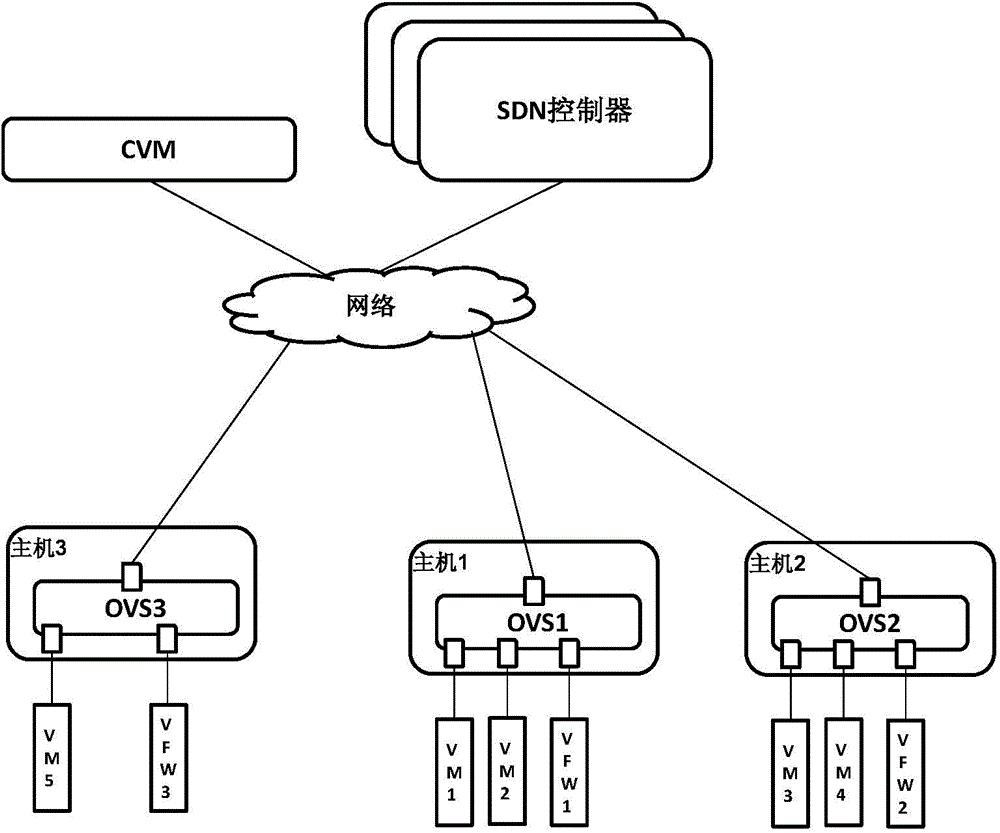
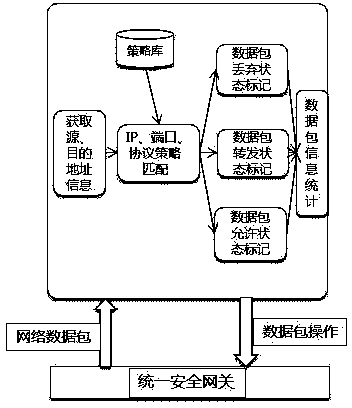
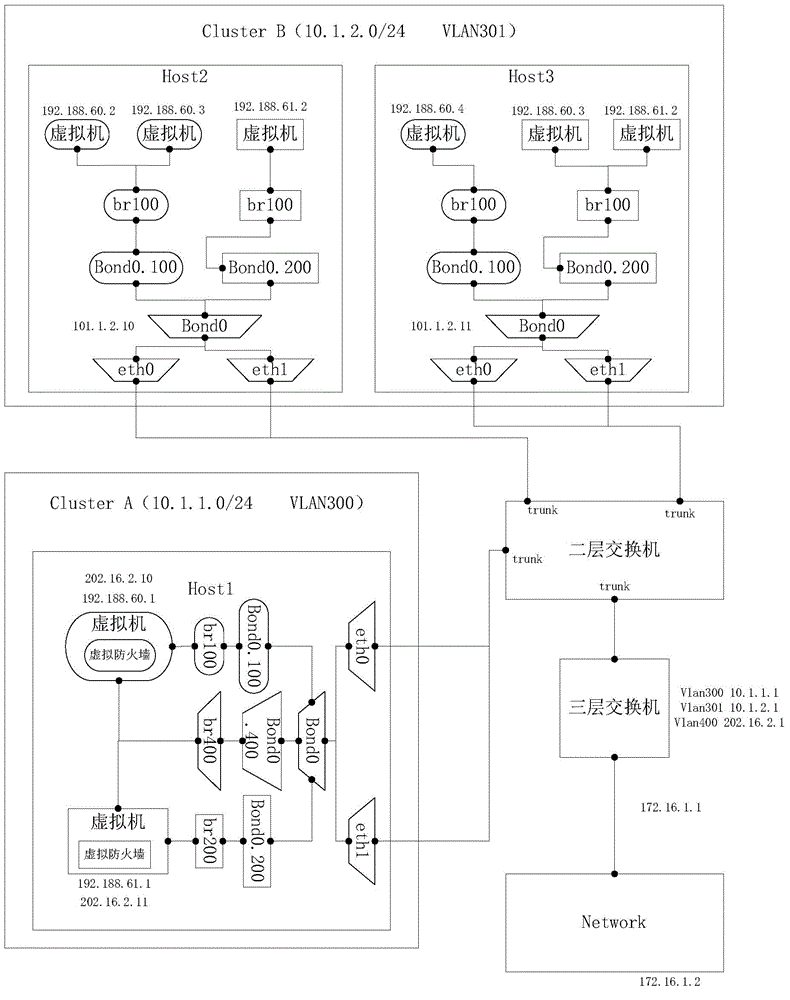
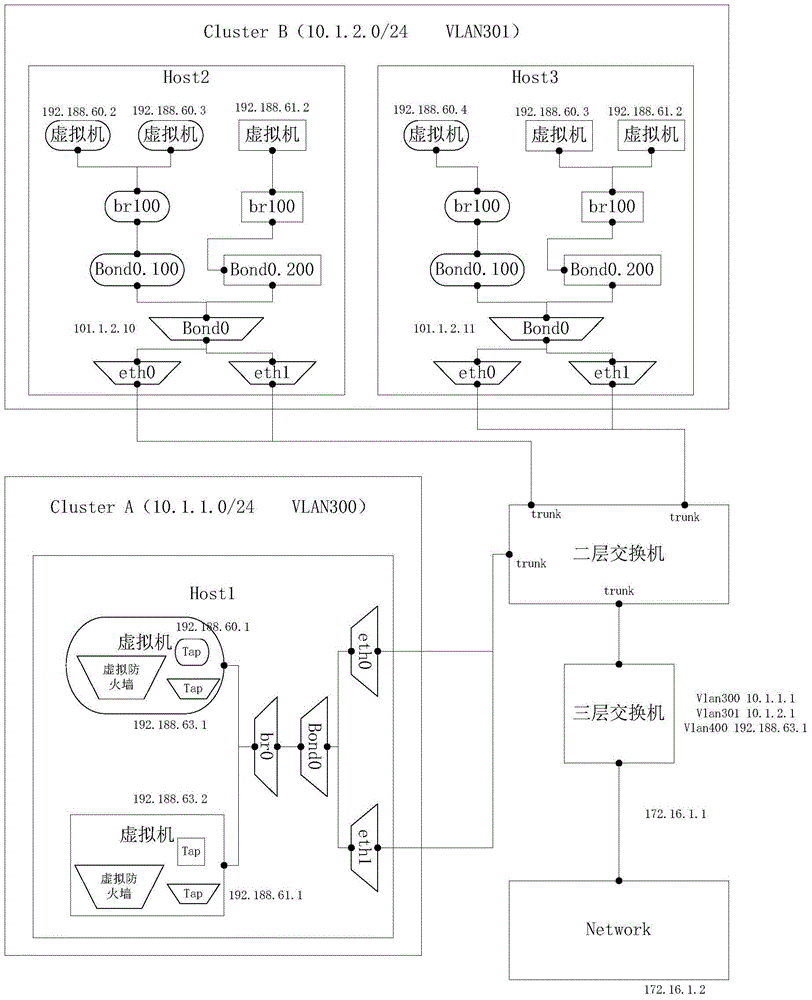
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
115 results about "Virtual firewall" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
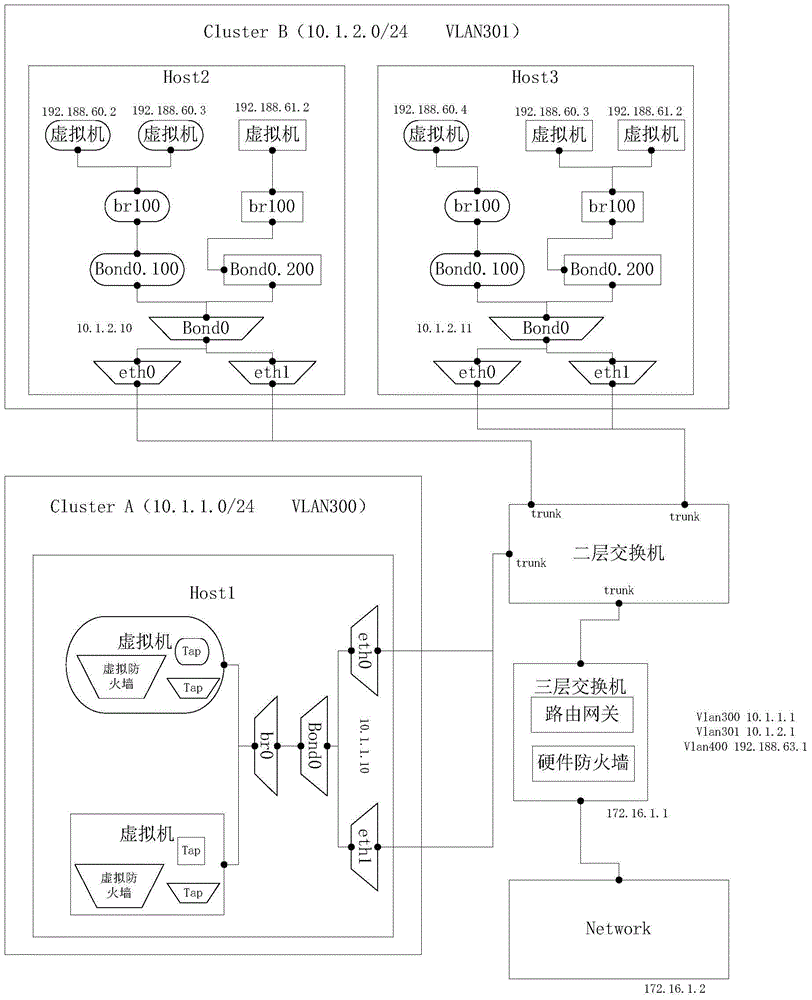
A virtual firewall (VF) is a network firewall service or appliance running entirely within a virtualized environment and which provides the usual packet filtering and monitoring provided via a physical network firewall. The VF can be realized as a traditional software firewall on a guest virtual machine already running, a purpose-built virtual security appliance designed with virtual network security in mind, a virtual switch with additional security capabilities, or a managed kernel process running within the host hypervisor.
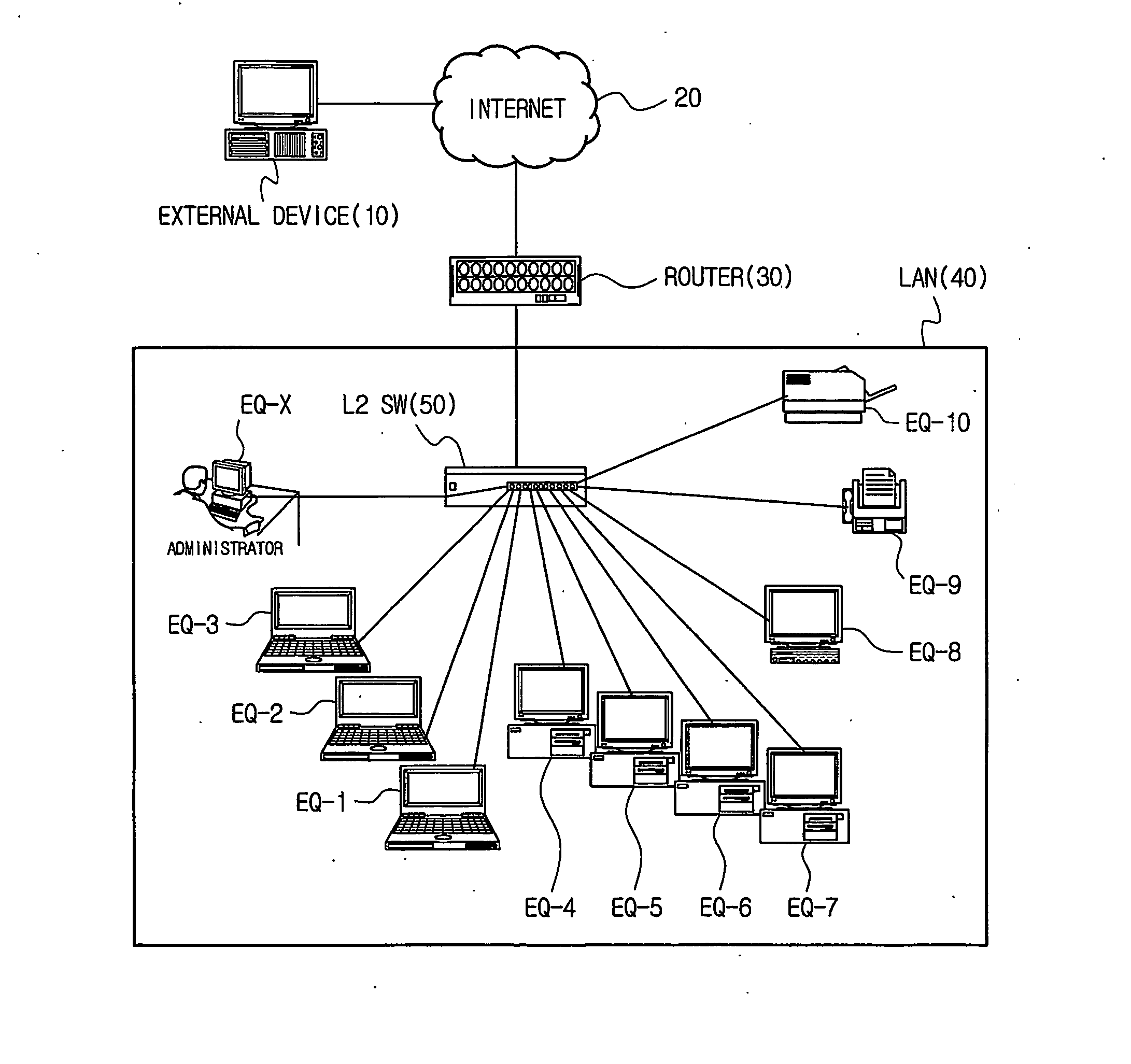
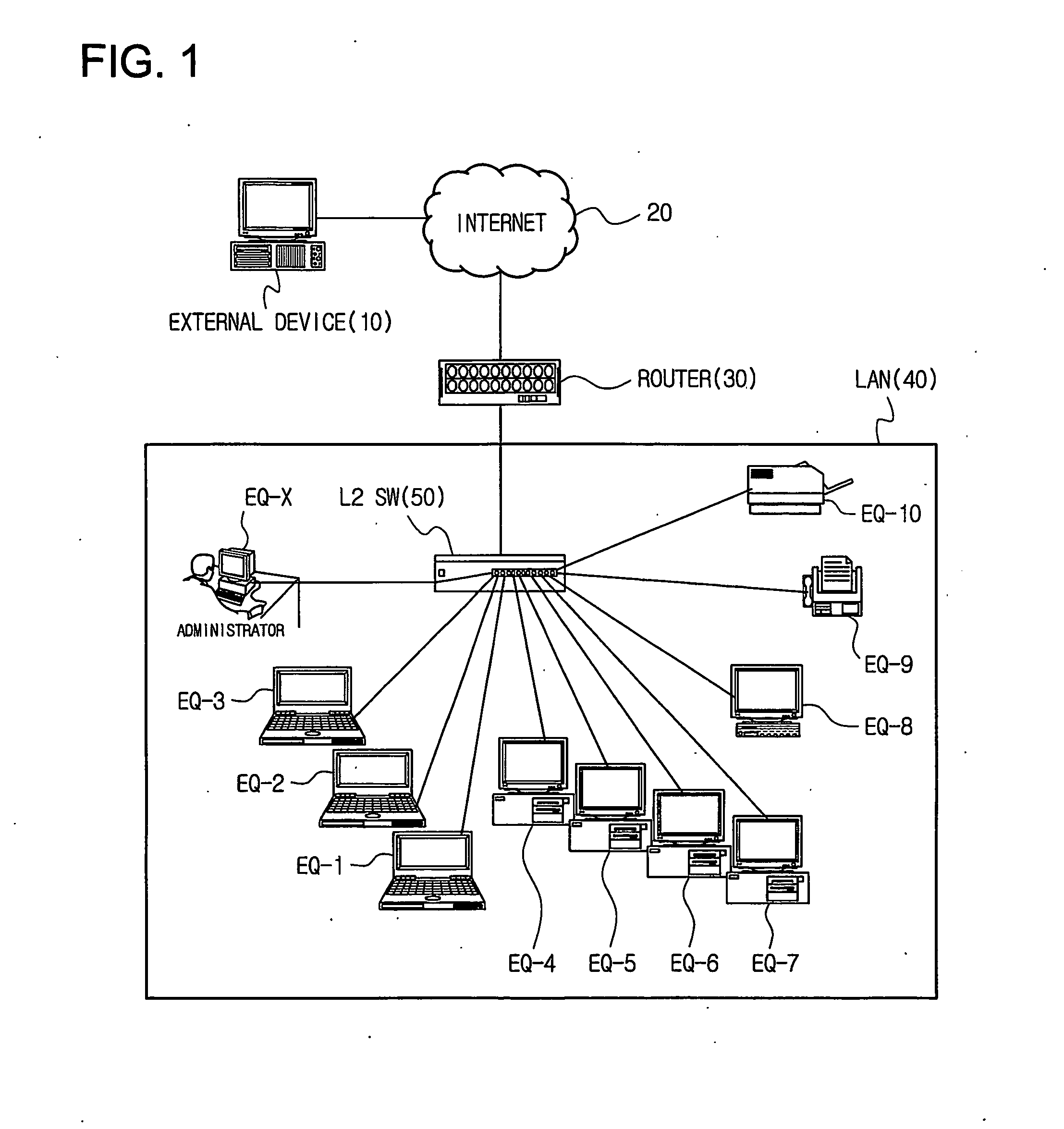
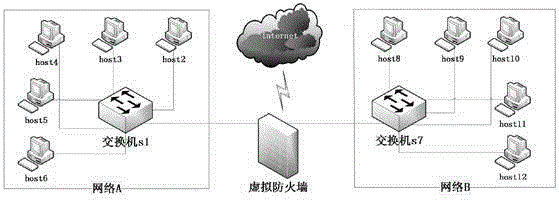
Method of controlling communication between devices in a network and apparatus for the same
InactiveUS20070064689A1Avoid collisionReduce communicationSpecial service provision for substationNetworks interconnectionAddress Resolution ProtocolVirtual firewall
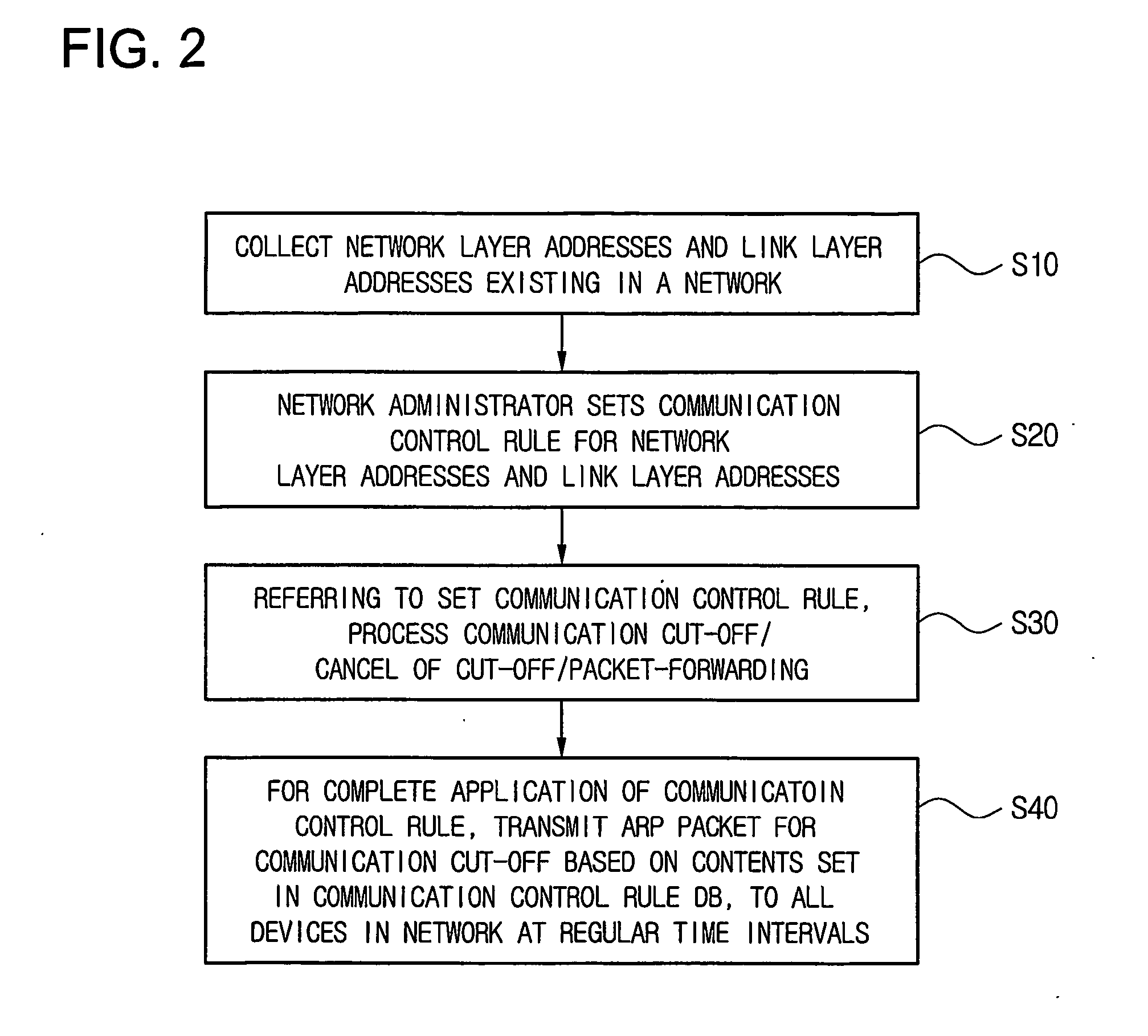
Disclosed is a technology by which rules on communication permission or control are enforced to network internal devices such that an environment which looks as if to have a virtual firewall existing between network internal devices can be established. A communication control apparatus for this is located on the same level in the network as other devices are located. By using this communication control apparatus, an address resolution protocol (ARP) packet in which a data link layer address is manipulated is provided to devices that are the objects of communication cut-off, such that data packets transmitted by the communication cut-off object devices are transmitted to manipulated abnormal addresses. By doing so, communication with the communication cut-off object devices is cut off. For a device which is in a communication cut-off state although the device is not an object of communication cut-off any more, the communication control apparatus transmits an ARP packet including normal address information to the device such that the communication cut-off state is canceled.
