Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
472 results about "Virtual target" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
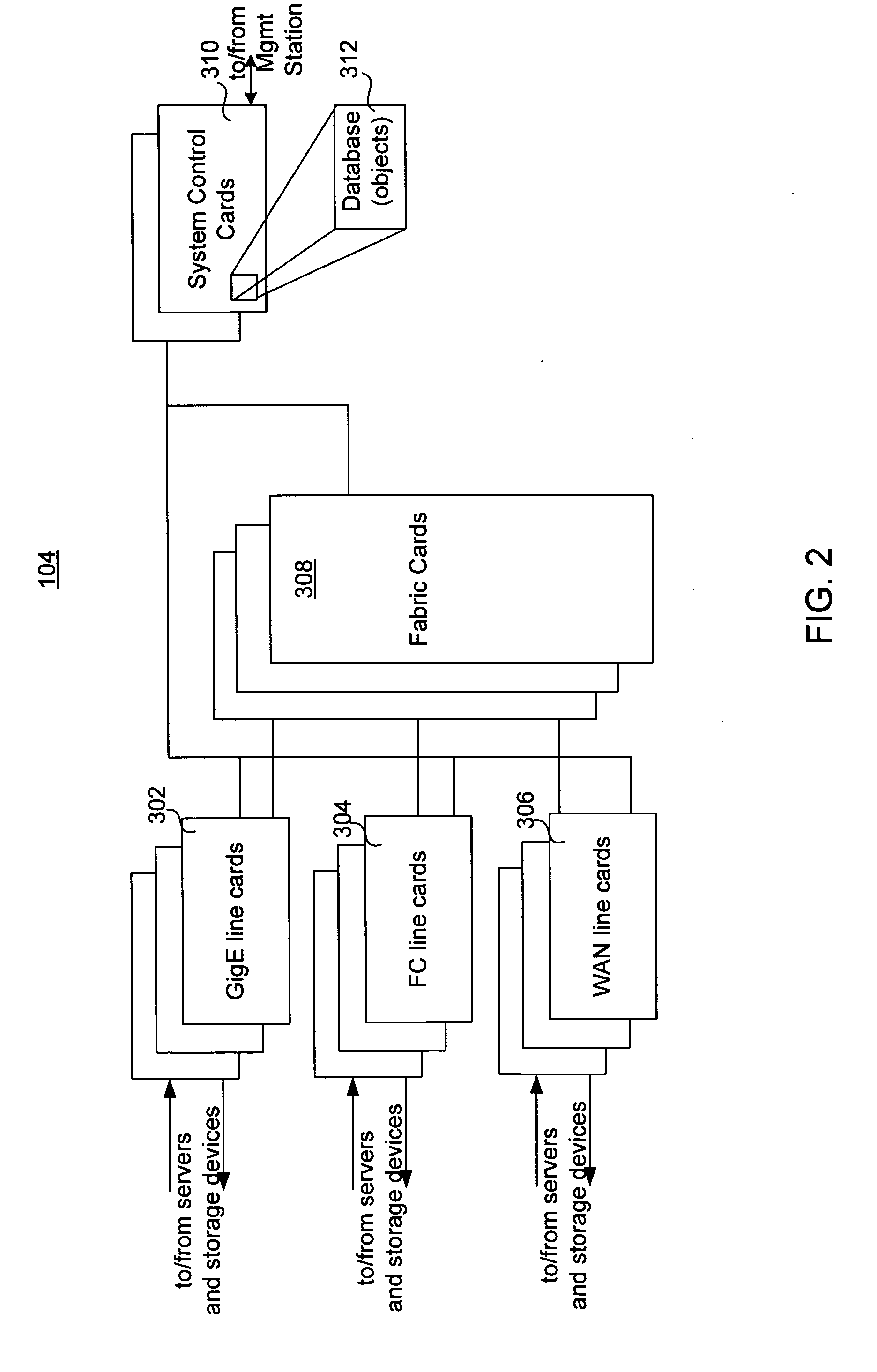
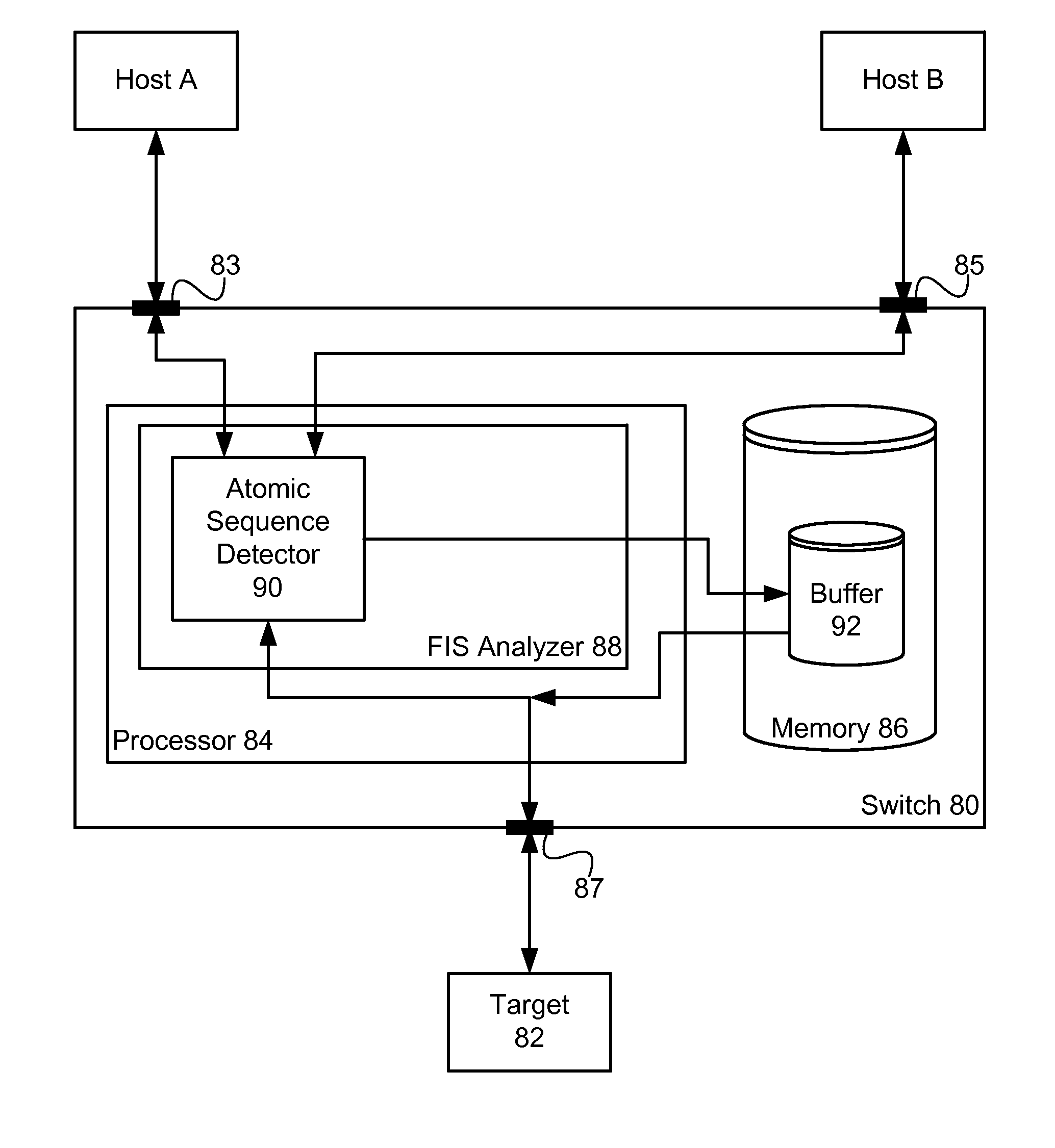
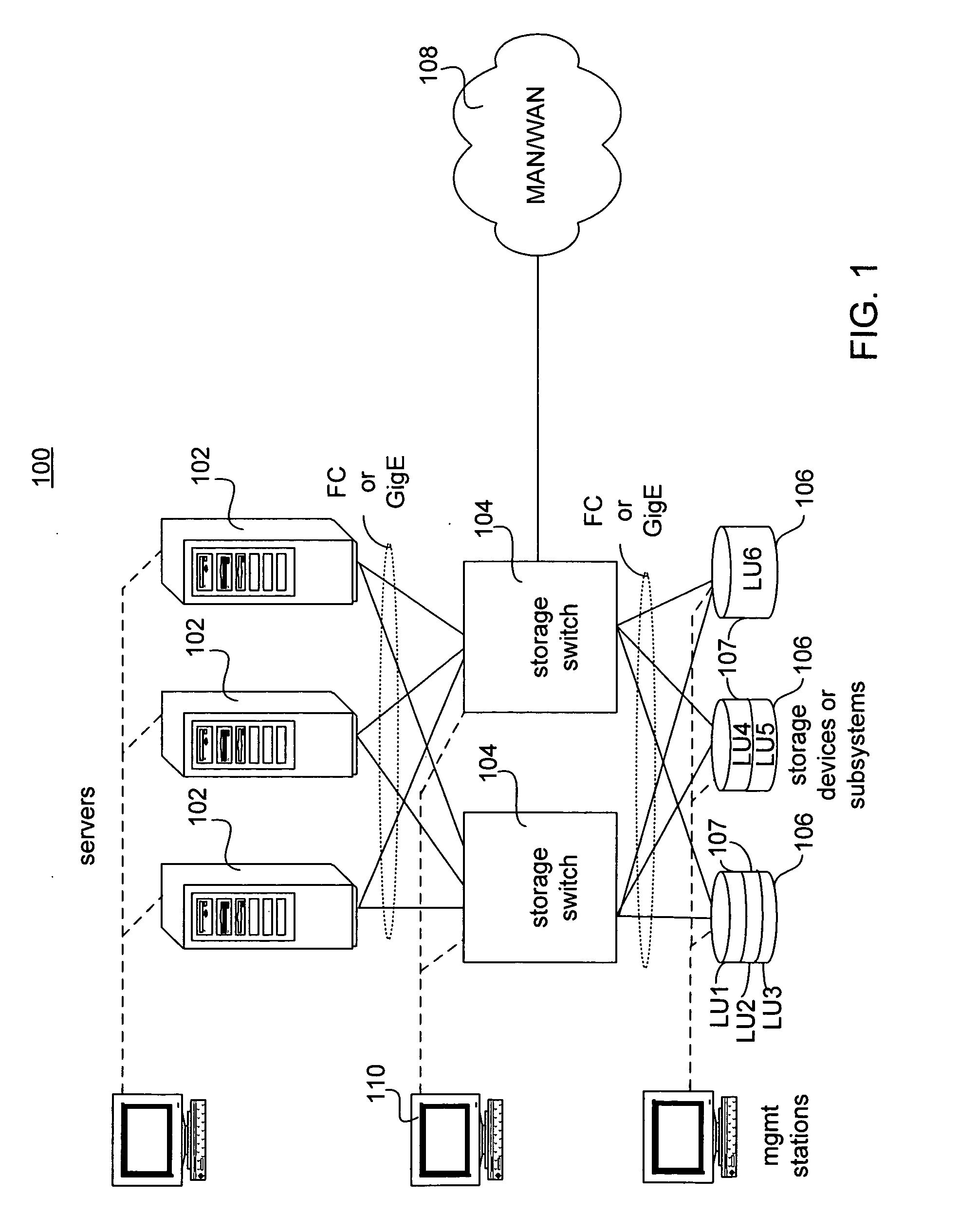
Apparatus for performing storage virtualization
ActiveUS20070239944A1Simplify writingIncrease overheadError detection/correctionMemory adressing/allocation/relocationVirtual targetData management
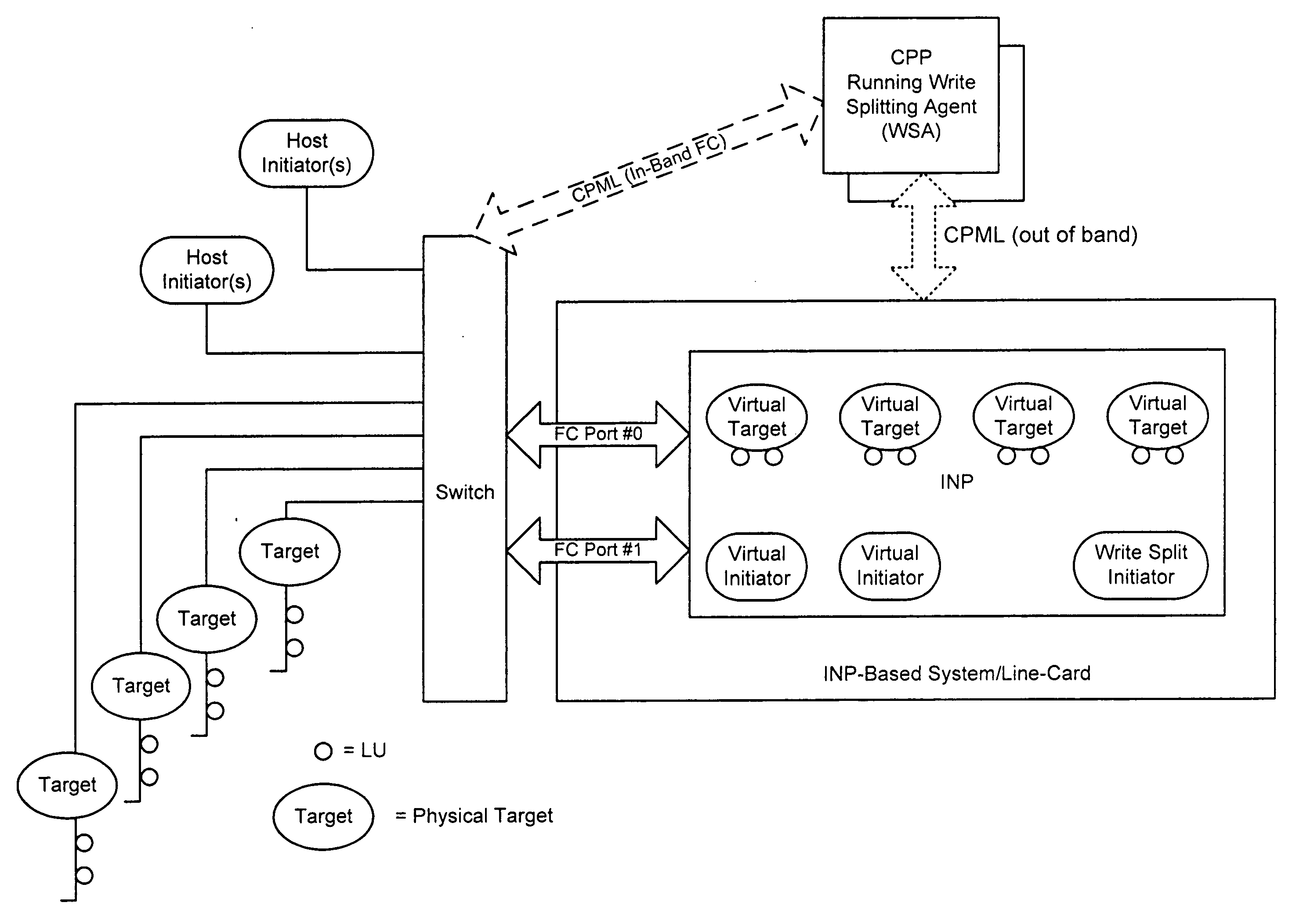
The splitting of storage applications and functions into a control path (CP) component and a data path (DP) component is disclosed. Reads and writes may be handled primarily in the DP. The CP may be responsible for discovery, configuration, and exception handling. The CP can also be enabled for orchestrating complex data management operations such as snapshots and migration. Storage virtualization maps a virtual I / O to one or more physical I / O. A virtual target (vTarget) in the virtual domain is associated with one physical port in the physical domain. Each vTarget may be associated with one or more virtual LUNs (vLUNs). Each vLUN includes one or more vExtents. Each vExtent may point to a region table, and each entry in the region table may contain a pointer to a region representing a portion of a pExtent, and attributes (e.g. read / write, read only, no access) for that region.
