality monitoring method and three-dimensional layered water quality monitoring system
ActiveCN106290770AMonitoring is automatic and accurateControl depthTesting waterAutomatic controlMean square
The invention provides a three-dimensional layered water quality monitoring method and a three-dimensional layered water quality monitoring system. The method comprises the following steps of collecting water quality information of each measurement point, calculating mean square deviation of water quality parameters of each measurement point in real time, and collecting positions underwater according to the mean square deviation value; automatically controlling the underwater collection speed according to the water-level fluctuation speed; and collecting water quality information at different underwater depths according to the mean square deviation of water quality information, measurement points with water-level fluctuation selective adaptability and underwater speed, and establishing water body information in a layered manner. The system comprises a lifting execution device, an underwater collection device arranged on the lifting execution device, and an overwater control device respectively connected with the lifting execution device and the underwater collection device. The method and the system are capable of automatically and accurately monitoring ocean water quality or surface water quality, intelligently controlling the collection depth, speed and interval, accurately, effectively and automatically dividing each water layer along the direction, and providing accurate and reliable data guarantee for water quality research.
Owner:CHINA AGRI UNIV
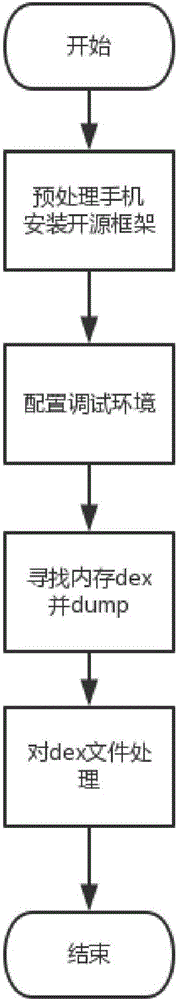
Dynamic shelling method for Android application
InactiveCN105930692ARealize security protectionNormal program functionProgram/content distribution protectionReverse analysisApplication software
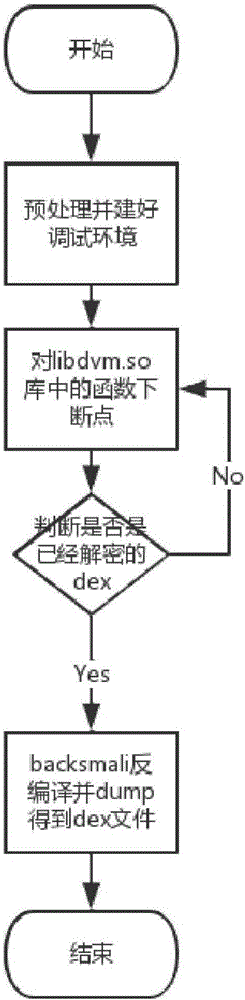
The invention discloses a dynamic shelling method for an Android application. A reinforced Android application is taken as a target program, and a dex file of the target program is obtained by utilizing an Xposed framework, so that the target program can be subjected to shelling. The dynamic shelling method comprises an Android mobile phone preprocessing process, a target program debugging process, a target program shelling process and a process of extracting the dex file in the target program and repairing the program. A library Libdvm.so in an Android system contains a function with a function parameter being the dex file, such as an openDexFile function, dex subjected to shelling serves as a parameter and is transmitted to the openDexFile function, and the dex subjected to the shelling is obtained by making a breakpoint at the openDexFile function. By utilizing the technical scheme provided by the method, a malicious Android program can be effectively subjected to reverse analysis to obtain a source code of the program so as to realize security protection of the system.
Owner:北京鼎源科技有限公司
Electric vehicle power battery safety monitoring device and method
PendingCN108357361ARealize security protectionRealize danger alarmElectric devicesElectric vehicle charging technologyFuzzy logic inferenceControl signal
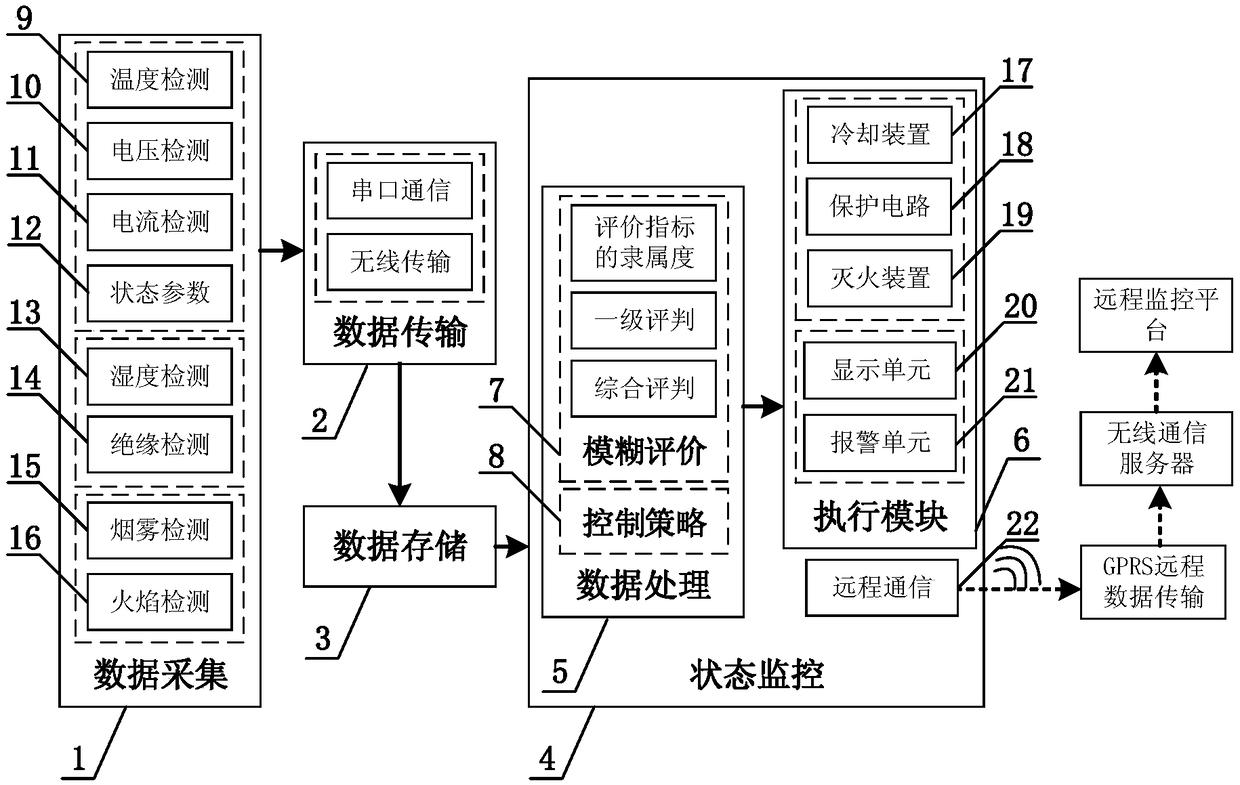
The invention discloses an electric vehicle power battery safety monitoring device and method. The monitoring device comprises a data acquisition system, a data transmission system, a data saving system and a state monitoring system. The state monitoring system comprises a data processing subsystem, an execution module and a remote communication unit. The data acquisition system sends the collected battery state data to the data saving system for caching through the data transmission system, and injects into the data processing subsystem to detect the internal resistance of a battery cell through an online parameter identification module. A evaluation index system combines the multi-factor and multi-level fuzzy logic reasoning to comprehensively evaluate the battery safety status; according to the evaluation result in combination with a corresponding control strategy, a control signal is injected into the execution module to achieve the battery safety monitoring and control. The devicehas the advantages of being systematic and intelligent, and the monitoring and troubleshooting of faulty vehicles are achieved through a remote communication technology in combination with a monitoring platform.
