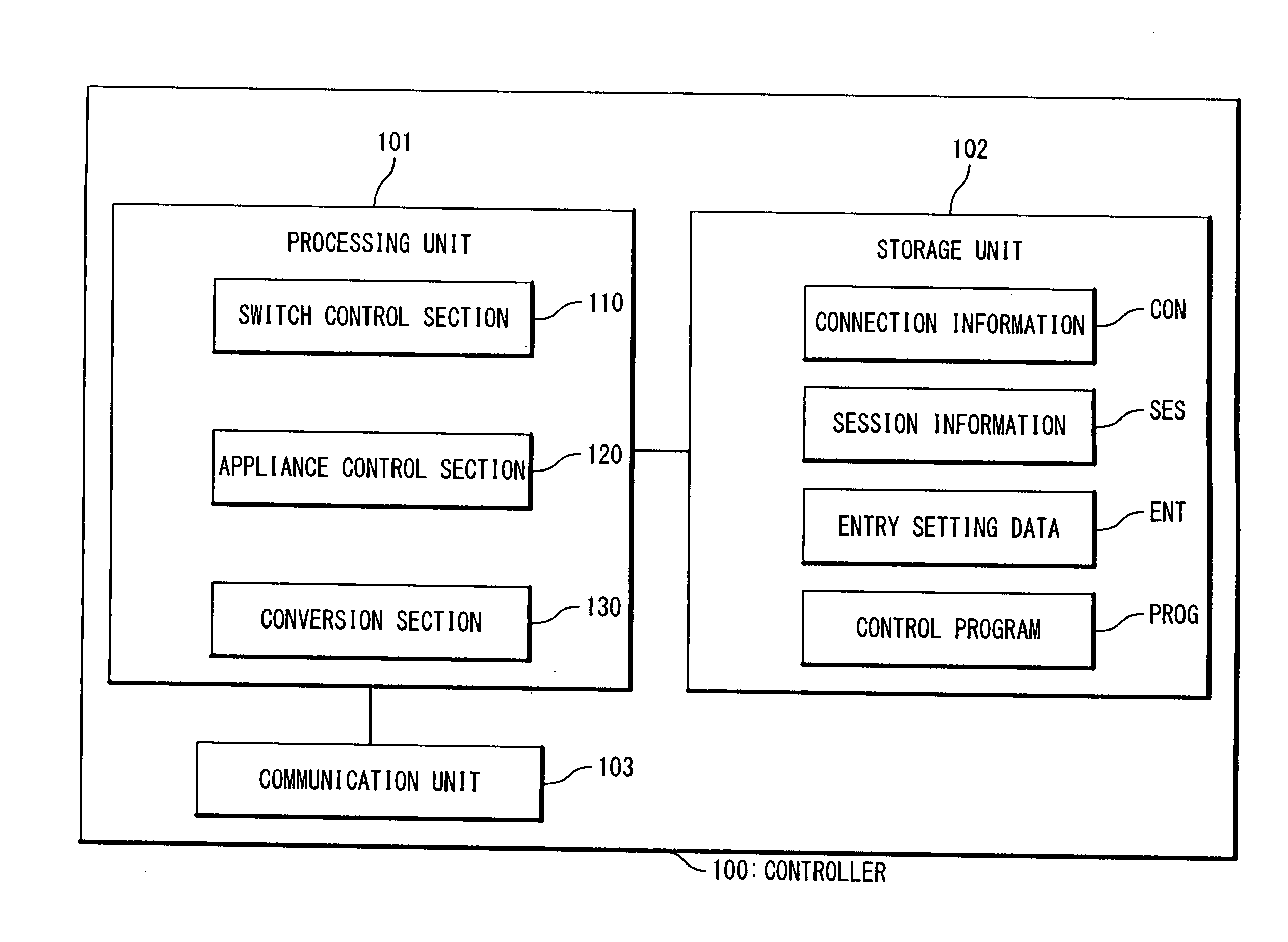
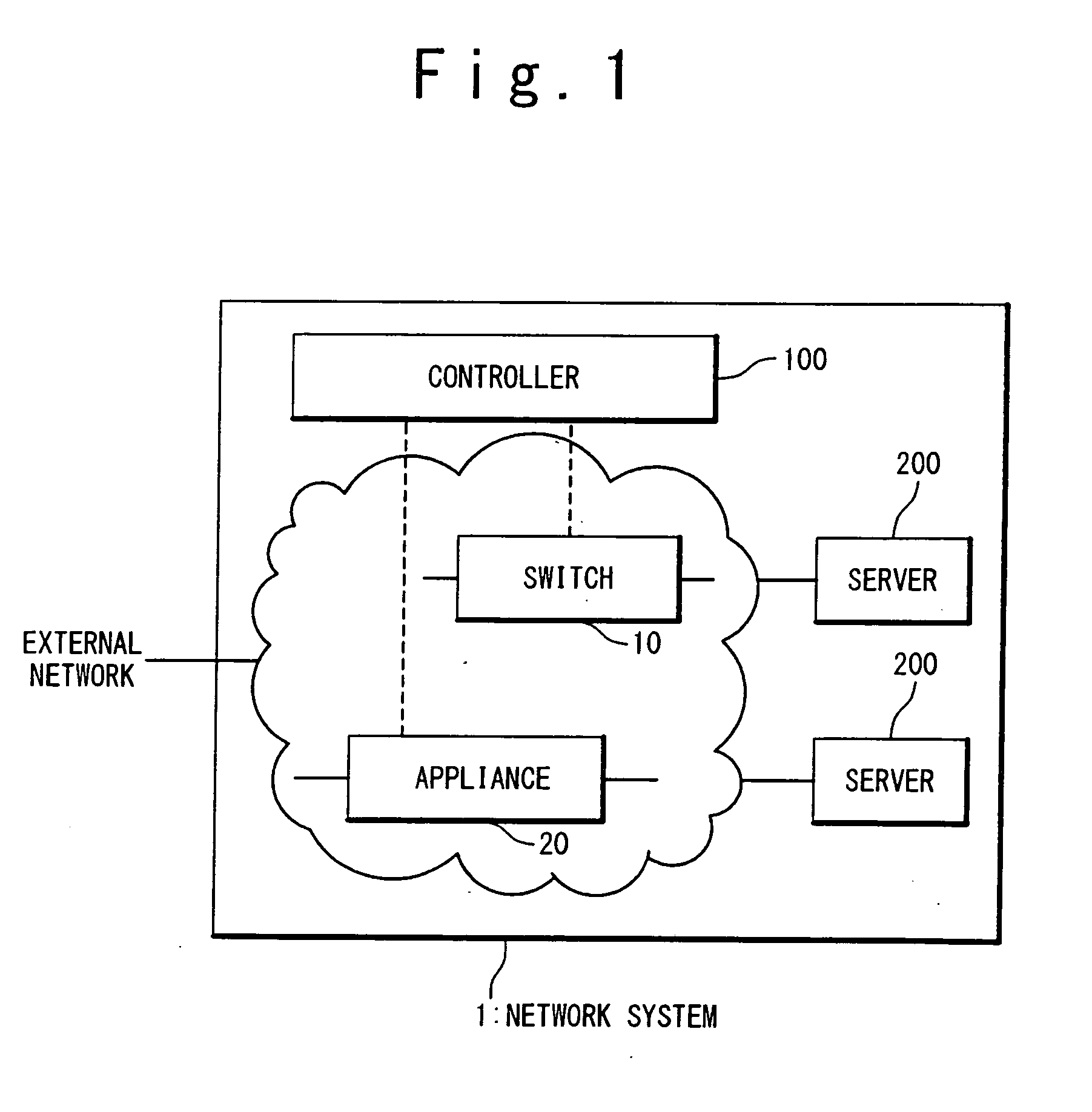
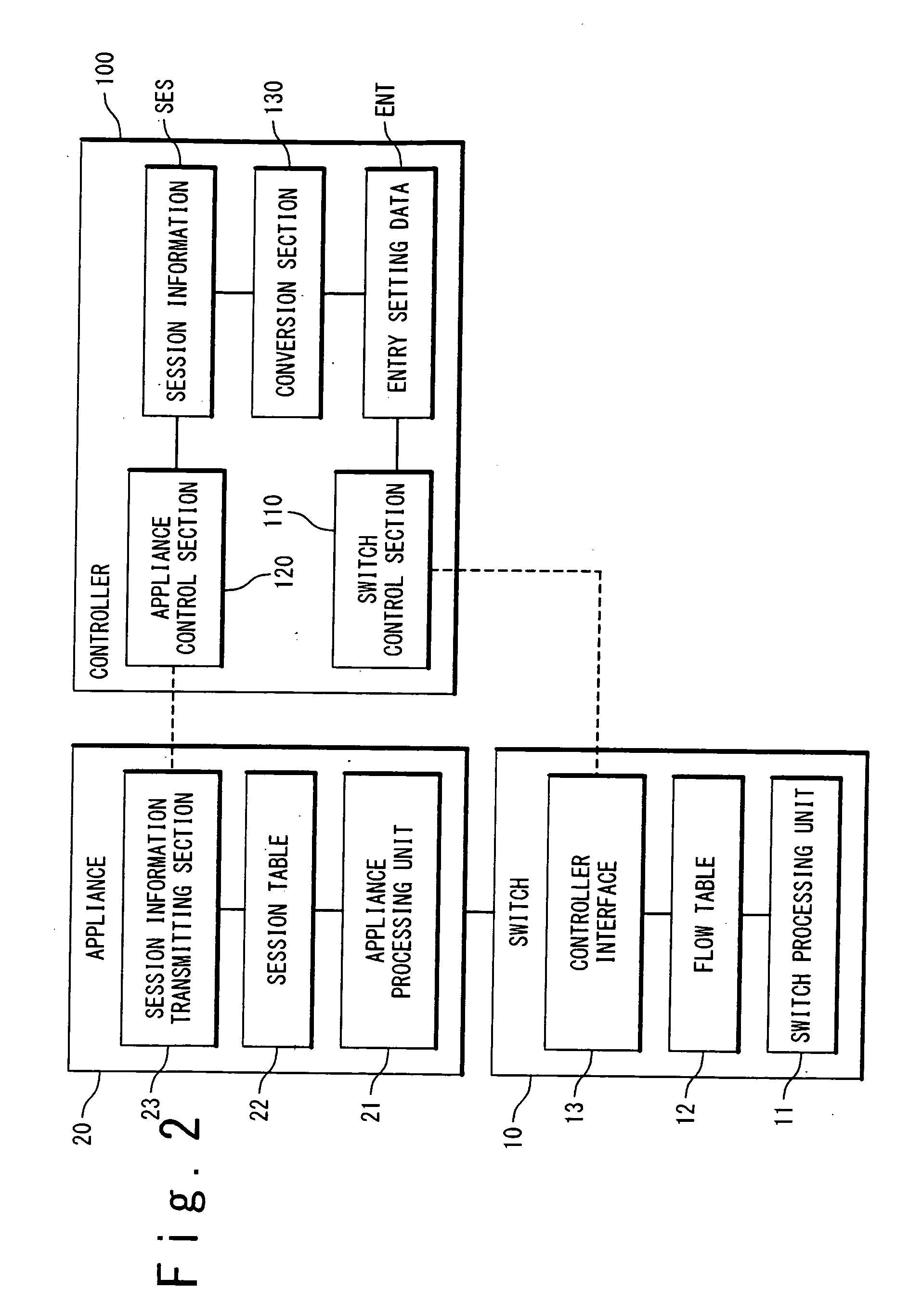
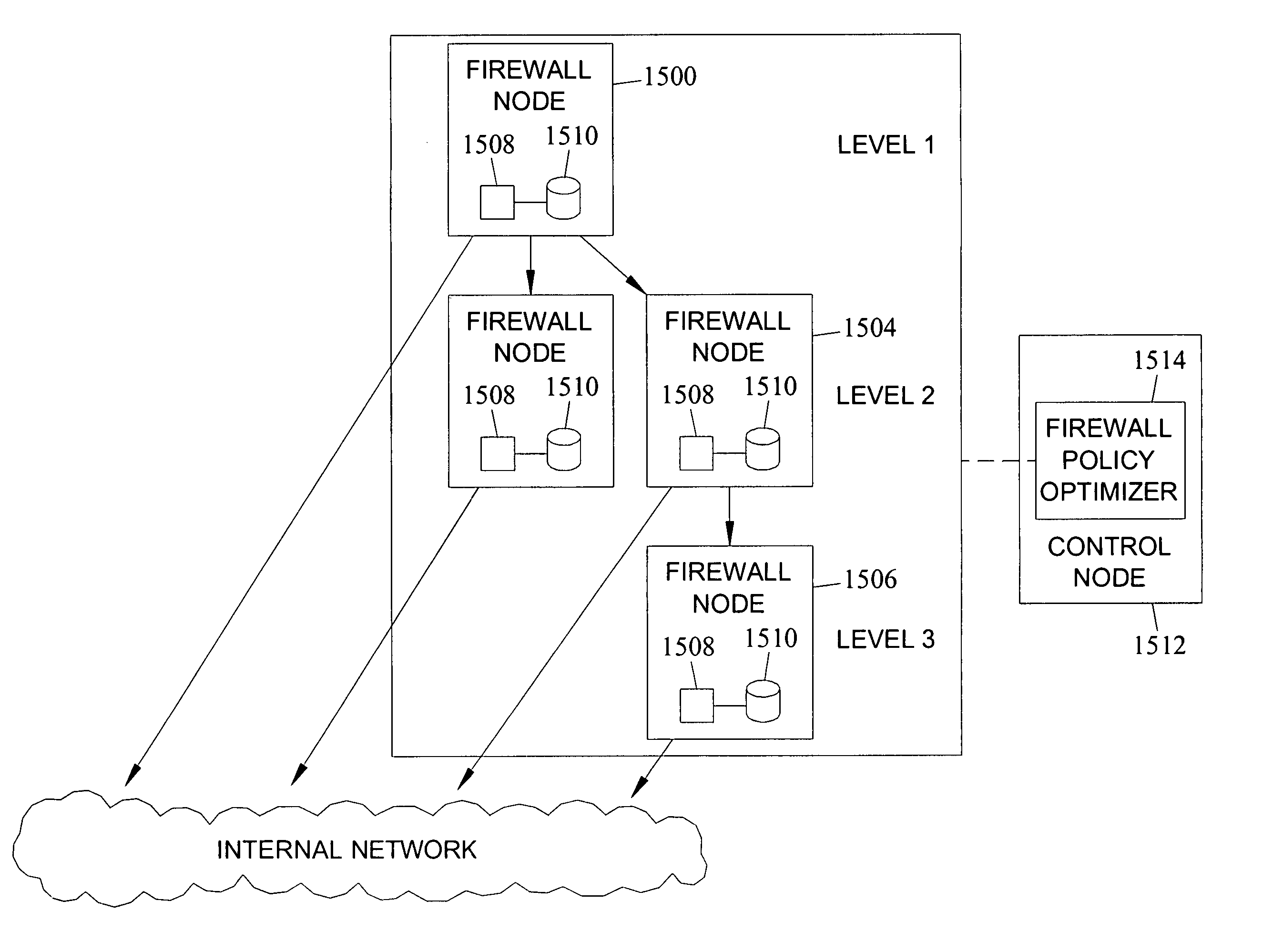
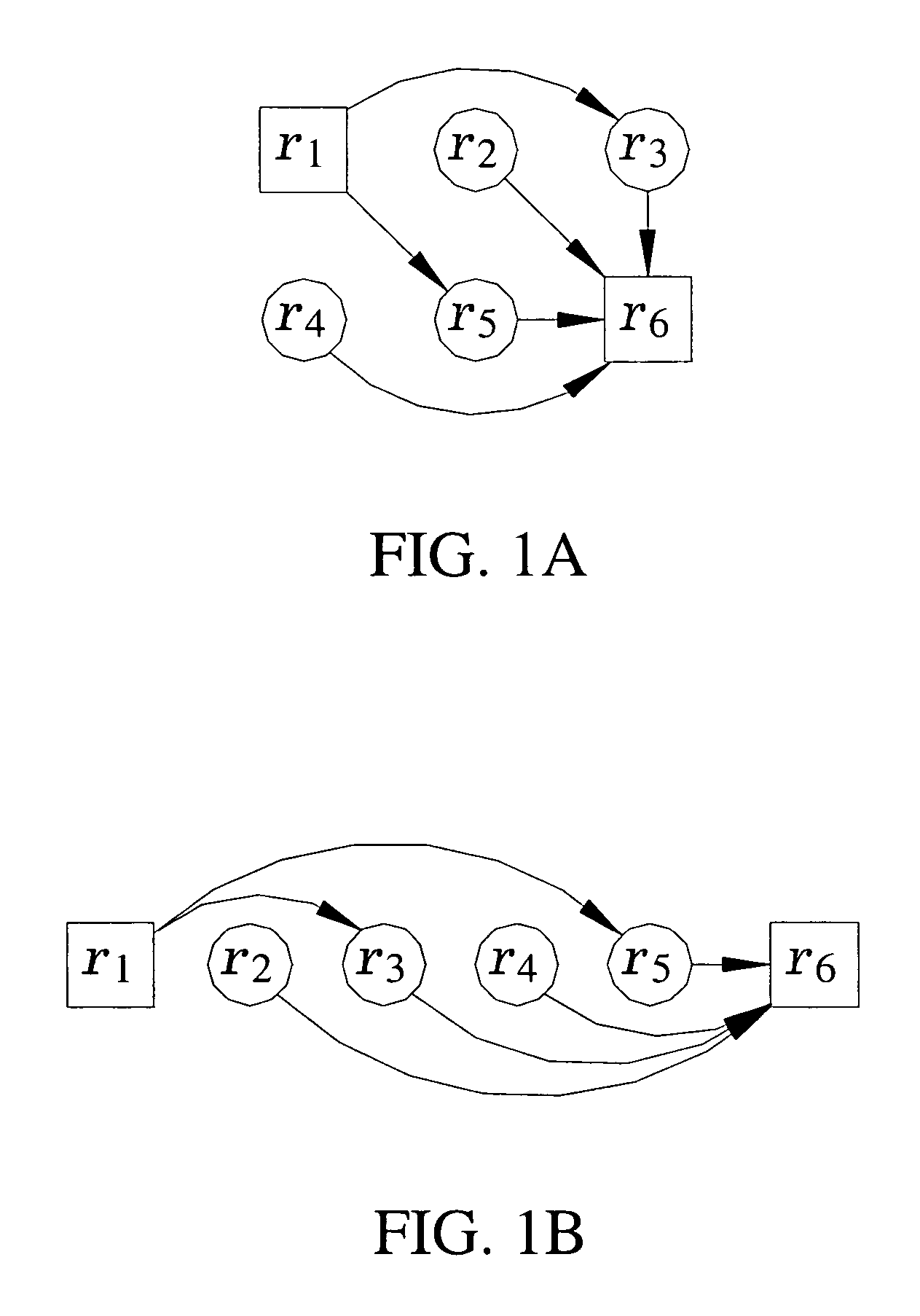
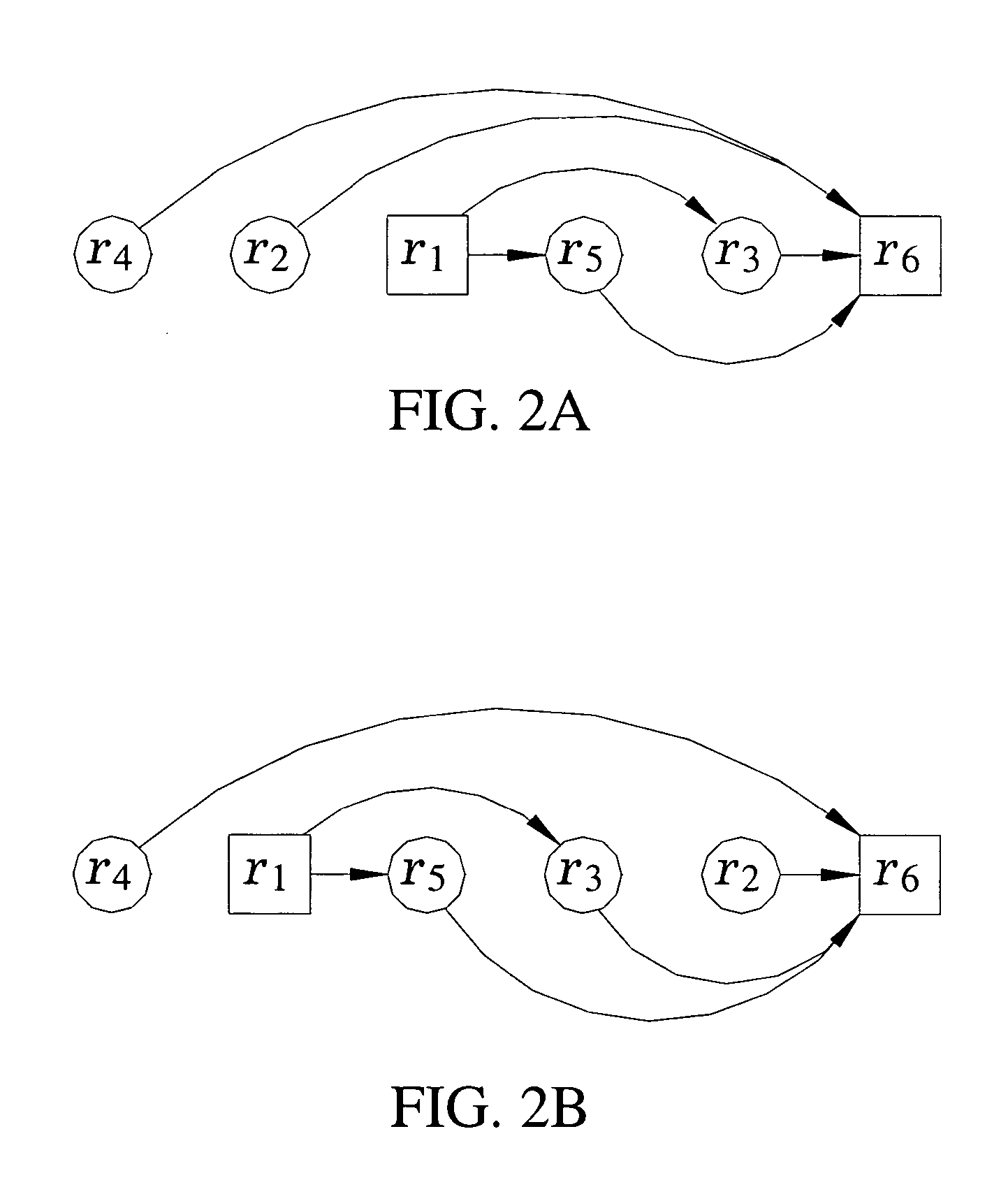
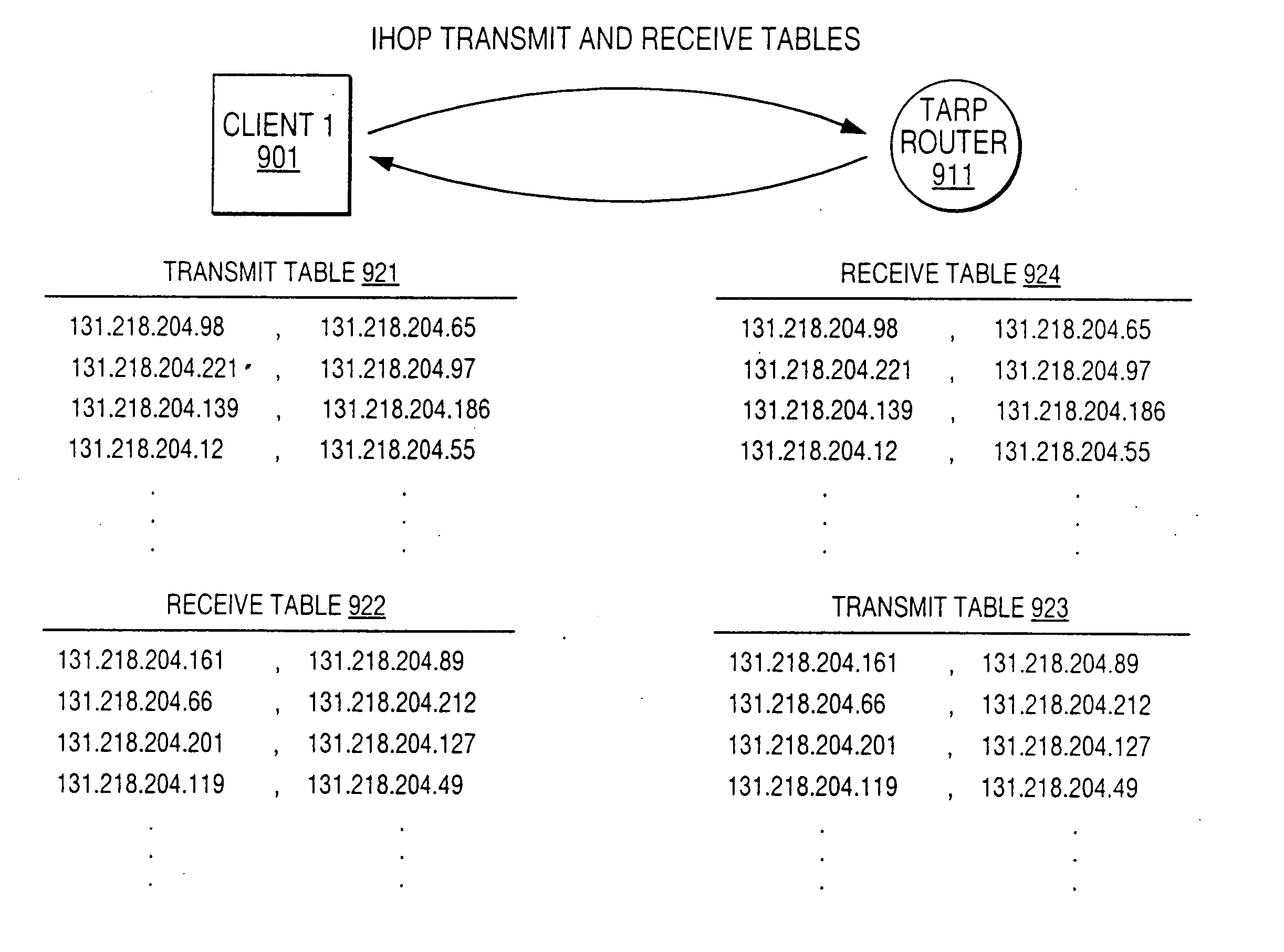
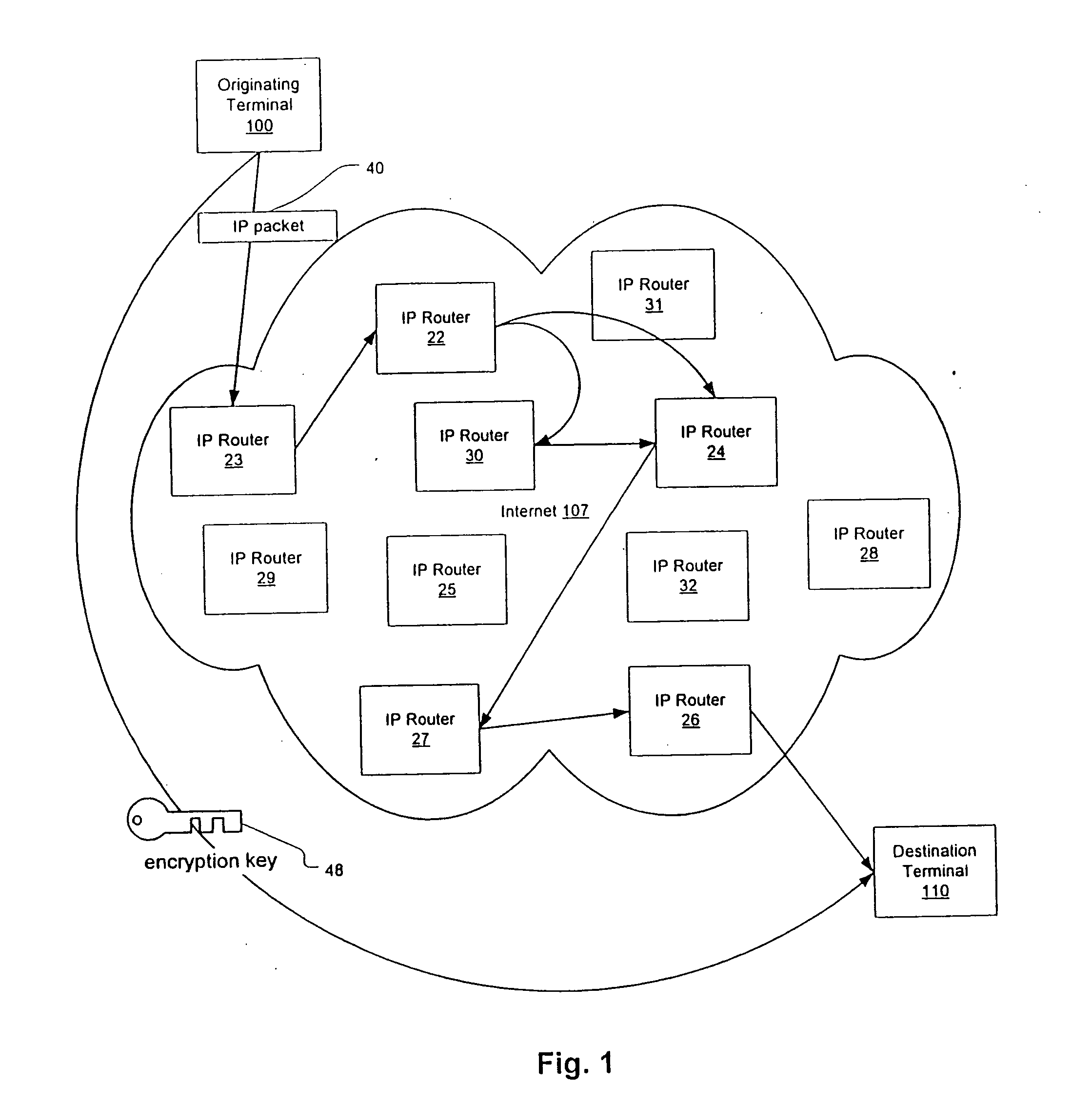
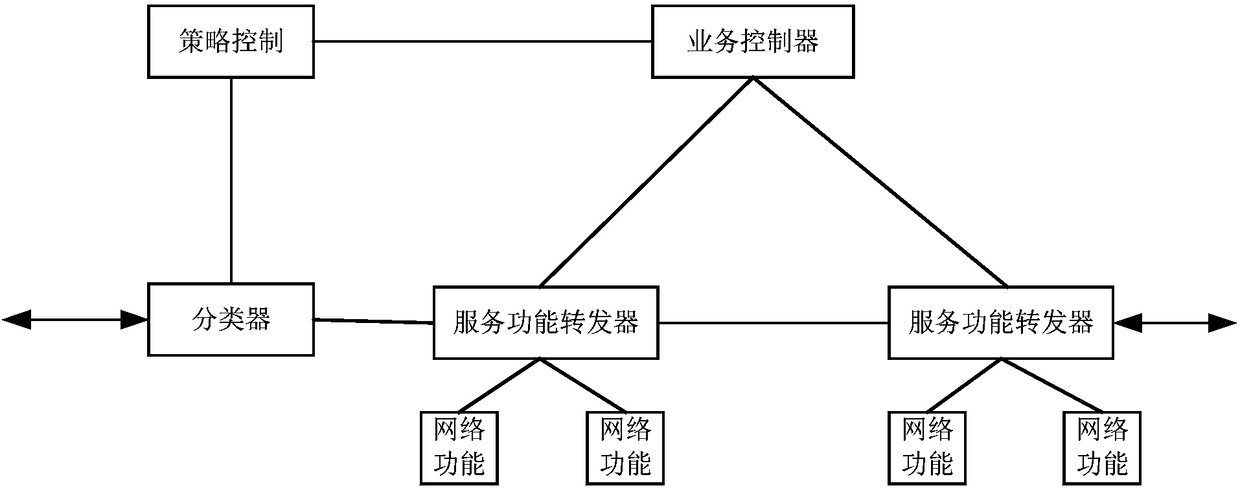
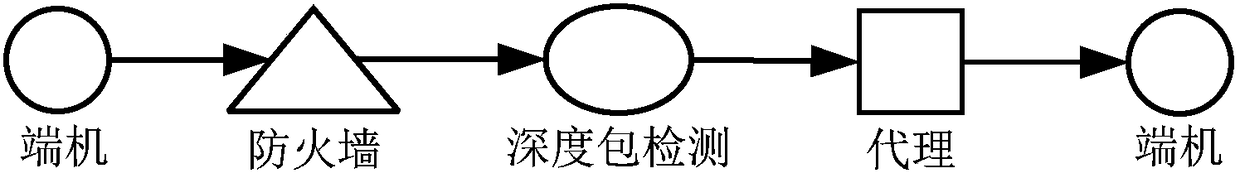
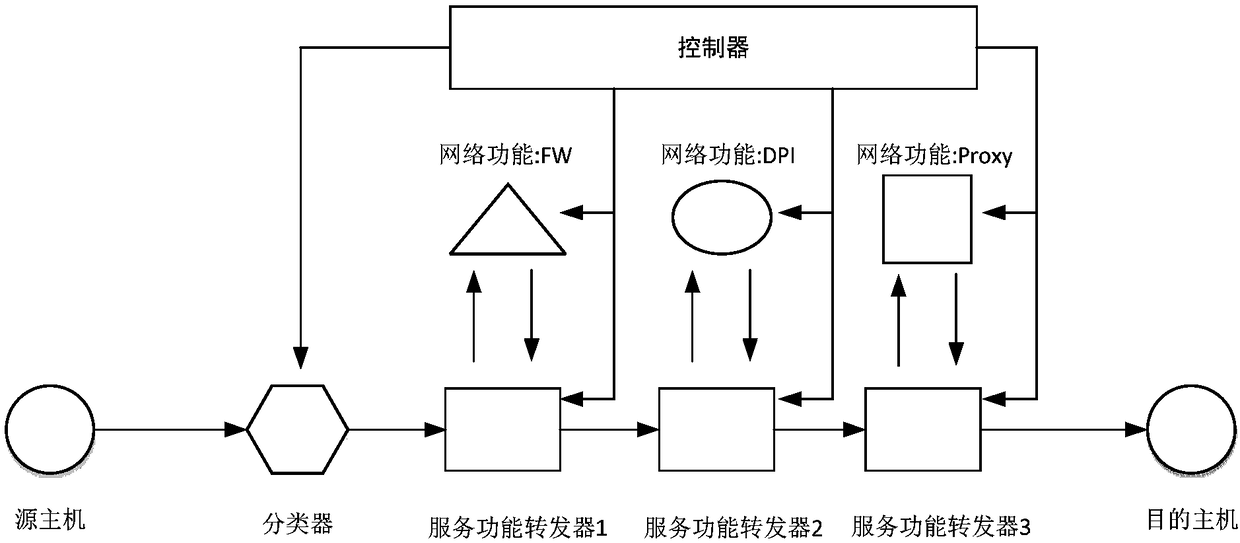
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
217 results about "Packet matching" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
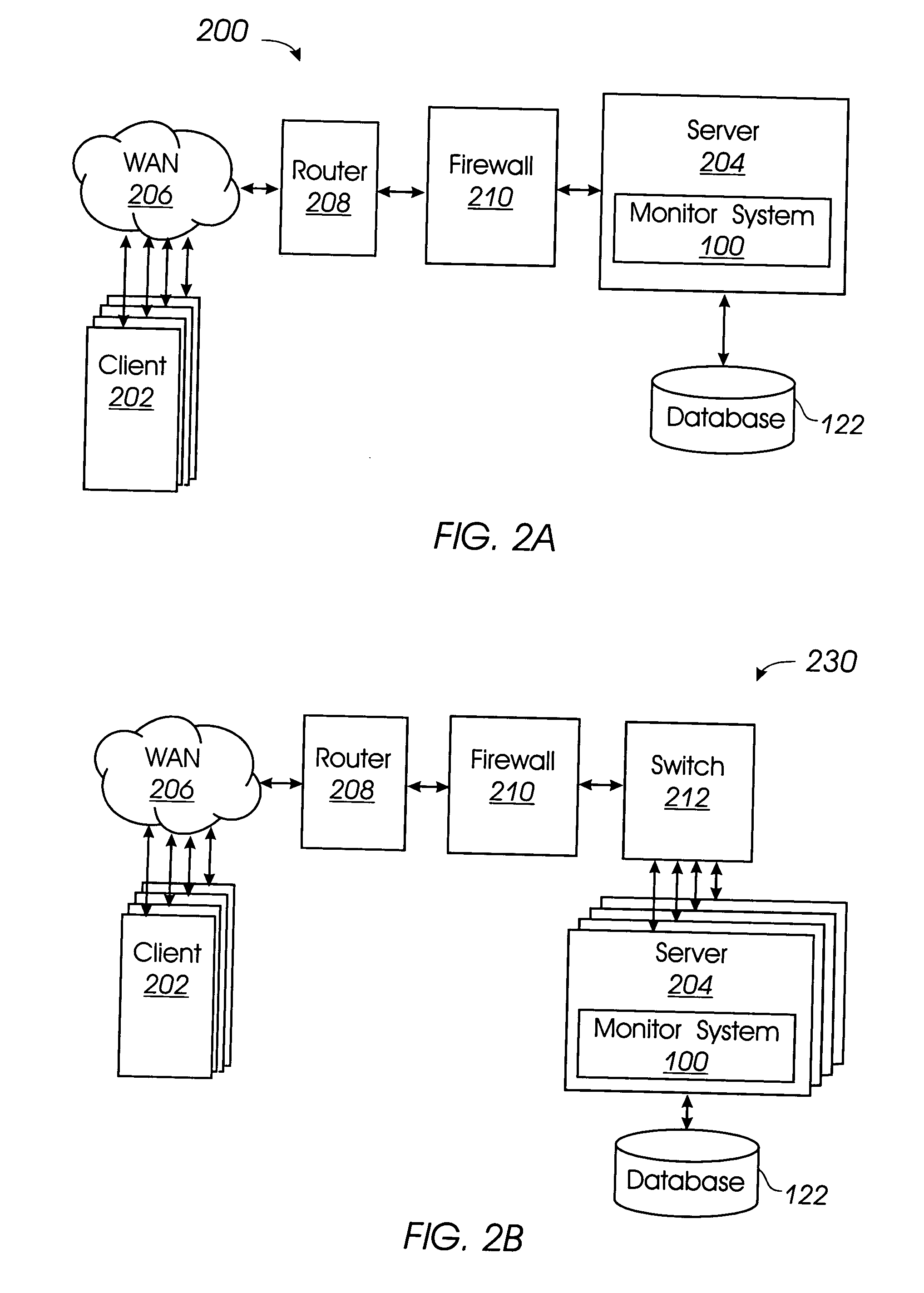
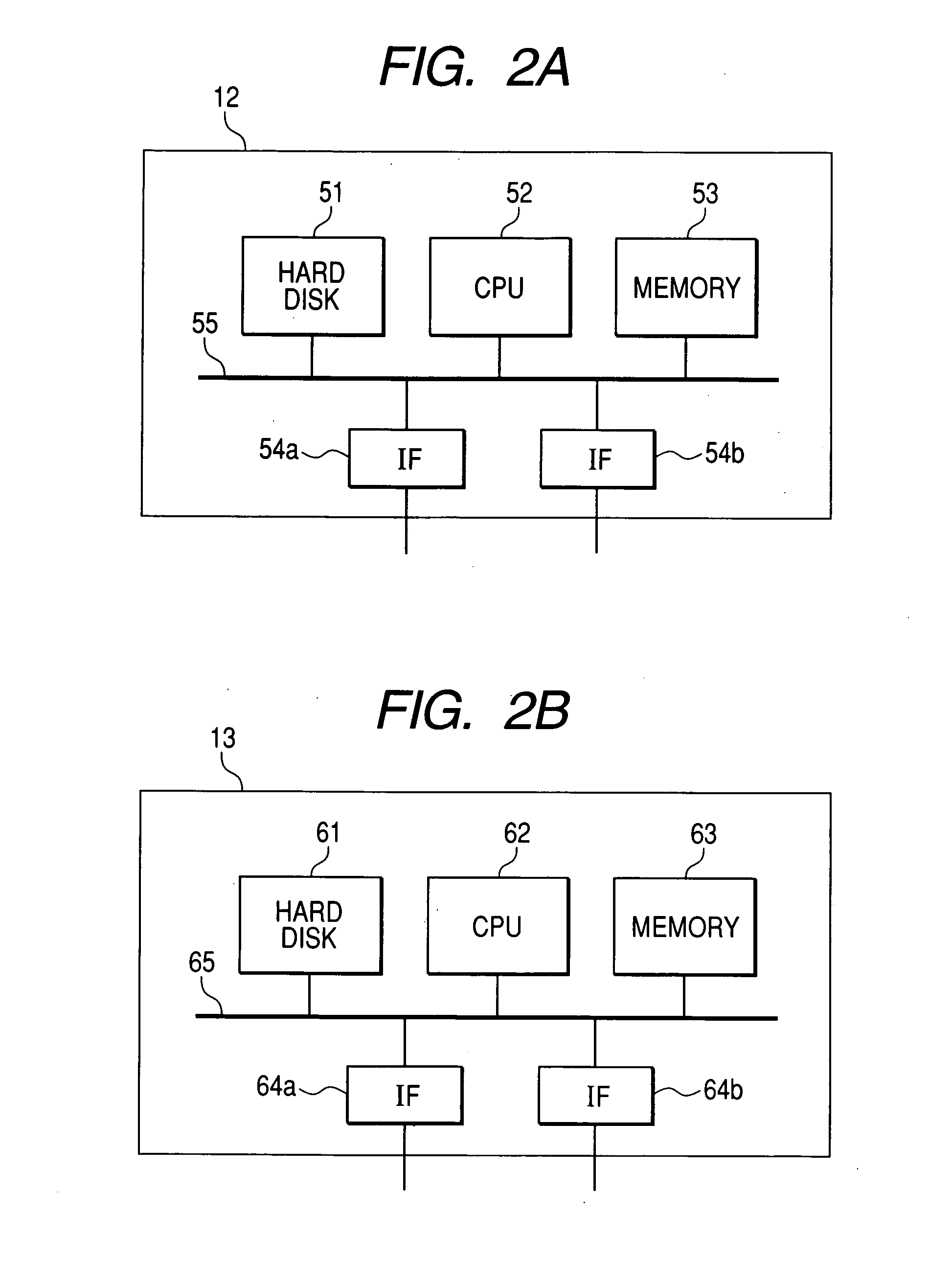
System and method for monitoring network traffic
ActiveUS20050063377A1Error preventionFrequency-division multiplex detailsInternet trafficComputer science
A system includes a packet reader configured to scan packets transmitted through a network for pre-specified criteria. The packets include endpoint information and data. A request / response matcher determines whether each packet meets pre-specified