Attack prevention practice method and device
A technology of attacking aircraft and attackers, applied in the network field, can solve the problems of inability to evaluate and improve the protection system, and not showing the protection effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
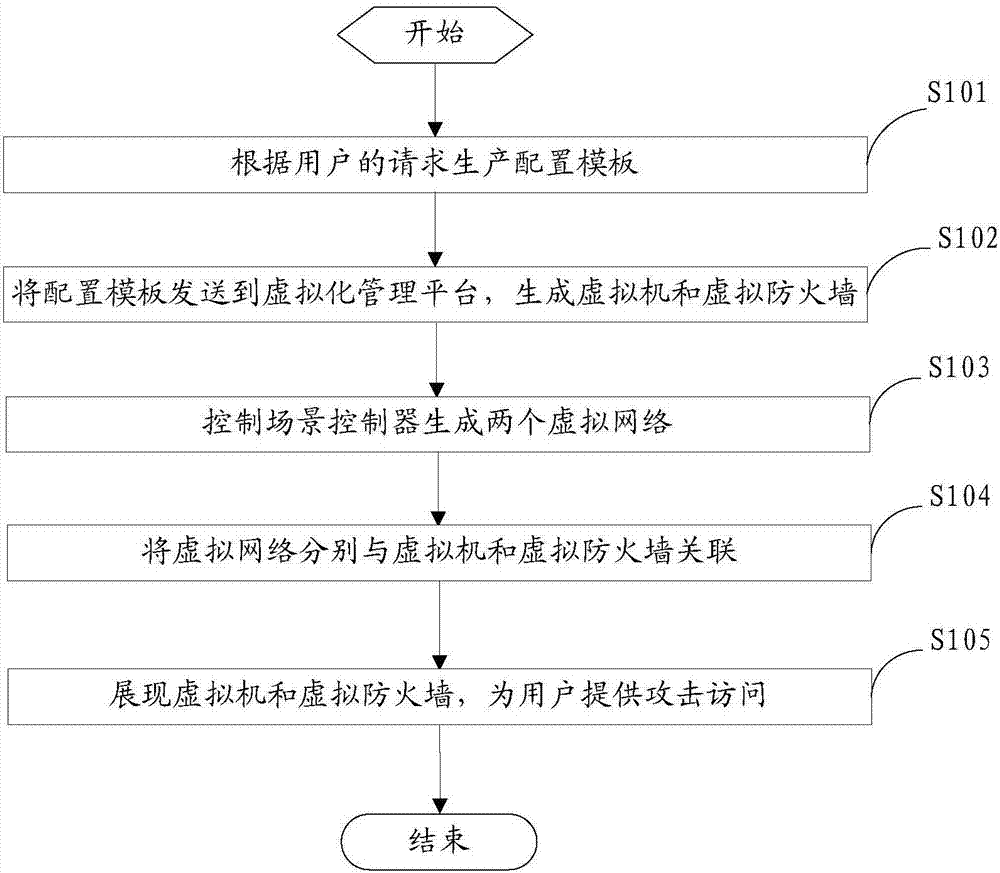
[0044] figure 1 A step flow chart of an embodiment of an attack prevention drill method provided for the invention.
[0045] Such as figure 1 As shown, the attack protection exercise method provided in this embodiment is applied to a network attack and defense laboratory, specifically, it is applied to a scene controller of an attack and defense exercise system in a network attack and defense laboratory, and is used to display firewalls or IPS in a simulated attack and defense exercise. For the protection effect, in this embodiment, cracking dvwa xss on owasp bwa is taken as an example. The attack protection drill method includes the following steps:
[0046] S101: Produce a configuration template according to the user's request.
[0047] When an offensive and defensive rehearsal is required, the user can send a corresponding offensive and defensive request to the scene controller. At this time, the scene controller produces a corresponding configuration template according to the req...
Embodiment 2
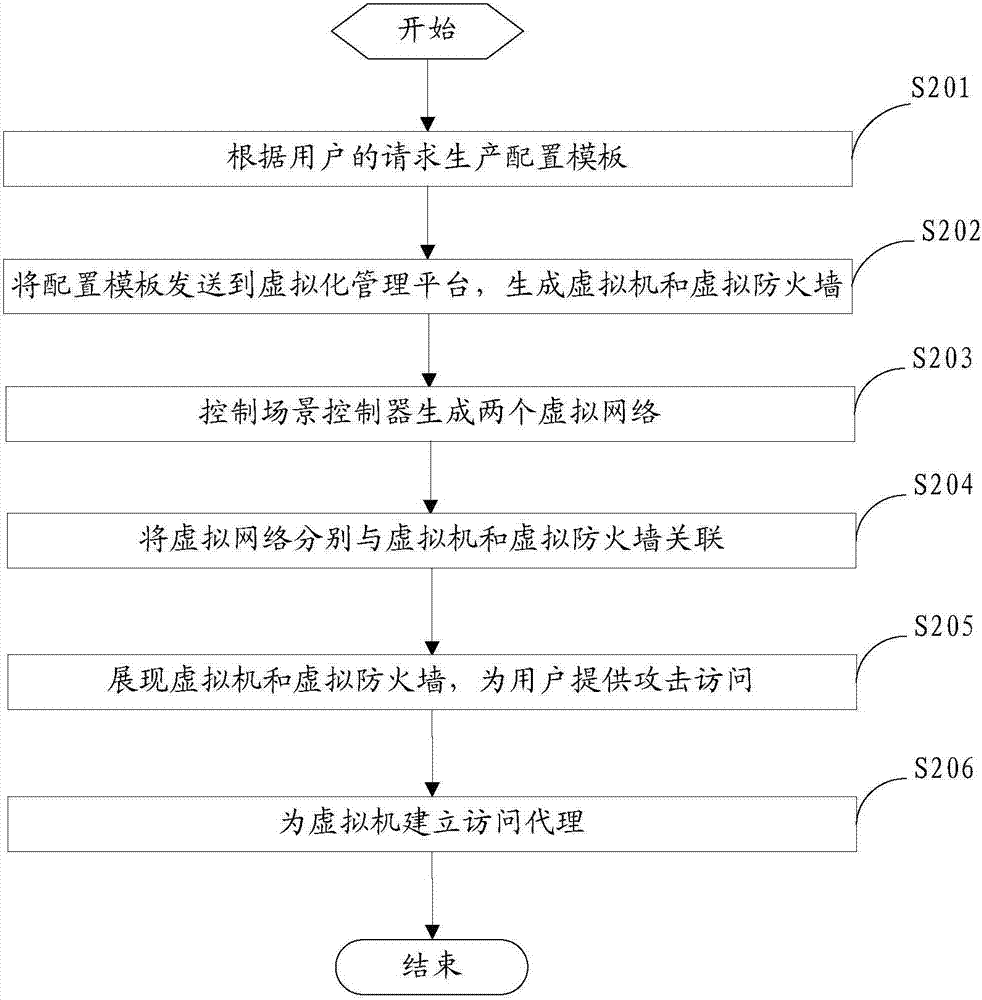
[0062] figure 2 A step flow chart of another embodiment of an attack prevention drill method provided for the invention.