Owner:UNIV OF SCI & TECH OF CHINA
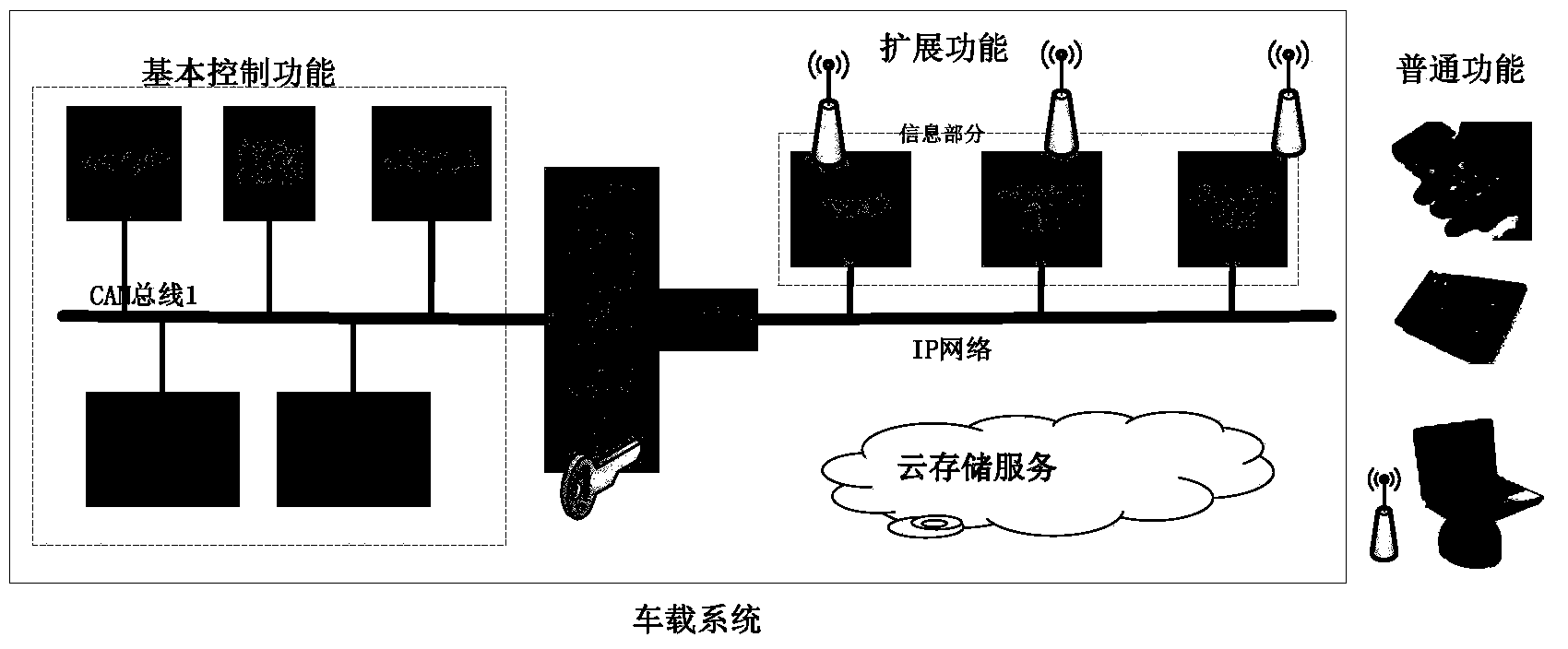
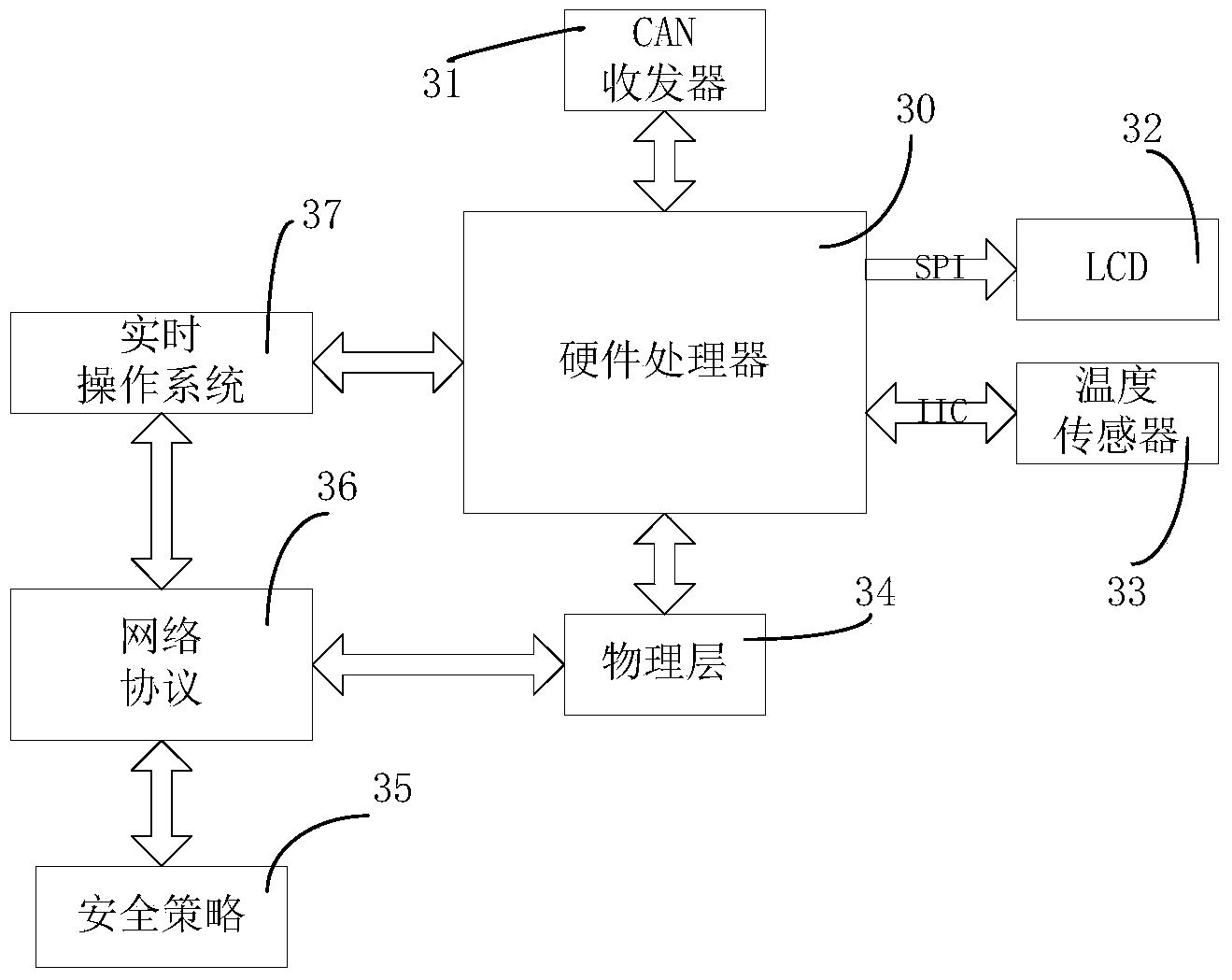
Method for achieving communication safety of vehicle-mounted electronic information system
InactiveCN103929428AEnsure safetyRealize security protectionTransmissionCommunications securityExternal data
The invention discloses a method for achieving communication safety of a vehicle-mounted electronic information system. The method includes the steps that when vehicle-mounted information is output, a corresponding authentication and / or encryption algorithm is searched for in a security strategy library, and a data package is output after being authenticated and / or encrypted and packaged; when external data packages are input into the vehicle-mounted information system, the authentication and / or encryption algorithm used by the data package is searched for in a rule library according to a parameter index, and de-encapsulation is carried out on the data package by means of a found result to obtain a verification value or plaintext data package; the plaintext data package is searched for again in the security strategy library, if a specific security rule in the security strategy library corresponds to that obtained according to the parameter index of the data package, it means that the data package has no fake or deceptive behaviors and the data package passes verification, and the data package after de-encapsulation is input to an upper layer protocol and continues to be decrypted. By means of the method, safe, reliable and confidential communication of the vehicle-mounted information system can be guaranteed.