Owner:INIMAX
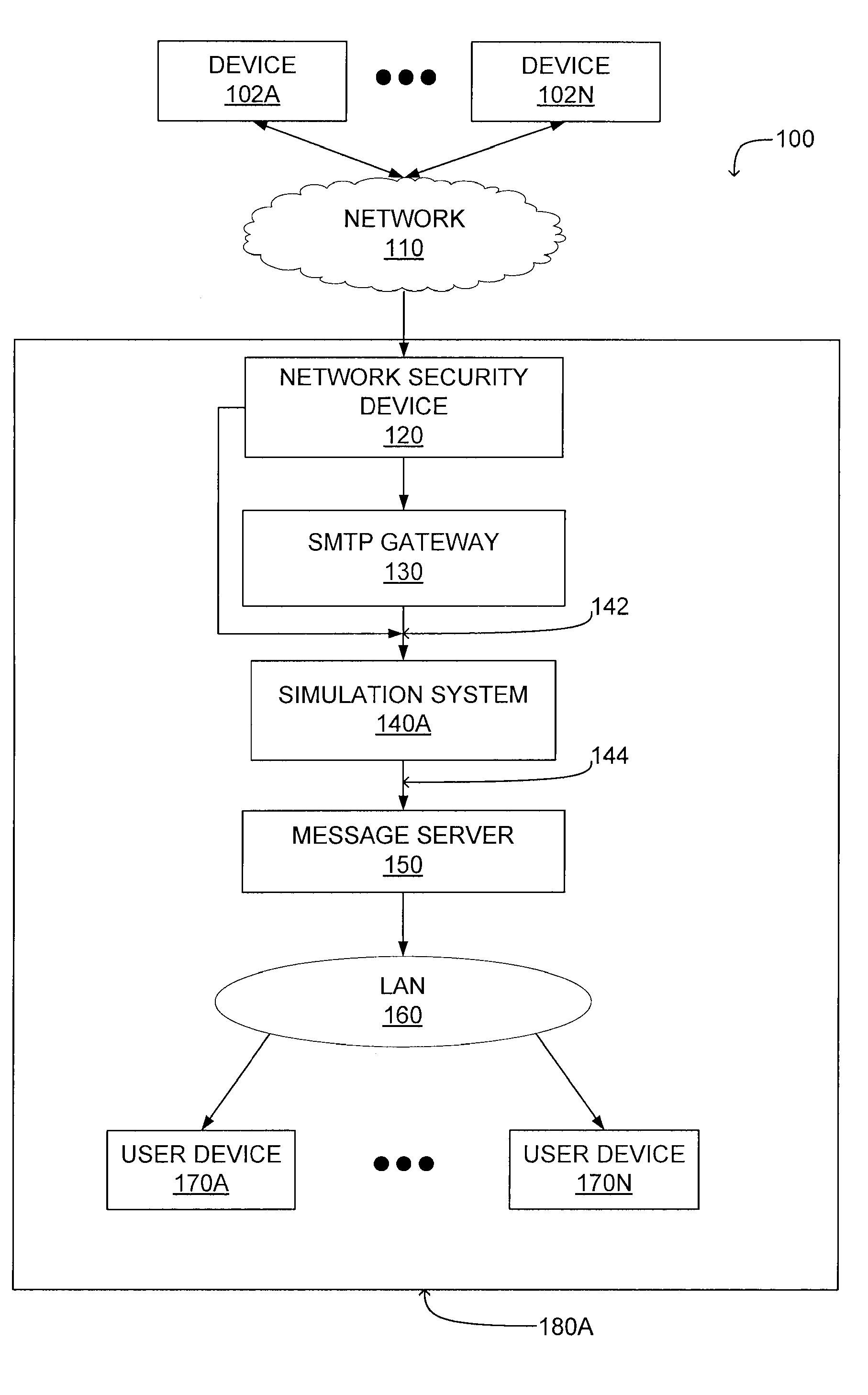
Preventing propagation of malicious software during execution in a virtual machine
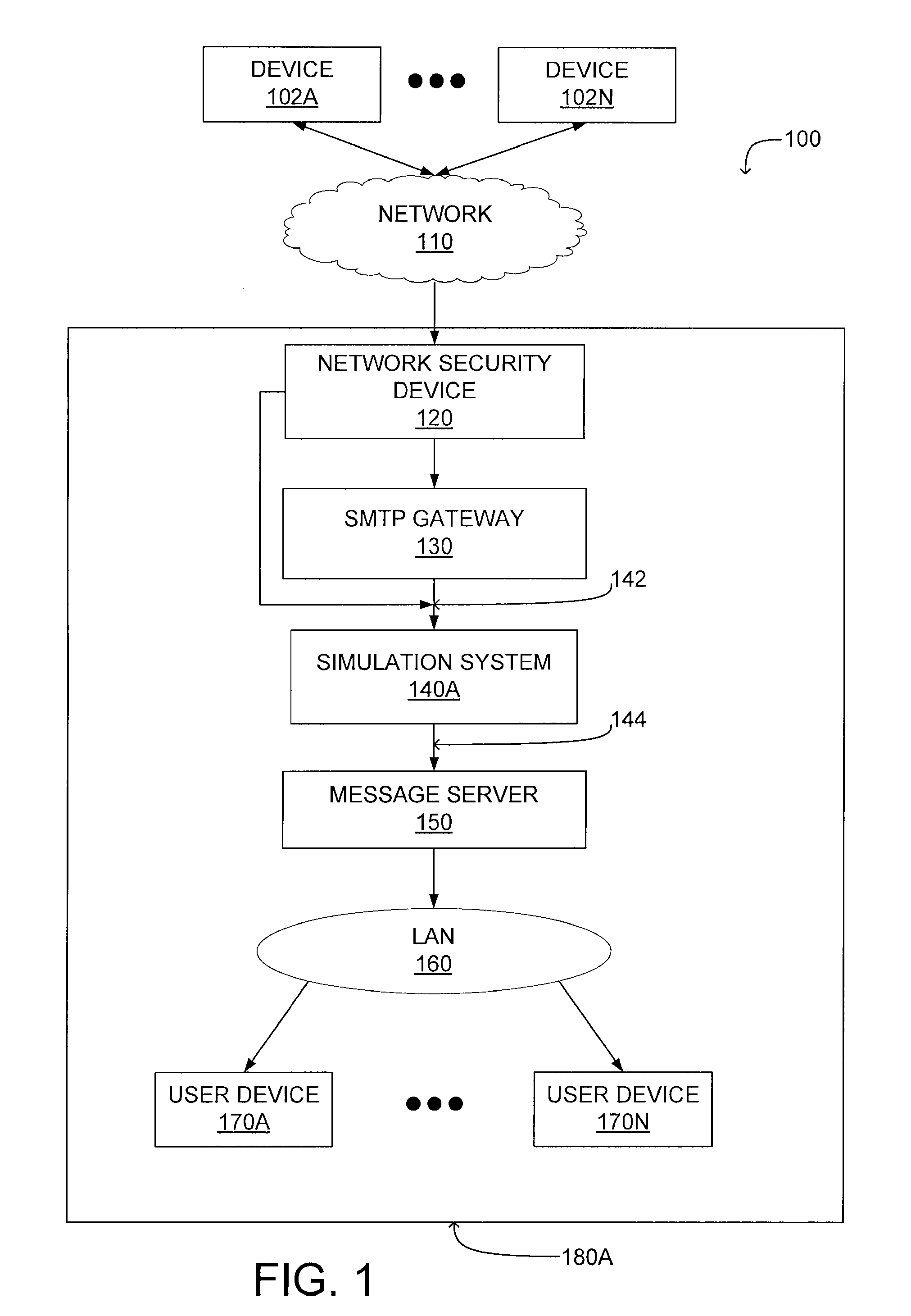
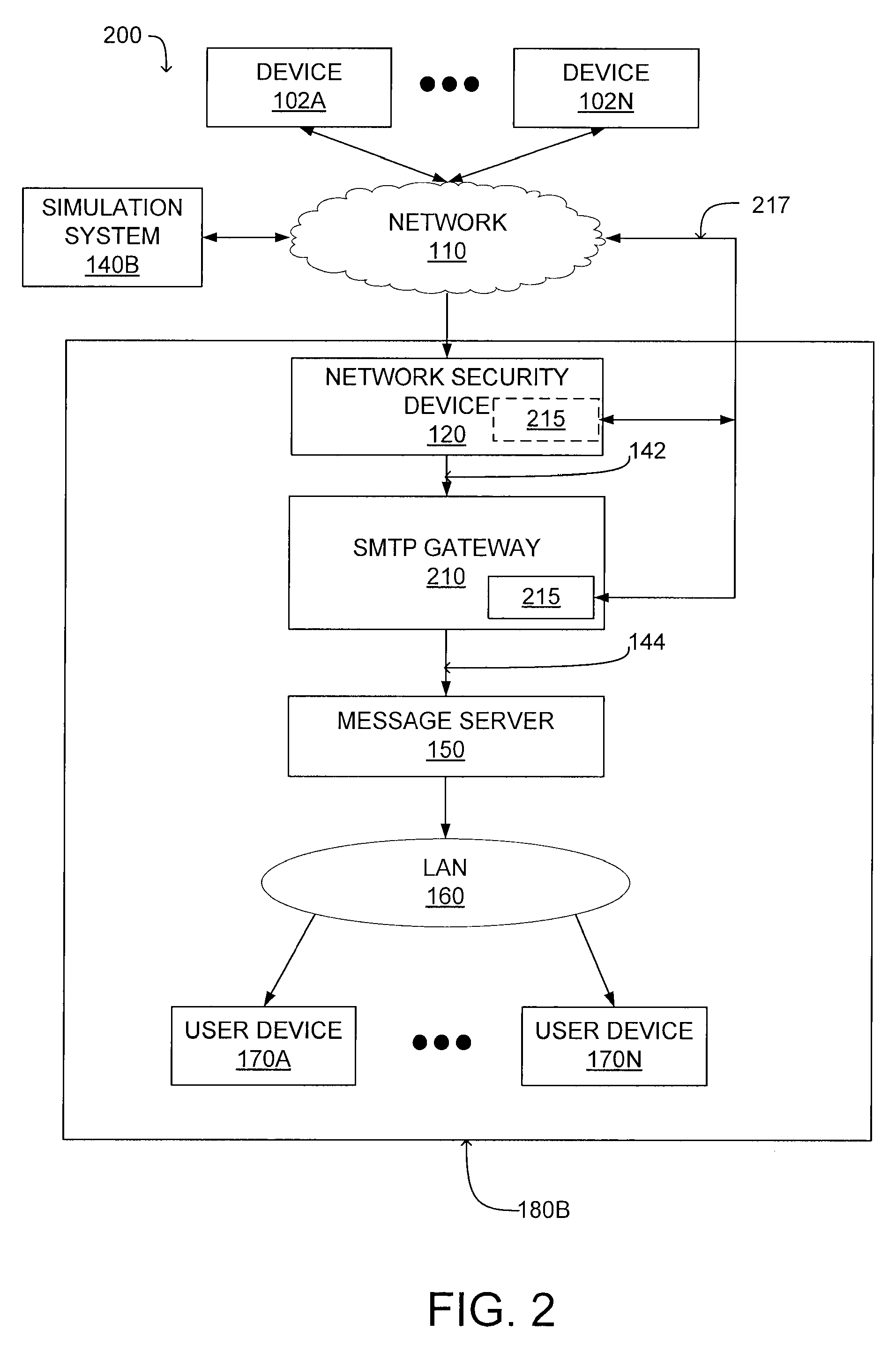
ActiveUS8402529B1Simulation is accurateOvercome limitationsMultiple digital computer combinationsProgram controlVirtual firewallNetwork connection
A system and method for preventing propagation of malicious content associated with an electronic message are disclosed. An electronic message and content associated with the electronic message is simulated in a virtual machine which emulates the destination computing device of the electronic message. A virtual firewall receives one or more commands as the electronic message or content associated with an electronic message is executed. Initially, the virtual firewall establishes a network connection and determines the type of action associated with the commands. If the type of action comprises a connection maintenance or configuration command, the network connection is maintained. If the type of action comprises a data transmission command, the network connection is terminated. This allows the virtual machine to simulate performance of a networked computer by transmitting a subset of the data through a network connection.
Owner:AVINTI CORP
Firewall device
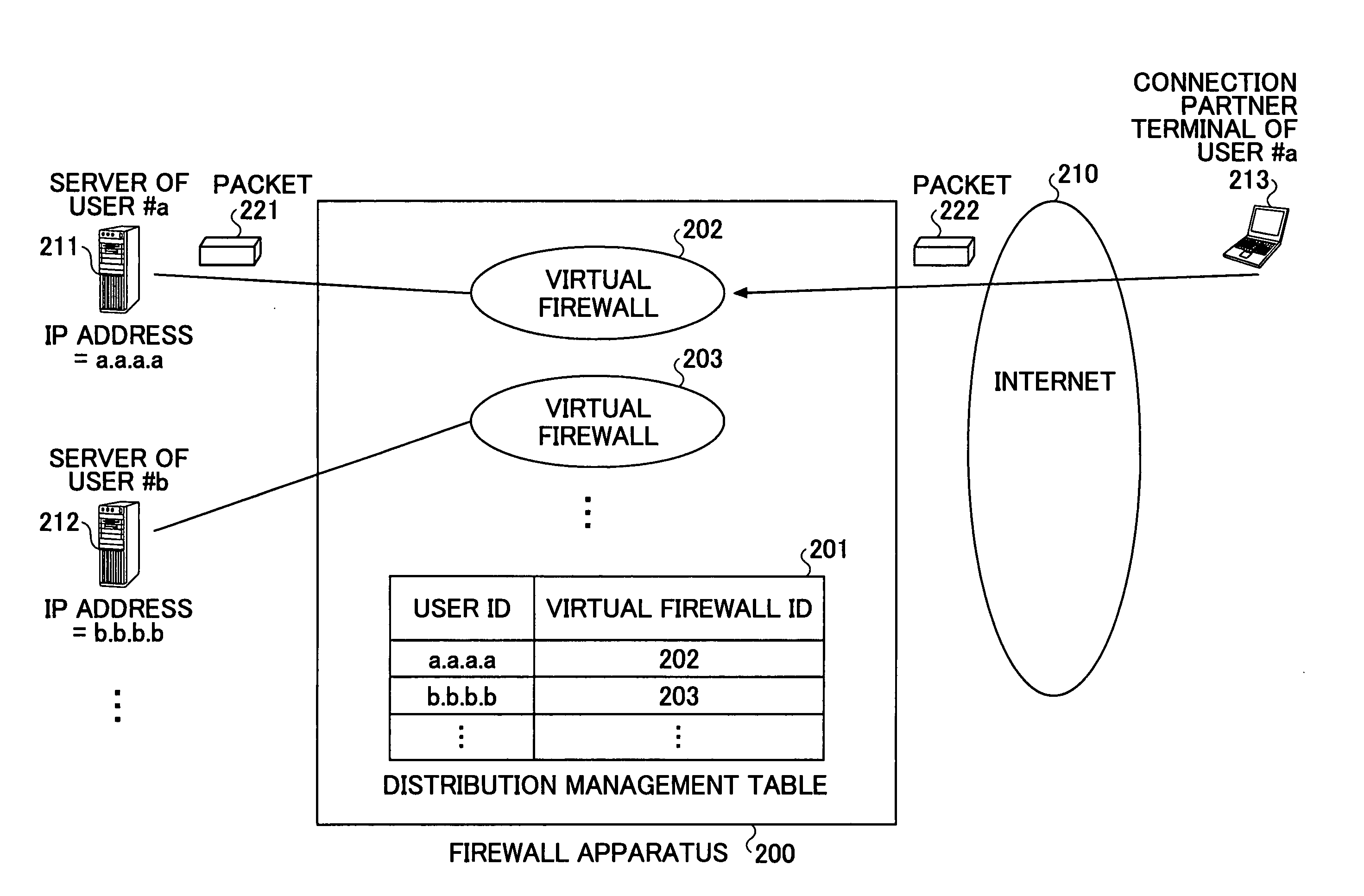
InactiveUS20060143699A1Load accuratelyIncrease the number ofMultiple digital computer combinationsProgram controlVirtual firewallNetwork connection
A firewall apparatus including plural virtual firewalls, each virtual firewall including a dependent firewall policy, is disclosed. The firewall apparatus includes: a distribution management table for managing a user name and a virtual firewall ID; a part configured to receive authentication information for network connection from a user terminal, and hold a user name included in the authentication information; a part configured to report the authentication information to the authentication server; and a part configured to receive an authentication response from the authentication server, and hold a user ID, included in the authentication response, to be provided to the user terminal. The firewall apparatus registers the user ID in the distribution management table associating the user ID with the user name.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Multi-tenant policy-driven type software-defined networking method for cloud data center
InactiveCN104092565AShorten the timeSave computing resourcesData switching networksVirtual firewallCloud data center
The invention belongs to the technical field of cloud computing and novel networks, and particularly provides a multi-tenant policy-driven type software-defined networking method for a cloud data center. The method includes the specific steps of tenant policy defining, user definition policy authority limiting, policy conflict solving and policy file parsing and executing. According to the method, a network is configured through policy defining, tenants can define virtual networks, virtual firewalls and the like of the tenants in a visual mode without writing programs or using a programming interface provided by a software-defined networking controller; management on a cloud computing platform and management on an SDN controller are unified; the networks are managed through policy parsing, so that higher efficiency can be achieved, computing resources, such as a CPU, of the software-defined networking controller are saved, and the time for processing requests of the tenants through the controller is shortened. On the premise that user friendliness is ensured, the performance can be close to the performance achieved when calling is conducted by a local API, and meanwhile the performance is quite better than the performance achieved when calling is conducted by an RESTAPI.
Owner:FUDAN UNIV
Virtual flow monitoring method based on cloud platform and device thereof
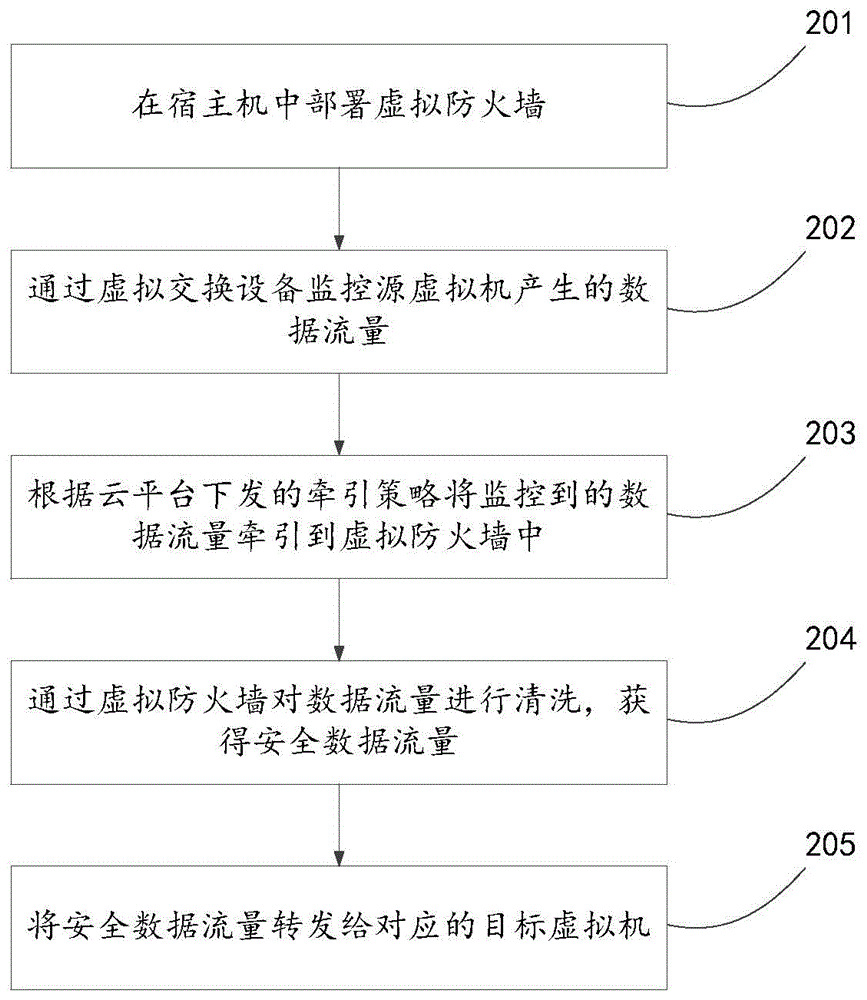
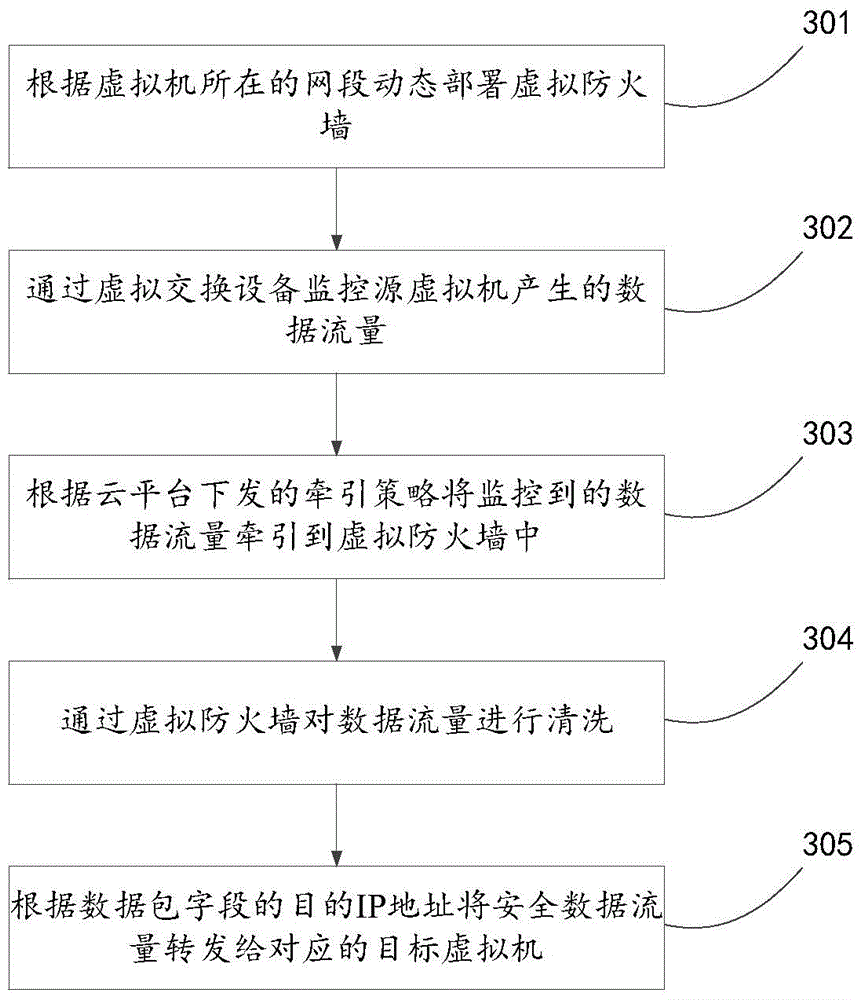
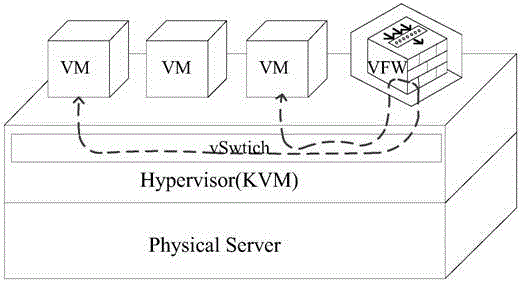
The present invention discloses a virtual flow monitoring method based on a cloud platform and a device thereof, relates to the field of network safety and aims to solve the problem that virtual machine flow safety can not be effectively monitored. The method comprises a step of deploying a virtual firewall at the middle of a host machine, a step of monitoring the data flow generated by a source virtual machine through virtual switching equipment and drawing the data flow monitored into the virtual firewall according to the draw strategy issued by the cloud platform, a step of cleaning the data flow through the virtual firewall and obtain safety data flow, and a step of forwarding the safety data flow to the corresponding target virtual machine. The method and the device are mainly applied to the virtual flow monitoring process in a web application environment.