Owner:AVAGO TECH INT SALES PTE LTD
Configuring vm and io storage adapter vf for virtual target addressing during direct data access
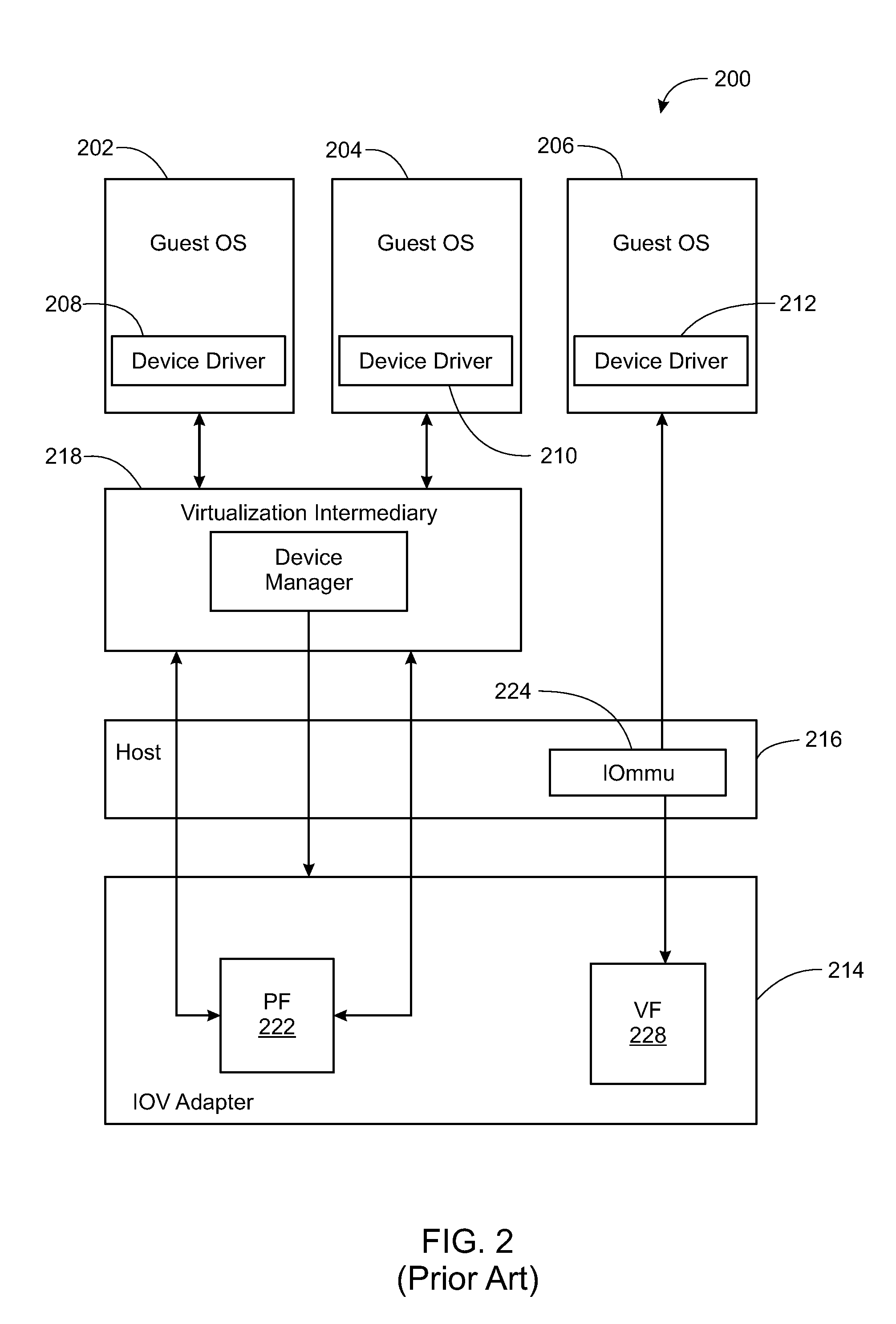
ActiveUS20110179414A1Multiprogramming arrangementsSoftware simulation/interpretation/emulationVirtualizationVirtual target
A method is provided for use in a system that includes a host computing machine configured to implement a virtualization intermediary and that includes a physical storage adapter, the configures a virtual machine (VM) and a virtual function (VF) to support IO operations to physical storage through a direct IOV path to the VF of the physical storage adapter, the method comprises: creating by the virtualization intermediary mapping information that includes a first mapping between virtual disks and physical regions of physical storage and that includes a second mapping between virtual disks and virtual disk addresses; transmitting the mapping information from the virtualization intermediary over the physical storage adapter from a physical function (PF) of the physical storage adapter to the VF; associating a virtual port with the mapping information within the virtualization intermediary; binding the virtual port to the VF; communicating virtual disk addresses indicated within the second mapping within the transmitted mapping information for the allocated virtual disks to the VM.
Owner:VMWARE INC
Apparatus and methods for facilitating data tapping with host clustering in a storage area network
InactiveUS20070011424A1Memory loss protectionData switching by path configurationVirtual targetStorage area network
Owner:CISCO TECH INC
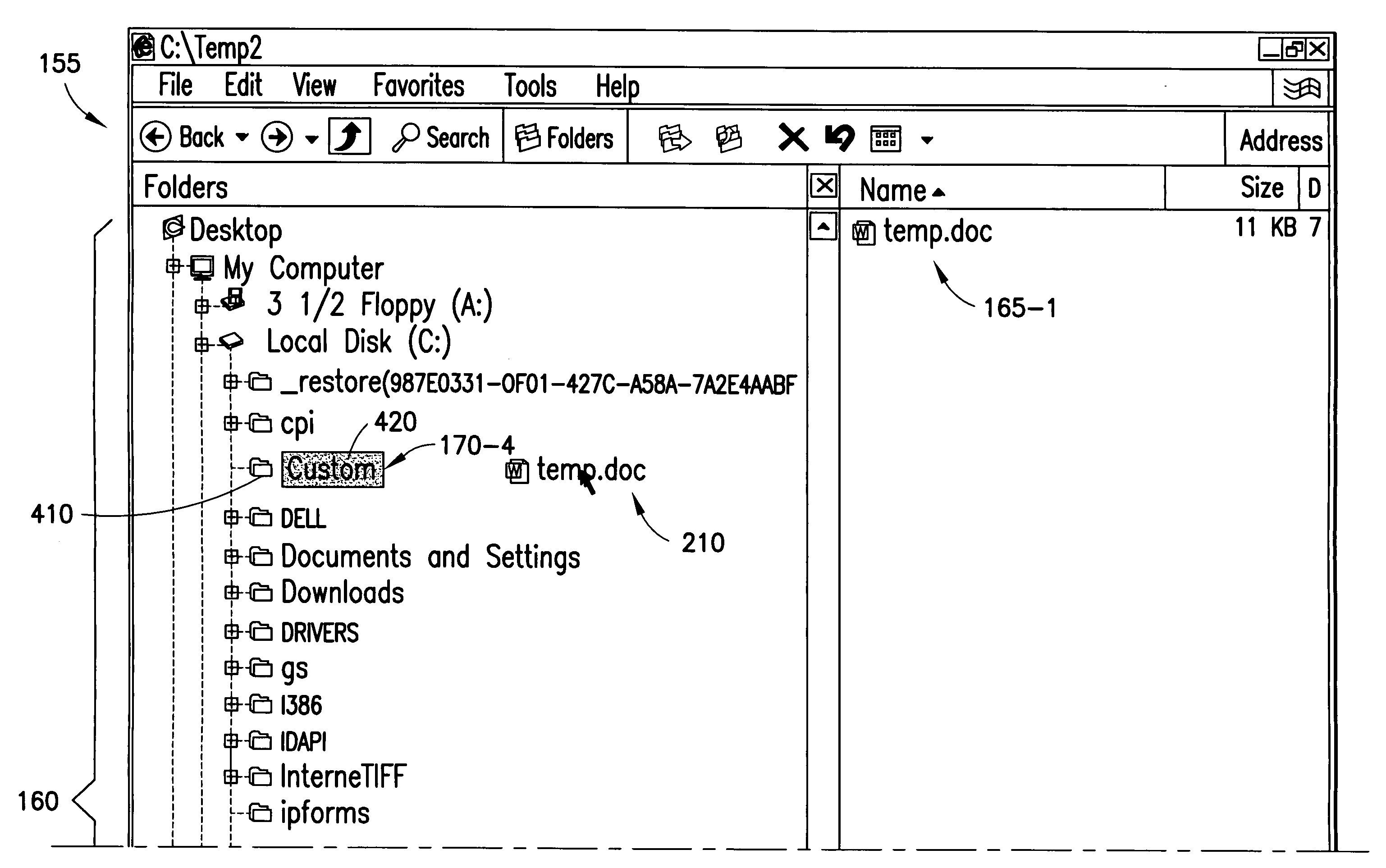
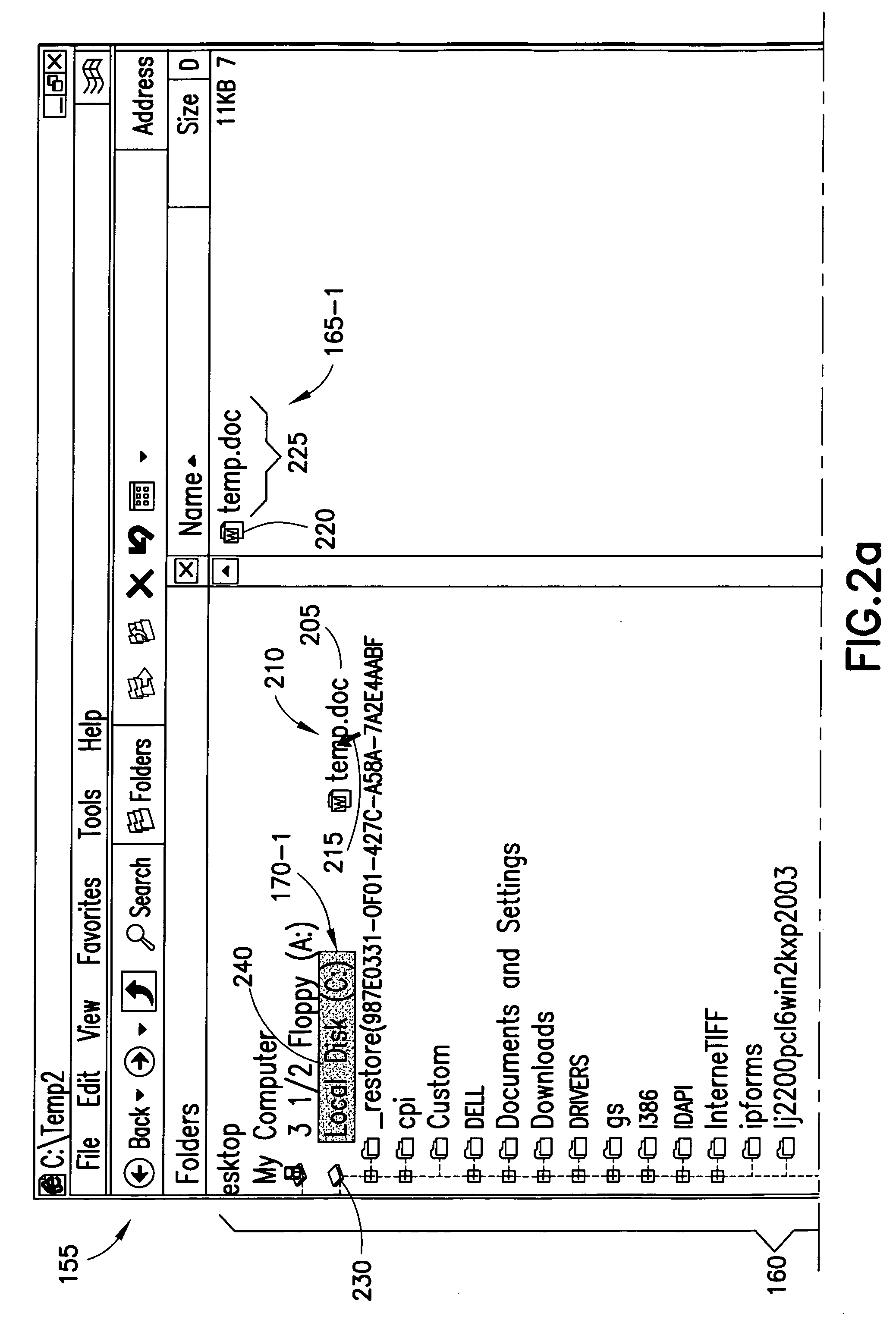
Creating virtual targets in directory structures
ActiveUS20080040668A1File/folder operationsSpecial data processing applicationsVirtual targetDirectory structure
A method includes detecting a first user operation corresponding to a first item in a directory structure. The directory structure represents a hierarchical arrangement of a plurality of items, including the first item, in a memory. The first user operation indicates a start of an item action with the first item. The method also includes, in response to detecting a second user operation corresponding to a second item in the directory structure, creating a virtual target in the second item in the directory structure. The virtual target is a possible location for completion of the item action with the first item. The method further includes, in response to a third user operation indicating completion of the item action with the first item in the virtual target, completing the item action with the first item in the virtual target.
Owner:NOKIA TECHNOLOGLES OY
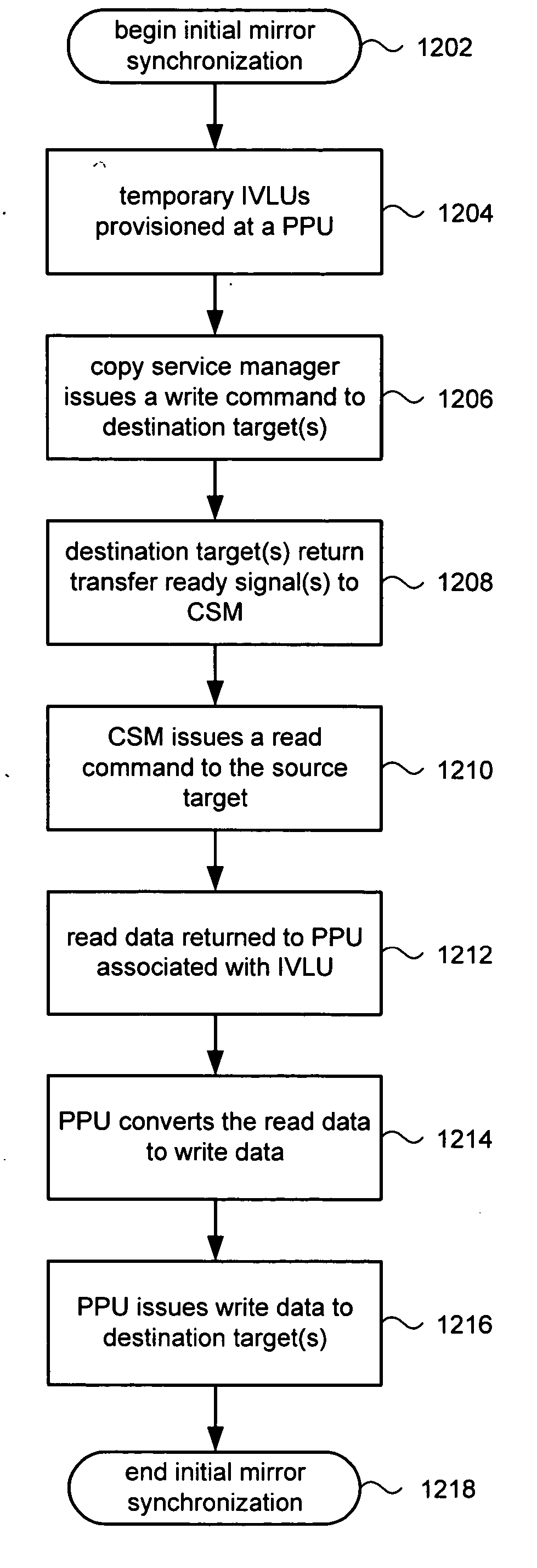
Online initial mirror synchronization and mirror synchronization verification in storage area networks
ActiveUS20060036648A1Unauthorized memory use protectionSpecial data processing applicationsVirtual targetStorage area network
Systems and methods in accordance with various disclosed embodiments can manage a mirrored virtual target to synchronize the members of the virtual target and / or to verify that the members of the virtual target are synchronized. In one embodiment, a mirrored virtual target is synchronized by first provisioning at least one first internal virtual logical unit (IVLU) corresponding to at least one destination target of the mirrored target and a second IVLU corresponding to a source target of the mirrored target. A write command is first issued, via one or more internal virtual logical units, to each of the destination target members of the mirrored target. When each destination target is available to receive data, as evidenced by a returned transfer ready signal, a read command is provided to the source target via the second internal virtual logical unit. In this manner, a data path between the source and destination targets is established prior to reading data from the source target. Accordingly, the data can be read from the source target, converted to write data, and routed to the destination targets at line speed without buffering of the data. A similar process is provided to verify that the members of a mirrored target are synchronized. In one embodiment, a system and method is provided to manage incoming commands for the mirrored target while synchronizing or verifying synchronization of the mirrored target. Incoming commands can be queued as they are received and provided to the mirrored target when pending synchronization or verification commands are completed.