Owner:吴刚 +3
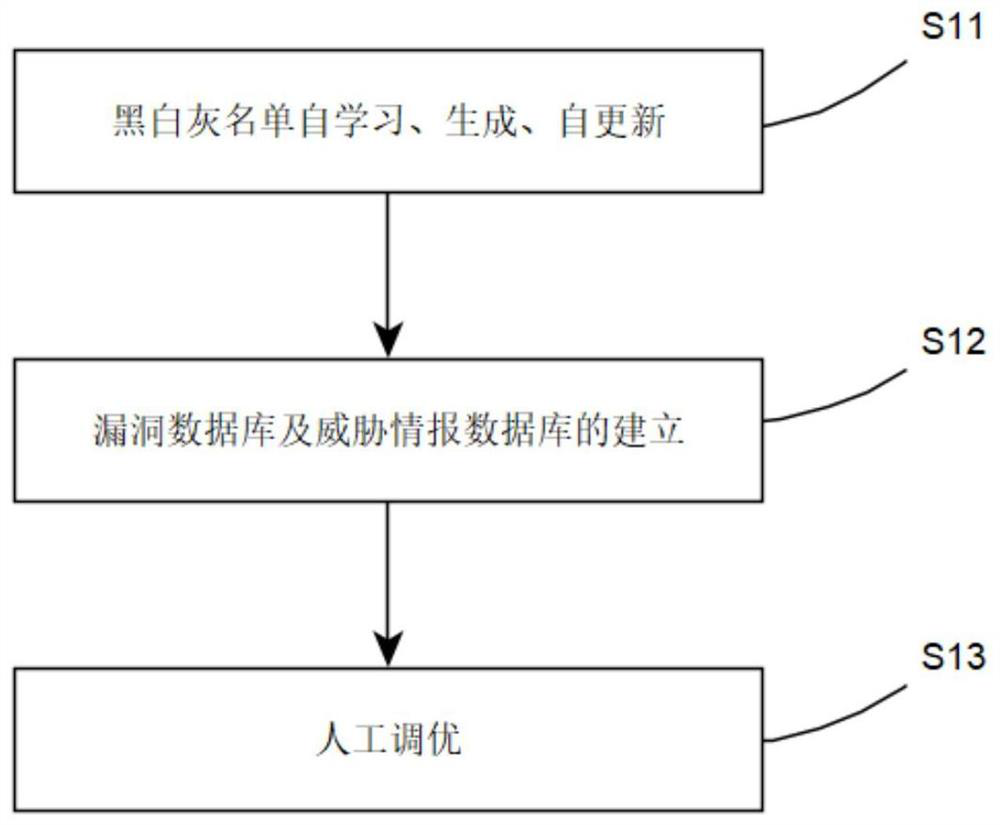
Industrial control system safety protection method and device
ActiveCN112637220ARealize security protectionImprove security levelTransmissionRisk identificationSecurity level
The invention discloses an industrial control system safety protection method and device, and the method comprises the steps: monitoring and obtaining the network information of an industrial control system in real time, and recognizing a safety risk according to an industrial control safety baseline, wherein the industrial control security baseline is established on the basis of a terminal layer security baseline and a network layer security baseline in combination with a vulnerability database and a threat intelligence database. According to the method, the industrial control security baseline is established, and security risk identification, prediction, disposal, transfer and the like are carried out on the industrial control system according to the industrial control security baseline, so that security protection of the industrial control system is realized, and the security level of the industrial control system is greatly improved.
Owner:中能融合智慧科技有限公司
North-south flow safety protection system in cloud computing network
InactiveCN105245504ARealize security protectionTransmissionSoftware simulation/interpretation/emulationTraffic capacityVirtual firewall
The invention discloses a north-south flow safety protection system in a cloud computing network. The system comprises a virtual machine occupied by a tenant, a virtual firewall for monitoring communication between the virtual machine currently occupied by the tenant and a Network, a first network forwarding layer and a second network forwarding layer, wherein the first network forwarding layer is used for judging a source of a message through recognizing a label of the received message, if the message is from the virtual machine, the message is forwarded to the virtual firewall corresponding to the tenant of the current virtual machine, and the message processed by the virtual firewall is sent to the Network via a second-layer switch and a third-layer switch; and the second network forwarding layer is used for receiving the message from the Network, judging the tenant to which the message belongs through recognizing the label of the message, issuing the message to the virtual machine corresponding to the tenant designated by the label of the message, and forwarding the message sent by the virtual machine to the second-layer switch.
Owner:北京汉柏科技有限公司
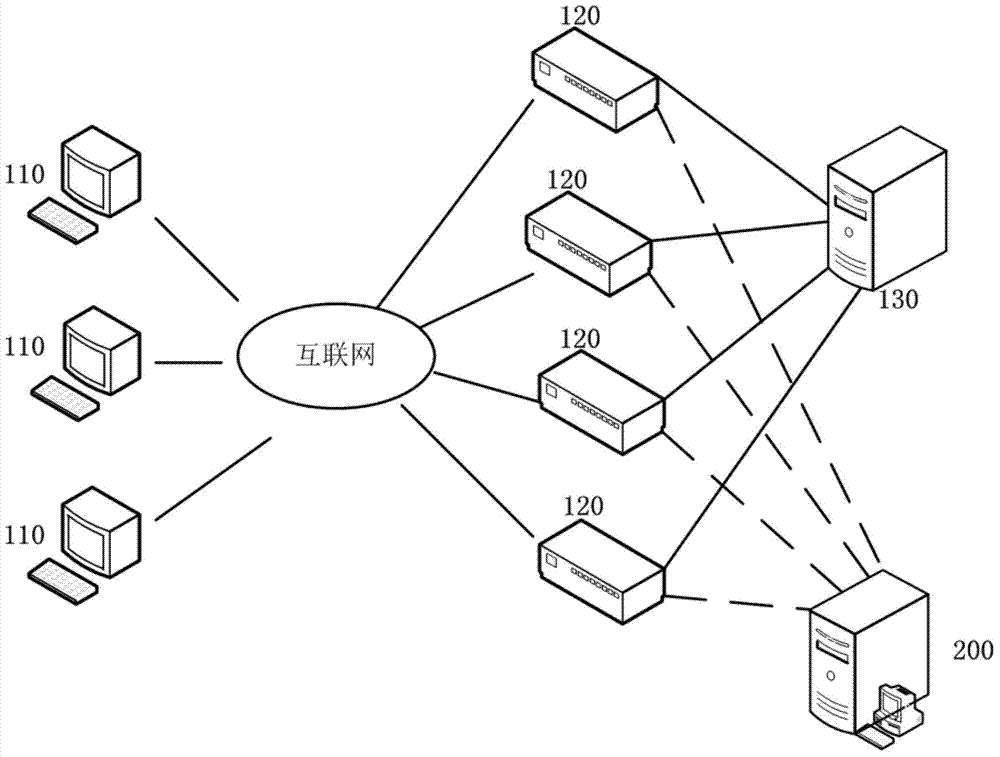
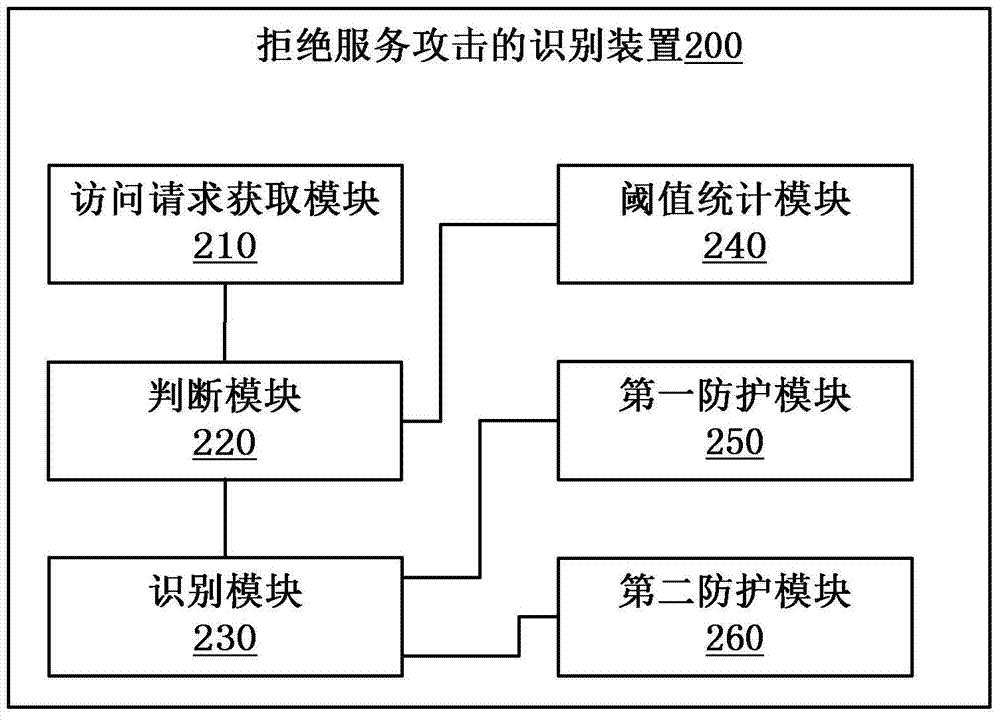
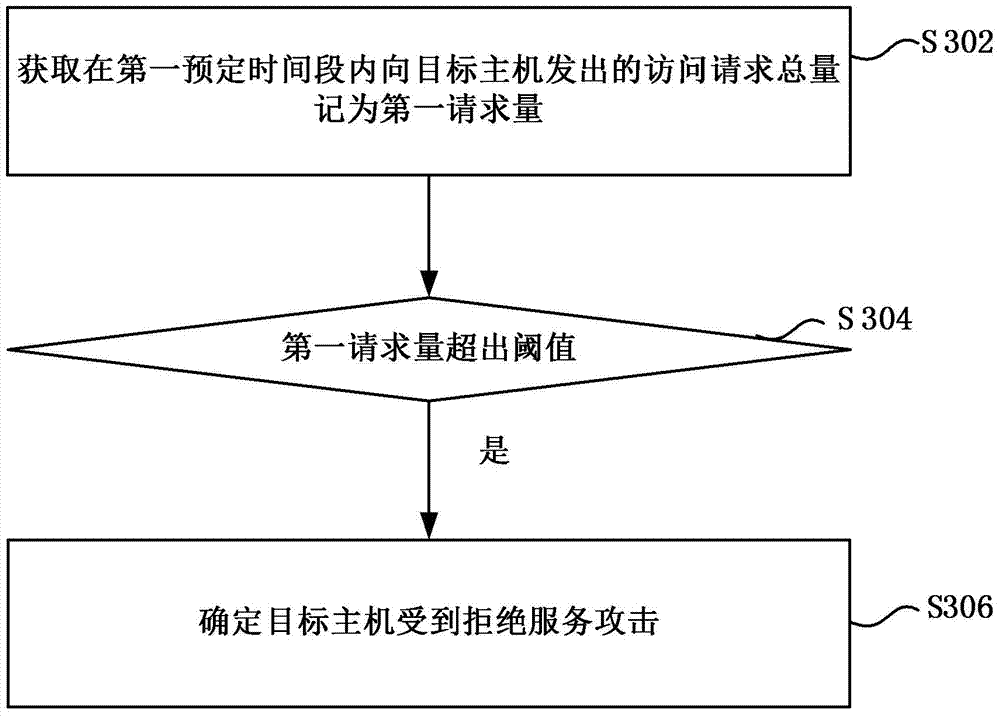
Identification method and device for denial of service attack
The invention provides an identification method and device for the denial of service attack. The identification method for the denial of service attack comprises the following steps of obtaining the total amount of access requests sent to a target host within a first preset time period, and recording as a first request amount; judging whether the first request mount exceeds a threshold value which is obtained by calculating the page view of the target host; and if so, determining that the target host is subjected to the denial of service attack. According to the