Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
116results about How to "Enable secure communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
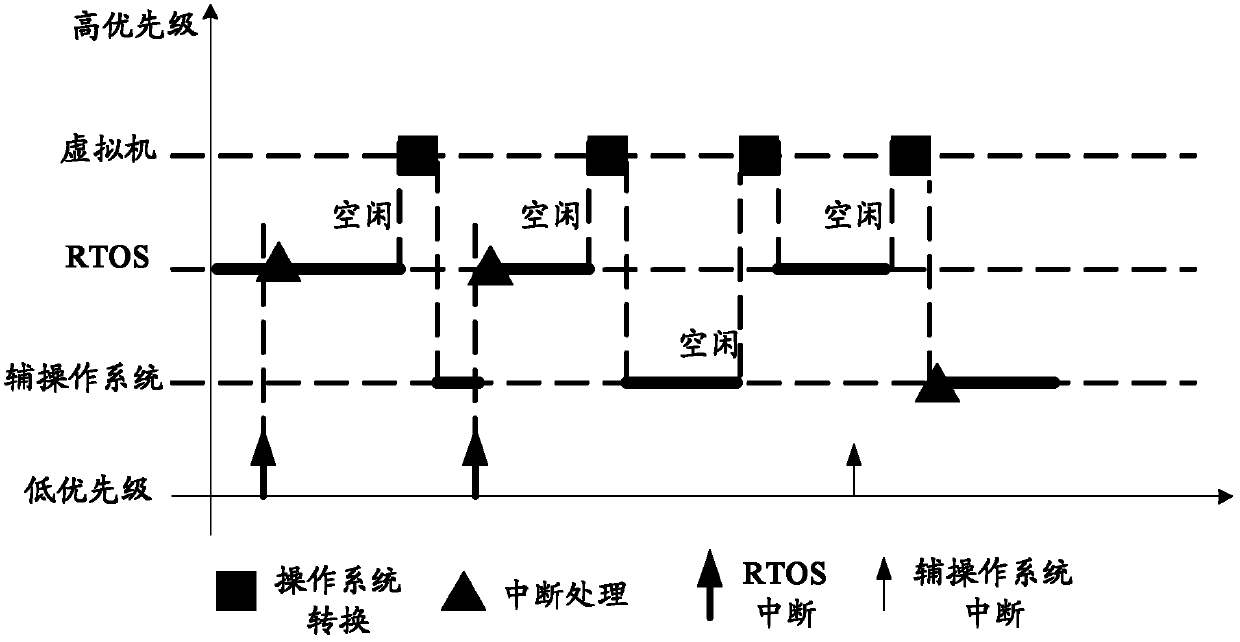
Mobile terminal and control method of mobile terminal provided with multiple operating systems
InactiveCN103136052AChoose accuratelySimple processProgram initiation/switchingSubstation equipmentOperational systemComputer terminal
The invention provides a mobile terminal and a control method of the mobile terminal provided with multiple operating systems. The multiple operating systems are mounted on the mobile terminal. The mobile terminal comprises an obtaining unit and a control unit, wherein the obtaining unit is suitable for obtaining selection signals corresponding to an operating system, and the control unit is suitable for suspending the running operating systems and running the operating system corresponding to the selection signals when the operating system corresponding to the selection signals is different from the running operating systems. The control method can obtain different selection signals corresponding to the different operating systems, achieves switching among the multiple operating systems based on the selection signals, achieves the purpose that the different operating systems are invoked according to demands, enables each operating system to play characteristics of each operating system, and reasonably uses system resources.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
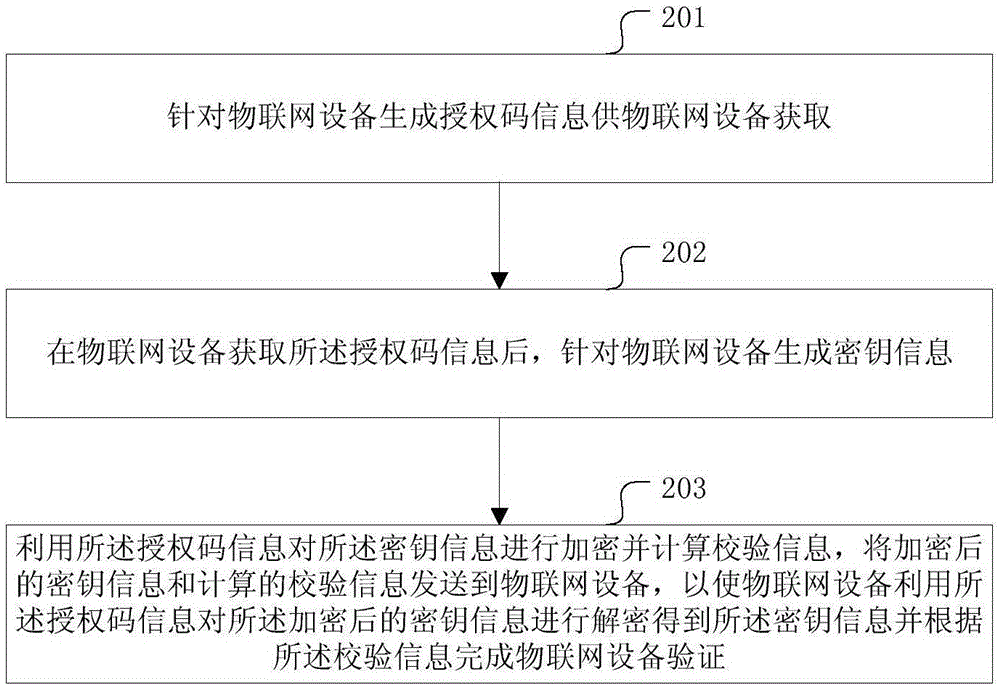
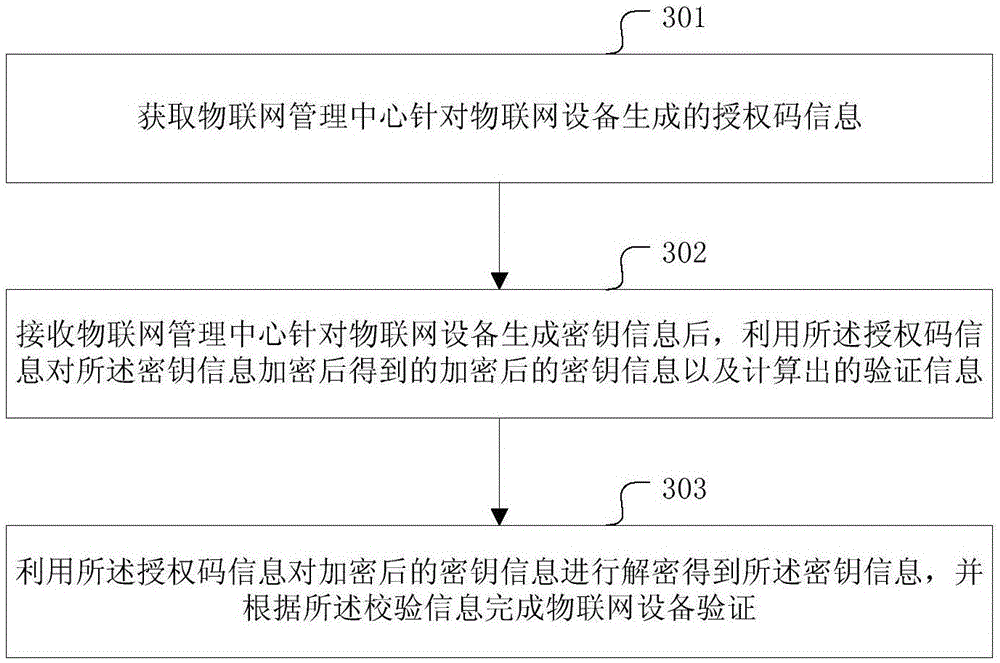
IoT equipment authentication and key agreement method and device
The invention provides an IoT (Internet of Things) equipment authentication and key agreement method and device. According to a technical scheme, an IoT control center generates an authentication code for the IoT equipment and sends the code to the IoT equipment, generates key information of the IoT equipment, utilizes the authentication code for encrypting the key information and thus obtains the cryptograph and calculates the verification information, and sends the cryptograph and the verification information to the IoT equipment. The IoT equipment utilizes the authentication code information cryptograph for decryption and obtains the key information, and implements IoT equipment authentication according to the verification information. The method and device can be used for realizing IoT communication security.
Owner:SAMSUNG ELECTRONICS CHINA R&D CENT +1
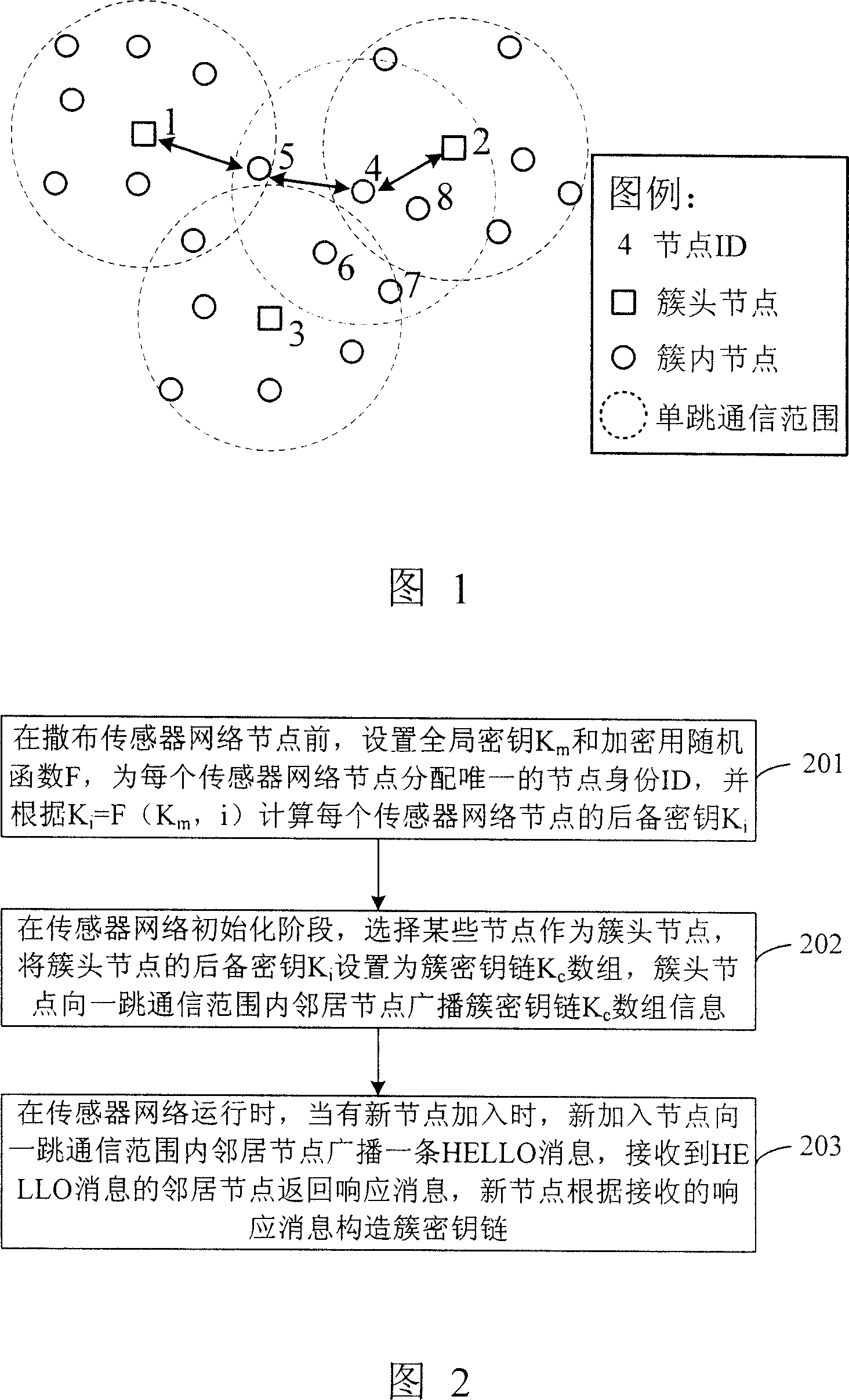
Allocation and management method of the secrete key in the sensor network
InactiveCN1996833AEnable secure communicationPrevent eavesdroppingKey distribution for secure communicationData switching by path configurationData setArray data structure
This invention discloses one method to align and manage in sensor network, which comprises the following steps: a, before distributing sensor network points to set whole key Km and coded random function F for each point with only identification and to compute point backup key Kid; b, in sensor initiating phase, establishing sensor network by cluster structure as cluster code key data set; c, in sensor operation, when there is new points, adding new communication range of HELLO information.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
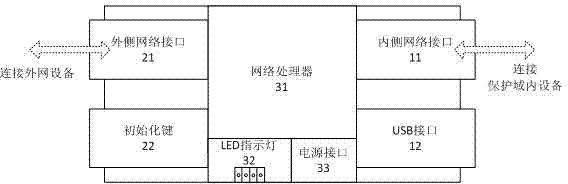
Device for establishing network isolated channel and method thereof
InactiveCN102316108AHighlight substantive featuresSignificant progressInternal/peripheral component protectionSecuring communicationThird partyVirtual network
The invention relates to a device for establishing a network isolated channel and a method thereof. A safe communication channel is established between two or multiple network devices through a network channel isolating device. The network channel isolating device is provided with an internal network interface and an external network interface. The internal network interface is connected with an internal network device. The external network interface is connected with an external network device. The network device which is connected with the internal network interface is protected by the network channel isolating device. A set of network devices protected by the network channel isolating device is called as a network channel isolating device protection domain. Host computers in different domains can communicate safely. By establishing a virtual network isolated channel through a public network among different geographic locations and by adopting an encryption algorithm recommended by the State Secrecy Bureau to conduct high-strength encryption to communication data, any third party cannot effectively decrypt the encrypted data and the communication data cannot be falsified; and the problem that different departments of small and medium enterprises cannot communicate safely through the public network is solved.
