Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
560 results about "Distributed management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Distributed management is a management method for people to work together over the web to accomplish desired goals. Management activities are distributed through the people doing the work.
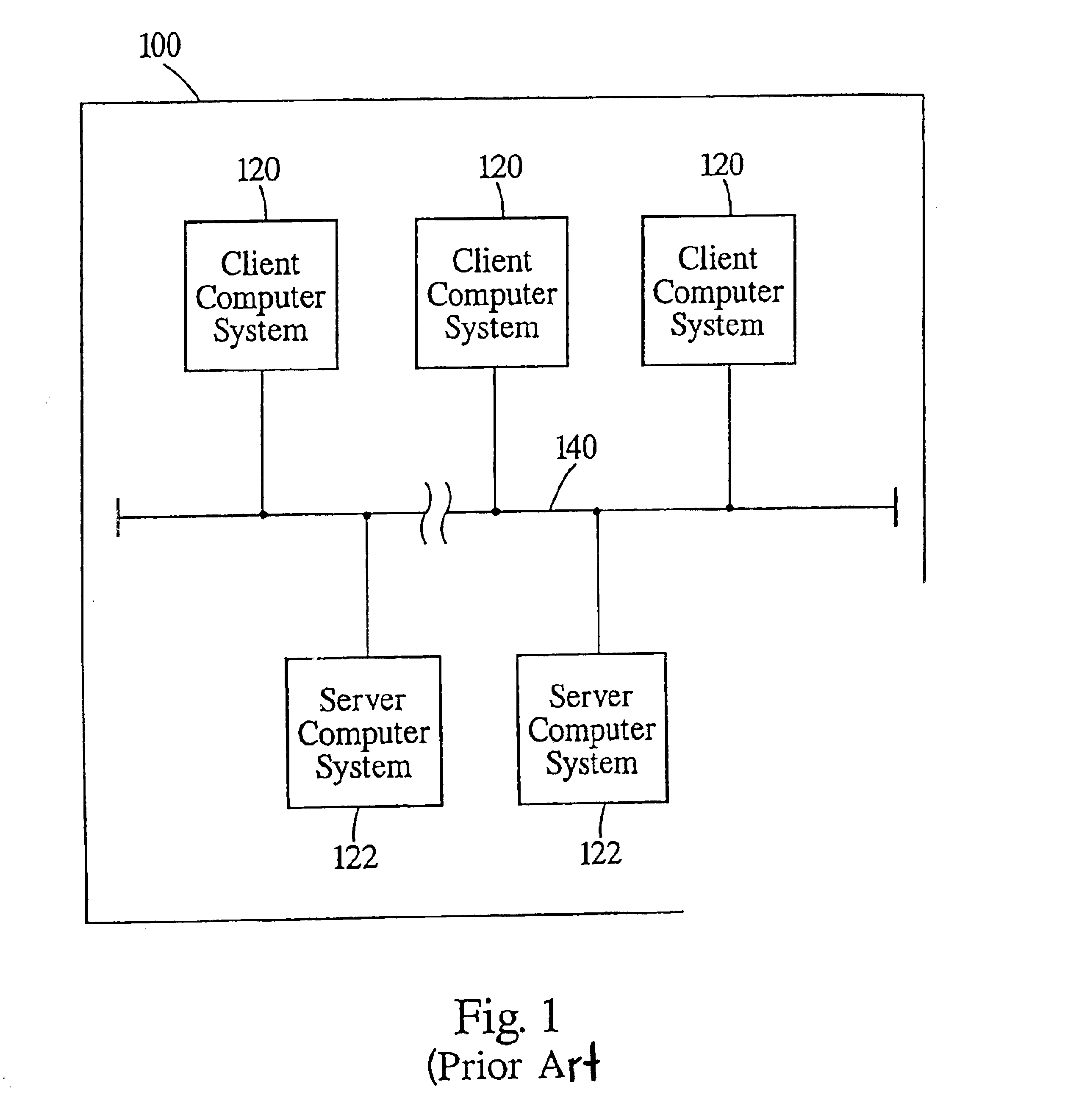
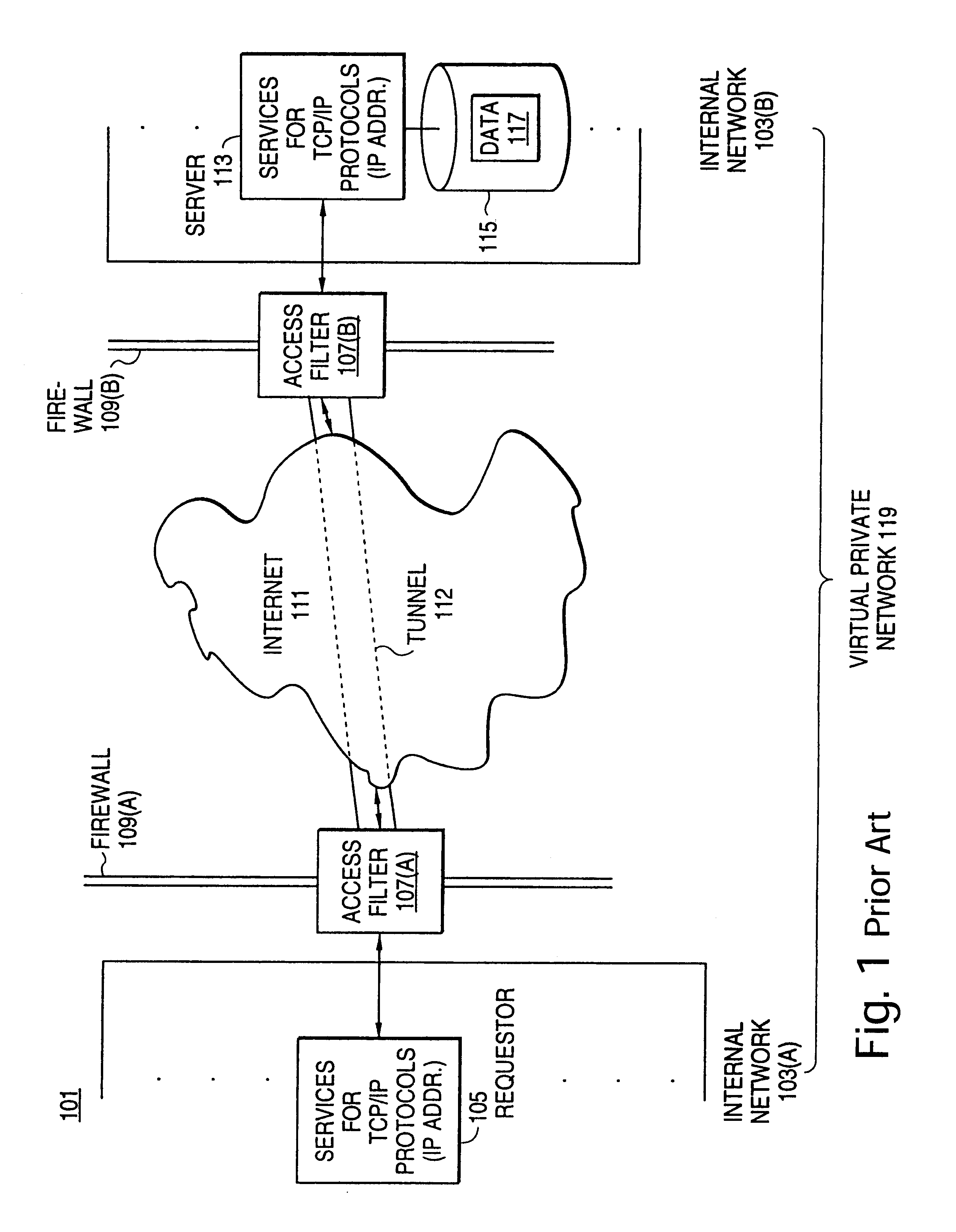
Distributed administration of access to information
InactiveUS6408336B1Digital data processing detailsMultiple digital computer combinationsPrivate networkInformation resource
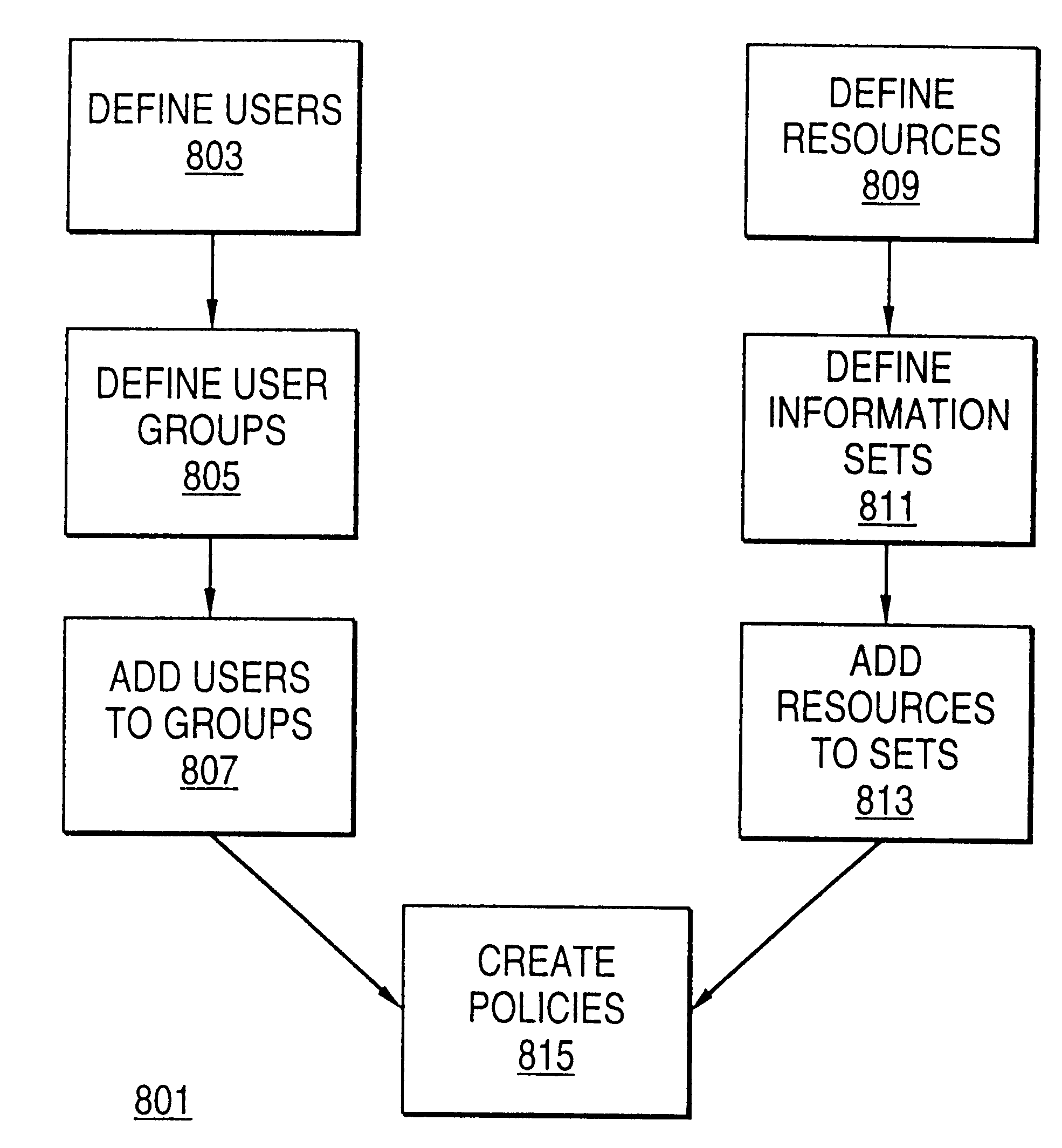
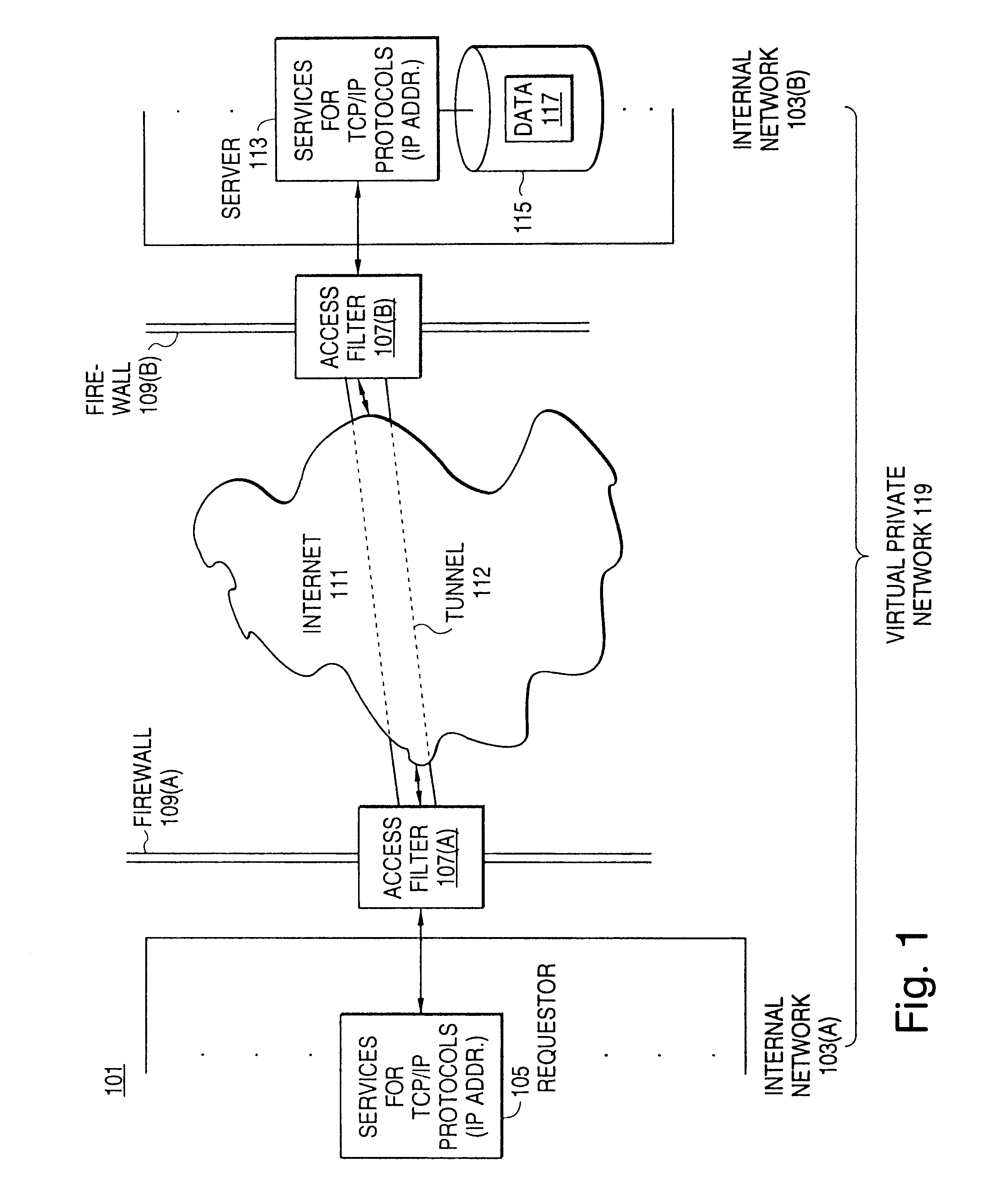
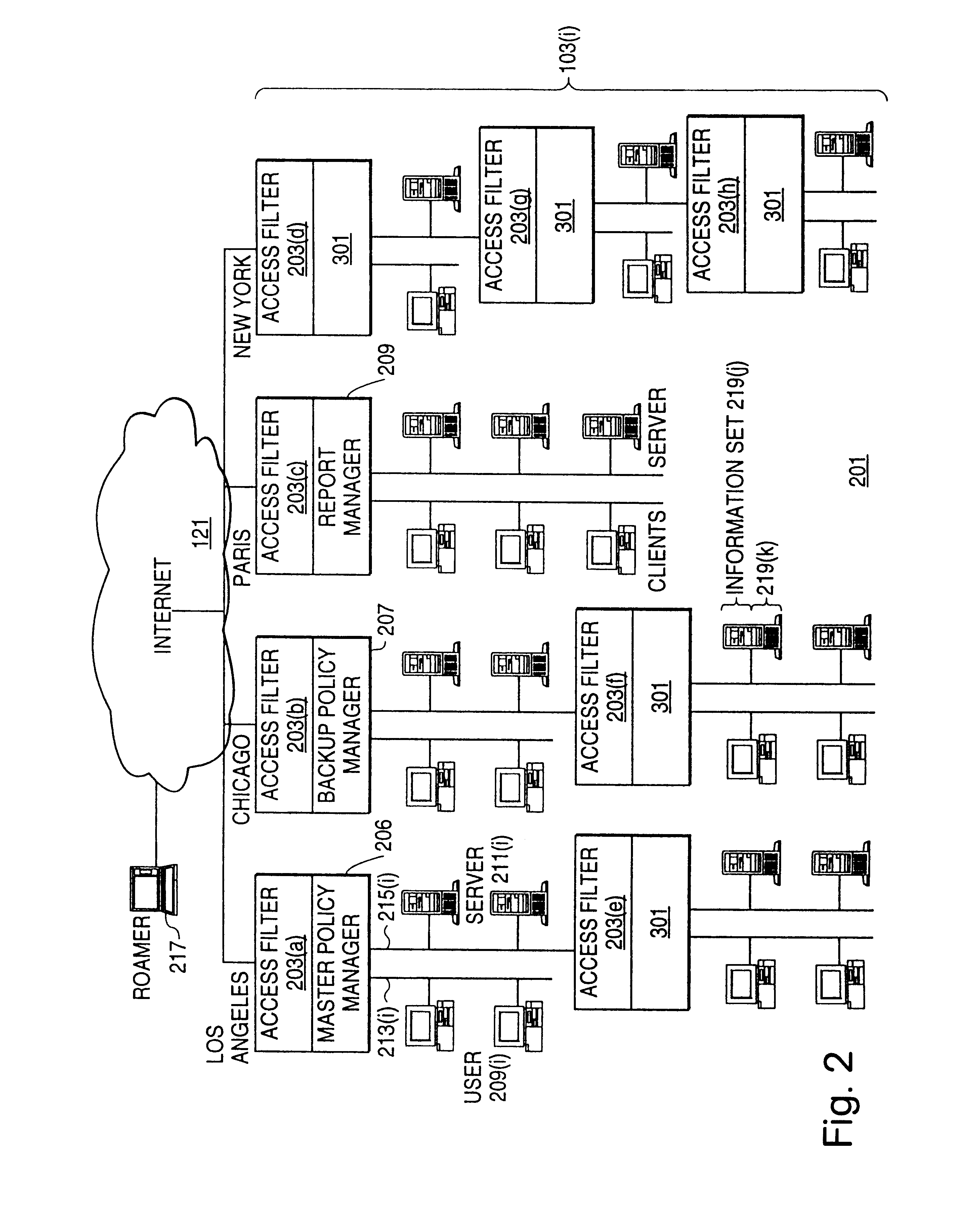
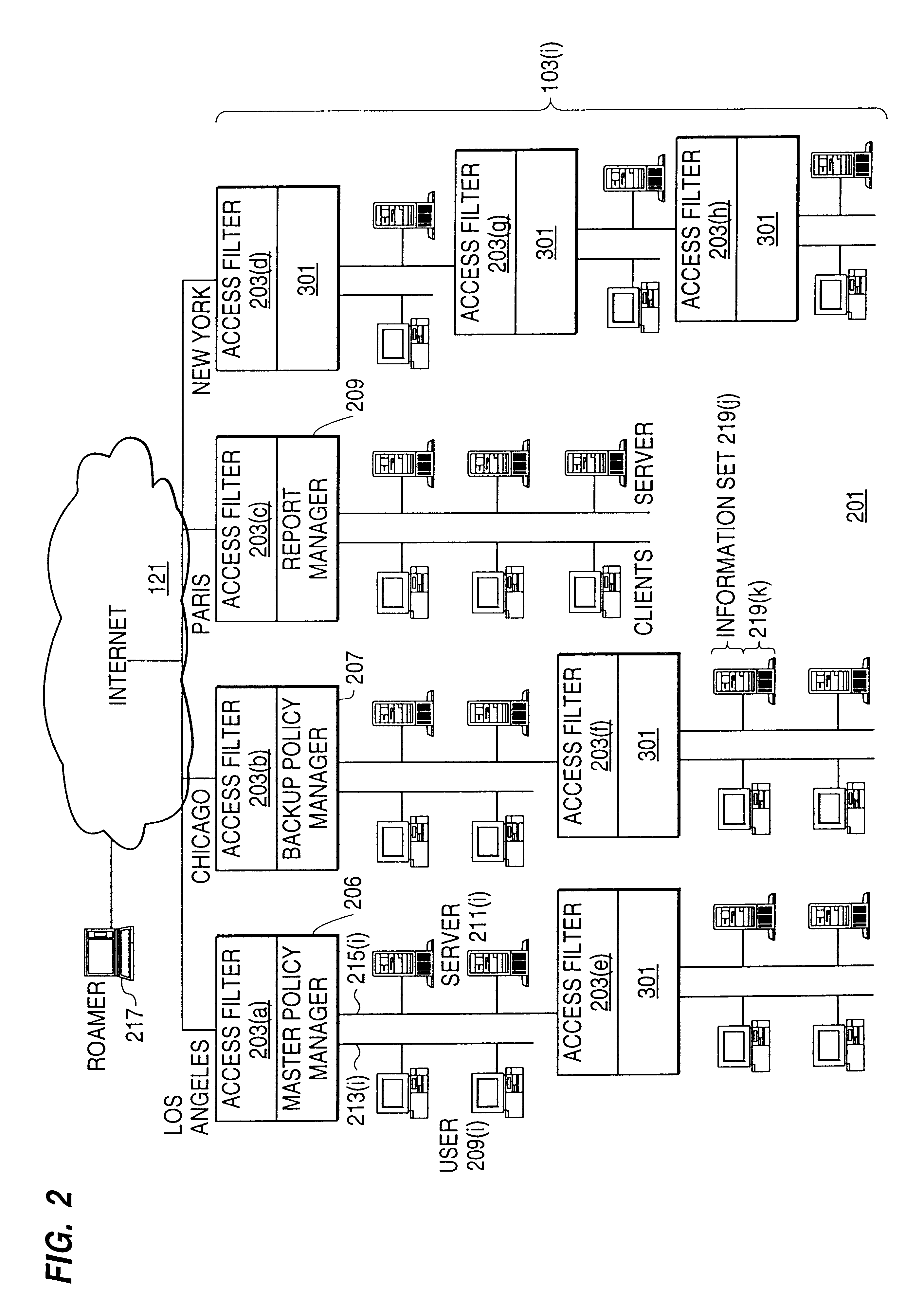
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
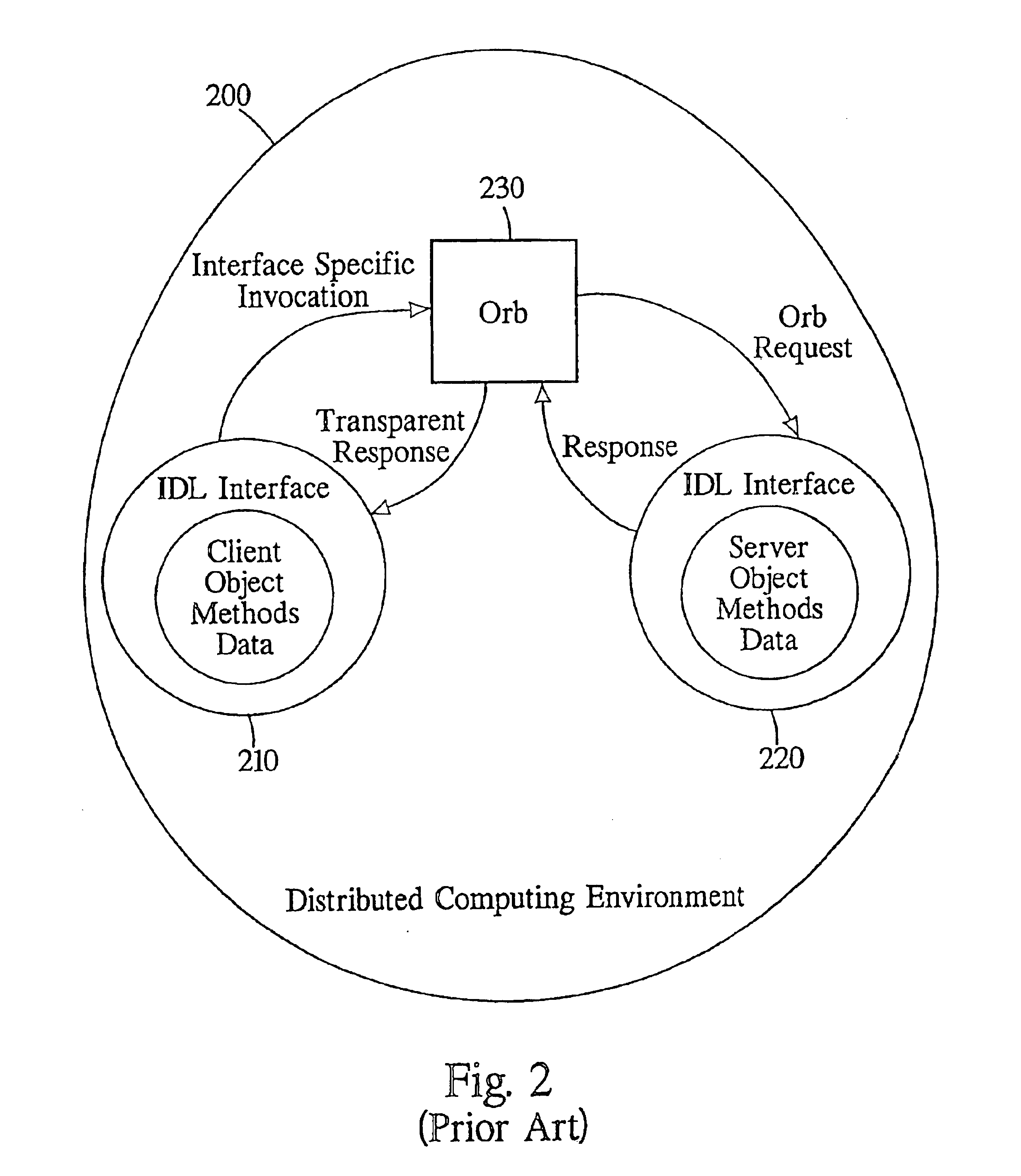
Extensible software-based architecture for communication and cooperation within and between communities of distributed agents and distributed objects
InactiveUS6859931B1Minimal effortIncrease flexibilityDigital data information retrievalInterprogram communicationIntelligent planningDistributed object systems
A distributed agent community is able to dynamically interact with alternative sofware technologies that manage distributed objects. The leveraging of capabilities of distributed object systems greatly expands the flexibility and capabilites of the distributed agent community. Through access to distributed object systems, the distributed agent community can draw on the capabilites of all the objects managed by the distributed object systems. The access to distributed systems by the distributed agent community allows for collaboration and intelligent planning that the distributed object systems do not themsleves provide.