technical scheme disclosed by the invention, the total amount of the access requests sent to the target host within the preset time is used as a judgment target, the threshold value is obtained by the page view statistics of the target host to serve as a criteria to judge whether denial of service attack is received, the denial of service attack phenomenon is concluded to identify the denial of service attack so as to bring convenience to take corresponding measures, the identification accuracy of the denial of service attack is greatly improved, and the safety protection of the host is realized.
Owner:BEIJING QIANXIN TECH
Data security protection method, network access equipment and terminal
InactiveCN108307389ARealize security protectionImprove securityConnection managementSecurity arrangementAir interfaceComputer terminal
The invention discloses a data security protection method, network access equipment and a terminal. The method comprises the following steps that the network access equipment receives an RRC connection request message sent by the terminal, wherein the RRC connection request message comprises a security capability algorithm supported by the terminal; the network access equipment determines a targetsecurity capability algorithm according to a security capability algorithm supported by the network access equipment and the security capability algorithm supported by the terminal; the network access equipment sends an RRC connection establishment message to the terminal, wherein the RRC connection establishment message comprises the target security capability algorithm; the network access equipment a downlink non-access layer direct transfer message sent by core network equipment, wherein the downlink non-access layer direct transfer message comprises a security key of the terminal; and data security protection is carried out on an AS layer message which is mutually received and sent between the network access equipment and the terminal by using the security key and the target securitycapability algorithm. By the adoption of the method, the network access equipment and the terminal, the transmission security of user data in an air interface can be improved.
Owner:ZTE CORP
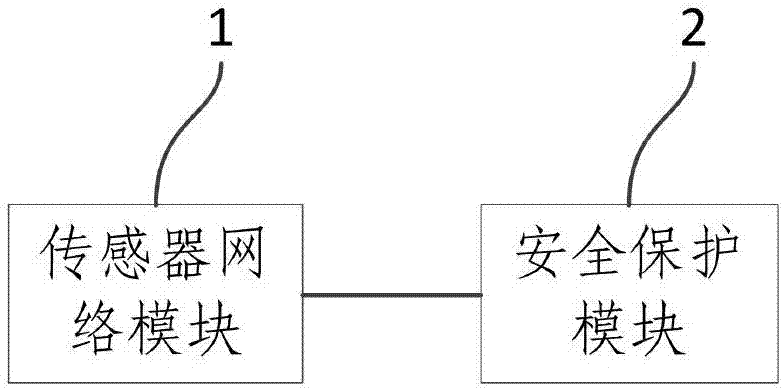
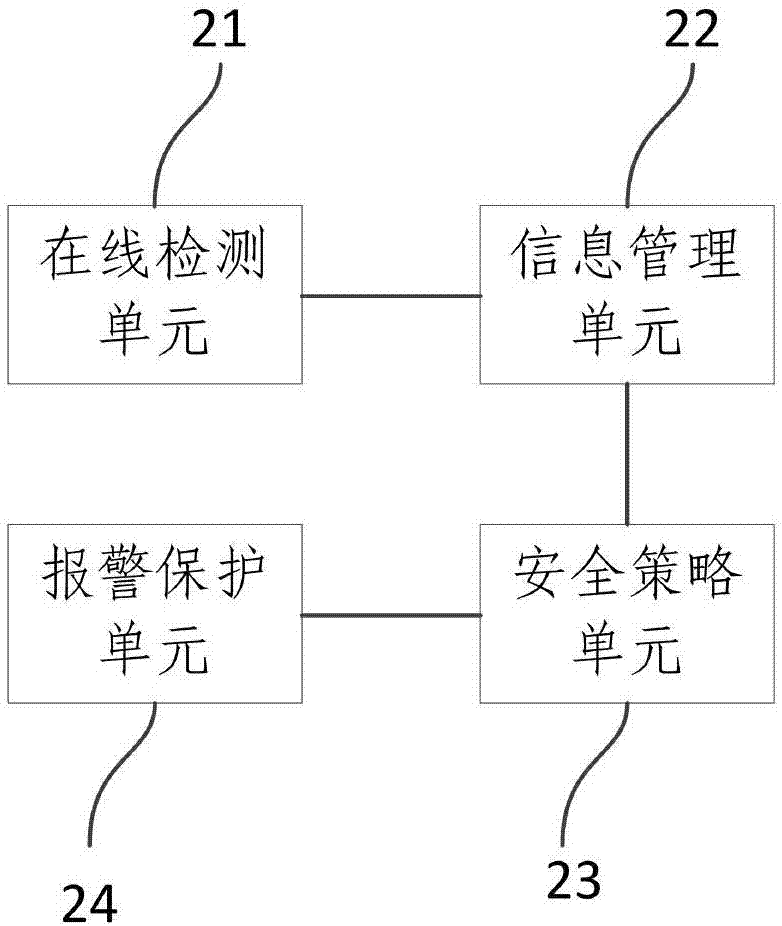
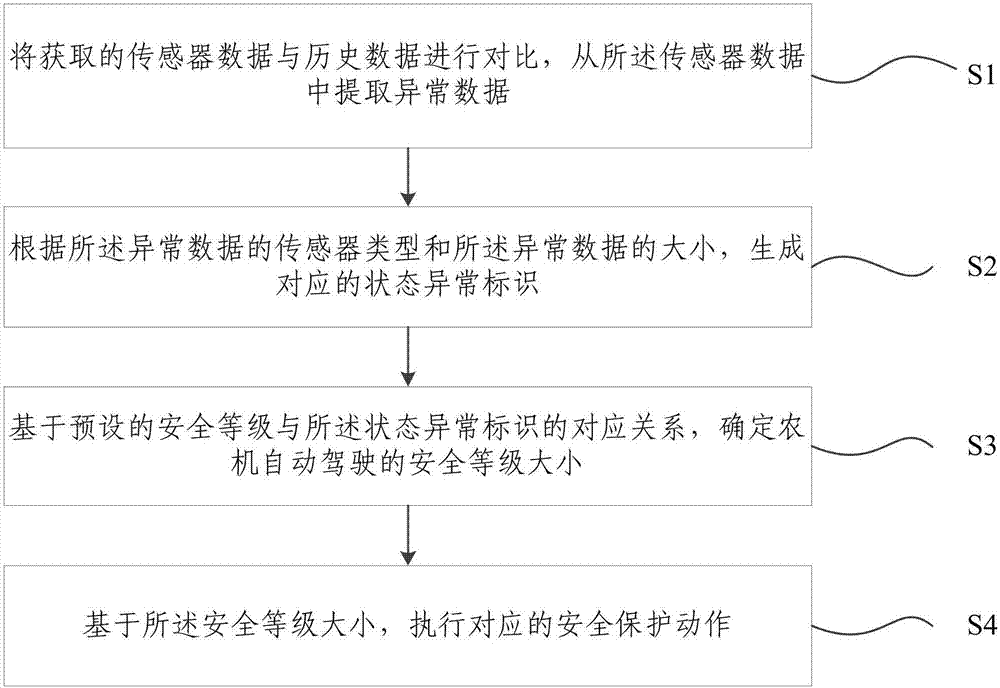
Safety protection system and method for automatic driving of agricultural machinery
InactiveCN107479562ARealize security protectionPosition/course control in two dimensionsVehiclesAgricultural engineeringFarm machine
The invention provides a safety protection system and method for automatic driving of agricultural machinery. The system comprises a sensor network module and a security protection module, wherein the sensor network module is a collection of various types of sensors. According to the safety protection system and method for automatic driving of agricultural machinery, through real-time detection of the sensor data in the automatic driving process of the agricultural machinery, the safety state of the automatic driving of the agricultural machinery is judged, and the security protection of the automatic driving process of the agricultural machinery is achieved through carrying out the corresponding safety protection operation according to the safety state.