Owner:周伯生
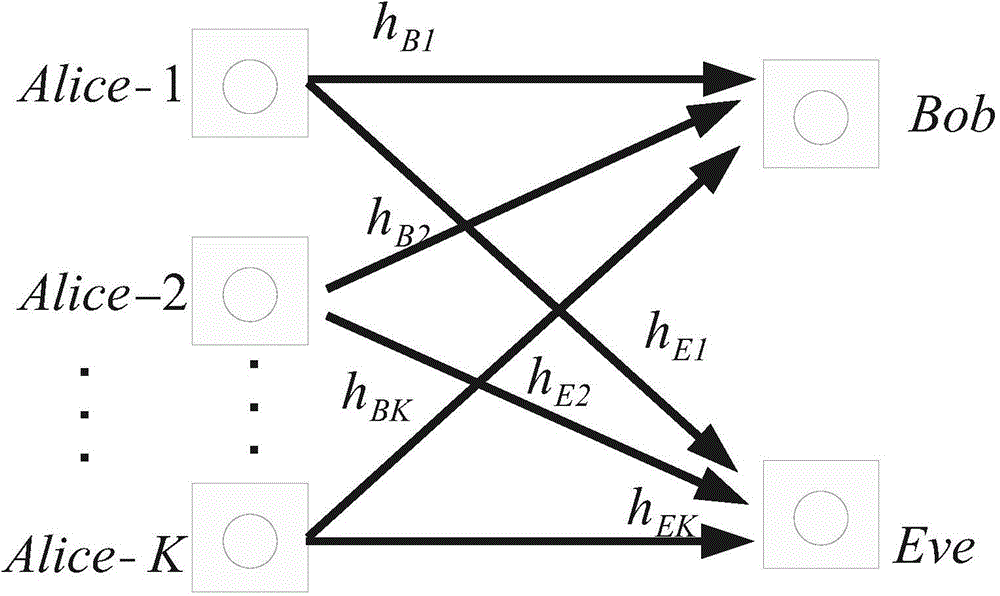
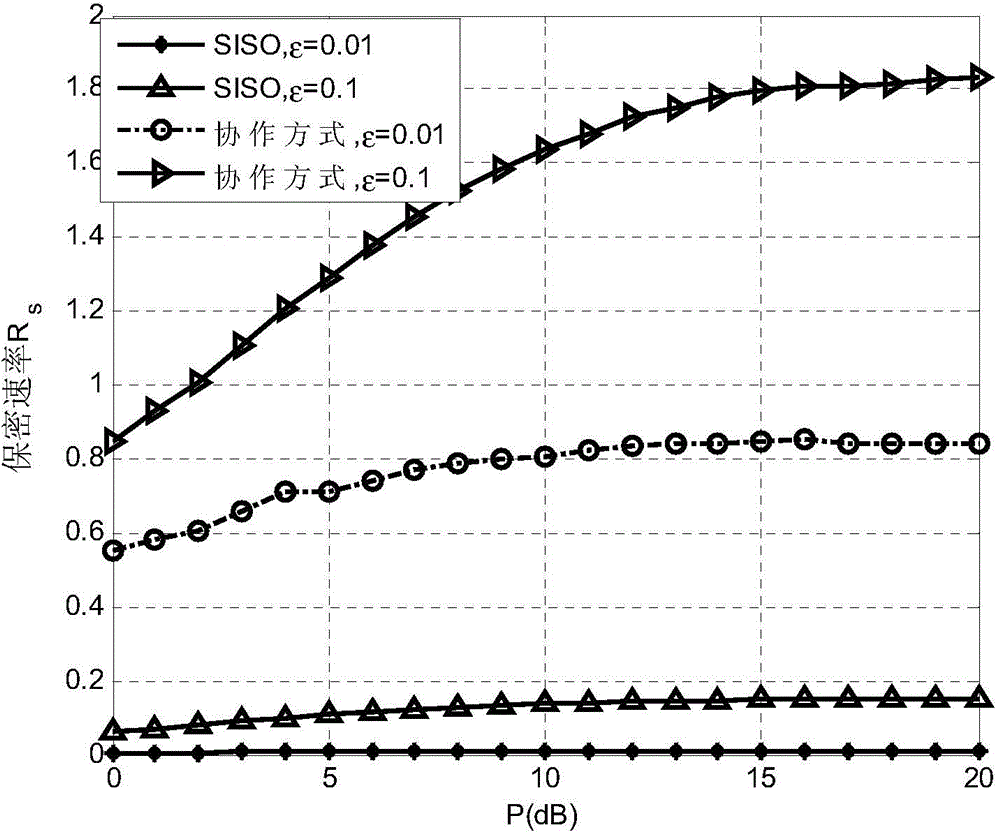
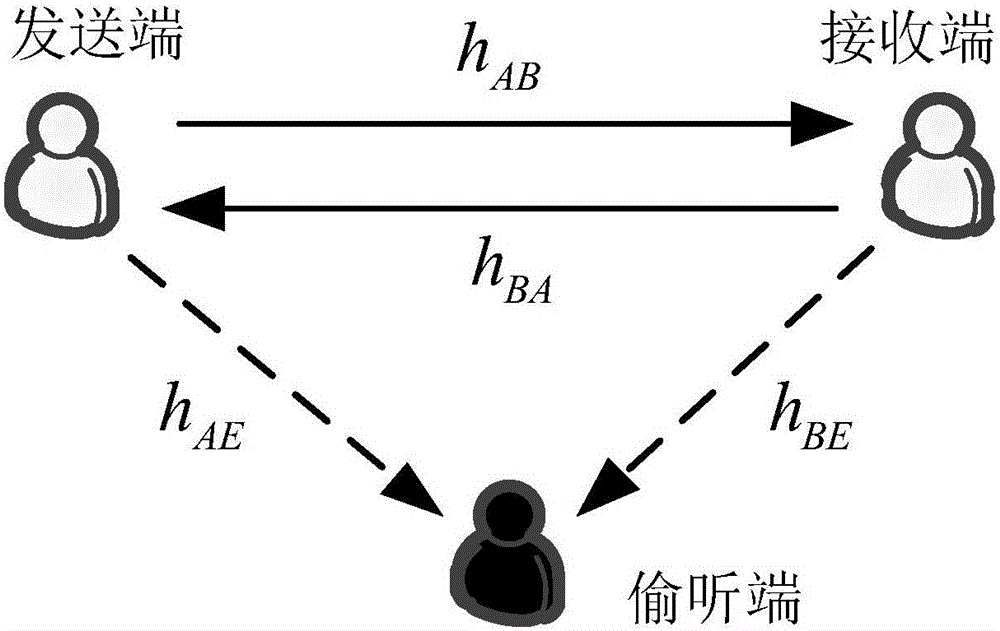
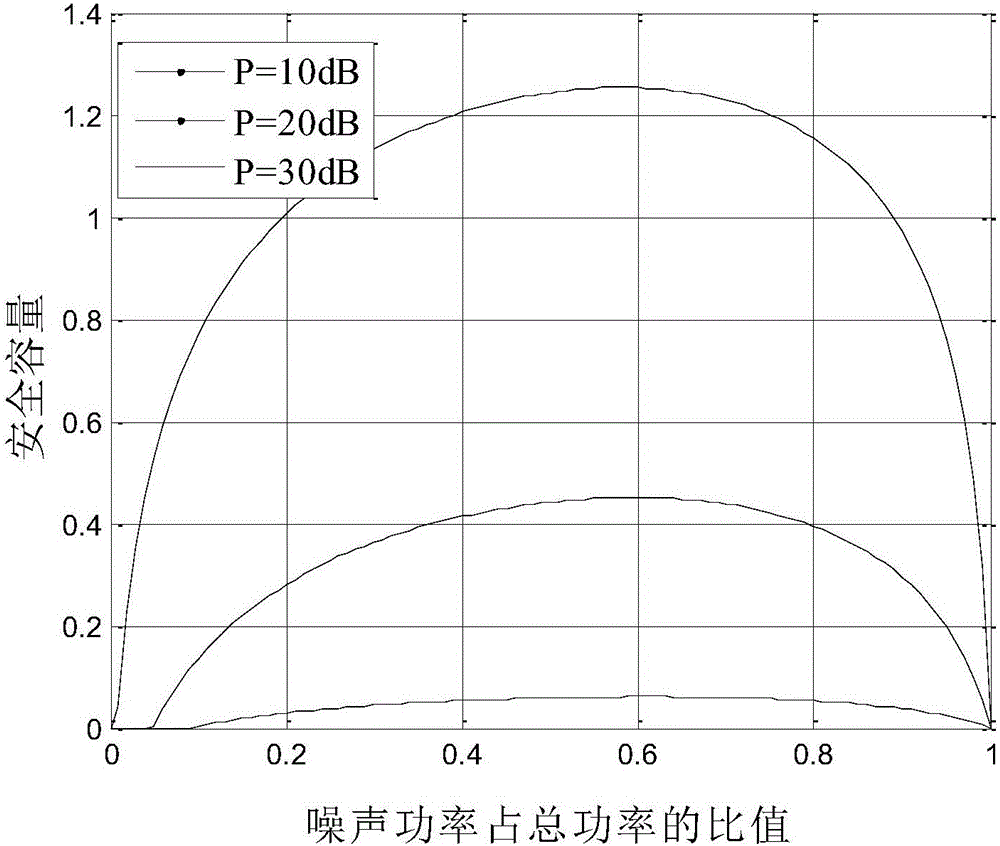
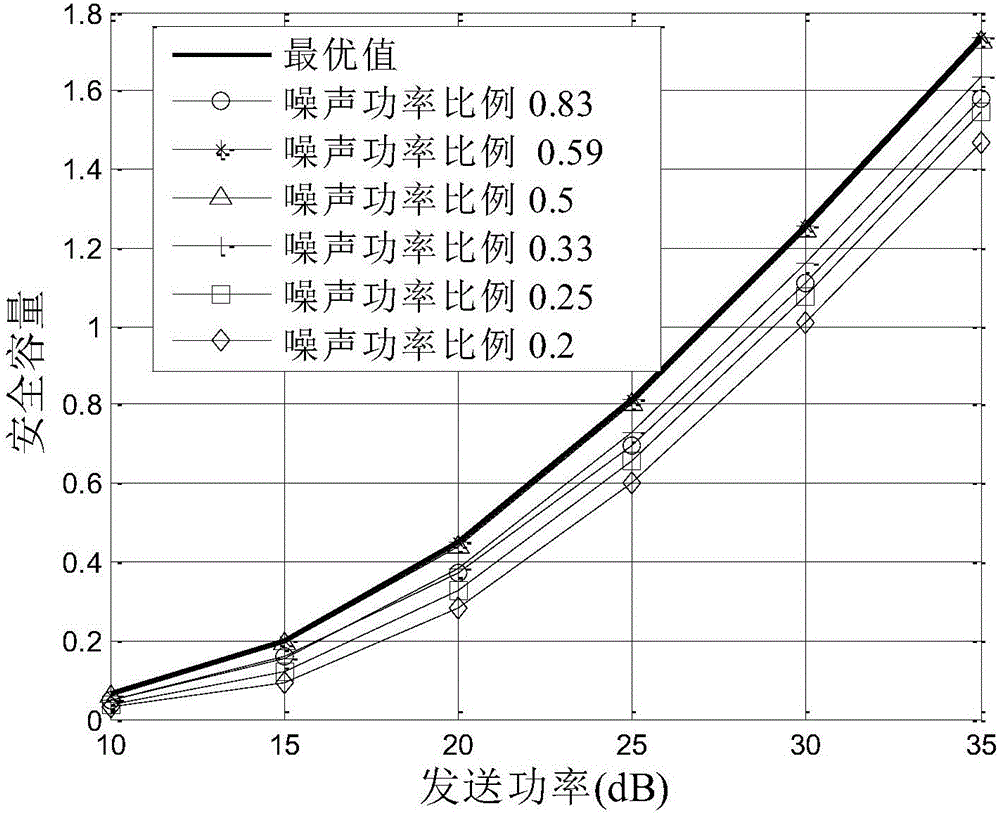
Multi-user collaboration jamming power distribution method under restraint of confidentiality interrupt probability
ActiveCN104581960AOptimize transmit powerEnable secure communicationSite diversityOrthogonal multiplexSecure communicationDistribution method
The invention discloses a multi-user collaboration jamming power distribution method under the restraint of confidentiality interrupt probability in a wireless wiretap channel. The Alice-1 user emits useful signals to an expected receiving end Bob, and remaining K-1 users emit collaboration jamming signals, and the wiretap end Eve of a single antenna wiretaps information sent by the Alice-1 user. By means of the method, the secure communication rate is improved by optimizing the emitting powers of all the jamming users, and the physical layer safe communication in the wireless wiretap channel is achieved.
Owner:XI AN JIAOTONG UNIV
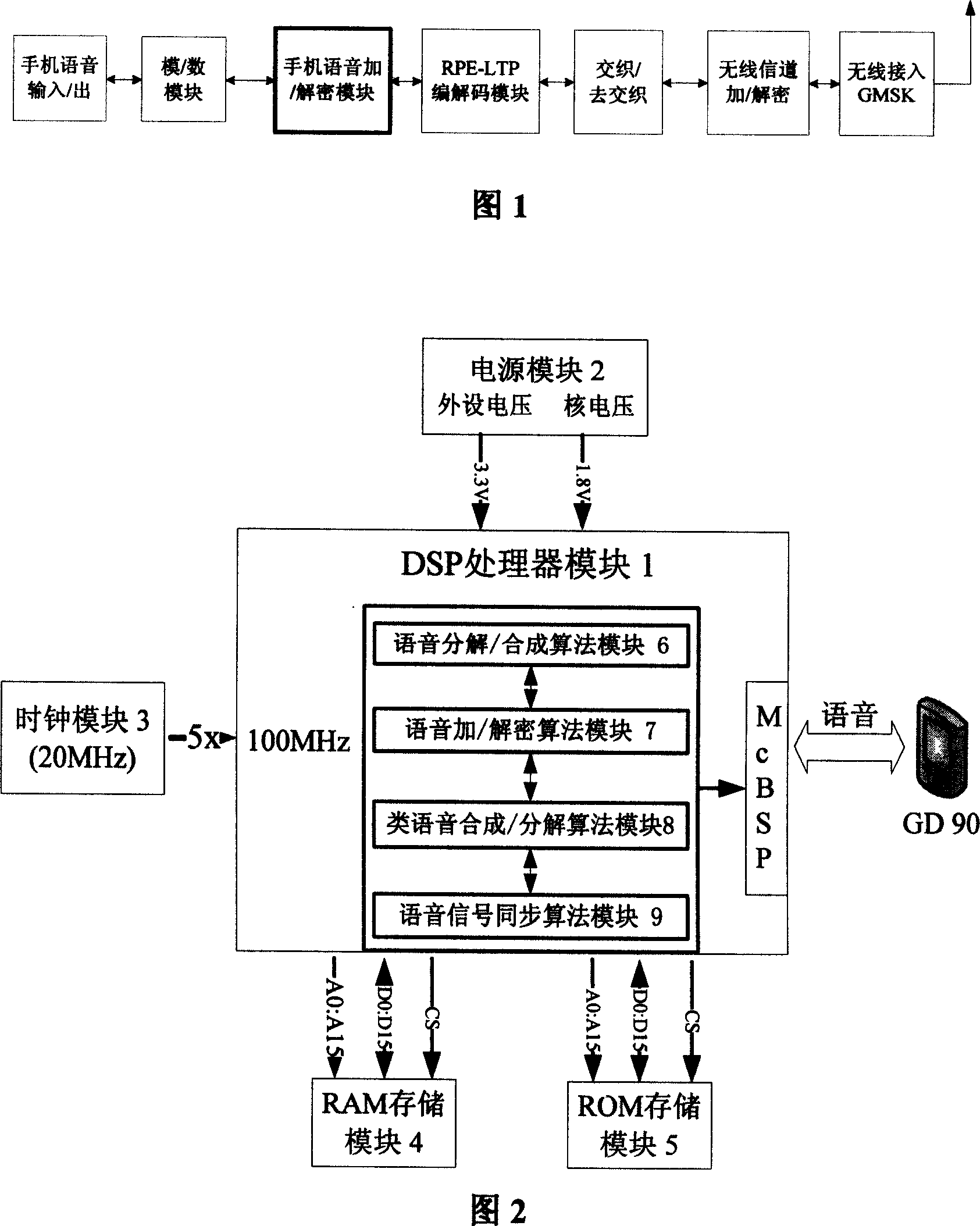
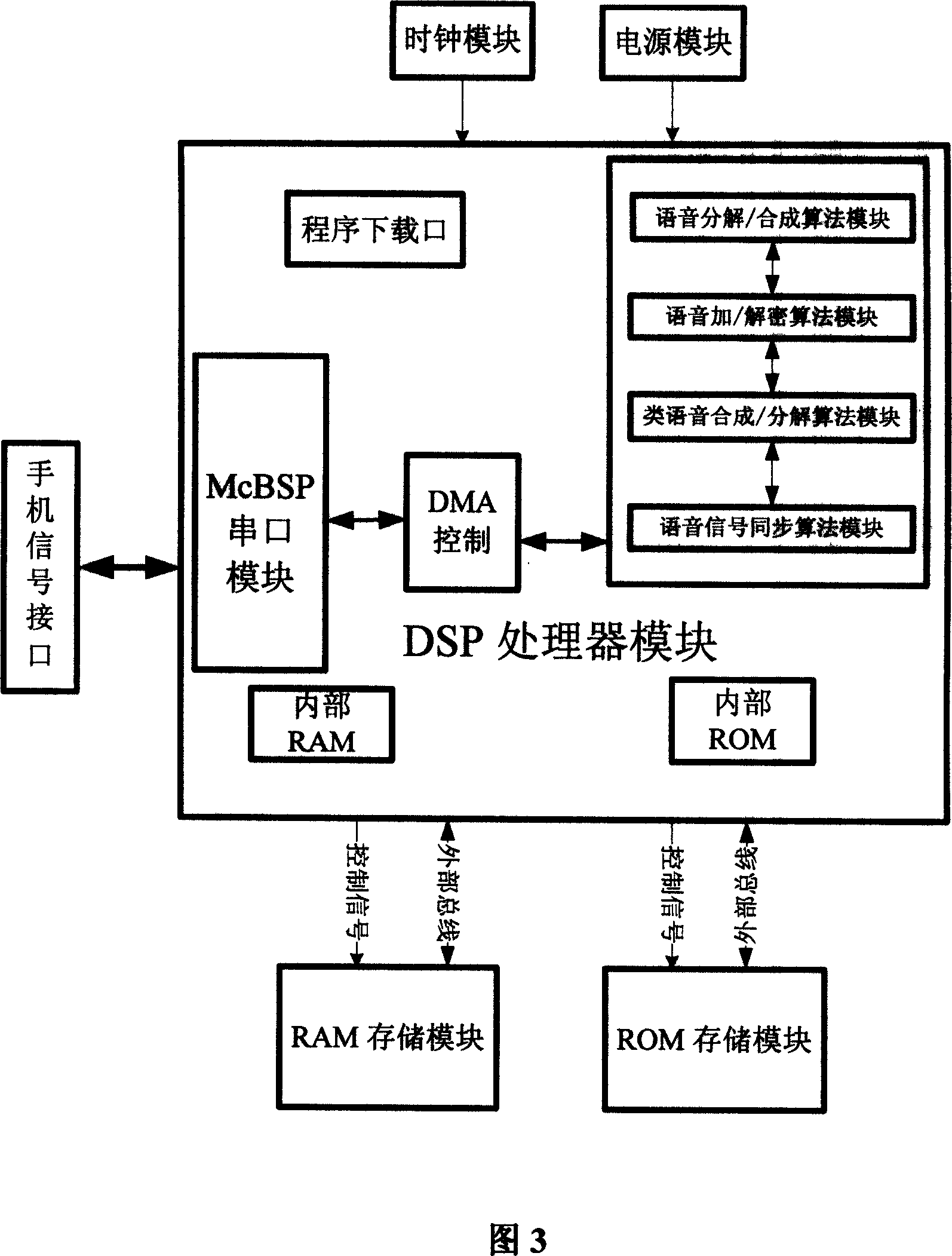
Voice encryption method for GoTone handset with anti longterm prediction rule pulse excitation compression coding
InactiveCN101014060AIntelligibility without lossImprove featuresEavesdropping prevention circuitsRadio/inductive link selection arrangementsCode moduleProcess module
The invention relates to one anti-long time prediction rules impulse excitation compression codes global cell phone language coding method, which comprises the following steps: connecting cell phone language coding and decoding modules for coding computation to realize decoding function between A / D module and decoding module, wherein, the said decoding and coding module is one digital signal minimum system hardware module and the DSP process module is to process language signals coding computation; the power module is connected to power interface of DSP process module.
