Virtual firewall configuration method based on OVS, electronic equipment and storage medium
A technology of virtual firewall and configuration method, applied in the field of virtual firewall configuration based on OVS, can solve problems such as poor performance, and achieve the effect of rich configuration strategies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] Below, the present invention will be further described in conjunction with the accompanying drawings and specific implementation methods. It should be noted that, under the premise of not conflicting, the various embodiments described below or the technical features can be combined arbitrarily to form new embodiments. .
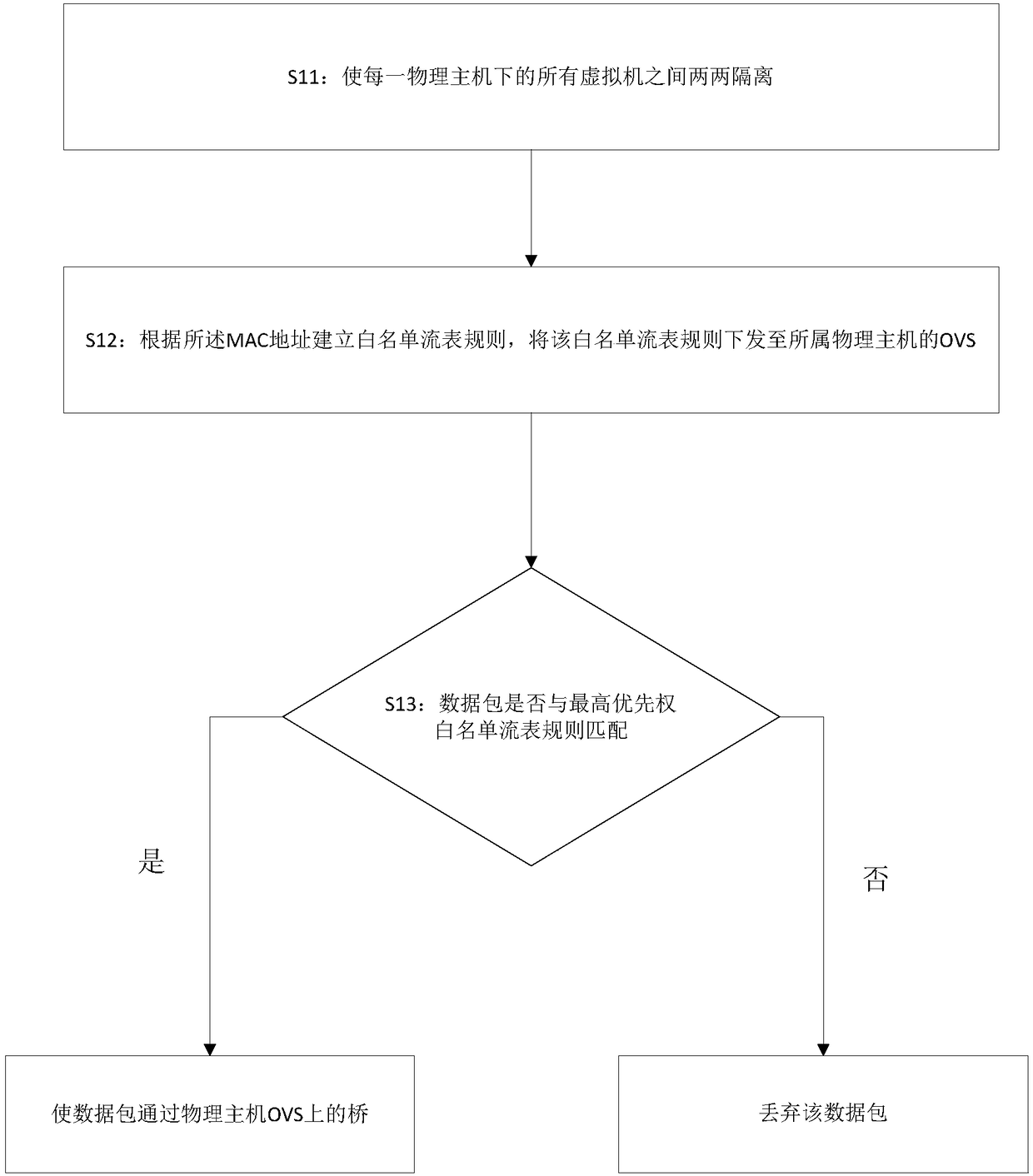