Owner:BEIJING QIANXIN TECH
Agentless Security of Virtual Machines using a Filtering Platform
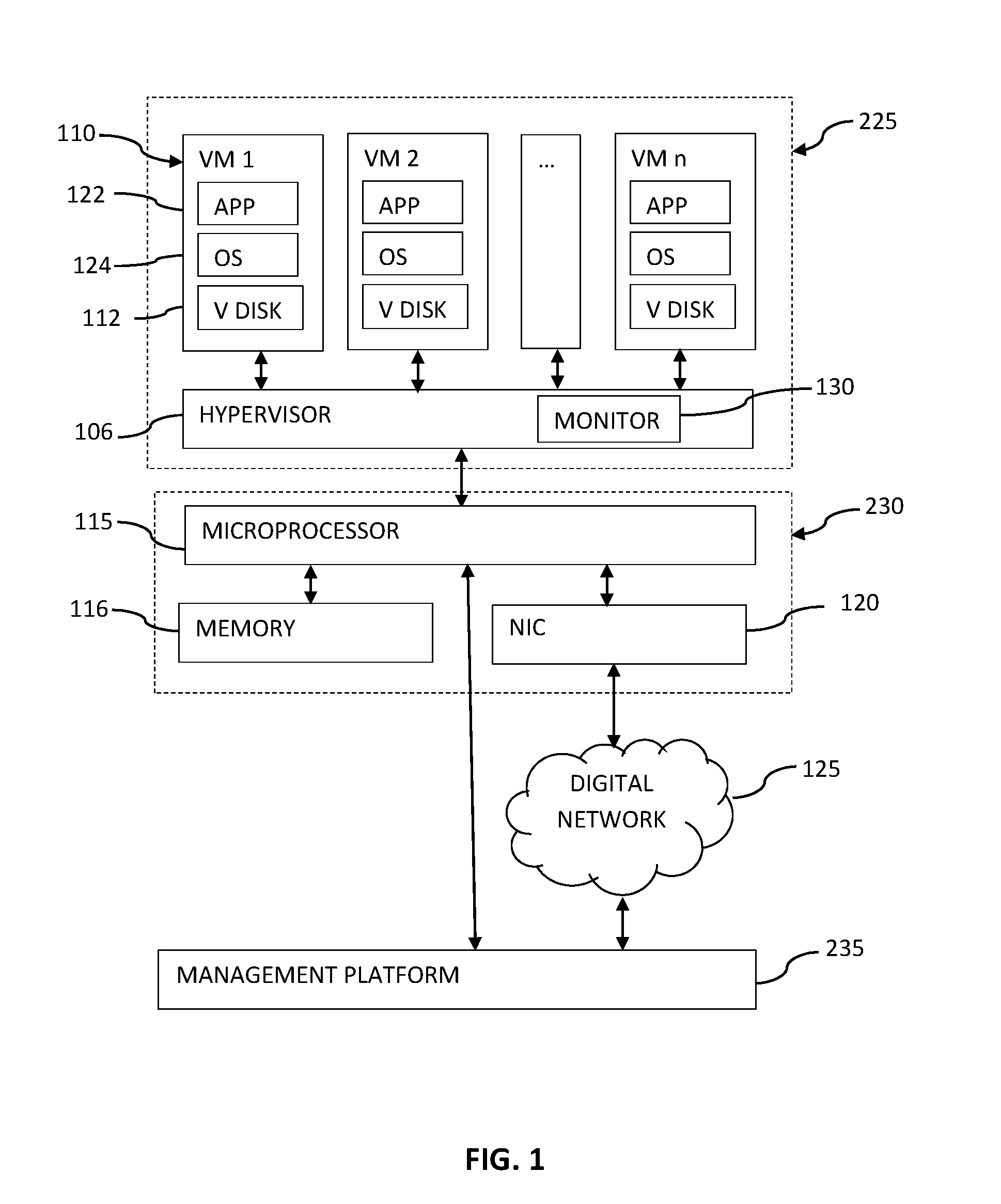
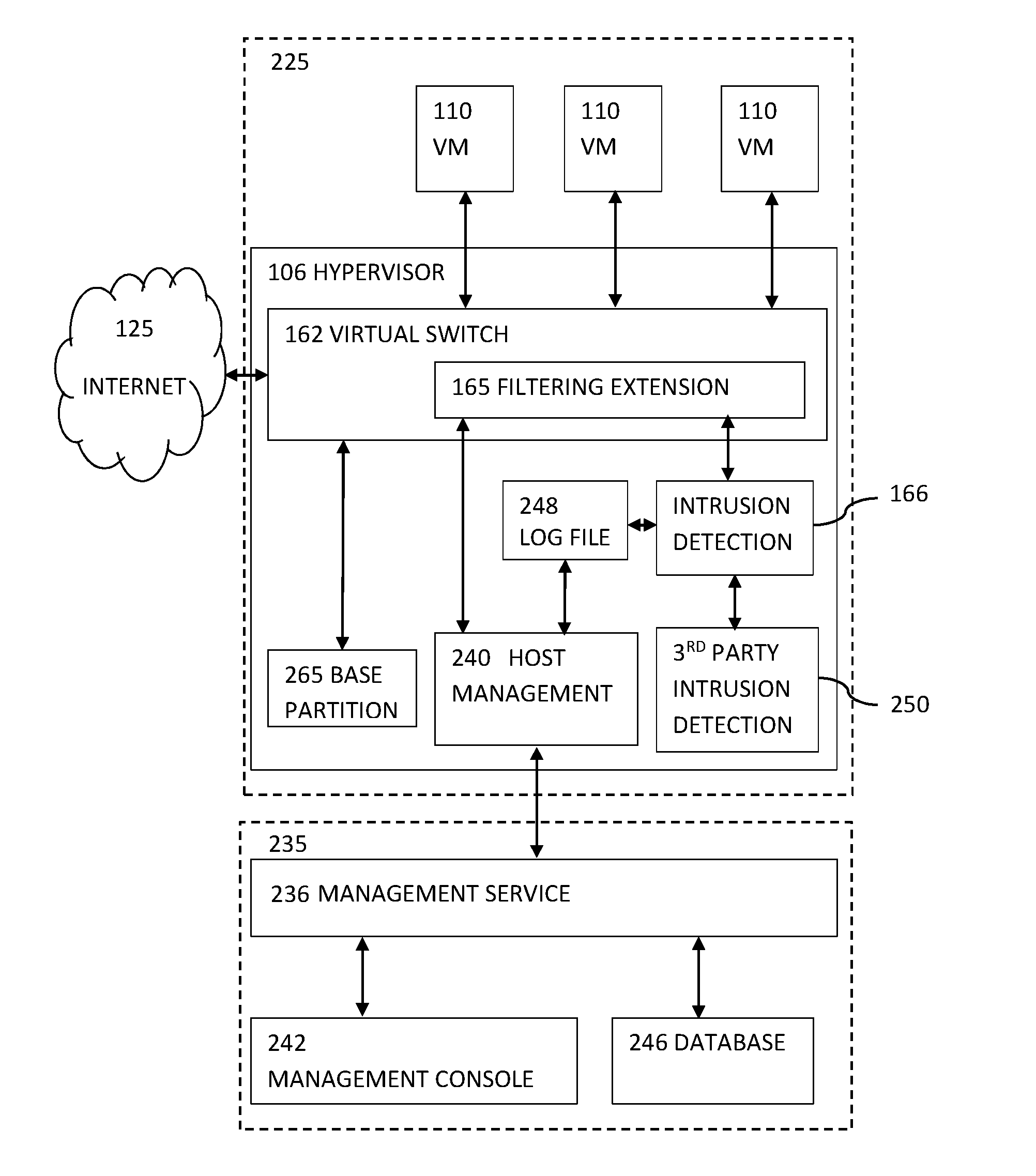
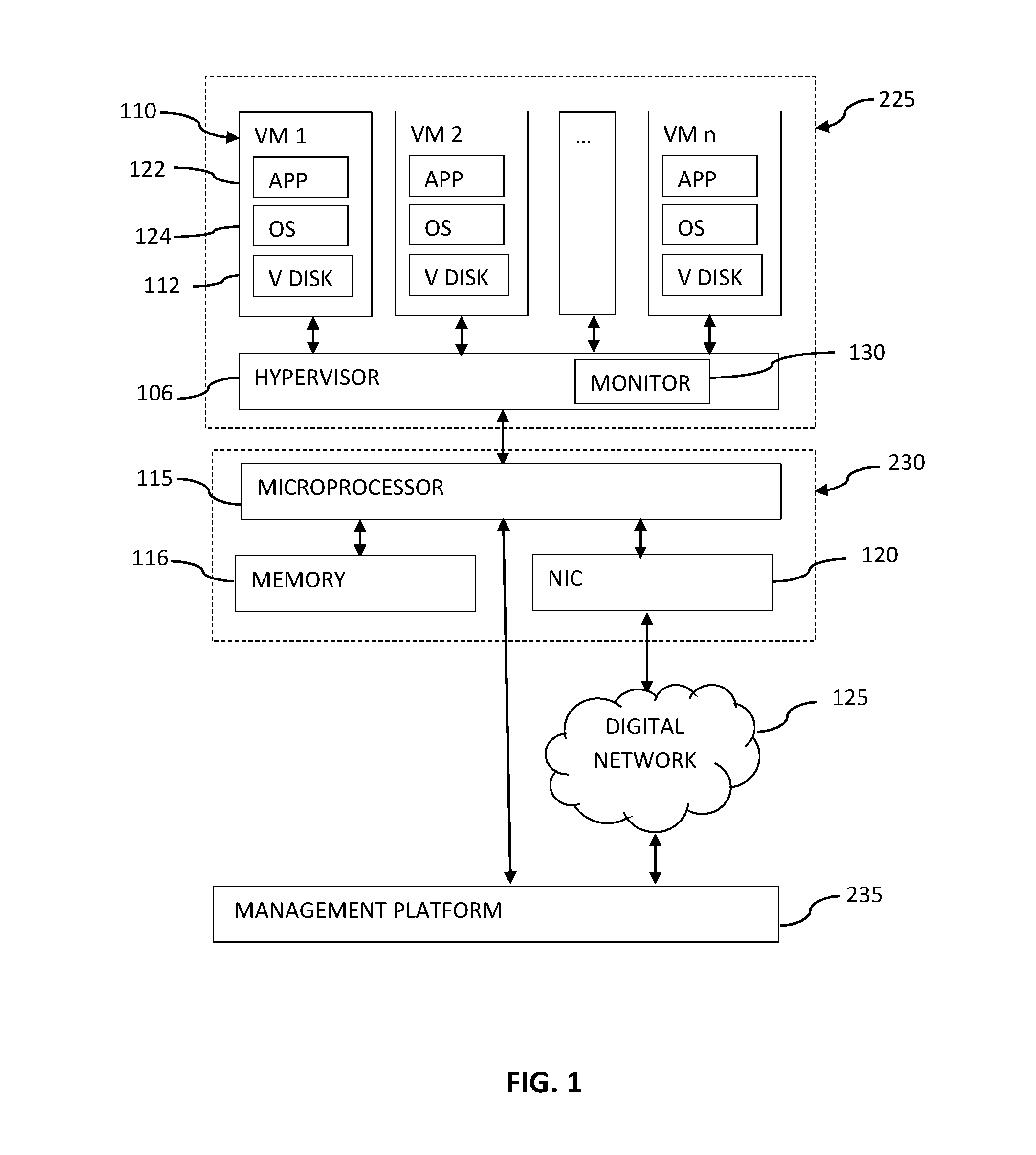
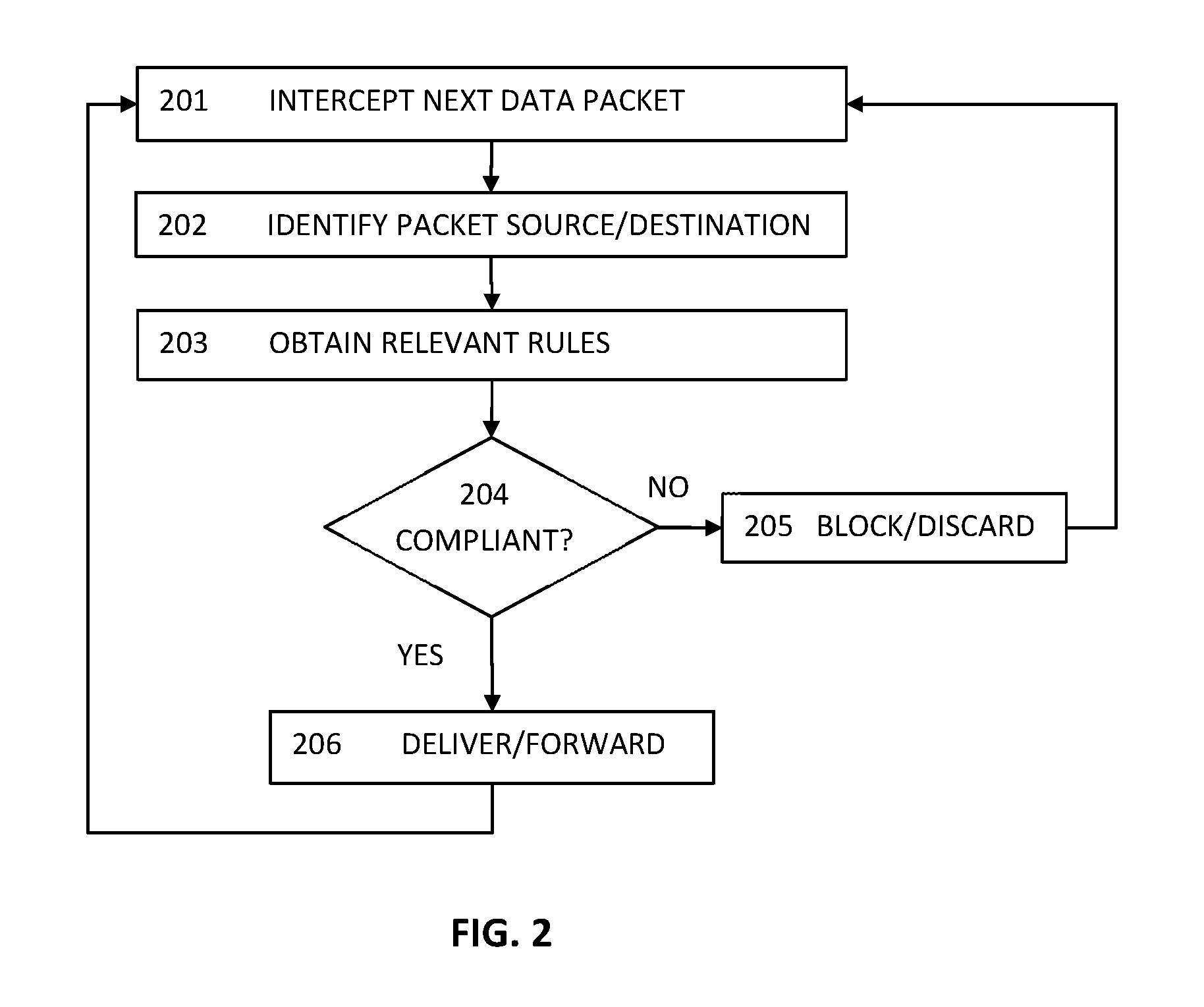
An agentless intrusion detection and prevention digital processing system and environment, or virtual firewall is disclosed. The agentless, virtual firewall monitors and controls digital data communications between a digital communications network and one or more virtual digital processing machines. The virtual digital processing machines, or virtual machines (VMs), are operative on a host digital processor under the supervision of a hypervisor software module. The agentless, virtual firewall is implemented as part of a virtual switch filtering extension to an extensible virtual switch running in a kernel mode as part of the hypervisor software module.
Owner:MALKOV KONSTANTIN +1
Method and system for achieving distributed network safety protection
ActiveCN104301321ATopological changes are smallLittle changeProgram controlTransmissionVirtual firewallVirtual switch
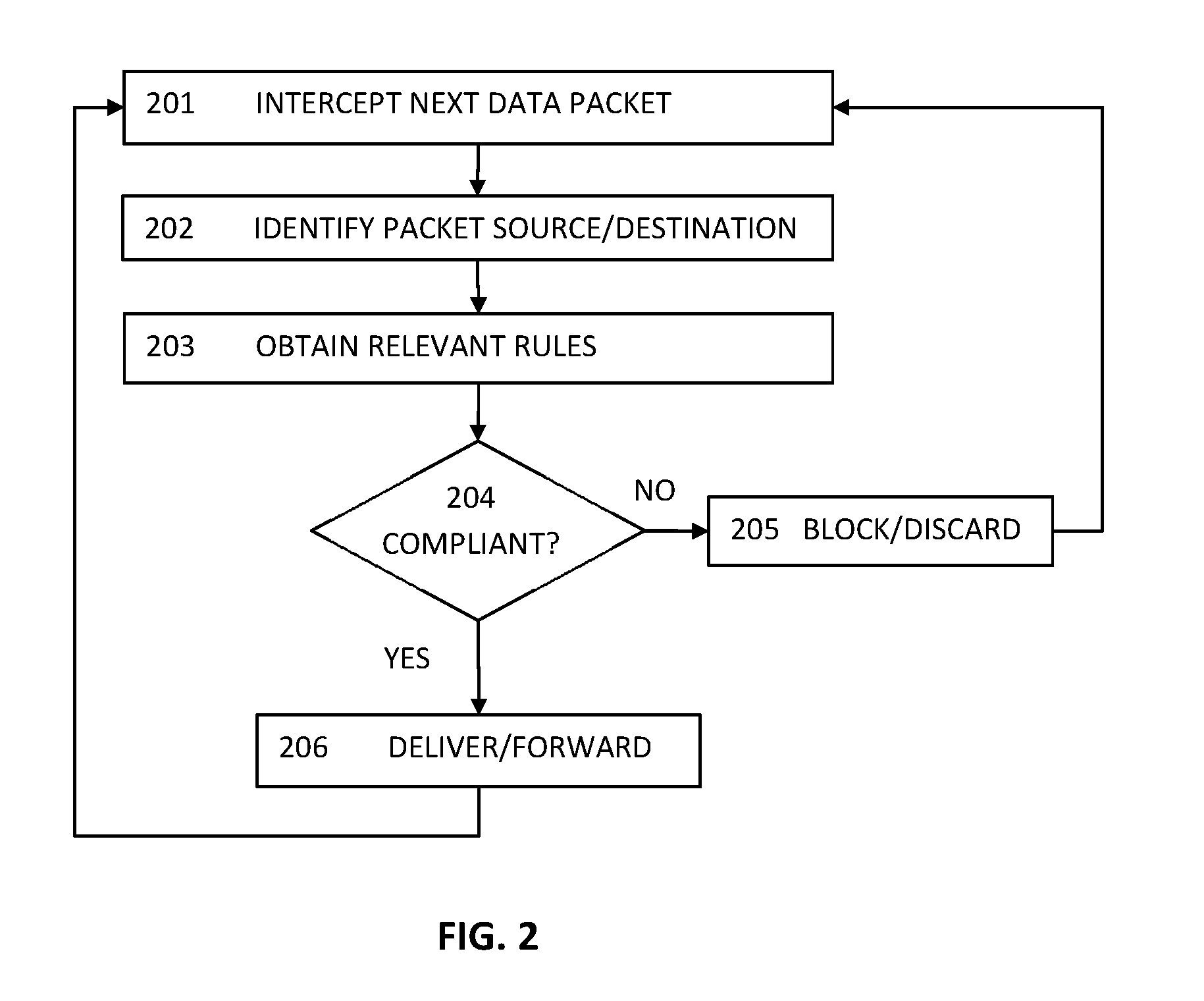
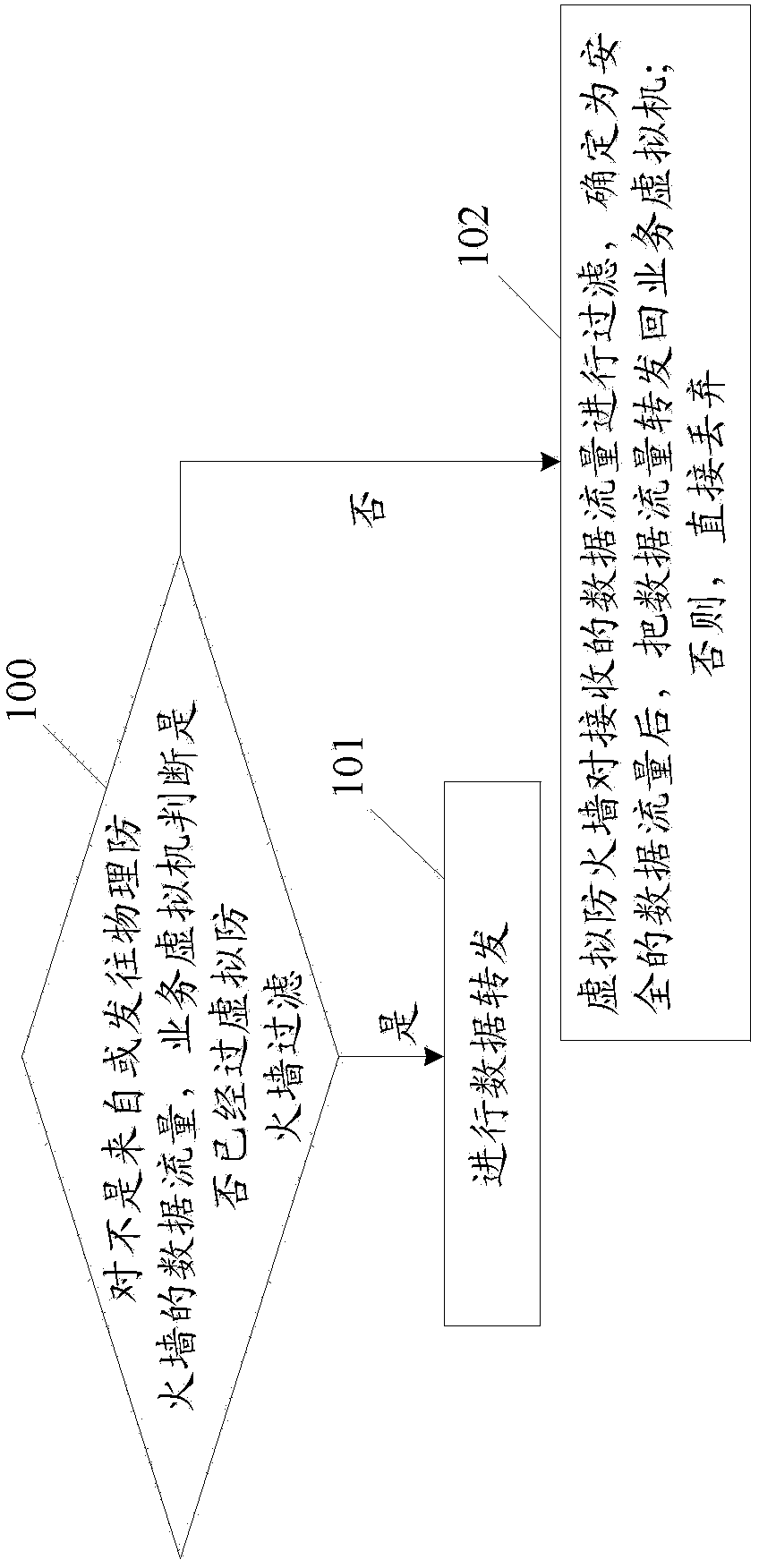
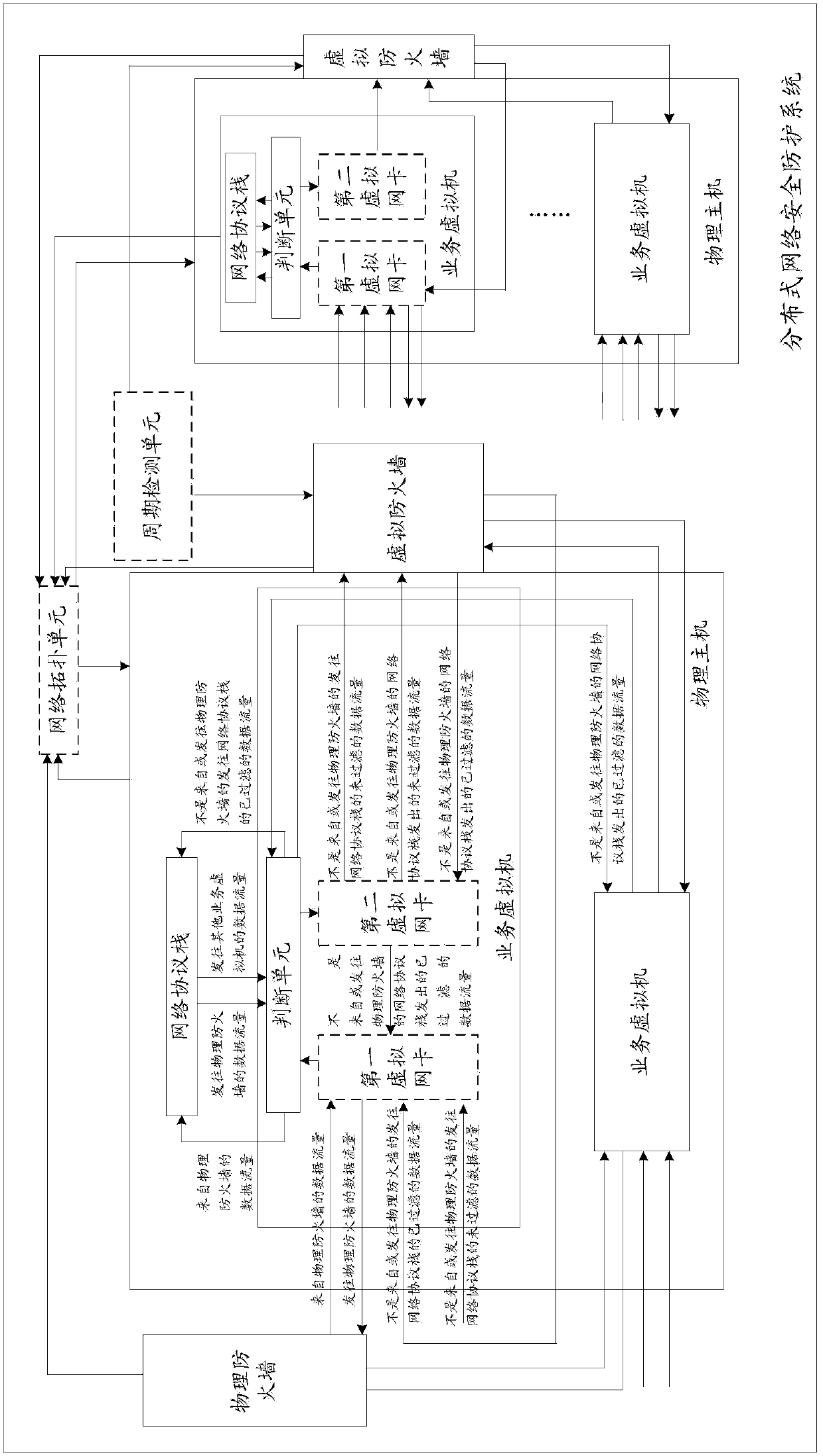
The invention discloses a method and system for achieving distributed network safety protection. The method comprises the steps that the side of a virtual firewall is hung on a virtual switch; whether data flow which is not from or sent to a physical firewall is filtered by the virtual firewall or not is judged through a service virtual machine, if yes, the data flow is forwarded, and otherwise, the data flow is sent to the virtual firewall; the received data flow is filtered through the virtual firewall, and after it is determined that the data flow is safe, the data flow is forwarded back to the service virtual switch, and otherwise the data flow is abandoned. According to the method and system, after the data flow which is not from or sent to the physical virtual wall is judged, the data flow needing to be filtered is sent to the side-hung virtual firewall to be filtered through the service virtual machine, and the data flow which does not need to be filtered is directly forwarded. Network topology is changed a little, it is guaranteed that all the data flow entering in a virtual machine system is filtered, and the resource consumed by the virtual firewall is reduced.
Owner:BEIJING VENUS INFORMATION TECH +1
Safe message forwarding method and safe message forwarding device
ActiveCN105100026ARealize security protectionAvoid forwardingHybrid transportVirtualizationVirtual firewall
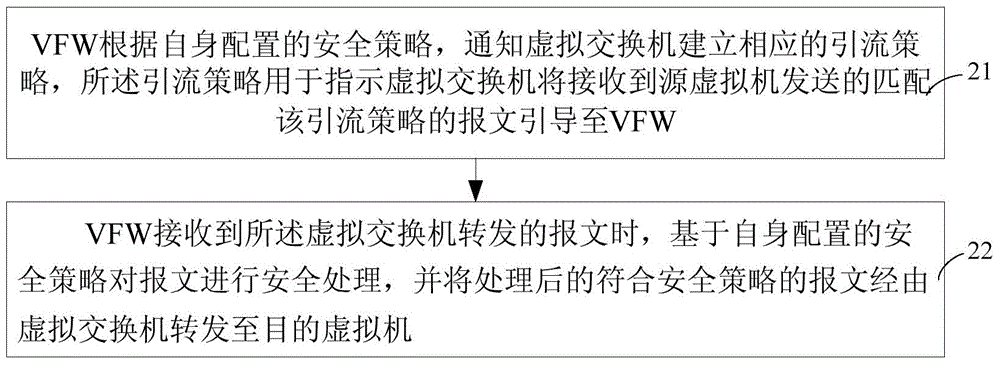
A virtual firewall (VFW) notifies a virtual switch (vSwitch) to establish a flow directing policy according to a security policy configured for the VFW. The vSwitch directs a received packet matching the flow directing policy to the VFW according to the flow directing policy. When receiving the packet forwarded from the vSwitch, the VFW performs security processing for the packet according to the security policy, and forwards the processed packet satisfying the security policy to a target virtual machine (VM). The VFW and the vSwitch are established in a same physical machine based on a virtual platform.