Owner:SOUTHEAST UNIV
Physical layer safe communication method designed by combining signal feedback and artificial noise in wireless communication network
ActiveCN106131824AEnable secure communicationHave superioritySecret communicationTransmitter/receiver shaping networksCommunications securityEavesdropping
The invention discloses a physical layer safe communication method designed by combining signal feedback and artificial noise in a wireless communication network. The method comprises a first stage that a sending end sends information needing to be kept secret to a legal receiving end; a second stage that after the legal receiving end receives the information, a certain amount of artificial noise is mixed in the received information, and the mixed signal is fed back to the sending end; and a third stage that the sending end sends feedback signal to the receiving end. The legal receiving end knows the artificial noise mixed in the second stage, so that the legal receiving end can eliminate the artificial noise; an eavesdropping end cannot eliminate the noise, so that the performance is weakened by the artificial noise; and the safe communication between the sending end and the receiving end is realized. According to the scheme, the safe communication between the legal devices can be realized under the condition that the legal communication devices have no antenna, no external helper and no any channel information of the eavesdropping end. The method has superiority in the communication safety aspect.
Owner:XI AN JIAOTONG UNIV
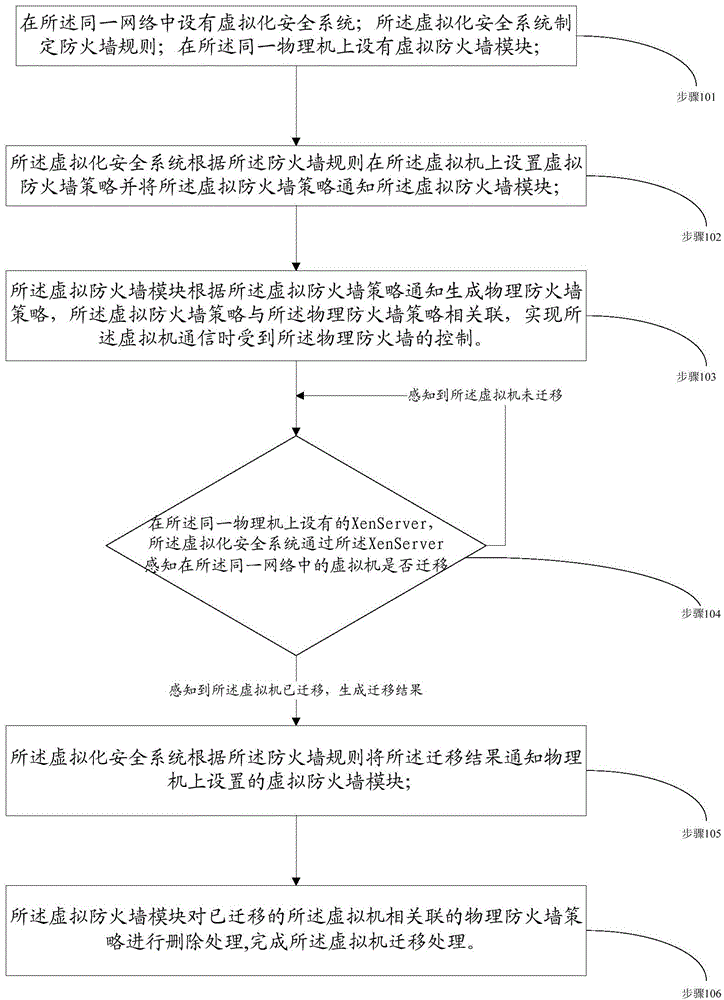
Implementation method of virtual firewall
InactiveCN104660553AEnable secure communicationEfficient use ofNetworks interconnectionVirtualizationSecure communication
The invention discloses an implementation method of a virtual firewall. Over two different virtual machines in an identical network are positioned on an identical physical machine. The implementation method comprises the following steps that: 101, a virtualization security system is arranged in the identical network, the virtualization security system makes up a firewall rule, and a virtual firewall module is arranged on the identical physical machine; 102, the virtualization security system sets a virtual firewall strategy on the virtual machines according to the firewall rule, and notifies the virtual firewall module of the virtual firewall strategy; and 103, the virtual firewall module generates a physical firewall strategy according to the virtual firewall strategy notification, and the virtual firewall strategy is correlated with the physical firewall strategy in order to implement control of the virtual machines under a physical firewall during communication. Through adoption of the implementation method, secure communication among the virtual machines is implemented; installation of firewall software for the virtual machines is simplified; and the physical firewall is efficiently utilized.
Owner:长城超云(北京)科技有限公司
Encrypting and authenticating equipment with dual safety chips
InactiveCN101667163ASafe and convenient multi-application formEnable secure communicationUnauthorized memory use protectionComputer security arrangementsRadio frequencyEngineering
The invention discloses an encrypting and authenticating equipment with dual safety chips, belonging to the technical field of identity authentication. The equipment comprises a shell, a USB plug outside the shell, a first safety chip, a second safety chip and a radio-frequency antenna, wherein the first safety chip, the second safety chip and the radio-frequency antenna are encapsulated in the shell; the first safety chip is connected with the USB plug, is connected with the second safety chip in the shell, and is also connected with an external system host computer by the USB plug; the second safety chip is connected with the radio-frequency antenna and is connected with a radio-frequency receiving terminal by the radio-frequency antenna; and the first safety chip and the second safety chip carry out communication with each other by an I / O interface. In the invention, two safety chips are used, the two safety chips are internally embedded in an intelligent card embedding software system respectively, thus realizing one corresponding application respectively; and the mutual independence of the two safety chips is effectively ensured, the safe and convenient multi-application formsare realized, furthermore, the two safety chips can realize the safe communication by the I / O interface.
Owner:BEIJING HUADA ZHIBAO ELECTRONICS SYST
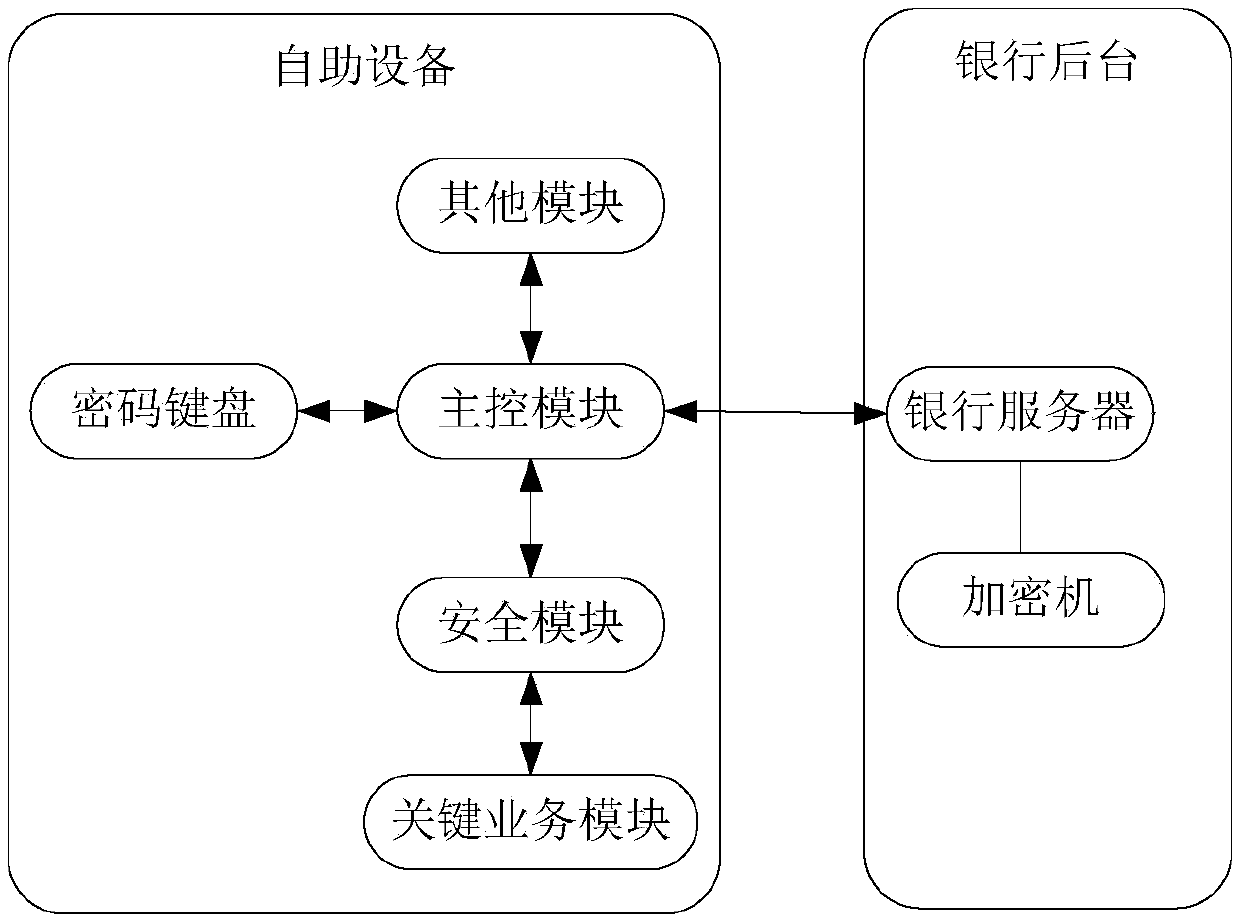
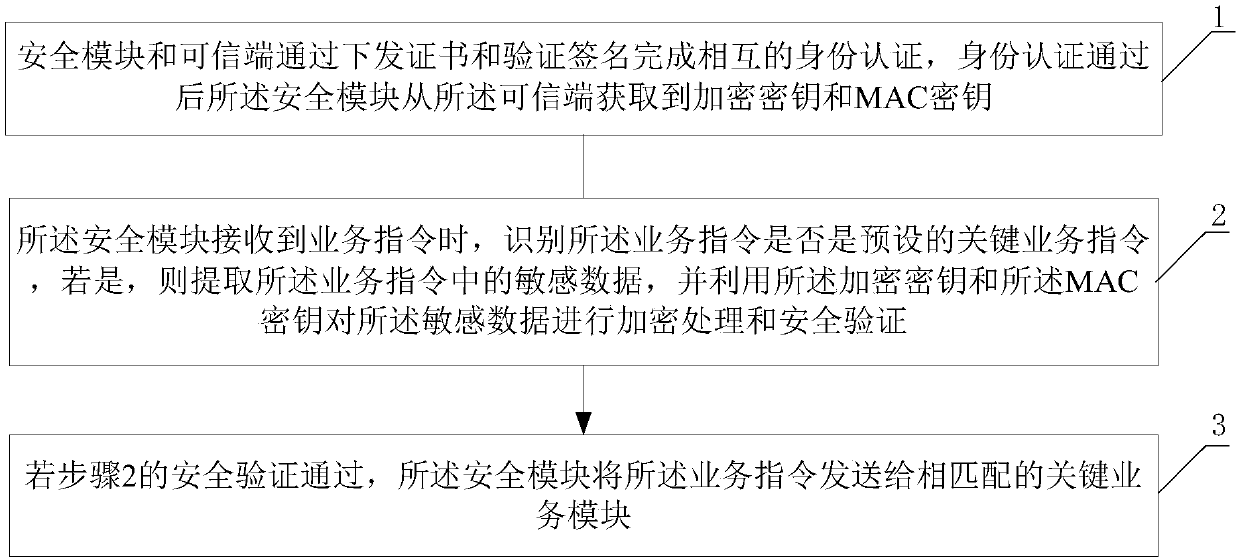
Secure communication method and secure communication system of self-service device, and self-service device
ActiveCN107786550AEnable secure communicationImprove securityComplete banking machinesKey distribution for secure communicationComputer moduleSecurity level
The invention discloses a secure communication method and a secure communication system of a self-service device, and the self-service device, wherein the method comprises the following steps: a step1, a security module and a trusted end perform interactive identity authentication through issuing certificates and verifying signatures, and after passing identify authentication, the security moduleobtains an encryption secret key and a MAC secret key from the trusted end; a step 2, when the security module receives a service instruction, the security module identifies whether the service instruction is a preset critical service instruction, if so, the security module extracts sensitive data in the service instruction, and performs encryption treatment and security verification through theencryption secret key and the MAC secret key; a step 3, if the security verification in the step 2 is passed, the security module sends the service instruction to a matched critical service module. According to the invention, by the method, security services are provided for the critical service module on the self-service device, and security level of the self-service device is improved.
Owner:CHINA ELECTRONICS GREAT WALL CHANGSHA INFORMATION TECH
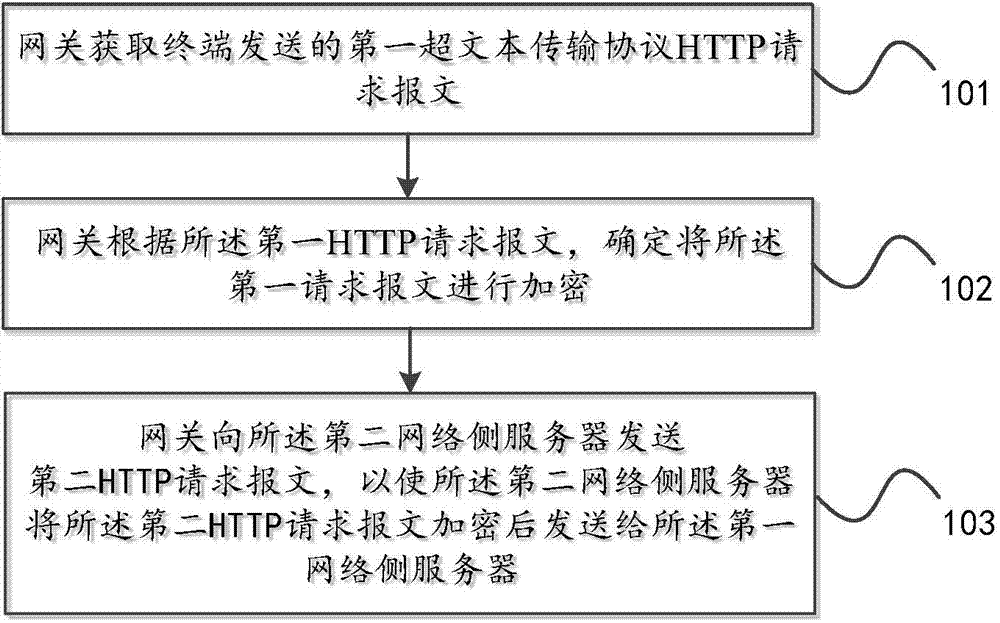
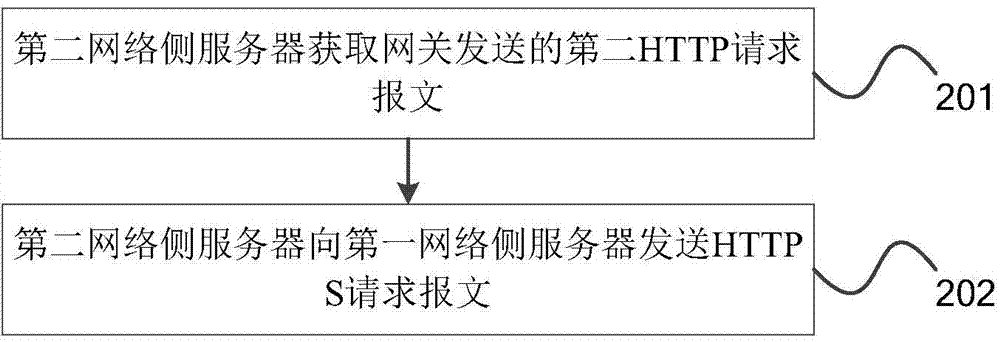
Safe communication method, gateway, network side server and system
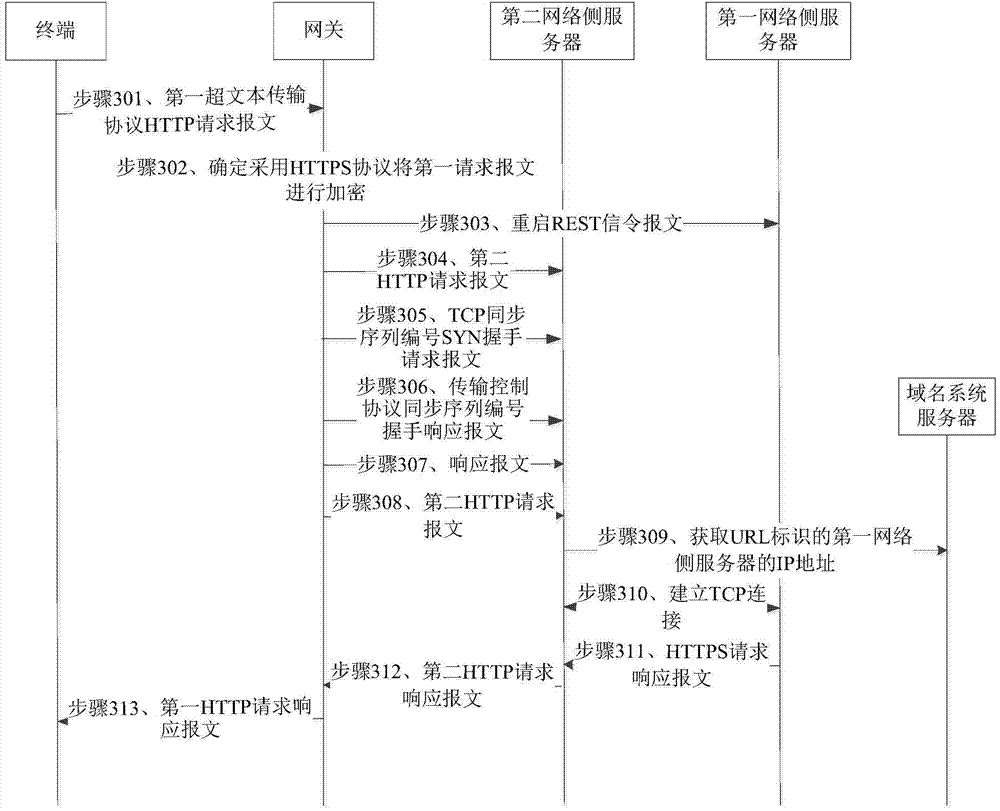
InactiveCN104767742AEnable secure communicationImplement encrypted communicationSecuring communicationTransmissionSecure communicationComputer terminal
The invention discloses a safe communication method, a gateway, a network side server and a system. The safe communication method comprises the steps that a first hypertext transport protocol HTTP request message sent by a terminal is obtained by the gateway, the first HTTP request message comprises that the terminal demands to visit a URL of a first network side server through the gateway; the gateway confirms conducting encryption on the first request message utilizing the HTTP protocol according to the first HTTP request message; the gateway send a second HTTP request message to a second network side server to enable the second network side server to sends the second HTTP request message to the first network side server after encryption, and the second request message comprises that the terminal visits the UCL of the first network side server. Encryption communication between the second network side server and the first network side server is achieved, and thereby the safety communication between the terminal and a server is achieved.