Owner:EMC IP HLDG CO LLC
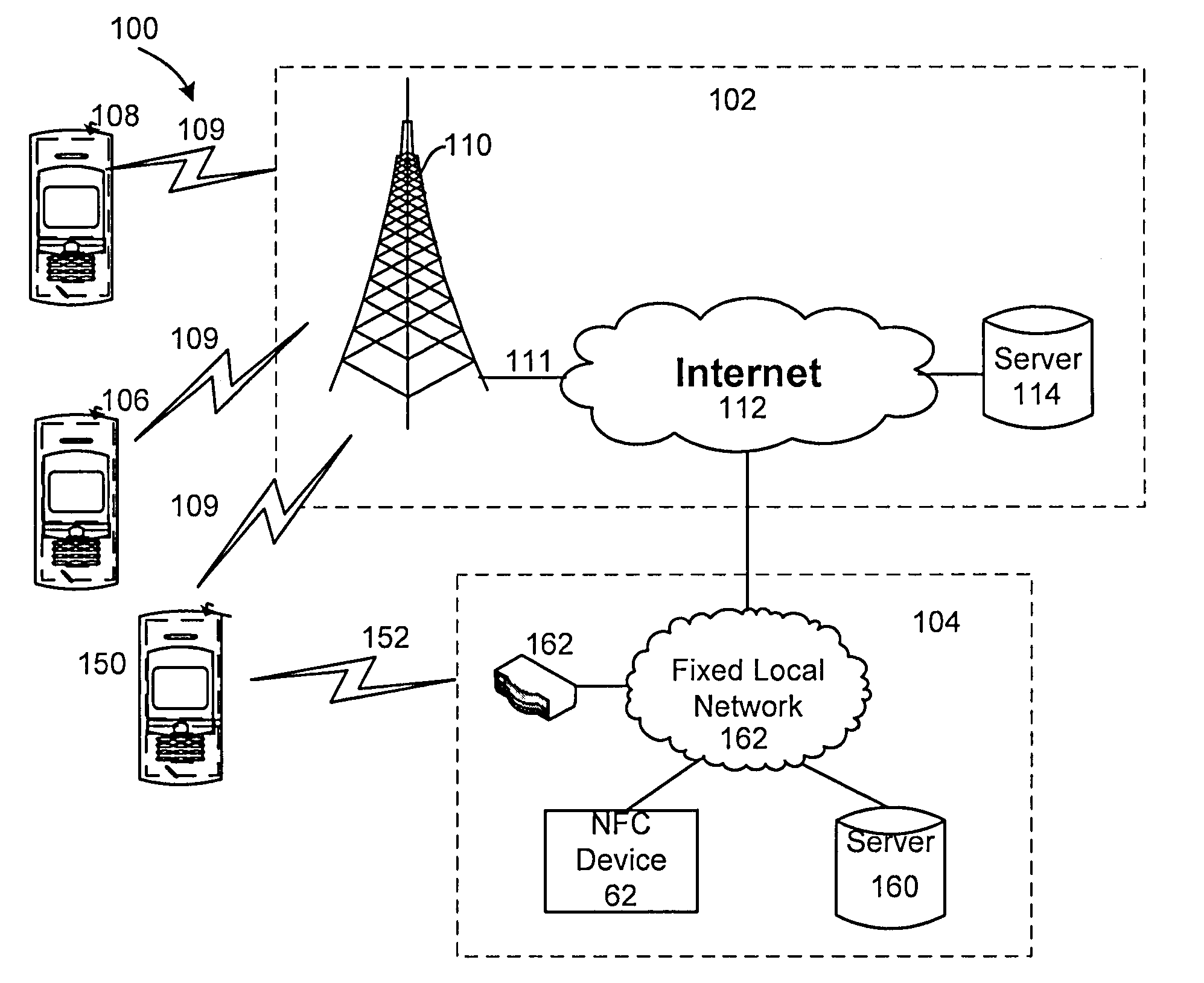
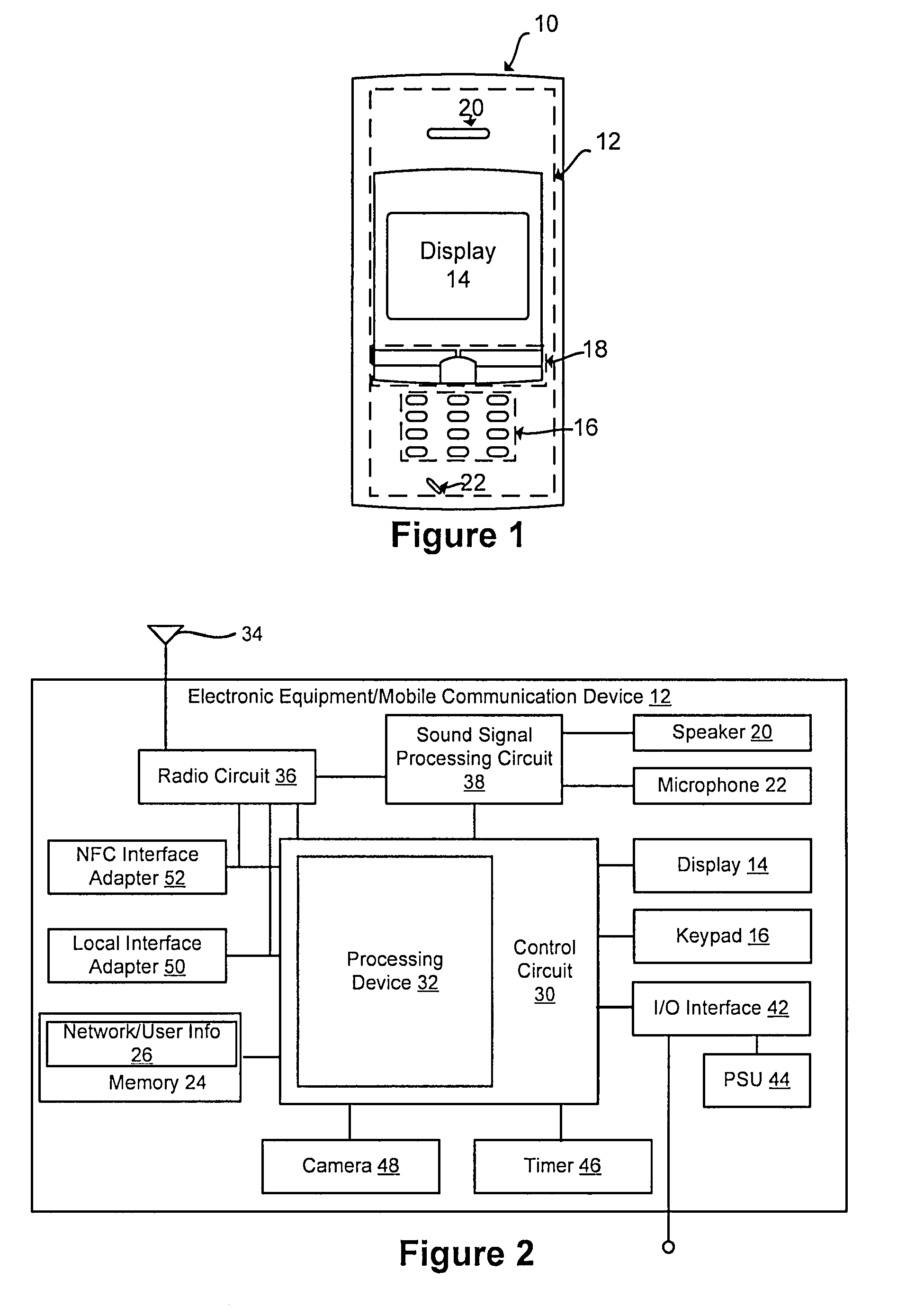
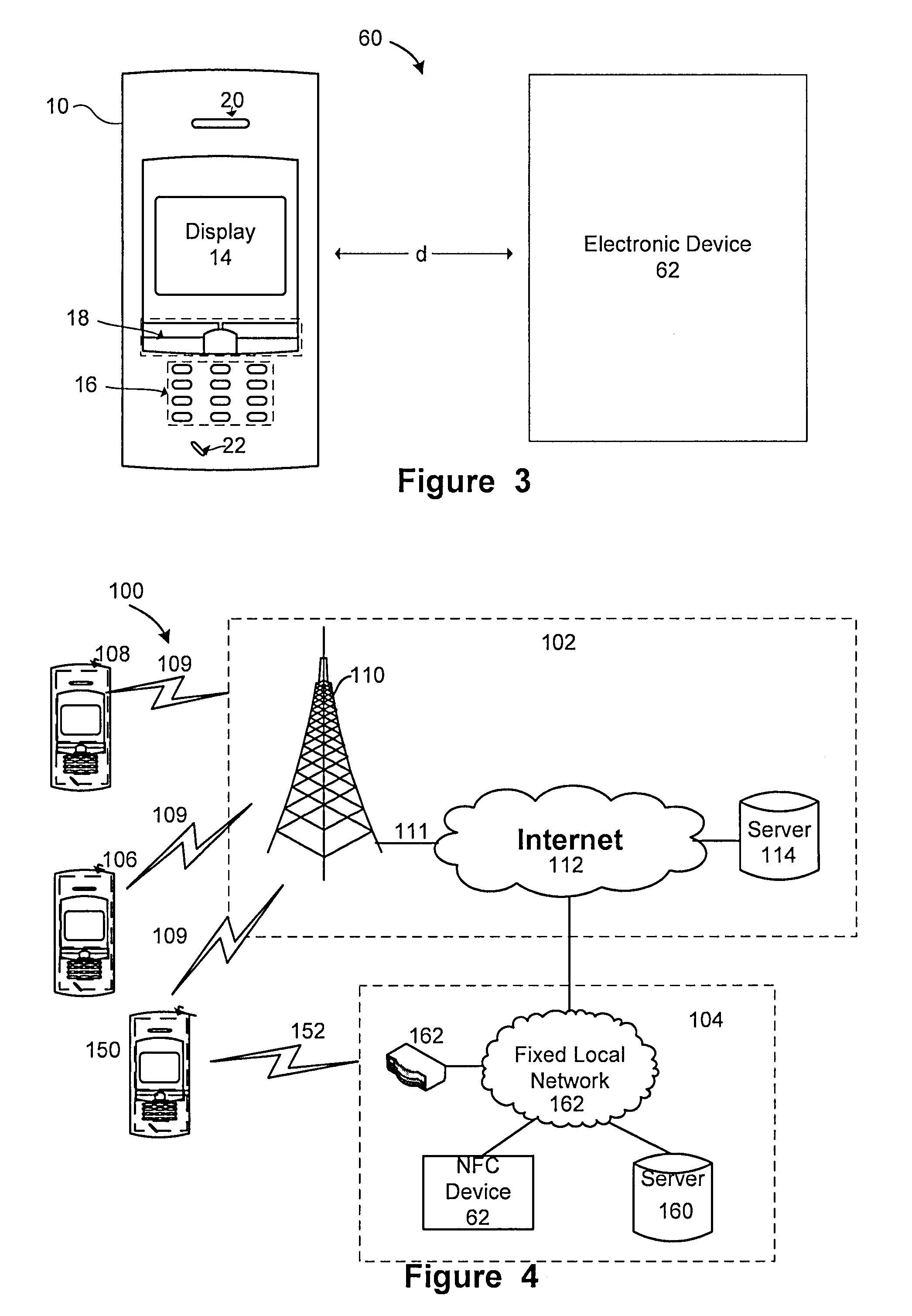
Near field communication for profile change in switching network acess
Disclosed is a system and method that utilizes near field communications (NFC) for establishing and / or controlling the routing of communications in a fixed mobile convergence environment. Electronic equipment is provided with an NFC adapter and a storage element (e.g., memory, disk drive, etc.) that has user's identity specific information (e.g., user's identity information, social security number, user's identity identification number, virtual target network (VPN) settings, etc.) stored in a suitable electronic format for transmission to a NFC reader that is coupled to a fixed local network (e.g., corporate enterprise network). The fixed local network authenticates the user and fixed mobile convergence is realized between a wide area communication network and the fixed local area network.
Owner:SONY ERICSSON MOBILE COMM AB
Coordinating processing for request redirection
ActiveUS8909980B1Redundant hardware error correctionInput/output processes for data processingVirtual targetVirtualization
Described are techniques for coordinating processing to redirect requests. First and second storage processors of a data storage system are provided. Requests are directed to a first set of physical target ports of the first storage processor. The second storage processor is unavailable and has a second set of virtual target ports. Each virtual port of the second set is virtualized by a physical port of the first set. First processing is performed to redirect requests from the second set of virtual ports to a third set of physical ports of the second storage processor. First processing includes booting the second storage processor, directing requests to the third set of physical ports of the second storage processor rather than second set of virtual ports, and queuing requests received at the third set of physical ports until completion of pending requests previously received at the second set of virtual ports.
Owner:EMC IP HLDG CO LLC
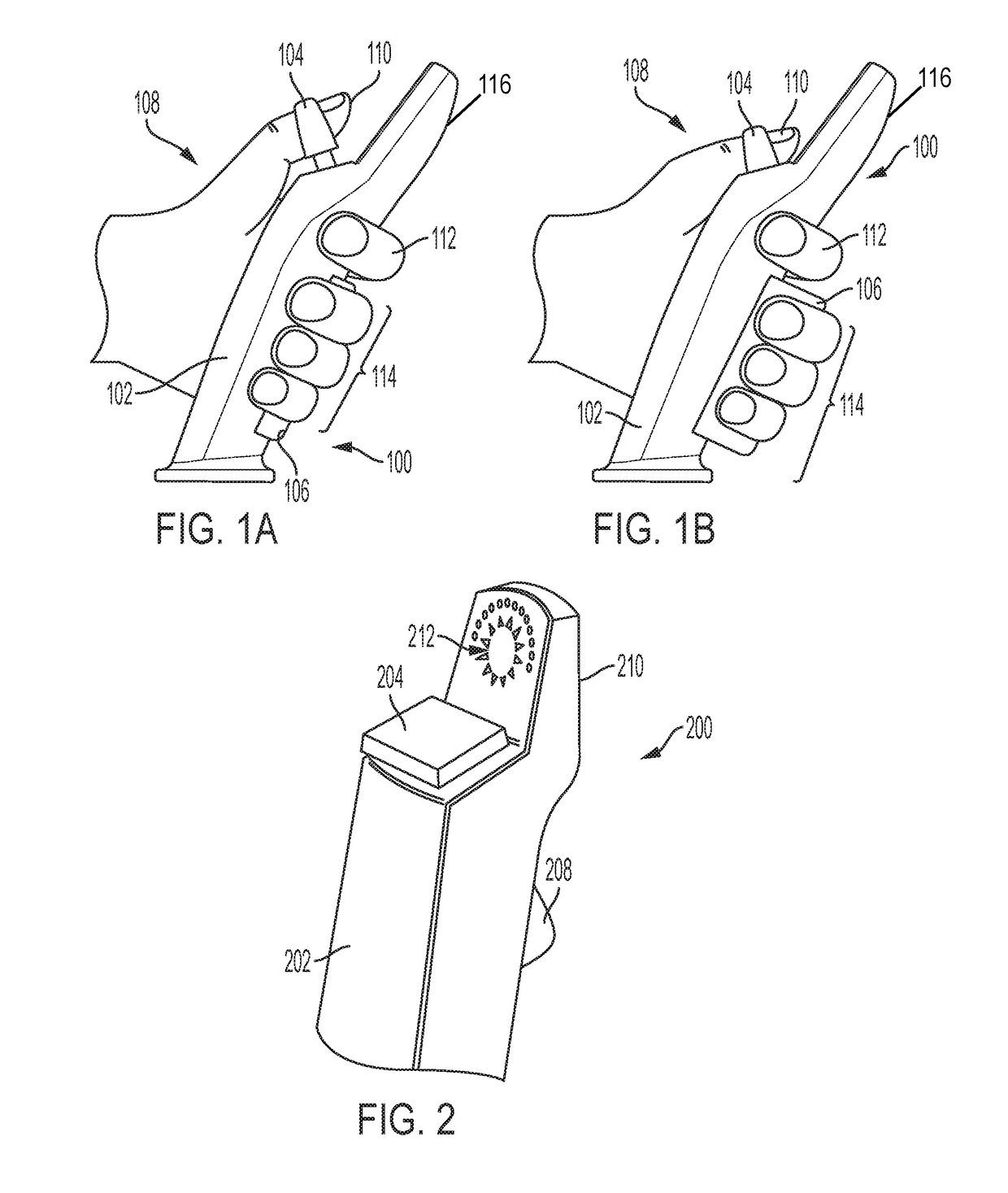
Controller with Situational Awareness Display
ActiveUS20190042003A1Visible signalling systemsVehicle position/course/altitude controlGraphicsVirtual target
A hand controller for commanding or controlling a target, such as a remote vehicle or a virtual target, includes a display mounted on a free end of a joystick for indicating graphically a direction of the remote vehicle from the hand controller and an orientation of the target relative to the hand controller's frame of reference, based on the location and orientation of the target received by the hand controller from the target and the location and orientation of the hand controller.