criteria, and matches request packets with corresponding response packets when the packets meet the pre-specified criteria. A message analyzer determines the format, or structure, of the data of the matched packets, and analyzes the data of the matched packets to generate at least a portion of a model of the data.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
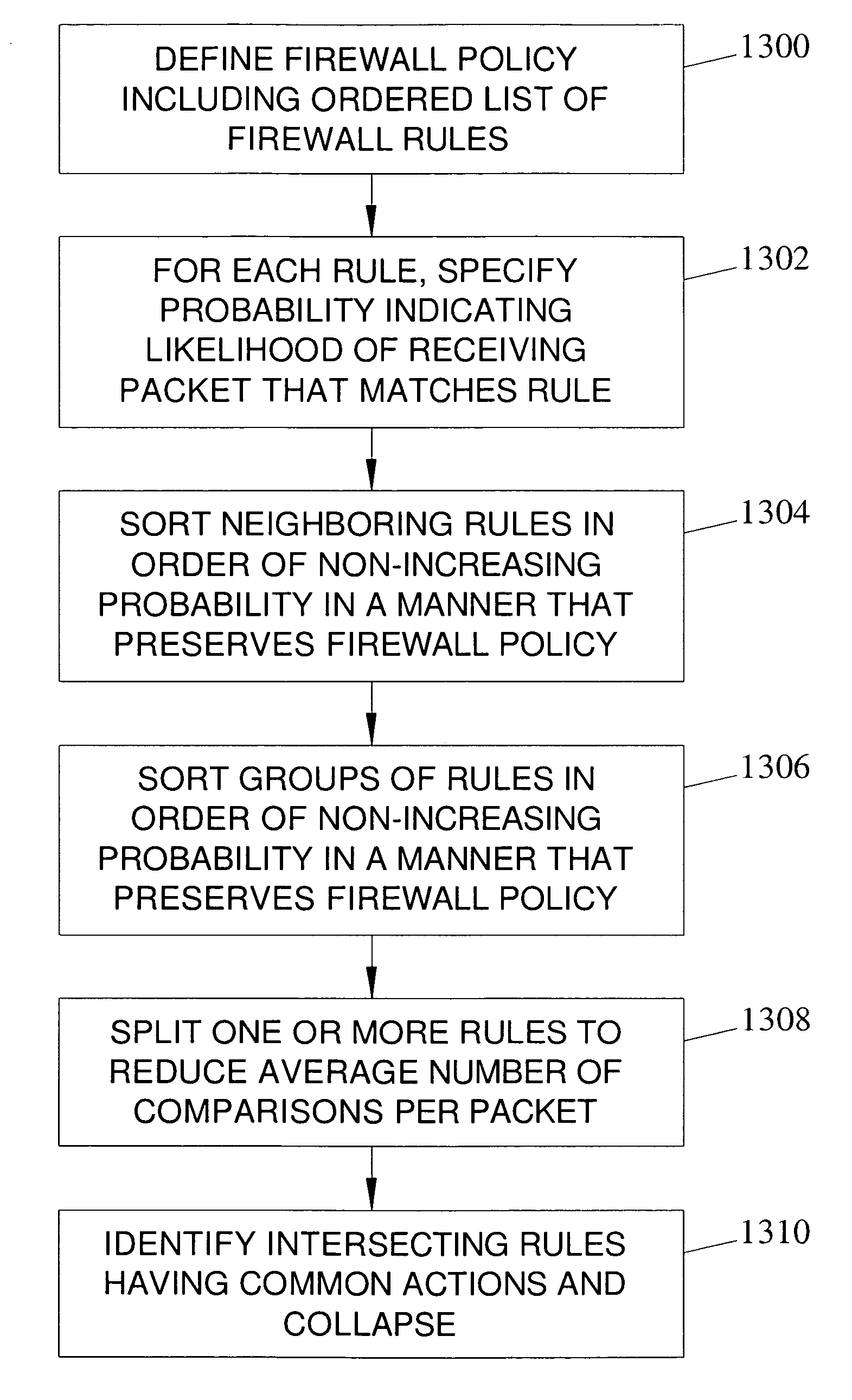
Methods, systems, and computer program products for network firewall policy optimization
ActiveUS20060248580A1Improve performanceLower latencyMultiplex system selection arrangementsData switching by path configurationComputer networkComputer program
Methods, systems, and computer program products for firewall policy optimization are disclosed. According to one method, a firewall policy including an ordered list of firewall rules is defined. For each rule, a probability indicating a likelihood of receiving a packet matching the rule is determined. The rules are sorted in order of non-increasing probability in a manner that preserves the firewall policy.