Owner:ZTE CORP
Intelligent home central control system and method based on user manipulation grade
ActiveCN106453331AEnable secure communicationHigh degree of humanizationUser identity/authority verificationMobile Telephone NumberControl system
The invention provides an intelligent home central control method based on user manipulation grade. The method comprises the steps that S0, a control privilege list of each formal family member and temporary visitor over each intelligent home device is configured, and the control privilege list is stored in a central controller of the intelligent home; privilege deadline information of a user terminal corresponding to the each formal family member and temporary visitor is configured in the central controller; S1, the central controller receives connection requirement information sent by the user terminal, and determines the type of the connection requirement information; S2, a connection record of the user terminal in the central controller is judged; S3, a mobile phone number of the user terminal is obtained, and whether the user terminal number exists in the list of formal family members or temporary visitors in the central controller or not is judged; S4, the central controller generates a random number, sends the random number after encryption to the user terminal, and the random number after being decoded by the user terminal is sent to the central controller after the random number is encrypted by an elliptic curve cryptography algorithm.
Owner:NINGBO HOPE INTELLIGENT TECH
Network system for secure communication
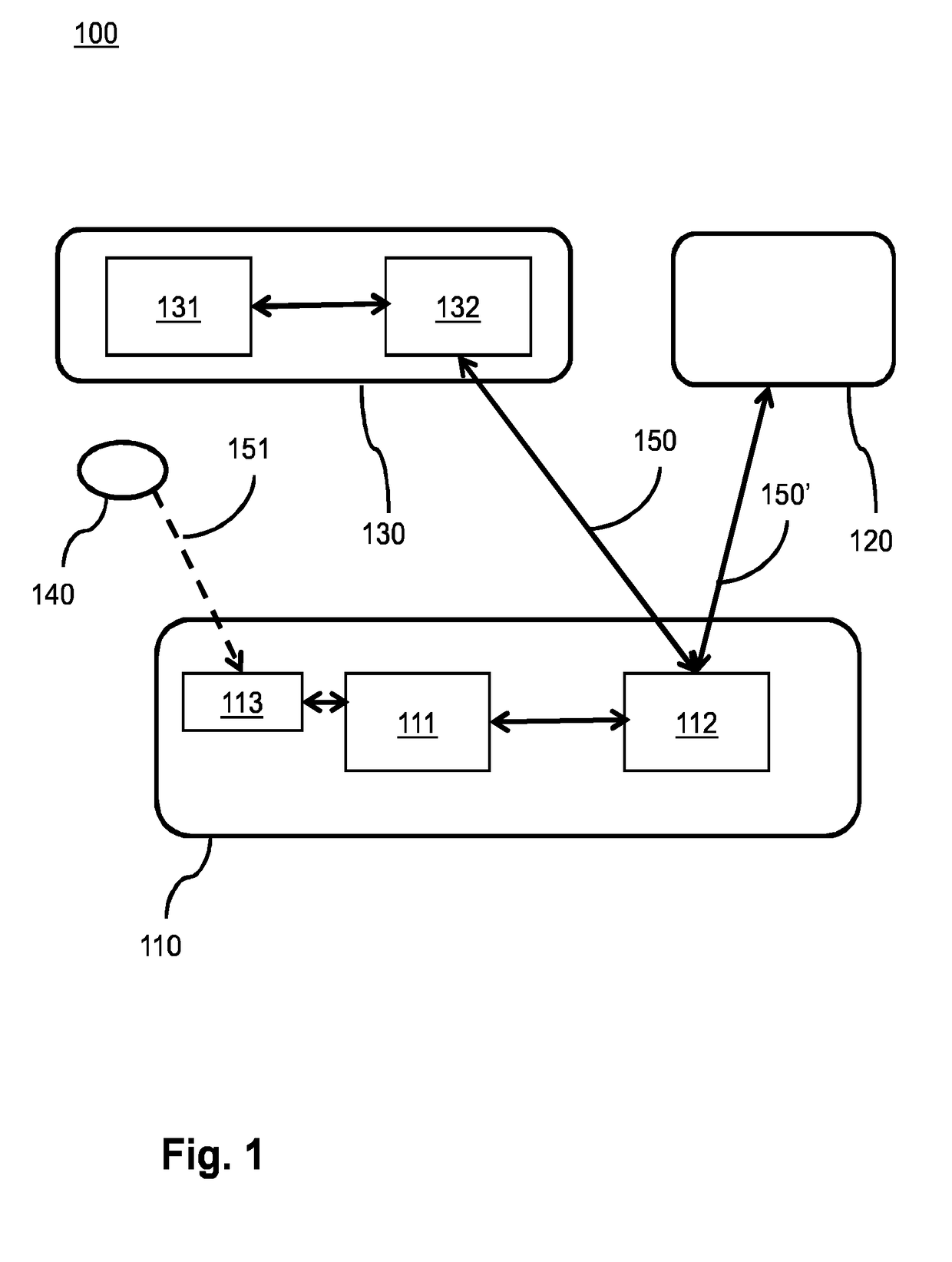
ActiveUS20180375870A1Communication securityEnable secure communicationKey distribution for secure communicationUser identity/authority verificationSecure communicationNetworked system
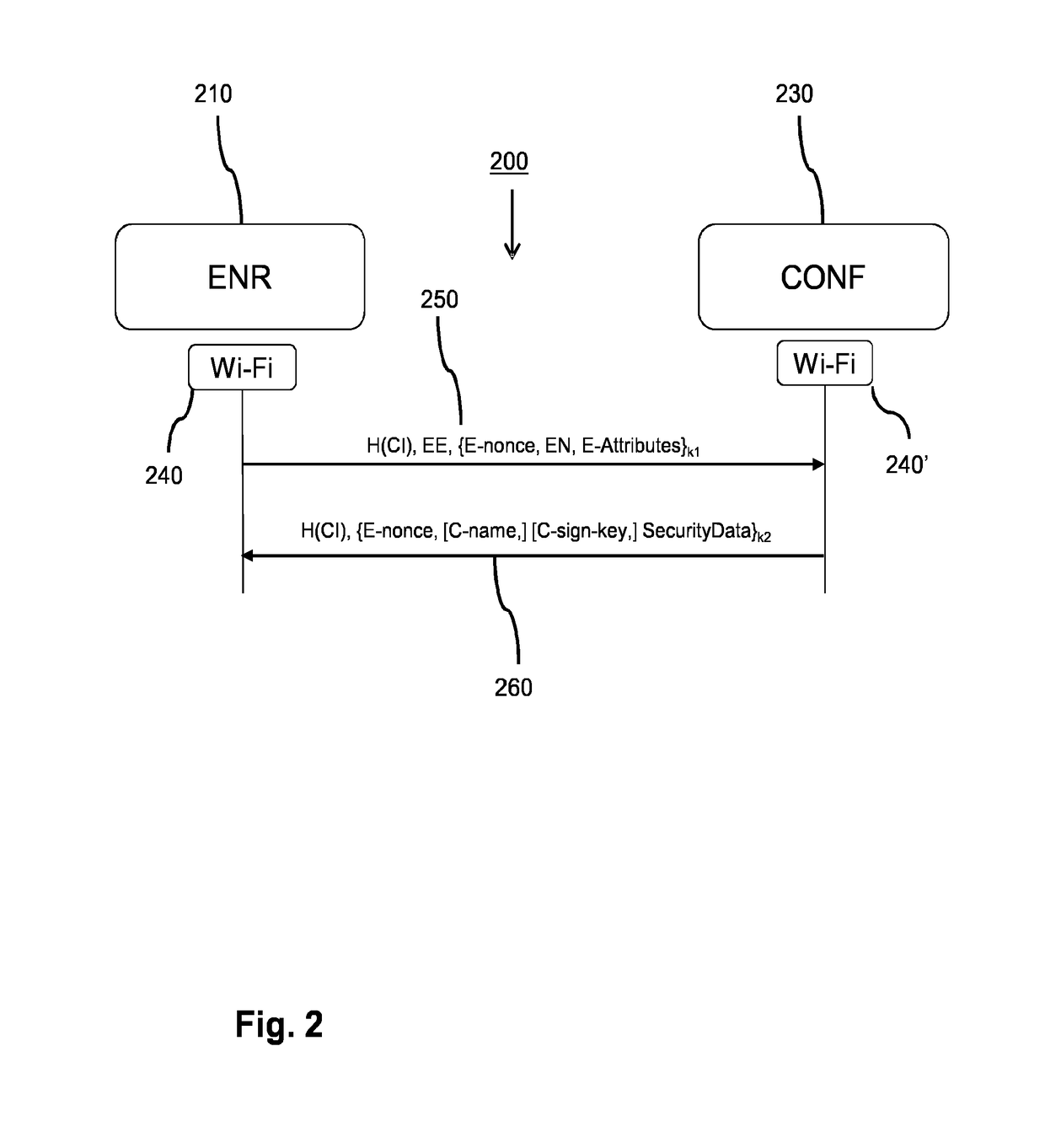
In a network system (100) for wireless communication an enrollee (110) accesses the network via a configurator (130). The enrollee acquires a data pattern (140) that represents a network public key via an out-of-band channel by a sensor (113). The enrollee derives a first shared key based on the network public key and the first enrollee private key, and encodes a second enrollee public key using the first shared key, and generates a network access request. The configurator also derives the first shared key, and verifies whether the encoded second enrollee public key was encoded by the first shared key, and, if so, generates security data and cryptographically protects data using a second shared key, and generates a network access message. The enrollee processor also derives the second shared key and verifies whether the data was cryptographically protected and, if so, engages the secure communication based on the second enrollee private key and the security data.
Owner:KONINKLJIJKE PHILIPS NV
Method and system for transmitting key information, transmitting end and receiving end
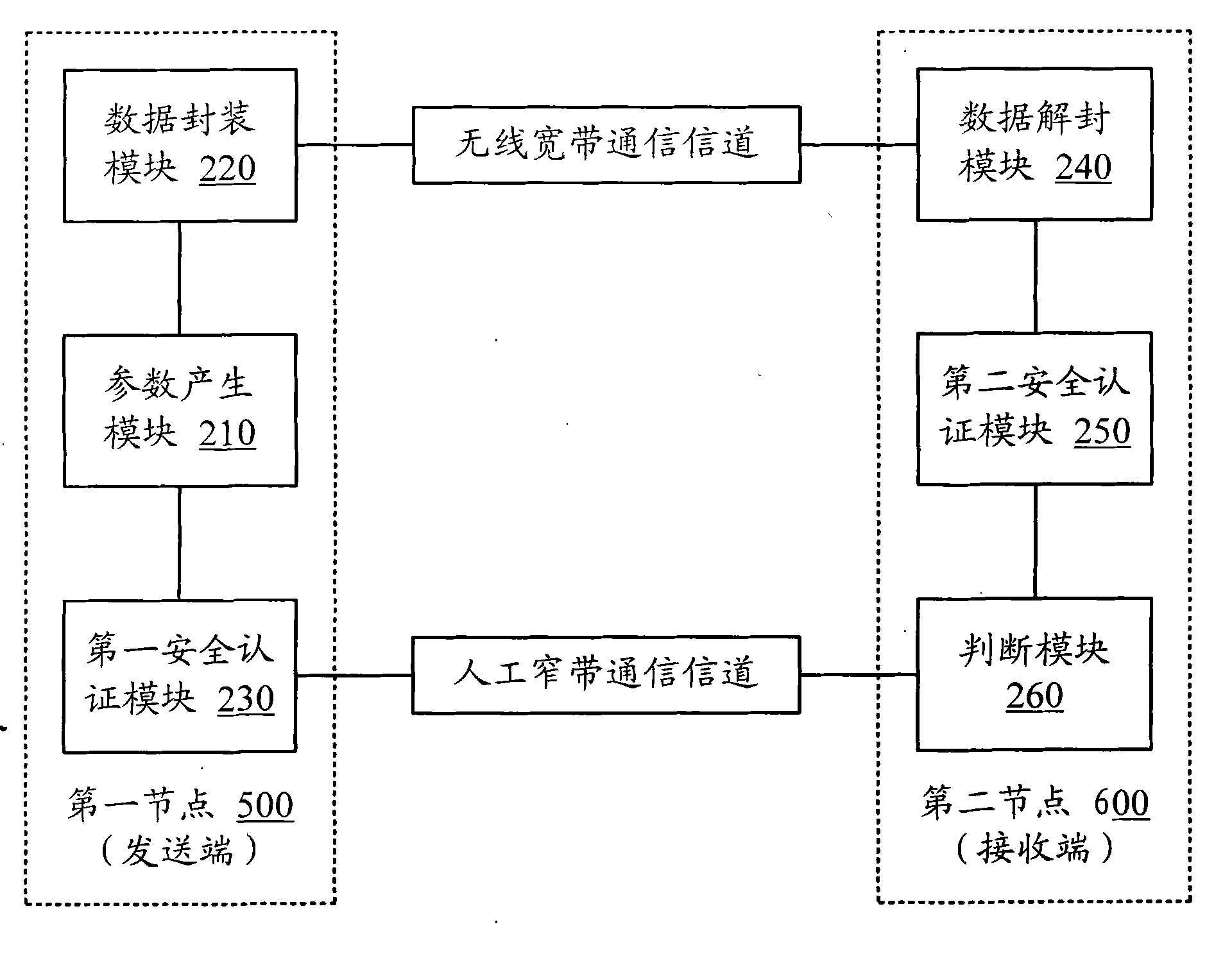
InactiveCN102098672AAchieve securityEnable secure communicationSecurity arrangementBroadbandNarrowband
The invention discloses a transmitting method and a transmitting system suitable for key information such as the public key of a wireless delay tolerant network in which people are involved, and the like, and can ensure safety when a node uses the public key of an opposite side. The public key or other key information of the node is transmitted through a wireless broadband communication channel, corresponding authentication information is transmitted through an artificial narrowband communication channel, and the information transmitted in two ways is compared at a receiving end, so that the reliability of key information transmission can be ensured. The key information transmitting technology realized by the invention is also suitable for the updating of the public keys and the application of abolished information or public key multi-node forwarding.