Owner:FLUIDITY TECH INC
Path planning for evasive steering maneuver in presence of target vehicle and surrounding objects
A method for calculating a virtual target path around a target object that includes providing scan points identifying detected objects and separating the scan points into target object scan points and other object scan points. The method identifies a closest scan point from the target object scan points and identifies a path point that is a predetermined safe distance from the closest scan point. The method determines a straight target line adjacent to the target object that goes through the path point, and determines a distance between the target line and each of the other objects and determines whether all of the distances are greater than a predetermined threshold distance. The method identifies curve points for each other object whose distance is less than the predetermined threshold distance, and identifies a curve path that connects the curve points to be the virtual target path using a quadratic polynomial function.
Owner:GM GLOBAL TECH OPERATIONS LLC
WLAN background scanning
InactiveUS20060171304A1Shorten the construction periodAvoid disruptionError preventionTransmission systemsVirtual targetComputer science
A wireless access point is operable to execute background scans of alternate channels by tuning to the alternate channel for short periods of time, thereby generating sub-windows of data. The sub-windows are calculated to have timing and duration that avoid disruption of communications on the active channel. Multiple background scan sub-windows are used to assemble a virtual target window of the alternate channel, e.g., a 100 mSec window, during which any periodic beacon within range might be expected to be received. The data such as beacon information is employed to generate a table ranking the alternate channels in terms of viability for communications.
Owner:PICCATA FUND LIABILITY
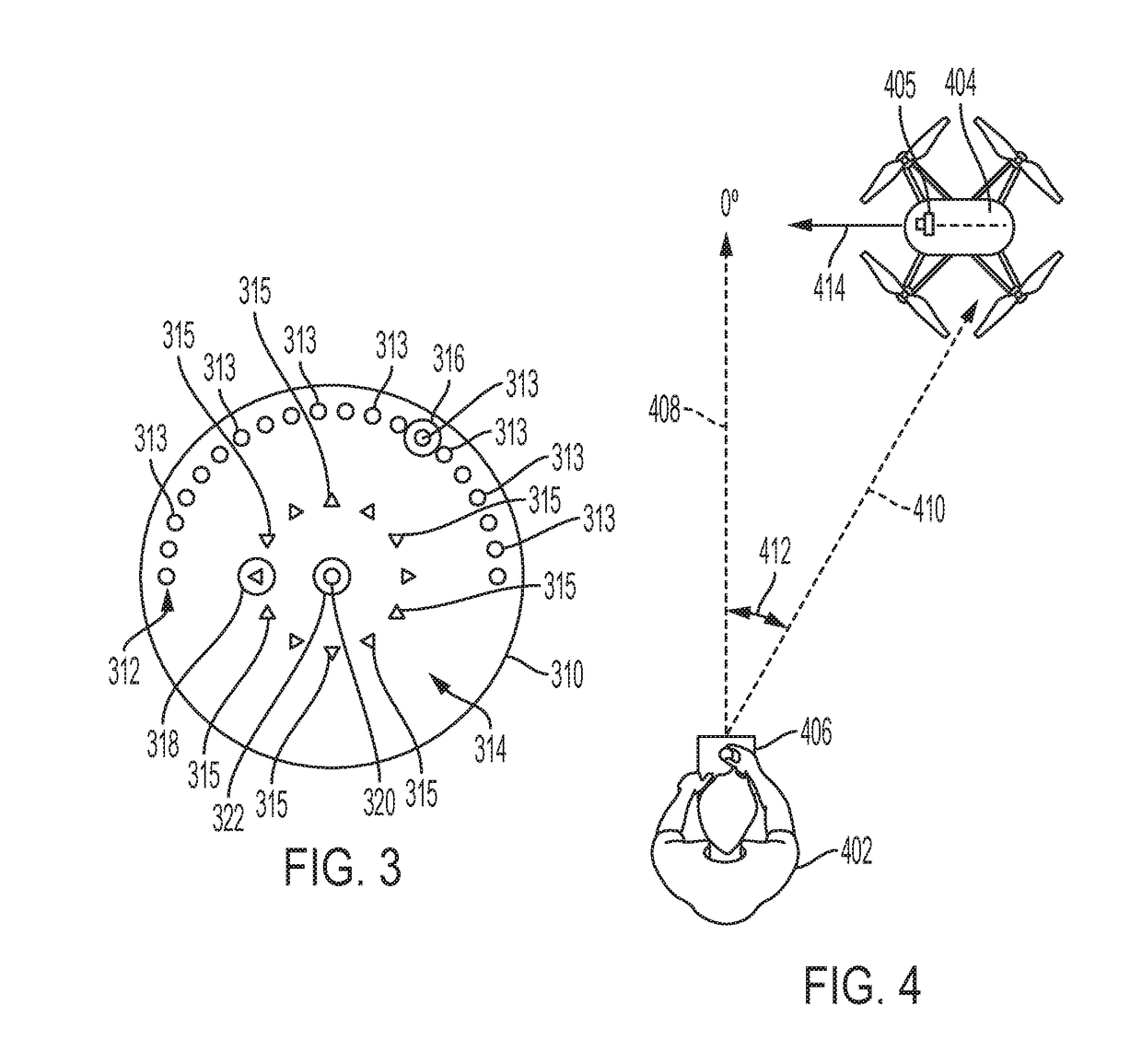
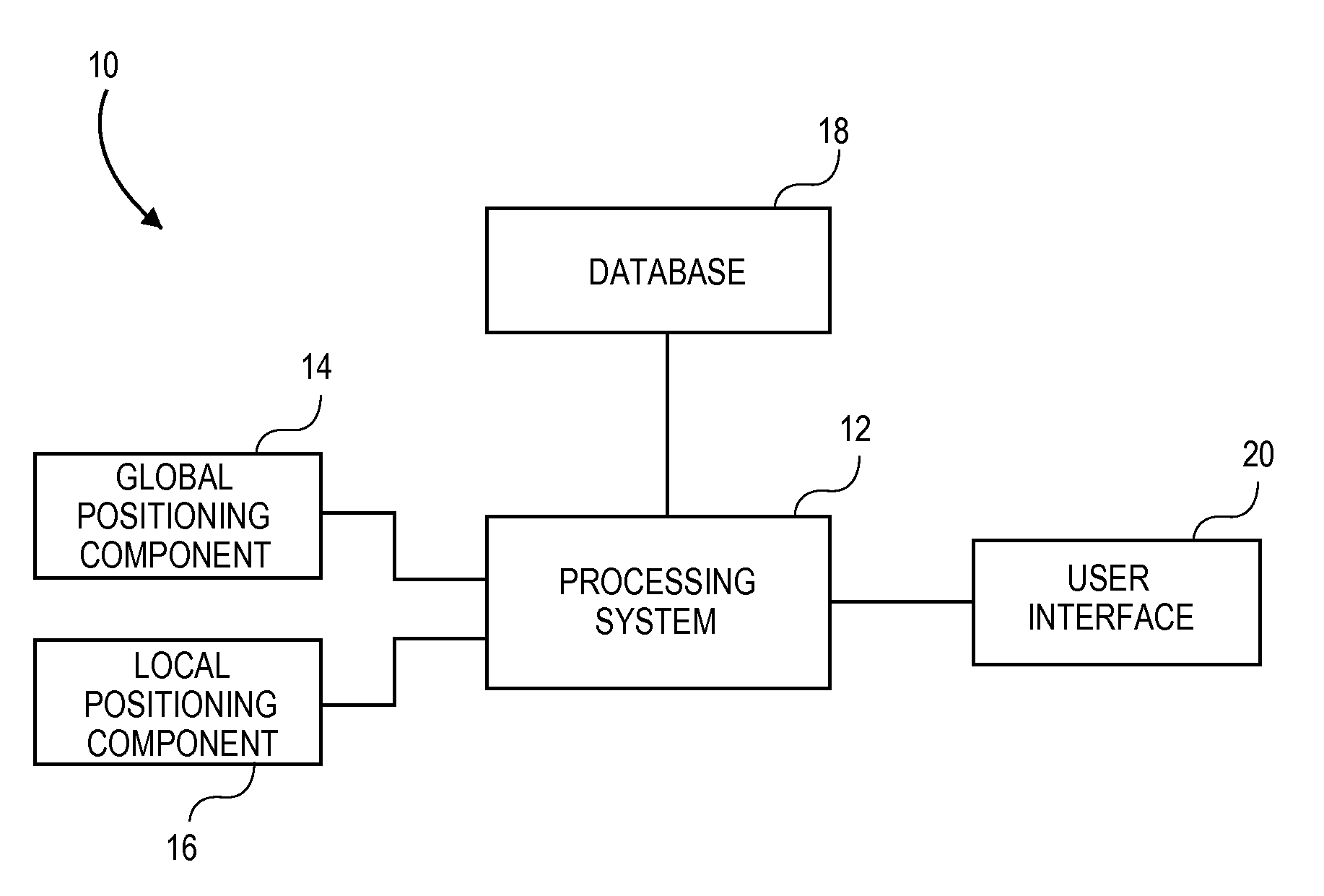
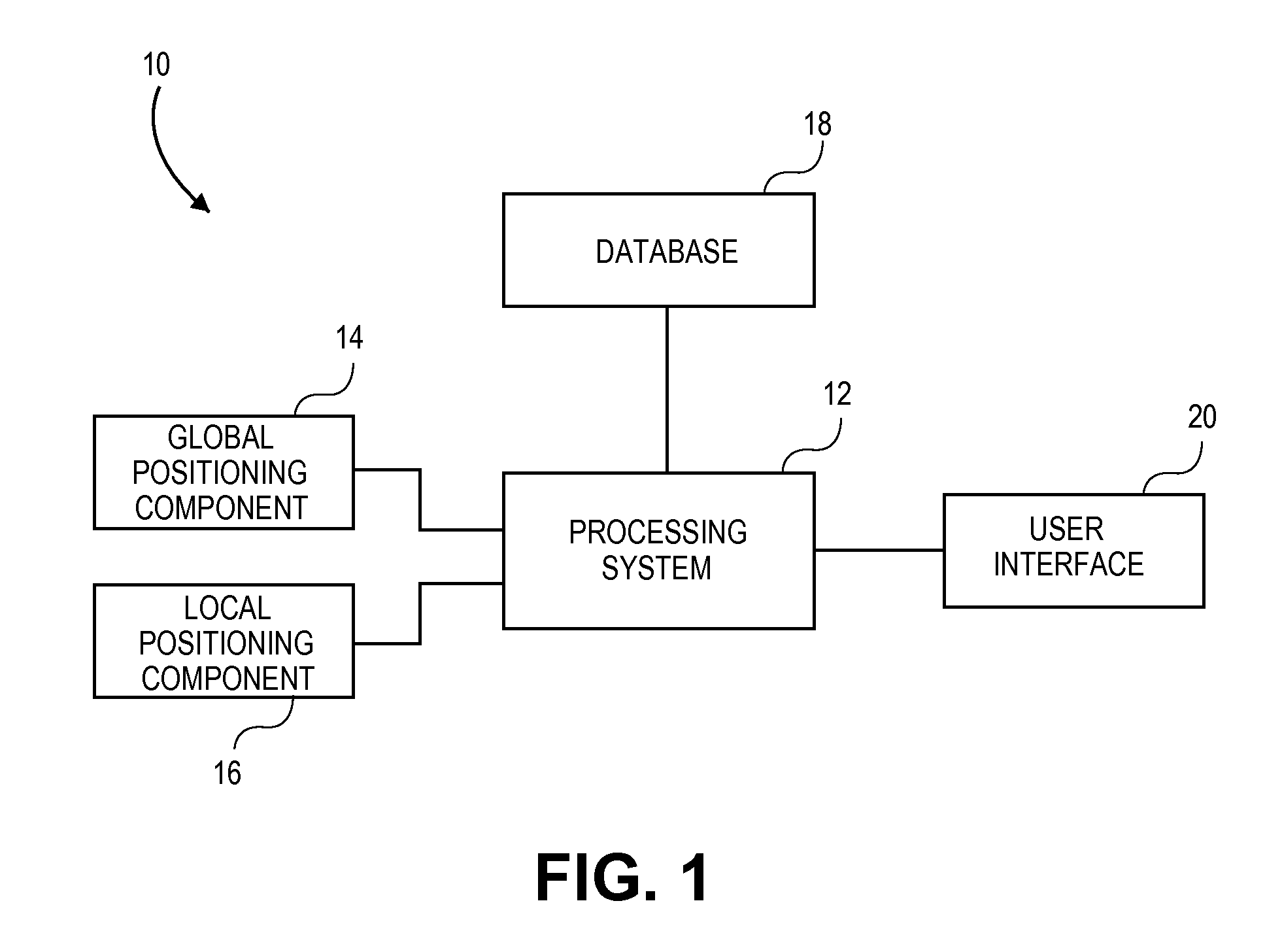
System and method of assisted aerial navigation
ActiveUS8035547B1Enhanced Situational AwarenessAnalogue computers for trafficRoad vehicles traffic controlVirtual targetAviation
A system and method of providing aerial navigation. Techniques are described for receiving global positioning system data, receiving local positioning system data such as instrument landing system data, generating a virtual target flight path using the global positioning system data and the local positioning system data, and presenting a virtual target flight path indicator corresponding to the virtual target flight path. In one implementation, the system includes a user interface, a global positioning component, a local positioning component, and a processing system.