Owner:IPA TECH INC
Distributed administration of access to information
InactiveUS6785728B1Cathode-ray tube indicatorsMultiple digital computer combinationsPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
System and method for transformation and analysis of messaging data
ActiveUS7231403B1Information can be usedData processing applicationsSupervisory/monitoring/testing arrangementsData transformationData warehouse
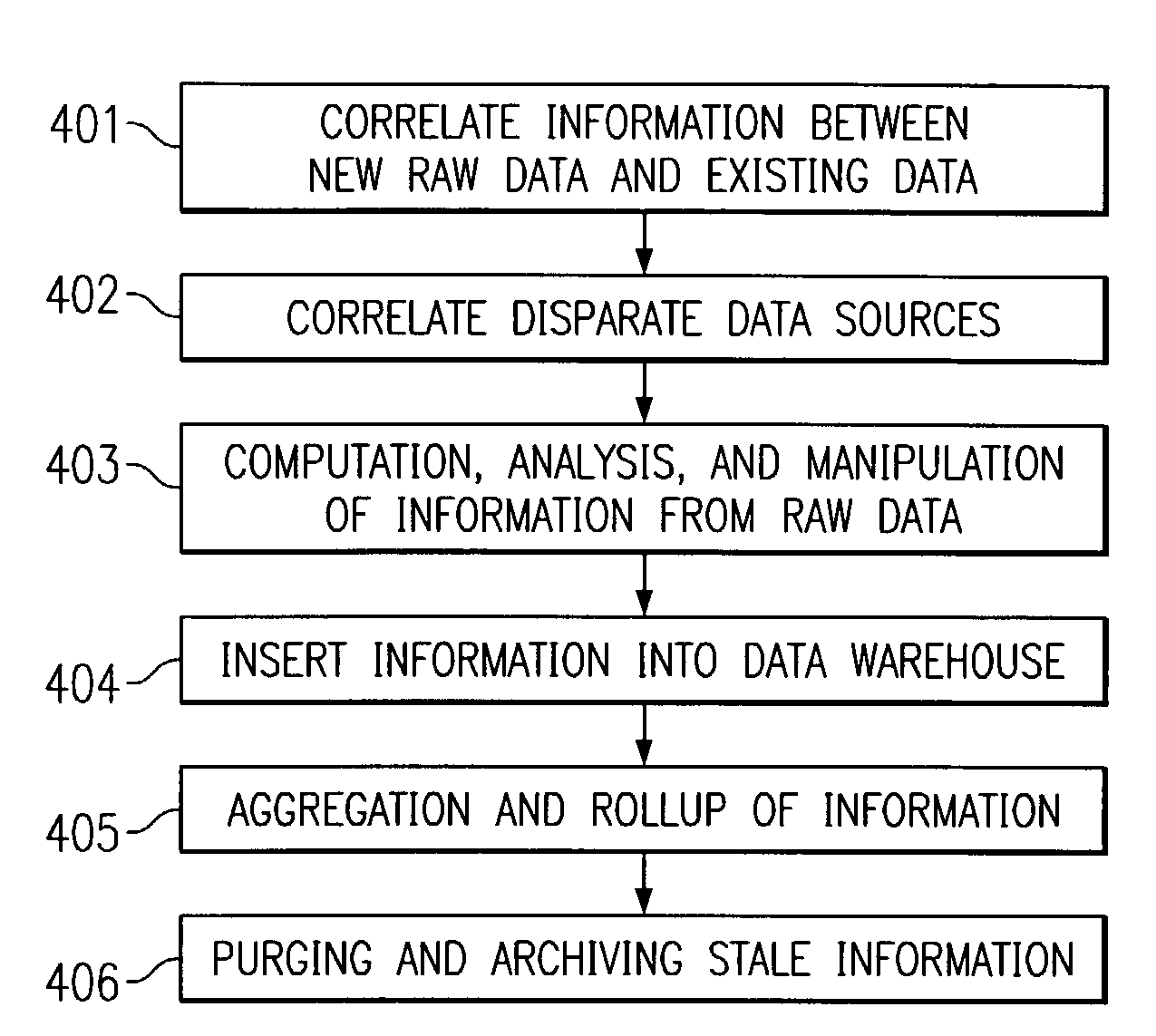
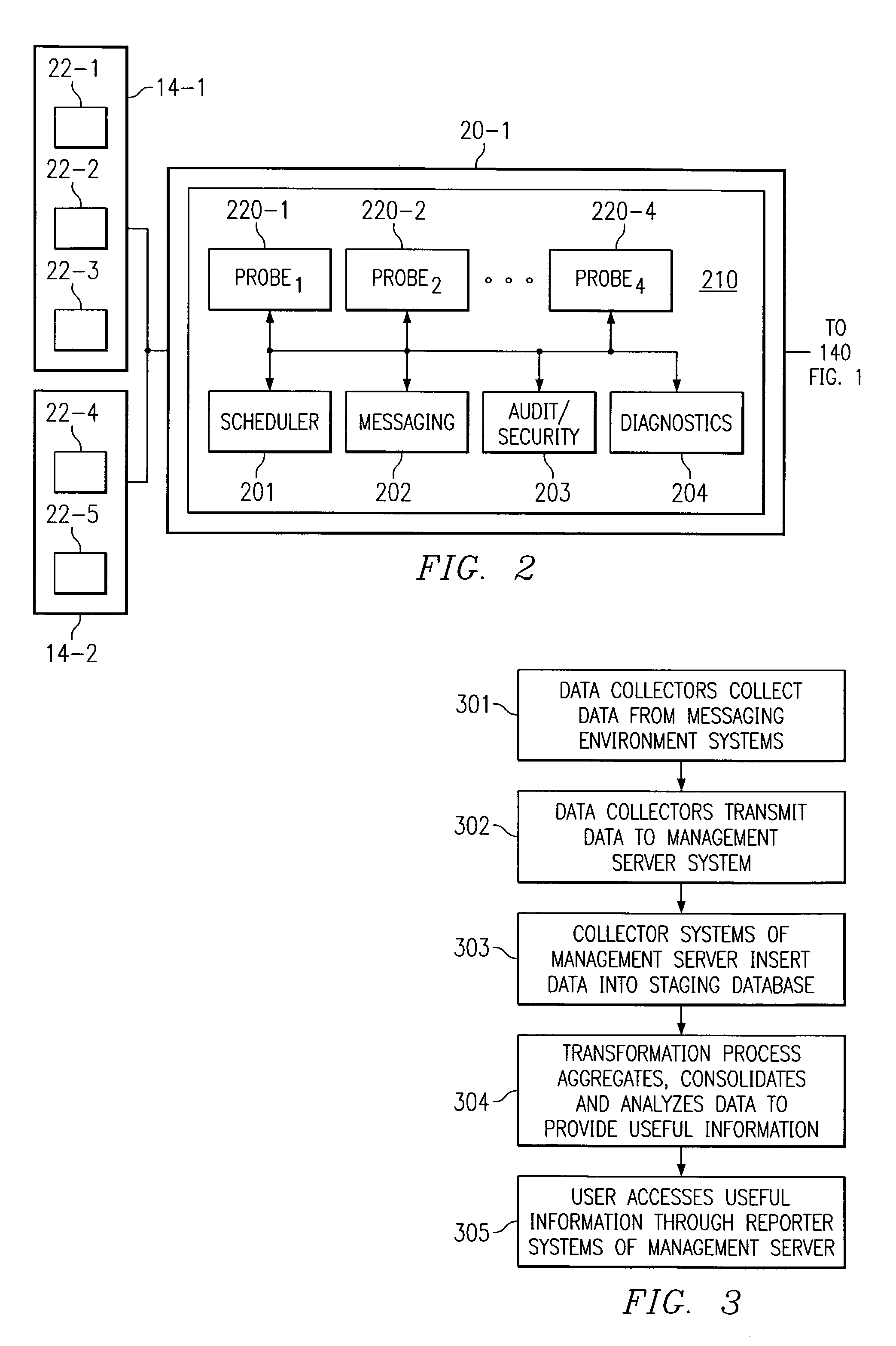
Systems and methods which provide translation and / or transformation of messaging data, such as that collected by a distributed management method, for collection, consolidation, processing, and / or analysis are shown. Preferred embodiments of the present invention provide data translation schema to manipulate raw data stored in a first database or databases, such as a staging database, to store useful information in appropriate locations of a second database or databases, such as a data warehouse. Preferably, for each data source monitored in a messaging environment, collected raw messaging data is parsed into appropriate positions of a staging database. Thereafter, data transforms of the present invention preferably manipulate and / or process data of the staging database and provide useful information for storage in a data warehouse.
Owner:MESSAGEONE INC
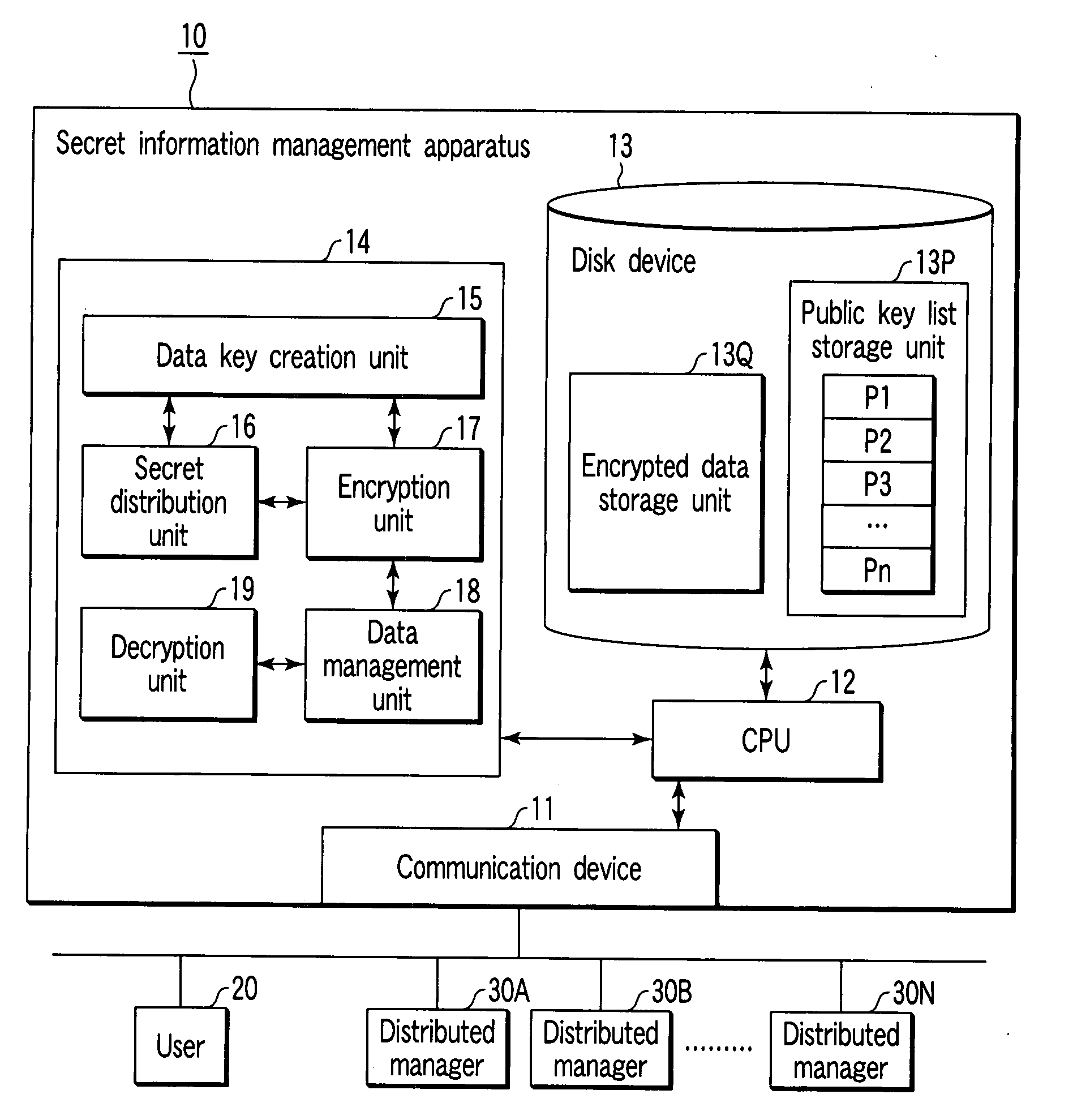
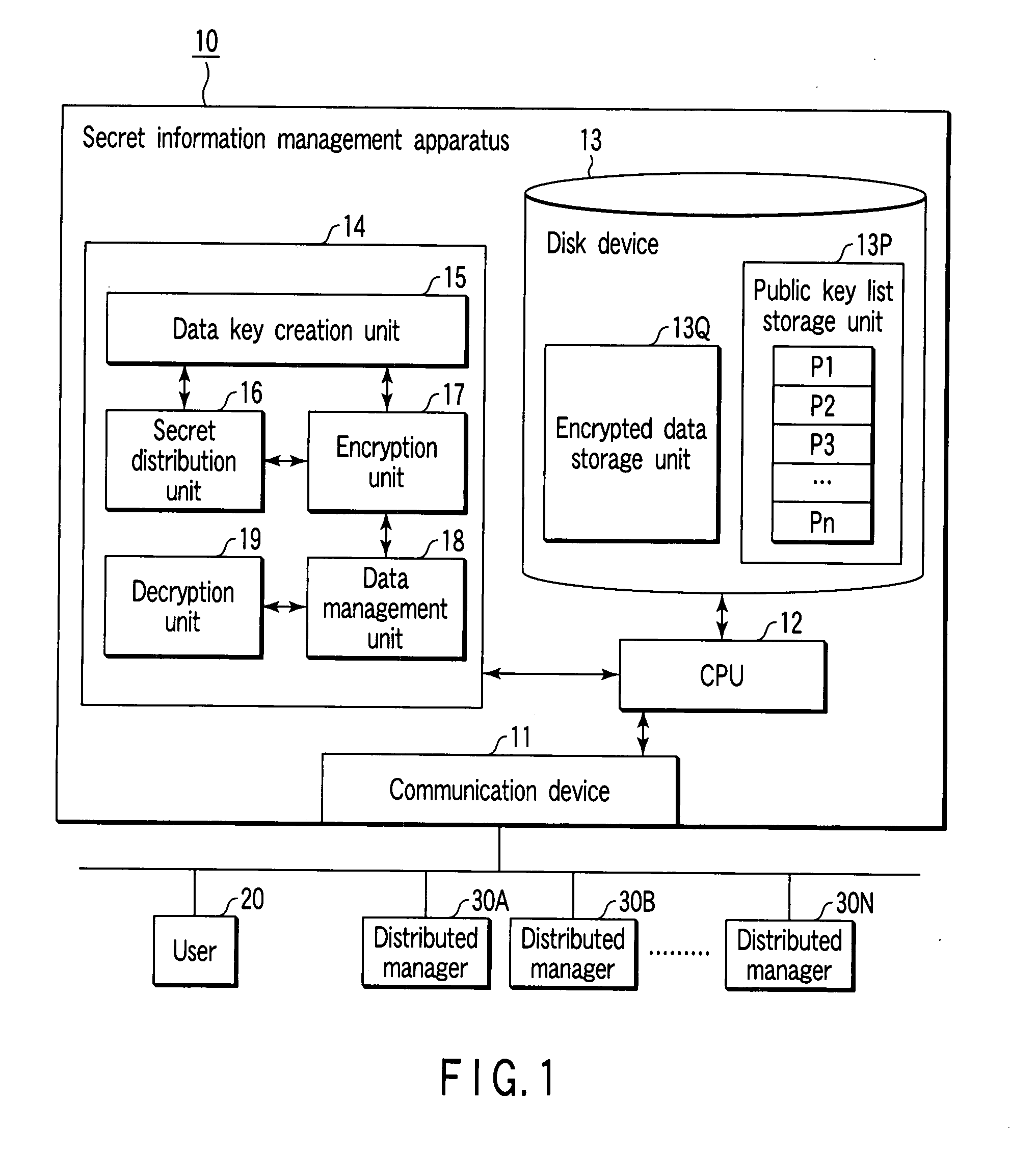
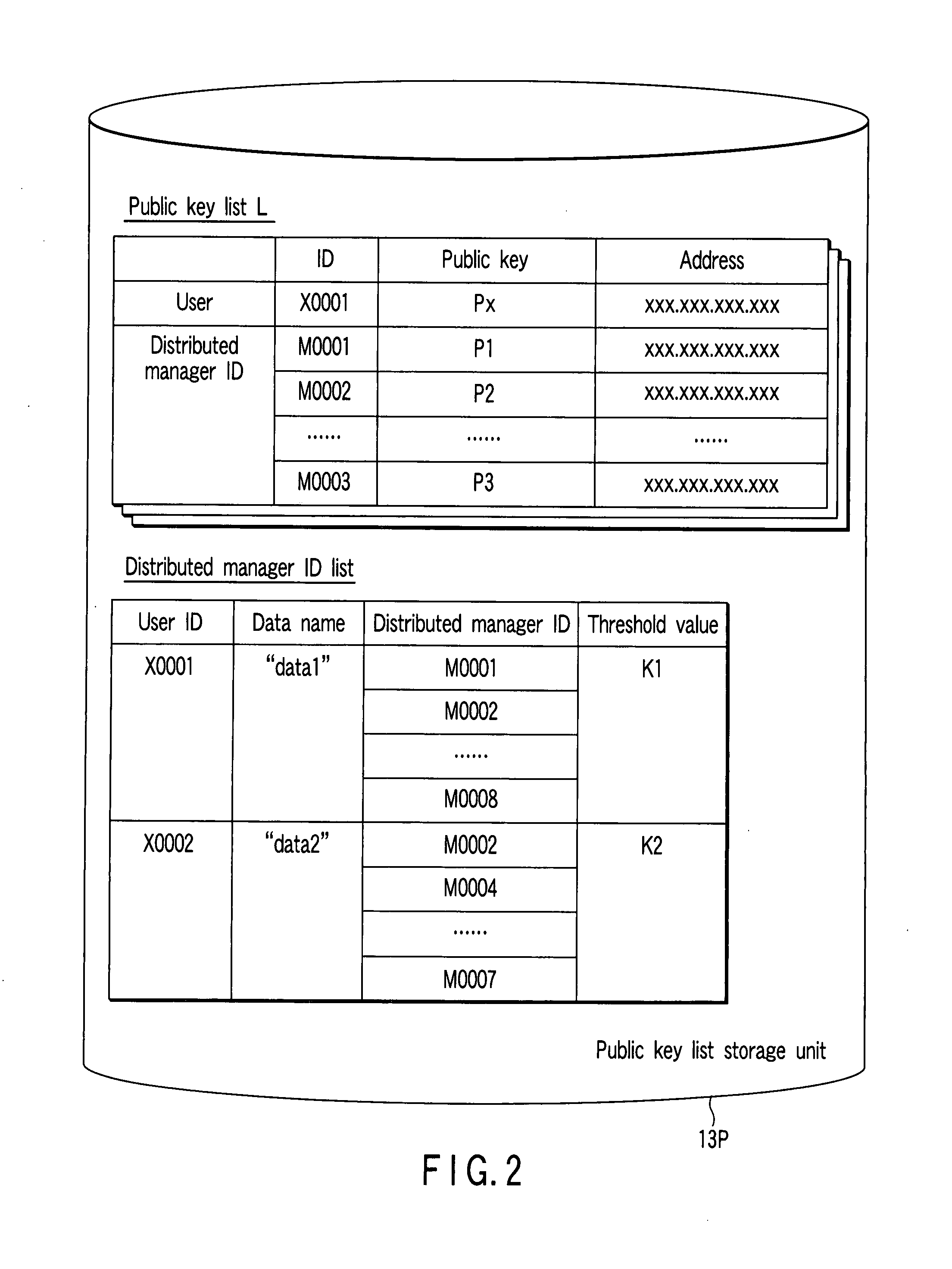
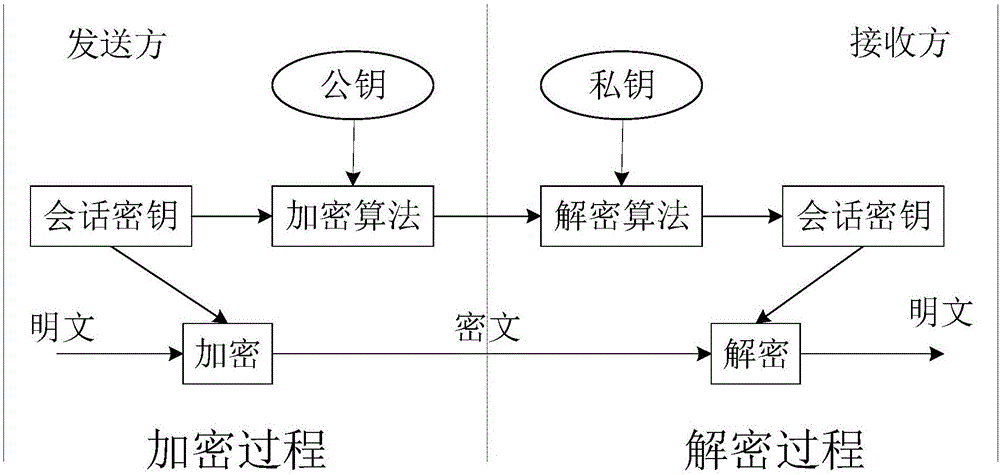
Secret information management apparatus and secret information management system
InactiveUS20080095375A1Key distribution for secure communicationPublic key for secure communicationManagement systemEncryption
In a secret information management system, a secret information management apparatus comprises a secret distribution unit which secretly distributes a data key k using a (k, n) threshold secret sharing scheme and creates n distributed keys B1, B2, . . . , Bn in the decryption of data D input from a user terminal, an encryption unit which creates n encrypted distributed keys EP1(B1), EP2(B2) . . . , EPn(Bn) using n distributed manager public keys P1, P2, . . . Pn, and an encrypted data storage unit which stores encrypted data EK(D), an encrypted data key EPx(K) and the n encrypted distributed keys in association with each other.
Owner:TOSHIBA DIGITAL SOLUTIONS CORP +1
Distributed data storage system and method
InactiveUS20030187853A1Maximum system efficiencyImprove efficiencyOffice automationSpecial data processing applicationsMass storageSoftware distribution
A distributed data storage system and method comprising a highly integrated mass storage controller system permitting distributed management and control of data storage is disclosed. The present invention in some preferred embodiments permits mass storage media to be made available on a network in a fashion to permit global access, while automatically handling many high-level file access and data integrity / security / control functions normally associated with a host operating system. This integration and redistribution of functionality permits spatial diversification of data resources, automatic mirroring of data, fault isolation, data security, and a plethora of other control functions to be integrated into the mass storage device. This integration permits peer-to-peer communication between mass storage devices to both unburden the host data consumers but also isolate the data management functions from the data presentation functions normally associated with host systems. Exemplary embodiments of the present invention as applied to specific preferred system contexts include but are not limited to distributed data storage in a networked environment, brokered data access metering, database access / control, data backup, journaling, checkpointing, and automated software distribution.
Owner:HENSLEY ROY AUSTIN +1
Method and system for grid-enabled virtual machines with distributed management of applications
InactiveUS20050160424A1Resource allocationSoftware simulation/interpretation/emulationLoad SheddingData processing system
A method, apparatus, computer program product, and data processing system provide for operation of a virtual machine with embedded functionality for interoperating with other virtual machines in a computational grid. A plurality of virtual machines are run on one or more devices within a data processing system; each virtual machine incorporates functionality for interoperating and associating with other virtual machines in a virtual machine cluster in a grid-like manner. Each virtual machine in the virtual machine cluster acts as a node within the virtual machine cluster. The virtual machines share information such that a virtual machine may be added to the virtual machine cluster or such that a virtual machine may be removed from the virtual machine cluster as the virtual machine cluster continues to run. Load-balancing operations may be performed within the virtual machine cluster, and threads and objects may be moved within the virtual machine cluster.