Owner:WAKE FOREST UNIV
Network system, controller, and network control method
InactiveUS20110295991A1Efficient switchingAvoid disconnectionDigital computer detailsNetwork connectionsNetwork controlNetworked system
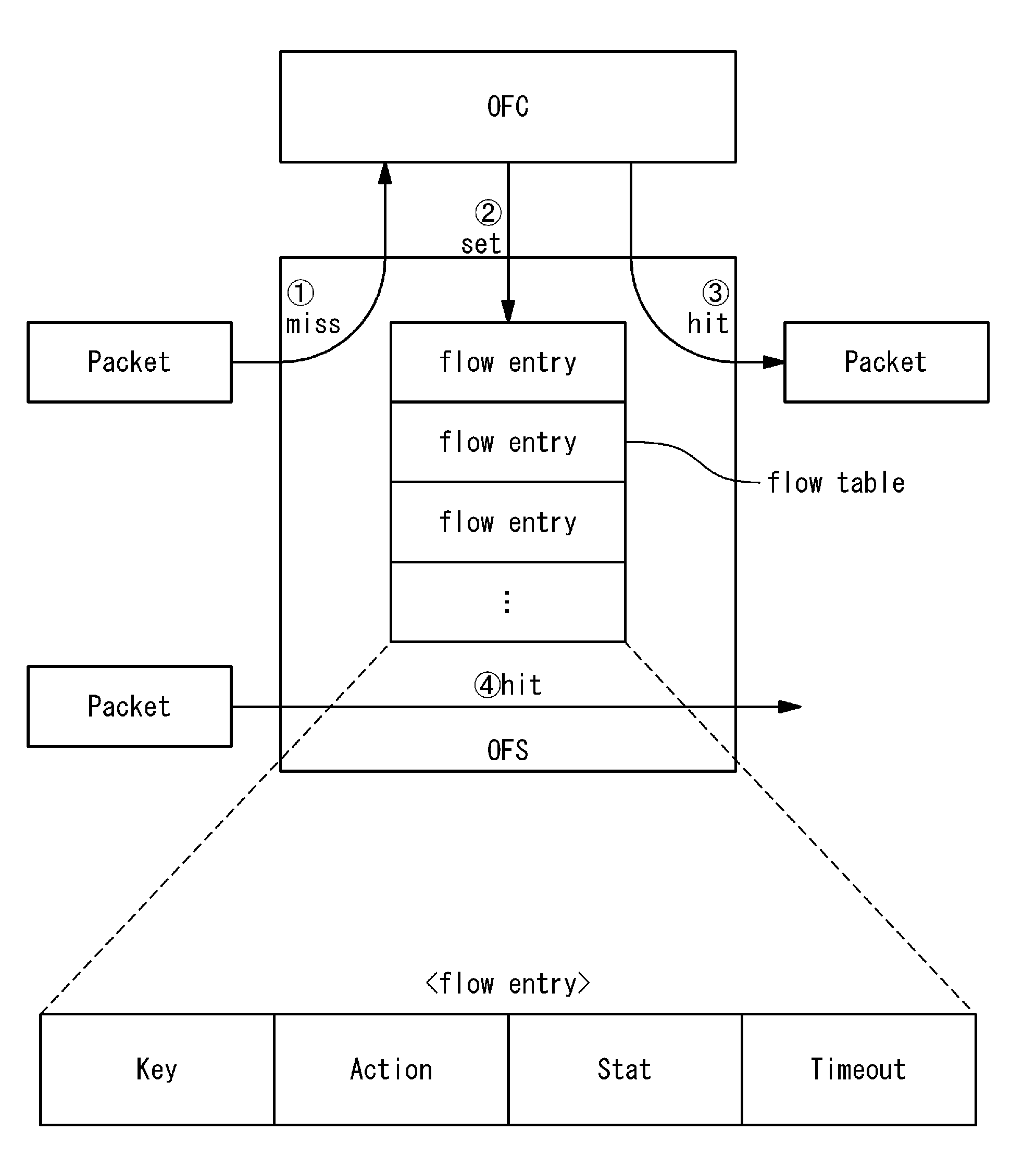
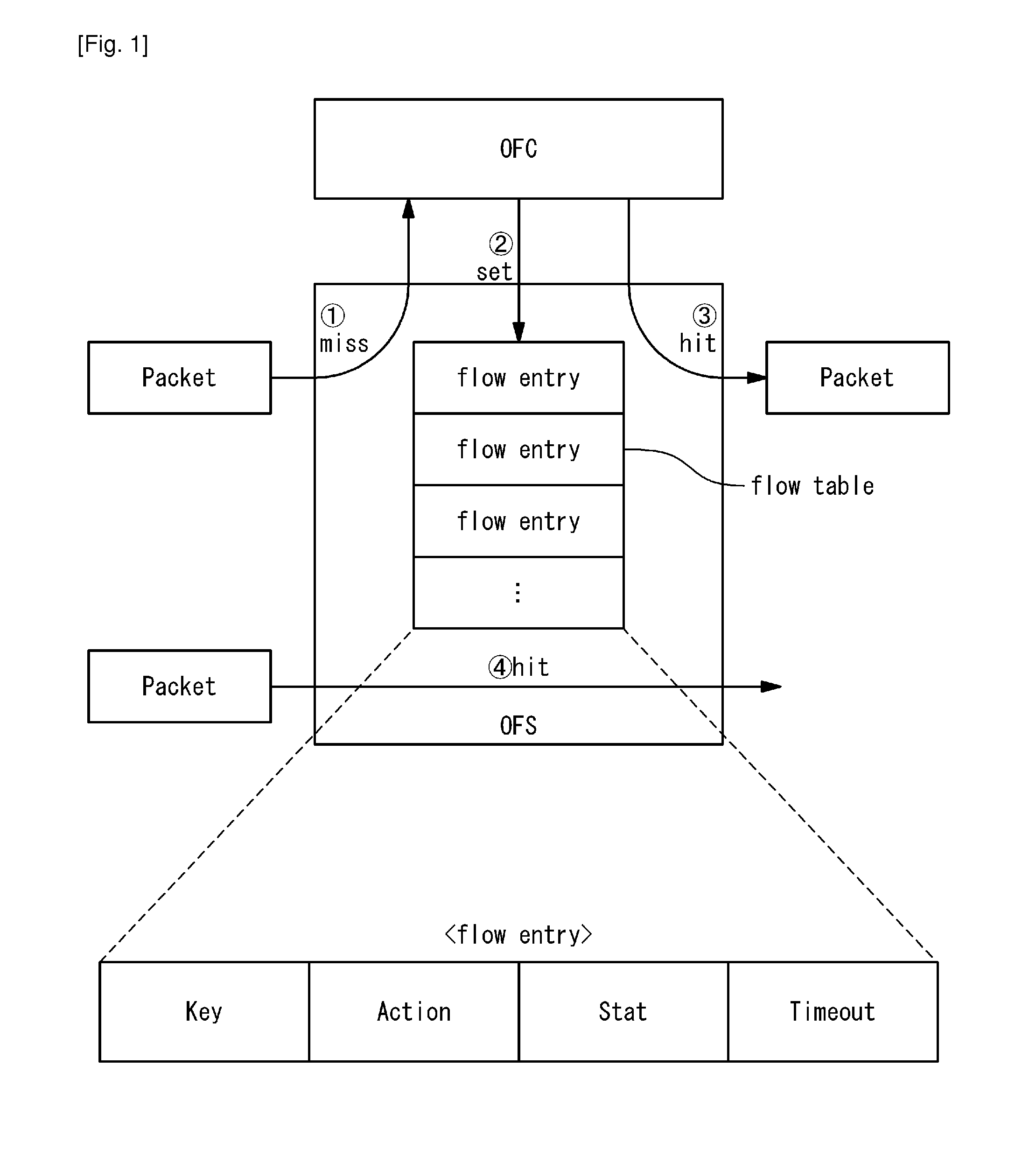
A network system includes appliances provided in a network; a switch provided in the network; and a controller connected to the appliances and the switch. The switch contains a flow table. Entries in the flow table each specify an action to be performed on a packet matching with a matching condition. Upon receiving a packet, the switch refers to the flow table and performs the action specified by matching one of the entries which matches the received packet, on the received packet. A first appliance of the appliances performs a first packet process on a packet belonging to an existing flow, when being selected as an active appliance. When the active appliance is switched from the first appliance to a second appliance of the appliances, the controller performs a switching process after performing a shortcut process. In the shortcut process, the controller instructs the switch to set a first entry into the flow table, the first entry specifying that the first packet process is to be performed on a packet belonging to the existing flow. In the switching process, the controller instructs the switch to set a second entry into the flow table, the second entry specifying that a packet which is addressed to the active appliance and belongs to a new flow other than the existing flow is to be transferred to the second appliance.
Owner:NEC CORP
Methods, systems, and computer program products for network firewall policy optimization
ActiveUS8042167B2Improve performanceLower latencyMultiplex system selection arrangementsData switching by path configurationComputer networkComputer program
Methods, systems, and computer program products for firewall policy optimization are disclosed. According to one method, a firewall policy including an ordered list of firewall rules is defined. For each rule, a probability indicating a likelihood of receiving a packet matching the rule is determined. The rules are sorted in order of non-increasing probability in a manner that preserves the firewall policy.
Owner:WAKE FOREST UNIV
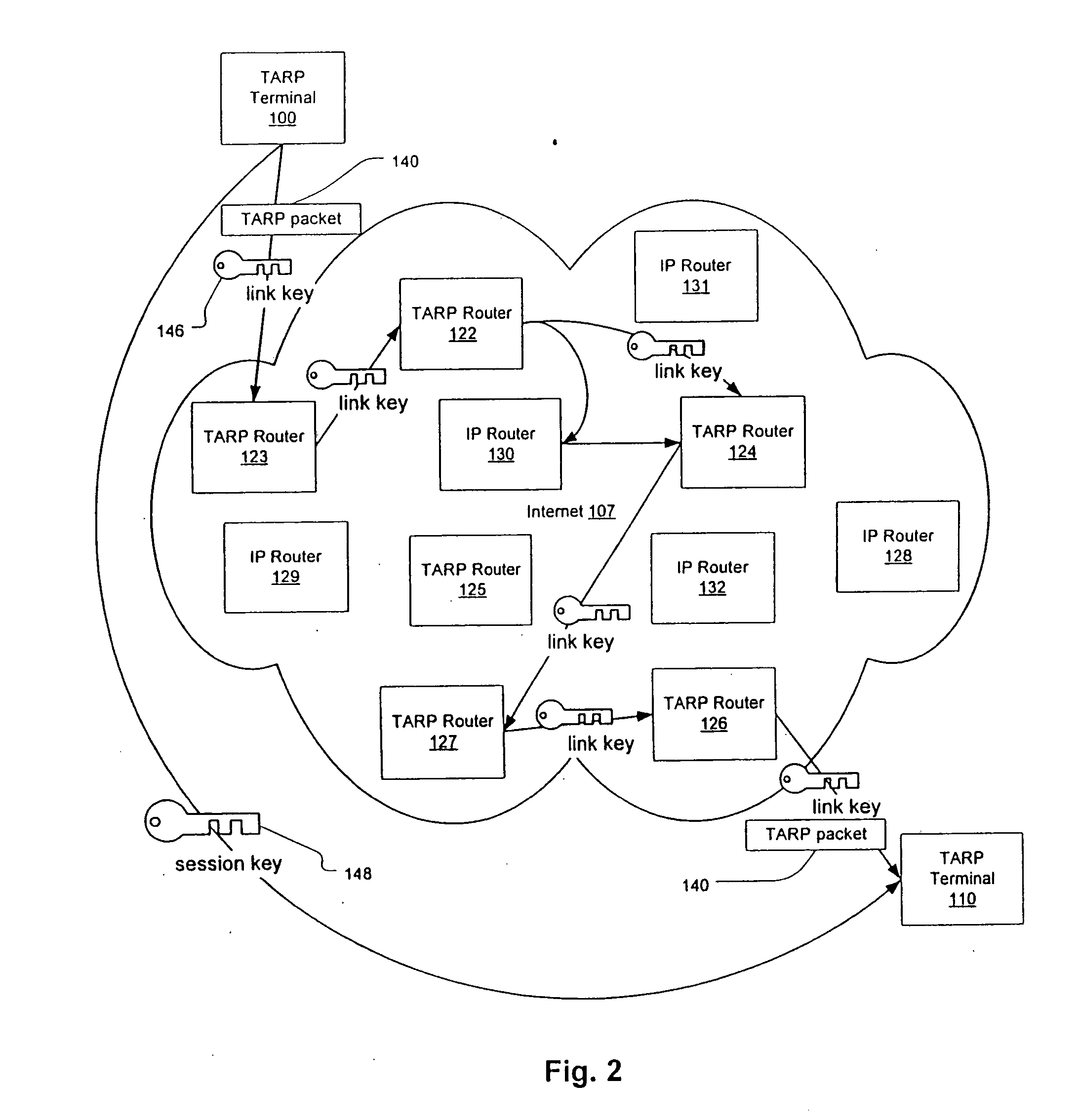
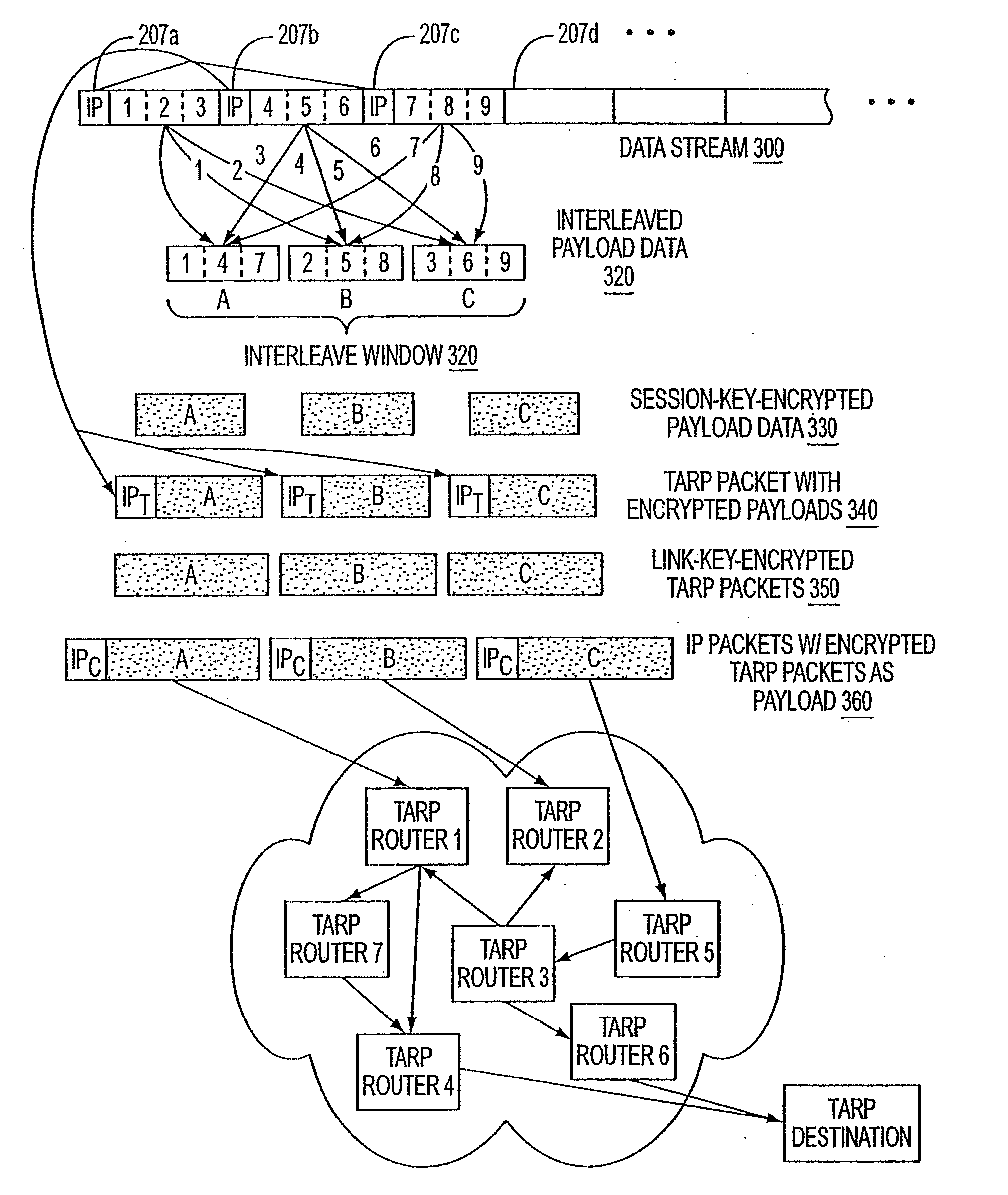
Agile network protocol for secure communications with assured system availability
InactiveUS20060123134A1Increase drop rateKey distribution for secure communicationData stream serial/continuous modificationSecure communicationDiscriminator
A plurality of computer nodes communicates using seemingly random IP source and destination addresses and (optionally) a seemingly random discriminator field. Data packets matching criteria defined by a moving window of valid addresses are accepted for further processing, while those that do not meet the criteria are rejected. In addition to “hopping” of IP addresses and discriminator fields, hardware addresses such as Media Access Control addresses can be hopped. The hopped addresses are generated by random number generators having non-repeating sequence lengths that are easily determined a-priori, which can quickly jump ahead in sequence by an arbitrary number of random steps and which have the property that future random numbers are difficult to guess without knowing the random number generator's parameters. Synchronization techniques can be used to re-establish synchronization between sending and receiving nodes.
Owner:VIRNETX
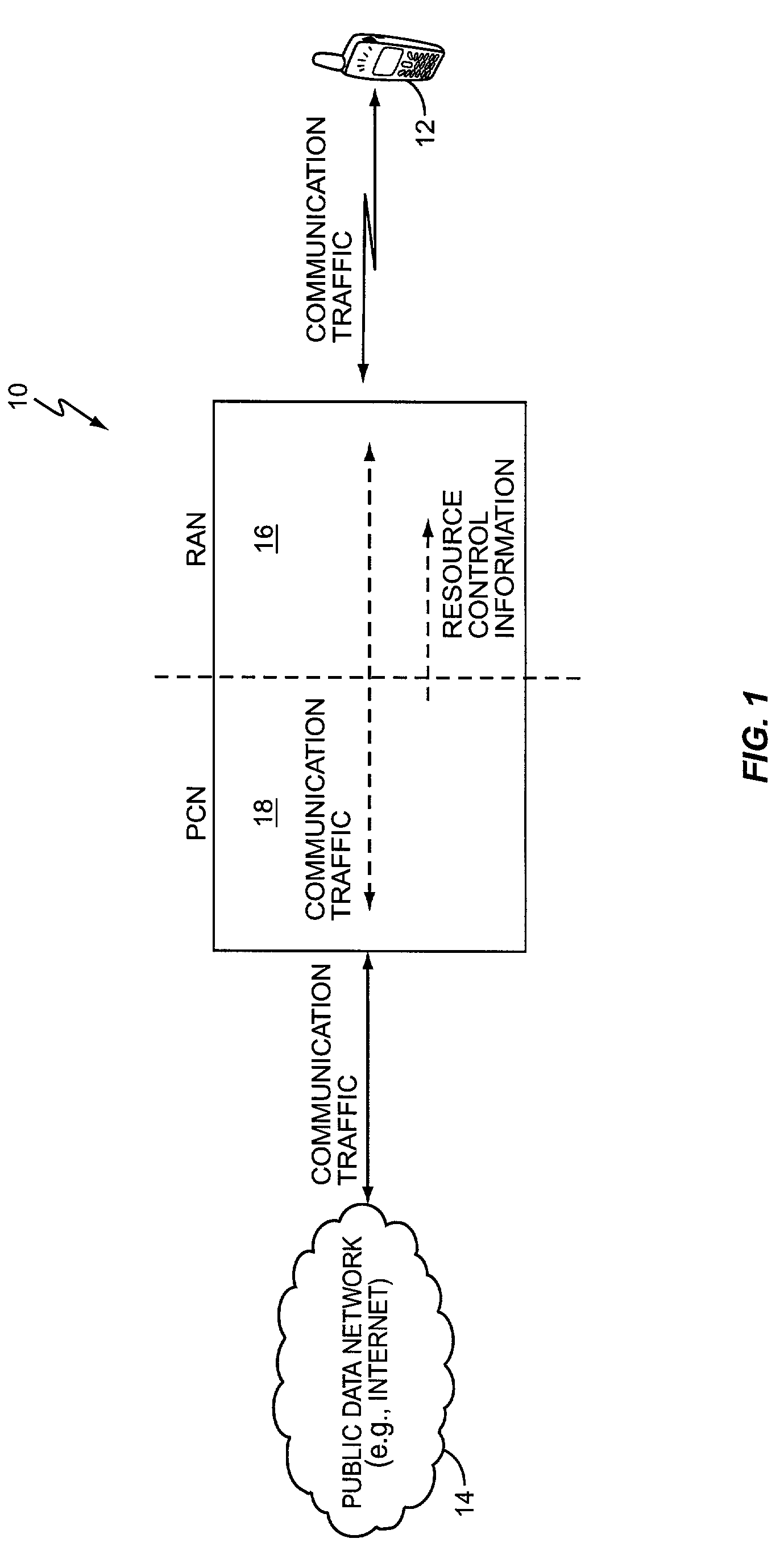
Applications based radio resource management in a wireless communication network
ActiveUS7289480B2Efficient managementMaintain balanceError preventionTransmission systemsValue setMobile station
A wireless communication network manages communication resources based on the types of packet data being carried by the network for each mobile station. Packet data for each use is matched to packet matching filters in defined flow type profiles. Each flow type profile corresponds to an expected application behavior and includes one or more resource control parameters having values set with regard to that expected behavior. An application activity profile is generated for each mobile station based on deriving resource control parameters using parameter values corresponding to the active flows for each mobile station. The network determines each mobile station's active flows based on matching that mobile station's packet data types to one or more of the defined flow type profiles. Thus, the network manages communication resources individually and / or jointly for its users based on the type of packet data traffic passing through the network for each of those users.
Owner:TELEFON AB LM ERICSSON (PUBL)
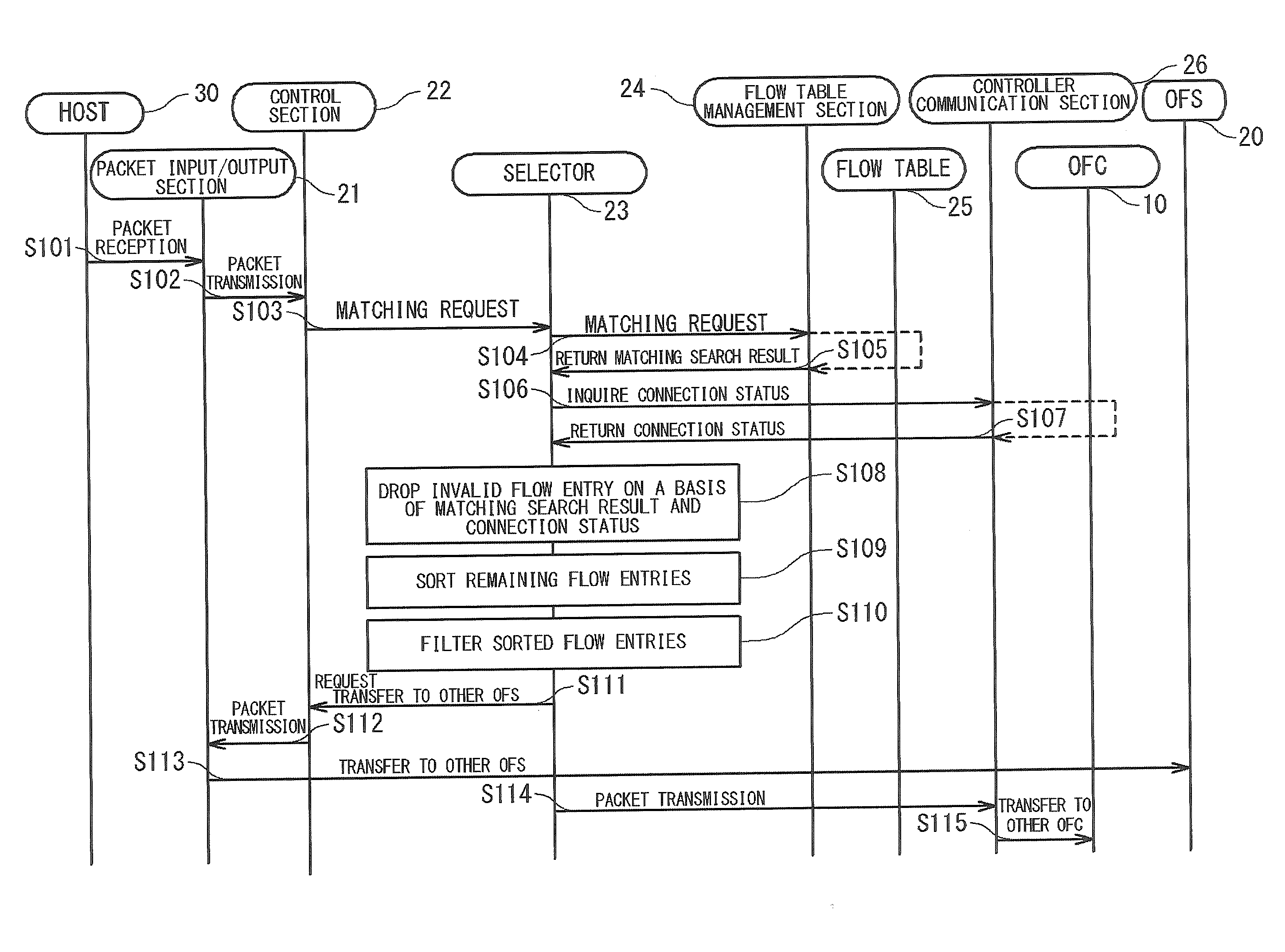
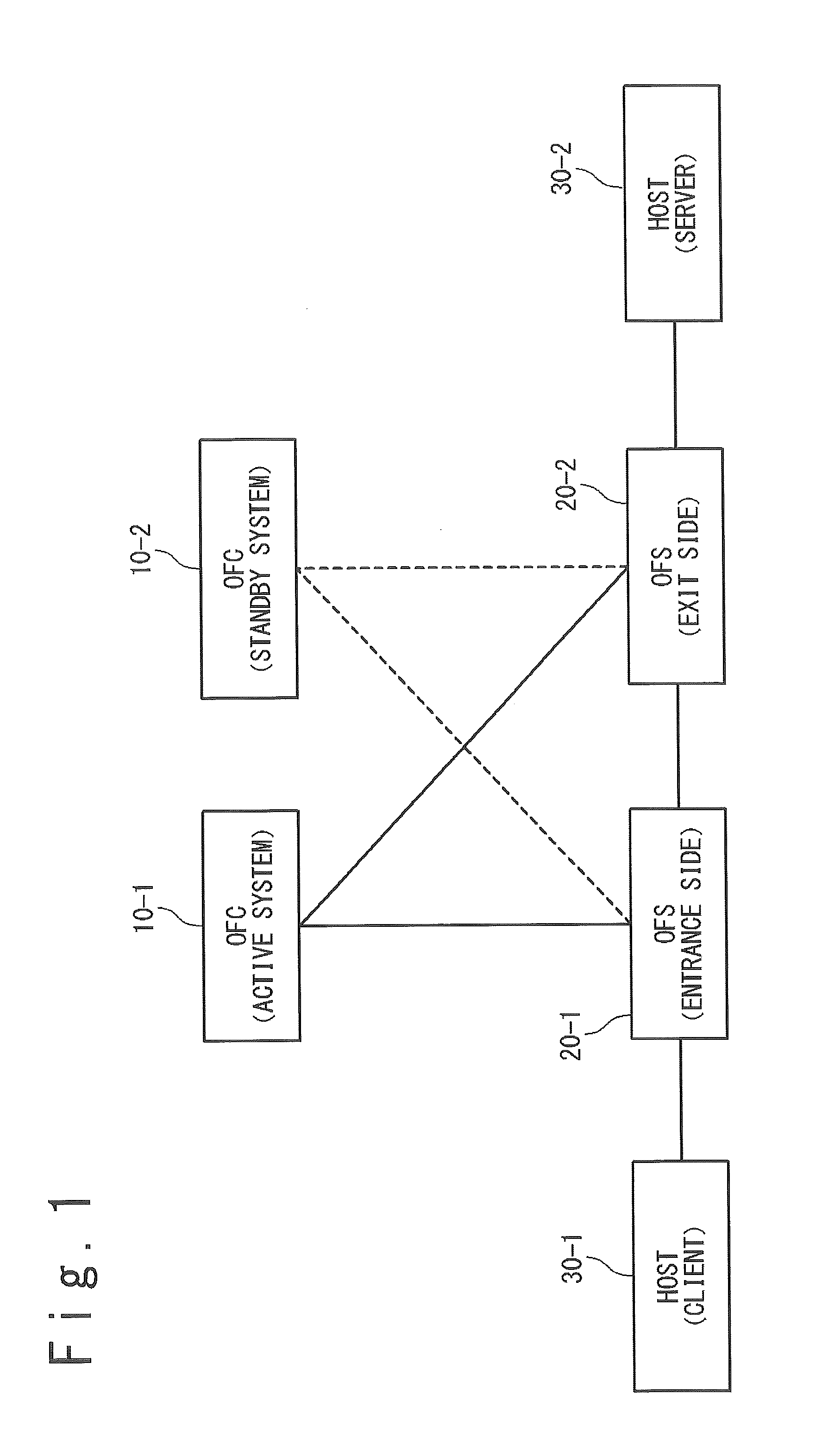
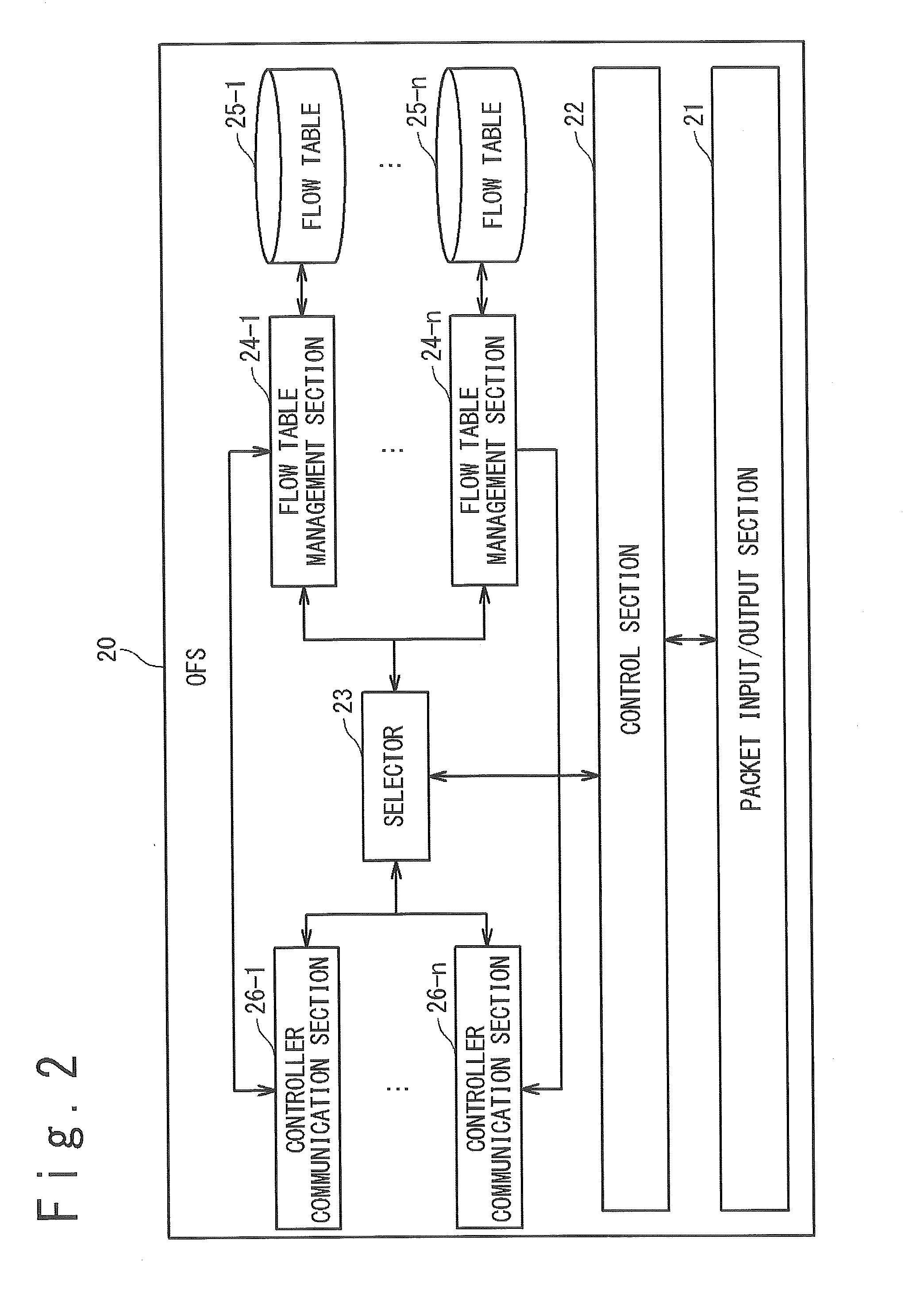
Network System, Switch and Method of Network Configuration
ActiveUS20150009828A1Accurate communicationError preventionTransmission systemsPacket matchingReal-time computing
A network system of the present invention includes a switch and controllers. The switch processes on a received packet in accordance with a flow entry in which are defined a rule and an action. The controllers set the flow entry to a flow table of the switch. The switch assigns a flow table to each controller, searches when receiving a packet from outside for a flow table matching with the packet in all flow tables, ignores a flow entry set by a controller of which a status of connection is invalid among flow entries matching with the packet and processes the packet in accordance with an action of a flow entry set by a controller of which a status of connection is valid.