Owner:GARMIN INT
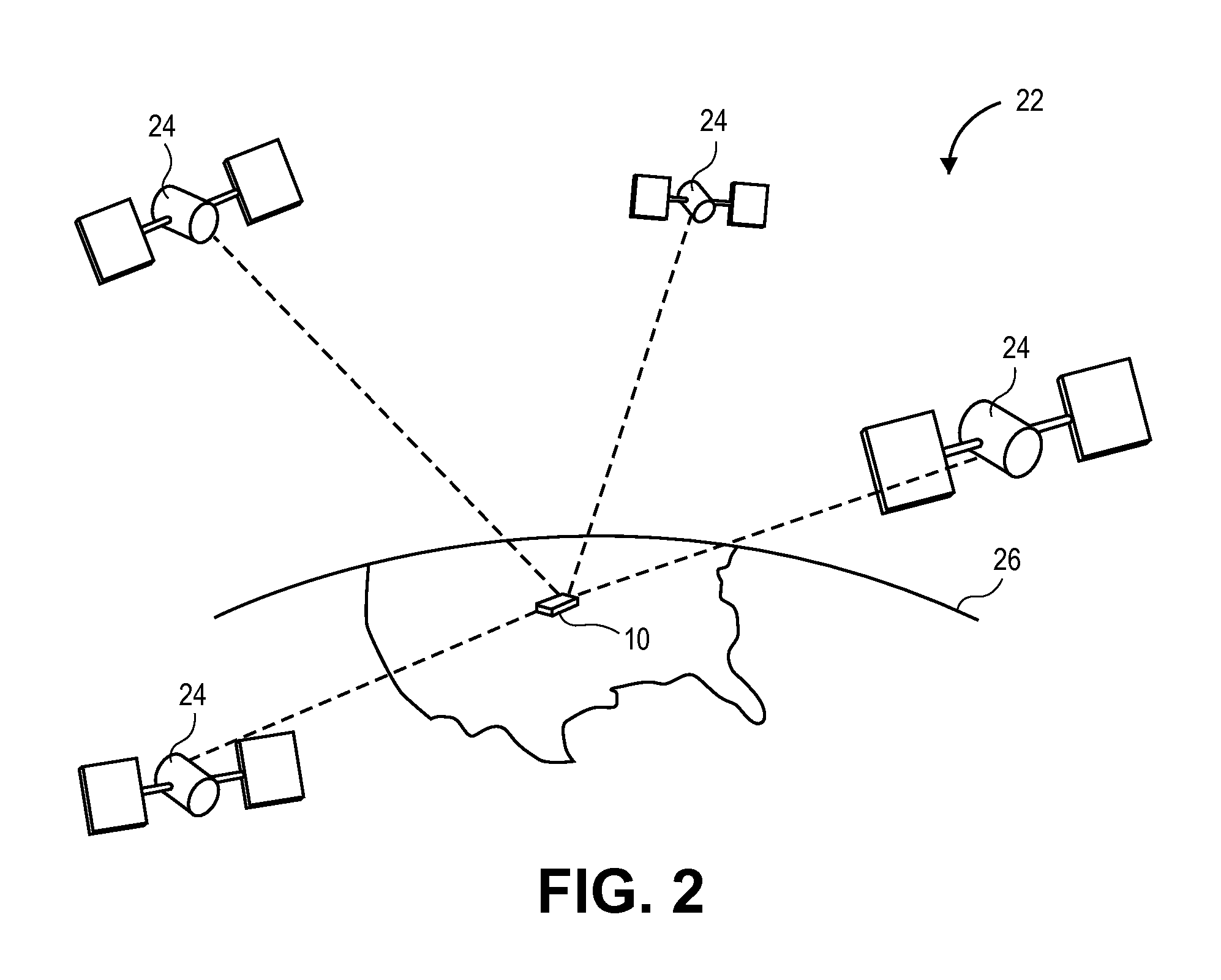
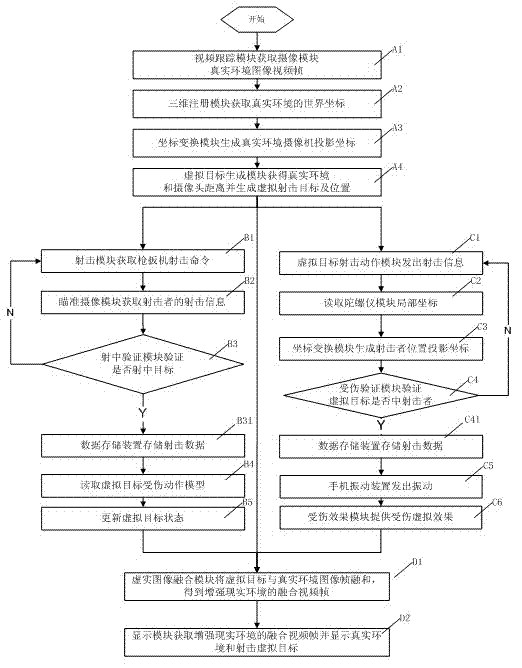
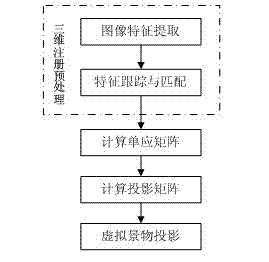
Individual light weapon shooting training method and system by using augmented reality technology
ActiveCN102735100AImprove accuracyImprove real-time performanceTraining adaptationVirtual targetFeedback effect
Owner:CHONGQING UNIV OF POSTS & TELECOMM
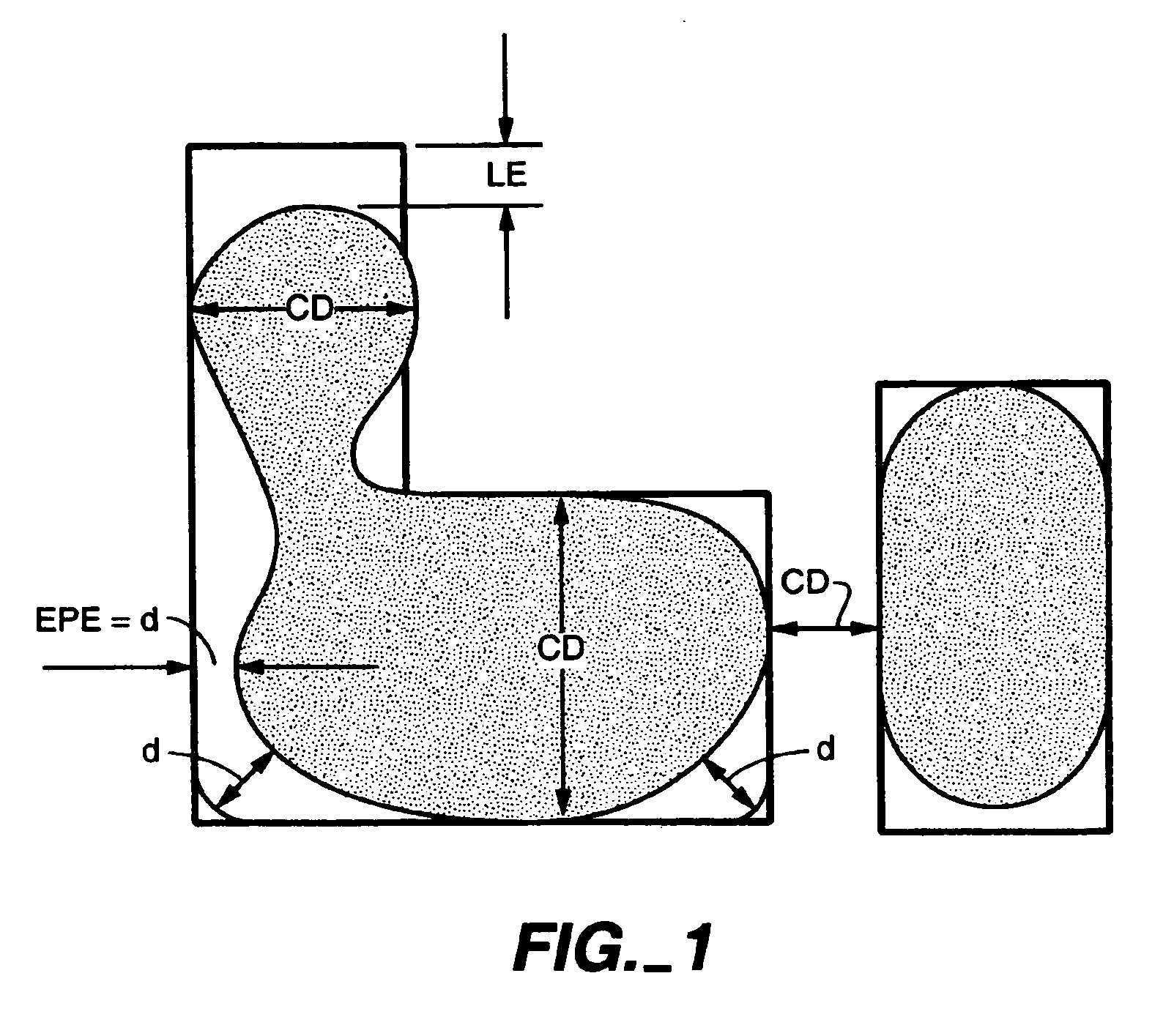
Method for post-OPC multi layer overlay quality inspection
A method for performing post-optical proximity correction (OPC) multi layer overlay quality inspection includes the steps of generating a virtual target mask for a first mask and a second mask overlay using design rules at least partially defining the relationship between the first mask and the second mask; creating a composite aerial image representing a first mask image formed from the first mask and a second mask image formed by the second mask by performing imaging of the first mask and the second mask and overlaying the second mask image onto the first mask image; generating an overlay image map of the composite aerial image using the design rules at least partially defining the relationship between the first mask and the second mask; and comparing the overlay image map area and the virtual target mask area.
Owner:BELL SEMICON LLC
Method for assessing and managing security risk for systems
A method, programmed digital computer and computer program product for assessing and managing security risks in an iterative fashion is provided. The invention is adaptable for use with any system with security targets that are accessible to a security threat. The invention is applicable to all systems with physical, electronic and virtual targets that can be accessed by a threat, thus creating a risk to the system, e.g., systems surrounding hospitals, blood banks, mass transit operations, power production and transmission facilities, communication systems, internet service providers, email and web hosting service providers, electronic commerce, financial institutions and school district lunch programs. Under the invention, if a security threat can access a security target within a system then a risk to the system is present. The invention provides an iterative process by which the system may be analyzed as an undivided whole or may, alternatively, be divided into discrete sections where all known security targets are identified within each section. All threats to each individual target are then identified and it is determined whether each threat has access to the associated target. If access is present, a qualitative or quantitative risk level is assigned. Then, appropriate countermeasures are considered and, where appropriate, implemented if the risk level is unacceptably high. A second inquiry is made regarding whether the particular threat has access to its identified target, considering the implemented countermeasure(s), and a second risk level assignment performed. If the risk level remains high, the process is repeated until the risk level for the subject target is acceptably low. All remaining targets are secured in this manner.
Owner:TRAP IT SECURITY
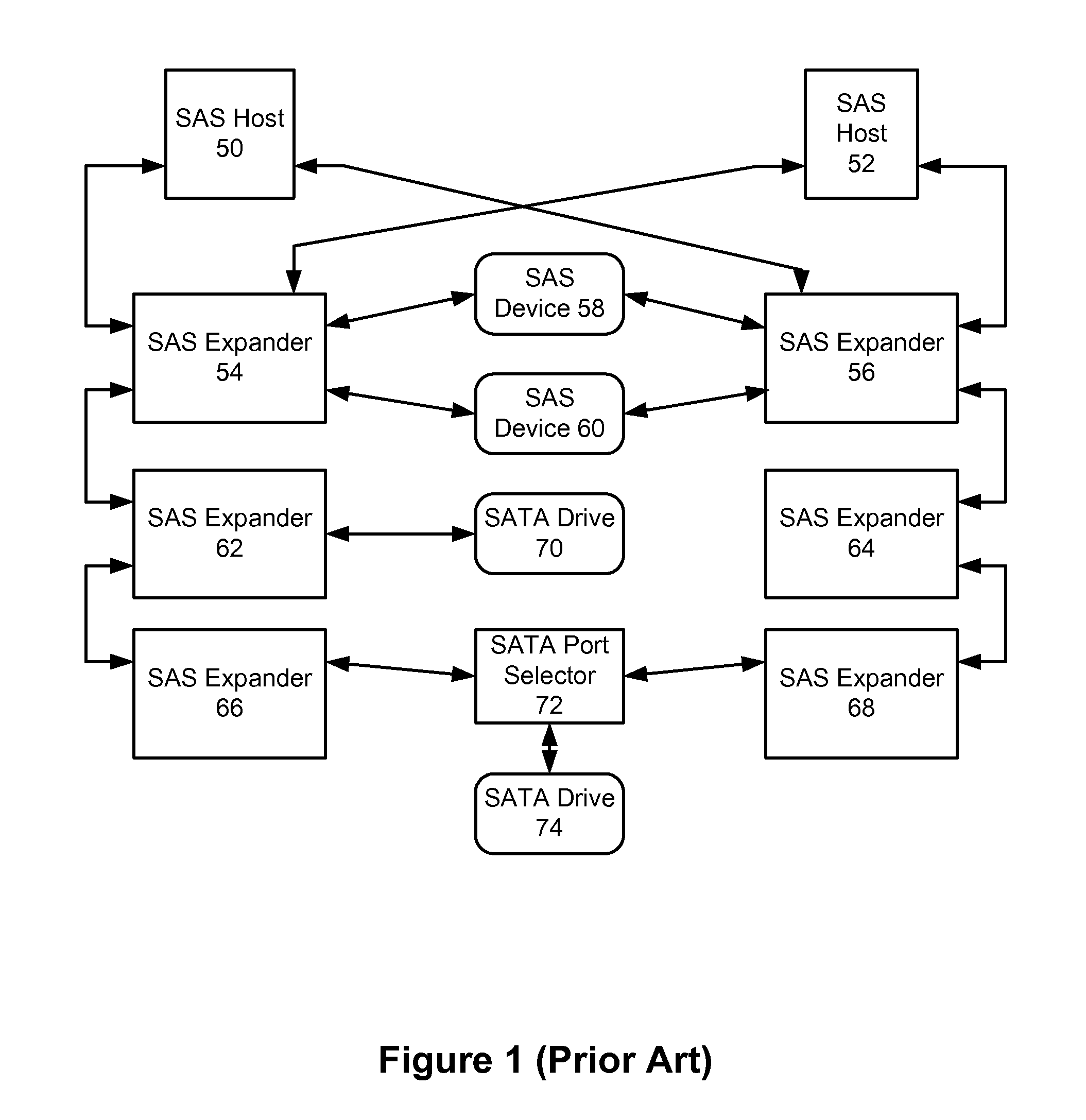
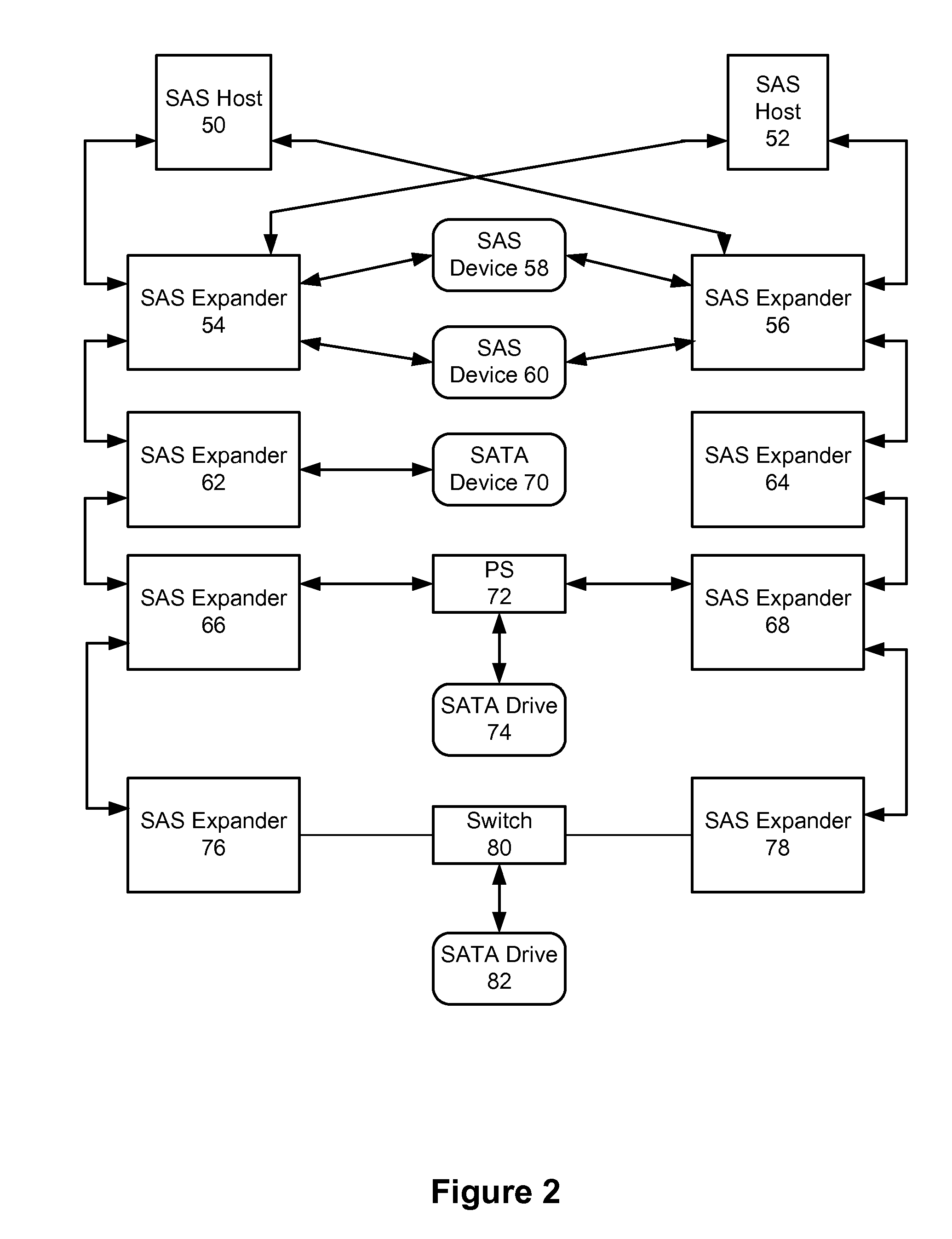
Command switching for multiple initiator access to a SATA drive
Owner:PMC-SIERRA
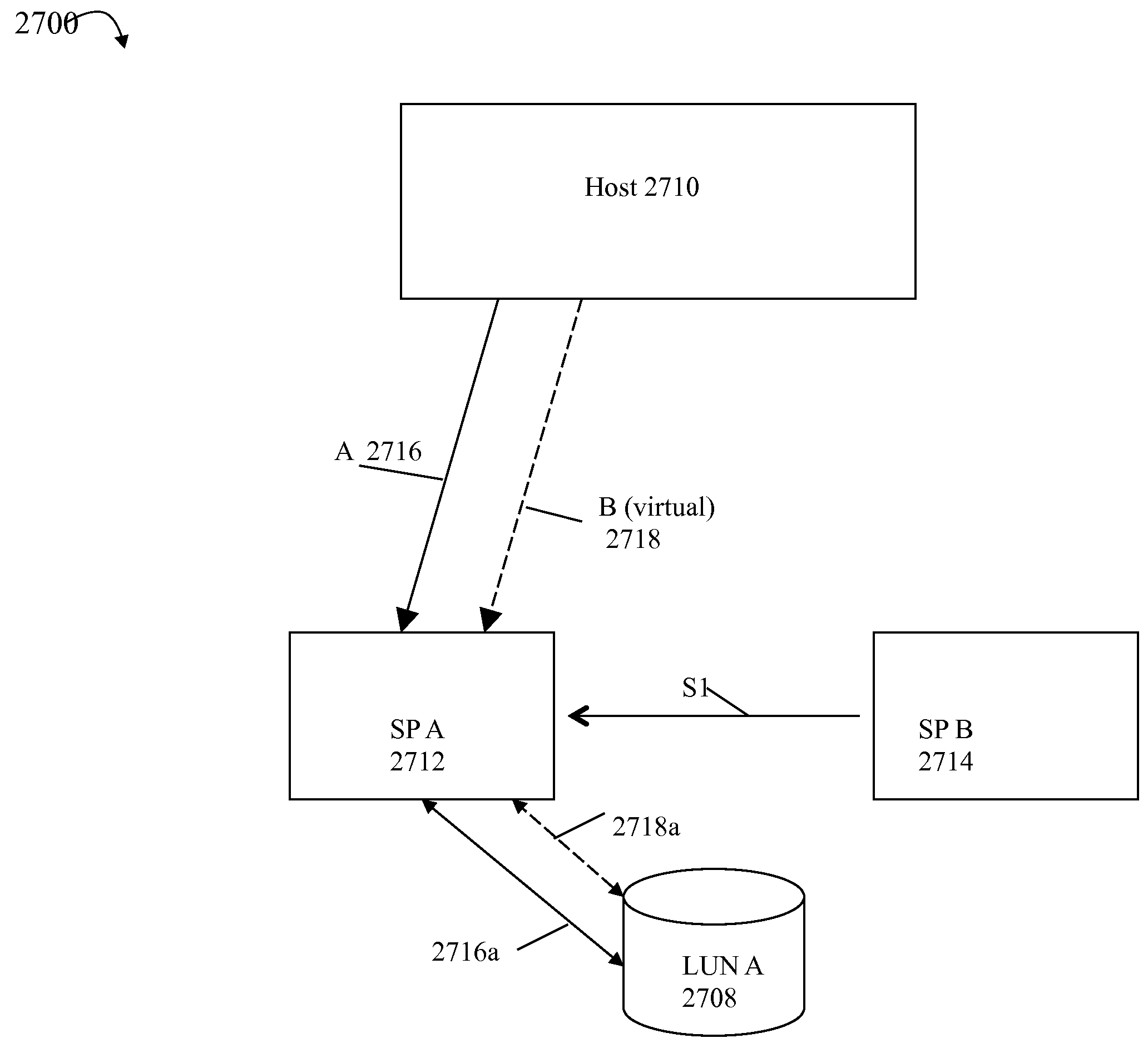
Virtualization of a storage processor for port failover
Described are techniques for processing requests. A request is received at a data storage system. The request is a command to perform first processing and the request is sent from a client over a virtualized path. The virtualized path includes a virtual target port of the data storage system. The virtual target port is a first physical target port that provides a virtualized counterpart port for a second physical target port whereby requests directed to the second physical target port are routed to the first physical target port rather than the second physical target port. First processing is performed and a response to the request is generated. The response includes first information consistent with sending the request over a non-virtualized path to the second physical target port. The response is sent to the client.