Owner:IBM CORP
Method of administering software components using asynchronous messaging in a multi-platform, multi-programming language environment
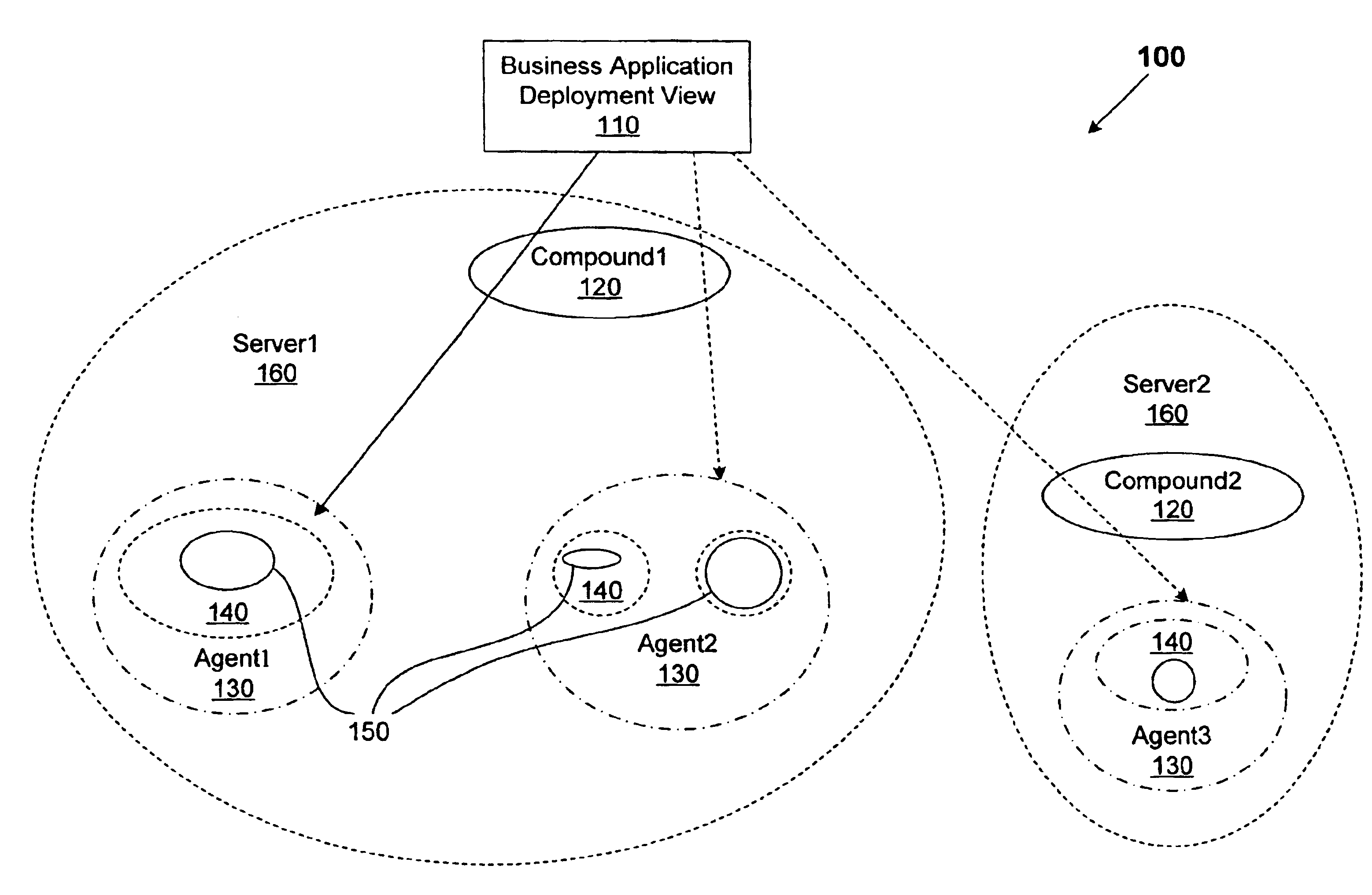
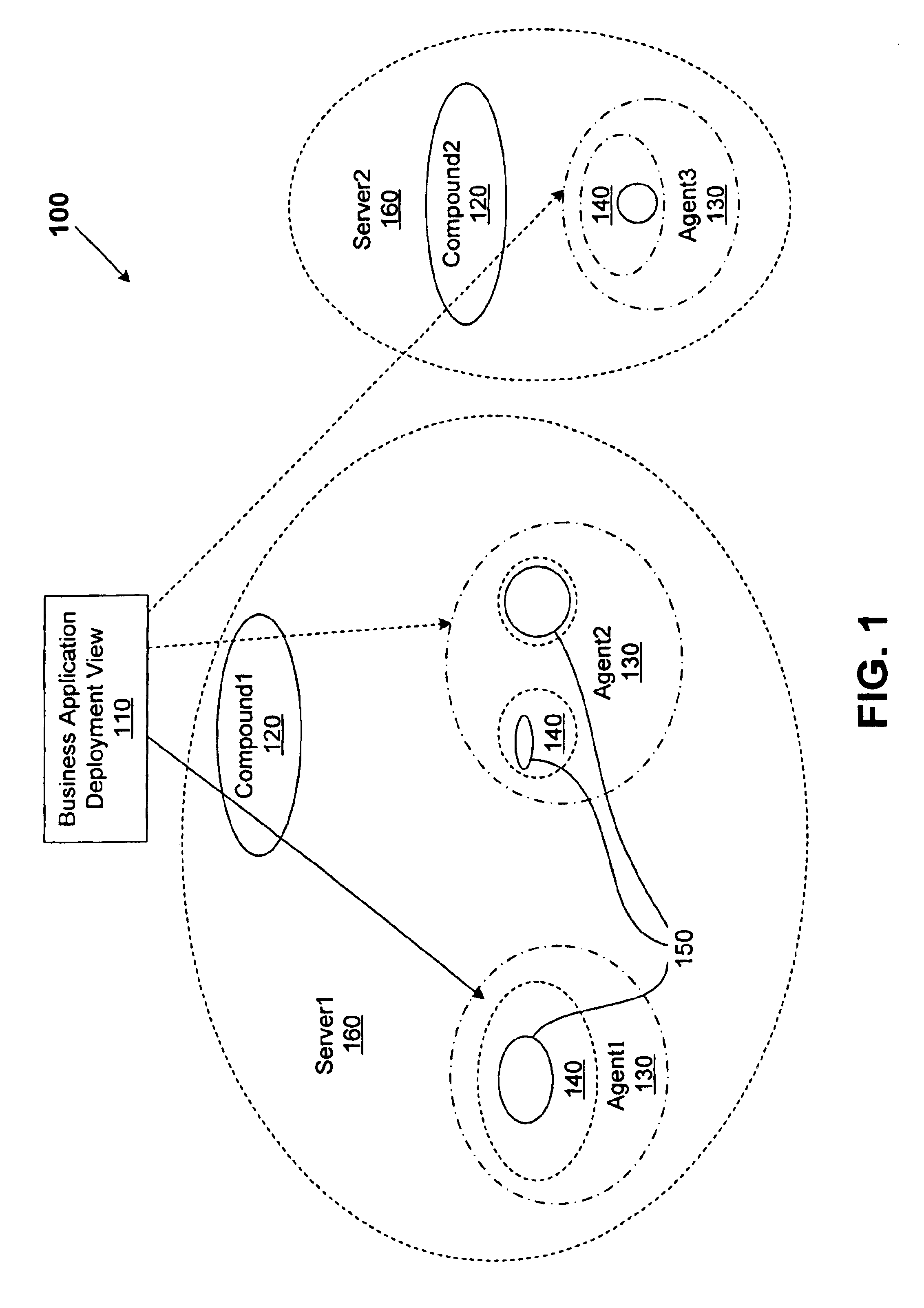
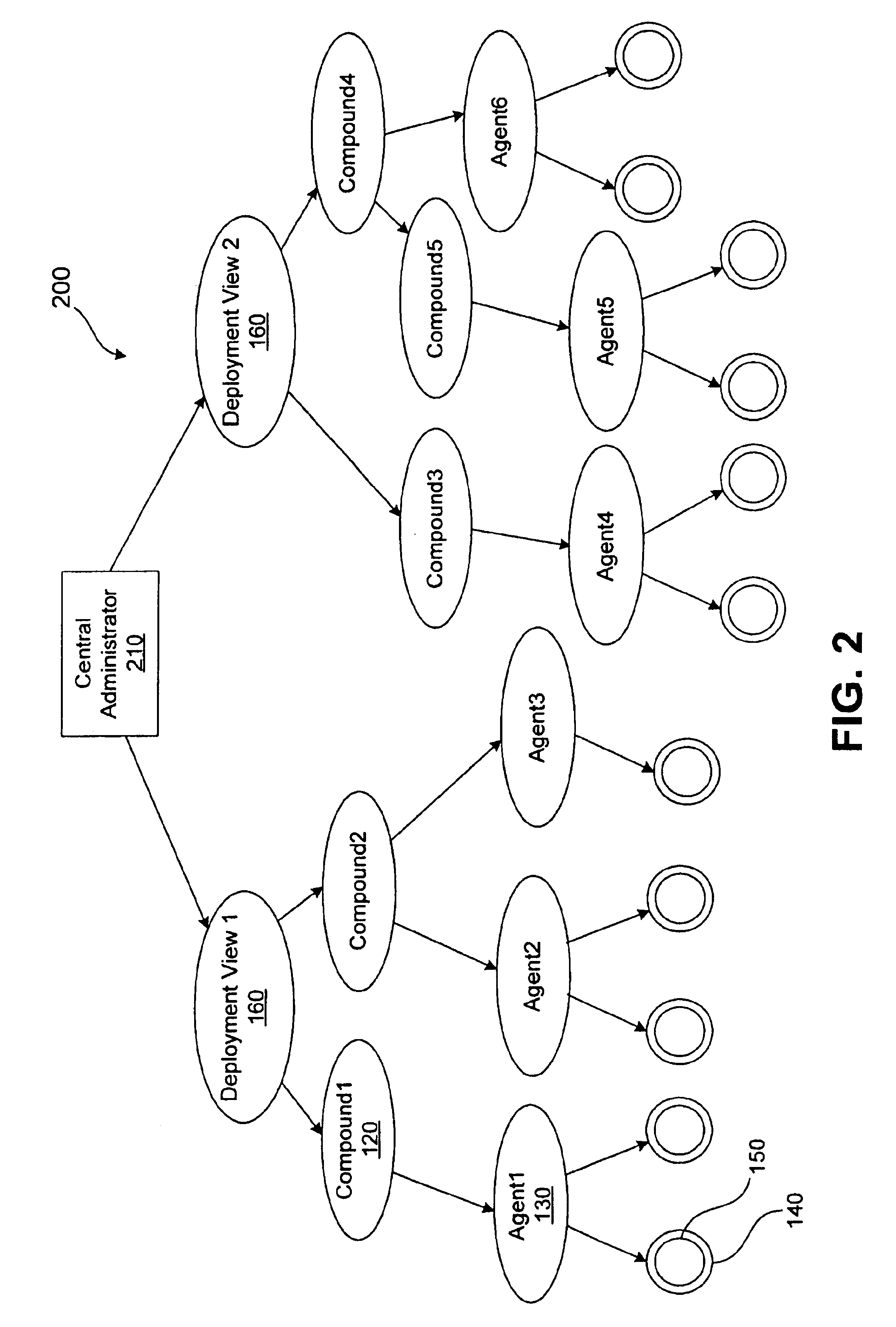
A method for performing life cycle management of business software applications and their components across a multiple-platform, multiple-language network. The method takes advantage of the inheritance properties of object-oriented programming (OOP) by developing all components of a business application from a set of base classes, thus deploying a common set of methods across all application components. The Central Administrator then determines when a need to reconfigure one or more components of the business application has arisen. The Central Administrator then modifies or replaces existing components of the business application or installs entirely new components over the network without end user interaction. In one embodiment of the present invention, the Central Administrator is aided by a set of Distributed Administrators located on each virtual node server / host computer of a business application operating over a network.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
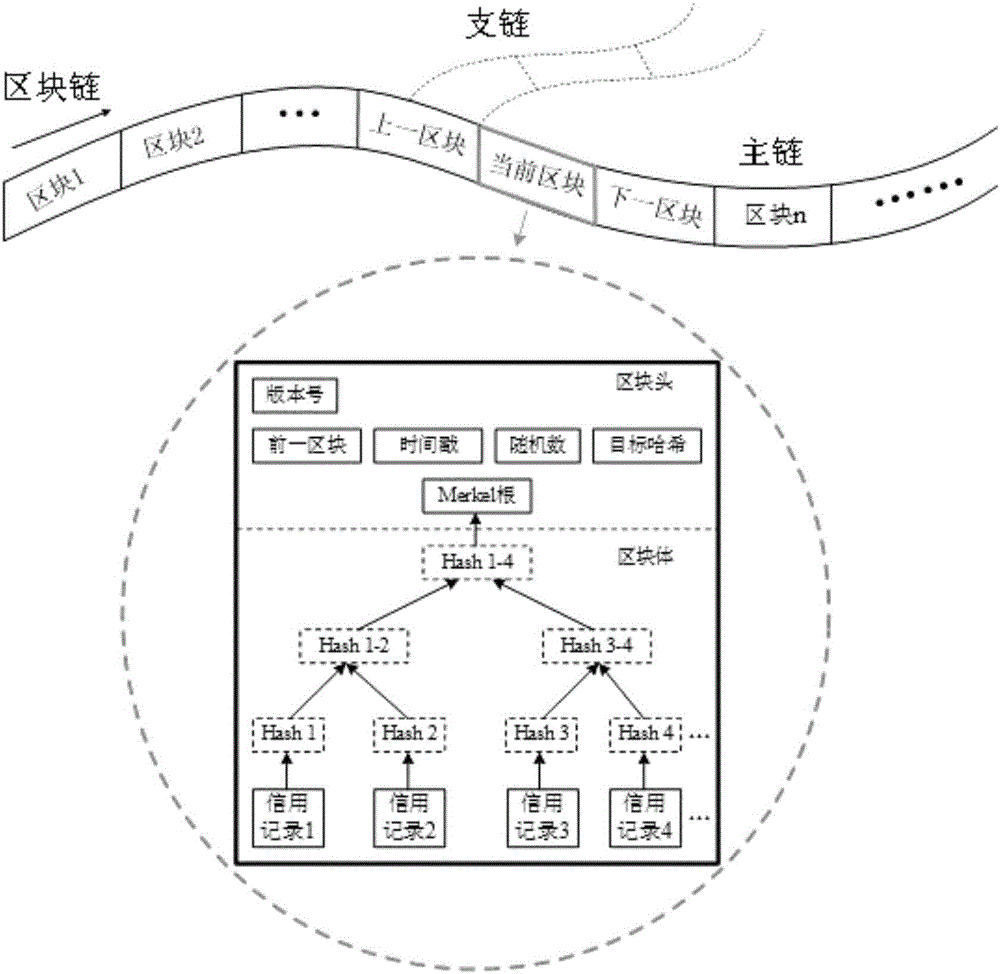
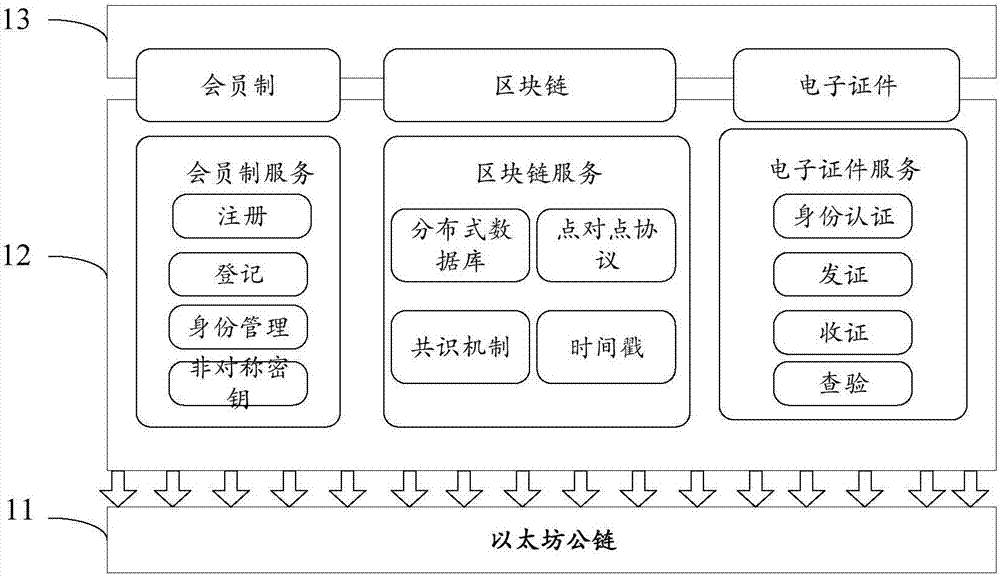
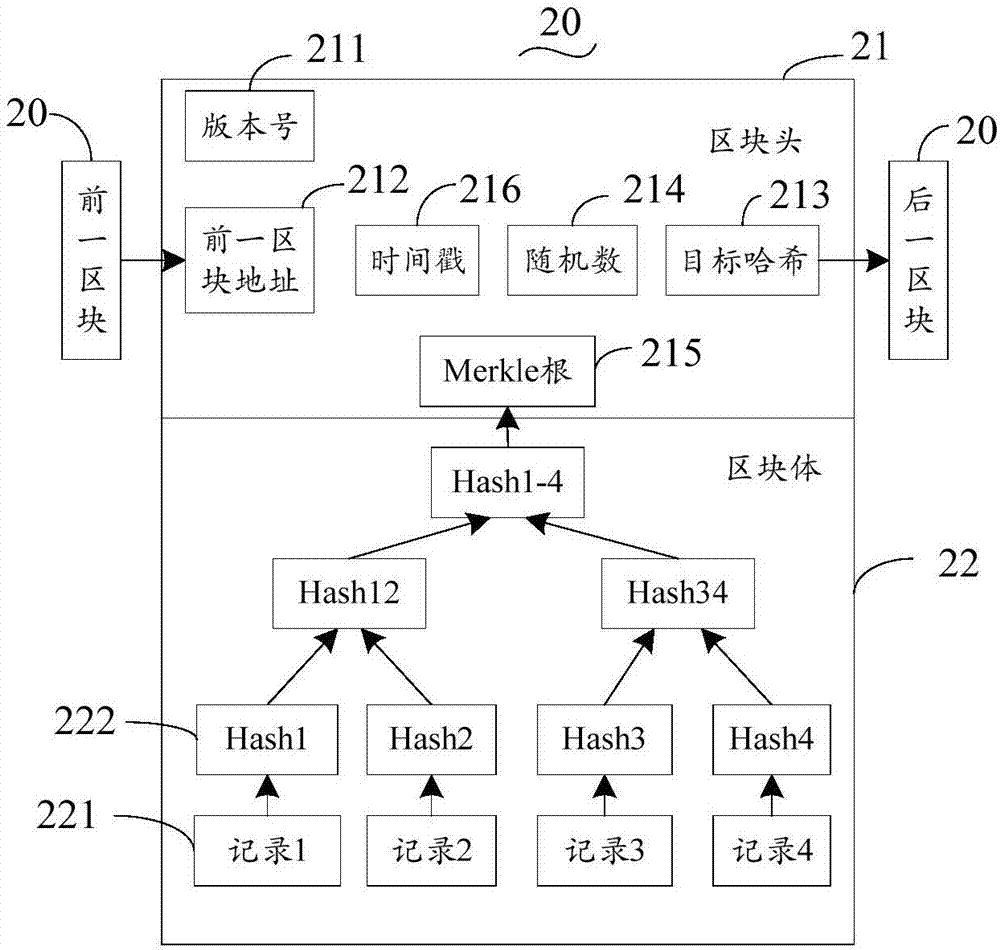
Individual credit reporting system establishment method based on block chain technology
InactiveCN106230808ARealize distributed managementAchieve sharingFinanceTransmissionData informationModel system
The invention discloses an individual credit reporting system establishment method based on a block chain technology. Block encapsulation and distributed management are carried out on individual credit data information by utilization of features of the block chain technology, and the defect that a management center is heavy in load and low in efficiency under intensive management of an individual credit reporting system can be removed. Moreover, an RSA asymmetric cryptographic algorithm is applied to a block chain, the system is very difficult to break by traversing all possible keys, the security of the individual credit reporting system is greatly ensured, and illegal tampering of the credit data can be effectively avoided. According to the method, high-security distributed data sharing among multiple credit databases can be realized, establishment of an intensive individual credit management center can be avoided, and the credit reporting cost is reduced. According to a model system structure with the complete block chain, the method has very wide application prospect in the field of individual credit reporting.
Owner:HANGZHOU YUNXIANG NETWORK TECH
Scalable communication within a distributed system using dynamic communication trees
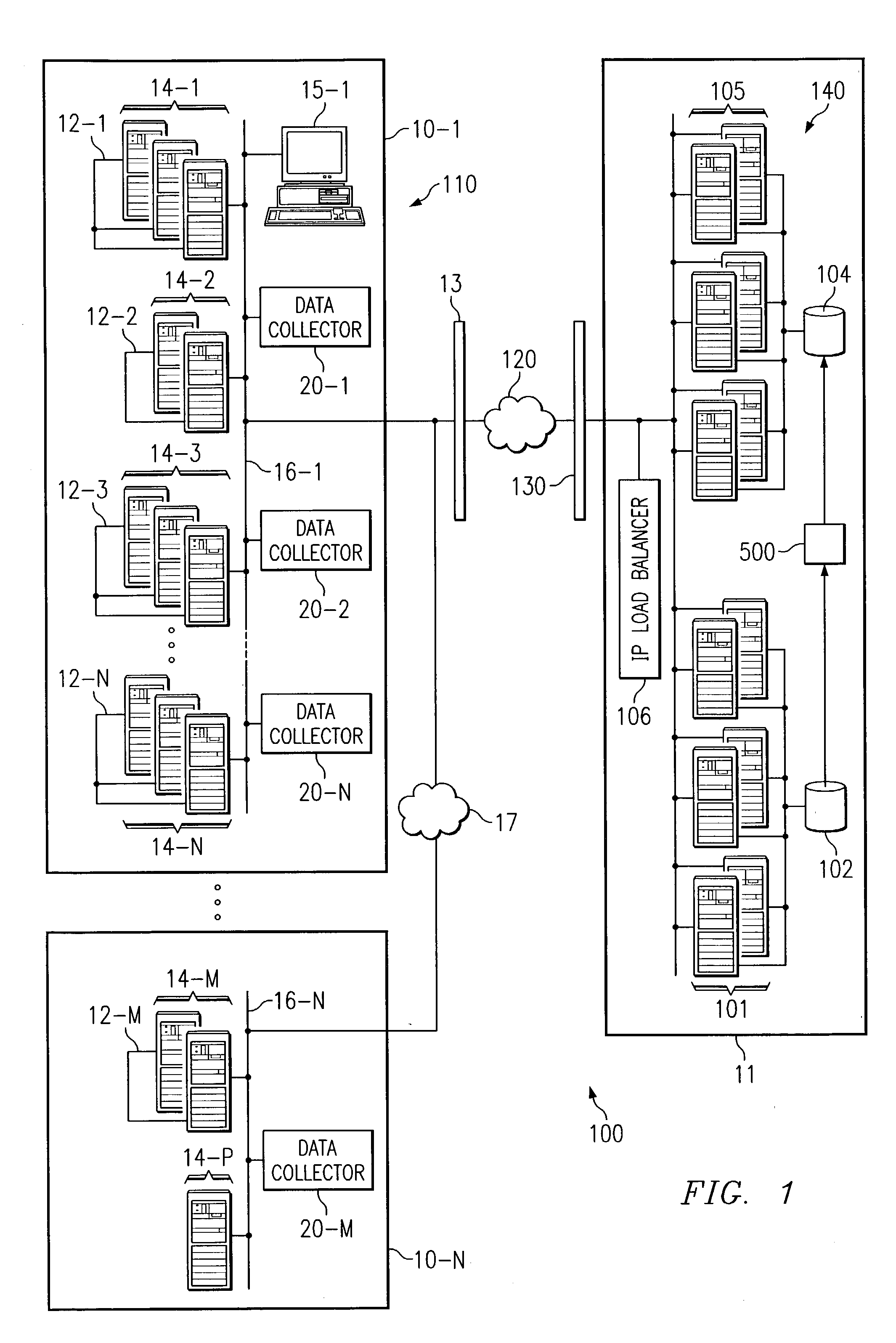
InactiveUS7010622B1Easy to useIncreased complexityData switching by path configurationMultiple digital computer combinationsStorage area networkHybrid storage system
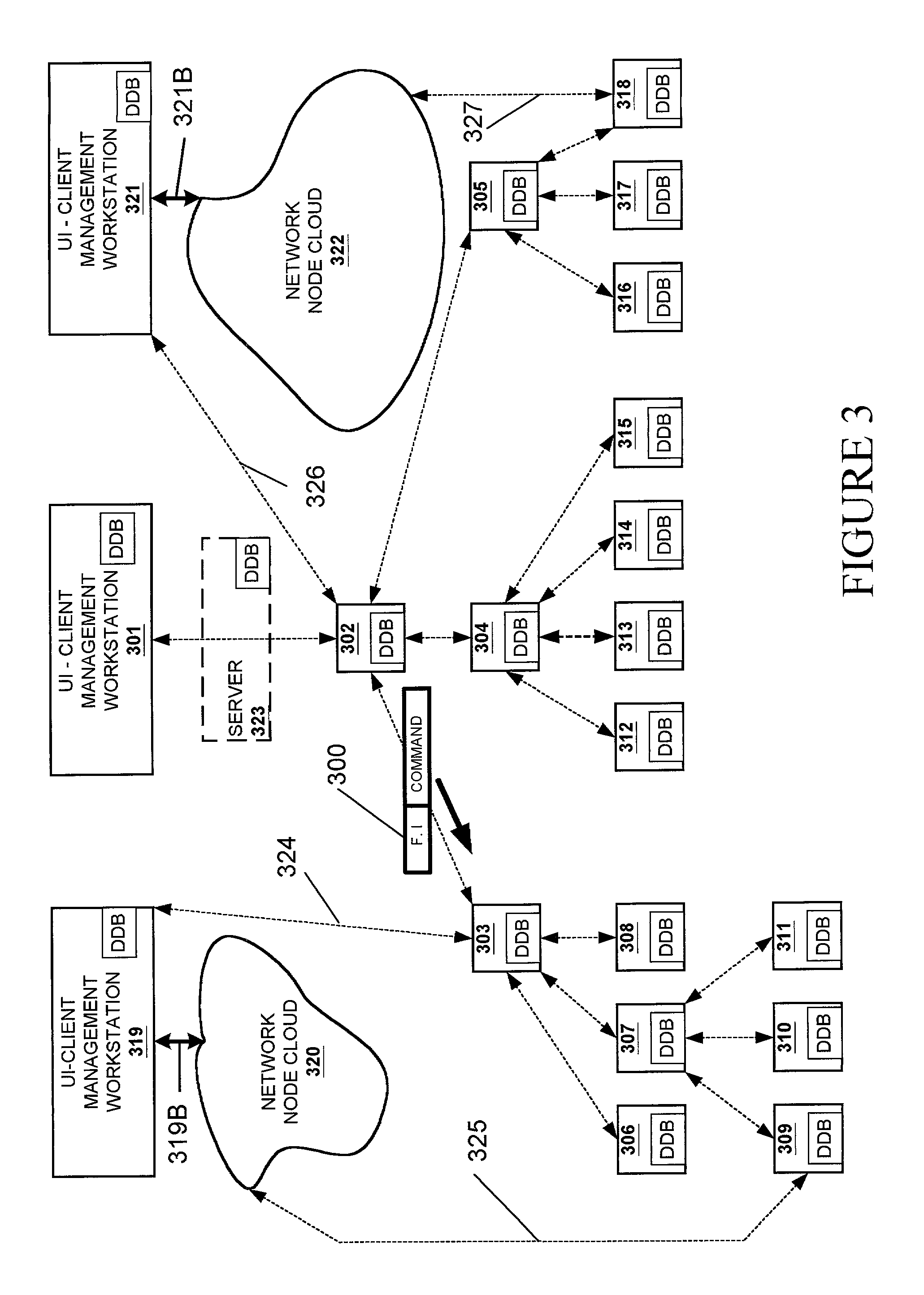
There is disclosed a technique for achieving scalable communication within a distributed system using dynamic communication trees. In a client server environment, and particularly in such an environment in which storage systems and storage area networks are managed by distributed management software, embodiments of the present invention are presented by which communication trees are built in a manner that evenly distributes load throughout nodes in the network, whereby scalability is enhanced allowing a larger number of nodes than otherwise allowable without such trees. Other advantages achievable by utilization of such trees are also disclosed.
Owner:EMC IP HLDG CO LLC
Electronic certificate management method and related equipment
ActiveCN107231351ARealize distributed managementImprove storage reliabilityMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesChain networkInformation security
The invention discloses an electronic certificate management method and related equipment. The method comprises the steps as follows: the electronic equipment processes an electronic certificate in response to a received processing command; an encrypted processing record is broadcasted into a block chain network, thus allowing a node of the block chain network to store the encrypted processing record into a block chain of the block chain network. According to the scheme of the method provided by the invention, distributed management of the electronic certificate is achieved, storage reliability of the electronic certificate is improved, the risk of tampering or leaking certificate information is reduced, and information security and credibility of the electronic certificate are effectively ensured.