Owner:NEW H3C TECH CO LTD
Method and system for transmitting and receiving data across virtual firewall
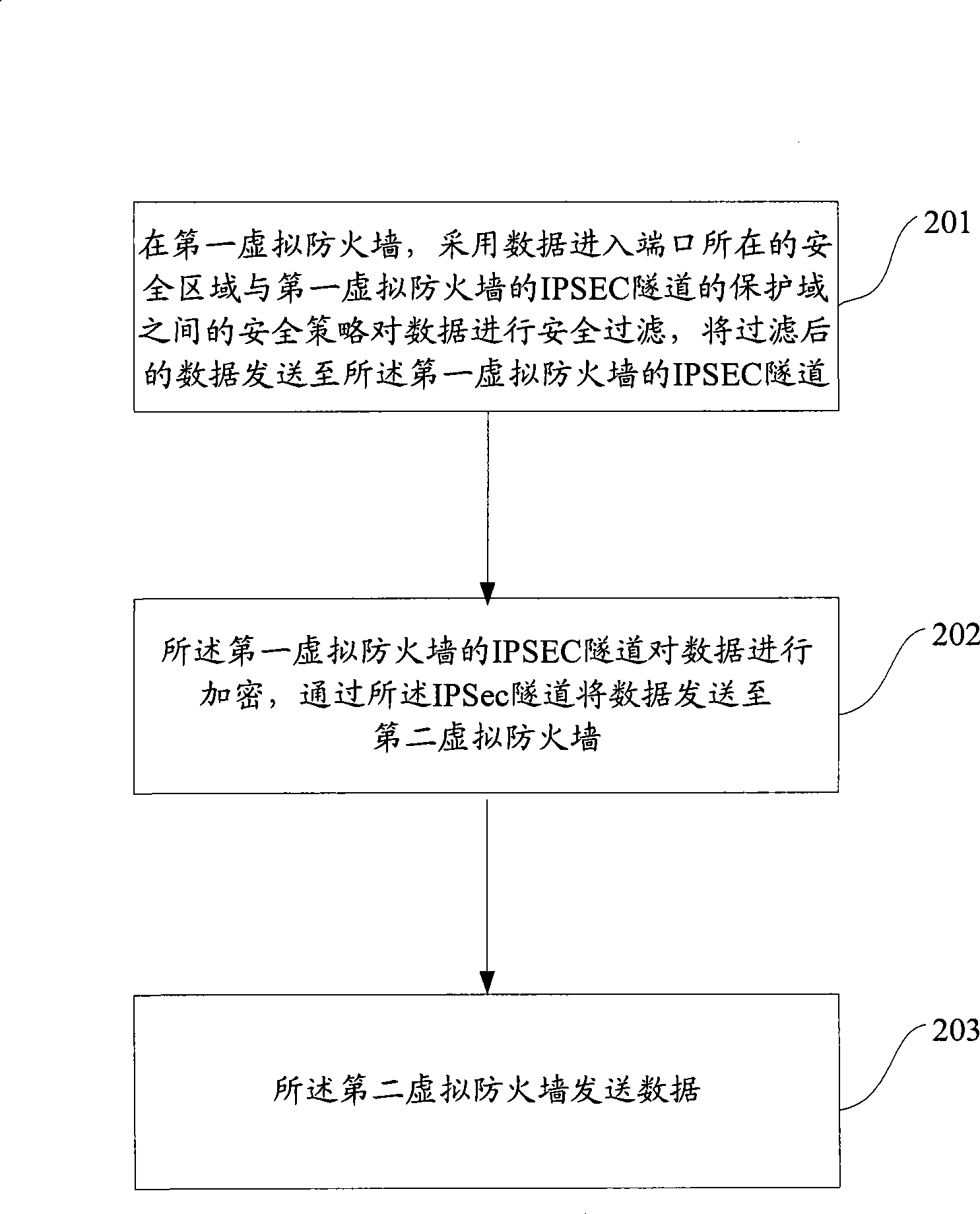
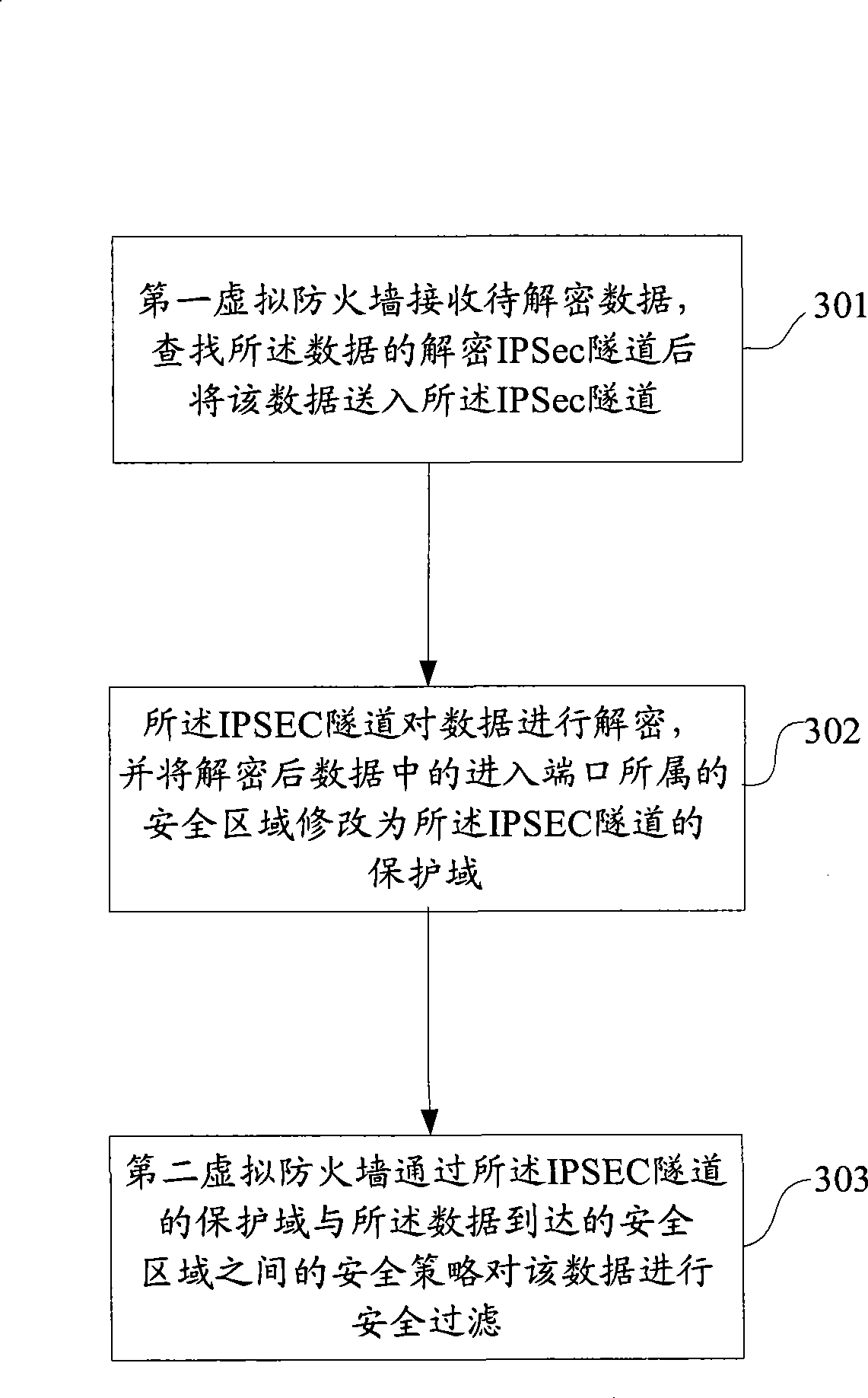
The invention discloses a method for transmitting data by spanning a virtual fireproof wall. The virtual fireproof wall has a corresponding security tunnel which has a protected field. When the data is transmitted, in a first virtual fireproof wall a security policy between the protected fields of a safety zone where data entrance port is and the security tunnel of the first virtual fireproof wall filters the data safety, transmits the safely filtered data to the security tunnel of the first virtual fireproof wall for encryption, and transmits the encrypted data through a second virtual fireproof wall. The method for transmitting data by spanning the virtual fireproof wall of the invention simplifies field relation management between the safe fields in the multiple different virtual fireproof walls, effectively implements repeated use of the virtual fireproof port and saves resource.
Owner:HUAWEI TECH CO LTD
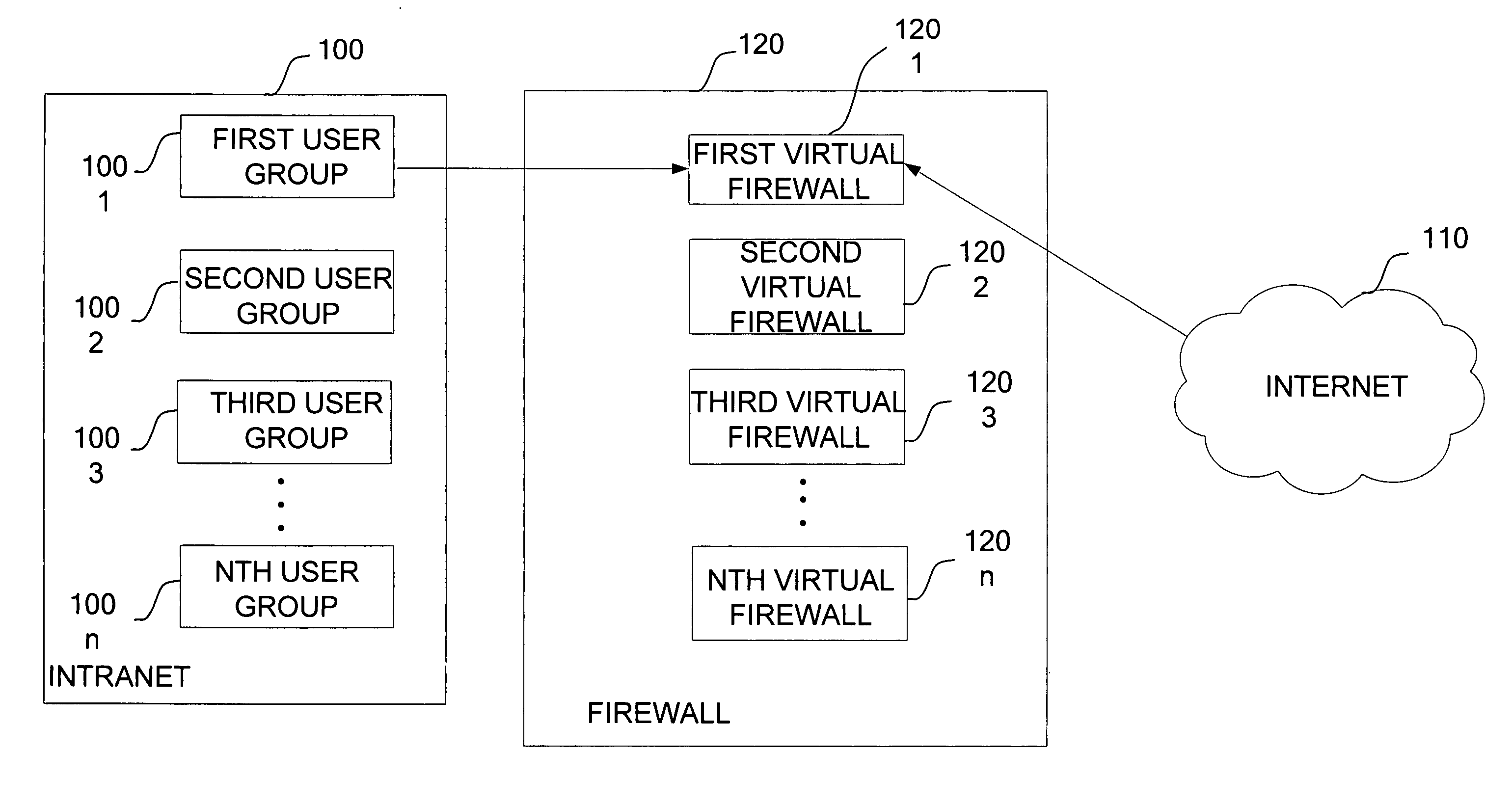
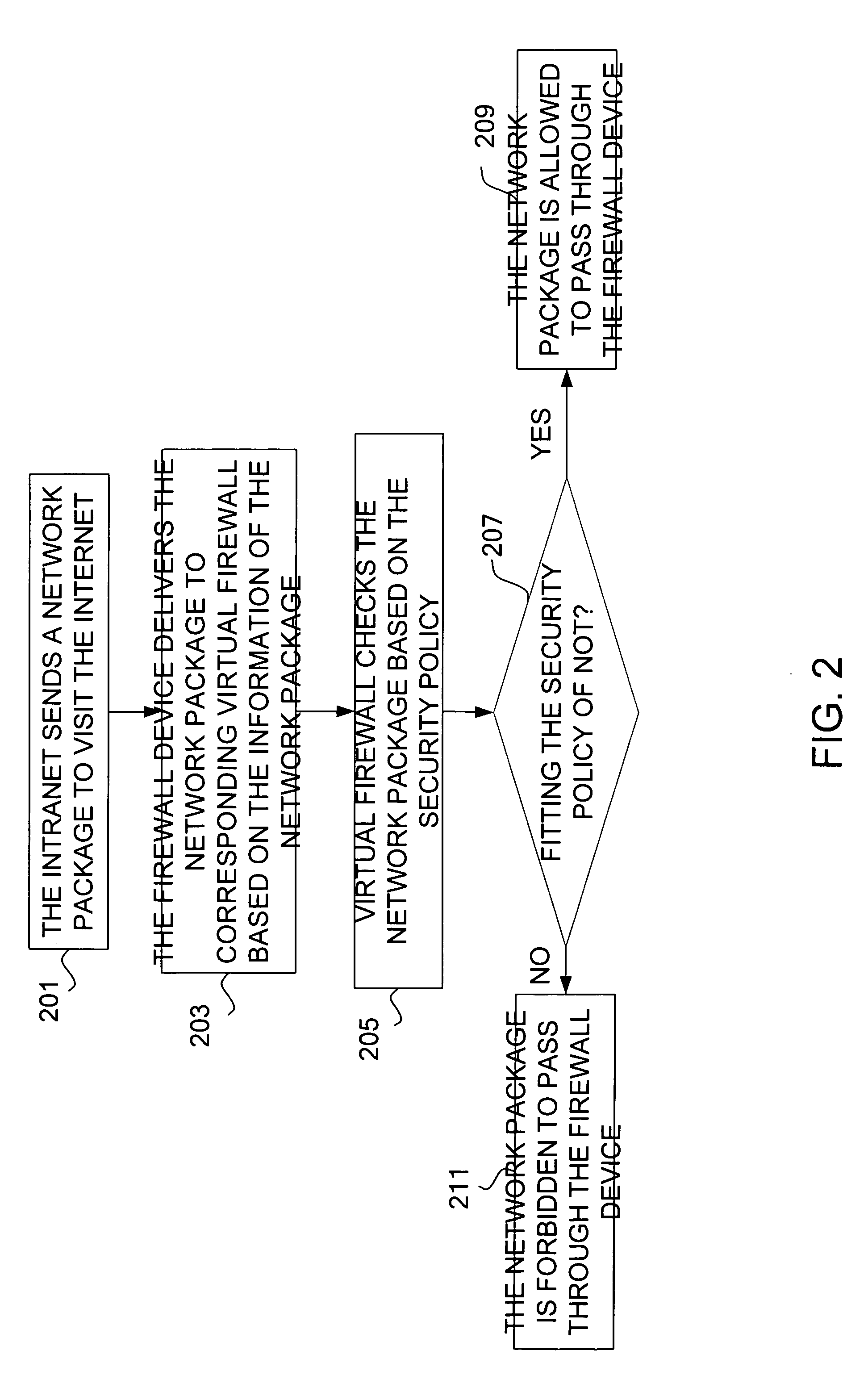
Network access control method and firewall device
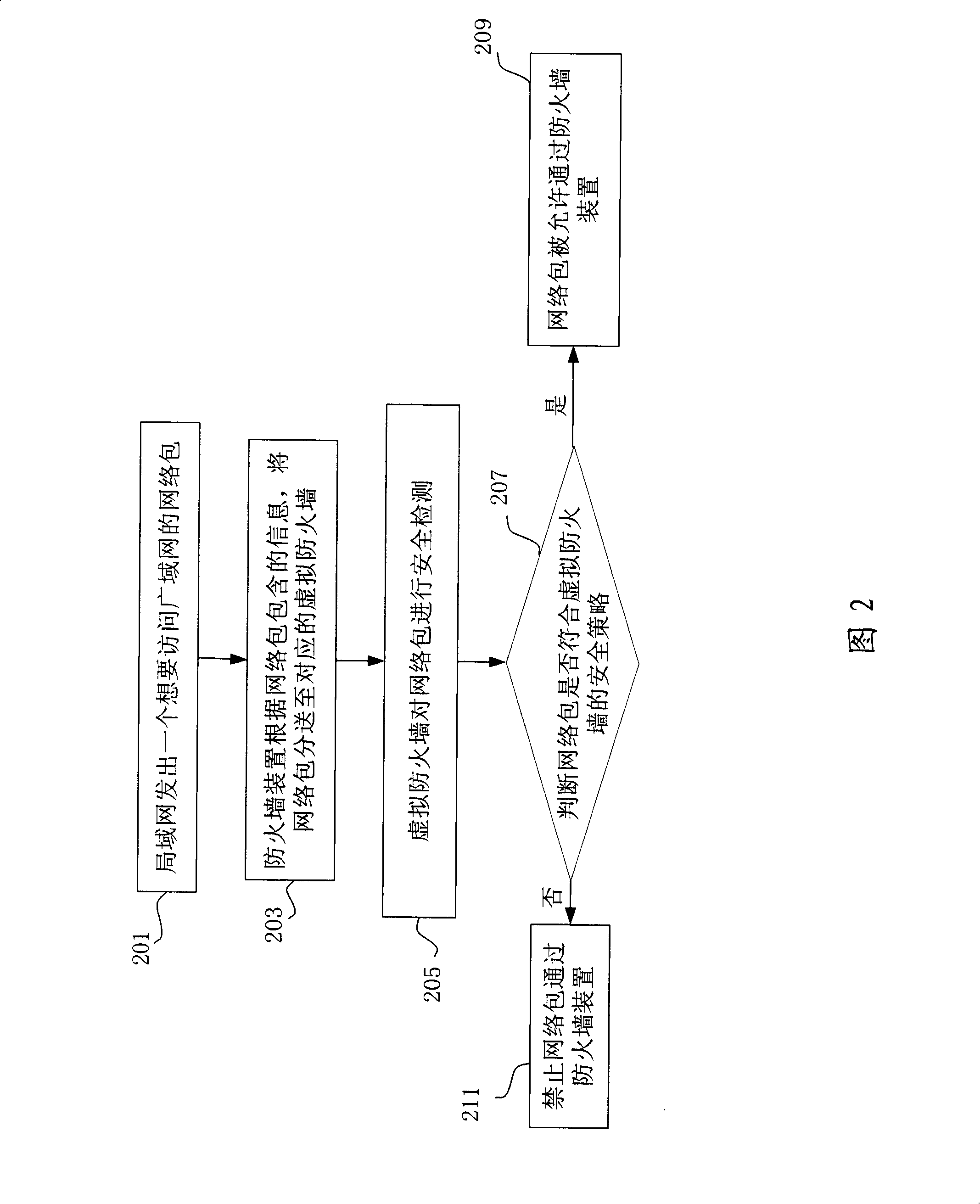
InactiveCN101212453AImprove work efficiencyReduce complexityData switching networksTraffic capacityVirtual firewall
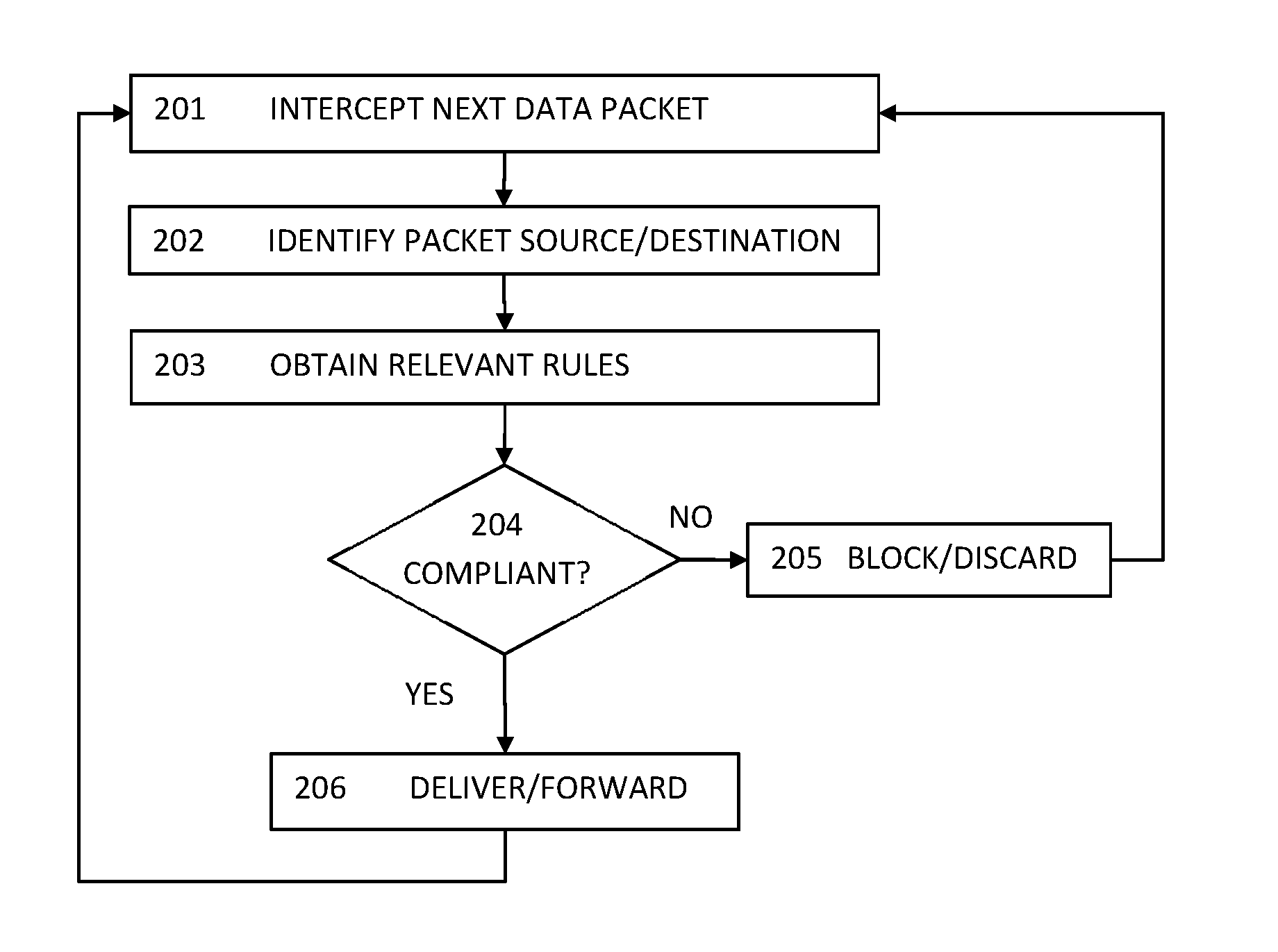
The invention discloses a method for realizing network access control and a firewall device thereof. The firewall device is arranged between a first network and a second network and the device comprises a plurality of virtual firewalls divided in logic. Each virtual firewall is provided with a safety strategy. The control method comprises the following steps: the first network send a network packet which accesses the second network; the firewall device, according to the contained information in the network packet, respectively sends the network packet to the corresponding virtual firewalls; the virtual firewall carries out a safety detection to the network packet; if the network conforms to the safety strategy of the virtual firewall, the network packet is allowed to pass through the firewall device; if the network fails to conform to the safety strategy of the virtual firewall, the network packet is prohibited from passing through the firewall device. As the network flow enters the firewall device, the network is divided and then is sent to the corresponding virtual firewall. Therefore, only the safety strategy in the corresponding virtual firewall is needed to look for, thus increasing working efficiency.