[0063] Such as figure 2 As shown, the attack protection exercise method provided in this embodiment is applied to a network attack and defense laboratory, specifically, it is applied to a scene controller of an attack and defense exercise system in a network attack and defense laboratory, and is used to display firewalls or IPS in a simulated attack and defense exercise. For the protection effect, in this embodiment, cracking dvwa xss on owasp bwa is taken as an example. The attack protection drill method includes the following steps:
[0064] S201: Produce a configuration template according to the user's request.
[0065] When an offensive and defensive rehearsal is required, the user can send a corresponding offensive and defensive request to the scene controller. At this time, the scene controller produces a corresponding configuration template according to ...
Embodiment 3
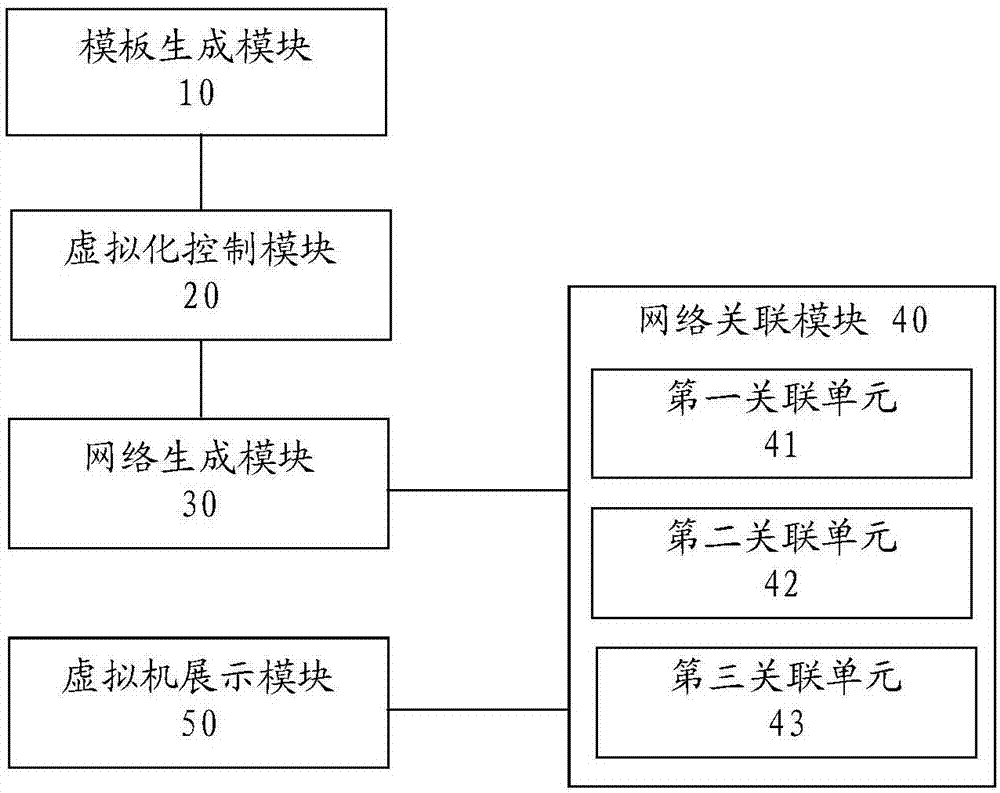
[0082] image 3 A structural block diagram of an embodiment of an attack protection drill device provided for the invention.
[0083] Such as image 3 As shown, the attack protection exercise device provided in this embodiment is applied to a network attack and defense laboratory, specifically, it is applied to a scene controller of an offense and defense exercise system in a network attack and defense laboratory, and is used to display firewalls or IPS in a simulated attack and defense exercise. For the protection effect, in this embodiment, cracking dvwa xss on owasp bwa is taken as an example. The attack protection drill device includes a template generation module 10, a virtualization control module 20, a network generation module 30, a network association module 40, and a virtual machine display module 50.
[0084] The template generation module is used to produce configuration templates according to user requests.
[0085] When an offensive and defensive rehearsal is required, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com