Owner:YGSOFT INC
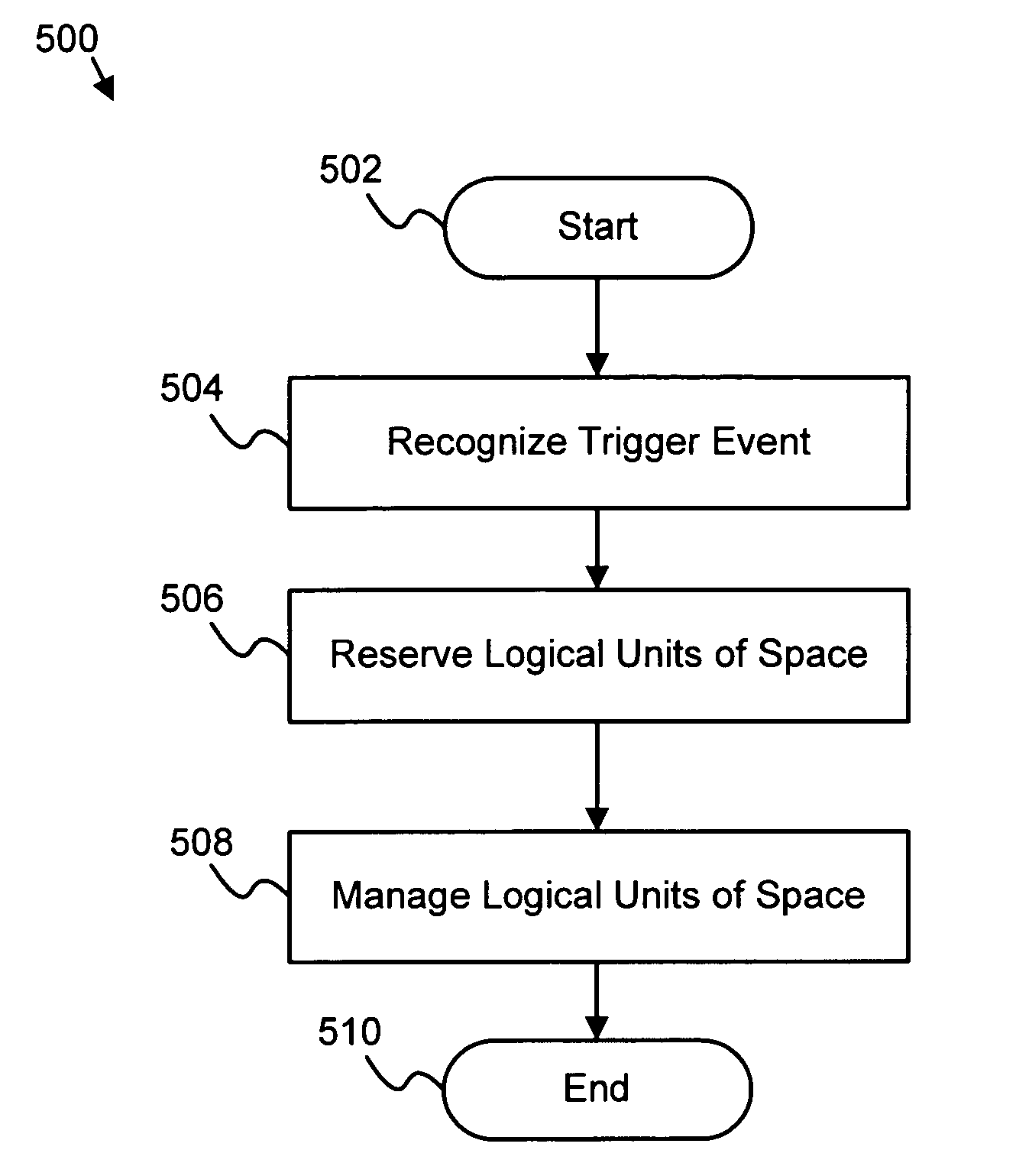
Apparatus, system, and method for managing storage space allocation
InactiveUS20060129778A1Multiple digital computer combinationsTransmissionStorage area networkFile system
An apparatus, system, and method are disclosed for managing storage space allocation. The apparatus includes a recognizing module, a reserving module, and a managing module. The recognizing module recognizes a trigger event at a client of the data storage system. The reserving module reserves logical units of space for data storage. The management module manages the logical units of space at the client. Such an arrangement provides for distributed management of storage space allocation within a storage area network (SAN). Facilitating client management of the logical units of space in this manner may reduce the number of required metadata transactions between the client and a metadata server and may increase performance of the SAN file system. Reducing metadata transactions effectively lowers network overhead, while increasing data throughput.
Owner:IBM CORP
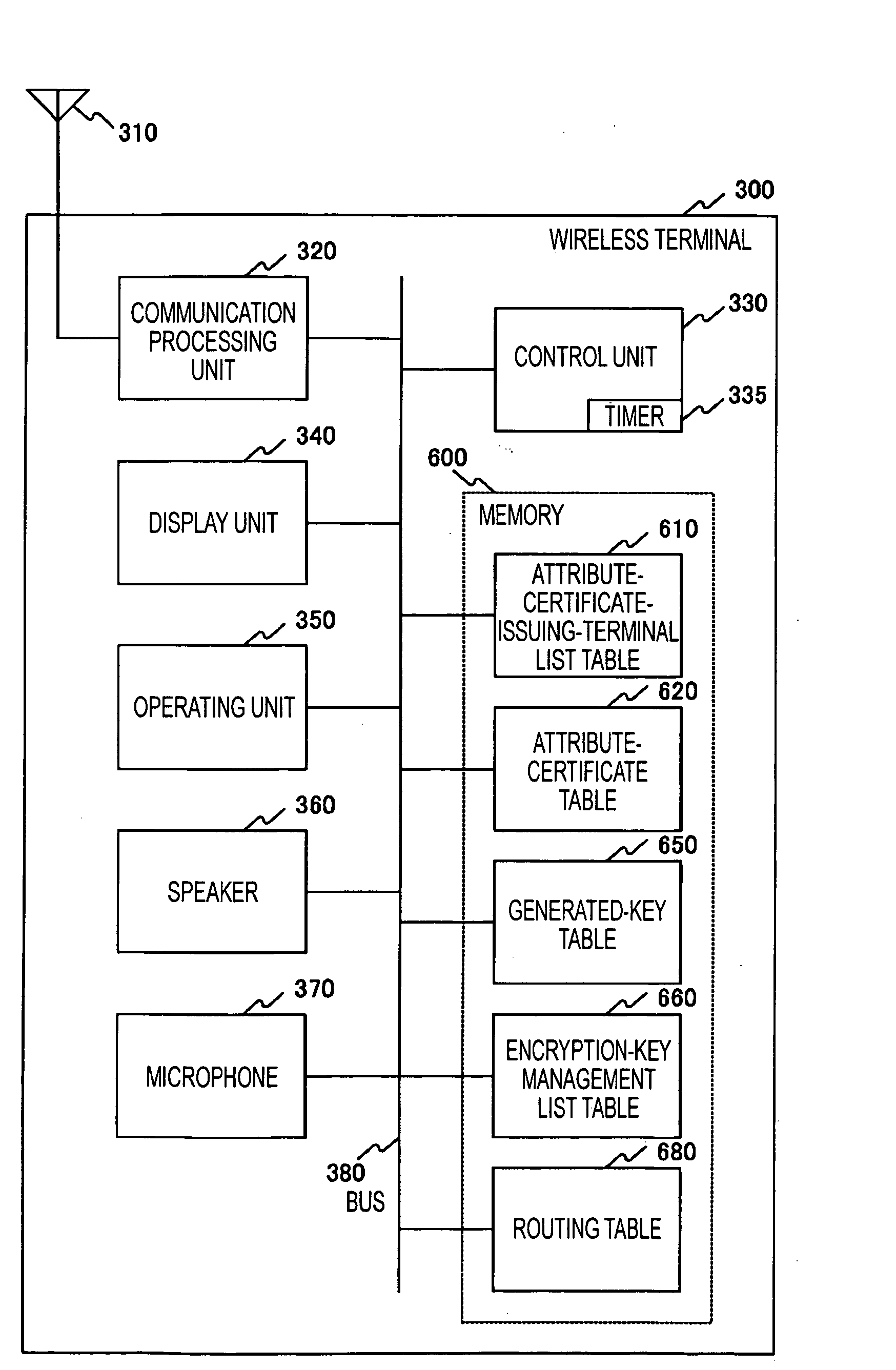
Broadcast encryption key distribution system
ActiveUS20050123141A1Key distribution for secure communicationUser identity/authority verificationKey distributionBroadcasting
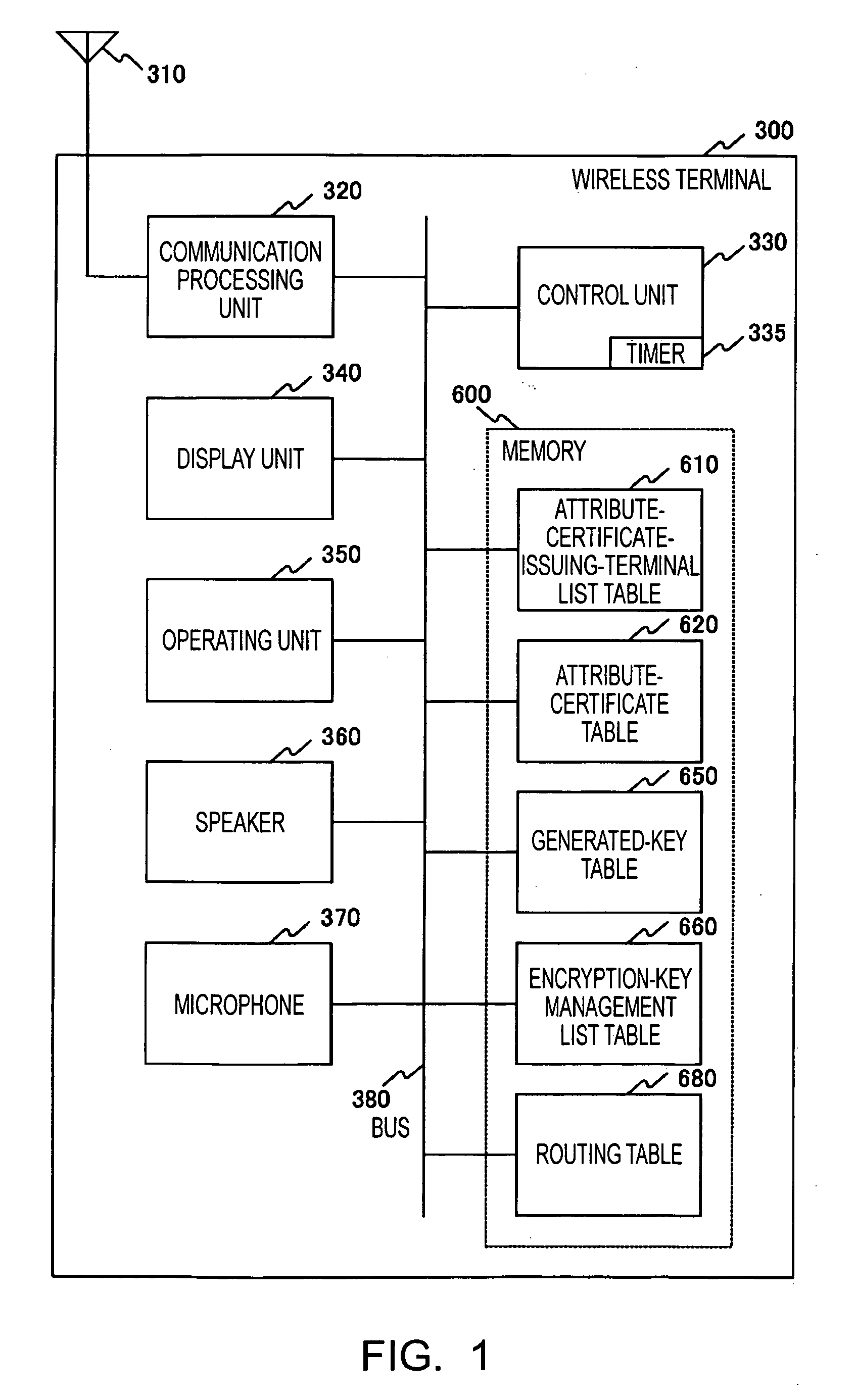
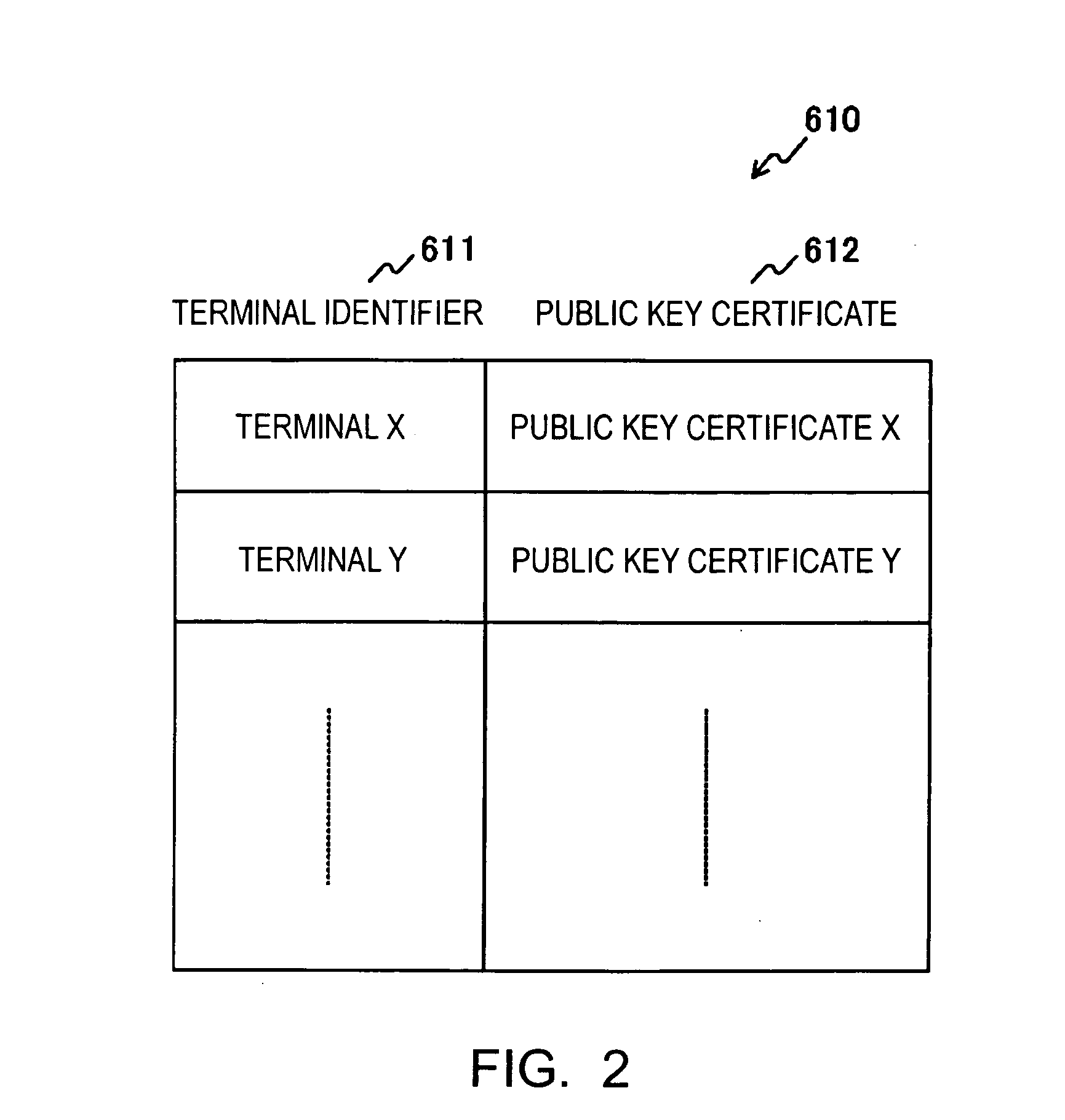
Each terminal in a wireless ad-hoc communication system includes an encryption-key management list table 660. The encryption-key management list table 660 stores, in association with a terminal identifier 661 such as a MAC address, a unicast encryption key 662 for use in unicast communication with a terminal identified by the terminal identifier 661, and a broadcast encryption key 663 used when the terminal identified by the terminal identifier 661 performs broadcast communication. Therefore, a broadcast encryption key is provided for each terminal that performs broadcast communication, and the broadcast encryption keys are managed by the individual terminals in an independent and distributed manner. This allows independent and distributed management of broadcast encryption keys in a wireless ad-hoc communication system.
Owner:SONY CORP
Vulnerability management system based on multi-engine vulnerability scanning association analysis
ActiveCN108737425AMeet safety construction requirementsEfficient and accurate executionTransmissionVulnerability managementOperational system
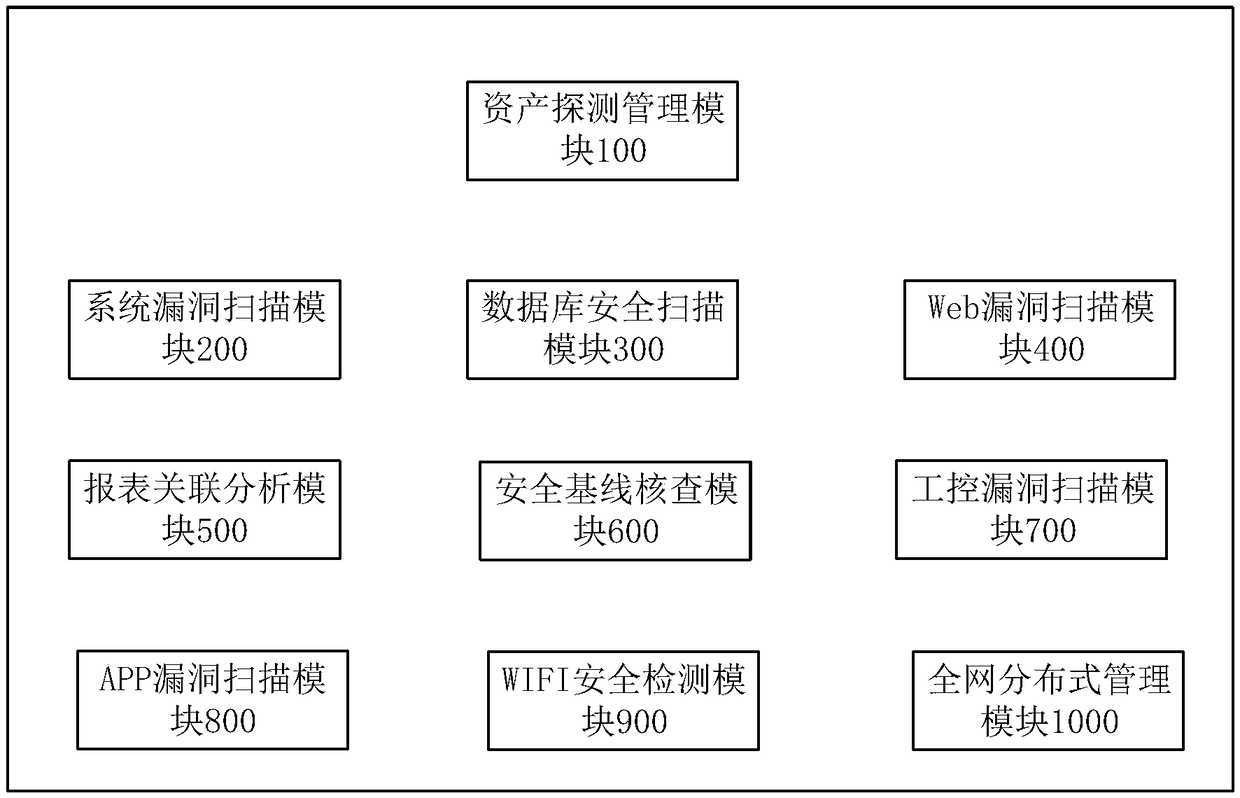
The invention provides a vulnerability management system based on multi-engine vulnerability scanning association analysis. The vulnerability management system comprises: an asset detection managementmodule used for detecting asset information in a scanning network; a system vulnerability scanning module used for performing vulnerability scanning and analysis on a network device, an operating system, application service and a database according to the asset information, and supporting intelligent service identification; a Web vulnerability scanning module used for automatically parsing data according to the asset information, scanning the data, verifying a discovered WEB vulnerability, and recording a test data packet discovered by vulnerability scanning; a database security scanning module; a security baseline verification module; an industrial control vulnerability scanning module; an APP vulnerability scanning module; a WIFI security detection module; a report association analysismodule; and a whole-network distributed management module. The vulnerability management system provided by the invention can perform association analysis on a detection result and a compliance libraryof information security level protection to generate a level protection evaluation report that meets the specification requirements, and the security requirements of different customers are comprehensively met.
Owner:北京凌云信安科技有限公司
Programmable lighting system
InactiveUS20160029464A1Discharge tube incandescent screensElectric discharge tubesEffect lightLighting system
Owner:HUGHES DAVID ANTHONY +1
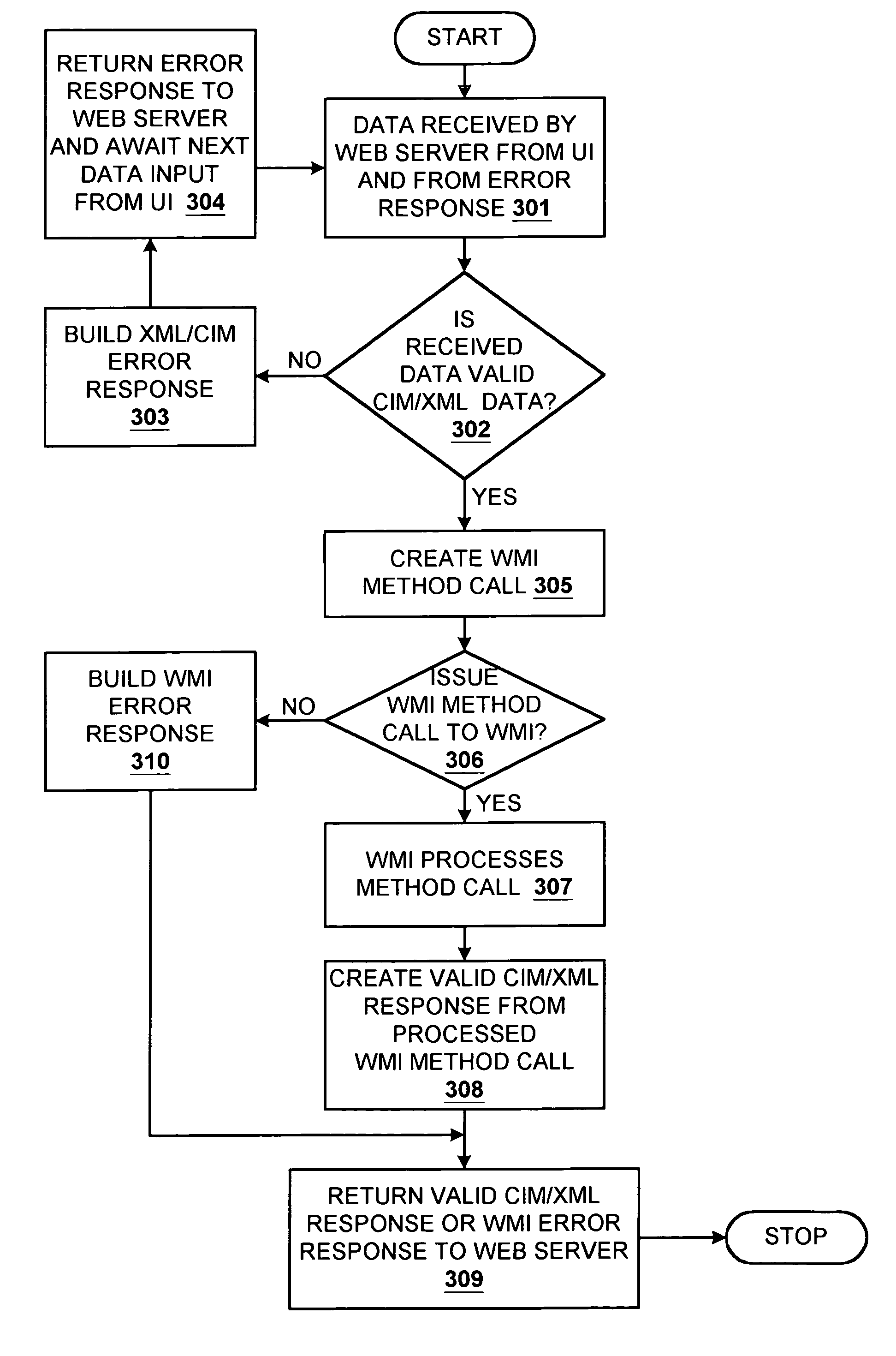
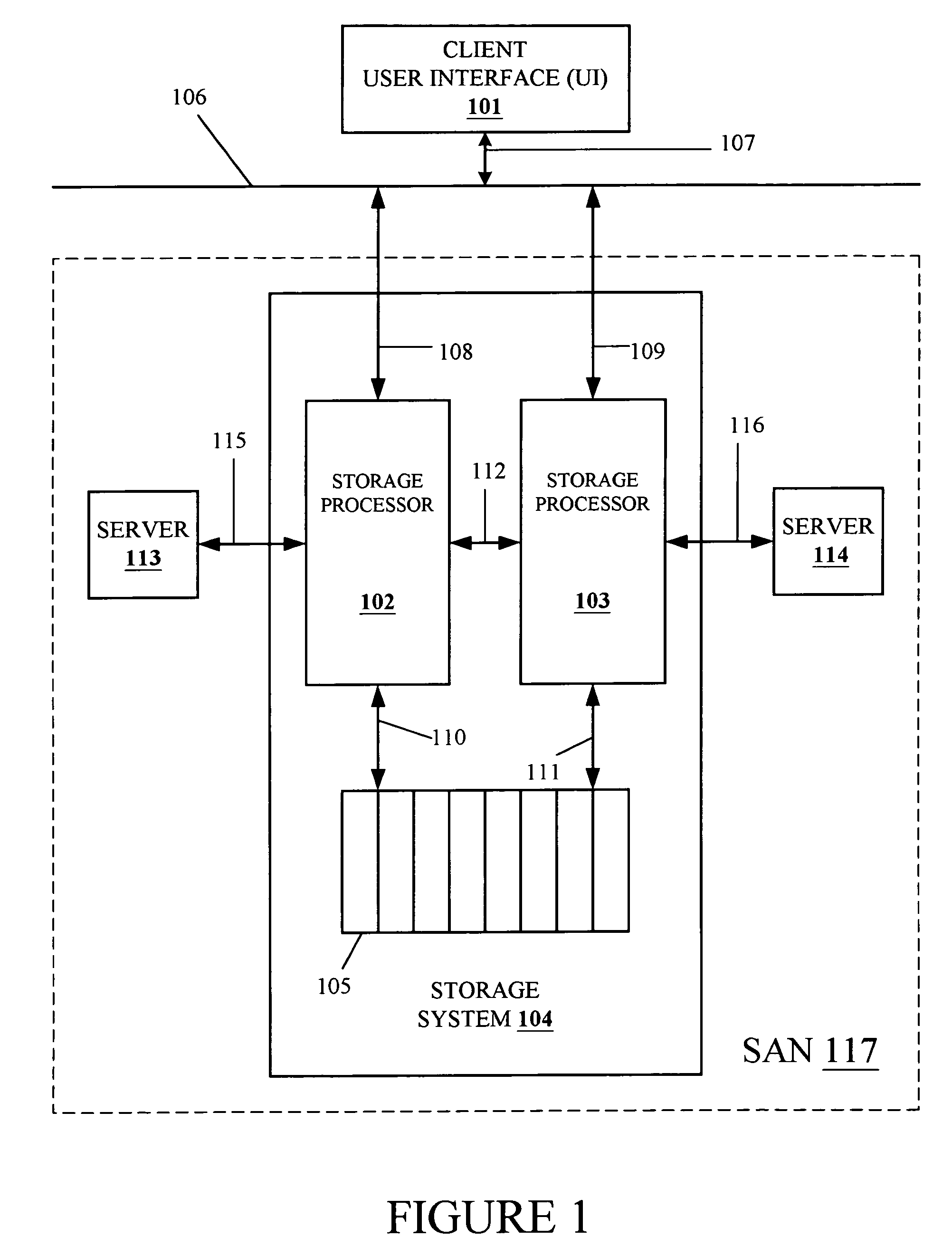
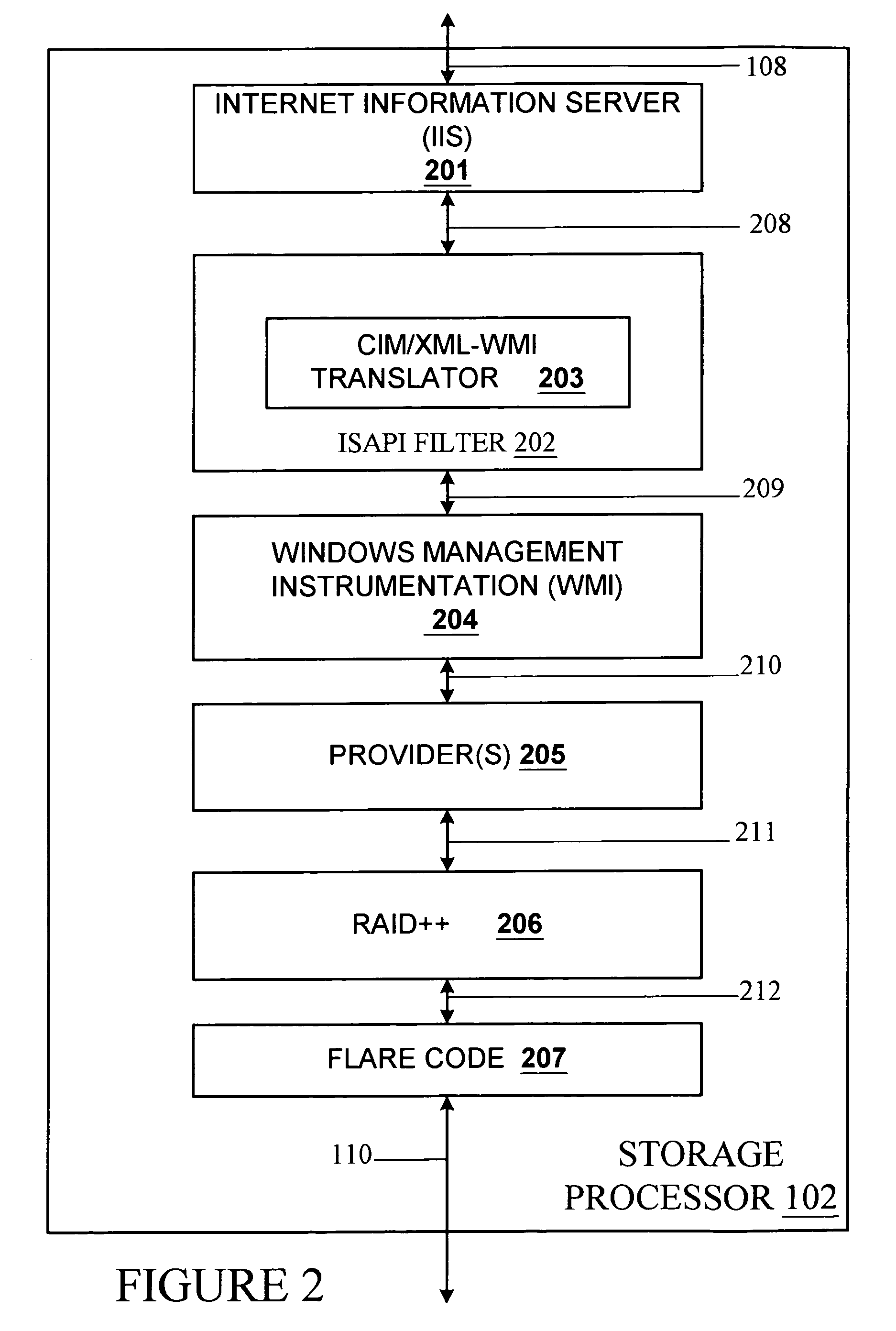
Common Information Model (CIM) translation to and from Windows Management Interface (WMI) in client server environment
InactiveUS6971090B1Interprogram communicationTransmissionComponent Object ModelDistributed Component Object Model
A protocol translator for use in a storage system or storage area network for translating between incompatible communication protocols. Apparatus, methodology, computer program product and interface embodiments are disclosed, and code examples are provided, for translating between Common Information Model / eXtensible Markup Language / Hyper Text Transfer Protocol (CIM / XML / HTTP) and Windows Management Interface / Distributed Component Object Model (WMI / DCOM) communication protocols for distributed management software used within a storage system or storage area network in a client server environment.