Owner:BEIJING UNIV OF POSTS & TELECOMM
OAM entanglement modulation key distribution network system and method with real-time tracking compensation
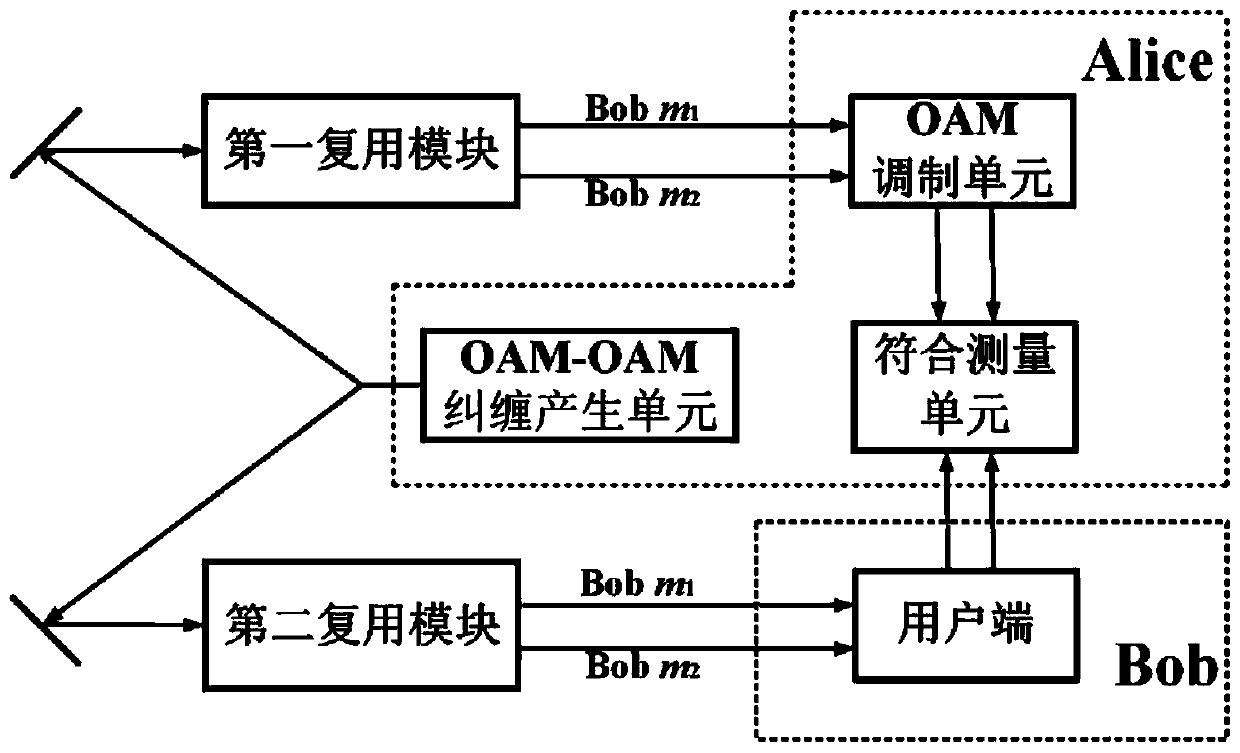
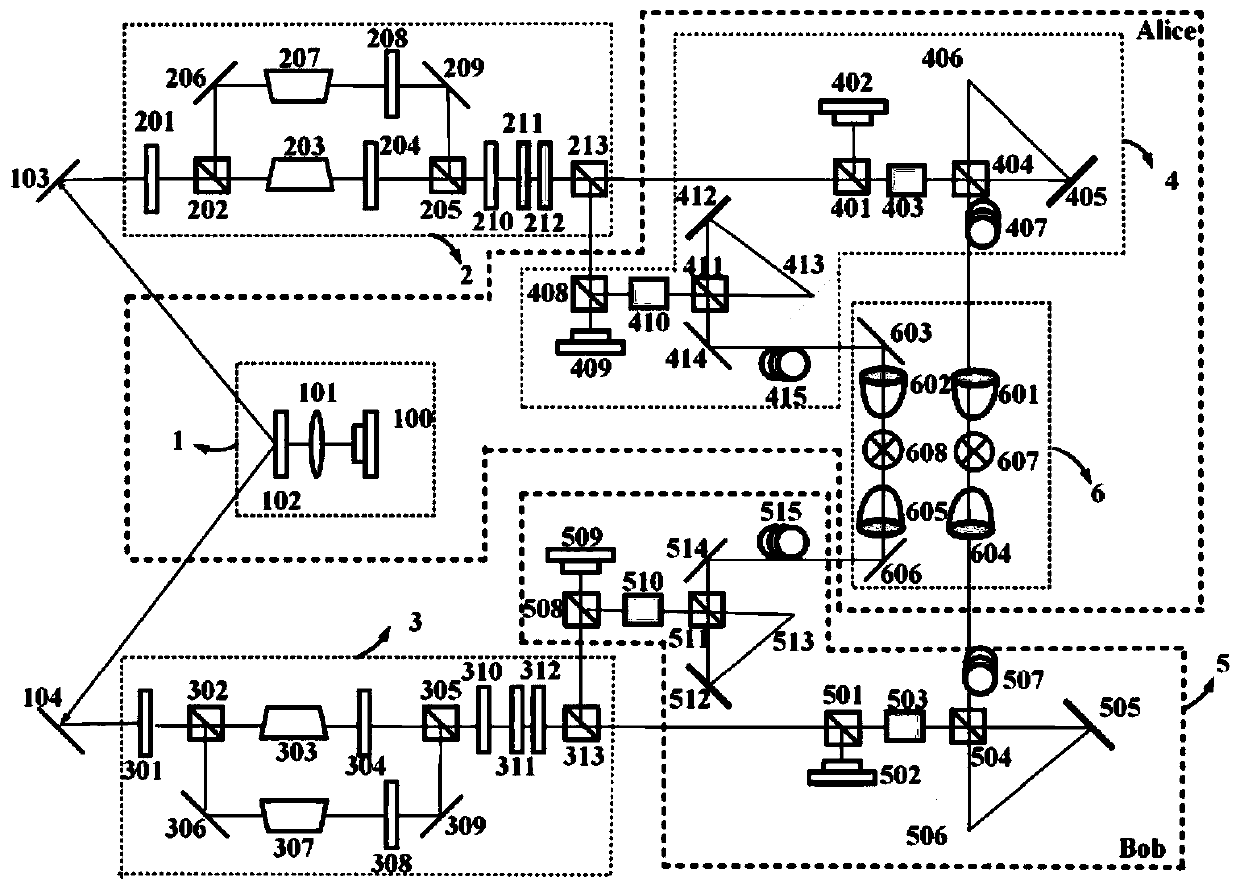
PendingCN111130779AImprove securityIncrease key rateKey distribution for secure communicationPhotonic quantum communicationMultiplexingPhase distortion
The invention provides an OAM entanglement modulation key distribution network system with real-time tracking compensation. The OAM entanglement modulation key distribution network system comprises anOAM-OAM entanglement generation unit, a first multiplexing module, a second multiplexing module, an OAM modulation unit, a Bob client and a coincidence measurement unit, wherein the OAM-OAM entanglement generation unit is used for generating an orbital angular momentum and an orbital angular momentum mixed entanglement quantum state; the first multiplexing module and the second multiplexing module are used for separating any OAM state; the OAM modulation unit is used for carrying out phase deflection modulation on the orbital angular momentum and loading coding information; and the coincidence measurement unit is used for performing coincidence measurement on signal light and idle light to decode the quantum bit information. According to the invention, the security of the quantum key distribution system is improved; an adaptive optical system is introduced, phase distortion caused by atmospheric turbulence is reduced, and the mode consistency during OAM light interference is guaranteed; an M-Z interferometer is used for separating any OAM, the quantum coding capacity is expanded, and an efficiently coded quantum key distribution system is obtained; and the engineering applicationrange is wide, the structure is simple, and the expandability is high.
Owner:GUANGDONG INCUBATOR TECH DEV CO LTD
Quantum repeater network coding scheme based on controller
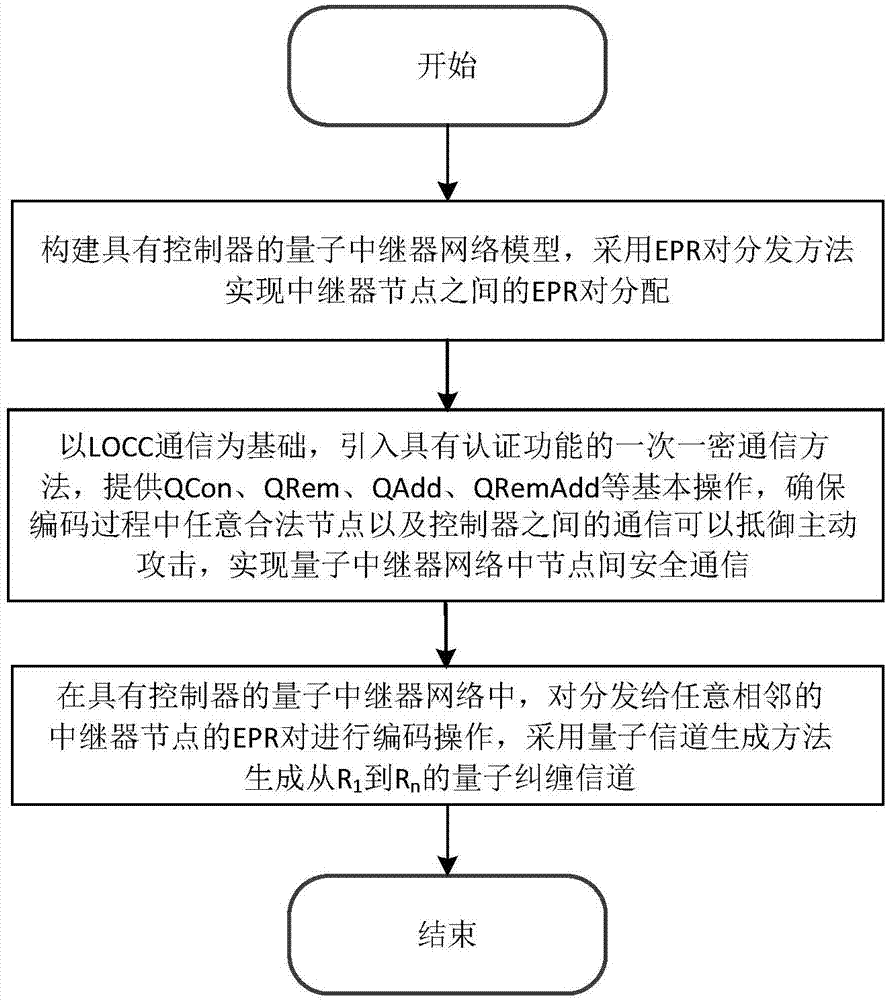
ActiveCN104780169AControllable consumptionImprove securityKey distribution for secure communicationQuantum entanglementDistribution method
A quantum repeater network coding scheme based on a controller comprises three main steps as follows: step 1, a quantum repeater network model provided with the controller is established, and EPR (einstein-podolsky-rosen) pair allocation among repeater nodes is realized with an EPR pair distribution method; step 2, an LOCC (local operation and classical communication) is taken as a basis, a one-time pad communication method with an authentication function is introduced, QCon, QRem, QAdd, QRemAdd basic operations are provided to ensure that communication between any legal node and the controller in the coding process can resist active attack, and safety communication among nodes of a quantum repeater network is realized; step 3, in the quantum repeater network provided with the controller, EPR distributed to any adjacent repeater nodes is coded, and R1-Rn quantum entanglement channels are generated with a quantum channel generation method. The quantum repeater network coding scheme has practical value in the technical field of the communication network.
Owner:苏州三六零智能安全科技有限公司
MAC secure network communication method and network device
InactiveCN101145899AEnsure normal communicationGuaranteed confidentialityData switching networksSecuring communicationNetwork communicationCommunication device
The invention discloses a MAC secure network communication method and communication equipment. The MAC secure network communication method includes that network equipment receive a MAC frame; if the MAC frame is of a MAC encrypted frame, decrypt the encrypted MAC frame, and if the network equipment in the next link where the encrypted MAC frame is to be forwarded does not support MAC security or MAC security can not be available, judge whether the link is reliable further, and if yes, forward to the link by using a MAC non-encrypted frame; otherwise, discard the MAC encrypted frame. The invention realizes to ensure the normal communication of network based on the security protection of the MAC frame.
Owner:HUAWEI TECH CO LTD
Secure communication method for vehicle-mounted TBOX and cloud server
PendingCN110753321AEnable secure communicationImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesSecure communicationData transmission
The invention discloses a safety communication method for a vehicle-mounted TBOX and a cloud server. The method comprises the following steps: a vehicle-mounted TBOX performs communication authentication with a cloud server, and acquires an RSA public key 2 from a CA certificate sent back by the cloud server; the vehicle-mounted TBOX negotiates with the cloud server to generate an AES key; the vehicle-mounted TBOX encrypts the plaintext message by using the AES key, and sends the encrypted message to the cloud server; meanwhile, the AES secret key is encrypted through an RSA public key 2, andthe encrypted AES secret key is sent to the cloud server; and the cloud server decrypts the received encrypted AES key by using the RSA private key 2 to obtain an AES key, and decrypts the received encrypted message by using the AES key to obtain a plaintext message. According to the invention, the AES secret key is generated through communication authentication and negotiation, the plaintext message is encrypted by using the AES secret key, and the encrypted AES secret key is sent, so that the safety of data transmission is greatly improved.
Owner:SAIC-GM-WULING AUTOMOBILE CO LTD
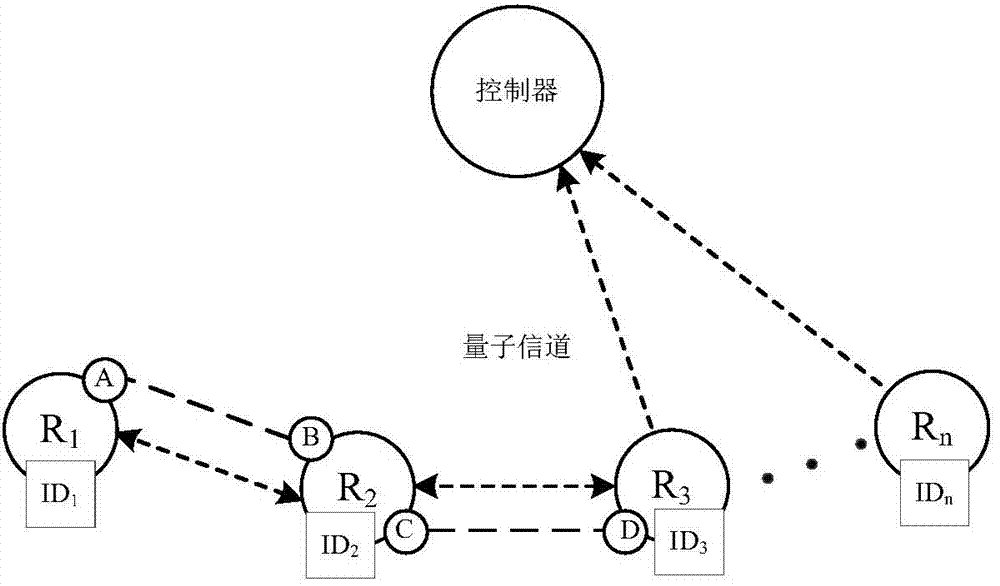
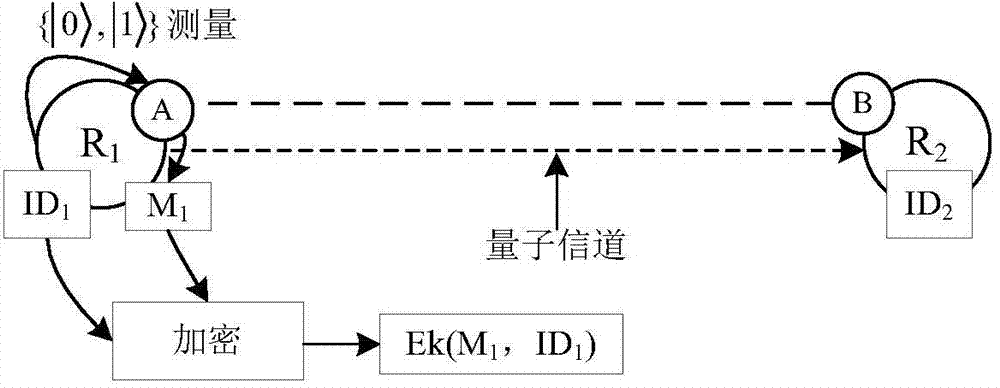
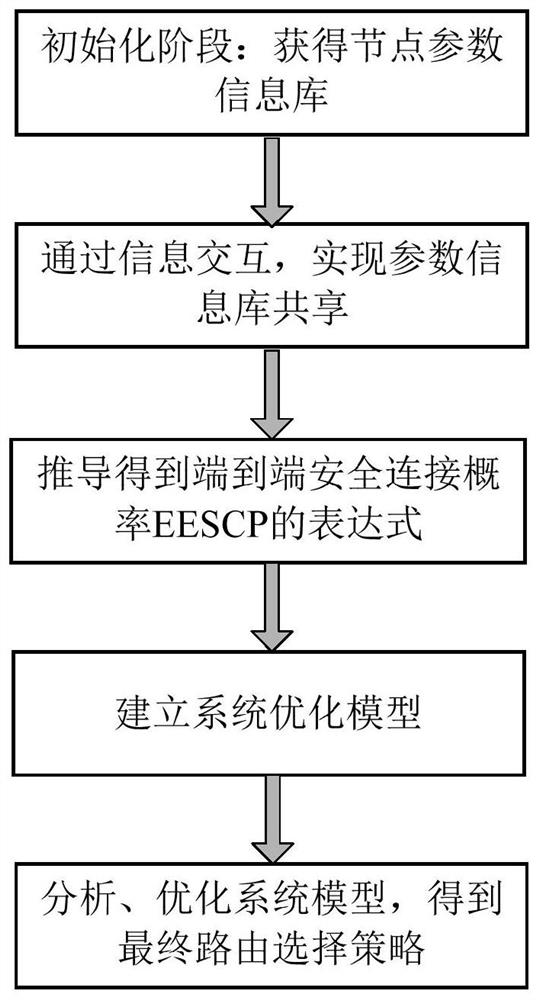
A safe routing method realized by aodv or dsdv protocol
InactiveCN108134772BEnable secure communicationImprove scalabilityData switching networksMulti hop relayEnd to end security
The invention discloses a safe routing method realized by using the AODV or DSDV protocol, comprising steps: S1: nodes obtain basic configuration information of the network and obtain parameters between nodes and system configuration parameters; The parameters and system configuration parameters are organized into a parameter library, and the sharing of nodes in the network is realized; S3: According to the definition of information theory security capacity, the expression of the system end-to-end secure connection probability EESCP is deduced; S4: According to the above expression Establishing a system optimization model, and deriving relevant parameter information from the parameter library, and substituting it into the optimization model; S5: analyzing and obtaining a routing selection strategy according to the optimization model. On the premise of assuming unknown eavesdropper's position and channel state information, the present invention combines physical layer security technology based on information theory, and obtains and uses end-to-end secure connection probability of multi-hop relay network.