Owner:北京耘华科技有限公司
Sounding rocket launching device
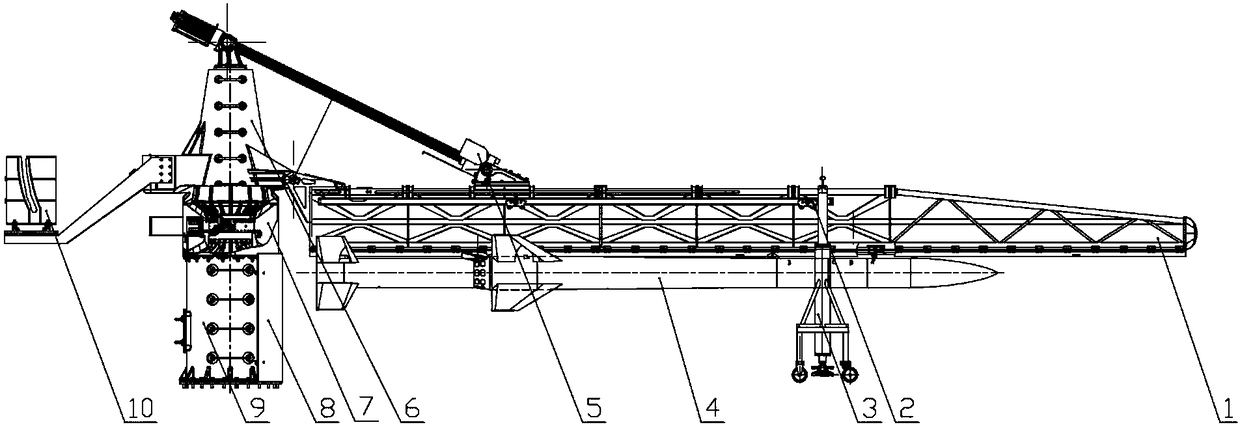
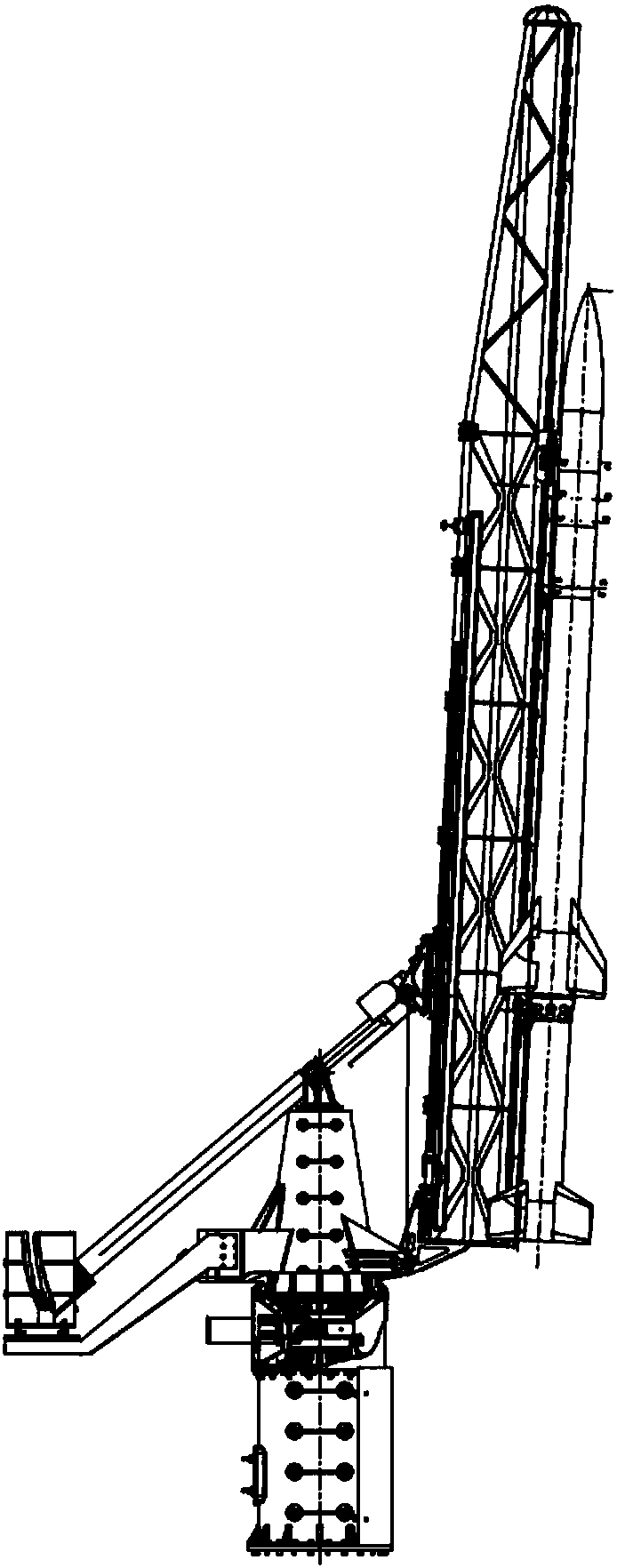
InactiveCN108562189AAvoid shocks under loadShorten working timeRocket launchersSounding rocketTrunnion
The invention provides a sounding rocket launching device. The launching device adopts downward hanging type loading, a spiral elevator is used for lifting, and the advantages of full-automatic lifting and rotating functions, simple operation, high reliability and the like are achieved. The sounding rocket launching device comprises a base, a rotary device, the spiral elevator, a lifting arm, an auxiliary supporting device and a transverse supporting device. The rotary device is installed on the base, and the rotary device can rotate relative to the ground, so that the launching device has thefunction of automatically adjusting the azimuth angle; and a trunnion supporting seat is fixed to the rotary device, the lifting arm is in pin joint with the trunnion supporting seat, and a rocket ishorizontally loaded under the lifting arm in a mechanical downward hanging mode, so that the lifting and vertical launching of the rocket can be realized through the spiral elevator.