Owner:EMC IP HLDG CO LLC
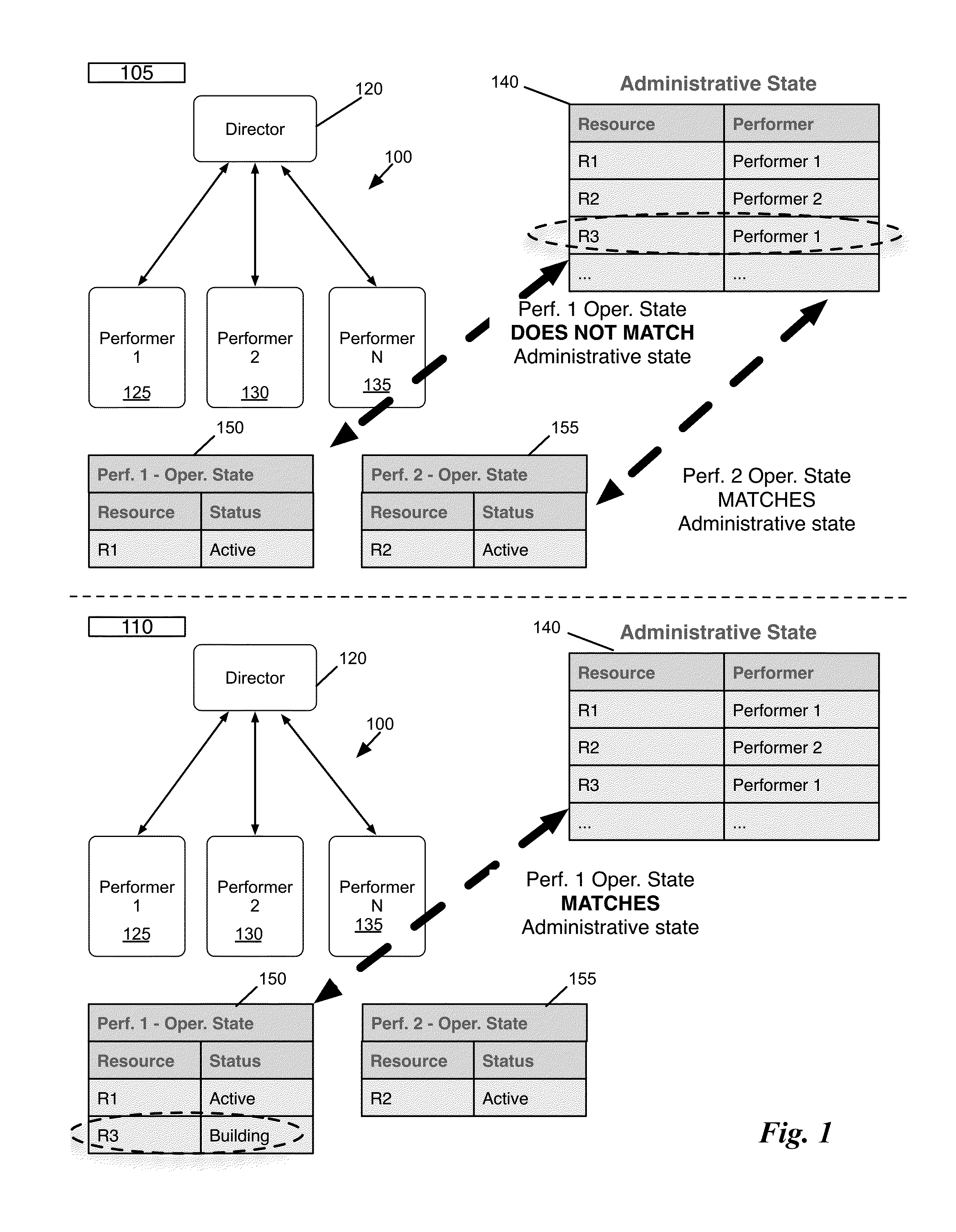
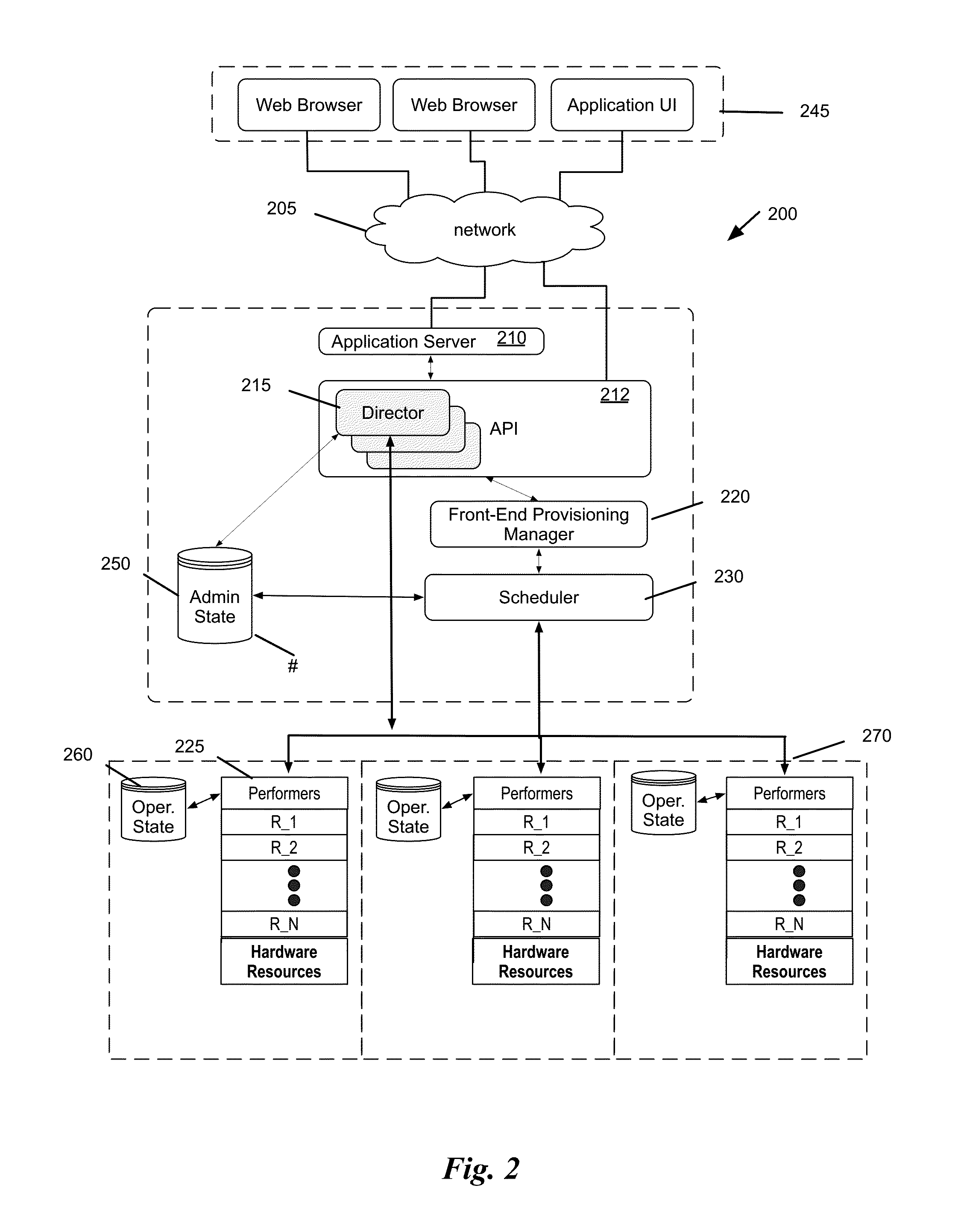
System and method for distributed management of cloud resources in a hosting environment
ActiveUS9350681B1Efficient managementDigital computer detailsData switching networksHosting environmentCloud resources
Some embodiments provide a method of managing cloud resources on several of nodes of a hosting system. The method receives a cloud resource configuration. The method identifies a particular node from the several nodes to host the cloud resource configuration. The method sets an administrative state of the hosting system to reflect the hosting of the cloud resource configuration on the particular node. The administrative state includes information for each node in the hosting system. Each node includes a performer operating on the node that manages an operational state of the node based on the administrative state of the node.
Owner:OPEN INVENTION NEWTORK LLC
Method and apparatus for providing dynamic group management for distributed interactive applications
InactiveUS20050114478A1Variable sizeSpecial service provision for substationData switching by path configurationSession controlClient-side
A method, computer readable media, and apparatus of hierarchical-based communication session and data distribution management that indexes client's communication preferences and network attribute information. Indexing is used to generate dynamic group membership lists that map into communication groups. Indexing is replicated at control nodes in the network overlay to allow distributed management of group membership. Send / receive operations are decoupled through data distribution and the indexing structure. Senders and receivers register their group communication interests to a parent node in the hierarchy. The session control structure aggregates client interest and dynamically updates replicas at control nodes which are selected according to the changes in registered client interest. The indexing structure has self-managing properties for automatic clustering based on client session and data interests, and dynamic partitioning of the session / data interest attribute space. Group membership is managed by querying the indexed session / data distribution management structure and mapping output to communication groups.
Owner:IBM CORP
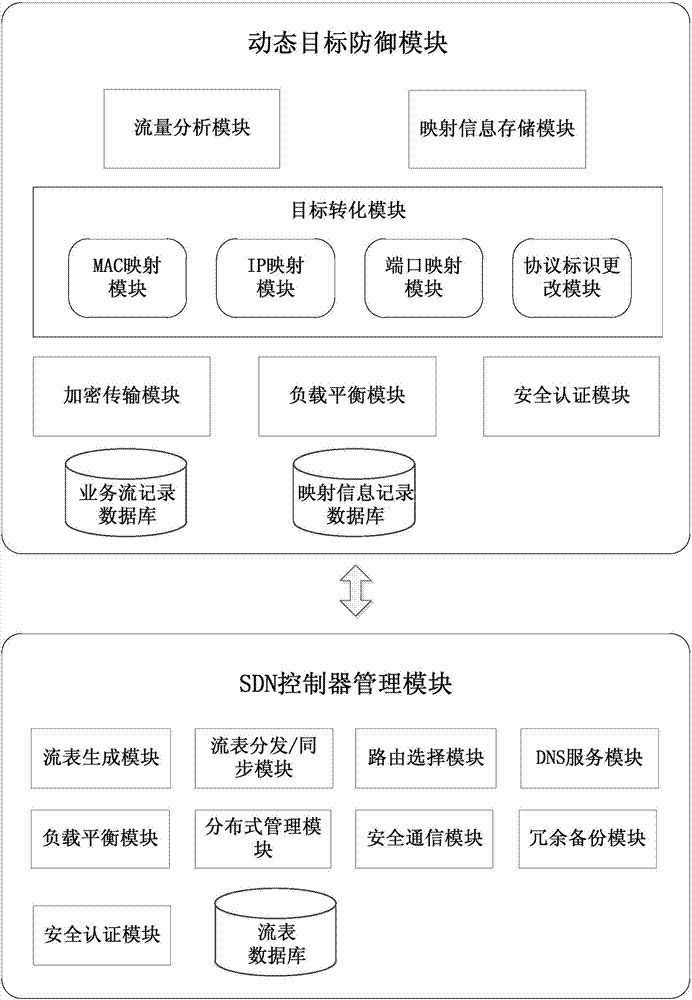
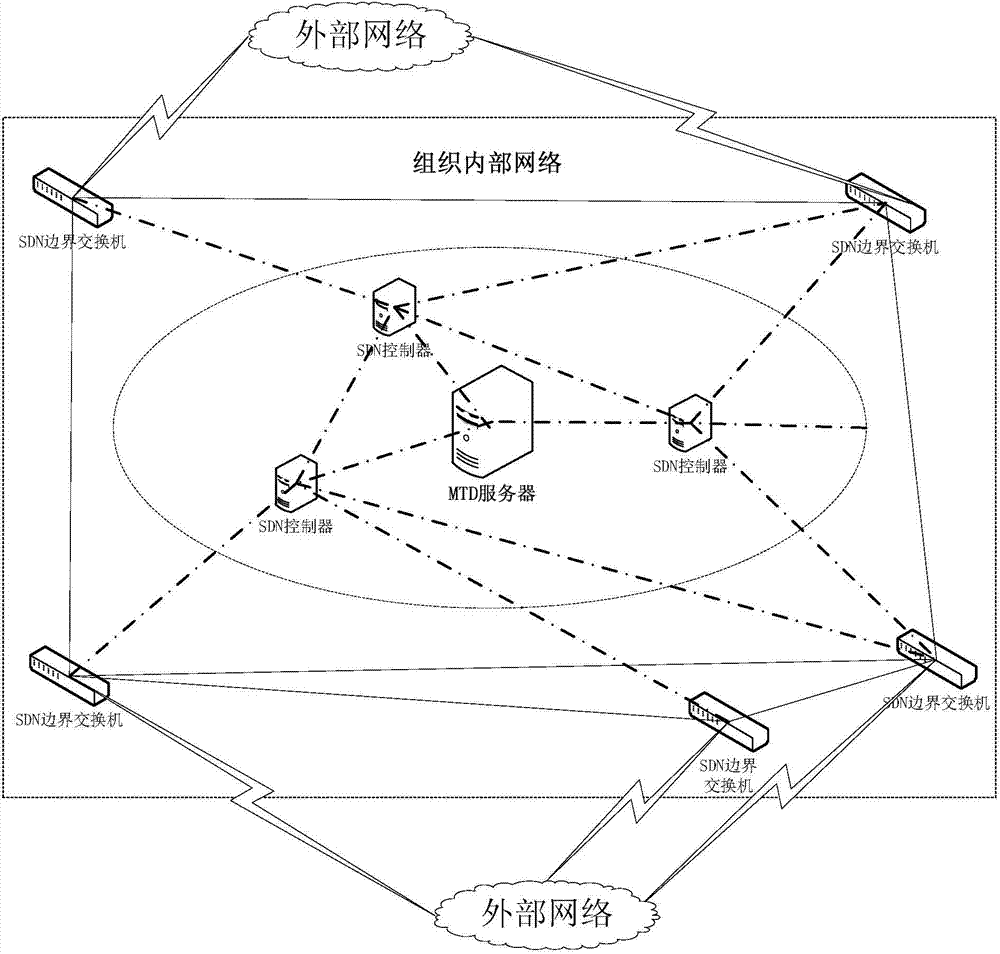
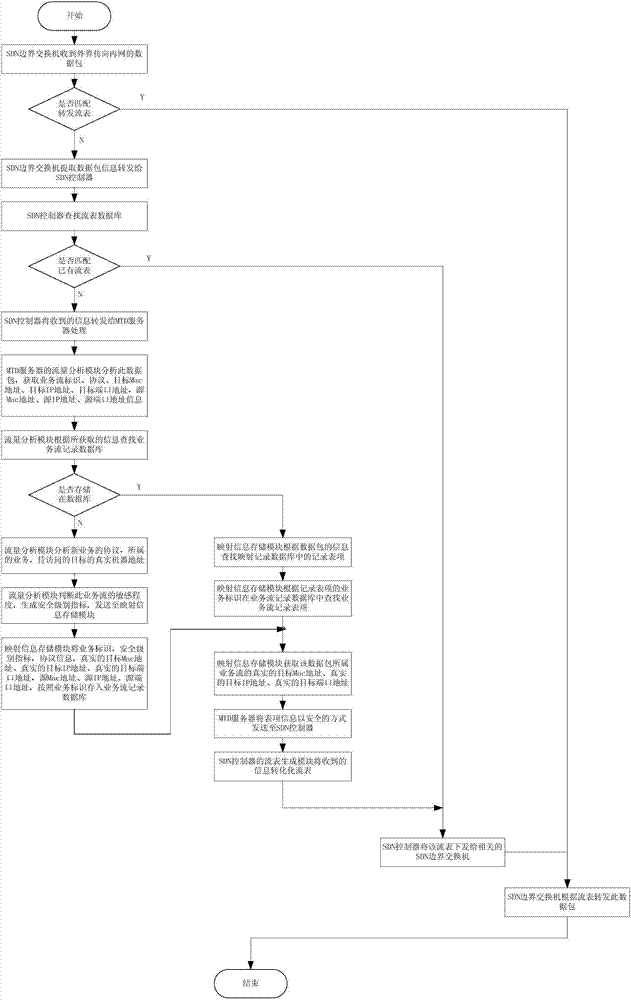
Moving target defense system and moving target defense method for SDN (self-defending network)
InactiveCN104506511AProtection securityIncrease the difficultyTransmissionTraffic flow analysisSafety Communications
The invention discloses a moving target defense system for an SDN (self-defending network). The system consists of a moving target defense module and an SDN controller management module; the moving target defense module comprises a flow analysis module, a mapping information storage module, a target conversion module, an encryption transmission module, a load balance module, a safety authentication module, a business flow recording database and a mapping information recording database; the SDN controller management module comprises a flow table generation module, a flow table distribution / synchronization module, a route selection module, a DNS service module, a load balance module, a distributed management module, a safety communication module, a redundant backup module, a safety authentication module and a flow table database; furthermore, the invention also discloses a moving target defense method for the SDN. Through the moving target defense system and the moving target defense method disclosed by the invention, the difficulty of an attacker to detect a target is increased further, and therefore the safety of an intranet is comprehensively protected.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
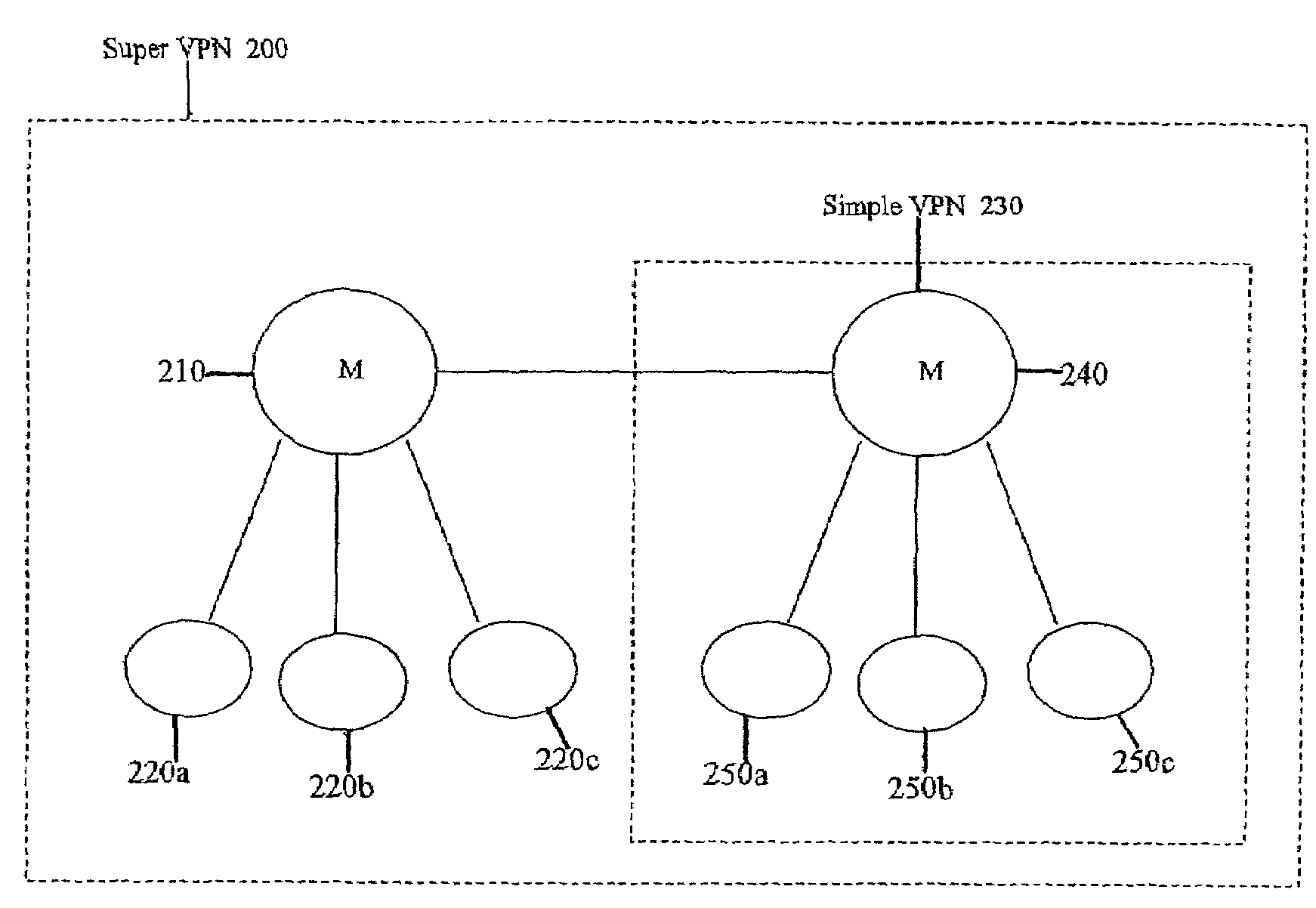
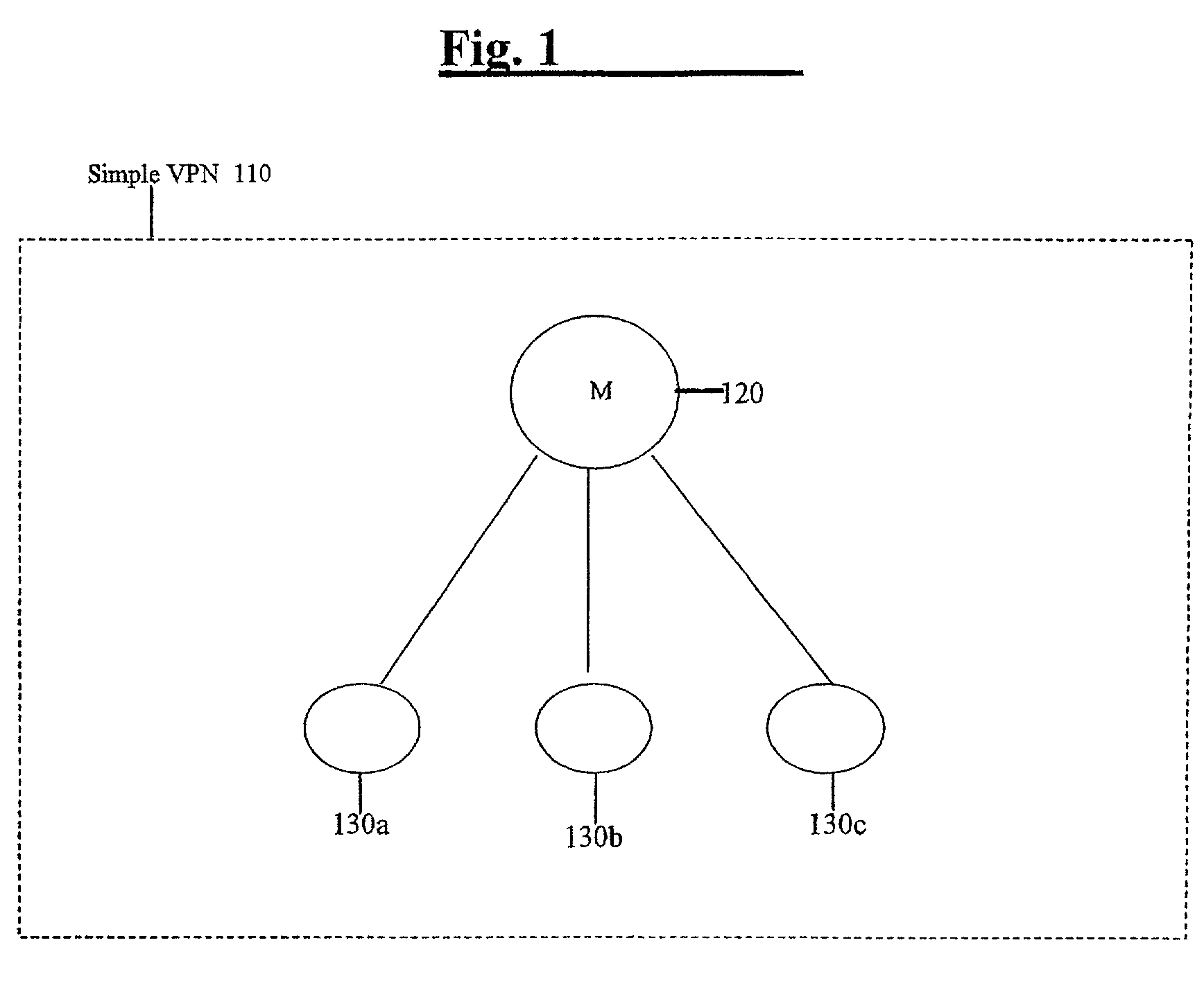
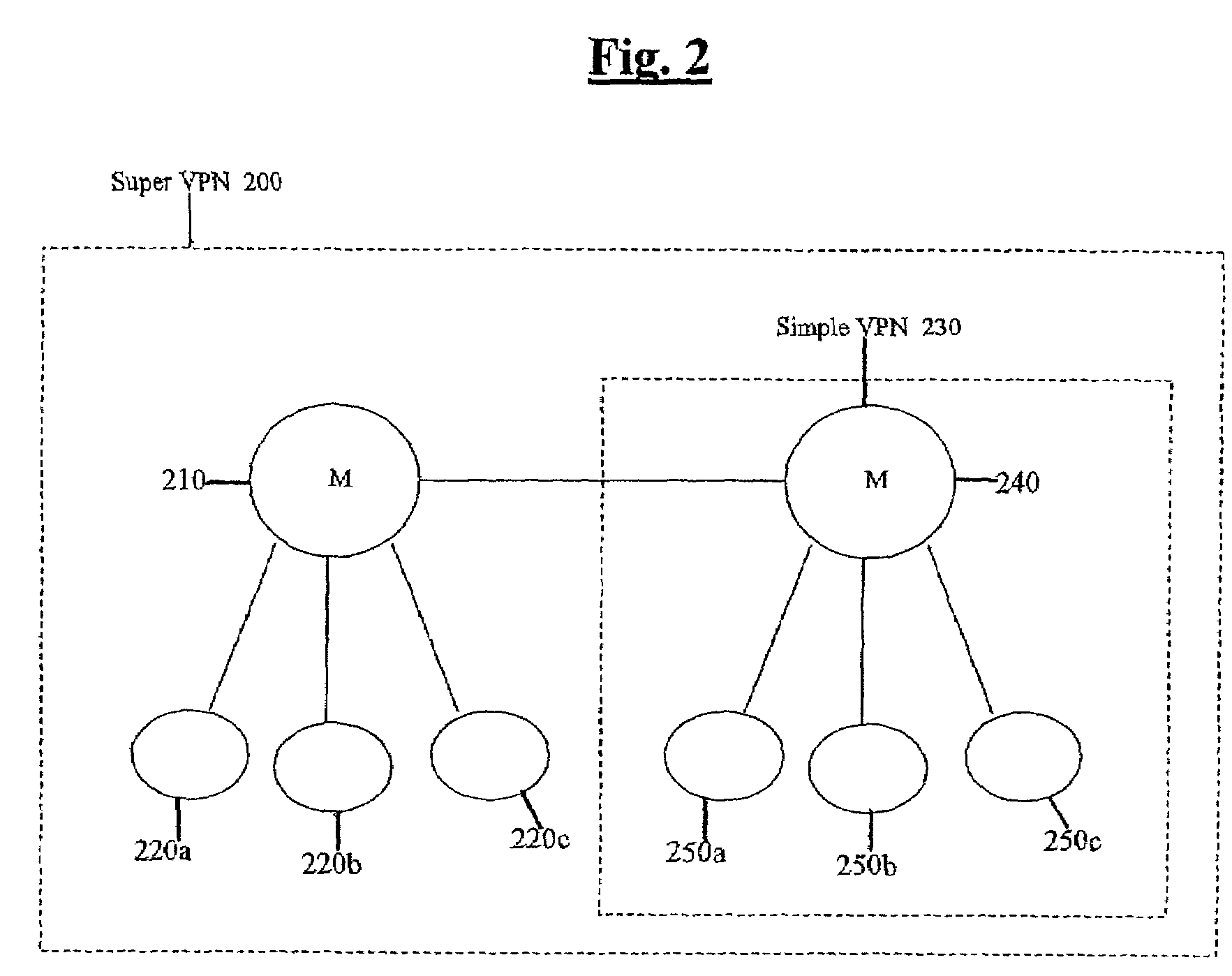
Methods and apparatus for scalable, distributed management of virtual private networks
InactiveUS7403980B2Improve reliabilityImprove efficiencyMultiple digital computer combinationsNetworks interconnectionFailoverGraphics
A groupware management system for collaborative groups is disclosed that is scalable to support large, dynamic, multiple, and other virtual VPNs. The system may introduce a graph (or hierarchical) structure to the VPN, providing multiple master nodes controlling membership in subsets of the collaborative group. Use of multiple master nodes in a graph-structured (or hierarchical) network topology often relaxes the need for a single, centralized, globally consistent view of VPN group membership, and enables distribution of the management burden among multiple master nodes. Membership in the VPN may be changed dynamically by the second master node for the member nodes of the second subset, without requiring the first master node to dynamically update its group membership records to reflect the change and in many cases without even having to notify the first master node (and vice versa), for example. In further embodiments, the use of multiple master nodes may increase the reliability and efficiency of VPNs, such as by enabling load balancing of master node tasks. Fail-over mechanisms may also be used to transparently re-route management tasks to an alternate master node especially in the case of failure of the current master node serving a given member node.