Owner:O2MICRO CHINA
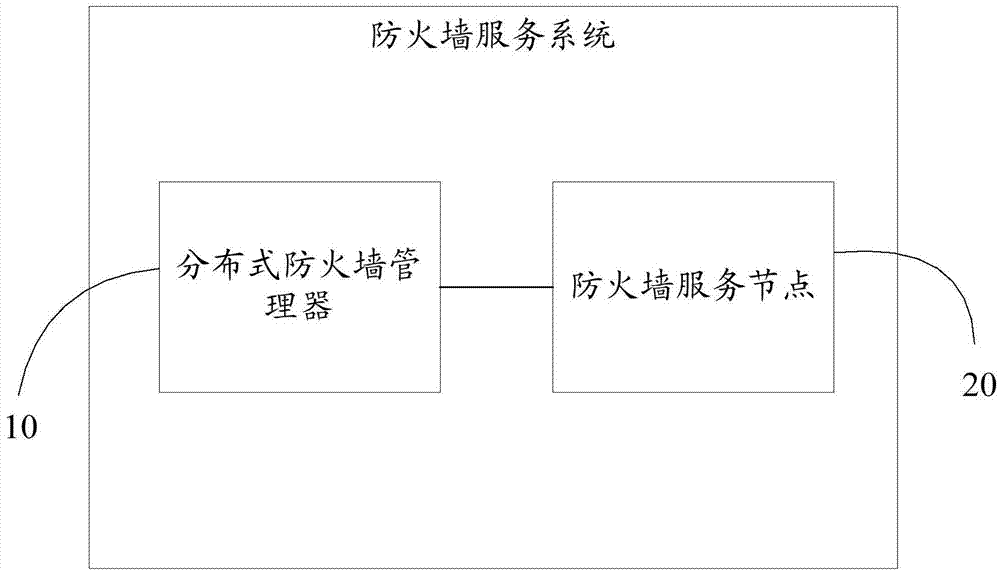
Firewall service system and method based on virtual network
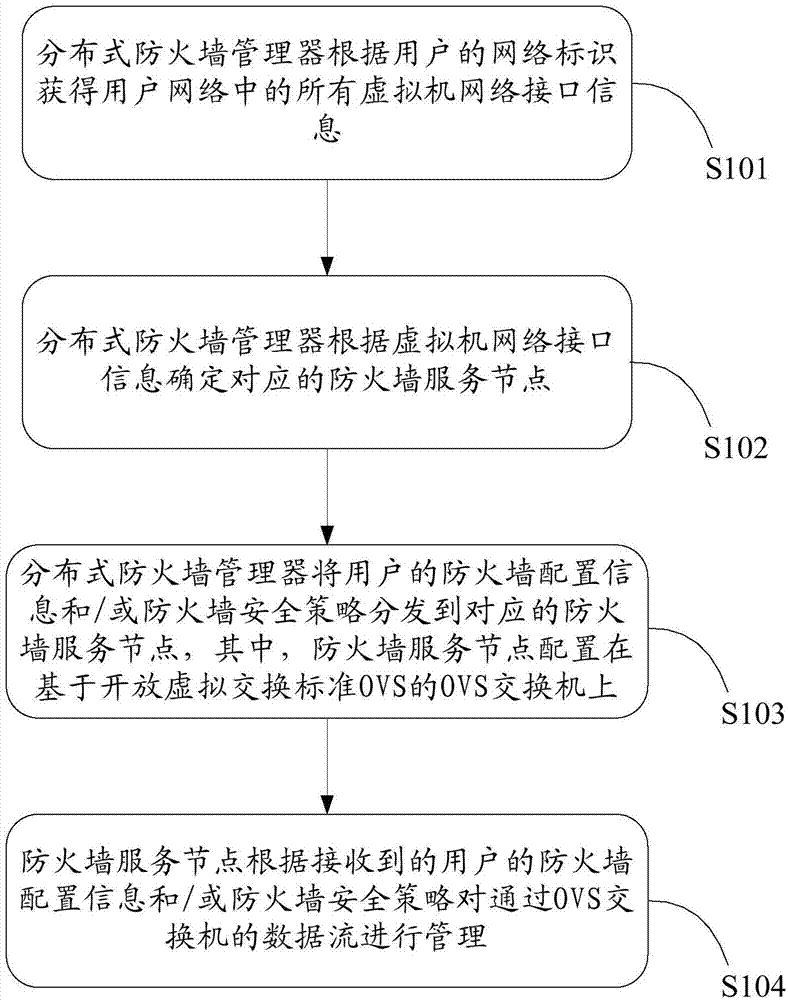
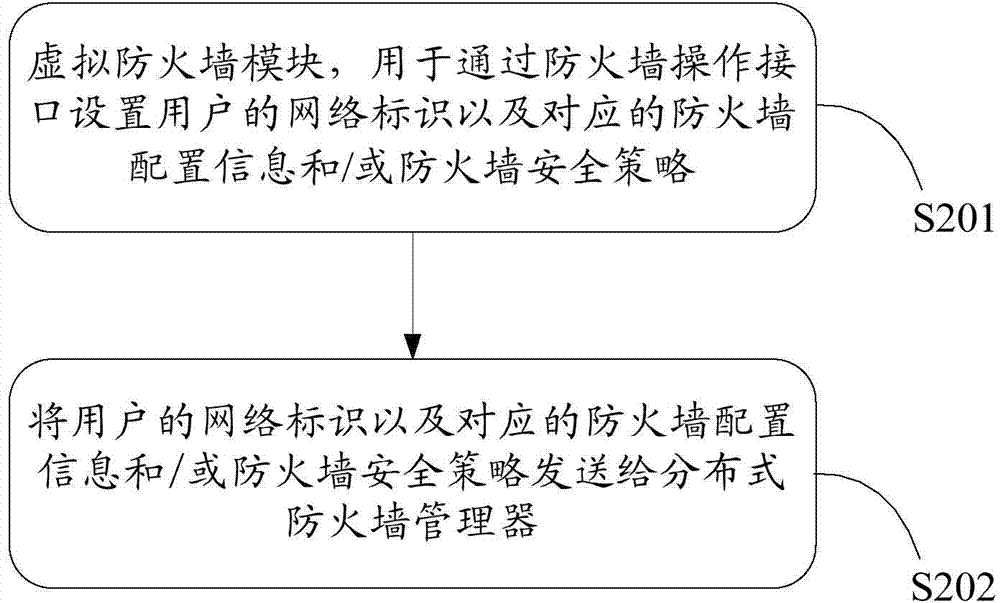
The invention provides a firewall service system based on a virtual network. The firewall service system based on the virtual network comprises a distributed type firewall manager and firewall service nodes, wherein the distributed type firewall manager is used for obtaining information of all virtual machine network interfaces in a user network according to the network identity of a user, determining the corresponding firewall service nodes according to the information of the virtual machine network interfaces, and distributing firewall configuration information and / or firewall security strategies of the user to the corresponding firework service nodes; the firewall service nodes are configured on an OVS switch based on OVS and are used for managing data flow passing through the OVS switch according to the received firewall configuration information and / or the received firewall security strategies of the user. The invention further provides a method for obtaining a virtual network firewall. By the adoption of the firewall service system based on the virtual network and the method for obtaining the virtual network firewall, through the deployment and the distributed management of the firewall service nodes, establishment of the distributed virtual network firewall is achieved.
Owner:DAWNING CLOUD COMPUTING TECH CO LTD
Distributed virtual firewall device and method
InactiveCN105141571ARapid detection filterAvoid performance bottlenecksSecuring communicationVirtual firewallVirtual switch
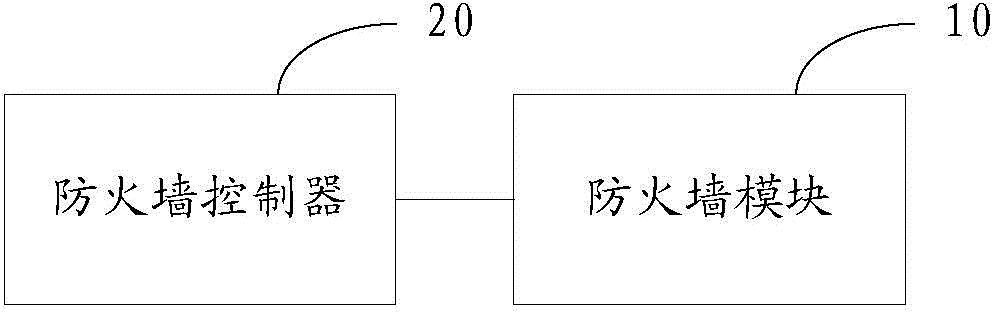
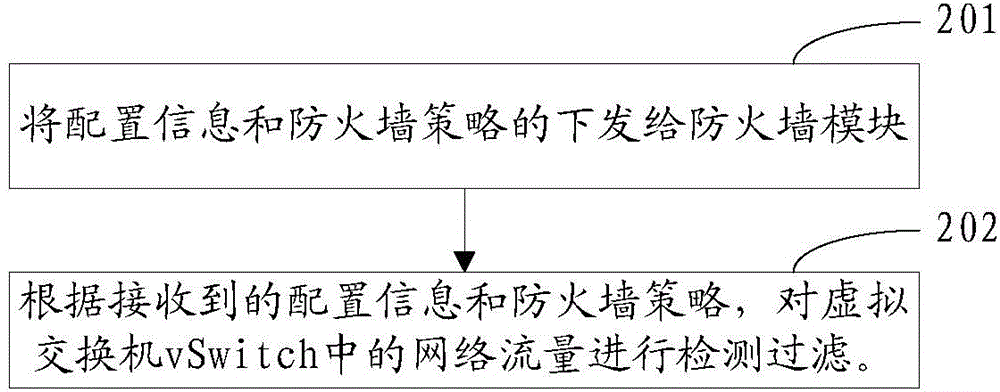
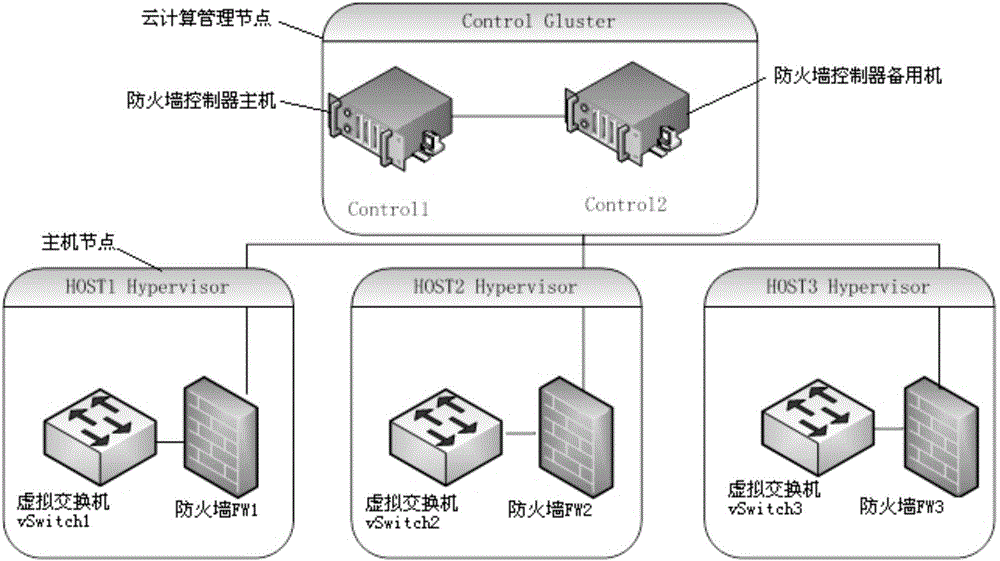
The invention provides a distributed virtual firewall device and a method. The device comprises a firewall controller and a firewall module, wherein the firewall controller is arranged on a cloud calculation management node and sends configuration information and firewall strategy information to the firewall module, the firewall module is arranged on a host node, and filtering detection on network flow in a virtual switch vSwitch is carried out according to the received configuration information and the firewall strategy information. Through the distributed virtual firewall device and the method, filtering detection on the network flow in the virtual switch vSwitch is carried out through the firewall module according to the received configuration information and the firewall strategy information, performance bottleneck in networking can be avoided, and the device further has advantages of abundant configuration strategy and flexible performance.
Owner:ZTE CORP
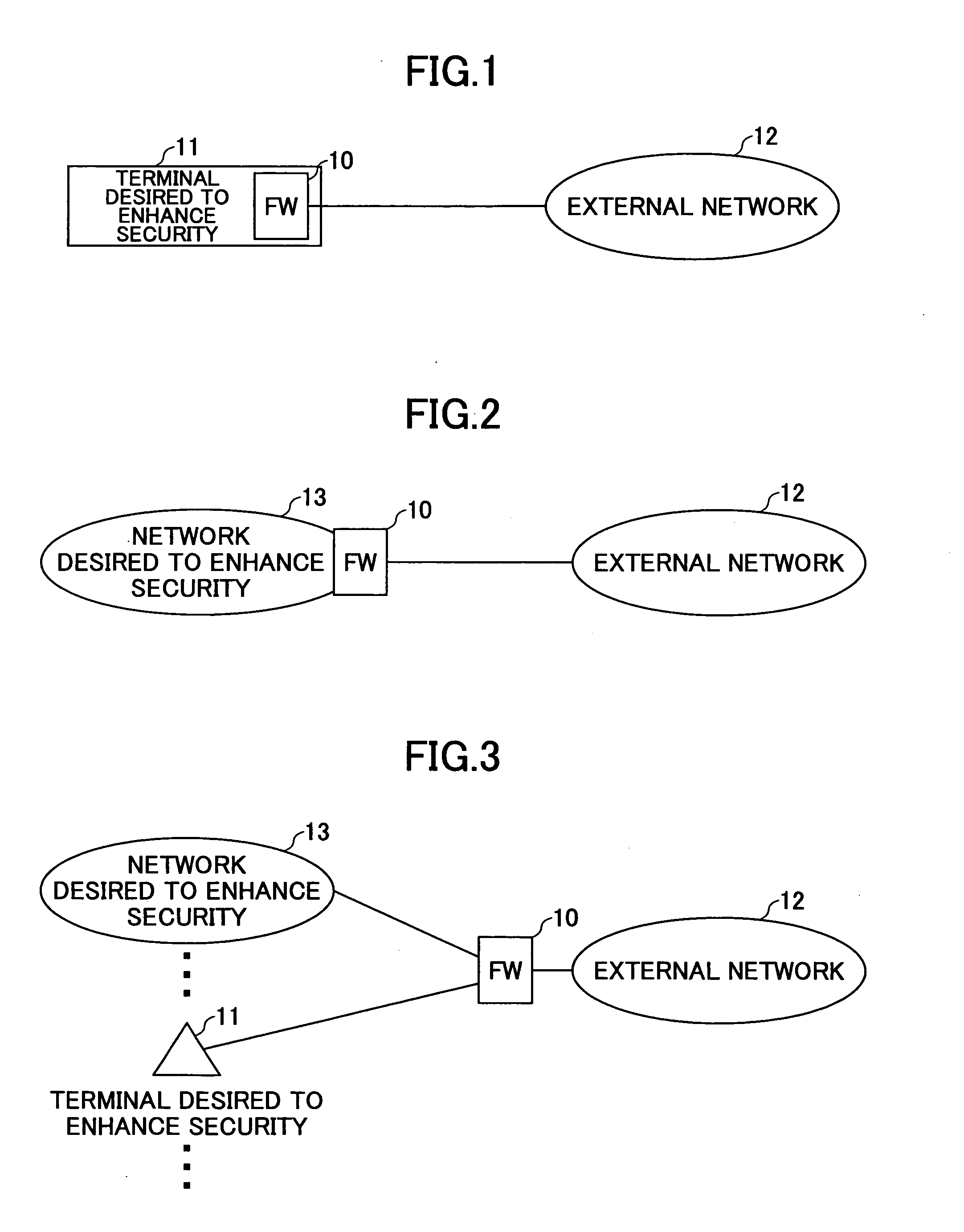
Virtual firewall
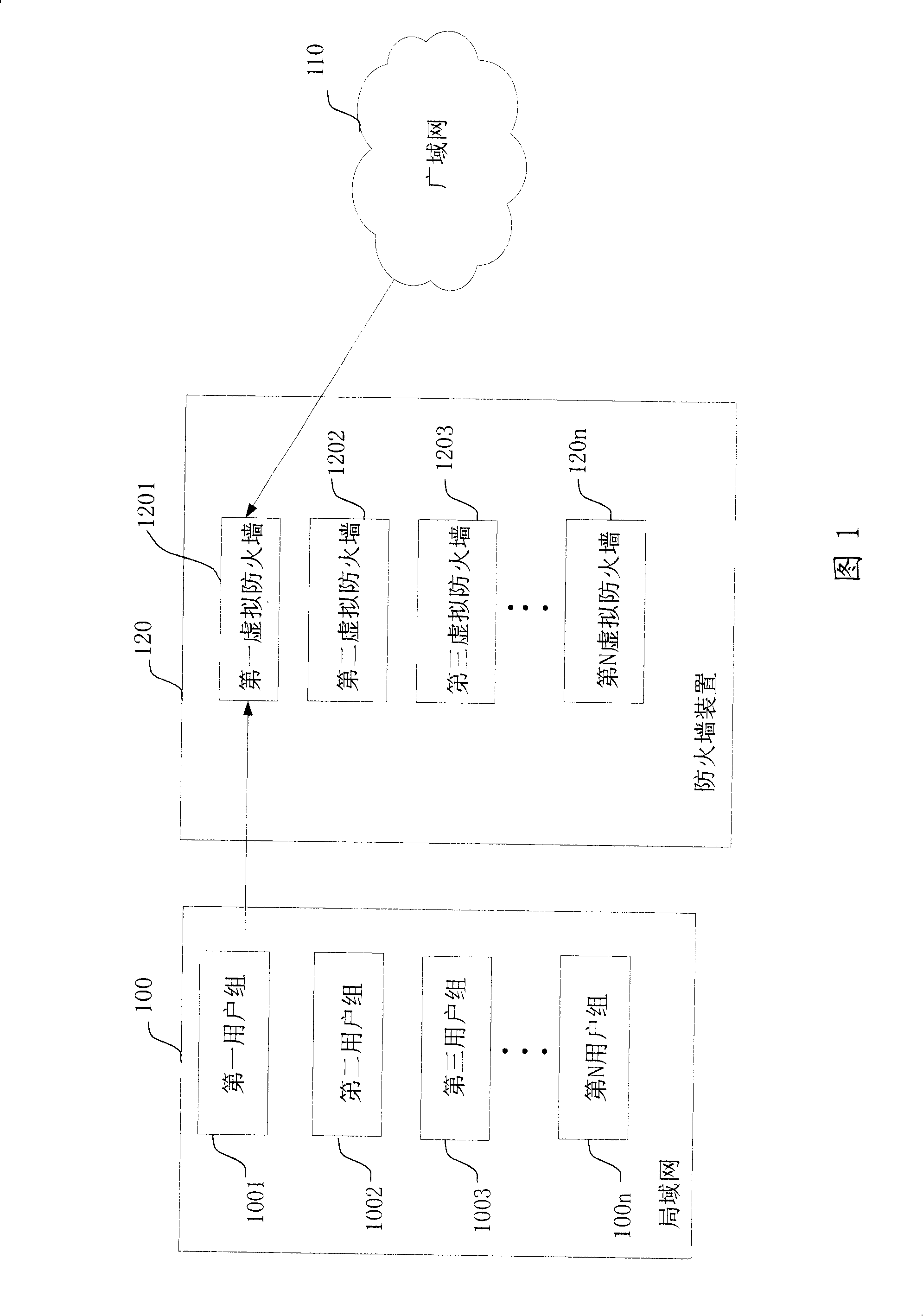
ActiveUS20080163357A1Digital data processing detailsMultiple digital computer combinationsVirtual firewallInternet privacy
The present invention provides a firewall device that is divided into several virtual firewalls. The users in the Intranet are divided into several user groups based on different security policy demands. Each virtual firewall is equipped with the security policy of the corresponding user group. Each firewall manages one user group in the Intranet. Thus, the present invention reduces the complex of the firewall management, reduces the extra cost of adding more firewalls and makes the management easier.
Owner:IYUKO SERVICES
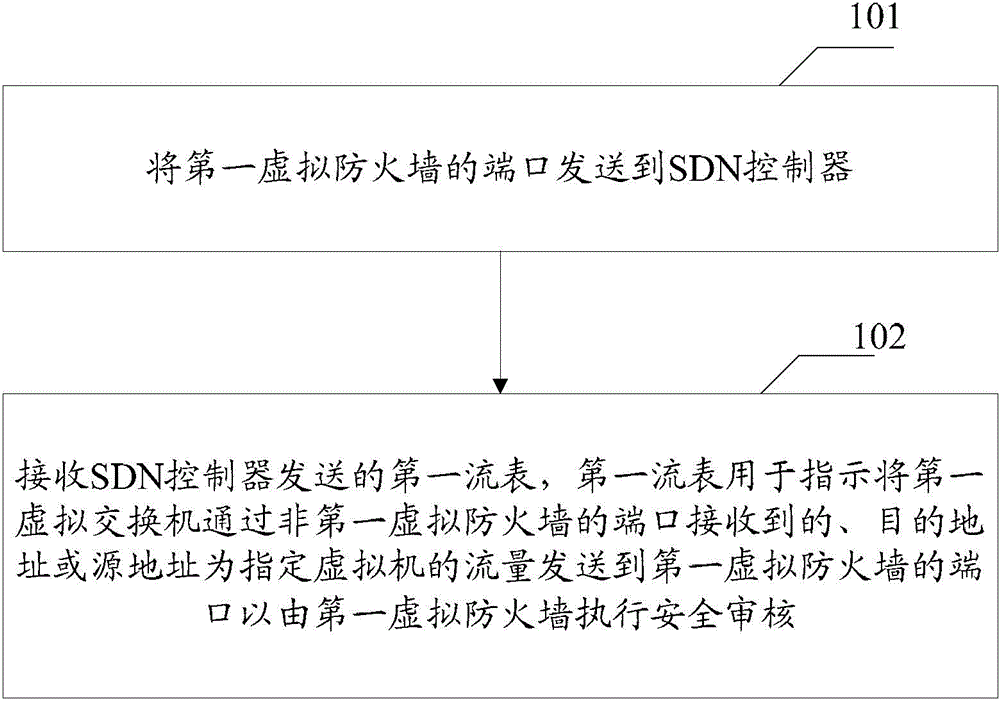
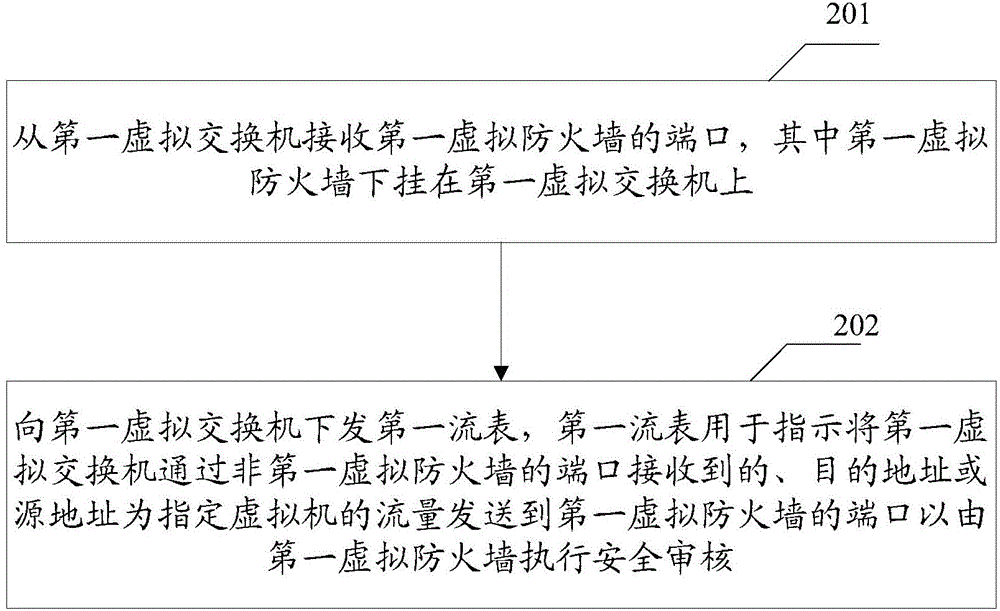
Method and device for realizing virtual firewall in software defined network
ActiveCN105656841AFlexible control of security policy inspectionGive full play to the function of the global managerTransmissionVirtual firewallVirtual switch
Embodiments of the invention provide a method and a device for realizing a virtual firewall in an SDN (Software Defined Network). The method is suitable for a first virtual switch, and a first virtual firewall is suspended under the first virtual switch. The method comprises the following steps of sending a port of the first virtual firewall to an SDN controller; and receiving a first flow table sent by the SDN controller, wherein the first flow table is used for indicating to send data to the port of the first virtual firewall to execute security auditing through the first virtual firewall, and the traffic is not received by the port of the first virtual firewall, and the target address or the source address of the data is an appointed virtual machine.
Owner:NEW H3C TECH CO LTD
Design of virtual firewall assembly acting on cloud computing data center security domain
Provided is a design of a virtual firewall assembly acting on a cloud computing data center security domain. The invention relates to Web direction network security production, and particular relates to a network security technology under a cloud computing environment. The technical scheme is that the firewall assembly is operated via a distributed deployment security gateway so that customized and distributed security protection of the overall data center is completed. A new firewall system structure comprises the following parts: the unified security gateway, the network firewall assembly and central management. The firewall assembly based on a data packet filtering technology is realized. The assembly operates in the unified security gateway. Network traffic is controlled by using the data packet filtering technology, distributed deployment is used and customized security protection of the overall data center is completed.
Owner:XIAN FUTURE INT INFORMATION CO LTD +1
North-south flow safety protection system in cloud computing network
InactiveCN105245504ARealize security protectionTransmissionSoftware simulation/interpretation/emulationTraffic capacityVirtual firewall
The invention discloses a north-south flow safety protection system in a cloud computing network. The system comprises a virtual machine occupied by a tenant, a virtual firewall for monitoring communication between the virtual machine currently occupied by the tenant and a Network, a first network forwarding layer and a second network forwarding layer, wherein the first network forwarding layer is used for judging a source of a message through recognizing a label of the received message, if the message is from the virtual machine, the message is forwarded to the virtual firewall corresponding to the tenant of the current virtual machine, and the message processed by the virtual firewall is sent to the Network via a second-layer switch and a third-layer switch; and the second network forwarding layer is used for receiving the message from the Network, judging the tenant to which the message belongs through recognizing the label of the message, issuing the message to the virtual machine corresponding to the tenant designated by the label of the message, and forwarding the message sent by the virtual machine to the second-layer switch.