Owner:EMC IP HLDG CO LLC
Transparent device switchover in a storage area network
Initiators and targets in a storage area network are presented as virtualized devices by a virtualization engine. An initiator accesses a virtualized target as though it was accessing a physical target. A target accesses a virtualized initiator as though it was accessing a physical initiator. A virtualization engine performs port World Wide Name (WWN) and FCID mapping to allow continued access to virtual initiators and virtual targets even if a particular physical initiator or physical target fails and the secondary is made active.
Owner:CISCO TECH INC
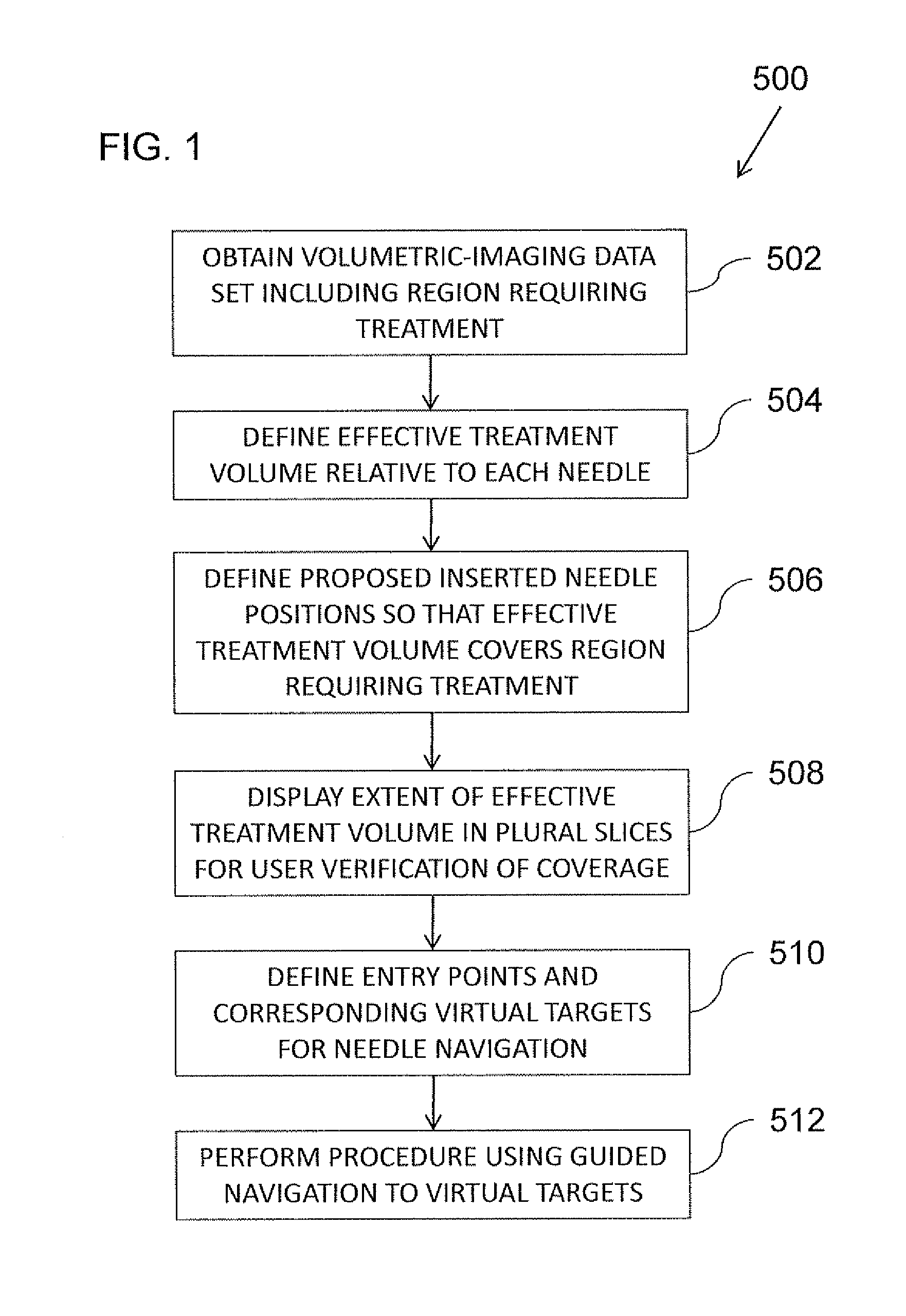
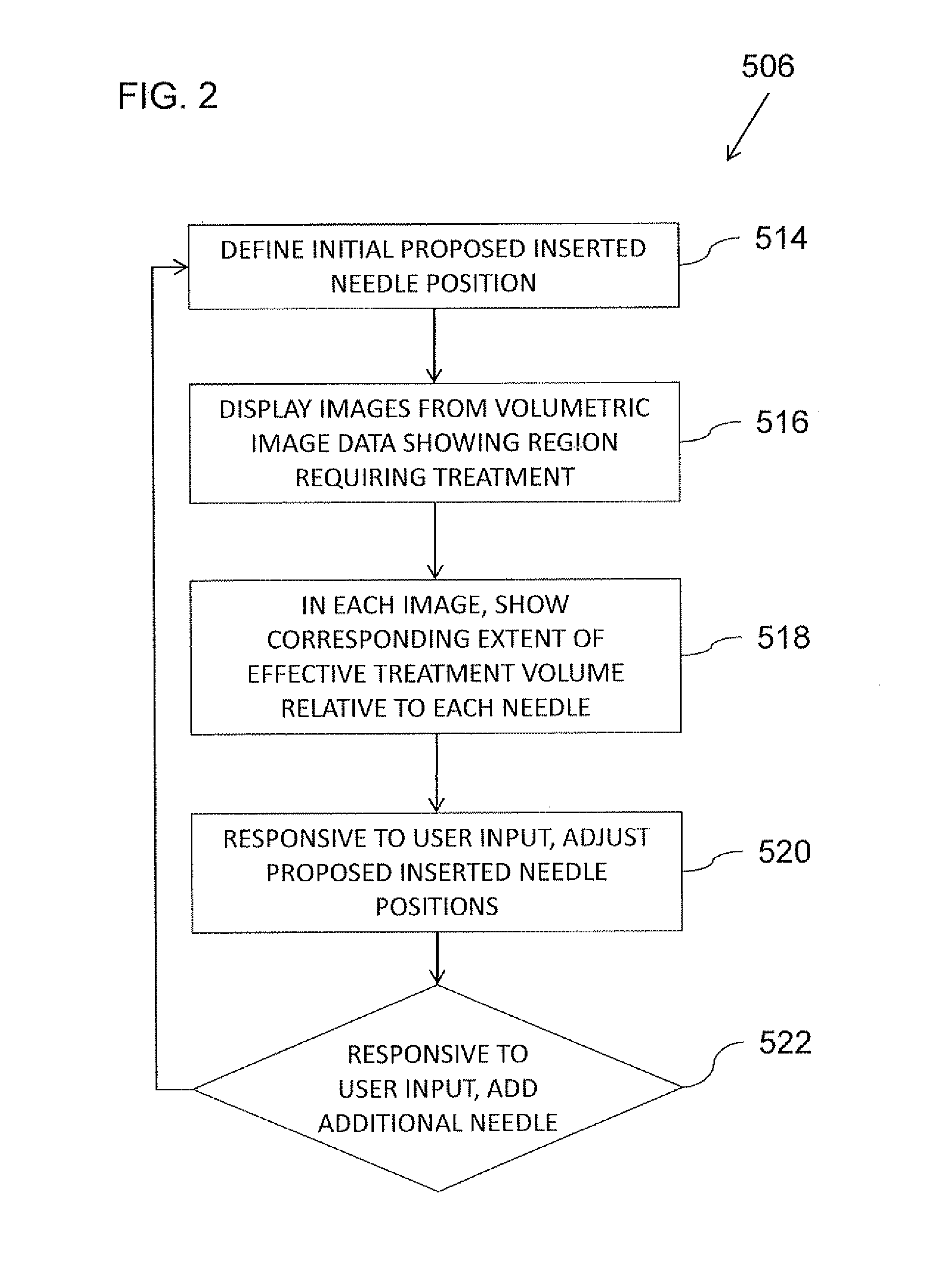
Systems & methods for planning and performing percutaneous needle procedures
ActiveUS20120215096A1Easily identifiablePrecise positioningSurgical navigation systemsDiagnostic markersVirtual targetData set
A system and method for planning volumetric treatment by percutaneous needle procedures obtains a volumetric image data set of a subject including an identifiable region requiring treatment. An effective treatment volume is defined relative to the needle position for at least one needle carrying a treatment applicator. One or more proposed inserted needle position is defined such that a effective treatment volume corresponding to the one or more proposed inserted needle position provides coverage of the region requiring treatment. The effective treatment volume for one or more needles can then be visualized in the context of slices of 3D image data. One or more entry point and corresponding virtual target are then defined relative to a frame of reference of the volumetric image data set for use in navigation of the at least one needle to the corresponding proposed inserted needle position.
Owner:STRYKER EURO OPERATIONS HLDG LLC
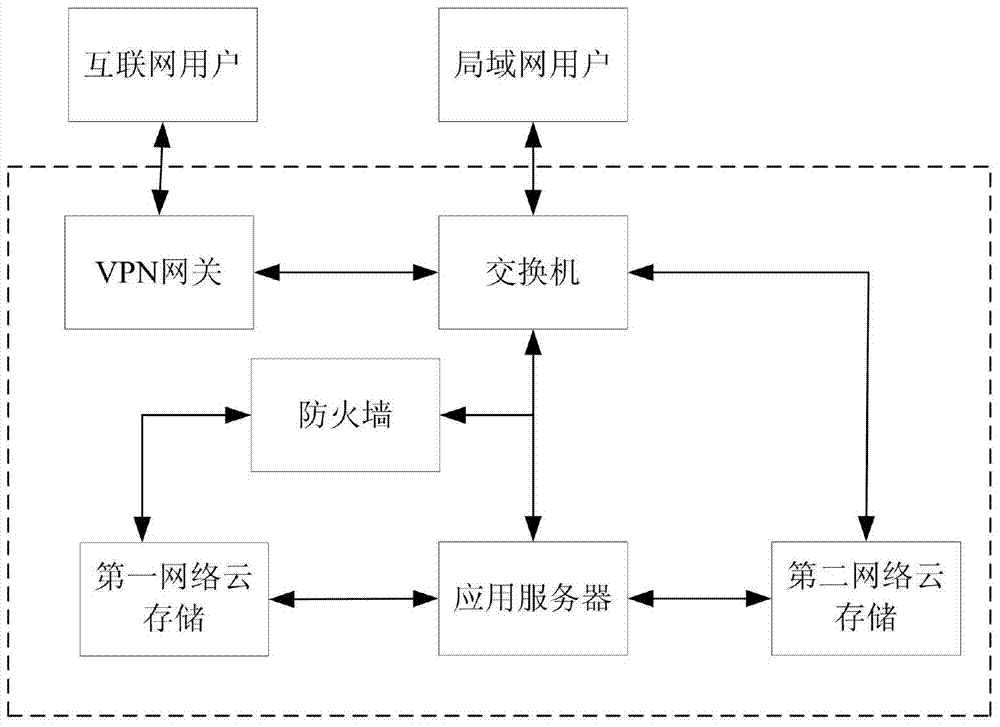
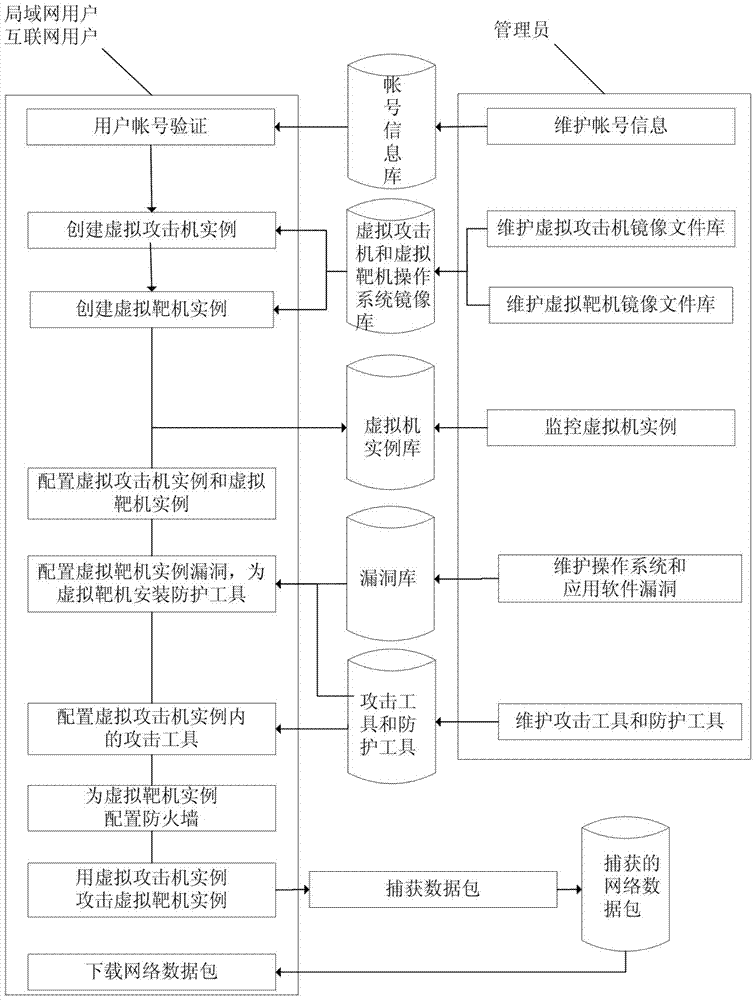
Remote network attack and defense virtual simulation system based on virtualization and cloud technology
ActiveCN103701777ARealize remote sharingAvoid duplication of investment in constructionTransmissionPrivate networkNetwork connection
The invention provides to a remote network attack and defense virtual simulation system based on virtualization and cloud technology, relates to the field of information safety and experimental system remote sharing, solves the problems of incapability of remotely sharing and building a network topology as well as a onefold attack and defense scene in the conventional network attack and defense virtual simulation system, and provides the remote network attack and defense virtual simulation system. According to the invention, virtualization and cloud technology are used to establish a virtual attacker and a virtual target airplane on cloud storage, network connection equipment and network guard equipment are configured for the virtual attacker and the virtual target airplane, and diversified network topologies and attack and defense scenes are established for users to carry out attack and defense experiment; the system comprises a remote access control module, an experimental configuration module, a virtual attacker cloud module, a virtual target drone cloud module, a monitoring center module, an expansion equipment configuration module and a management center module; users are allowed to use the virtual simulation system remotely through a VPN (Virtual Private Network), repeated investment and construction to the attack and defense virtual simulation system are avoided, and the use ratio of experimental facilities is improved.