Owner:NAVY SEC OF THE UNITED STATES +1
JMX based network service management method and its application system
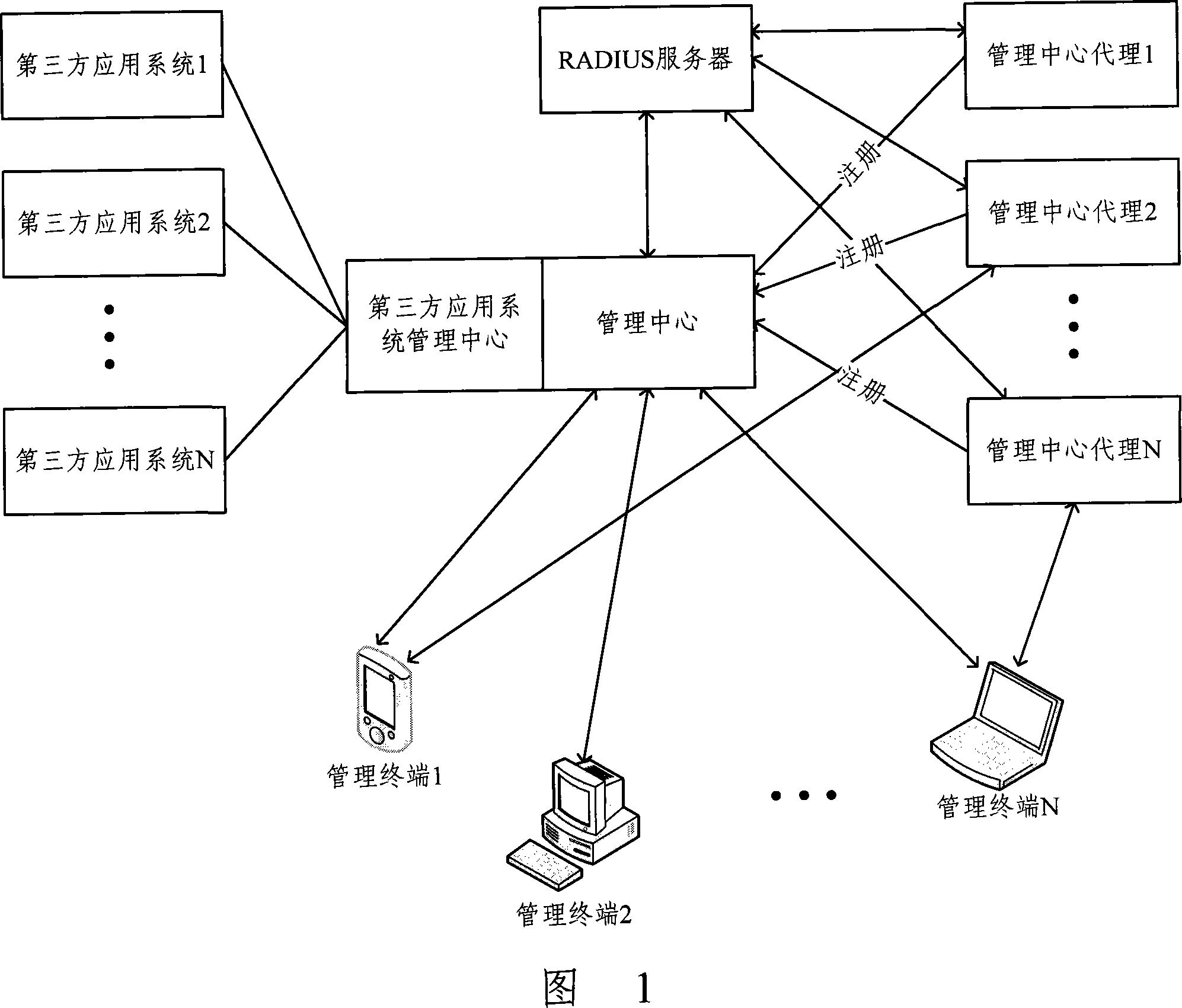
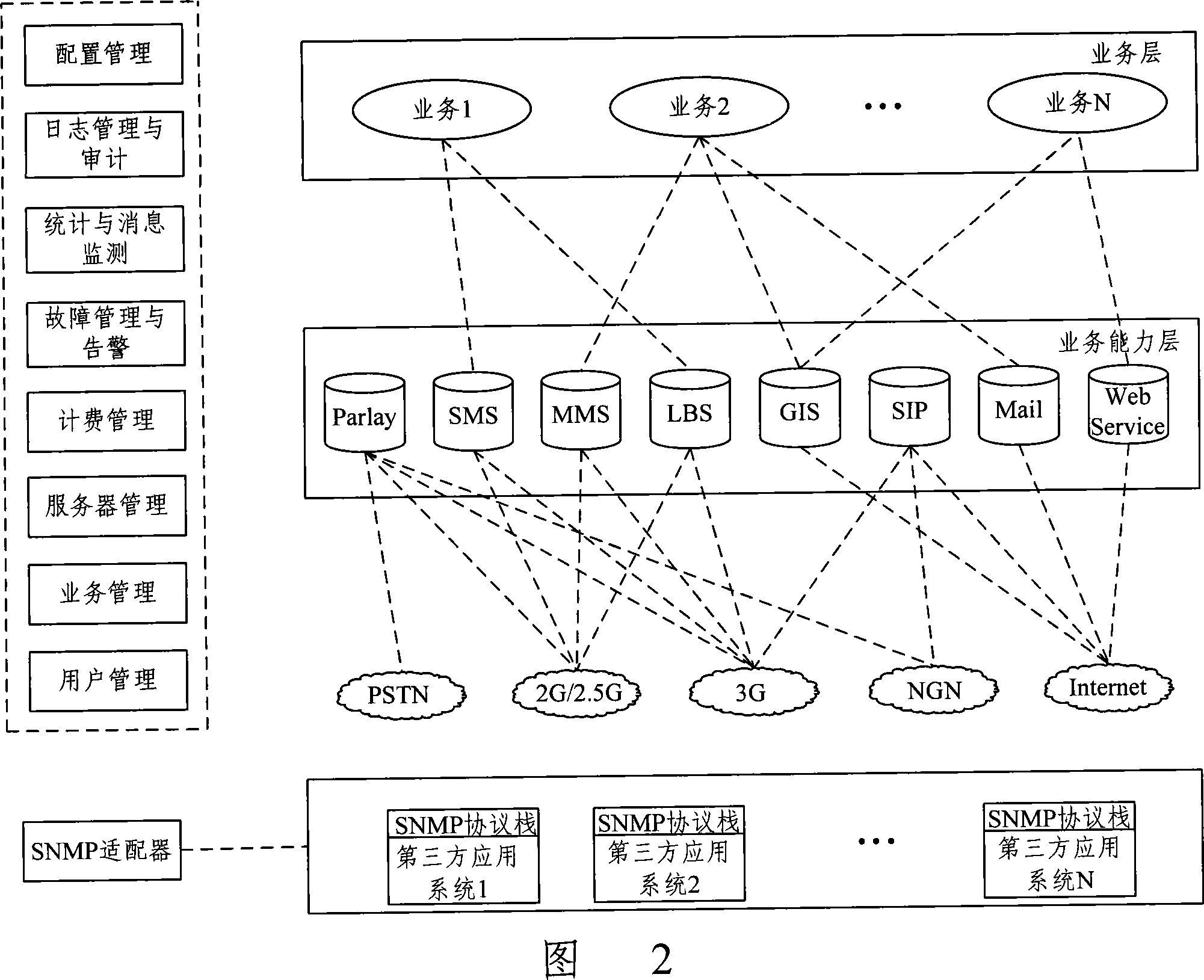
InactiveCN101072129AAvoid complicated settingsAchieve intelligenceData switching networksSelection arrangementsThird partySystems management
Using administrator - agent mode, the system can carries out distribution type management for multiple telecom services and service capabilities across platforms. Logging on management center (MC) in the method, management terminal (MT) configures global basic settings of system. Being registered on MC, agent of MC is managed by MC. Based on command of MT, MC carries out managing one or more functions of resources of each server in system by calling each agent of MC. Based on call from MC, each agent of MC executes managing operations, and feeds back accomplishing situation to MT. MC is possible to be integrated to application system in third party. Application system includes MC, MC of application system in third party, at least one agent of MC, and at least one MT. Advantages are: supporting multiple kinds of user interface, and unified charging for services.
Owner:BEIJING UNIV OF POSTS & TELECOMM
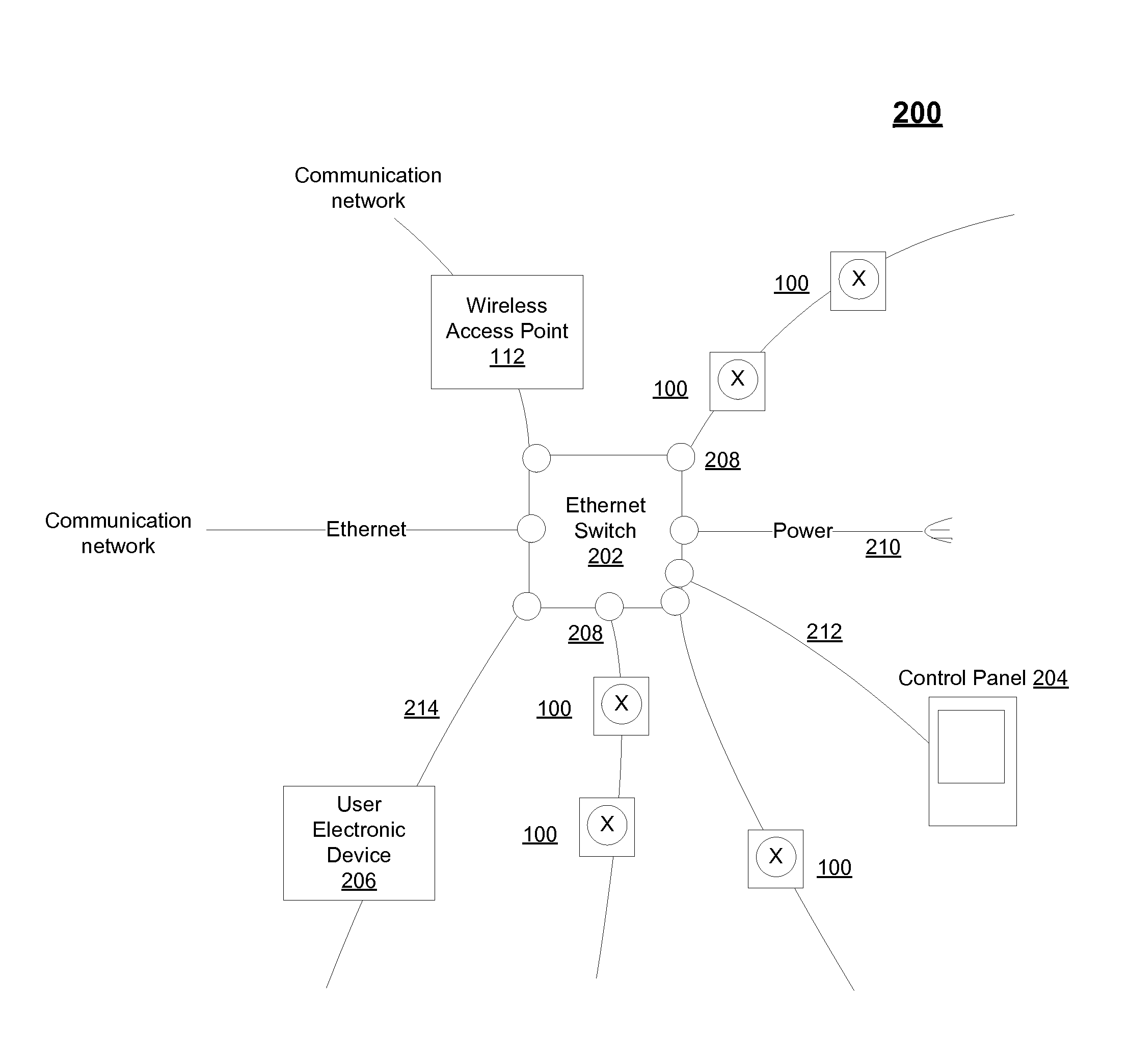
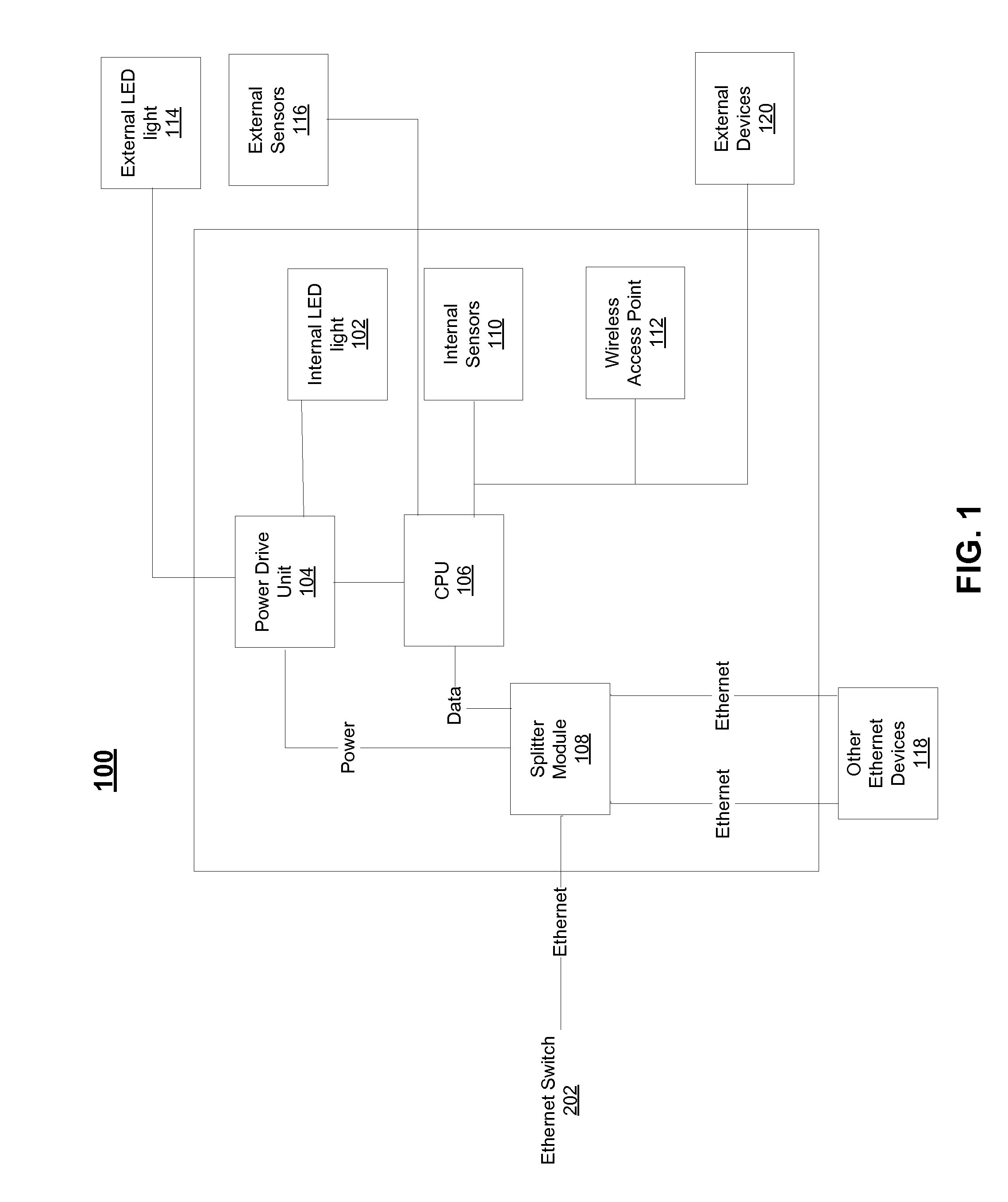
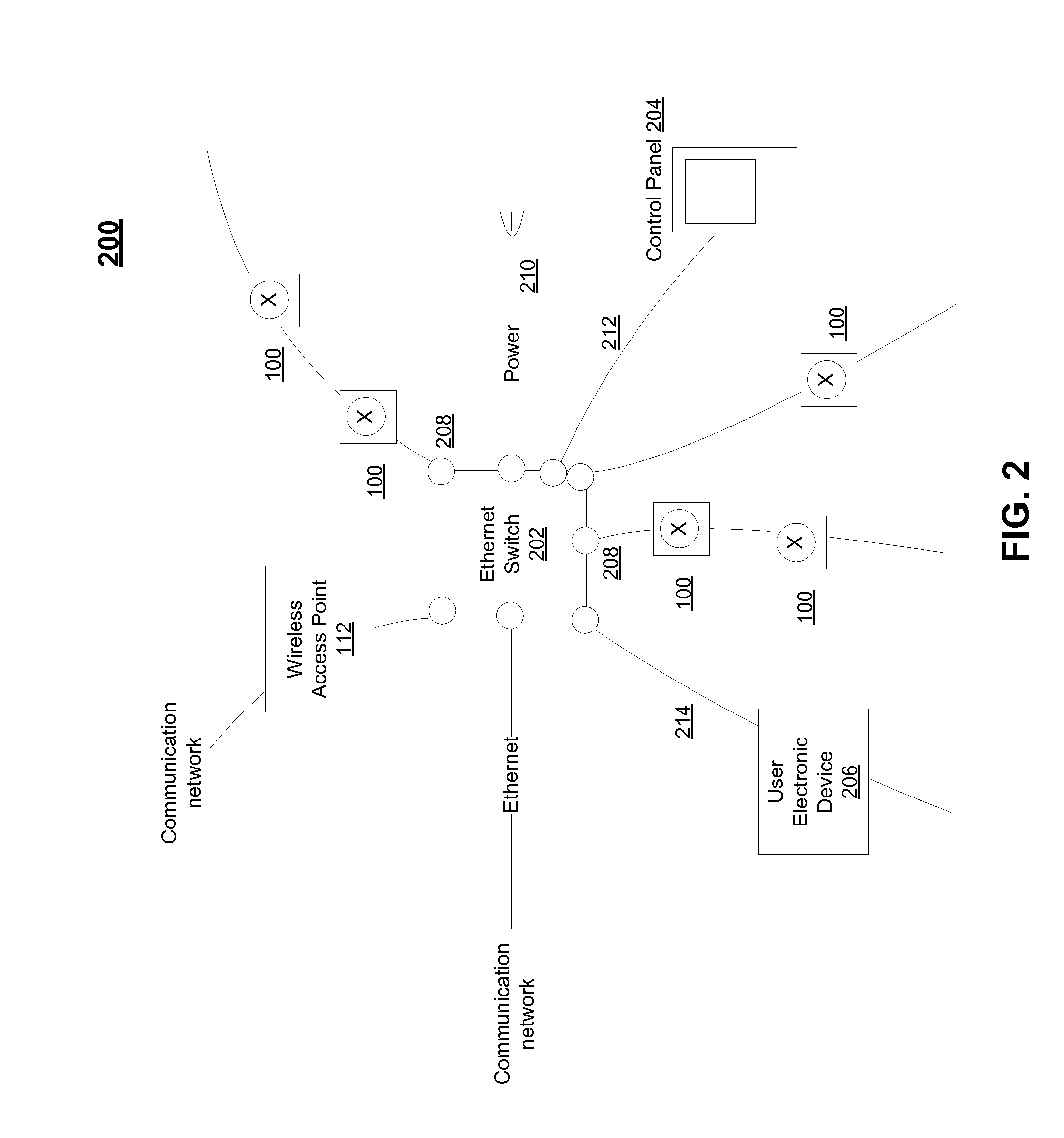
Power over ethernet lighting system
ActiveUS9155171B1Electrical apparatusElectroluminescent light sourcesStructure of Management InformationLighting system
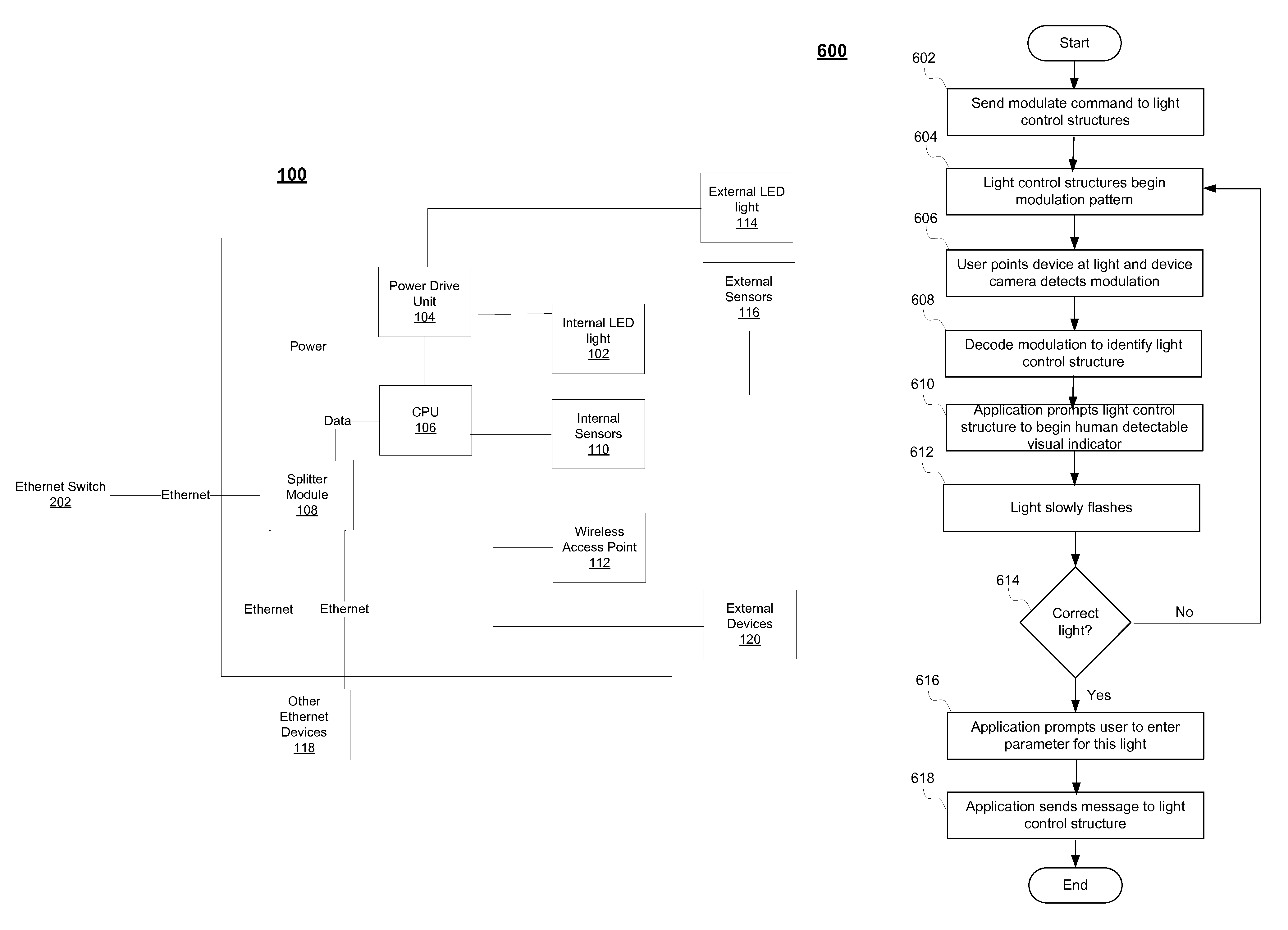
A system, method, and computer program for deploying a lighting system throughout a building using power over Ethernet is provided. In exemplary embodiments, one or more LED lighting structures may be powered using Ethernet cable in a building, and may be controlled by a distributed management system throughout a communication network.