Owner:NEC CORP
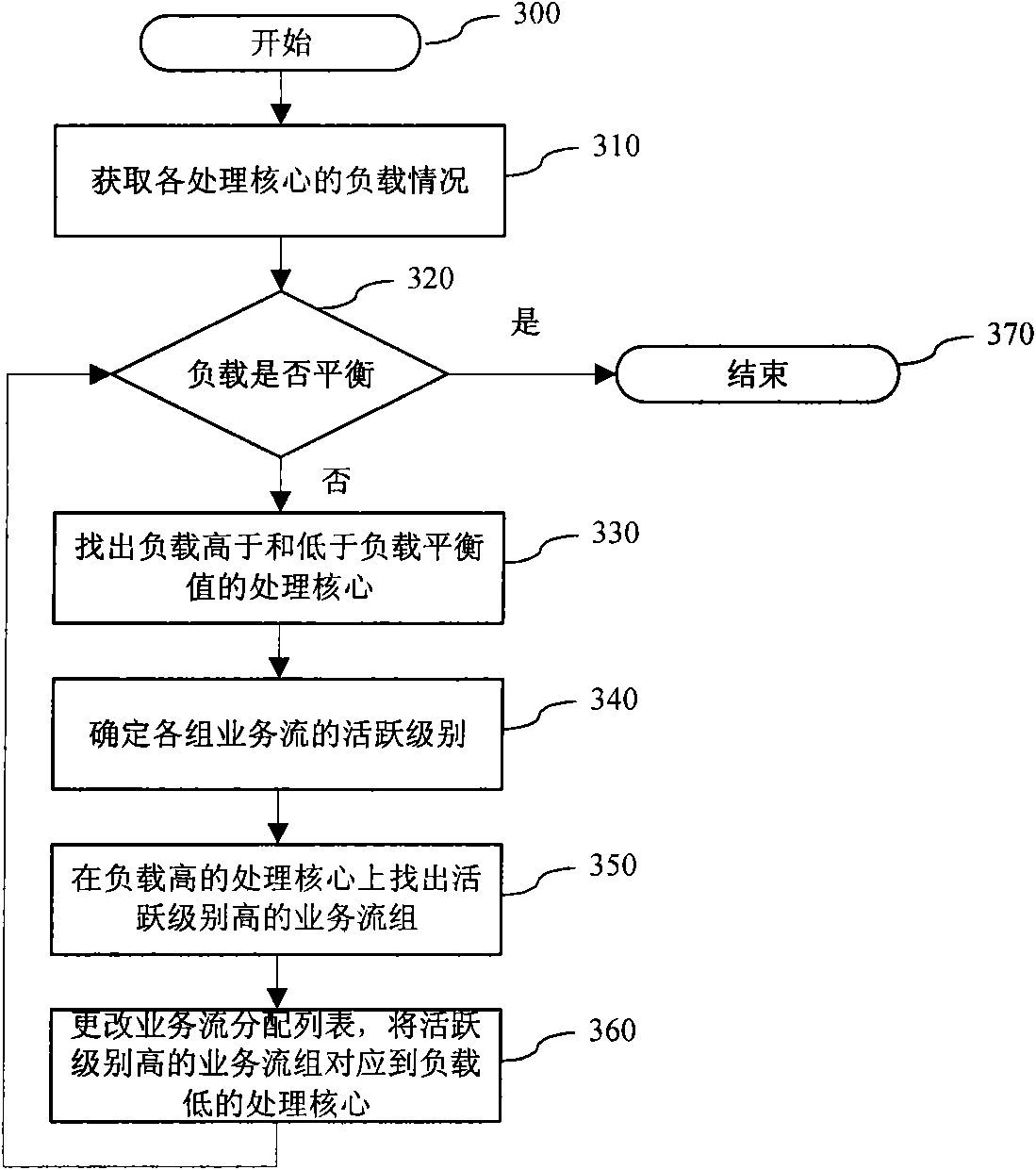
Method and device for multi-core parallel concurrent processing of network traffic flows
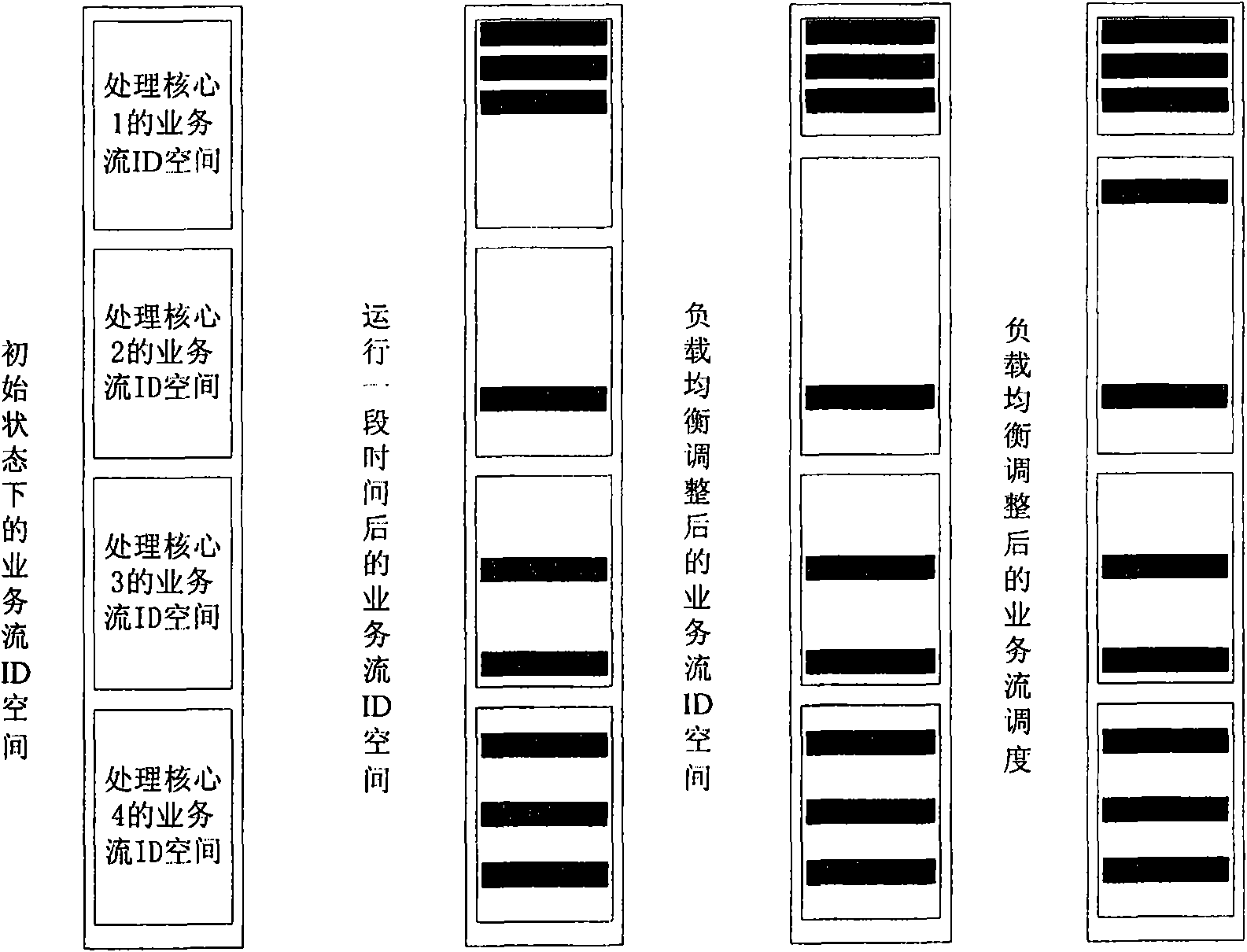
ActiveCN101610209ARegulating loadTake advantage of processingData switching networksProcessing coreTraffic flow
The invention relates to a method and a device for the multi-core parallel concurrent processing of network traffic flows. The method comprises the following steps: capturing a data pocket from a network; and unpacking the data pocket into a plurality of traffic flows and generating a traffic flow distribution list so that a multi-core processor processes the traffic flows according to the traffic flow distribution list. The method is characterized by also comprising following steps: acquiring the load condition of each processing core; and confirming the active level of each traffic flow after generating the traffic flow distribution list which is changed according to the load conditions and the active levels so as to dynamically distribute the traffic flows. The invention effectively adjusts the load of each processing core and fully utilizes the processing performance of the multi-core processor by dynamically distributing the network traffic flows into a plurality of processing cores.
Owner:BEIJINGNETENTSEC
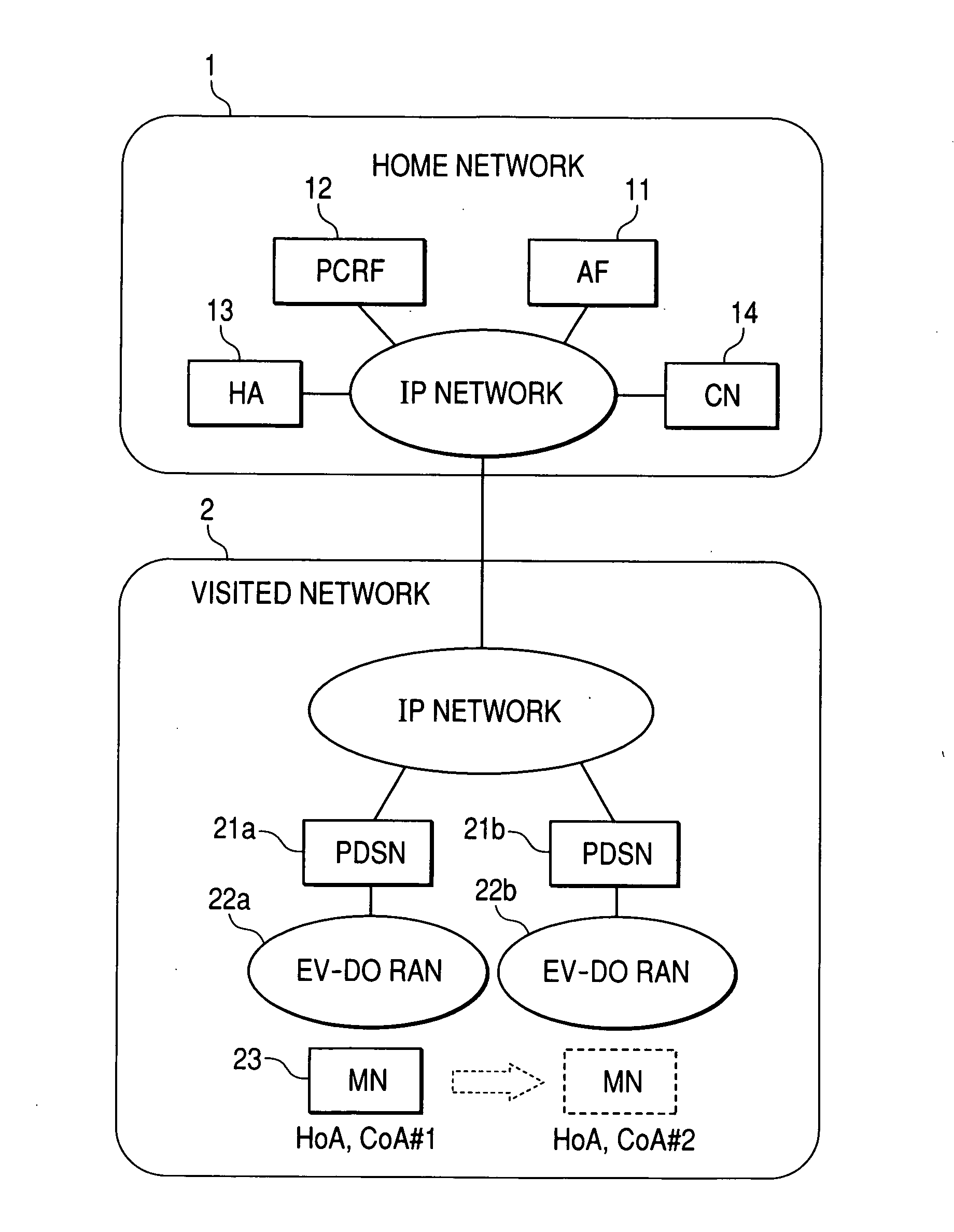
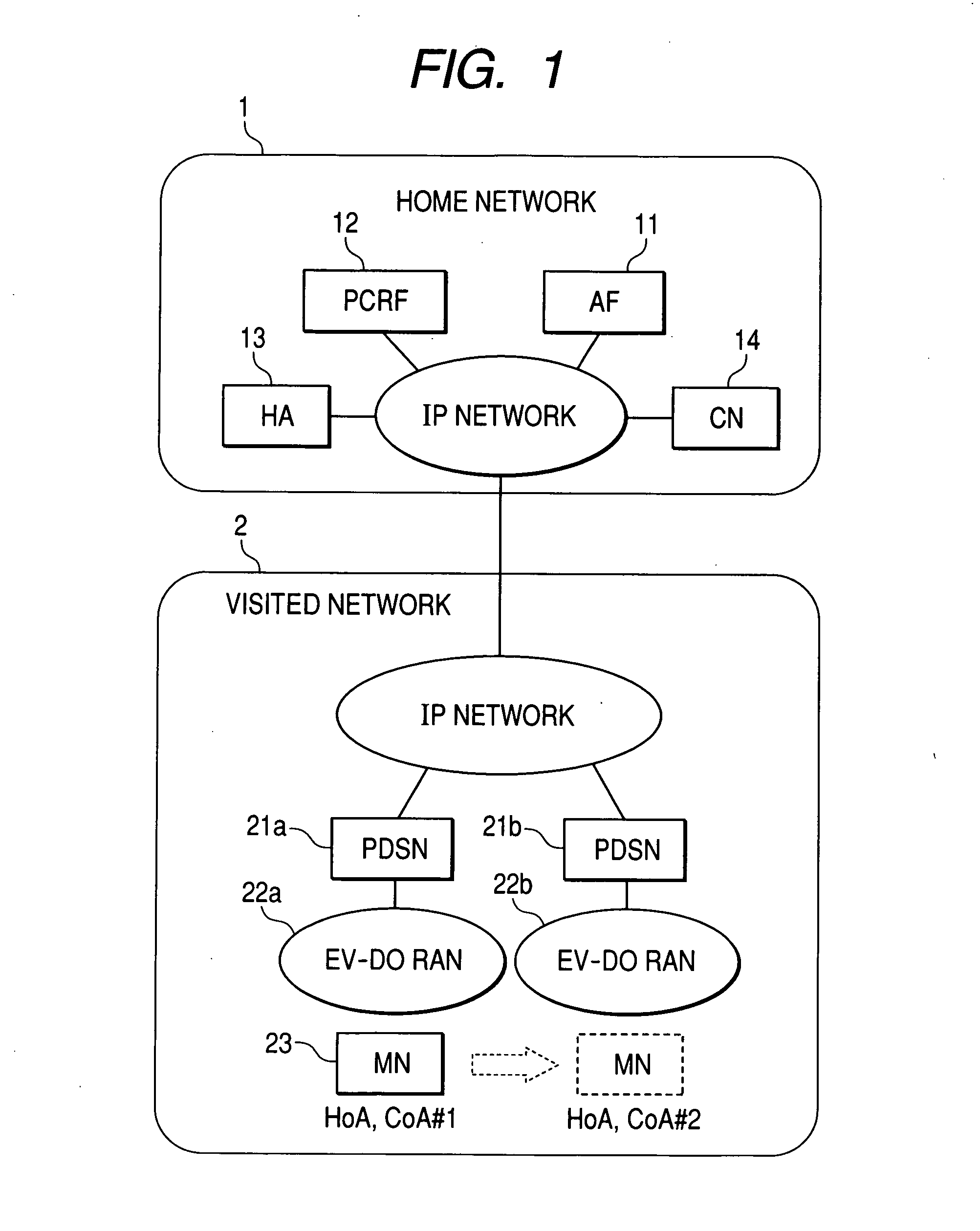
Communication system, server, control apparatus and communication apparatus
InactiveUS20080310334A1Network traffic/resource managementWireless network protocolsCommunications systemCommunication device
Disclosed herewith is a communication system, which can solve the following conventional problem that if packets exchanged between a terminal and an HA are encapsulated with use of the mobile IPv6 protocol, the PDSN cannot identify any IP flows in the mobile IPv6 tunnel. Consequently, there is no QoS usable appropriately to the services in the EV-D0 RAN. To solve such a problem, the PCRF notifies the HA of the filter information used to specify each IP flow and the flow label assigned to each IP flow. The HA then sets the flow label in the outer IPv6 header of the packet matching with the filter information and transfers the packet to the object unit. The PDSN then refers to the flow label set in the outer IPv6 header to identify the object IP flow in the mobile IPv6 tunnel. Consequently, a proper QoS can be usable for the services respectively in the EV-D0 RAN.