Owner:CHANGCHUN UNIV OF SCI & TECH
Adaptative cruise control
ActiveUS20140005908A1Reduce steering input burdenReduce negative impactDigital data processing detailsAutomatic initiationsVirtual vehicleControl signal
An adaptive cruise control system for a motor vehicle includes a forward looking object detecting arrangement for simultaneously detecting several target objects moving in the predicted path and adjacent paths of the equipped vehicle. The detecting arrangement is arranged to continuously monitor velocity and distance to each of the target objects, and a processing arrangement processes signals from the detecting means to provide information of distance to and relative speed of vehicles travelling in front of the equipped vehicle. The processing arrangement repeatedly generates velocity control signals based on the information of distance to and relative speed of vehicles travelling in front of the equipped vehicle. An arrangement controls velocity of the vehicle in response to the control signals from the processing arrangement. The processing arrangement calculates a distance in time from the equipped vehicle to a virtual target vehicle, the distance to and velocity of the virtual target vehicle being calculated on basis of the number of vehicles in the group, the spread in distance of the group, and thus the vehicle density of the group, and the variability of positions in the group, such that the algorithm of the processing means decides from the above parameters on the allowed deviations in time distance, wherein the processing arrangement is arranged to produce a signal to the velocity control arrangement based on the calculated distance in time between the equipped vehicle and the virtual vehicle.
Owner:VOLVO LASTVAGNAR AB
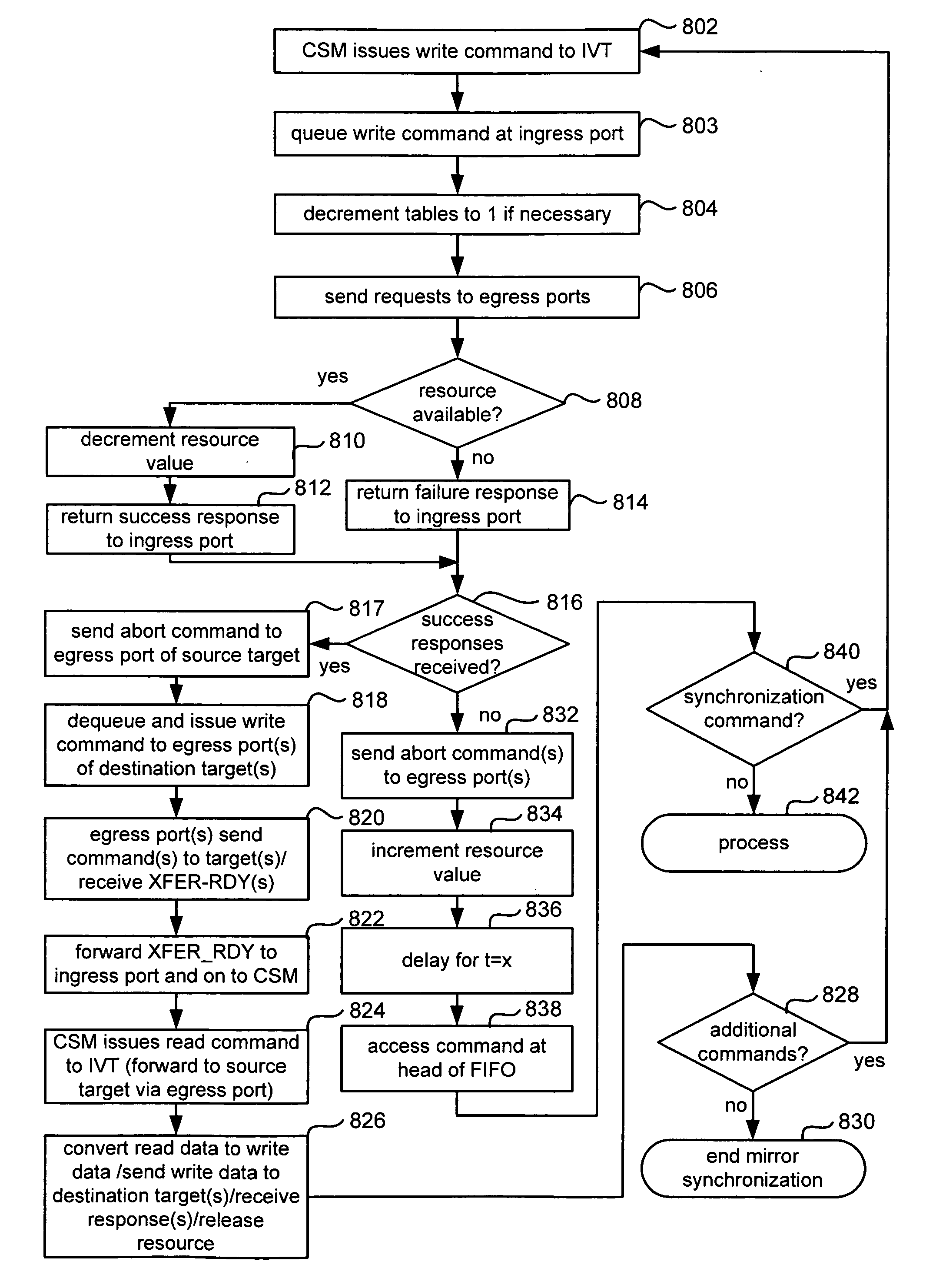
Systems and methods to avoid deadlock and guarantee mirror consistency during online mirror synchronization and verification
ActiveUS20060010299A1Memory loss protectionError detection/correctionVirtual targetVerification system
Systems and methods can provide mirrored virtual targets and online synchronization and verification of the targets while avoiding deadlock, inconsistencies between members of the target, and false verification failures. A lock within the storage switch can limit the number of outstanding commands for a physical target to one during synchronization and verification operations. In one embodiment, a lock can be implemented as one or more resource tables maintaining an indication of the number of transfer ready signals available from physical targets. During typical write operations, deadlock can be avoided by determining whether each physical target for the mirrored operation can issue a transfer ready signal prior to issuing a command to the physical target. When a synchronization or verification operation begins, the maximum available number of transfer ready signals for each target can be decremented to one in order to limit the total number of outstanding commands for each target to one.
Owner:EMC IP HLDG CO LLC
System and method for marksmanship training
A system and method for simulating lead of a target includes a network, a simulation administrator and a user device connected to the network, a database connected to the simulation administrator, and a set of position trackers positioned at a simulator site. The user device includes a virtual reality unit and a computer connected to the set of virtual reality unit and to the network. A generated target is simulated. The target and the user are tracked to generate a phantom target and a phantom halo. The phantom target and the phantom halo are displayed on the virtual reality unit at a lead distance and a drop distance from the target as viewed through the virtual reality unit.
Owner:SHOOTING SIMULATOR
Real time holographic projection method, device and system
The invention provides a real time holographic projection method, a device and a system; the method comprises the following steps: capturing and collecting first motion data of a target in real time, wherein the first motion data comprises at least one of the following list: expression data, movement data, special effect data and a control order; receiving and processing the first motion data in real time so as to generate first motion driving data, driving and rendering a virtual target to generate first animation image data according to the first motion driving data, wherein a visual angle number of the first animation image data is between 1 and N, and the N is a natural number; projecting the first animation image data on a holographic device. The real time holographic projection method solves the problems that image data needed by holographic projection cannot be generated in real time in the prior art, thus affecting comprehensive application of the holographic projection technology; the real time holographic projection method, device and system can real time generate the image data needed by holographic projection, thus expanding holographic projection technology application effect.
Owner:世优(北京)科技有限公司
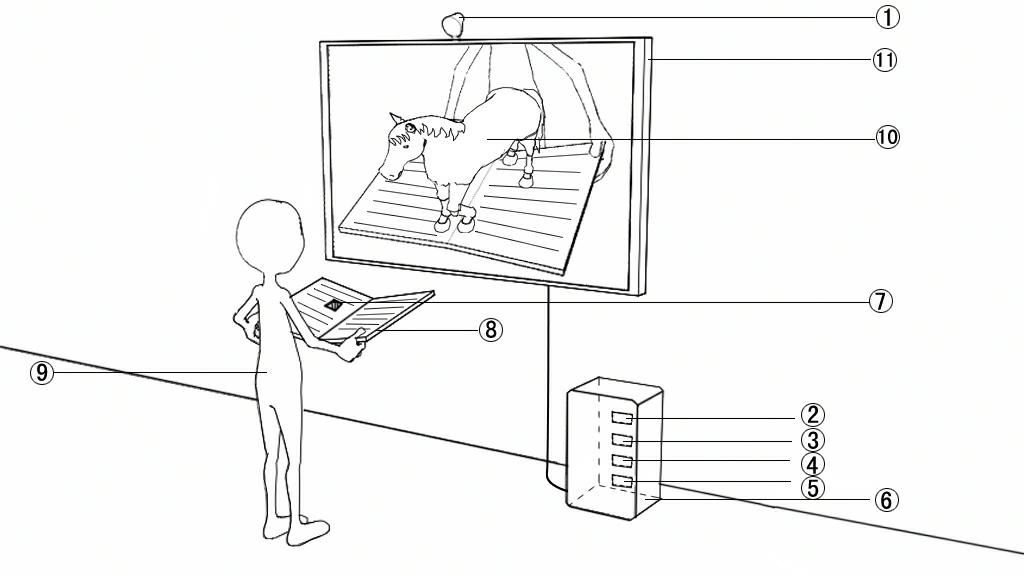
Multimedia reading matter giving readers enhanced feeling of reality
The invention relates to an image processing technology, particularly to a multimedia reading matter giving readers an enhanced feeling of reality. The multimedia reading matter comprises identification marks, an image processing module, an image positioning module and an image generating module. After a camera acquires one identification mark, an image recognition module and the image processing module analyze, compare and process the identification mark, the image positioning module accurately analyzes and positions the three-dimensional coordinates of the identification mark, the image generating module generates a virtual target which does not exist in reality and accurately places on the reading matter, and a display device displays the virtual target. The traditional reading matter is displayed by the multimedia content, and the virtual target and the real environment are integrated, thereby giving users a new environment with a real sensory effect. The multimedia reading matter provided by the invention has the characteristics of integration of virtual target and real environment, real-time interaction and three-dimensional positioning.
Owner:黄振强
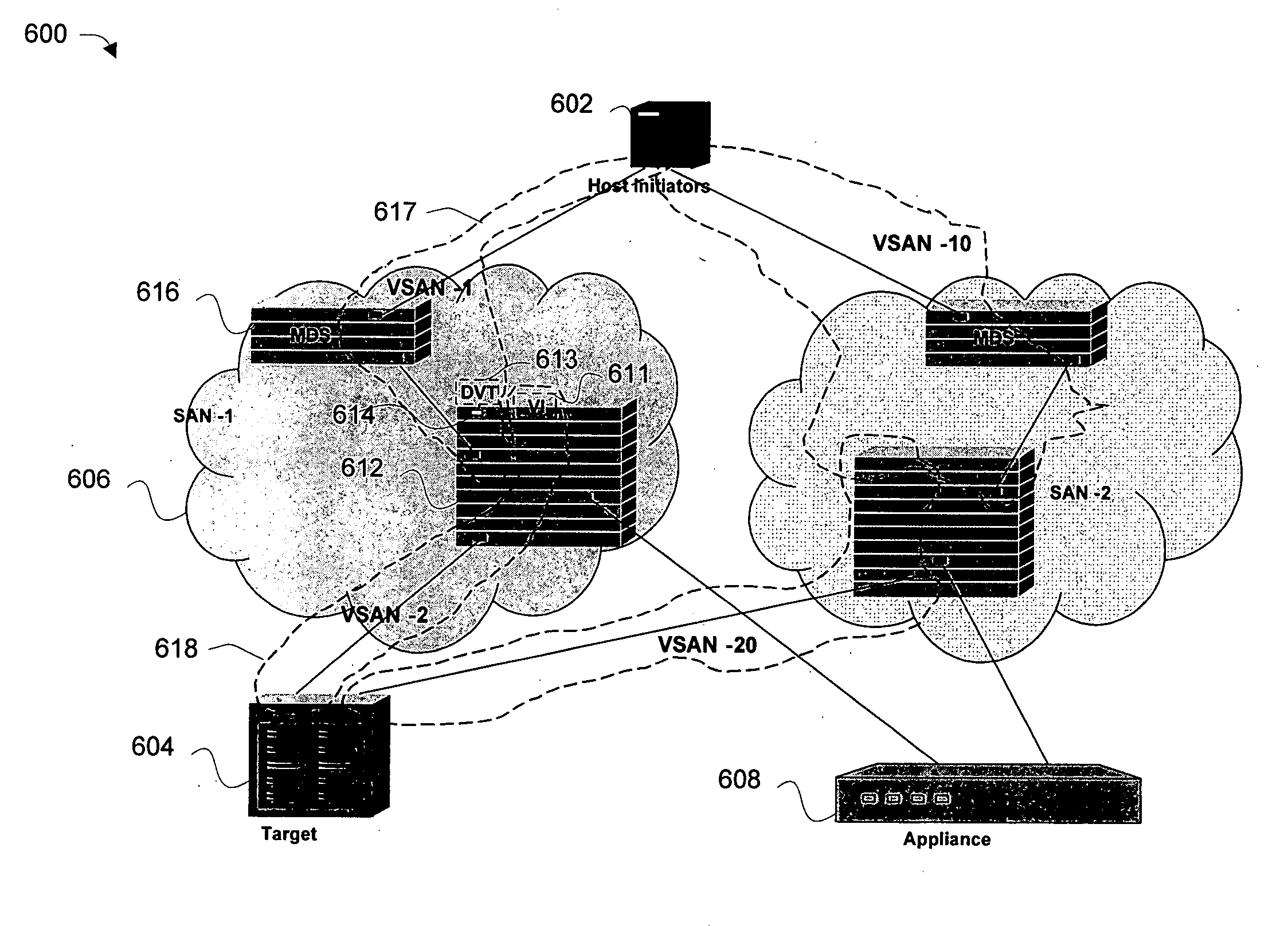
Apparatus and methods for data tapping in a storage area network
ActiveUS20070011276A1Multiplex system selection arrangementsCircuit switching systemsThird partyVirtual target
Disclosed are methods and apparatus for data tapping within a storage area network (SAN) and providing tapped data to a third party device, such as an appliance. In general, mechanisms are provided in a SAN to allow a data tap of data flowing between an initiator and a target. In one implementation, a data virtual target (DVT) in created in a network device to intercept data sent by a specific initiator to a specific logical unit of a specific target. The data or a copy of the data is sent to both the specific logical unit of the specific target and to an appliance. The data routing may be accomplished by use of a virtual initiator (VI), which is configured to send the data (or a copy of the data) to the specific target and the appliance. In a transparent mode of operations, the DVT has a same PWWN (port world wide name) and FCID (fibre channel identifier) as the specific target. In a first proxy mode of operation, the DVT has a different PWWN and FCID than the specific target. In a second proxy mode of operation, the DVT has a same PWWN and different FCID than the specific target.