Owner:HUGHES DAVID ANTHONY +1
System and method for distributed management of shared computers
ActiveUS20050091078A1Key distribution for secure communicationDigital computer detailsApplication softwareServer
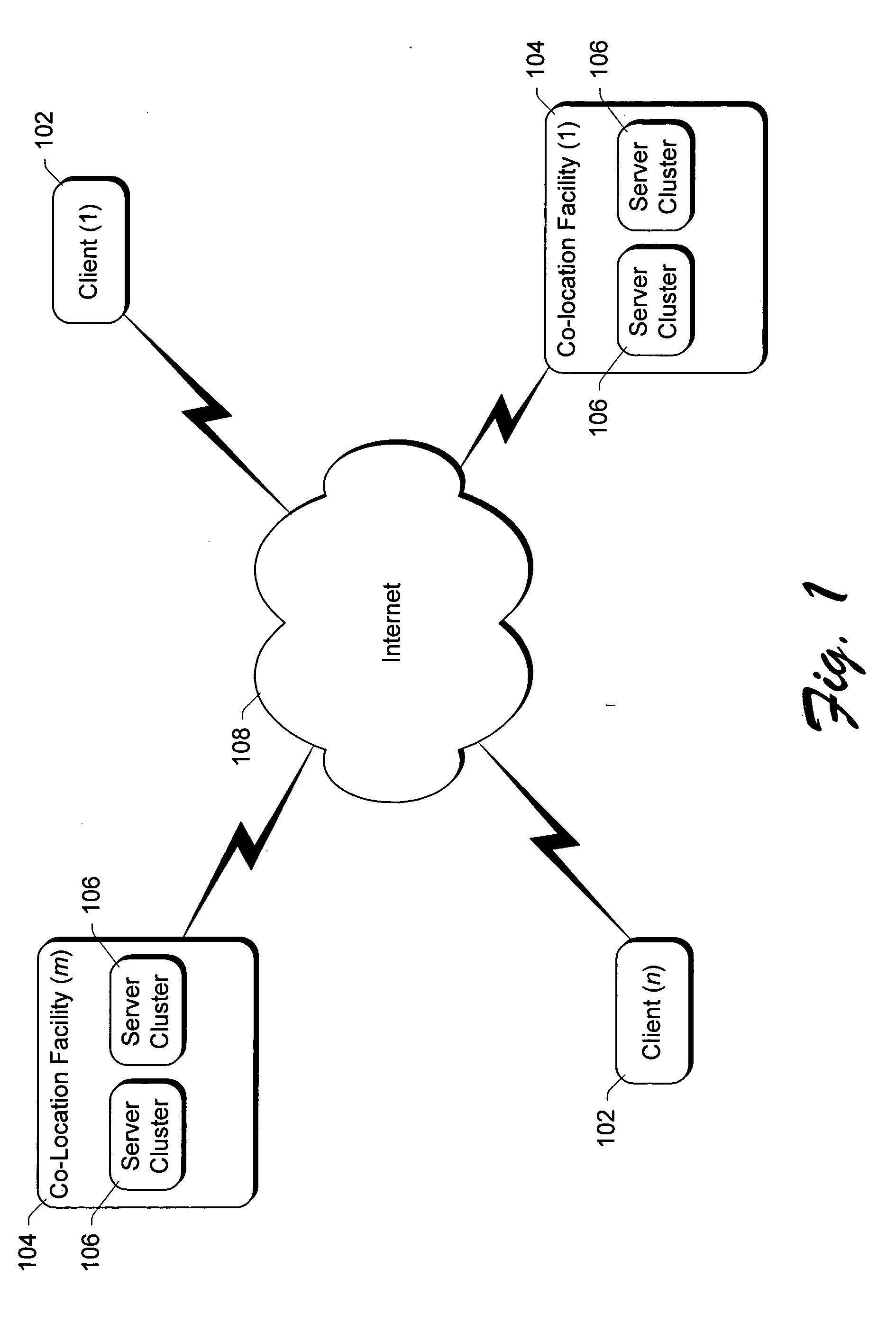
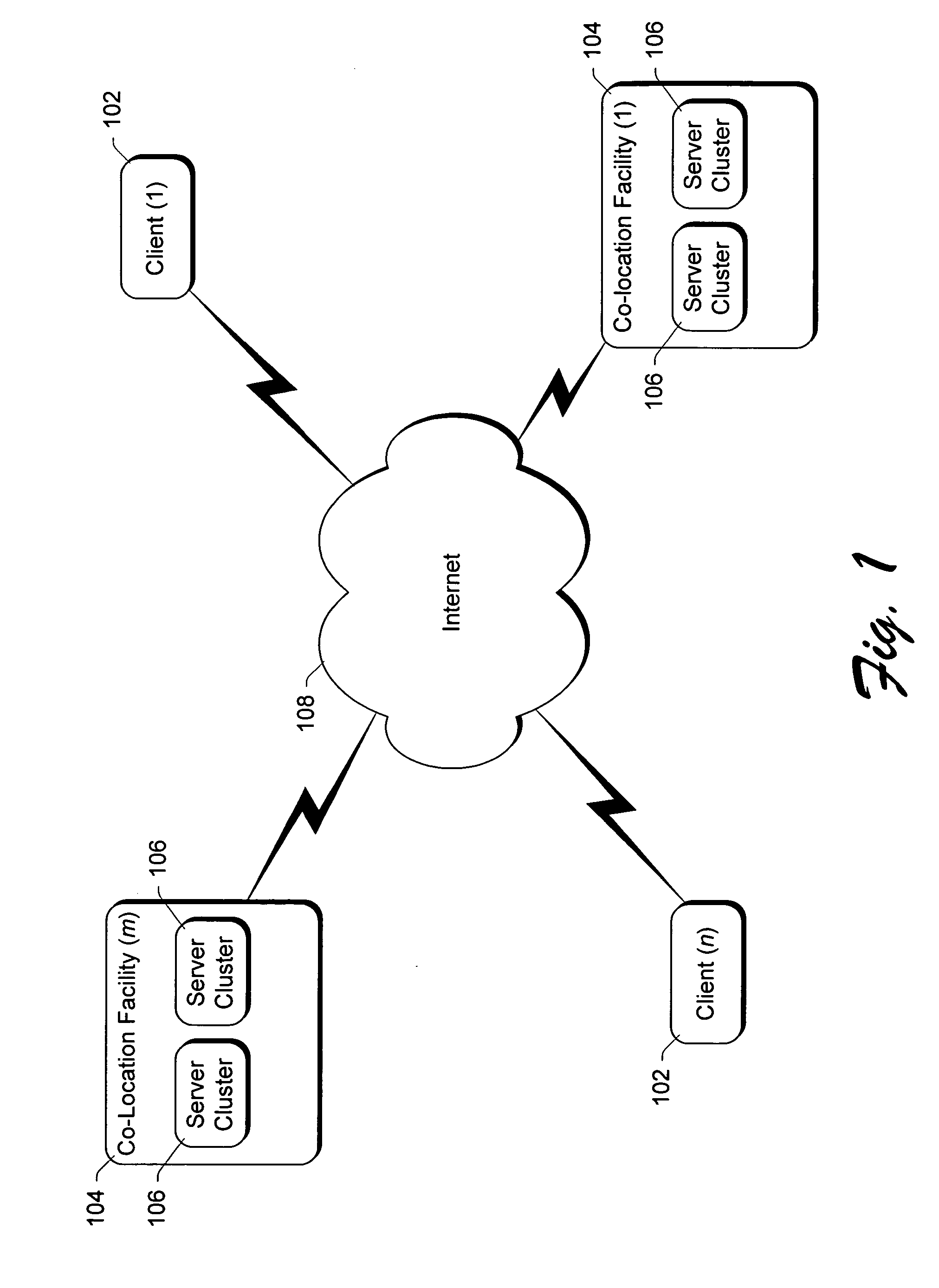
A multi-tiered server management architecture is employed including an application development tier, an application operations tier, and a cluster operations tier. In the application development tier, applications are developed for execution on one or more server computers. In the application operations tier, execution of the applications is managed and sub-boundaries within a cluster of servers can be established. In the cluster operations tier, operation of the server computers is managed without concern for what applications are executing on the one or more server computers and boundaries between clusters of servers can be established. The multi-tiered server management architecture can also be employed in co-location facilities where clusters of servers are leased to tenants, with the tenants implementing the application operations tier and the facility owner (or operator) implementing the cluster operations tier.
Owner:ZHIGU HLDG
Concurrent connections performance testing system and method for file system
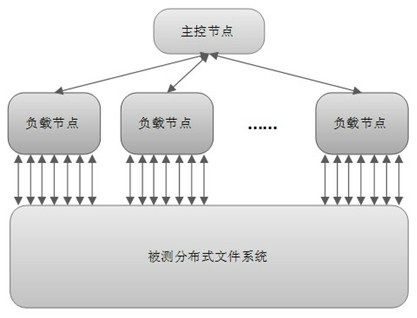
ActiveCN102035697AUnderstand the actual situationIncrease profitData switching networksSystem under testTask management
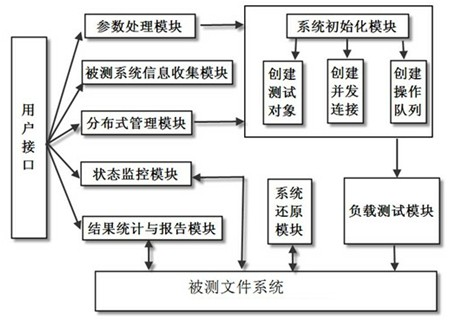
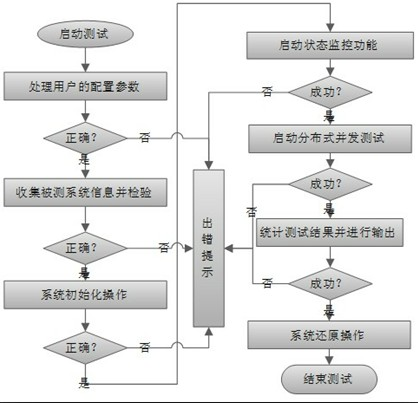
The invention discloses a concurrent connections performance testing system and a concurrent connections performance testing method for a file system. A master control node and at least one testing node are arranged, wherein the testing node is arranged on an application server of a storage system, is mainly used for simulating an application load to test a tested system, is connected with the tested file system through a storage network, and is used for testing the tested system; and the master control node performs centralized management which comprises process scheduling and task management on the testing node through a local area network, and is used for performing centralized management on all testing nodes and counting a test result. The system comprises a parameter processing module, a tested system information collecting module, a system initialization module, a condition monitoring module, a distributed management module, a load testing module, a result counting and reporting module and a system recovery module, solves the problems that the concurrent connections of the file system are not definitely defined and a detailed and useable testing method is lacked in the prior art, and is particularly suitable for the concurrent connections performance test of a distributed file system.
Owner:NO 15 INST OF CHINA ELECTRONICS TECH GRP
System and method for distributed management of shared computers
ActiveUS20050097097A1Key distribution for secure communicationDigital computer detailsApplication softwareServer
A multi-tiered server management architecture is employed including an application development tier, an application operations tier, and a cluster operations tier. In the application development tier, applications are developed for execution on one or more server computers. In the application operations tier, execution of the applications is managed and sub-boundaries within a cluster of servers can be established. In the cluster operations tier, operation of the server computers is managed without concern for what applications are executing on the one or more server computers and boundaries between clusters of servers can be established. The multi-tiered server management architecture can also be employed in co-location facilities where clusters of servers are leased to tenants, with the tenants implementing the application operations tier and the facility owner (or operator) implementing the cluster operations tier.
Owner:ZHIGU HLDG
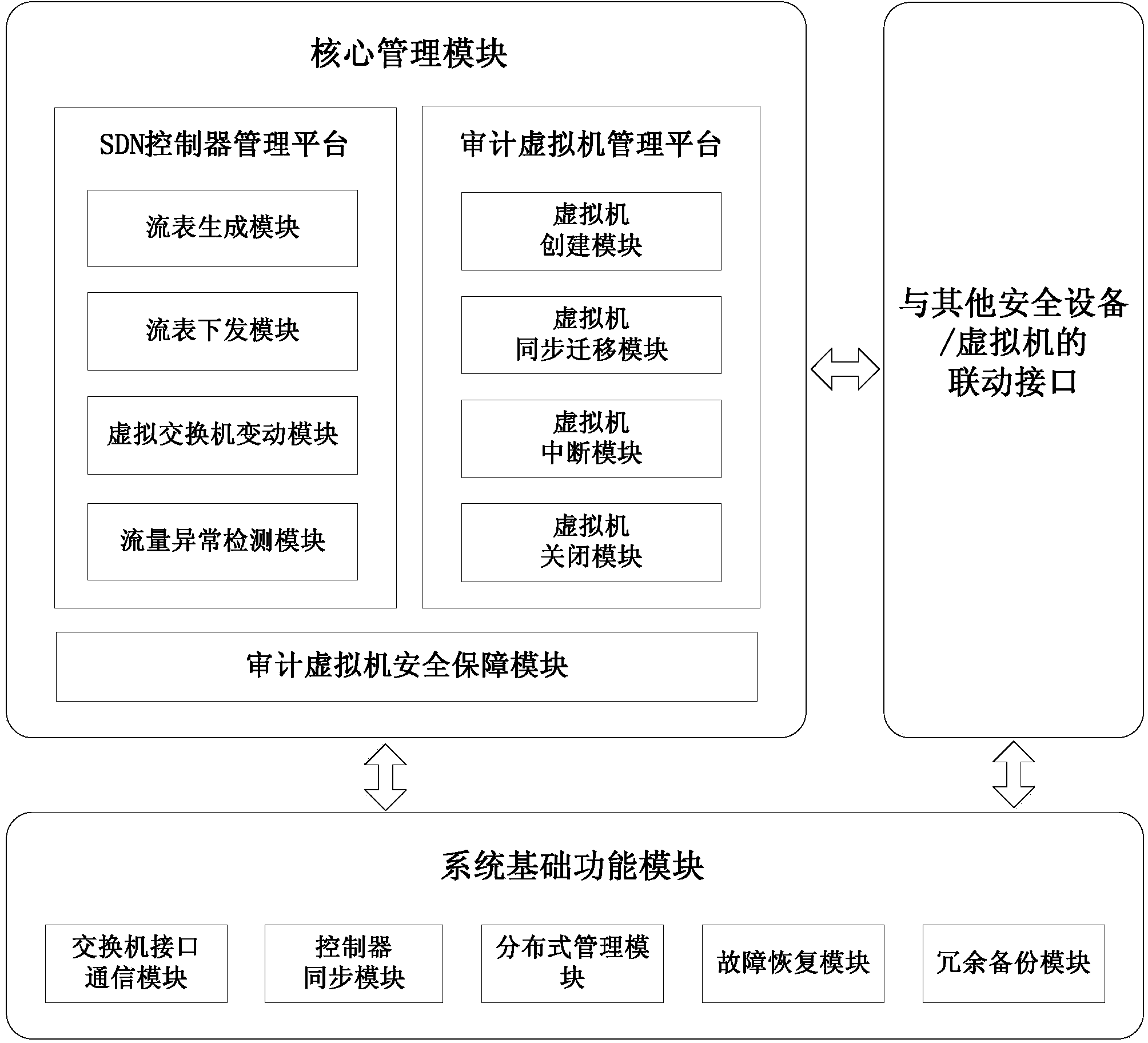
System and method for auditing cloud computing data center based on SDN
InactiveCN103973481AGuaranteed validityCustomizable Virtual Audit ServicesData switching networksCloud data centerSecurity management
The invention discloses a system for auditing a cloud computing data center based on an SDN. The system comprises a core management module, a system basic function module and a linkage interface for connecting the system with other safety equipment or virtual machines. The core management module is the core of the whole system and comprises an SDN controller management platform module, an auditing virtual machine management platform module and an auditing virtual machine safety guarantee module. The system basic function module conducts coordinated management on multiple controllers in a cloud data center environment and comprises a switch interface communication module, a controller synchronization module, a distributed management module, a fault recovery module and a redundant backup module. The linkage interface for connecting the system with other safety equipment or virtual machines is used for connecting the system for auditing the cloud computing data center based on the SDN with other auditing virtual safety management platforms or other network safety products. According to the system and method, customizable and extensional virtual auditing services are provided in the cloud computing data center under the condition that normal operation of the services is not affected.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
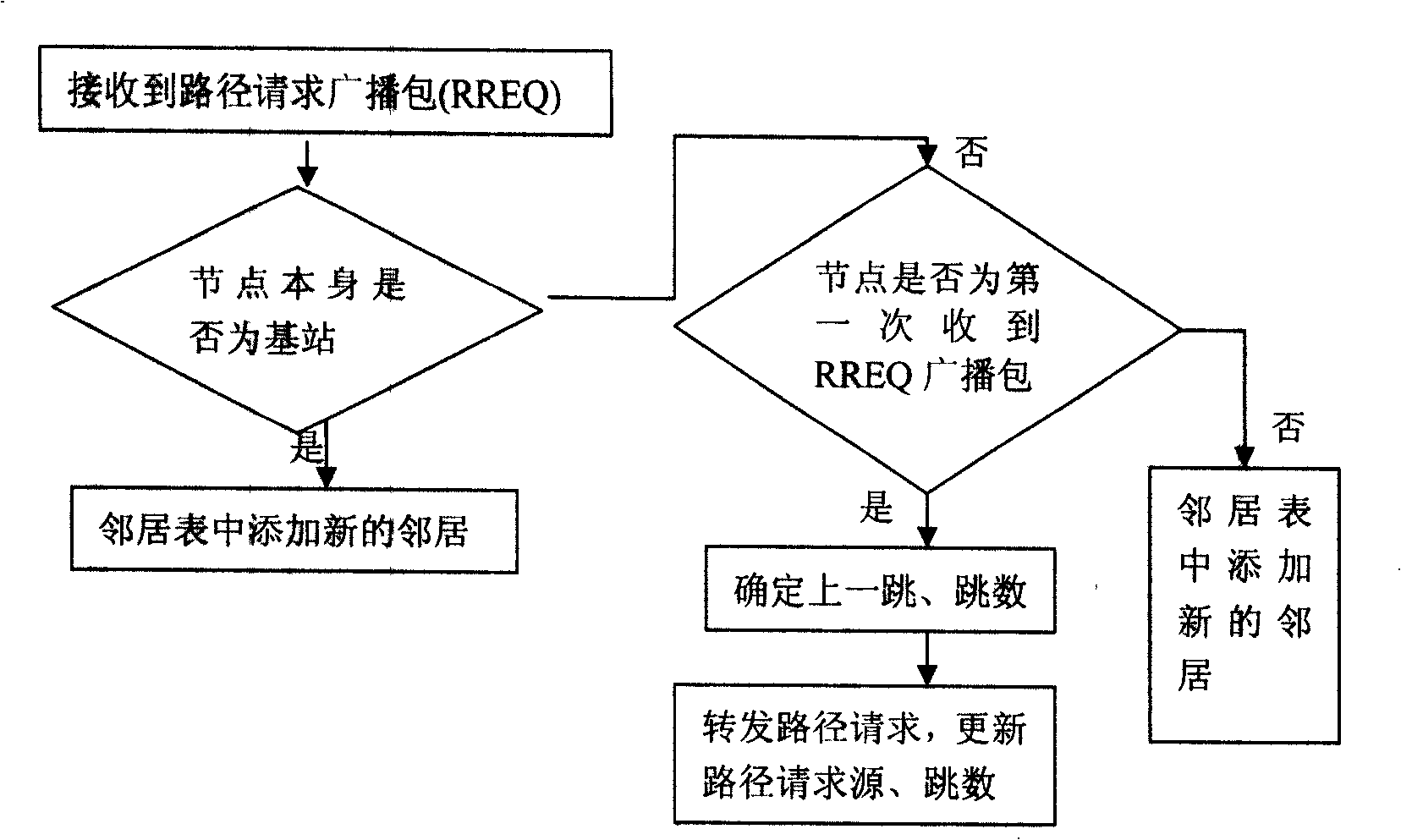
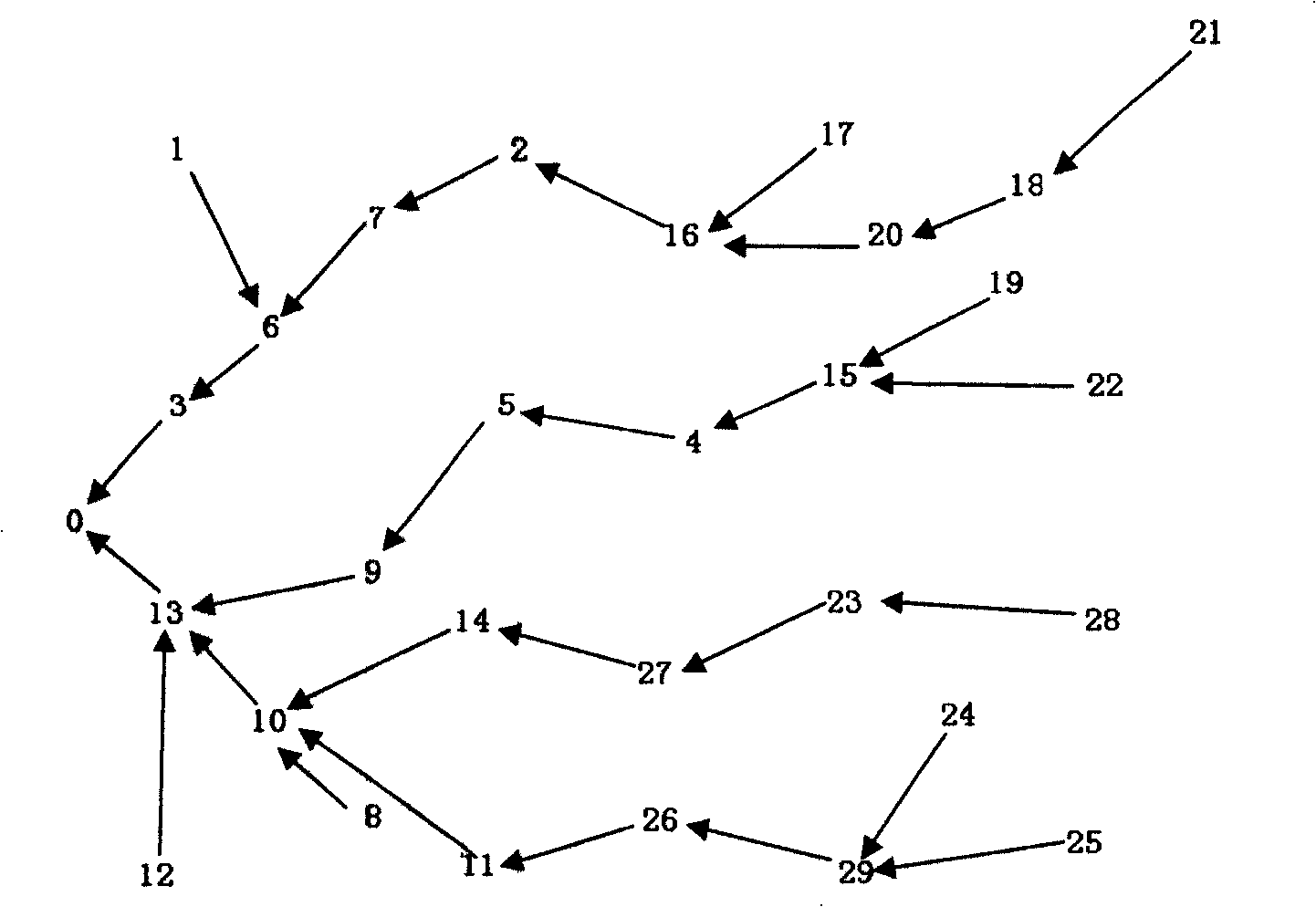
Multi-hop clustering route protocol initiated by base station
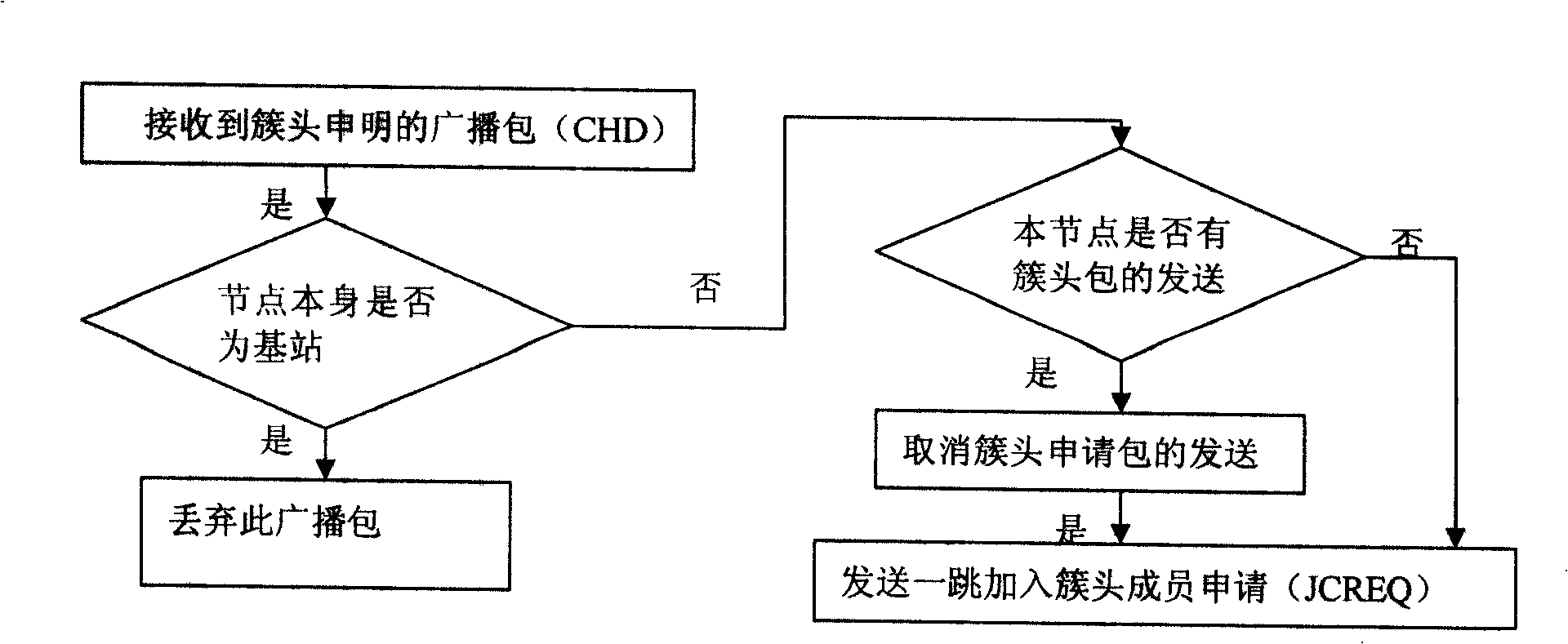
The invention discloses a multi-hop clustering routing protocol initiated on the basis of a base station. The routing protocol mainly comprises three steps: (1) a flooding process from the base station to other nodes, (2) forming process of a cluster; and (3) a data transmitting process and path maintenance, wherein each node establishes a pervious hop of a planar route of the node during the flooding process; according to received information, the node determines the number of adjacent nodes so as to determine whether to act as a cluster head; the forming process of the cluster ensures that the cluster head can identify in-cluster members, realize distributed management of the in-cluster members and ensure that the in-cluster members can confirm identities of the members; and when network path failure occurs caused by node failure on a data transmission path, network nodes can realize self organization to recover a disconnected link through cooperation. After the base station receives a first data packet uploaded by each node, information of an entire routing list is established so as to carry out fixed-point inquiry for any member node during subsequent operation without carrying out renetworking or flooding process.