Owner:XIAN AEROSPACE PROPULSION TECH INST
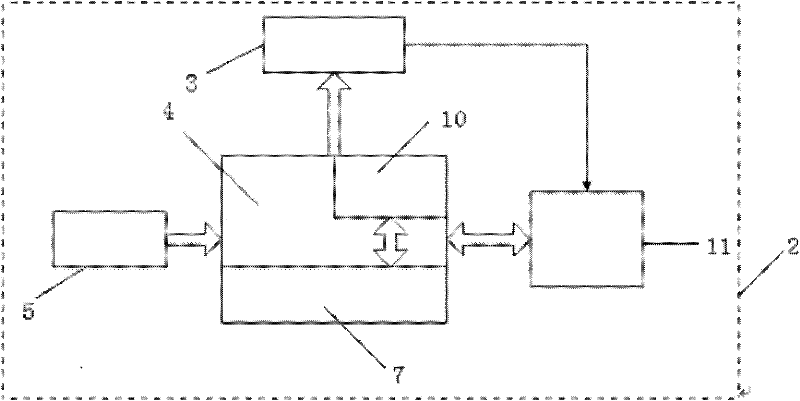
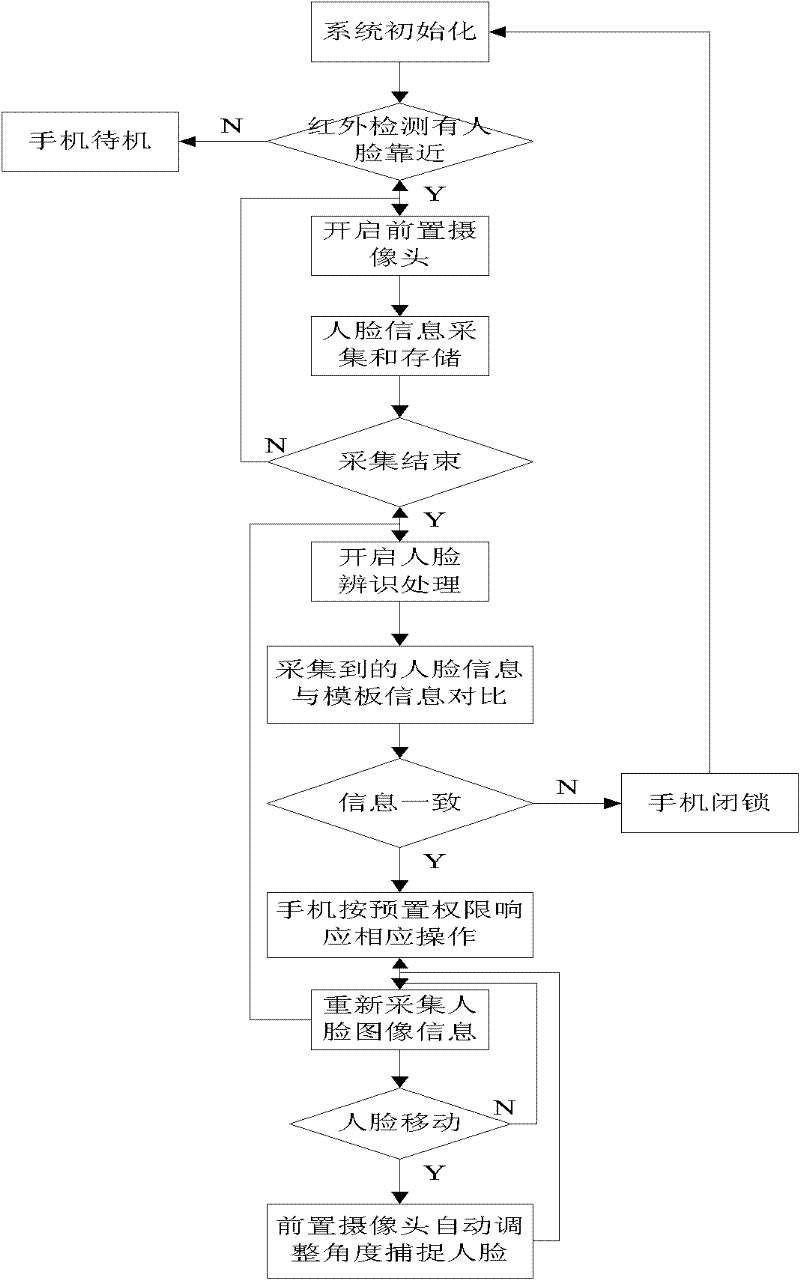
Cell phone capable of realizing safety protection by means of intelligently capturing human face images by aid of front-facing camera
InactiveCN102546938ARealize security protectionEasy to useCharacter and pattern recognitionSubstation equipmentDigital signal processingControl system
The invention discloses a cell phone capable of realizing safety protection by means of capturing human face images by the aid of a front-facing camera, which structurally comprises a cell phone shell, a cell phone control system and the front-facing camera. The front-facing camera is arranged on the surface of the cell phone shell. The cell phone control system consists of a cell phone processor, an infrared detection device, a cell phone memory, a cell phone CPU (central processing unit), an output control device and a control circuit. The cell phone processor comprises a digital signal processor DSP. The cell phone capable of realizing safety protection by means of capturing human face images by the aid of the front-facing camera has the advantages that the cell phone is safe and stable, and is convenient in use and remarkable in effect. Besides, safety and stability of the cell phone are greatly improved as compared with common digitally encrypted and unlocking devices and identification devices with application of other human biological characteristics.
Owner:GUANGDONG BUBUGAO ELECTRONICS IND
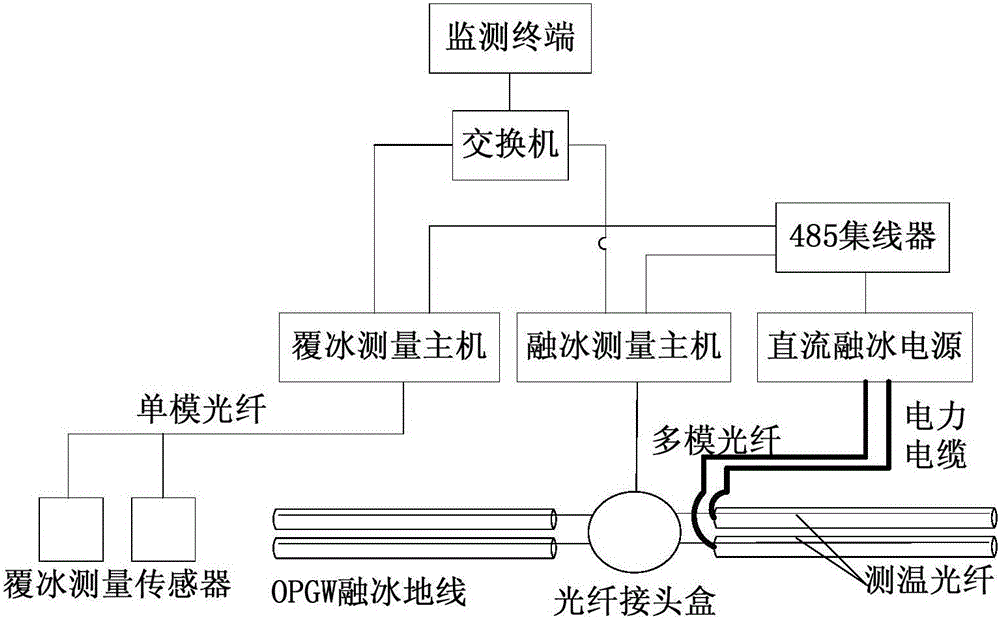
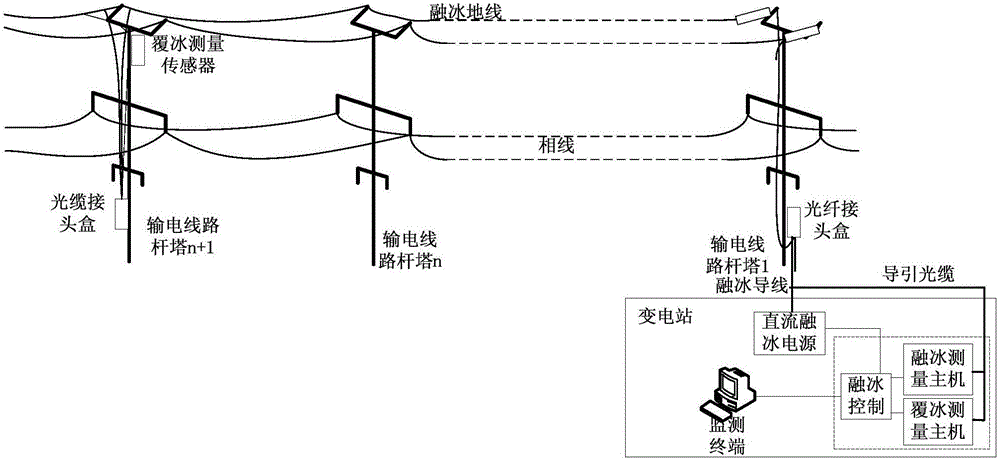
OPGW DC ice-melting system
ActiveCN105119227AEnhance the effectiveness of disaster resistance and mitigationStrong practical application valueOverhead installationThermometers using physical/chemical changesSingle-mode optical fiberTemperature measurement
The invention discloses an OPGW DC ice-melting system, and the system comprises an ice-melting ground line, an ice covering measurement sensor, an ice covering measurement host, an ice-melting measurement host, a DC ice-melting power supply, a 485 concentrator, a switcher, a monitoring terminal, and an optical cable joint box. The ice-melting ground line is connected with the ice covering measurement host through the optical cable joint box, and the ice covering measurement sensor is connected with the ice covering measurement host through a single-mode optical fiber. The ice covering measurement host, the ice-melting measurement host and the DC ice-melting power supply are respectively connected with the 485 concentrator. The ice covering measurement host and the ice-melting measurement host are connected with the monitoring terminal through the switcher. The system achieves the overtemperature monitoring in a long-distance circuit ice melting process and circuit ice melting control under the different conditions in a deicing period through employing the technology of distributed optical temperature measurement and the technology of on-line analysis. The system achieves the ice covering monitoring of a power transmission rod tower under the on-site passive conditions, electromagnetic radiation resistance conditions and severe monitoring conditions through employing the technology of optical fiber grating ice covering measurement, and has a higher practical value.