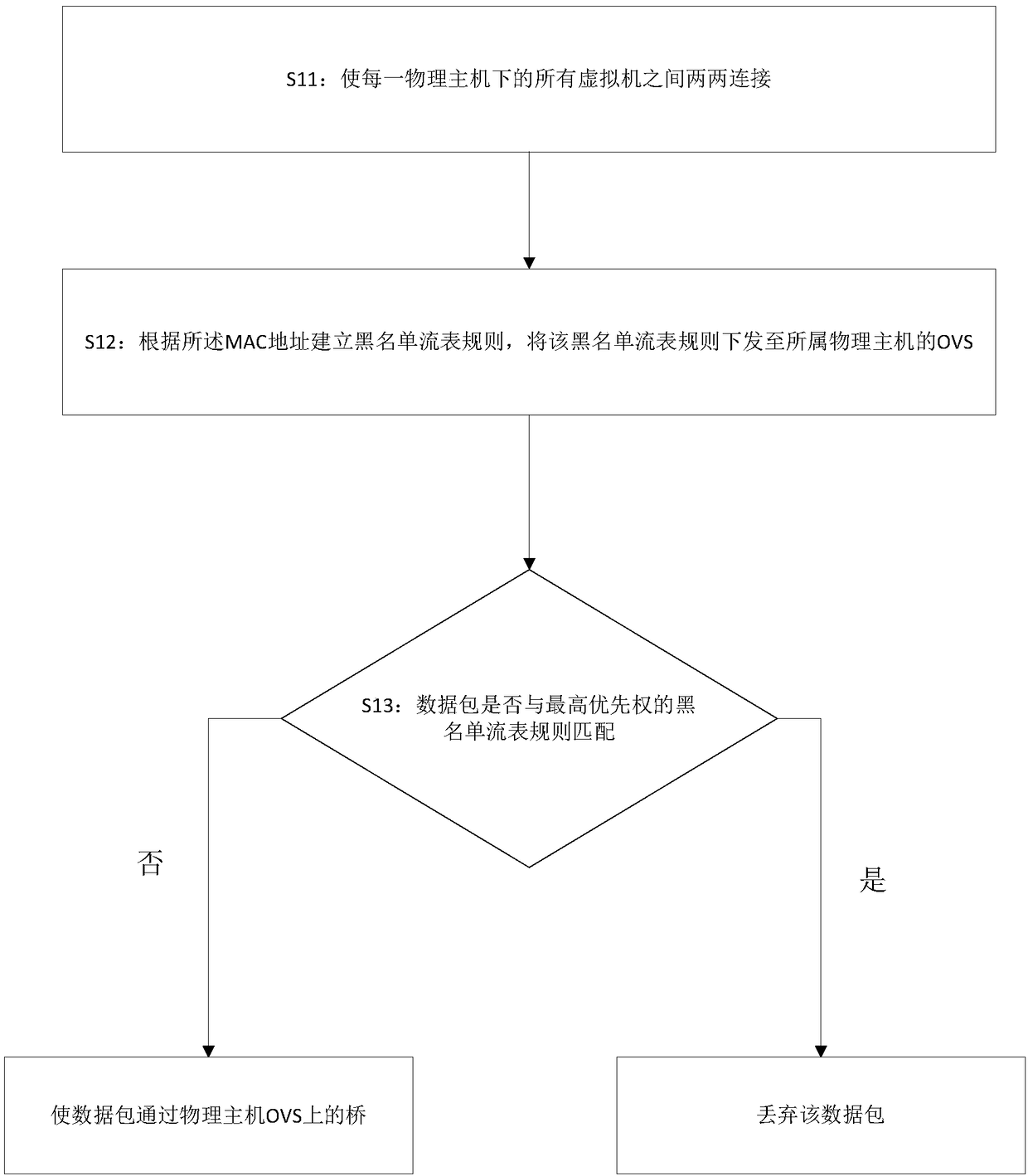
[0031] The present invention provides a kind of virtual firewall configuration method based on OVS, mainly comprises following key steps:
[0032] 1. Load the firewall rules saved in the system database. When the system starts, the firewall rules saved by the system are checked out from the database and loaded into the memory. Firewall rules belong to the physical host, source type (IP, IP segment, MAC), source object value, protocol, port number, target type (IP, IP segment, MAC), target object value, and unidirectional and bidirectional information. 2. Send the rules to the OVS of the physical host. When the system starts, establish an ssh (ssh is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com