Owner:CISCO TECH INC
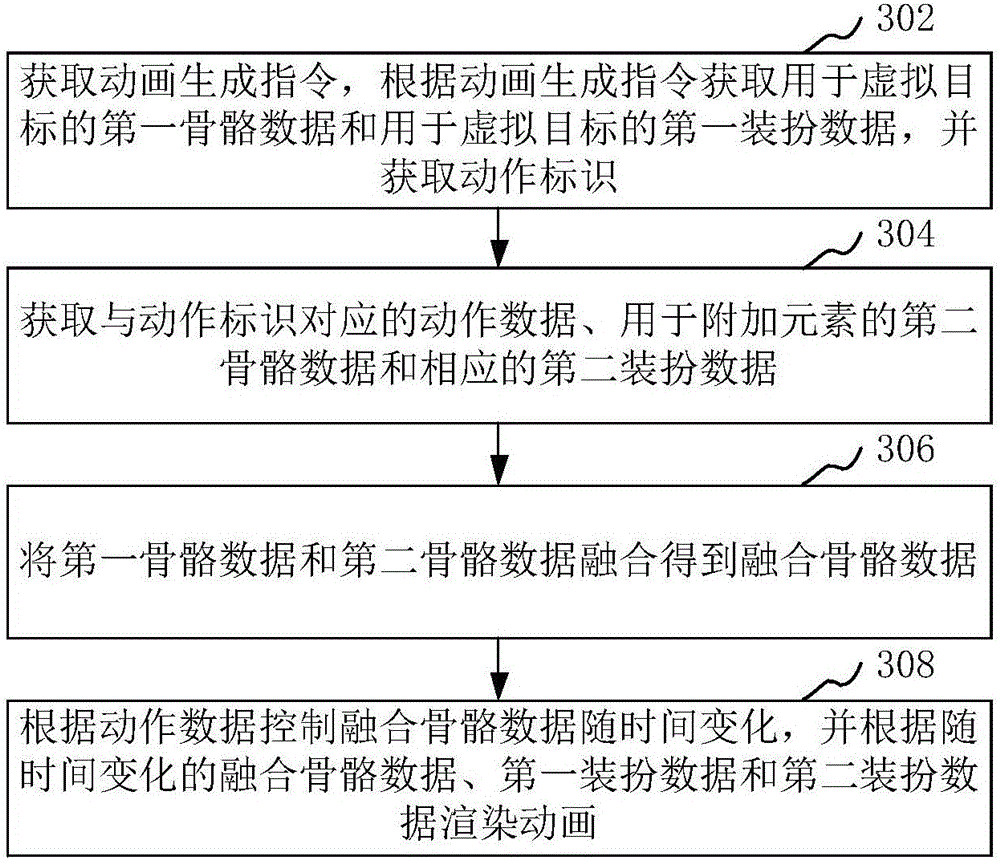
Animation generating method and apparatus
The invention relates to an animation generating method and apparatus. The method comprises: an animation generating instruction is obtained, first skeleton data for a virtual target and first dress-up data for the virtual target are obtained based on the animation generating instruction, and an action identifier is obtained; action data corresponding to the action identifier, and second skeleton data for an additional element and corresponding second dress-up data are obtained; the first skeleton data and the second skeleton data are fused to obtain fused skeleton data; and according to the action data, the fused skeleton data are controlled to change with time and animation rendering is carried out based on the fused skeleton data changing with time, the first dress-up data, and the second dress-up data. According to the invention, with the provided method and apparatus, consumption of stored resources is reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Vehicle-pedestrian detecting, tracking and early-warning device and method
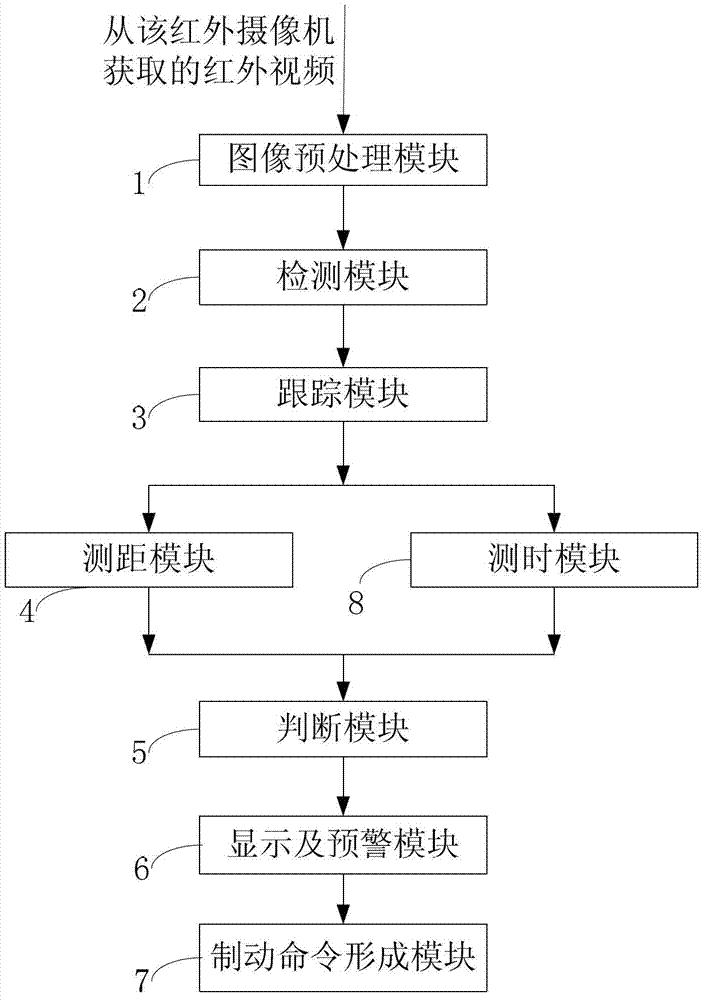
ActiveCN103204123AAvoid accidentsBraking element arrangementsPedestrian/occupant safety arrangementVirtual targetDisplay device
The invention discloses vehicle-pedestrian detecting, tracking and early-warning device and method. The method includes that the early-warning device preprocesses infrared videos obtained by an infrared camera through an image preprocessing module, detects vehicles and pedestrians through a detecting module, forecast-tracks the vehicles and pedestrians through a tracking module to eliminate interference influences of vehicle vibration and virtual targets, calculates the distance between each target and the infrared camera according to corresponding relationship between world coordinates and image coordinates through a distance measuring module, judges an early-warning standard through a judging module, and displays the infrared videos carrying target identifiers and distance information on a display. The vehicle-pedestrian detecting, tracking and early-warning device has the advantages that driving safety is improved, most traffic accidents are effectively avoided, and life and property loss is lowered. The invention further discloses the vehicle and pedestrian detecting, tracking and early-warning method using the early-warning device.
Owner:CHINA ELECTRONIC TECH GRP CORP NO 38 RES INST +1
Colour calibration of emissive display devices
ActiveUS20050174309A1Extend potential colour gamutImprove color gamutCathode-ray tube indicatorsDriving currentVirtual target
A calibration method for calibrating a fixed format emissive display device having a plurality of pixels is described In the display each pixel comprises at least three sub-pixels for emitting light of different real primary colours. The method comprises determining, for each real primary colour separately, a virtual target primary colour which can be reached by at least 80% of the pixels of the display, determining a colour gamut defined by the determined virtual target primary colours, and adjusting the drive currents to the sub-pixels to achieve a colour inside the determined colour gamut. A display having an extended range of colours is described, i.e. a gamut of colours that is more than the gamut provided by an n virtual primary colour based electronic multicolour display, as measured on a chromaticity diagram, for example. A color and / or brightness uniform image can be produced with this fixed format emissive display device.
Owner:BARCO NV
Variable focus imaging lens assembly for an imaging-based bar code reader
A variable focus imaging lens assembly (50) for an imaging-based bar code reader (10) including: a lens assembly (52) focusing light from a field of view (FV) onto a sensor array (28), the lens assembly (52) including a lens (53) movable along a path of travel; a drive mechanism (58) to drive the moving lens (53); a focusing system (60) for establishing a reference point (RP) for the moving lens (53) along the path of travel corresponding to a reference focal plane (RFP) within the field of view; and a projection assembly (62) projecting a virtual target image (64a) of a reference target light source (64) to a predetermined position (P) within the field of view and coincident with the reference focal plane (RFP), the predetermined position (P) being a known distance (D) from the lens assembly (52) along its optic axis (OA).
Owner:SYMBOL TECH LLC
Guidance method with terminal restraint based on virtual target point
InactiveCN102353301ASolve the problem of skimming attackMeet the detonation height requirementsAiming meansVirtualizationVirtual target
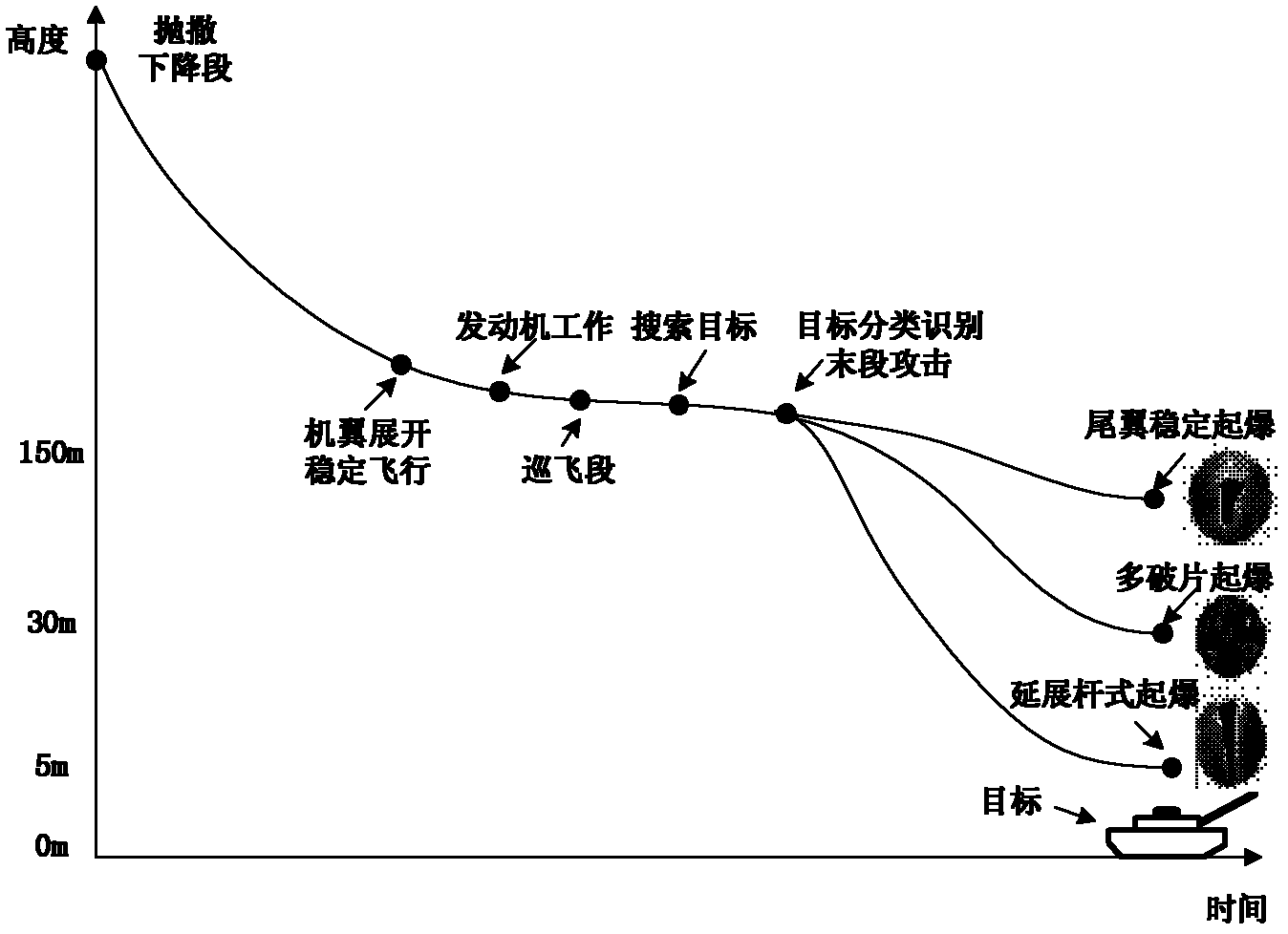
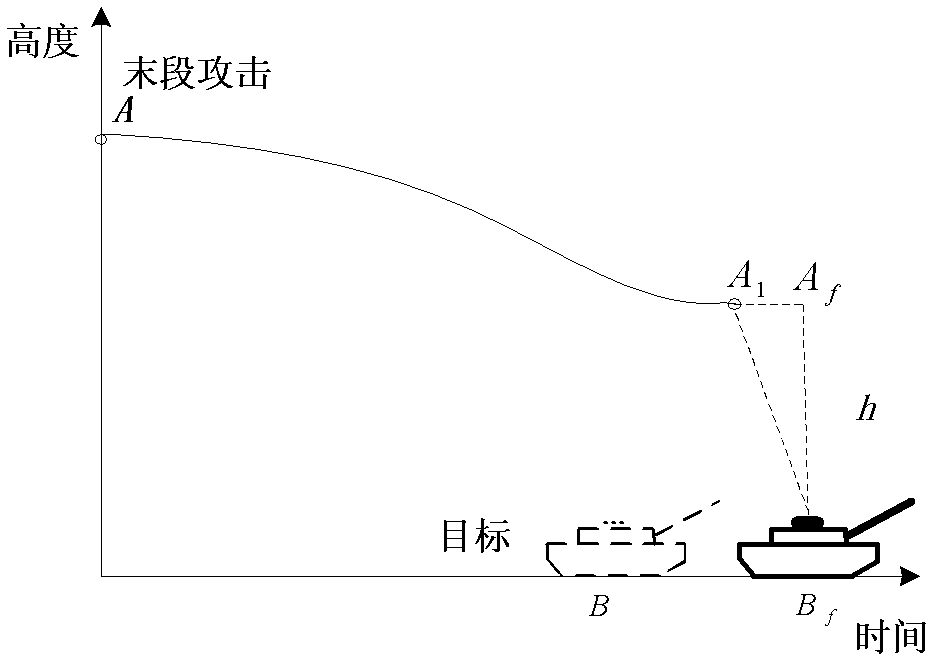
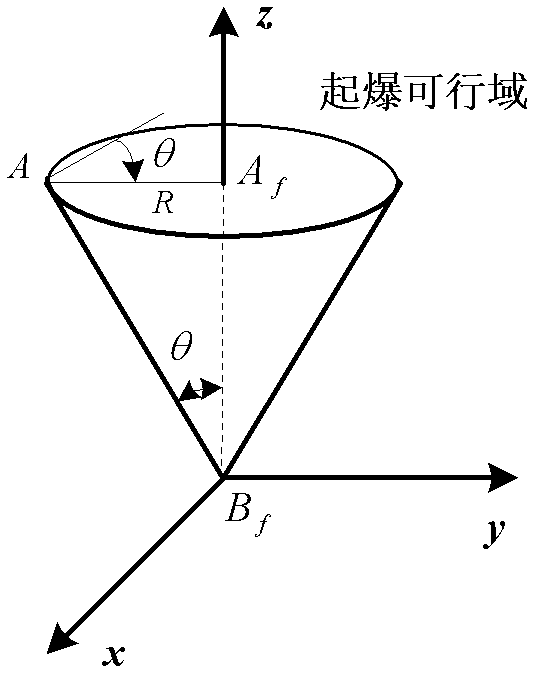
The invention discloses a guidance method with terminal restraint based on a virtual target point and belongs to the technical field of aircraft guidance and control systems. By using a target virtualization method, an aircraft can fly in the optimum height to attack a target; a virtualized target is positioned, above a real target, in the height, namely a detonation height which is required for a damage element; by designing a guidance law, when the aircraft reaches an imaginary target, a warhead detonates; and the conventional mode of attacking the real target by flying is changed into a guidance mode of flying to the virtualized target and detonating according to a required attitude angle. By adoption of the guidance law of the method, the aim that the aircraft with the explosion-formed damage element flies and attacks in an expected height can be fulfilled, the requirement of the optimum detonation height of the damage element is met, the problem of the attitude angle of the aircraft with the explosion-formed damage element during end attacking can be solved, and the requirement of the detonation moment of the damage element on the attitude angle of the aircraft is met.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com