Owner:CHINA ELECTRIC POWER RES INST +2
Virtual machine image file exporting and importing method and device
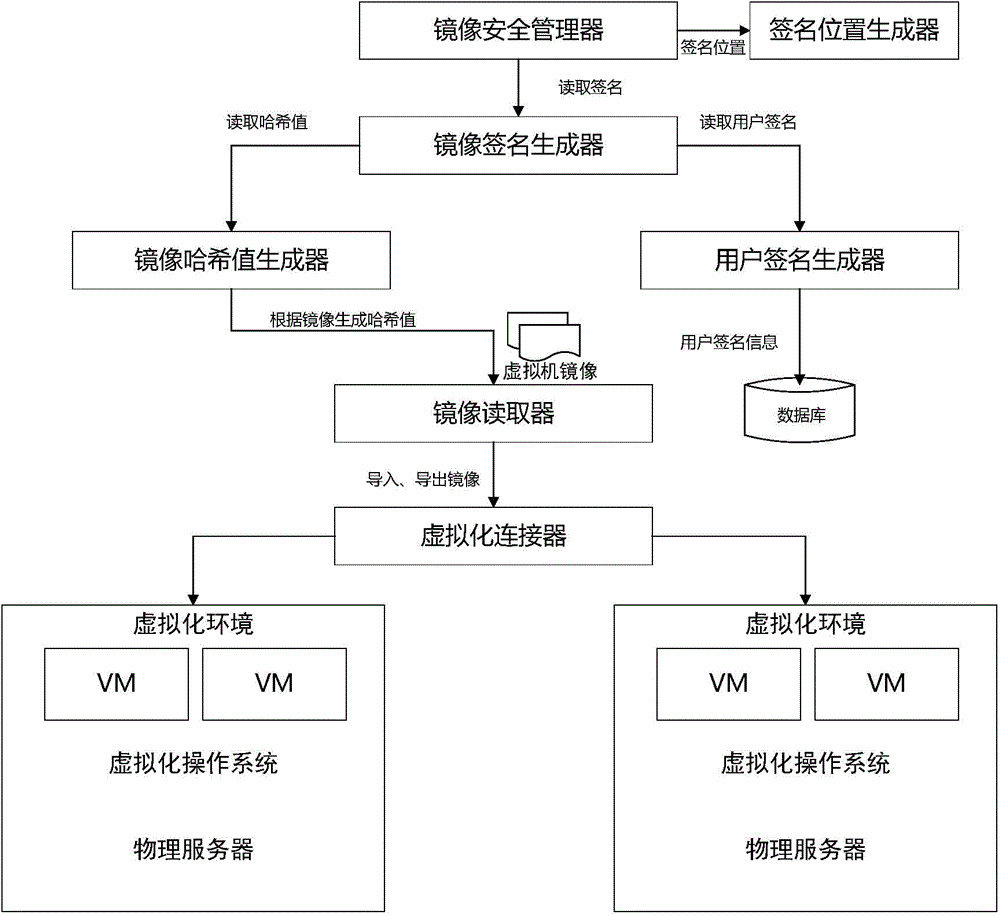
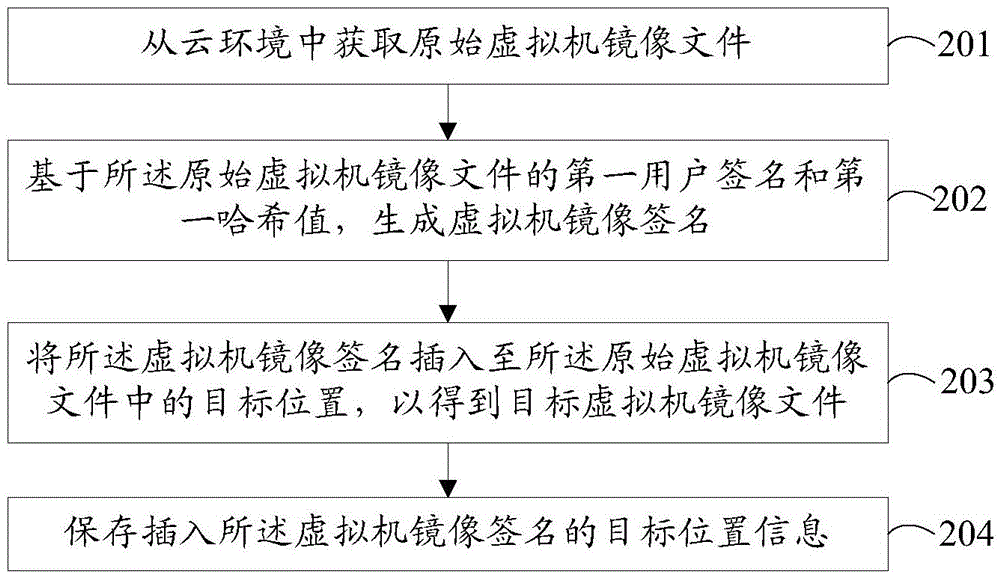
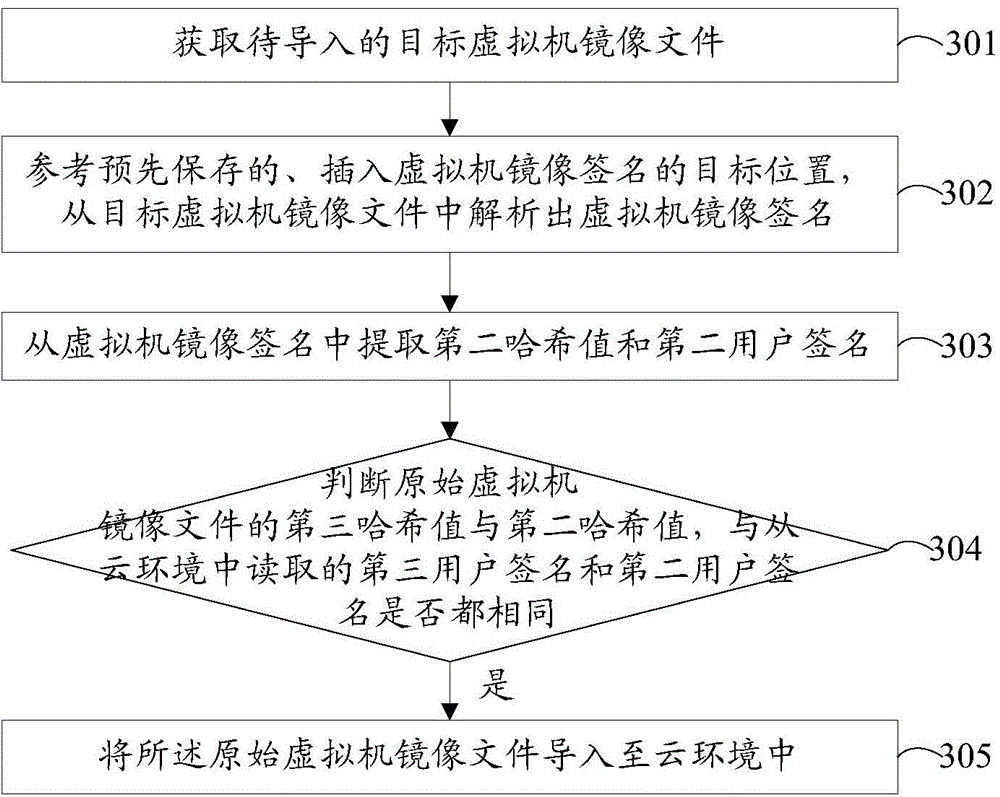
InactiveCN104463012AImprove user experienceImprove export efficiencyDigital data protectionVirtual machine
The invention provides a virtual machine image file exporting and importing method and device. The exporting method comprises the steps of obtaining an original virtual machine image file from a cloud environment; generating a virtual machine image signature based on a first user signature and a first Hash value of the original virtual machine image file; inserting the virtual machine image signature into the target position of the original virtual machine image file to obtain a target virtual machine image file, and saving the information of the target position where the original virtual machine image signature is inserted. According to the embodiment, safety protection of the virtual machine image file in the cloud environment can be achieved, it is guaranteed that only the user and cloud environment to which the virtual machine image file belongs can use the file, and the safety of the virtual machine image file and the safety of the cloud environment are improved.