Owner:HITACHI LTD
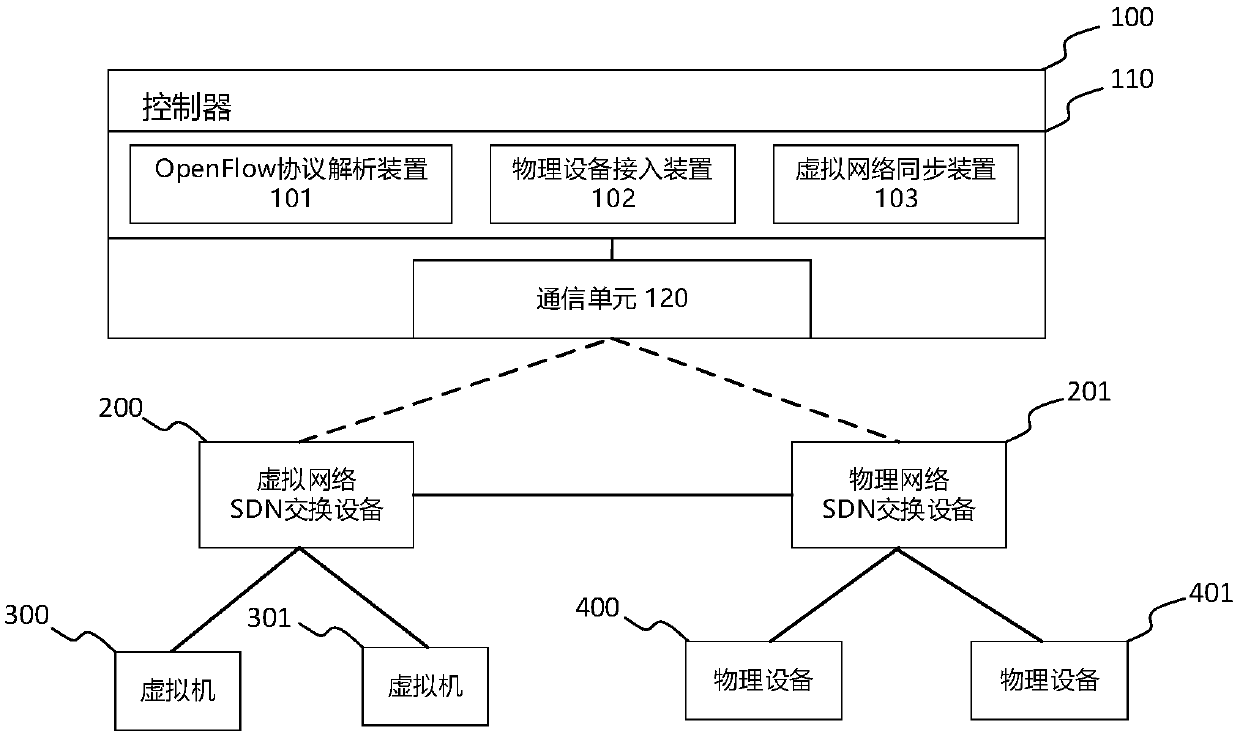
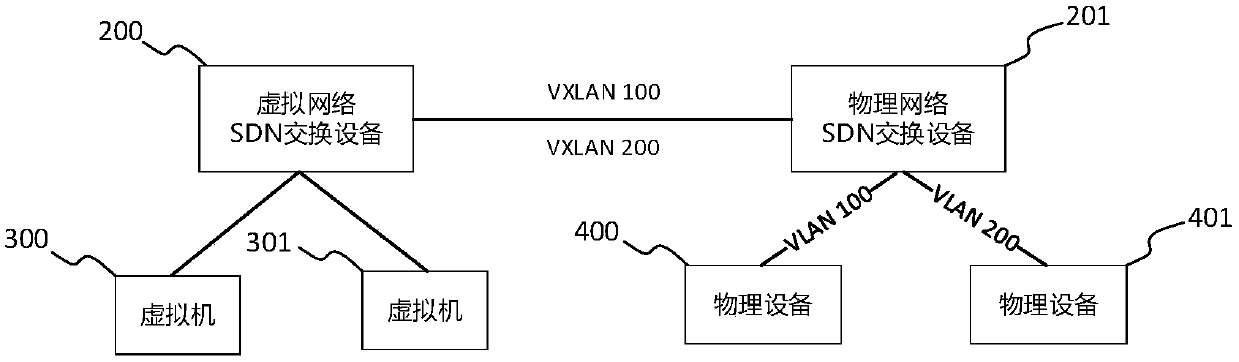
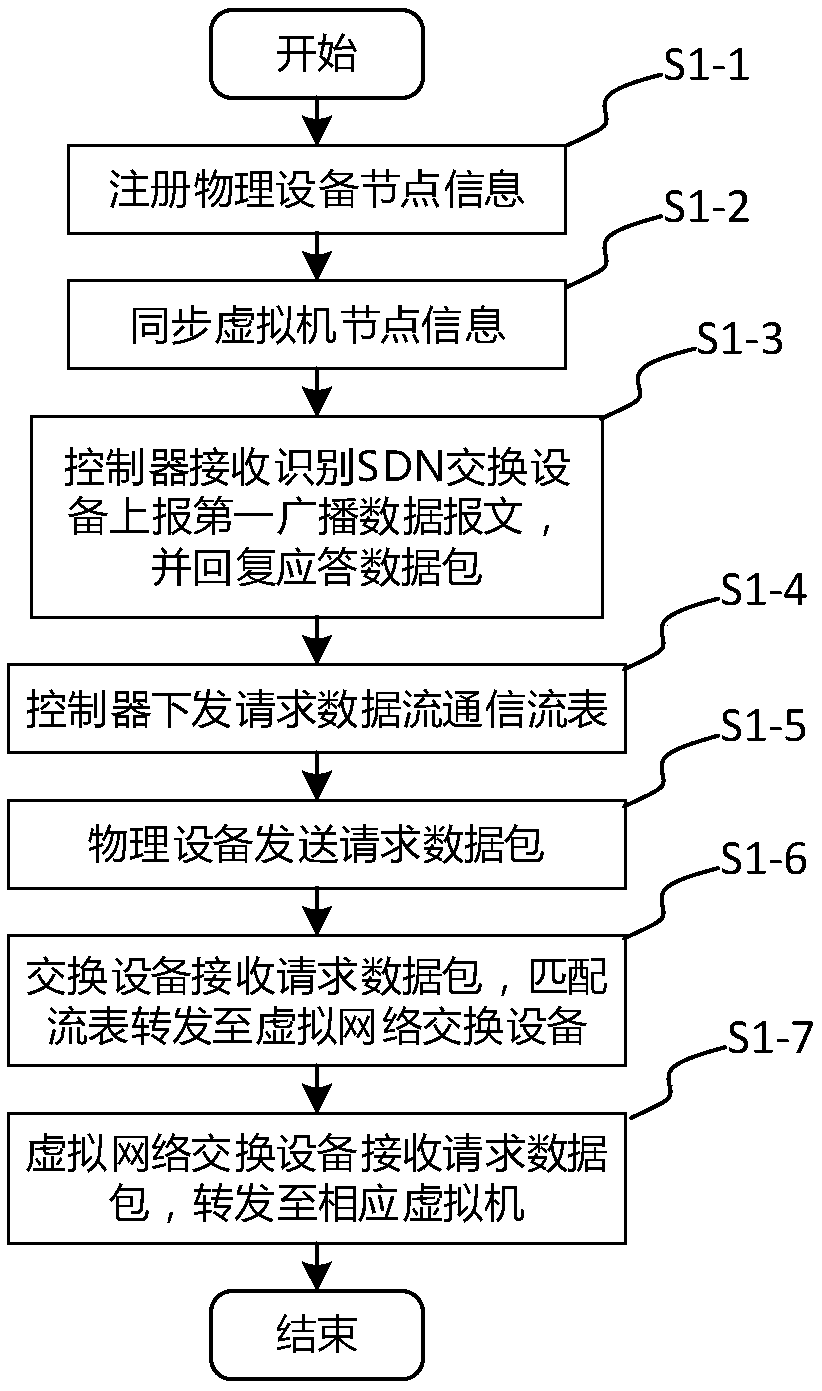
Physical device and virtual network communication method and system based on SDN (Software Defined Network)
ActiveCN109660443AAchieve isolationDifferent business functionsSpecial service provision for substationNetworks interconnectionComputer hardwareIp address
The invention discloses a physical device and virtual network communication method and system based on an SDN (Software Defined Network). The communication method comprises the following steps that physical device nodes are registered, and virtual node information is synchronized; physical devices which access for the first time are authenticated, thereby enabling the physical devices to access data; a controller issues flow tables to a physical network SDN switch and a virtual network switch and instructs a communication process of the physical devices and virtual machines; the physical devices send request data packets, wherein destination IP addresses and destination MAC addresses are the virtual machines; the physical network SDN switch receives the request data packets from the physical devices, matches the flow tables, packages the request data packets into VXLAN (Virtual Extensible Local Area Network) tunnels and forwards packaged data packets to the virtual network SDN switch corresponding to the virtual machines; and the virtual network SDN switch receives the packaged data packets through utilization of the VXLAN tunnels, matches the flow tables and forwards the request data packets to corresponding interfaces of the virtual machines. According to the method and the system, the physical devices and the virtual machines are located in the same subnetwork, and the access of the physical devices to layer 2 and layer 3 networks through utilization of a virtual network is supported.
Owner:JIANGSU FUTURE NETWORKS INNOVATION
Safe message forwarding method and safe message forwarding device
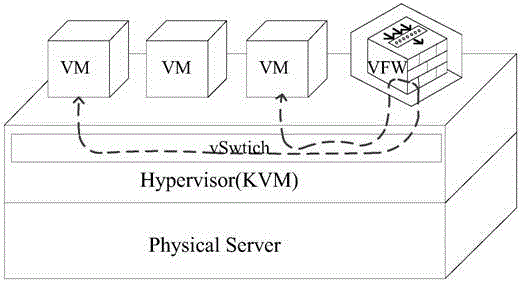
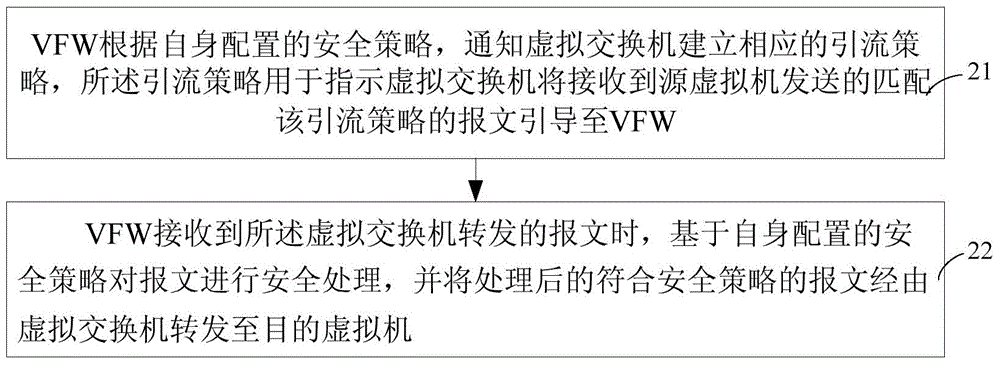
ActiveCN105100026ARealize security protectionAvoid forwardingHybrid transportVirtualizationVirtual firewall
A virtual firewall (VFW) notifies a virtual switch (vSwitch) to establish a flow directing policy according to a security policy configured for the VFW. The vSwitch directs a received packet matching the flow directing policy to the VFW according to the flow directing policy. When receiving the packet forwarded from the vSwitch, the VFW performs security processing for the packet according to the security policy, and forwards the processed packet satisfying the security policy to a target virtual machine (VM). The VFW and the vSwitch are established in a same physical machine based on a virtual platform.
Owner:NEW H3C TECH CO LTD
Method and system of controlling spam
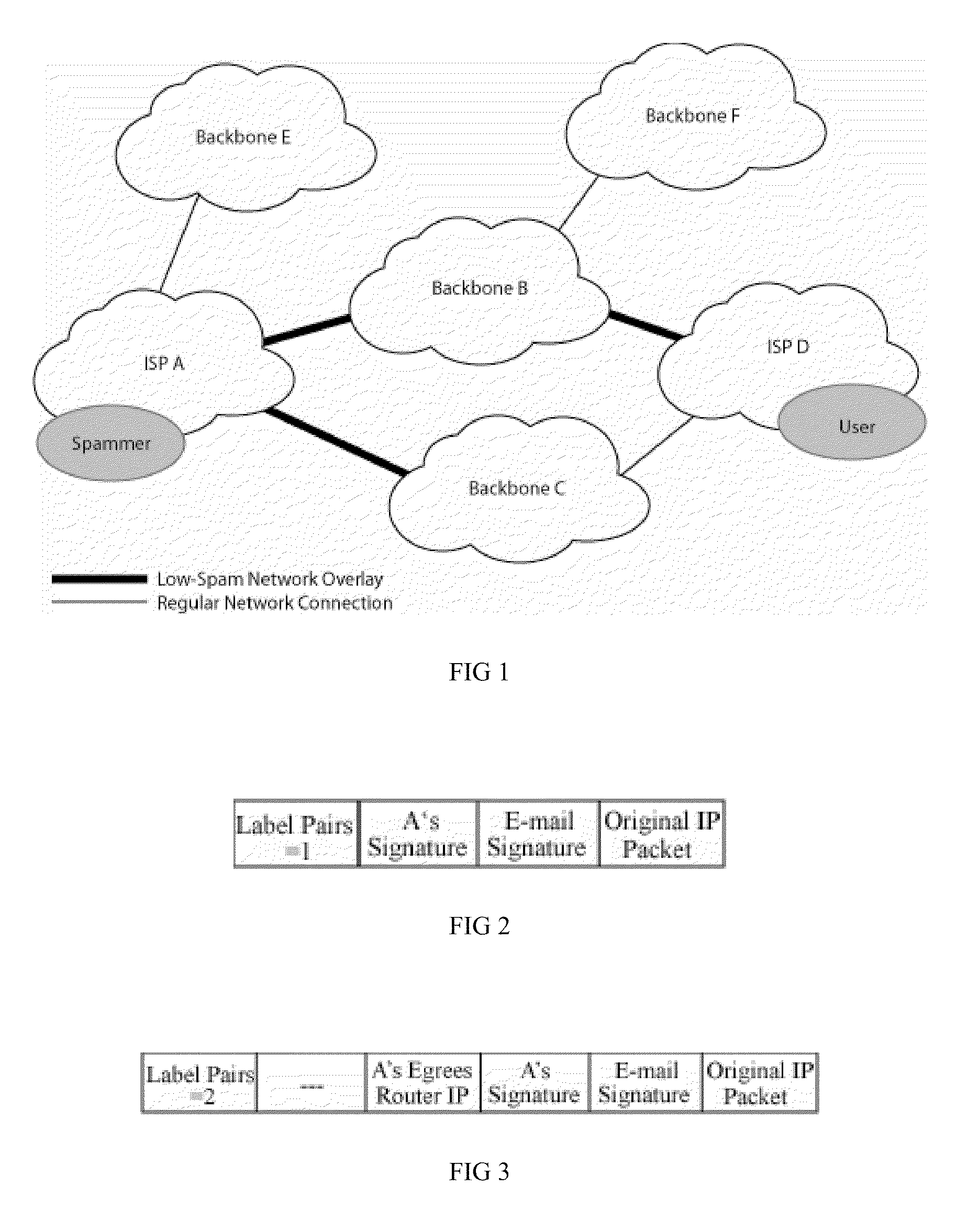
ActiveUS20100138539A1Improve trustPositive feedbackUser identity/authority verificationDigital computer detailsPacket matching
A method for a first network to receive a packet from a second network is provided, including a router at the first network receiving the packet from the second network, the packet addressed to a client reachable through the first network; the router inspecting the packet for a nonrepudiable marking provided by the second network; if the nonrepudiable marking is present and matches the packet, adding an indicator pointing to the second network in the packet; adding a second nonrepudiable marking to the packet, and transmitting the packet to a destination; and otherwise, dropping the packet.
Owner:NEVILLE STEPHEN W +1
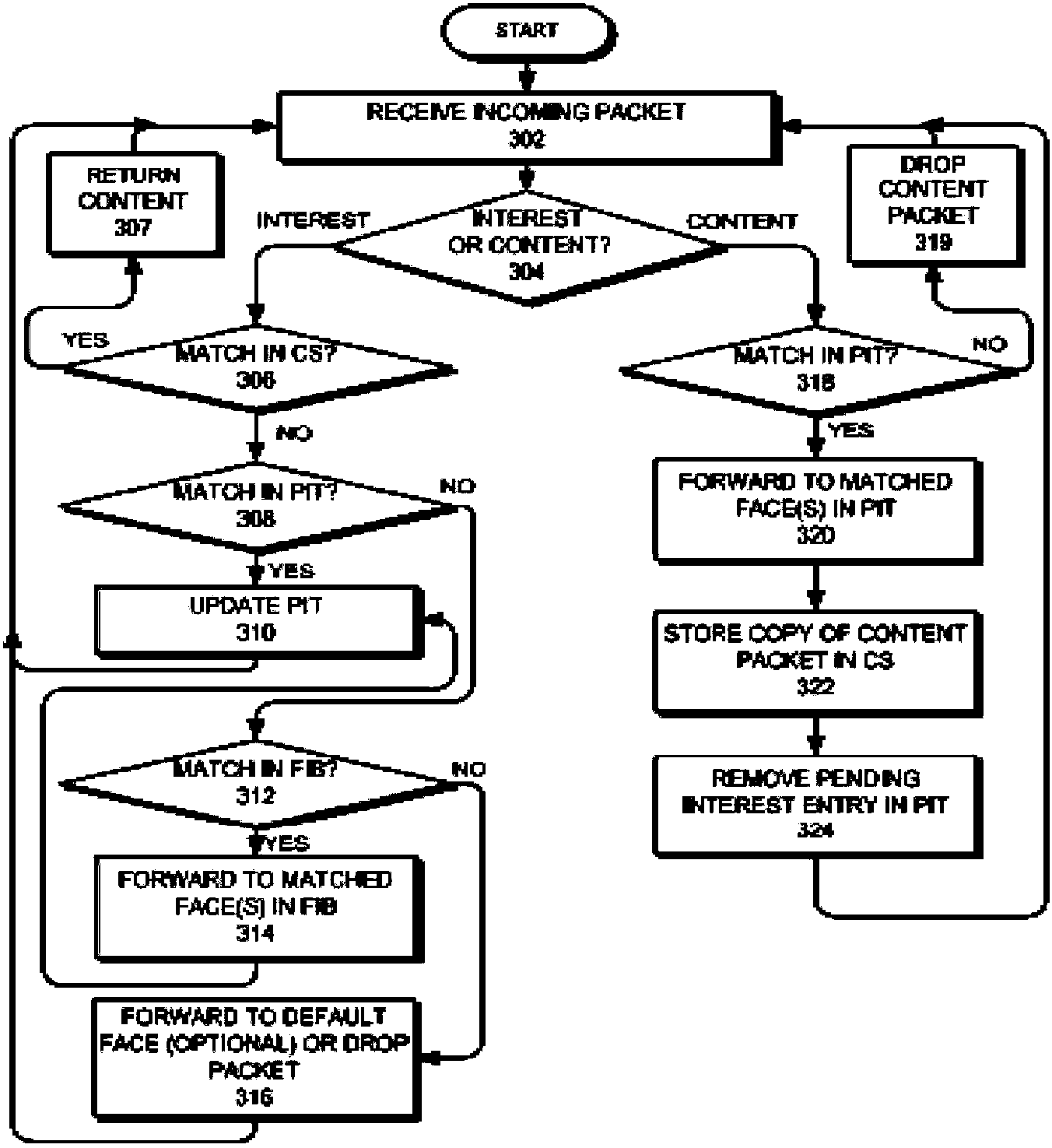
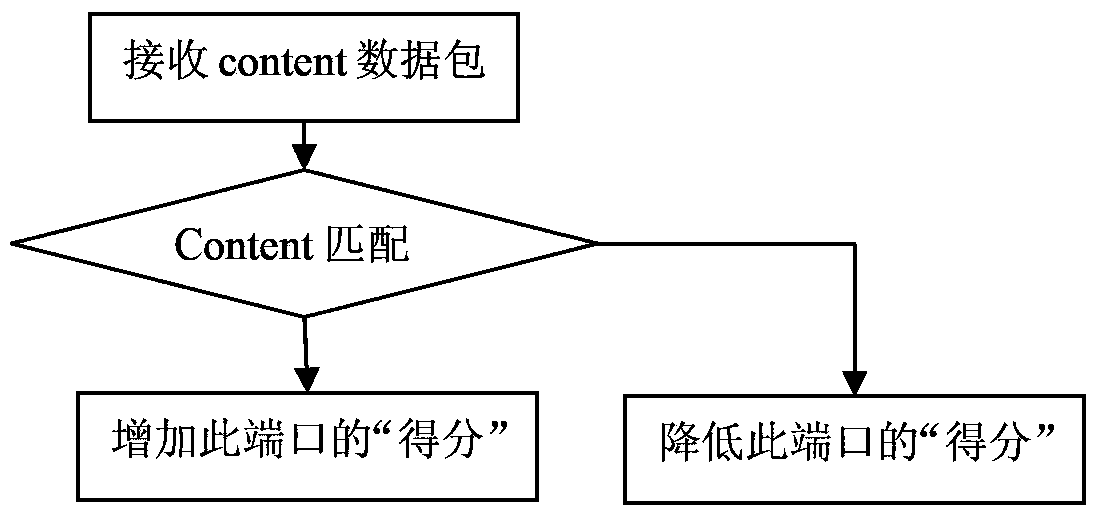
Content centric network multiport forwarding method and router
The invention is applicable to the communication field, and provides an NDN multiport forwarding method and a router. The method comprises the following steps: when an interest packet is forwarded, a matching item matching the interest packet is queried in a local forwarding information table (FIB), so as to acquire a plurality of ports corresponding to the matching item; according to weighted values of the plurality of ports, several ports are selected from the plurality of ports for forwarding the interest packet; and based on whether a port of a forwarded interest packet receives a returned content packet matching the interest packet, the weight value of the port of the forwarded interest packet is updated. According to the technical scheme of the invention, the advantages of reducing the interest packet flooding and improving the forwarding efficiency are realized.
Owner:浙江杭海新城控股集团有限公司
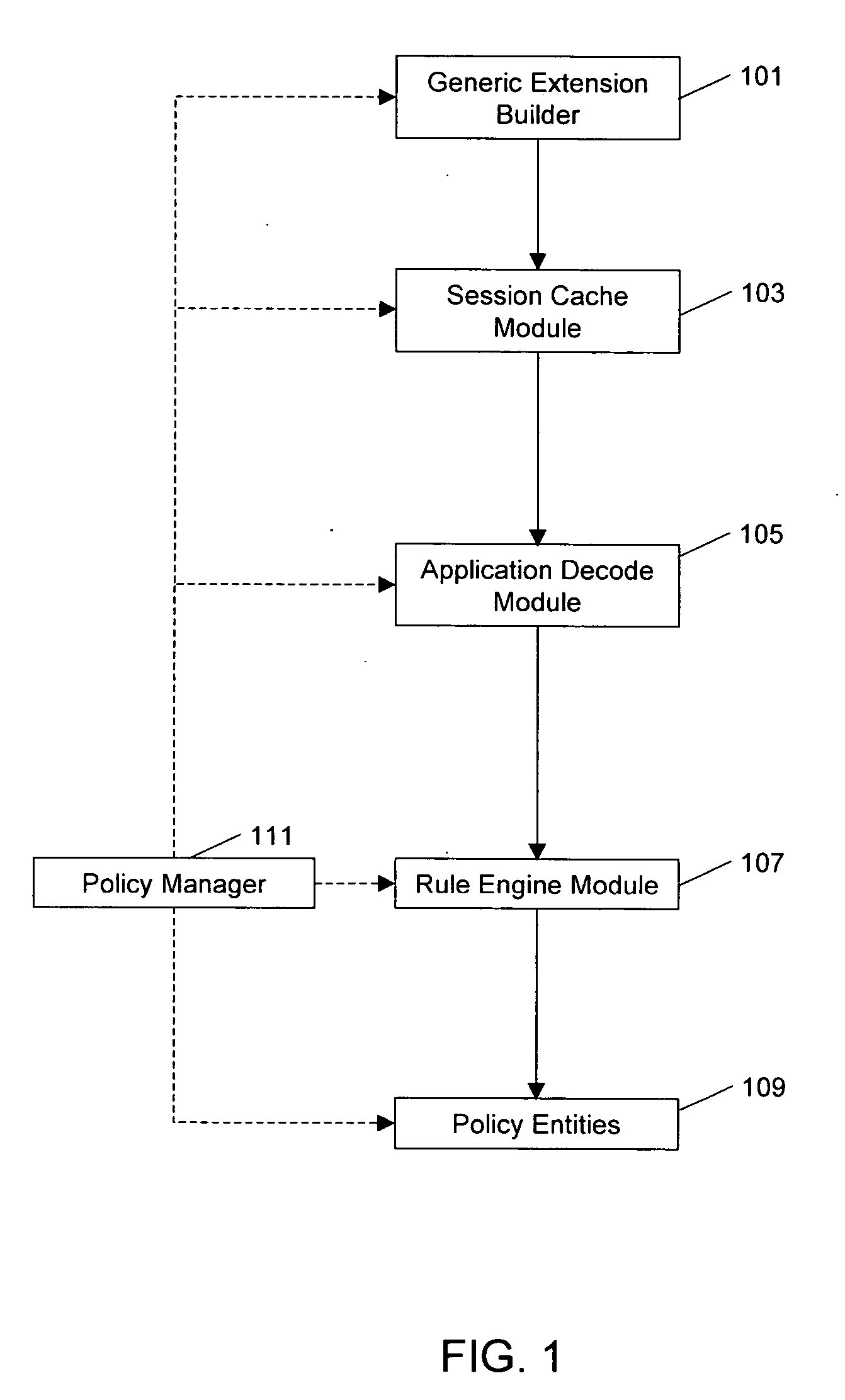
Rule engine
InactiveUS20070038775A1Improve efficiencyDigital computer detailsTransmissionGraphicsProgramming language
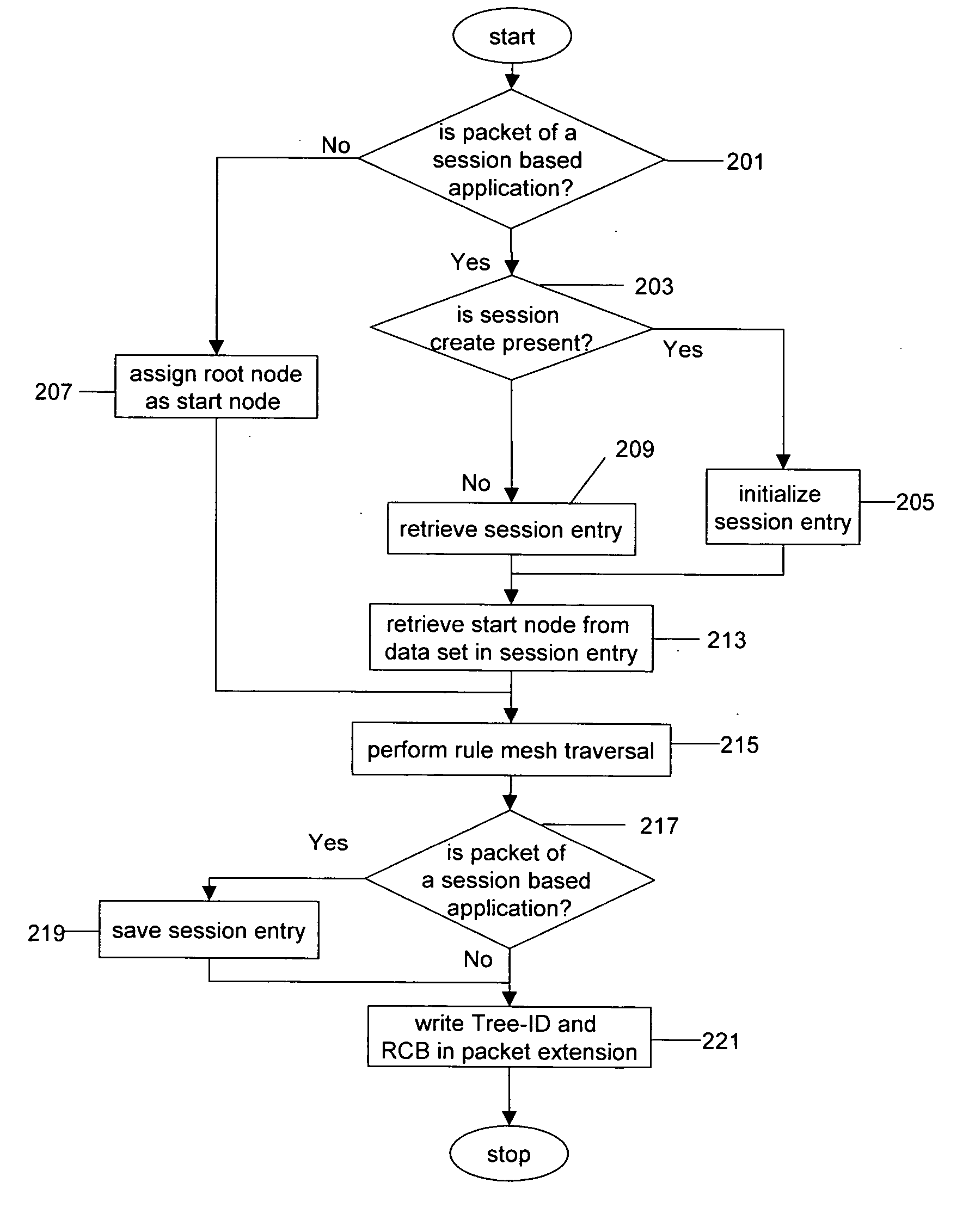
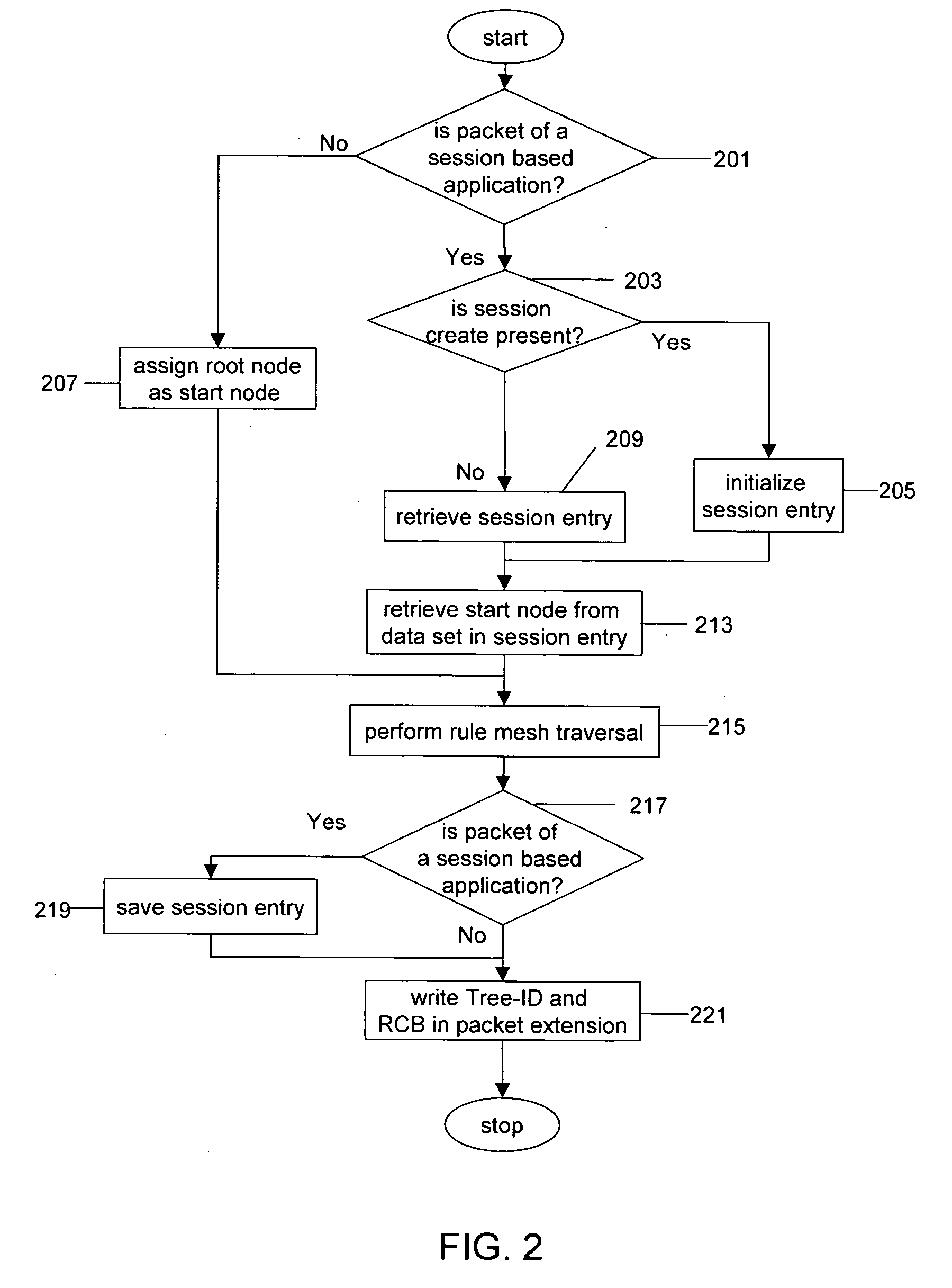
A rule engine for a computer network traverses a rule mesh having path nodes and path edges in form of a tree part and a graph part. The rule engine evaluates data packets flowing through a network to determine rules matched for every packet. Subsequent packets having same expression values as an already checked packet are not rechecked against the same nodes in the rule mesh through the use of a session entry. The rule engine performs a search on every path node of rule mesh to determine the next path edge to traverse. A Tree-Id and Rule Confirmation Bitmap that are indicative of path traversed and rules matched by a packet are generated at the end of rule mesh traversal. These are appended in the packet extension for subsequent modules of Policy Agent.