Owner:杭州缤构网络科技有限公司
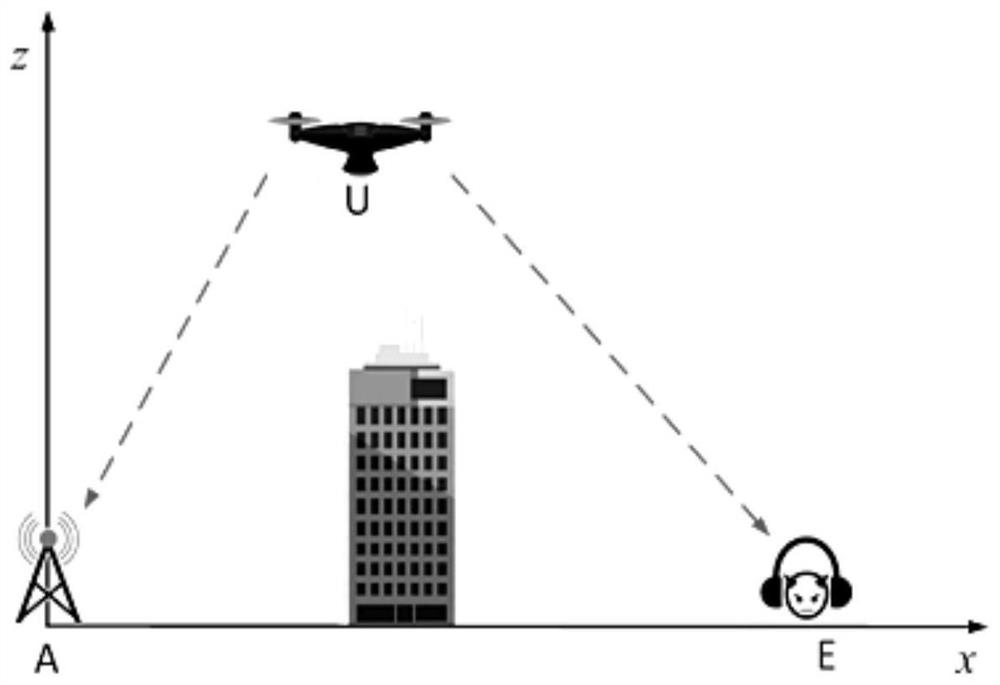
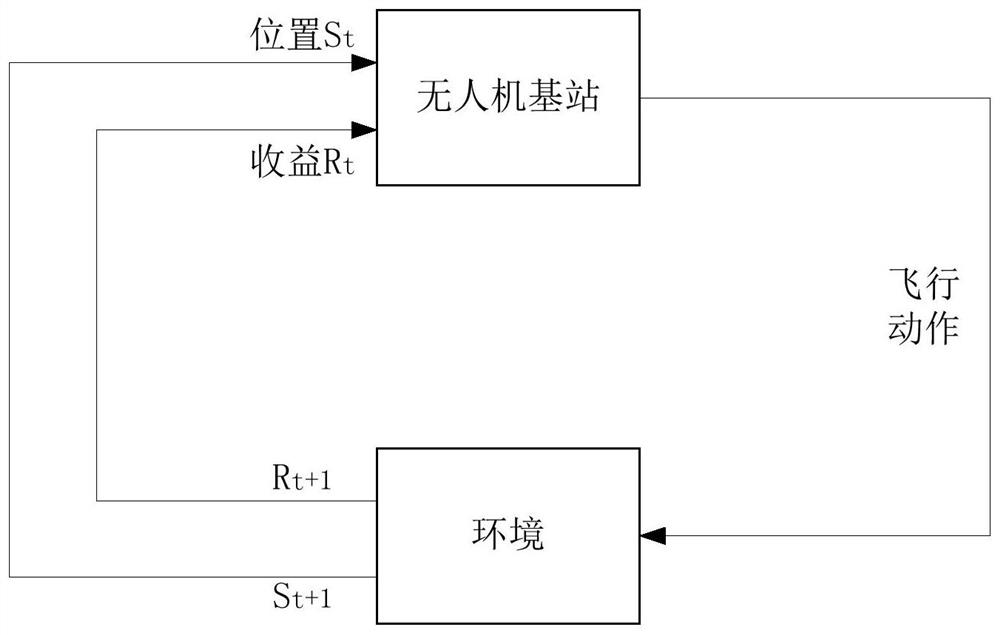
Unmanned aerial vehicle base station flight planning method and system, storage medium and unmanned aerial vehicle base station
PendingCN112068590AThe average confidentiality rate is highHigh confidentiality rateParticular environment based servicesFor mass transport vehiclesSimulationUncrewed vehicle
The invention provides an unmanned aerial vehicle base station flight planning method and system, a storage medium and an unmanned aerial vehicle base station. The method comprises the following steps: obtaining the instantaneous secrecy rate of the unmanned aerial vehicle base station and the distance from the unmanned aerial vehicle base station to the end point position in real time through anunmanned aerial vehicle base station operation model adopting a sight distance and non-sight distance mixed channel; performing reinforcement learning by taking the instantaneous secrecy rate as an income, and obtaining an optimized flight path of the unmanned aerial vehicle base station flying from an initial position to a maximum position of the instantaneous secrecy rate; and carrying out reinforcement learning by taking the instantaneous secrecy rate in combination with the distance from the unmanned aerial vehicle base station to the final position as an income, and obtaining an optimizedflight path of the unmanned aerial vehicle base station flying from the position with the maximum instantaneous secrecy rate to the final position.
Owner:GUANGDONG UNIV OF TECH
Safety communication implementation of next generation wireless network
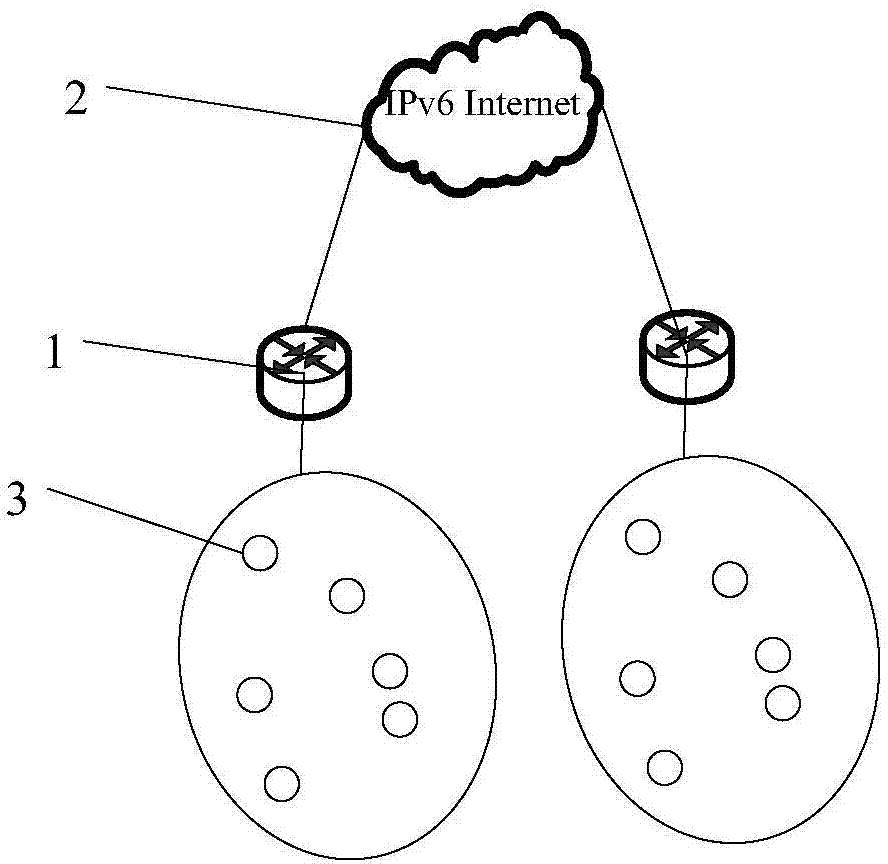
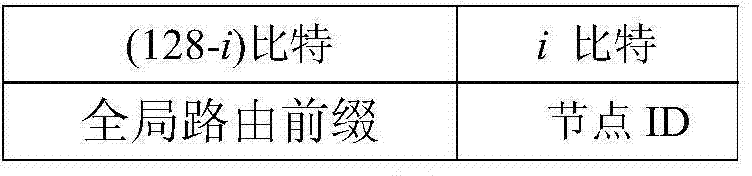
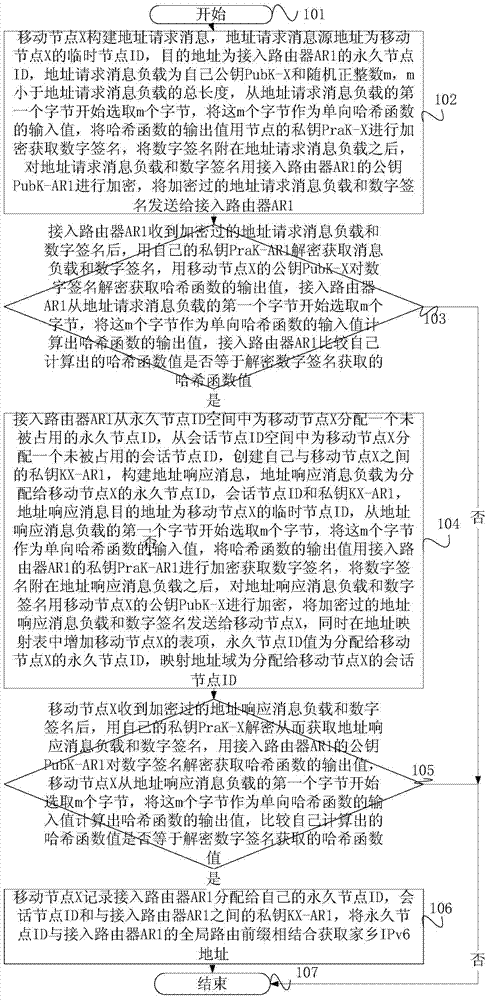
ActiveCN104243504AEnable secure communicationProtect private informationTransmissionSecurity arrangementWireless mesh networkThe Internet
The invention provides a communication implementation of a next generation wireless network. The method is characterized in that the wireless network is connected to the internet as an end network by an access router, wherein each mobile node with IPv6 address in the wireless network has the routing forwarding function; the mobile nodes move from one wireless network to another wireless network; the wireless network of home address is obtained by each mobile node as the home network of the mobile node, wherein the access router connected by the home network is treated as the home access router of the mobile node; the wireless network is called the external network of the mobile node when the mobile node is moved from the home network to another wireless network, and the access router connected by the external network is called the external access router of the mobile node. According to the safety communication implementation of the next generation wireless network, the privacy of a user can be protected while the safety communication is implemented when moving the nodes in either home network or external network.
Owner:HUAWEI TEHCHNOLOGIES CO LTD
User pairing method for non-orthogonal multiple access system
ActiveCN107612669AEnable secure communicationImprove performanceTransmission path multiple useSecurity arrangementSecure communicationInequation
The invention discloses a user pairing method for a non-orthogonal multiple access system. The method comprises the following steps of step 1) establishing a multi-user non-orthogonal multiple accessdownlink system model; step 2) obtaining a user scheduling predicate between users in the multi-user non-orthogonal multiple access downlink system model according to an average bit error rate threshold requirement inequation of the users in multi-slot transmission and the multi-user non-orthogonal multiple access downlink system model established in the step 1); and step 3) judging whether the users can be paired according to the user scheduling predicate obtained in the step 2). Through the method of the invention, the secure communication between the users can be realized.
Owner:XI AN JIAOTONG UNIV
Internet of Things equipment safety communication system and method, networking equipment and server
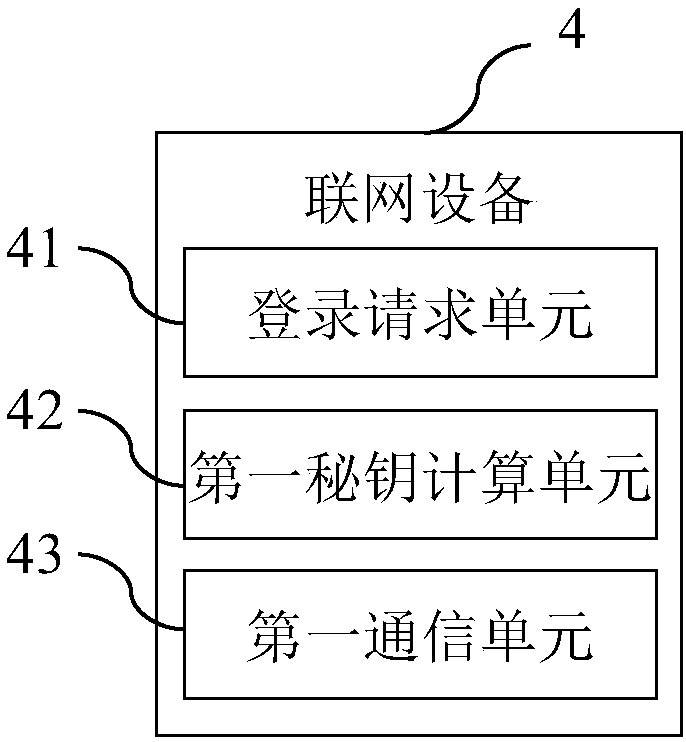
InactiveCN108076062AEnable secure communicationSimplify the authentication processKey distribution for secure communicationCommunications systemCommunication unit
The invention provides an Internet of Things equipment safety communication system and method, networking equipment and a server, which are used for achieving safe communication between the networkingequipment and the server in Internet of Things; the networking equipment comprises a login request unit, a first secret key calculation unit and a first communication unit, wherein the server comprises a login authentication unit, a login feedback unit and a second communication unit, wherein the login request unit is used for sending login request information; the login authentication unit is used for carrying out authentication on the login request information; the login feedback unit is used for generating login feedback information and a session key and sending the login feedback information to the networking equipment; the first secret key calculation unit is used for generating the session key; and the first communication unit and the second communication unit communicate through the session key. According to the Internet of Things equipment safety communication system and method, the networking equipment and the server, the session key is generated in a login authentication process, and safe communication of the Internet of Things equipment can be realized only by occupying a small amount of resources.
Owner:SHENZHEN INOVANCE TECH
Network isolation device and method for nuclear power plant
InactiveCN106972969AEnable secure communicationAchieve isolationData switching networksNuclear powerComputer module
The invention discloses a network isolation device for a nuclear power plant. The device comprises a safety side communication module, a non-safety side communication module, and a master control module, wherein information can be transmitted between the safety side communication module and the non-safety side communication module, and the modules can process signals according to respective communication protocols; and the master control module controls the safety side communication module and the non-safety side communication module, and monitors working statuses of the safety side communication module and the non-safety side communication module. The device has the advantages that safe communication between a safety system and a non-safety system of the nuclear power plant is achieved; and the safety system and the non-safety system can be isolated from each other, so that the phenomenon that a failure of one of the two systems leads to a failure of the other system is avoided.