Owner:NEUSOFT CORP
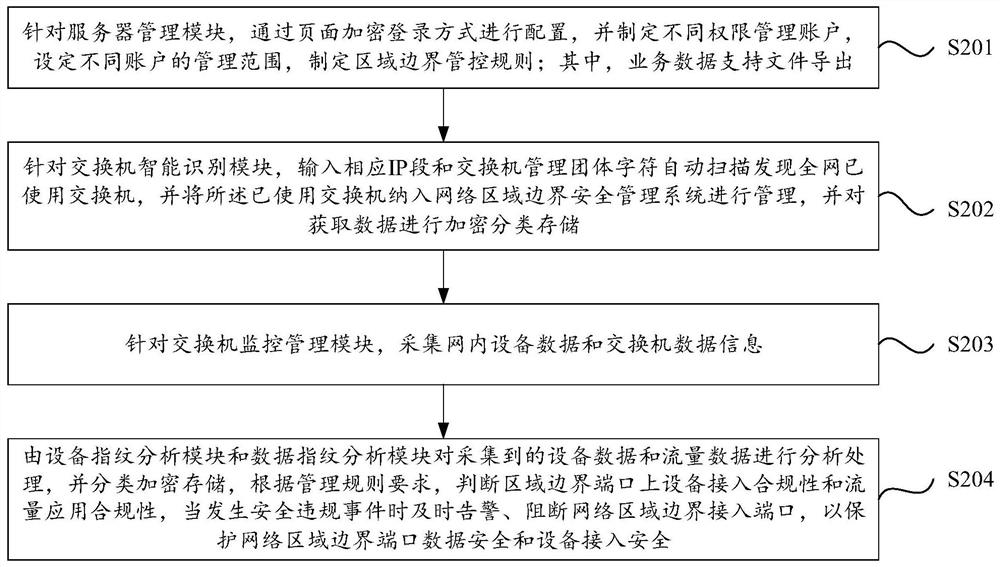
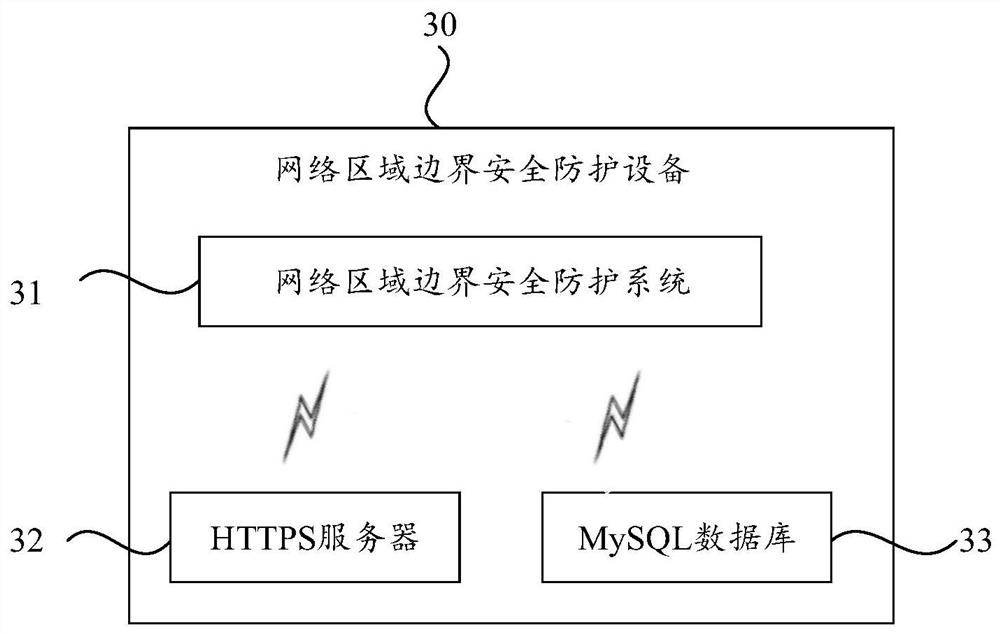
Network area boundary security protection system, method and equipment
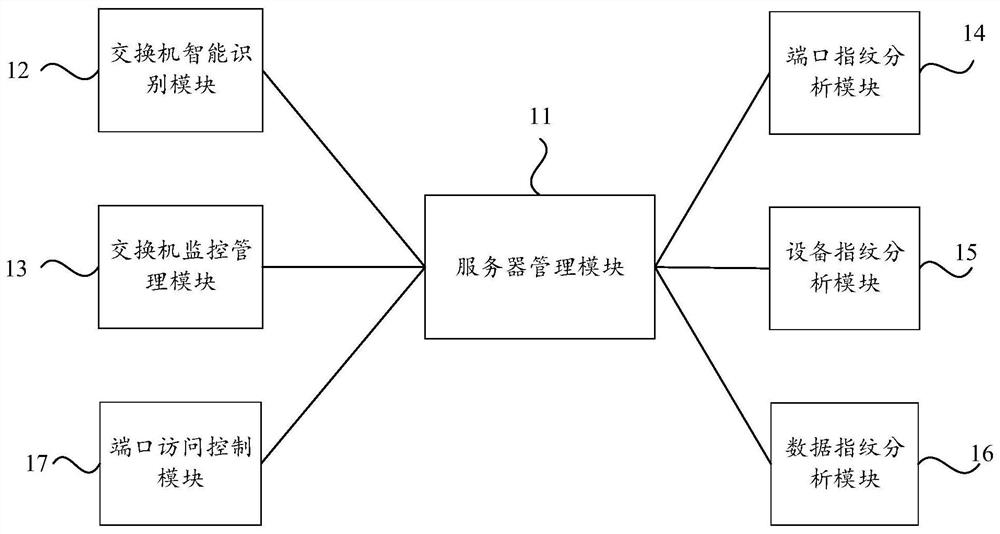
ActiveCN111711616ARealize security protectionMake up for the lack of protectionTransmissionData streamAnalysis data
The invention relates to a network area boundary security protection system, method and device. The method comprises the steps that a server management module monitors the operation condition of the system, formulates a security management strategy, and carries out the collection, storage and calculation of associated data; a switch intelligent identification module identifies equipment information of the switch; the switch monitoring management module acquires corresponding information and generates alarm information when the protocol state information of the switch is abnormal; a port fingerprint analysis module performs unique fingerprint identity identification and calibration on physical ports of all switches; an equipment fingerprint analysis module acquires related information of the network access equipment and then calibrates the related information; a data fingerprint analysis module performs fingerprint calibration on all data streams in the network, and analyzes the source,destination, type and content of the data to release and block the data; and a port access control module is used for monitoring the operation state and the data throughput condition of the access port in the regional boundary so as to close or open the port. And basic guarantee and protection are provided for boundary protection of the network area.
Owner:蜘易唐平(北京)科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com