Owner:北京汉柏科技有限公司
Method and apparatus for realizing high availability
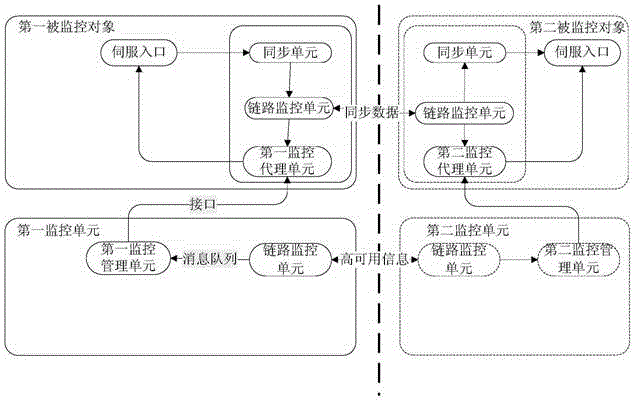
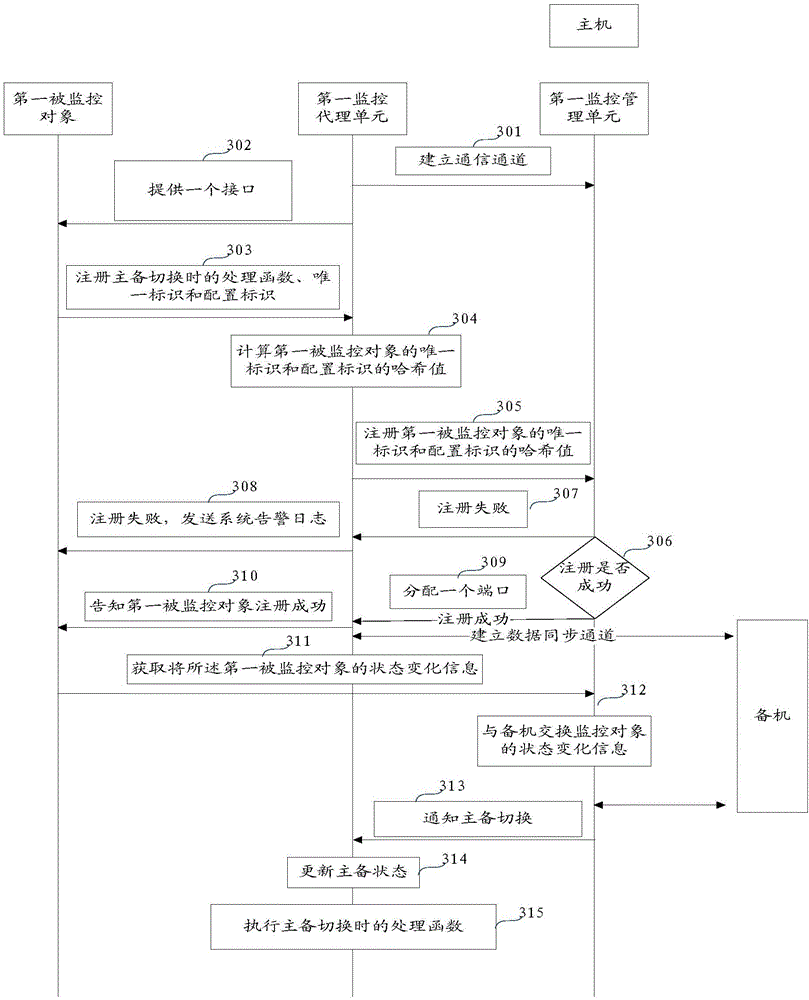
InactiveCN106411589ALow running costImprove work efficiencyData switching networksState variationVirtual firewall
The embodiment of the invention relates to the field of network security, and particularly relates to a method and apparatus for realizing high availability. The method and apparatus is used for realizing the high availability of a plurality of network security devices. The method comprises the following steps: a first monitoring unit acquires state change information of a first monitored object and receives the state change information of a second monitored object sent by a second monitoring unit, wherein the second monitored object is a master device or a slave device of the first monitored object; the first monitoring unit updates an active / standby state of the first monitored object when the state change information of the first monitored object and the state change information of the second monitored object satisfy a preset active / standby switching condition; a next generation firewall / intrusion prevention system and an ATCA distributed firewall and virtual firewall under the ''parallel forwarding engine'' architecture are compatible at the same time; and when the network security device needs to be changed, the device or the system of the device does not need to be changed or replaced, thereby reducing the operation cost and improving the working efficiency.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Implementation method of virtual firewall
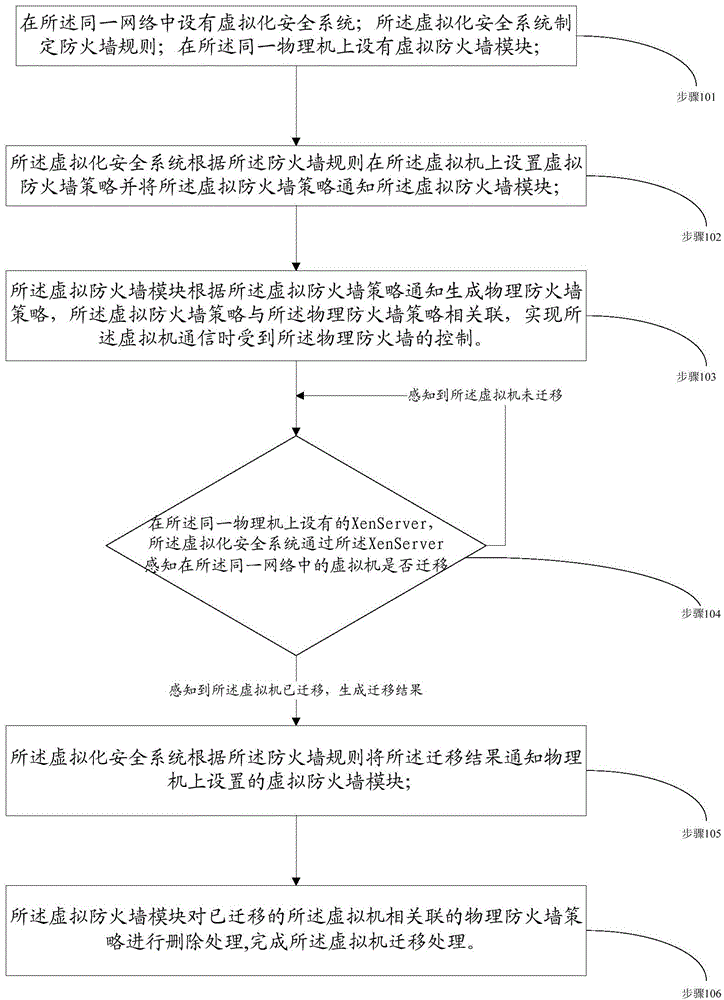
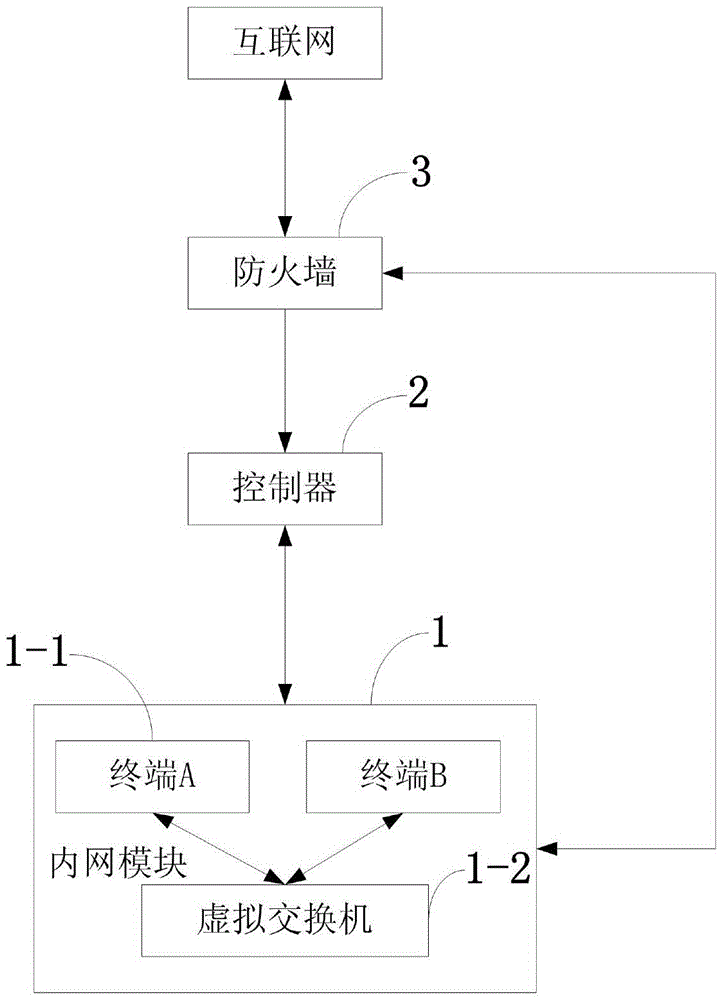
InactiveCN104660553AEnable secure communicationEfficient use ofNetworks interconnectionVirtualizationSecure communication
The invention discloses an implementation method of a virtual firewall. Over two different virtual machines in an identical network are positioned on an identical physical machine. The implementation method comprises the following steps that: 101, a virtualization security system is arranged in the identical network, the virtualization security system makes up a firewall rule, and a virtual firewall module is arranged on the identical physical machine; 102, the virtualization security system sets a virtual firewall strategy on the virtual machines according to the firewall rule, and notifies the virtual firewall module of the virtual firewall strategy; and 103, the virtual firewall module generates a physical firewall strategy according to the virtual firewall strategy notification, and the virtual firewall strategy is correlated with the physical firewall strategy in order to implement control of the virtual machines under a physical firewall during communication. Through adoption of the implementation method, secure communication among the virtual machines is implemented; installation of firewall software for the virtual machines is simplified; and the physical firewall is efficiently utilized.
Owner:长城超云(北京)科技有限公司
Openflow based virtual firewall transmission control method and system
InactiveCN105471907AIncrease flexibilityImprove controllabilityTransmissionPaper documentControllability
The invention discloses an Openflow based virtual firewall transmission control method and system. The Openflow based virtual firewall transmission control method comprises the steps of after a data packet is sent from a host, extracting key information of the data packet by a firewall core module through a virtual network card configured on a virtual firewall, and performing basic mapping for the key information of the data packet by the virtual firewall through a firewall definition rule; and after a rule document is filtered by the firewall and the data packet reaches to a port, intercepting the data packet and performing grammatical analysis for the packet header, and extracting a packaging protocol, an IP source address, an IP destination address, an Mac address, and information of a packet input port and a packet output port; and forwarding and matching. According to the Openflow based virtual firewall transmission control method and system, flexibility and controllability of a network are improved, the bottleneck problems of high implementation cost and low processing efficiency of massive data are solved, safety of an internal network and a terminal is guaranteed, scanning and monitoring for transmission data of multiple networks, monitoring management of a specific service port and access control of a special website are realized, and the whole network can be protected.
Owner:YUNNAN UNIV
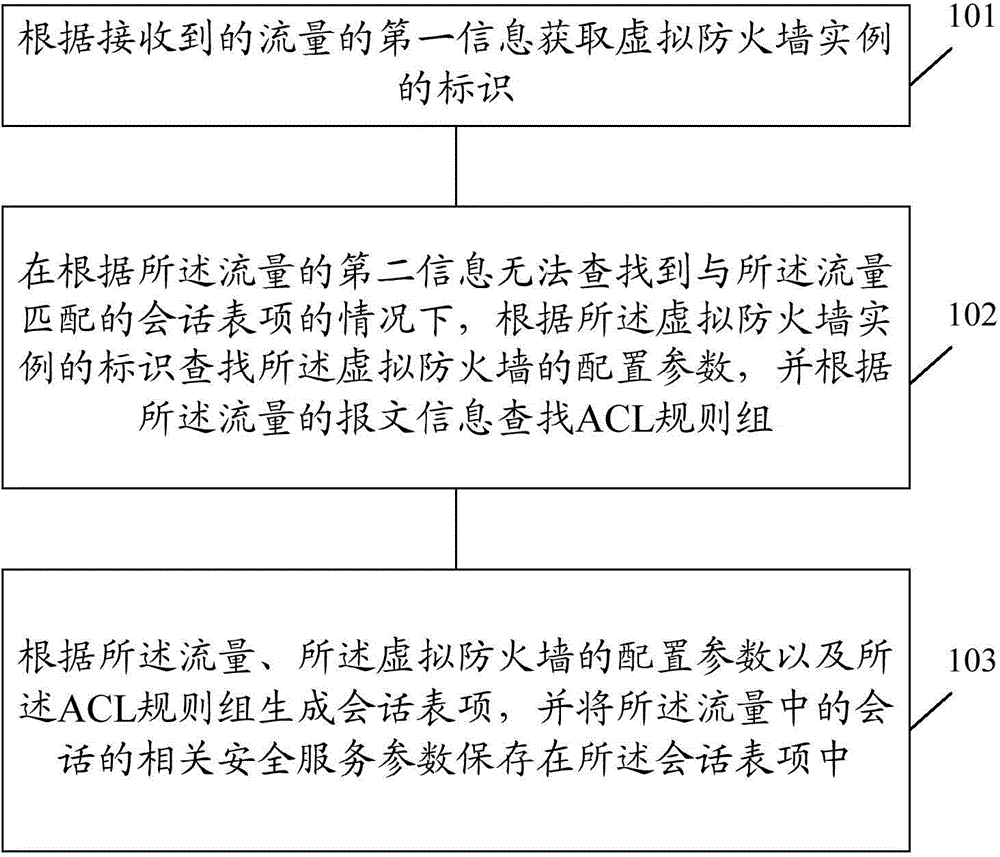
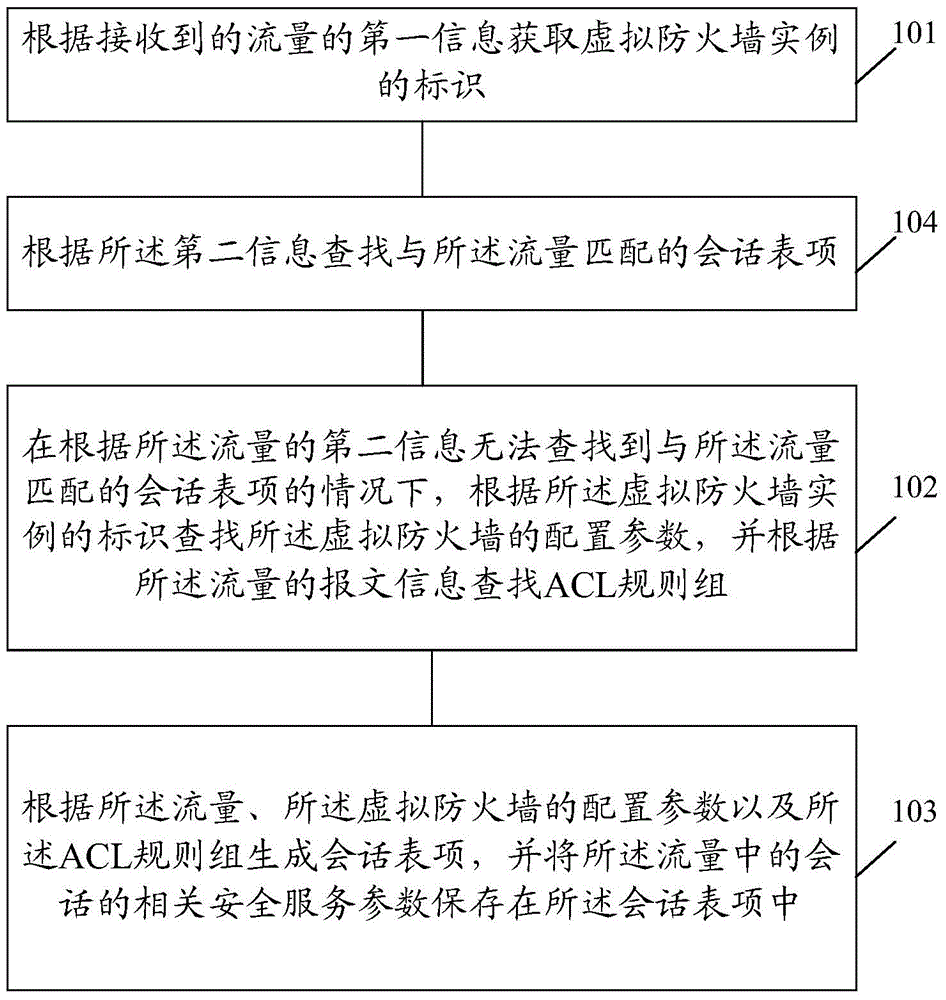
Method and device for realizing virtual firewall
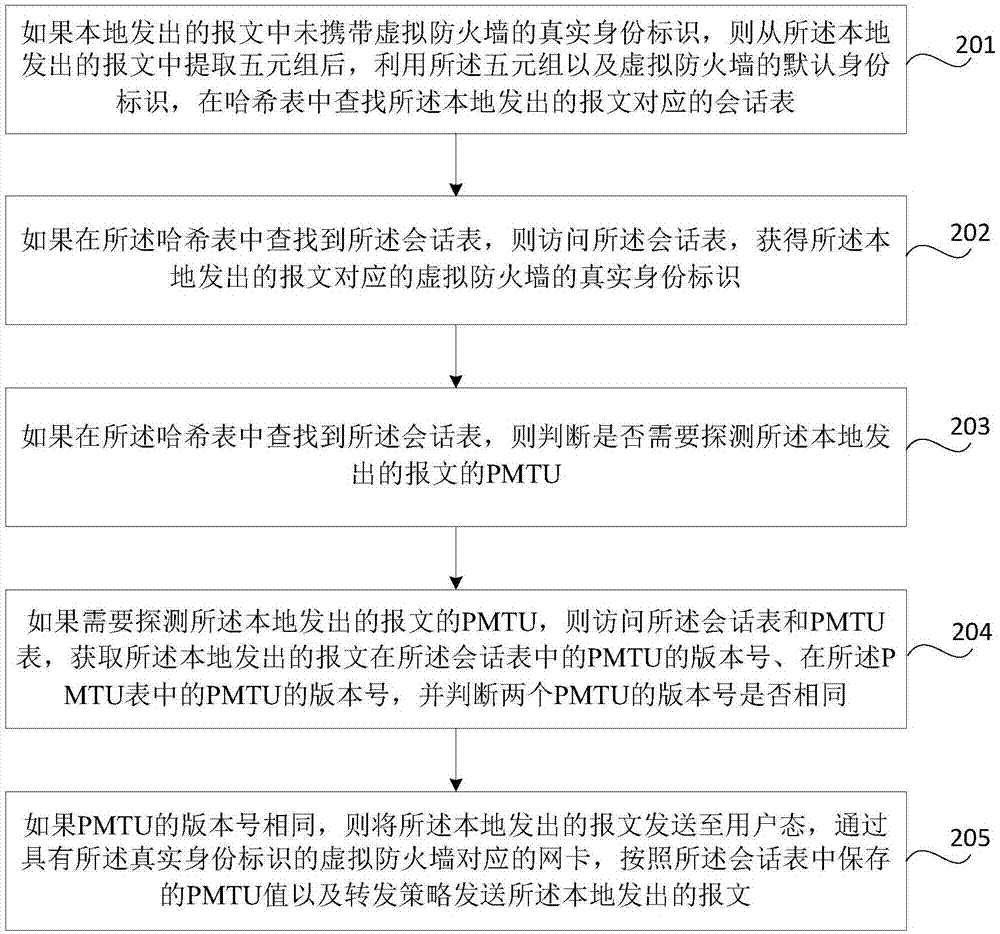
ActiveCN105577628AMeet different security needsAddress deployment deficienciesSecuring communicationVirtual firewallData traffic
The invention discloses a method for realizing a virtual firewall. The method includes the following steps that: the identifier of a virtual firewall instance is obtained according to the first information of received data flow; the configuration parameters of the virtual firewall are searched according to the identifier of the virtual firewall instance, and an ACL rule group is searched according to the message information of the data flow; and session table entries are generated according to the data flow, the configuration parameters of the virtual firewall and the ACL rule group, relevant security service parameters of sessions in the data flow are saved in the session table entries. The invention also discloses a device for realizing a virtual firewall. With the method and device for realizing the virtual firewall of the invention adopted, a physical firewall can be divided into a plurality of logical firewalls for use, and each logical firewall can independently apply for resources; and at the same time, the disadvantages of traditional firewall deployment can be eliminated, and independent security service strategies can be provided for different users under the premise that maintenance and management cost can be greatly reduced.
Owner:ZTE CORP
Agentless Security of Virtual Machines Using a Network Interface Controller
ActiveUS20170054685A1TransmissionSoftware simulation/interpretation/emulationDigital dataVirtual firewall
An agentless intrusion detection and prevention digital processing system and environment, or virtual firewall is disclosed. The agentless, virtual firewall monitors and controls digital data communications between a digital communications network and one or more virtual digital processing machines. The virtual digital processing machines, or virtual machines (VMs), are operative on a host digital processor under the supervision of a hypervisor software module. The agentless, virtual firewall is implemented as part of a virtual switch filtering extension to an extensible virtual switch running in a kernel mode as part of the hypervisor software module.
Owner:MIDCAP FINANCIAL TRUST
Cloud data center service subnet security management method and system
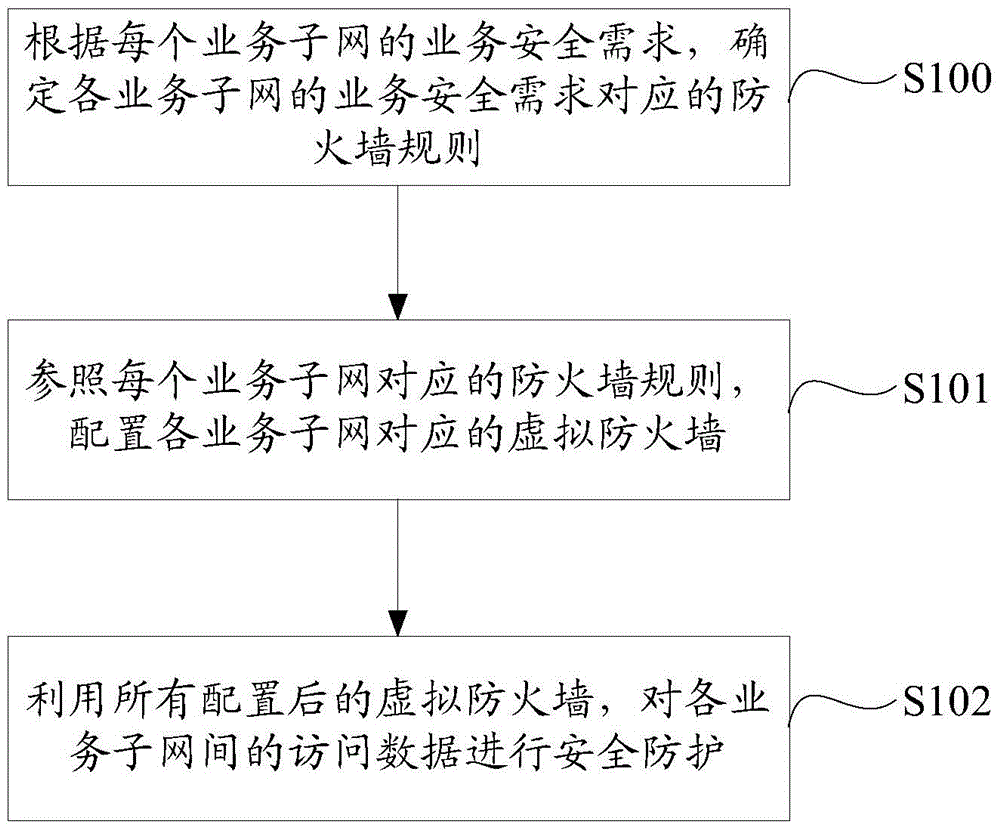
InactiveCN105656916ARealize security protection functionImprove securityTransmissionVirtual firewallData access
The invention discloses a cloud data center service subnet security management method and system. The cloud data center service subnet security management method comprises the steps: according to service security requirements of each service subnet, determining a firewall rule corresponding to the service security requirements of each service subnet; by referring to the firewall rule corresponding to each service subnet, configuring a virtual firewall corresponding to each service subnet; by utilizing all configured virtual firewalls, performing security protection on access data of each service subnet; wherein the service security requirements of each service subnet are data access security requirements between a service subnet and another service subnet in a cloud data center. According to the cloud data center service subnet security management method and system, the virtual firewalls capable of being configured in the interior of a physical server are introduced; furthermore, each virtual firewall can be configured with the self corresponding firewall rule according to the service security requirements of different service subnets; therefore, a purpose that a security protection function is provided for different service subnets in the data center so as to improve the security of internal data in the cloud data center is implemented.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
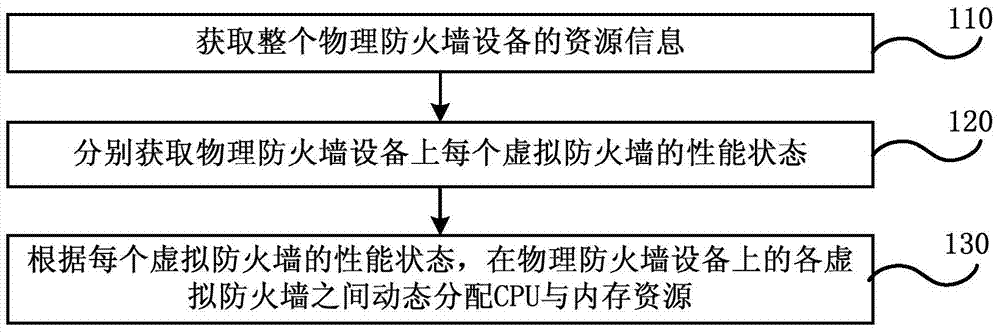
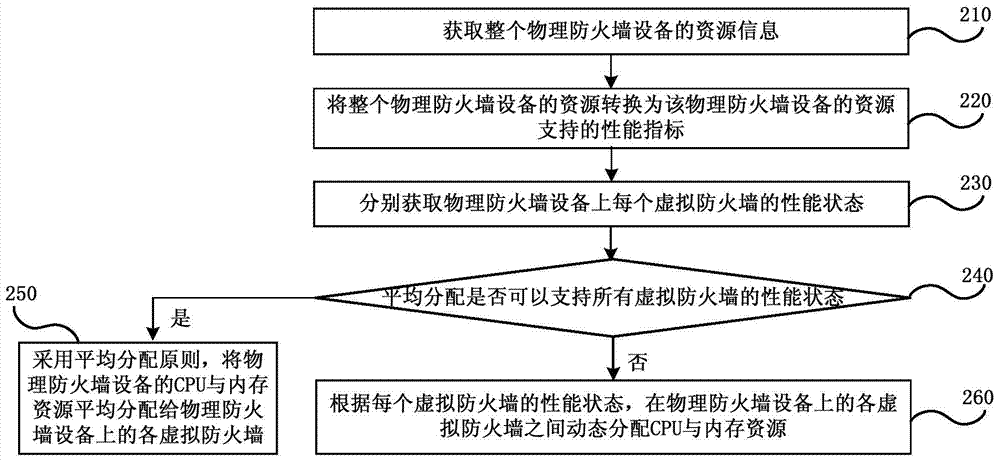
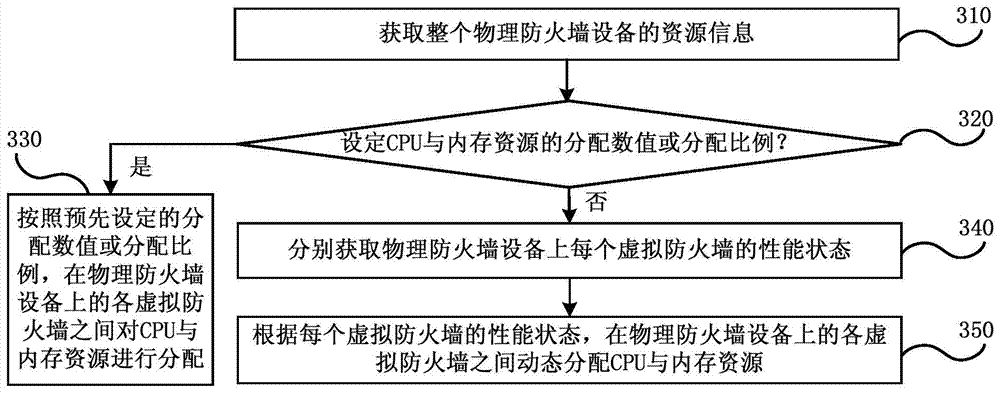
Resource management optimization processing method and resource management optimization processing device for virtual firewalls
InactiveCN104518897AEnsure safety and stabilityReasonable distributionData switching networksVirtual firewallResource information
An embodiment of the invention discloses a resource management optimization processing method and a resource management optimization processing device for virtual firewalls. The resource management optimization processing method includes acquiring resource information of integral physical firewall equipment; respectively acquiring a performance state of each virtual firewall on the physical firewall equipment; dynamically distributing CPU (central processing unit) and memory resources between the various virtual firewalls on the physical firewall equipment according to the performance state of each virtual firewall. The resource information includes information of the CPU and memory resources. The resource management optimization processing method and the resource management optimization processing device in the embodiment of the invention have the advantages that the resources can be reasonably distributed for the various virtual firewalls in a single physical firewall, and accordingly the safety and the stability of the integral physical firewall can be effectively guaranteed.