Owner:IPOLICY NETWORKS
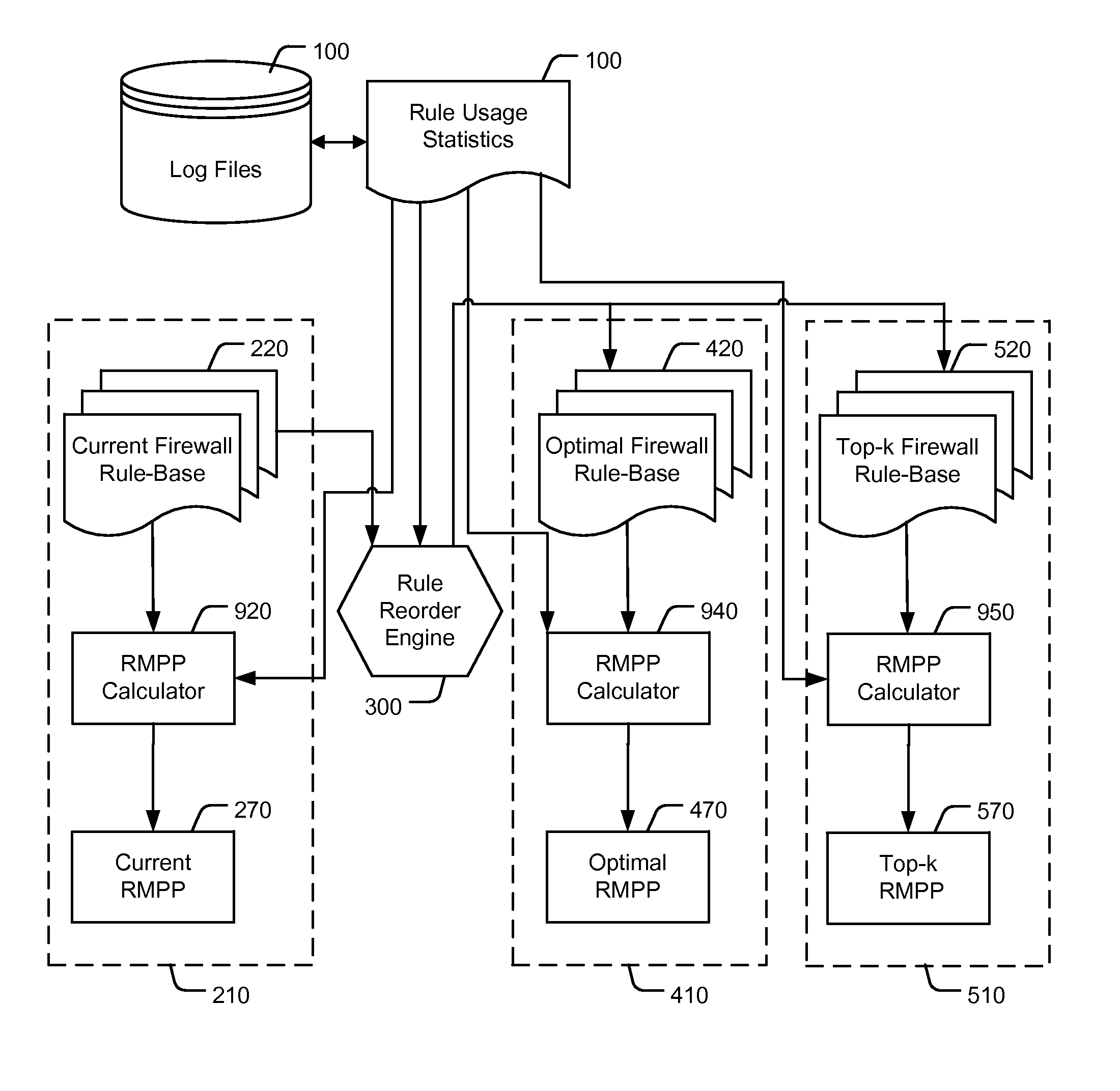
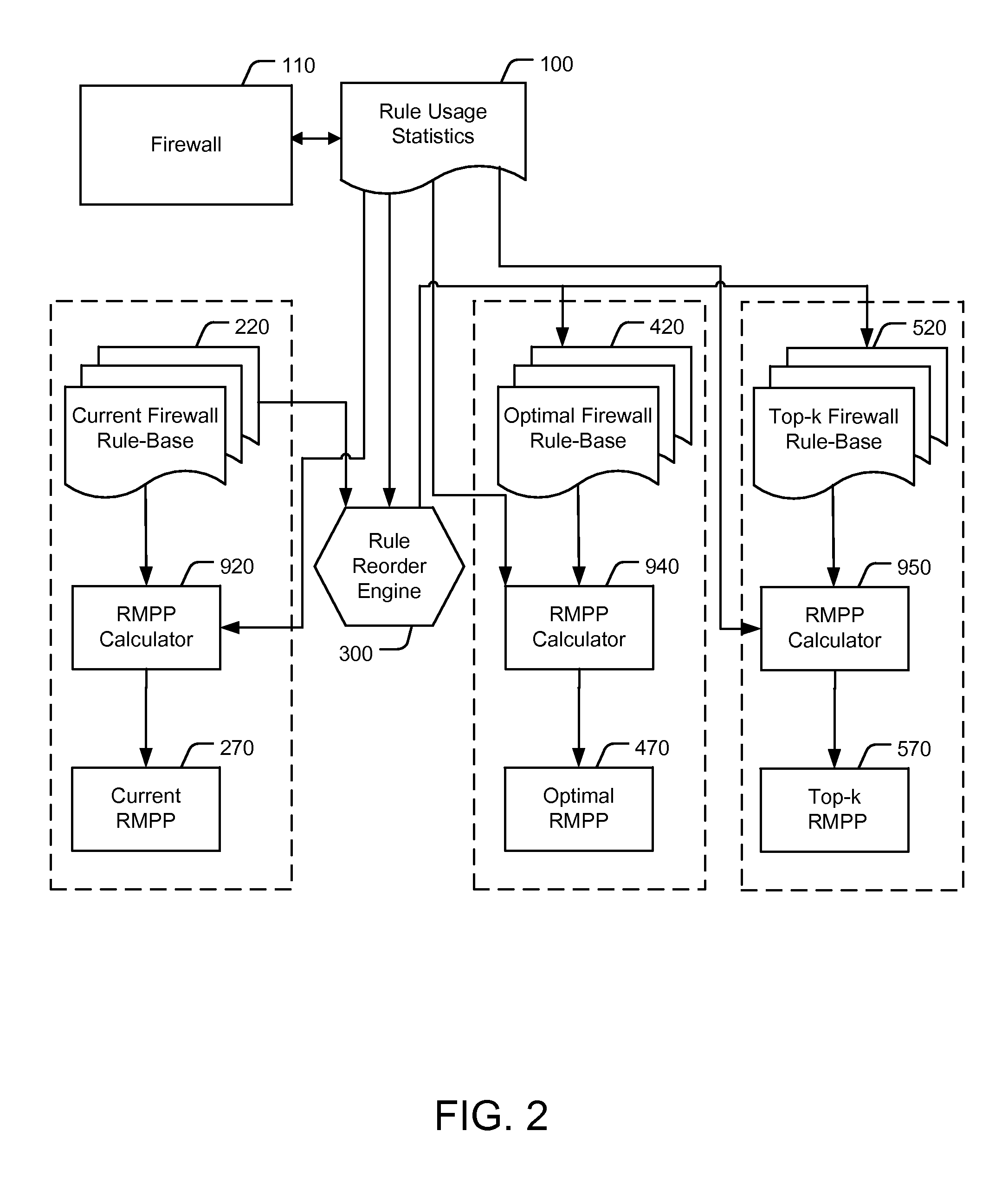
Reordering a firewall rule base according to usage statistics
ActiveUS8418240B2Reduce processReduction of the RMPPComputer security arrangementsMultiple digital computer combinationsNetwork connectionDisjoint-set
A computer implemented method of reducing central processing unit (CPU) usage of a firewall by safe reordering a current firewall's rule-base exhibiting N rules. The method comprising: receiving rule usage statistics exhibiting usage frequency of each rule on the current firewall's rule-base; calculating a rules matched per packet (RMPP) parameter, being a summation of products of each rule identifier and the corresponding usage frequency for all the N rules; determining an alternative order of the rule base by repositioning rules, wherein the repositioned rules perform the same action on the firewall, or wherein the repositioned rules act on disjoint sets of network connections, and wherein the repositioning results in a reduction of the RMPP of the reordered rule base, thereby reducing the CPU usage of the firewall in implementing the alternative order of rules.
Owner:ALGORITHMIC SECURITY ISRAEL
Screening of data packets in a gateway
InactiveUS6996573B2Efficient screeningEfficient processingData processing applicationsTransmissionInformation dataData structure
A method for processing data packets in a gateway element comprises the steps of: comparing a data packet to screening information comprising a set of rules, and processing a data packet according to a rule belonging to the set of rules, the header information of said data packet matching the header information of said rule. The method is characterized in that said screening information is hierarchically structured so that it comprises a first rule, which specifies first header information, and a subset of rules relating to said first rule, and in that in said step of comparing a data packet, said data packet is compared to said subset of rules only if the header information of the data packet matches the header information of the first rule. A gateway element, an arrangement, and a data structure comprising screening information are also presented.
Owner:FORCEPOINT LLC
Multi-core paralleled network traffic load balancing method and system
InactiveCN101577705AEasy to handleSolving Parallel Processing Scheduling ProblemsData switching networksProcessing coreSpatial mapping
The invention discloses a multi-core paralleled network traffic load balancing method and a multi-core paralleled network traffic load balancing system, which can equally share network traffic load on processing cores of a processer according to the actual network loading condition. The system and the method mainly comprises the following steps: matching data packets in a network into the traffic; generating a traffic record according to a traffic spacial mapping mechanism to make the traffic uniformly mapped into an ID space; and according to the network loading condition, dividing the traffic space, and dispatching the traffic load to different processing cores by a dispatching core. The method utilizes the appeared multi-core technology to effectively meet the requirements on parallel processing and dispatching of the data packets and the traffic under high-speed links.
Owner:DHC SOFTWARE
Flow communication system
A flow communication system has: a node having a flow table; and a controller configured to set a flow entry in the flow table. Each flow entry that is set in the flow table specifies packet processing which is performed with respect to a packet matching a match condition. If a hit entry exists in the flow table, the node performs the packet processing specified by the hit entry with respect to a received packet. If a deletion condition with regard to a first flow entry in the flow table is satisfied, the node deletes the first flow entry from the flow table. The deletion condition includes that a sum of packet lengths of all the received packets matching the first flow entry after the first flow entry is set up exceeds a predetermined deletion unit length.
Owner:NEC CORP
Agile network protocol for secure communications with assured system availability
InactiveUS20080040791A1Avoid attackUser identity/authority verificationMultiple digital computer combinationsDomain namePrivate network
A plurality of computer nodes communicate using seemingly random Internet Protocol source and destination addresses. Data packets matching criteria defined by a moving window of valid addresses are accepted for further processing, while those that do not meet the criteria are quickly rejected. Improvements to the basic design include (1) a load balancer that distributes packets across different transmission paths according to transmission path quality; (2) a DNS proxy server that transparently creates a virtual private network in response to a domain name inquiry; (3) a large-to-small link bandwidth management feature that prevents denial-of-service attacks at system chokepoints; (4) a traffic limiter that regulates incoming packets by limiting the rate at which a transmitter can be synchronized with a receiver; and (5) a signaling synchronizer that allows a large number of nodes to communicate with a central node by partitioning the communication function between two separate entities.
Owner:VIRNETX
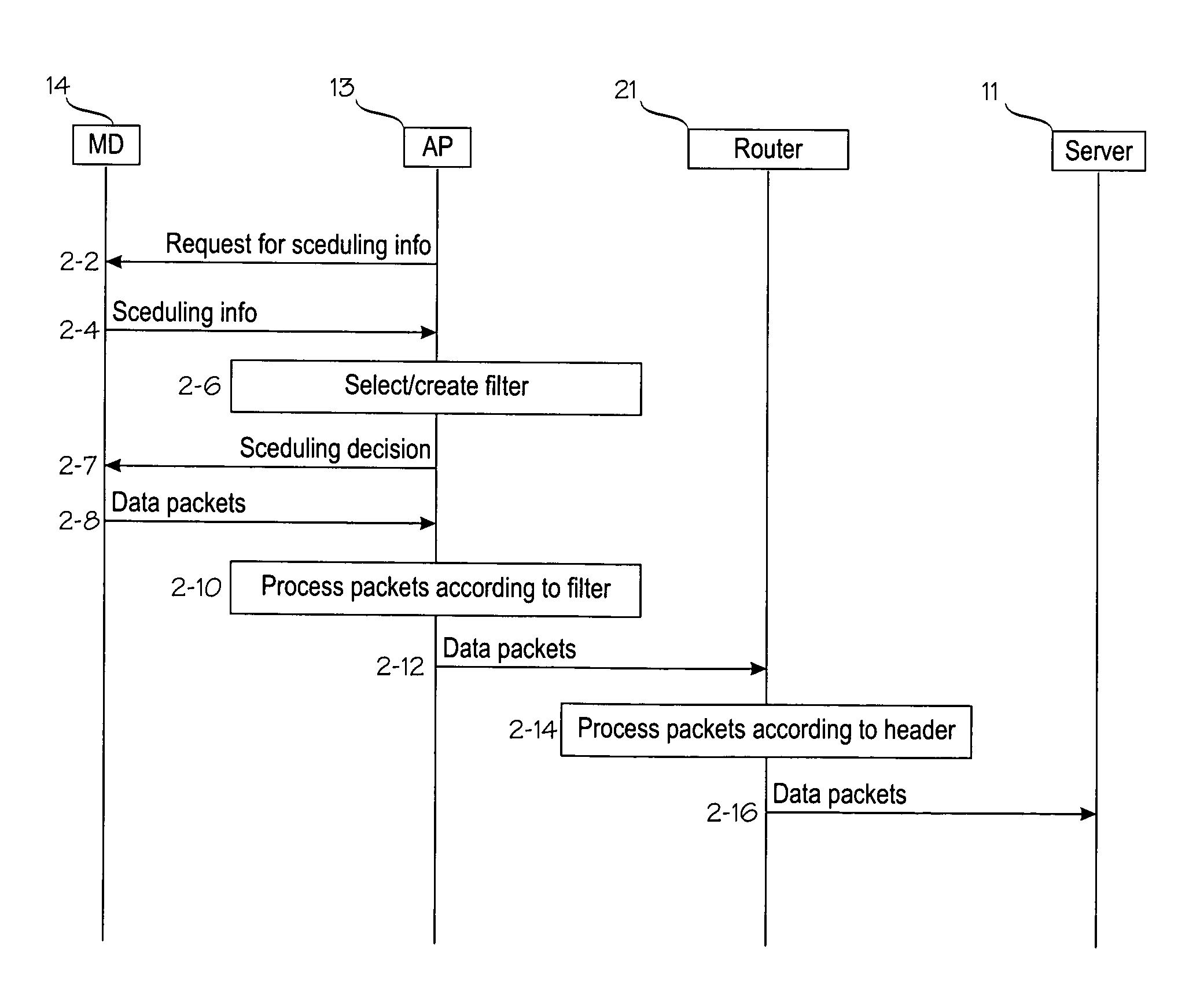
Scheduling technique for mobile uplink transmission
InactiveUS20060198378A1Easy to manageSave capacityData switching by path configurationRadio/inductive link selection arrangementsComputer networkUplink transmission
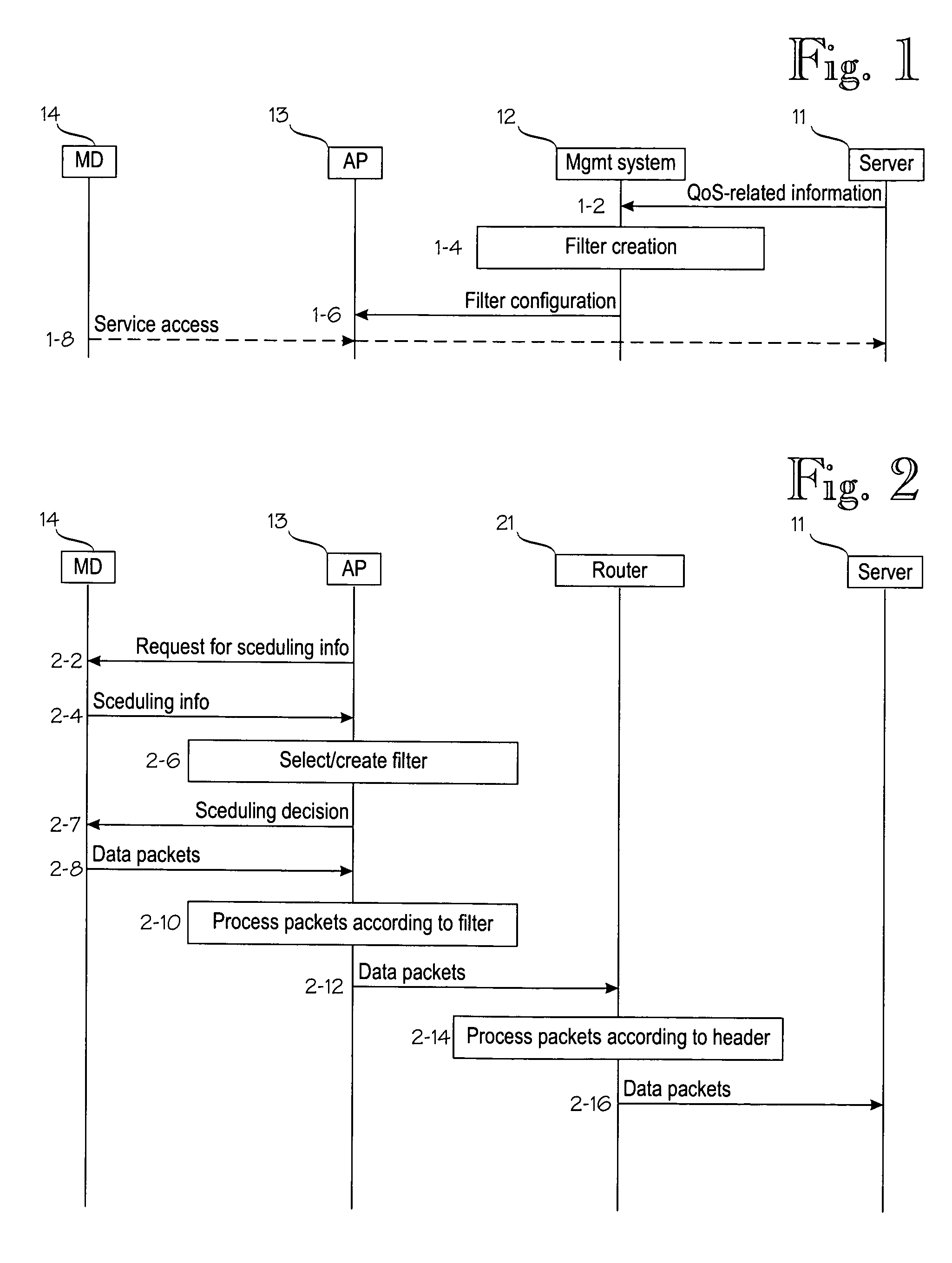
An uplink scheduling technique for accessing a priority service from a mobile device (14) via a network access point (13). The access point (13) sends a request for scheduling information (2-2) to the mobile device. The mobile device (14) returns the requested scheduling information (2-4). The access point uses the requested scheduling information to determine (2-6) a filter configured for a priority service which implies better than best-effort scheduling priority for the data packets related to the priority service. The access point sends a scheduling decision (2-7) to the mobile device. The mobile device sends data packets (2-8) to the access point according to the scheduling decision. The access point receives from the mobile device an uplink data packet, the received uplink data packet matching the filter configured for the priority service.