Owner:CHINA NUCLEAR CONTROL SYST ENG
Rapid authentication method and system for trusted execution environment
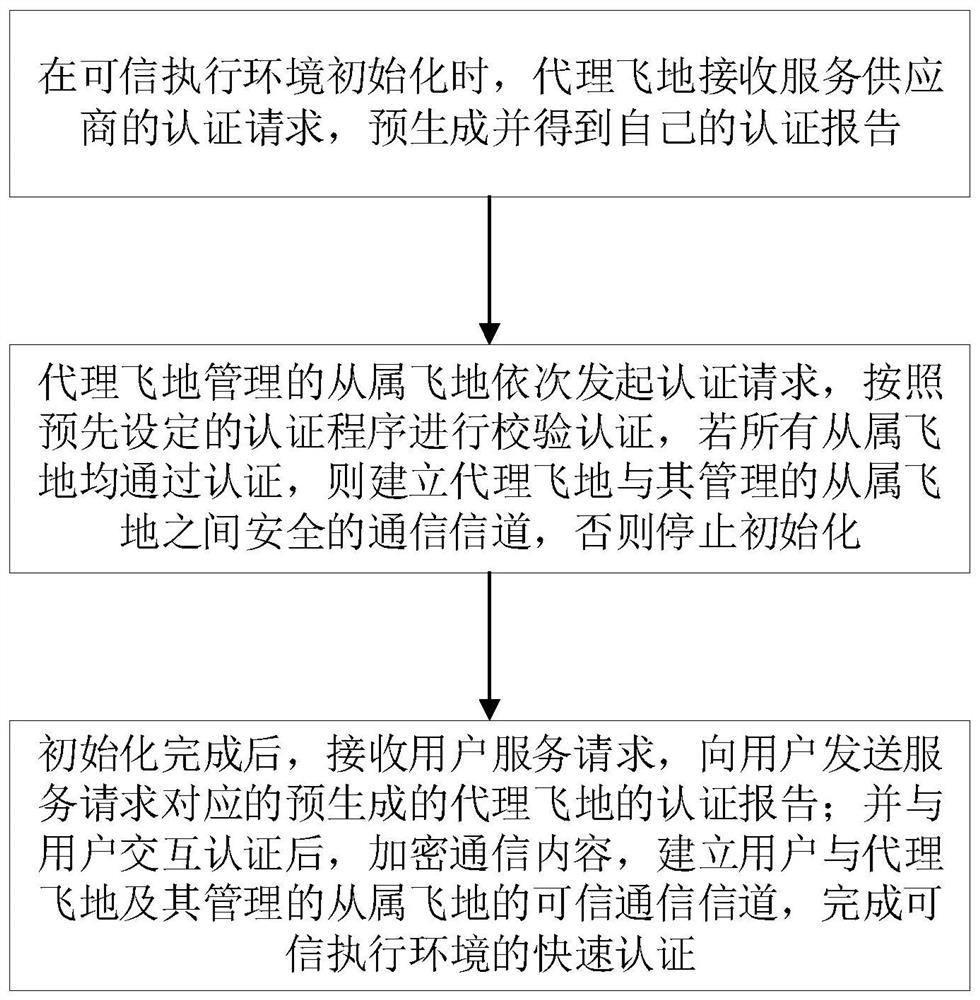
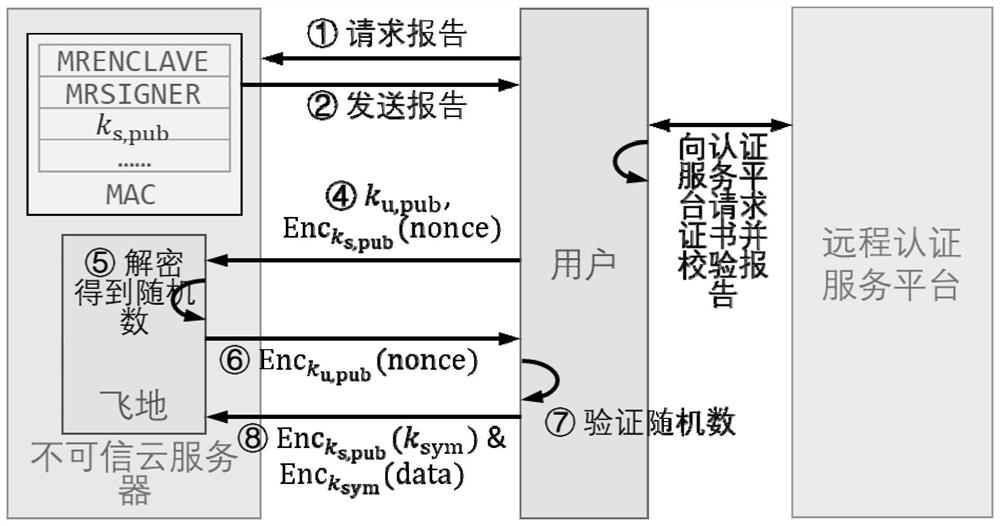
ActiveCN113329012AQuickly build trustEnable secure communicationKey distribution for secure communicationUser identity/authority verificationEngineeringCommunication channel
The invention provides a rapid authentication method and system for a trusted execution environment, which are reasonable in design, fast in enclave authentication speed, small in calculation overhead and capable of rapidly establishing a trusted communication channel. The method comprises the following steps: when a trusted execution environment is initialized, an agent enclave receives an authentication request of a service provider, and pre-generates and obtains an own authentication report; the subordinate enclaves managed by the agent enclave sequentially initiate authentication requests, verification authentication is carried out according to a preset authentication program, if all the subordinate enclaves pass authentication, a safe communication channel between the agent enclave and the subordinate enclaves managed by the agent enclave is established, and otherwise, initialization is stopped; after initialization is completed, a user service request is received, and a pre-generated proxy enclave authentication report corresponding to the service request is sent to the user; and after interactive authentication with the user, the communication content is encrypted, a trusted communication channel between the user and the agent enclave and the slave enclave managed by the agent enclave is established, and rapid authentication of the trusted execution environment is completed.
Owner:INST FOR INTERDISCIPLINARY INFORMATION CORE TECH XIAN CO LTD
M2M (Machine-to-Machine) terminal security access method and terminal and management platform
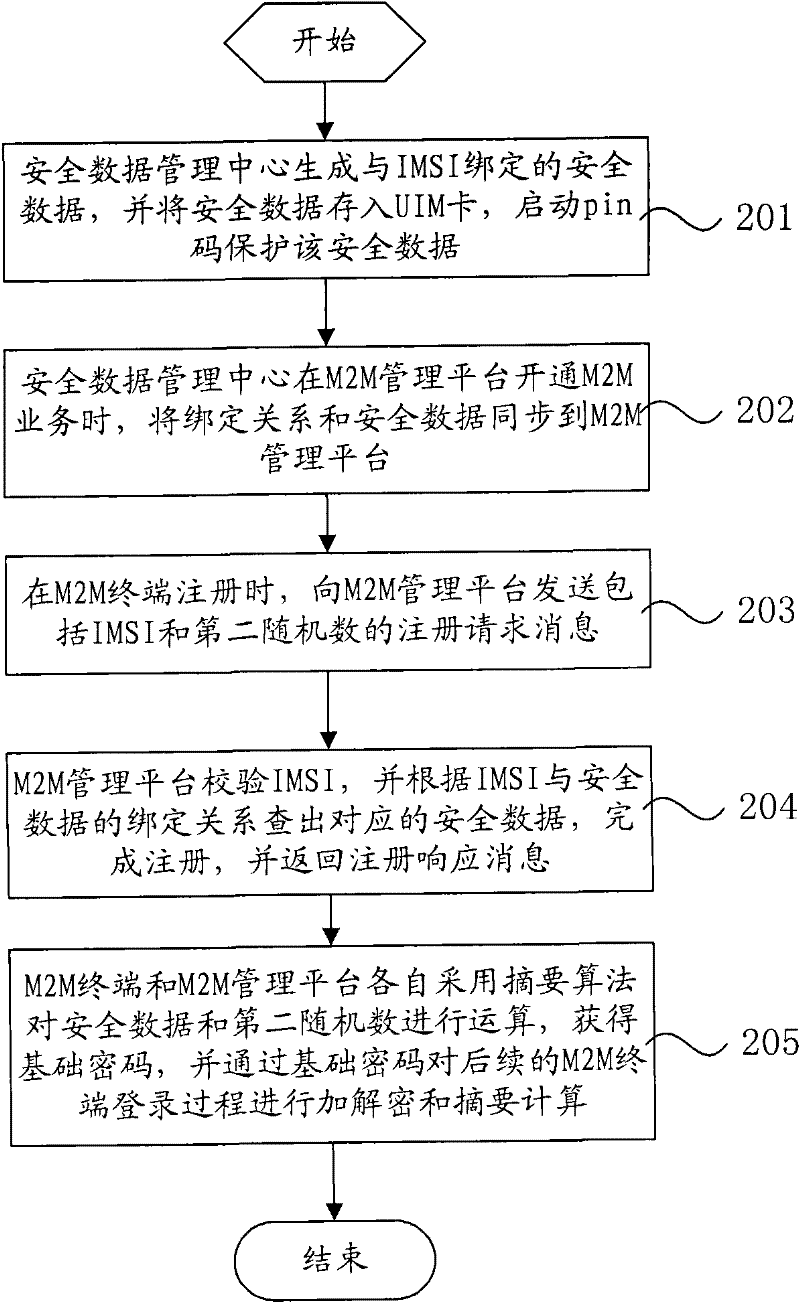
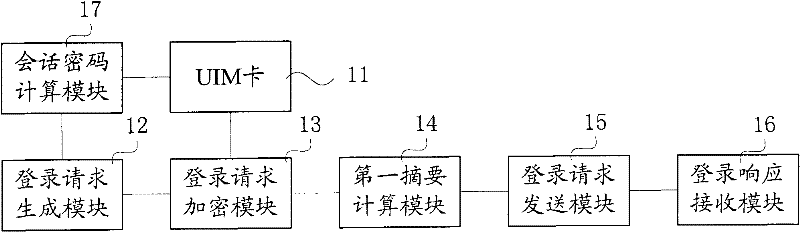
ActiveCN102547686AEnable secure communicationMeet security needsSecurity arrangementAccess methodCiphertext
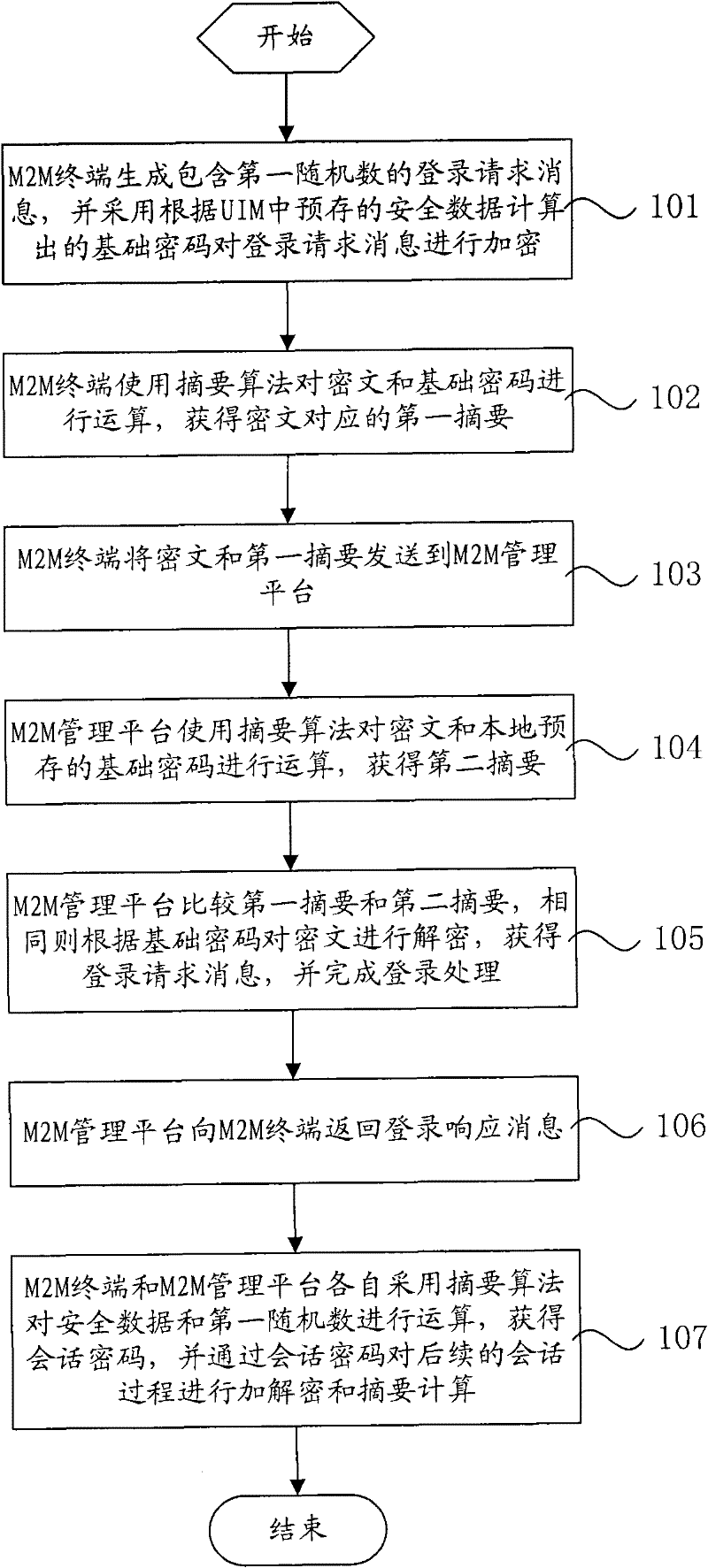
The invention relates to an M2M (Machine-to-Machine) terminal security access method. The method comprises the following steps that: the M2M terminal generates login request information including a first random number and encrypts the login request information by using a base password calculated according to security data pre-stored in a UIM (User Identifier Module); the M2M terminal calculates a ciphertext and the base password by using a digest algorithm so as to obtain a first digest; the M2M terminal transmits the ciphertext and the first digest to the M2M management platform; the M2M management platform adopts the digest algorithm to calculate and obtain a second digest; the first digest is compared with the second digest, if the first digest is the same as the second digest, the ciphertext is decrypted according to the base password, thereby obtaining the login request information and accomplishing the login; and the M2M terminal and the M2M management platform adopt the digest algorithm to calculate the security data and the first random number, respectively, thereby obtaining a session password and decrypting a subsequent session process by using the session password. The invention further relates to an M2M terminal and a management platform. According to the invention, a relatively perfect application security mechanism is provided for communication between the M2M terminal and the M2M management platform.