Owner:CHINA TELECOM CORP LTD
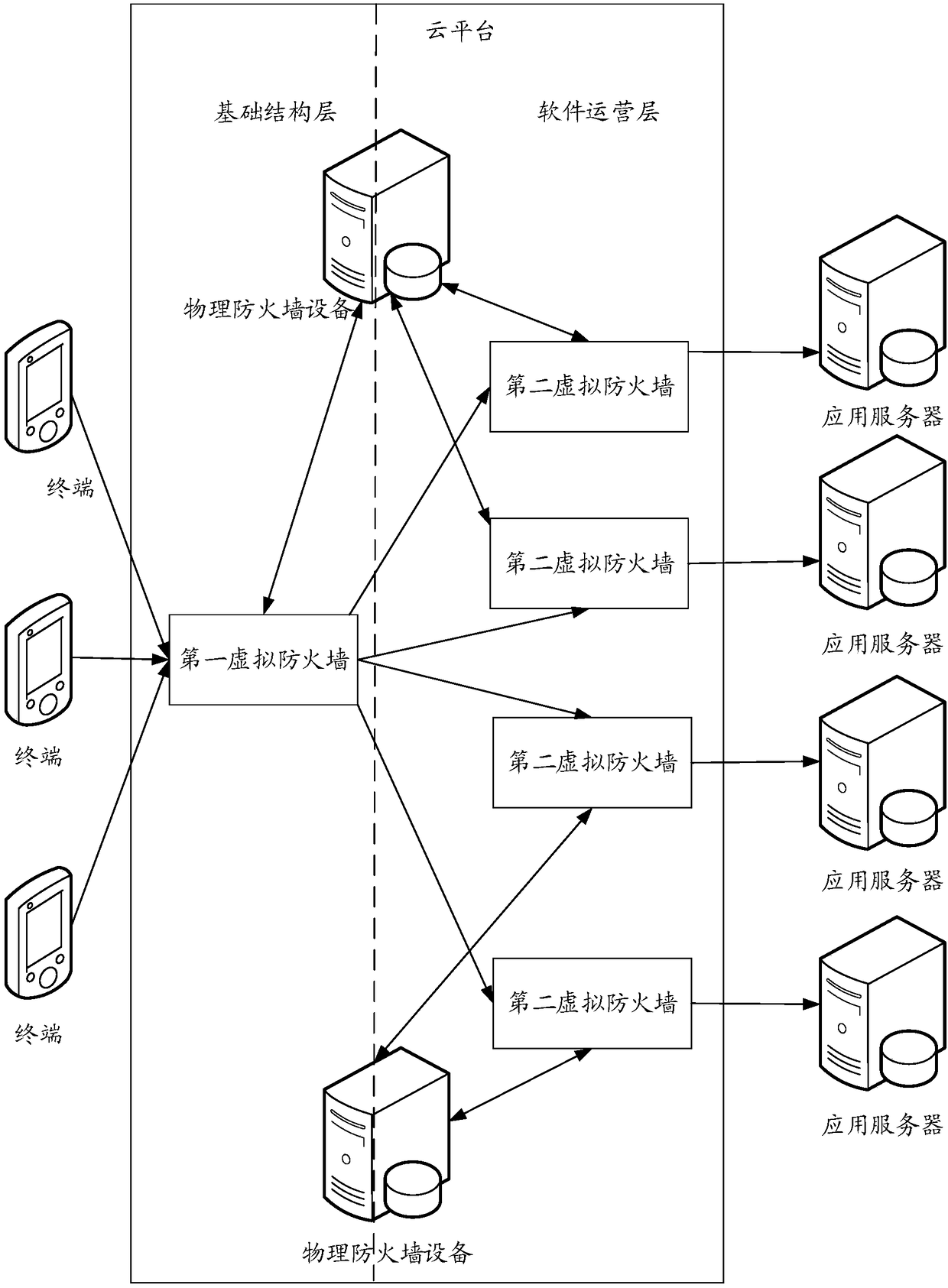
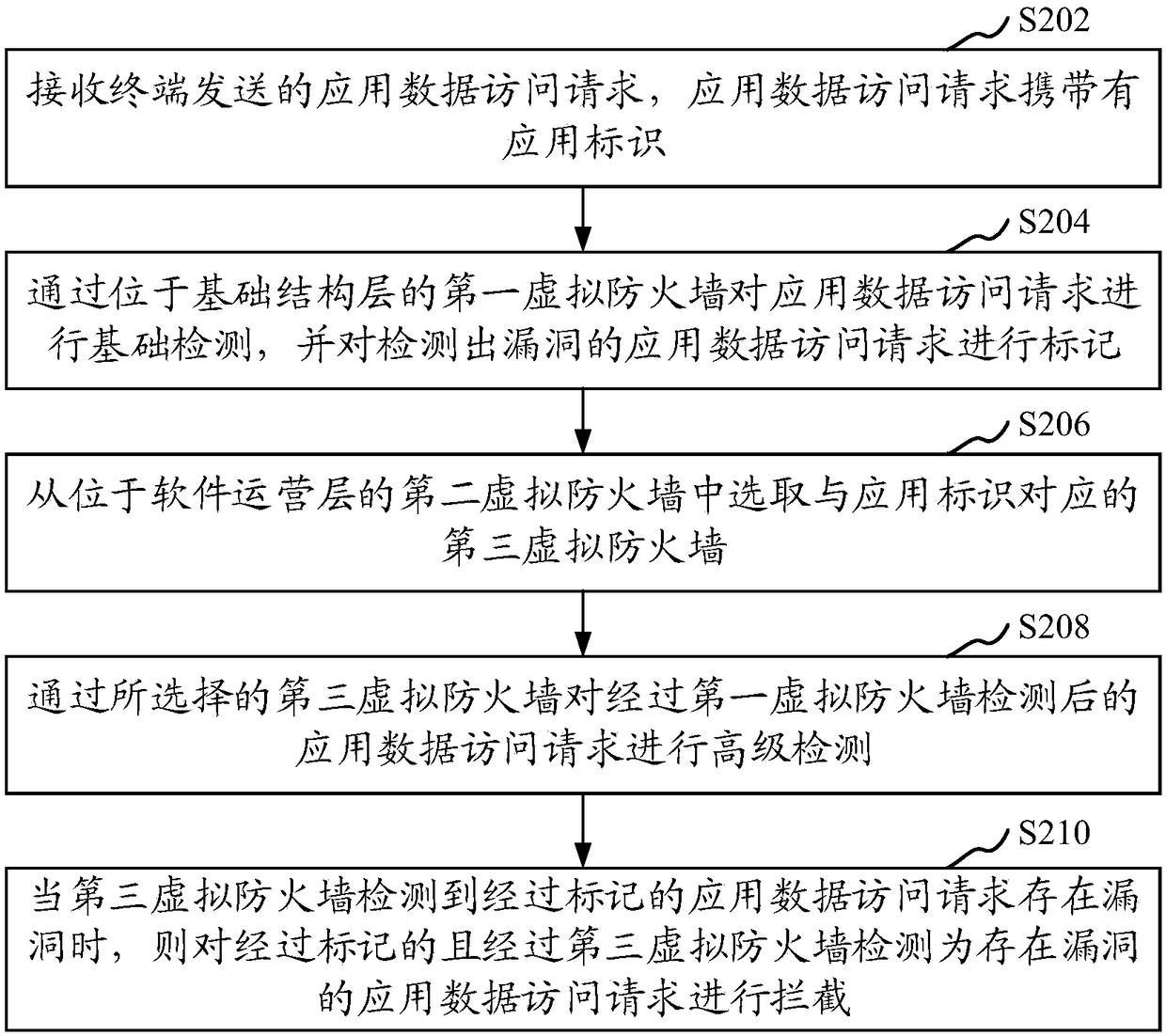
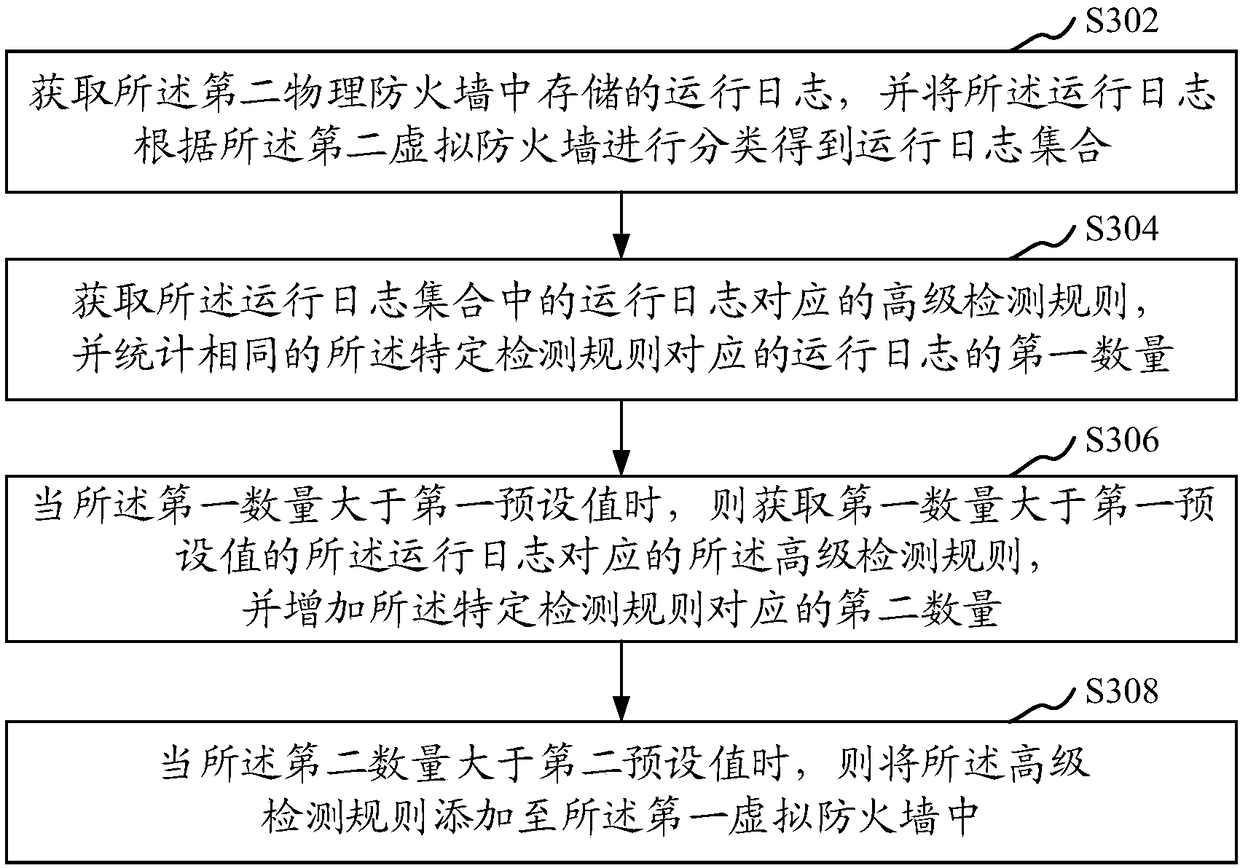
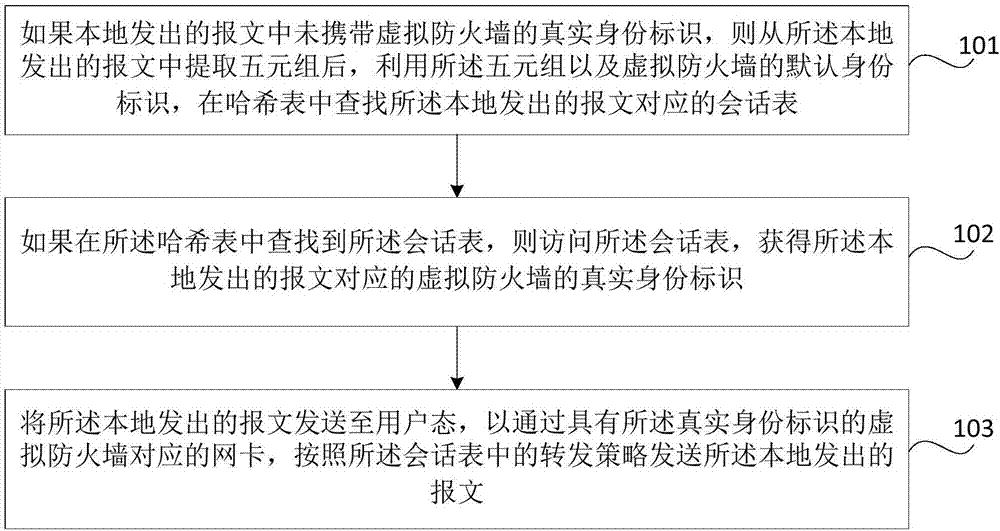
Vulnerability detection method and device, computer equipment and memory medium
The invention relates to a vulnerability detection method and device, computer equipment and a memory medium. The method comprises the steps of receiving application data access requests sent by terminals, wherein the application data access requests carry application identities; carrying out basic detection on the application data access requests through utilization of a first virtual firewall located in an infrastructure layer and marking the application data access requests with vulnerabilities; selecting third virtual firewalls corresponding to the application identities from second virtual firewalls located in a software operation layer; carrying out advanced detection on the application data access requests detected by the first virtual firewall through utilization of the selected third virtual firewalls; and intercepting the marked application data access requests in which the vulnerabilities exist when the third virtual firewalls detect that the vulnerabilities exist in the marked application data access requests, wherein the application data access requests are the requests detected by the third virtual firewalls. According to the method, the security of application servers can be improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Message forwarding method and device, memory medium and electronic device
ActiveCN107888500AImprove forwarding performanceData switching networksVirtual firewallNetwork interface controller
Owner:NEUSOFT CORP
Virtual firewall configuration method based on OVS, electronic equipment and storage medium
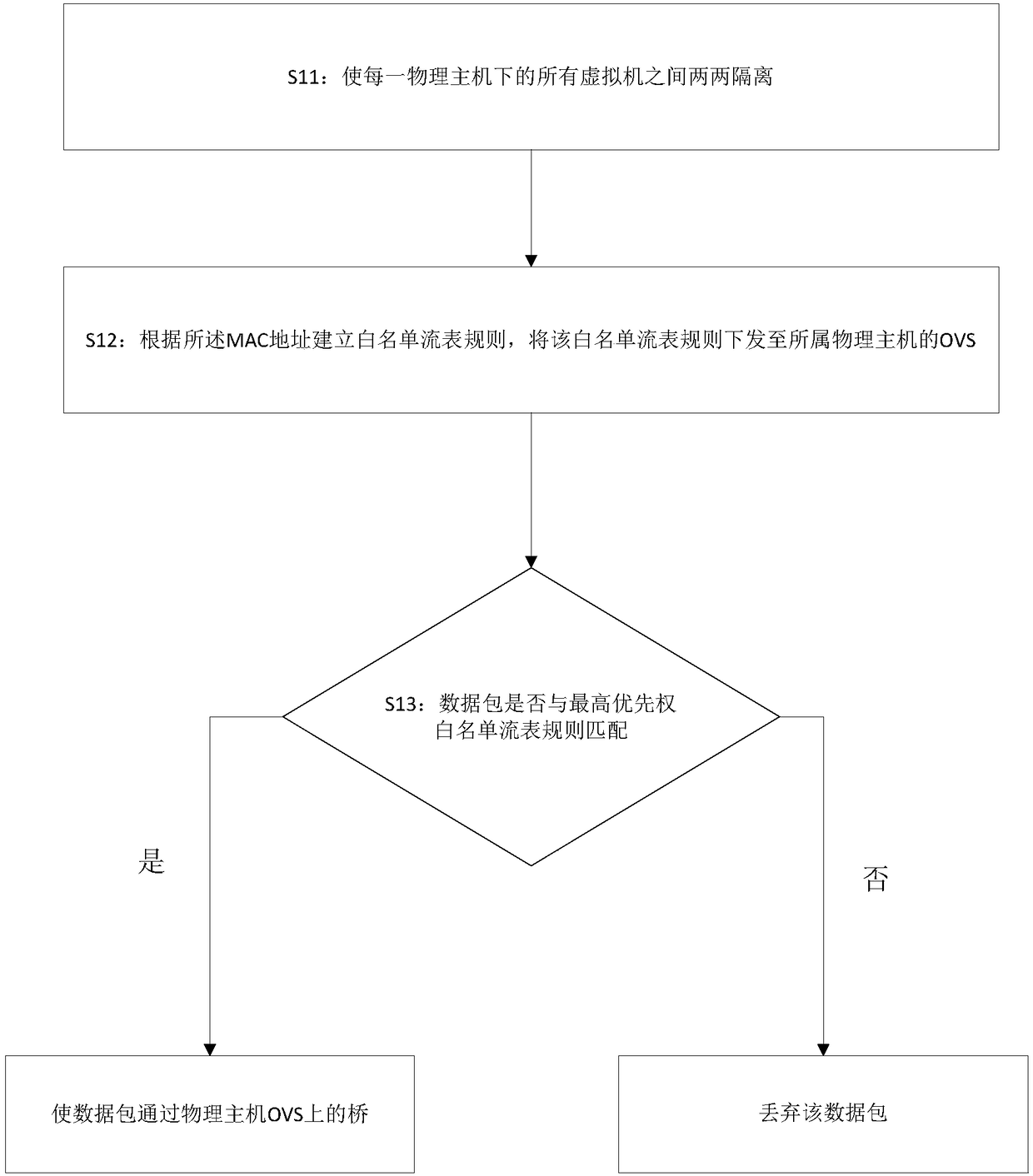
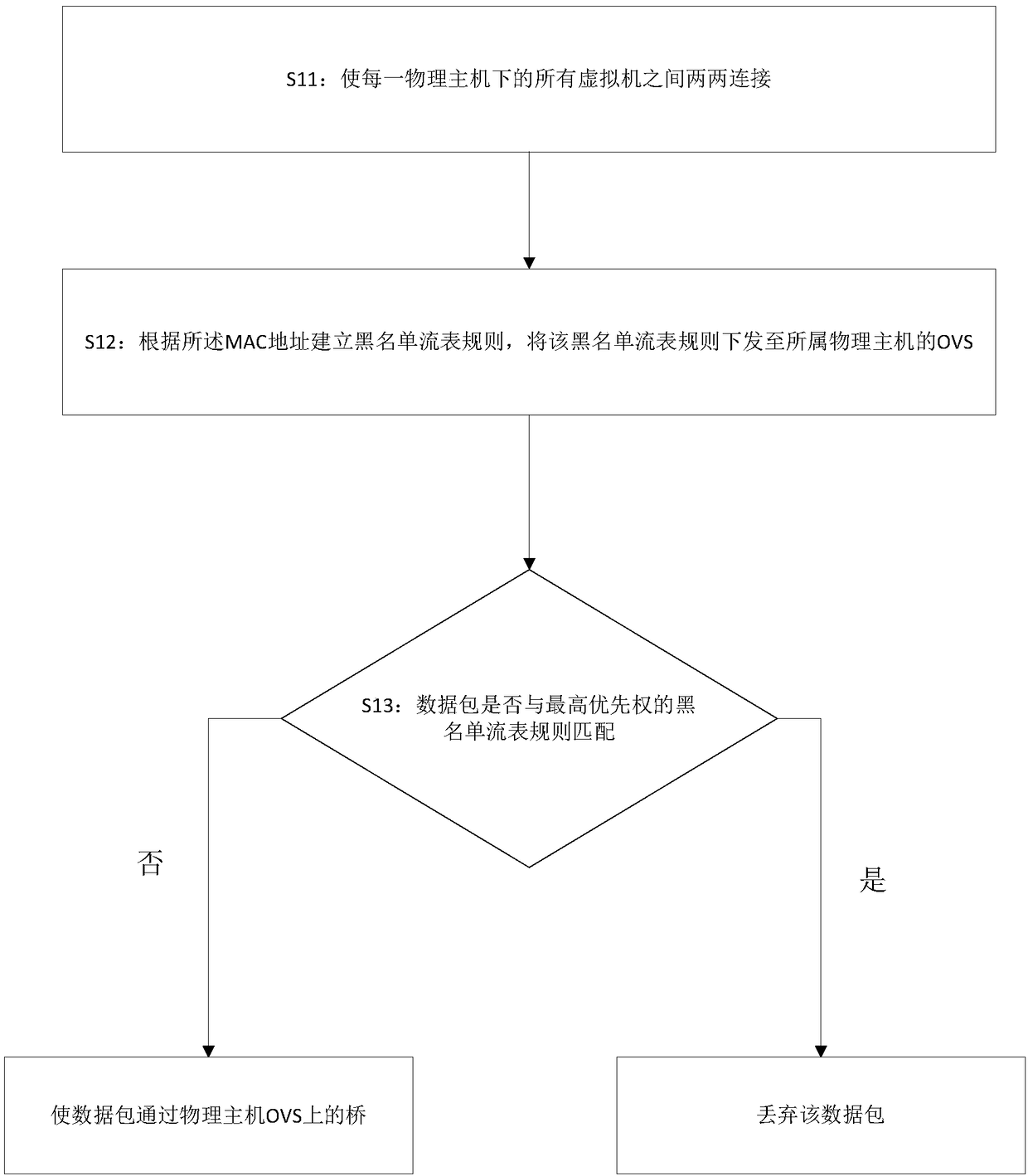
ActiveCN108322467AAvoid disadvantagesRich configuration strategiesTransmissionVirtual firewallNetwork packet
The invention discloses a virtual firewall configuration method based a OVS. The method comprises the following steps: enabling all virtual machines under each physical host to be isolated or connected in pairs, and writing a MAC address of a virtual machine into an openflow table; establishing a white list flow table rule or a blacklist flow table rule according to the MAC address, issuing the white list flow table rule or the blacklist flow table rule to the OVS of the homed physical host; judging whether the attribute of a data packet flowing through the OVS is matched with the white list flow table rule with the highest priority; if the attribute of the data packet flowing through the OVS is matched with the white list flow table rule with the highest priority, enabling the data packetto pass through a bridge on the physical host OVS; or abandoning the data packet. The function of the virtual firewall can be realized by configuring a network traffic filtering rule based on the openflow table of the OVS, the situation that the traditional virtual firewall configuration needs a firewall controller or firewall software is avoided, thereby achieving the aim of evading the defectsof the traditional virtual firewall, and the configuration policy is abundant and flexible.