Owner:NOKIA CORP
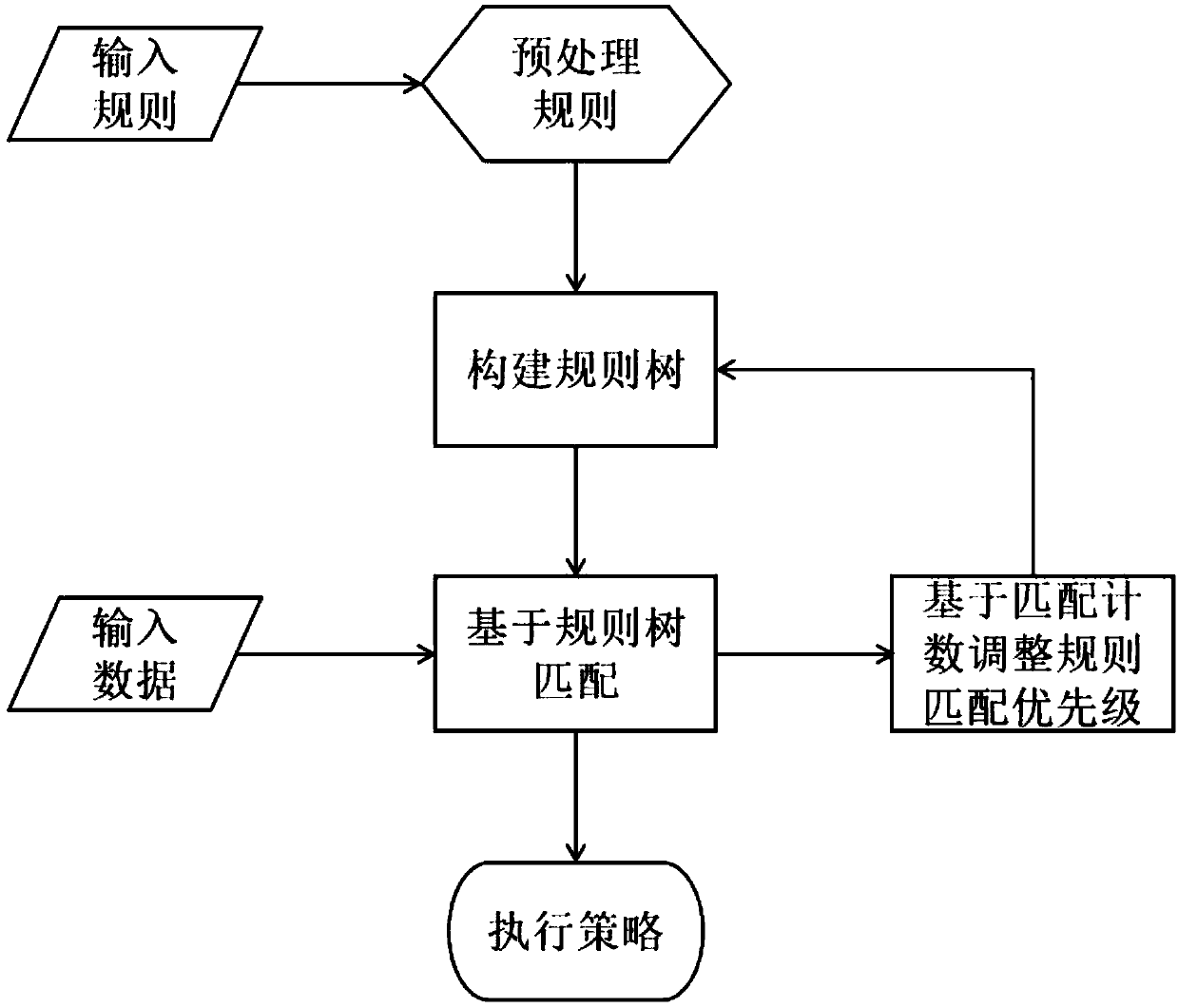
Firewall data packet matching algorithm based on rule tree retrieval
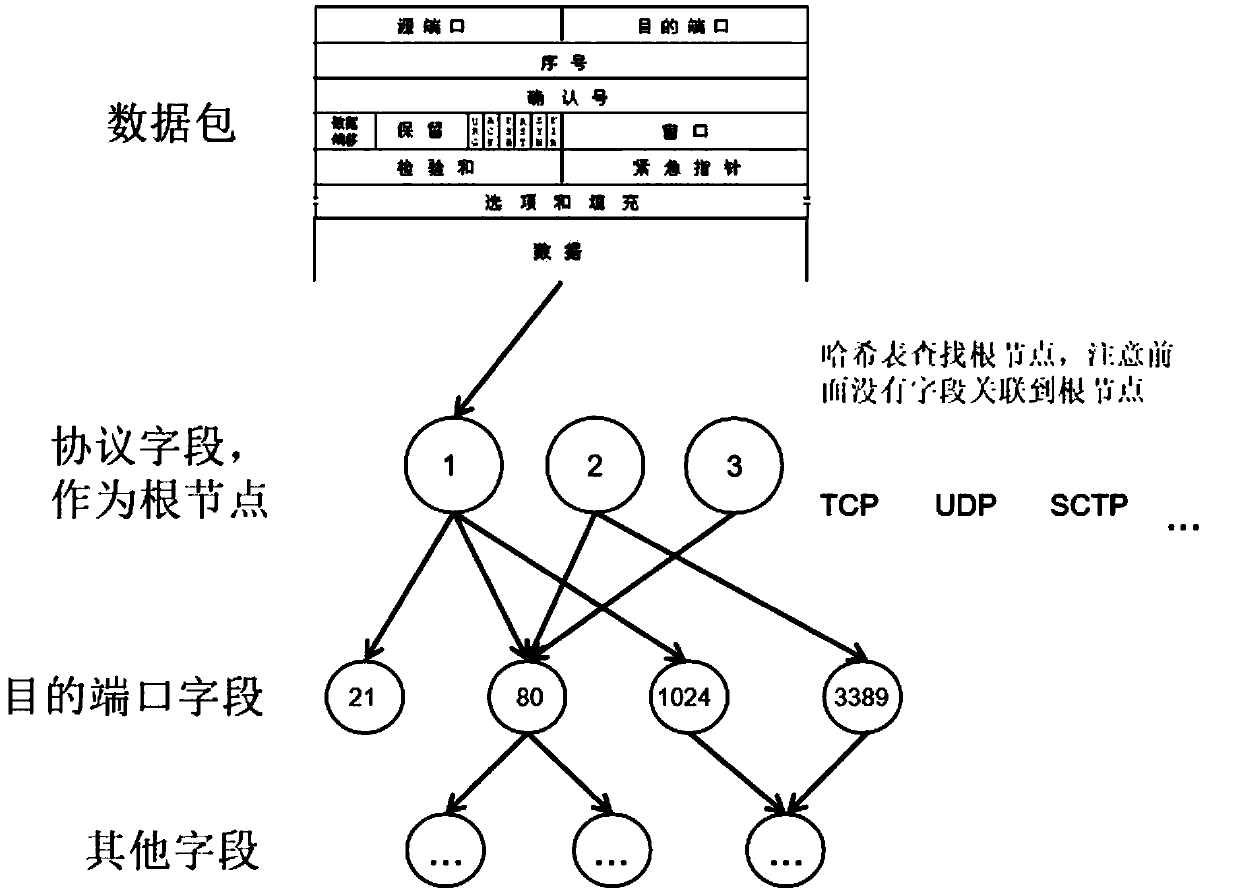
The invention relates to a firewall data packet matching algorithm based on rule tree retrieval. The method provided by the invention comprises the step of a preprocessing rules, constructing a rule tree and matching a data packet; the step of processing the rules is to perform formalization and standardization processing on the rules to generate a rule set with a complete and uniform structure; the step of constructing the rule tree is to process all rules to generate a tree data structure that is organized, stores all rule information and is easy to be retrieved quickly; and the step of matching the data packet comprises: 1. parsing the data packet to be matched to obtain data packet features; 2. performing retrieval matching on each feature of the data packet one by one according to theconstructed rule tree to finally match a certain rule; recording a matching count and a backtracking count; and 3. executing a policy set by the matched rule, or, executing a default policy if the rule is not matched. The invention provides a firewall data packet matching algorithm having excellent performance and controllable space complexity and friendly supporting the increase and decrease ofthe rules.
Owner:G CLOUD TECH
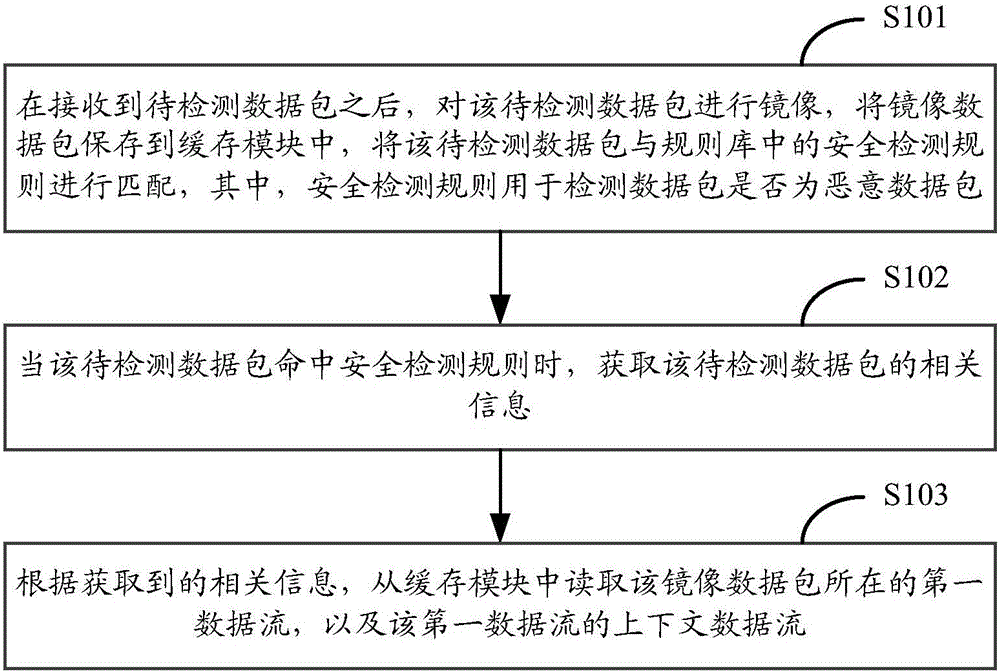
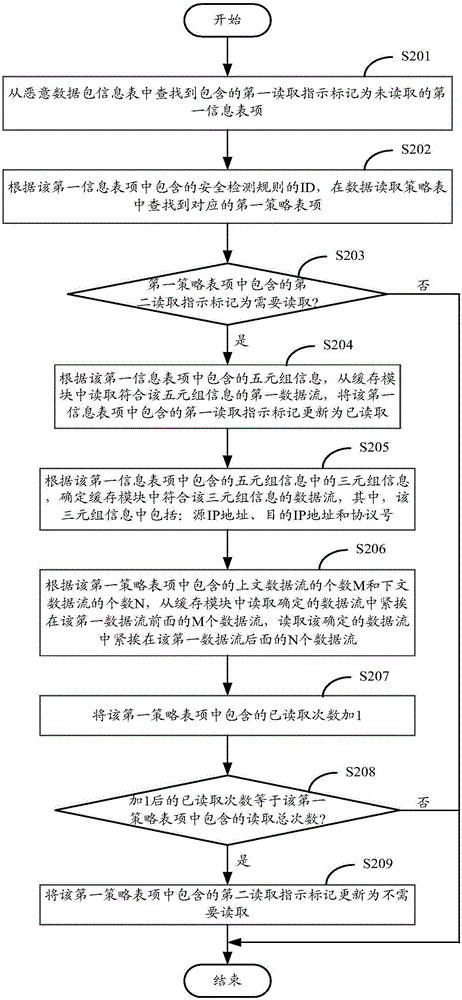
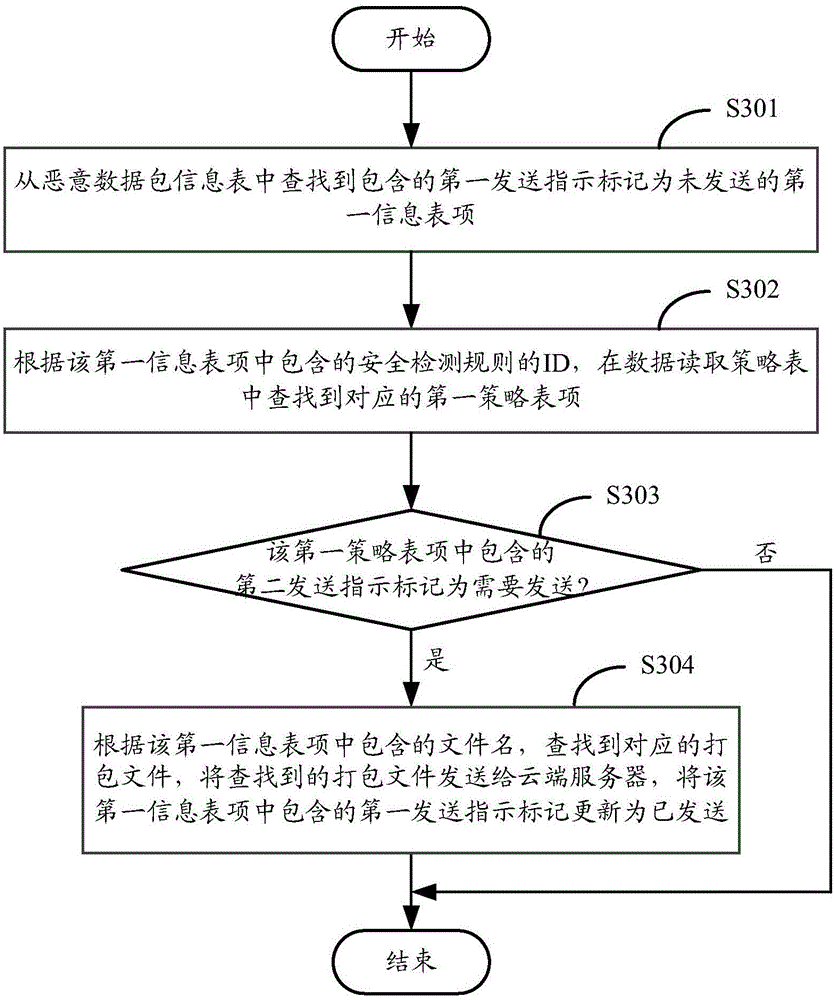
Security-detection-based data flow obtaining method and apparatus
ActiveCN105915516AThe analysis result is accurateData switching networksData streamRelevant information
The application provides a security-detection-based data flow obtaining method and apparatus. The method comprises: after a to-be-detected data packet is received, mirror image processing is carried out on the to-be-detected data packet, a mirror image packet is stored into a buffer module, and matching of the to-be-detected data packet and a security detection rule in a rule base is carried out, wherein the security detection rule is used for detecting whether the data packet is a malicious packet; when to-be-detected data packet matches the security detection rule, relevant information of the to-be-detected data packet is obtained, wherein the relevant information includes five-element information; according to the relevant information, a first data flow where the mirror image data packet is located and a context data flow of the first data flow are read from the buffer module. According to the application, a malicious data packet matching the rule, a data flow of location of the malicious data packet, and a context data flow can be obtained; and on the basis of complete attack information provided by the data flows, an accurate analysis result can be obtained.
Owner:NEW H3C TECH CO LTD
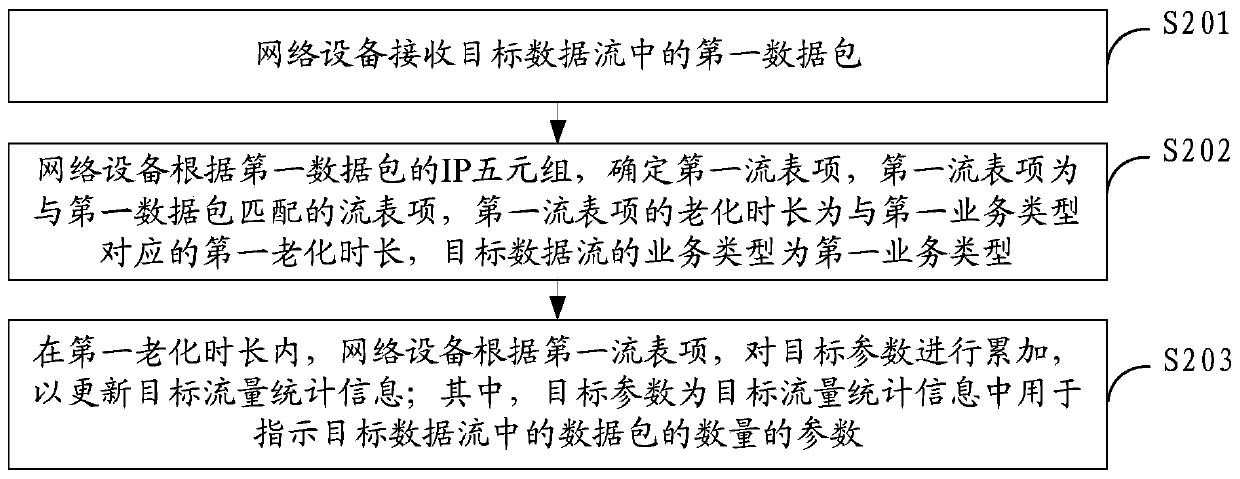
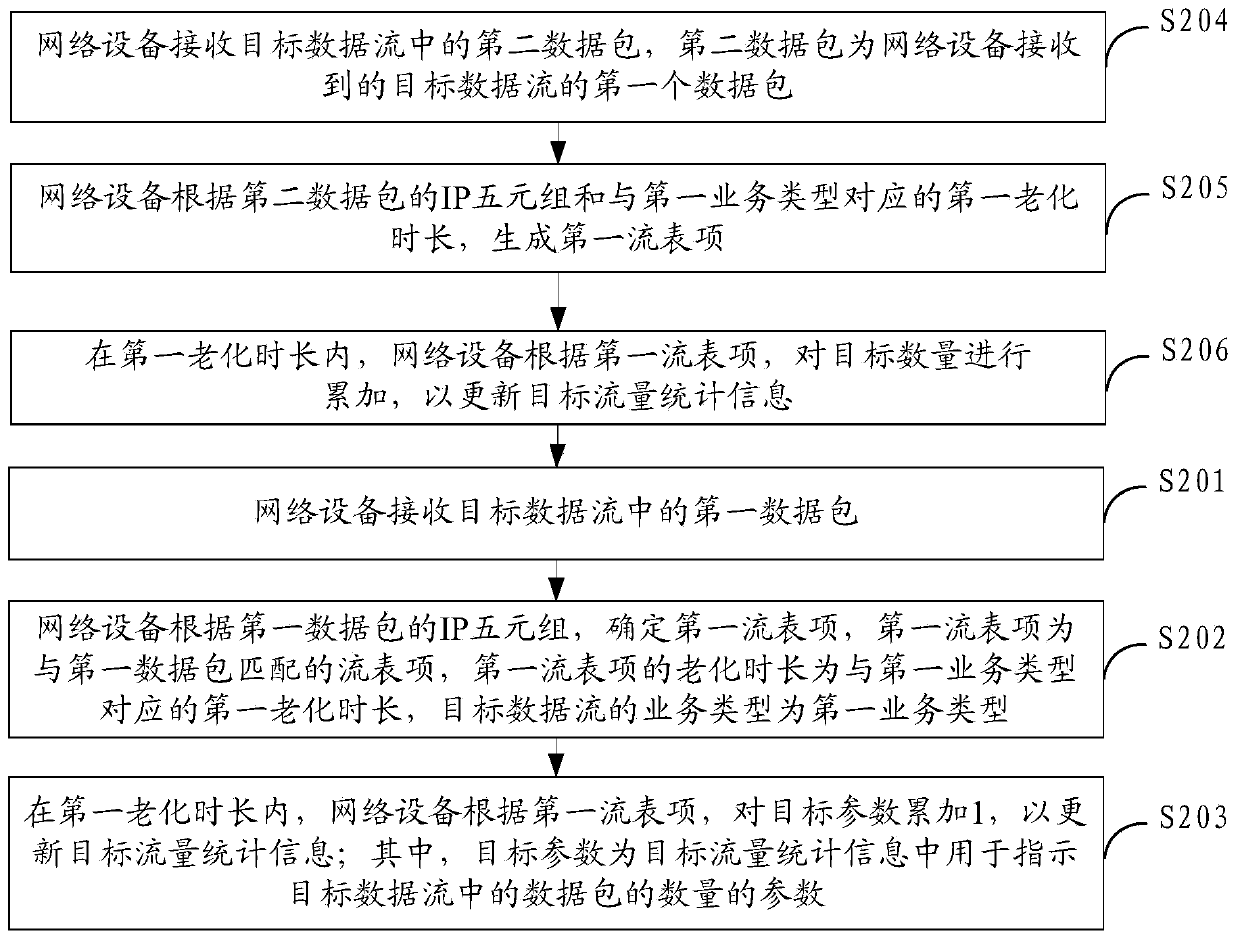
A data processing method and network equipment
The embodiment of the invention provides a data processing method and network equipment, is applied to the technical field of communication, and aims to solve the problem of contradiction between statistical accuracy determination and statistical real-time performance of IPFIX flow monitoring analysis. Specifically, the method is applied to network equipment, and comprises the following steps: receiving a first data packet in a target data stream; Determining a first flow table entry according to the IP quintuple of the first data packet, the first flow table entry being a flow table entry matched with the first data packet, the aging duration of the first flow table entry being a first aging duration corresponding to the first service type, and the service type of the target data flow being the first service type; And accumulating the target parameters in the first aging duration according to the first flow table entry, the target parameters being parameters used for indicating the number of data packets in the target data flow in the target flow statistical information. The scheme is specifically applied to the process of determining the aging duration corresponding to the service type of the data stream before the network equipment reports the traffic statistical information of the data stream to the management equipment.
Owner:MAIPU COMM TECH CO LTD
Internet of things environment large data-based information safety monitoring and managing method and system
InactiveCN107592306AEnsure safetyImprove performanceTransmissionCloud processingInformation security
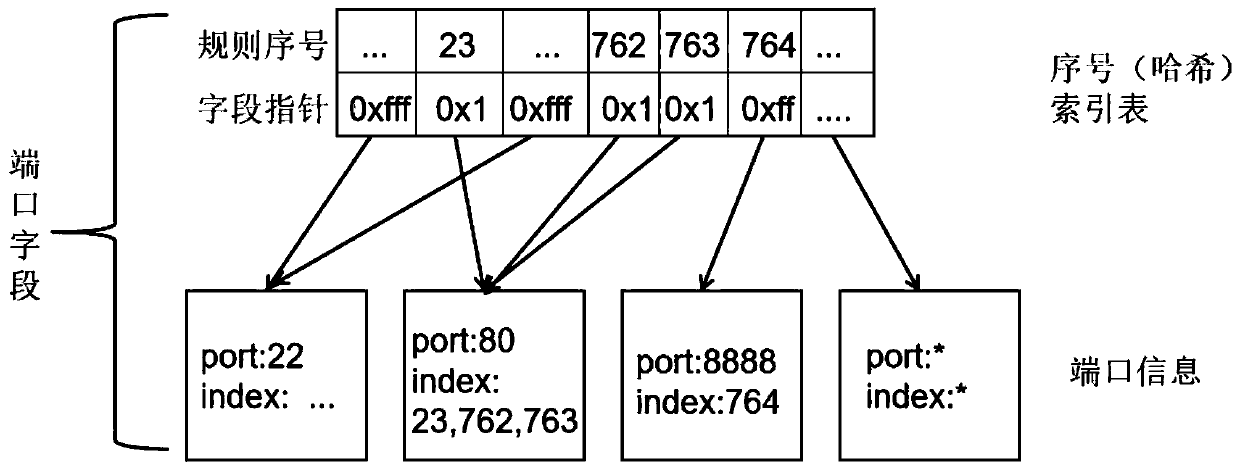
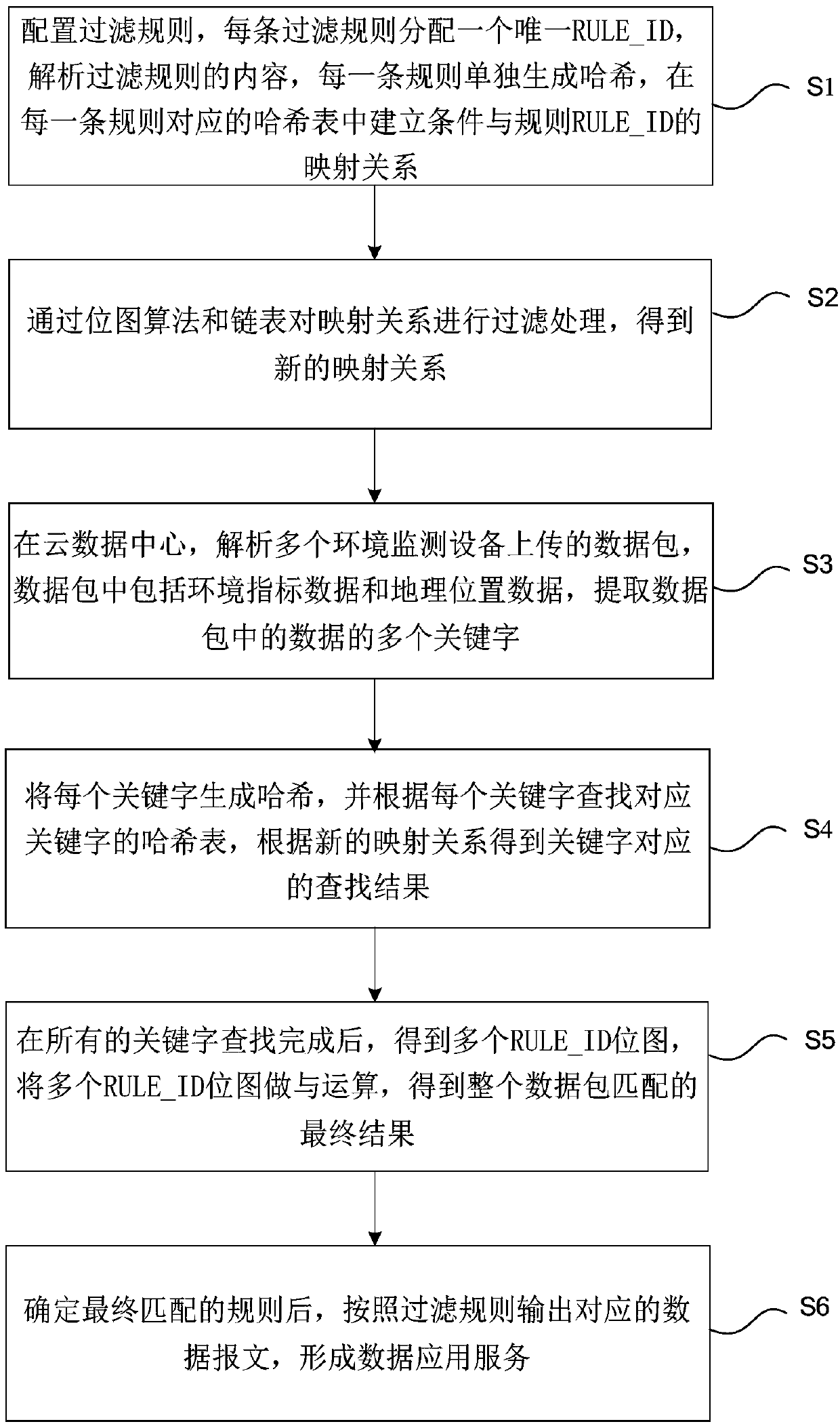
The present invention provides an internet of things environment large data-based information safety monitoring and managing method and system. The method comprises the steps of configuring the filtering rules, and establishing the mapping relation of the condition and the rule RULE_ID in a Hash table corresponding to each rule; analyzing the data packets uploaded by a plurality of environment monitoring devices, and extracting a plurality of keywords of the data in the data packets; generating each keyword into a Hash, and searching the Hash tables of the corresponding keywords to obtain thesearch result corresponding to the keywords; after all keywords are searched, obtaining a plurality of RULE_ID bitmaps, and carrying out the AND operation on the plurality of RULE_ID bitmaps to obtainthe final results matching the whole data packets; determining a final matching rule, and then outputting the corresponding data messages according to the filtering rules. According to the present invention, a cloud processing technology is utilized in a cloud data center to filter the environment index data, the performances of a multi-core processor are utilized fully, the real-time data filtering of high performance is realized, and the data safety is guaranteed.