Owner:CHINA TELECOM CORP LTD
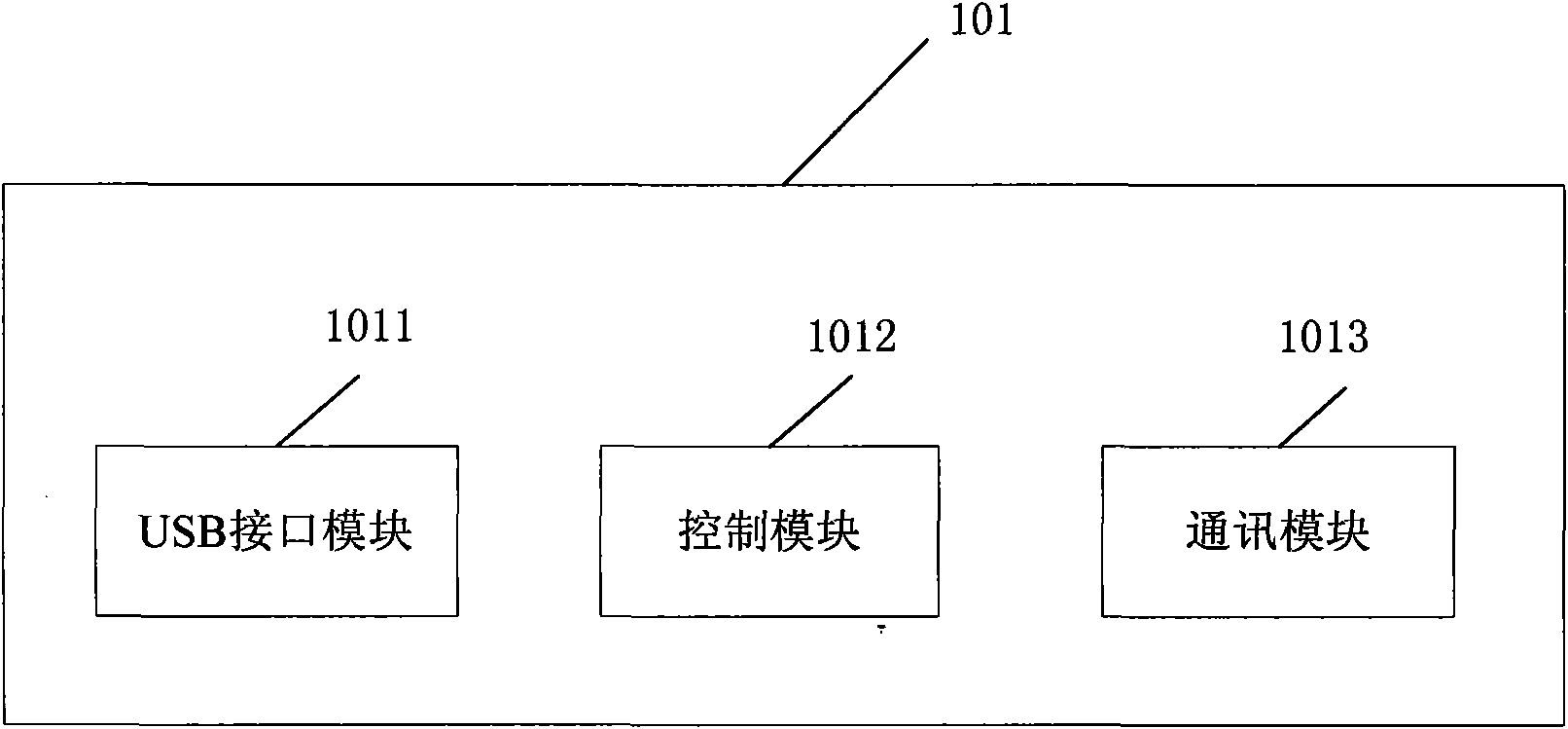
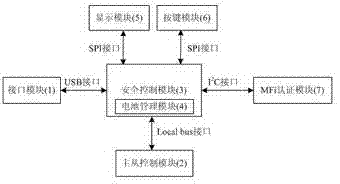
Second generation USB (Universal Serial Bus) key system for implementing safety pavement of mobile terminals
InactiveCN102819707AAddress limitationsAchieve securityComputer security arrangementsPaymentCoprocessor
The invention relates to a second generation USB (Universal Serial Bus) key system for implementing the safety pavement of mobile terminals, which comprises a USB interface module, a master-slave control module, a safety control module, a battery management module, a display module and a key module. The USB interface module adopts a standard mini UBS3.0 interface; an interface A is a USB2.0 interface for being connected with iOS (Internetwork Operating System)-series and Android-series mobile equipment; an interface B is a USB3.0 interface for being connected with a PC (Personal Computer); the master-slave control module adopts a CH374 chip; the safety control module uses a 3272L chip as a master control chip; the display module uses an A514 chip as a display chip; according to an MFi (Made for iPod / iPhone / iPad) authentication module, an IPOD_AC_2.0C Apple authentication coprocessor is connected with the 3272L chip by an I2C (Inter-Integrated Circuit) interface so as to implement the authentication on the iOS-series equipment; and by the interfaces, the master-slave control module, an online second generation key is connected into the PC, the Android equipment, the iOS-series equipment and OTG (On-The-Go) equipment to implement safety communication among various mobile terminal equipment. The problem of the limitation that the existing second generation key can only be connected into the PC to carry out network payment is solved.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
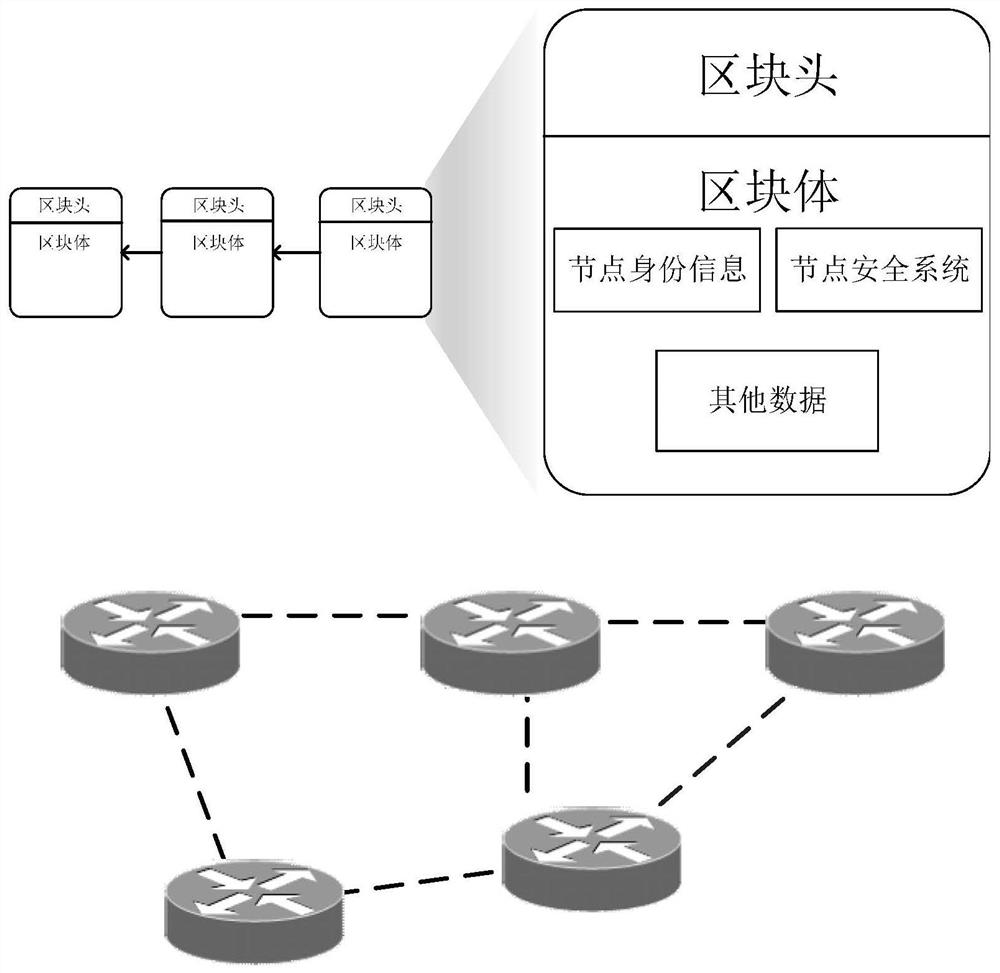
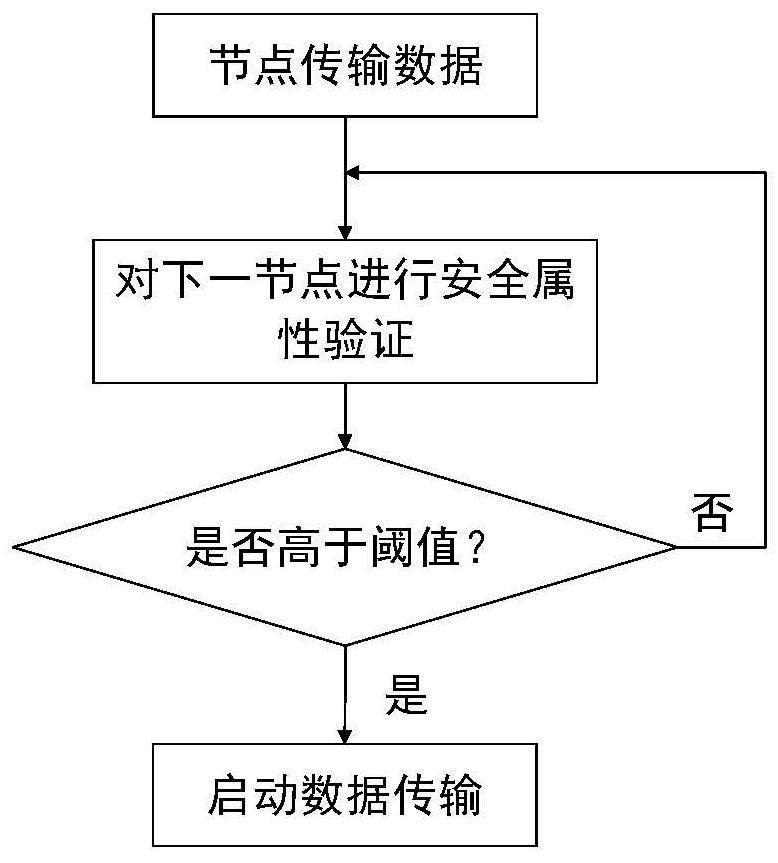
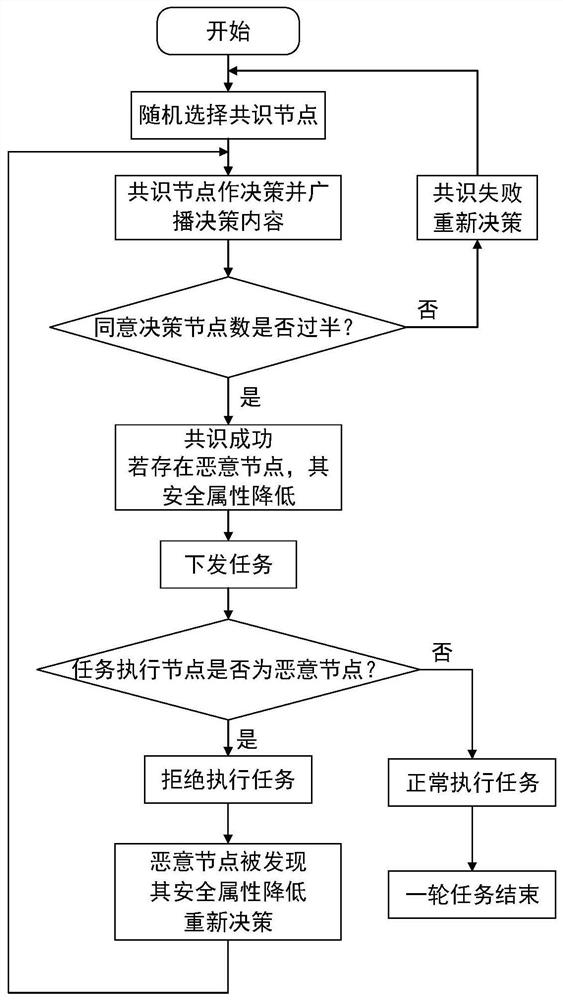
Network node security attribute evaluation method based on blockchain consensus result feedback
ActiveCN111770103AIncrease credibilityEnable secure communicationDatabase distribution/replicationDigital data protectionSecure communicationComputer network
The invention discloses a network node security attribute evaluation method based on blockchain consensus result feedback, which enhances the credibility between network nodes by combining a consensusmechanism of a blockchain, and has the characteristics of tamper resistance, traceability, decentration and the like. By establishing a security attribute evaluation mechanism based on a trust mechanism, security attribute evaluation is carried out to judge the security of each network node, and secure communication between the nodes is realized.
Owner:UNIV OF SCI & TECH OF CHINA
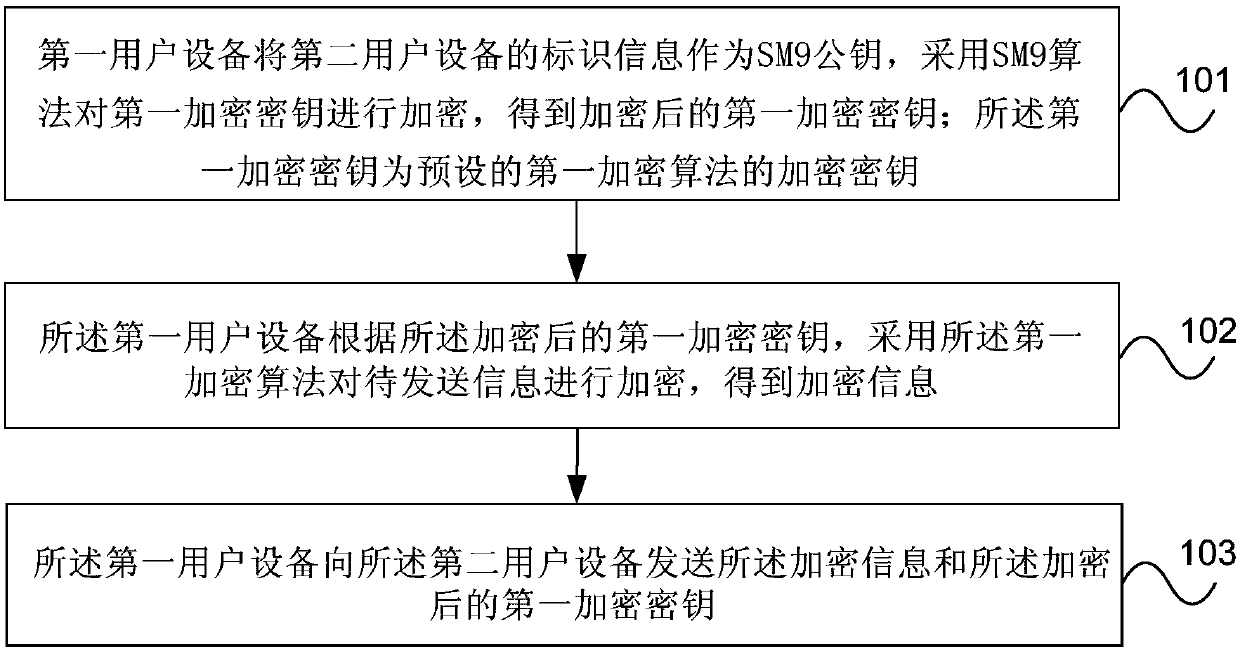
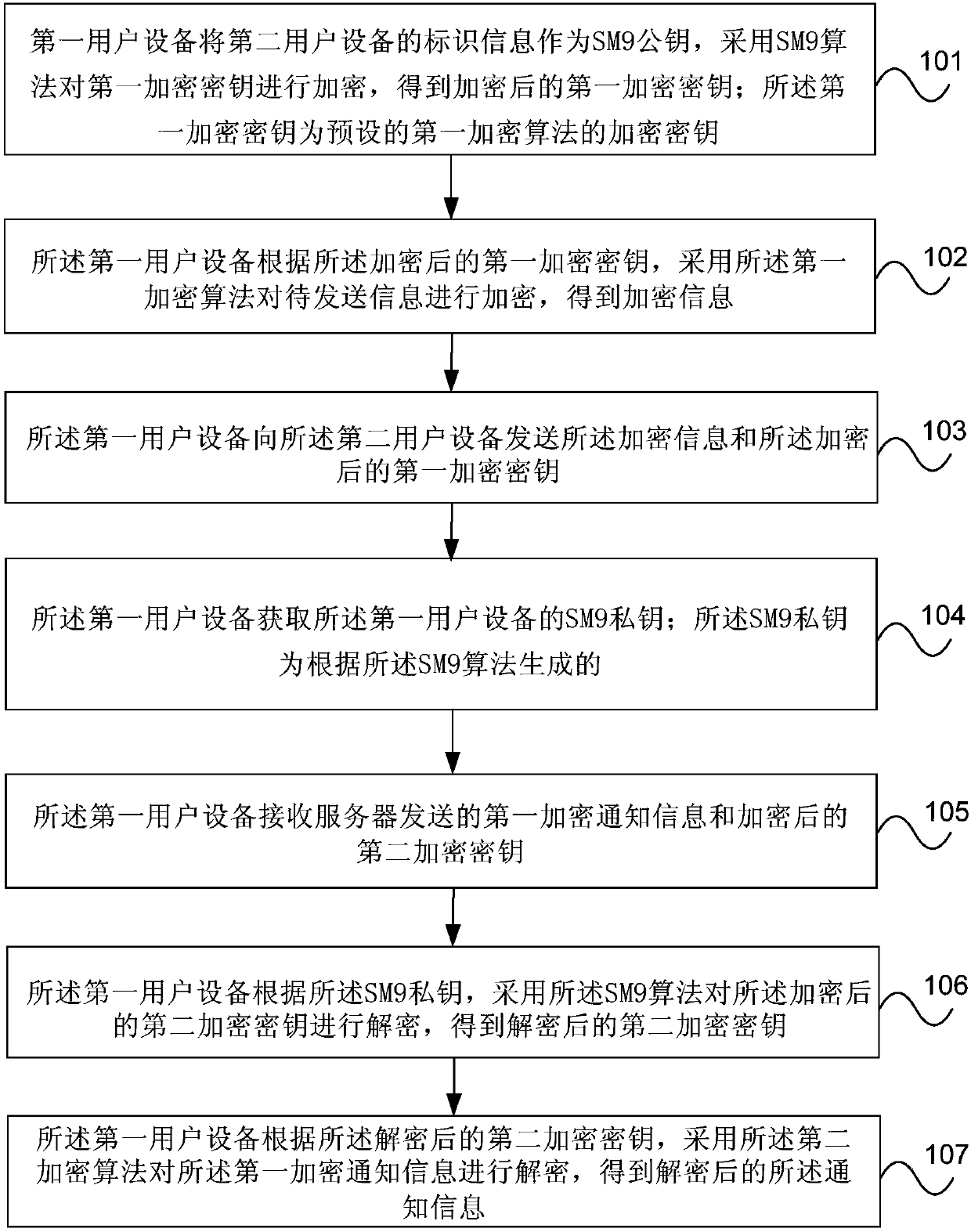
Encryption communication method and device based on SM9 algorithm
InactiveCN107682156AEnable secure communicationEasy to operateKey distribution for secure communicationPublic key for secure communicationSecure communicationUser equipment
The invention provides an encrypted communication method and device based on the SM9 algorithm. The method includes: the first user equipment uses the identification information of the second user equipment as the SM9 public key, and uses the SM9 algorithm to encrypt the first encryption key to obtain an encrypted first encryption key; the first encryption key is an encryption key of a preset first encryption algorithm; the first user equipment uses the first encryption algorithm to encrypt information to be sent according to the encrypted first encryption key to obtain encrypted information; the The first user equipment sends the encrypted information and the encrypted first encryption key to the second user equipment. The embodiment of the present invention realizes the safe communication between multiple user equipments and the function of safe group sending of messages.
Owner:Fisherman Information Technology Co Ltd
Method for security encryption and signing based on identity file
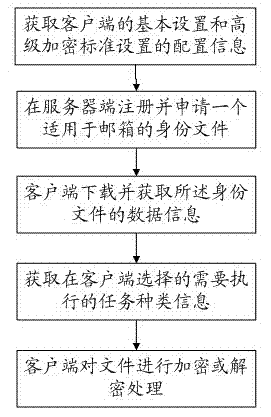
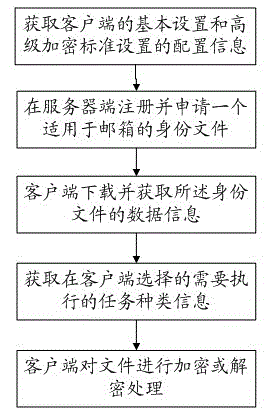
InactiveCN102710601ANot viewedNot modifiedUser identity/authority verificationData informationAdvanced Encryption Standard
The invention discloses a method for security encryption and signing based on an identity file. The method includes: obtaining configuration information of basic setting of a client and configuration information of advanced encryption standard setting of the client; registering and applying the identity file applicable to a mailbox at a server end; downloading data information of the identity file through the client; obtaining type information of a task to be executed selected by the client; and performing encryption and decryption to files through the client according to the identity file. By the method, important data of a user can be protected from being viewed or modified, safe communication on an originally unsafe channel can be achieved, and denial behaviors after using the user's identity to receive and transmit information can be avoided.
Owner:SUZHOU UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com