Owner:云宏信息科技股份有限公司 +1
Attack prevention practice method and device
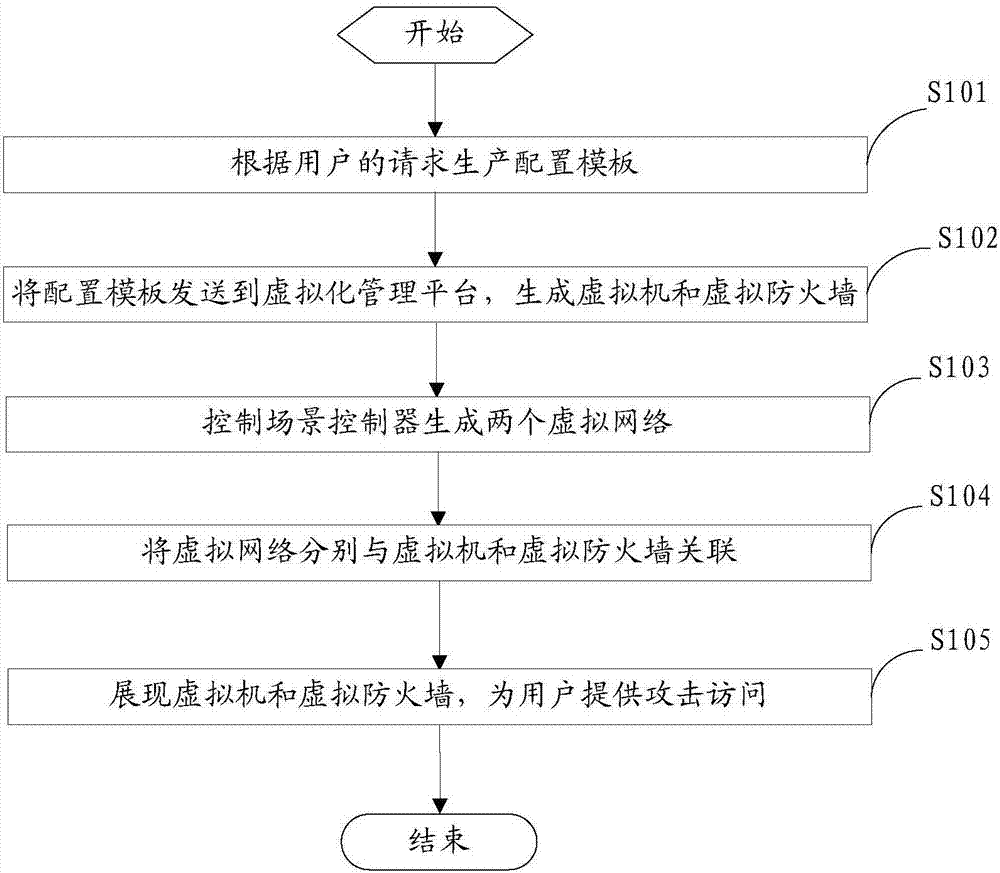
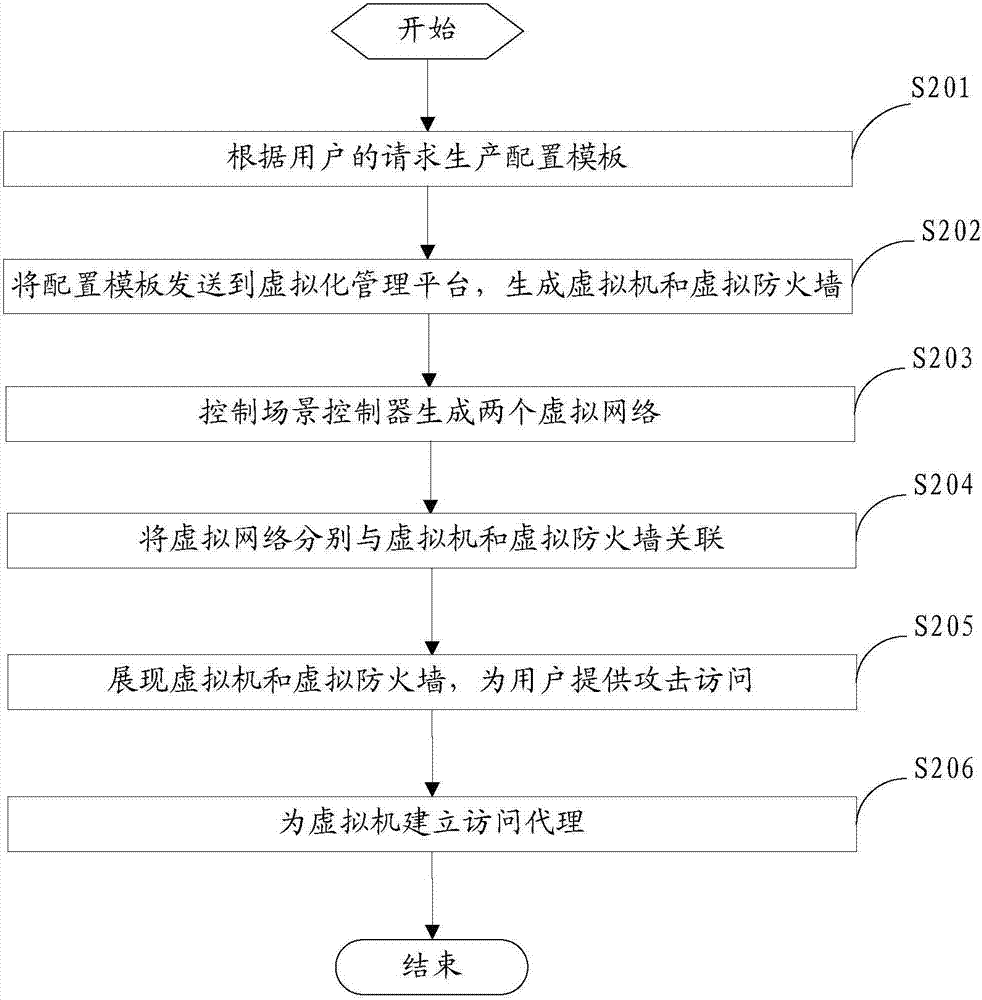
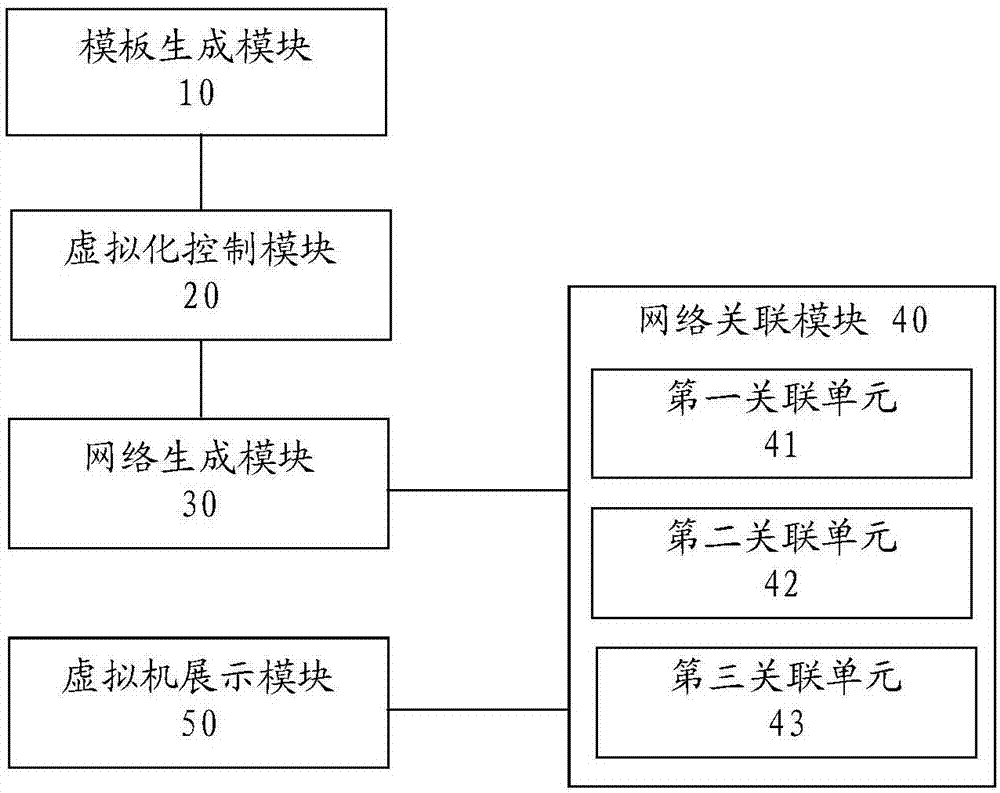
The invention provides an attack prevention practice method and an attack prevention practice device. The method and the device are applied to a scene controller of an attack prevention practice system. the method specifically comprises the steps of generating a configuration template in response to an attack prevention request of a user, wherein the configuration template comprises an attacker clone parent, a target clone parent and a firewall clone parent; sending the configuration template to a virtualized management platform of the attack prevention practice system, and controlling the virtualized management platform to clone virtual machines and a virtual firewall according to the configuration template, wherein the virtual machines comprise a virtual attacker and a virtual target; generating two virtual networks including an attacker network and a target network; associating the virtual networks with the virtual machines and the virtual fire wall; displaying the virtual machines and the virtual firewall, and providing an attack access for a user, wherein a log of the virtual firewall is used for recording attack effect of attacks initiated by the user and prevention effect. The user can acquire the prevention effect of the firewall by checking the log report.
Owner:北京椰子树信息技术有限公司
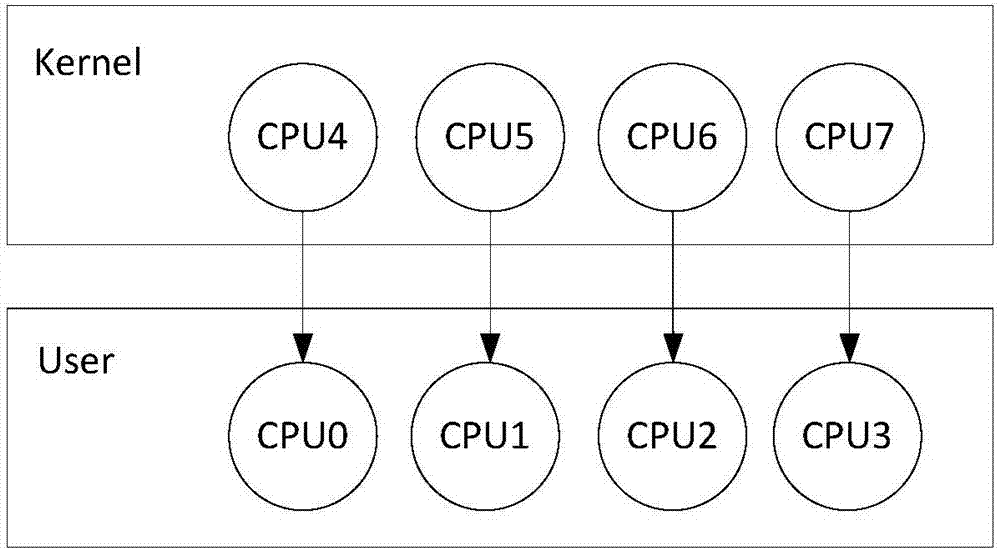
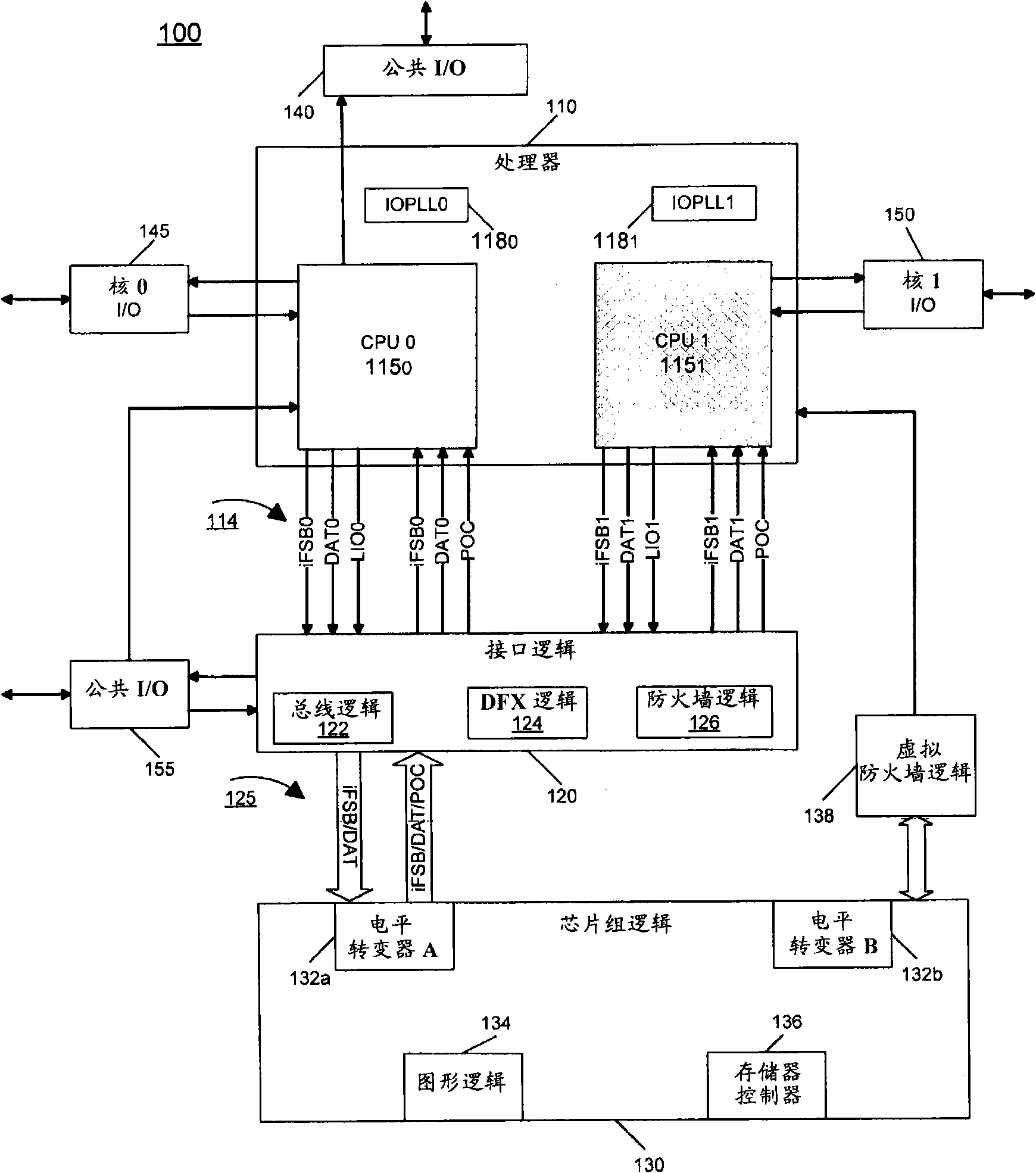
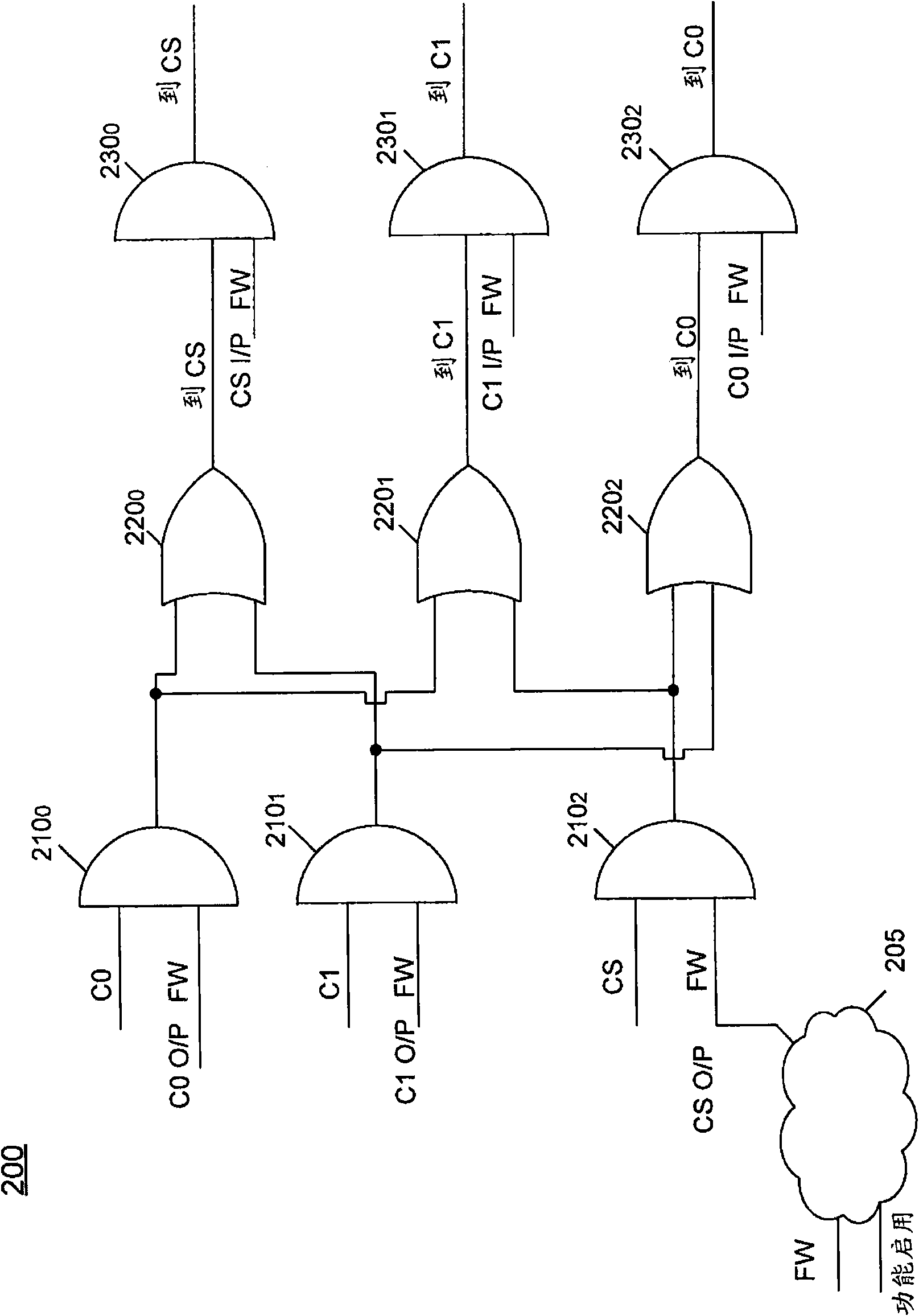
Interface logic for a multi-core system-on-a-chip (SOC)
In one embodiment, the present invention includes a system-on-a-chip (SoC) with first and second cores, interface logic coupled to the cores, chipset logic coupled to the interface logic, and a virtual firewall logic coupled between the chipset logic and the second core. The interface logic may include a firewall logic, a bus logic, and a test logic, and the chipset logic may include a memory controller to provide for communication with a memory coupled to the SoC. In some system implementations, both during test operations and functional operations, the second core can be disabled during normal operation to provide for a single core SoC, enabling greater flexibility of use of the SoC in many different implementations. Other embodiments are described and claimed.
Owner:INTEL CORP
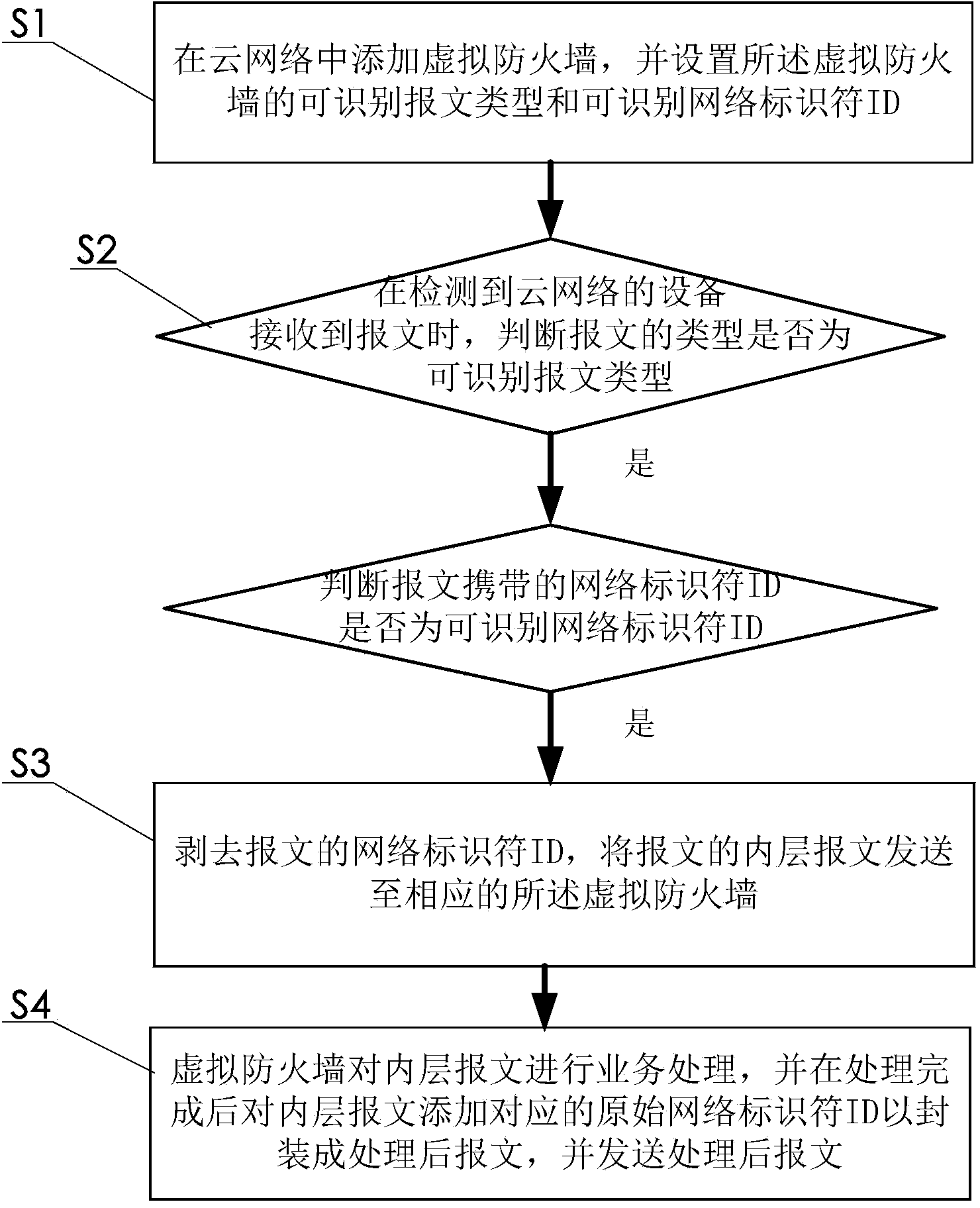
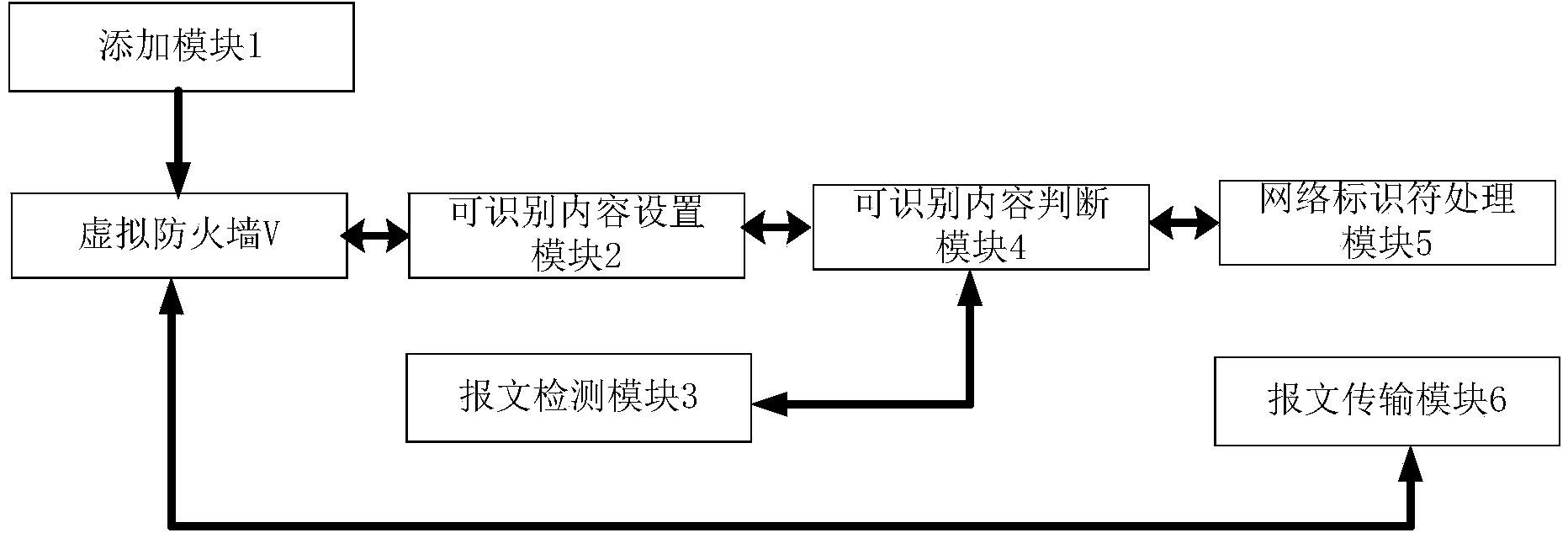
Virtual firewall partitioning method and equipment
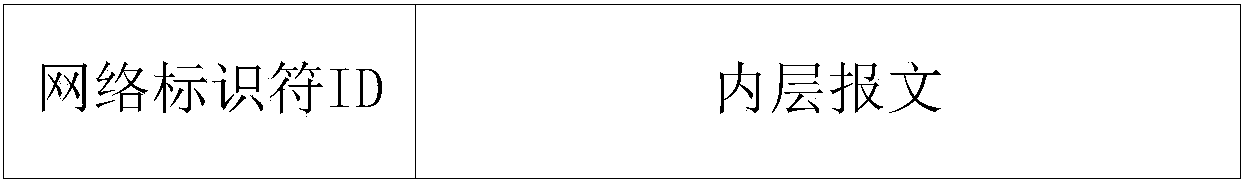
ActiveCN103973673ALower deployment costsAvoid the problem of reduced utilizationNetworks interconnectionVirtual firewallMessage type
The invention discloses a virtual firewall partitioning method and equipment. The virtual firewall partitioning method includes steps of adding many virtual firewalls into a cloud network and setting identifiable message types and identifiable network identifiers ID of the virtual firewalls; judging whether types of messages are identifiable message types or not when detecting that the equipment of the cloud network receives the messages, if yes, judging whether the network identifiers ID carried by the messages are the identifiable network identifiers ID or not; removing the network identifiers ID if the network identifiers ID carried in the messages are the identifiable network identifiers ID, and transmitting inner messages of the messages to the corresponding virtual firewalls; subjecting the inner messages to service processing by the virtual firewalls, adding the corresponding original network identifiers into the inner messages after processing to be packaged into processed messages and transmitting the processed messages. By the virtual firewalls, safety services are isolated, hardware configuration cost is reduced and the requirements of the large cloud network are met.
Owner:OPZOON TECH
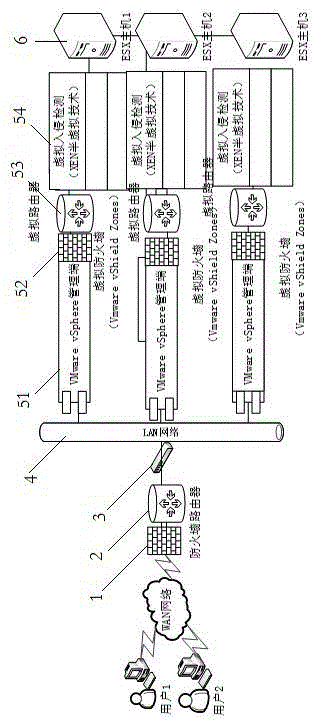
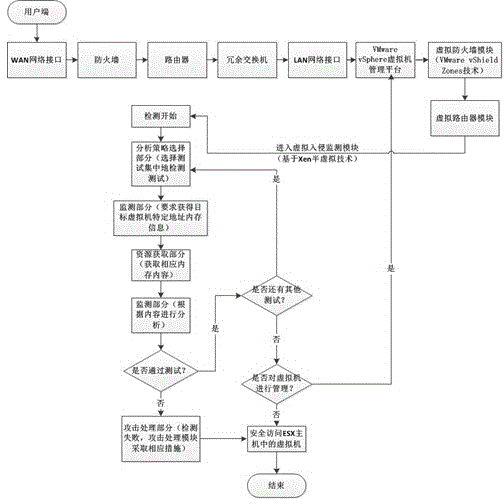
Device for realizing network security management based on virtualization and management method
The invention discloses a device for realizing network security management based on virtualization and a management method. The device comprises a firewall function module, a routing function module and a redundancy-supporting switch module; the device further comprises an LAN virtual network security management platform control and ESX hosts; and the LAN virtual network security management platform control is composed of virtual machine management ends, virtual firewall modules, virtual routing modules and virtual intrusion monitoring modules. According to the device and the method provided by the invention, virtual firewalls are built based on VMware vShield Zones, and therefore, isolation of virtual machines can be realized through security and gateway services, and functions such as control area, extranet and parameter protection functions are provided, so that support for a multi-user application environment can be realized; based on a VMware vSphere platform, a virtual routing function can be realized, and the virtual machines in the ESX hosts can be controlled; and a network intrusion detection function is realized in a virtual machine environment through adopting an Xen-based para-virtualization, so that network security can be enhanced.
Owner:甘肃省科学技术情报研究所
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com