Owner:SICHUAN MIANYANG TAIKOO SOFTWARE
Method for classifying data packets
ActiveCN105897587AClassification is flexibleClassification can be extendedData switching networksAlgorithmPacket matching
The invention discloses a method for classifying data packets. The method comprises preprocessing a rule set by a CPU and classifying data packets by a GPU. The preprocessing is executed before the data packet classification, preprocesses the rule set in order that subsequent packet classification can be operated, and is completed in the CPU. The data packet classification is the core of the method, classifies the data packets, and outputs rule numbers with the highest priority and matching the data packets, and is completed in the GPU. The method fully utilizes the hardware features and advantages of the GPU and is superior to a conventional data packet classifying algorithm in performance.
Owner:HUNAN UNIV
SDN-based security service chain system and data packet matching and forwarding method
PendingCN109495391AImprove monitoring efficiencyRealize linkageData switching networksUser needsOpenFlow
The invention discloses a SDN-based security service chain system. The system comprises a control plane, flow classification nodes, service nodes and a service chain. The control plane mainly comprises core control components of the SDN service chain that are a SDN controller and an OpenFlow 1.3 switch. The SDN controller creates a service chain according to user requirements and deploys service logics of each service node on the service chain. The controller sends the characteristics of user messages that need to be processed in the service chain to the OpenFlow 1.3 switch. The OpenFlow 1.3 switch introduces data messages into the service chain according to the corresponding message characteristics. The invention also discloses a packet matching and forwarding method of the SDN-based security service chain system. The network service chain is constructed and deployed based on SDN technology, and the linkage between network visualization and service chain is realized through the feedback of information. Therefore, in the case of massive data and multi-service nodes, the method has high data forwarding efficiency and low processing time to improve network monitoring efficiency. Theinvention designs a SDN-based service chain architecture and provides a matching and forwarding process of the service chain data packets based on the architecture.
Owner:TIANJIN CHENGJIAN UNIV +1
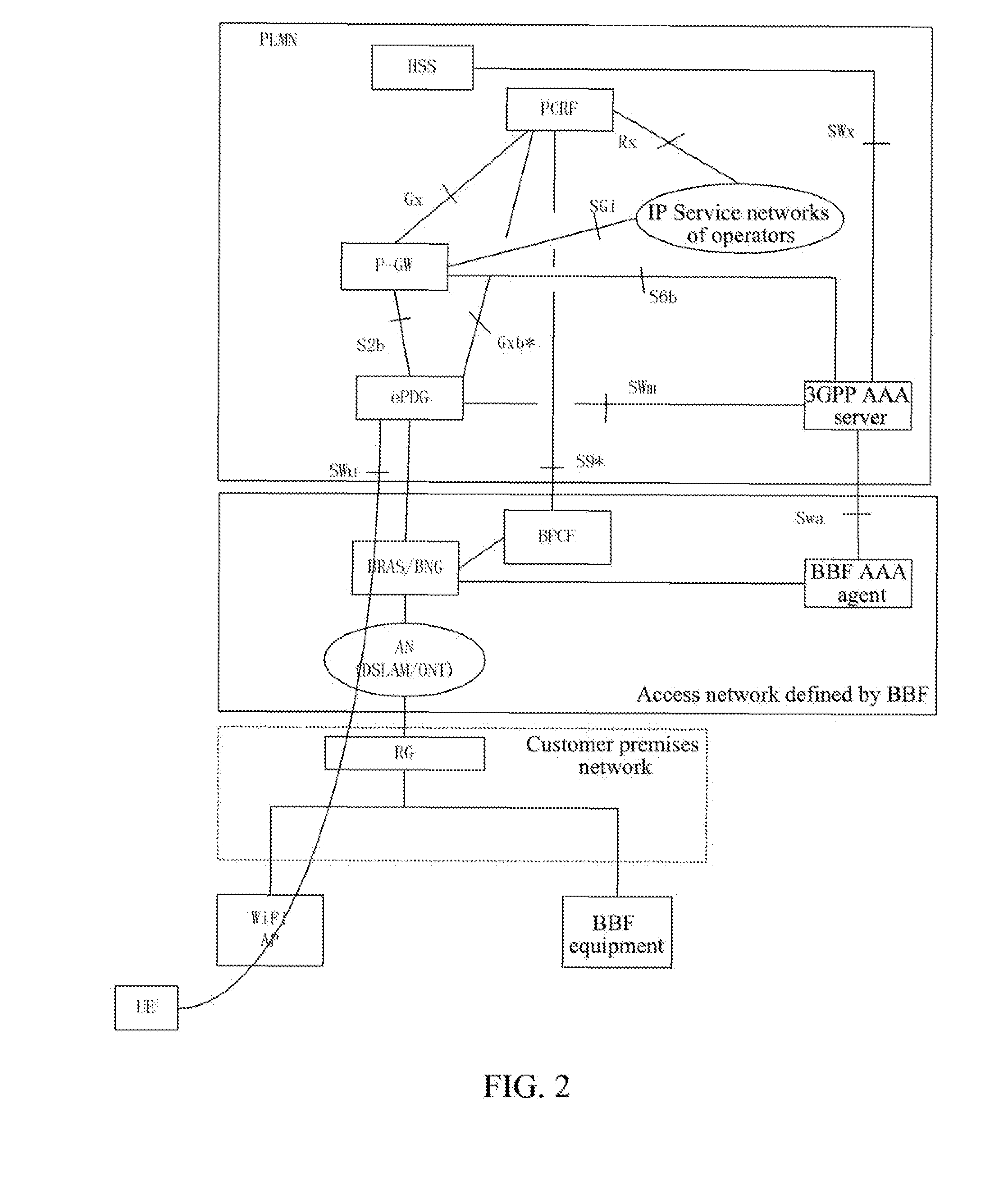
Policy Control Method and System
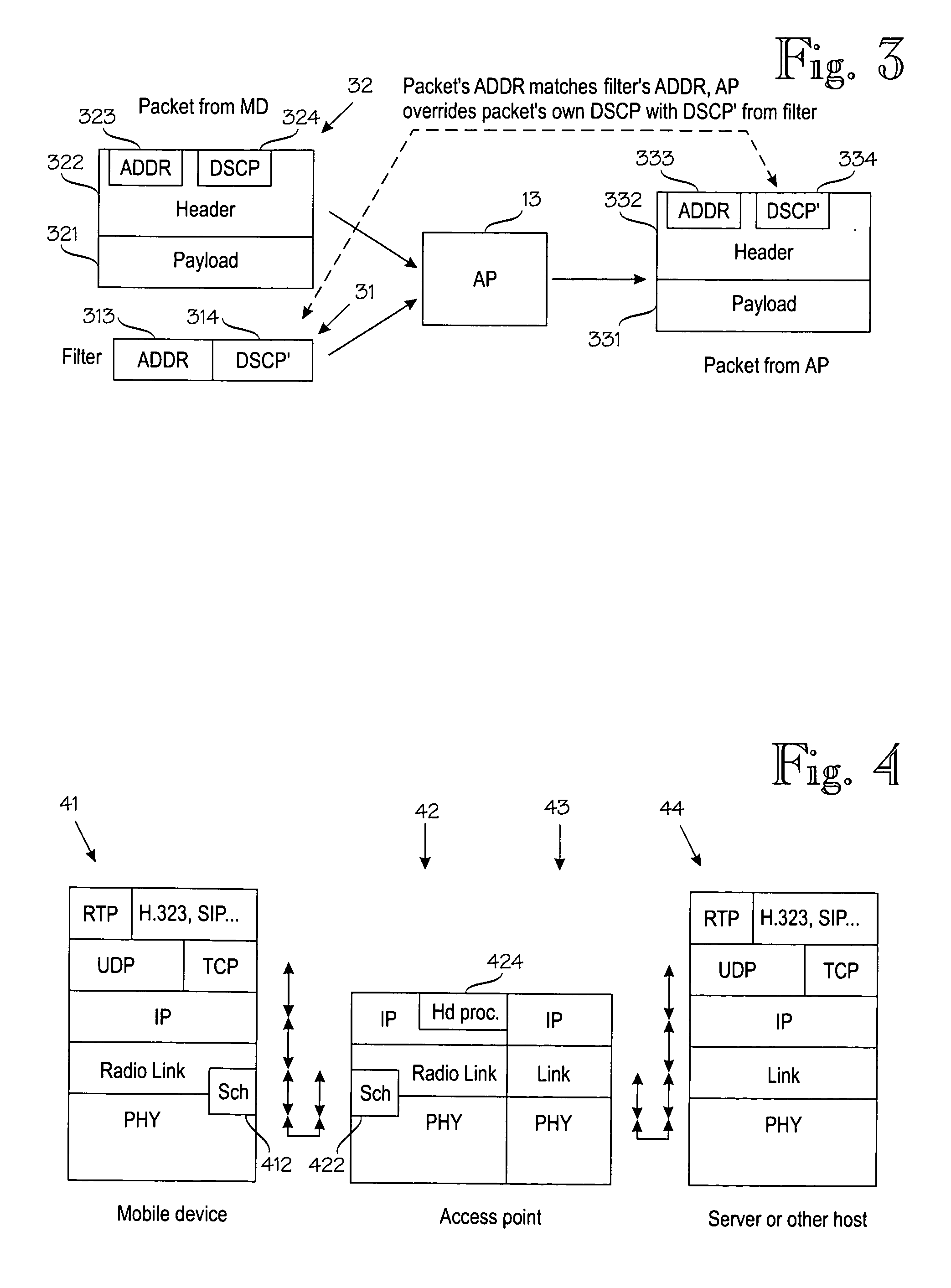
A policy control method and system are disclosed. The method includes: a 3rd Generation Partnership Project (3GPP) network entity sending outer IP packet header information to a Broadband Forum (BBF) access network entity; and the BBF access network entity scheduling a data packet matching the outer IP packet header information according to a Differentiated Services Code Point (DSCP) of the data packet. With the above technical scheme, service data flows without going through admission control will not occupy resources of other service data flows going through the admission control.
Owner:XIAN ZHONGXING NEW SOFTWARE
Method and device for filtering data packets
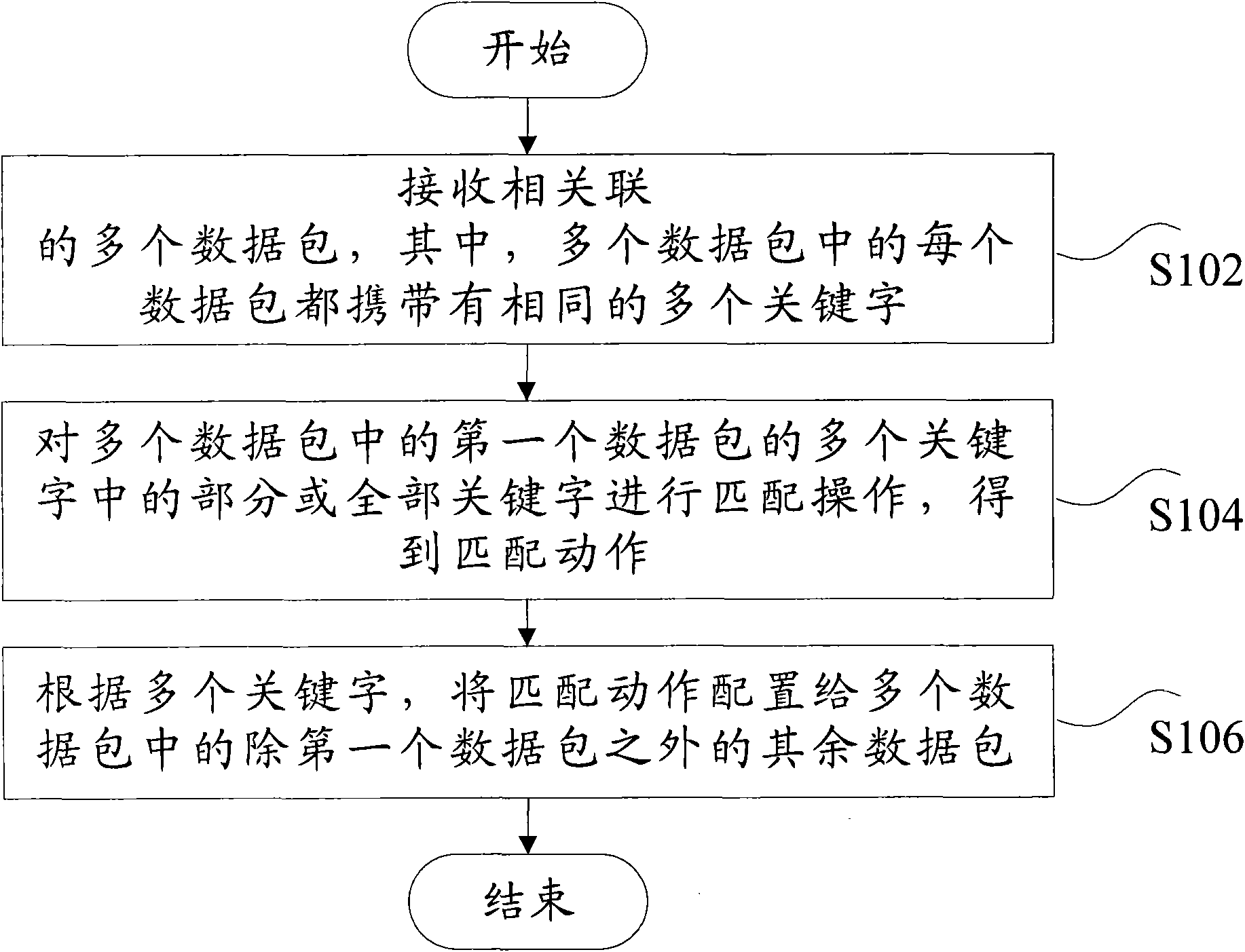
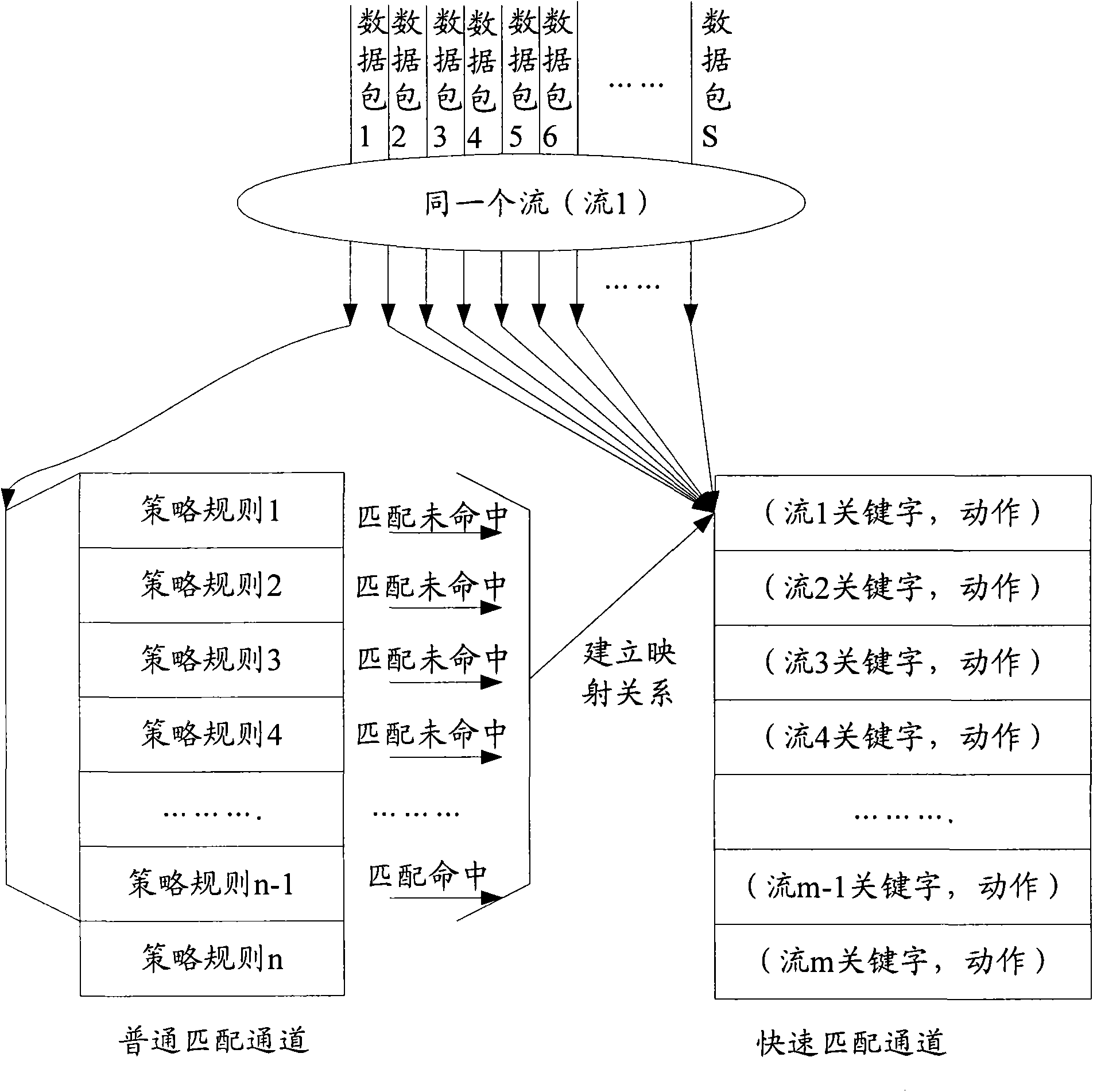
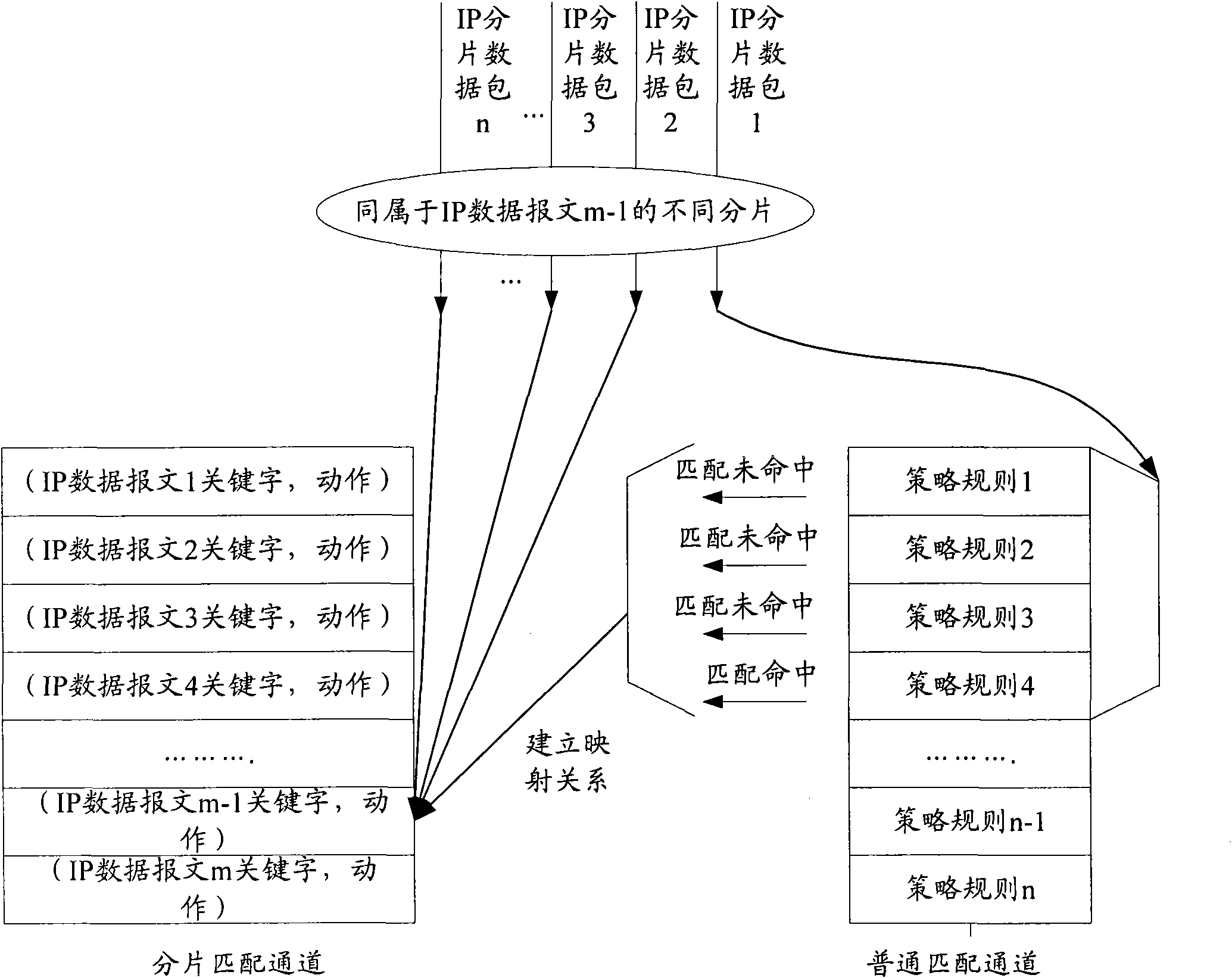
InactiveCN101783786AImprove matching speedIncrease filter speedError preventionSpecial data processing applicationsPacket filteringPacket matching
The invention discloses a method and a device for filtering data packets. The method comprises the following steps: receiving a plurality of related data packets, wherein each of the plurality of data packets carries a plurality of same key words; performing a matching operation on part or all of the key words in a first word packet in the plurality of the data packets to acquire a matching action; and according to the plurality of key words, configuring the matching action to the other data packets besides the first data packet in the plurality of data packets. In the method and the device for filtering the data packets, by performing the matching operation on the first data packet in the plurality of related data packets which contain the same key words, the acquired matching action is configured to other data packets which contain the same key words, and a data packet matching speed can be increased, so that the problem that the data packet filtering speed is slow in the related technique is solved, and system cost is saved and system processing efficiency is improved.
Owner:OPEN INVENTION NEWTORK LLC
Switch system based on service function chain
ActiveCN108471389AProgrammableSupport complex network functionsData switching networksGeneral functionOperational costs
The invention discloses a switch system based on a service function chain. For the problems that a switch node data plane is fixed, the function expansibility is bad and the resource is over-configured, a flexible network processing function is provided for a data packet in a network function pool way by separating a non-general function from a line card. The data packet is divided into differenttypes by a classifier through a matching rule, for the data packet needing the non-general network function processing, the network function instance (non-general network function) needing to be processed is found in a network function instance list of a flow table according to a data packet matching domain, and the processing is performed by a service function chain composed of corresponding different network functions in the network function pool. Compared with the traditional switch system, P4 architecture and like existing research techniques, the switch system disclosed by the invention has the following advantages: the high-level network function is supported, the data traffic processing rule can be flexibly extended, the change is dynamic, the resource utilization efficiency is improved, and the capital expenditure and the operation cost are reduced.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Methods and devices for configuring and issuing Open Flow items
ActiveCN104796336ASave configuration timeReduce forwarding delayData switching networksDistributed computingPacket matching
The present application provides a method and an apparatus for configuring and delivering a flow table entry. The method comprises: a switch sending, to a controller, a request message for requesting delivering a flow table entry, the request message carrying a to-be-forwarded data packet; after the controller receives the request message, the controller generating all flow table entries matching the to-be-forwarded data packet, and returning, to the switch, a response message carrying all the flow table entries matching the to-be-forwarded data packet; after then switch receives the response message, the switch extracting all the flow table entries matching the to-be-forwarded data packet from the response message; and aggregating all the extracted flow table entries into flow table entries of a hardware layer, and when the switch supports the flow table entries of the hardware layer, the switch configuring the flow table entries of the hardware layer into a flow table of the hardware layer. The method and the apparatus for configuring and delivering a flow table entry in the present application can shorten the time of configuring flow table entries of a hardware layer into a flow table of the hardware layer, can shorten the delay of forwarding the data packets, and can reduce the number of lost packets of the data packets.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com