Owner:WUHAN UNIV
Blockchain-based medical electronic medical record distributed management system and construction method thereof
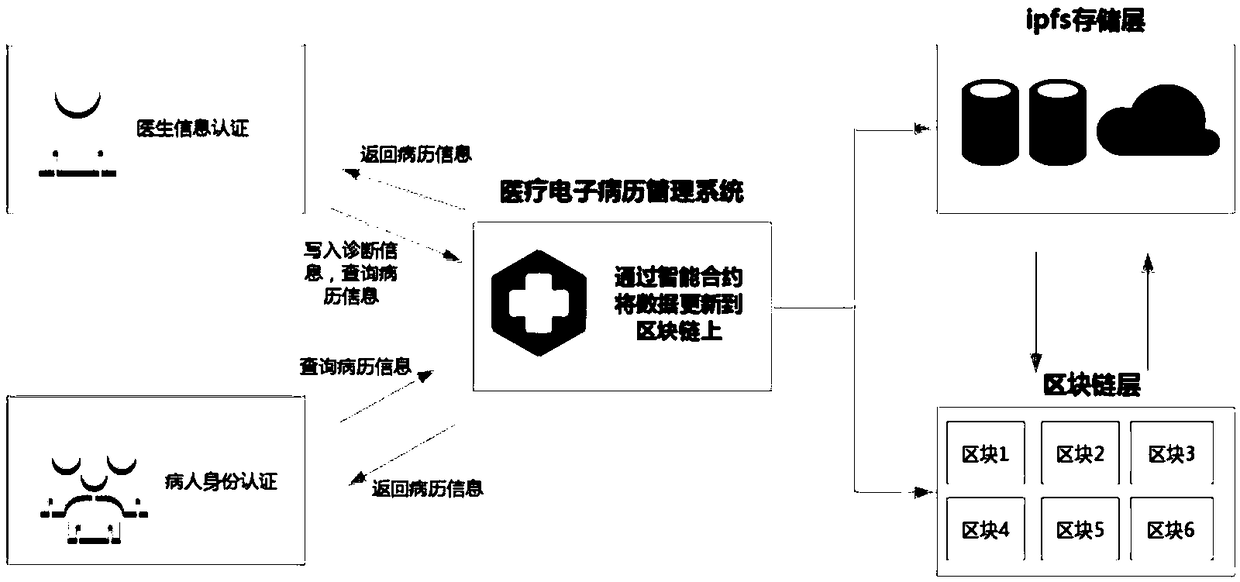
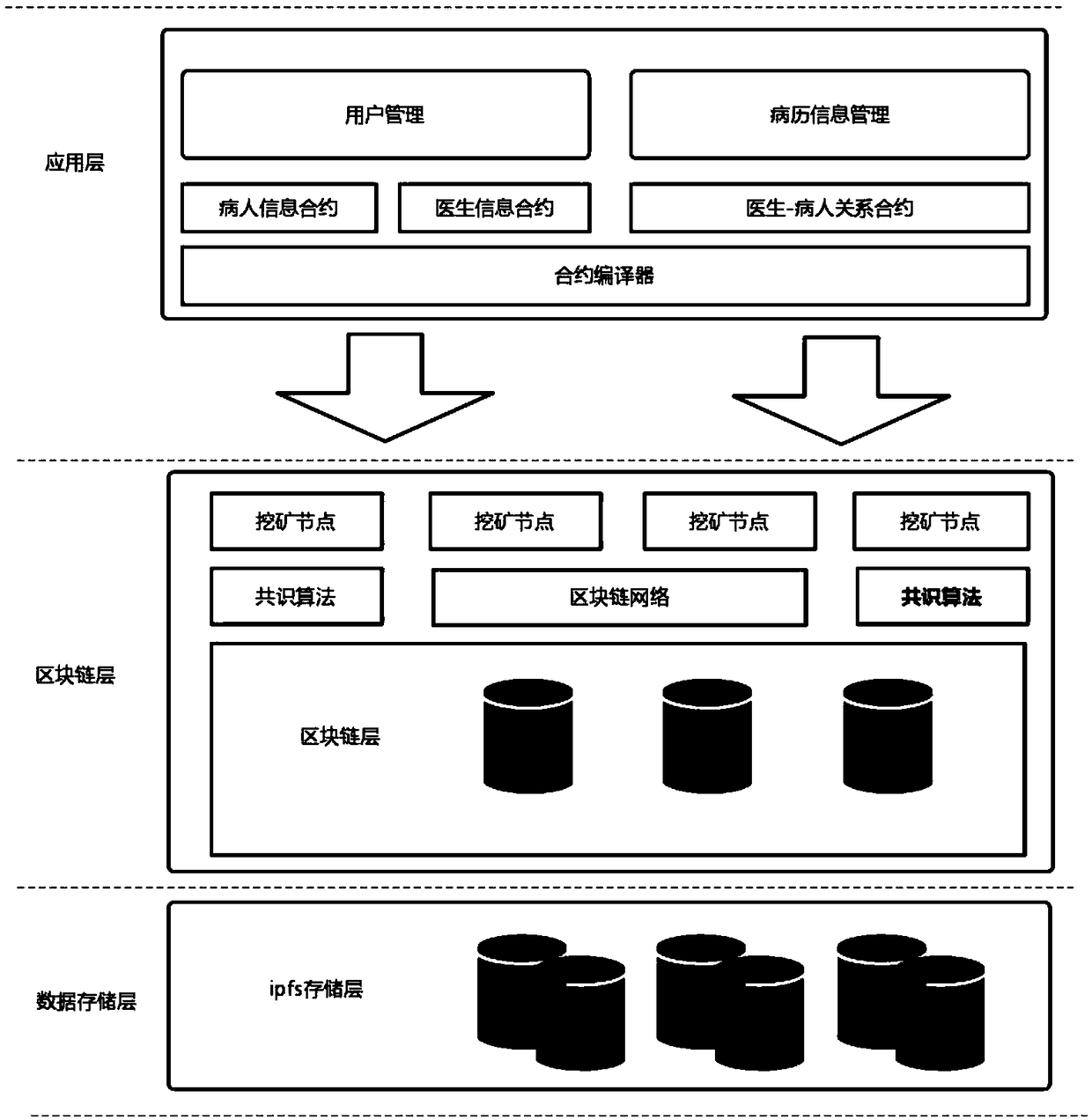
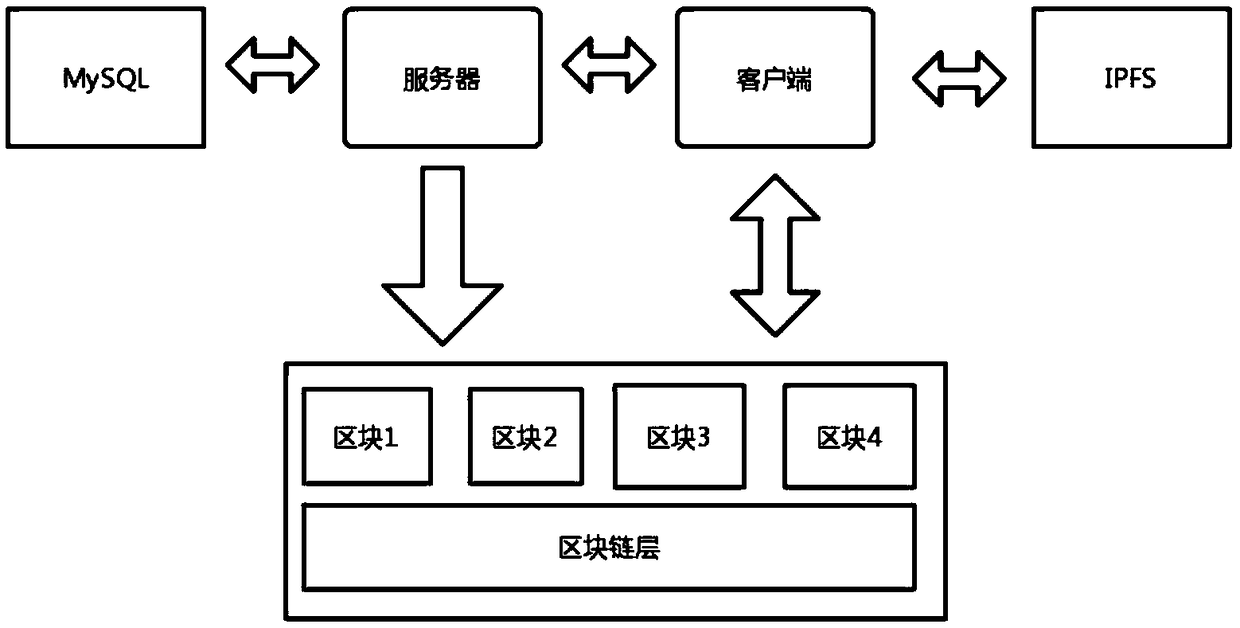
InactiveCN109215751AAvoid lostReduce maintenance costsMedical communicationDigital data protectionMedical recordSystem maintenance
The invention discloses a blockchain-based medical electronic medical record distributed management system and a construction method thereof. According to the blockchain-based medical electronic medical record distributed management system and the construction method thereof, the diagnosis processes of patients, such as medical records and prescriptions, are written into a blockchain in the form of smart contracts, so that a relevant hospital does not need to rely on a centralized server to manage the medical record information of the patients, and single-point failures common to the centralized server can be avoided; the data stored in the blockchain cannot be tempered and are traceable, and therefore, illegal tampering can be prevented; and a series of information such as the physical health, medical histories, and personal data of the patients, which concern personal privacy, can be effectively protected through an ABE encryption algorithm. With the system and method of the invention adopted, data loss caused by the single-point failures can be avoided, system maintenance cost can be decreased, and a condition that the diagnosis records of the patients are falsified during medical disputes can be avoided.
Owner:JINAN UNIVERSITY
Data transaction credit investigation platform and method on supply chain
PendingCN107423980AImprove maintainabilityImprove portabilityElectronic credentialsTamper resistanceOnline signature
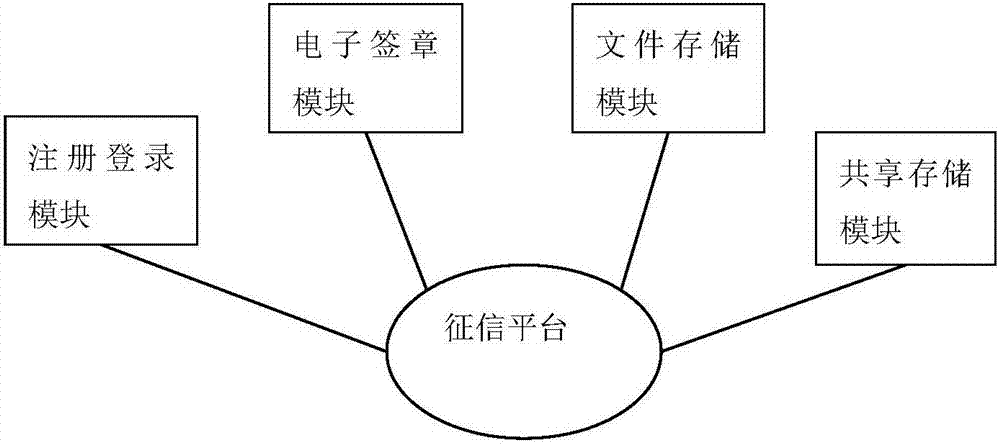
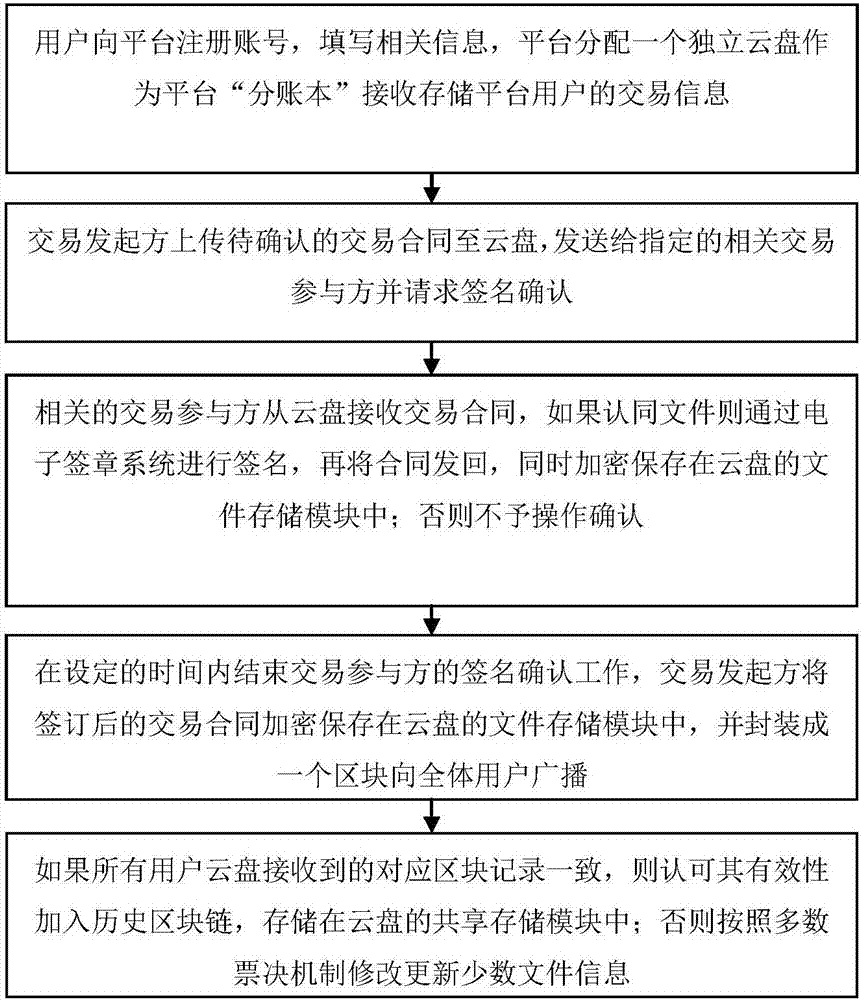
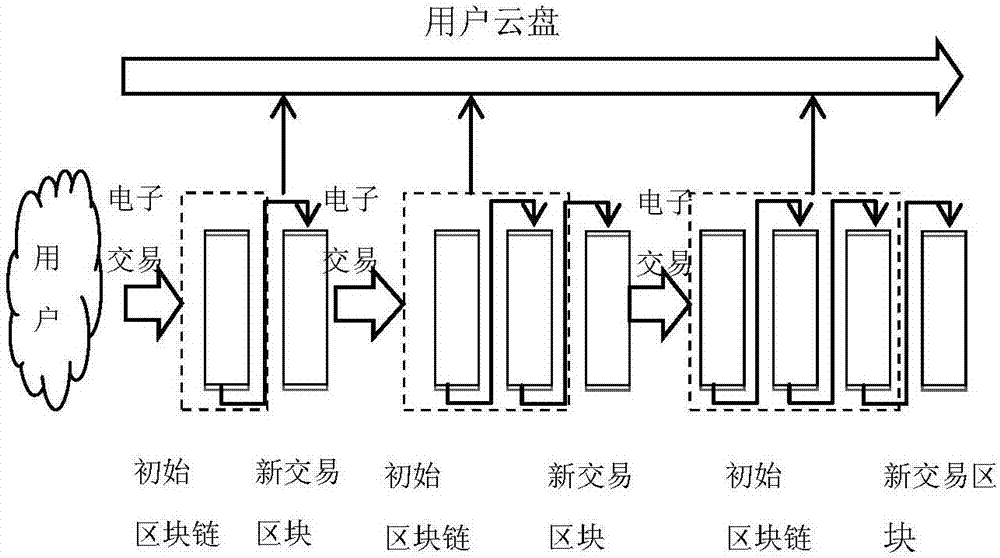
The invention discloses a data transaction credit investigation platform on a supply chain. The platform comprises a registration and login module which allows a user to register and use a platform function after login, an electronic signature module which allows the user to carry out online signature on a transaction contract, an encryption and authentication module which allows the user to authenticate the contract for a third party, a file storage module which is used for the encryption and storage of a contract file of the user, and a sharing storage module for storing shared contract abstract information. According to the platform architecture, the distributed management and sharing of credit data can be realized, and the querying, unforgeability and tampering resistance of data are ensured. The invention also discloses a data transaction credit investigation method on a supply chain.
Owner:易信(厦门)信用服务技术有限公司
Method for integrating distribution type isomerization information resource
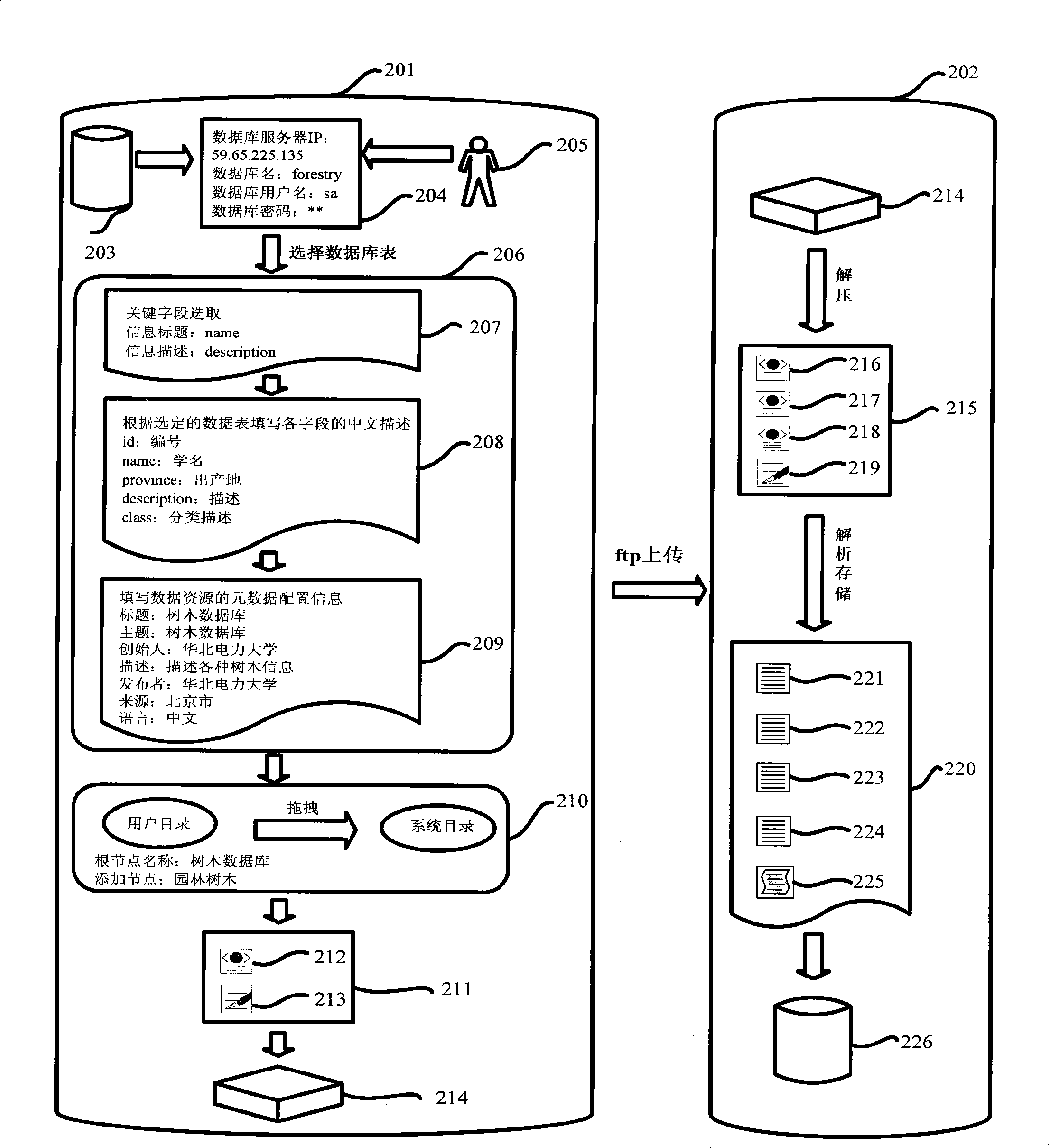
InactiveCN101329682ARealize a high degree of sharingAchieve integrationSpecial data processing applicationsInformation processingIsomerization
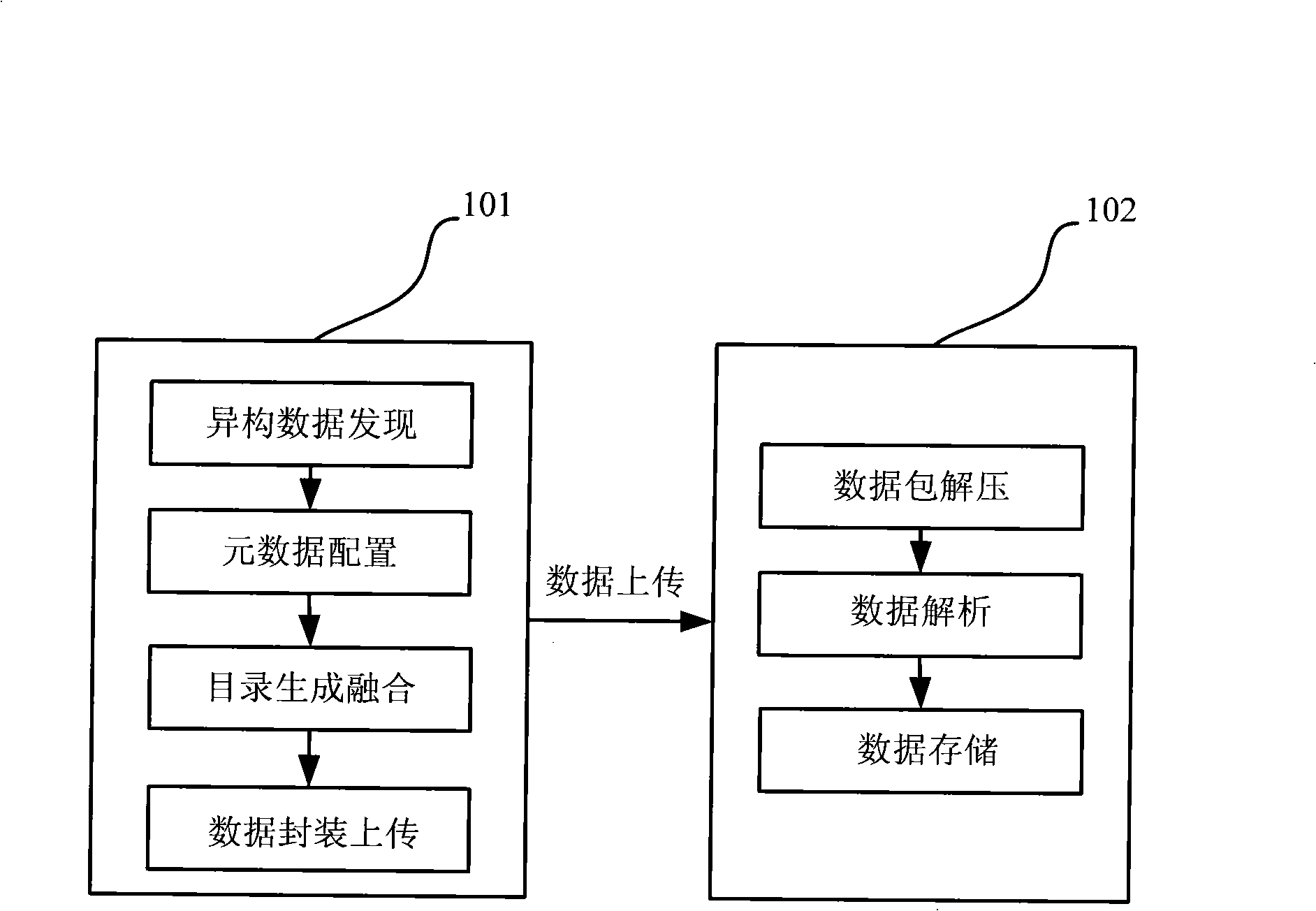
The invention pertains to the technical field of information processing, in particular relates to an integration method of distributed heterogeneous information resources. The method of the invention realizes the integration and share of the distributed heterogeneous information resources through the operations of an information resource provider end and an information resource collection end. The realization steps are as follows: (1) the following steps are carried out in sequence at the information resource provider end: heterogeneous data discovery, metadata configuration, catalog generation, catalog integration, data package as well as data upload that is uploading the packaged data in the form of data packet to the information resource collection end; (2) when the information resource collection end receives the data packet sent by the information resource provider end, data packet decompression, the analysis of configuration files and data storage are carried out. The method of the invention takes full consideration of the flexibility and scalability of structure; database type heterogeneity and data table heterogeneity are solved; centralized storage or distributed management of the distributed information sources is solved; the unified catalog storage of distributed heterogeneous information resources is realized; the problem of 'Information Island' that is increasingly serious is solved; the integration and share of the distributed heterogeneous information resources are effectively finished.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com